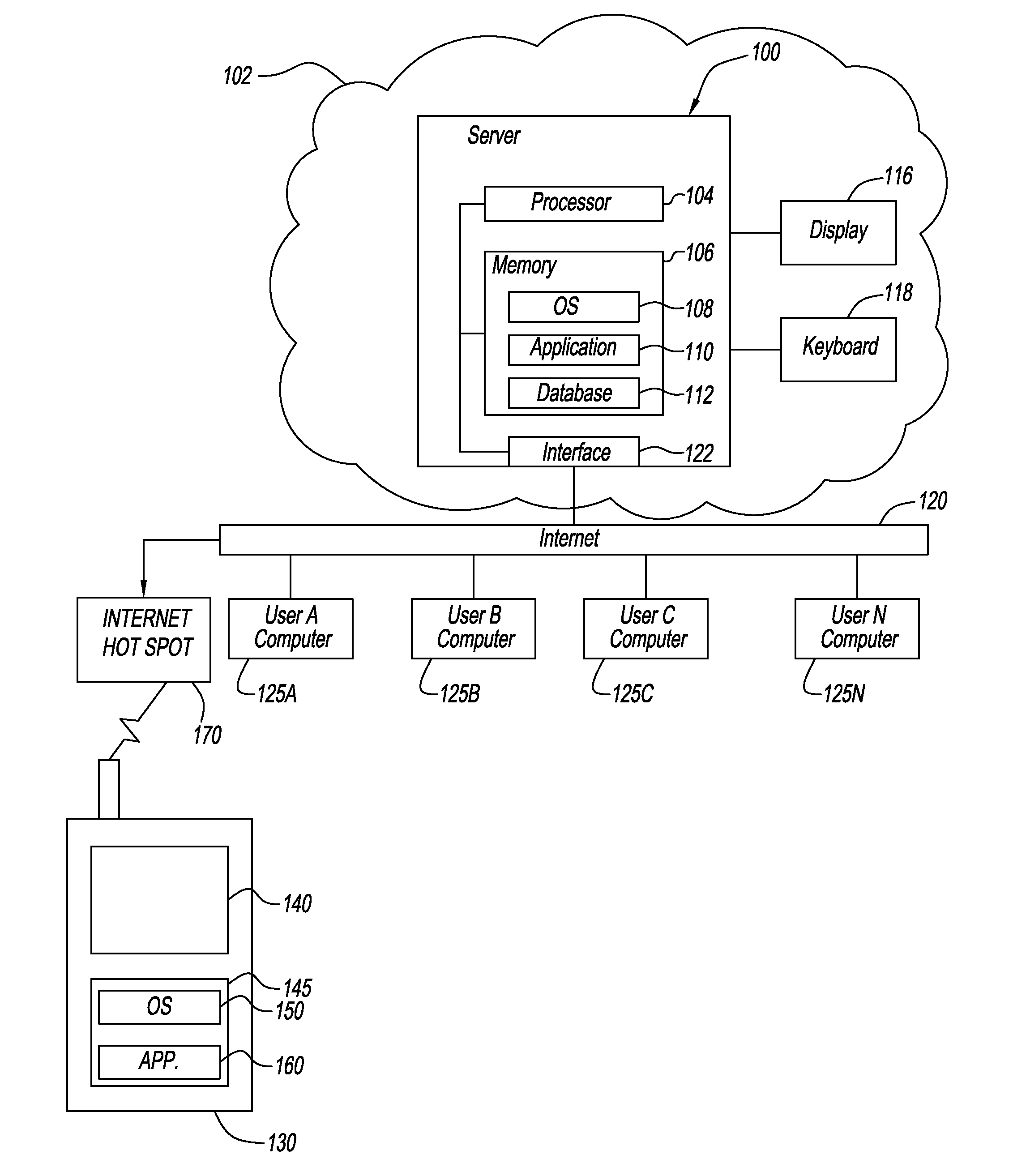
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
53 results about "SMS phishing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computing, SMS phishing or smishing is a form of criminal activity using social engineering techniques. Phishing is the act of attempting to acquire personal information such as passwords and details by masquerading as a trustworthy entity in an electronic communication. Short Message Service (SMS) is the technology used for text messages on cell phones.
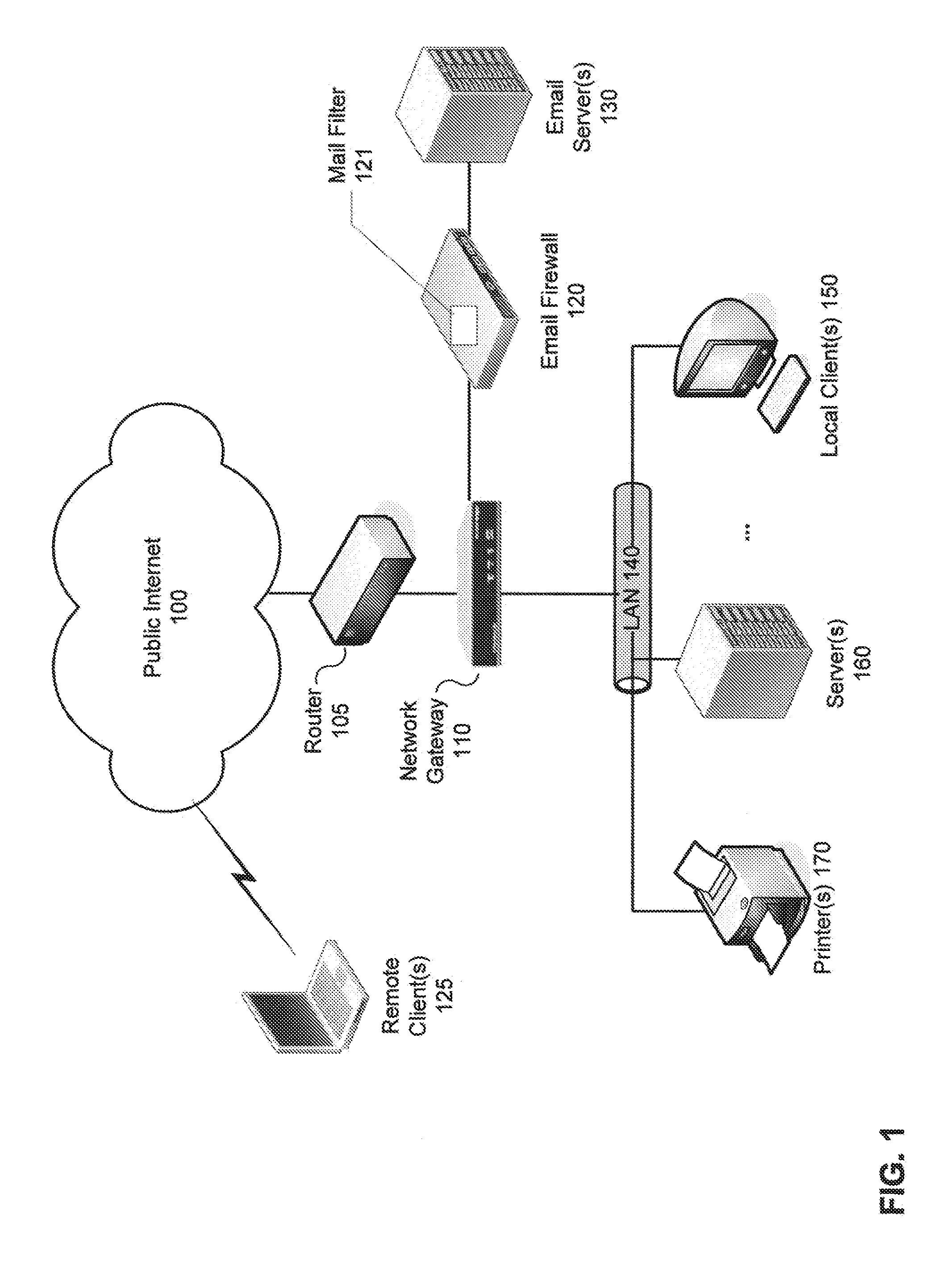
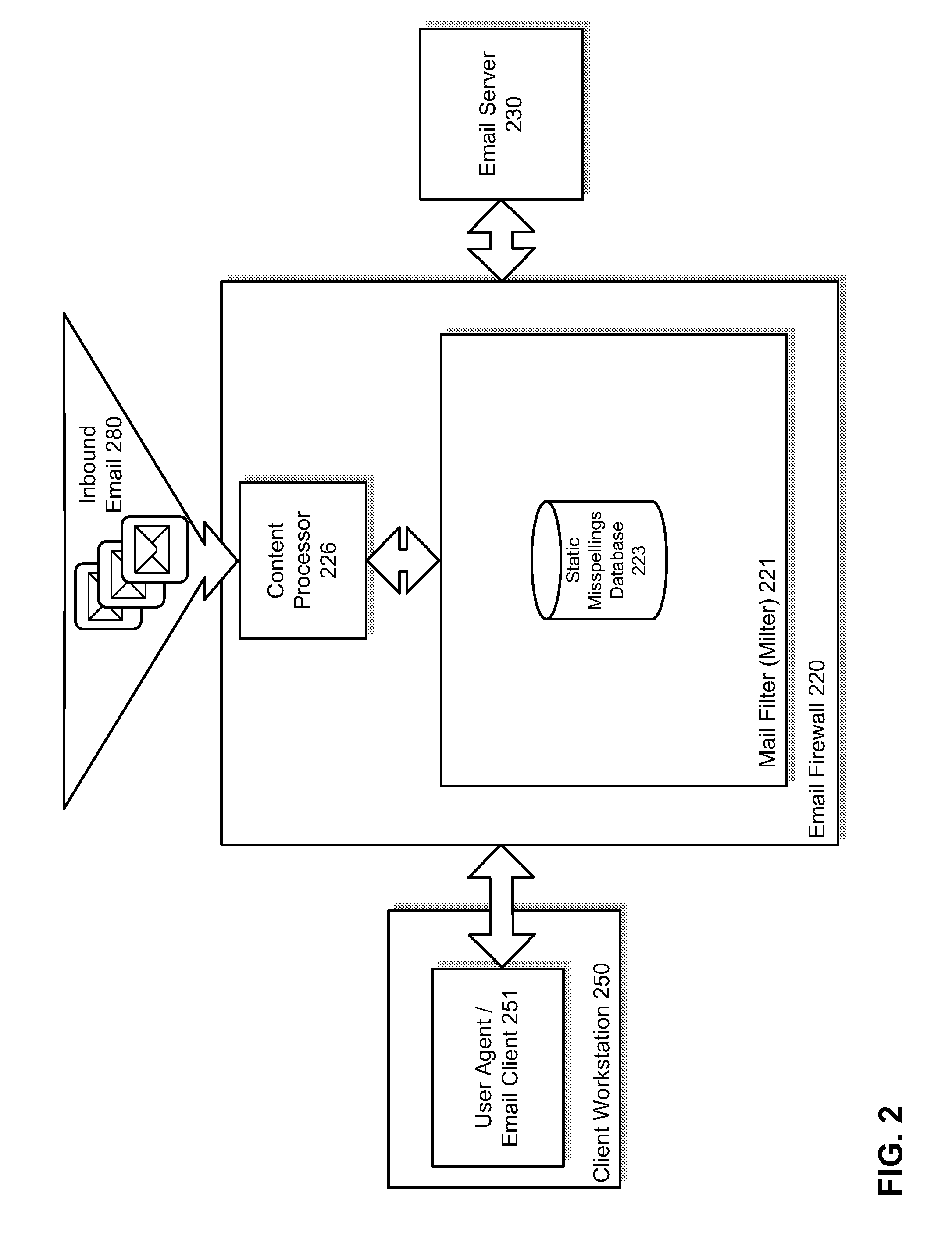
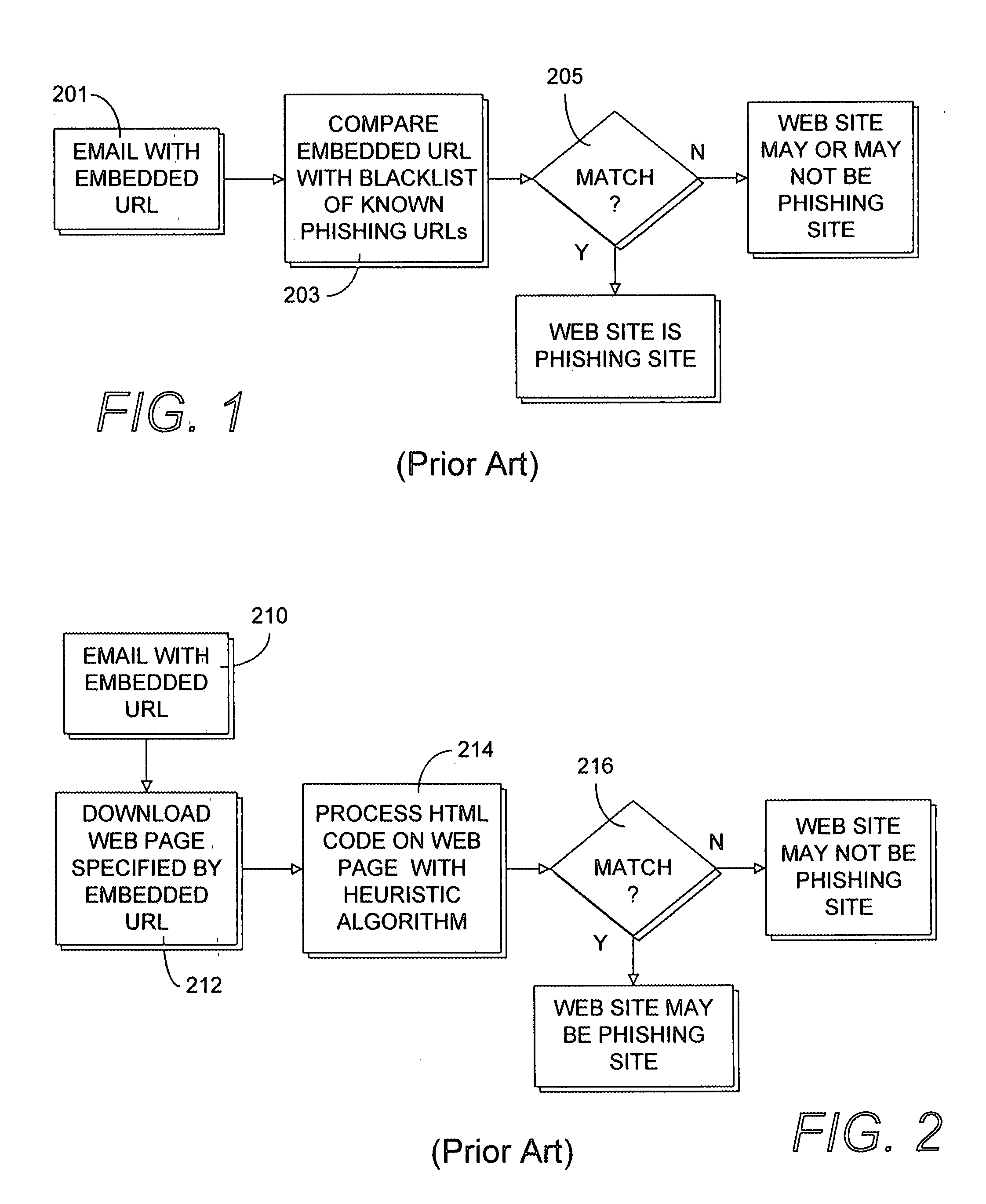
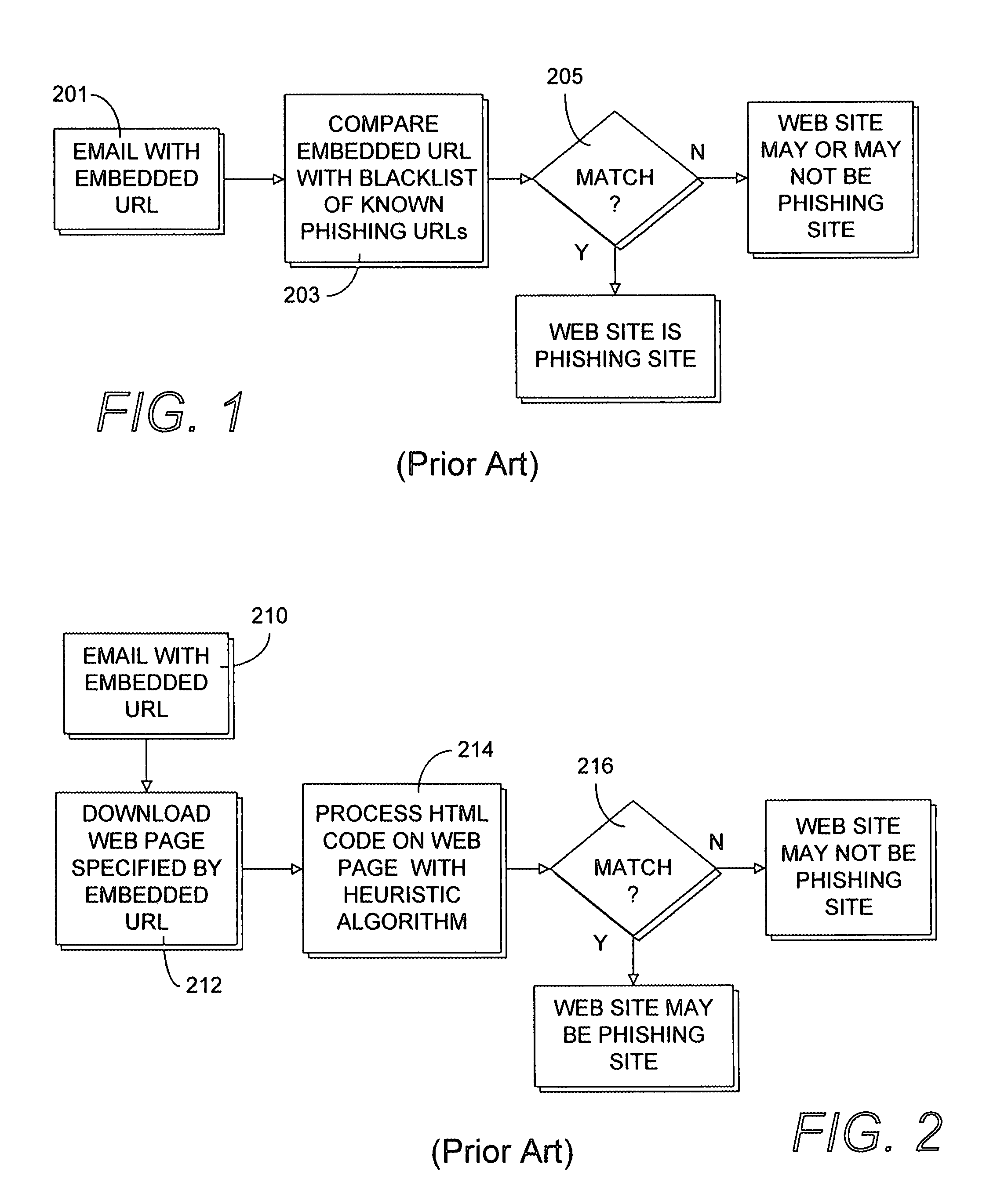
Heuristic detection of probable misspelled addresses in electronic communications
Methods and systems for detecting suspicious electronic communications, such as electronic mail (email) messages containing, originated or purportedly originated from misspelled and / or deliberately misleading addresses, are provided. According to one embodiment, an electronic communication, such as an electronic mail (email) message, is scanned to determine whether the electronic communication contains one or more suspicious addresses or represents a suspicious traffic pattern. If the electronic communication is determined to contain one or more suspicious addresses or is determined to represent a suspicious traffic pattern, then the electronic communication is handled in accordance with an electronic communication security policy associated with suspicious electronic communications. For example, an event may be logged, the electronic communication may be dropped or quarantined, the communication may be tagged as spam or possible phishing and / or an end user may be alerted to the existence of the one or more suspicious addresses.
Owner:FORTINET
Protecting computer users from online frauds
Protecting computer users from online frauds, such as phishing and pharming. A client computer may include a page signature extractor and a policy enforcer. The page signature extractor may encode a web page to generate its signature, which may be provided to a remote server computer for comparison with signatures of phishing pages. The client computer and the server computer may communicate using the DNS protocol. The policy enforcer may perform one or more predetermined actions when a match is found. Examples of such actions include replacing the web page with a blocking page, displaying a warning message, or both. The policy enforcer may be configured to determine if the web page is part of a phishing or pharming attack by comparing the URL of the web page to URLs of legitimate web pages.
