Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
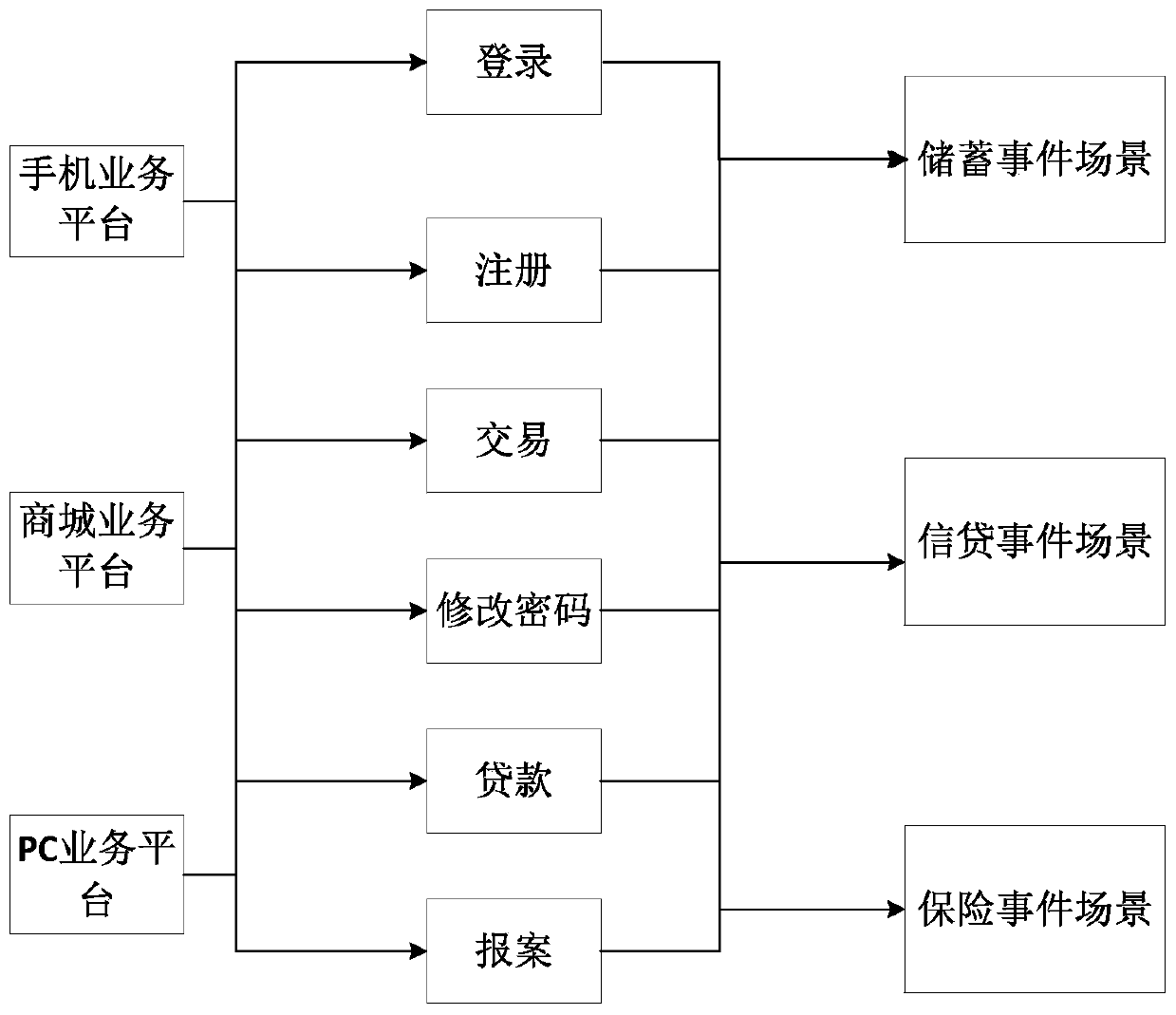
90 results about "Risk behavior" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
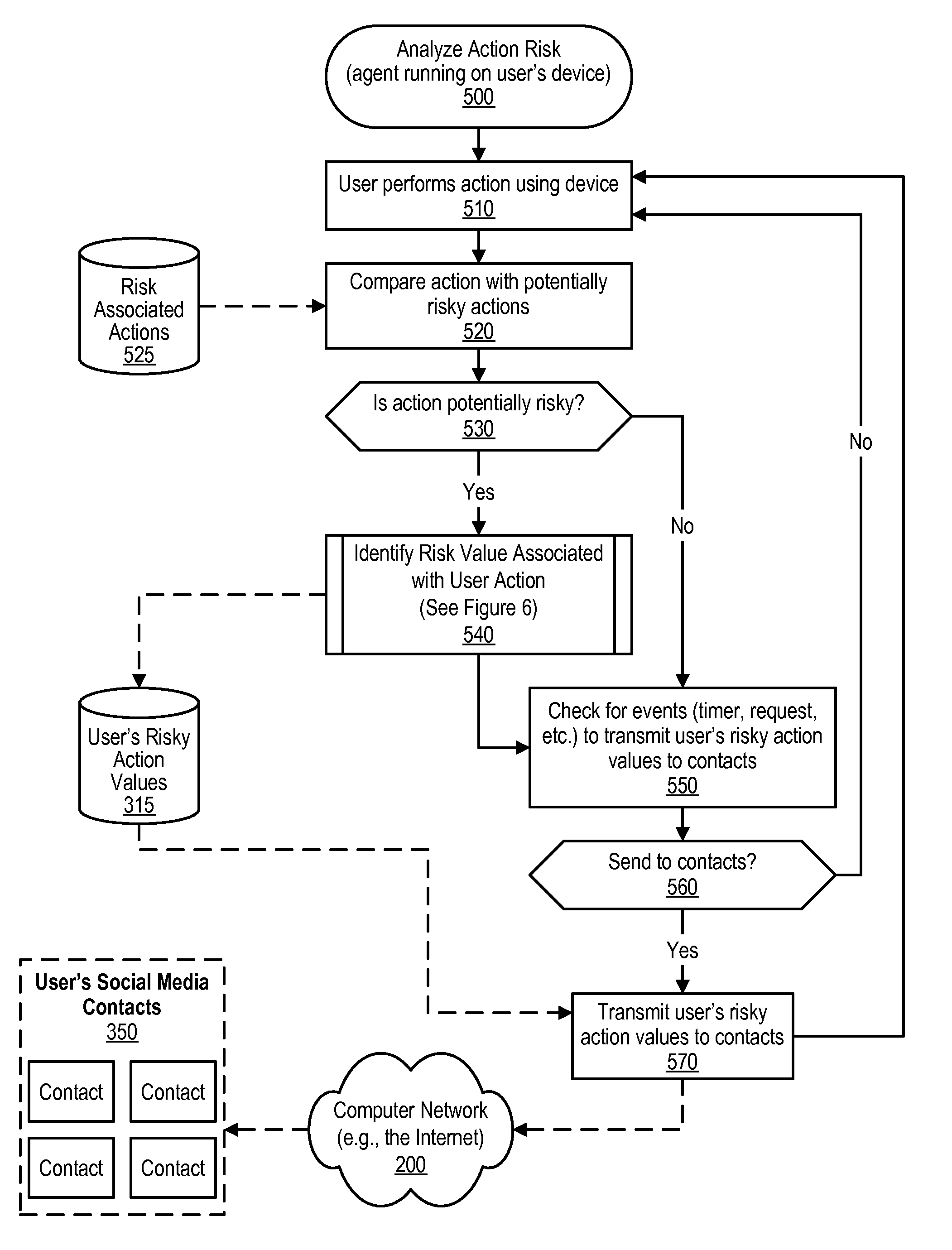
Assessing Social Risk Due To Exposure From Linked Contacts
An approach is provided in which a risk assessment is performed that accesses the risk to a user of an information handling system due to the user's link to a social network contact. Risky action values is received with the values corresponding to the social network contact. A risk level is calculated with the risk level corresponding to one or more of the risky action values. A preventative security action is then performed based on the calculated risk level. In another embodiment, an approach is provided in which the potential risks posed by a user are transmitted to the user's social network contacts. In this approach, potentially risky actions that are performed by the user are detected. Risky action values are identified that correspond to the detected potentially risky actions. The risky action values are then transmitted to the user's social network contacts over a computer network.
Owner:IBM CORP
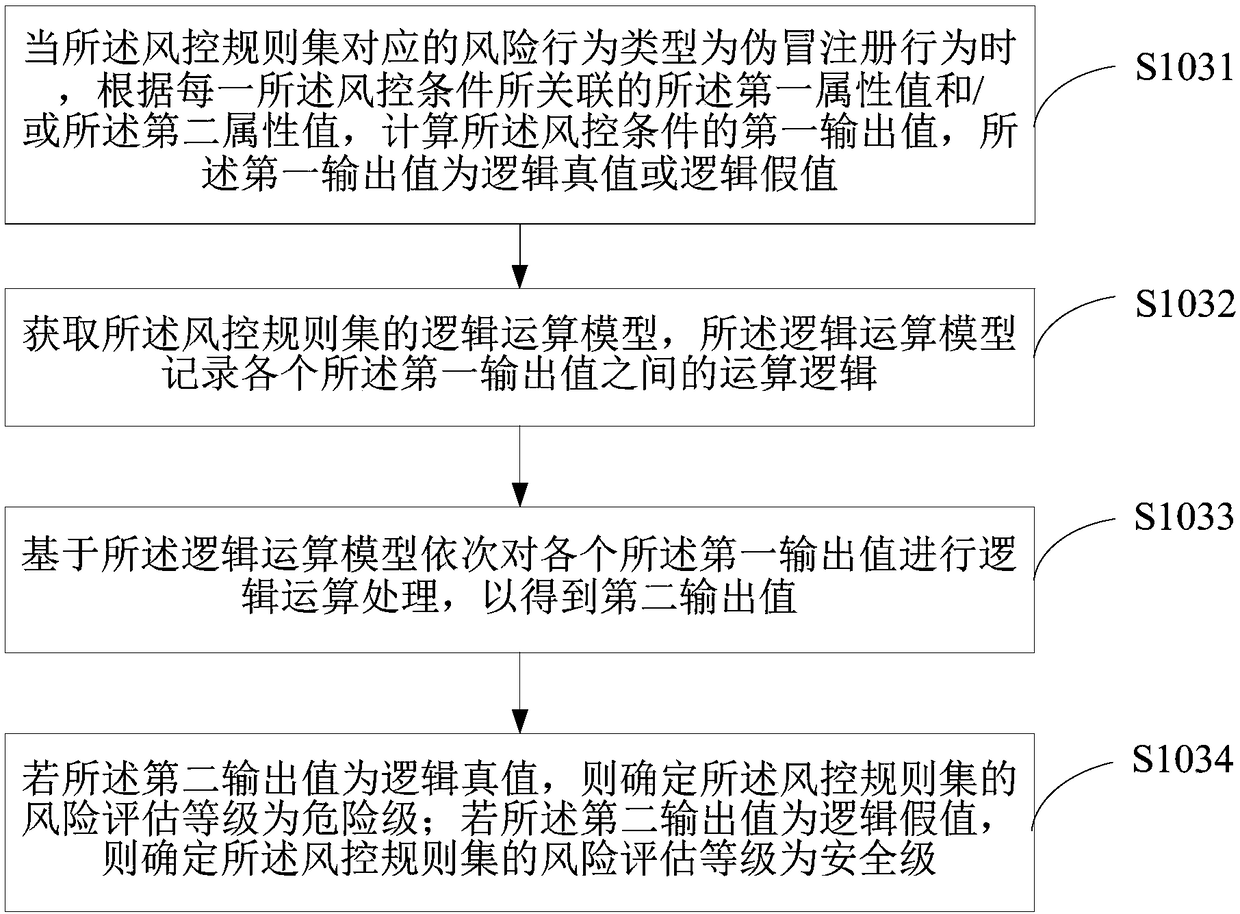
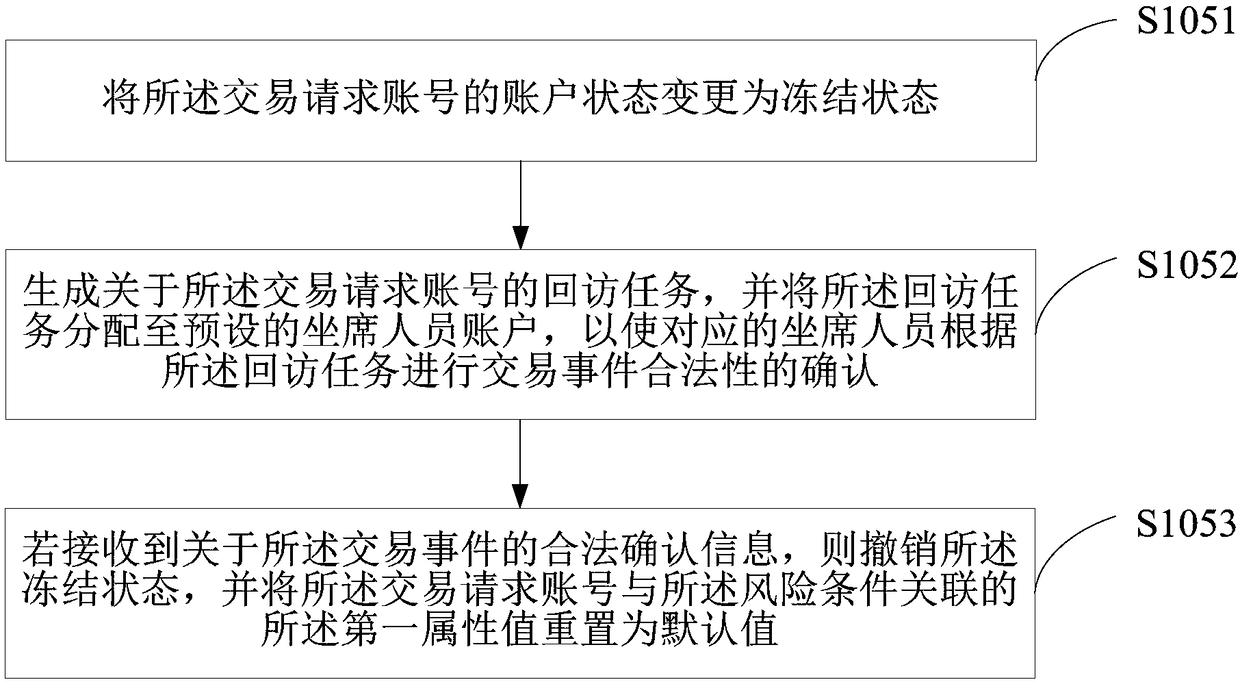
Transaction event processing method, terminal equipment and medium
ActiveCN108062629AImprove recognition accuracyEfficient detectionPayment protocolsResourcesRisk behaviorPayment
The invention is suitable for the field of Internet technology, and provides a transaction event processing method, terminal equipment and a medium. The method comprises the steps of acquiring a plurality of preset risk management rule sets; acquiring a first attribute value and a second attribute value, which are related with a risk management condition, of a transaction request account number; performing operation processing on the first attribute value and the second attribute value which correspond with the risk management condition in each risk management rule set for outputting the riskevaluation grade of each risk management rule set; if the risk evaluation grade of a random risk management rule set is a dangerous grade, determining the risk behavior type which corresponds with therisk management rule set as the risk behavior type that exists in a transaction event; and according to a preset feedback manner of the determined risk behavior type, performing a feedback operationon the transaction request account number. The transaction event processing method, the terminal equipment and the medium have advantages of improving identification accuracy for abnormal transactionbehaviors, realizing preliminary evaluation to the risk state of the transaction request account number on the condition of a non-payment scene, and realizing active risk management processing.
Owner:PING AN TECH (SHENZHEN) CO LTD
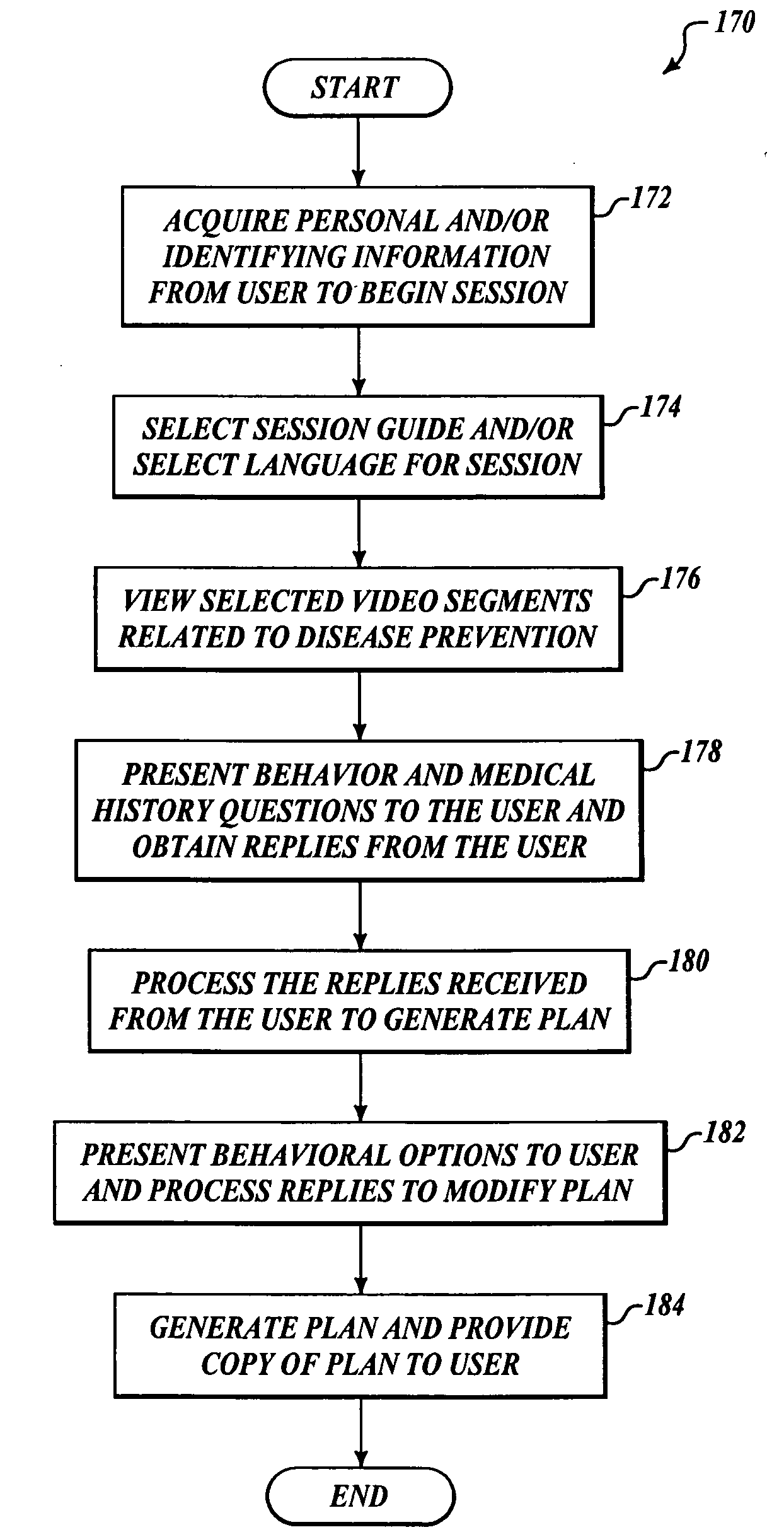
Systems, methods and computer product for disease risk reduction, education and assessment
Systems, methods and a software product for disease reduction education and risk assessment are disclosed. In one embodiment, a system for computer-assisted disease risk assessment and education includes a processor that generates at least a plurality of questions directed to a disease risk assessment for a user. Based upon responses received from a user, the processor is further operable to generate one or more plans configured to prospectively guide the risk behavior and sexual activity of the user. At least one personal data entry and display device (PDDA) is communicatively coupled to the processor, that is operable to at least display the plurality of questions and to accept corresponding responses from the user.
