Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
42results about How to "Not easy to attract attention" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
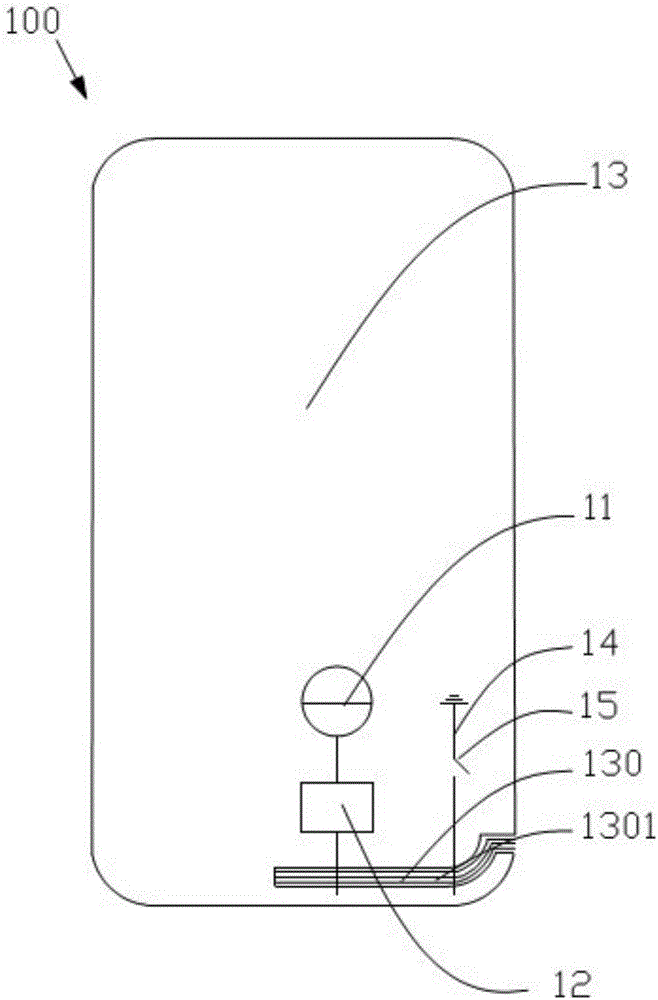
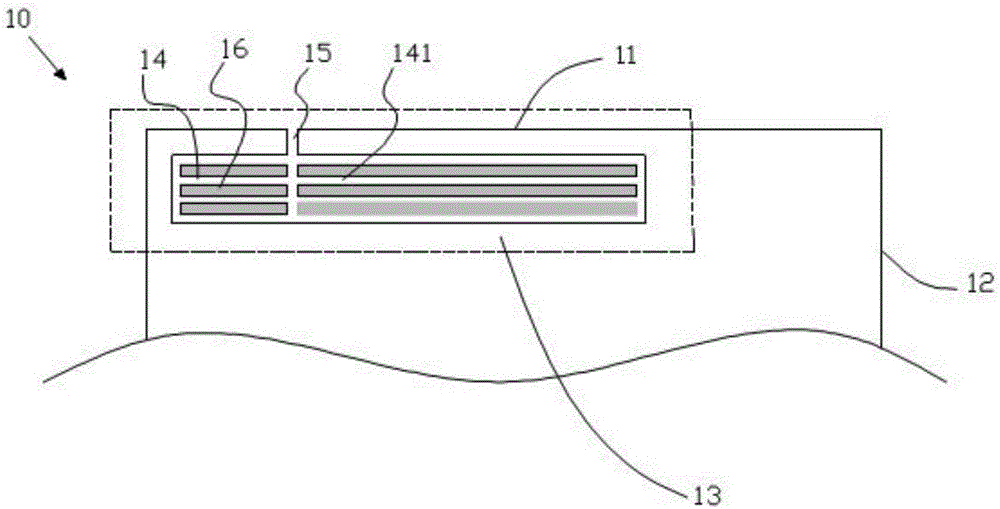
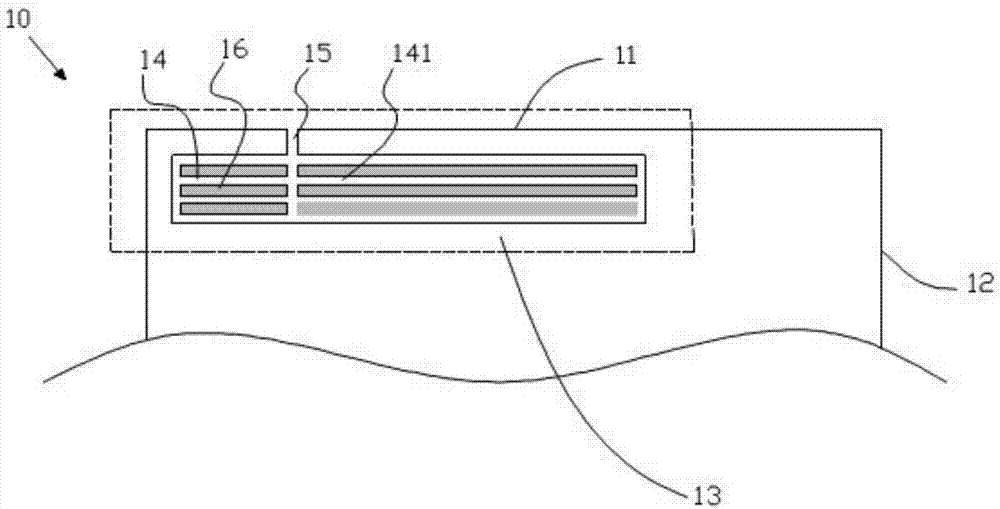
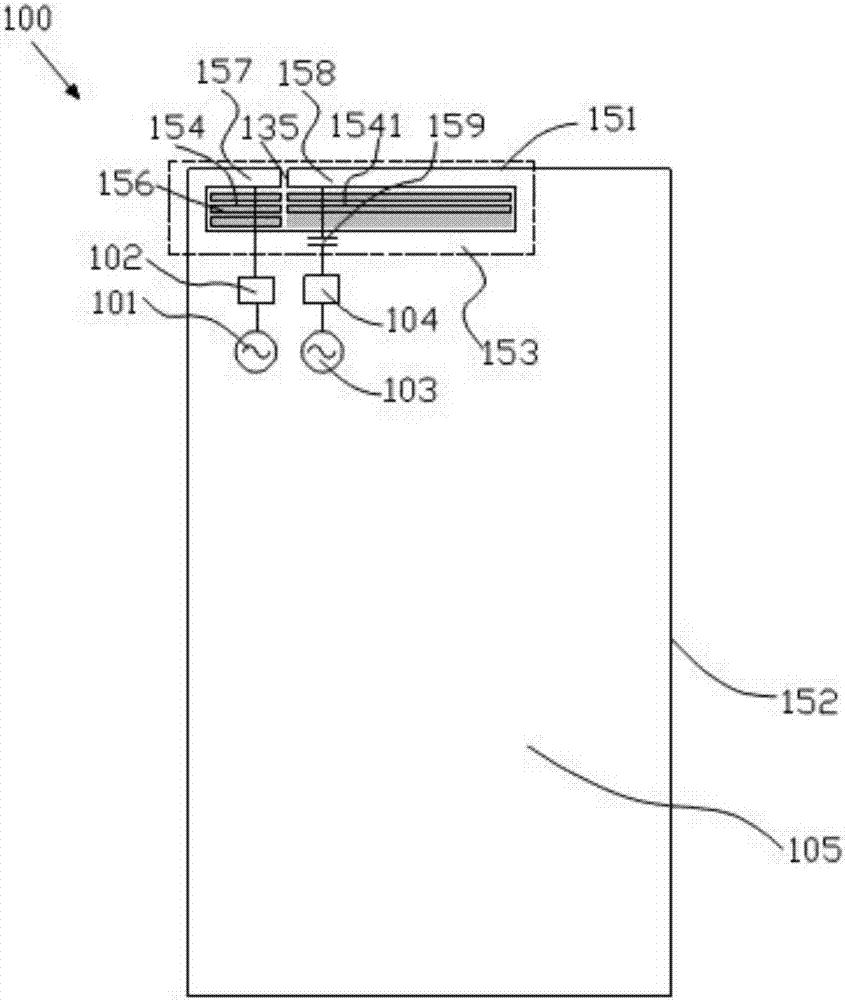
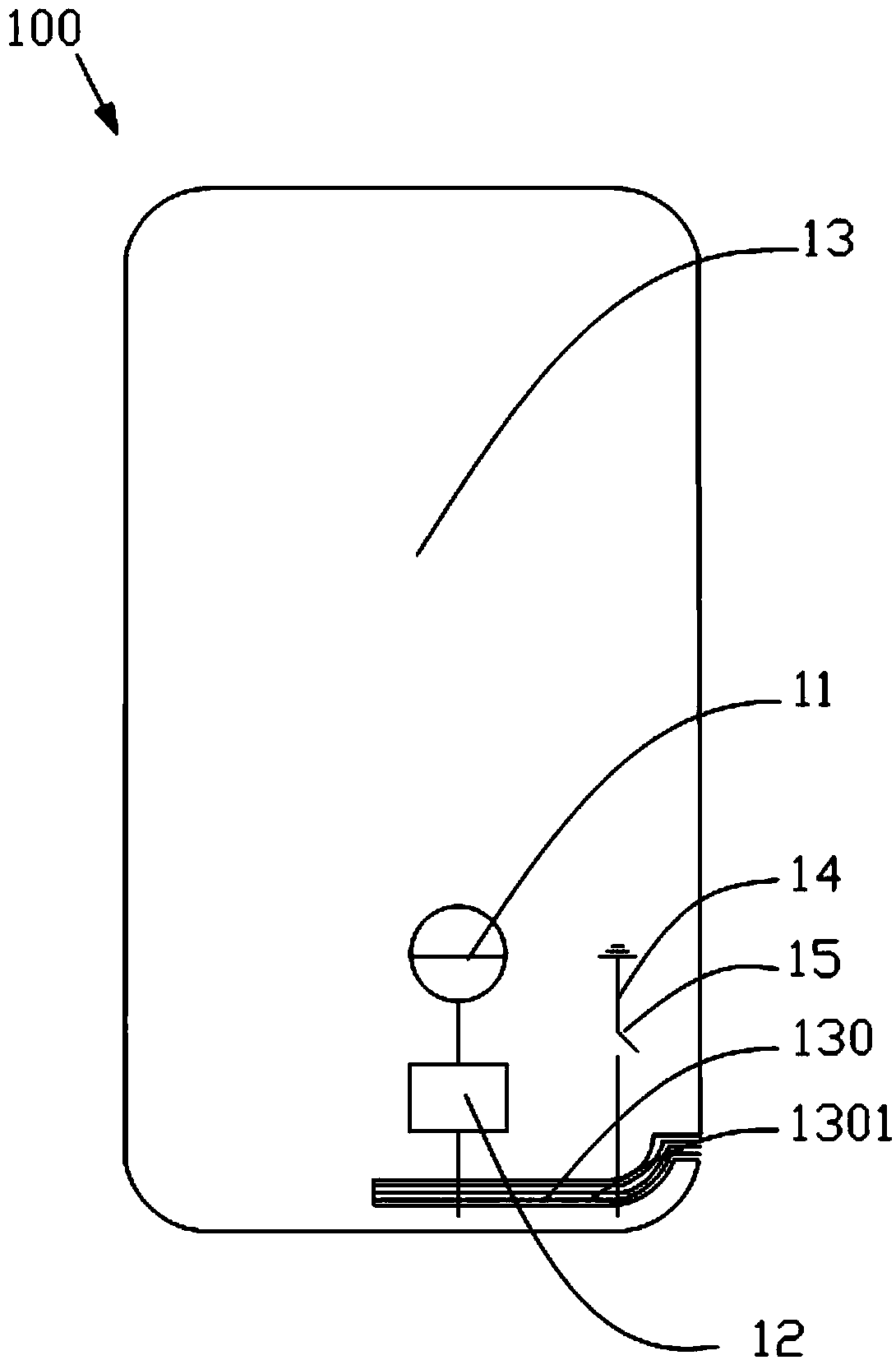
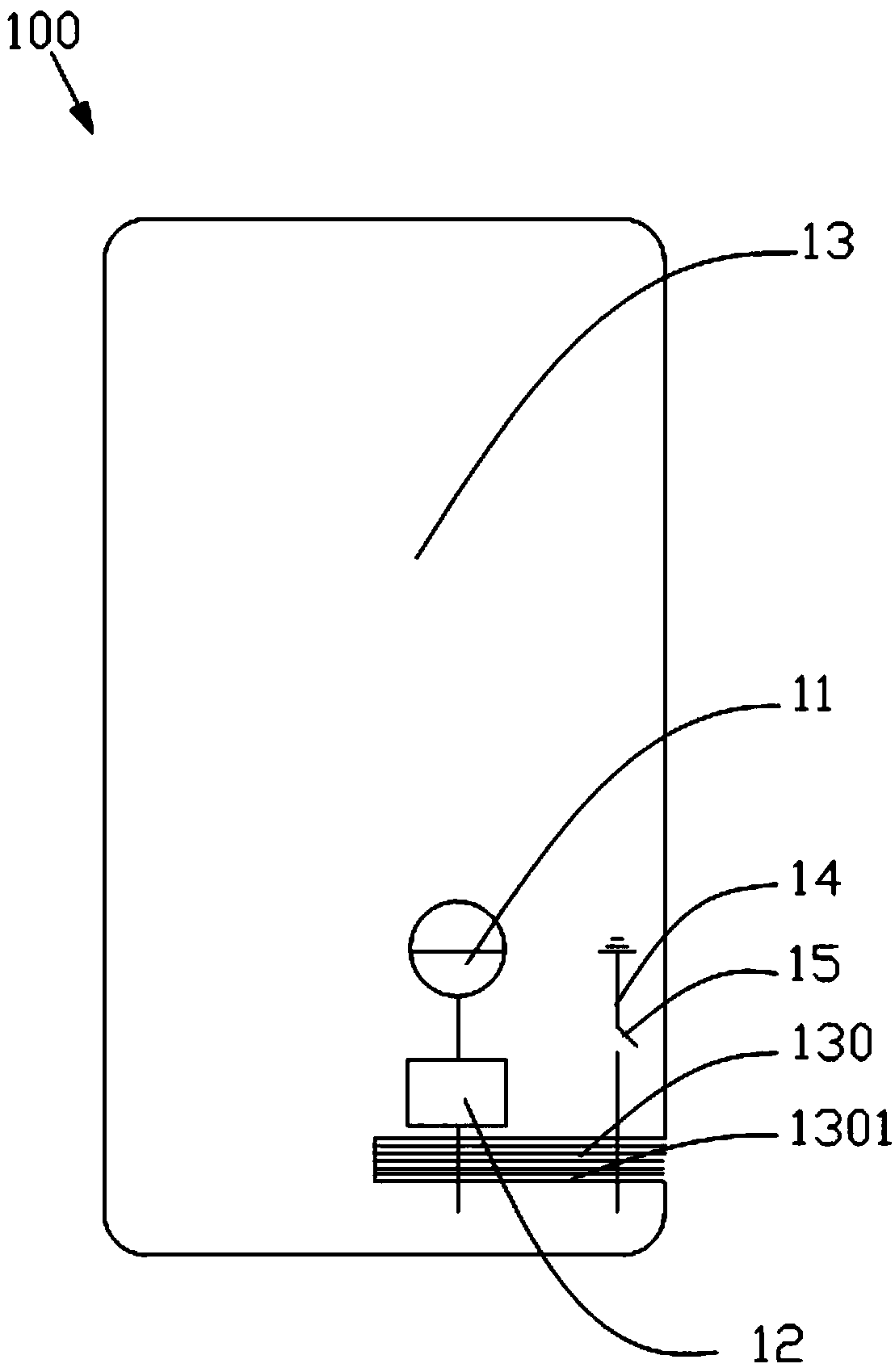
Antenna device and mobile terminal
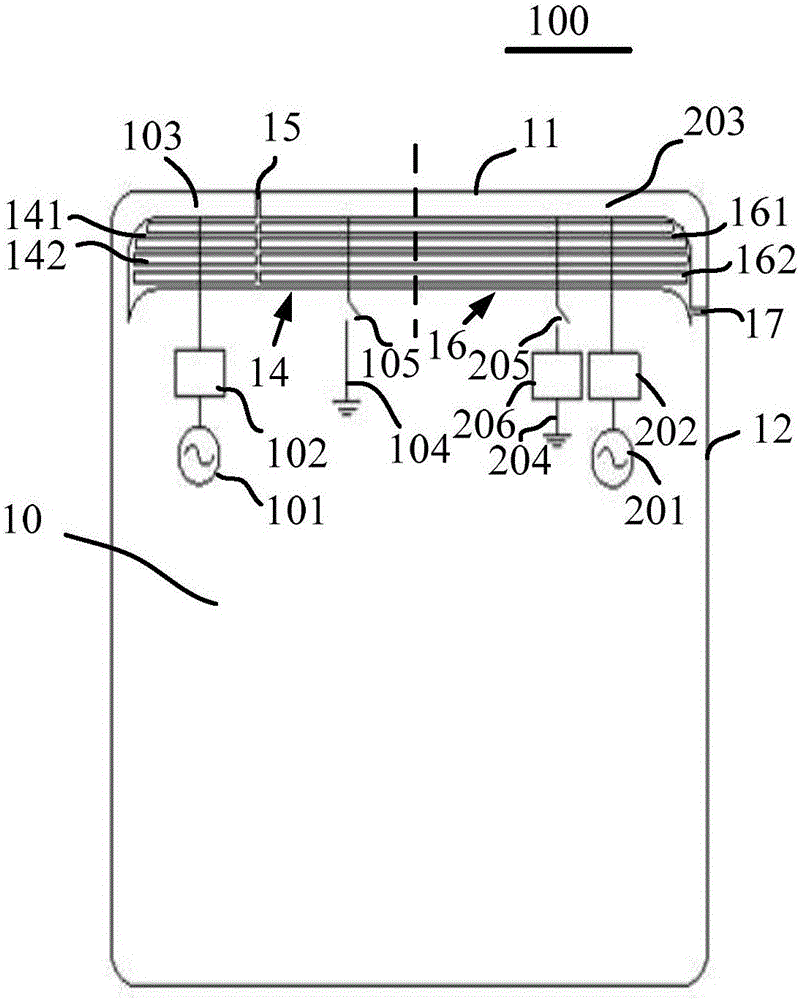
ActiveCN105789827AGuaranteed integrityImprove Radiation PerformanceAntenna supports/mountingsRadiating elements structural formsRadio frequencyElectricity
The invention provides an antenna device. The antenna device comprises a radio frequency transceiving circuit, a matching circuit and a metal shell, wherein the matching circuit is electrically connected to the radio frequency transceiving circuit, the edge of the metal shell comprises an arc segment, the metal shell is provided with at least one micro-slot belt, the at least one micro-slot belt comprises an arc part, the arc part is matched with the arc segment of the metal shell, the radio frequency transceiving circuit is electrically connected with the metal shell through the matching circuit so that the metal shell is used as a radiation body of the antenna device, the metal shell is grounded by a grounding line, and a switch is arranged on the grounding line and is used for controlling on / off of the grounding line. With the antenna device according to the invention, the comprehensive appearance effect of a mobile terminal can be ensured, meanwhile, a signal of the antenna device can be prevented from being intervened, and the bandwidth of the antenna device is improved. The invention also provides the mobile terminal.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
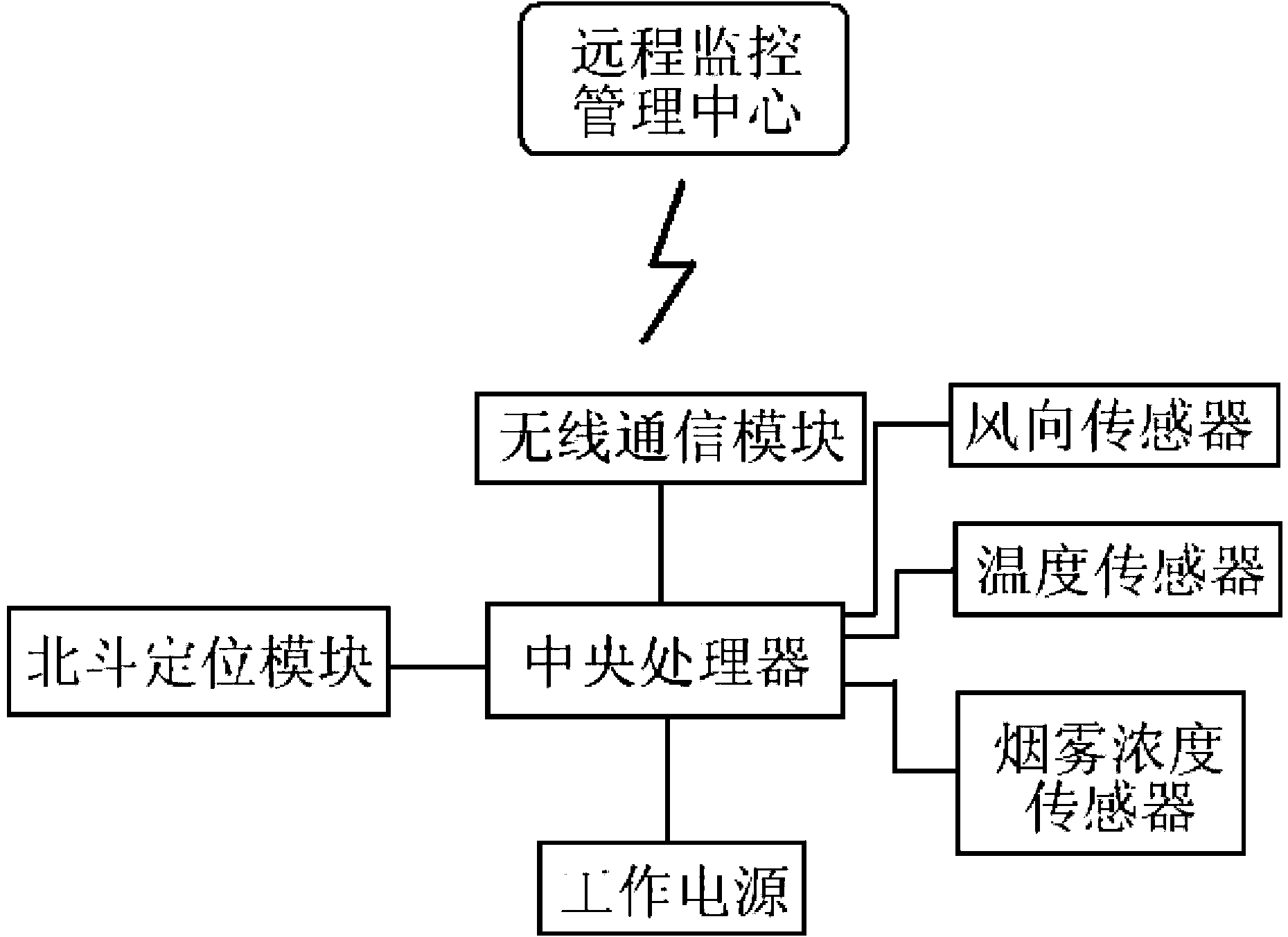
Method for designing forest fire prevention early warning system
InactiveCN103514700ARun smoothlyReliable monitoringClimate change adaptationFire alarm electric actuationMonitoring dataData processing
The invention discloses a method for designing a forest fire prevention early warning system. The method comprises the following steps that (1) monitoring terminals are distributed at all monitoring points of a forest so as to collect environment information around the monitoring points and then the environment information and position information of the monitoring points are sent to a remote monitoring center in a binding mode; (2) the remote monitoring center is provided with a monitoring data base server and a monitoring software platform and a forest fire alarm model which is set in advance is further stored in the monitoring data base server; (3) the monitoring software platform reads the environment information, newly received by the monitoring data base server, around the monitoring points and conducts data processing, then analysis and comparison are conducted on the forest fire alarm model and the processed environment information, if the forest fire alarm model is matched with the processed environment information, the situation that corresponding forest fire occurs to the monitoring point is judged, an alarming sound is emitted, meanwhile, warning information is generated and a pre-protocoled fire prevention measure scheme is sent to a forest fire prevention center. The method for designing the forest fire prevention early warning system is reasonable in design, low in erection cost, stable in running and reliable in monitoring.
