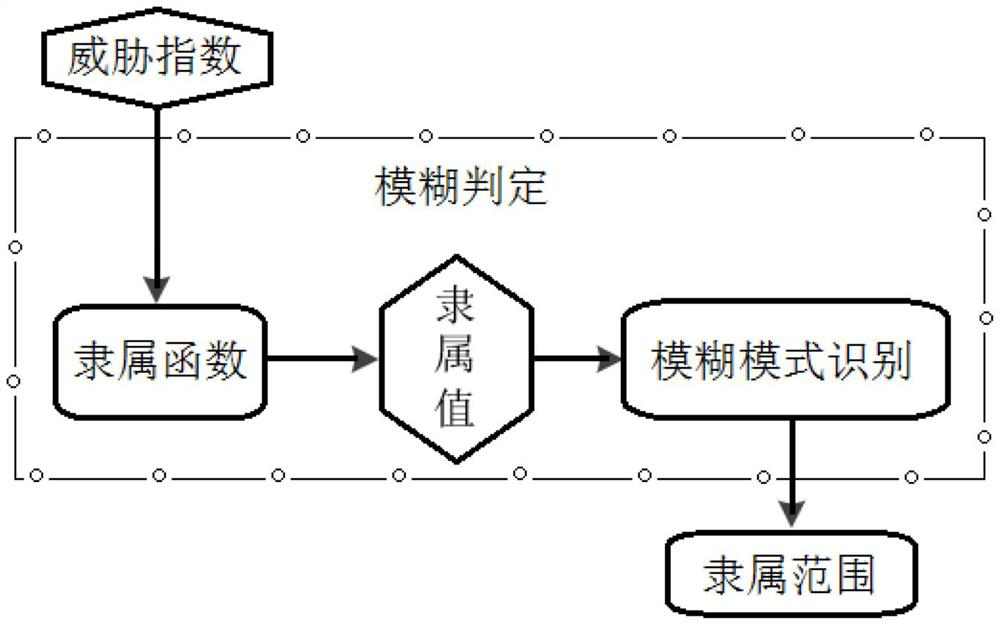
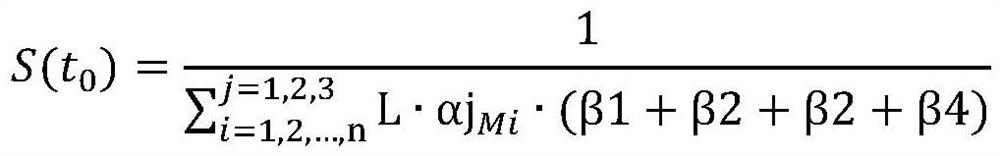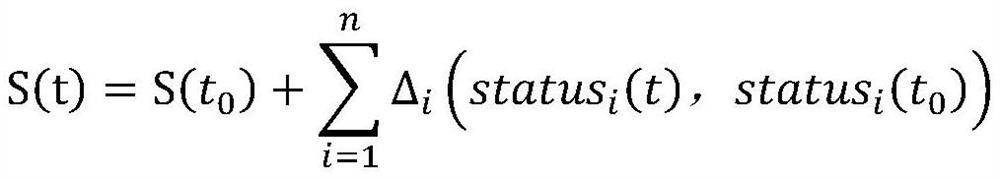Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
51 results about "Right to privacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The right to privacy is an element of various legal traditions to restrain governmental and private actions that threaten the privacy of individuals. Over 150 national constitutions mention the right to privacy.
Method and system for protecting privacy of users in social network
InactiveCN102253952AGuarantee recognitionImprove recognitionDigital data authenticationSpecial data processing applicationsInternet privacyDatabase server
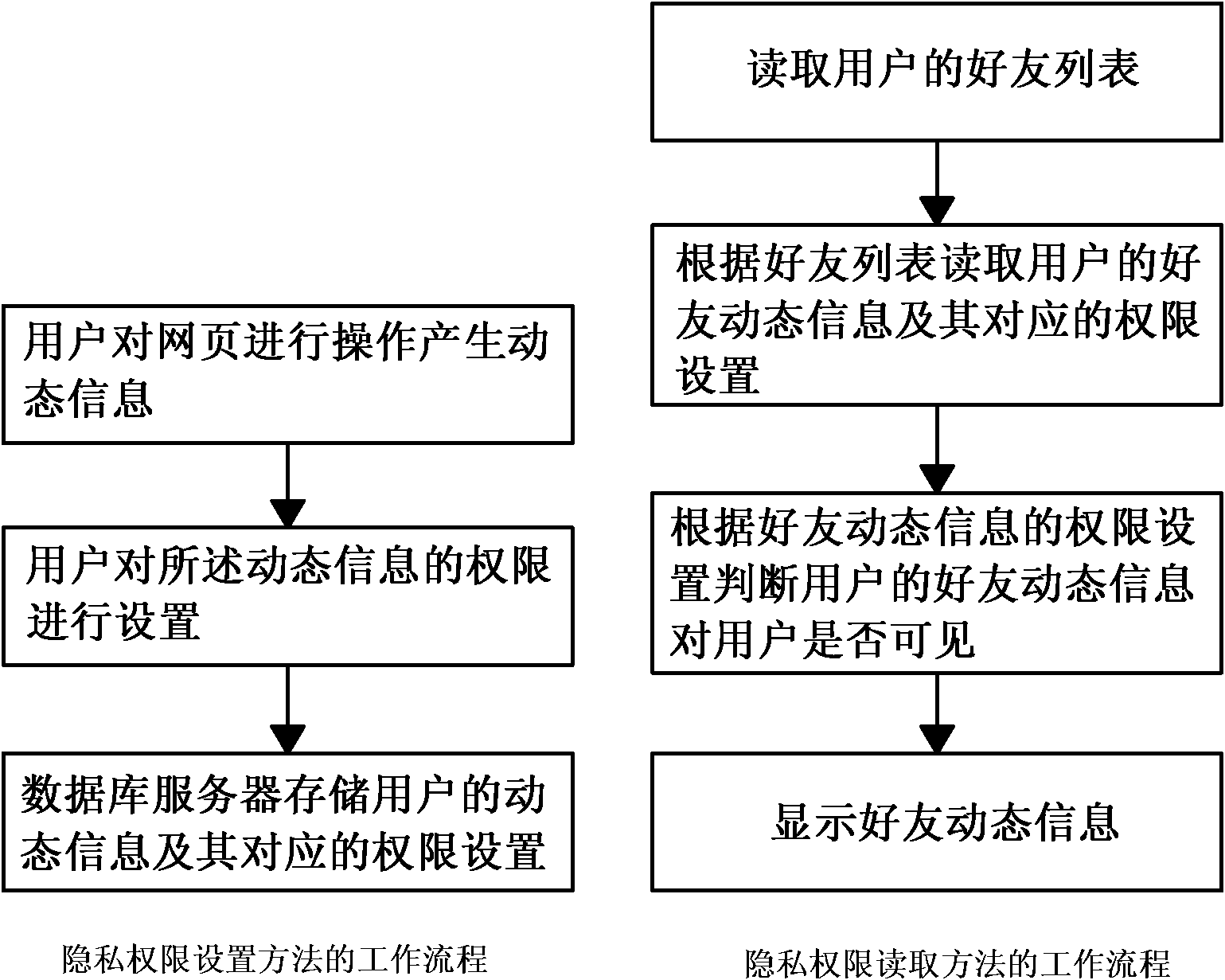
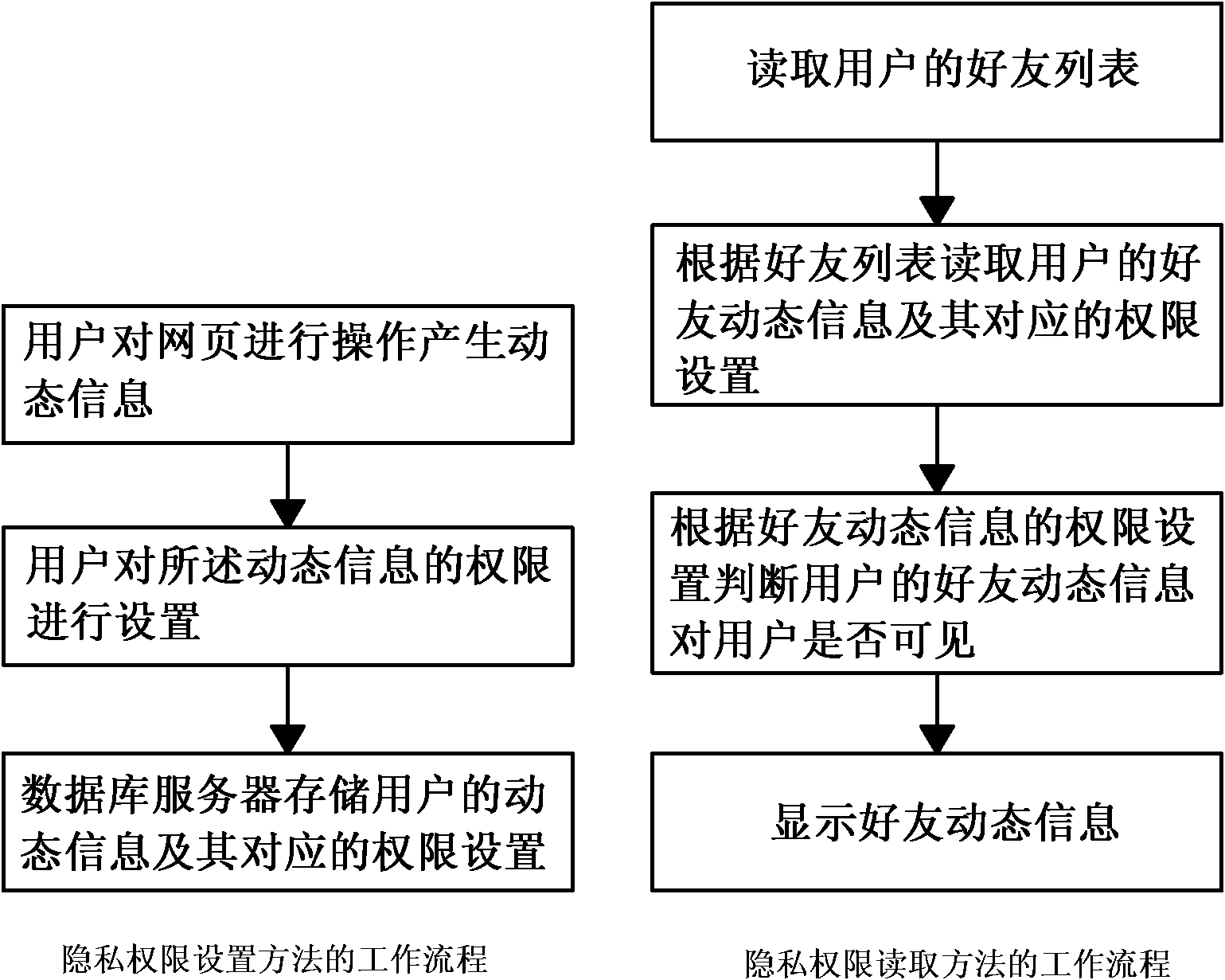
The invention discloses a method and system for protecting the privacy of users in a social network. The method comprises a privacy authority setting method and a privacy authority reading method, wherein the privacy authority setting method comprises the following steps of: S1, operating a webpage by a user to generate dynamic information; S2, setting the authority of the dynamic information by the user; and S3, storing the dynamic information of the user and the corresponding authority setting by a database server. The privacy authority reading method comprises the following steps of: S4, reading a user's friend list; S5, reading friend dynamic information of the user and the corresponding authority setting according to the friend list; S6, judging whether the friend dynamic information of the user is visible to the user according to the authority setting of the friend dynamic information, if so, turning to a step S7, and if not, requiring no treatment; and S7, displaying the friend dynamic information. According to the method and system disclosed by the invention, the access authority to dynamic information generated by users in a social network site can be controlled.
Owner:BEIJING PEOPLE HAPPY INFORMATION TECH
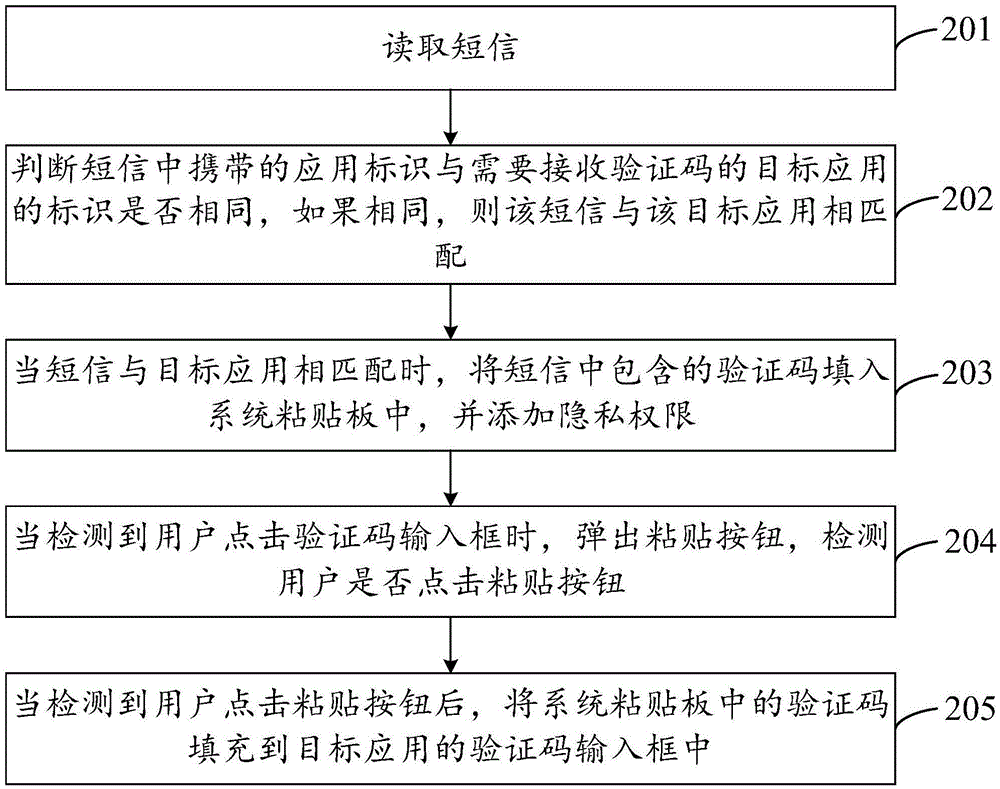
Verification code input method and device
InactiveCN105553663AIncrease privacy permissionsEasy to operateUser identity/authority verificationMessaging/mailboxes/announcementsComputer hardwareFilling-in
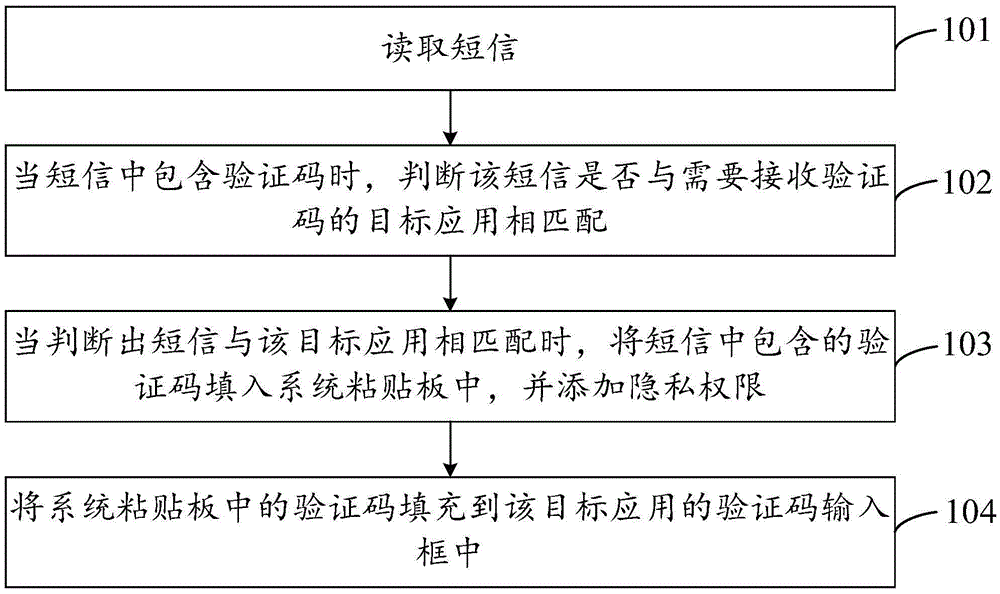
The invention provides a verification code input method and device, and the method comprises the steps: reading a short message; judging whether the short message is matched with a target application which needs to receive a verification code or not when the short message contains the verification code; enabling the verification code in the short message to be filled in a system paste board when the short message is matched with the target application, and adding privacy authority, wherein the privacy authority is used for shielding other applications different from the target application; and enabling the verification code in the system paste board to be filled in a verification input frame of the target application. In conclusion, the method can automatically analyzes the verification code, matched with the target application which needs to receive the verification code, from the content of the short message, and fills the verification code into the corresponding verification input frame. A user does not need to specially search the verification code from the short message, so the method and device are relatively simple in operation. In addition, the method adds privacy authority to the content of the system paste board, thereby preventing the leakage of the privacy of the user.
Owner:XIAOMI INC
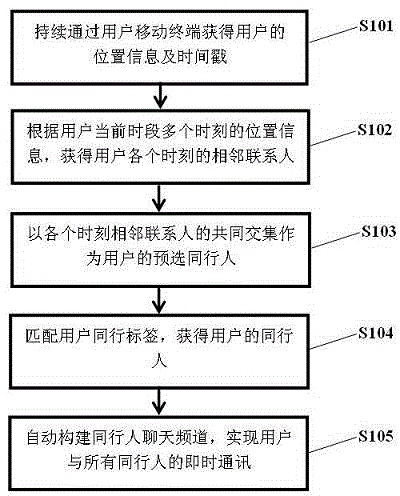
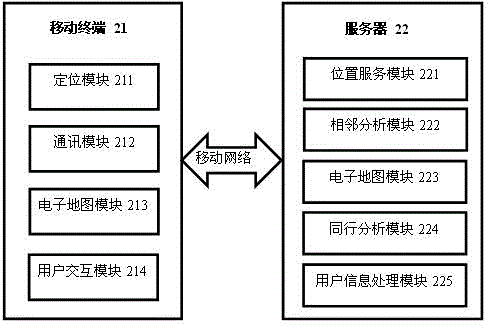
Method and system for realizing instant messaging among persons travelling together
InactiveCN104954984ARealize instant messagingMeet instant messaging needsLocation information based serviceData switching networksTimestampRight to privacy
The invention relates to a method for realizing instant messaging among persons travelling together. The method includes the steps: acquiring position information and timestamps of a user continuously through a mobile user terminal; acquiring adjacent contact persons of the user at every moment according to the position information of the user at multiple moments of the current time period; taking persons having common intersections of the adjacent contact persons at every moment as preselected persons travelling together of the user; matching user travelling-together tags, and acquiring the persons travelling together of the user; automatically building a chat channel for the persons travelling together to realize instant messaging of the user and all the persons travelling together. By the method, the persons travelling together can be automatically searched and added for the user, the instant messaging channel is built, and communication among the persons travelling together is facilitated greatly. Meanwhile, unless the user selects shared position information, the other users cannot know the position information of the user, so that instant messaging requirements of the user is met, and the right of privacy of the user is protected effectively.
