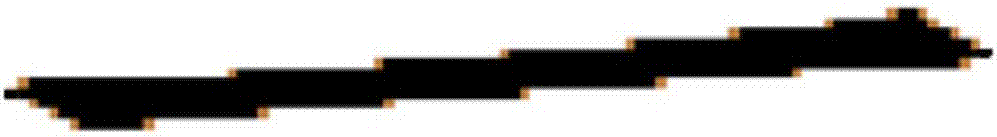Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
268results about How to "Imperceptible" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Information privacy method and electronic terminal
InactiveCN103177206AAvoid identificationConfidentiality is concealedDigital data protectionDigital data authenticationComputer terminalInformation confidentiality
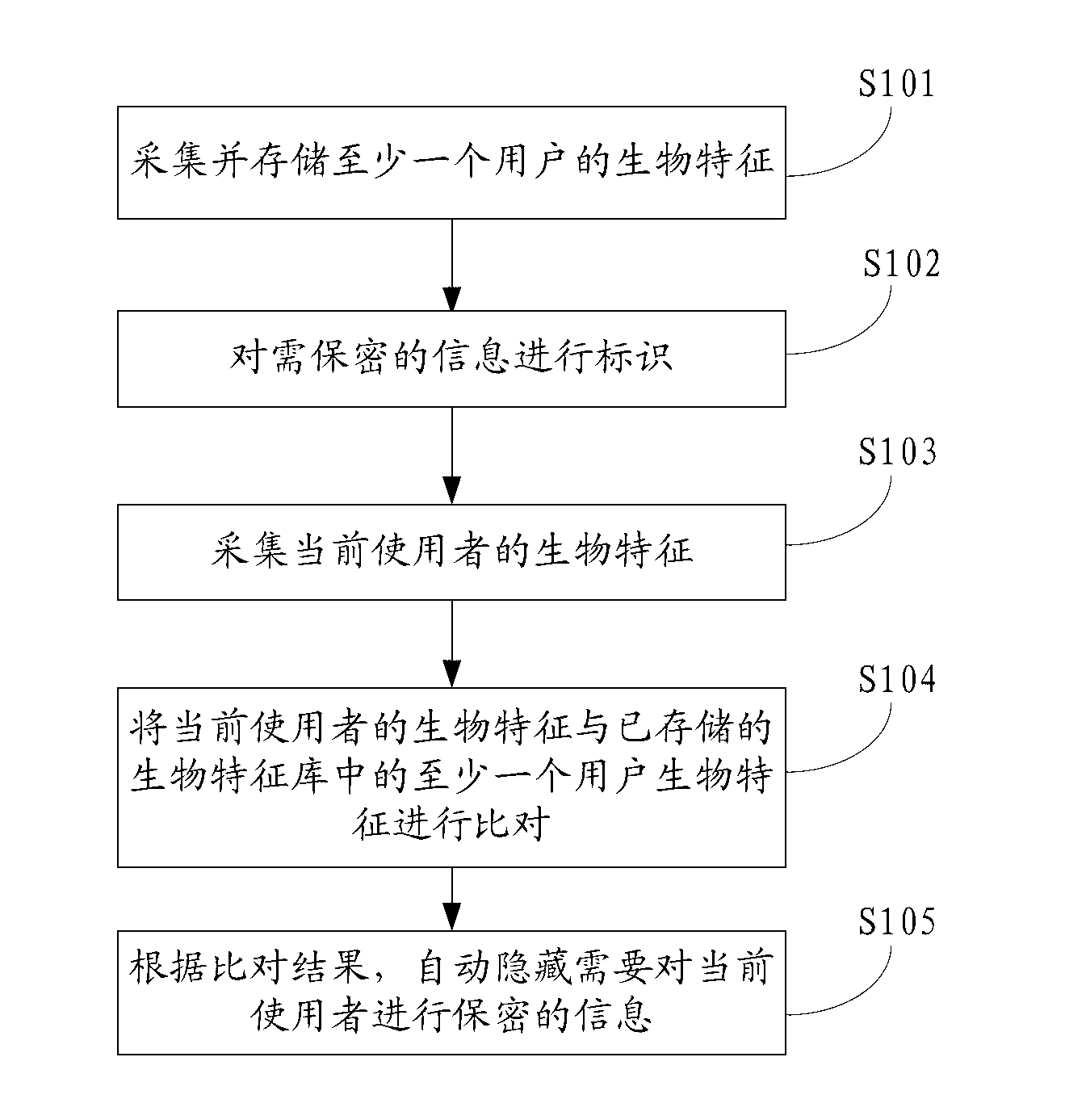
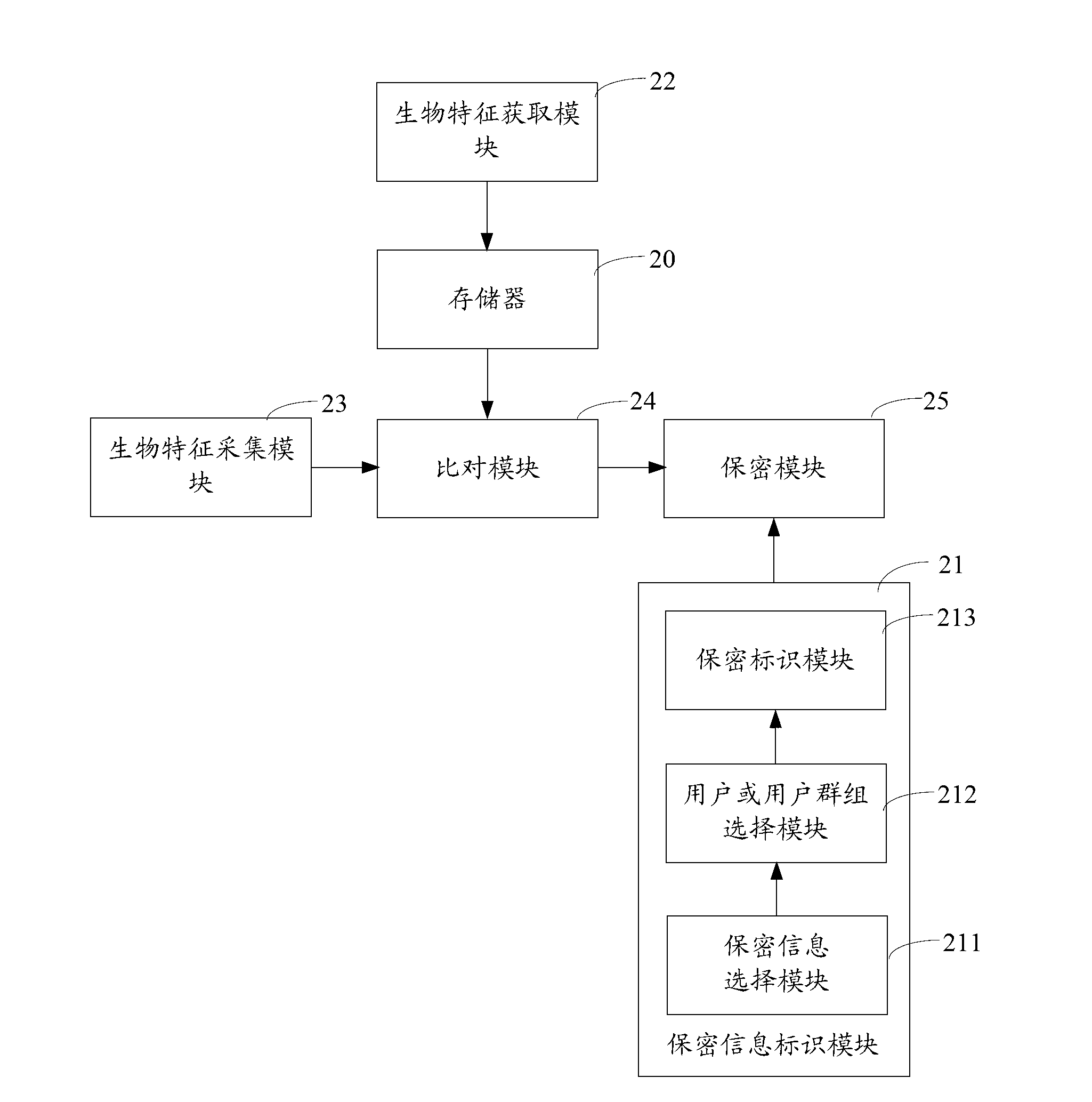
The invention belongs to the field of communication and provides an information privacy method and an electronic terminal. The information privacy method includes the following steps. Biological characteristics of a current user are collected. The biological characteristics of the current user are compared with at least one user biological characteristic stored in a biological characteristic base. The user biological characteristic is correlated with operation authority of information privacy. According to a comparison result, information that the current user is not supposed to know is automatically hidden. The biological characteristics of the current user are collected and compared with the stored biological characteristics. Based on the comparison result, the information that the current user is not supposed to know is automatically hidden. Thus, automatic identification can be performed without tedious log-in and code entering. Private information can be automatically hidden and a privacy manner is invisible and not easily observed by people.
Owner:NUBIA TECHNOLOGY CO LTD
Method and device for speed measurement based on geomagnetic sensing
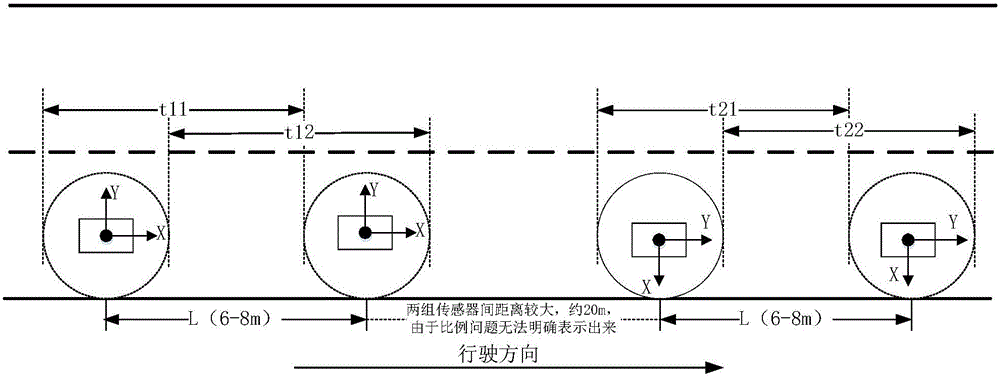
The invention discloses a method and a device for speed measurement based on geomagnetic sensing. The method comprises the following steps of: arranging multiple groups of geomagnetic sensor nodes on a same lane of a road, each group comprising two geomagnetic sensors with a fixed distance and in the same direction; detecting, by the geomagnetic sensors, a passing situation of vehicles by using a fixed threshold value method: setting a fixed geomagnetic strength as a threshold value, and determining the arrival of a vehicle when detecting that the magnetic field strength is changed and continuously exceeds the threshold value; determining the departure of the vehicle when the magnetic field strength is changed and is continuously smaller than the threshold value; and according to the distance between two geomagnetic sensors in each group of the geomagnetic sensor nodes, and the times of the arrival and departure of the vehicle, calculating the driving speed of the vehicle in this period of time, wherein the average value of the driving speeds of the vehicle, calculated by the multiple groups of geomagnetic sensor nodes, is a finally measured driving speed of the vehicle. By use of the method and the device disclosed by the invention, overspeed phenomena on a common road or an expressway can be effectively detected and corrected in time, so that the method and the device have the characteristics of strong function, low price, convenience, flexibility and the like.
Owner:NANJING UNIV OF SCI & TECH +1
Electronic device unlocking method and device
InactiveCN103488404AImprove experienceImprove securityInput/output for user-computer interactionDigital data authenticationComputer scienceElectronic equipment
Owner:GUANGDONG WEICHUANG ELECTRIC CO LTD
Mobile phone fingerprint recognition alarm system and alarm method
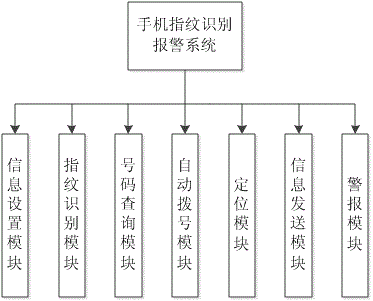
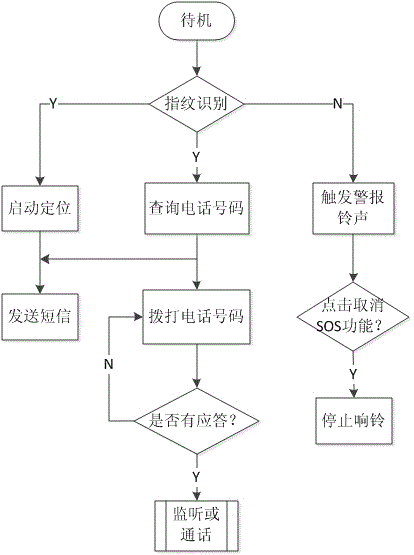
The invention discloses a mobile phone fingerprint recognition alarm system and alarm method. The system comprises an information setting module which is used for setting fingerprint information, multiple groups of phone numbers and help calling information; a fingerprint recognition module which is used for comparing the collected fingerprint information of a user with the fingerprint information stored by the setting module and judging whether the information is consistent or not; a number search module which is used for automatically searching a phone number matching with the fingerprint; an automatic dialing module which is used for automatically dialing the phone number; a location module which is used for marking the geographical location of the user; an information sending module which is used for sending the geographical location information and help calling information of the user; and an alarm module which is used for triggering alarm bell. According to the system and the method, an SOS help calling function is started through fingerprint recognition; the system can automatically dial the phone number, send a short message and so on; the help calling information of the user can be rapidly and effectively sent in a hidden mode; the system and the method are applied to the smart phone; and the demands of the user group of the smart phone can be satisfied.
