Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
57 results about "User exit" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
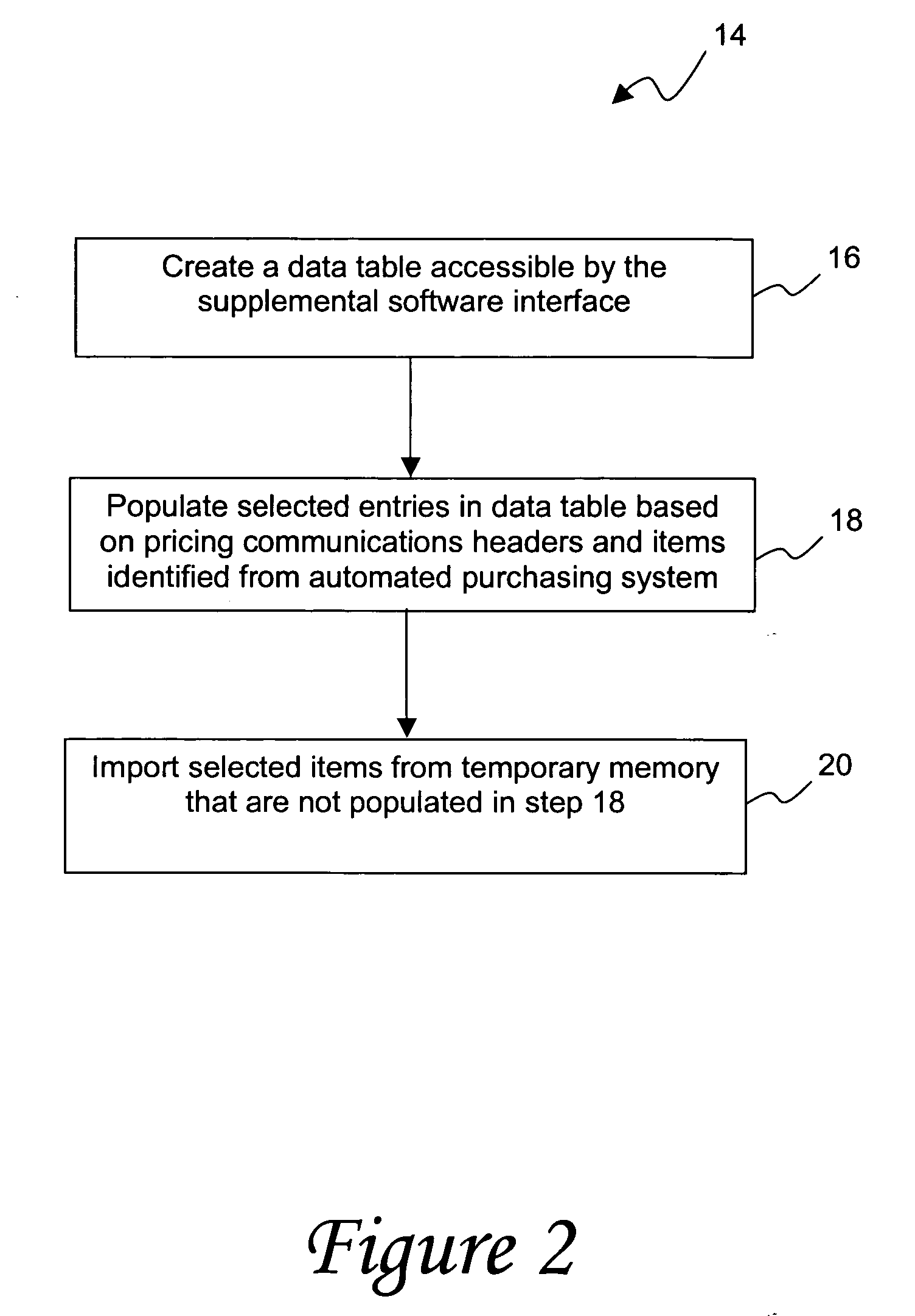
A user exit is a subroutine invoked by a software package for a predefined event in the execution of the package. Clients of the package can substitute their own subroutines in place of the default ones provided by the package vendor to provide customized functionality.
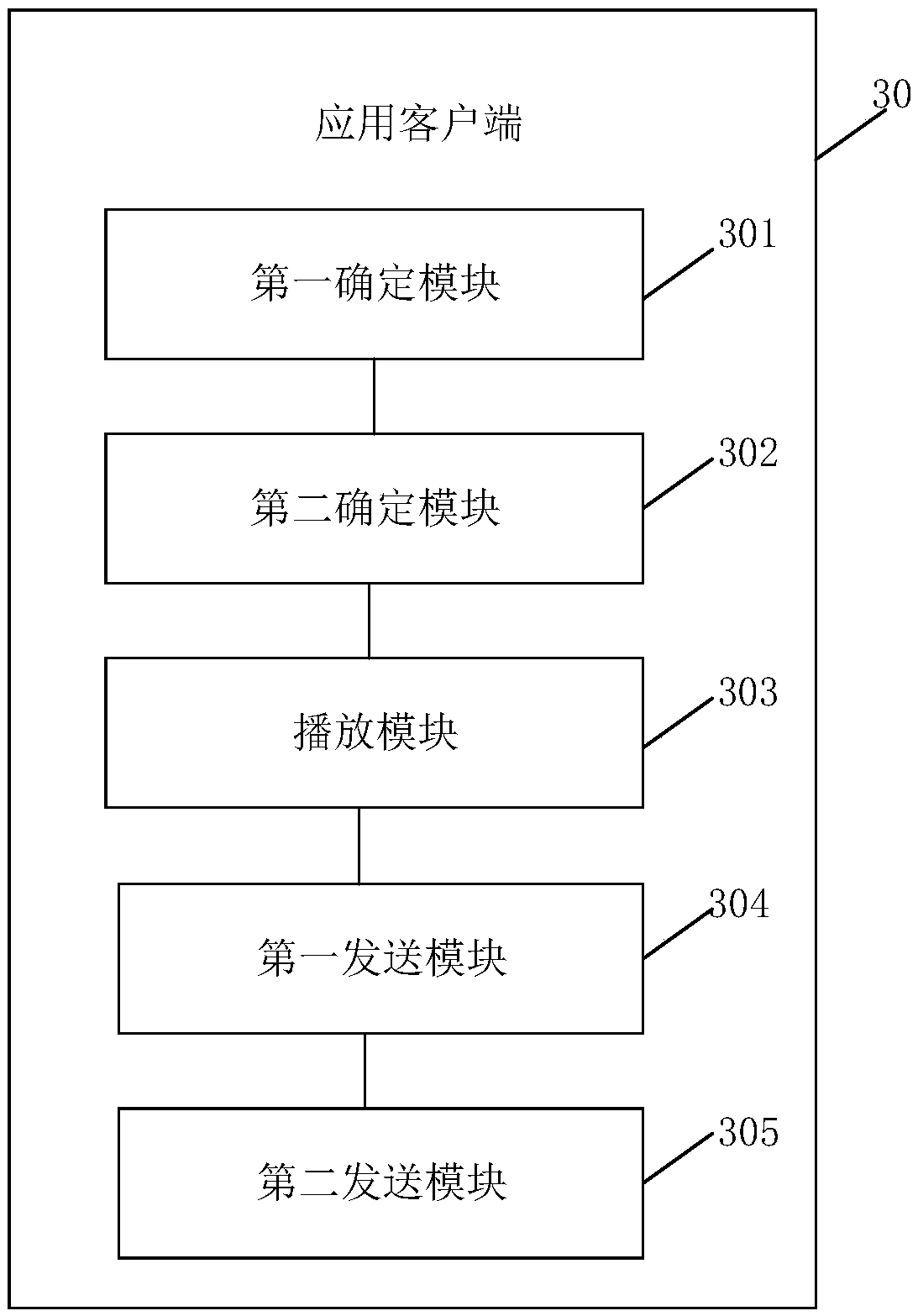
Multimedia program bookmarking system
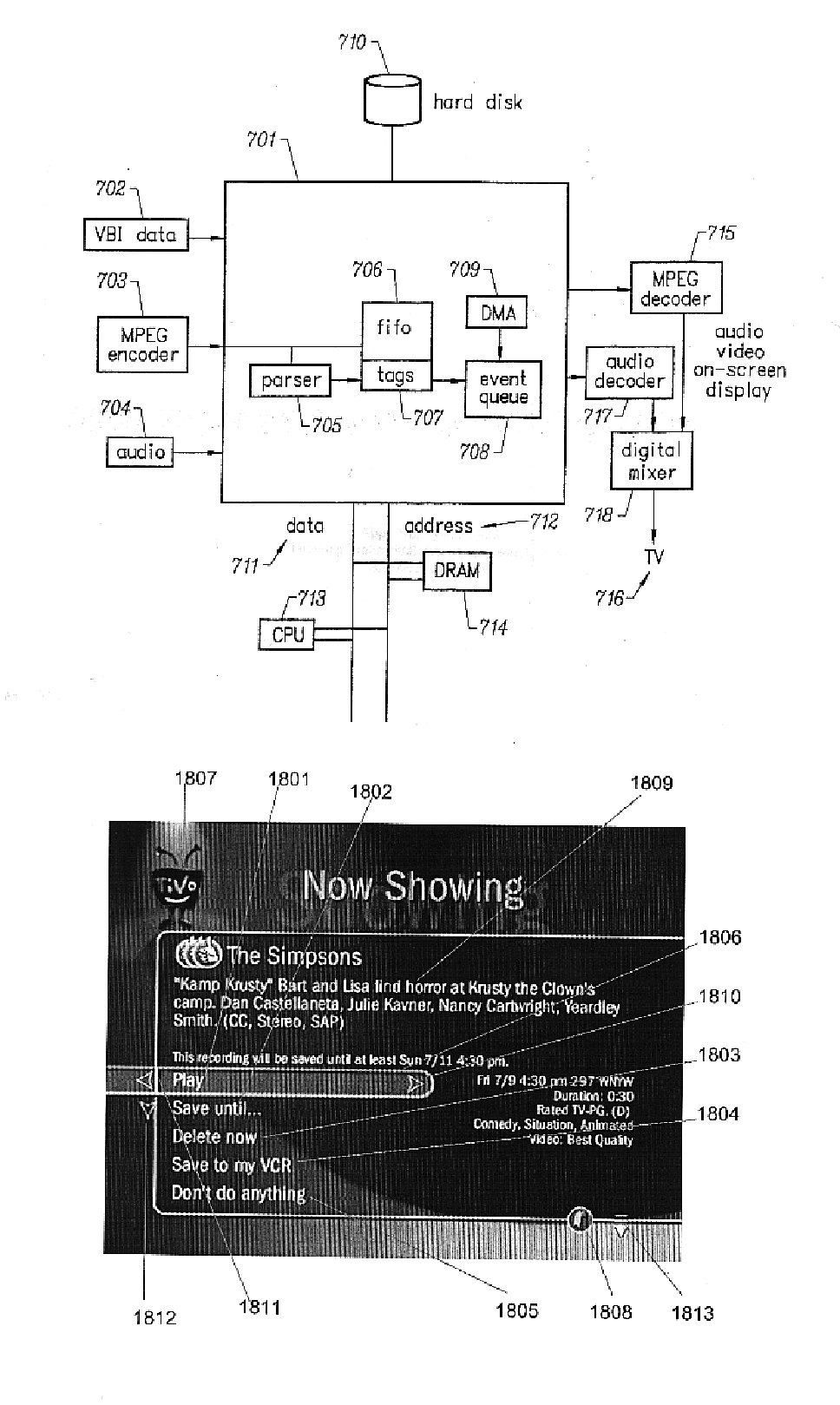
A multimedia program bookmarking system provides a bookmark function that allows the user to bookmark a program where he left off. The invention records the frame of the program where the user stopped when the user commands the system to do so. Alternatively, the invention automatically bookmarks the program for the user if the user exits viewing the program. The invention displays an indicator indicating that a bookmark has been saved and the user can, at any time, access his bookmark and continue playback of the program from where he left off. Bookmarks within a single program can be set for different users. Remote controls are encoded for a specific user in a household, allowing each person in the household to have a personal remote control and therefore, personal bookmarks. The invention notes that a set of bookmarks belongs to a certain encoded remote control. The user can alternatively select a specific set of bookmarks manually, through a menu. The system loads the associated bookmark information for the user and any bookmarks that do not have associated programs stored on the storage device are ignored and deleted, otherwise programs are played backed starting from the associated bookmarks, if they exist. Multiple bookmarks for a program are transparent to the user because the remote control that the user uses tells the system to only display and activate that particular user's bookmarks.
Owner:TIVO SOLUTIONS INC
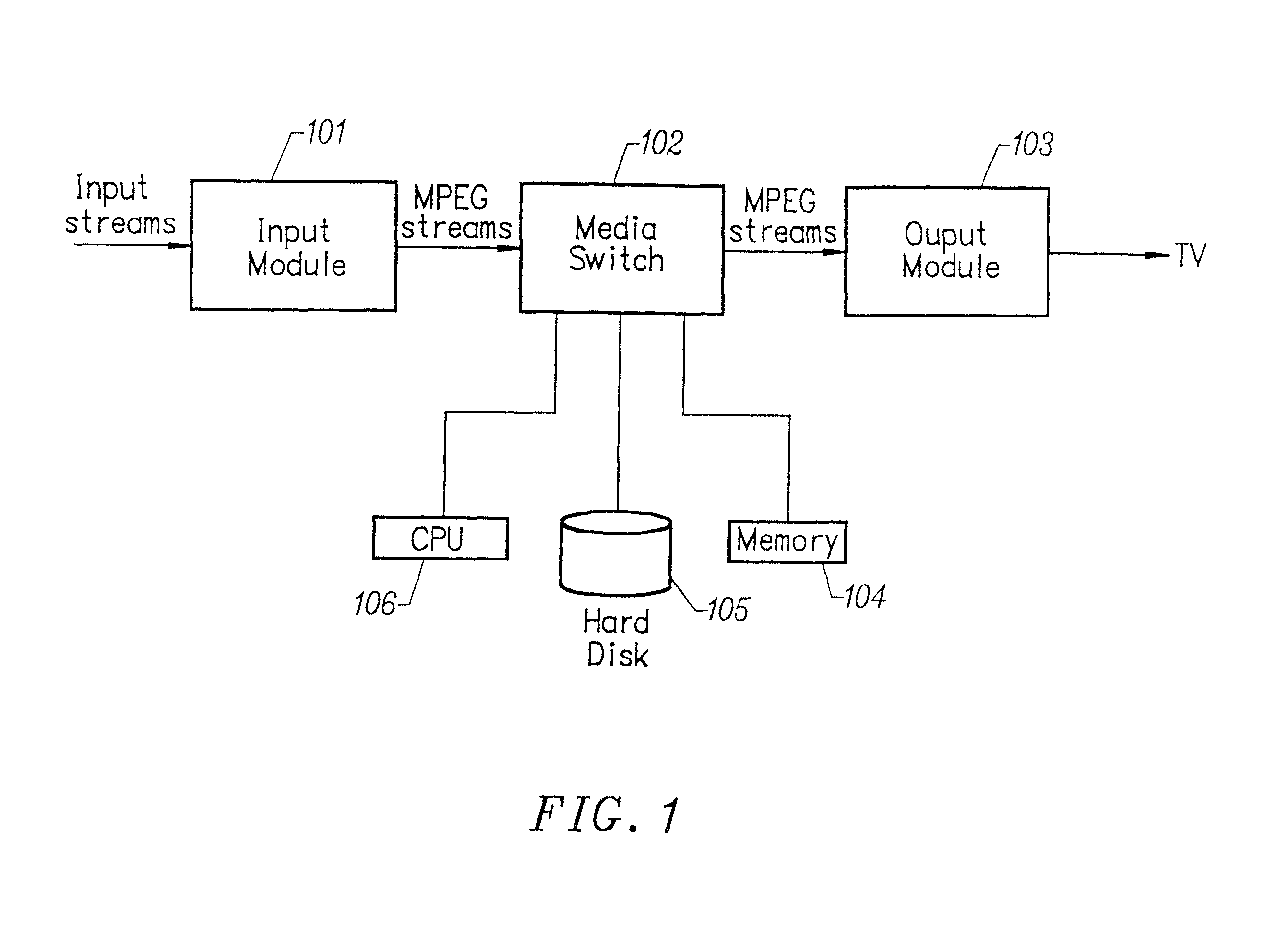
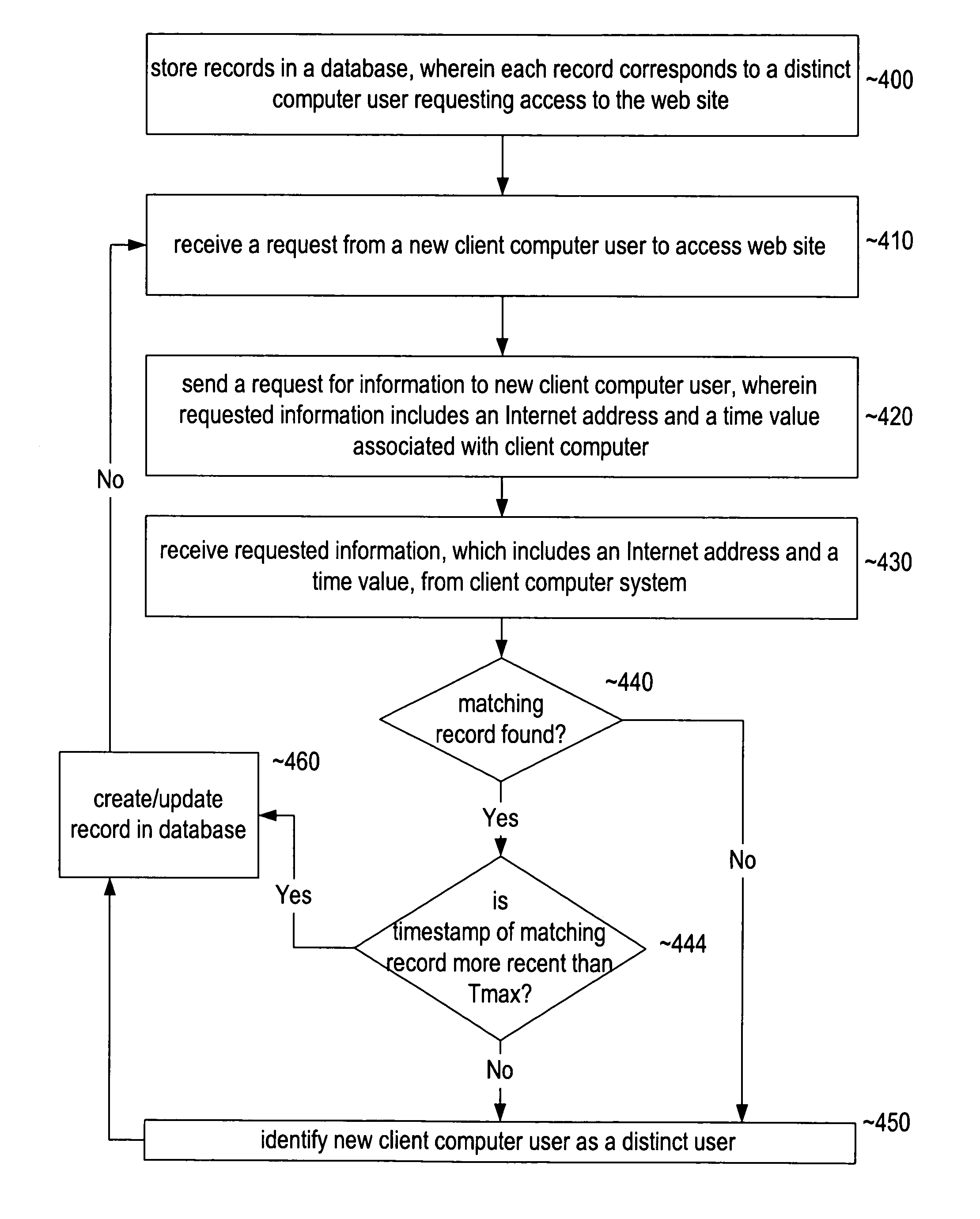
System and method for identifying individual users accessing a web site
ActiveUS7962603B1Digital computer detailsWebsite content managementUser identifierApplication software
An improved method and system for identifying individual users accessing a web site. A web site server is able to identify distinct users by using a unique identifier associated with each client computer system requesting access to the web site. The unique identifier comprises an Internet address, such as an Internet Protocol (IP) address, and a time value associated with each client computer system requesting access to the web site. On starting up a web browser, an application program or browser plug-in may synchronize the internal clock included with the client computer system with a global time standard. The synchronized time value may be based on an event associated with the client computer system, such as the start of a web browser. A web site server may determine the uniqueness of the client computer system by comparing unique identifier records of users accessing the web site. A user may be identified as distinct if no matching record exists in the database. Multiple client computer systems having a common Internet address may be identified by using this method. Users privacy is also protected as the unique identifiers are erased when the client computer system's user exits the web browser or powers down the computer.
