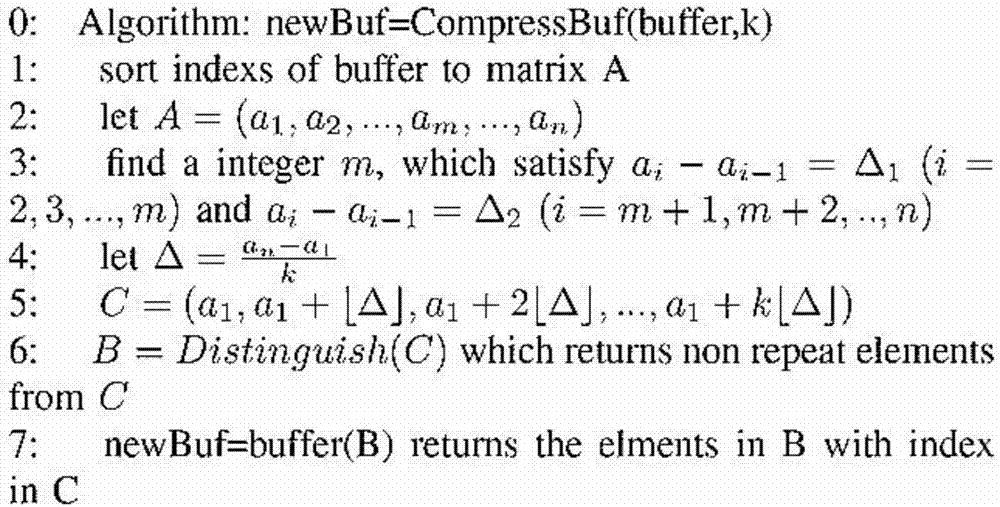Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
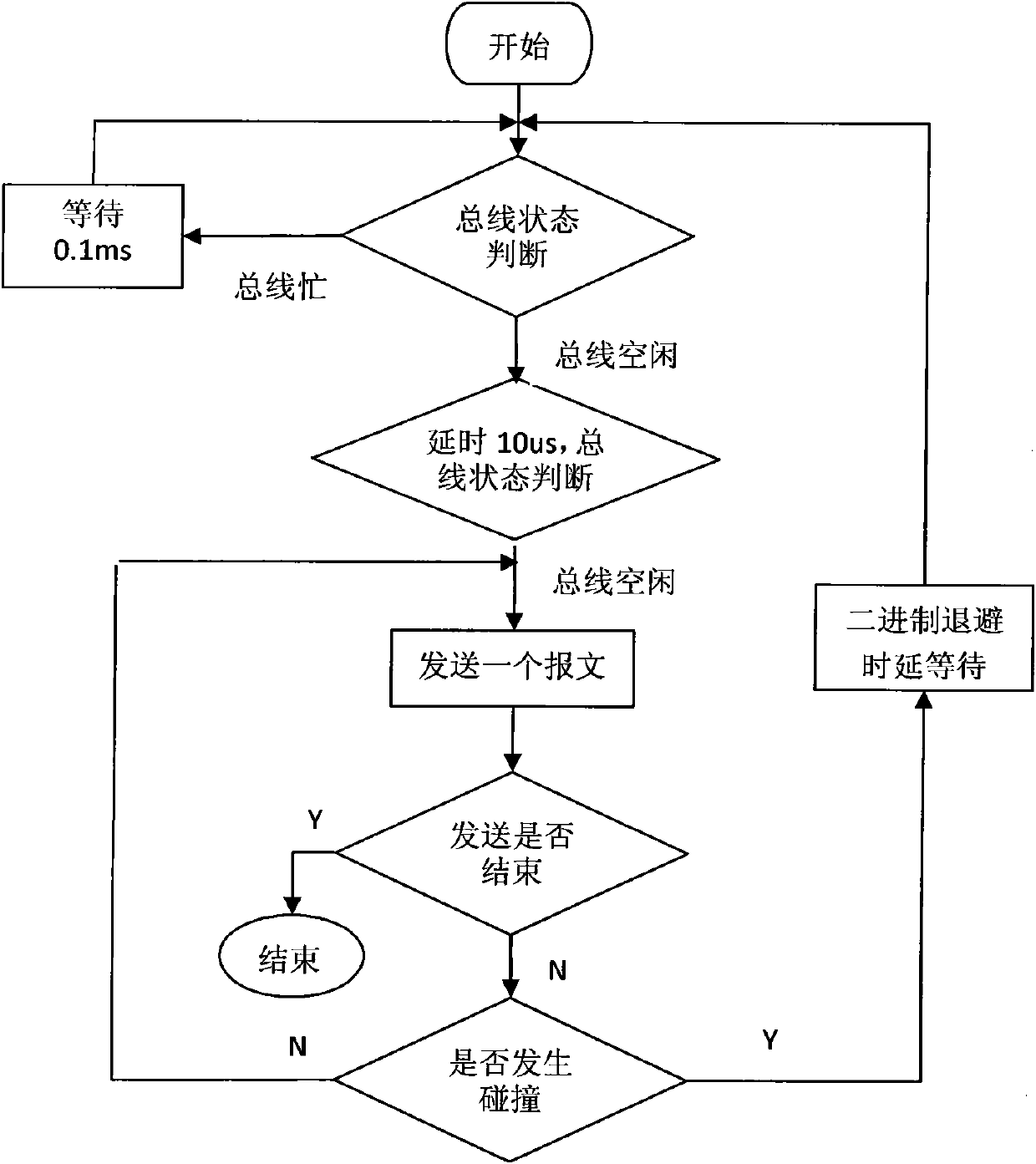
34 results about "Exponential backoff" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Exponential backoff is an algorithm that uses feedback to multiplicatively decrease the rate of some process, in order to gradually find an acceptable rate.
Modified backoff mechanism for wireless networks
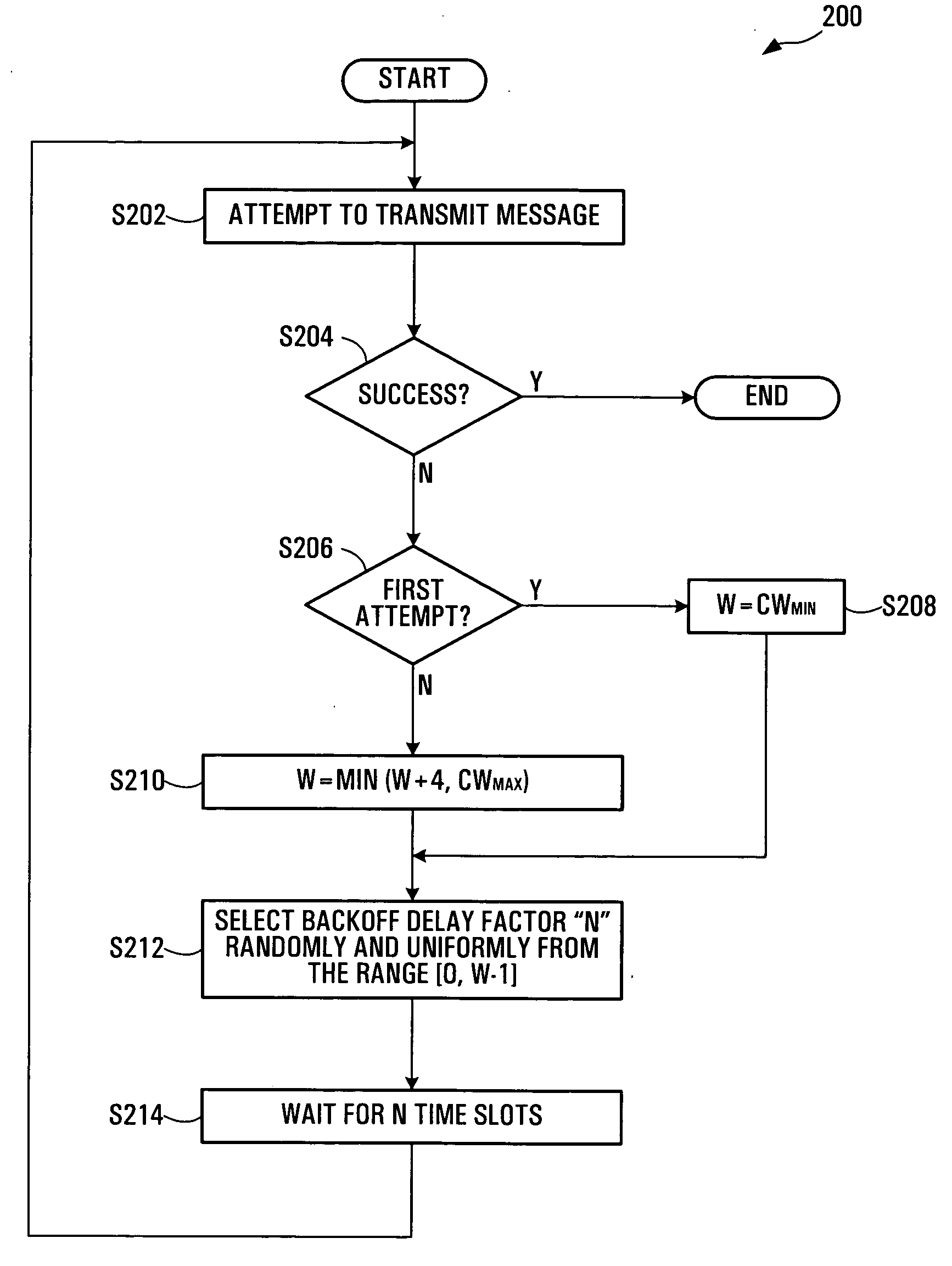
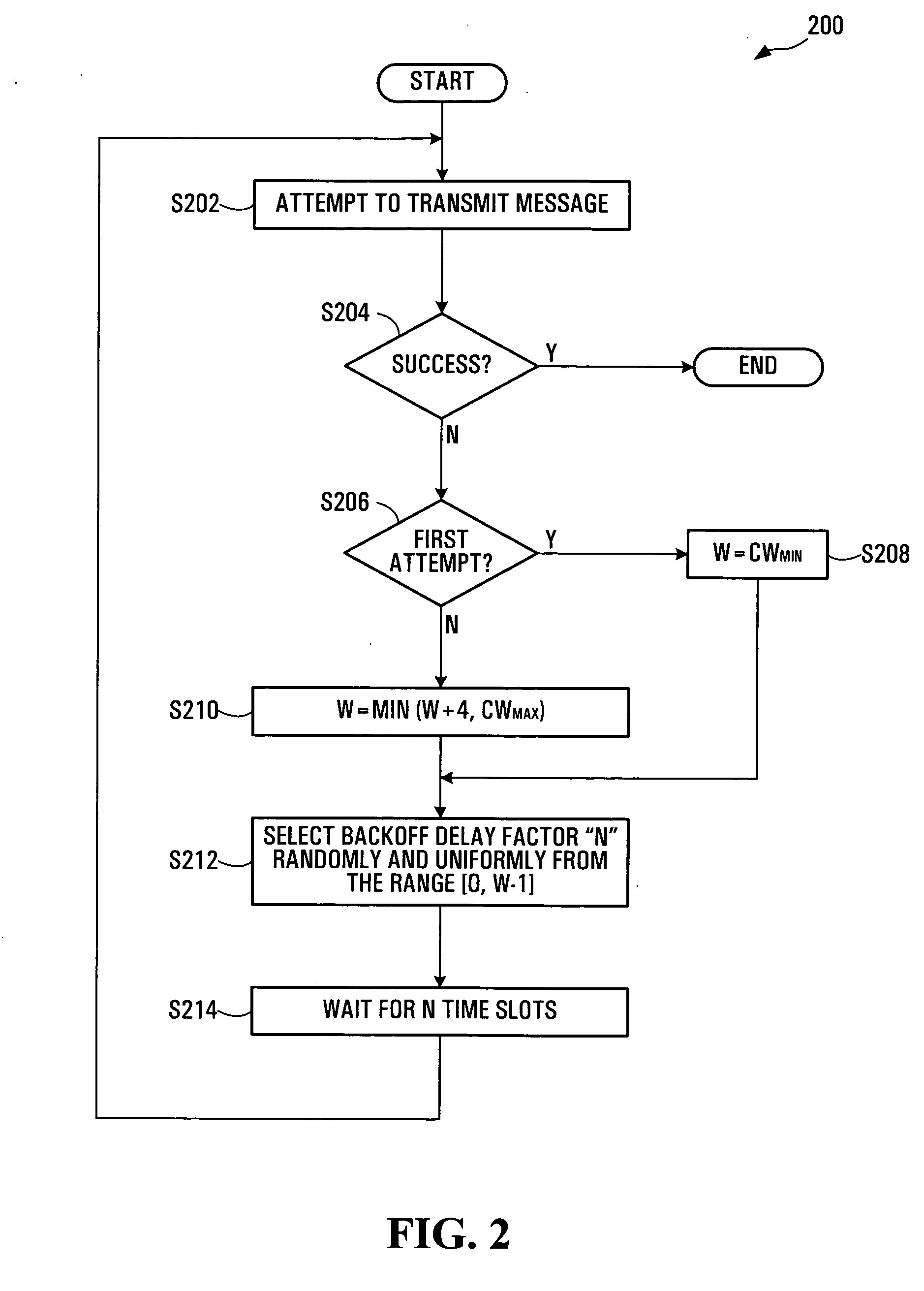
InactiveUS20060034208A1Increase in sizeError preventionNetwork traffic/resource managementDelay periodsTime segment
In a scheme for accessing a wireless network, a backoff delay time period representing a duration of time that is to elapse before a station is permitted to attempt a retransmission is selected from a group of delay periods. The group of delay periods grows at a rate that is less than exponentially (e.g. linearly) based on the number of attempted retransmissions. Selection of the backoff delay time period may entail random selection of an integer N from a contention window and multiplication of N by a slot time duration. The contention window may be a range of integers [0, W-1]. The contention window size W may be initialized to a predetermined minimum value upon a first attempted transmission and may be capped at a predetermined maximum value. Average backoff delay may be reduced in comparison to a binary exponential backoff approach.
Owner:NORTEL NETWORKS LTD
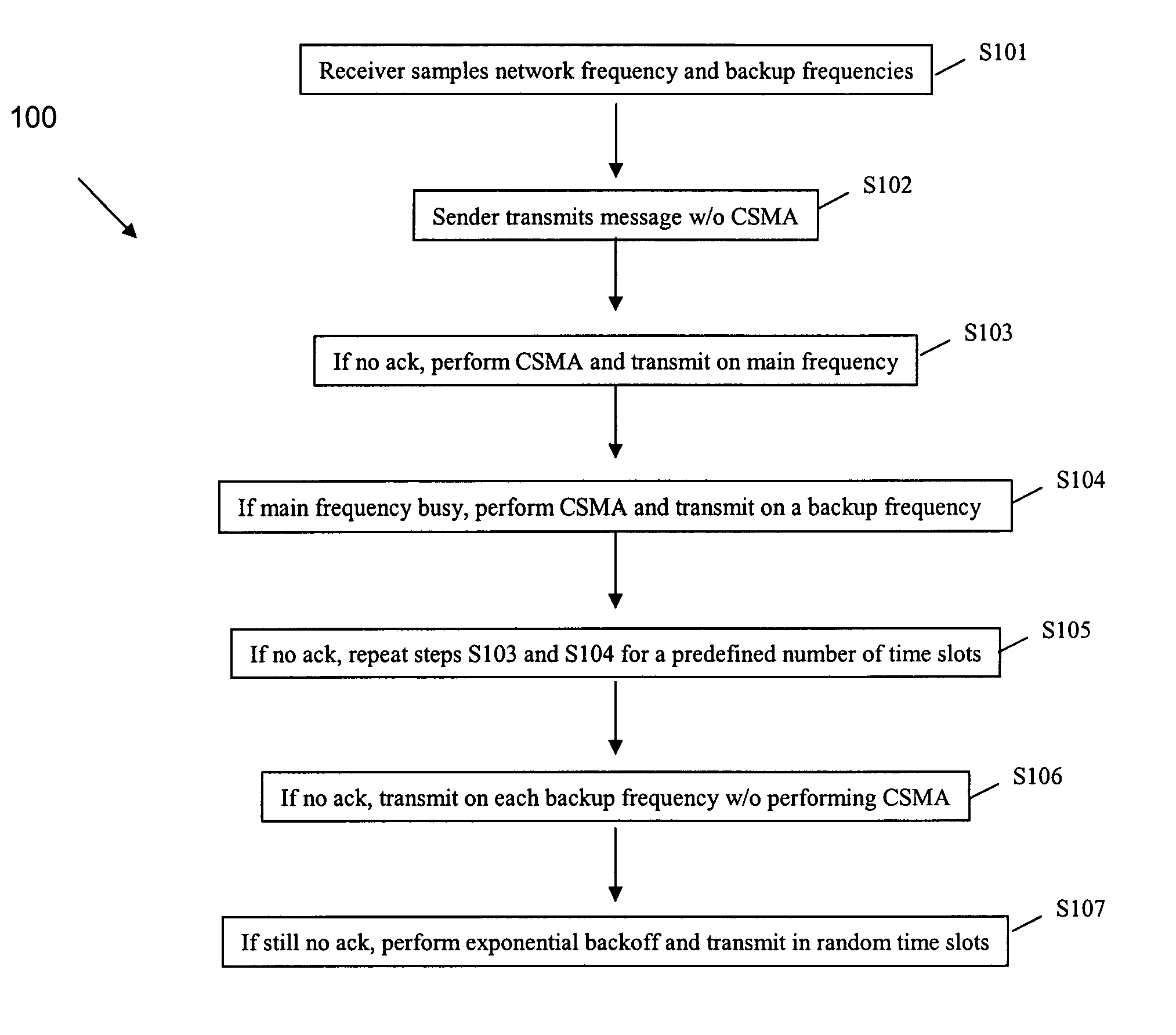
Method and system for reliable data transmission in wireless networks
ActiveUS20070076745A1Improve coordinationReduce delaysError preventionFrequency-division multiplexExponential backoffRemote data transmission
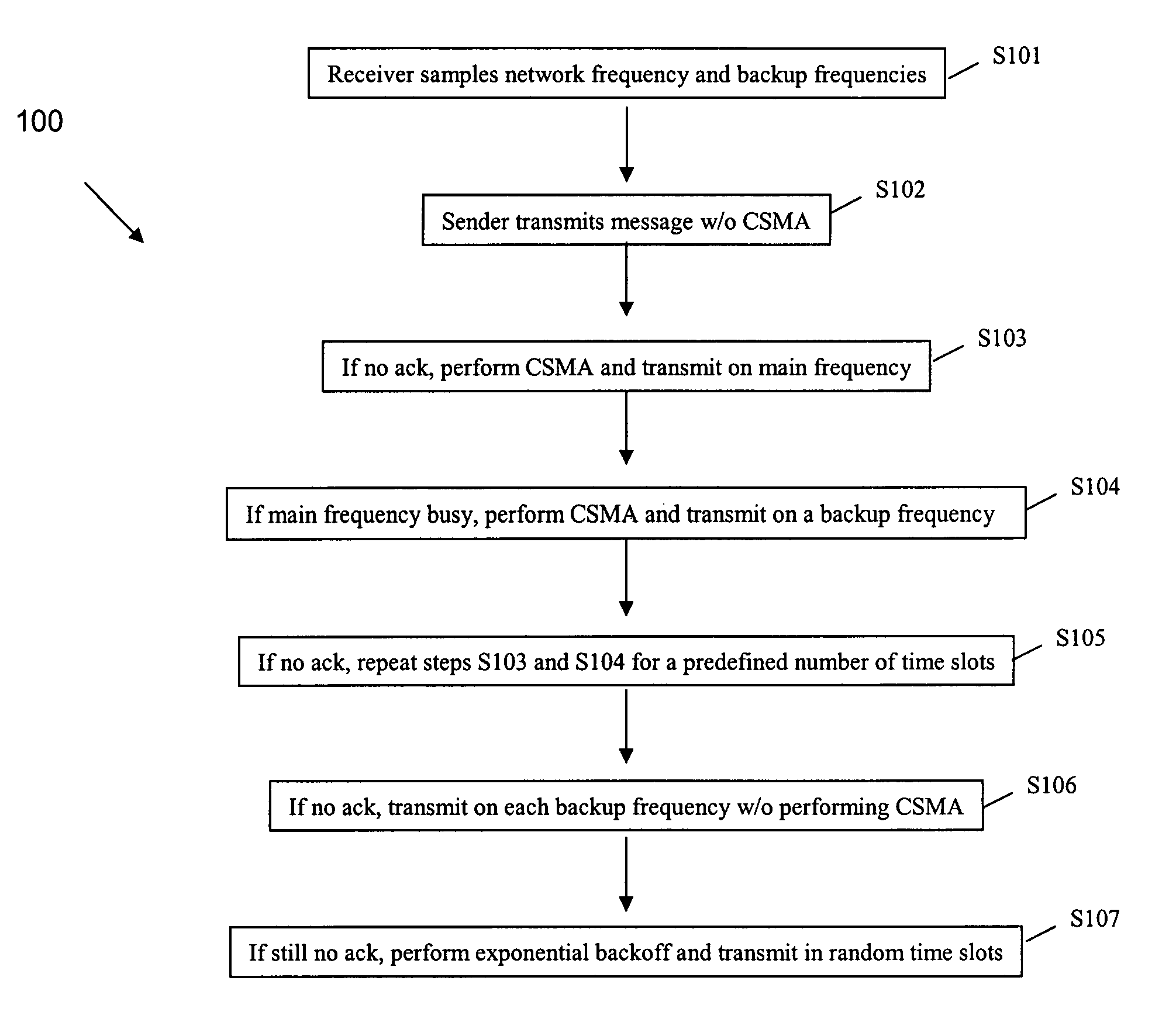
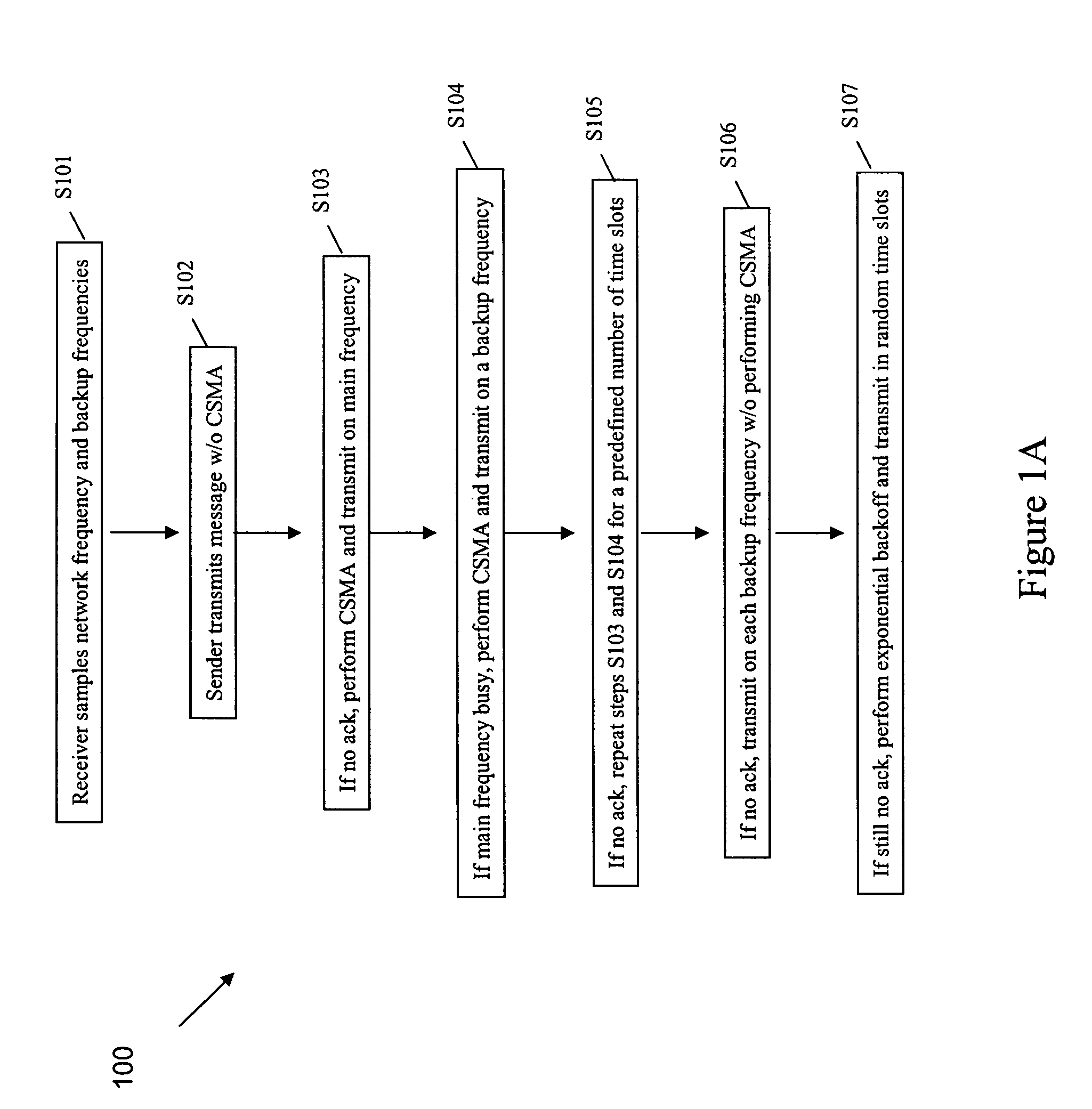
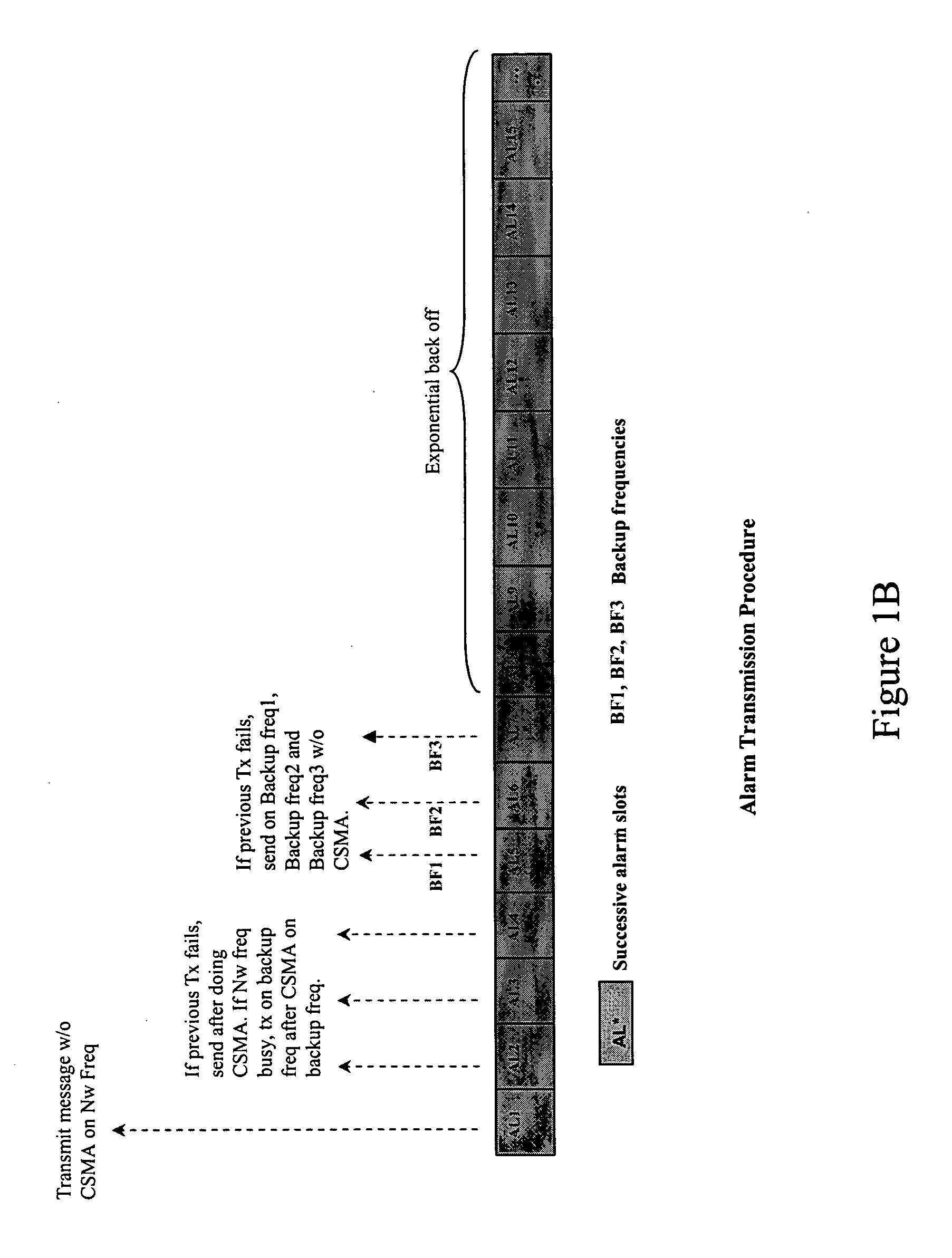
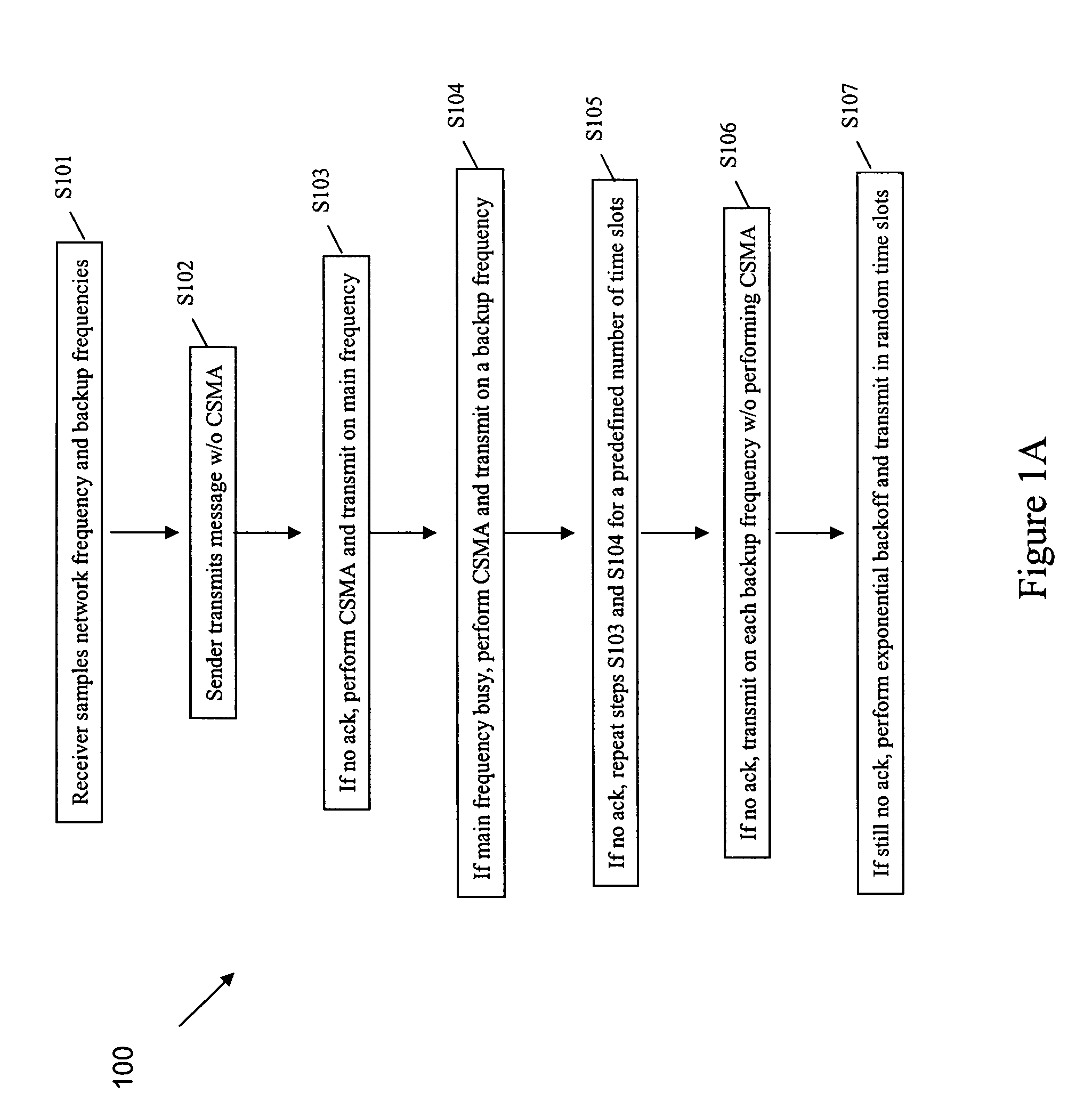
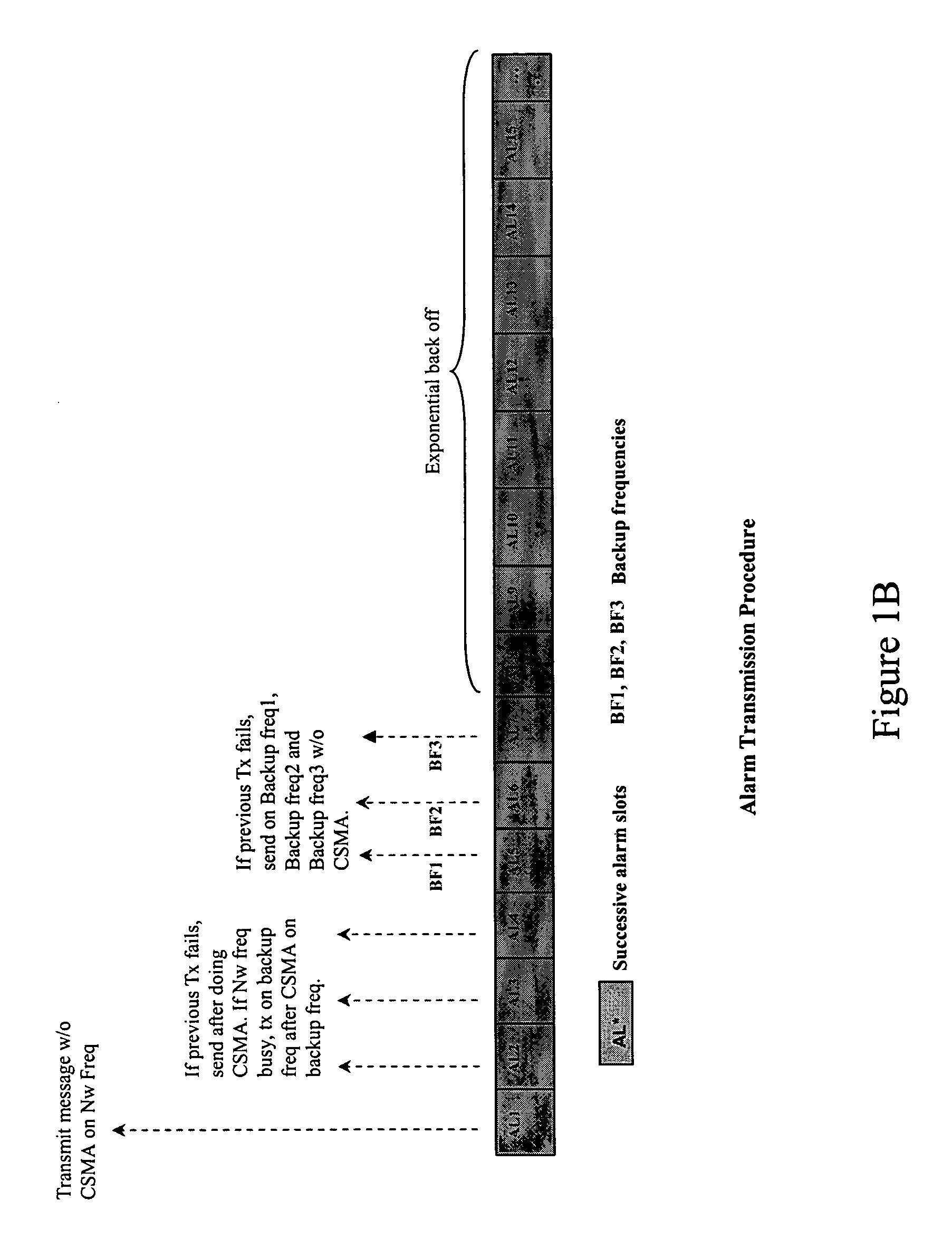
A method for transmitting data from a sender node from among at least one sender node to a receiver node in a wireless network, the method including (a) sampling, by the receiver node, in each time slot, a main network frequency and at least one backup frequency, (b) transmitting, by the sender node, a message on the main network frequency in a first time slot, without using a multiple access protocol, (c) transmitting, by the sender node, the message on the main network frequency in a next time slot, using the multiple access protocol exchange, if an acknowledgement of the message is not received from the receiver node, (d) transmitting, by the sender node, the message on at least one backup frequency in the next time slot, using a multiple access protocol, if the main network frequency is busy after performing step (c), (e) repeating steps (c) and (d) for a predefined number of time slots, unless or until an acknowledgement is received from the receiver node, (f) transmitting, by the sender node, the message on each backup frequency, using the multiple access protocol, unless or until an acknowledgment is received from the receiver node, and (g) performing an exponential backoff and subsequent transmission of the message, by the sender node, if an acknowledgement is still not received from the receiver node after performing steps (a) through (f)
