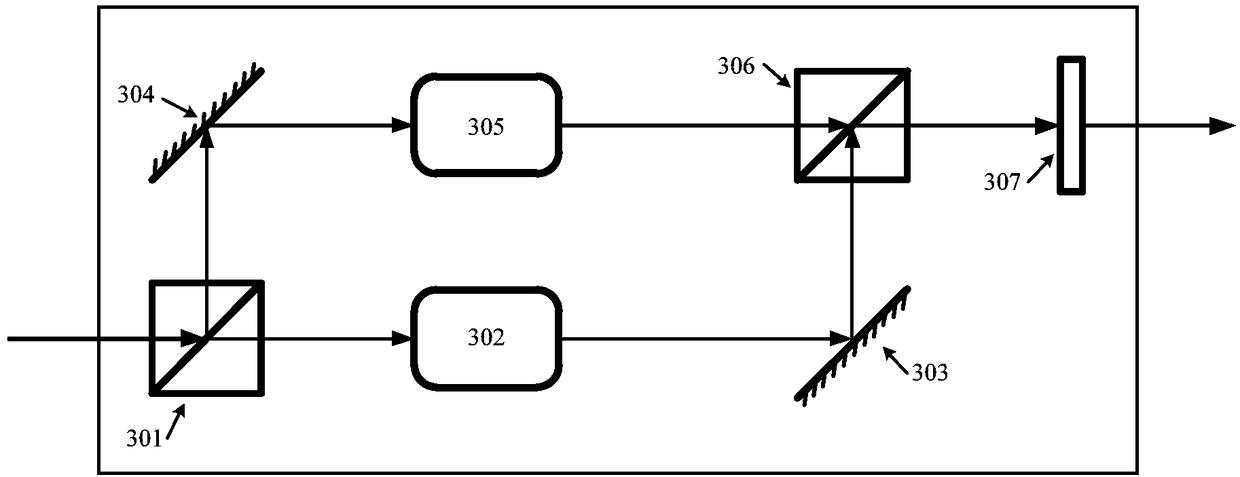
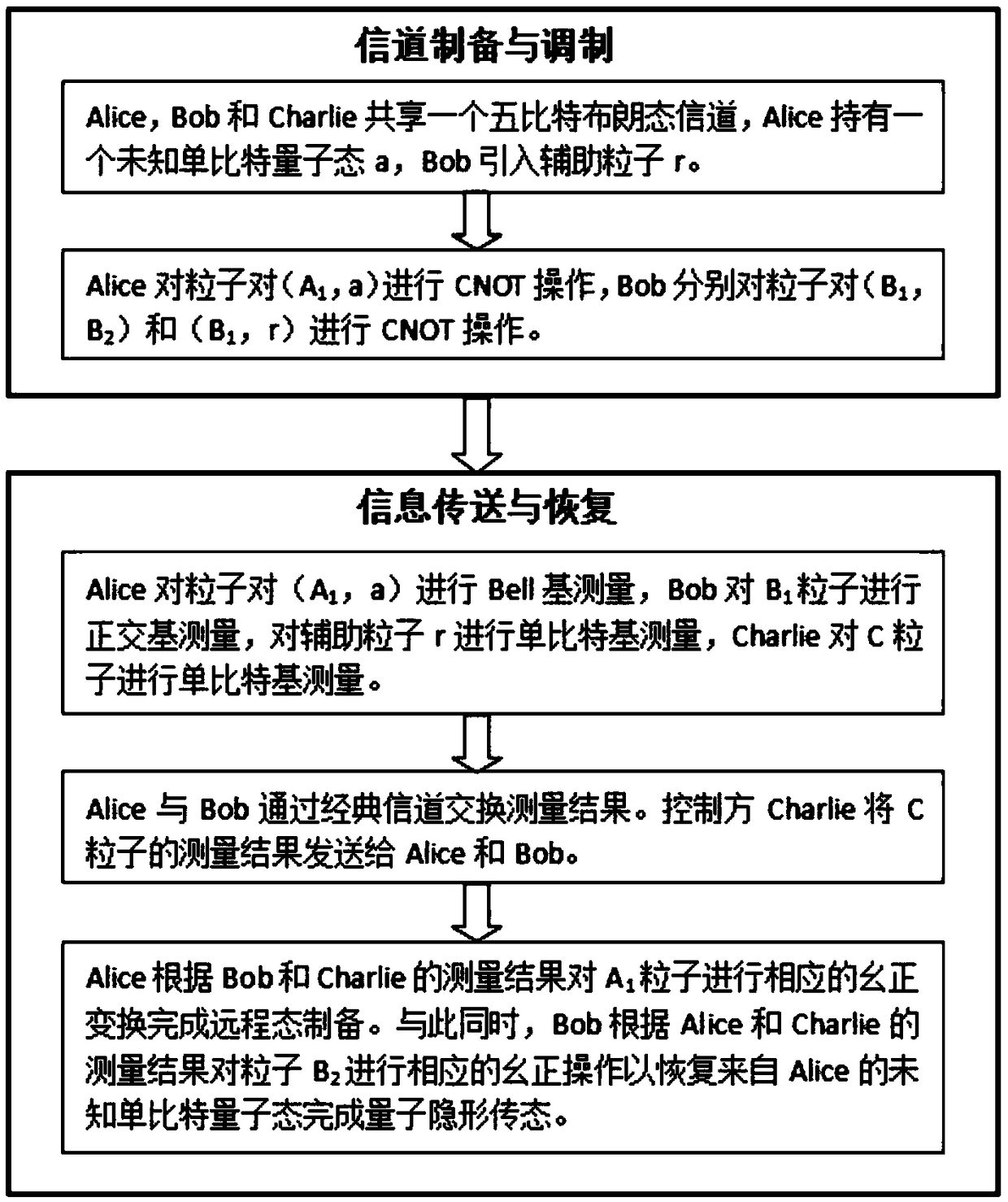
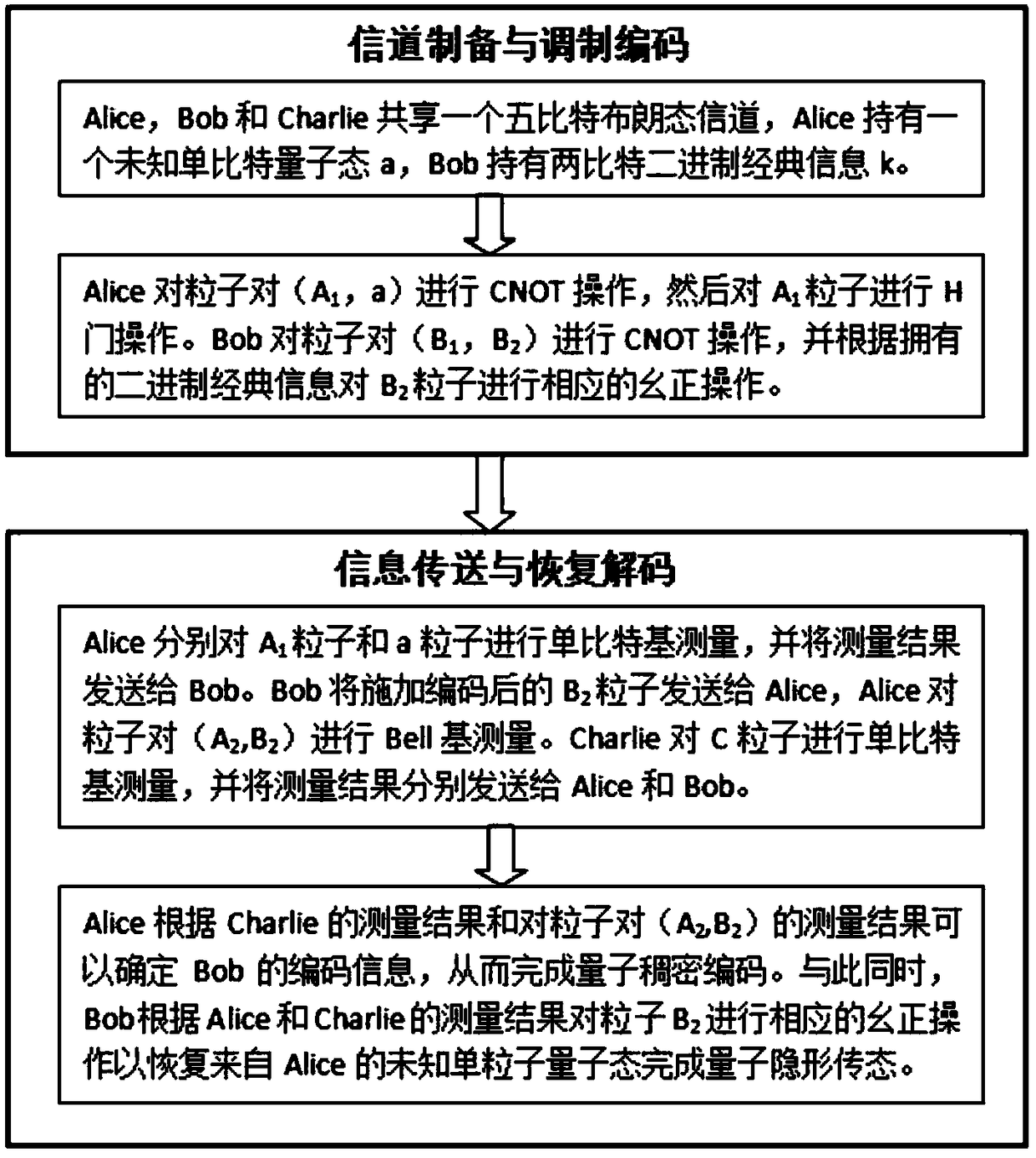
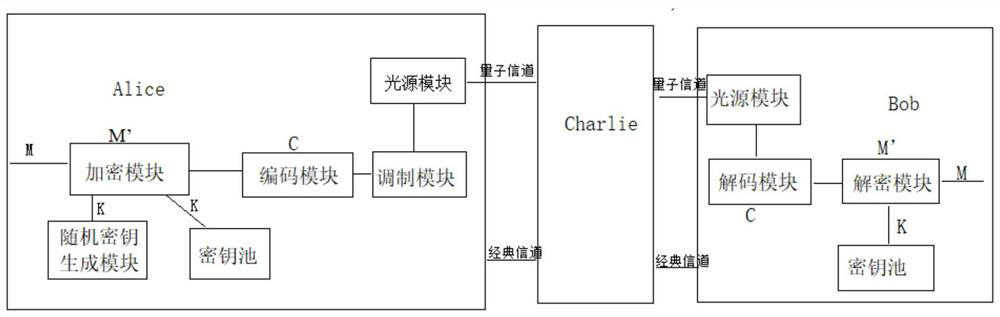
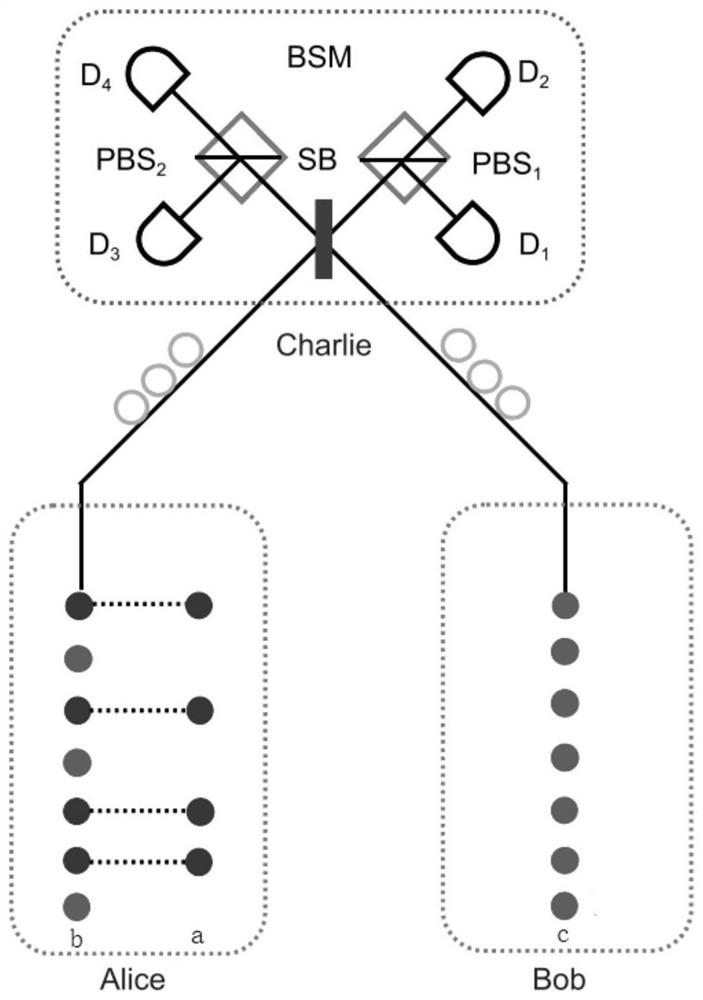
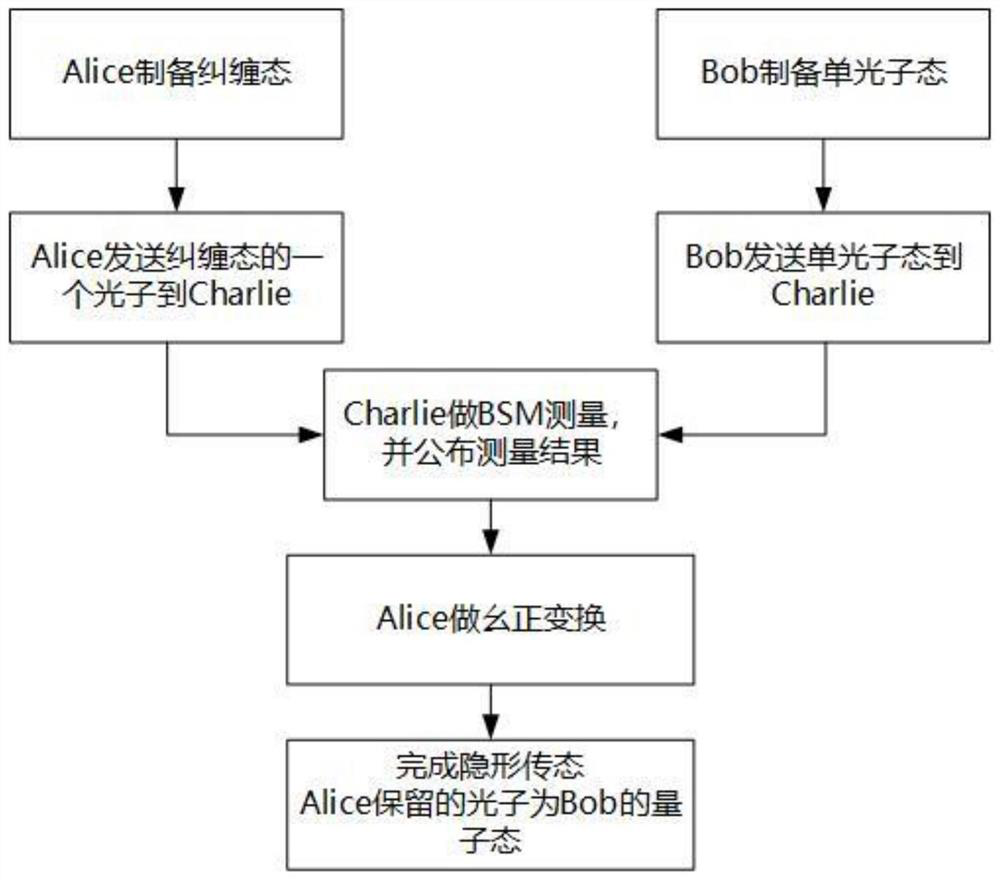
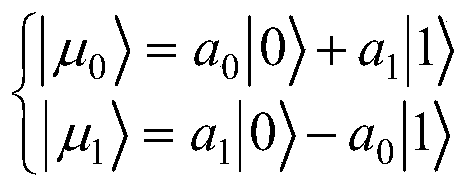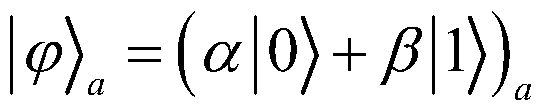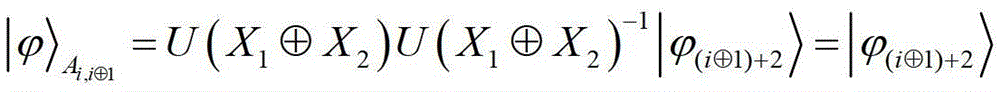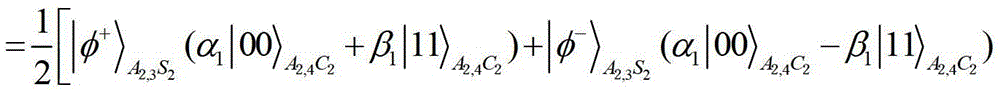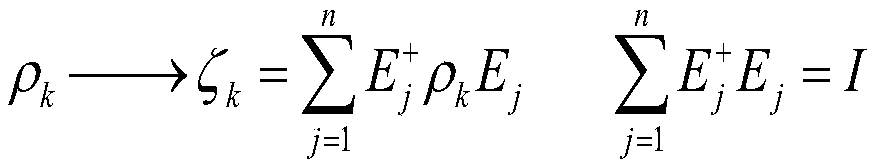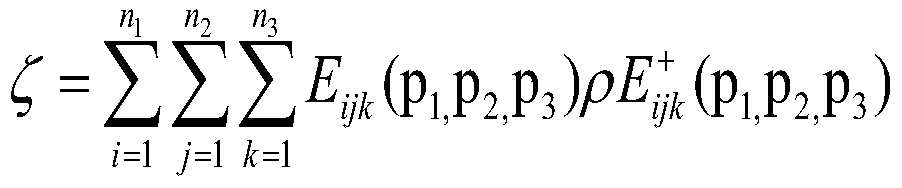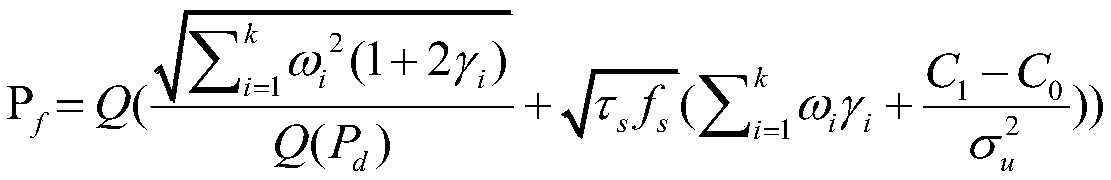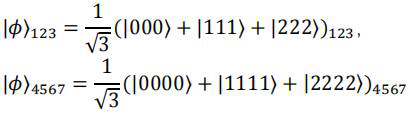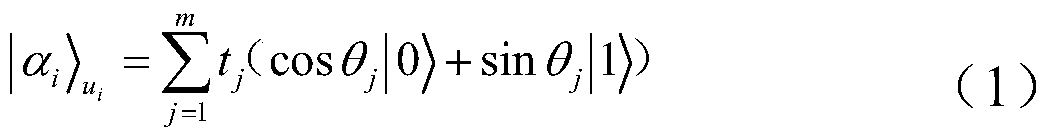Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
47 results about "Quantum teleportation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
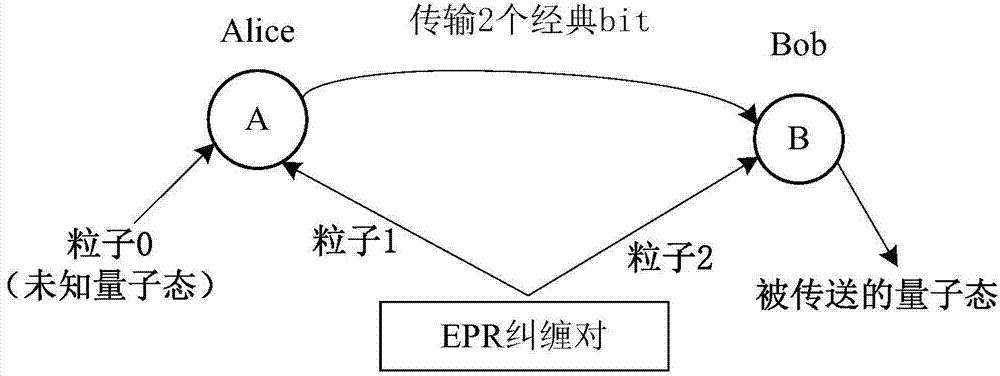
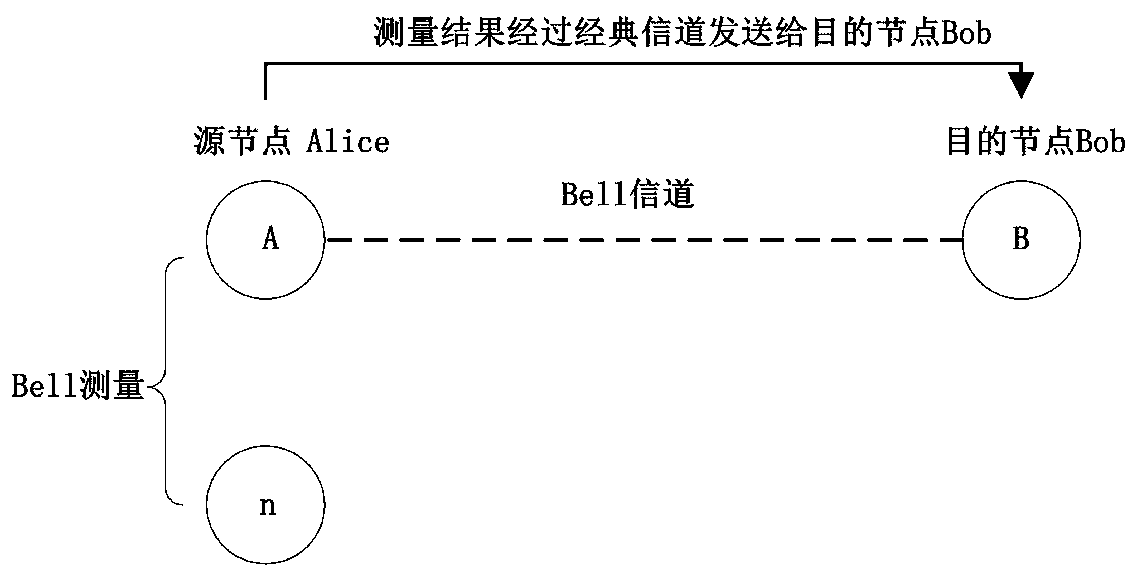
Quantum teleportation is a process in which quantum information (e.g. the exact state of an atom or photon) can be transmitted (exactly, in principle) from one location to another, with the help of classical communication and previously shared quantum entanglement between the sending and receiving location. Because it depends on classical communication, which can proceed no faster than the speed of light, it cannot be used for faster-than-light transport or communication of classical bits. While it has proven possible to teleport one or more qubits of information between two (entangled) quanta, this has not yet been achieved between anything larger than molecules.
