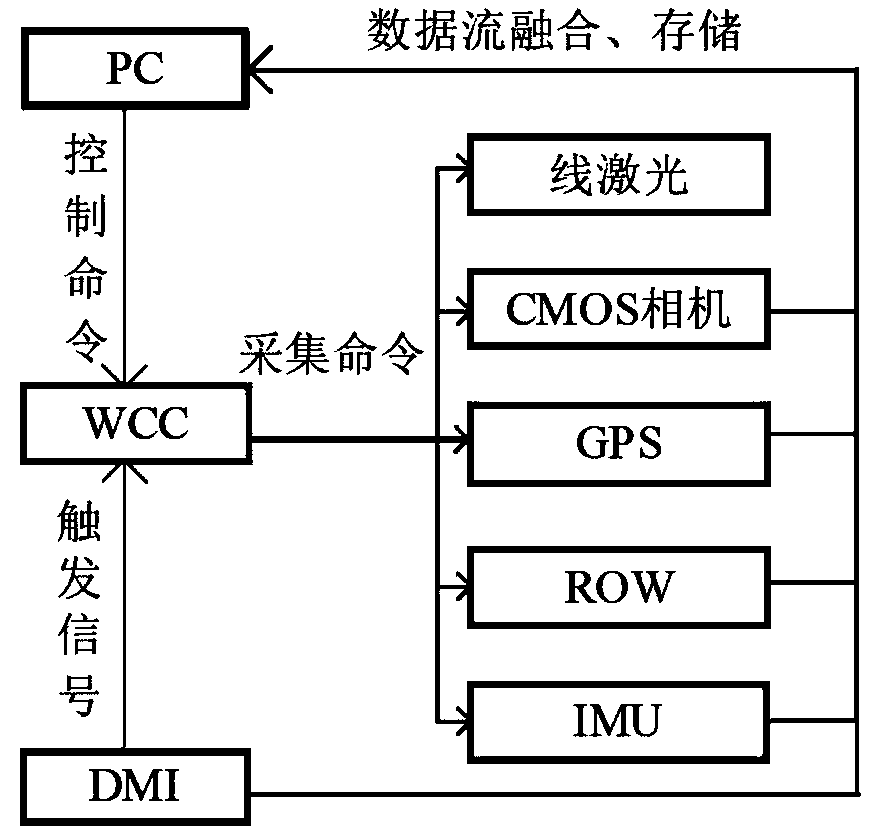
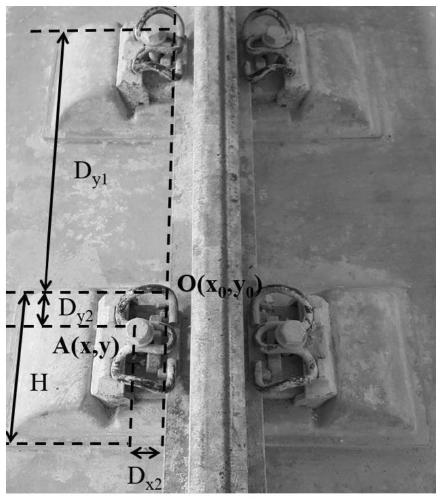
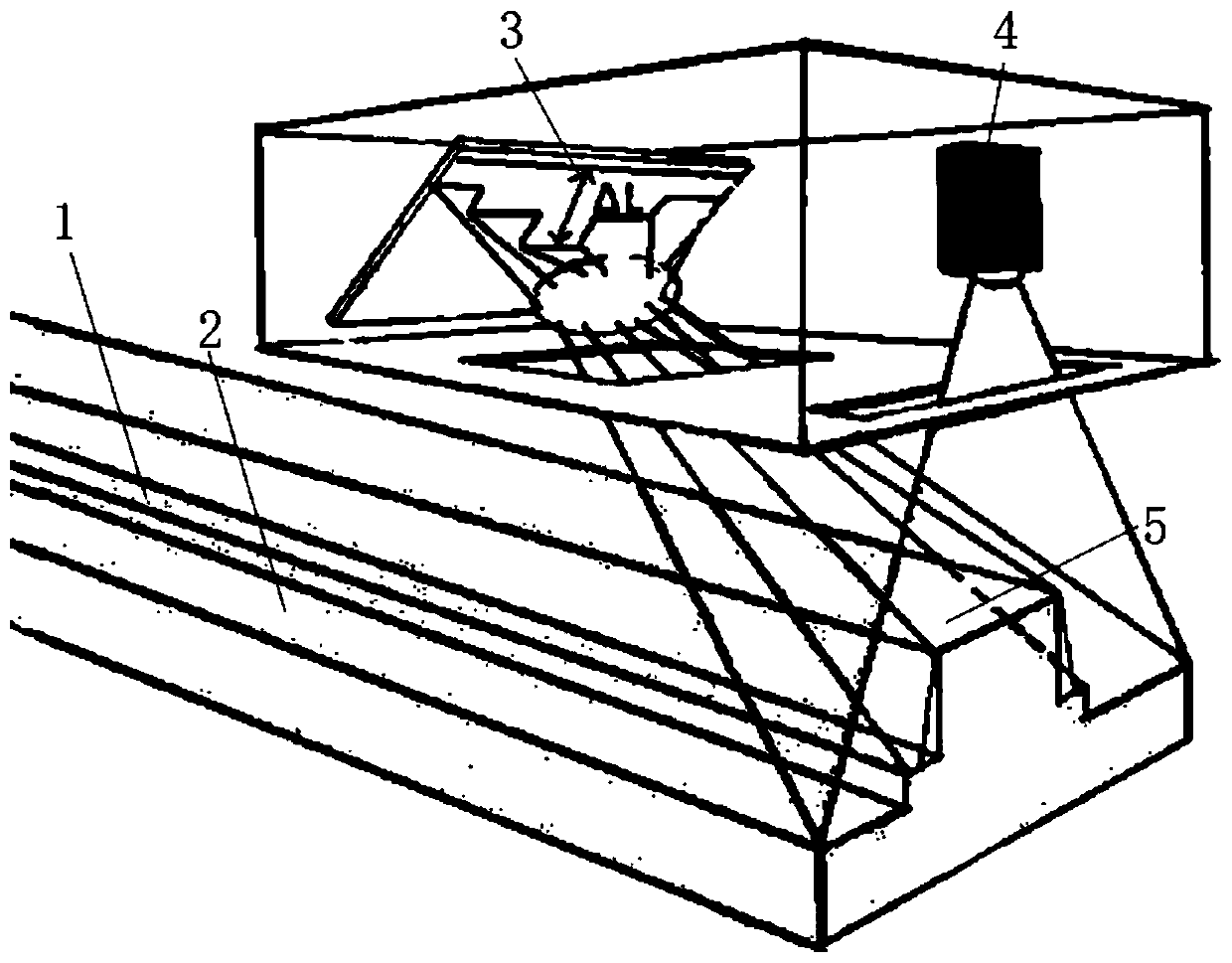
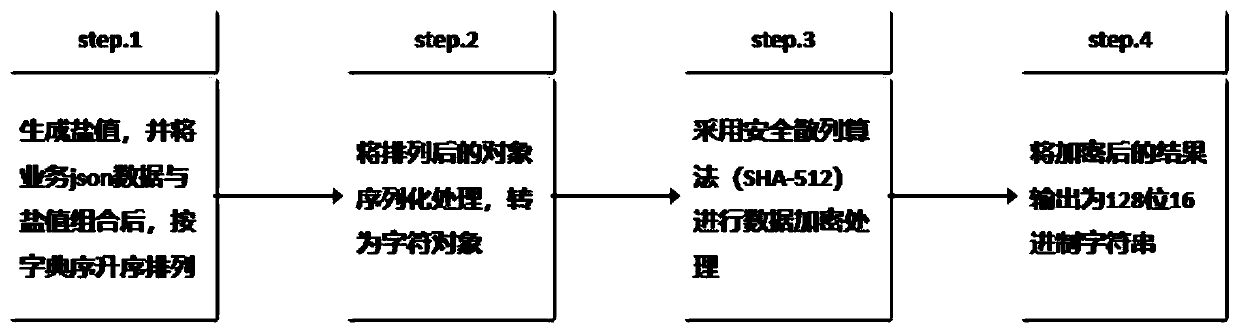
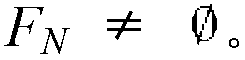Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
40 results about "Knowledge validation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
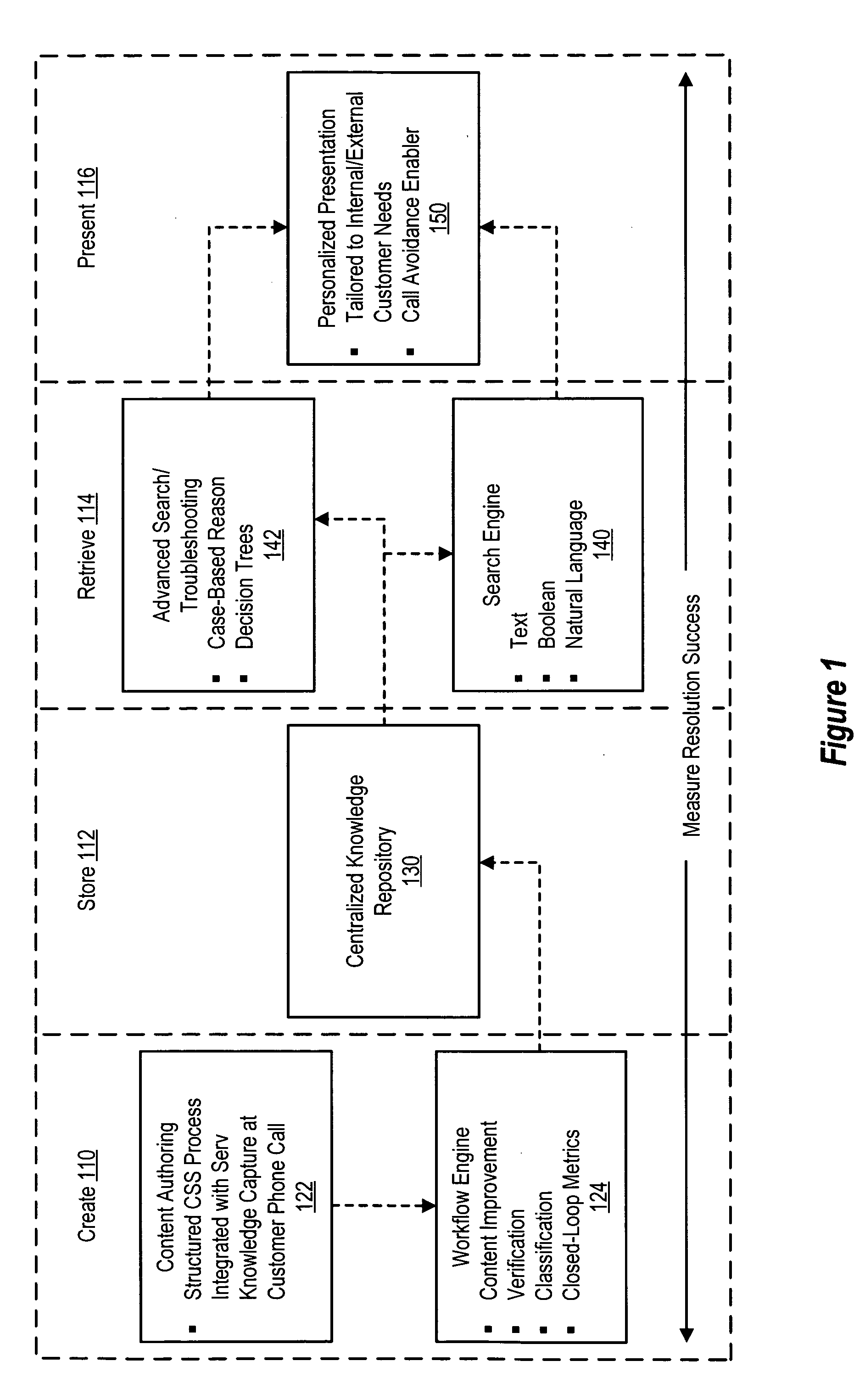
Validation is a critical process in the whole knowledge-based system life cycle. A knowledge base incorporated into such systems has to be verified or (more generally) validated.
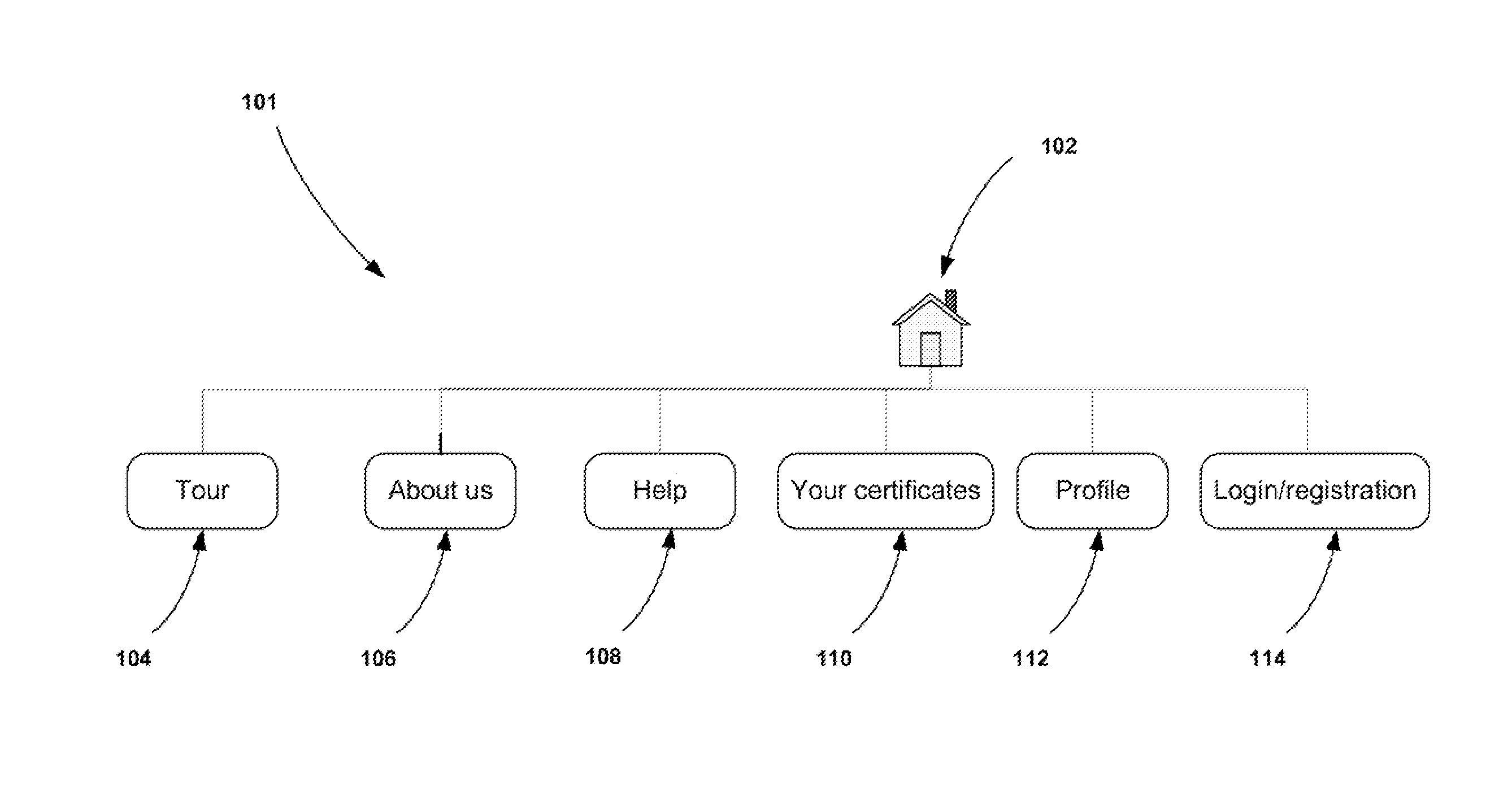
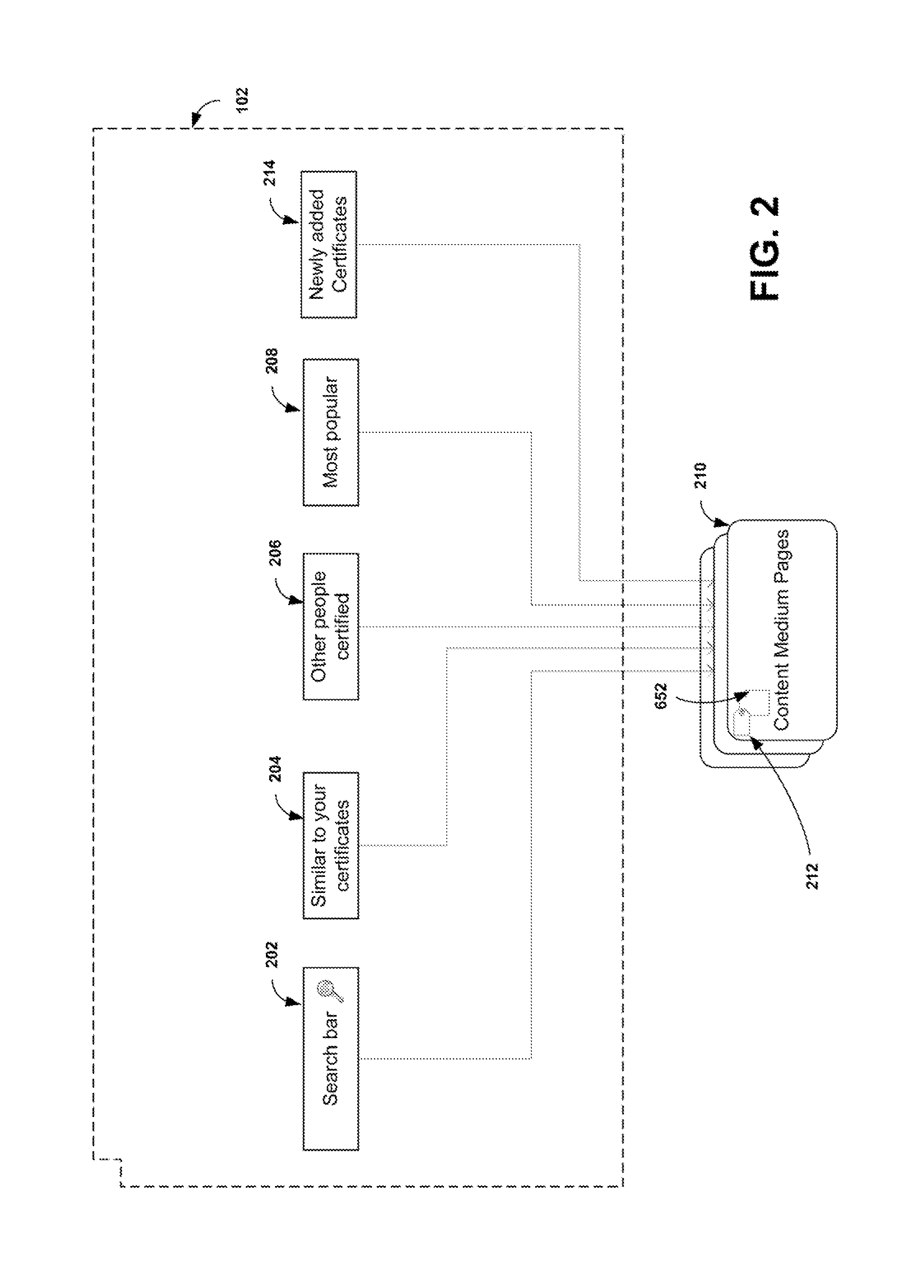
Online community-based knowledge certification method and system
InactiveUS20150262189A1Facilitates knowledge verificationCommerceElectrical appliancesCommunity basedSocial media
An online knowledge verification system, method and software system product provides self-generating community-based knowledge certification. The system can be web-based and includes an infrastructure that allows users to identify and import into the system information descriptive of virtually unlimited content media for which knowledge certification can be established. The system includes a Question Preparation Engine by which questions and answers for an identified content medium are prepared for supporting the certification process. A Question Judgment Engine permits users to provide endorsement scores for the value of questions provided by other users for each content medium. Testing Engines are provided for testing the knowledge of users, using the prepared questions and answers having sufficient endorsement from the community and providing certificates for users who pass the tests for that particular content medium. The system permits users to share those certificates with other users of the community, as well as contacts on social media websites.