Owner:柳州市宏亿科技有限公司
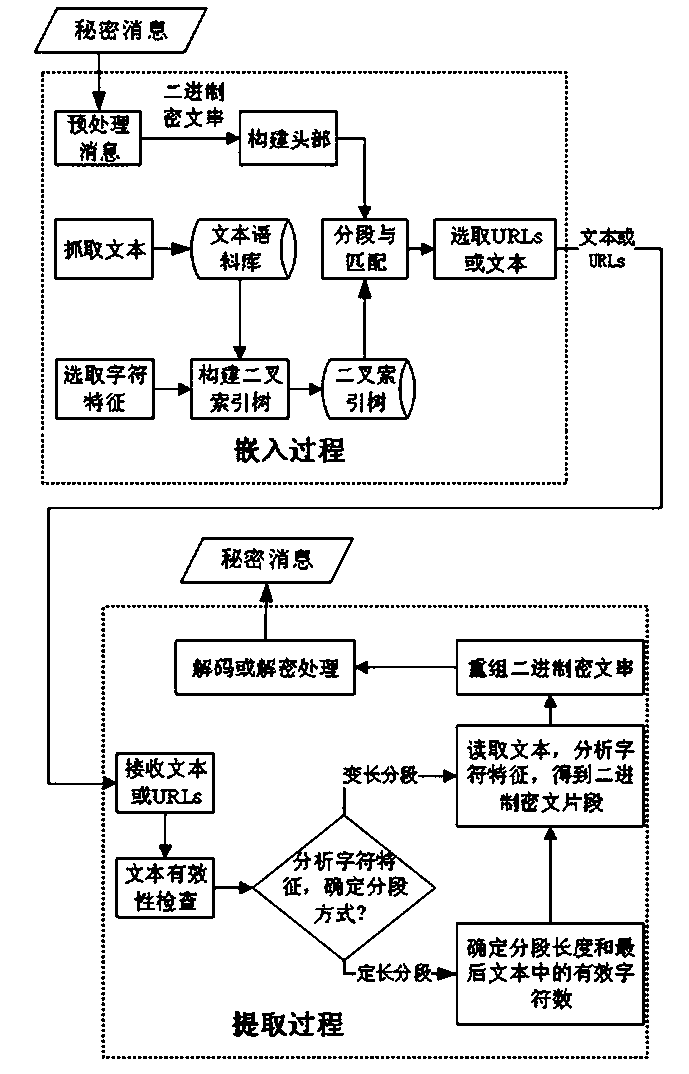
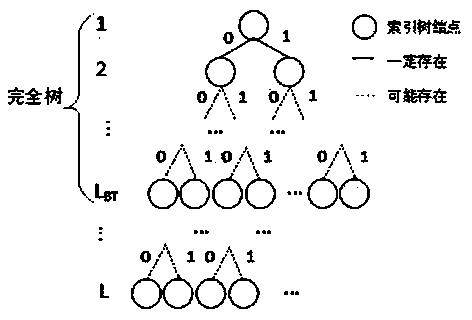
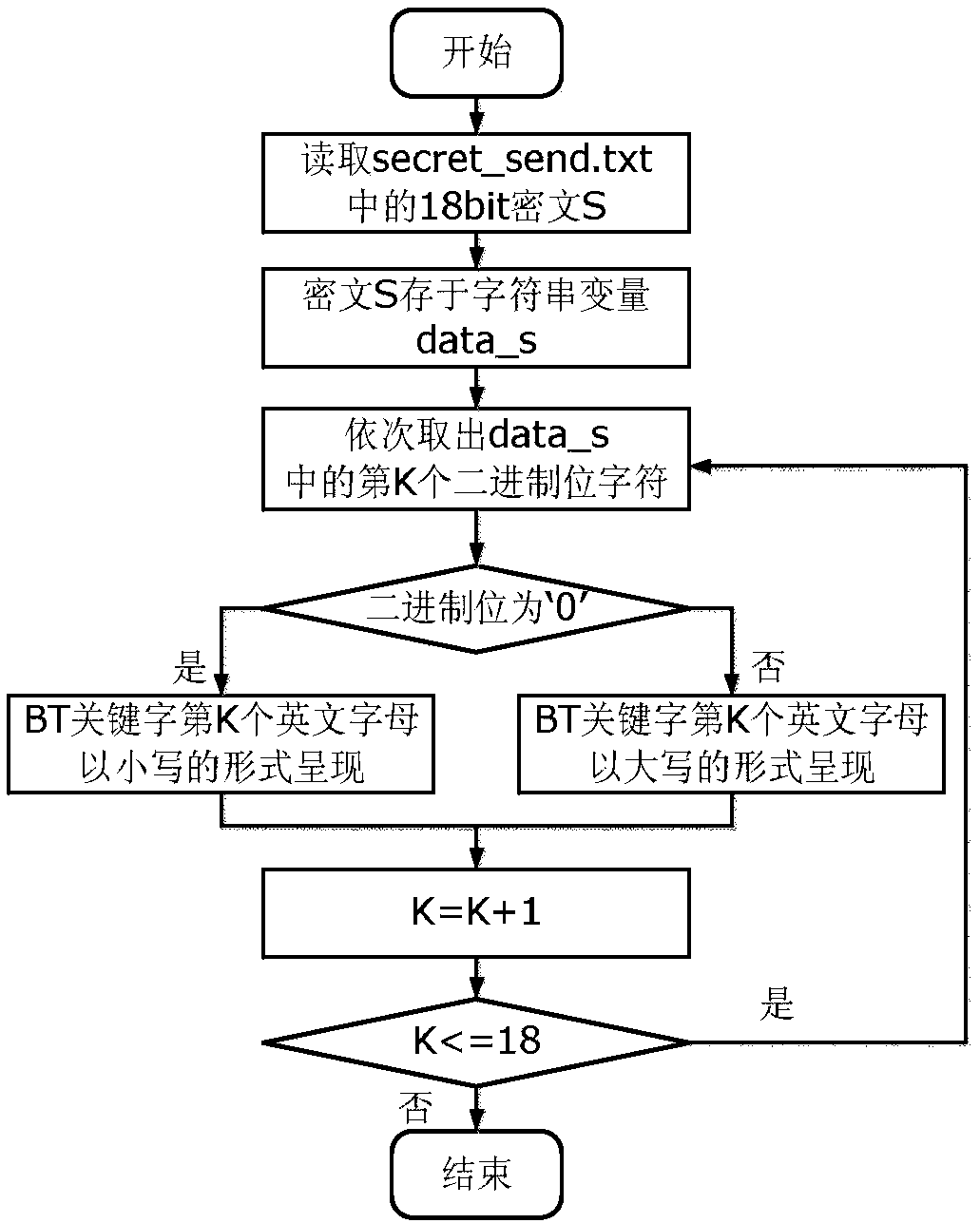
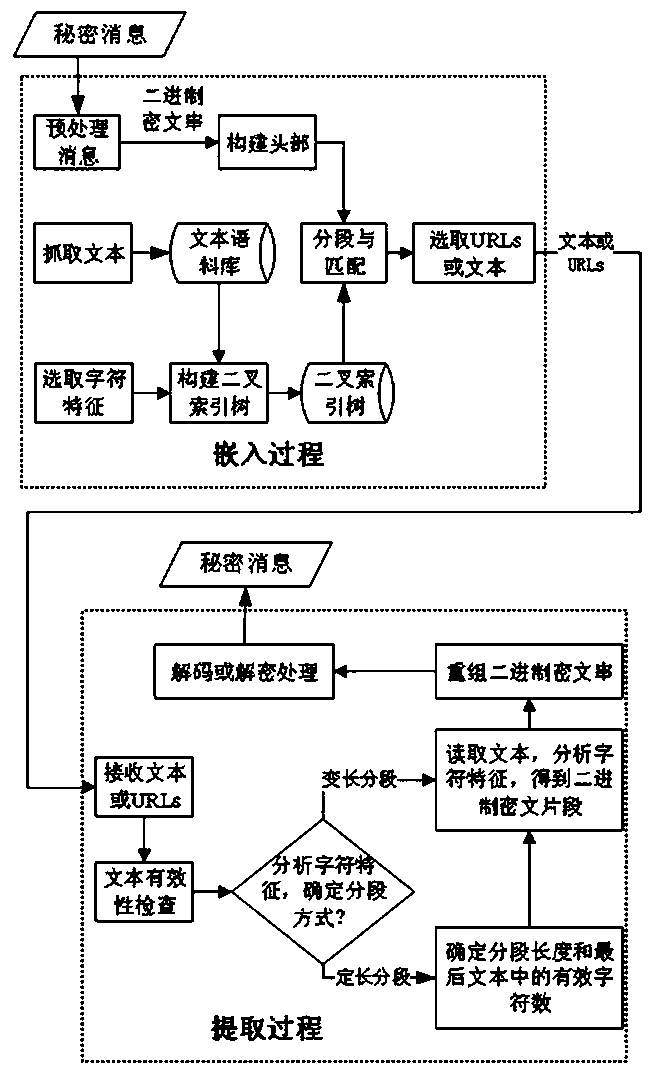
Carrier-free text steganography method based on character features
ActiveCN107947918AAvoid distortionNot easy to attract attentionKey distribution for secure communicationEncryption apparatus with shift registers/memoriesAlgorithmCiphertext
The invention discloses a carrier-free text steganography method based on character features. Binary digits are expressed through the character features; secret information is processed into a binaryciphertext string and then is packaged and segmented; mapping between texts and binary ciphertext string segments is established by taking abundant webpage texts in a network big data environment as candidate carriers; corresponding texts are found for the secret information through the mapping relationship; and the texts or the corresponding URLs are sent, thereby finishing secret information interaction. After a receiving end receives the texts, the character features of a first text are analyzed to obtain head information; a binary ciphertext segmentation mode and length are determined; thefollow-up text character features are analyzed to obtain binary ciphertext segments; the segments are recombined to form the complete binary ciphertext string; and decoding or decryption is carried out to obtain the secret information. The method has the advantages of high stealthiness, high expandability and high embedded capacity, and the application and development of a steganography technology in various fields are facilitated.
Owner:QINGDAO UNIV
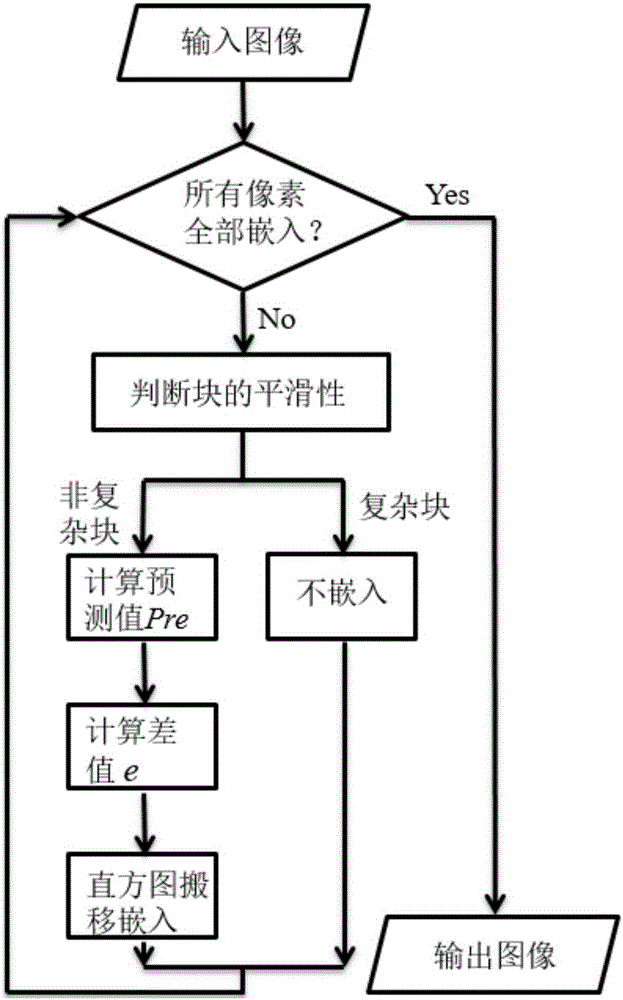
Reversible data hiding method based on eight neighborhood pixels
InactiveCN106097241ASmall distortionImprove forecast accuracyImage data processing detailsLow distortionInformation hiding
The invention discloses a reversible data hiding method based on eight neighborhood pixels. According to the method, a gray image of a space domain is predicted using eight neighborhood pixels of a pixel to be embedded and a prediction difference is calculated, and then, secret data is embedded based on the difference and a histogram removal algorithm. The method specifically comprises the steps as follows: first, the smoothness of a current block is predicted based on the characteristics of eight neighborhood pixels of a pixel to be embedded to get the characteristics of smoothness; then, the pixel to be embedded is predicted to get a difference, and different secret data embedding modes are adopted according to the smoothness in the hope of reducing distortion caused by secret data embedding; and finally, an embedding template is used to embed all pixels in the scope of the template in sequence to achieve high embedding capacity. Because of the characteristics of natural gray images, that embedded images have low distortion is ensured while a lot of secret data is embedded, and the security of data hiding is improved.
