Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
30results about How to "Build trust" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
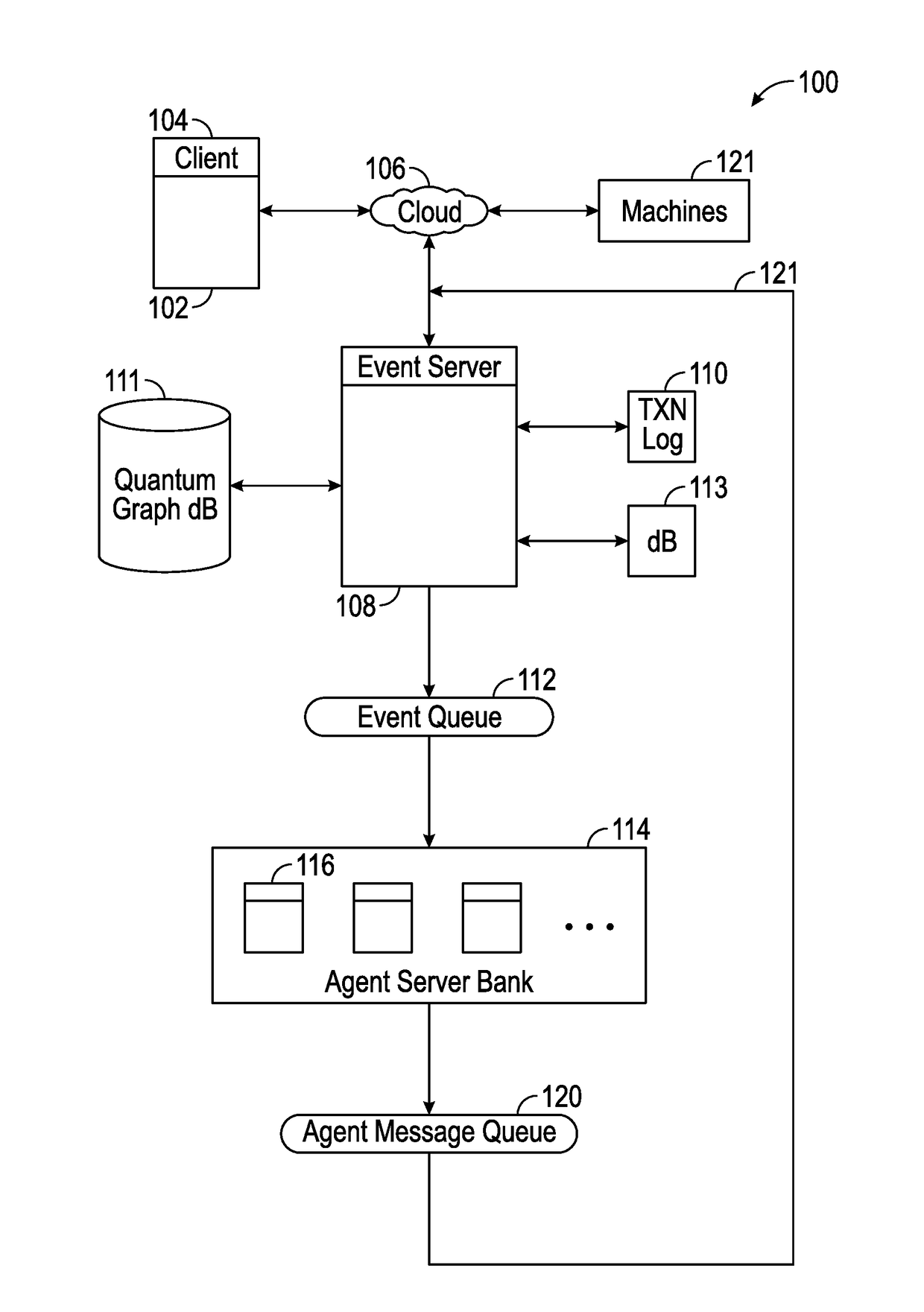
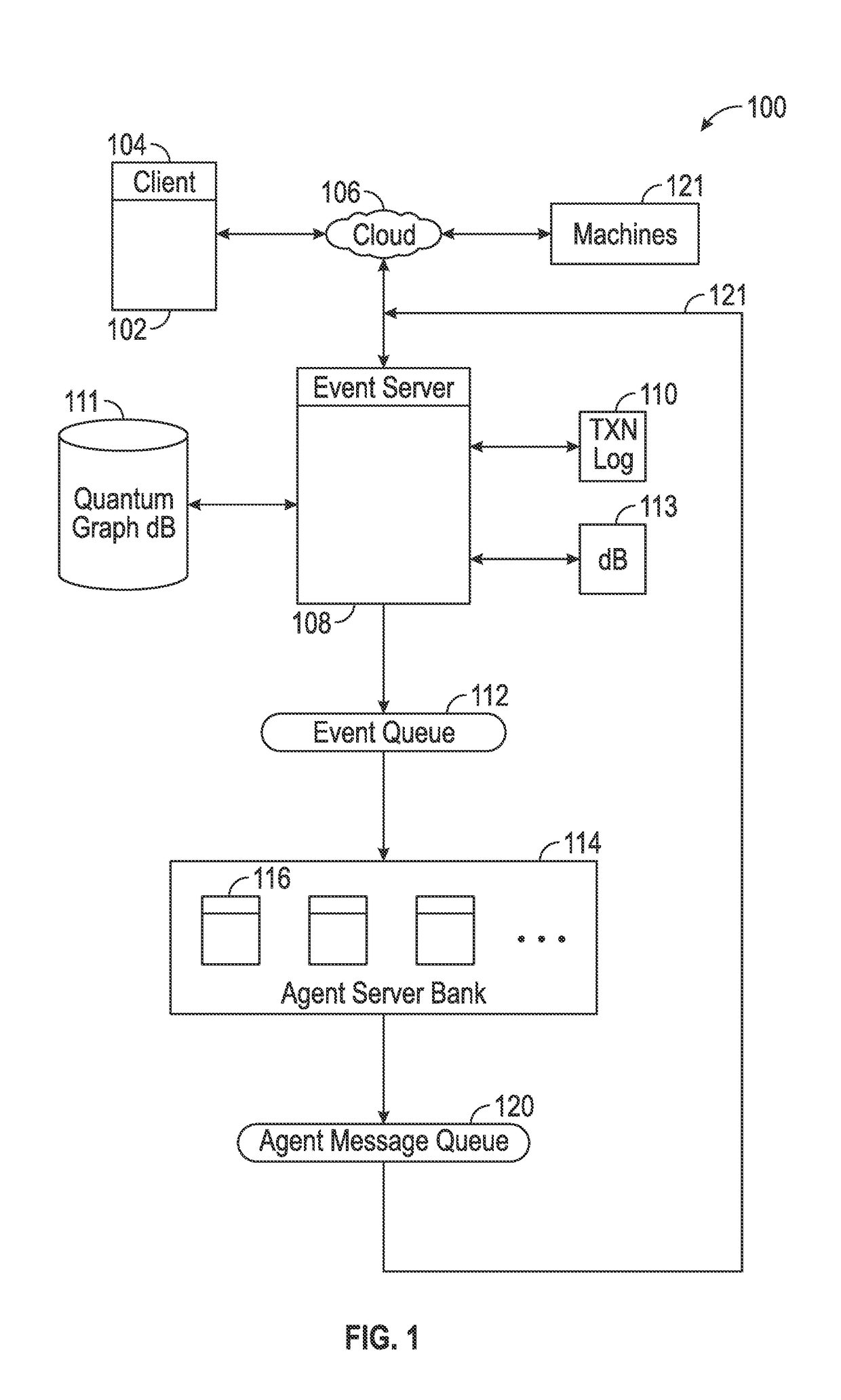
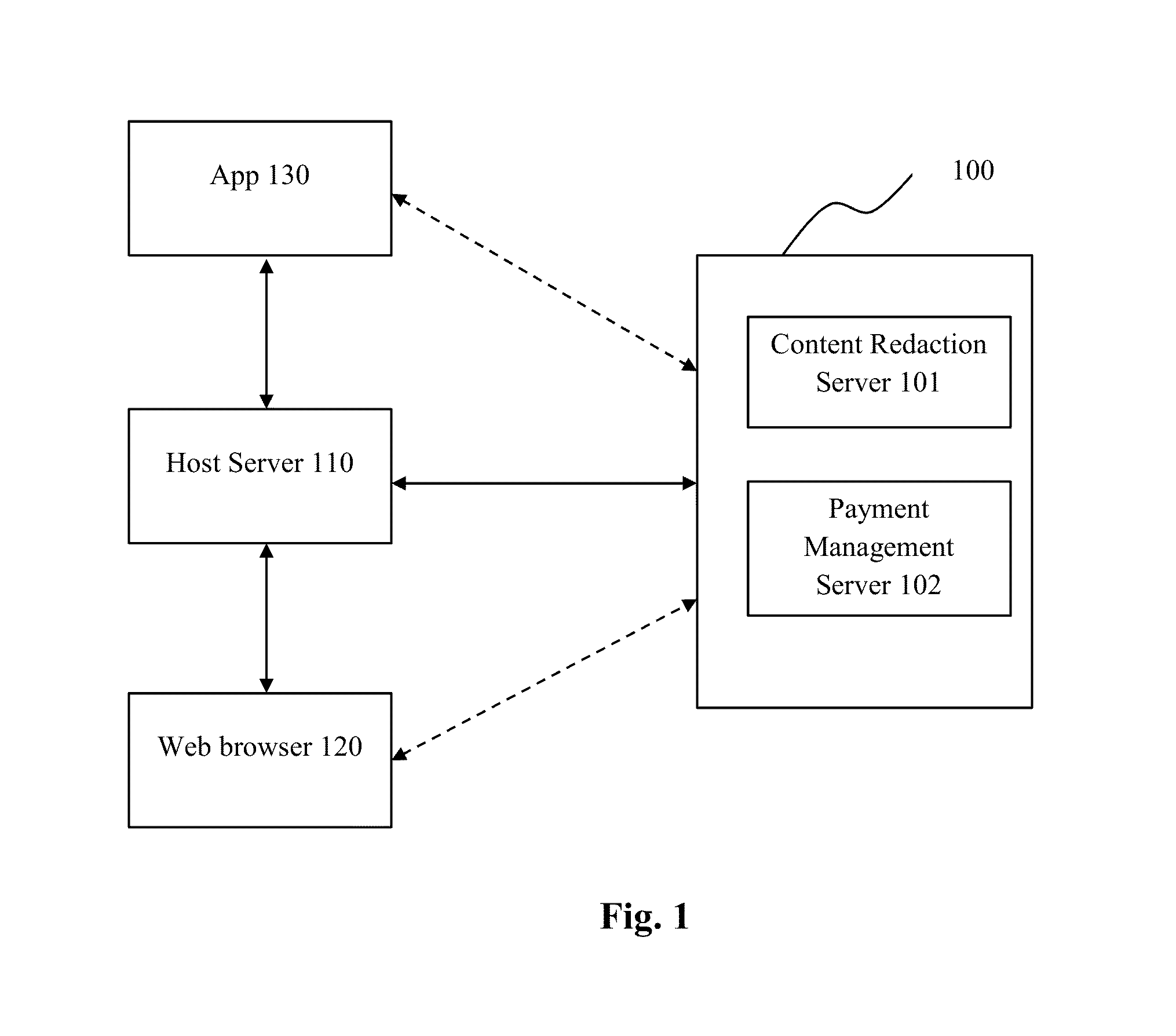
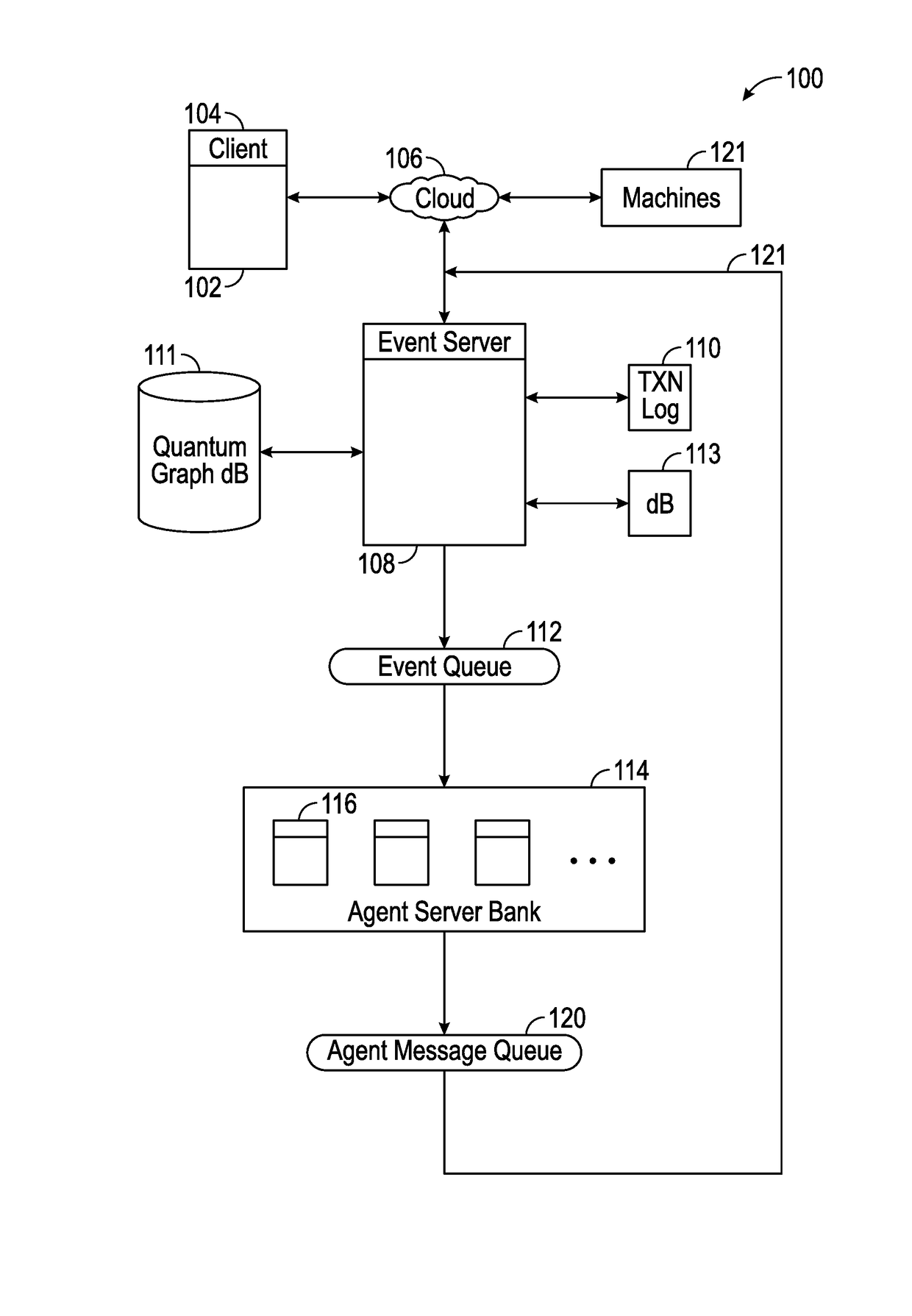
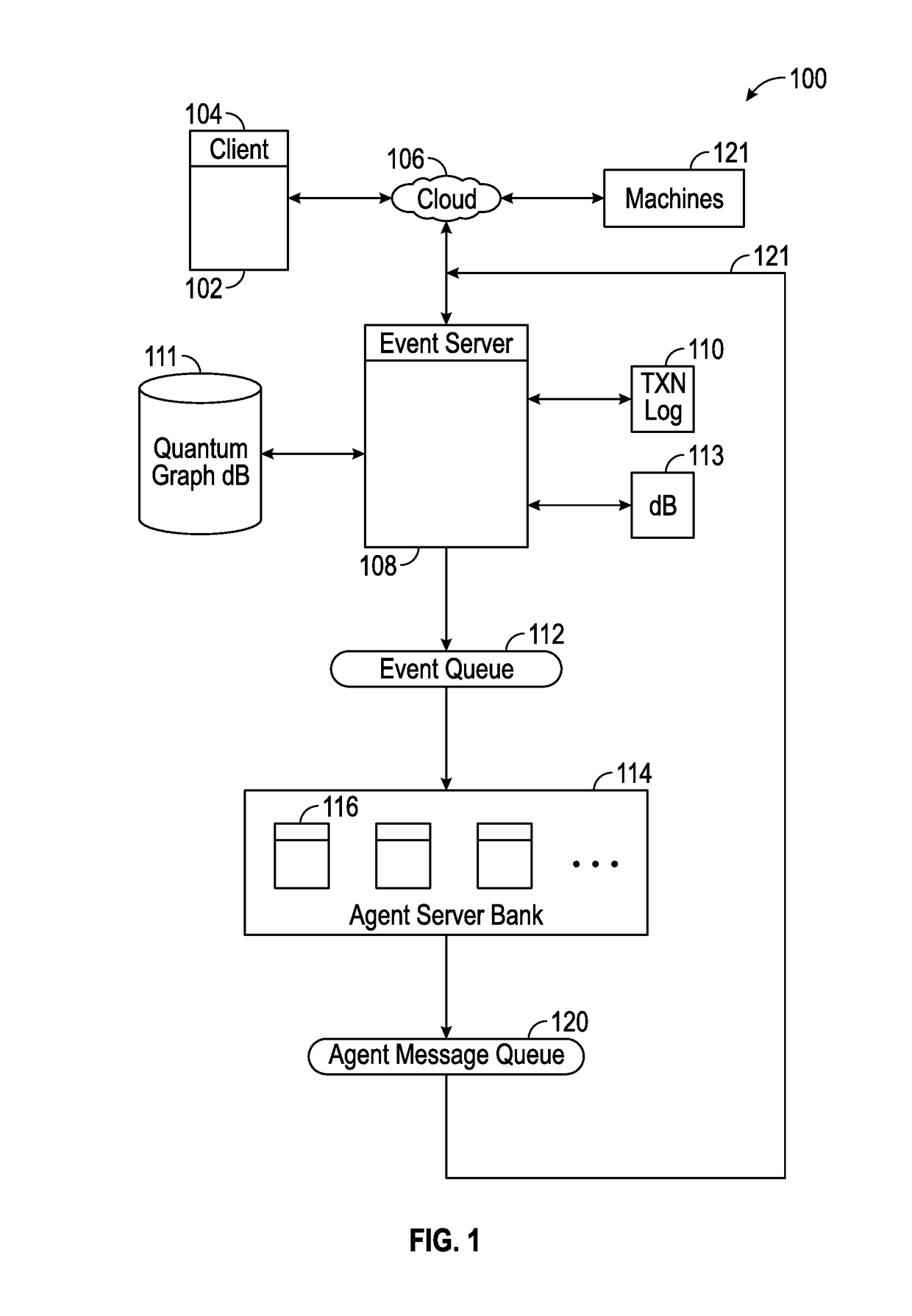
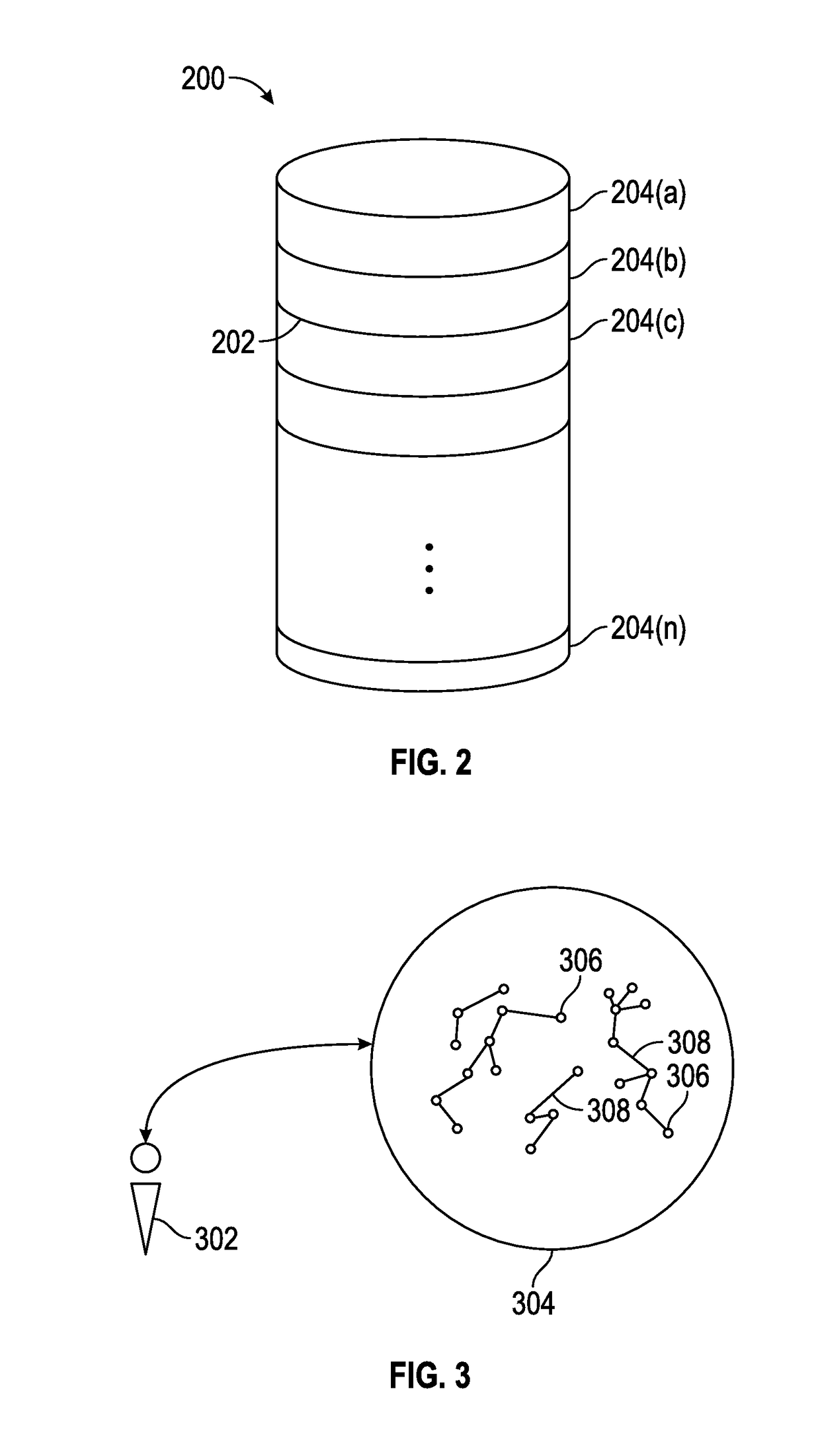
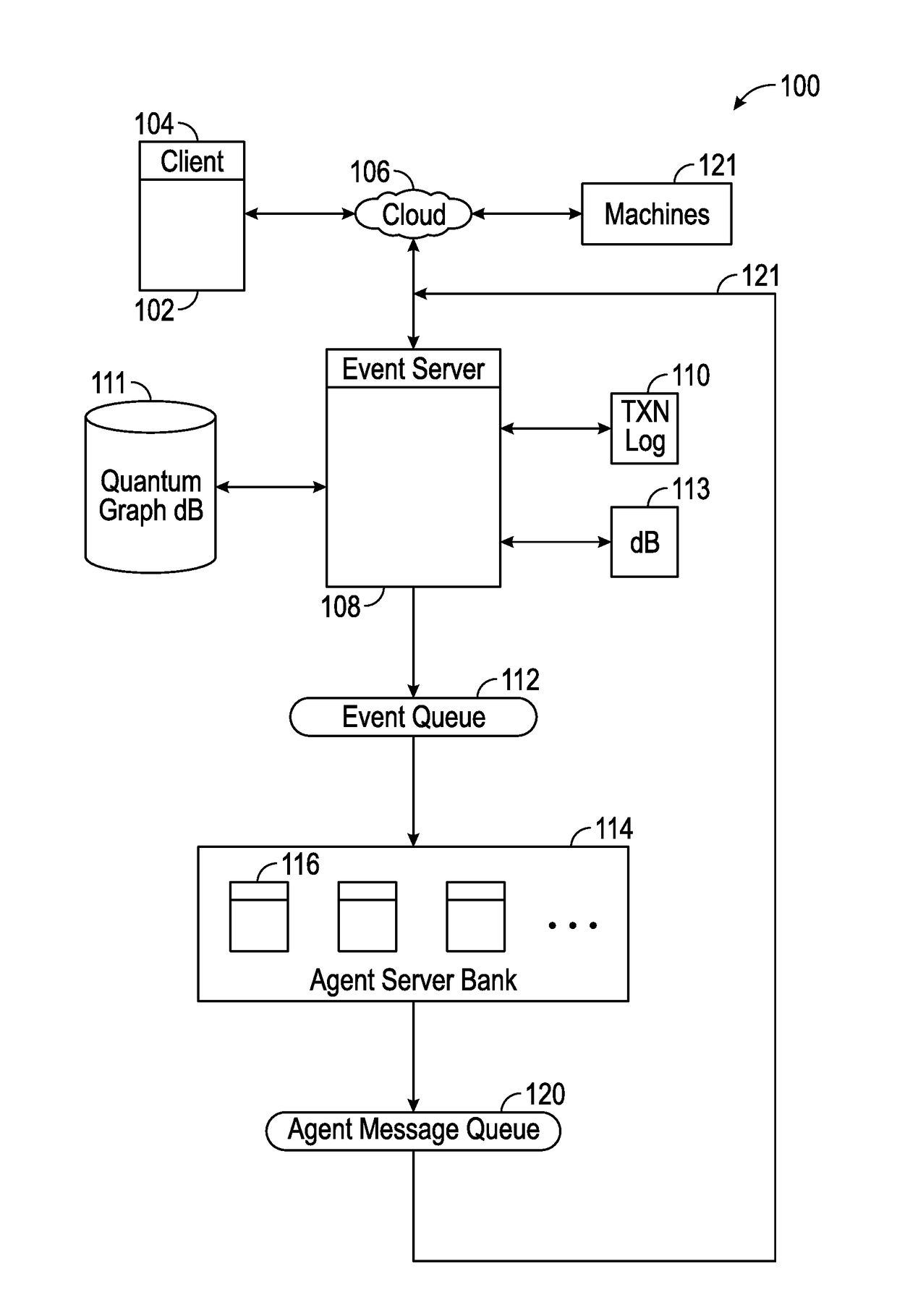
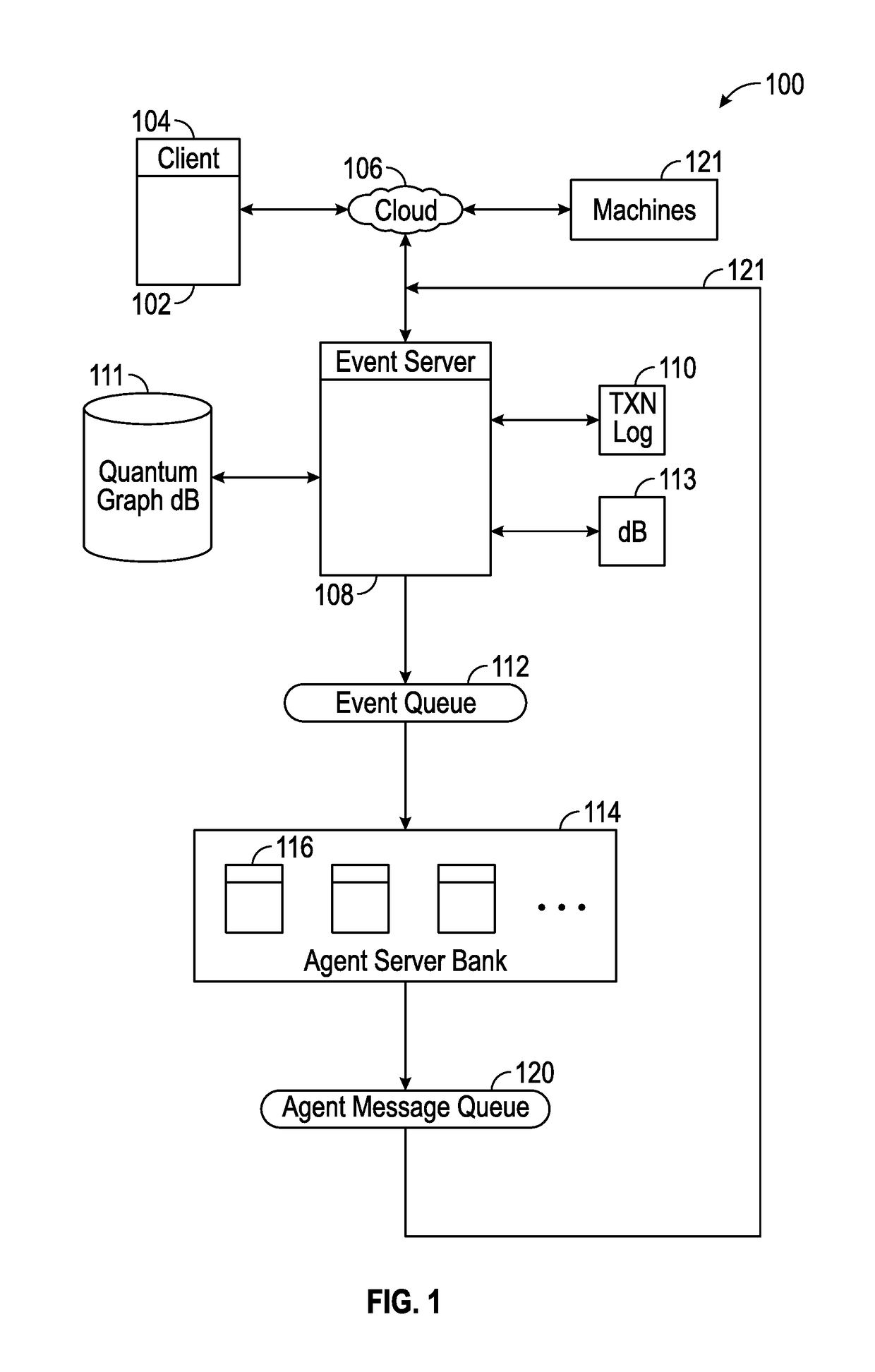
Systems and Methods For Socializing Machines Using Autonomous Software Agents
InactiveUS20170078448A1Build trustData processing applicationsServices signallingMessage queueSocial devices
A platform for socializing devices includes a knowledge database, a rules database, an event processor, an event queue, an advocate message processor, and an advocate message queue. A plurality of software advocates, each corresponding to a respective one of the devices, resides on the advocate message processor. The knowledge database includes a plurality of private social graphs, each corresponding to a respective one of the advocates. A policy database includes rules governing the relationships between and among the advocates and devices. The event processor is configured to process incoming payloads based on the knowledge database and the policy database.
Owner:OVERMAN STEPHEN E +1
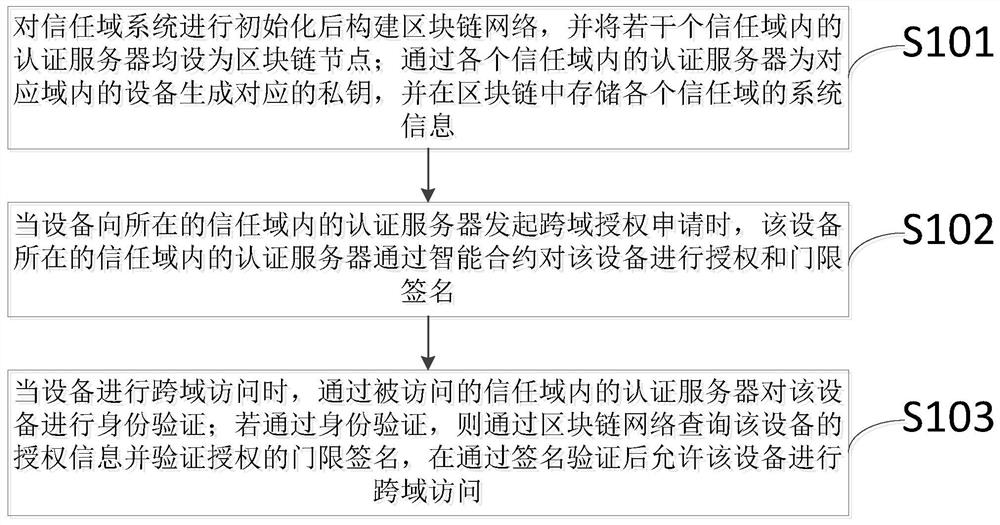
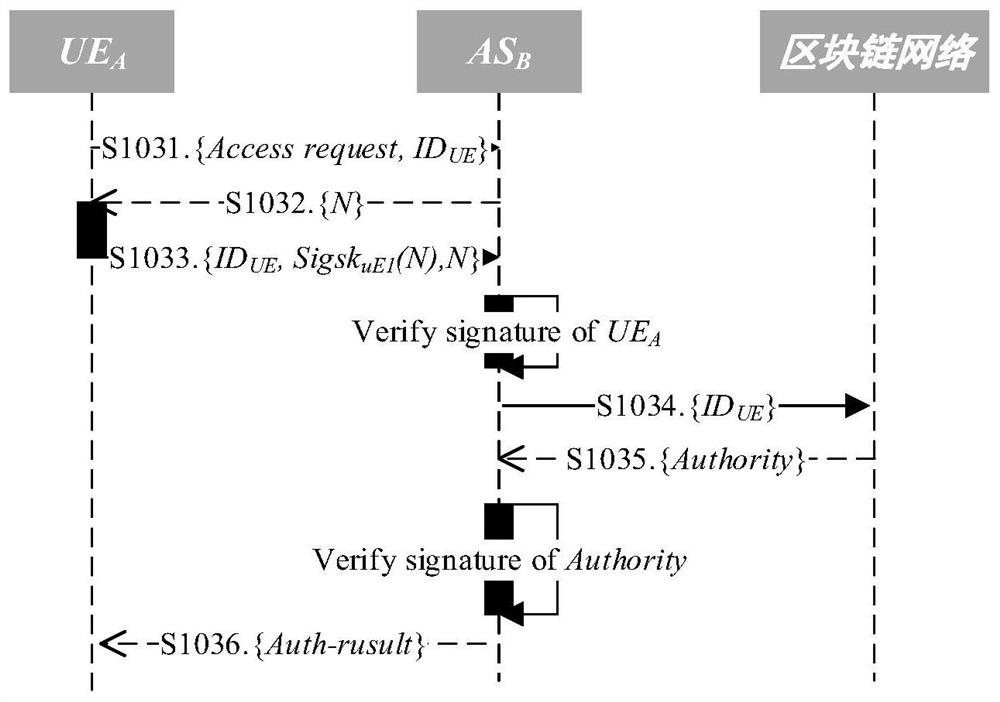
Decentralized Internet-of-Things cross-domain access authorization method and system
PendingCN111835528AEasy to deployEasy maintenanceKey distribution for secure communicationUser identity/authority verificationDomain AuthoritySystem information
The invention discloses a decentralized Internet-of-Things cross-domain access authorization method and system, and the method comprises the steps: building a blockchain network after initializing a trust domain system, and setting authentication servers in a plurality of trust domains as blockchain nodes; generating a private key for the equipment in the corresponding domain through the authentication server in each trust domain, and storing the system information of each trust domain in the