Owner:VERGEER ADRIANUS MARINUS HENDRIKUS MENNO
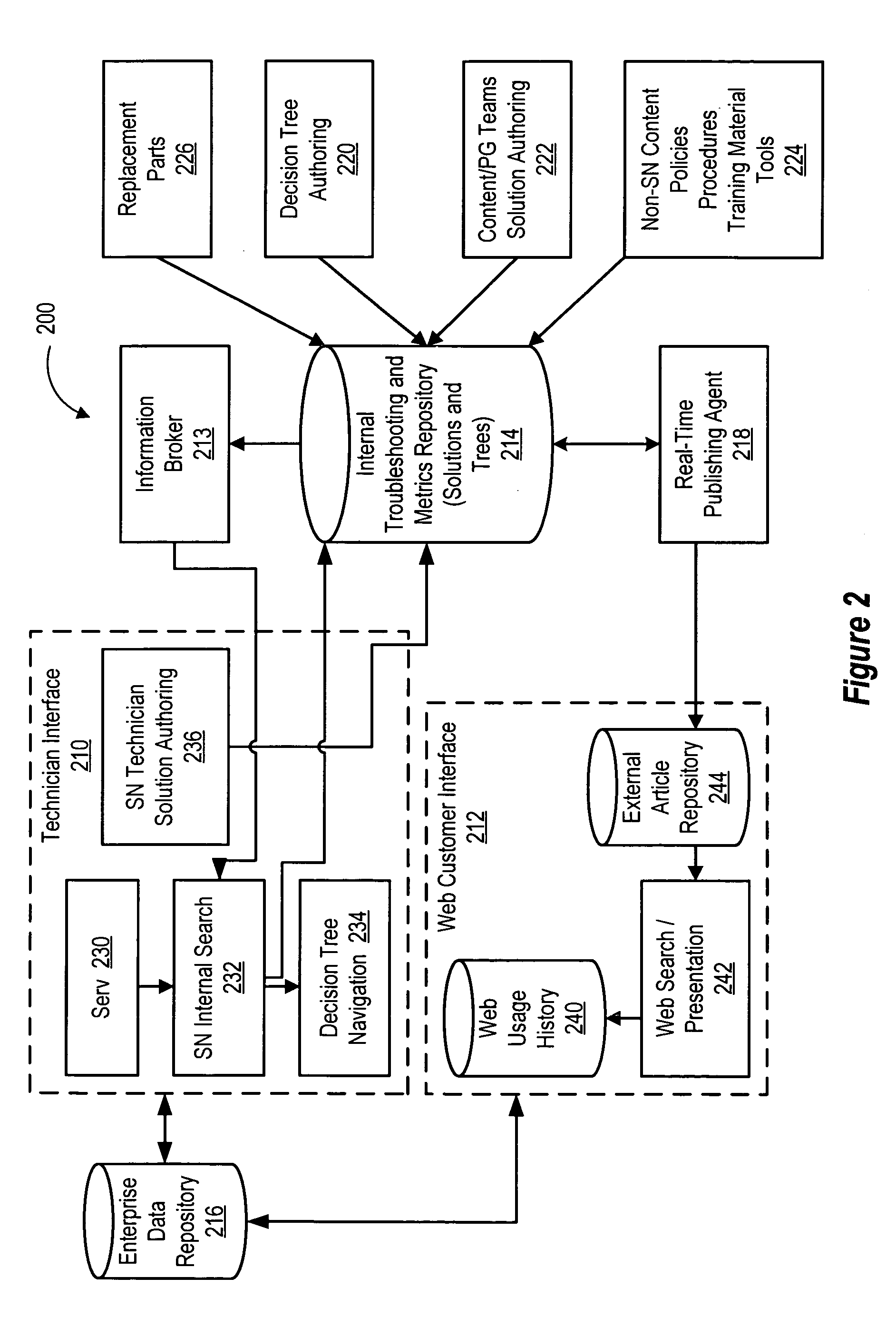
Solution network knowledge verification
InactiveUS20050097507A1MarketingSpecific program execution arrangementsKnowledge levelKnowledge validation
Owner:DELL PROD LP
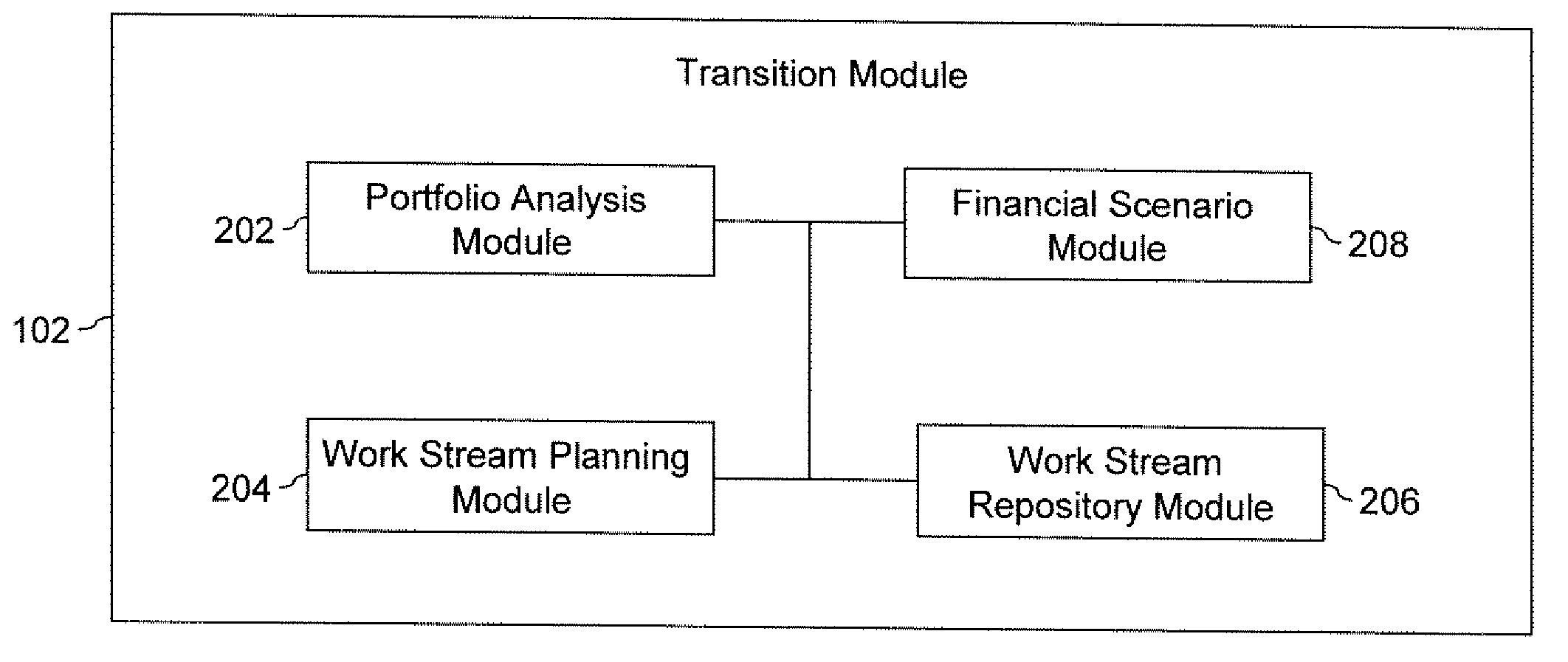
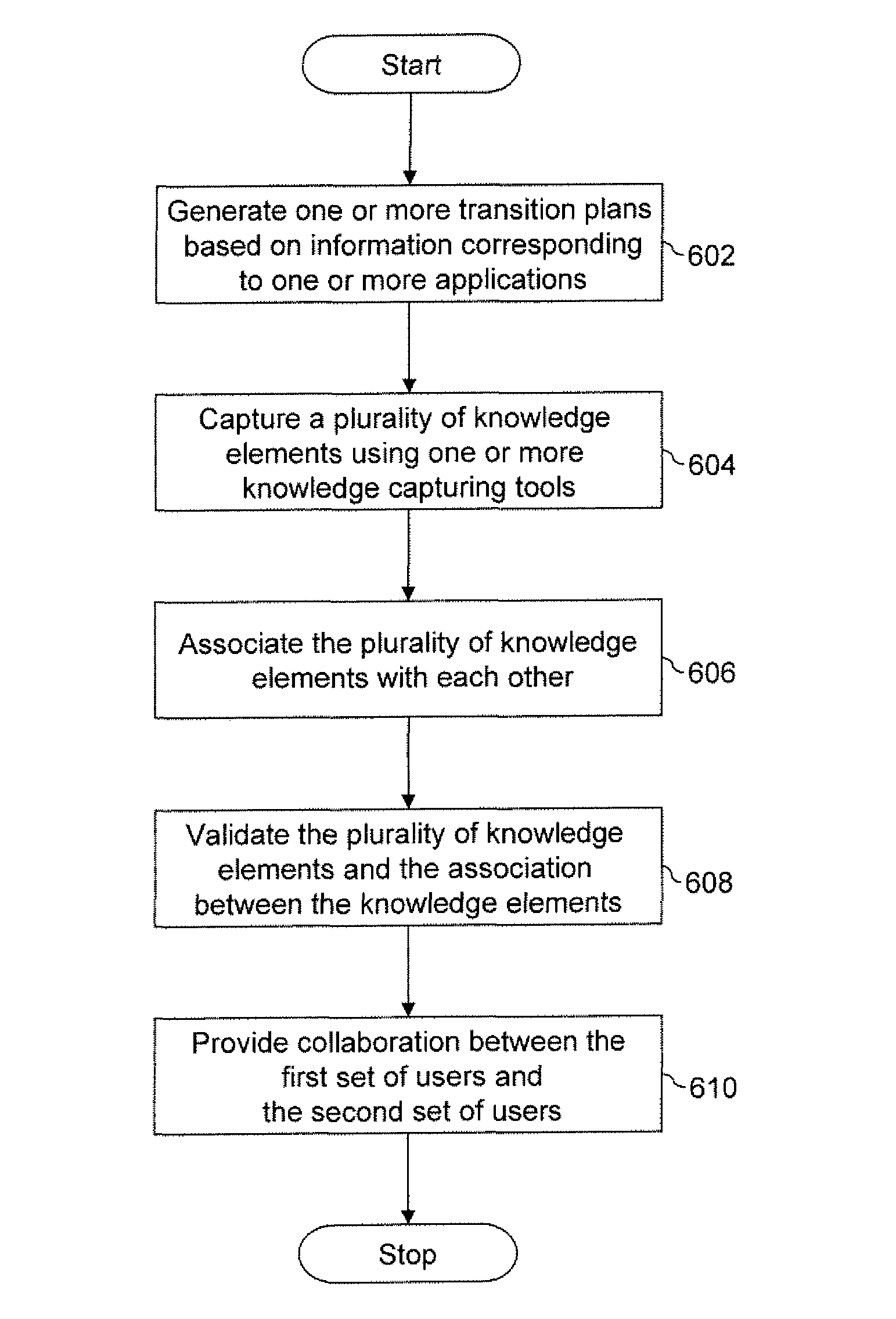
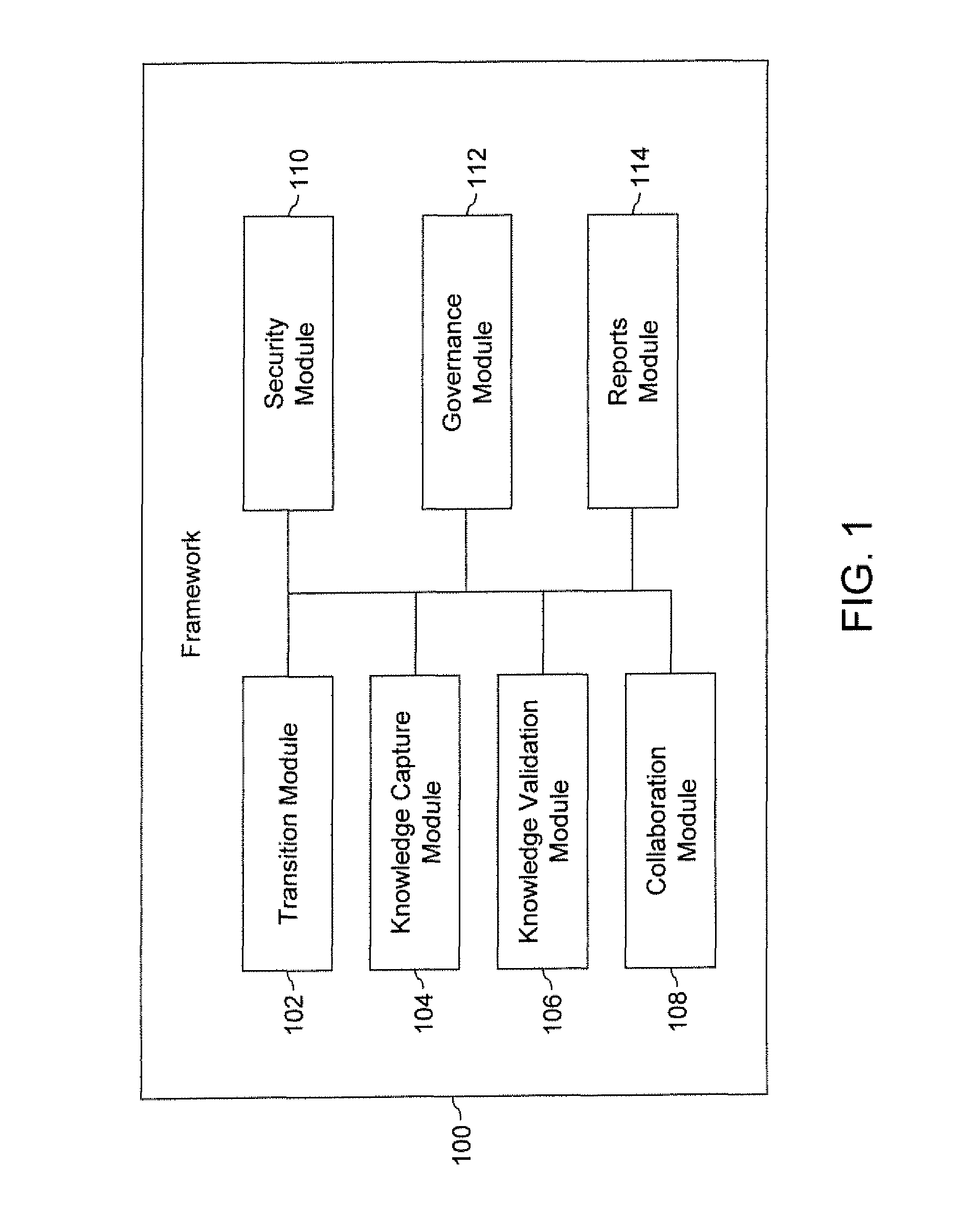
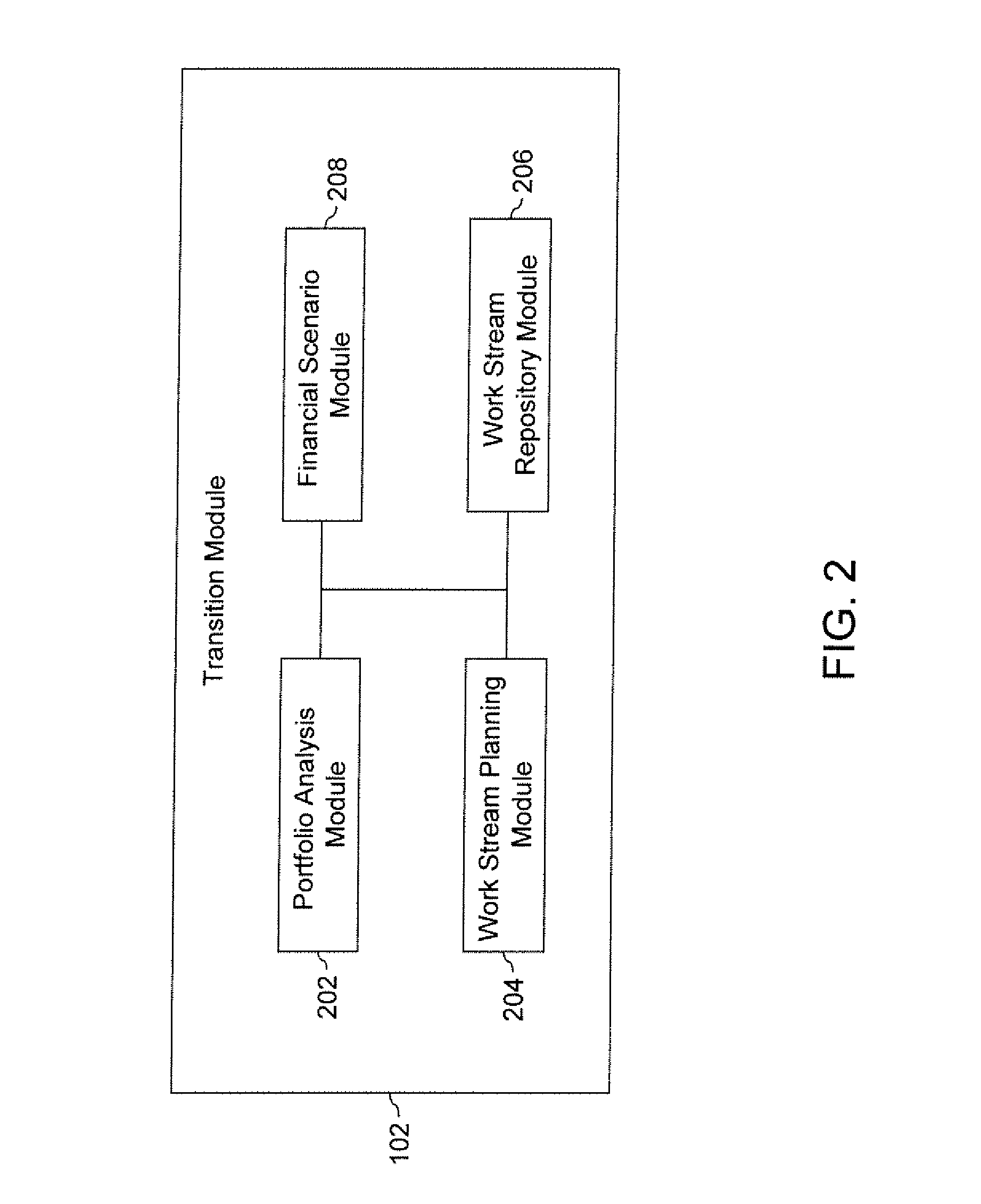
Framework for supporting transition of one or more applications of an organization
ActiveUS20090288018A1Promote collaborationMeet cutting requirementsInput/output for user-computer interactionOffice automationKnowledge elementMultiple applications
A framework for supporting transition of one or more applications of an organization is provided. The one or more applications are transitioned from a first set of users to a second set of users. The framework includes a transition module, a knowledge capture module, a knowledge validation module, and a collaboration module. The transition module generates one or more transition plans based on information corresponding to the one or more applications. The knowledge capture module captures a plurality of knowledge elements corresponding to the one or more applications. The knowledge capture module further establishes association between the plurality of knowledge elements. The knowledge validation module validates the plurality of knowledge elements and their association. The collaboration module provides collaboration between the first set of users and the second set of users during the transition of the one or more applications.
Owner:INFOSYS LTD
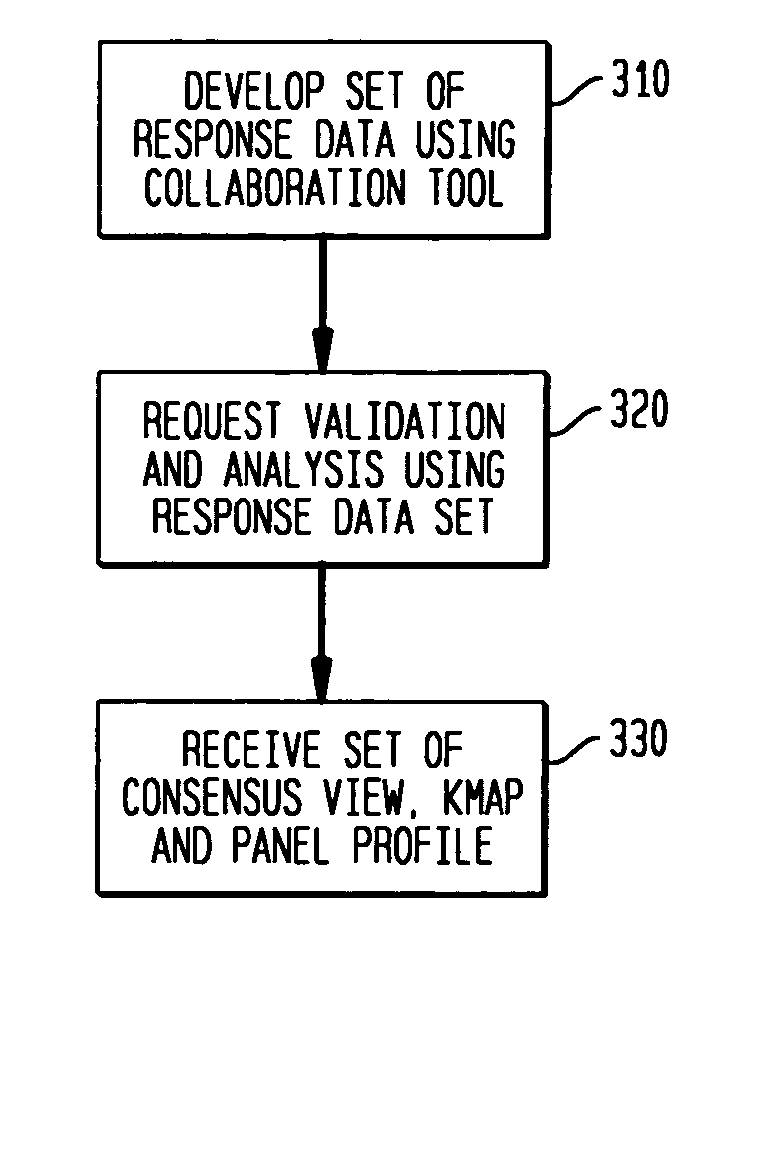
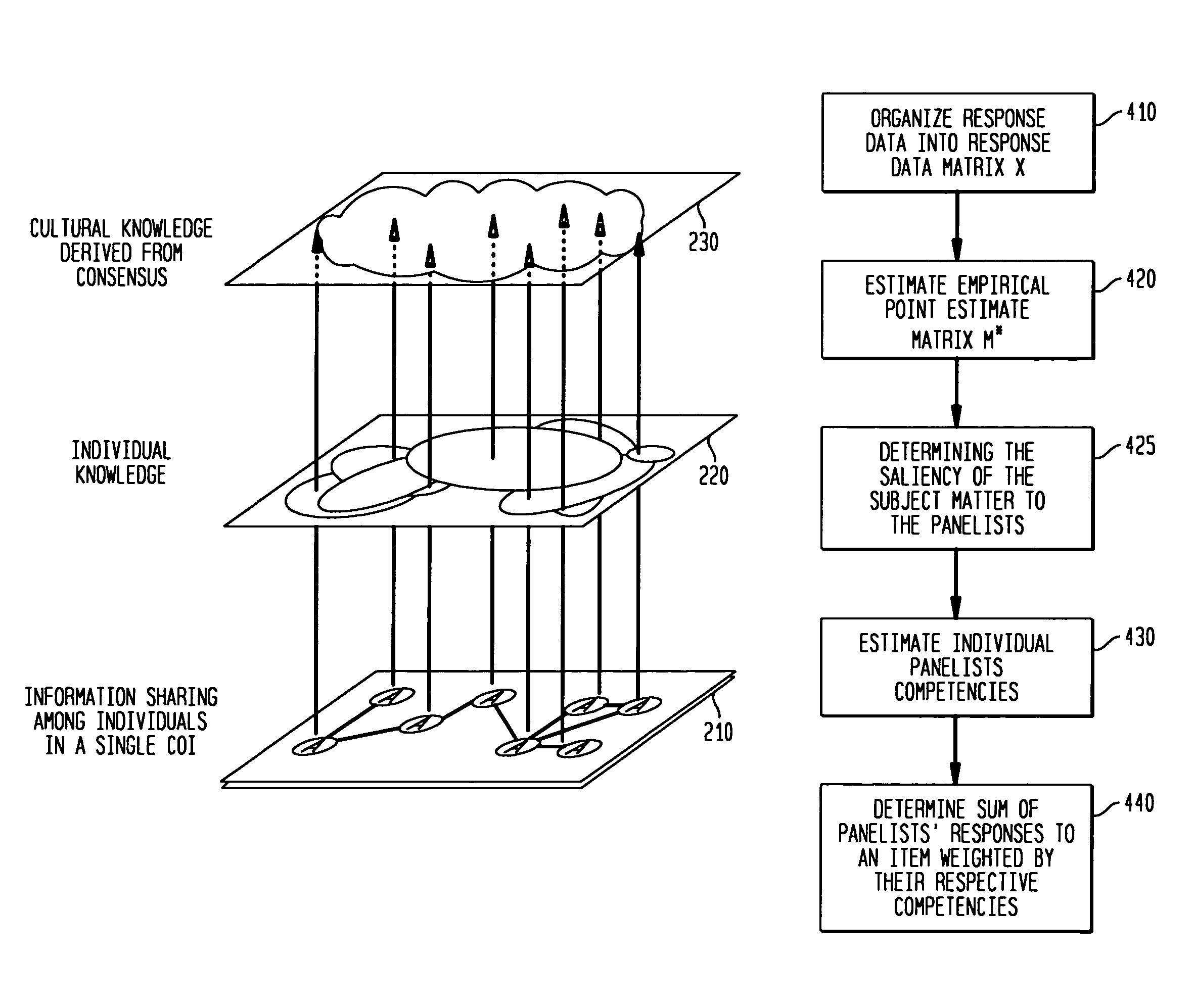
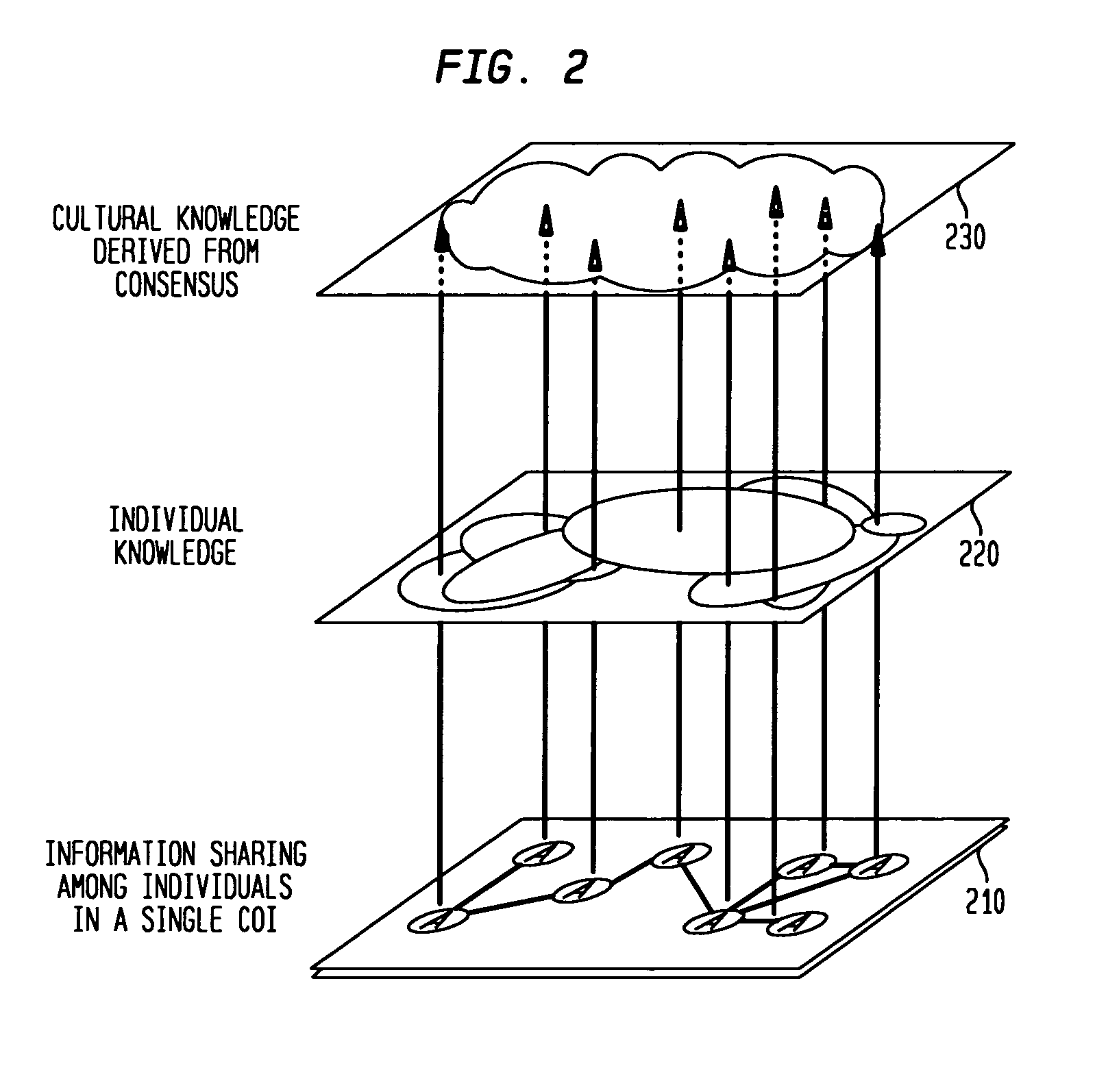
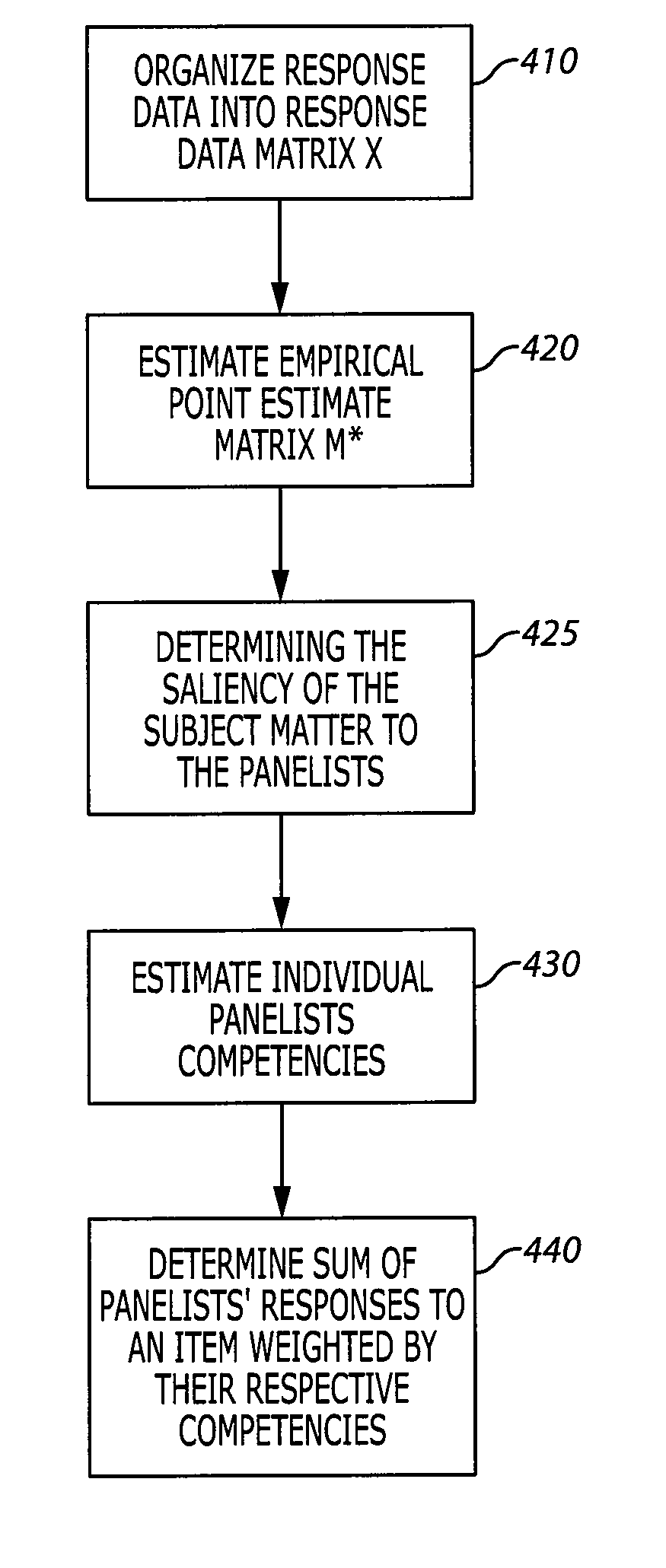
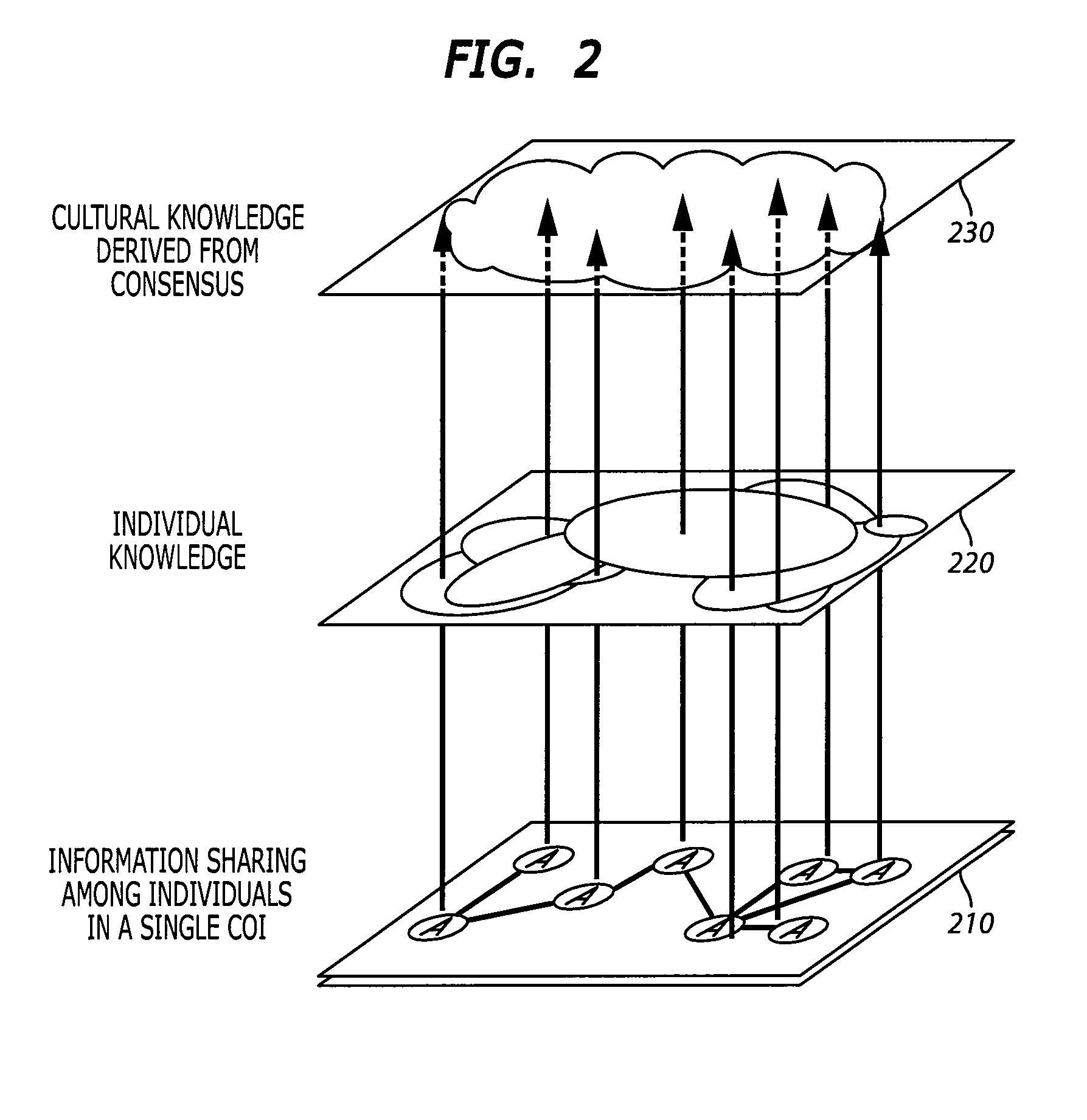
System and method for consensus-based knowledge validation, analysis and collaboration
ActiveUS20070239405A1Easy to useEncourage further collaborationNuclear monitoringDigital computer detailsData setPrivate network
A consensus-based knowledge validation and analysis system provides a way to increase use of collaboration tools among panels of experts by providing a system for analyzing and validating the responses of such experts to a set of questions. The system uses a set of response data input by a panel of experts with respect to a particular subject matter formatted in accordance with a data model as input. The response data set is used to estimate an empirical point estimate matrix indicative of the amount of agreement in the responses on all items between the panelists. The empirical point estimate matrix is used to estimate the saliency of the subject matter to panelists, the competency of each panelist and a consensus model of correct answers is based on the estimated competency of each panelist and the of responses for each item in the response data set. This consensus model is used to generate a knowledge map to aid visualization of the consensus data and encourage further collaboration and consensus building. The method is implemented in a web-based system that enables users of collaboration tools to send response data sets to the tool via the Internet or virtual private network and to likewise retrieve knowledge maps, panelist information and consensus data. An interactive feature enables users / panelists to collaborate with other panelists using the knowledge map as an interface to one or more collaboration tools such as instant messaging.
Owner:NYTELL SOFTWARE LLC
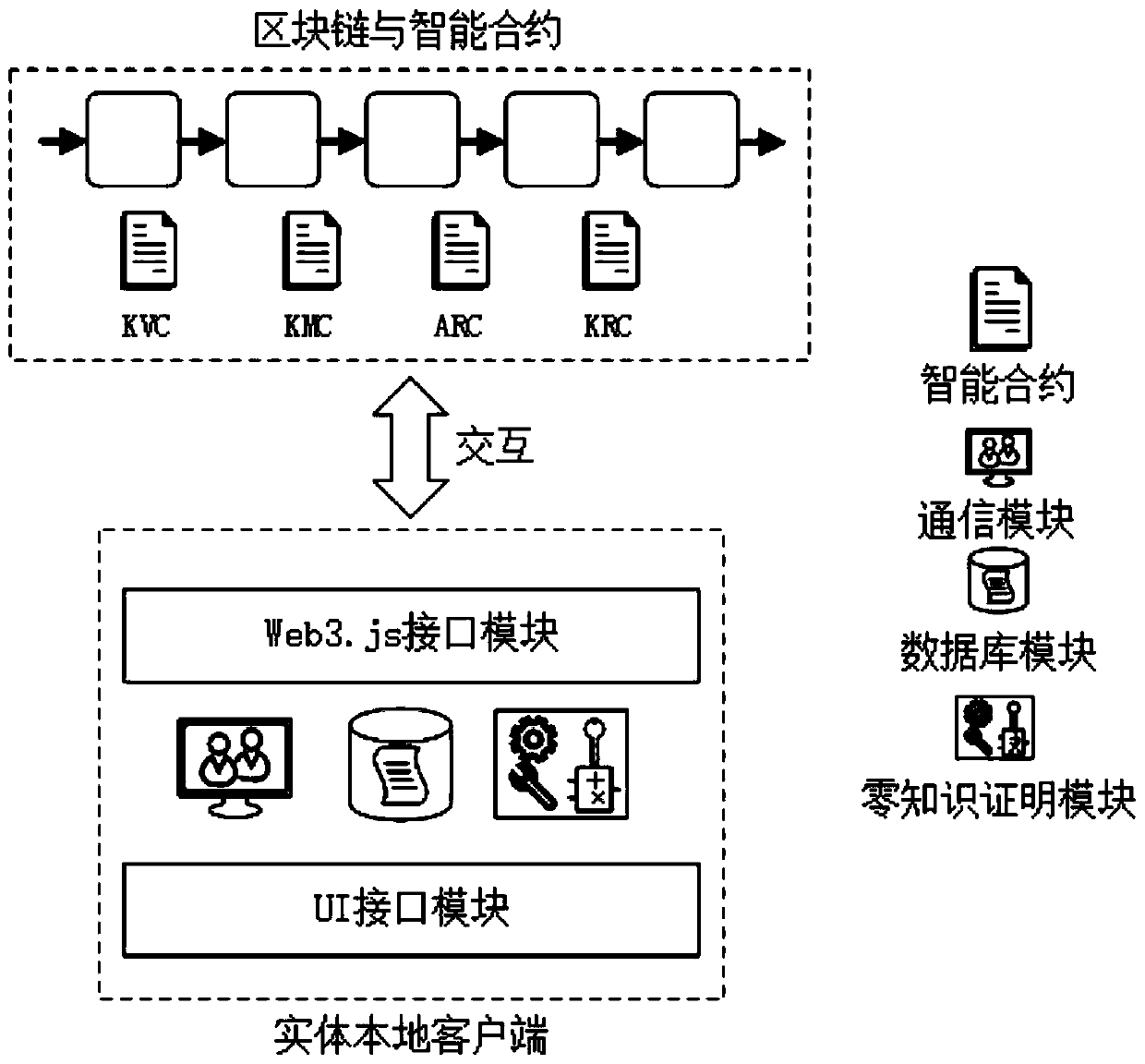
Identity management and authentication system and method based on block chain and zero knowledge proof
ActiveCN111447073AImplement anonymous authenticationSolve the problem that the mapping relationship is exposed to everyoneDatabase management systemsUser identity/authority verificationEngineeringSmart contract
The invention provides an identity management and authentication system and method based on a block chain and zero knowledge proof. The identity management and authentication system comprises an on-chain smart contract and an off-chain entity local client. The on-chain intelligent contract comprises the following contracts: an attribute warehouse contract, a knowledge management contract, a knowledge verification contract and a key warehouse contract. The off-chain entity local client comprises the following modules: a UI interface module, a web3.js interface module, a zero knowledge proof module, a communication module and a database module. The identity management and authentication method comprises the steps of attribute token creation, attribute hidden token creation, identity information authentication and attribute token logout. According to the invention, the ownership of the user to the attribute is not disclosed in the blockchain, the problem that the identity management system in the blockchain discloses the mapping relationship between the personal identifier and the personal identity information to the owner is solved, and the privacy of the user identity information isensured.
Owner:HEBEI UNIVERSITY
Rail fastener defect recognition algorithm based on deep learning
PendingCN111080597AGuaranteed accuracyImprove accuracyImage enhancementImage analysisFeature extractionAlgorithm
