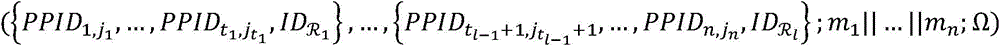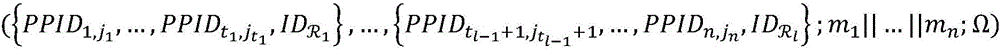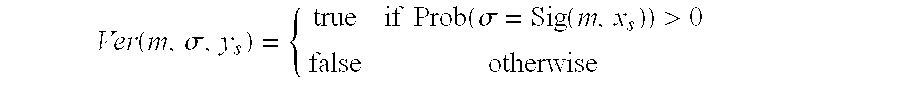Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
220 results about "Pseudonymization" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
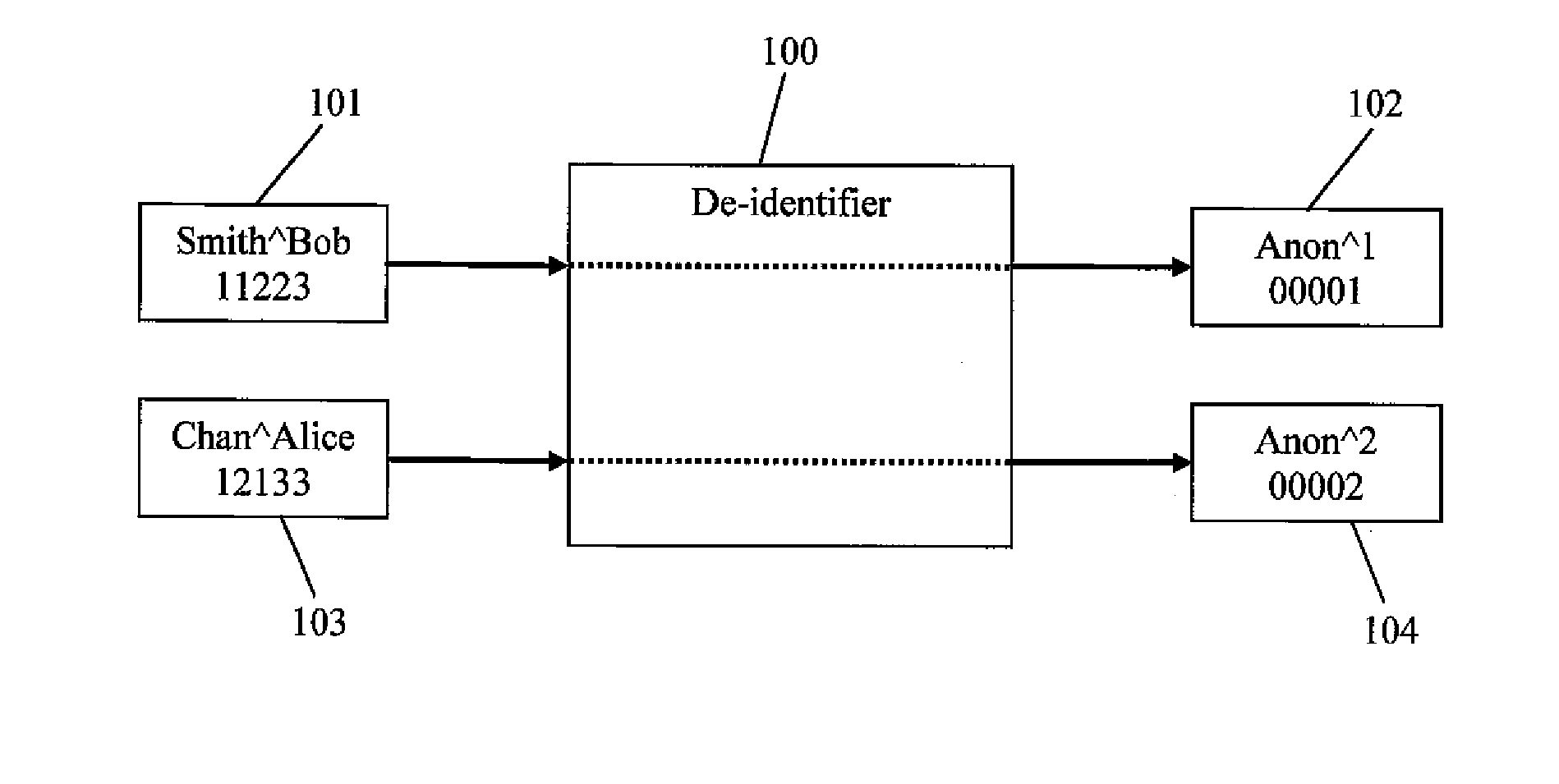
Pseudonymization is a data management and de-identification procedure by which personally identifiable information fields within a data record are replaced by one or more artificial identifiers, or pseudonyms.
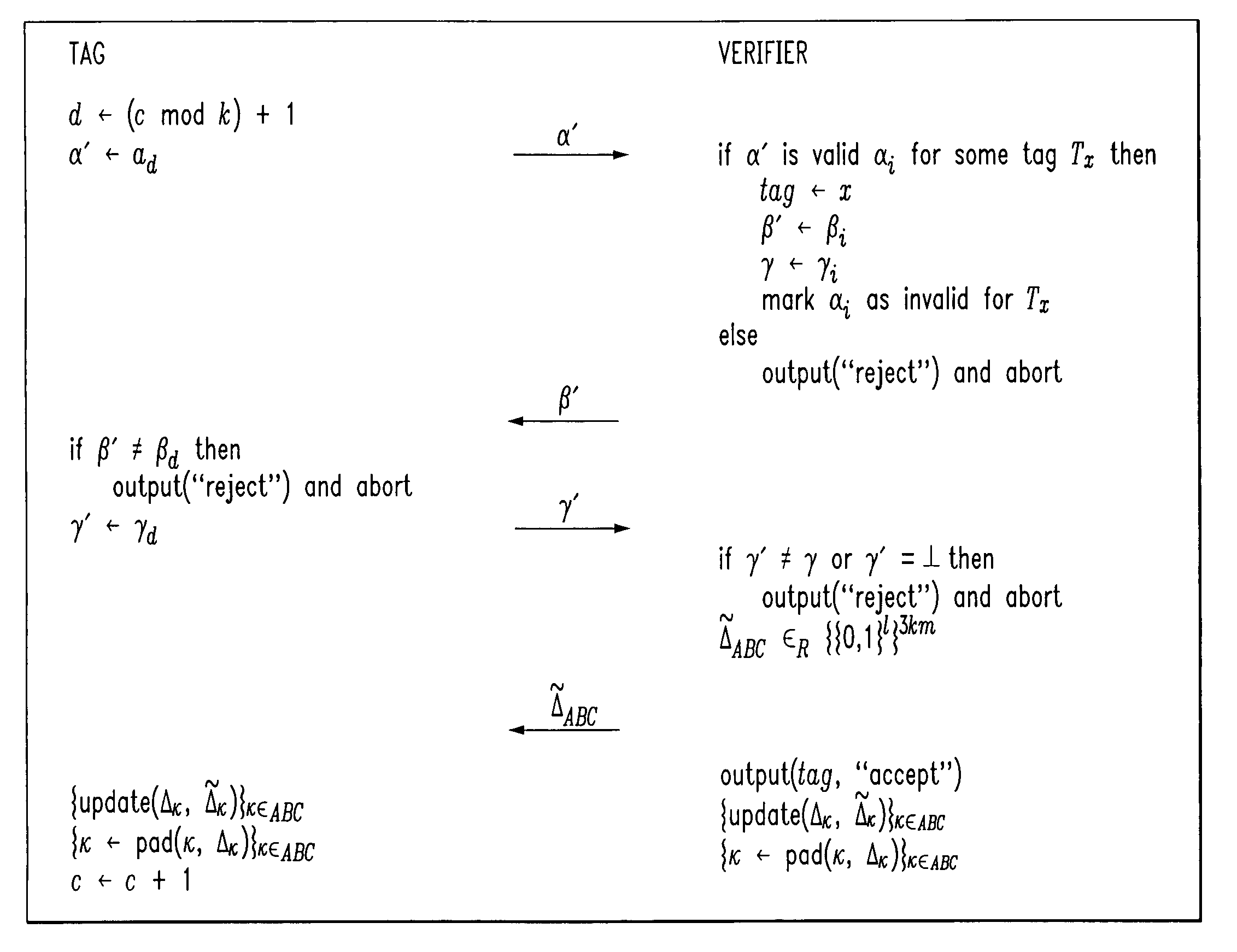
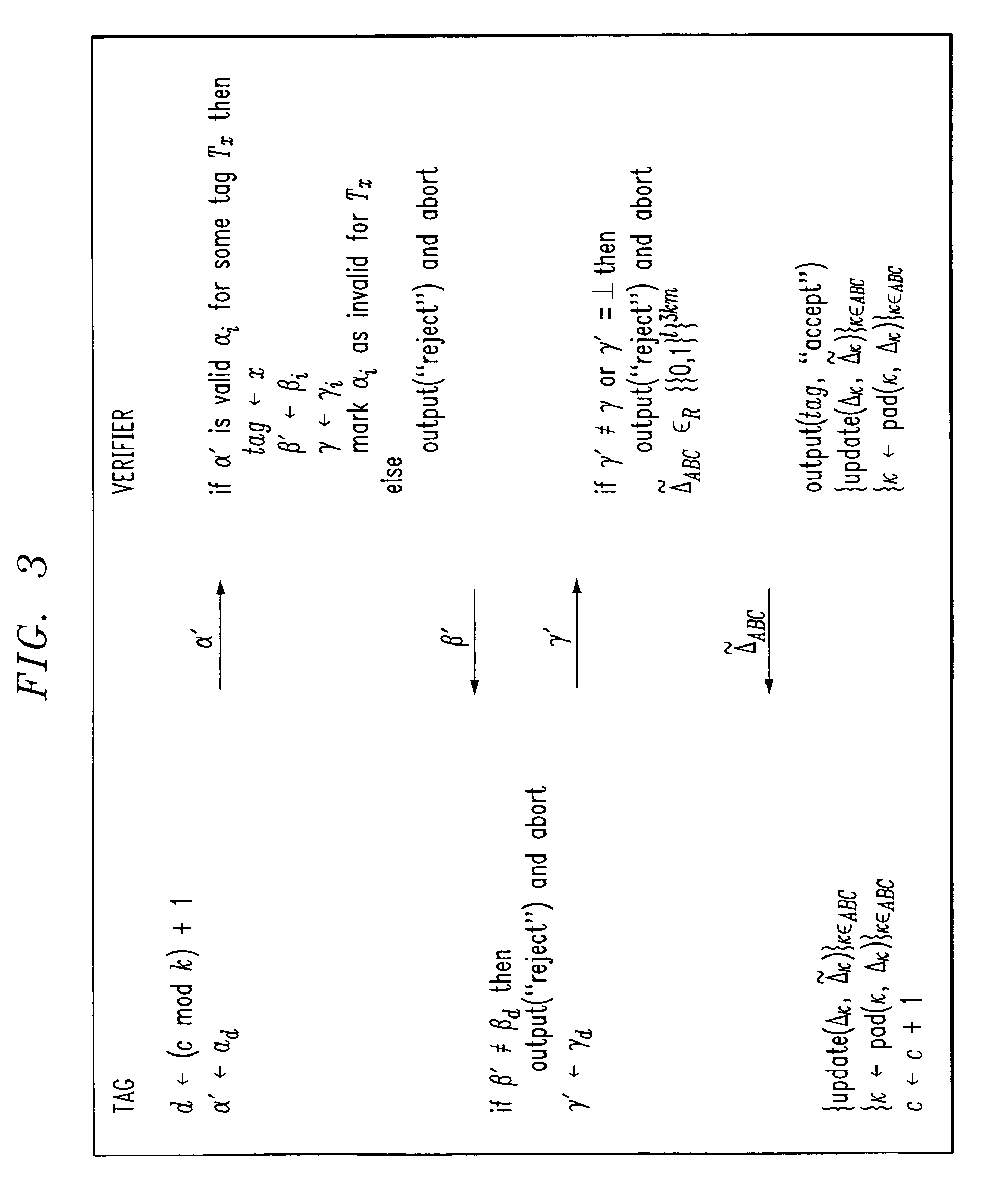
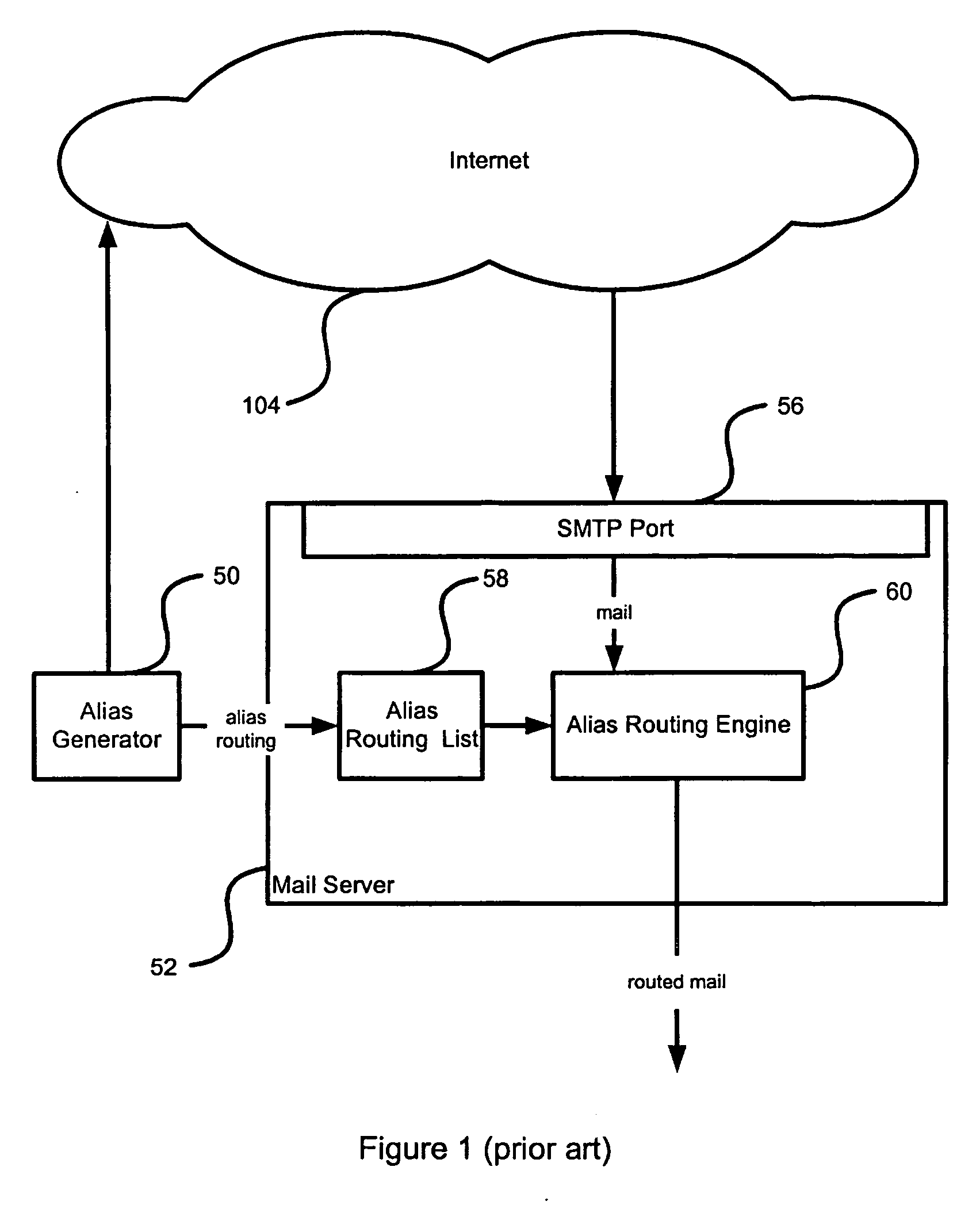
Low-complexity cryptographic techniques for use with radio frequency identification devices
ActiveUS7532104B2Easy authenticationElectric signal transmission systemsMultiple keys/algorithms usageComputer hardwareRadio frequency
Cryptographic techniques are provided having a complexity level which permits their implementation in inexpensive radio frequency identification (RFID) tags or other RFID devices. In an RFID system comprising one or more RFID devices and at least one reader that communicates with the devices, a plurality of pseudonyms is associated with a given one of the RFID devices. The RFID device transmits different ones of the pseudonyms in response to different reader queries, and an authorized verifier is able to determine that the different transmitted pseudonyms are associated with the same RFID device.
Owner:EMC IP HLDG CO LLC
Pseudonymous email address manager
ActiveUS20050114453A1Memory loss protectionError detection/correctionDisposable email addressElectronic mail
A system and method of automated pseudonymous email address creation and management is disclosed herein. The use of the disclosed system provides users the ability to create disposable email addresses, so that if a pseudonymous email address is placed on an unsolicited commercial email distribution list, the unsolicited email message can be prevented from reaching the user.
