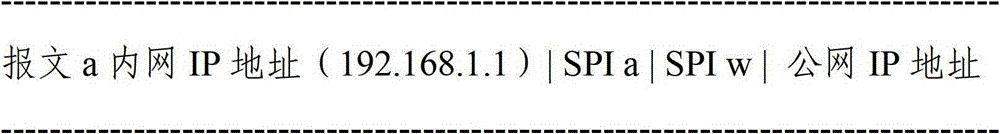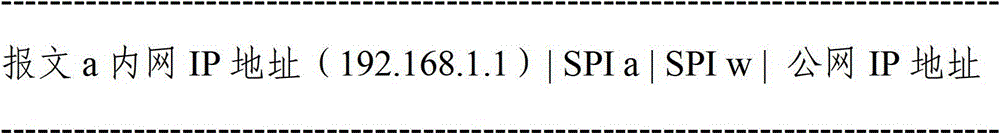Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
49 results about "Security Parameter Index" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
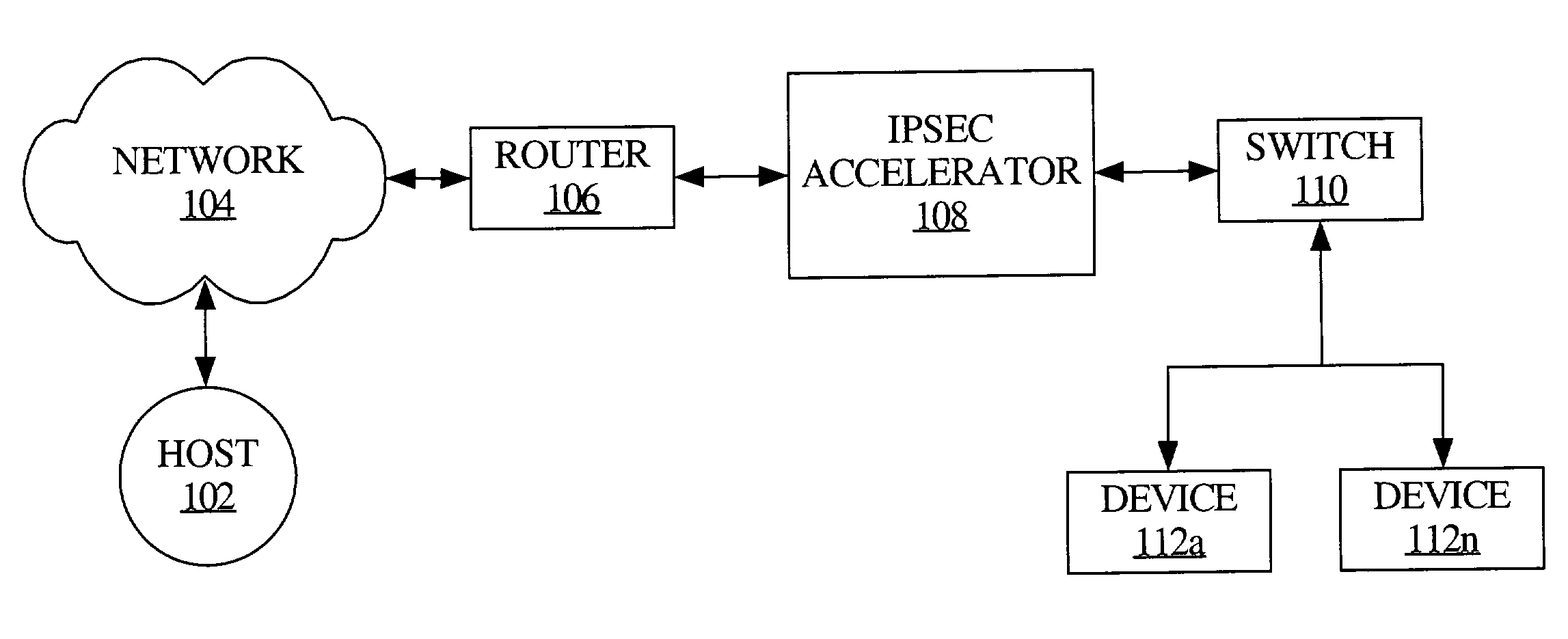
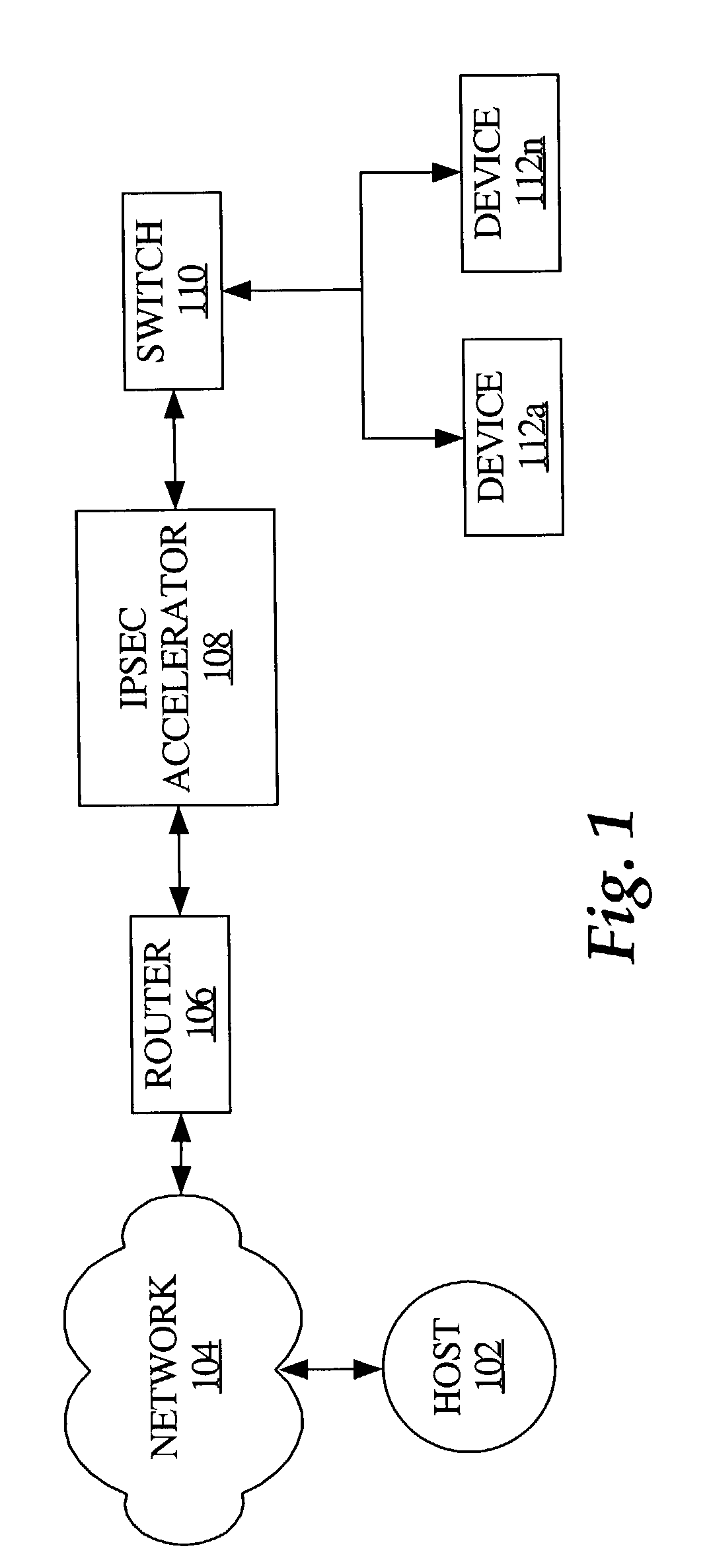
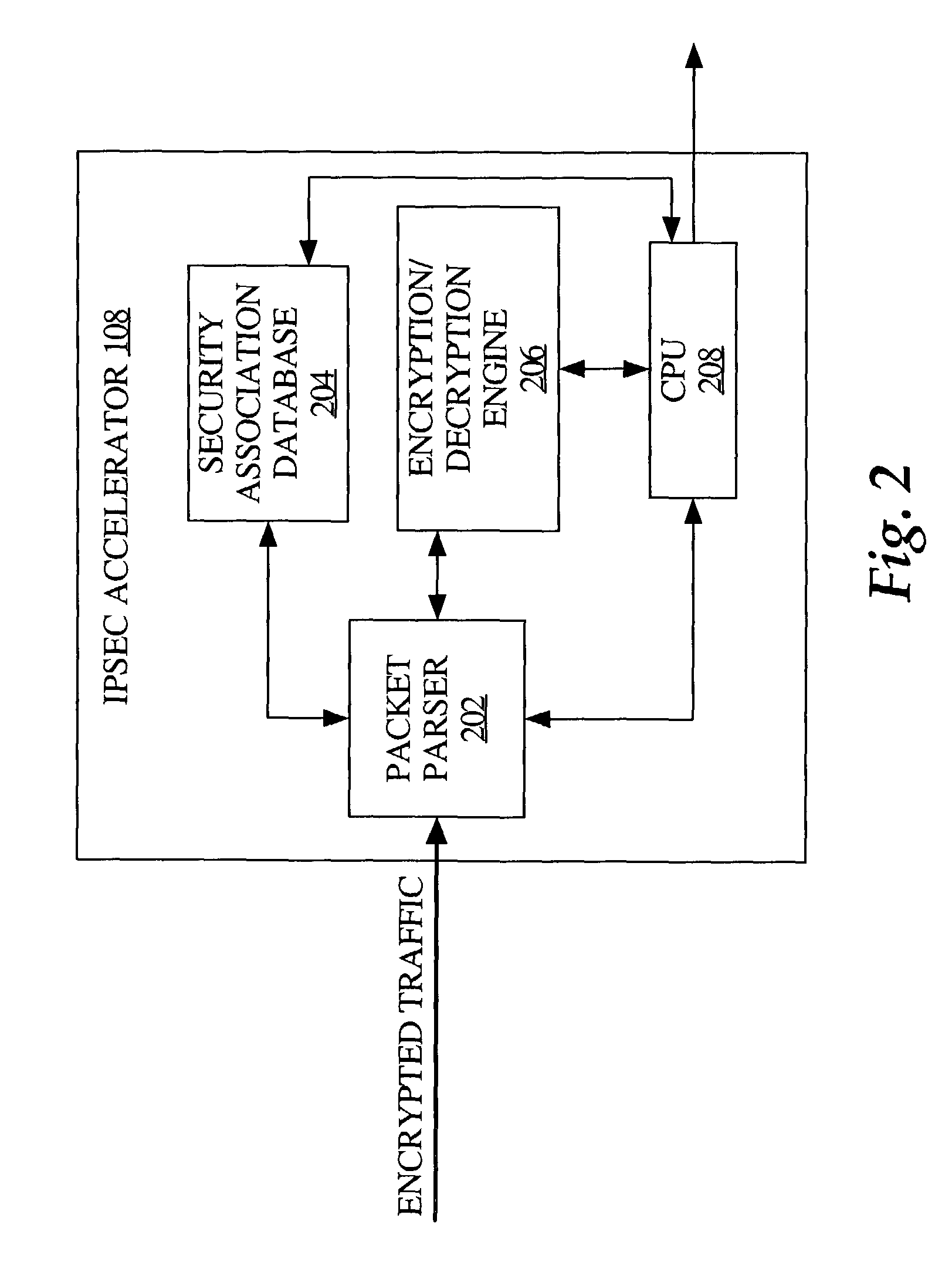
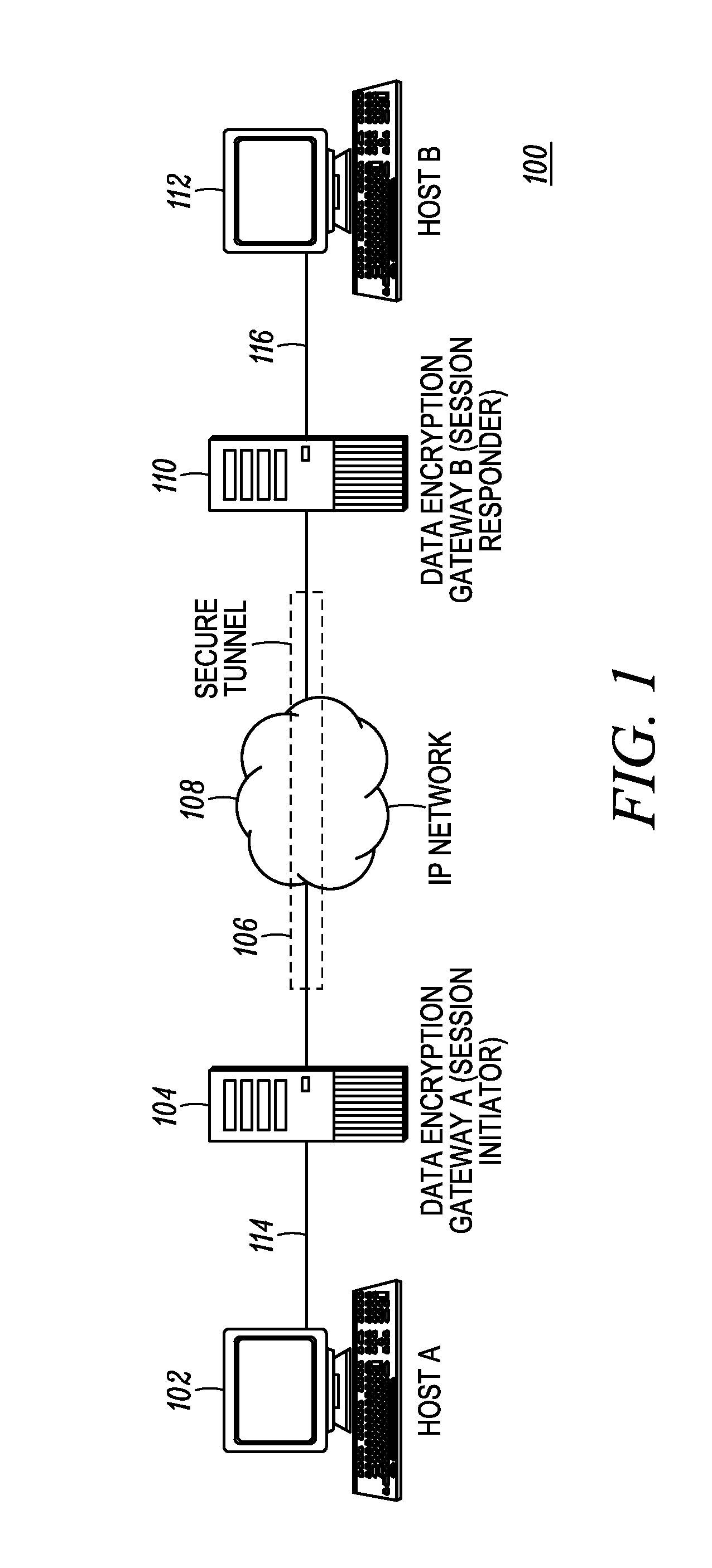
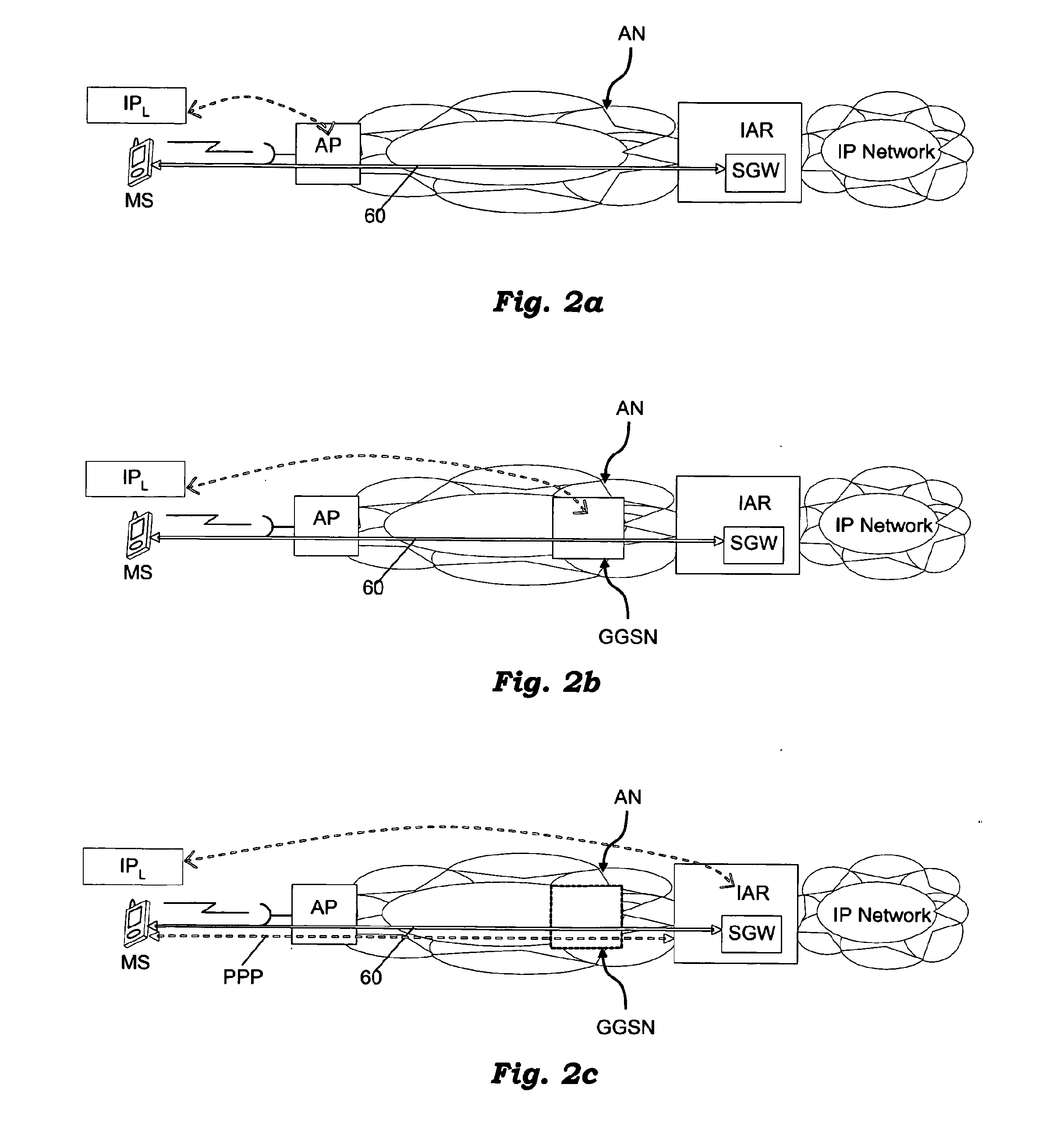
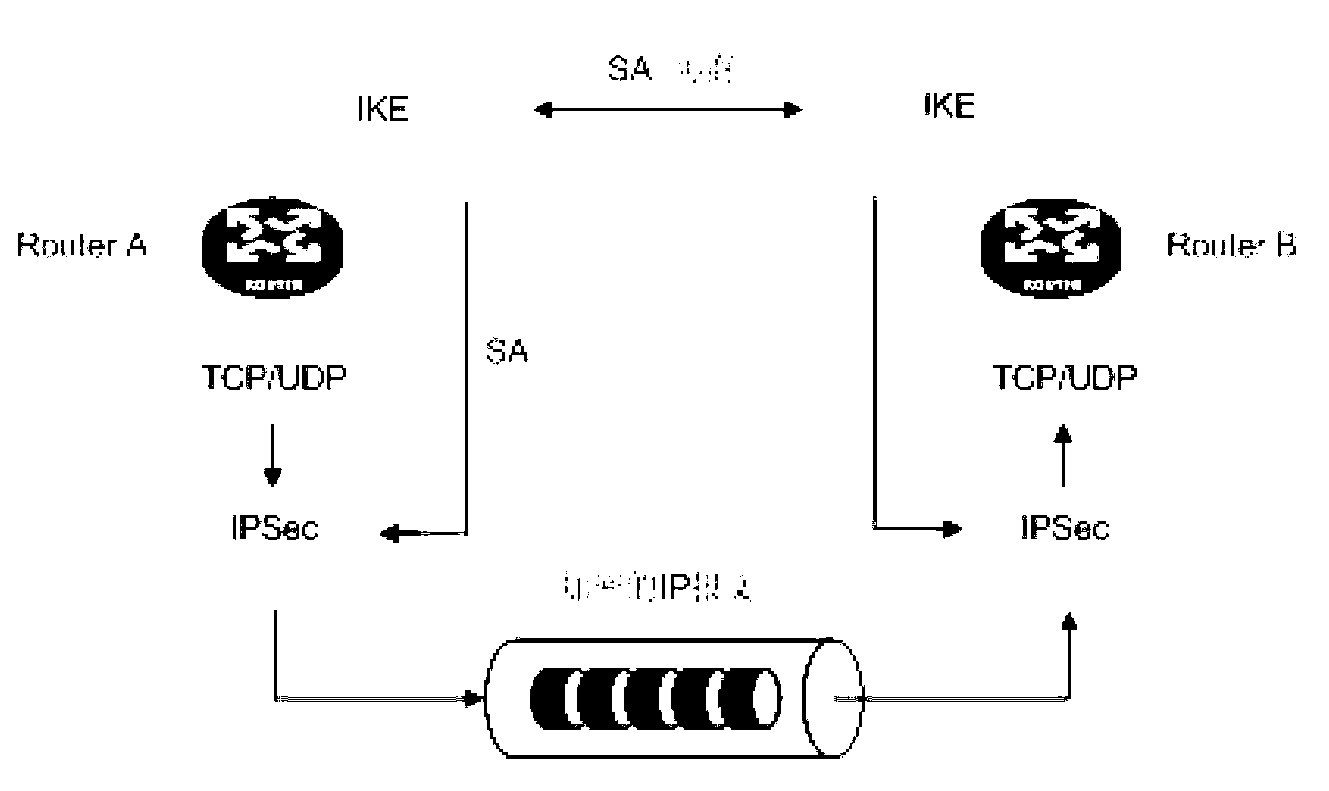
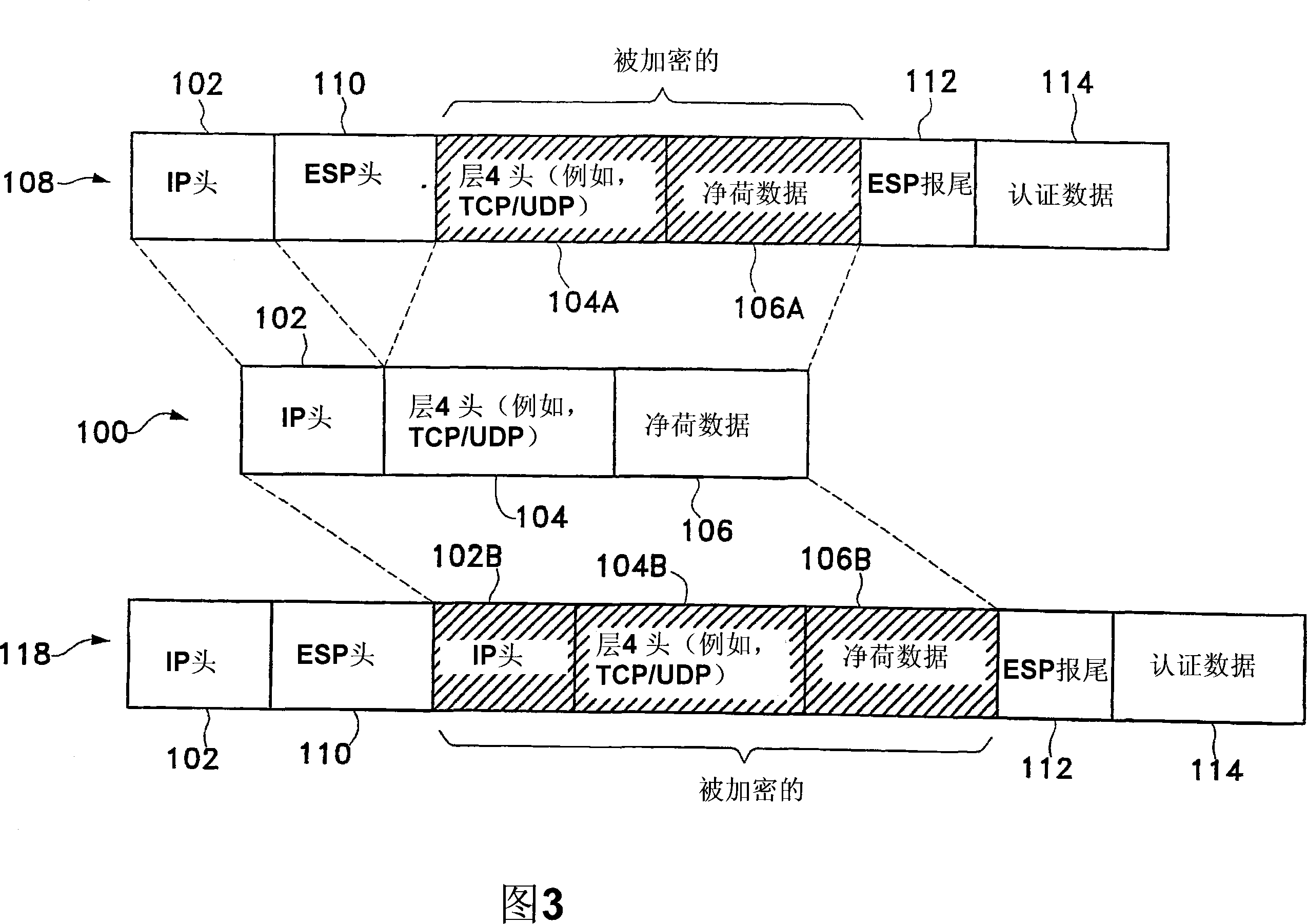
The Security Parameter Index (SPI) is an identification tag added to the header while using IPsec for tunneling the IP traffic. This tag helps the kernel discern between two traffic streams where different encryption rules and algorithms may be in use.