Owner:蔡宏铭
Method of and system for conducting mobile video/audio surveillance in compliance with privacy rights
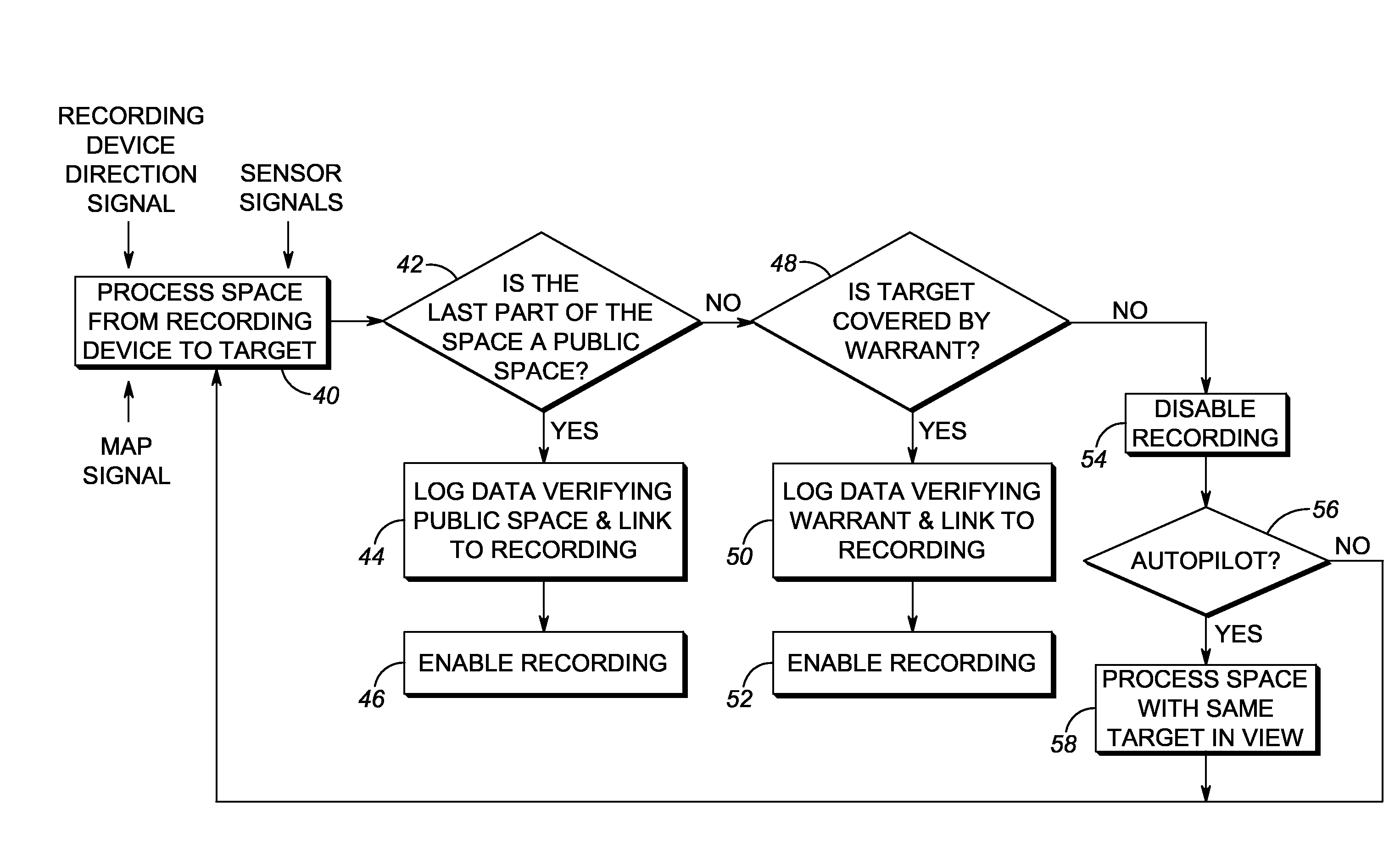
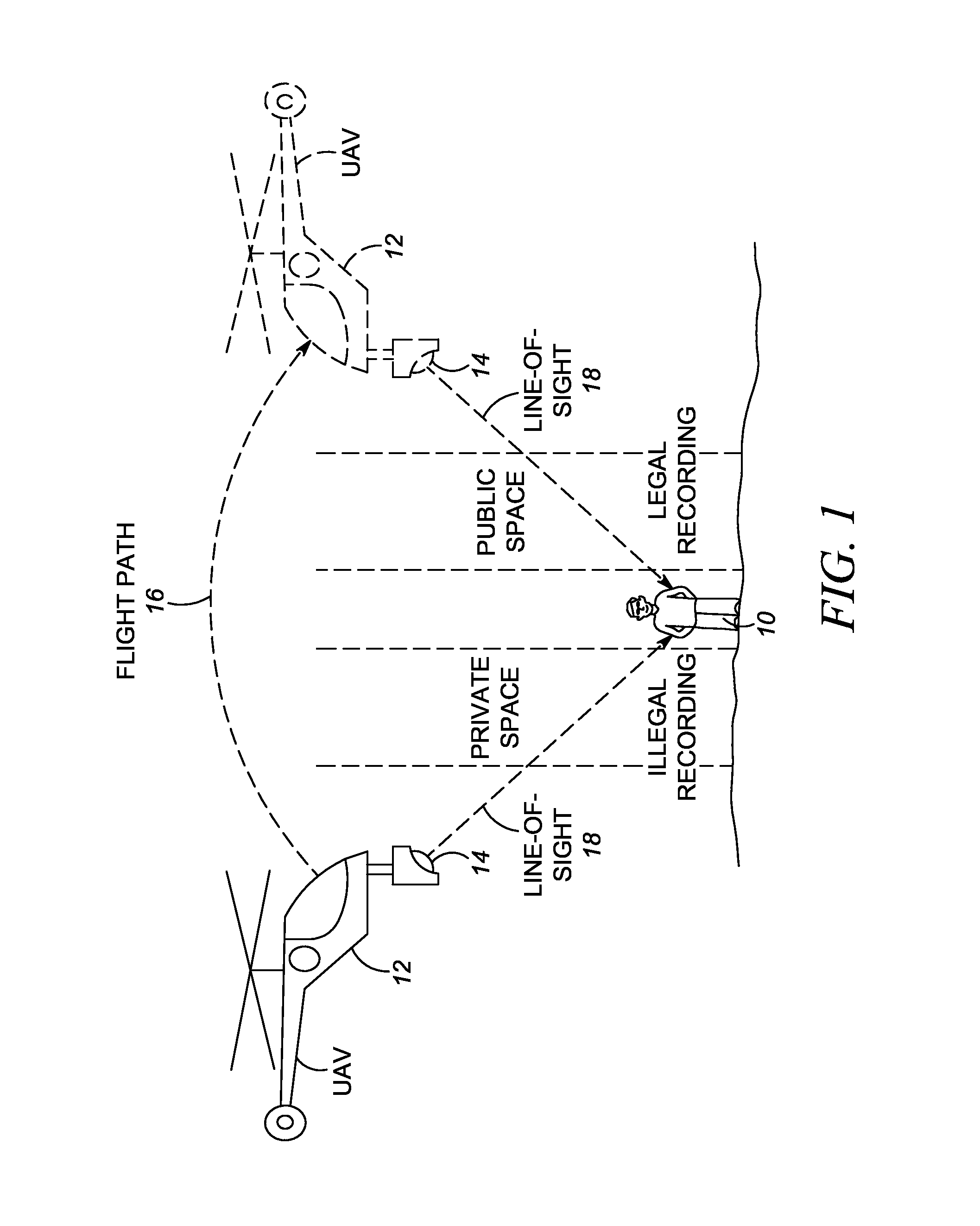
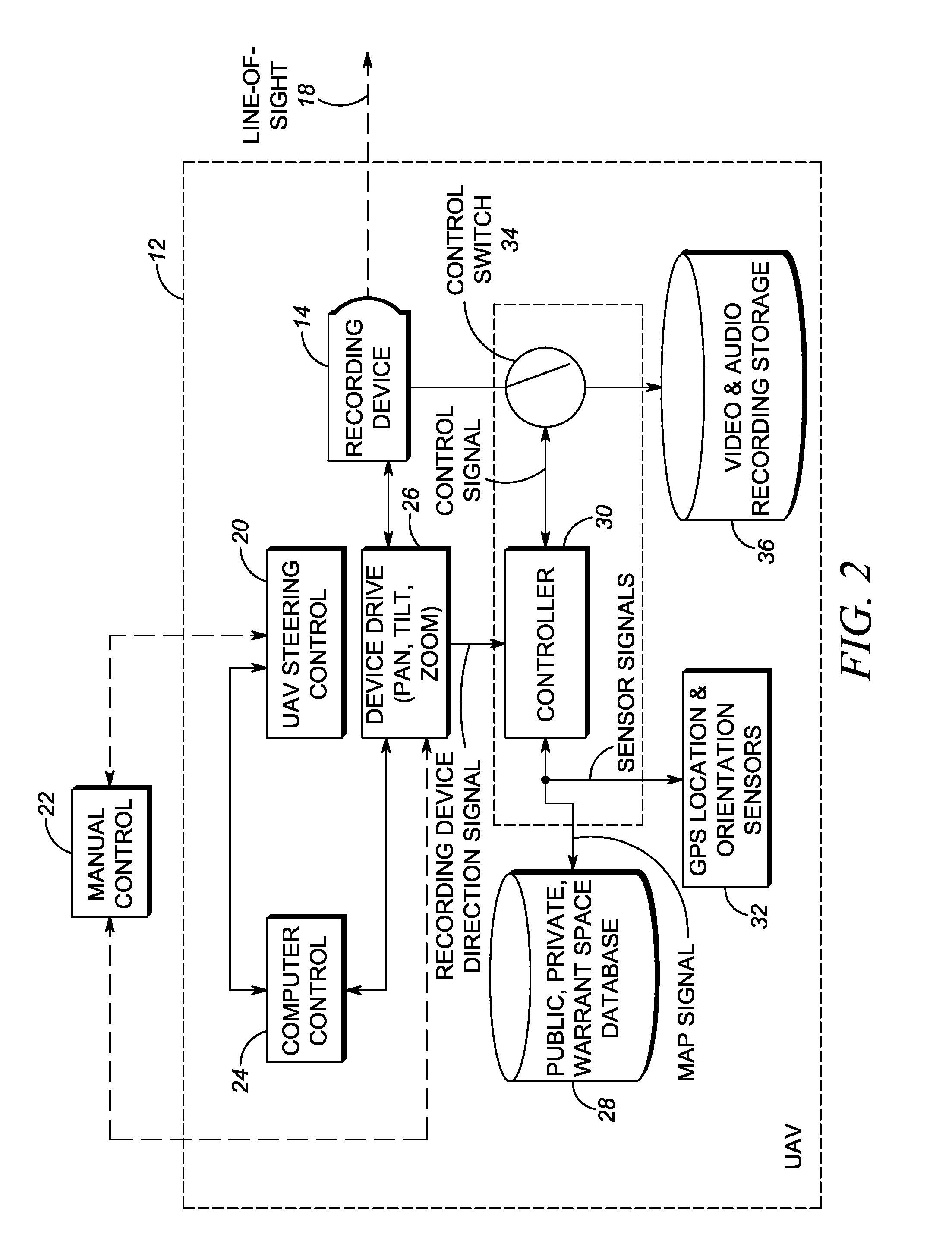
A video / audio recording device is mounted on a mobile support for recording surveillance information. The recording device is movable relative to the mobile support to adjustably position the recording device to face the target along a line-of-sight during recording. A database stores public map spaces, private map spaces, and warrant spaces that exist in a geographic area to be surveilled. A programmed controller accesses the database, determines whether the target is recordable from a public map space along the line-of-sight between the recording device and the target and / or whether the target is covered by a warrant space, and controls the recording device to record the surveillance information upon a successful determination that the target is so recordable or so covered.
Owner:MOTOROLA SOLUTIONS INC
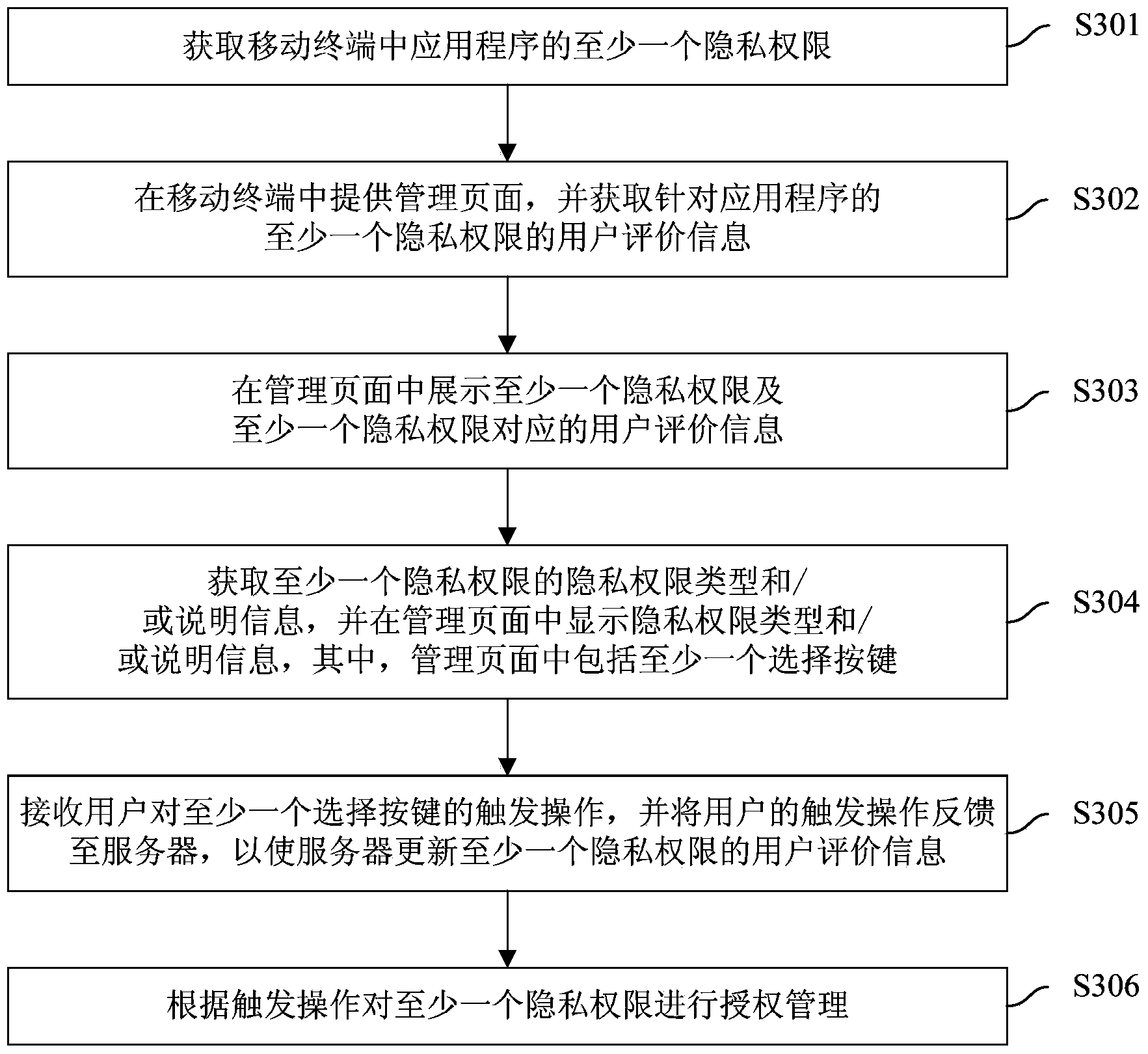
Application program privacy authority management method and device
ActiveCN103886255AEasy to manageImprove privacy and securityDigital data protectionPlatform integrity maintainanceApplication softwareAuthorization
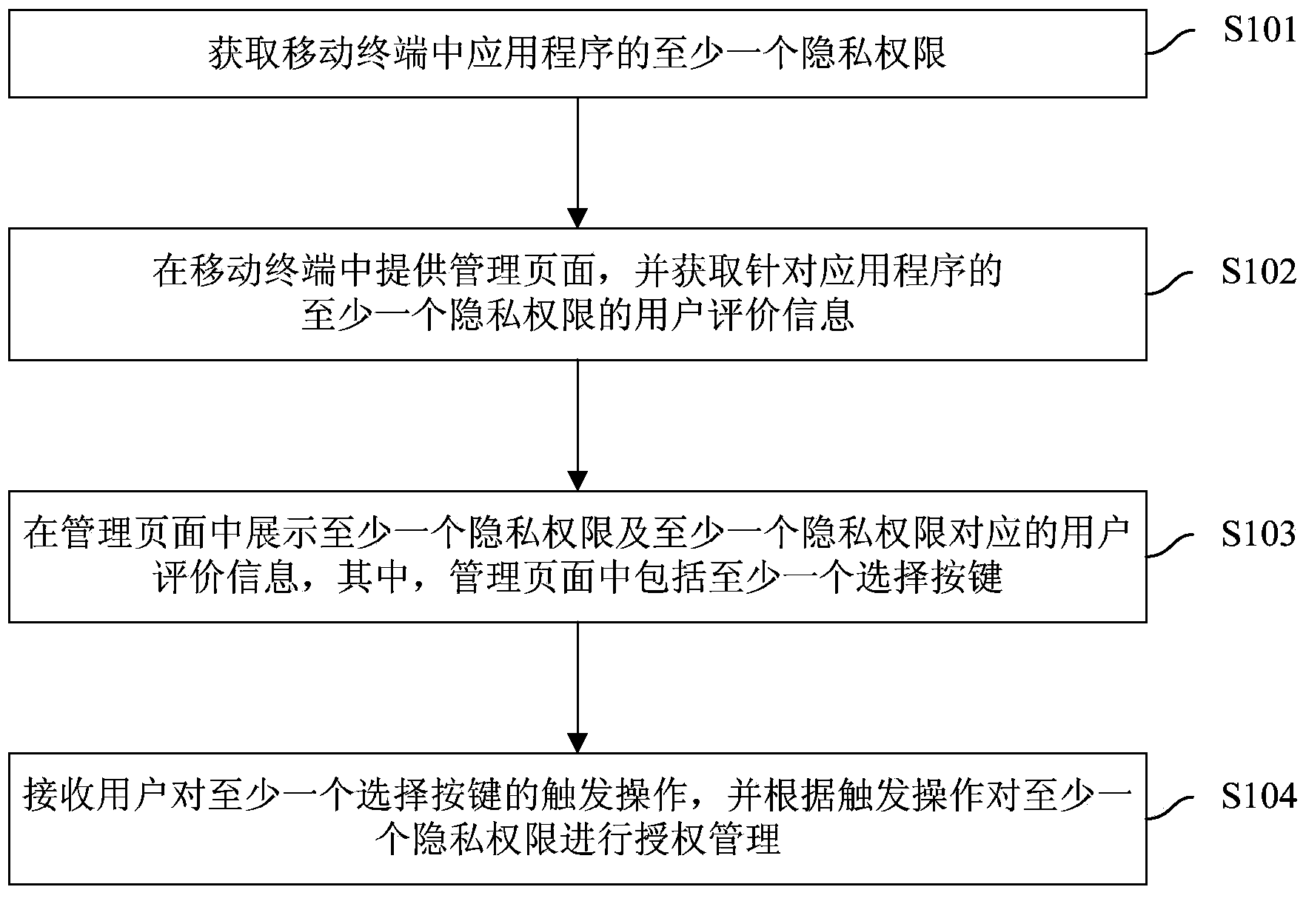
The invention discloses an application program privacy authority management method and device. The method comprises the steps that at least one privacy authority of an application program in the mobile terminal is obtained; a management page is provided in the mobile terminal, and user assessing information of the at least one privacy authority corresponding to the application program is obtained; the at least one privacy authority and the user assessing information corresponding to the at least one privacy authority are shown in the management page, wherein at least one selecting key is included in the management page; and triggering operation on the at least one selecting key of a user is received, and according to the triggering operation, authorization management is carried out on the at least one privacy authority. According to the management method, the user can clearly know which application programs obtain the privacy authority excessively, the user can conveniently manage the privacy authority, the privacy safety of the user is improved, user experience is improved, manual analysis is of no need, and labor cost is greatly lowered.