Owner:SHENZHEN ARTS CHANGHUA INTELLIGENT TECH CO LTD
Automobile anti-theft alarm system
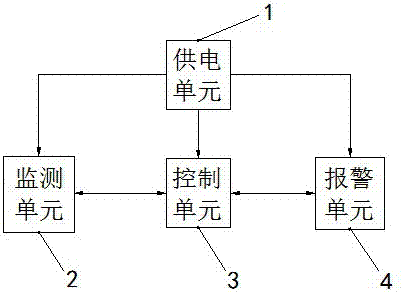
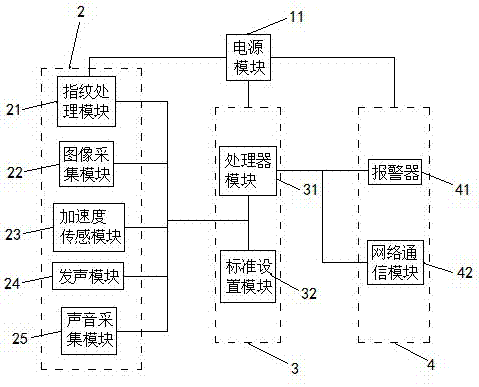
The invention provides an automobile anti-theft alarm system. The system comprises a power supplying unit, a monitoring unit, a control unit and an alarm unit, and a power supply module is arranged in the power supplying unit; the system is characterized in that the monitoring unit is arranged outside an automobile and used for sensing the safety around an automobile body; the control unit is arranged inside the automobile, electrically connected with the monitoring unit, and used for receiving monitoring information sent by the monitoring unit and sending alarm information according to the monitoring information; the alarm unit is electrically connected with the control unit and used for receiving the alarm information sent by the control unit and performing an alarm action according to the alarm information. The automobile anti-theft alarm system is provided with a fingerprint and sound double unlocking system, the unlocking system is not easy to break, the installation position is hidden and is not easily sensed, false alarming is avoided, the theft mode of trailing the automobile or carrying the whole automobile can be sensed, and the property loss of an owner is reduced.
Owner:合肥佳洋电子科技有限公司
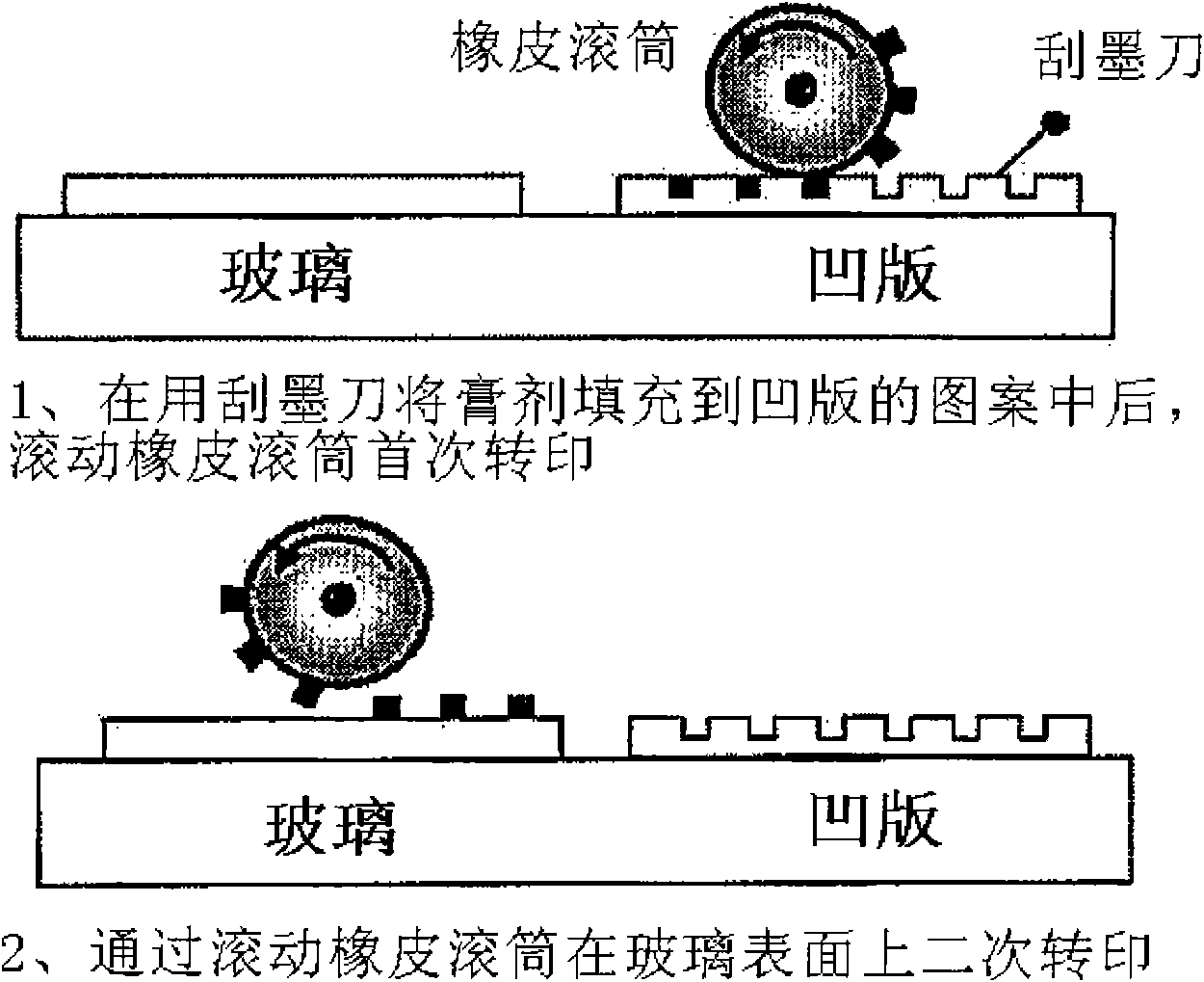
Text digital water printing technology based on character topoloical structure
InactiveCN1684115AImperceptibleReduce visual impactImage data processing detailsCoding/ciphering apparatusDigital watermarkingGlyph
The present invention provides a digital text watermark technology based on topological character structure and has the basic principle that by means of altering the topological structure of character, different character fonts with the same semanteme are designed and properly coded to carry digital watermark information. The present invention includes several methods of designing character font and coding character font and watermark forming and detecting technology. The digital text watermark technology of the present invention has the features of less visual influence, simple and reliable detection, high robustness, great watermark information capacity, etc.
Owner:刘东
Method and device for information hiding in text document
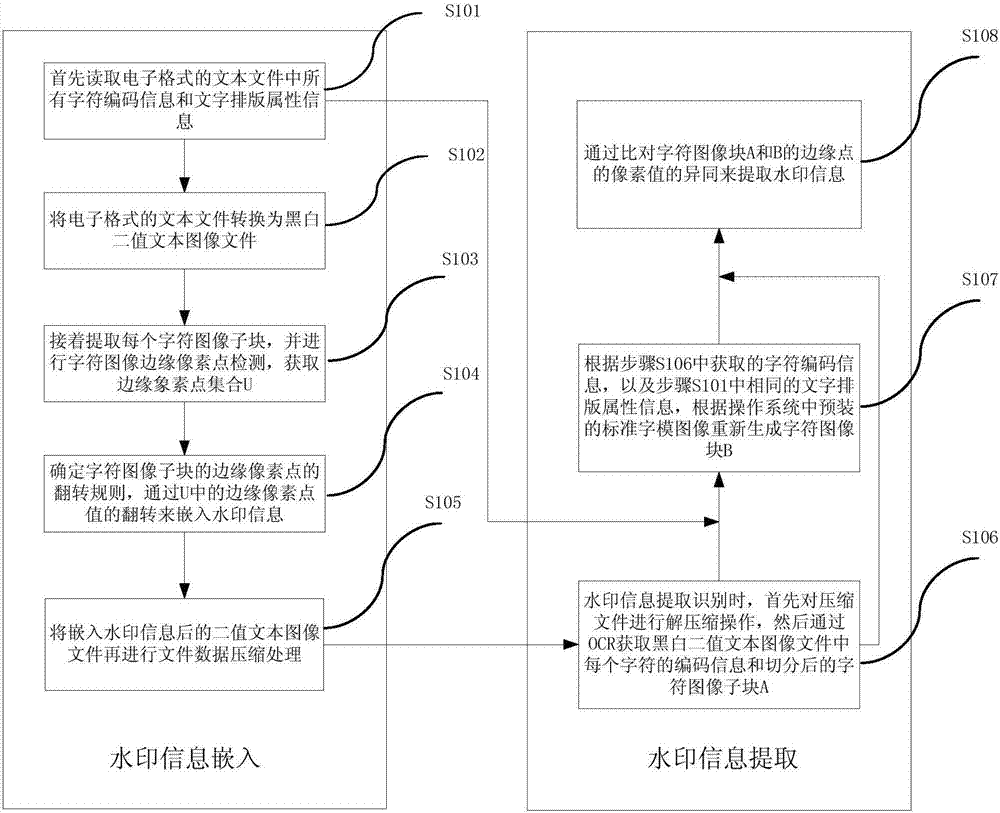
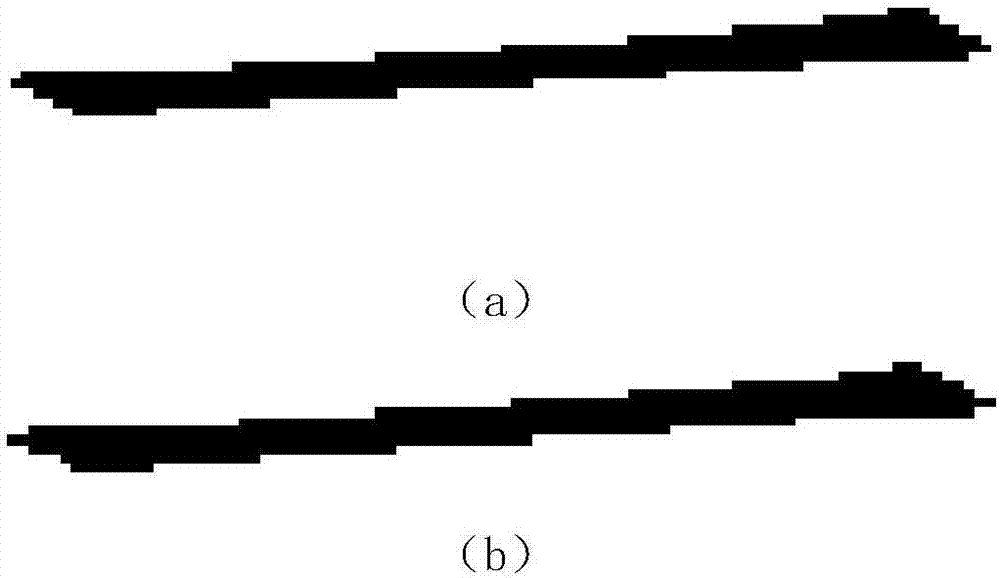
ActiveCN107248134AImprove securityIncrease capacityImage analysisImage data processing detailsComputer graphics (images)Information embedding
The invention relates to a method and a device for information hiding in a text document. The method includes the following steps: (1) reading all character coding information and text layout attribute information in an electronic text file; (2) converting the electronic text file into a black-and-white binary text image file according to the character coding information and the text layout attribute information; (3) extracting each character image sub-block from the black-and-white binary text image file, detecting the edge pixels of the character image, and getting an edge pixel set; and (4) determining the turning rules of the edge pixels of the character image sub-blocks, and embedding watermark information by turning the values of the edge pixels in the edge pixel set, thus realizing information hiding in a text document. According to the invention, watermark information is embedded by modifying the edge of the character image, the text image embedded with the watermark information has a good visual effect, and the information embedding capacity can be greatly increased.
Owner:李晓妮
Device and method for monitoring telephone number of user
InactiveCN103260172AQuick release in timeImperceptibleWireless communicationMobile Telephone NumberSecurity policy
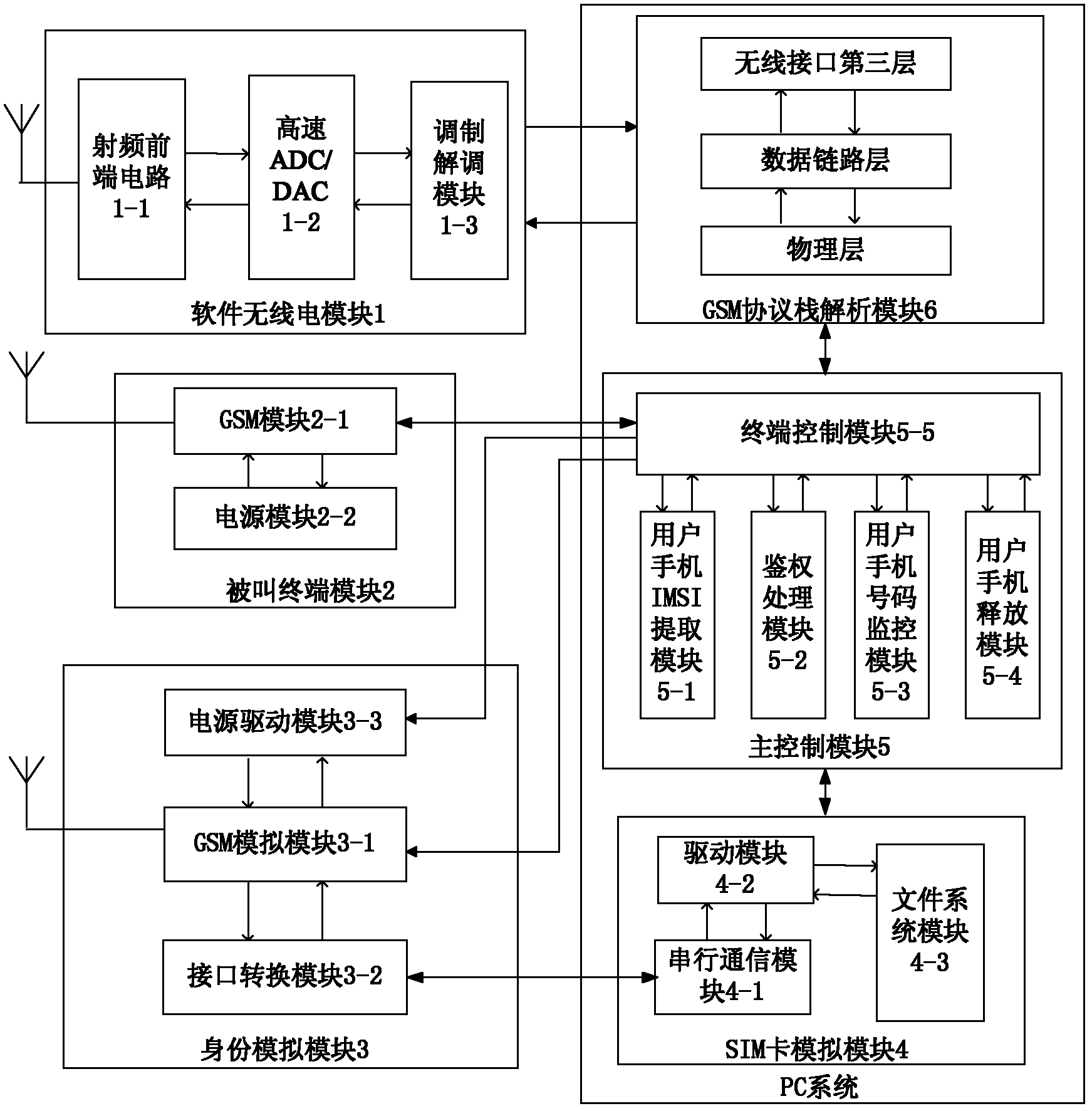
The invention relates to a device and method for monitoring a telephone number of a user. A software radio platform and a global system of mobile communication (GSM) protocol stack program are utilized by the device and method to build a regulation base station system which has a base transceiver station (BTS) function of a GSM network, and the regulation base station system is used for conducting wireless communication with a telephone of the user and extracting identification information, like an international mobile subscriber identification number (IMSI), of the telephone of the user. According to the IMSI of the telephone of the user, a subscriber identity module (SIM) card simulation program is used for achieving SIM card simulation on the telephone of the user, the SIM card simulation program completes operations, such as network authentication and position updating, and then is attached to a normal network through information interaction between identity simulation equipment and a simulation user telephone SIM card, finally the telephone number of the user is extracted by dialing of a called terminal, and monitoring of the telephone number of the user is achieved according to a preset security policy. The device and method is mainly composed of six components including a software radio module, a called terminal module, an identity simulation module, an SIM card simulation module, a main control module and a GSM protocol stack analysis module.