Owner:ROBERT BOSCH GMBH
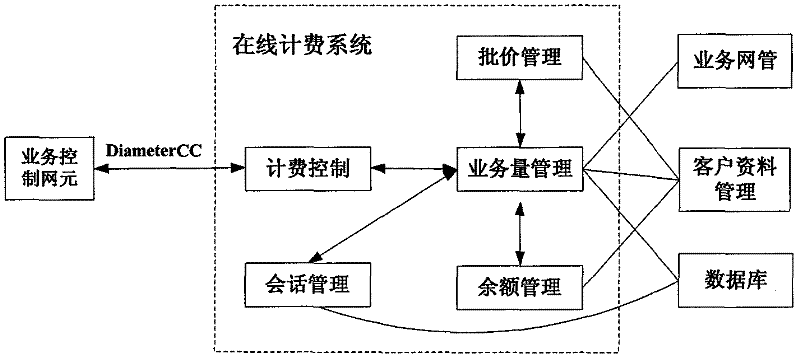
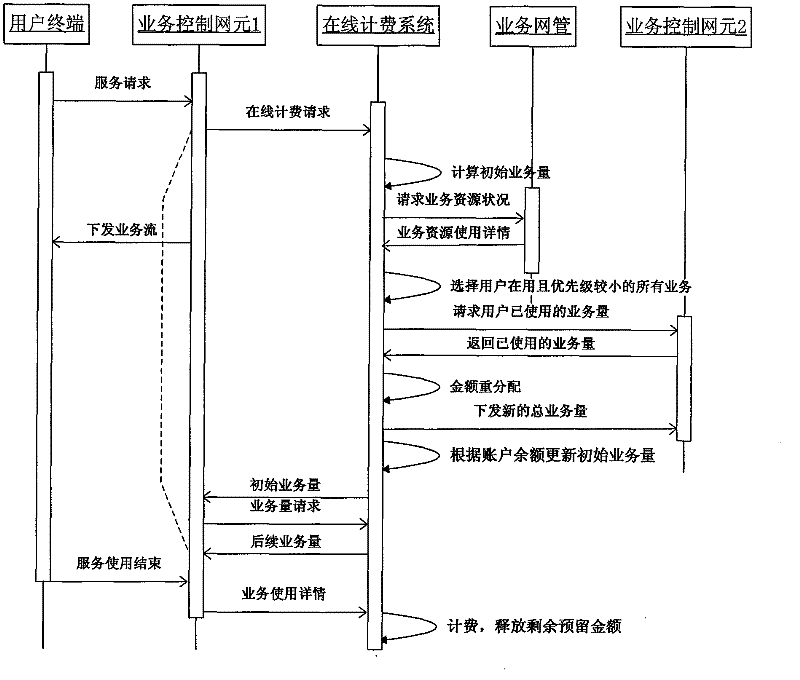
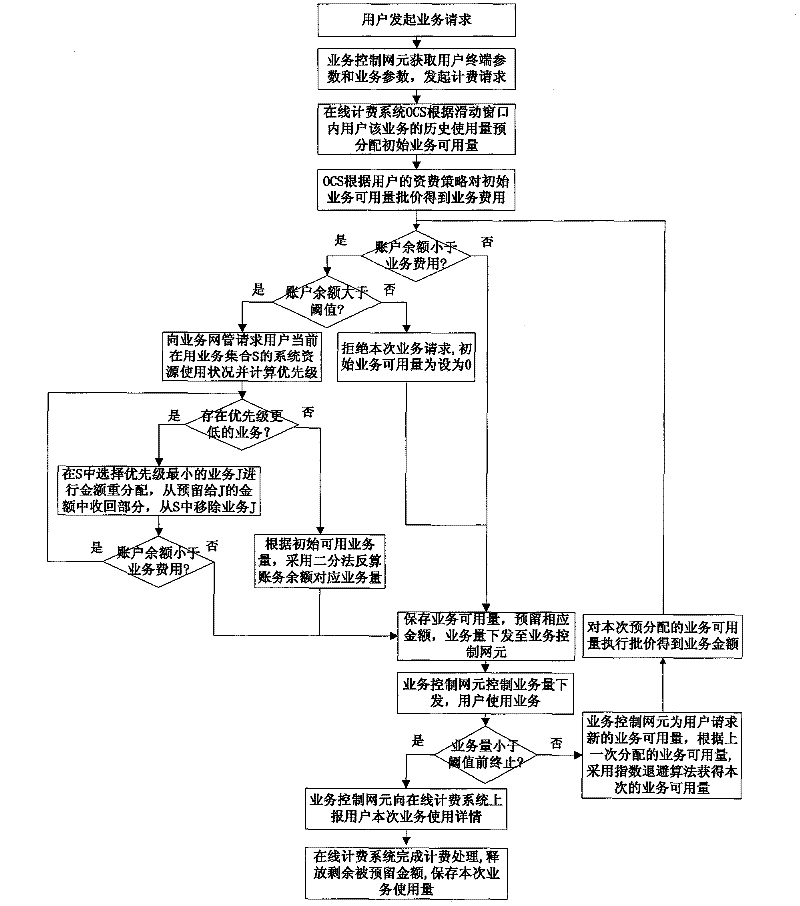
Online billing method and system based on user traffic volume
InactiveCN101645782AReduce the number of expected interactionsIncrease profitMetering/charging/biilling arrangementsAccounting/billing servicesInteraction timeComputation complexity
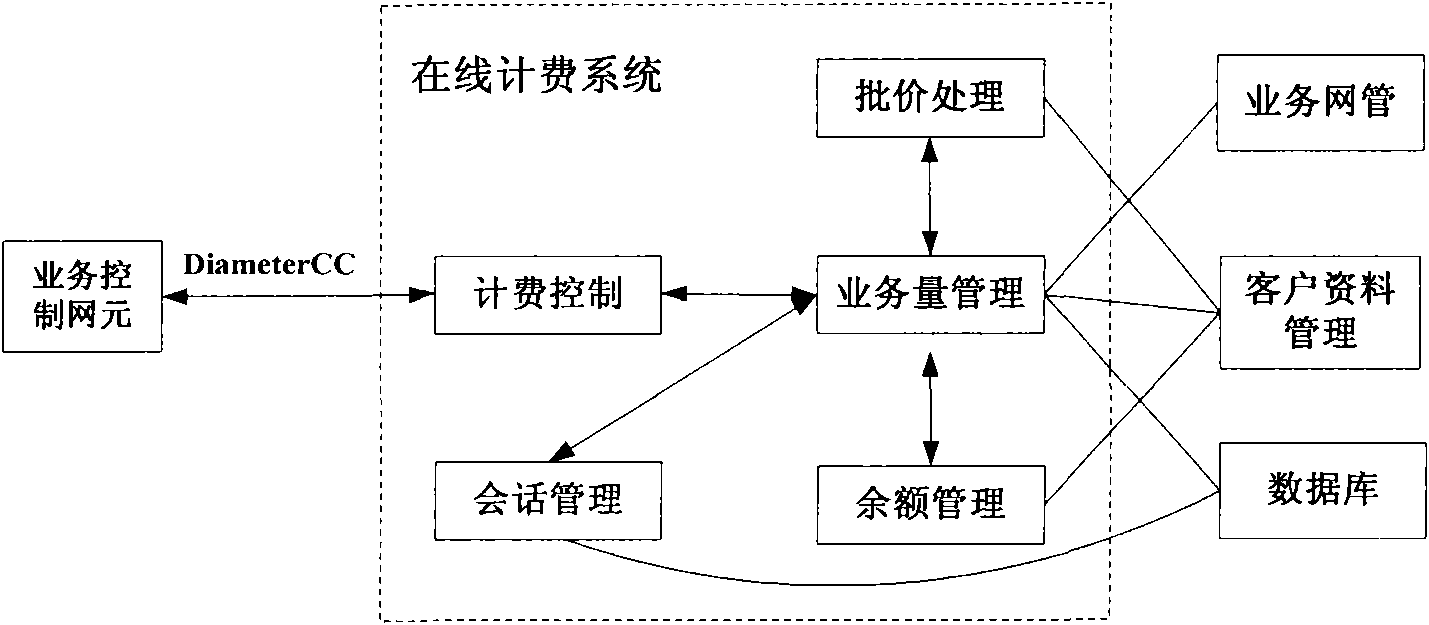
The invention provides an online billing method and a system based on user traffic volume. The online billing method is applied in a business operation support system, and the online billing method adopts the using frequency sliding window technology, pre-distributes usable traffic volume based on historical using amount of user business, realizes the function of online billing, reduces the repeattimes from amount to the usable traffic volume during the online billing process and improves the billing efficiency, thereby leading the distributed initial traffic volume to be in line with the using habits of a user as far as possible, reducing the expected interaction times between a business control network element and the online billing system during the online billing process to a constantand reducing the concurrent pressure of the online billing system. The usable volume of the follow-up business in the conversation is computed by adopting the exponential backoff algorithm with a threshold, thereby reducing computational complexity; and balances of pre-reserved accounts are re-distributed according to the using status of system resources of various businesses in a business system, thereby improving the utilization rate of idle business resources. The method can be directly applied in the existing online billing system and have higher application values.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI
Adaptive carrier sense multiple access (CSMA)/conditional access (CA) method based on institute of electrical and electronics engineers (IEEE)802.15.4
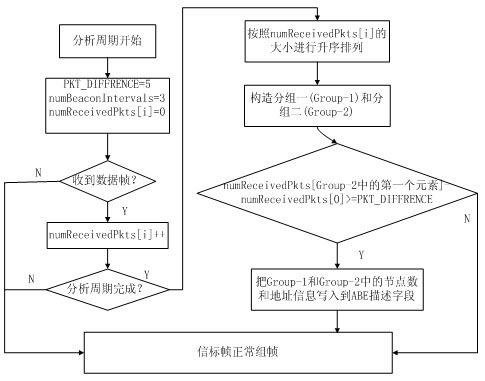
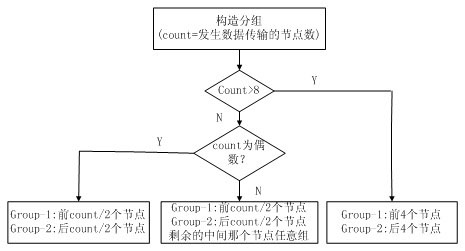
ActiveCN102595648AImprove fairnessImprove throughputNetwork topologiesWireless network protocolsBeacon frameNetwork conditions
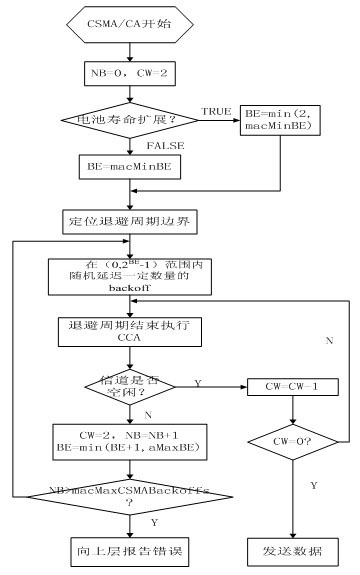
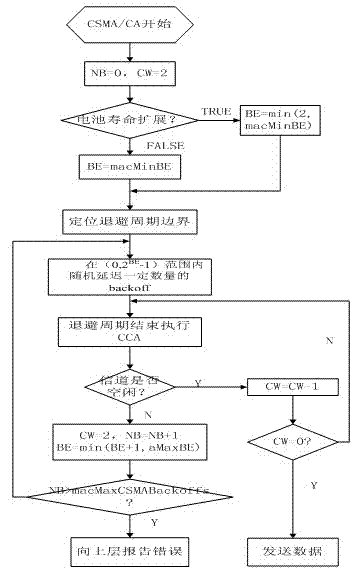
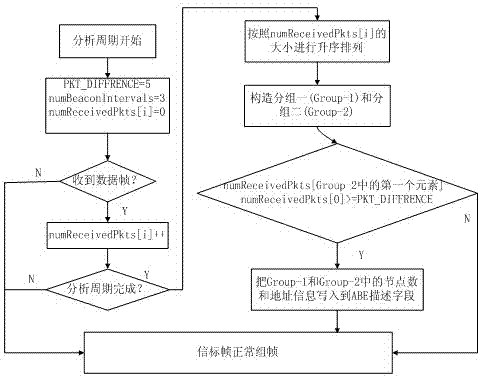