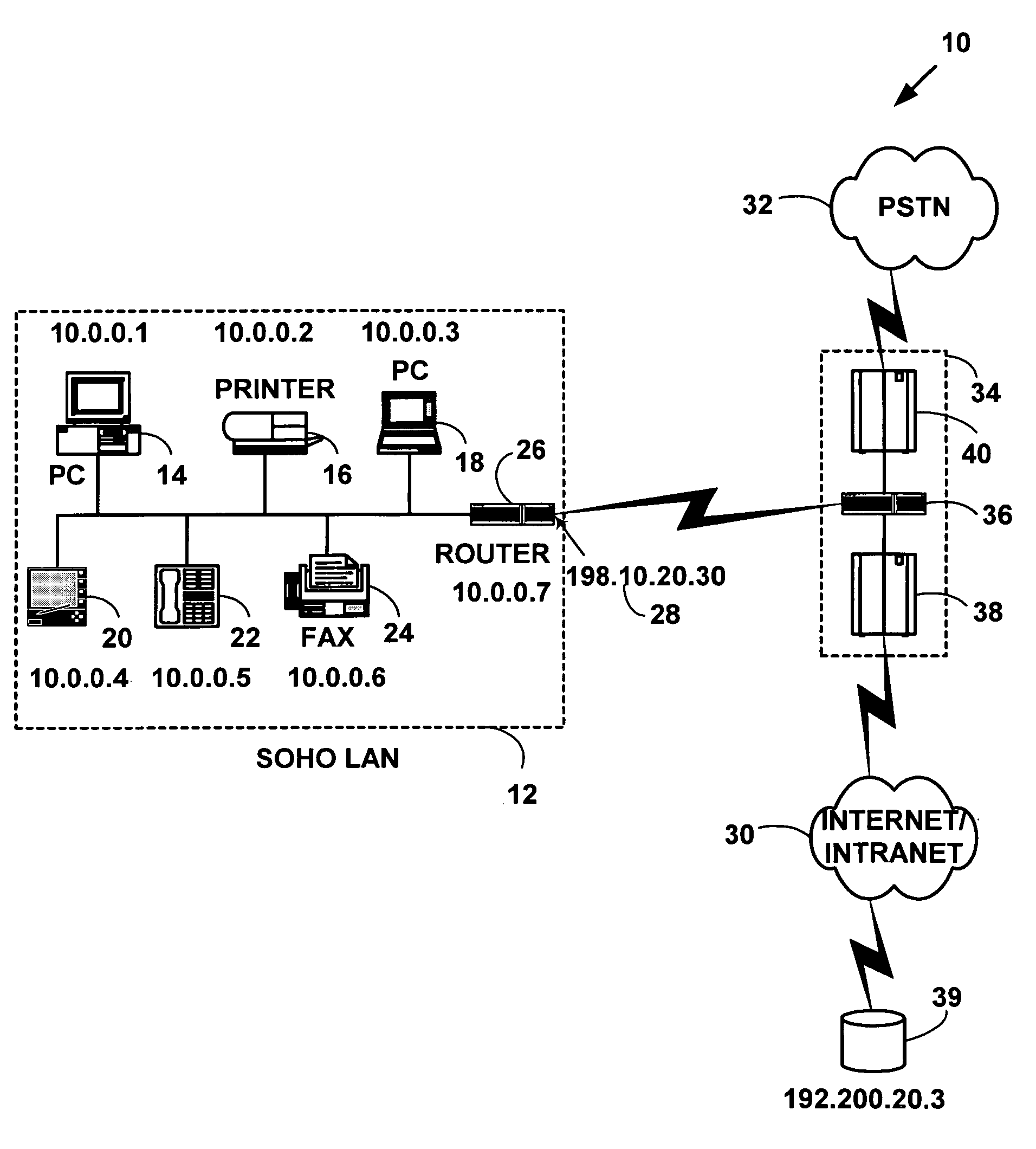
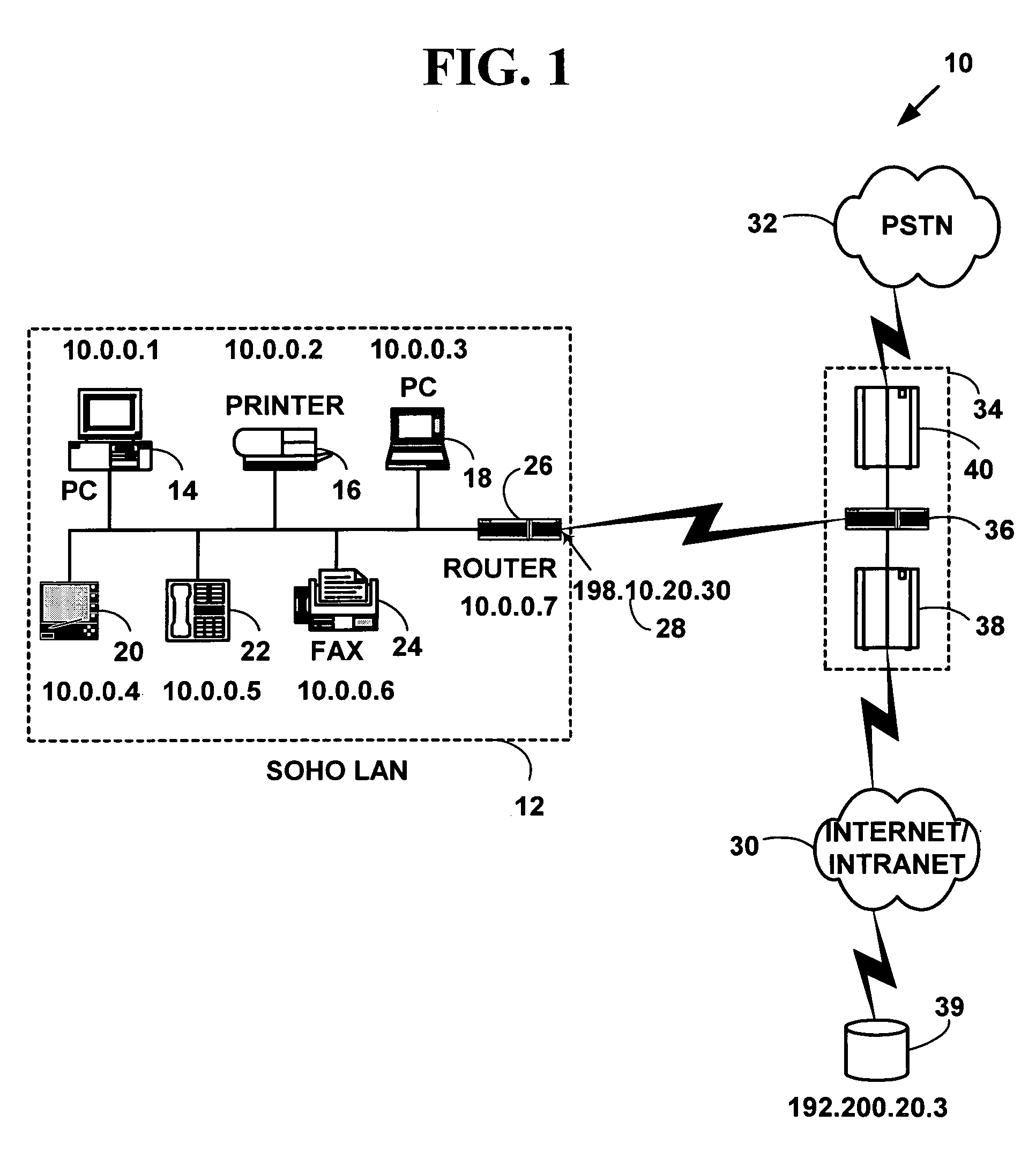
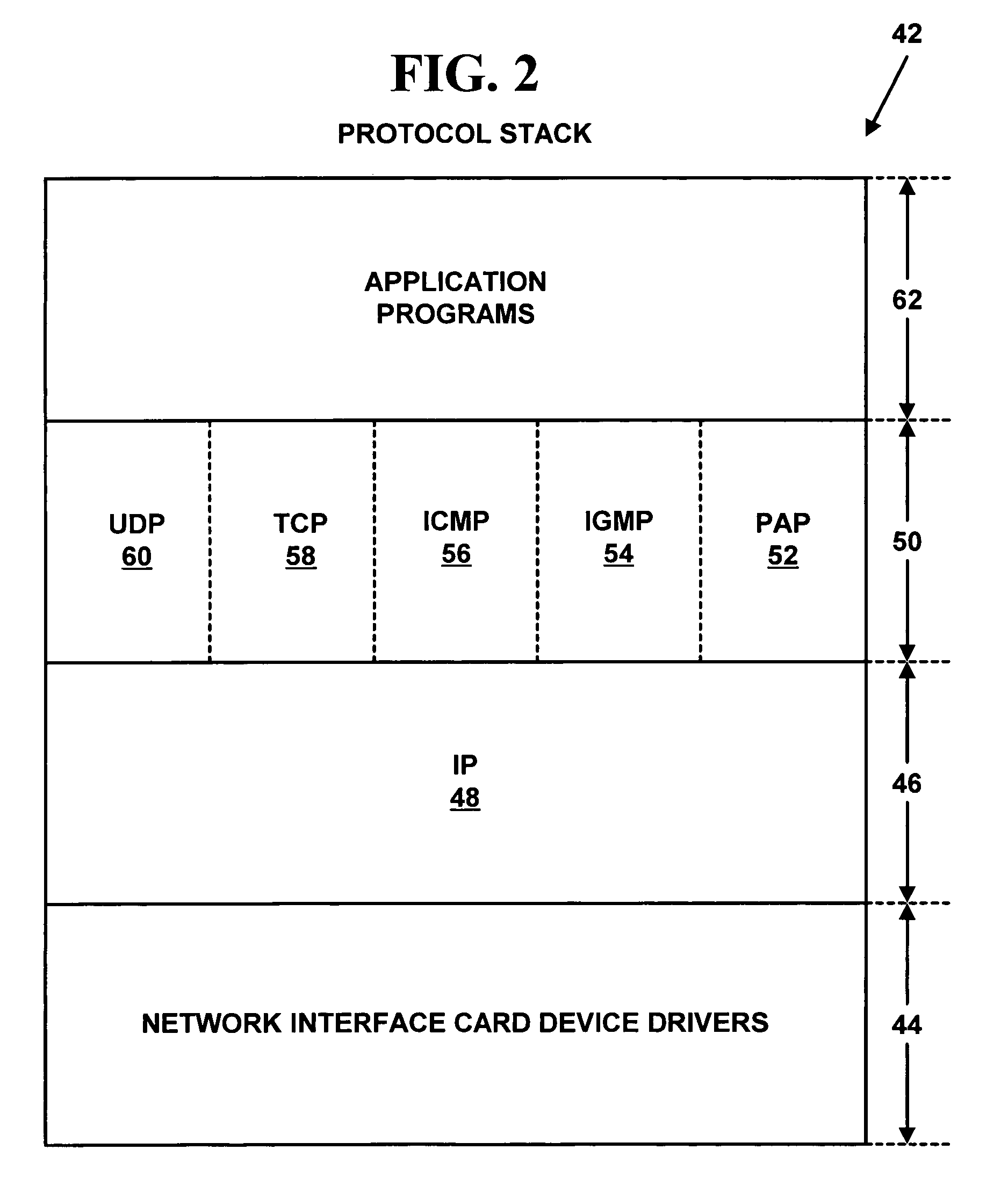
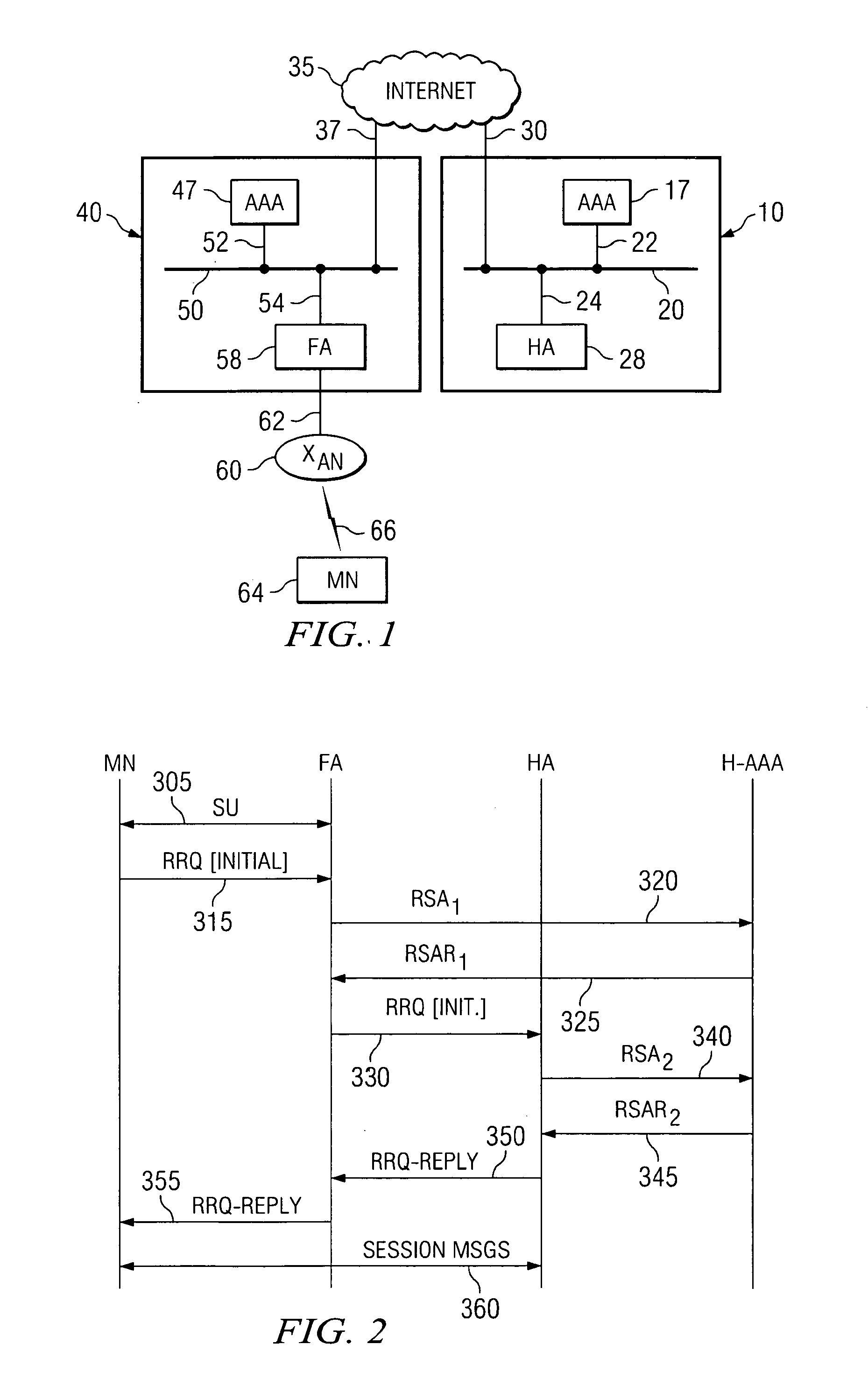
Method and system for distributed network address translation with network security features
InactiveUS7032242B1Digital data processing detailsUser identity/authority verificationSecurity associationIp address
A method and system for distributed network address translation with security features. The method and system allow Internet Protocol security protocol (“IPsec”) to be used with distributed network address translation. The distributed network address translation is accomplished with IPsec by mapping a local Internet Protocol (“IP”) address of a given local network device and a IPsec Security Parameter Index (“SPI”) associated with an inbound IPsec Security Association (“SA”) that terminates at the local network device. A router allocates locally unique security values that are used as the IPsec SPIs. A router used for distributed network address translation is used as a local certificate authority that may vouch for identities of local network devices, allowing local network devices to bind a public key to a security name space that combines a global IP address for the router with a set of locally unique port numbers used for distributed network address translation. The router issues security certificates and may itself be authenticated by a higher certificate authority. Using a security certificate, a local network device may initiate and be a termination point of an IPsec security association to virtually any other network device on an IP network like the Internet or an intranet. The method and system may also allow distributed network address translation with security features to be used with Mobile IP or other protocols in the Internet Protocol suite.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Method and apparatus for security protocol and address translation integration
ActiveUS7143137B2Add significant overheadImprove securityMultiple digital computer combinationsProgram controlInternet Security Association and Key Management ProtocolTTEthernet
Method and apparatus for Internet Protocol Security (IPSec) and Network Address Translation (NAT) integration is described. A client obtains a public address from a gateway for IPSec communication. A mapping table is used to form associations between a local address for the client and a destination address for a peer, an Internet Security Association and Key Management Protocol (ISAKMP) Initiator Cookie and a Security Parameters Index associated with communication between the client and the peer. Incoming and outgoing routing may be done at the gateway using the mapping table.
Owner:NVIDIA CORP
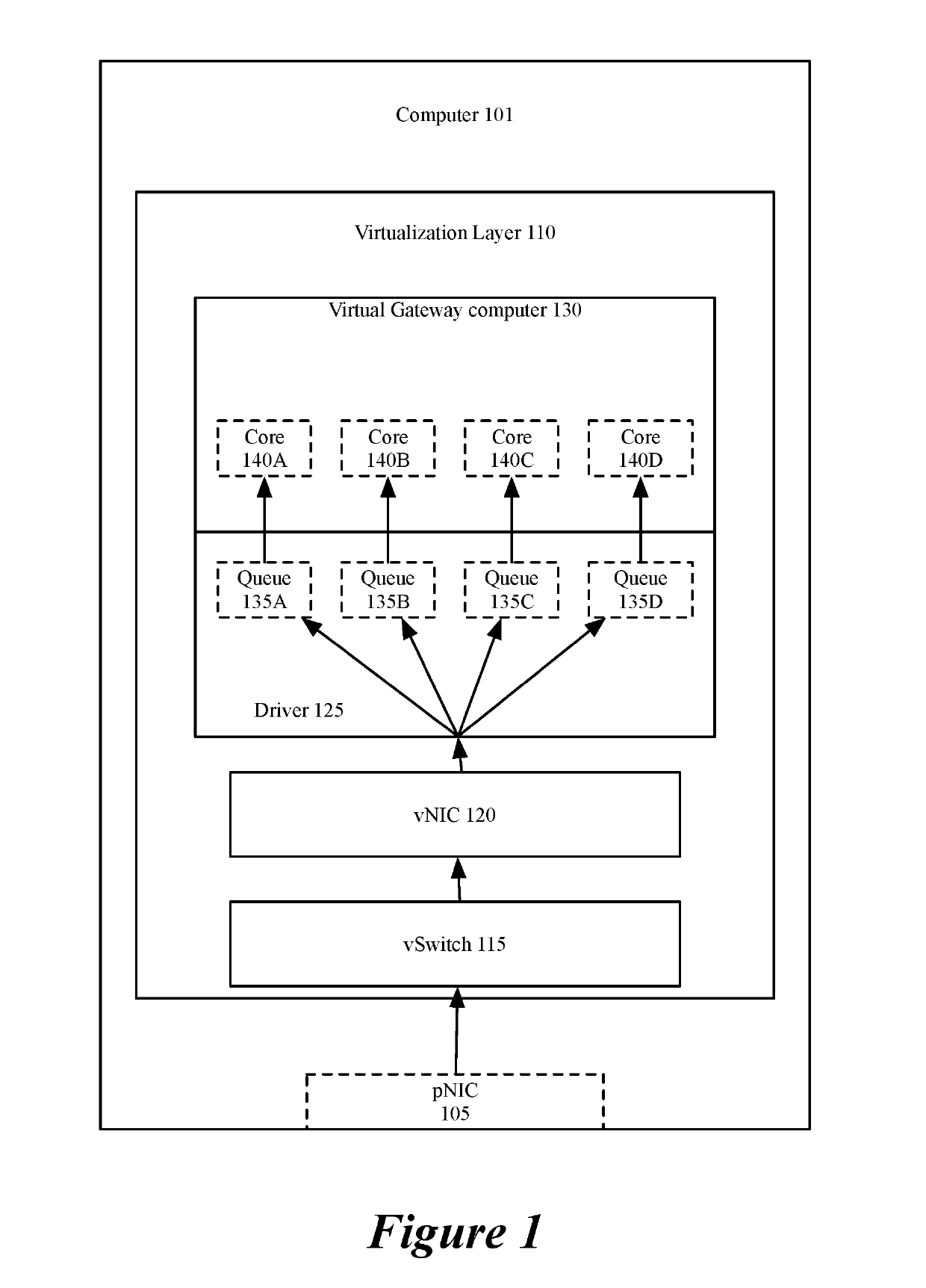
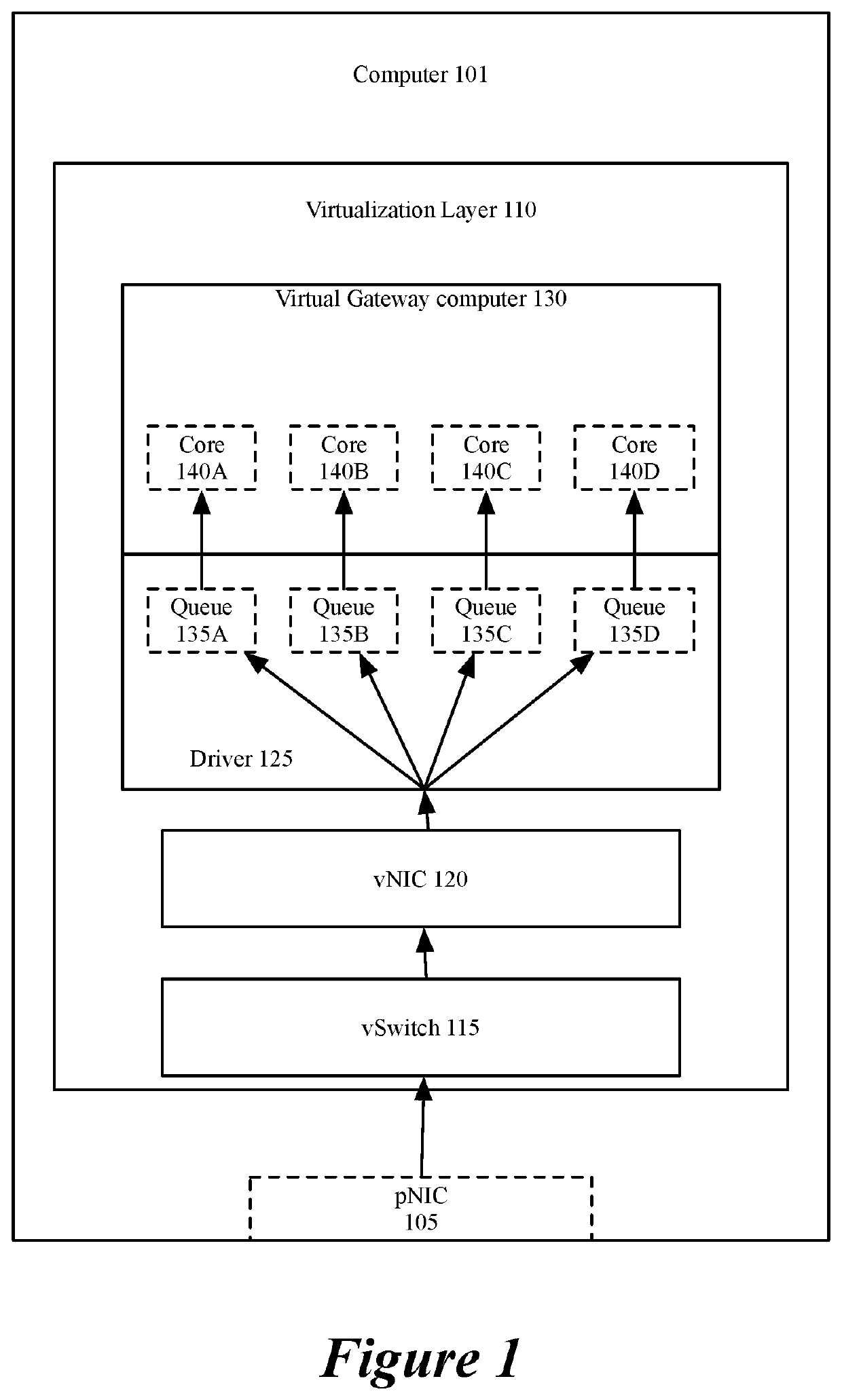
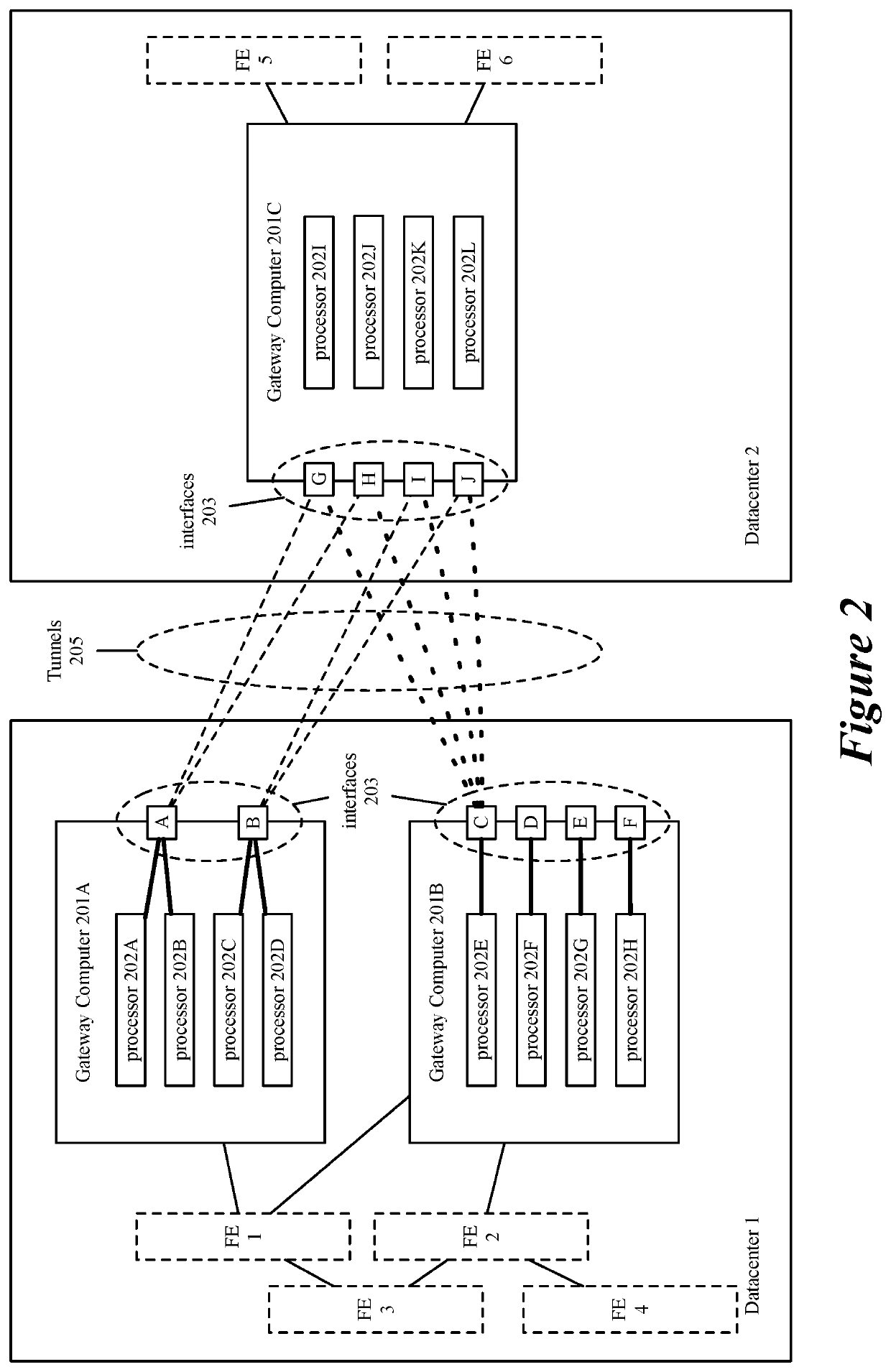
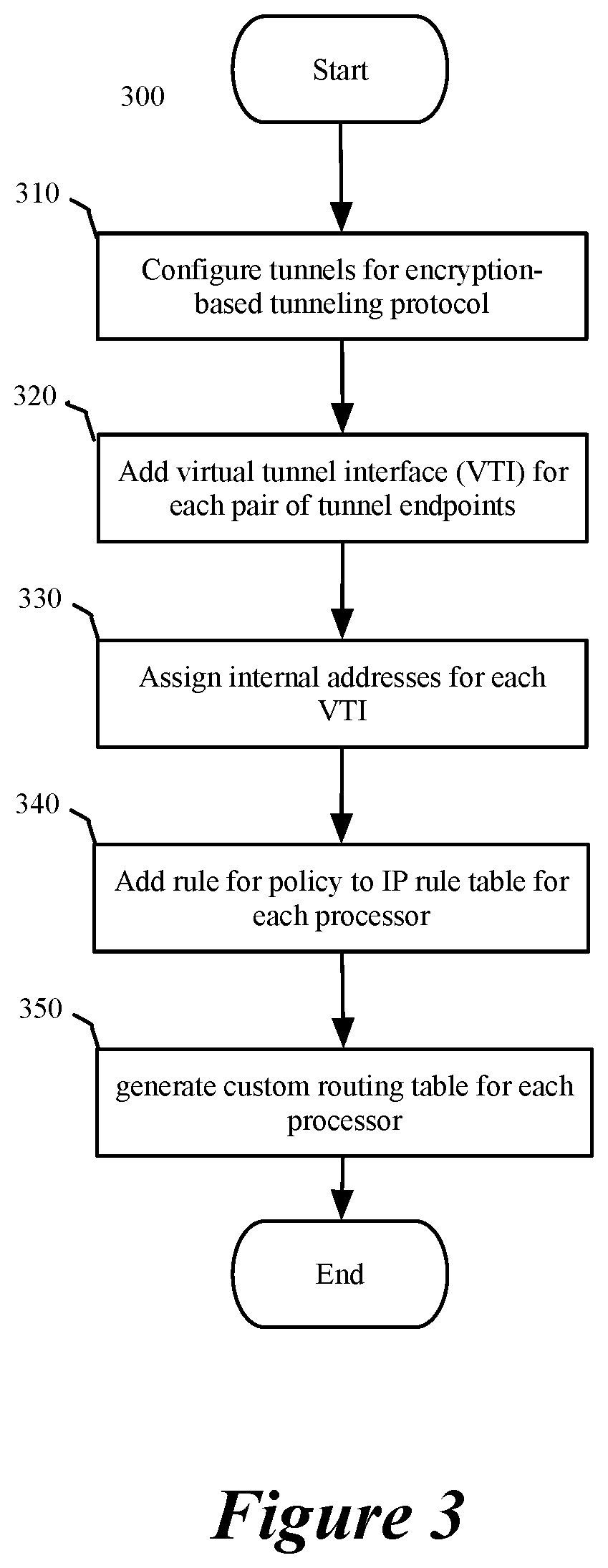
Scaling gateway to gateway traffic using flow hash
ActiveUS20190173851A1Increase probabilityEncryption apparatus with shift registers/memoriesNetworks interconnectionDistributed computingEncryption
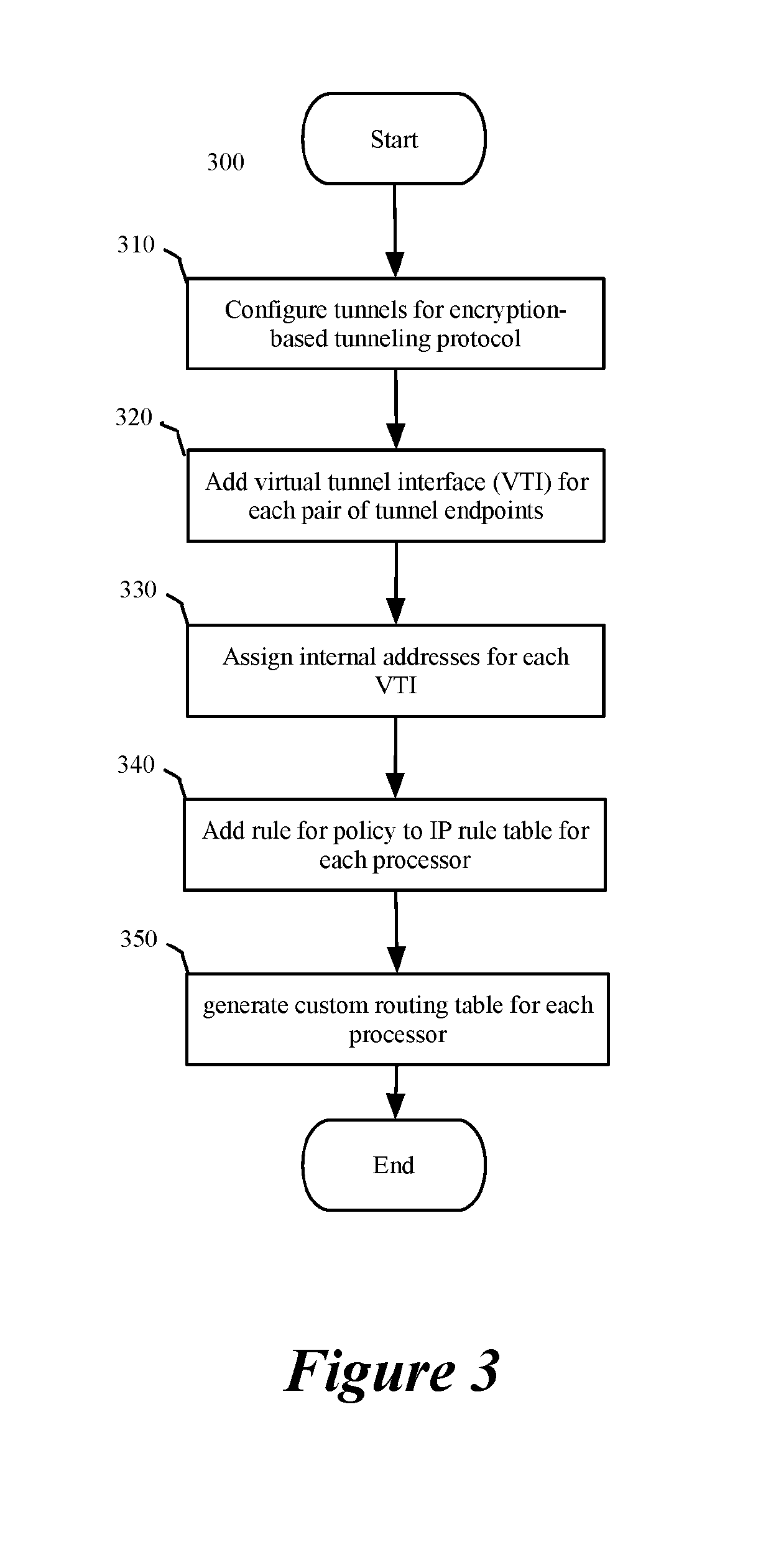
For a network including multiple computers acting as tunnel endpoints in a network, some embodiments provide a method for distributing data messages among processors of a destination computer that receives encrypted data messages from a source computer. Each computer in some embodiments has a set of interfaces configured as tunnel endpoints connecting to multiple tunnels. The encrypted data messages are received at multiple interfaces of the destination computer and in some embodiments, include an identifier for a set of encryption parameters (e.g., a security parameter index). The encryption-parameter-set identifier is used to distribute encrypted data messages among processors of the destination computer.