Owner:CALLAHAN CELLULAR L L C
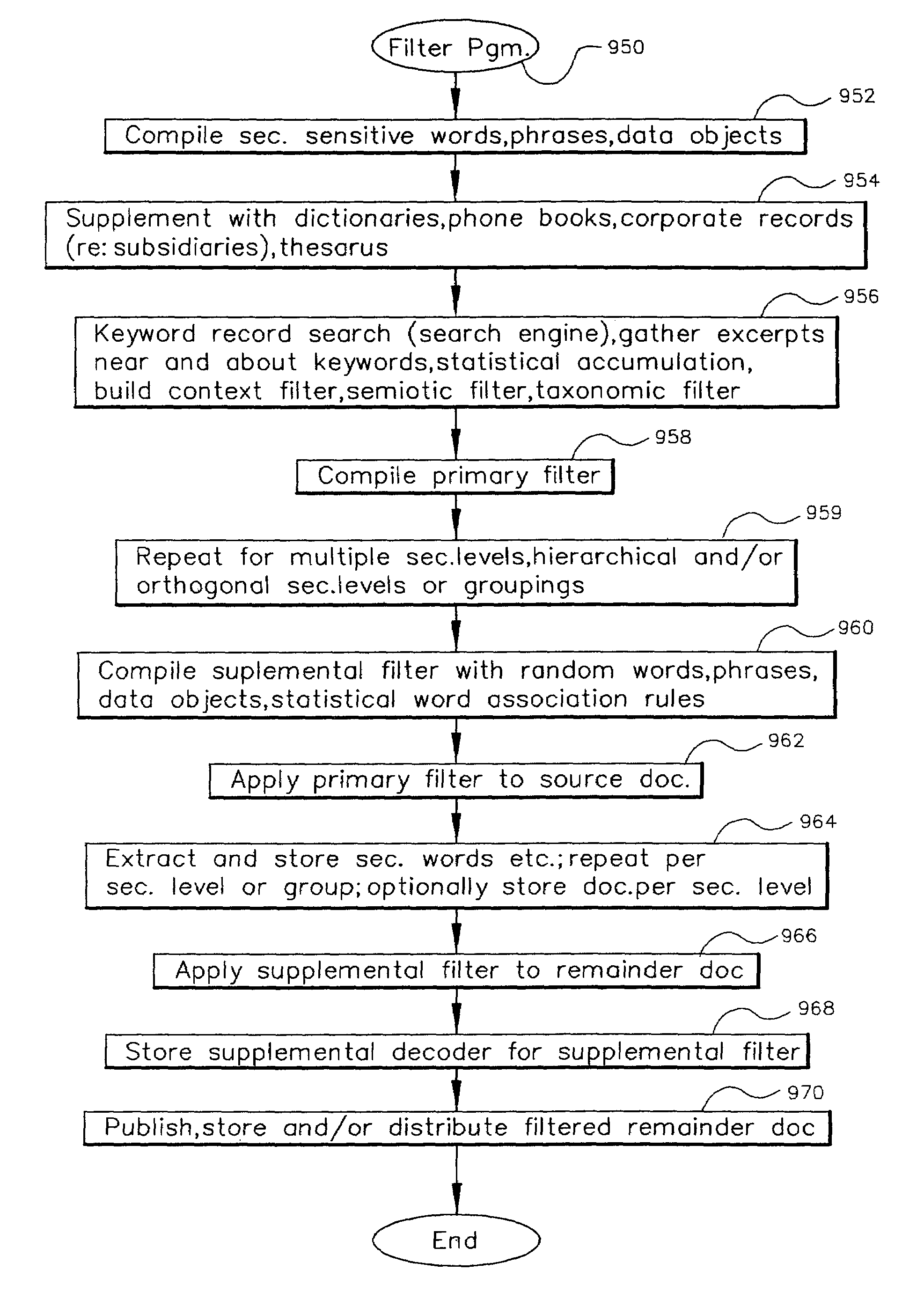
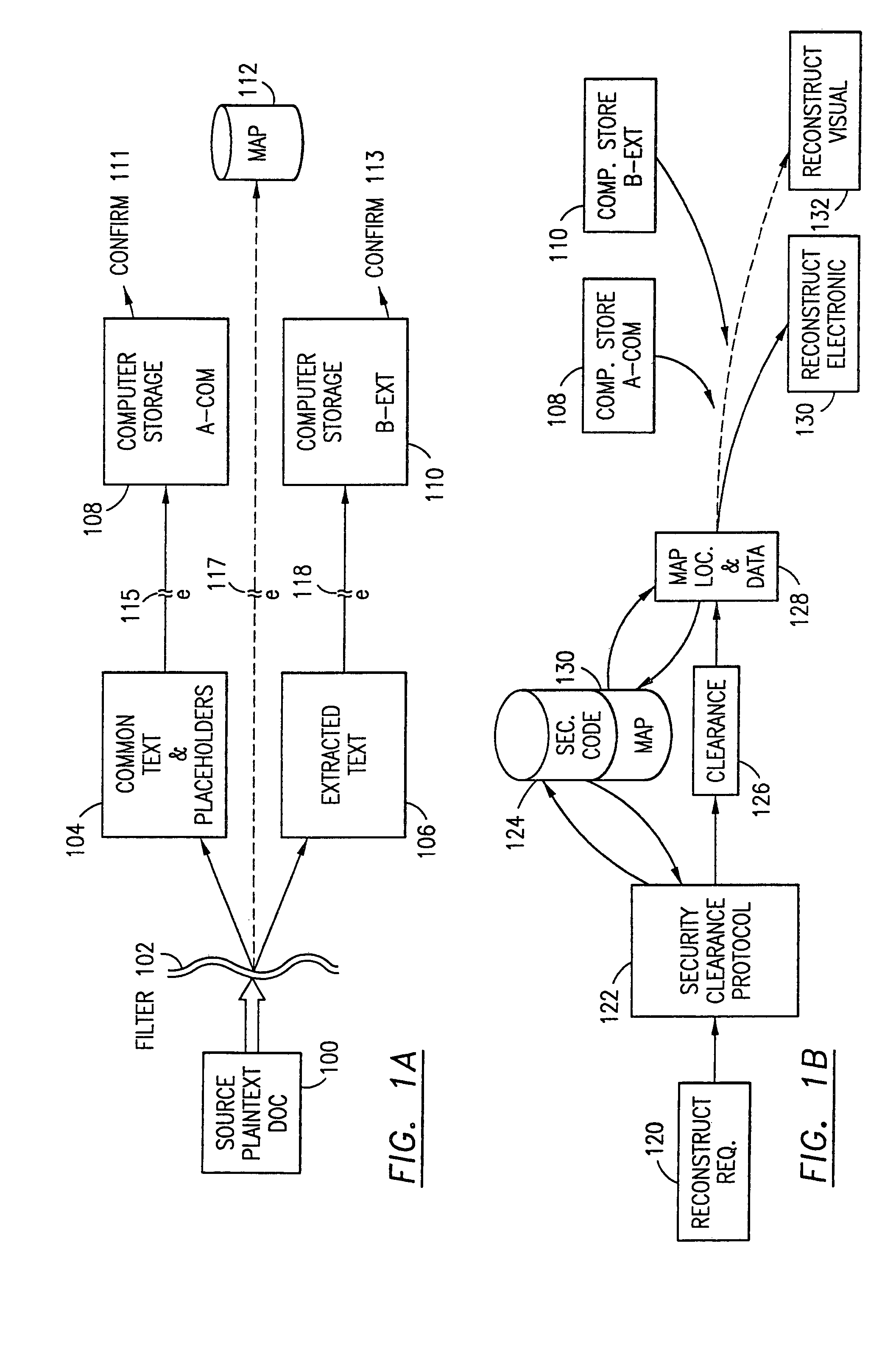
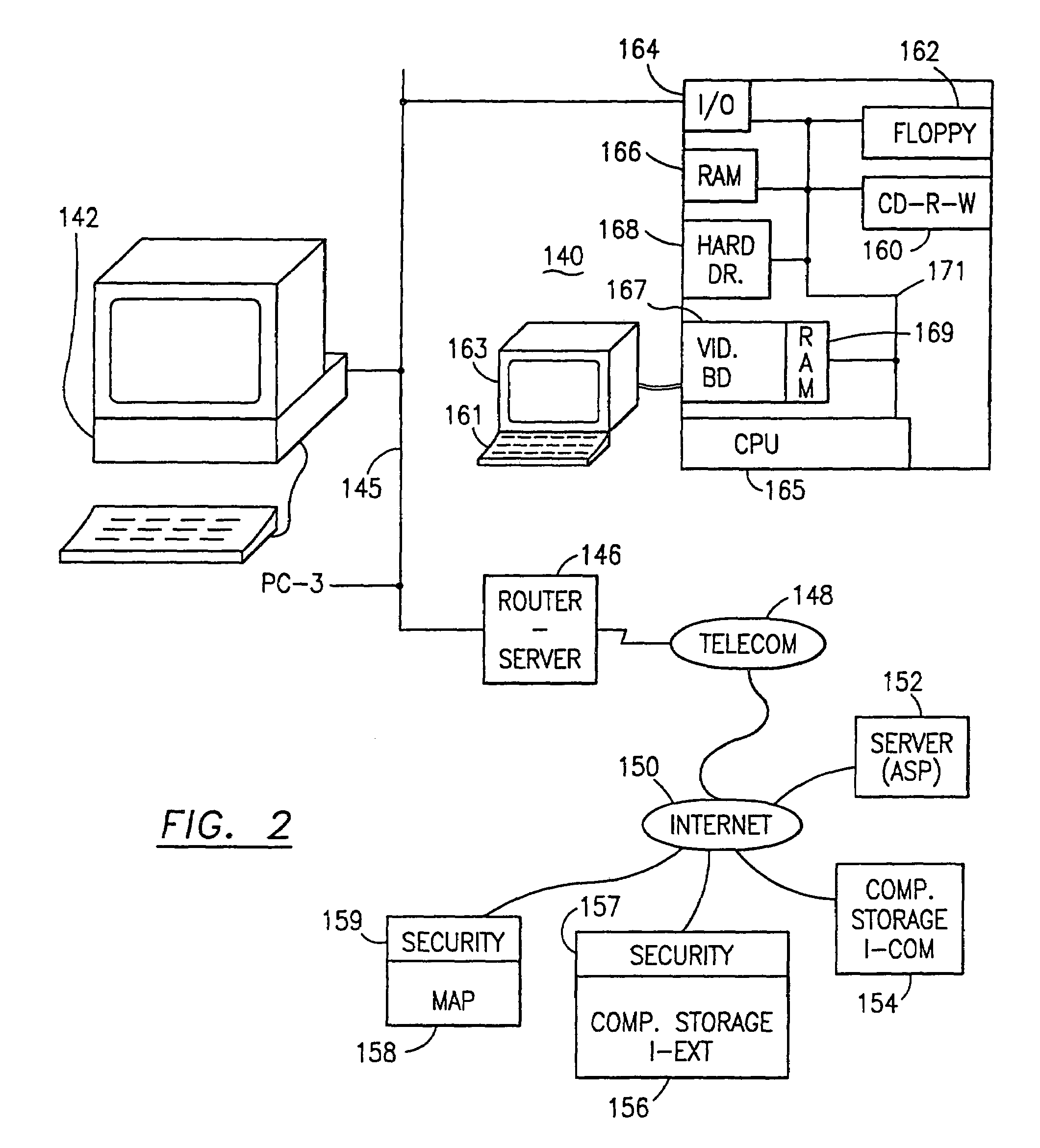
Data security system and method with adaptive filter
ActiveUS7546334B2Digital data information retrievalDigital data processing detailsInformation processingAdaptive filter
A method, program and information processing system filters and secures data (security sensitive words-characters-data objects) in a source document. The adaptive filter uses a compilation of additional data (typically networked) and identifies the sensitive words / objects in the compilation of additional data, and retrieves contextual, semiotic and taxonomic words / objects from the compilation related to the sensitive words / objects. The resulting compiled filter is used to extract sensitive words / objects and retrieved data (words / objects) from the source document to obtain extracted data and remainder data therefrom. Contextual words, related to the security sensitive words / objects, are based upon statistical analysis of the additional data compilation. Semiotic words related words are synonyms, antonyms, and pseudonyms, syntactics relative to the target words and retrieved words, and pragmatics relative to the sensitive words and retrieved words.
Owner:DIGITAL DOORS
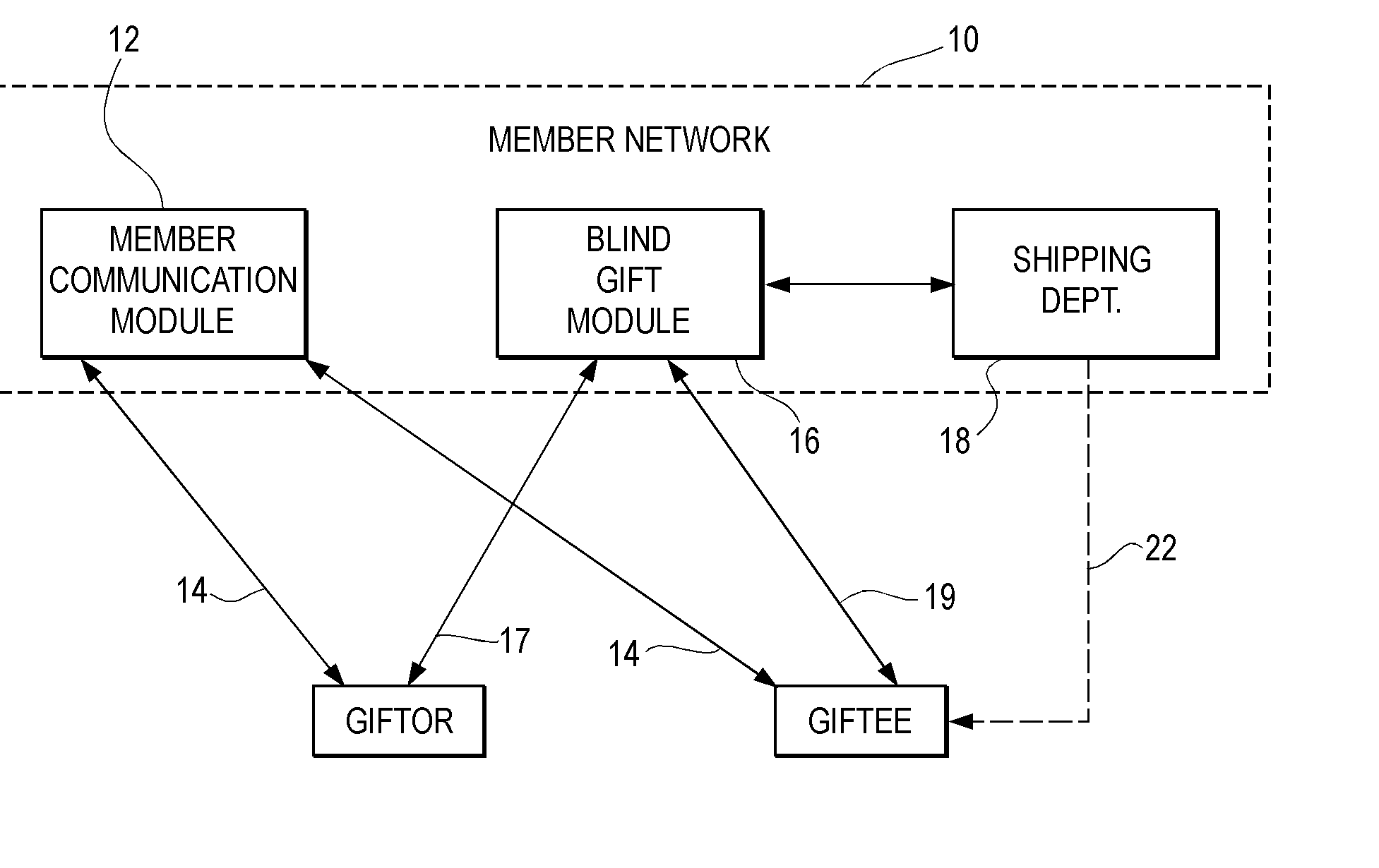
Blind Gift Method and System
InactiveUS20020095298A1Overcomes shortcomingAvoid disadvantagesBuying/selling/leasing transactionsMarketingThe InternetComputer science
<heading lvl="0">Abstract of Disclosure< / heading> This is a method and system whereby parties who know each other only by pseudonyms, such as by Internet e-mail addresses, may send and receive gifts while maintaining anonymity behind their pseudonyms. Steps of the method include receiving a request from a first pseudonymous party to take an order for a gift to be sent to a second party; obtaining from the first party an identification of the intended gift, and the pseudonym of the second party; and, looking up a non-pseudonymous name and address associated with the second in a database. Alternatively, the second party may be contacted and asked to confidentially reveal his or her name and mailing address for gift delivery purposes. While the second party's information is kept confidential from the first party, the second party has various choices including accepting the gift, accepting it upon certain conditions, or refusing it. The system of the invention includes components for permitting the first party to enter the second party's pseudonym; for determining the second party's true name and mailing address from his or her pseudonym; and, for sending the gift to the second party's true name and mailing address.
Owner:JOVIAN HLDG
Pseudonymous email address manager
ActiveUS7783741B2Memory loss protectionError detection/correctionDisposable email addressElectronic mail
Owner:CALLAHAN CELLULAR L L C
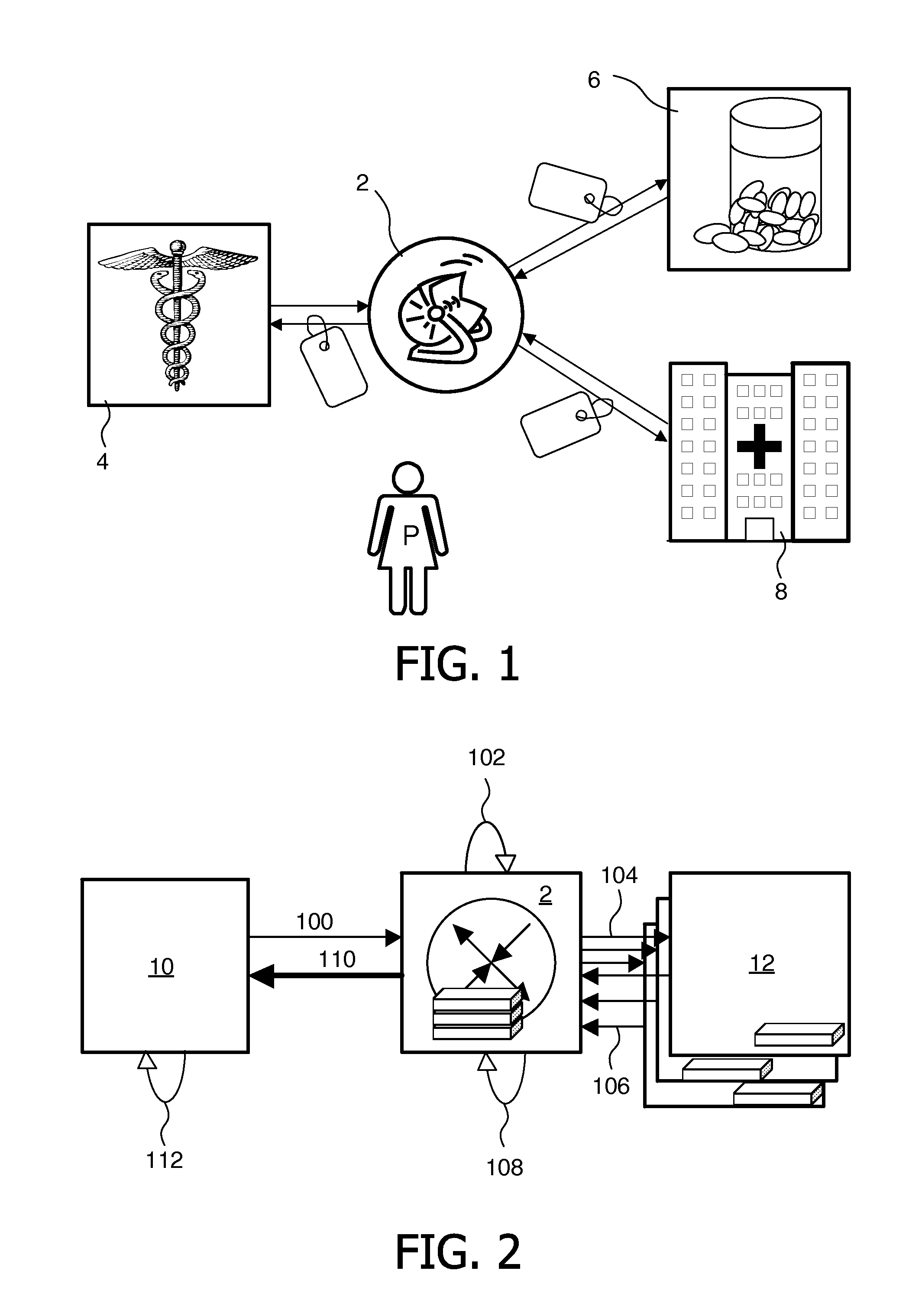
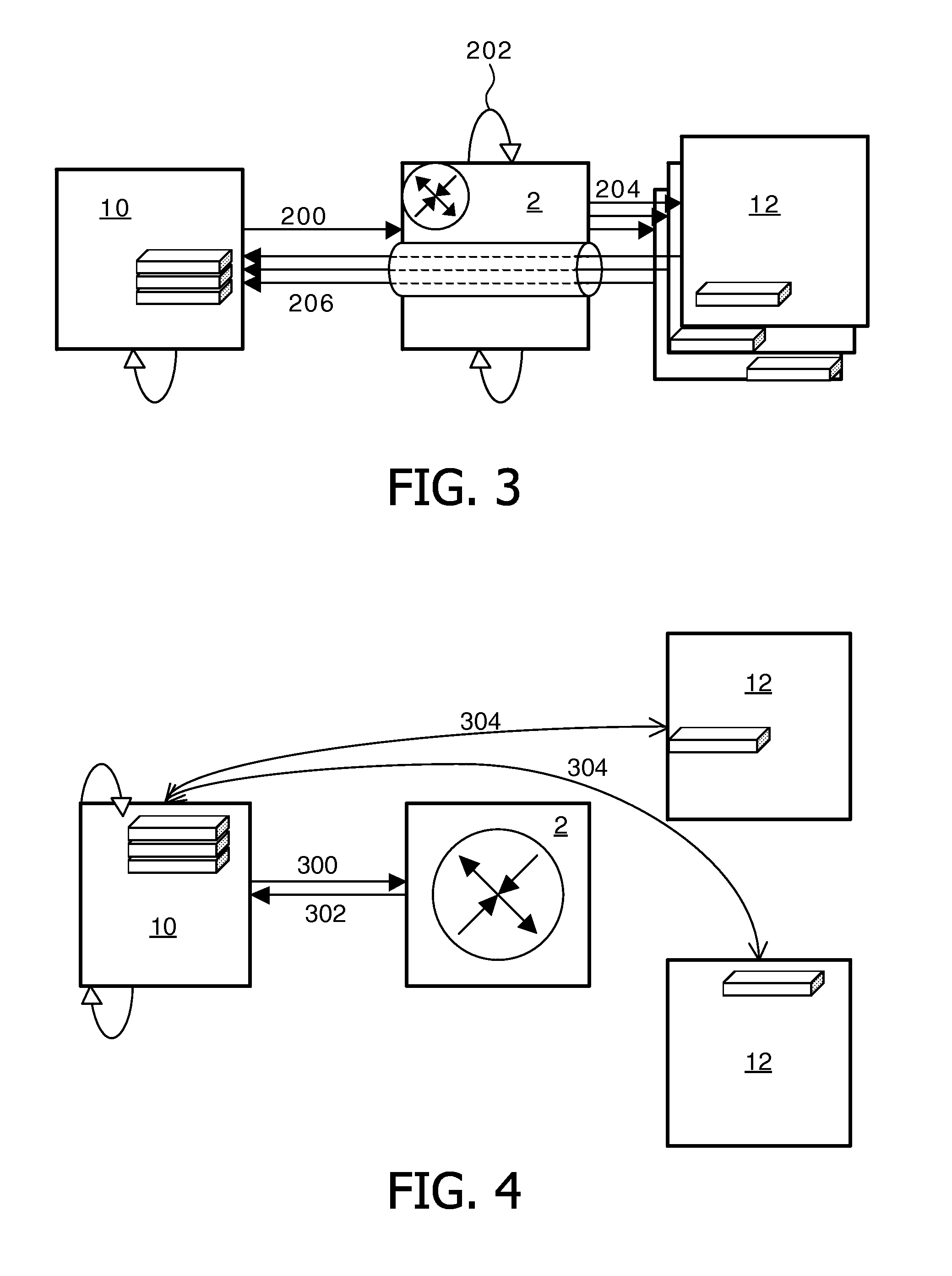
Method for exchanging data
ActiveUS20110264809A1Privacy protectionEfficient methodInterprogram communicationMultiple digital computer combinationsComputer networkPatient data
The present invention relates to a method for exchanging data between at least two servers with use of a gateway. Preferably the method is applied to healthcare systems. Each server holds a unique federated identifier, which identifier identifies a single patient (P). Thus, it is possible for the servers to communicate with each other without having to reveal the true identity of patient. By creating one session pseudonym for each pair of providing server (12) holding relevant patient data and a requesting server (10) and by formatting an inbound session identifier related to the requesting server and an outbound session identifier related to the providing server for each session pseudonym the servers may communicate anonymous data with each other. The patient data is transferred from the at least one providing server to the requesting server and all session pseudonyms are replaced, in the requesting server, with the identifier of the requesting server for the patient (P).