Owner:东南大学常州研究院
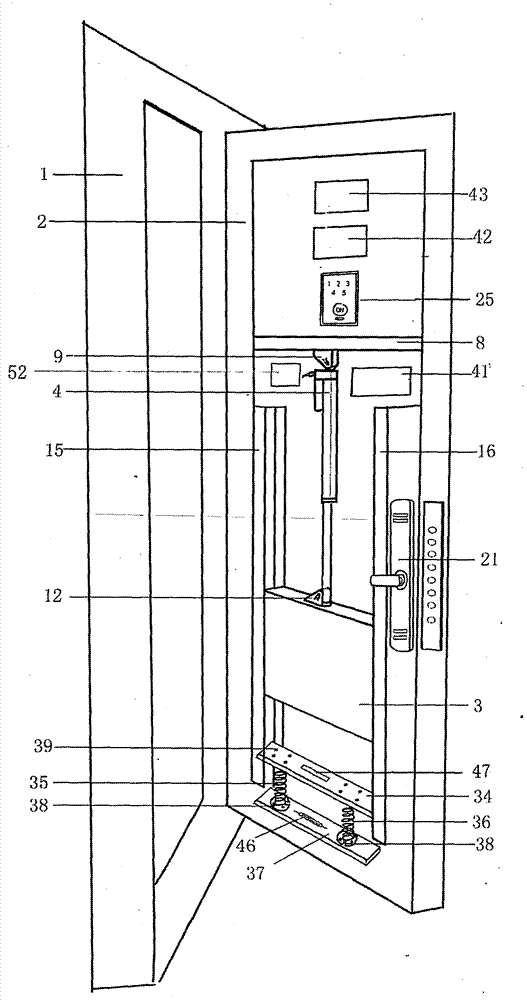
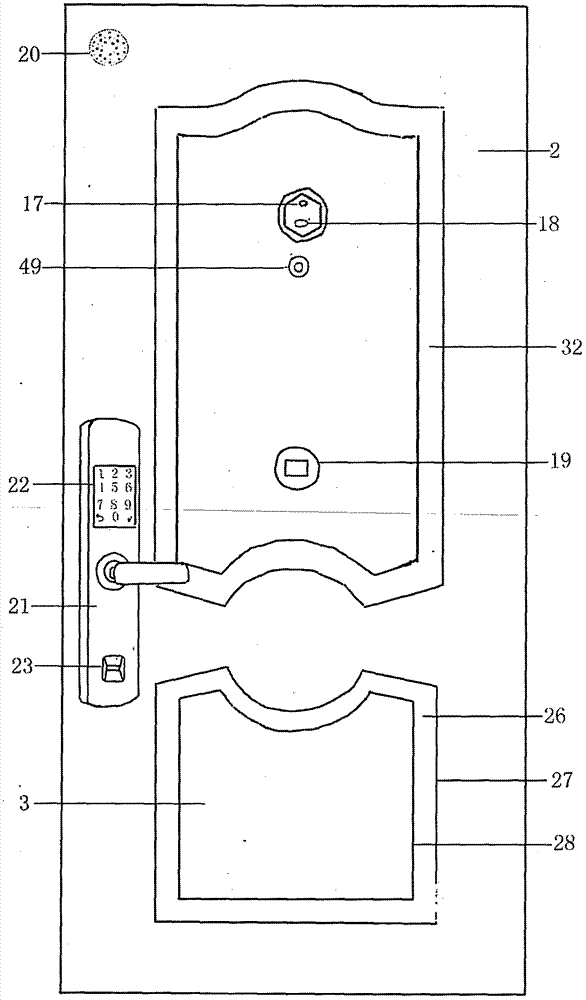
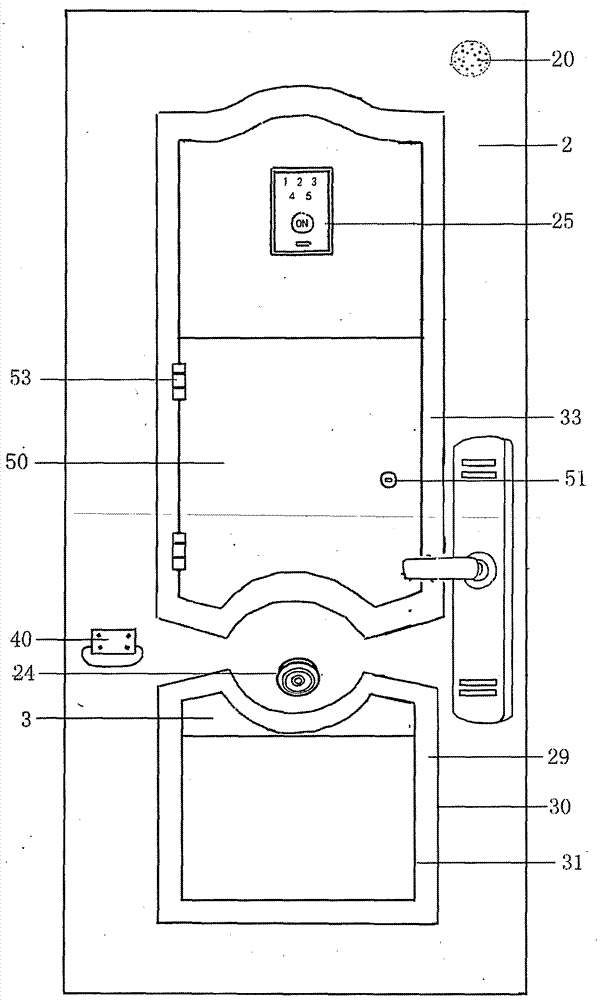
Intelligent remote control anti-theft door with internally hidden invisible door capable of receiving express deliveries and for pets passing through
PendingCN107191110AEnsure safetyImperceptiblePower-operated mechanismServing doorsMicrocontrollerDoorbell
The invention discloses an intelligent remote control anti-theft door with an internally hidden invisible door capable of receiving express deliveries and for pets passing through. The intelligent remote control anti-theft door comprises a door frame, a door leaf, and an intelligent electric lock. The invisible door is hidden below the door leaf, the invisible door is arranged in an interlayer between an iron plate which is located below the front face of the door leaf facing outdoors and an iron plate below the reverse face of the door leaf facing indoors, the invisible door is tightly attached to a guide rail to slide up and down, the invisible door is connected with an electric pushing rod, and the electric pushing rod operates according to orders from a single-chip controller. A door bell button, a front camera, a back camera, an audio collector, a pyroelectric infrared sensor, a horn alarm, and an electric intelligent lock are arranged on the front face of the door leaf. The intelligent lock comprises a password, and a fingerprint reader. A touching screen, an audio and video module, a wireless communication send-receive device and the single-chip controller are arranged on the reverse face of the door leaf. When express delivery personnel get through the call and require to open the door, under the cell phone remote monitoring, users can control the risen height of the invisible door according to the size of goods, so that the opening safety of the invisible door is ensured. The invisible door is imperceptible if not opened, and integrated with the whole anti-theft door, the overall attractiveness of the anti-theft door is not influenced at all, and the problem of express delivery receiving and pets passing through the anti-theft door are solved well.
Owner:赵莉生
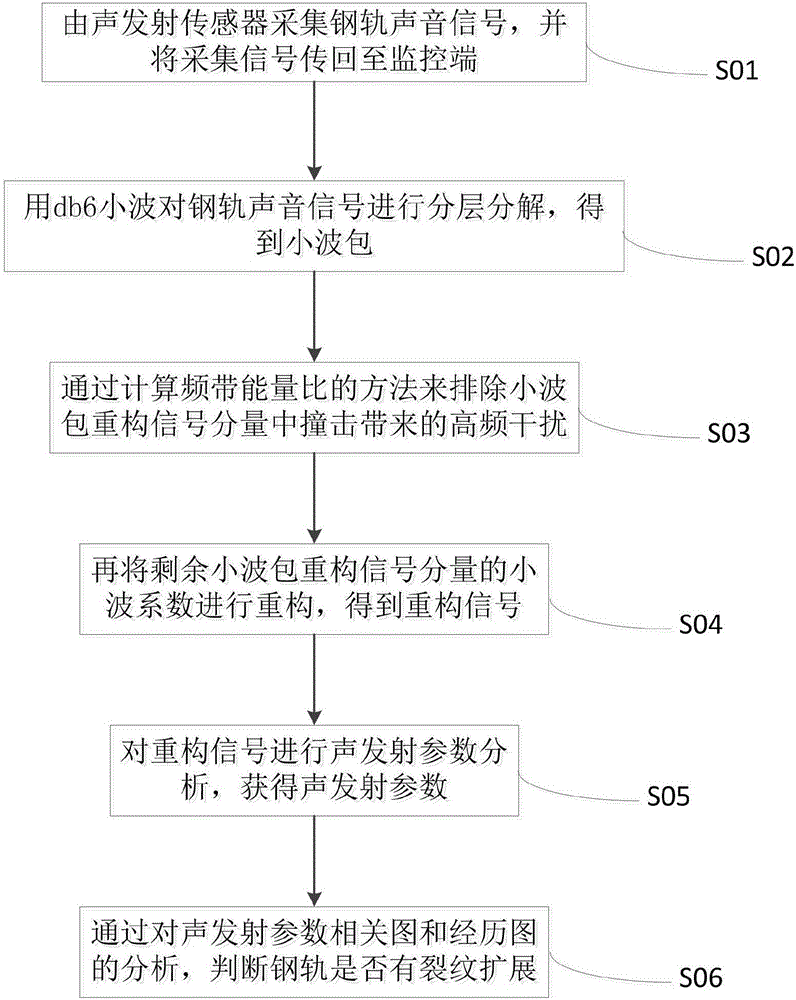
Method and system for filtering online monitored noise of steel rail cracks and judging cracks
ActiveCN106645424AEfficient removalHigh separation precisionMaterial analysis using acoustic emission techniquesProcessing detected response signalAcoustic emissionEngineering
The invention discloses a method for filtering online monitored noise of steel rail cracks and judging the cracks. The method comprises the following steps: collecting steel rail sound signals by virtue of an acoustic emission sensor, and transferring the steel rail sound signals back to a monitoring terminal by virtue of a collection controller, and processing; carrying out hierarchical decomposition on the steel rail sound signals by virtue of a db6 wavelet, so as to obtain a wavelet packet reconstruction signal component, time, frequency and a wavelet coefficient; calculating a frequency band energy ratio, so as to eliminate high-frequency interference in the wavelet packet reconstruction signal component caused by striking; reconstructing the wavelet coefficient of the rest wavelet packet reconstruction signal component, so as to obtain reconstruction signals; carrying out classical acoustic emission parameter analysis on the reconstruction signals, so as to obtain acoustic emission parameters; and analyzing correlation diagrams and experience diagrams, so as to judge whether the cracks are expanded. By virtue of the method, noise interference signals in acoustic emission signals can be effectively removed, crack signals can be separated from the interference signals, and the separation precision is high; and the method can be used for processing smooth signals and has a local analysis function to non-smooth signals.
Owner:SICHUAN SOUTHWEST JIAOTONG UNIV RAILWAY DEV
Capacitive touch panel and production method thereof
InactiveCN102968232AGood lookingImperceptibleInput/output processes for data processingOptical propertyTouch Senses
The invention relates to the technical field of flat-panel display, in particular to a capacitive touch panel and a production method thereof. The capacitive touch panel comprises a substrate with a first surface, a first functional layer and a touch sensing layer, the first functional layer and the touch sensing layer are sequentially formed on the first surface, the first surface at least comprises a first area, and the first functional layer is formed on the first surface, and at least covers the first area; the touch sensing layer is formed on the first functional layer in the first area, and moreover, in the first area, at least the area at least with the first functional layer and the touch sensing layer and the area only with the first functional layer have the same or similar optical characteristics. In addition, the invention also provides the production method for the capacitive touch panel.
