Efficient anonymous authentication method and system suitable for alliance chain and capable of supporting identity traceability
An anonymous authentication and traceable technology, applied in the field of blockchain, can solve the problems of unforgeability and inability to obtain the real identity of members
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0104] In order to make the above objects, features and advantages of the present invention more comprehensible, the present invention will be further described in detail below through specific embodiments and accompanying drawings.
[0105] Embodiments of the present invention: a distributed, traceable anonymous authentication method suitable for consortium chains, comprising the following steps:
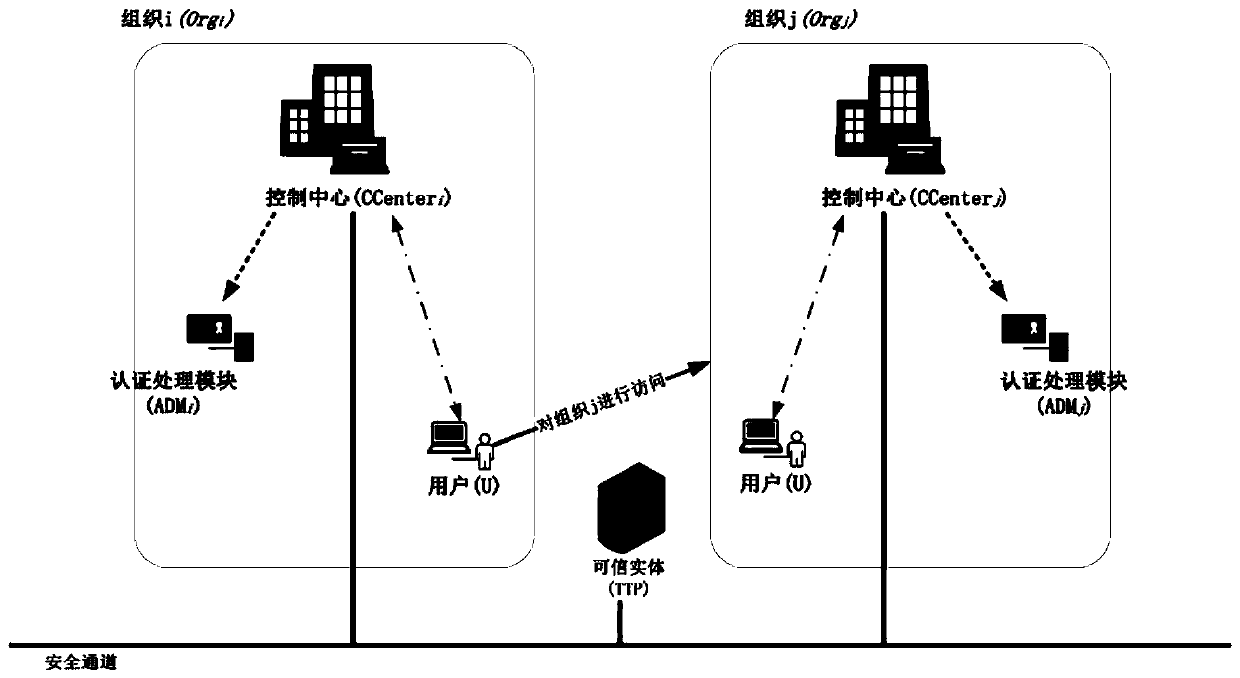
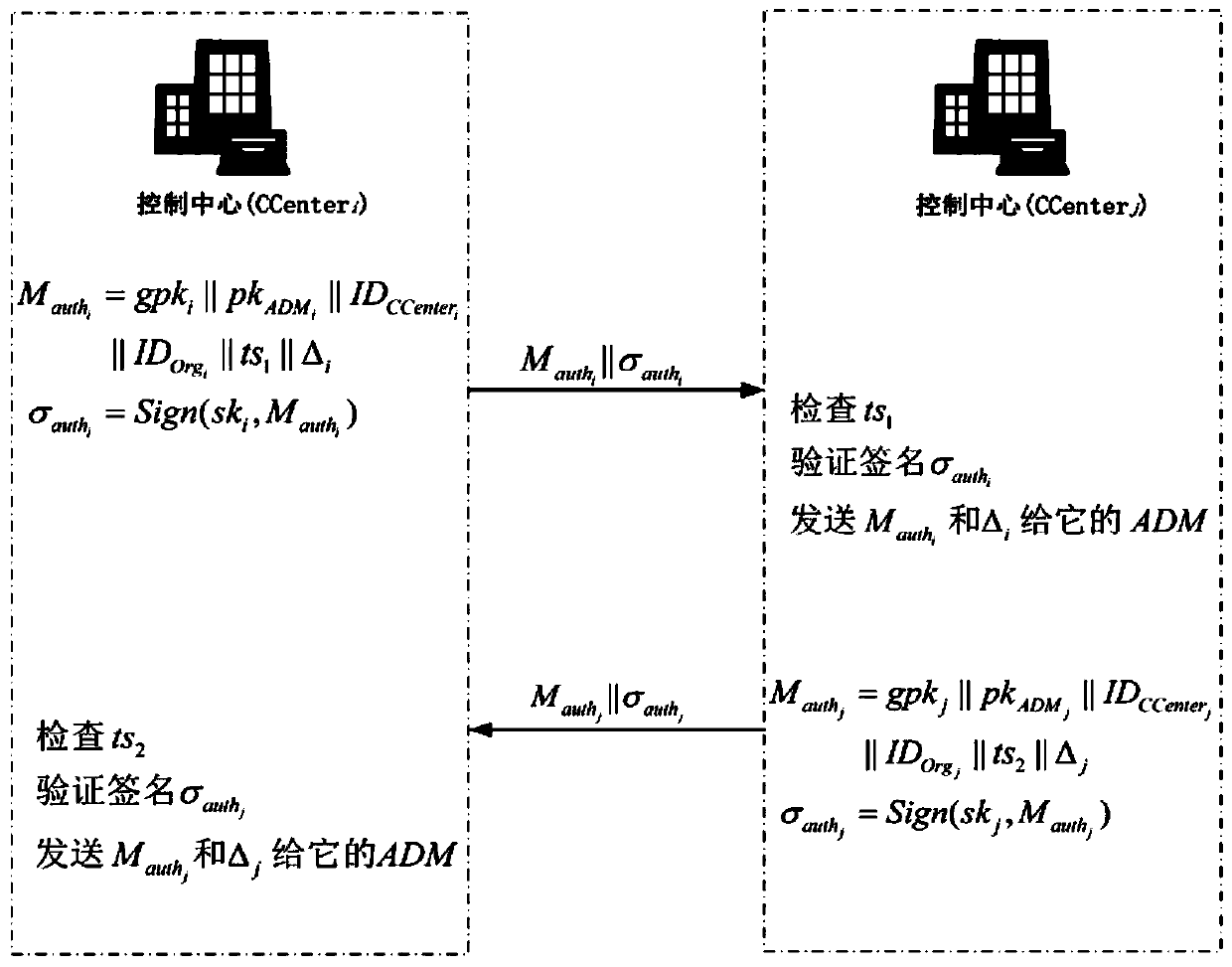
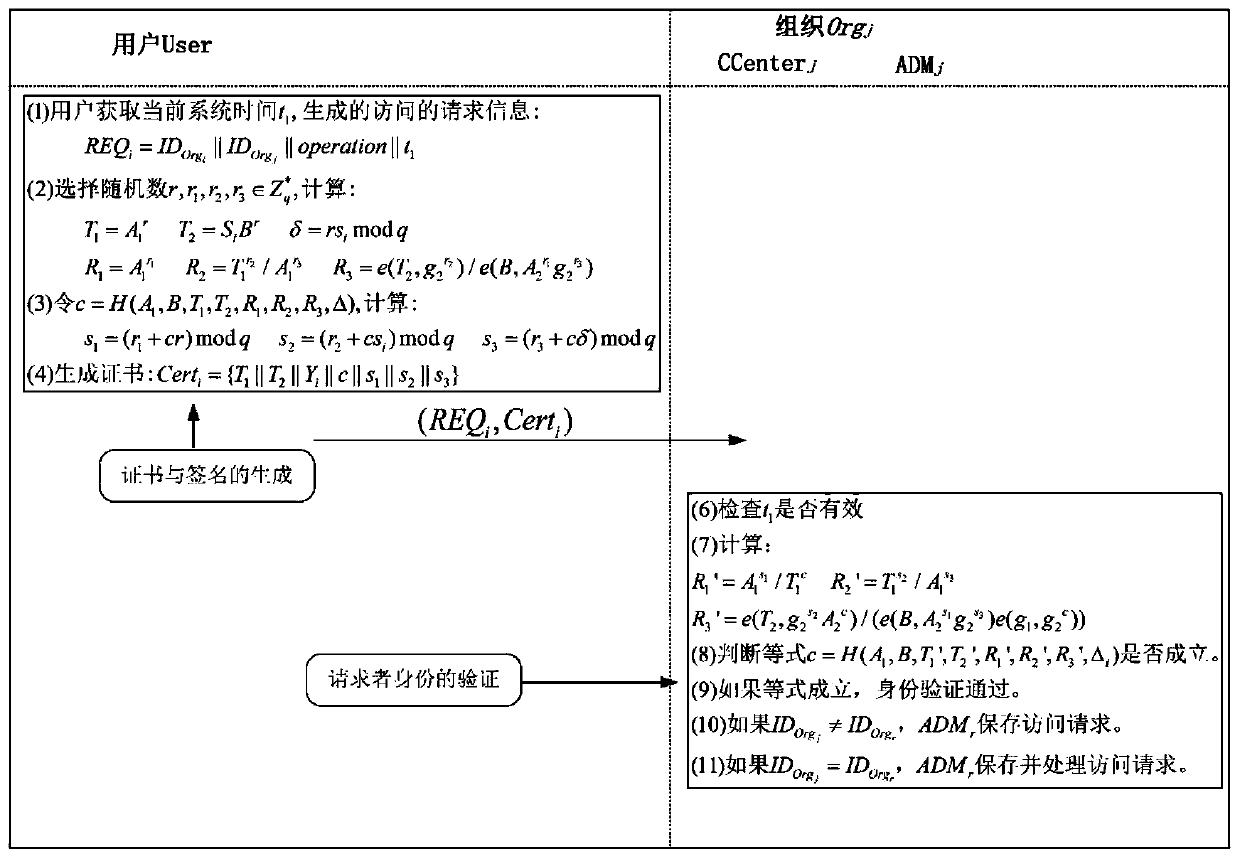
[0106] S1. System initialization: figure 1 is a schematic diagram of the system model. The system includes 1 trusted entity TTP, organization members of N alliances Org i (i=1,2,...,N), each organization can contain M users U j (j=1,2,...,M). Each organization Org i Have 1 control center CCenter i and 1 message authentication processing module ADM i . CCenter is responsible for managing all users in the organization, and generates public parameters gpk and master key gmsk for the organization it belongs to. TTP is CCenter i distribution key pair (pk i ,sk i ), used when ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com