Security parameter index management method and apparatus
A security parameter index and management method technology, which is applied in the field of security parameter index management methods and devices, can solve problems such as low search efficiency, achieve high search efficiency, reduce memory usage, and avoid allocation conflicts
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
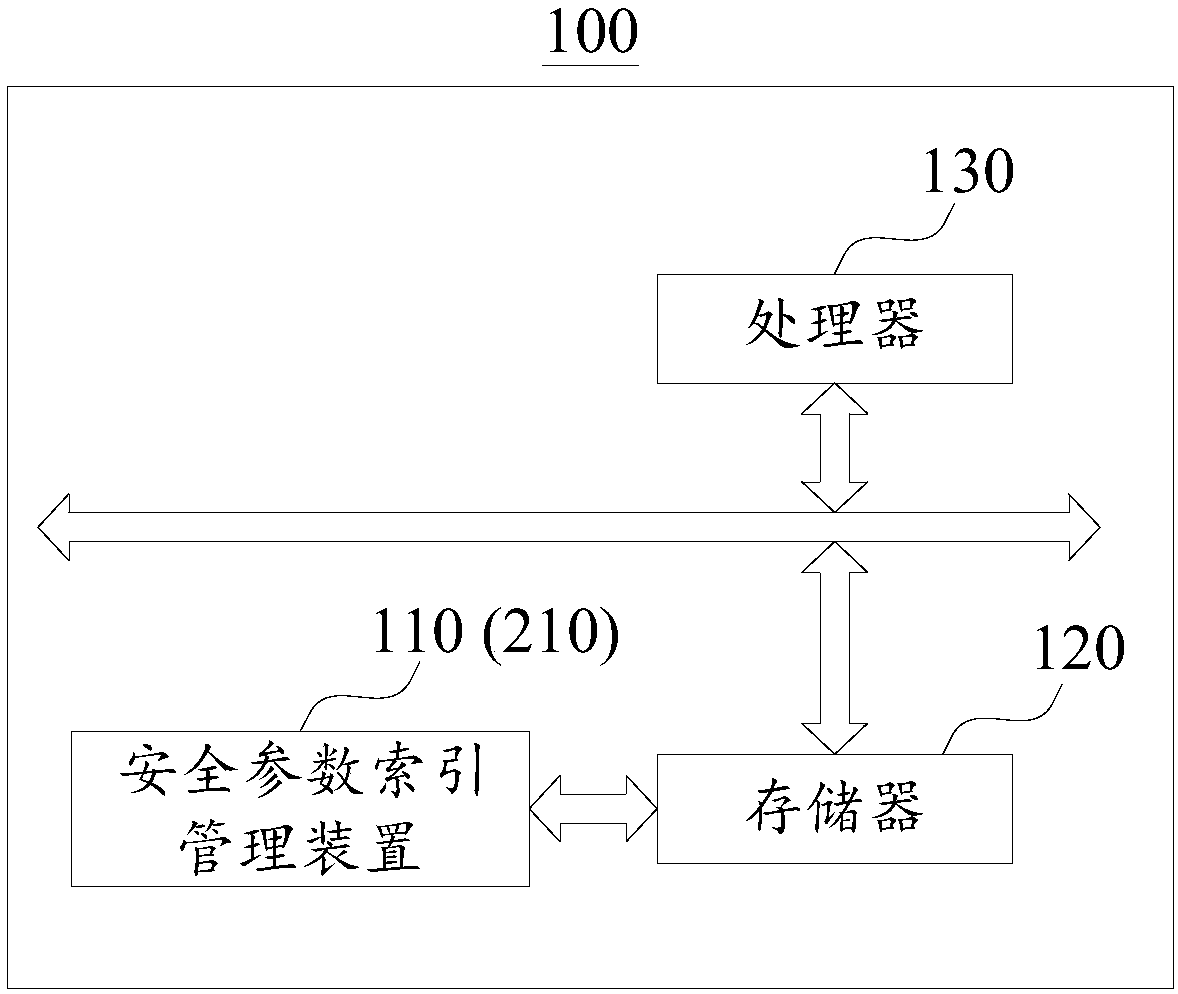
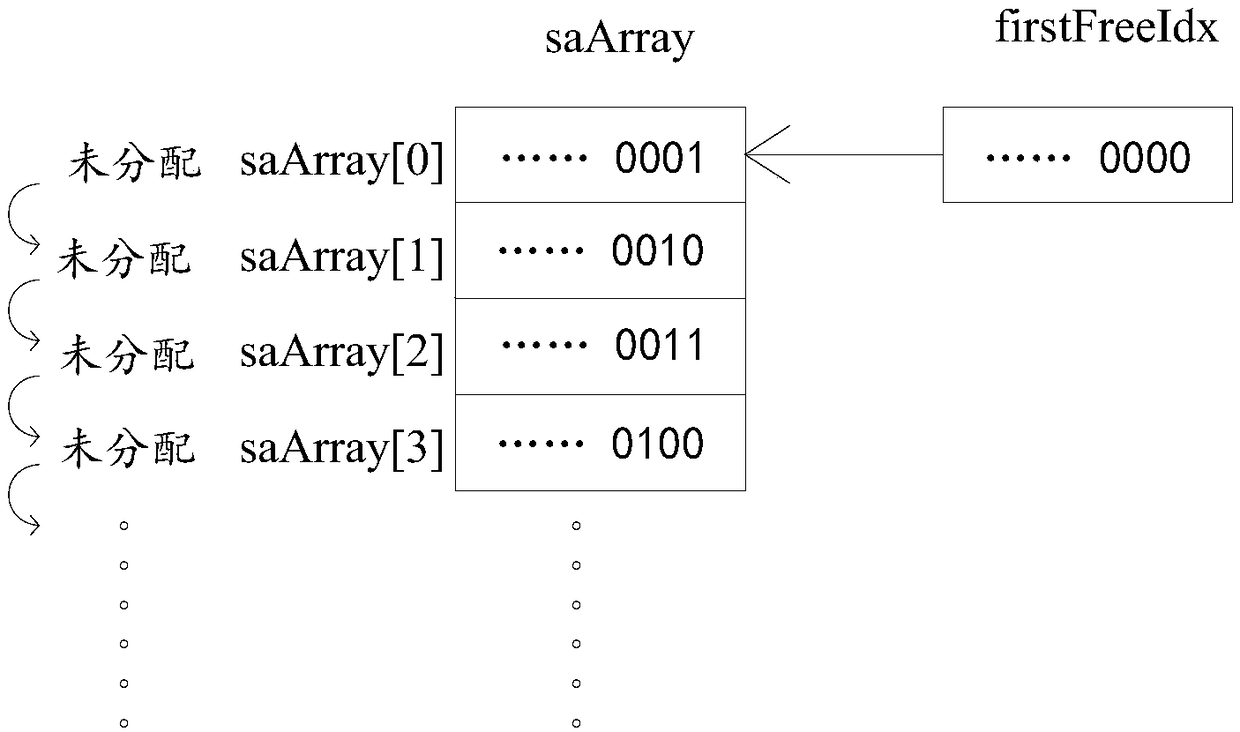
[0047] The security parameter index management method provided in this embodiment is applied to figure 1 A communication device 100 is shown. The communication device 100 includes an index array, and the array elements in the index array that do not store security parameter indexes are free array elements.
[0048] In this embodiment, the security parameter index is generated based on the array subscript of the relevant array element in the index array and assigned to the security association, and the address pointer pointing to the security association is stored in the array element.
