Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
62 results about "False path" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
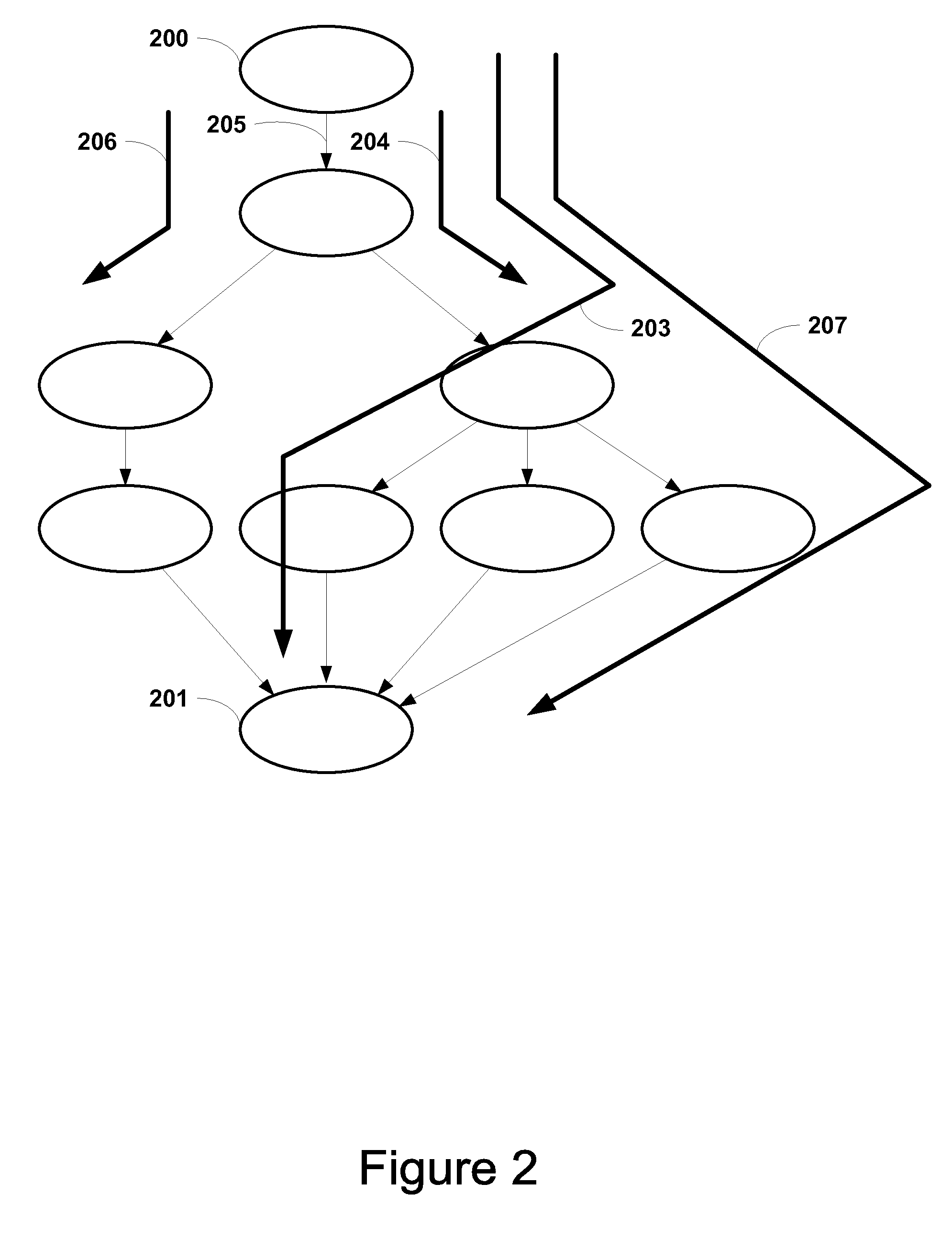
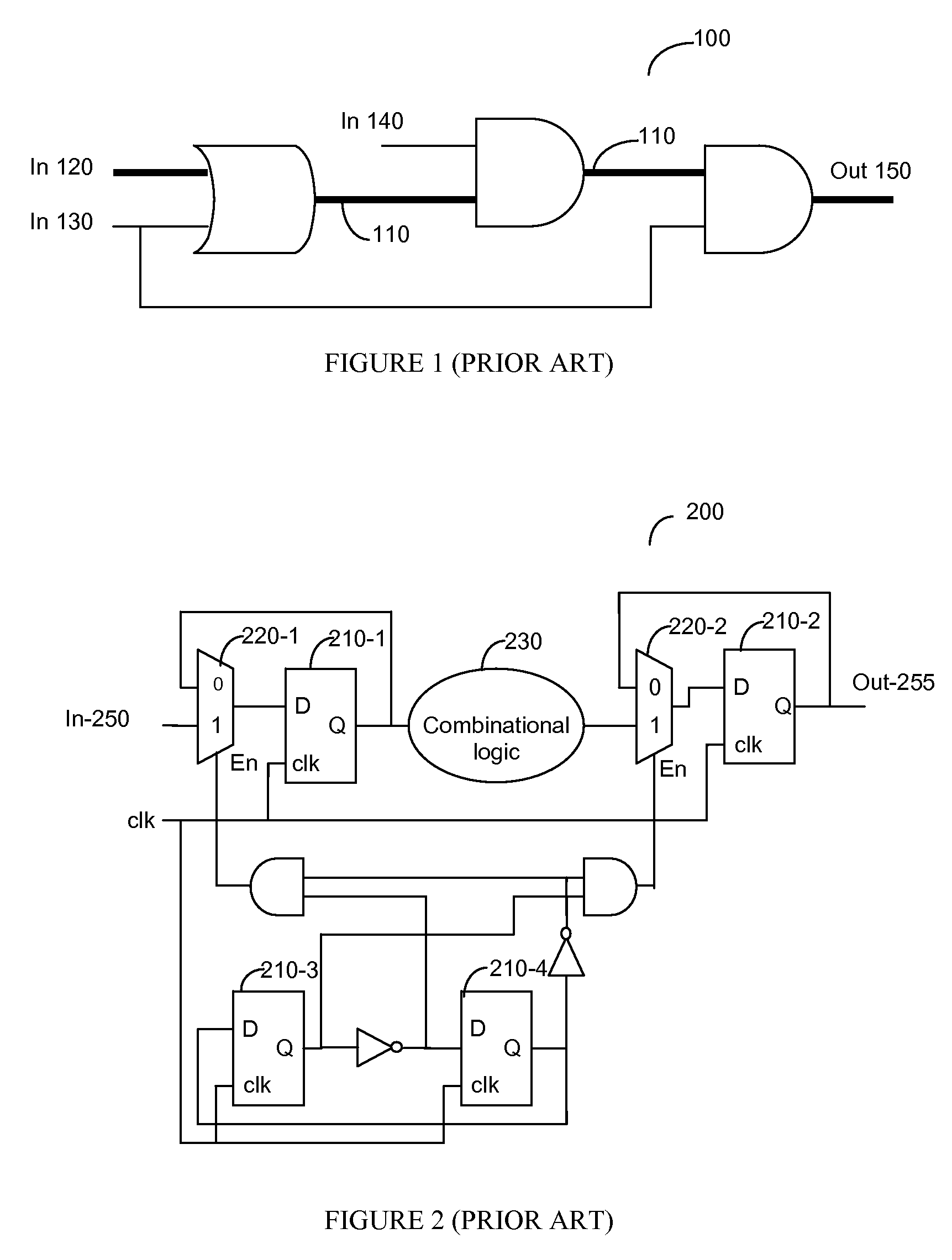
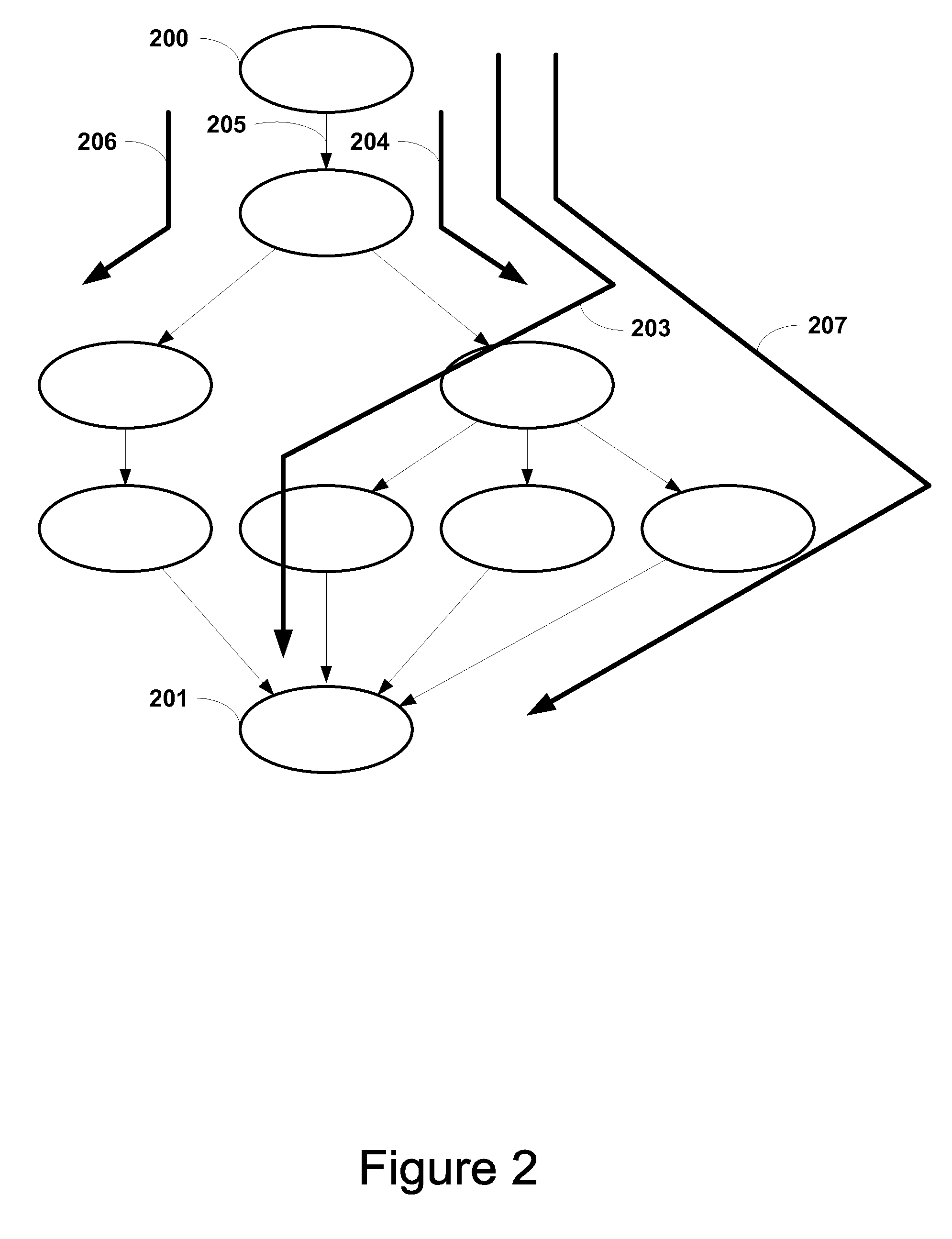
False Paths are those timing arcs in design where changes in source registers are not expected to get captured by the destination register within a particular time interval. False Paths can be categorized in the following design topologies.