The invention relates to a carrier sense multiple access (CSMA) / conditional access (CA) mechanism optimization method in a new institute of electrical and electronics engineers (IEEE)802.15.4 standard. An analysis stage, a determination stage and an execution stage are involved. An initial value of macMinBE in the CSMA / CA is retained, but the backoff index macMinBE is dynamically adjusted according to contention network flow of each node in a certain number of beacon frame intervals, so that a proper backoff range can be dynamically selected by a sensor node according to the condition of a network. Due to optimization, macMinBE can reflect the current network condition accurately, and network use rights among the nodes are balanced. Therefore, the network justice of the nodes is improved, the network throughput is increased, and the network load is reduced. A simulation result shows that: compared with the conventional binary exponential backoff (BEB) algorithm in the IEEE802.15.4, the optimization method for a BEB algorithm with adaptive adjustment capacity has the advantage that under the condition that the network input service amount is relatively large, the network throughput is increased obviously, and the network working load is reduced.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
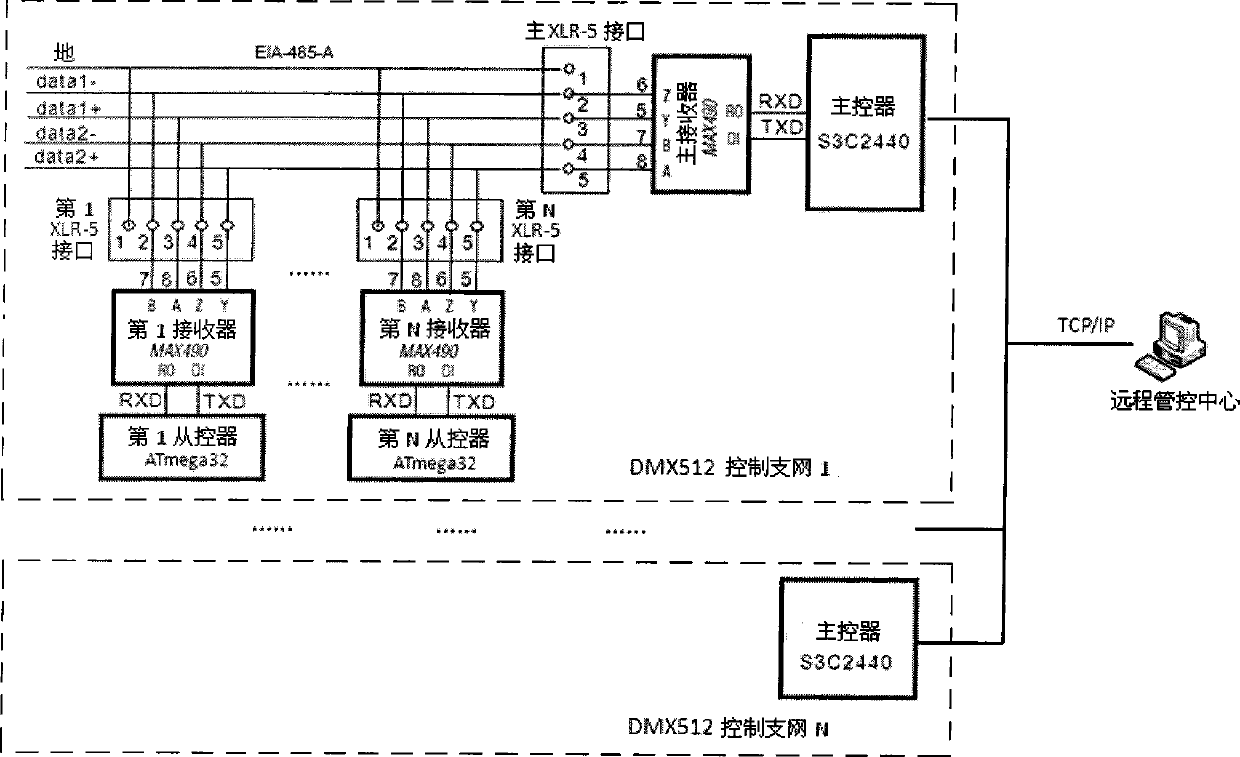
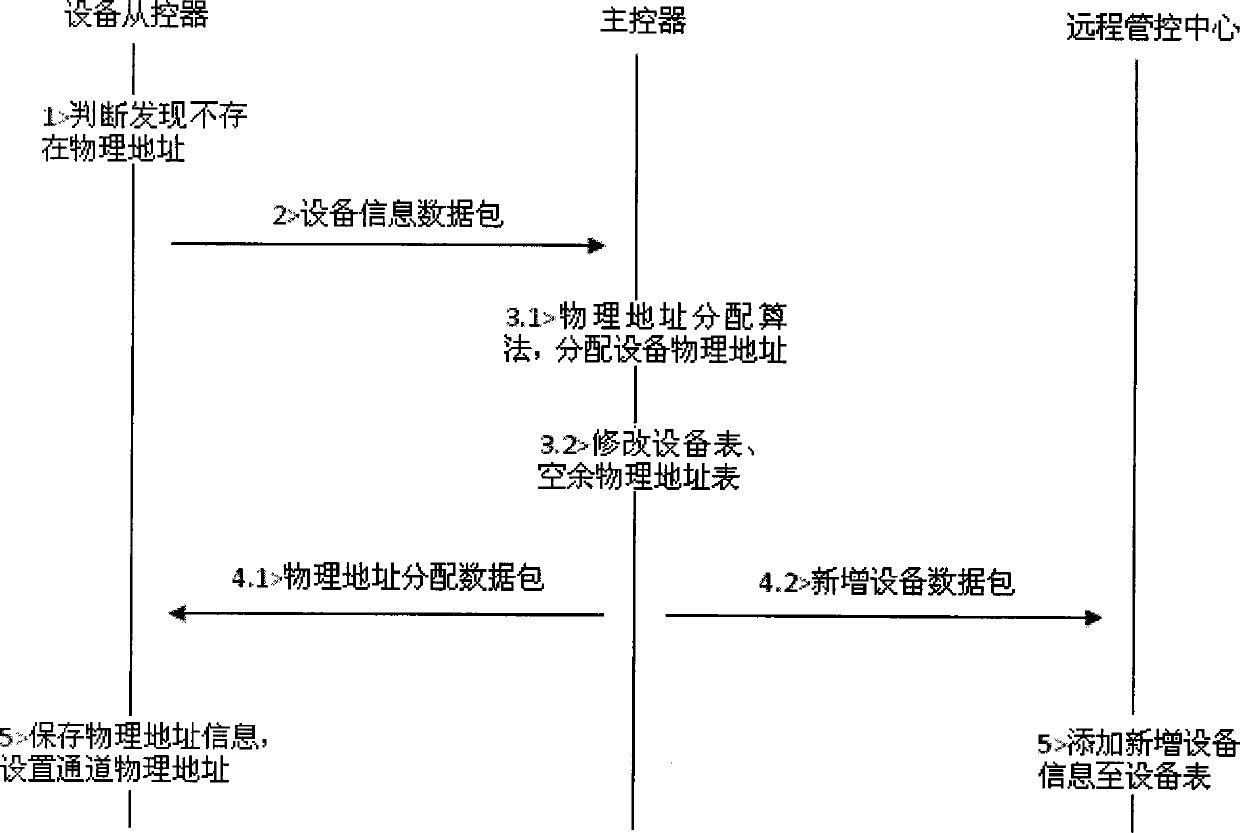
Automatic equipment identification and maintenance supported DMX512 (Digital Multiplex 512) landscape lighting control system and method
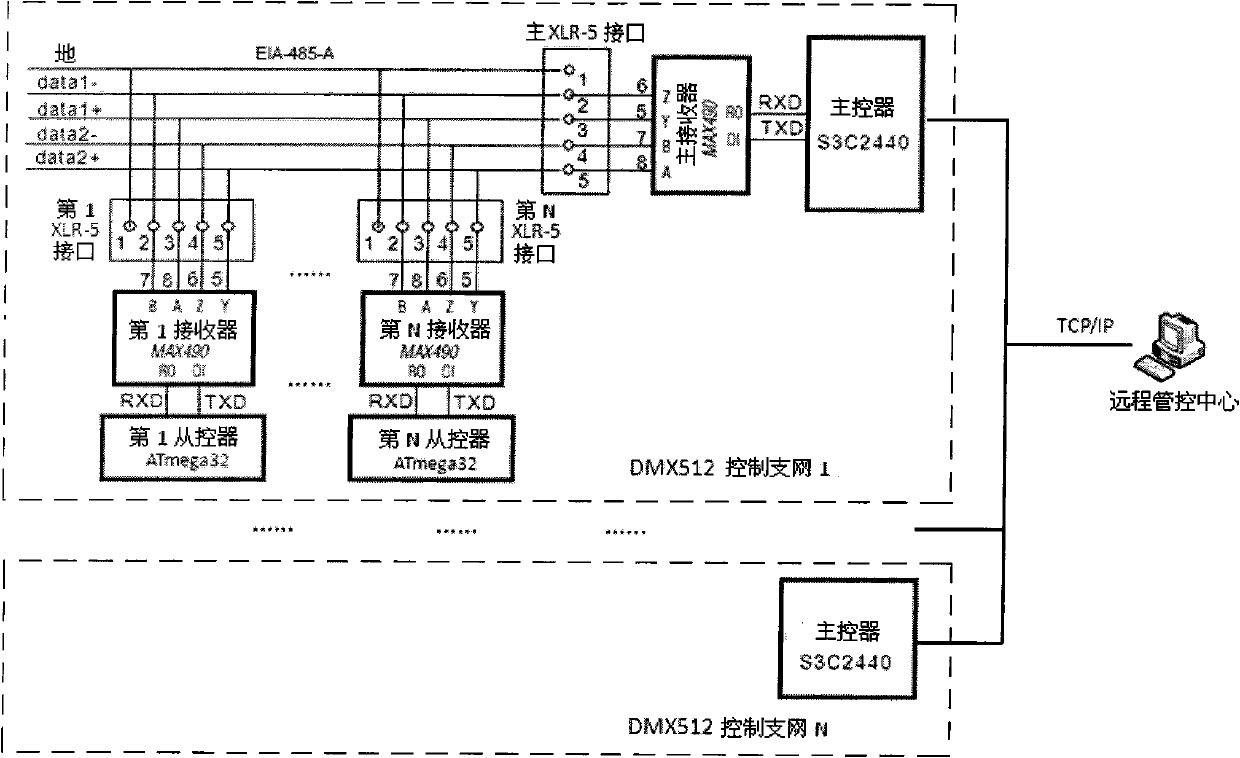
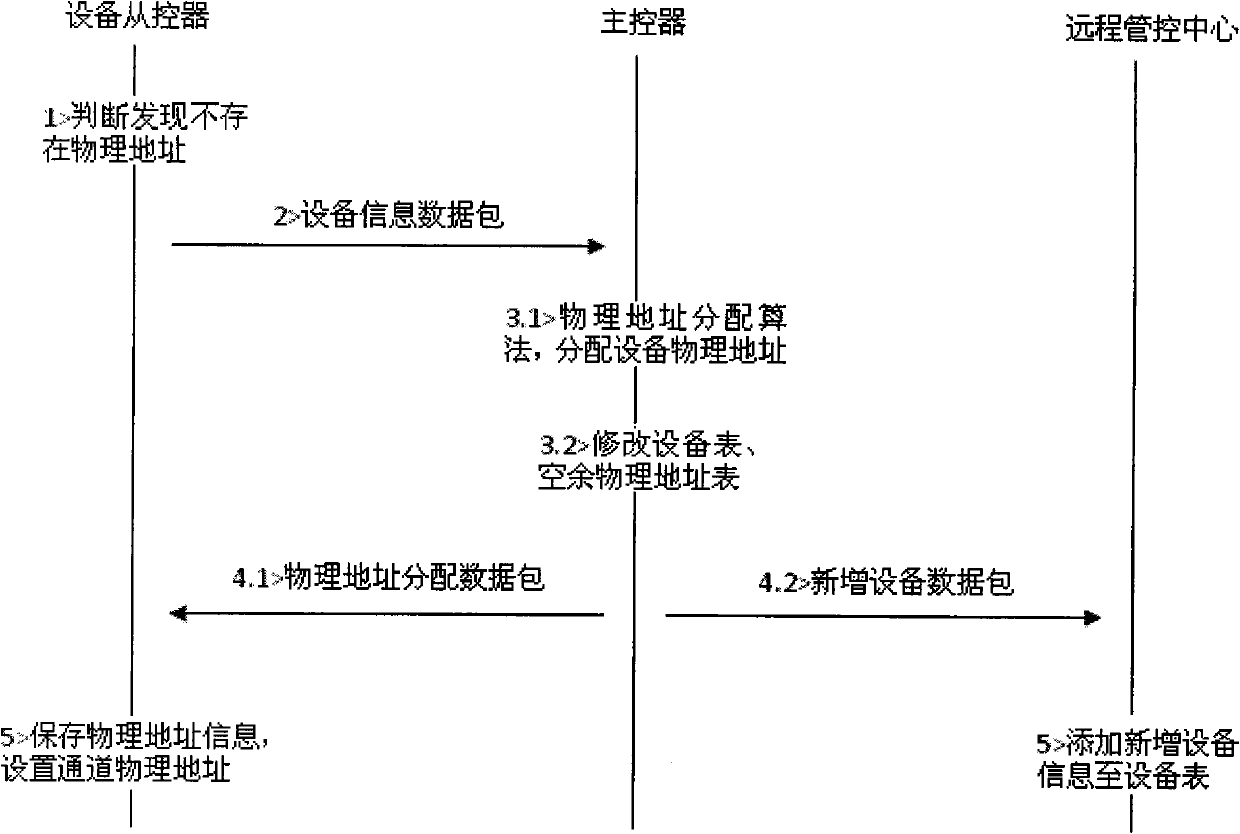
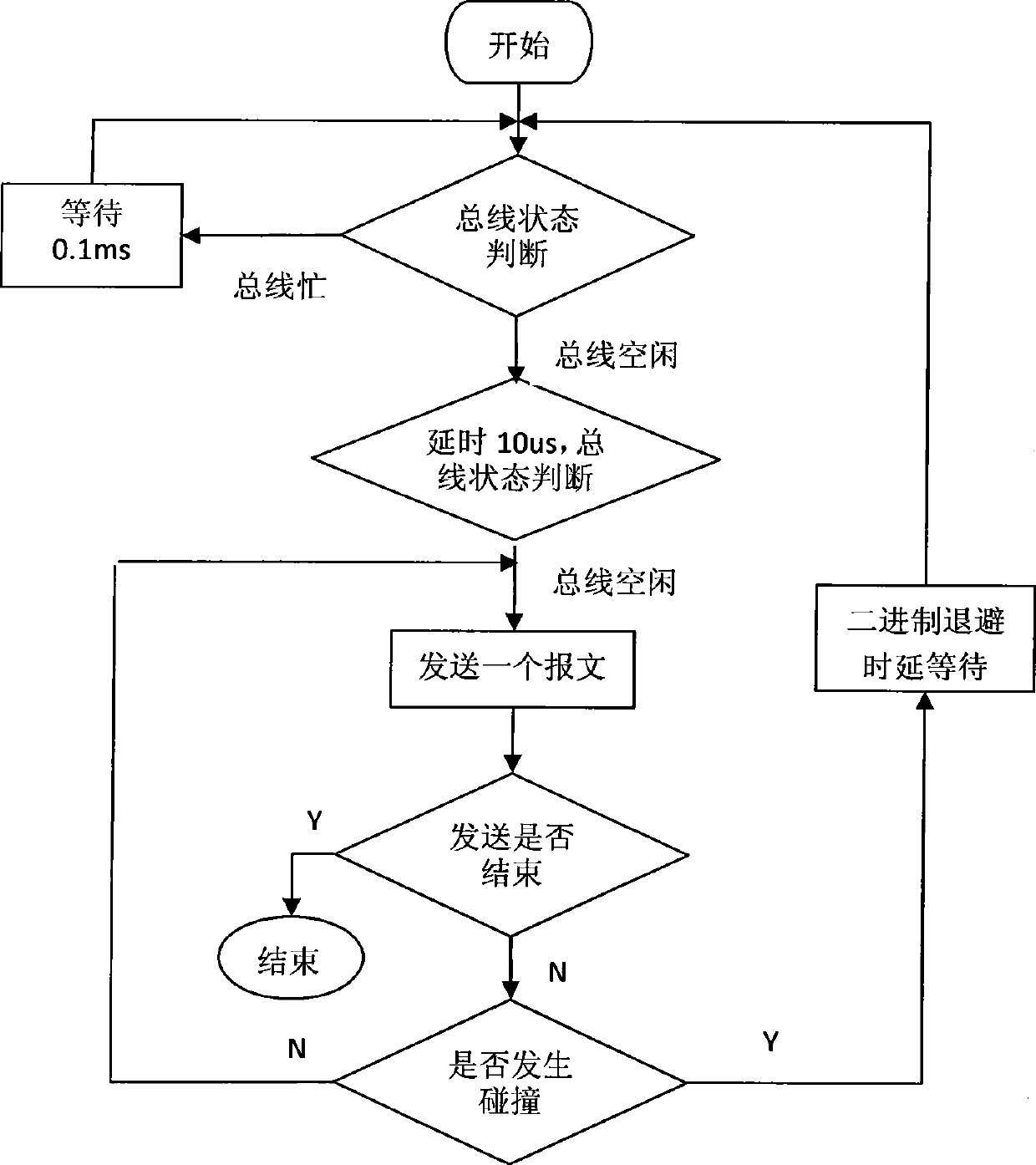
InactiveCN102036439AEliminate manual operationPrevent reporting conflictsElectric light circuit arrangementEnergy saving control techniquesRemote controlDMX512
The invention discloses an automatic equipment identification and maintenance supported DMX512 (Digital Multiplex 512) landscape lighting control system and method. The system consists of a remote control center and a DMX512 control network, wherein the DMX512 control network is downwards compatible with standard DMX512 products occupying the market dominant position; a corresponding slave controller reports equipment identification information when DMX512 equipment is networked for the first time, and a master controller automatically allocates a physical address to the equipment by a physical address allocation algorithm, thus manual operation is avoided; the slave controller prevents from reporting conflicts by adopting a carrier sense and binary exponential backoff algorithm; by virtue of an automatically created equipment list, the master controller detects the status of the equipment regularly, reports the status of the equipment in the DMX512 control network to the remote control center and automatically updates the equipment list; and operating personnel can also manually add new equipment and remove the original equipment as required or modify the physical address of the equipment.
