Extension visual encryption and decryption method
An encryption method and secret image technology, applied in the field of extended visual decryption, can solve the problems of carrier image interference, meaningless image sharing, and no tampering authentication function, so as to reduce storage capacity requirements, transmission bandwidth requirements, and The effect of the probability of interception and analysis
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] Below in conjunction with accompanying drawing and specific embodiment the present invention is described in further detail:
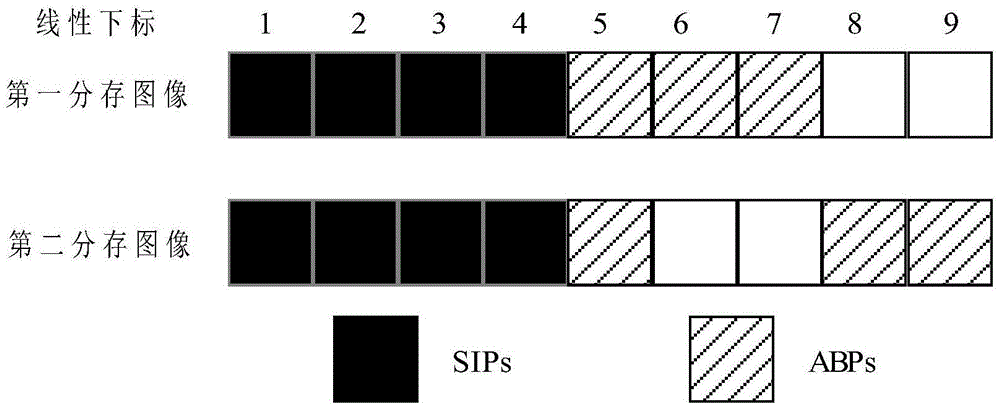
[0055] In the embodiment of the present invention, the binary secret image and watermark image used are as figure 2 shown.
[0056] It should be noted that, in the embodiment of the present invention, any size conforms to Binary images of any size can be used as secret images, and any size conforms to Binary images of any size can be used as watermark images, where Indicates that x is rounded towards -∞.
[0057] The parameters used in the embodiment of the present invention are shown in Table 1.
[0058] The parameters used in the specific embodiment of table 1
[0059]
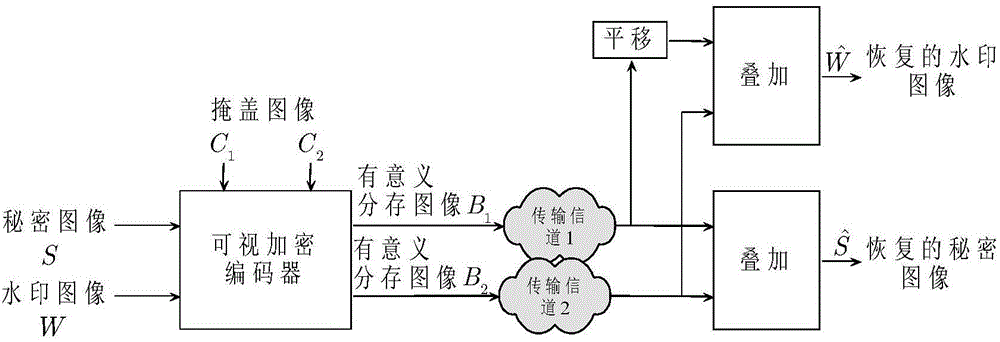
[0060] The overall block diagram of the extended visual encryption and decryption process is as follows figure 1 shown.
[0061] The extended visual encryption process includes three stages: (1) pixel division, (2) embedding of secret image and watermark, (3) res...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com