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
System for verification of pseudonymous credentials for digital identities with managed access to personal data on trust networks
InactiveUS20190333054A1Key distribution for secure communicationUser identity/authority verificationDigital identityThird party
The invention advantageously provides a system for the verification a user's identity and qualifications and authentication of credentials associated with a user's digital identity on a trust network (where service providers involved in a transaction may be independent parties operating with limited trust), in which a pseudonymized transaction record may be created for that digital identity and stored in a shared ledger; identifying information for a user may be retained in a custodial escrow account for that user; and transactions may be re-correlated with identifying information for authorized third parties under established “due process” rules that are appropriate for the applicable jurisdiction(s).
Owner:INFONETWORKS LLC
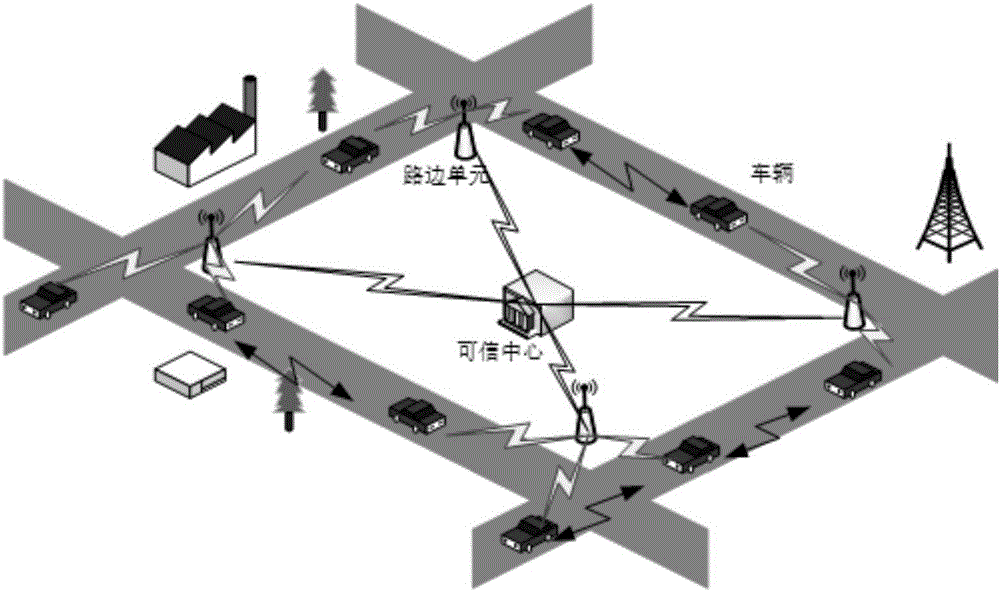
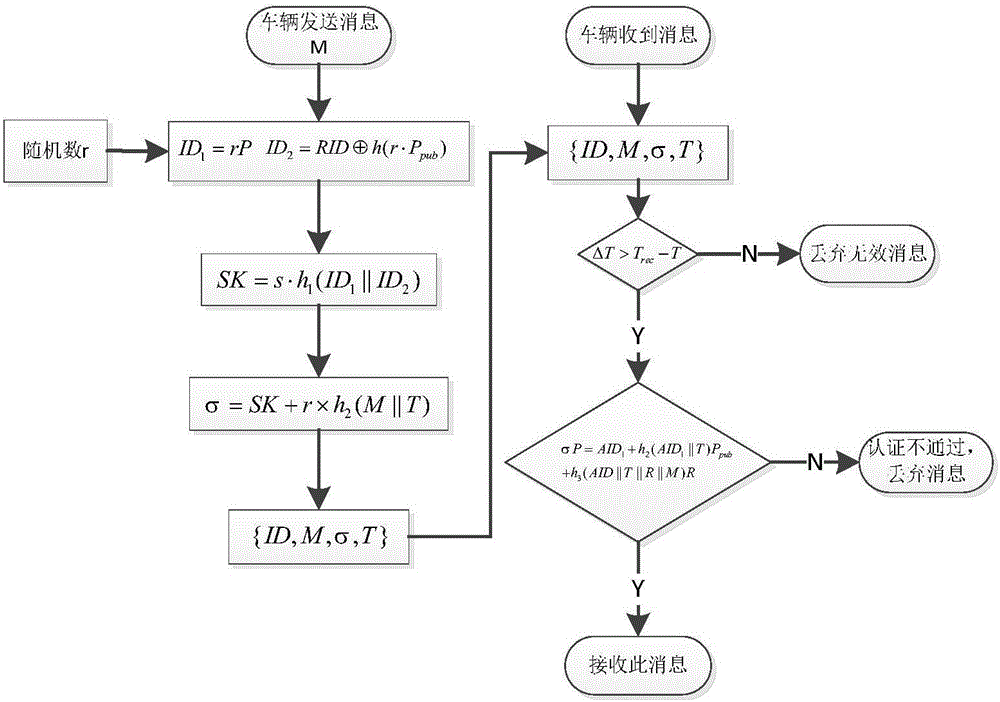
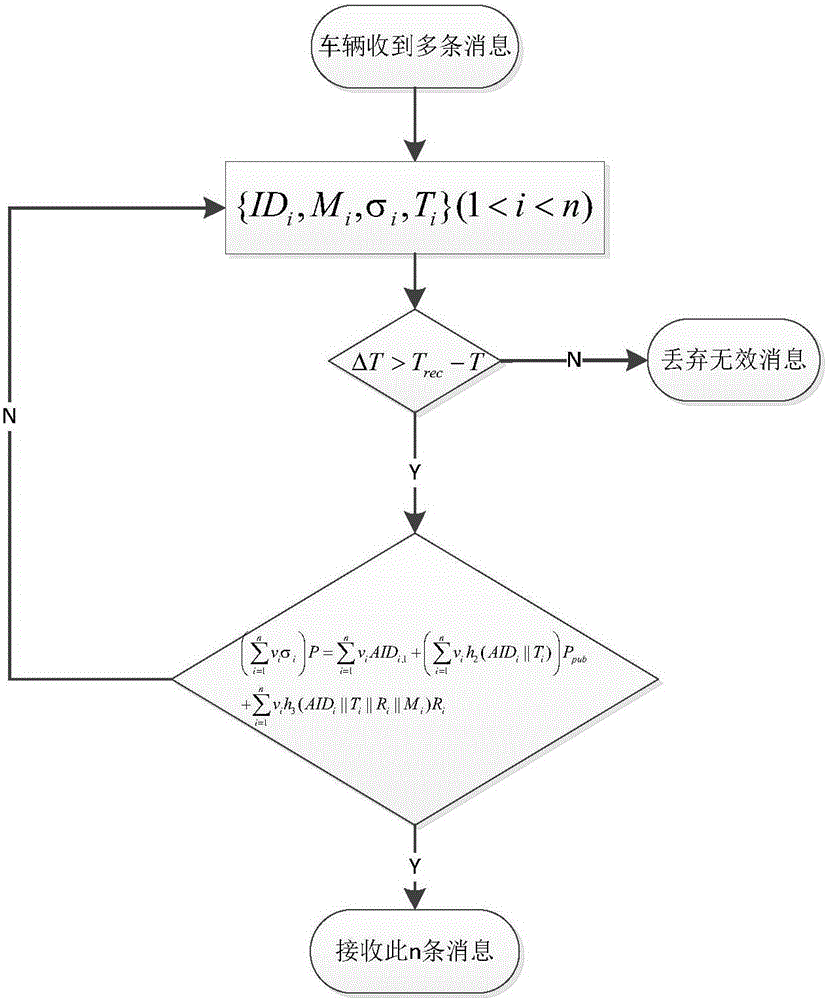
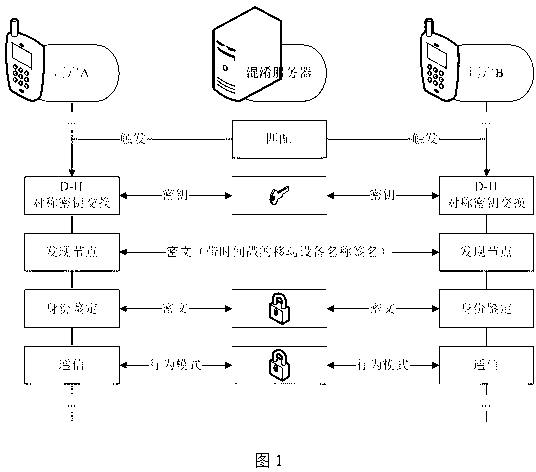
Identity based efficient anonymous batch authentication method in IOV (Internet of Vehicles) environment
ActiveCN105847235AAchieve authenticationImprove securityUser identity/authority verificationTrusted authorityTamper resistance
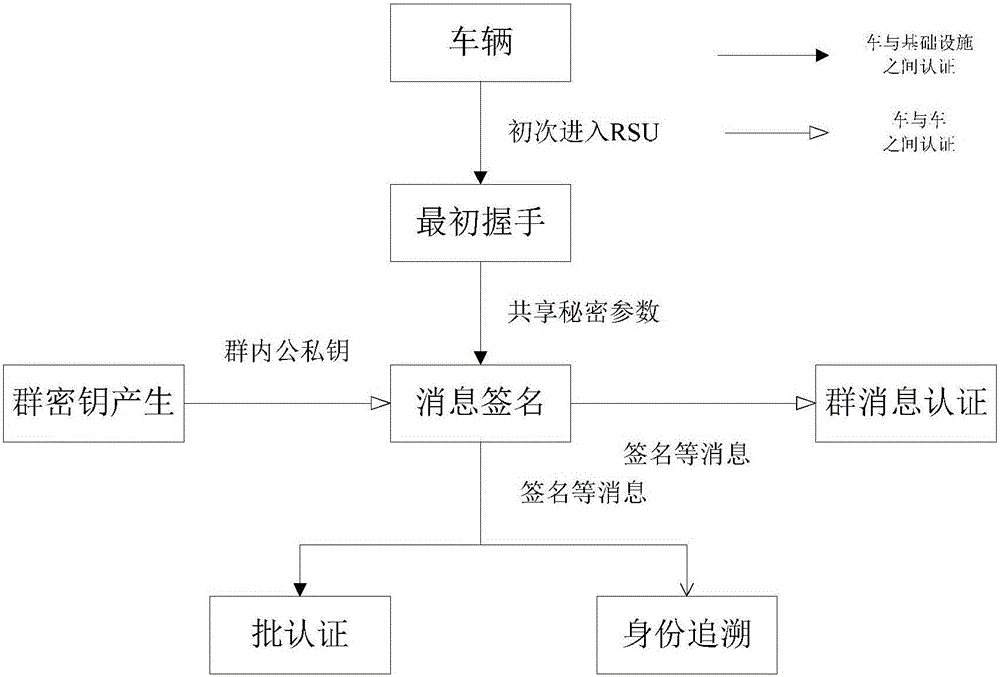
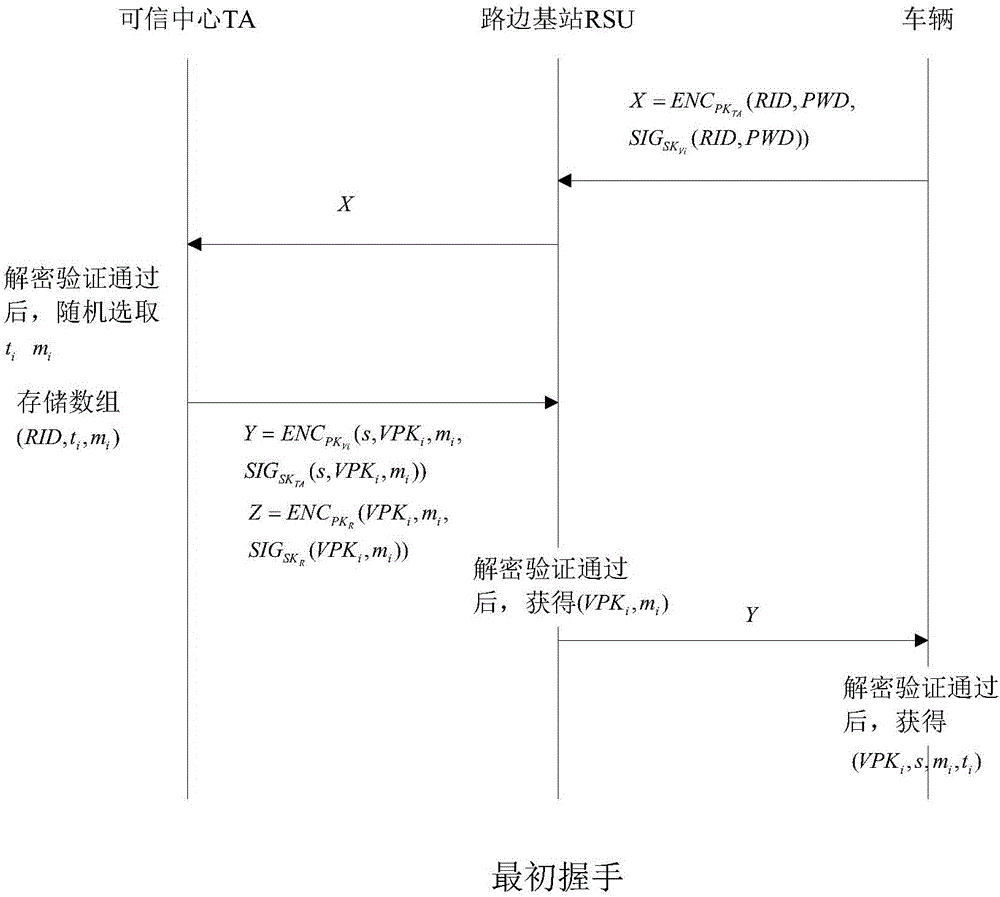
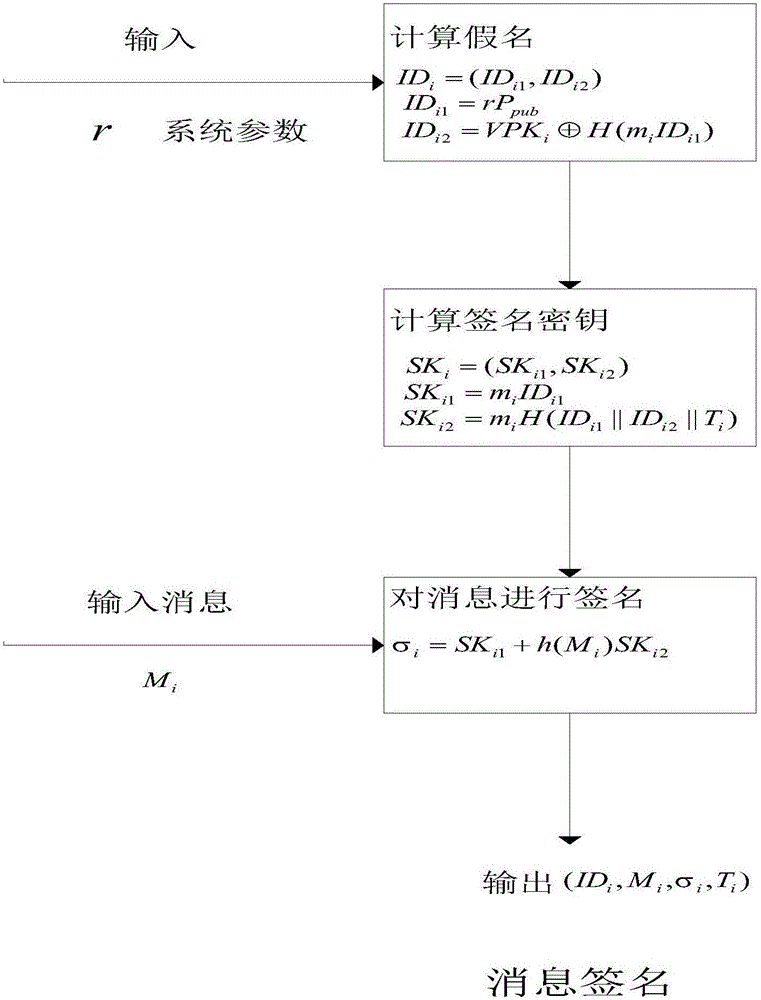
The invention discloses an identity based efficient anonymous batch authentication method in an IOV (Internet of Vehicles) environment. The identity based efficient anonymous batch authentication method in the IOV environment comprises an initial handshake module, a message signature module, a batch authentication module, an identity tracing module, a group key generation module and a group message signature and authentication module. According to the identity based efficient anonymous batch authentication method in the IOV environment, authentication between vehicles and infrastructures and authentication between vehicles can be realized, no tamper-proofing device is depended, privacy protection is realized by utilizing a pseudonymous name, conditional privacy protection is realized as a TA (Trusted Authority) can trace the real identity of each vehicle if necessary, the efficiency is improved as batch authentication is adopted, and the authentication process is simple and efficient. The message signature process and the group message signature process are same, the operating cost is low, and a replay attack can be borne as a time stamp is added.
Owner:南京秉蔚信息科技有限公司
Distributed aggregation authentication method having privacy protection function for vehicle-mounted self-organizing network
InactiveCN105763558ASatisfy unlinkable privacyKey distribution for secure communicationSecurity arrangementPrivate communicationPrivacy protection
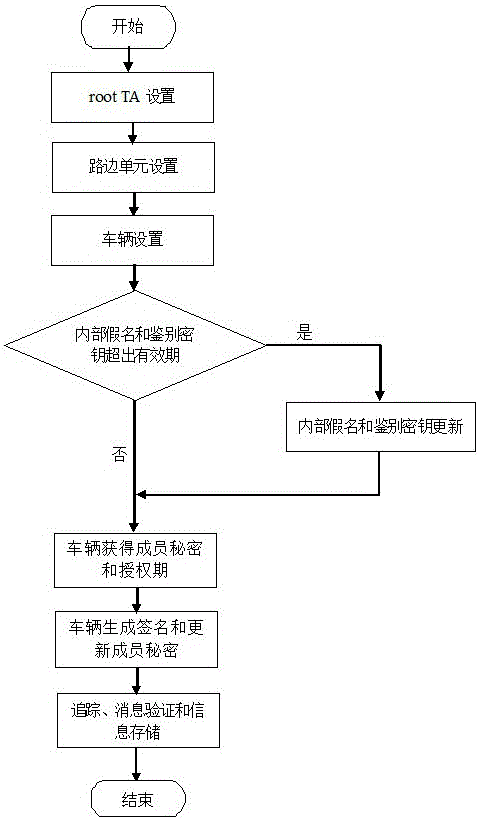
The invention discloses a distributed aggregation authentication method having a privacy protection function for a vehicle-mounted self-organizing network. The method comprises the following steps: a step of trusted root mechanism arrangement, a step of road side unit arrangement, a step of vehicle arrangement, a step of internal pseudonym and authentication key updating, a step of a vehicle obtaining secrets of members and authorization terms, a step of the vehicle generating signatures and updating the secrets of the members, a step of tracking and a step of message verification and information storage. The distributed aggregation authentication method is characterized in that conditional privacy is not associable, the method is independent of an ideal and strict anti osmosis device, and no secret key trusteeship problem can be caused. Safe and private communication of a the vehicle-mounted self-organizing network can be realized through the distributed aggregation authentication method.
Owner:EAST CHINA NORMAL UNIV
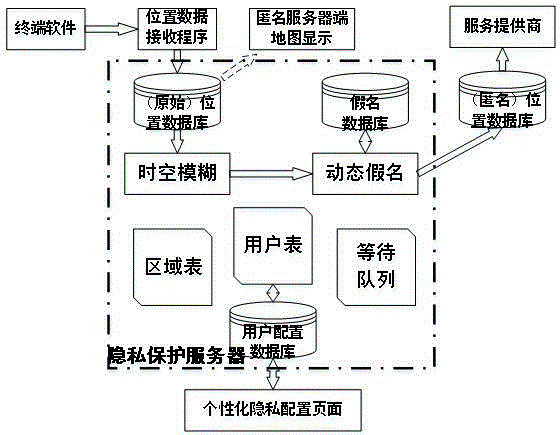
Position privacy protection method based on dynamic pseudonyms
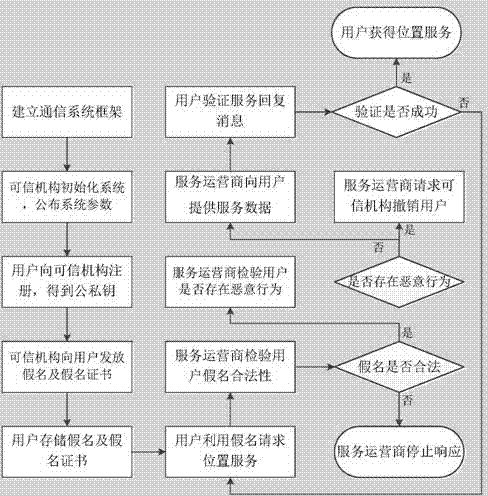
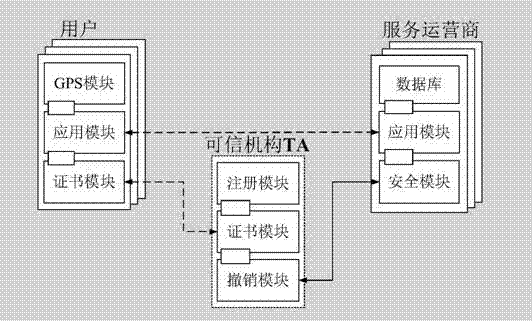
ActiveCN103618995AAddress privacy breachesIncreased level of privacyLocation information based serviceSecurity arrangementCommunications systemSide information
The invention discloses a position privacy protection method based on dynamic pseudonyms. The position privacy protection method mainly overcomes the defect that the position privacy protection degree in an existing position pseudonym method based on position services is too low. The position privacy protection method comprises the steps that a communication system composed of users, a credible mechanism and a service provider is built; the system is initialized through the credible mechanism; the users sign in the credible mechanism on line to obtain public and private keys; the credible mechanism updates the pseudonyms and pseudonym certificates of the users regularly; the users use the dynamic pseudonyms to request position services from the service provider; the service provider provides service data for legal users and requests the credible mechanism to revoke malicious users; the legal users obtain the position service data. According to the position privacy protection method, identity anonymity is achieved by using the dynamic pseudonyms, the relation between identity information and spatiotemporal information is cut off, and therefore it is difficult for the service provider to speculate position information of the specific users by means of side information, position privacy of the users is protected effectively, and the position privacy protection method can be used for position privacy protection based on the position services in social networking services.