Owner:LARKIN JAMES D +5
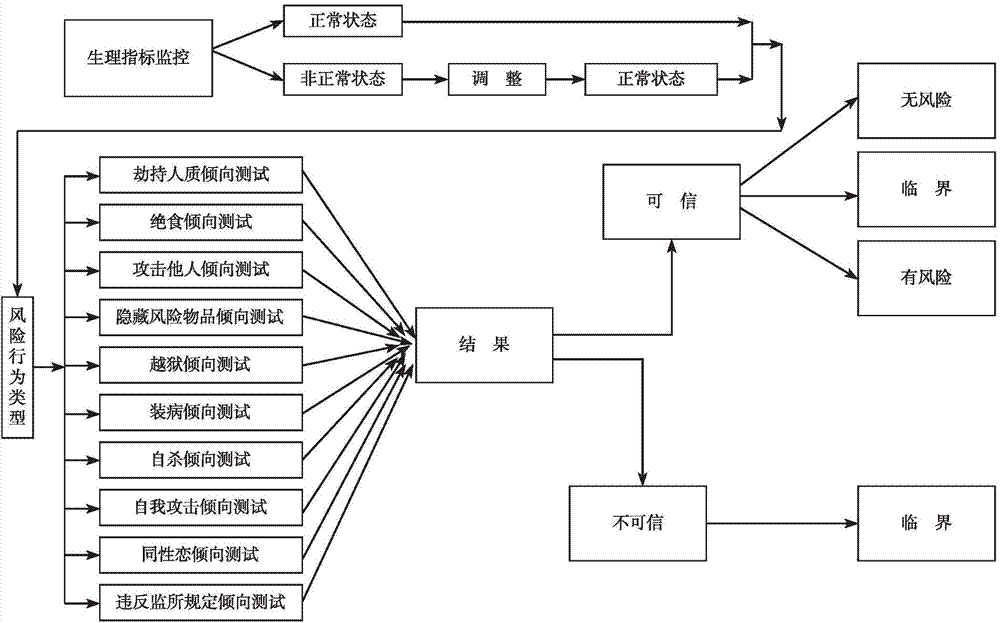
Special person risk behavior evaluation method
ActiveCN104715139ASolve the lying problemImprove the level of scientific managementSpecial data processing applicationsEvaluation resultRisk behavior
A special person risk behavior evaluation method comprises the following steps of obtaining physical sign monitoring data of a tested person; obtaining personal factor data of the tested person; obtaining risk behavior disposition data of the tested person; obtaining interview data of the tested person; obtaining risk behavior type data of the tested person; conducting comprehensive computation on an evaluation result of objective circumstances in personal factors, risk behavior disposition evaluation results and an evaluation result of personal social circumstances and personal subjective factors, and the result obtained after computation is used as a special person risk behavior disposition evaluation result; the risk behavior disposition evaluation results are computed respectively, and the result obtained after computation is used as a risk behavior type evaluation result. According to the special person risk behavior evaluation method, the problem that a special person tells a lie is solved scientifically, the risk behavior disposition is accurately judged, the risk behavior type is predicted, and the scientific management level of the special person is improved.
Owner:张振声
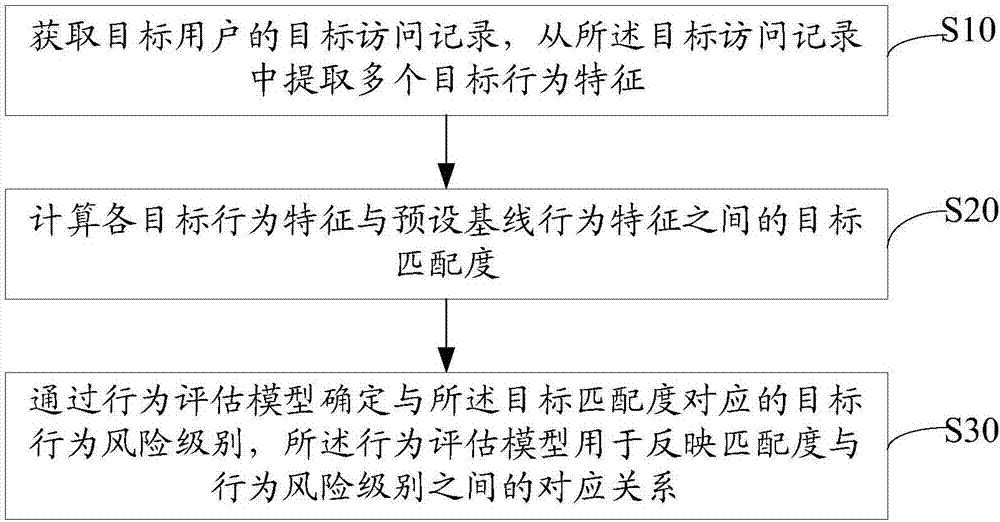
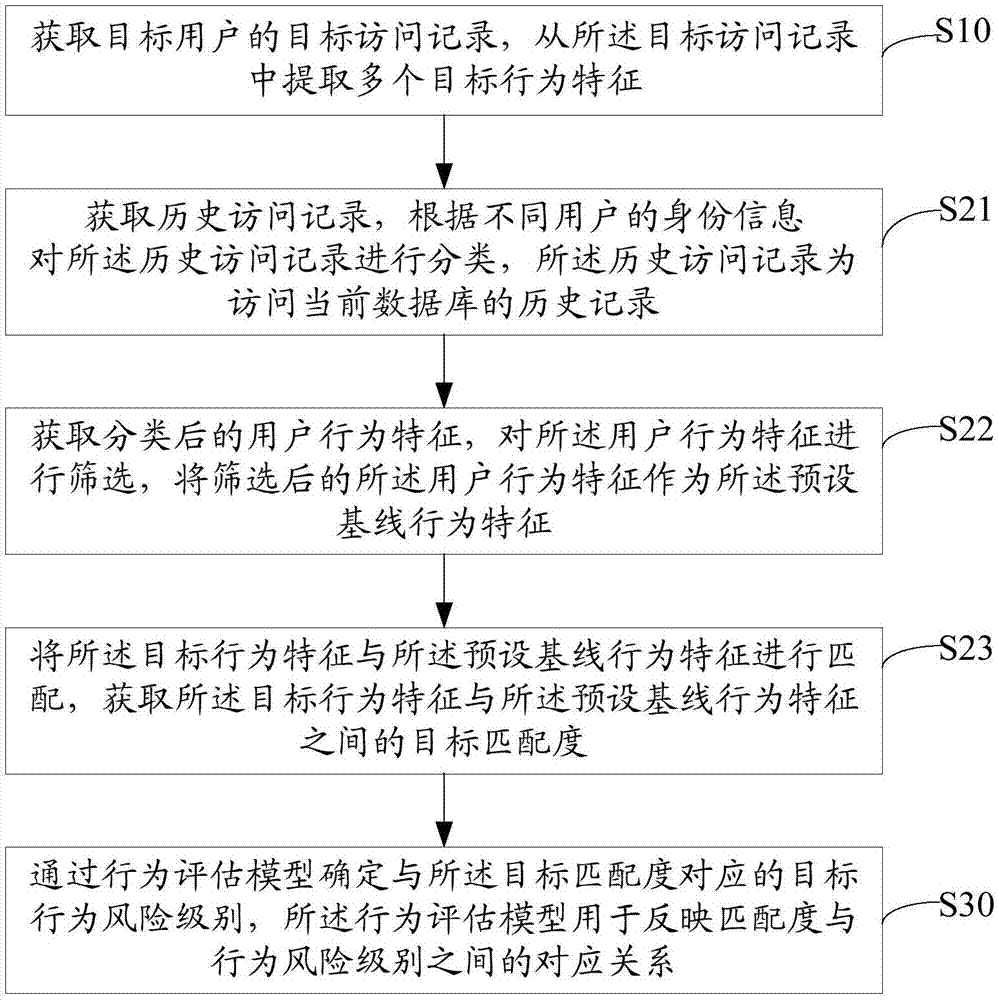
Method for detecting database risk, server and storage medium
The invention discloses a method for detecting a database risk, a server and a storage medium. The method comprises the steps of obtaining a target access record of a target user; extracting multipletarget behavior characteristics from the target access record; calculating a target matching degree between each target behavior characteristic and a preset baseline behavior characteristic; determining a target behavior risk level corresponding to the target matching degree through a behavior estimation model, wherein the behavior estimation model is used for reflecting a corresponding relationship between the matching degree and the behavior risk level. Based on the preset baseline behavior characteristic, the method for detecting the database risk can detect external attacks and internal threats, also can detect variable attacks efficiently without updating the database repeatedly and in real time, avoids data leakage caused by risky behavior of internal personnel, can detect threatening access to the database more comprehensively, can protect the database more efficiently, improves the database risk detection efficiency and accuracy and improves the database security.
Owner:SANGFOR TECH INC
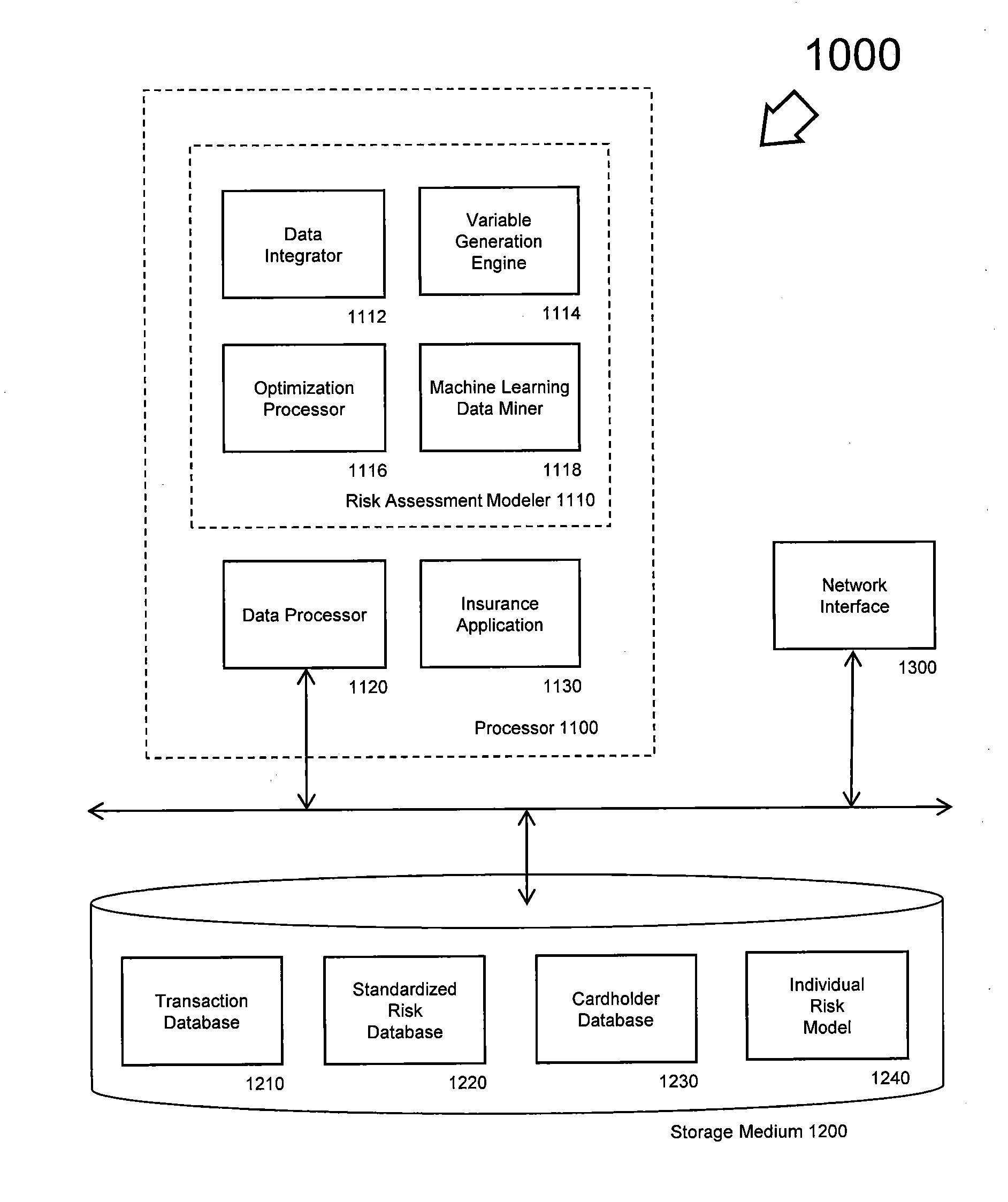
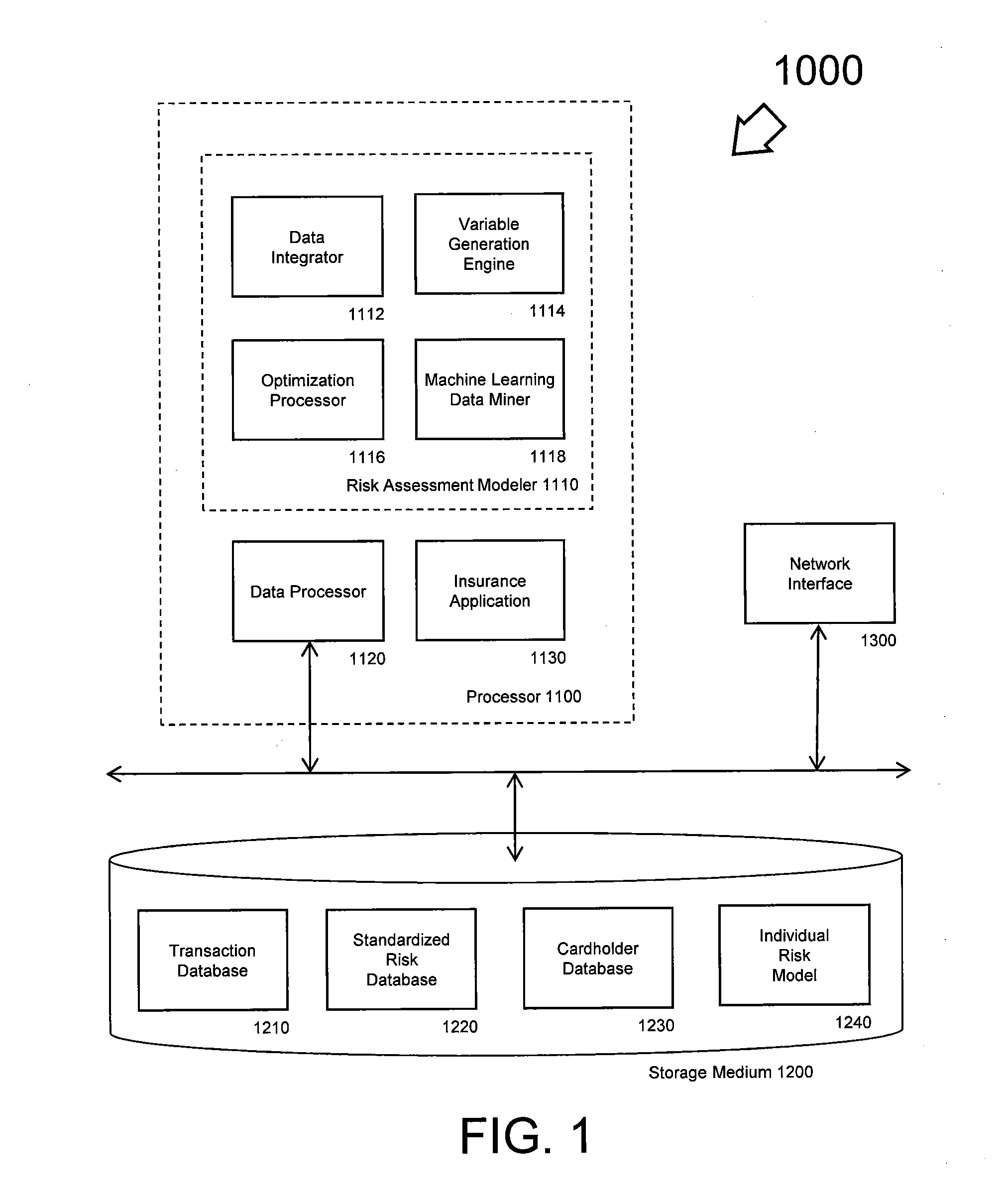
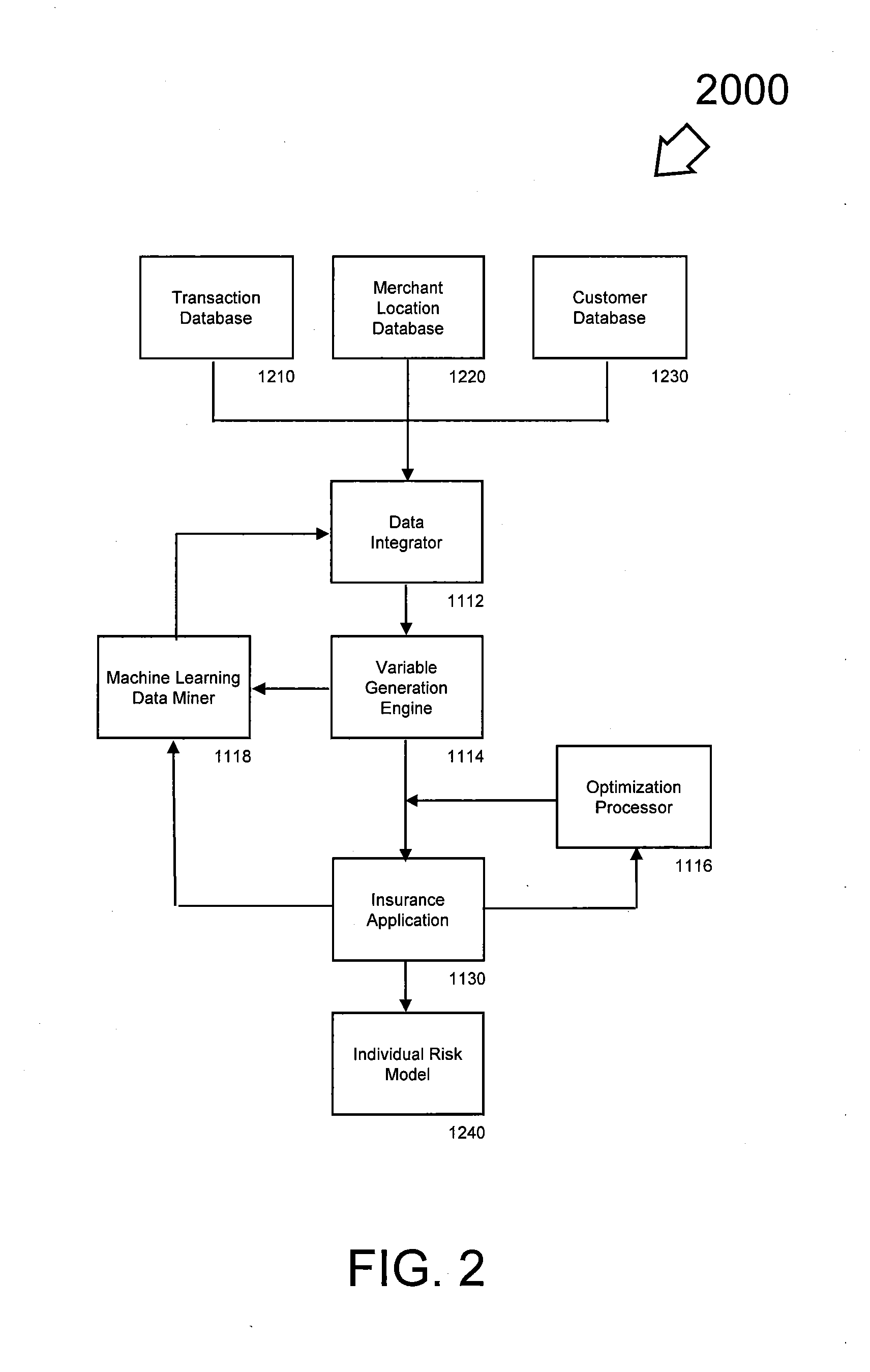
Insurance risk modeling method and apparatus
A system, method, and computer-readable storage medium configured to enable insurance-related risk behavior modeling of individuals based on their payment card purchases.
