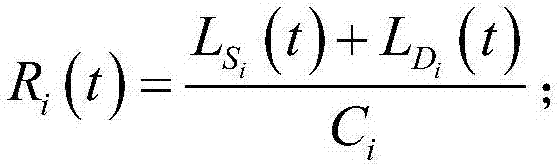Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
35results about How to "Improve lookup rate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
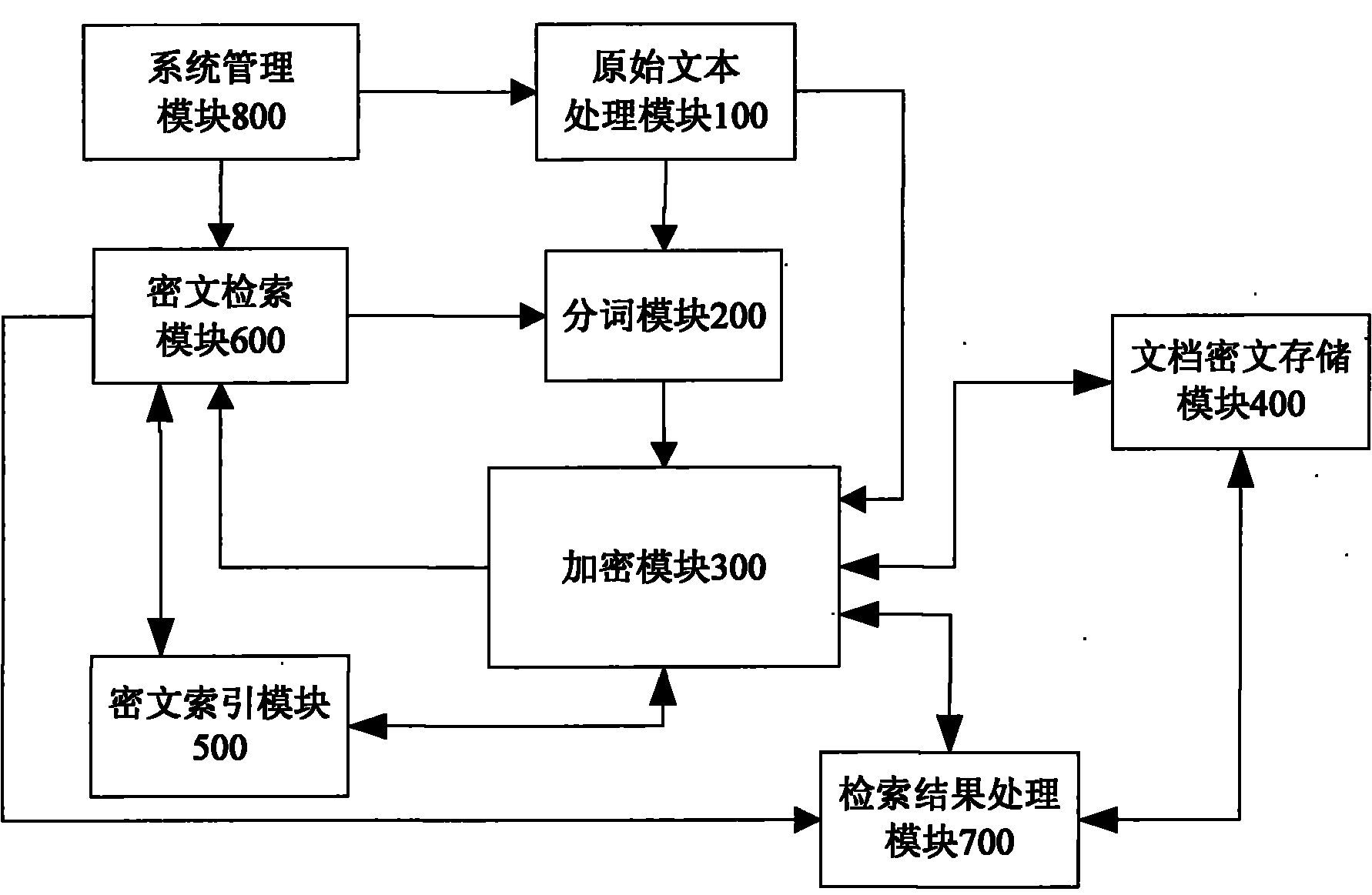
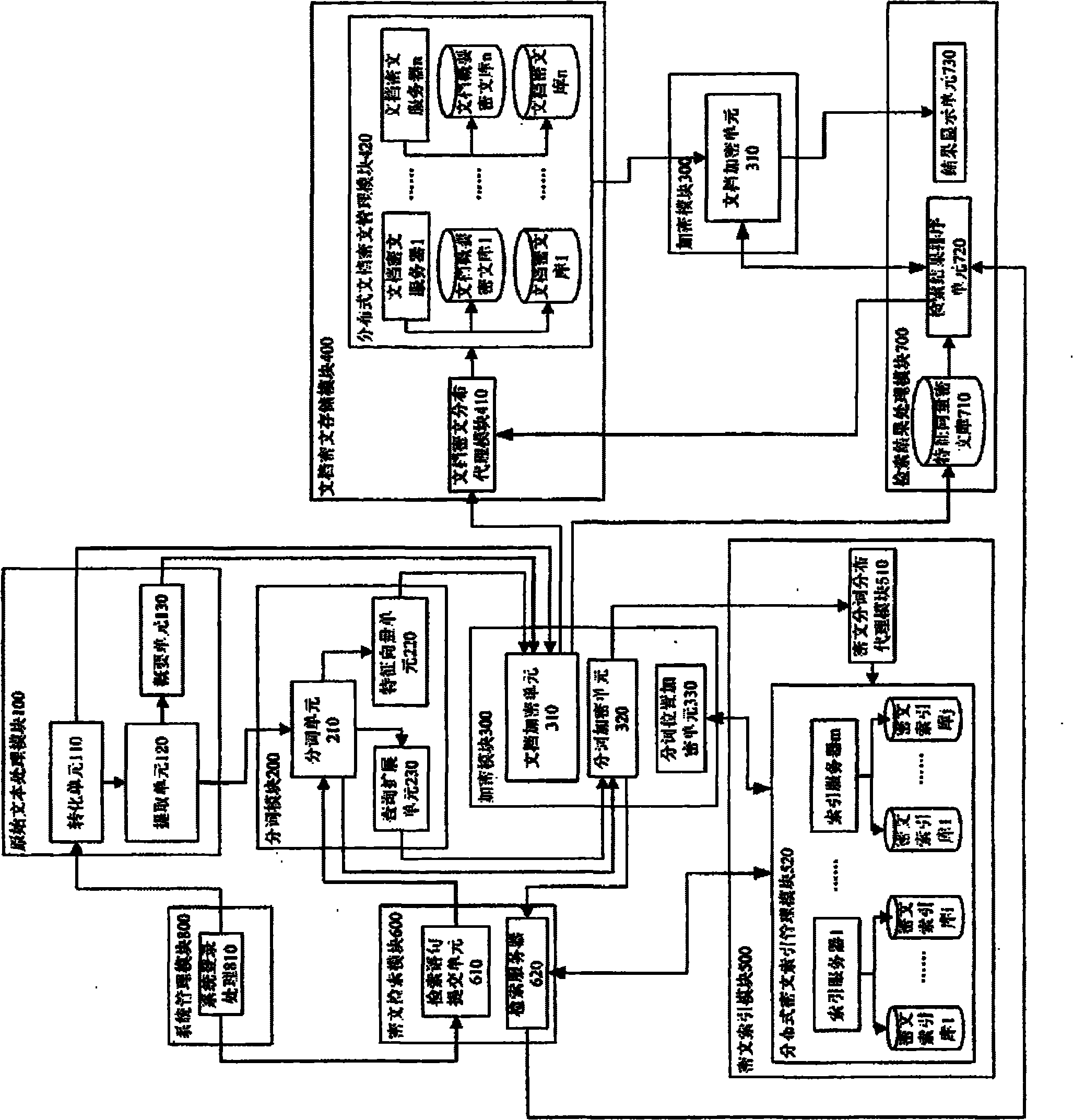
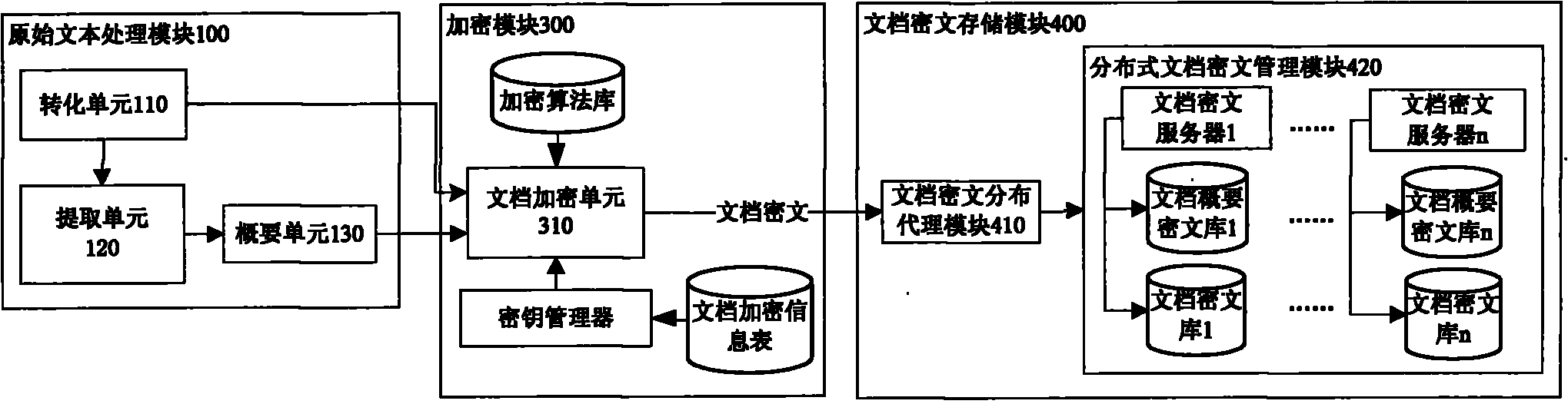
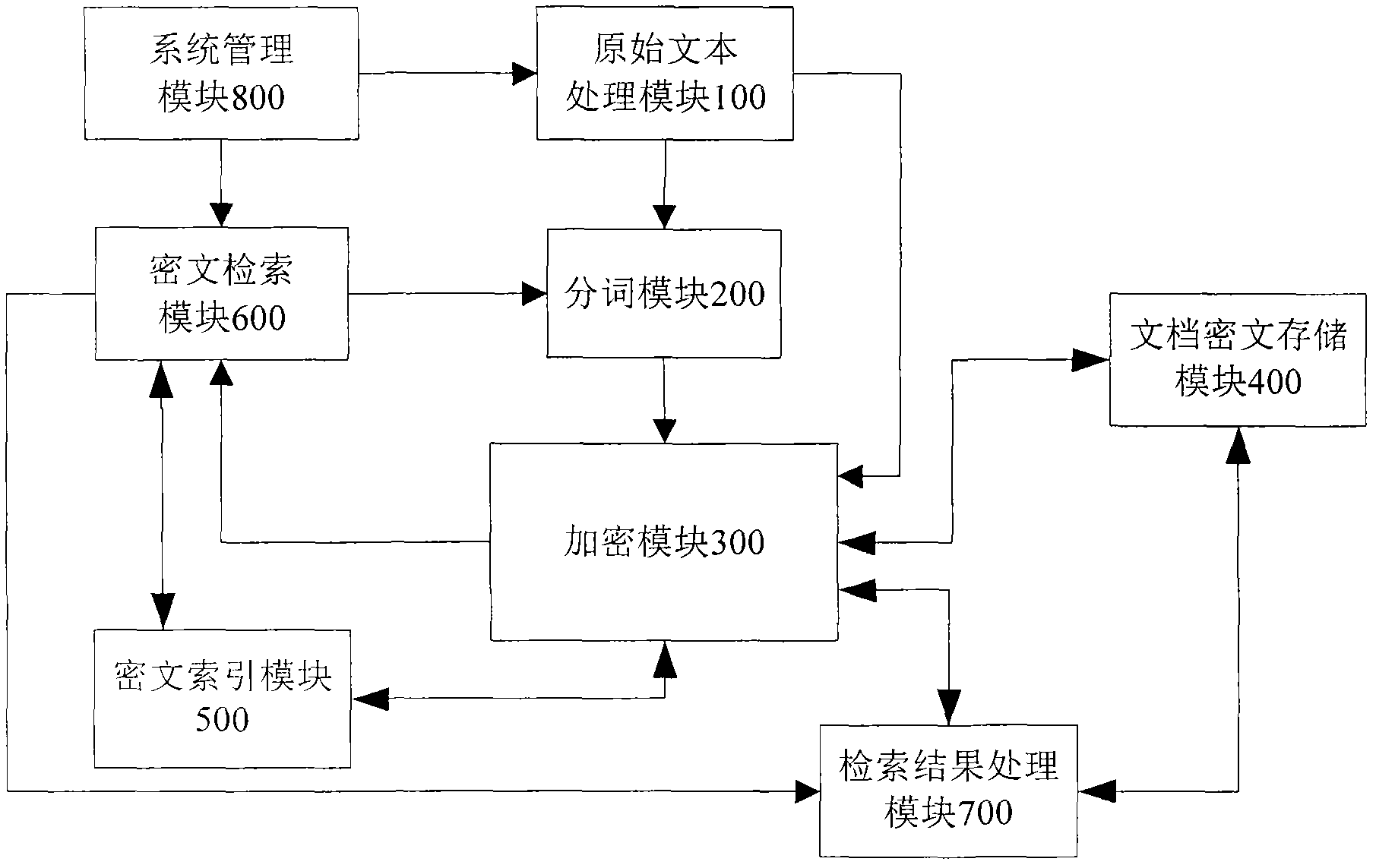
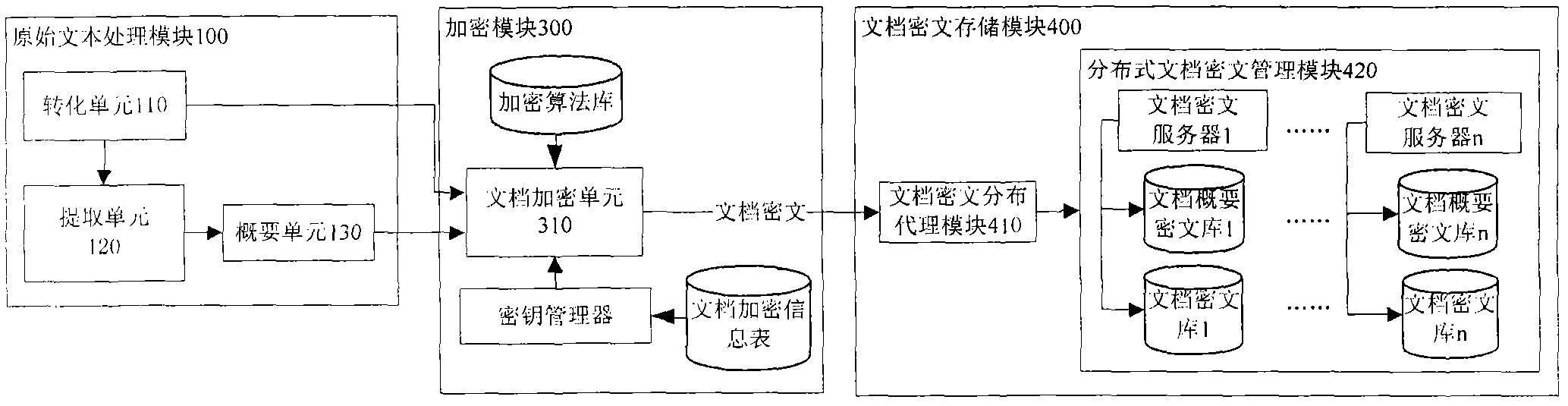
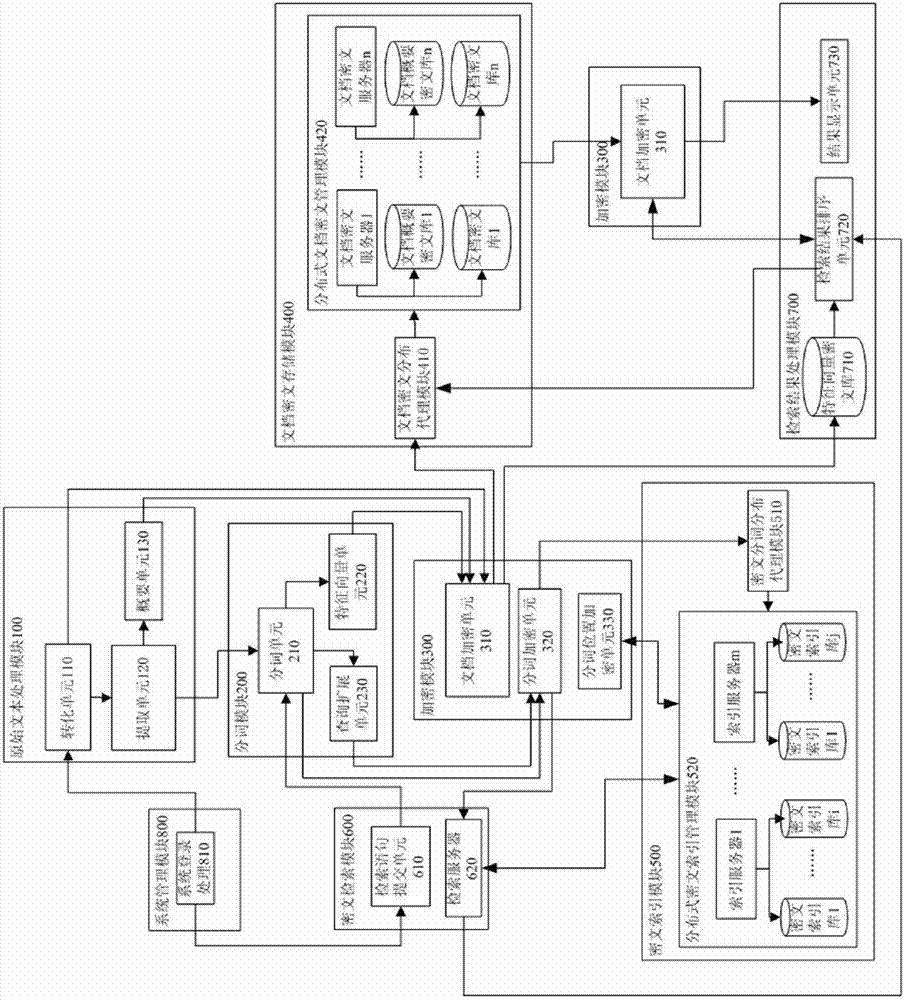
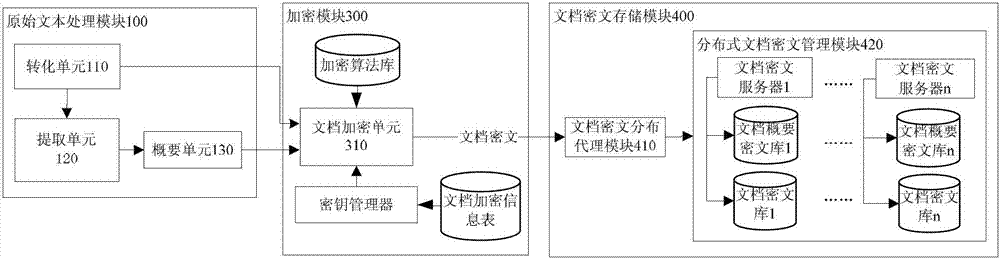
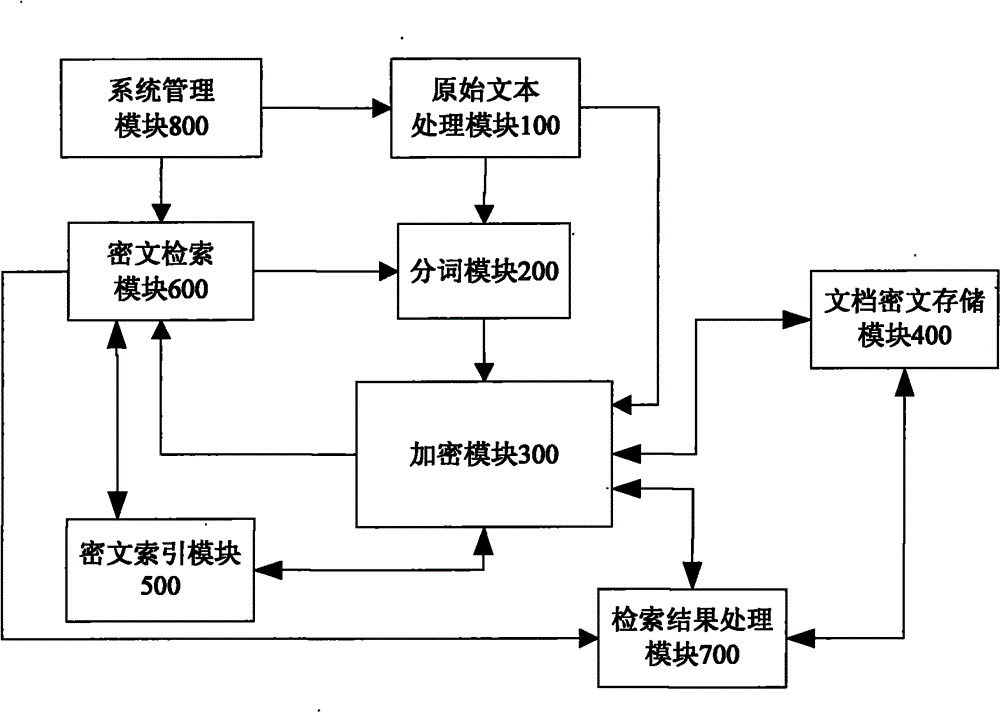
Ciphertext full-text search system
InactiveCN101859323ASafe and efficient dynamic updateSafe and efficient creationSpecial data processing applicationsFull text searchResource utilization
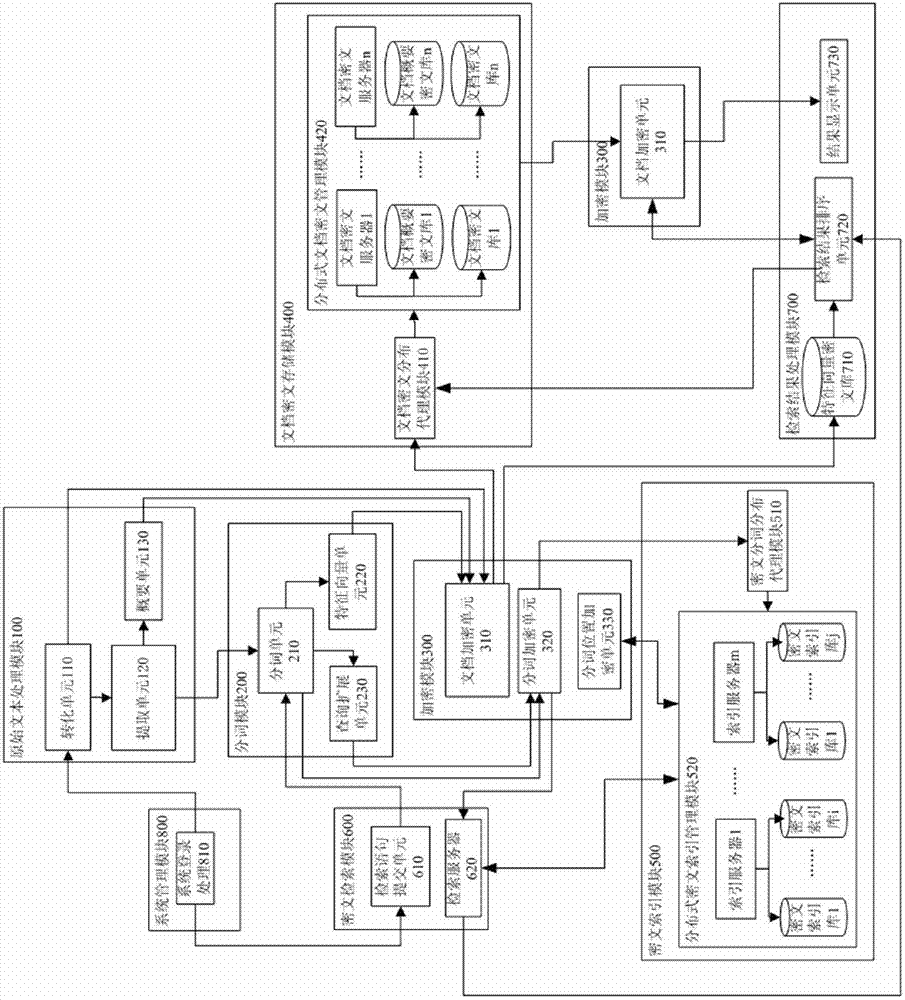
The invention discloses a ciphertext full-text search system, comprising an original text processing module, a word segmentation module, an encrypting module, a file ciphertext storage module, a ciphertext index module, a ciphertext search module, a search result processing module and a system management module. The system adopts a ciphertext dynamic sequential tree index structure, a word segmentation group technology and a file local ciphertext dynamic sequential tree index updating method, and can realize index establishment, dynamic index updating, full-text search and substring query under a ciphertext state. The system also can realize peer-to-peer full text research for a safety overlay network in a P2P network and introduces an index file carbon copy replication mechanism based ona peer-to-peer network hubs and nodes. In addition, the ciphertext full-text search system has good expandability, solves the problems of distribution storage and search of massive data index files, increased no occupation of network bandwidth, and has high network resource utilization ratio.