Owner:NIHON DOT COM
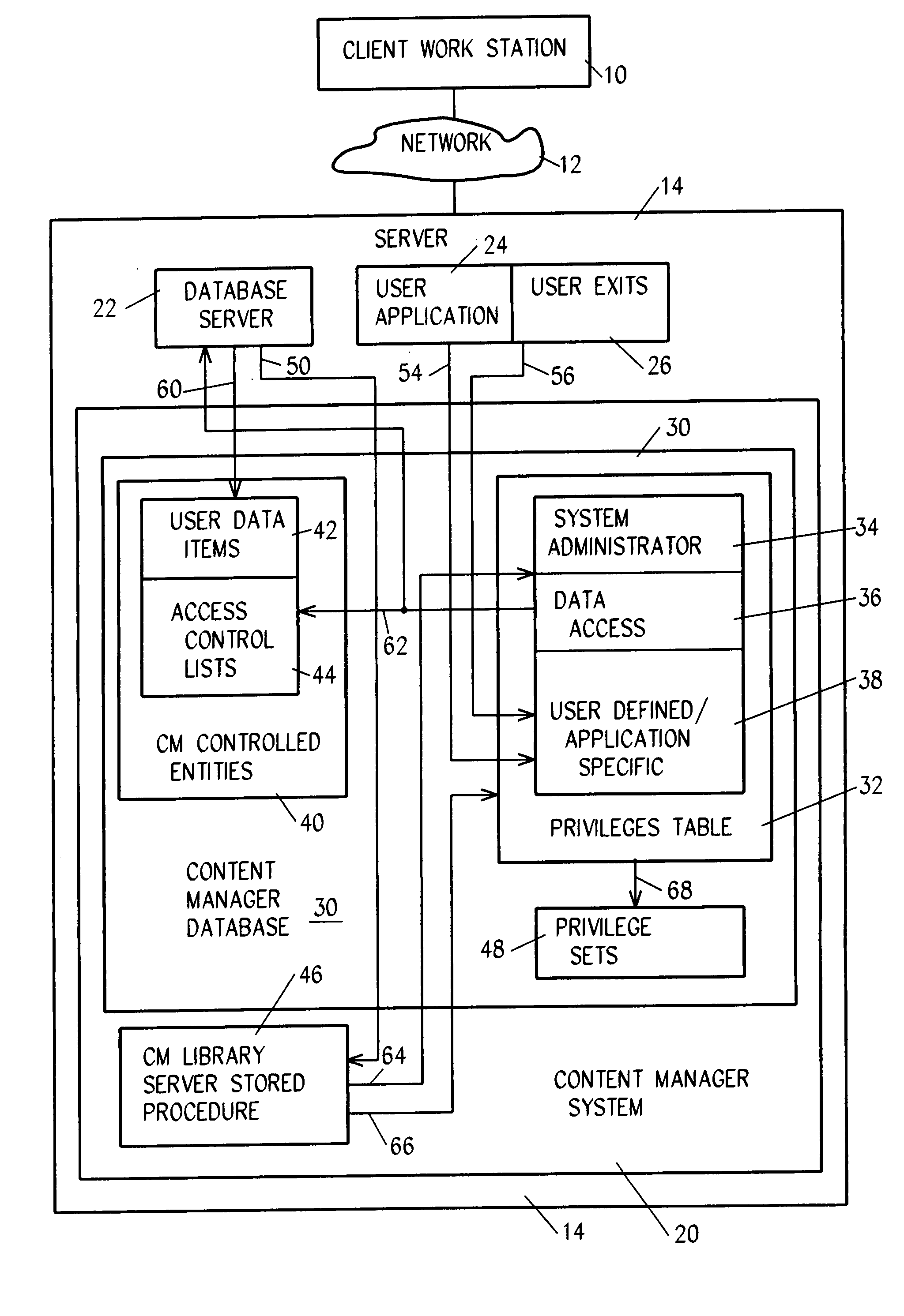
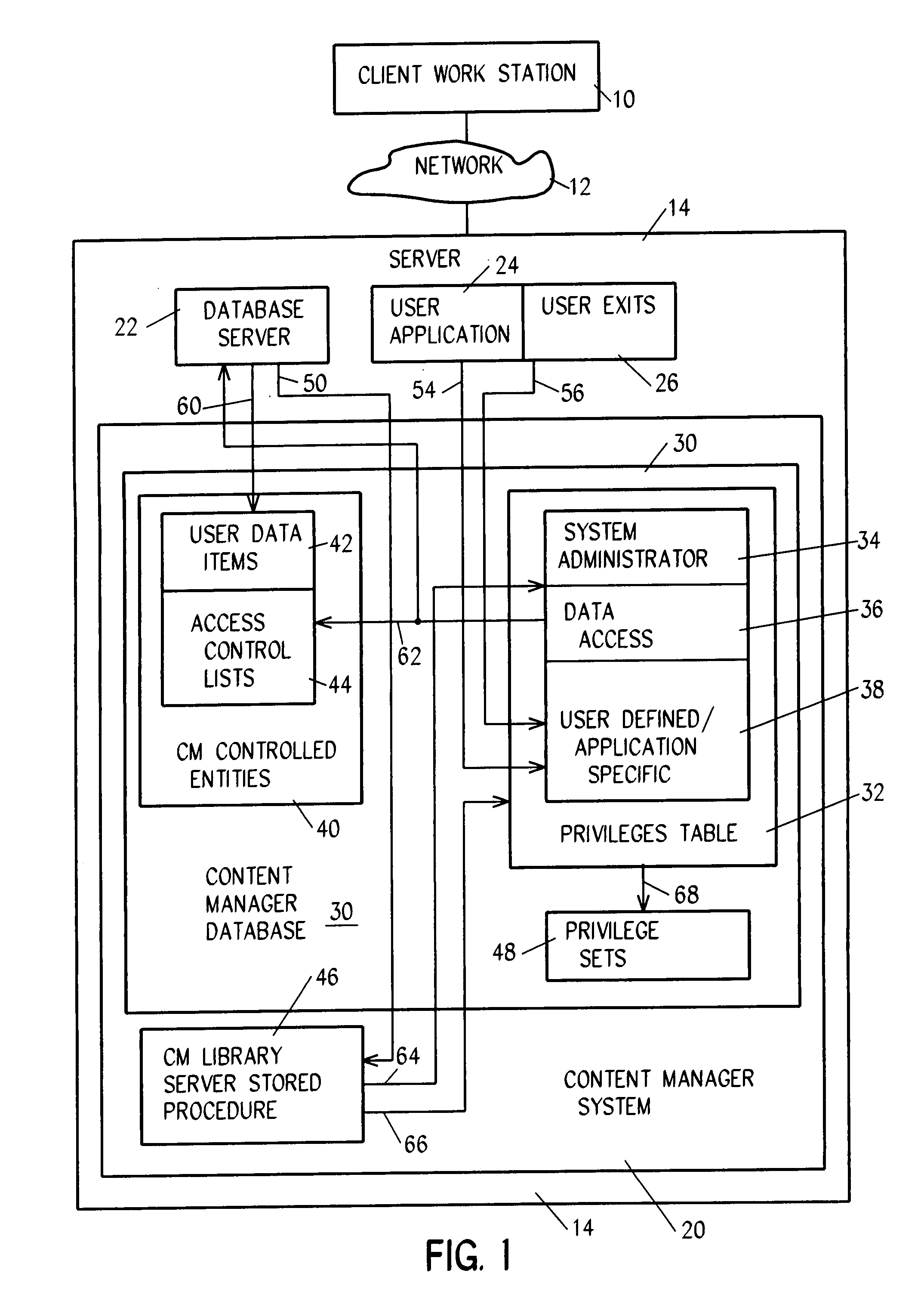
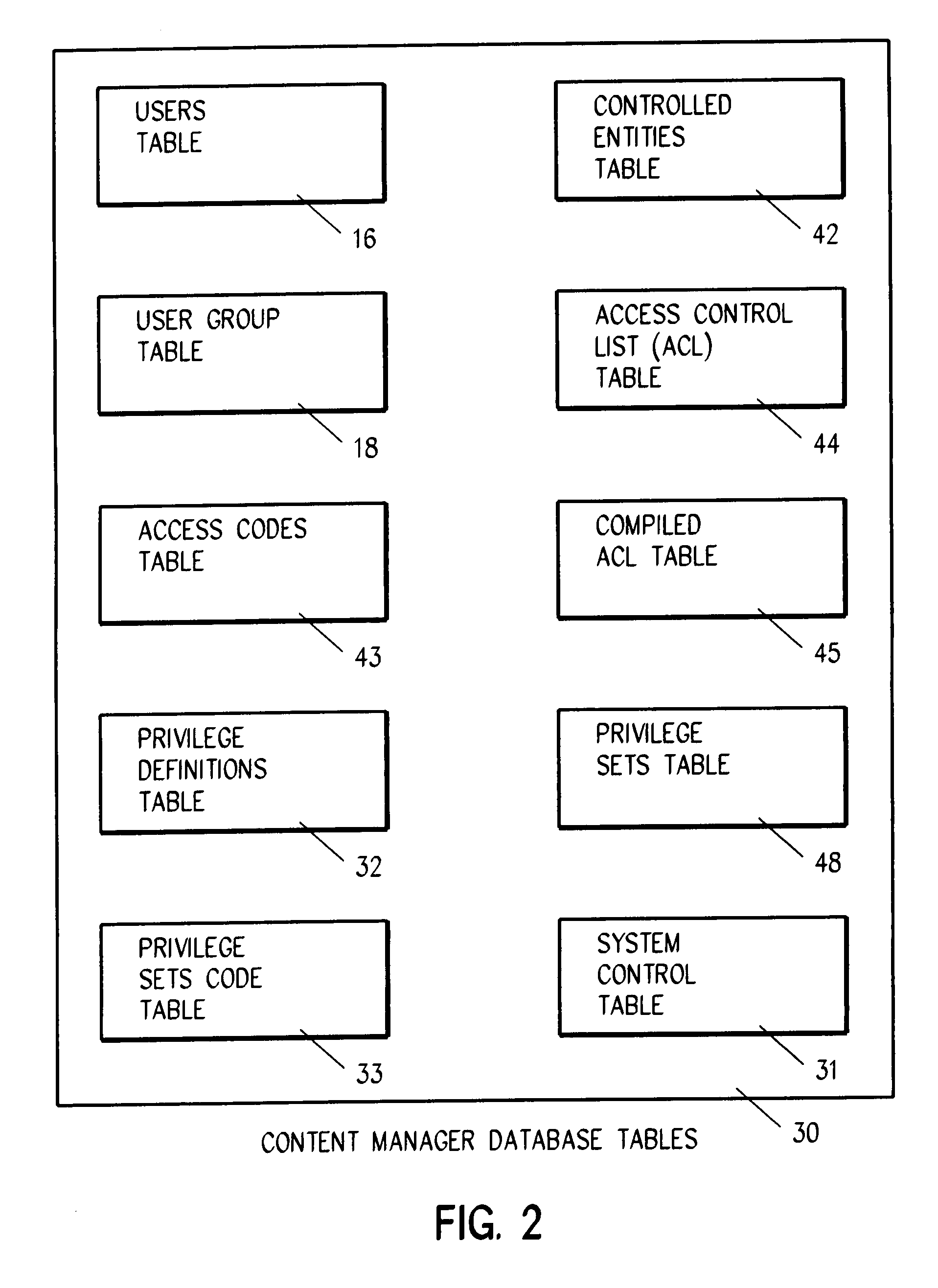
System and method for ensuring security with multiple authentication schemes
InactiveUS7308580B2Data processing applicationsDigital data processing detailsThird partyInternet privacy
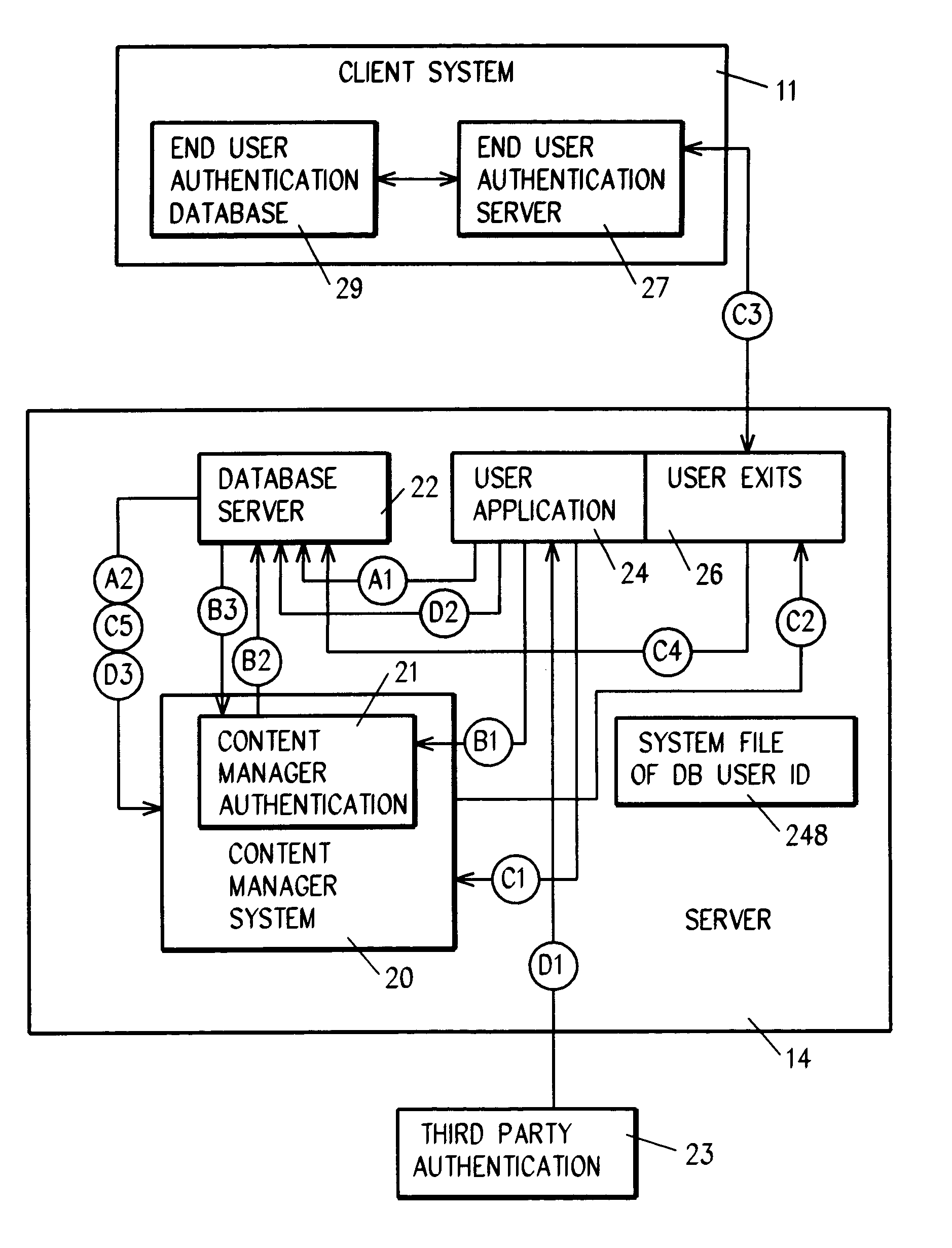
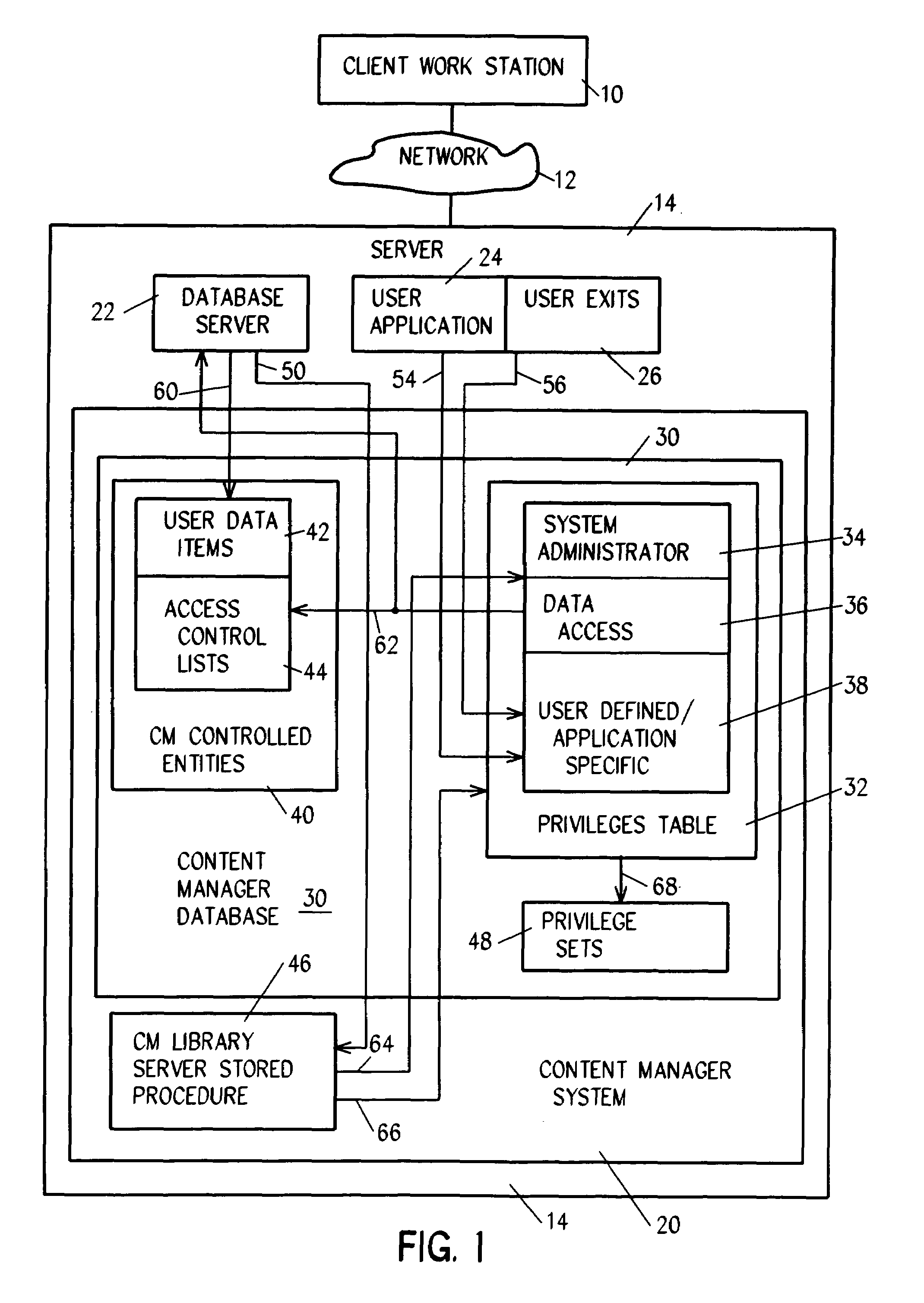
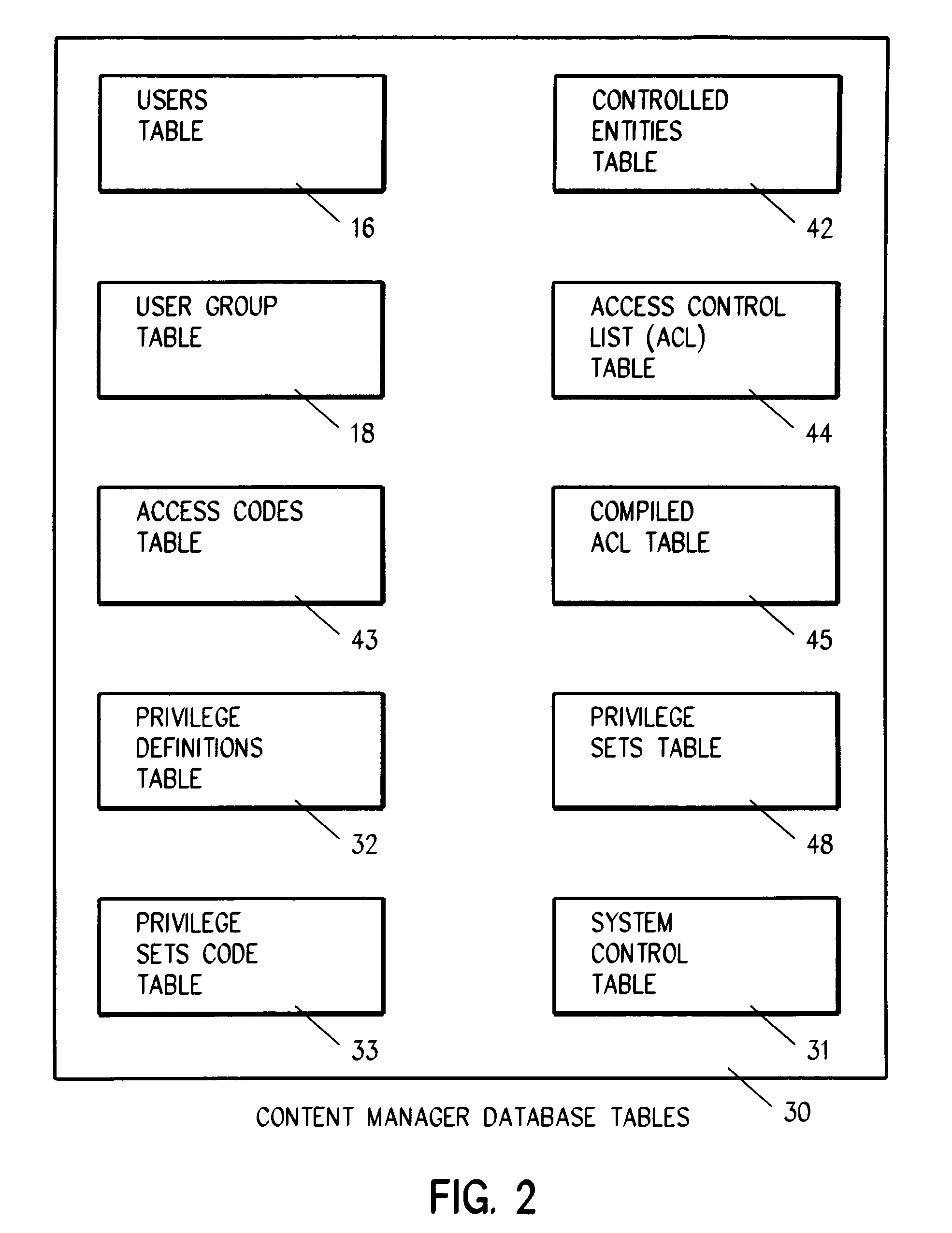
System for authenticating a user for logon to a content manager running on top of a database manager. A connect procedure connects the user to a database manager; and then a logon procedure logs on the user to the content manager selectively responsive to the user connecting to the database manager; the user being authenticated by a third party by way of a user exit or a trusted logon environment and privilege; or the user being authenticated by the content manager.