Owner:SHENZHEN LAIBAO HI TECH
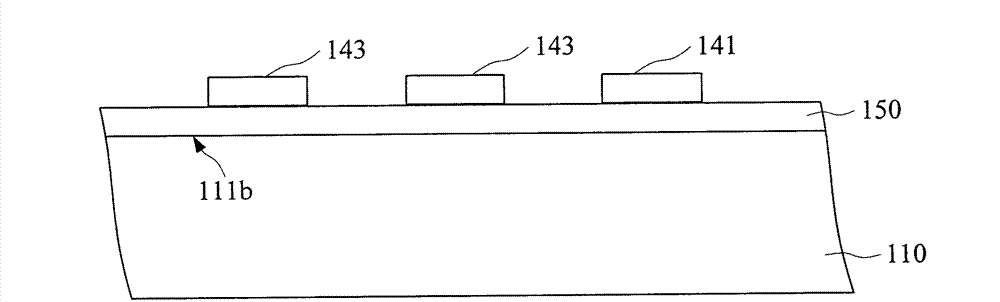
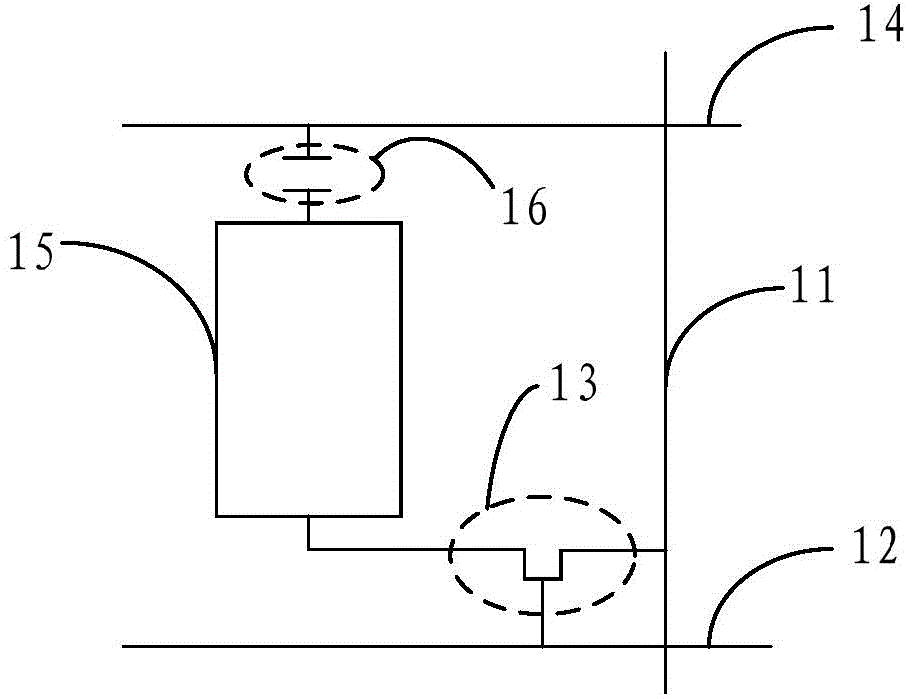
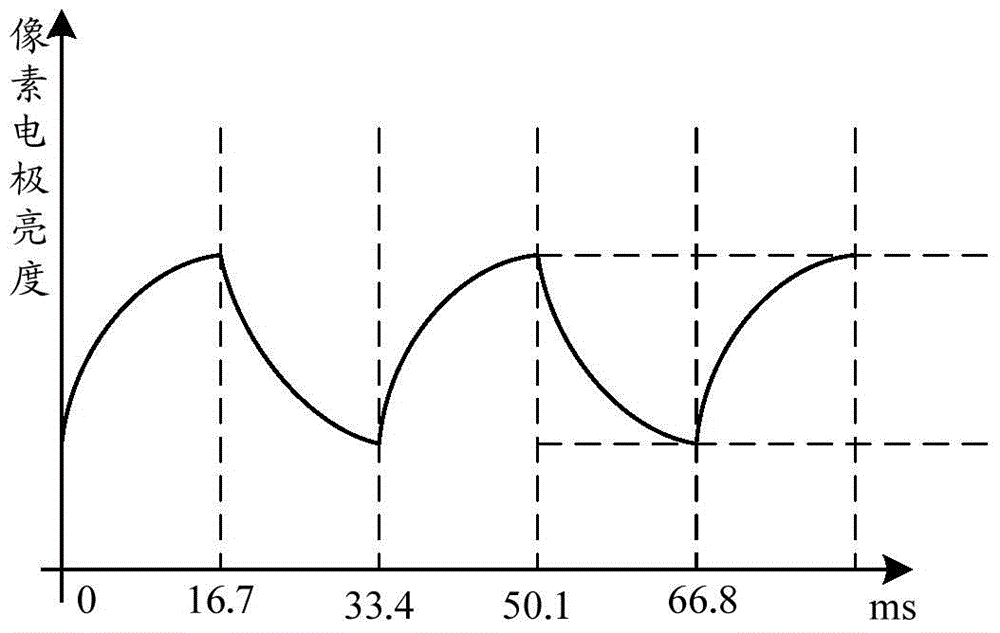
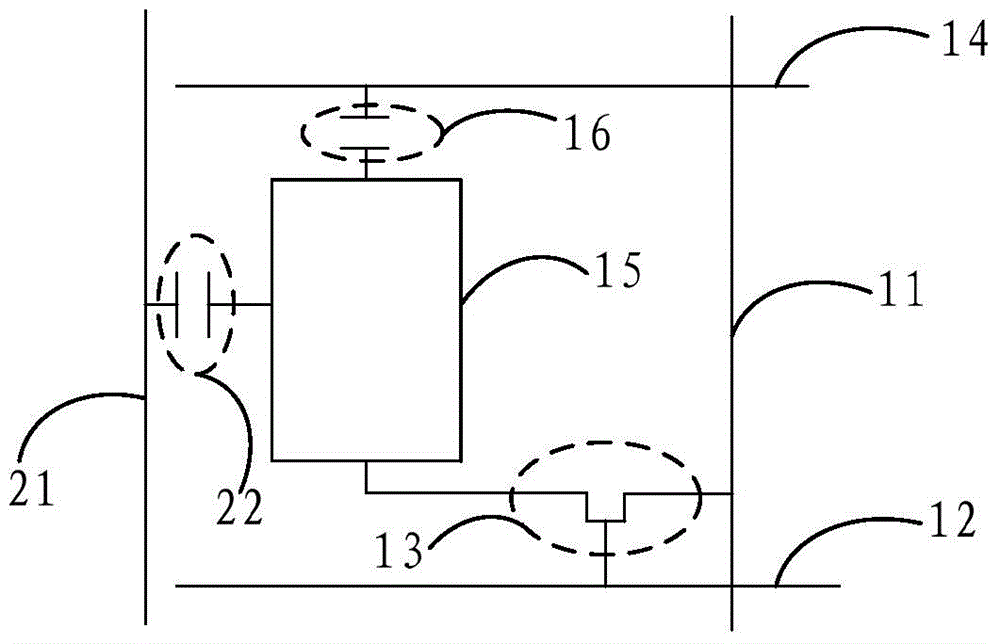
Display panel, method and device for debugging flicker, and display device
ActiveCN104834132AHigh frequencyImprove flickeringStatic indicating devicesElectrical testingDisplay deviceAlternating current
The invention provides a display panel, a method and a device for debugging a flicker, and a display device; the method and the device for debugging the flicker are used for improving the flicker phenomenon in the display panel under the condition that the frequency of a pixel electrode to drive a liquid crystal to turn over is unchanged so that the flicker is not perceived easily by human eyes; the display panel comprises a substrate, data lines and grid lines arranged on the substrate crossly, and sub-pixel units enclosed by the data lines and the grid lines; the display panel is characterized in that each of the sub-pixel units comprises a TFT (thin film transistor), a pixel electrode, a first common electrode and a second common electrode, and the second common electrodes are connected with the input end used for providing an alternating current voltage of a first frequency, wherein projections, on the substrate, of the second common electrodes and the pixel electrodes have an overlapping area.
Owner:BOE TECH GRP CO LTD
Portable telescopic spherical throwing detection robot
The invention discloses a portable telescopic spherical throwing detection robot which comprises a stander, a left driving wheel, a right driving wheel, a telescopic system and a control system, wherein the left driving wheel and the right driving wheel are fixed at both ends of the stander respectively; the telescopic system is used for stretching and contracting the left driving wheel, the right driving wheel and a supporting tail, and is arranged on the stander; and the control system is fixedly connected with the center of the stander. The robot has a certain pretending property during folding, so that the robot cannot be perceived easily; a wheel housing of the robot has a shock absorption property, so that the robot can bear impact of several-meter free fall; and the portable telescopic spherical throwing detection robot can be applied to detection and acquisition of information in dangerous environments.
Owner:BEIHANG UNIV
Text digital Watermark tech using character's features for carrying watermark information
InactiveCN1601956AReduce error rateEasy to detectMultiple keys/algorithms usageSpecial data processing applicationsGlyphComputer science
Owner:刘东
Function level packing-oriented unpacking method and system
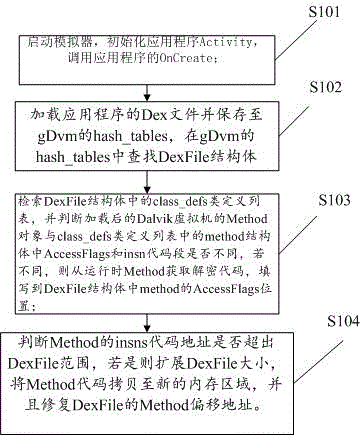
ActiveCN105989252AVersatileFunction increasePlatform integrity maintainanceProgram/content distribution protectionInitVirtual machine
The invention discloses a function level packing-oriented unpacking method and system. The method comprises the following steps: starting a simulator, initiating an application program and calling OnCreate of the application program; loading and storing a Dex file of the application program and searching a DexFile structural body; and retrieving a class-defs class definition list, judging whether a loaded Method object in a Dalvik virtual machine is different from a specific code segment in the class definition list or not, and judging whether a code address exceeds a range or not. According to the function level packing-oriented unpacking method and system, initiative decryption can be realized when calling is carried out from the system layer; and meanwhile, for the similar reinforcing technologies, similar unpacking methods can be used, so that the universality problem is effectively solved.
Owner:WUHAN ANTIY MOBILE SECURITY
Heater and manufacturing method for same
InactiveCN101977863AImprove the heating effectImperceptibleTransparent/reflecting heating arrangementsMicrometerEngineering
The present invention relates to a method for manufacturing a heater that includes: a step of determining a form of a pattern in which the line width of the pattern is 100 micrometers or lower and the aperture ratio of the pattern is 70% or higher and 99% or lower; a step of printing a paste containing a conductive heating material onto at least one surface of a resin film in accordance with the pattern determined in the previous step; a step of firing the printed paste containing the conductive heating material to form a conductive heating pattern; a step of forming bus bars at both ends of the conductive heating pattern; a step of bonding a transparent base to at least one surface of the resin film having the conductive heating pattern; and a step of preparing a power source connected to the bus bars. The invention also relates to a heater manufactured by said method.
Owner:LG CHEM LTD
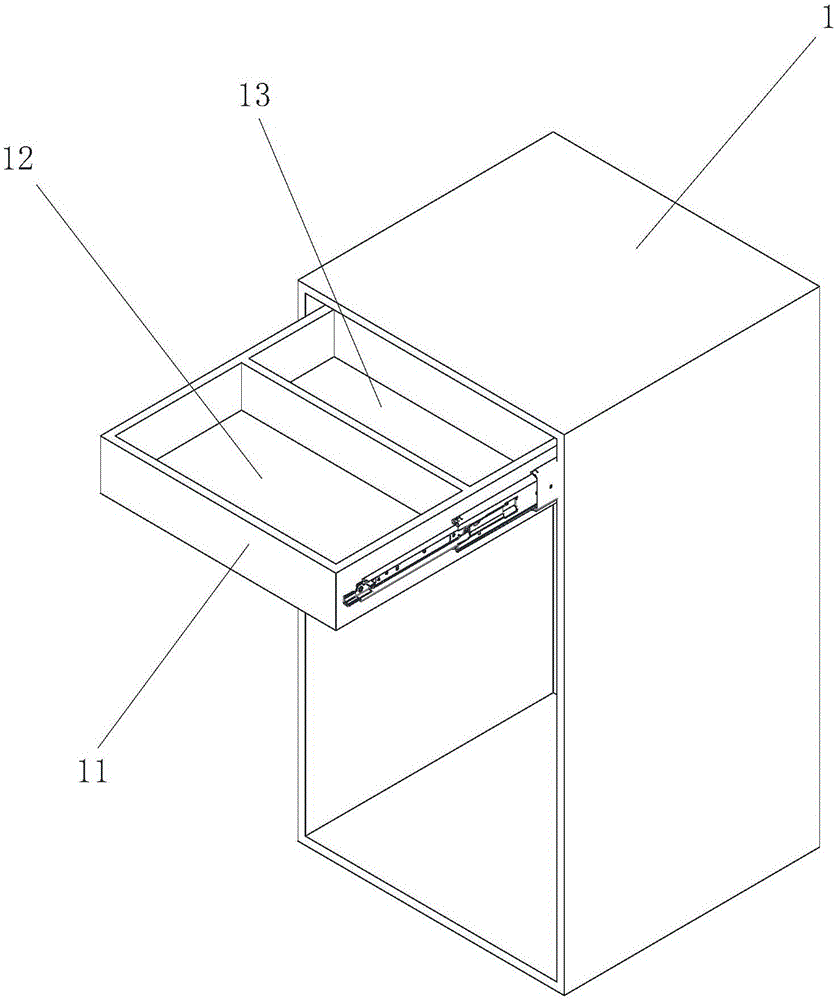
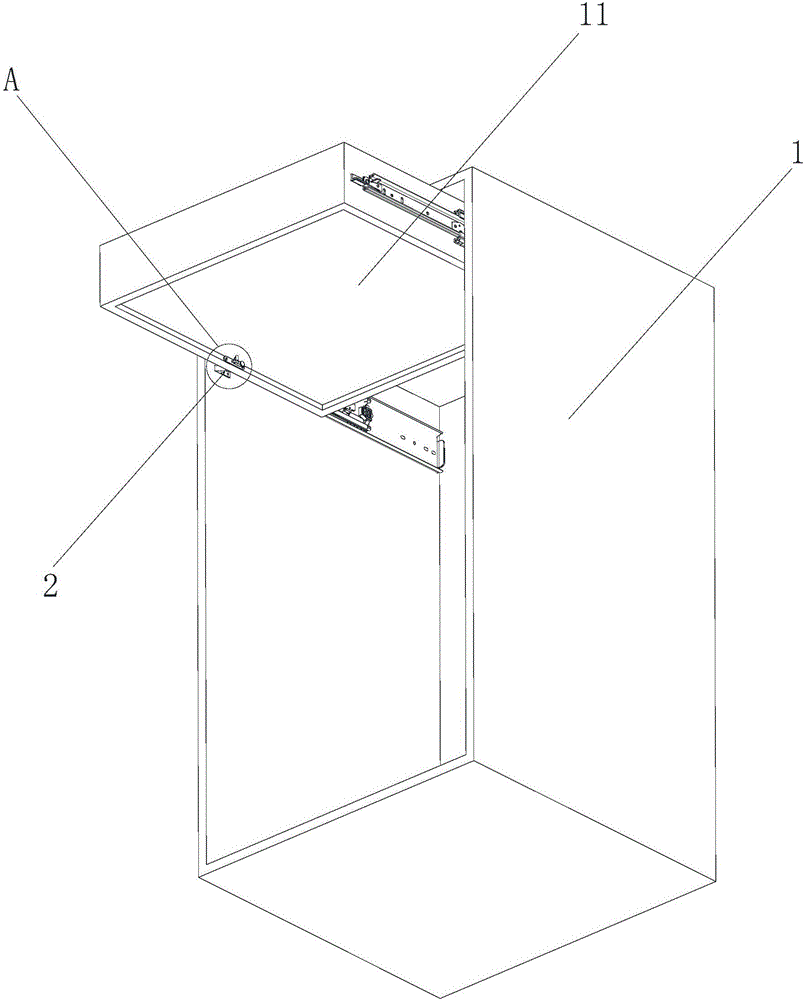
Hidden drawer cabinet
ActiveCN106562588AGood concealmentImprove securityDrawersEngineeringElectrical and Electronics engineering
The invention provides a hidden drawer cabinet. The hidden drawer cabinet includes a cabinet body; a plurality of drawers are arranged in the cabinet body; each drawer has a first accommodation chamber and a second accommodation chamber which are used for holding articles and arranged successively in the opening direction of each drawer; the bottom end of each drawer is provided with a limiting assembly, the limiting assembly has a first working state and a second working state, when the limiting assembly is in the first working state, the limiting assembly limits a outward sliding distance of the drawer so as to allow the first accommodation chamber to freely slide out of the cabinet, and when the limiting assembly releases a limit to the outward sliding distance of the drawer so as to allow the first accommodation chamber and the second accommodation chamber to slide out of the cabinet. The second accommodation chambers are used as hidden spaces, the security is high, the limiting assemblies are positioned on the bottom ends of the drawers and are difficult to aware, and the security of the hidden drawer cabinet can be improved further.