Owner:XIDIAN UNIV
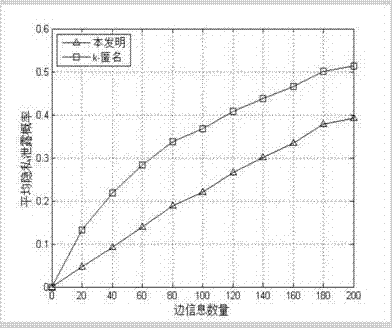
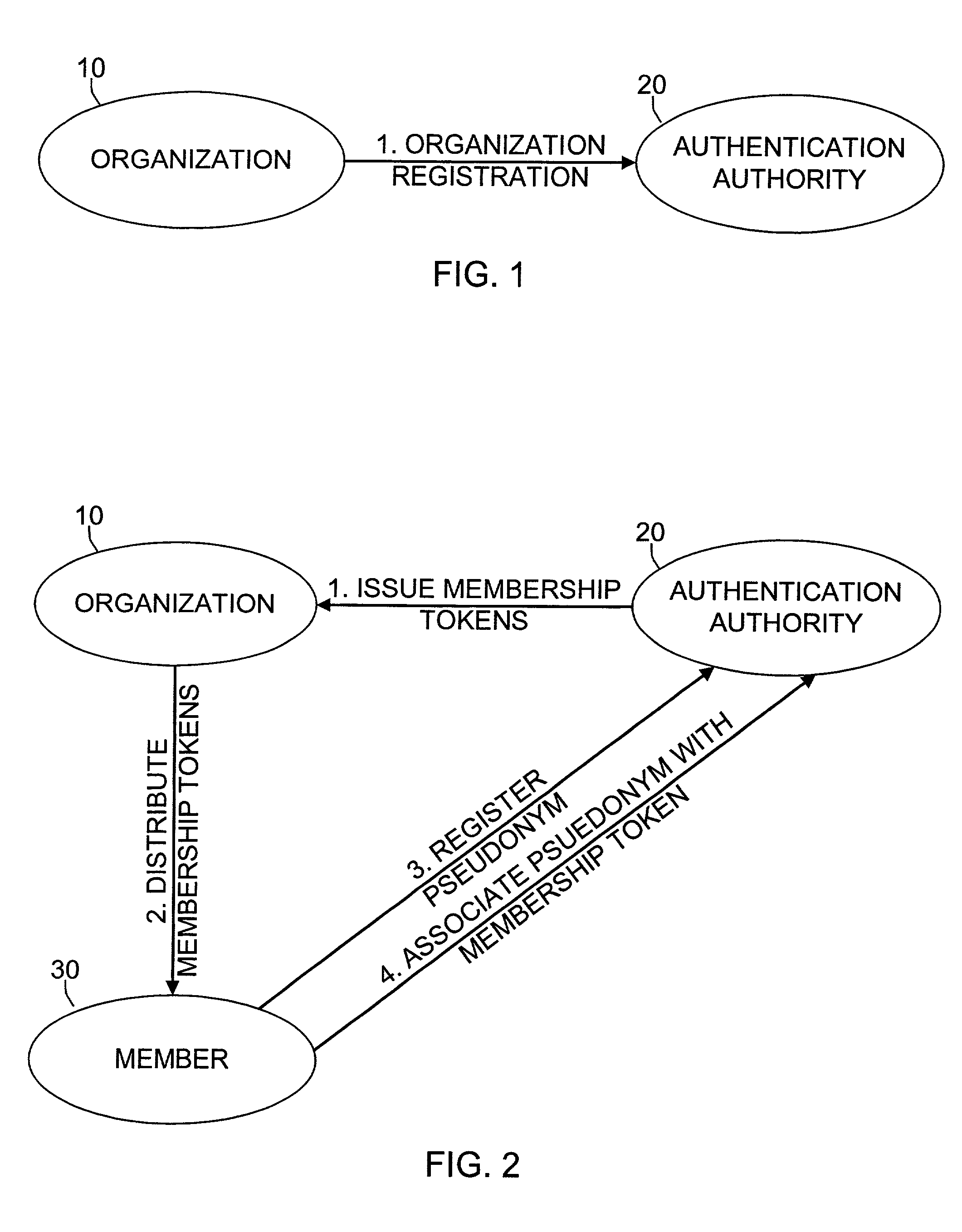
System and method for establishing and managing relationships between pseudonymous identifications and memberships in organizations
A system and method for bonding a pseudonymous identity to an organization to provide assurance that a user claiming to be a member or representative of the organization may anonymously post messages or documents to electronic forum. The system and method includes distribution of tokens from an authentication authority to the organization which can then be provided by the organization to its members. Members register with the authentication authority and designate a pseudonym to associate with the organization and also provide the membership token as proof of membership in the organization.
Owner:PSEUDS
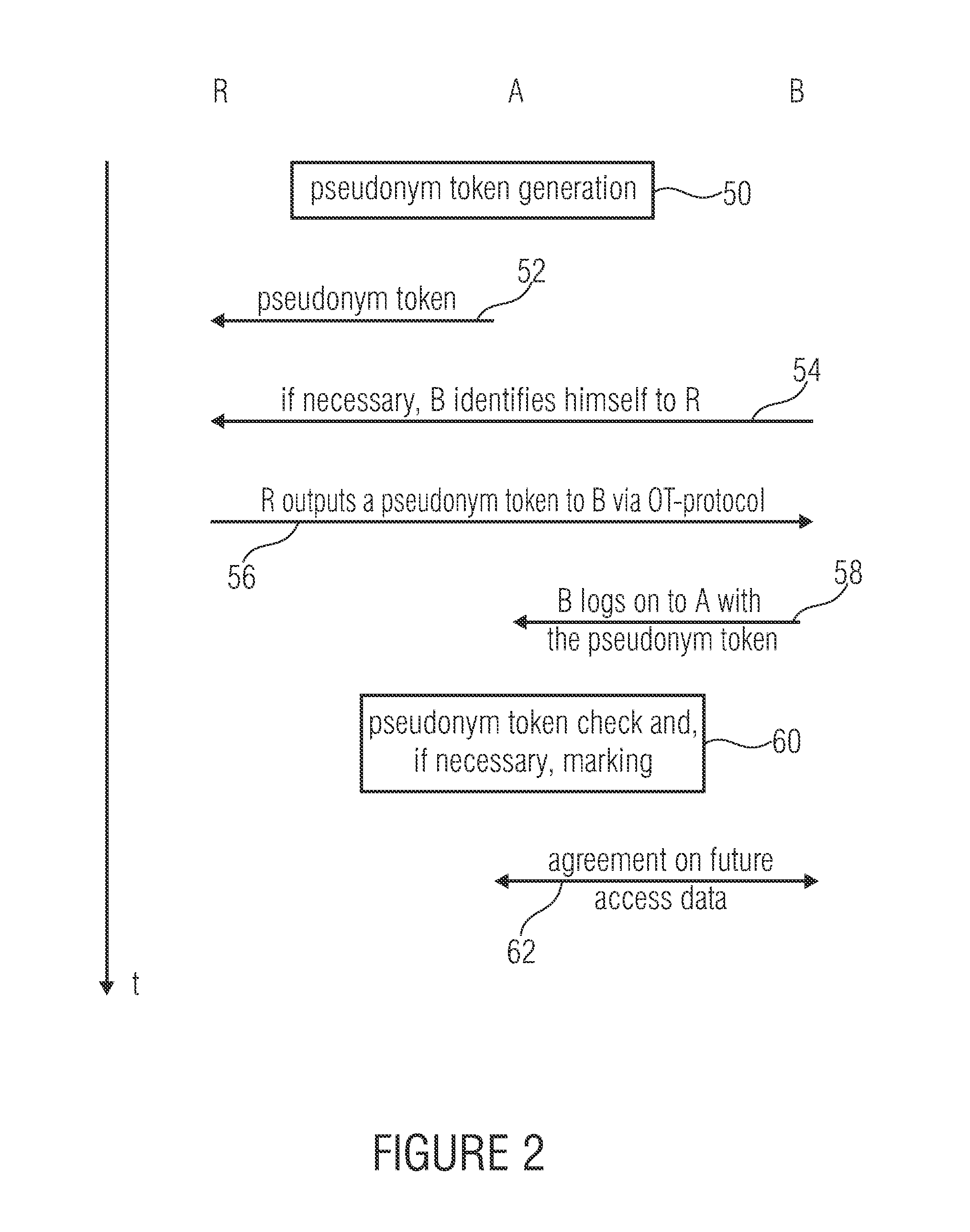
Pseudonymized authentication
ActiveUS20120167189A1Digital data processing detailsComputer security arrangementsProtocol for Carrying Authentication for Network AccessPseudonymity
An OT or Oblivious Transfer protocol is used to output pseudonym tokens from a list of pseudonym tokens to user entities such that it is possible to obtain pseudonymized authentication by a preceding verification of proof of identity of the respective user entities and marking pseudonym tokens as used as soon as the same are used for authentication by means of the OT protocol after the output.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
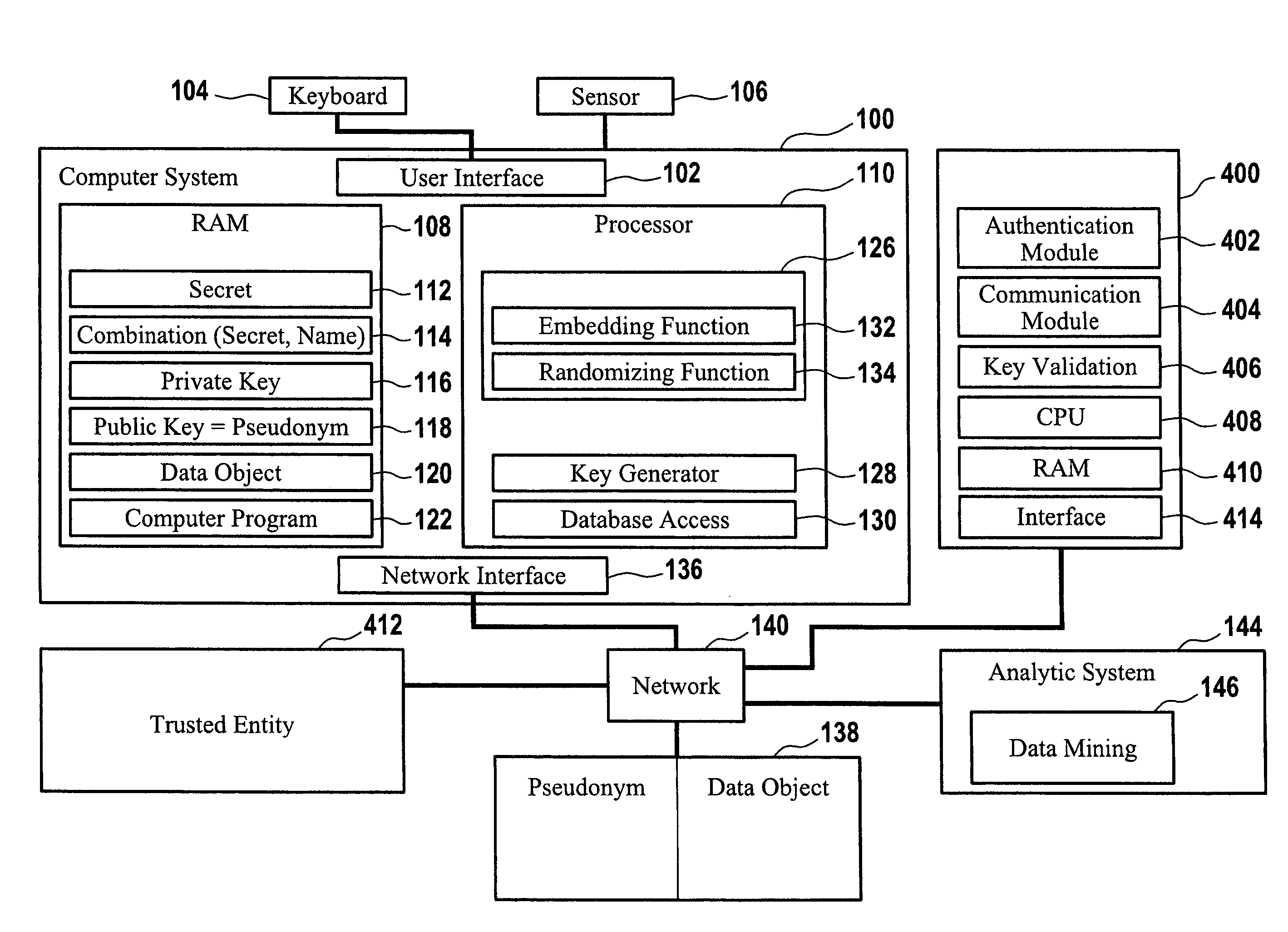
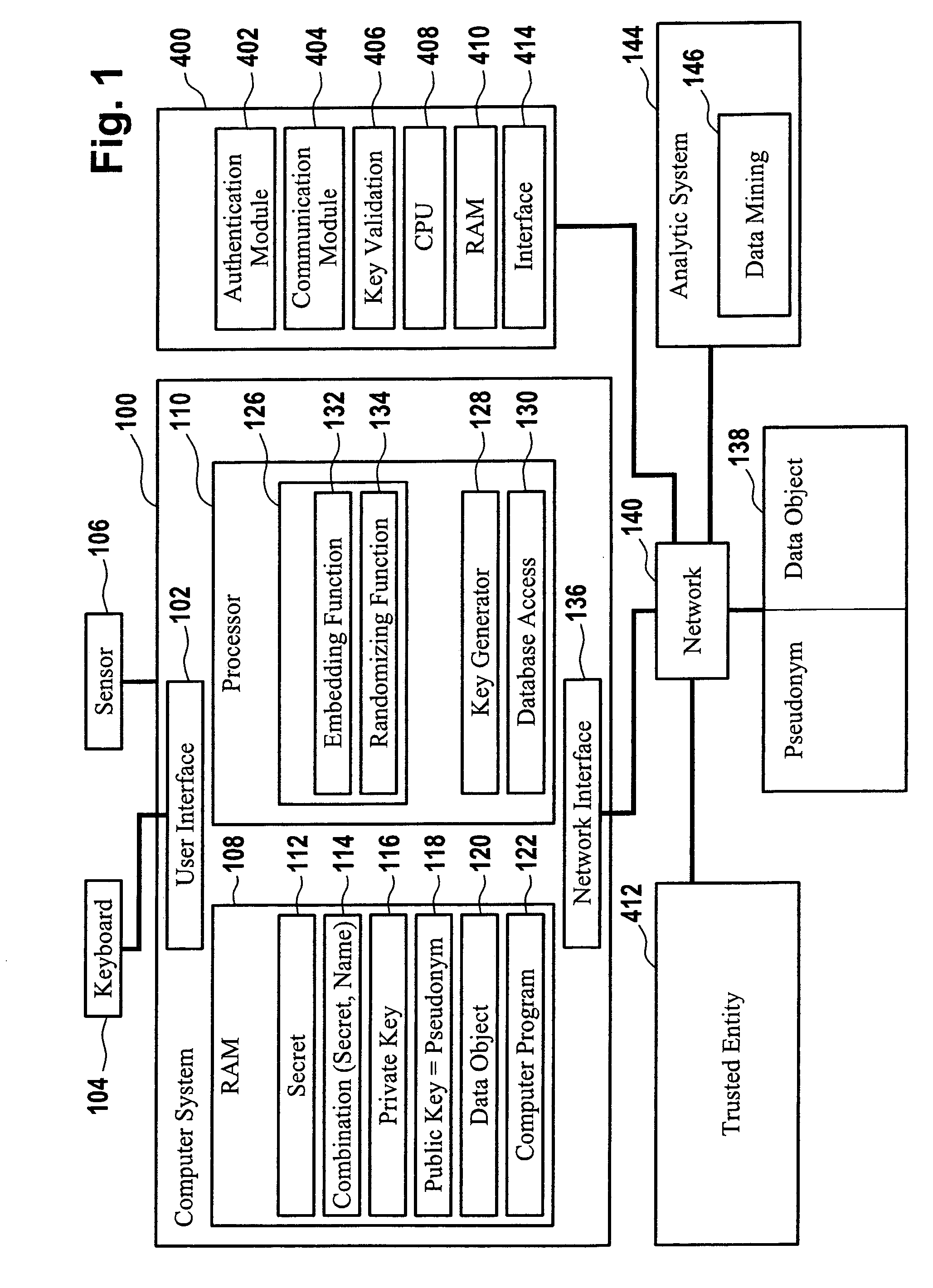
Computer implemented method for performing cloud computing on data being stored pseudonymously in a database
ActiveUS20110179286A1Enhanced anonymityEfficient implementationPublic key for secure communicationUnauthorized memory use protectionComputer scienceCloud computing
The invention relates to a computer implemented method for performing cloud computing on data of a first user employing cloud components, the cloud components comprising a first database and a data processing component, wherein an asymmetric cryptographic key pair is associated with the first user, said asymmetric cryptographic key pair comprising a public key and a private key, the data being stored pseudonymously non-encrypted in the first database with the data being assigned to an identifier, wherein the identifier comprises the public key, the method comprising retrieving the data from the first database by the data processing component, wherein retrieving the data from the first database comprises receiving the identifier and retrieving the data assigned to the identifier from the first database, wherein the method further comprises processing the retrieved data by the data processing component and providing a result of the analysis.
Owner:SPALKA ADRIAN +1
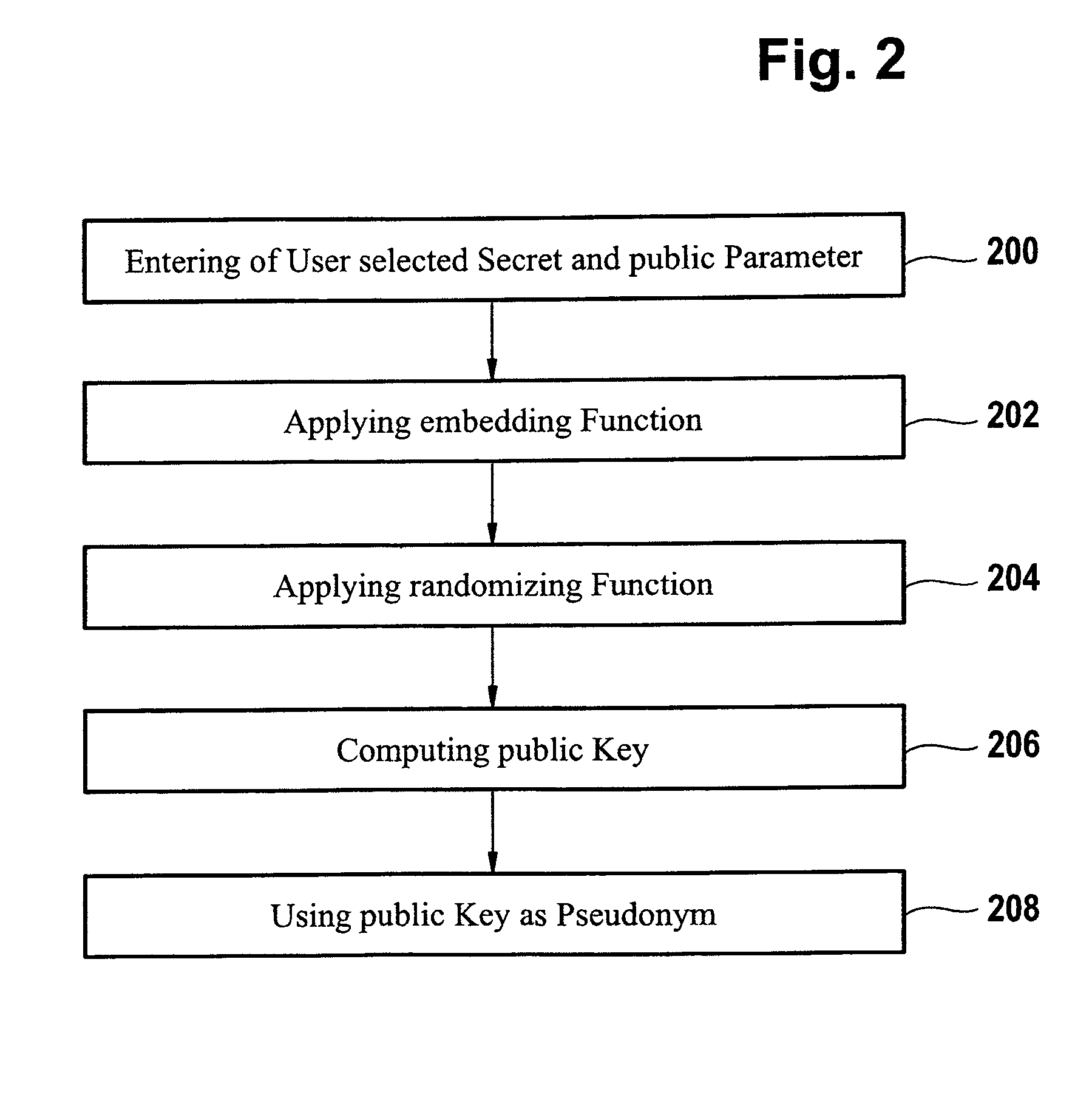
Computer implemented method for authenticating a user
ActiveUS8522011B2Simplify the authentication processEfficient implementationKey distribution for secure communicationPublic key for secure communicationUser authenticationComputer science
The invention relates to a computer implemented method for performing a user authentication, wherein an asymmetric cryptographic key pair is associated with the user, said key pair comprising a public key and a private key, wherein the method comprises selecting the user to be authenticated using a pseudonym of said user, wherein said pseudonym comprises the public key of the user, the method further comprising performing a cryptographic authentication of the user using the asymmetric cryptographic key pair.