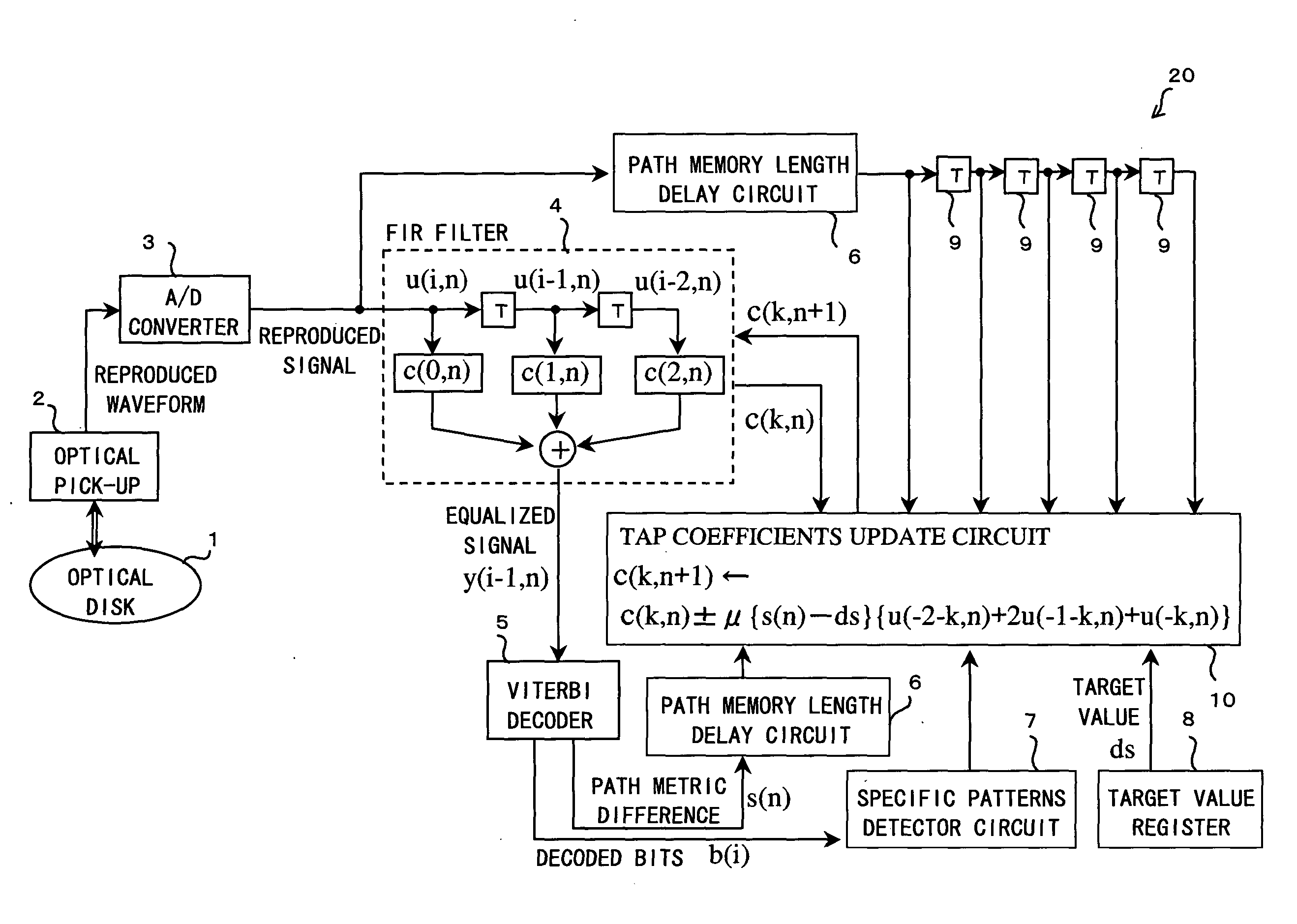
Adaptive waveform equalization for viterbi-decodable signal and signal quality evaluation of viterbi-decodable signal
InactiveUS20050193318A1Convenient ArrangementEvaluate qualityMultiple-port networksData representation error detection/correctionMean squareSignal quality
The waveform equalizing device includes: an FIR filter for generating an equalized signal pattern y(i, n) on the basis of equalization of a waveform of the reproduced signal pattern u(i, n); a Viterbi decoding circuit for detecting a path metric difference s(n) between a correct path determined as a survivor path and an error path which fails to survive the correct path in Viterbi decoding based on the equalized signal pattern y(i, n); a target register for setting a target value ds for the path metric difference s(n); and a tap coefficients update circuit for adapting the equalization according to an error of the detected path metric difference from the target value. The tap coefficients update circuit adapts equalization properties so that the mean square error is minimized, thereby achieving a satisfactory result in lowering the error rate.
Owner:SHARP KK
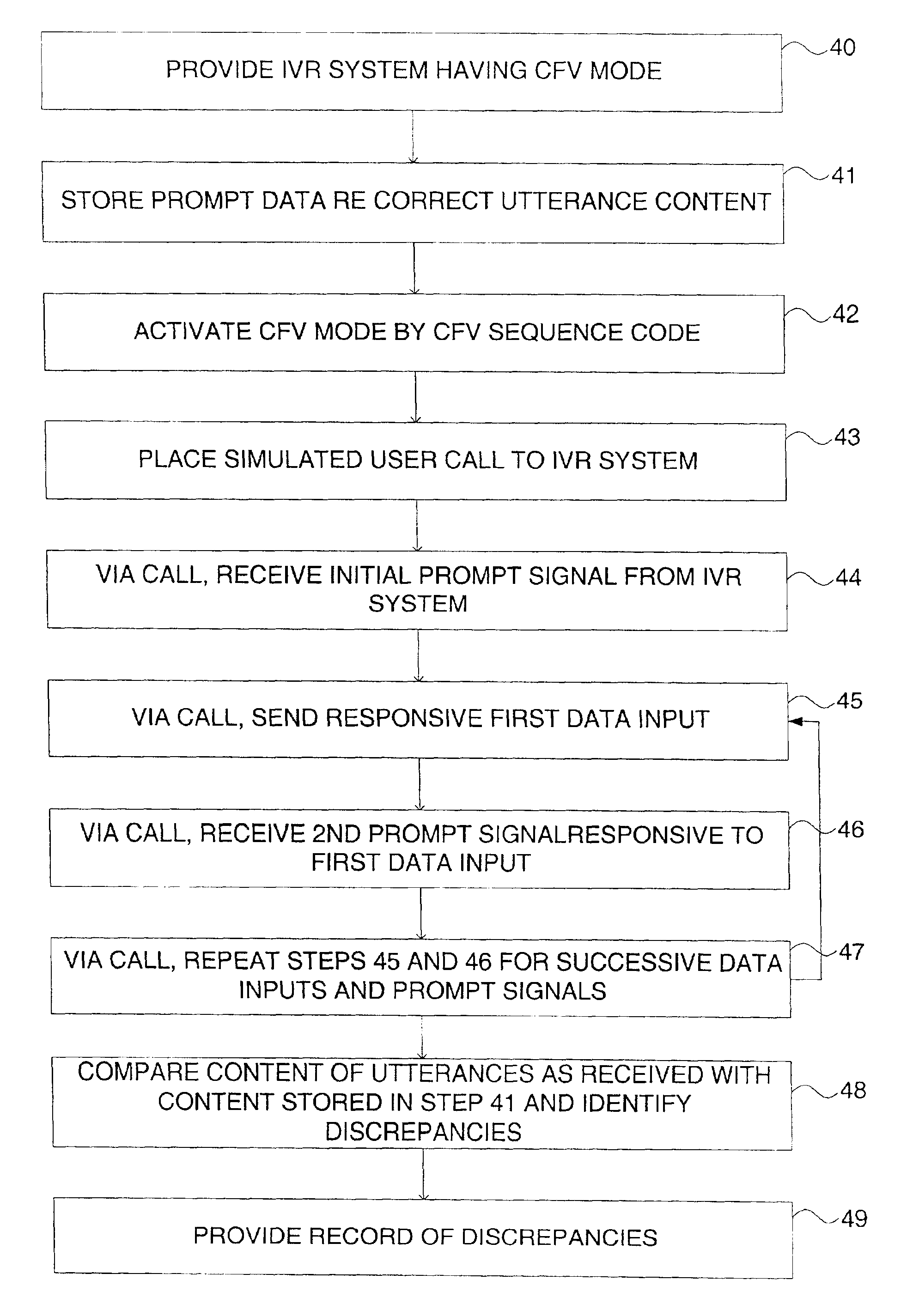
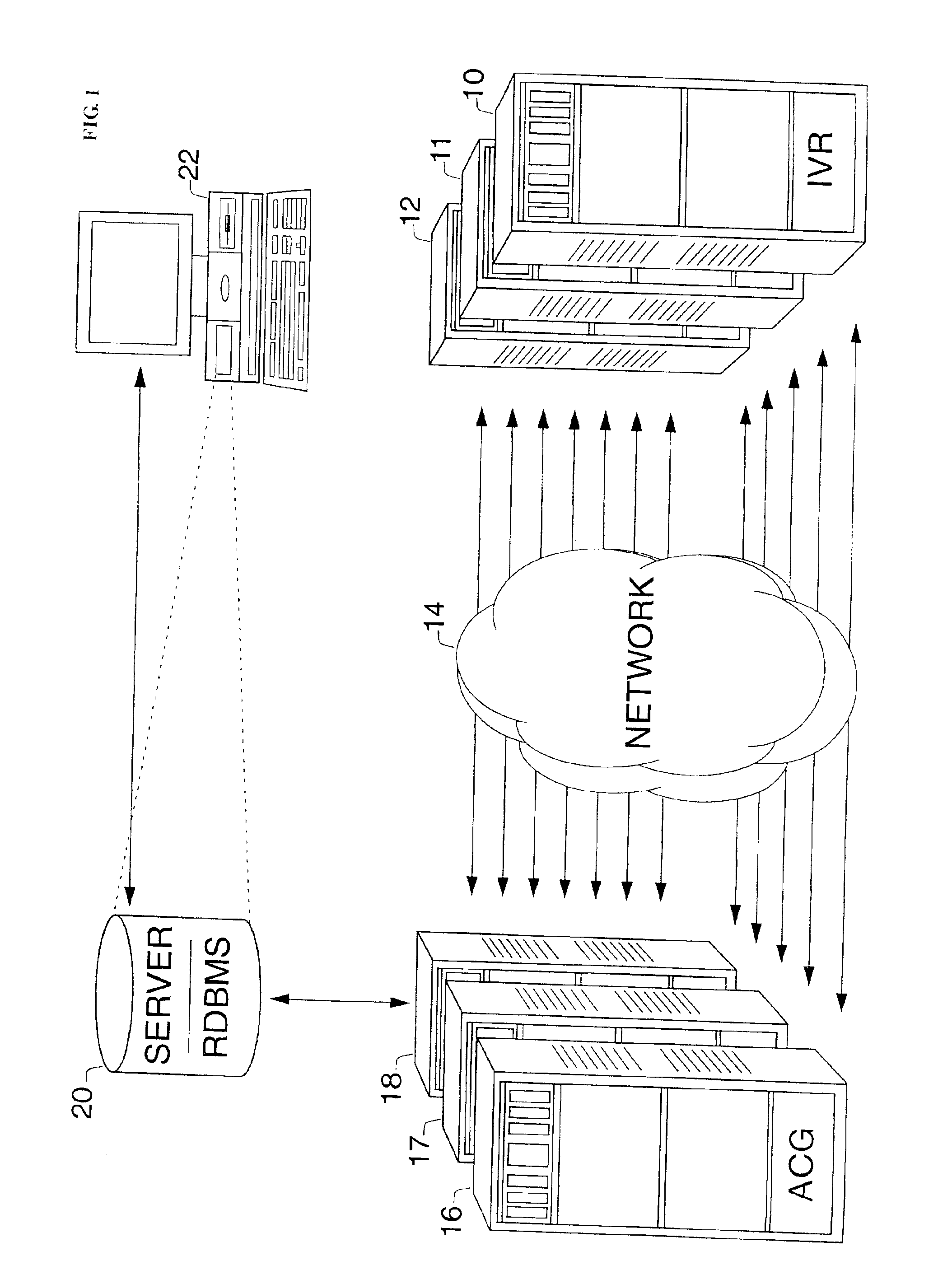
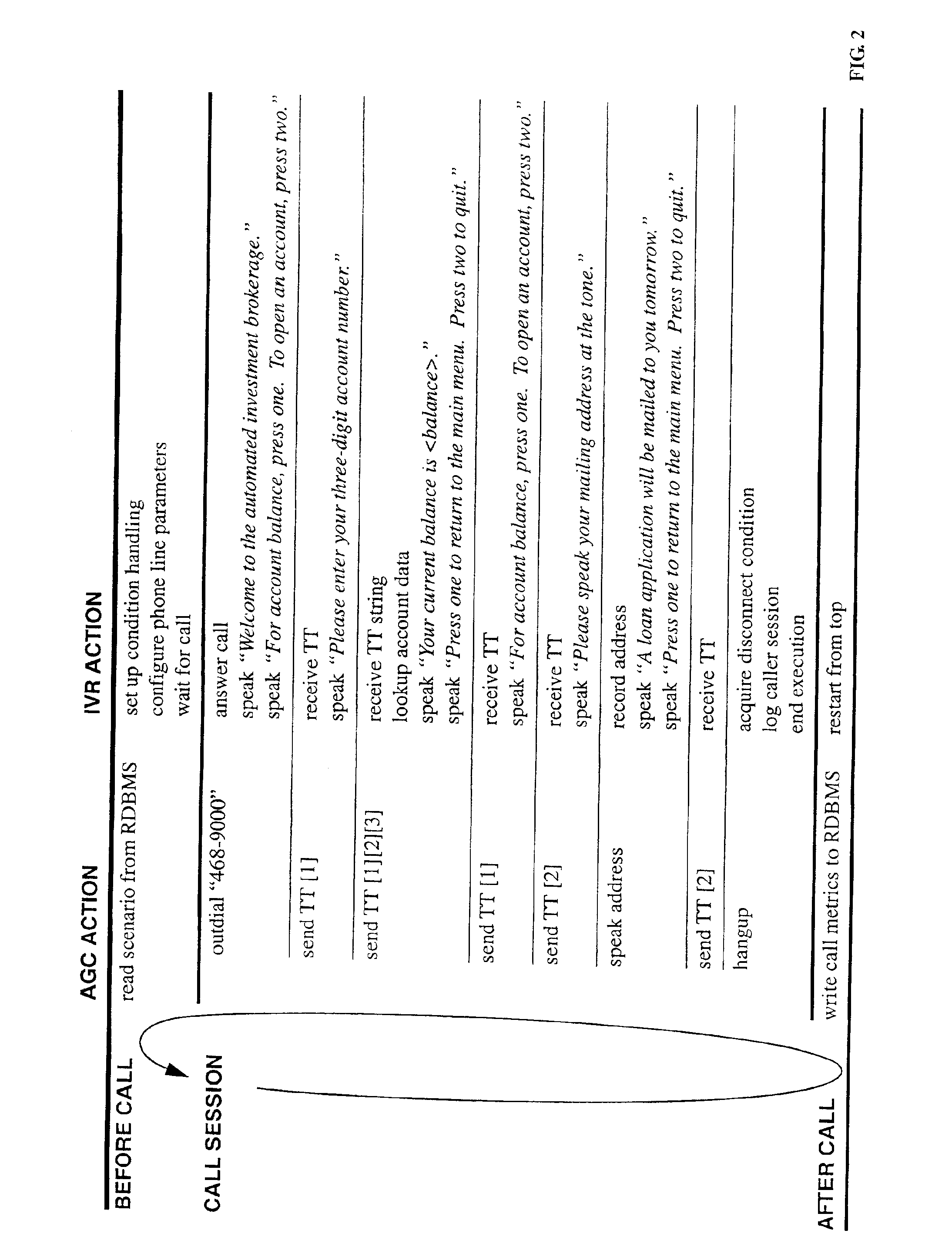
Call-flow verification method and apparatus
InactiveUS6914962B2Automated verificationResistance/reactance/impedenceAutomatic call-answering/message-recording/conversation-recordingValidation methodsFalse path
After implementation of an interactive voice response (IVR) system providing voice prompts (i.e., utterances) to aid a telephone caller, it is desirable to provide call-flow verification to validate system accuracy, particularly under high-volume or saturation calling conditions. An IVR system has a call-flow verification (CFV) mode which can be activated for this purpose. In the CFV mode, the IVR system provides prompt signals which include coded signals representing the content of utterances. An automated call generator (ACG) unit places simulated user calls to the IVR system. The content of utterances is represented by coded signals included in prompt signals sent by the IVR system during the course of the simulated call and stored by the ACG unit. Verification can be applied for all possible paths an application might take (to check all possible go-right and error paths). By comparing content of received utterances represented by such coded signals with previously stored data representative of correct utterances, discrepancies are identified for call-flow verification. DTMF signals can be used to represent characters of an utterance in a coded format.