blockchain; when the equipment authentication server initiates a cross-domain authorization application, enabling the authentication server to perform authorization and threshold signature on the equipment through the intelligent contract; when the equipment performs cross-domain access, performing identity authentication on the equipment through an authentication server in an accessed trust domain; and if the identity verification is passed, querying authorization information of the equipment through the blockchain network, verifying an authorized threshold signature, and allowing the equipment to perform cross-domain access after the signature verification is passed. According to the invention, decentralized cross-domain access authorization of the Internet-of-Things equipment can be realized, and the autonomy and initiative of the trust domain are ensured.
Owner:GUANGZHOU UNIVERSITY
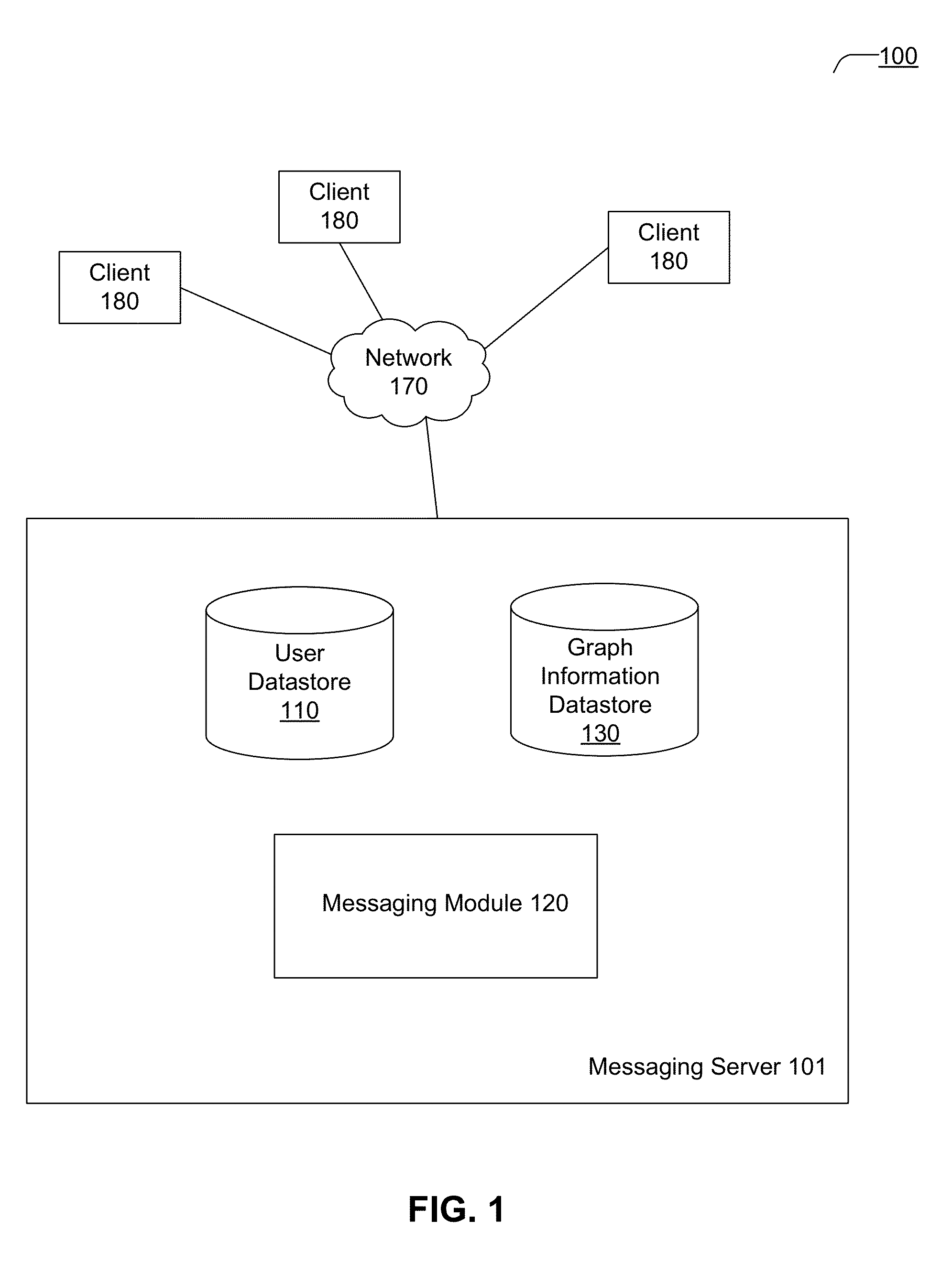
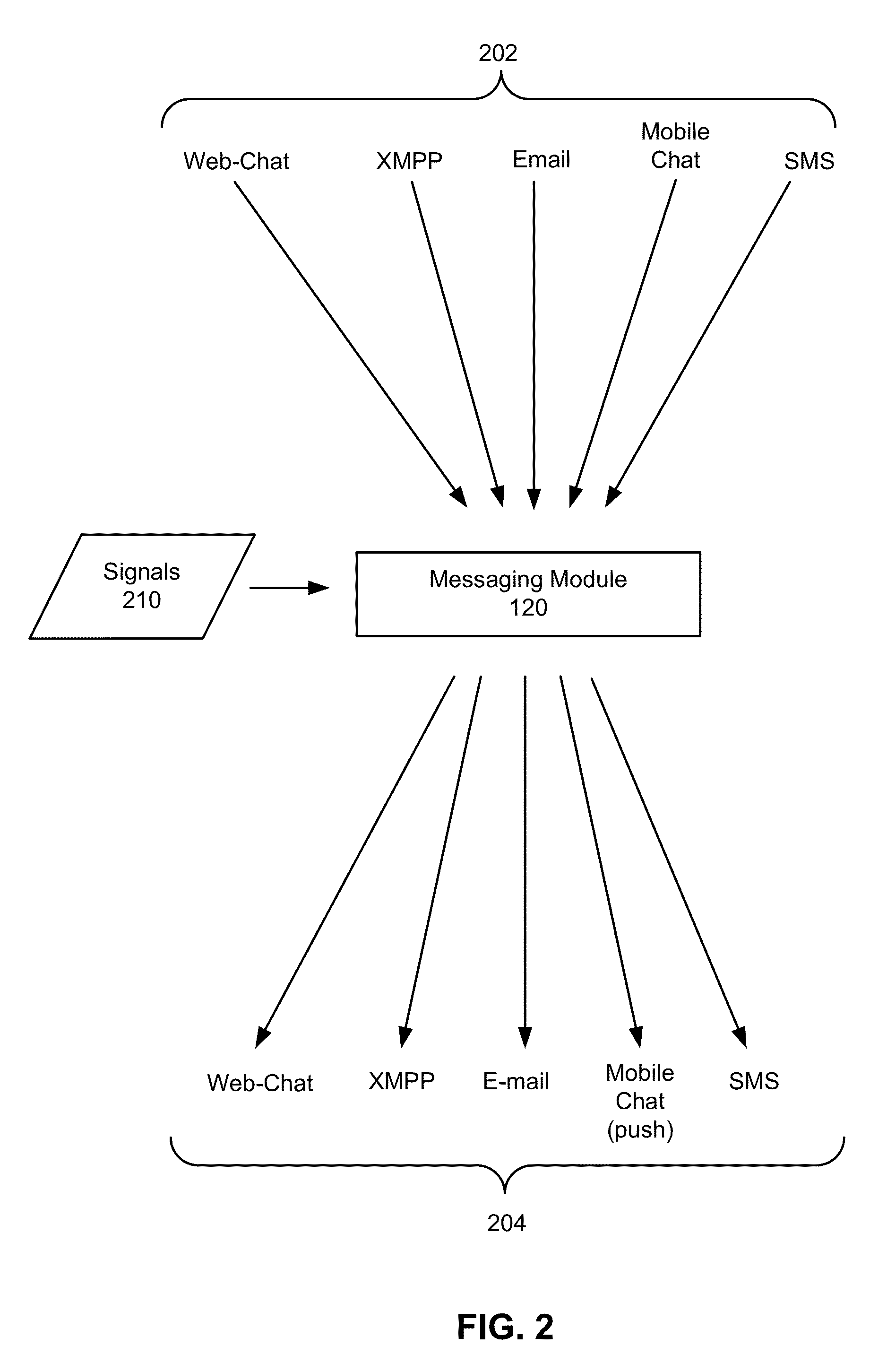
Rescinding messages in a messaging system with multiple messaging channels
ActiveUS8706824B2Build trustAvoids overwhelming the recipient with duplicate messagesMultiple digital computer combinationsTransmissionUser interfaceFacilitated communication
A messaging system facilitates communication between users through various messaging channels. The messaging system supports multiple communication channels and includes a messaging module that automatically selects one or more of the messaging channels for delivering a message to a recipient of the message using, for example, a set of policy rules or a trained model. The messaging module may also provide, in a user interface for sending and receiving messages, a visual indication of the selected messaging channel to the sender of the message to provide the user with transparency about how the message will be delivered. Additionally, the message may be delivered via multiple messaging channels, where the messaging module may rescind messages from some of the messaging channels upon receiving a reply from the recipient of the message or other confirmation that the recipient has seen the message via one of the communication channels.