Owner:XI AN JIAOTONG UNIV
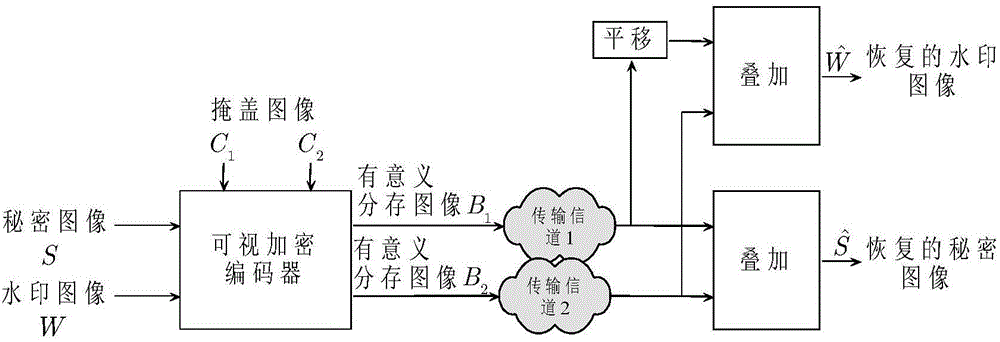
Extension visual encryption and decryption method
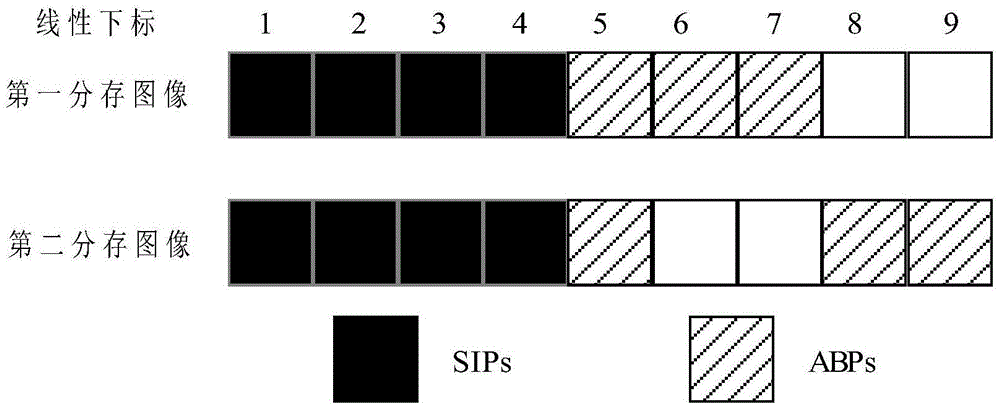
InactiveCN104574262ANot easy to attract attentionReduce computational complexityImage data processing detailsError diffusionImage sharing
The invention discloses an extension visual encryption and decryption method. In the extension visual encryption process, a cover image is chunked first, and pixels in each block are divided into secret information pixels, auxiliary black pixels and common pixels; then (2,2) lines of a visual cryptography fundamental matrix are filled at the position of secret information, share images are divided into four areas, and secret images and watermark images are sequentially embedded into the four areas; at last, limited error diffusion is used for incorporating the characteristics of the cover image. In the extension visual decryption process, the two share images are overlaid in a staggered mode, and watermarks are recovered; then the two images align to each other to recover secret images. The extension visual encryption and decryption method has the advantages that image sharing is meaningful, the dimension is not extended, decryption does not need a computer, a tampering authentication function is achieved, and the recovered secrete images and the watermarks can be free of interference of the cover images at the same time.
Owner:SHANDONG UNIV OF SCI & TECH
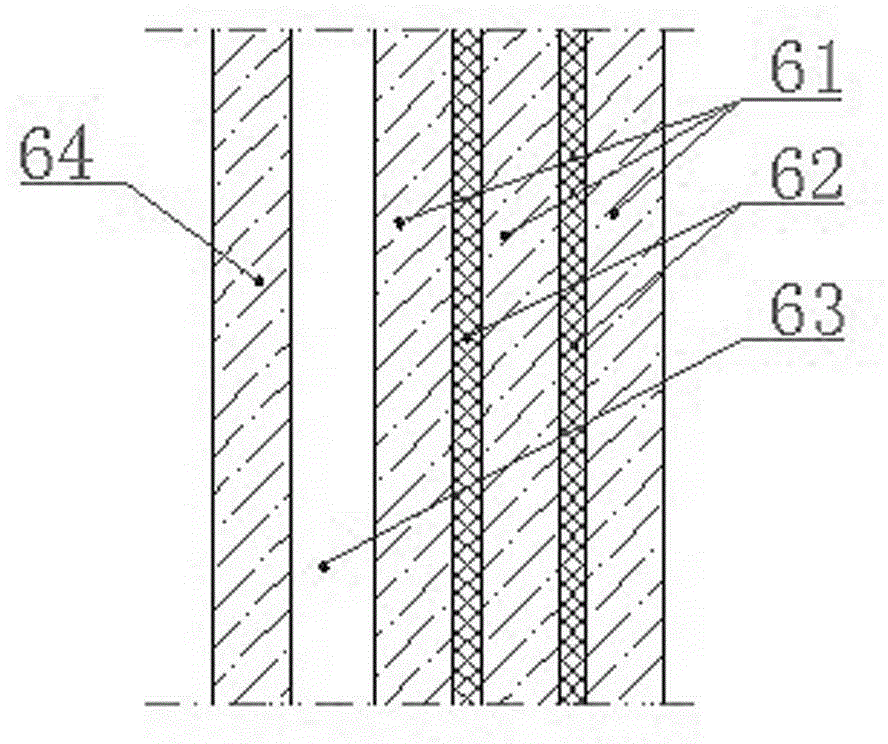
Shell, antenna device, mobile terminal and shell processing method
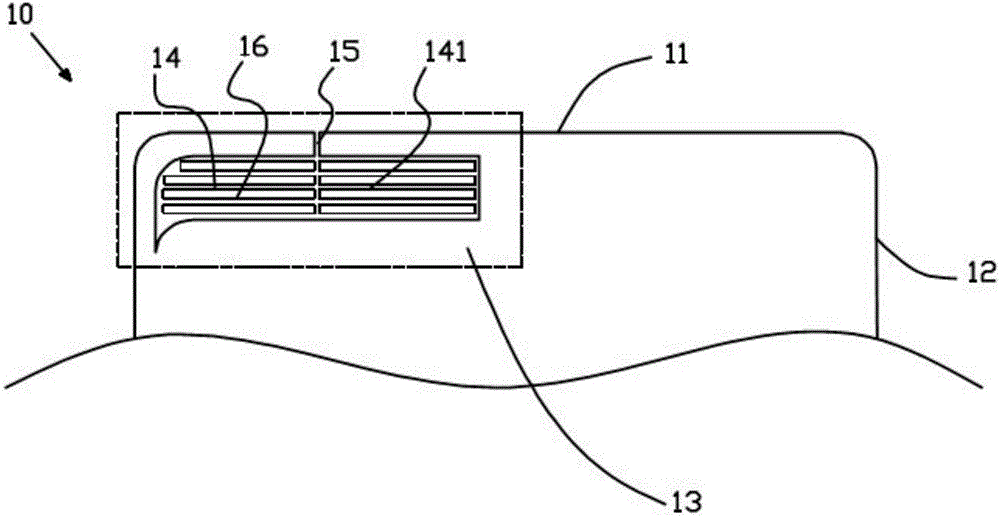
InactiveCN107394349AImprove structural strengthNot easy to attract attentionAntenna supports/mountingsRadiating element housingsComputer terminalEngineering
The invention discloses a shell. The shell is provided with at least two conducting parts and at least one insulating part for partitioning the at least two conducting parts; each insulating part is provided with two micro gap belts arranged at an interval and a gap connected between the two micro gap belts; each micro gap belt is provided with a plurality of micro gaps; each micro gap is communicated to the gap respectively; and each micro gap and the gap are filled with an insulating material respectively. The shell is relatively high in structural strength. The invention also discloses an antenna device, a mobile terminal and a shell processing method.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Antenna device and terminal device
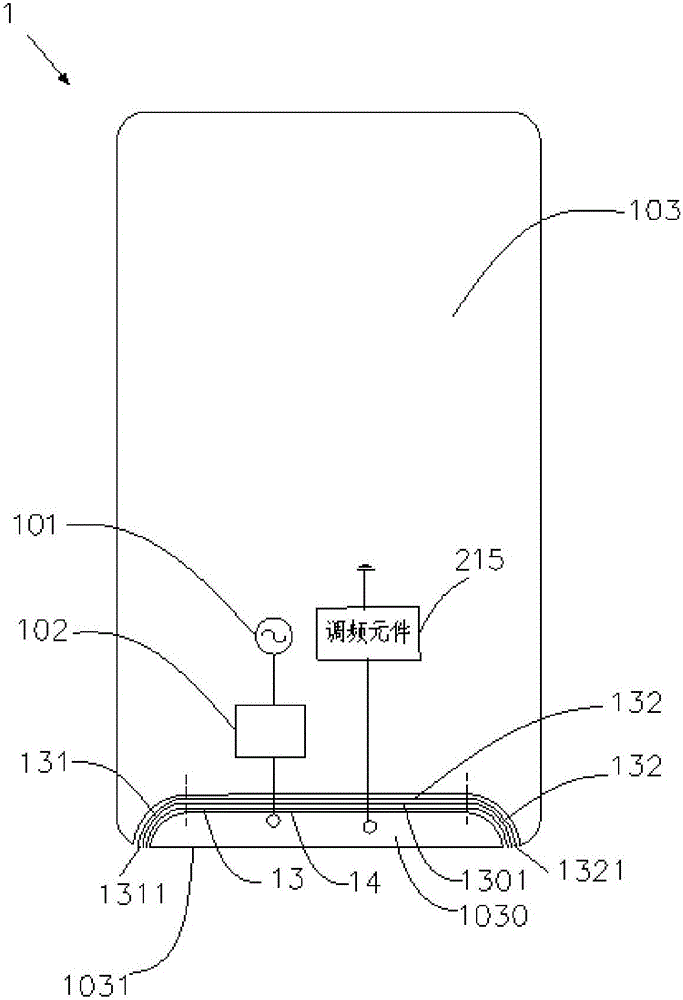
ActiveCN106025508AAvoid contactNot easy to attract attentionAntenna supports/mountingsAntennas earthing switches associationElectricityTransceiver
The invention provides an antenna device comprising a first radio frequency transceiver circuit, a first matching circuit, a housing, and a frequency modulation element. The housing includes a first side and a conductive area with a micro-slit tape formed by a plurality of micro slits; the micro-slit tape is adjacent to the first side of the housing; and the opening of the micro-slit tape is arranged on the first side of the housing. The first radio frequency transceiver circuit is connected with the conductive area electrically by the first matching circuit. The frequency modulation element is connected between the conductive area and the ground. In addition, the invention also provides terminal equipment. According to the invention, the overall appearance effect of the terminal equipment can be guaranteed; and the adverse effect on the antenna performance by hand holding by a user can be reduced.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
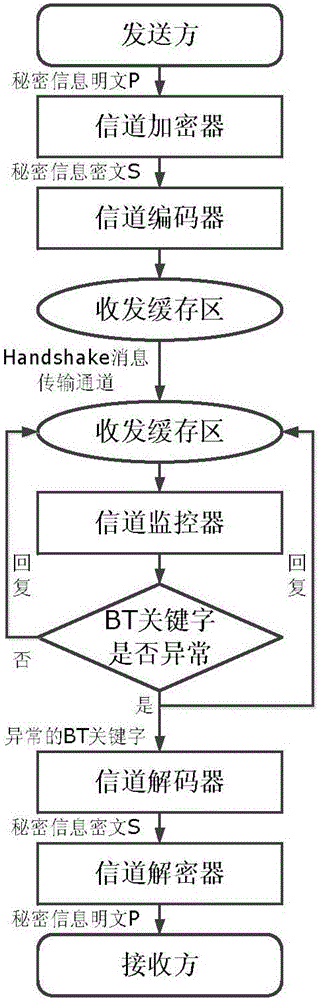
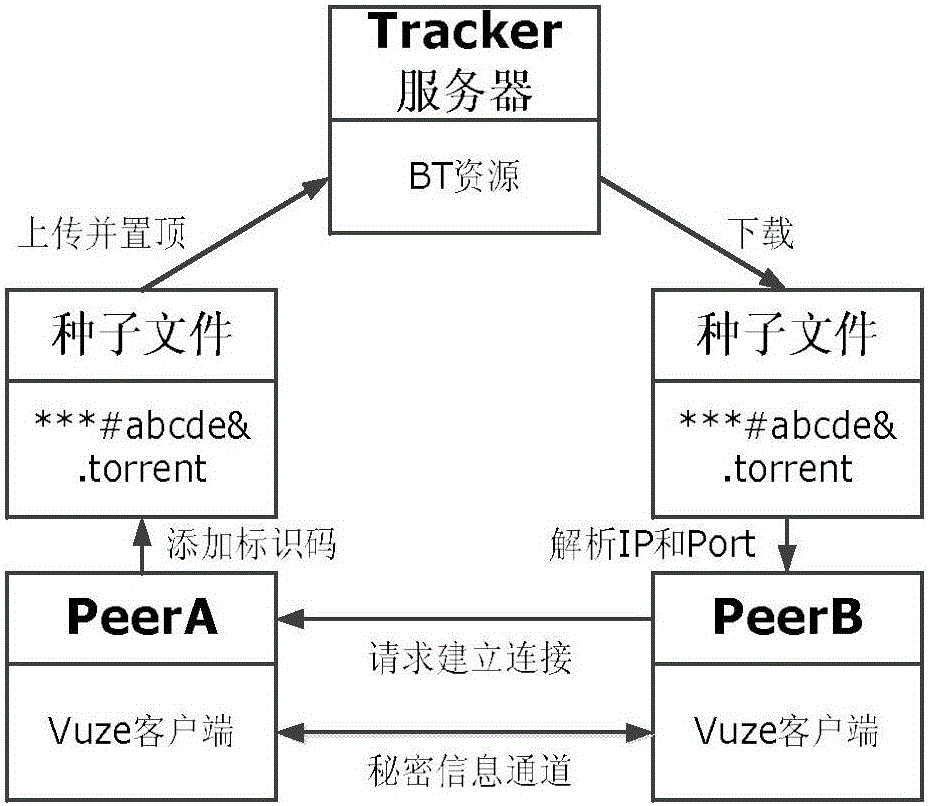
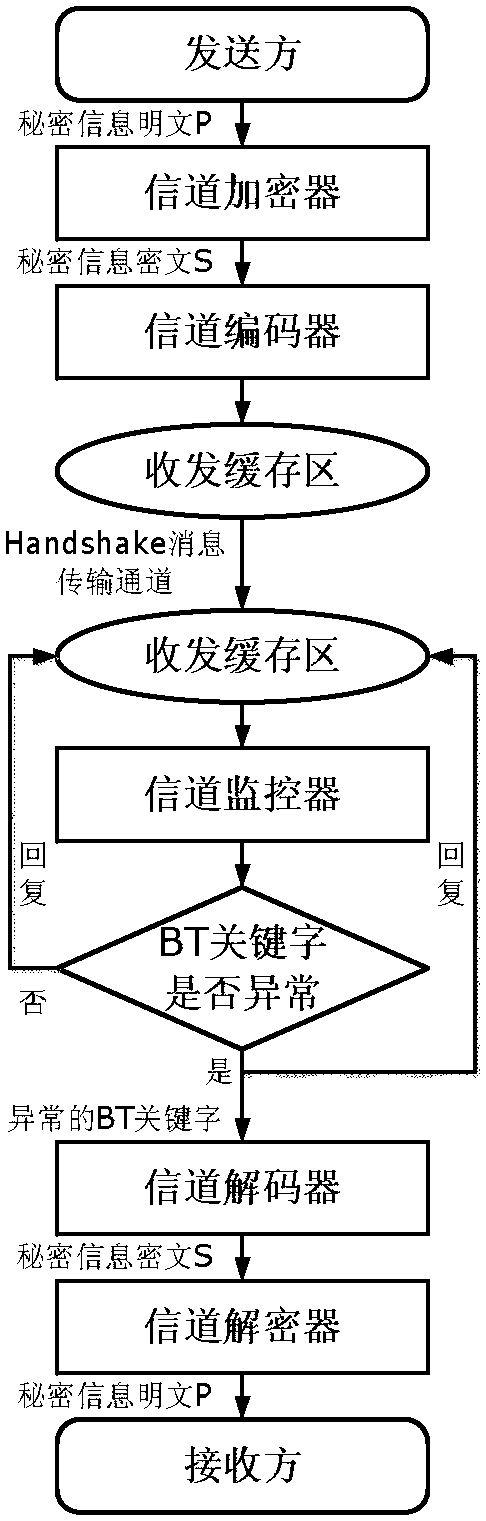
Confidential information transmission method in P2P network based on BitTorrent protocol
ActiveCN105959355ASimple transfer methodNot easy to attract attentionTransmissionInformation transmissionTransmission channel
The invention belongs to the computer network and information safety technology field, and discloses a confidential information transmission method in a P2P network based on a BitTorrent protocol. A covert transmission channel is established based on Handshake information transmission in the P2P network, and by adopting the established covert transmission channel, confidential information is embedded in BT key words of Handshake information in an information coding way, which is not sensitive to case, for transmission. The covert transmission is carried out by introducing the information coding way, which is not sensitive to the case, to the BT key words of the handshake information. The confidential information transmission method provided by the invention is simple and effective, is low in realization cost, is safer and more reliable, and is not easy to crack.