Owner:ZHEJIANG UNIV
Method for optimizing passing rate performance in wireless ad hoc network
InactiveCN102104447AShorten the timeIncrease the probability of conflictError prevention/detection by using return channelWireless communicationDistributed coordination functionEngineering
The invention discloses a method for optimizing passing rate performance in a wireless ad hoc network. By adopting the method, the following defects are overcome: the traditional IEEE802.11DCF (distributed coordination function) mechanism adopts the minimum contention window of the BEB (binary exponential backoff) algorithm, so the processing nodes are not timely enough to contend and are too passive. The method has the following beneficial effects: dynamically detecting the number of the transmitting nodes of the contention channels, then computing the next minimum contention window after the transmitting nodes successfully complete the current transmission according to the frame error rate of the RTS (request to send) packet, optimizing the backoff timeslot and reducing the average time of access of the nodes to the channels. The backoff mechanism is superior to the traditional BEB algorithm.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
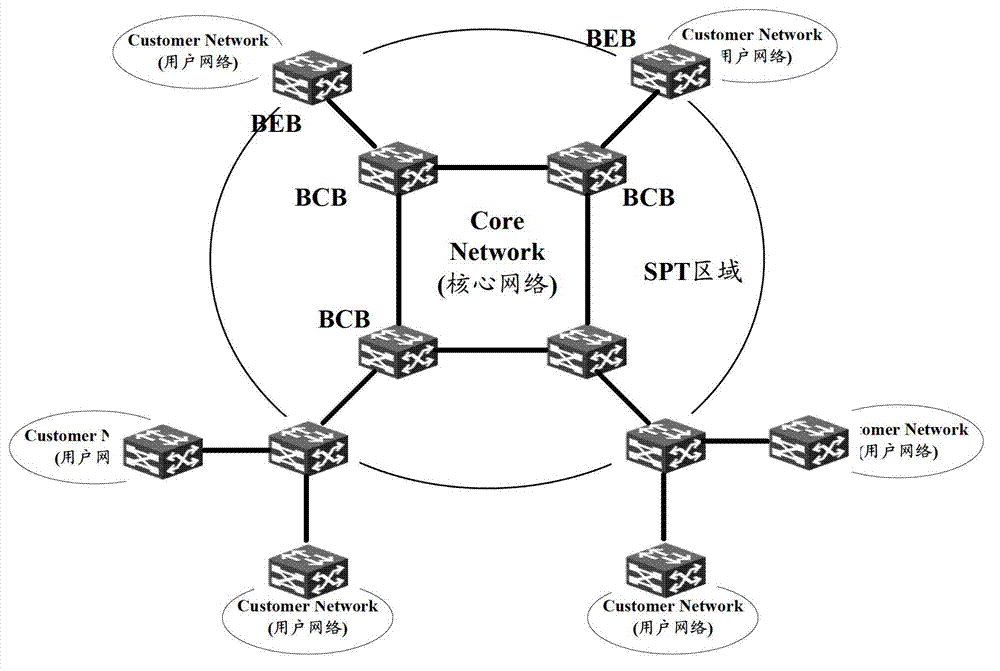
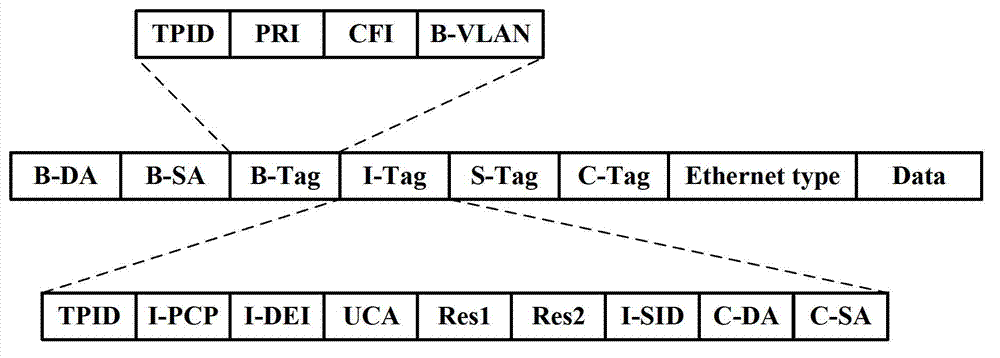
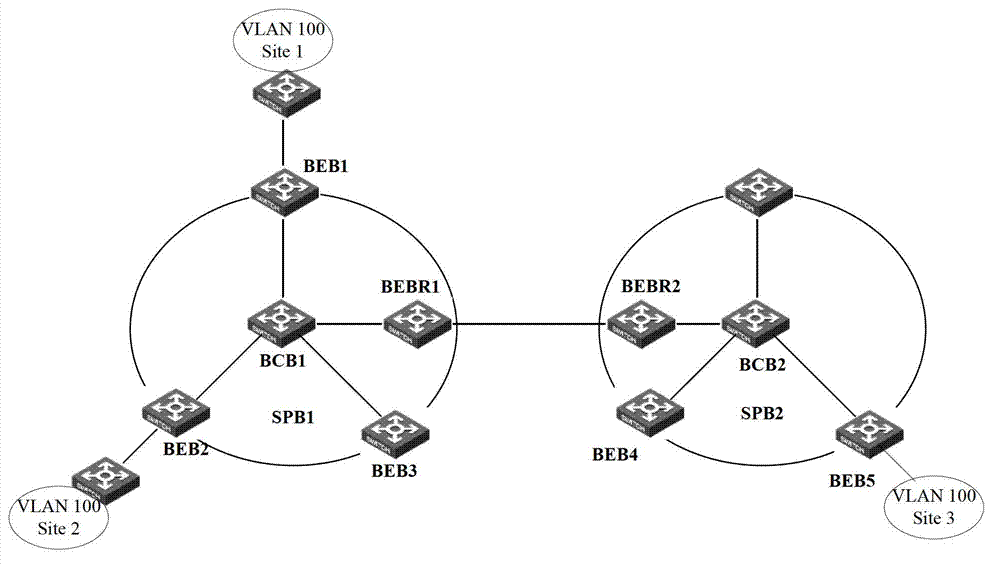
Cross-space Builder (SPB)-network access implementing method and cross-SPB-network access implementing equipment
ActiveCN103200095AReduce configurationReduce resource requirementsData switching networksNetwork access serverExponential backoff
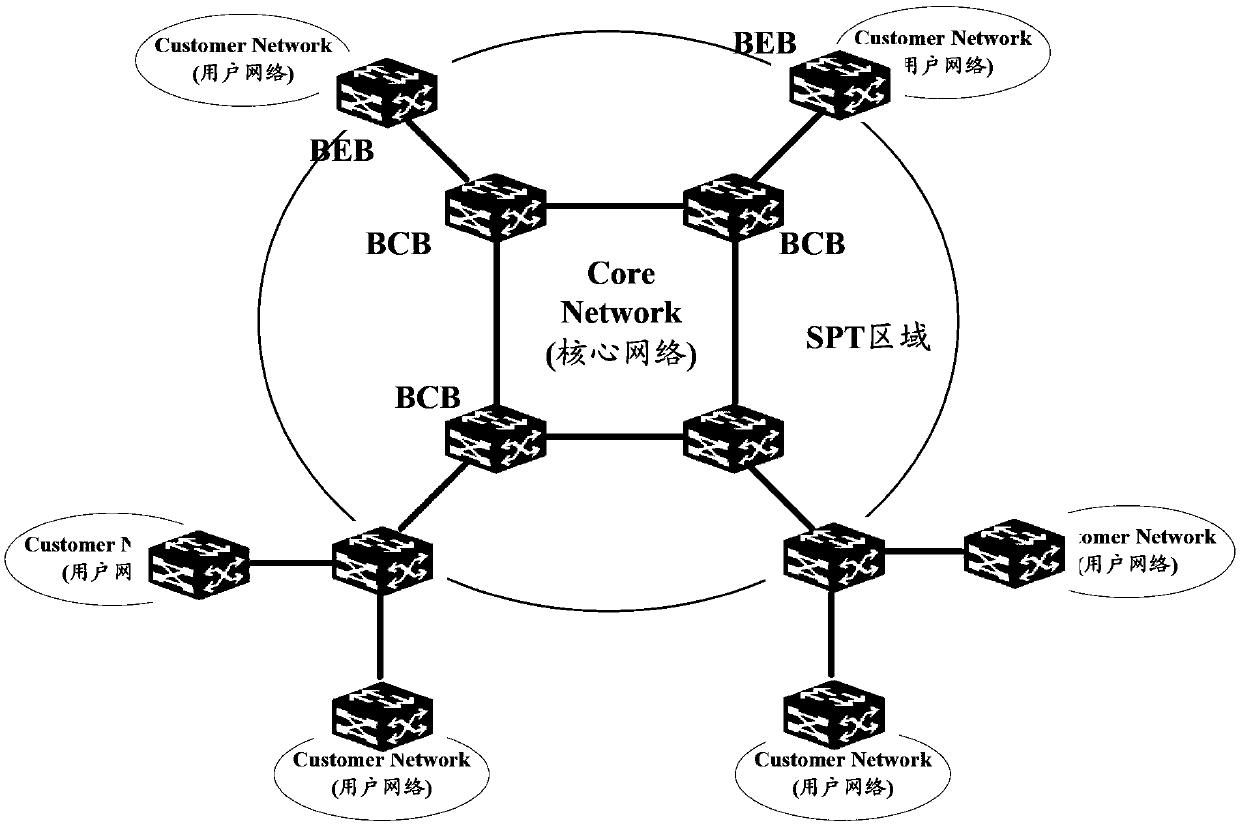
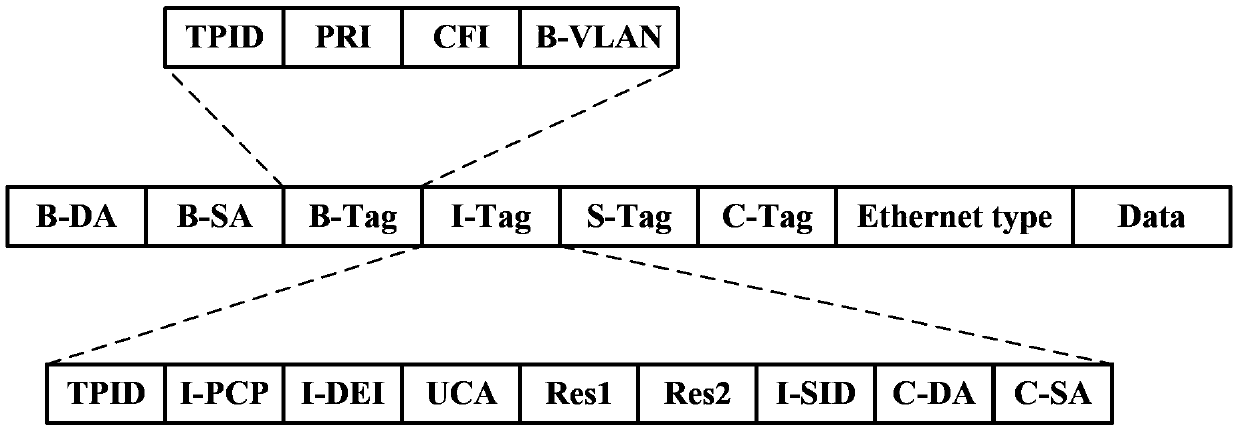
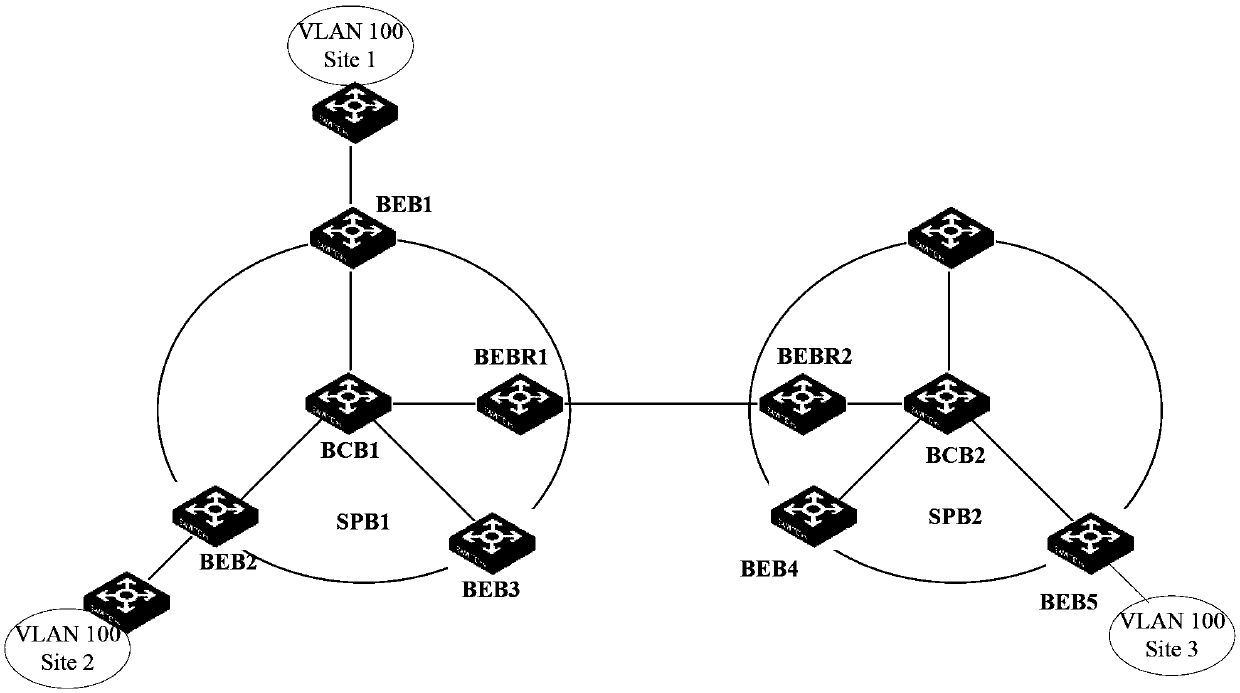
The invention discloses a cross-space Builder (SPB)-network access implementing method and cross-SPB-network access implementing equipment. The method comprises the following steps: after binary exponential backoff (BEB) confirms a user service instance which is in an SPB network where the equipment is located and needs accessing cross the SPB network so as to map the user service instance to a transmission service instance and tell an opposite-end boundary BEB the transmission service instance to trigger the boundary BEB to calculate a forward path from the equipment to the boundary BEB aiming at the transmission service instance; the boundary BEB calculates a forwarding path from the equipment to other BEBs in the SPB network aiming at the user service instance needing accessing cross the SPB network, and tells the other BEBs in the SPB network where the equipment is located the user service instance needing accessing cross the SPB network so as to trigger the other BEBs to calculate a forwarding path from the equipment to the boundary BEB aiming at the user service instance. The cross-SPB-network access implementing method and the cross-SPB-network access implementing equipment can reduce configuration expenses and resource expenses of the boundary BEB aiming at implementing of cross-SPB-network access.