Owner:AVAYA INC
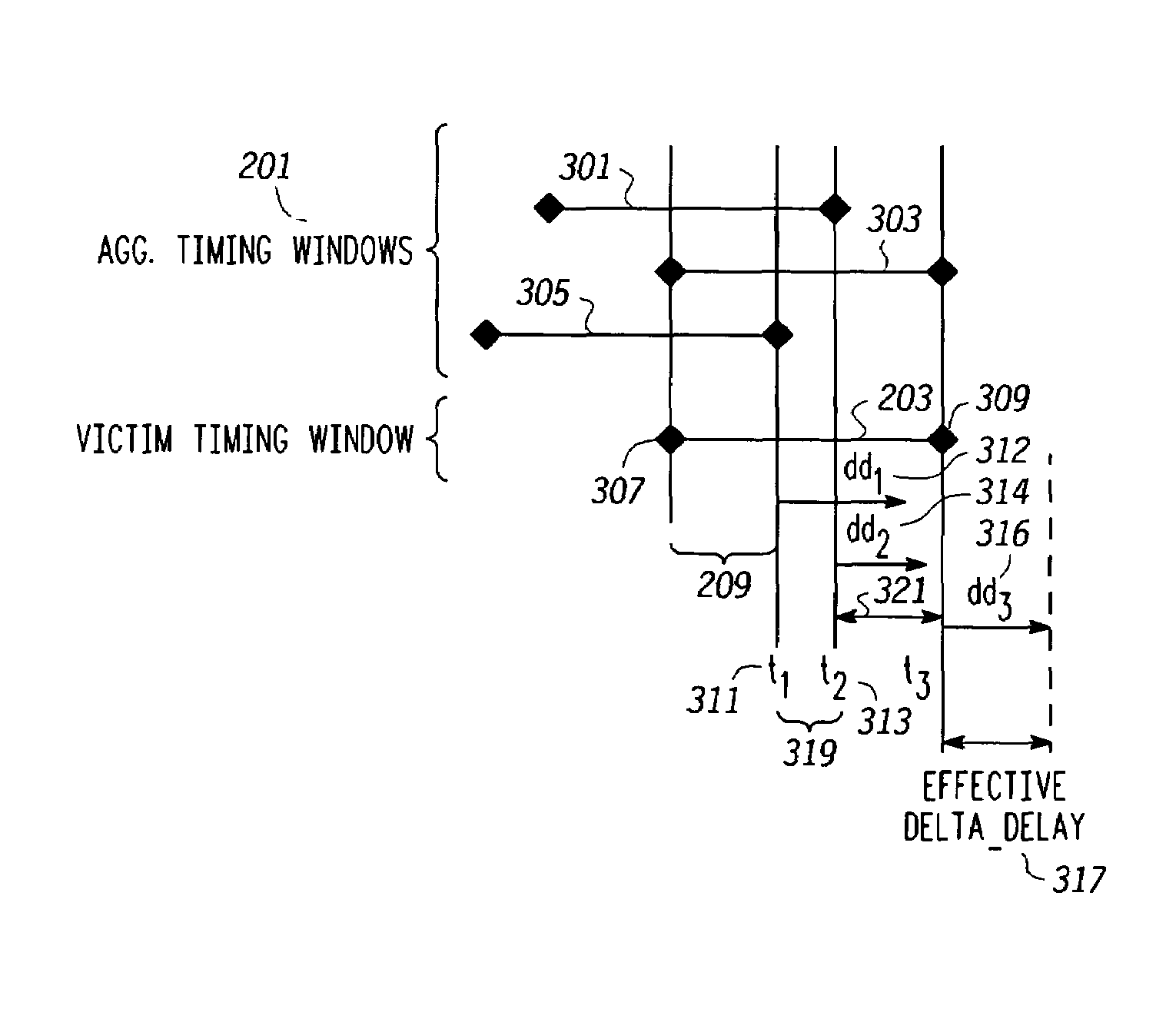
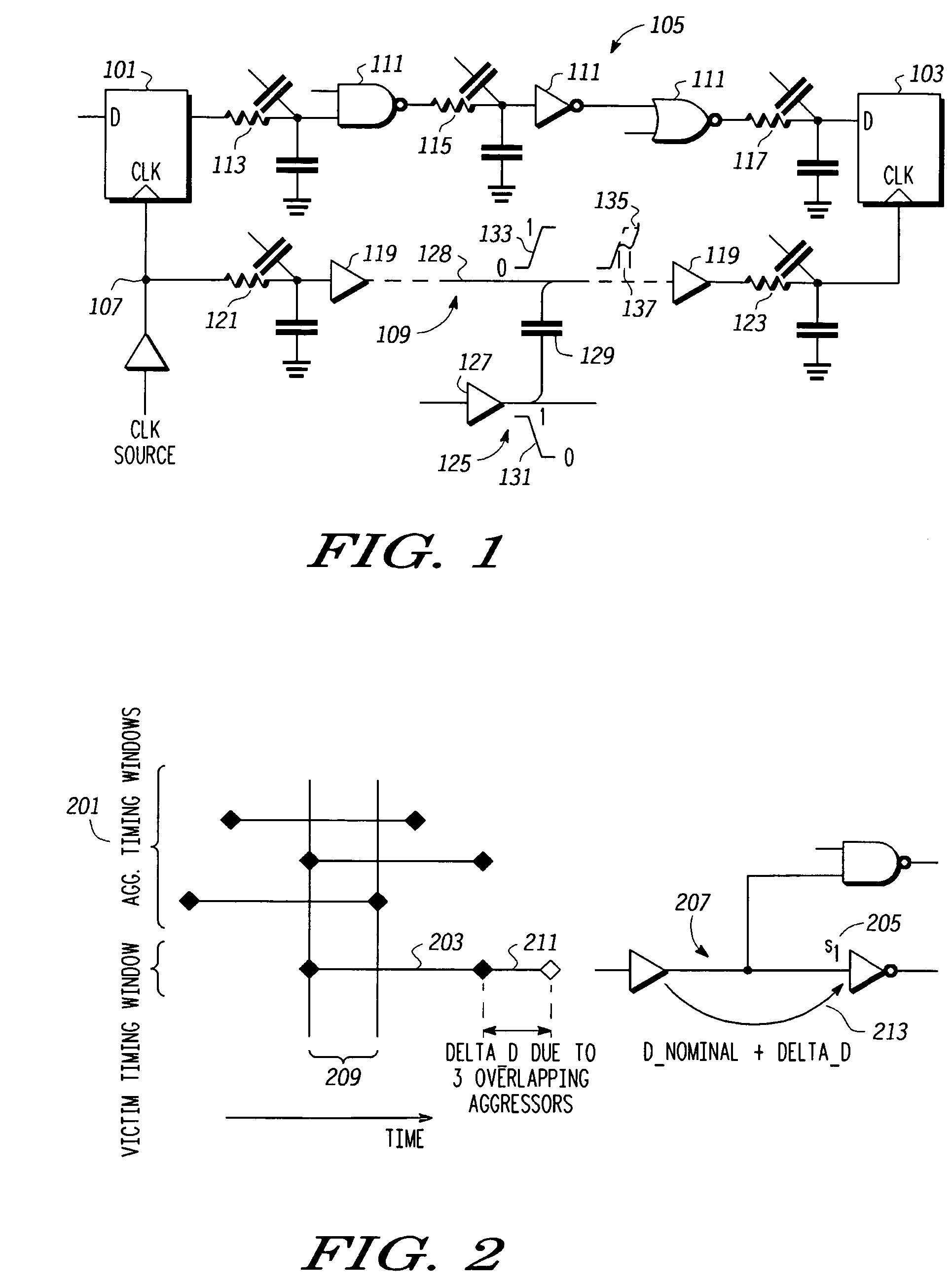
Pessimism reduction in crosstalk noise aware static timing analysis
InactiveUS20060112359A1Computer aided designSoftware simulation/interpretation/emulationEngineeringFalse path
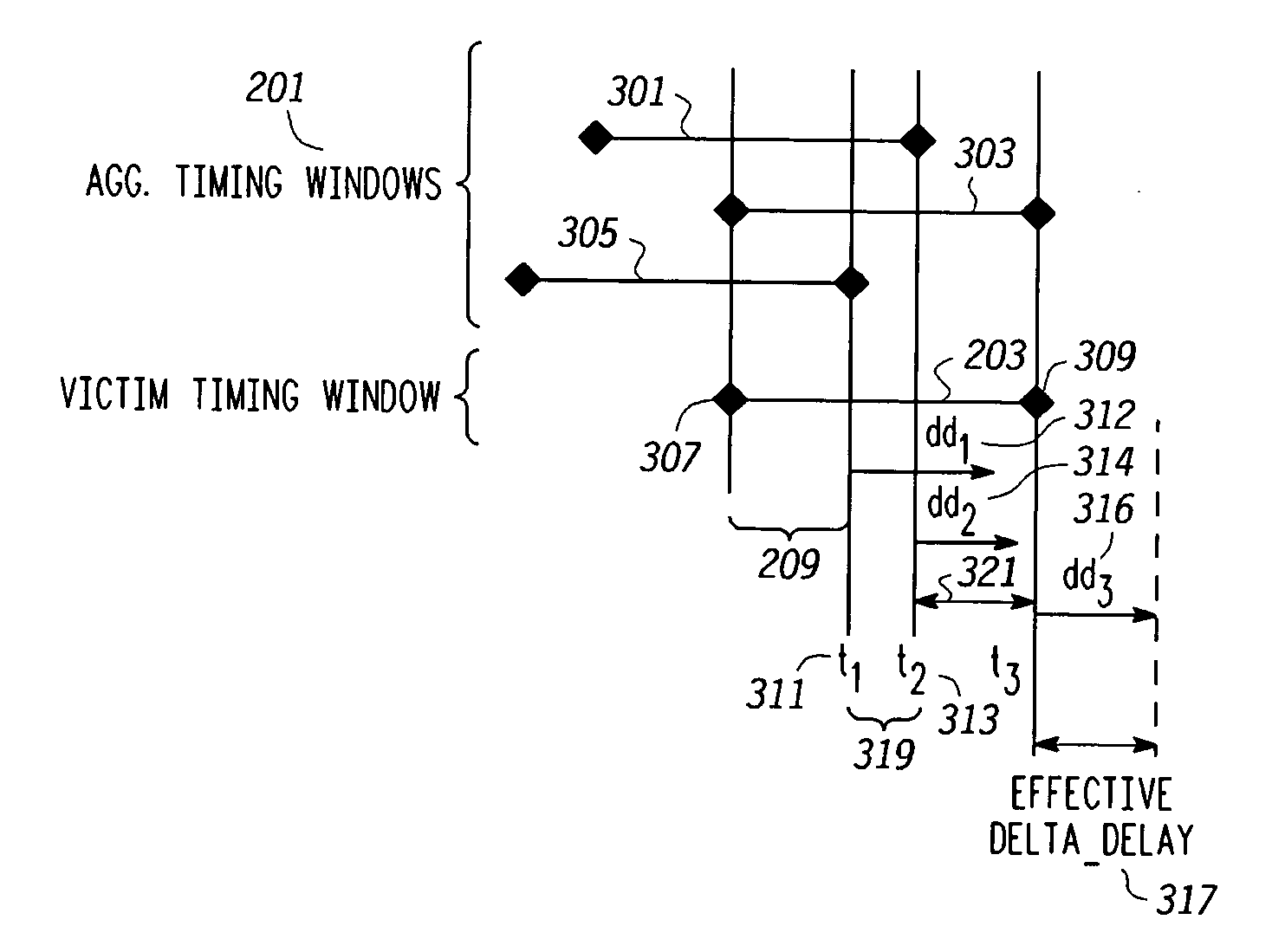
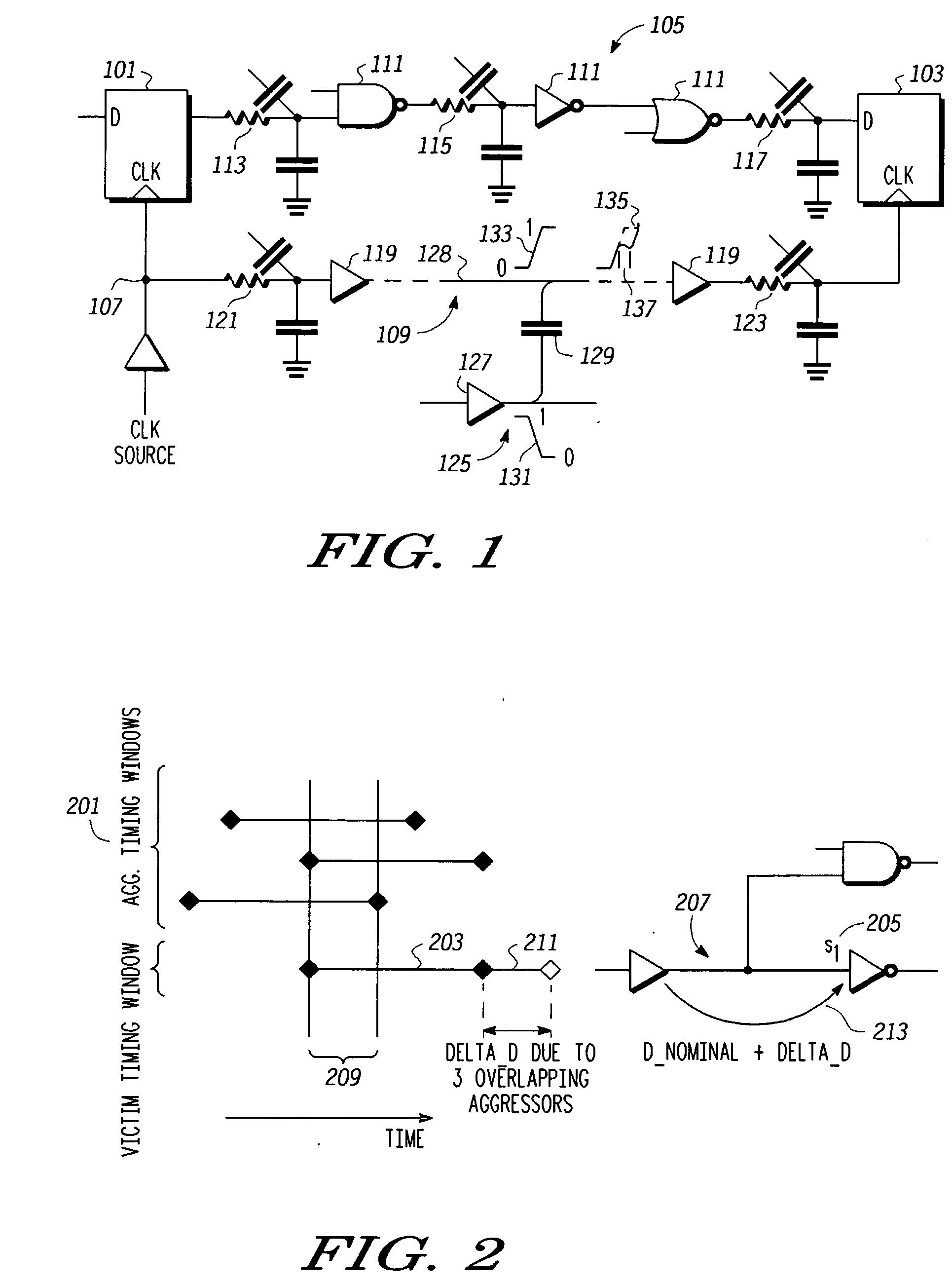
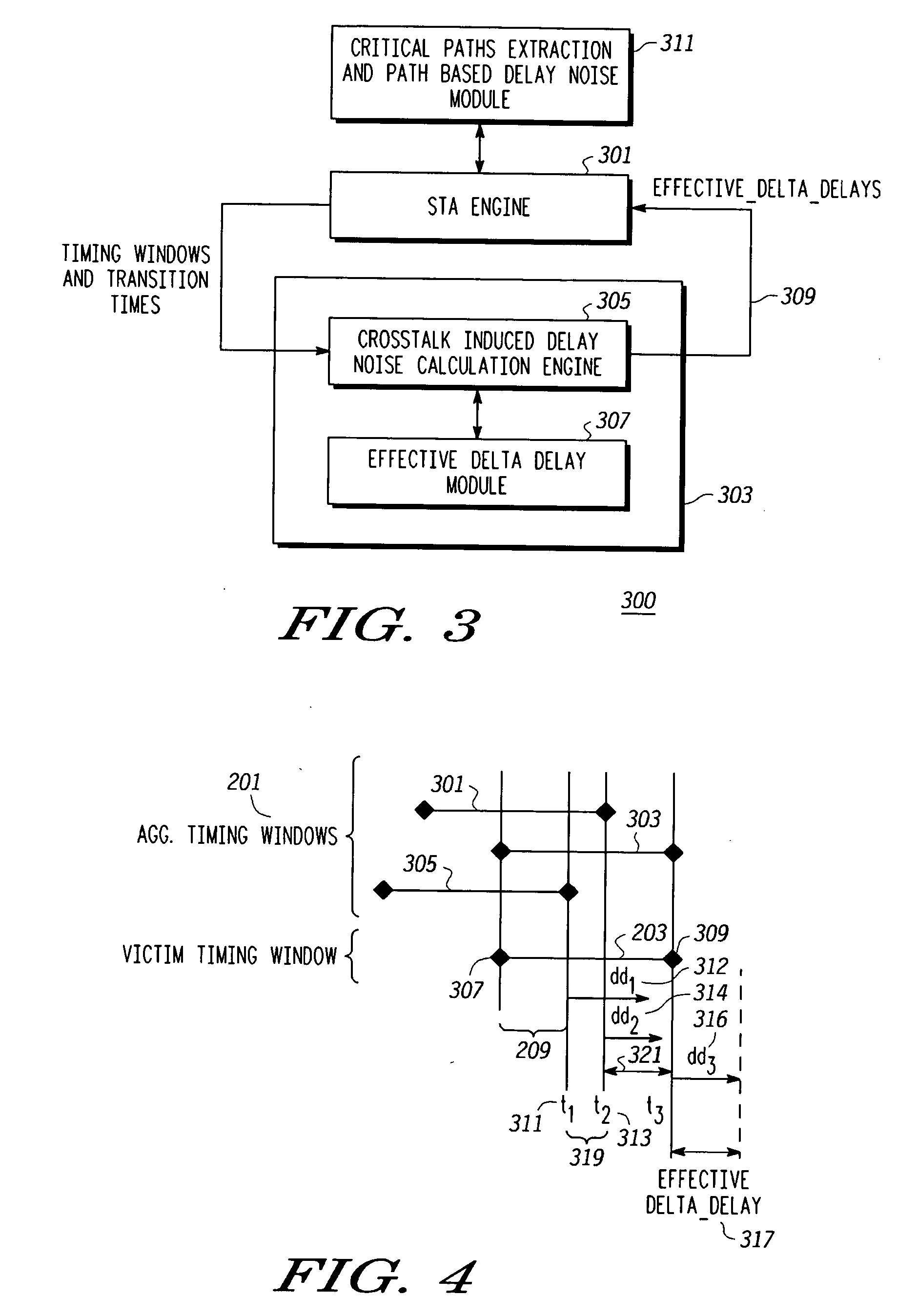
Processes and systems (300) for reducing pessimism in cross talk noise aware static timing analysis and thus resulting false path failures use either or both of effective delta delay noise (307) and path based delay noise (311) analysis. Effective delta delay determines an impact (312, 314, 316) on victim timing of an action by aggressors that occur during a region (209, 319, 321) where victim and aggressor timing windows overlap and determines an effective delta delay 317 corresponding to any portion 316 of the impact on victim timing that extends beyond the victim timing window. The effective delta delay is used to adjust the victim timing window. Path based delta delay determines an uncertainty (627, 637) in a switching time corresponding to a particular path for a victim resulting from an action (switching) by aggressors that occurs at the switching time 607, 613, i.e. during a switching time window (a2 to a2+u1) (613, 625) when uncertainty is included.