Owner:SPALKA ADRIAN +1
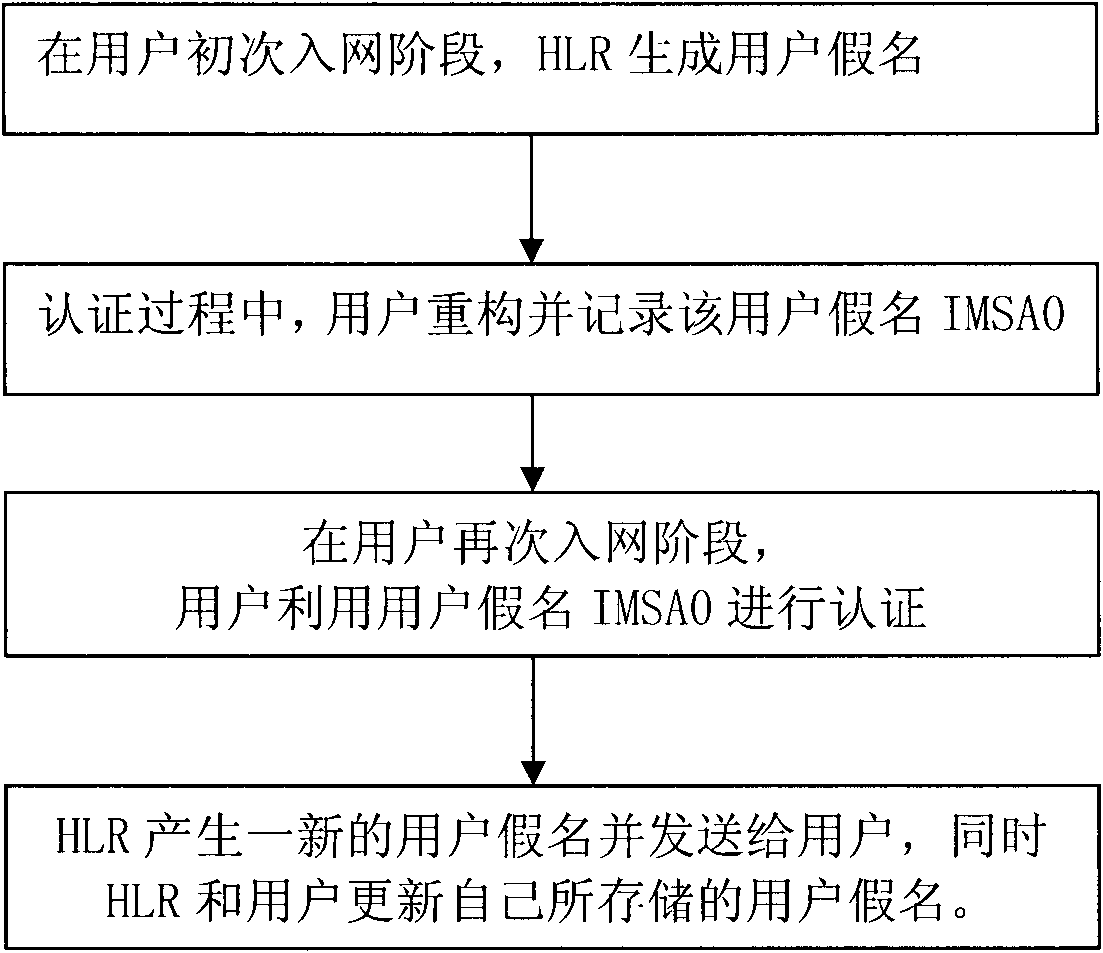
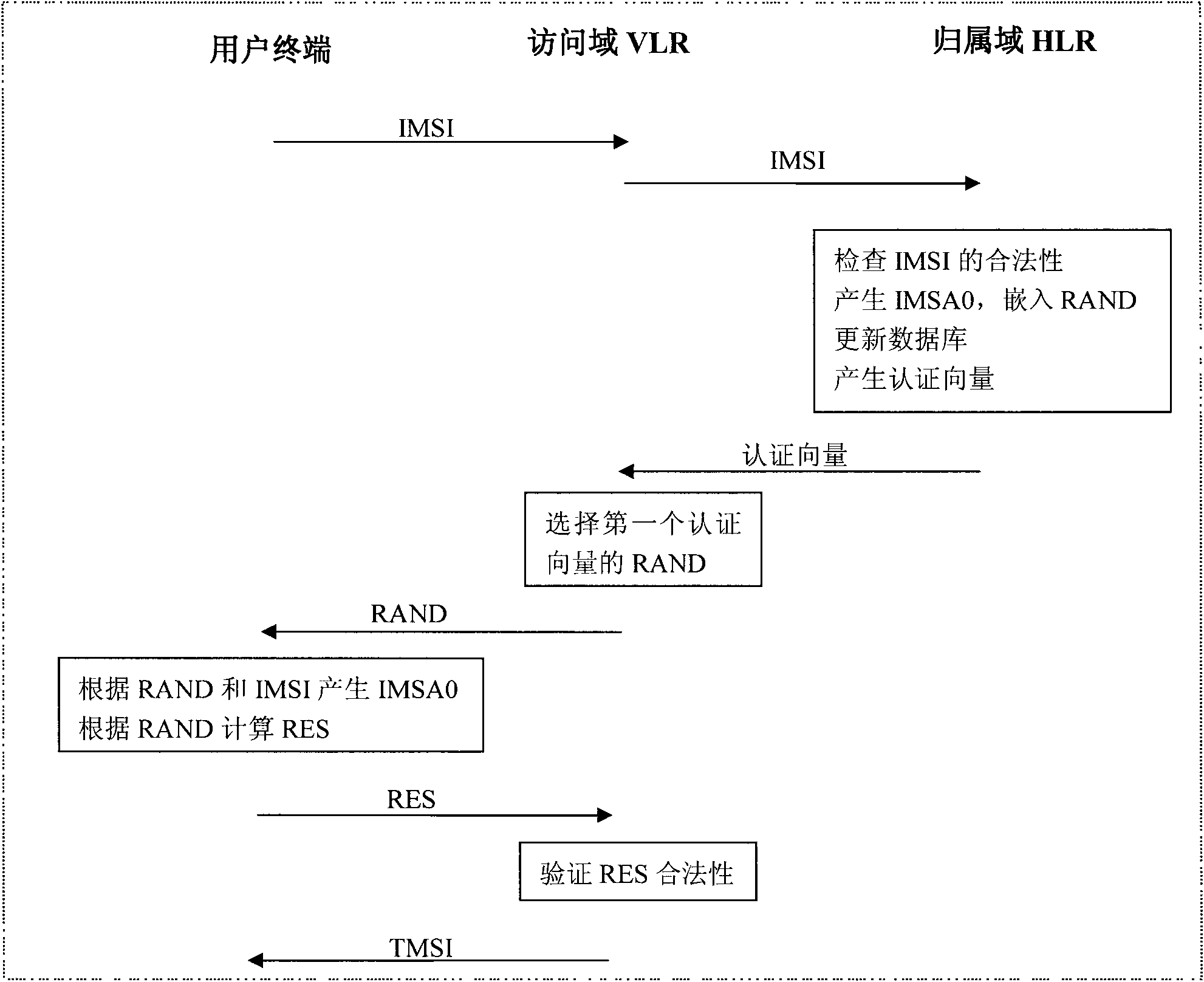
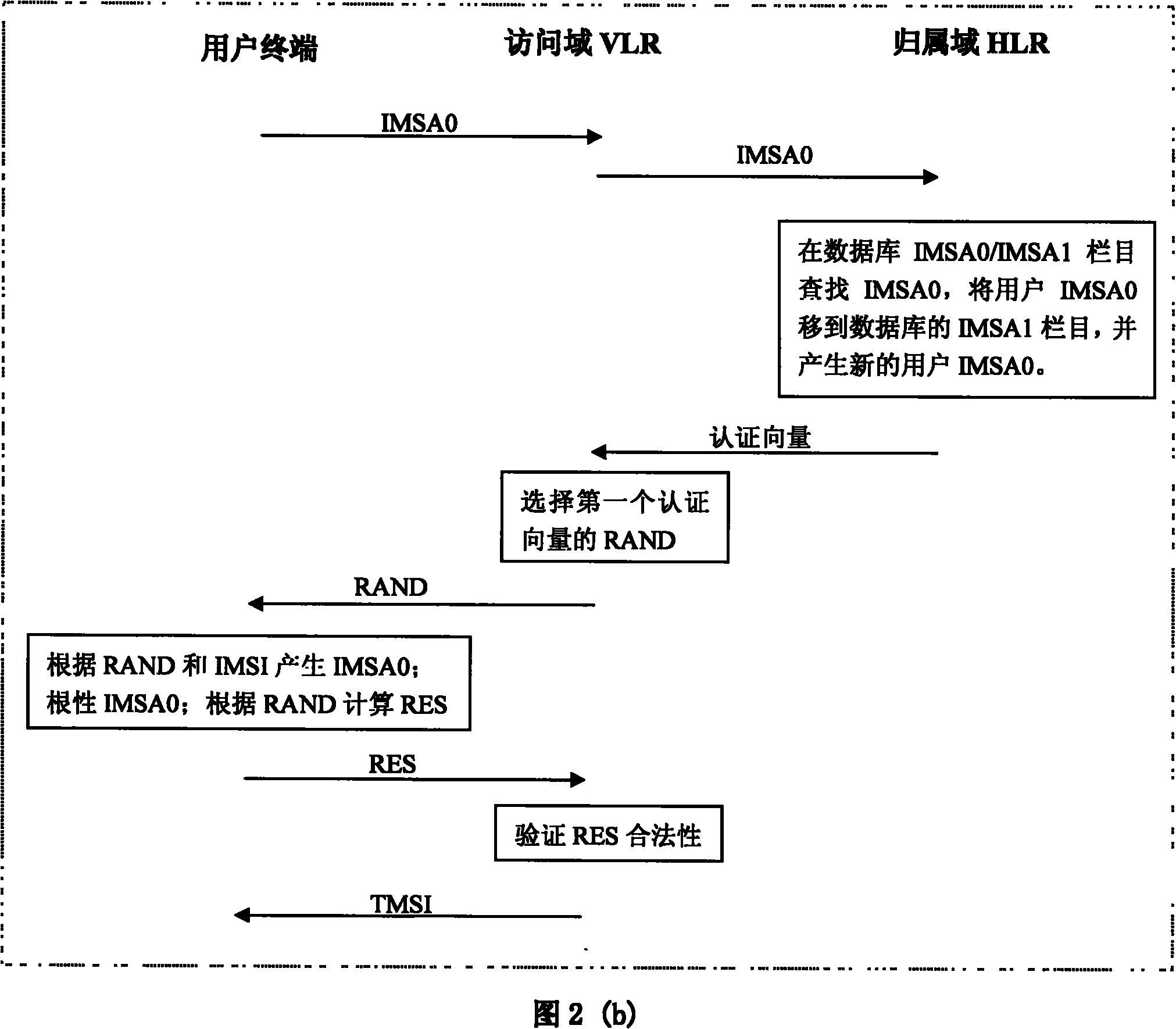
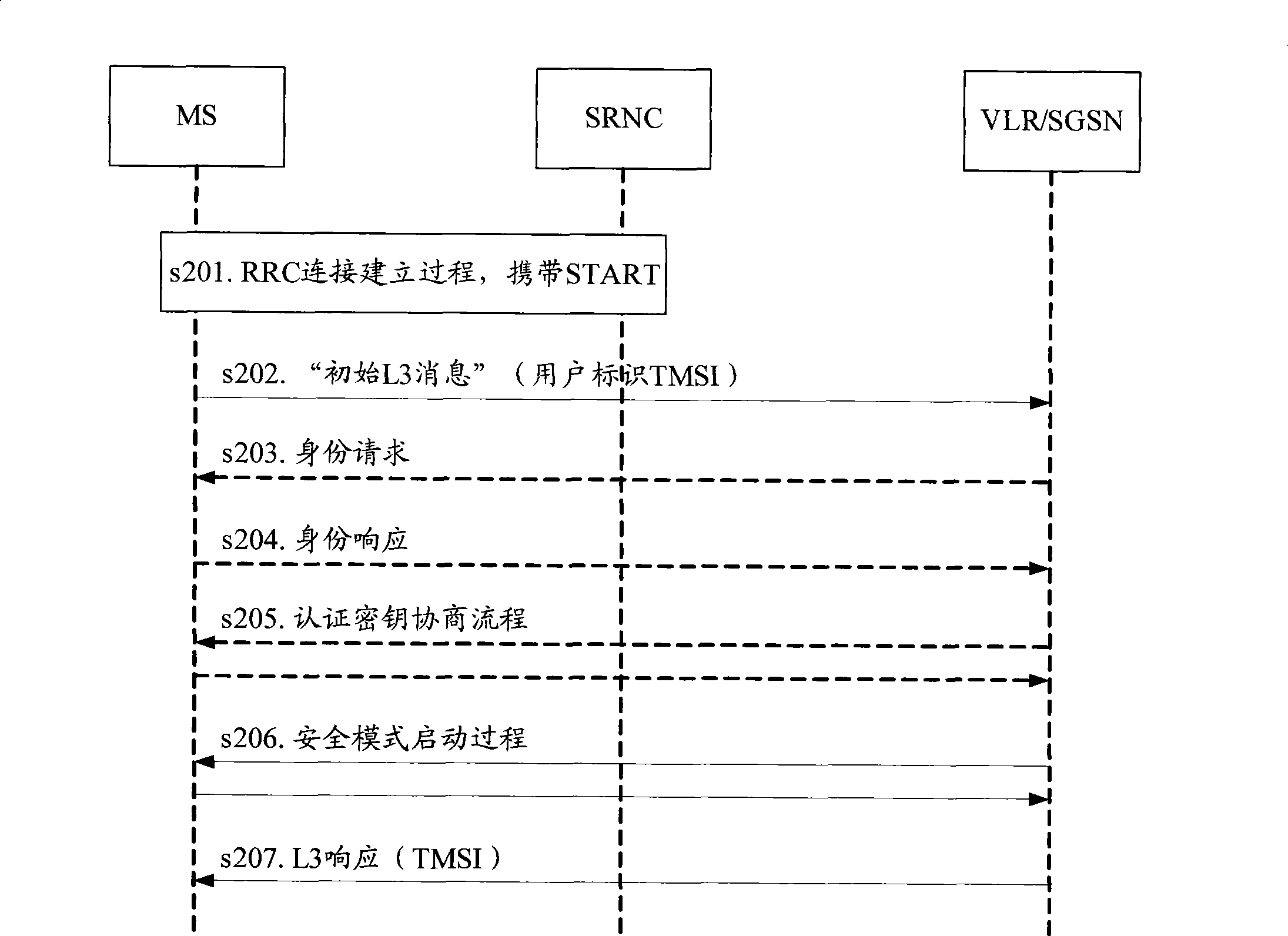
Mobile user identification code IMSI protection method based on pseudonym
ActiveCN101959183ASeamlessly compatibleInvariant communication protocolSecurity arrangementNetwork data managementCommunications securityAuthentication
The invention discloses an IMSI protection method based on pseudonym, belonging to the field of communication safety. The method comprises: in an initial network accessing stage for a user, the user sends IMSI to HLR for authentication; after authentication, a pseudonym is generated for the user and is recorded into a database; then, according to the user pseudonym, HLR generates an authentication vector and authenticates the user by VLR; finally HLR sends a user pseudonym field in the user pseudonym to the user; and the user reconstructs and records the user pseudonym. In a secondary networkaccessing stage for the user, the user sends the user pseudonym to the HLR for authentication; if a database does not have the user pseudonym, authentication is reported to fail, otherwise, HLR generates a new user pseudonym and updates the database; then, the user is authenticated like initial network accessing; finally, HLR sends the user pseudonym field in the user pseudonym which is newly generated to the user; and the user reconstructs and records the user pseudonym. The method greatly improves the safety of IMSI, and the system is convenient to update.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
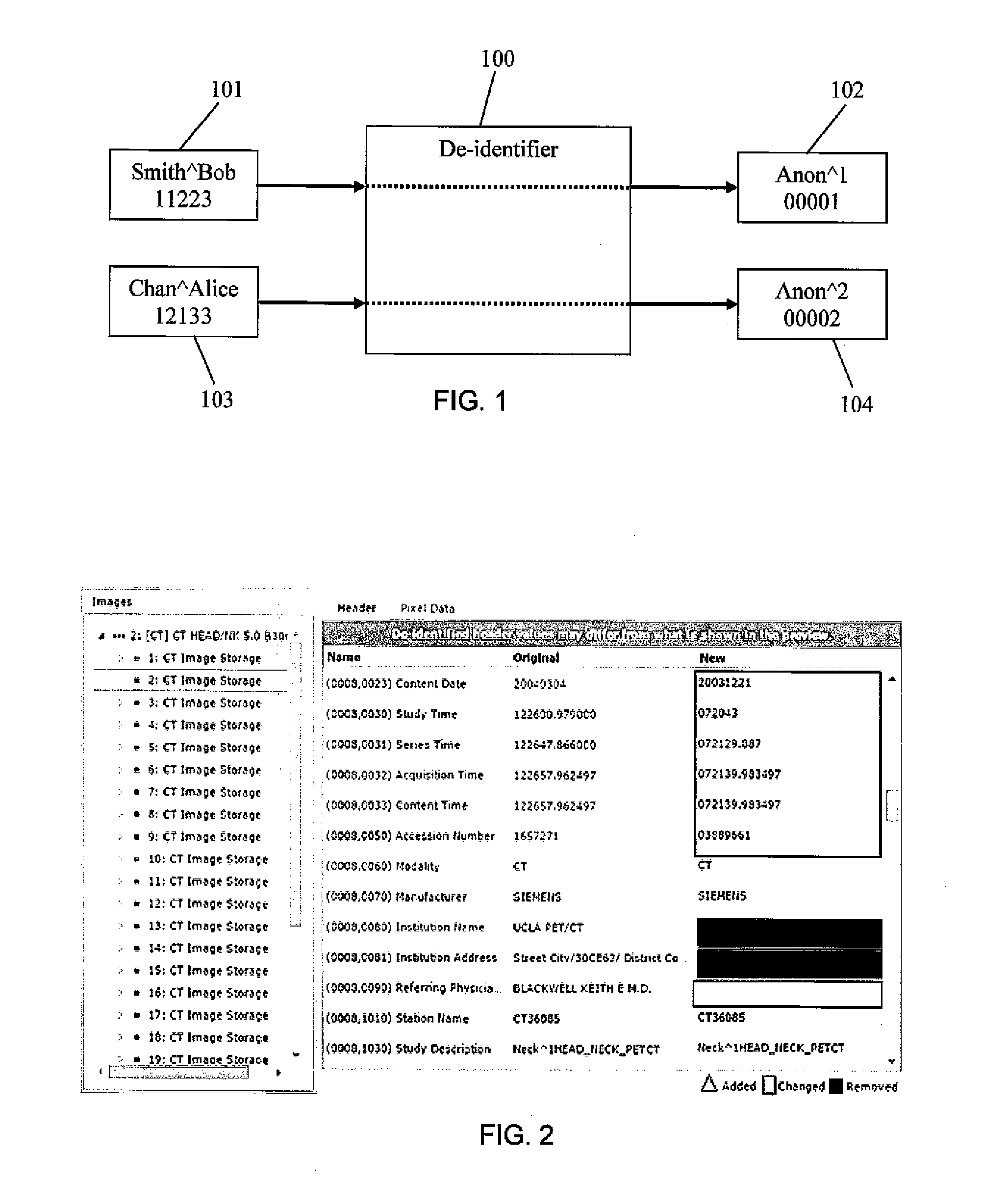
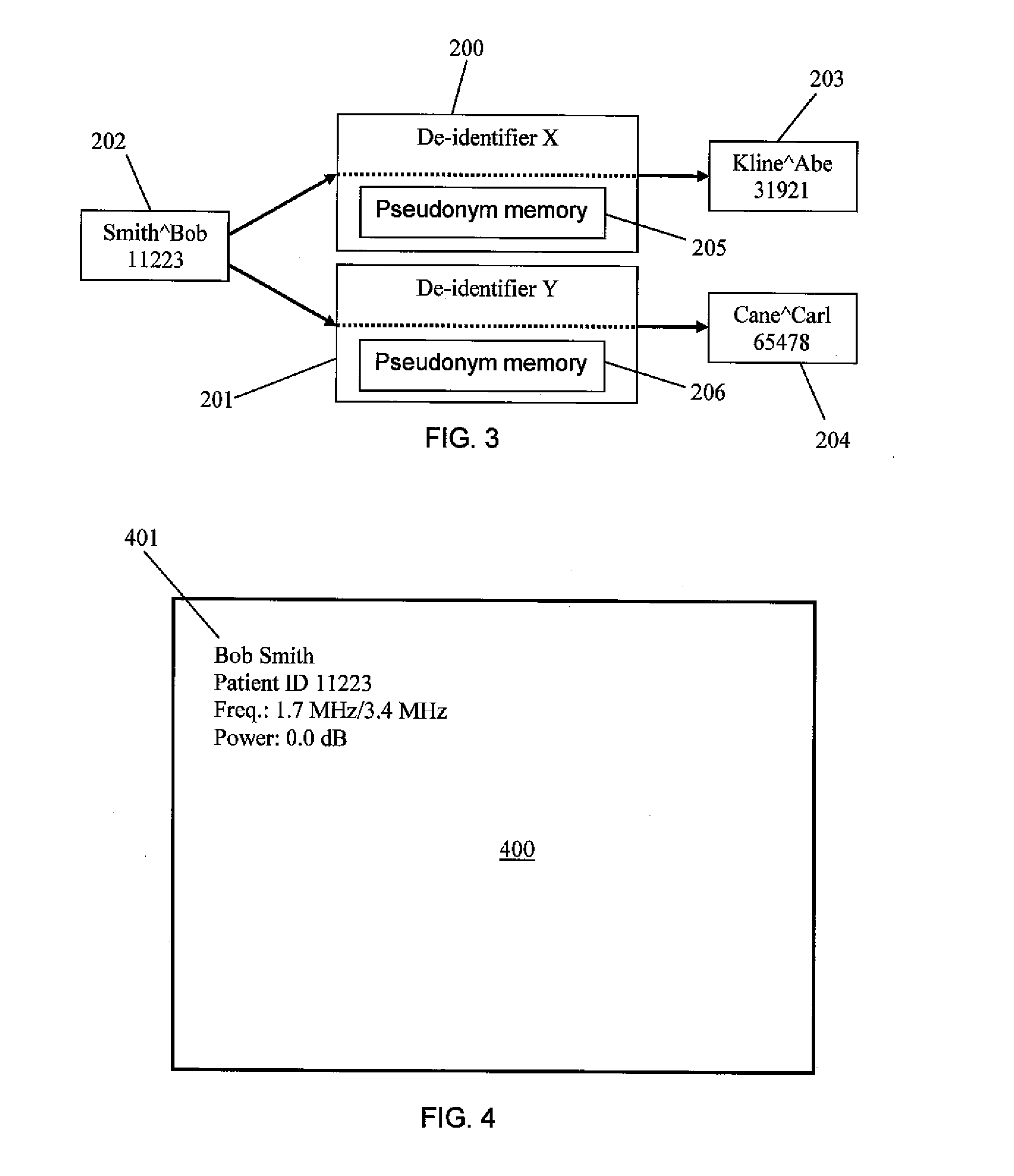
Dicom de-identification system and method
A system for creating de-identification programs for de-identifying DICOM image files containing DICOM images and metadata. The system provides a user interface that allows users to create de-identification programs. Each program has redaction rules specifying redaction regions in normalized coordinates defining a region of a DICOM image to be redacted to obfuscate content in the redaction region, and metadata substitution rules specifying metadata elements to be substituted with pseudonyms. The user may modify the redaction rules and metadata substitution rules, and preview the effect of the de-identification program by applying the de-identification program to DICOM images and associated metadata and displaying the resulting modified DICOM image and associated metadata. The system maintains a pseudonym memory to determine if a pseudonym has been stored for each metadata element specified by the substitution rule so that the same pseudonym is consistently used for the same element values.