Owner:IBM CORP
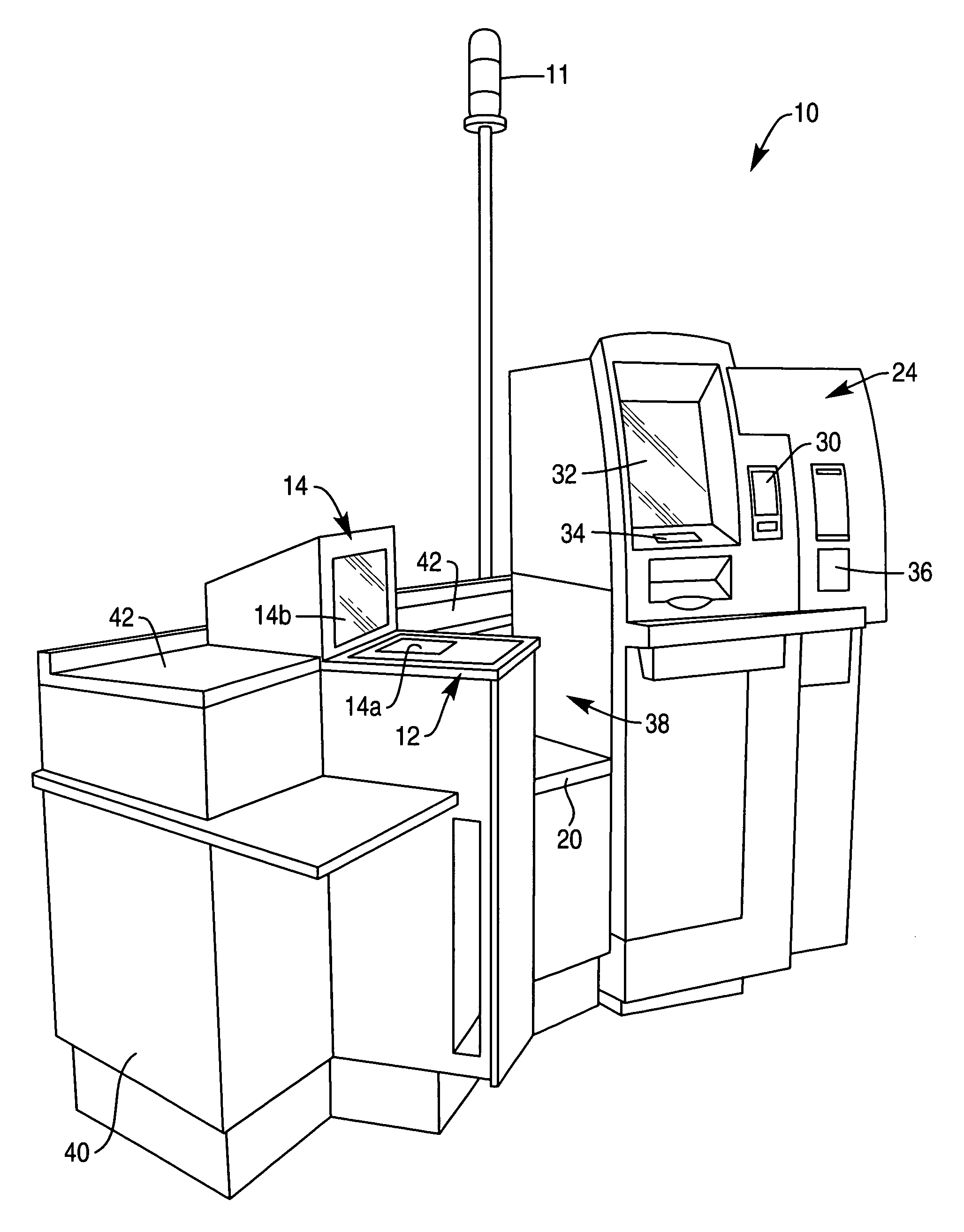
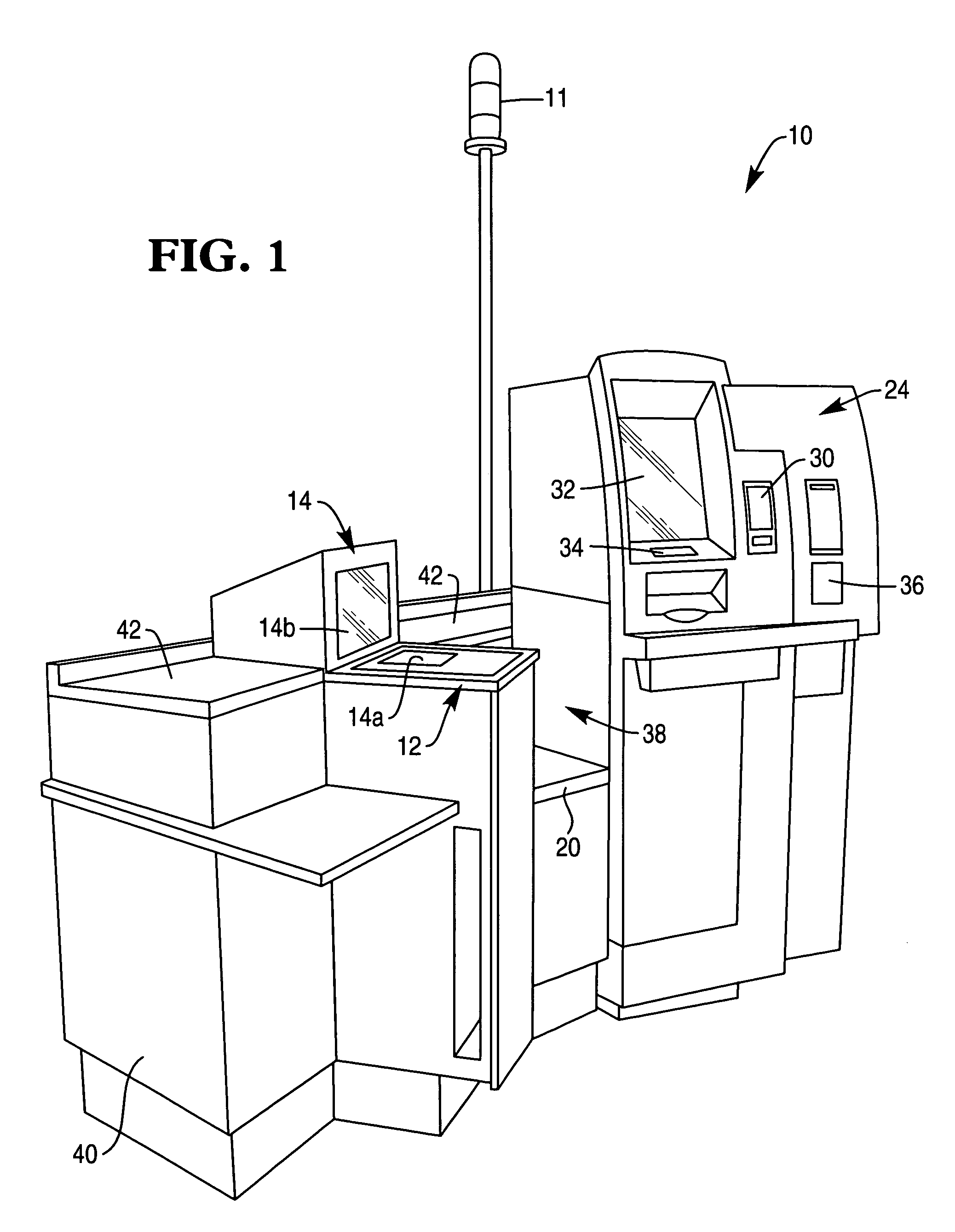
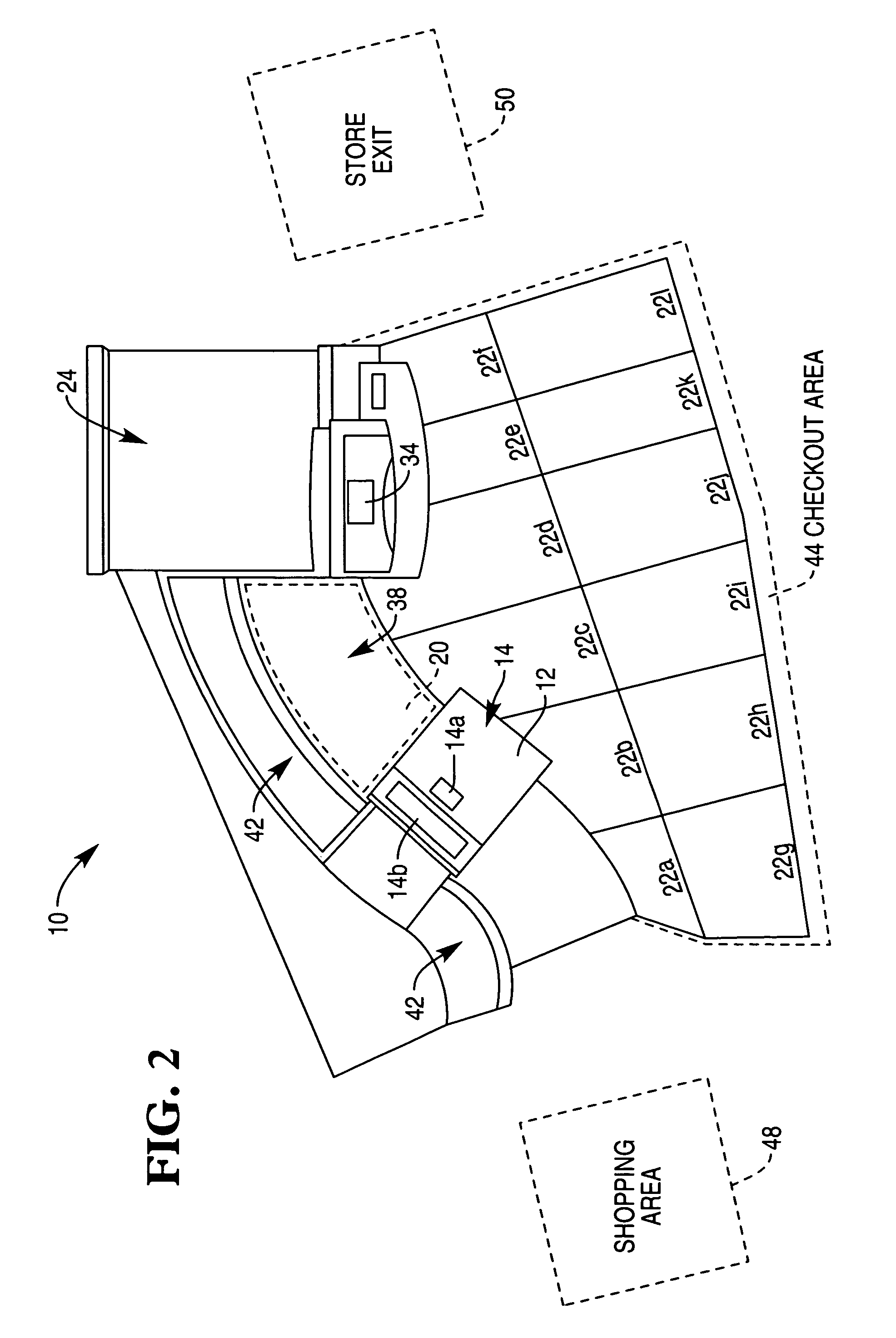
Method and apparatus for determining if a user walks away from a self-service checkout terminal during operation thereof
A method of operating a self-service checkout terminal located in a checkout area of a retail store includes the step of generating a payment-tendered control signal when a user of the self-service checkout terminal tenders payment for a number of items for purchase. The method also includes the step of detecting movement of the user on a movement detection floor mat and generating a walk-away control signal if the user exits the checkout area of the retail store. Moreover, the method includes the step of generating a personnel-request control signal if the walk-away control signal is generated prior to generation of the payment-tendered control signal. A self-service checkout terminal is also disclosed.
Owner:NCR CORP
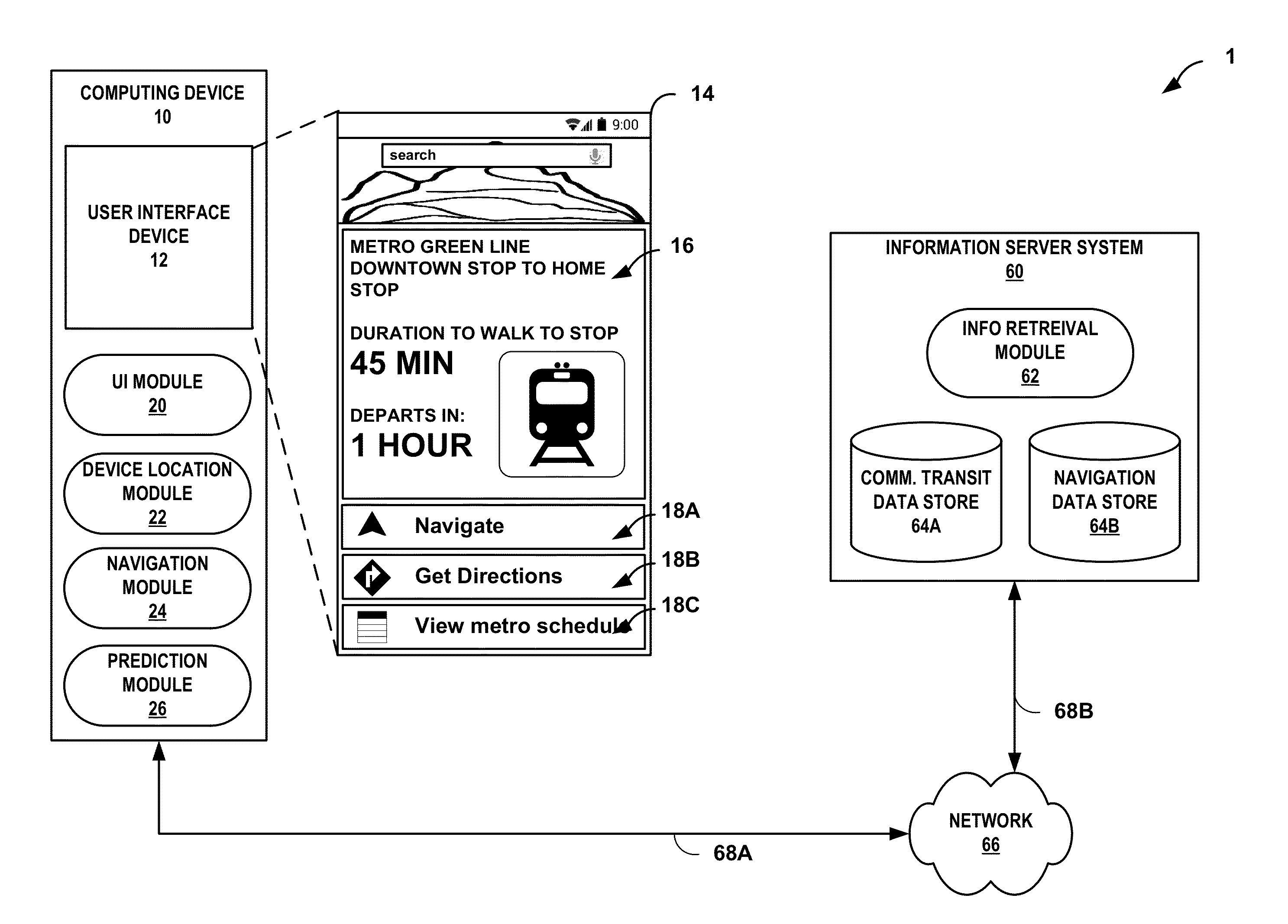
Predictive transit calculations
ActiveUS8738292B1Analogue computers for vehiclesInstruments for road network navigationUser exitReal-time computing
Owner:GOOGLE LLC
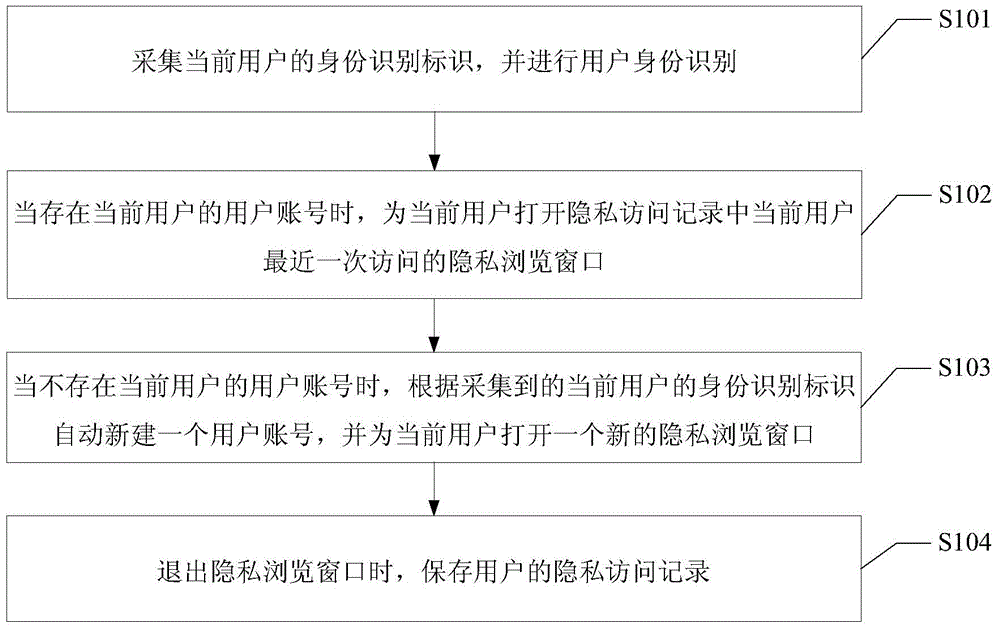
Method and device for providing InPrivate browsing
The invention discloses a method and a device for providing InPrivate browsing. The method comprises steps as follows: an identity recognition mark of a current user is acquired, and identity recognition of the user is performed; when a user account of the current user exists, an InPrivate browsing window, accessed last time by the current user, in InPrivate access records is opened for the current user; when the user account of the current user doesn't exist, a new user account is automatically created according to the acquired identity recognition mark of the current user, and a new InPrivate browsing window is opened for the current user; the InPrivate access records of the user are saved when the user exits from the InPrivate browsing window. By means of the technical scheme, privacies of all users can be effectively protected, accordingly, the users can directly open the corresponding InPrivate access records when accessing the records next time, and the use experience of the users is improved.
Owner:XIAOMI INC
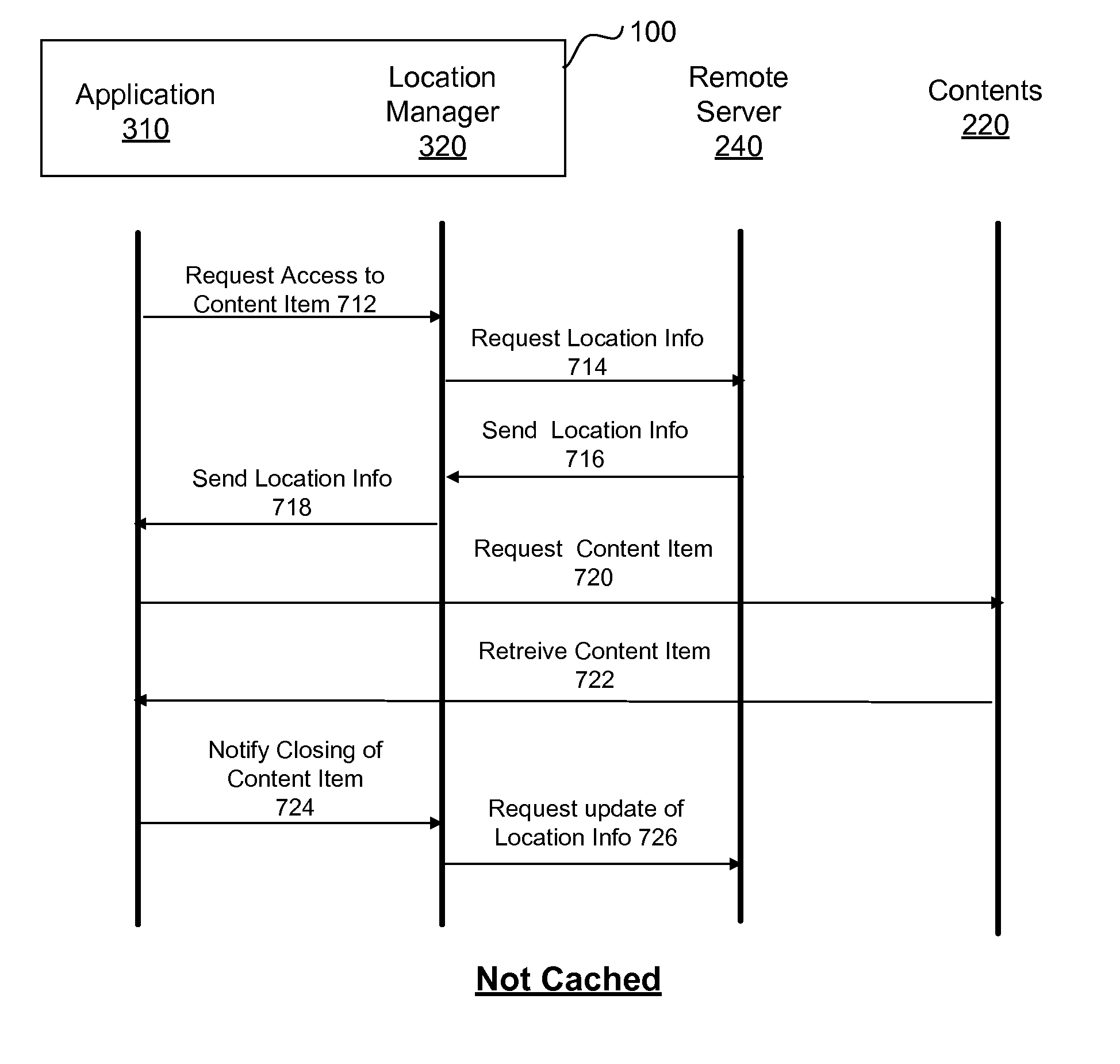
Preserving a user experience with content across multiple computing devices using location information
ActiveUS7870272B2Improve access speedAvoid confictMultimedia data retrievalMultiple digital computer combinationsSystem usageUser exit
A content management system stores location information indicating a location within a content item where a user exited from or last-accessed the content item. This location information is synchronized or otherwise shared between or among a plurality of devices associated with the user. With this information stored on or accessible to these multiple devices, the system enables the user to start from that location when subsequently accessing the content item on any of these devices. The user's experience with the content item is thus preserved over time and independently of the device on which the content item is accessed.
Owner:QUALCOMM INC
Minimizing message flow wait time for management user exits in a message broker application
InactiveUS20090070779A1Minimizing message flow wait timeProgram controlTransmissionMessage flowApplication software
A method for minimizing the message flow wait time for management user exits in a message broker application. A message broker application processes a request in a request and a response message flow. The request message flow generates a request identifier, collects information about the request message flow, and stores the request identifier and information in a global data map. The response message flow uses the request identifier to access the map and read the collected information without having to acquire a lock on the map. The response message flow also collects information about the response message flow, and generates management information about the request based on the information about the request message flow and the information about the response message flow. A dedicated clean up thread in the message broker application is used to remove used items from the global data map.