Owner:XINHUASAN INFORMATION TECH CO LTD
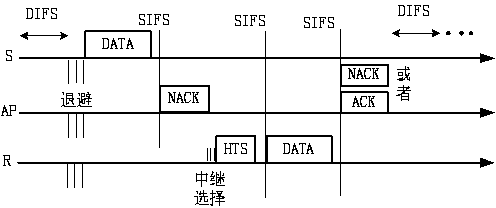
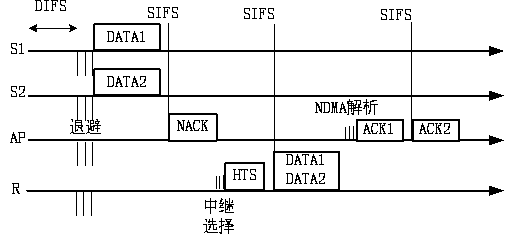
Stable Internet of Vehicles relay node selection method
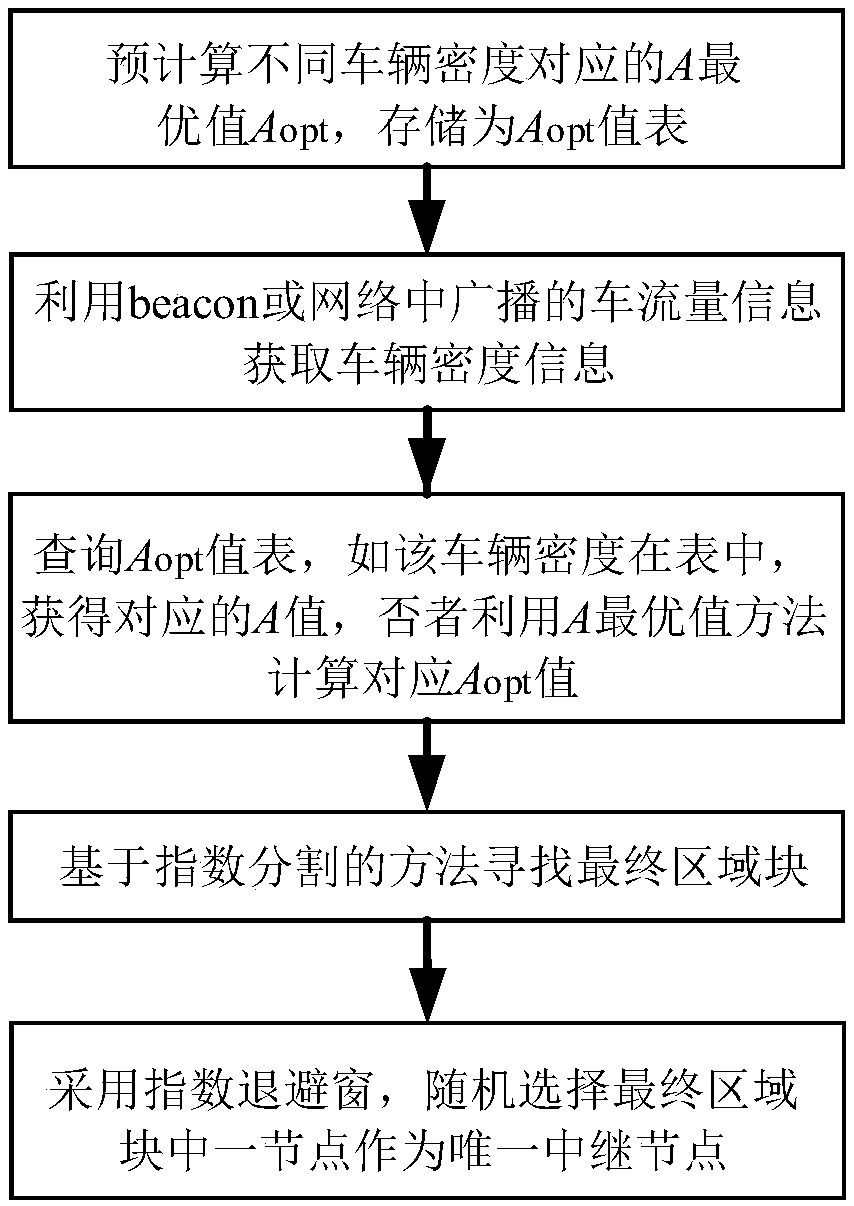
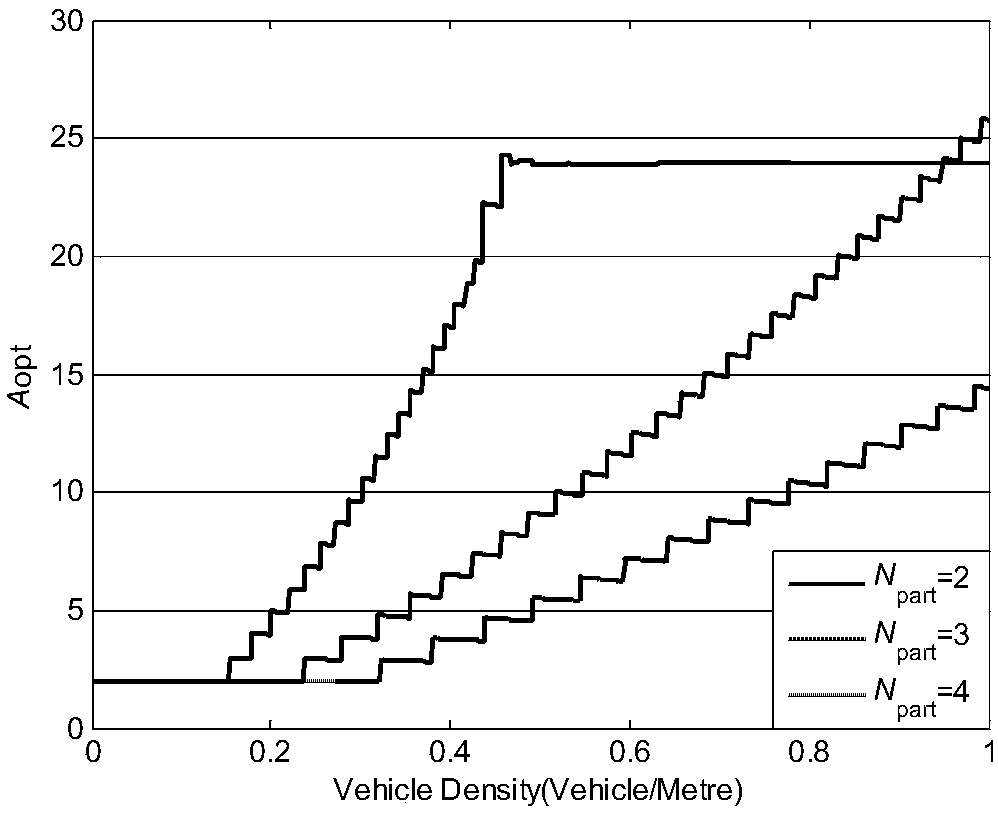
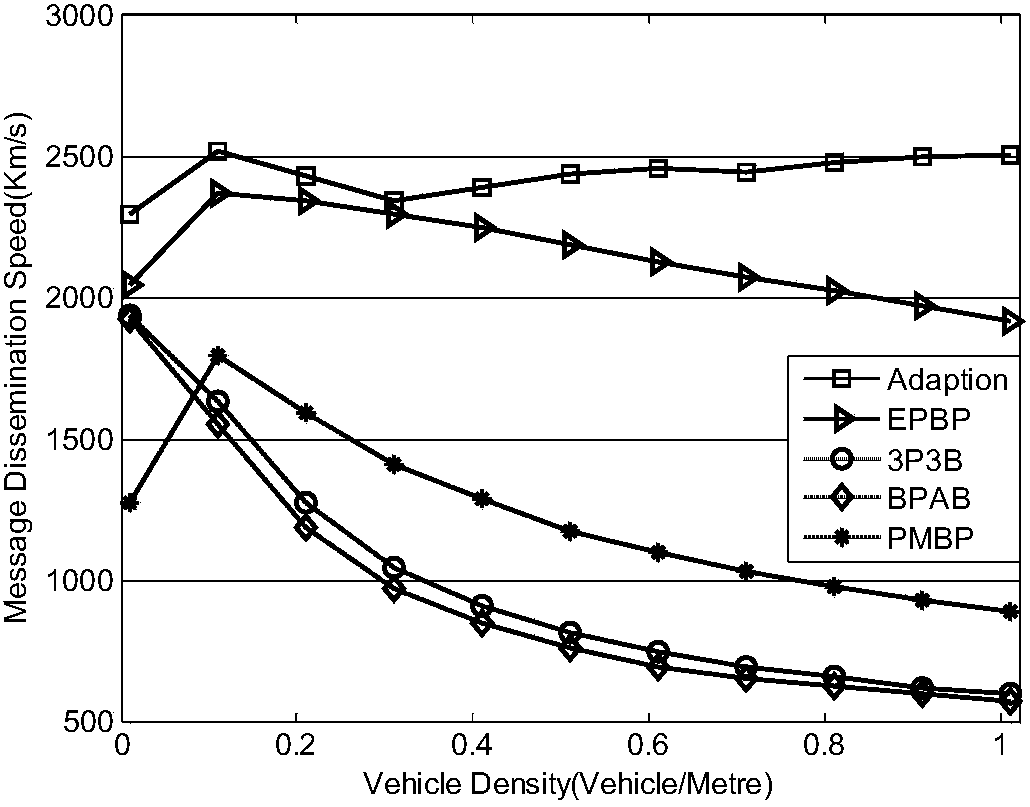
ActiveCN107659911AStable transmission speed performanceAvoid performance bottlenecksParticular environment based servicesVehicle-to-vehicle communicationAlgorithmThe Internet
The invention provides a stable Internet of Vehicles relay node selection method for selecting relay nodes in a single-hop area and accomplishing multi-hop transmission of message. The stable Internetof Vehicles relay node selection method specifically comprises the following steps: 1) obtaining optimal values Aopt of compression coefficients A under different vehicle density lambda by using an optimization method A in advance, and storing the optimal values Aopt as a data table of vehicles; 2) querying an Aopt value table by using the lambda estimation value of a selected area; if the lambdais not in the table, using the optimization method A to obtain the Aopt corresponding to the lambda; 4) performing iterative segmentation on the selected area by using a segmentation method based onindexes to find the final area block; and 5) selecting a unique node in the final area block by using an exponential backoff window to serve as a relay node so as to accomplish the selection of the relay node. The message transmission speed achieved by the method is independent from the vehicle density, and the performance bottle neck caused by overlarge or too small vehicle density in the traditional method is overcome, and the requirements for the computing performance of the local vehicles and the computing time consumption are reduced by budgeting the Aopt value table and using a query method.
Owner:CHANGSHA UNIVERSITY OF SCIENCE AND TECHNOLOGY
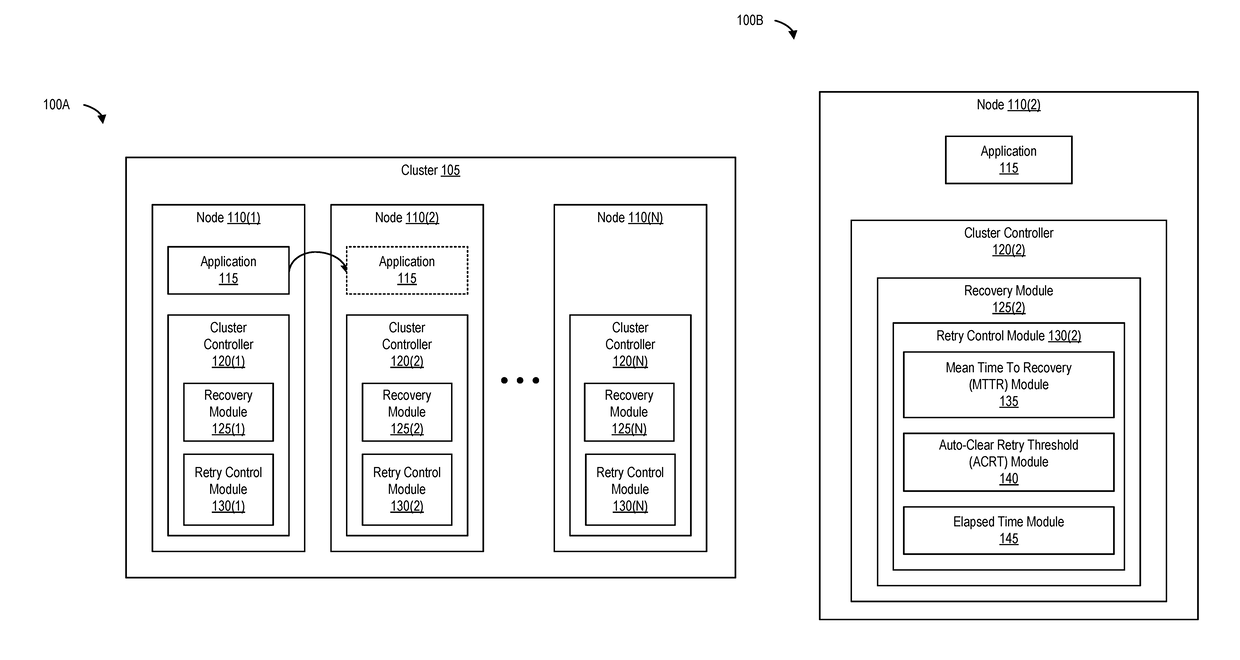
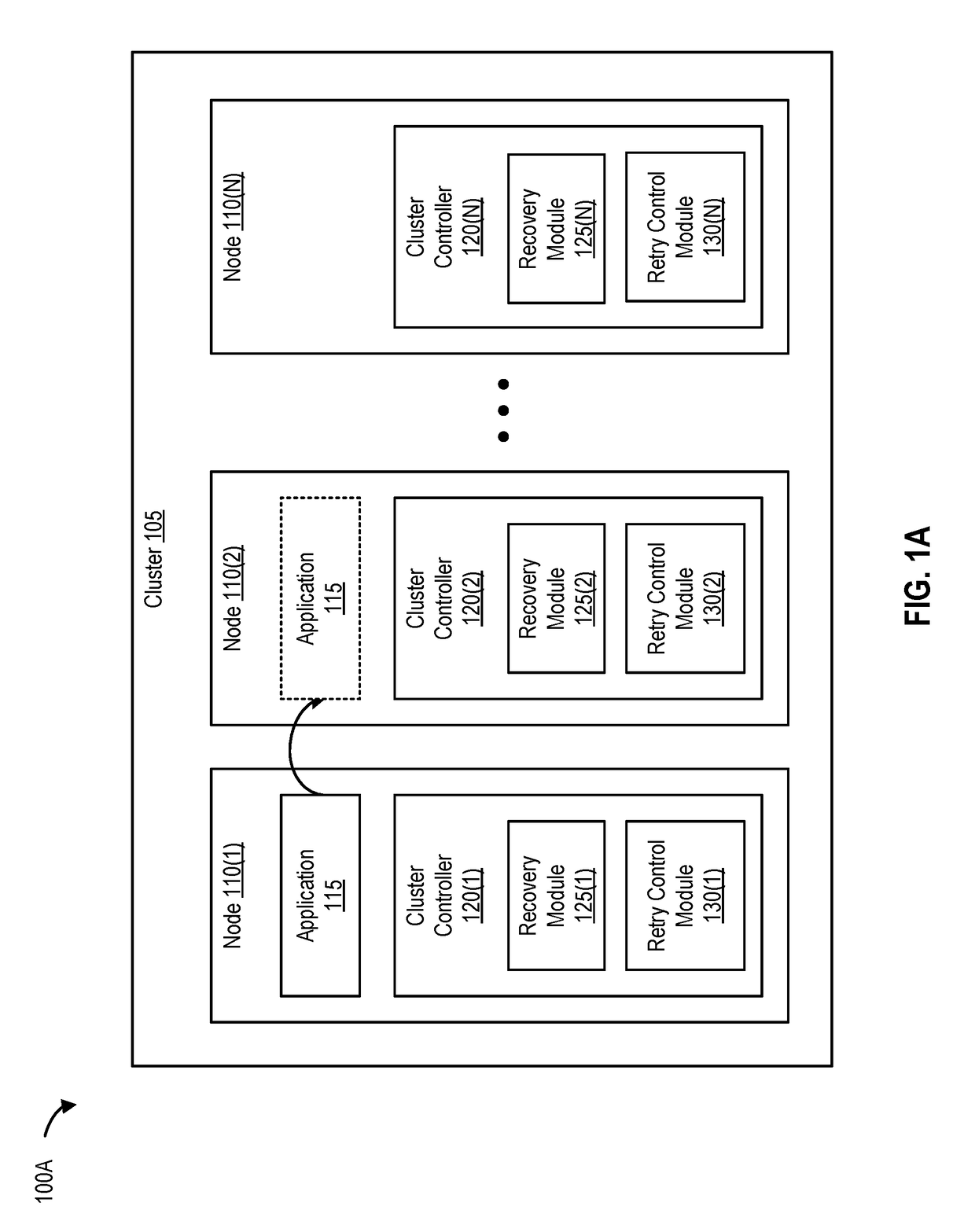
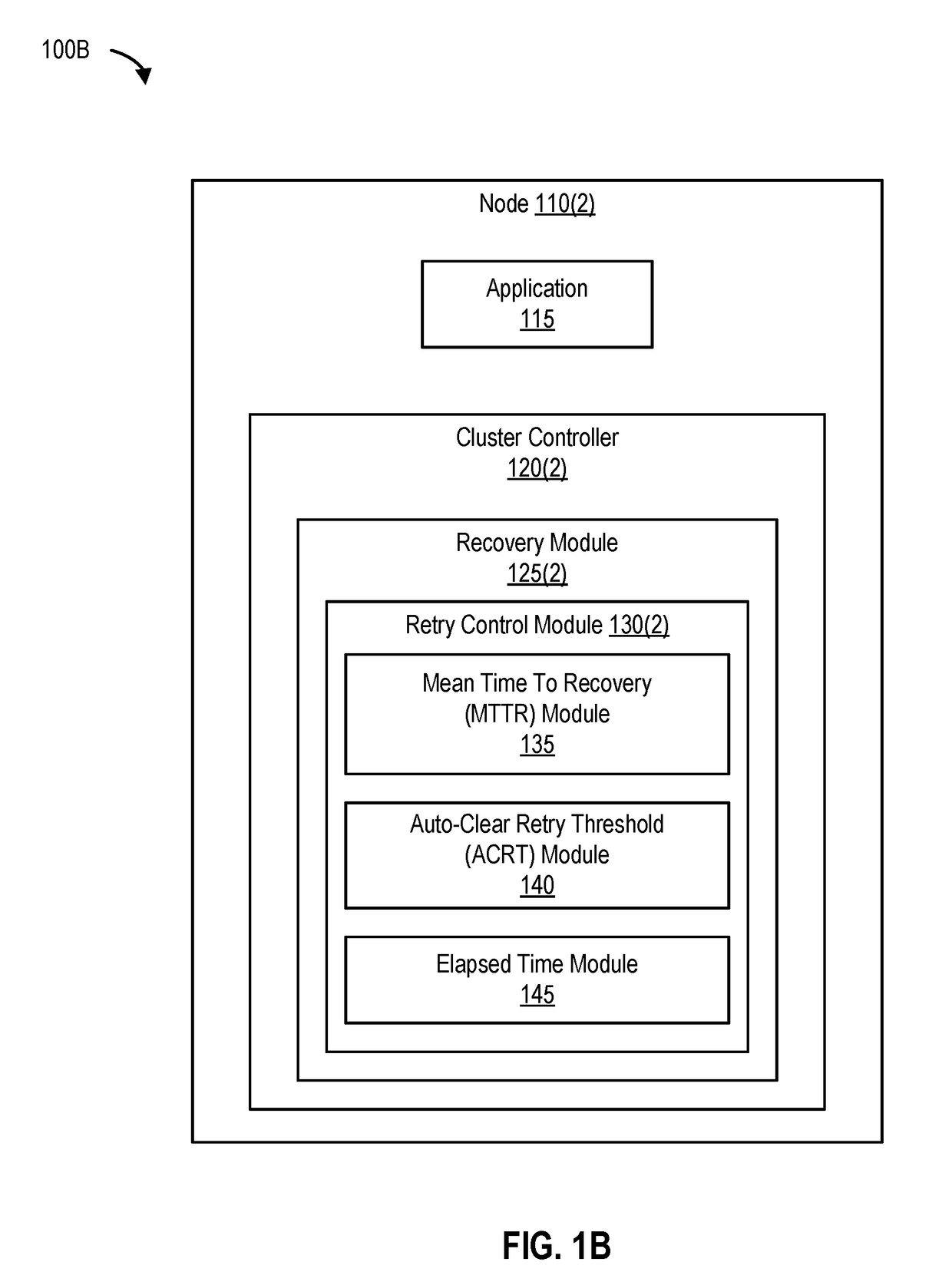
Optimizing application recovery in unmanaged clusters
ActiveUS10049023B1Data switching networksRedundant hardware error correctionExponential backoffCluster based
Various systems, methods, and processes to perform recovery operations in a cluster based on exponential backoff models are disclosed. A node failure is detected. The node is one of multiple nodes in a cluster. In response to the node failure, an application executing on the node is failed over to another node in the cluster. In response to the detecting the node failure, recovery operations are automatically performed to determine whether the node is recovered. A subsequent recovery operation is performed after a prior recovery operation. The subsequent recovery operation is performed periodically based on a frequency that decreases exponentially after performing the prior recovery operation.
Owner:VERITAS TECH
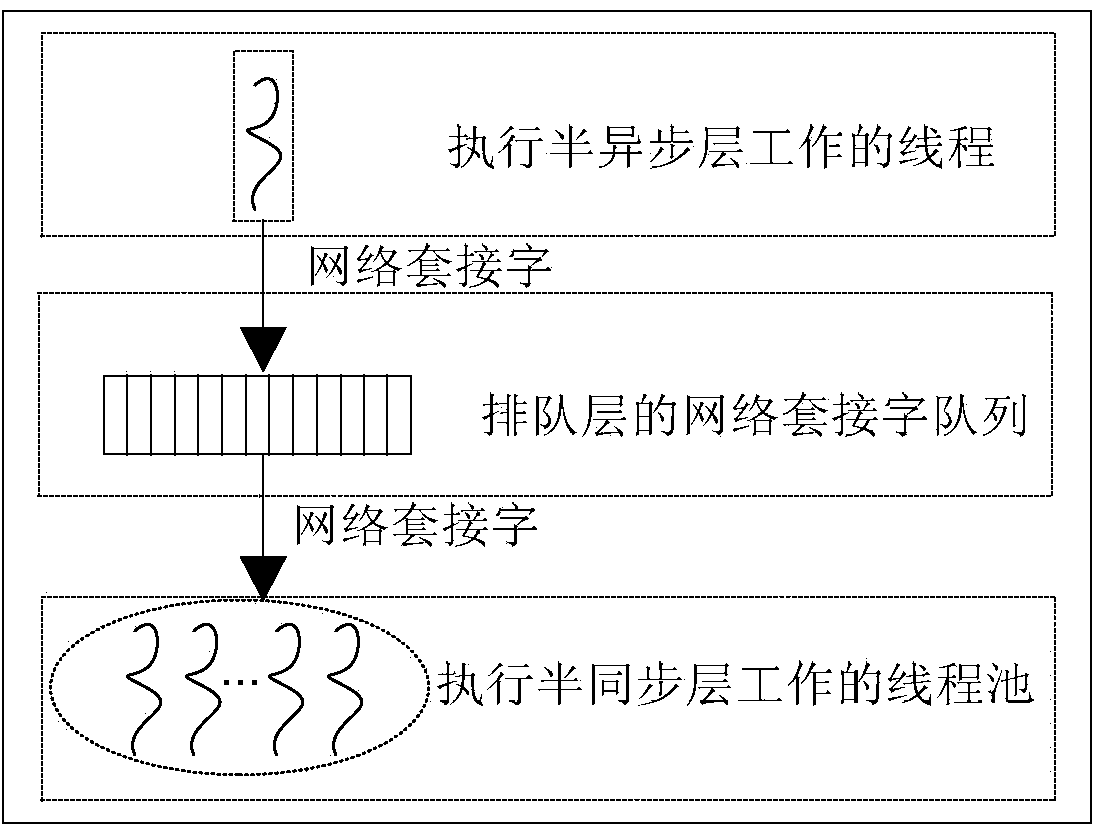
Server designing method based on semi-synchronization, semi-synchronization and pipe filter mode
InactiveCN104219284AAdd dynamicallyDelete dynamicallyResource allocationProgram synchronisationComputer moduleExponential backoff
The invention provides a server designing method based on semi-synchronization, semi-synchronization and a pipe filter mode. The method includes the steps of firstly, allowing a semi-synchronization layer to comprise a plurality of data processing modules; secondly, applying the pipe filer mode to the data processing modules of the semi-synchronization layer; thirdly, sequentially linking the data processing modules through a link table; fourthly, applying a binary exponential backoff policy to the application layer of a client. By the method, a whole server system has the advantages that system concurrency is increased greatly, and good system expansibility is achieved; the data processing modules can be dynamically added or deleted, and efficient and flexible data processing is achieved; server pressure can be effectively relieved by the binary exponential backoff policy, and server operation capability is increased at the same time.
Owner:HUAQIAO UNIVERSITY
Exponential backoff multiple access method in cooperation with network-assisted diversity
InactiveCN102665287AImprove throughputImprove spectral efficiencyHigh level techniquesWireless communicationAccess methodTelecommunications
The invention discloses an exponential backoff multiple access method in cooperation with network-assisted diversity. The method comprises: (1) allocation of an orthogonal overlapping pilot sequence to nodes requesting for access, including: selecting an orthogonal overlapping pilot sequence and allocating the orthogonal overlapping pilot sequence to the node requesting for access to the network for the first time as the identity identification and channel estimation of the node; (2) the access channel backoff, including: monitoring the channel when a data packet in the network nodes needs to be transmitted, and subjecting the node to countdown backoff when the idle period of the monitored channel lasts for an interval length between distributed frames; and (3) data packet transmission, including: transmitting the data packet of the node needing to transmit the data packet in step (2) by the exponential backoff multiple access method in cooperation with network-assisted diversity. The exponential backoff multiple access method provided by the invention is high in throughput, reliability and efficiency, and has excellent burst traffic handling ability.