Owner:NICIRA
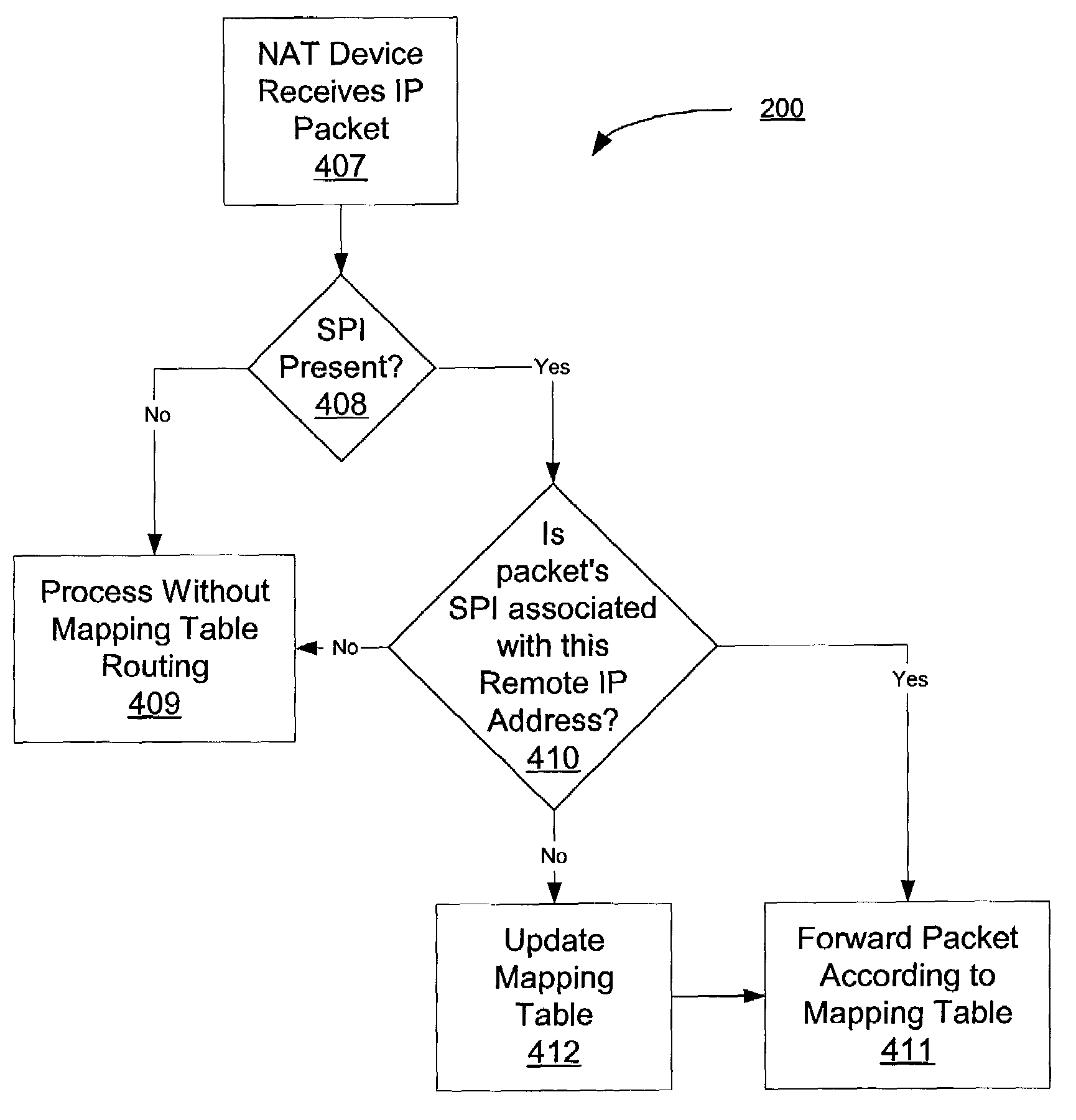
Method and apparatus for indexing an inbound security association database
ActiveUS7434045B1Digital data processing detailsSpecial data processing applicationsComputer networkSecurity association
Processes are disclosed in which an index value is generated for locating a security association in a security association database, such as an inbound SAD associated with the IPsec set of protocols. The index value is specified for insertion into a Security Parameter Index (SPI) field of a packet header, such as an IPsec header. For packets that are to be secured according to the policies and protocols identified in the header and the security association and that are transmitted to a particular network device or host, the index value is inserted into the SPI field of the packets by a packet sender. The packet is then parsed by a packet receiver, the index value determined from the SPI and used to identify the security association in the SAD, based solely on the index value determined from the SPI. Hence, a simple and efficient mechanism is provided for fast inbound security association lookups.
Owner:CISCO TECH INC
Method and apparatus for control of security protocol negotiation
ActiveUS7120930B2Add significant overheadMultiple digital computer combinationsProgram controlPlaintextPrivate network
Method and apparatus for enhanced security for communication over a network, and more particularly to control of security protocol negotiation to enable multiple clients to establish a virtual private network connection with a same remote address, is described. A mapping table accessible by a gateway computer is used to form associations between a local address for the client and a destination address for a peer and a Security Parameters Index associated with IPSec-protected traffic from the peer. When a packet is received at the gateway from a client it is checked to determine if it is an Internet Key Exchange (IKE) packet, whether an IKE session has already been recorded from this client in the mapping table for the destination address in the IKE packet, whether a Security Parameters Index has been observed in the clear from a remote computer associated with the destination address.
Owner:NVIDIA CORP
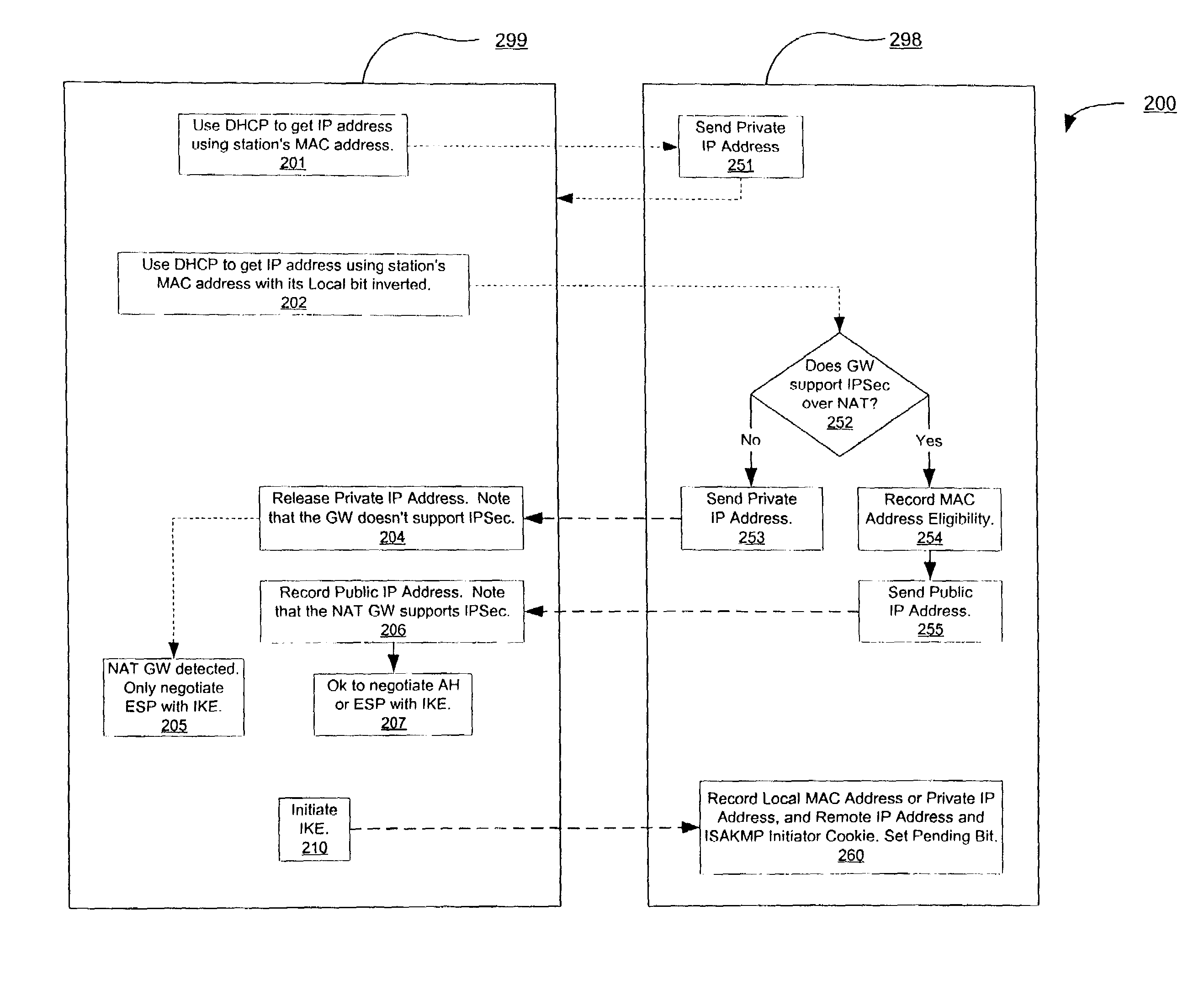
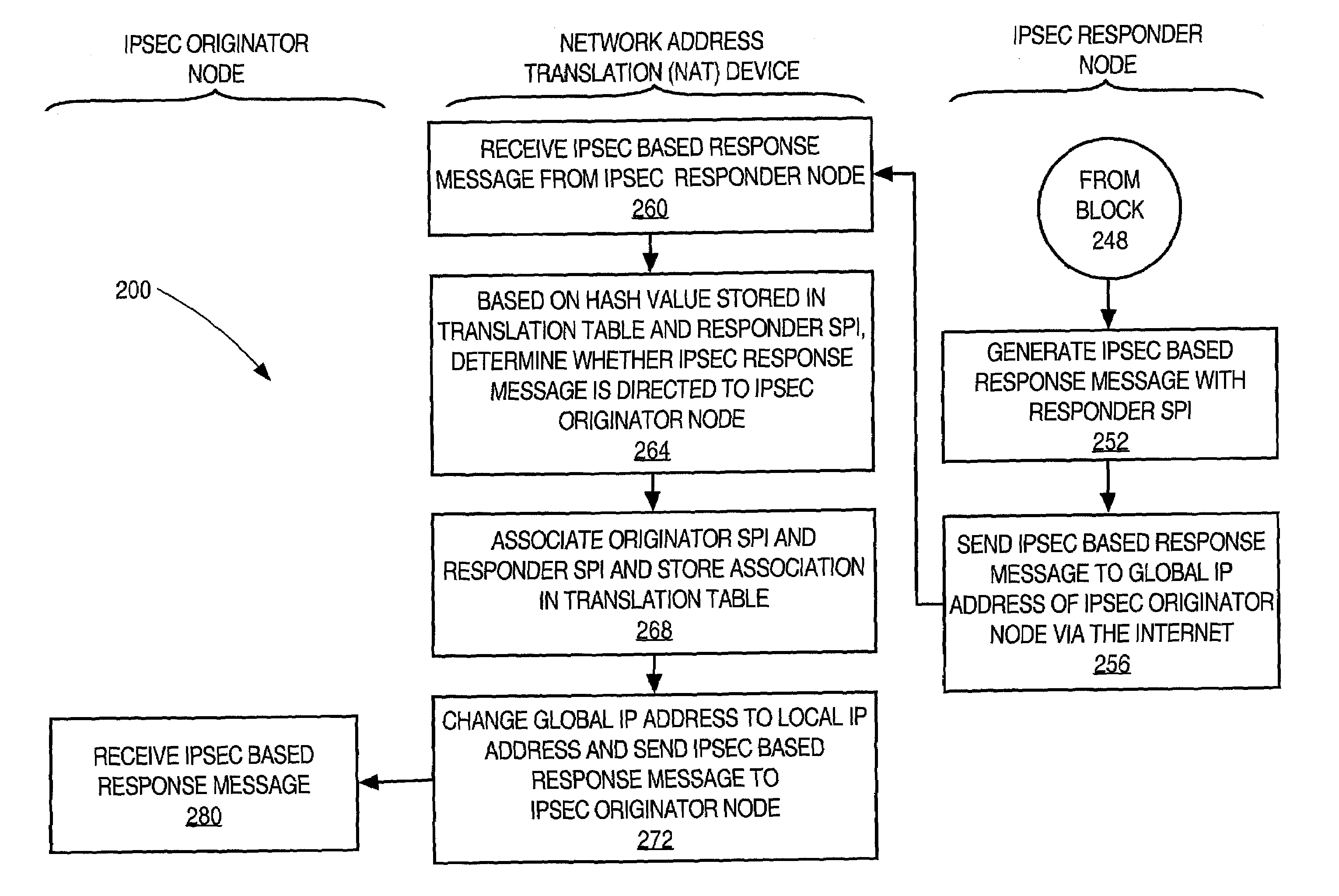
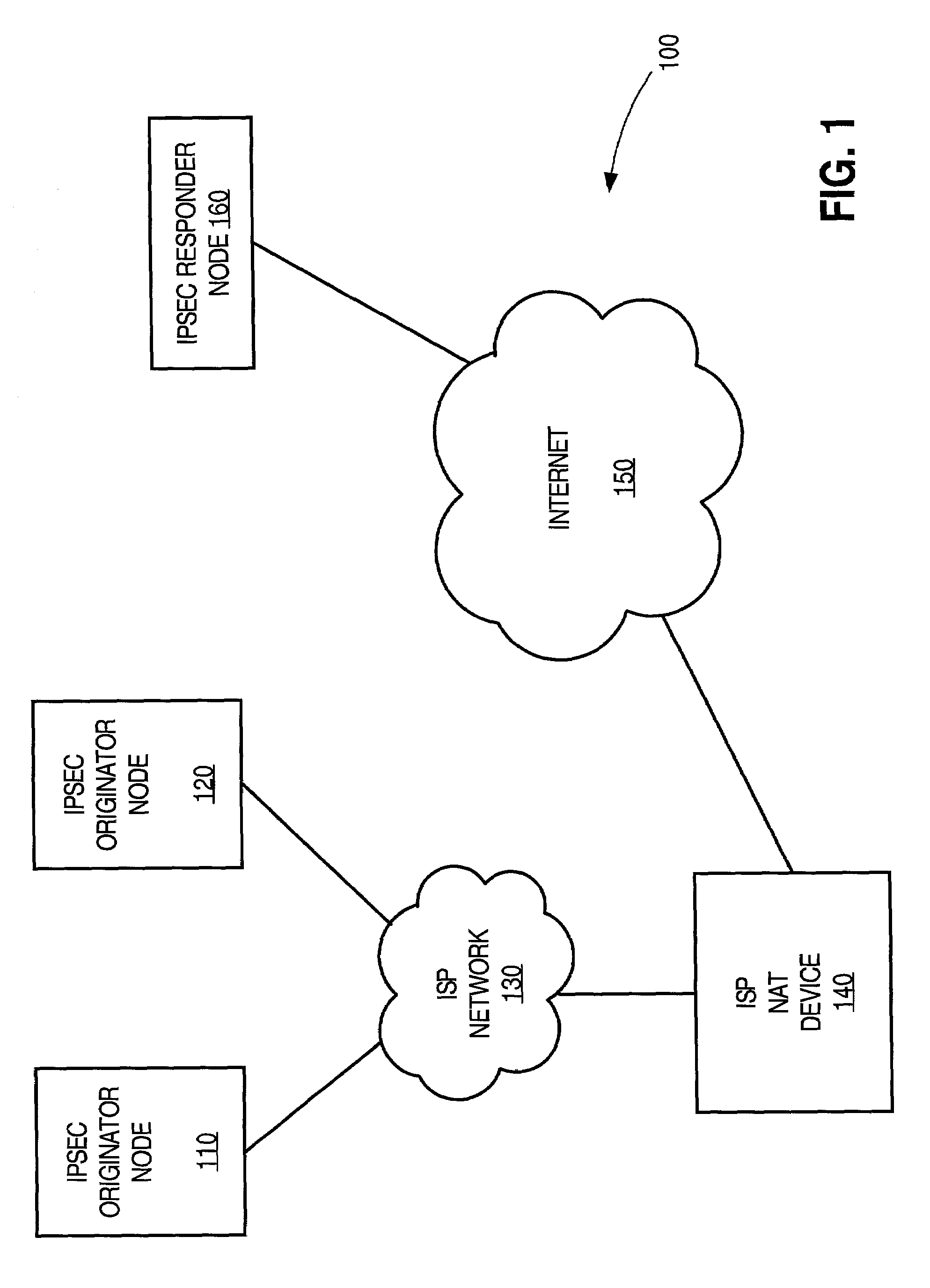
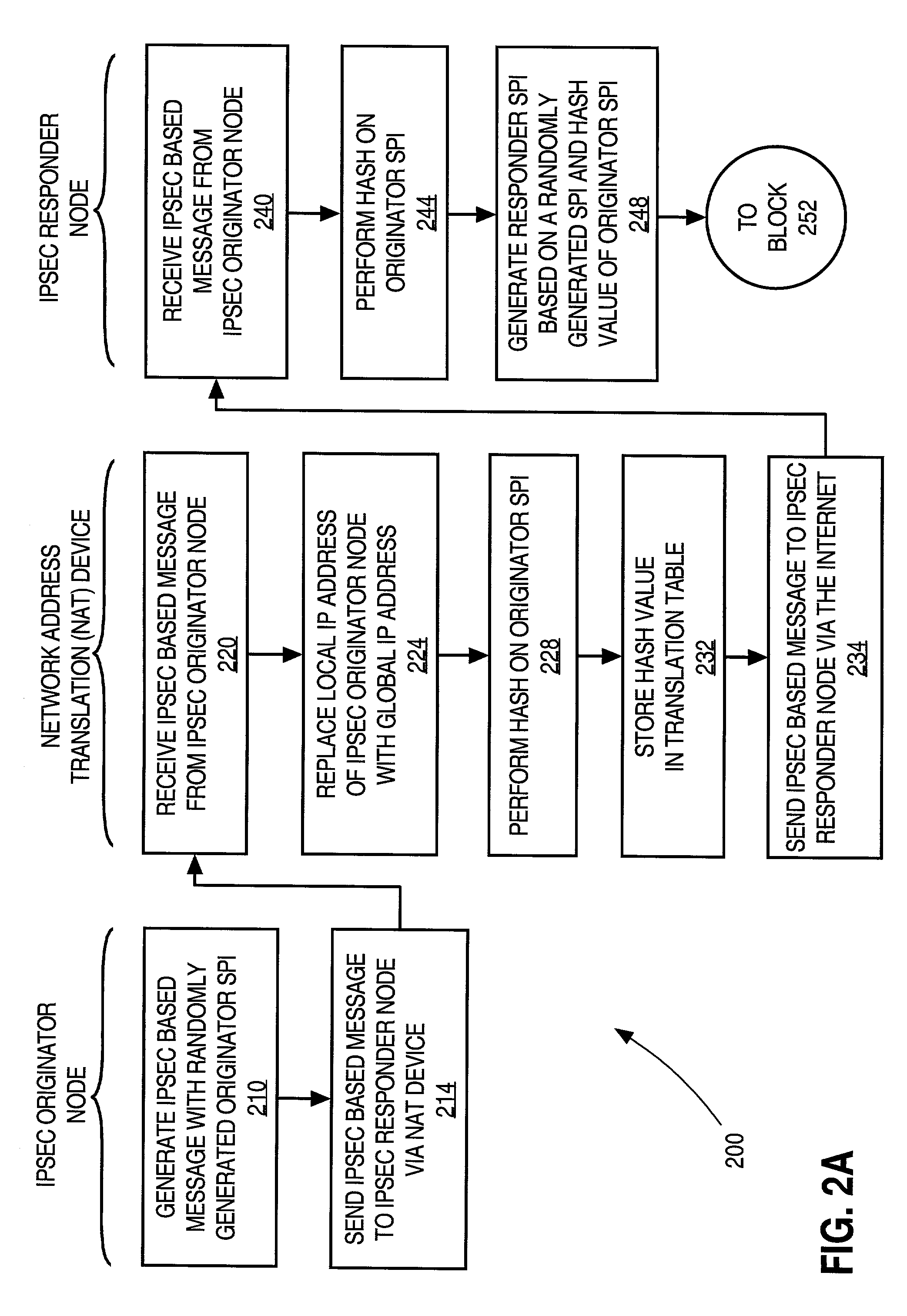
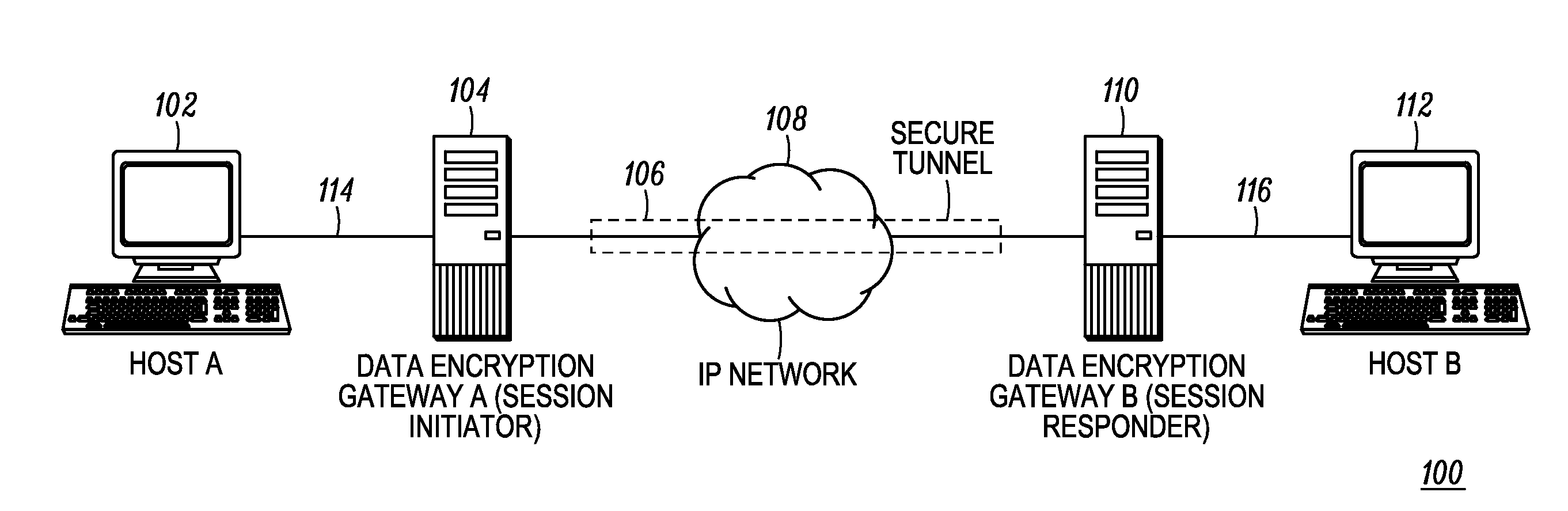
Facilitating IPsec communications through devices that employ address translation in a telecommunications network
InactiveUS7181612B1Easy to set upMultiple digital computer combinationsProgram controlTelecommunications networkTelecommunications link
A method and apparatus for facilitating Internet Security Protocol (IPsec) communications through devices that employ address translation in a telecommunications network is disclosed. A device that employs address translation, such as a router using Network Address Translation (NAT), receives IPsec based messages from originator nodes in a network and generates a result value for each message based on an initial identifier for each message. The messages are sent to a responder node that generates a response message to each originator node with a subsequent identifier that is based on the corresponding initial identifier. The device matches each response messages to the appropriate originator node within the network based on the result values and the subsequent identifiers. For example, the initial identifiers may be originator Security Parameter Indexes (SPI), and the subsequent identifiers may be responder SPI's that are each based on a hash value of the corresponding originator SPI.