Owner:IBM CORP
Control method and device for game application
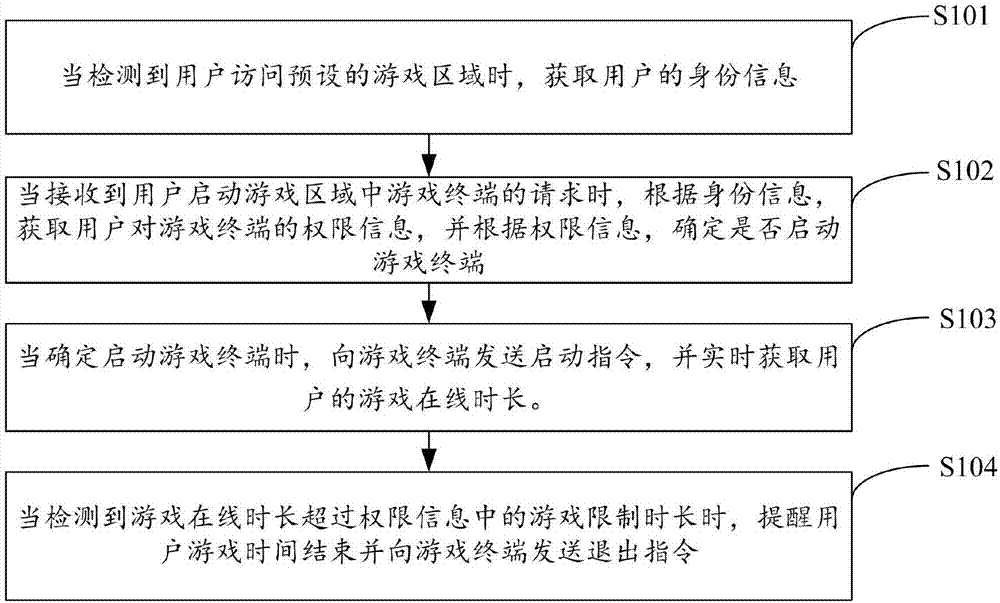
InactiveCN107137929AGood prevention effectImplement Differentiation LimitsVideo gamesComputers technologyUser exit
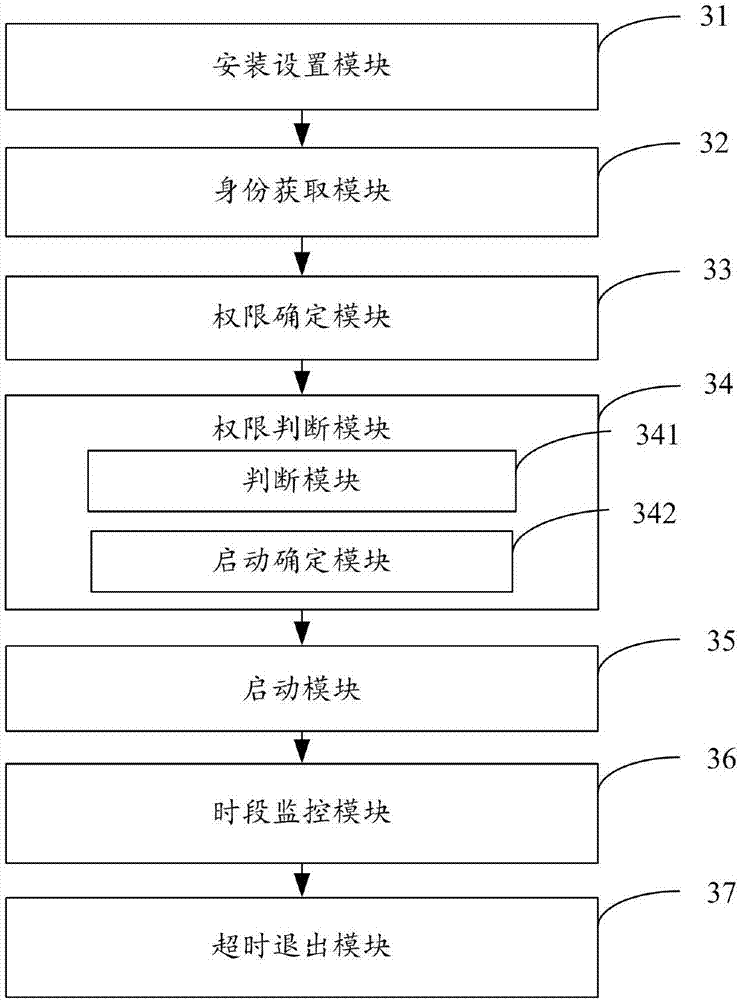
The invention is applicable to the field of computer technologies, and provides a control method and a control device for a game application. The method comprises the following steps: when detecting that a user visits a preset game area, acquiring the identity information of the user, when receiving the request that the user starts the game application in the game area, according to the identity information, acquiring the authority information for the game application of the user, according to the authority information, determining that whether the game application needs to be started or not, when determining that the game application needs to be started, starting the game application, acquiring the game on-line duration of the user in real time, when detecting that the game on-line duration exceeds the preset game limited duration, reminding the user that the game time ends so that the user exits the game application, therefore, differentiated limiting is carried out on playing of the game application of different users, and the effect of preventing addiction to games is effectively improved.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
Order optimization in hybrid cloud networks
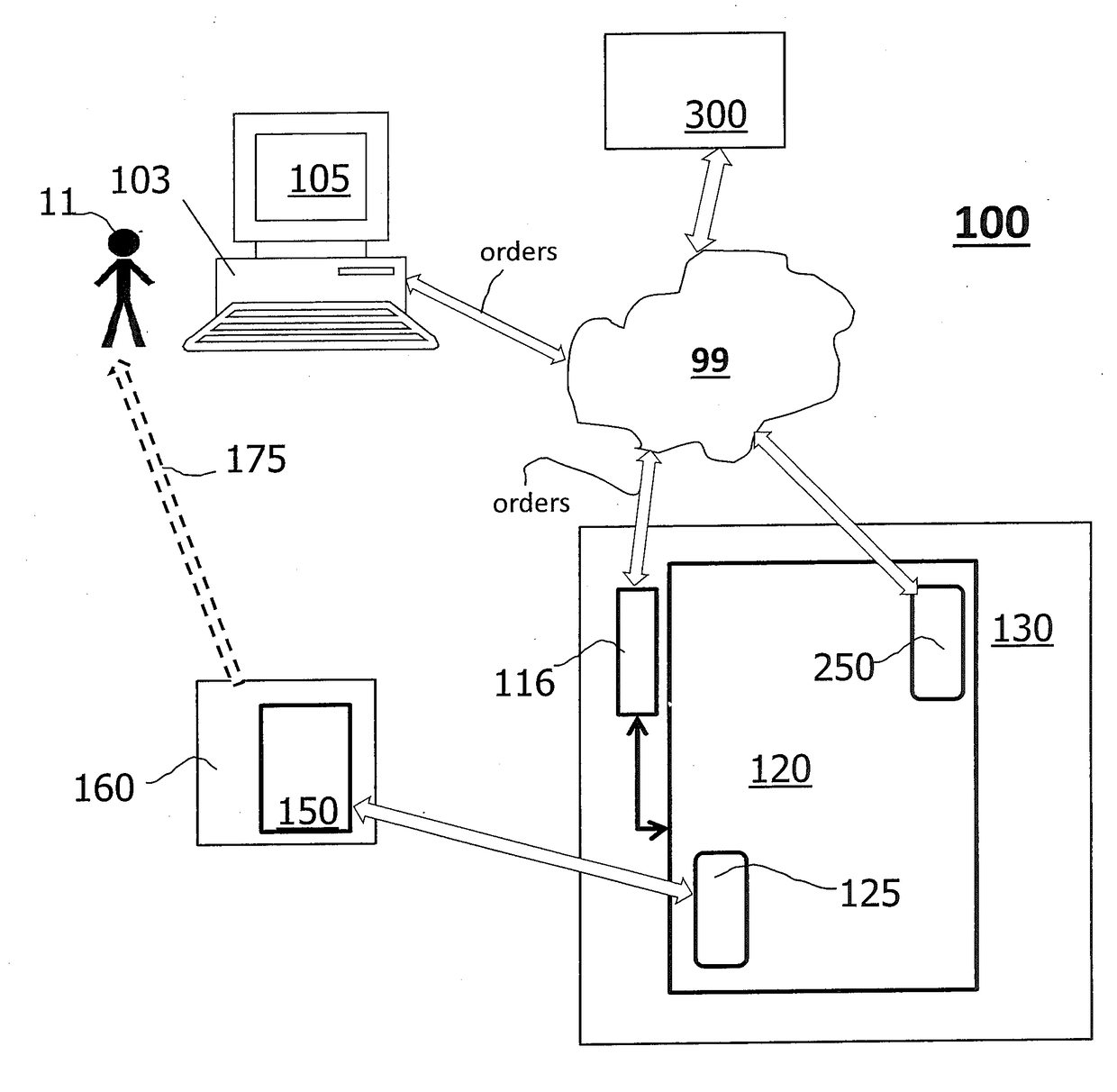
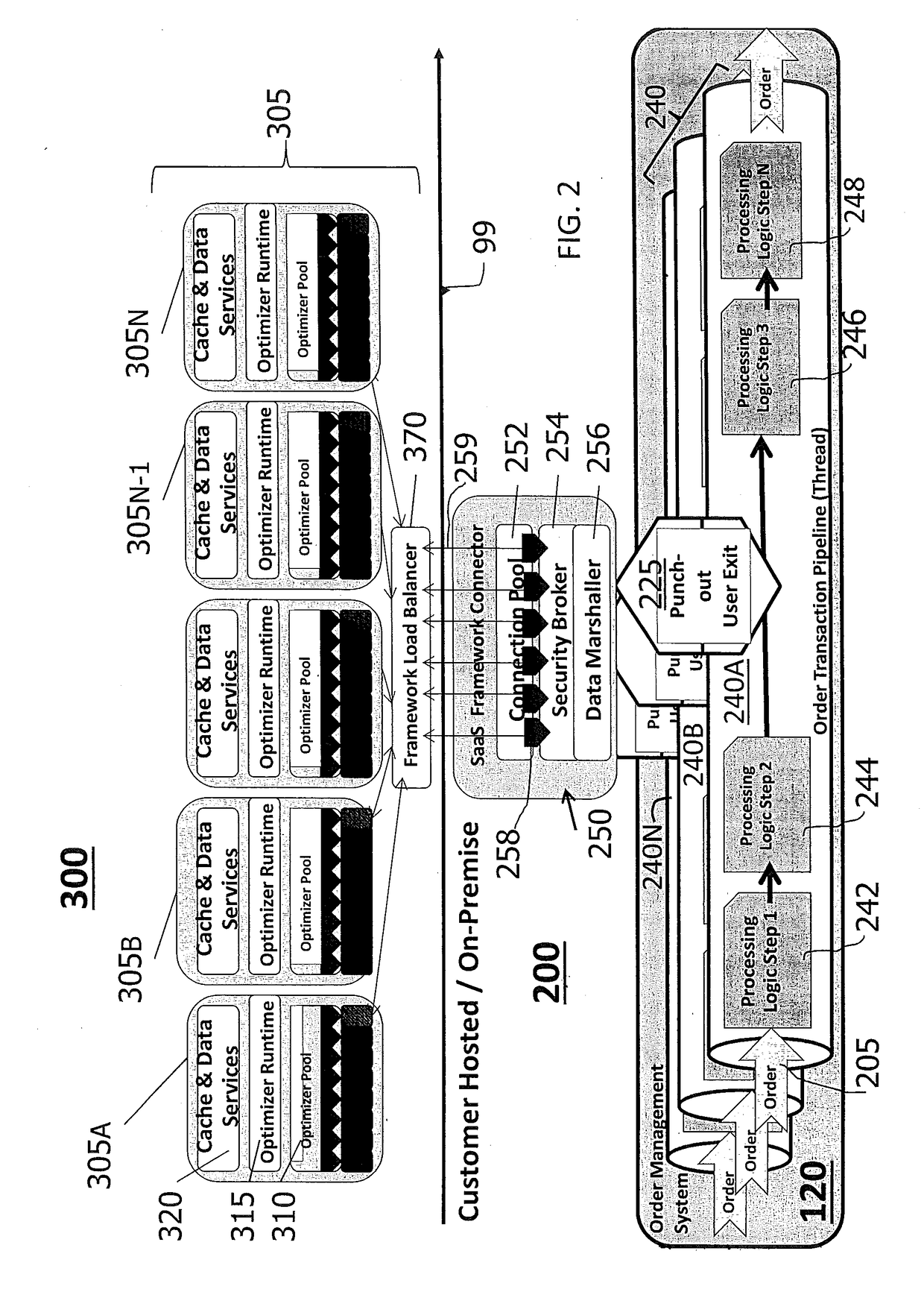
A system, method and computer program product for enhancing on-premise order management systems (OMS) designed for fulfillment transactions with analytic and optimization technologies and services hosted in a shared multi-tenant software-as-a-service (SaaS) environment, such as a hybrid cloud. The computer-implemented method improves an order management system by leveraging a “punch-out” approach based on user exits to integrate with and augment currently implemented order management processing and transaction flows. Using the hybrid cloud, an entity may retain data such as its accumulated business, sales, test and other data, and then run analytical queries, which can scale to support distributed computing tasks. A framework adaptor / connector is leveraged by the OMS to provide a web client for communicating with and integrating to the SaaS analytics runtime environment, encapsulating all necessary connection pooling, security, and data marshaling complexity away from the order management system to meet strict service response time windows.
Owner:DOORDASH INC
Efficient anonymous authentication method and system suitable for alliance chain and capable of supporting identity traceability
ActiveCN110149304APrivacy protectionImplement identity revocationUser identity/authority verificationThird partyUser needs
The invention relates to an efficient anonymous authentication method and system suitable for an alliance chain and capable of supporting identity traceability. According to the method, an anonymous authentication technology is utilized to grant a corresponding key to a legal user, so that the user can generate a certificate for authentication in an interaction process, and identity authenticationis successful if the authentication is passed; the anonymous authentication technology is constructed based on the group signature technology, so that the privacy of the user identity can be protected while the identity traceability is supported. The key granted to the user is divided into two components: an anonymous key and a time component. And when the user exits, only the time component which does not exit the user needs to be updated, and identity revocation of the user can be realized. According to the method, authentication can be achieved without depending on a third party, privacy of a user can be protected in the authentication process, the identity of the user can be exposed when disputes occur, traceability can be achieved, and dynamic joining and exiting of alliance membersand members in an organization can be efficiently achieved after system initialization.
Owner:INST OF INFORMATION ENG CAS
System and method for program execution
InactiveUS20050223356A1Digital data authenticationSpecific program execution arrangementsClient-sideUser exit
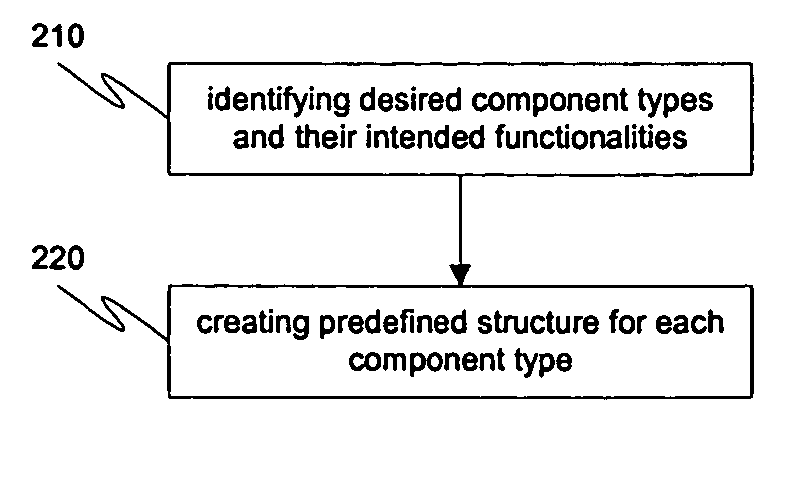
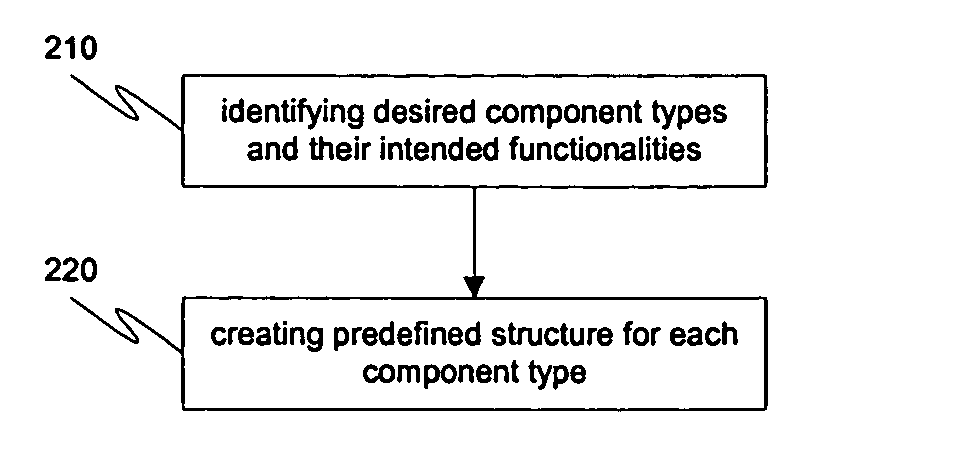
The invention pertains to a method and system that uses similar functionalities of different components within a software application when executing the application and application components. In one embodiment, predefined structures are created for a component type, where each component type has a similar functionality when executed. Parameter information is received at a client and linked with the predefined to provide a script specific predefined structure. The component is executed by executing the script specific predefined structure. After a user exits the component, the script specific predefined structure is automatically deleted.
Owner:VAAKYA TECH PRIVATE
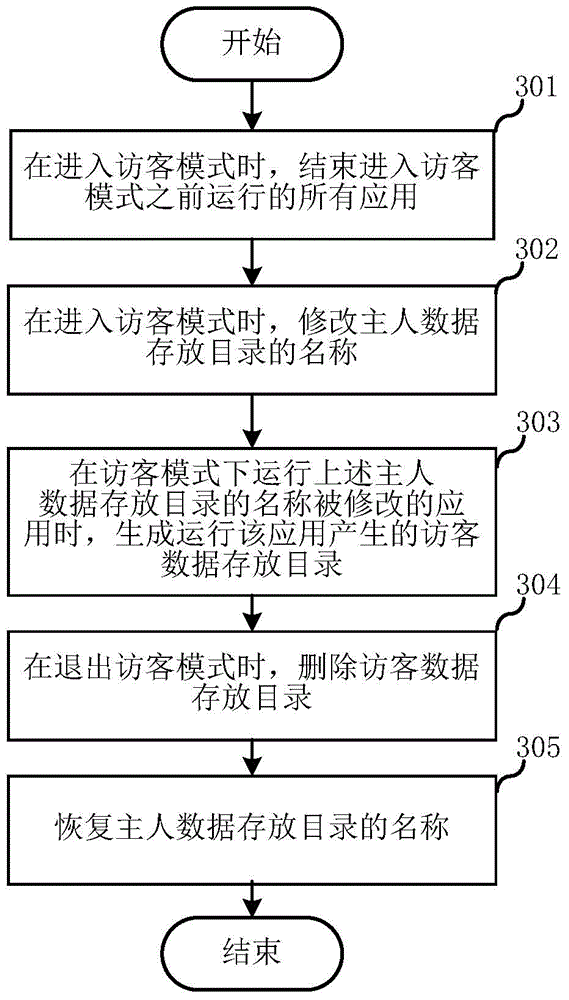
Method and system for isolating applications through data
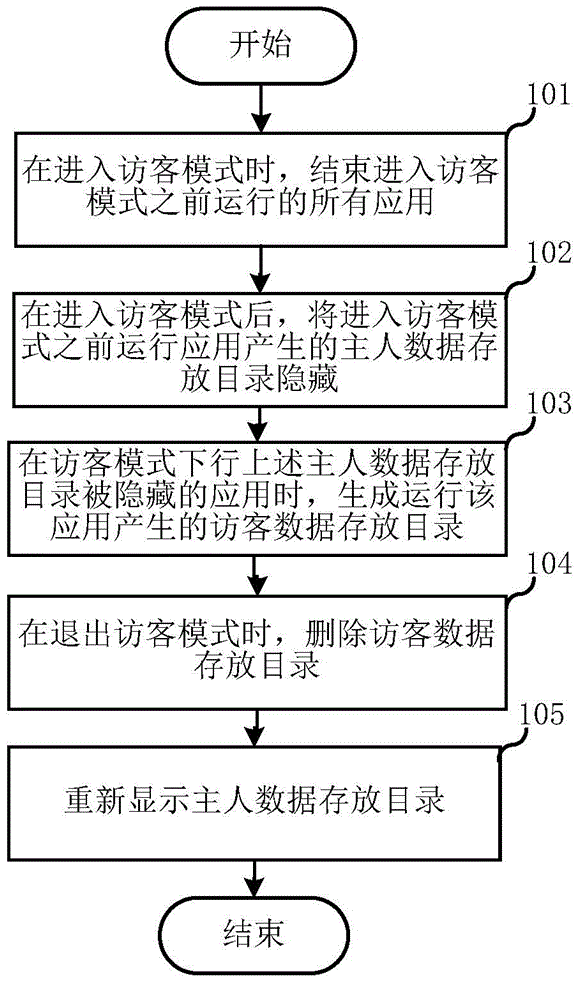
The invention relates to the field of communications and discloses a method and system for isolating applications through data. The method includes the following steps that when a user enters a visitor mode, all the applications running before the user enters the visitor mode are ended; after the user enters the visitor mode, a directory for storing host data generated in the application running process before the user enters the visitor mode is hidden; when the hidden applications of the directory for storing host data are run in the visitor mode, a directory for storing visitor data generated by running the applications is generated; before the user exits the visitor mode, the directory for storing visitor data is deleted; the directory for storing host data is displayed again. Compared with the prior art, not only does a terminal reserve data used when the applications are run by a terminal host, but also the privacy of the terminal host can be effectively protected.
Owner:SHANGHAI ZHUO YOU NETWORK TECH
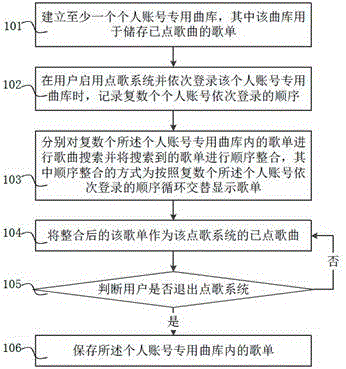
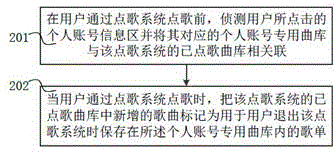
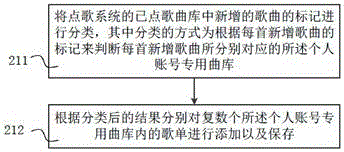
Method and system for associating karaoke song menu with personal account
ActiveCN104820689AEasy to viewEasy to manageSpecial data processing applicationsPersonal accountUser exit
The invention relates to a method and a system for associating a karaoke song menu with a personal account. The method comprises the steps of establishing at least one personal account private song library, wherein the song library is used for storing a song menu of requested songs; when a user exits from a song request system, storing the song menu in the personal account private song library; when the user starts the song request system and sequentially logs in the personal account private song libraries, recording the login sequence of a plurality of personal accounts; performing song searching on the song menu of each of the plurality of personal account private song libraries, and performing sequence integration on the searched song menus, wherein the manner of sequence integration is to display the song menu alternately and circularly according to the login sequence of the plurality of personal accounts; and taking the integrated song menu as requested songs of the song request system. The method can effectively solve the problem in the prior art that song request is inconvenient when multiple people sing in the KTV.