Owner:META PLATFORMS INC
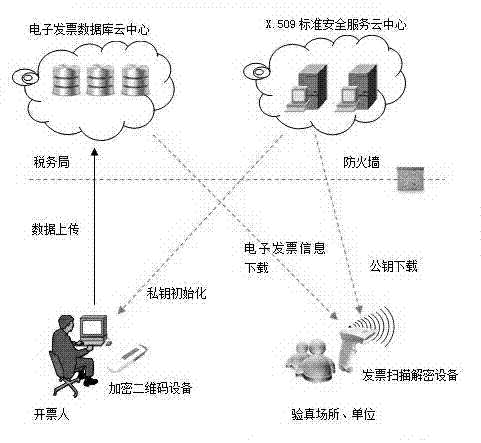
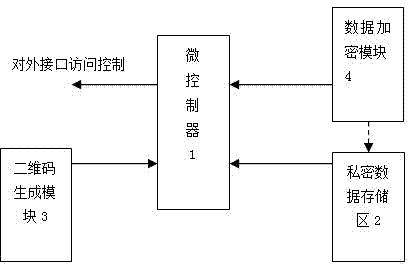
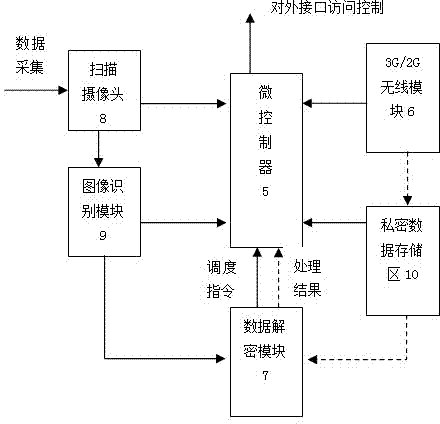
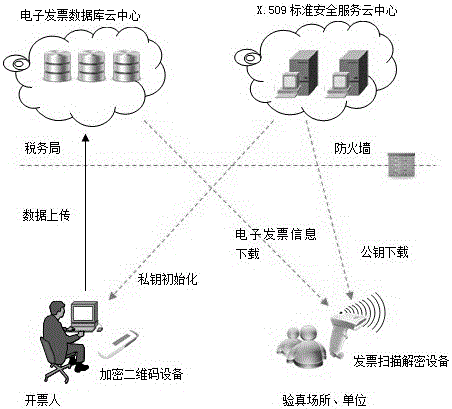
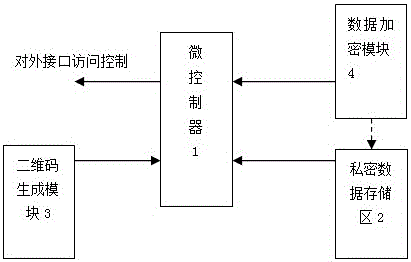
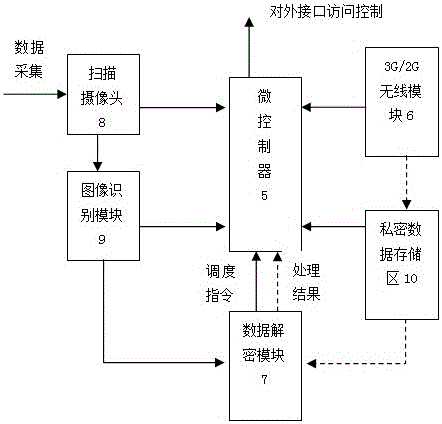
Invoice true check system based on cloud computing and encrypted two-dimensional codes
ActiveCN102930634AMeet the needs of invoice verificationEnsure information securityPaper-money testing devicesCharacter and pattern recognitionComputer hardwareInvoice
The invention discloses an invoice true check system based on cloud computing and encrypted two-dimensional codes and belongs to a tax invoice true check system. The invoice true check system comprises a tax office cloud computing platform, an encrypted two-dimensional code device and an invoice scanning decrypting device. The tax office cloud computing platform is used for managing the encrypted two-dimensional code device and the invoice scanning decrypting device. The encrypted two-dimensional code device is used for printing the encrypted two-dimensional codes on physical invoices when invoicing invoices for drawers. The invoice scanning decrypting device is used for scanning, decrypting and comparing the invoices needing true check and outputting processing results according to grades to serve as true check basis. Compared with the prior art, the invoice true check system based on cloud computing and the encrypted two-dimensional codes can solve the problems of trust issue and data safety of the existing invoice true check results, and restrains invoice counterfeiting and false invoice using to a certain extent.
Owner:INSPUR SOFTWARE TECH CO LTD
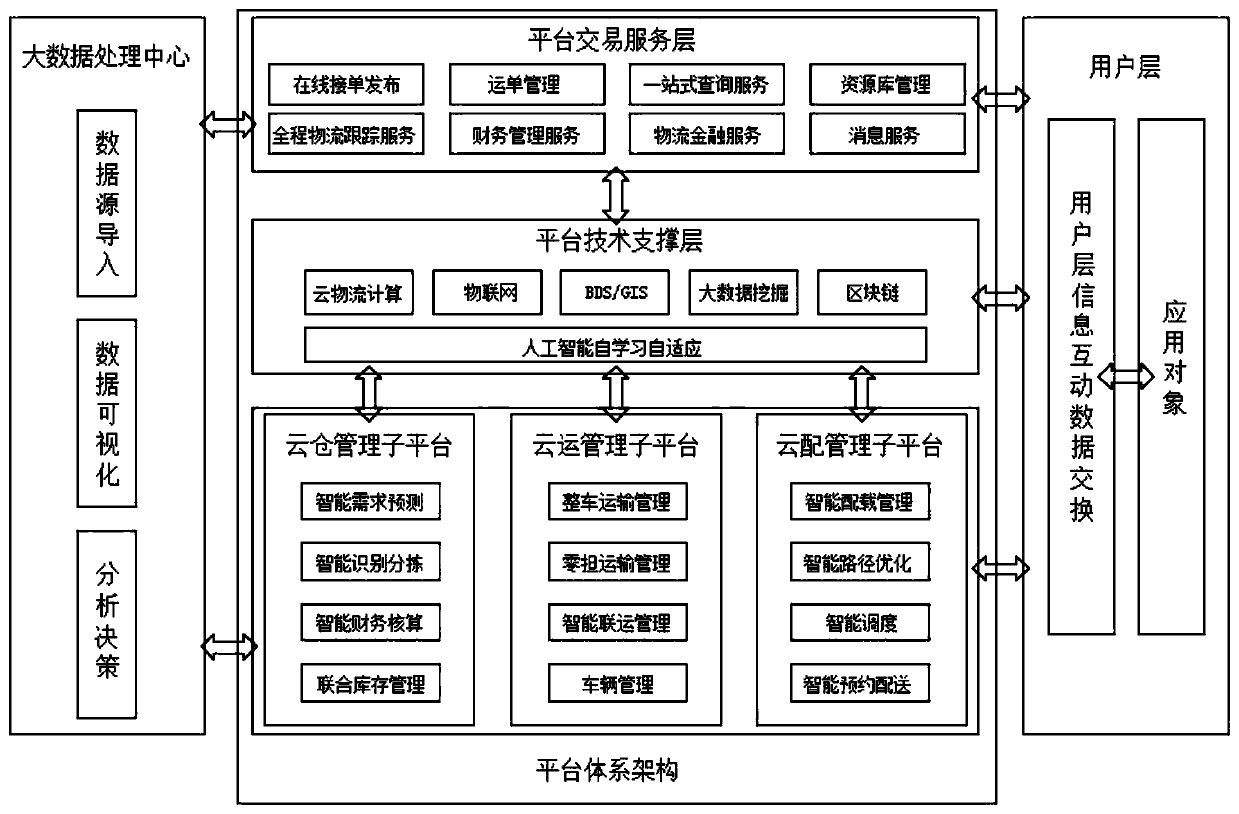
Cloud logistics platform and construction method
PendingCN110717716ARealize reasonable storageIncrease stickinessLogisticsLogistics managementBusiness enterprise
The invention discloses a cloud logistics platform and a construction method, and belongs to the technical field of cloud logistics. The invention provides the cloud logistics platform and the construction method of the logistics platform, and the logistics platform comprises a platform system architecture, a big data processing center and a user layer. The construction method of the logistics platform comprises the following steps: S1, constructing a logistics task; S2, establishing a service resource library; S3, constructing a logistics task and cloud logistics service resource combinationmodel; S4, performing big data mining and logistics demand prediction; S5, performing logistics storage planning and joint inventory optimization; and S6, performing logistics transportation and terminal distribution optimization. Through the cloud logistics platform, the relationship between the logistics resource provider and the logistics demand can be well communicated. Sharing and on-demand using of logistics resources, logistics capacity and logistics knowledge are achieved, selection, communication and service matching are provided for enterprises and individuals with logistics demandsthrough a public cloud logistics service platform, and logistics services which are obtained by users at any time, serve on demand, safe, reliable, high in quality and low in price are achieved.
Owner:安徽九州通智能科技有限公司
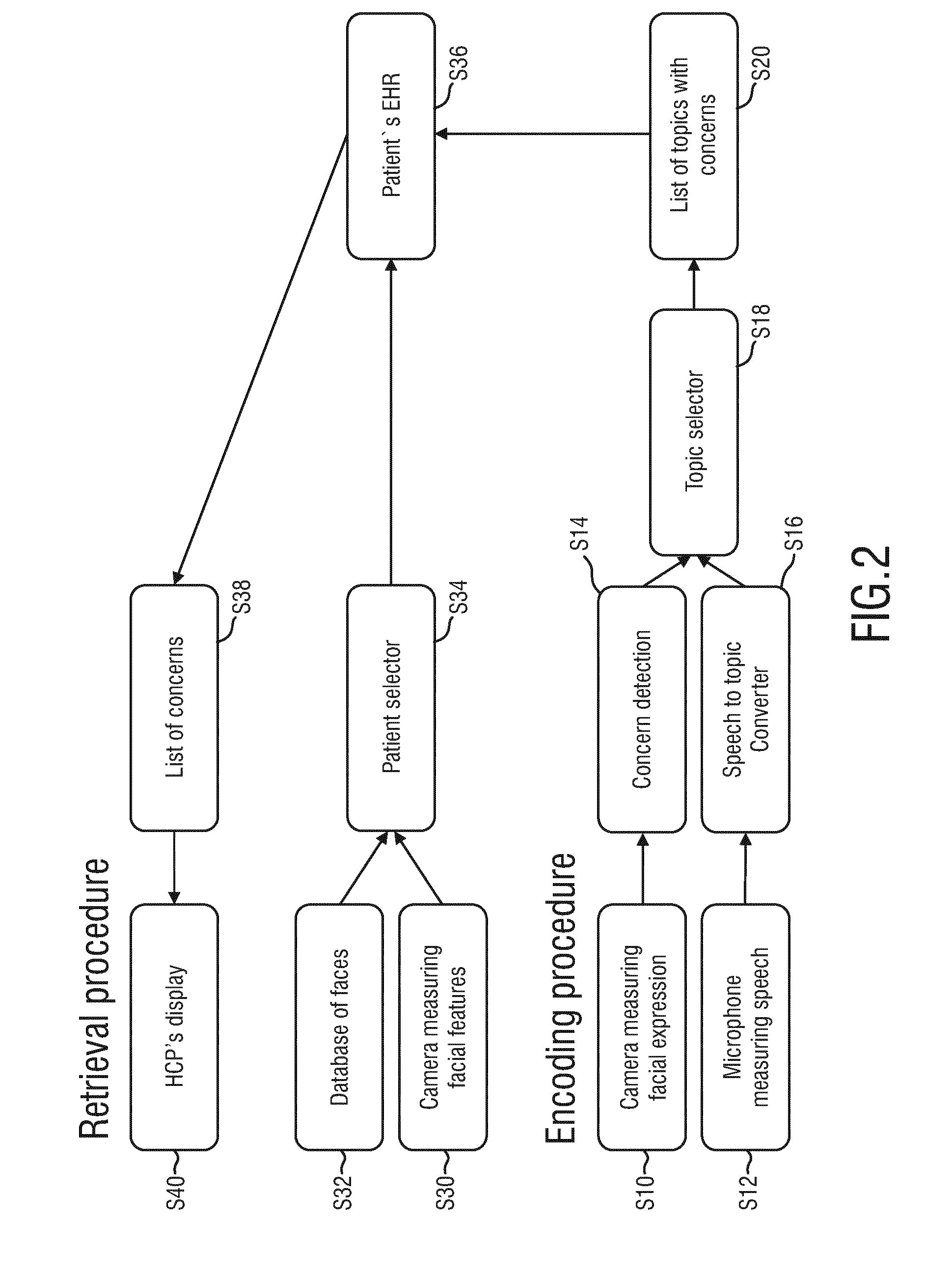
System and method for topic-related detection of the emotional state of a person
InactiveUS20160321401A1Impaired relationshipImprove relationshipLocal control/monitoringTelemedicineMood stateComputer science
The present invention relates to a system and method for unobtrusive topic-related detection of the emotional state of a person, in particular of a patient's concerns. In order to provide a user with information about the persons emotional state of a current topic in an unobtrusive way at the right time the system comprises a data recorder (10) for recording person-related data, a data analyzer (20) for analyzing said person-related data to detect, at a given moment, the emotional state of the person and a topic dealt with by the person at the given moment, a topic representing a subject of conversation, a storage unit (30), a retrieval unit (40) for accessing said storage unit i) to check if it comprises an entry for a current topic that the person currently deals with and retrieve a stored emotional state of the person for the current topic and / or ii) to retrieve one or more topics, for which the storage unit comprises entries for the person with respect to one or more predetermined emotional states, and a user interface (50) for outputting the result.
Owner:KONINKLJIJKE PHILIPS NV
Systems and Methods For Socializing Machines Using Autonomous Software Agents
InactiveUS20170075944A1Build trustPrivacy protectionData processing applicationsServices signallingMessage queueSocial devices
A platform for socializing devices includes a knowledge database, a rules database, an event processor, an event queue, an advocate message processor, and an advocate message queue. A plurality of software advocates, each corresponding to a respective one of the devices, resides on the advocate message processor. The knowledge database includes a plurality of private social graphs, each corresponding to a respective one of the advocates. A policy database includes rules governing the relationships between and among the advocates and devices. The event processor is configured to process incoming payloads based on the knowledge database and the policy database.
Owner:OVERMAN STEPHEN E +1
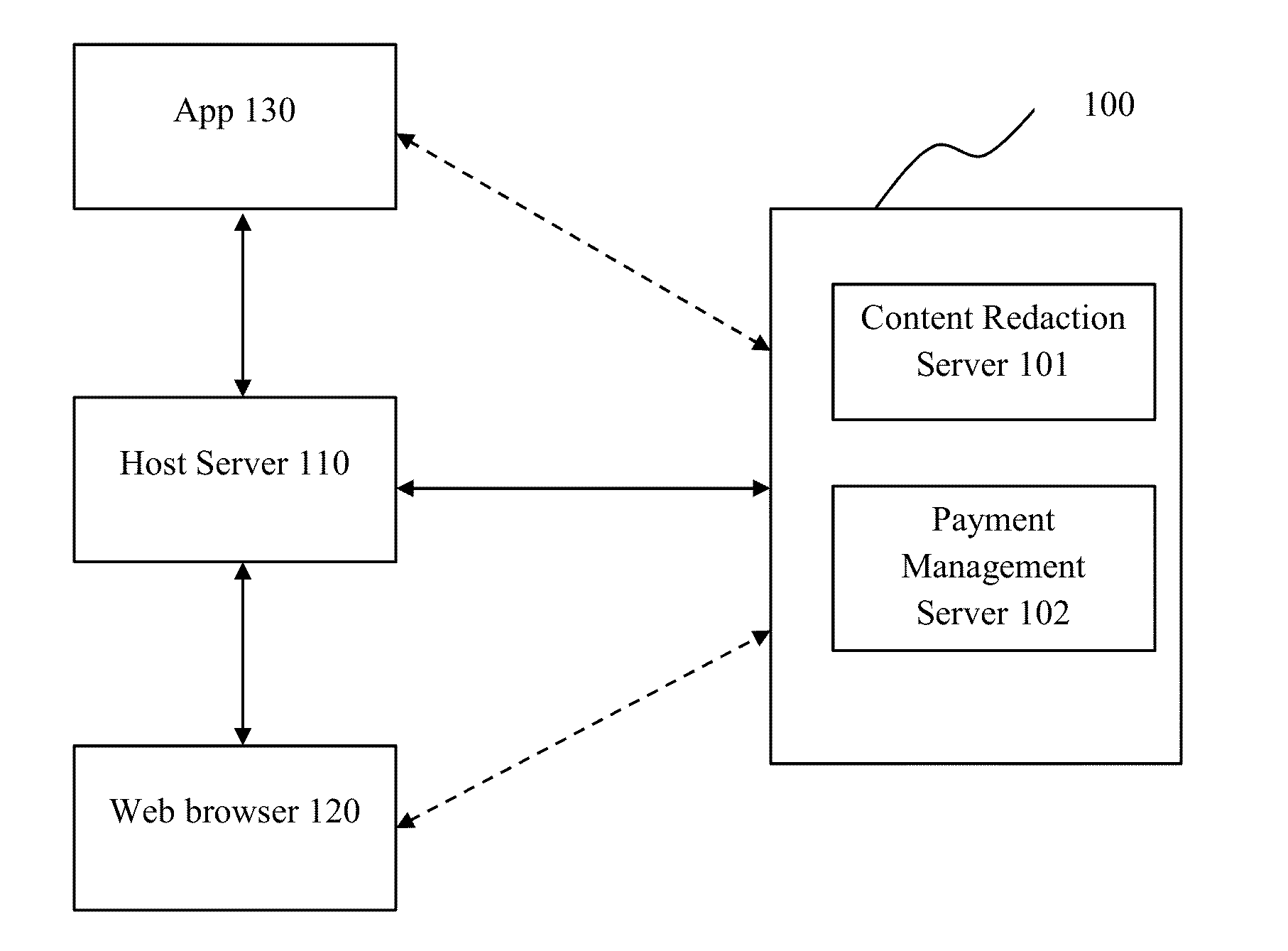
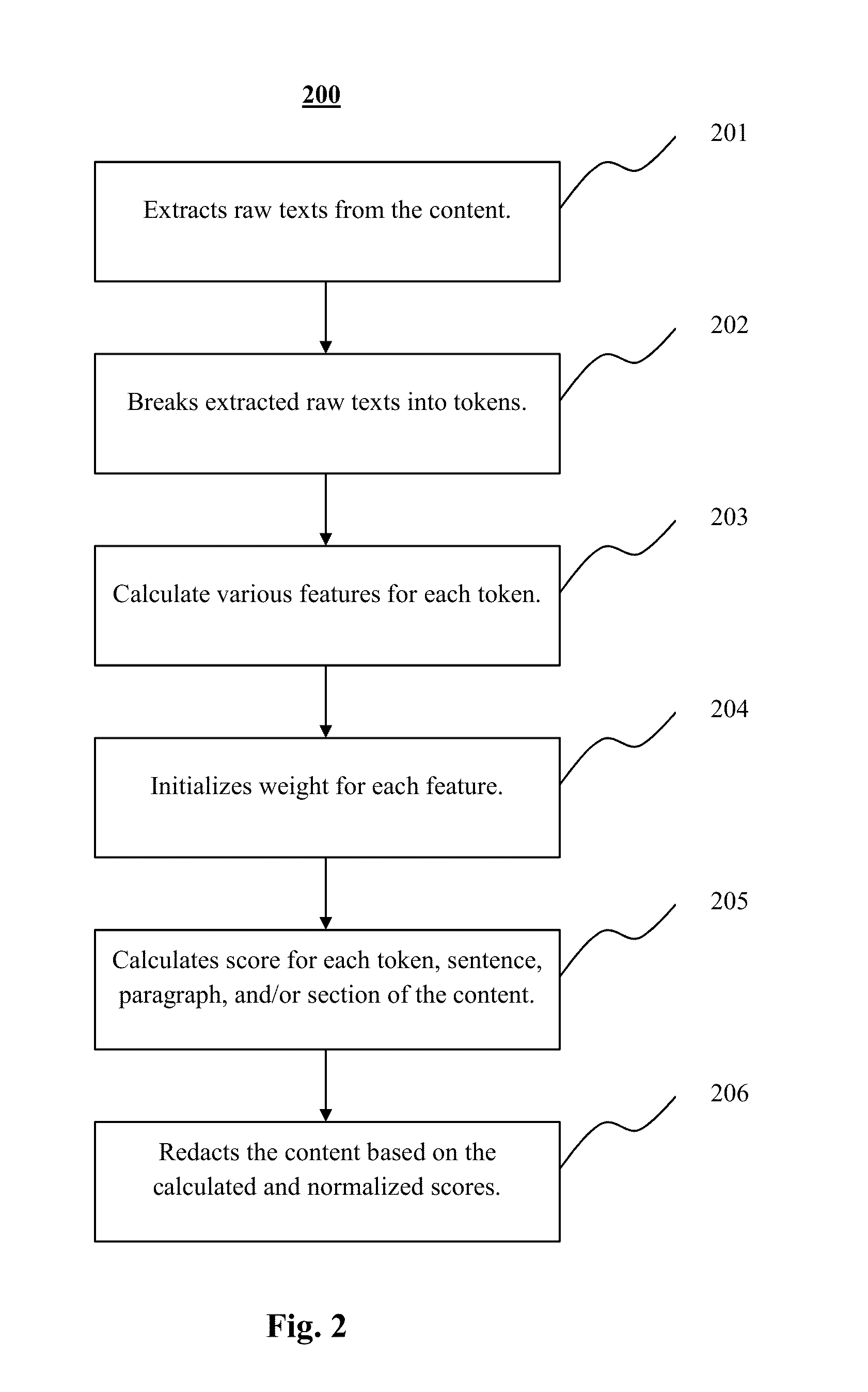
Content Monetization System
InactiveUS20160004977A1Build trustReduce fraudComputing modelsDigital computer detailsDigital contentParagraph
A system and method are provided to monetize content by redacting the content with machine learning algorithms. This invention increases the conversion rate of website surfers to paid customers. Extracted texts of the content are tokenized and then scored with normalized value [0, 1] to measure their significance. Intra-token, inter-token, extra-token, and tagged token features are used to characterize each individual token. Scores of sentences, paragraphs, sections, and even chapters can be calculated with various methods based on the scores of tokens. Then, the content is redacted according to the calculated scores. Customers can view the redacted content for free. If interested, they can purchase the content and view the full, non-redacted version of the content. The present invention is useful in publication and monetization of digital contents such as e-books.