Owner:TREND MICRO INC
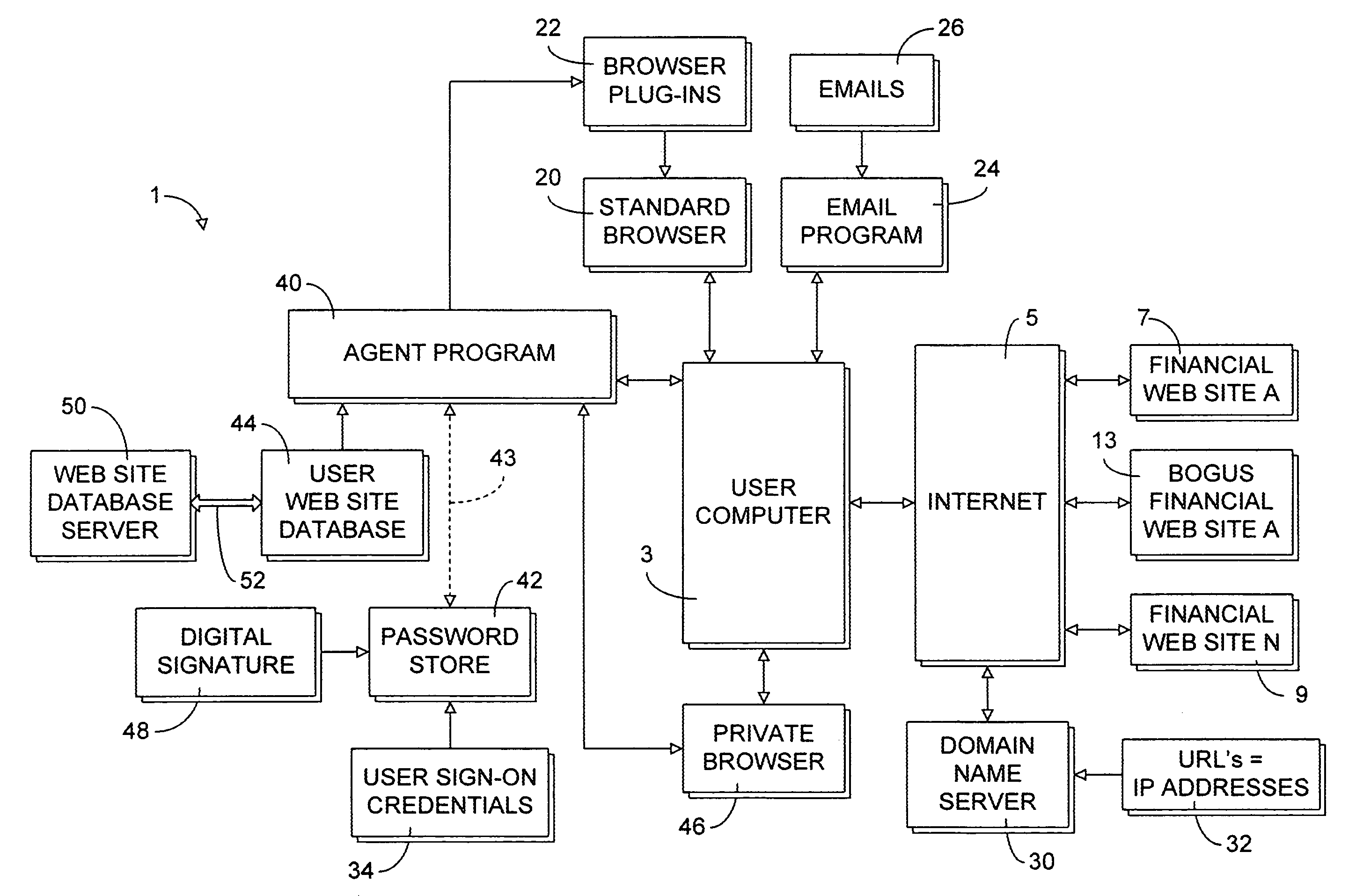
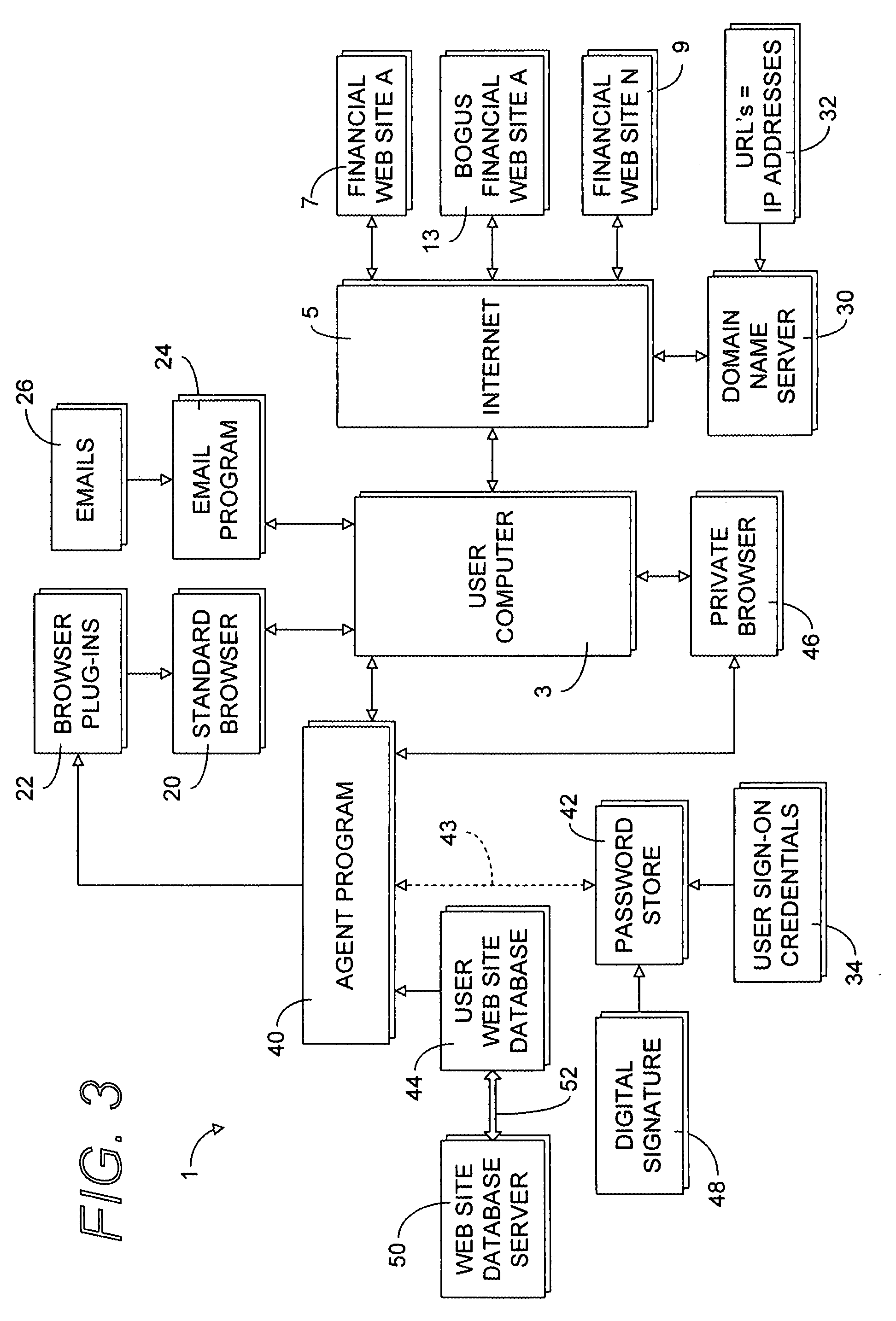
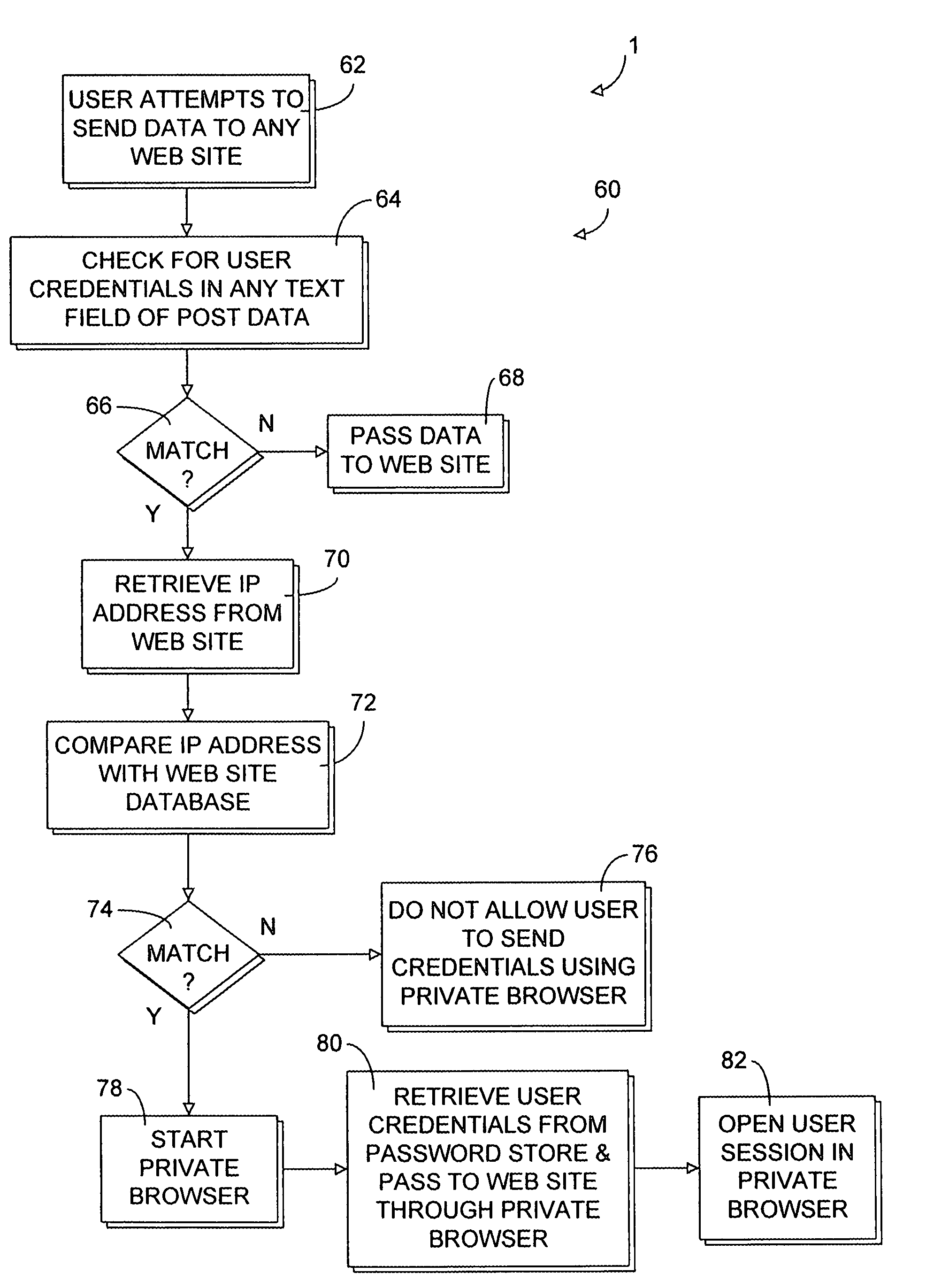
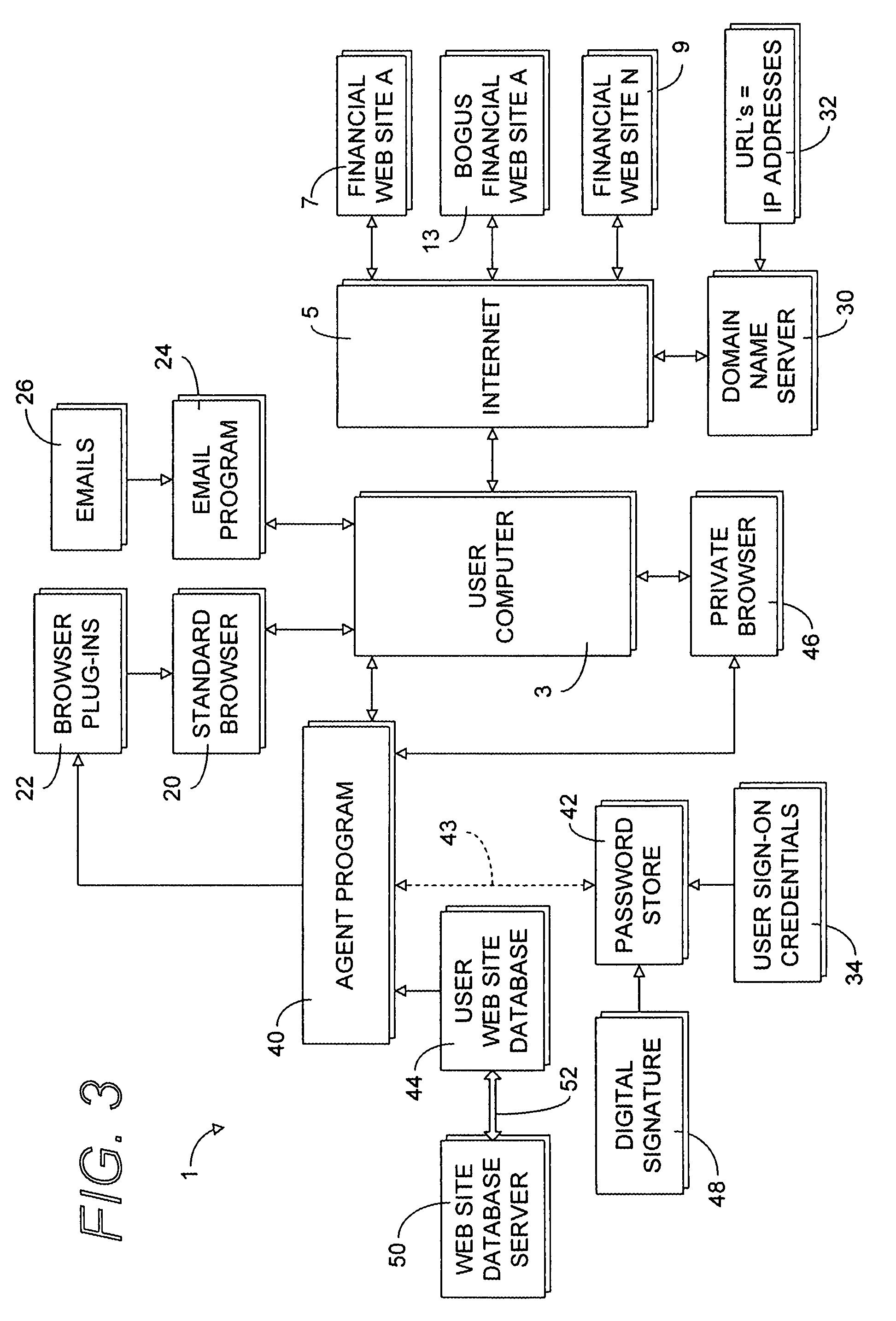
Secure web site authentication using web site characteristics, secure user credentials and private browser
ActiveUS20080028444A1Overcome deficienciesImprove approachDigital data information retrievalMemory loss protectionWeb siteIp address
A secure authentication process detects and prevents phishing and pharming attacks for specific web sites. The process is based on a dedicated secure hardware store for user sign-in credentials, a database of information about specific web sites, and a private secure browser. All user web activity is monitored by an agent program. The agent program checks to make sure that user attempts to send any sign-in credentials stored in secure hardware store of user sign-in credentials, to any web site accessed by the user, is allowed only if the IP address of the web site accessed by the user matches at least one of the IP addresses stored web site database associated with the sign-in credential the user is attempting to send. The process also detects mismatches between a URL and the actual IP address of the web site associated with the URL.
Owner:AURA SUB LLC +1
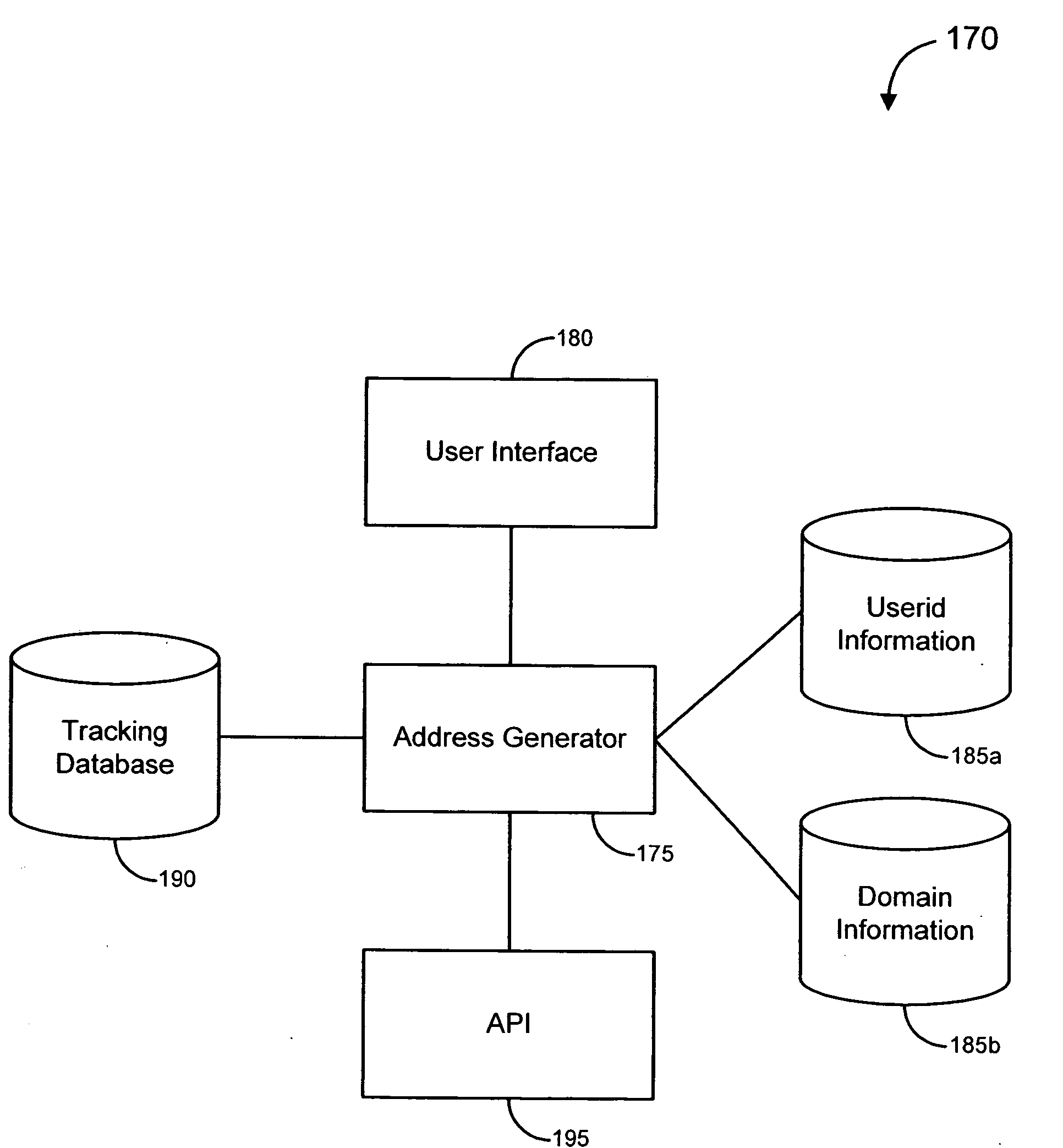
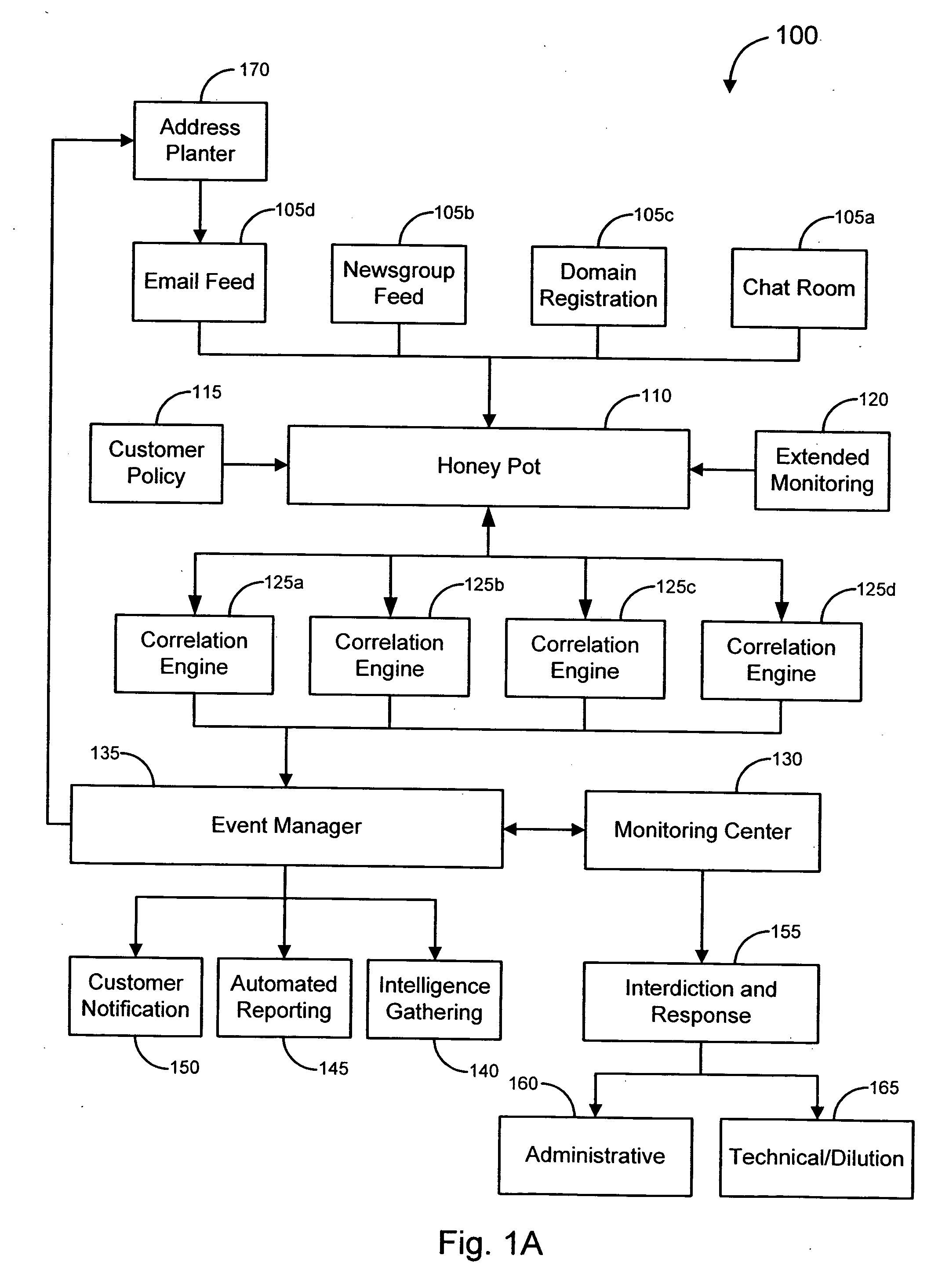
Generating phish messages
ActiveUS20070294352A1Multiple digital computer combinationsData switching networksWeb siteEmail address
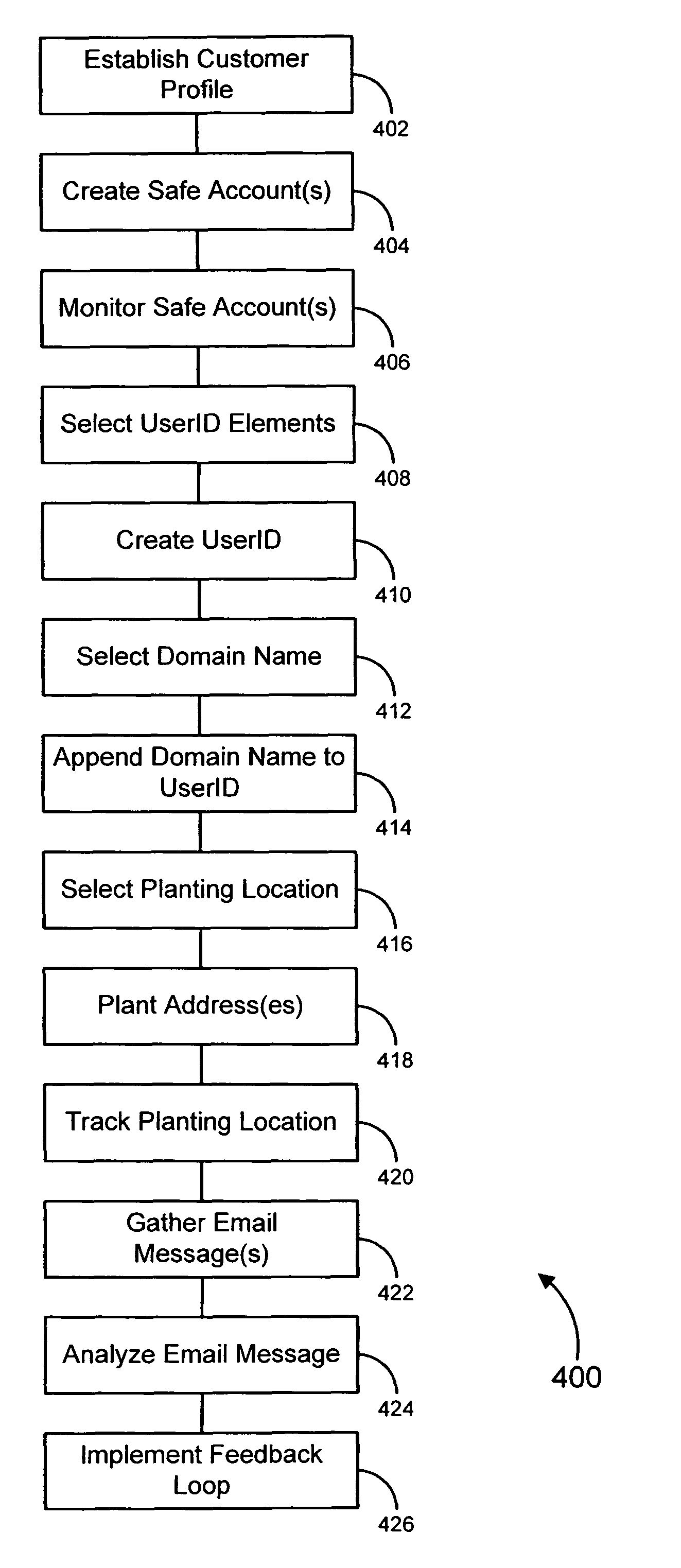
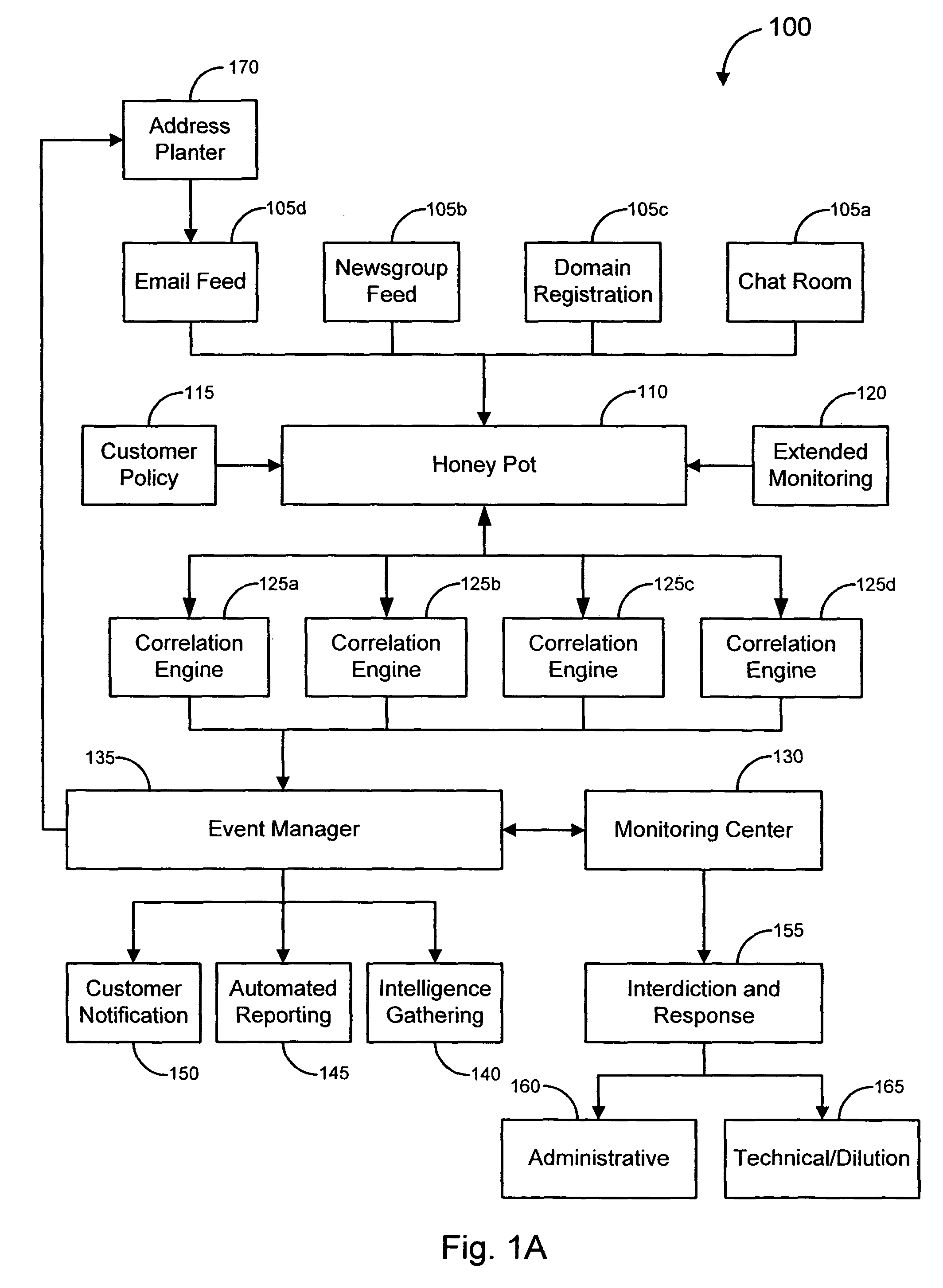
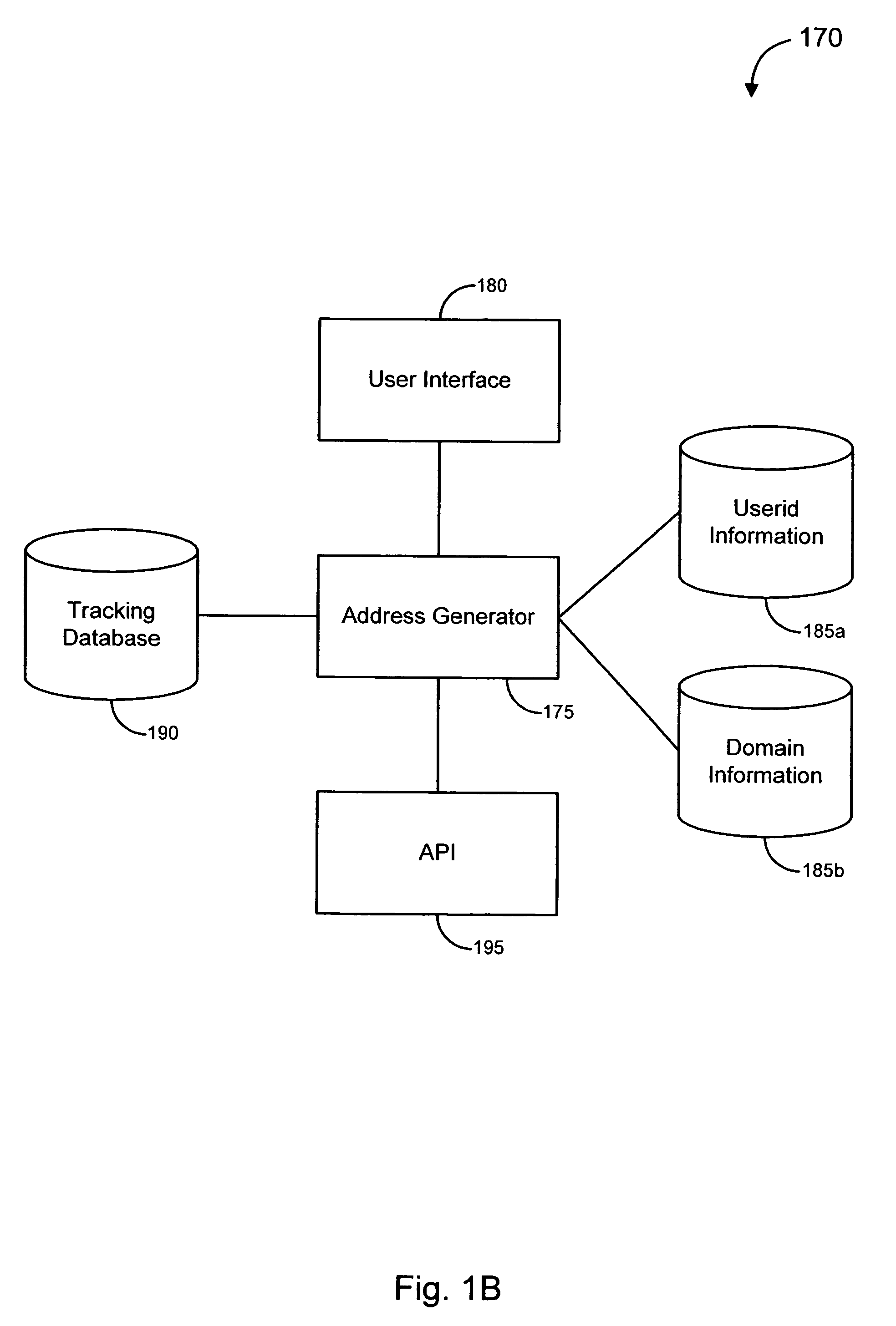
Various embodiments of the invention provide solutions (including inter alia, systems, methods and software) for dealing with online fraud. In particular, various embodiments of the invention provide ways to incite unsolicited email messages (such as spam messages, phish messages, etc.). In accordance with some embodiments, a bait email address may be planted in a particular location on the Internet. In particular embodiments, the location of the planted email address may be tracked in order to determine which locations are relatively more likely to generate unsolicited email messages. In other embodiments, domains likely to host the bait email addresses receiving unsolicited messages may be obtained. In some cases, unsolicited messages may be analyzed and / or otherwise processed to determine whether the messages are possibly associated with a fraudulent activity. Such analysis may lead to the investigation of one or more web sites and / or to the initiation of a response against a fraudulent activity.