Owner:MASTERCARD INT INC
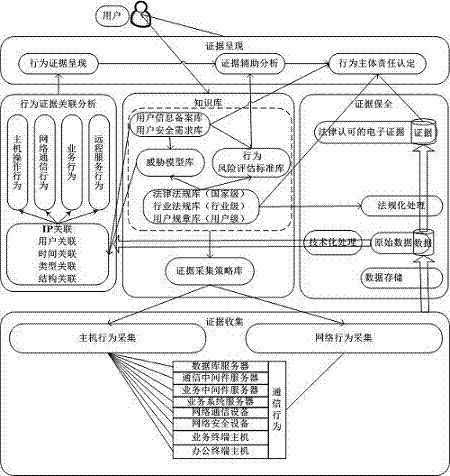
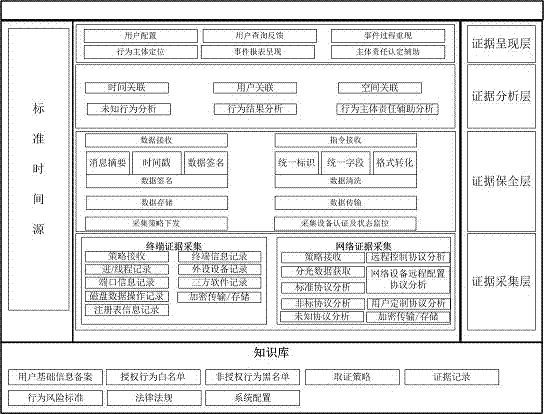
APT detection method and system based on invasion route
ActiveCN107172022ALow costImprove efficiencyData switching networksRisk behaviorKnowledge based modeling
The invention relates to an APT detection method and system based on an invasion route. The APT detection method based on the invasion route comprises the following steps: S1, carrying out knowledge base modeling on an invasion route area; S2, acquiring behavior data, i.e., acquiring host behavior data and acquiring network behavior data; S3, carrying out association analysis on results obtained through the behavior data acquisition; S4, preserving evidence, i.e., recovering attack risk behaviors for evidence preservation; and S5, presenting the evidence. The APT detection system based on the invasion route comprises an evidence presentation module, a behavior evidence association analysis module, a knowledge base module, an evidence preservation module, and an evidence collection module. The method and system provided by the invention has the beneficial effects that invasion by an APT attacker is intercepted at a source, so that preventive measures can be taken for the invasion route, and low-cost and highly-efficient construction can be achieved; an acquisition process is concealed and totally transparent, so that network loads are avoided; and evidence presentation is easy to use and can be simply operated.
Owner:CHENGDU GOLDTEL IND GROUP
Behavior detection method, server and system for application installation package
InactiveCN106162648AEffective protectionEasy to deploySecurity arrangementRisk behaviorComputer terminal
The invention provides a behavior detection method, server and system for an application installation package. The method comprises the following steps: 1) obtaining the application installation package to be detected; 2) extracting behavioral feature information in the application installation package to be matched with a preset behavioral feature database, performing risk behavior detection and obtaining a behavioral feature matching result, wherein multiple behavioral feature data are saved in the behavioral feature database, and each behavior feature datum is used for identifying at least one risk behavior feature; 3) generating a behavior detection result of the application installation package according to the behavioral feature matching result. According to the behavior detection method, server and system provided by the invention, fast detection can be performed on the application installation package in multiple aspects, so that a user quickly understands whether malicious or all kinds of risk behaviors exist in an APK to be detected or not as well as existing malicious behavioral features, therefore, a terminal used by the user is effectively protected.
Owner:上海墨贝网络科技有限公司
Ambulatory blood pressure joint detection and analysis system
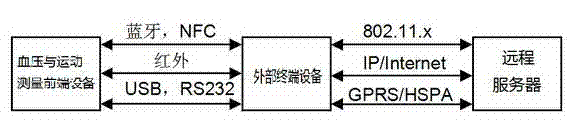
InactiveCN103892811ARealize dynamic monitoringRealize analysisDiagnostic recording/measuringSensorsSoftware analyticsContact behavior
An ambulatory blood pressure joint detection and analysis system comprises a hardware system and a software analysis system. The hardware system is composed of a blood pressure and motion measurement front end device, an external terminal device and a remote server. The software analysis system collects data of the blood pressure, motion and social contact through the hardware system. According to an ambulatory blood pressure model and an algorithm, the system is operated in an application layer. The ambulatory blood pressure joint detection and analysis system has the advantages that various sensors and data sources are used and ambulatory detection and analysis of the blood pressure are achieved with lower cost; motion modes and social contact behaviors which lead to blood pressure fluctuation are reasonably distinguished and a user is guided to avoid high-risk behaviors; the medicine use effect is reasonably analyzed and differentiation of influences, caused by the medicine effect and other factors, on the blood pressure fluctuation is facilitated.
Owner:HANGZHOU UTEAMTEC
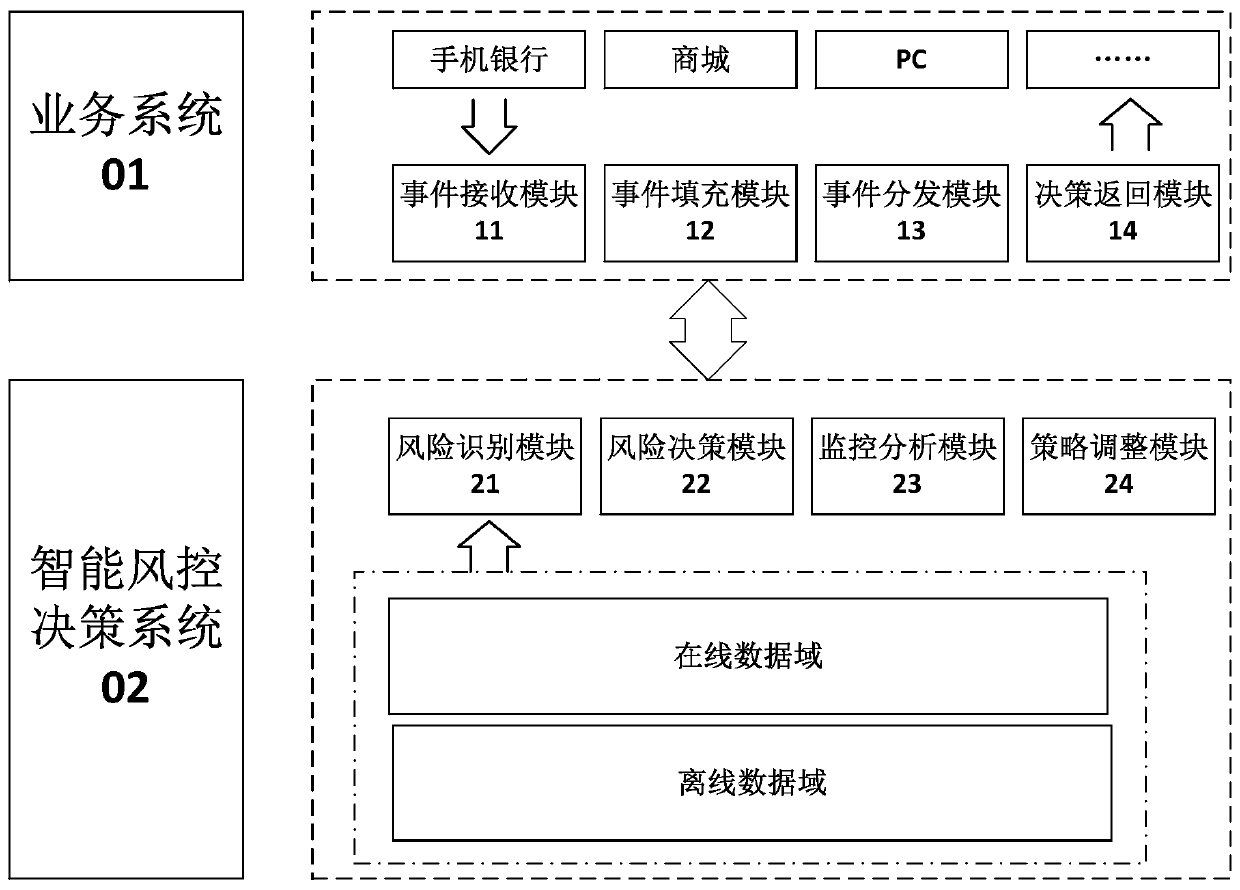
Intelligent risk control decision-making method and system, business processing method and system
ActiveCN110827032AImprove accuracyReduce misjudgmentFinanceProtocol authorisationRisk ControlRisk behavior
The invention discloses an intelligent risk control decision-making method and a system, a business processing method and a system, and the method comprises the steps: calling a recognition strategy to carry out the risk recognition of an event set, obtaining the risk behaviors of the event set, and generating a response decision according to the risk behaviors of the event set. After an event setis identified and decided, the risk behavior and the response decision of the event set can be monitored and analyzed to obtain the analysis result of the event set, and the identification strategy and the response decision can be adjusted according to the analysis result of the event set, so that the strategy (decision) can be flexibly changed according to the actual situation, the risk situation can be quickly responded, the misjudgment is reduced, and the risk identification accuracy is improved.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
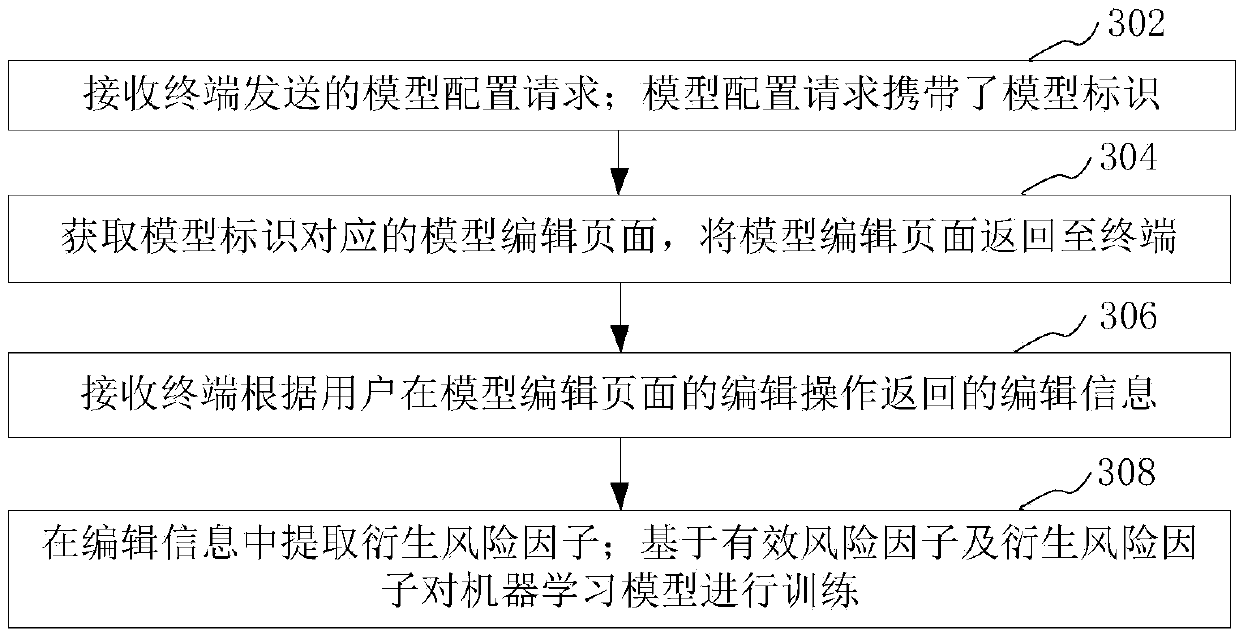
Risk prediction method and apparatus based on machine learning, computer device and storage medium
ActiveCN109543925AExpand the dimension of risk predictionExpand the forecast dimensionForecastingResourcesRisk behaviorData mining
The present application relates to a risk prediction method and apparatus based on machine learning, a computer device and a storage medium. The method includes obtaining first risk data of a trainingsample; Preprocessing the first risk data to obtain a plurality of basic risk factors; Identifying an associated sample of the training sample and climbing the second risk data of the associated sample; Preprocessing the second risk data to obtain a plurality of associated risk factors; Screening the basic risk factors and associated risk factors to obtain a variety of effective risk factors; training The machine learning model based on the effective risk factors, and obtaining the risk prediction model; Based on the risk prediction model, monitoring the existence of risk behaviors of monitoring objects. The method can improve the risk prediction efficiency.
Owner:PING AN TECH (SHENZHEN) CO LTD
Risk behavior recognition method, storage medium, device and system
The invention discloses a risk behavior recognition method, a storage medium, a device and a system, and relates to the field of big data risk control. The method comprises the steps of extracting, according to behavior log data, each specific behavior of each user in a set user set, and obtaining a specific behavior sequence for each user; using pre-defined strong rules to find high-risk suspected users in the set user set, recording the suspected users as a first user set, and recording the remaining users in the set user set as a second user set; setting specific behavior pairs, and calculating a first transition probability and a second transition probability; for the same specific behavior pair, judging whether the difference between the first transition probability and the second transition probability is within a preset range, and if not, recording the specific behavior pair as a risk specific behavior pair; and calculating the information entropy of each risk specific behaviorpair group, and judging whether the user is a suspected user according to the size of the information entropy. The risk behavior recognition method in the invention can find malicious users whose cheating characteristics are not obvious.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Risk behavior detection method, device, equipment and computer storage medium
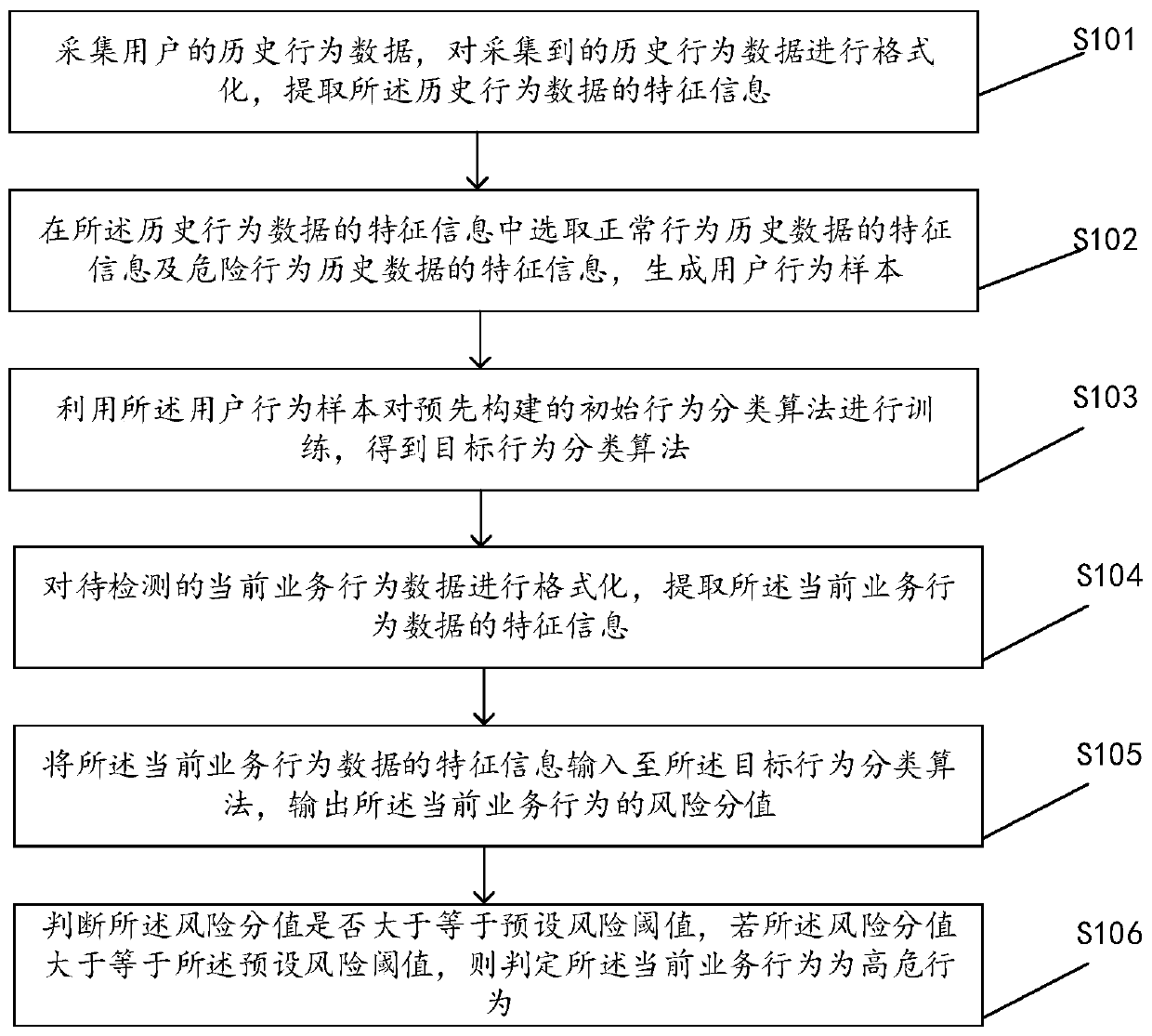
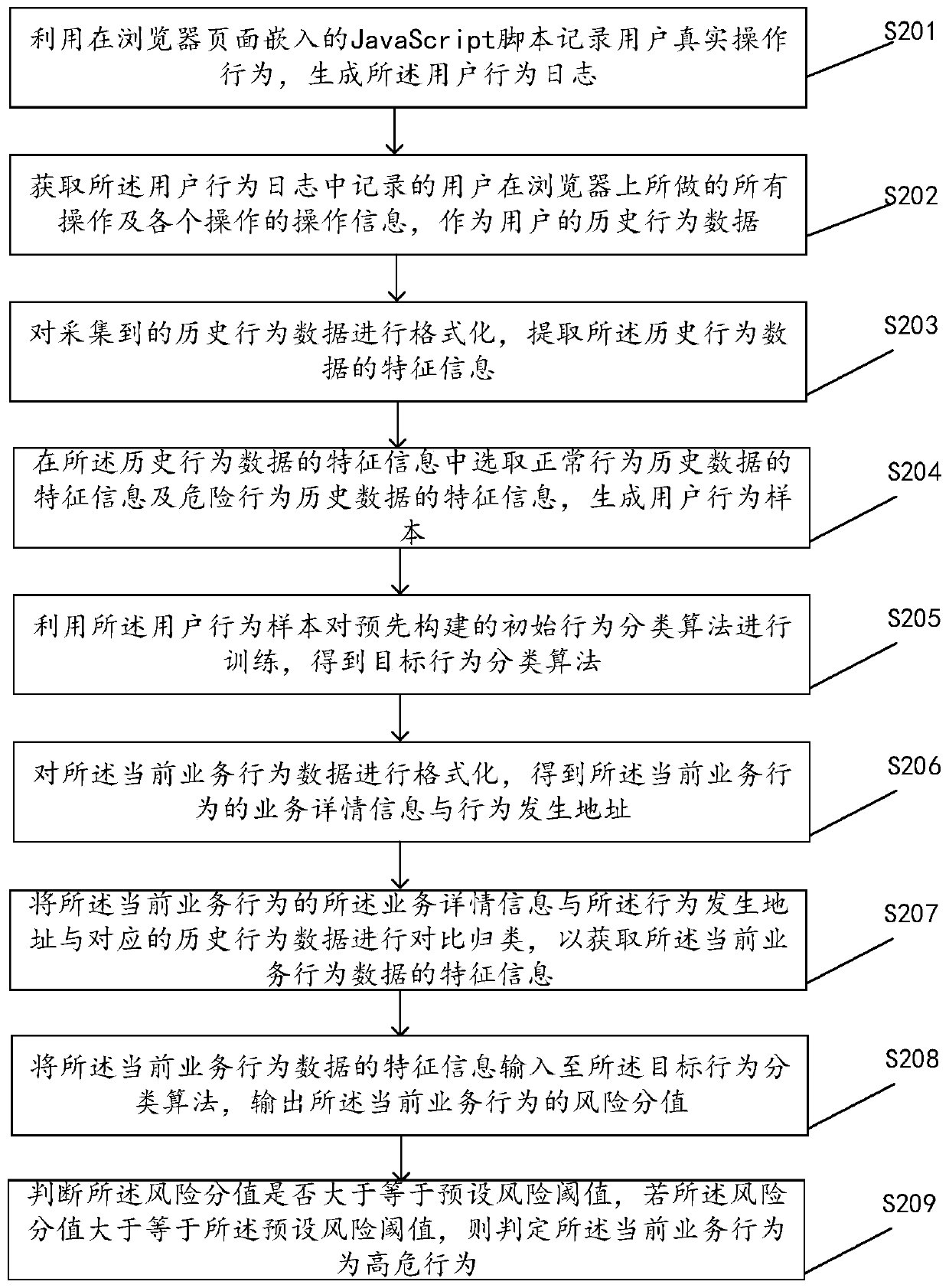
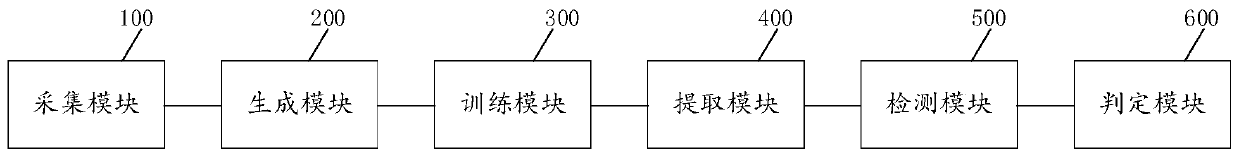
PendingCN111143175AImprove real-time performanceHardware monitoringProtocol authorisationRisk behaviorBehavioral data
The invention discloses a risk behavior detection method, a device, equipment and a computer readable storage medium, and the method comprises the steps: collecting historical behavior data of a user,carrying out the formatting of the historical behavior data, and extracting the feature information of the historical behavior data; selecting the feature information of the normal behavior historical data and the feature information of the dangerous behavior historical data from the feature information of the historical behavior data to generate a user behavior sample; training a classificationalgorithm by using the user behavior sample to obtain a target behavior classification algorithm; formatting the current business behavior data, and extracting feature information of the current business behavior data; inputting the feature information of the current business behavior data into a target behavior classification algorithm, and outputting a risk score of the current business behavior; and if the risk score is greater than or equal to the threshold, determining that the current business behavior is a high-risk behavior. According to the method, the device, the equipment and the computer readable storage medium provided by the invention, the efficiency, the accuracy and the real-time performance of risk behavior detection are improved.