Owner:广东顶固集创家居股份有限公司
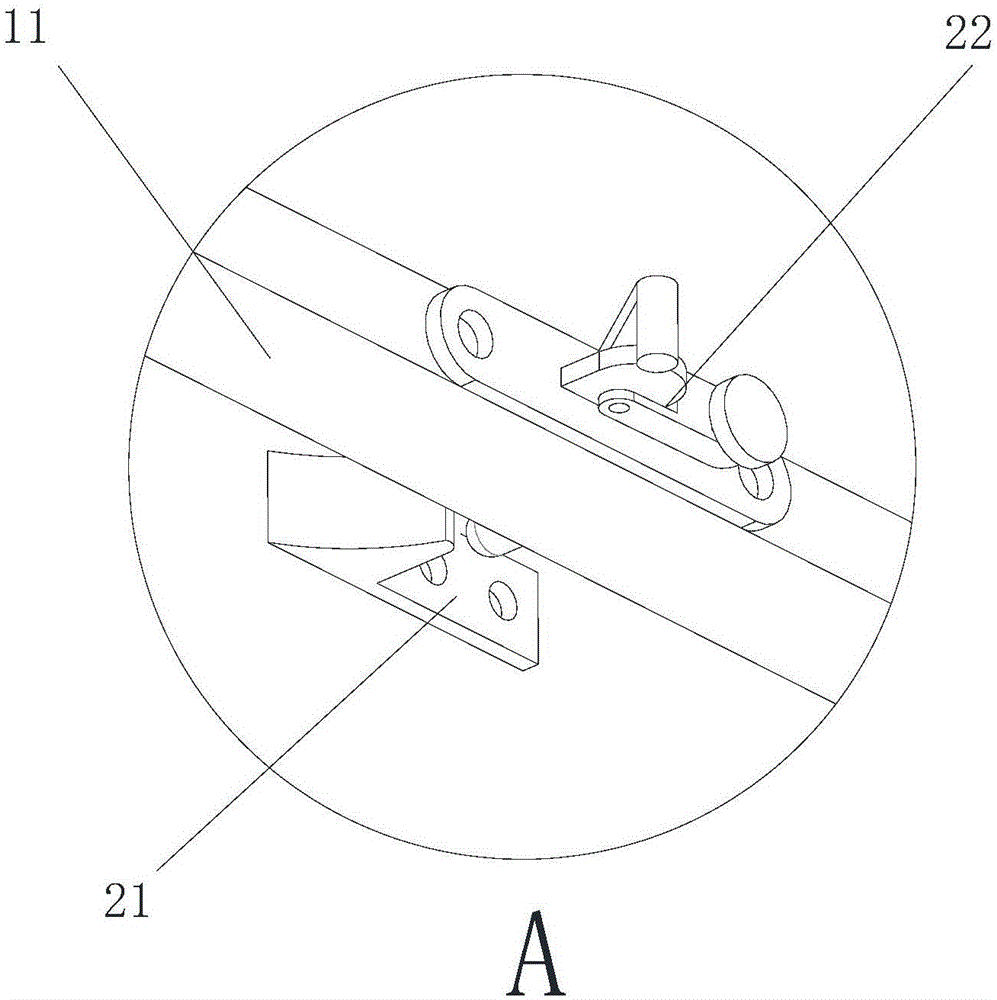
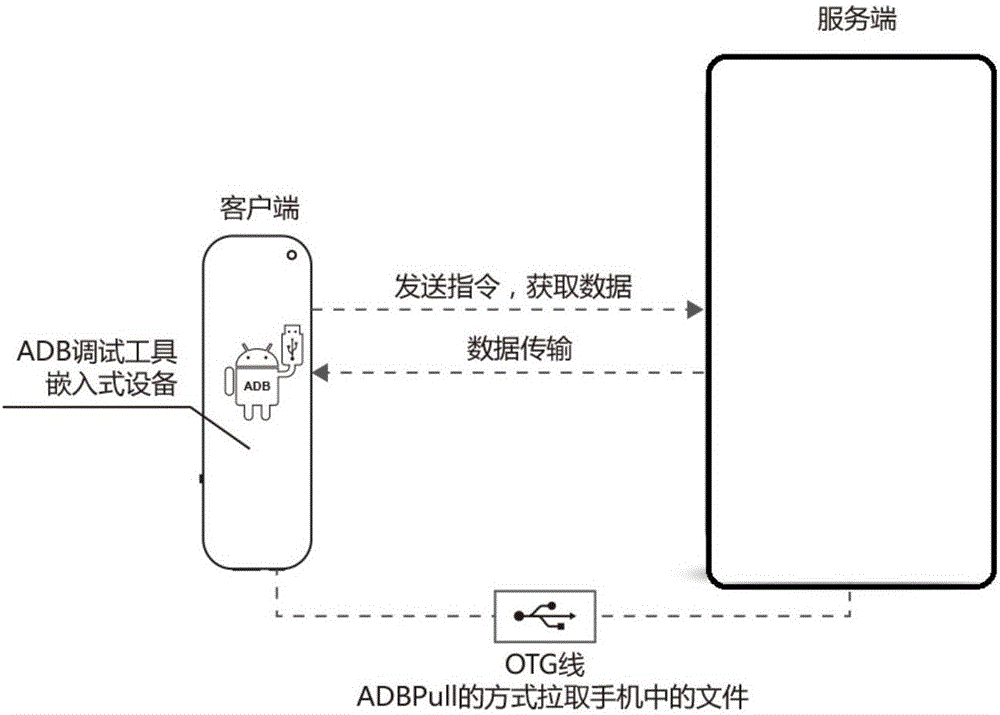
Microdevice for secretly extracting information of Android mobile phone and extraction method
ActiveCN105005474AQuick extractionStrong concealmentSpecific program execution arrangementsComplete dataComputer science
The present invention discloses a microdevice for secretly extracting information of an Android mobile phone and an extraction method. The method comprises: firstly, connecting a microdevice with data of an Android mobile phone from which electronic evidence is to be extracted; secondly, communicating with an externally connected target Android mobile phone by using a pulling file interface provided by an adb debugging tool and an interface of establishing Socket communication; and then, acquiring a root access privilege out of the target mobile phone by using an adb root interface provided by the abd debugging tool: if the root access privilege can be acquired, directly and rapidly extracting a corresponding file according to settings of a user, and if the root access privilege can not be acquired, installing a plug-in that can communicate with the microdevice in the target mobile phone, and completing data extraction by using the plug-in. According to the solution provided by the present invention, the microdevice is very small in volume, convenient to hide and not easy to notice; without the need for operation of the user, automatic extraction is performed after a target device is connected to the microdevice; and an extraction speed is high, extraction of key data can be completed within a few seconds or tens of seconds and time of contact with the target device is short.
Owner:PANSAFE SOFTWARE SHANGHAI
Chilli sauce preparing method and chilli sauce
The invention discloses a chilli sauce preparing method and chilli sauce. Dry vegetable powder and dry fruit powder are used as raw materials and are obtained by dewatering and drying fresh fruits and fresh vegetables with a vacuum freeze dryer without adding any preservative, water in fresh fruits and fresh vegetables is directly sublimated into water vapor from solid ice in the vacuum freezing environment to be evaporated, dried fresh fruit particles and fresh vegetable particles are obtained, and nutrients in fresh fruits and fresh vegetables are not damaged. The chilli sauce prepared from dry vegetable powder and dry fruit powder does not require preservative and is easy to store. The dry vegetable powder and dry fruit powder can be easily matched with meat to obtain different kinds of chilli sauce products, nutrients are more balanced, and diversified development of chilli sauce products can be achieved.
Owner:宋军兴
Wrinkle removing cosmetic
InactiveCN101627958AIncrease brightnessImperceptibleCosmetic preparationsToilet preparationsWrinkle skinVisual perception
The invention relates to preparation of wrinkle removing cosmetic, and aims to provide users with a formulation of a cosmetic for removing skin wrinkles on the face and a preparation method. The cosmetic uses PVA wrapped optical active grains [disulfonic acid triazanaphthlene polydodecyl amide (and) polyethylene] to emit visible light so as to increase brightness at hollowness of wrinkles; therefore, the gloss of the wrinkle part is close to the surrounding skin, the vision effect that the wrinkles 'disappear' is produced, and the grains have the function as lightening 'faint bulbs' at the wrinkles and achieve the effect of 'soft focus' by scattering the surrounding visible light so that the wrinkles are not easy to be discovered.
Owner:孙海
Touch panel
InactiveCN104345991AGood visual effectImprove the problem of high reflectivityDigital data processing detailsInput/output processes for data processingEngineeringTouch panel
Owner:WINTEK CORP
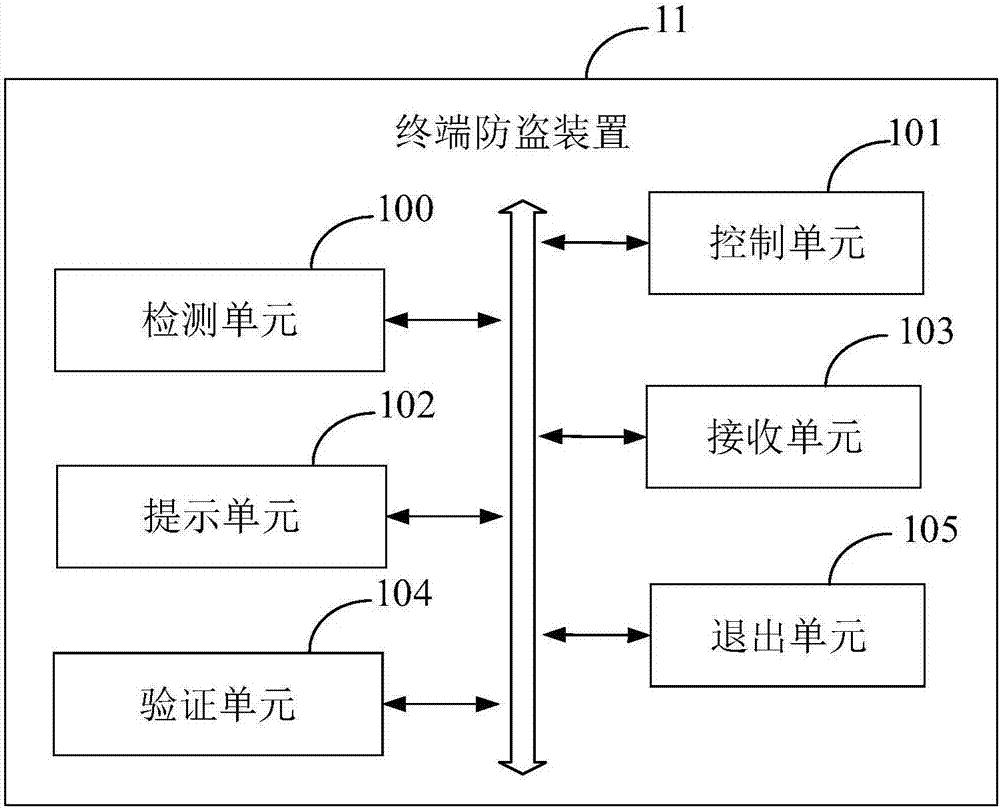
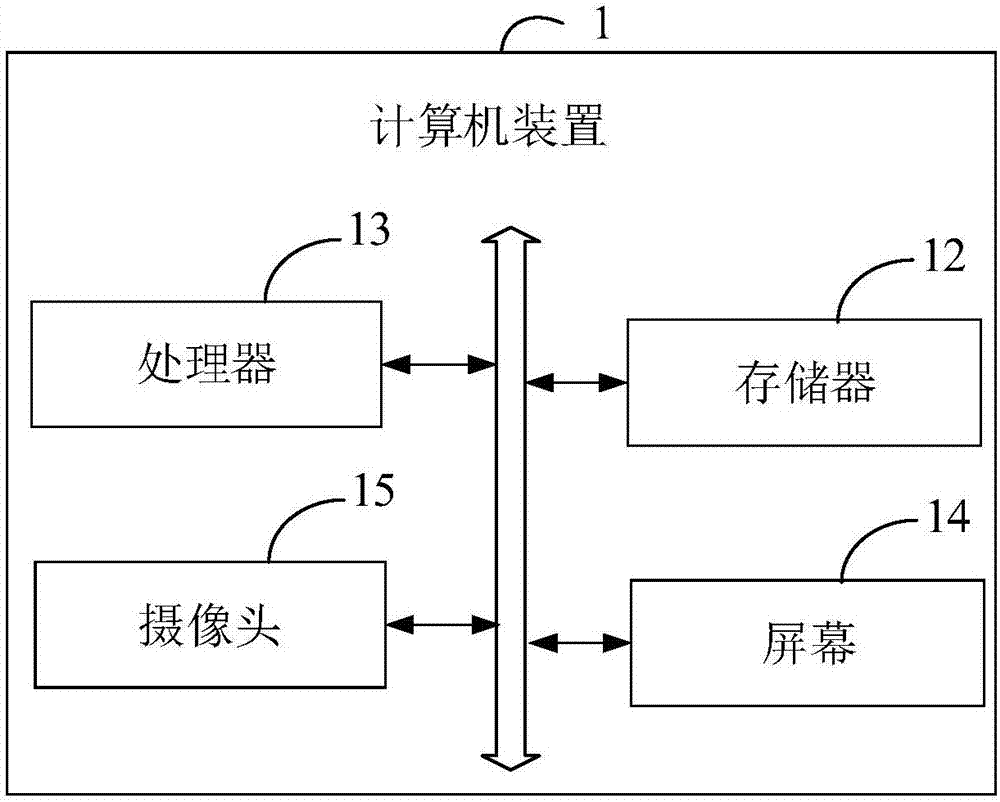
Terminal anti-theft method and device, computer device and computer readable storage medium
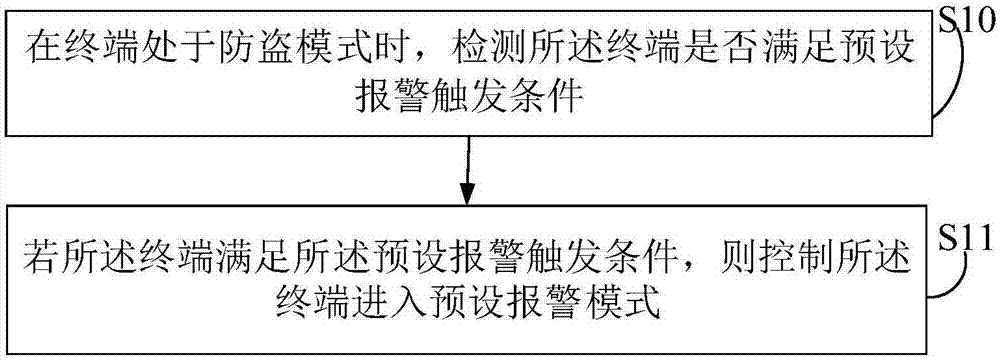
InactiveCN107979692APlay a warning roleImperceptibleSubstation equipmentComputer terminalComputer engineering
The invention provides a terminal anti-theft method and device, a computer device and a computer readable storage medium. The terminal anti-theft method comprises the steps of detecting whether the terminal meets a preset alarm triggering condition when the terminal is in an anti-theft mode; and if the terminal meets the preset alarm triggering condition, controlling the terminal to enter a presetalarm mode. The terminal anti-theft method has a good anti-theft effect and brings about greater guarantee to users.