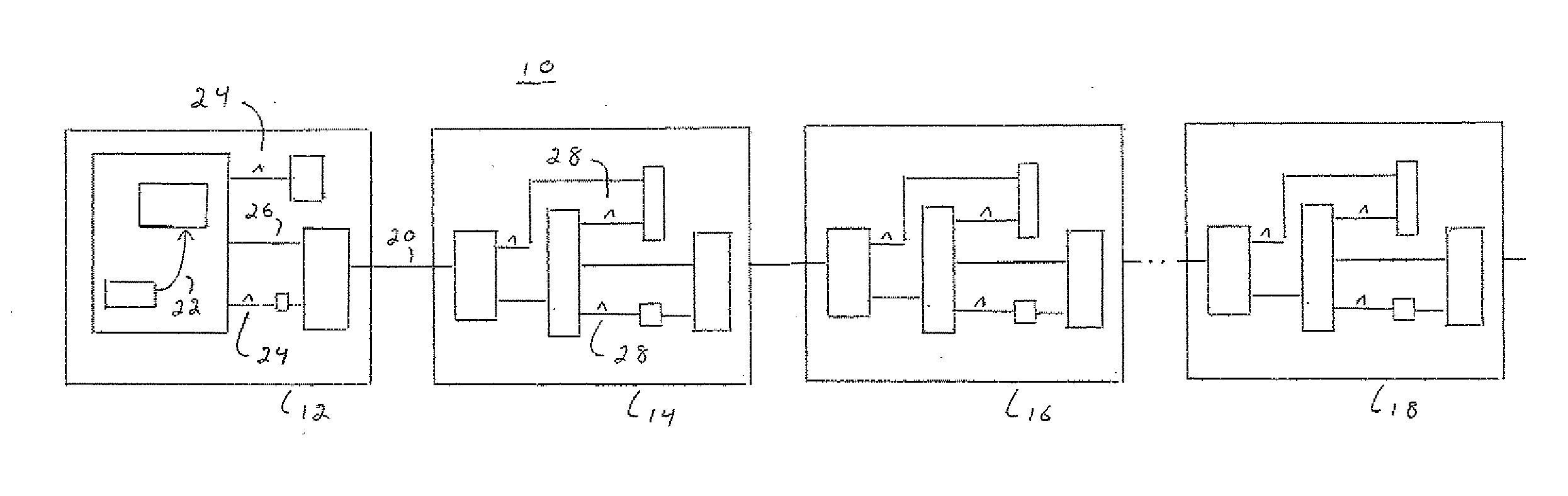
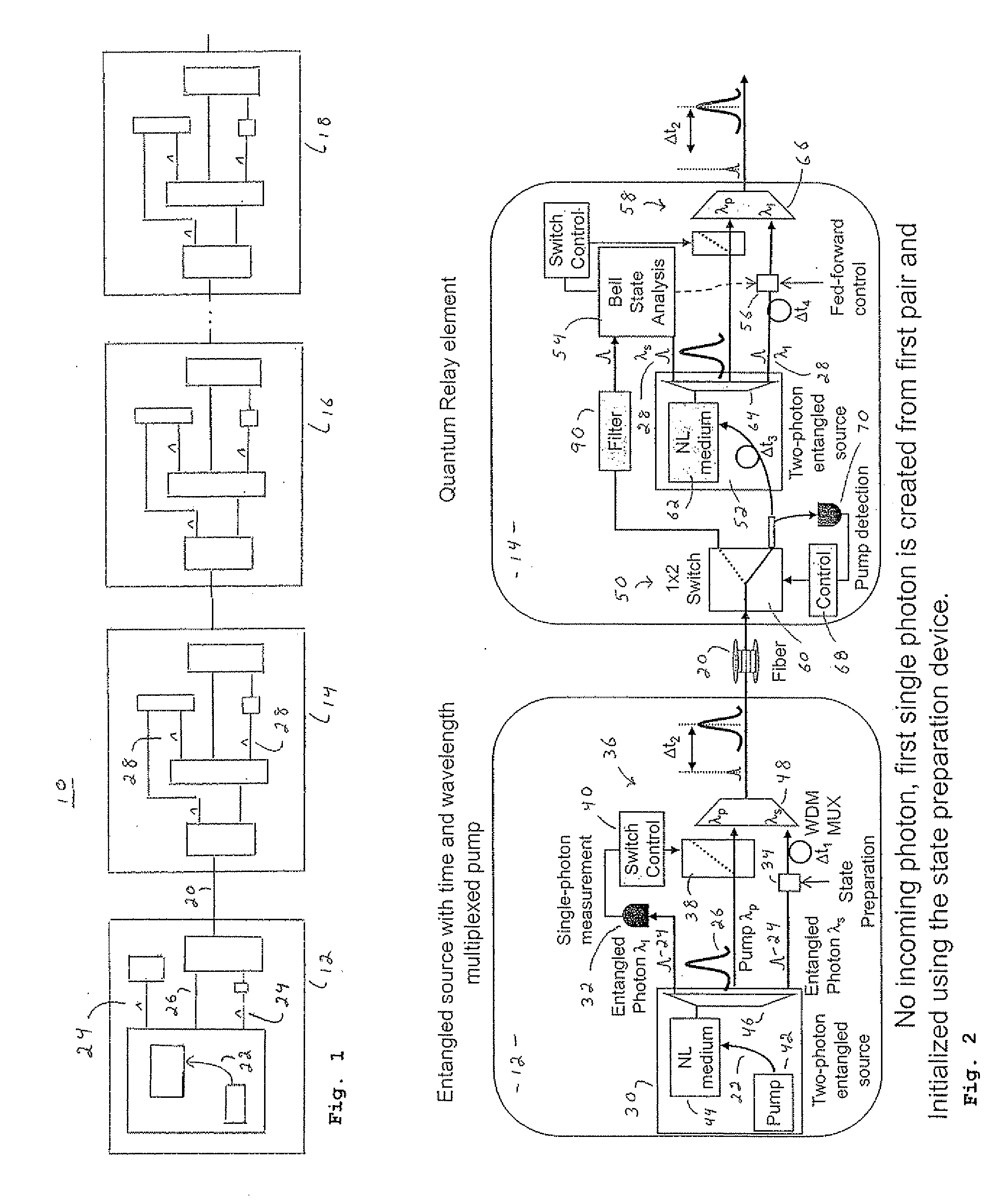
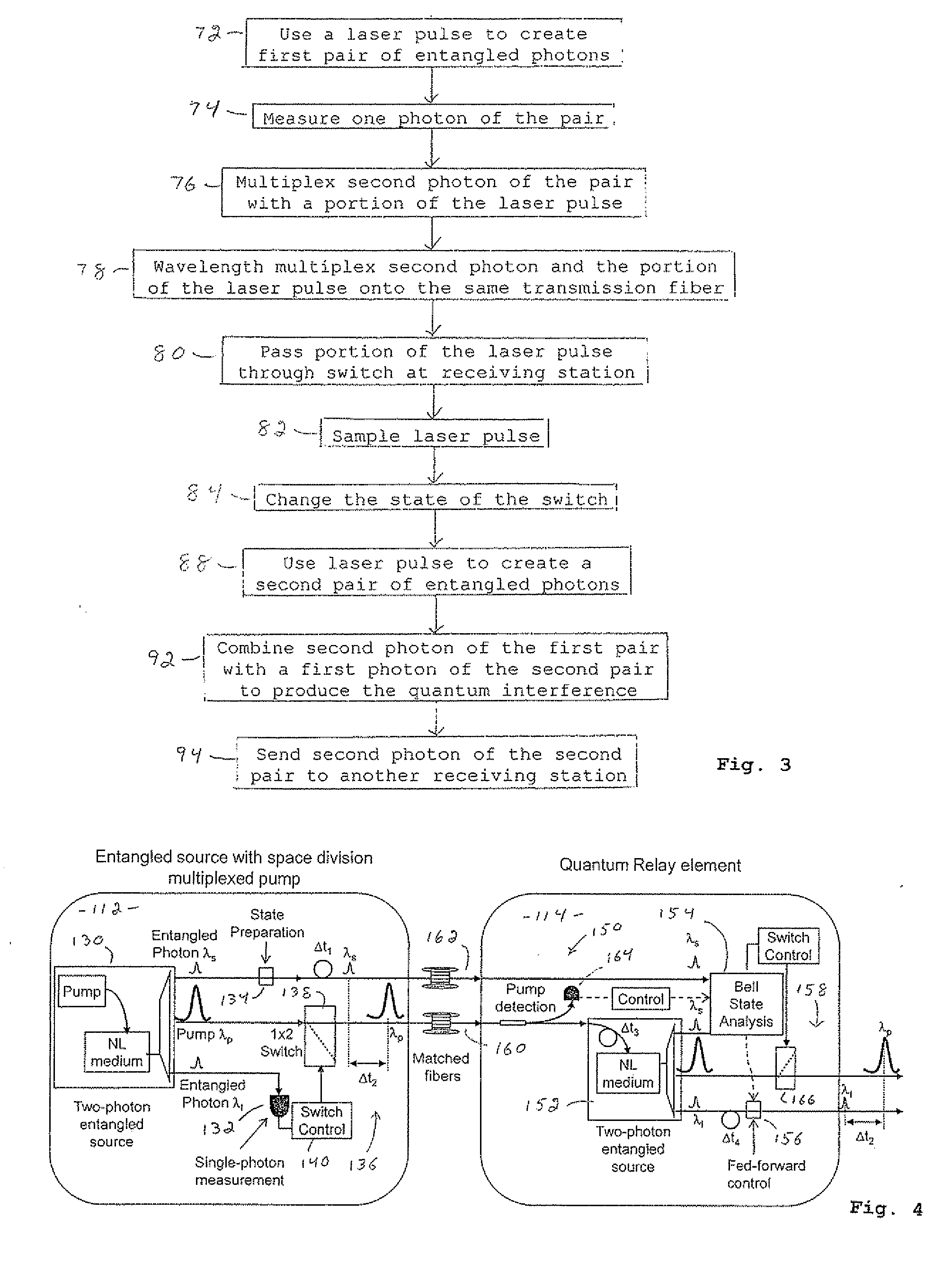
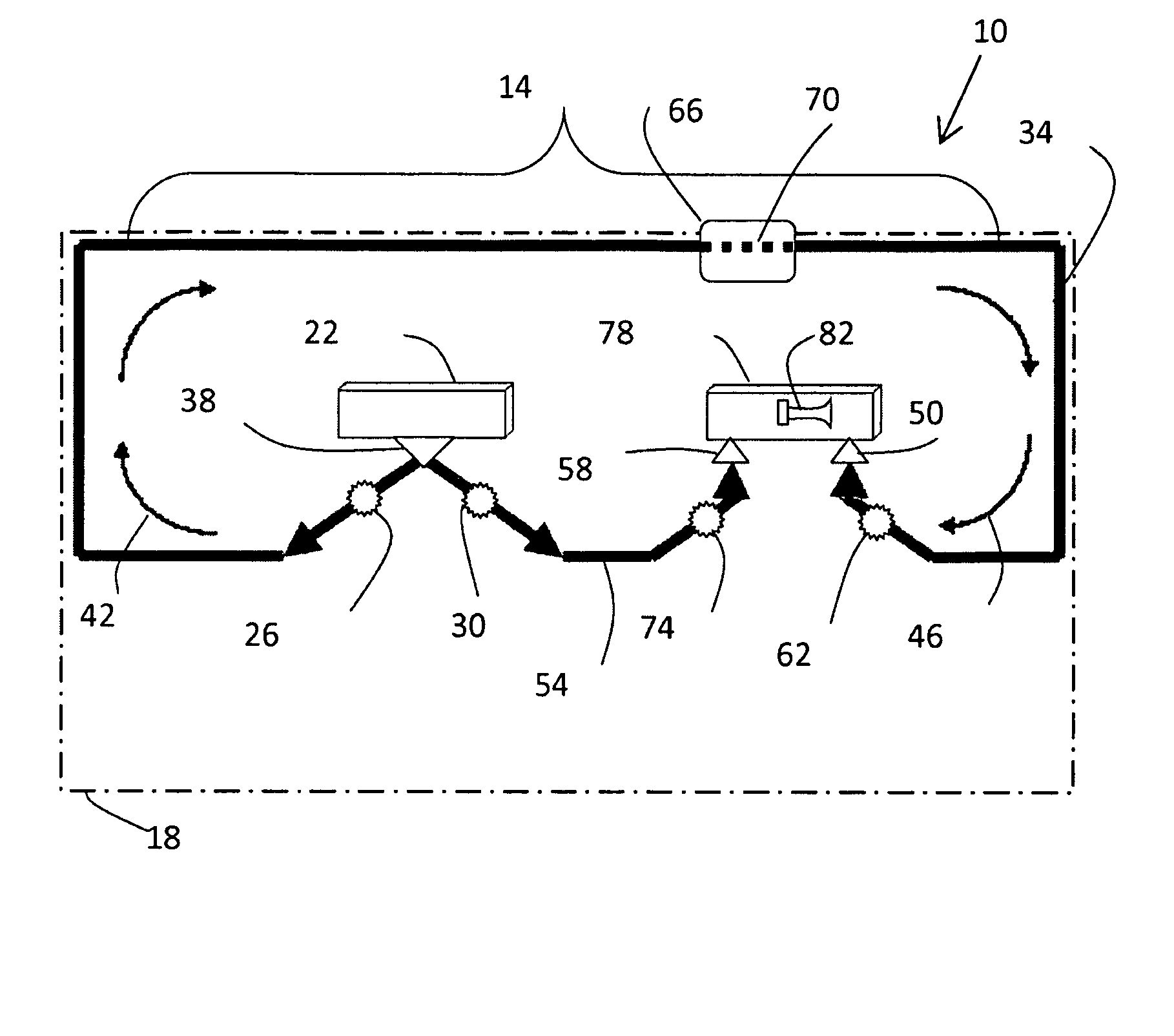
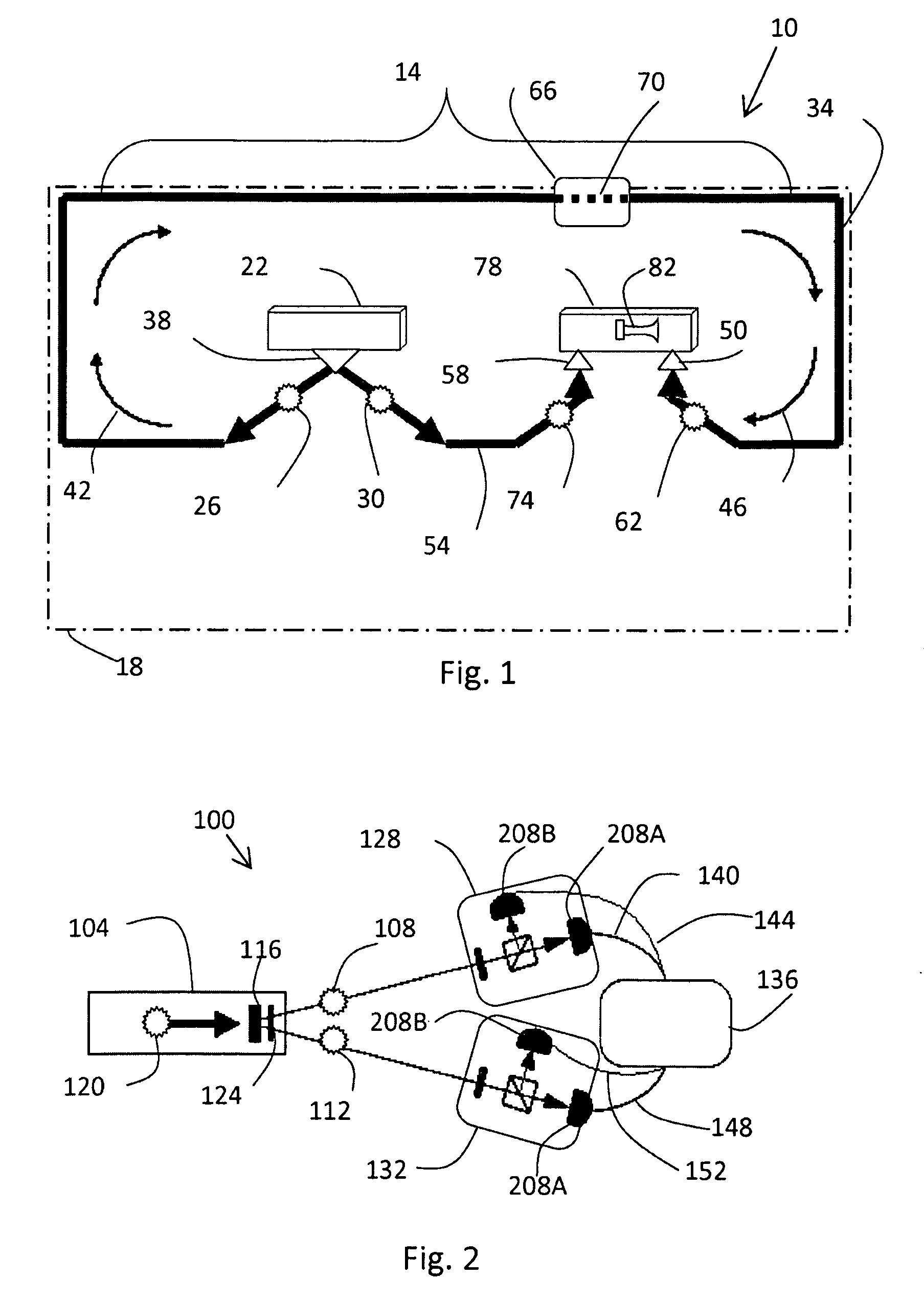
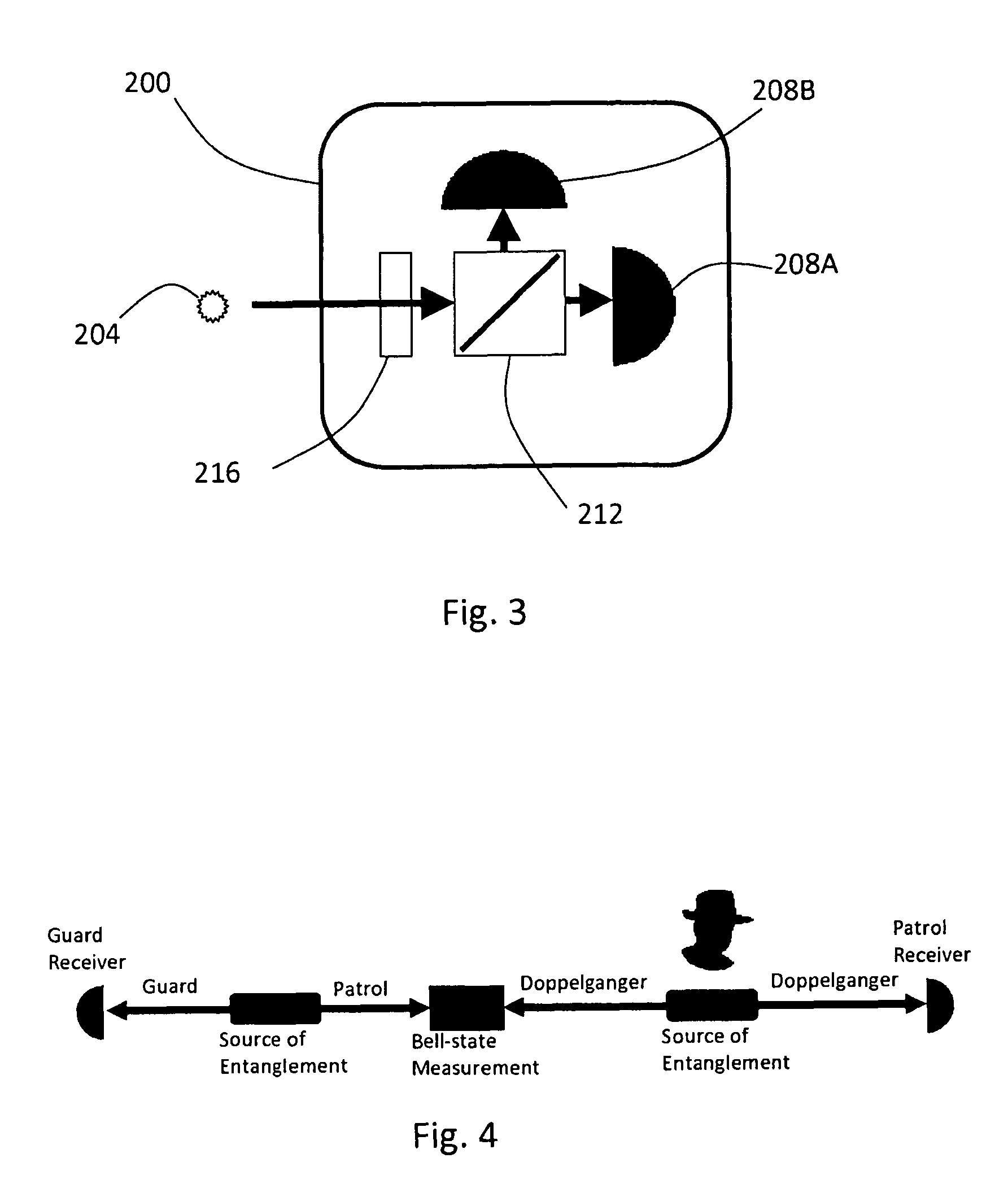
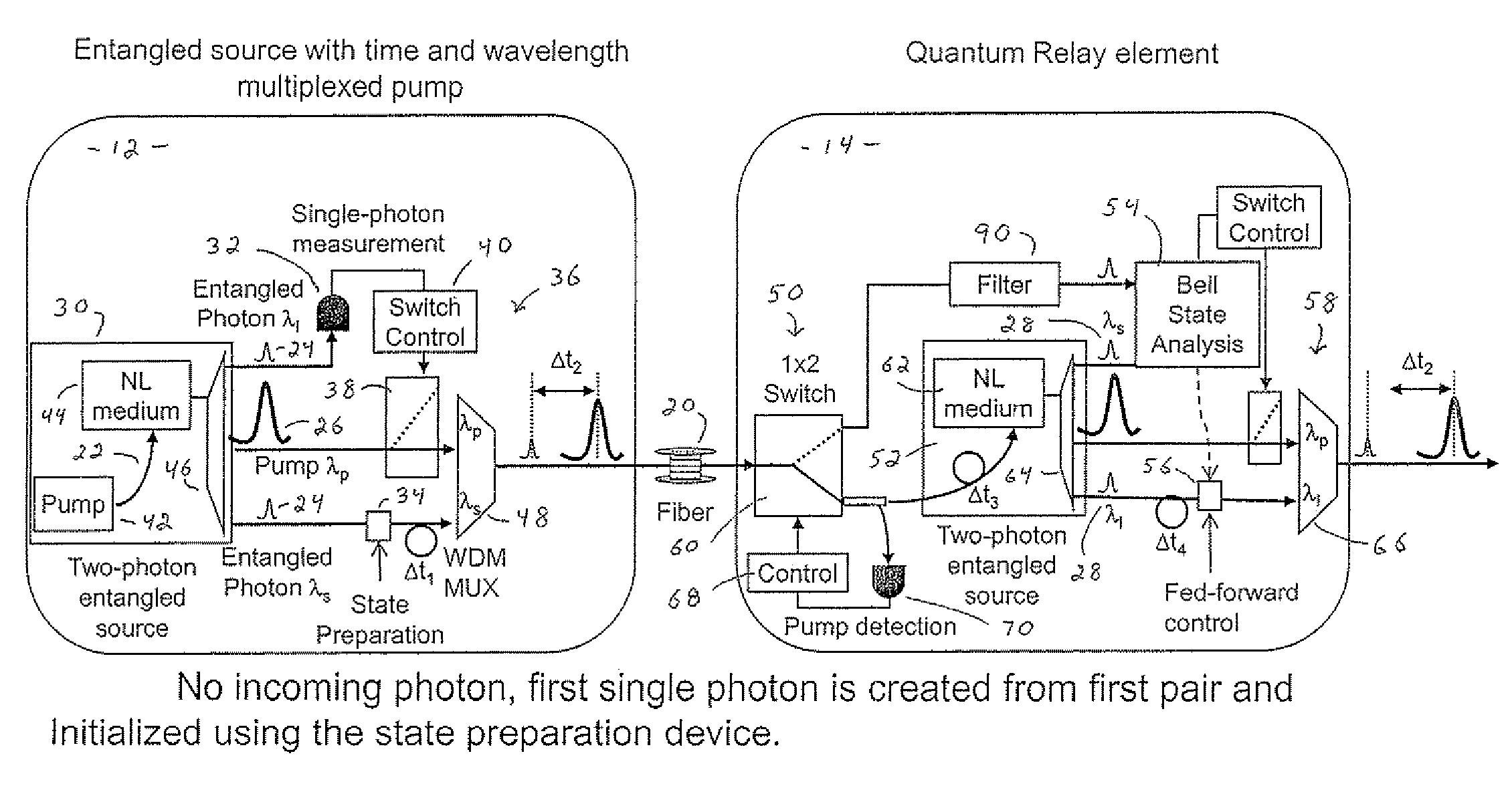
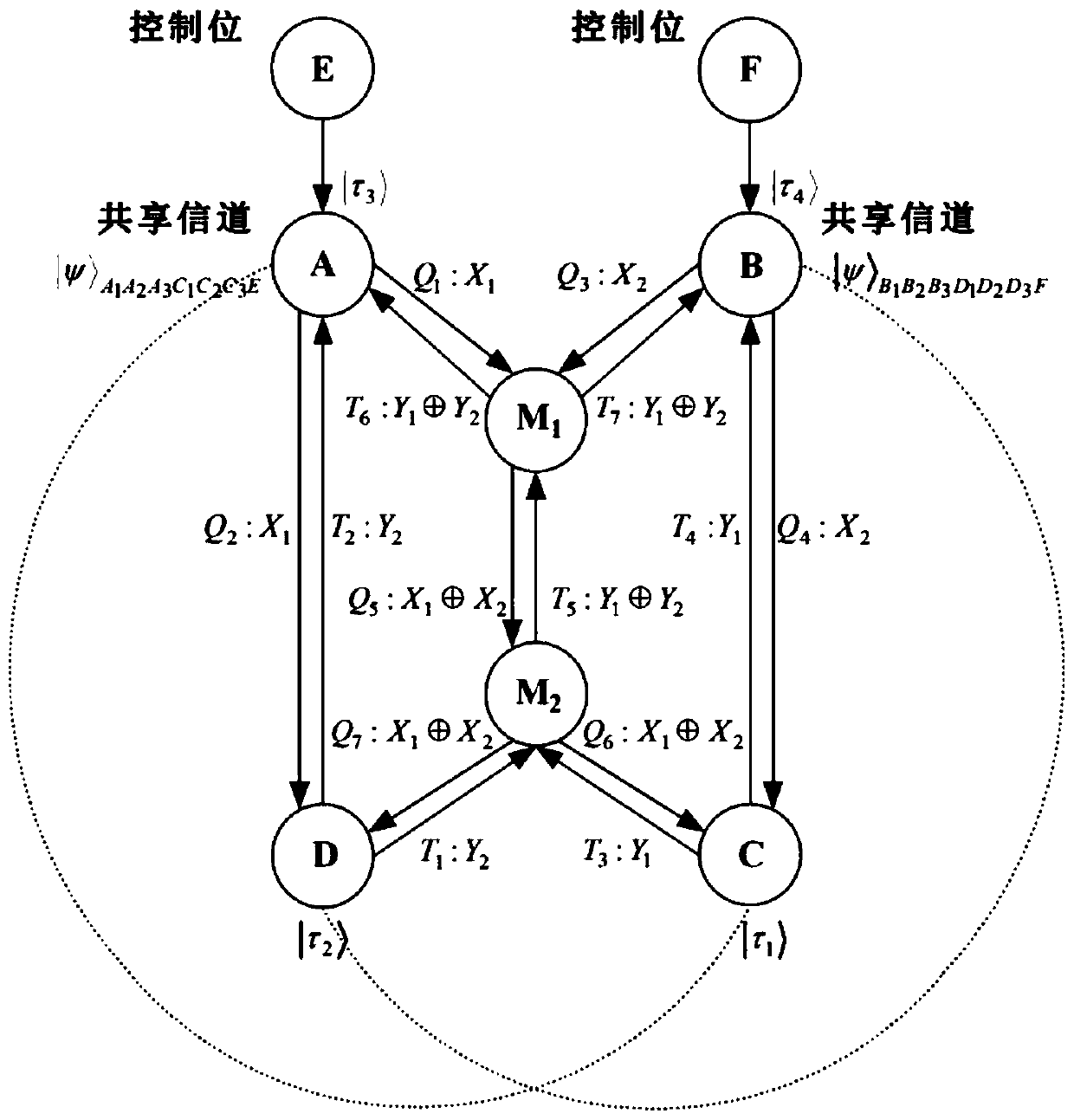
Distributable Quantum Relay Architecture
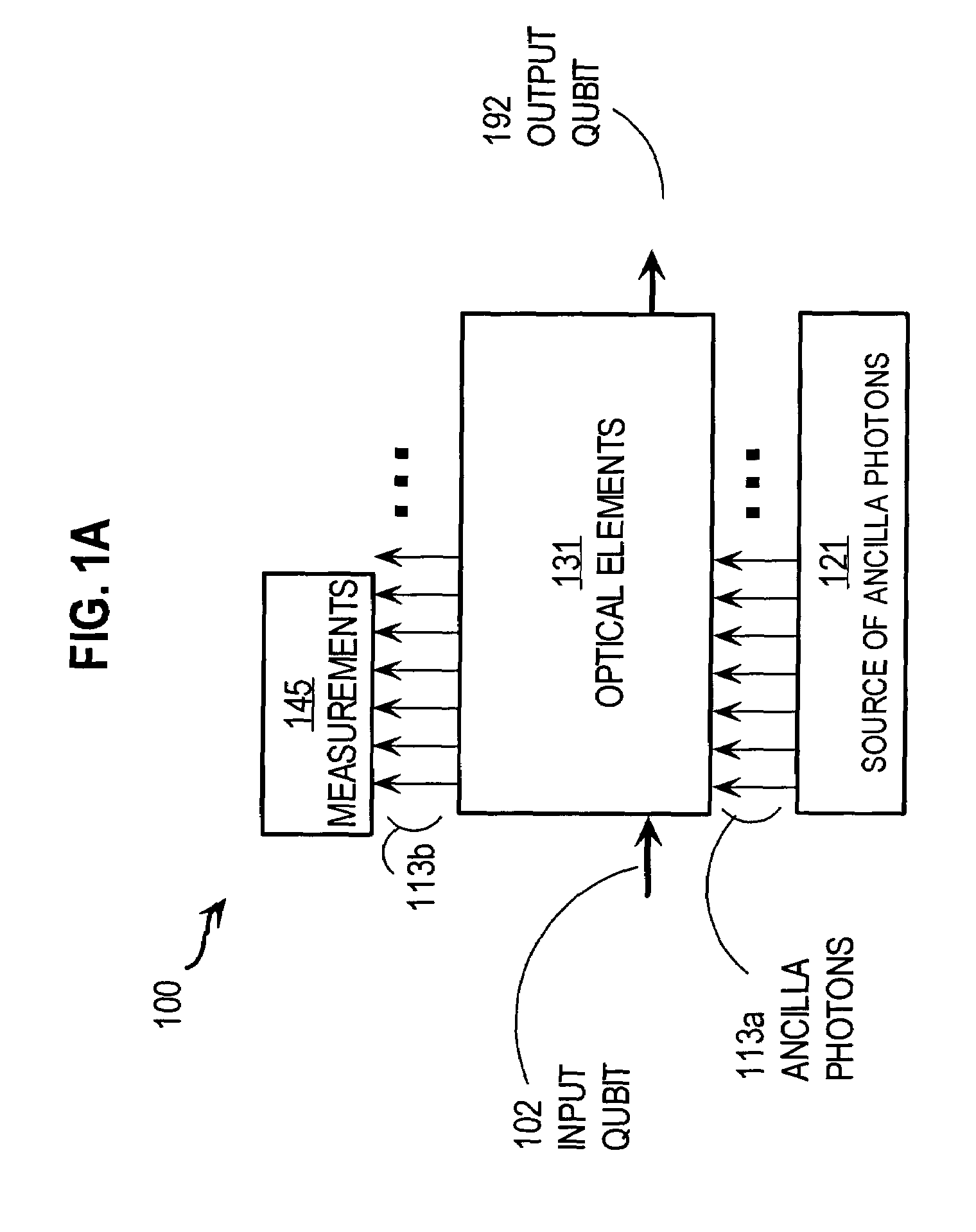
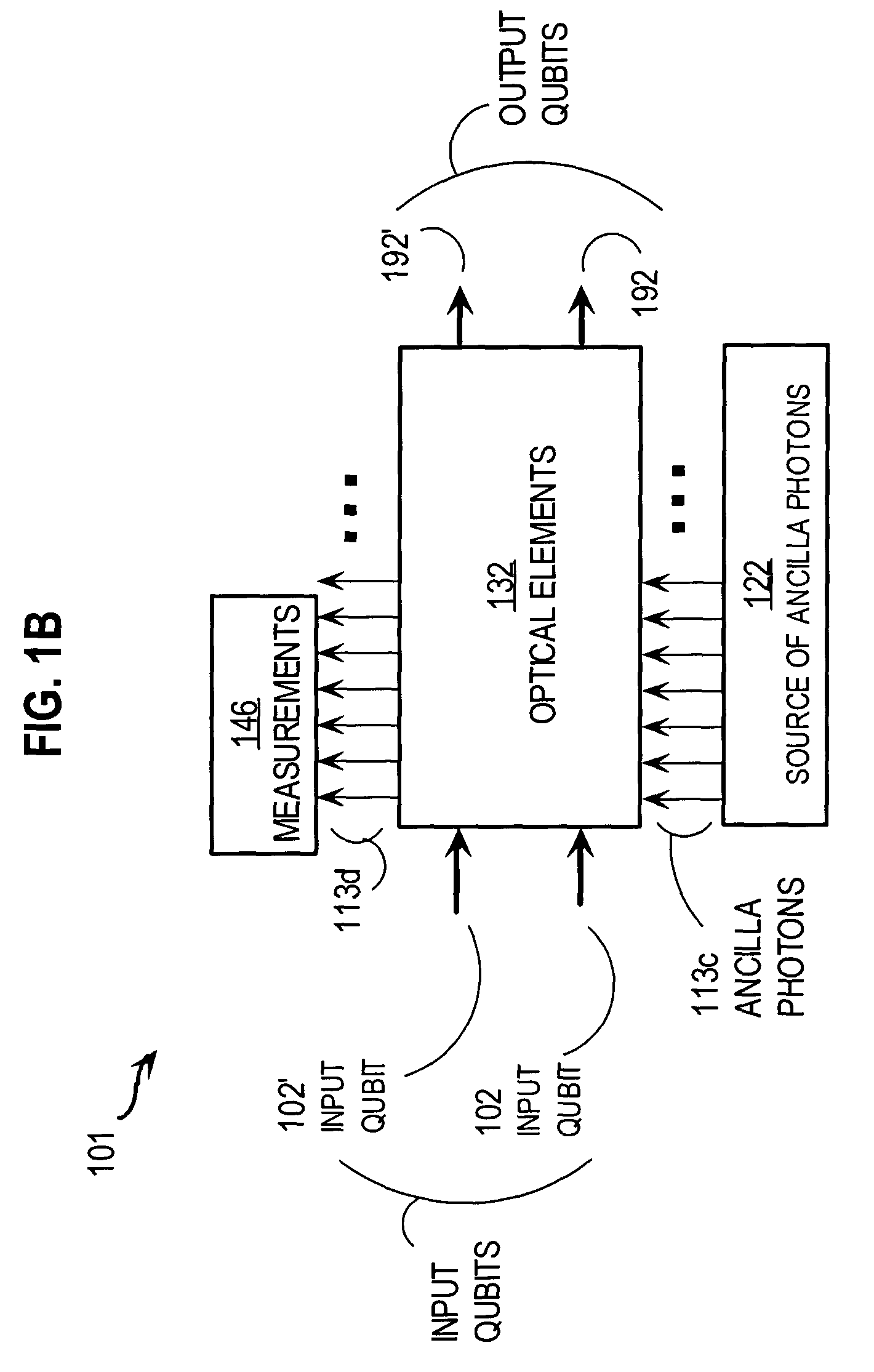
ActiveUS20090317089A1Increase indistinguishabilityPhotonic quantum communicationSecuring communicationQuantum teleportationCost savings
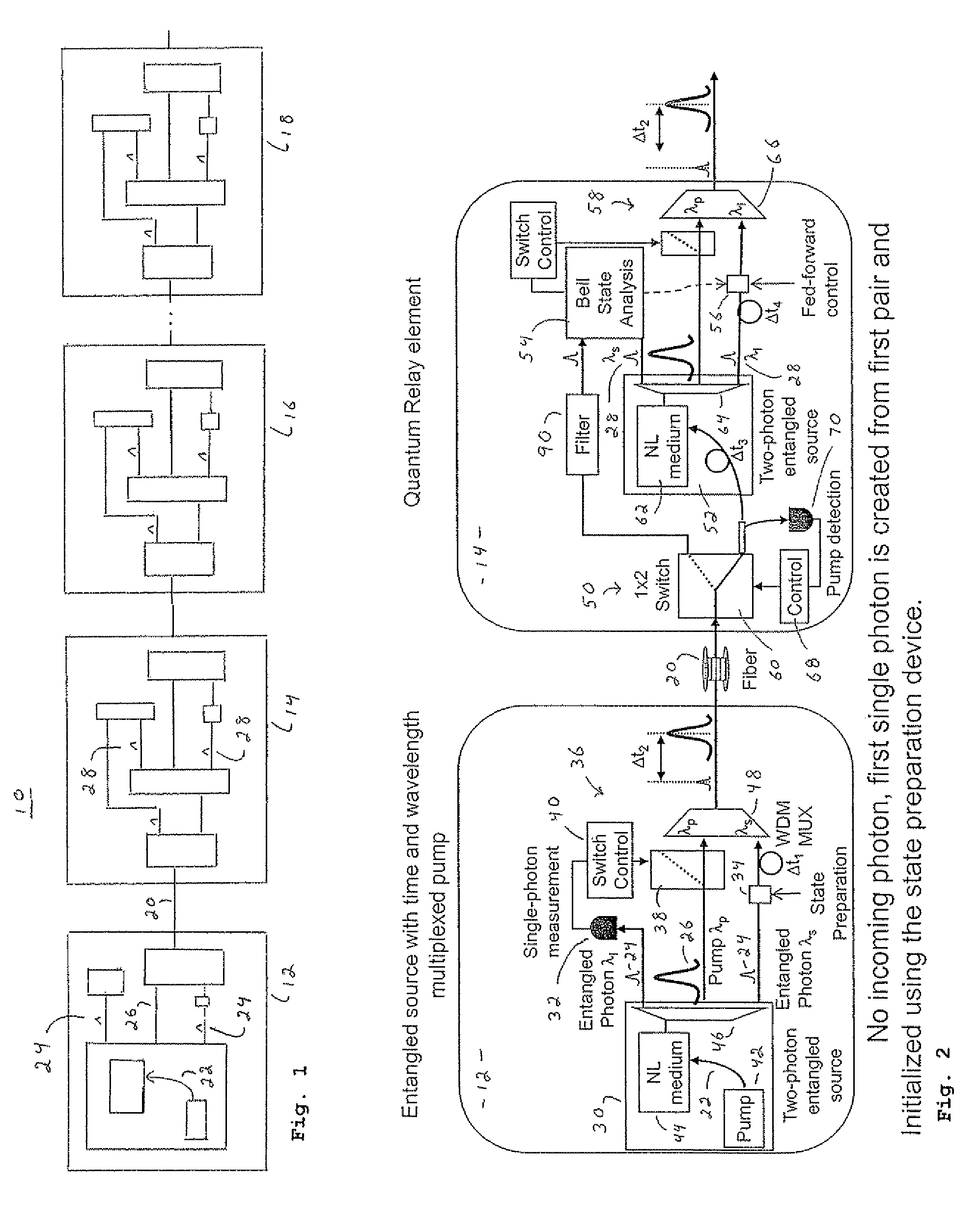
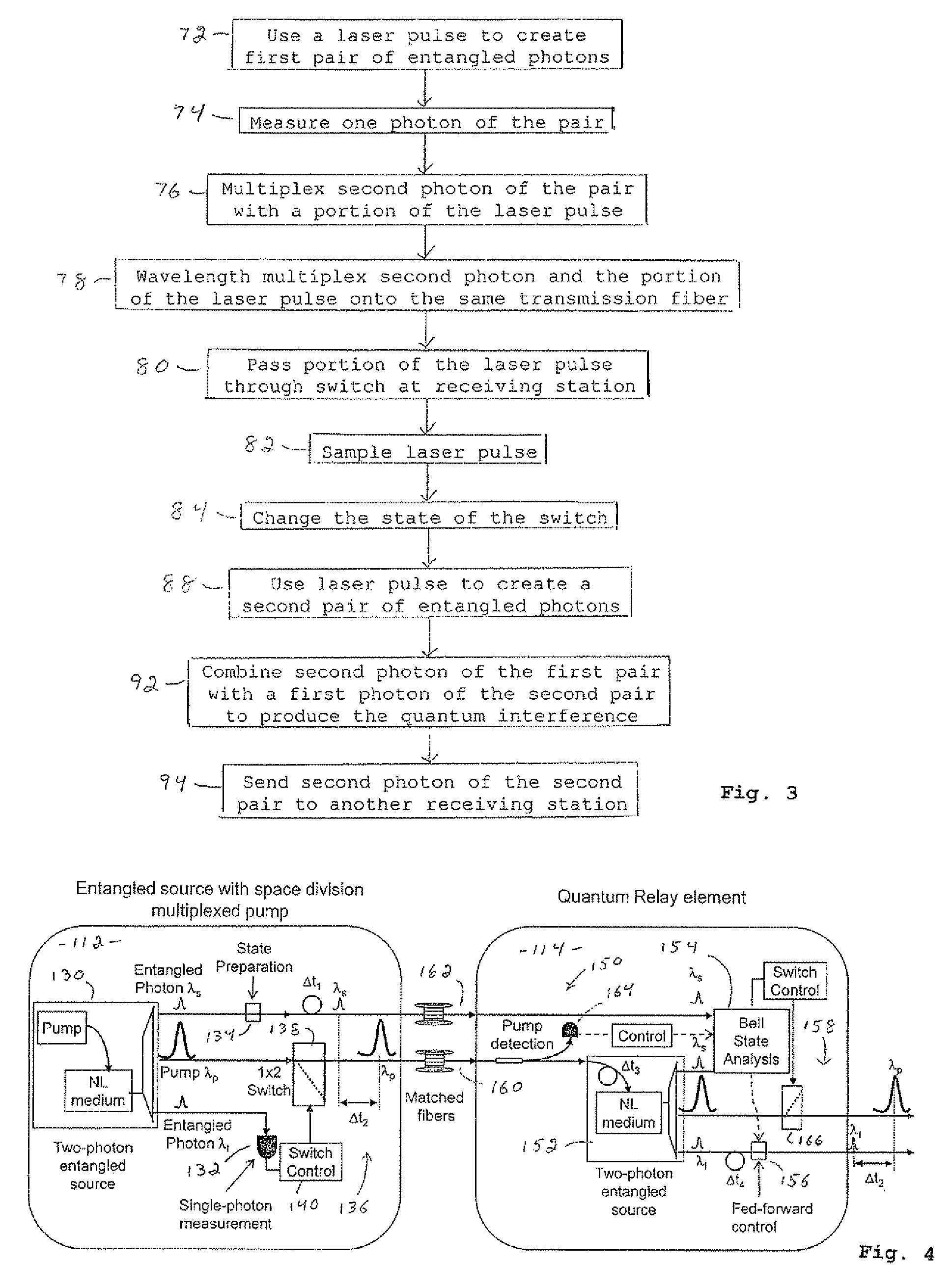
A distributed quantum relay architecture is disclosed. In one embodiment of this architecture, time and wavelength division multiplexing are used to enable a laser pump pulse, already used to create an initial entangled photon pair, to be distributed to a remote relay site, on the same optical fiber as a photon from that initial pair. At that remote site, the pump pulse is amplified and used to locally create the second entangled photon pair that is required for quantum teleportation. This embodiment enables the placement of quantum repeater stations at remote locations without complicated dedicated channels to distribute the pump or electronics. In addition, as lasers are generally among the most expensive components, a significant cost savings is gained, in this embodiment, by using only one pump laser instead of two (or more) as in previous quantum teleportation efforts.
Owner:PERSPECTA LABS INC
Techniques for high fidelity quantum teleportation and computing
ActiveUS7006267B2Sufficient error reductionIncrease opportunitiesQuantum computersKey distribution for secure communicationQuantum teleportationQuantum logic
Owner:THE JOHN HOPKINS UNIV SCHOOL OF MEDICINE
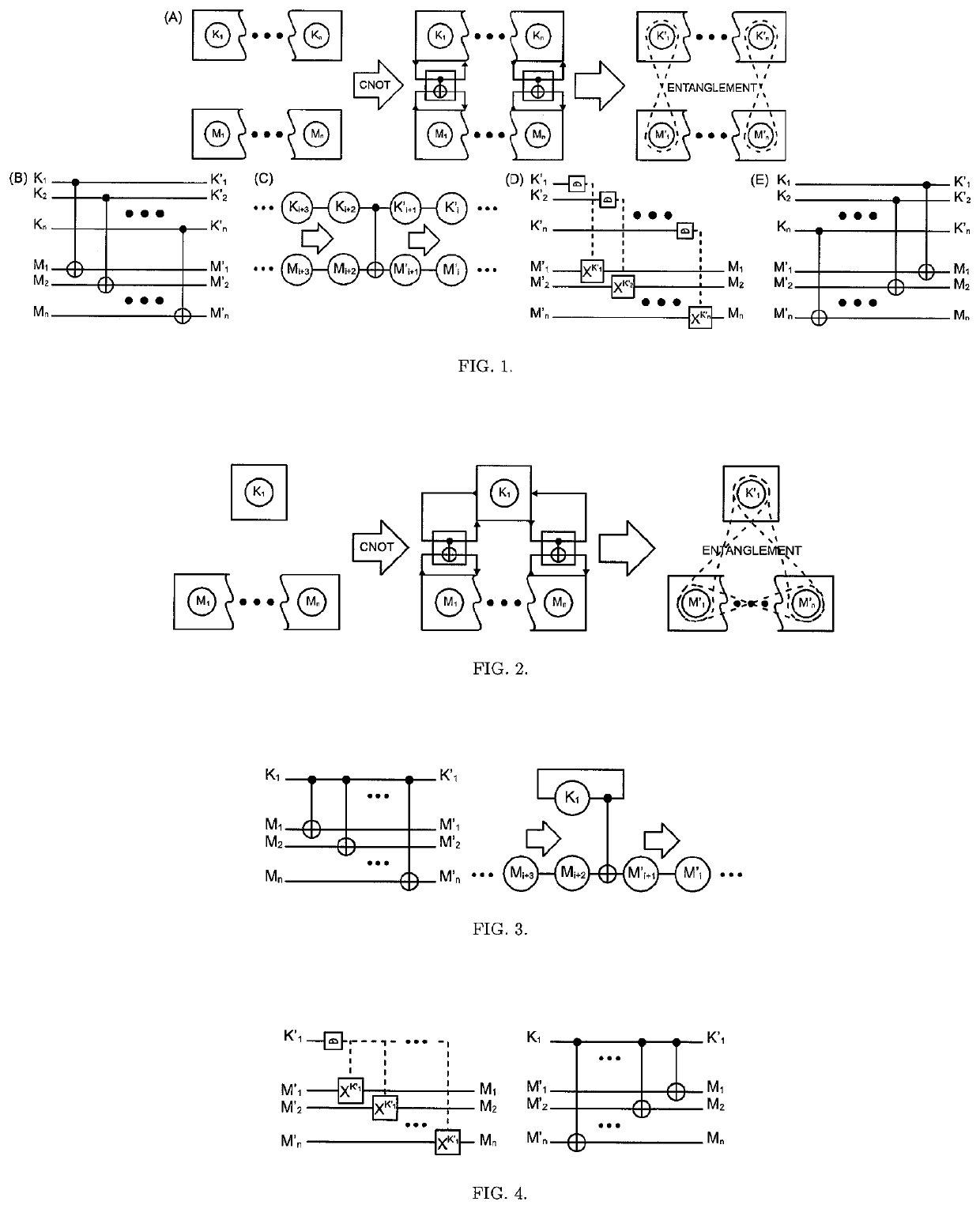
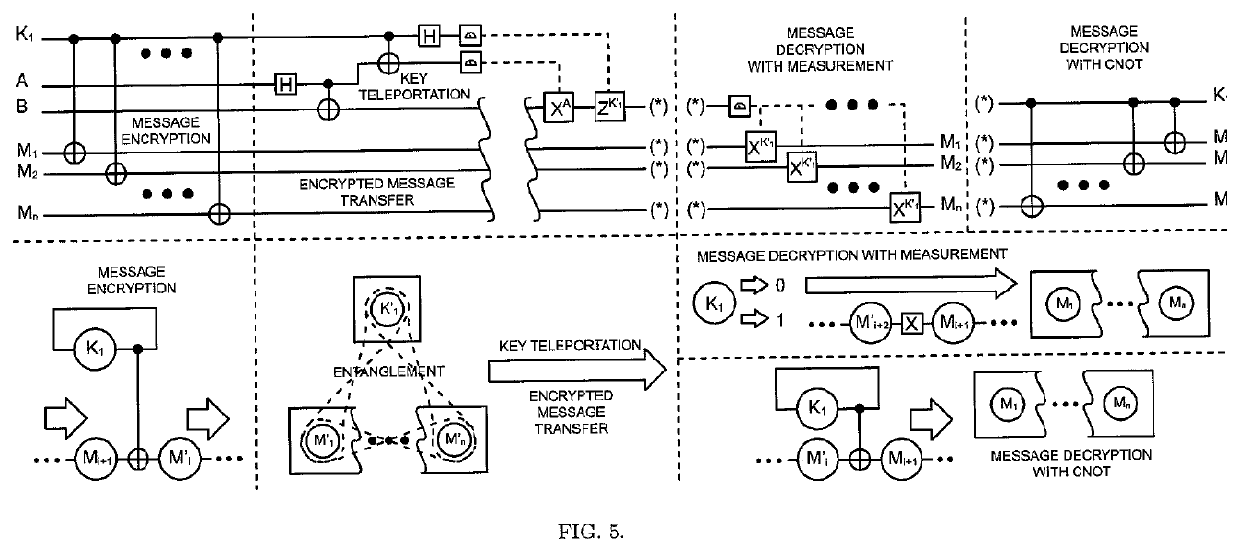
The One-Qubit Pad (OQP) for entanglement encryption of quantum information
InactiveUS20210058244A1Quantum computersKey distribution for secure communicationInformation processingQuantum teleportation
The One-Qubit Pad (OQP) protocol and its generic implementing device constitute a novel, maximally efficient scheme for encryption of quantum information with a quantum key of just a single qubit in an arbitrary unknown quantum state. The OQP enables encryption of the quantum information of n qubits register with a single qubit key upon provision of a multi-qubit entanglement between the single qubit key and the n qubits of the quantum message by the iterative