Owner:GUANGXI UNIV
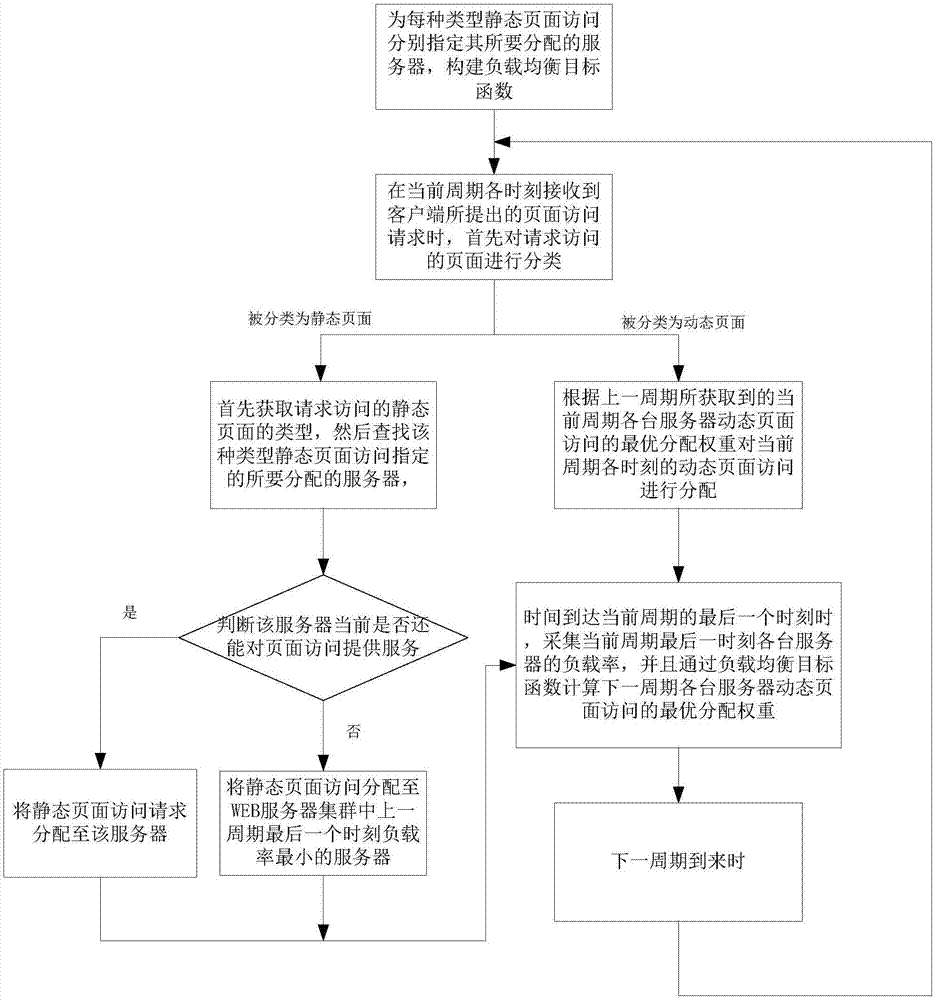
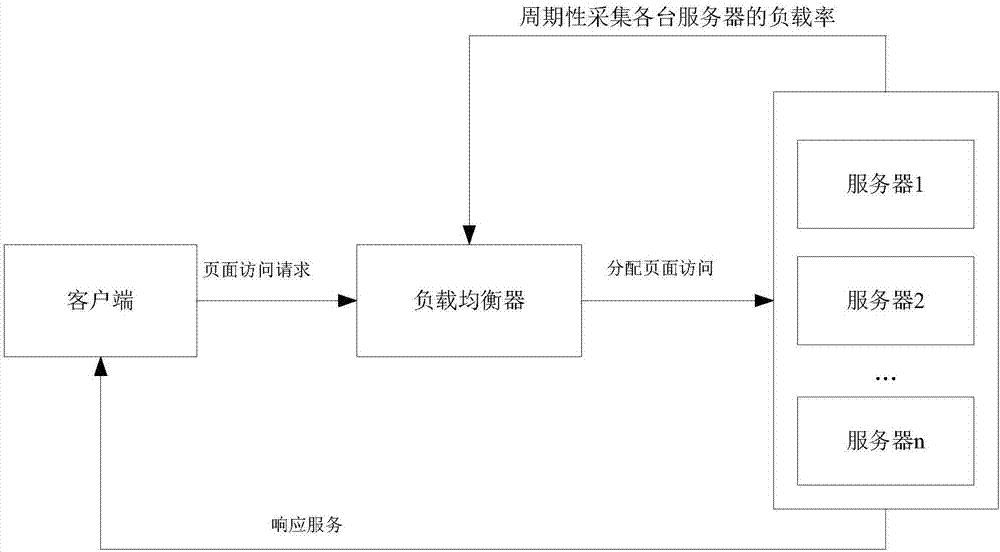
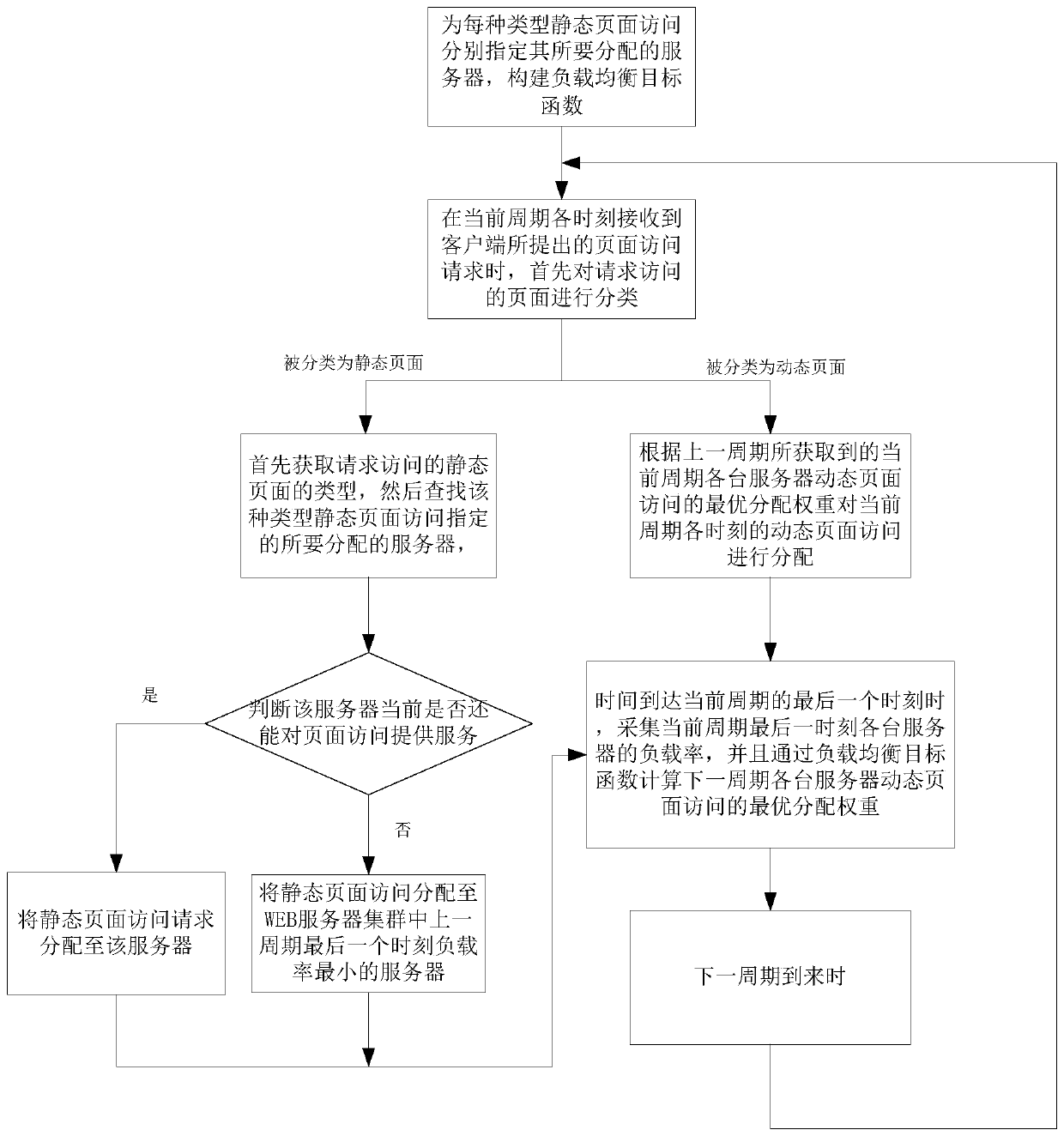
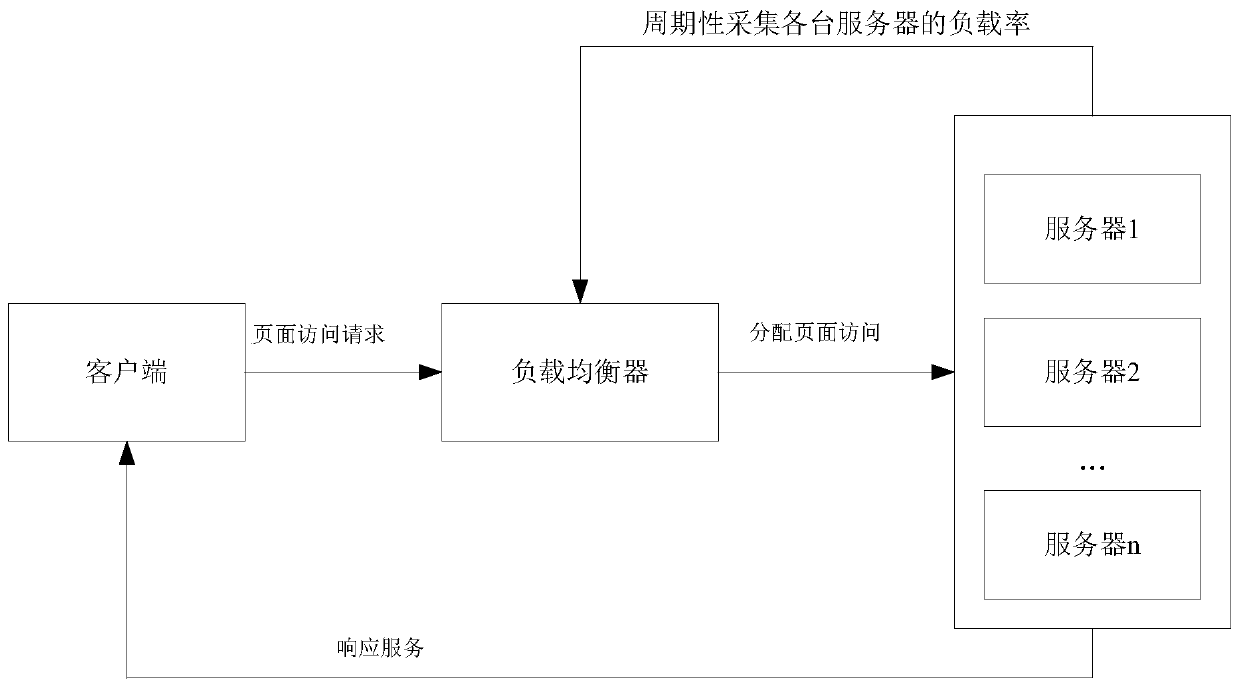
Load balancing method and system of WEB server cluster
ActiveCN107426332AMake full use of resourcesImprove experienceTransmissionStatic web pageOperating system
The invention discloses a load balancing method and system of a WEB server cluster. The method comprises the following steps: firstly, separately specifying a to-be-allocated server for each type of static page access, meanwhile constructing a load balancing target function, when a page method request is received, classifying the page method request, and when the page method request is a static page access request, allocating the page method request to a corresponding server according to the type of the page method request; when the page method request is a dynamic page access request, allocating the dynamic page access at various moments within a current period according to an optimum allocation weight of the dynamic page access of the servers within the current period obtained within the previous period; and when the time arrives at the last moment of the current period, obtaining the optimum allocation weight of the dynamic page access of the servers within the next period through the load balancing target function. According to the load balancing method and system disclosed by the invention, different processing modes are respectively provided for static pages and dynamic pages, so the server resources can be fully used, and a load balancing effect can still be achieved under complex access situations.
Owner:SOUTH CHINA UNIV OF TECH
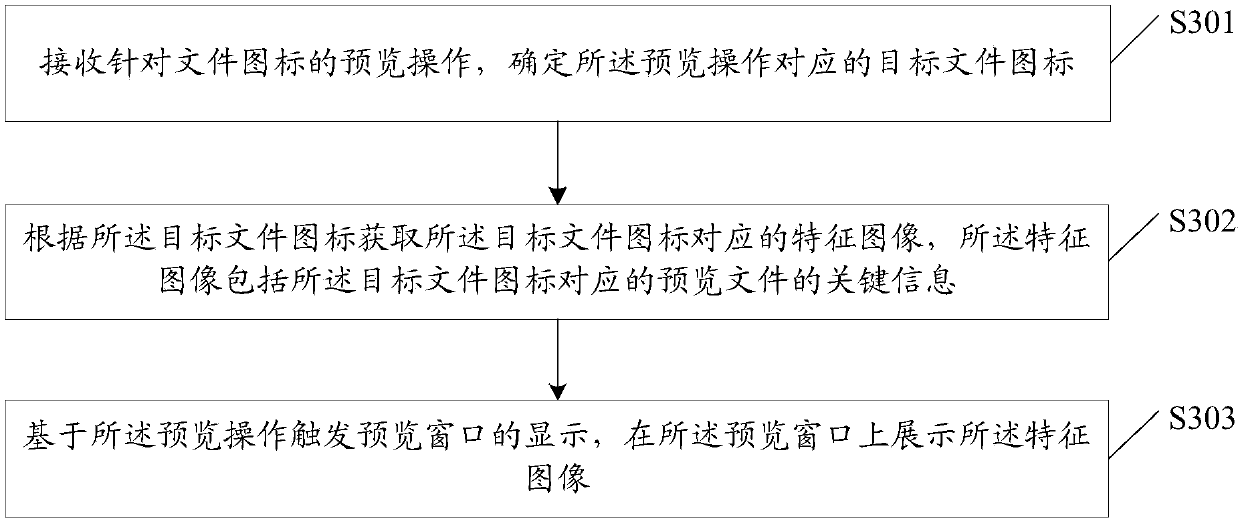
File preview method, device and computer readable storage medium
InactiveCN107659729ADisplay is intuitive and fastQuick showSubstation equipmentInput/output processes for data processingComputer terminalComputer science
The invention discloses a file preview method, comprising the steps of: receiving a preview operation for a file icon, and determining a target file icon corresponding to the preview operation; acquiring a feature image corresponding to the target file icon according to the target file icon, wherein the feature image comprises key information of a preview file corresponding to the target file icon; and based on the display of a preview window triggered by the preview operation, displaying the feature image on the preview window. The embodiments of the invention further provide a device for implementing the method and a computer readable storage medium. By adopting the method, a user can accurately learn the main content of files that are not opened at a terminal and quickly find the required file, and the operating resource of a system is saved at the same time.
Owner:NUBIA TECHNOLOGY CO LTD
Bit vector-based high-speed routing lookup apparatus and method
ActiveCN105959224AOvercome the problem of lookup delayLookup delay is smallData switching networksCode moduleTheoretical computer science
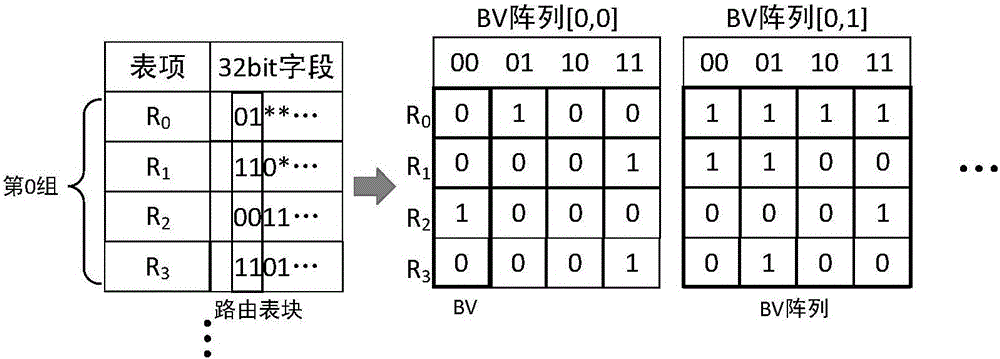
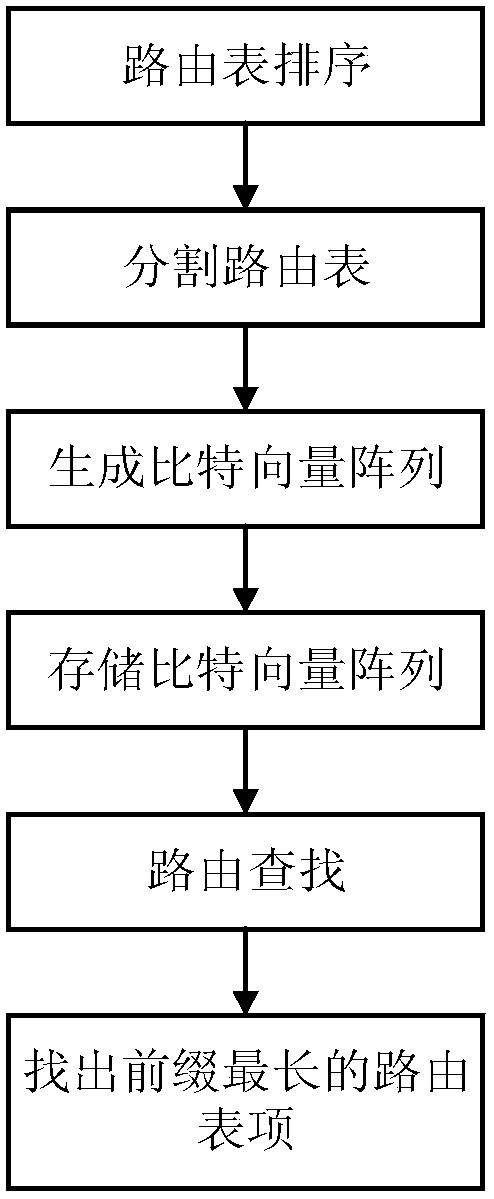
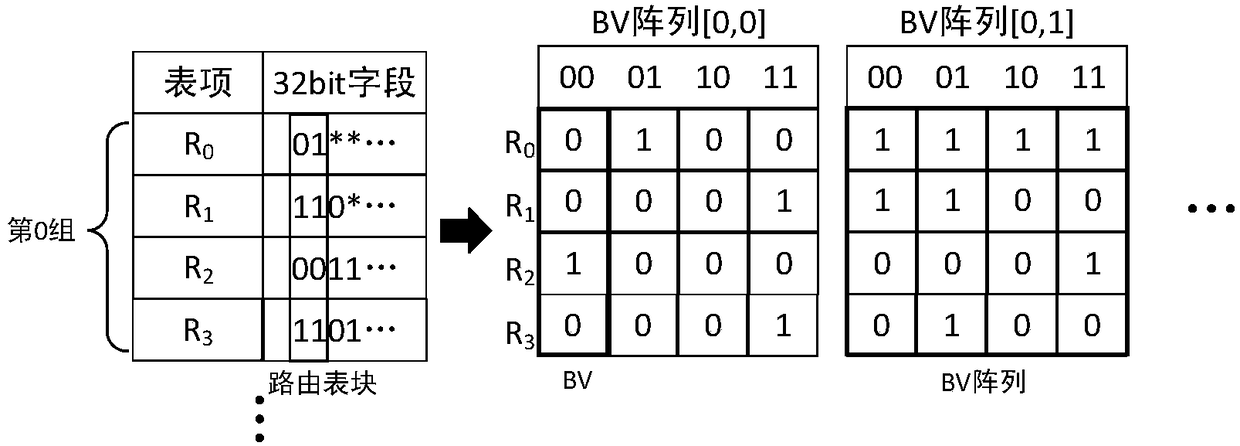
The present invention discloses a bit vector-based high-speed routing lookup apparatus and method, which mainly solves problems in the existing routing lookup methods that a data structure and a lookup operation are complex, hardware is hard to realize, and lookup speed is low. The apparatus includes a routing table coding module, a routing lookup module and an advanced coder module. The method includes the steps of ranking all routing table items stored in a routing table in a descending manner according to lengths of network prefixes; segmenting the routing table into multiple routing table blocks; converting the routing table blocks into bit vector arrays and storing the bit vector arrays in a memory; reading bit vector ''AND'' by bit in a corresponding sub address in the memory; and finding a routing table item matching with the longest prefix. The method has the advantages that the data structure and the lookup operation are simple, the hardware is easy to realize, and the lookup speed is high.