Owner:PLA UNIV OF SCI & TECH
Data transmission method and device
ActiveCN103152257AForwarding control implementationData switching networksComputer hardwareExponential backoff
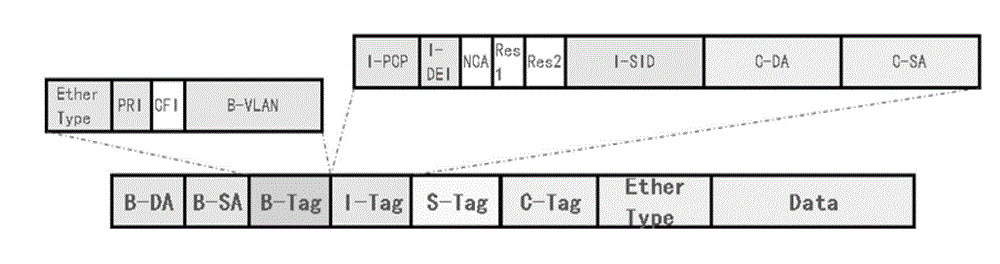
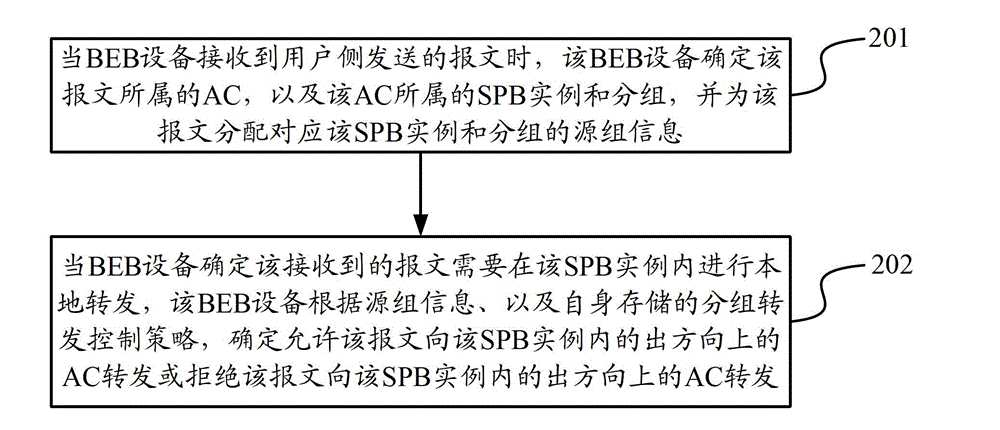
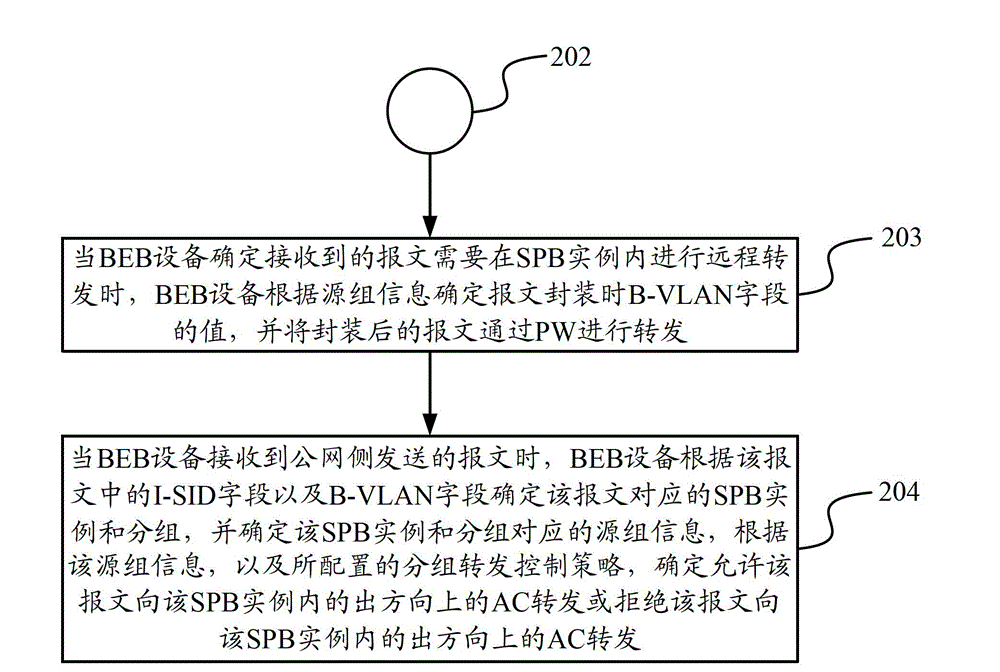
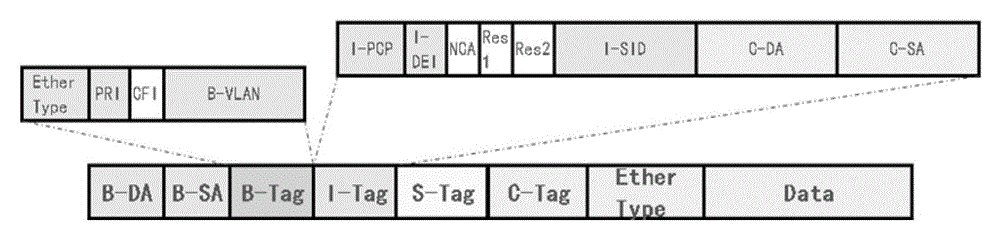
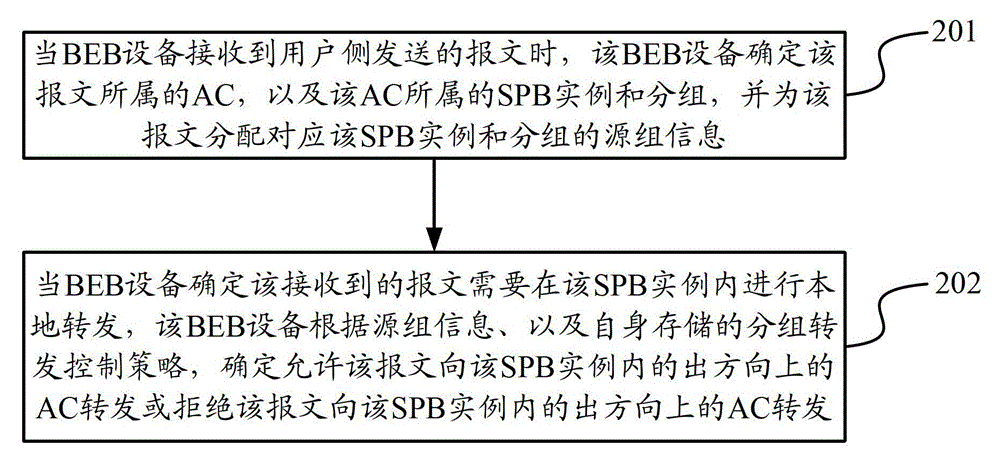
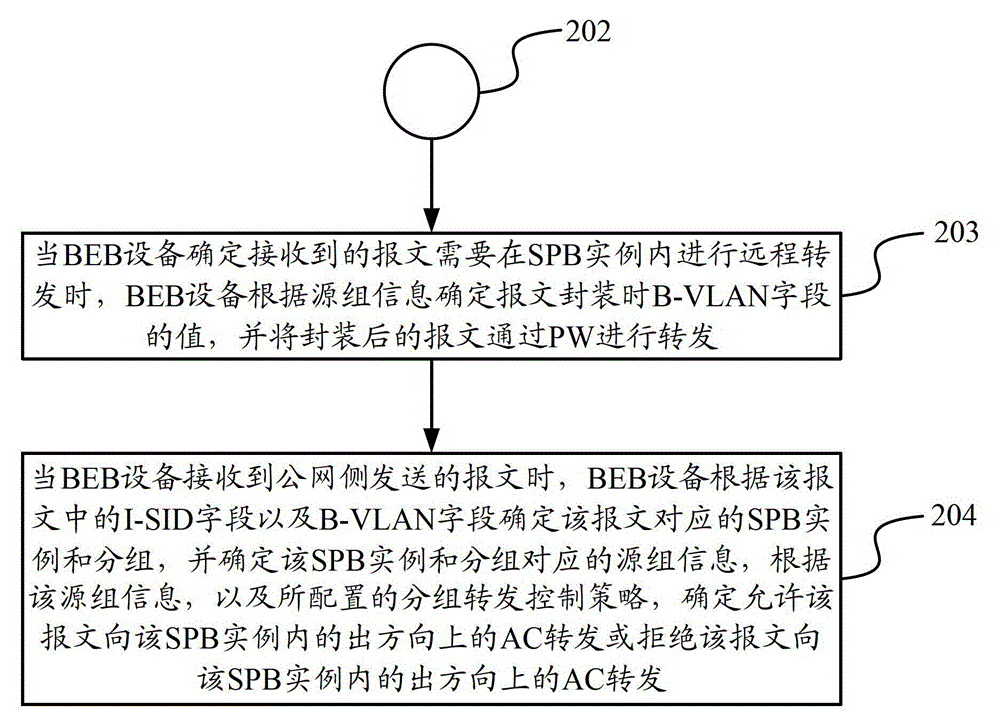
The invention discloses a data transmission method and device. The data transmission method comprises the following steps of: when BEB (Binary Exponential Backoff) equipment receives a message transmitted by a user side, determining an attachment circuit (AC) belonging to the message as well as an SPB (Shortest Path Bridging) case and groups belonging to the AC and allocating source group information corresponding to the SPB case and the groups for the message by the BEB equipment; and when the BEB equipment determines that the received message is required to be locally forwarded in the SPB case, determining to allow the message to be forwarded towards the AC in an egress direction in the SPB case or reject the message to be forwarded towards the AC in an egress direction in the SPB case according to the source group information and a grouping forwarding control strategy by the BEB equipment. According to the data transmission method and device disclosed by the invention, the message forwarding control over the AC in the SPB case is realized.
Owner:XINHUASAN INFORMATION TECH CO LTD
Communication device and communication method
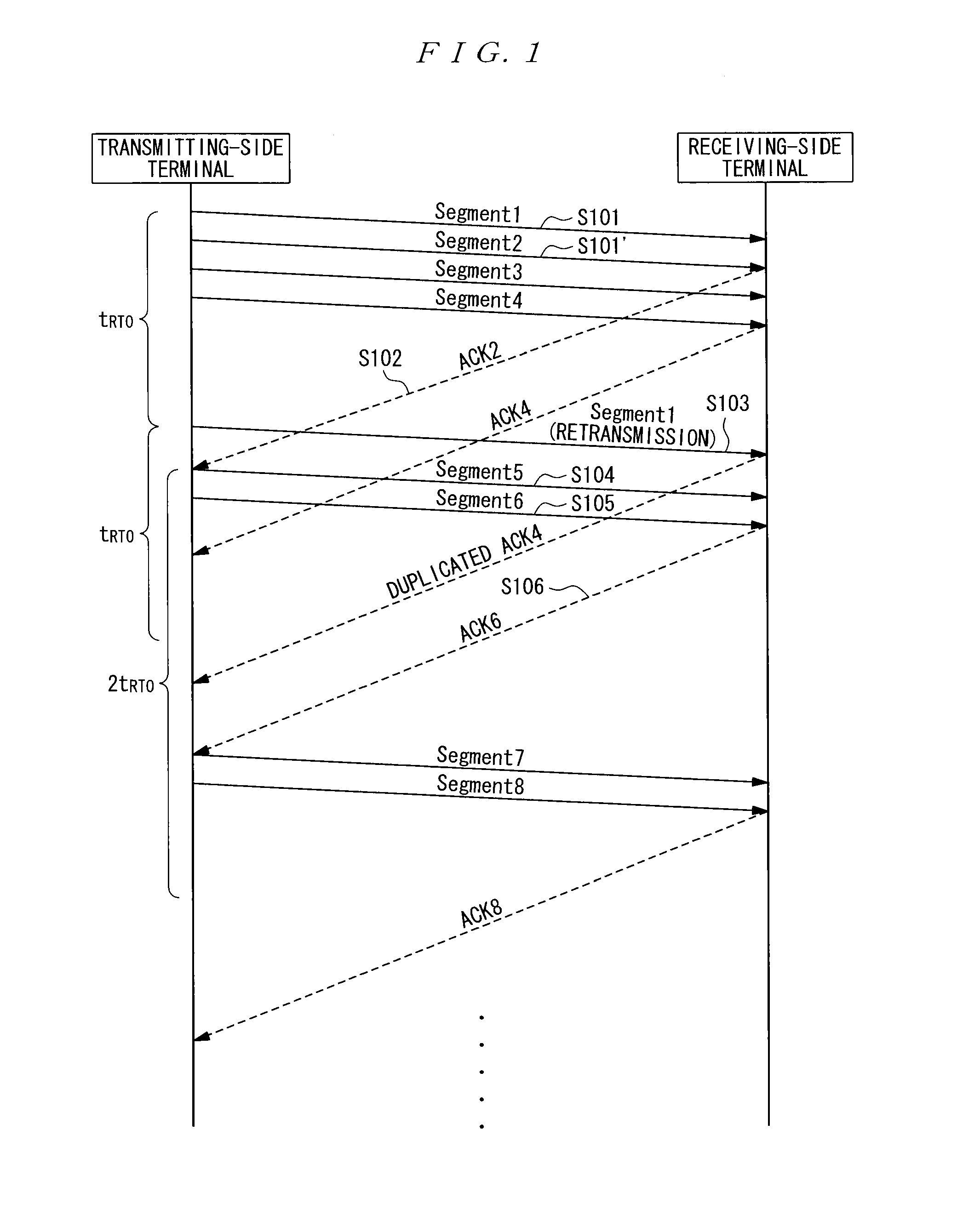
InactiveUS8607114B2Preventing situationError prevention/detection by using return channelFrequency-division multiplex detailsData segmentExponential backoff
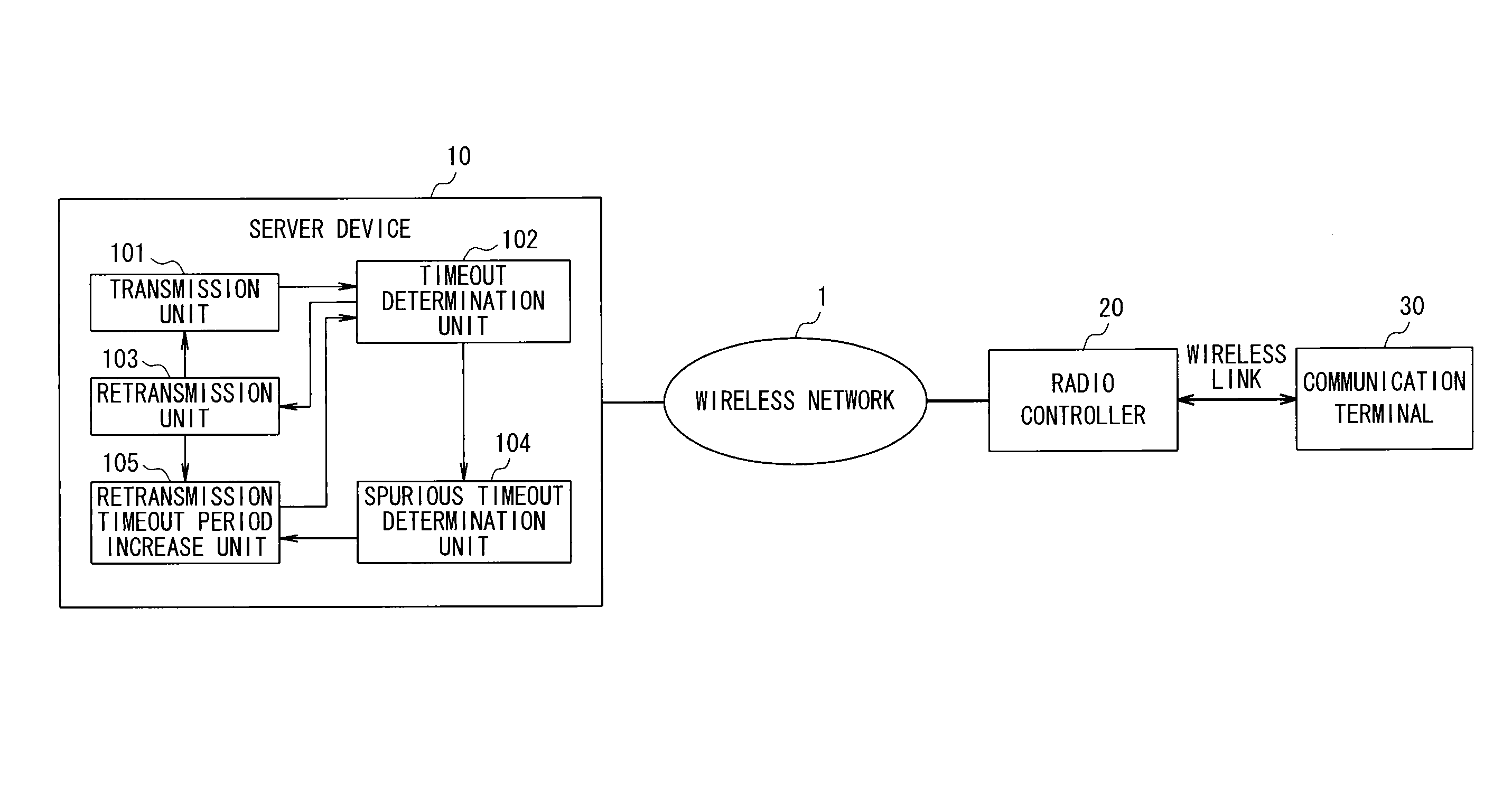
In a case where the F-RTO algorithm is simply combined with the exponential backoff algorithm which is being suppressed, there is a problem in that once a spurious timeout occurs, the spurious timeout continuously occurs since then. In order to solve the above problem, according to the present invention, in a communication device for transmitting data segments and receiving acknowledgements in response to the data segments, respectively and sequentially, suppressing an application of a backoff algorithm for increasing a retransmission timeout period at the time of retransmitting a data segment, and controlling the retransmission timeout period to retransmit the data segment, the spurious timeout is determined based upon the acknowledgement received immediately after the retransmission of the data segment. In an event of determining the occurrence of the spurious timeout, the retransmission timeout is increased.
Owner:NTT DOCOMO INC
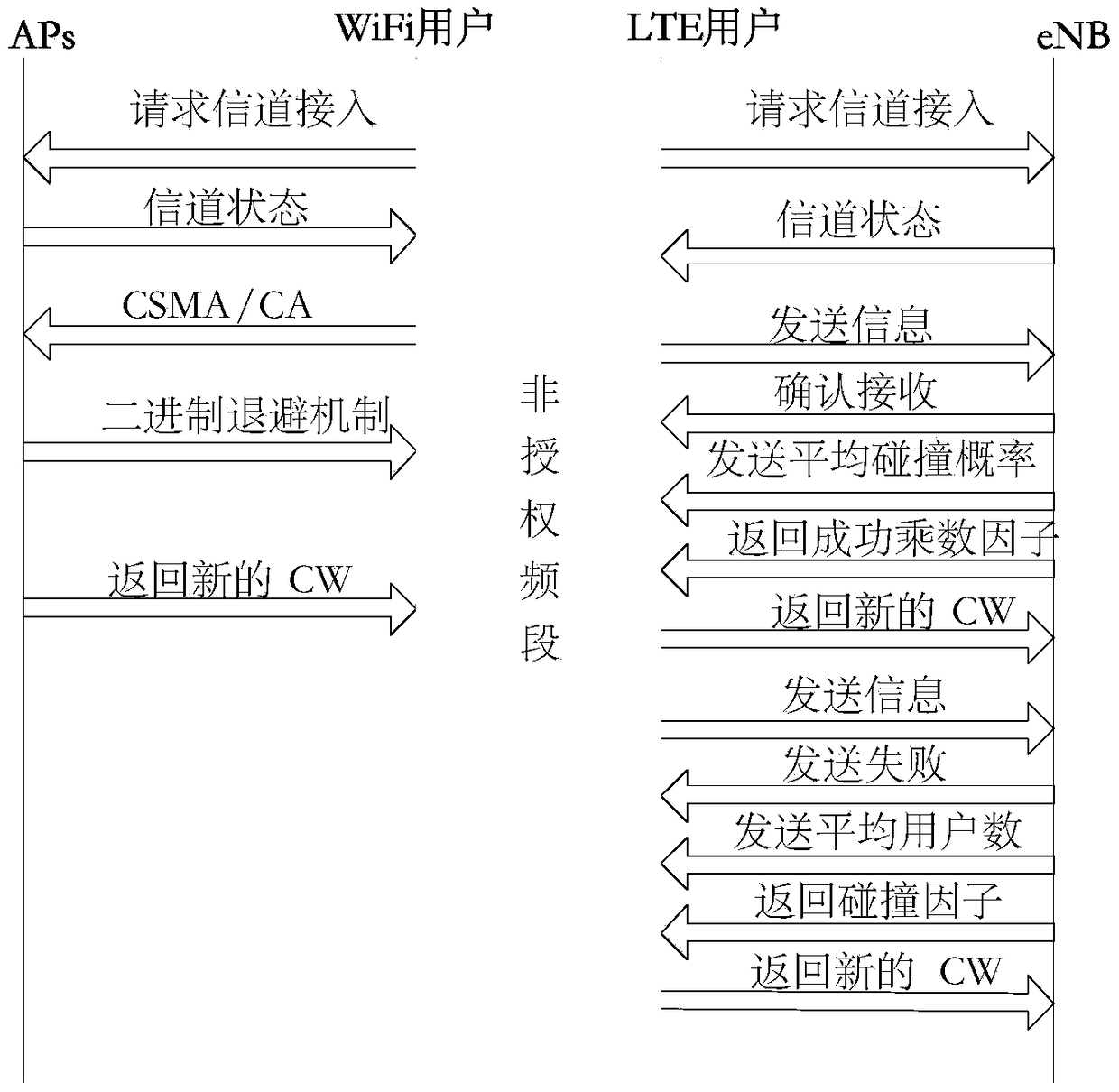
Method for transmitting data under coexistence of LTE system and WiFi system on unlicensed frequency band
InactiveCN108966360AGuarantee friendly coexistenceGuaranteed normal transmissionWireless communicationWi-FiData stream
The invention provides a method for transmitting data under the coexistence of an LTE system and a WiFi system on an unlicensed frequency band. The method includes the following steps that: when the LTE system and the WiFi system coexist in the unlicensed frequency band, the user equipment of the WiFi system performs data transmission with a binary exponential backoff mechanism, and the LTE systemperforms data transmission with an EDCA(Enhanced Distributed Channel Access)-based ALBT mechanism; and the EDCA-based ALBT mechanism includes a backoff mechanism after successful data transmission and a backoff mechanism after data collision. According to the method of the present invention, the EDCA-based ALBT mechanism is adopted, different types of data services use different parameters to complete channel access of different priorities, and small AIFSs and CWs are allocated to data services of higher priority; and therefore, it can be ensured that data of high priority can preferentiallyaccess channels, so that data transmission can be completed, and at the same time, the transmission of services of low priority can be ensured to the greatest extent, the coexistence performance of the Wi-Fi system is improved, and the friendly coexistence of the LTE system and the Wi-Fi system on the unlicensed frequency band can be ensured.