application of the CNOT gate on the same key qubit (control input) and subsequent qubits of the message (target input). This results in an entanglement of all n+1 qubits, which locks original quantum information qubits and the single qubit of the key in a jointly entangled state that cannot be disentangled without the single qubit key. In order to decrypt the quantum message (by its disentanglement) one needs to have the qubit key and either reverse the protocol (applying CNOT operations in the reversed order) or simply measure the entangled key qubit and then depending on the outcome either straightforwardly obtain the decrypted quantum message or its quantum negation (dealt with by again applying quantum negation on all of the message qubits thus restoring their original states). The OQP protocol and its implementing device is proposed one hundred years after the classical One-Time Pad (Vernam cipher) was invented in 1917. The main differences between two schemes show how much quantum and clasical information differ. It is of course impossible to unconditionally securely encrypt classical sequence of n bits with just 1 bit of a key or guarantee that the random key that can be used for this purpose of n bits length (same as of the message) could not be copied. In contrast both these features are possible for the quantum information as described upon the proposed invention. The main characteristic of the OQP protocol to use only a single qubit as the key to enable information-theoretic security of n qubits quantum information encryption follows from the introduction in the invention of the multi-qubit entanglement, which is a non-local, topological and non-classical phenomenon giving quantum information significant edge over its classical counterpart. The main application of the OQP protocol and its implementing generic device is to lock quantum information with the single key qubit in order to prevent any unauthorized access to it (not only a classical access upon a measurement, but more importantly a quantum access by a quantum information processing device). This application can be also extended to communication scenario jointly with the Quantum Teleportation, which without OQP requires pre-sharing of n pairs of Bell states between Alice and Bob to securely communicate n qubits long quantum message, whereas in contrast with the OQP protocol just one pair of Bell state is required to securely teleport only the single qubit key for the OQP encrypted quantum message sent through an insecure quantum channel and still be access-protected from Eve (an adversary).