Owner:XIDIAN UNIV +1
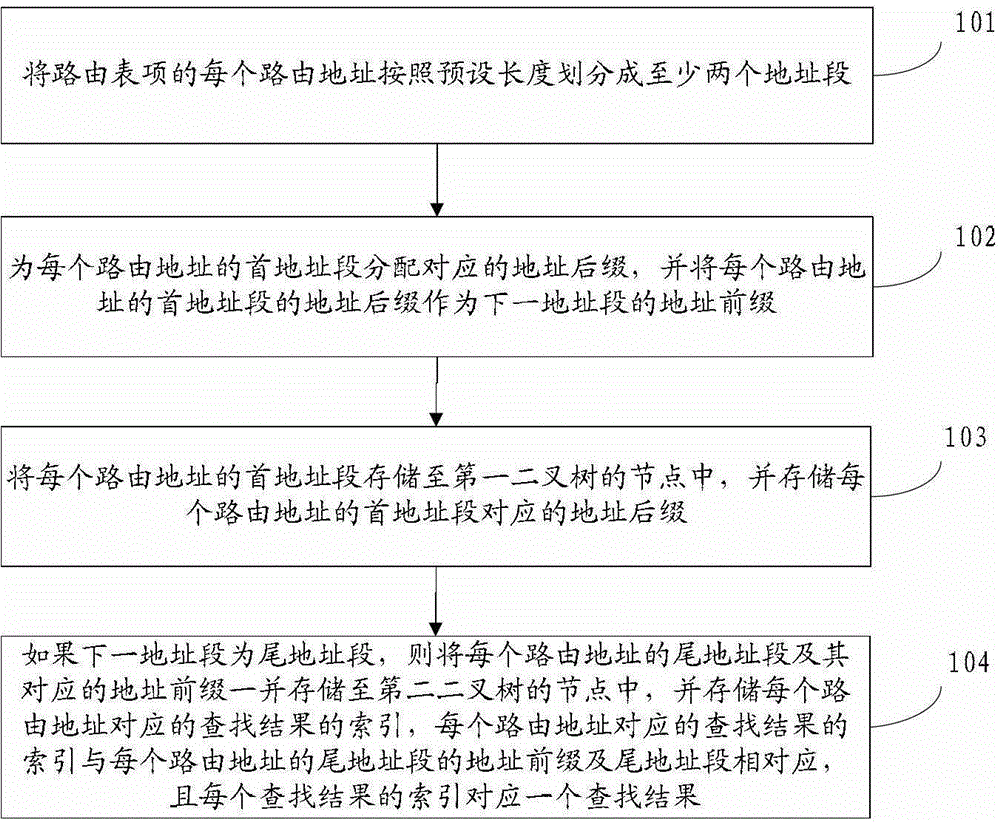
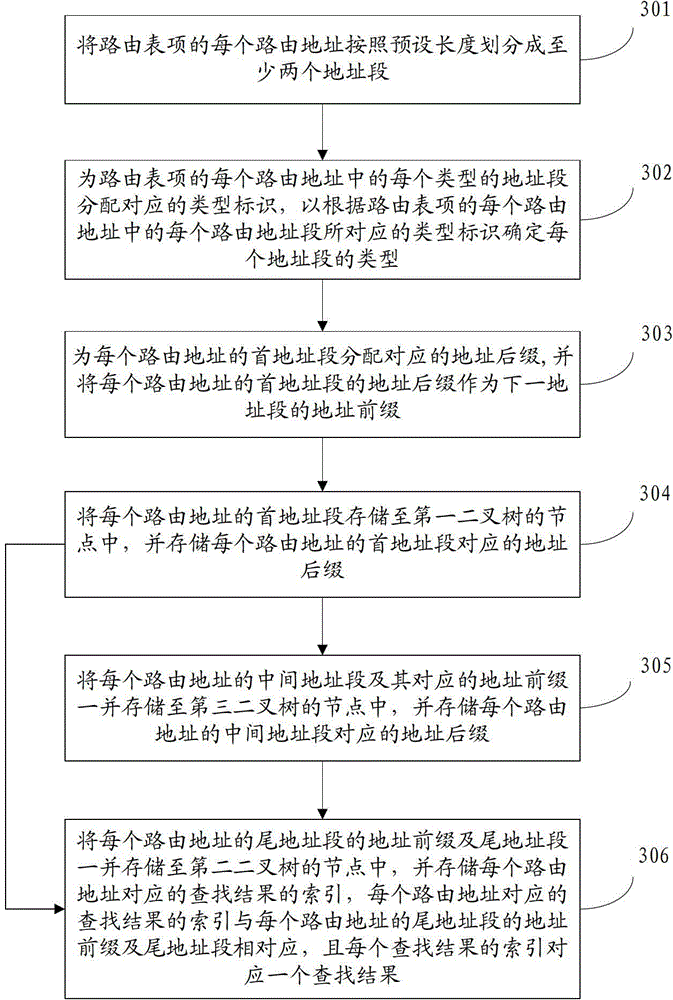
Storage method, search method, device and system of routing table entries
ActiveCN102904812AStorage flexibly appliesStorage applicableData switching networksRouting tableBinary tree
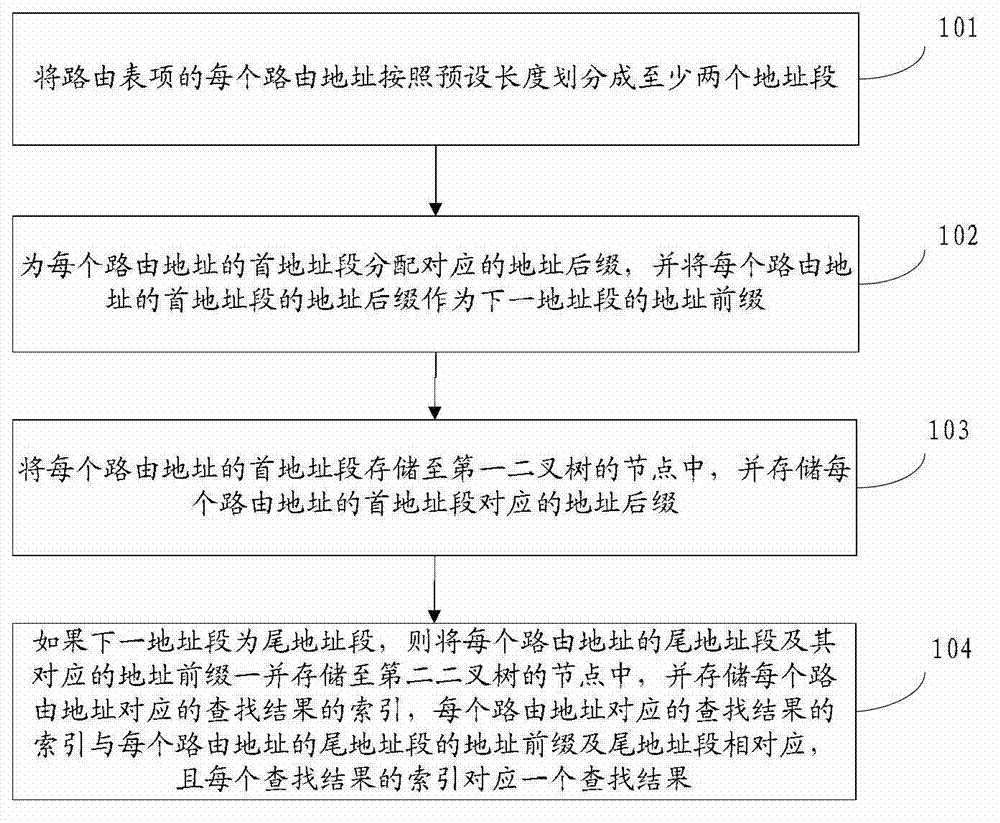
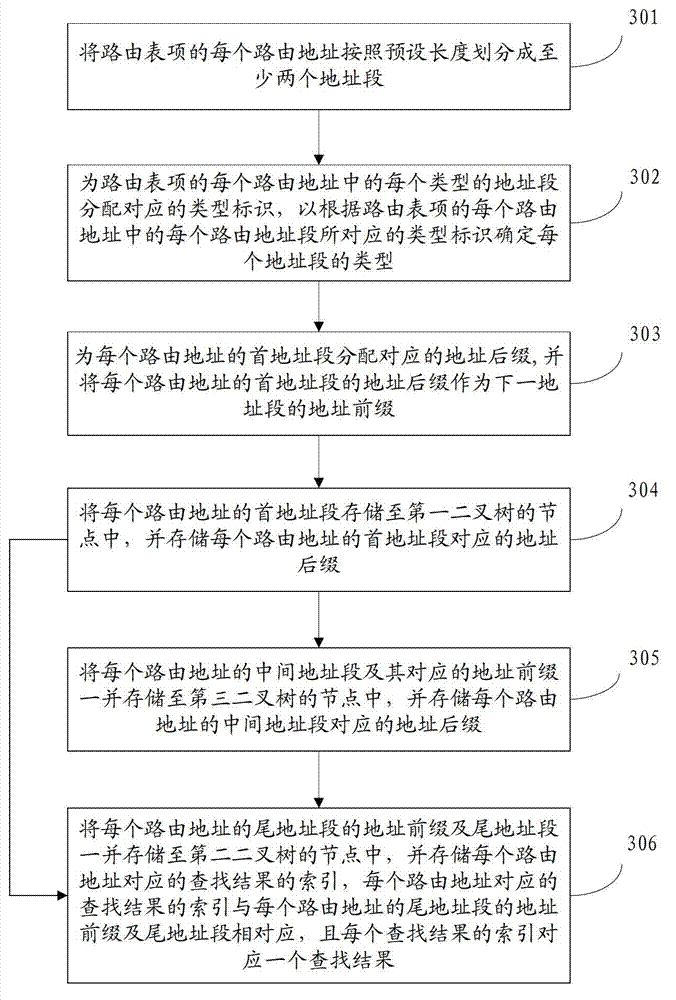
The invention discloses a storage method, a search method, a device and a system of routing table entries, belonging to the computer field. The search method comprises the following steps of: dividing a search address into at least two address fields; searching a head address field matched with the head address field of the search address in a first binary tree according to the head address field of the search address; taking the address suffix of the head address field found out as the address prefix of the tail address field of the search address; according to the address prefix of the tail address field of the search address and the tail address field, searching the matched address prefix of the tail address field and the matched tail address field in a second binary tree; and obtaining the search result according to the obtained address prefix of the tail address field and the tail address field. The method saves storage space compared with the prior art by sectionally storing and searching the routing address, thus being flexibly suitable for storing and searching the routing addresses of various bit widths; and the search rate is increased.
Owner:HUAWEI TECH CO LTD
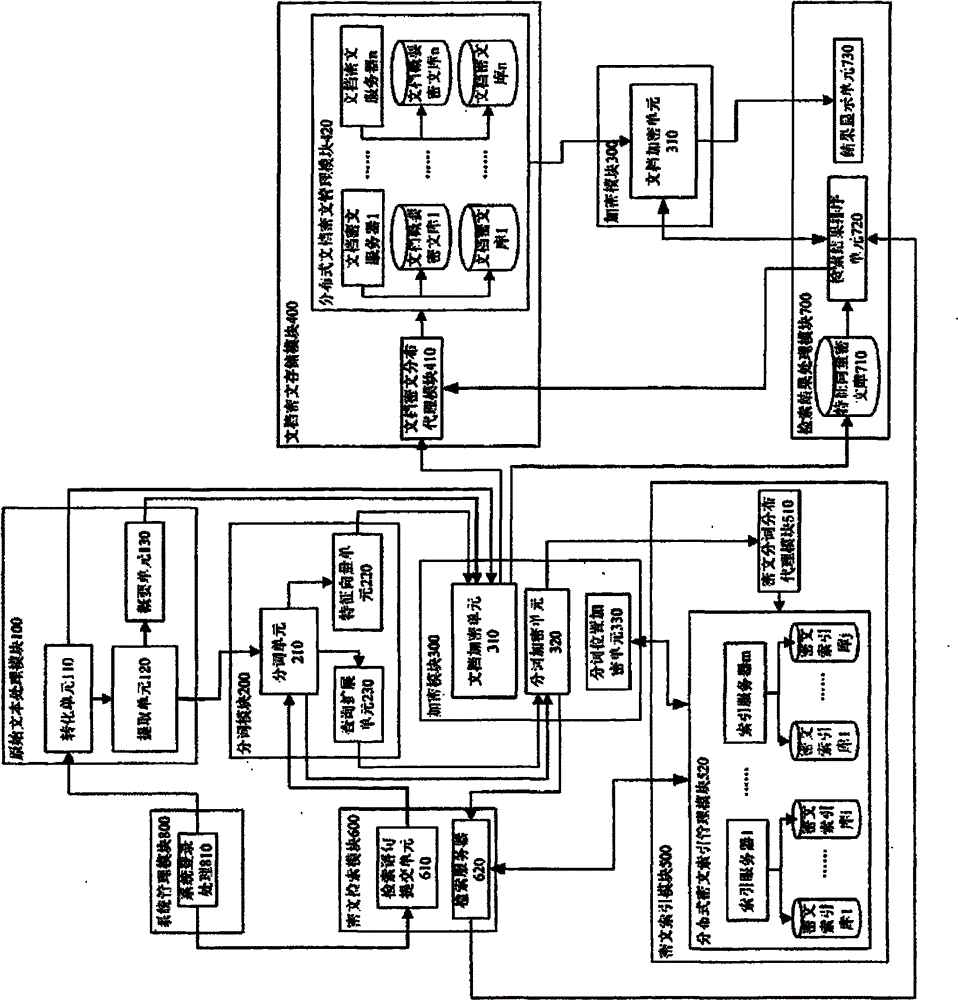
Safety overlay network constructing method of ciphertext full text search system and corresponding full text search method
ActiveCN102855292ASafe and efficient dynamic updateSafe and efficient creationSpecial data processing applicationsFull text searchCiphertext
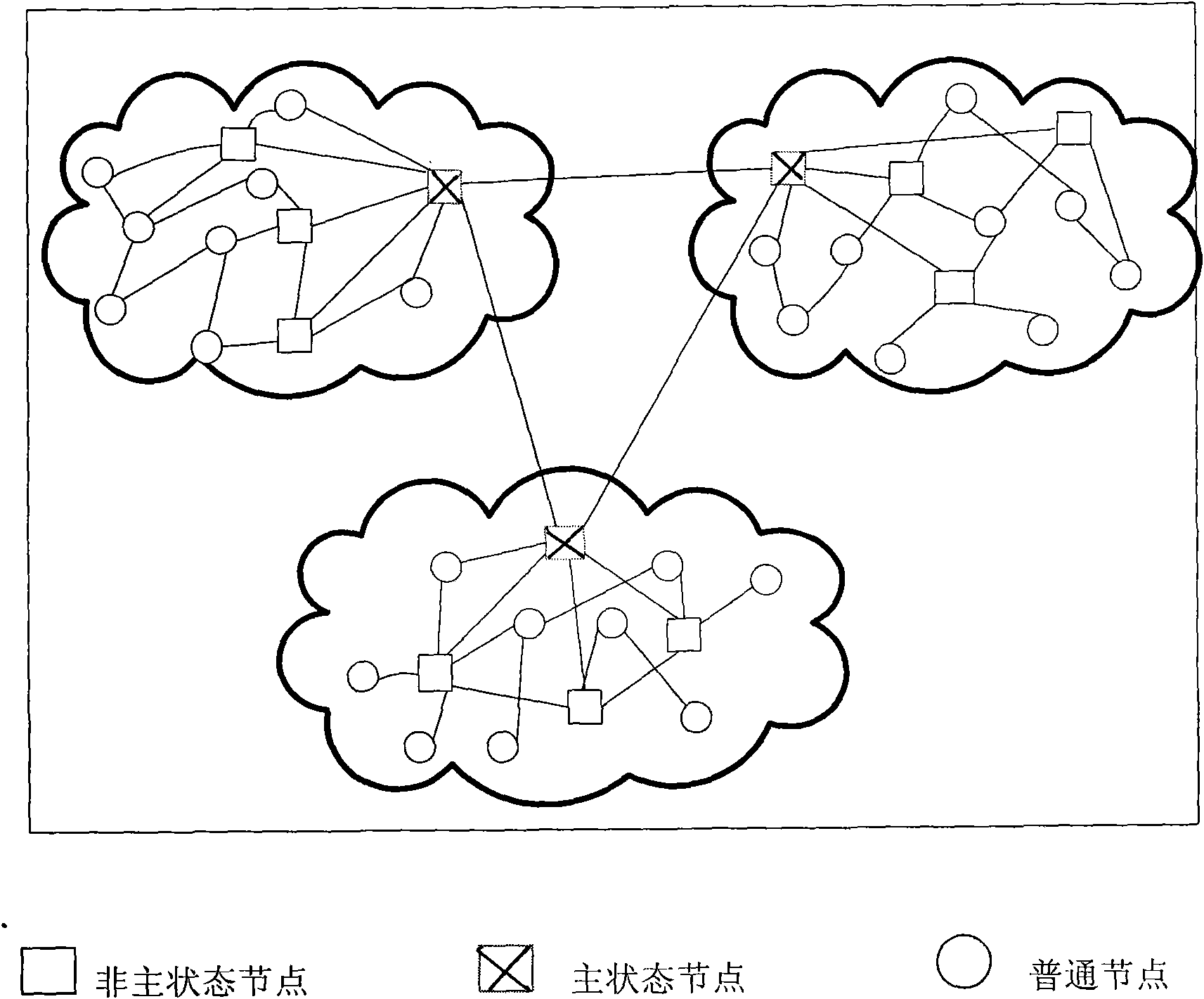
The invention relates to a safety overlay network constructing method of ciphertext full text search system and a corresponding full text search method. The invention initially provides a safety overlay network concept used for peer-to-peer full test search, solves the problems of distribution, storage and search of massive ciphertext data index files under the premise that recall ratio and precision ratio are not influenced, realizes storage and search of massive data to peer-to-peer nodes of a distributed P2P (peer-to-peer) network and introduces an index file duplicate copying mechanism based on a pivot node, wherein the mechanism ensures that resource can be rapidly obtained by searches in different directions by virtue of a duplicate of the pivot node without increasing occupation of network bandwidth, so that the safety overlay network constructing method and the corresponding full text search method disclosed by the invention are more applicable to peer-to-peer full text search when information amount is large, and efficiency of full text search under the peer-to-peer network environment is further improved.
Owner:GUANGXI UNIV
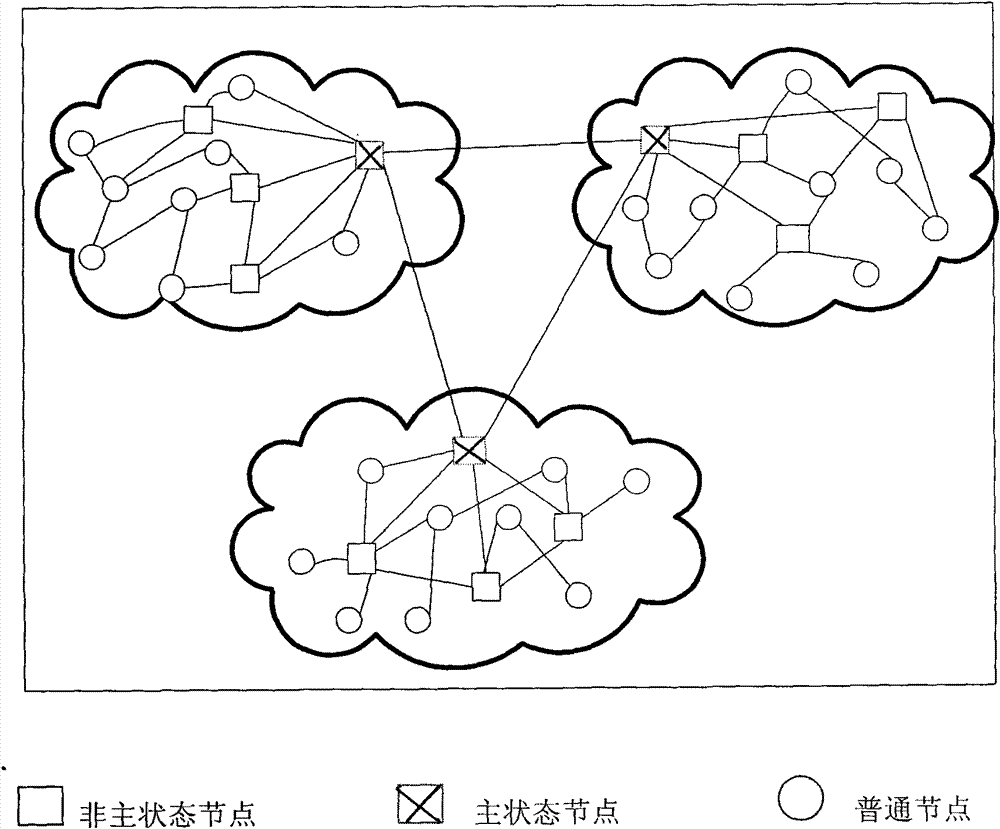
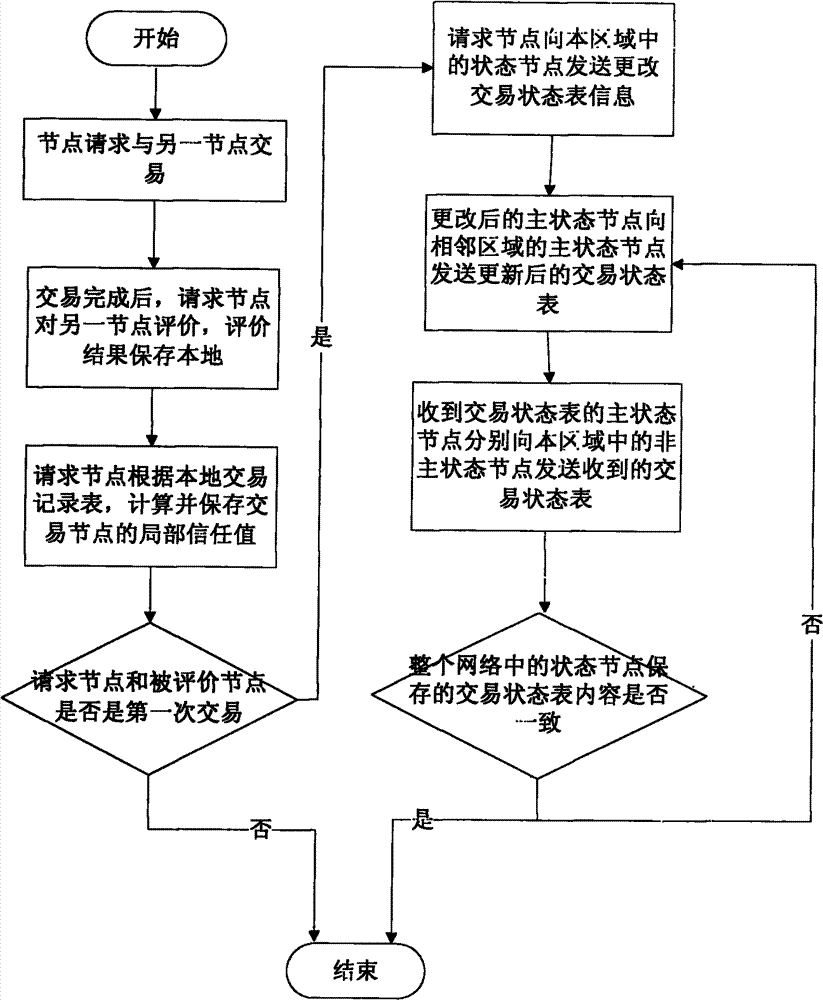
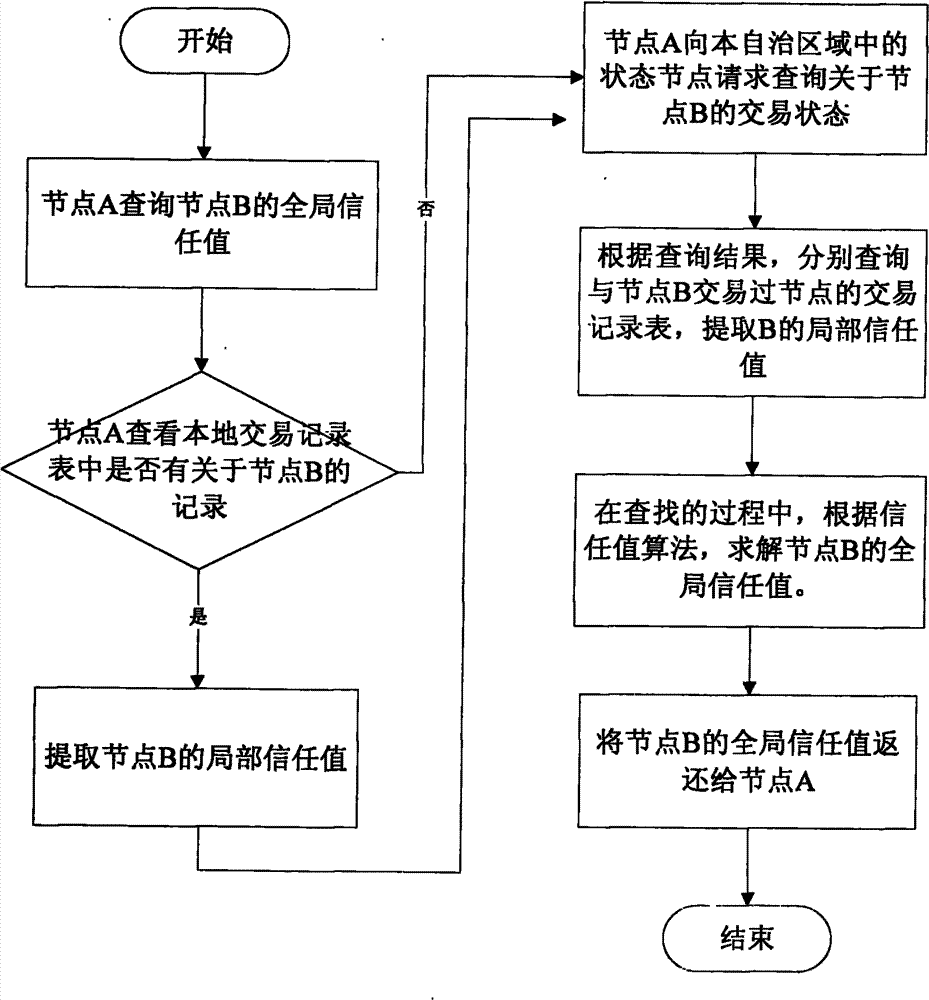
Trust data management method in peer-to-peer network
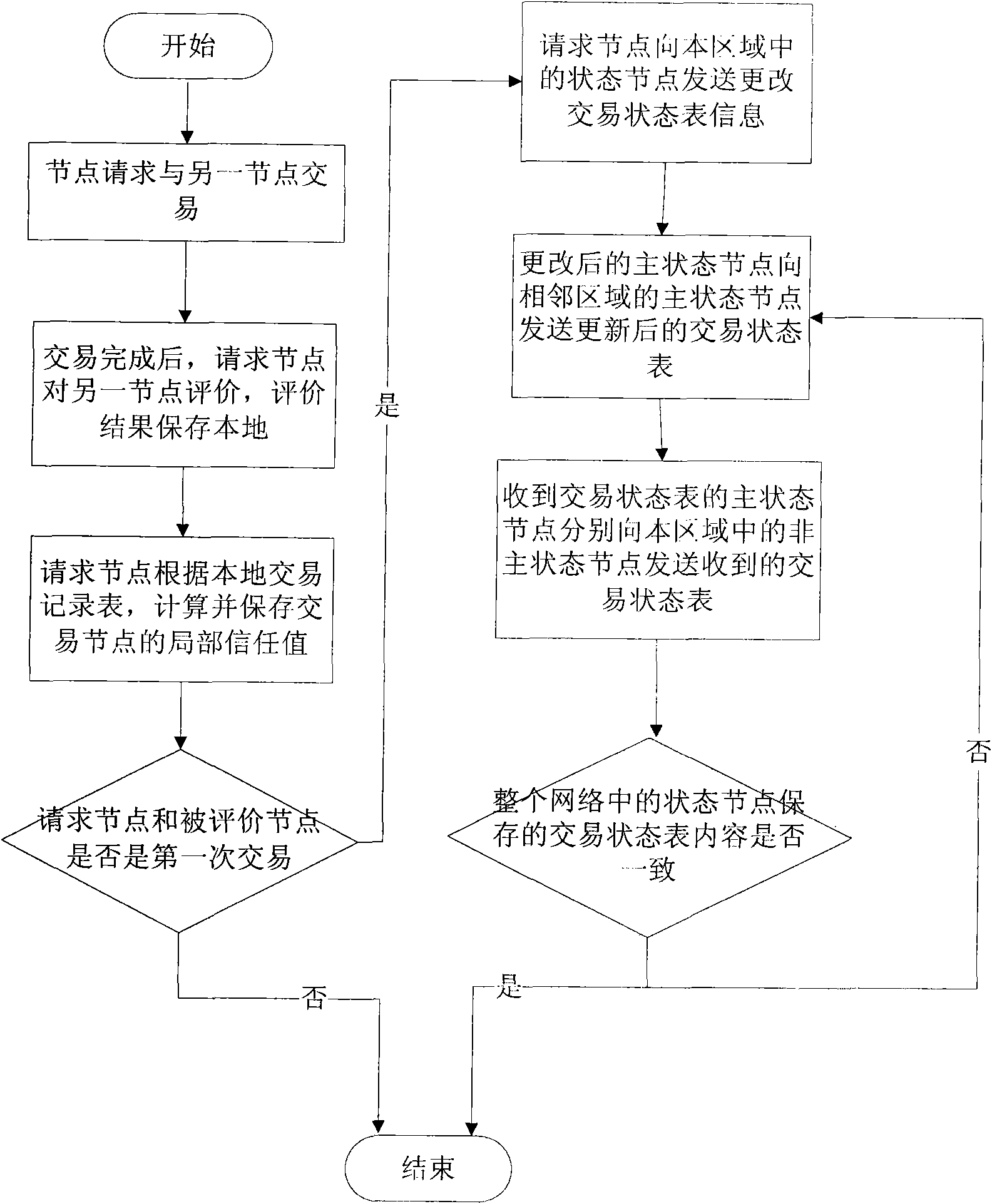
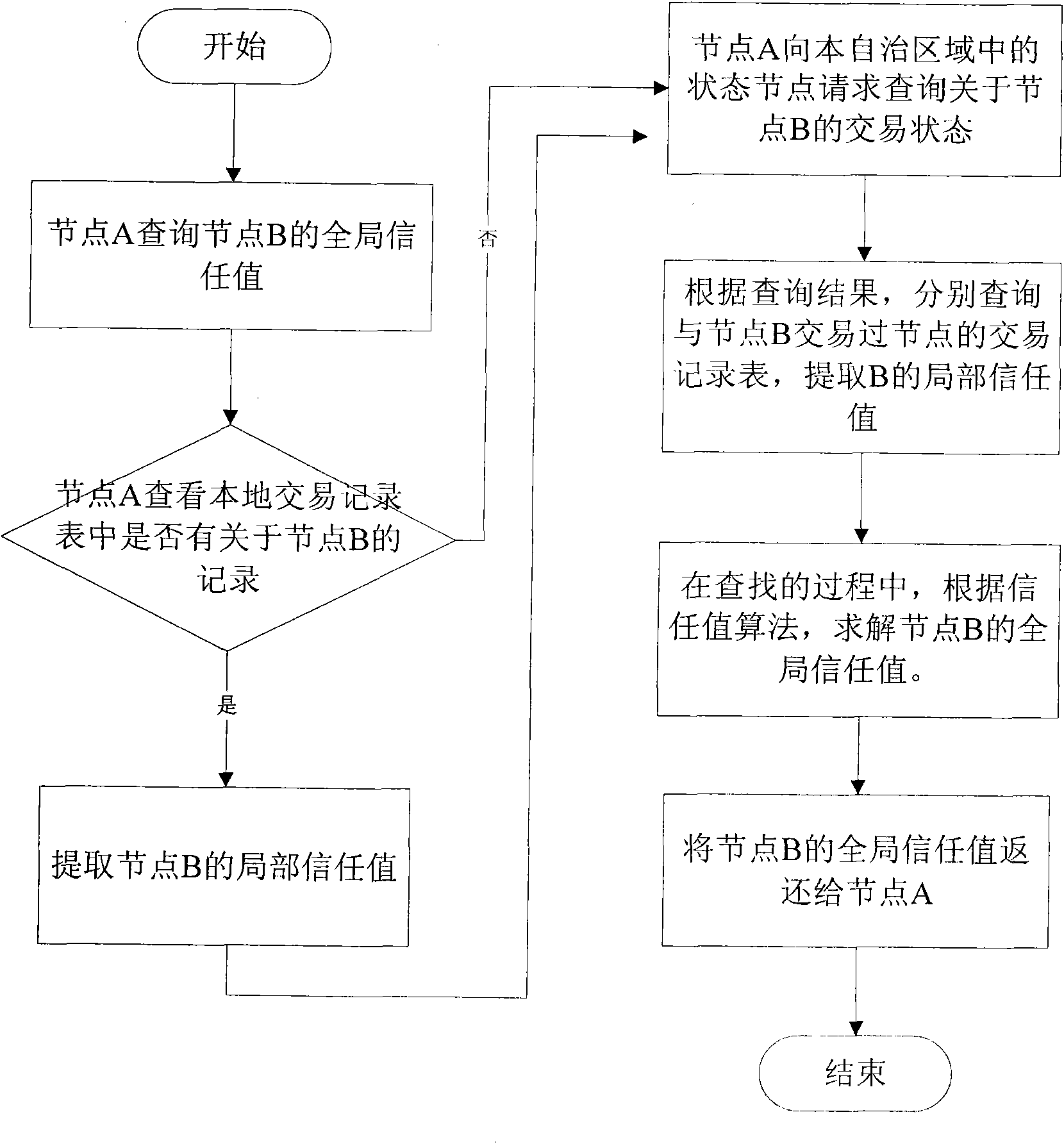