Owner:CISCO TECH INC
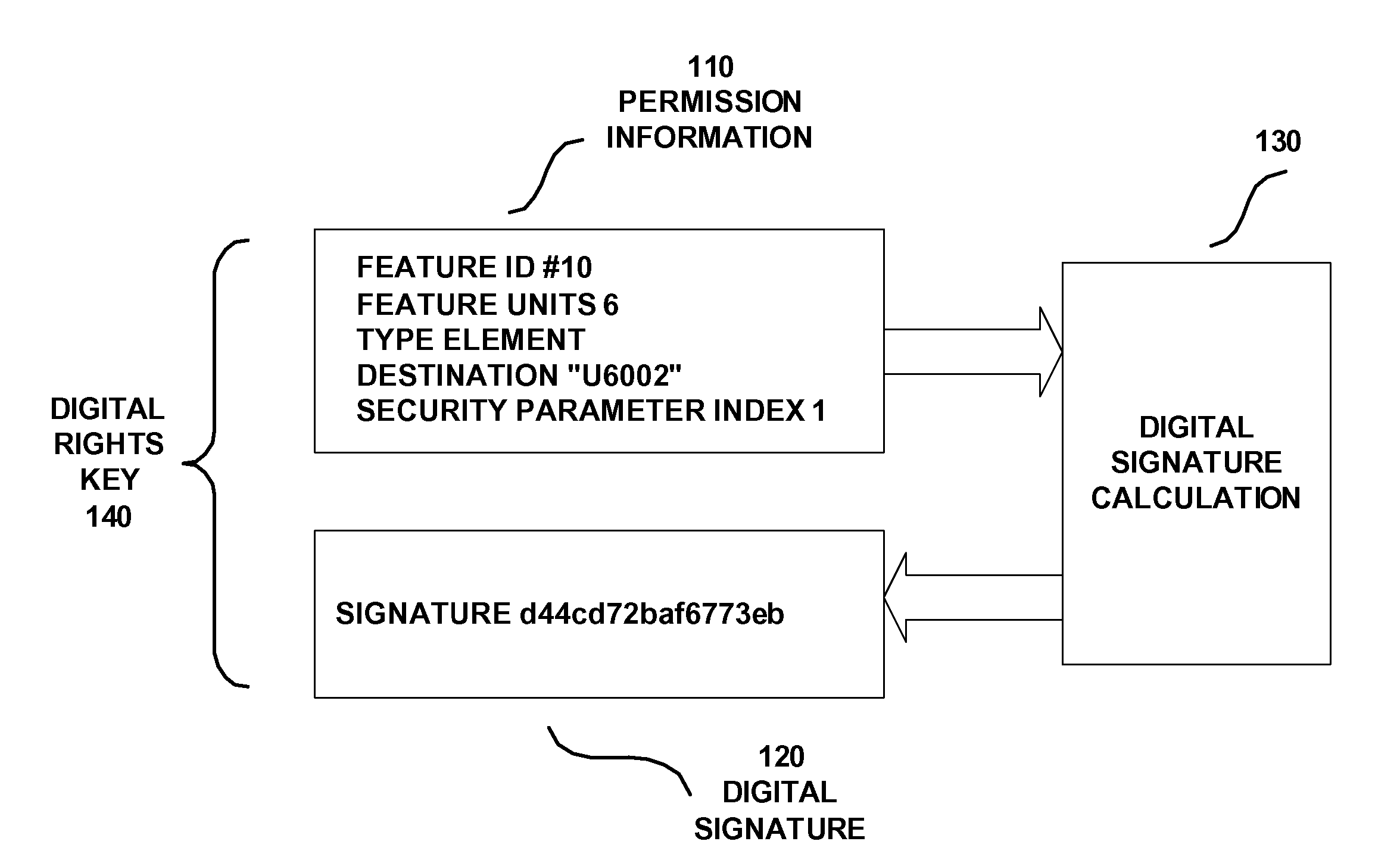
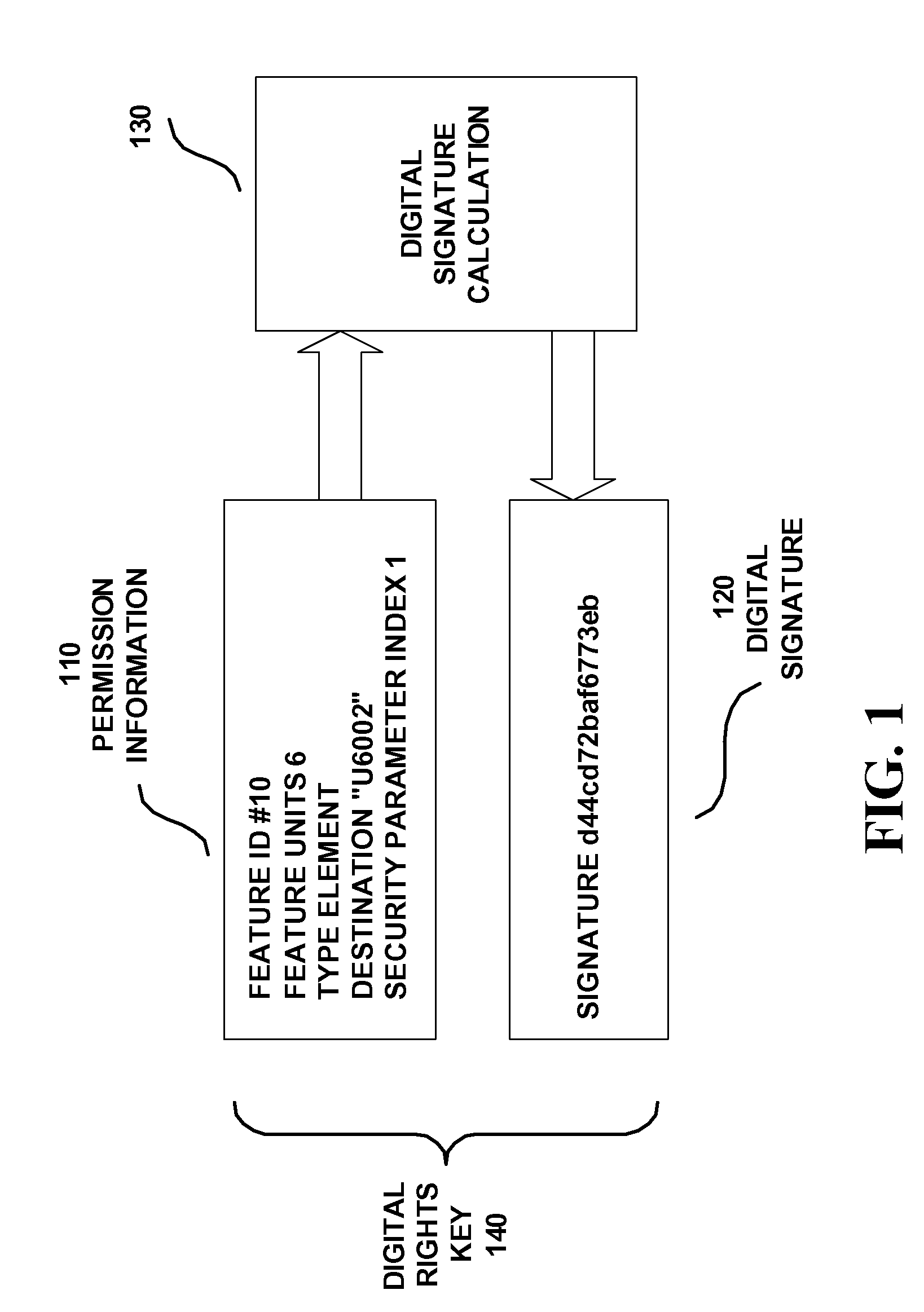
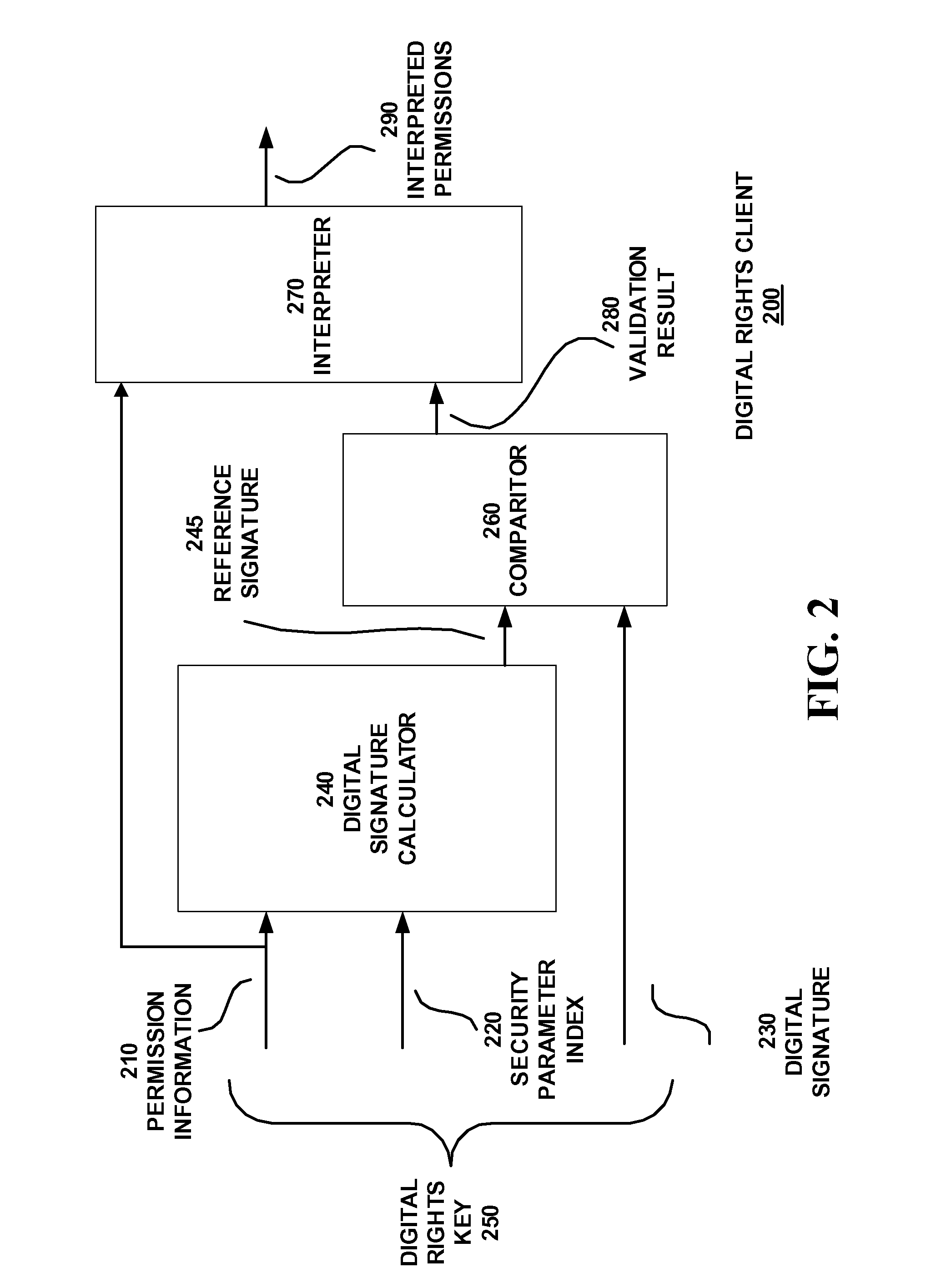
Method and Apparatus in a Digital Rights Client and a Digital Rights Source and associated Digital Rights Key
InactiveUS20050071274A1User identity/authority verificationDigital data protectionDigital signatureDigital rights management system
Permission information (110), including a security parameter index SPI and a digital signature (120), form a digital rights key (140) in a digital rights management system. The security parameter index SPI identifies and algorithm for digital signature calculation (130) and of the digital rights key (140). A digital rights source generates the digital rights key (140) using the security parameter index SPI for digital rights management of licenses to an application. A digital rights client receives the digital rights key (140) and interprets it using an algorithm identified by the security parameter index SPI.
Owner:UTSTARCOM INC
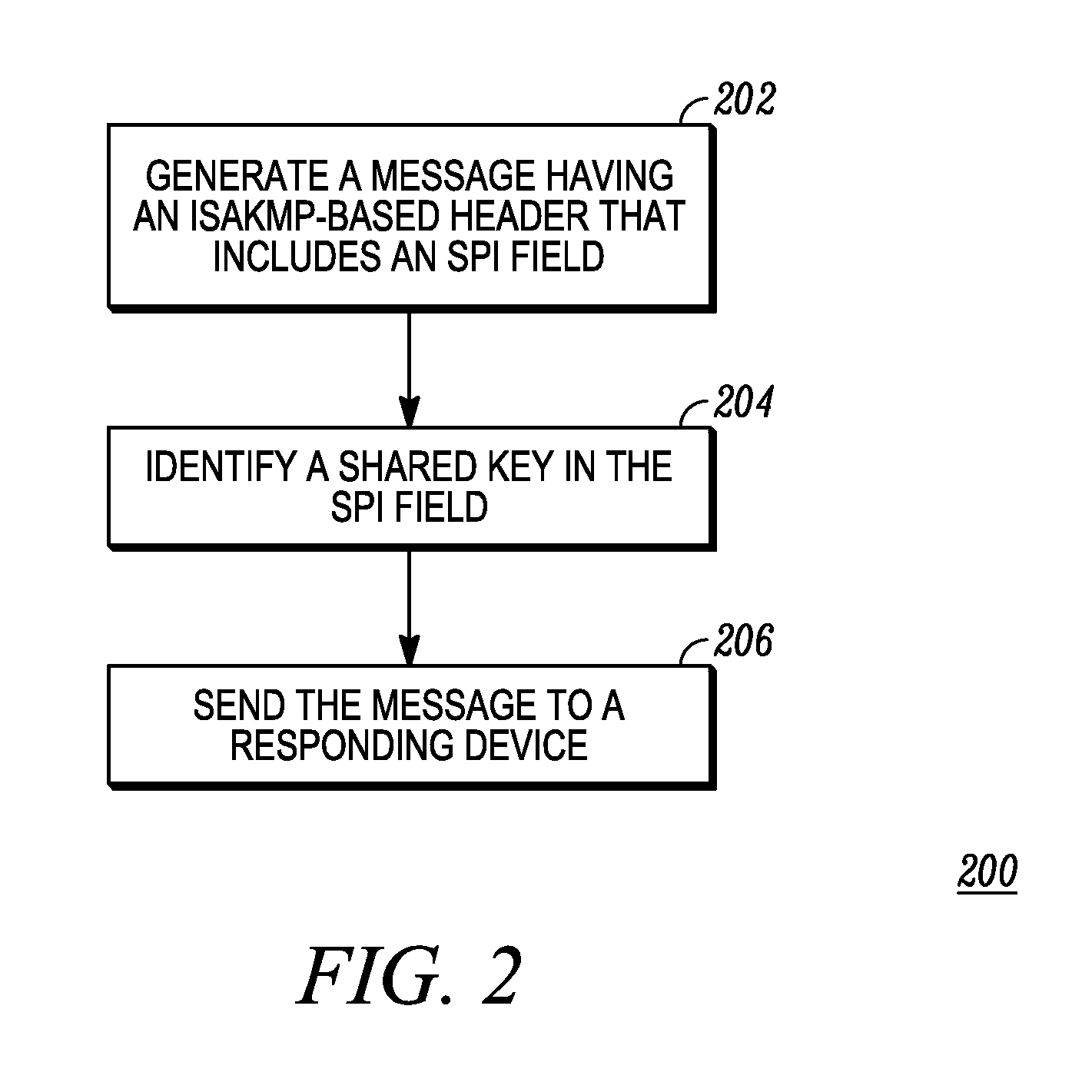
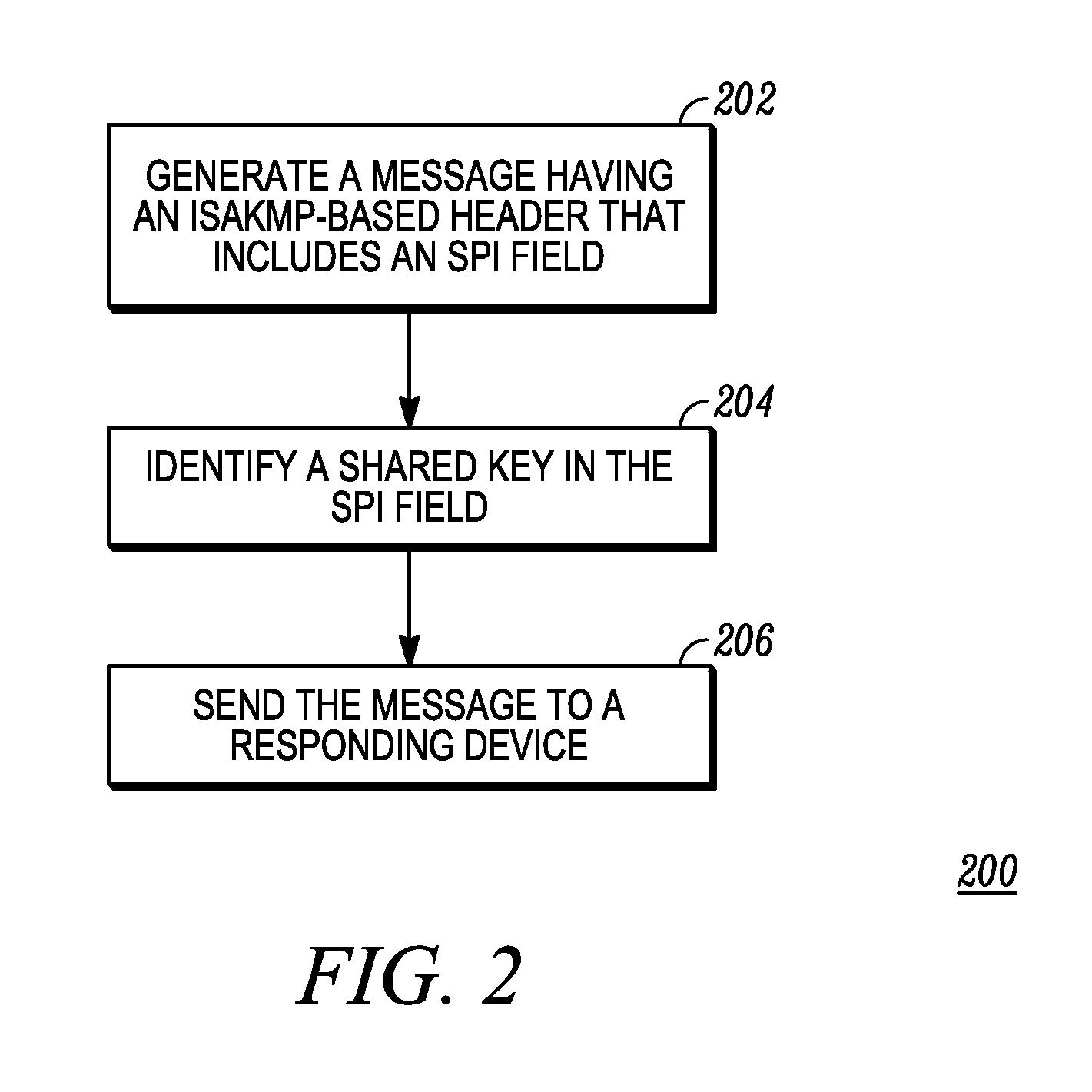
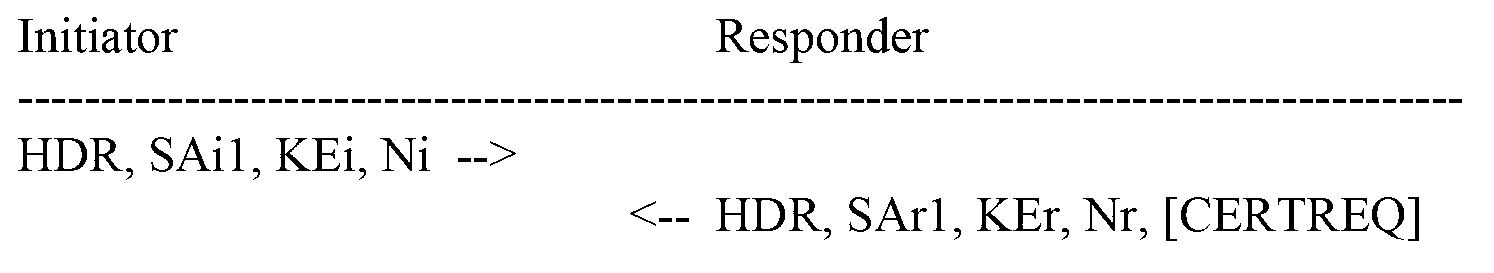
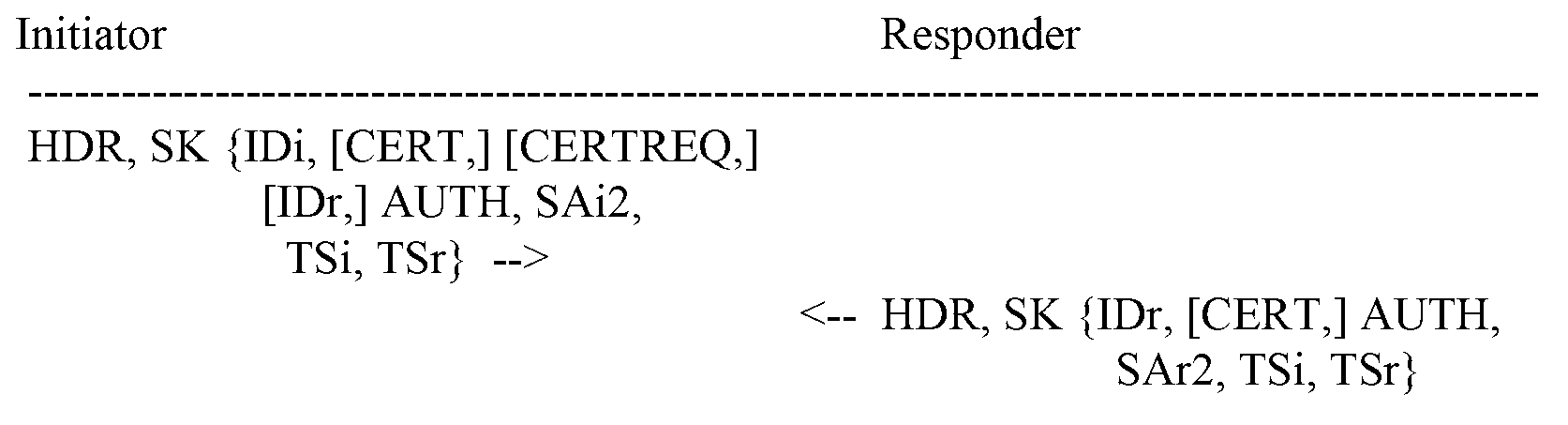
Method for key identification using an internet security association and key management based protocol
ActiveUS20120036363A1User identity/authority verificationMultiple digital computer combinationsSecurity associationProtocol for Carrying Authentication for Network Access
An initiating device: generates a message having an ISAKMP-based header that includes a security parameter index (SPI) field; identifies a key in the SPI field of the ISKMP-based header; and sends the message to a responding device. The responding device: receives the message; extracts the key identifier; and when a shared key is selected using the key identifier, uses the selected shared key to establish, with the initiating device, a session having a secure tunnel.
Owner:MOTOROLA SOLUTIONS INC
Efficient security parameter index selection in virtual private networks
InactiveUS20060005012A1Special data processing applicationsSecuring communicationData packPrivate network
A solution is provided for manual configuration of SPIs without requiring time-consuming checks for overlapping allocations between multiple customers by utilizing a unique decryption process. In this process, the data available in the incoming encrypted packets is considered to uniquely identify the different traffic streams even with overlapping SPIs. The destination address, SPI, and source address parameters present in the outer header of received encrypted packets may be hashed to yield an index, which may be used for searching a security association database to uniquely identify the properties of the security association. Using this process, customer administrators can configure manual SPIs without concern for any overlap or duplication by other customer administrators.
Owner:IPOLICY NETWORKS
Method for key identification using an internet security association and key management based protocol
ActiveUS8448235B2User identity/authority verificationMultiple digital computer combinationsSecurity associationProtocol for Carrying Authentication for Network Access
Owner:MOTOROLA SOLUTIONS INC
Method and system for managing mobility in a mobile communication system using mobile internet protocol
ActiveUS20090052379A1Improve mobilityPerforming secure and efficientServices signallingData switching by path configurationCommunications systemIp address
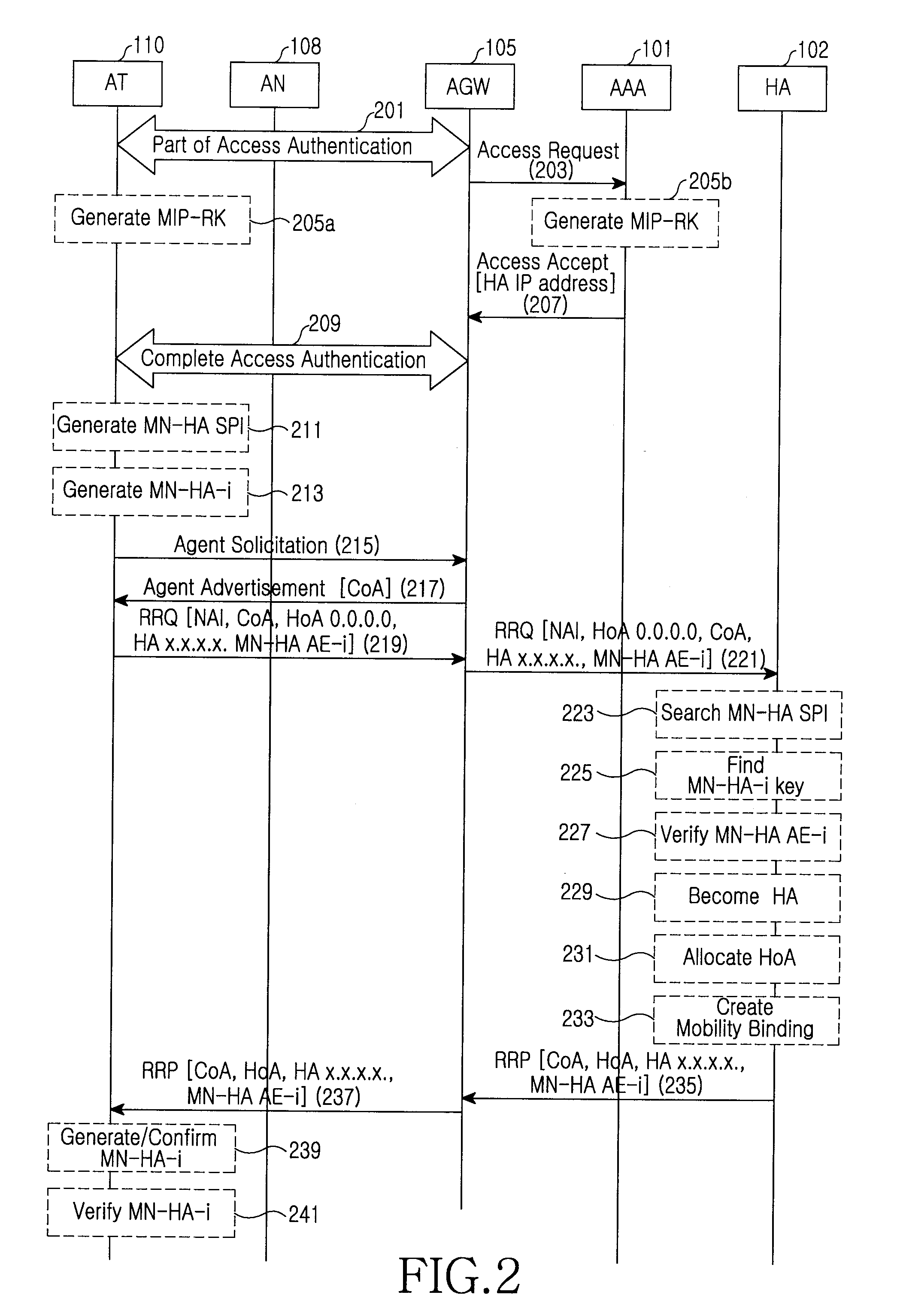
A method is provided for managing mobility of an Access Terminal (AT) in a mobile communication system using a Mobile Internet Protocol (MIP). The method includes generating, by an AT that has entered a new network, a Security Parameter Index (SPI) and a security key for mutual authentication with a Home Agent (HA) of the new network, sending, by the AT, a registration request message including authentication information including the SPI, the authentication information being generated using the security key, upon receipt of the registration request message, searching, by the HA, a database for the SPI included in the authentication information, verifying the authentication information according to the search result, upon successful verification of the authentication information, generating, by the HA, mobility binding information of the AT, and sending, by the HA, a registration response message including the HA's IP address.