Owner:COMPSECUR SP ZOO
Tampering detection system using quantum-mechanical systems
ActiveUS8077047B2Using optical meansBurglar alarm electric actuationTelecommunications linkQuantum mechanical system
The use of quantum-mechanically entangled photons for monitoring the integrity of a physical border or a communication link is described. The no-cloning principle of quantum information science is used as protection against an intruder's ability to spoof a sensor receiver using a ‘classical’ intercept-resend attack. Correlated measurement outcomes from polarization-entangled photons are used to protect against quantum intercept-resend attacks, i.e., attacks using quantum teleportation.
Owner:UT BATTELLE LLC
Distributable quantum relay architecture
ActiveUS8103172B2Increase indistinguishabilityPhotonic quantum communicationSecuring communicationQuantum teleportationCost savings
A distributed quantum relay architecture is disclosed. In one embodiment of this architecture, time and wavelength division multiplexing are used to enable a laser pump pulse, already used to create an initial entangled photon pair, to be distributed to a remote relay site, on the same optical fiber as a photon from that initial pair. At that remote site, the pump pulse is amplified and used to locally create the second entangled photon pair that is required for quantum teleportation. This embodiment enables the placement of quantum repeater stations at remote locations without complicated dedicated channels to distribute the pump or electronics. In addition, as lasers are generally among the most expensive components, a significant cost savings is gained, in this embodiment, by using only one pump laser instead of two (or more) as in previous quantum teleportation efforts.
Owner:PERSPECTA LABS INC
Controlled quantum safe and direct communication method and system for preventing tampering
ActiveCN108092771AFew constraintsVerify identidyKey distribution for secure communicationPhotonic quantum communicationSecure communicationQuantum secure direct communication
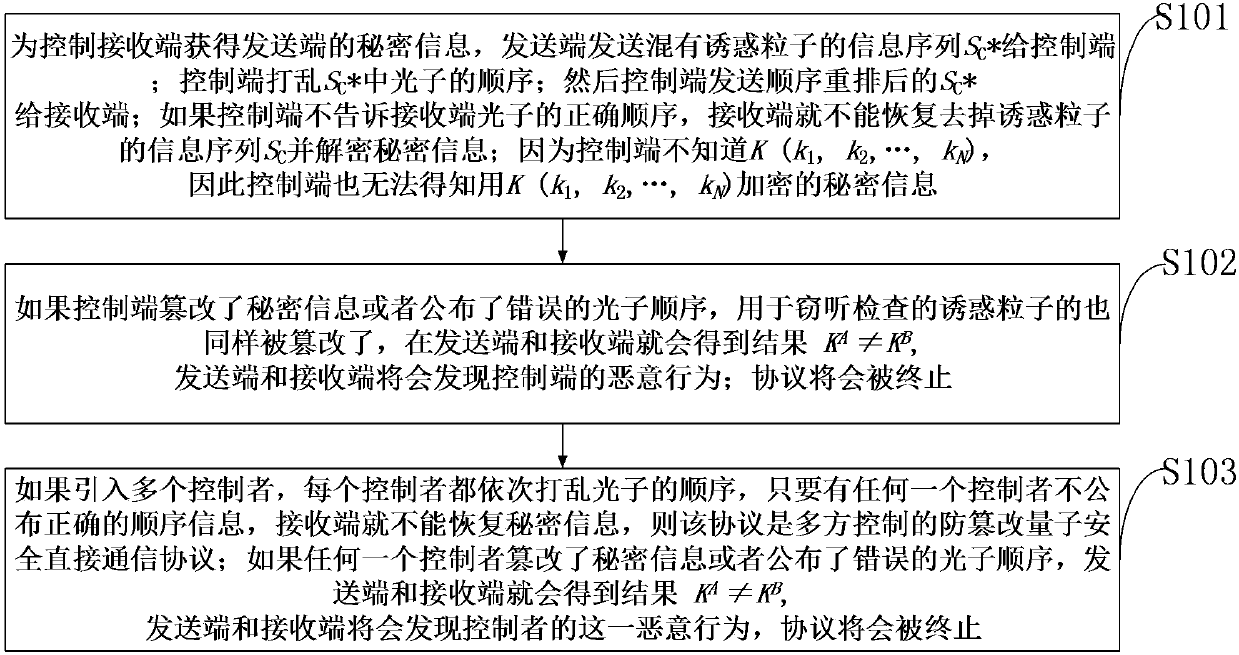
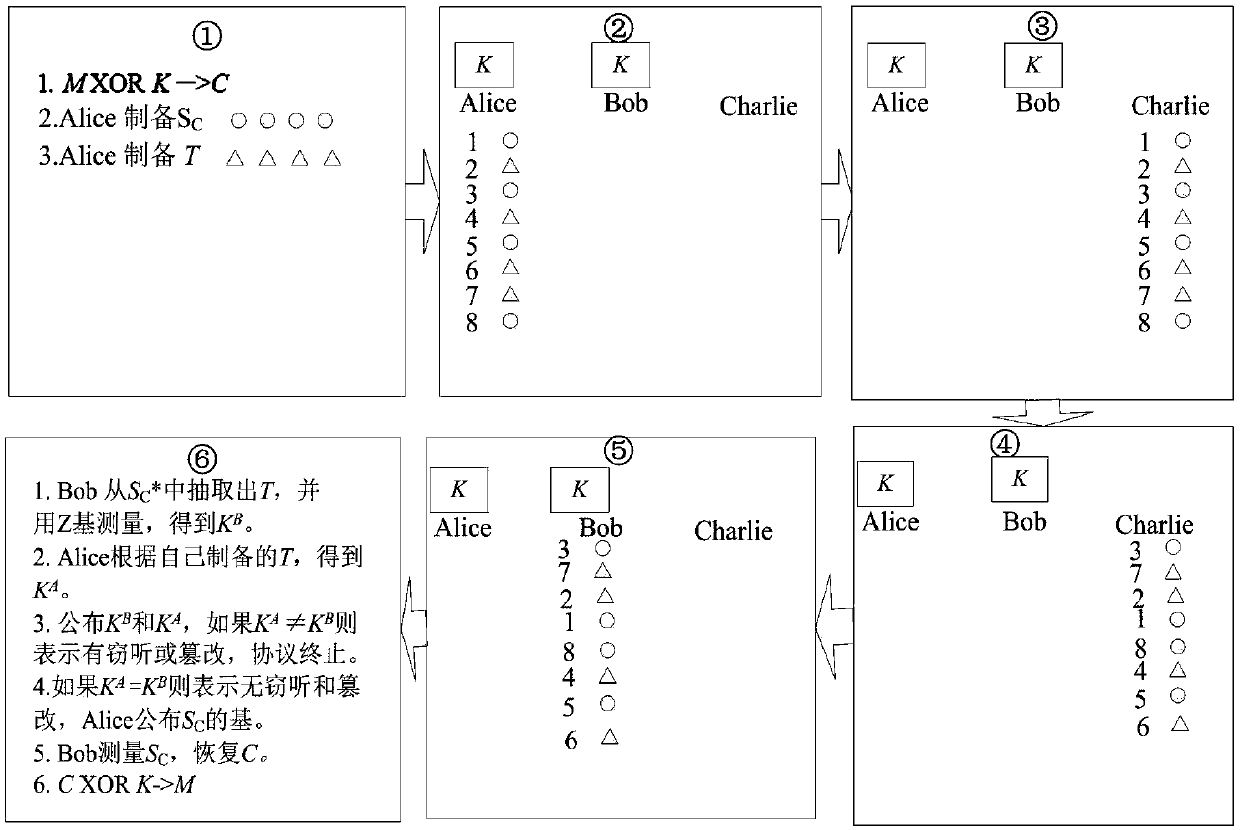
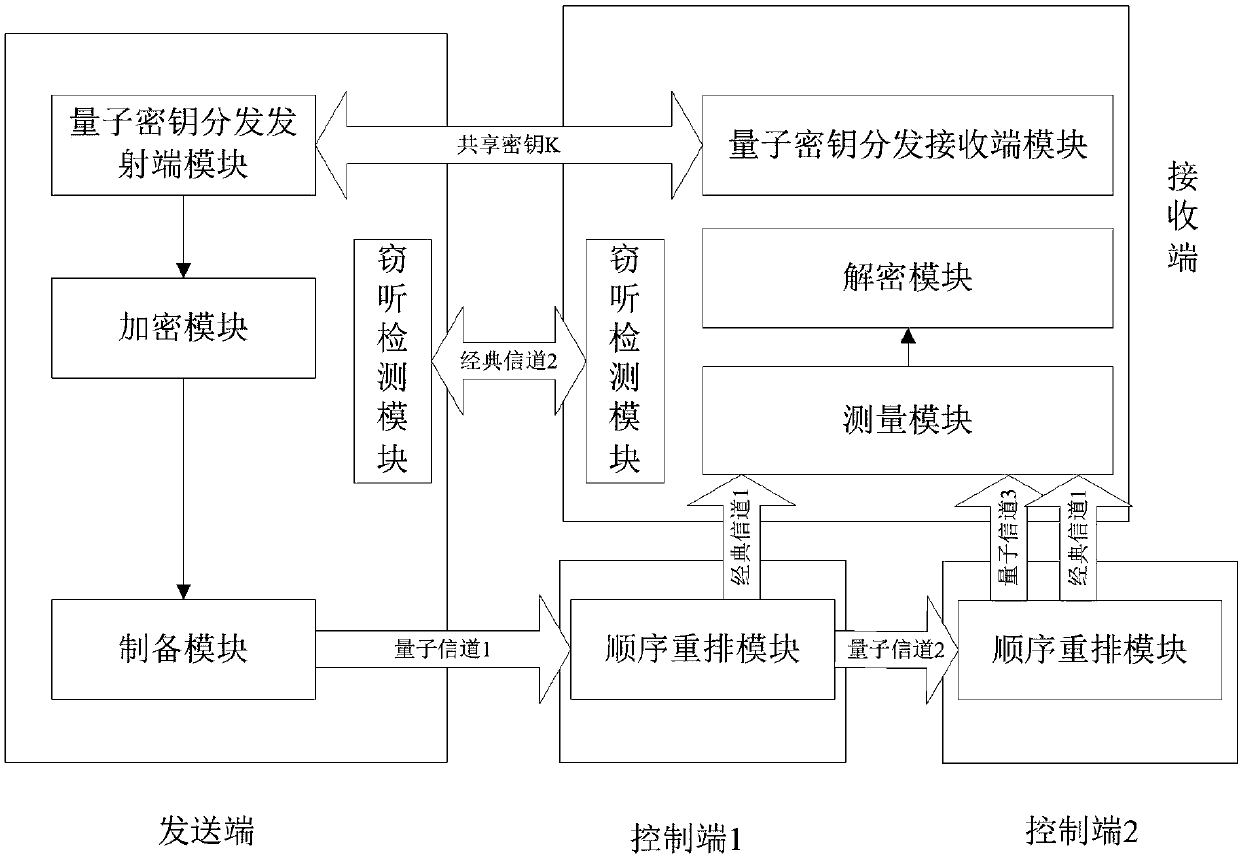
The invention belongs to the technical field of safety communication, and discloses a controlled quantum safe and direct communication method and system for preventing tampering. A receiving end is controlled to obtain secret information of a sending end, and the sending end sends SC* to a control end; the control end disorganizes photons in SC*; then the control end sends rearranged SC* to the receiving end; if the control end does not tell the accurate sequence of the photons to the receiving end, the receiving end cannot resume SC and decrypt the secret information; the control end cannot know the secret information encrypted through K(k1, k2, ..., kN). The premise that a controller is honest is not needed; even under the condition that the controller is dishonest, the proposed protocolis still safe, and any tampering of the secret information can be easily found. By means of the controlled quantum safe direct communication method and system for preventing tampering, attack of fakephotons based on quantum teleportation can be resisted, and meanwhile, identities of two participants, namely, the sender and the receiver, can also be verified.
Owner:武汉飞信云科技有限公司
Quantum voting system and method based on quantum teleportation
PendingCN108880790AGuaranteed legalityEnsure safetyKey distribution for secure communicationUser identity/authority verificationBell stateMeasurement device
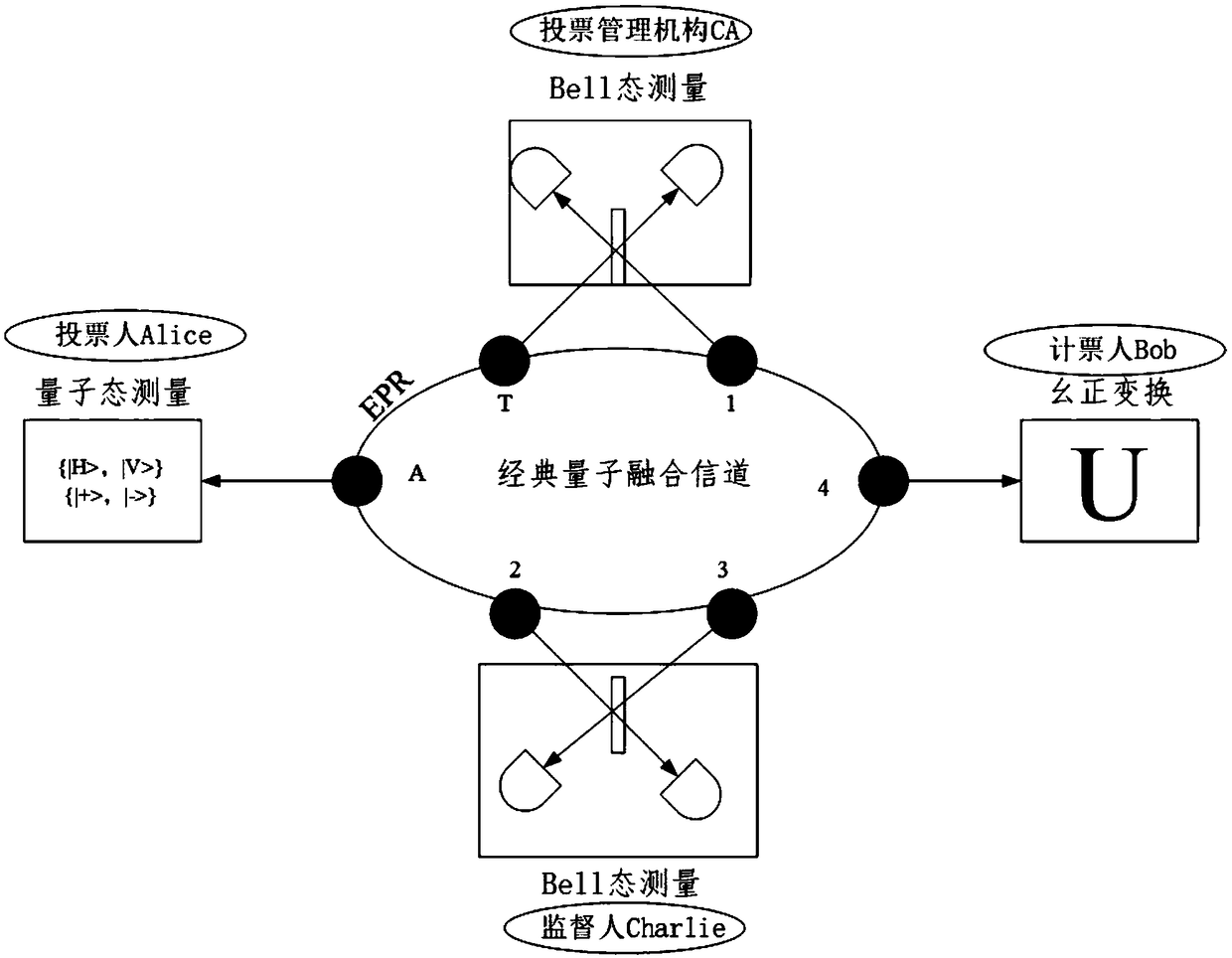
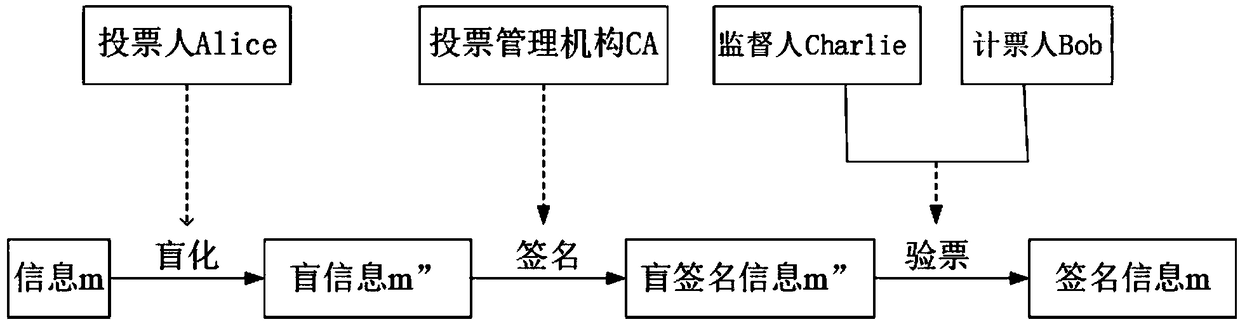
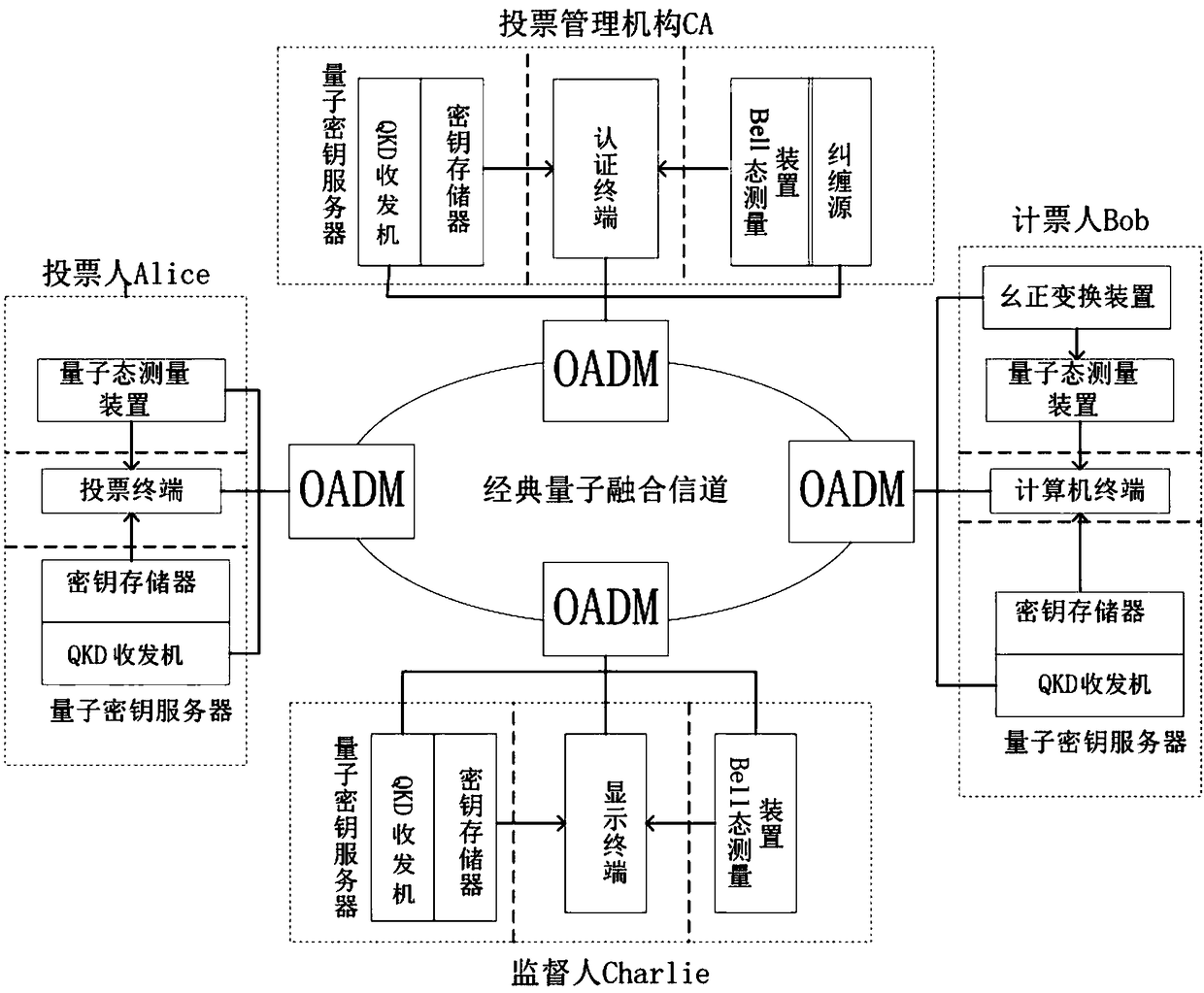
The invention discloses a quantum voting system and method based on quantum teleportation. The quantum voting system comprises a voter Alice, a voting management organization CA, a supervisor Charlie,a teller Bob and four OADMs, wherein the voter Alice comprises a first a quantum key server, a voting terminal and a first quantum state measurement device; the voting management organization CA comprises a second quantum key server, an authentication terminal, an entanglement source and a first Bell state measurement device; the supervisor Charlie comprises a third quantum key server, a displayterminal and a second Bell state measurement device; and the teller Bob comprises a fourth quantum key server, a computer terminal, a unitary transformation device and a second quantum state measurement device. The quantum voting system disclosed by the invention ensures the security of the whole voting process by the coherence of entangled particles, a QKD protocol, a one-time-one-encryption encryption algorithm and quantum channel eavesdropping detection. In addition, the quantum voting system disclosed by the invention transmits the classical and quantum information through different wavelengths in the same optical fiber, so that the cost of an application can be greatly reduced, and the practicability is improved