Owner:SYNAPTIVE MEDICAL INC
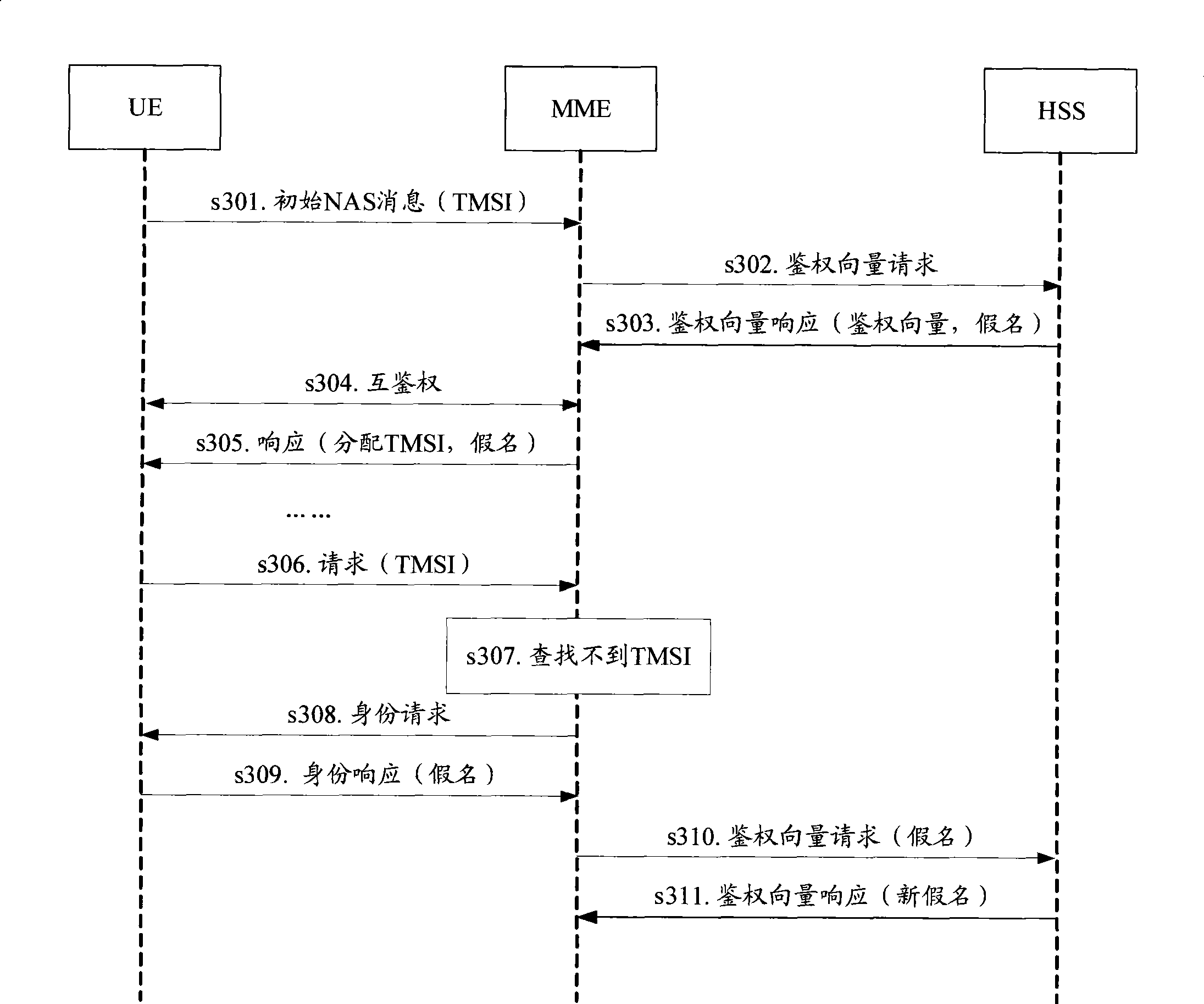
Pseudonym-based anonymous authentication and key negotiation optimization method and optimized authentication analysis method for Internet of Things
ActiveCN106657124AAchieve non-traceabilityAvoid attackTransmissionKey-agreement protocolThe Internet
The invention provides a pseudonym-based anonymous authentication and key negotiation optimization method and optimized authentication analysis method for the Internet of Things. The method comprises the following steps: S1, a user and a sensor node separately register a gateway node, and for the difference of the user and the sensor node, a user registration protocol and a sensor node registration protocol different from each other are adopted; and S2, after the registration, the user logs in the system through a user login protocol and an authentication and key negotiation protocol, and under the assistance of the gateway node, the sensor node requiring access realizes mutual authentication and a negotiation shared session key. By adoption of the method provided by the invention, better anonymity, non-traceability and security are realized.
Owner:YICHUN UNIVERSITY
Method, system and device for protecting privacy of customer terminal
The invention discloses a method for protecting user terminal comprising following step: network side successfully accesses to network at user terminal and assigns a false name to the user terminal; the network side receives the user terminal using the false name as information for marking user identity. The invention also discloses a method for protecting user terminal privacy comprising following steps: when the user terminal successfully access at user terminal, the user terminal receives temporary identity mark sent by network side and retention period of the identity mark; the user terminal receives request for reporting permanent identity mark sent by the network side; the user terminal judges if reporting response to permanent identity mark. The invention also discloses a system and device for protecting privacy of user terminal. The invention can effectively avoids attacker to take advantage of identity request information for acquiring permanent identity mark of user terminal, thereby protects privacy of user terminal.
Owner:HUAWEI TECH CO LTD
Efficient condition privacy protection and security authentication method in internet of vehicles
ActiveCN106027519AReduce computational overheadWill not be tampered withKey distribution for secure communicationPublic key for secure communicationOn boardThe Internet
The invention discloses an efficient condition privacy protection and security authentication method in an internet of vehicles. The efficient condition privacy protection and security authentication method comprises the following steps of: system initialization, generation of pseudonym identities and signature private keys of vehicles, signing and authentication of a message and tracing of real identities of the vehicles. The vehicles carry out cooperative communication with surrounding vehicles and roadside units deployed at both sides of a road by on-board units assembled on the vehicles, driving security of the vehicles can be effectively improved, and vehicle users can more conveniently and rapidly acquire related traffic services. The efficient condition privacy protection and security authentication method disclosed by the invention not only can meet security requirements in the internet of vehicles, but also optimizes the computing process of signature generation and verification in the communication. The efficient condition privacy protection and security authentication method is greatly improved on the aspect of efficiency of computing cost, communication cost and the like, and is more applicable to communication and application in the internet of vehicles.
Owner:ANHUI UNIVERSITY
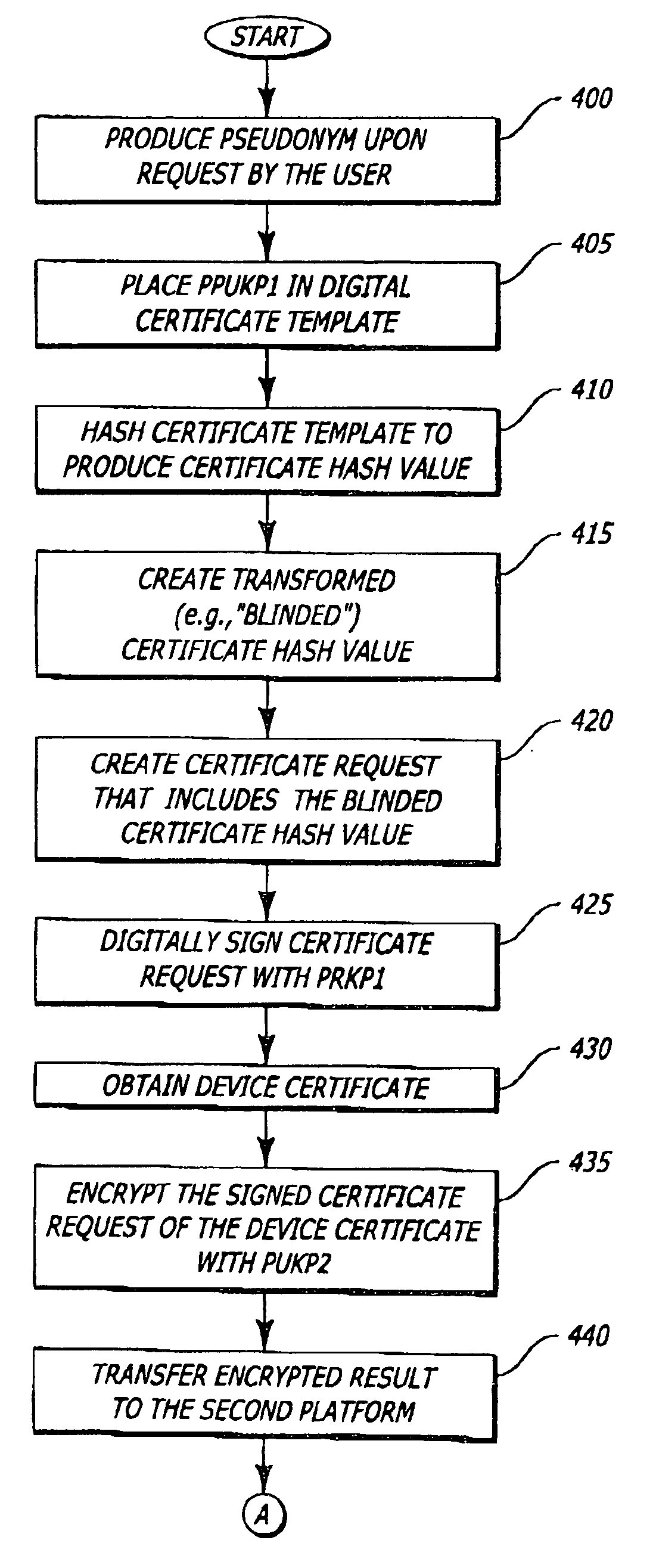
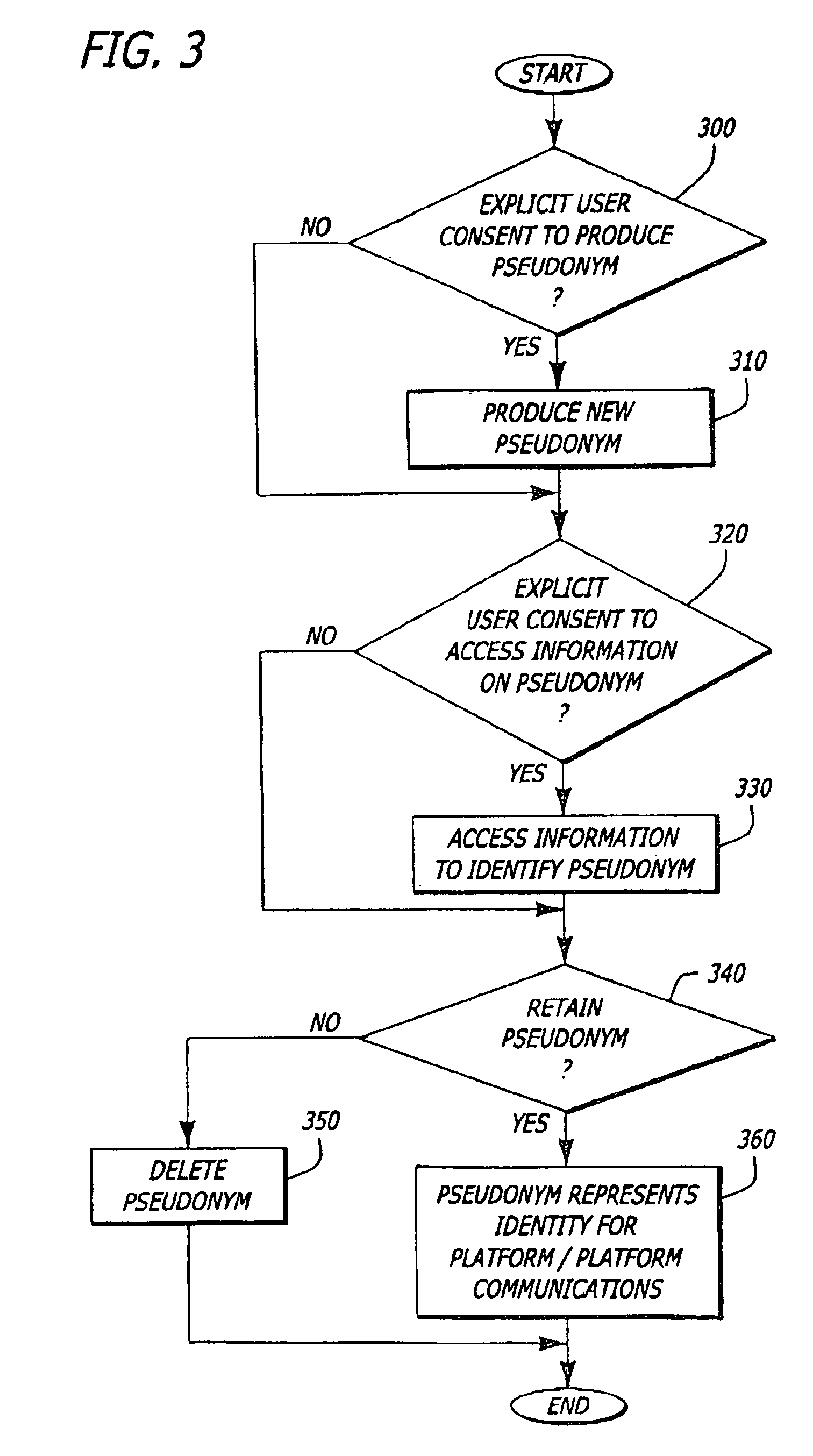
Platform and method for establishing provable identities while maintaining privacy
InactiveUS6976162B1Multiple keys/algorithms usageUser identity/authority verificationData integrityDigital signature
In one embodiment, a method for utilizing a pseudonym to protect the identity of a platform and its user is described. The method comprises producing a pseudonym that includes a public pseudonym key. The public pseudonym key is placed in a certificate template. Hash operations are performed on the certificate template to produce a certificate hash value, which is transformed from the platform. Thereafter, a signed result is returned to the platform. The signed result is a digital signature for the transformed certificate hash value. Upon performing an inverse transformation of the signed result, a digital signature of the certificate hash value is recovered. This digital signature may be used for data integrity checks for subsequent communications using the pseudonym.
Owner:INTEL CORP
Method for protecting position privacy by mobile terminals
InactiveCN103281672AImplement location privacy protectionRealize privacy protectionLocation information based serviceTransmissionPrivacy protectionMarine navigation
The invention discloses a method for protecting position privacy by mobile terminals. According to the method, the mobile terminals are used for forecasting moving tracks of terminal owners in a period and refining and amending the moving tracks according to a local map. For the terminal owners which are close to each other, each mobile terminal takes a position where the owner of the mobile terminal exists as a start point, and positions forecast by the other owners are taken as terminal points. A map navigation service is utilized to generate a fake route, the fake route is mixed with a true route, and the fake route and the true route are combined to generate complete two branch route pictures. Each terminal owner performs fake name replacement at end points of the complete two branch pictures, the owners can be mutually indistinguishable, and therefore privacy protection is achieved. According to the method for protecting the position privacy by the terminal mobile, the position privacy of the mobile users is protected, meanwhile, reduction of precision in issuing position information is not needed, and therefore the functionality for accessing the LBS service by mobile users based on the position information is ensured.