Owner:KENIU NETWORK TECH BEIJING
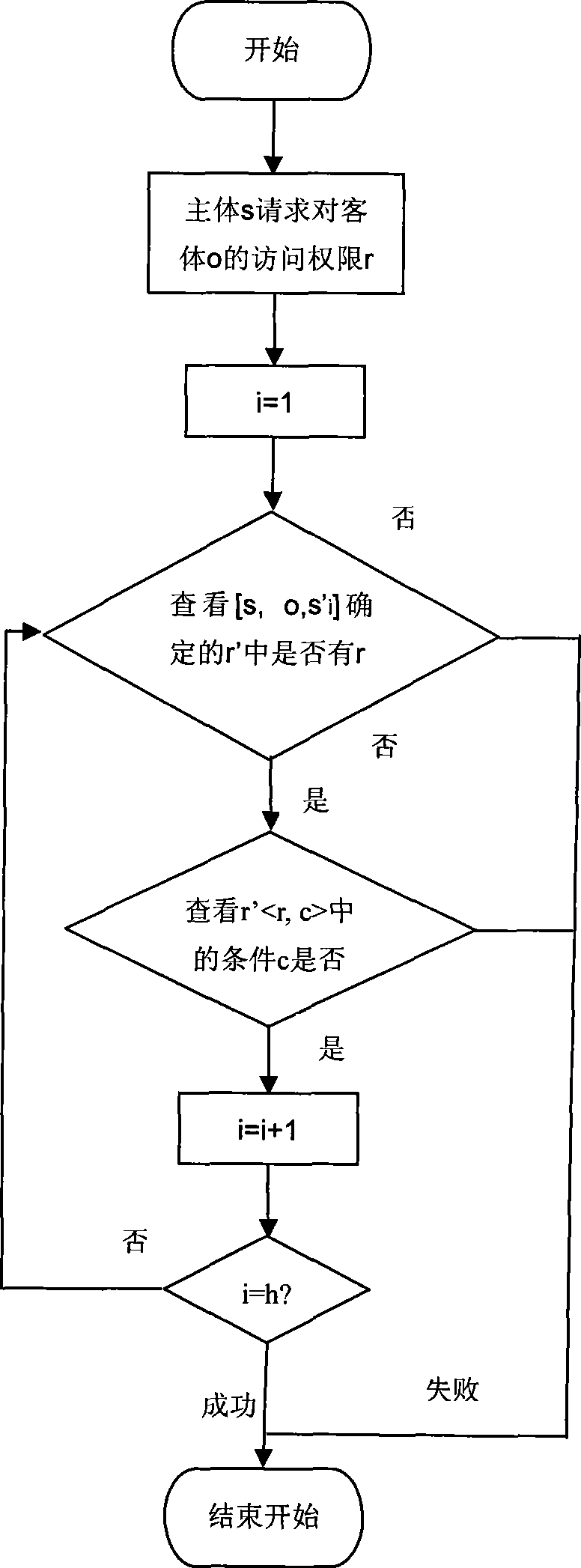
Method for protecting privacy based on access control
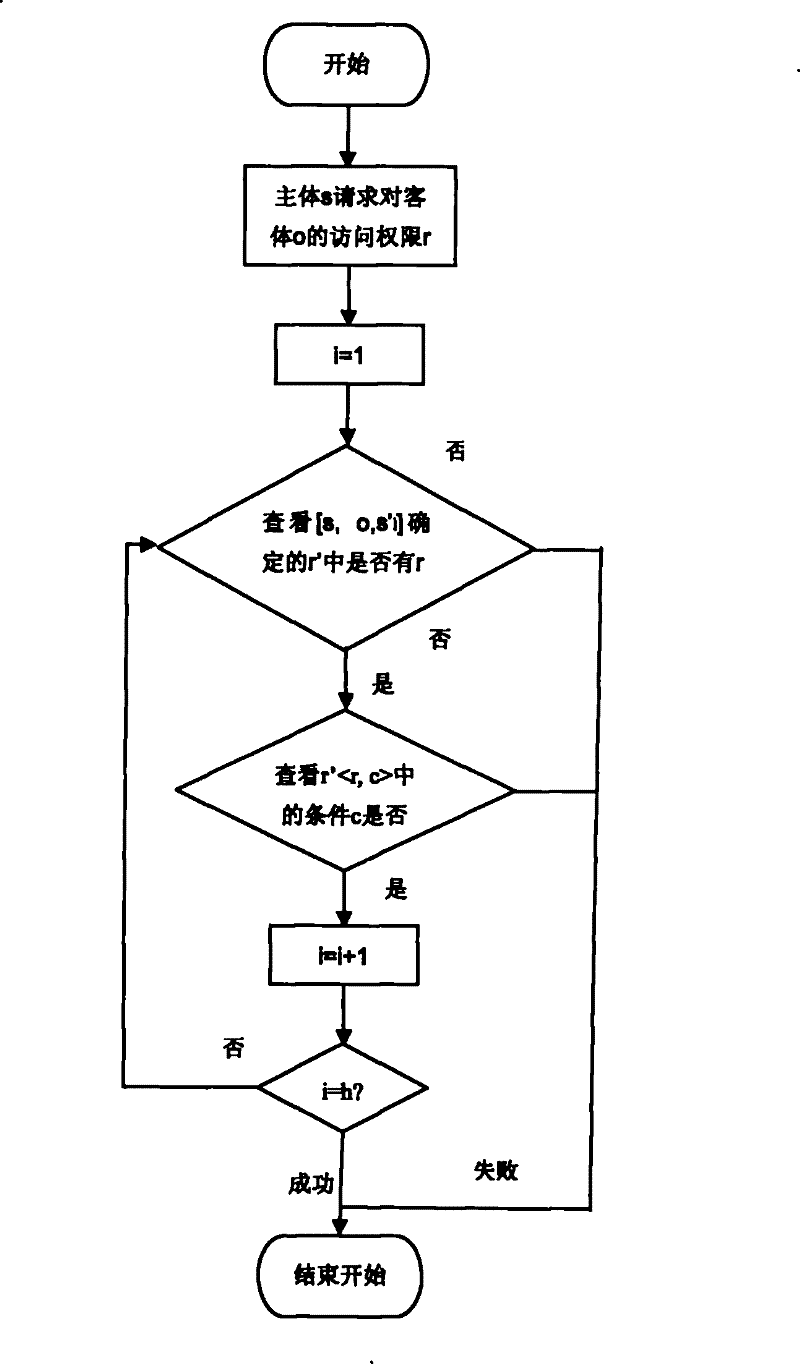
InactiveCN101465853AAvoid the risk of leakageEasy to implementData switching networksThe InternetPrivacy protection
A privacy information protecting method based on access control belongs to computer network security field and is used in network application whose privacy information needs to be protected in the Internet. The invention expands the access right to privacy access right; when setting the right, conditions which need to be satisfied when authorizing the right are added; and a user is allowed to control the privacy information at real time, thus increasing the flexibility of the user to control the privacy information. Furthermore, all the entities relevant to the privacy information are added into the access control as privacy subjects, so that all the relevant subjects can set access control strategies for privacy information protection according to privacy information protection requirements. Accesses to the privacy information are controlled according to the strategies of the privacy subjects, which makes the privacy information protection method more perfect, thus avoiding all invasions of privacy of the user. The privacy information protecting method gives consideration to the distinctive features of privacy information protection, namely the flexibility and integrity required in privacy protection, and fully guarantees the rights and interests of the user.
Owner:BEIJING UNIV OF TECH
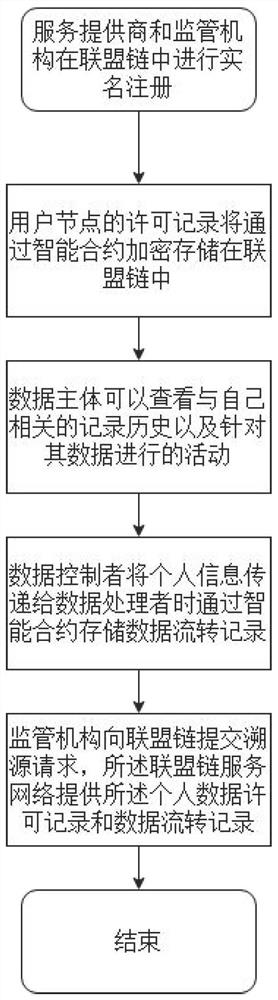
GDPR compliance supervision method and system based on alliance chain
ActiveCN112073484AImprove efficiency in complying with GDPR complianceReduce complianceUser identity/authority verificationData streamEngineering
The invention provides a GDPR compliance supervision method and system based on an alliance chain, and the method comprises the steps: enabling a service provider and a supervision mechanism to carryout the real-name registration in the alliance chain, enabling the service provider to be registered as a service node, and carrying out the accounting node election and block generation according tothe credibility of the service node; the permission record of the data subject is encrypted and stored in the alliance block chain through the smart contract; the data subject is granted permission toaccess the alliance block chain, and when the data controller transmits personal information to the data processor, the agreement of the related data subject is needed, and the transaction also stores a data flow record through the smart contract; and during compliance investigation, submitting a traceability request to the alliance block chain by the supervision institution, and tracing to obtain a record by the alliance block chain service network according to the request. According to the method, the expansibility and the tamper resistance of the block chain are utilized so that the privacy right endowed by the user to drive the GDPR and the efficiency of a service provider to abide by the GDPR compliance can be effectively improved from the aspect of technical support, and the compliance and supervision cost is reduced.
Owner:WUHAN UNIV
Privacy processing method and device, computer readable storage medium and electronic medium
InactiveCN111885339ASolving the inability to make an effective statement on one's own privacy rightsSolve protection problemsGeometric image transformationBiometric pattern recognitionElectronic mediaRight to privacy
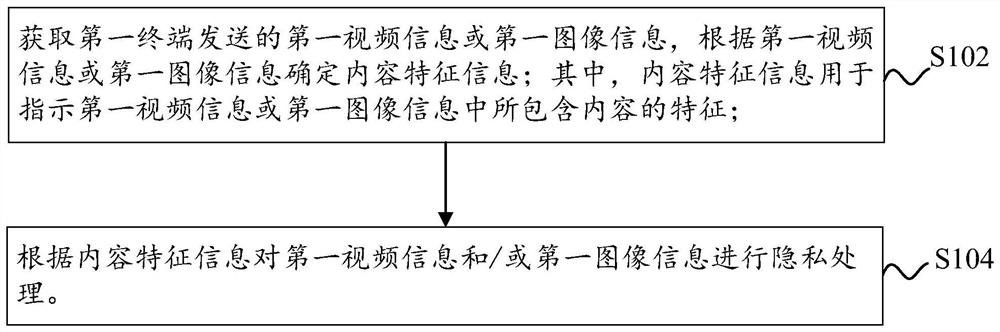
The invention provides a privacy processing method and device, a computer readable storage medium and an electronic medium, and the privacy processing method comprises the steps: obtaining first videoinformation or first image information sent by a first terminal, and determining content feature information according to the first video information or the first image information, wherein the content feature information is used for indicating features of content contained in the first video information or the first image information; and performing privacy processing on the first video information and / or the first image information according to the content feature information. Through the embodiment of the invention, the problem that the user cannot effectively declare or protect the own privacy rights in the related art can be solved, so that the effect of declaring or protecting the privacy according to the own requirements of the user can be achieved.
Owner:HAIER YOUJIA INTELLIGENT TECH BEIJING CO LTD
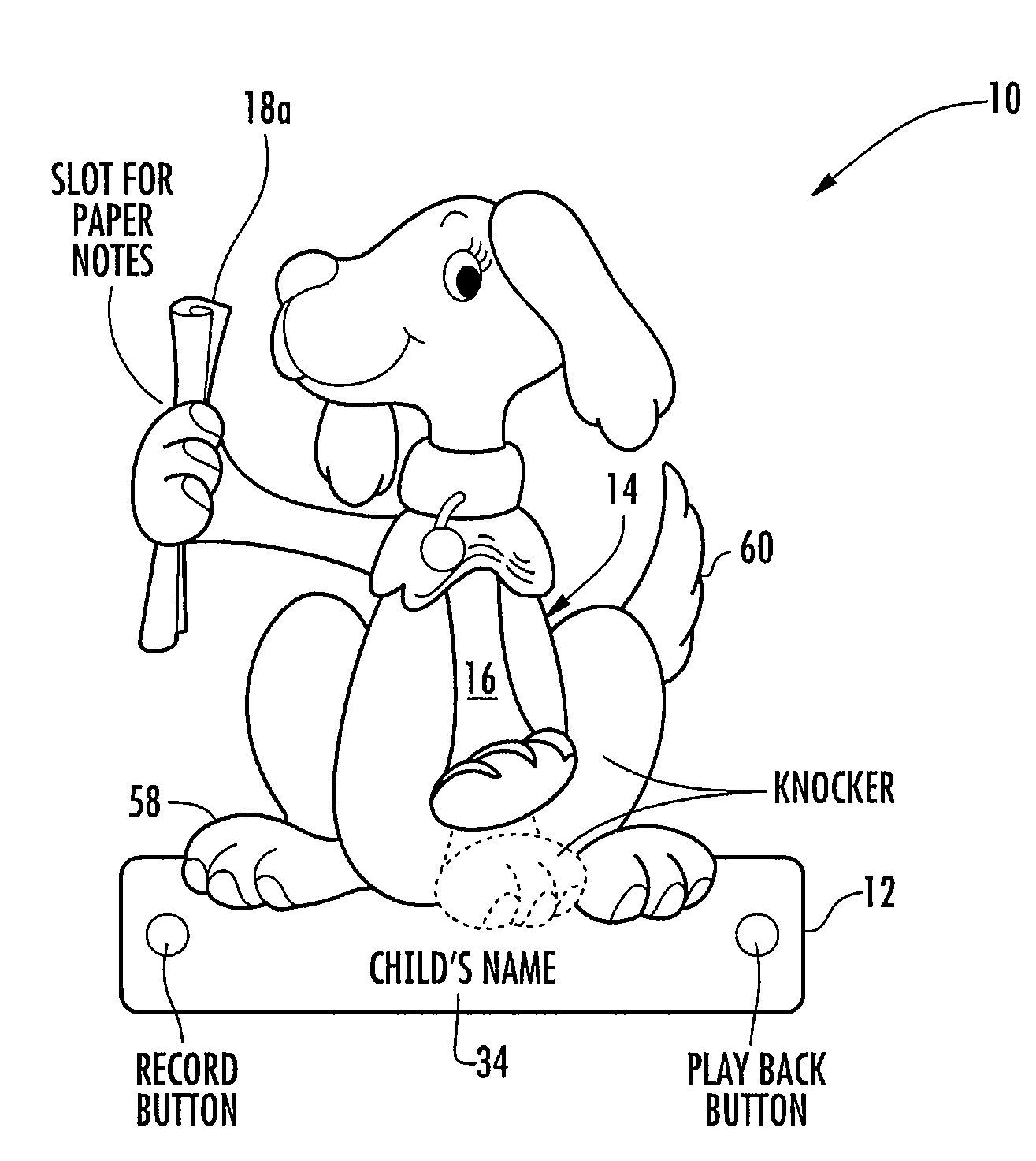
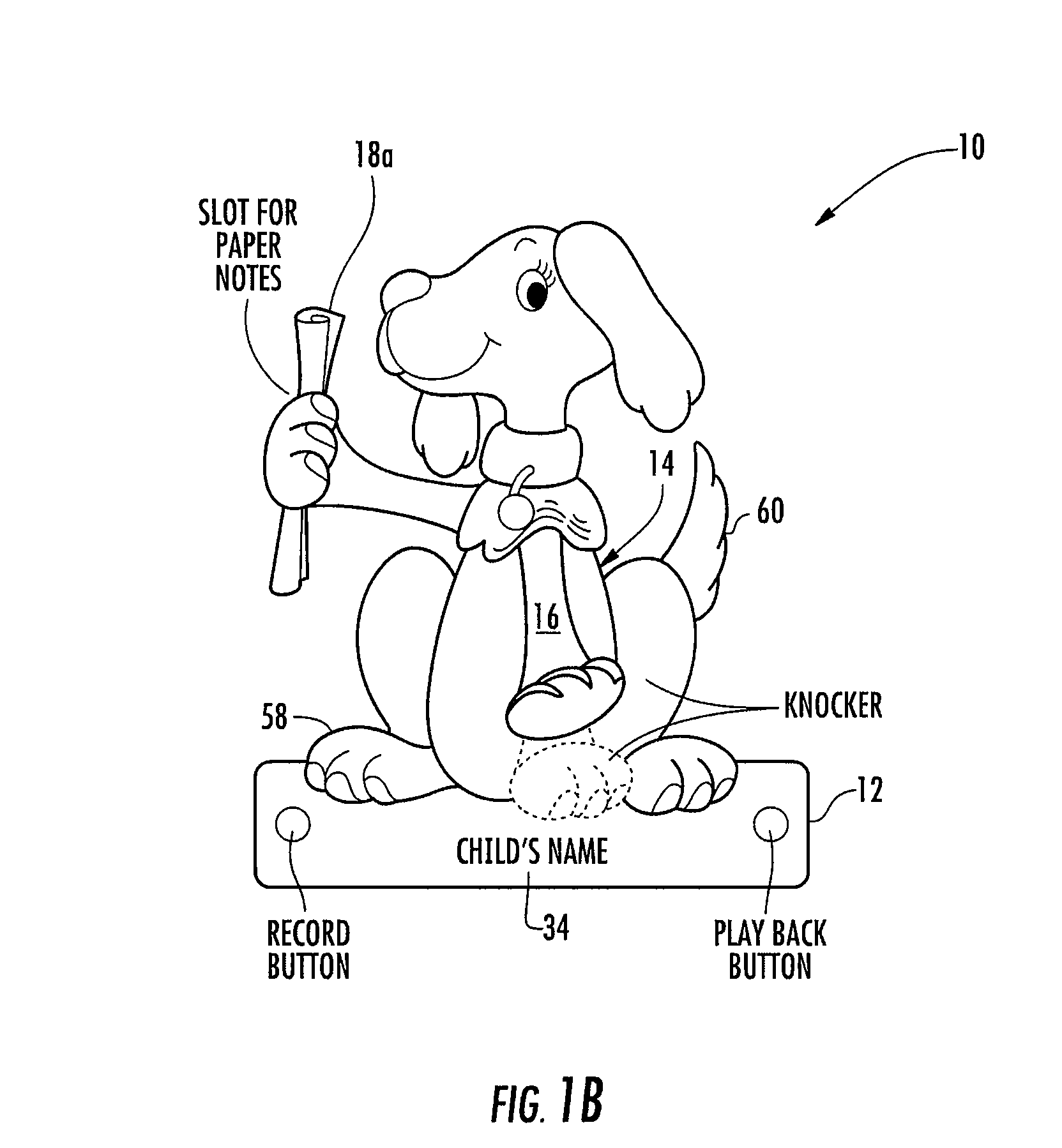
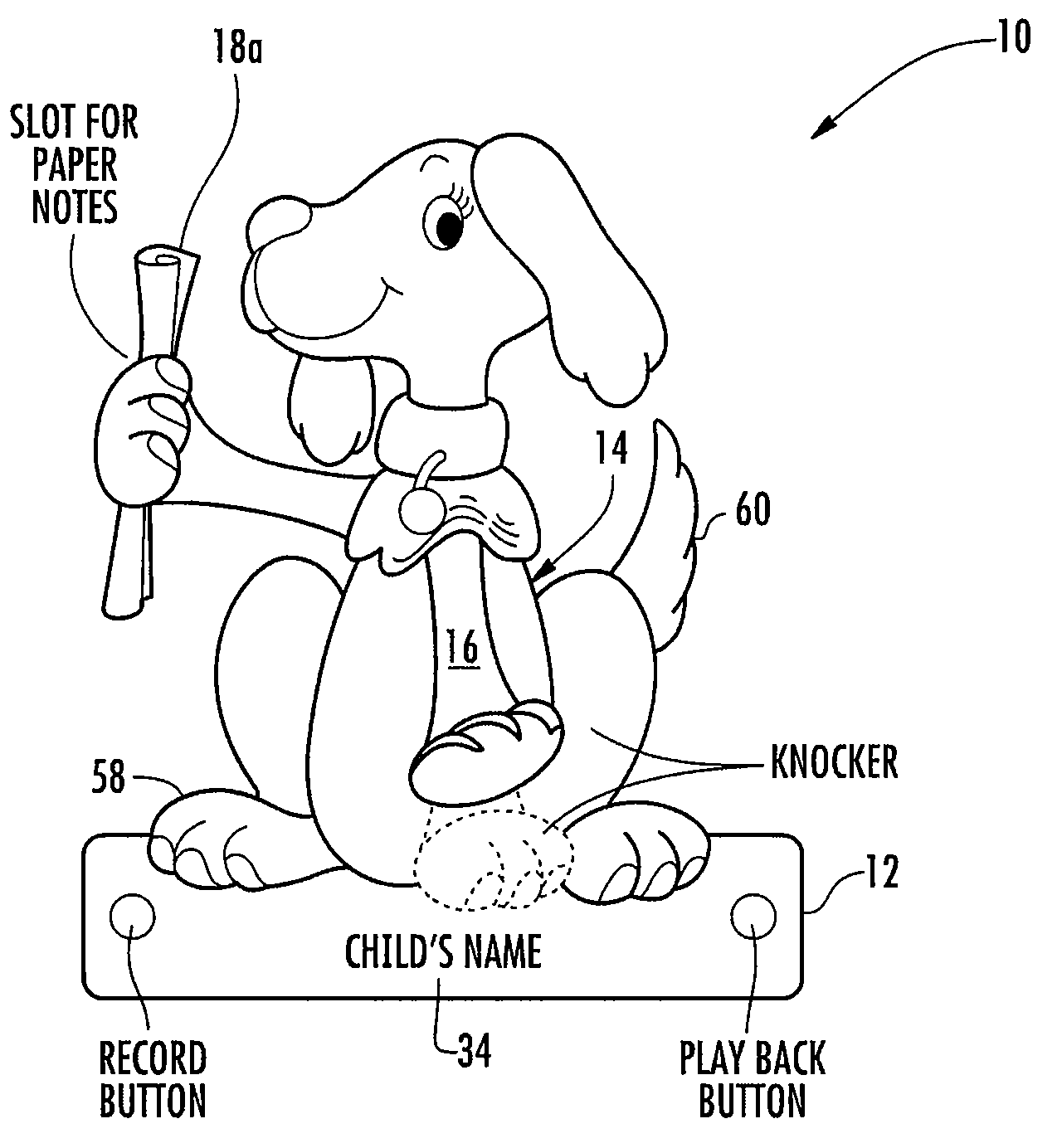
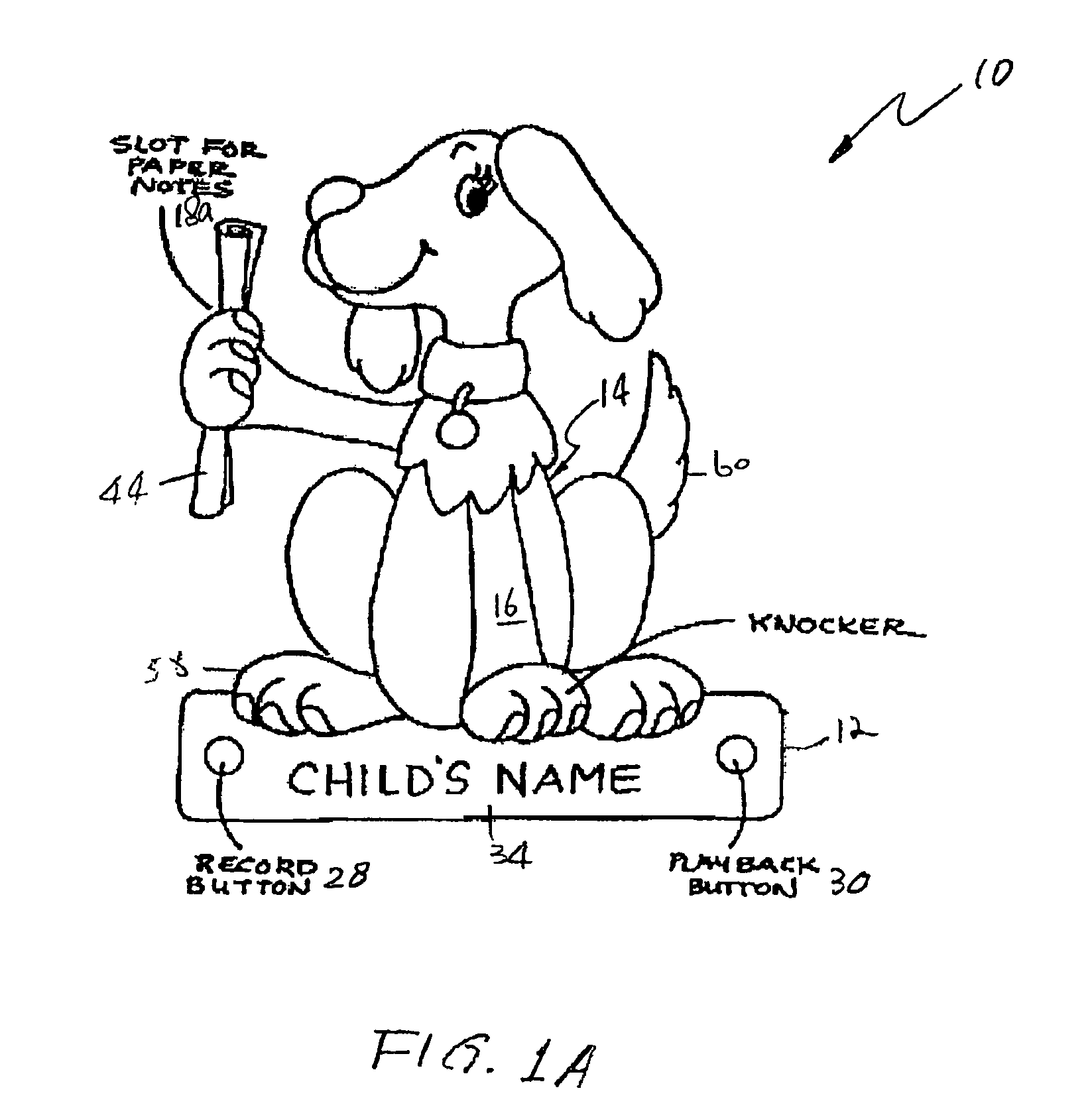
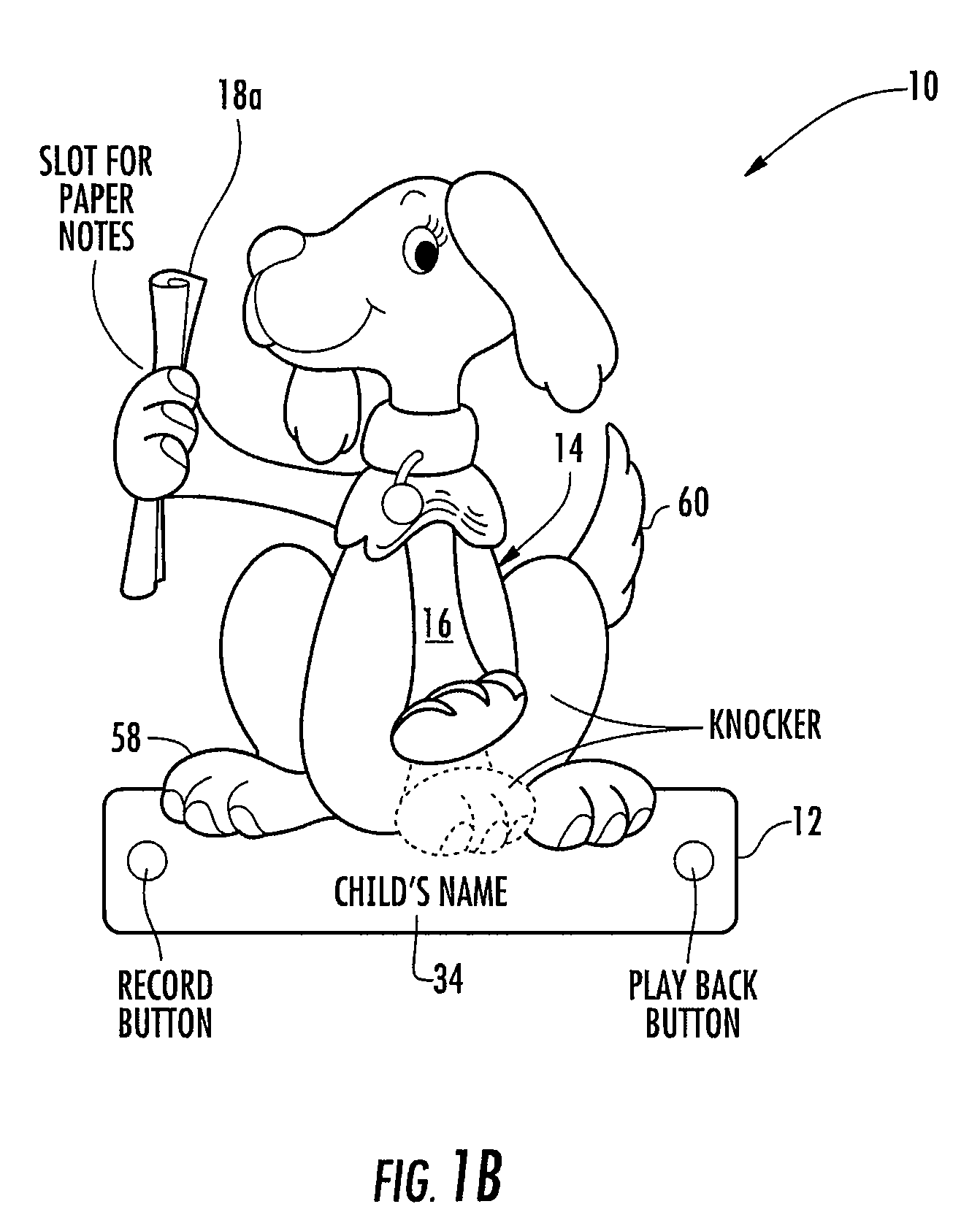
Toy door knocker, and construction and educational kits including a door knocker