Owner:BOOGOO INTPROP +2
Systems and Methods For Socializing Machines Using Autonomous Software Agents
InactiveUS20170076111A1Build trustPrivacy protectionData processing applicationsServices signallingMessage queueSocial devices
A platform for socializing devices includes a knowledge database, a rules database, an event processor, an event queue, an advocate message processor, and an advocate message queue. A plurality of software advocates, each corresponding to a respective one of the devices, resides on the advocate message processor. The knowledge database includes a plurality of private social graphs, each corresponding to a respective one of the advocates. A policy database includes rules governing the relationships between and among the advocates and devices. The event processor is configured to process incoming payloads based on the knowledge database and the policy database.
Owner:OVERMAN STEPHEN E +1
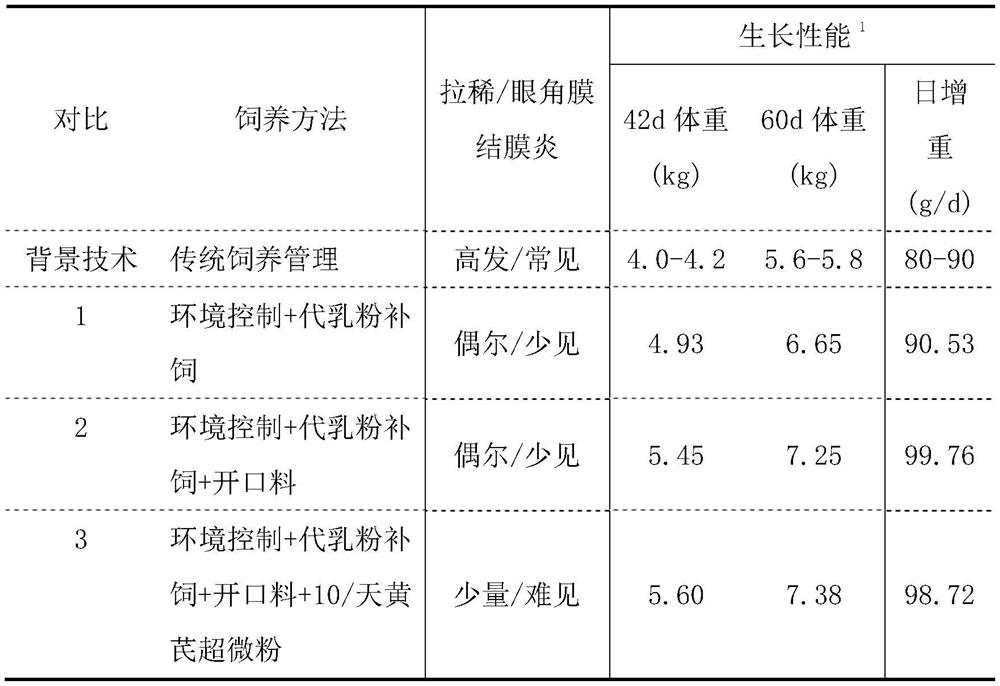
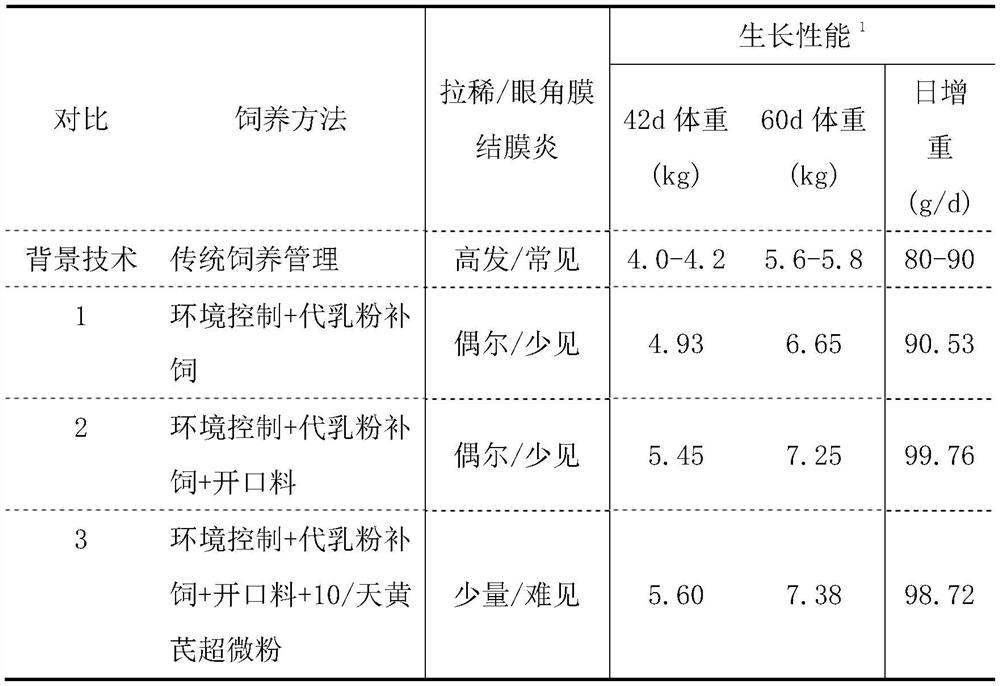
Feeding method for increasing survival rate of Southern lambs
ActiveCN111631189AImprove survival rateFeed management is highly operableAnimal feeding stuffWeaningMedicine
The invention relates to a feeding method for increasing the survival rate of Southern lambs. The method comprises the steps of nursing new-born lambs, performing artificial supplementary feeding withpowdered milk substitute, performing early induction for feeding, adopting a raising management scheme, controlling breeding environment, performing regular disinfection, performing mother and son transitional isolation, performing mild weaning, improving immunity with Chinese herbal medicines, preventing diseases and the like. Six measures are taken, i.e. borne lambs are nursed, the powdered milk substitute is subjected to supplementary feeding, early starting is induced, environment is controlled, favorable weaning is performed, and supplementary feeding is performed with Chinese medicinalherbs, so that the survival rate of the Southern lambs can achieve 95% or above, the immunity and the productive potential of the lambs are improved, and the economic benefits for breeding Southern goats are increased.
Owner:INST OF SUBTROPICAL AGRI CHINESE ACAD OF SCI
Systems and Methods For Socializing Machines Using Autonomous Software Agents
InactiveUS20170075979A1Build trustPrivacy protectionData processing applicationsRelational databasesMessage queueSocial devices
A platform for socializing devices includes a knowledge database, a rules database, an event processor, an event queue, an advocate message processor, and an advocate message queue. A plurality of software advocates, each corresponding to a respective one of the devices, resides on the advocate message processor. The knowledge database includes a plurality of private social graphs, each corresponding to a respective one of the advocates. A policy database includes rules governing the relationships between and among the advocates and devices. The event processor is configured to process incoming payloads based on the knowledge database and the policy database.
Owner:OVERMAN STEPHEN E +1
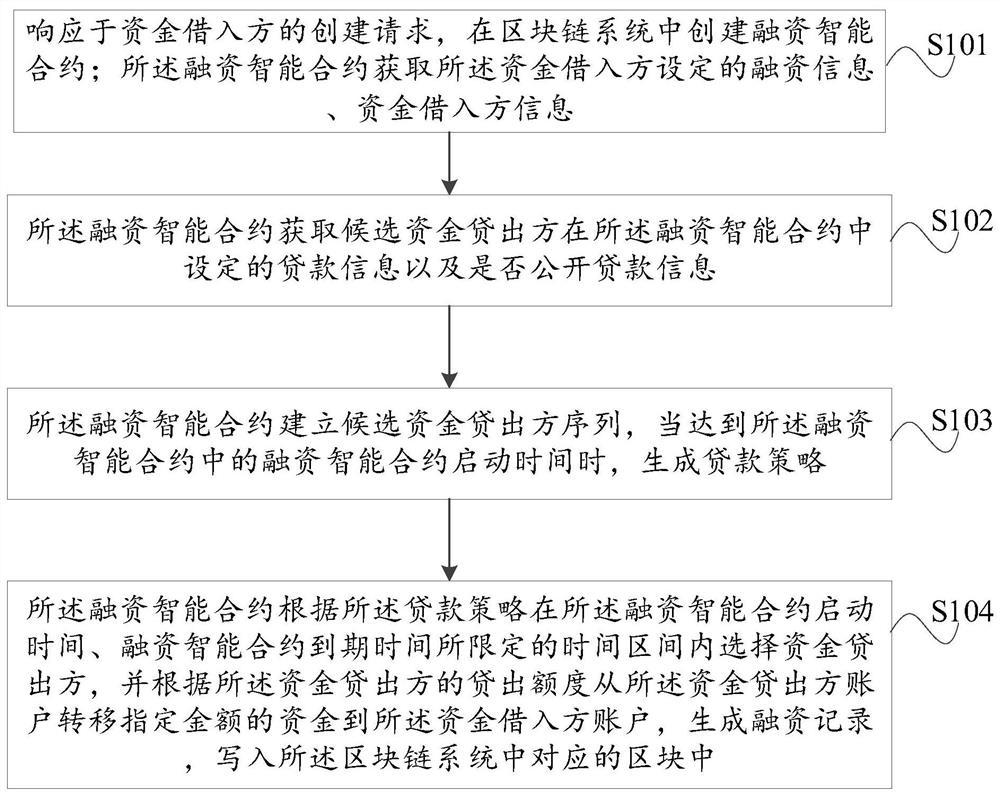
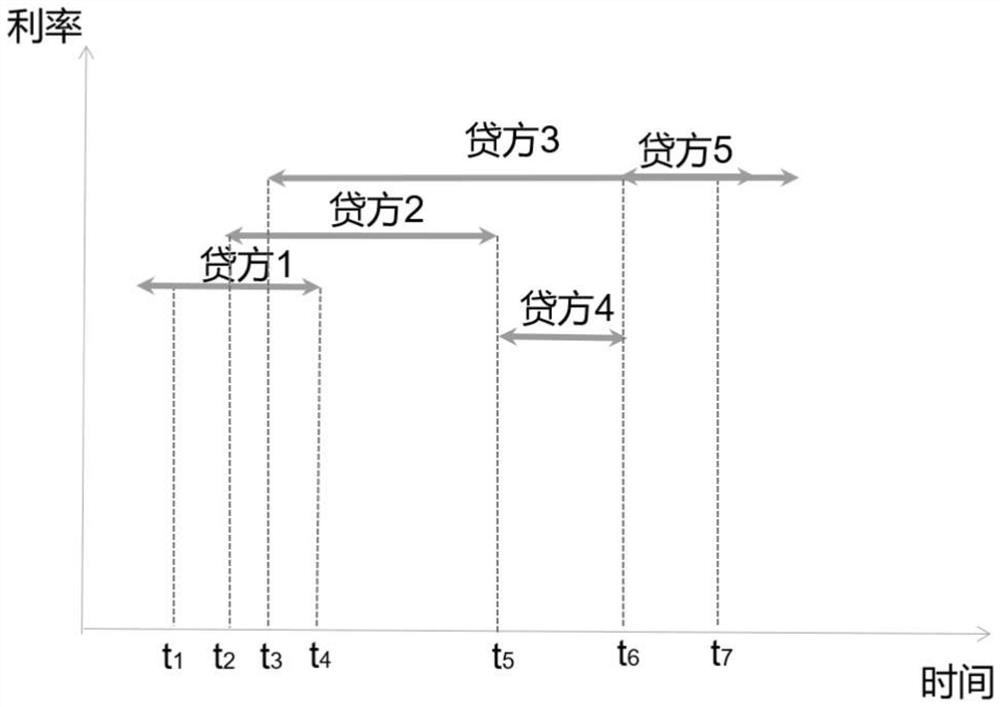
Financing method and equipment based on block chain intelligent contract technology
ActiveCN113240530AImprove turnover rateReduce malicious disruption of the financing marketDatabase updatingFinanceSmart contractOperations research
The invention provides a financing method and device based on a block chain intelligent contract technology. The method comprises the following steps: in response to a creation request of a fund borrower, creating a financing smart contract in a block chain system; enabling the financing intelligent contract to obtain financing information set by the fund borrowing party, fund borrowing party information and loan information set by the candidate fund loaning party; establishing a candidate fund loan party sequence, and when the financing smart contract starting time in the financing smart contract is reached, generating a loan strategy; and enabling the financing intelligent contract to select a fund loaning party according to the loan strategy, transfer a specified amount of fund from the account of the fund loaning party to the account of the fund borrowing party, generate a financing record, and write the financing record into the block chain system. In this way, more investors are promoted to participate in the financing plan, and financing activities are transparent and open, cannot be tampered and are more flexible; and a trust mechanism is established, so that the default rate, the investment threshold and the investment difficulty are reduced, and the fund flow rate, the financing efficiency and the social resource utilization rate are improved.
Owner:中通服创发科技有限责任公司
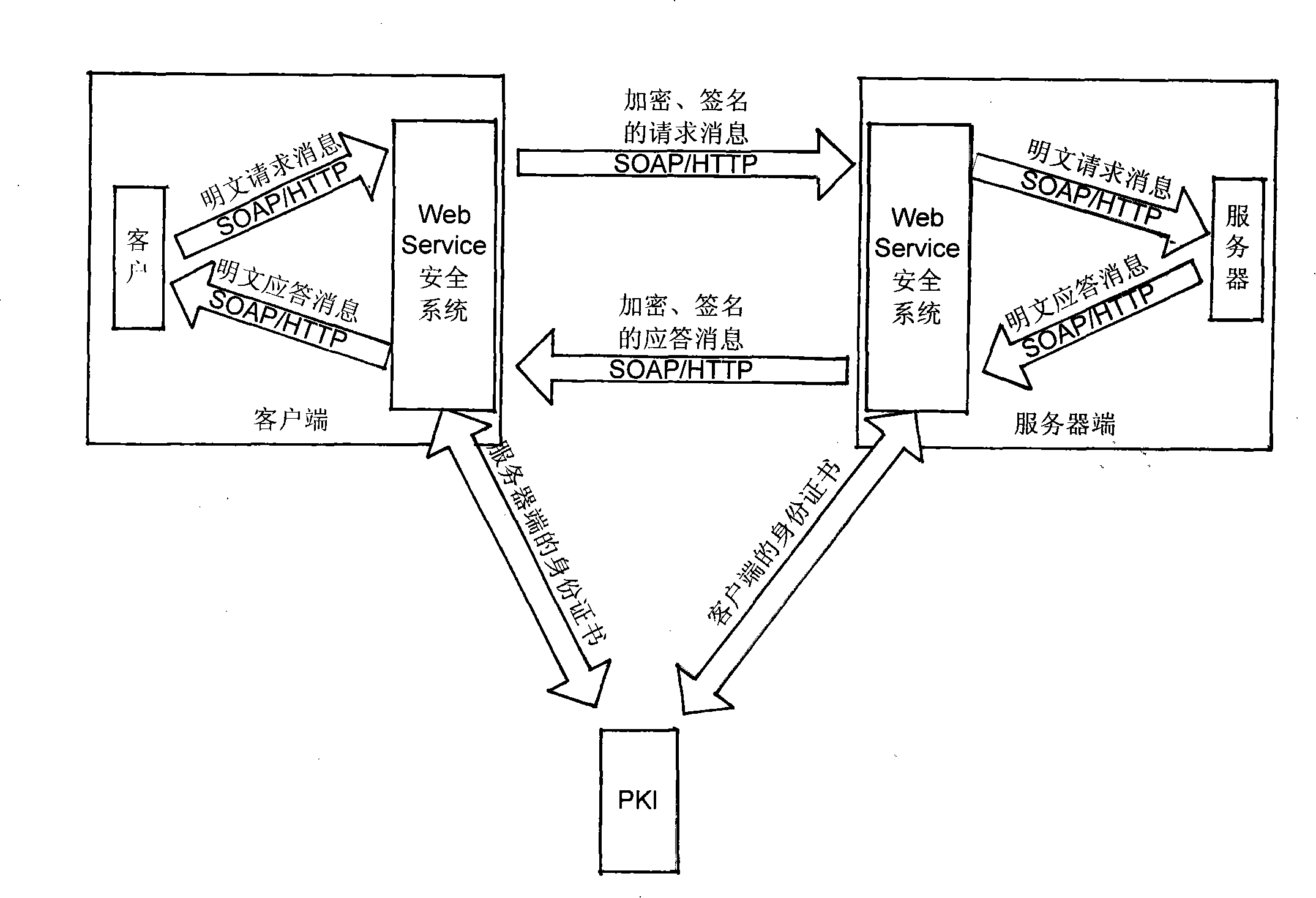
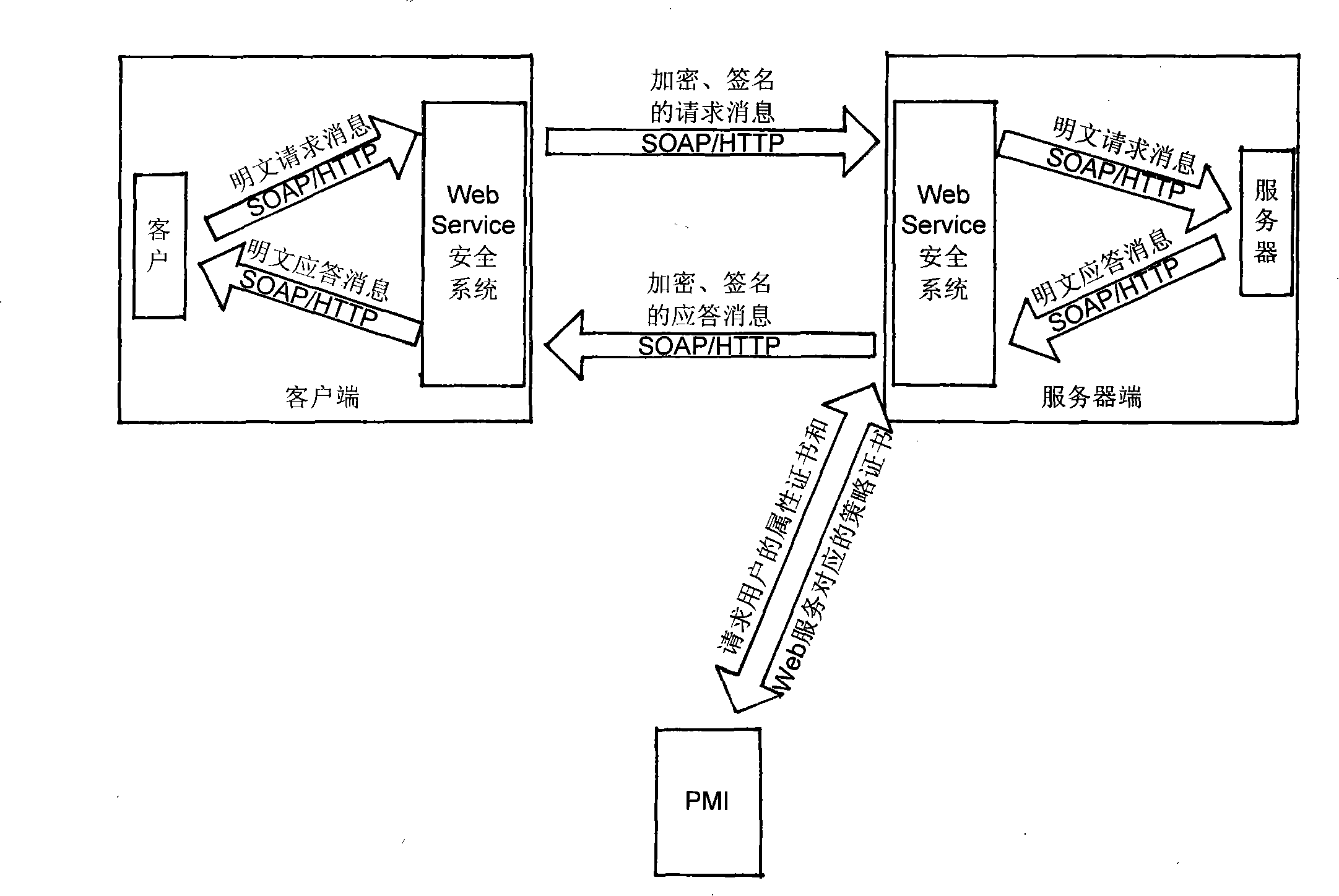
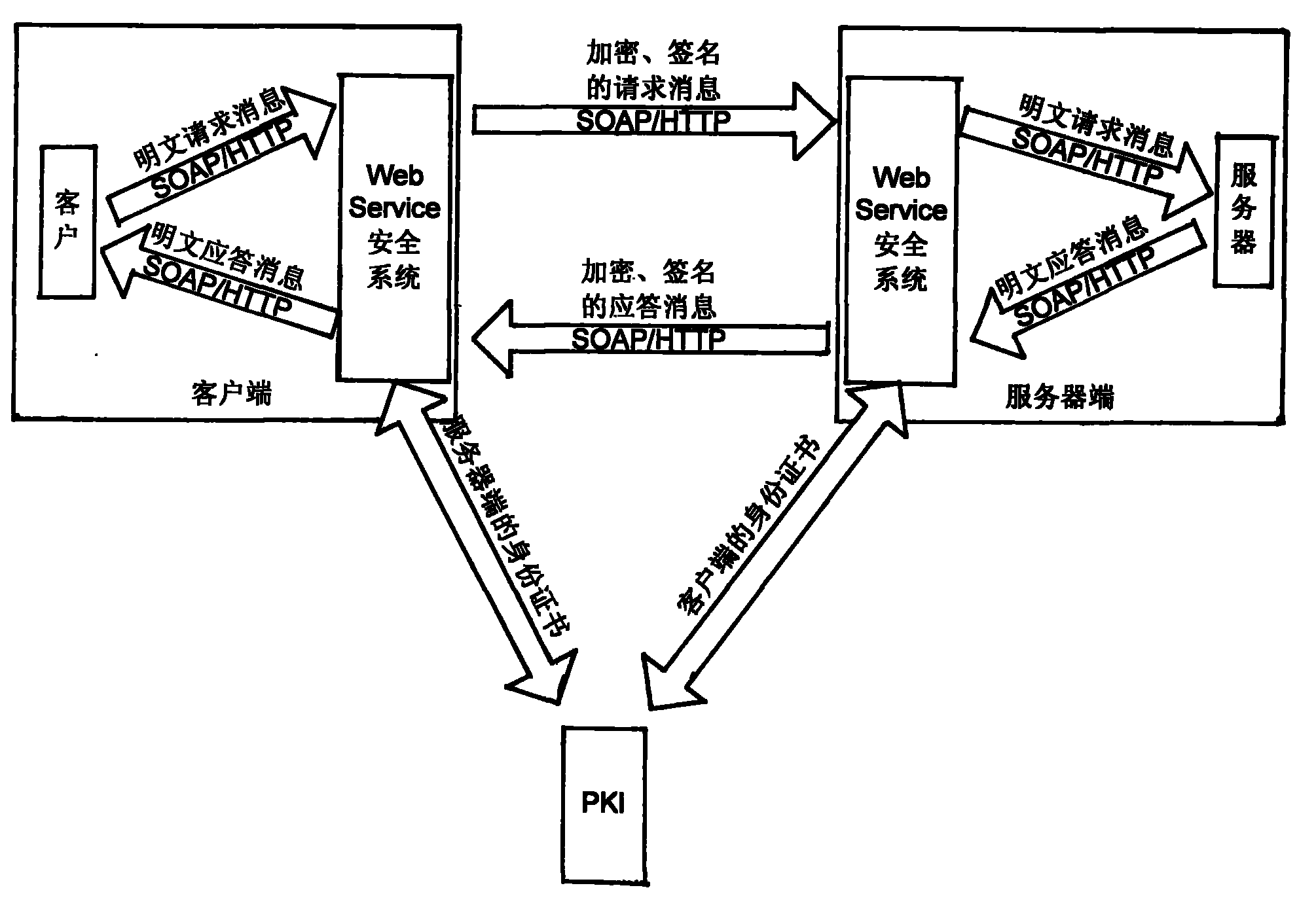
Web service security control mechanism based on PKI and PMI
InactiveCN101296230BQuick responseHigh precisionKey distribution for secure communicationUser identity/authority verificationControl systemWeb service
The invention discloses a safety control method based on the Web service of PKI and PMI, which comprises a PKI system, a PMI system and a safety system of the Web service. Users apply for a letter of identification by the PKI system, and then apply for an attribute certificate in the PMI system according to the letter of identification. The attribute certificate relates to the user identification with one or more roles. The roles are then bond to one or more Web services by a strategy certificate pre-defined by the PMI system. When the users use the Web service, the safety system of Web helps the PKI system to check the legality of the letter of identification and helps the PMI system to check whether the user has the right to call the Web service or not. When all checks pass through successfully, the user can access the Web service so as to realize the safety calling of the Web service. The mechanism of the invention provides a set of identification authentication and access control system with strong integrity, thereby ensuring the confidentiality, the integrity and the non-repudiation of the calling information of the Web service.