Owner:JIANGSU UNIV OF SCI & TECH
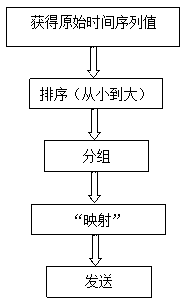
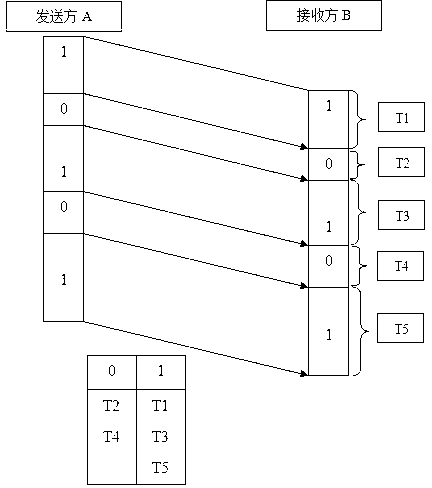
Optical fiber web encryption communication system based on time hidden signal channel
InactiveCN103138913AImperceptibleNot easy to attract attentionSecuring communicationCommunications systemAnti jamming
The invention belongs to the field of encryption communications of an optical fiber web, and discloses an optical fiber web encryption communication system based on a time hidden signal channel. A sender sorts obtained time sequence value, the time sequence value after sorted is divided into groups, the sender conducts one-to-one correspondence on data to be sent and the time sequence value which is sorted and divided into the groups, the sender controls sending rate, and a receiver conducts decoding. Compared with the prior art, the optical fiber web encryption communication system has the obvious advantages of hiding information which is not easily observed by an observer, not enabling carrier data to generate big changes, not easily attracting attention of an aggressor, being strong in anti-jamming capability, and being capable of well keeping integrity and reliability of information.
Owner:CHANGSHU RES INSTITUE OF NANJING UNIV OF SCI & TECH
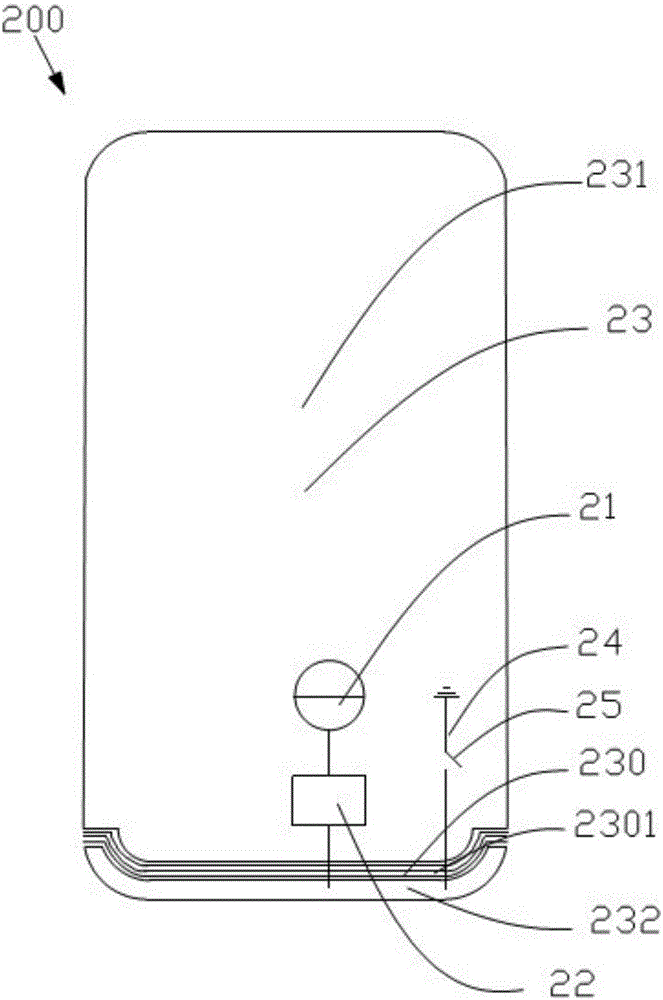
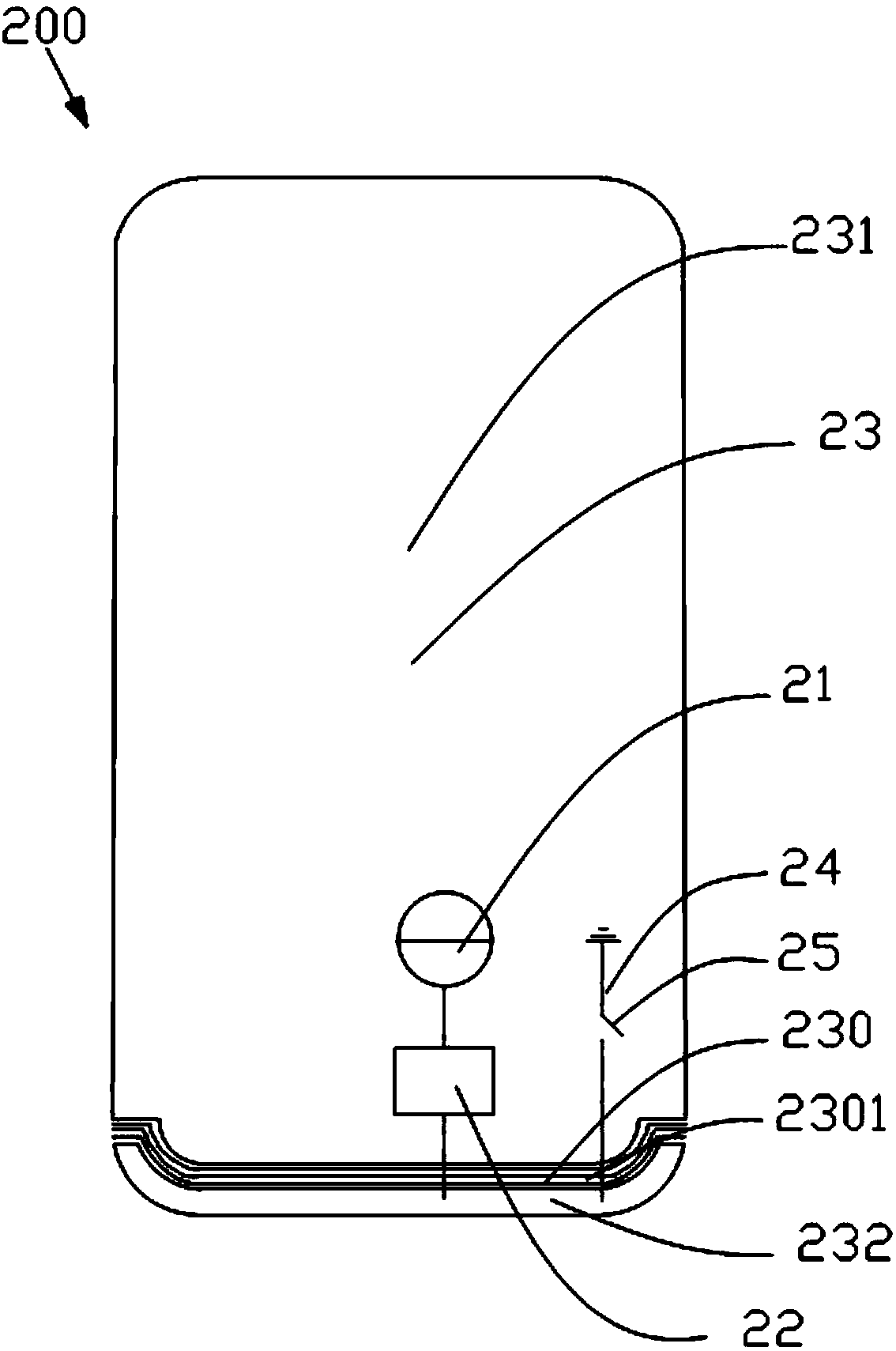
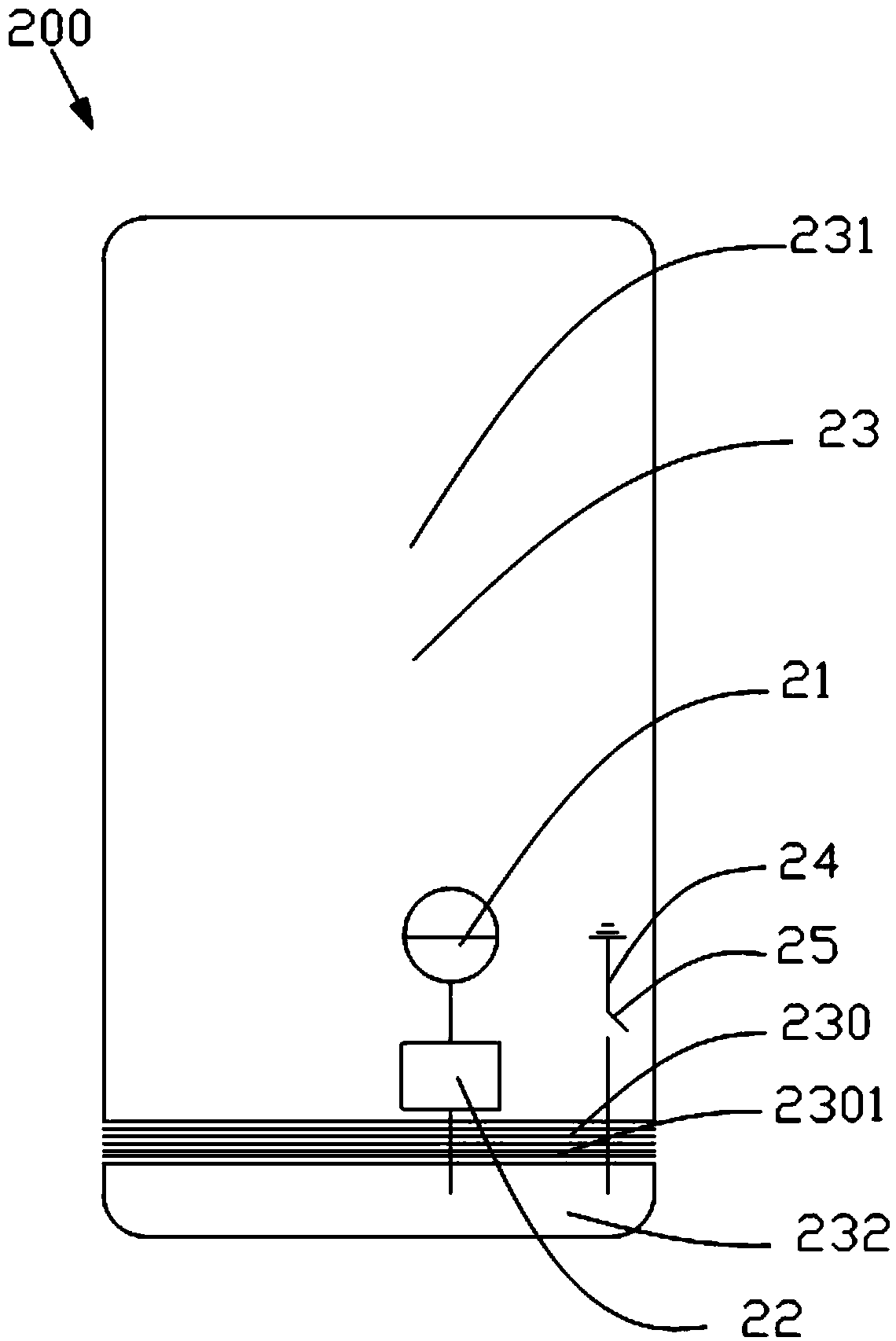
Antenna device and mobile terminal
ActiveCN105896085ANot easy to attract attentionGuaranteed integritySimultaneous aerial operationsRadiating elements structural formsElectricityMicro gap
The invention provides an antenna device for a mobile terminal. The antenna device comprises first radio-frequency receiving and transmitting circuit, a first matching circuit, a second radio-frequency receiving and transmitting circuit, a second matching circuit and a shell, wherein the shell comprises a first conducting region; the first conducting region is provided with a first micro-gap strip and a first gap; the first micro-gap strip comprises a plurality of first micro-gaps; the first micro-gap is intersected with the plurality of first micro-gaps; the first radio-frequency receiving and transmitting circuit is electrically connected with the first conducting region through the first matching circuit; and the second radio-frequency receiving and transmitting circuit is electrically connected with the first conducting region through the second matching circuit. According to the antenna device provided by the invention, the overall appearance effect of the mobile terminal can be ensured; and meanwhile, receiving and transmitting of a high-frequency signal and a low-frequency signal can be achieved. The invention further provides the mobile terminal.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Method for carrying out secret communication by using word document
The invention provides a method for carrying out secret communication by using a word document. The method mainly comprises the following three steps of: manufacturing secret characters by using a True Type character-formation program and generating a secret key; embedding the secret characters into the word document; and extracting the secret characters by using the secret key. According to the method disclosed by the invention, the True Type character-formation program in the conventional general windows operation system, display characters of a window word base and certain functions of word character processing software are designed and integrated so as to realize a function of performing the secret communication by using the word document. The method disclosed by the invention has the advantages of smart conception, simple method, low cost, good commonality and easiness of operation. Therefore, the method can be accessibly used by any operator familiar with windows.
Owner:XIAN UNIV OF SCI & TECH
Dangerous chemical safety inspection device and gate system
PendingCN111815830ANot easy to attract attentionReduce sampling costsIndividual entry/exit registersMaterial analysisChemical safetySecurity check
The invention relates to a dangerous chemical safety inspection device and a gate system. The dangerous chemical safety inspection device comprises a first machine body and a second machine body whichare oppositely arranged at a certain interval to form a security check channel, an air blowing module is arranged in the first machine body and blows air into the security check channel, and an air suction module is arranged in the second machine body and sucks in gas in the security check channel to detect dangerous chemicals in the gas.