Owner:GUANGDONG INCUBATOR TECH DEV CO LTD
Quantum communication using quantum teleportation
ActiveUS9264225B1Key distribution for secure communicationQuantum teleportationQuantum key distribution
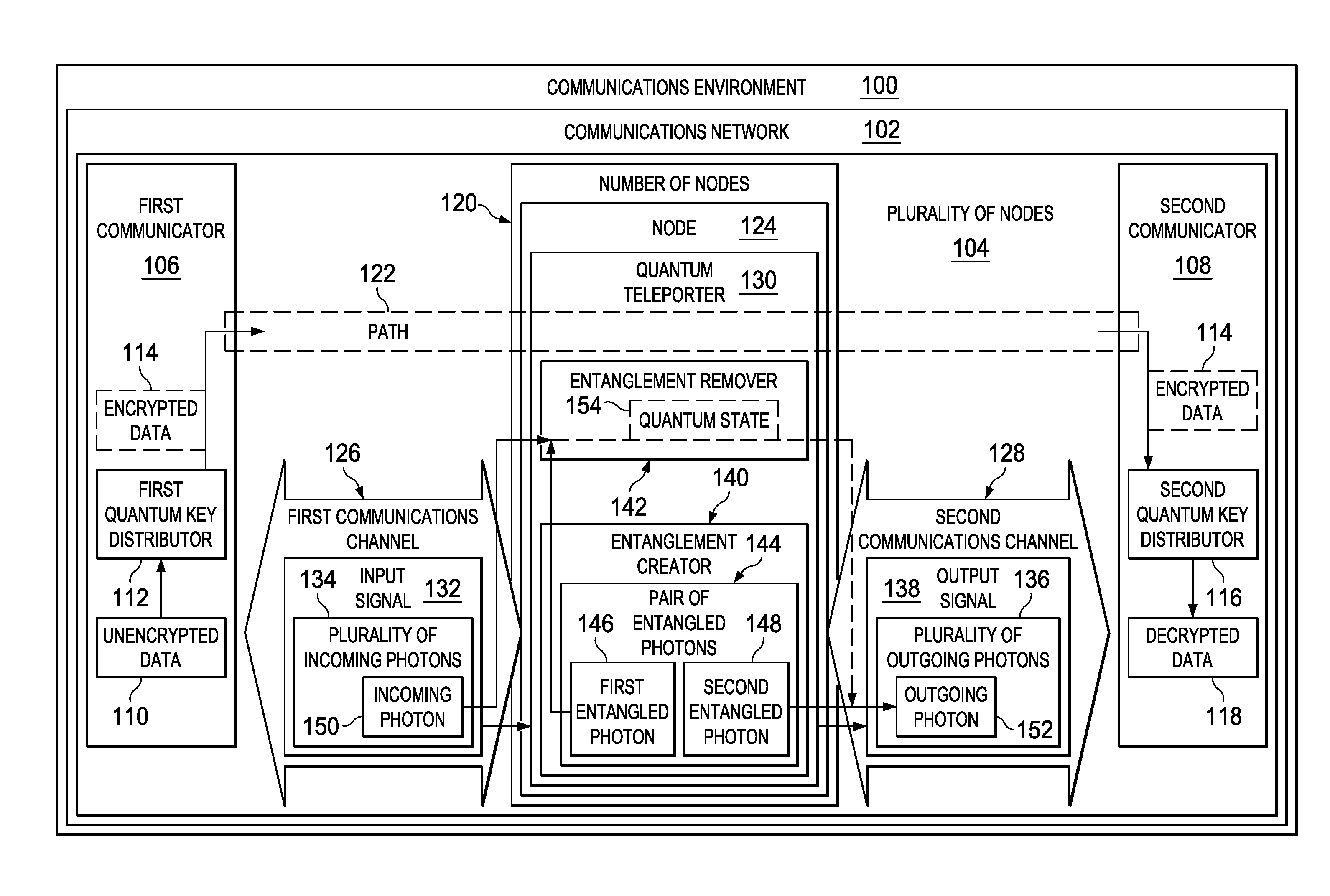
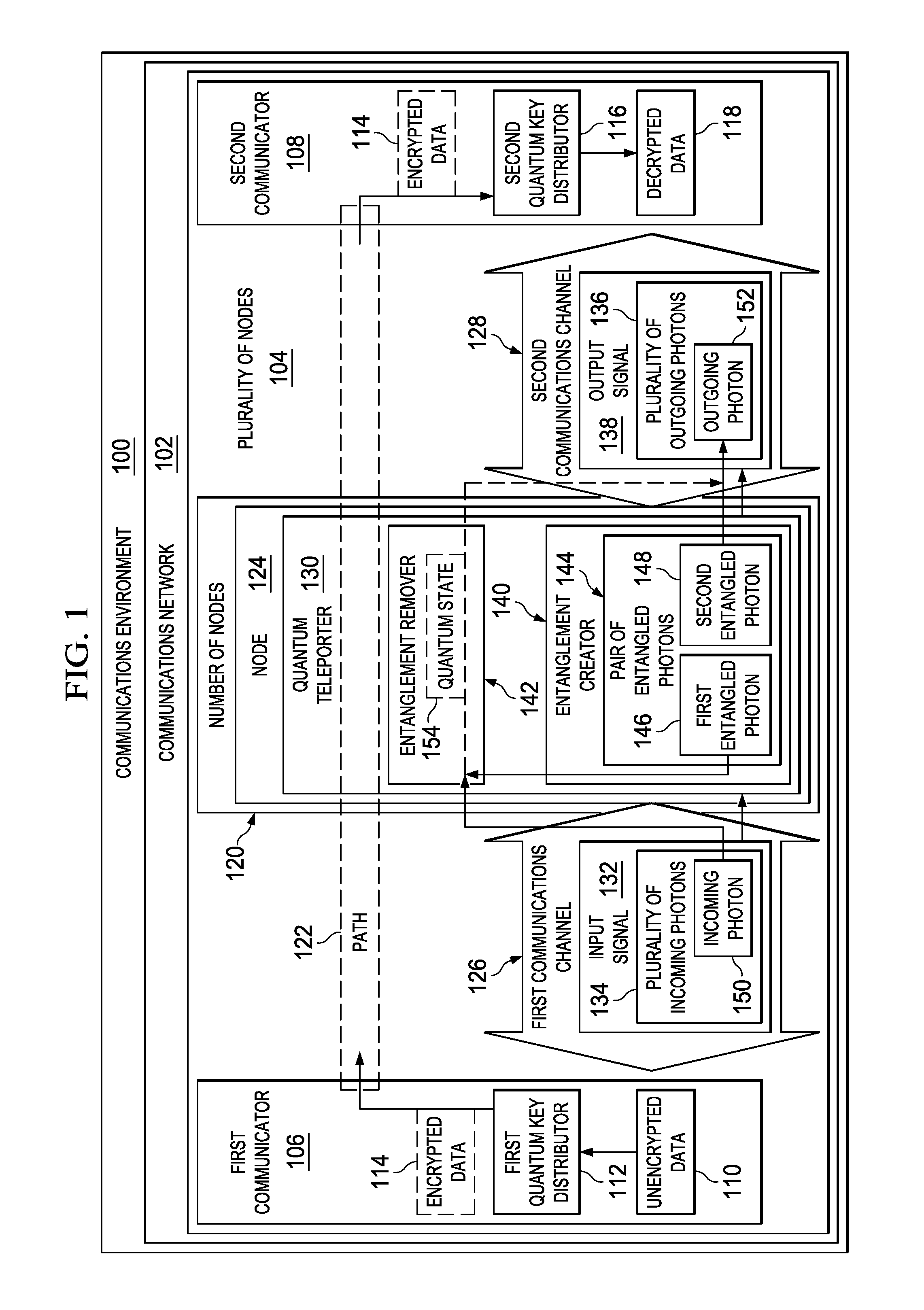
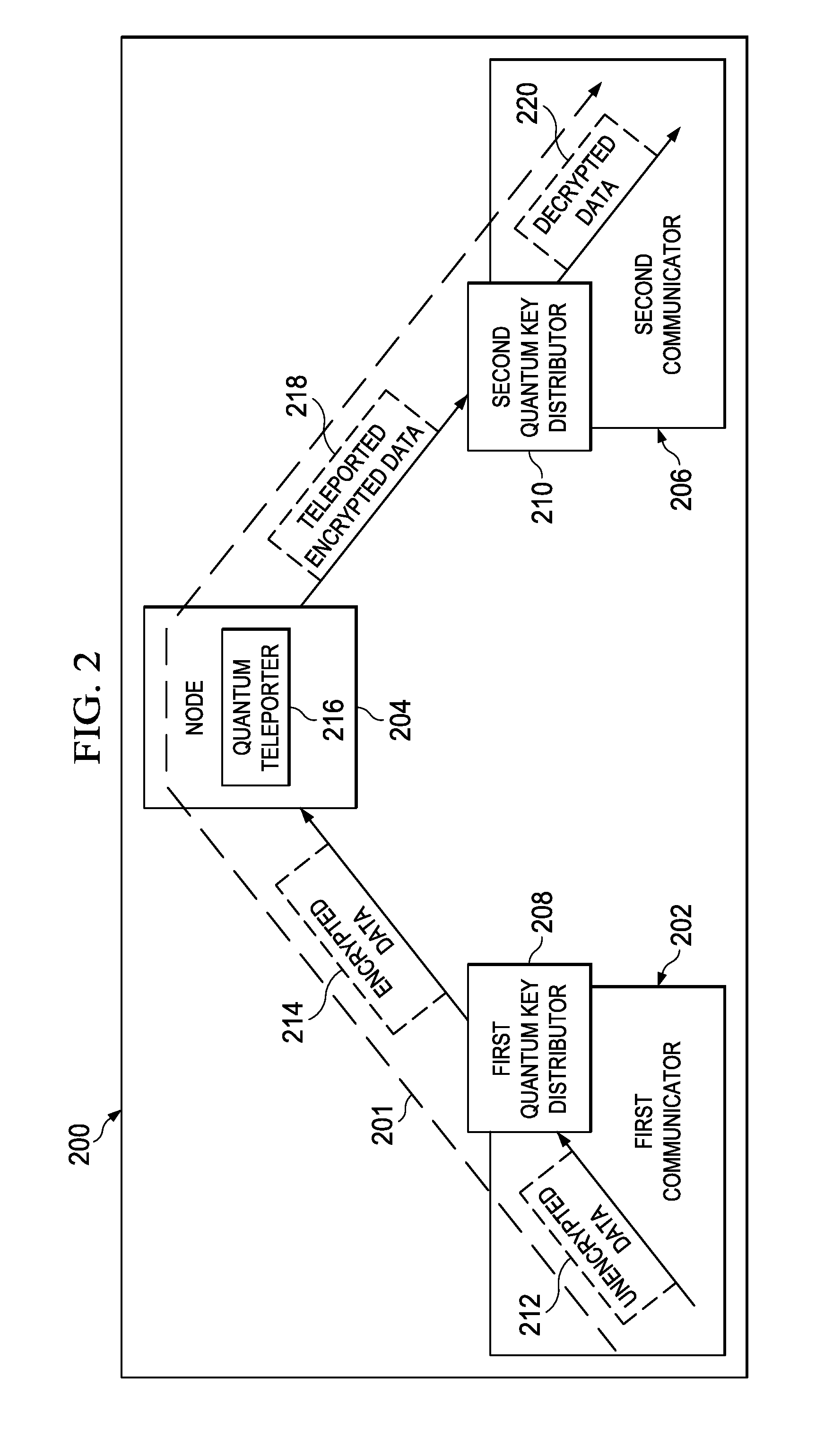
A method and apparatus for sending encrypted data across a node in a communications network. In one illustrative embodiment, an apparatus comprises a first communicator, a second communicator, and a number of nodes. The first communicator is configured to encrypt unencrypted data to form the encrypted data using a first quantum key distributor. The second communicator is configured to decrypt the encrypted data using a second quantum key distributor. The number of nodes is configured to receive the encrypted data sent from the first communicator and send the encrypted data to the second communicator using quantum teleportation. The encrypted data remains encrypted as the encrypted data passes through each of the number of nodes.
Owner:THE BOEING CO
Opportunistic quantum network coding method
ActiveCN104301098AAchieve absolute securityEmbody opportunistic characteristicsKey distribution for secure communicationData switching networksNetwork codeQuantum teleportation
The invention provides an opportunistic quantum network coding method. The opportunistic quantum network coding method is characterized by being designed by giving full play to the characteristics of quantum teleportation, specific classical information is characterized by means of quantum states and transferred through a quantum teleportation method, opportunistic monitoring is achieved through classical channels, and opportunistic characteristics of quantum network coding are achieved; the method includes ten steps. According to the opportunistic quantum network coding method, the classical opportunistic network coding thought is applied to quantum network coding, the absolute security of communication is guaranteed by means of the quantum channels, and thus by means of the character that the classical channels can be monitored, quantum network coding with opportunistic characteristics is achieved; as a result, the security of quantum information transmission in a quantum network coding model is enhanced, and the transmission performance of the quantum network is further improved beneficially.
Owner:BEIHANG UNIV
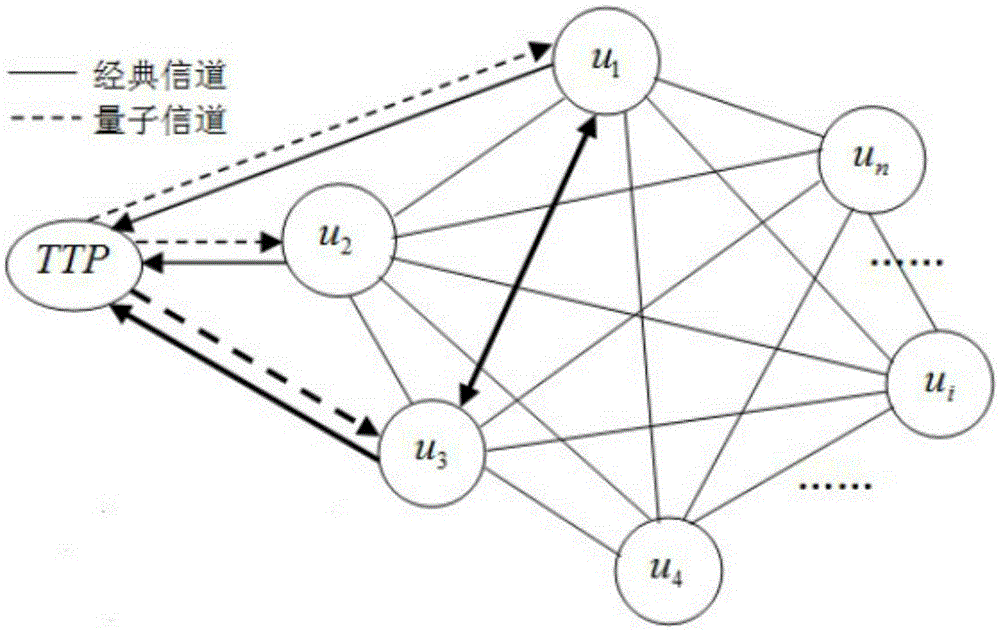
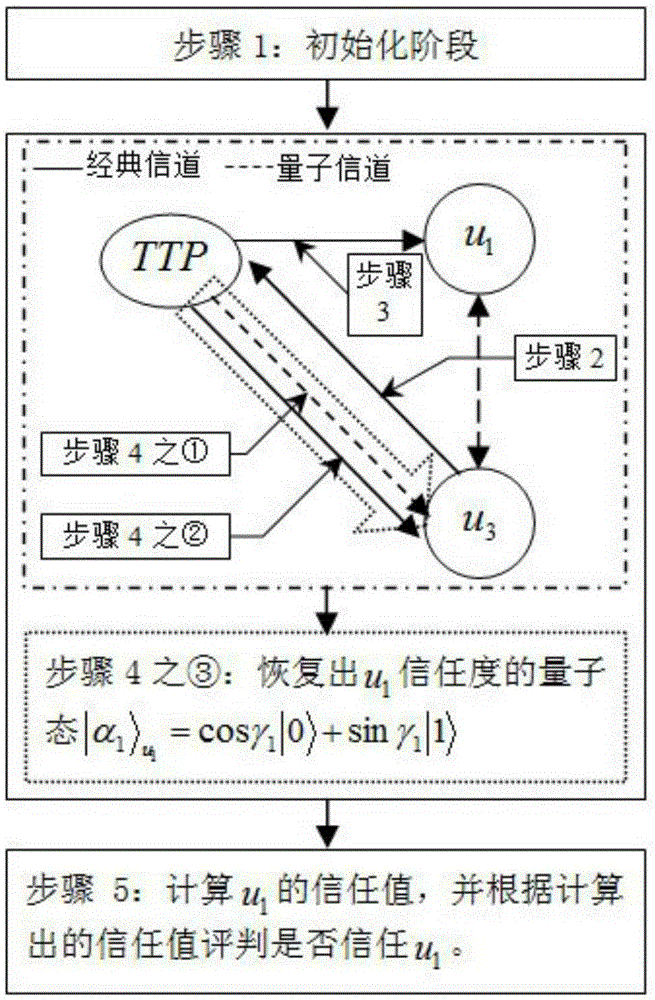
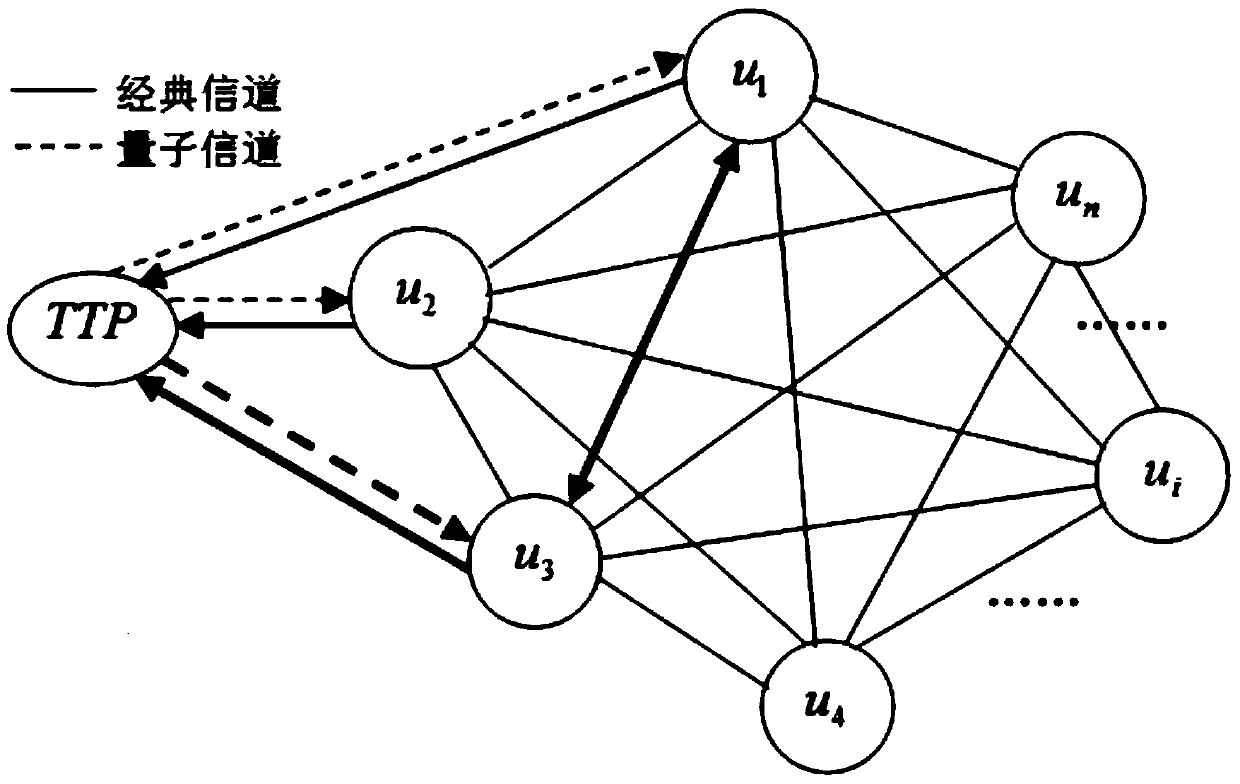
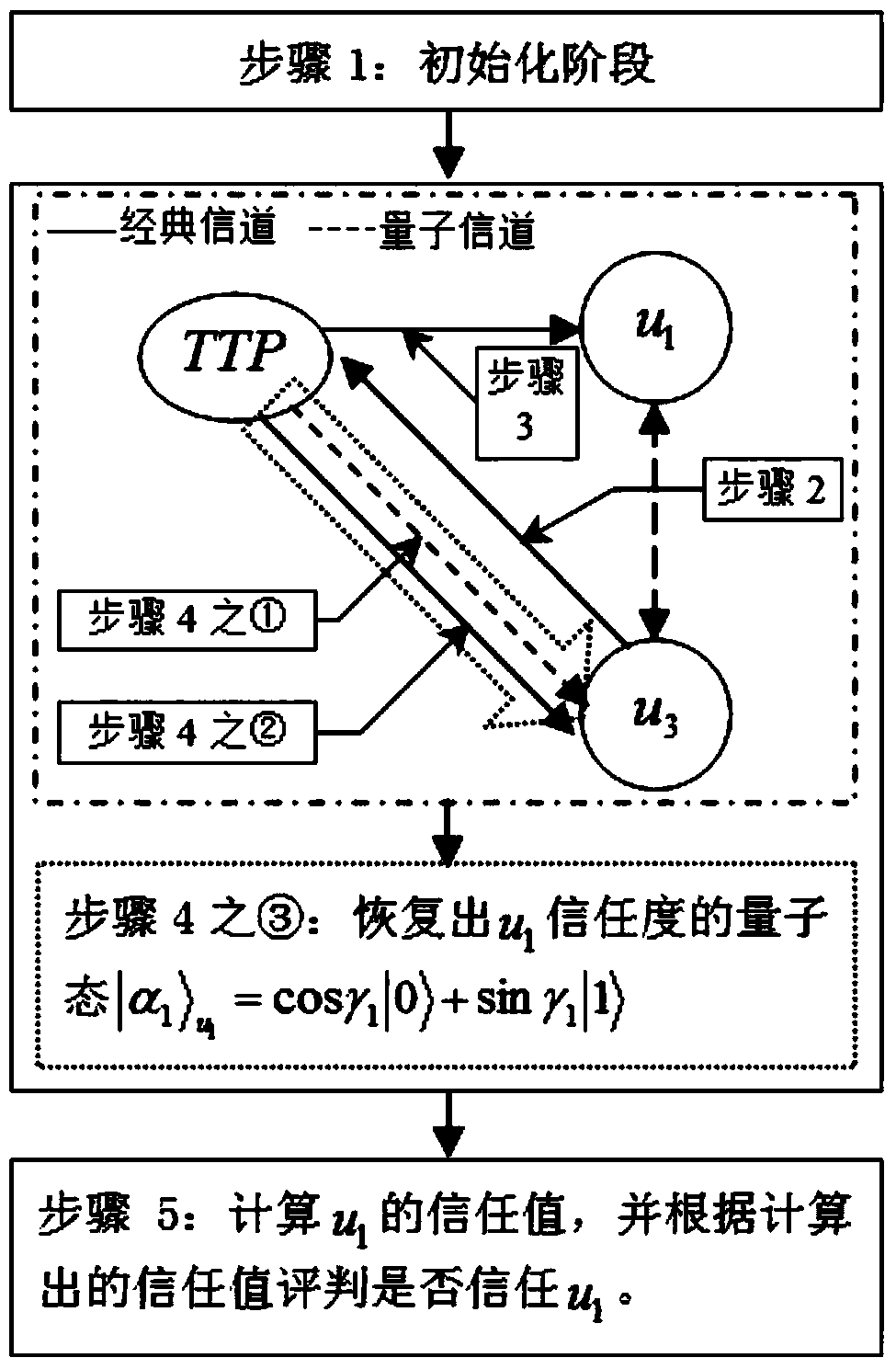
Node trust-based quantum trust assessment method
ActiveCN105391548AKey distribution for secure communicationPhotonic quantum communicationQuantum entanglementResearch Object
The invention discloses a node trust-based quantum trust assessment method, including modeling of a quantum trust model and a method for quantum trust assessment. Compared with the prior art, the method uses a trust node-based credible quantum relay network as a research object, introduces trust management into a quantum communication network, uses assessment of a trust value of a node as a basis to build a safe and credible quantum communication network, and uses the trust value as a basis for judging whether users in the quantum communication network are credible; by means of unique characteristics of a quantum entanglement effect and quantum teleportation, the node trust-based quantum trust assessment method is researched and proposed, and the idea and the process of quantum trust assessment are explained in detail; and finally feasibility, reasonability and safety of the node trust-based quantum trust assessment method proposed by the invention are analyzed, thereby providing a valuable new idea and new method for building a safe and credible quantum communication network.