Owner:北京浪潮数据技术有限公司
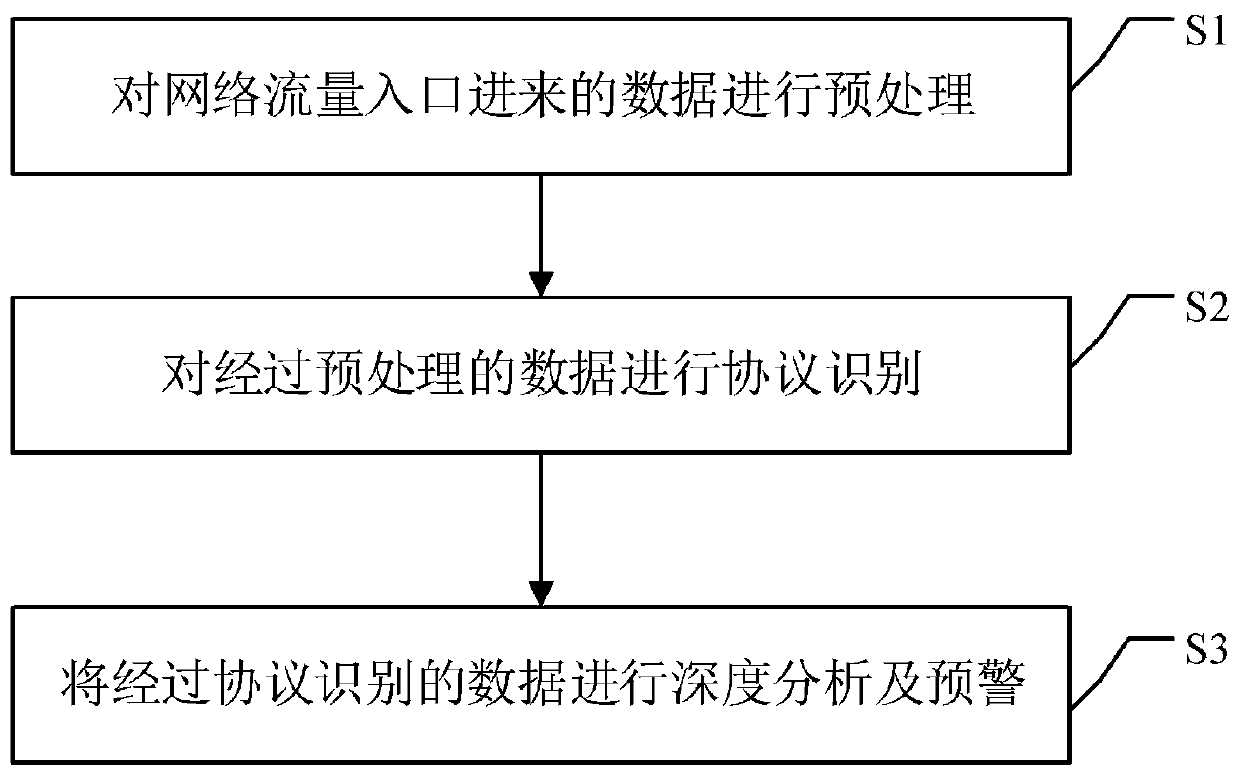
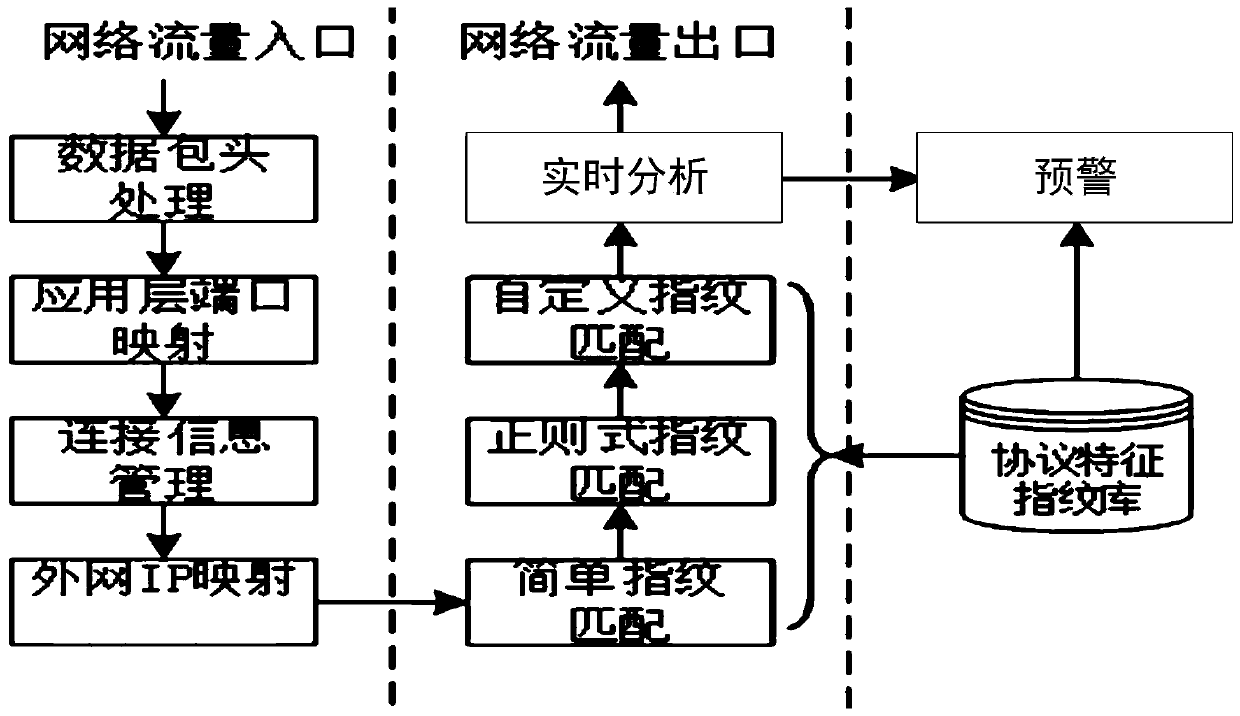
Security early warning method and device based on protocol identification in scheduling data network
The invention discloses a security early warning method and device based on protocol identification in a scheduling data network. The method comprises the following steps: preprocessing data coming from a network traffic entrance; performing protocol identification on the preprocessed data; performing deep analysis and early warning on the data subjected to protocol identification; the method hasthe advantages that data in the whole scheduling data network is monitored and subjected to safety protection, and safety early warning is carried out on malicious invasion and other risk behaviors existing in the scheduling data network.
Owner:HEFEI YOUO ELECTRONICS TECH
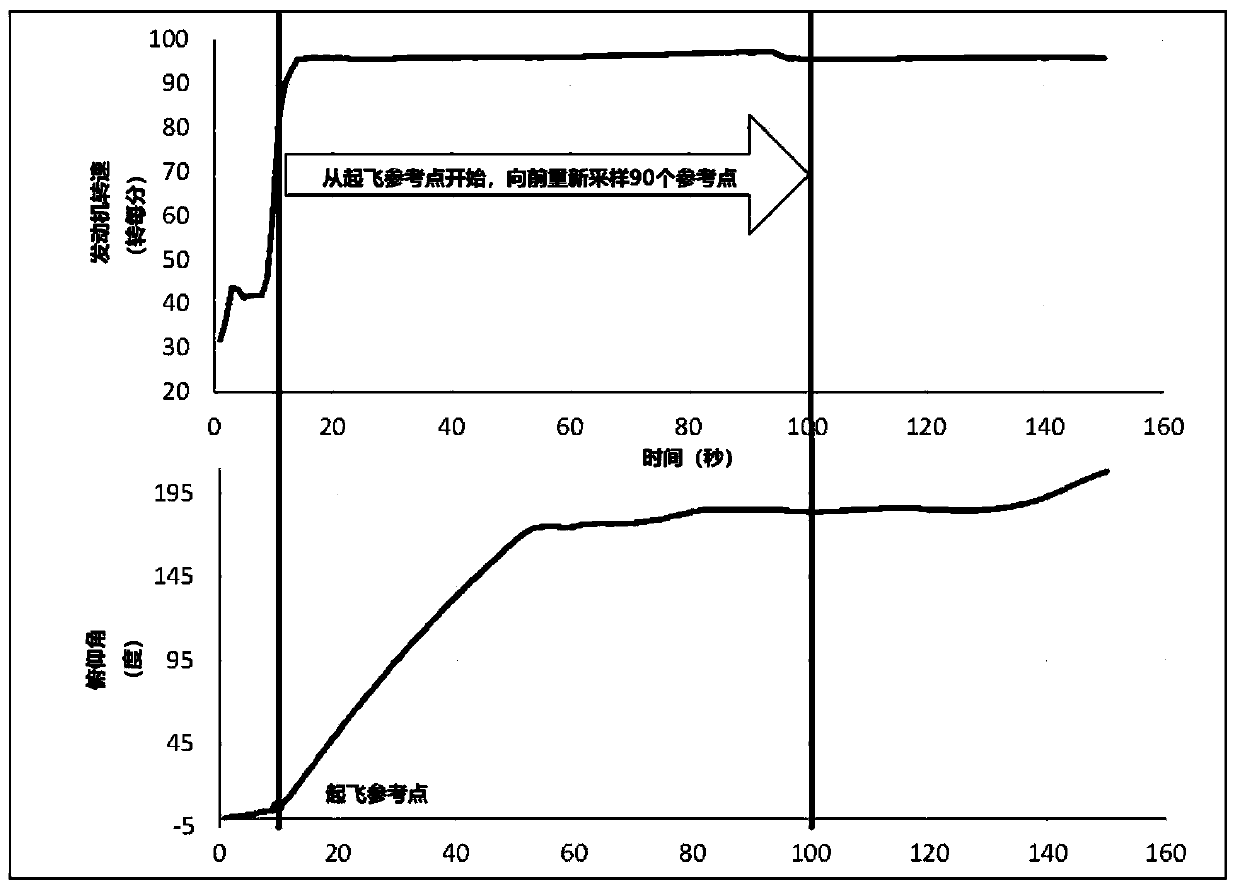
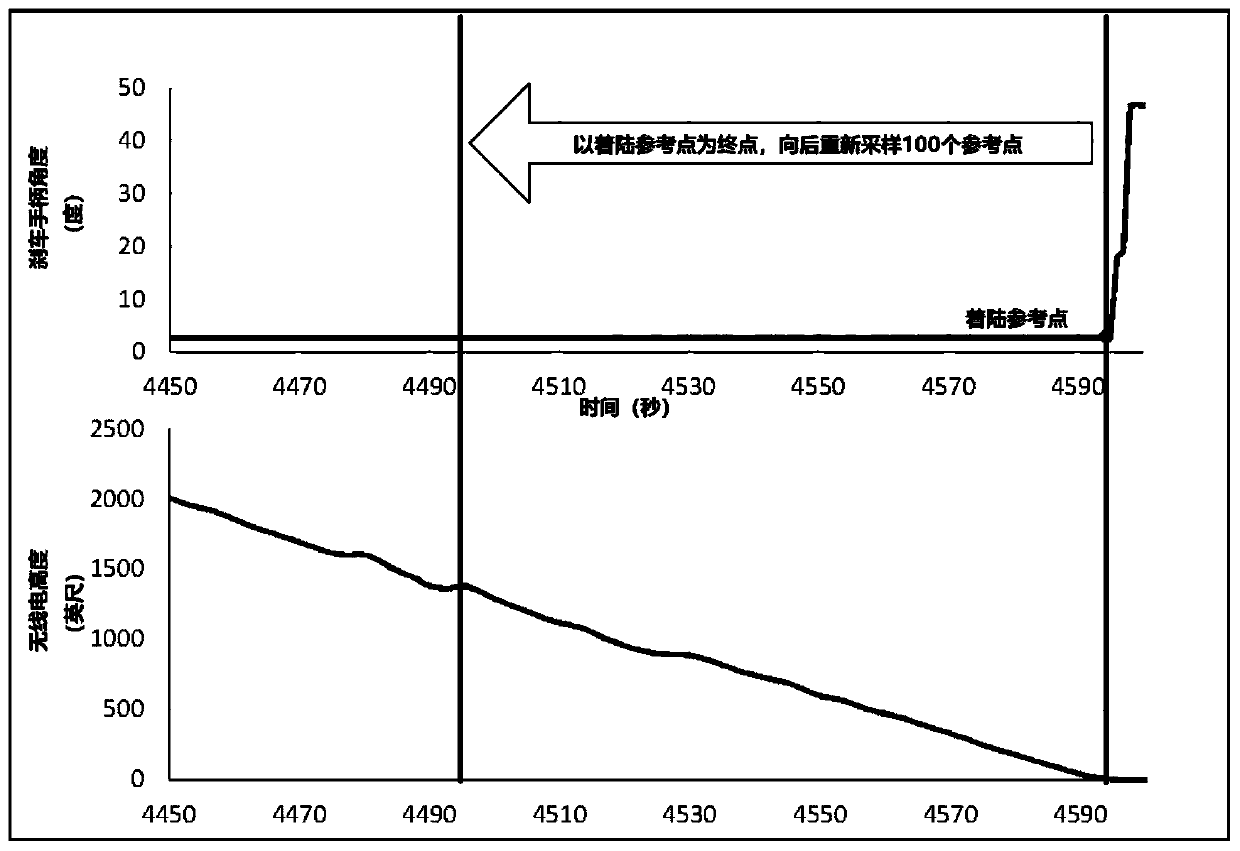
Flight risk behavior identification method based on improved random forest
ActiveCN110533095ATake it easyEasy to takeCharacter and pattern recognitionFeature vectorRisk behavior
The invention discloses a flight risk behavior identification method based on an improved random forest. The method comprises the steps of calibrating and resampling original QAR data and acquiring feature vectors of each sortie flight take-off and landing stage; performing dimension reduction and feature extraction on the feature vector to obtain a final feature vector; constructing a high-riskover-limit event judgment data set in the take-off and landing stages, and improving the high-risk over-limit event judgment data set to obtain an improved high-risk over-limit event judgment data set; building a high-risk over-limit event recognition model based on the improved random forest; and classifying and identifying the data in the improved high-risk over-limit event judgment data set byutilizing an identification model, and making secondary discrimination on unknown risk events. According to the invention, common high-risk over-limit events in take-off and landing stages can be accurately identified; according to the invention, flights with potential flight risks can be screened out for secondary discrimination by safety management personnel, so that pilots can improve technicalactions more timely, and the management personnel can make decisions more leisurely.
Owner:CIVIL AVIATION UNIV OF CHINA
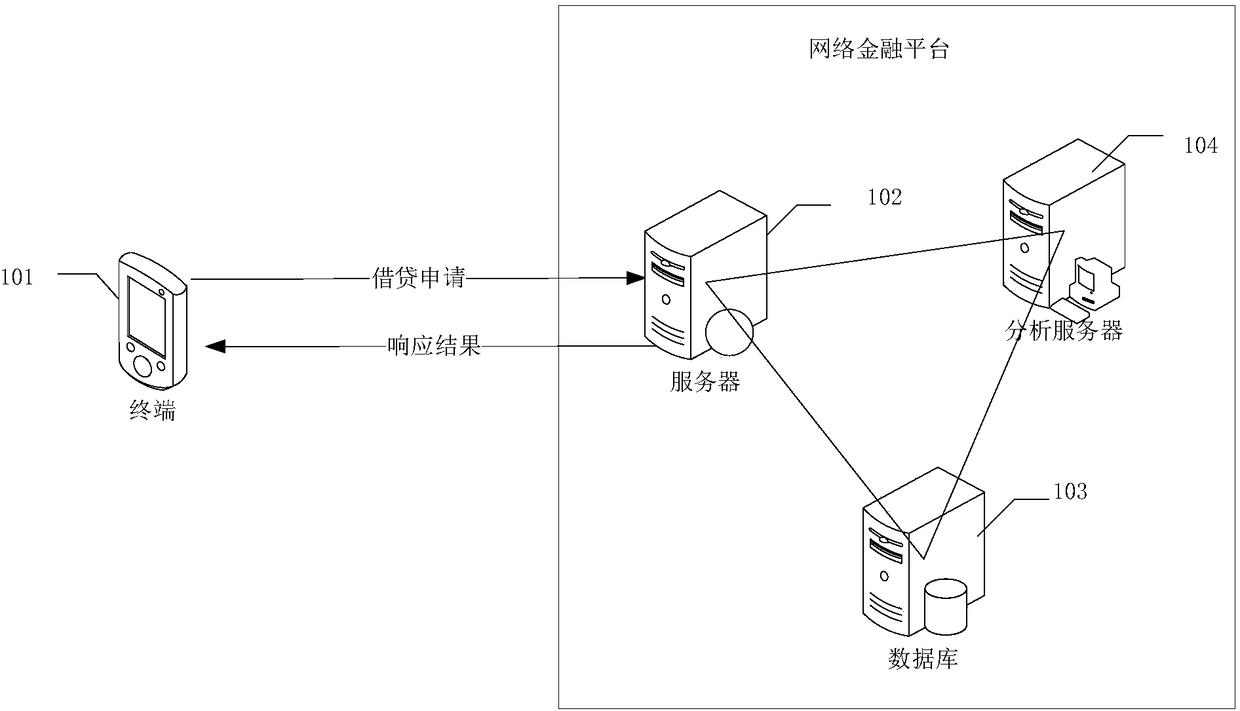
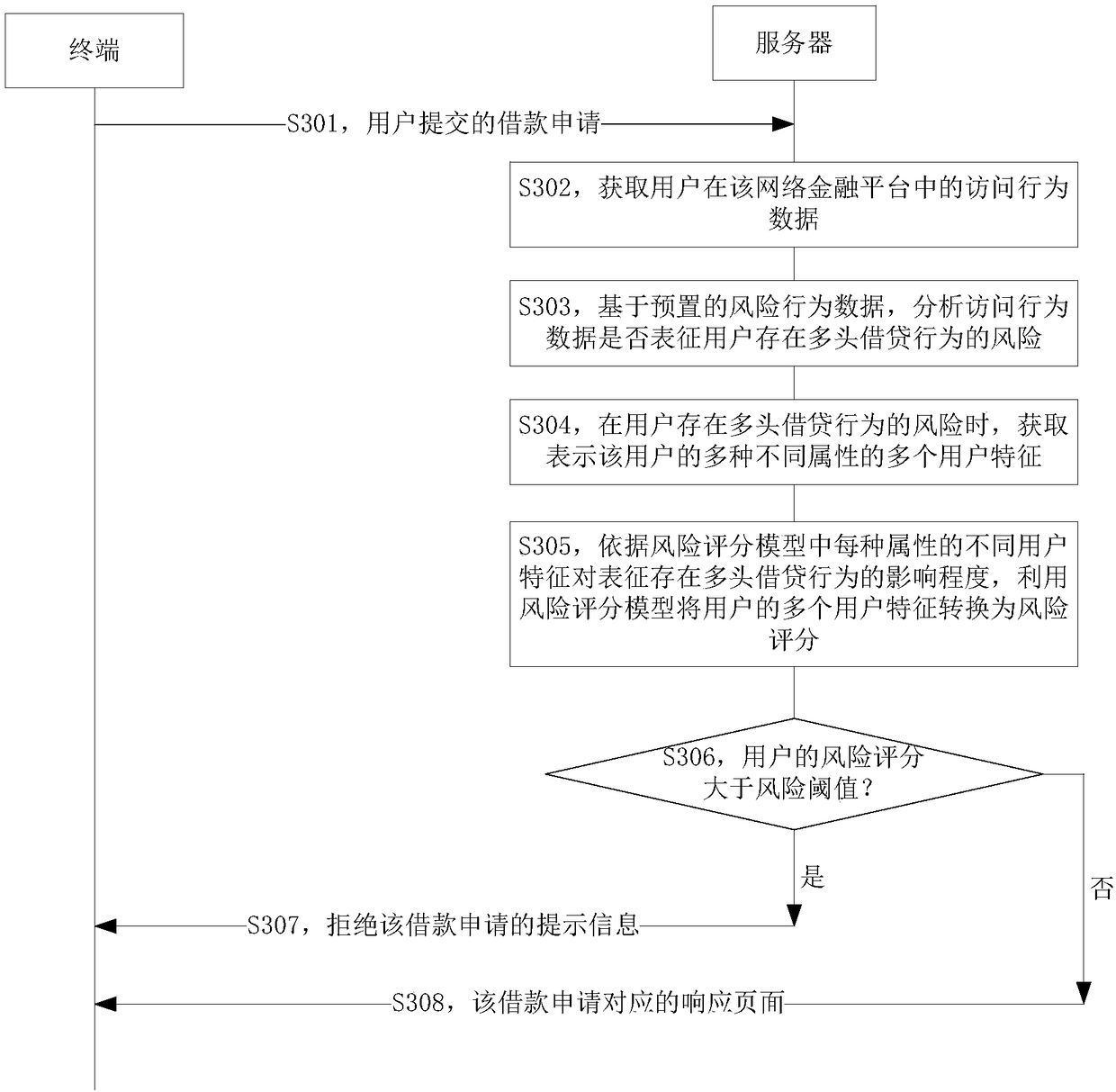
Loan processing method and apparatus, and server
The invention discloses a loan processing method and apparatus, and a server. The loan processing method includes the steps: receiving a loan application submitted to a network financial platform by auser; giving a response to the loan application, acquiring access behavior data of the user in the network financial platform; based on preset risk behavior data, and when knowing that the access behavior data represents that the user has a bull loan behavior risk through analysis, acquiring a plurality of user characteristics of a plurality of different attributes of the user; according to the influence degree, on the representation that a bull loan behavior exists, of different user characteristics contained in each attribute in a risk evaluation mode which is obtained through pre-training,and utilizing the risk evaluation model to convert the plurality of user characteristics of the user into a risk score for representing that the user has a bull loan behavior; and according to the risk score, processing the loan application submitted by the user. The loan processing method and apparatus can reduce the situation that loans are supplied to a lender having a fund risk, and can improve the fund safety of the internet financial platform.