Owner:ZHEJIANG UNIV
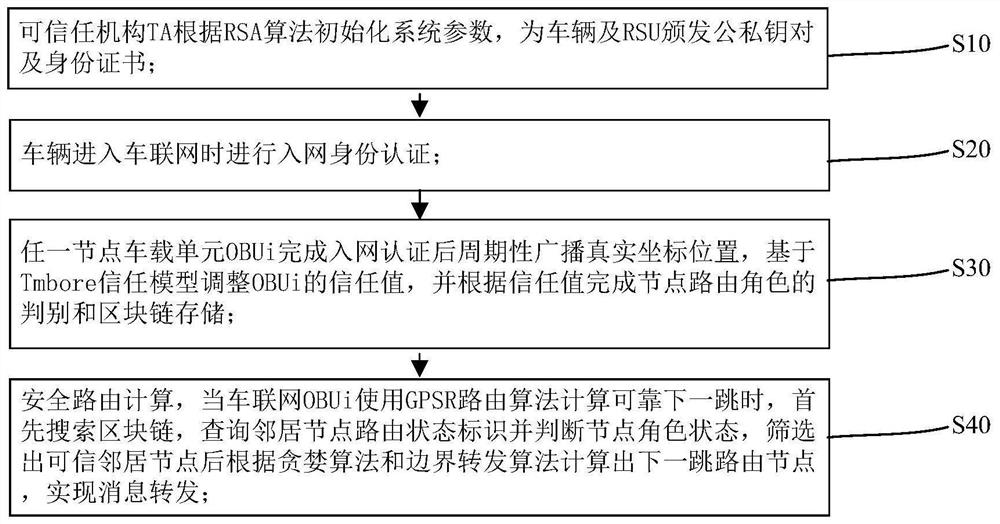
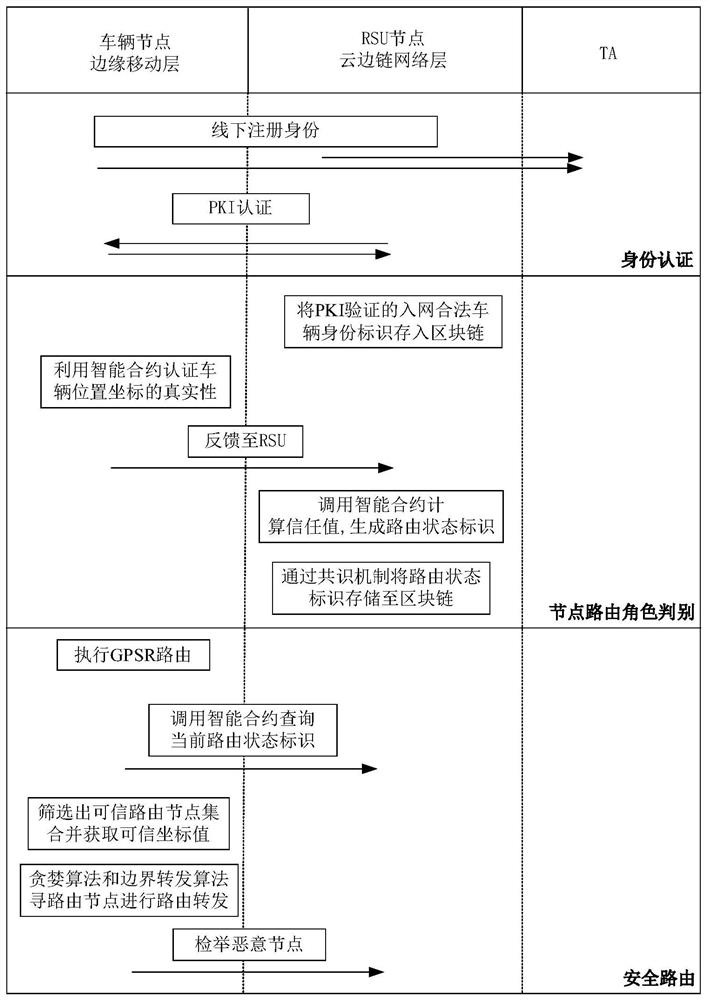
GPSR secure routing protocol implementation method based on block chain trust model
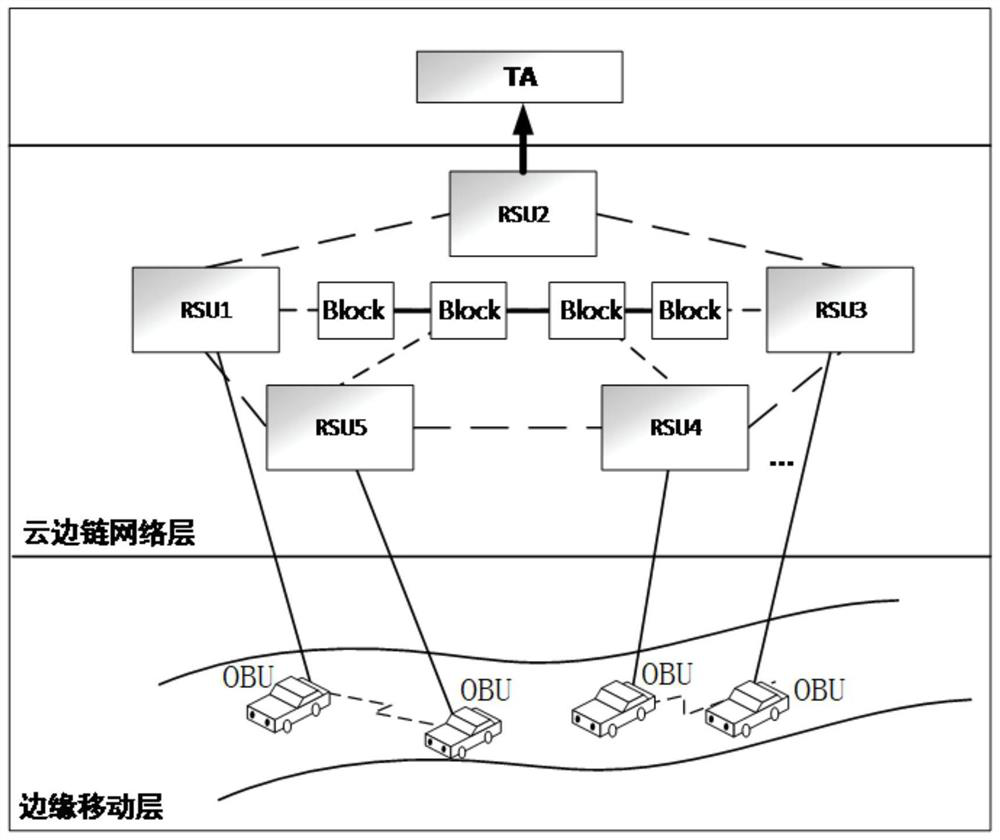
PendingCN112911549AImprove securityReliable storageParticular environment based servicesVehicle wireless communication serviceIn vehicleBlockchain
The invention provides a GPSR security routing protocol implementation method based on a block chain trust model. The method comprises the following steps of: S10, enabling a trusted authority (TA) to initialize vehicle network system parameters according to an RSA algorithm; S20, when the vehicle enters the Internet of Vehicles, performing network access identity authentication; S30, periodically broadcasting a real coordinate position after any node vehicle-mounted unit OBUi completes network access authentication, adjusting a trust value of the OBUi based on a Tmbore trust model, and completing node routing role judgment and block chain storage according to the trust value; and S40, performing secure routing calculation. According to the GPSR secure routing protocol implementation method based on the block chain trust model, the mobile edge computing technology and the block chain technology are combined, and the Tmbore trust model is designed and used for improving the security of a GPSR routing protocol, realizing secure and reliable storage of trust values and lightweight discrimination of authenticity and reliability of routing nodes, and improving the security of the GPSR routing protocol, and improving the security of the GPSR routing protocol is improved.
Owner:NANTONG UNIVERSITY +1
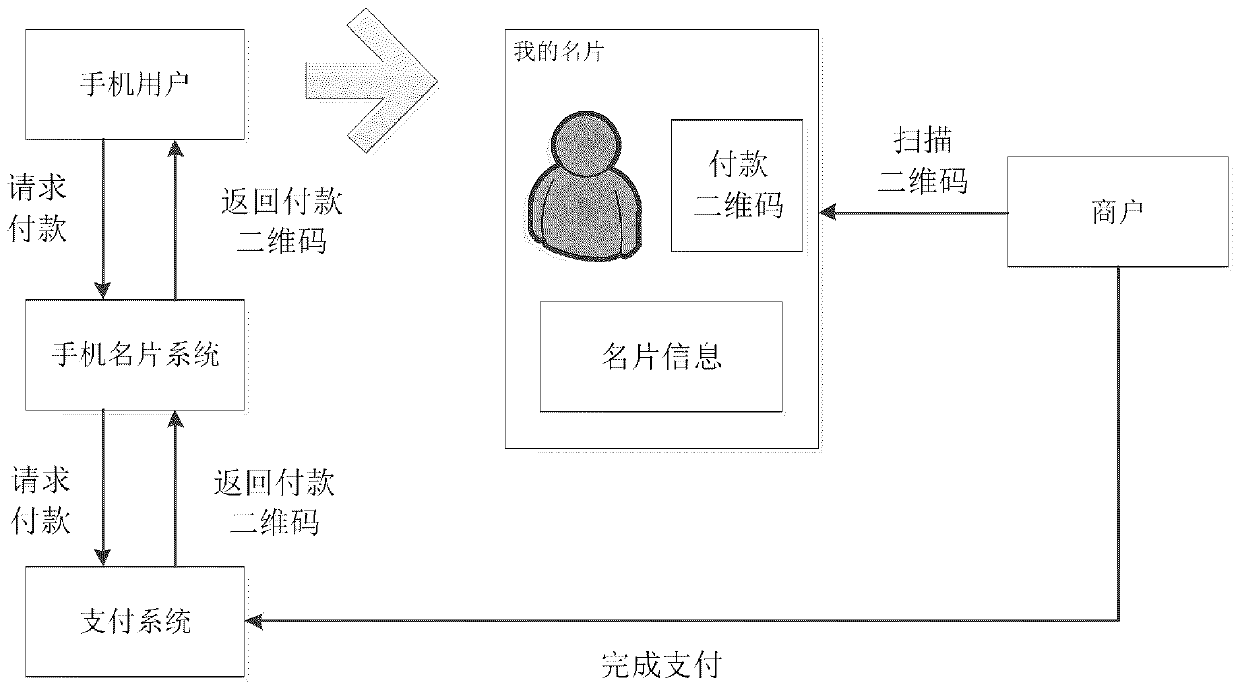
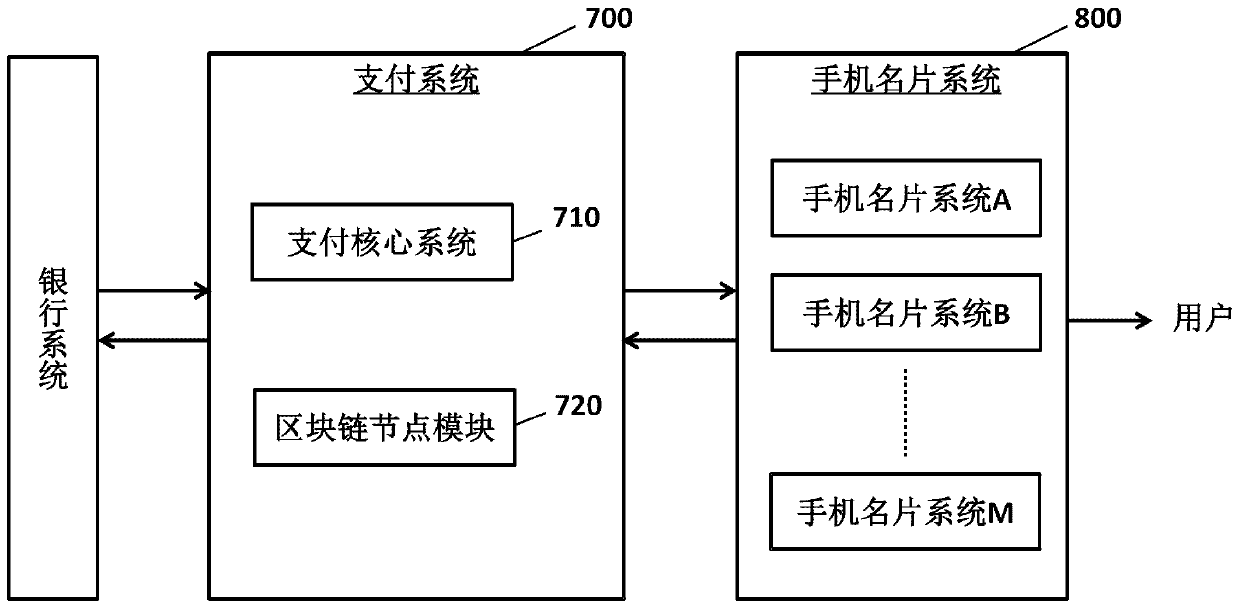
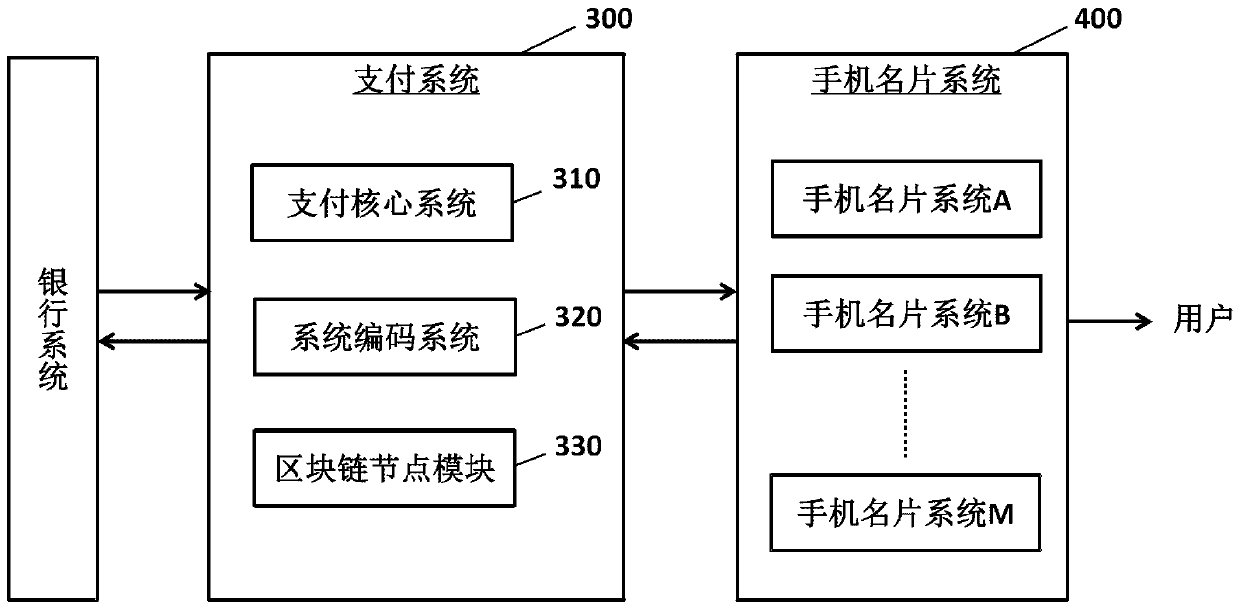
QR code payment method based on mobile phone business card, and system thereof
PendingCN111553678ASave operating timeReduce transaction implementation costsPayment protocolsBusiness cardComputer security
The invention relates to a QR code payment method based on a mobile phone business card, and a system thereof. The QR code payment method is realized by a payment system and a mobile phone business card system, and comprises the following steps: a request receiving step, a mapping establishment step, a distribution step, an account acquisition step, and a binding step. Therefore, the binding of the bank card information and the user business card can be realized. According to the QR code payment method based on the mobile phone business card and the QR code payment system based on the mobile phone business card, compared with traditional QR code card binding opening, a user does not need to download a client or input bank card information in the card binding work, and the user operation time is greatly shortened, and the card binding threshold is reduced, and the use willingness is improved.