Owner:NUCTECH CO LTD +1
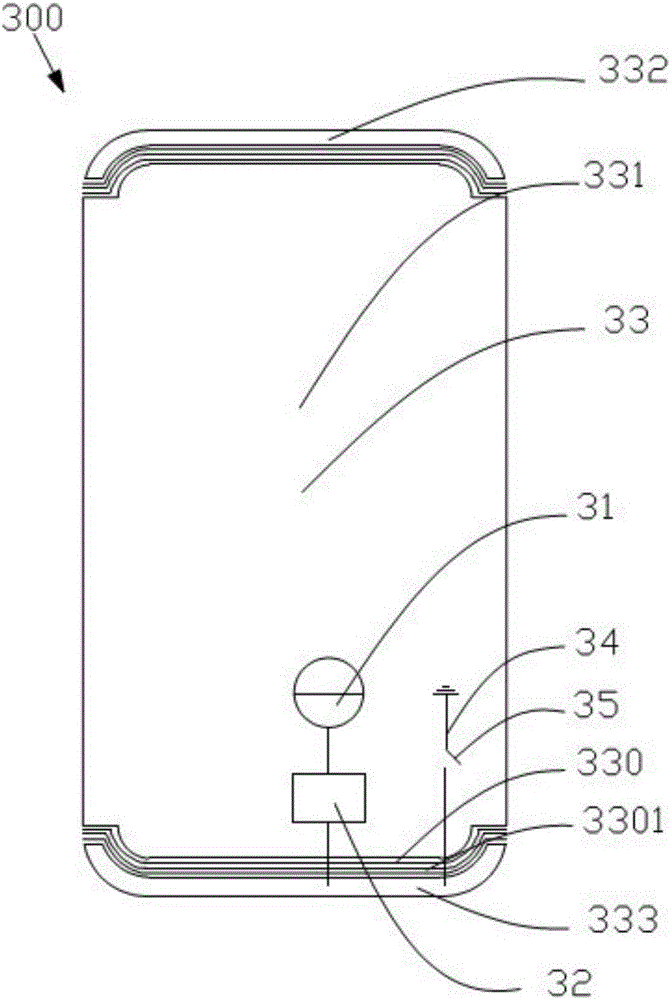
Shell, antenna device and terminal equipment
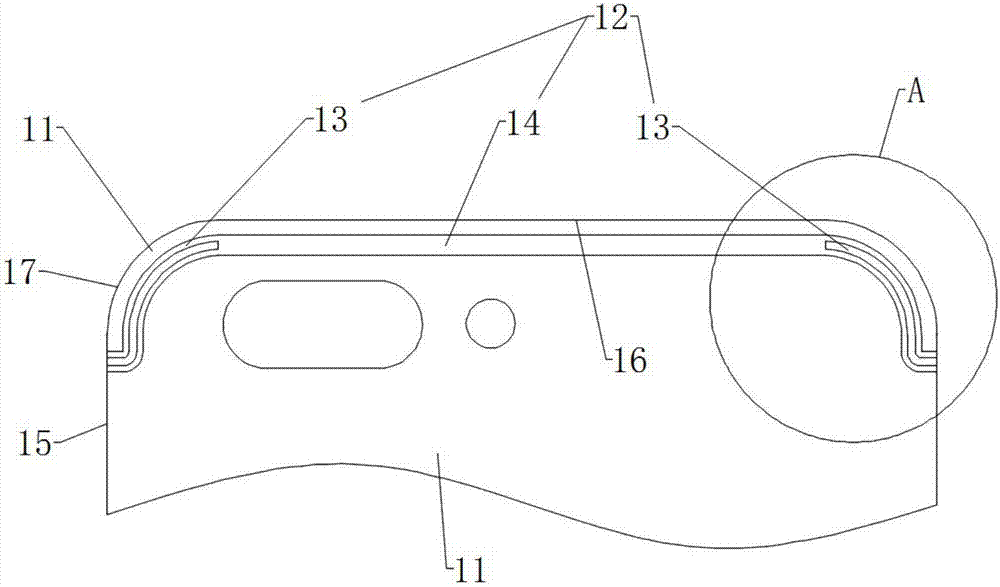
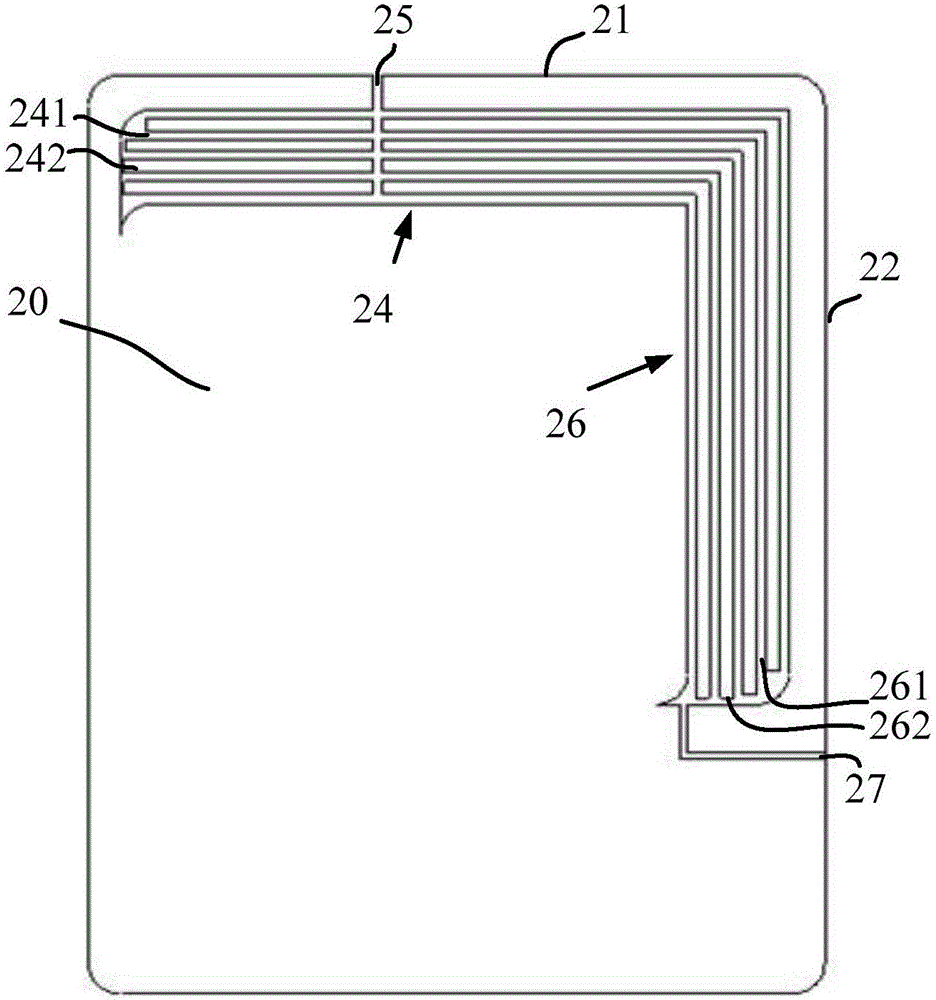
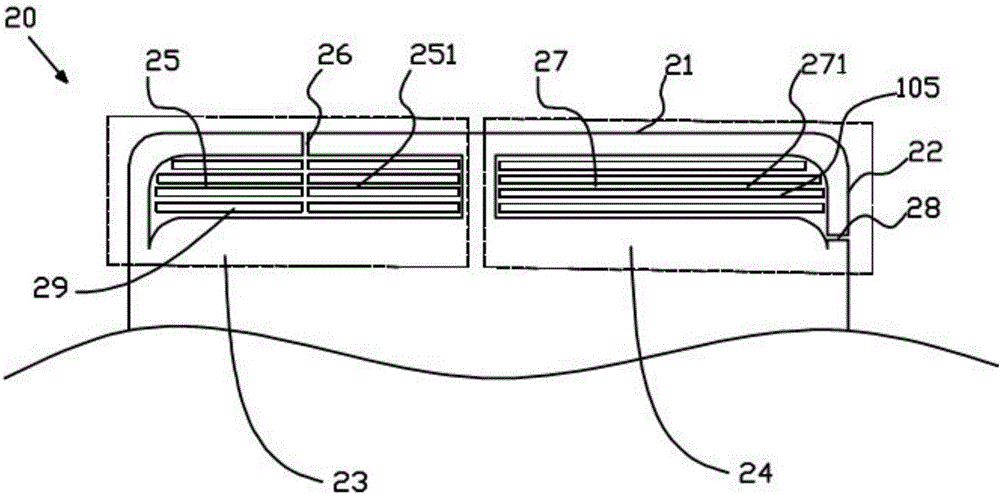
ActiveCN105932396ANot easy to attract attentionGuaranteed integrityAntenna supports/mountingsTerminal equipmentMicro gap
The invention provides a shell. A first micro-gap belt, a second micro-gap belt and a first gap are arranged on the shell; the first micro-gap belt comprises multiple first micro-gaps; the second micro-gap belt comprises multiple second micro-gaps; the first gap is intersected with the multiple first micro-gaps; and the multiple first micro-gaps of the first micro-gap belt are respectively communicated with the multiple second micro-gaps in the second micro-gap belt. The invention further provides an antenna device comprising the shell, and terminal equipment comprising the antenna device. According to the shell, the antenna device and the terminal equipment disclosed by the invention, the overall appearance effect of the terminal equipment can be ensured; and simultaneously, transceiving of high-frequency signals and GPS signals can be realized.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Shell, antenna device and mobile terminal
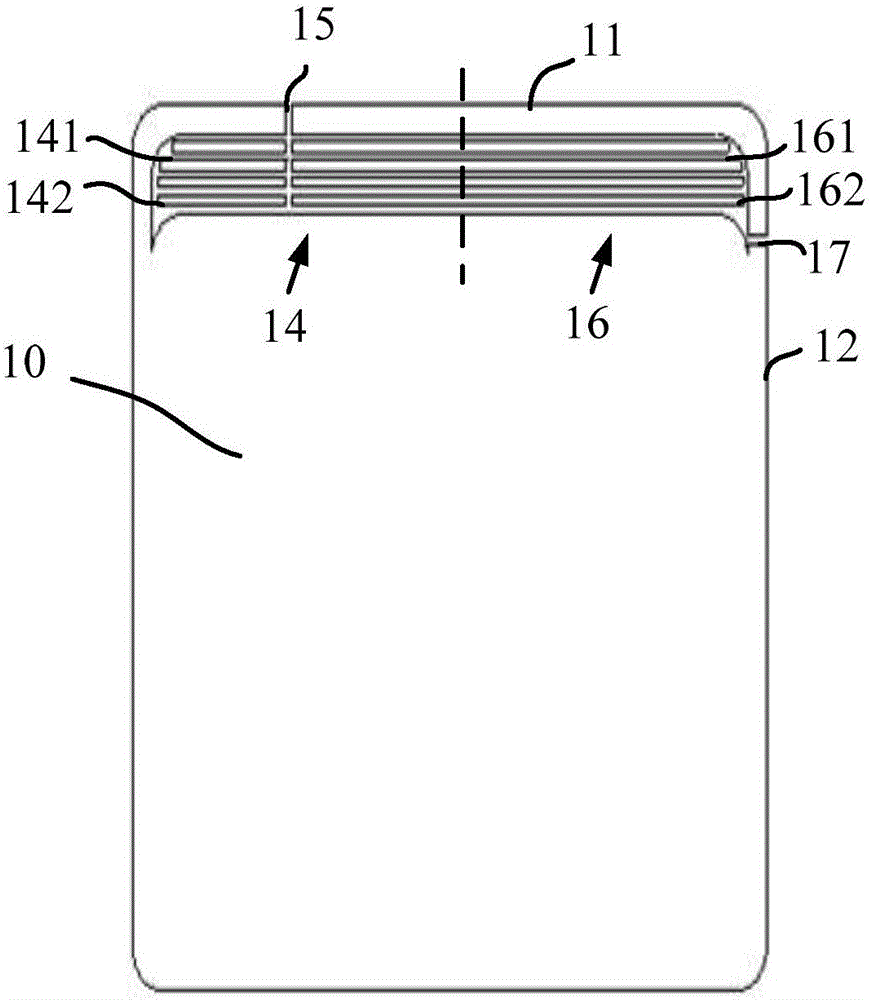
ActiveCN105789885ANot easy to attract attentionGuaranteed integrityAntenna supports/mountingsAntenna equipments with additional functionsEngineeringComputer terminal
The invention provides a shell which is used for a mobile terminal. The shell comprises a first conductive area. The first conductive area is provided with a first micro seam band and a first seam. The first micro seam band comprises multiple first micro seams. The first seam is intersected with the multiple first micro seams. According to the shell, the overall appearance effect of the mobile terminal can be guaranteed, and transmitting and receiving of high-frequency signals and GPS signals can also be realized. The invention also provides an antenna device and the mobile terminal.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
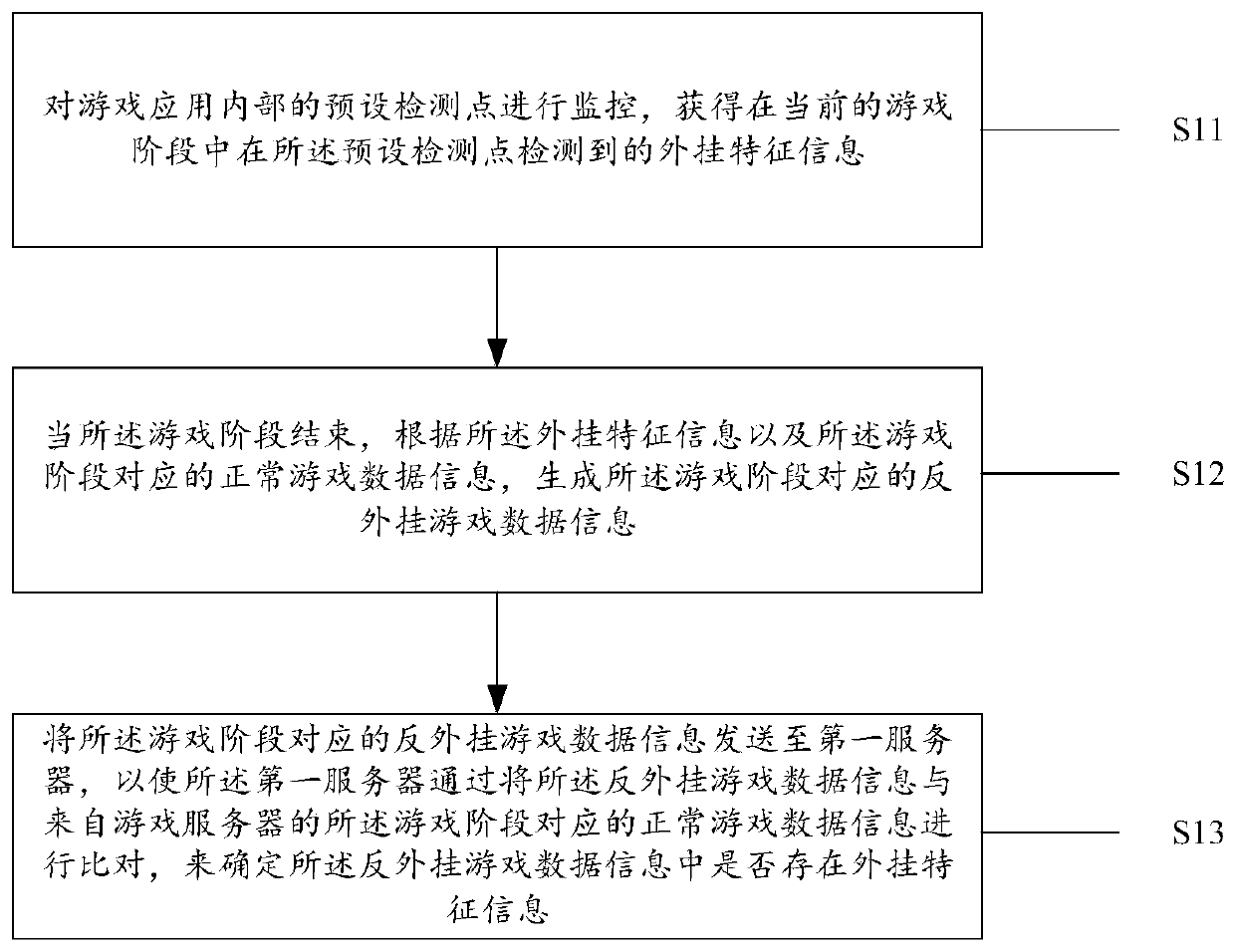
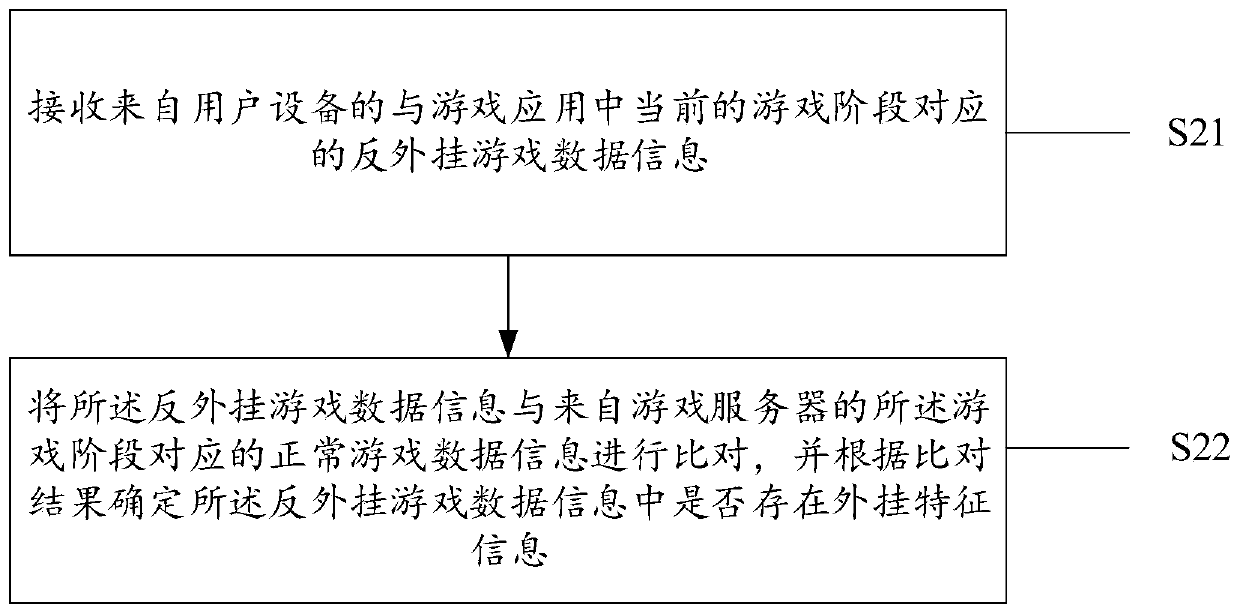
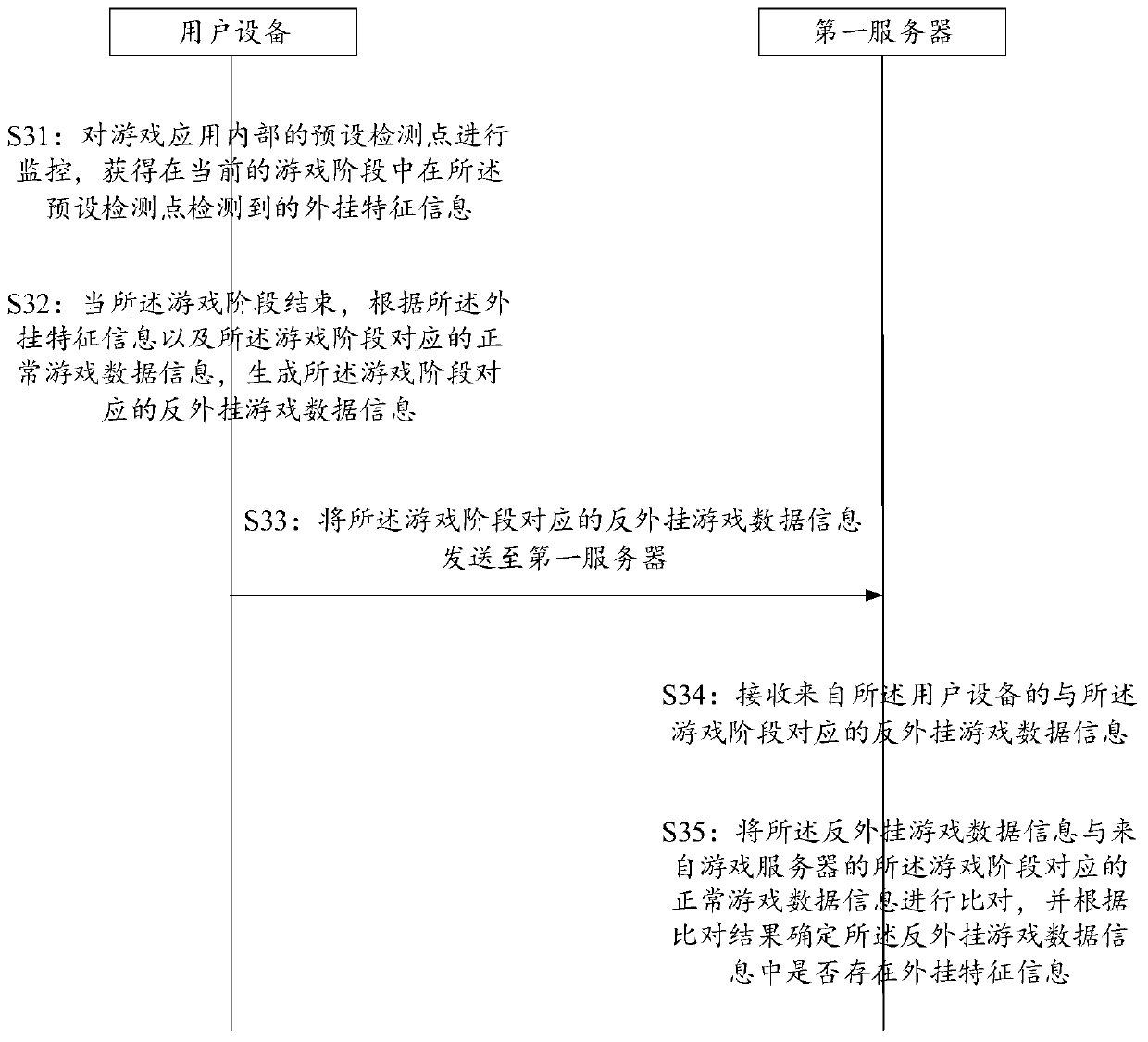
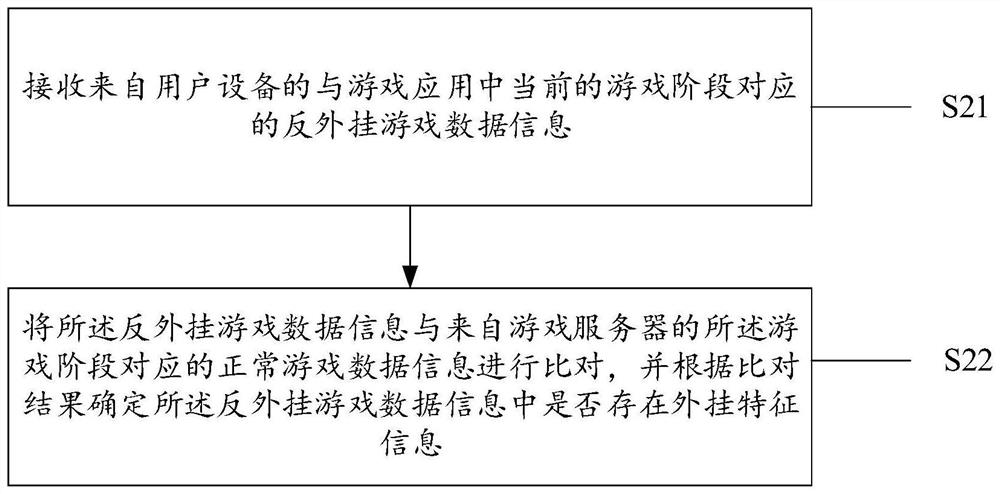
Anti-plug-in method, device and system
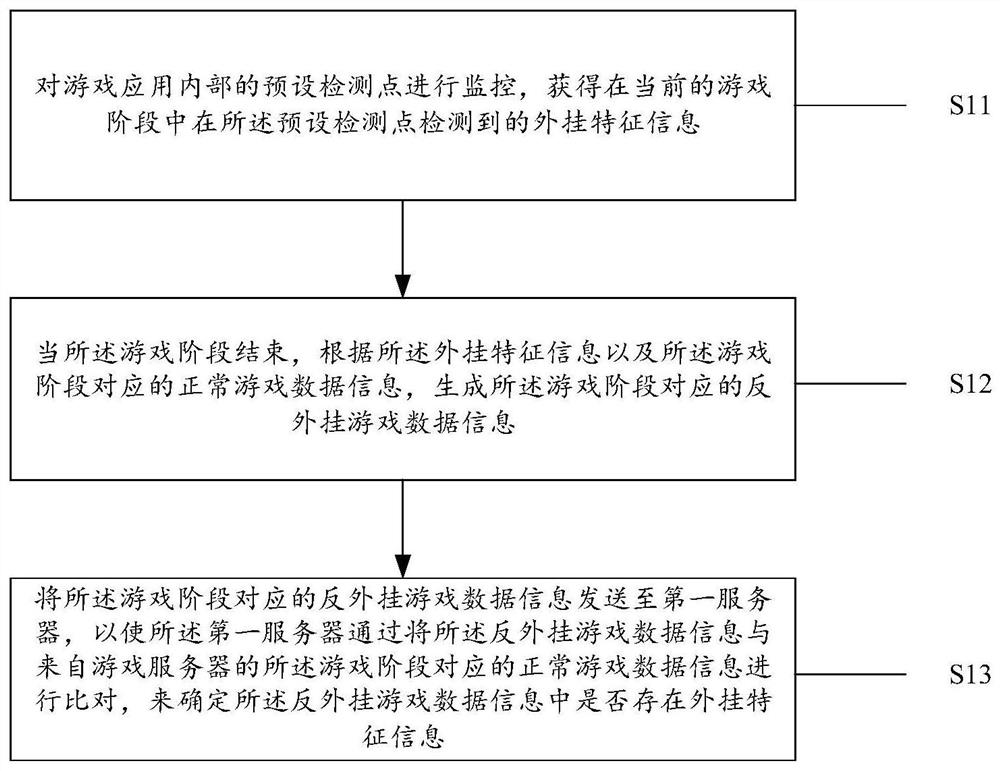
ActiveCN111389012ANot easy to attract attentionIncrease the difficultyVideo gamesReal-time computingData pack
The invention provides an anti-plug-in method, device and system, and the method comprises the steps: monitoring a preset detection point in a game application, and obtaining plug-in feature information detected at the preset detection point in a current game stage; when the game stage is finished, generating anti-plug-in game data information corresponding to the game stage according to the plug-in feature information and normal game data information corresponding to the game stage; and sending the anti-plug-in game data information corresponding to the game stage to a first server, so that the first server determines whether plug-in feature information exists in the anti-plug-in game data information or not by comparing the anti-plug-in game data information with normal game data information corresponding to the game stage from a game server. According to the scheme of the invention, a confused and hidden anti-plug-in mechanism is adopted, so that the difficulty in counterfeiting a data packet by a plug-in developer can be greatly increased.