Owner:SAMSUNG ELECTRONICS CO LTD
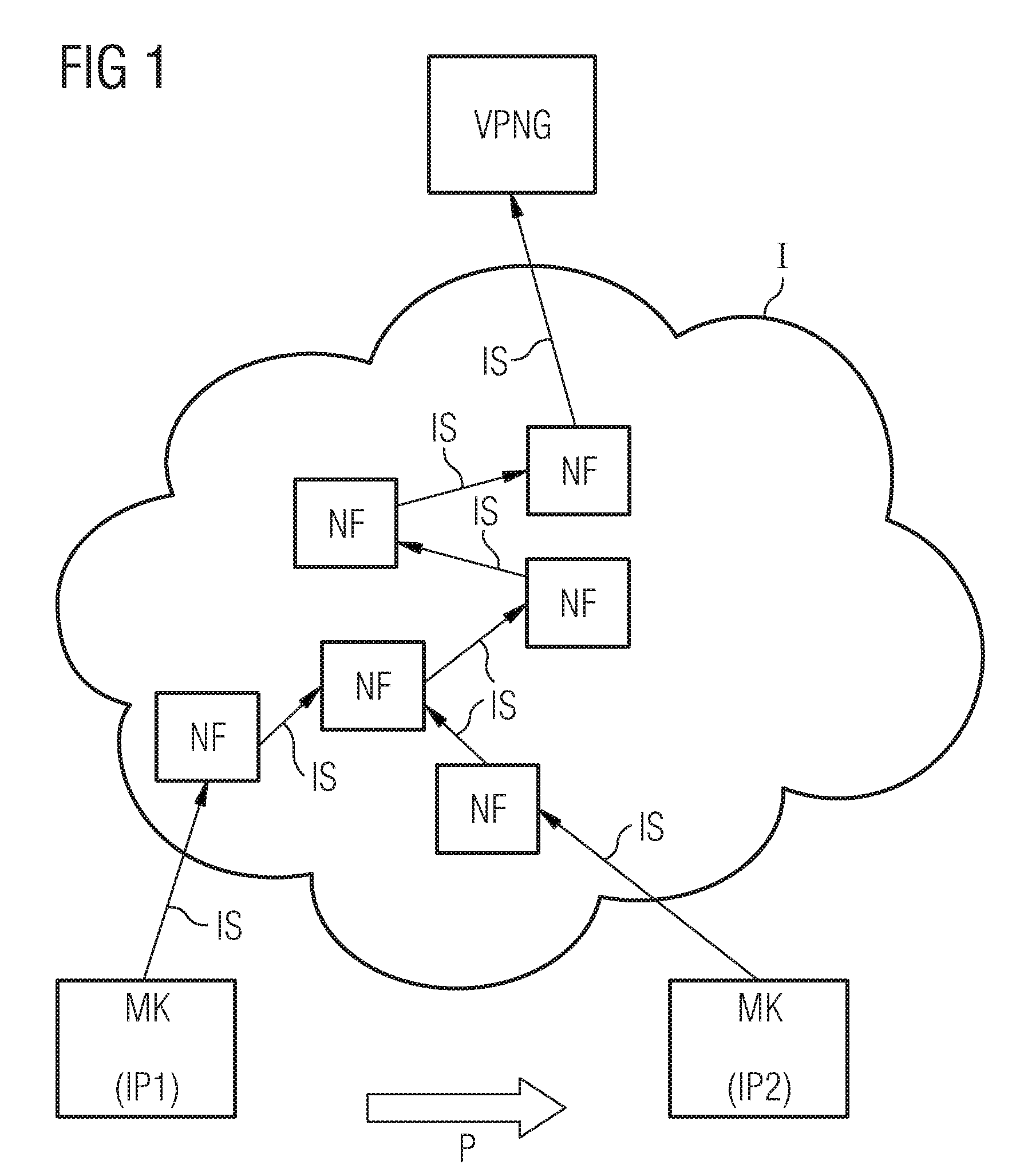
Method for achieving message-crossing network address translation device
The invention provides a method for achieving message-crossing network address translation device. The method comprises (S1) enabling an intranet to send a message to the network address translation device, and enabling the message to carry an intranet internet protocol (IP) address, an intranet safety parameter index and an extranet safety parameter index; (S2) enabling the network address translation device to receive the message, and building a mapping table according to the intranet IP address, the intranet safety parameter index and the extranet safety parameter index which the message carries and a public network IP address; and (S3) enabling the intranet IP address of the message to be converted into the public network IP address according to the mapping table, and sending the message to an extranet device through the public network IP address; and enabling the extranet safety parameter index to be the safety parameter index of the extranet device. By building a network address translation (NAT) device address mapping, when the message in an internet protocol security (IPSec) tunnel undergoes NAT crossing, port address conversion can be performed without adding a user datagram protocol (UDP).
Owner:OPZOON TECH
Method and device of obtaining IPSec SA (Internet Protocol Security Association)
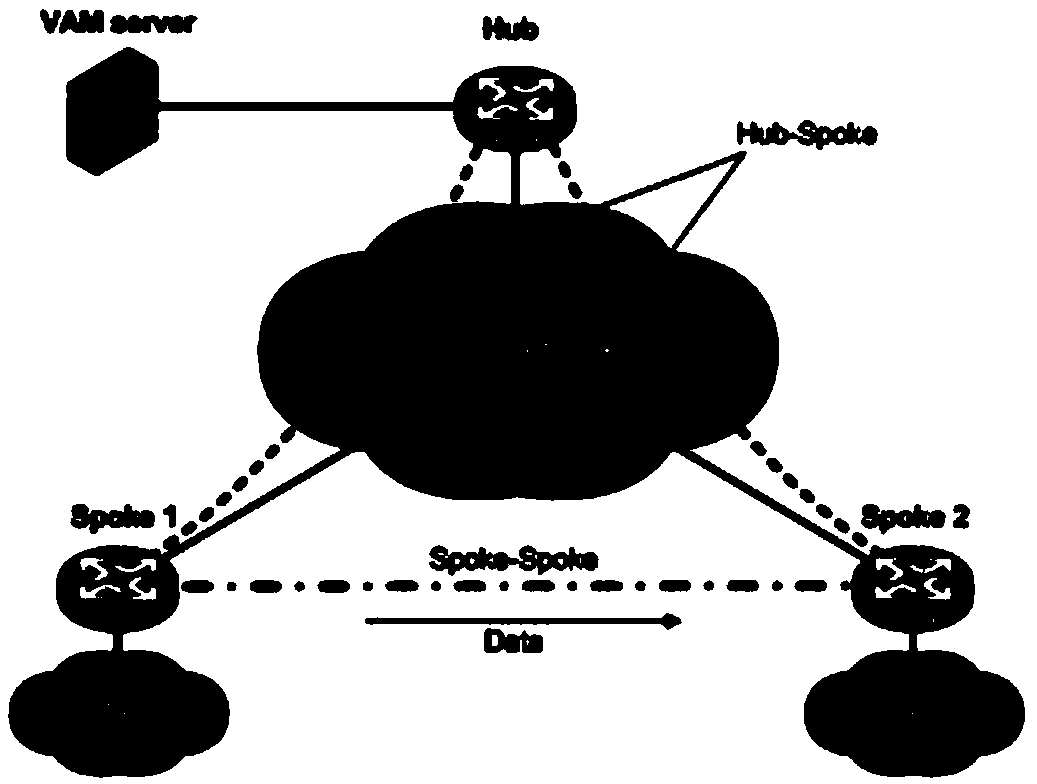
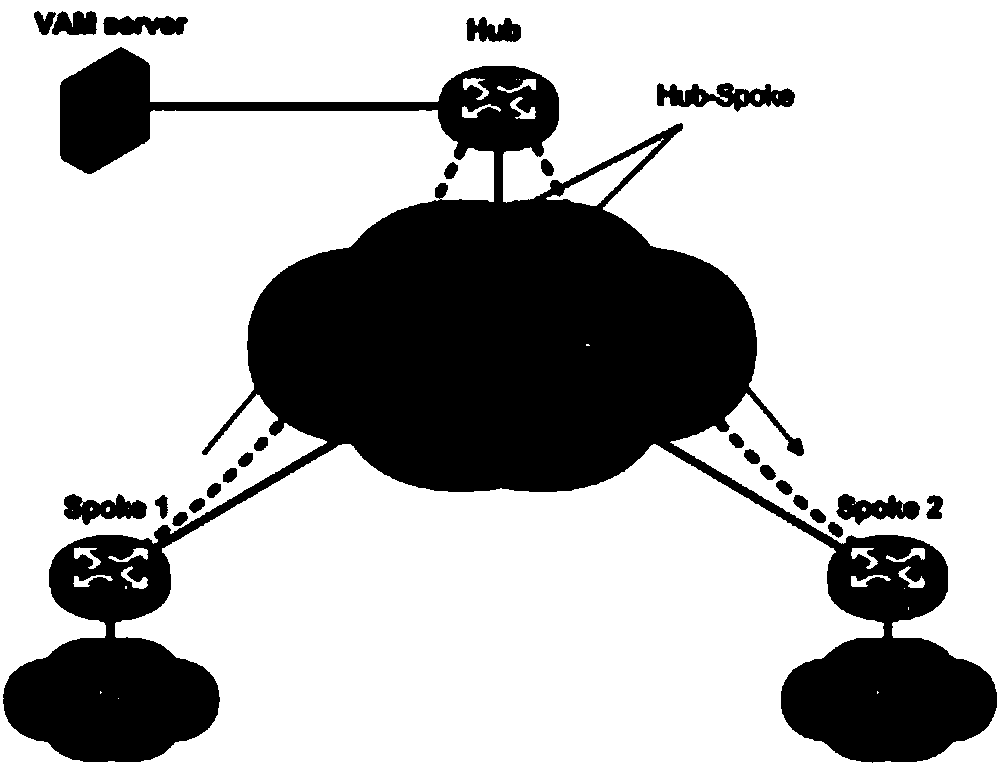
The invention provides a method and a device of obtaining IPSec SA (Internet Protocol Security Association). The method comprises the following steps that: a VAM (Virtual Private Network Address Management) client registers with a VAM server; the VAM server issues the corresponding IPSec SA to the VAM client according to the registration information of the VAM client; the VAM client transmits a keepalive message to the VAM server; the keepalive message comprises an SPI (Security Parameter Index) of the local newest IPSec SA of the VAM client; the VAM server judges whether the SPI of the newest IPSec SA of the VAM client is equal to the SPI of the local newest IPSec SA; if the SPI of the newest IPSec SA of the VAM client is not equal to the SPI of the local newest IPSec SA, the local newest IPSec SA is issued to the VAM client. Through the method and the device, the centralized management and issuing of the IPSec SA in an ADVPN (Auto Discovery Virtual Private Network) network can be implemented, and meanwhile, the keepalive message is initiated by the VAM client, so that when the local IPSec SA of the VAM client is updated by the VAM server, the newest IPSec SA, which is issued by the VAM server, can normally pass through an NAT (Network Address Translator).
Owner:NEW H3C TECH CO LTD
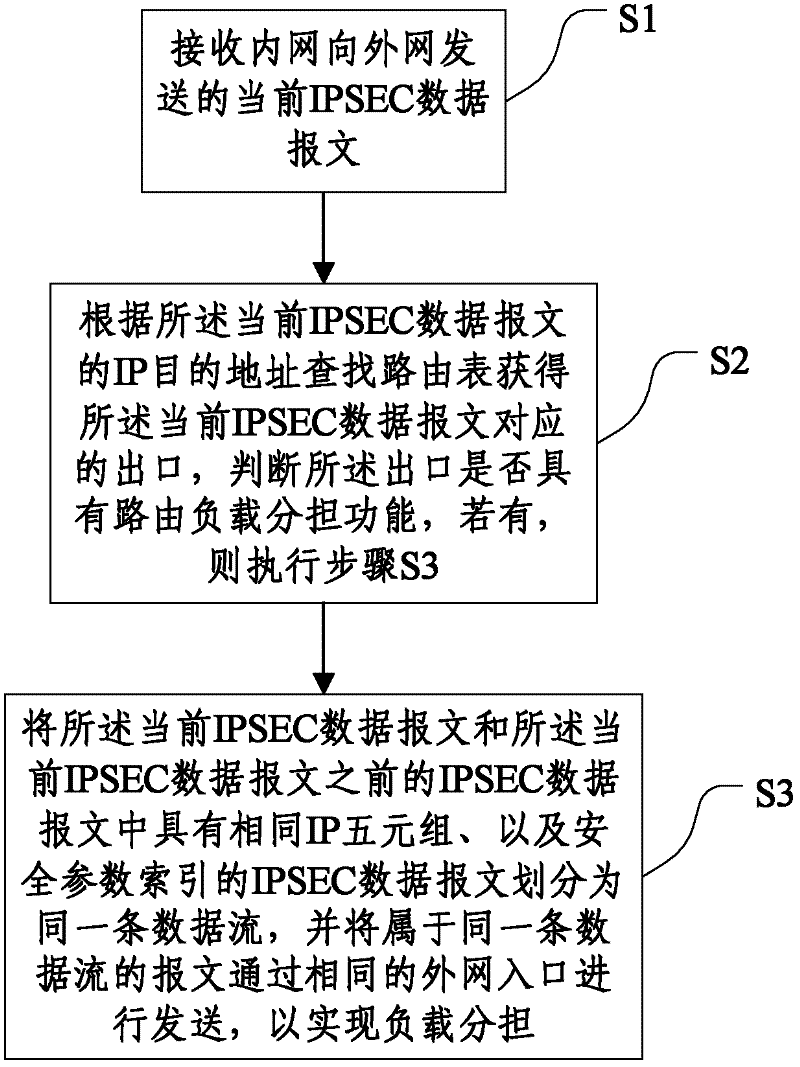
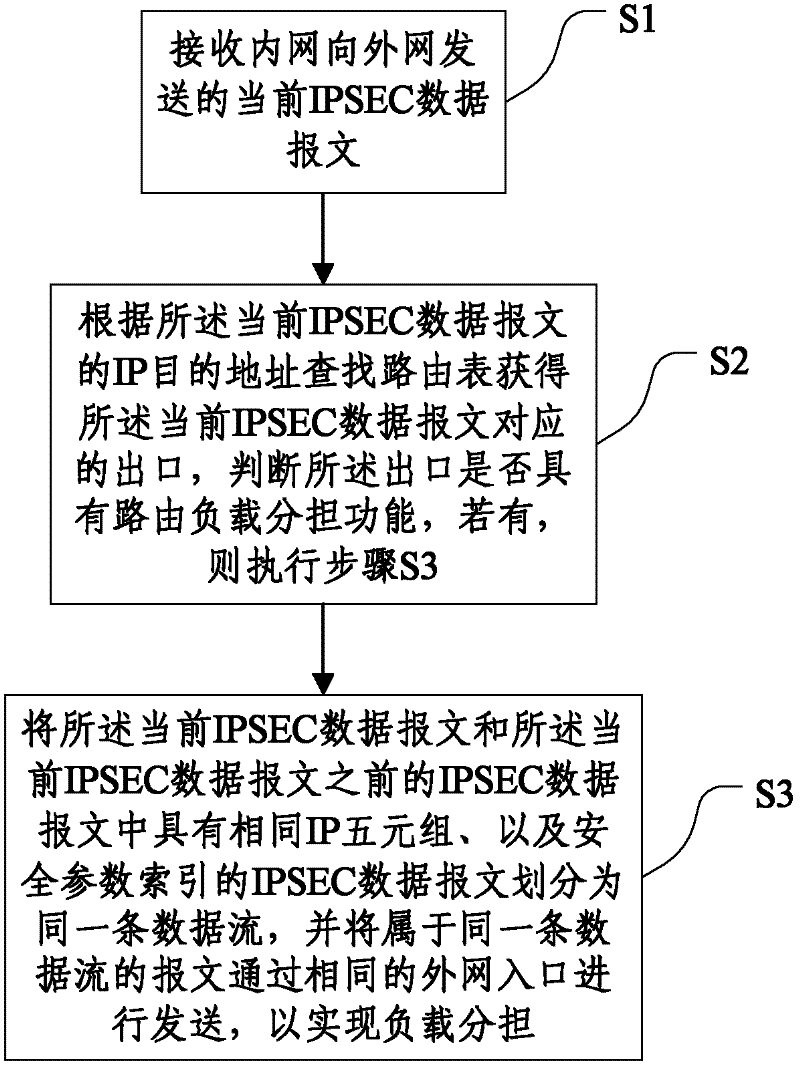
Load sharing method and system for IPSEC (Internet Protocol Security) data message
The invention discloses a load sharing method and system for an IPSEC (Internet Protocol Security) data message, belonging to the technical field of network communication. The load sharing method comprises the following steps of: S1, receiving a current IPSEC data message sent by an intranet to an extranet; S2, searching a route list to obtain an exit corresponding to the current IPSEC data message, and judging whether the outlet has a load sharing function or not; and if the outlet has the load sharing function, executing step S3; and S3, classifying the IPSEC data message with same IP (Internet Protocol) five-element group and safe parameter index as a same data stream, and sending the message of the same data stream through the same extranet entrance, so as to share a load. According to the load sharing method and system provided by the invention, the IPSEC data message is branched by using the IP five-element group and the safe parameter index, and data are sent according to a branching result, so that the precision of branching the IPSEC data message and the properties of the entire machine can be improved.
Owner:OPZOON TECH
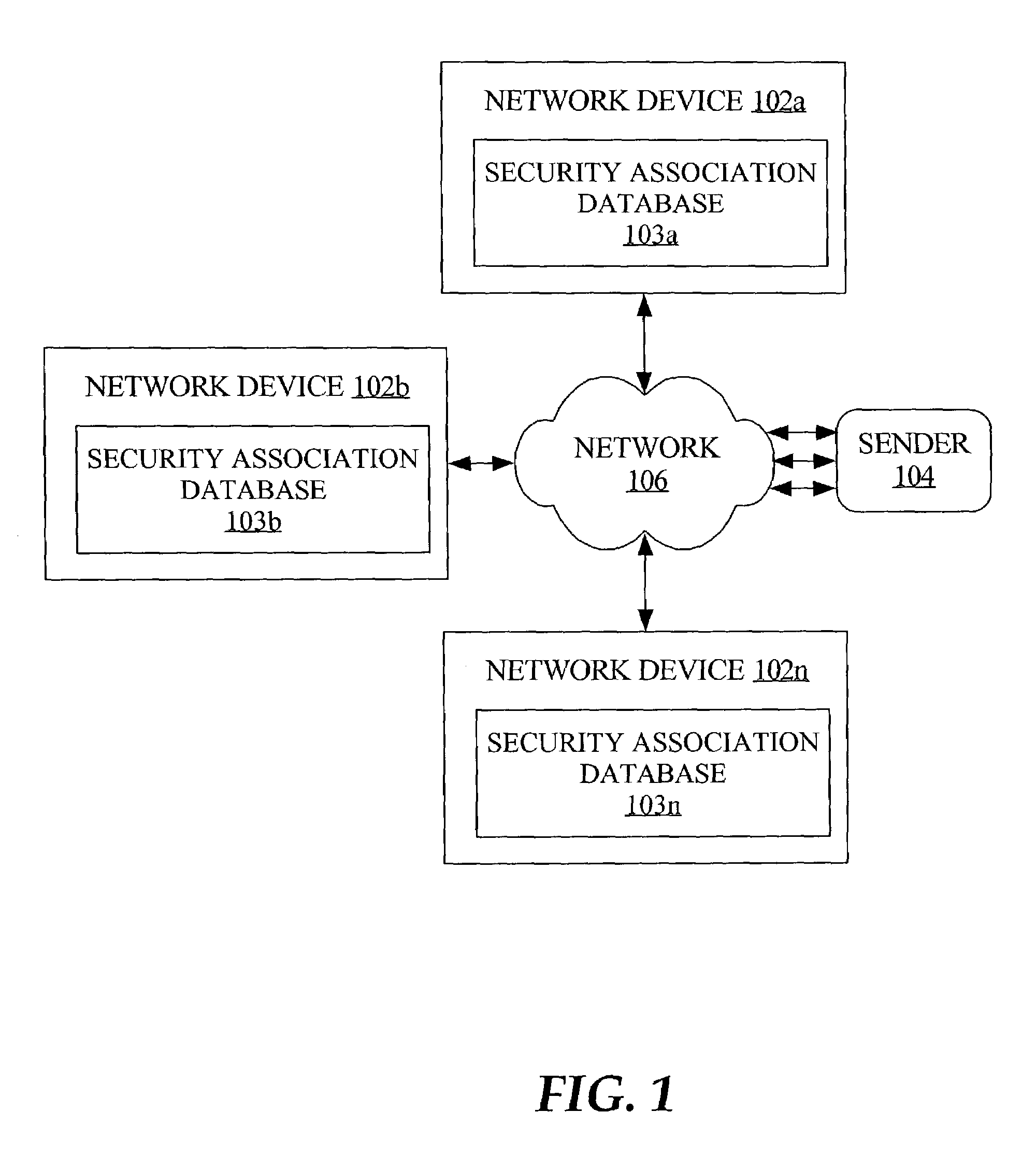
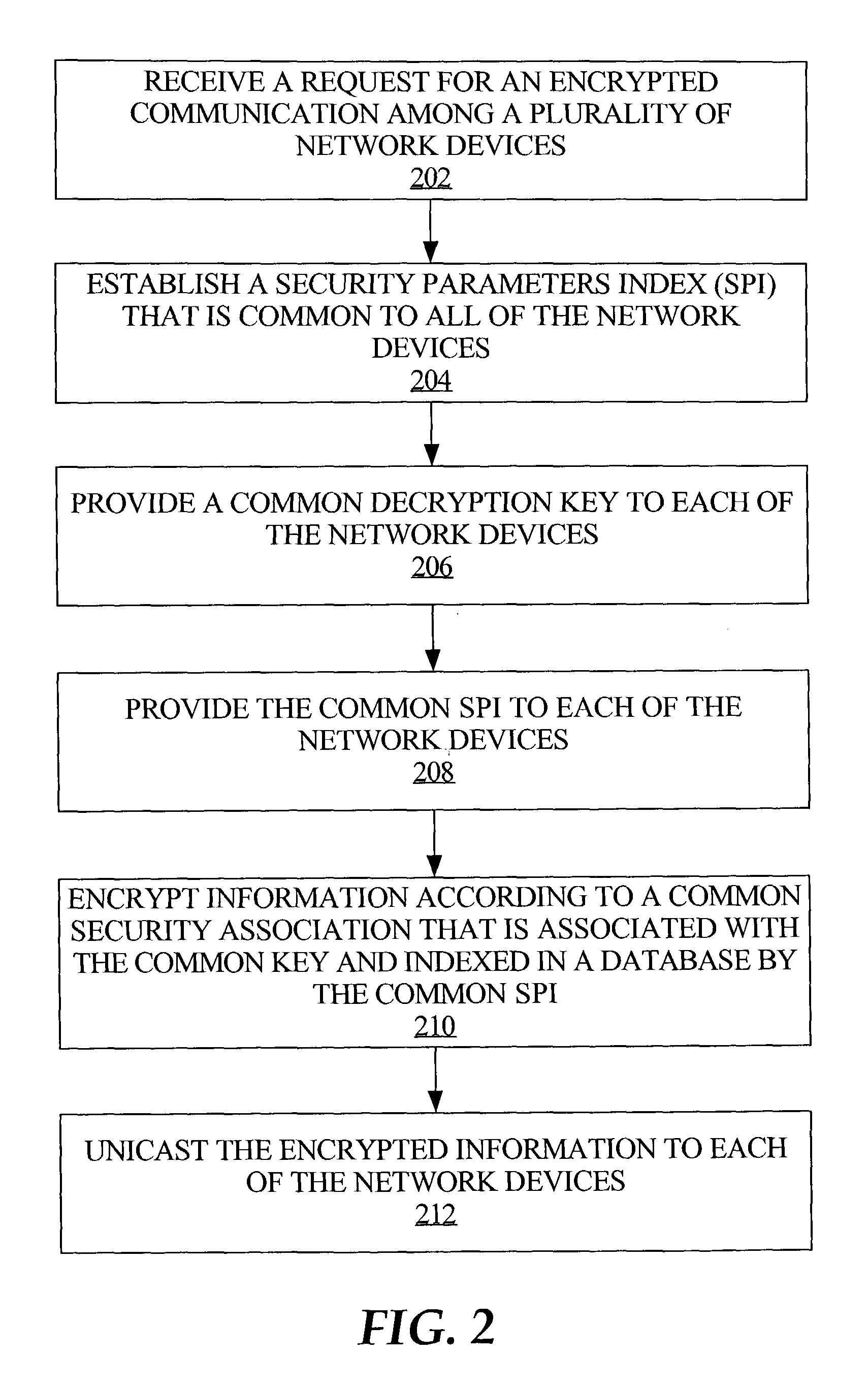
Method and apparatus for encrypted unicast group communication
ActiveUS7577837B1Precise positioningMultiple digital computer combinationsProgram controlComputer networkSecurity association
A process for managing encrypted group communication according to a single security association (SA) for network traffic from a sender includes receiving a request for an encrypted communication among a plurality of network devices. A common decryption key and a common security parameters index (SPI) are provided to each of the network devices participating in the communication. The common security parameters index facilitates locating, in respective databases associated with each of the network devices, security association information that is associated with the common security association. Information is encrypted based on the common security association, and unicasted to each of the network devices. In an embodiment, the common security parameters index provided to each network device is established by the sender. For example, the SPI is established by a conference server and sent to each device participating in a voice conference.