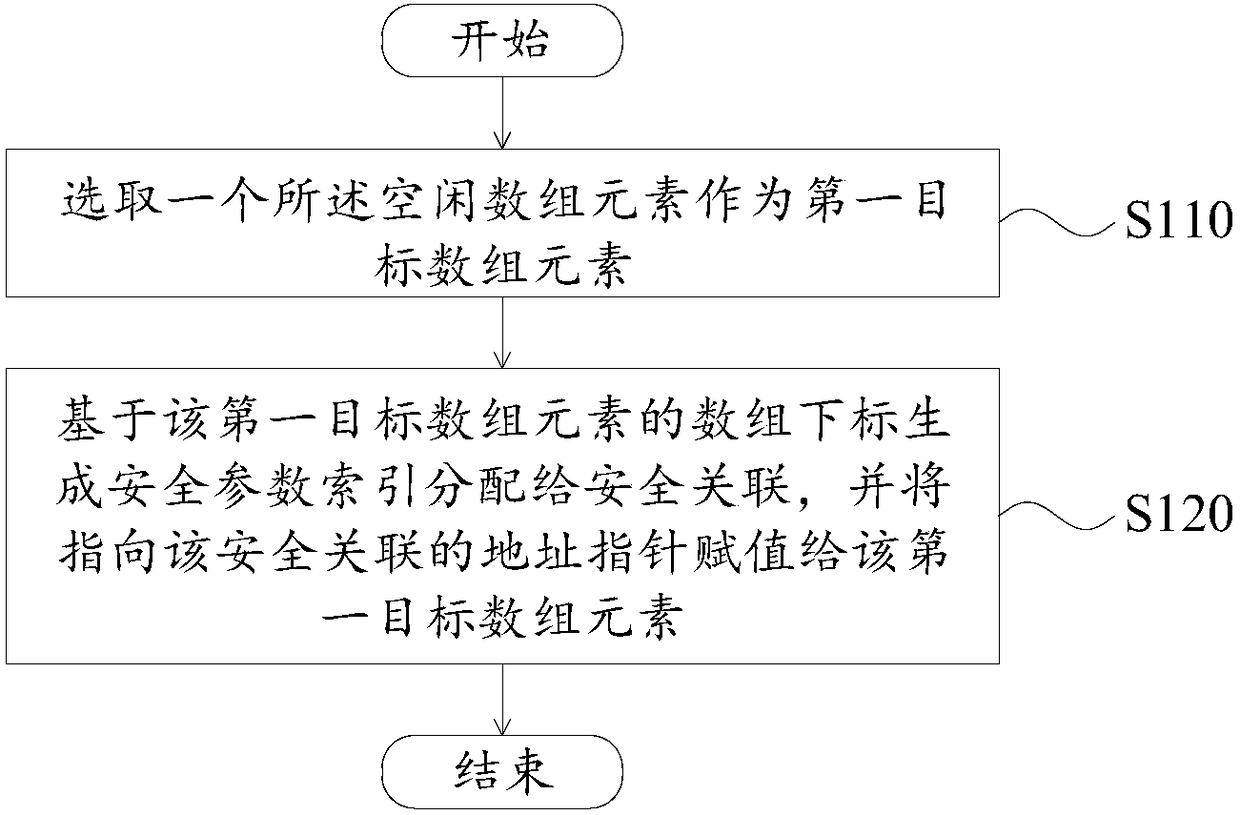
[0049] Accordingly, when the communication device 100 allocates array elements, please refer to figure 2 , the method includes the following steps.
[0050] Step S110, selecting one of the free array elements as the first target array element.
[0051] Specifically, in this embodiment, when the system is initialized, the array elements in the index array are all free array elements, and the...
no. 2 example
[0122] This embodiment provides a security parameter index management method, which is applied to a communication device 100, and the communication device 100 includes an idle identification array and at least one index array. The index array includes free array elements not used for generating security parameter indexes, and the free array elements form a chain of free elements. The array elements of the free identifier array point to the elements in the index array.
[0123] The difference between this embodiment and the first embodiment is that in this embodiment, the security parameter index is generated according to the array subscripts of the allocated index array and the array subscripts of the related array elements of the idle identification array and assigned to the security association, and the And store the address pointer pointing to the security association in the array element.
[0124] Please refer to Figure 15 , the method includes the following steps.
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com