The invention relates to a trust data management method in a peer-to-peer network, which provides a safer, available and highly efficient trust data management mechanism for solving the problem of some defects exiting in a traditional data management mode. Differing from past pure centralized type and scattered type management mechanisms, the centralized type and the scattered type are effectively combined by the management mechanism and mutually make up for deficiencies. The equilibrium, the safety and the high efficiency of data access can be achieved by using the trust data management mechanism disclosed by the invention. The method is a method that the centralized type and the scattered type are effectively combined, mutually make up for deficiencies and are improved, and two nodes logically exist in the network. One is a state node which is used for managing a trading state table; and the other is an ordinary node which is a basic element for forming the network and is used for storing a trading record table per se. Trust data management can be safely and efficiently realized by quoting the trading state table and the trading record table.
Owner:NANJING UNIV OF POSTS & TELECOMM
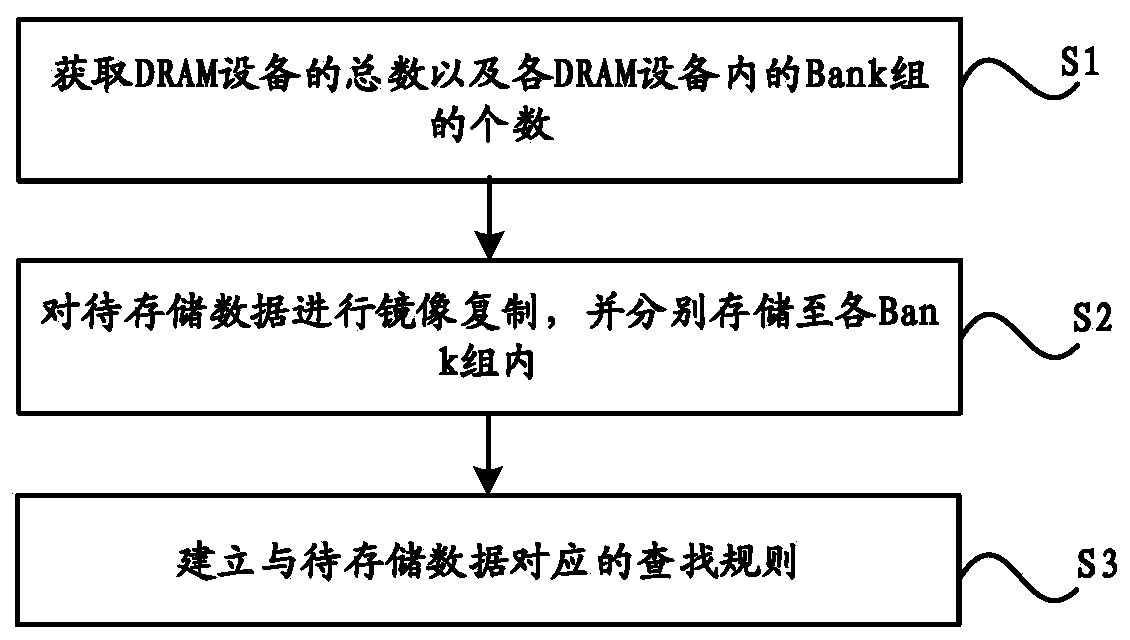
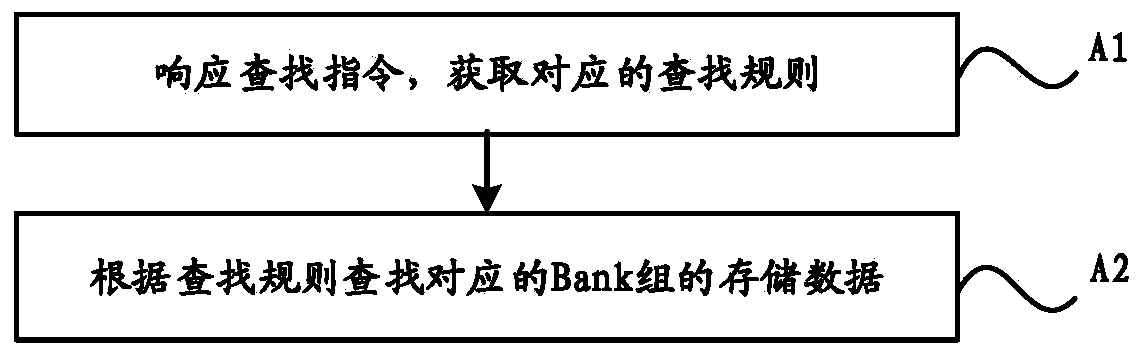
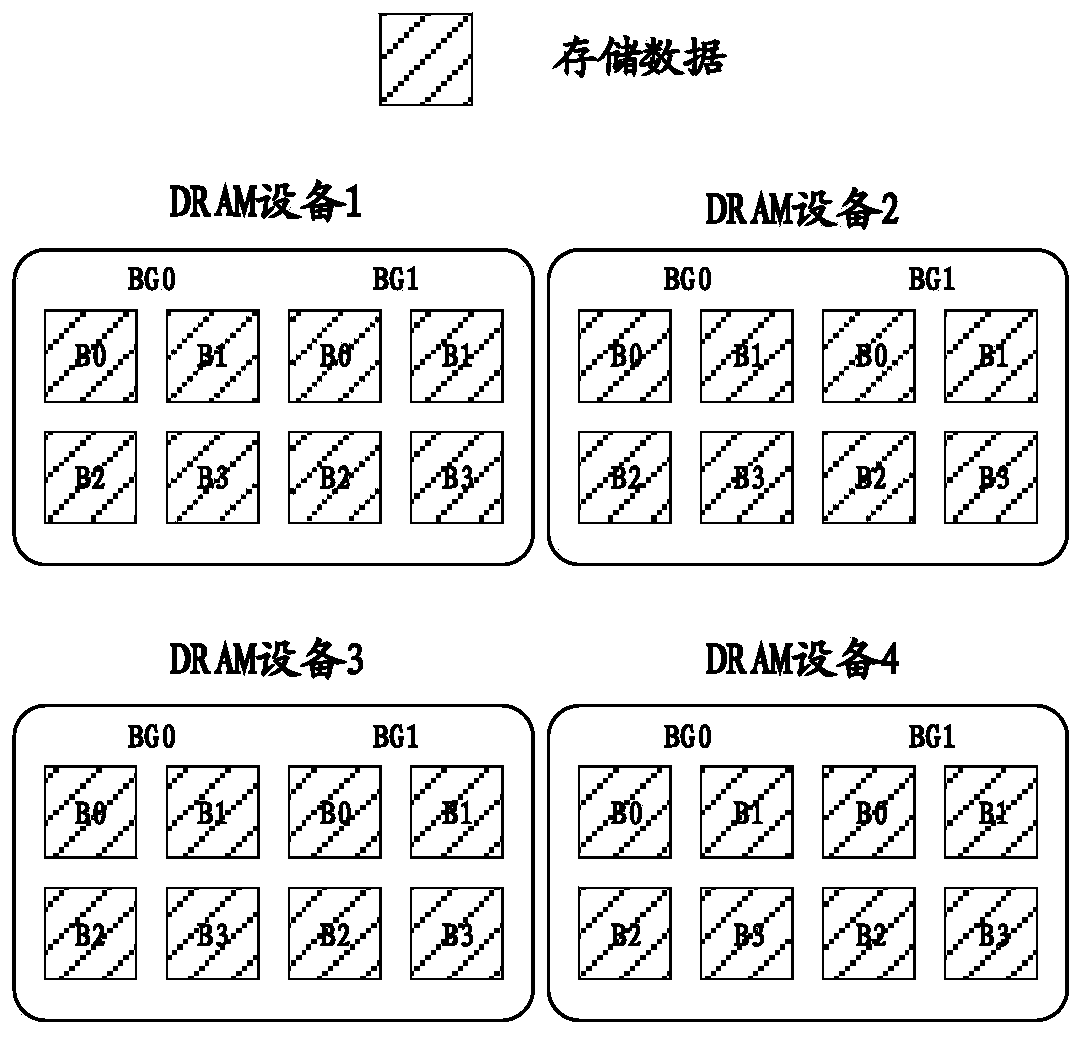
Method and system for improving data search rate in DRAM
PendingCN111459408AImprove lookup rateImprove reading and writing efficiencyInput/output to record carriersDigital data information retrievalAccess timeMirror image
The invention discloses a method and system for improving the data search rate in a DRAM, and relates to the technical field of memories. An execution device for data search is provided with a plurality of DRAM devices. The method comprises the following steps: obtaining the total number of the DRAM devices and the number of Bank groups in each DRAM device, wherein each Bank group at least comprises one Bank; performing mirror image copying on the to-be-stored data, and respectively storing the to-be-stored data into each Bank group; and establishing a search rule corresponding to the to-be-stored data, wherein the search rule records the storage addresses of the to-be-stored data and the search sequence corresponding to the storage addresses. According to the invention, the access time sequence limitation of the DRAM equipment is broken through, the data search rate in the DRAM is effectively improved, and the read-write working efficiency of the memory is further effectively improved.
Owner:武汉二进制半导体有限公司
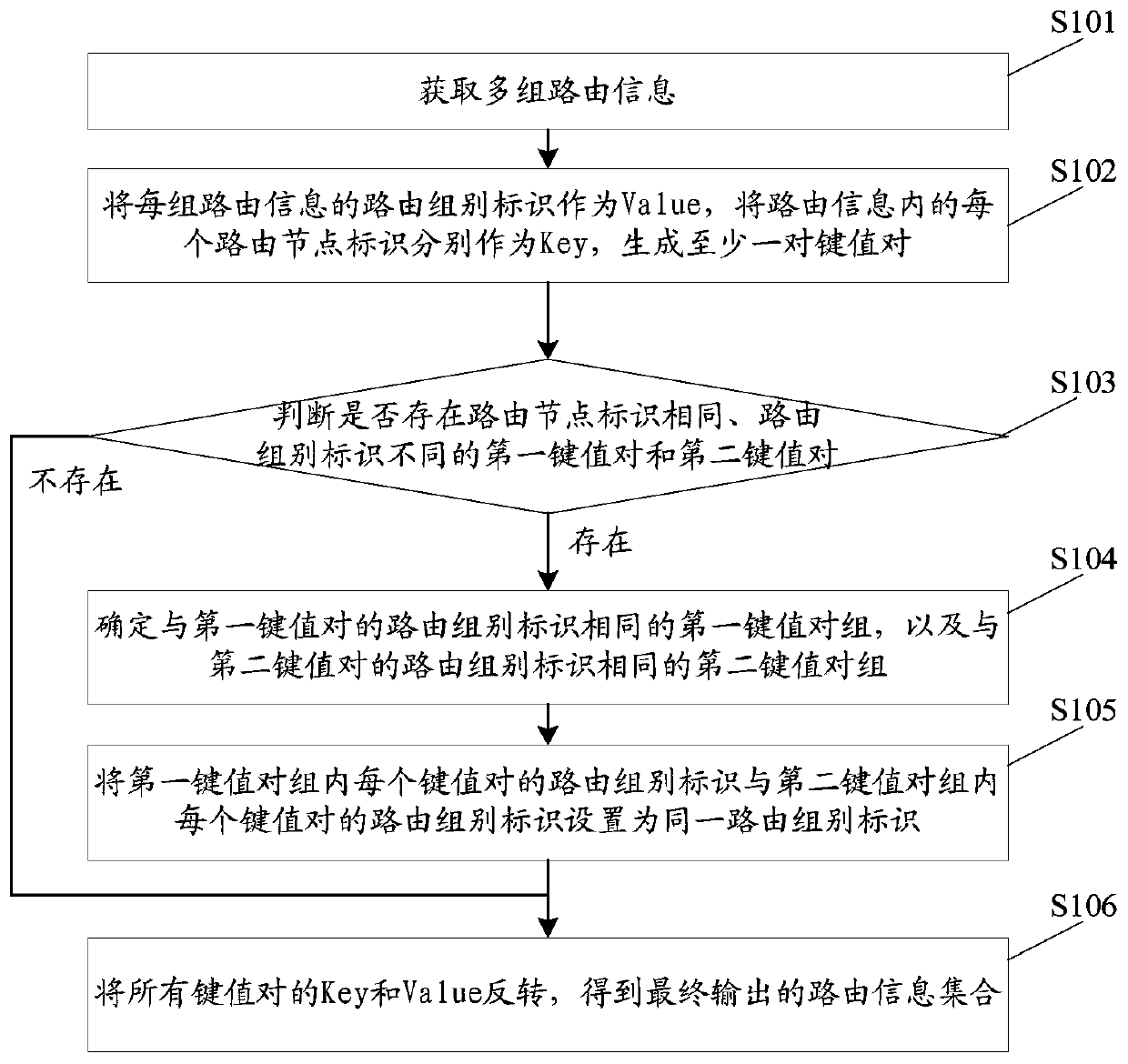
Routing information processing method, device and equipment and readable storage medium
ActiveCN110266598AImprove lookup rateSave search timeData switching networksInformation processingComputer engineering
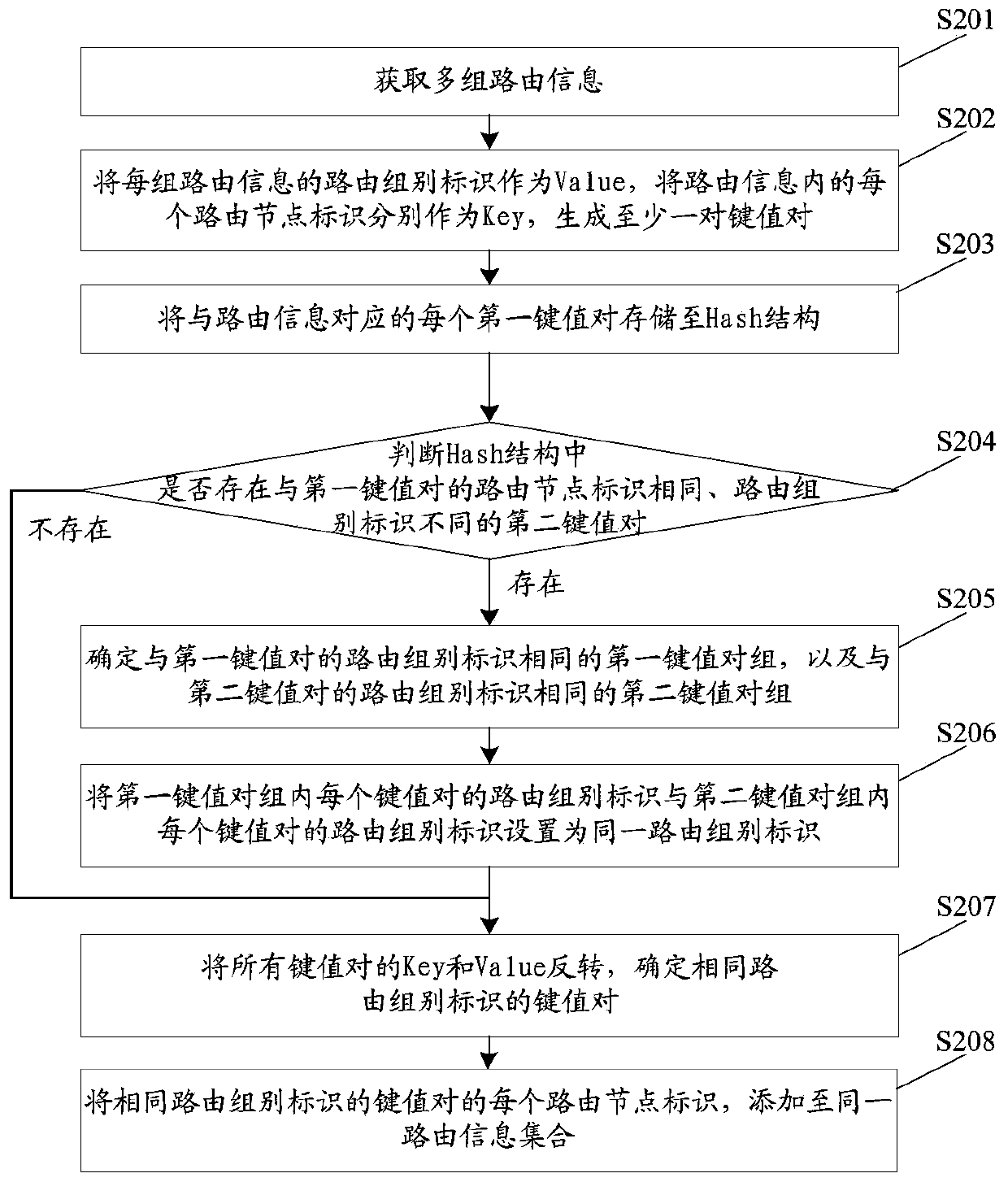
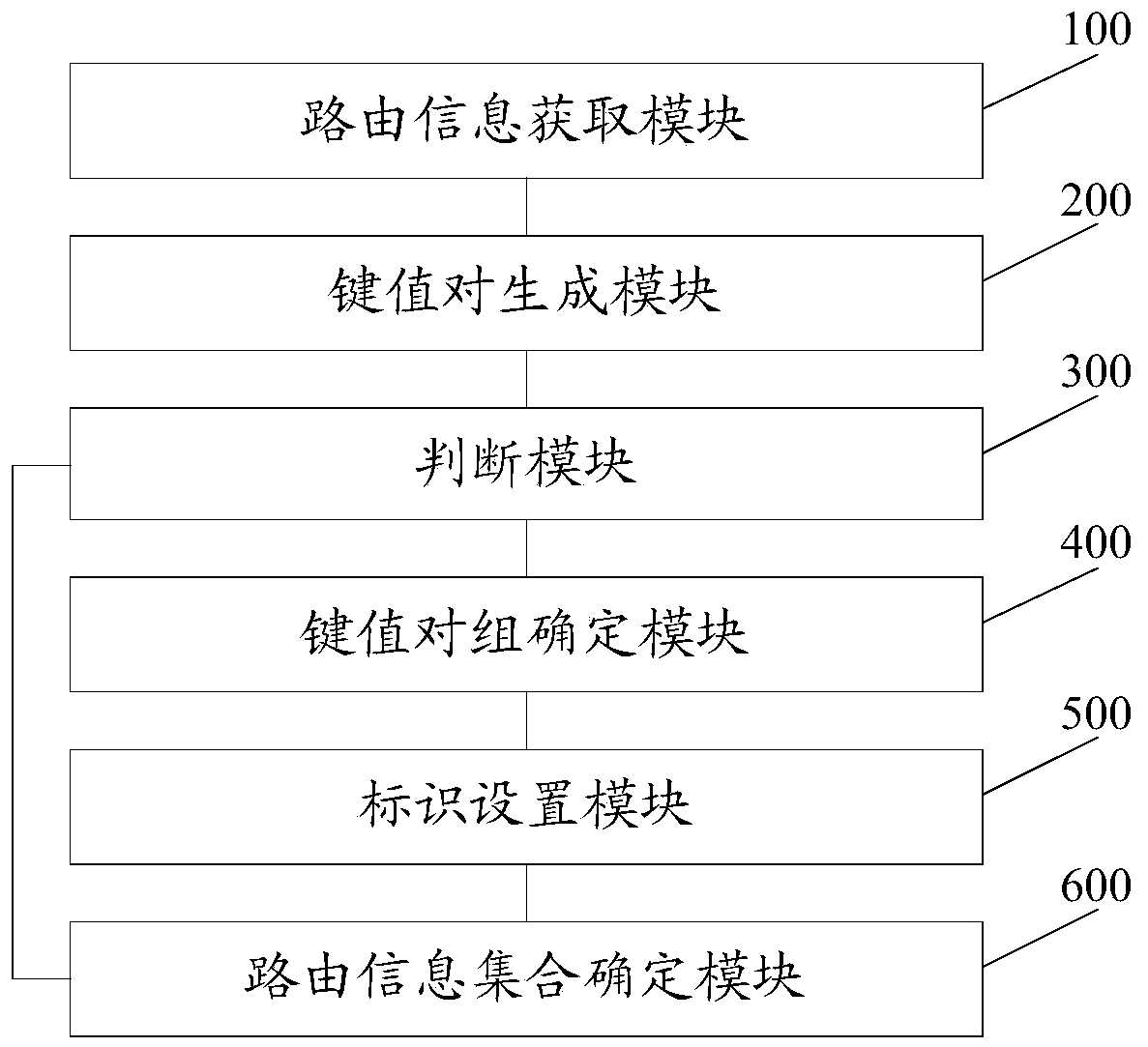
The invention discloses a routing information processing method, device and equipment and a computer readable storage medium. The routing information processing method comprises the following steps: generating a key value pair of each group of routing information; if a first key value pair and a second key value pair exist, wherein the routing node identifiers are the same and the routing group identifiers are different, setting the routing group identifier of the key value pair which is the same as the routing group identifier of the first key value pair and the routing group identifier of a second key value pair group which is the same as the routing group identifier of the second key value pair as the same routing group identifier; otherwise, inverting all the key value pairs to obtain a finally output routing information set. Thus, in the scheme, after each group of routing information is converted into a corresponding key value pair, the key value pairs can be utilized to quickly retrieve the key value pairs with the same routing node identifier and different routing group identifiers, and after the routing group identifiers of the key value pairs are updated, a final required routing information set is obtained through inversion, so that the searching speed is increased, and the searching time is shortened.