Owner:CHINA UNIONPAY
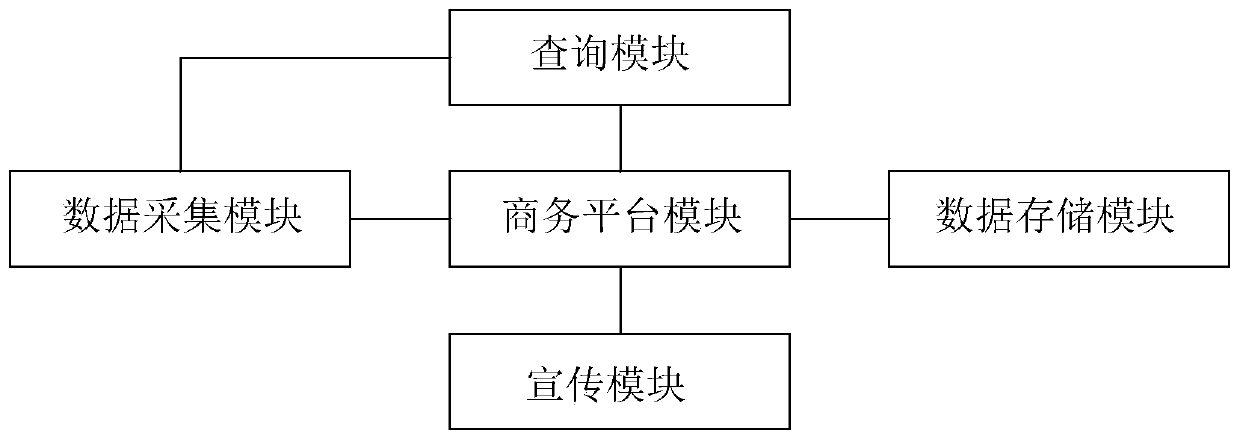
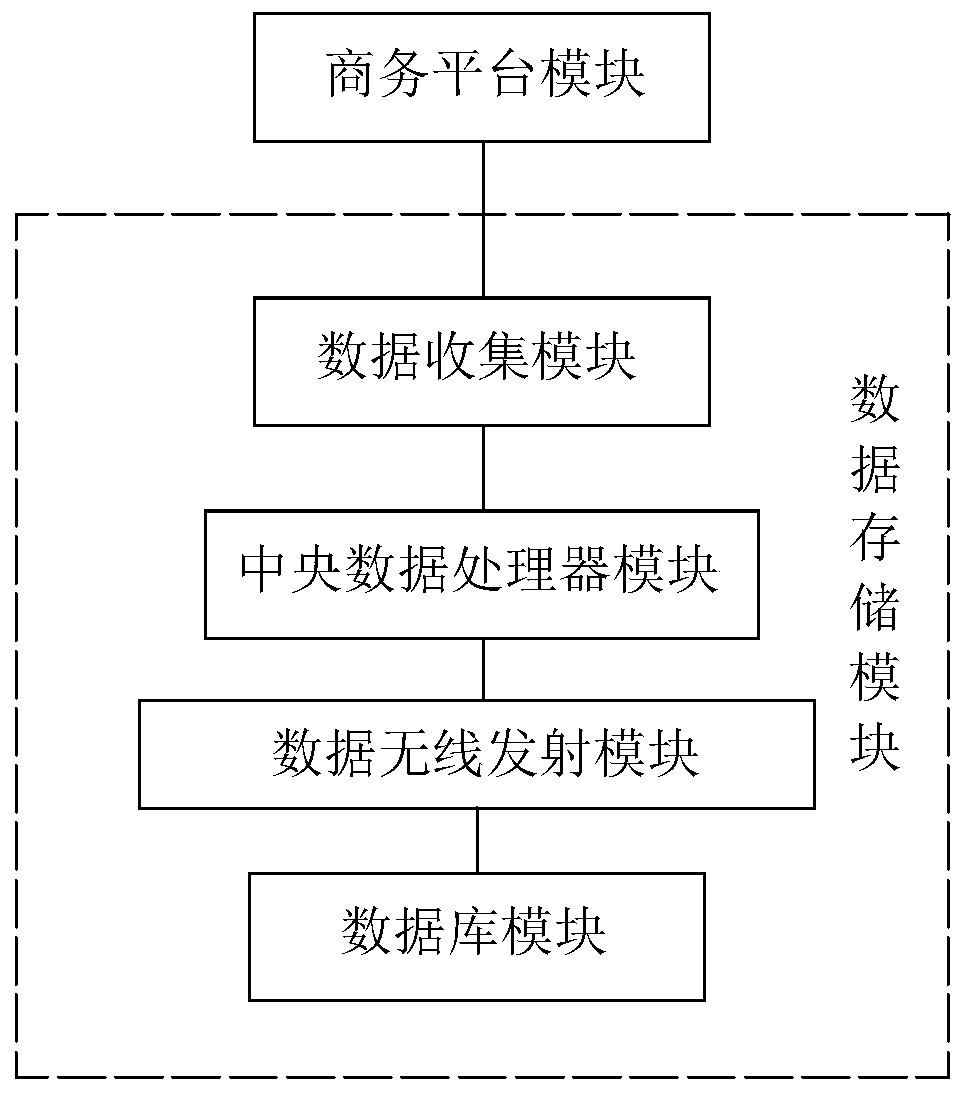
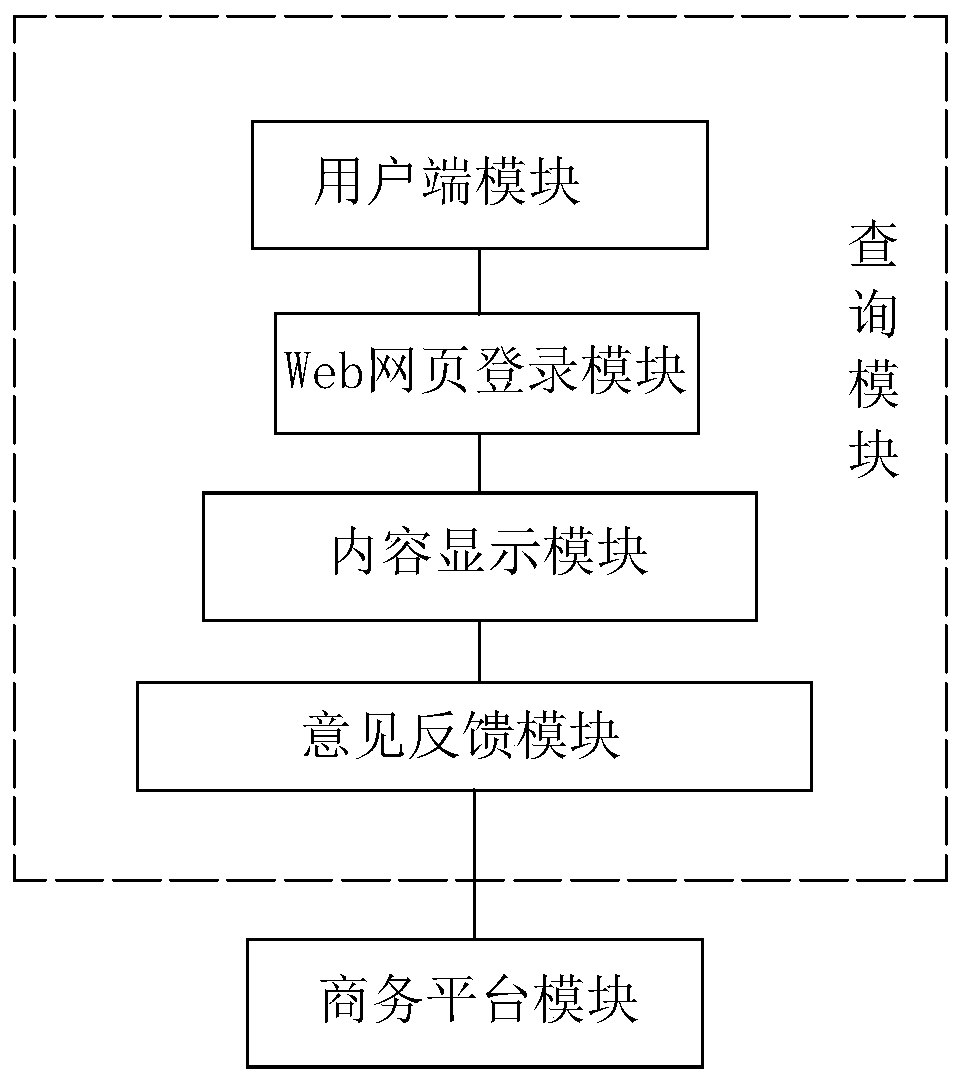
Big data e-commerce shopping guide system
InactiveCN110827081AIncrease publicityImprove protectionCustomer communicationsMarket data gatheringData scienceE-commerce
The invention relates to the technical field of business shopping guide, in particular to a big-data e-commerce shopping guide system. The big-data e-commerce shopping guide system includes a data acquisition module, the data acquisition module is connected with the business platform module in a signal connection mode. Meanwhile, the business platform module is in signal connection with the data storage module; data information in the business platform module is transmitted to the data storage module to be stored; the business platform module is in signal connection with the propaganda module;the business platform module comprises a mobile base station module. The mobile base station module receives the data information collected by the data acquisition module; the data is transmitted tothe cloud big database module through the wireless transmission module to be processed, the processed data is transmitted to the internal server module, and the data information is transmitted to theinternal computer control module through the internal server. Propaganda strength on commodities can be improved, and meanwhile the sales volume of the commodities is increased.
Owner:温州红秀招信息科技有限公司
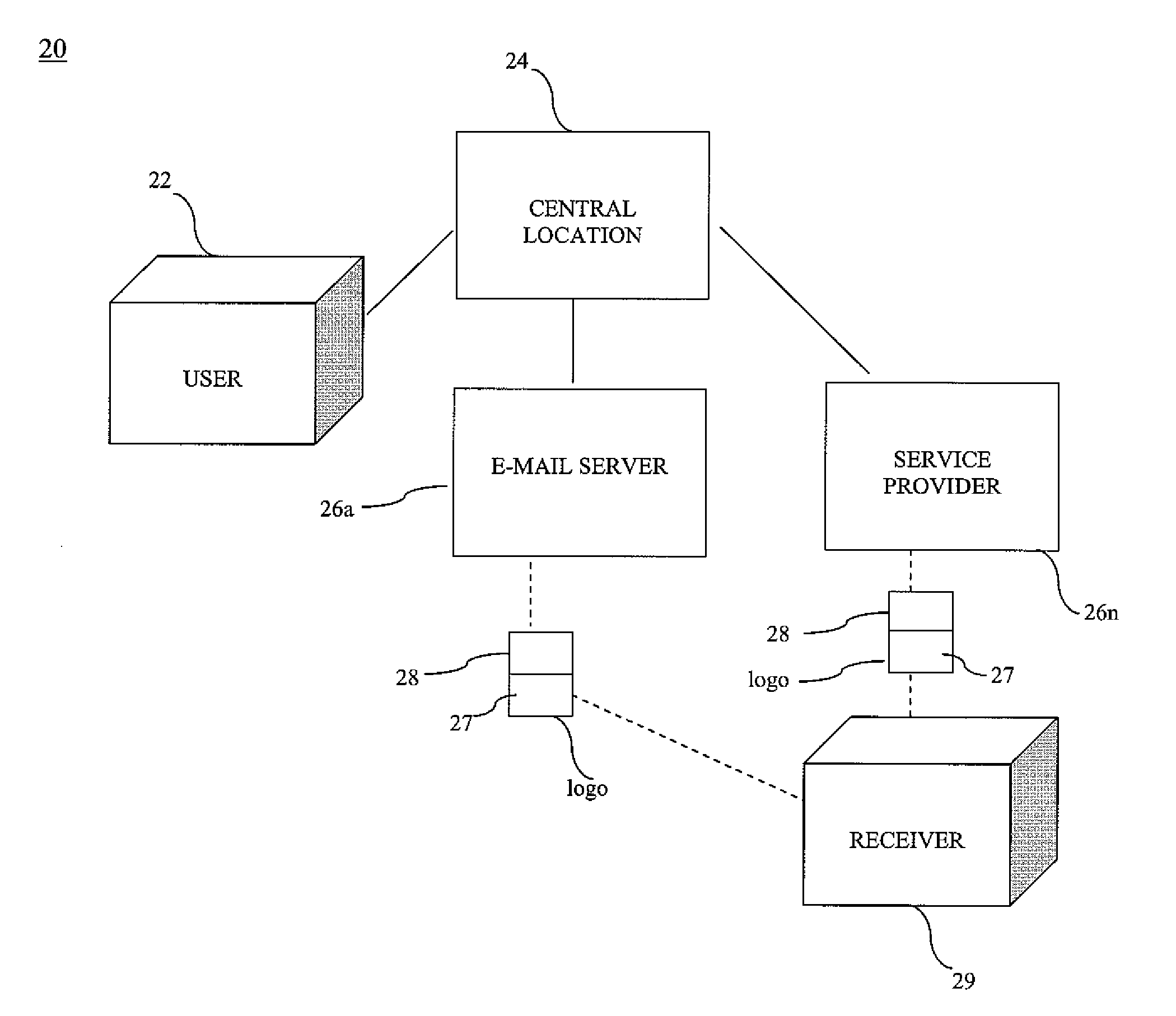
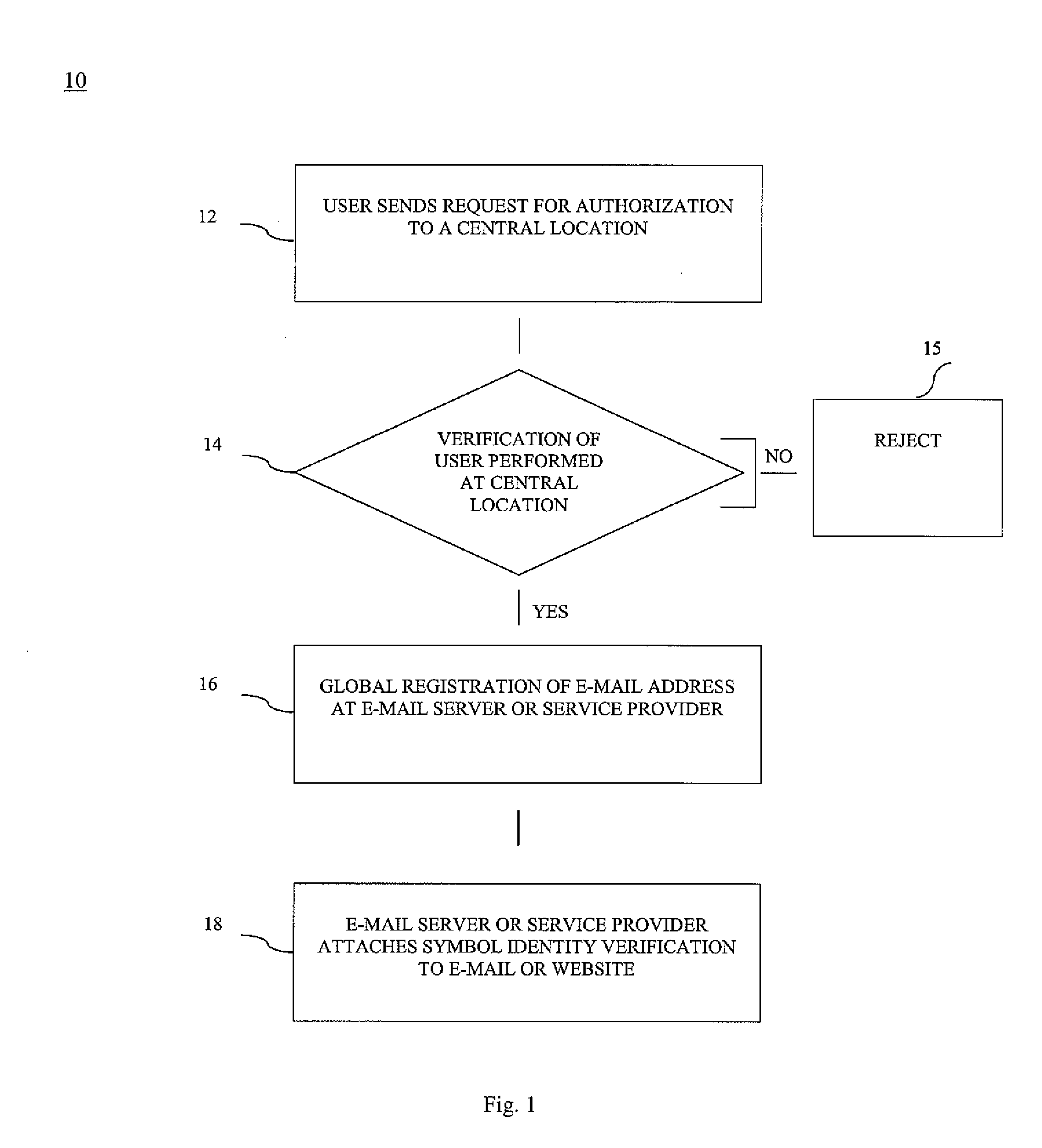
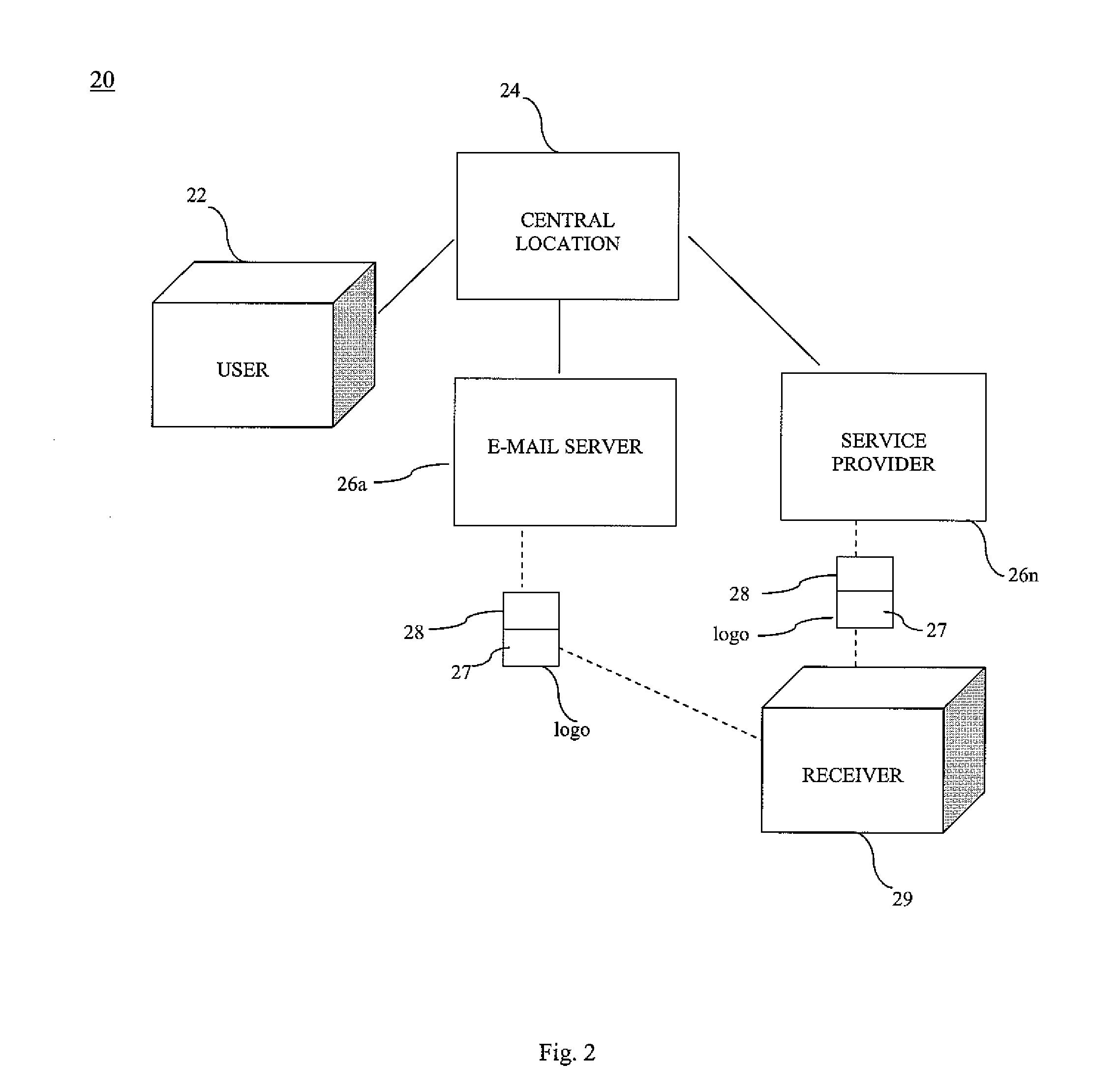
Method and system for real world verification of a person and/or business identity at a central location for real and virtual world
InactiveUS20080301789A1New of revenueEffectively deter potential fraudDigital data processing detailsUser identity/authority verificationService provisionVirtual world
The method and system of the present invention provides a central location, such as the United States Postal Service® (USPS), a product that will advance them into the world of internet business and will in turn offer the opportunity for new sources of revenue. The method and system of the present invention has the facilities to verify a person's and / or businesses identity. The verification process can be done in the same manner as money order, check cashing and real P.O. boxes, which are currently limited to availability in the post office. If the user is verified at the central location, the user's e-mail address, domains, ISP, WSP, and Web Sites can be globally registered at one or more e-mail servers or service providers that participate with the verification. The e-mail server or service providers can attach a symbol of the identity verification on all e-mail sent by the e-mail server or service provider from the verified customer.
Owner:FOSTER FREDERICK D
Cigarette specially-made packing box capable of being made into 3D VR stereo imaging glasses
InactiveCN107128610AWith functionUsableContainers for flexible articlesPackage recyclingStereo imagingEyewear
The invention discloses a cigarette specially-made packing box capable of being made into a 3D VR stereo imaging glasses helmet. The cigarette specially-made packing box comprises a paper box body and a forehead point-pressed line, an eye point-pressed line and a nose point-pressed line of the paper box body. The forehead point-pressed line is located on the top of the paper box body. The eye point-pressed line and the noise point-pressed line are located on the front portion of the paper box body. More than one crease is arranged at the bottom of the paper box body. The creases and the front portion of the paper box body are matched in shape. According to the cigarette specially-made packing box capable of being made into the 3D VR stereo imaging glasses helmet, an original paper box discarded after used can be changed into a reusable storage box for storing objects or a garbage box, so that the original scrapped paper box is recycled and creates subsequent value.
Owner:CHINA TOBACCO YUNNAN IND
Method for recording product packaging process by using nested digital twinning body
PendingCN111507736AEffective traceabilityImprove efficiencyDigital data protectionCommerceComplete dataData pack
The invention provides a method for recording a product packaging process by using a nested digital twinning body. Based on the packaging process, data generated in each operation node is signed to obtain an electronic tag, the data and the electronic tag are included in a data packet and are sent to the next operation node, and each operation node except the first operation node includes the datapacket sent by the previous operation node in the sent data packet. The method can effectively help governments, enterprises, logistics and other parties to provide complete data traceability, provide simple and verifiable evidences for auditing, problem investigation and the like, help all parties to clarify responsibility boundaries and establish trust relationships among the parties; data counterfeiting events are greatly reduced, and the efficiency of manually tracing risk events is greatly improved; the requirements of services needing data anti-counterfeiting traceability are met; and the implementation is simple, the data traceability is effective, and the service requirements are met.
Owner:GUIZHOU UNIV +1
Method, device and system for delivering network information
InactiveCN103491146BPrecise deliveryResolve trust issuesTransmissionSpecial data processing applicationsInformation repositoryTrust relationship
The embodiment of the invention provides a method, device and system for releasing network information. The problems that the accuracy of releasing the network information is lowered, and the releasing effect is poor are solved. The method comprises the steps of receiving a network information scheduling request sent by a demand side platform, wherein the network information scheduling request comprises the corresponding cookie_1, of a user, in the demand side platform; seeking cookie_2 related to the cookie_1 in a prestored cookie association table; seeking user attributes corresponding to the cookie_2 in a pre-generated user attribute database; retrieving the corresponding network information in a network information base according to the user attributes and returning the network information to the demand side platform. According to the method, device and system for releasing the network information, user data collected through a data side can be fully utilized, the user-oriented network information can be accurately released, and the releasing effect is improved; the data privacy of all sides is fully protected, and the trust relationship of a whole industry chain is built.