Owner:王桂英
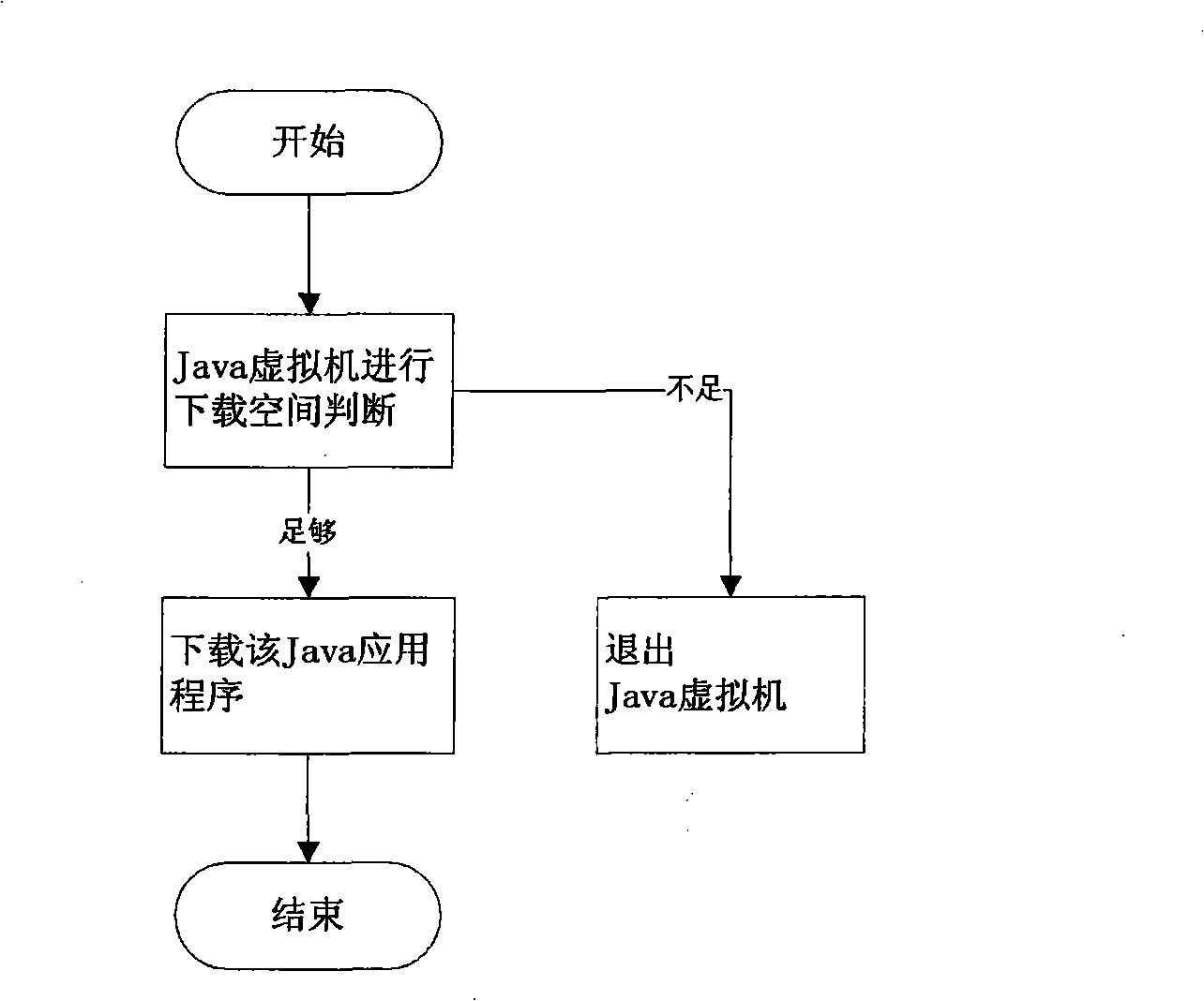
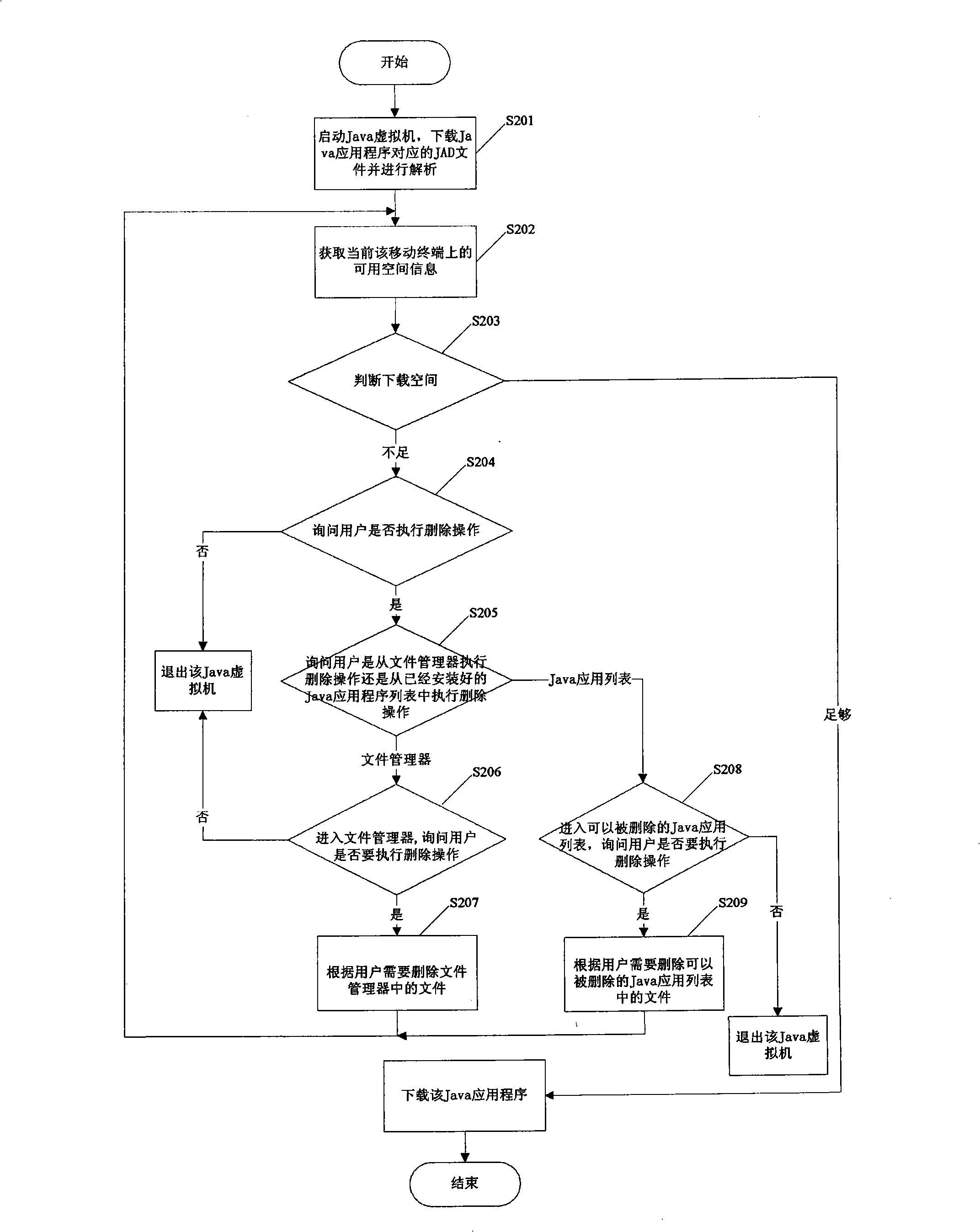
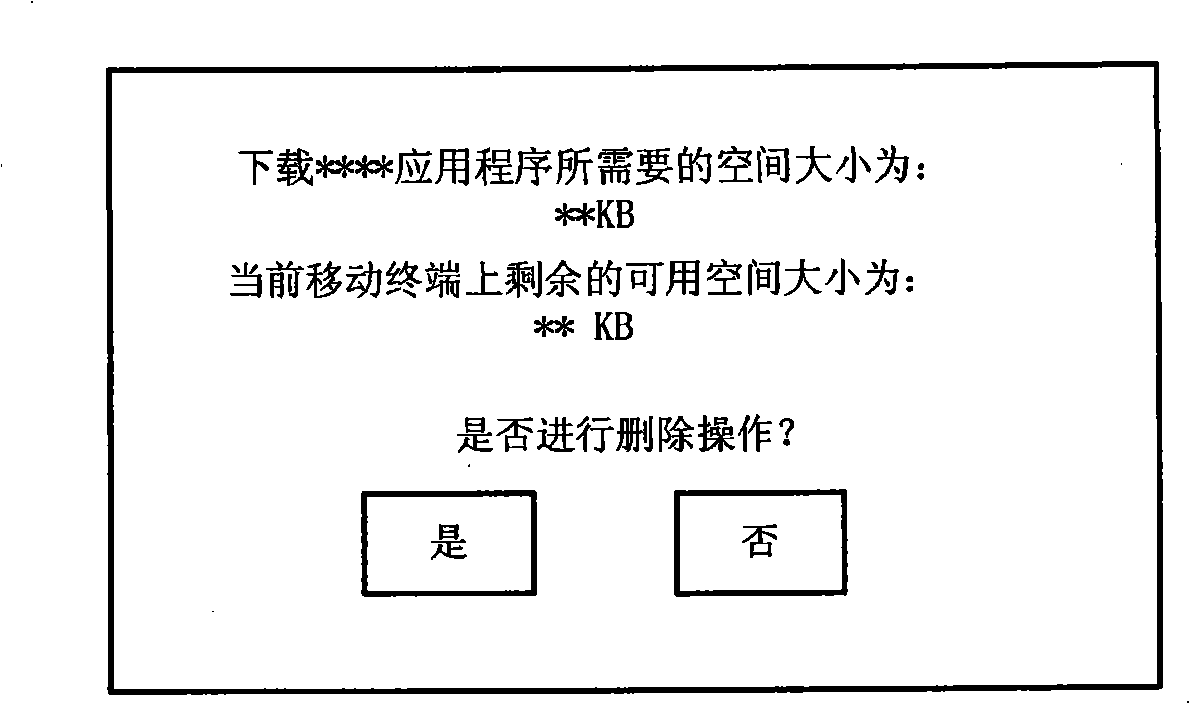
Method for supporting Java application download spacing detection
InactiveCN101321353AIncrease success rateAdd supportRadio/inductive link selection arrangementsProgram loading/initiatingApplication softwareUser exit
The invention provides a method that supports Java application download space detection: when downloading a Java application software, if a Java virtual machine detects low Java application download space, the Java virtual machine prompts a user to execute delete operation; if the user chooses not to execute the delete operation, the user exits the Java virtual machine; if the user chooses to execute the delete operation, download space is detected again after completing the delete operation every time; when detecting that the download space is enough, the Java virtual machine downloads the Java application software, and then the Java virtual machine quits. When the Java application download space is low, the method is capable of effectively guiding a user to obtain the space for downloading.
Owner:OX MOBILE TECH LLC
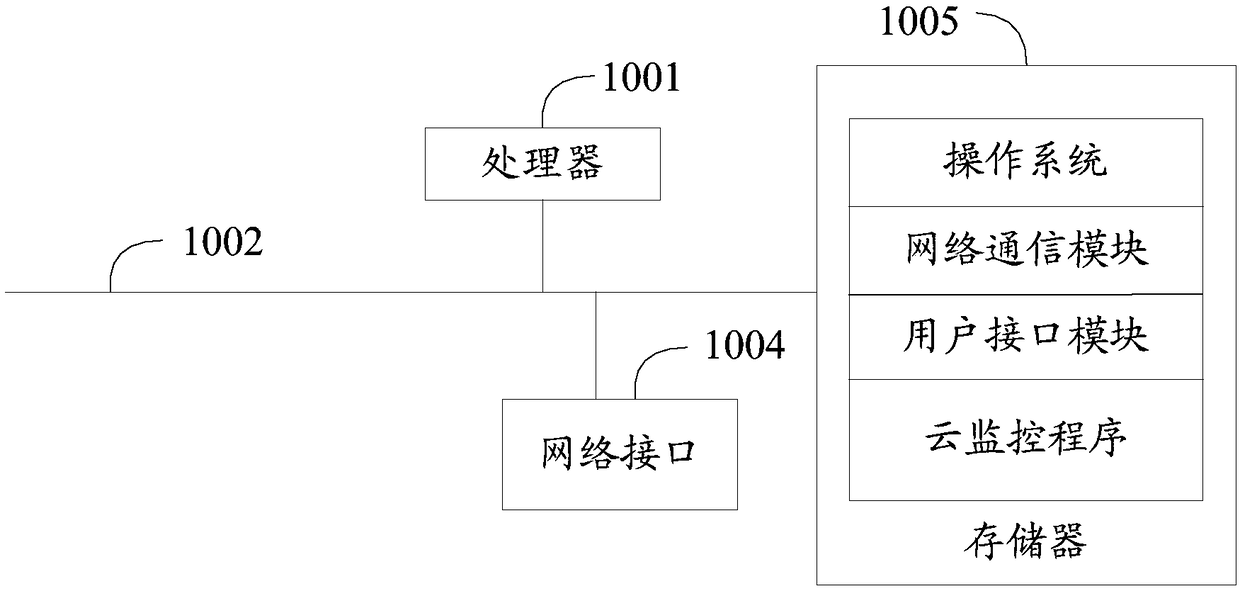
Cloud monitoring method, cloud server and computer-readable storage medium
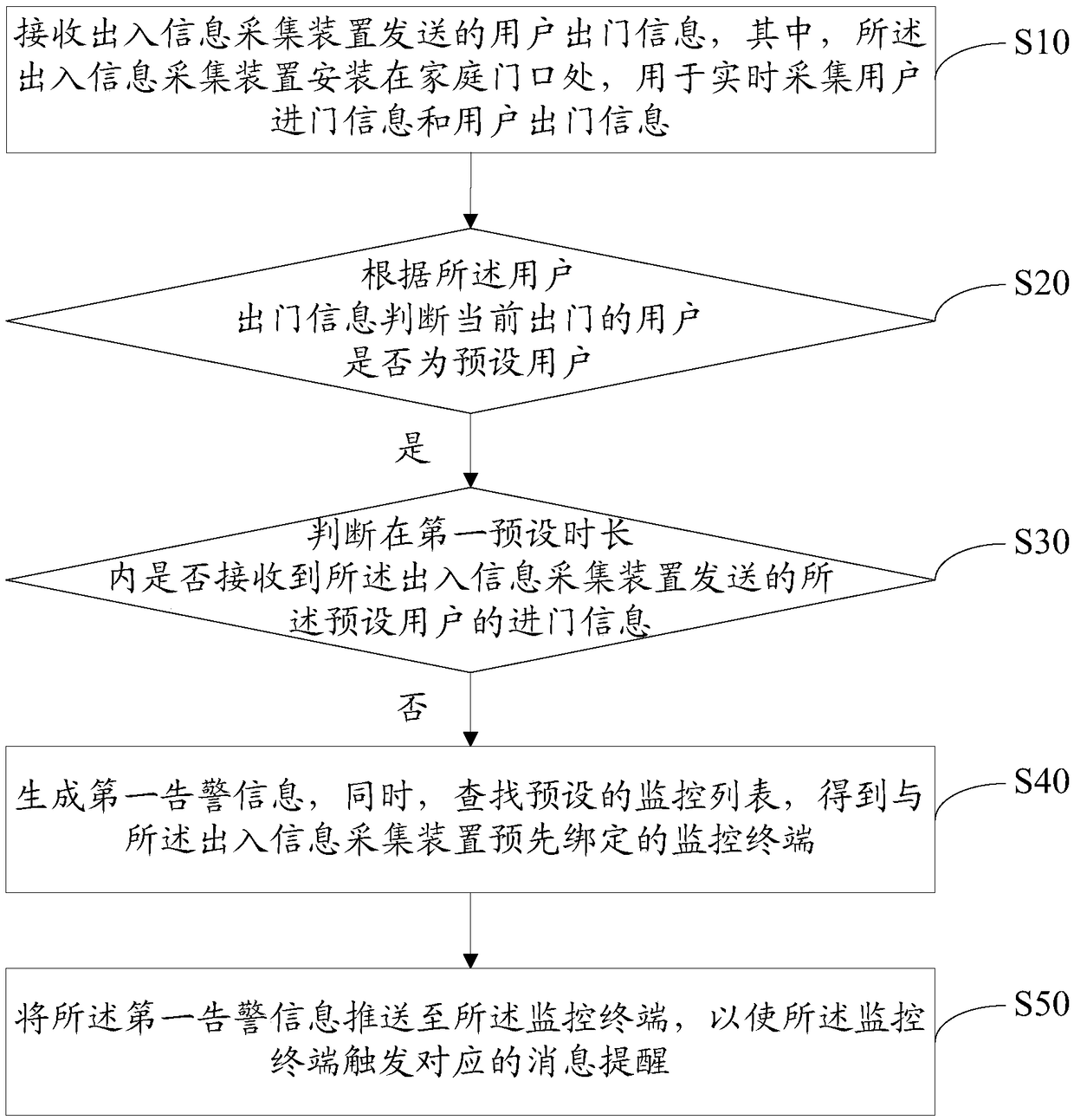
InactiveCN108696723AMonitor travelImprove securityCharacter and pattern recognitionClosed circuit television systemsReal time acquisitionUser exit
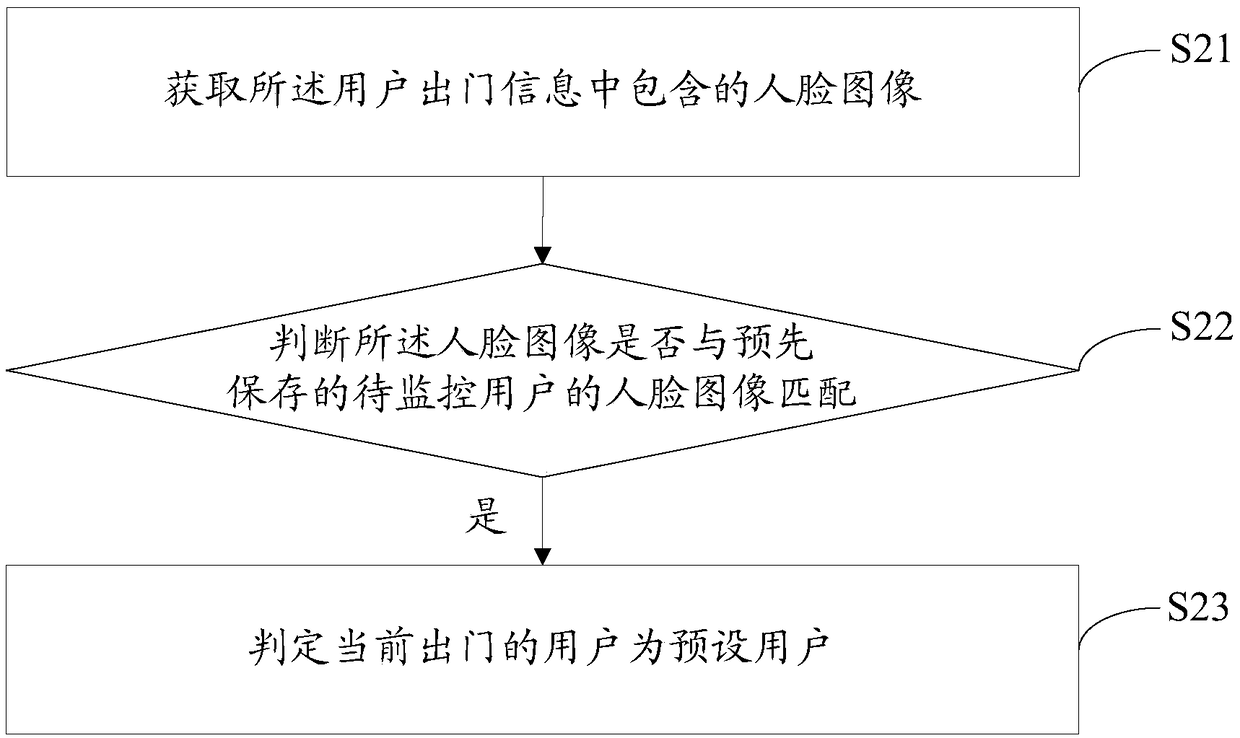
The invention discloses a cloud monitoring method. The method comprises the steps of: receiving user exit information sent by an exit and entry information acquisition device, wherein the exit and entry information acquisition device is installed at a family gate, and used for acquiring user entry information and user exit information in real time; judging whether the current exit user is a pre-set user or not according to the user exit information; if so, judging whether the entry information of the pre-set user sent by the exit and entry information acquisition device is received or not within the first pre-set time; if not, generating first alarm information, and simultaneously, searching a pre-set monitoring list to obtain a monitoring terminal bound with the exit and entry informationacquisition device in advance; and pushing the first alarm information to the monitoring terminal, so that the monitoring terminal triggers corresponding message reminding. The invention further discloses a cloud server and a computer-readable storage medium. By means of the cloud monitoring method, the cloud server and the computer-readable storage medium disclosed by the invention, the travel situation of family members can be monitored; and thus, the family monitoring security is improved.