The invention discloses a rail fastener defect recognition algorithm based on deep learning. The rail fastener defect recognition algorithm comprises the following steps that 1, a fastener detection system is adopted; step 2, data preprocessing is carried out; and step 3, feature extraction and classification is carried out. According to the method, the position of the fastener area is verified byutilizing priori knowledge, so that the accuracy of fastener positioning is ensured; the elastic strip sub-images is extracted by using the depth information of the three-dimensional data, and the information of the model input image is successfully simplified; in addition, in order to solve the problem that the number of positive and negative samples is unbalanced, the invention provides a method for creating real simulated fastener fracture data. In the aspect of feature extraction and classification, the feature automatically extracted from the training data by using the deep convolutionalneural network is stronger in expressive force and higher in stability, and the strategy of training feature extraction and classification at the same time is more beneficial to improving the accuracy and stability of the algorithm.
Owner:SOUTHWEST JIAOTONG UNIV
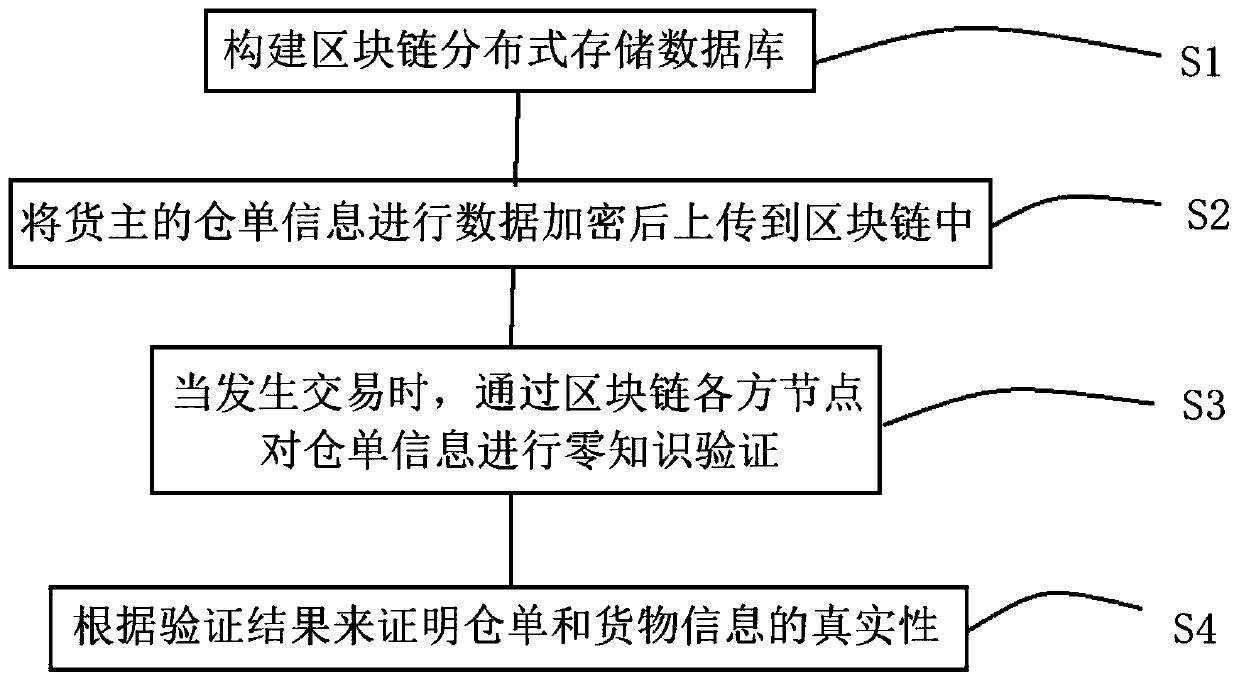
Warehouse receipt verification method based on block chain and zero knowledge proof
ActiveCN109858852AIncrease credibilityGuaranteed safe storagePayment protocolsLogisticsValidation methodsZero-knowledge proof
The invention discloses a warehouse receipt verification method based on a block chain and zero knowledge proof. The warehouse receipt verification method comprises the following steps: constructing ablock chain distributed storage database; the warehouse receipt information of the cargo owner is subjected to data encryption and then is uploaded to the block chain; when a transaction occurs, zero-knowledge verification is carried out on warehouse receipt information through nodes of each party of the block chain; the authenticity of the warehouse receipt and the cargo information is proved according to a verification result; and the authenticity, accuracy and privacy of warehouse receipt information in the transaction market can be ensured.
Owner:SHANGHAI YUANLU JIAJIA INFORMATION SCI & TECH CO LTD
System and method for consensus-based knowledge validation, analysis and collaboration
ActiveUS7630867B2Easy to useDetermine the saliency of the subject matterDigital computer detailsNuclear monitoringData setPrivate network
A consensus-based knowledge validation and analysis system provides a way to increase use of collaboration tools among panels of experts by providing a system for analyzing and validating the responses of such experts to a set of questions. The system uses a set of response data input by a panel of experts with respect to a particular subject matter formatted in accordance with a data model as input. The response data set is used to estimate an empirical point estimate matrix indicative of the amount of agreement in the responses on all items between the panelists. The empirical point estimate matrix is used to estimate the saliency of the subject matter to panelists, the competency of each panelist and a consensus model of correct answers is based on the estimated competency of each panelist and the of responses for each item in the response data set. This consensus model is used to generate a knowledge map to aid visualization of the consensus data and encourage further collaboration and consensus building. The method is implemented in a web-based system that enables users of collaboration tools to send response data sets to the tool via the Internet or virtual private network and to likewise retrieve knowledge maps, panelist information and consensus data. An interactive feature enables users / panelists to collaborate with other panelists using the knowledge map as an interface to one or more collaboration tools such as instant messaging.
Owner:NYTELL SOFTWARE LLC
Federation learning modeling method, device and readable storage medium
ActiveCN111598254AAccurate identificationImprove model qualityDigital data protectionMachine learningAlgorithmTheoretical computer science
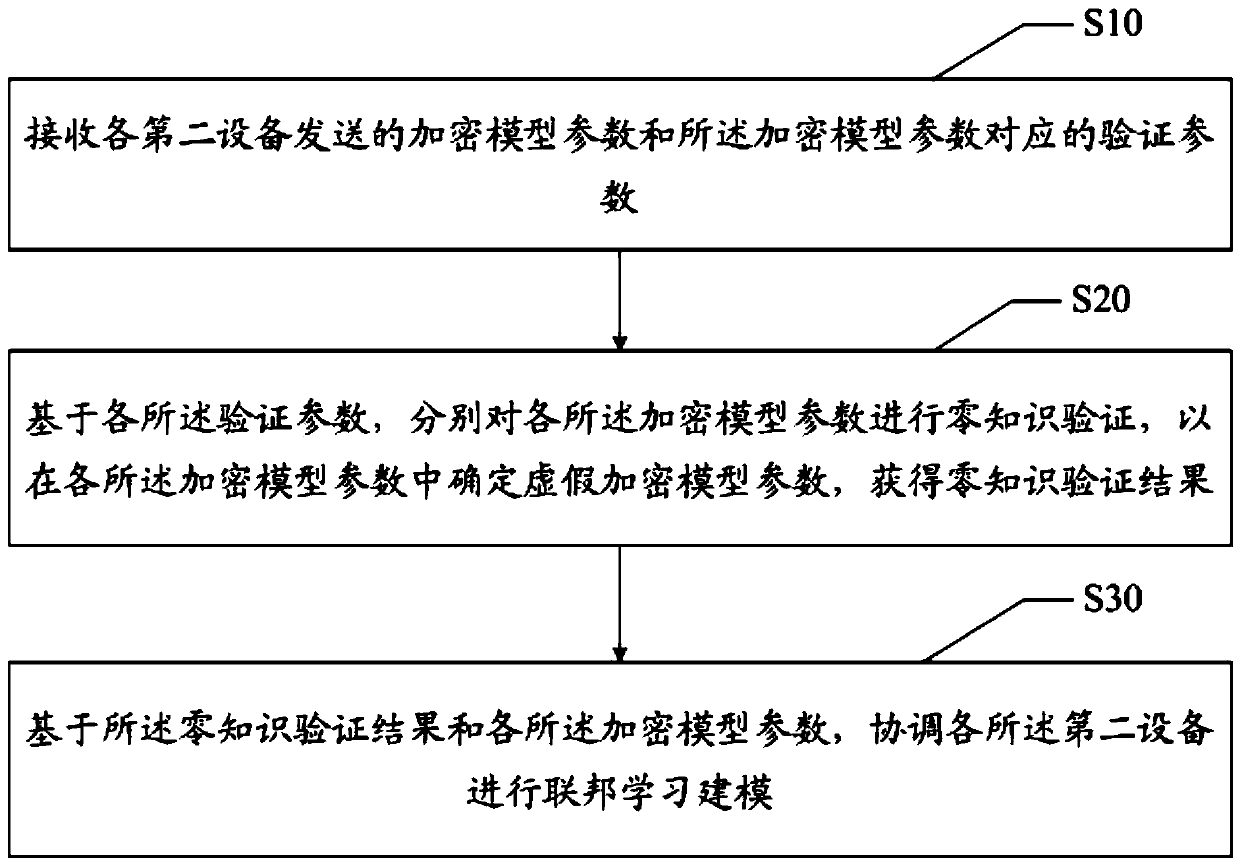
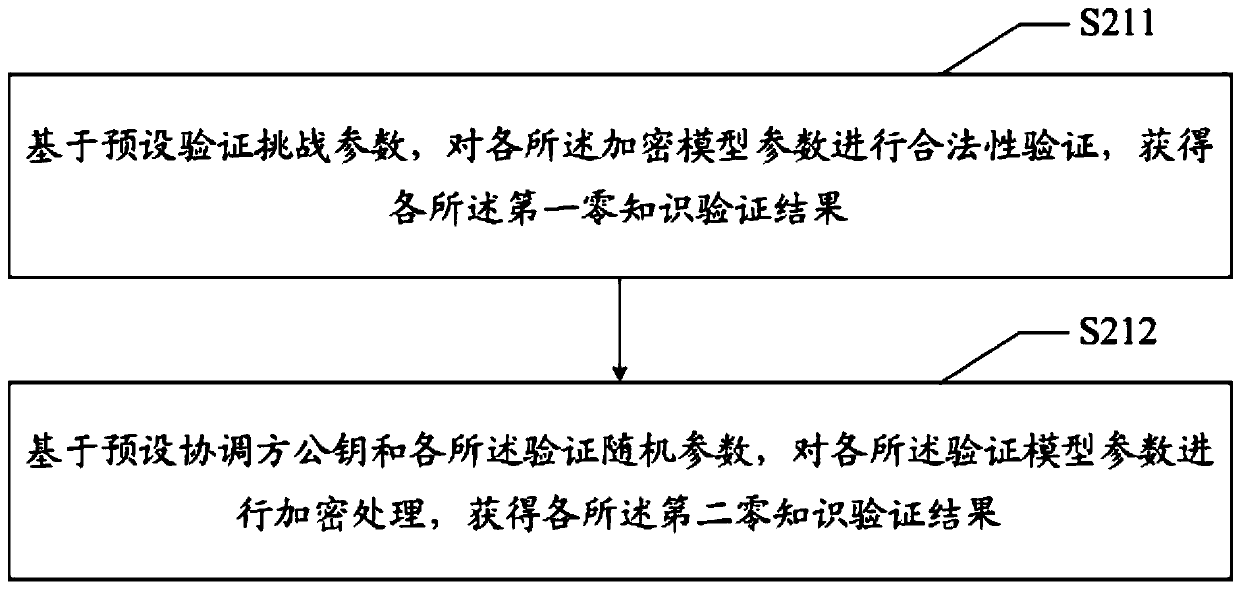
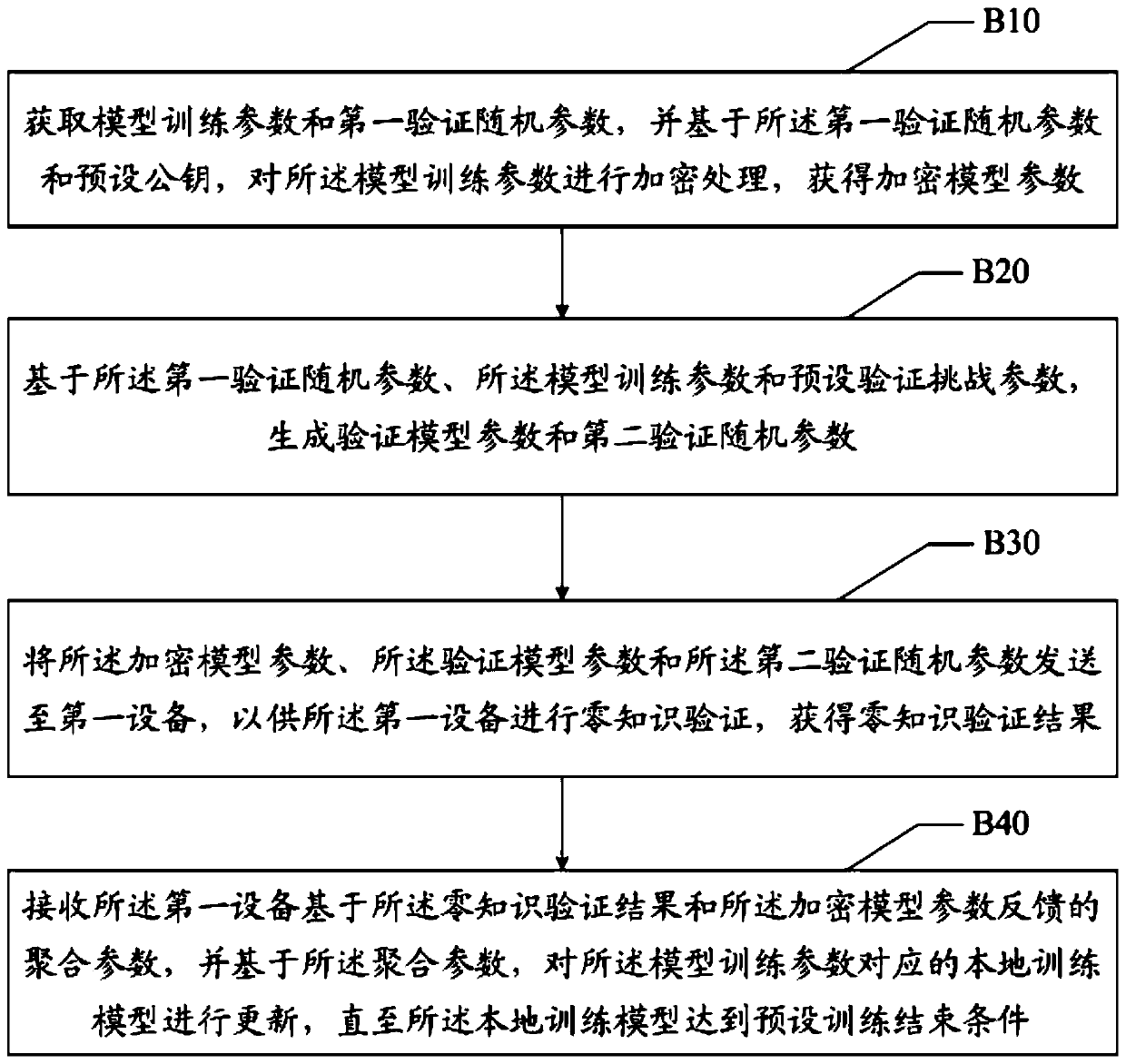
The invention discloses a federation learning modeling method, a device and a readable storage medium. The federation learning modeling method comprises the steps of carrying out federation learning modeling, receiving encryption model parameters sent by each second device and verification parameters corresponding to the encryption model parameters, based on each verification parameter, obtaininga verification result; and performing zero knowledge verification on each encryption model parameter to determine a false encryption model parameter in each encryption model parameter to obtain a zeroknowledge verification result, and then coordinating each second device to perform federation learning modeling based on the zero knowledge verification result and each encryption model parameter. The technical problems that federation learning modeling is low in efficiency and poor in accuracy are solved.