Owner:CHENGDU UNIV OF INFORMATION TECH +1
Quantum network coding method based on quantum discord
ActiveCN109379144AImprove robustnessImprove throughputPhotonic quantum communicationForward error control useSeparated stateInformation transmission
The invention discloses a quantum network coding method based on quantum discord. Characteristics of the quantum discord are brought into full play, entanglement distribution based on the separated state is combined, and the quantum network coding method based on the quantum discard is designed, thus the quantum resource consumption of the entanglement distribution is reduced, and the robustness and the throughput of a communication network are improved. Compared with the prior art, the quantum network coding method based on the quantum discard provided by the invention has the following advantages: (1), the quantum discard is adopted as a measure of quantum correlation to perform the entanglement distribution from the perspective of taking the quantum correlation as a communication resource, thereby reducing the quantum resource consumption of the entanglement distribution and improving the robustness and the throughput of the communication network; and (2), the quantum network codingmethod is designed by adopting the entanglement distribution based on the separated state, no quantum entanglement is involved in an entanglement establishment process, and an entangled particle pairis generated between a source node and a destination node only at the end, so that the advantages of the quantum invisible transmission state in the aspect of information transmission are fully exerted.
Owner:BEIHANG UNIV
Bidirectional single-bit state preparation method based on Brown state and network coding
ActiveCN111510289AAchieve bidirectional preparationReduce resource consumptionKey distribution for secure communicationTelecommunicationsNetwork code
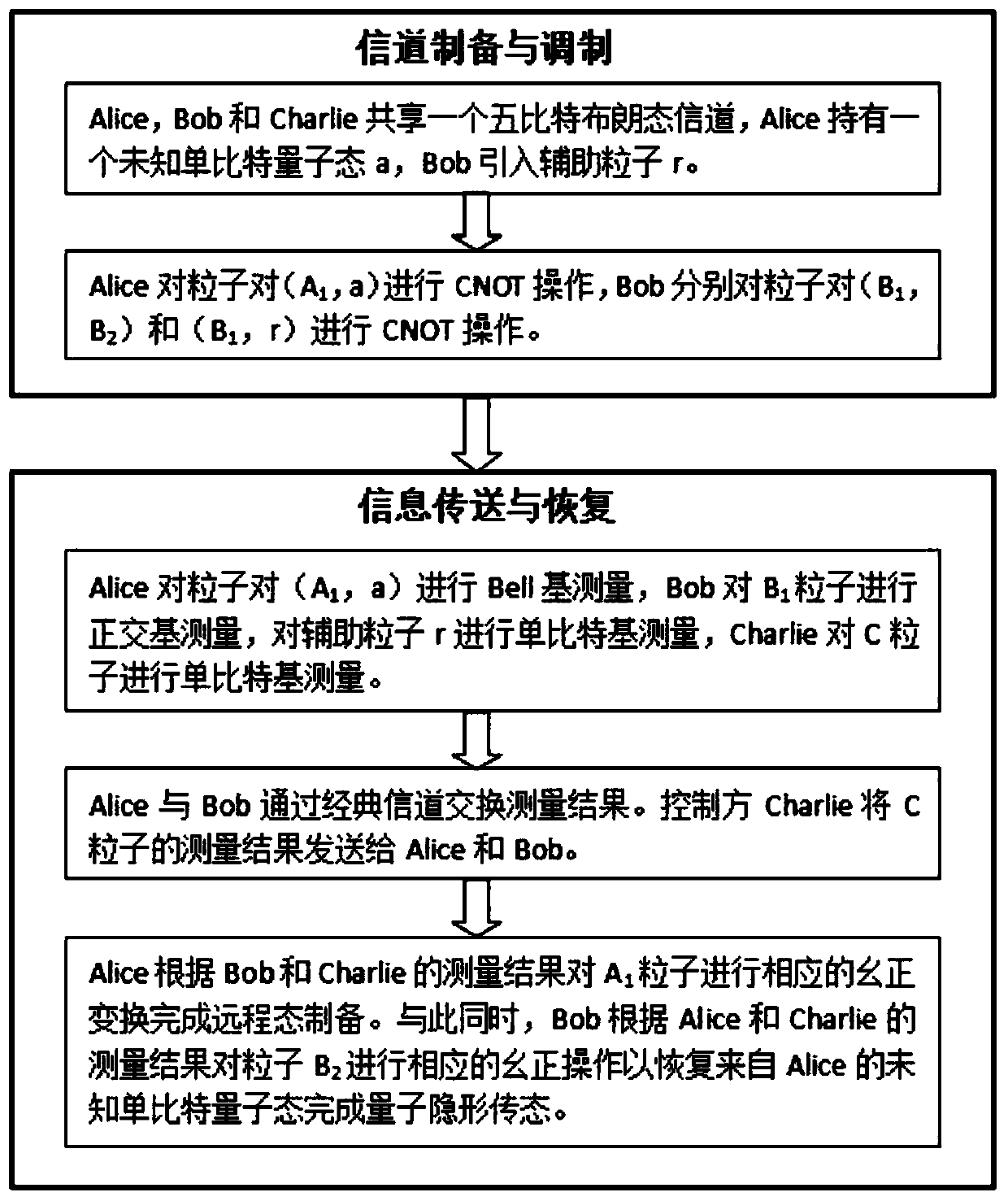
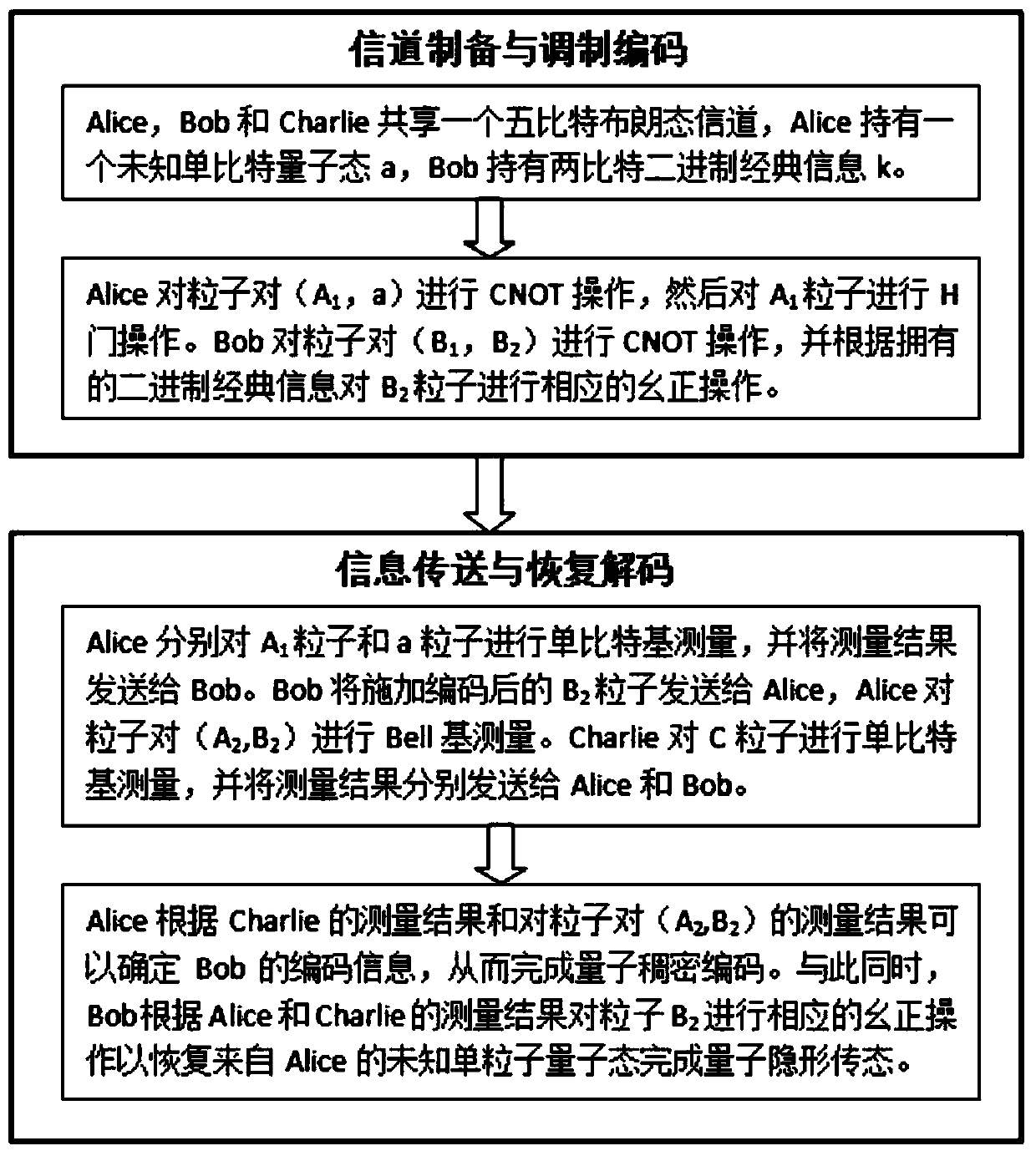
The invention discloses a bidirectional single-bit state preparation method based on a Brown state and network coding. According to the bidirectional single-bit state preparation method, state preparation based on the Brown state and network coding are combined for the first time, cross transmission is carried out between a sender and a receiver through a butterfly network and a five-bit Brown state, and an arbitrary single-bit quantum state scheme is prepared bidirectionally. The bidirectional single-bit state preparation method is mainly characterized in that a quantum network coding model is established through state preparation on the basis of a butterfly network coding protocol. A channel shared by a source node and a destination node is obtained by adding auxiliary particles in the five-bit Brown state and performing channel modulation through CNOT operation. The transmission of known information in the whole network model is realized, compared with a quantum stealth transmissionscheme, the resource consumption is lower, the transmission efficiency reaches a higher level, the bidirectional preparation is innovatively realized, and the communication capacity reaches four bitsper round. The bidirectional single-bit state preparation method has a wide application prospect in the technical field of quantum communication networks.
Owner:SUZHOU UNIV
Phase entangled encoding method and device
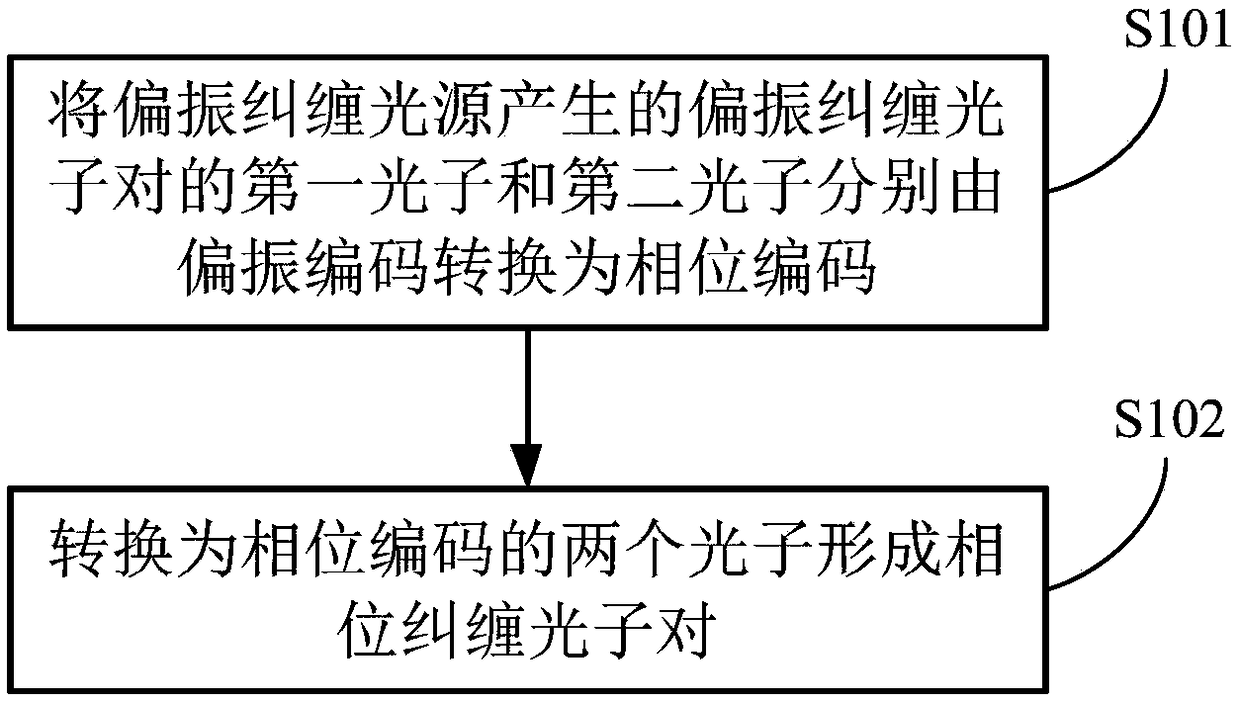
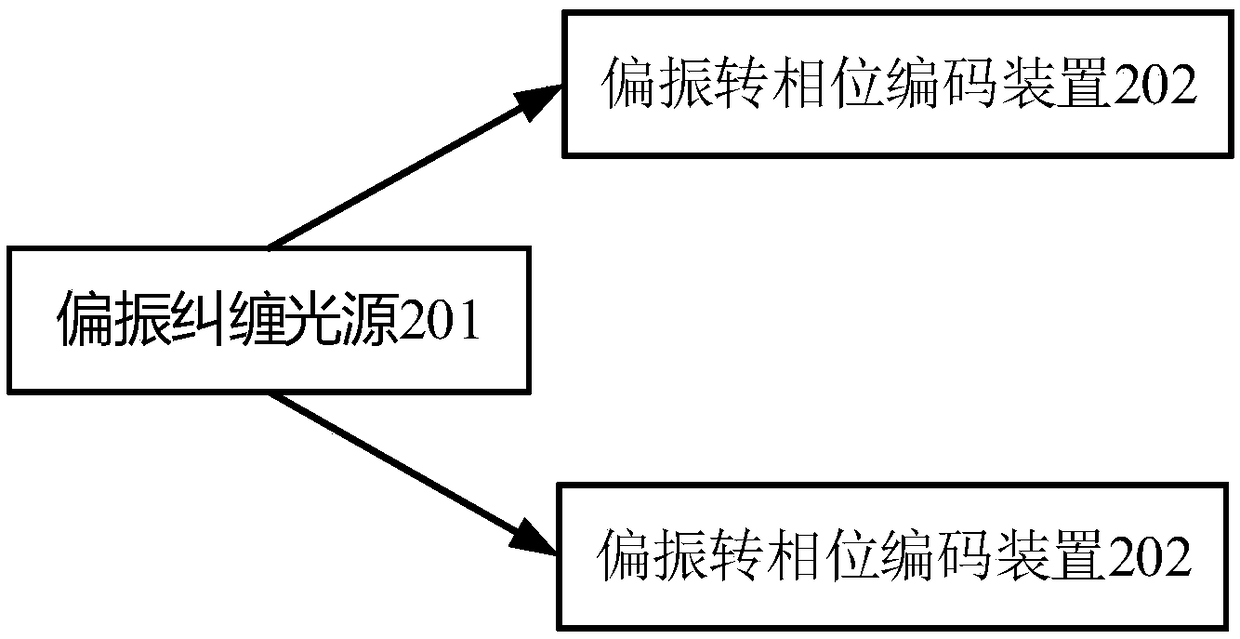
ActiveCN108712249AGood anti-environmental interference advantageSimple methodKey distribution for secure communicationPhotonic quantum communicationQuantum entanglementQuantum teleportation
The invention relates to a phase entangled encoding method for a photon pair and a phase entangled encoding device for the photon pair. The method comprises the steps of: respectively converting a first photon and a second photon in a polarization-entangled photon pair generated by a polarization-entangled light source into phase encoding from polarization encoding; and forming a phase entangled photon pair by the first photon and the second photon converted into the phase encoding. The phase encoding has the advantages of resistance to environment interference and stable transmission in an optical fiber channel; and utilization of the phase entangled encoding device provided by the invention is helpful for implementing application requirements of the optical fiber channel for quantum entanglement distribution, quantum teleportation, quantum key distribution and the like for resistance to environment interference.
Owner:CHINA ACADEMY OF ELECTRONICS & INFORMATION TECH OF CETC
Channel multiplexing method based on 5-bit brown state
The invention discloses a channel multiplexing method based on a 5-bit brown state. The method comprises three parts consisting of a channel multiplexing method in which quantum teleportation and remote state preparation coexist, a channel multiplexing method in which quantum teleportation and quantum dense coding coexist, and a channel multiplexing method in which remote state preparation and quantum dense coding coexist. According to the channel multiplexing method provided by the invention, quantum information can be simultaneously sent and received by two parties of communication, and thequantum information exchange modes are effectively enriched.
Owner:SUZHOU UNIV
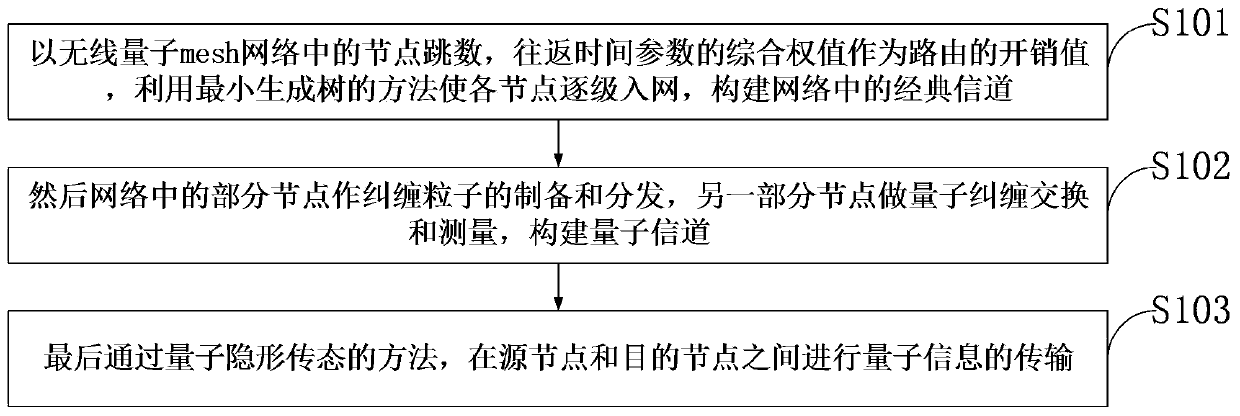
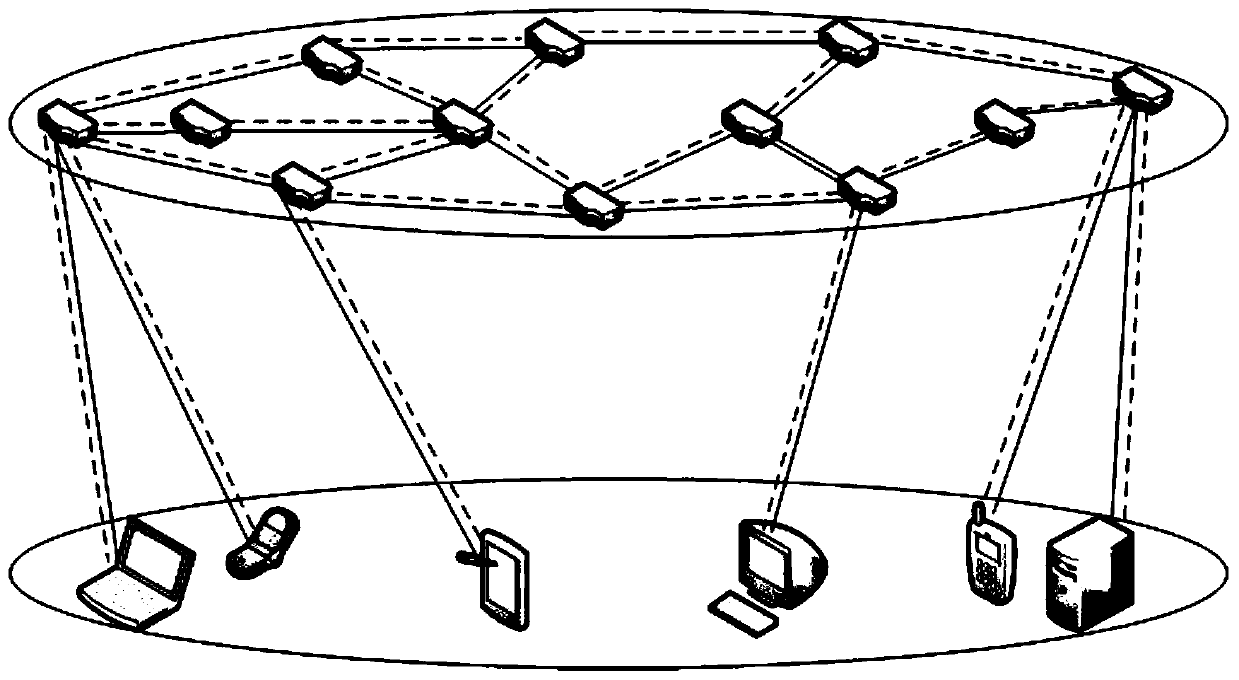
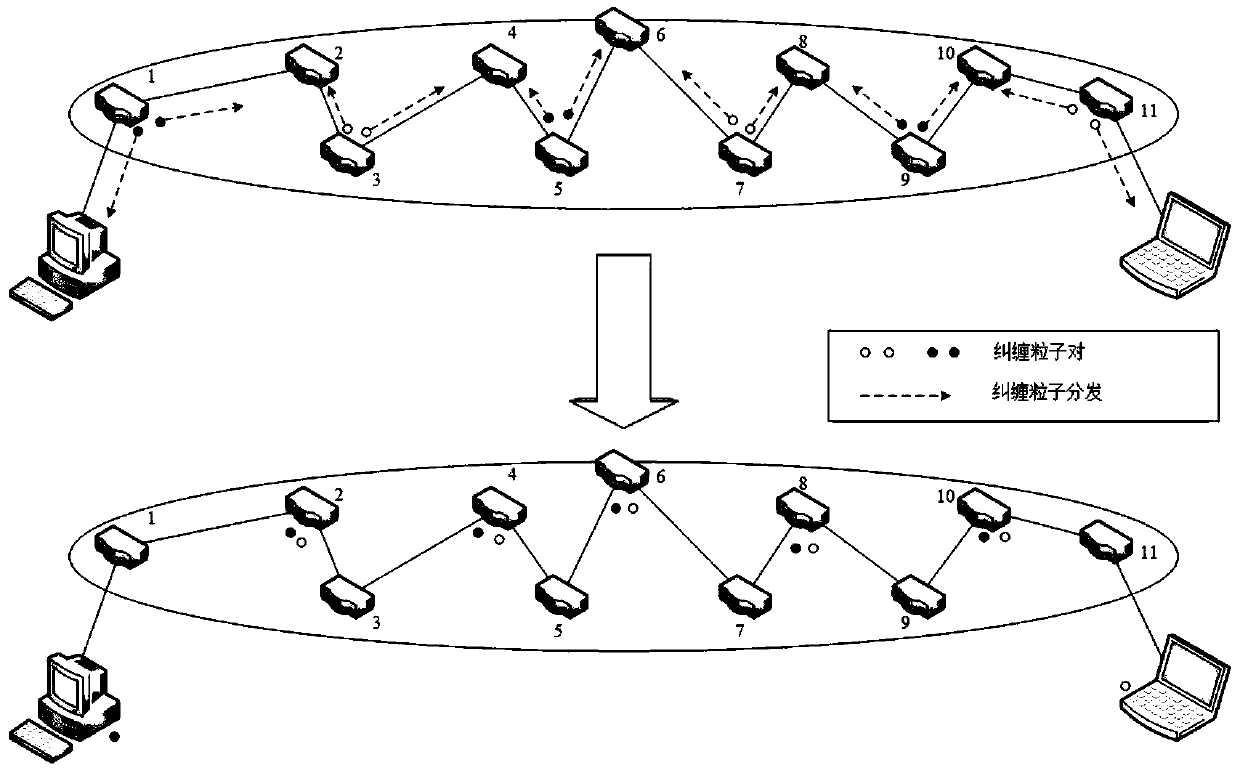
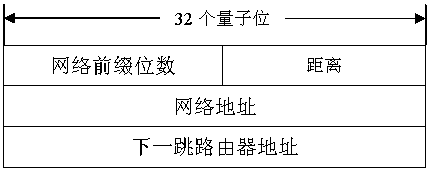
Quantum wireless mesh network routing method and architecture based on entanglement exchange
ActiveCN109982410AAvoid cyber stormPromote growthWireless communicationWireless mesh networkQuantum entanglement
The invention belongs to the technical field of quantum communication, and discloses a quantum wireless mesh network routing method and architecture based on entanglement exchange. The method comprises the following steps: taking a comprehensive weight value of node hops and round-trip time parameters in a wireless quantum mesh network as an overhead value of a route, enabling each node to be accessed to the network step by step by using a minimum spanning tree method, and constructing a classical channel in the network; then preparing and distributing entangled particles by a part of nodes inthe network, and performing quantum entanglement exchange and measurement by the other part of nodes to construct a quantum channel; and finally, carrying out quantum information transmission betweenthe source node and the destination node through a quantum stealth state transfer method. According to the method, the wireless quantum mesh network with a complex structure can be logically regardedas a tree-shaped ring-free network topology, so that the generation of network storms is avoided; a ''pairwise combination'' scheme is proposed to establish a quantum channel between a source node and a destination node.