Owner:SHENZHEN LINGDU INTELLIGENT CONTROL TECH CO LTD
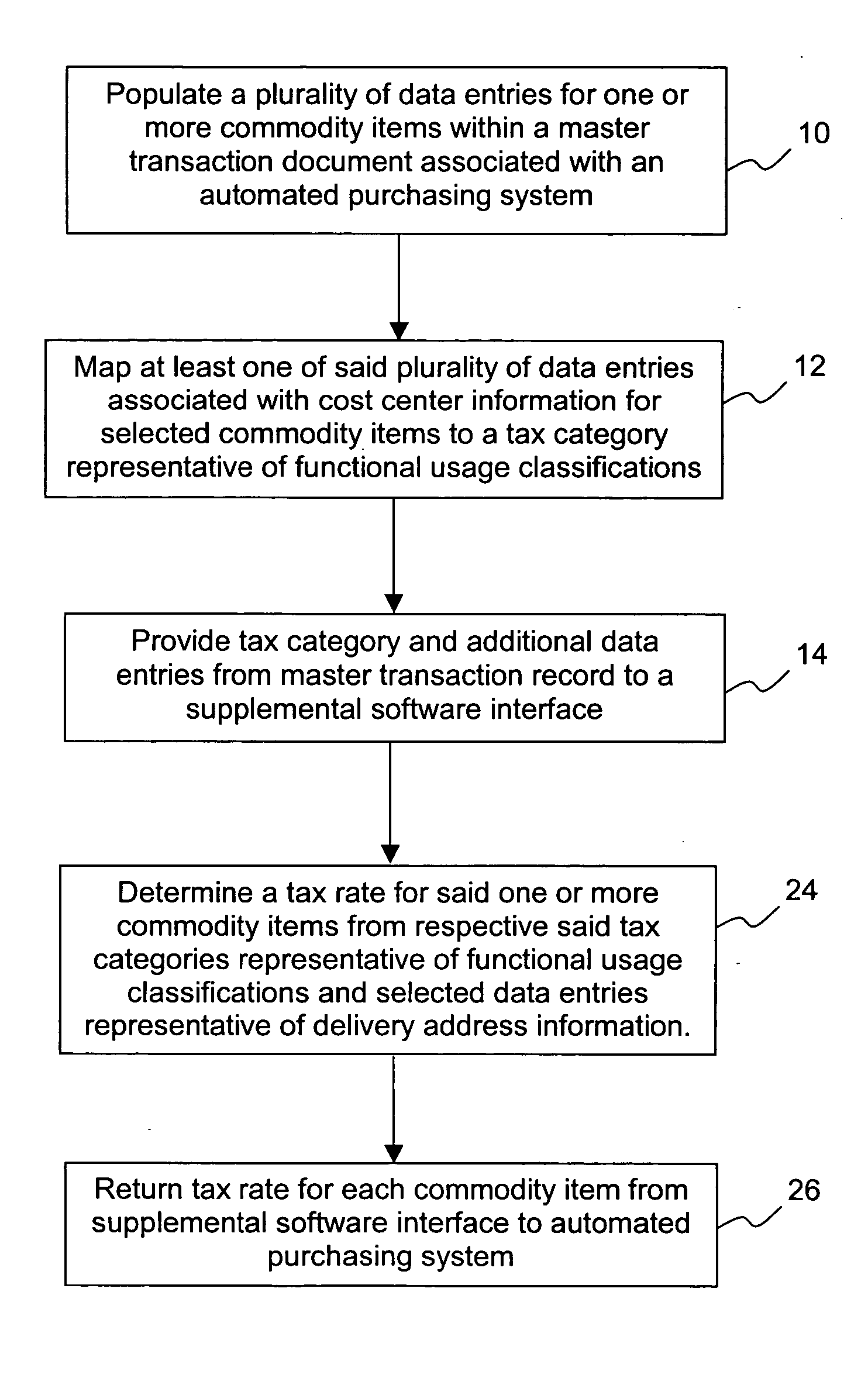
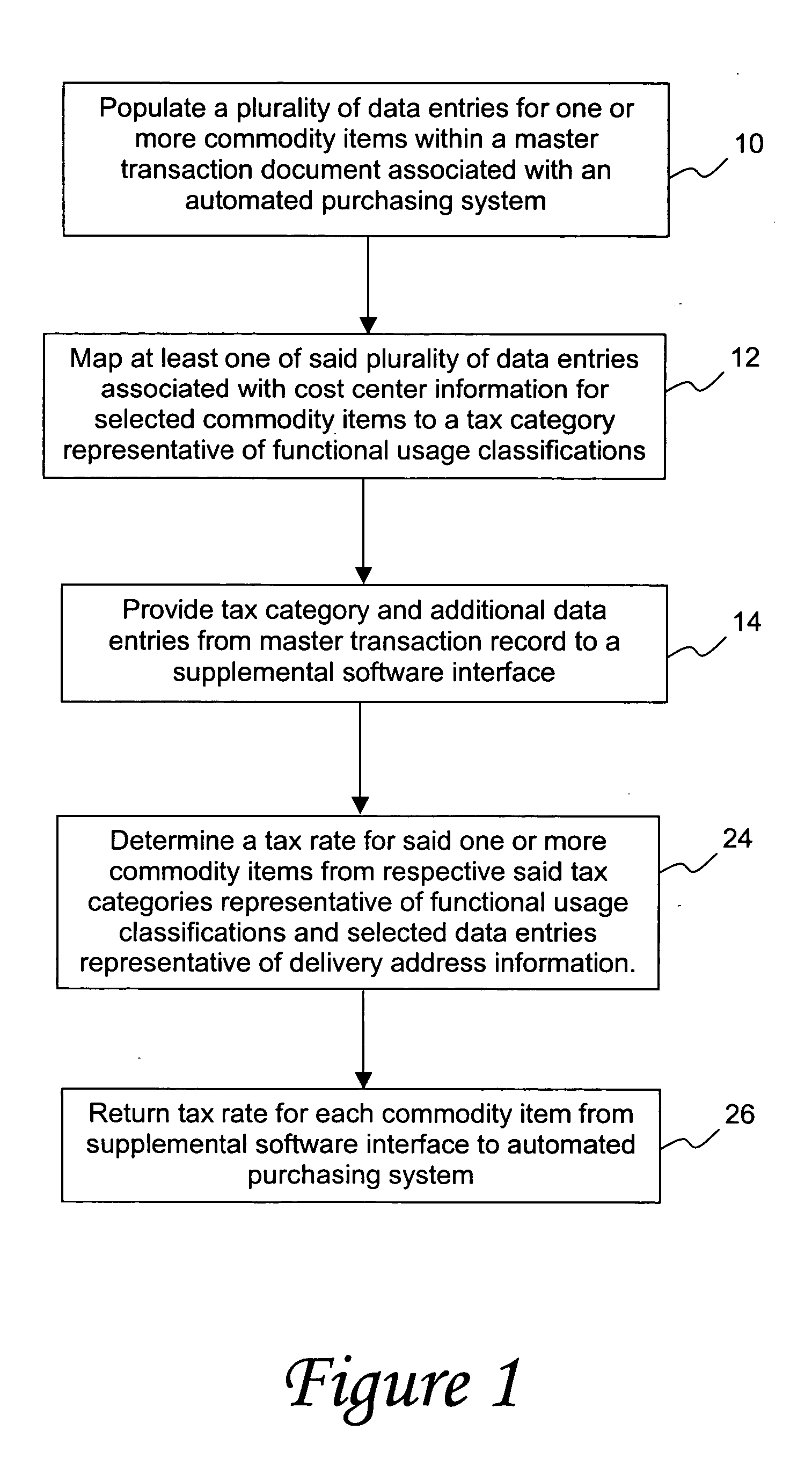
Method for determining sales tax in automated purchasing systems
A method for determining sales tax in an automated purchasing system includes the steps of populating data entries in a master transaction record for one or more commodity items. Exemplary populated data entries include material group, cost center code and delivery address. Data corresponding to cost centers are mapped to tax categories representative of abridged functional use classifications. The tax category, material group, and physical location information determined either from the delivery address or from the cost center code are provided from the automated purchasing system to a supplemental software interface. Such data availability is enabled by various combination of user exits, data tables, and importation from temporary memory associated with the automated purchasing system. A tax rate (e.g., state, county, city and / or district tax) is then determined for each commodity item based on the tax categories representative of various functional use information and selected data representative of physical location. Such tax rates may then be returned from the supplemental software interface to the automated purchasing system.
Owner:ZITI TECH LIABILITY
Method, apparatus and system for automatically exiting instant messaging session group
ActiveCN108734186ASimplify the execution of ungroup operationsTechnical effects that enhance the experienceCharacter and pattern recognitionData switching networksUser exitInstant messaging
The invention discloses a method, apparatus and system for automatically exiting an instant messaging session group. The method comprises the following steps: traversing at least one session group, and obtaining a user behavior feature of each user included in the session group; obtaining a probability that each user exits the session group according to the user behavior feature of each user contained in the session group; and determining whether to output a prompt message of exiting the session group according to the probability of exiting the session group. By adoption of the method, apparatus and system disclosed by the invention, the technical problem that the group exiting operation of the existing instant messaging tool is cumbersome to affect the user experience is solved.
Owner:ALIBABA GRP HLDG LTD
System and method for program execution
InactiveUS7685230B2Multiple digital computer combinationsDigital data authenticationClient-sideUser exit
The invention pertains to a method and system that uses similar functionalities of different components within a software application when executing the application and application components. In one embodiment, predefined structures are created for a component type, where each component type has a similar functionality when executed. Parameter information is received at a client and linked with the predefined to provide a script specific predefined structure. The component is executed by executing the script specific predefined structure. After a user exits the component, the script specific predefined structure is automatically deleted.
Owner:VAAKYA TECHNOLOGIES PRIVATE LIMITED
Play control method of video preview information, application client and electronic equipment
ActiveCN109462779AImprove experienceImprove controllabilitySelective content distributionInput/output processes for data processingComputer graphics (images)Client-side
The invention provides a play control method of a video preview information, an application client and electronic equipment. The play control method is applied to the technical field of the video, andcomprises the following steps: determining sliding track information corresponding to a touch operation when detecting the touch operation on a display screen by a user, and then determining play control information corresponding to at least one video preview information in the display screen based on the sliding track information, and playing the corresponding video preview information based onthe play control information. Through the play control method provided by the invention, the user can browse video preview information corresponding to at least one video before clicking to watch thecorresponding video, and then understand more content of the corresponding video, and then determine the interested video to click and watch; the operation that the user exits when discovering that the video is uninterested after clicking to watch the corresponding video is avoided; furthermore, the play control is performed on the corresponding video preview information according to the sliding track information in the display screen by the user, and the user controllability on the pre-display of the video content is improved.
Owner:BEIJING MICROLIVE VISION TECH CO LTD
System and method for ensuring security with multiple authentication schemes
InactiveUS20080307520A1Data processing applicationsDigital data processing detailsThird partyInternet privacy
System for authenticating a user for logon to a content manager running on top of a database manager. A connect procedure connects the user to a database manager; and then a logon procedure logs on the user to the content manager selectively responsive to the user connecting to the database manager; the user being authenticated by a third party by way of a user exit or a trusted logon environment and privilege; or the user being authenticated by the content manager.
Owner:INT BUSINESS MASCH CORP
Application abnormal exit handling method and device
PendingCN111221671AReduce stepsImprove user experienceHardware monitoringNon-redundant fault processingApplication procedureUser exit
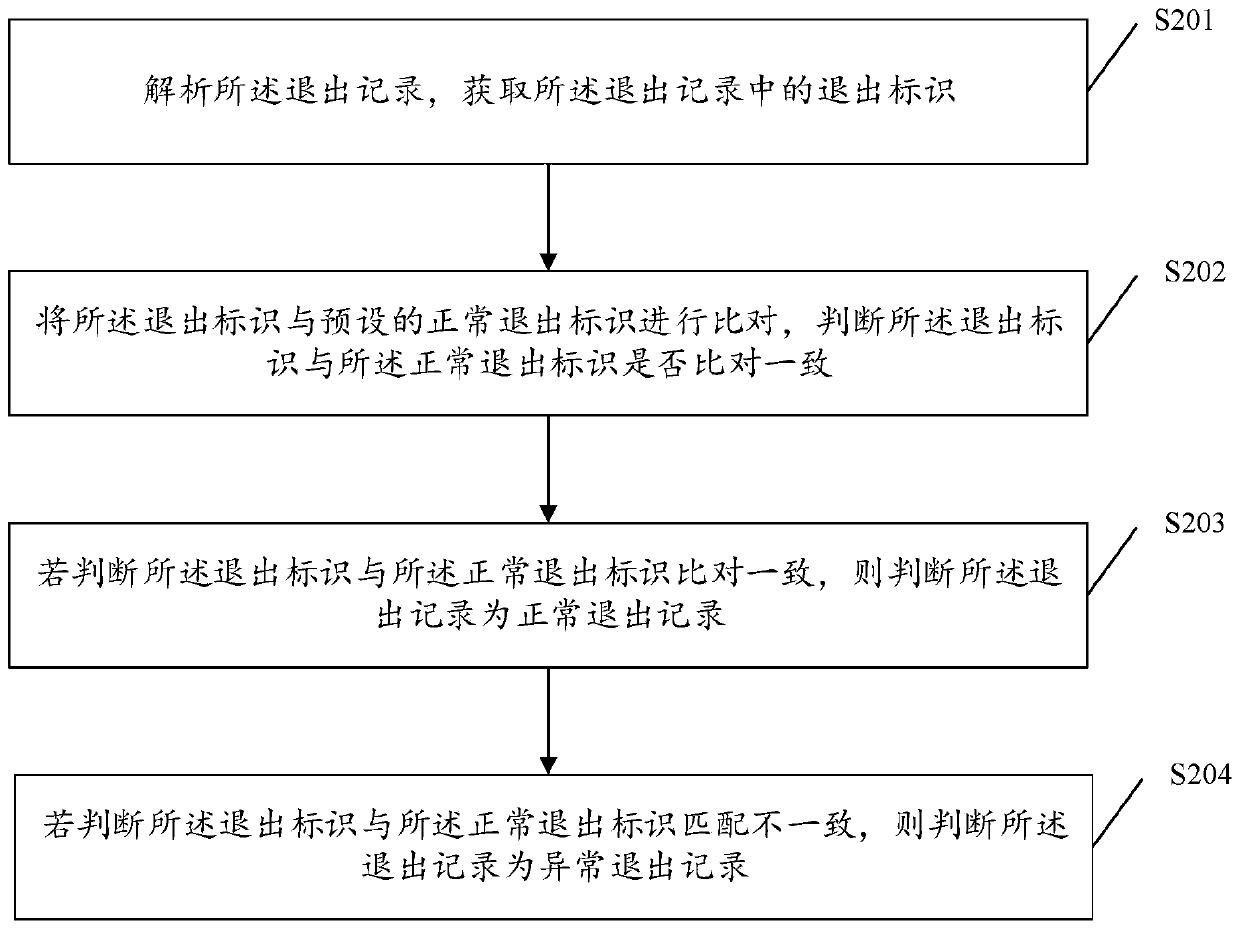
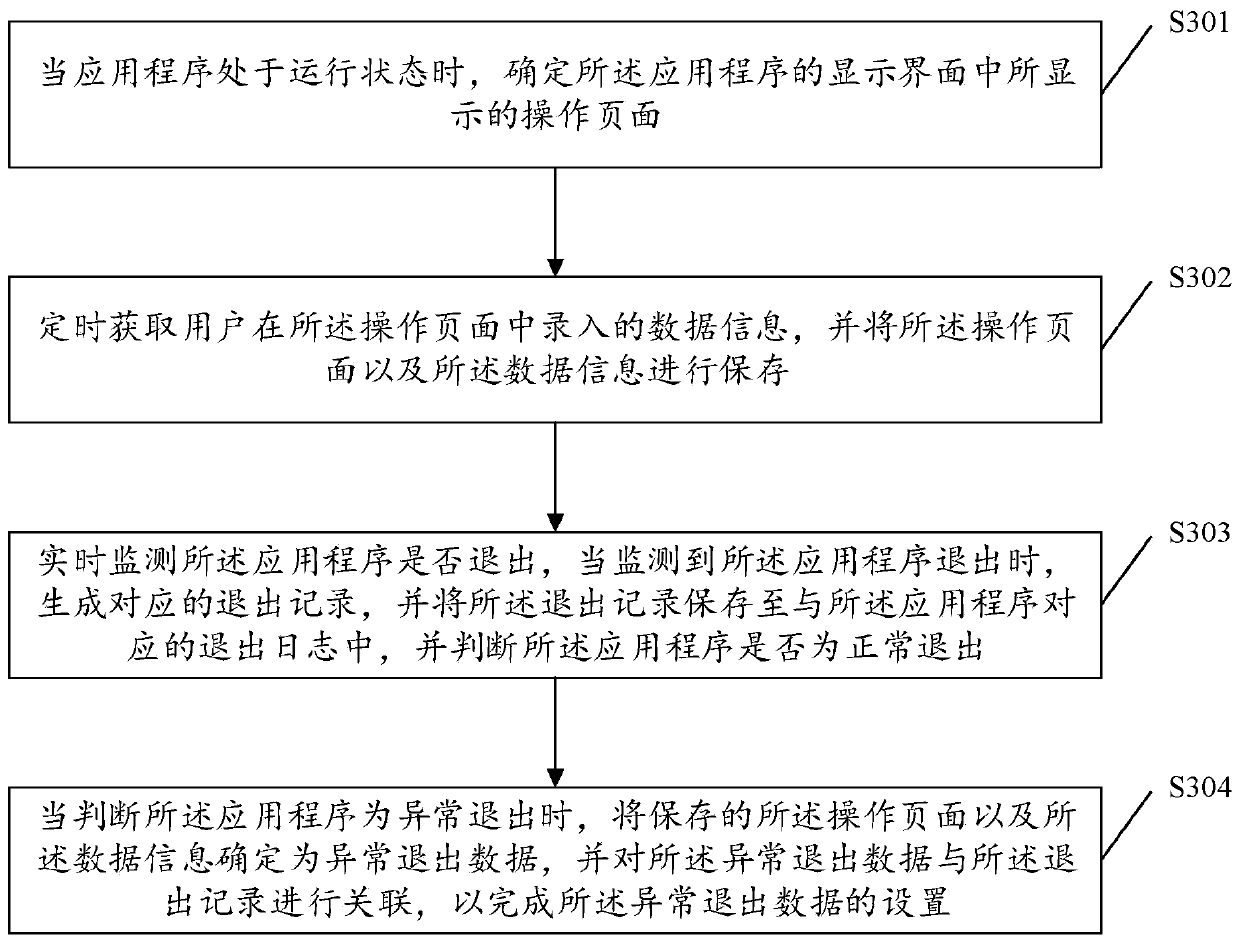
The invention provides an application abnormal exit handling method and device. The method comprises the following steps: receiving a request instruction for running an application program sent by a user, obtaining an exit log corresponding to the application program, acquiring a recently stored quit record in the quit log, judging whether the exit record is an abnormal exit record or not, if it is judged that the exit record is the abnormal exit record, prompting a user whether to recover page content corresponding to the exit record in a display interface of the application, and when a recovery instruction is received, obtaining abnormal exit data corresponding to the exit record, and recovering the abnormal exit data to the display interface of the application. By applying the method and the device, when the application program used by the user exits abnormally and is then run again, the page content during abnormal exit is recovered to the display interface, so that the user can continue to operate from an interrupted place during abnormal exit of the application program, and the experience of using the application program by the user is improved.
Owner:BANK OF CHINA
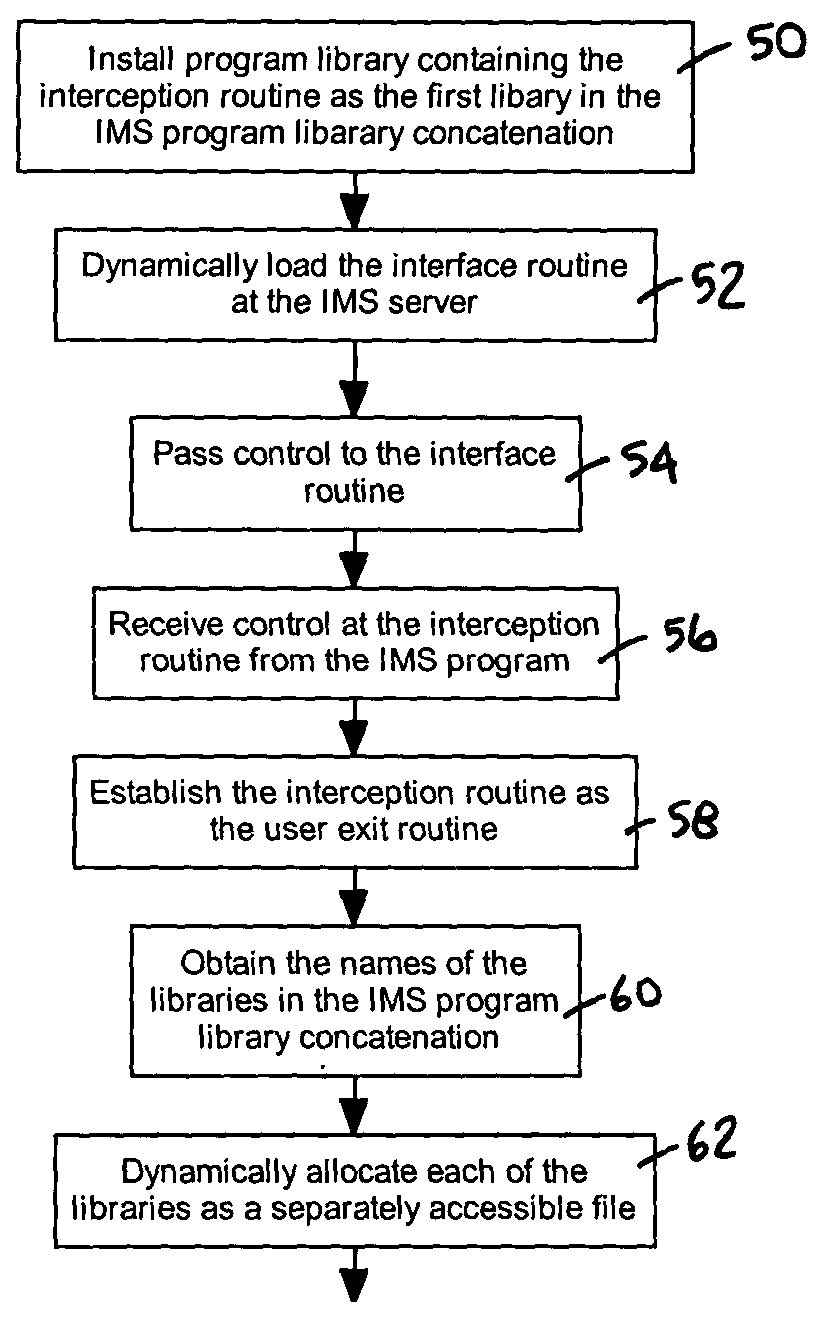
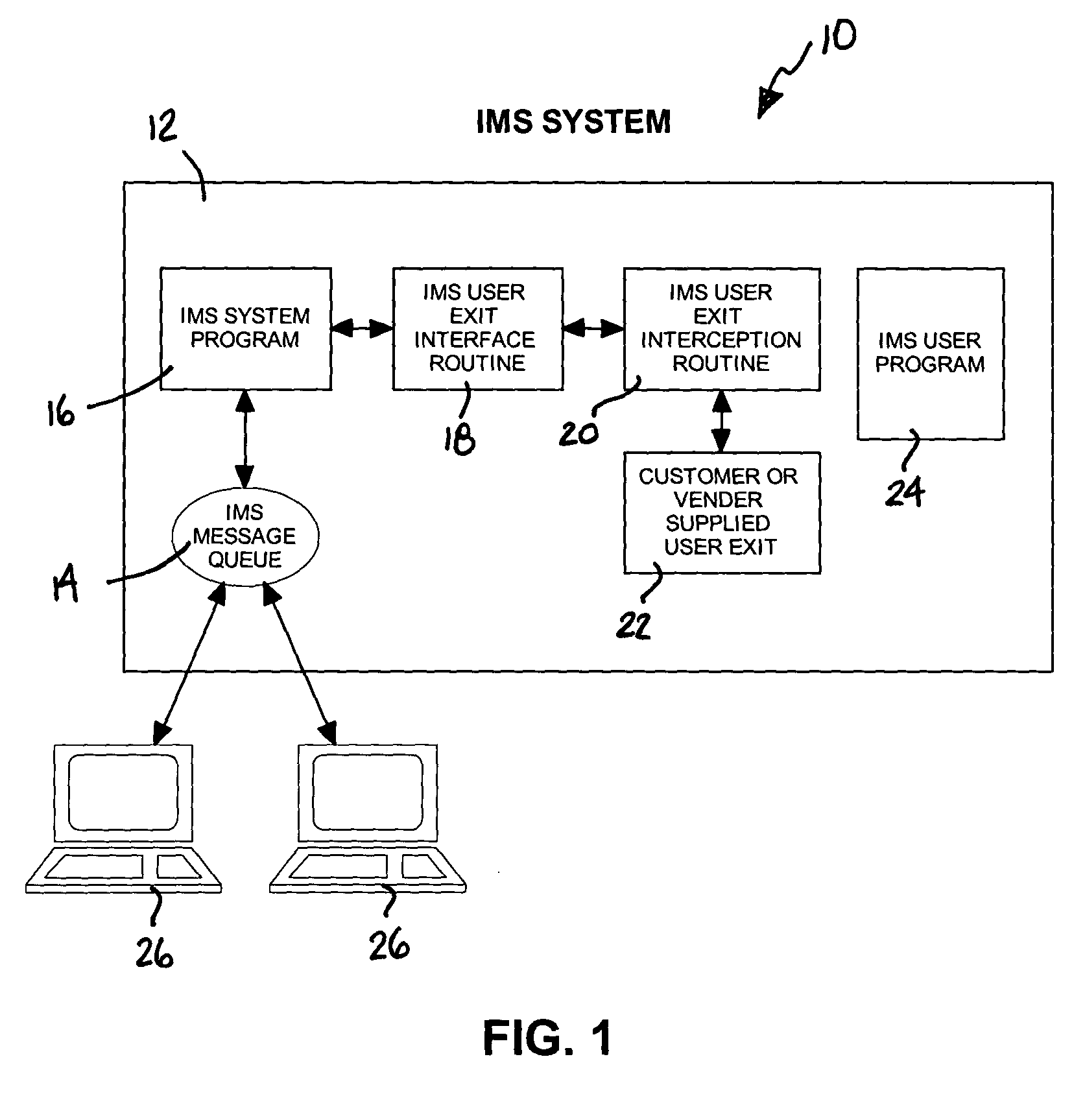
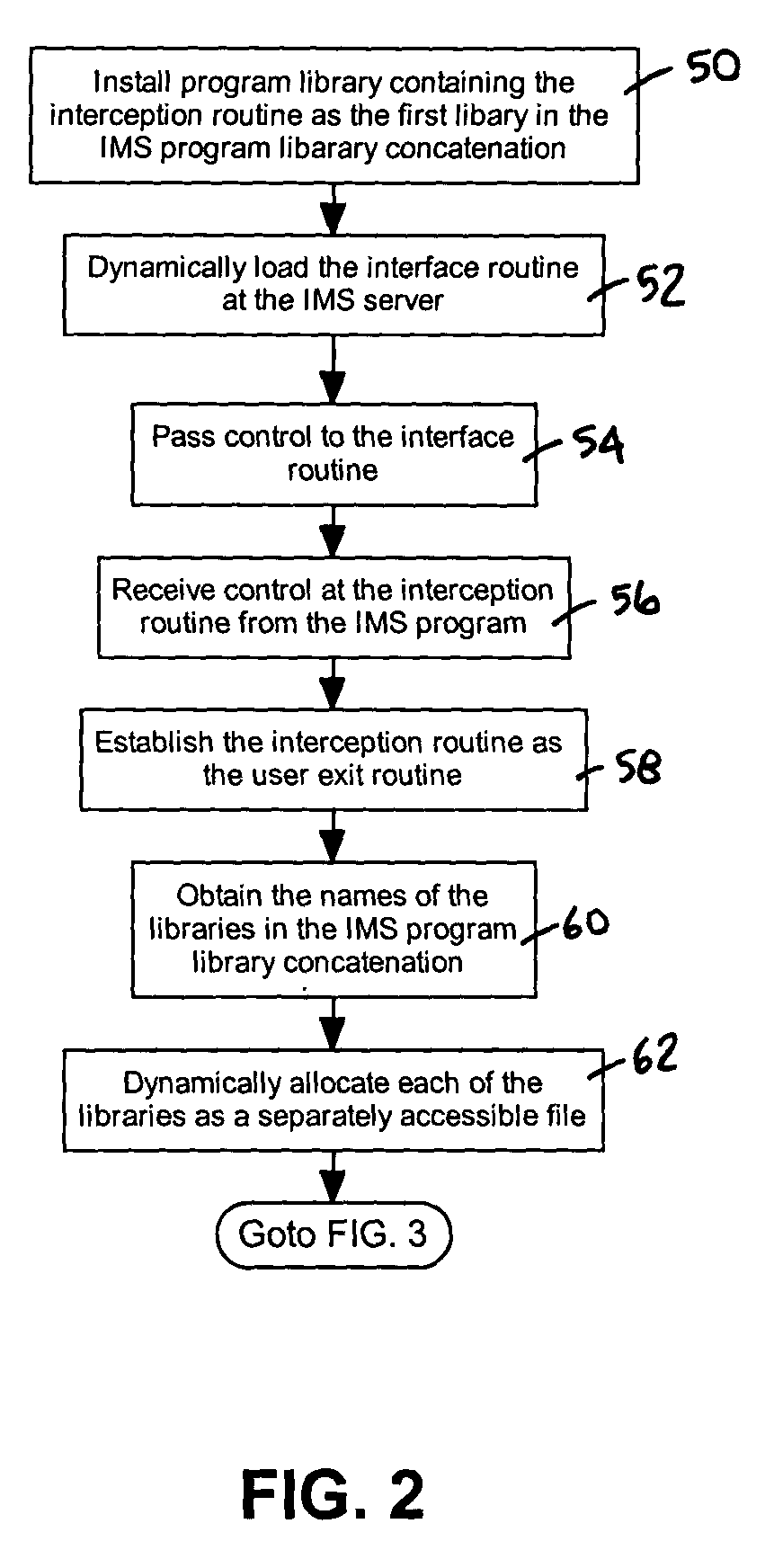
System and method for intercepting user exit interfaces in IMS programs
A system and method for intercepting user exit interfaces in IMS programs includes installing a program library at an IMS system server as the first library in an IMS program library concatenation. The program library includes an interception routine. An interface routine resides at an IMS system server and can be dynamically loaded. During operation, the interception routine communicates with the interface routine to resolve name ambiguity and enable simultaneous use of a single exit by plural users.