Owner:CISCO TECH INC
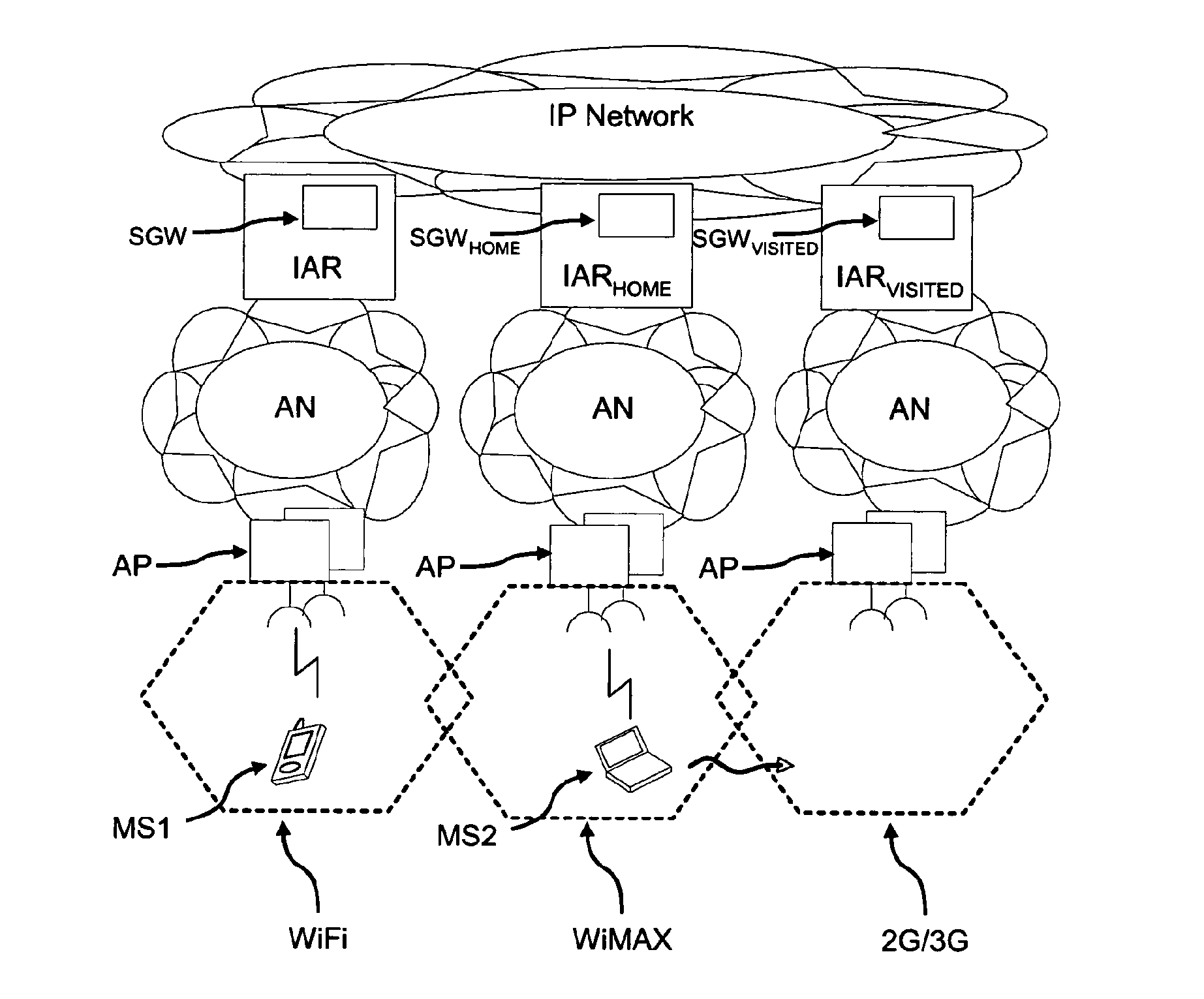
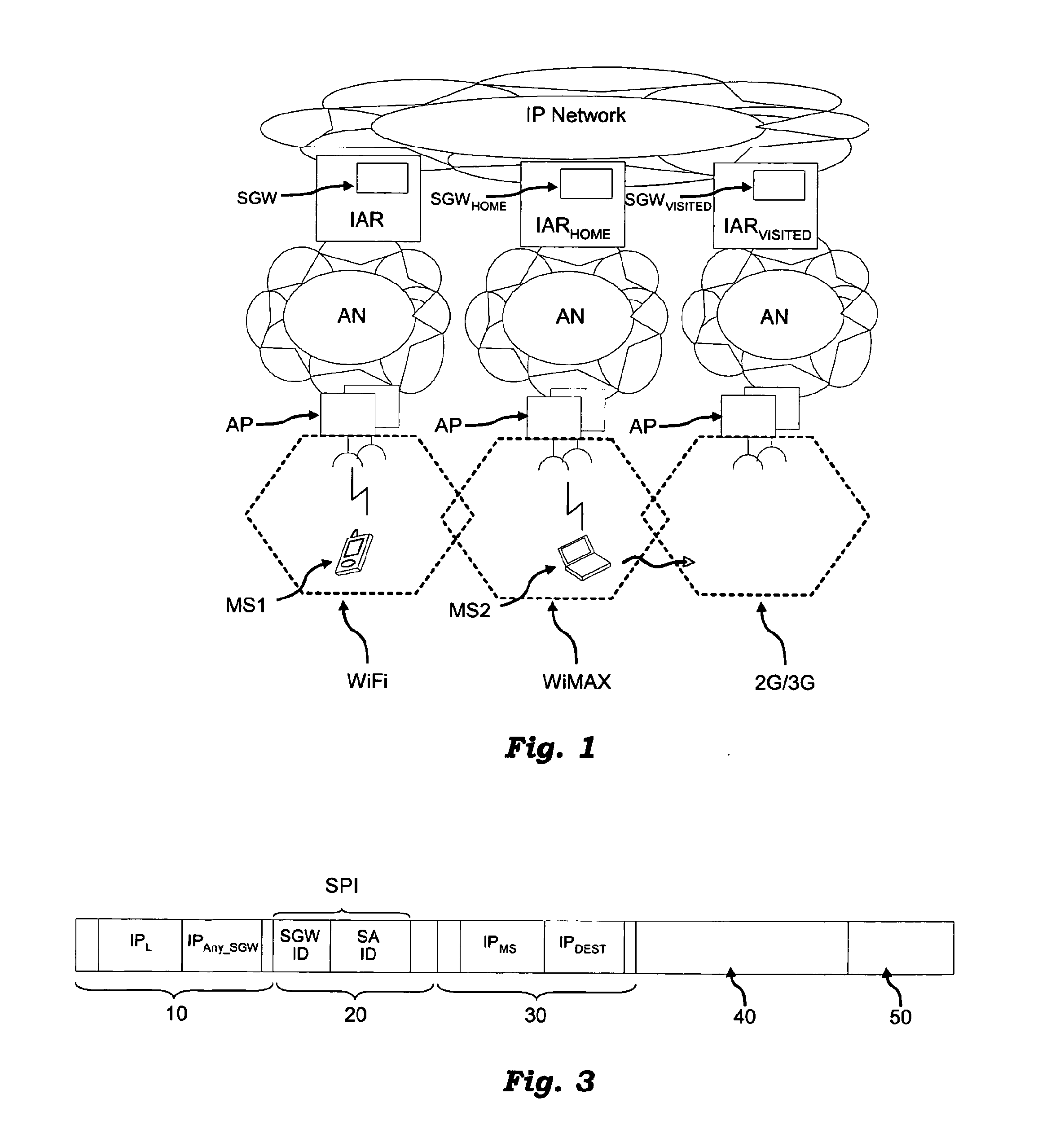
Method for Network Access, Related Network and Computer Program Product Therefor
ActiveUS20110047612A1Computer security arrangementsMultiple digital computer combinationsComputer networkSecurity association
A method of providing access of a mobile terminal to an IP network includes establishing a security association between the mobile terminal and a first security gateway of a first router in said plurality of routers. The mobile terminal is provided access to the IP network via the first router, and the data exchanged between the mobile terminal and the first router is encapsulated by using the security association. The security association is made available to at least one second router having a second security gateway. The mobile terminal is provided access to the IP network via said the second router, and data exchanged between the mobile terminal and the second router is encapsulated by using the same security association. Establishing the security association includes assigning a Security Parameter Index that identifies univocally the first security gateway and the security association. Making the security association available to the second router includes making available to the second router the Security Parameter Index. The second router may thus have access to the security association either by requesting it from the first router or by identifying it in a set of security associations sent from the first router to a set of routers candidate to become the second router as result of the mobility of the mobile terminal.
Owner:TELECOM ITALIA SPA
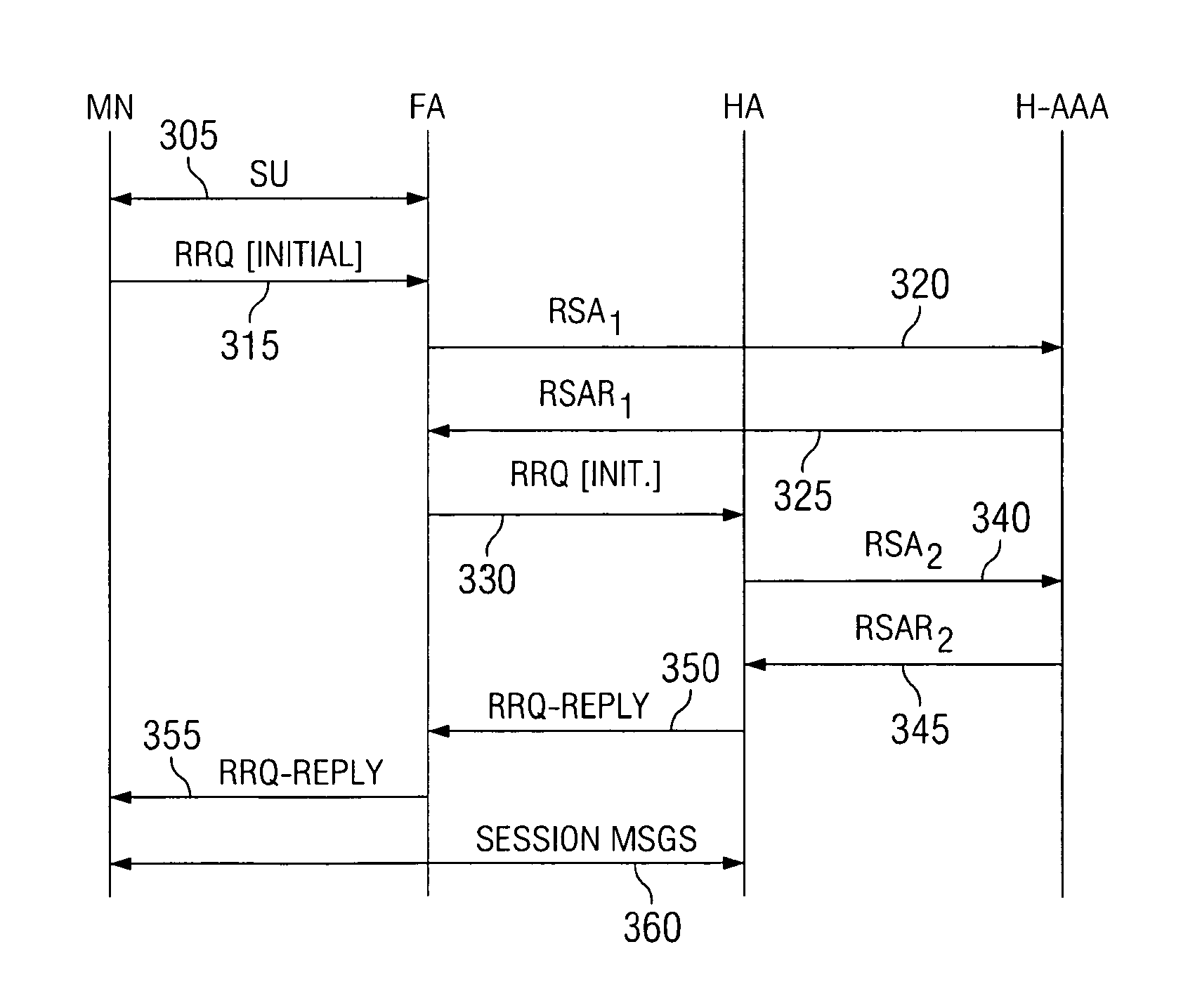
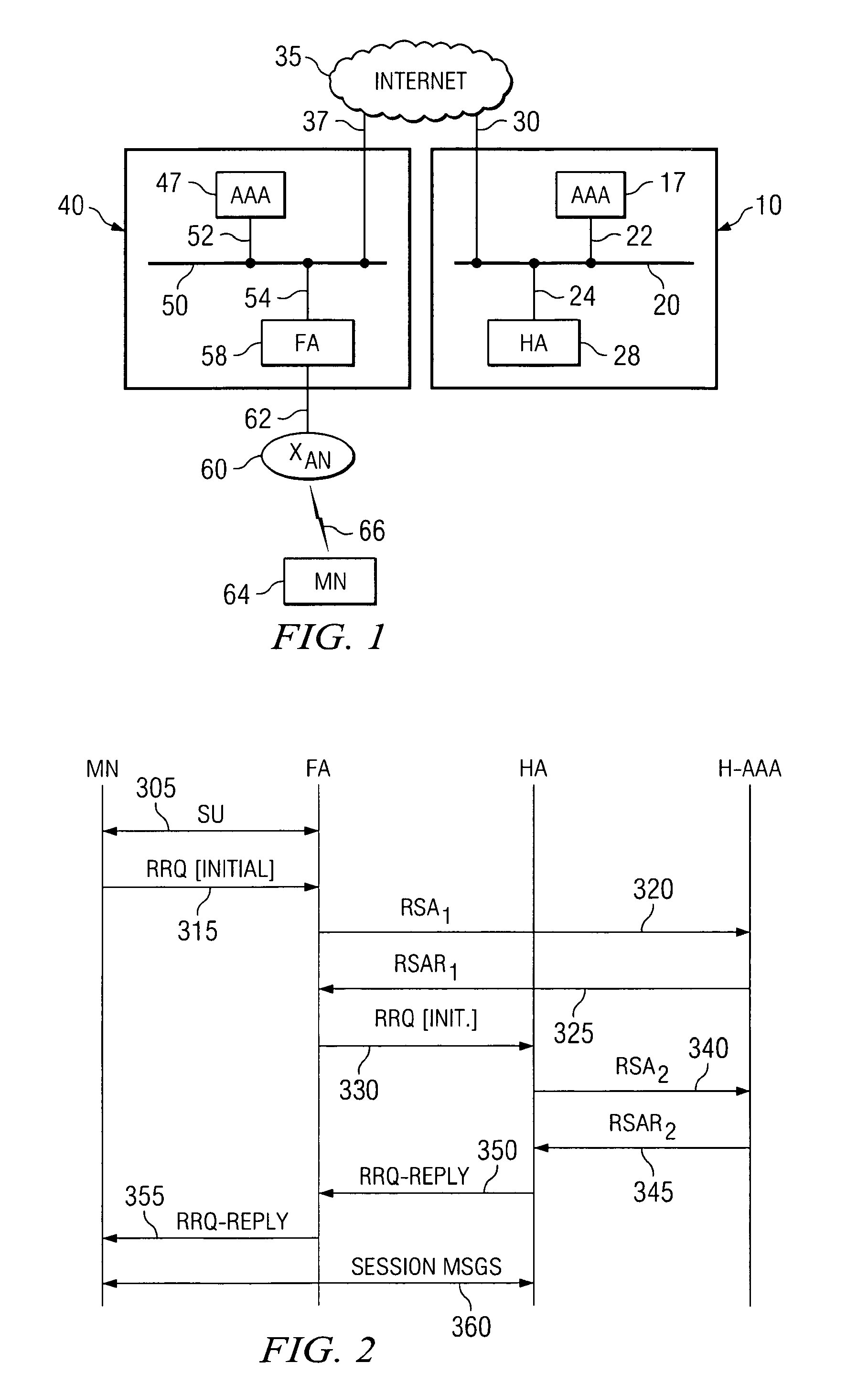
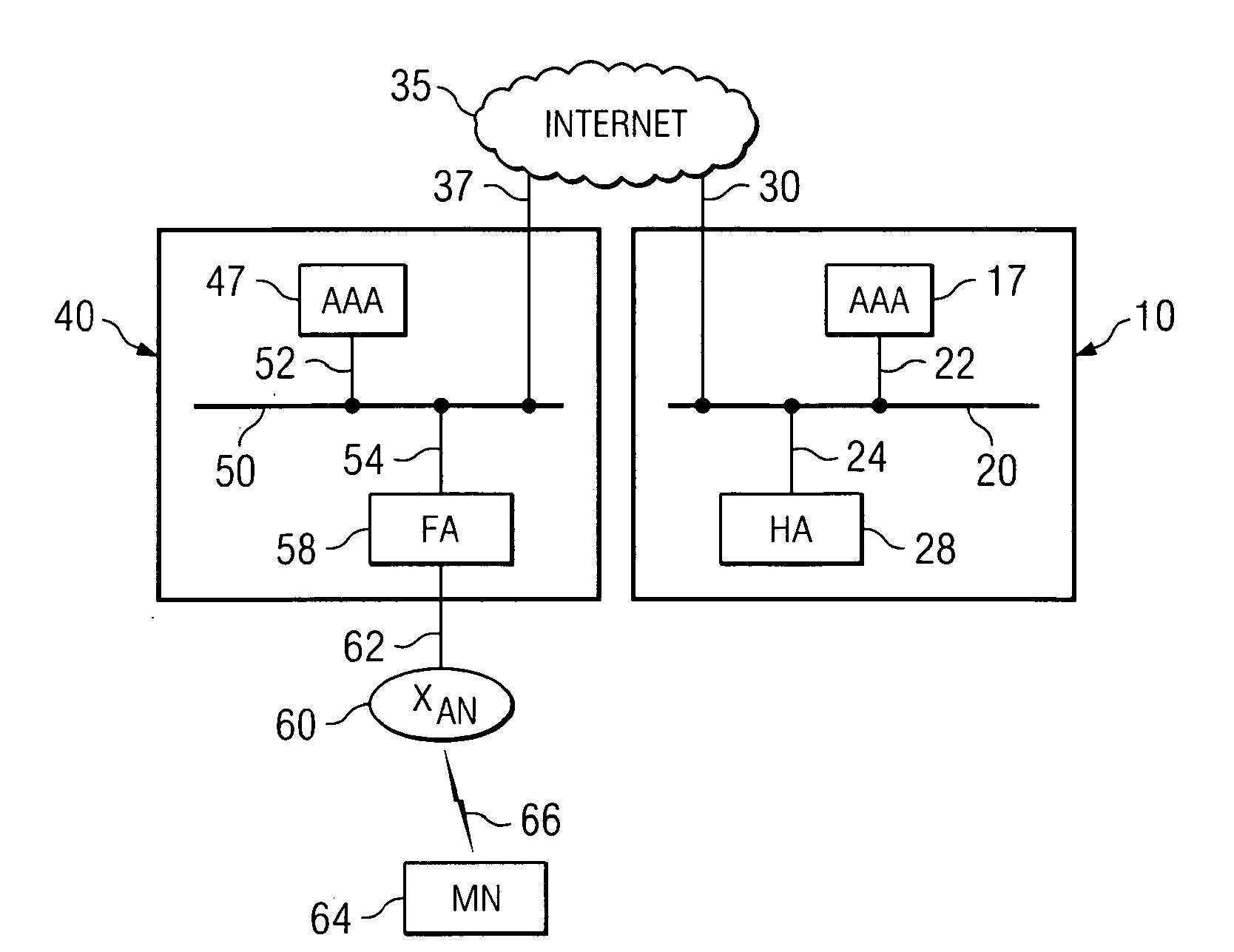
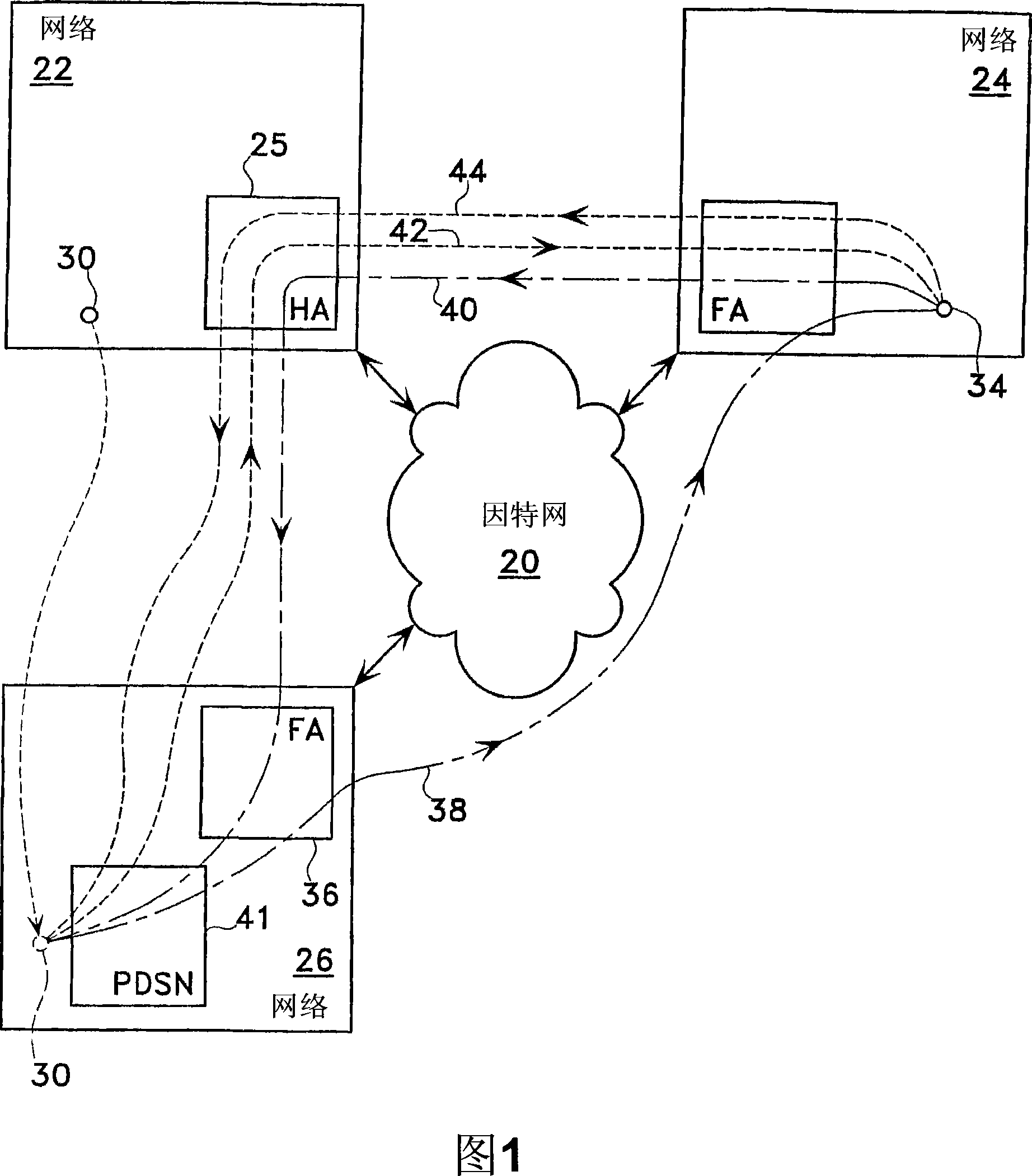
Dynamic foreign agent-home agent security association allocation for IP mobility systems
ActiveUS8411858B2Network traffic/resource managementAssess restrictionSecurity associationForeign agent
The present invention utilizes the AAA infrastructure to dynamically allocate the various parameters needed to establish the security association between the Foreign Agent and the Home Agent. The present invention uses the AAA server as a central entity to dynamically generate and distribute the chosen security association parameters needed to support the Foreign Agent and Home Agent security association based on a request from the Foreign Agent. The AAA server can also dynamically assigns a unique SPI value to the Foreign Agent and Home Agent pairs. The various parameters that can be allocated in the present invention include a FA-HA shared secret key or a public / private key pair, an authentication algorithm and mode, a FA-HA secret key lifetime, and security parameter index or security index values. The present invention also can assist in making sure that the Foreign Agent and the Home Agent stay synchronized with respect to their security association.
Owner:APPLE INC
System for negotiating security association on application layer
ActiveUS8028161B2Reduce data rateCost efficientDigital data processing detailsUser identity/authority verificationSecurity associationProtocol for Carrying Authentication for Network Access
A first computer sends a list of possible security associations to a second computer in a message according to a protocol of an application layer, a security parameter index being contained in the message for each security association. The second computer selects a security association and transmits it or an indication of the security association selected by it to the first computer.
Owner:SIEMENS AG
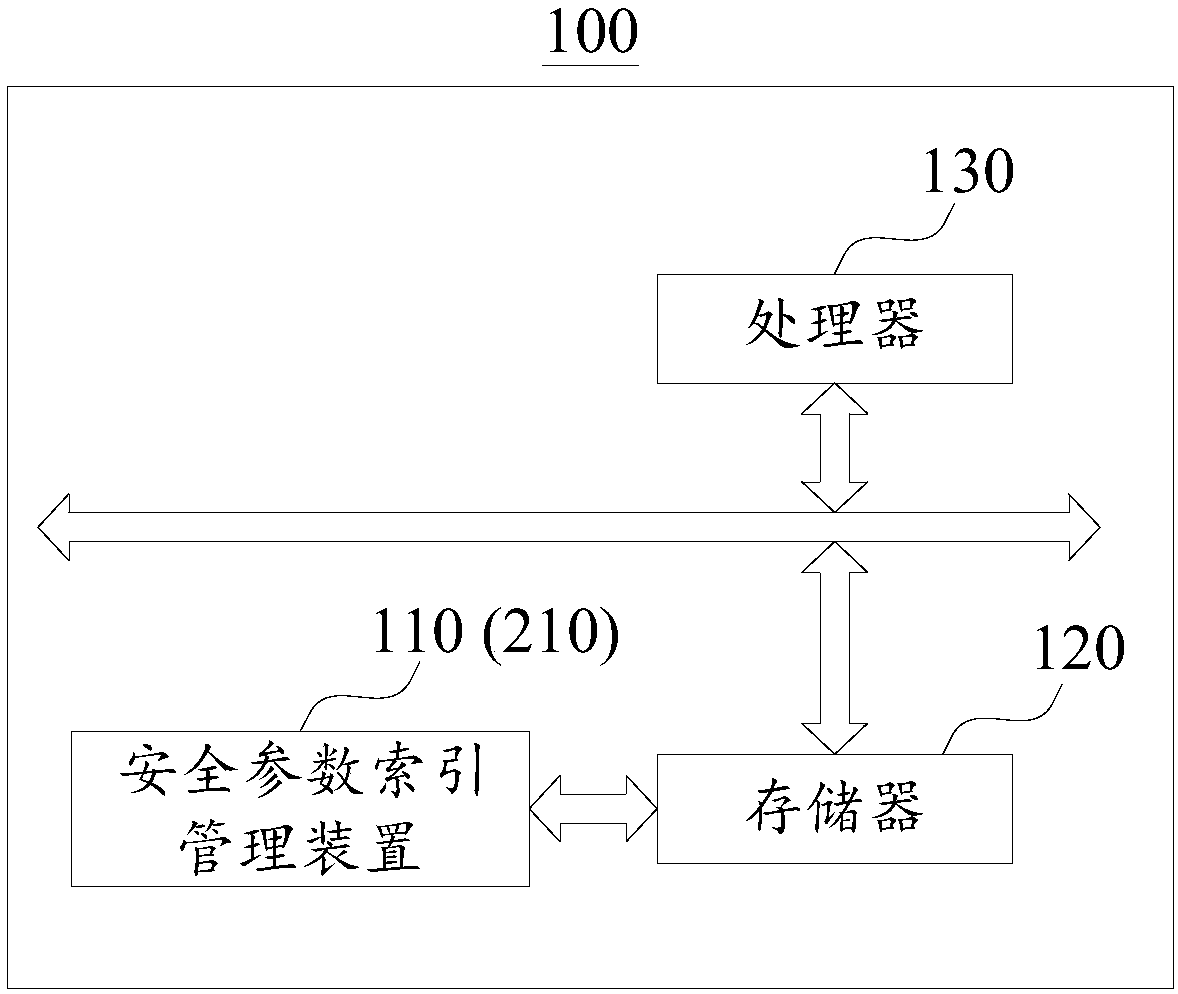
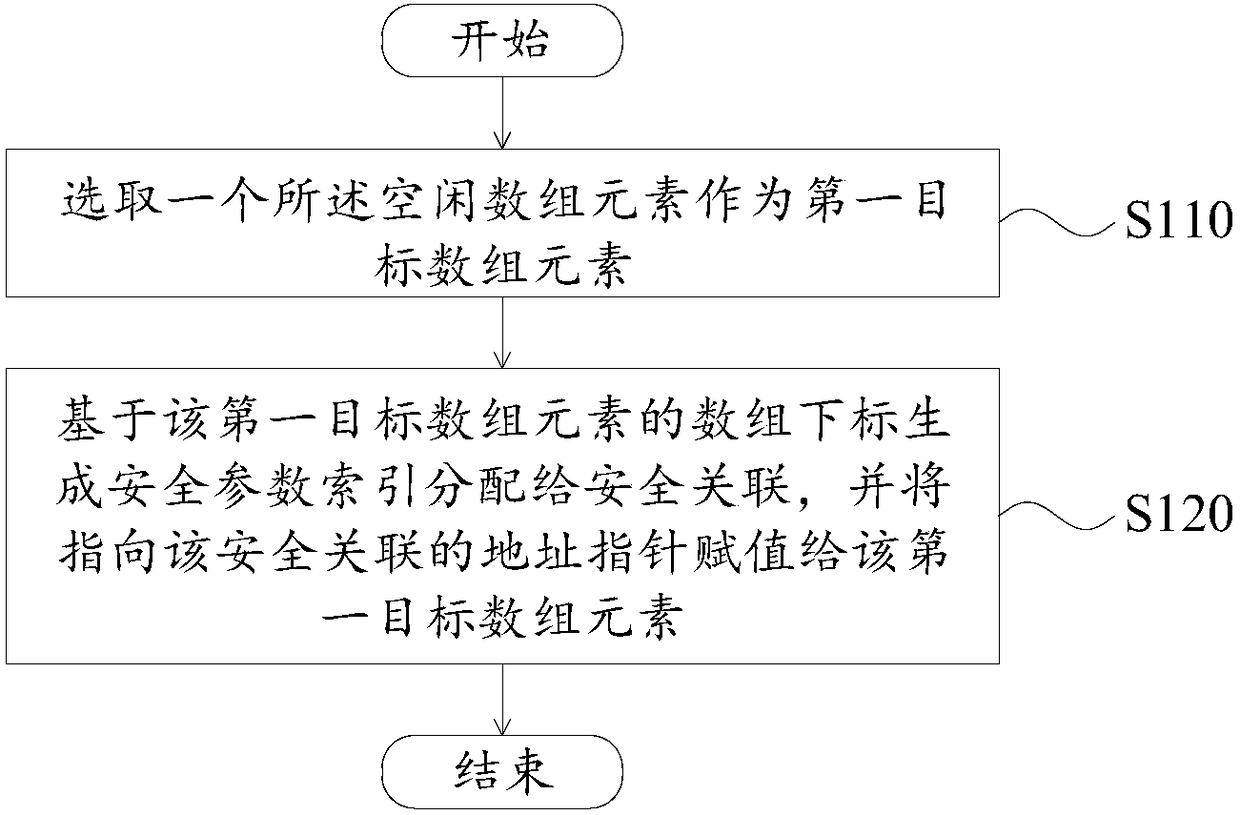
Security parameter index management method and apparatus
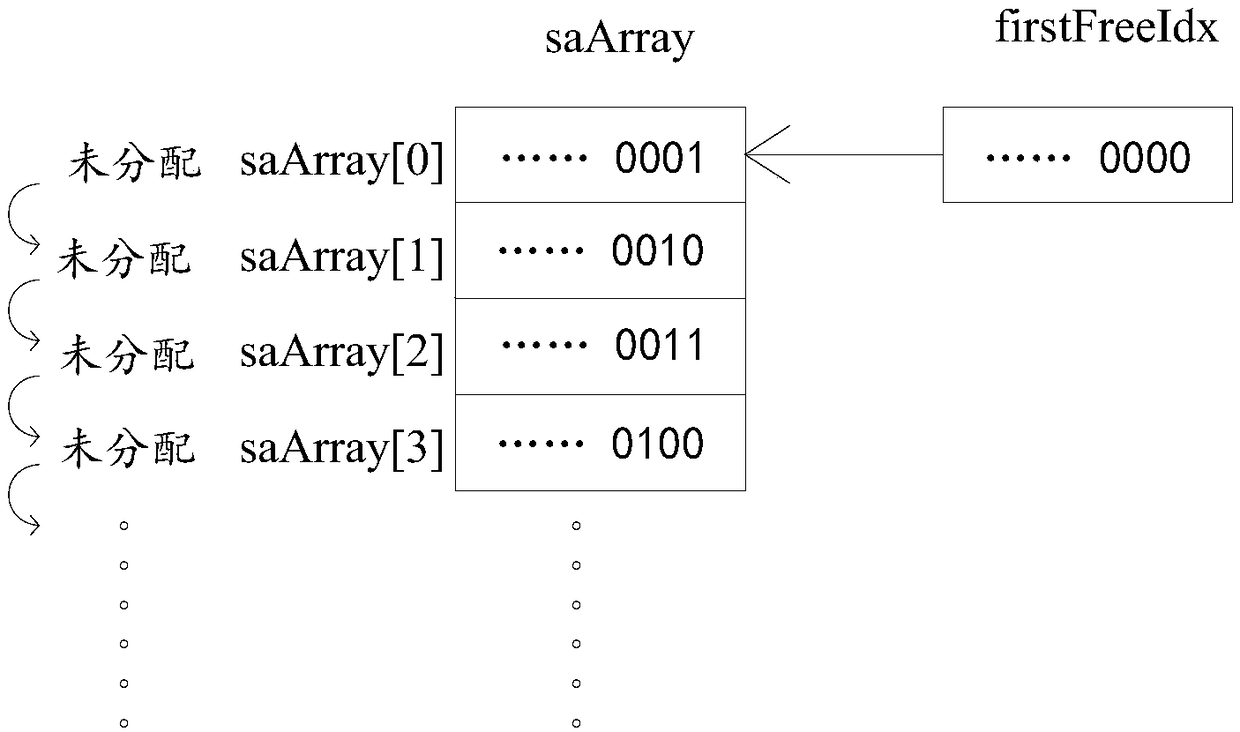
ActiveCN108614734AAvoid allocation conflictsReduce memory usageResource allocationSpecial data processing applicationsTarget arrayArray data structure
The invention provides a security parameter index management method and apparatus, which is applied to a communication device. The apparatus is characterized in that the communication device comprisesan index array; and the index array comprises idle array elements not used for generating security parameter indexes. The method comprises the steps of selecting an idle array element as a first target array element; and based on an array subscript of the first target array element, generating the security parameter index to be allocated to security association, and assigning an address pointer pointing to the security association to the first target array element. The security parameter indexes are allocated in an array form, and the security parameter indexes are generated based on the array subscripts of the idle array elements, so that the generated security parameter indexes are ensured not to be used certainly and the problem of security parameter index allocation conflict is avoided. The security parameter indexes are organized by adopting the array; and compared with a mode using a HASH table in the prior art, fewer memories are occupied and the search efficiency is higher.
