Trust data management method in peer-to-peer network
A technology for trusting data and management methods, applied in the cross-application field of computing and resource management technology, to achieve the effect of solving security problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
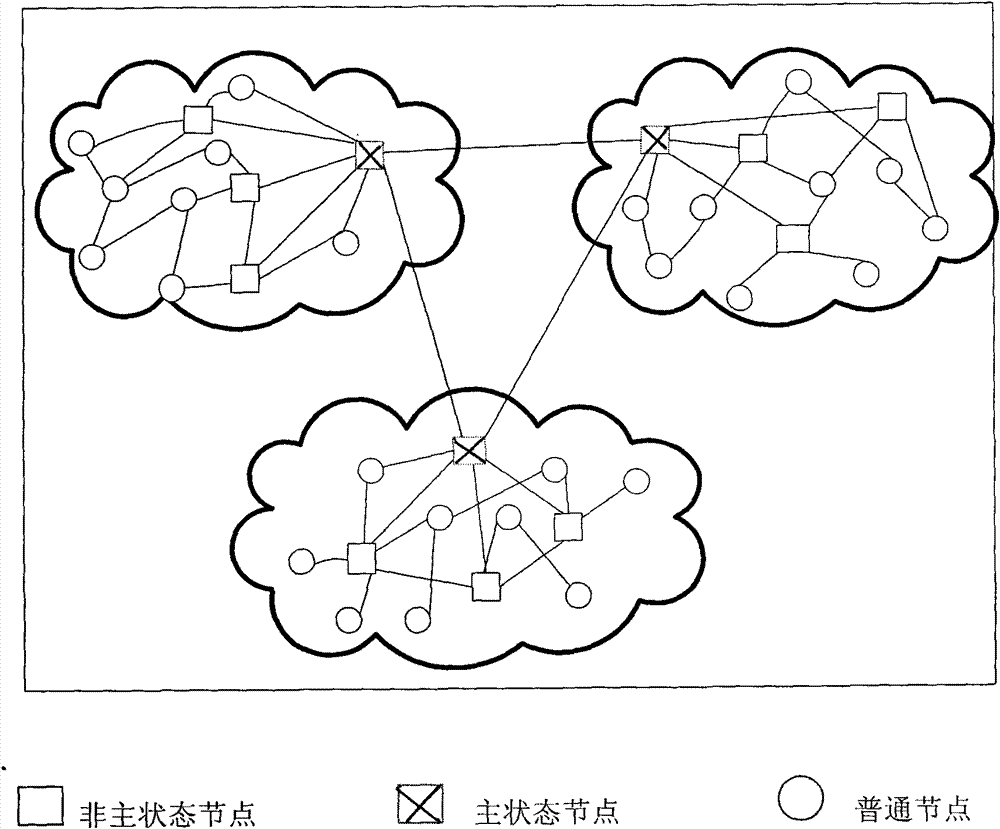
[0055] For the convenience of description, we assume the following application examples: Assume that the autonomous area A is adjacent to the autonomous area B, and there are state nodes D and E in the autonomous area A, where D is the main state node, E is the non-main state node, and the ordinary node F, G; There are state nodes H and I in the autonomous area B, where H is the main state node, I is the non-main state node, and ordinary nodes J and K.
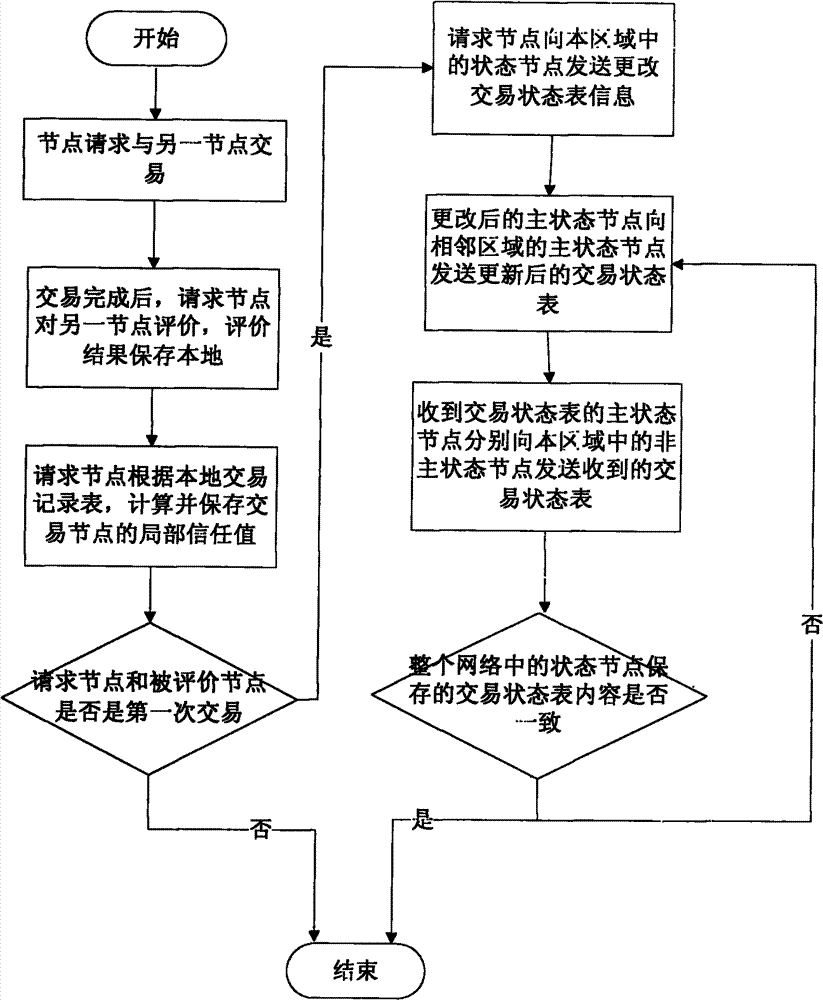
[0056] 1: Trust the workflow of data storage:
[0057] Step 1: Ordinary node F in autonomous area A requests a transaction with ordinary node J in autonomous area B.
[0058] Step 2: After the transaction, node F evaluates node J according to the service quality provided by the node, and the evaluation result is saved in the local (node F) transaction record table.
[0059] Step 3: After the transaction record table is updated, node F updates the local trust value of node J in the table according to the evaluation records o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com