Owner:OPSEC ONLINE LTD
Generating phish messages
Owner:OPSEC ONLINE LTD
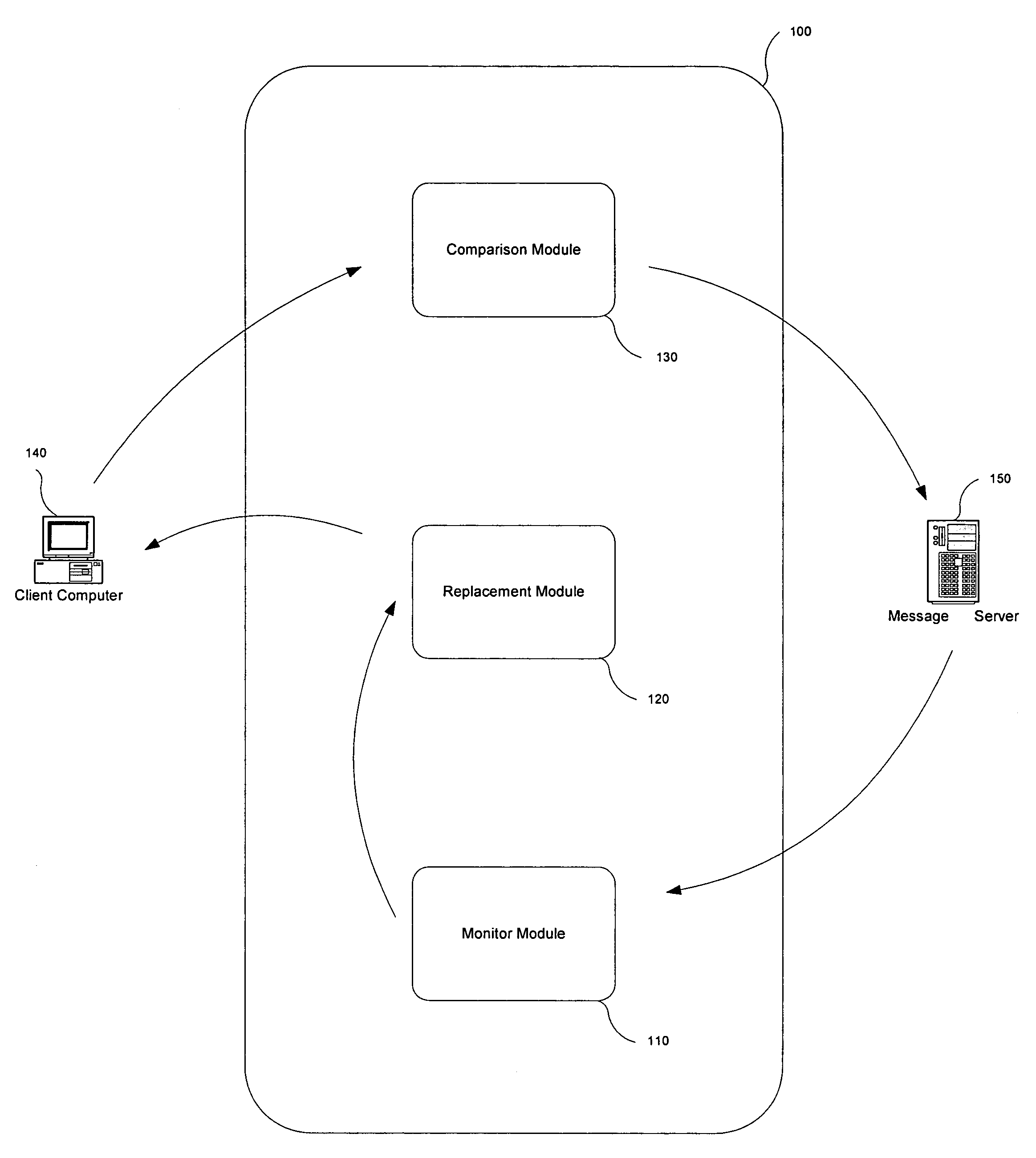
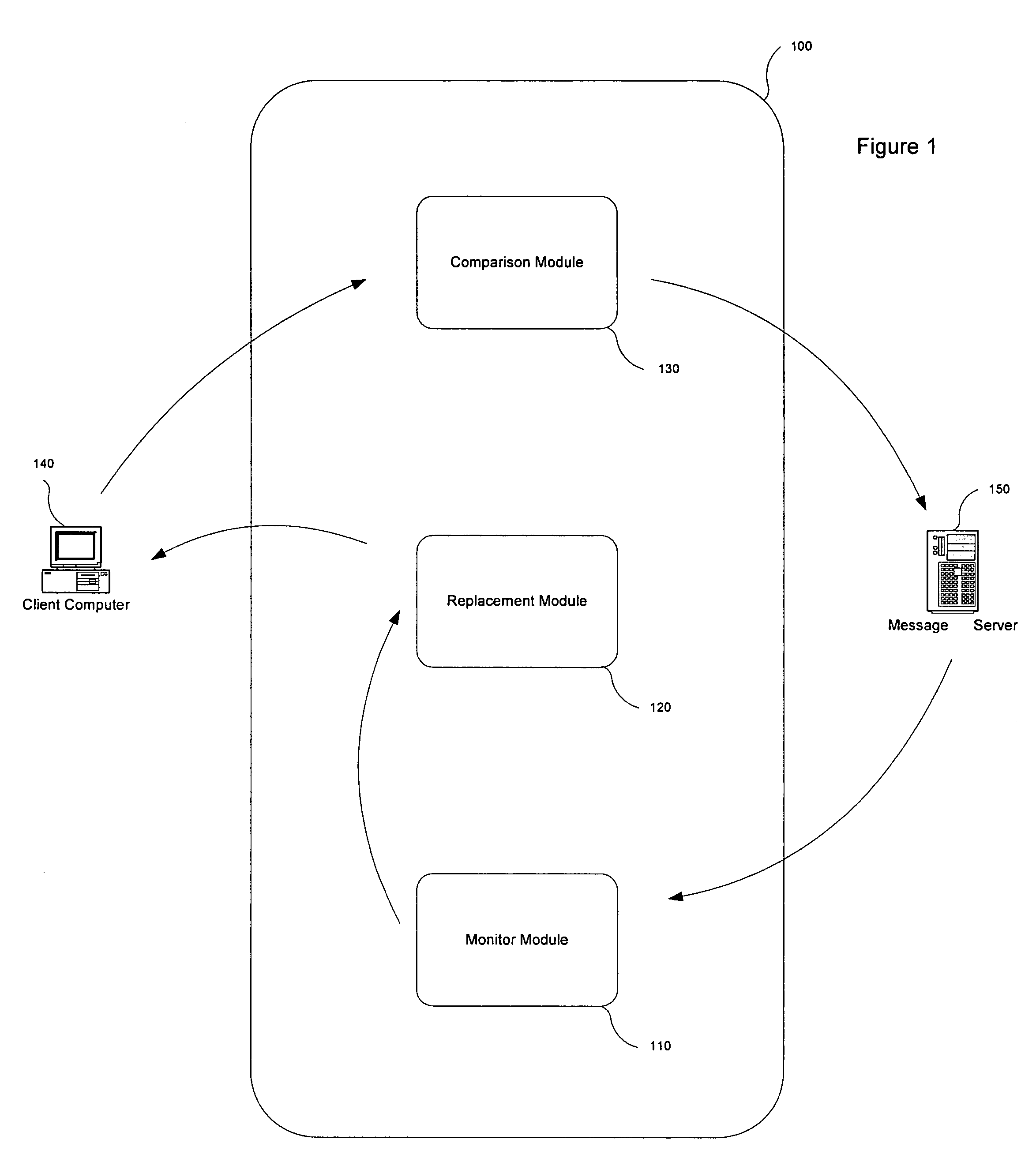
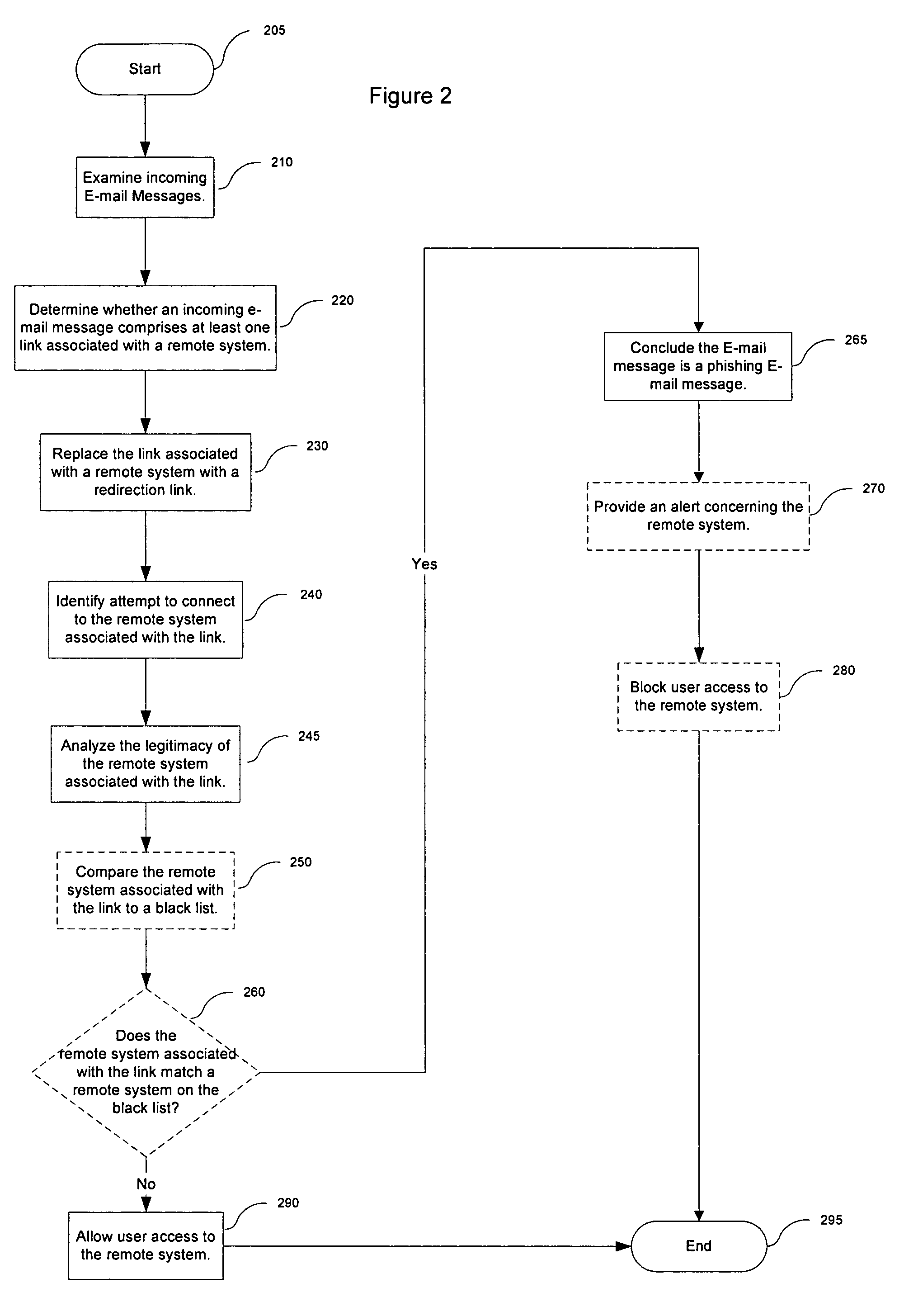
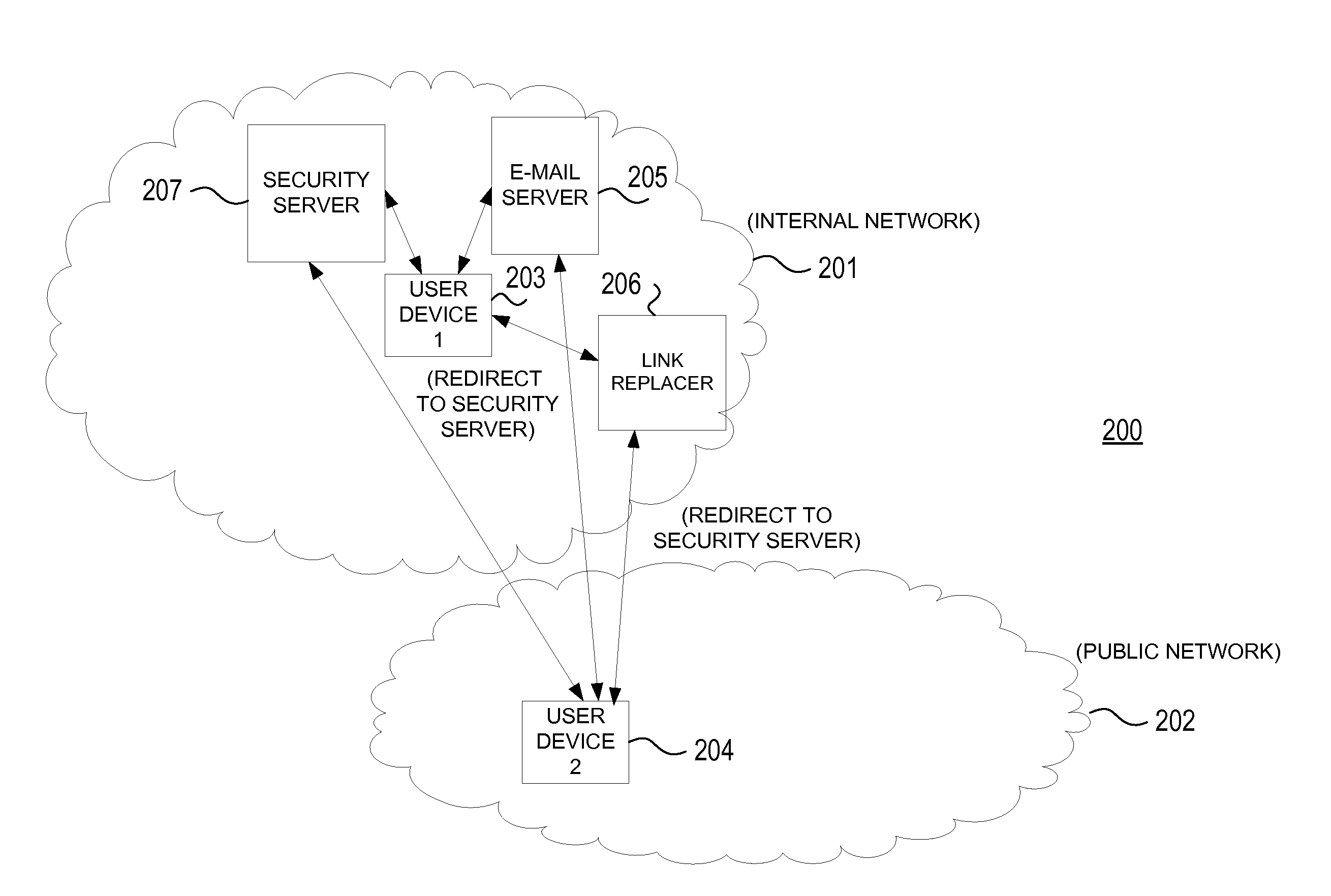
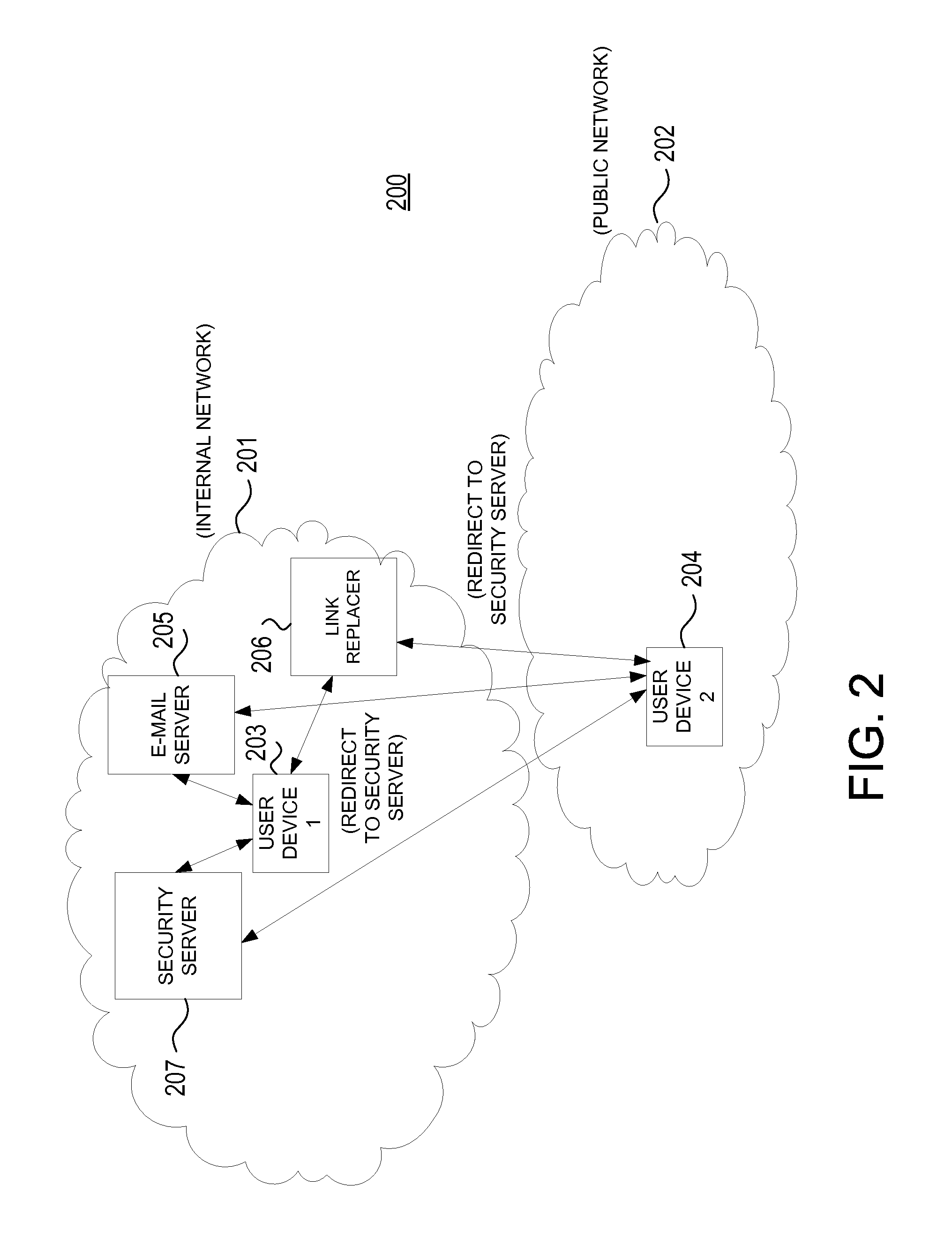
Preventing data from being submitted to a remote system in response to a malicious e-mail
An electronic message manager (100) examines (210) incoming electronic messages and determines (220) whether an incoming electronic message comprises at least one suspect link associated with a remote system. In response to the determination (220) that the incoming message comprises at least one suspect link, the electronic message manager (100) replaces (230) each suspect link with a redirection link. In response to a user attempting (240) to connect to the remote system by clicking on the redirection link, the electronic message manager directs the user to a remote analysis site for deciding (260) whether that incoming message comprises a phishing message.