Modular constructional toy kit and instructional story book, for use in forming a customized and personalized privacy guard in the form of a door knocker and learning the importance of protecting and respecting a persons right to privacy. The constructional toy kit allows children to build and decorate their own door knockers. Each door knocker has a base unit and a pivotal member hinged at one end to the base unit allowing the pivotal member to swing in a short arc away from the base unit. When released, the pivotal member swings back to make contact with the base unit emitting a loud sound. The constructional toy kit can also have an integrated holder to store written messages, integrated electronic recording and playback device for personalized audio messages, a smooth flat surface at the lower portion of the base unit suitable for imprinting a child's name, assorted decorations and attachable components to allow for the creation of animals or creatures, paints and commercially available hardware and adhesives.
Owner:WICHARD SHEREE +1
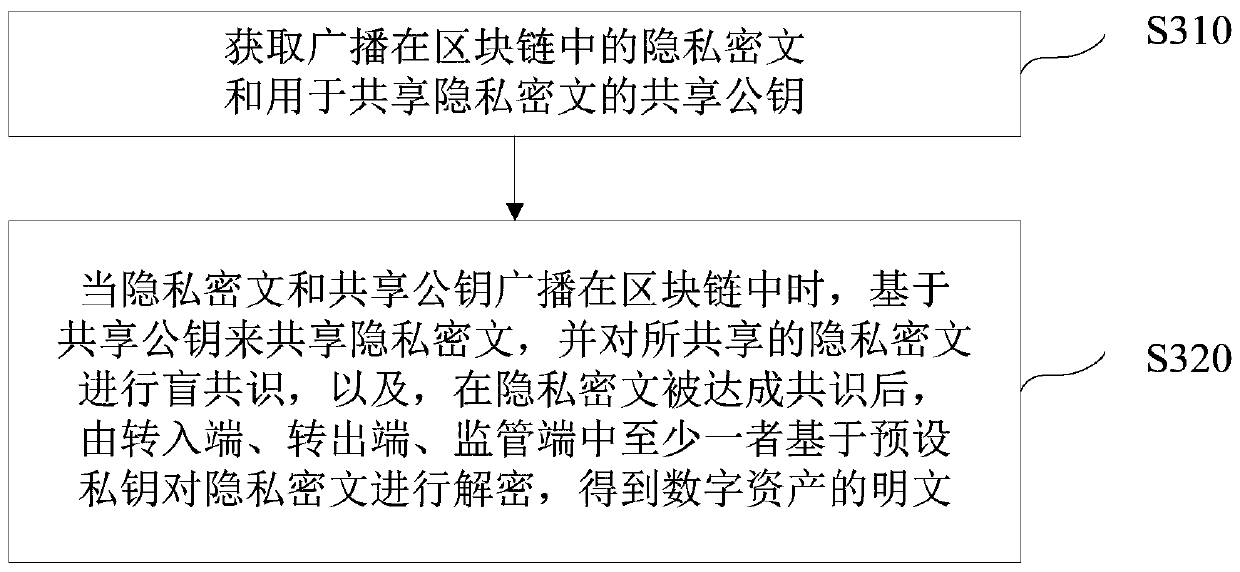
Blockchain-based digital asset processing method and device
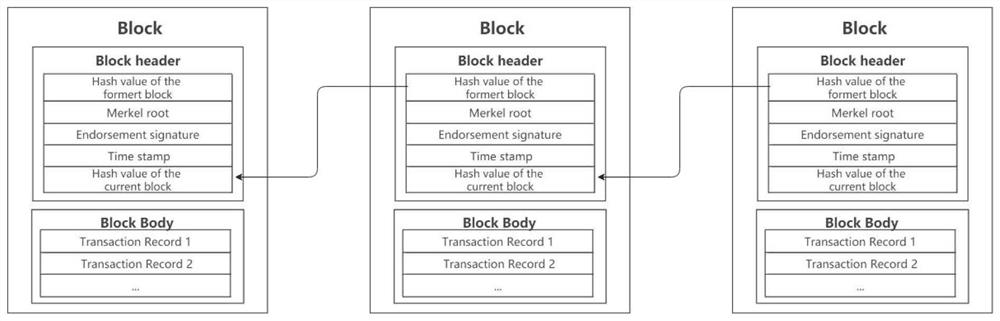
ActiveCN106982205BProtection of privacySmooth circulationKey distribution for secure communicationDigital data protectionPlaintextComputer network
The invention discloses a blockchain-based digital asset processing method and device. The method comprises the following steps: receiving private ciphertext for a digital asset circulated from a sending end to a receiving end through a blockchain, and a preset public key; and obtaining a sharing public key for sharing the private ciphertext based on the preset public key, so that when the private ciphertext and the sharing public key are broadcast in the blockchain, blockchain nodes on the blockchain can share the private ciphertext based on the sharing public key and reach a blind consensus on the shared private ciphertext, and after the consensus on the private ciphertext is reached, the private ciphertext can be decrypted by at least one of three parties, i.e., the sending end, the receiving end and a monitoring end, based on a preset private key to obtain plaintext of the digital asset. The method and device provided by the embodiment of the invention has the advantages that the privacy right of a user is protected; under the premise of privacy protection, the single general digital asset can be smoothly circulated within one blockchain or among multiple blockchains, and a total currency amount remains unchanged; and a monitoring party other than the transaction parties can monitor transaction information at any time.
Owner:中钞信用卡产业发展有限公司杭州区块链技术研究院 +1
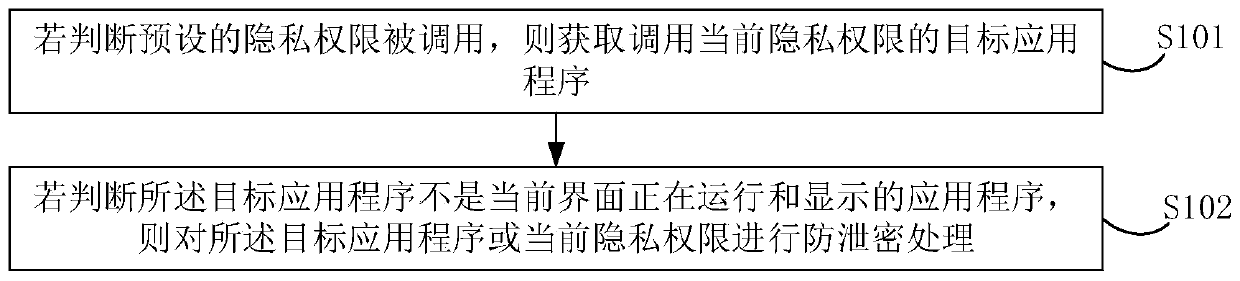
Secret divulgence prevention processing method and device for privacy authority, electronic equipment and storage medium
The embodiment of the invention discloses an anti-disclosure processing method and device for a privacy authority, electronic equipment and a storage medium, and the method comprises the steps: obtaining a target application program for calling a current privacy authority if the preset privacy authority is judged to be called; if it is judged that the target application program is not the application program which is being operated and displayed on the current interface, performing anti-disclosure processing on the target application program or the current privacy authority; wherein the presetprivacy authority comprises at least one of the following items: a camera shooting authority, a recording authority, a positioning authority and a calling authority of a privacy application program.According to the method, after it is judged that the target application program calling the current privacy authority is not the application program running at the foremost end, secret leakage prevention processing is conducted on the target application program or the current privacy authority, and secret leakage caused by the privacy authority can be effectively prevented.
Owner:BEIJING QIANXIN TECH +1
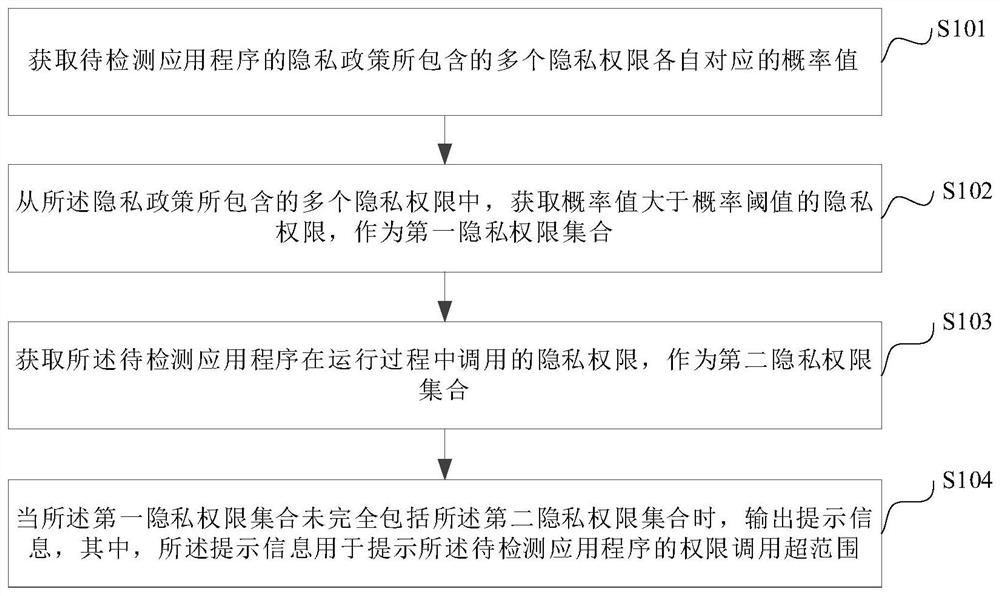
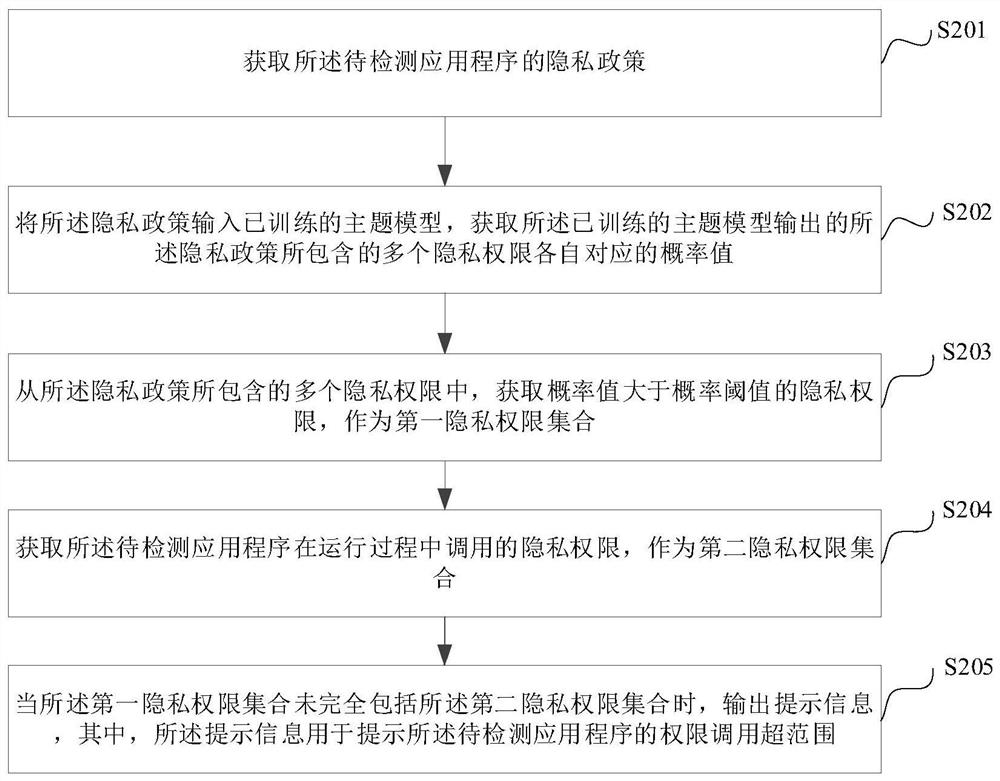
Private authority detection method and device, electronic equipment and storage medium
PendingCN113849852ARealize detectionImprove accuracyDigital data protectionPlatform integrity maintainanceApplication procedureEngineering
The invention discloses a privacy authority detection method and device, electronic equipment and a storage medium, and relates to the technical field of data safety. The method comprises the steps of obtaining probability values corresponding to a plurality of privacy permissions contained in a privacy policy of a to-be-detected application program, obtaining privacy permissions of which the probability values are greater than a probability threshold value from the plurality of privacy permissions contained in the privacy policy, and taking the obtained privacy permissions as a first privacy permission set, the privacy authority called by the to-be-detected application program in the running process is obtained to serve as a second privacy authority set, and when the first privacy authority set does not completely comprise the second privacy authority set, prompt information is output and used for prompting that authority calling of the to-be-detected application program is out of range, privacy authority detection of the application program is achieved, and the privacy authority of the to-be-detected application program is detected. The accuracy of privacy authority detection is improved, and the duration of privacy authority detection is shortened.