Owner:BEIJING JIAOTONG UNIV
Online billing method and system based on user traffic volume
InactiveCN101645782BReduce the number of expected interactionsIncrease profitMetering/charging/biilling arrangementsAccounting/billing servicesInteraction timeComputation complexity
The invention provides an online billing method and a system based on user traffic volume. The online billing method is applied in a business operation support system, and the online billing method adopts the using frequency sliding window technology, pre-distributes usable traffic volume based on historical using amount of user business, realizes the function of online billing, reduces the repeat times from amount to the usable traffic volume during the online billing process and improves the billing efficiency, thereby leading the distributed initial traffic volume to be in line with the using habits of a user as far as possible, reducing the expected interaction times between a business control network element and the online billing system during the online billing process to a constant and reducing the concurrent pressure of the online billing system. The usable volume of the follow-up business in the conversation is computed by adopting the exponential backoff algorithm with a threshold, thereby reducing computational complexity; and balances of pre-reserved accounts are re-distributed according to the using status of system resources of various businesses in a business system, thereby improving the utilization rate of idle business resources. The method can be directly applied in the existing online billing system and have higher application values.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI
Automatic equipment identification and maintenance supported DMX512 (Digital Multiplex 512) landscape lighting control system and method
InactiveCN102036439BEliminate manual operationPrevent reporting conflictsElectric light circuit arrangementEnergy saving control techniquesRemote controlDMX512
Owner:ZHEJIANG UNIV
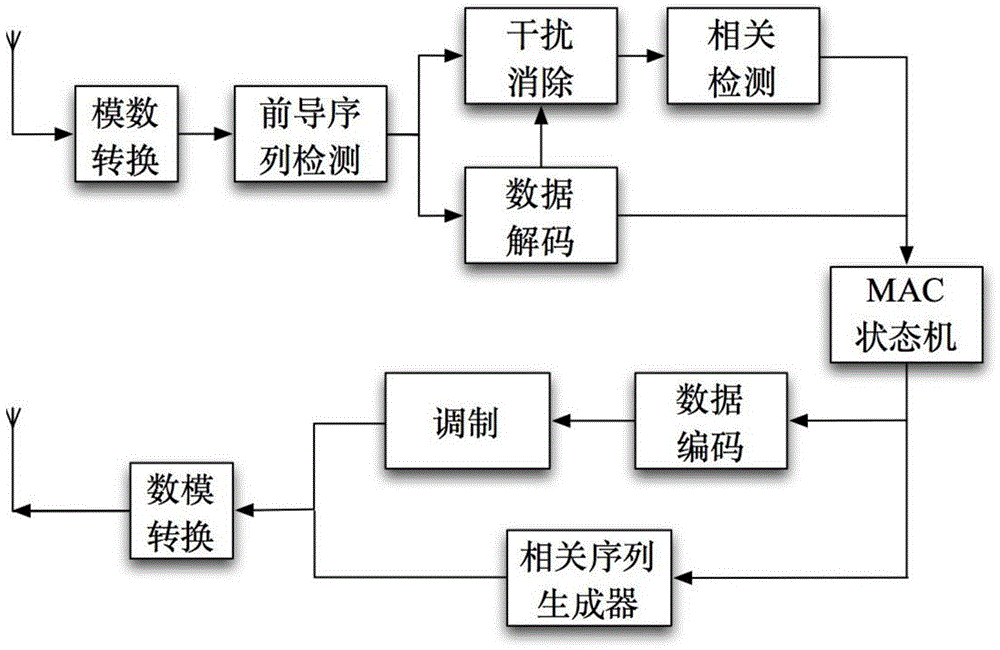
Media access control method based on recognition of correlative sequences
InactiveCN104378834ALow signal to noise ratioImprove reliabilityWireless communicationInterference eliminationMedia access control
The invention provides a media access control method based on recognition of correlative sequences. Different nodes are recognized through correlative sequences, different control messages are transmitted through the combination of the correlative sequences and a micro-timeslot mechanism, and the contradiction between high-speed data and low-speed control messages in the traditional MAC (media access control) protocol is relieved. The control messages are transmitted through the correlative sequences, control sequences and data packets are transmitted in the same time by the aid of the interference elimination technology, the explicit competition process of the traditional media access control protocol is eliminated, expenditure on conventional control message transmission and time of binary exponential backoff are reduced, and channel utilization rate and network throughput are increased.
Owner:PLA UNIV OF SCI & TECH
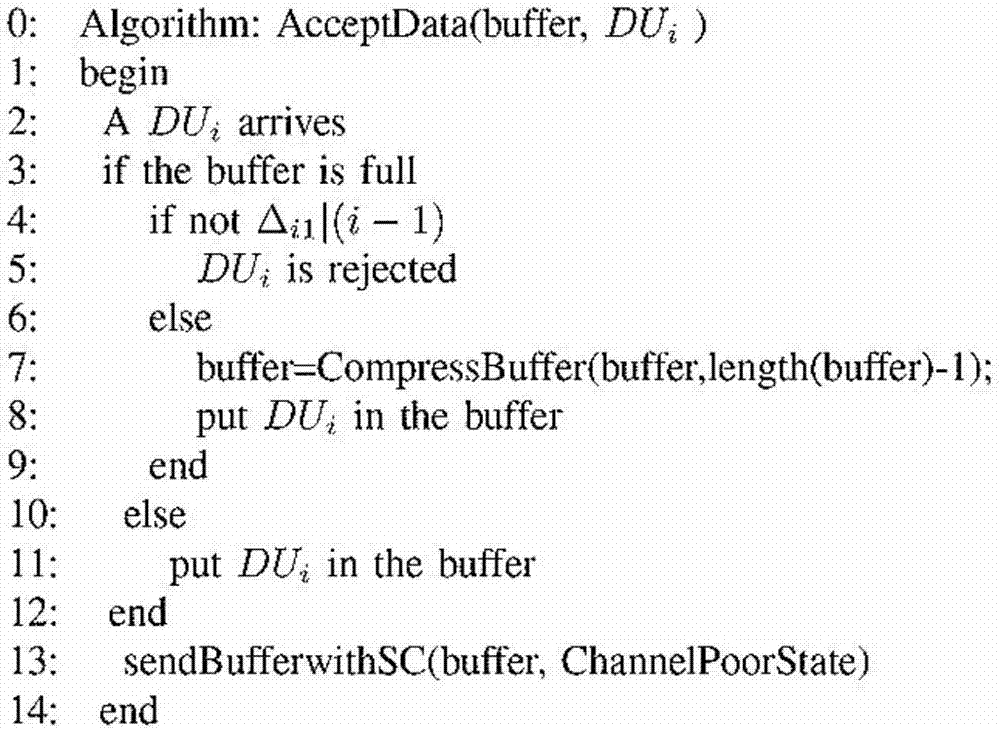
Intelligent power grid electronic data compression access algorithm for cognitive radio based on binary exponential backoff
The invention provides an intelligent power grid electronic data compression access algorithm for cognitive radio based on binary exponential backoff. The algorithm comprises the following steps of S1, monitoring that data packets are generated per te seconds (te is a random variable), and numbering according to an index mode of a following text; S2, if the number is accordant with an algorithm requirement of the following text, being ready to put the data packet into a buffer, and otherwise directly ignoring; S3, if the buffer is not full, directly putting the data packet into the buffer, and if the buffer is full, compressing the buffer at first to make room for the new data packet; S4, starting a sending process, being ready to send the new buffer; and S5, if sending is successful, emptying the buffer, and numbering the data packets from 0; if sending is failed due to lack of channel, keeping the buffer unchanged, keeping the currently increased data packet numbers unchanged, and restarting from the step S1 until the new data packet reaches.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Method and system for reliable data transmission in wireless networks
ActiveUS7613146B2Reliable data transmissionImprove coordinationError preventionBroadcast transmission systemsExponential backoffData transmission
A method for transmitting data from a sender node to a receiver node in a wireless network including (a) sampling a main network frequency and at least one backup frequency, (b) transmitting a message on the main network frequency without using a multiple access protocol, (c) transmitting the message on the main network frequency, using the multiple access protocol exchange, if an acknowledgement is not received, (d) transmitting the message on at least one backup frequency, using a multiple access protocol, if the main network frequency is busy after (c), (e) repeating (c) and (d) for a predefined number of time slots, until an acknowledgement is received, (f) transmitting the message on each backup frequency, using the multiple access protocol, until an acknowledgment is received, and (g) performing an exponential backoff and subsequent transmission of the message if an acknowledgement is still not received after (a) through (f).
Owner:ROBERT BOSCH GMBH
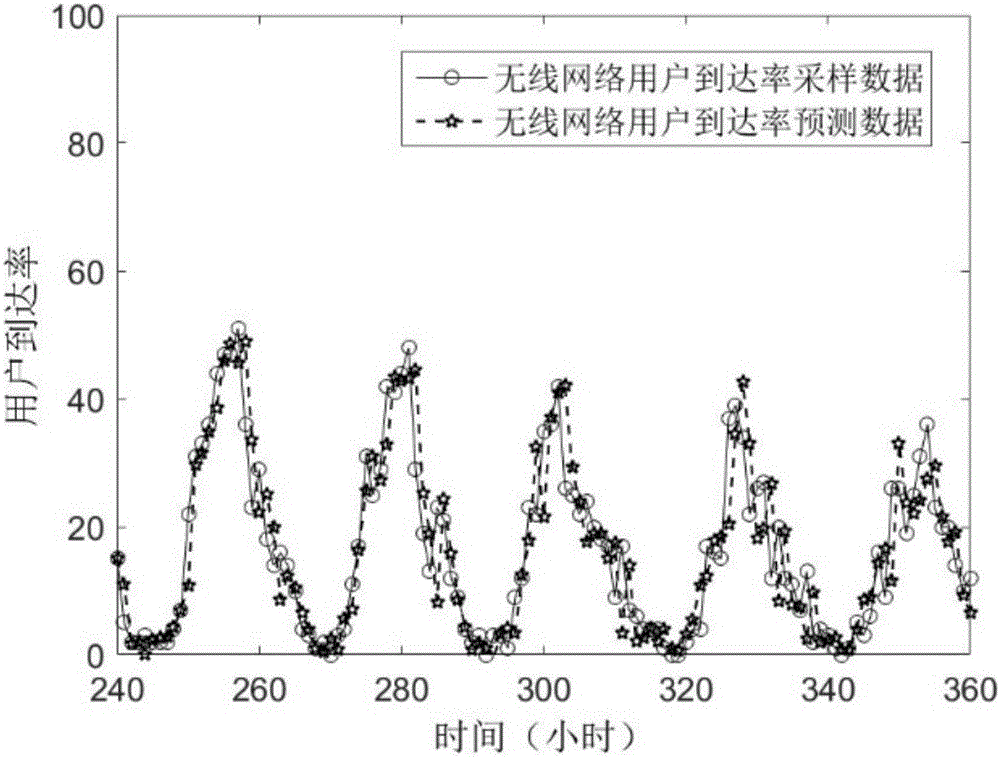
Network user arrival rate prediction method based on binary exponential backoff deviation correction
InactiveCN105933152ATroubleshoot issues that depend on specific networksCan't solveData switching networksUltrasound attenuationExponential backoff
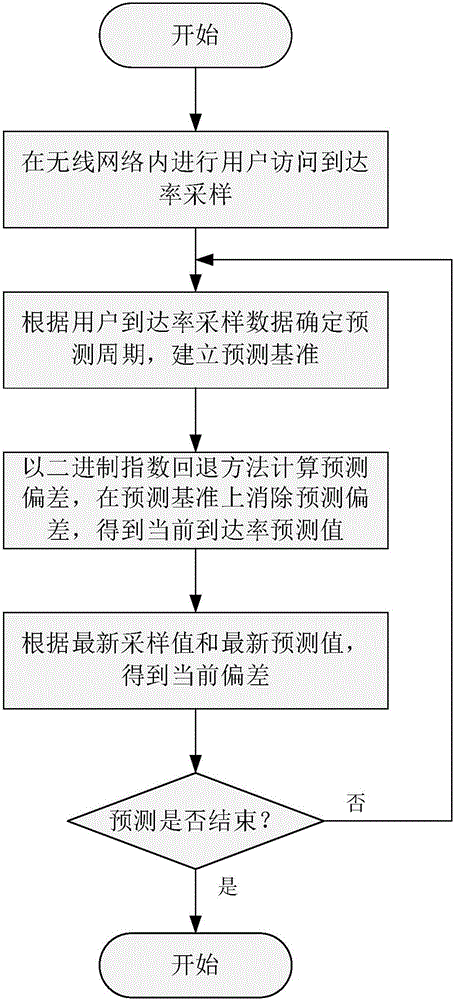
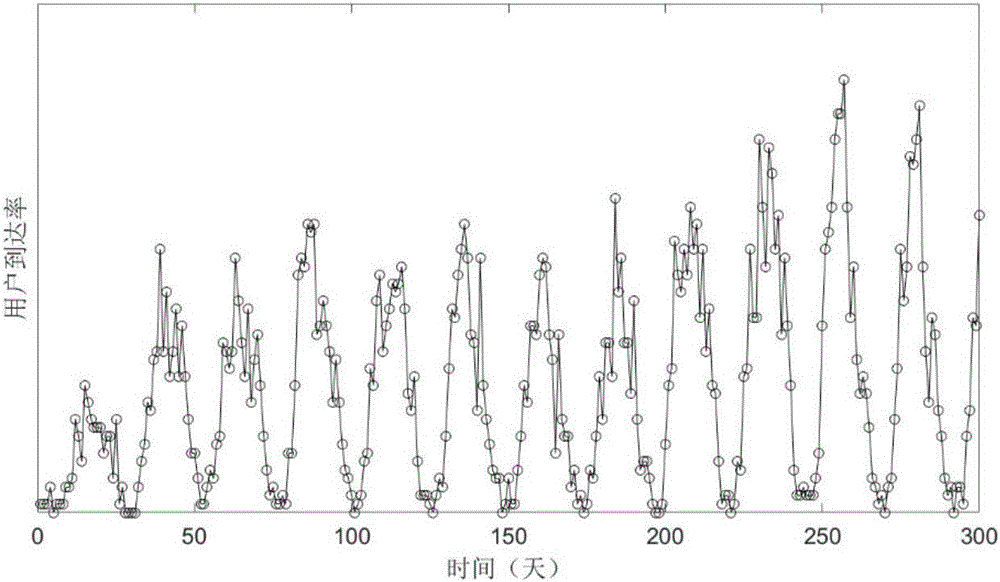
The invention discloses a network user arrival rate prediction method based on binary exponential backoff deviation correction, belonging to the technical field of wireless networks. The method sets up a prediction reference on the basis of sample data of the user arrival rate in an actual wireless network, determines an updating period of a prediction parameter on the basis of user data analysis, determines that the difference between prediction data and actual data is a deviation, carries out attenuation estimation of a burst factor affecting the user arrival rate by means of a binary exponential backoff factor, thus eliminates influence of the burst factor on a user behavior prediction result, and achieves advance prediction of the user arrival rate of the wireless network. The method can provide basis for wireless network strategies in resource allocation, rate standard adjustment and other aspects.
Owner:BEIHANG UNIV
Low Temperature Drift High Power Supply Rejection Ratio Bandgap Reference Circuit Based on Exponential Compensation
ActiveCN110362144BAvoid the problem of introducing excessive errorReduce temperature drift coefficientElectric variable regulationHemt circuitsComputational physics
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
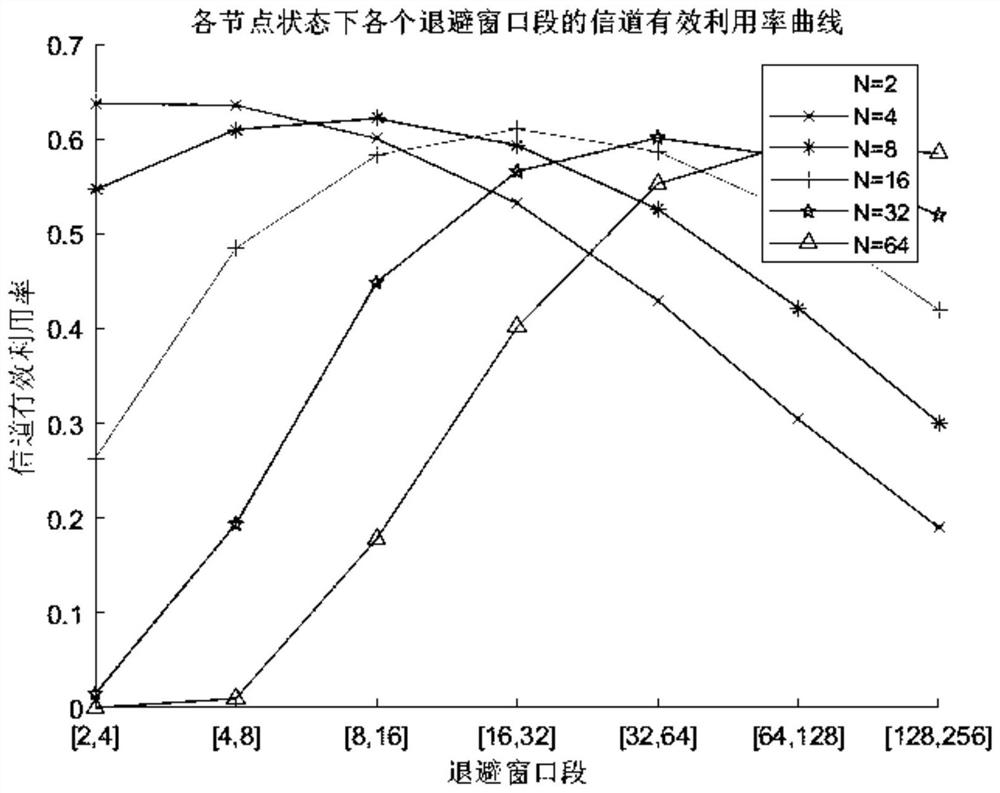
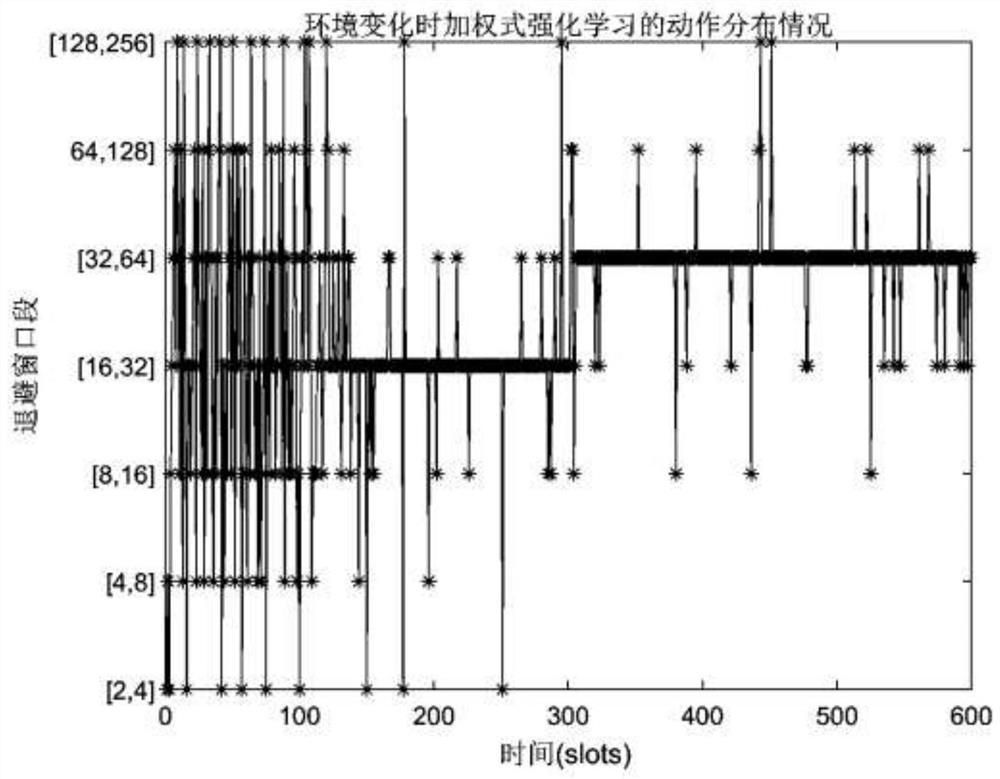
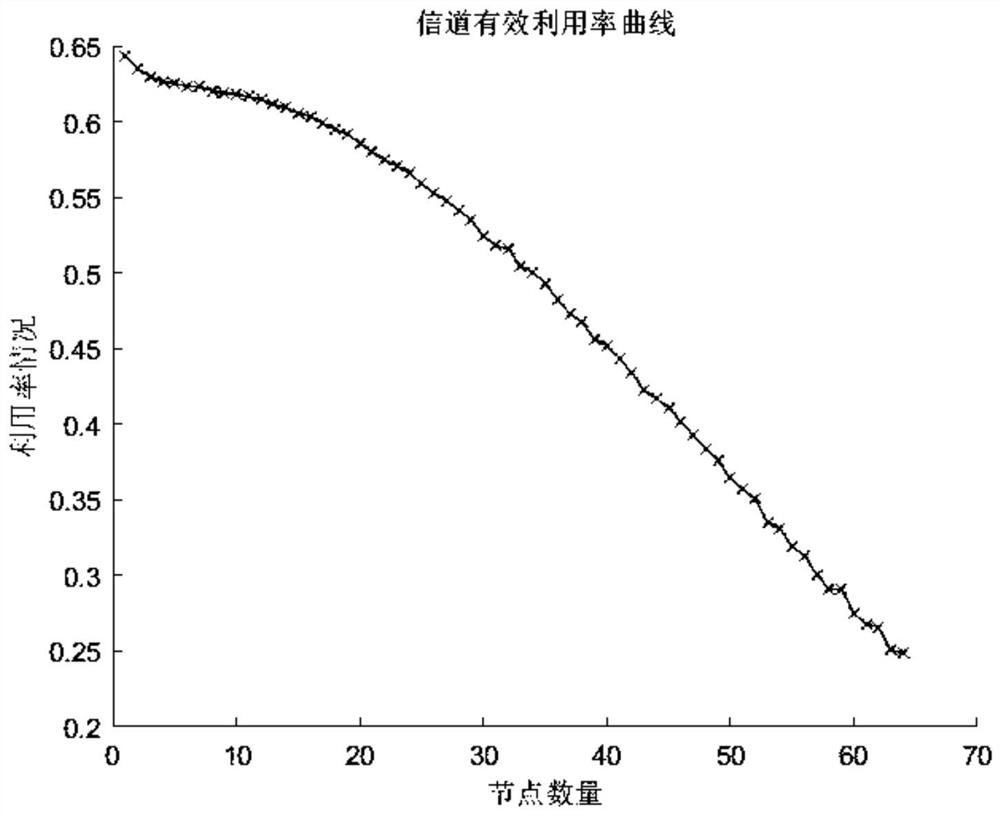
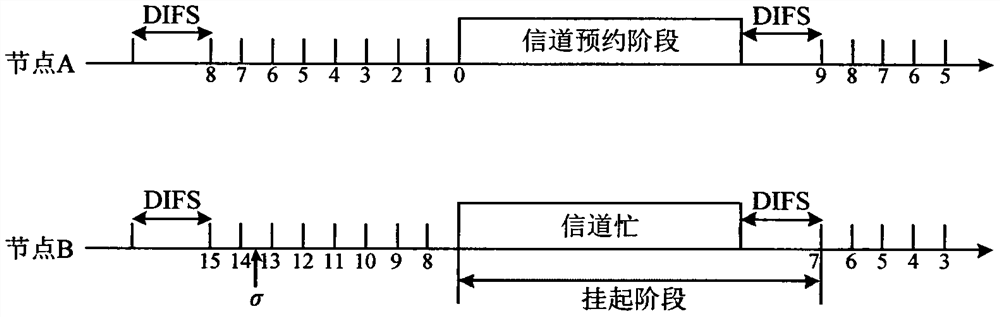
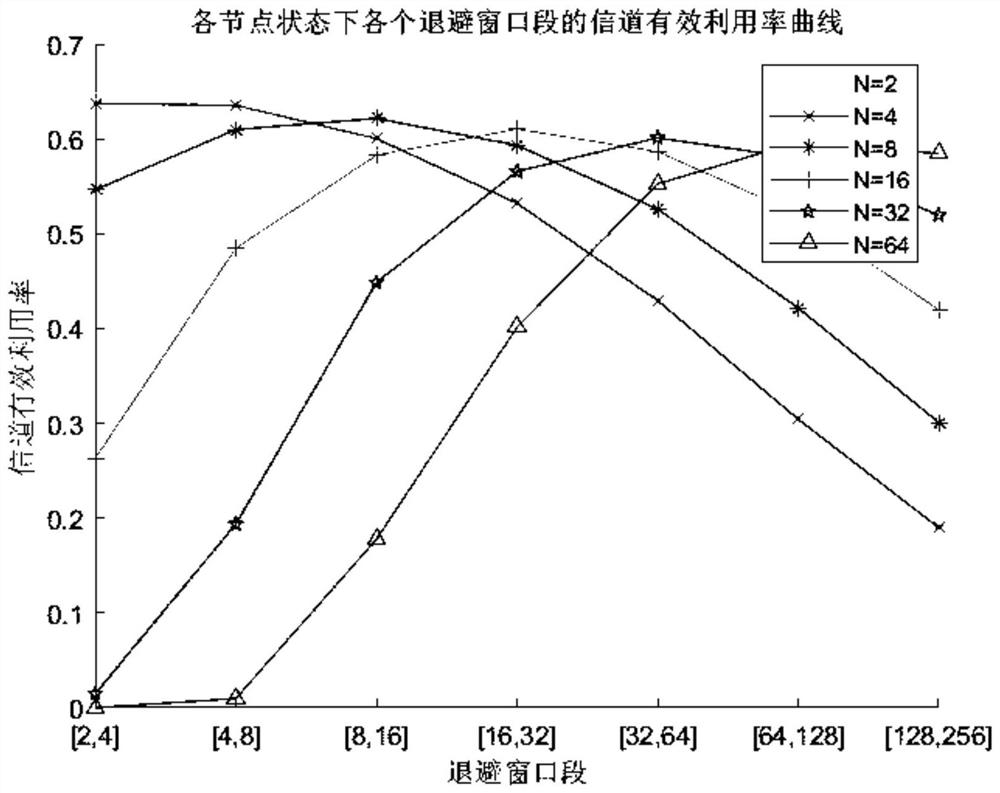
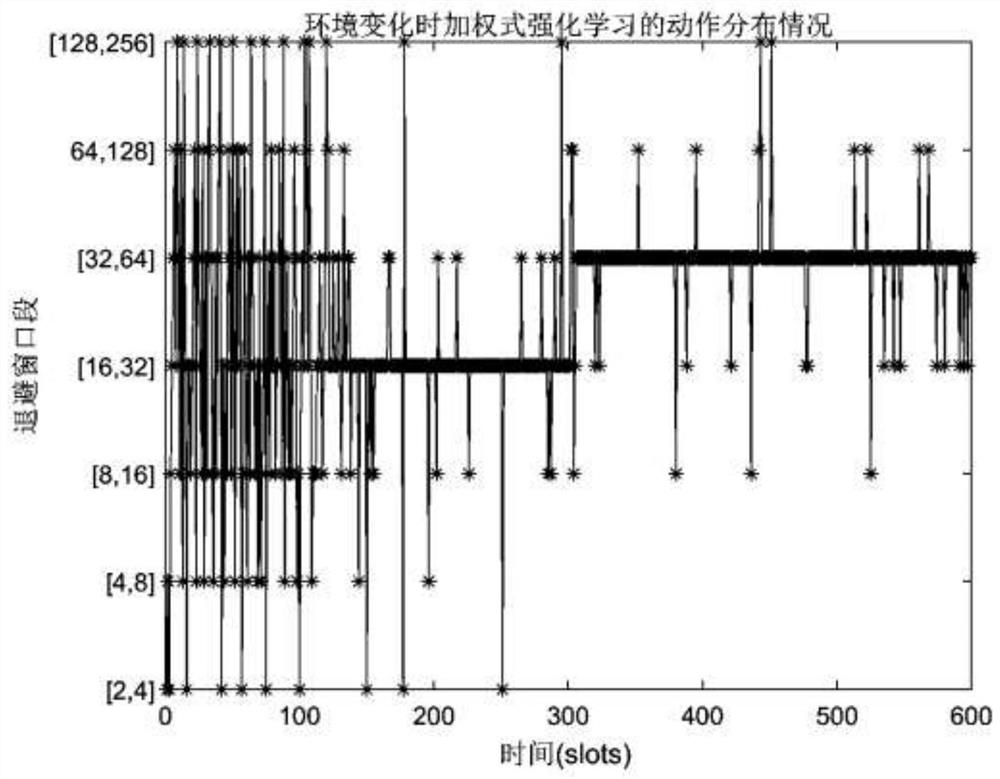
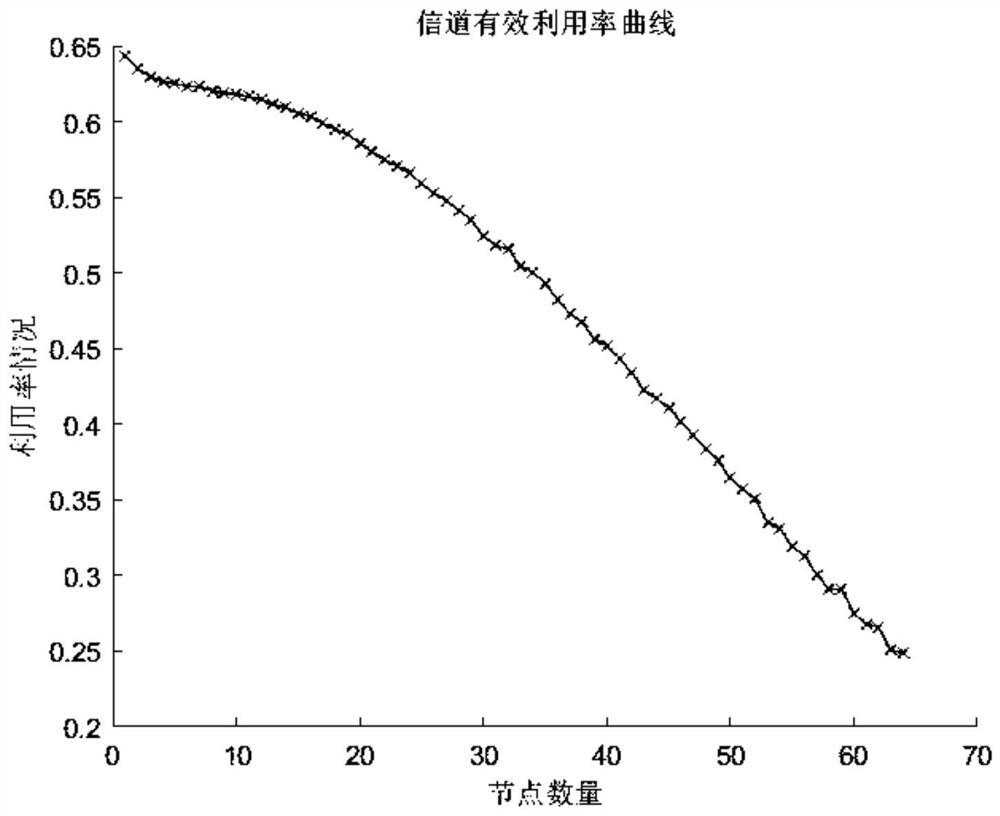
Segmented backoff algorithm based on weighted reinforcement learning
The invention discloses a segmented backoff algorithm based on weighted reinforcement learning, which comprises the following steps: S1, establishing a binary exponential backoff algorithm model, analyzing the condition that the channel effective utilization rate and the data packet loss rate of a wireless sensor network change along with the increase of data traffic in the network, establishing a segmented backoff window, and setting different numbers of nodes to change the data flow condition in the network so as to obtain the channel effective utilization rate of each segment of backoff window under the condition of different numbers of nodes. According to the weighted reinforcement learning-based segmented backoff algorithm disclosed by the invention, the channel access mode of the network access control layer is adjusted through the weighted reinforcement learning model; and therefore, the effective utilization rate of the channel of the wireless sensor network is improved and the packet loss rate is reduced while the fairness of competitive access of the node to the channel is ensured.
Owner:JIAXING UNIV
Method for optimizing passing rate performance in wireless ad hoc network
InactiveCN102104447BShorten the timeIncrease the probability of conflictError prevention/detection by using return channelWireless communicationDistributed coordination functionPass rate