Owner:SHENZHEN ONETHING TECH CO LTD
Method and system for classification of network data flow
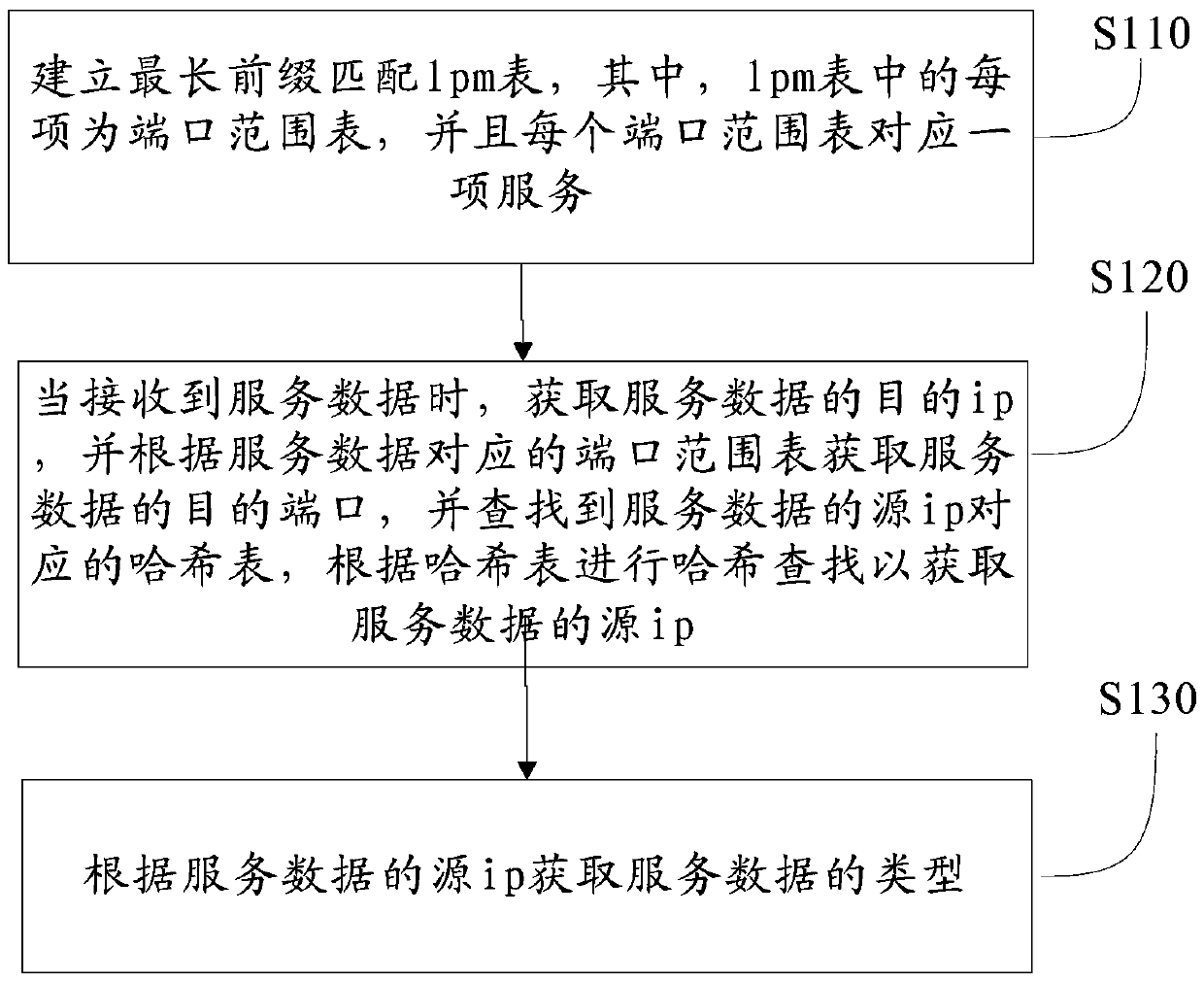
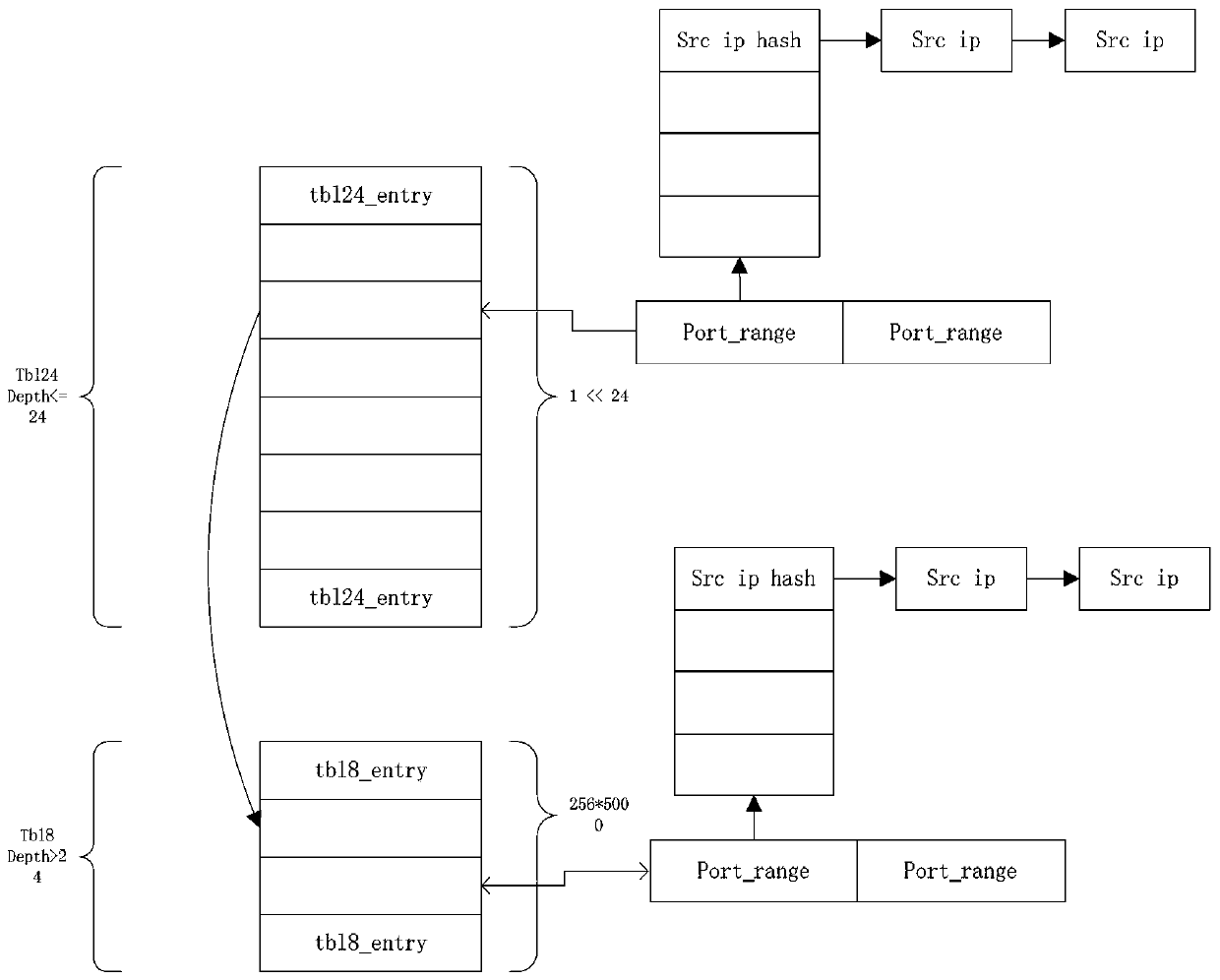
ActiveCN103220223AGood scalabilityFast searchData switching networksHash tableClassification methods
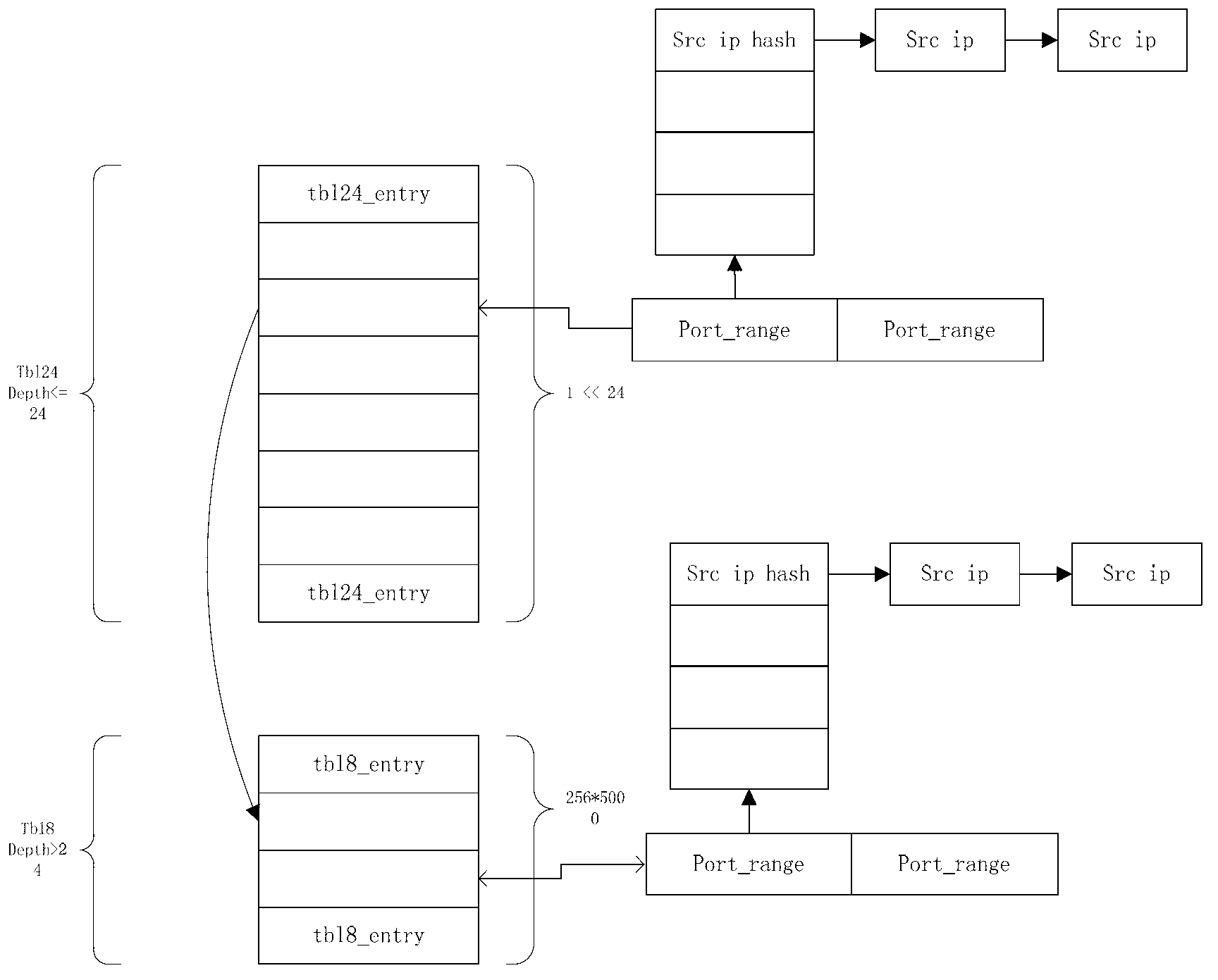
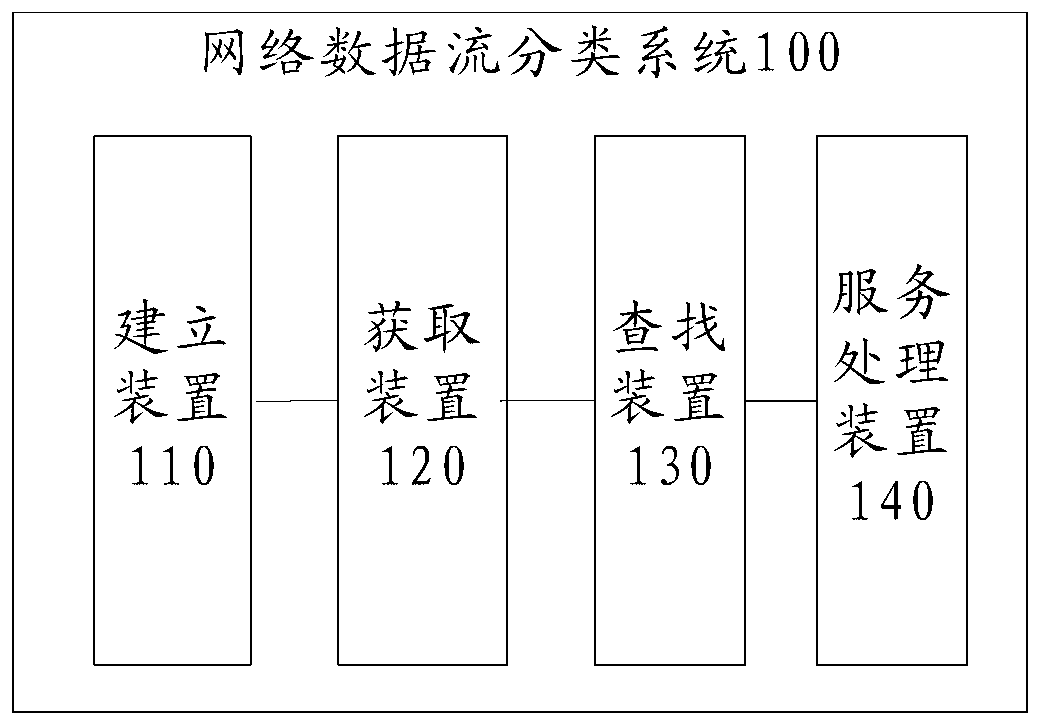
The invention provides a method for classification of network data flow. The method for the classification of the network data flow comprises building a longest prefix matching (lpm) table, wherein each item in the lpm table is a port range table, and each port range table corresponds to a service; acquiring the destination internet protocol (ip) of service data when receiving the service data, acquiring the destination port of the service data according to the port range tables corresponding to the service data, finding a hash table corresponding to the source ip of the service data, carrying out hash searching according to the hash table to obtain the source ip of the service data, and obtaining the types of the service data according to the source ip of the service data. According to the method for the classification of the network data flow, an lpm algorithm is combined with the hash table, searching speed is high, scalability is good, transmission quality is improved, and transmission cost is reduced. The invention further discloses a system for the classification of the network data flow.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
Index update method for ciphertext full-text searching system based on dynamic succeed tree index structure
ActiveCN102629274ASafe and efficient dynamic updateImprove securitySpecial data processing applicationsFull text searchGranularity
The invention discloses an index update method for a ciphertext full-text searching system based on a dynamic-succeed tree- index structure. The method comprises the followings: add operation, delete operation and modify operation, and the updating granularity is in a file section grade. The adding operation comprises the followings: building leaf information in a relative position for a new added text; deciphering a leaf information set influenced by the added text; inserting new built leaf information into an original index; only altering the related position of the front drive leaf of the added text during the inserting process, so as to enable the position to point to the leaf position of the first character of the added text, and meanwhile writing the original related position value of the front drive leaf into the related position of the last character leaf of the added text; and after each insertion of the new position information, judging the length of the leaf information set, if the length is larger than a preset value, leaf information set division is performed; and encrypting the obtained leaf information. After the adoption of the method, the system is enabled to achieve index creation and dynamic update safely and efficiently under a ciphertext state.
Owner:GUANGXI UNIV
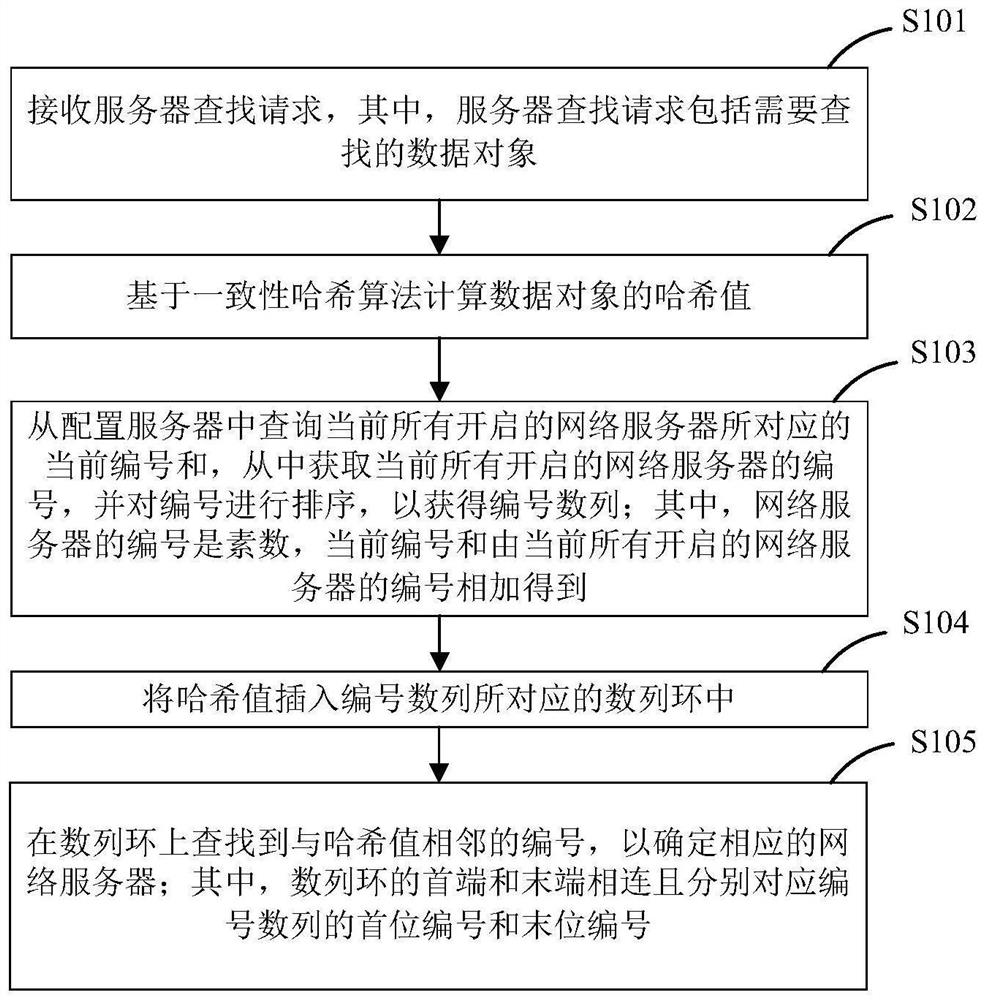
Optimization method and device for searching network server, computer equipment and storage medium
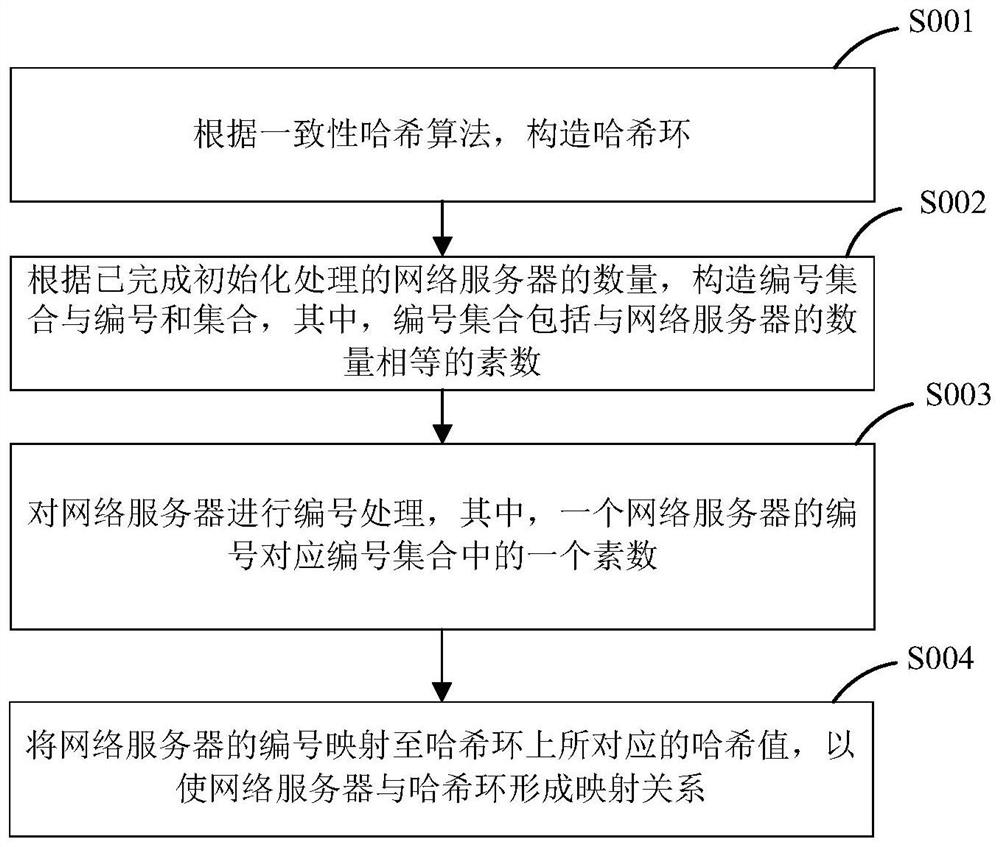
PendingCN112650451AImprove lookup rateSimple structureInput/output to record carriersOther databases indexingComputer equipmentTheoretical computer science
The invention discloses an optimization method for searching a network server based on a consistent hash algorithm, which is applied to the field of network servers and is used for solving the problems of more occupied network resources, high complexity and high implementation difficulty in the existing technology for searching the network server. The method provided by the invention comprises the following steps: receiving a server search request, wherein the server search request comprises a data object to be searched; calculating a hash value of the data object based on a consistent hash algorithm; querying the sum of the current numbers corresponding to all the currently opened network servers from the configuration server, obtaining the numbers of all the currently opened network servers from the sum, and sorting the numbers to obtain a number sequence; inserting the hash value into a sequence ring corresponding to the serial number sequence; and searching a serial number adjacent to the hash value on the sequence ring to determine a corresponding network server.