Owner:MEIZU TECH CO LTD
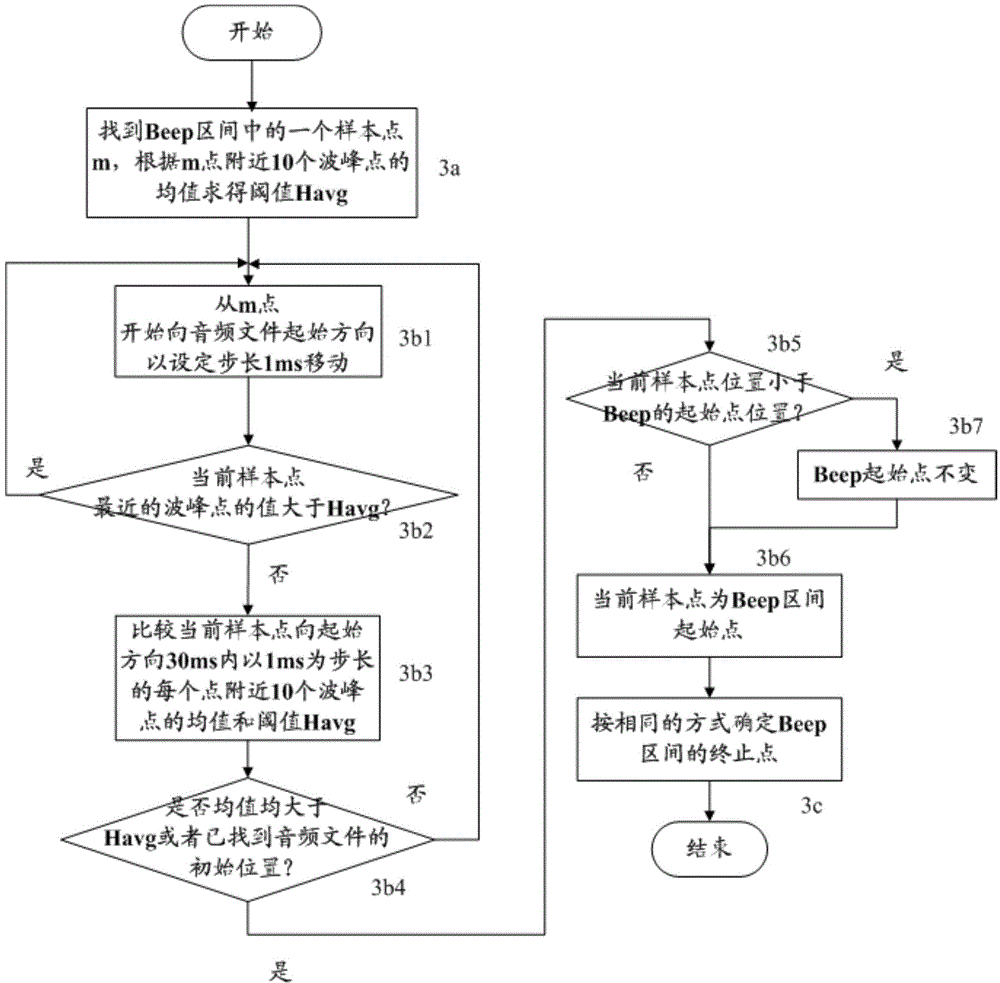
Ranging method based on sound sensor and system thereof
ActiveCN104155644AEquipment limitations are smallThe method is robustUsing reradiationHome positionStart time
The invention relates to a ranging method based on a sound sensor and a system thereof. The method comprises the steps: (1) a ranging server generates the audio recording start time and the play start time and play time length of playing a Beep signal of each mobile terminal in a plurality of mobile terminals involved in ranging, each mobile terminal plays the Beep signal according to the play start time and play time length generated by the ranging server, and each mobile terminal in the plurality of mobile terminals records the respective audio file respectively, (2) the recorded original audio file is read, original audio data is obtained, and the noise removing is carried out on the original audio data, (3) based on the original audio data which is subjected to noise removing, a Beep interval is determined, (4) the audio file of each of the mobile terminals has a plurality of Beep signals, each audio file is subjected to multiple cycle calculation, and the start position of each Beep signal is calculated, (5) according to the calculated Beep signal start position, the actual distances between mobile terminals in the plurality of mobile terminals are calculated.
Owner:XIDIAN UNIV
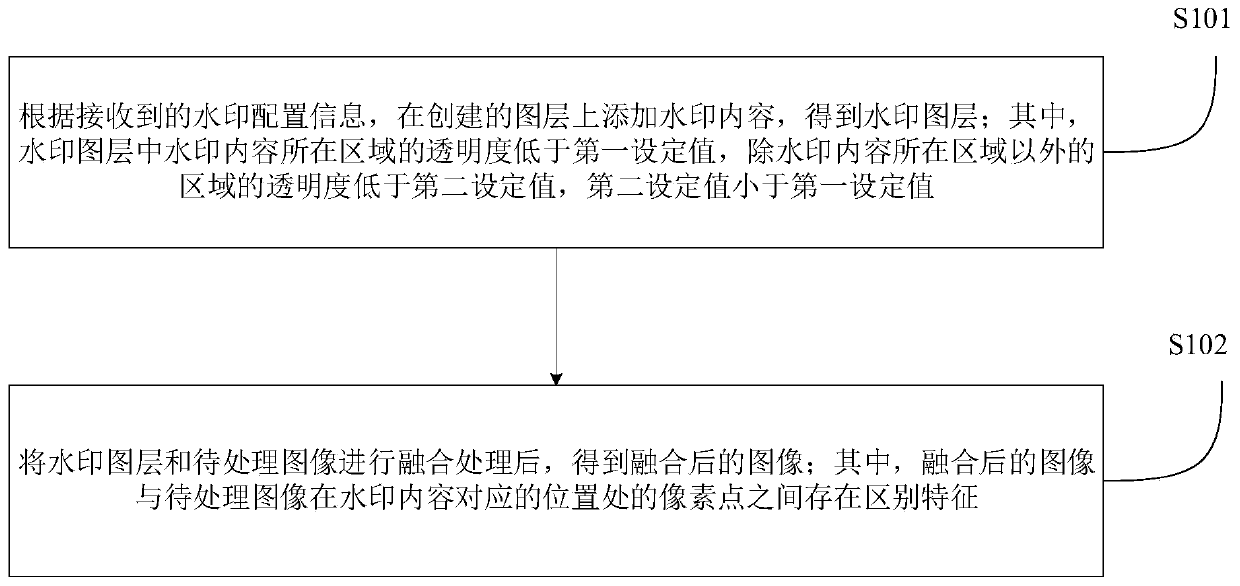
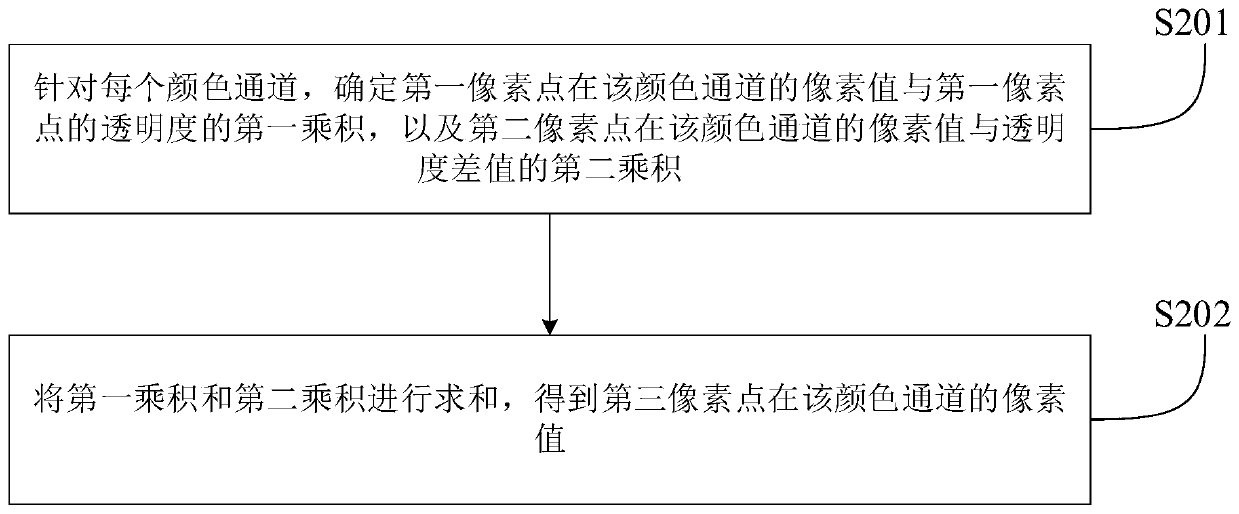
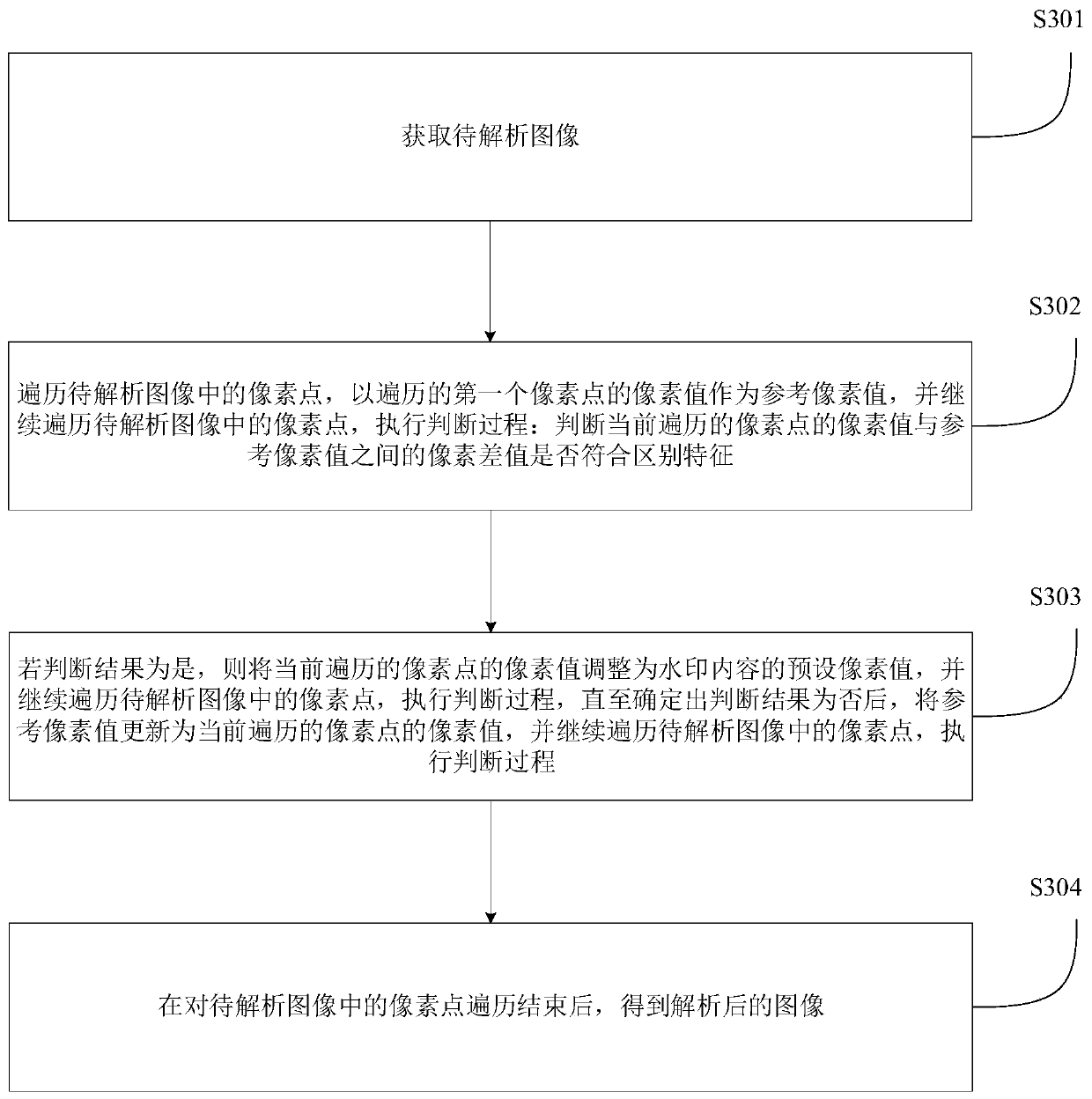
Watermark adding method and device, watermark analyzing method and device, electronic equipment and storage medium
InactiveCN110084735AAchieve safety protectionImperceptibleImage data processing detailsComputer visionAnalysis method
The invention relates to the technical field of computers, in particular to a watermark adding method and device, an analysis method and device, electronic equipment and a storage medium, and aims toadd and analyze watermarks and save time and labor. The watermark adding method comprises the following steps: adding watermark content on a created layer according to received watermark configurationinformation to obtain a watermark layer; carrying out fusion processing on the watermark layer and the to-be-processed image to obtain a fused image, wherein the fused image and the to-be-processed image have a distinguishing feature between pixel points at a position corresponding to the watermark content.