Owner:WEBANK (CHINA)
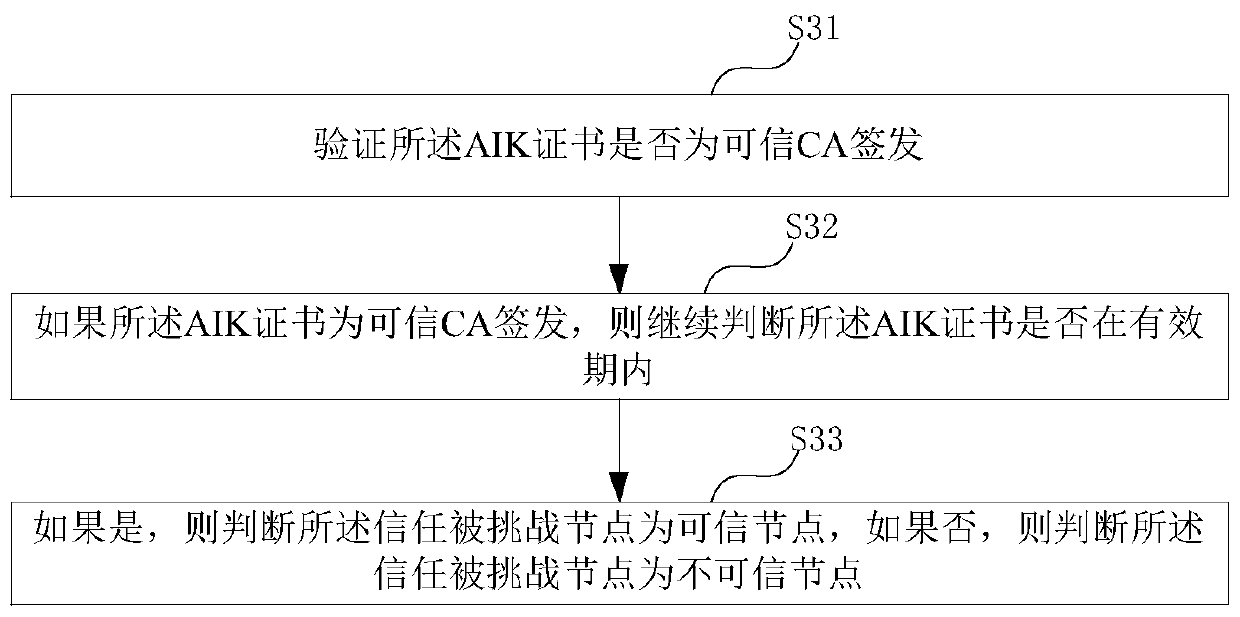
Zero-knowledge proof data interaction method, node and equipment
ActiveCN110768791AKey distribution for secure communicationUser identity/authority verificationComputer networkTrusted Platform Module
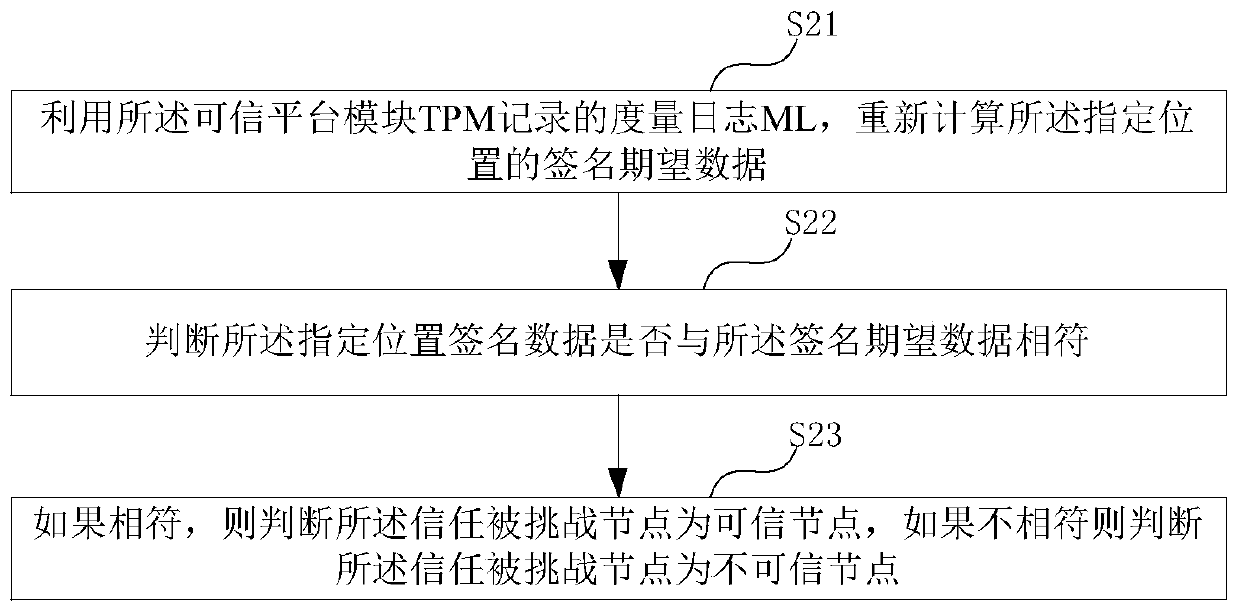
The embodiment of the invention provides a zero-knowledge proof data interaction method, which is used for a trust challenge node and comprises the following steps of sending a zero-knowledge challenge request to a trust challenged node, wherein the challenge request comprises a random number and specified position data, so that the trusted challenged node signs the data of the specified positionby using a trusted platform module (TPM) of the trusted challenged node and the random number to obtain specified position signature data; receiving the specified position signature data sent by the trusted challenged node, and a measurement log ML and an AIK certificate recorded by the trusted platform module TPM; verifying whether the trust challenge node verifies that the specified position signature data and the measurement log ML recorded by the trusted platform module TPM are consistent with the AIK certificate or not; and according to the verification result, determining whether the trusted challenged node is trusted or not, so as to determine whether to transmit the (pk, vk) in the zero-knowledge verification application stored in the TEE security area to the trusted challenged node or not.
Owner:北京八分量信息科技有限公司
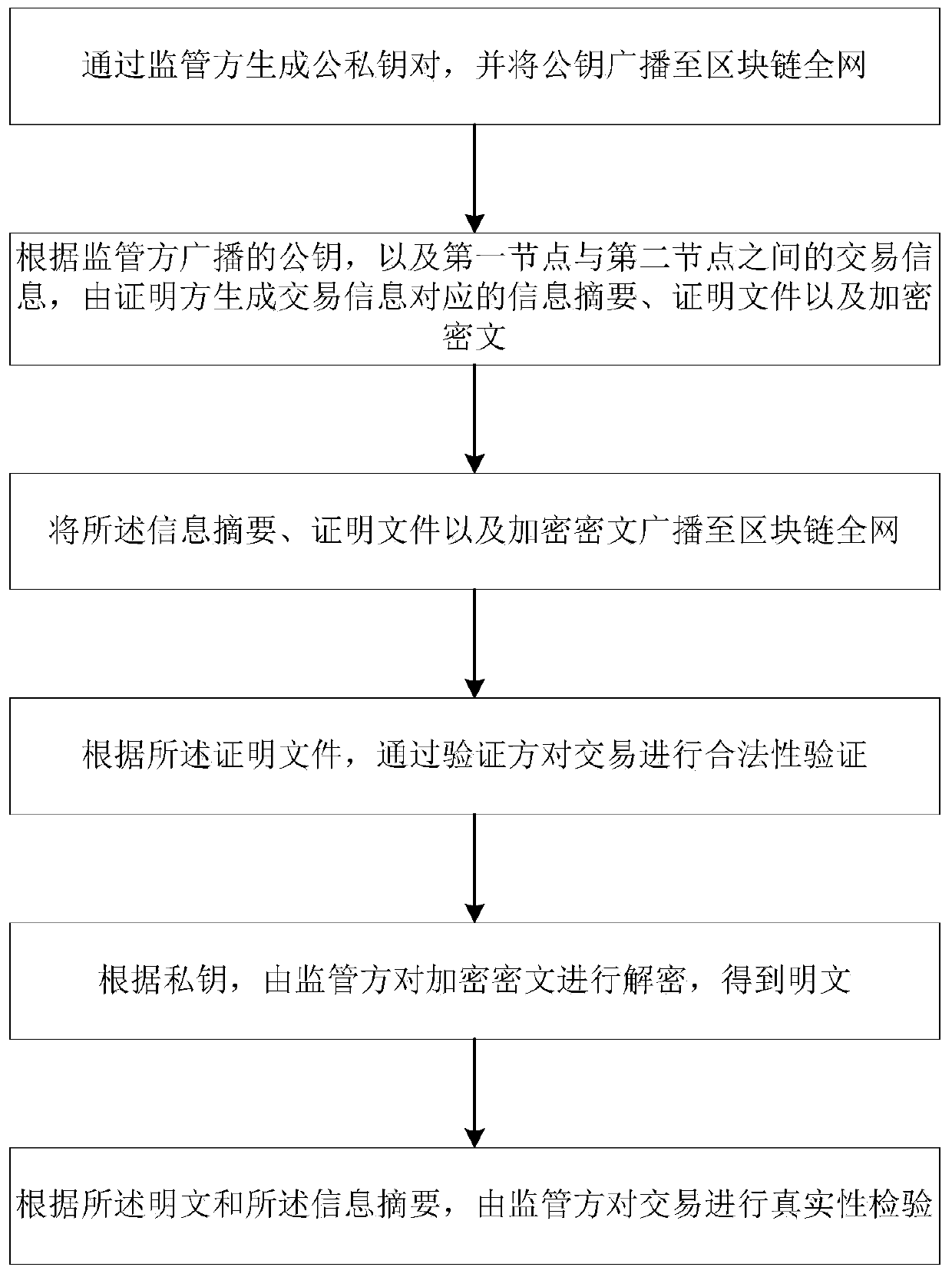
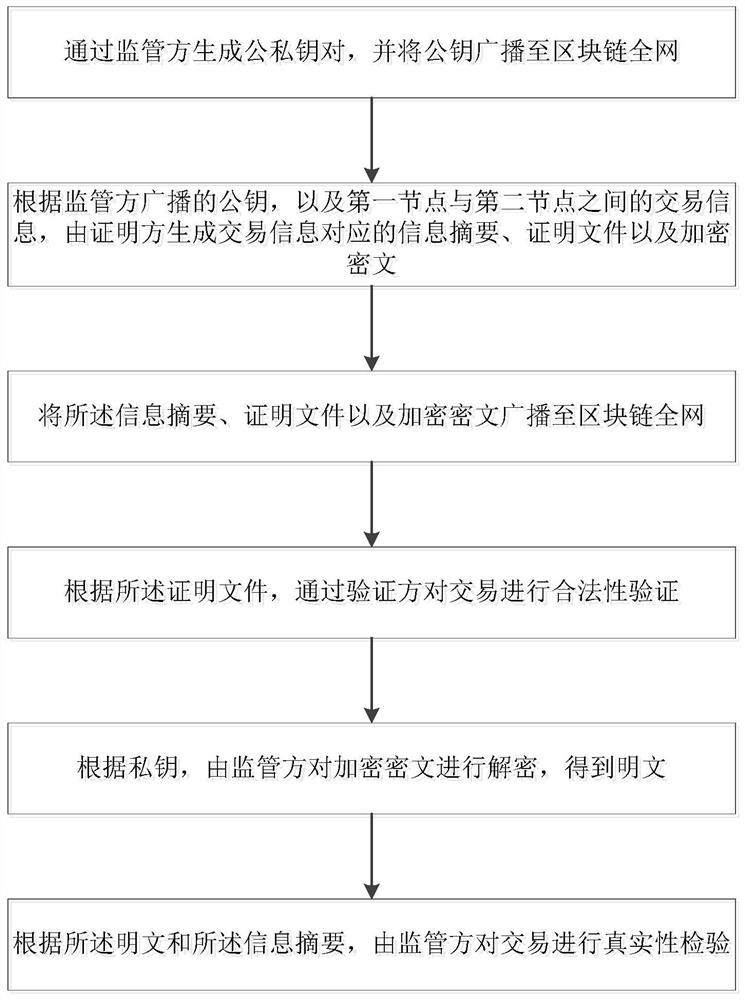
Supervisable zero-knowledge verification method and system in block chain and storage medium
ActiveCN110855631AGuaranteed correctnessSmall amount of calculationKey distribution for secure communicationPlaintextComputer network
The invention discloses a supervisible zero-knowledge verification method and system in a block chain and a storage medium. The method comprises the following steps: generating a public and private key pair through a supervisor, and broadcasting a public key to the whole network of the block chain; according to the public key broadcasted by the supervisor and the transaction information between the first node and the second node, the certification party generates an information abstract, a certification file and an encrypted ciphertext corresponding to the transaction information; broadcastingthe information abstract, the proof file and the encrypted ciphertext to the whole network of the block chain; verifying the legality of the transaction through a verifier according to the certification file; decrypting the encrypted ciphertext by the supervisor according to the private key to obtain a plaintext; According to the plaintext and the information abstract, performing authenticity verification on the transaction by a supervisor. According to the method, the privacy of the proving party is guaranteed, the calculated amount of the verifying party is reduced, the supervising party can effectively meet the supervising requirement. Meanwhile, the correctness of the information is guaranteed, and the method can be widely applied to the technical field of block chains.
Owner:南京可信区块链与算法经济研究院有限公司
System and method for consensus-based knowledge validation, analysis and collaboration
ActiveUS20100305915A1Easy to useDetermine the saliency of the subject matterDigital computer detailsNuclear monitoringData setPrivate network
A consensus-based knowledge validation and analysis system provides a way to increase use of collaboration tools among panels of experts by providing a system for analyzing and validating the responses of such experts to a set of questions. The system uses a set of response data input by a panel of experts with respect to a particular subject matter formatted in accordance with a data model as input. The response data set is used to estimate an empirical point estimate matrix indicative of the amount of agreement in the responses on all items between the panelists. The empirical point estimate matrix is used to estimate the saliency of the subject matter to panelists, the competency of each panelist and a consensus model of correct answers is based on the estimated competency of each panelist and the of responses for each item in the response data set. This consensus model is used to generate a knowledge map to aid visualization of the consensus data and encourage further collaboration and consensus building. The method is implemented in a web-based system that enables users of collaboration tools to send response data sets to the tool via the Internet or virtual private network and to likewise retrieve knowledge maps, panelist information and consensus data. An interactive feature enables users / panelists to collaborate with other panelists using the knowledge map as an interface to one or more collaboration tools such as instant messaging.
Owner:NYTELL SOFTWARE LLC
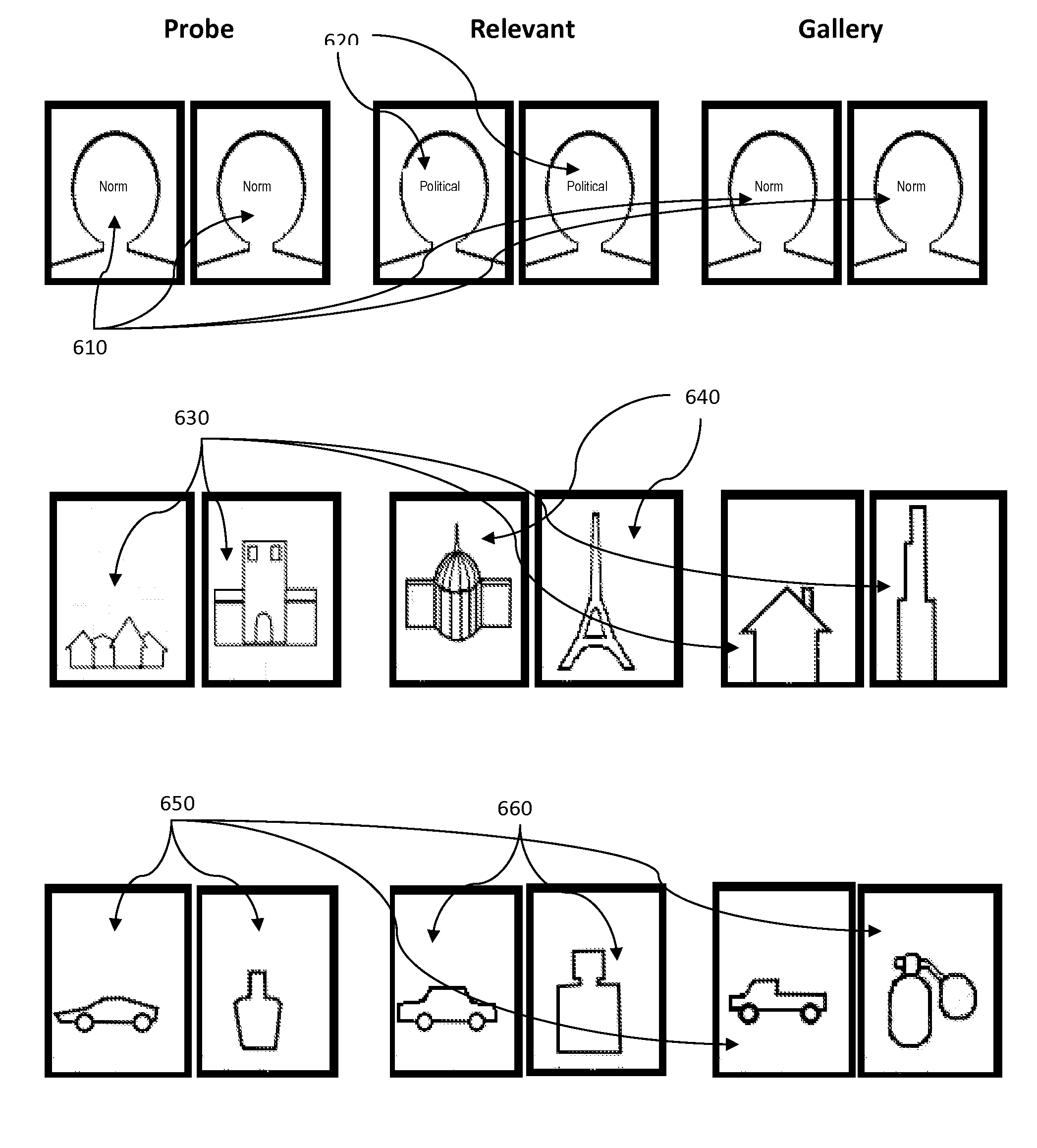
System and method for knowledge verification utilizing biopotentials and physiologic metrics
A system and method for knowledge verification utilizing biopotentials and physiologic metrics, which includes a computer-based device having stored thereon Probe, Relevant and Gallery image data, and a biopotential amplifier removably connected to a human subject via disposable Ag / Ag—Cl electrodes. Furthermore, the system comprises an analog-to-digital (A / D) converter to digitize said biopotential data for subsequent storage on said computer-based device, analysis software for discriminating said subject's event-related response to the exogenous stimuli, a visual display system comprising an LCD video monitor, and control software for presenting the Probe, Relevant and Gallery visual stimuli in a weighted, pseudo-random sequence which can be modulated by the outcome of said analysis software. Probe image data are not generally known to said human subjects but relevant to the knowledge to be verified; Relevant image data are generally known to said human subjects but not relevant to the knowledge to be verified; and Gallery image data are not generally known to said human subjects and not relevant to the knowledge to be verified. Said knowledge verification system can utilize parametric or non-parametric, e.g., artificial neural networks, analysis to provide an output of verification, or non-verification of knowledge of interest. Exemplary headband and electrode configurations optimized to produce the desired signals are disclosed.