Owner:HANGZHOU DOUKU SOFTWARE TECH CO LTD
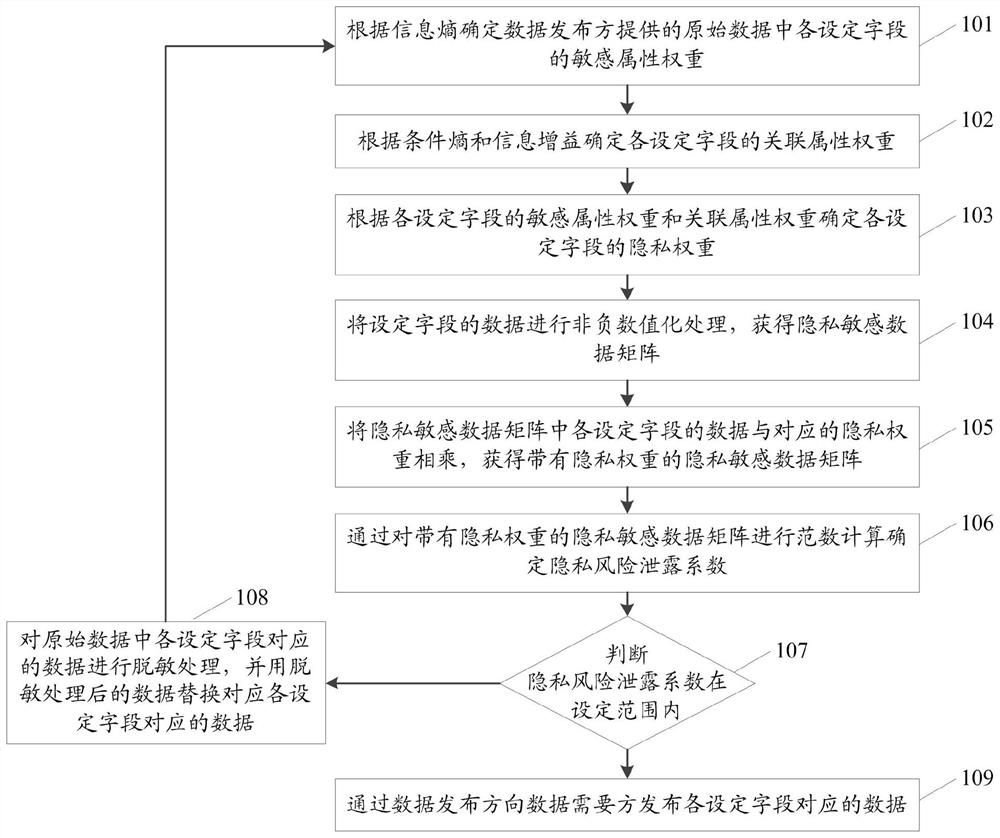
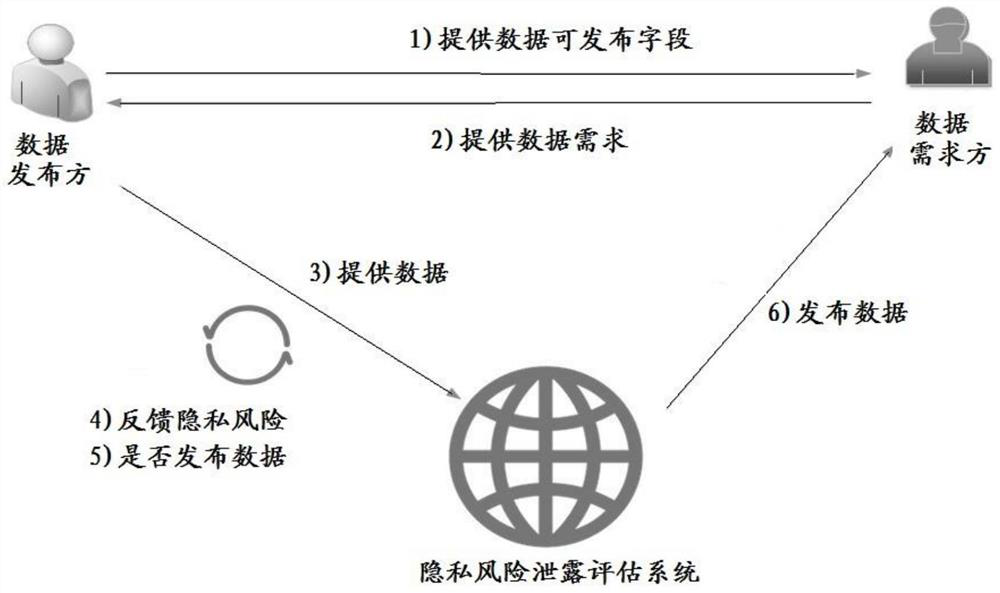
Data publishing method and system
PendingCN114117525AReduce risk of leakageDigital data protectionComplex mathematical operationsConditional entropyOriginal data
The invention relates to a data publishing method and system. The method comprises the steps that sensitive attribute weights of all set fields in original data provided by a data publisher are determined according to information entropy; determining an association attribute weight of each set field according to the conditional entropy and the information gain; determining a privacy weight of each set field according to the sensitive attribute weight and the associated attribute weight; performing non-negative numeralization processing on the data of the set field to obtain a privacy sensitive data matrix; obtaining a privacy sensitive data matrix with a privacy weight; performing norm calculation on the privacy sensitive data matrix with the privacy weight to determine a privacy risk leakage coefficient; judging whether the privacy risk leakage coefficient is within a set range or not; and if the privacy risk leakage coefficient is not within the set range, desensitizing the data corresponding to each set field in the original data, replacing the data corresponding to the set fields with the desensitized data, and recalculating the privacy risk leakage coefficient until the privacy risk leakage coefficient conforms to the set range. According to the invention, the risk of data privacy leakage is reduced.
Owner:GUIZHOU UNIV
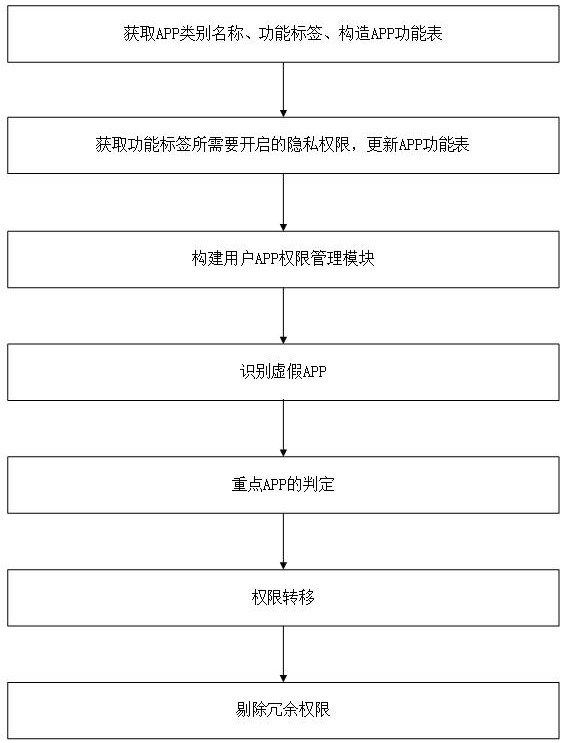
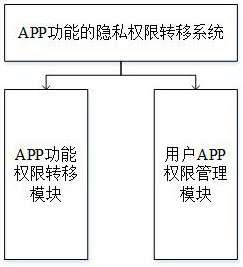
Privacy authority transfer method based on APP function
ActiveCN113157210AImprove service experienceAchieve transferInput/output to record carriersCharacter and pattern recognitionUser PrivilegeService experience
The invention discloses a privacy authority transfer method and system based on an APP function, and the method comprises the steps: obtaining various APPs and corresponding various function types according to various APPs in the market; according to different functions of the APP, determining which privacy authorities need to be started when a user uses a certain function, and carrying out importance degree grading on the privacy authorities; according to the type of a certain APP used by a user, counting functions under the type, and constructing a user APP authority management table; according to different conditions such as false APPs, key APPs, carrying out function labels of the APPs and importance of permissions corresponding to the functions, permission transfer, so that good service experience of a user is guaranteed, it is guaranteed that when the user uses a certain function of the APPs, only necessary privacy permissions need to be granted to the current function, and unimportant privacy permissions are filtered out.
Owner:深圳季连科技有限公司
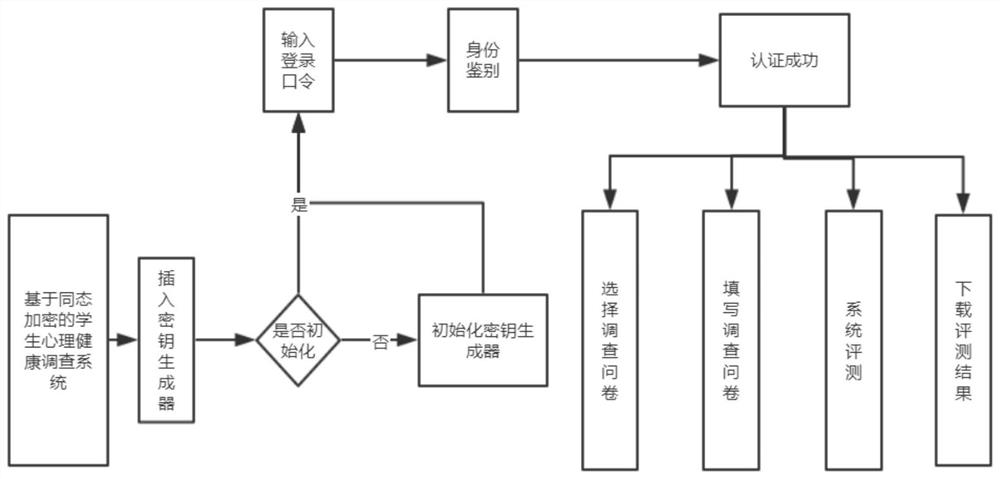
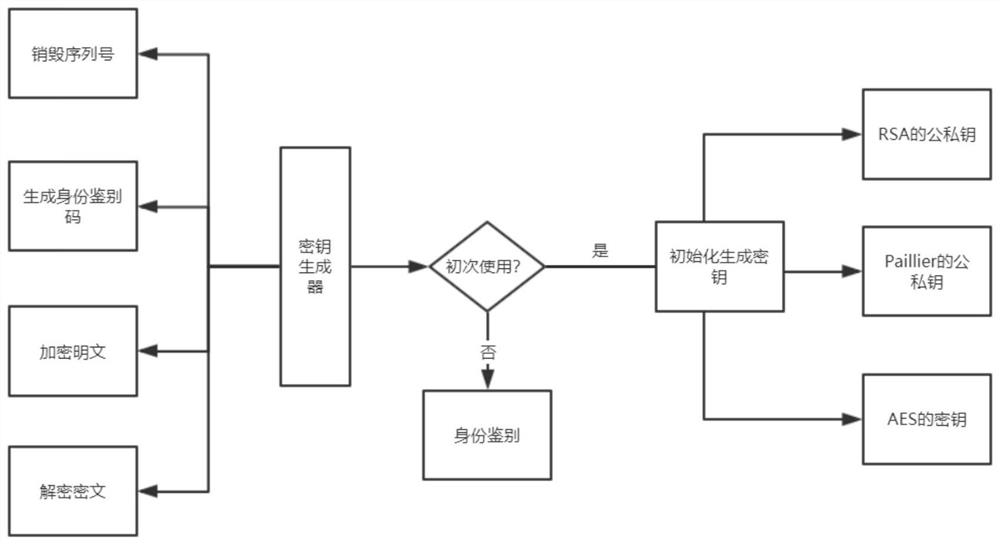
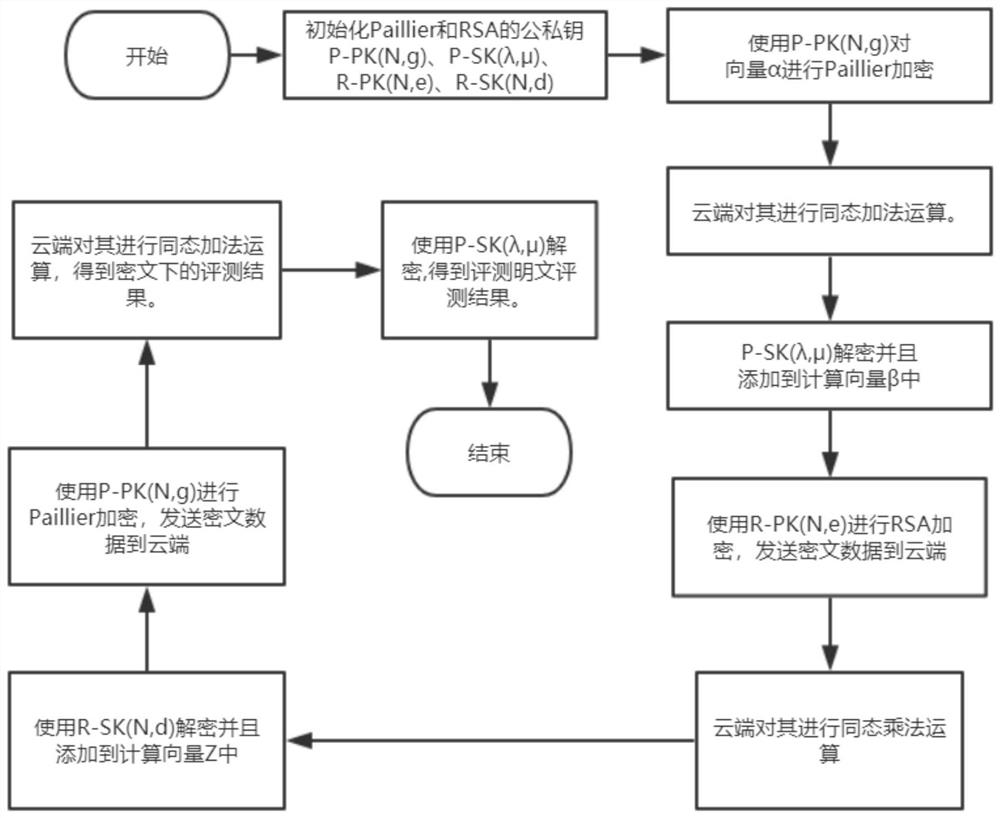
System design and implementation method of homomorphic encryption in student mental health investigation
ActiveCN113141246AMeet privacy protection needsProtection of privacyEncryption apparatus with shift registers/memoriesPublic key for secure communicationKey (cryptography)Systems design
The invention discloses a system design and implementation method of homomorphic encryption in student mental health investigation, and belongs to the field of symmetric key cryptography and public key cryptography. According to the method, firstly, a user uses a key generator to generate an identity authentication code, then, the user logs in a system to fill in a survey report, then, the system ensures full homomorphic calculation of a cloud end by using a full homomorphic algorithm (somewhat algorithm) constructed by a pallier addition homomorphic structure and an RSA multiplication homomorphic structure, and finally, the user inquires and detects a ciphertext result through a ciphertext index, and exports and decrypts by using a private key to obtain the mental health assessment. The student trust psychological health evaluation system can be guided to obtain a real test effect. Therefore, the system can meet the privacy protection requirement of mental health evaluation in an online environment, and the privacy right of the user is better protected. The method not only can be applied to the mental health evaluation level, but also has a good application prospect in various online surveys such as occupational attainment evaluation and the like.
Owner:山东凌瑞市场调查有限公司
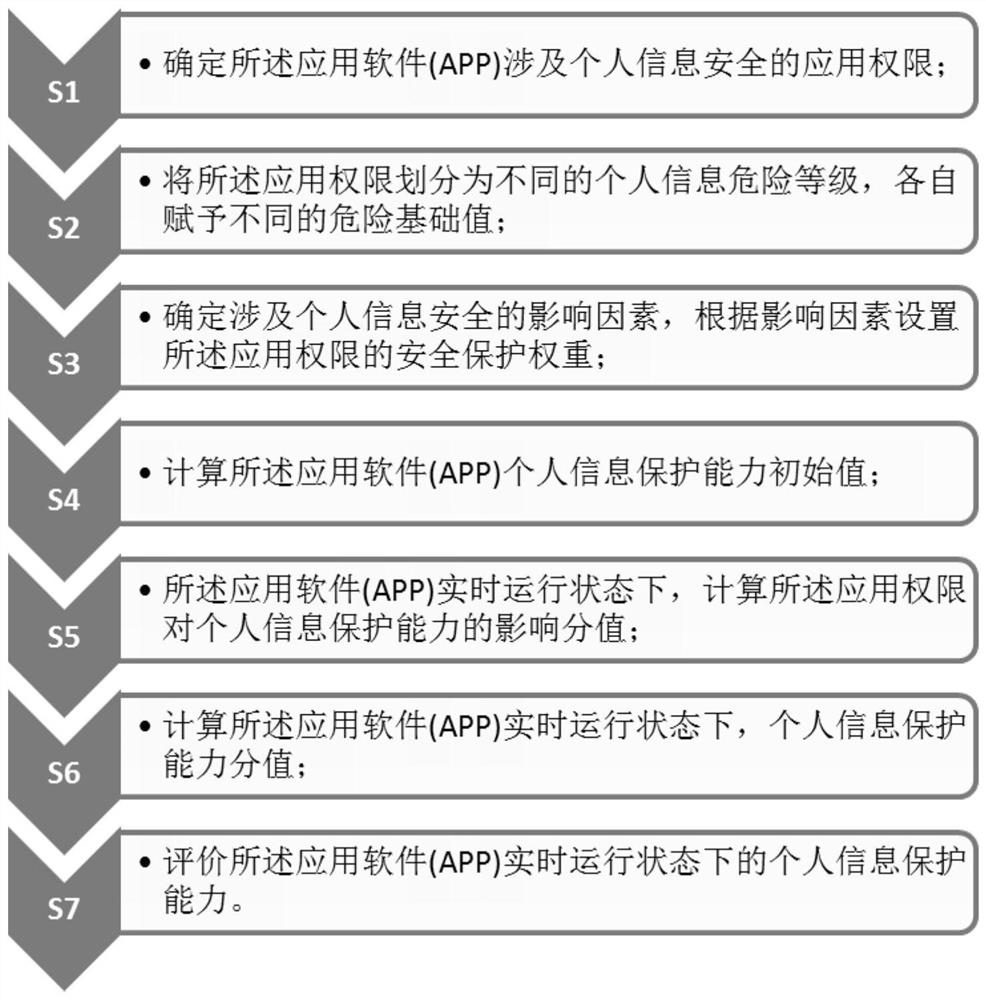
Method for evaluating personal information protection capability of application software in real-time running state
PendingCN113158236ADigital data protectionPlatform integrity maintainanceApplication softwareRight to privacy
The invention provides a method for evaluating personal information protection capability of an APP in a real-time running state, according to application behaviors and influence factors of personal information security related to the application software (APP), a personal information security calculation strategy of the application software (APP) is generated, and according to different application behaviors and influence factors, each application permission is assigned; an APP static personal information protection capability score is calculated and taken as an initial value; then the influence of the important privacy authority obtained by the APP on the personal information protection capability of the APP is analyzed and calculated; and finally, the score of the personal information protection capability of the APP during real-time operation is calculated, guidance is provided for evaluating the personal information protection capability of the APP, a user to select and use the APP is guided, the user can be assisted to fully understand the influence of opening / closing of different permissions on the personal information protection capability of the APP, and therefore, the user can be guided to carefully open the APP permission or timely close the permission for use compensation.
