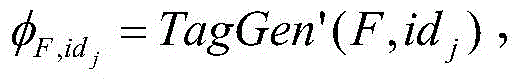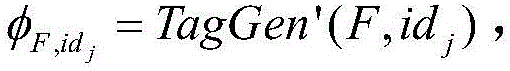A Safe Distributed Data Deduplication Method
A data deduplication and distributed technology, applied in the field of cloud storage services, can solve the problems of data inaccessibility, hidden dangers, data loss, etc., and achieve the effect of protecting data confidentiality, high reliability, high reliability and confidentiality level
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0066] System settings: In our construction, it is assumed that the number of S-CSPs storage servers is n, and the identities are represented as id 1 ,id 2 ...,id n . Define the security parameter as 1 λ , and initialize the secret sharing mechanism SS=(Share, Recover), a tag generation algorithm TagGen. The file storage system of the storage server is set to ⊥.
[0067] File upload: upload a file F, and the user interacts with S-CSPs to achieve deduplication. More precisely, the user first computes and sends the file label φ F =TagGen(F) for S-CSPs to perform deduplication check.
[0068] If a duplicate is found, the user calculates and sends Give the jth owning identity id j The S-CSP server. The purpose of introducing index j is to prevent servers from fetching the same file or block from other S-CSPs. if with metadata φ F match, the user will be given a pointer to the server id j Our Shared Data in .
[0069] Otherwise, if no duplication is found, the user ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com