Owner:IBM CORP
Game charging method in network video chatting system
InactiveCN101753321AAccurate billingSimplify the billing processMetering/charging/biilling arrangementsSystem callPurchasing
The invention relates to a game charging method in a network video chatting system, which belongs to the field of network video games; the method comprises that a user purchases a game ticket, the system transfers a charging interface to deduce from the user account; the user invites others to play the game, and the number of the game tickets is reduced by 1; after the game is over, the user exits the game or goes to the next step; the user starts the game again, the system checks if the number of game ticket which corresponds to the user account is 0; if not, the number of the game ticket is reduced by 1, the game is continued, otherwise, the user goes to the next step; the system checks if the number of game ticket which corresponds to the user account is 0, and further checks if the user account has enough balance to purchase game tickets; if yes, money is deduced from the user account, the game ticket purchasing succeeds, otherwise, the user goes to the next step; and the user exits the game. The method has the advantages of realizing the accurate charging of games in the network video chatting, and greatly simplifying the charging process from a complicated control process.
Owner:GUANGZHOU WONDERS INFORMATION
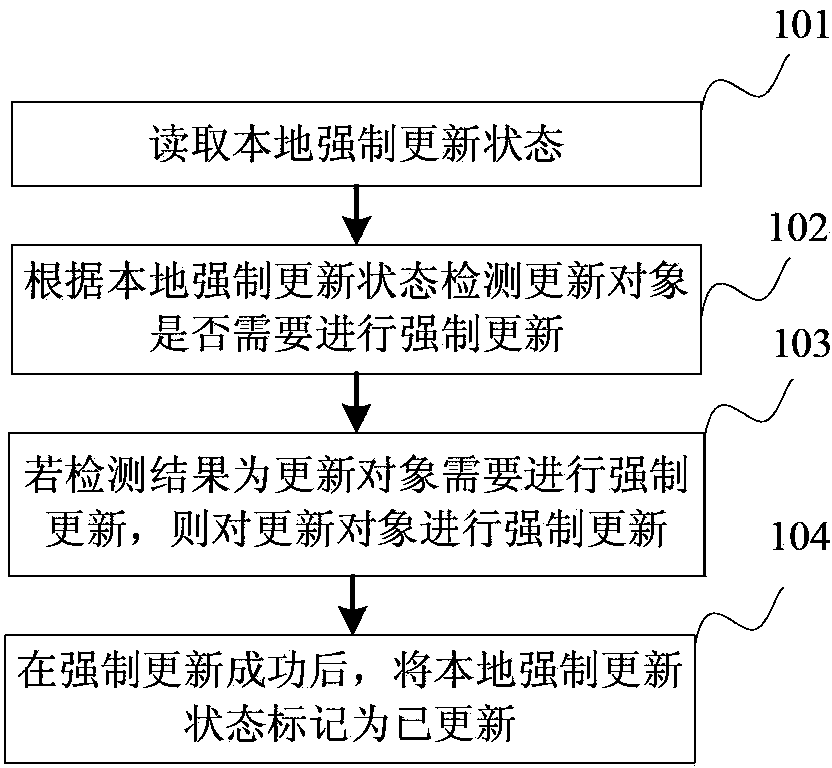
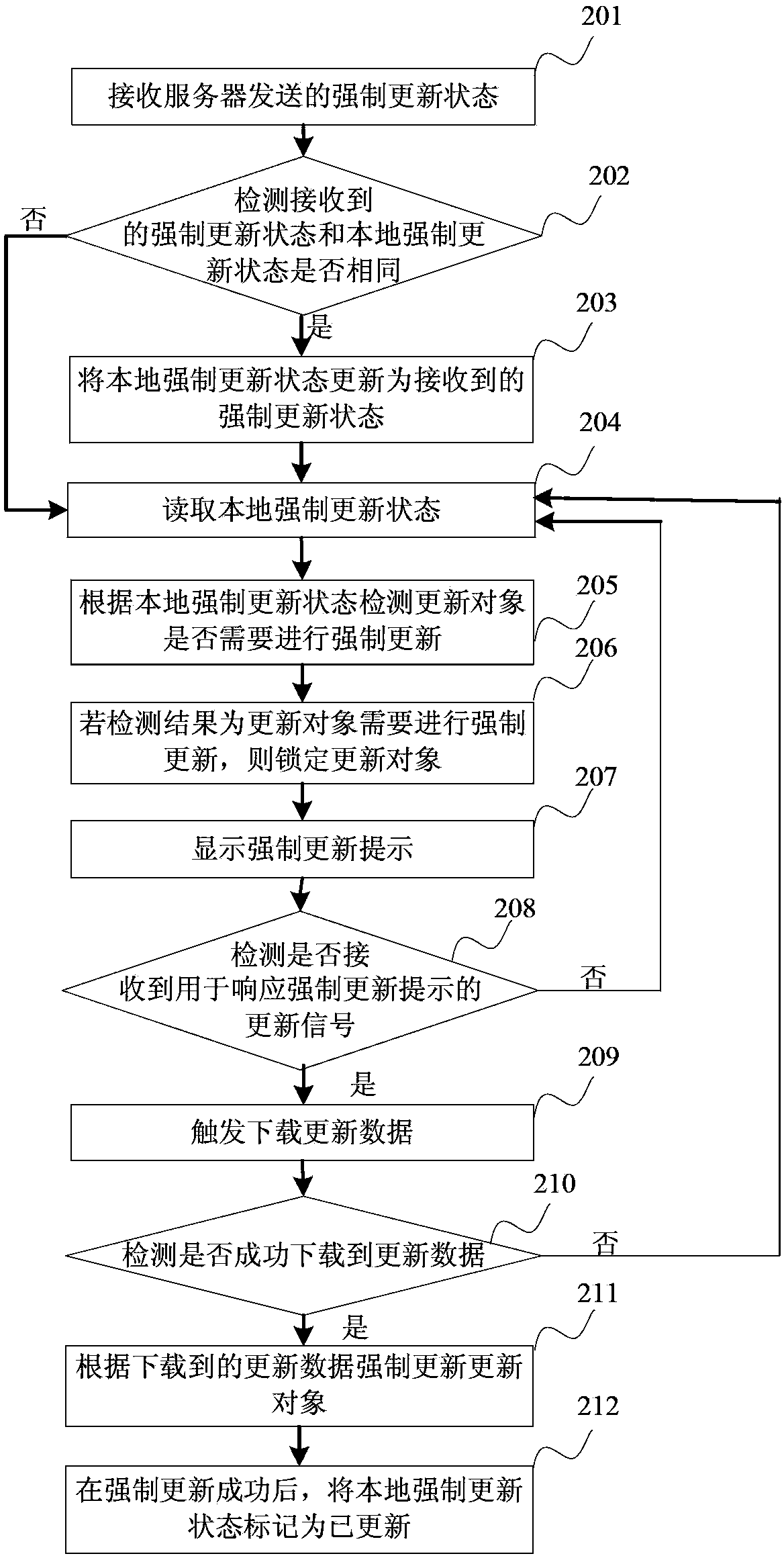
Forced updating method and forced updating device
The invention discloses a forced updating method and a forced updating device and belongs to the technical field of networks. The forced updating method includes: reading a local forced updating status, and detecting whether a to-be-updated object needs to be subjected to forced updating or not according to the local forced updating status; if the to-be-updated object needs to be subjected to forced updating, subjecting the to-be-updated object to forced updating; after forced updating is successful, marking the local forced updating status as 'updated'. The forced updating method and the forced updating device have the advantages that the problem in the prior art that forced updating of an existing version cannot be completed due to the fact that a client side is disconnected with a server or a user exit from the client side after the client side receives a forced updating prompt is solved, and forced updating can be still completed under the circumstance.
Owner:TENCENT TECH (SHENZHEN) CO LTD
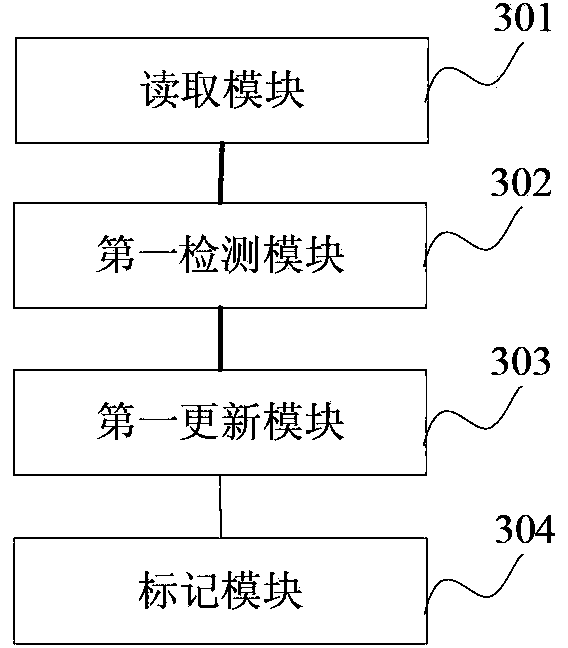
User access authorization control method, device and system and medium
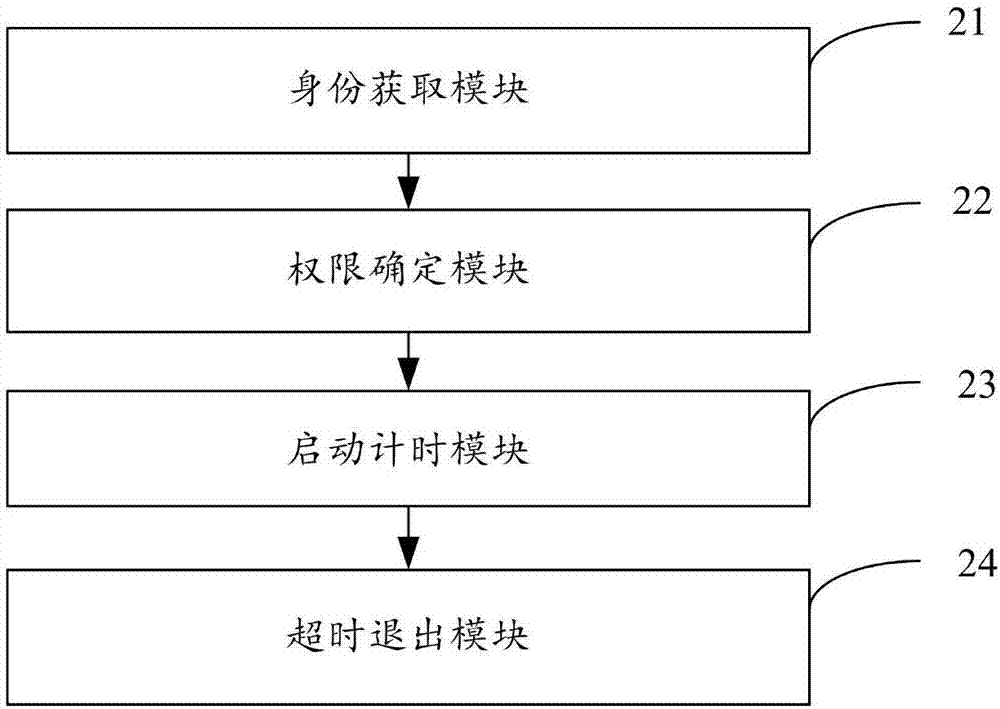
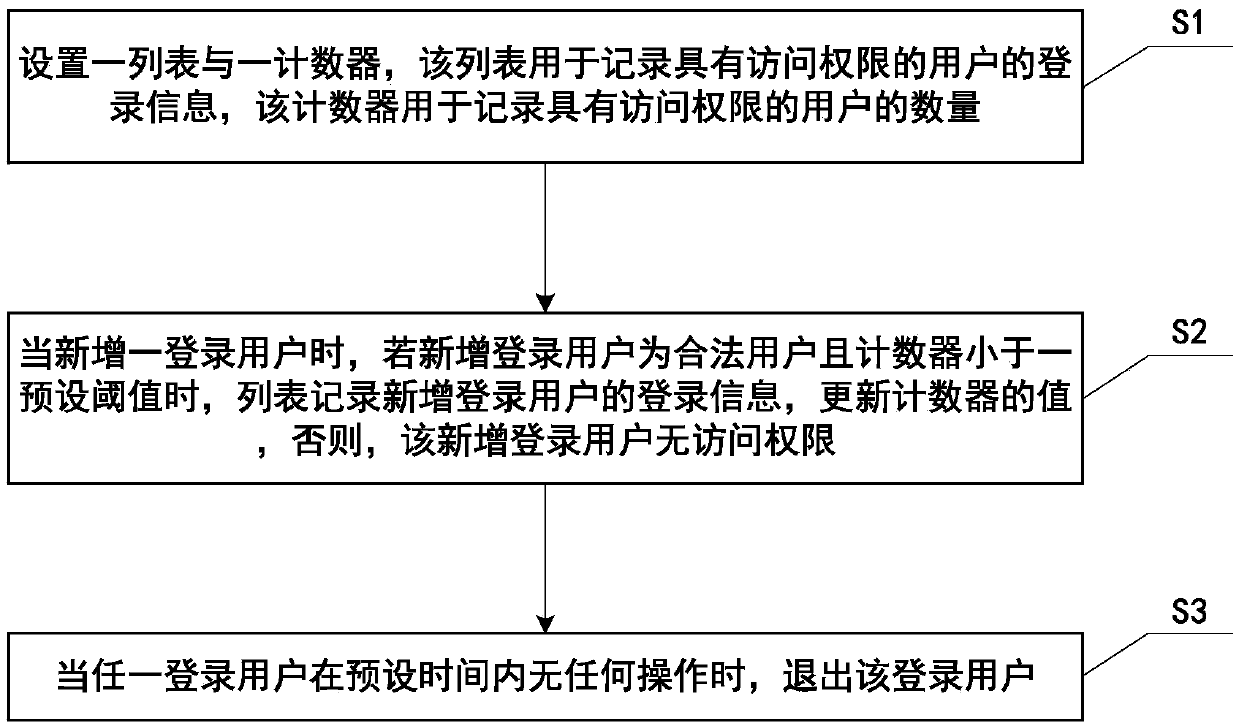
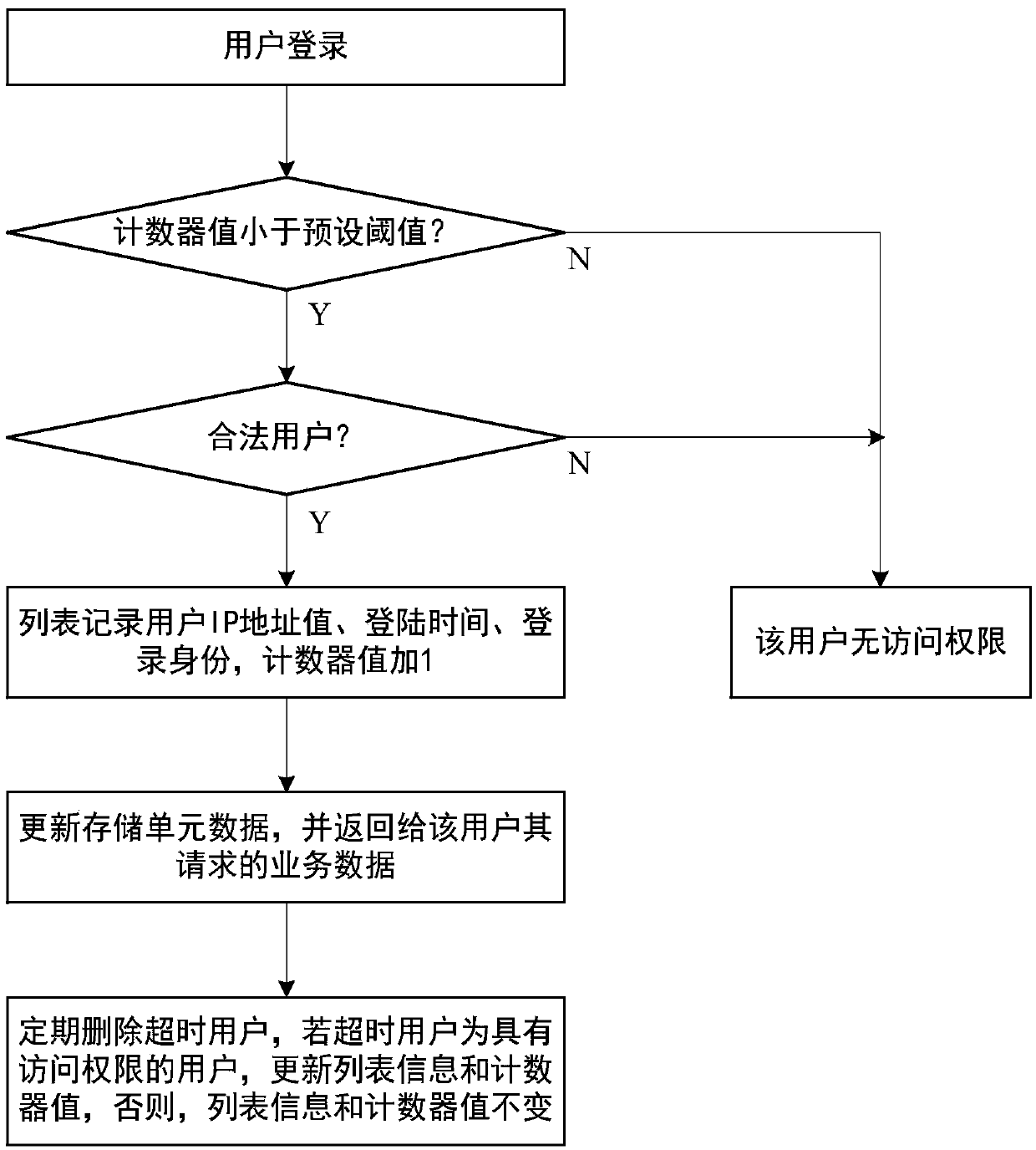
The invention provides a user access authorization control method, which comprises the following steps that: S1, a list and a counter are set, the list is used for recording login information of a user with access authority, and the counter is used for recording the number of the users with the access authority; S2, when a login user is newly added, if the newly added login user is a legal user and the counter is smaller than a preset threshold value, login information of the newly added login user is recorded by the list, the value of the counter is updated, otherwise, the newly added login user is enabled to have no access permission; And S3, when any login user has no operation within the preset time, the login user exits.