Owner:PERFECT WORLD ZHENGQI SHANGHAI MULTIMEDIA TECH CO LTD
Antenna device and mobile terminal
ActiveCN105896085BNot easy to attract attentionGuaranteed integritySimultaneous aerial operationsRadiating elements structural formsElectricityMicro gap
The invention provides an antenna device for a mobile terminal. The antenna device comprises first radio-frequency receiving and transmitting circuit, a first matching circuit, a second radio-frequency receiving and transmitting circuit, a second matching circuit and a shell, wherein the shell comprises a first conducting region; the first conducting region is provided with a first micro-gap strip and a first gap; the first micro-gap strip comprises a plurality of first micro-gaps; the first micro-gap is intersected with the plurality of first micro-gaps; the first radio-frequency receiving and transmitting circuit is electrically connected with the first conducting region through the first matching circuit; and the second radio-frequency receiving and transmitting circuit is electrically connected with the first conducting region through the second matching circuit. According to the antenna device provided by the invention, the overall appearance effect of the mobile terminal can be ensured; and meanwhile, receiving and transmitting of a high-frequency signal and a low-frequency signal can be achieved. The invention further provides the mobile terminal.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
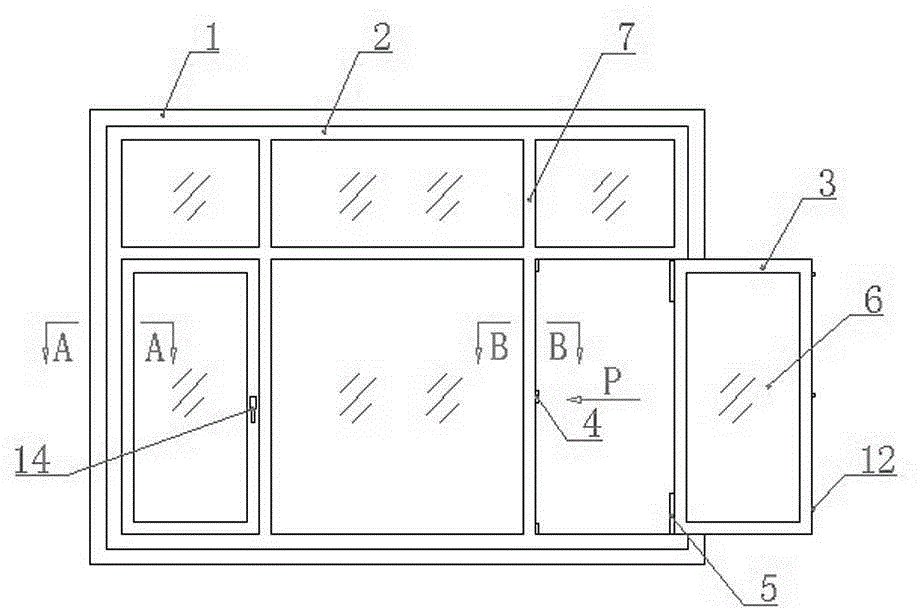
Concealed protective anti-theft anti-riot casement window without guardrail
InactiveCN102678018BHigh strengthImprove impact resistancePin hingesSealing arrangementsEnergy absorptionEngineering
The invention discloses a concealed protective anti-theft anti-riot casement window without a guardrail. The concealed protective anti-theft anti-riot casement window without the guardrail is characterized in that an anti-theft frame is arranged at the periphery of a window frame, a protective convex edge is arranged at the inner edge of an outdoor side of the anti-theft frame, and the window frame is embedded in the anti-theft frame and is mutually fastened and connected with the anti-theft frame by using bolts. The concealed protective anti-theft anti-riot casement window with the guardrail has the advantages that the anti-theft frame can be accurately fixed, when in use, firstly the anti-theft frame is arranged in a window of a wall, then the embedded window frame is fixed by the anti-theft frame, and the anti-theft frame and the window frame are sequentially and successfully arranged and do not need to rework, thereby greatly increasing the operating efficiency and installing accuracy; a gap between the anti-theft frame and the window frame is covered by the protective convex edge arranged at the inner edge of the outer side of the anti-theft frame, and therefore, the protective convex edge has the pry-proof effect; the strength and the anti-impact property of the window frame are increased through steel pipes and energy absorption materials in the window frame; a glass film composite layer is used for effectively preventing thieves from breaking up or gashing glass to enter a room and has the functions of anti-theft, temperature preservation and heat insulation; and stoppers and hinges of window sashes are also used for increasing the strength and anti-theft performance.
Owner:高林
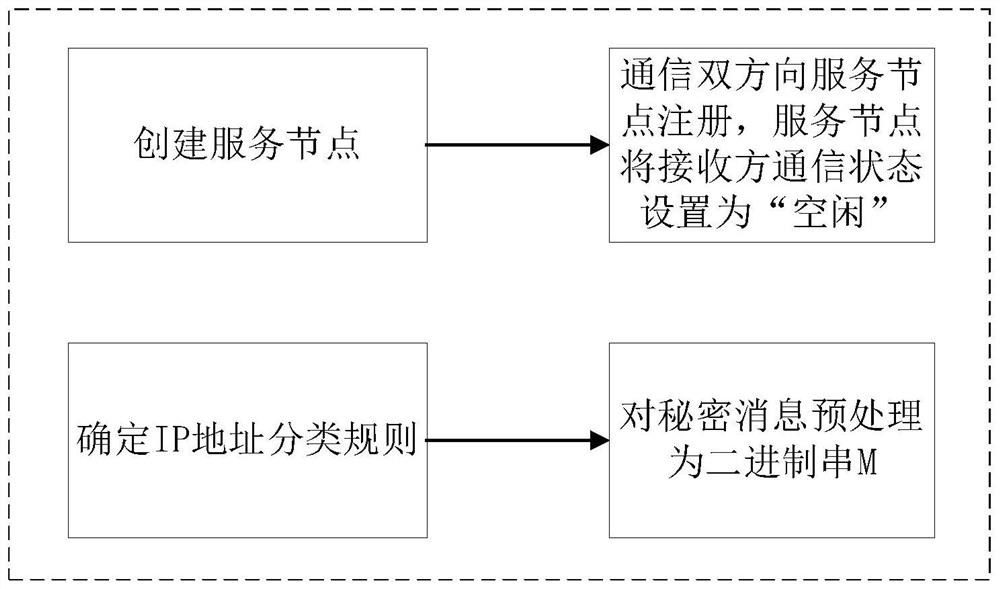
A Reliable Network Steganography Method Based on IP Source Address
ActiveCN112422511BNot easy to attract attentionReliable communicationSecuring communicationData packReliable transmission
A reliable network steganography method based on IP source address, which mainly consists of three parts: preparation process, embedding process and extraction process. A service node is set to record the basic information and communication status of both parties in communication, and both parties use different IP source addresses. The type represents the binary digits "0" and "1", and the service node completes the auxiliary confirmation of the integrity of the secret message and realizes the reliable transmission of the secret information. The advantages are: the entire steganography process only hides the secret message by classifying the source address field of the data packet, and chooses to use the IP address that exists in the public network. It actually exists in the network, so it is not easy to attract the attention of the attacker; the service node is A network node independent of the receiver and sender of a secret message to record the state used for covert communication to ensure reliable communication. The sender and receiver of the secret message do not communicate directly, so that the attacker cannot detect the communication process between the two, which helps to improve the concealment.
Owner:QINGDAO UNIV
Voice encryption method and voice sending terminal
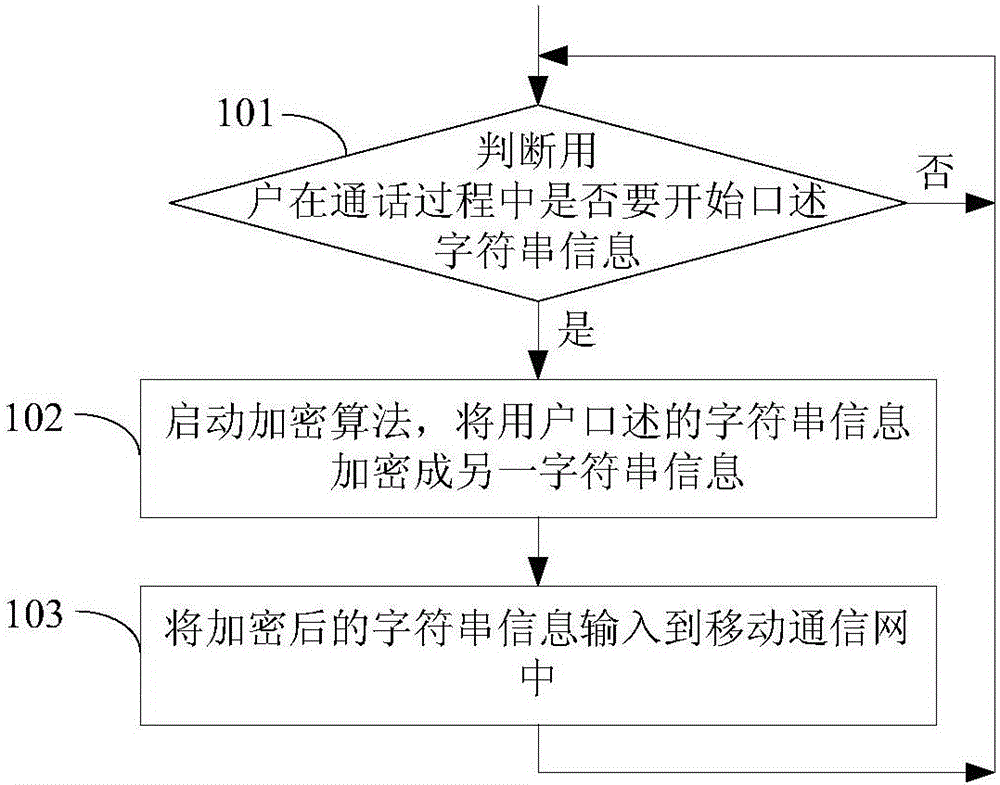
ActiveCN105743912ANot easy to attract attentionImprove securitySecurity arrangementSecuring communicationComputer hardwareVoice communication
The invention discloses a voice encryption method and a voice sending terminal. The method is applied in the voice sending terminal. The method comprises following steps of judging whether a user starts dictating character string information or not in a call process; if the user starts dictating the character string information, encrypting the user dictated character string information into another piece of character string information; and inputting the encrypted character string information in a mobile communication network. According to the method and the terminal, the voice communication security is improved.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Method for carrying out secret communication by using word document
The invention provides a method for carrying out secret communication by using a word document. The method mainly comprises the following three steps of: manufacturing secret characters by using a True Type character-formation program and generating a secret key; embedding the secret characters into the word document; and extracting the secret characters by using the secret key. According to the method disclosed by the invention, the True Type character-formation program in the conventional general windows operation system, display characters of a window word base and certain functions of word character processing software are designed and integrated so as to realize a function of performing the secret communication by using the word document. The method disclosed by the invention has the advantages of smart conception, simple method, low cost, good commonality and easiness of operation. Therefore, the method can be accessibly used by any operator familiar with windows.
Owner:XIAN UNIV OF SCI & TECH
Directed attack anti-patch generation method and device
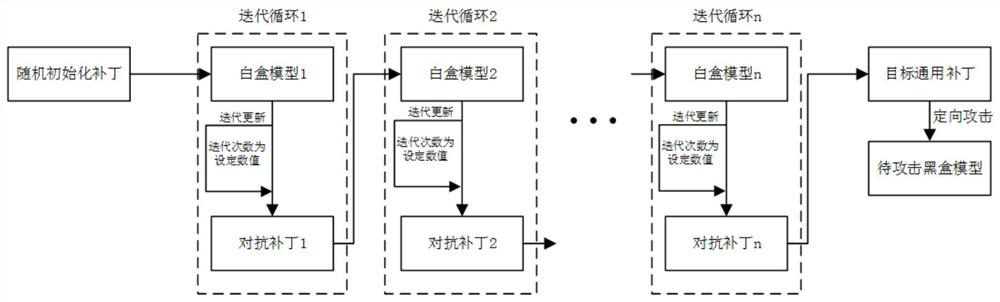
ActiveCN113255816BGood attack performanceIncrease success rateCharacter and pattern recognitionNeural architecturesAlgorithmBox model
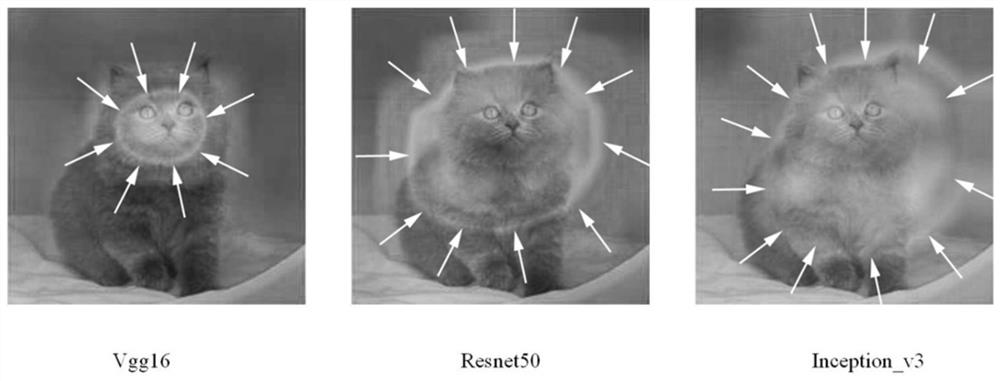
The present invention provides a method and device for generating a directional attack adversarial patch. The method adopts a plurality of consecutive white-box models with different structures to iteratively update the adversarial patch, so that the obtained target general adversarial patch can be better for the black-box model with unknown structure. attack effect. By introducing the triplet loss, the success rate of the output target category can be improved during the directed attack. By introducing the attention shift loss, the migration effect of the target general adversarial patch to the model attention area can be improved, so as to greatly improve the directional attack effect of the target general adversarial patch. By introducing a smoothing loss, it is possible to reduce the gap between the pixel points of the target common adversarial patch, which is not easy to attract the attention of the human eye. Furthermore, by adding anti-patches, targeted attacks can be carried out at the physical and digital levels at the same time, which is easier to implement.