Owner:IDEAL INNOVATIONS
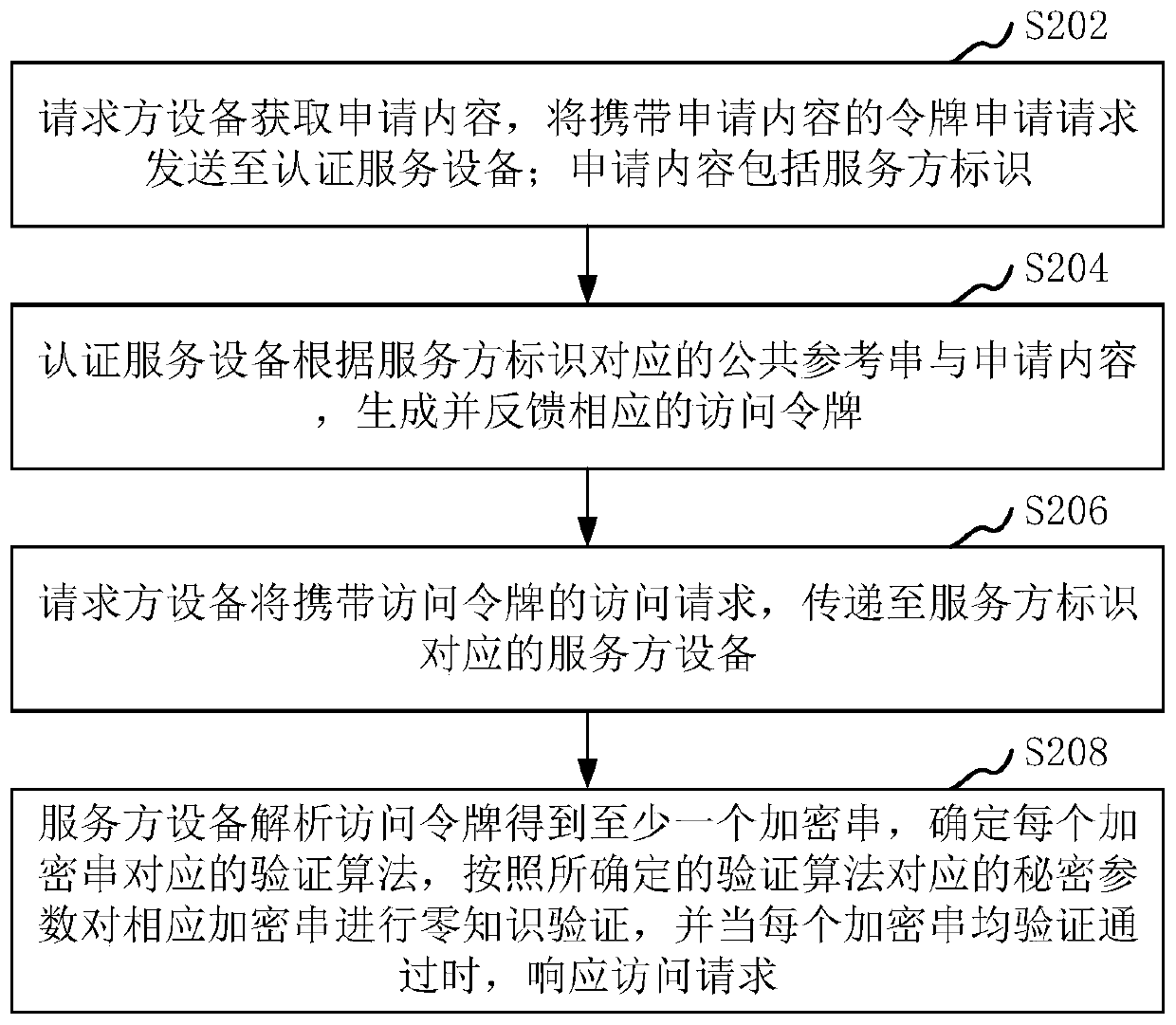
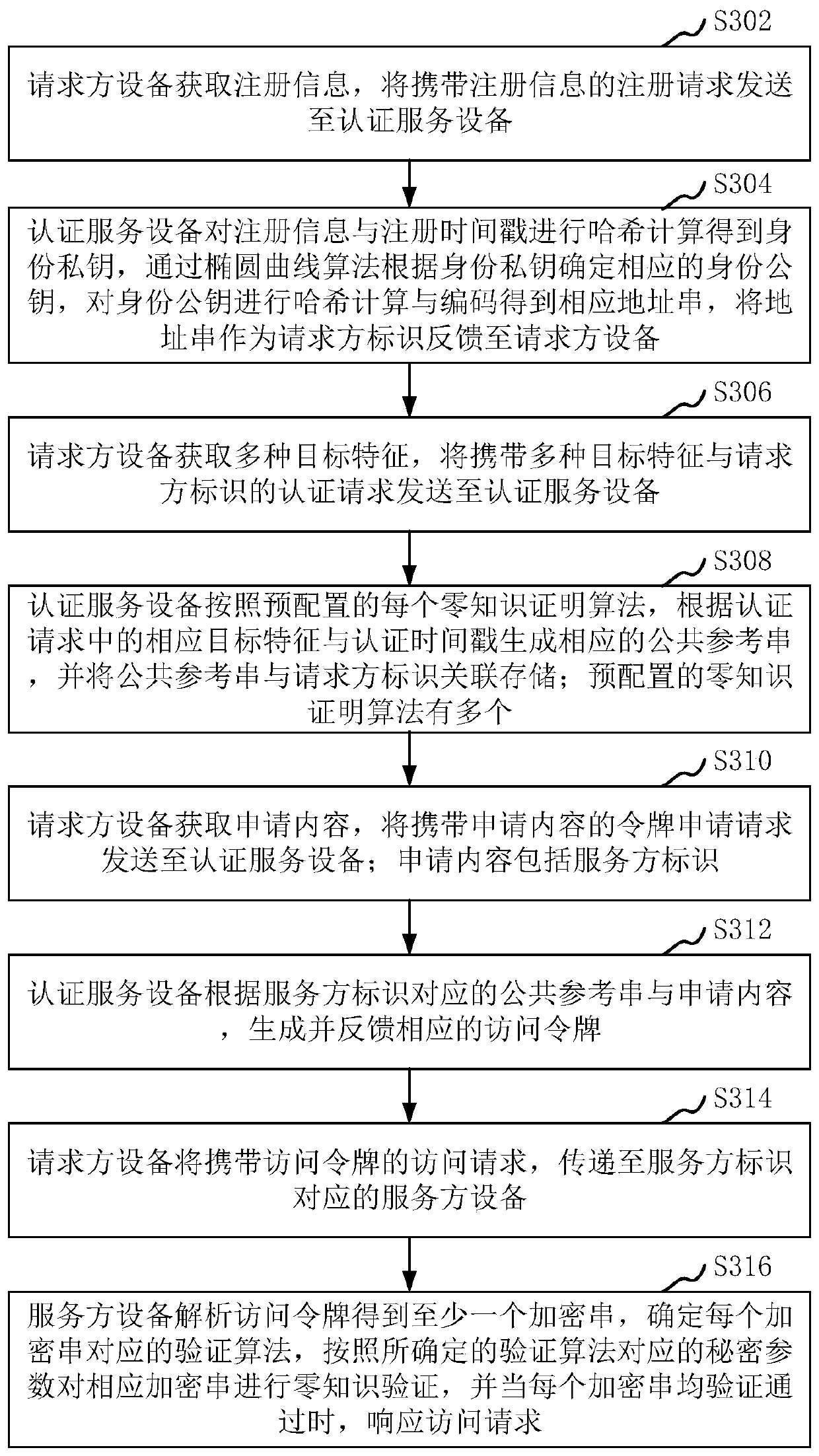
Access control method and system, computer equipment and storage medium
ActiveCN111211908AEnsure safetyAvoid interactionUser identity/authority verificationInstrumentsThe InternetEngineering
The invention relates to an access control method and system, computer equipment and a storage medium. The method comprises the steps that requester equipment acquires application content and sends atoken application request carrying the application content to authentication service equipment, wherein the application content comprises a service party identifier, the authentication service equipment generates and feeds back a corresponding access token according to a public reference string corresponding to the service party identifier and the application content, the requester equipment transmits the access request carrying the access token to service party equipment corresponding to the service party identifier, and the service equipment analyzes the access token to obtain at least one encrypted string, determines a verification algorithm corresponding to each encrypted string, performs zero knowledge verification on the corresponding encrypted string according to a secret parametercorresponding to the verification algorithm, and responds to the access request when each encrypted string passes the verification. By the adoption of the method, effective control over access of theInternet of Things equipment can be achieved, and therefore the safety of the Internet of Things equipment can be guaranteed.
Owner:SHENZHEN POWER SUPPLY BUREAU
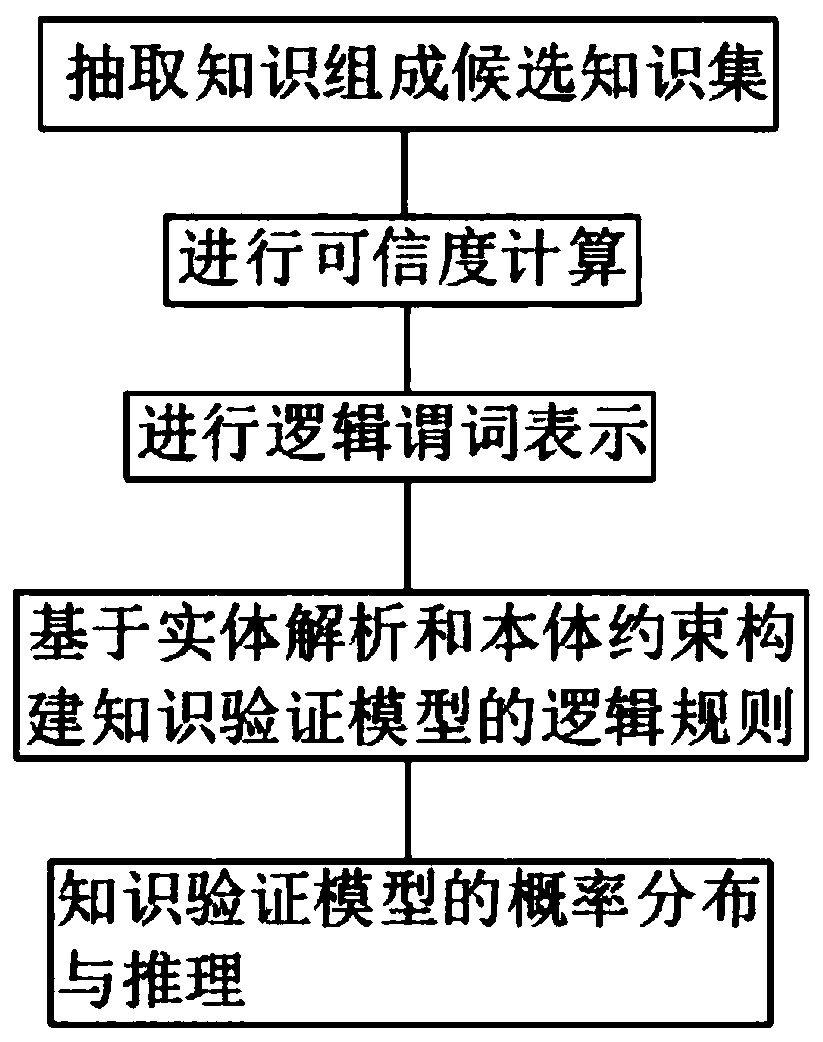
Knowledge verification model construction and analysis method based on probability soft logic
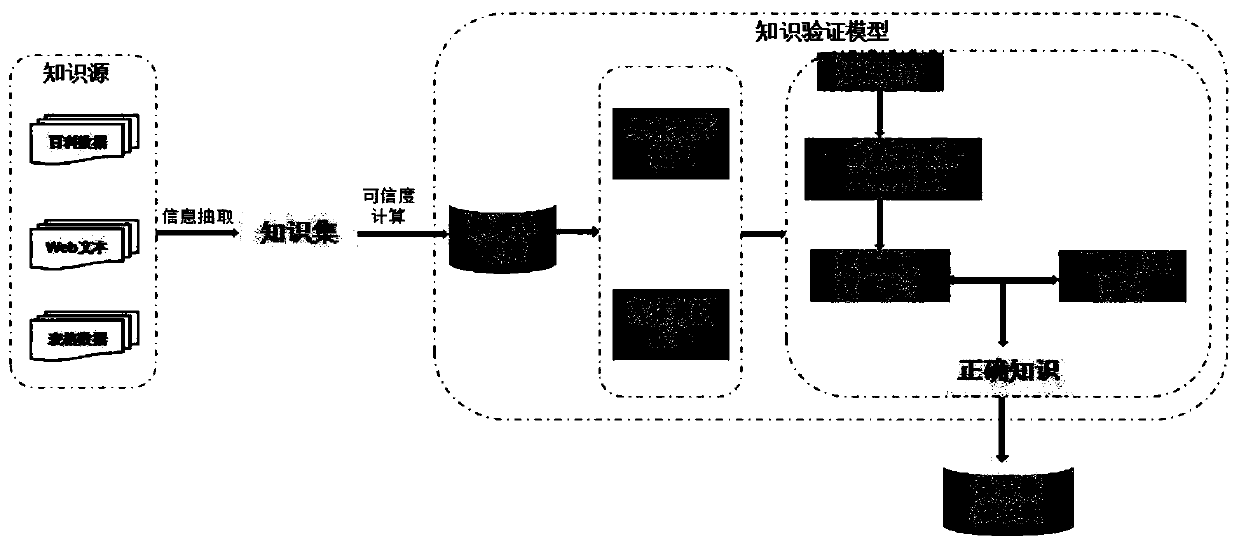
PendingCN111026877AImprove accuracyTroubleshoot issues such as errorsMathematical modelsKnowledge representationTheoretical computer scienceEngineering
The invention belongs to the technical field of information extraction, and particularly relates to a knowledge verification model construction and analysis method based on probability soft logic, which comprises the following steps of: a, forming a candidate knowledge set by knowledge extracted from webpage web texts of a plurality of data sources by an information extraction system; b, carryingout credibility calculation on the candidate knowledge set; c, performing logic predicate representation on each entity in the candidate knowledge set; d, constructing a first-order logic rule of theknowledge verification model based on the entity analysis and the ontology constraint, generating the first-order logic rule in the probability soft logic model through the constructed logic rule, andachieving entity relationship and entity label verification in the candidate knowledge set; and e, setting probability distribution of the knowledge verification model, and calculating and selectingcorresponding knowledge to be updated through an inference algorithm. According to the method, the candidate knowledge set is verified, so that the accuracy of the candidate knowledge set is greatly improved.
Owner:INST OF ELECTRONICS & INFORMATION ENG OF UESTC IN GUANGDONG
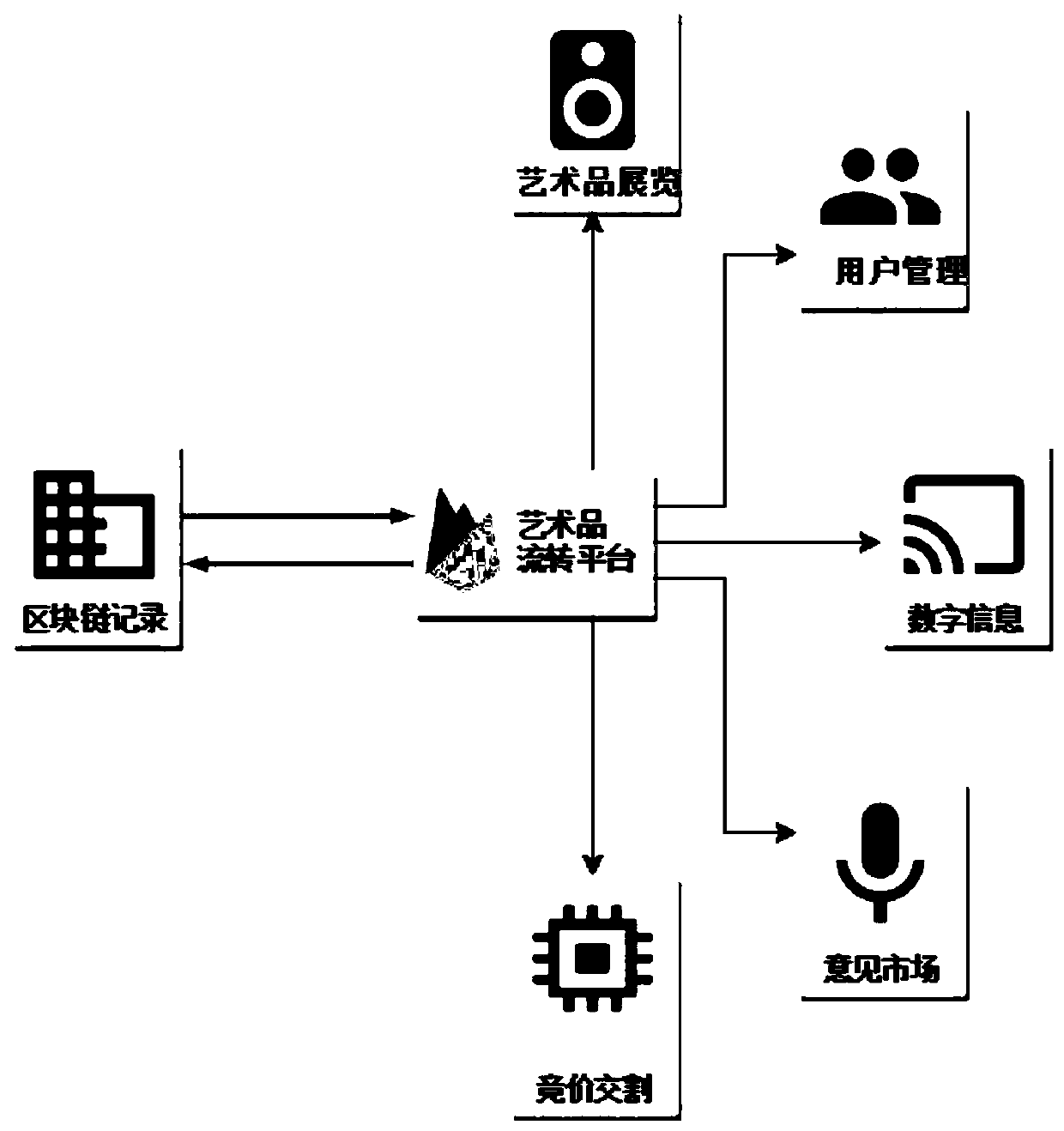
Artwork circulation platform based on block chain technology
InactiveCN110009377AResolve asymmetrySettle the priceFinanceCommerceLogistics managementRelevant information
Owner:北京一三链科技有限公司
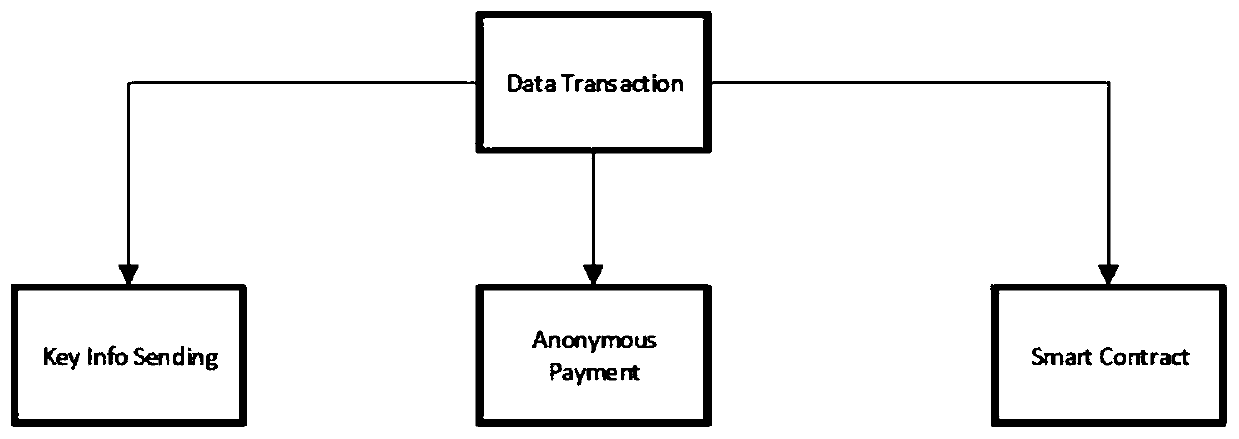
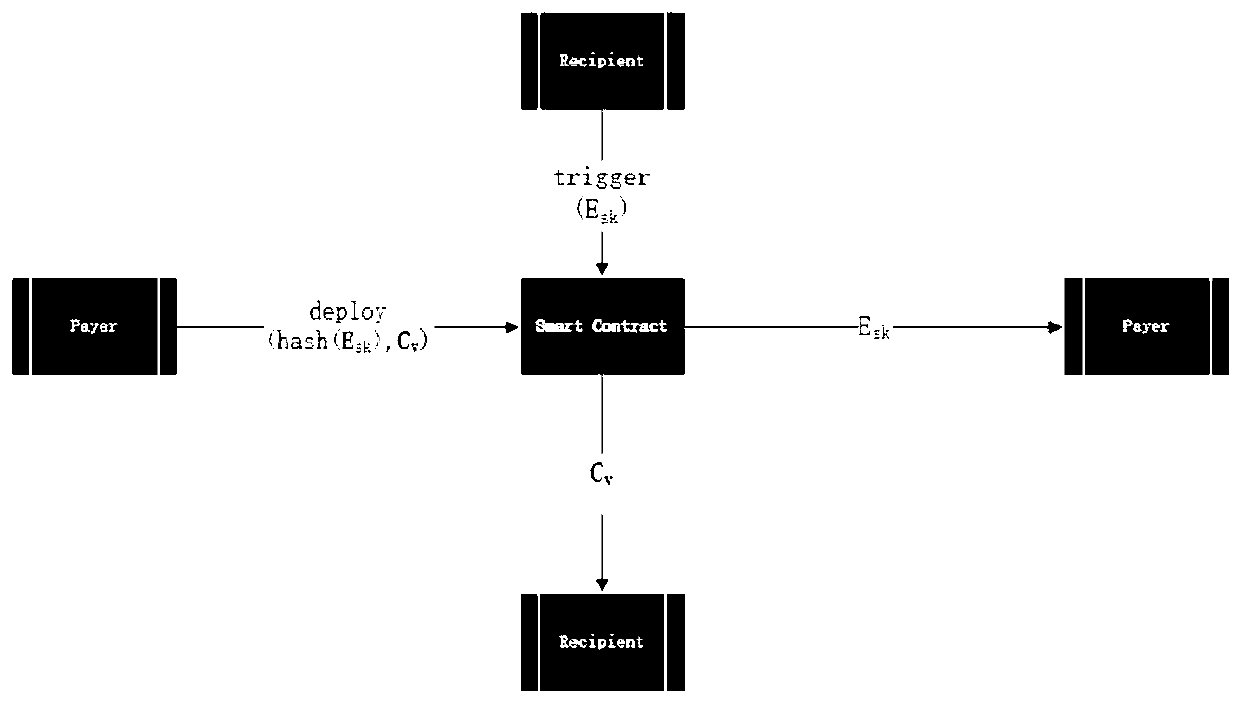
Decentralized anonymous data transaction method based on zero knowledge proof
PendingCN110728576ASpecial service provision for substationKey distribution for secure communicationComputer networkEngineering
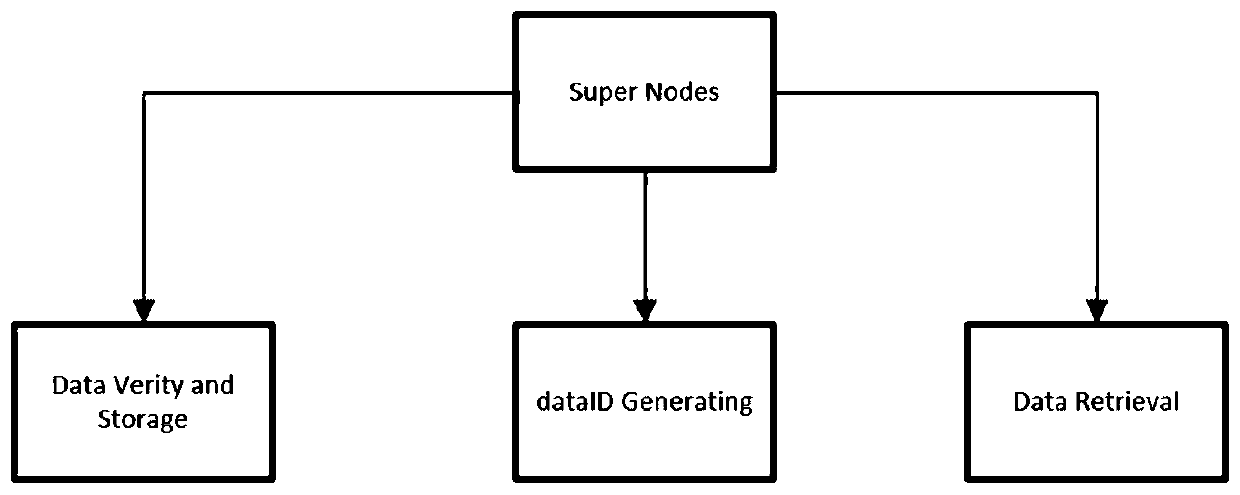
The invention discloses a decentralized anonymous data transaction method based on zero knowledge proof. The decentralized anonymous data transaction method guarantees the authenticity of data throughthe erection of super nodes, builds the anonymity of transaction based on a zero knowledge verification technology (ZK-SNARKs) and a Zerocash DAP scheme, and ensures the interests of the buyer and the seller by deploying the intelligent contract. The technical effect of the decentralized anonymous data transaction method is that by implementing the present invention, decentralized and anonymous transactions can be brought to data sellers and data purchasers. Specifically, data transaction can be completed by sending information by a seller and deploying an intelligent contract by a buyer, which is simple and convenient for both parties. Moreover, the anonymity of the transaction is provided by utilizing a DAP scheme, and an experiment shows that the scheme has almost the same performanceas Zerocash, which means that the scheme is a practical scheme in the data transaction.