Owner:NEW H3C CLOUD TECH CO LTD
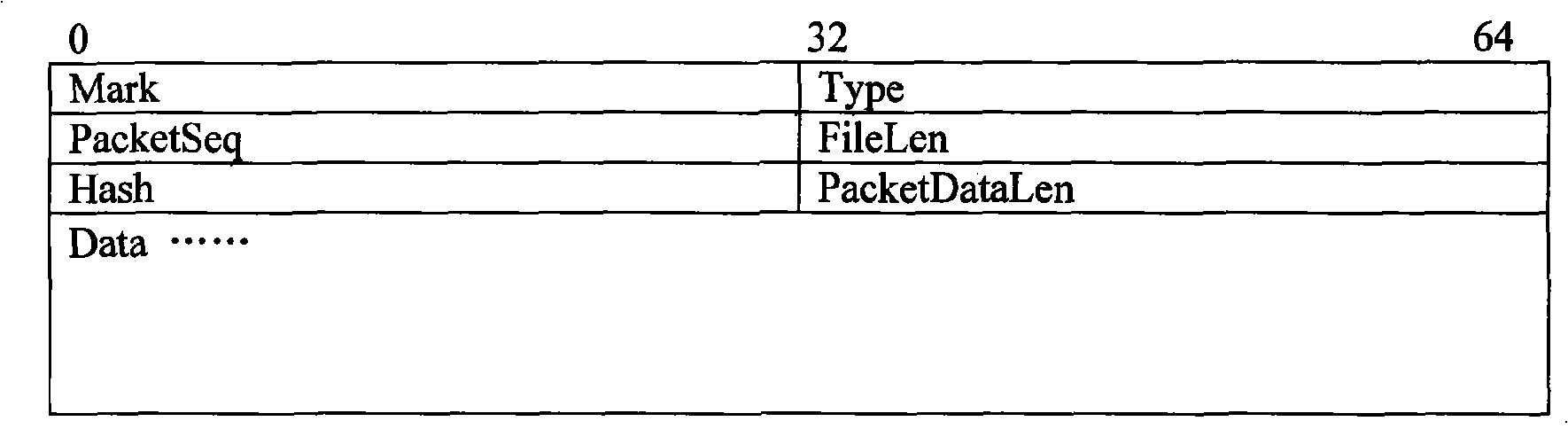
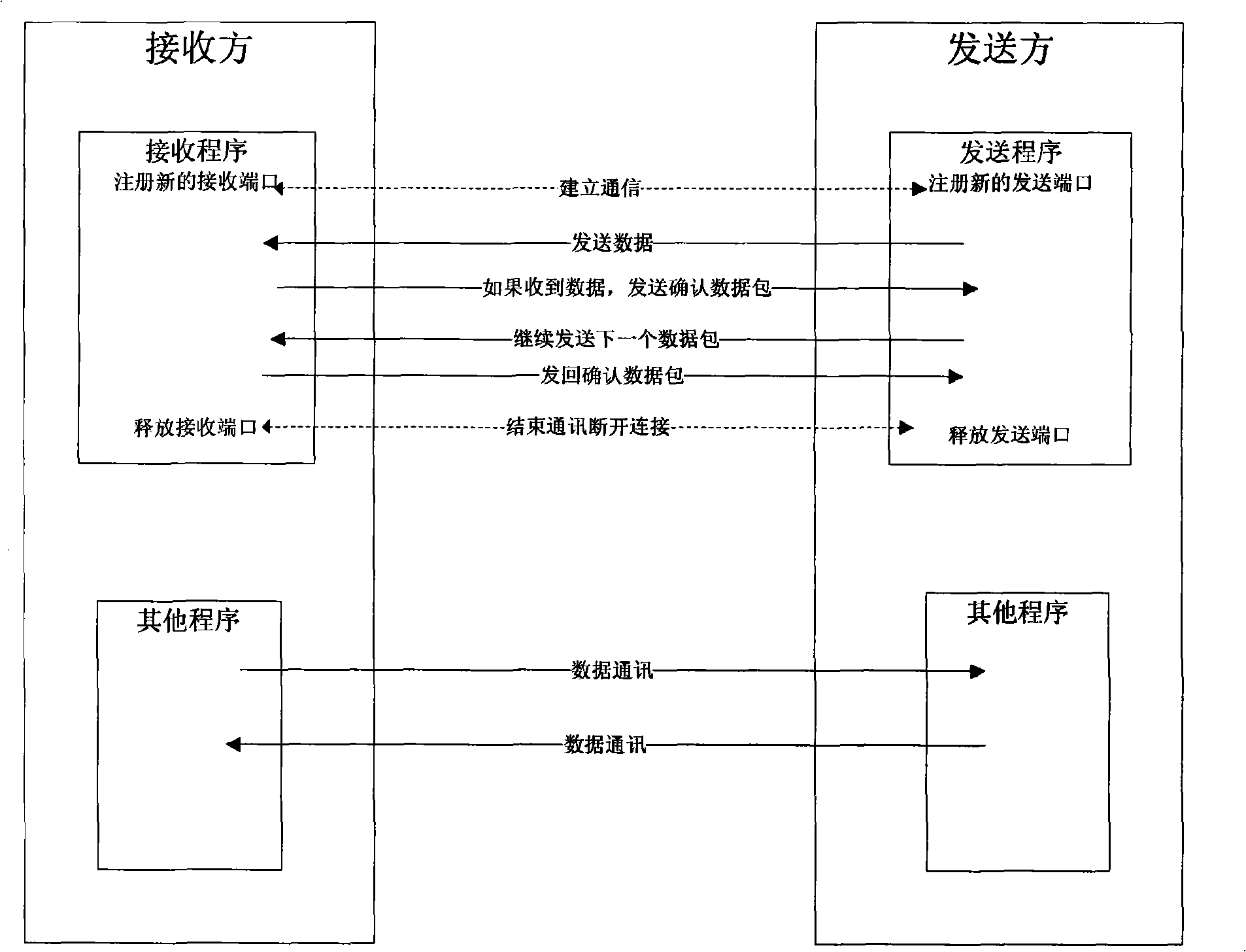
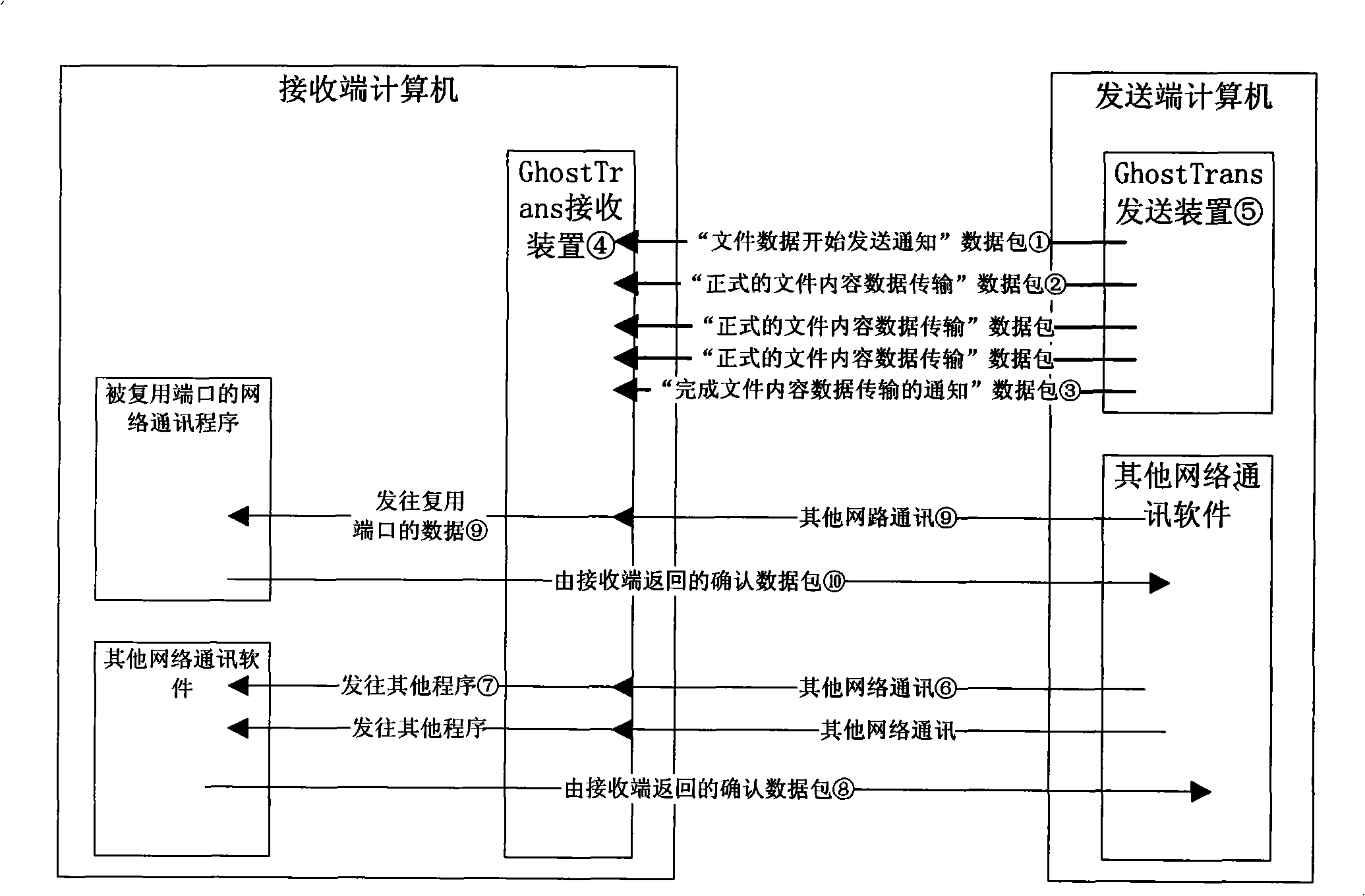
Method and system for silent hiding network transmission
The invention discloses a silent and invisible network transmission method and a system, which belong to the computer network communication technical field; the method defines the communication protocol which satifies the characteristics as the followings: the header feature code is used for distinguishing from other protocols; the type is used for identifying the data packet; the serial number is used for recoding the data packet; the sending device in the sender end selects the port with opened receiving end as the destination port and loads the sent data; a , a and a are sequentially constructed and sent to the receiver end; the receiver end snoops the data packets received from the ports and analyzes the acquired data packets to recover the data packets to raw data. The network transmission method and the system has the advantages of multiplexing general port, one-side data-sending, enabling the receiver device to be in the silent mode, uneasy discovering of the existence of the receiver device and preventing the monitoring devices from noticing the data transmission in the network.
Owner:RUN TECH CO LTD BEIJING
A controlling method and electronic apparatus
InactiveCN104468943AGood reminderImprove prompt effectSubstation equipmentElectric equipmentComputer science
Owner:LENOVO (BEIJING) CO LTD
Alarm and alarming method for mobile phone
InactiveCN102724366AShorten the alarm timeImprove alarm efficiencySubstation equipmentAlarmsMobile phoneAlarm signal
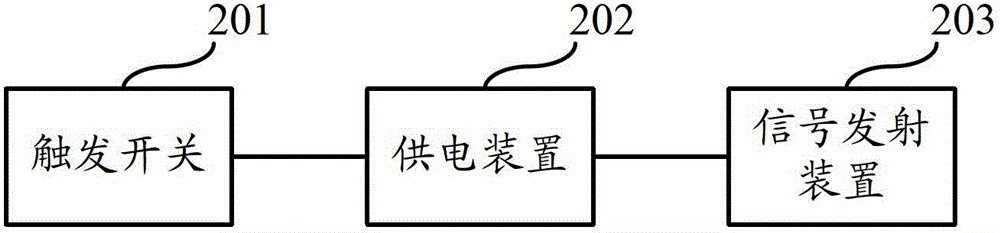
The invention discloses an alarm for a mobile phone. The alarm comprises an alarm signal transmission module and an alarm implementation module, wherein the alarm signal transmission module is arranged outside the mobile phone, and is used for transmitting an alarm signal to the alarm implementation module when an alarm signal triggering condition is satisfied; and the alarm implementation module is arranged in the mobile phone, receives the alarm signal through the mobile phone, and controls the mobile phone to give an alarm according to a preset rule. The invention also discloses an alarming method for the mobile phone. According to the alarm and the alarming method, the mobile phone is not required to be operated, only the alarm signal transmission module outside the mobile phone is required to transmit the alarm signal, and then the mobile phone can be automatically used for automatically giving the alarm, so that alarming time is greatly reduced.