Owner:BEIJING UNIV OF POSTS & TELECOMM
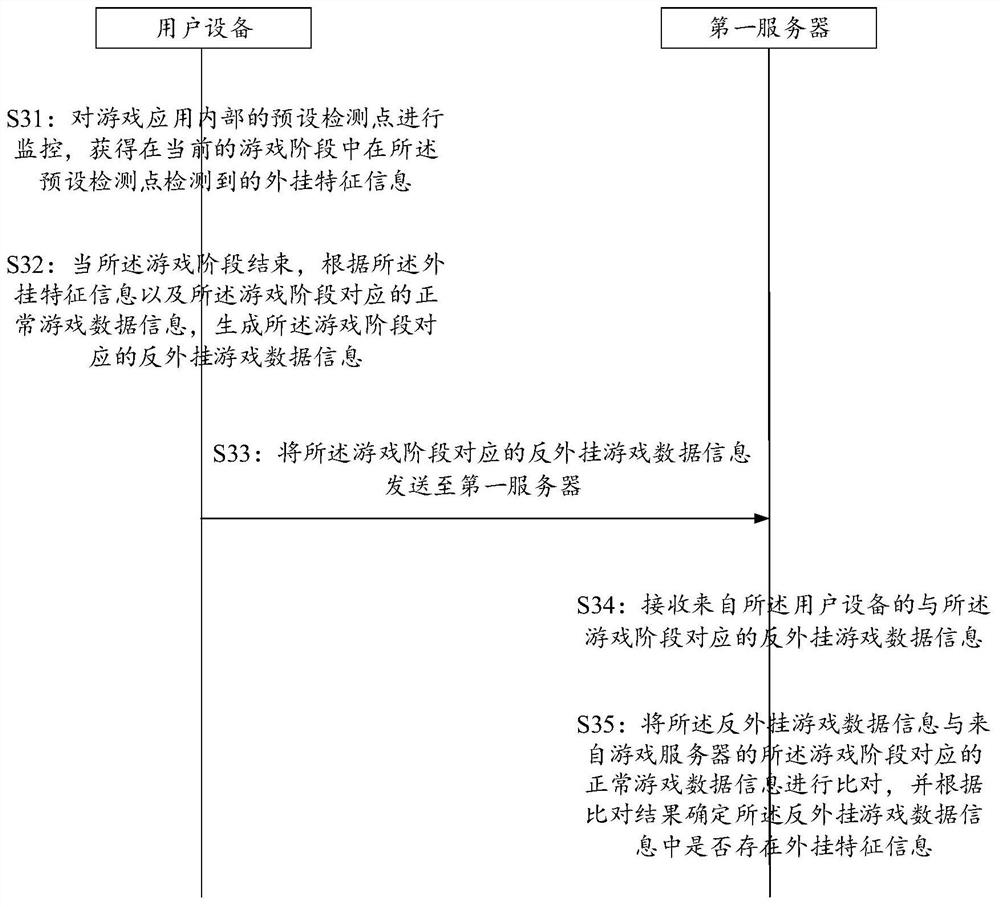
A method, device and system for anti-cheat
ActiveCN111389012BNot easy to attract attentionIncrease the difficultyVideo gamesData packSimulation
The present application provides a method, device and system for anti-cheat. The method includes: monitoring the preset detection points inside the game application, and obtaining the The plug-in feature information; when the game stage is over, according to the plug-in feature information and the normal game data information corresponding to the game stage, generate the anti-cheat game data information corresponding to the game stage; The anti-cheat game data information is sent to the first server, so that the first server determines the Whether there is cheat feature information in the anti-cheat game data information. According to the solution of the present application, the use of a deceptive and concealed anti-cheat mechanism can greatly increase the difficulty for a cheat developer to forge data packets.
Owner:PERFECT WORLD ZHENGQI SHANGHAI MULTIMEDIA TECH CO LTD
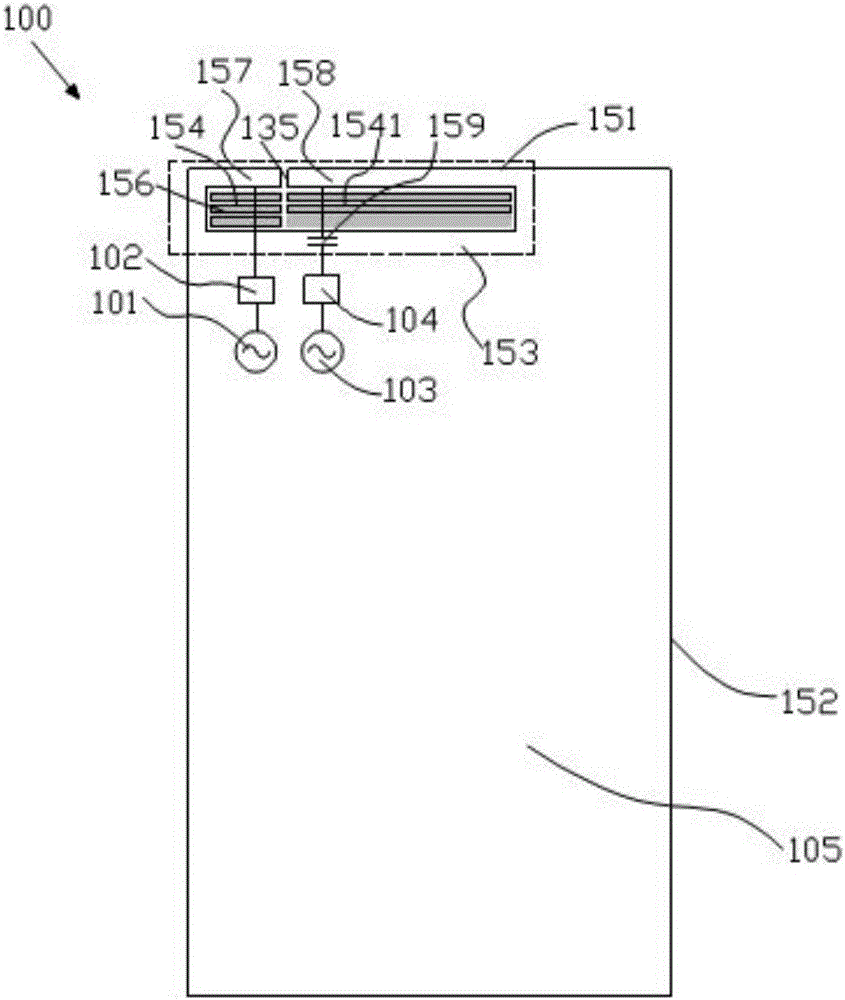
Antenna device and mobile terminal
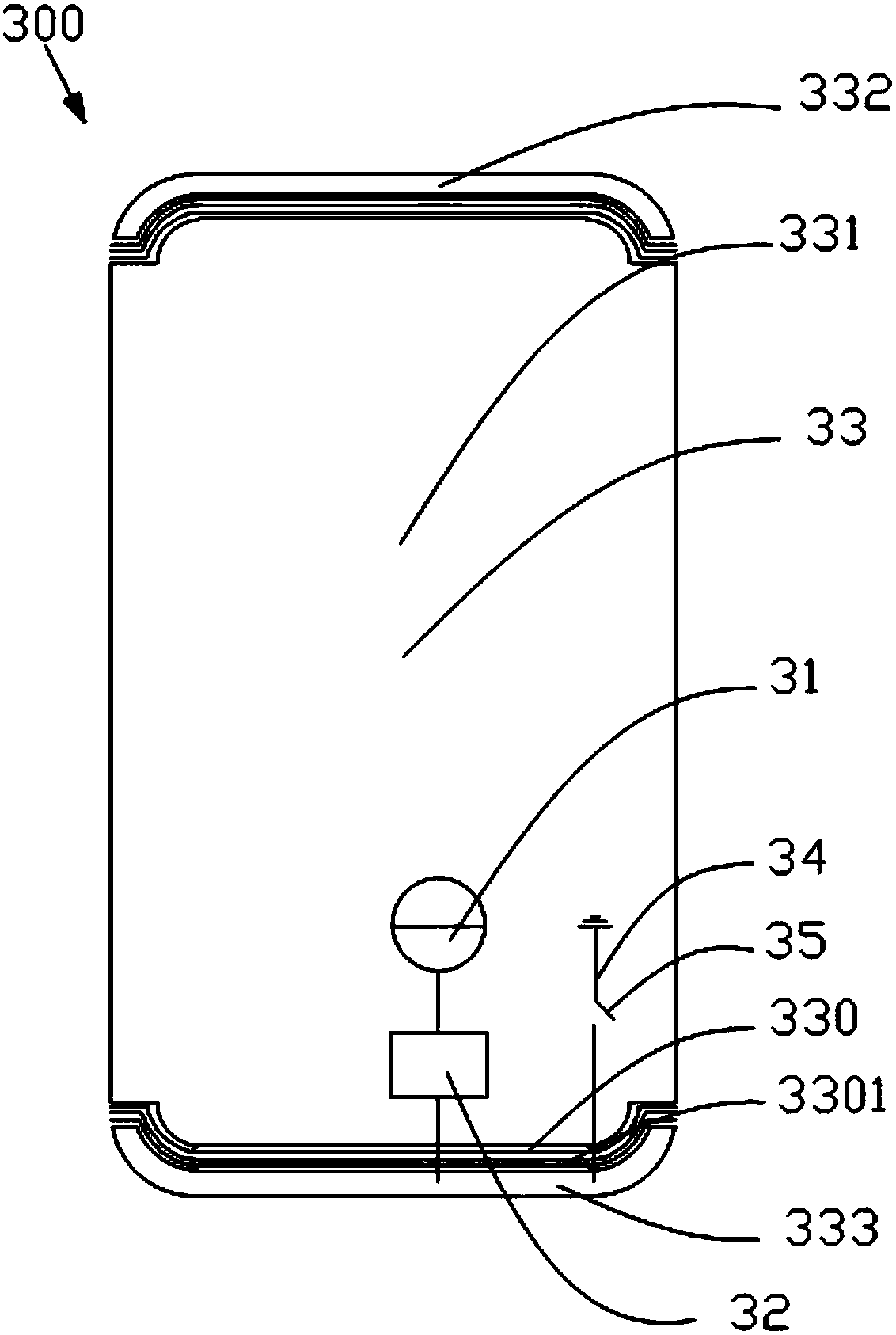
ActiveCN105789827BGuaranteed integrityIncrease the lengthAntenna supports/mountingsRadiating elements structural formsMetallic enclosureTransceiver
The present invention provides an antenna device, comprising a radio frequency transceiver circuit; a matching circuit electrically connected to the radio frequency transceiver circuit; The seam belt, the at least one micro-slit belt includes an arc portion, the arc portion matches the arc segment of the metal casing, and the radio frequency transceiver circuit is electrically connected to the metal casing through the matching circuit connected, so that the metal casing is used as a radiator of the antenna device, wherein the metal casing is grounded through a ground wire, and a switch for controlling the on-off of the ground wire is provided on the ground wire. The antenna device according to the present invention can ensure the overall appearance effect of the mobile terminal, and at the same time prevent the signals of the antenna device from being interfered and improve the bandwidth of the antenna device. The invention also provides a mobile terminal.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
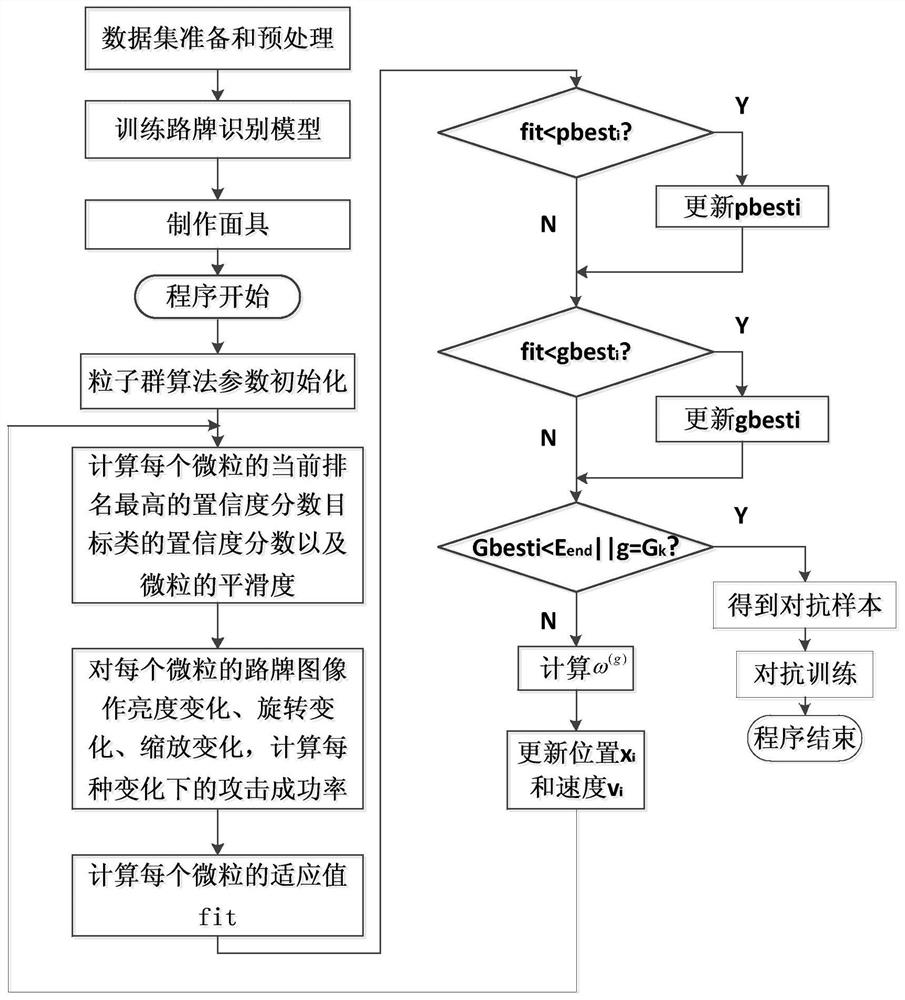
A road sign recognition attack defense method based on multi-objective road optimization
ActiveCN110175513BImprove defenseImprove the degree of physicalizationCharacter and pattern recognitionArtificial lifeAlgorithmEngineering
Owner:ZHEJIANG UNIV OF TECH
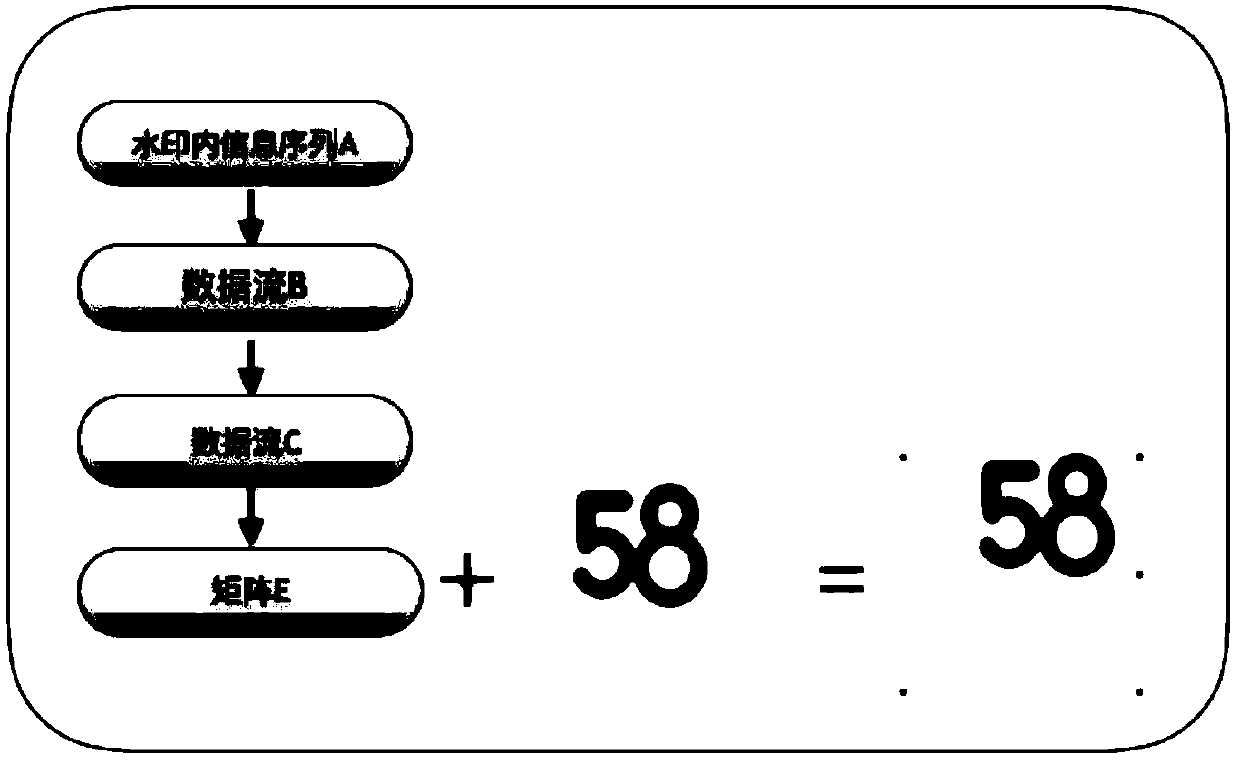
A method for displaying a dark watermark at a moving end
InactiveCN109543152ANot easy to attract attentionInterfere with readingNatural language data processingImage data processing detailsMobile endComputer science
The invention discloses a method for displaying a dark watermark at a mobile end, which comprises the following steps: 1, after the watermark content is encoded and converted, the watermark content isplaced in a matrix; Step 2: the matrix is drawn onto the application interface. By adopting the method, the invention can avoid interfering with the normal reading of the user, ensure the user experience, prevent the illegal elements from forging the watermark content, and bring the safe experience to the user.