Owner:深圳鼎智达表计信息科技有限公司
Adaptive RIP routing selection protocol based on quantum teleportation
The invention discloses an adaptive RIP routing selection protocol based on quantum teleportation. Efficient, safe and rapid update of routing information in an autonomous system can be achieved, and consumption of entanglement resources can also be reduced as much as possible; a RIP message transmitted by a classical RIP protocol during an information exchange process is subjected to data transmission in a plaintext manner, so that security of the exchanged routing information cannot be ensured; the RIP message is still able to be eavesdropped, tampered and counterfeited; in order to further improve security of exchange of the RIP protocol routing information, the adaptive RIP routing selection protocol based on quantum teleportation provided by the invention provided by the invention introduces a quantum communication technology into a routing selection protocol RIP, and thus security transmission of the routing information is achieved.
Owner:HENAN POLYTECHNIC UNIV
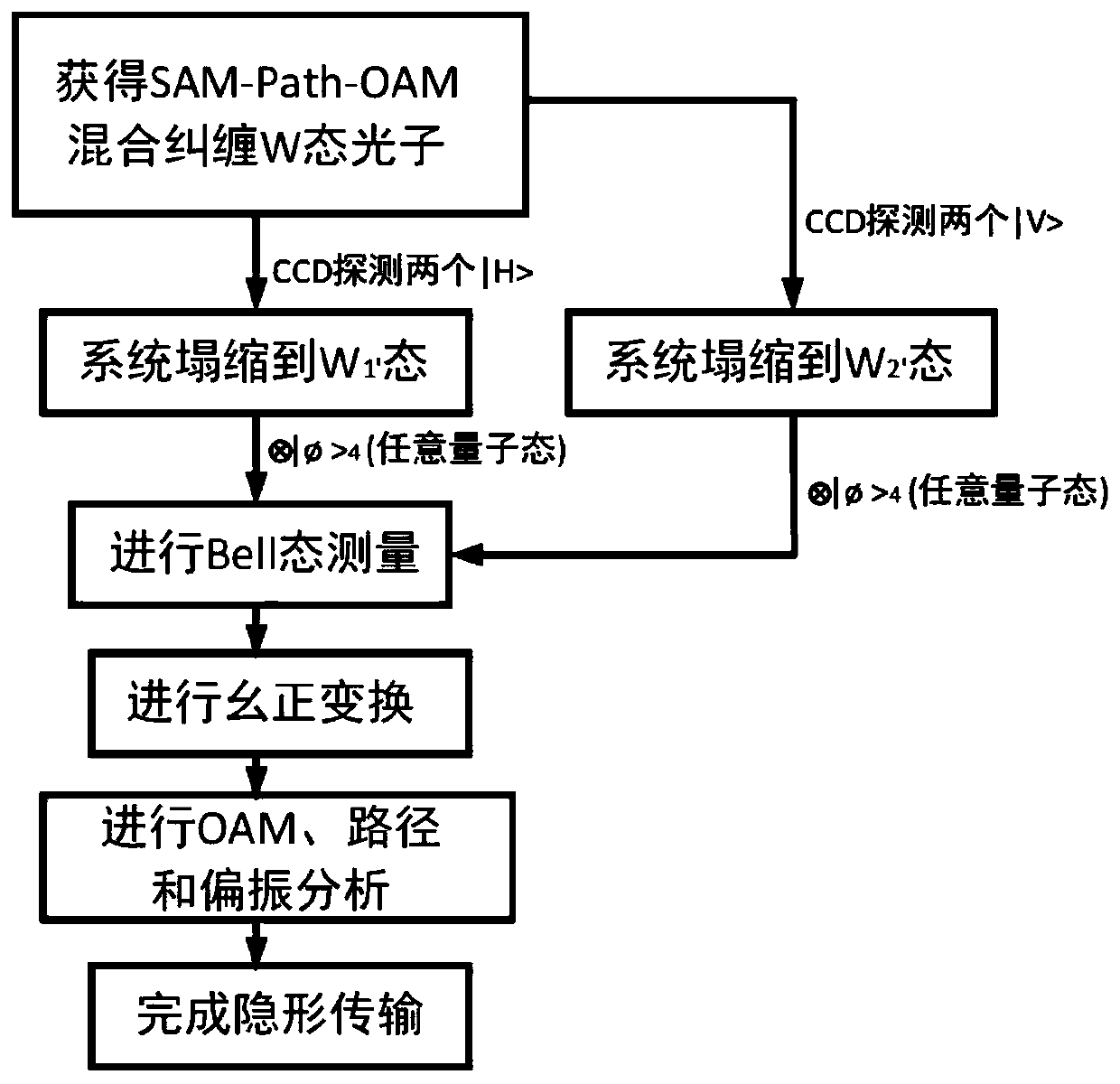
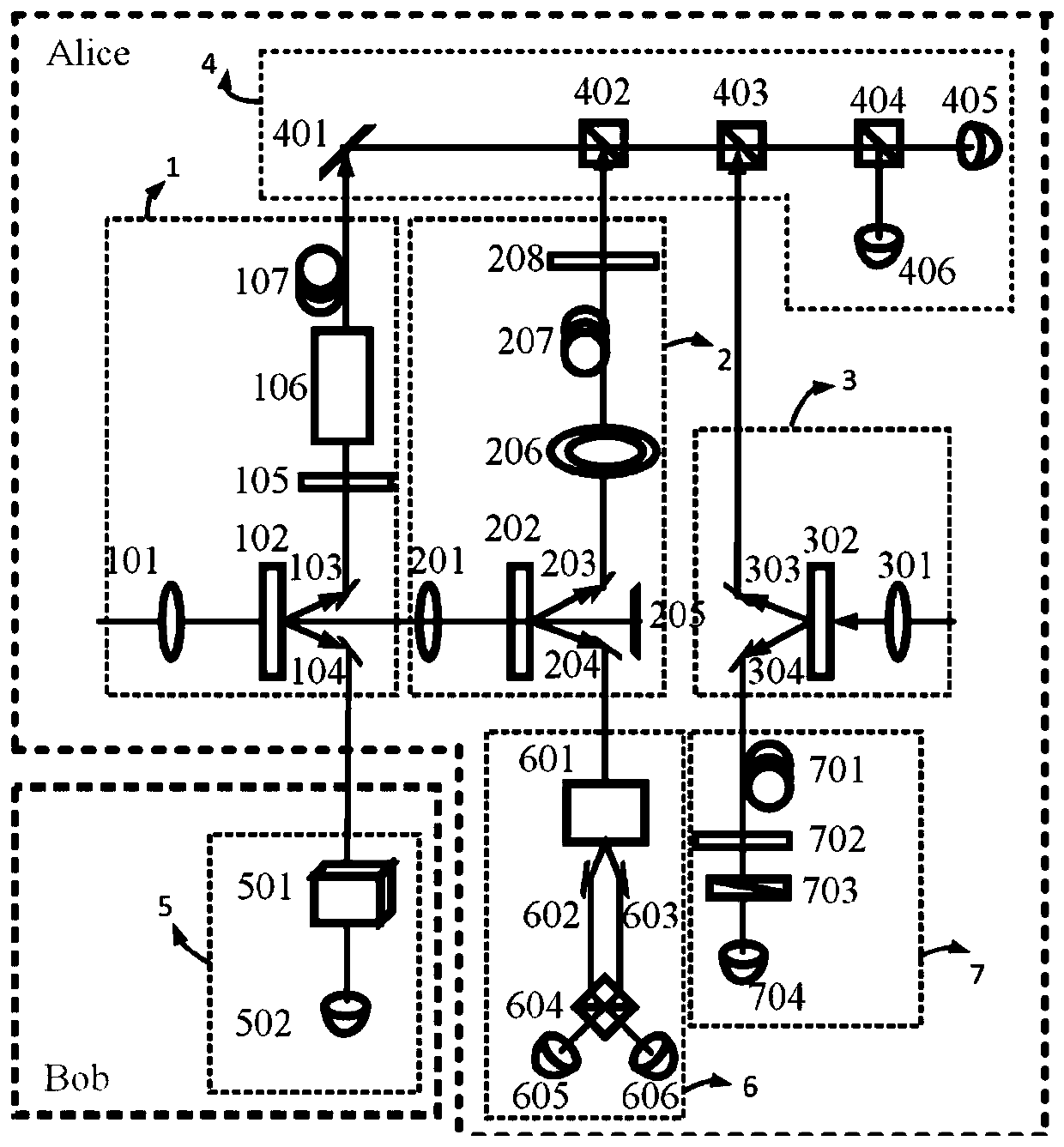
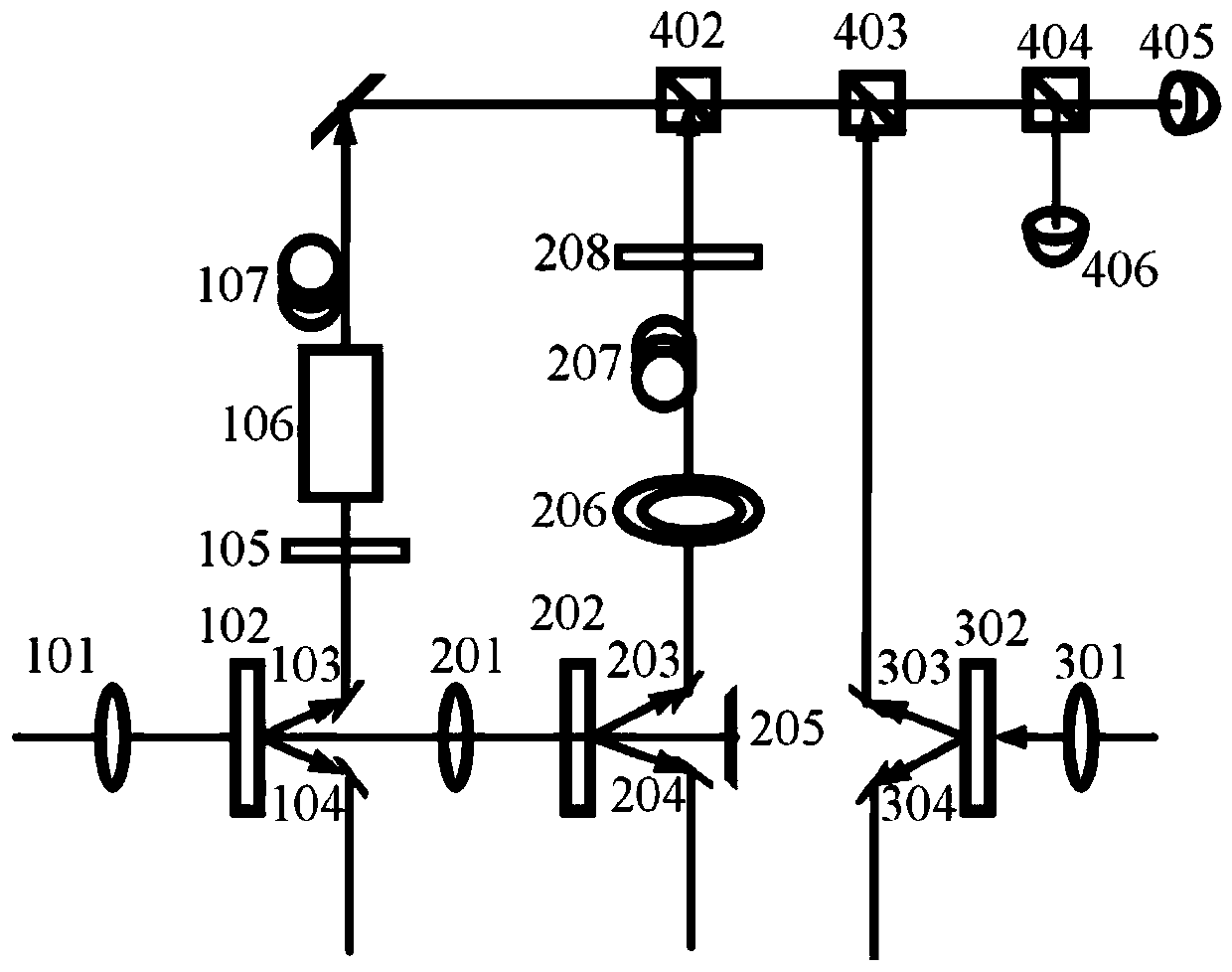
A controllable OAM quantum invisible state transfer system and method based on a W state
ActiveCN109714110AImprove communication securityIncrease channel capacityPhotonic quantum communicationNon symmetricRemote control
The invention discloses a controllable OAM quantum invisible state transfer system based on a W state. the system comprises an Alice sending end and a Bob receiving end. Alice comprises a mixed entanglement unit, an entanglement exchange unit, a Path analysis unit and an SAM analysis unit. the Bob comprises an OAM analysis unit. The Entanglement exchange unit is used for Performing entanglement exchange on the SAM- OAM entangled photon pair, SAM- Path entangled photon pair and SAM-SAM entanglement photon pairs to obtain two W states which are equal in probability and symmetrical to each other,and randomly selecting one W state as a quantum channel; The OAM analysis unit is used for OAM analysis, and Alice can remotely control OAM generation of Bob photons through electric field tuning. The method is an open type target invisible transmission state, an asymmetric light quantum network can be formed, remote control, high-dimensional, expandable and safer quantum invisible transmission state can be realized, and the method has a great application prospect.
Owner:GUANGDONG INCUBATOR TECH DEV CO LTD
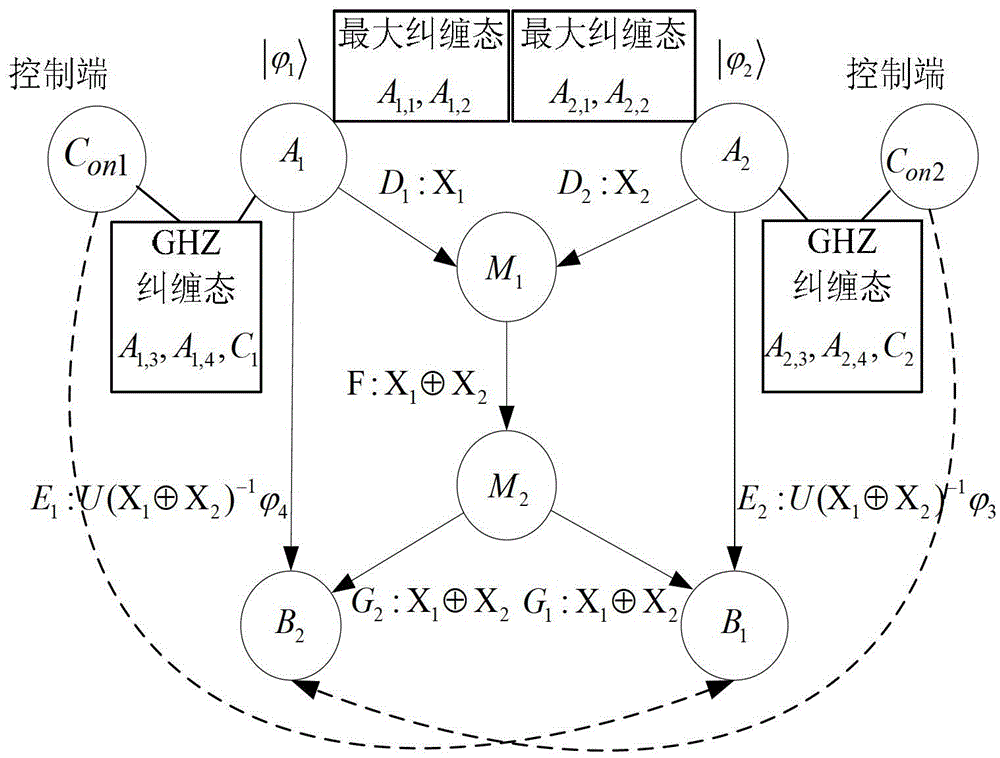
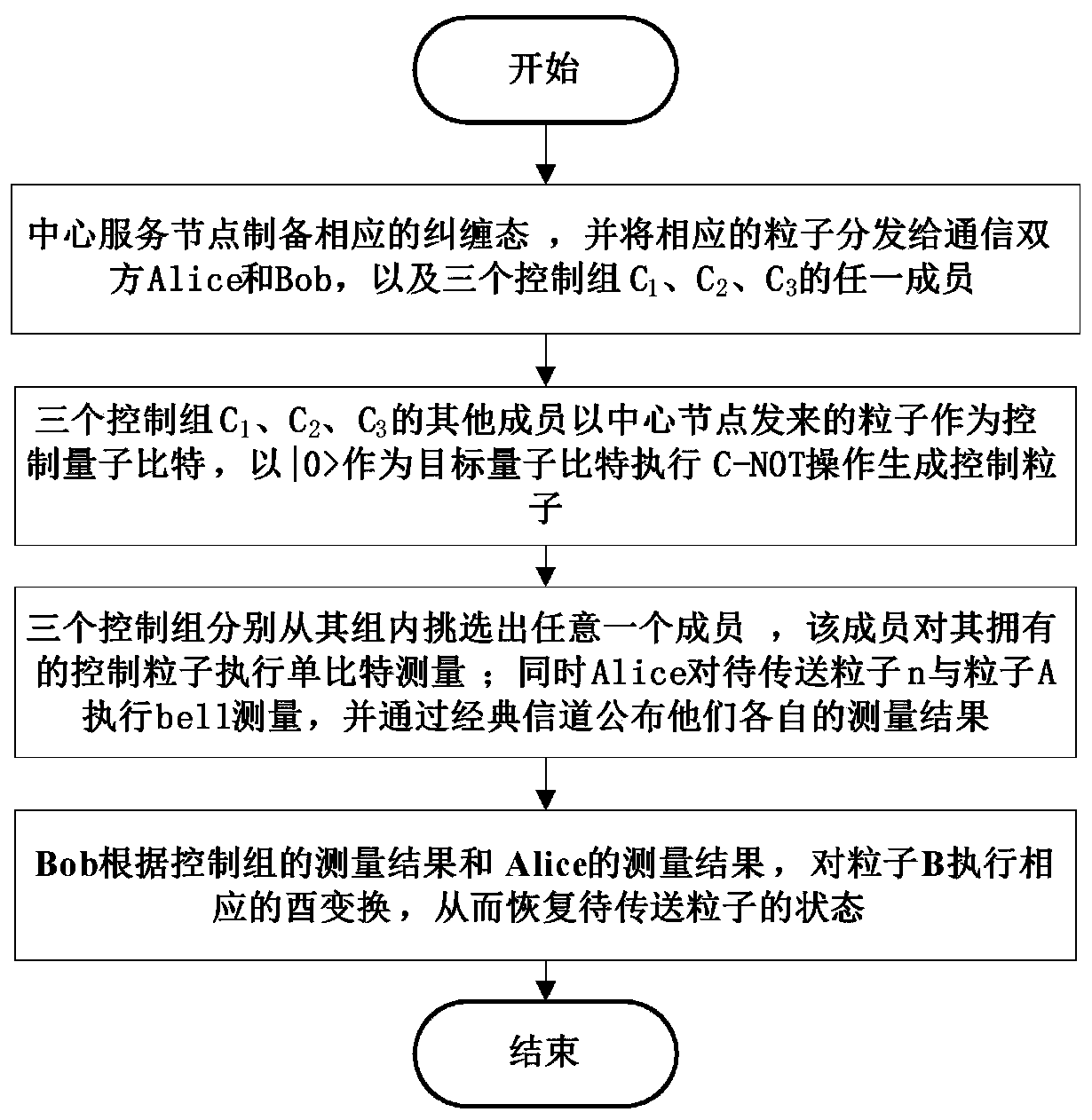
Optimal controlled quantum stealth state transfer method with an adjustable threshold value for any unknown n particles
ActiveCN110086547AAchieve securityIncrease flexibilityPhotonic quantum communicationAlice and BobInformation transmission
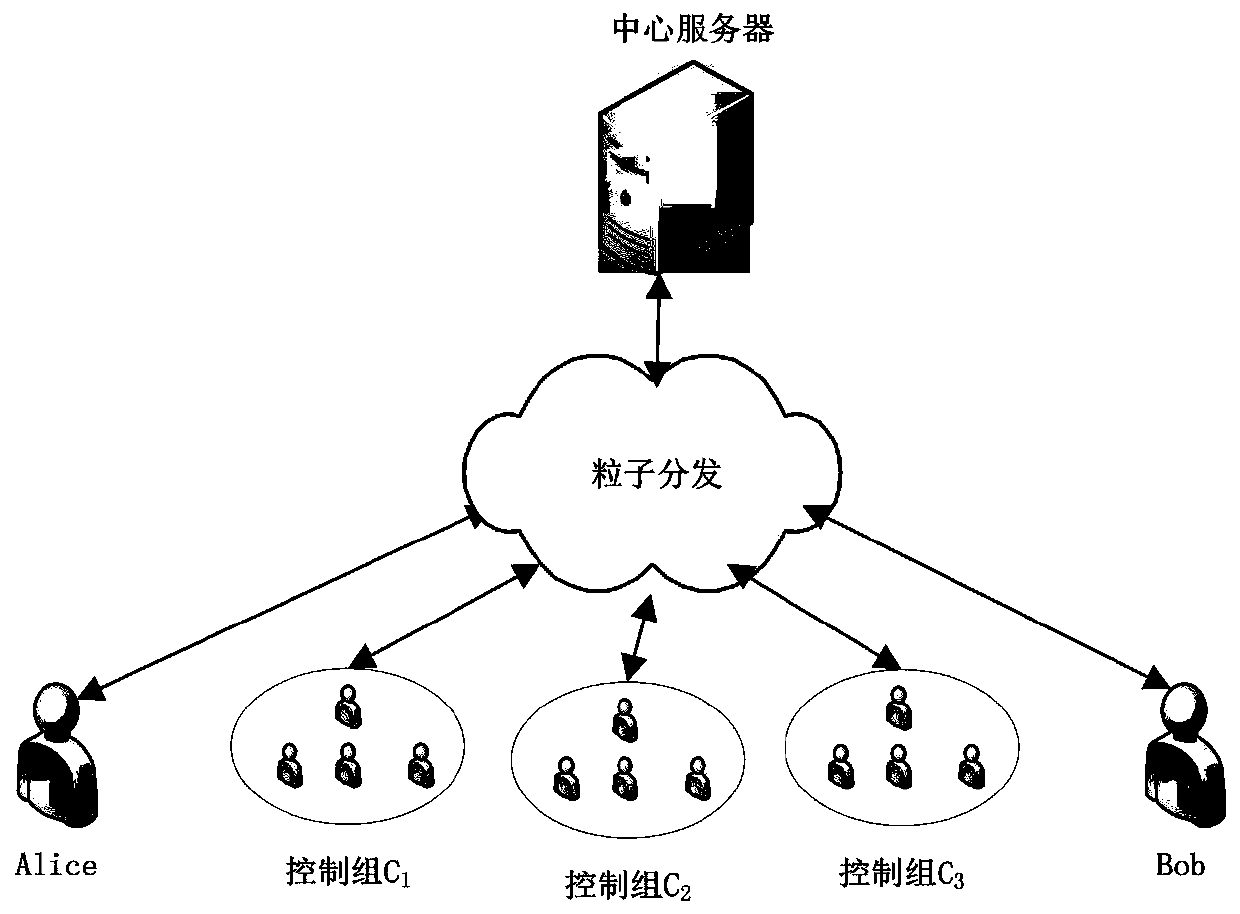
The invention discloses an optimal controlled quantum stealth state transfer method with an adjustable threshold value for any unknown n particles. The invention discloses an optimal controlled quantum stealth state transfer method for any unknown n particles with an adjustable threshold value. The method is characterized by comprising the following steps that: a central service node prepares a corresponding entanglement state, and distributes corresponding entanglement particles to Alice and Bob of two communication parties and any one member of three control groups C1, C2 and C3 through a quantum channel; and other members of the three control groups C1, C2 and C3 execute C-by taking the particles sent by the central service node as control quantum bits and | 0) as target quantum bits. The NOT operation generates control particles. The threshold-adjustable optimal controlled quantum stealth transmission method for any unknown n particles has the advantages that the threshold-adjustable optimal controlled quantum stealth transmission method for any unknown n particles realizes the safety and flexibility of information transmission.