Owner:TENCENT TECH (SHENZHEN) CO LTD
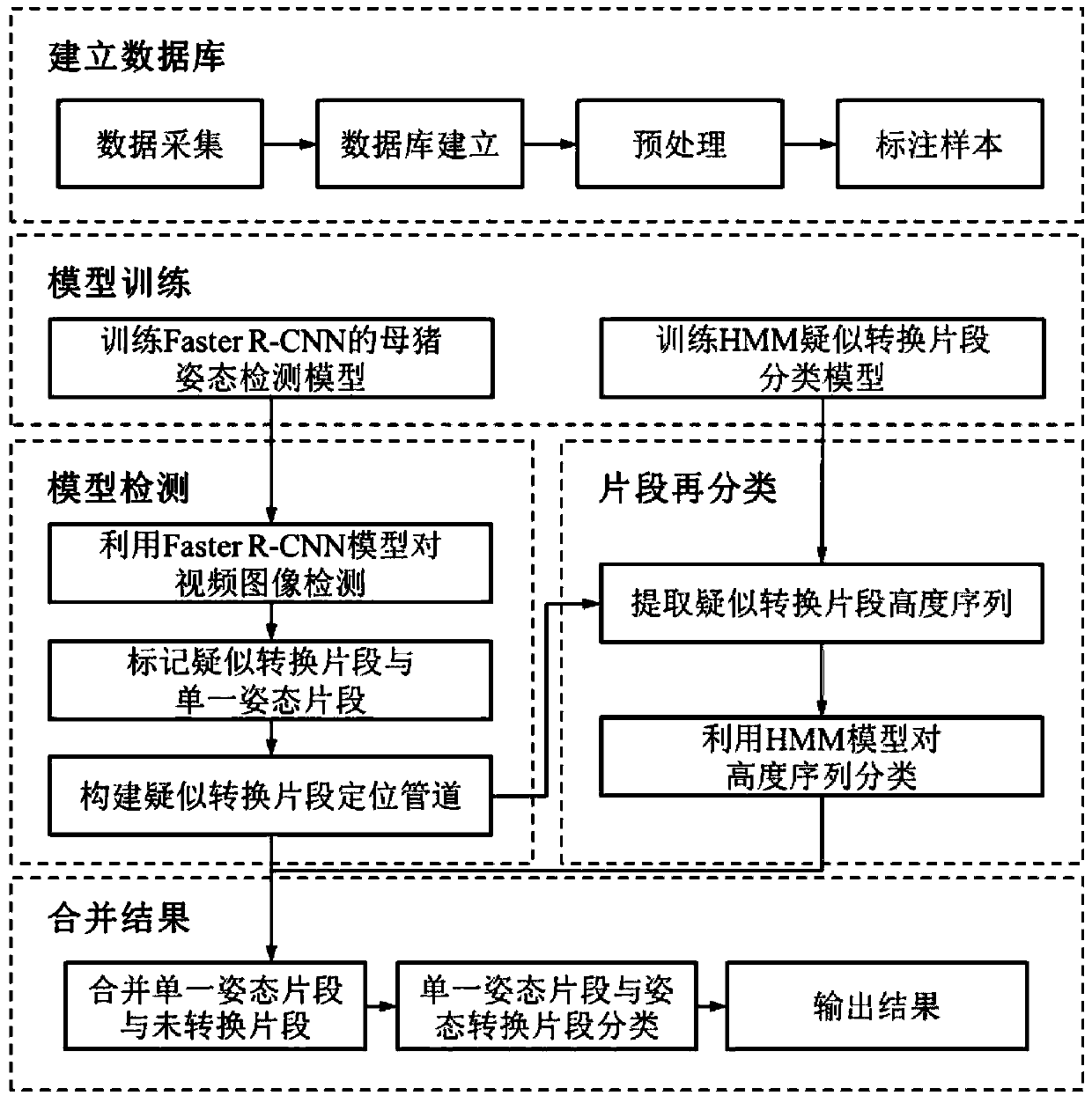
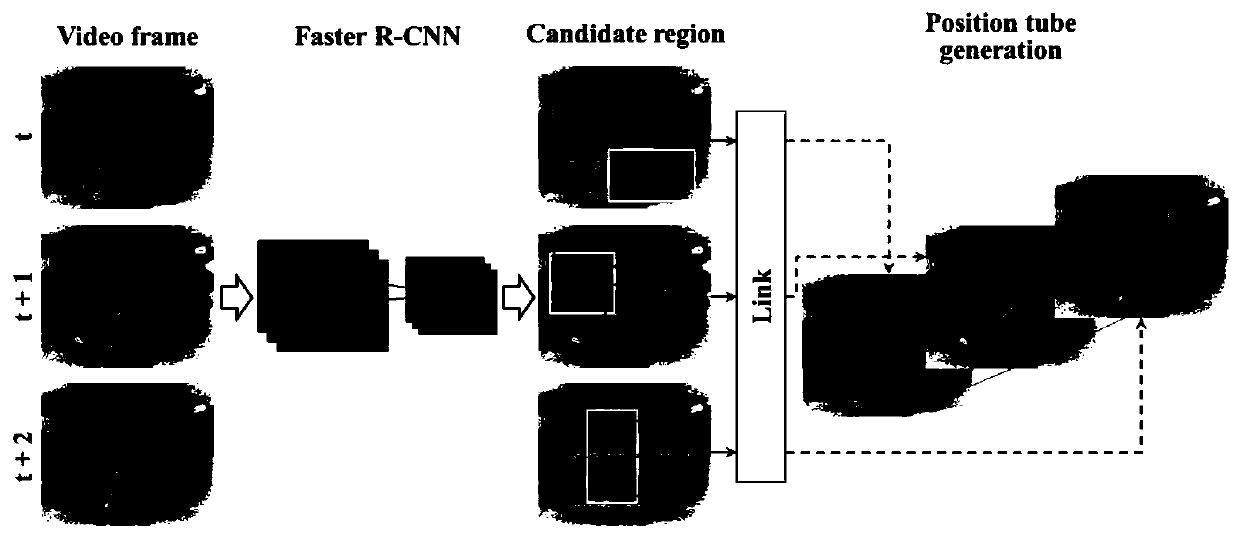
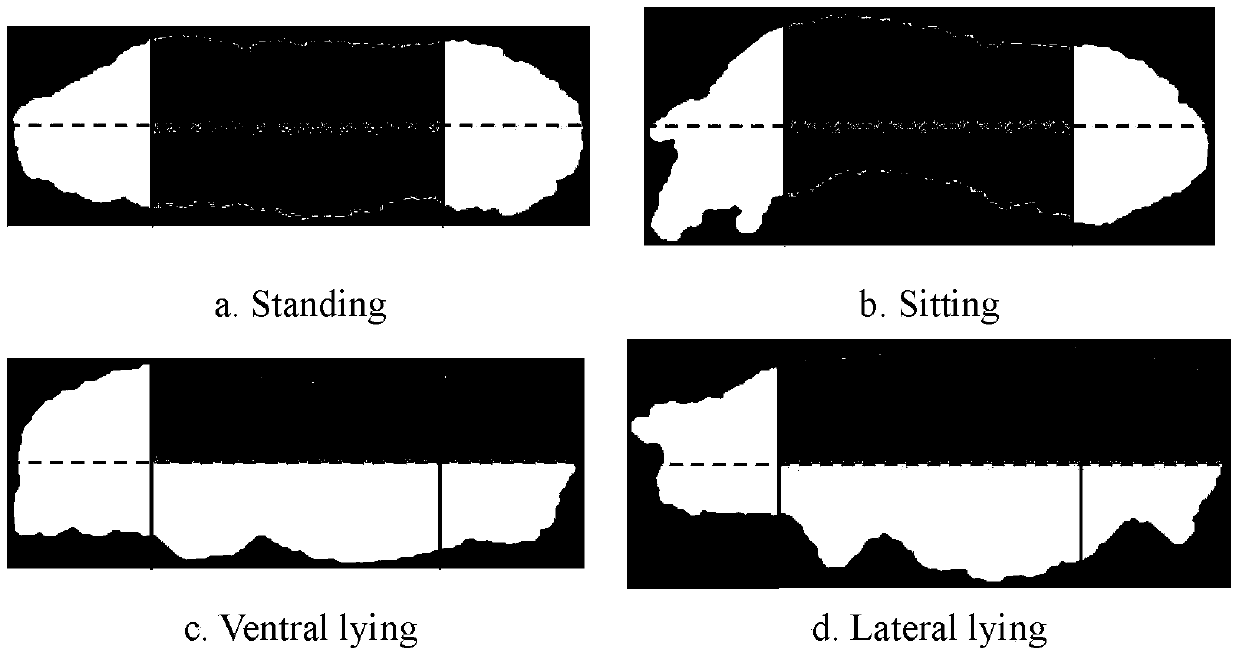
A lactating sow posture conversion identification method based on Faster R-CNN and HMM
ActiveCN109711389AImprove generalization abilitySolve the problem of difficult recognition of sow posture transformationCharacter and pattern recognitionNeural architecturesRisk behaviorVariance method
The invention discloses an R-based on a Faster. The CNN and HMM lactating sow posture conversion identification method comprises the following steps: 1, enhancing the quality of a depth image; 2,usingan improved Faster R-CNN to identify the postures of the sows, and take the posture with the maximum probability per frame as a posture sequence; taking the first five detection frames with the maximum probability as candidate areas; 3, correcting an attitude sequence classification error by using median filtering with the length of 5; detecting a suspected conversion segment by using the video segment attitude conversion times; In the suspected conversion segment, constructing a sow positioning pipeline according to the candidate area by using a Viterbi algorithm; 4, in the positioning pipeline, segmenting each frame of sow by using a maximum between-class variance method, and calculating the height of each part of the sow body to form a height sequence; 5, inputting the height sequenceinto an HMM model, and dividing a suspected conversion segment into an attitude conversion segment and an unconverted segment; and classifying the single posture segment and the posture conversion segment to obtain a recognition result. The sow posture recognition system can automatically convert and recognize the posture of the sow under the conditions of light change and nighttime, and lays a foundation for high-risk behavior recognition.
Owner:SOUTH CHINA AGRI UNIV
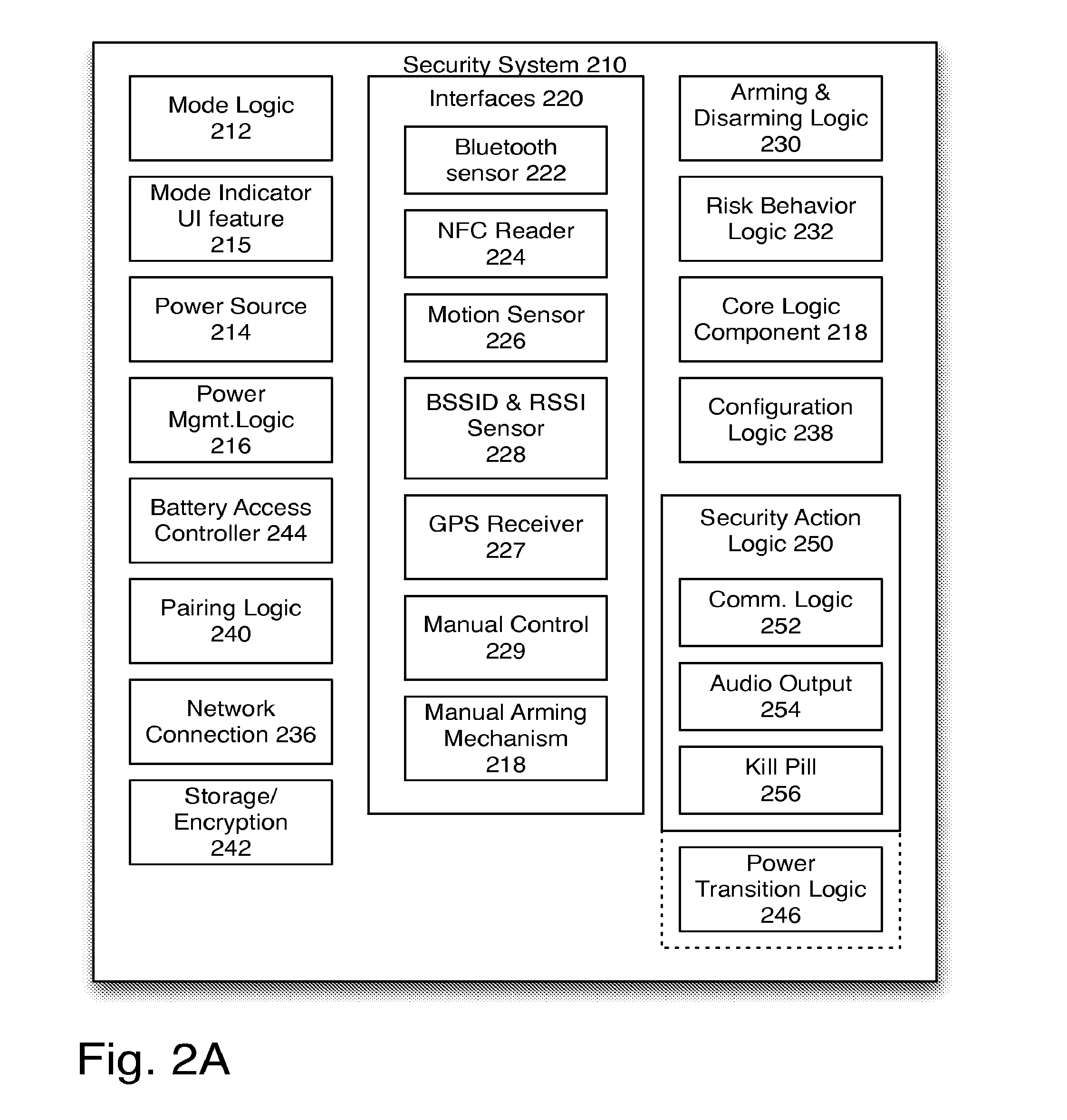
Always-available embedded theft reaction subsystem
InactiveUS20140123328A1Error detection/correctionVolume/mass flow measurementEmbedded systemRisk behavior
A platform including an always-available theft protection system is described. In one embodiment, the system comprises a power management logic to selectively power elements of the system, a disarming logic to disarm the platform from an armed mode when a disarming command is received via an interface, the interface powered when the platform is in the armed and suspecting modes to detect the disarming command. The system further comprises, in one embodiment, a risk behavior logic to detect a potential problem via a interface, the interface powered when the platform is in the armed mode to detect the potential problem, and a core logic component to provide logic to analyze the potential problem, and to move the platform to a suspecting mode, when the potential problem indicates a theft suspicion, the core logic powered when the risk behavior logic detects the potential problem.
Owner:INTEL CORP
Method and device for identifying risk behaviors
ActiveCN105989155AAvoid the drawbacks of consuming additional computer resourcesReduce the burden onPlatform integrity maintainanceTransmissionRisk behaviorNetwork behavior
Owner:ADVANCED NEW TECH CO LTD
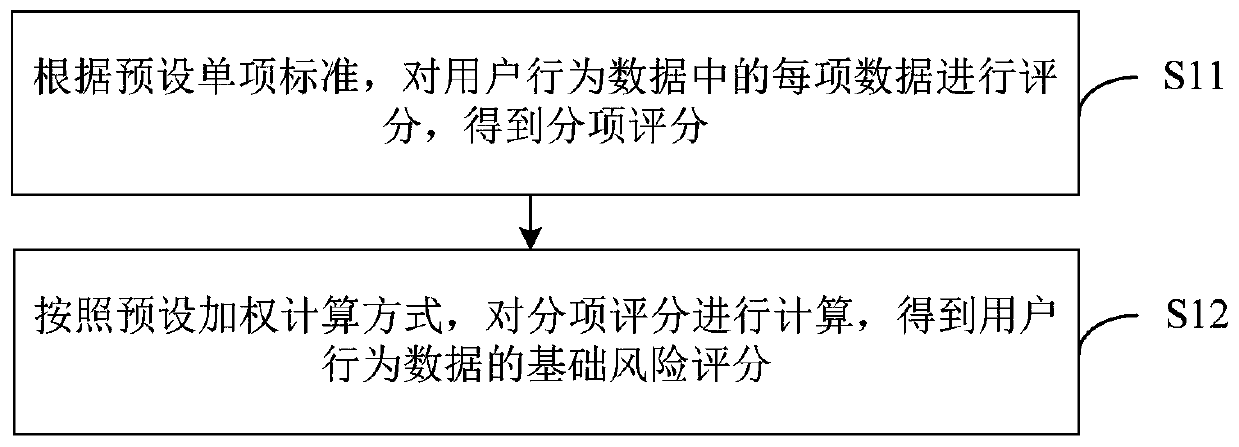
User behavior detection method and device, computer equipment and storage medium
ActiveCN110493181AReduce false alarm rateImprove accuracyHardware monitoringTransmissionRisk behaviorNormal behaviour
The invention discloses a user behavior detection method and device, computer equipment and a storage medium, and the method comprises the steps: obtaining user behavior data, carrying out the calculation of the user behavior data according to a preset score calculation mode, and obtaining a basic risk score of the user behavior data; comparing the basic risk score with a preset standard score, and if the basic risk score exceeds the preset standard score, determining a user behavior corresponding to the user behavior data as a risk behavior; and if the basic risk score is lower than a presetstandard score, performing data intersection operation on the user behavior data and a risk behavior template in a preset reference risk library, and determining whether a user behavior correspondingto the user behavior data belongs to a risk behavior or a normal behavior according to a numerical relationship between an operation result and a preset threshold. According to the technical scheme, the probability of missing report and false report in the user behavior detection process is reduced, and the accuracy of risk behavior recognition is improved.