Owner:NORTONLIFELOCK INC
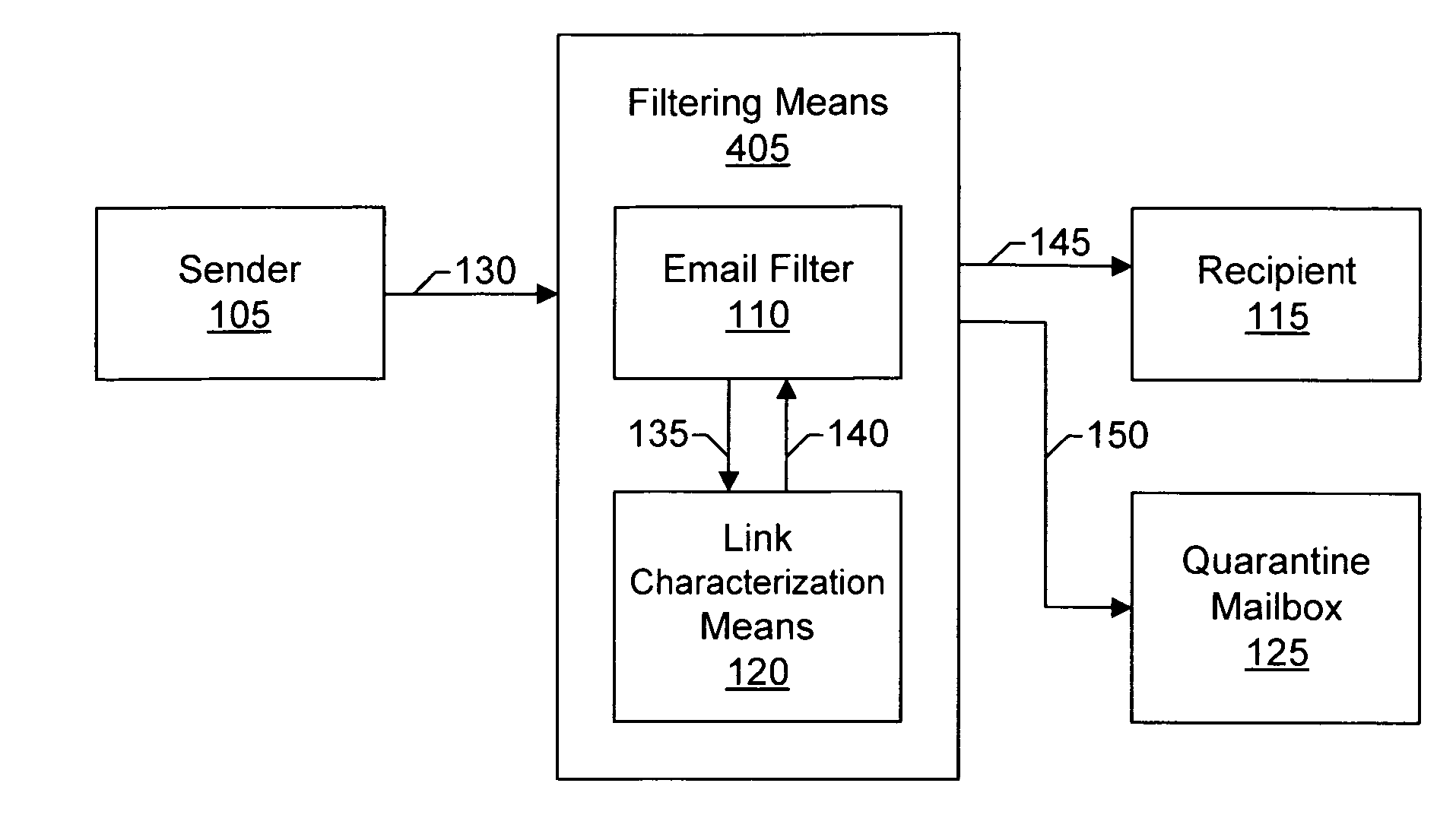
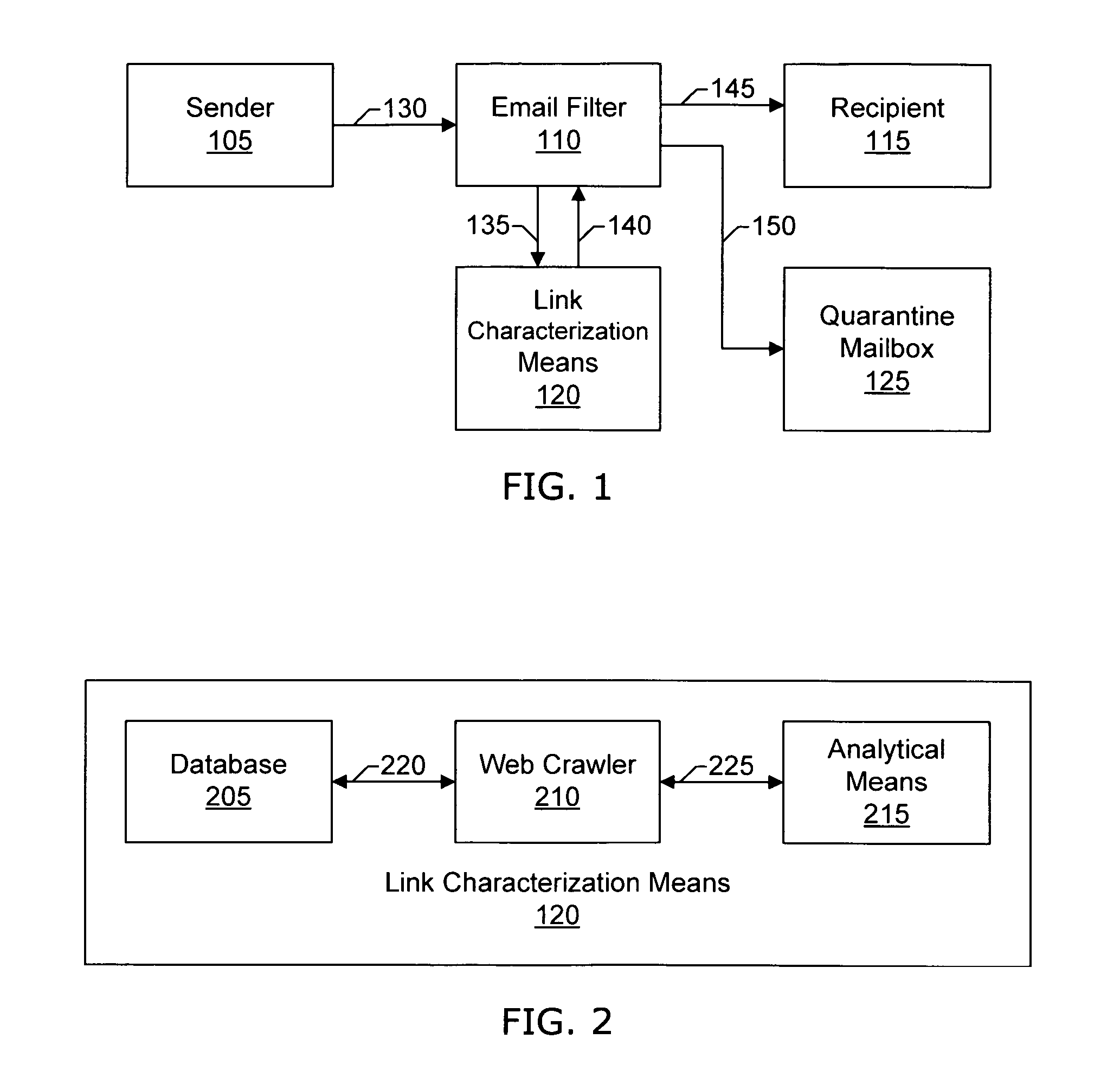
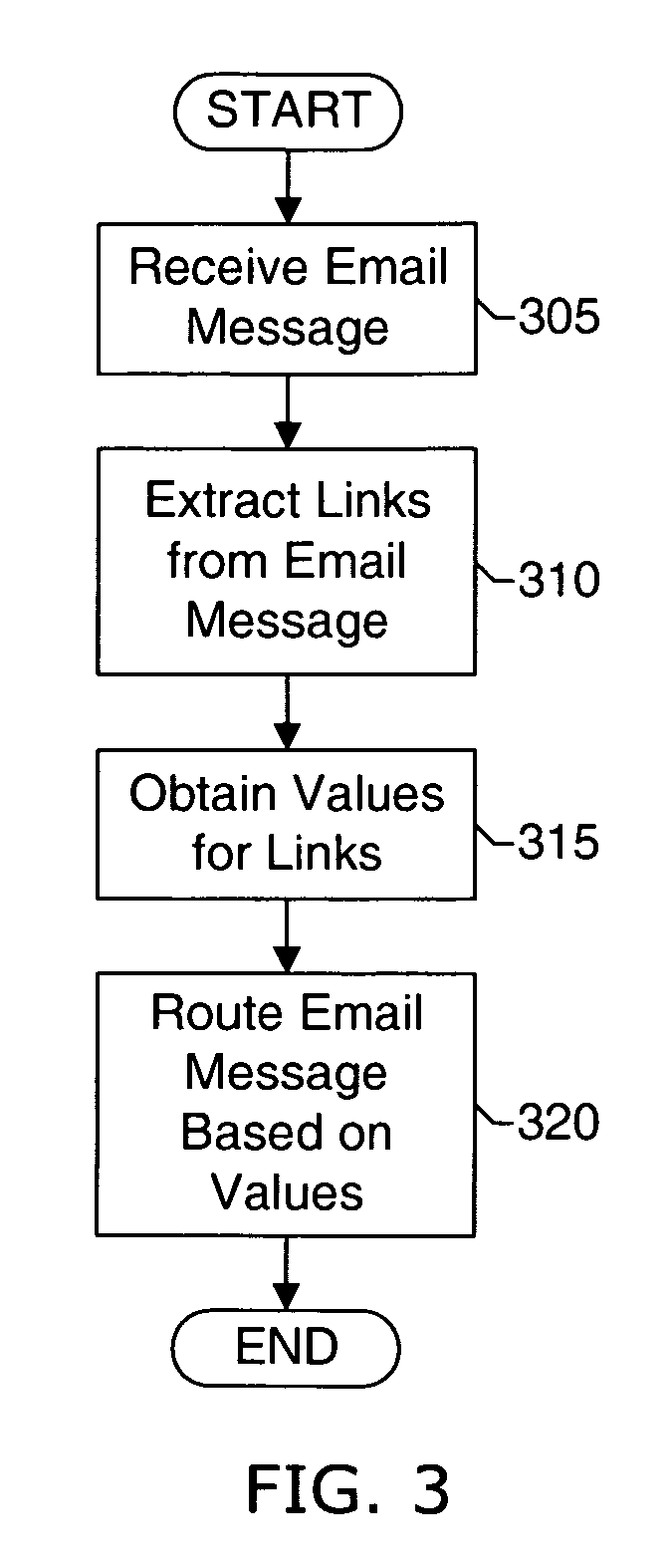
Email filtering system and method
ActiveUS7580982B2Effective filteringMultiple digital computer combinationsData switching networksFilter systemSMS phishing
Systems and methods of the present invention allow filtering out spam and phishing email messages based on the links embedded into the email messages. In a preferred embodiment, an Email Filter extracts links from the email message and obtains desirability values for the links. The Email Filter may route the email message based on desirability values. Such routing includes delivering the email message to a Recipient, delivering the message to a Quarantine Mailbox, or deleting the message.
Owner:GO DADDY OPERATING
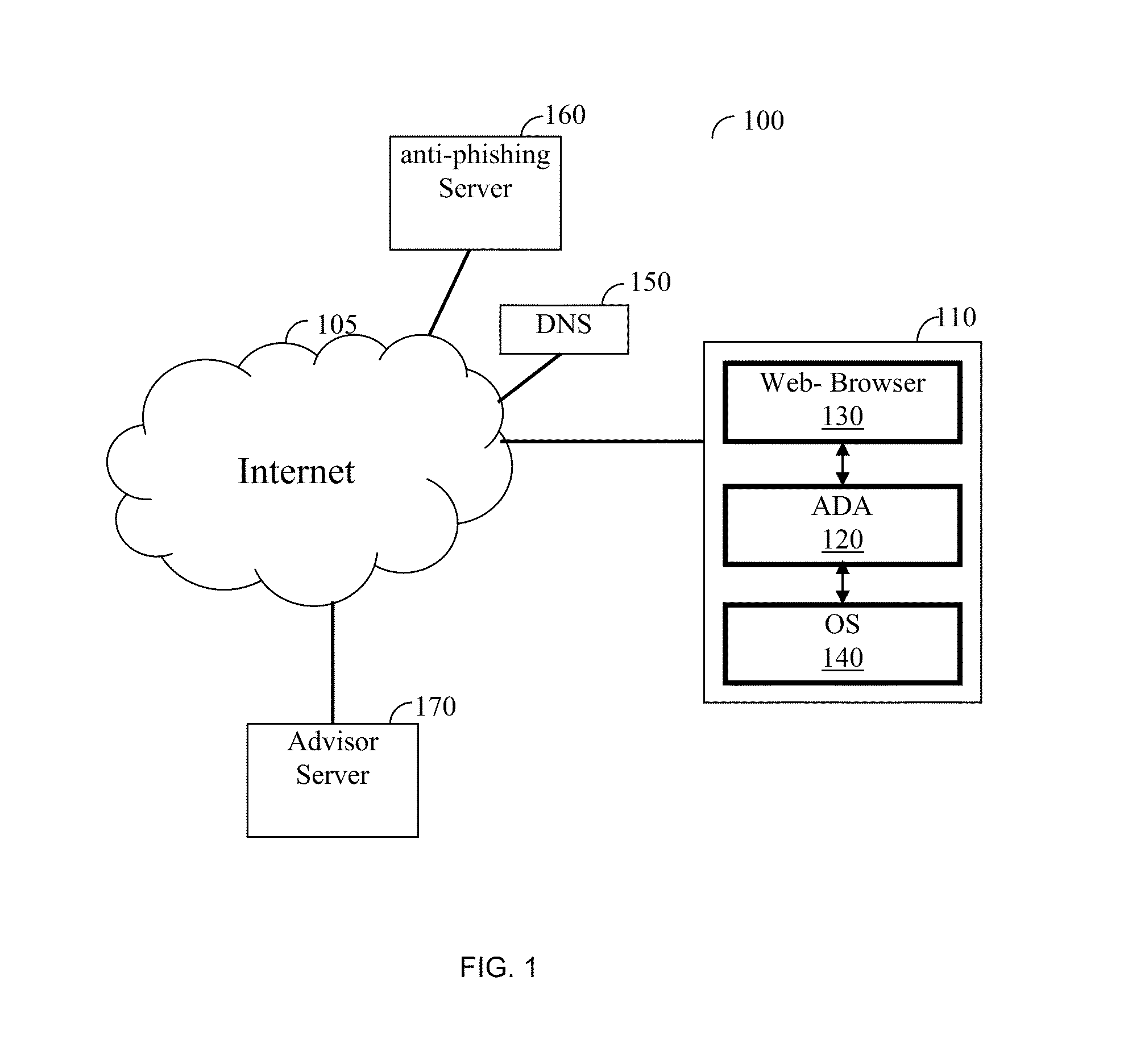
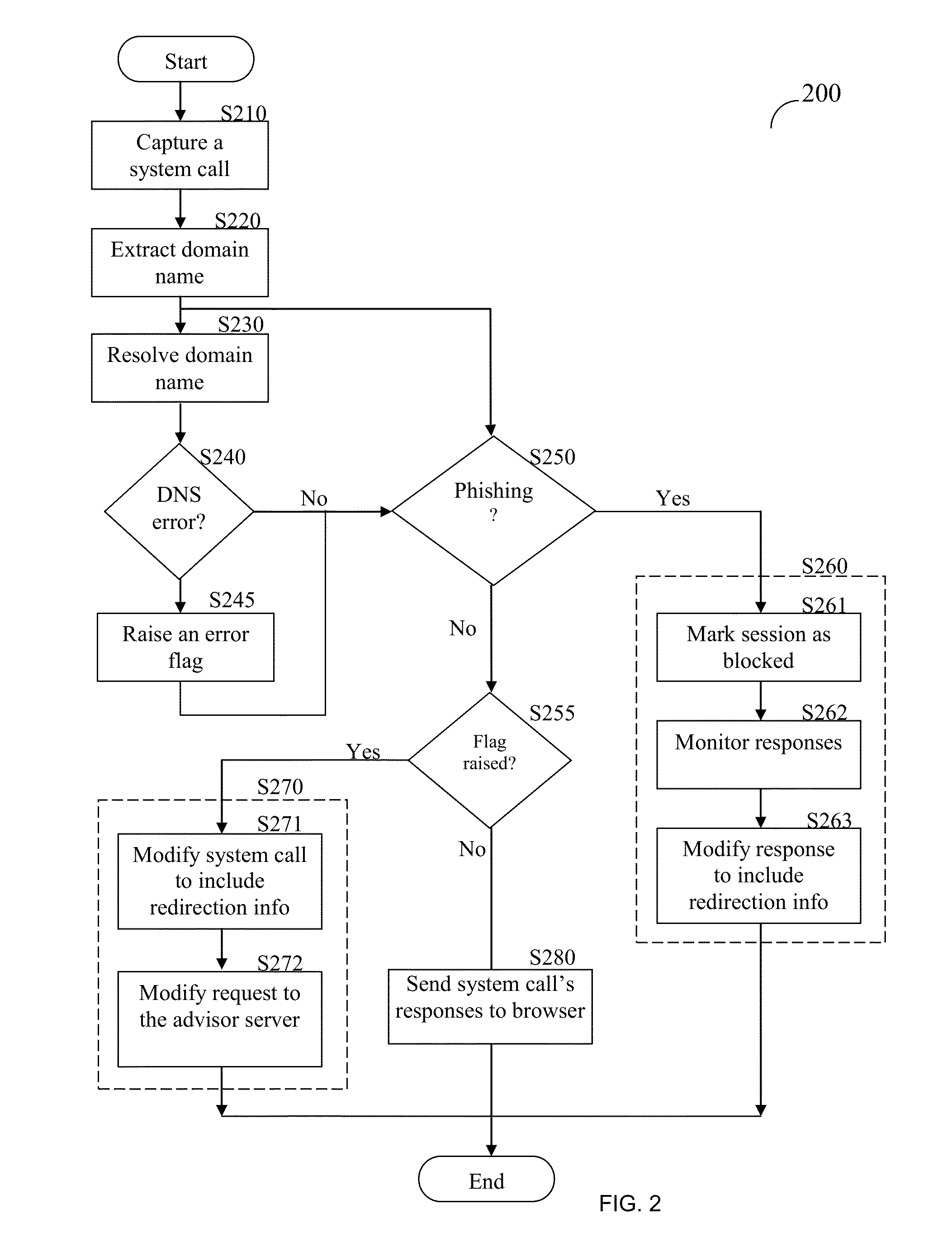
Anti-phishing domain advisor and method thereof
A method of anti-phishing and domain name protection. The method comprises capturing a system call sent to an operating system of a client by an application requesting an access to an Internet resource; extracting a URL included in the captured system call; capturing a response to the system call sent from operating system to the application; determining if the system call's response includes any one of a domain name system (DNS) error code and fake internet protocol (IP) address; checking the extracted URL against an anti-phishing blacklist to determine if the Internet resource is a malicious website; performing a DNS error correction action if any one of the DNS error code and the fake IP address was detected; and performing an anti-phishing protection action if the internet resource is determined to be a malicious website.
Owner:VISICOM MEDIA
Risk Ranking Referential Links in Electronic Messages
ActiveUS20140259158A1Reduce riskMemory loss protectionError detection/correctionRisk rankingComputerized system
A computer system enables a business to reduce risks from phishing electronic messages. One or more original web links embedded in the electronic message may be replaced with a replacement web link. If the determined risk score for the original webpage is large enough webpage and the user clicks on the embedded web link, a user is directed to an intermediate webpage rather than to the original webpage. The intermediate webpage may provide details about the original webpage so that the user can make an informed choice whether to proceed to the original website. For example, the intermediate webpage may provide pertinent information to a user such as the actual domain of the remote site, the country the site is hosted in, how long the site has been online, and a rendered screen capture of the remote website, and / or a confidence score.
Owner:BANK OF AMERICA CORP
Anti-phishing filter
ActiveUS20080276315A1Memory loss protectionUnauthorized memory use protectionInternet privacyElectronic communication
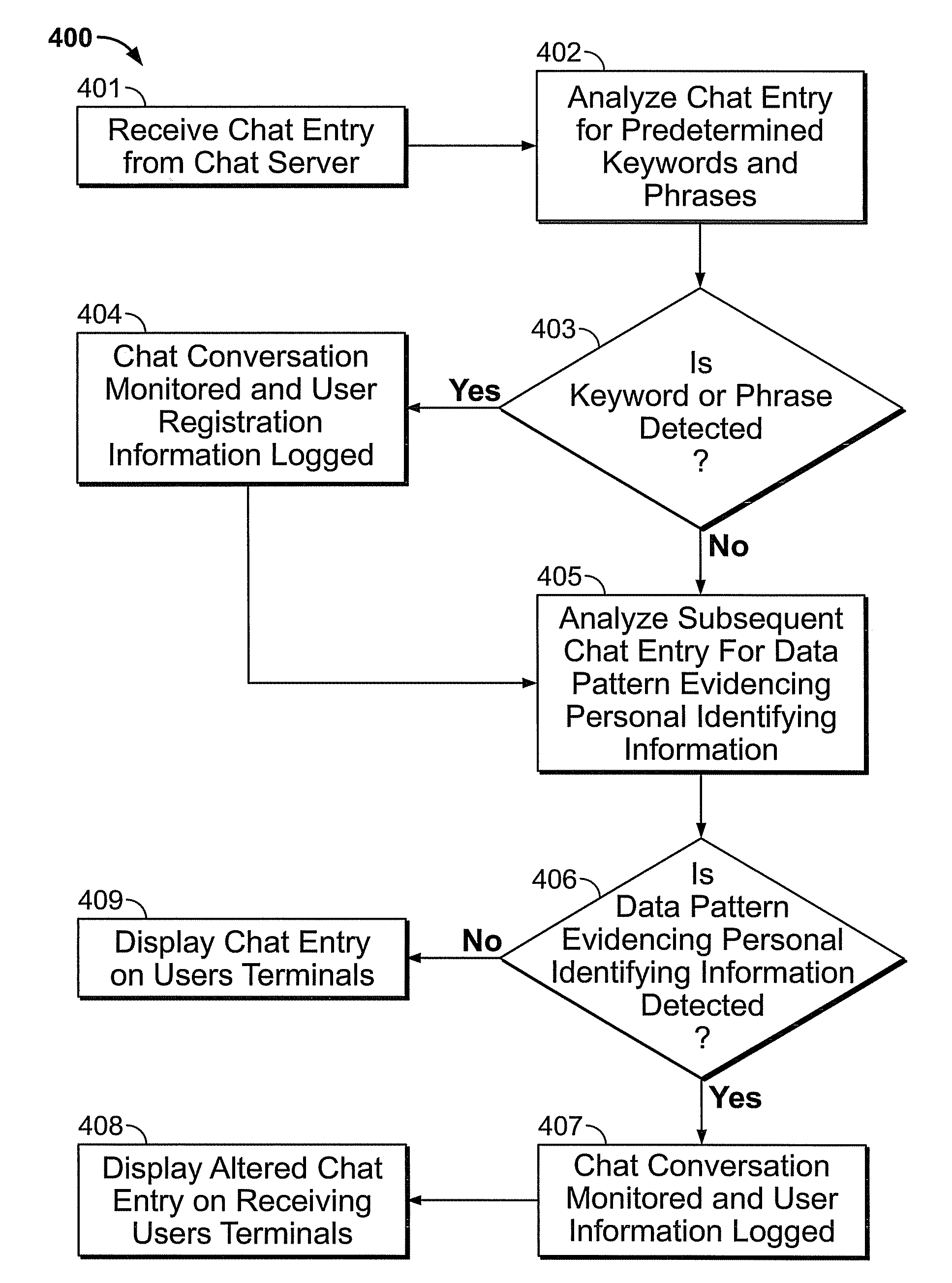
A method operates to detect personal identifying or account information exchanged in a real-time electronic communication occurring between computer network users, such as electronic chat. A detected personal identifier may be recognized as an attempt on the part of one user to engage in a phishing attack upon another user or to otherwise steal the other user's sensitive personal information. Upon recognizing the communication as an unwarranted attempt to collect such information, the electronic communication may be monitored, and communication of the personal information may be prevented.
Owner:SHUSTER GARY STEPHEN
Method and system for phishing detection
InactiveUS7668921B2Multiple digital computer combinationsData switching networksSMS phishingSource code
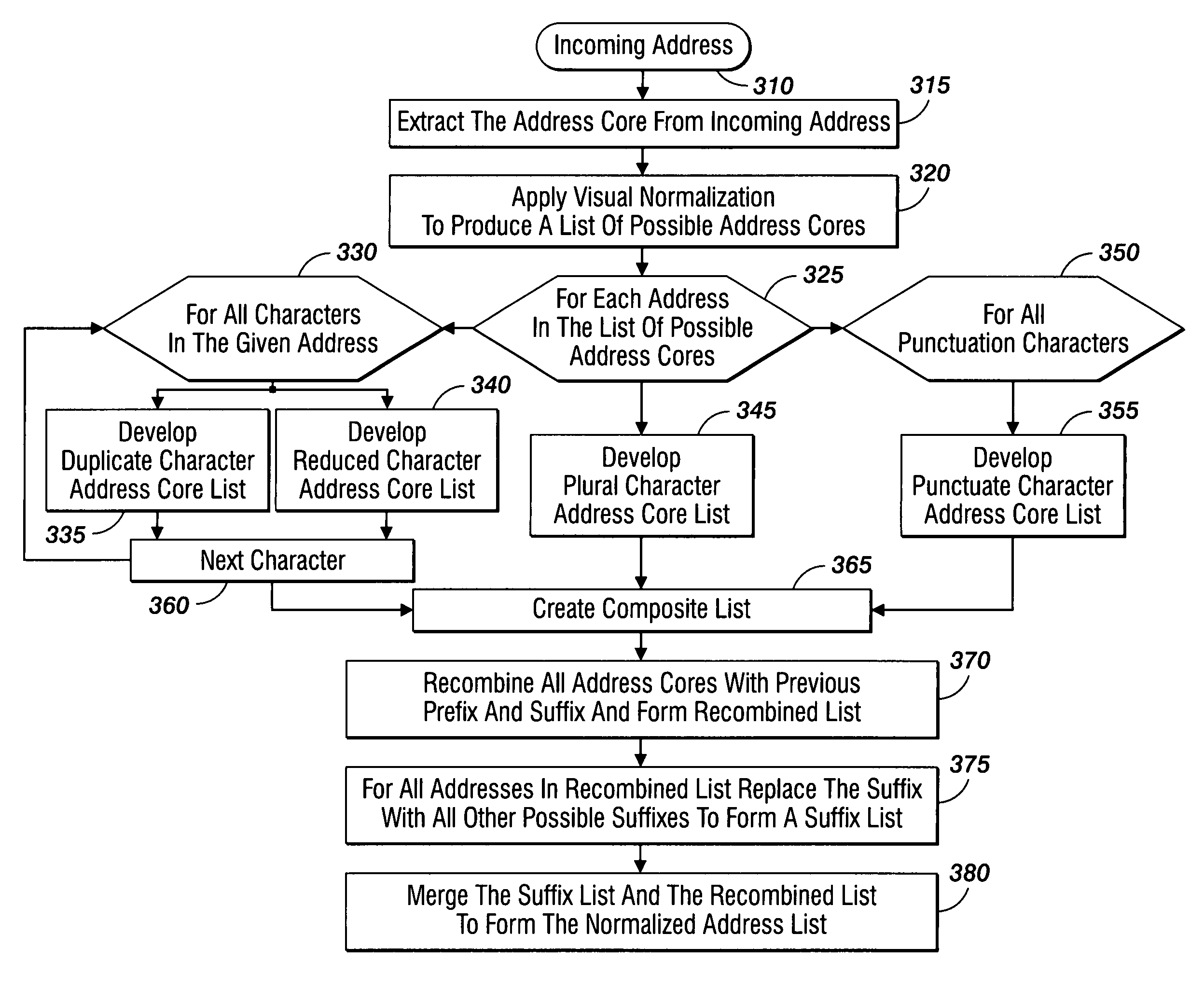
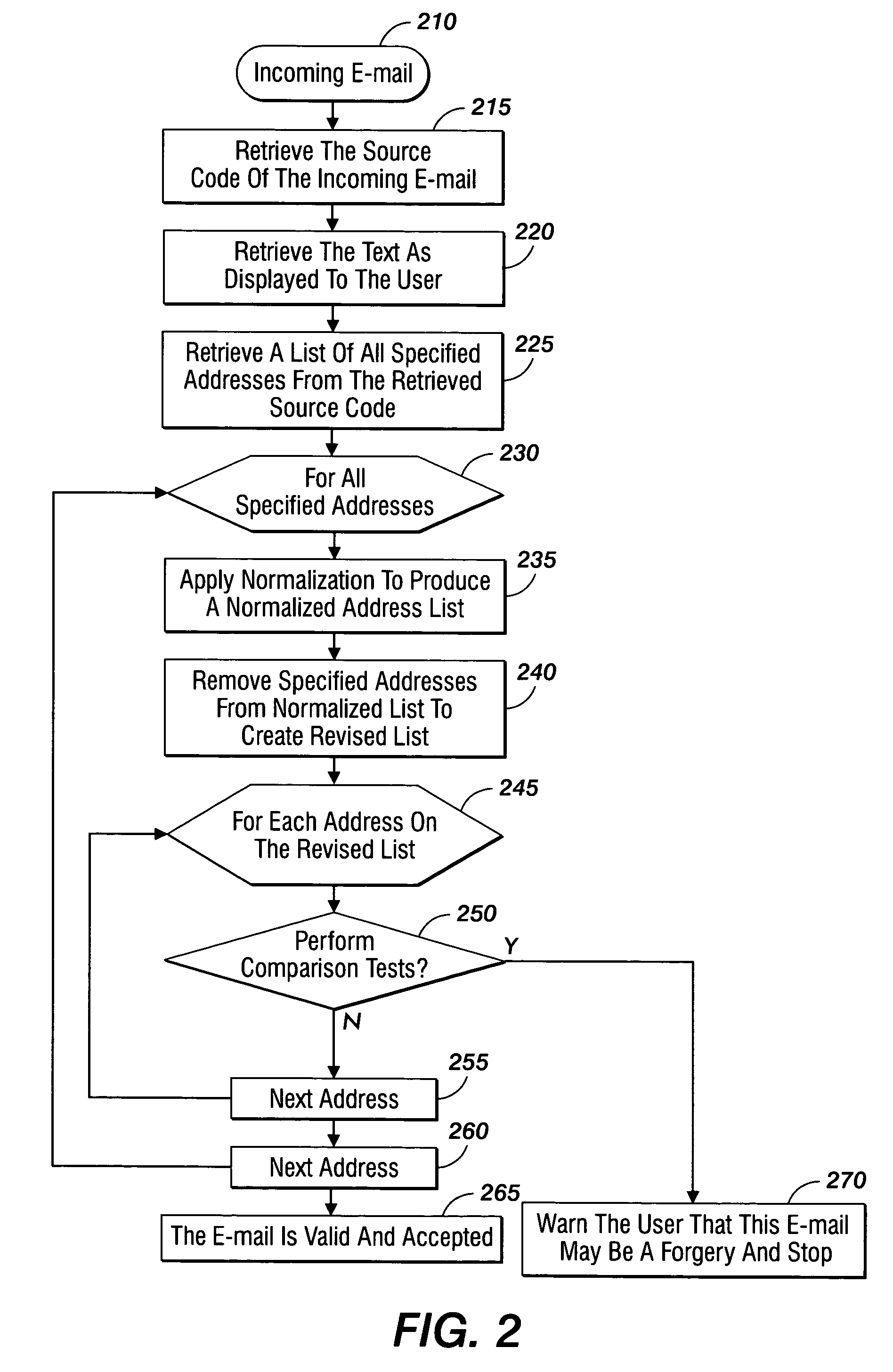
A method for detection of phishing attempts in received electronic mail messages includes retrieving the source code, displayed text, and a list of all specified addresses contained within the source code of a received electronic message. Visual character normalization is applied to each specified address to develop all possible address combinations and to form a normalized address list. The specified addresses are removed from the normalized address list to create a revised address list, upon which comparison tests are performed to determine if each address in the revised address list is from a valid source. The recipient of the electronic message is informed of any message found to be from an invalid source.