Owner:FREESCALE SEMICON INC
Multi-phase models for timing closure of integrated circuit designs
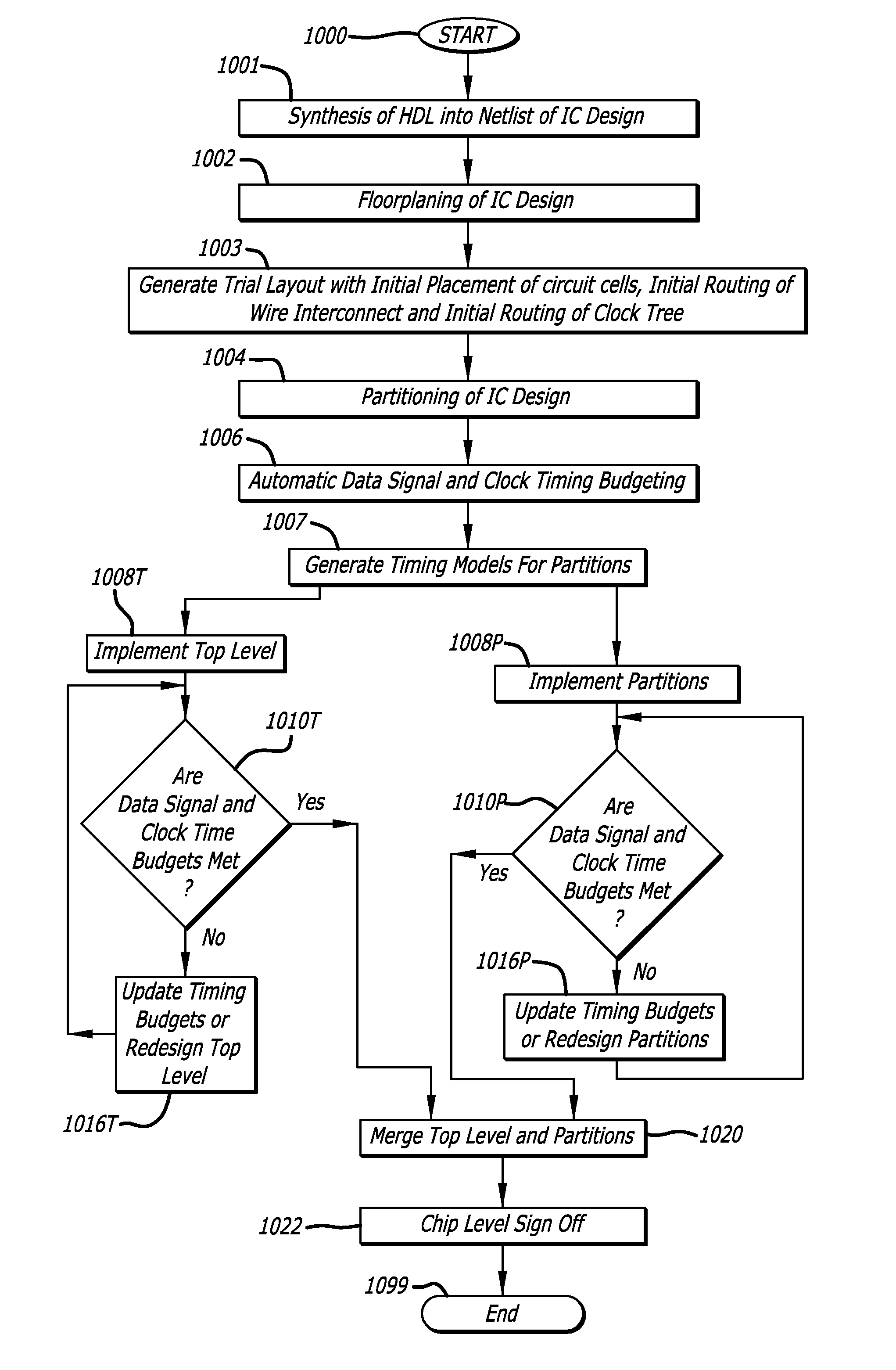
ActiveUS8640066B1Accurate modelingDetecting faulty computer hardwareComputer aided designFalse pathHierarchical design
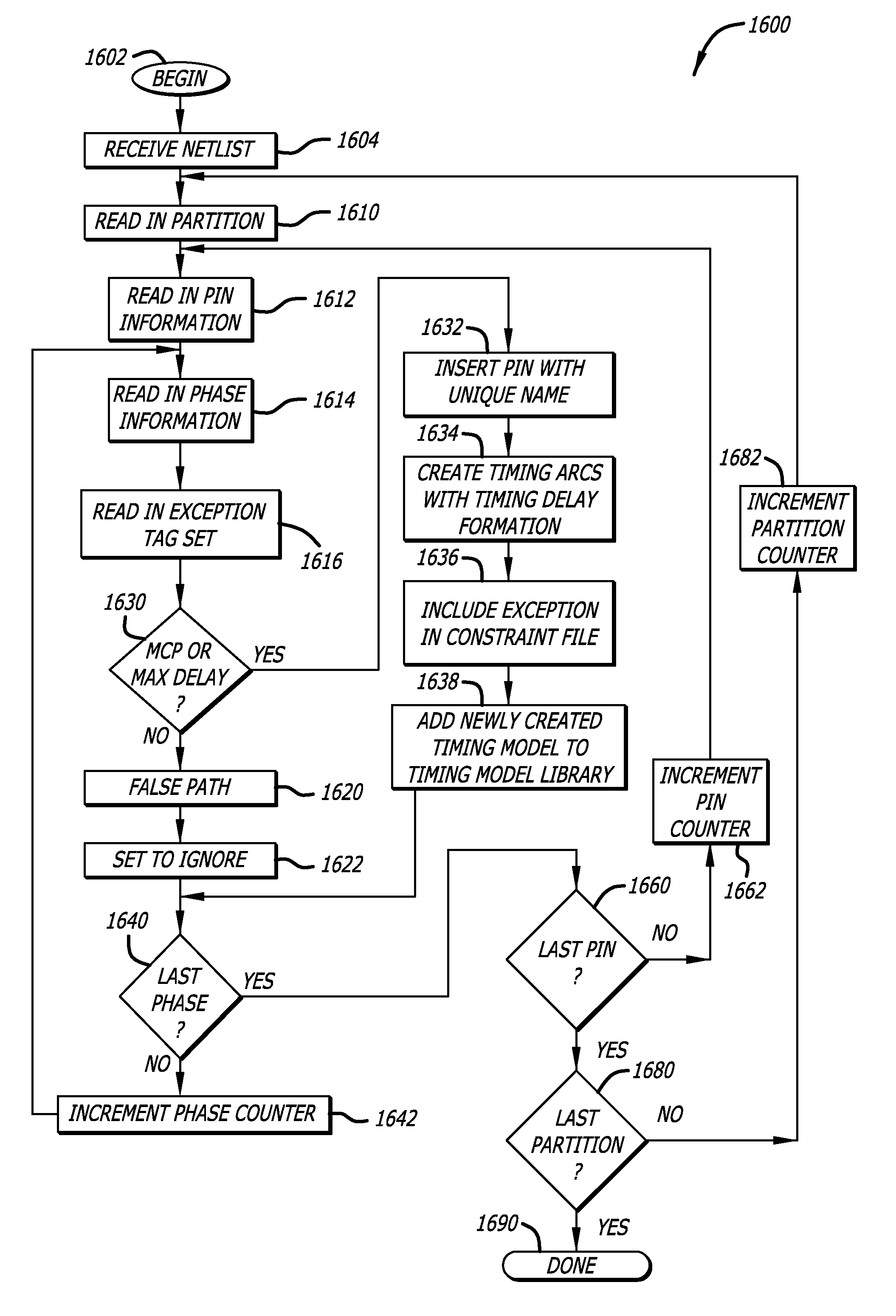
In one embodiment, a method of designing an integrated circuit is disclosed, including receiving a first partition block for a top level of a hierarchical design of an integrated circuit; analyzing each pin of the first partition block for an attribute associated with the pin indicating a timing exception; and if a timing exception other than false path is indicated then generating an internal timing pin in a first timing graph model of the first partition block for each timing exception, and adding a timing arc and a dummy arc coupled to the internal timing pin in the first timing graph model of the first partition block. The internal timing pin adds a timing exception constraint for each timing exception. Timing of the top level may then be analyzed with the first timing graph model to determine if timing constraints, including the added timing exception constraints, are met.