Owner:付弦
Optical fiber web encryption communication system based on time hidden signal channel
InactiveCN103138913AImperceptibleNot easy to attract attentionSecuring communicationCommunications systemAnti jamming
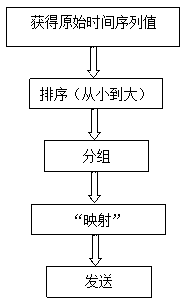
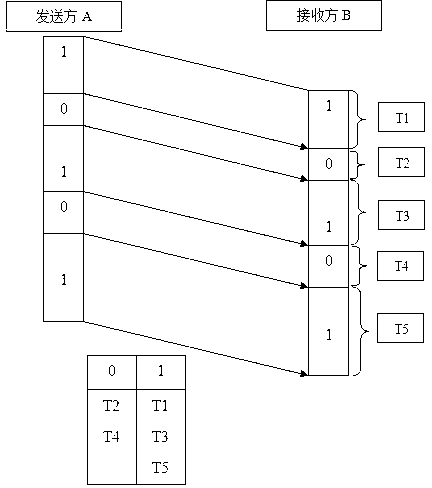
The invention belongs to the field of encryption communications of an optical fiber web, and discloses an optical fiber web encryption communication system based on a time hidden signal channel. A sender sorts obtained time sequence value, the time sequence value after sorted is divided into groups, the sender conducts one-to-one correspondence on data to be sent and the time sequence value which is sorted and divided into the groups, the sender controls sending rate, and a receiver conducts decoding. Compared with the prior art, the optical fiber web encryption communication system has the obvious advantages of hiding information which is not easily observed by an observer, not enabling carrier data to generate big changes, not easily attracting attention of an aggressor, being strong in anti-jamming capability, and being capable of well keeping integrity and reliability of information.
Owner:CHANGSHU RES INSTITUE OF NANJING UNIV OF SCI & TECH
Cellphone full-system information collection and human face recognition analysis comparison system and usage
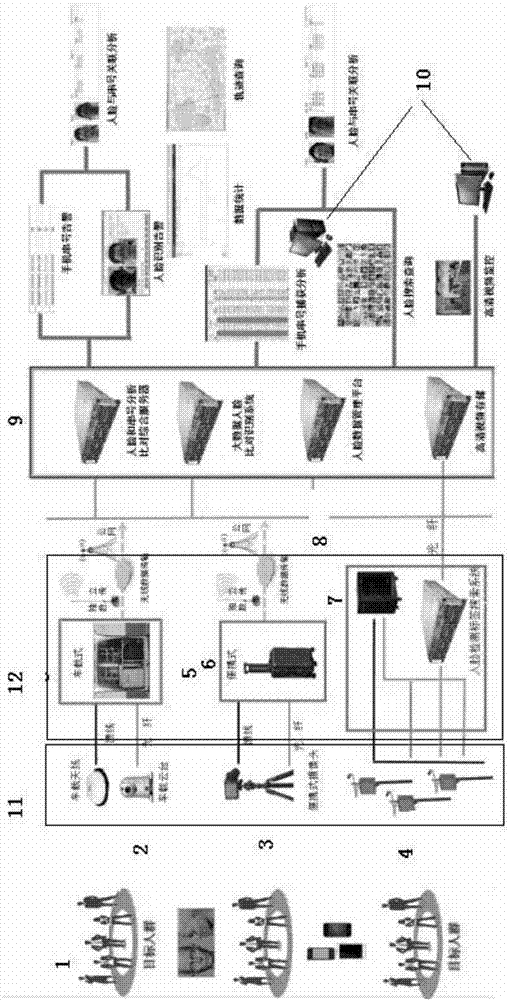
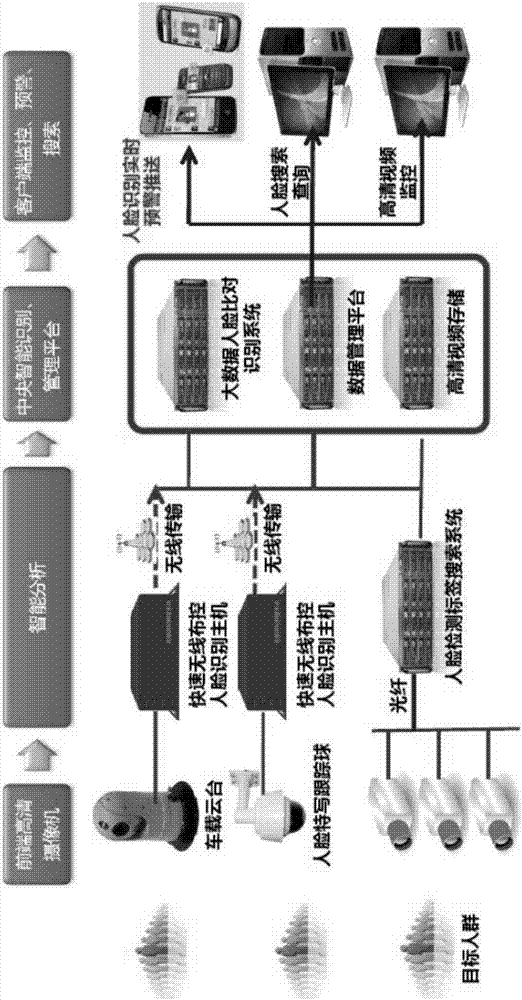
PendingCN107426442AReduce perceptionImprove integrityCharacter and pattern recognitionSubstation equipmentFace detectionAnalysis data
The invention discloses a cellphone full-system information collection and human face recognition analysis comparison system. The system comprises a target crowd, a collection device, an analysis device, a transmission device, an analysis comparison system, and a display terminal, wherein collection objects of the target crowd comprise a cellphone serial number and facial characteristics; the collection device comprises and uses one or more of an on-board device, a portable camera, and a fixed camera simultaneously; the analysis device comprises and uses one or more of on-board collection, portable collection, and a human face detection tag search system simultaneously; the transmission device comprises an optical fiber transmission mode and a wireless transmission mode, and according to the wireless transmission mode, independent data is transmitted wirelessly through a public network; the analysis comparison system comprises a human face and serial number analysis comparison comprehensive server, a big data human face comparison recognition system, a human face data management platform, and a high definition video memory; and the display terminal is used for displaying warning, statistics, searching, monitoring and analysis data results.
Owner:SHANDONG CHUANGHUI TECH CO LTD
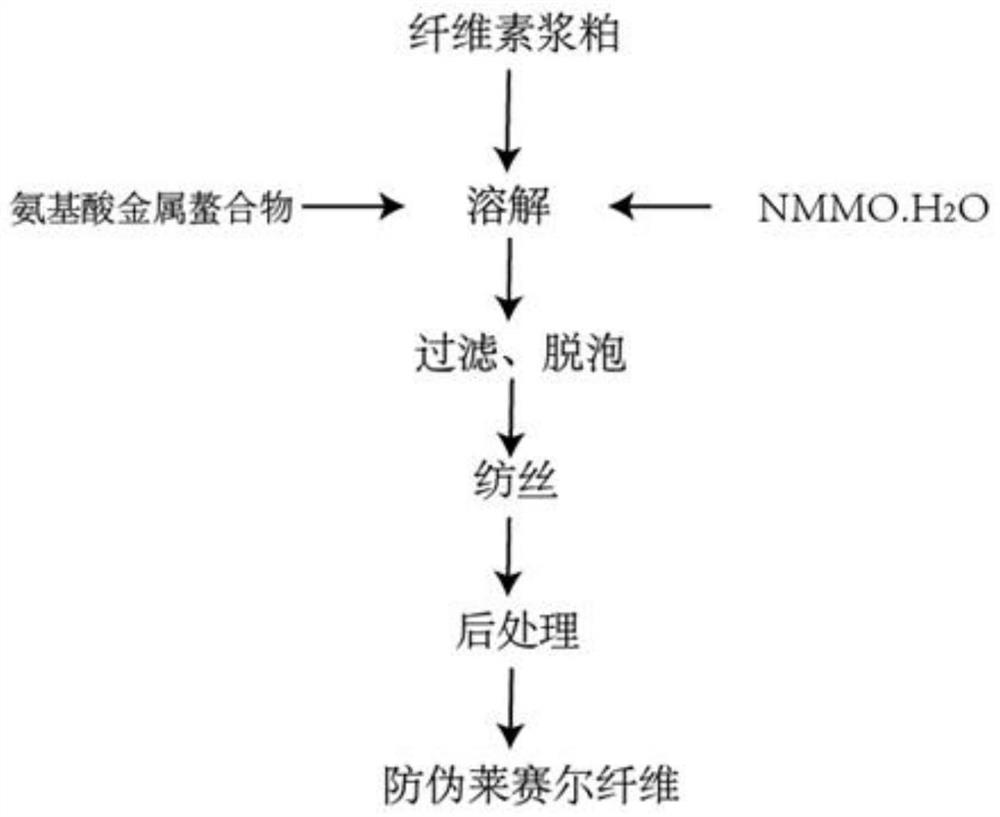
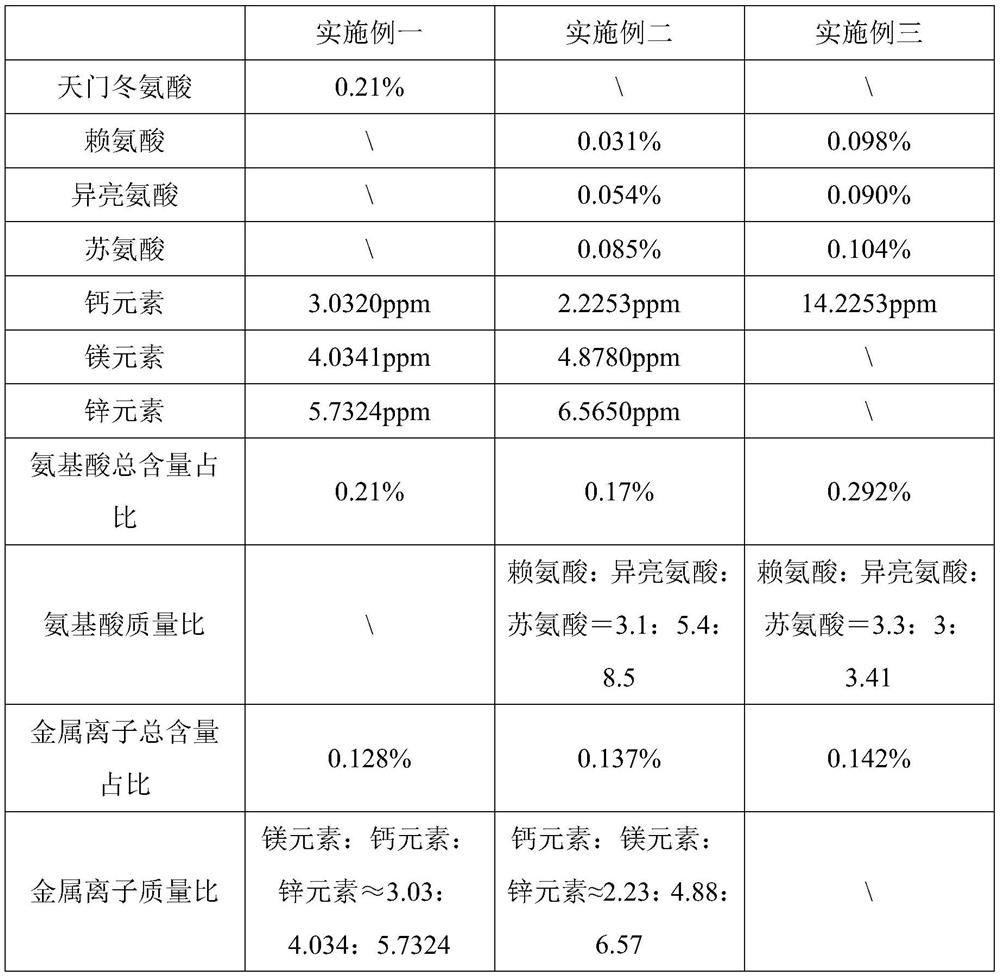
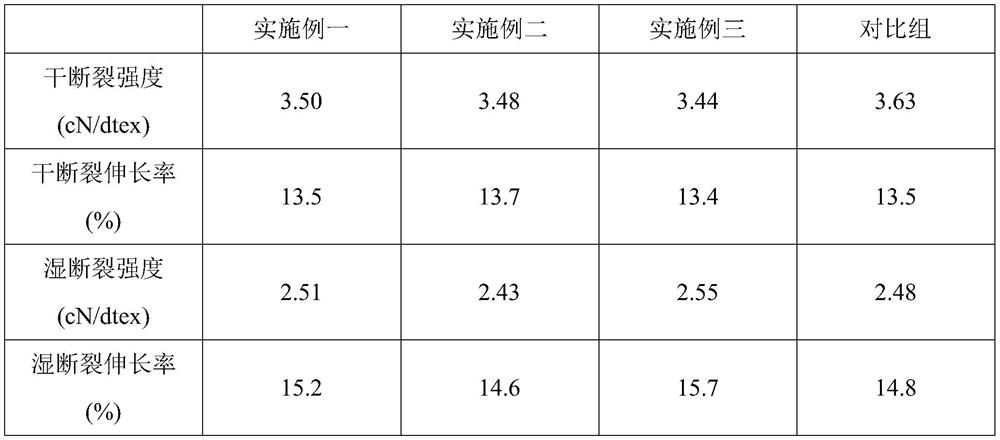
Anti-counterfeiting Lyocell fiber, preparation method and anti-counterfeiting method
The invention relates to a preparation method of an anti-counterfeiting Lyocell fiber. The method comprises the following steps of dissolving at least one amino acid metal chelate and cellulose pulp in an aqueous solution of a cellosolve to obtain a spinning solution, and then carrying out wet spinning by utilizing the spinning solution to obtain the anti-counterfeiting Lyocell fiber, wherein the amino acid metal chelate accounts for 0.2%-0.6% of the total mass of the anti-counterfeiting Lyocell fiber. The anti-counterfeiting Lyocell fiber disclosed by the invention is encrypted by utilizing the amino acid metal chelate, the process flow is simple and convenient, and the prepared Lyocell fiber can be provided with one or two passwords according to the ratios of metal ions to amino acids contained in the Lyocell fiber, so that a product prepared from the fiber has the advantages of memory tracking property, recognition function and high anti-counterfeiting degree.
Owner:NANTONG TEXTILE & SILK IND TECH RES INST +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com