Owner:CHINA PING AN PROPERTY INSURANCE CO LTD
Receiving Security Risk Feedback From Linked Contacts Due to a User's System Actions and Behaviors
An approach is provided in receiving risk feedback from a social network. Feedback transmissions are received by a user's system with each of the feedback transmissions being received over a computer network from a social network contact. The received feedback transmissions are analyzed and, based on the analysis, a risky action that was performed by the user is identified. The user performs a risk avoidance measure to counteract the identified risky action. In one embodiment, the risk avoidance measure is reported back to the user's contacts.
Owner:INT BUSINESS MASCH CORP
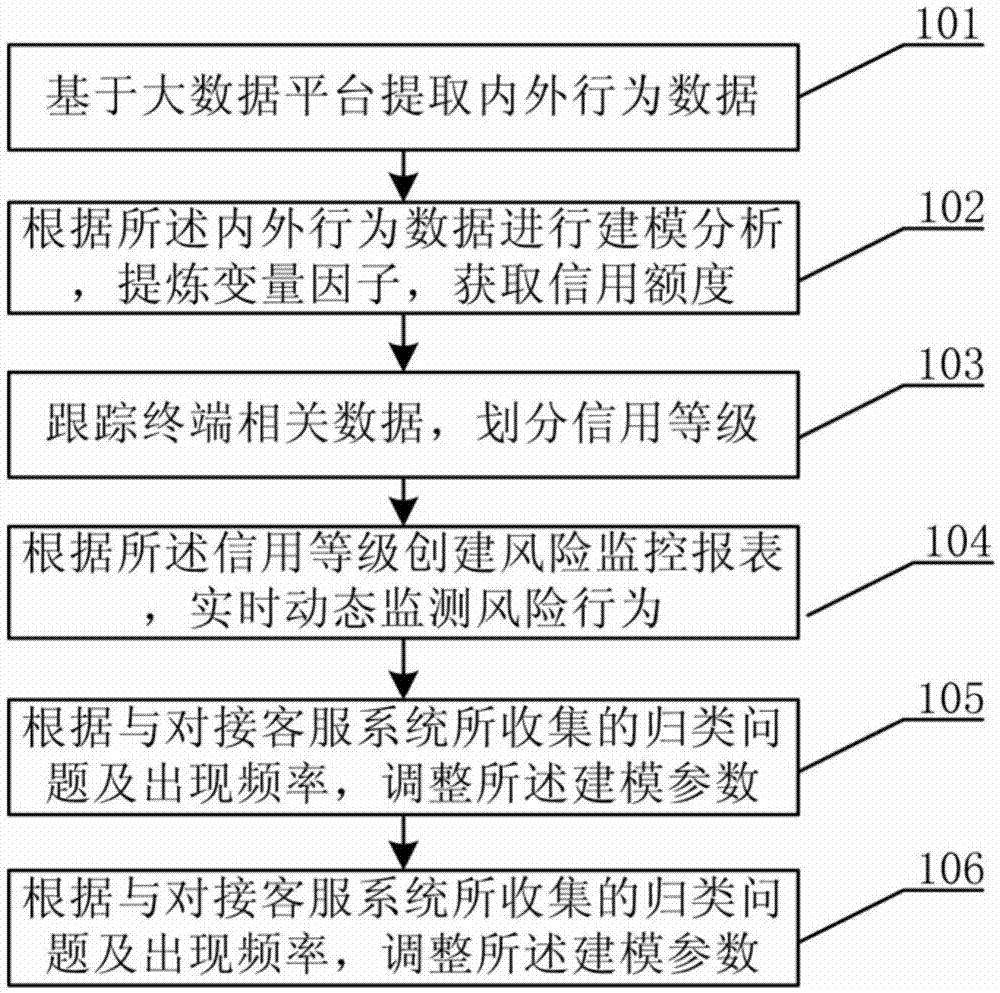
Real-time risk control method based on big data platform and system thereof
A real-time risk control method based on big data is disclosed. The method comprises the following steps of extracting internal and external behavior data based on a big data platform; according to the internal and external behavior data, carrying out modeling analysis, refining a variable factor and acquiring a credit limit; tracking terminal correlation data and dividing a credit grade; according to the credit grade, creating a risk monitoring statement and dynamically monitoring a risk behavior in real time; according to a classification problem collected with a butt joint customer service system and an appearance frequency, adjusting a modeling parameter; carrying out correlation data query on a determined loss asset and acquiring a list. In the invention, a risk control system and the big data platform carry out seamless joint. A risk control model can rely on real-time data high-efficiently collected by the big data platform so that inaccurate and non-real-time problems in risk control are effectively solved. Game risk control is effectively, quantitatively and professionally realized in a programming, productization and marketization mode. A complete risk tracking system after credit extension, a loss asset claim system and a virtual reconciliation system are possessed.
Owner:SNAIL GAMES
Identity verification method and device
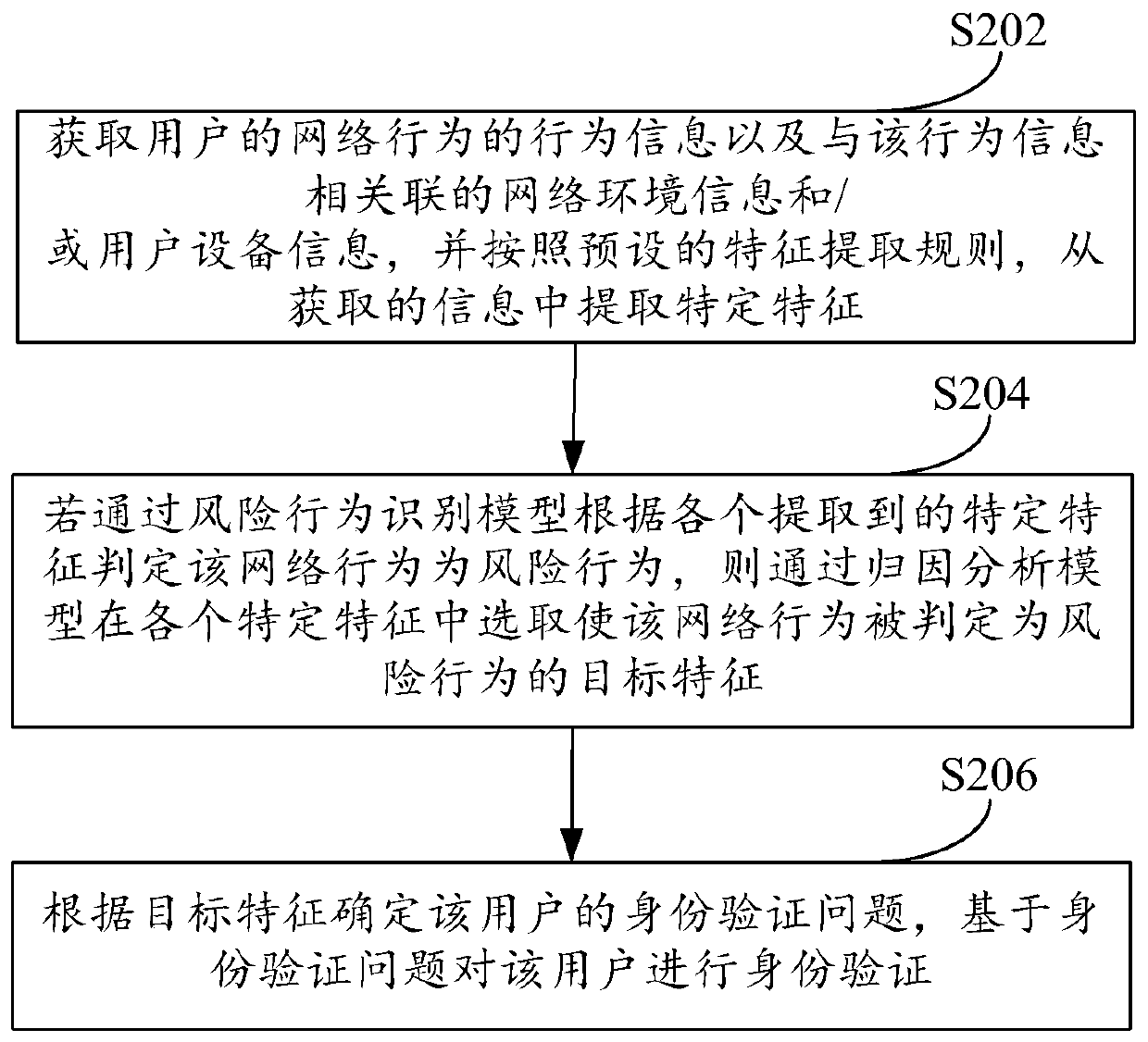
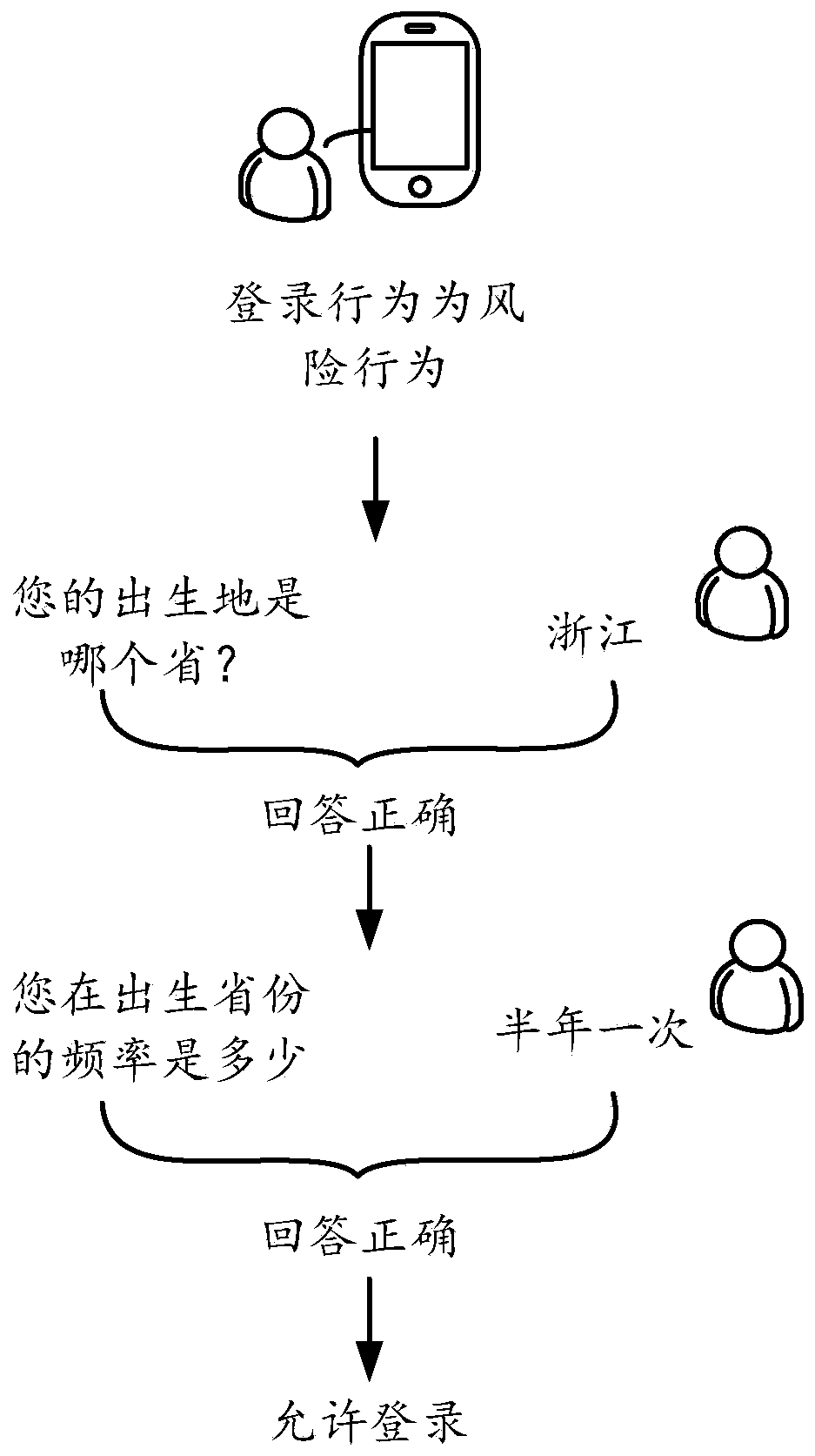
ActiveCN110245475AImprove securityDigital data authenticationPlatform integrity maintainanceRisk behaviorFeature extraction
The embodiment of the invention provides an identity verification method and device which aims to improve the security of the user identity verification. The method comprises the following steps of firstly, acquiring the behavior information of a network behavior of a user and the network environment information and / or the user equipment information associated with the behavior information, according to a preset feature extraction rule, extracting the specific features from the acquired information, then, judging whether the network behavior is a risk behavior or not through a risk behavior recognition model according to each extracted specific feature; and if yes, selecting a target feature enabling the network behavior to be judged as a risk behavior from all specific features through an attribution analysis model, and finally, determining an identity verification problem of the user according to the target feature and carrying out identity verification on the user.
Owner:ADVANCED NEW TECH CO LTD
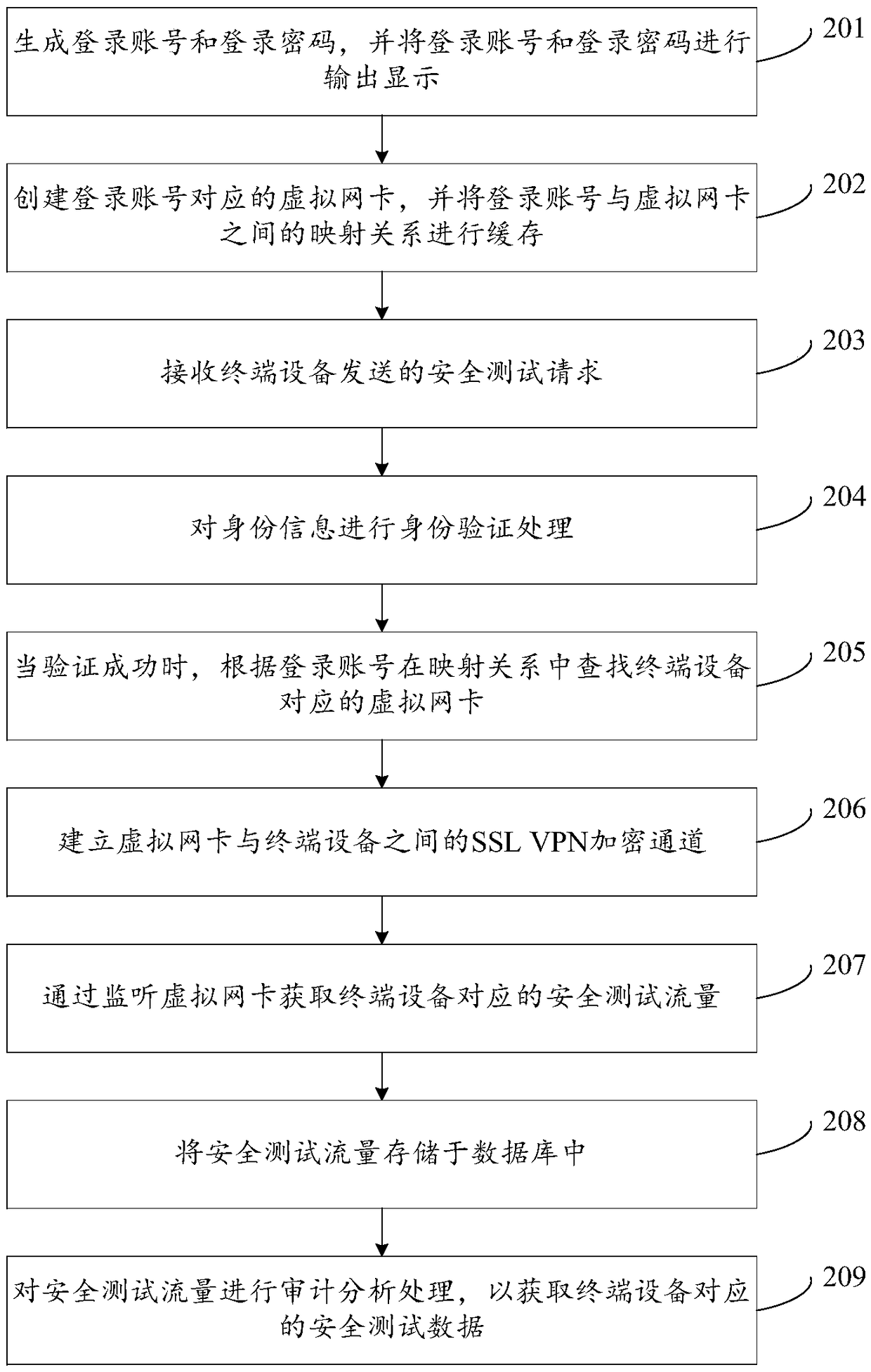
Acquisition and audit analysis method and device for safety test data
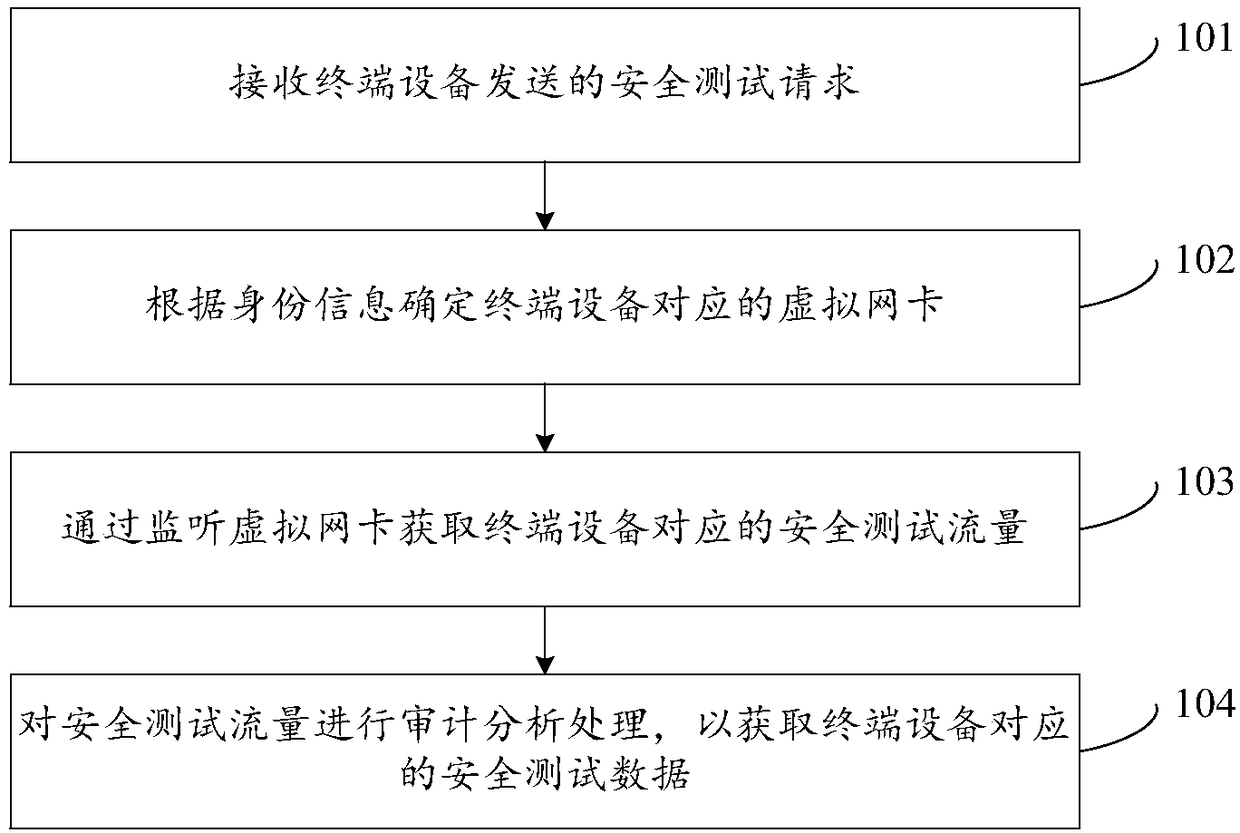
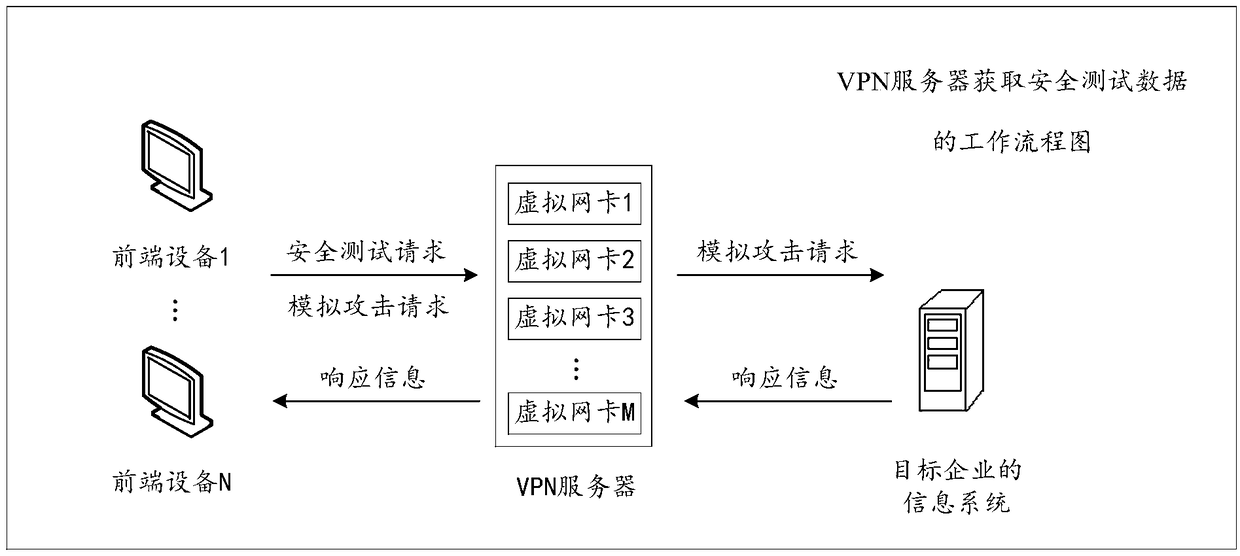
The invention discloses an acquisition and audit analysis method and device for safety test data, relates to the technical field of the internet, and improves safety of a process of carrying out a safety test on an information system of an enterprise. The method disclosed by the invention comprises the steps of: receiving a safety test request sent by terminal equipment, wherein the safety test request comprises identity information corresponding to the terminal equipment; according to the identity information, determining a virtual network card corresponding to the terminal equipment; by monitoring the virtual network card, acquiring safety test traffic corresponding to the terminal equipment; and carrying out audit analysis processing on the safety test traffic to acquire safety test data corresponding to the terminal equipment, wherein the safety test data is used for quantizing the safety test process corresponding to the terminal equipment and auditing a high-risk behavior operation corresponding to the terminal equipment. The acquisition and audit analysis method and device are applicable to the process that a third-party tester carries out the safety test on the informationsystem of the enterprise.