Owner:XEROX CORP
Controlling hostile electronic mail content
InactiveUS7461339B2Reduce harmSimple technologyComputer security arrangementsNatural language data processingHyperlinkJScript
Owner:TREND MICRO INC
Apparatus and method for analyzing and filtering email and for providing web related services
InactiveUS7904518B2Software engineeringMultiple digital computer combinationsTraffic capacityService provision
The inventive methodology provides an integrated plug and play solution designed to protect home networks against spam, phishing emails, viruses, spyware as well as other similar threats. The described content filtering appliance can be used for processing of web and email traffic implemented and can be deployed as a stand-alone appliance. In one implementation, the content processing appliance utilizes backend content filtering provided by a remote scanning service accessed via a network. The system employs network level analysis and translation of content and executes various procedures to handle the network traffic. In an embodiment of the invention, the appliance is provided with an automatic remote updating capability, wherein the software and data used by the appliance can be updated remotely via a network. Finally, the appliance may also implement parental controls.
Owner:MARINO JOSEPH P
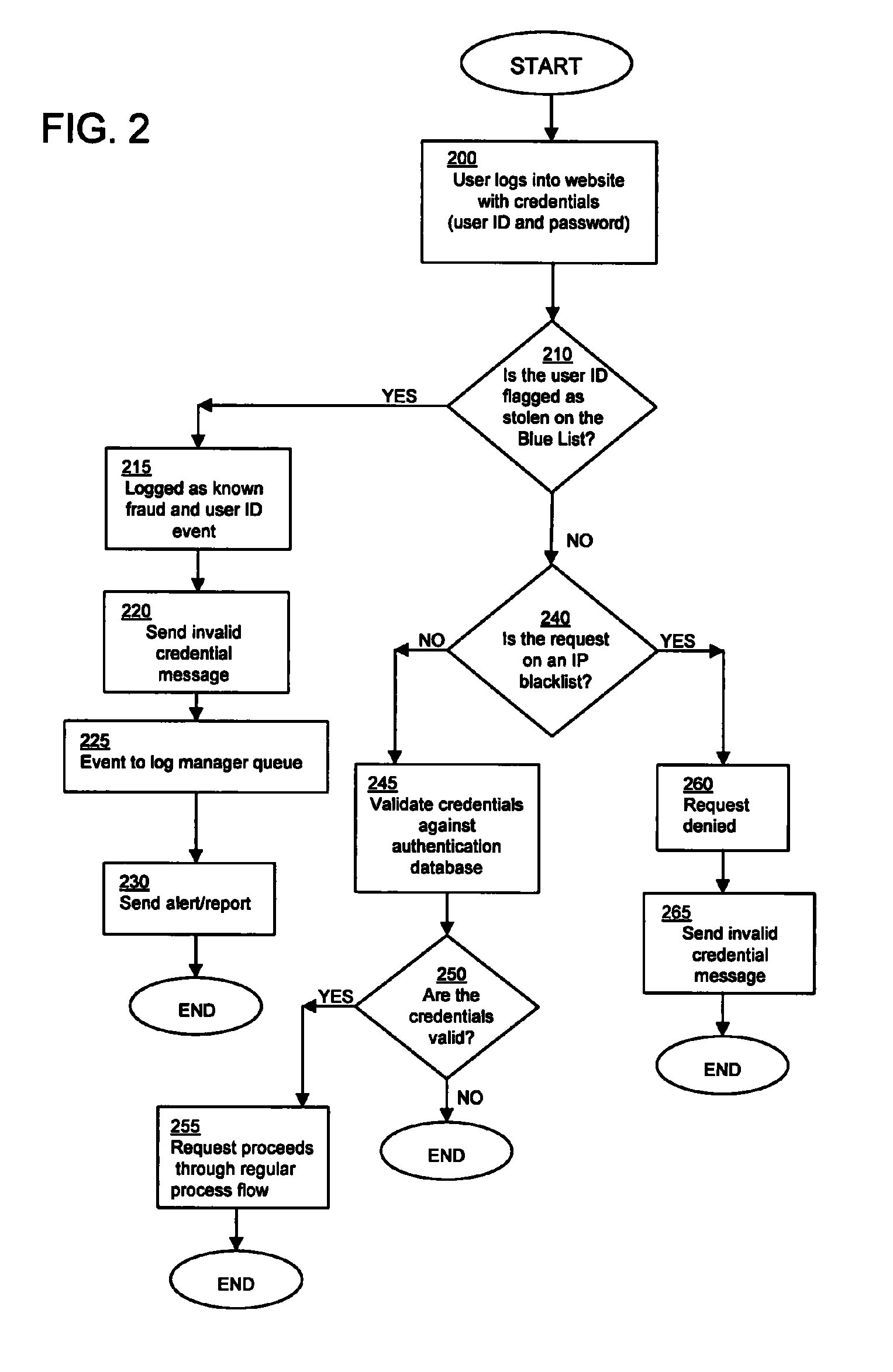
System and method for detection and prevention of computer fraud
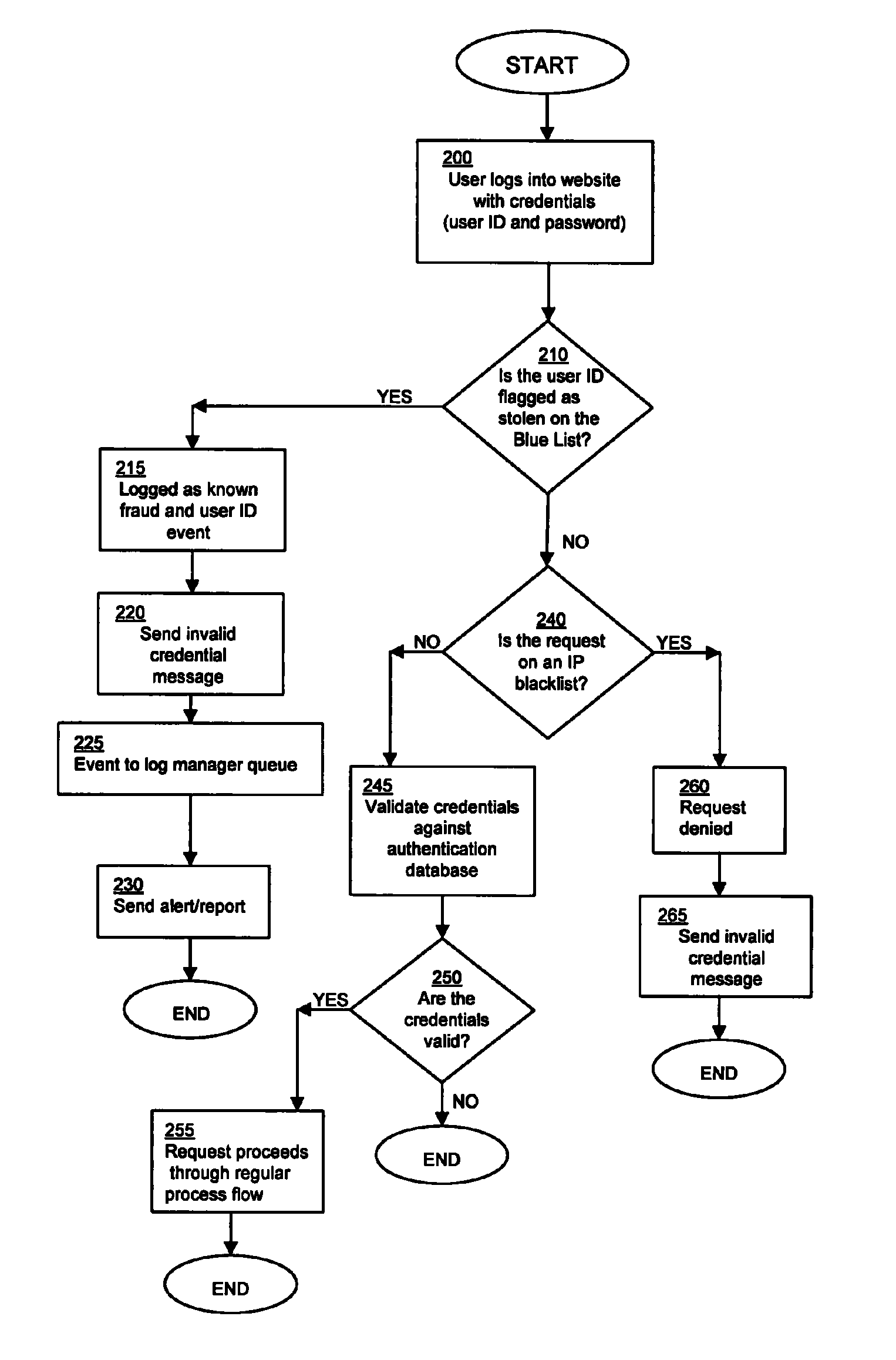
ActiveUS8695097B1Memory loss protectionDigital data processing detailsComputer fraudApplication server
In a networked computer system, a user accesses a webserver via a web interface presenting credentials comprising a user identification. The webserver is communicatively connected to an application server. If fraud with respect to the user identification is detected, the application server sends a notification or alert to add the user identification to a list of compromised user identifications. The system also comprises a database for storing the list of compromised user identifications on a computer. Another category of user identifications is created referred to as phish phood which is comprised of fabricated user identifications.
Owner:WELLS FARGO BANK NA
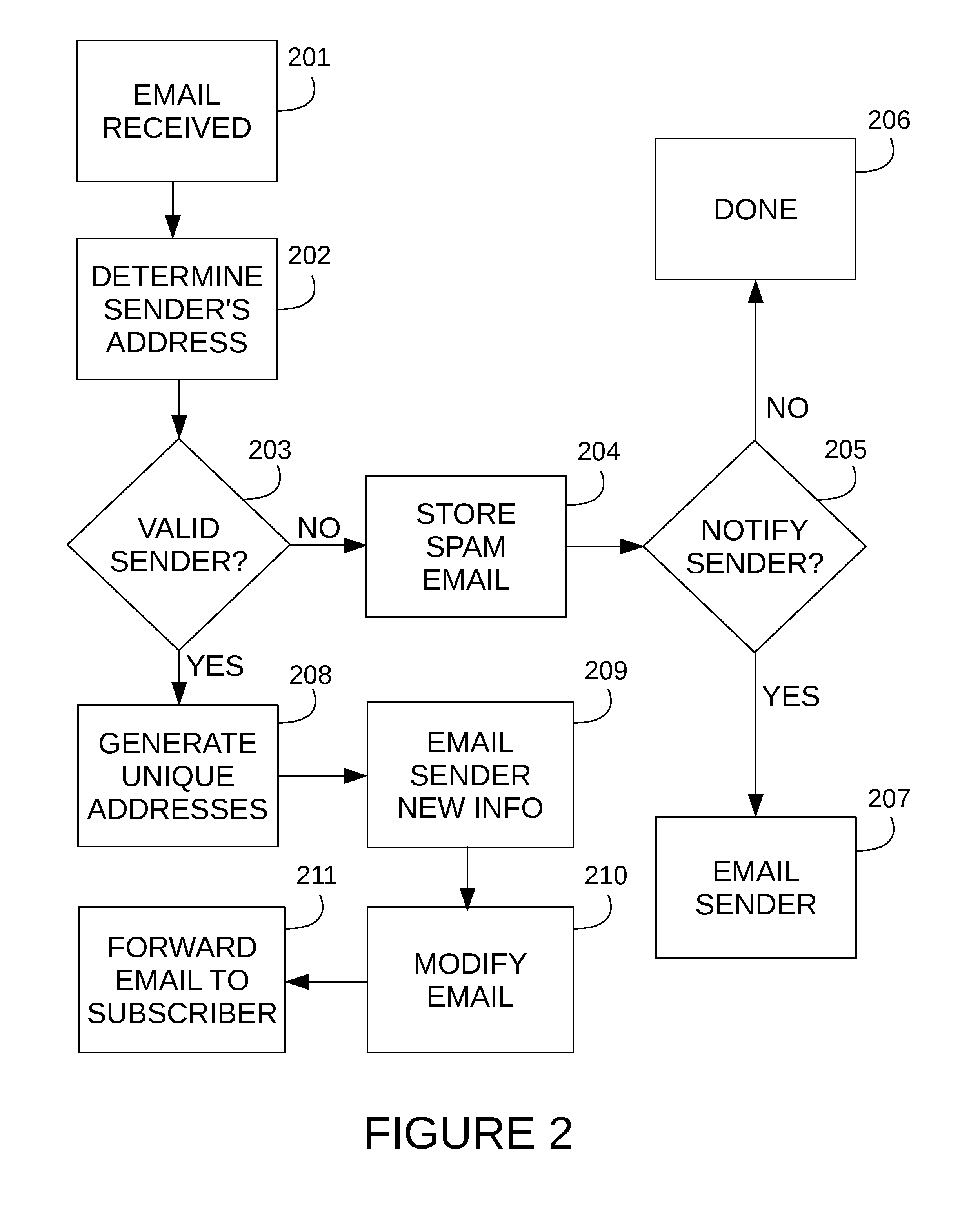
Method and system for email privacy, security, and information theft detection
ActiveUS20160094566A1Provide privacyProvide securityDigital data authenticationData switching networksEmail privacyEmail address
A system and method is proposed for managing email messages across a network. The system provides multiple means of verifying an originating sender of email. In addition, the system automatically generates unique email addresses as a means mask the email address of an original sender and shield users from unwanted email. The system may also be configured to block email security threats (e.g. phishing, spear phishing, etc.). Further, the system provides means of processing email messages to enable encryption, spam detection, geographical location identification of users, and social networking
Owner:MIRAGE DATA INC
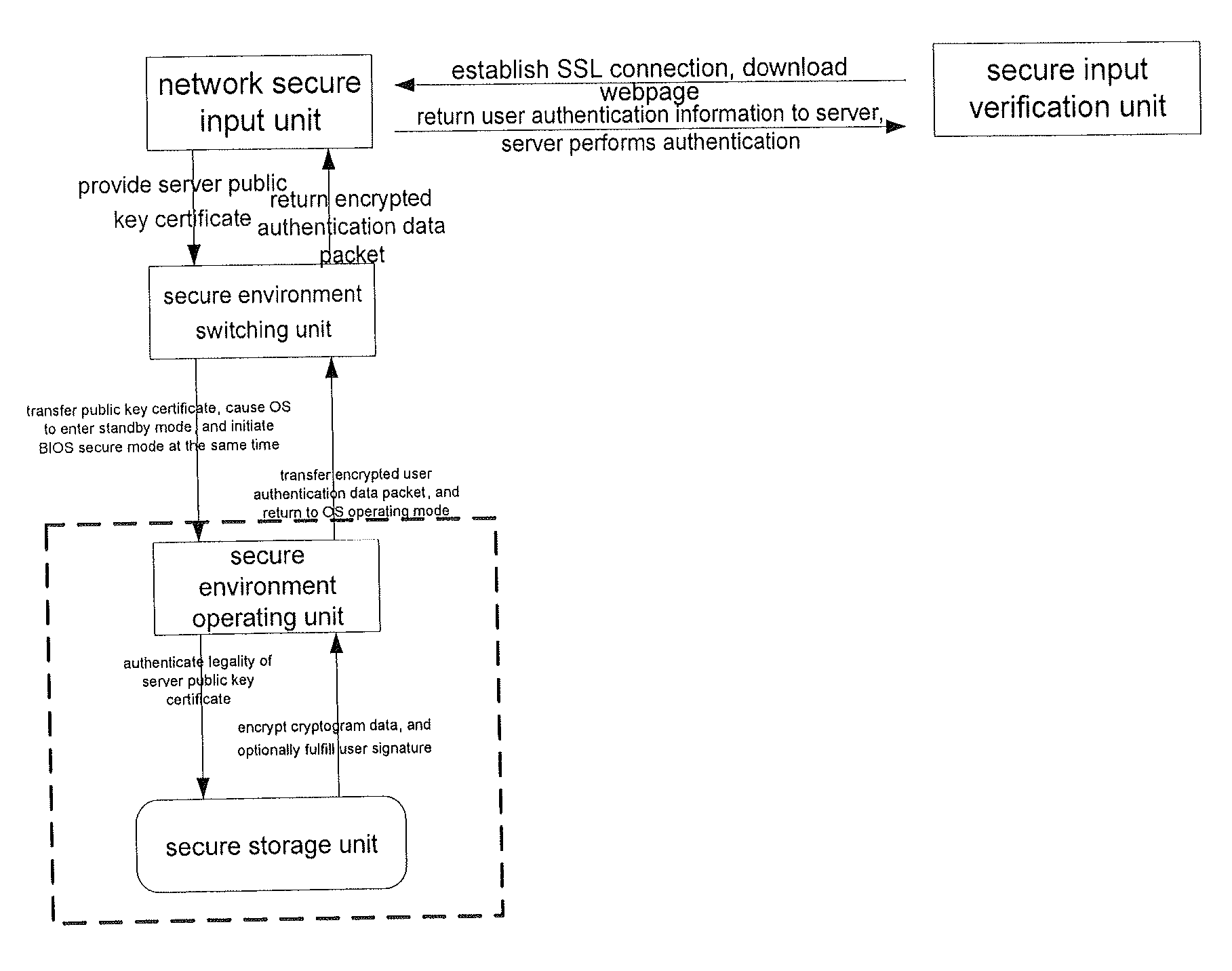
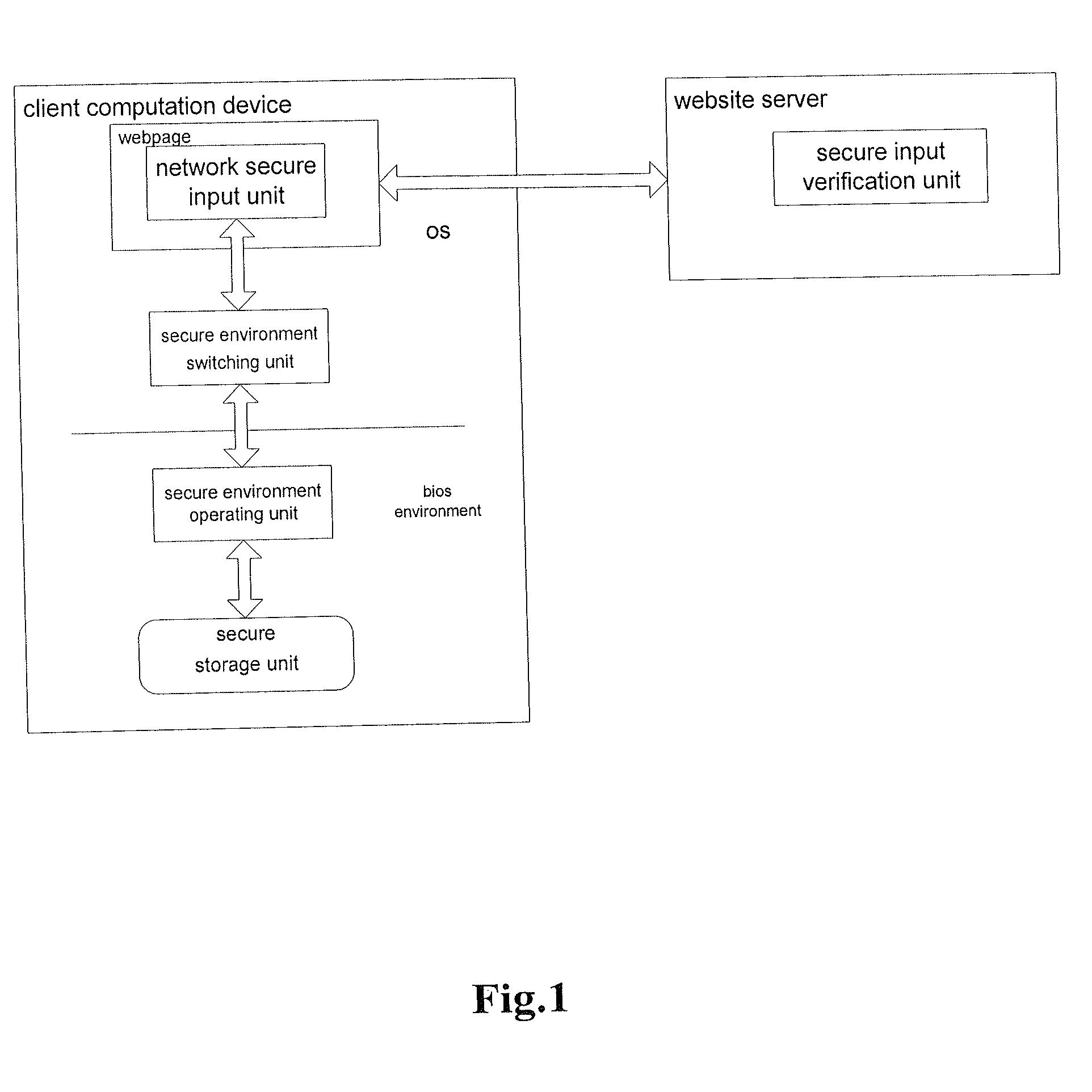
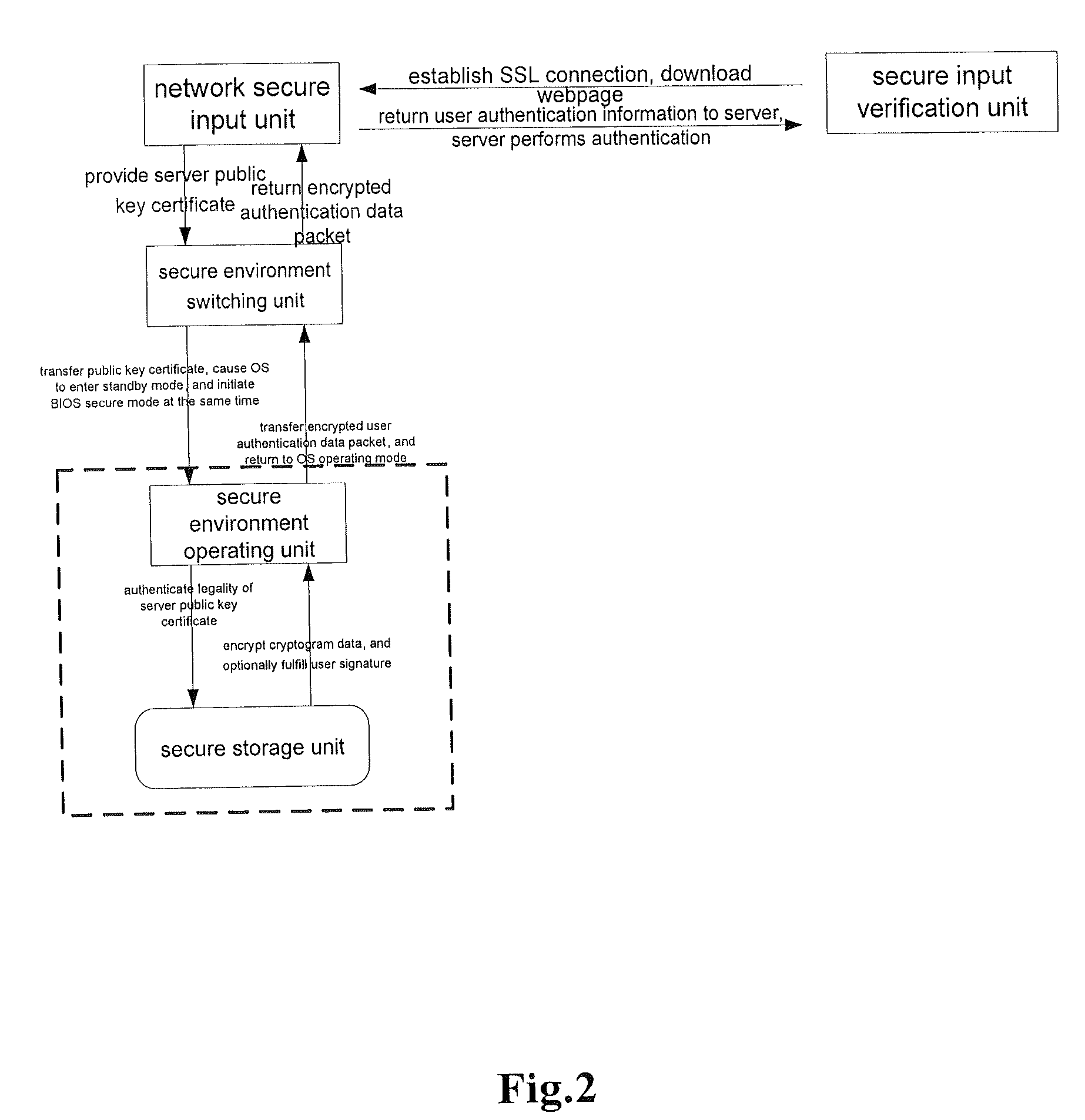
Method and system for performing secure logon input on network
ActiveUS20090013393A1Solve the real problemKey distribution for secure communicationMemory loss protectionPlaintextSchema for Object-Oriented XML
A trusted input technique in which switching is made between an OS environment unreliable in security and a BIOS reliable in security. Rapid switching to a secure environment, such as BIOS mode, upon request for secure input, is enabled. An OS environment of a user can be quickly resumed after the user completes the input of a cryptogram. The technique does not and will not have any influence on secure transaction architecture. The identification of a server is authenticated in a trusted secure environment, and thus it is possible to prevent such problem as “phishing” websites. The user cryptogram is present as plaintext only in a BIOS environment and server and as encrypted during intermediate transmission. Thus, it is impossible to be intercepted by any virus such as a “Trojan horse”.