Owner:MAIPU COMM TECH CO LTD
Data transmission method and device, related equipment and storage medium
PendingCN111385259AEasy to handleAvoid disorderData switching networksData streamNetworking protocol
Owner:ZTE CORP
Dynamic foreign agent-home security association allocation for IP mobility systems
ActiveUS20100106969A1Network traffic/resource managementAssess restrictionSecurity associationSecurity index
The present invention utilizes the AAA infrastructure to dynamically allocate the various parameters needed to establish the security association between the Foreign Agent and the Home Agent. The present invention uses the AAA server as a central entity to dynamically generate and distribute the chosen security association parameters needed to support the Foreign Agent and Home Agent security association based on a request from the Foreign Agent. The AAA server can also dynamically assigns a unique SPI value to the Foreign Agent and Home Agent pairs. The various parameters that can be allocated in the present invention include a FA-HA shared secret key or a public / private key pair, an authentication algorithm and mode, a FA-HA secret key lifetime, and security parameter index or security index values. The present invention also can assist in making sure that the Foreign Agent and the Home Agent stay synchronized with respect to their security association.
Owner:APPLE INC
Method for optimizing nsis signaling in mobike-based mobile applications
InactiveUS20090241181A1Avoid delayPrevents waste of resourceComputer security arrangementsData switching by path configurationPrivate networkIp address
A method reduces signaling overhead of a mobile node that maintains at least one active Next Steps in Signaling session. The mobile node has a MOBIKE connection to a virtual private network gateway, and changes its link to the Internet. At least the IP address of the VPN gateway and / or an address space corresponding to the subnetwork of the VPN gateway is / are inserted into the message routing information object contained in the NSIS message. A value is defined for a security parameter index. The SPI value is inserted into the MRI object. The S flag is set in the MRI object. An address space that refers to the IP address of the mobile node is inserted into the MRI object.
Owner:SIEMENS AG
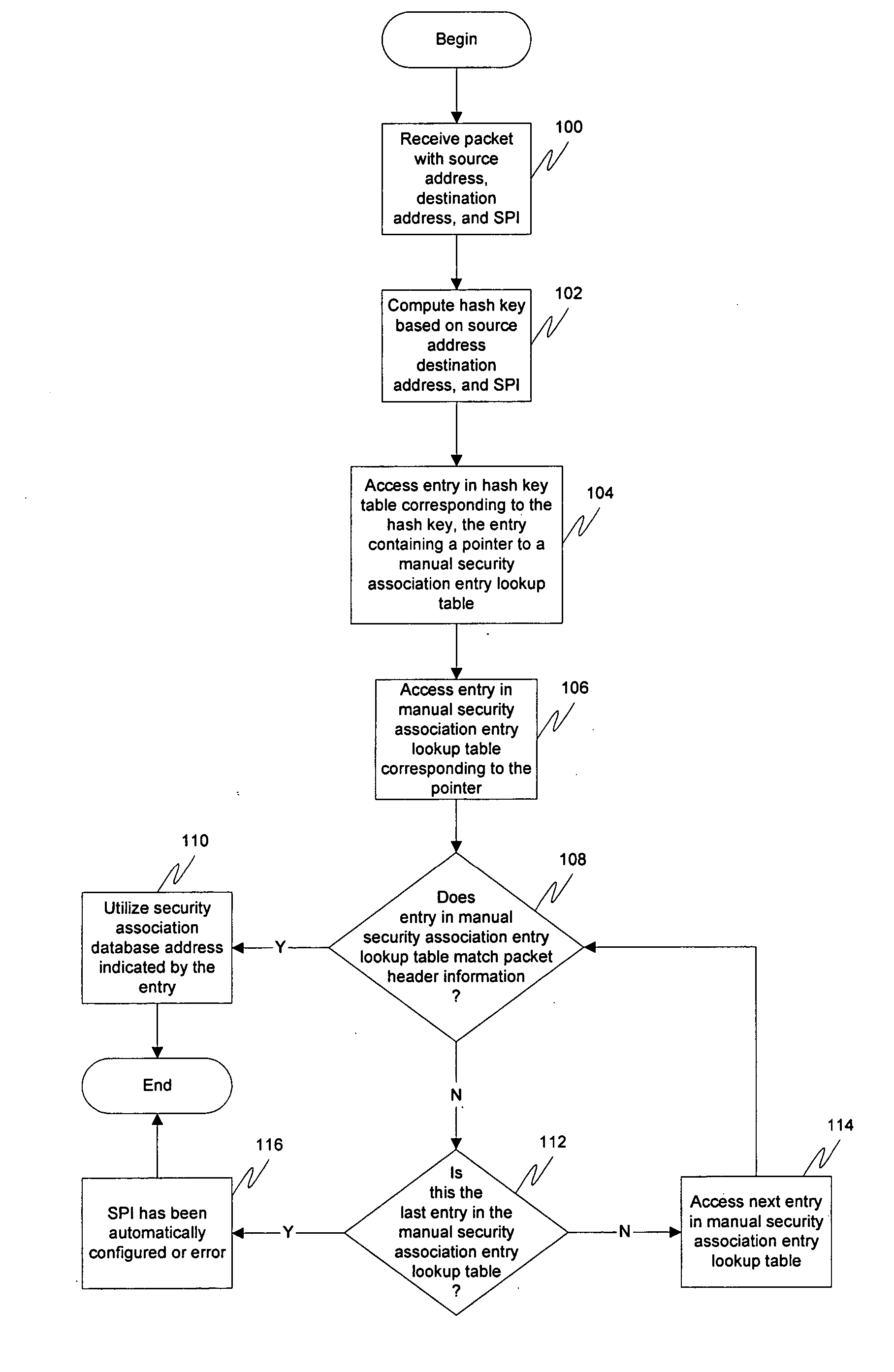
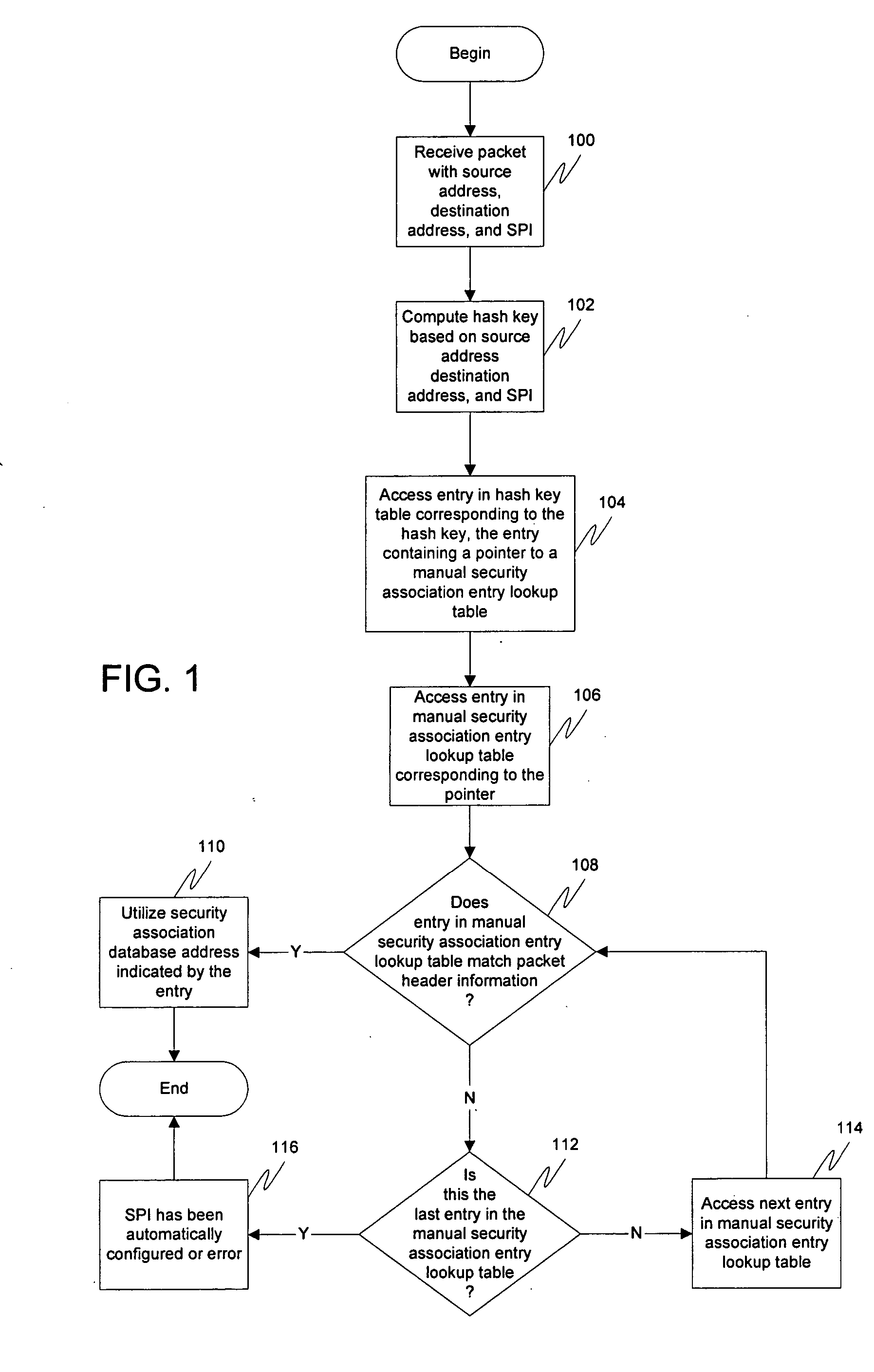
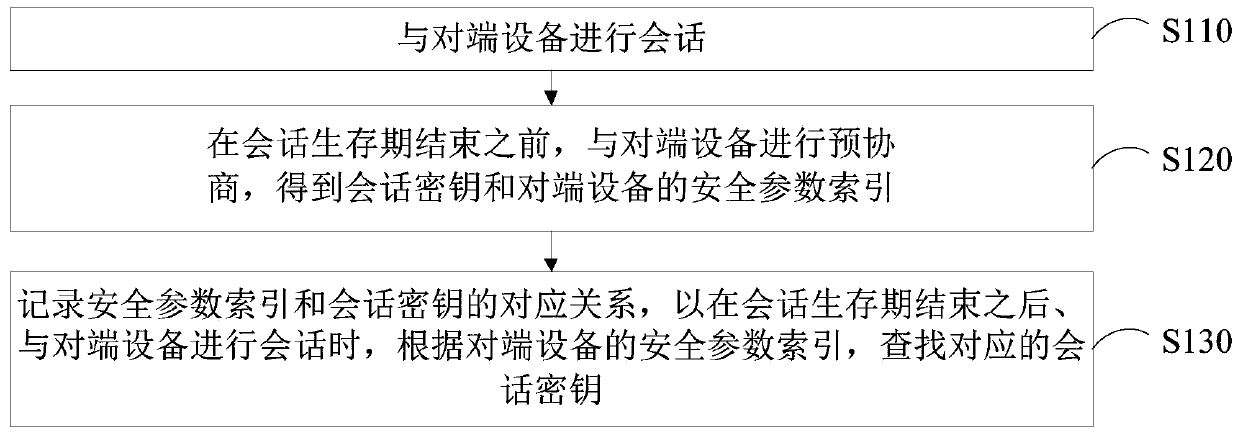
Key negotiation method and device, computer equipment and storage medium
ActiveCN109981272AAvoid lossImprove stabilityKey distribution for secure communicationNetworks interconnectionData lossSession key
The invention relates to a key negotiation method and device, computer equipment and a storage medium. The method comprises the following steps: carrying out session with opposite-end equipment; pre-negotiating with the opposite-end equipment before the end of the session lifetime to obtain a session key and a security parameter index of the opposite-end equipment; and recording a corresponding relation between the security parameter index and the session key, so as to find the corresponding session key according to the security parameter index of the opposite end equipment when the session with the opposite end equipment is carried out after the session lifetime is finished. By adopting the method, the problem of communication data loss caused by asynchronous session key switching can beavoided, and the communication stability is improved.
Owner:SHENZHEN COMTOP INFORMATION TECH
Process method, apparatus and system for controlling data stream
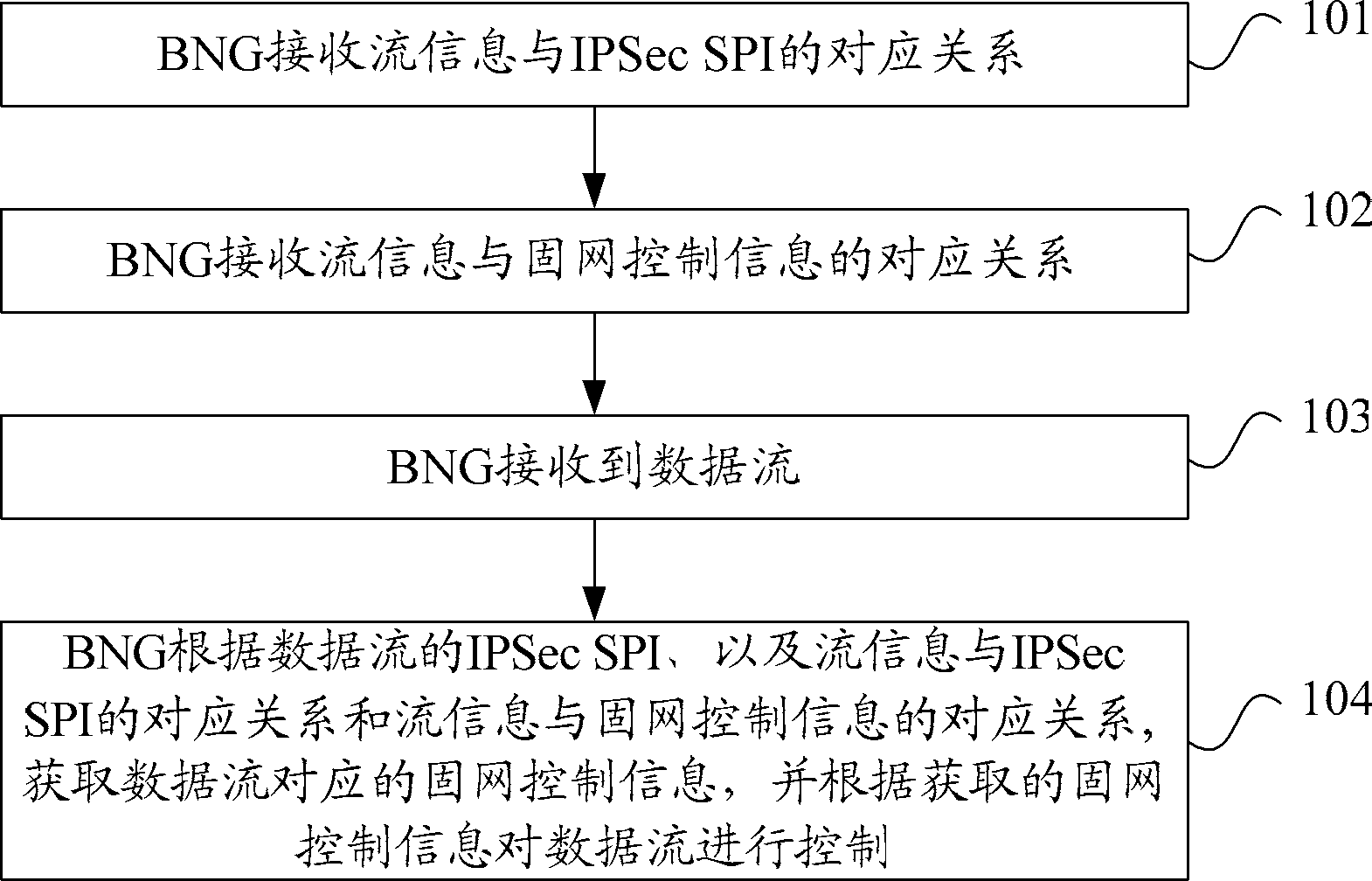
InactiveCN102907056BRealize flow control processingNetwork traffic/resource managementConnection managementIPsecNetwork control
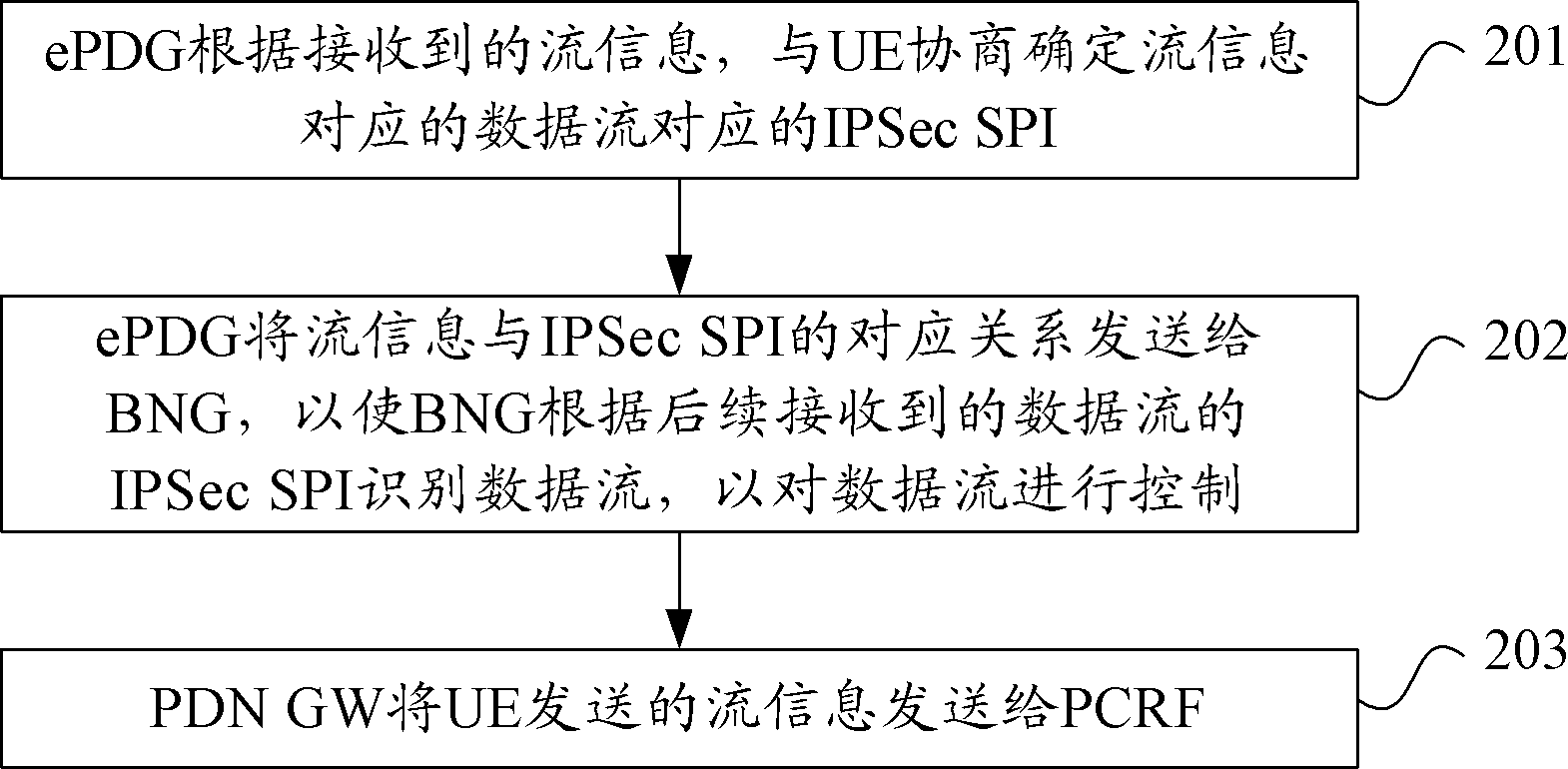
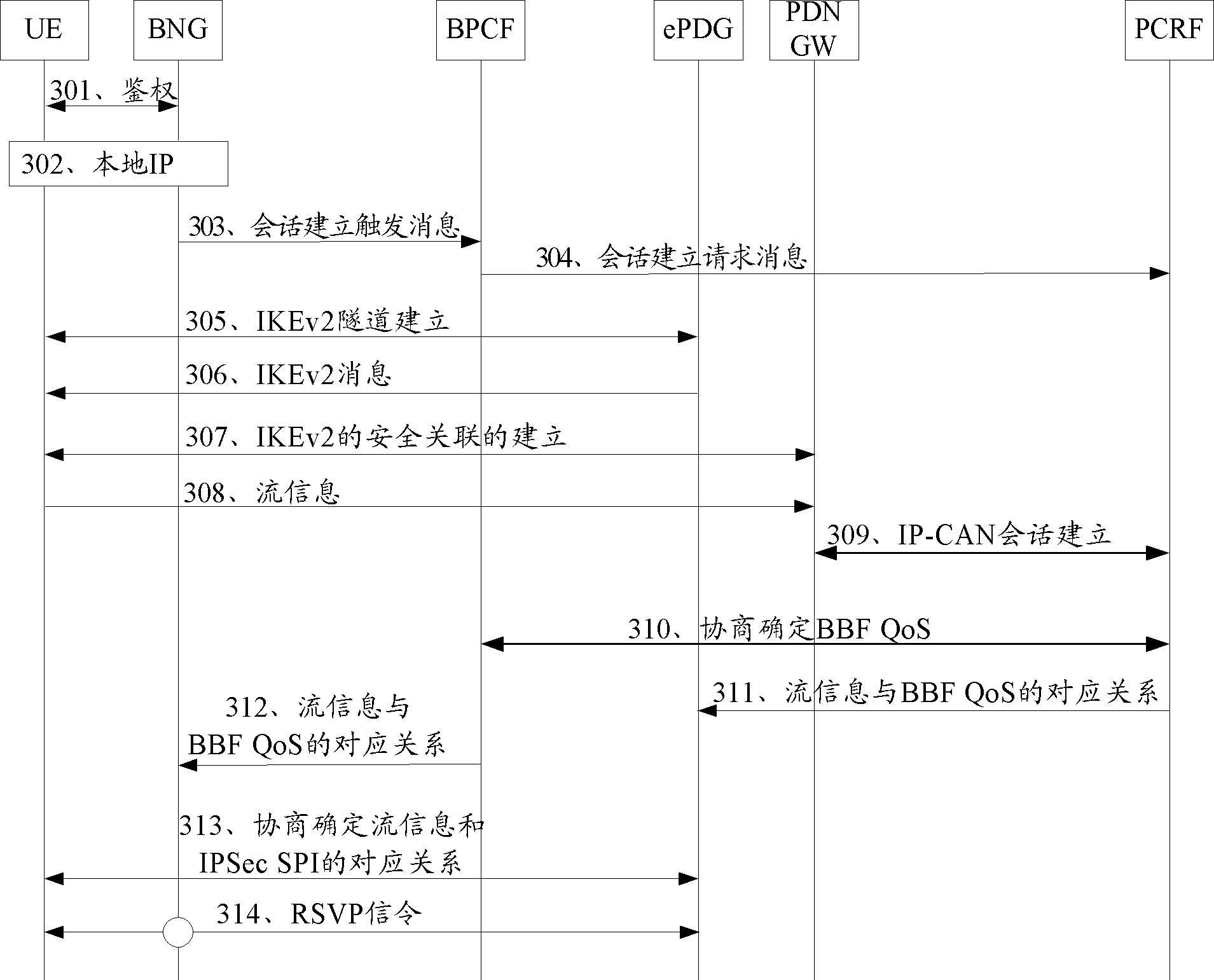
A process method, apparatus and system for controlling data stream are provided. The method includes: a Broadband Network Gateway (BNG) receives relationship between stream information and an Internet protocol security security parameter index (IPSec SPI); the BNG receives relationship between the stream information and fixed network control information; the BNG receives data stream; and the BNG acquires the fixed network control information corresponding to the data stream according to the IPSec SPI of the data stream, the relationship between the stream information and the IPSec SPI and the relationship between the stream information and the fixed network control information, and controls the data stream according to the acquired fixed network control information. After receiving the data stream subsequently, the BNG acquires the fixed network control information corresponding to the data stream according to the stream information of the data stream and the aforementioned relationships, and controls the data stream according to the acquired fixed network control information, thereby enabling the BNG to control the data stream and implementing the process for controlling stream on data stream of multiple services of an identical User Equipment (UE).