Owner:CADENCE DESIGN SYST INC
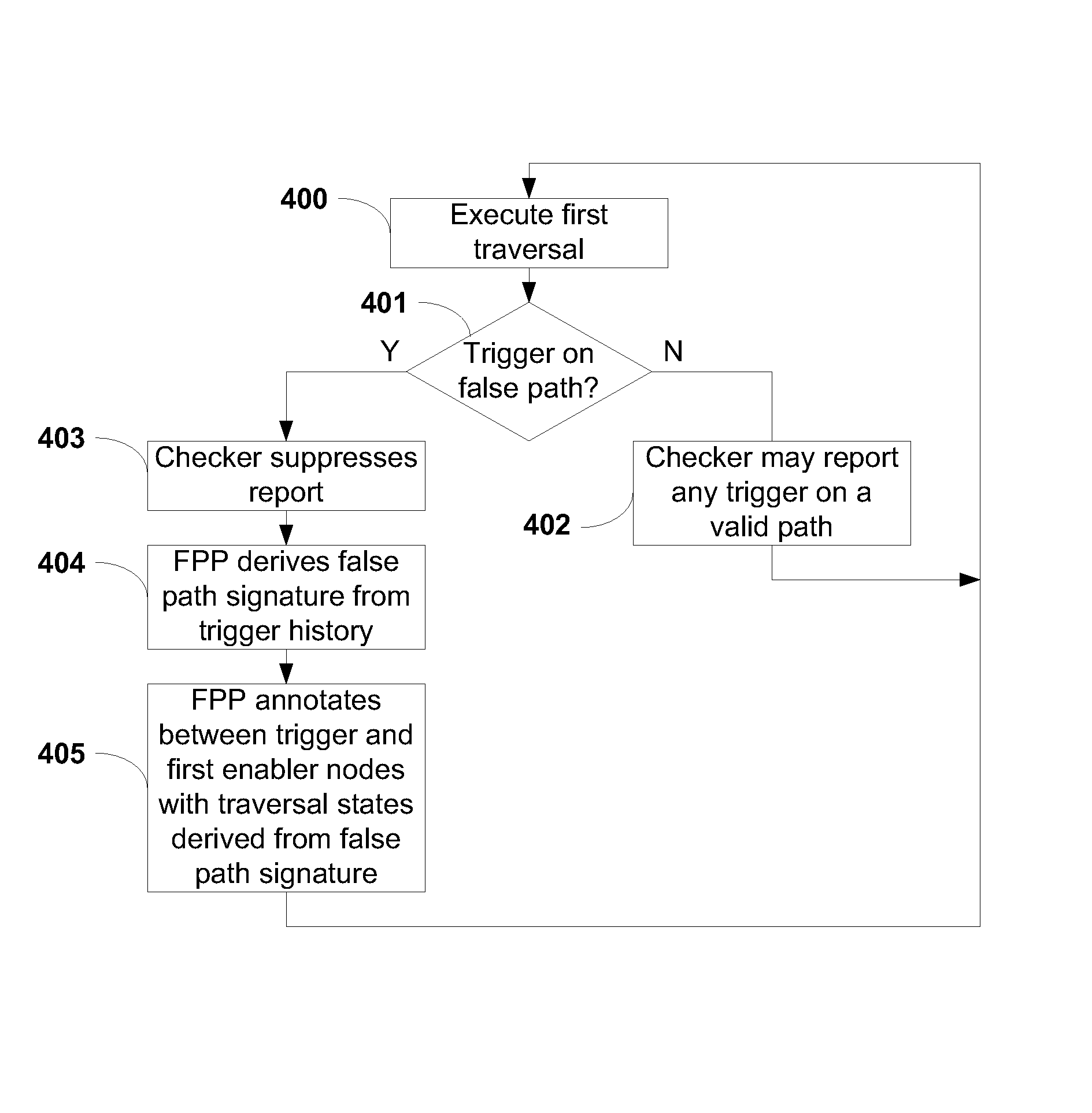
Methods for selectively pruning false paths in graphs that use high-precision state information
Methods are provided that allow a false path pruner to traverse a directed acyclic graph in conjunction with one or more checker programs that are analyzing a program for defects or other artifacts of interest. While the checkers may have ways of avoiding re-traversal of portions of the graph that have already been traversed, the false path pruner may override such decisions made by the checkers as a result of a false path in order to allow re-traversal during a future different traversal when that same defect or artifact may not lie along a false path, and therefore avoid missing a valid defect or artifact. Computer programs stored on tangible media are provided that implement the methods of the invention.
Owner:SYNOPSYS INC
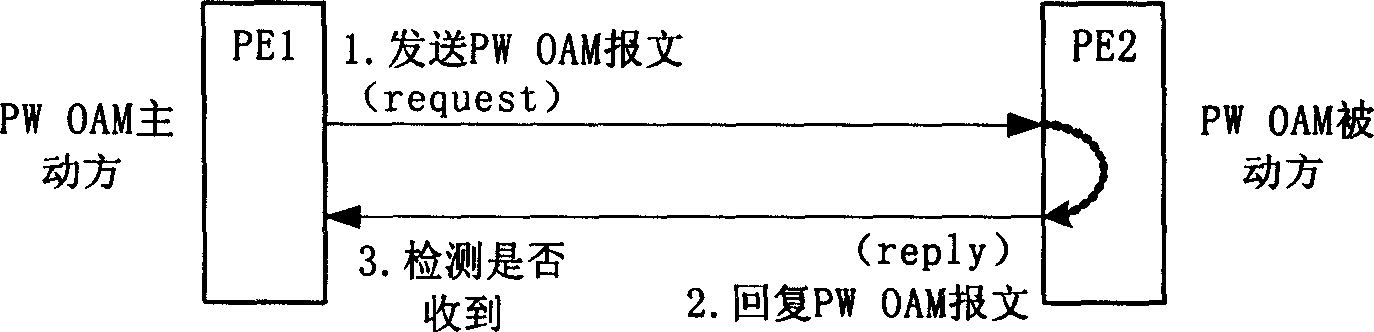
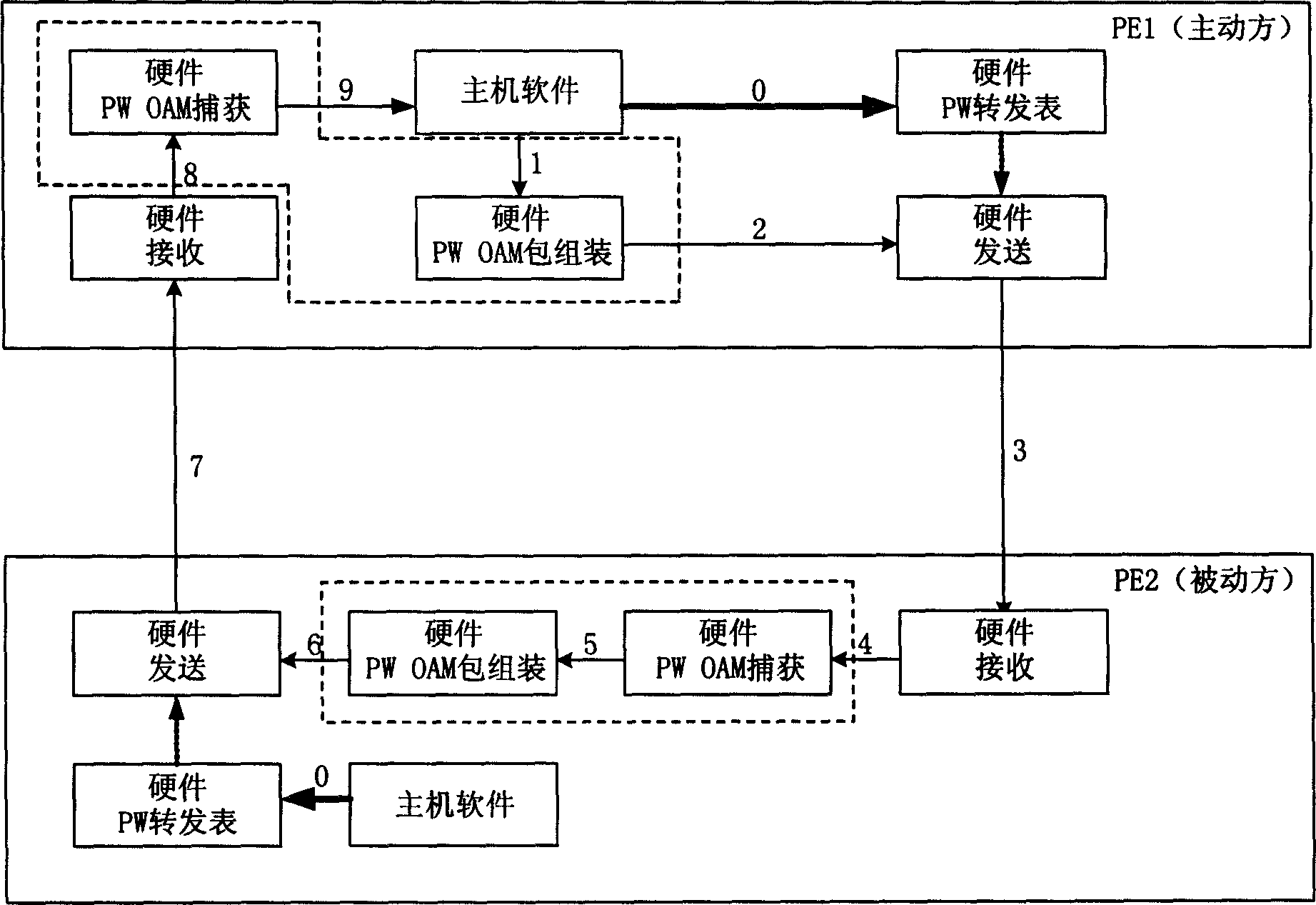
Method for judging pseudo wire connection state in packet-switching network and service apparatus
InactiveCN1878135AThe detection is effectively completedRealize the function of PW connection on and offData switching networksExchange networkInterconnection
The invention discloses a judging method of false path connecting condition in the packet-switching network, which is characterized by the following: increasing false path operational management and maintenance report to detect the interconnection condition of false path; receiving the report through end service equipment; responding corresponding report; regarding the false path normal among service equipments after the local end service equipment receives the respond report within preset time. The invention proceeds operational management and maintenance report sending, receiving and disposal for false path through OAM mode, which finishes detecting connectivity of PW data plane effectively.