Owner:北京中金安服科技有限公司
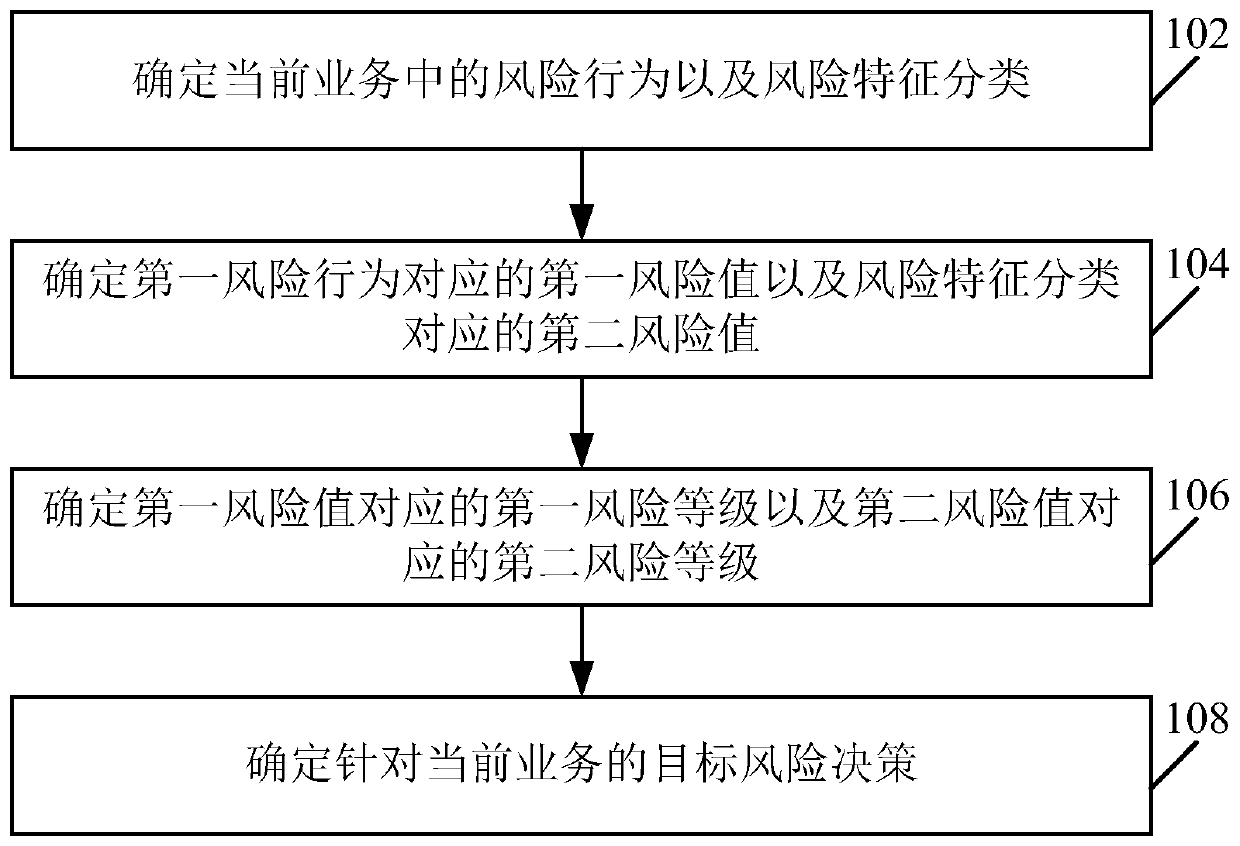
Risk control method and device
ActiveCN110245954AReduce consumptionSimplify the risk control processProtocol authorisationRisk levelRisk Control
The embodiment of the invention provides a risk control method and device, a computing device and a machine readable storage medium. The method comprises the following steps of determining a risk behavior and the risk feature classification in a current service; determining a first risk value corresponding to the risk behavior and a second risk value corresponding to the risk feature classification; determining a first risk level corresponding to the first risk value and a second risk level corresponding to the second risk value; and determining a target risk decision for the current service based on the predetermined risk strategies corresponding to various combinations of the first group of risk levels and the second group of risk levels and the first risk level and the second risk level.
Owner:ADVANCED NEW TECH CO LTD
Judgment method for motor vehicle driving state by applying intelligent cell phone
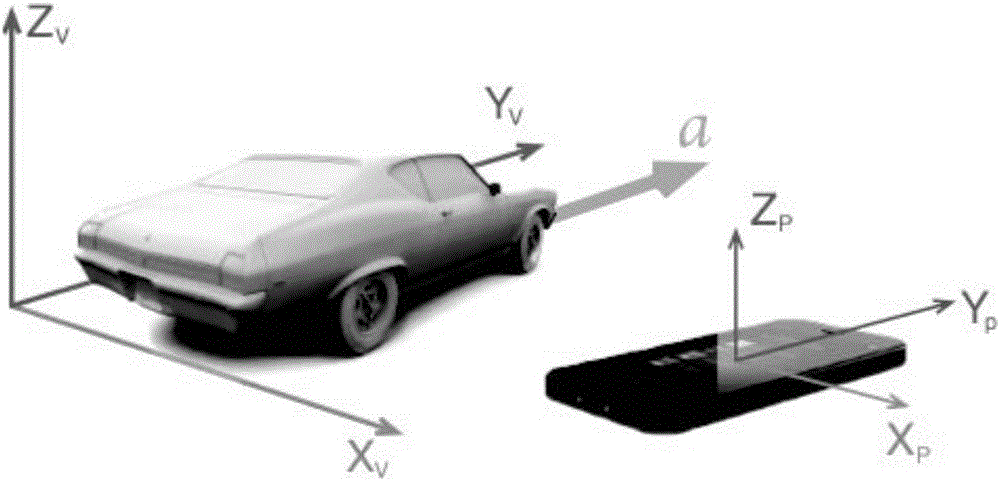
InactiveCN106840192AReduce mistakesImprove experienceNavigation instrumentsSubstation equipmentRisk behaviorDriving risk
The invention discloses a judgment method for a motor vehicle driving state by applying an intelligent cell phone. Acceleration values of three directions under a cell phone coordinate system are read through a G-sensor, and speed information read by a GPS (Global Positioning System) module is comprehensively considered to judge whether a motor vehicle is at an unstable acceleration process, an unstable deceleration process and a sudden turning process with extremely great risks or not. According to the judgment method, GPS data and G-sensor data are fused to obtain more accurate acceleration and speed values and errors caused by sensor data are reduced. According to the judgment method, the intelligent cell phone does not need to be fixed on the motor vehicle and whether acceleration data fluctuation is caused when a user utilizes the cell phone or caused by risk driving behaviors can be distinguished; when the user utilizes the cell phone, analysis can also be carried out so that the customer experience is improved. According to a data analysis method and a driving behavior judgment model, the accuracy of recognizing the risk behaviors is improved.
Owner:上海评驾科技有限公司
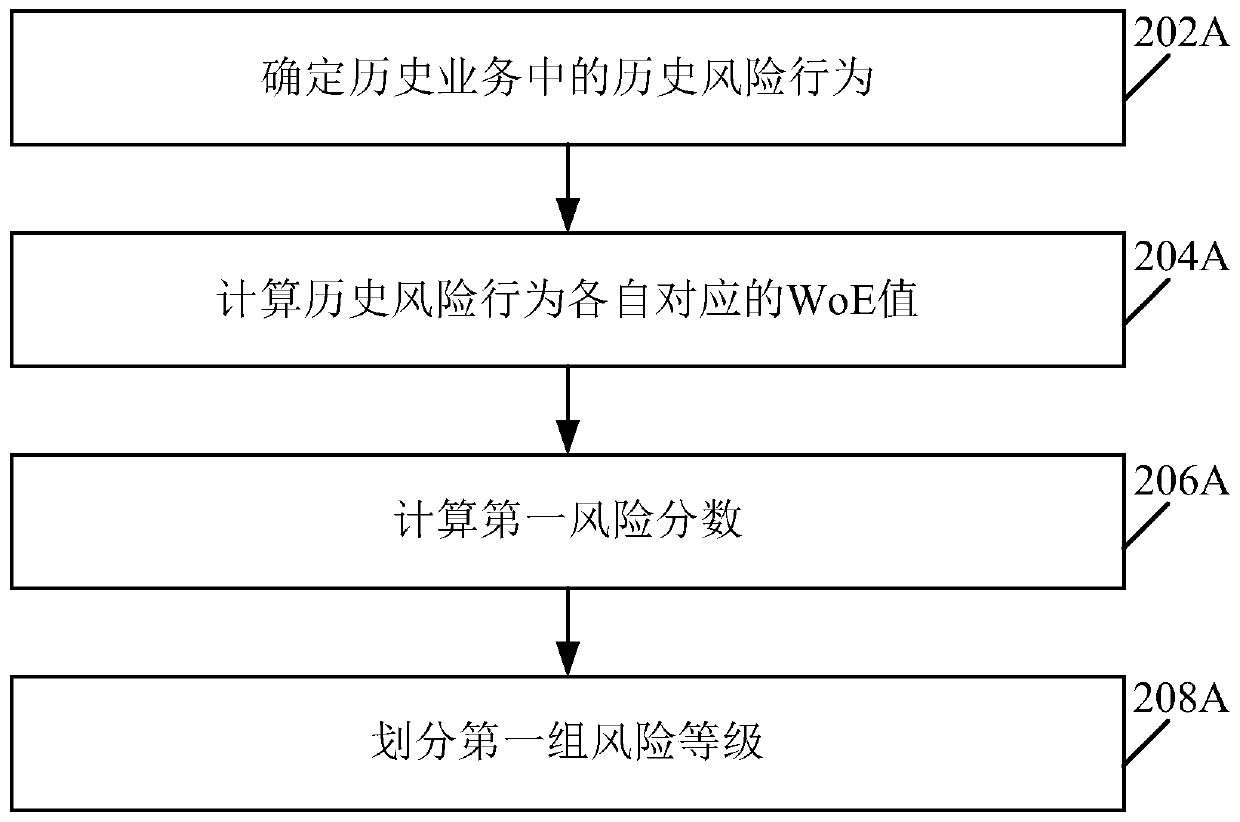
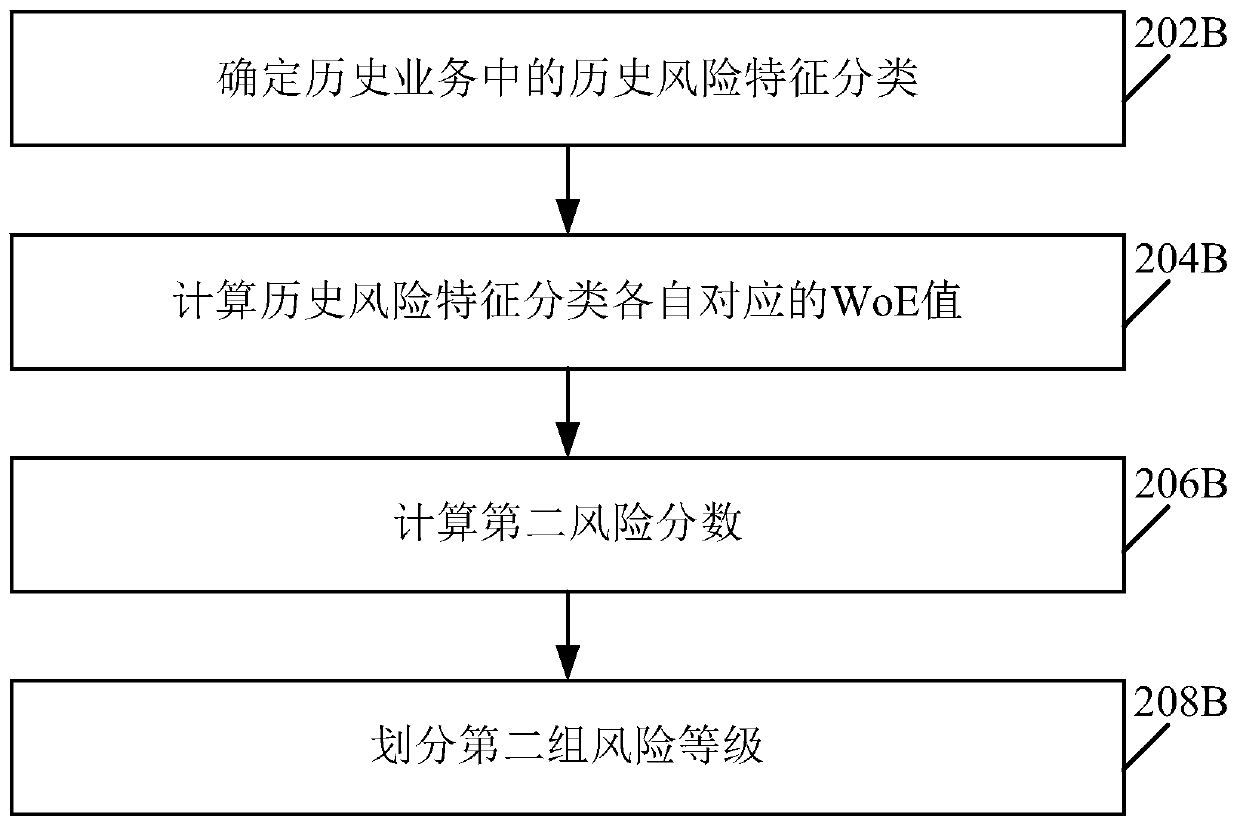
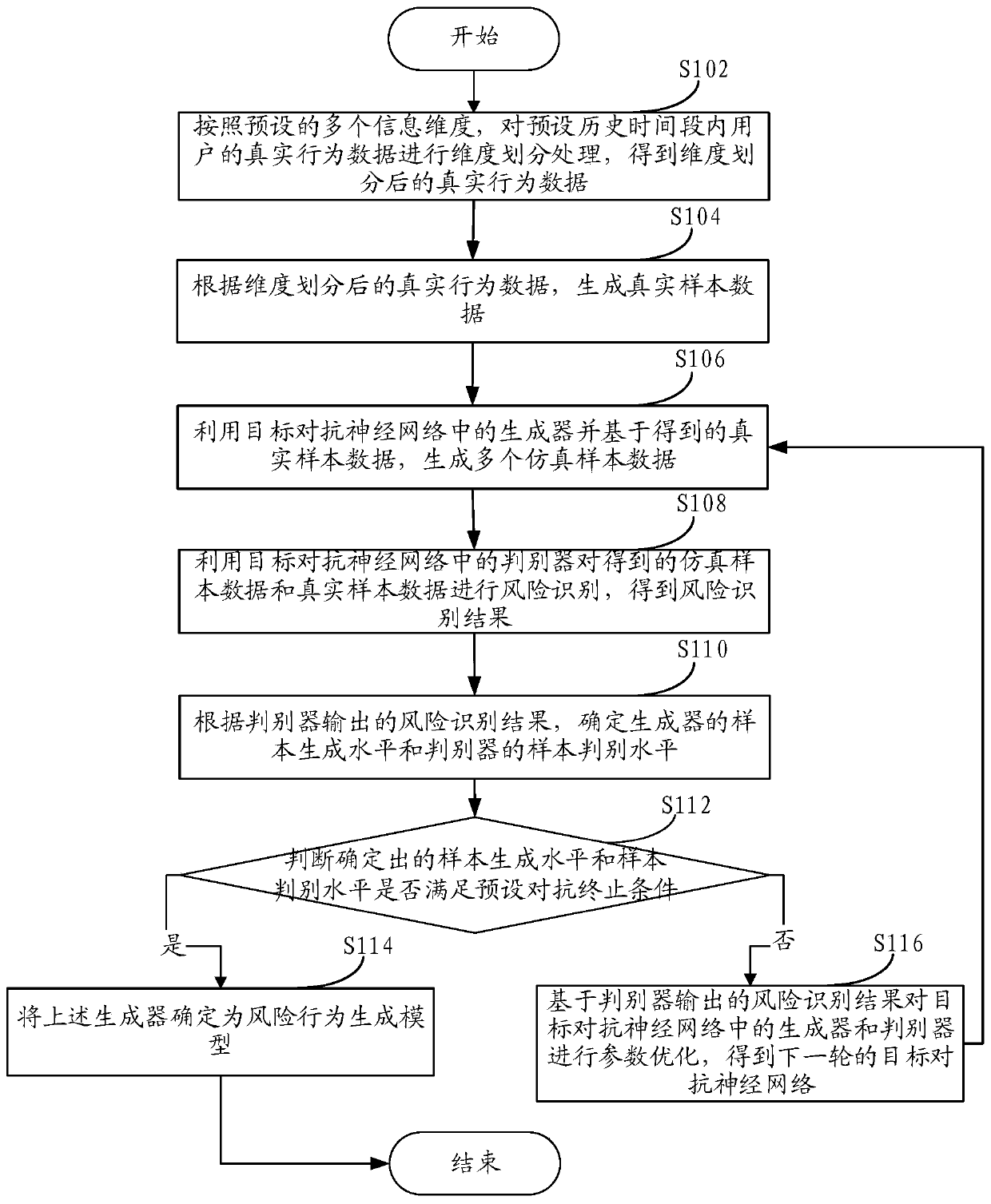
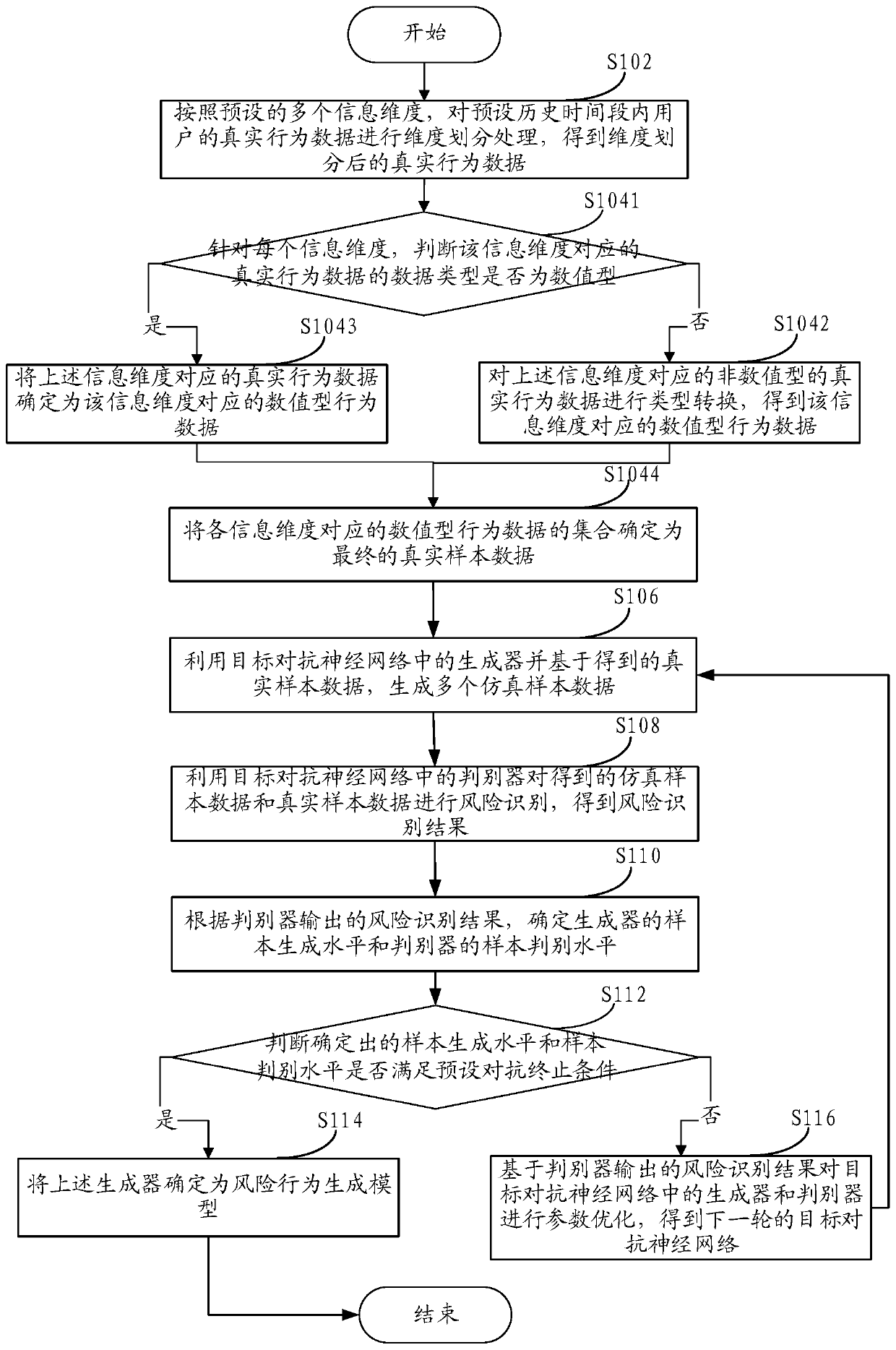
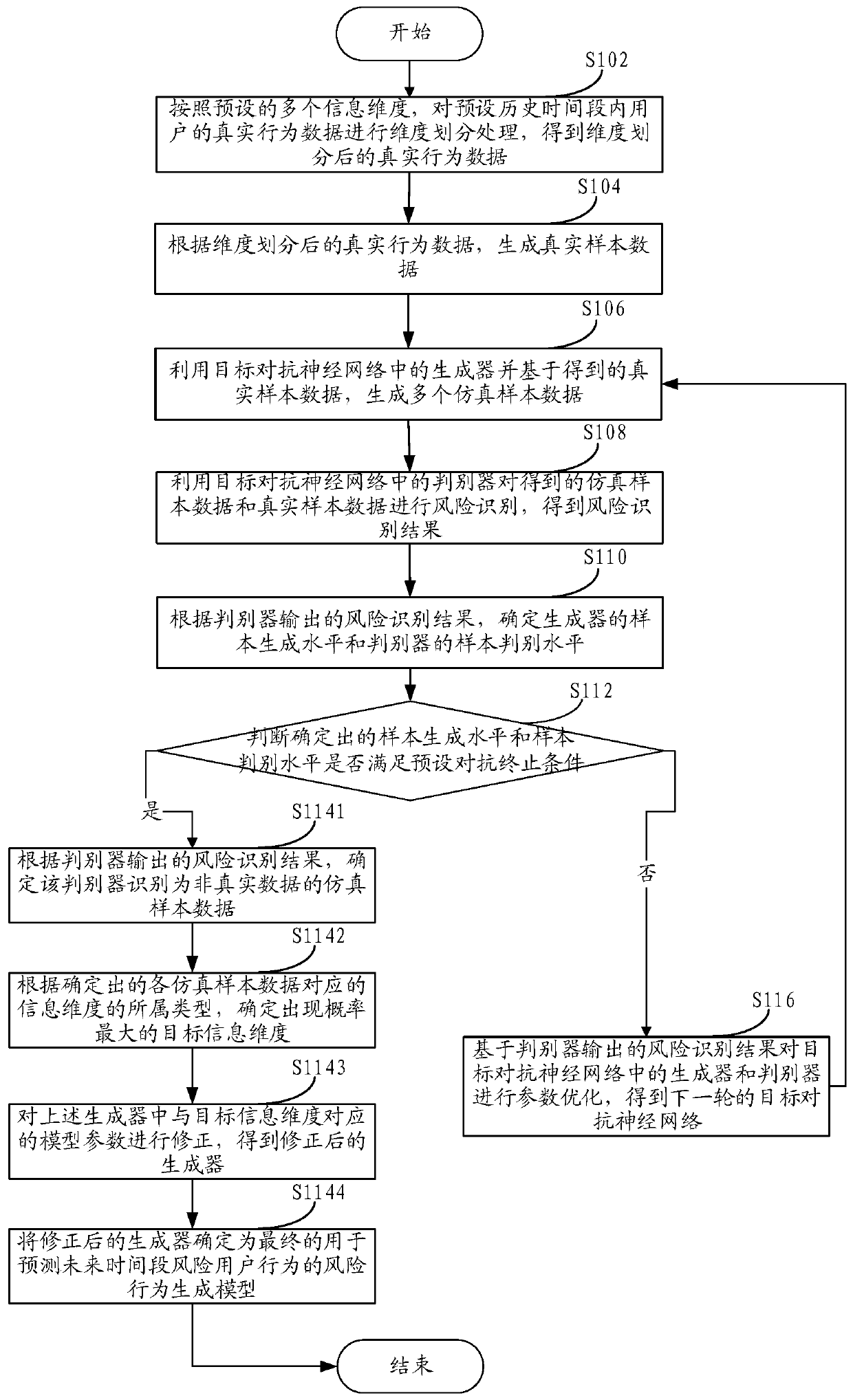
Method and device for determining risk behavior generation model
ActiveCN110633989AImprove timelinessImprove accuracyFinanceCharacter and pattern recognitionDiscriminatorRisk prevention
One or more embodiments of the invention provide a risk behavior generation model determination method and device, and the method comprises the steps: carrying out the dimension division of the real behavior data of a historical user according to a plurality of preset information dimensions; utilizing a generator in the target adversarial neural network to automatically generate a plurality of simulation sample data based on the real sample data obtained by dimension division, and utilizing a discriminator in the target adversarial neural network to perform risk identification on the simulation sample data and the real sample data; according to risk identification result, judging whether the sample generation level of the generator and the sample discrimination level of the discriminator meet a preset adversarial termination condition or not; and if so, determining the final generator as a risk behavior generation model so as to update the online risk control strategy based on the riskbehavior data generated by the risk behavior generation model, and performing risk prevention and control on the behavior data of the online user based on the updated risk control strategy.