Owner:HUNAN UNIV OF SCI & ENG
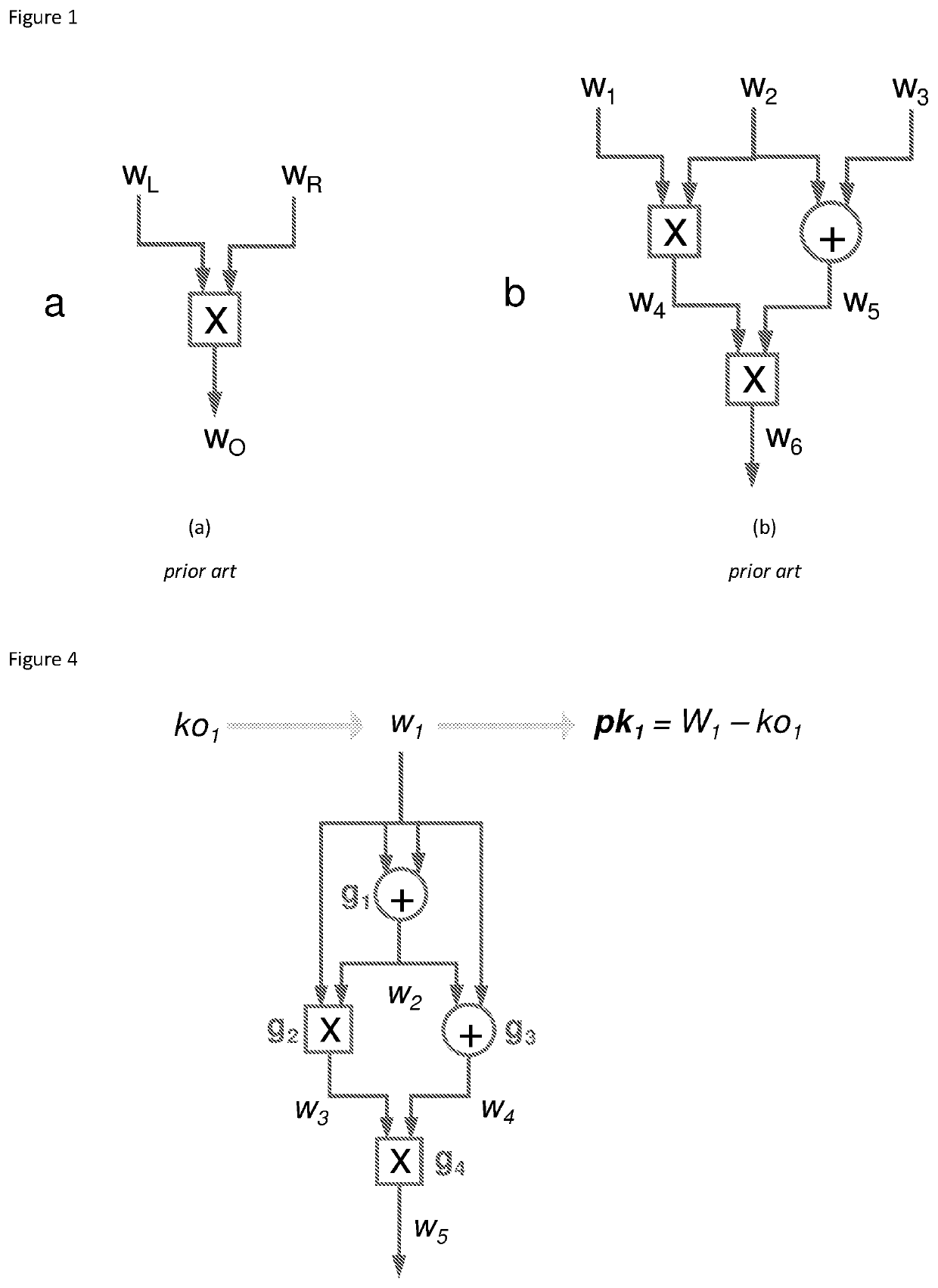
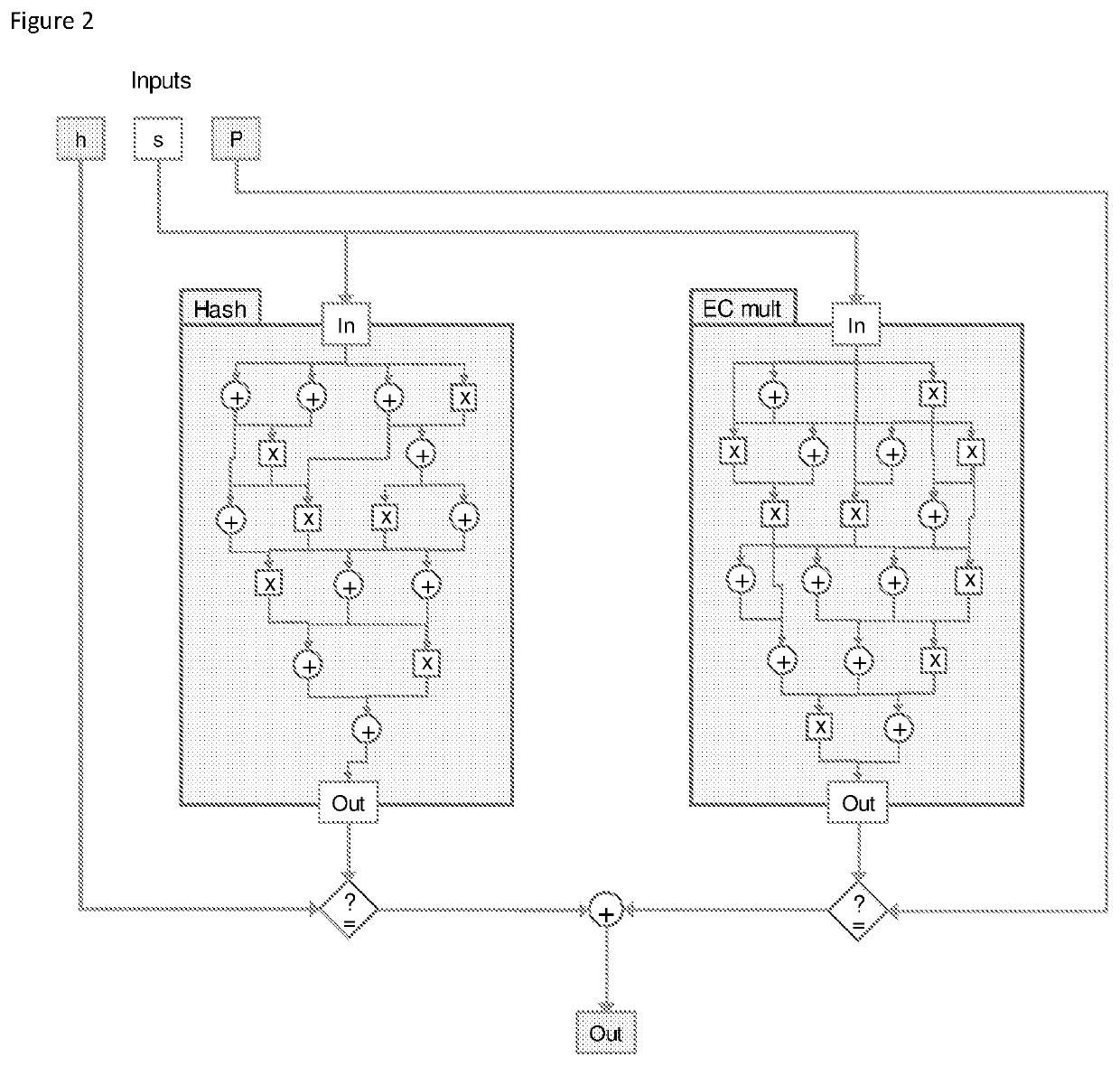
Computer-implemented system and method for trustless zero-knowledge contingent payment
PendingUS20210027294A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesPaymentAlgorithm
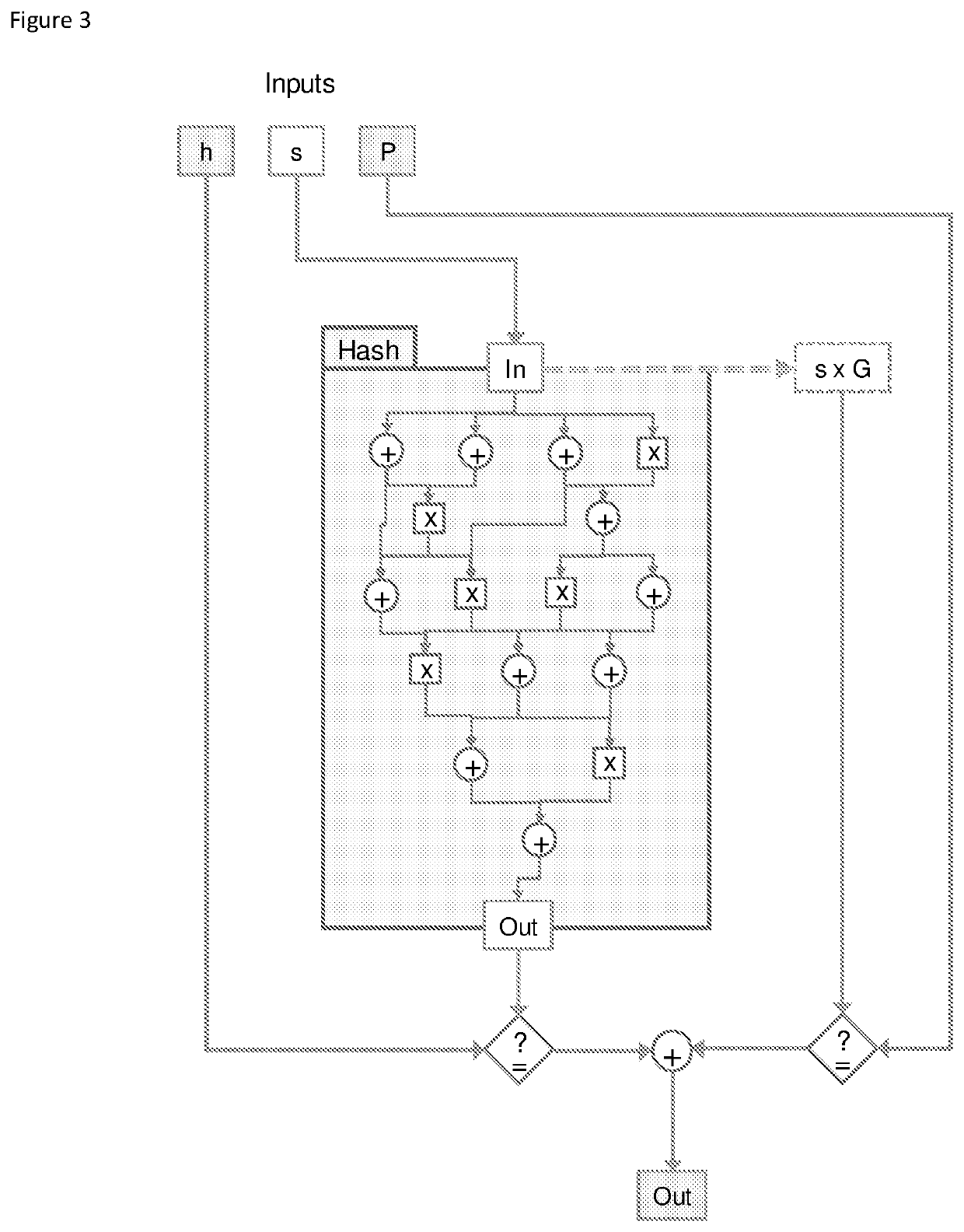
The invention relates to efficient zero knowledge verification of composite statements that involve both arithmetic circuit satisfiability and dependent statements about the validity of public keys (key-statement proofs) simultaneously. The method enables a prover to prove this particular statement in zero-knowledge. More specifically, the invention relates to a computer-implemented method for enabling zero-knowledge proof or verification of a statement (S) in which a prover proves to a verifier that a statement is true while keeping a witness (W) to the statement a secret. The invention also relates to the reciprocal method employed by a verifier who verifies the proof. The method includes the prover sending to the verifier a statement (S) having an arithmetic circuit with m gates and n wires configured to implement a function circuit and determine whether for a given function circuit output (h) and an elliptic curve point (P), the function circuit input (s) to a wire of the function circuit is equal to the corresponding elliptic curve point multiplier (s). The prover also sends individual wire commitments and / or a batched commitment for wires of the circuit, an input for a wire in the arithmetic circuit; and a function circuit output (h). The prover receives from the verifier a challenge value (x) and responding with an opening or additionally sends a proving key (PrK) to the verifier. The statement and the data enables the verifier to determine that the circuit is satisfied and calculate the elliptic curve point (P) and validate the statement, thus determining that the prover holds the witness (W) to the statement.
Owner:NCHAIN LICENSING AG
Information validation
ActiveCN103218288AEasy to debugSoftware testing/debuggingKnowledge representationAutomatonKnowledge level
A computer implemented method for knowledge validation includes identifying a fact for validation. A semantic model representing the fact for validation can be created. A context associated with the fact can be identified, and an automaton can be created based at least in part on the identified context. The fact can be validated using the automaton.
Owner:SAP AG
Case-based design knowledge description method and system
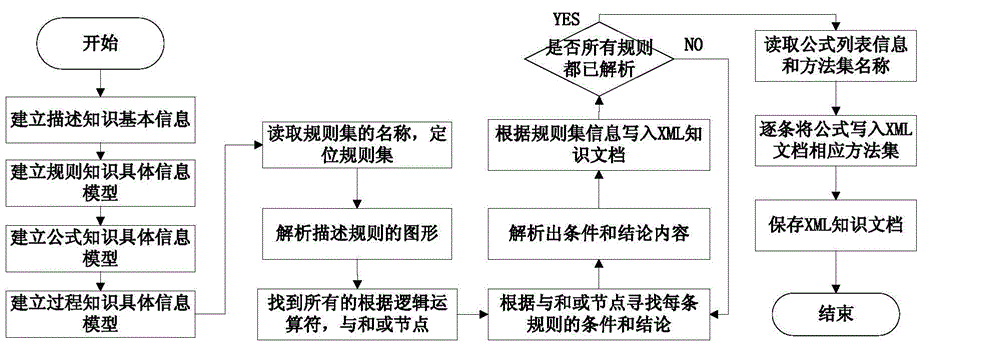
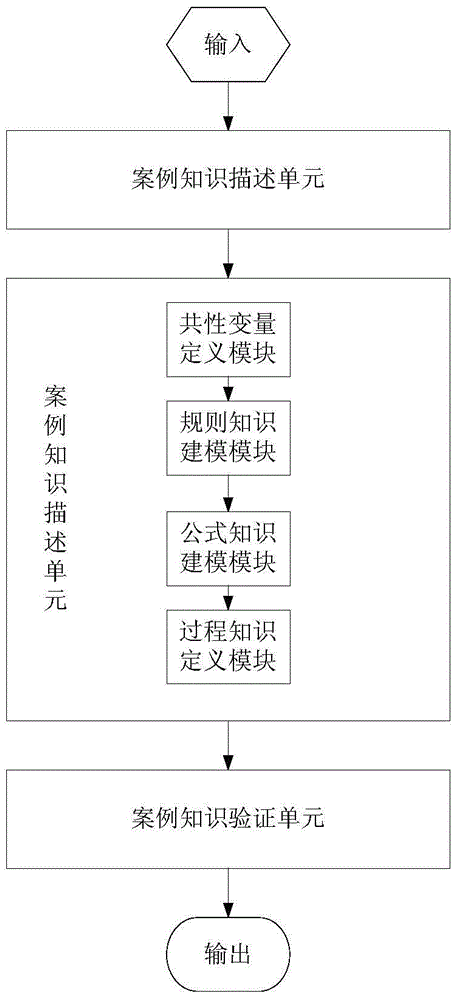
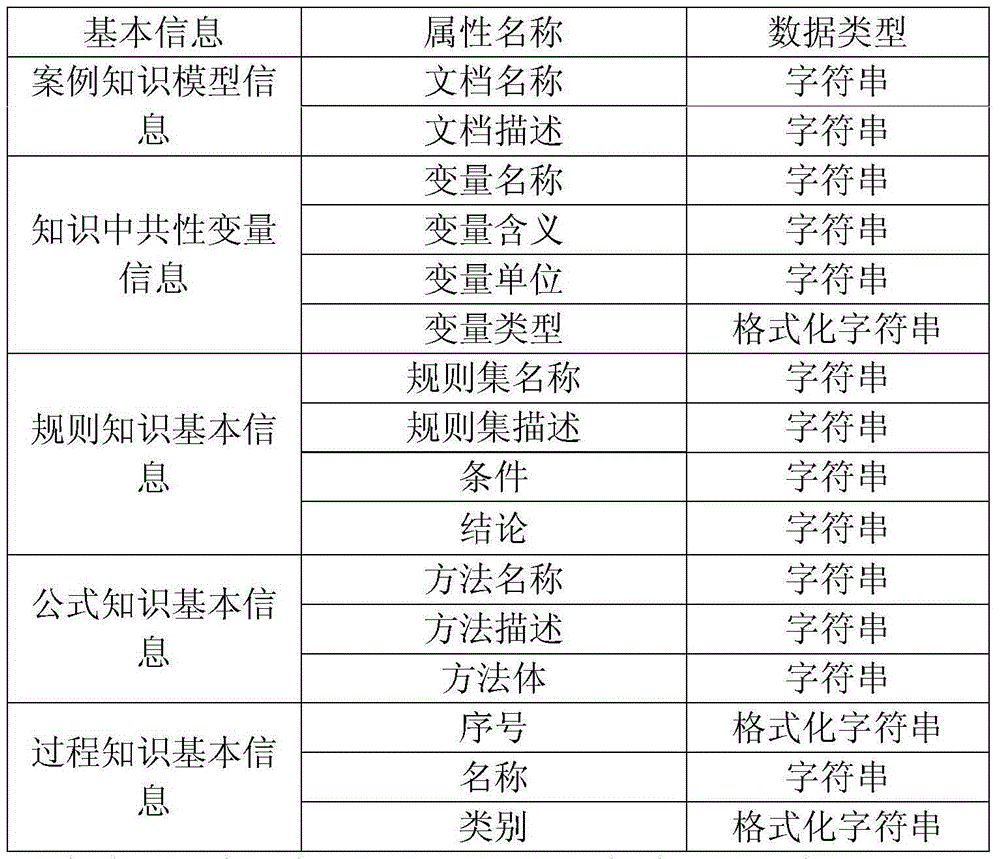
ActiveCN105843973AConvenient timeLow costSpecial data processing applicationsCase based designKnowledge management
The invention discloses a case-based design knowledge description method and system. The method includes the steps: describing basic information of case knowledge according to an XML-based case knowledge information description specification; establishing a specific information model of the case knowledge according to the basic information of the case knowledge; and checking grammar and logic of the specific information of the case knowledge in the specific information model of the case knowledge. According to the technical scheme, XML-based uniform description grammar is established, the heterogeneity of knowledge such as formulas, rules, and processes in a case can be shielded, and uniform basic information of the case knowledge can be supported and formed; through the method for modeling formulas, rules, and processes which are integrated with EXCEL, acquisition and formalized description of the knowledge can be supported; and through verification of the case knowledge, checking and verification of logic among lots of heterogeneous knowledge can be supported.
Owner:BEIJING SIMULATION CENT
Grid operation KPI (key performance indicator) data self-learning method and system
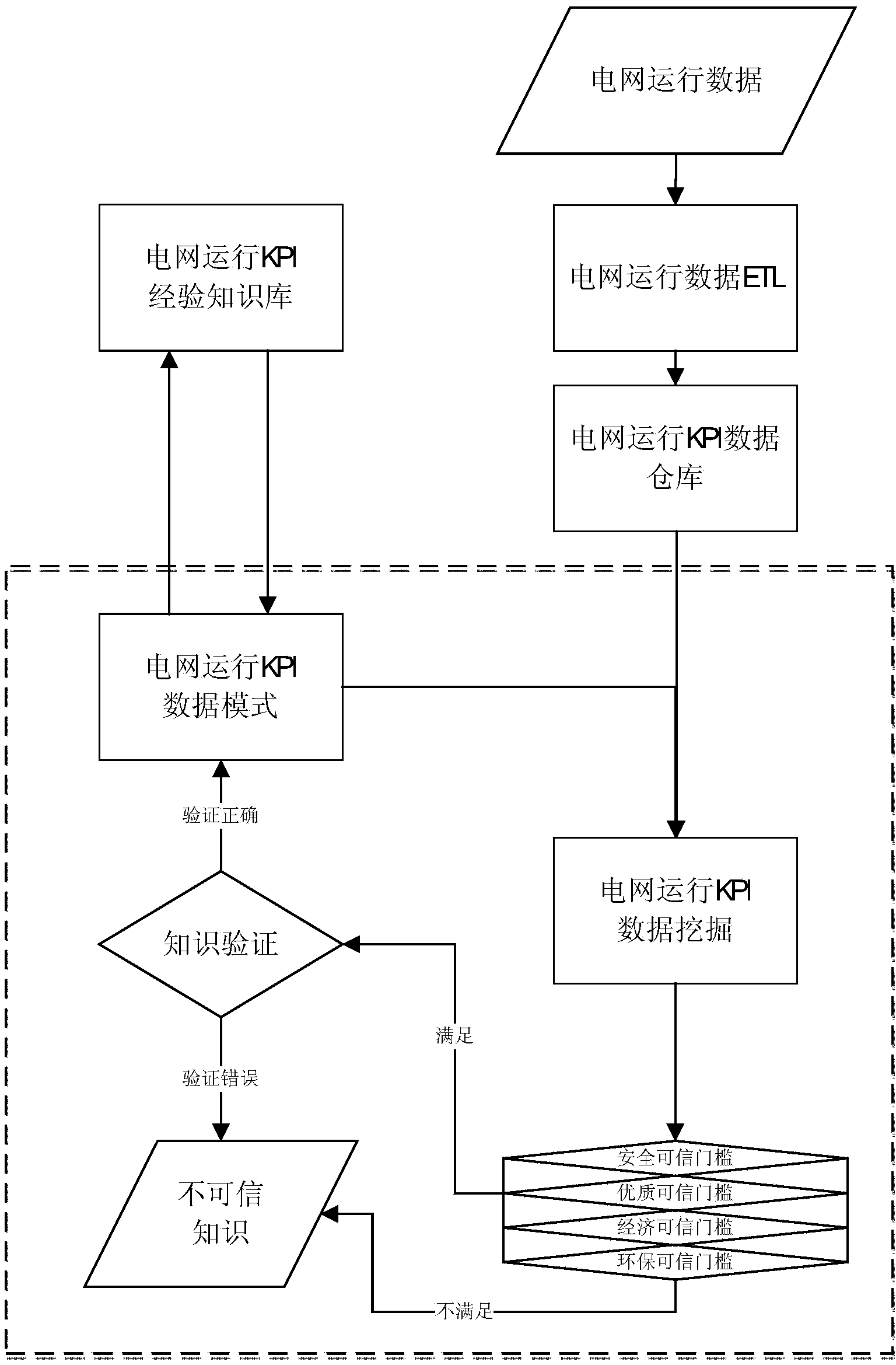
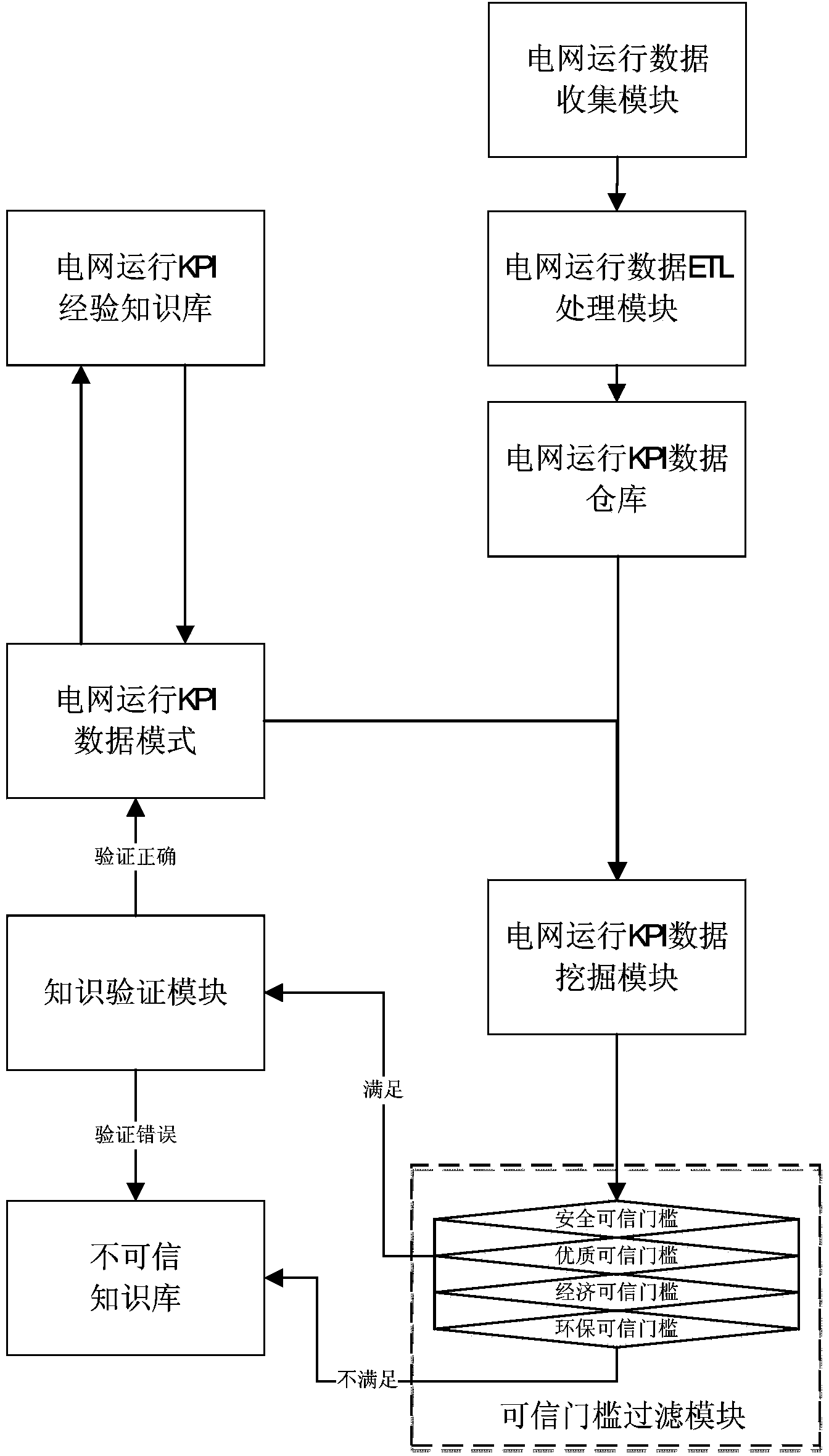
InactiveCN104361433ASolve the problem of low operation management efficiency and impossibility of refined managementImprove management efficiencyResourcesData transformationData warehouse
The invention relates to a grid operation KPI (key performance indicator) data self-learning method and system. Through the ETL (extract, transform and load) technology, collected grid operation data is subjected as required to data extraction, data transformation and washing to obtain grid operation KPI data; the washed grid operation KPI data is loaded to a grid operation KPI data warehouse; the data loaded to the grid operation KPI data warehouse is subjected to grid operation KPI data mining through a C4.5 algorithm; a KPI data correlation relationship is obtained through feature analysis, correlation analysis and clustering decision analysis; an accepted KPI data correlation relationship is obtained through trusted threshold filtering; after knowledge verification, a new grid operation KPI data mode is obtained and stored in a grid operation KPI experience and knowledge base. According to the method, knowledge expansion surely available and undiscovered by the traditional grid operation research theories, basis for enriching and improving specialized knowledge and capacities of grid operation personnel is provided, and fine management is achieved accordingly.