Owner:北京指掌易科技有限公司
Secret information transmission method in p2p network based on bittorrent protocol
ActiveCN105959355BSimple transfer methodNot easy to attract attentionTransmissionInformation transmissionInternet privacy
The invention belongs to the technical field of computer network and information security, and mainly discloses a secret information transmission method under the P2P network based on the BitTorrent protocol. The secret transmission channel is established on the basis of the Handshake message transmission channel in the P2P network, relying on the established secret transmission method. channel, and embed the secret information into the BT keyword of the Handshake message for transmission by means of case-insensitive information encoding. The present invention introduces a case-insensitive information encoding method into the BT keyword of the Handshake message to implement secret communication. The secret information transmission method provided by the present invention is not only simple and efficient, but also has low implementation cost, and is more secure and reliable, and is not easy to be cracked.
Owner:JIANGSU UNIV OF SCI & TECH
A Character-Based Steganographic Method for Plain Text
ActiveCN107947918BAvoid distortionNot easy to attract attentionKey distribution for secure communicationEncryption apparatus with shift registers/memoriesAlgorithmCiphertext
The invention discloses a carrier-free text steganography method based on character features. Binary digits are expressed through the character features; secret information is processed into a binaryciphertext string and then is packaged and segmented; mapping between texts and binary ciphertext string segments is established by taking abundant webpage texts in a network big data environment as candidate carriers; corresponding texts are found for the secret information through the mapping relationship; and the texts or the corresponding URLs are sent, thereby finishing secret information interaction. After a receiving end receives the texts, the character features of a first text are analyzed to obtain head information; a binary ciphertext segmentation mode and length are determined; thefollow-up text character features are analyzed to obtain binary ciphertext segments; the segments are recombined to form the complete binary ciphertext string; and decoding or decryption is carried out to obtain the secret information. The method has the advantages of high stealthiness, high expandability and high embedded capacity, and the application and development of a steganography technology in various fields are facilitated.
Owner:QINGDAO UNIV
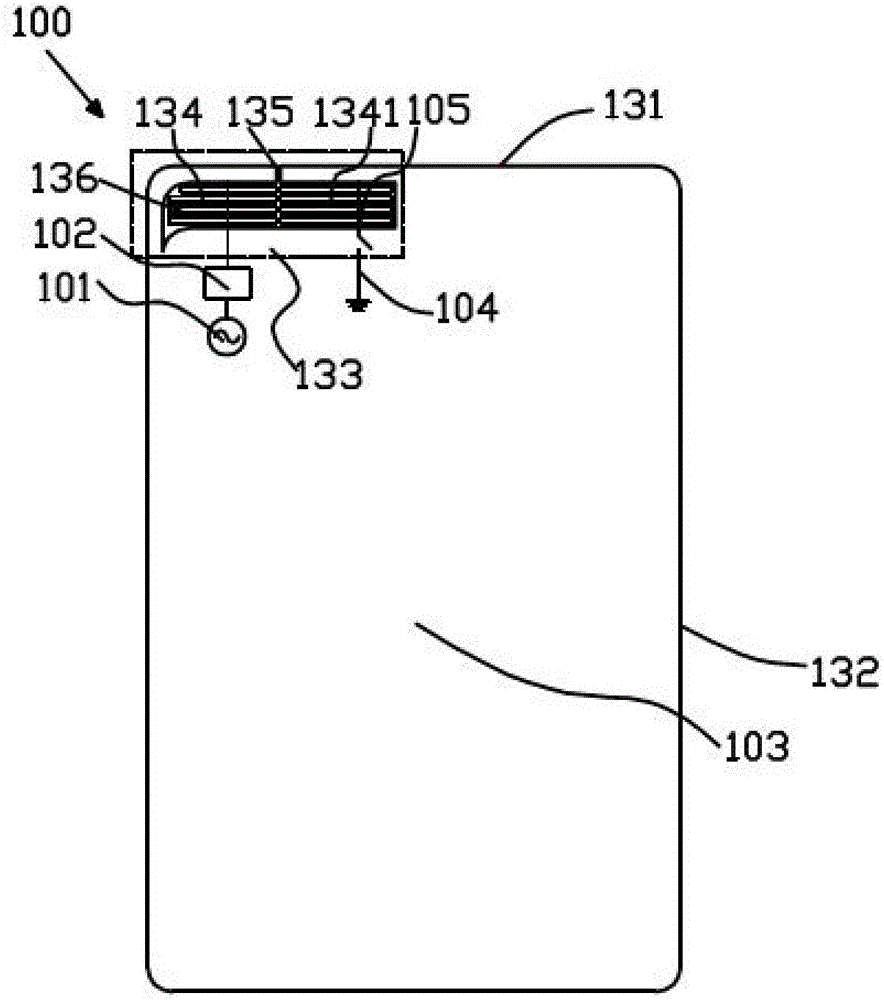
Antenna device and mobile terminal
ActiveCN105655704BGuaranteed integrityNot easy to attract attentionSimultaneous aerial operationsMetal casingsElectricityTransceiver
Provided in the present invention is an antenna device, comprising: a radio frequency transceiver circuit; a match circuit, which is electrically connected to the radio frequency transceiver circuit; and a metal cover, which is provided with at least one band of micro seams. The radio frequency transceiver circuit is electrically connected to the metal cover by means of the match circuit, such that the metal cover is used as a radiating body of the antenna device. The metal cover is grounded by means of a grounding wire, the grounding wire being provided with a switch thereon for connecting / disconnecting the grounding wire. The antenna device according to the present invention can guarantee the overall appearance of a mobile terminal, and meanwhile, can prevent signals of the antenna device from being interfered and improve the bandwidth of the antenna device. Further provided in the present invention is a mobile terminal.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Hidden information transmission method and transmission system based on biological sound
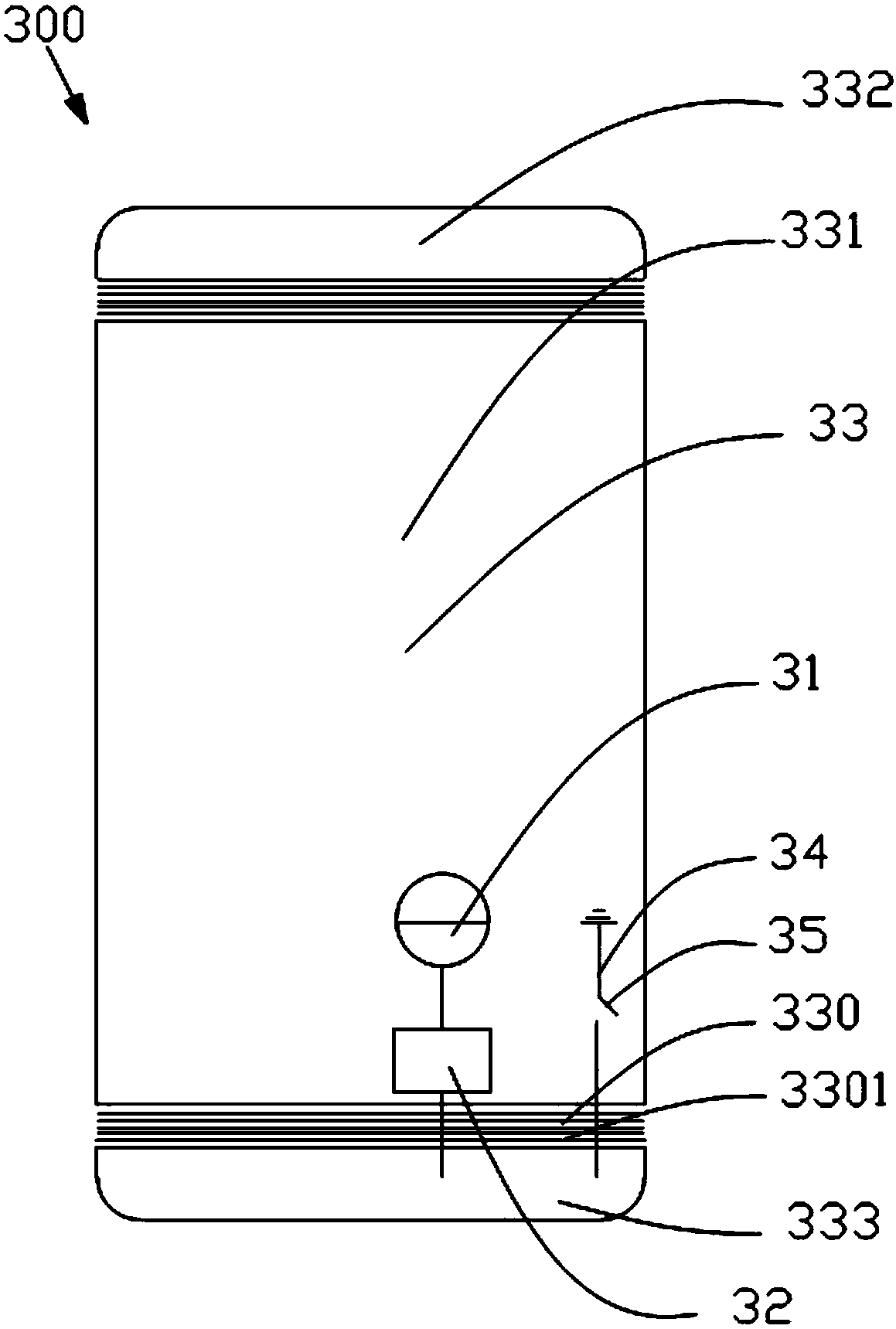
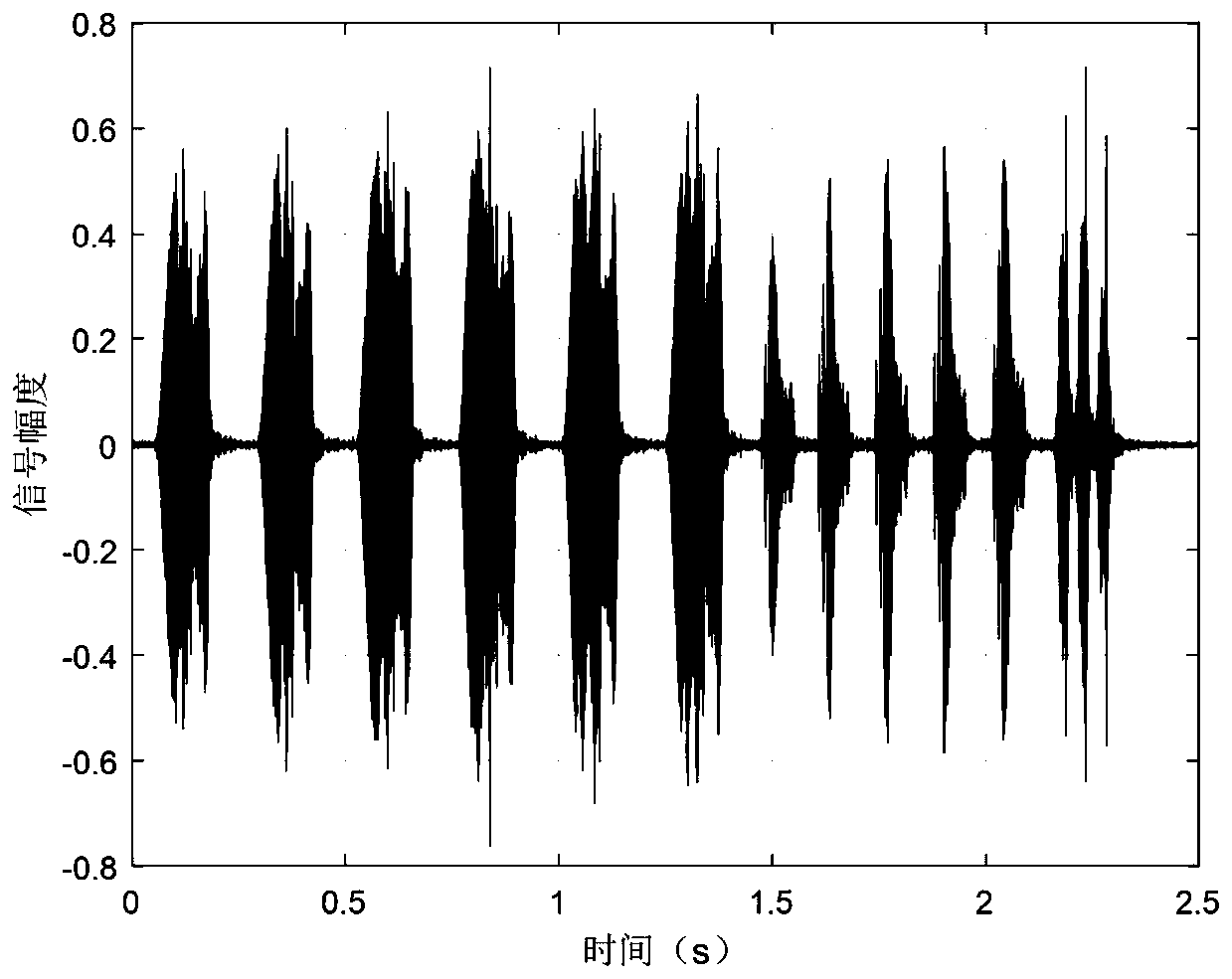
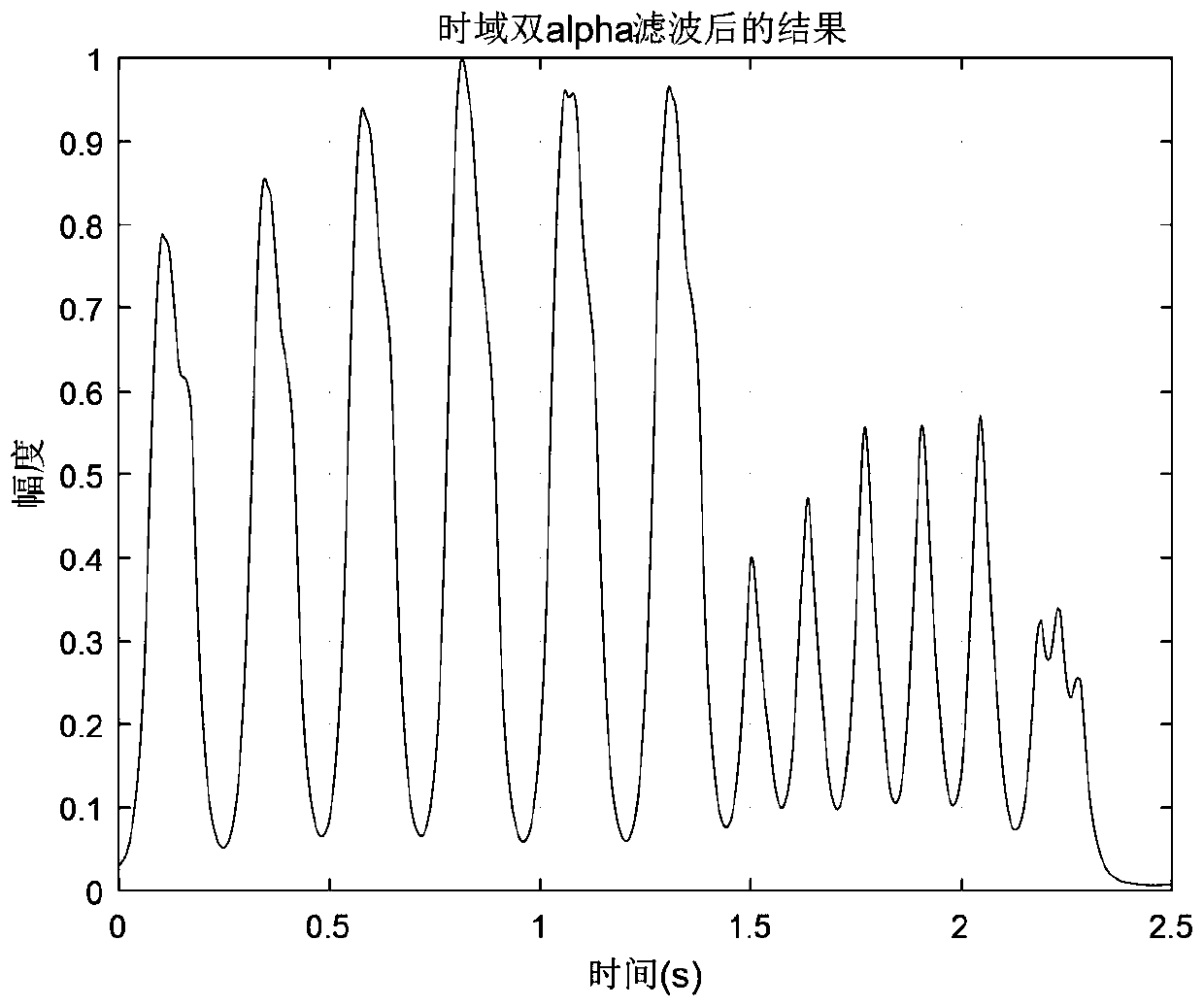
ActiveCN111181656AImprove delivery reliabilityNot easy to attract attentionSonic/ultrasonic/infrasonic transmissionSpeech analysisTime rangeInformation transmission
The invention discloses a concealed information transmission method and transmission system based on biological sound, and the method comprises the steps: 1, enabling a transmitting end to collect a biological sound pulse signal x(t), and extracting an envelope es(t); 2, acquiring the time range of each biological sound pulse in es(t); 3, when an i-th code element to be sent is B1, embedding an identification signal into an i-th biological sound pulse signal xi(t) in the x(t), and when the i-th code element to be sent is B2, performing no processing on the xi(t) signal; 4, enabling the transmitting end to send out the processed biological sound signal; 5, extracting an enveloper(t) from a received biological sound signal y(t) by the receiving end, and obtaining the time range of each biological sound pulse; 6, judging whether embedded information exists or not for each biological sound pulse yj(t) in the y(t): if the embedded information exists, determining that the j-th code element sent by the sending end is B1. According to the method, the requirement for transmitting the hidden information in a specific occasion can be met, and the probability that the secret information is intercepted and captured is reduced through the hidden communication behavior.
Owner:JIANGSU UNIV OF SCI & TECH +1
A voice encryption method and voice sending terminal
ActiveCN105743912BNot easy to attract attentionImprove securitySecurity arrangementSecuring communicationCommunications securityVoice communication
The present application discloses a voice encryption method and a voice sending terminal. The method is applied to the voice sending terminal. The method includes: judging whether the user wants to start dictating character string information during a call; if so, start an encryption algorithm The character string information dictated by the user is encrypted into another character string information; the encrypted character string information is input into the mobile communication network, thereby improving the security of the voice communication.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com