Owner:BAICHUAN TONGLIAN BEIJING NETWORK TECH
Membership system community store operation method and platform
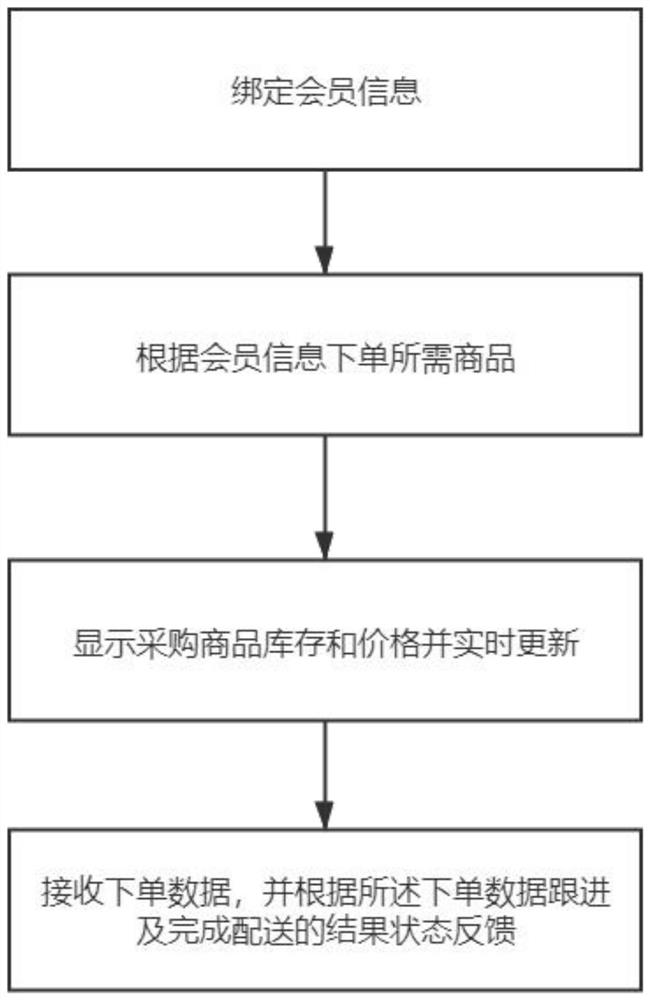
PendingCN112488653ARealize the bindingReduce inventory costsOffice automationBuying/selling/leasing transactionsCommunity settingEngineering
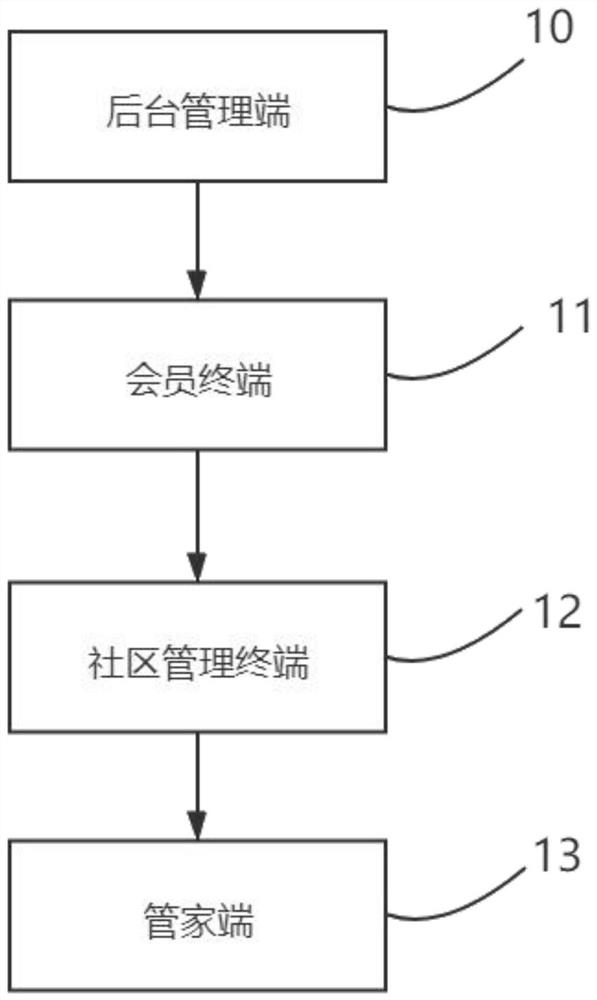
The invention discloses a membership system community store operation method. The method comprises the following steps: binding member information; ordering required commodities according to the member information; displaying the stock and price of the purchased commodity and updating in real time; and receiving order placing data, and performing follow-up according to the order placing data and completing result state feedback of distribution. The invention further discloses a membership system community store operation platform which comprises a background management terminal, a member terminal, a community management terminal and a housekeeper terminal. Members are bound through household registration, community management is facilitated, illegal registration of individual users is avoided, the management cost is reduced, users in a community can visually feel the service value of the community by disclosing the purchase price and showing the service concept of zero profit in the sales stage. The business mode of the invention can effectively enhance the recognition degree of the users in the community to the managers, and facilitates the managers to provide more services to theusers in the community.
Owner:宜宾幸雅物业管理有限公司
Device and method for realizing offline social contact
PendingCN111464604AFull trust relationshipFully build trustSubstation equipmentData switching networksEmbedded systemInternet of Things
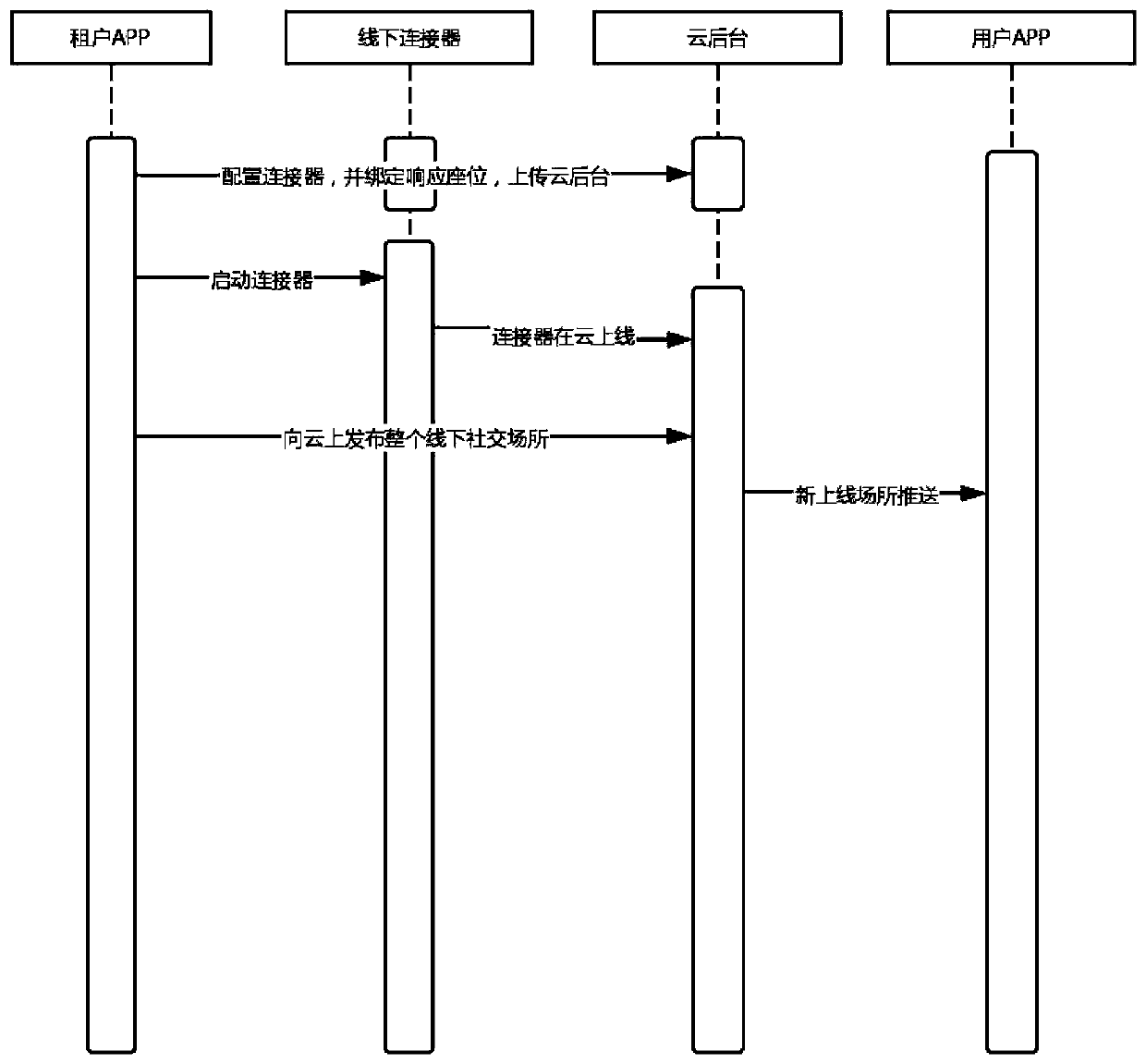
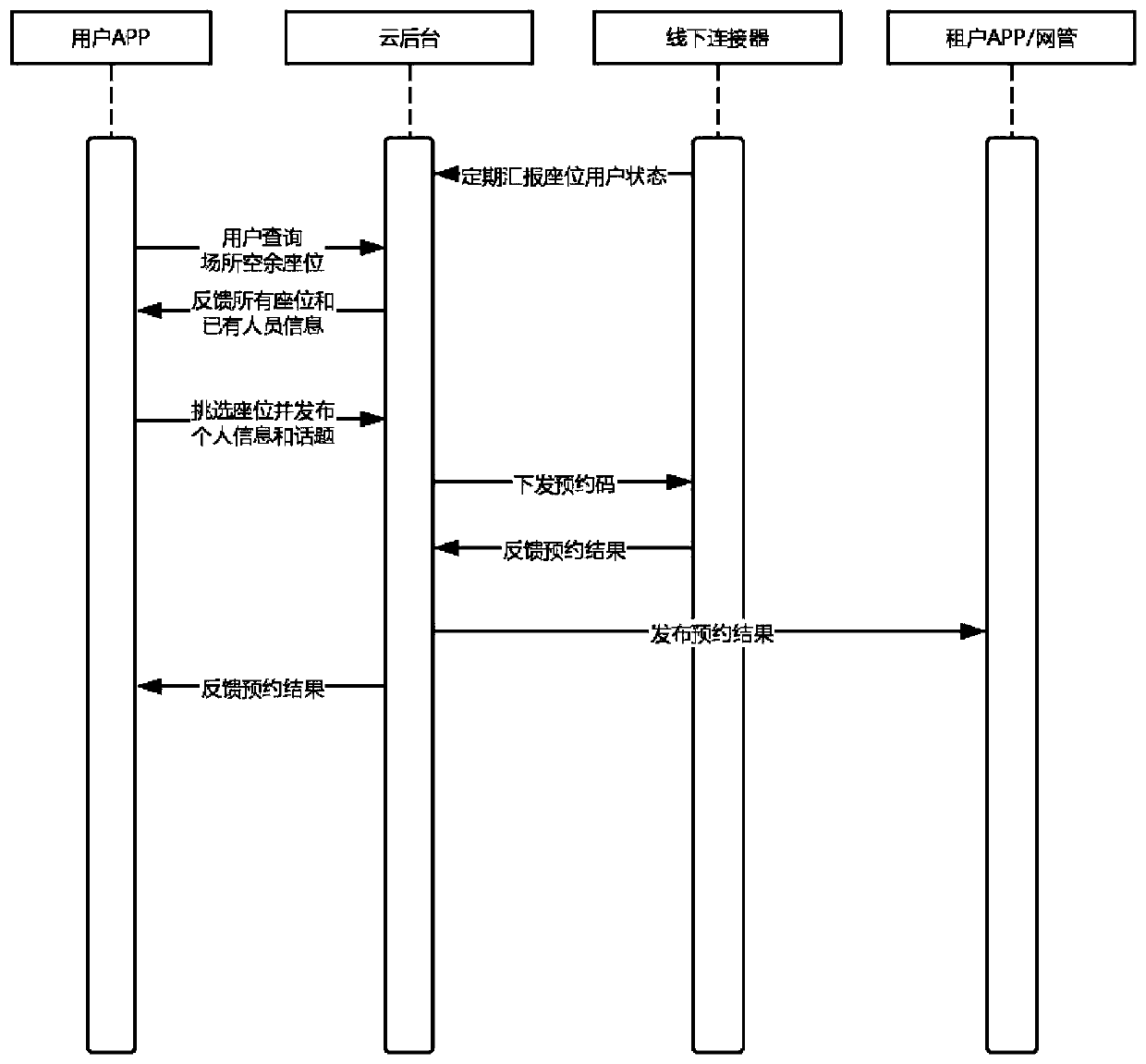
The invention discloses a device and a method for realizing offline social contact. The device comprises an offline connector module, an on-cloud service platform module and a terminal service module.The method is characterized in that the offline connector module comprises a mainboard part, a lithium battery, a GPS antenna, a charging coil, a shielding layer, a Bluetooth antenna and a GSM antenna. The mainboard part is designed based on a PCB, Bluetooth, a GPS module and GSM communication are additionally arranged on the PCB, a GSM antenna is arranged on one side of the GSM communication. The method comprises the steps that S1, bounding a seat; S2, reserving 'seats' online; S3, making an online seat appointment; S4, fulfilling offline appointment. A position function is used for reference, Internet of Things hardware is newly added as an anchor point, a B2B2C offline communication system is provided for merchants, an offline connector is used as a core device of the device and the method, and a position-based authentication effect is mainly provided.
Owner:杭州雄芯物联科技有限公司
Calculation method and calculation system of social-network user trust
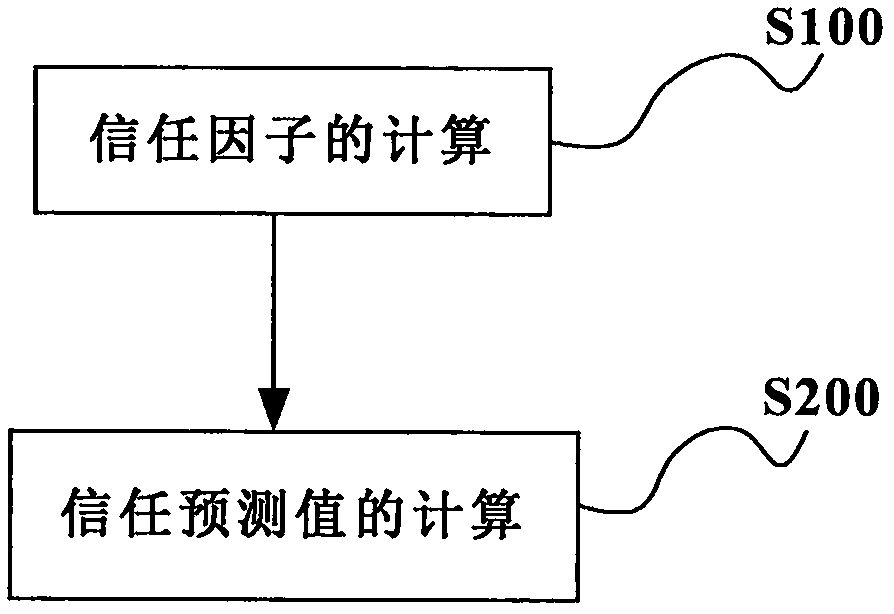
InactiveCN107609002AFast predictionImprove forecast accuracyData processing applicationsSpecial data processing applicationsComputing systemsInternet privacy
The invention discloses a calculation method and a calculation system of social-network user trust. The calculation method of the social-network user trust includes: S100, calculation of a trust factor; and S200, calculation of a trust prediction value. By utilizing the calculation method and the calculation system of the social-network user trust of the invention, a trust relationship between users can be established without the need for providing trust attribute information of the users by the users. The calculation method has a very high prediction speed and higher prediction precision; successfully explains technical problems of trust propagation and trust imbalance in trust chains; successfully solves a technical problem that transmission of the trust often fails, and can ensure thattransmission of the trust always succeeds; can effectively filter out malicious users, is higher in security, and thus can ensure that a social network is more secure; and is more wider in a scope ofapplication , and has a huge market promotion value.
Owner:HENAN UNIV OF SCI & TECH
A feeding method to improve the survival rate of southern lambs
ActiveCN111631189BImprove survival rateFeed management is highly operableAnimal feeding stuffWeaningZoology
The invention relates to a feeding method for improving the survival rate of southern lambs, said method comprising nursing of newborn lambs, artificial feeding of milk replacer, early induced feeding and feeding management scheme, breeding environment control and regular disinfection, transitional isolation of mother and child and Mild weaning, Chinese herbal medicine to enhance immunity and prevent diseases. The present invention makes the survival rate of the southern lamb reach more than 95% and increases the immunity of the lamb through six measures, such as birth care of the lamb, supplementary feeding of milk replacer, induction of early feeding, environmental control, benign weaning and supplementary feeding of Chinese herbal medicine. and production potential, improving the economic benefits of southern goat breeding.
Owner:INST OF SUBTROPICAL AGRI CHINESE ACAD OF SCI
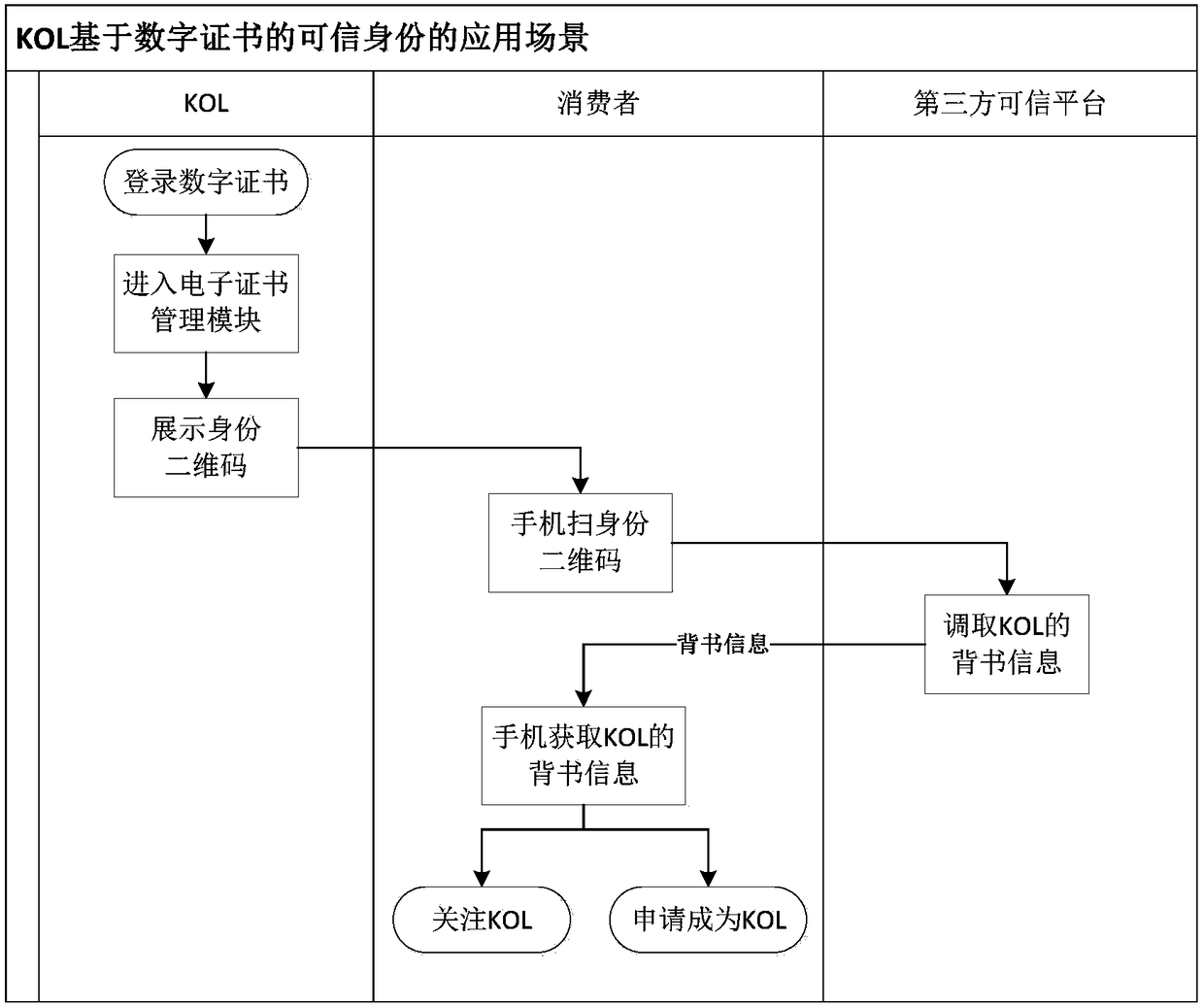
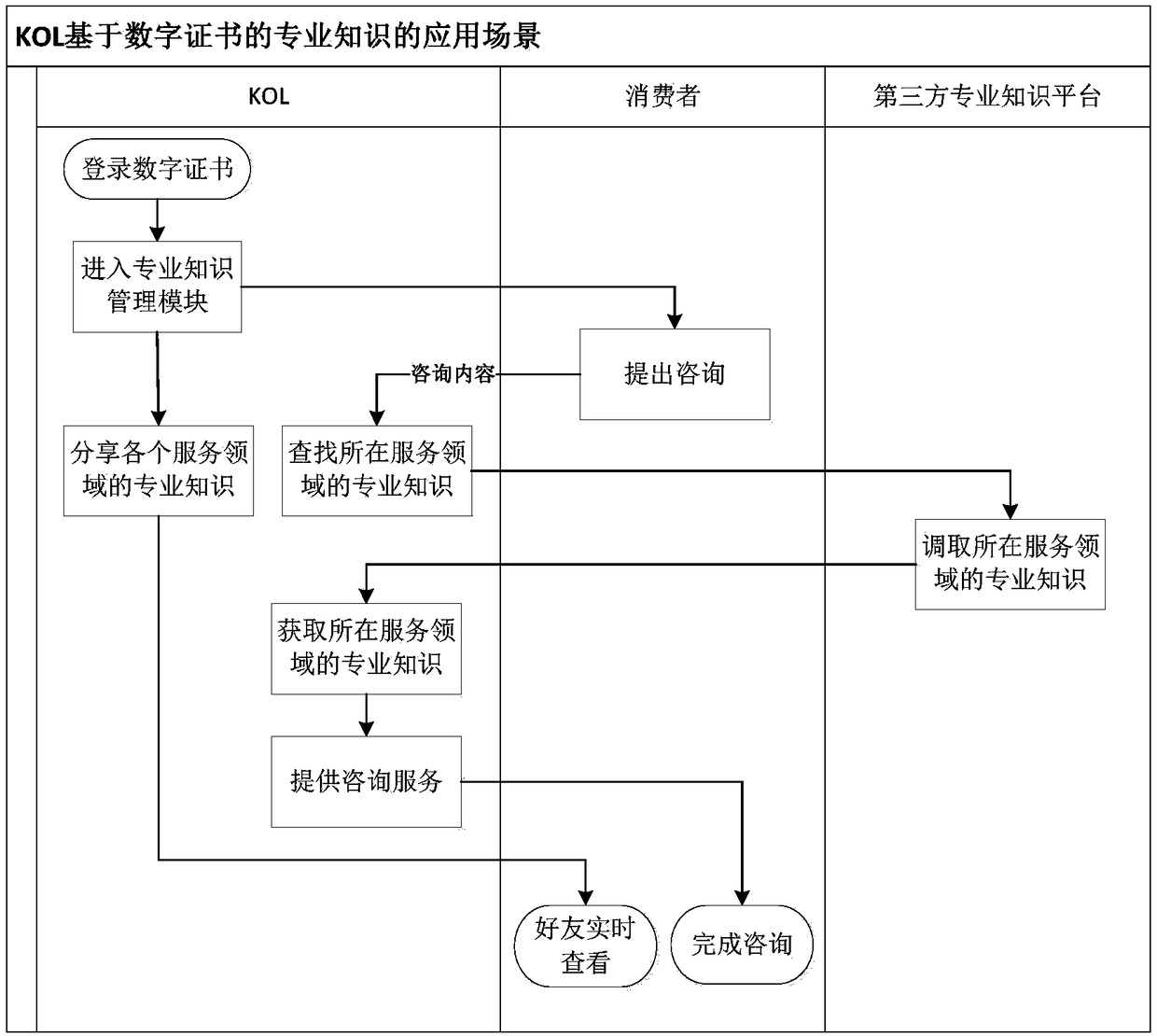
Community service system and method based on KOLs
InactiveCN108205785AImprove trustEfficient use ofData processing applicationsTransmissionData processing systemLibrary science
The invention discloses a community service system based on KOLs (key opinion leaders) and relates to the field of management-dedicated data processing systems. The system comprises an electronic certificate management module and a professional knowledge management module, wherein the electronic certificate management module is used for community service personnel to register as the KOLs, and unique identification codes, used for proving KOL identities, in one-to-one correspondence with the KOLs are provided for all the KOLs; and the professional knowledge management module comprises pre-stored professional knowledge of all domains and is used for the KOLs to perform query. On the basis of the KOLs, the community service system serves as support to overcome defects of the community servicepersonnel through the professional knowledge management module, therefore, the community service personnel can carry out service work more smoothly, and meanwhile higher service quality is provided.