Owner:ELECTRIC POWER SCHEDULING CONTROL CENT OF GUIZHOU POWER GRID CO LTD +1
Crowdsourcing worker reliability model establishing method and device in crowdsourcing knowledge verification environment
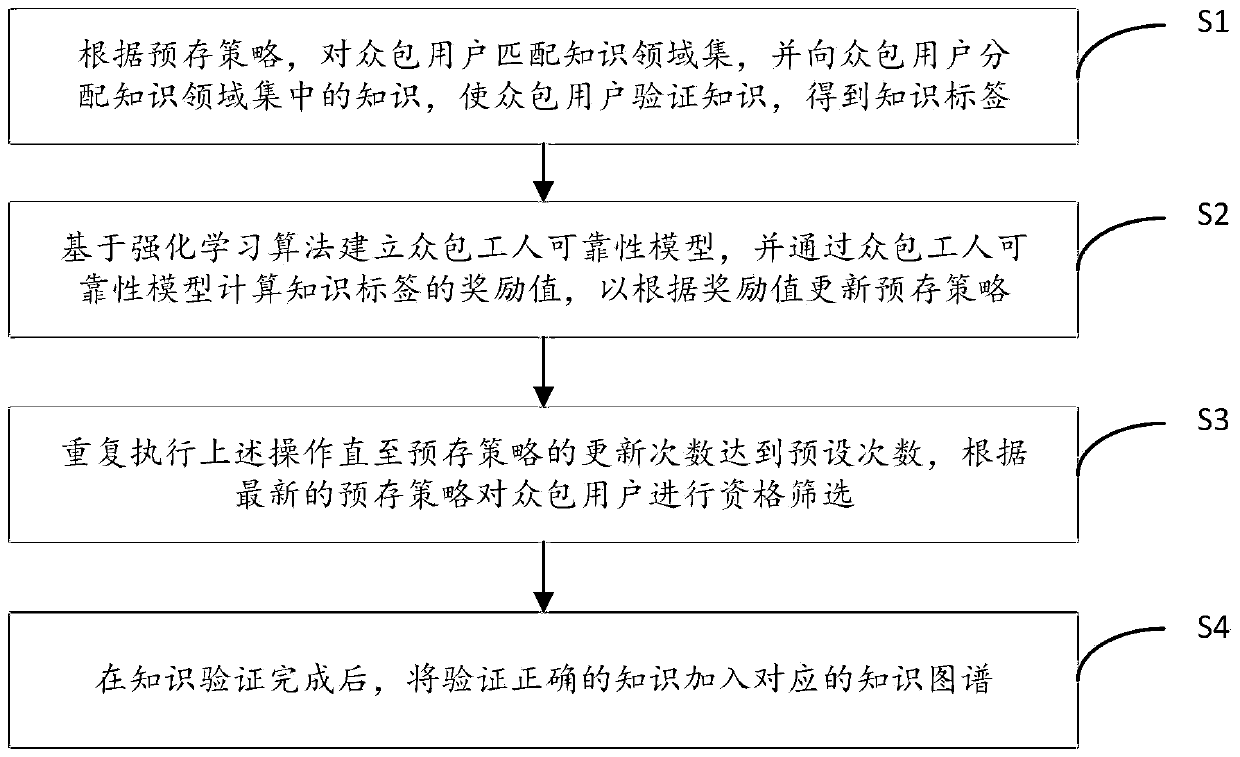
ActiveCN111444332AImprove verification efficiencyQualification Screening ImplementationSpecial data processing applicationsSemantic tool creationReinforcement learning algorithmEngineering
The invention discloses a crowdsourcing worker reliability model establishing method and device in a crowdsourcing knowledge verification environment. The method comprises the following steps of: matching a knowledge domain set for crowdsourcing users according to a pre-stored strategy, and allocating knowledge in the knowledge domain set to the crowdsourcing users, so that the crowdsourcing usersverify the knowledge to obtain knowledge tags; establishing a crowdsourcing worker reliability model based on a reinforcement learning algorithm, and calculating a reward value of the knowledge labelthrough the crowdsourcing worker reliability model so as to update the pre-stored strategy according to the reward value; repeatedly executing the above operation until the updating frequency of thepre-stored strategy reaches the preset frequency, and carrying out qualification screening on the crowdsourcing users according to the latest pre-stored strategy; and adding the knowledge which is verified to be correct into the corresponding knowledge graph after knowledge verification is completed. According to the method, the crowdsourcing worker reliability model can be established in the crowdsourcing verification environment based on reinforcement learning, qualification screening of crowdsourcing workers is achieved, and therefore the crowdsourcing knowledge verification efficiency is improved.
Owner:GUANGZHOU UNIVERSITY
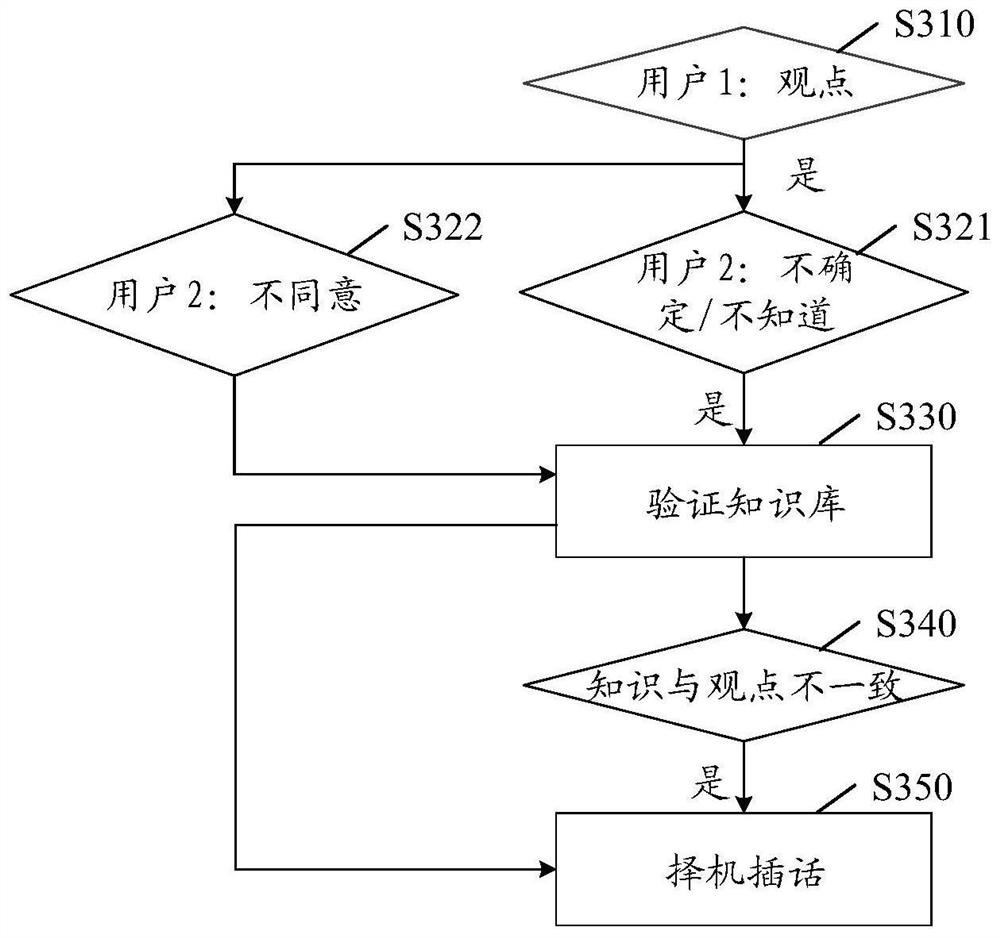
Dialogue interaction method and device, electronic equipment and computer readable storage medium
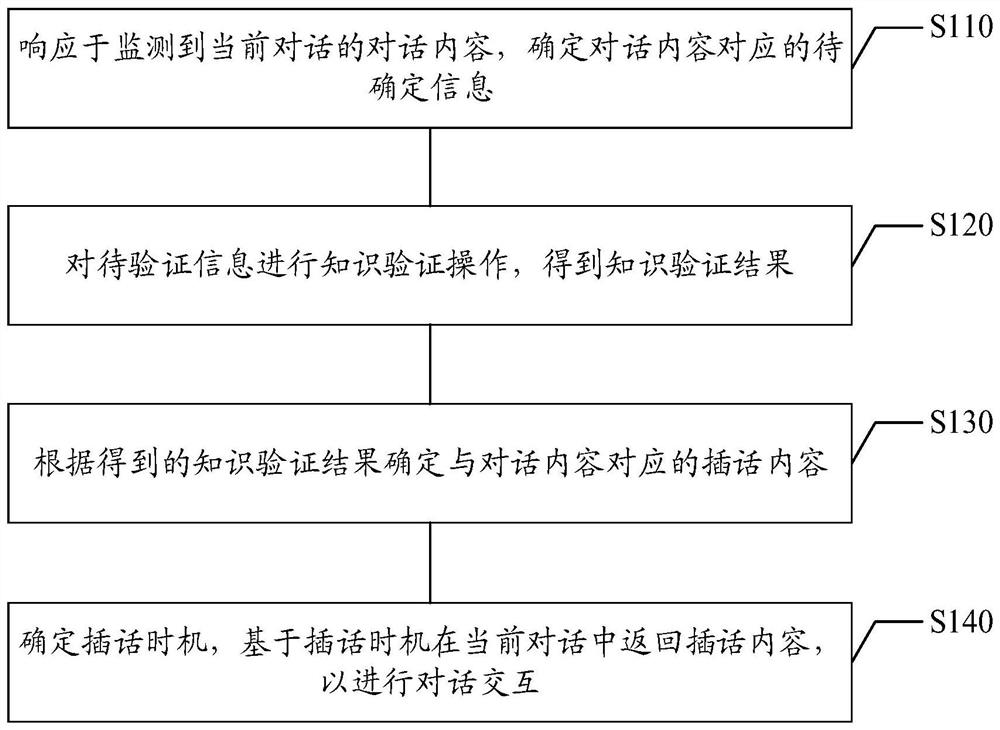
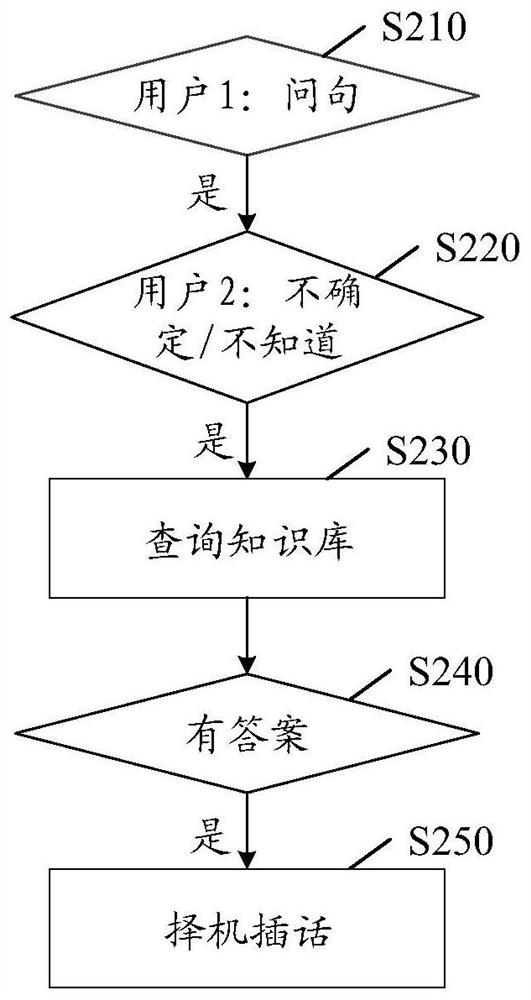
PendingCN113468894ACharacter and pattern recognitionNatural language data processingEngineeringHuman–computer interaction
The invention relates to a dialogue interaction method and device, electronic equipment and a computer readable storage medium, which relate to the technical field of natural language processing, and can be applied to a scene in which an intelligent dialogue robot initiatively inserts to provide knowledge for a user. The method comprises the steps of determining to-be-determined information corresponding to a dialogue content in response to the monitored dialogue content of a current dialogue, performing knowledge verification operation on the to-be-determined information to obtain a knowledge verification result, determining an insert content corresponding to the dialogue content according to the obtained knowledge verification result, and determining an insert opportunity, and returning insert content in the current session based on the insert opportunity to perform dialogue interaction. According to the method and the device, knowledge query and verification operation can be performed according to the dialogue content in multi-person chat, the related knowledge corresponding to the dialogue content is determined, and dialogue interaction is performed in an active insertion mode.
Owner:TAIKANG LIFE INSURANCE CO LTD
Malignant tumor diagnosis and treatment aid decision generation method and device
PendingCN112735584AImprove the efficiency of knowledge acquisitionImprove applicabilityMedical data miningMedical automated diagnosisReasoning algorithmKnowledge extraction
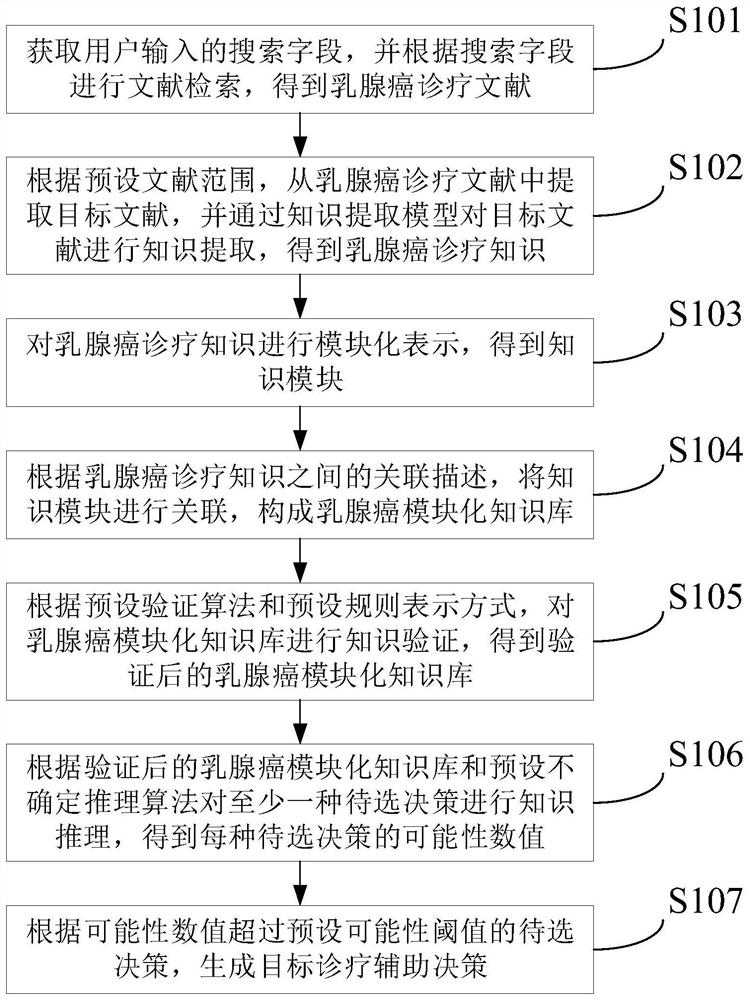
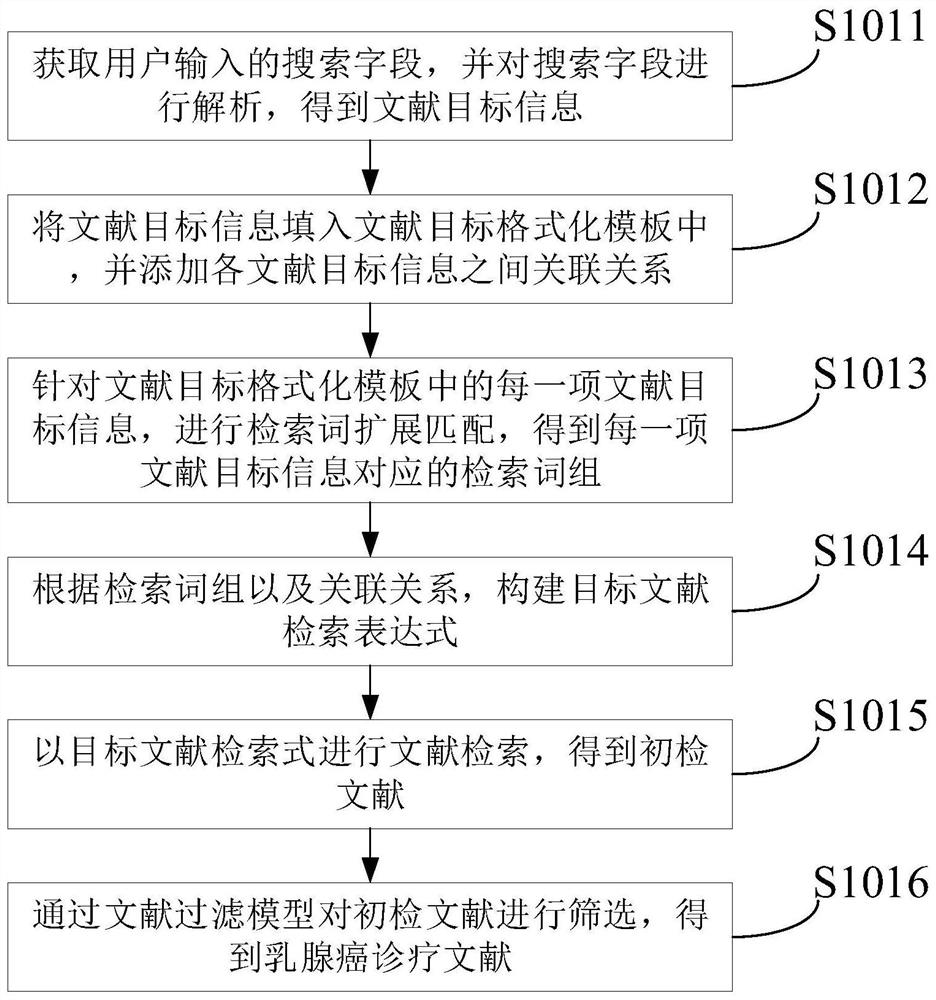
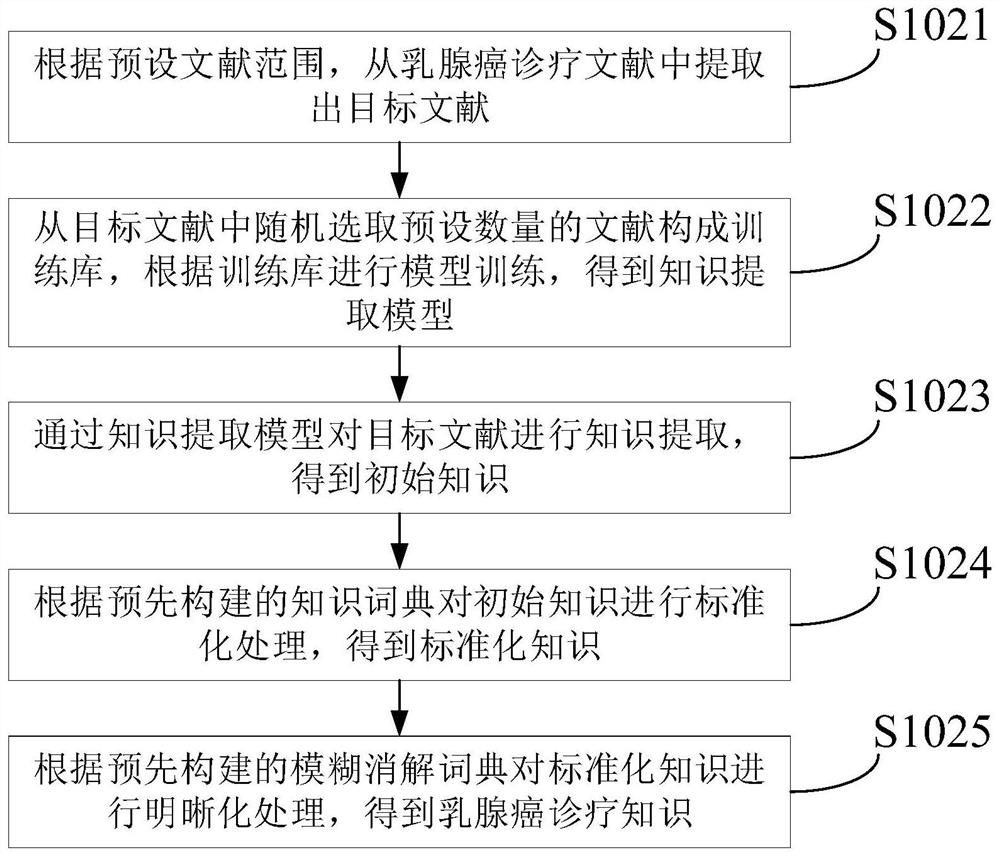
The invention provides a malignant tumor diagnosis and treatment aid decision generation method and device, and the method comprises the steps: obtaining a search field inputted by a user, carrying out document retrieval according to the search field, and obtaining a breast cancer diagnosis and treatment document; according to a preset literature range, extracting a target literature from the breast cancer diagnosis and treatment literature, and performing knowledge extraction on the target literature through a knowledge extraction model to obtain breast cancer diagnosis and treatment knowledge; performing modular representation on the breast cancer diagnosis and treatment knowledge to obtain a knowledge module; associating the knowledge modules to form a breast cancer modular knowledge base; performing knowledge verification on the breast cancer modular knowledge base according to a preset verification algorithm and a preset rule representation mode; performing knowledge reasoning on the at least one to-be-selected decision according to the verified breast cancer modular knowledge base and a preset uncertainty reasoning algorithm to obtain a possibility value of each to-be-selected decision; and generating a target diagnosis and treatment aid decision according to the to-be-selected decision with the possibility value exceeding a preset possibility threshold.