Owner:BEIJING QIANXIN TECH
Enterprise business management system
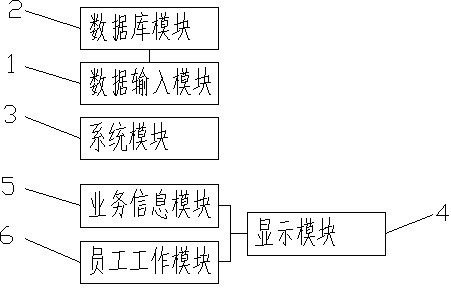
InactiveCN102708459AUnderstand the working statusEasy to make an appointmentResourcesRelevant informationBusiness management
The invention discloses an enterprise business management system, which comprises a data input module, a data base module, a system module, a display module, a business information module and a crew working module, wherein the data base module is used for storing data input by the data input module, the display module is used for displaying relative information of the business information module and the crew working module, and the system module is used for user login, user operating authorization setting and user exit. By the method, the enterprise business management system can perform statistics on business of enterprises in real time, understand working condition of crew, and facilitate clients in making appointment.
Owner:SUZHOU WANTUMING ELECTRONICS SOFTWARE
Account information association method and device, electronic equipment and storage medium
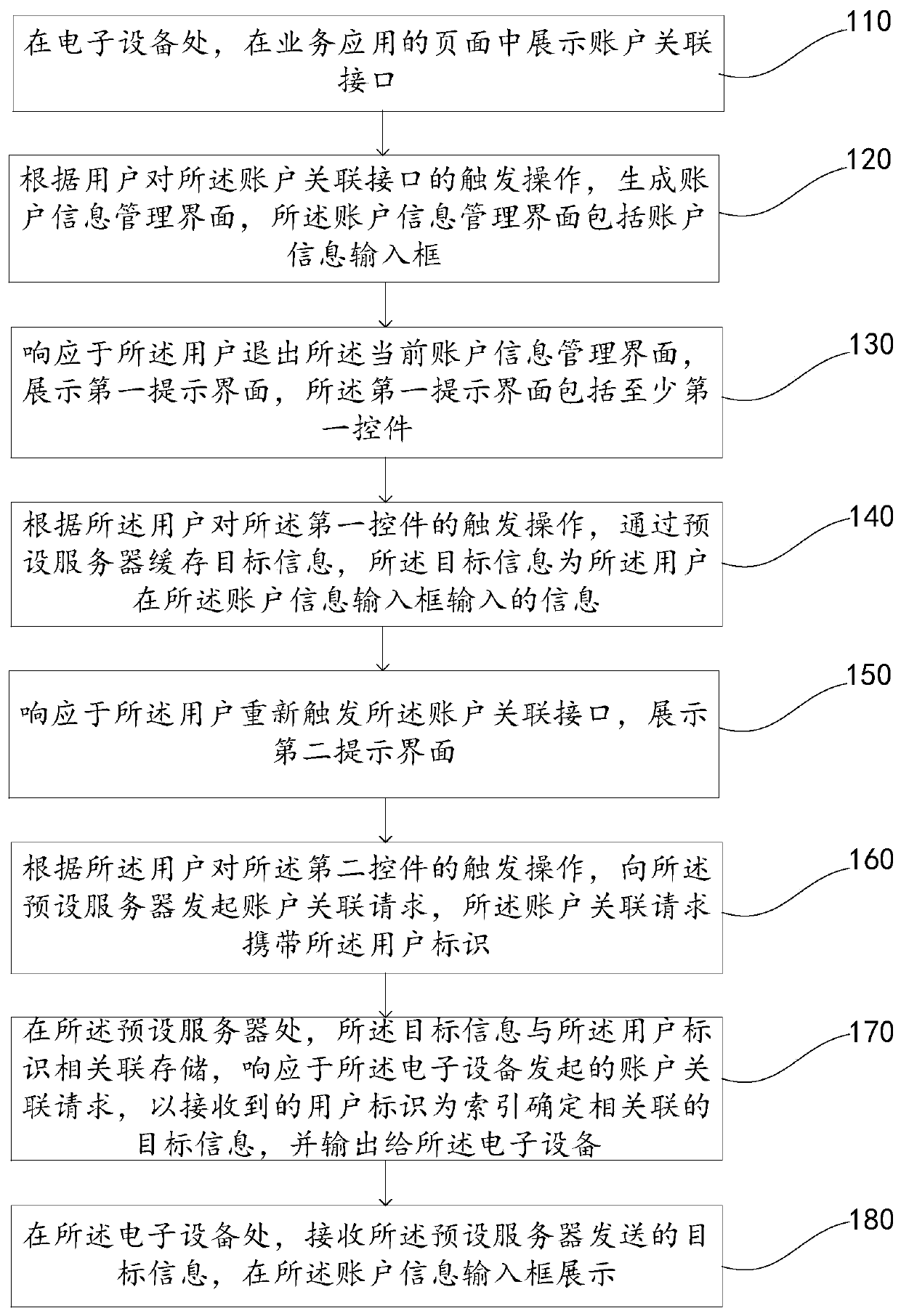
PendingCN110807536AImprove the efficiency of linked account informationAvoid double typingReservationsBuying/selling/leasing transactionsEngineeringHuman–computer interaction
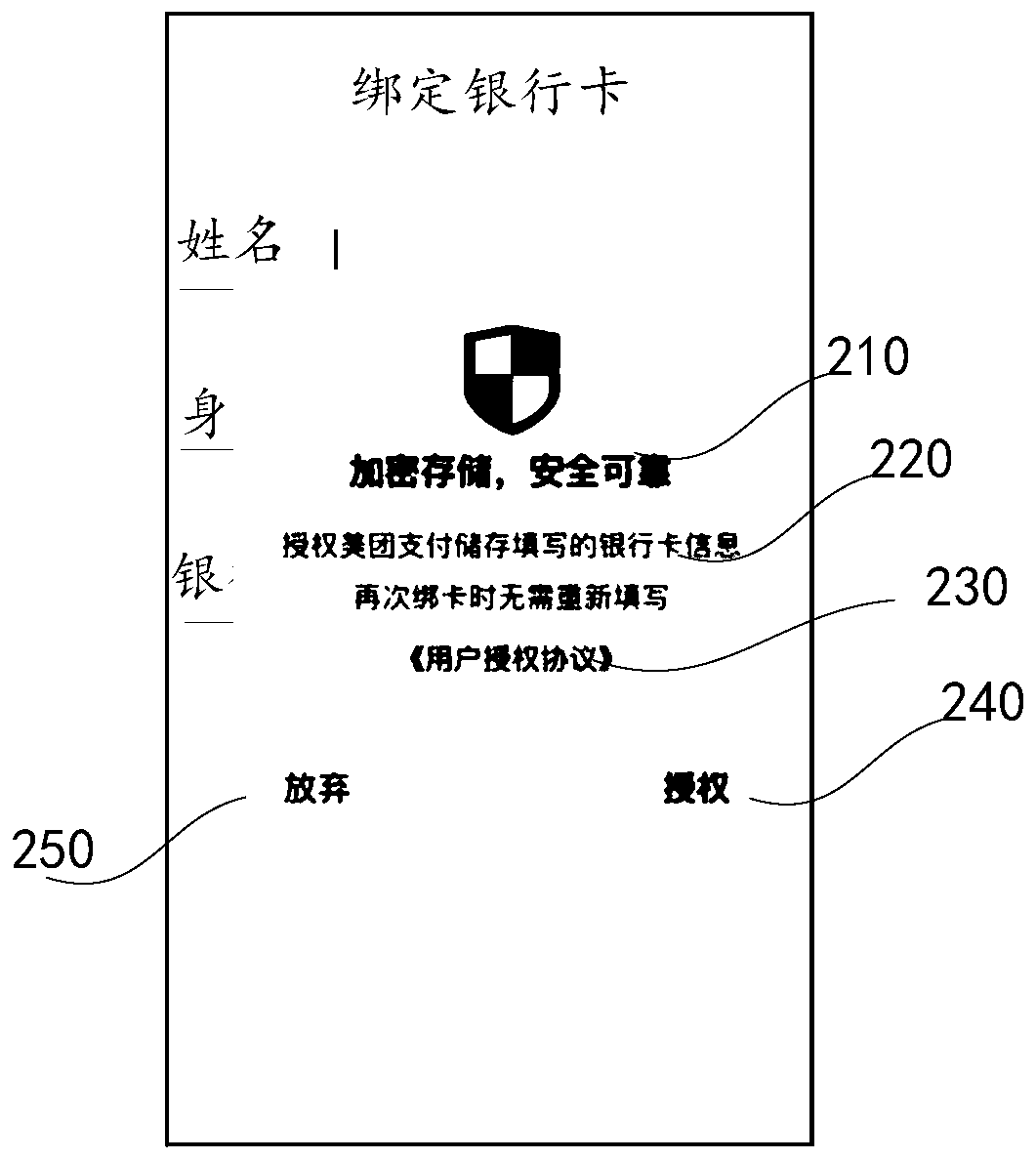
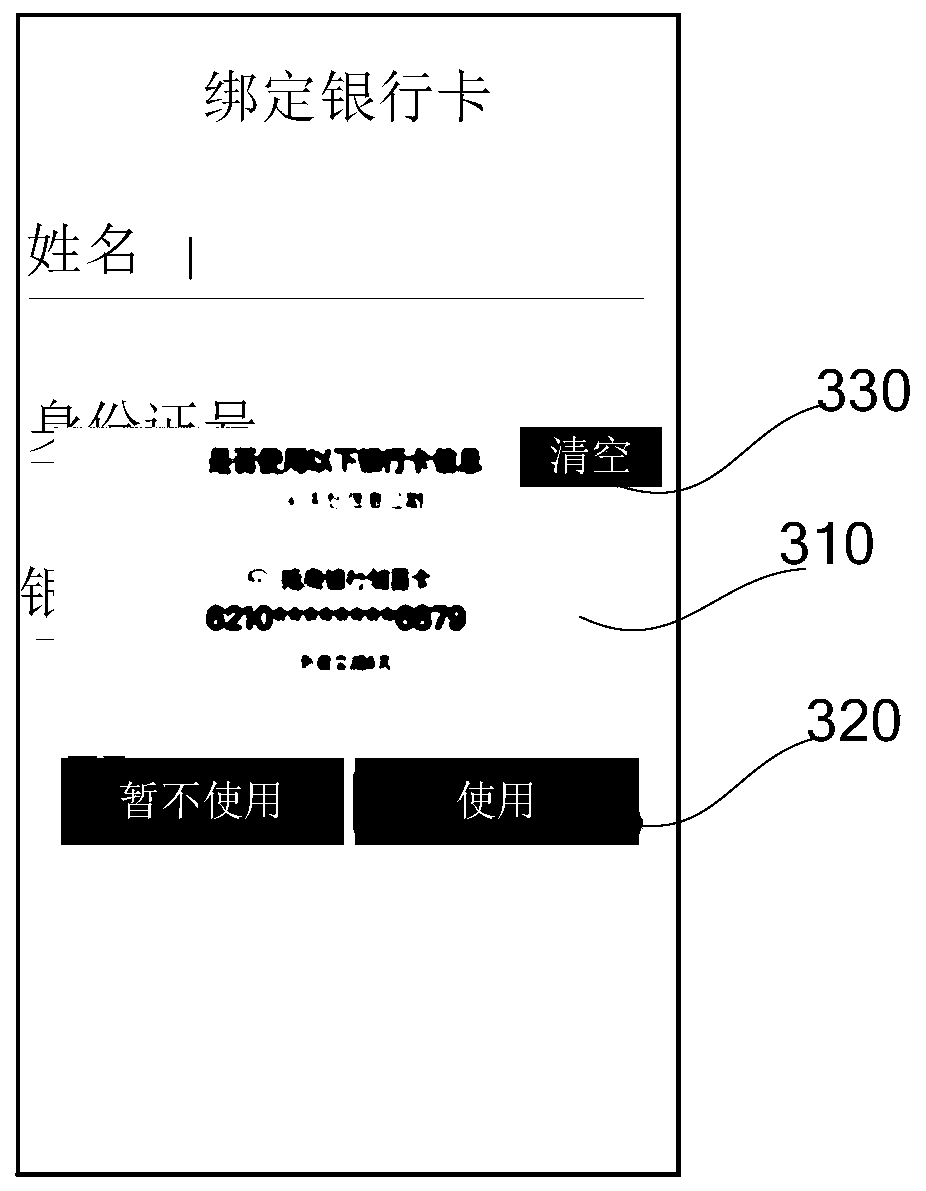
The invention discloses an account information association method, belongs to the technical field of computers, and the method is helpful for improving the efficiency of associating account information by a user. The method comprises the following steps: displaying an account association interface in a page of a service application at the electronic equipment; generating an account information management interface and displaying an account information input box according to a triggering operation of a user on the account associated interface; in response to the situation that the user exits from the current account information management interface, displaying a first control; caching information input by the user in the account information input box through a preset server according to a triggering operation of the user on a first control; in response to the situation that the user triggers the account association interface again, displaying a second control used for indicating to usethe account information; and obtaining the target information cached by the preset server according to the triggering operation of the user on the second control, and displaying the target informationin the account information input box, so that the user can be prevented from repeatedly inputting the account information, and the efficiency of associating the account information by the user is improved.
Owner:BEIJING SANKUAI ONLINE TECH CO LTD
Mode determination method and device, equipment, and readable storage medium
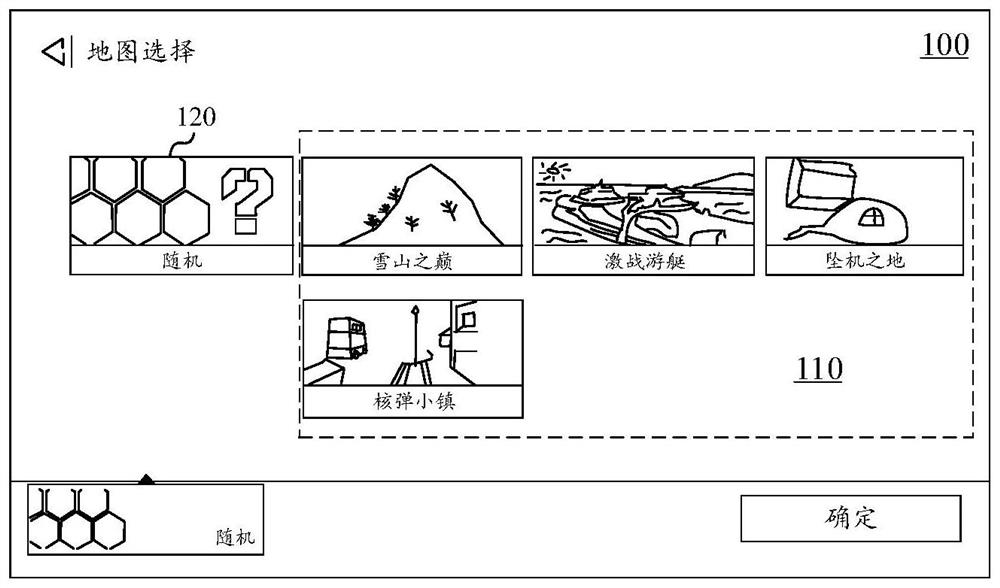
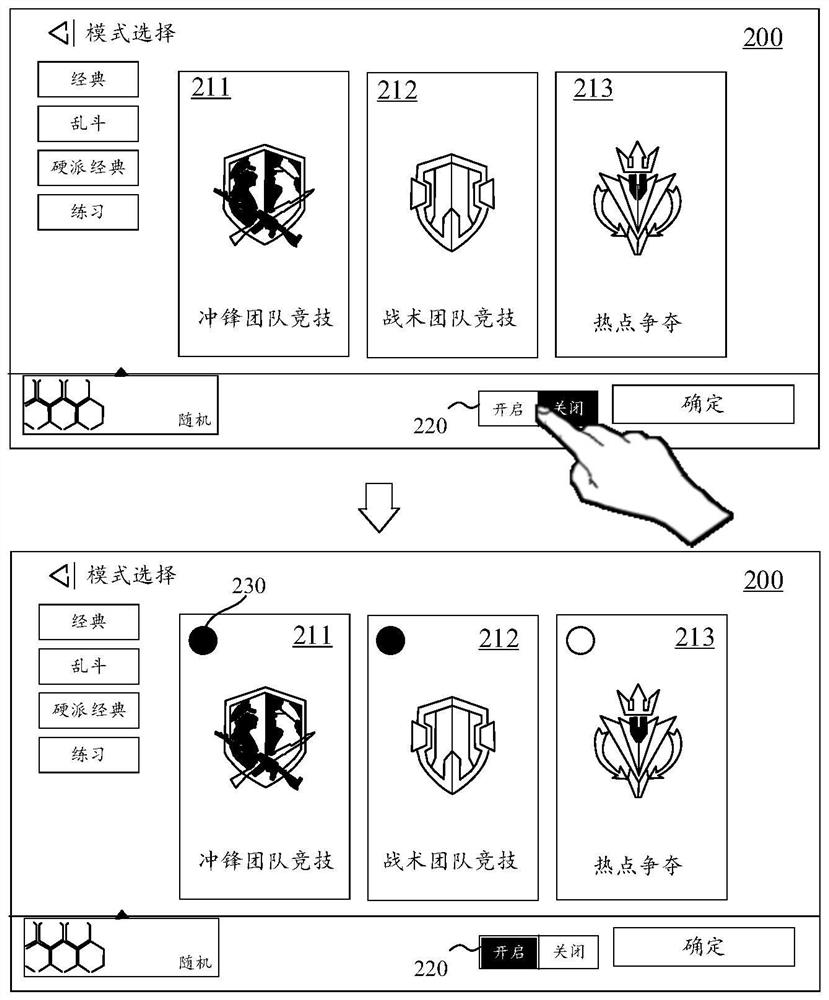
ActiveCN112169321AAvoid problems that increase server computing pressureImprove matching accuracyVideo gamesComputer hardwareMode control
The invention discloses a mode determination method and device, equipment and a readable storage medium, and relates to the field of interface display. The method comprises the following steps: displaying at least two candidate modes and a random mode control; in response to switching of the random mode control to the open state, displaying a selection marker box on the at least two candidate modes; determining a marked mark candidate mode from the at least two candidate modes; and determining a target mode from the mark candidate modes. The random mode control control is displayed when the mode selection interface is displayed, so that the random mode is controlled to be opened and closed, and the selection mark box is displayed on the candidate mode when the random mode is opened, so that a user can select the candidate mode needing to participate in random matching through the selection marker box, the matching accuracy is improved And the problem that the calculation pressure of the server is increased due to the fact that the user exits from the virtual game for multiple times for re-matching is solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Enterprise business process management system
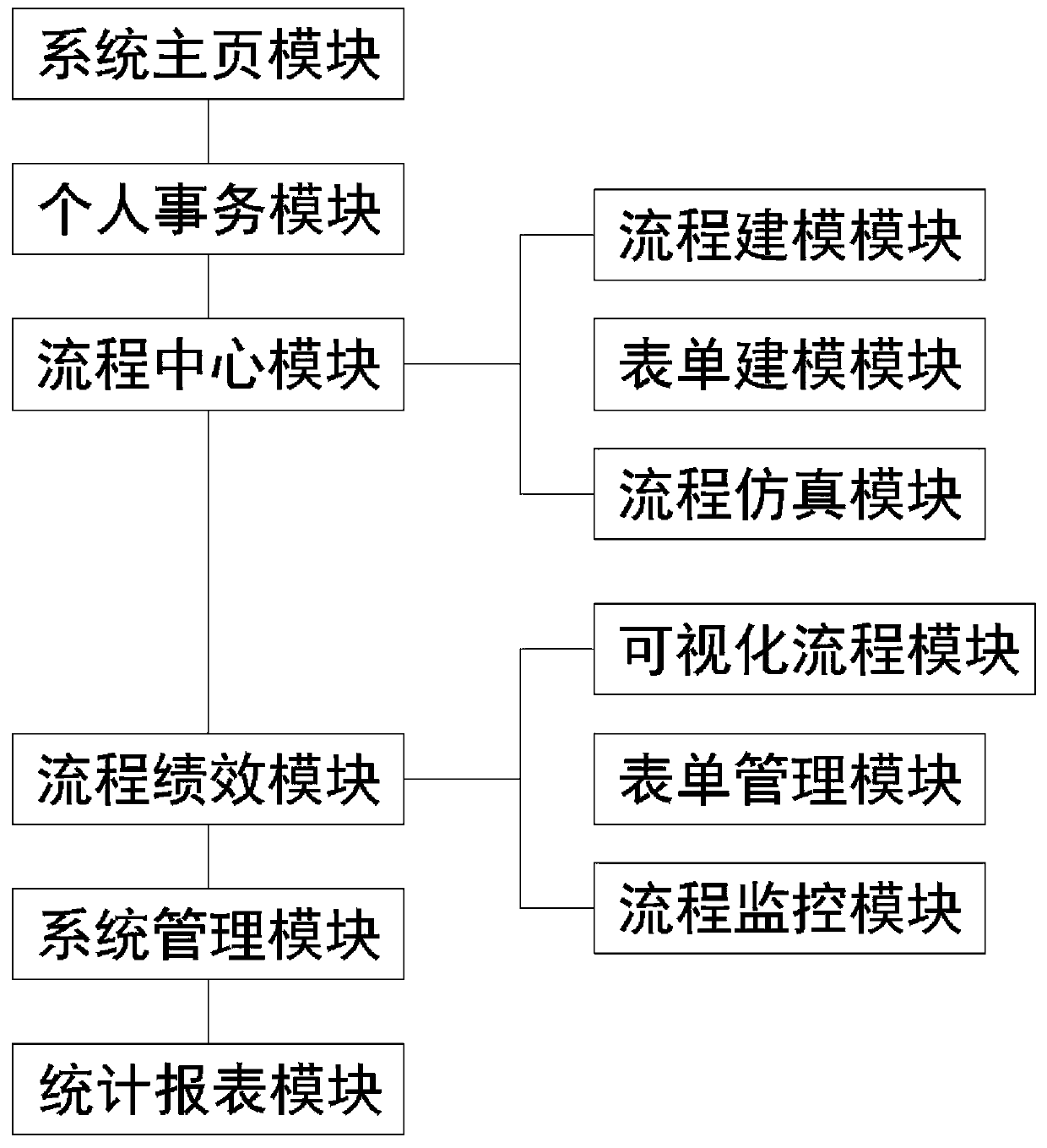
InactiveCN110782106ASave human effortLower cost of capitalOffice automationResourcesSystems managementSoftware engineering
The invention discloses an enterprise business process management system, which comprises a system homepage module, a personal affair module, a process center module, a process performance module anda system management module, wherein the system homepage module is used for operations of user login and user exit; the personal affair module is used for operating the personal work progress and the obtained business situation; the process center module is used for process carding, process optimization and process capitalization operation; the process performance module is used for seamless and efficient work cooperation between enterprise department personnel; and the system management module is used for setting user operation authority and setting other modules. Enterprises and users thereofdo not need to set through a large number of complex code programming, and customers completely perform fool-type operation in use, and professional software engineers do not need to compile source program codes, and software development efficiency is greatly improved, and manpower, capital and time costs of companies for process management are greatly reduced.
Owner:广州市联科软件股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com