Owner:LENOVO (BEIJING) CO LTD
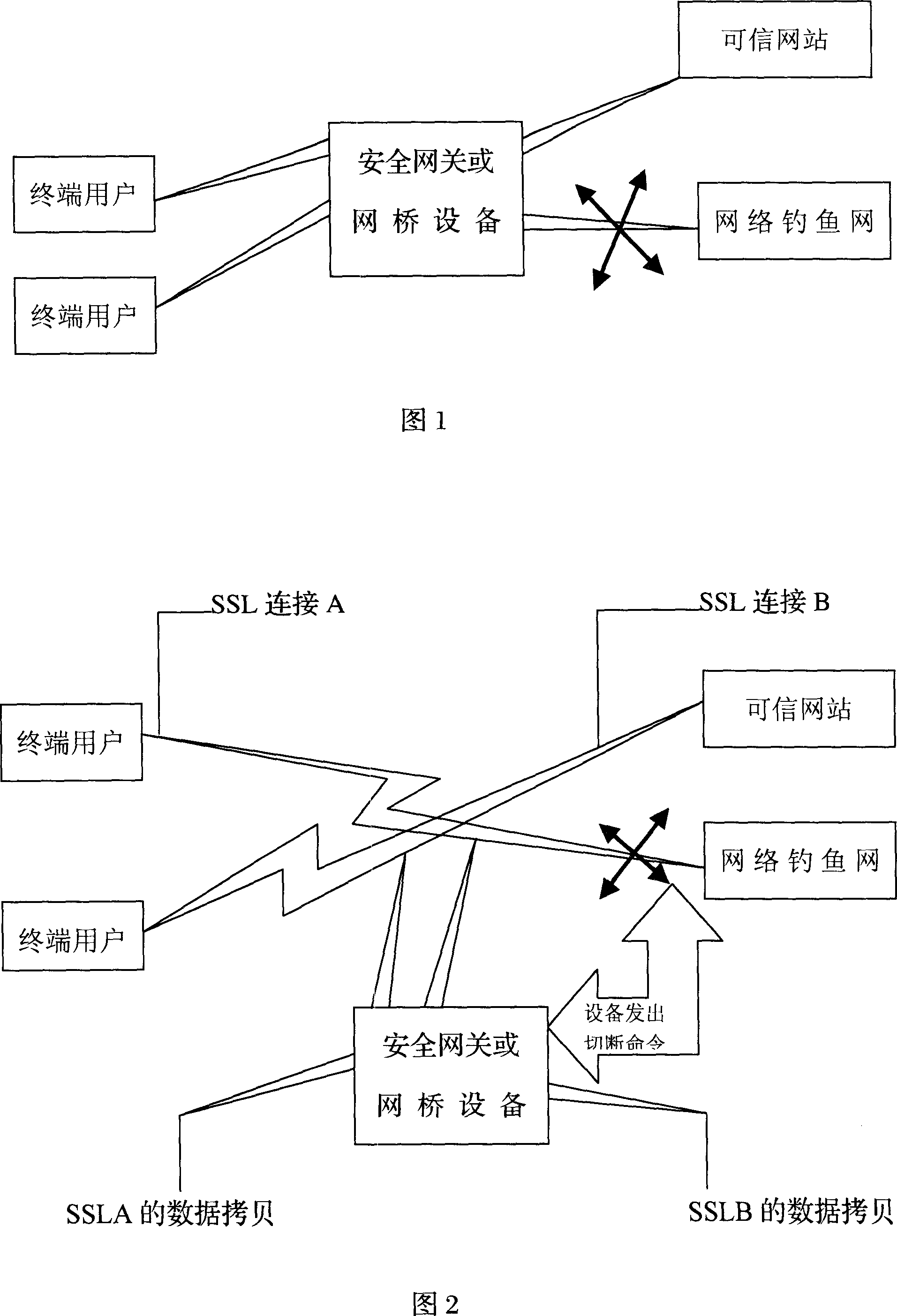
Method for guarding phishing website based on gateway, bridge
ActiveCN101026599APrevent leakageUser identity/authority verificationNetworks interconnectionSMS phishingFishing
The method includes steps: (1) being added between terminal for logging network and network station to be accessed, secure gateway (SG) captures data encrypted by SSL; (2) interface for settings provided on SG lets user induct credible X.509 certificate list; (3) capturing handshaking procedure (HP) in SSL protocol, SG picks up X.509 certificate link transferred by HP; (4) filtering out and stopping illegal SSL connection in certificate link. Or the method uses following steps: (a) connecting SG to device able to monitor user's online data; SG captures a copy of data from normal network station or fishing network station accessed through SSL encrypted tunnel by internal user; (b) interface for settings provided on SG inducts credible X.509 certificate list; (c) capturing HP in SSL protocol, SG picks up X.509 certificate link transferred by HP; (d) validating validity of certificate link; SG sends out command to cut off illegal SSL connection in certificate link.
Owner:SANGFOR TECH INC
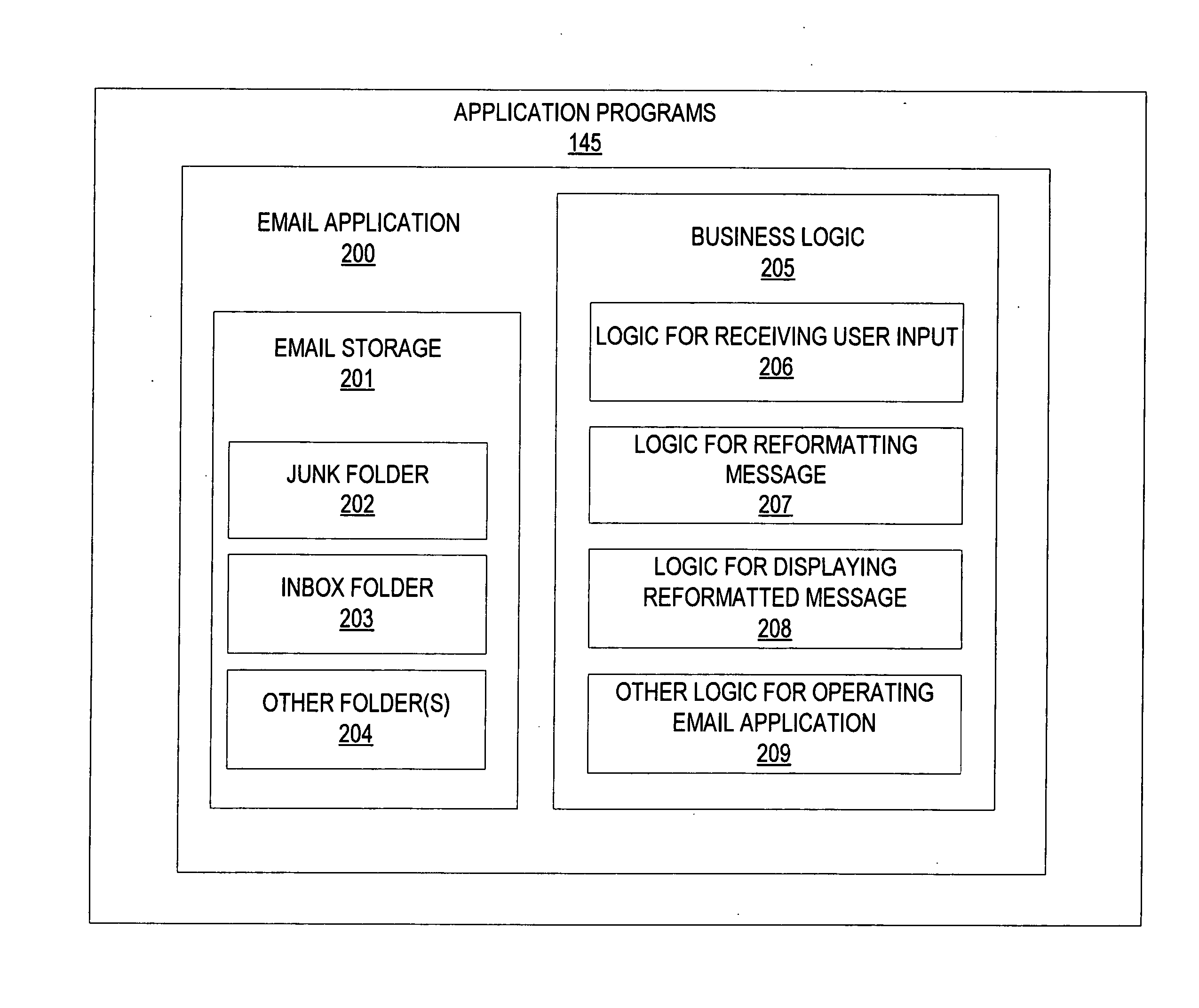
Enhanced e-mail folder security
InactiveUS20070043815A1Improve securityHigh security riskData processing applicationsComputer security arrangementsHyperlinkSMS phishing
Various technologies and techniques are disclosed that enhance the security of electronic mail messages and folders. Messages that are deemed to be less secure and have a higher security risk, such as unsolicited commercial e-mail (i.e. SPAM) and phishing messages, are reformatted and displayed in plain text with hyperlinks disabled in certain circumstances. For example, messages in a junk e-mail folder may be reformatted and displayed in plain text with hyperlinks disabled to make them safer for the user to interact with.
Owner:MICROSOFT TECH LICENSING LLC
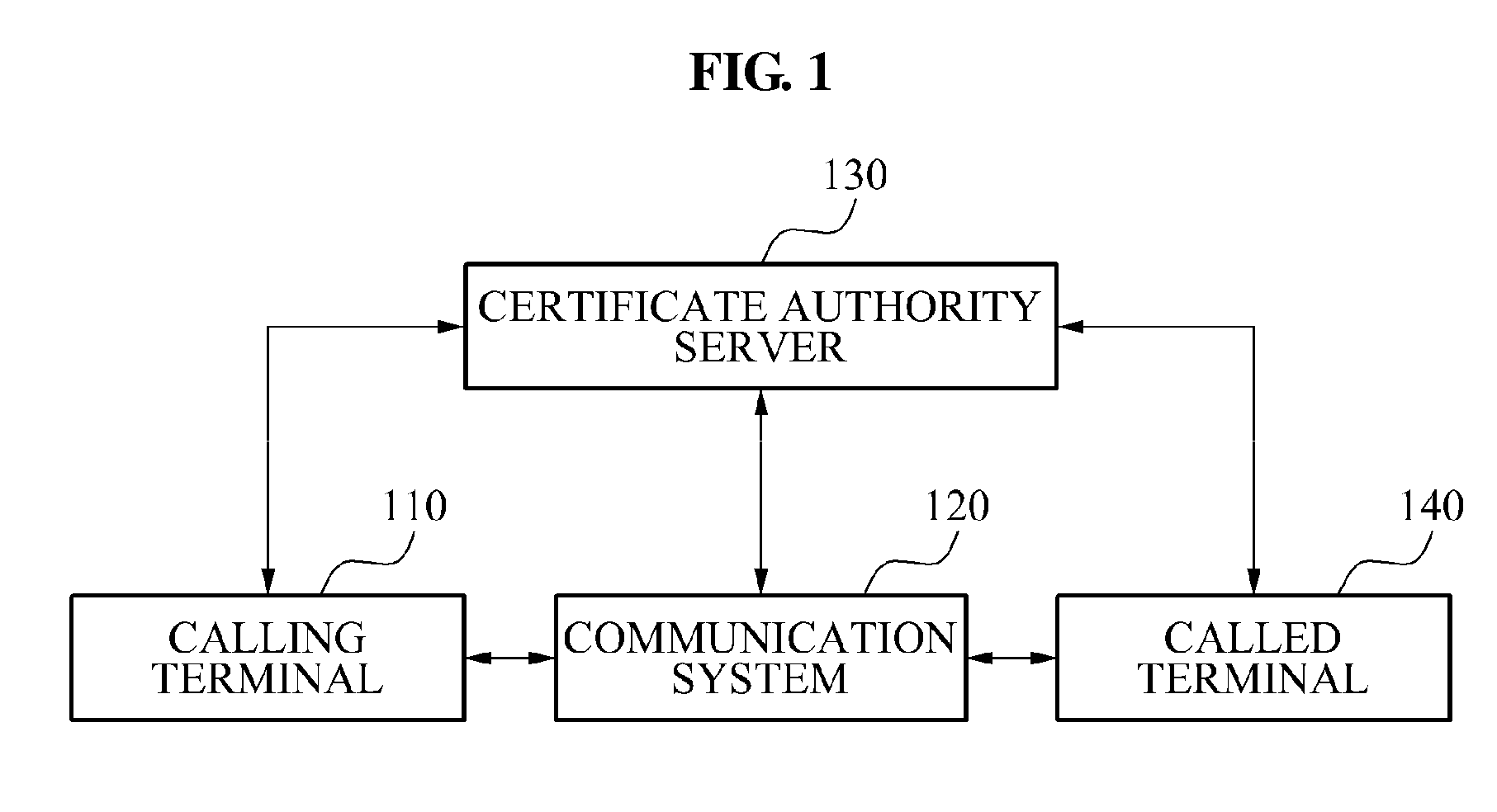
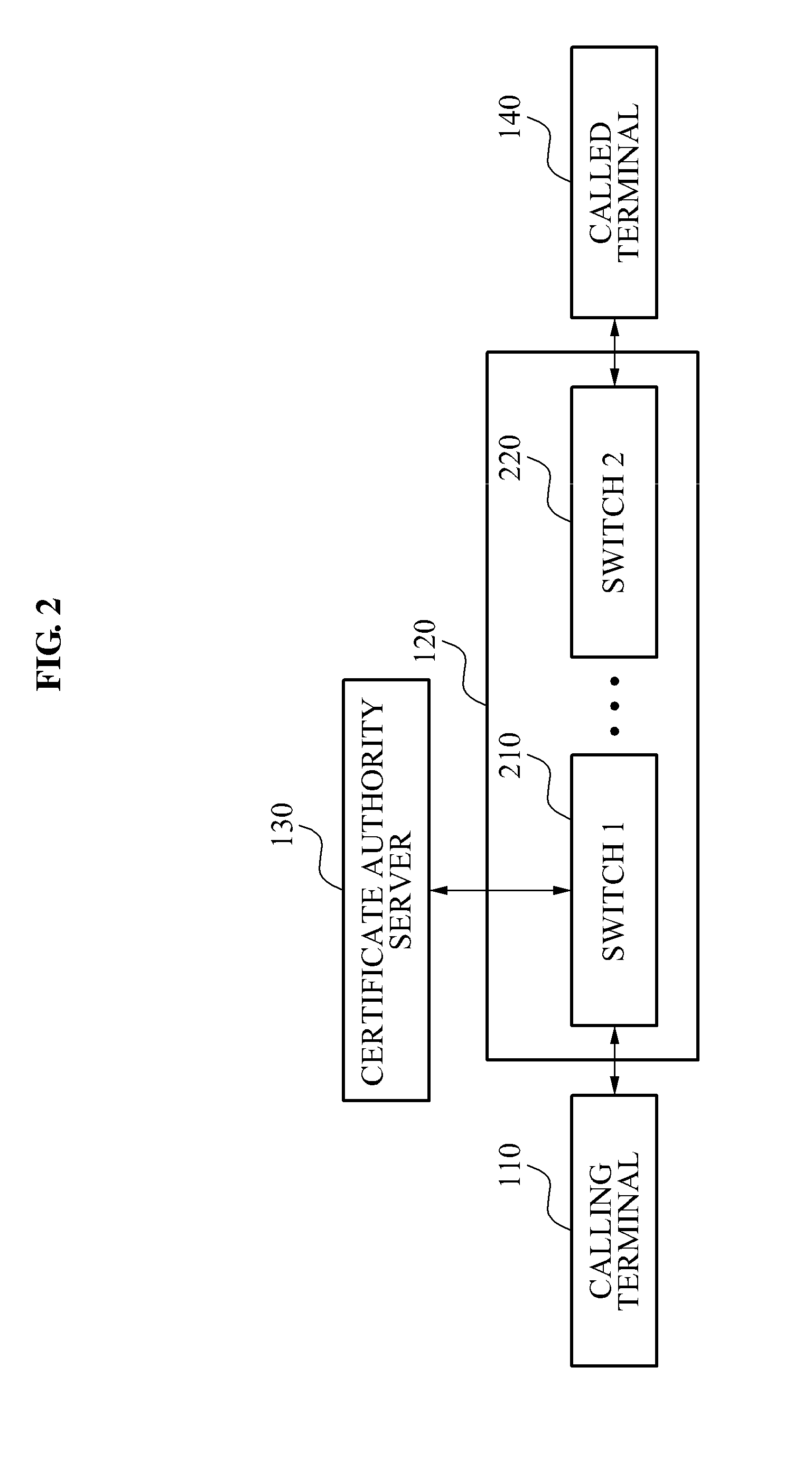
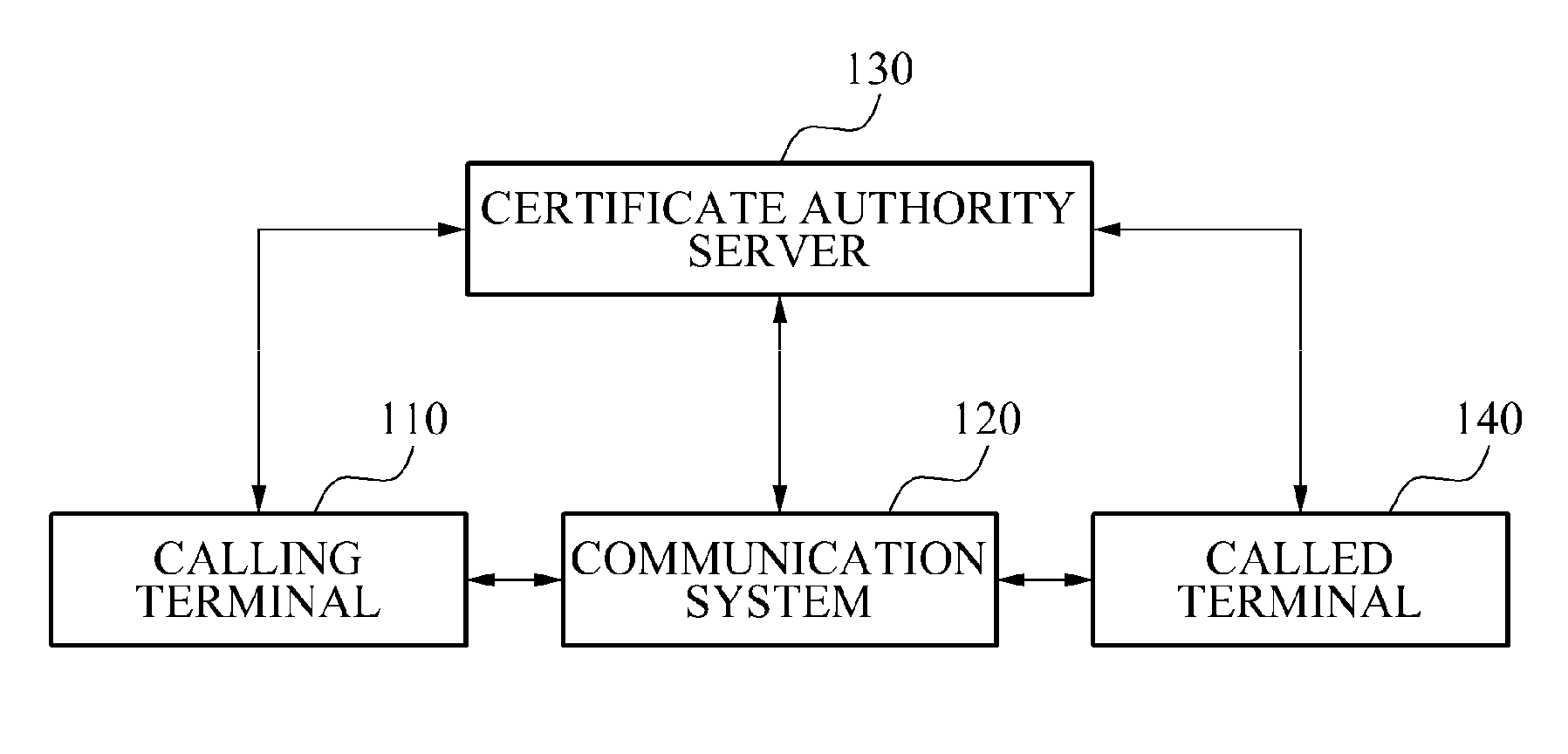
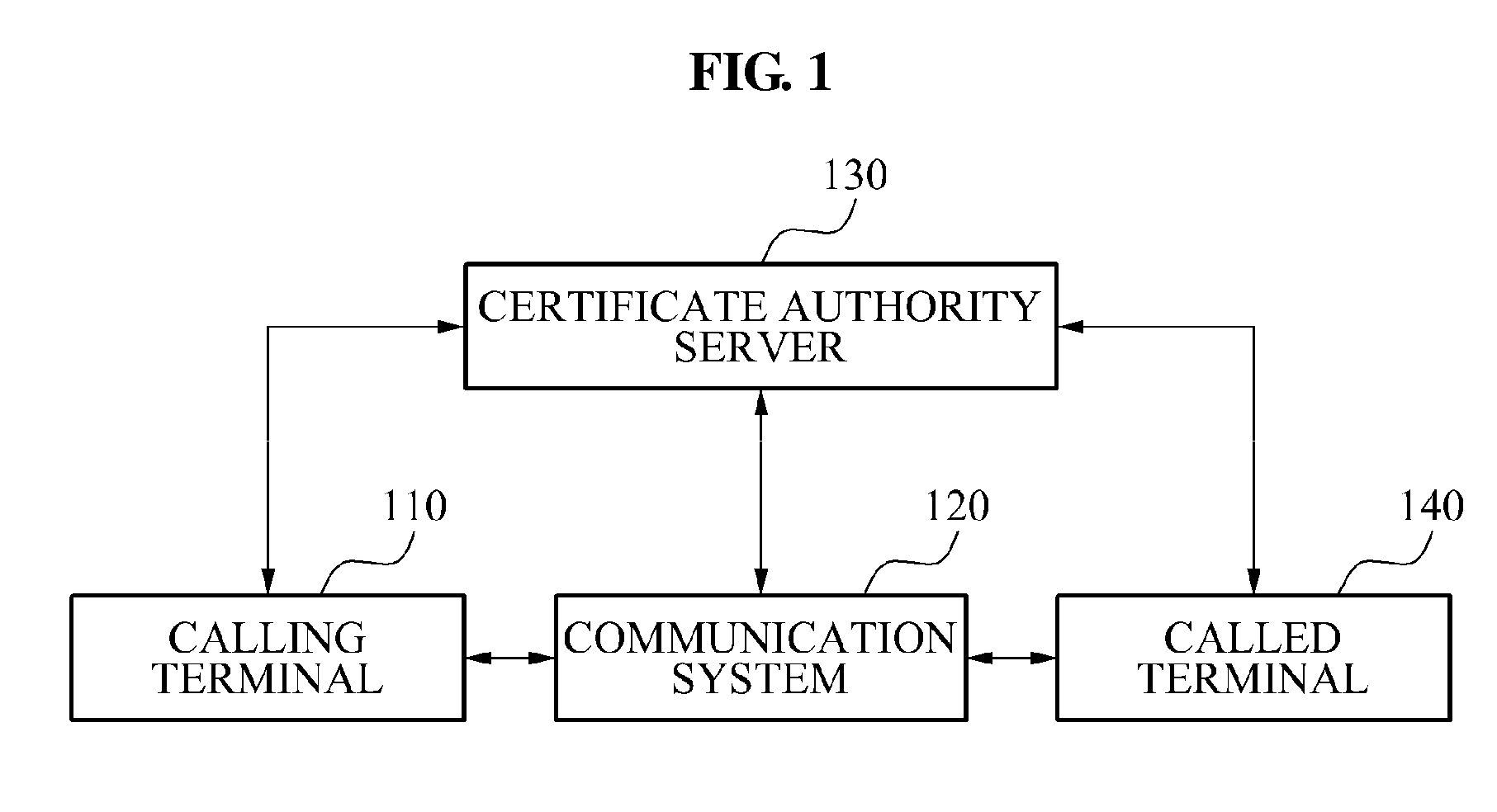
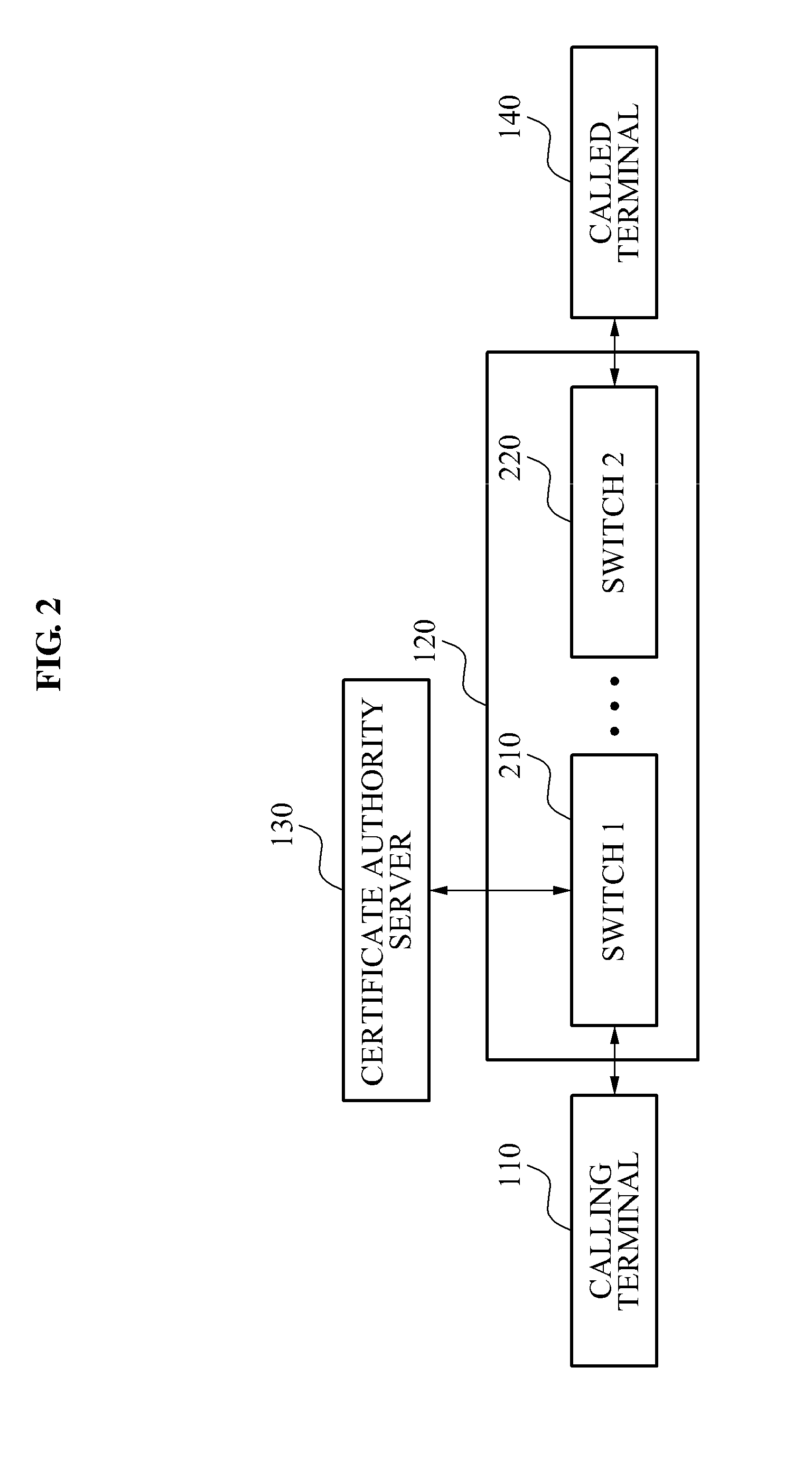
Caller authentication system and method for phishing prevention
InactiveUS20110085650A1Prevent phishing fraudSpecial service for subscribersCalled number recording/indicationCommunications systemComputer terminal
A caller authentication system that may enable a called party to be provided with identification information of a caller may be provided. The caller authentication system, including: a communication system to transmit, when a call request signal is received from a calling terminal of a caller, network information and a telephone number of the calling terminal to a certificate authority server, and to request identification of the caller, the network information and the telephone number being included in the call request signal, to transmit, when identification information of the caller is received from the certificate authority server in response to the identification request, the identification information to a called terminal of a called party, and to enable the identification information to be displayed on the called terminal.