Owner:HANGZHOU QULIAN TECH CO LTD
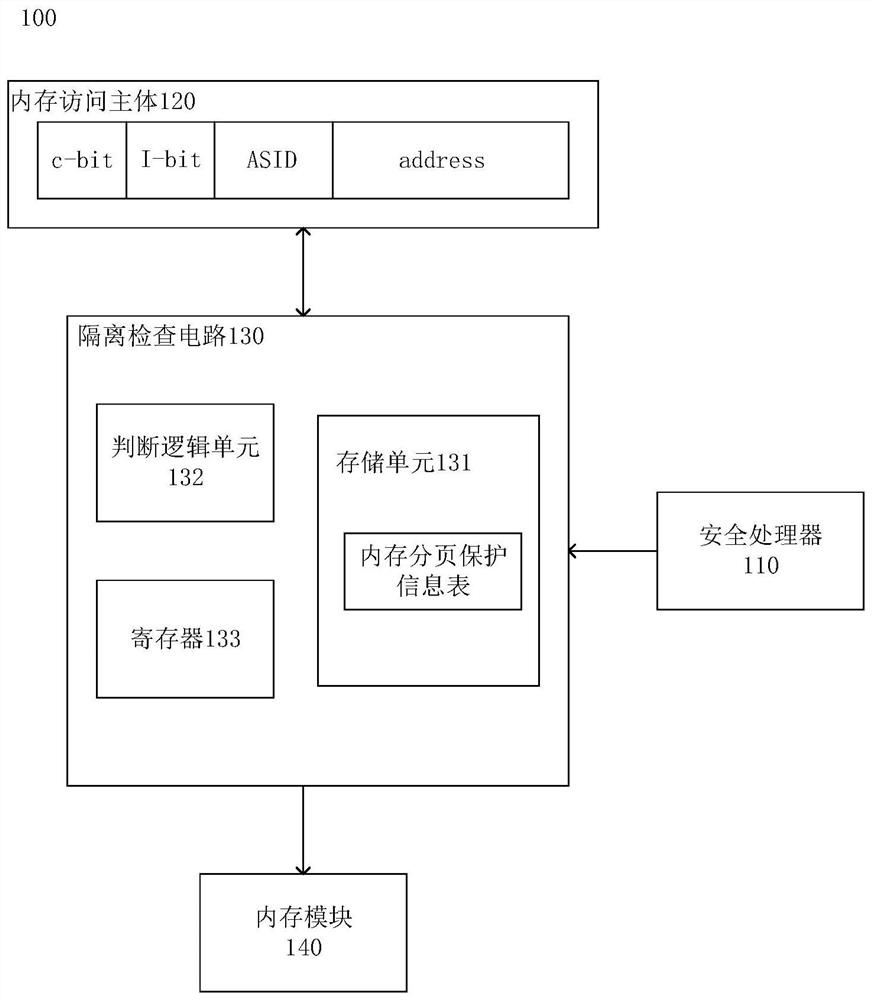
Memory isolation method, isolation check circuit and CPU chip
PendingCN111857947AMeet the needs of the number of security applicationsImprove lookup rateMemory adressing/allocation/relocationSoftware simulation/interpretation/emulationTerm memoryLookup table
The invention relates to a memory isolation method which comprises the following steps: receiving a memory access request which comprises an access address of a memory page requested to be accessed; searching a table entry corresponding to the access address in a memory paging protection information table, wherein the index value of the table entry corresponding to the access address is determinedaccording to the access address; and performing isolation check on the memory access request based on the access address and the table entry, and when the isolation check succeeds, allowing the memory page to be accessed by the access request. The memory isolation method at least has one of the following technical effects: the address space is divided into the memory pages equal in size in a paging mode, the number of the memory pages can meet the requirement for the number of security virtual machines or security applications of the virtual machines, the index value of the lookup table itemis determined according to the access address in the access request, and the lookup rate of the table item can be remarkably increased.
Owner:HYGON INFORMATION TECH CO LTD
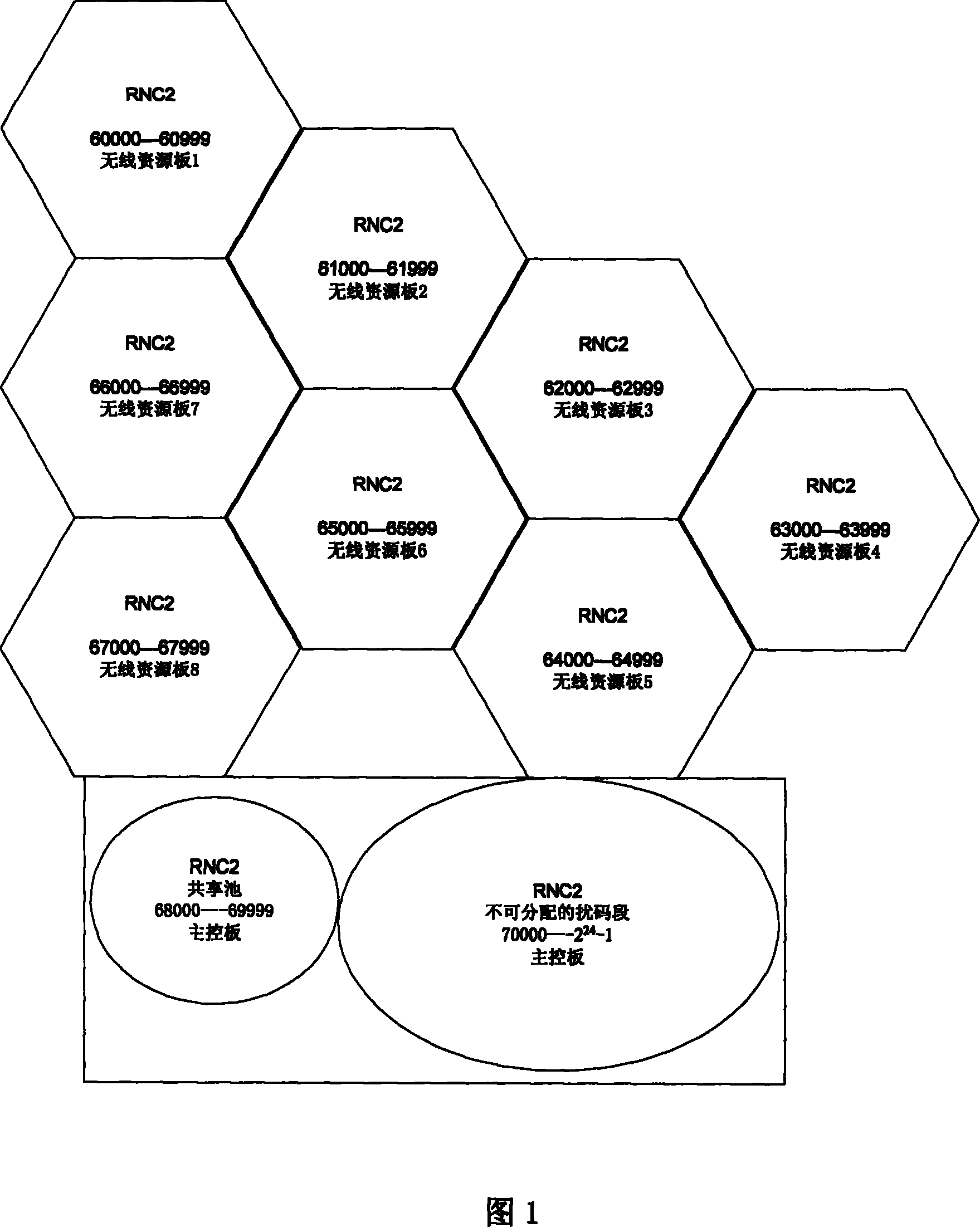
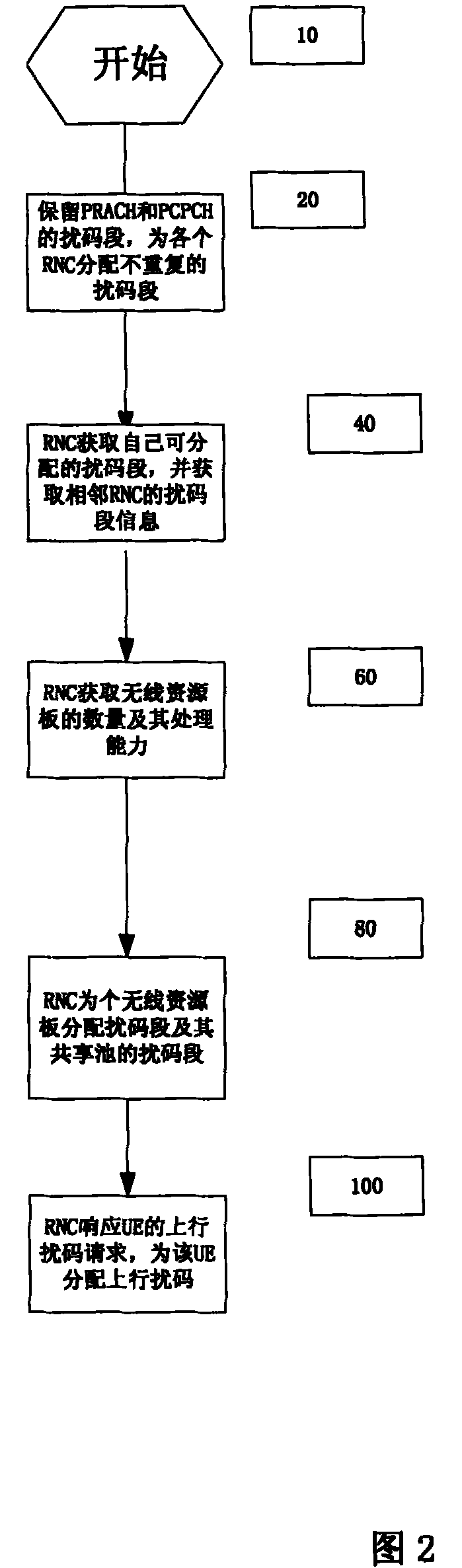
Method for distributing graded distribution type ascending scramble in wideband code division multiple access
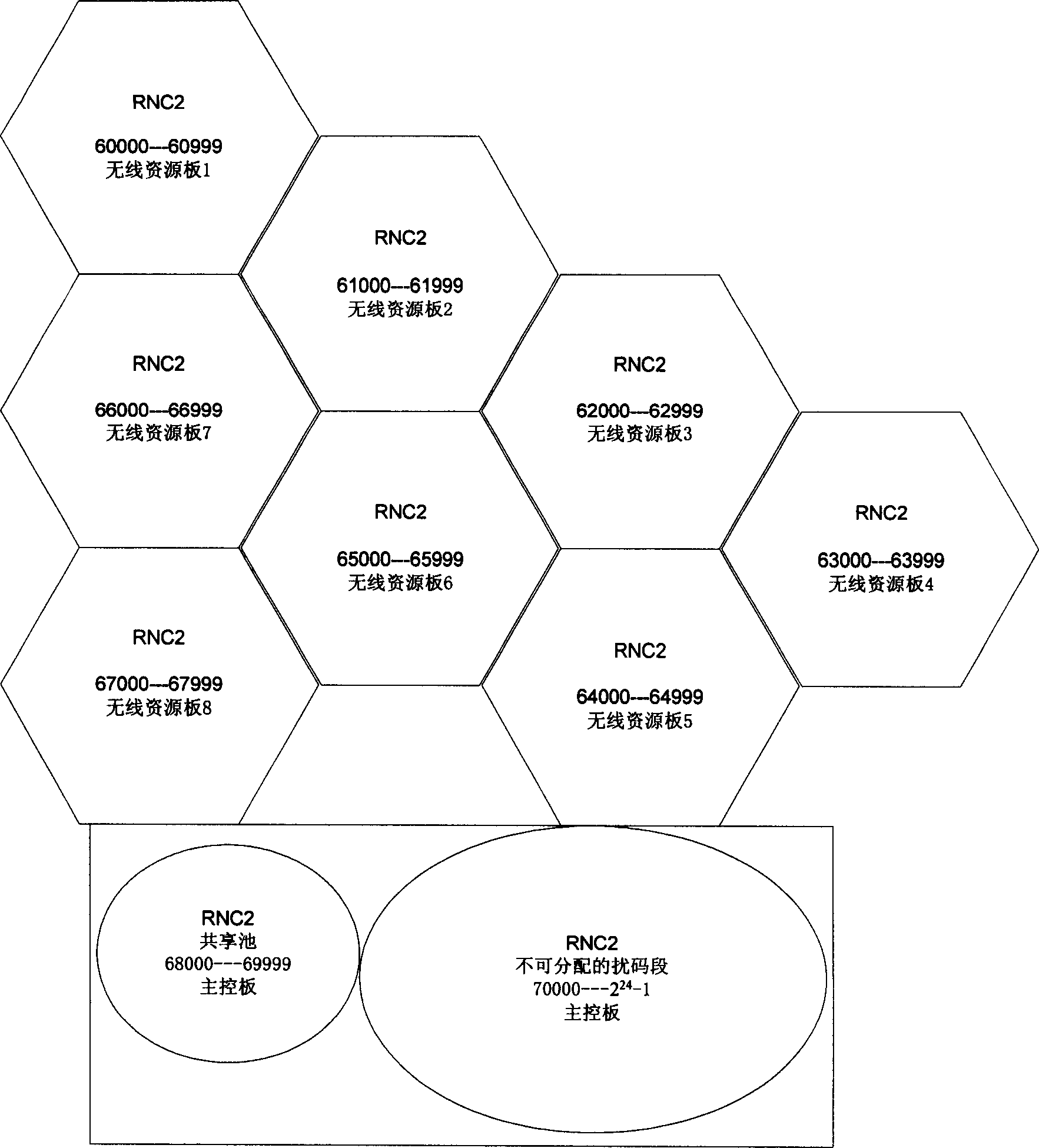
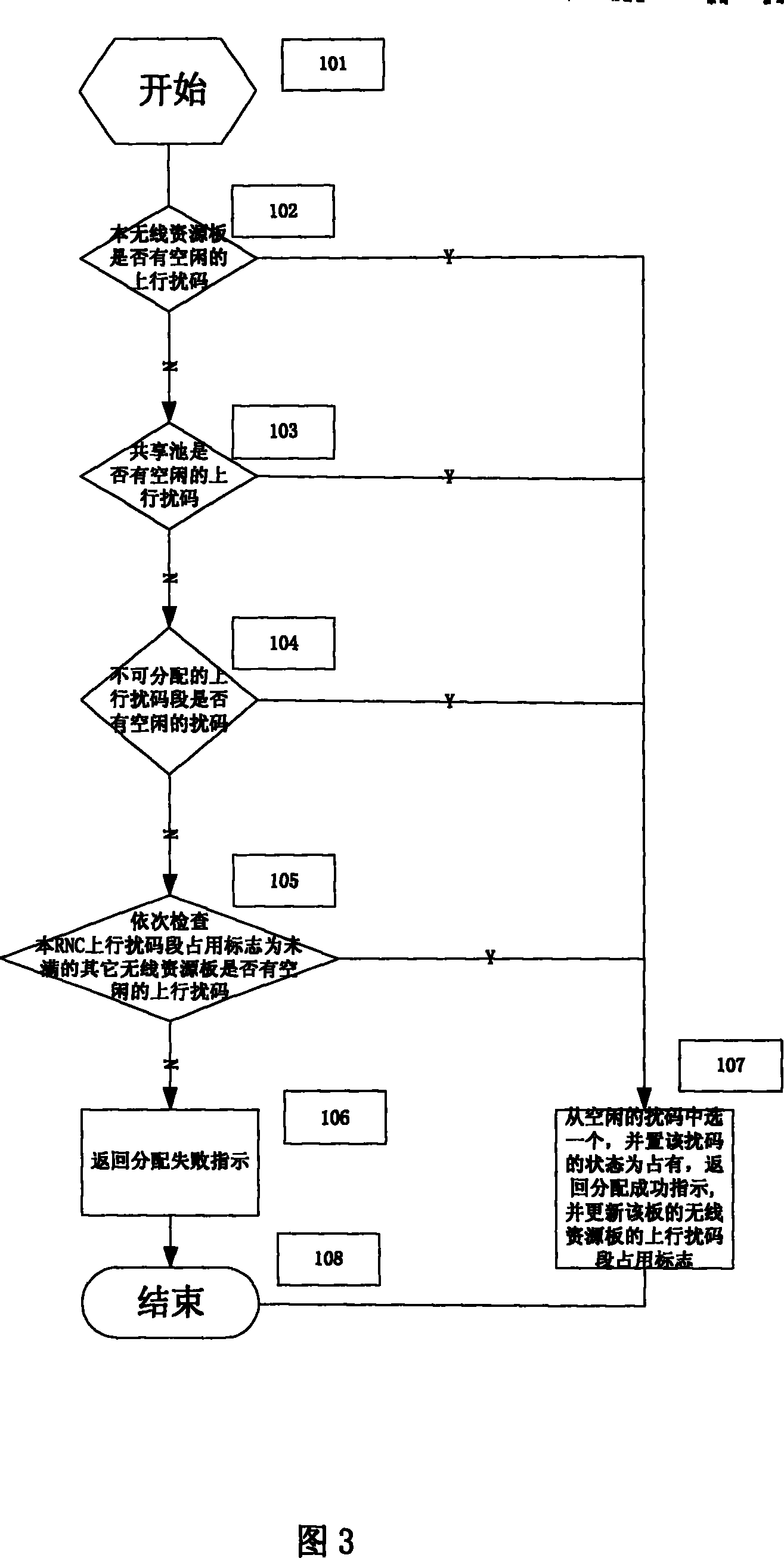
ActiveCN1674479AImprove lookup rateImprove the connection rateMultiplex code allocationCode division multiple accessCode segment
The present invention relates to a hierarchical distributed up-going scramble code divison multiple address system. Said invention comprehensively considers the up-going scramble code characteristics and its several factors of calculation, search, maintenance complexity and communication between plates so as to adopt the invented hierarchical distributed up-going scramble code distribution method, and make the main control plate and every wireless resource plate process up-going scramble code request of user terminal according to management level, and make every wireless resource plate process the scramble code in respective scramble code segment, so that it can reduce communication between main control plate and every wireless resource plate and can raise up-going scramble code distribution efficiency.
Owner:WUHAN HONGXIN TELECOMM TECH CO LTD
Method, device and equipment for generating active peptide fragment and storage medium
PendingCN114783521AImprove lookup rateShort time consumingBiostatisticsCharacter and pattern recognitionPeptide fragmentBioinformatics
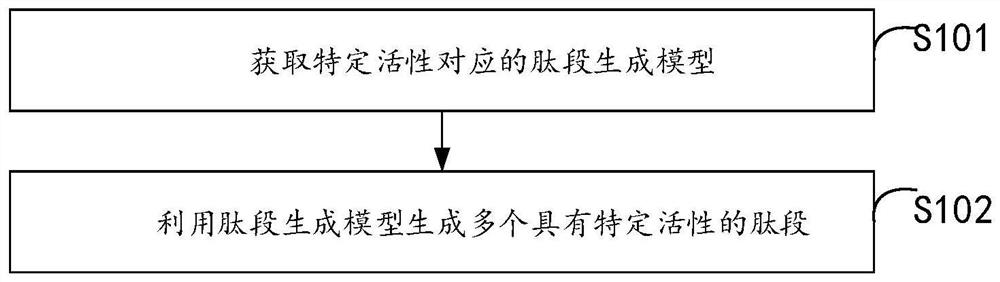
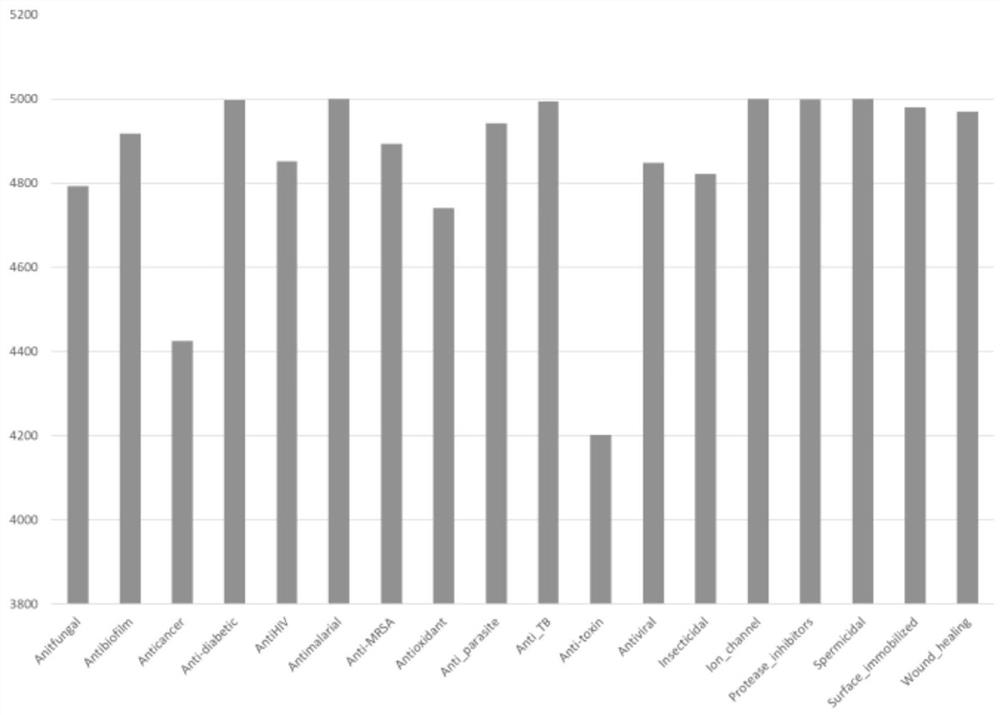
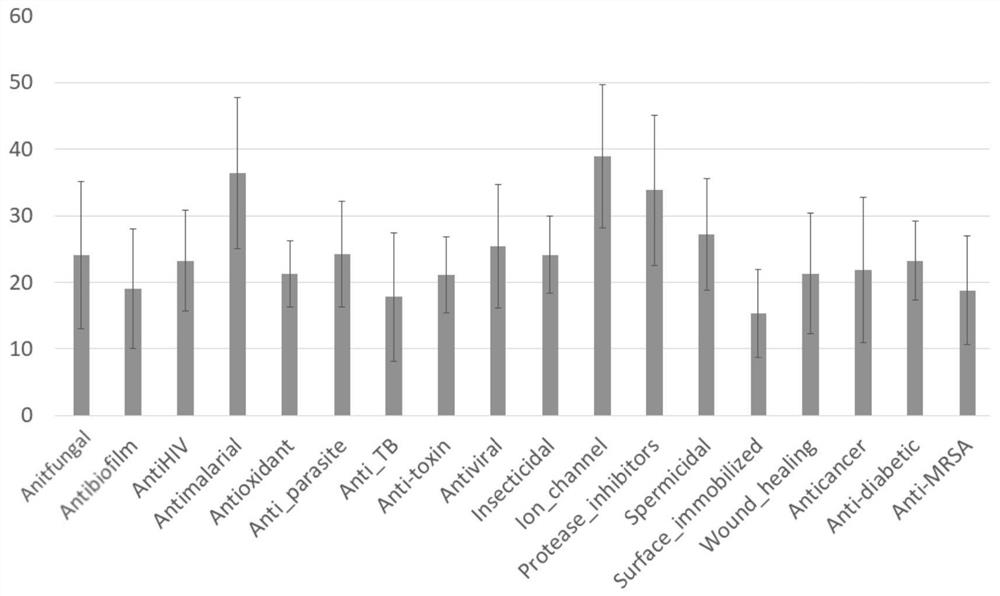
The invention is applicable to the field of biological medicine, and provides a method, device and equipment for generating an active peptide fragment and a storage medium, and the method comprises the following steps: obtaining a peptide fragment generation model corresponding to specific activity, the peptide fragment generation model is obtained by training an LSTM network by using a general peptide data set and a preset active peptide data set corresponding to the specific activity, the universal peptide data set comprises a plurality of universal peptide fragments; and generating a plurality of peptide fragments with specific activity by using the peptide fragment generation model. In the scheme, the peptide fragment generation model is obtained by training the LSTM network by using the general peptide data set and the preset active peptide data set corresponding to the specific activity, and can learn potential characteristics in the general peptide fragment and potential activity rules in the known active peptide fragment in the training process, so that the potential activity of the active peptide fragment is improved. Therefore, in the process of actually using the peptide fragment generation model, the peptide fragments with different specific activities and abundant diversity can be generated according to different specific activity requirements.