Owner:中电数据服务有限公司
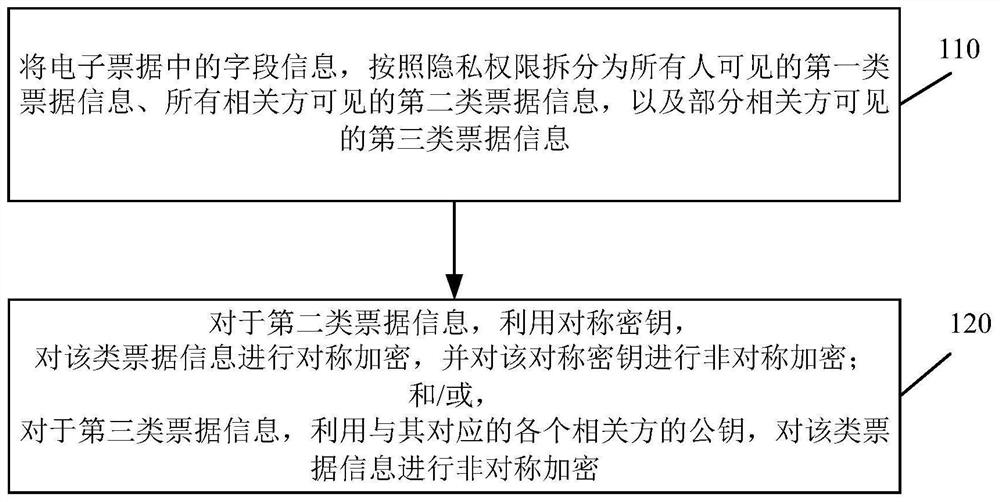
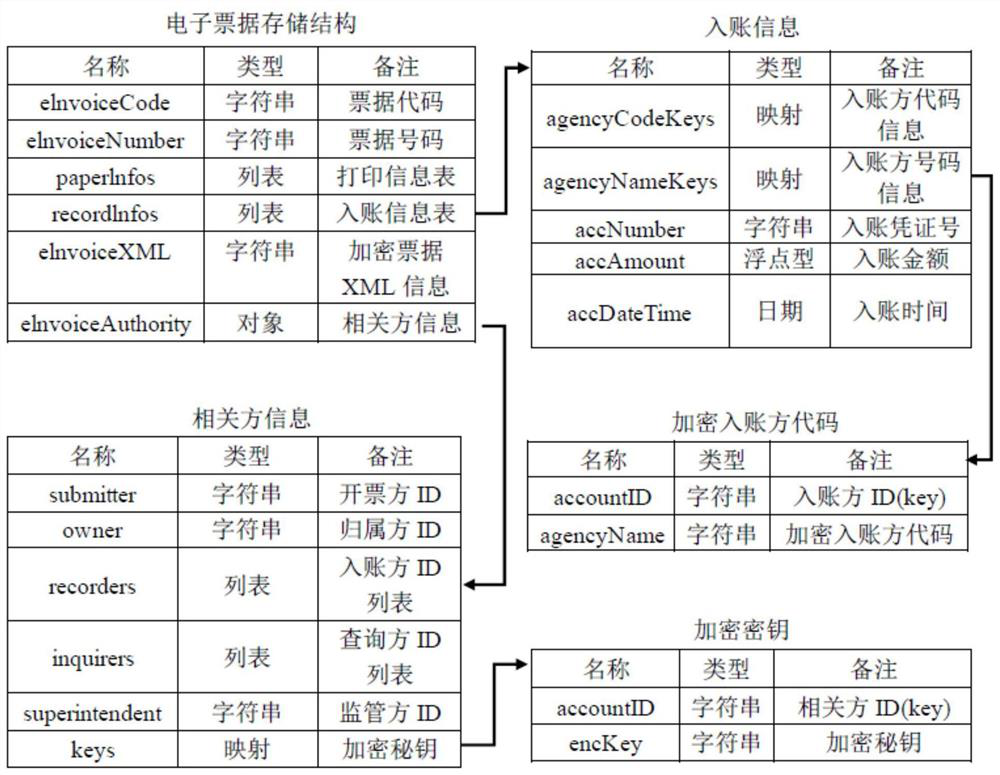
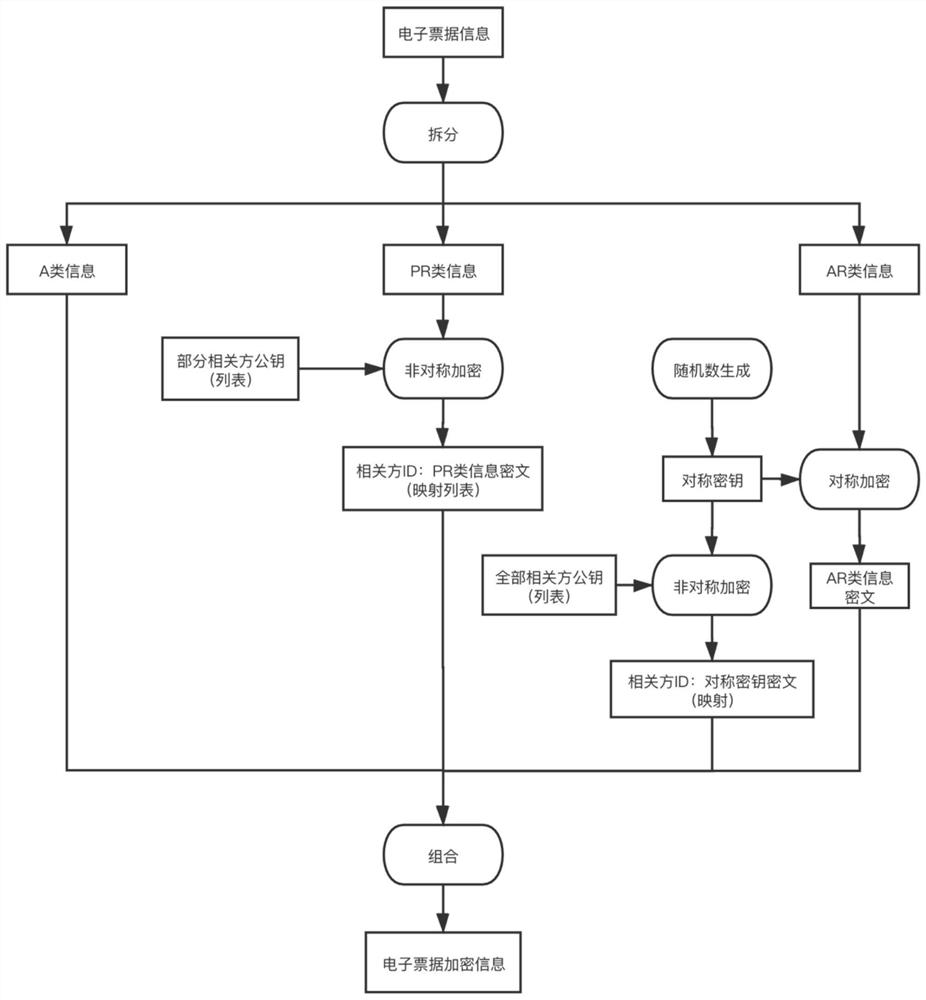
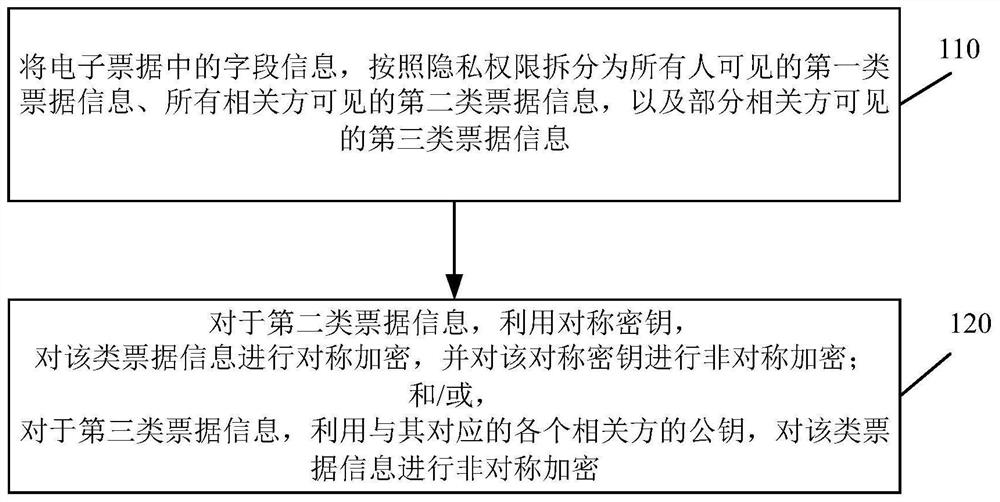
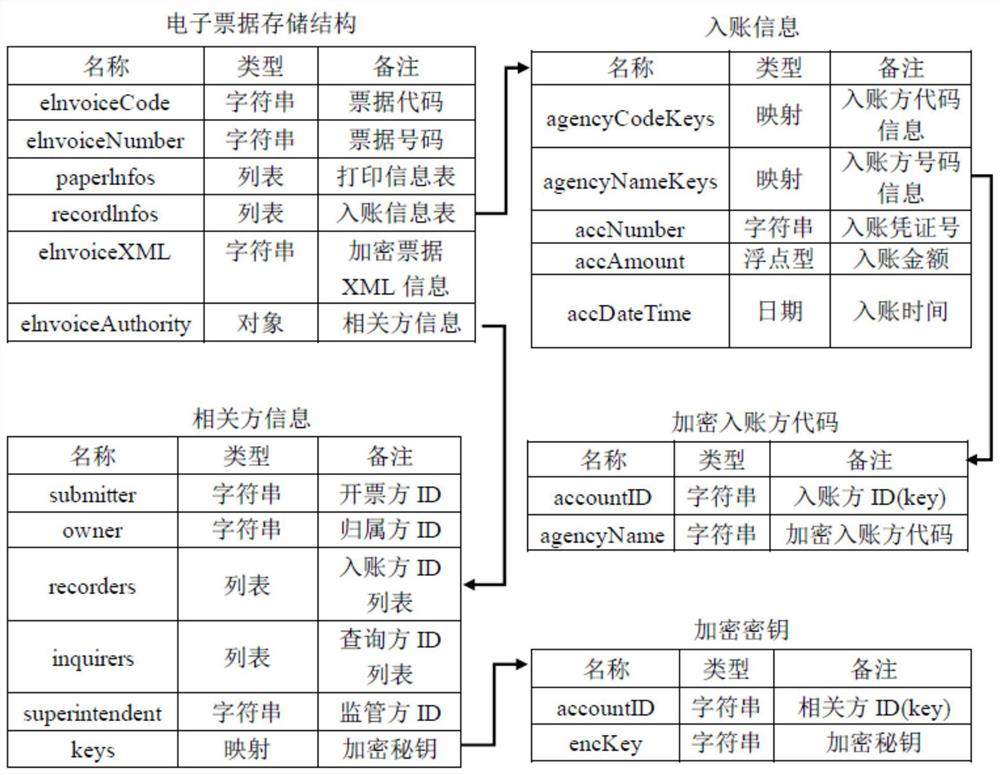
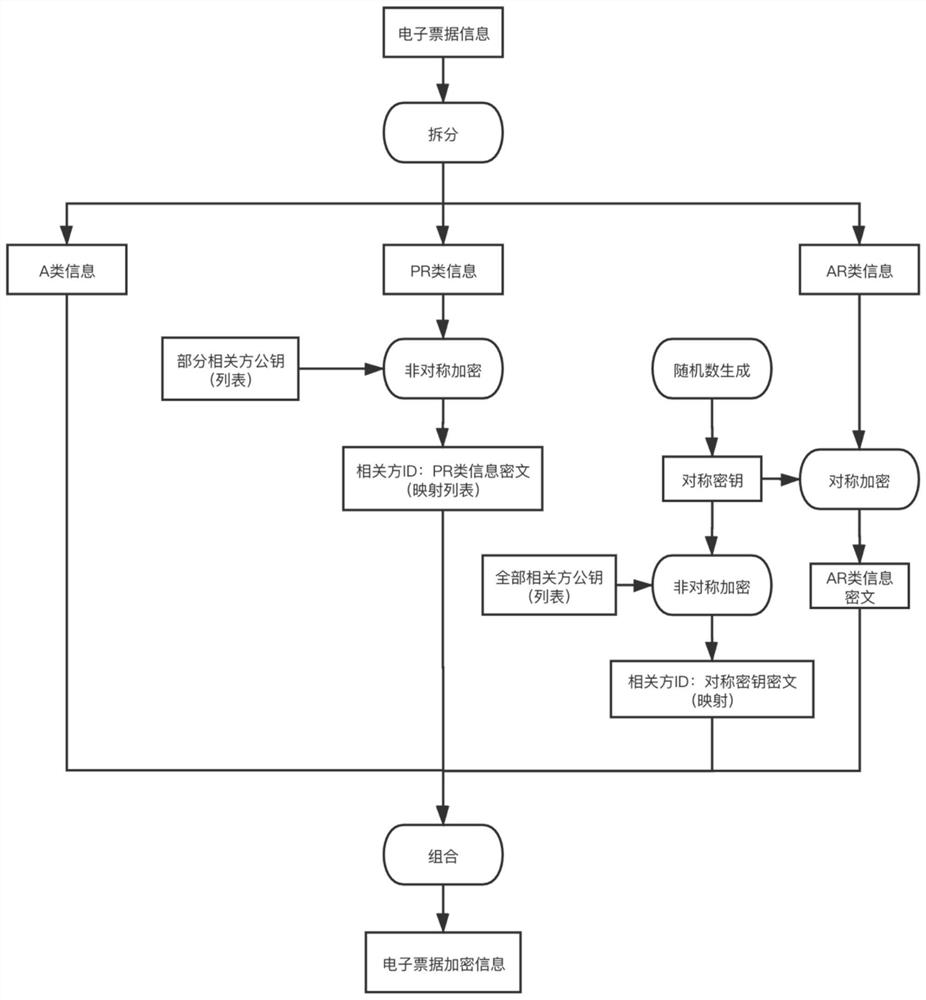
Electronic bill encryption and decryption method and device based on related parties
ActiveCN112332989AReduce redundancyMeet the needs of actual businessMultiple keys/algorithms usageDigital data protectionEngineeringEncryption decryption
The embodiment of the invention discloses an electronic bill encryption and decryption method and device based on related parties, and the method comprises the steps: dividing field information in anelectronic bill into first-type bill information visible to all people and second-type bill information visible to all related parties according to a privacy authority, wherein the third type of billinformation is visible to a part of related parties; for the second type of bill information, based on a symmetric key, performing symmetric encryption on the second type of bill information, and performing asymmetric encryption on the symmetric key; and / or for the third type of bill information, asymmetrically encrypting the third type of bill information by utilizing the public key of each related party corresponding to the third type of bill information. By the adoption of the technical scheme, on the premise that data safety is guaranteed, the requirements of actual services can be well met, and the redundancy of the data can be reduced to the maximum extent.
Owner:TSINGHUA UNIV
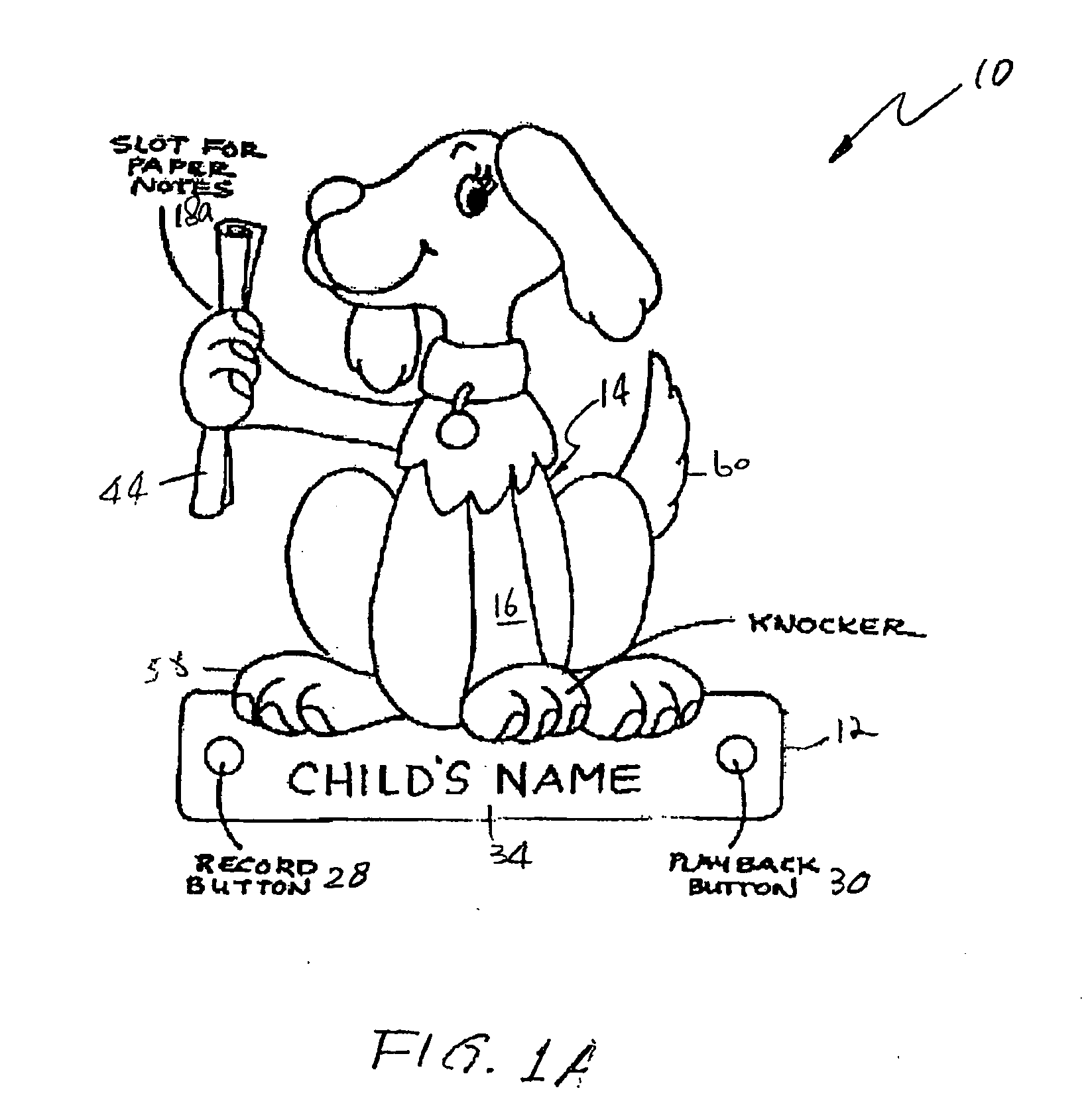
Toy door knocker, and construction and educational kits including a door knocker
Modular constructional toy kit and instructional story book, for use in forming a customized and personalized privacy guard in the form of a door knocker and learning the importance of protecting and respecting a persons right to privacy. The constructional toy kit allows children to build and decorate their own door knockers. Each door knocker has a base unit and a pivotal member hinged at one end to the base unit allowing the pivotal member to swing in a short arc away from the base unit. When released, the pivotal member swings back to make contact with the base unit emitting a loud sound. The constructional toy kit can also have an integrated holder to store written messages, integrated electronic recording and playback device for personalized audio messages, a smooth flat surface at the lower portion of the base unit suitable for imprinting a child's name, assorted decorations and attachable components to allow for the creation of animals or creatures, paints and commercially available hardware and adhesives.