Owner:NANJING UNIV
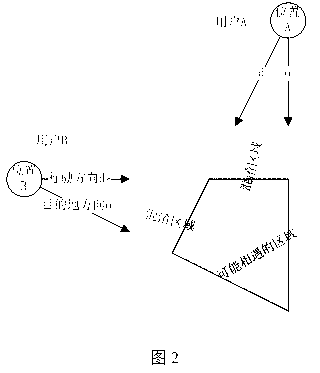
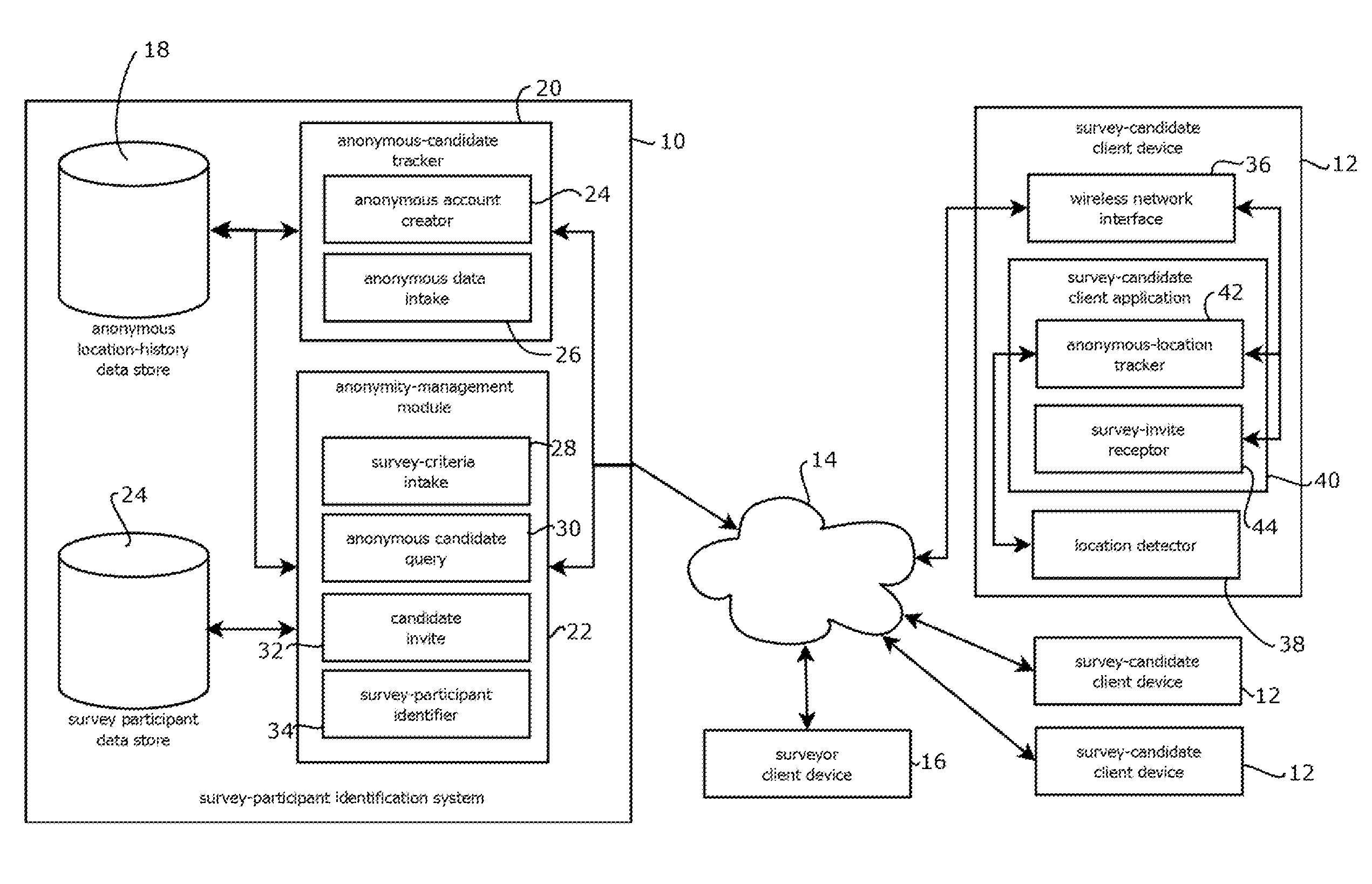
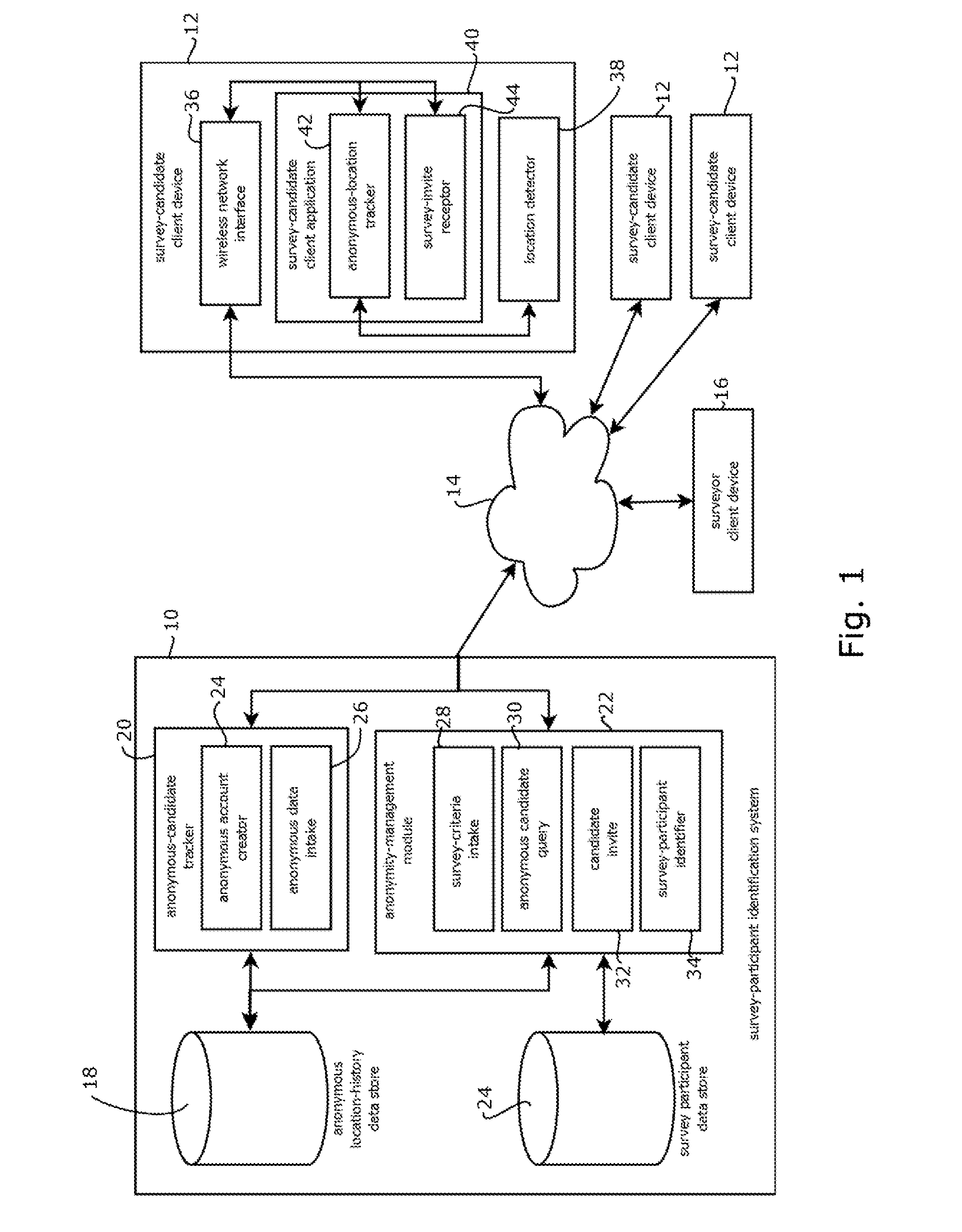
Selecting anonymous users based on user location history
Provided is a process for selecting candidates for participating in a market-research survey, or receiving other offers, based on location history while protecting privacy of the candidates. In some cases, the process includes: obtaining, at a survey-participant identification system, location histories from client devices, and the location histories indicating locations of the client device over time; associating each of the location histories with an anonymous pseudonym of the survey candidate; storing the location histories and the association with the anonymous pseudonyms in memory accessible to the server; obtaining, at the survey-participant identification system, criteria by which to select survey candidates, the criteria specifying locations relevant to a survey; selecting, with the survey-participant identification system, anonymous pseudonyms in memory that are associated with a location history that satisfies the criteria; and sending messages to the client devices inviting survey candidates corresponding to the selected anonymous pseudonyms to further identify themselves to participate in the survey.
Owner:CRISTOFARO DAVID
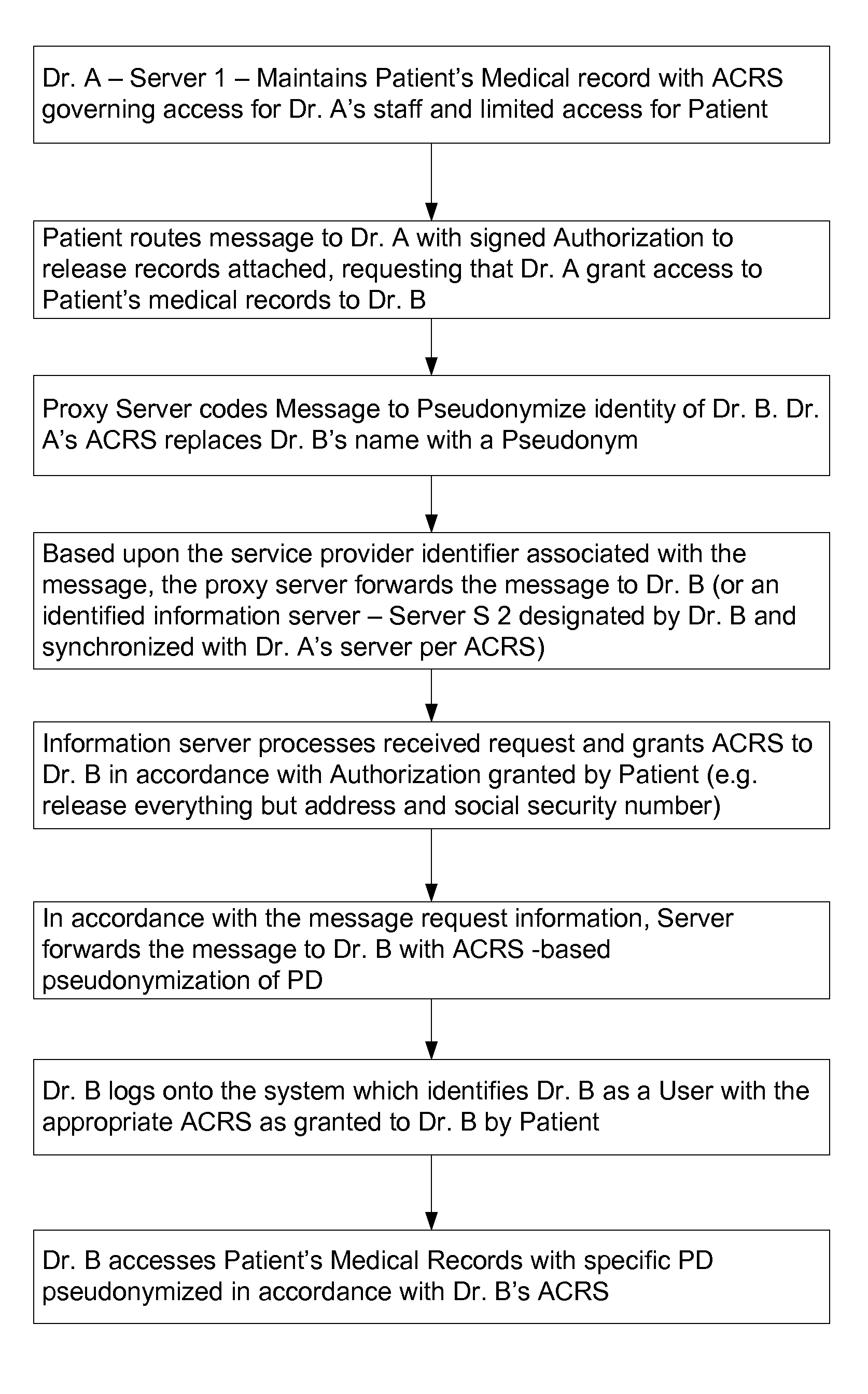
Use of proxy servers and pseudonymous transactions to maintain individual's privacy in the competitive business of maintaining personal history databases
InactiveUS7844717B2Protect data privacyPrivacy can be assuredComputer security arrangementsMultiple digital computer combinationsData accessProxy server
A system is provided that preserves data privacy for the Individual-I and Private Data Owner (PDO) while granting data access to the User-U and Accessor who need such data to perform their usual and customary business functions. The method and system completely control the User's access to the Private Data Owner's Private Data by replacing Identifying Information for the User-U, Individual-I, Accessor and PDO with pseudonyms. This assures the overall privacy of individuals, throughout the course of collecting, storing, accessing, analyzing and sharing detailed private records among different organizations engaged in providing and / or consuming services and / or products. Access Control Rule Sets (“ACRS”) consist of instructions which prescribe the terms and conditions for permitting Users to access the PDO's Pseudonymized and Actual Private data in accordance with the rules governing their authorization to access such data.
Owner:HERZ FREDERICK S M +2
Dynamic pseudonymization method for user data profiling networks and user data profiling network implementing the method
A users' data profiling network implementing a method of dynamic pseudonymization of users for ensuring user privacy, including: receiving at a data node new input data related to a user along with an associated new user pseudonym and an old user pseudonym; in the data node, finding user data record, corresponding to the received new input data, having stored therein a dynamic input user pseudonym equal to the old user pseudonym received together with the new input data or to one user pseudonym; temporarily storing, in the found user data record, the new input data; setting the dynamic input user pseudonym stored in the user data record equal to the last received new user pseudonym associated with the received input data related to the user; computing and storing an output user data profile in the user data record, and then erasing accumulated new input data from the user data record.
Owner:TELECOM ITALIA SPA
Computer implemented method for authenticating a user
ActiveUS20110154025A1Simplify the authentication processEfficient implementationKey distribution for secure communicationPublic key for secure communicationMethod selectionUser authentication
The invention relates to a computer implemented method for performing a user authentication, wherein an asymmetric cryptographic key pair is associated with the user, said key pair comprising a public key and a private key, wherein the method comprises selecting the user to be authenticated using a pseudonym of said user, wherein said pseudonym comprises the public key of the user, the method further comprising performing a cryptographic authentication of the user using the asymmetric cryptographic key pair.
Owner:SPALKA ADRIAN +1
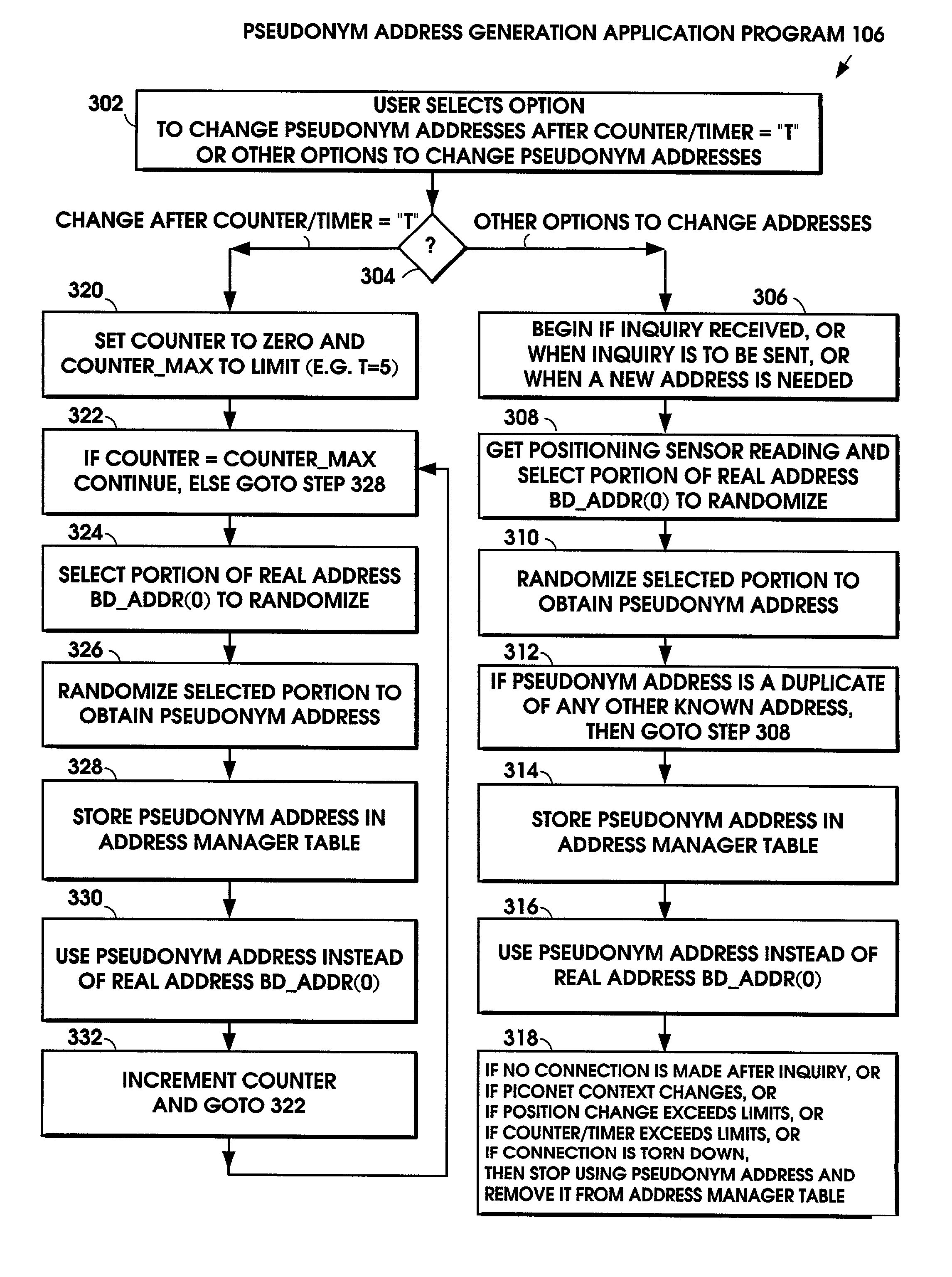
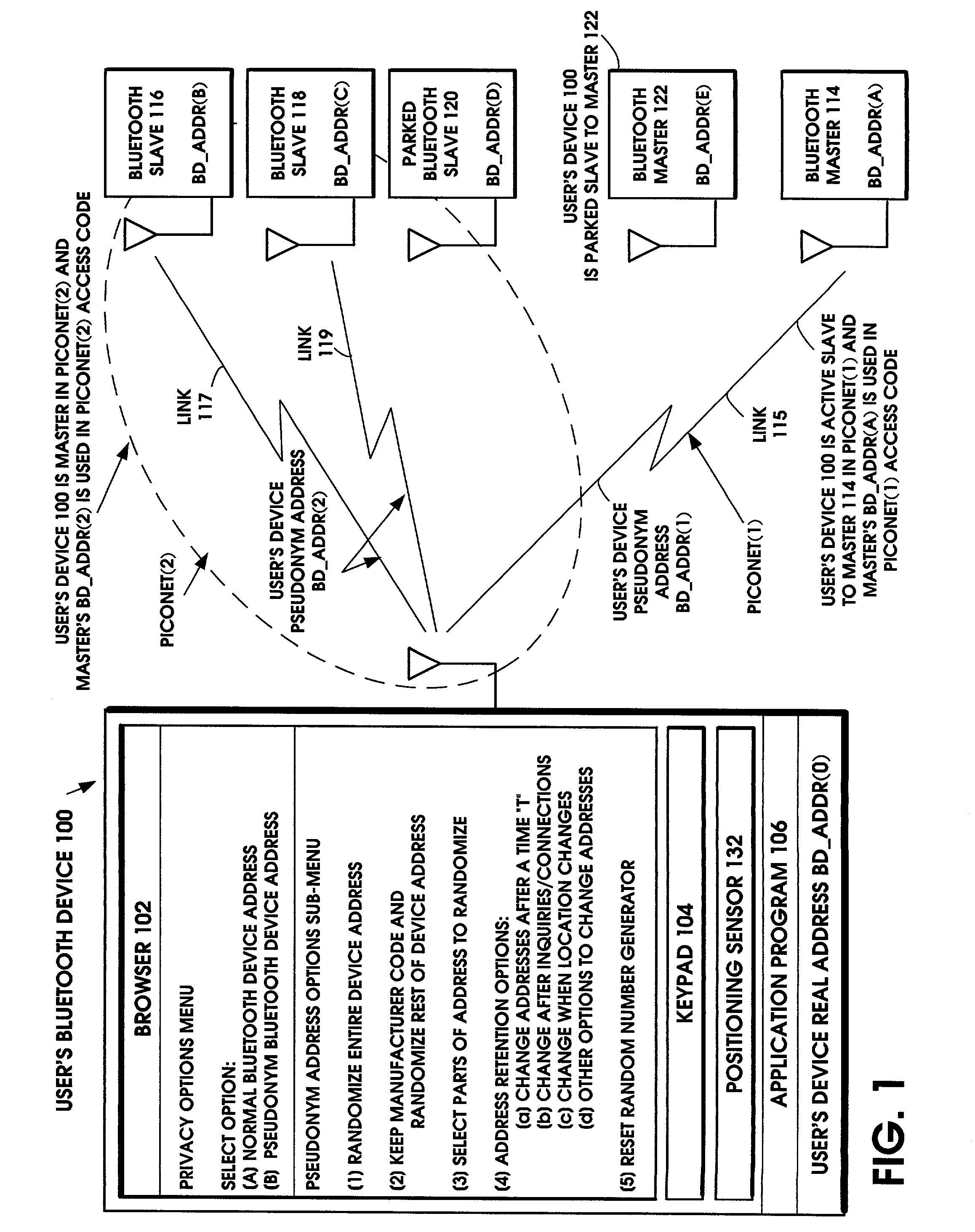
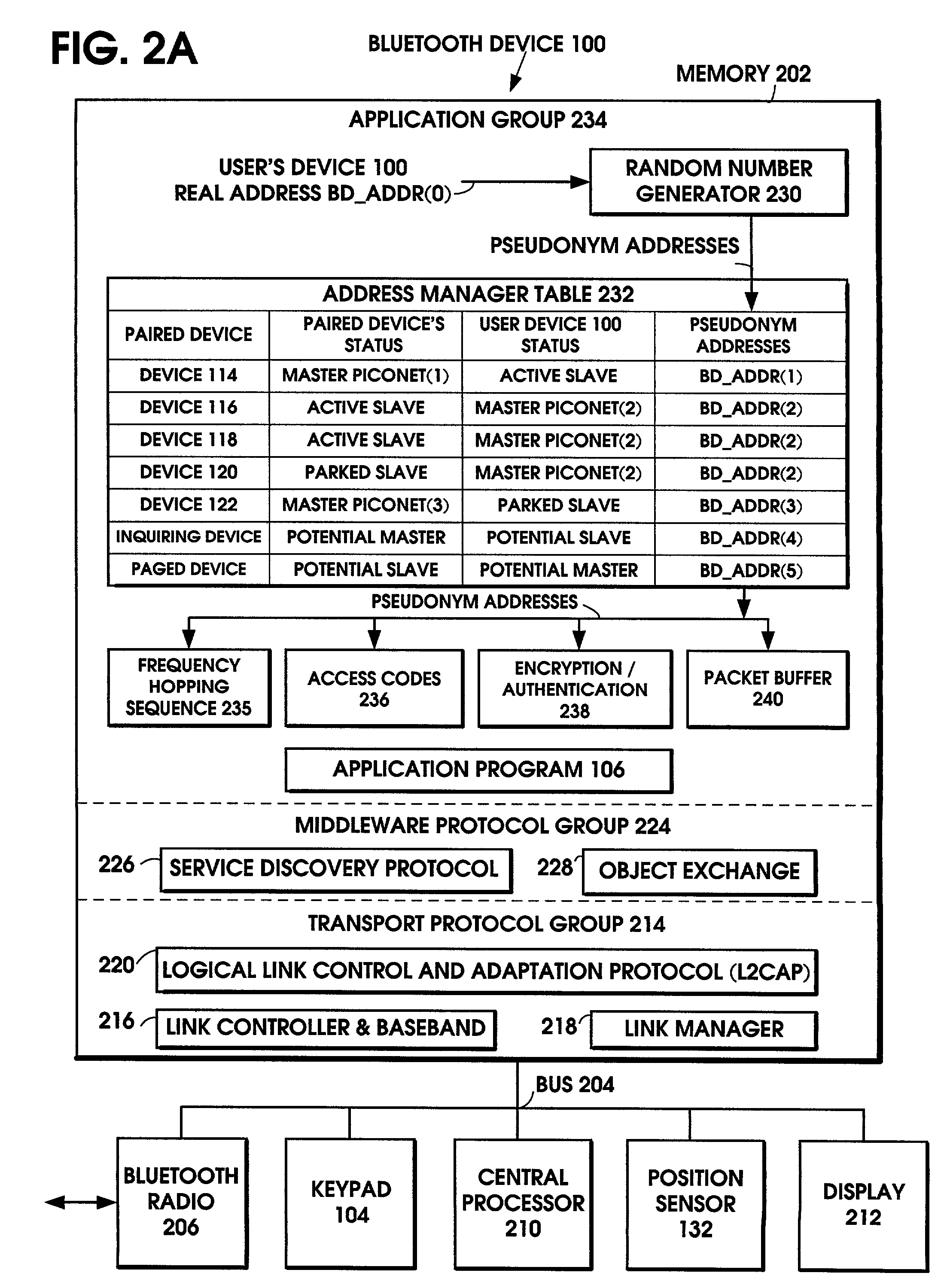
Method for protecting privacy when using a Bluetooth device
InactiveUS7194760B2Privacy protectionDigital data processing detailsNetwork topologiesComputer hardwareBluetooth
The user's Bluetooth device substitutes a pseudonym address for the Bluetooth Device Address (BD_ADDR). The pseudonym address is a randomized version of the BD_ADDR. The pseudonym address is used in all the functions of the Bluetooth device that normally use the BD_ADDR, including the frequency hopping sequence, the device access code, the initialization key in link encryption, the authentication code, and the various packet addresses. In this manner, the user's privacy is protected by preventing the user's identity, routes, and activities from being correlated with his / her device's address. In addition to the Bluetooth standard, the technique also applies to other wireless standards.