Owner:中国科学院深圳理工大学筹 +1
High-speed routing search device and method based on bit vector
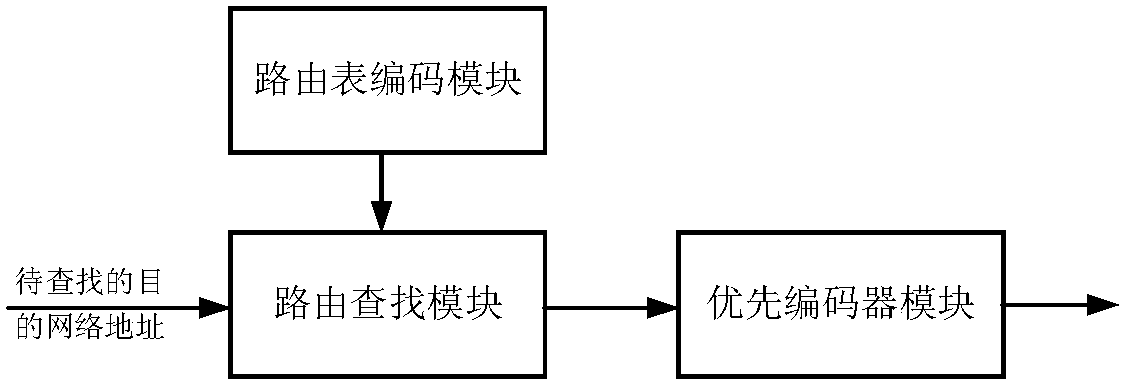
ActiveCN105959224BOvercome the problem of lookup delayLookup delay is smallData switching networksCode moduleTheoretical computer science
The invention discloses a high-speed route search device and method based on bit vectors, which mainly solve the problems of complex data structure and search operation, difficult hardware implementation and low search speed in the existing route search method. The device includes a routing table coding module, a routing lookup module and a priority encoder module. The steps of the method include: sorting all routing table items stored in the routing table in descending order according to the length of the network prefix; dividing the routing table into multiple routing table blocks; converting the routing table block into a bit vector array and storing it in the memory; Read out the bit vector in the corresponding sub-address in bit-wise "AND"; find out the routing table entry that matches the longest prefix. The invention has the advantages of simple data structure and search operation, easy hardware realization and high search speed.
Owner:XIDIAN UNIV +1
A method and terminal for quickly finding contacts based on edge touch
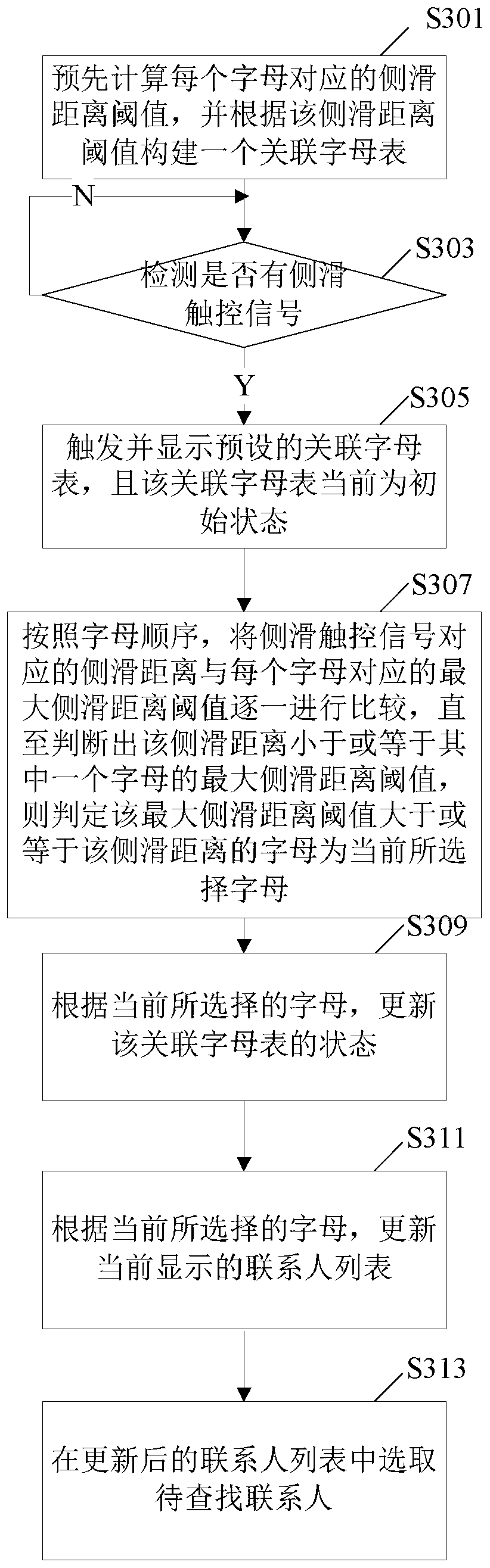
The invention discloses a method for quickly searching contacts based on edge touch. The method comprises the following steps: when detecting a sideslip touch signal, comparing a sideslip distance corresponding to the sideslip touch signal with a maximum sideslip distance threshold corresponding to each letter in a prebuilt associated alphabet one by one, so as to match a corresponding letter with the sideslip touch signal, wherein the letter is an initial letter of a contact name to be searched; and after that, updating the state of the associated alphabet and a currently displayed contact list according to the initial letter, so as to quickly enter the contact list to which the contact name to be searched belongs. According to the method for quickly searching the contacts based on the edge touch provided by the invention, the user does not need to slide ceaselessly from the first letter A until sliding to the contact list to which the contact name to be searched belongs, so that the search speed is improved and user experience is also improved. Correspondingly, the invention further provides a mobile terminal.
Owner:NUBIA TECHNOLOGY CO LTD
Information searching method and device, equipment and storage medium
PendingCN113535171AImprove lookup rateSoftware engineeringSpecial data processing applicationsInformation findingEngineering
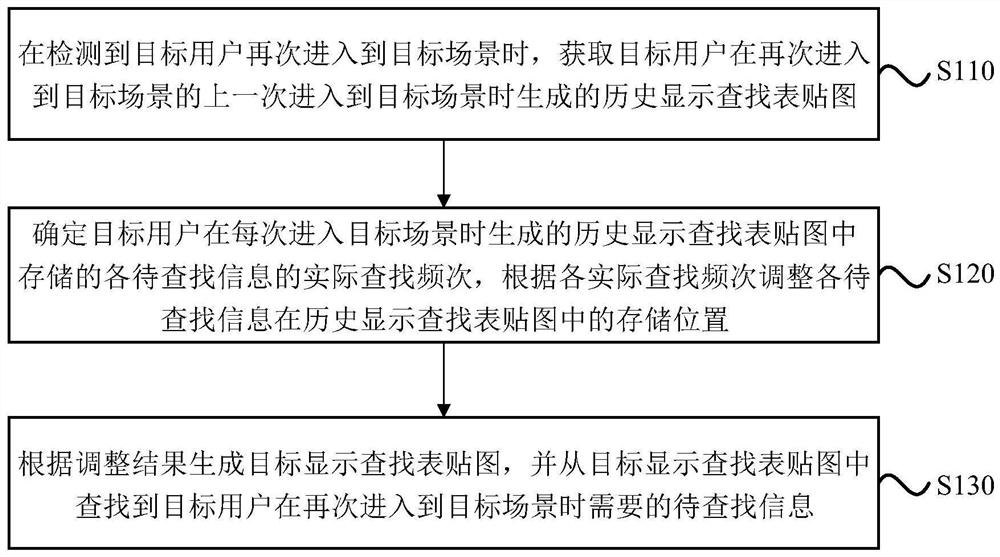
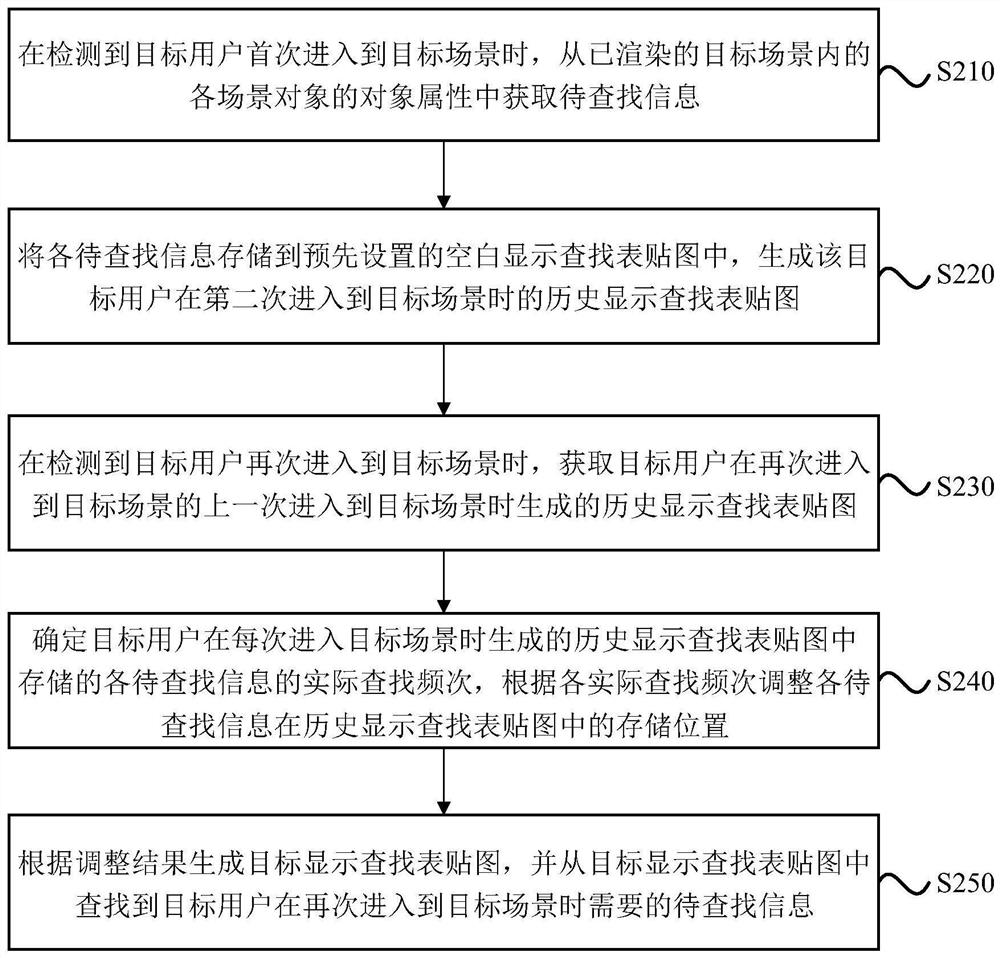
The embodiment of the invention discloses an information searching method and device, equipment and a storage medium. The method comprises the steps: when it is detected that a target user enters a target scene again, acquiring a historical display lookup table map generated when the target user enters the target scene again and enters the target scene last time; determining the actual searching frequency of each piece of to-be-searched information stored in a historical display searching table map generated when the target user enters the target scene every time, and adjusting the storage position of each piece of to-be-searched information in the historical display searching table map according to each actual searching frequency; and according to the adjustment result, generating a target display lookup table map, and finding out the information to be looked up required when the target user enters the target scene again from the target display lookup table map. According to the technical scheme, the information searching efficiency can be improved.
Owner:上海米哈游璃月科技有限公司
Safety overlay network constructing method of ciphertext full text search system and corresponding full text search method
ActiveCN102855292BSafe and efficient dynamic updateSafe and efficient creationSpecial data processing applicationsFull text searchCiphertext
The invention relates to a safety overlay network constructing method of ciphertext full text search system and a corresponding full text search method. The invention initially provides a safety overlay network concept used for peer-to-peer full test search, solves the problems of distribution, storage and search of massive ciphertext data index files under the premise that recall ratio and precision ratio are not influenced, realizes storage and search of massive data to peer-to-peer nodes of a distributed P2P (peer-to-peer) network and introduces an index file duplicate copying mechanism based on a pivot node, wherein the mechanism ensures that resource can be rapidly obtained by searches in different directions by virtue of a duplicate of the pivot node without increasing occupation of network bandwidth, so that the safety overlay network constructing method and the corresponding full text search method disclosed by the invention are more applicable to peer-to-peer full text search when information amount is large, and efficiency of full text search under the peer-to-peer network environment is further improved.
Owner:GUANGXI UNIV
A load balancing method and system for a web server cluster
ActiveCN107426332BTake advantage ofTo achieve the effect of load balancingTransmissionParallel computingEngineering
The invention discloses a load balancing method and system of a WEB server cluster. Firstly, for each type of static page access, the server to be allocated is respectively designated, and at the same time, a load balancing target function is constructed. When a page method request is received, it is classified, When it is a static page access request, it is allocated to the corresponding server according to its type; when it is a dynamic page access request, it is obtained according to the optimal allocation weight of each server's dynamic page access in the current cycle obtained in the previous cycle Allocate the dynamic page access at each moment of the current cycle; when the time reaches the last moment of the current cycle, obtain the optimal allocation weight of each server's dynamic page access in the next cycle by balancing the objective function; the present invention is aimed at static pages and dynamic pages Different processing methods are proposed respectively, so that server resources can be fully utilized, and load balancing effects can still be achieved under complex access situations.
Owner:SOUTH CHINA UNIV OF TECH
Ciphertext full-text search system
InactiveCN101859323BSafe and efficient dynamic updateSafe and efficient creationSpecial data processing applicationsFull text searchResource utilization
The invention discloses a ciphertext full-text search system, comprising an original text processing module, a word segmentation module, an encrypting module, a file ciphertext storage module, a ciphertext index module, a ciphertext search module, a search result processing module and a system management module. The system adopts a ciphertext dynamic sequential tree index structure, a word segmentation group technology and a file local ciphertext dynamic sequential tree index updating method, and can realize index establishment, dynamic index updating, full-text search and substring query under a ciphertext state. The system also can realize peer-to-peer full text research for a safety overlay network in a P2P network and introduces an index file carbon copy replication mechanism based ona peer-to-peer network hubs and nodes. In addition, the ciphertext full-text search system has good expandability, solves the problems of distribution storage and search of massive data index files, increased no occupation of network bandwidth, and has high network resource utilization ratio.
Owner:GUANGXI UNIV
Method for distributing graded distribution type ascending scramble in wideband code division multiple access
ActiveCN1674479BImprove lookup rateImprove the connection rateMultiplex code allocationCommunications systemCode division multiple access
Owner:WUHAN HONGXIN TELECOMM TECH CO LTD
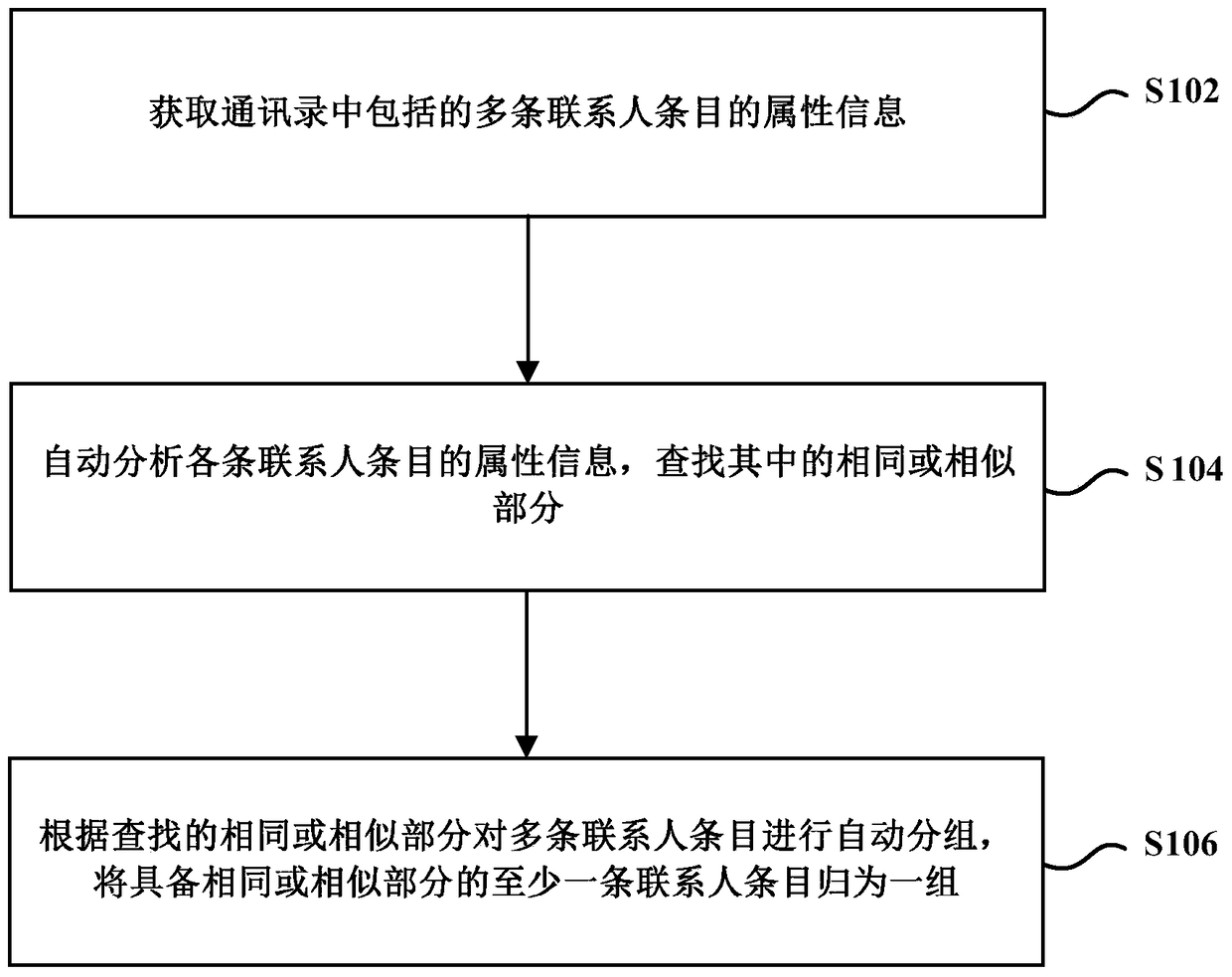
Method and device for grouping contact entries in address book
The invention provides a method and a device for grouping contact entries in a contact list. The method comprises the steps of: obtaining attribute information of multiple contact entries included in the contact list; analyzing the attribute information of each contact entry automatically and finding same or similar parts therein; grouping the contact entries automatically based on the found same or similar parts, and putting at least one contact entry with the same or similar parts in a group. By adopting the method and the device for grouping the contact entries in the contact list, a new function of automatically grouping the contact entries based on the attribute information is added for the contact list.
Owner:北京鸿享技术服务有限公司
Trust data management method in peer-to-peer network
InactiveCN101834895BImprove efficiencyImprove lookup rateTransmissionCommerceData accessData management
Owner:NANJING UNIV OF POSTS & TELECOMM
Storage method, search method, device and system of routing table entry
ActiveCN102904812BStorage flexibly appliesStorage applicableData switching networksRouting tableBinary tree
The invention discloses a storage method, a search method, a device and a system of routing table entries, belonging to the computer field. The search method comprises the following steps of: dividing a search address into at least two address fields; searching a head address field matched with the head address field of the search address in a first binary tree according to the head address field of the search address; taking the address suffix of the head address field found out as the address prefix of the tail address field of the search address; according to the address prefix of the tail address field of the search address and the tail address field, searching the matched address prefix of the tail address field and the matched tail address field in a second binary tree; and obtaining the search result according to the obtained address prefix of the tail address field and the tail address field. The method saves storage space compared with the prior art by sectionally storing and searching the routing address, thus being flexibly suitable for storing and searching the routing addresses of various bit widths; and the search rate is increased.
Owner:HUAWEI TECH CO LTD
Method for quickly searching contacts based on edge touch and terminal
The invention discloses a method for quickly searching contacts based on edge touch. The method comprises the following steps: when detecting a sideslip touch signal, comparing a sideslip distance corresponding to the sideslip touch signal with a maximum sideslip distance threshold corresponding to each letter in a prebuilt associated alphabet one by one, so as to match a corresponding letter with the sideslip touch signal, wherein the letter is an initial letter of a contact name to be searched; and after that, updating the state of the associated alphabet and a currently displayed contact list according to the initial letter, so as to quickly enter the contact list to which the contact name to be searched belongs. According to the method for quickly searching the contacts based on the edge touch provided by the invention, the user does not need to slide ceaselessly from the first letter A until sliding to the contact list to which the contact name to be searched belongs, so that the search speed is improved and user experience is also improved. Correspondingly, the invention further provides a mobile terminal.