Owner:WICHARD SHEREE +1
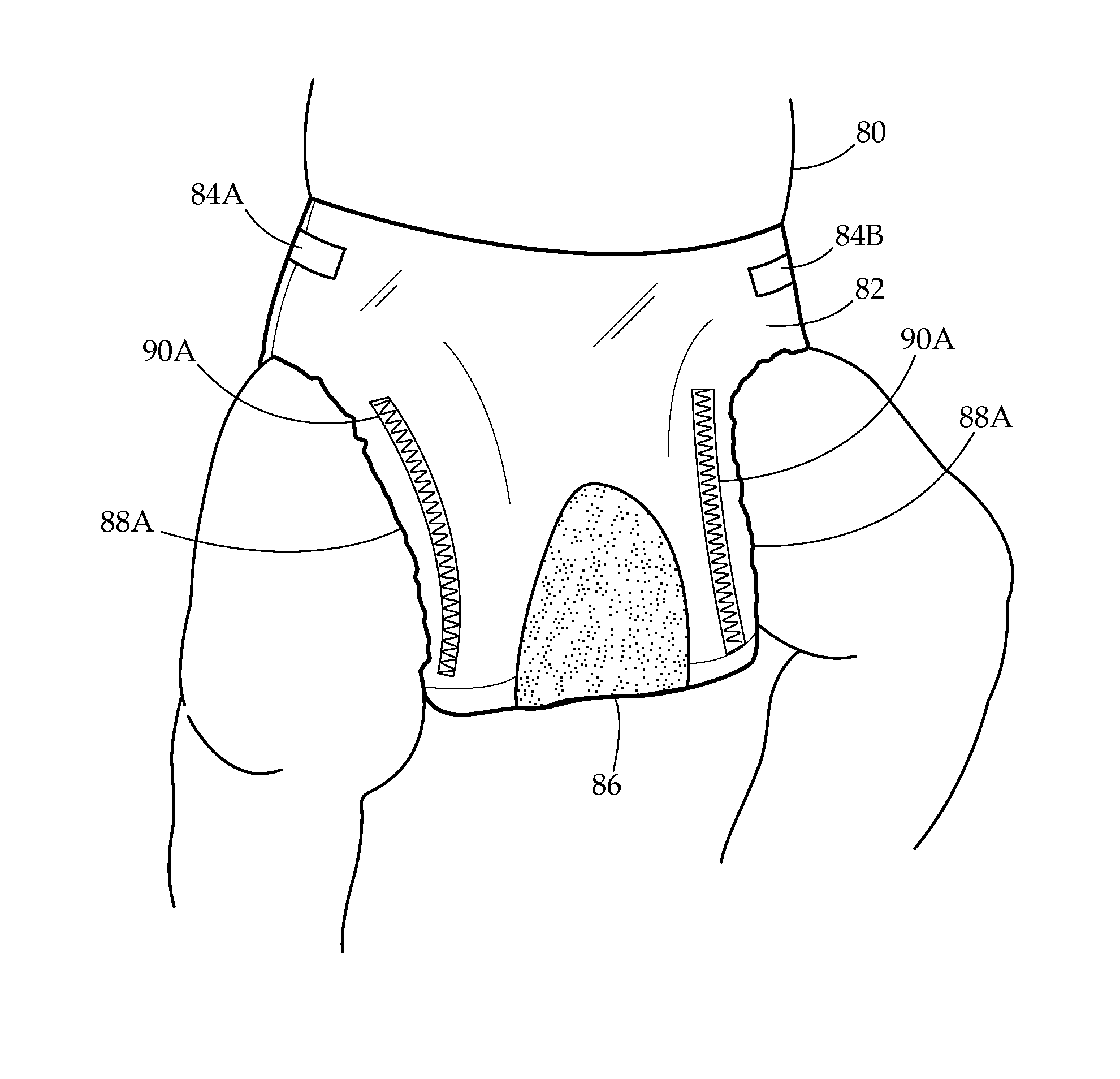
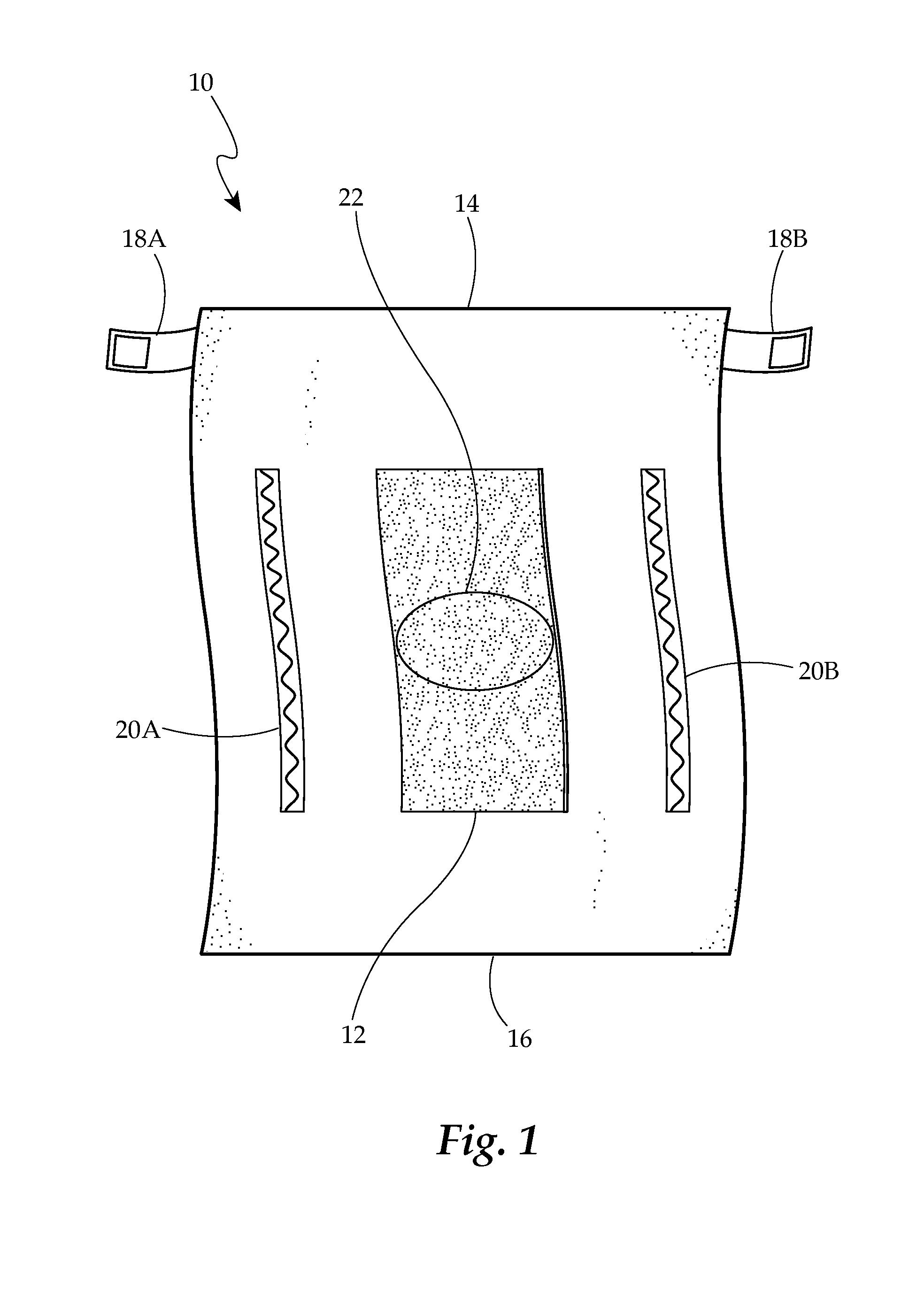
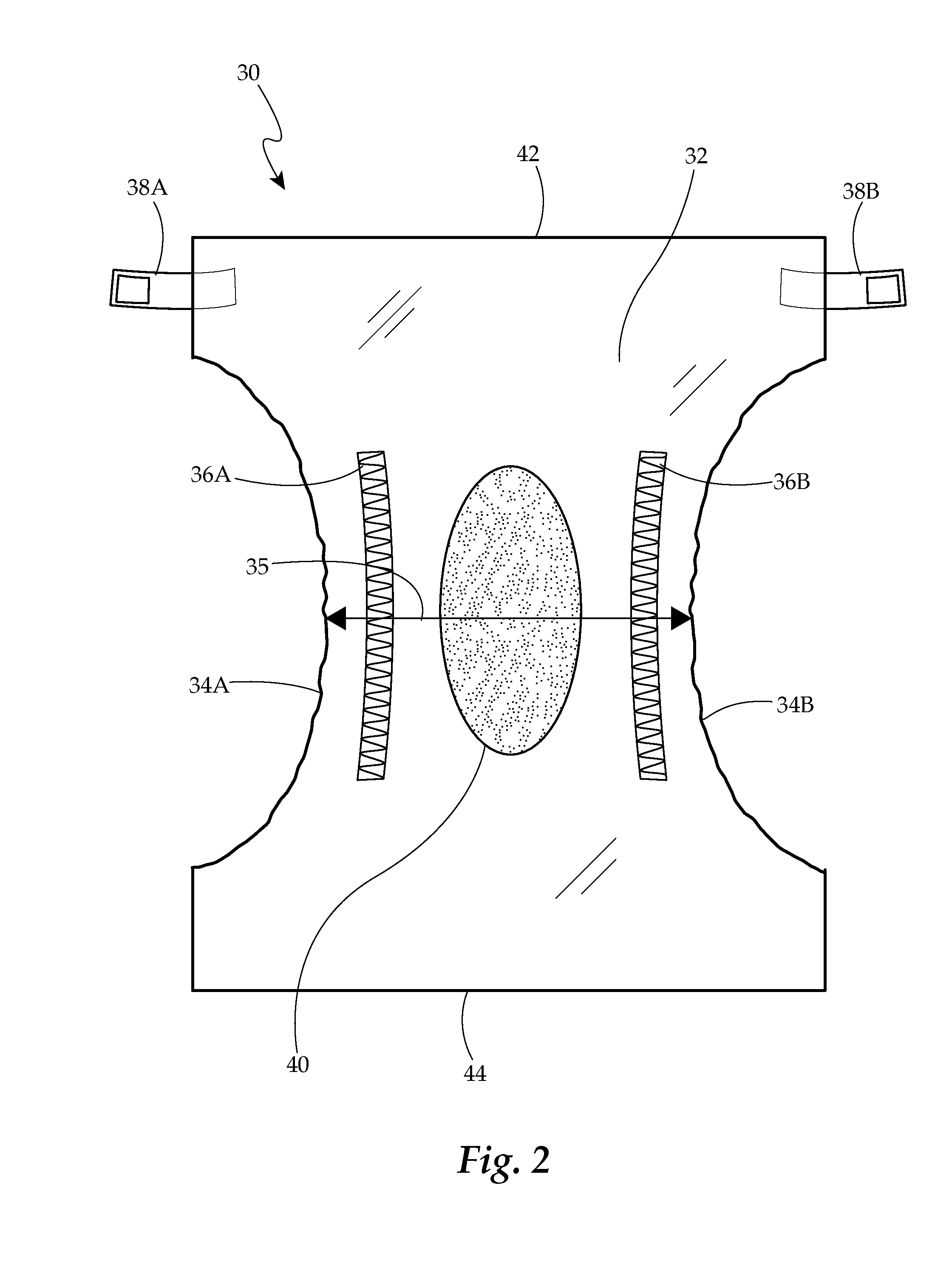
Phototherapy Diaper
InactiveUS20140074054A1Quantity maximizationImprove the degradation problemBaby linensLight therapyLight treatmentRight to privacy
A versatile containment system and apparatus for enclosing urine, fecal matter, bodily excretions, which additionally acts as a disposable phototherapy diaper intended primarily to maximize the surface area of an infant's skin available to light in order to assist in phototherapy, while protecting individuals rights to privacy, is presented. The system additionally includes versatile affixing mechanisms.
Owner:DAVENPORT NATALIE LORENE
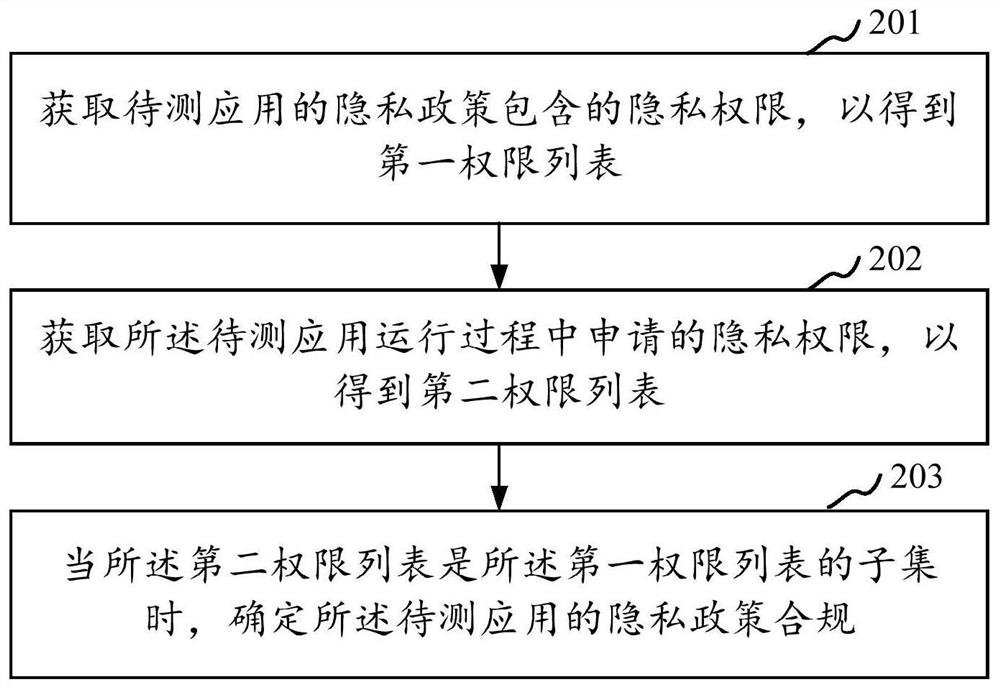
Privacy policy detection method and device, electronic equipment and readable storage medium
PendingCN113051613AImprove securityProtect personal privacyDigital data protectionProgram/content distribution protectionEngineeringRight to privacy
The embodiment of the invention provides a privacy policy detection method and device, electronic equipment and a readable storage medium. The electronic equipment obtains a first permission list used for indicating privacy permissions contained in a privacy policy of a to-be-detected application and a second permission list used for indicating the privacy permissions used in the actual running process of the to-be-detected application; when the second permission list is the subset of the first permission list, determining that the privacy policy of the to-be-tested application is qualified. By adopting the scheme, the privacy authority in the privacy policy is compared with the privacy authority actually involved in the use process of the to-be-tested application, so that whether the privacy policy of the to-be-tested application is compliant or not is determined under the condition that normal use of the to-be-tested application by a user is not influenced, the personal privacy of the user is effectively protected, and the security of the electronic equipment is improved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
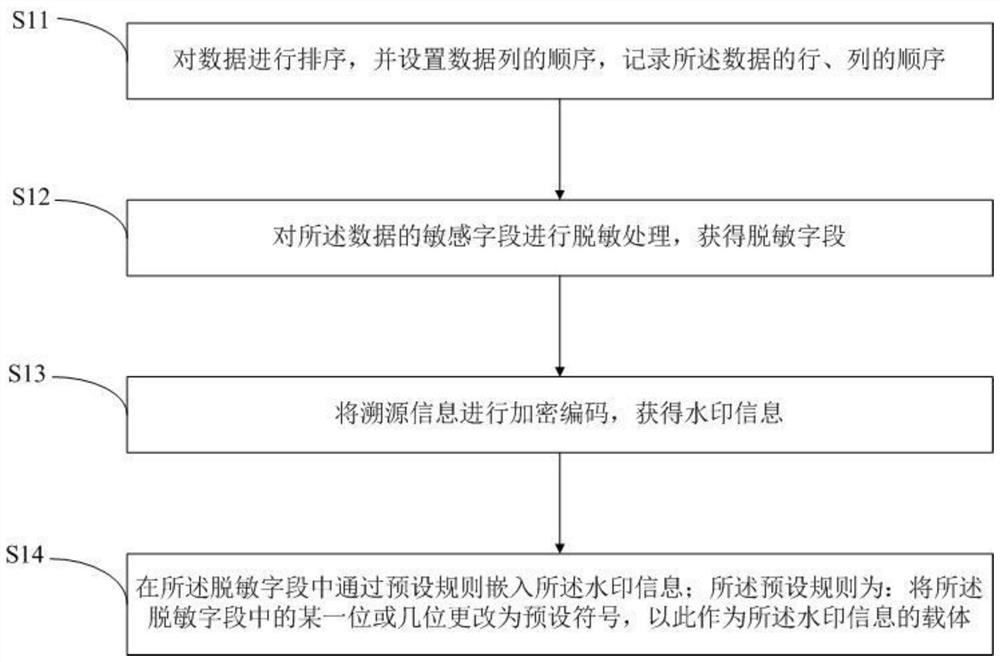
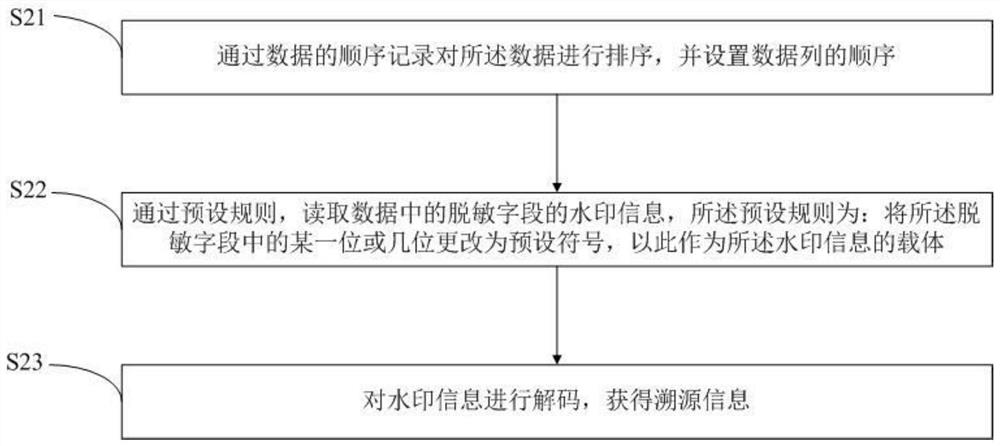
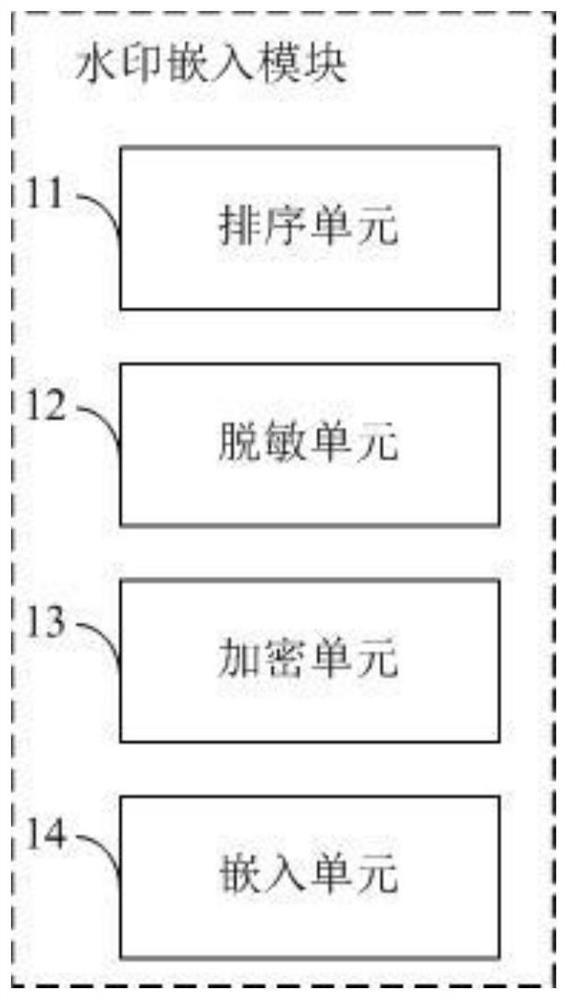
Watermark embedding method, watermark reading method and watermark system based on desensitized data
ActiveCN111831982AEasy to confirmProtection of Privacy InterestsDigital data protectionProgram/content distribution protectionAlgorithmData information
The invention discloses a watermark embedding method, watermark reading method and watermark system based on desensitized data. The watermark embedding method based on desensitized data comprises thesteps: sorting data, setting the sequence of data columns, and recording the sequence of rows and columns of the data; performing desensitization processing on the sensitive field of the data to obtain a desensitization field; encrypting and encoding the traceability information to obtain watermark information; and embedding watermark information into the desensitization field through a preset rule, the preset rule being that one or more bits in the desensitization field are changed into preset symbols to serve as carriers of the watermark information. According to the technical scheme, data can be traced back effectively, more data information cannot be lost when watermarks are added in the encryption method, the watermark removing cost is low, sensitive information can be effectively protected, leakers can be traced back, and privacy rights and interests of enterprises and individuals are protected.