Owner:北京万方数据股份有限公司
Block chain-based private data mapping method and device, medium and electronic equipment
ActiveCN113536384AImprove data securityEasy to set upDigital data protectionEngineeringZero-knowledge proof
The invention provides a block chain-based private data mapping method, which is applied to a private data mapping publisher, and comprises the following steps: generating published data corresponding to private data based on the held private data, and publishing the published data to a block chain for evidence storage; acquiring application data which is stored in a block chain and issued to the block chain by the applicant; and in response to the obtained application data, performing zero-knowledge verification on the zero-knowledge proof, and when the verification is passed, issuing indication information for indicating that the verification of the zero-knowledge proof is passed to the block chain for evidence storage. According to the technical scheme, on one hand, the privacy data held by the two mapping parties can be effectively protected, and the data security of the two mapping parties during mapping is improved; and on the other hand, a mapping relationship can be more conveniently established among a plurality of service providers with the same privacy data, and multi-party cooperation is realized.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
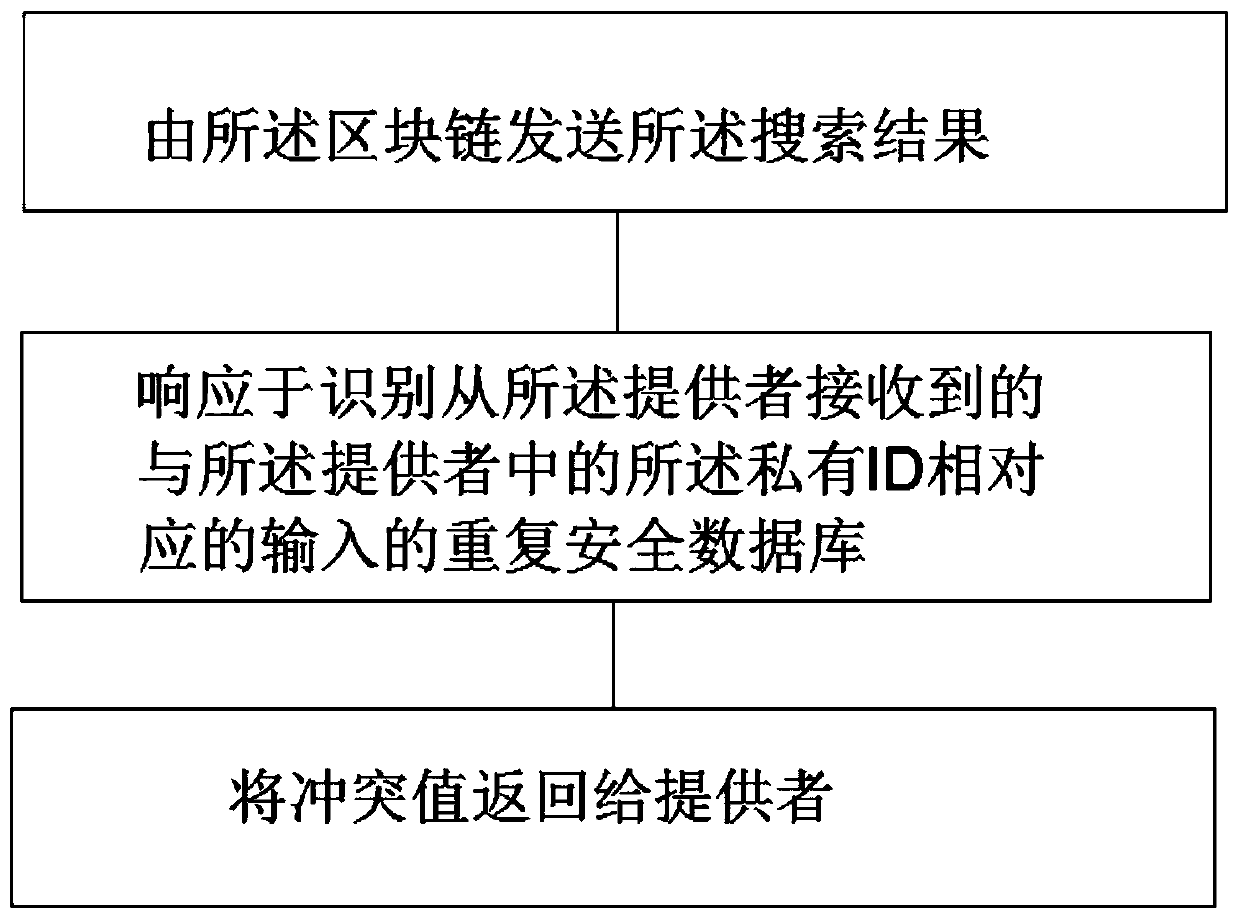
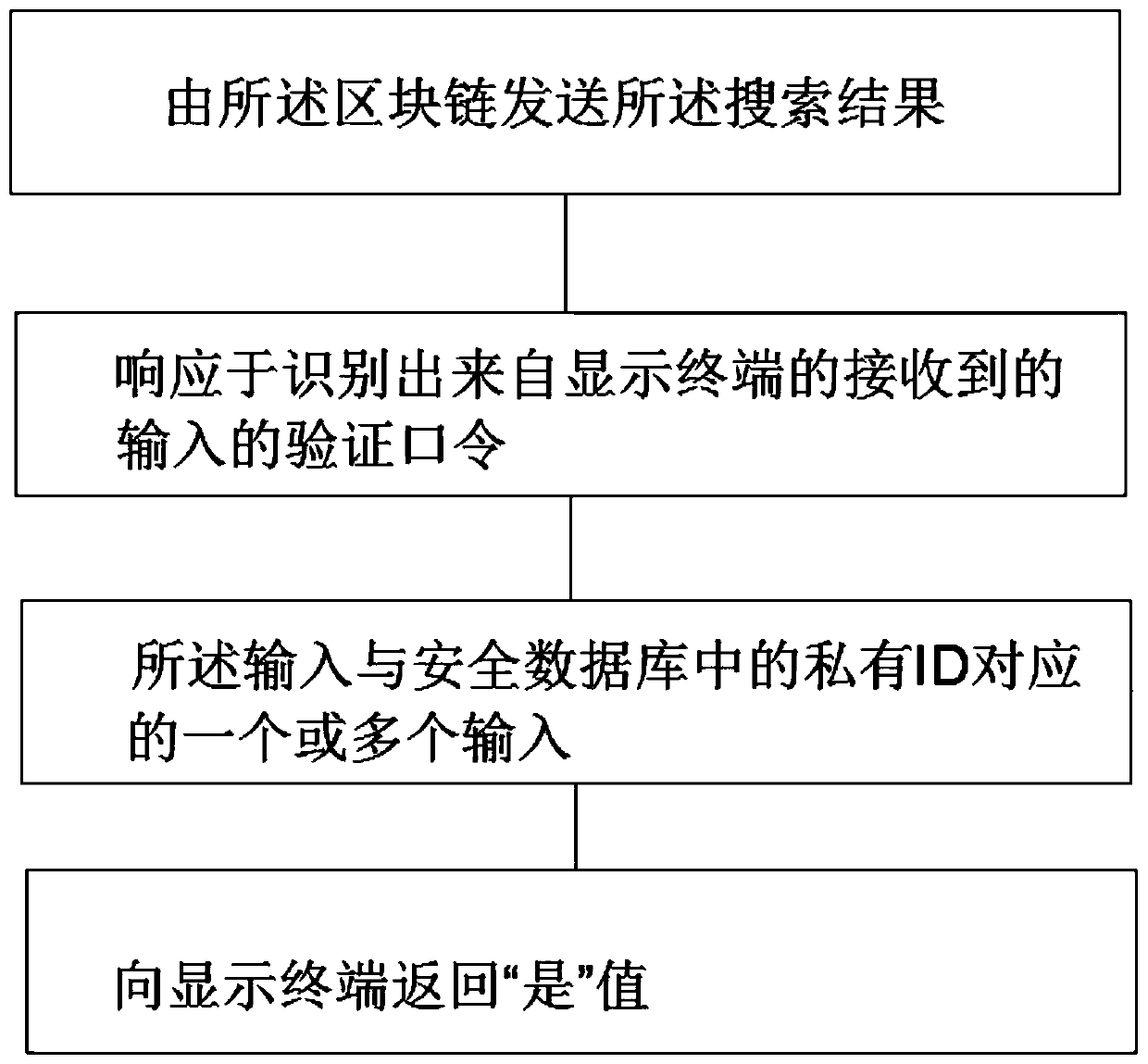
Zero-knowledge verification method based on block chain
ActiveCN111125741AImprove securitySecurityDigital data protectionPayment protocolsPasswordEngineering
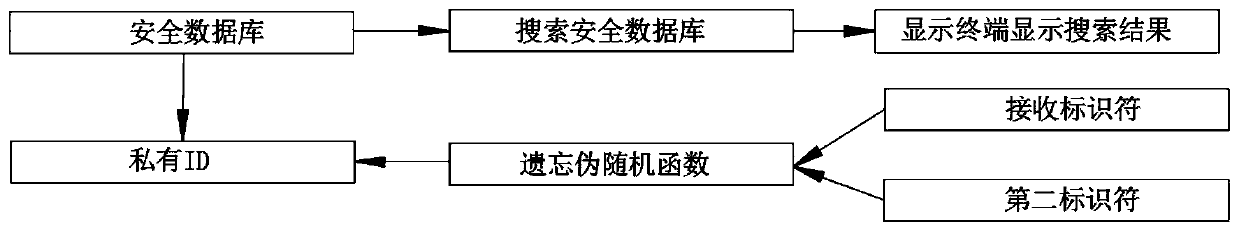
The invention provides a zero-knowledge verification method based on a block chain, wherein the method comprises the steps: acquiring a receiving identifier from a provider through the block chain, and enabling the receiving identifier to correspond to the access of a block chain authentication provider; acquiring a second identifier by the block chain, wherein the second identifier corresponds toa receiving identifier, and the receiving identifier is different from the second identifier; accessing a secure database containing the stored private identifier by the block chain, wherein the stored private ID is a combination of the received identifier and the retrieved second identifier. In the method, by accessing a security database containing stored private IDs by adopting a block chain,the stored private ID is a combination of such that the received identifier and the retrieved second identifier are combined, and the security database includes data relating thereto such that a password of the private ID has higher security performance.
Owner:广东卓启云链科技有限公司
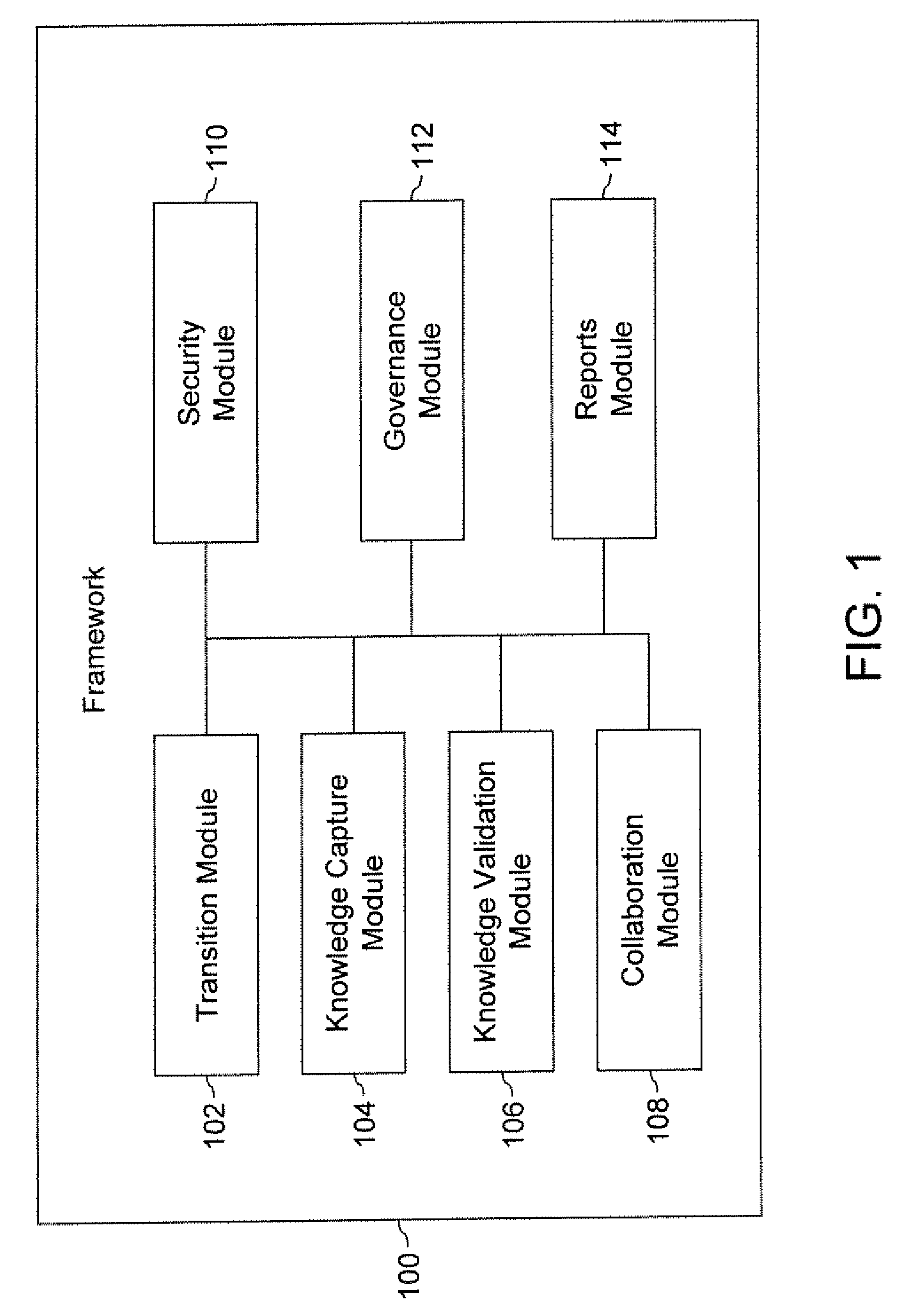
Framework for supporting transition of one or more applications of an organization
ActiveUS8799210B2Promote collaborationLow costDigital data processing detailsOffice automationComputer moduleApplication software
A framework for supporting transition of one or more applications of an organization is provided. The one or more applications are transitioned from a first set of users to a second set of users. The framework includes a transition module, a knowledge capture module, a knowledge validation module, and a collaboration module. The transition module generates one or more transition plans based on information corresponding to the one or more applications. The knowledge capture module captures a plurality of knowledge elements corresponding to the one or more applications. The knowledge capture module further establishes association between the plurality of knowledge elements. The knowledge validation module validates the plurality of knowledge elements and their association. The collaboration module provides collaboration between the first set of users and the second set of users during the transition of the one or more applications.
Owner:INFOSYS LTD
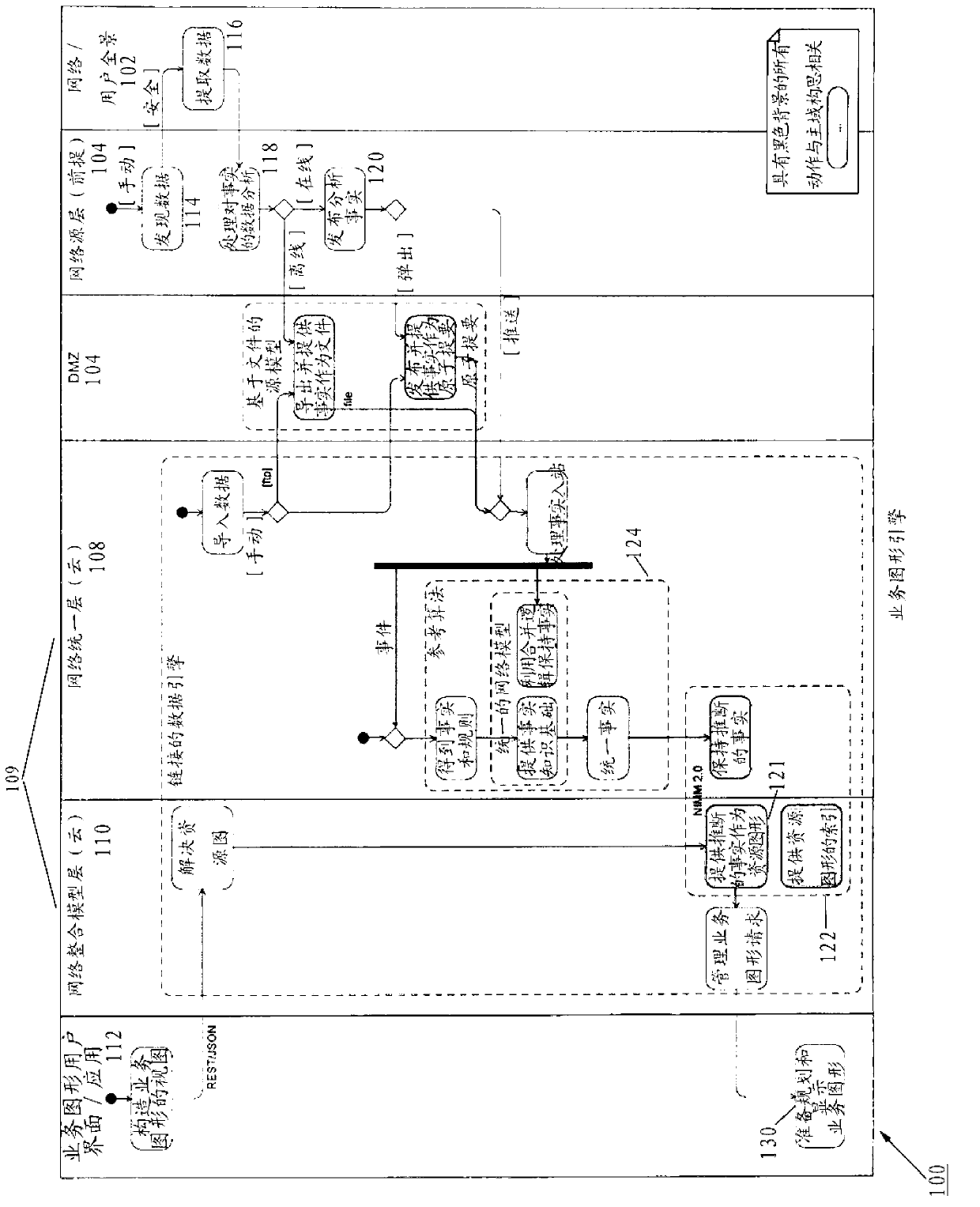
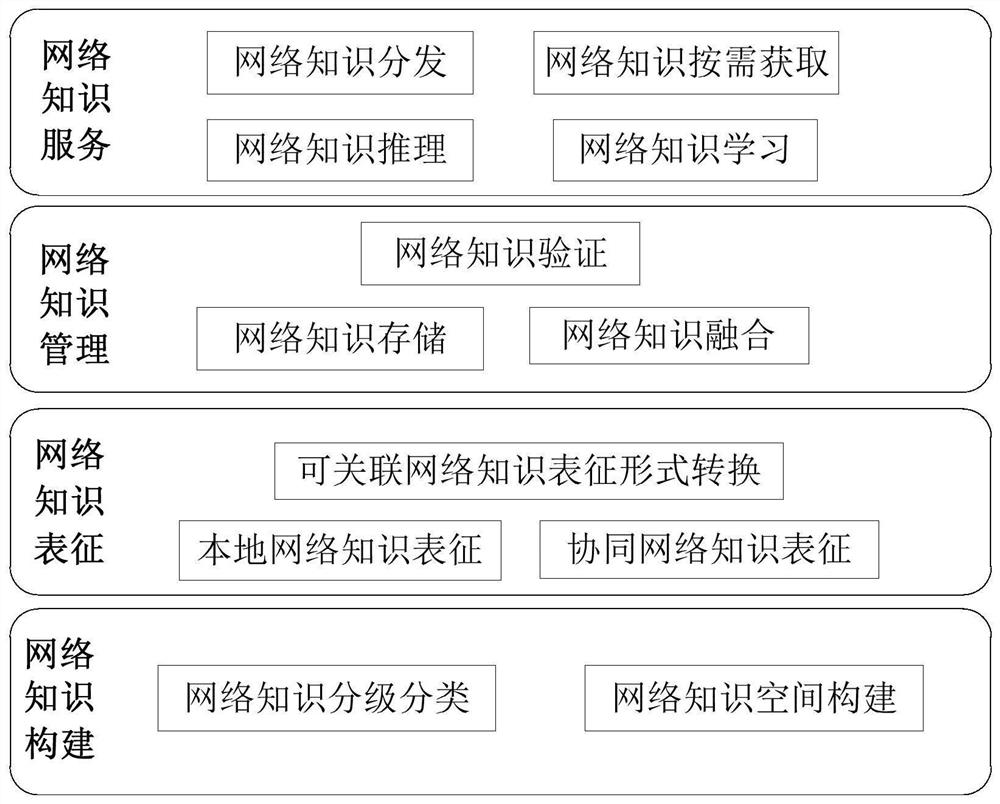
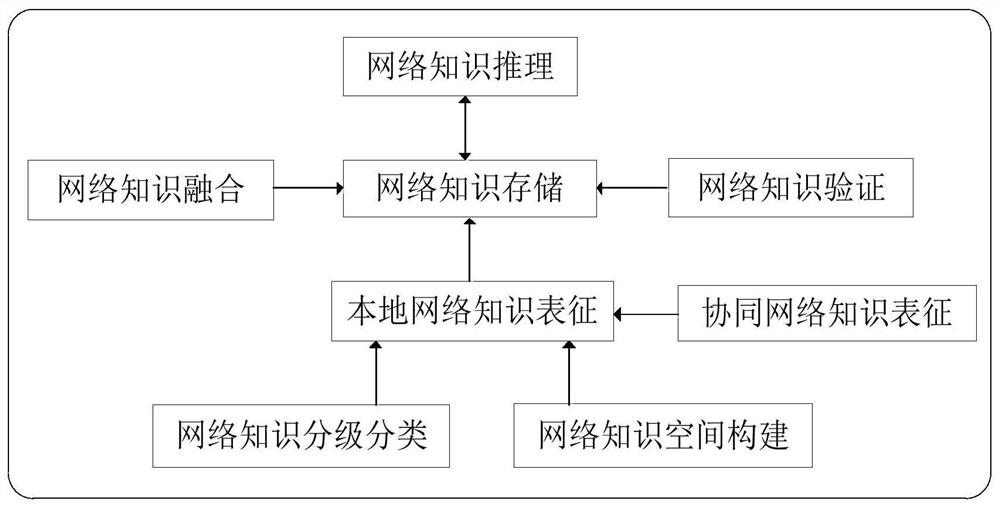
Network knowledge unified representation architecture in Internet of Things and implementation method thereof
The invention discloses a network knowledge unified representation architecture in the Internet of Things and an implementation method thereof. The architecture comprises a network knowledge classification module, a network knowledge space construction module, a local network knowledge representation module, a collaborative network knowledge representation module, a network knowledge storage module, a network knowledge fusion module, a network knowledge verification module and a network knowledge reasoning module. The method comprises the following steps: setting a network knowledge construction layer, a network knowledge representation layer, a network knowledge management layer and a network knowledge service layer, wherein the network knowledge construction layer is responsible for determining the category of network knowledge in the multi-domain environment, the network knowledge representation layer is responsible for systematic identification of network knowledge structures, modes and contents, the network knowledge management layer is responsible for network knowledge storage, fusion and verification under the condition that network communication resources are limited, and the network knowledge service layer is responsible for network knowledge learning, reasoning, distribution and on-demand acquisition. The method can support network elements to complete routing addressing, management control, security and other functions by using network knowledge, thereby reasonably deploying network resources.
Owner:军事科学院系统工程研究院系统总体研究所
An organization identity encryption and decryption method
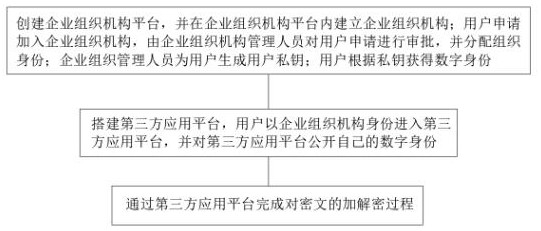
ActiveCN113630260BSolve the problem of unauthorized accessUser identity/authority verificationThird partyInternet privacy
The invention discloses an organization identity encryption and decryption method, which relates to the technical field of encryption and decryption. It generates the public key of the enterprise organization and the private key of the enterprise organization, and then forms the user's private key through the attribute label in the organization identity, thereby completing the user's authentication. To determine the organization identity, in the process of encrypting and decrypting the ciphertext, the third-party application platform uses "zero-knowledge" verification to verify the user's organization identity, and then authorizes the user through the access policy of the organization structure, thereby Enabling users to complete the encryption and decryption process of ciphertexts; the present invention encrypts enterprise organizations and individual users using attribute tags, thereby enabling the verification of organizational identities, one-to-many authorization and access control to be completed, and at the same time through "Zero-knowledge" verification enables users to complete all verification and authorization processes in third-party application platforms without providing personal privacy.
Owner:JIANGSU RONGZE INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com