Owner:NOKIA TECHNOLOGLES OY
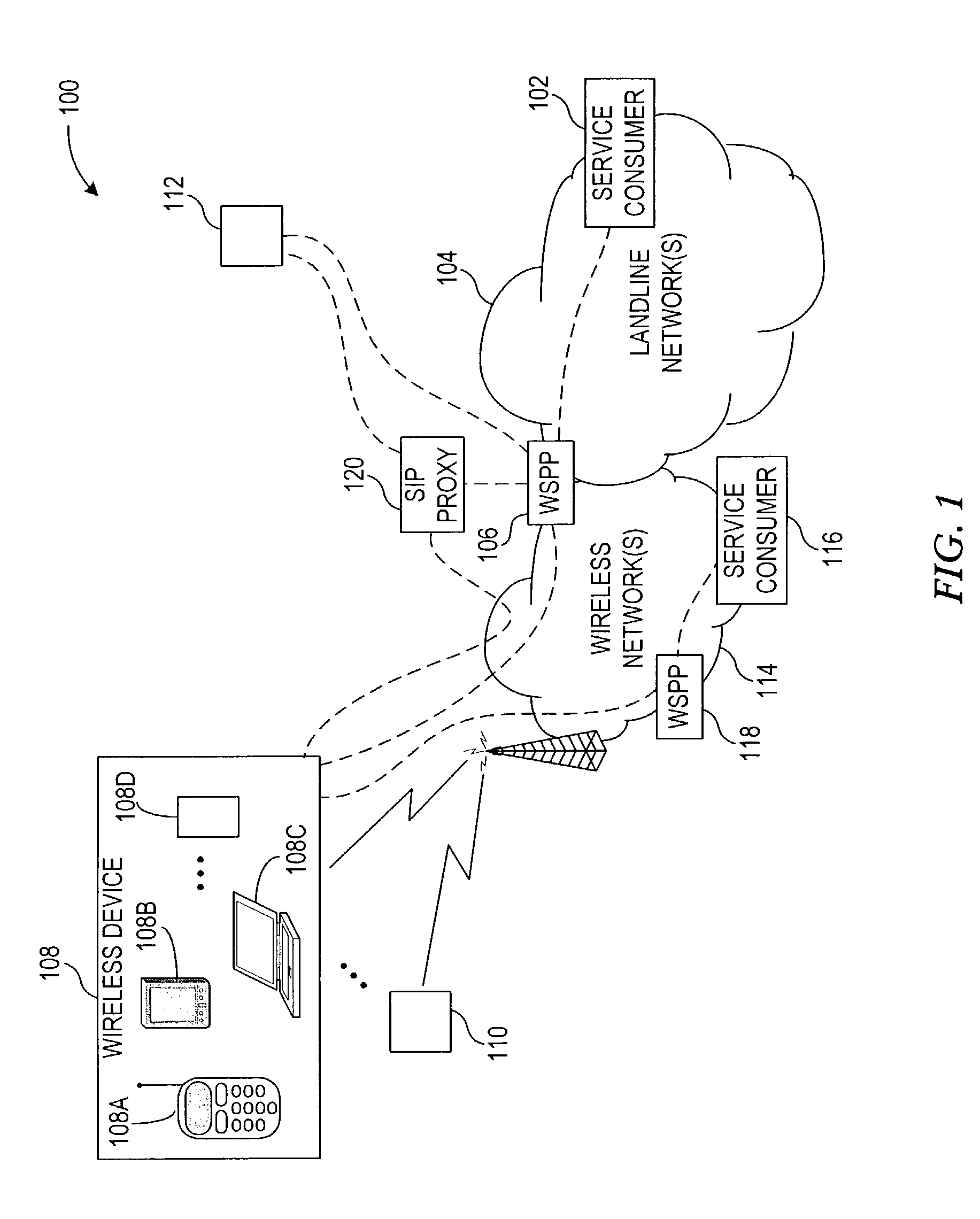
System and method for addressing networked terminals via pseudonym translation
A system, apparatus, and method for performing terminal address translation, and more particularly for identifying addresses of mobile terminals in a mobile network in order to communicate messages with the mobile terminals. Messages are received from a service consumer at a pseudonymity proxy operable within the mobile network, where the message includes an information exchange message including a pseudonym locally identifying a target mobile terminal. The pseudonym is translated into an address of the target mobile terminal unknown to the service consumer. The information exchange message is forwarded from the pseudonymity proxy to the address of the target mobile terminal.
Owner:RPX CORP
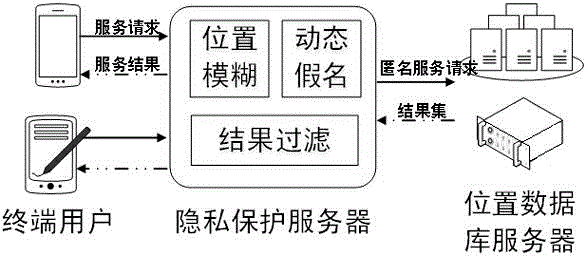
Method and system for protecting location service privacy based on grid density
ActiveCN104618896AReduce risk of leakageAchieve controllable and adjustable privacy protectionLocation information based serviceSecurity arrangementGrid densityPrivacy protection
The invention discloses method and system for protecting location service privacy based on grid density. The method comprises the steps of receiving a location query request of a user through a privacy protection server; creating and maintaining a user state table and a block information table based on a grid density model through the privacy protection server; finding out k adjacent cell covering the user as a location fuzzy area by the grid-based minimum inclusion region; assigning a pseudonym to the query request of the user; exchanging the pseudonyms of adjacent high-risk users according to the trajectory privacy measurement; transmitting the query request to a location service supplier server; filtering and returning the obtained query result to the query user.
Owner:SHANGHAI JIAO TONG UNIV +1
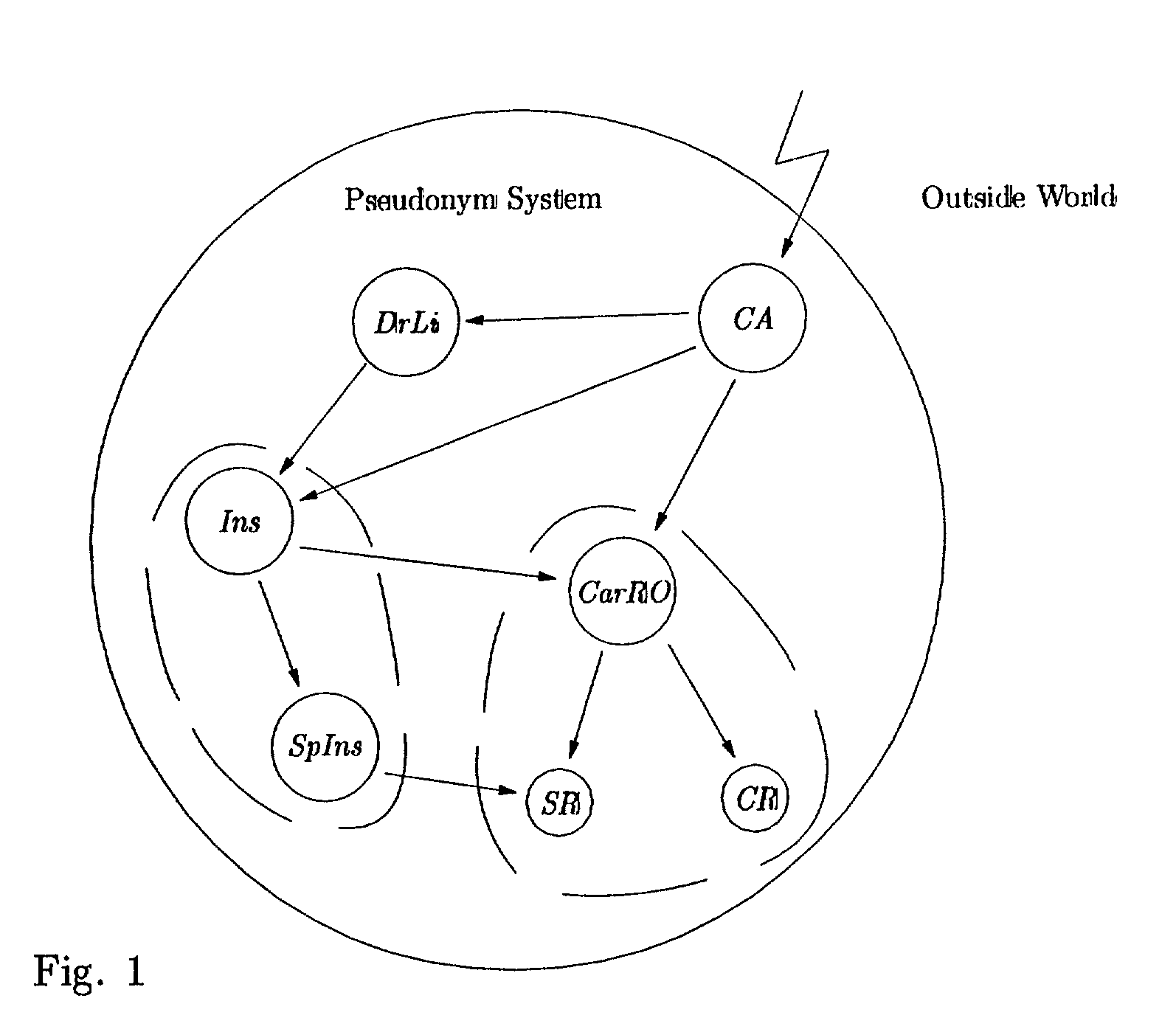
Non-transferable anonymous credential system with optional anonymity revocation
InactiveUS7360080B2SpeedUser identity/authority verificationAnonymous user systemsAnonymity revocationPseudonymity
The present invention relates to a method and system for securely proving ownership of pseudonymous or anonymous electronic credentials. A credential system is described consisting of users and organizations. An organization knows a user only by a pseudonym. The pseudonyms of the same user, established for use with different organizations, cannot be linked. An organization can issue a credential to a pseudonym, and the corresponding user can prove possession of this credential to another organization that knows him under another pseudonym. During the prove of possession of the credential nothing besides the fact that he owns such a credential is revealed. A refinement of the credential system provides credentials for unlimited use, so called multiple-show credentials, and credentials for one-time use, so called one-show credentials.
Owner:GOOGLE LLC
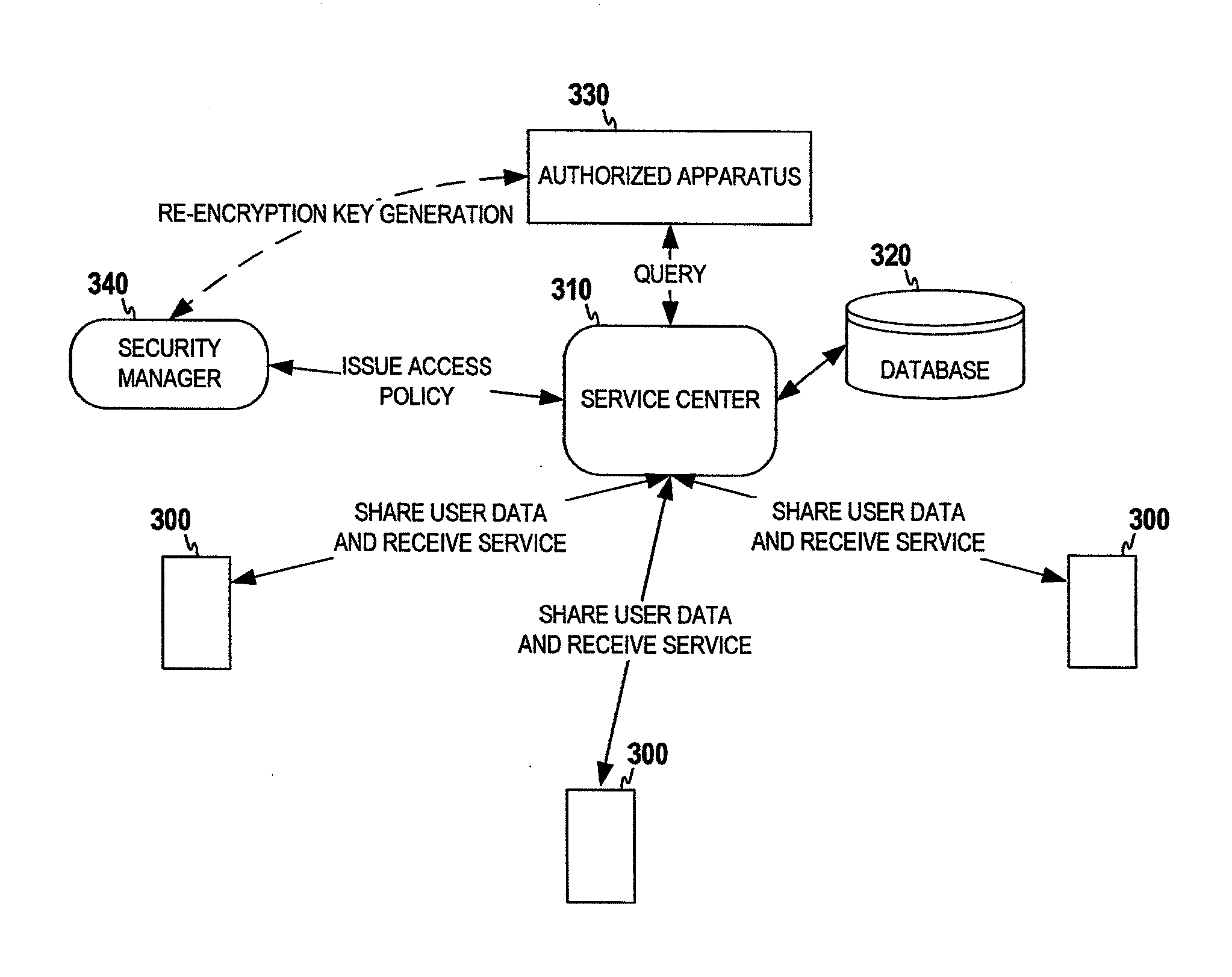
Preservation of User Data Privacy in a Network
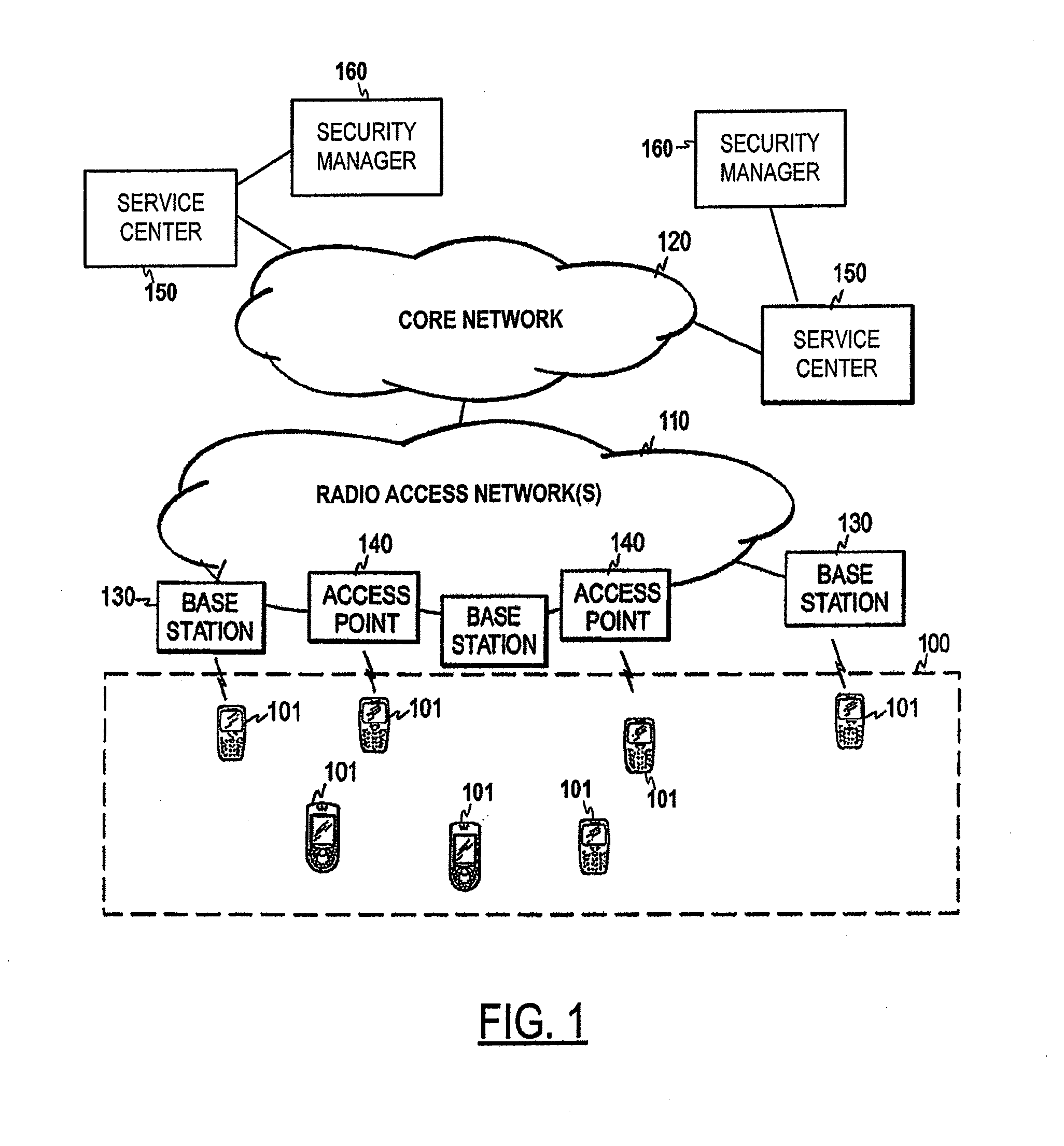
ActiveUS20120239942A1Privacy protectionLow costUnauthorized memory use protectionHardware monitoringProxy re-encryptionEncryption
An example apparatus is provided that receives a pseudonym and encrypted identifier, where the pseudonym is of a user's personal data. The pseudonym has been generated using a first secret key, and the encrypted identifier has been generated by encrypting the identifier using a second secret key. The first and second secret keys are known to other user(s) authorized to access the data, and are unknown to the apparatus. The operations also include storing the personal data in a database under the pseudonym, and indexed by the encrypted identifier. The keys used for encryption and pseudorandom generation can be provided by a second apparatus (e.g. an offline security manager), which may employ a proxy re-encryption scheme to provide proper keys to the apparatus based on access policies. Only the authorized users can decrypt the keys with their private keys, thus can query the user records stored in the apparatus.
Owner:NOKIA TECHNOLOGLES OY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com