Owner:ADVANCED NEW TECH CO LTD
Investment Risk Modeling Method and Apparatus
A system, method, and computer-readable storage medium configured to enable investment-related risk behavior modeling of individuals based on their payment card purchases.
Owner:MASTERCARD INT INC
Automobile monitoring method and system
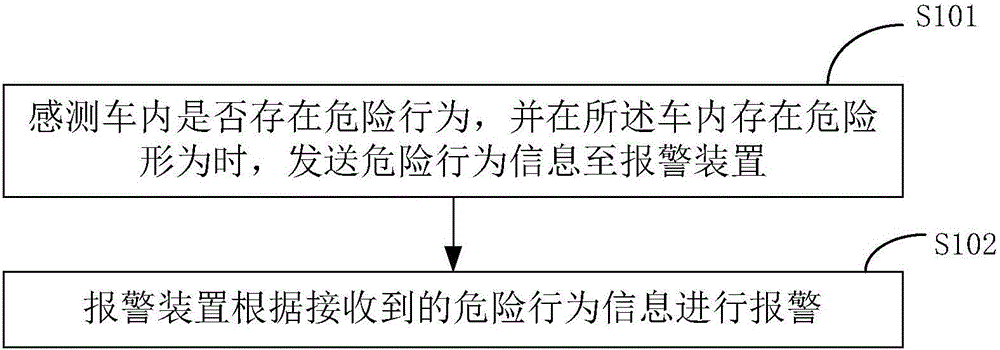
InactiveCN104527548AAvoid distractionProtection from dangerous situationsSignalling/lighting devicesElectric/fluid circuitRisk behaviorEngineering
The invention discloses an automobile monitoring system, including an automobile control device and an alarm device, wherein the automobile control device is used for sensing whether risk behaviors exist in the automobile, and sending a risk behavior message to the alarm device when risk behaviors exist in the automobile; the alarm device is in communication connection with the automobile control device, and used for giving an alarm when receiving the risk behavior message sent by the automobile control device, and the alarm device is a wearing type intelligent device. The invention also correspondingly provides an automobile monitoring method. According to the automobile monitoring system and method, the risk behaviors of riders in the automobile can be monitored and reminded, to prevent a driver from distracting attention when driving, and thereby avoid the happening of traffic accidents.
Owner:DONGGUAN YULONG COMM TECH
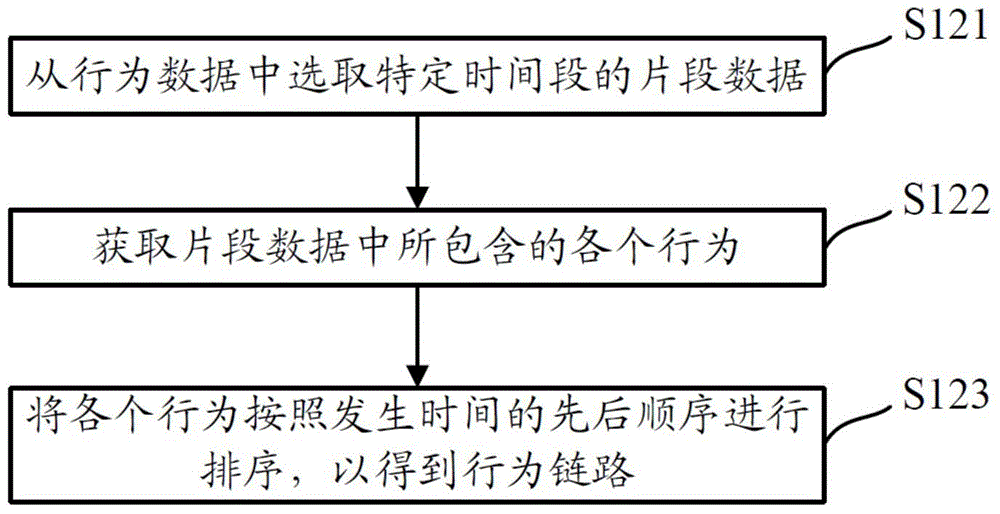
Risk identification method and equipment, storage medium and electronic equipment
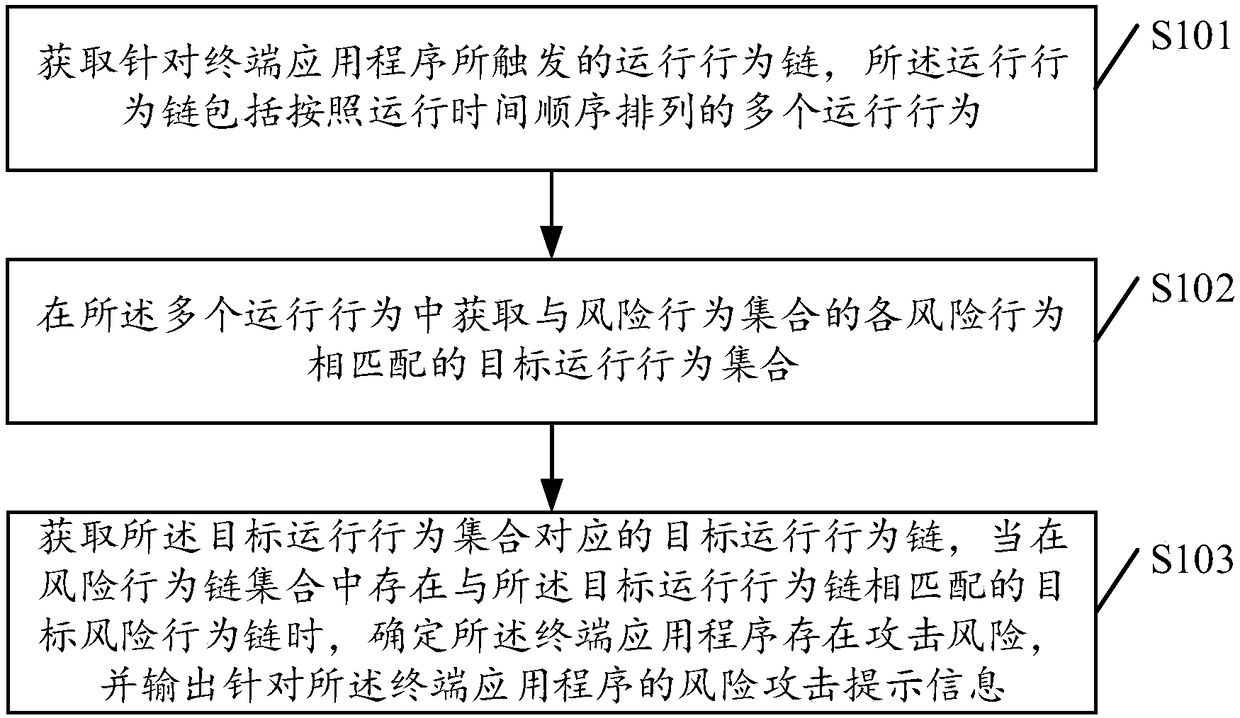
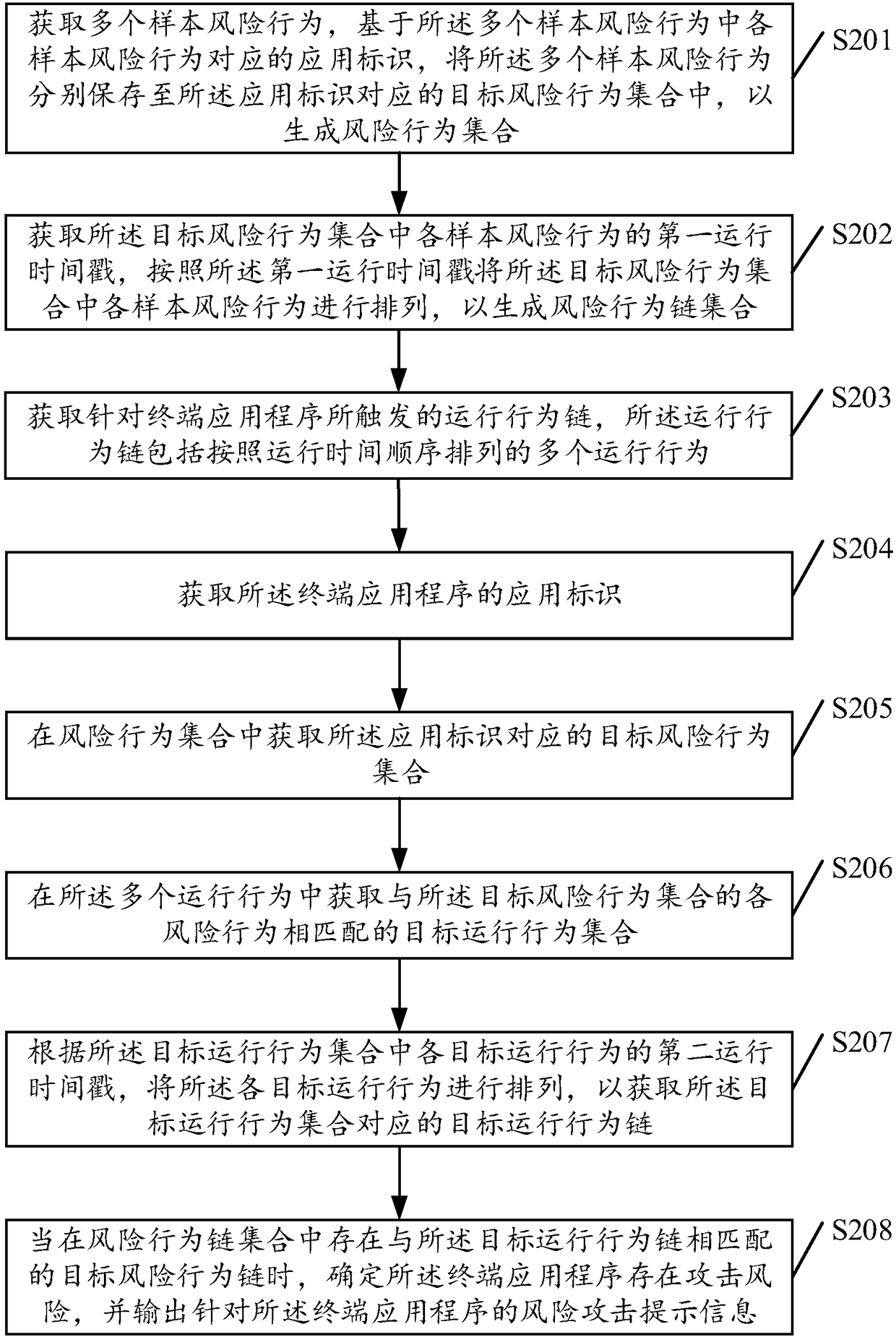
PendingCN108182360AGuarantee the safety of useImprove perceptionPlatform integrity maintainanceRisk behaviorRisk identification
The embodiment of the invention discloses a risk identification method and equipment, a storage medium and electronic equipment. The method includes the following steps that an operation behavior chain triggered aiming at a terminal application is acquired, wherein the operation behavior chain comprises multiple operation behaviors arranged according to the operation time sequence; a target operation behavior set matched with all risk behaviors in a risk behavior set is acquired from the operation behaviors; a target operation behavior chain corresponding to the target operation behavior set is acquired, when a target risk behavior chain matched with the target operation behavior chain exists in the risk behavior chain set, it is determined that an attack risk exists in the terminal application, and risk attack prompt information aiming at the terminal application is output. By the adoption of the risk identification method and equipment, the storage medium and the electronic equipment, hostile attack behaviors aiming at the terminal application can be accurately sensed and identified without being limited by detection environments, and the use security of the terminal applicationis fundamentally guaranteed.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com