Owner:广州美诚汇信息科技有限公司 +1
An intelligent monitoring system for hazardous agricultural inputs based on dbn-softmax
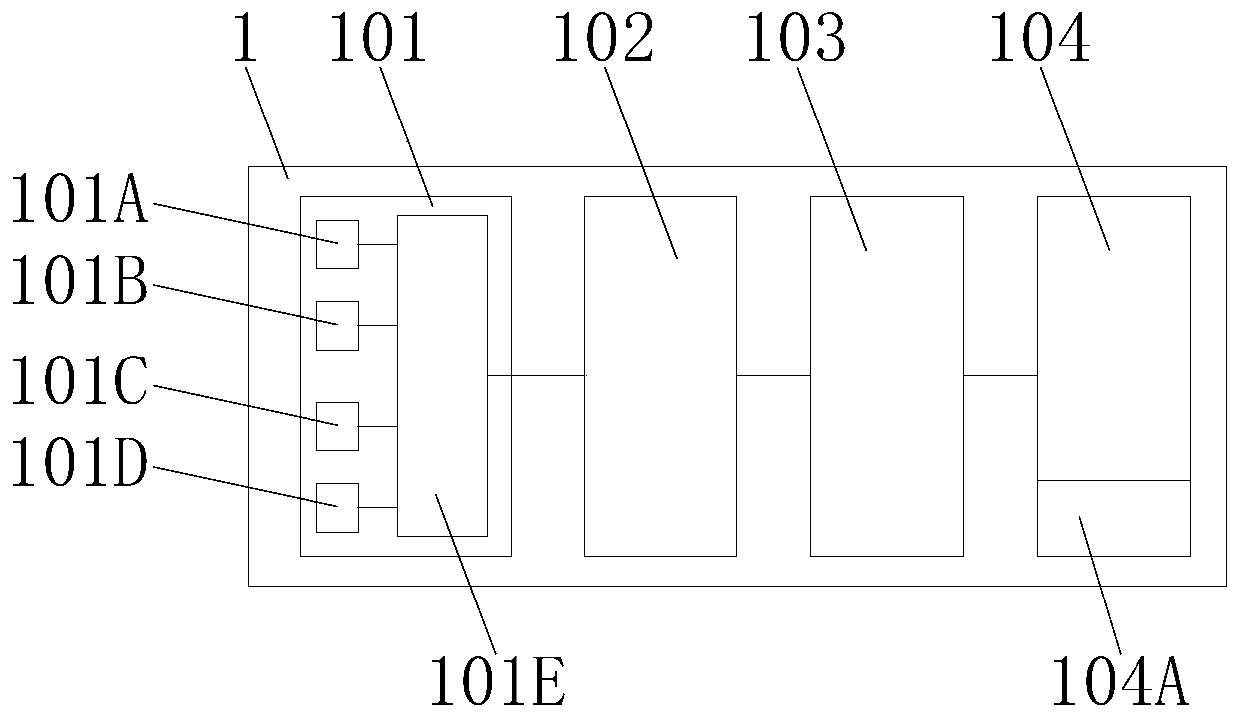
ActiveCN109669403BBuild trustEasy constructionProgramme total factory controlMonitoring systemModule network
The invention discloses a dangerous agricultural input intelligent monitoring system based on DBN-SOFTMAX. The dangerous agricultural input intelligent monitoring system comprises a monitoring centerand a LORA gateway, wherein a cloud server, an intelligent equipment module, a DBN-SOFTMAX network and a database are arranged in the monitoring center, an input prediction module and a SOFTMAX classifier are arranged in the DBN-SOFTMAX network, a plurality of LoRa nodes are connected with one side of the LORA gateway, the other side of the LORA gateway is connected with the cloud server and the database through a data receiving service end, one side of the cloud server is connected with the input prediction module, one side of the input prediction module is connected with one side of the intelligent equipment module, and the database is connected with the SOFTMAX classifier. The dangerous agricultural input intelligent monitoring system based on DBN-SOFTMAX can monitor agricultural inputsof a planting base in real time.
Owner:ZHONGKAI UNIV OF AGRI & ENG
Special packaging box capable of being manufactured into LED lamp box for cigarettes and manufacturing method for special packaging box
InactiveCN106185053AWith functionUsableContainers for flexible articlesPackaging cigaretteEngineeringLED lamp
The invention discloses a special packaging box capable of being manufactured into an LED lamp box for cigarettes and a manufacturing method for the special packaging box. The special packaging box comprises a packaging box body, wherein the packaging box body comprises a bottom box part and a box body part, wherein both the bottom box part and the box body part are arranged in a rectangular form and are detachably connected; the inside diameter of the bottom box part is matched with the outside diameter of the box body part; and both the top and the bottom of the box body part are arranged in a hollow manner. According to the special packaging box capable of being manufactured into the LED lamp box for the cigarettes, originally-scrapped paper boxes can be recycled, and subsequent higher value is created.
Owner:CHINA TOBACCO YUNNAN IND
An invoice verification system based on cloud computing and encrypted two-dimensional code
ActiveCN102930634BMeet the needs of invoice verificationEnsure information securityPaper-money testing devicesCharacter and pattern recognitionComputer hardwareInvoice
The invention discloses an invoice true check system based on cloud computing and encrypted two-dimensional codes and belongs to a tax invoice true check system. The invoice true check system comprises a tax office cloud computing platform, an encrypted two-dimensional code device and an invoice scanning decrypting device. The tax office cloud computing platform is used for managing the encrypted two-dimensional code device and the invoice scanning decrypting device. The encrypted two-dimensional code device is used for printing the encrypted two-dimensional codes on physical invoices when invoicing invoices for drawers. The invoice scanning decrypting device is used for scanning, decrypting and comparing the invoices needing true check and outputting processing results according to grades to serve as true check basis. Compared with the prior art, the invoice true check system based on cloud computing and the encrypted two-dimensional codes can solve the problems of trust issue and data safety of the existing invoice true check results, and restrains invoice counterfeiting and false invoice using to a certain extent.
Owner:INSPUR SOFTWARE TECH CO LTD
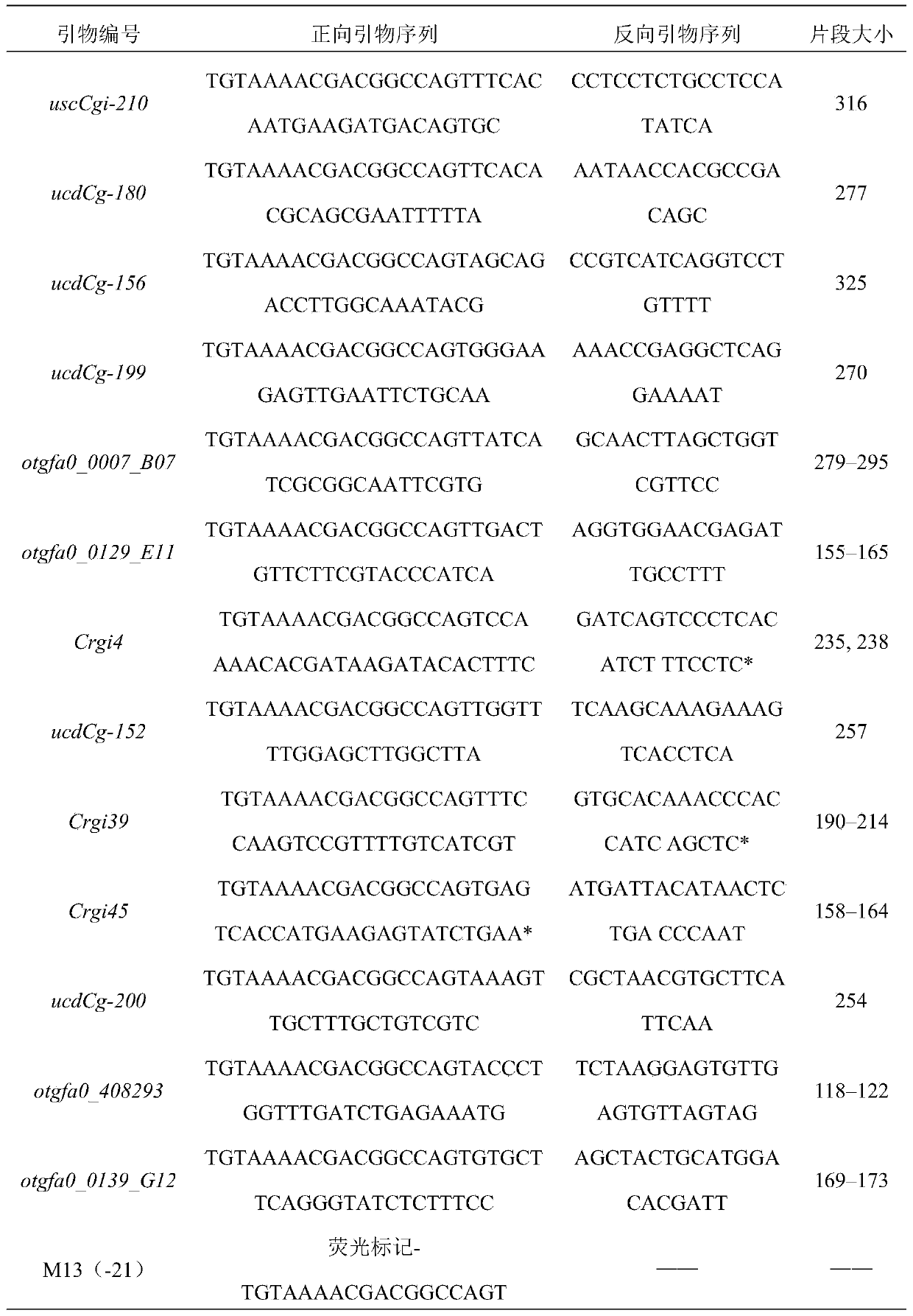
A microsatellite multiplex pcr method for paternity identification of oyster oyster
ActiveCN105441576BImprove analysis accuracyImprove experimental efficiencyMicrobiological testing/measurementFluorescenceOyster
Owner:OCEAN UNIV OF CHINA
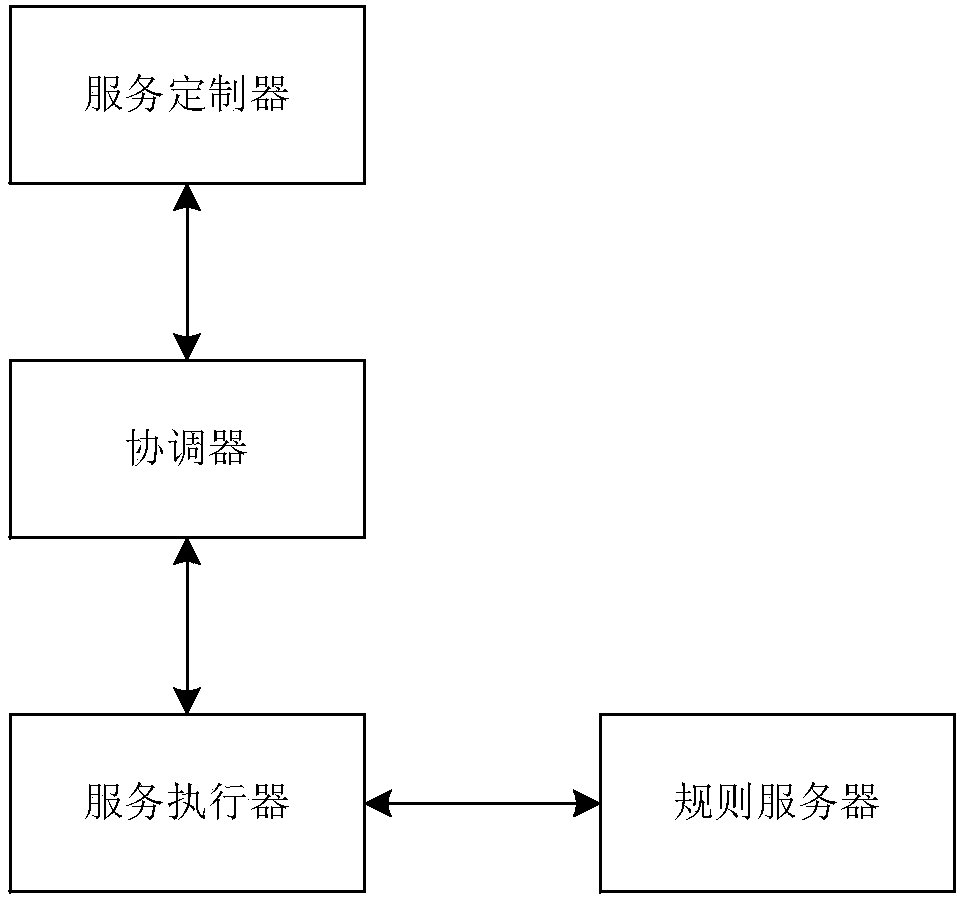
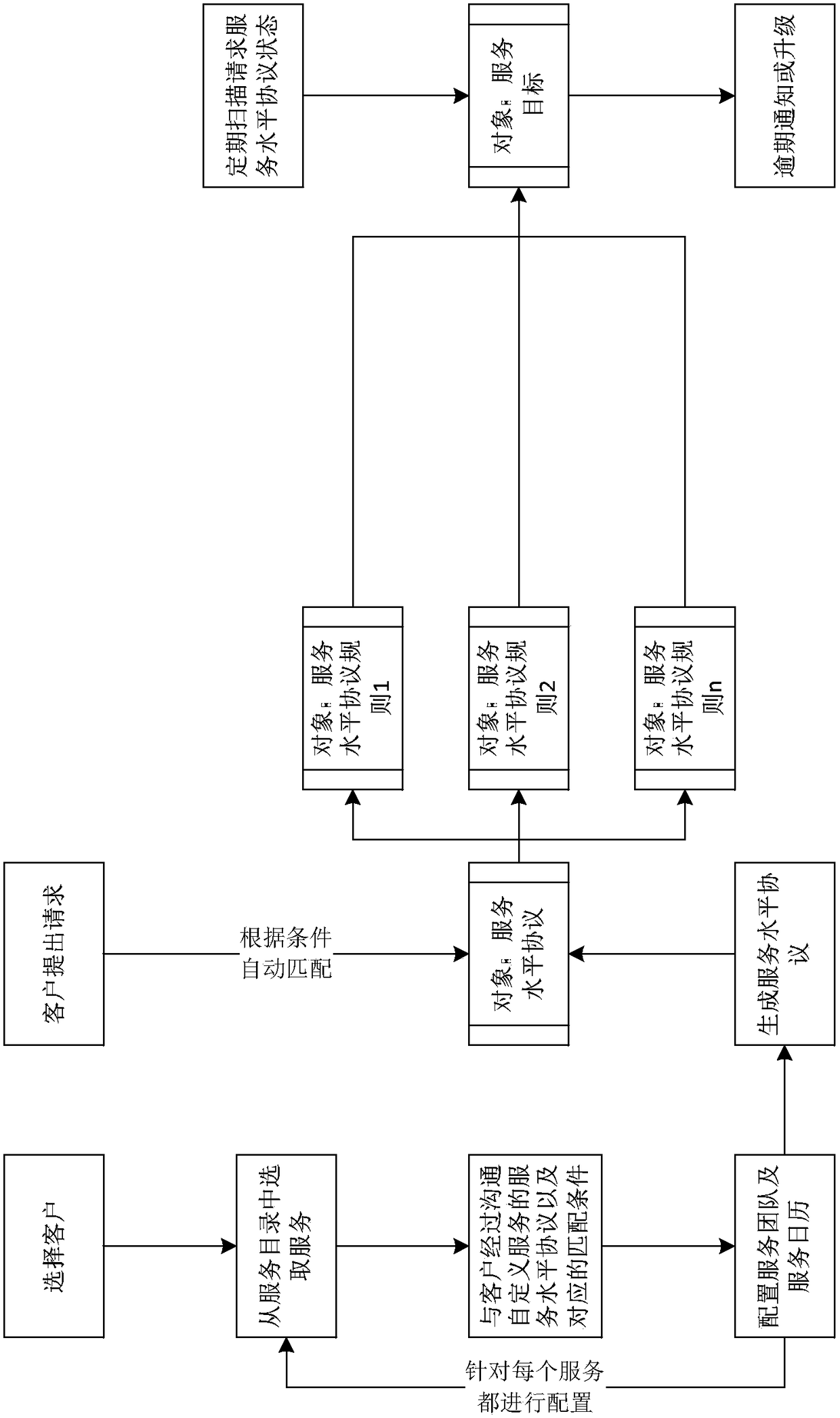
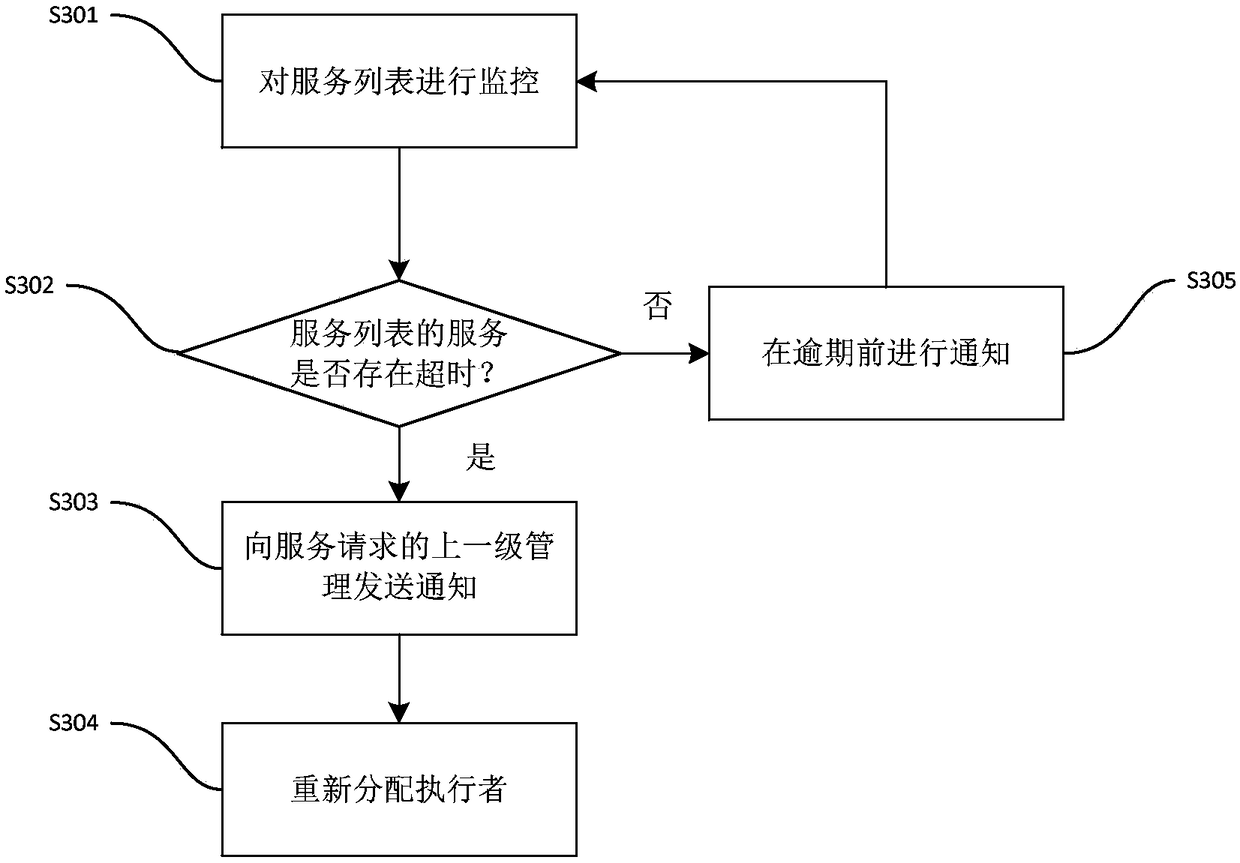
Rule based service level protocol management system and method
InactiveCN108270612AHelp assessmentQuick responseData switching networksService-level agreementService provider
The invention relates to a rule based service level protocol management system and method. The method comprises that an interaction interface capable of customizing services is provided for a servicerequester, and a service level protocol in which services are selected is customized; a service request submitted by a user is received, a corresponding service level protocol matches the service request automatically, and a corresponding executer and execution time are configured according to the service level protocol; and a rule server provides a rule set for executing the service request and the service level protocol for the rule executer. The system and method have the advantages that different customized services and service strategies can be configured for different users flexibly, response time, update strategy, notification before overdue and the like can be configured, and rapid response to the users can be ensured; and the service level is quantified so that the users rely on aservice provider, and the service provider is helped to check service groups.
Owner:珠海国津软件科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com