Owner:SUZHOU UNIV
Method for estimating multi-degree-of-freedom stealth state transmission efficiency under quantum noise
ActiveCN111355537AIncrease channel capacityReduce transmission efficiencyPhotonic quantum communicationChannel estimationNoise generationQuantum teleportation
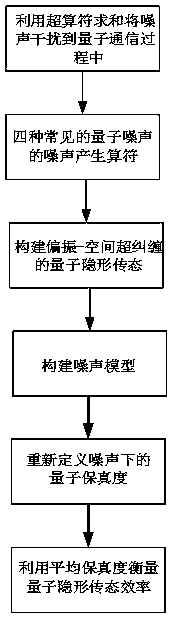
The invention discloses a method for estimating multi-degree-of-freedom stealth state transmission efficiency under quantum noise. The method comprises the following specific steps: interfering noiseinto a communication process, describing noise generation operators of different types of noise, constructing a polarization space hyper-entangled quantum stealth transfer state, constructing a quantum noise model, calculating quantum fidelity under the noise, and measuring quantum stealth transfer state efficiency by utilizing average fidelity. According to the invention, a superoperator summation method is used; four kinds of common quantum noise are superposed to act on quantum bits; a noise model is established by considering the influence of noise on three different photons in the quantumstealth transfer process; due to the fact that space entanglement is not easily affected by noise, the quantum in the default space freedom degree is in the maximum entanglement state, the situationthat polarization entanglement is affected by noise is mainly considered, the average fidelity is redefined, and according to the specific situation, the proper quantum state is selected to ensure that quantum stealth transfer achieves the optimal efficiency.
Owner:XIDIAN UNIV
Measurement equipment-independent quantum direct communication method
InactiveCN113612601AEliminate dependenciesKey distribution for secure communicationPhotonic quantum communicationBell stateQuantum teleportation
The invention discloses a measurement equipment-independent quantum direct communication method, which comprises the following steps of: randomly preparing an entangled quantum bit in a two-photon state through Alice, and randomly preparing a quantum bit in a single-photon state in one of four quantum states of {|0>, 1>, |+> and |->} through Bob; the Alice sends the quantum bit of one photon in the entangled state to the Charlie and keeps the quantum bit of the remaining entangled state of one photon, and the Bob sends the randomly prepared quantum bit of the single photon state to the Charlie; after the Charlie receives the quantum bits sent by the Alice and the Bob, Bell state measurement is executed, then a measurement result is published through a classical channel, and the Alice executes unitary operation to complete quantum teleportation. According to the coding mode, quantum storage can be removed.
Owner:NAT QUANTUM COMM GUANGDONG CO LTD
Integrated optical chip system for distributed security quantum information processing
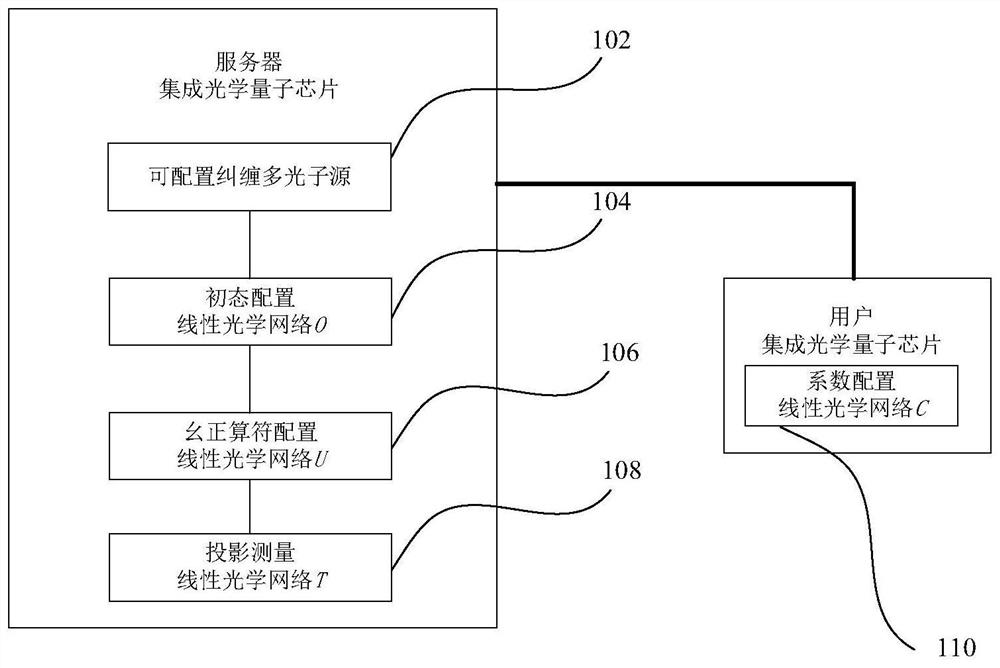
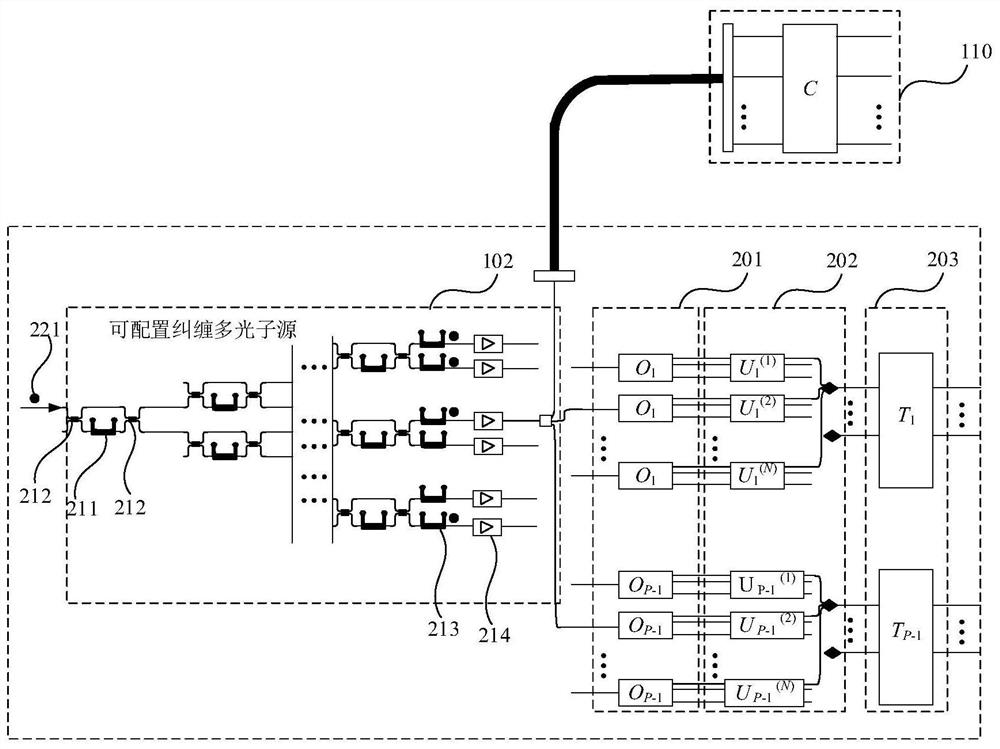
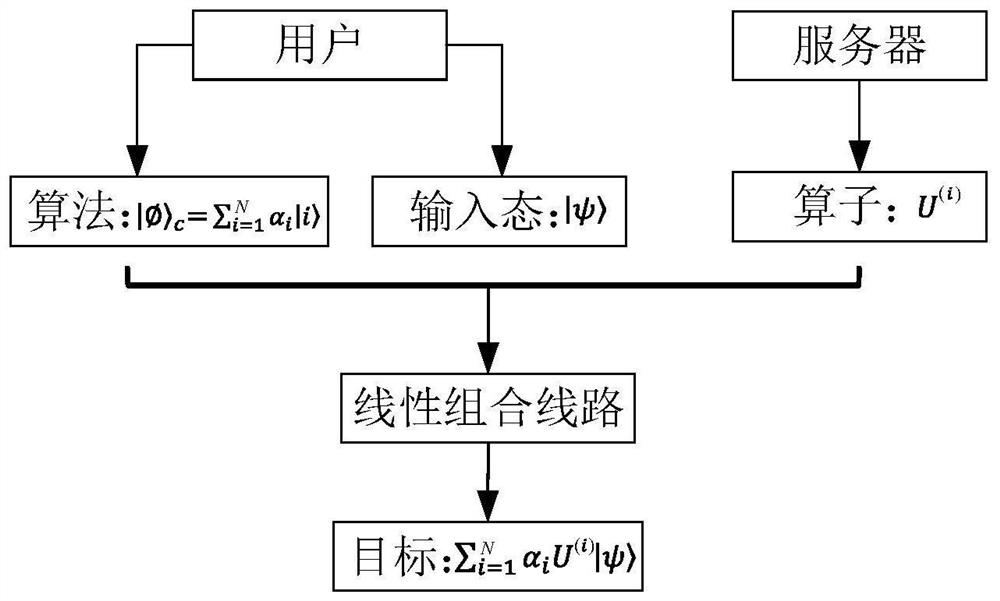
PendingCN113935494ARealize the quantum computing processRealize remote quantum information processingQuantum computersEngineeringQuantum teleportation
The invention provides an integrated optical chip system for distributed security quantum information processing. The integrated optical chip system comprises a server integrated optical quantum chip and a user integrated optical quantum chip. The server integrated optical quantum chip comprises a configurable entanglement multi-photon source which is used for generating a plurality of photons and outputting the photons to a server linear optical network and a user linear optical network according to wavelengths; the server linear optical network which is used for preparing an initial state for the photons output by a wavelength division multiplexer, carrying out unitary transformation and linear combination, carrying out combination and carrying out projection measurement on the combined photons; and a user integrated optical quantum chip which transmits linear term coefficients through quantum teleportation so as to linearly combine each term of unitary transformation in the server integrated optical quantum chip. The server cannot know the specific computing task of the user, and the user is informed of the result through a classic channel after computing is completed. By using the technical scheme of the invention, the computing privacy of the user can be protected.
Owner:NAT INNOVATION INST OF DEFENSE TECH PLA ACAD OF MILITARY SCI
A method and system for increasing the number of quantum entanglement interfaces
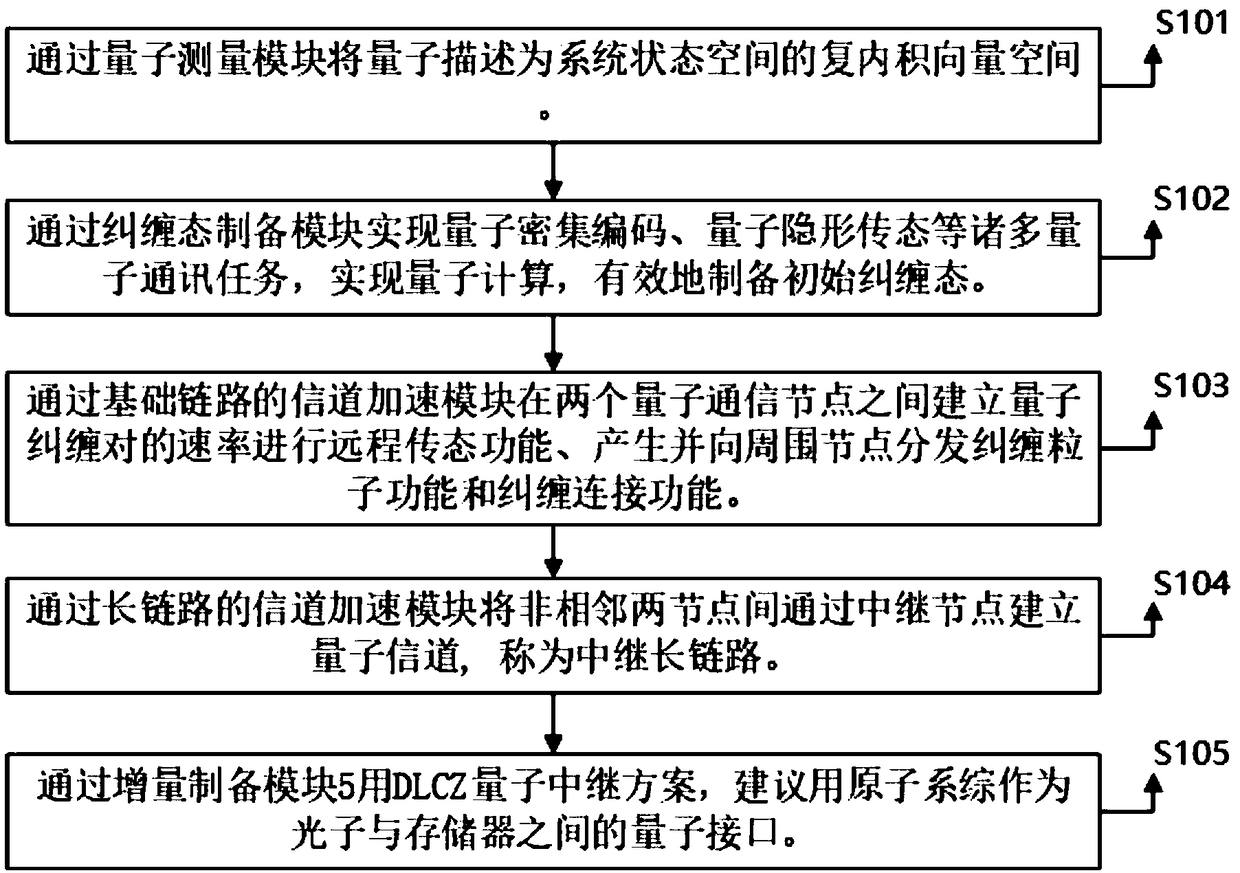
InactiveCN109257171AEfficient manufacturingEnabling Quantum ComputingKey distribution for secure communicationPhotonic quantum communicationQuantum teleportationQuantum state
The invention belongs to the technical field of computer software and discloses a method and a system for increasing the number of quantum entanglement interfaces. The system comprises a quantum measurement module, an entanglement state preparation module, a channel acceleration module of a basic link, a channel acceleration module of a long link and an incremental preparation module. The quantumis described as the complex inner product vector space of the system state space by the quantum measurement module. The entanglement generation module realizes many quantum communication tasks, such as dense quantum coding, quantum teleportation and so on, realizes quantum computation and prepares the initial entanglement effectively. The whole process of quantum computation deals with the information encoded in quantum states. The invention establishes a quantum channel between two non-adjacent interfaces through a relay interface through a channel acceleration module of a long link.
Owner:GUANGDONG TECHN COLLEGE OF WATER RESOURCES & ELECTRIC ENG
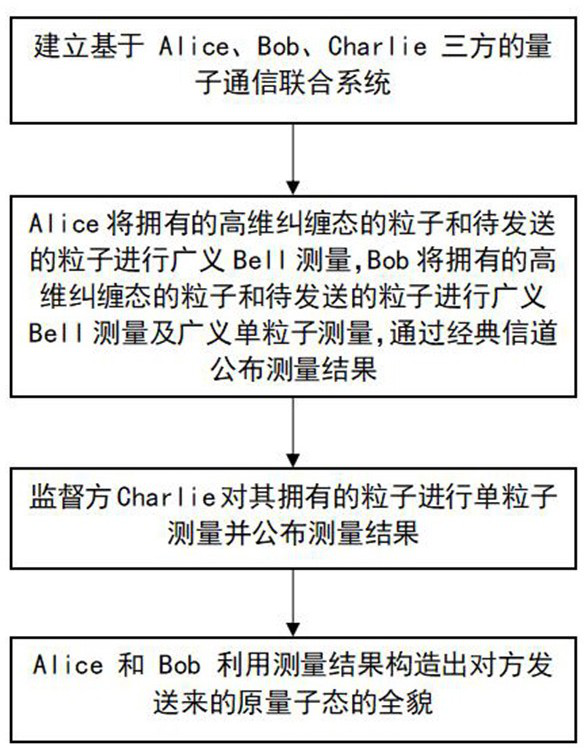
High-dimensional asymmetric bidirectional controlled quantum teleportation method
PendingCN114598396AImplement two-way transmissionLarge amount of informationPhotonic quantum communicationHigh level techniquesAlice and BobBidirectional transmission
The invention discloses a high-dimensional asymmetric bidirectional controlled quantum teleportation method. The method comprises the following steps: step 1, establishing a quantum communication joint system based on three parties of Alice, Bob and Charlie; step 2, Alice and Bob respectively carry out generalized Bell measurement and generalized single particle measurement on particles owned by Alice and Bob, and publish measurement results; 3, the supervisor Charlie carries out single particle measurement on particles owned by the supervisor Charlie and publishes a measurement result; and step 4, the Alice and the Bob construct a full view of the original quantum state sent by the opposite side by using the measurement result. Bidirectional transmission of quantum information can be realized; the success probability of transmission and restoration of quantum information is 1, the difficulty of specific communication control is greatly reduced, and bidirectional controlled invisible state transmission is easier to physically realize.
Owner:SICHUAN NORMAL UNIVERSITY +1
Quantum Trust Evaluation Method Based on Node Trust
ActiveCN105391548BKey distribution for secure communicationPhotonic quantum communicationQuantum entanglementResearch Object
The invention discloses a quantum trust evaluation method based on node trust, including the modeling of the quantum trust model and the method of quantum trust evaluation. Compared with the prior art, the invention takes the trusted quantum relay network based on trust nodes as the research object , introduce trust management into the quantum communication network, build a safe and credible quantum communication network based on the trust value of the evaluation node, and use the trust value as the basis for judging whether each user in the quantum communication network is credible; with the help of quantum Unique characteristics such as entanglement effect and quantum teleportation, research and propose a quantum trust evaluation method based on node trust, and describe the idea and process of quantum trust evaluation in detail; finally analyze the node trust based on the present invention. The feasibility, rationality and security of the quantum trust evaluation method provide a valuable new idea and new method for establishing a safe and credible quantum communication network.
Owner:CHENGDU UNIV OF INFORMATION TECH +1
An adaptive rip routing method based on quantum teleportation
The invention discloses an adaptive RIP routing selection method based on quantum teleportation, which can not only realize the effective, safe and fast update of routing information in the autonomous system, but also reduce the consumption of entanglement resources as much as possible; the classic RIP protocol The RIP message transmitted in the routing information exchange process is transmitted in plain text, and the security of the exchanged routing information cannot be guaranteed; the RIP message still has the possibility of being eavesdropped, tampered with and forged; in order to further improve For the security of RIP protocol routing information exchange, the self-adaptive RIP routing protocol based on quantum teleportation proposed by the present invention realizes the safe transmission of routing information by introducing quantum communication technology into the routing protocol RIP.
Owner:HENAN POLYTECHNIC UNIV
A mdi-qkd method based on quantum network
ActiveCN108847939BIncrease distanceGuaranteed independenceKey distribution for secure communicationPhotonic quantum communicationCommunications securityAttack
The invention discloses an MDI-QKD (Measurement-Device-Independent Quantum Key Distribution Protocol) based on a quantum network. According to the protocol, quantum teleportation in the quantum network is applied to a traditional unilateral MDI-QKD. Advantages of an original MDI-QKD are kept. Independence of a security protocol for measurement equipment is ensured. All attacks at a measurer side in a QKD system are effectively avoided. According to the quantum teleportation in the quantum network, communication secure distance can be greatly extended. According to the protocol, the quantum teleportation in the quantum network is applied to the MDI-QKD, the communication security is ensured, and moreover, the distance of the MDI-QKD is greatly extended.
Owner:南京南瑞网络安全技术有限公司 +4
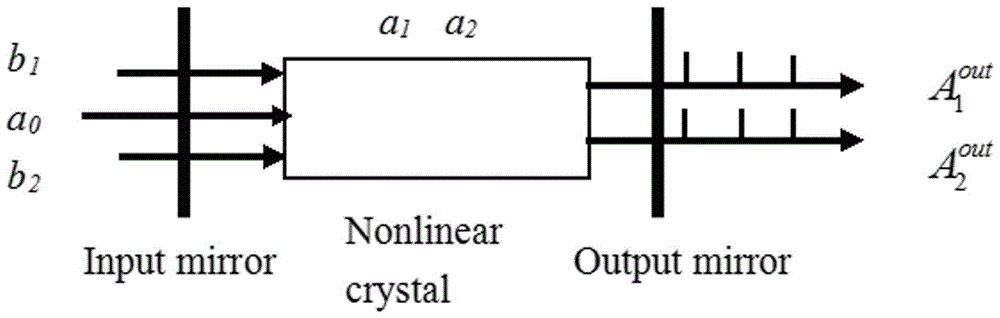
Device and method for generating multi-frequency point two-component entangled light field with continuous wave laser
Owner:太原市和信无双科技有限责任公司
A Channel Multiplexing Method Based on Five-bit Brown State
Owner:SUZHOU UNIV
An Opportunistic Quantum Network Coding Method
ActiveCN104301098BAchieve absolute securityEmbody opportunistic characteristicsKey distribution for secure communicationData switching networksNetwork codeQuantum teleportation
The invention provides an opportunistic quantum network coding method. The opportunistic quantum network coding method is characterized by being designed by giving full play to the characteristics of quantum teleportation, specific classical information is characterized by means of quantum states and transferred through a quantum teleportation method, opportunistic monitoring is achieved through classical channels, and opportunistic characteristics of quantum network coding are achieved; the method includes ten steps. According to the opportunistic quantum network coding method, the classical opportunistic network coding thought is applied to quantum network coding, the absolute security of communication is guaranteed by means of the quantum channels, and thus by means of the character that the classical channels can be monitored, quantum network coding with opportunistic characteristics is achieved; as a result, the security of quantum information transmission in a quantum network coding model is enhanced, and the transmission performance of the quantum network is further improved beneficially.
Owner:BEIHANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com