Owner:ELECTRONICS & TELECOMM RES INST
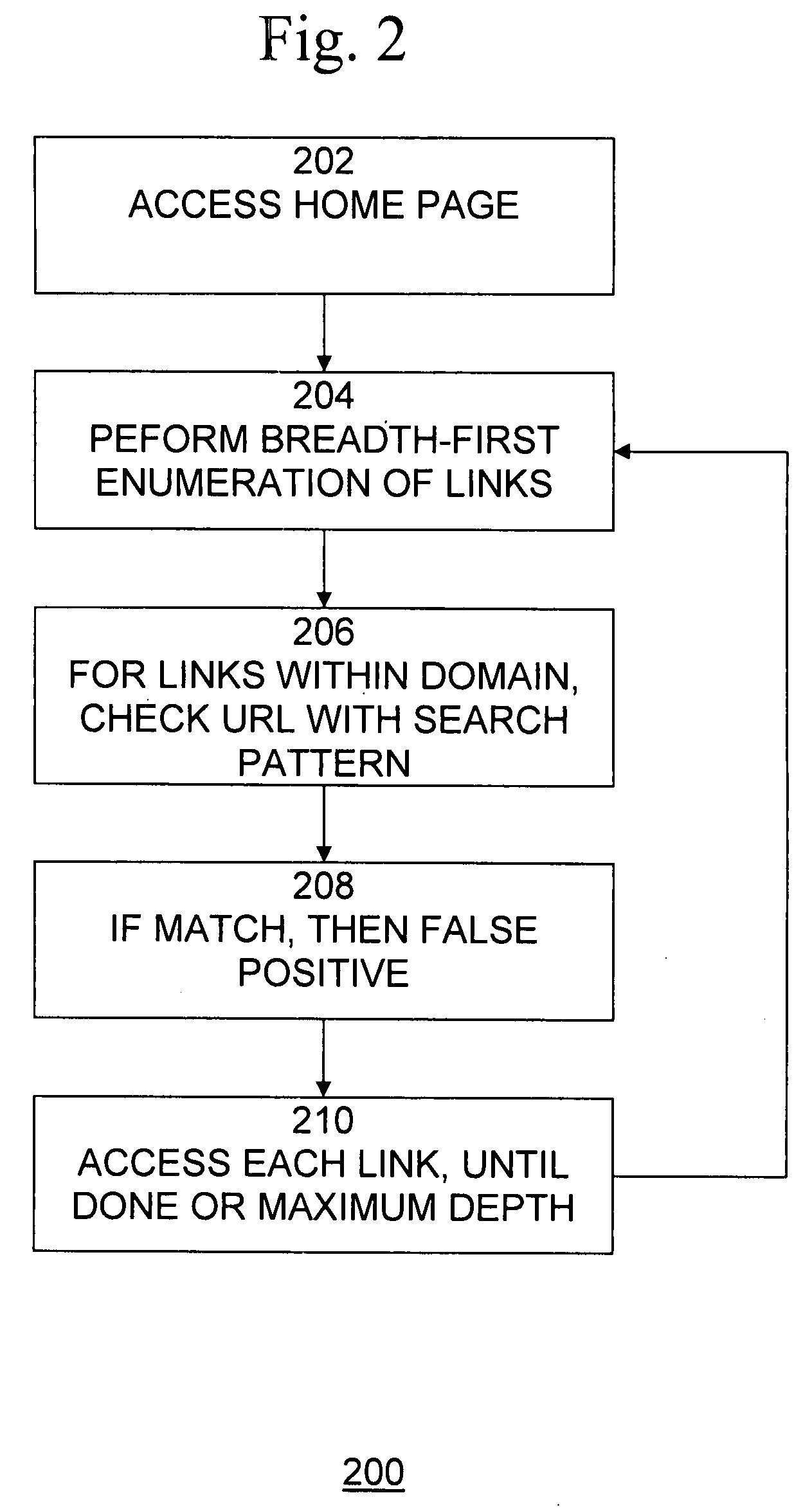
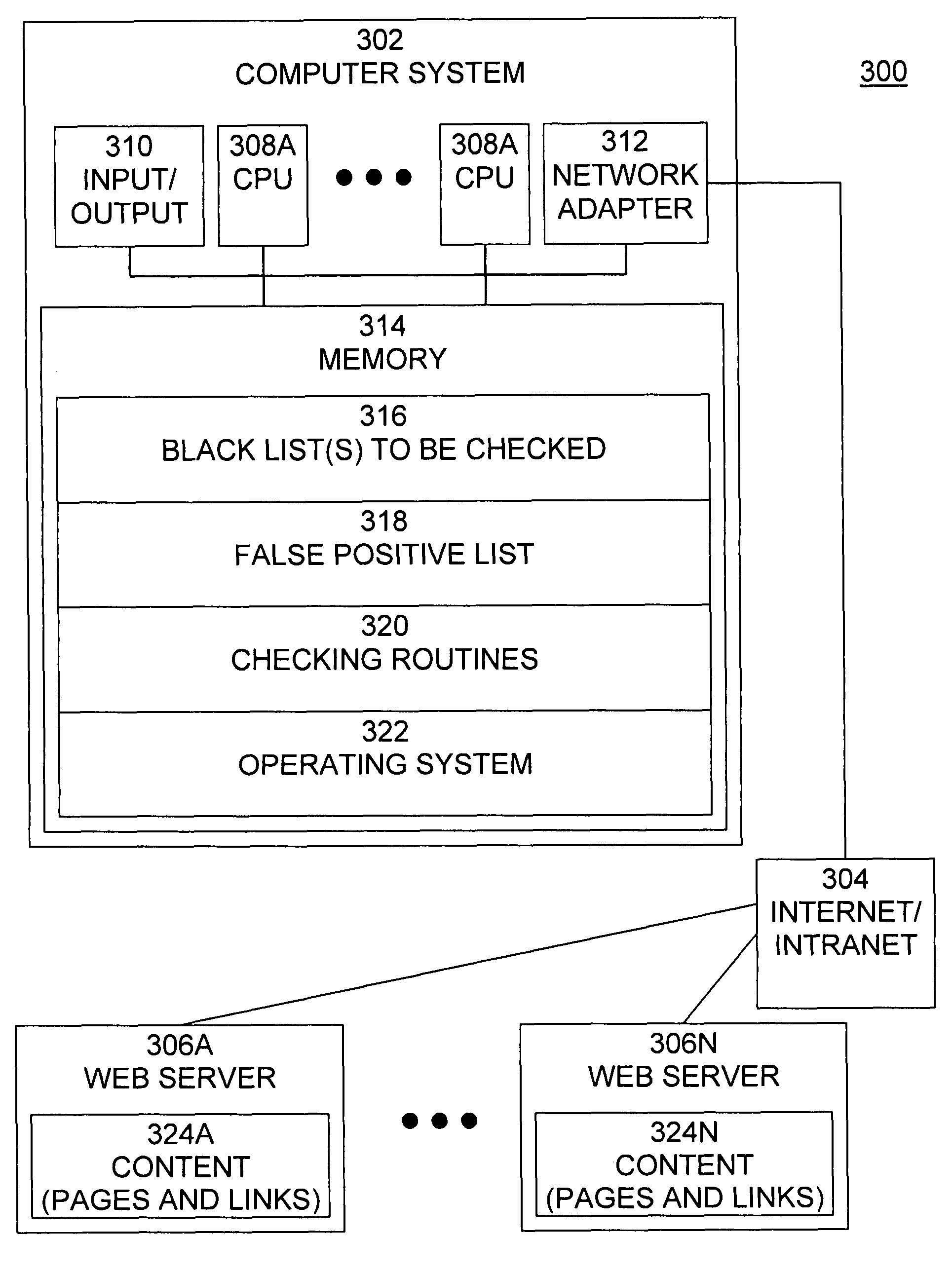
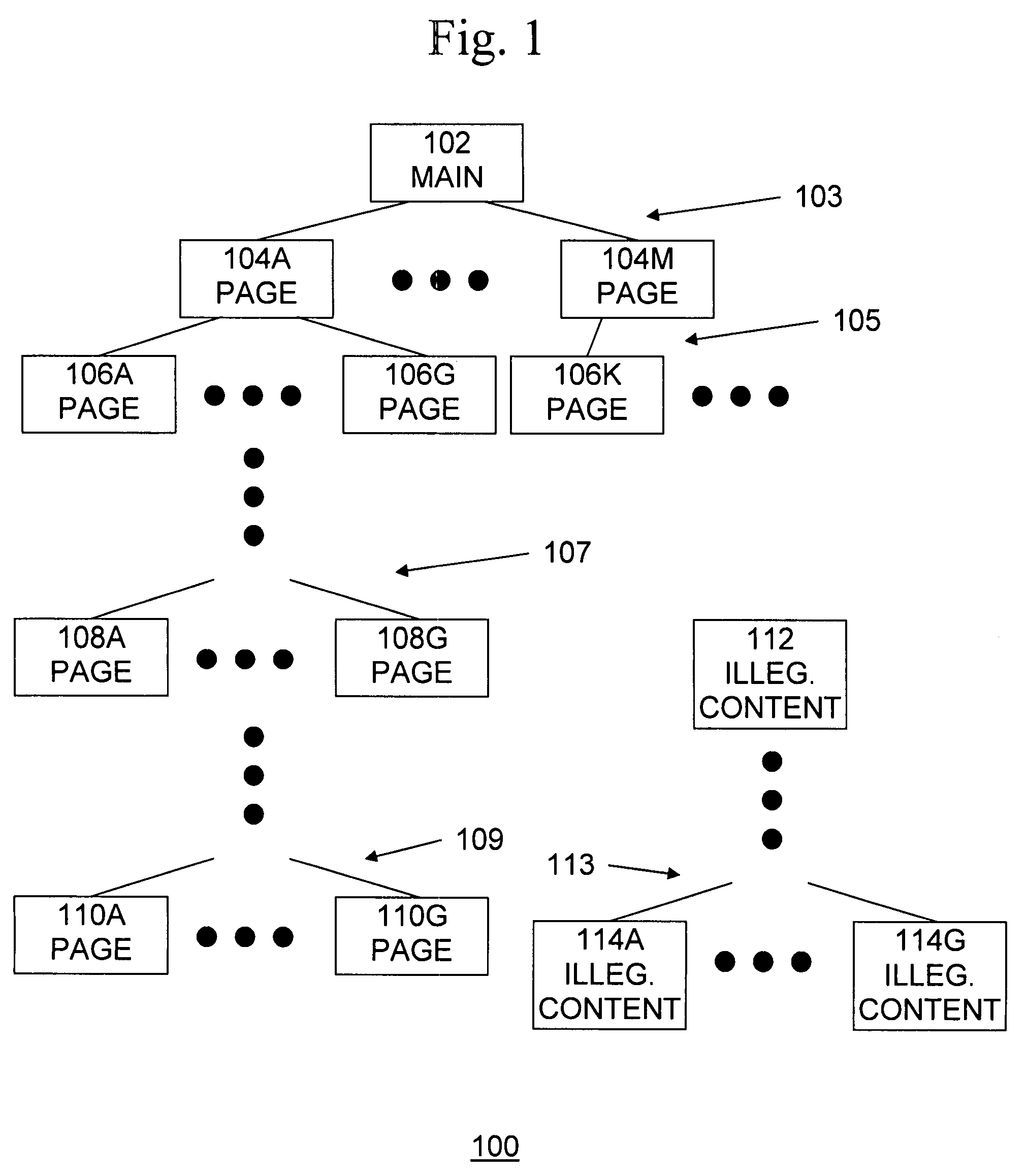
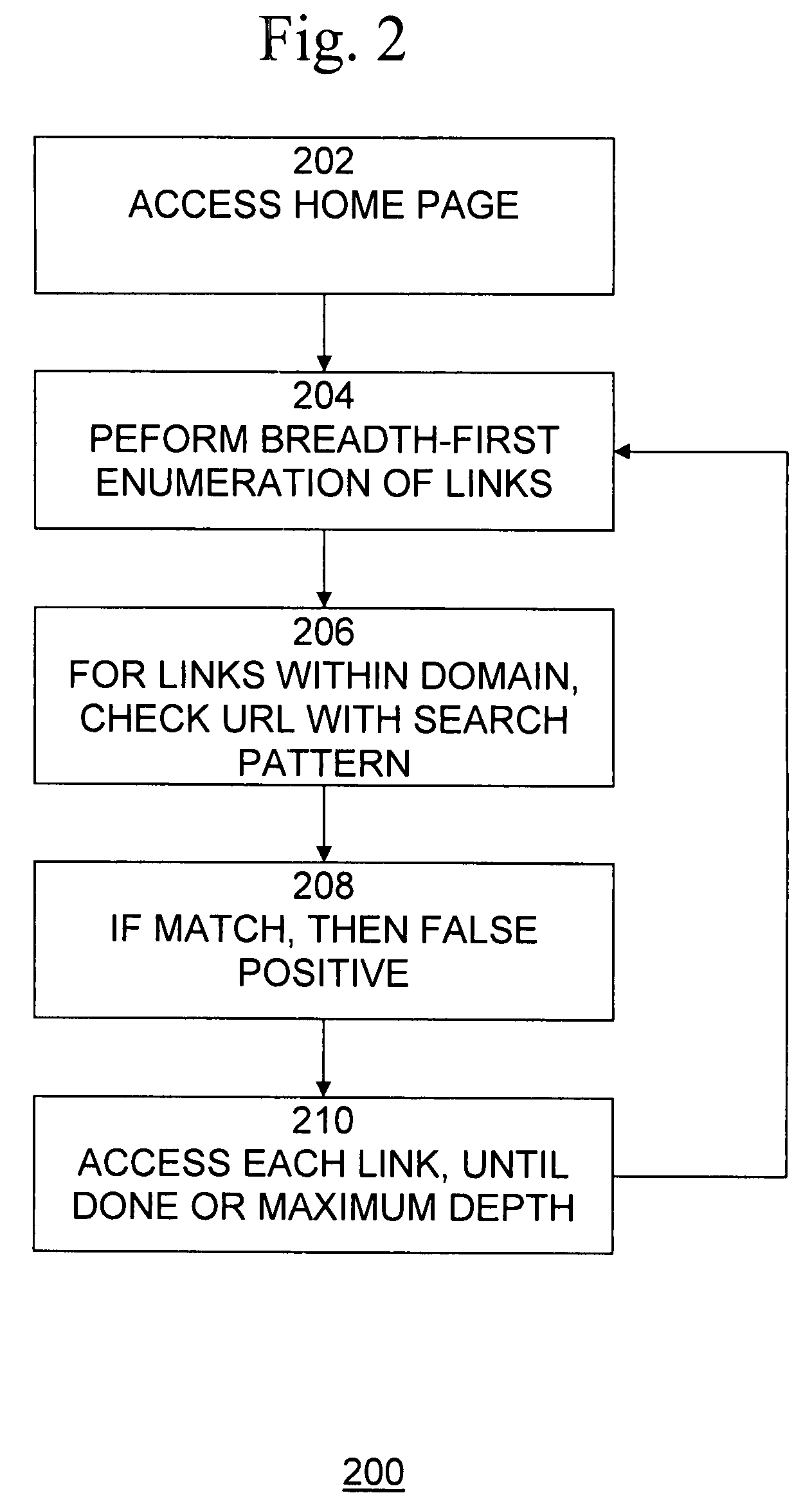
Automatically verifying that anti-phishing URL signatures do not fire on legitimate web sites
ActiveUS20090089287A1Take more riskLow costDigital data information retrievalDigital data processing detailsWeb sitePattern matching
A method and computer program product prevent false positives from occurring by reducing or preventing legitimate web site content from triggering matches to phishing black lists, but provides time and cost savings over manual review of black lists. A method implemented in a computer system for detecting false positives among a plurality of search patterns of web sites that include illegitimate content comprises accessing a first page of a legitimate web site, obtaining all links included in the first page, for each link included in the first page that points to a page on the web site, determining whether the link matches at least one of the plurality of search patterns, and for each link that matches the search pattern, indicating that the search pattern is a false positive.
Owner:MCAFEE LLC
System and method providing secure access to a computer system
InactiveUS20070150743A1Digital data processing detailsUser identity/authority verificationNetwork packetPassword
A system and method for providing secure access to a computer system. An access device divides the password into multiple segments and places them in data packets. In one embodiment, an authentication server has multiple addresses, and each packet is sent to a different address. The server then reassembles the password. In another embodiment, when the server receives a password, the server sends an index value back to the access device, which then accesses the server on another address indicated by the index value. Alternatively, the password is sent to multiple addresses for the server, and the server determines whether any of the received packets have been altered. The multiple password packets may be forced to follow different paths to the server, thereby denying hackers the ability to intercept all of the password characters or determine the inter-packet timing factor. The system is effective against passive and active hackers, Trojans, and phishing techniques.
Owner:JSM TECH
Client Side Phishing Avoidance
In one implementation, a phishing scam involves a communication sent to a user by an impersonator. Rather than detect the communication and verify the identity of the sender, the data entry of the user is monitored. For example, an example embodiment scans data entry from a user for a security word and queries a list of authorized terms for the security word. In response to the security word being included in the list of authorized terms, a destination address associated with the security word is identified. A list of authorized destination addresses is queried with the destination address associated with the security word.
Owner:CISCO TECH INC
Systems and methods for discovering suspect bot IP addresses and using validated bot IP address to ignore actions in a simulated phishing environment
Methods, systems and apparatus are provided which allow a server of a security awareness system to associate IP addresses with events representing user interactions with simulated phishing campaigns. The server receives a plurality of events related to one or more simulated phishing campaigns for a plurality of accounts. The server determines if an IP address of the plurality of IP addresses is associated with one or more events for multiple accounts of the plurality of accounts. Based upon this determination, the server provides identification of the IP address as suspected as having the one or more events associated with it not originating from any user of the multiple accounts. The server receives an indication of whether the IP address is validated as having the one or more events originating from a bot instead of a user of one of the multiple accounts.
Owner:KNOWBE4 INC
Secure web site authentication using web site characteristics, secure user credentials and private browser
ActiveUS8095967B2Defeat both phishing and pharming attacksOvercome deficienciesDigital data information retrievalMemory loss protectionWeb siteIp address
A secure authentication process detects and prevents phishing and pharming attacks for specific web sites. The process is based on a dedicated secure hardware store for user sign-in credentials, a database of information about specific web sites, and a private secure browser. All user web activity is monitored by an agent program. The agent program checks to make sure that user attempts to send any sign-in credentials stored in secure hardware store of user sign-in credentials, to any web site accessed by the user, is allowed only if the IP address of the web site accessed by the user matches at least one of the IP addresses stored web site database associated with the sign-in credential the user is attempting to send. The process also detects mismatches between a URL and the actual IP address of the web site associated with the URL.
Owner:AURA SUB LLC +1
Secondary authentication method based on out-of-band authentication and enhanced OTP (One-time Password) mechanism
ActiveCN105357186AEliminate the threat of attackSignificantly progressiveTransmissionMan-in-the-middle attackControl communications
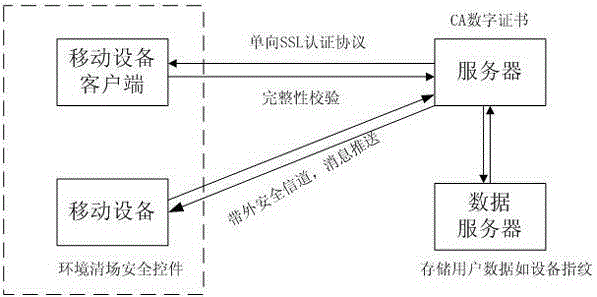
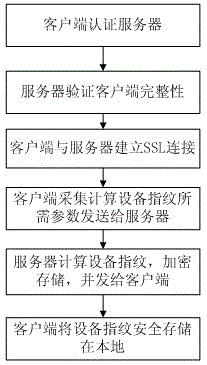
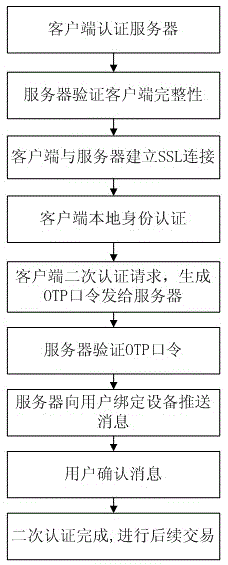
The invention discloses a secondary authentication method based on out-of-band authentication and an enhanced OTP (One-time Password) mechanism. Authentication of a client to a server is added based on a common OTP mechanism, and the client and the server are communicated based on PKI / CA (Public Key Infrastructure / Certificate Authority) by adopting a one-way SSL (Secure Socket Layer) authentication protocol; after secondary authentication is completed, the server adopts an out-of-band secure channel to push a business authentication message to equipment bound to a user based on an equipment fingerprint. After the user affirms the push message on the equipment, a business party can proceed. Meanwhile, mobile equipment of the user is provided with an environment site-cleaning control to prevent Trojan from controlling communication to destroy business security. Through the whole secondary authentication method, threats from phishing and a man-in-the-middle attack of a common OTP token are eliminated, and the method is a good replacement for commonly used short message verification codes in business, such as quick payment, on-line payment and mobile payment.