Owner:HUAWEI TECH CO LTD
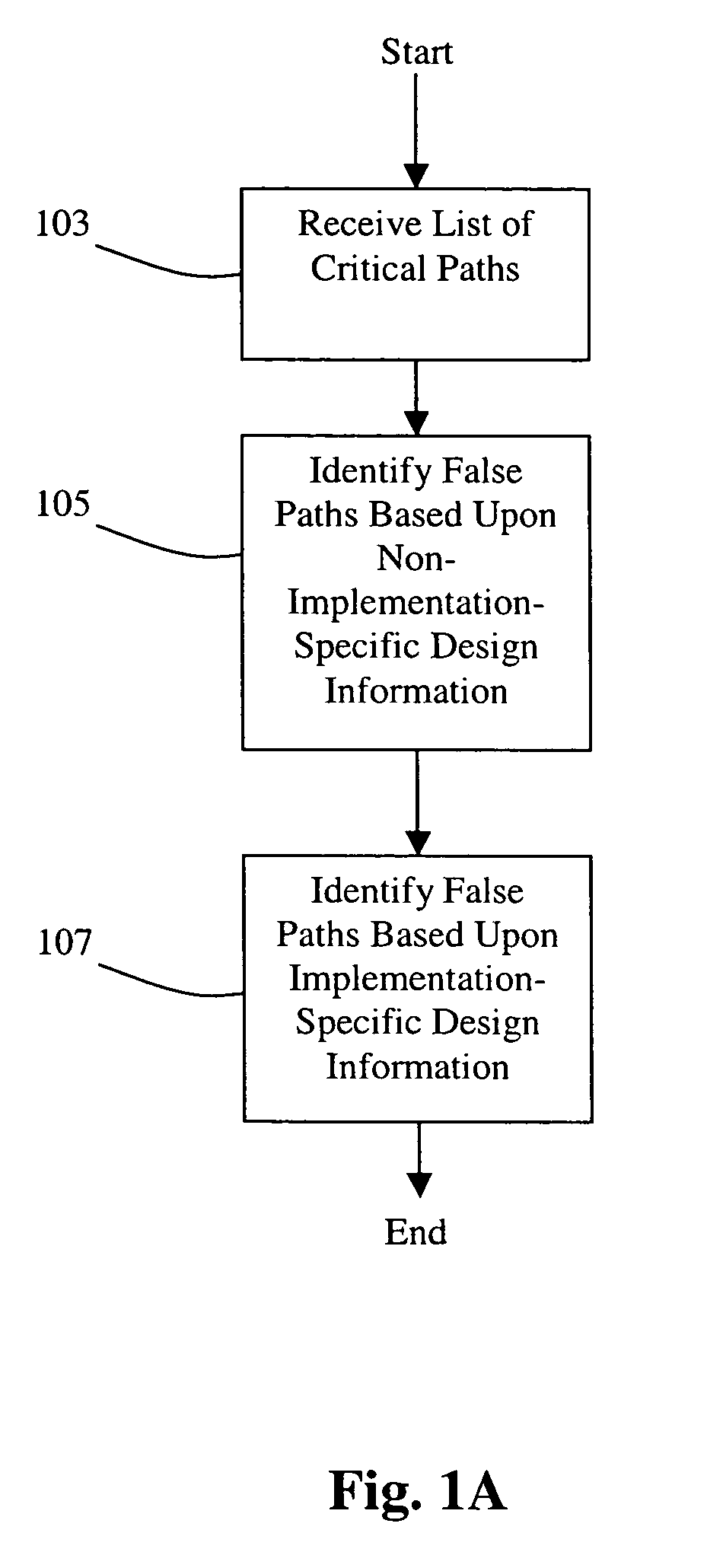
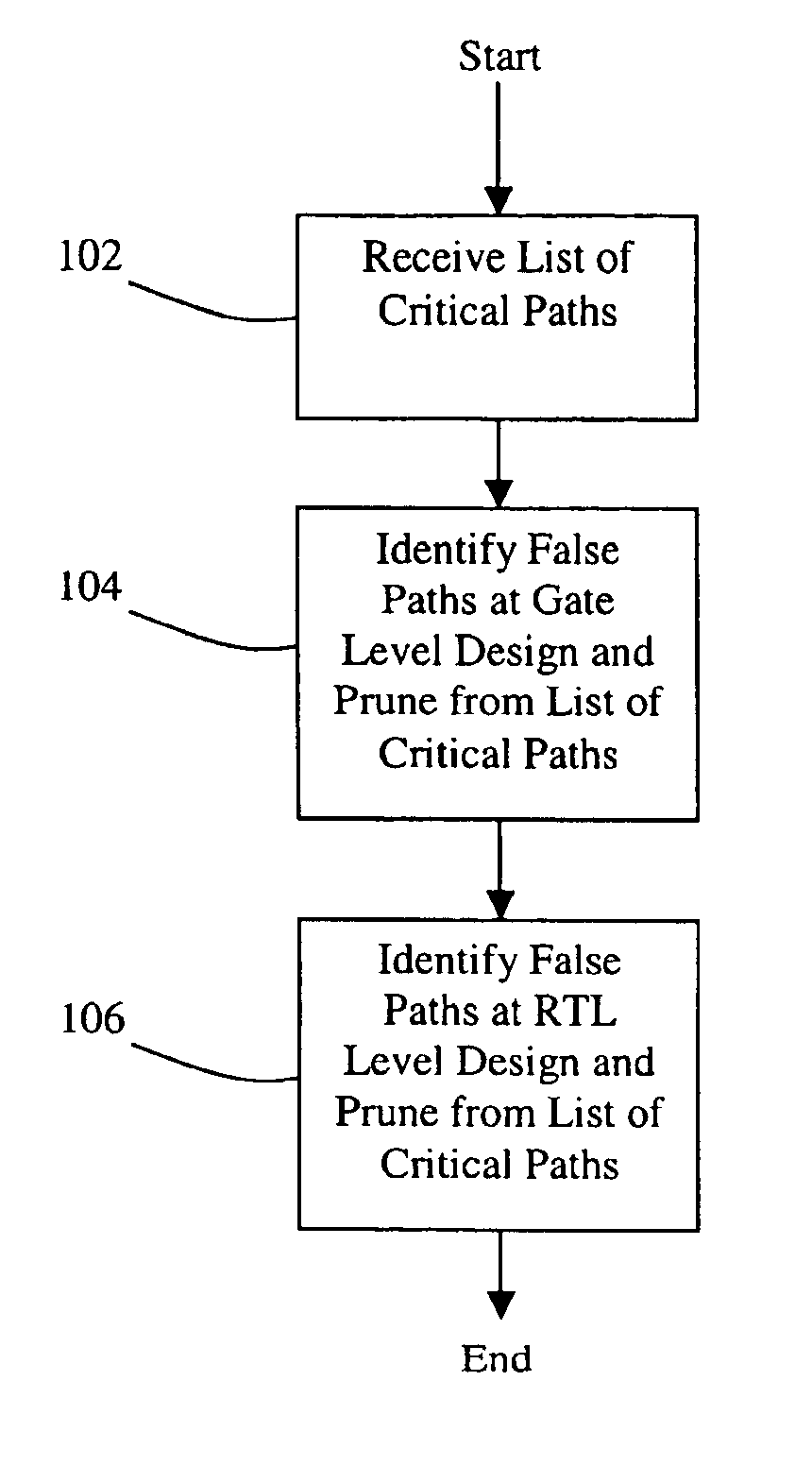
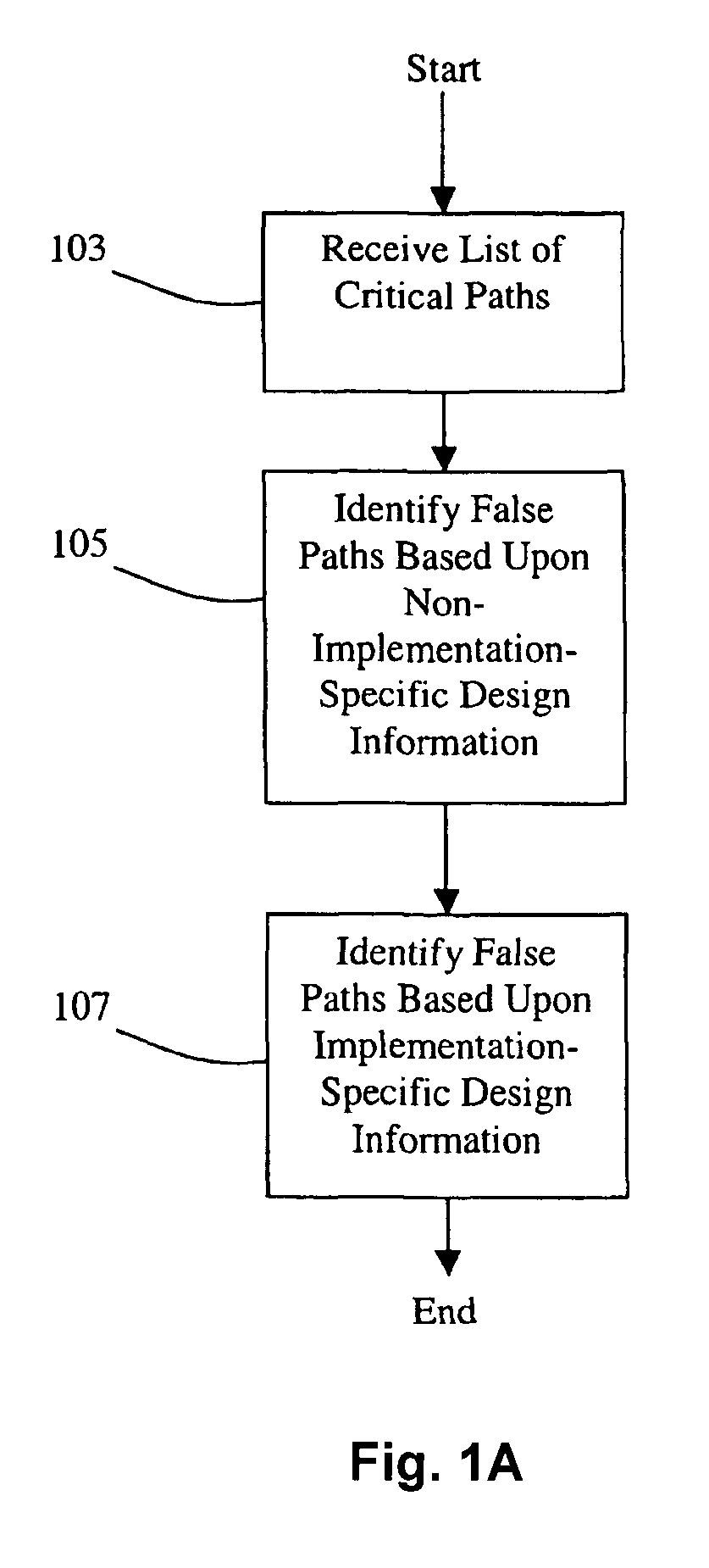
Method and system for false path analysis
InactiveUS7216318B1Accurate identificationPromote resultsComputer aided designSoftware simulation/interpretation/emulationTheoretical computer scienceMapping techniques
Disclosed are methods and systems for performing false path analysis. In one approach, the methods and systems identify a set of zero or more false paths based upon both implementation-specific design data and non-implementation-specific design data. In some approaches, disclosed are methods and systems for performing automated gate-level static timing false path analysis, identification, constraint generation, and / or verification using architectural information. Static timing paths at the gate-level can be linked to the architectural information via mapping techniques found in equivalence checking (EC). The gate level static timing paths can be analyzed in the context of the architectural information to identify false paths.
Owner:CADENCE DESIGN SYST INC
Pessimism reduction in crosstalk noise aware static timing analysis
InactiveUS7251797B2Computer aided designSoftware simulation/interpretation/emulationFalse pathSwitching time
Processes and systems (300) for reducing pessimism in cross talk noise aware static timing analysis and thus resulting false path failures use either or both of effective delta delay noise (307) and path based delay noise (311) analysis. Effective delta delay determines an impact (312, 314, 316) on victim timing of an action by aggressors that occur during a region (209, 319, 321) where victim and aggressor timing windows overlap and determines an effective delta delay 317 corresponding to any portion 316 of the impact on victim timing that extends beyond the victim timing window. The effective delta delay is used to adjust the victim timing window. Path based delta delay determines an uncertainty (627, 637) in a switching time corresponding to a particular path for a victim resulting from an action (switching) by aggressors that occurs at the switching time 607, 613, i.e. during a switching time window (a2 to a2+u1) (613, 625) when uncertainty is included.
