Method for guarding phishing website based on gateway, bridge
A phishing and network bridge technology, applied in network interconnection, network connection, user identity/authority verification, etc., can solve problems such as security flaws, personal confidential data fraud, and inability to filter phishing websites, so as to prevent economic damage Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
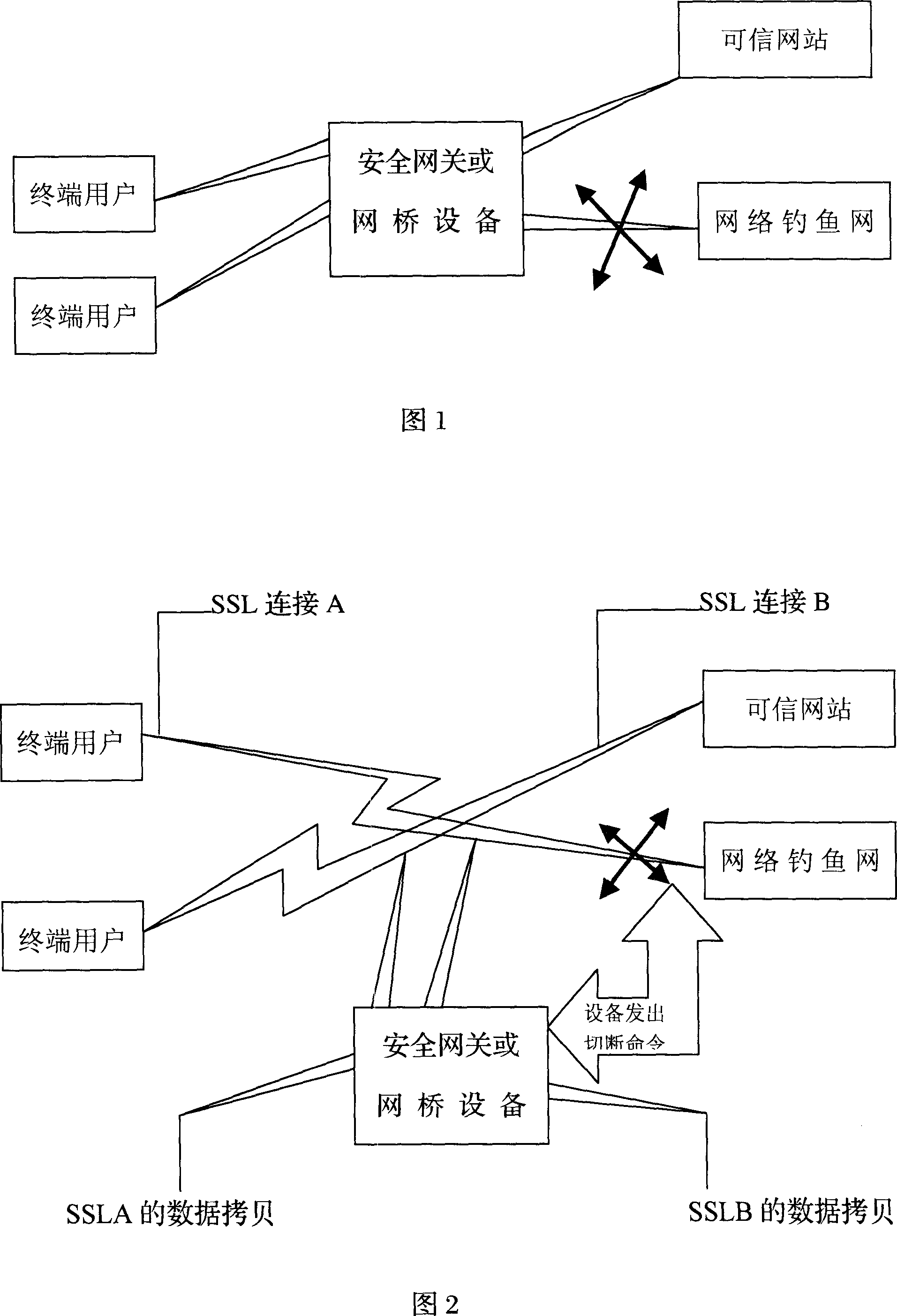
[0020] The first implementation method of the present invention is shown in Figure 1, the electrical characteristics of its security gateway or network bridge are the same as those of general Internet gateways.
[0021] First, let's explain how the method works. As shown in Figure 3, the security gateway or bridge captures the data encrypted by SSL, captures the handshake process of the SSL protocol, and extracts the X.509 certificate chain. Verify the legitimacy of the X.509 certificate chain transmitted during the extracted handshake process according to the relevant PKI standards and the trusted certificate list provided by the user. The security gateway or bridge allows the certificate chain to pass through the legal SSL connection, filters and blocks the certificate chain invalid SSL connection.
[0022] As shown in Figure 1, the security gateway or network bridge is arranged between the user's Internet access terminal and the network link of the visited website. The dat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com