Owner:NUBIA TECHNOLOGY CO LTD
Method of uplink scrambling code distribution in WCDMA system
InactiveCN100369401CImprove lookup rateReduce handover failure rateCode division multiplexTelecommunicationsCommunications system
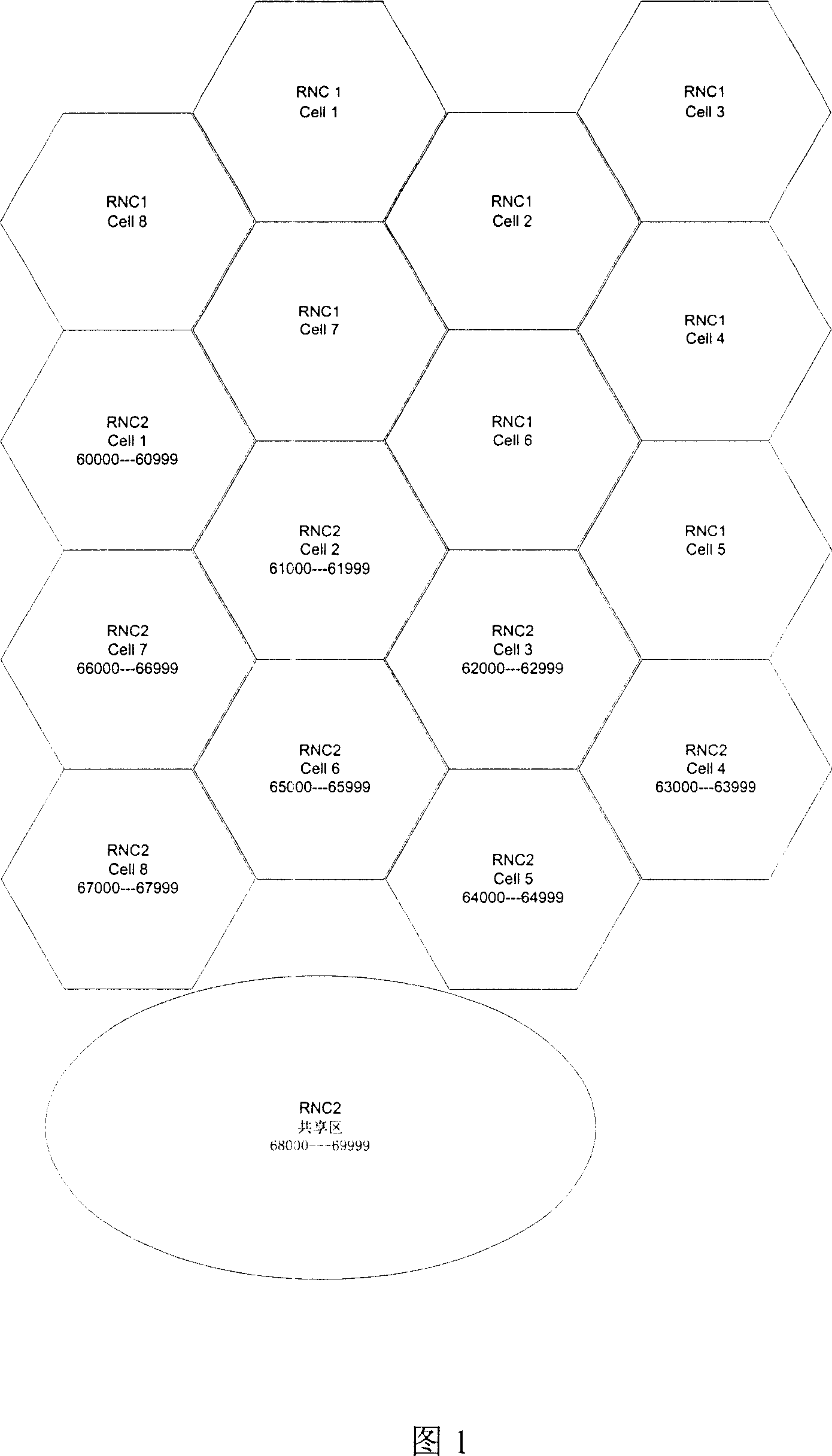
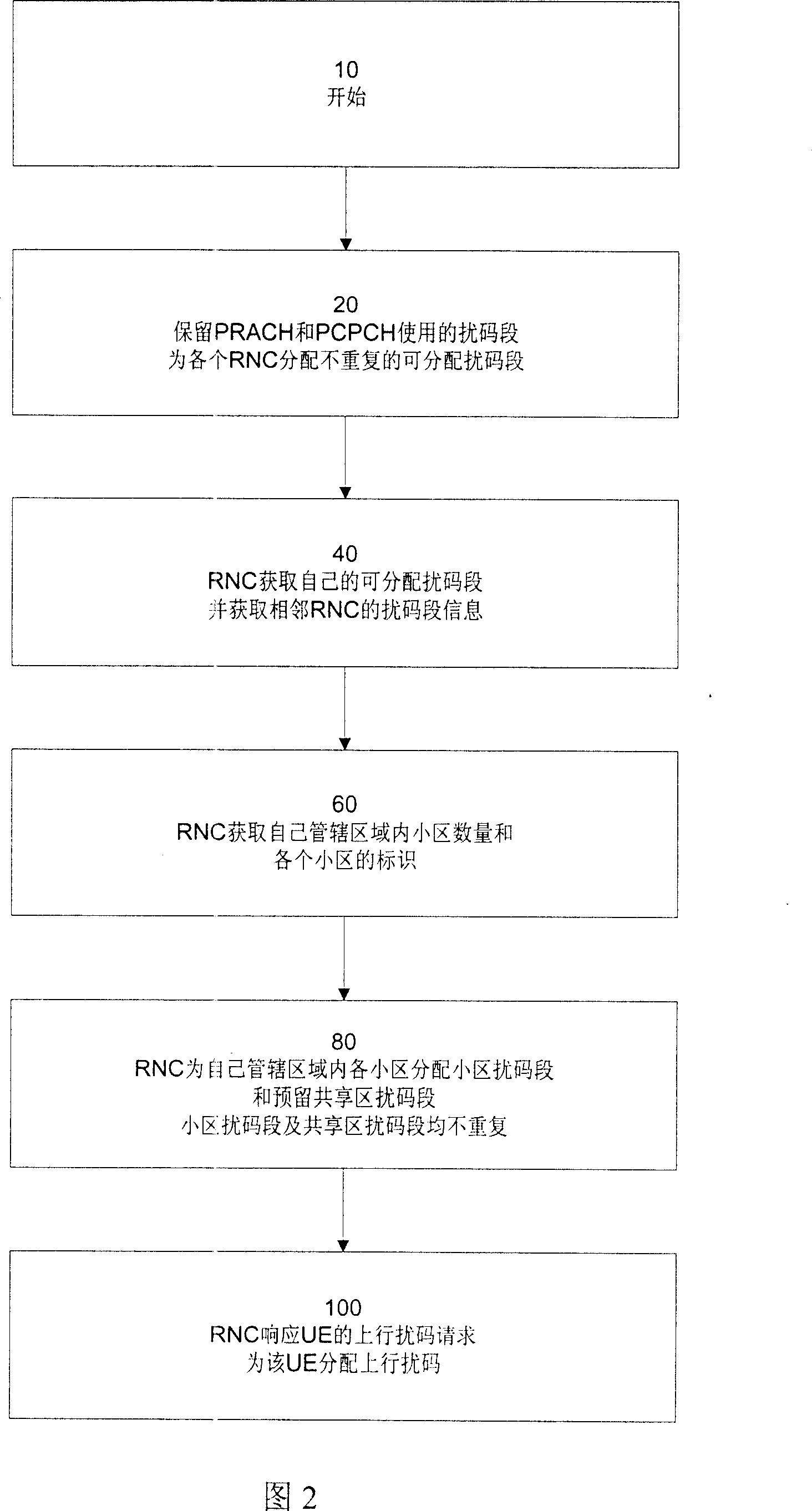
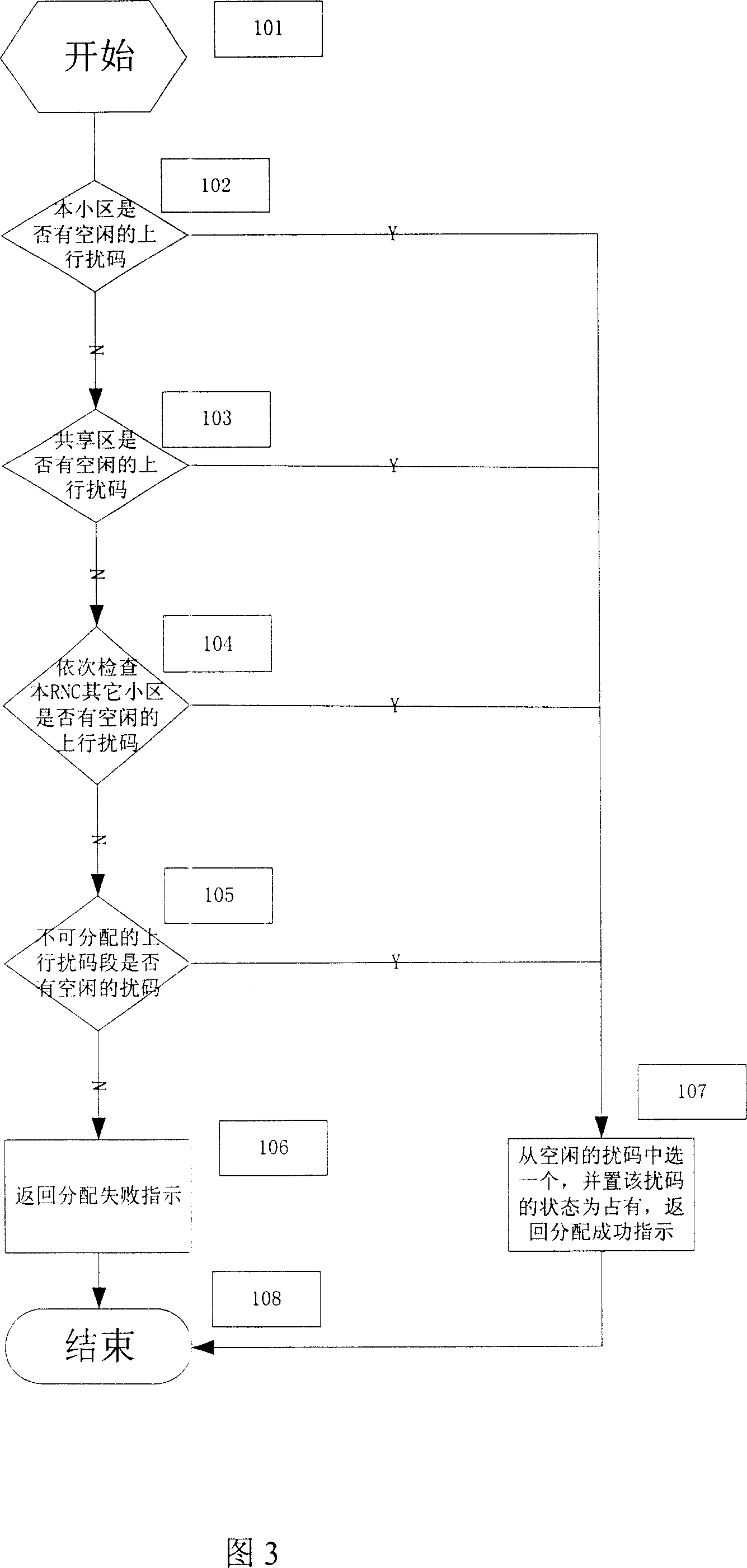
This invention relates to a distribution method for up scrambling code in WCDMA, which distributes non-repeated distributed scrambling code segments for adjacent radio network controller (RNC) and divides each RNC administrative zone to small areas and shared zones to assign non-repeated scrambling codes segments for them. The method can increase the distribution effect of up scrambling codes and reduces probability of failure switch when UE crosses over RNC zone.
Owner:BEIJING NORTHEN FIBERHOME TECH CO LTD
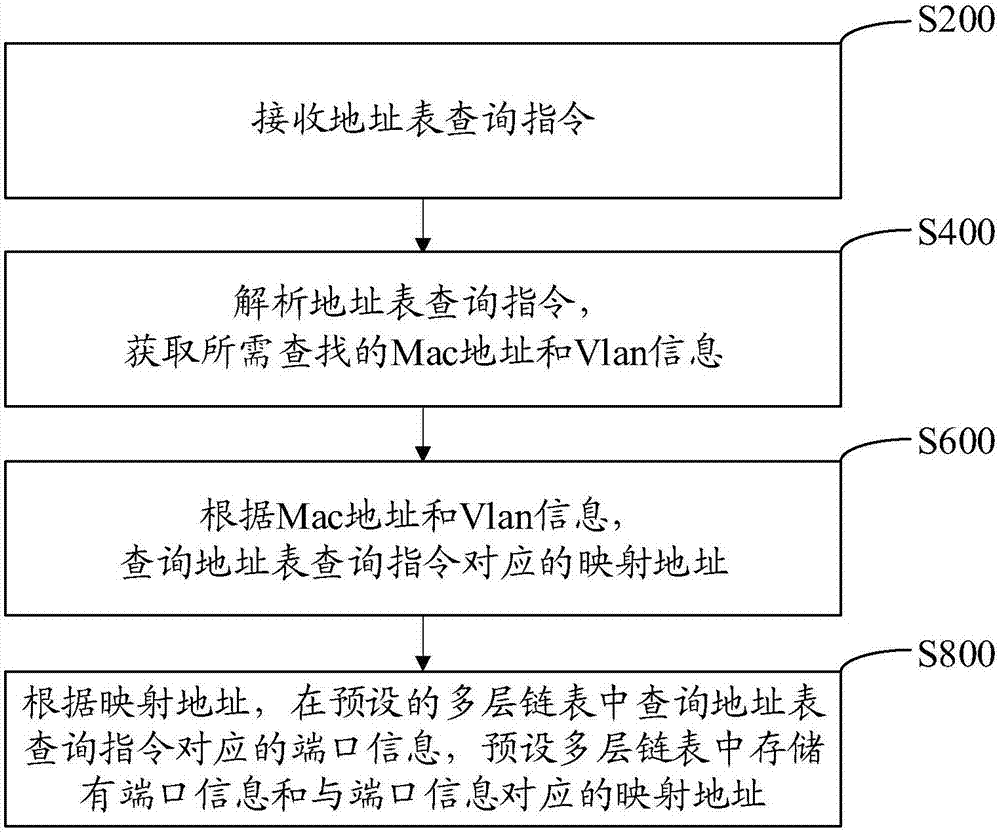
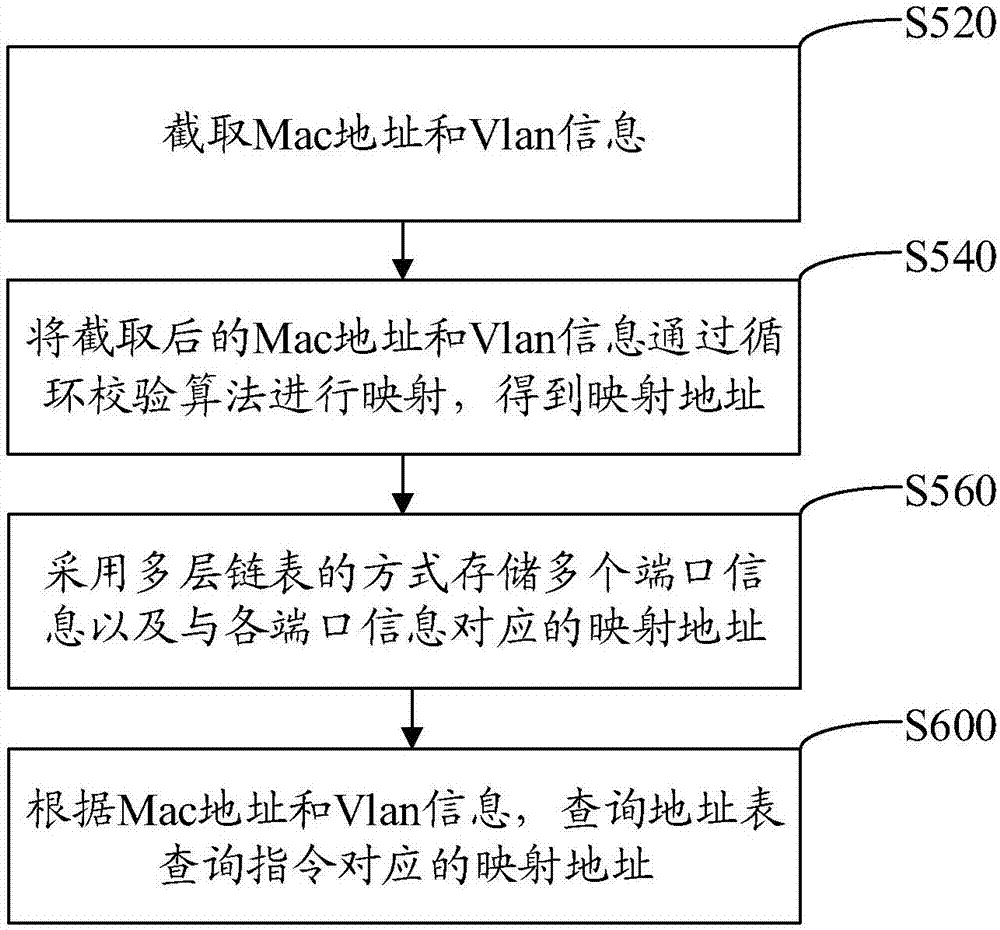
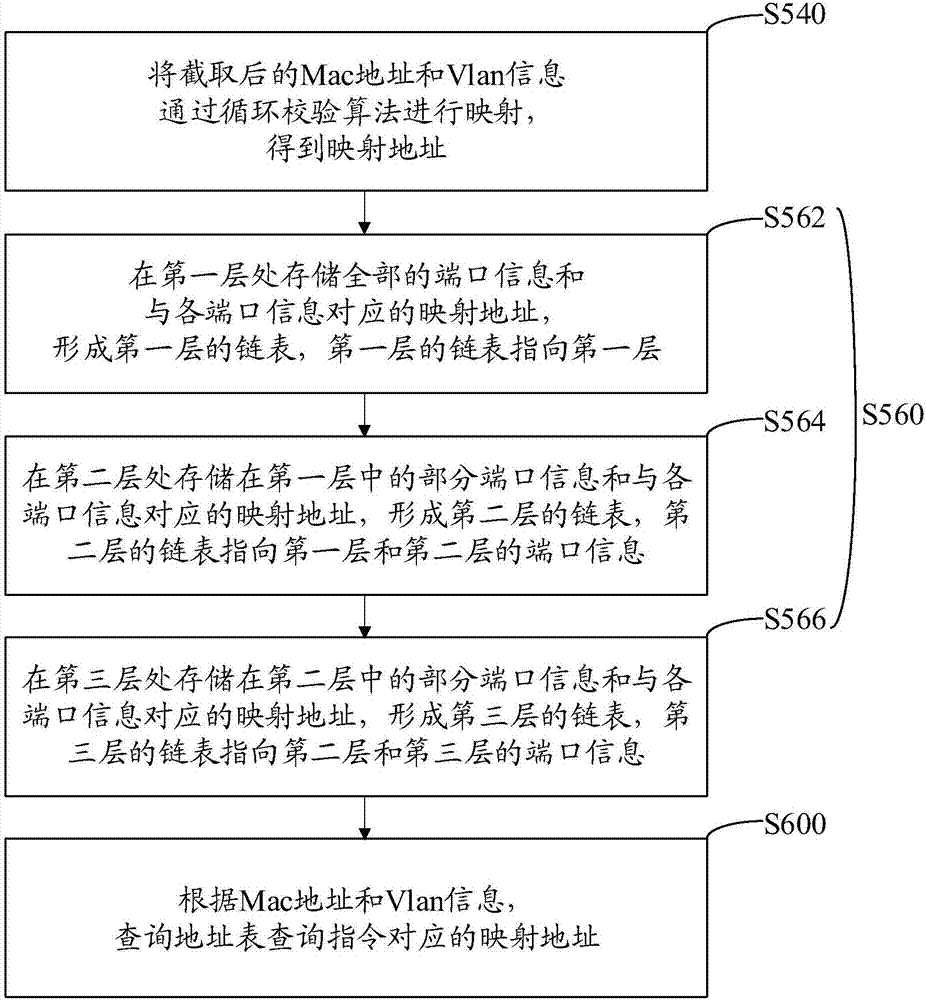
Address table storage and lookup method, device, computer equipment and readable storage medium
The invention provides an address table storage and lookup method, applied to a switch. The method comprises the following steps: receiving an address table query instruction; parsing the address table query instruction to obtain an Mac address and Vlan information to be looked up; querying a mapping address corresponding to the address table query instruction according to the Mac address and the Vlan information; and querying port information corresponding to the address table query instruction in a preset multi-layer chain table according to the mapping address, wherein the port information and the mapping address that corresponds to the port information are stored in the preset multi-layer chain table. The invention also provides an address table storage and lookup device, computer equipment and a readable storage medium. According to the invention, after an address table query instruction is received, the query instruction is parsed to acquire the Mac address and the Vlan information, the corresponding mapping address is queried, and the port information is queried in the preset multi-layer chain table to ensure that the retrieval for the Mac address and the Vlan information can be quickly performed, and the lookup speed can be increased.
Owner:LILING FULLRIVER ELECTRONICS & TECH LTD
Network data flow classification method and system
ActiveCN103220223BImprove lookup rateImprove scalabilityData switching networksData streamClassification methods
The invention provides a method for classification of network data flow. The method for the classification of the network data flow comprises building a longest prefix matching (lpm) table, wherein each item in the lpm table is a port range table, and each port range table corresponds to a service; acquiring the destination internet protocol (ip) of service data when receiving the service data, acquiring the destination port of the service data according to the port range tables corresponding to the service data, finding a hash table corresponding to the source ip of the service data, carrying out hash searching according to the hash table to obtain the source ip of the service data, and obtaining the types of the service data according to the source ip of the service data. According to the method for the classification of the network data flow, an lpm algorithm is combined with the hash table, searching speed is high, scalability is good, transmission quality is improved, and transmission cost is reduced. The invention further discloses a system for the classification of the network data flow.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
Information presentation manner change method and device
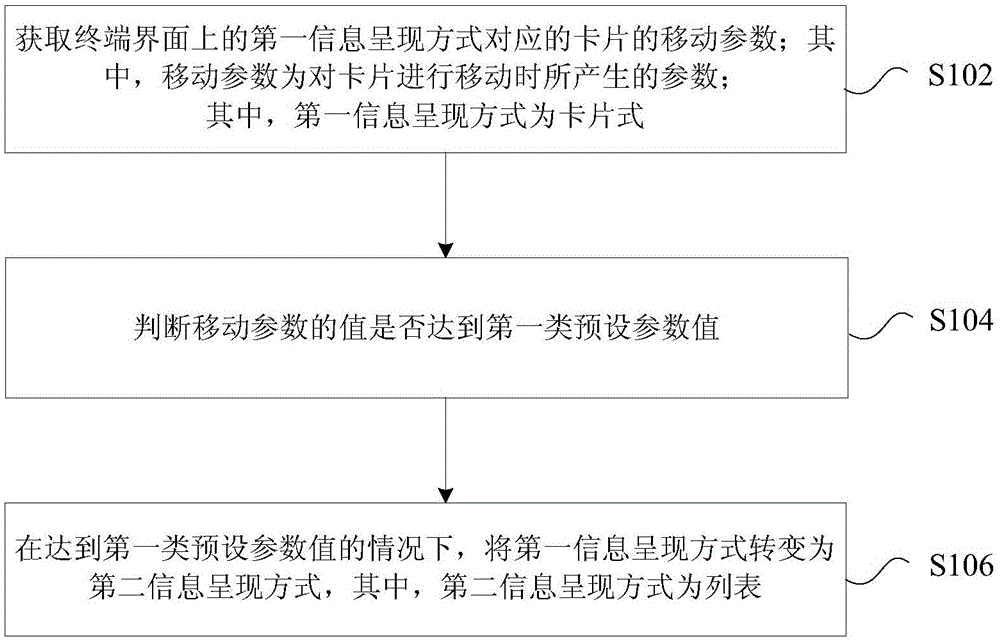
InactiveCN106484372ASolve the problem that scrolling to find content takes a long timeTime-consuming to resolveSpecific program execution arrangementsSimulationInformation presentation
The invention provides an information presentation manner change method and device. The method is applied to a terminal, and comprises the following steps of: obtaining a motion parameter of a card corresponding to a first information presentation manner on a terminal interface, wherein the motion parameter is generated when the card is moved, and the first information presentation manner is a card manner; judging whether the value of the motion parameter achieves a first type of preset parameter value; and when the value of the motion parameter achieves the first type of preset parameter value, converting the first information presentation manner into a second information presentation manner, wherein the second information presentation manner is a list manner. Through the method and device provided by the invention, the problem that the consumed time is long as a card type list is adopted to carry out rolling type search on content in the prior art is solved, and the search speed is improved.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com