Owner:FREESCALE SEMICON INC
Static timing analysis and dynamic simulation for custom and ASIC designs
ActiveUS20060200786A1CAD circuit designSoftware simulation/interpretation/emulationFull customFalse path
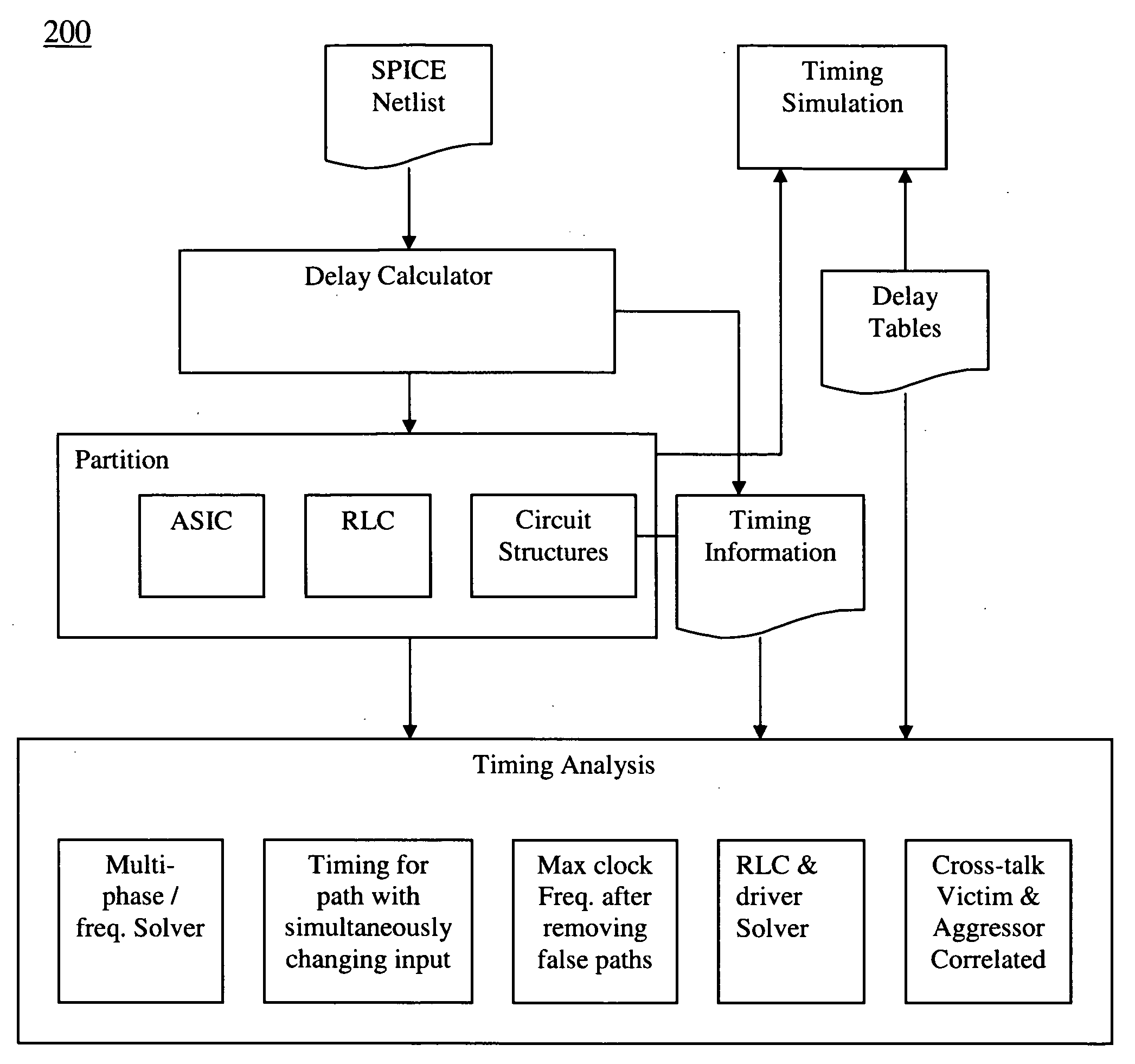
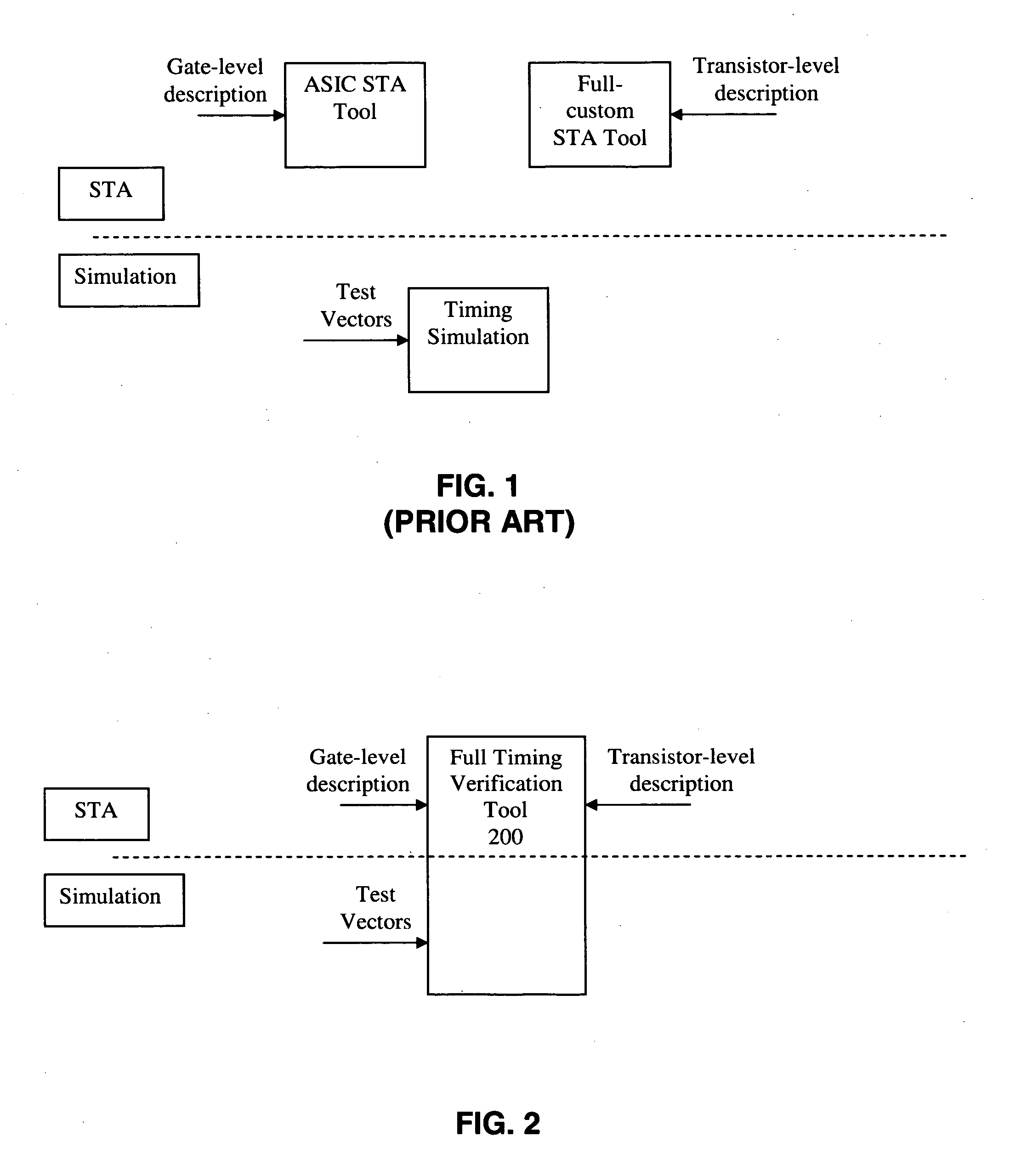
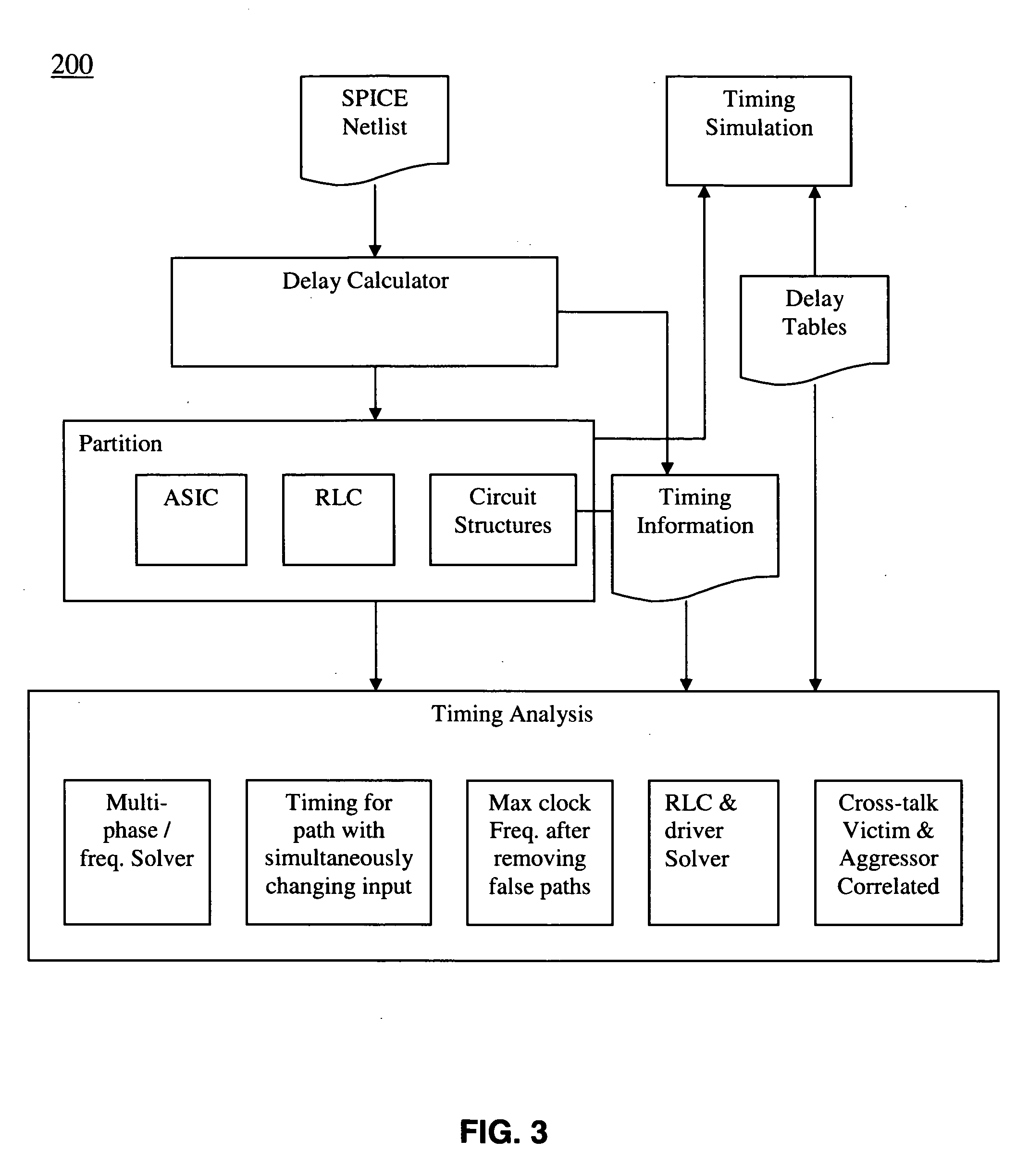
A single verification tool provides both static timing analysis and timing simulation capabilities targeted at both full-custom and ASIC designs in a unified environment. In various embodiments the verification tool includes the following features: (a) Integrating both static timing analysis and dynamic simulation tools into a single tool, (b) Efficient path search for multi-phase, multi-frequency and multi-cycle circuit in the presence of level sensitive latch, (c) Automatically identifying circuit structure, e.g. complex gate, for timing characterization, (d) Circuit structures at transistor level solved by incorporating function check, (e) Carrying out functional check to filter out failing path and identifying gate with simultaneously changing inputs, (f) Finding maximum operation frequency in the presence of level sensitive latches after filtering out false paths, (g) Crosstalk solver by utilizing the admittance matrix and voltage transfer of RLC part in frequency domain coupled with the non-linear driver in time domain implemented in spice-like simulator, (h) Making use of the correlation between inputs of aggressors and victim to determine switching time at victim's output iteratively.