The invention discloses a method for optimizing passing rate performance in a wireless ad hoc network. By adopting the method, the following defects are overcome: the traditional IEEE802.11DCF (distributed coordination function) mechanism adopts the minimum contention window of the BEB (binary exponential backoff) algorithm, so the processing nodes are not timely enough to contend and are too passive. The method has the following beneficial effects: dynamically detecting the number of the transmitting nodes of the contention channels, then computing the next minimum contention window after the transmitting nodes successfully complete the current transmission according to the frame error rate of the RTS (request to send) packet, optimizing the backoff timeslot and reducing the average time of access of the nodes to the channels. The backoff mechanism is superior to the traditional BEB algorithm.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
A conversion method of a protocol conversion gateway
ActiveCN109510827BReduce latency jitterImprove real-time performanceNetwork connectionsHigh level techniquesEngineeringCD protocol
The invention discloses a conversion method of a protocol conversion gateway. The conversion method mainly improves the Binary Exponential Backoff (BEB) algorithm of the CSMA / CD protocol in the existing gateway, and re-constrains the message backoff time. In order to realize the protocol conversion transmission. The method can effectively reduce the delay jitter under data overload and improve the real-time performance of data transmission. The invention also has the characteristics of strong anti-interference and suitable for marine use.
Owner:JIANGSU UNIV OF SCI & TECH
Exponential backoff multiple access method in cooperation with network-assisted diversity
InactiveCN102665287BImprove throughputImprove spectral efficiencyEnergy efficient ICTError prevention/detection by using return channelTelecommunicationsAccess method
The invention discloses an exponential backoff multiple access method in cooperation with network-assisted diversity. The method comprises: (1) allocation of an orthogonal overlapping pilot sequence to nodes requesting for access, including: selecting an orthogonal overlapping pilot sequence and allocating the orthogonal overlapping pilot sequence to the node requesting for access to the network for the first time as the identity identification and channel estimation of the node; (2) the access channel backoff, including: monitoring the channel when a data packet in the network nodes needs to be transmitted, and subjecting the node to countdown backoff when the idle period of the monitored channel lasts for an interval length between distributed frames; and (3) data packet transmission, including: transmitting the data packet of the node needing to transmit the data packet in step (2) by the exponential backoff multiple access method in cooperation with network-assisted diversity. The exponential backoff multiple access method provided by the invention is high in throughput, reliability and efficiency, and has excellent burst traffic handling ability.
Owner:PLA UNIV OF SCI & TECH
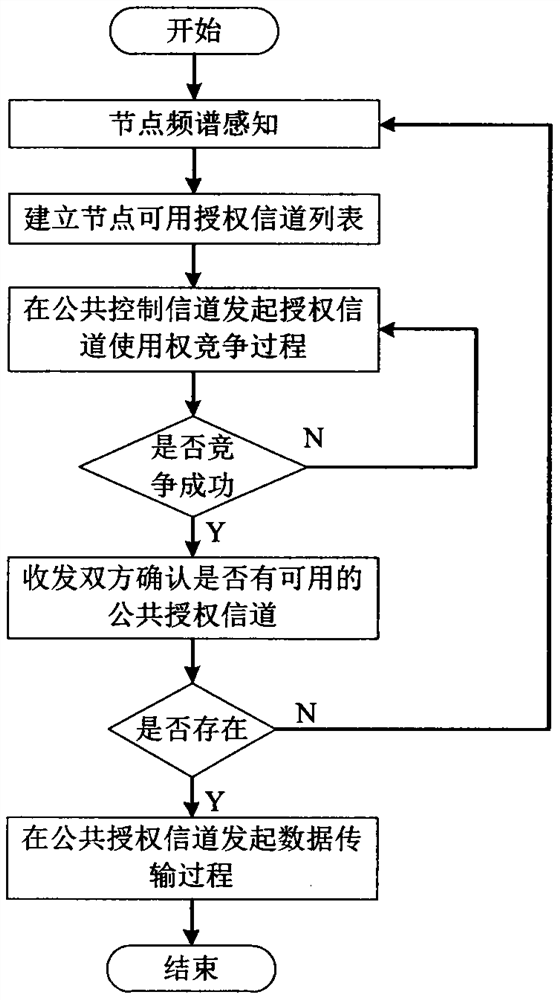
A Cognitive Wireless Network Access Method Based on Common Control Channel
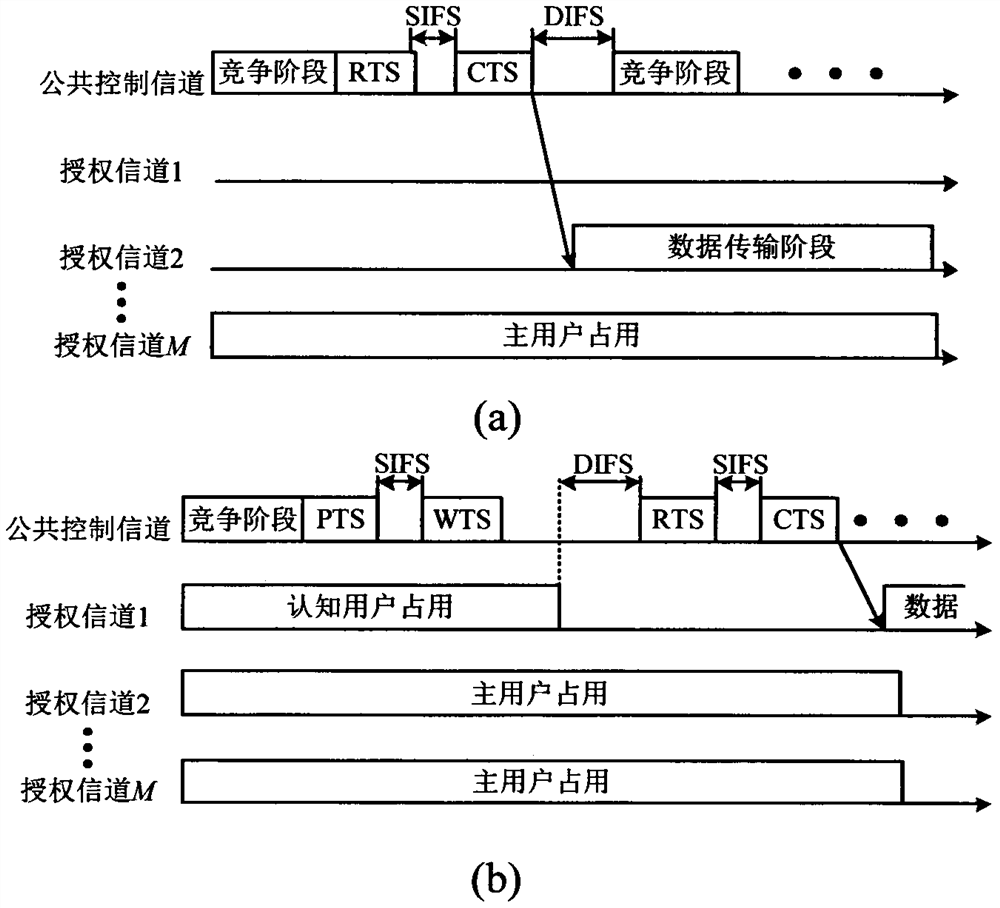
InactiveCN109714807BImprove performanceAssess restrictionTransmission monitoringCognitive userQuality of service
The invention discloses a cognitive wireless network access method based on a common control channel. The method can be divided into a channel competition process, a channel reservation process and adata transmission process. Wherein the channel competition process is mainly that cognitive users compete for authorization channel use rights on a public control channel in a distributed mode, the channel reservation process is a link of information confirmation between cognitive user receiving and transmitting node pairs, and the data transmission process is a process of tuning the cognitive user receiving and transmitting node pairs to an authorization channel for data transmission. The method is aimed at reducing channel bandwidth wasted by cognitive users due to the fact that waiting authorization channels are idle and conflicts between the cognitive users and main users through an improved binary exponential backoff algorithm, a four-handshake mechanism and a main user priority classification mechanism, and service quality guarantee of the users is improved as much as possible while network saturation throughput performance is improved. A simulation result in an EXata network simulation environment proves the effectiveness of the protocol.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
A Segmented Backoff Algorithm Based on Weighted Reinforcement Learning
The invention discloses a segmented backoff algorithm based on weighted reinforcement learning, comprising step S1: establishing a binary exponential backoff algorithm model, and analyzing the channel effective utilization rate and data packet loss rate of a wireless sensor network with the increase of data traffic in the network If the situation changes, a segmented backoff window is established, and different node numbers are set to change the data flow in the network, so as to obtain the channel effective utilization of each segment backoff window under different node numbers. The invention discloses a segmented backoff algorithm based on weighted reinforcement learning, which adjusts the channel access mode of the network access control control layer through the weighted reinforcement learning model, so as to ensure the fairness of nodes competing for access channels At the same time, it can improve the effective utilization of the wireless sensor network channel and reduce the packet loss rate.
Owner:JIAXING UNIV
A data transmission method and device thereof
ActiveCN103152257BForwarding control implementationData switching networksComputer hardwareExponential backoff
The invention discloses a data transmission method and device. The data transmission method comprises the following steps of: when BEB (Binary Exponential Backoff) equipment receives a message transmitted by a user side, determining an attachment circuit (AC) belonging to the message as well as an SPB (Shortest Path Bridging) case and groups belonging to the AC and allocating source group information corresponding to the SPB case and the groups for the message by the BEB equipment; and when the BEB equipment determines that the received message is required to be locally forwarded in the SPB case, determining to allow the message to be forwarded towards the AC in an egress direction in the SPB case or reject the message to be forwarded towards the AC in an egress direction in the SPB case according to the source group information and a grouping forwarding control strategy by the BEB equipment. According to the data transmission method and device disclosed by the invention, the message forwarding control over the AC in the SPB case is realized.
Owner:XINHUASAN INFORMATION TECH CO LTD
A method and device for implementing cross-spb network access
ActiveCN103200095BReduce configurationReduce resource requirementsData switching networksAccess methodExponential backoff
The invention discloses a cross-space Builder (SPB)-network access implementing method and cross-SPB-network access implementing equipment. The method comprises the following steps: after binary exponential backoff (BEB) confirms a user service instance which is in an SPB network where the equipment is located and needs accessing cross the SPB network so as to map the user service instance to a transmission service instance and tell an opposite-end boundary BEB the transmission service instance to trigger the boundary BEB to calculate a forward path from the equipment to the boundary BEB aiming at the transmission service instance; the boundary BEB calculates a forwarding path from the equipment to other BEBs in the SPB network aiming at the user service instance needing accessing cross the SPB network, and tells the other BEBs in the SPB network where the equipment is located the user service instance needing accessing cross the SPB network so as to trigger the other BEBs to calculate a forwarding path from the equipment to the boundary BEB aiming at the user service instance. The cross-SPB-network access implementing method and the cross-SPB-network access implementing equipment can reduce configuration expenses and resource expenses of the boundary BEB aiming at implementing of cross-SPB-network access.
Owner:XINHUASAN INFORMATION TECH CO LTD
Adaptive carrier sense multiple access (CSMA)/conditional access (CA) method based on institute of electrical and electronics engineers (IEEE)802.15.4
ActiveCN102595648BImprove fairnessImprove throughputNetwork topologiesWireless network protocolsBeacon frameNetwork conditions
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com