Owner:JIANGSU PAYEGIS TECH CO LTD
Automatically verifying that anti-phishing URL signatures do not fire on legitimate web sites
ActiveUS7831611B2Prevents false positivesLow costDigital data information retrievalDigital data processing detailsWeb sitePattern matching
A method and computer program product prevent false positives from occurring by reducing or preventing legitimate web site content from triggering matches to phishing black lists, but provides time and cost savings over manual review of black lists. A method implemented in a computer system for detecting false positives among a plurality of search patterns of web sites that include illegitimate content comprises accessing a first page of a legitimate web site, obtaining all links included in the first page, for each link included in the first page that points to a page on the web site, determining whether the link matches at least one of the plurality of search patterns, and for each link that matches the search pattern, indicating that the search pattern is a false positive.
Owner:MCAFEE LLC
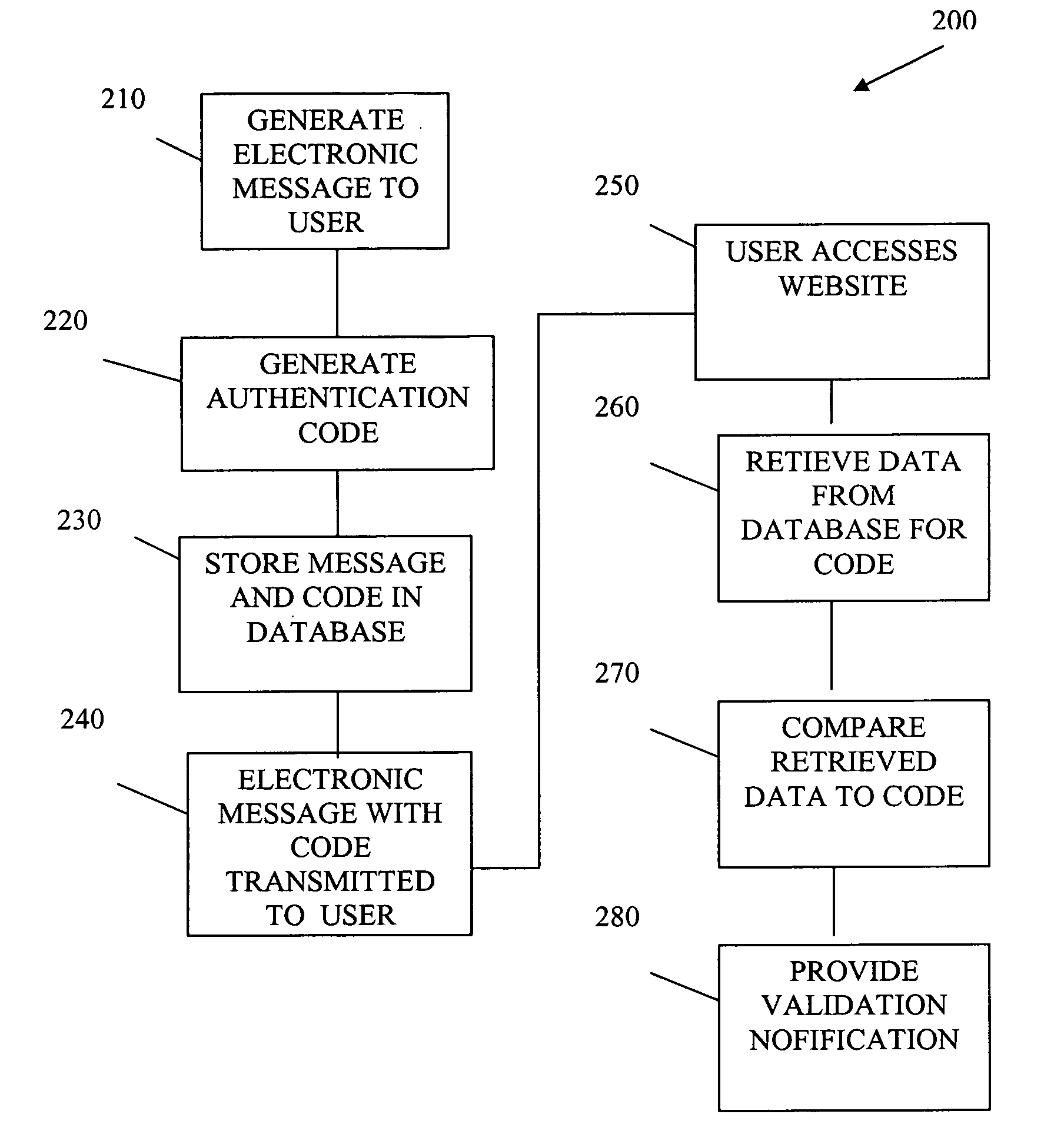
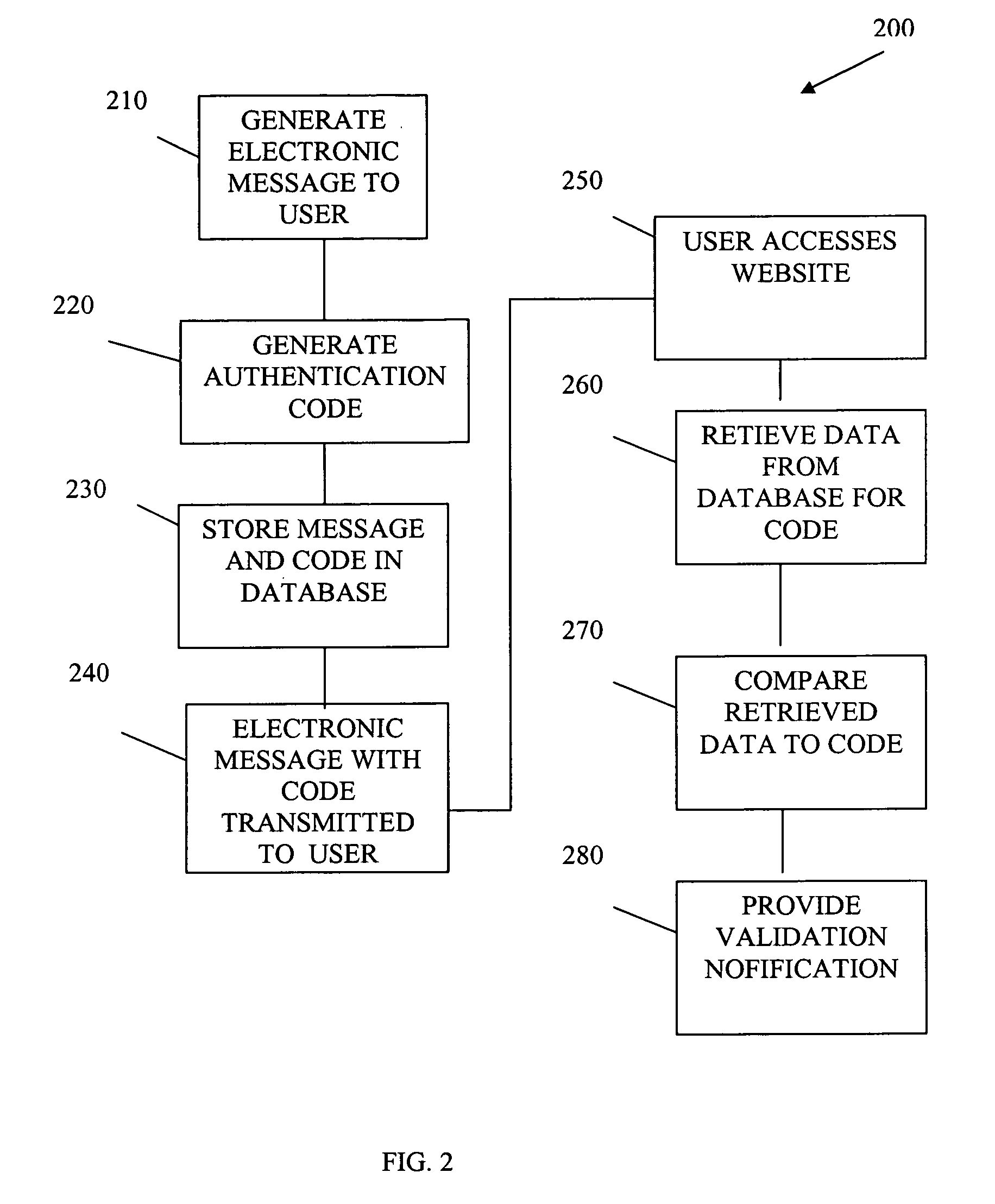
Anti-phishing communication system
A system and method for electronic message verification are described. One embodiment adds a unique code to electronic messages which a user can provide to a financial services company website. The code can be verified and a verification notice is provided to the user if the message was authentic. Authentication can be based upon both the code and the user's identification relative to the financial services company.
Owner:EBAY INC
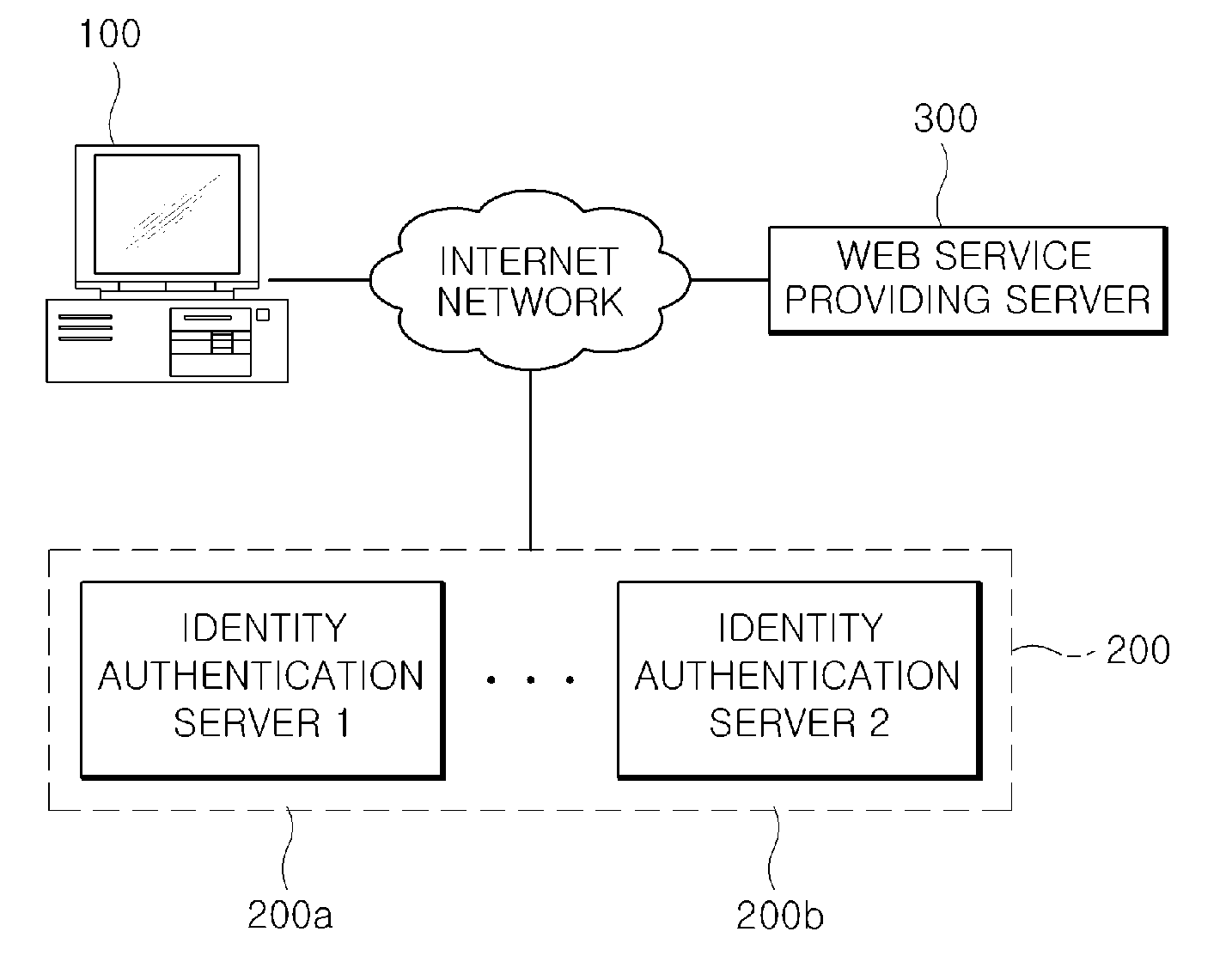
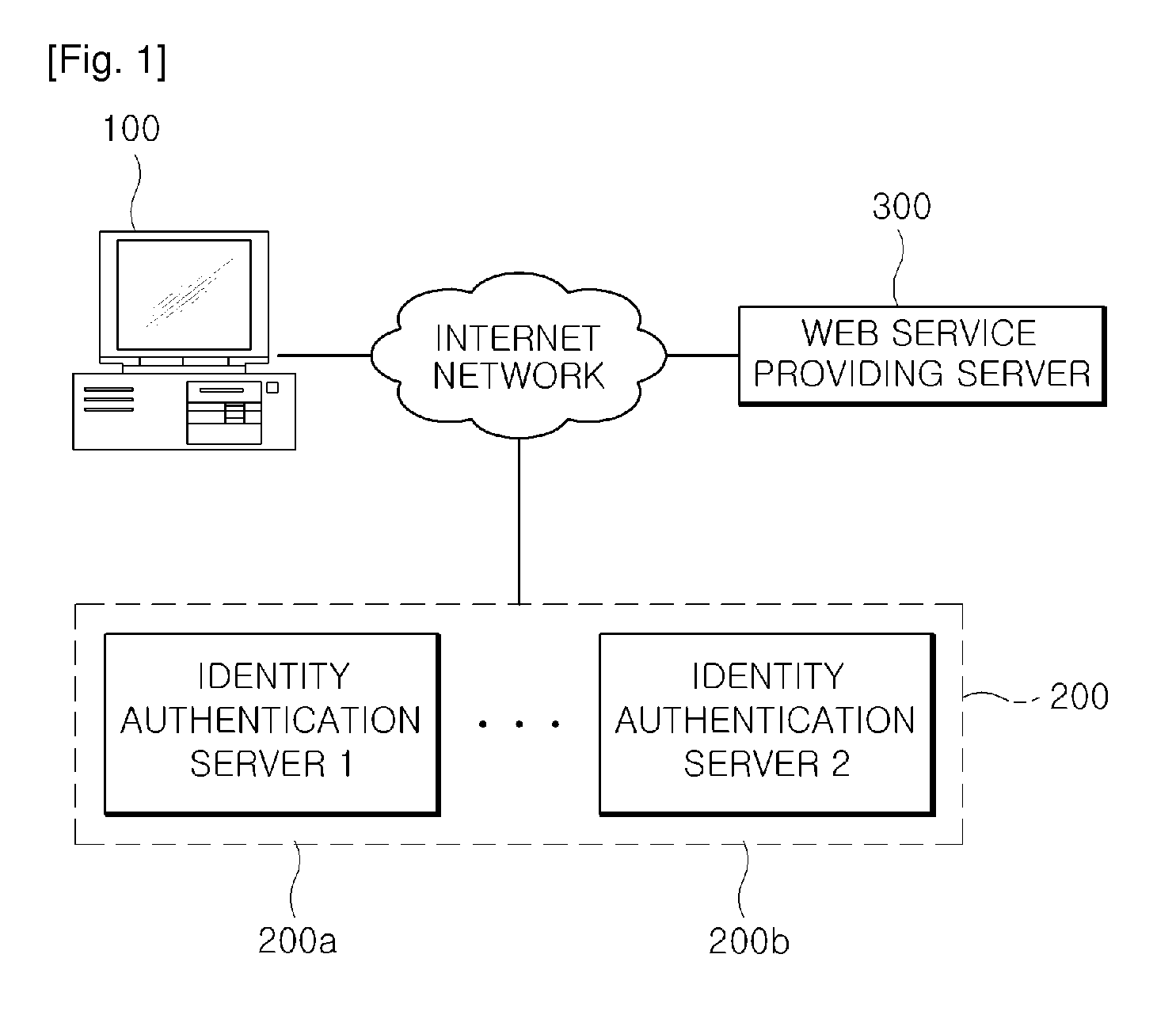
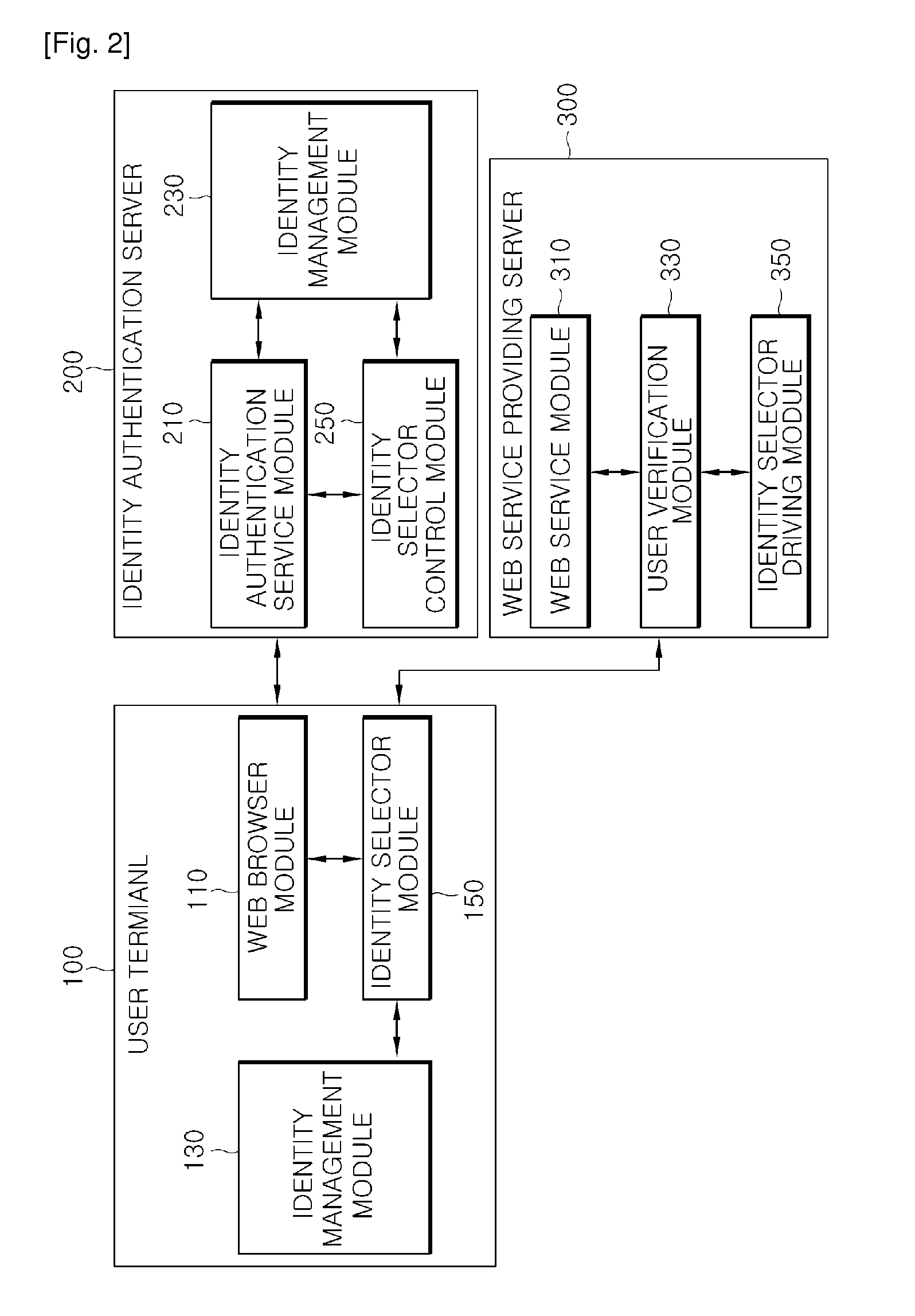
User terminal with identity selector and method for identity authentication using identity selector of the same
InactiveUS20110023099A1Difficult to rememberSolve the real problemDigital data processing detailsUser identity/authority verificationService protocolPassword
The present invention relates to a user terminal (100) with an identify selector and a method for an identity authentication using the identify selector of the same, in which when a web service makes a request to a web service providing server (300) using a virtual personal identification information issued from an identity authentication server (200), a corresponding user identity is authenticated between the user terminal and the identity authentication server (200) using the identity selector according to the request of the web service providing server (300). The present invention has advantages that it can solve the problem of inputting an ID and password within the range such that the I-PIN or SMAL service protocol is not changed, but the subscribed I-PIN or SAML service providing site cannot be easily copied and a phishing problem by simplifying a log-in process for identity authentication by adding the identity selector.
Owner:ELECTRONICS & TELECOMM RES INST
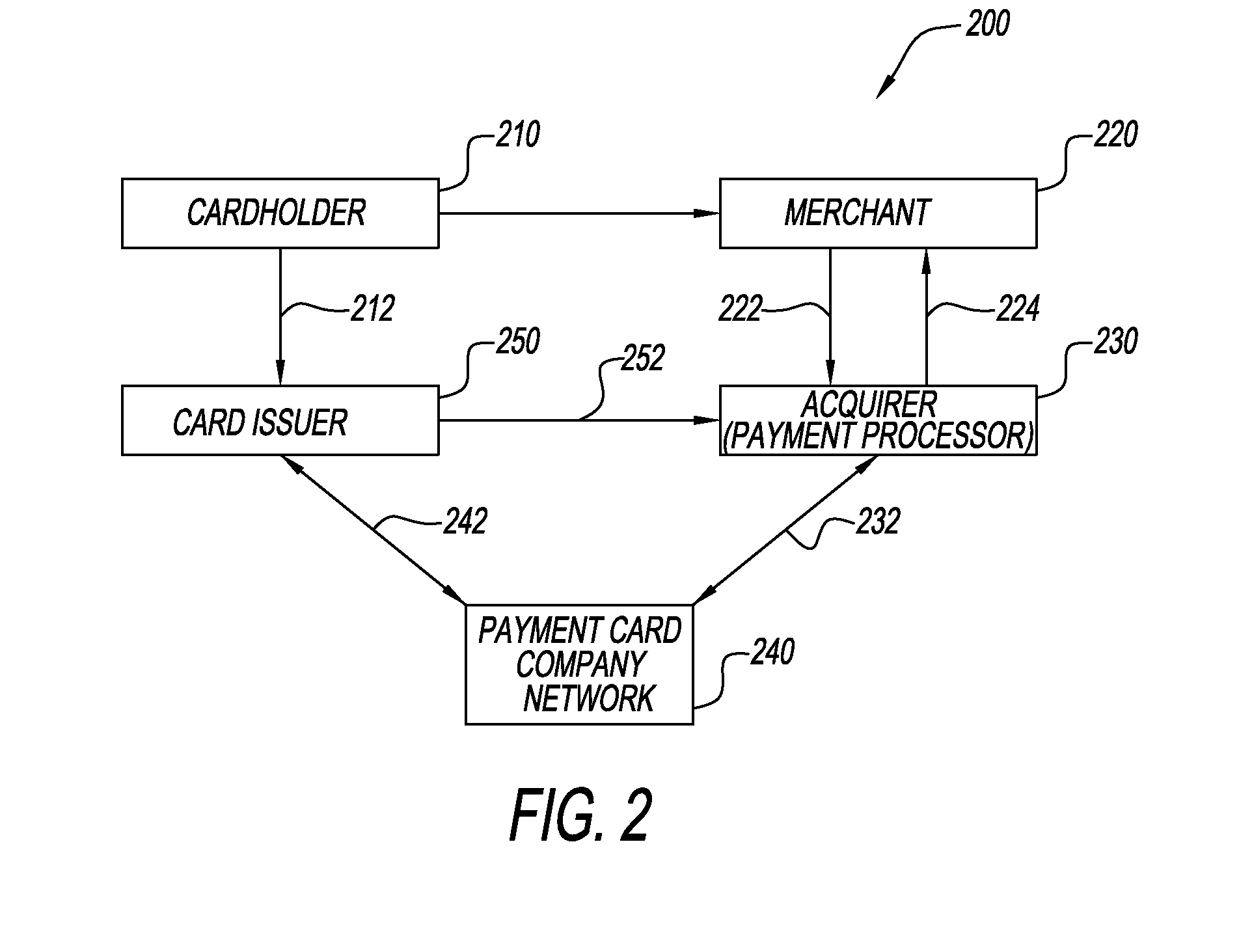
Internet site authentication with payments authorization data
A system for identification by a payment cardholder of phishing and / or deceptive Websites is provided. The system includes an electronic storage device having a database of merchant or financial institution Website registration with a payment card network information stored therein. The system includes an access path for allowing access to the merchant or financial institution Website registration with a payment card network information. The system includes a processor for assembling the merchant or financial institution Website registration with a payment card network information in the database, and for communicating the assembled merchant or financial institution Website registration with a payment card network information to a payment cardholder that has been granted access to the database.
Owner:MASTERCARD INT INC
Caller authentication system and method for phishing prevention
InactiveUS8290130B2Prevent phishing fraudSpecial service for subscribersCalled number recording/indicationCommunications systemComputer terminal
A caller authentication system that may enable a called party to be provided with identification information of a caller may be provided. The caller authentication system, including: a communication system to transmit, when a call request signal is received from a calling terminal of a caller, network information and a telephone number of the calling terminal to a certificate authority server, and to request identification of the caller, the network information and the telephone number being included in the call request signal, to transmit, when identification information of the caller is received from the certificate authority server in response to the identification request, the identification information to a called terminal of a called party, and to enable the identification information to be displayed on the called terminal.
Owner:ELECTRONICS & TELECOMM RES INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com