Owner:HUAWEI TECH CO LTD
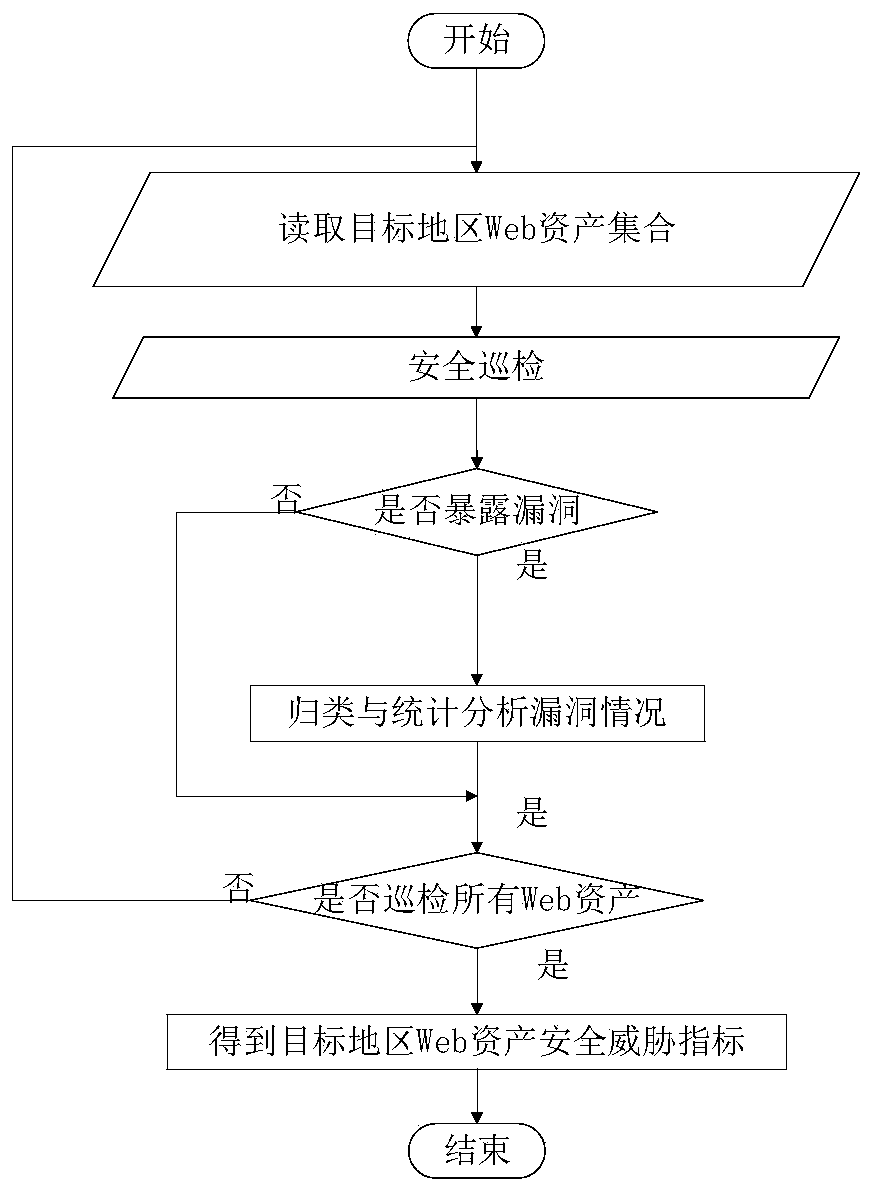
Industrial internet security situation evaluation method based on multiple attributes
ActiveCN109962916AImprove the level ofImprove accuracyResourcesData switching networksWeight coefficientThe Internet
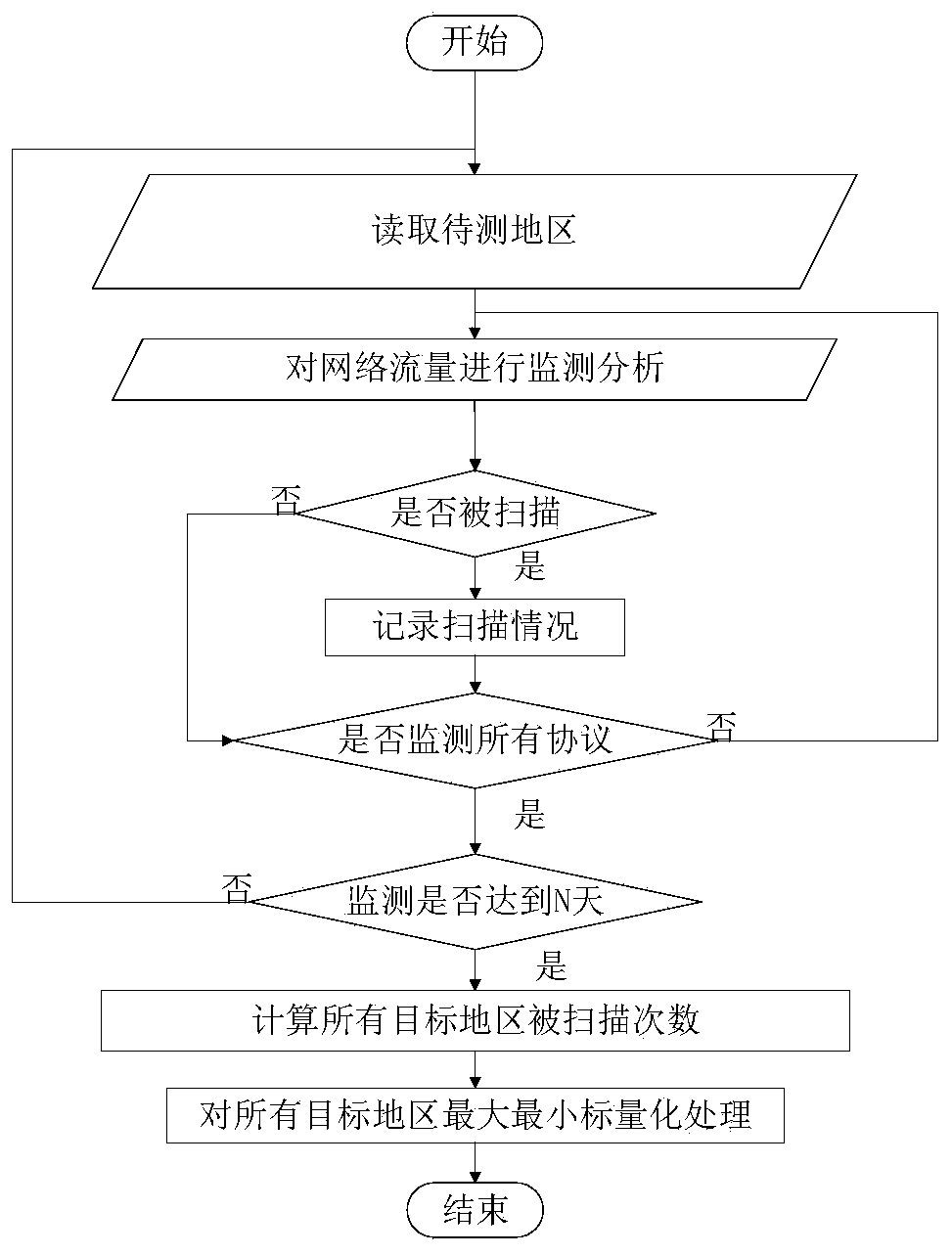
The invention relates to an industrial internet security situation evaluation method based on multiple attributes. The method comprises the steps of constructing target industrial internet related software and hardware; monitoring and analyzing the network flow of the international Internet gateway; taking the Web asset set of each target region as a target to obtain a security threat index of theWeb assets of the target region; obtaining hardware of a target area and security threat indexes of related systems by taking a set of the hardware of each area and the related systems as a target, and obtaining comprehensive security threat evaluation indexes of all the target areas according to the number of scanning times of an industrial internet related protocol port of each target area. Theinvention provides an industrial internet security situation evaluation method based on multiple attributes in the technical scheme. The problems that the weight coefficient is unreasonable and the decision accuracy and reliability are slightly poor due to the fact that the existing industrial internet security situation evaluation technology bureau is limited to objective evaluation or subjective evaluation are effectively solved, and the level and accuracy of industrial internet security situation evaluation are effectively improved.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT
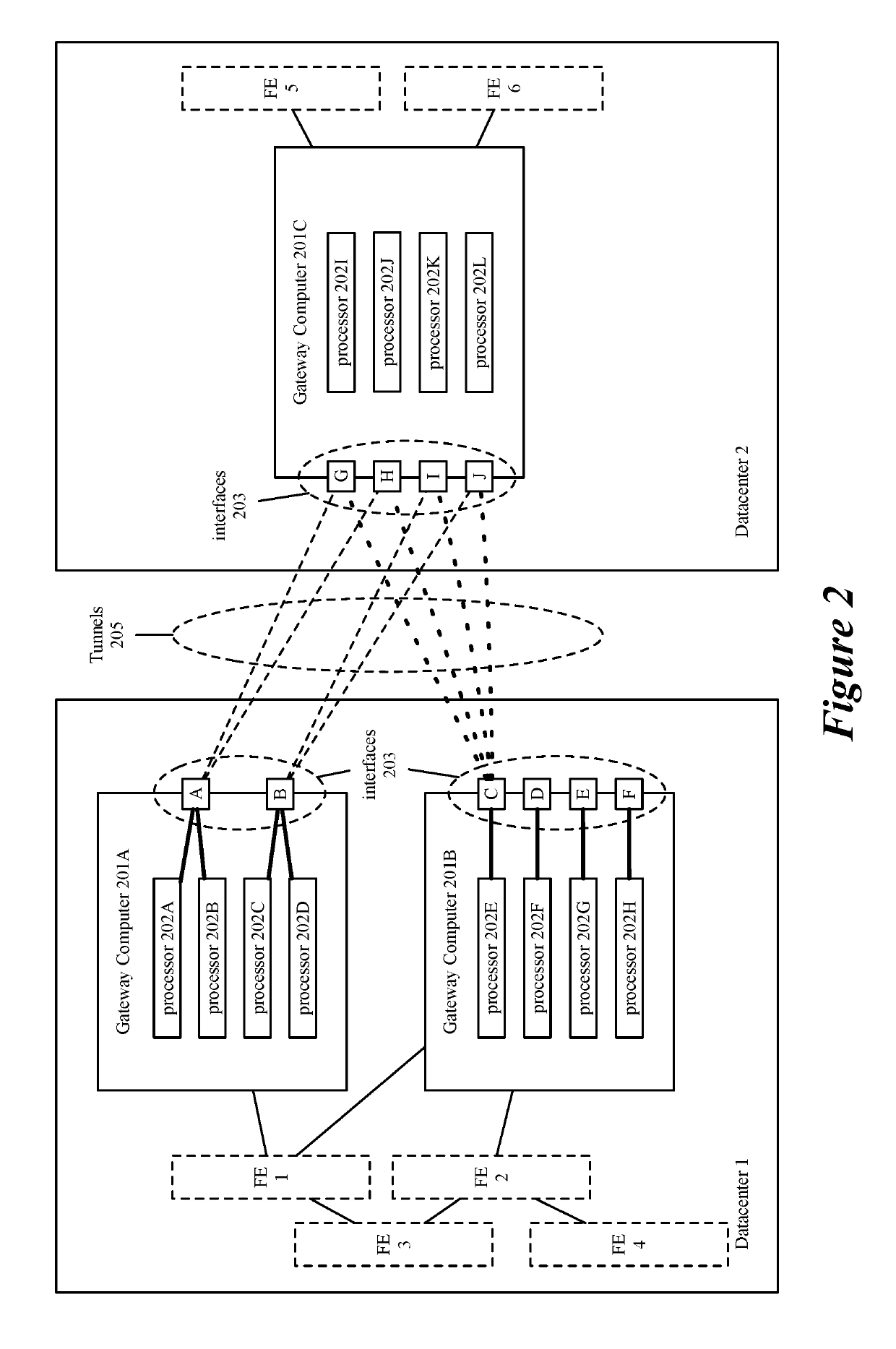
Scaling gateway to gateway traffic using flow hash
ActiveUS11075888B2Increase probabilityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesEngineeringDistributed computing
For a network including multiple computers acting as tunnel endpoints in a network, some embodiments provide a method for distributing data messages among processors of a destination computer that receives encrypted data messages from a source computer. Each computer in some embodiments has a set of interfaces configured as tunnel endpoints connecting to multiple tunnels. The encrypted data messages are received at multiple interfaces of the destination computer and in some embodiments, include an identifier for a set of encryption parameters (e.g., a security parameter index). The encryption-parameter-set identifier is used to distribute encrypted data messages among processors of the destination computer.
Owner:NICIRA
Method for realizing packet traversal of network address translation equipment
The present invention provides a method for realizing message passing through a network address translation device, including: S1, the intranet sends a message to the network address translation device, and the message carries the internal network IP address, the internal network security parameter index and the external network security Parameter index; S2. The network address translation device receives the message, and according to the internal network IP address carried in the message, the internal network security parameter index and the external network security parameter index and the public network Establish a mapping table for the IP address; S3. Convert the internal network IP address of the message to the public network IP address according to the mapping table, and send the message to the public network IP address through the public network IP address An external network device; the external network security parameter index is the security parameter index of the external network device. The present invention establishes NAT device address mapping, so that when the message in the IPSec tunnel performs NAT traversal, the port address translation can be performed without adding UDP.
Owner:OPZOON TECH
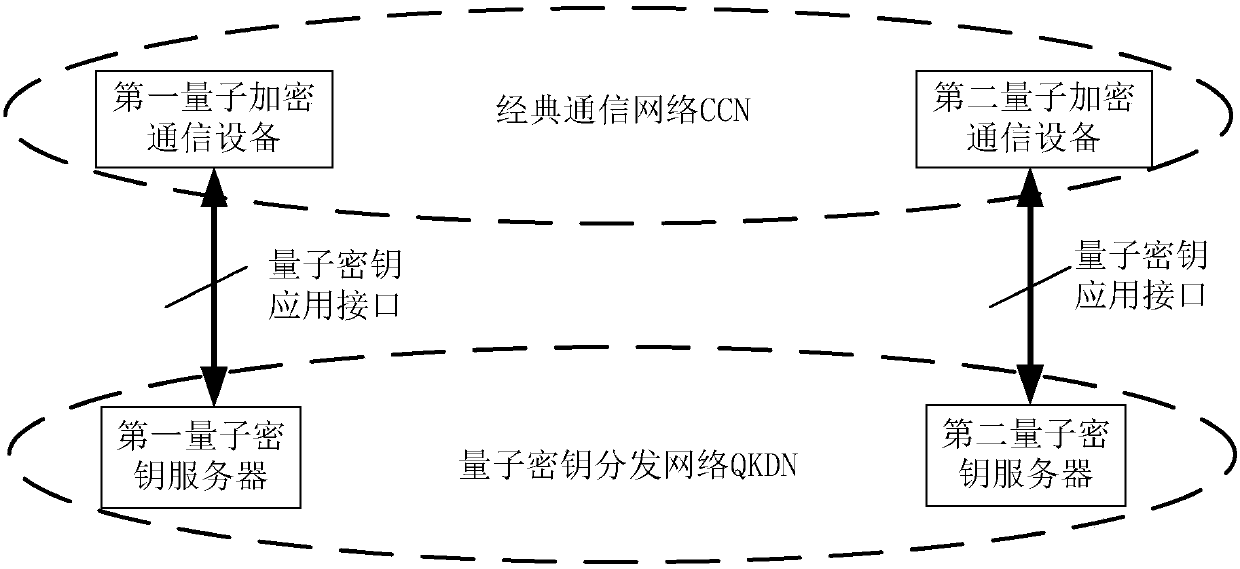
Quantum encryption communication method and device and computer readable storage medium
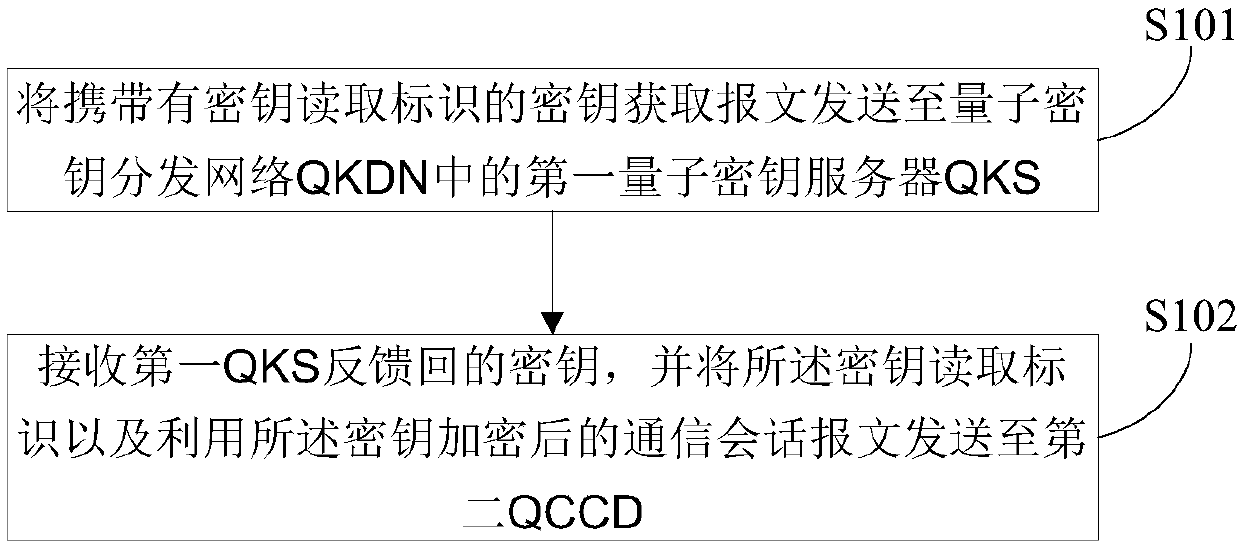
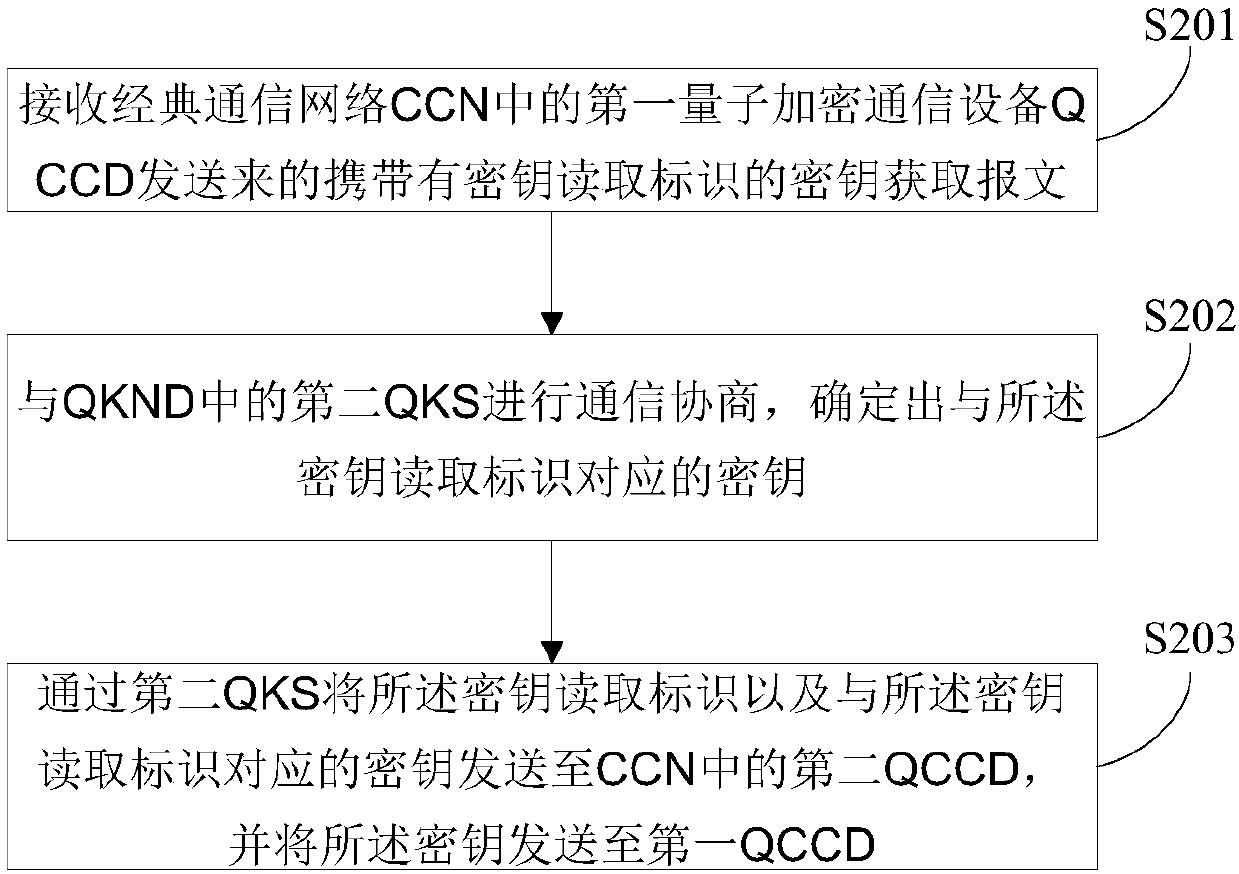
ActiveCN109756326ASave resourcesSimplify the interaction processKey distribution for secure communicationComputer hardwareSecurity parameter
The invention discloses a quantum encryption communication method and device and a computer readable storage medium. The method comprises the following steps of: obtaining a sample; sending the key acquisition message carrying the key reading identifier to a first quantum key server QKS in a quantum key distribution network QKDN, sending the key reading identifier and a key corresponding to the key reading identifier to a second QCCD in the CCN by the first QKS through a second QKS in the QKDN; receiving a secret key fed back by the first QKS, and sending the secret key reading identifier andthe communication session message encrypted by using the secret key to a second QCCD, so that the second QCCD searches the secret key corresponding to the secret key reading identifier, and decrypts the encrypted communication session message by using the searched secret key; Wherein the key reading identifier comprises a security parameter index SPI bit and an SPI round digit. The quantum encryption communication method and device solve the problem that in the existing quantum encryption communication process, an old session is frequently terminated, and a new session is generated.
Owner:ZTE CORP
Method and device for deleting Child SAs
ActiveCN103237028ATransmissionSpecial data processing applicationsCryptographic protocolSecurity parameter
The invention discloses a method and device for deleting Child SAs. The method includes the following steps: when needing to delete a Child SA, the device sets the outbound Child SA corresponding to the Child SA to be deleted to be unavailable, and sends a deletion message carrying the security parameter index (SPI) and security protocol of the Child SA to be deleted to the peer device; and when the deletion response message returned by the peer device is received by the device, the Child SA to be deleted and the outbound Child SA corresponding to the Child SA to be deleted are deleted by the device. In the invention, the probability of deleting Child SAs by mistake is decreased.
Owner:XINHUASAN INFORMATION TECH CO LTD
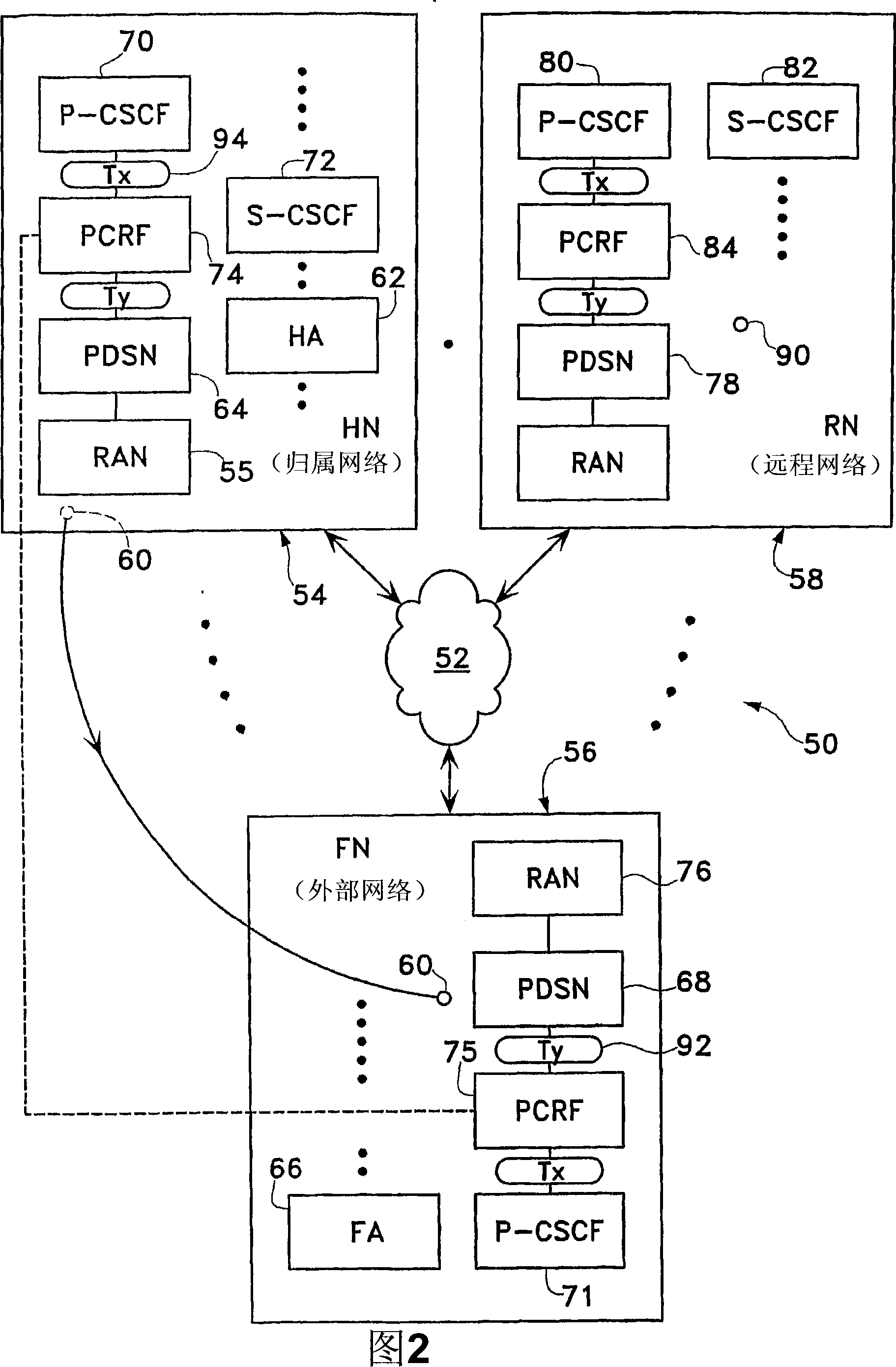
Bearer control of encrypted data flows in packet data communications
In a communication session in which data flows with encrypted data packets pass through a monitoring intermediary for data traffic control. The encrypted data packets include SPIs (Secured Parameter Indexes) which are used to identify SAs (Security Associations) for data decryption. During the initial signaling process for the communication session, the nodes seeking the communication session include the SPIs in the signaling messages and send the signaling messages through the monitoring intermediary which in turn matches the SPIs of the signaling messages with the corresponding SPIs extracted from the data packets. In enforcing data traffic control, the monitoring intermediary allows data flows to pass through if comparison matches in the SPIs are found. Otherwise, the data flows are rejected.
Owner:QUALCOMM INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com