Owner:NEWLAND DIGITAL TECH CO LTD
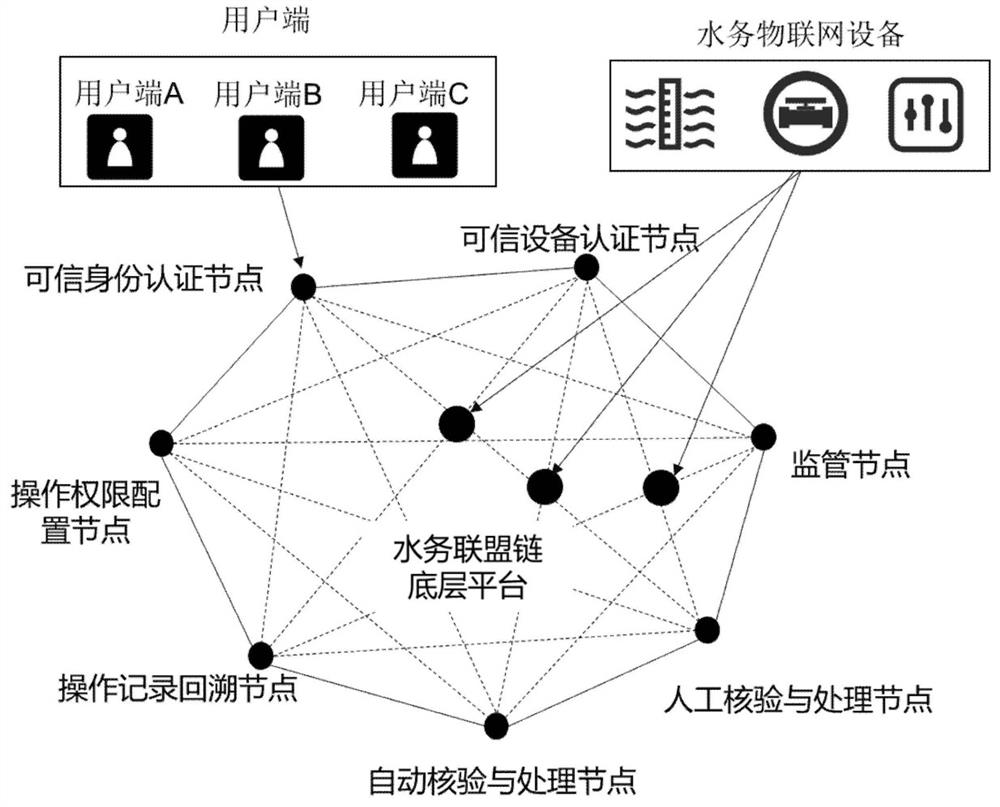
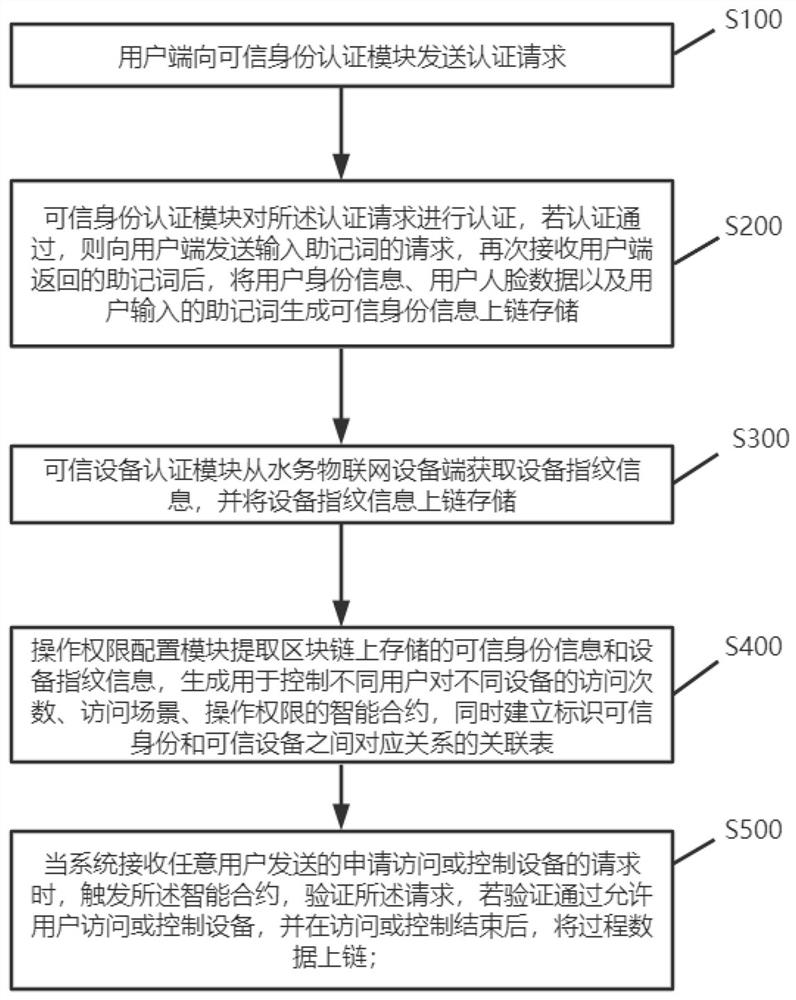
Intelligent water affair Internet of Things remote monitoring control method and system and block chain system
ActiveCN113849796ATroubleshoot rights management issuesMaintain Privacy PermissionsDigital data protectionDigital data authenticationTimestampRight to privacy
The invention discloses an intelligent water affair internet-of-things remote monitoring control method and system and a block chain system, solves the problems of non-circulation and data islanding of water affair data in the whole water affair monitoring control process by using distributed nodes, and builds a technical basis for water affair data tracing. The time tracing problem in the tracing process is solved by using a timestamp. The authority management problem of the water affair equipment is solved by using the intelligent contract, and the privacy authority of sensitive information is maintained. The water affair data operated by the whole system is ensured to be true and credible by utilizing the non-tampering characteristic of the block chain bottom layer platform, and the problem that the water affair equipment is maliciously controlled and the water affair data is maliciously tampered due to the fact that the user side and the water affair equipment are not uniquely identified in the prior art can be greatly solved.
Owner:南京可信区块链与算法经济研究院有限公司
A method and device for encrypting and decrypting electronic bills based on related parties
ActiveCN112332989BReduce redundancyMeet the needs of actual businessMultiple keys/algorithms usageDigital data protectionTicketEngineering
The embodiment of the present invention discloses a method and device for encrypting and decrypting electronic notes based on related parties, wherein the encryption method for electronic notes includes: splitting the field information in the electronic notes into the first One type of bill information, the second type of bill information visible to all related parties, and the third type of bill information visible to some related parties; for the second type of bill information, based on the symmetric key, the type of bill information is encrypted symmetrically, and Asymmetric encryption is performed on the symmetric key; and / or, for the third type of bill information, asymmetric encryption is performed on this type of bill information by using the corresponding public keys of each related party. By adopting the above-mentioned technical solution, under the premise of ensuring data security, it can well meet the needs of actual business, and at the same time, it can also reduce the redundancy of data to the greatest extent.
Owner:TSINGHUA UNIV
Method for protecting privacy based on access control
InactiveCN101465853BAvoid the risk of leakageEasy to implementData switching networksData access controlThe Internet
A privacy information protecting method based on access control belongs to computer network security field and is used in network application whose privacy information needs to be protected in the Internet. The invention expands the access right to privacy access right; when setting the right, conditions which need to be satisfied when authorizing the right are added; and a user is allowed to control the privacy information at real time, thus increasing the flexibility of the user to control the privacy information. Furthermore, all the entities relevant to the privacy information are added into the access control as privacy subjects, so that all the relevant subjects can set access control strategies for privacy information protection according to privacy information protection requirements. Accesses to the privacy information are controlled according to the strategies of the privacy subjects, which makes the privacy information protection method more perfect, thus avoiding all invasions of privacy of the user. The privacy information protecting method gives consideration to the distinctive features of privacy information protection, namely the flexibility and integrity requiredin privacy protection, and fully guarantees the rights and interests of the user.
Owner:BEIJING UNIV OF TECH
Cloud native task allocation system, method and device based on block chain
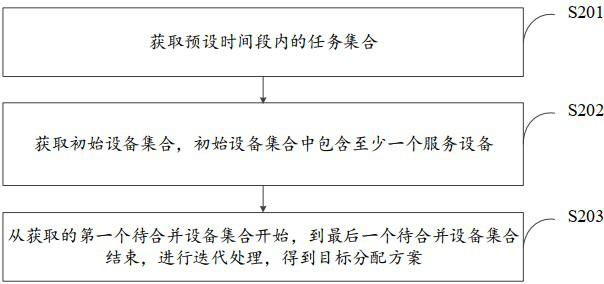
ActiveCN114048018AProtection of Privacy Interest InformationEfficient allocationProgram initiation/switchingResource allocationResource utilizationRight to privacy
The invention discloses a cloud native task allocation system, method and device based on a block chain. The method comprises following steps: acquiring a task set within a preset time period, and acquiring an initial device set comprising at least one service device; performing iterative processing from the acquired first to-be-merged device set to the end of the last to-be-merged device set to obtain a target allocation scheme; and based on incomplete information of a plurality of service facilities of a multi-party service provider, according to the comprehensive resource utilization rate of all the devices in the device set, the income of the service provider and the deployment cost of all the devices, determining the device set, carrying out task allocation in the device set. Multiple optimization objectives of the user and the service provider are comprehensively considered, and a task allocation problem is abstracted into an incomplete information game problem, so privacy right information of all parties is protected, efficient allocation of user tasks is completed based on an alliance decentralization mode, effectiveness of all service providers is improved to the maximum extent, and overall effectiveness maximization is achieved.
Owner:PEKING UNIV SHENZHEN GRADUATE SCHOOL +4
A Dynamic Analysis System for Android Platform Applications Based on Permission Usage Behavior
The invention belongs to the technical field of Android platform application security analysis, and specifically relates to a dynamic analysis system for Android platform application programs based on authorization usage behavior. The system includes: core explicit permission usage point recognizer and implicit permission usage point tracker, auxiliary application driver and behavior analyzer; explicit permission usage point identifier and implicit permission usage point tracker based on Android permissions Implement the system; the explicit permission use point recognizer fully records the explicit permission use point when the application is running, and the privacy permission use point tracker tracks the implicit permission use point when the application is running. The present invention can fully identify all authority usage points and associated authority information when the application program is running, so as to describe the internal authority use behavior of the application program.
Owner:FUDAN UNIV
Android application classification authorization method for quantitative judgment of suspicious behaviors
PendingCN113326502AImprove securityProtect private informationDigital data protectionDigital data authenticationAuthorization ModeSoftware engineering
The invention discloses an android application classification authorization method for quantitative judgment of suspicious behaviors. According to the android application classification authorization method for quantitative judgment of suspicious behaviors, an existing android system authorization mechanism is improved from two aspects of assisting user authorization and refining authorization modes, wherein firstly, aiming at the situation that a large number of user privacy permissions are obtained by application programs and cross-border obtaining is very serious, from the aspects of safety and privacy, a suspicious behavior quantitative judgment scheme is provided, and when an application program is installed, a judgment result is presented to a user in a simple, concise and direct expression by checking an applied permission list and judging the security threat degree of the application program, so that the user is helped to make an authorization decision; and secondly, an existing coarse-grained authorization mode of full selection or non-full selection is improved, a classification authorization method is provided, for some privacy permissions, the user is allowed to flexibly authorize each permission, and meanwhile, the privacy information of the user is protected from being leaked while normal operation of the application program is ensured in a replacement mode.
Owner:刘秀萍
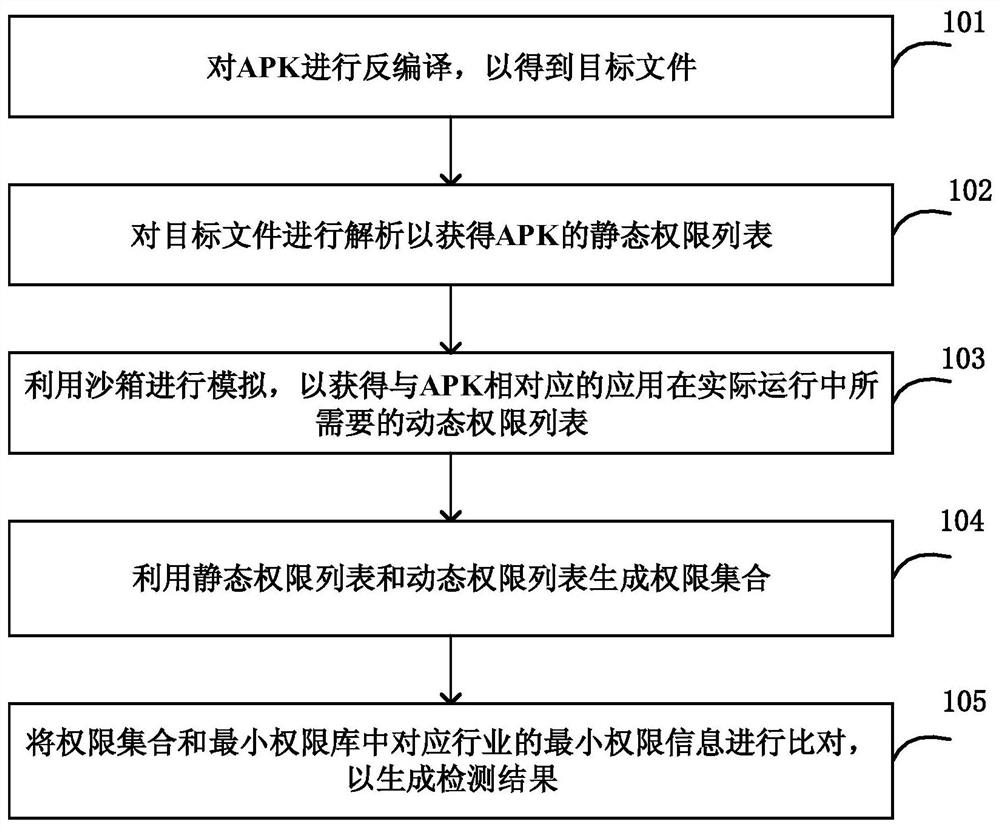
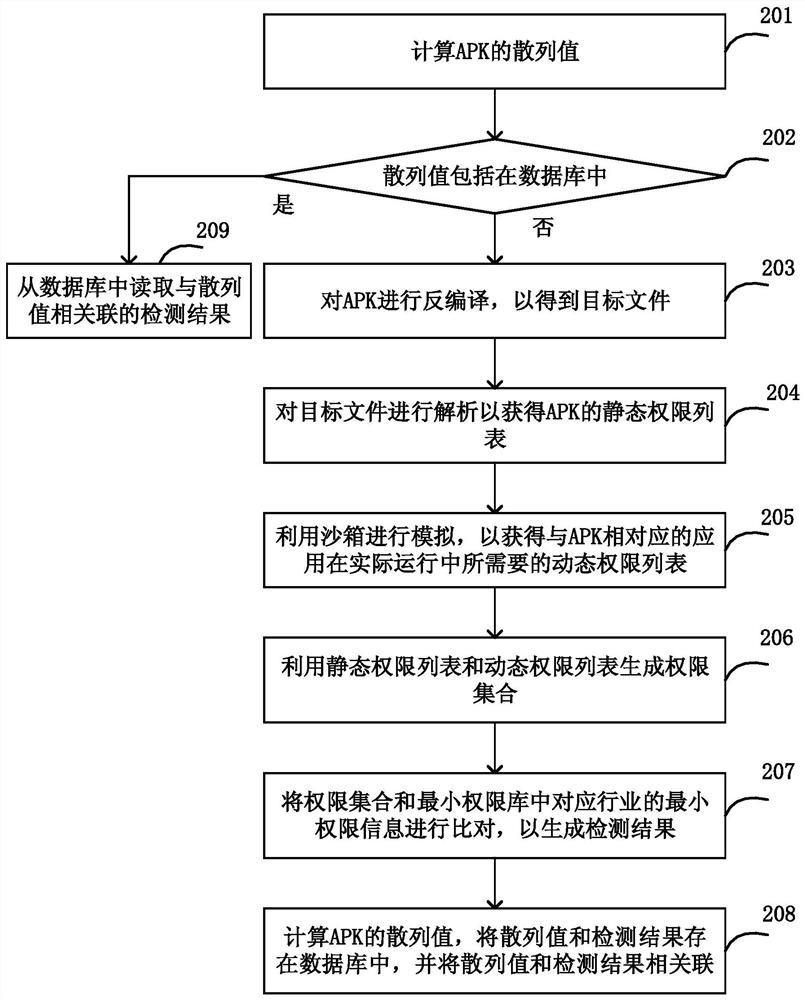
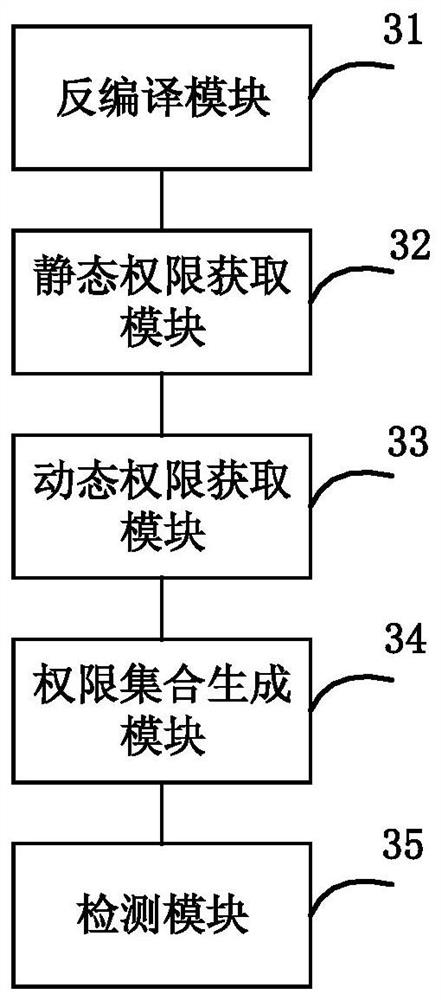
Private authority detection method and device
The invention provides a privacy authority detection method and device. The privacy authority detection device decompiles the APK to obtain a target file; analyzing the target file to obtain a static permission list of the APK; simulating by utilizing a sandbox to obtain a dynamic permission list required by an application corresponding to the APK in actual operation; generating a permission set by using the static permission list and the dynamic permission list; and comparing the permission set with the minimum permission information of the corresponding industry in the minimum permission library to generate a detection result. According to the method and the device, the Android application permission detection accuracy can be effectively improved.
Owner:CHINA TELECOM CORP LTD
Application control method and device and electronic equipment
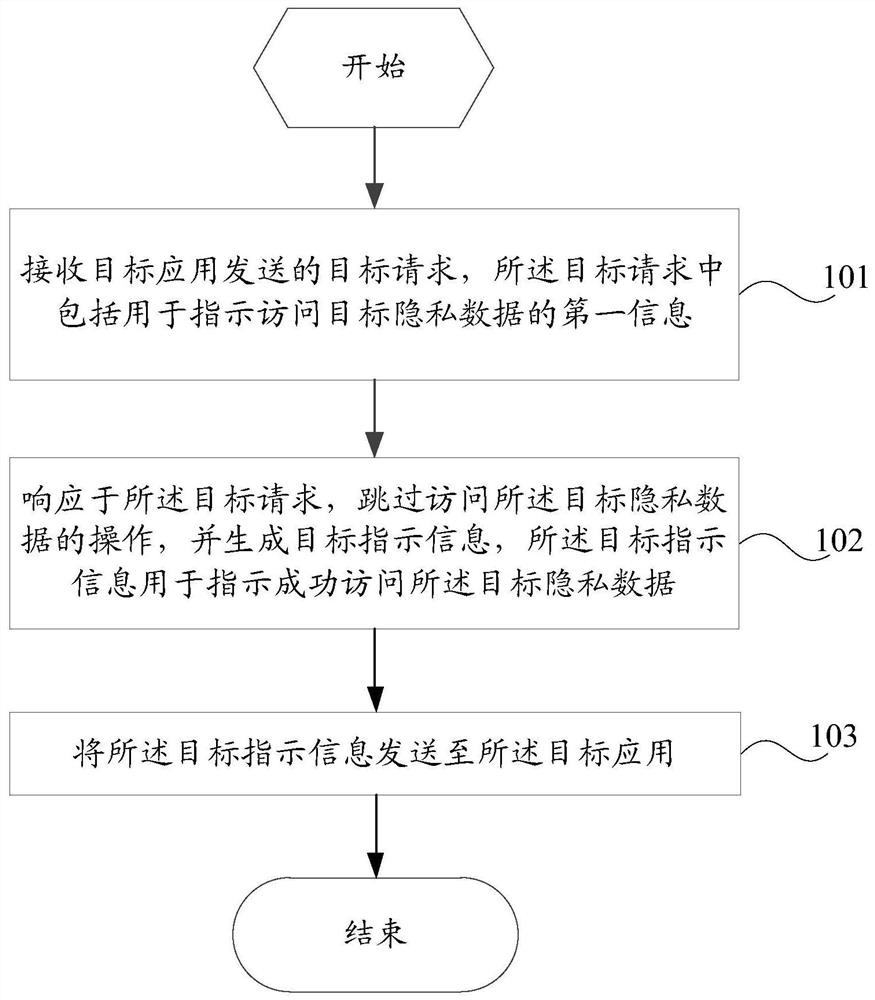
PendingCN111814135AAvoid violationsReduce the risk of leaking private informationDigital data protectionUser privacyEngineering
The invention discloses an application control method and device and electronic equipment, and belongs to the technical field of computers. The method comprises the steps of receiving a target requestsent by a target application, wherein the target request comprises first information used for indicating access to target private data; in response to the target request, skipping an operation of accessing the target private data, and generating target indication information, the target indication information being used for indicating that the target private data is successfully accessed; and sending the target indication information to the target application. According to the embodiment of the invention, the problem that in the prior art, an APP forcibly requires user authorization to obtainuser privacy information by denying service, so that the privacy right of a user is invaded, and the privacy information is leaked is solved.
Owner:VIVO MOBILE COMM CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com