Owner:SAGE SOFTWARE
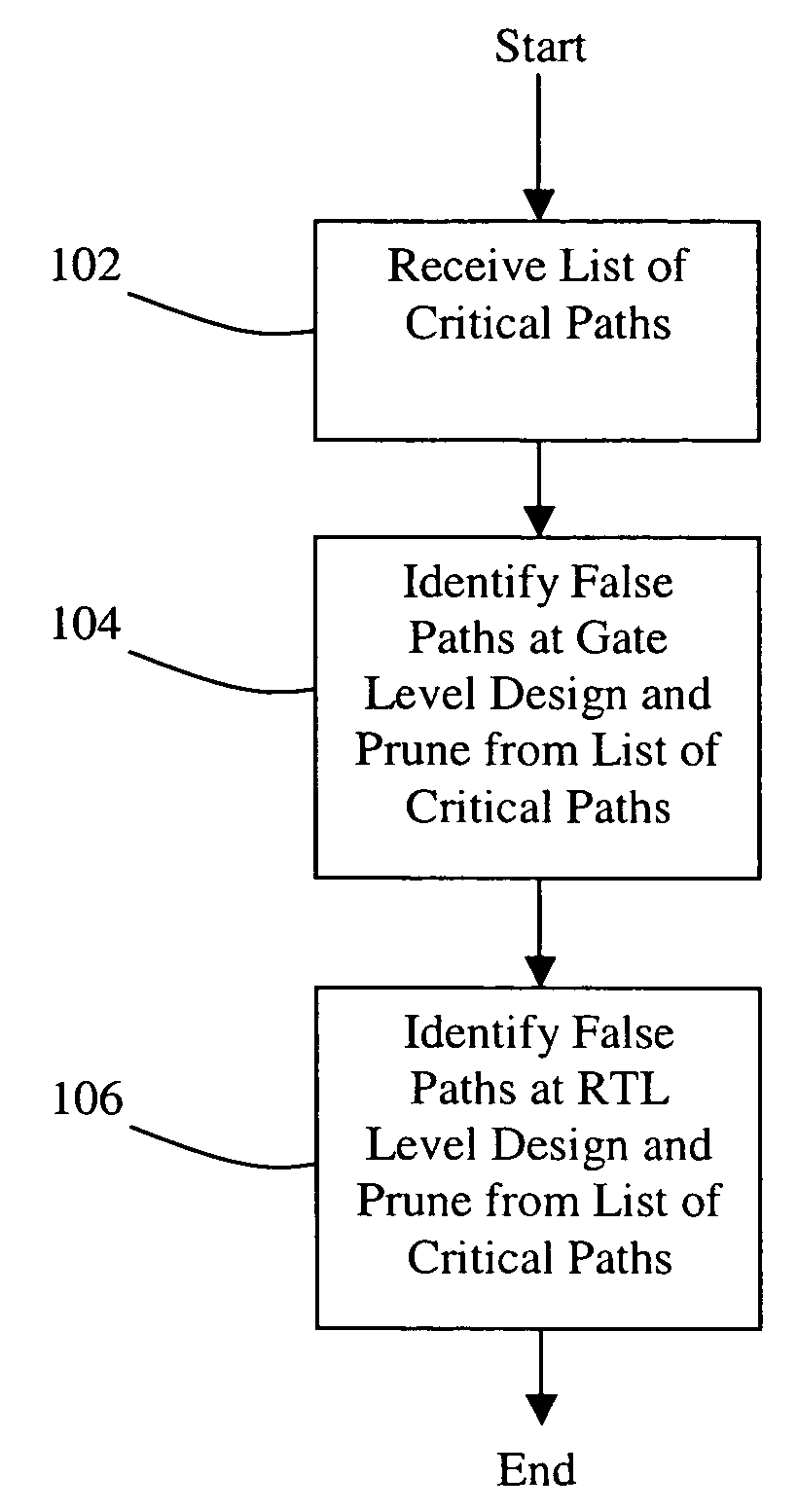
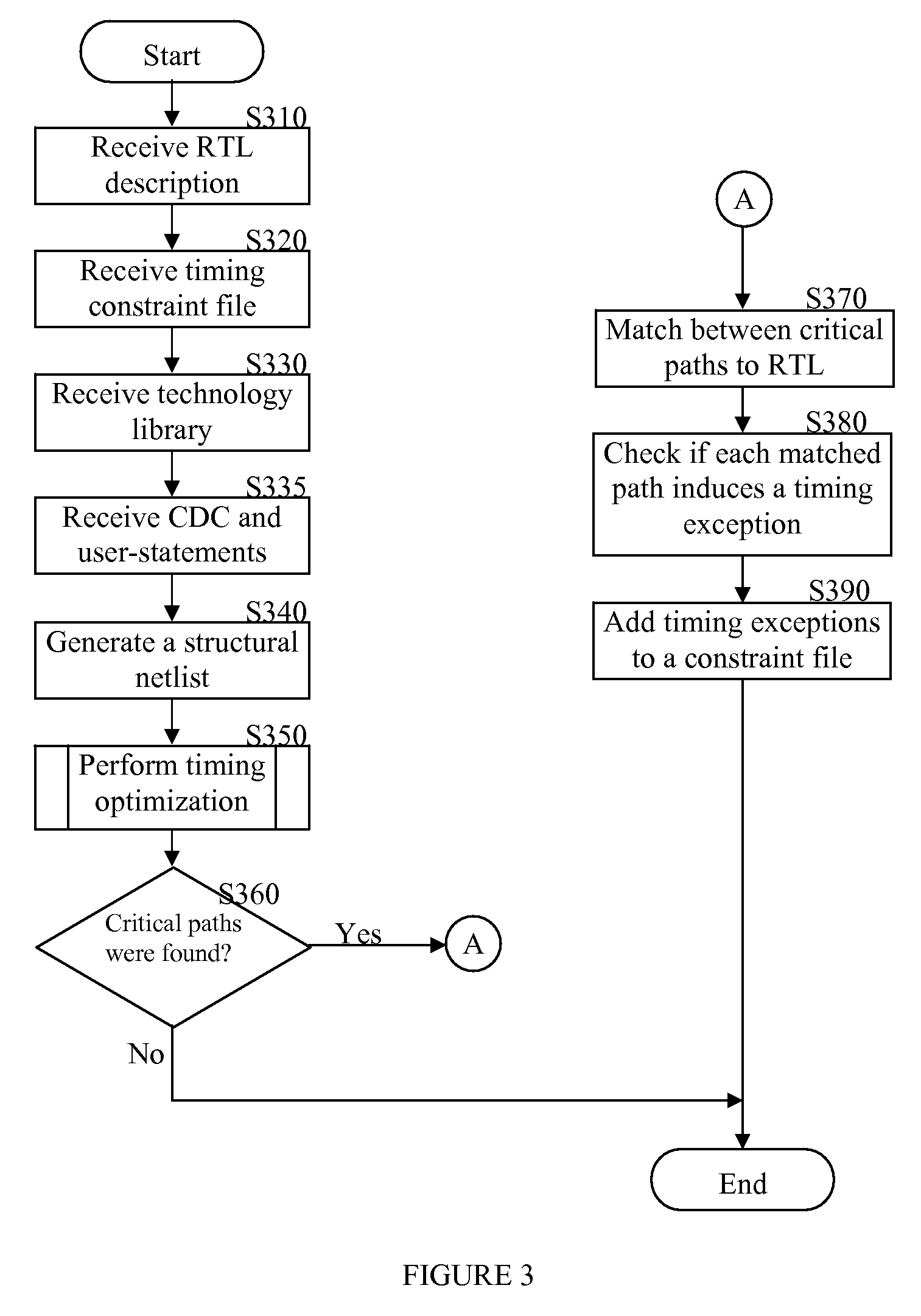
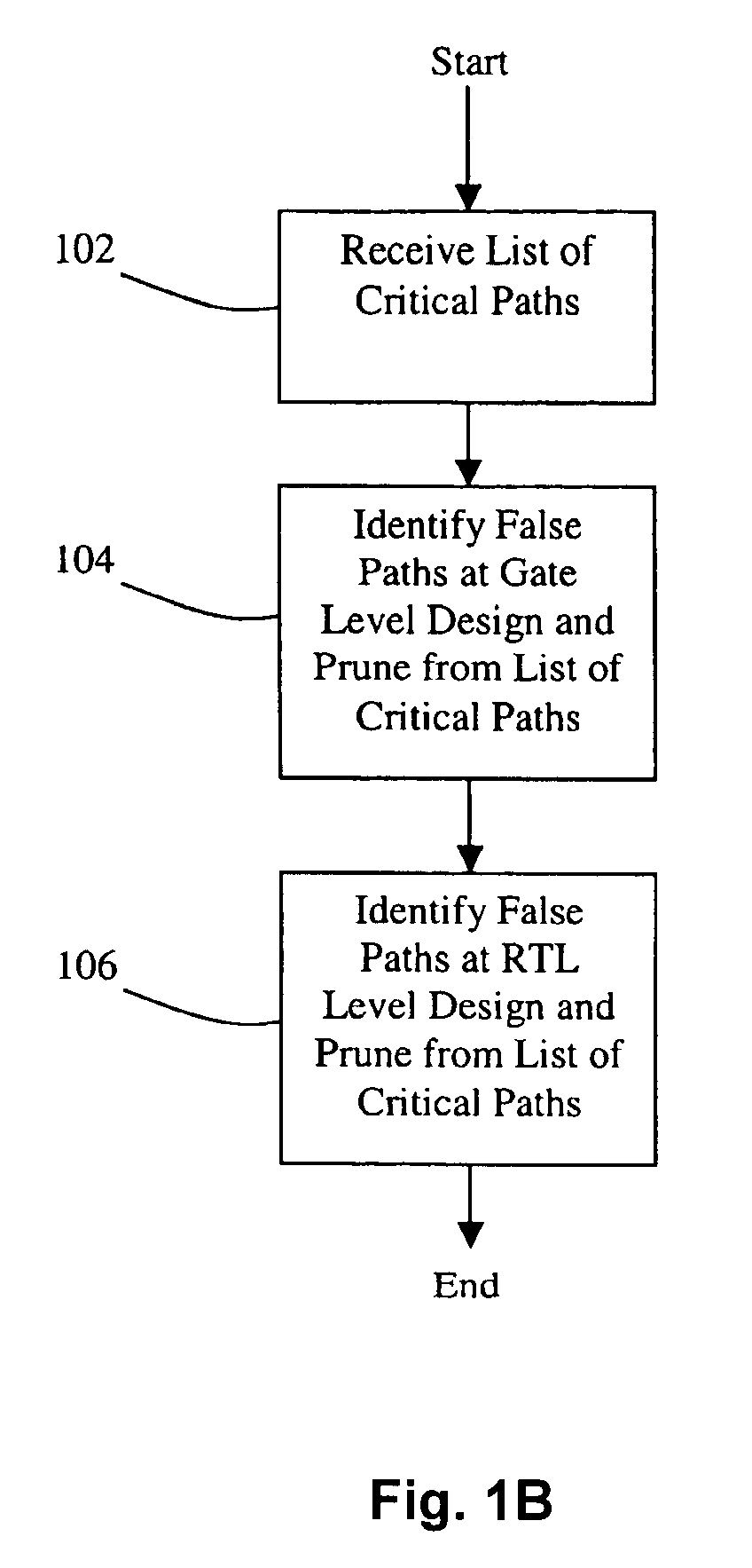
Method for generating timing exceptions
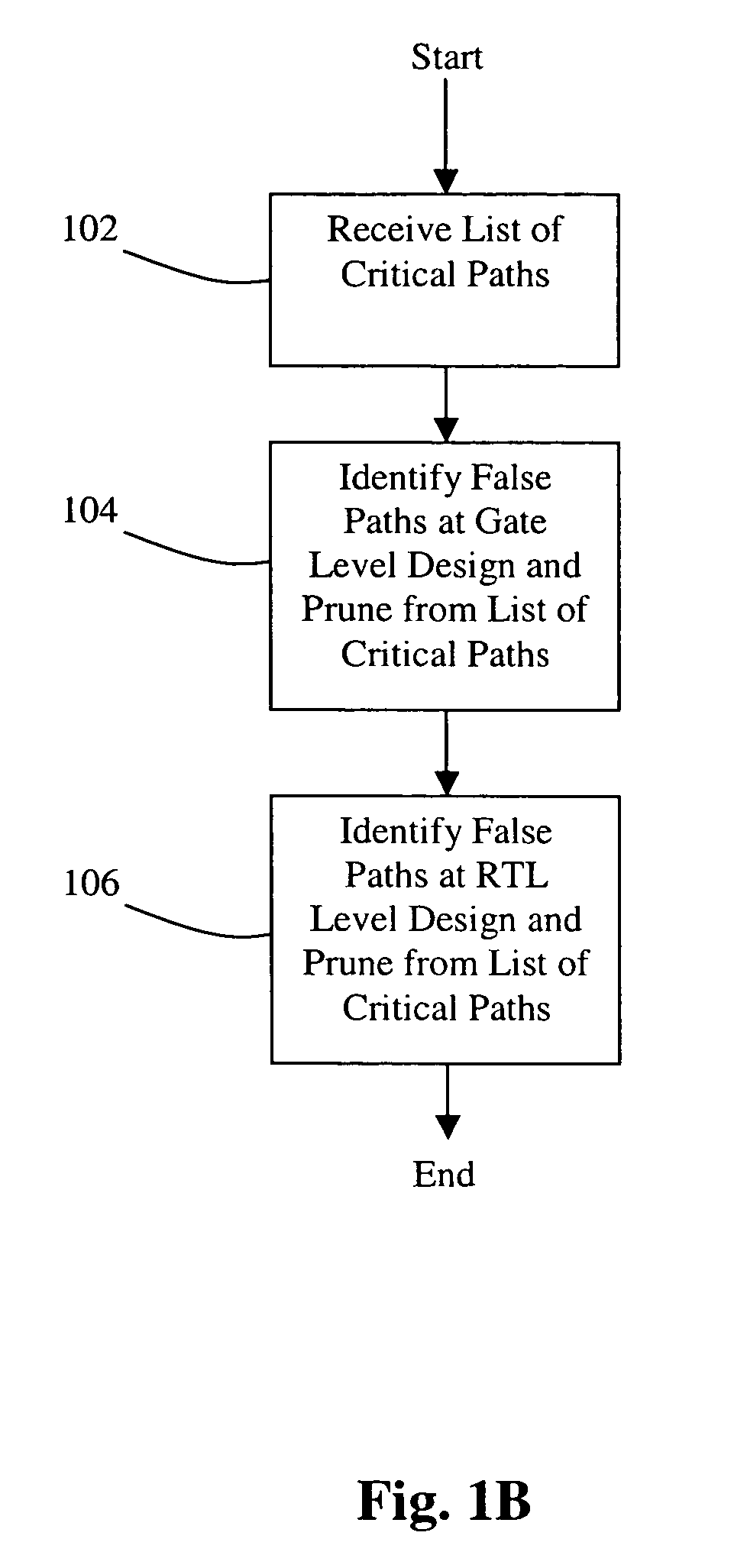
InactiveUS20080201671A1Computer aided designSoftware simulation/interpretation/emulationFalse pathComputer science
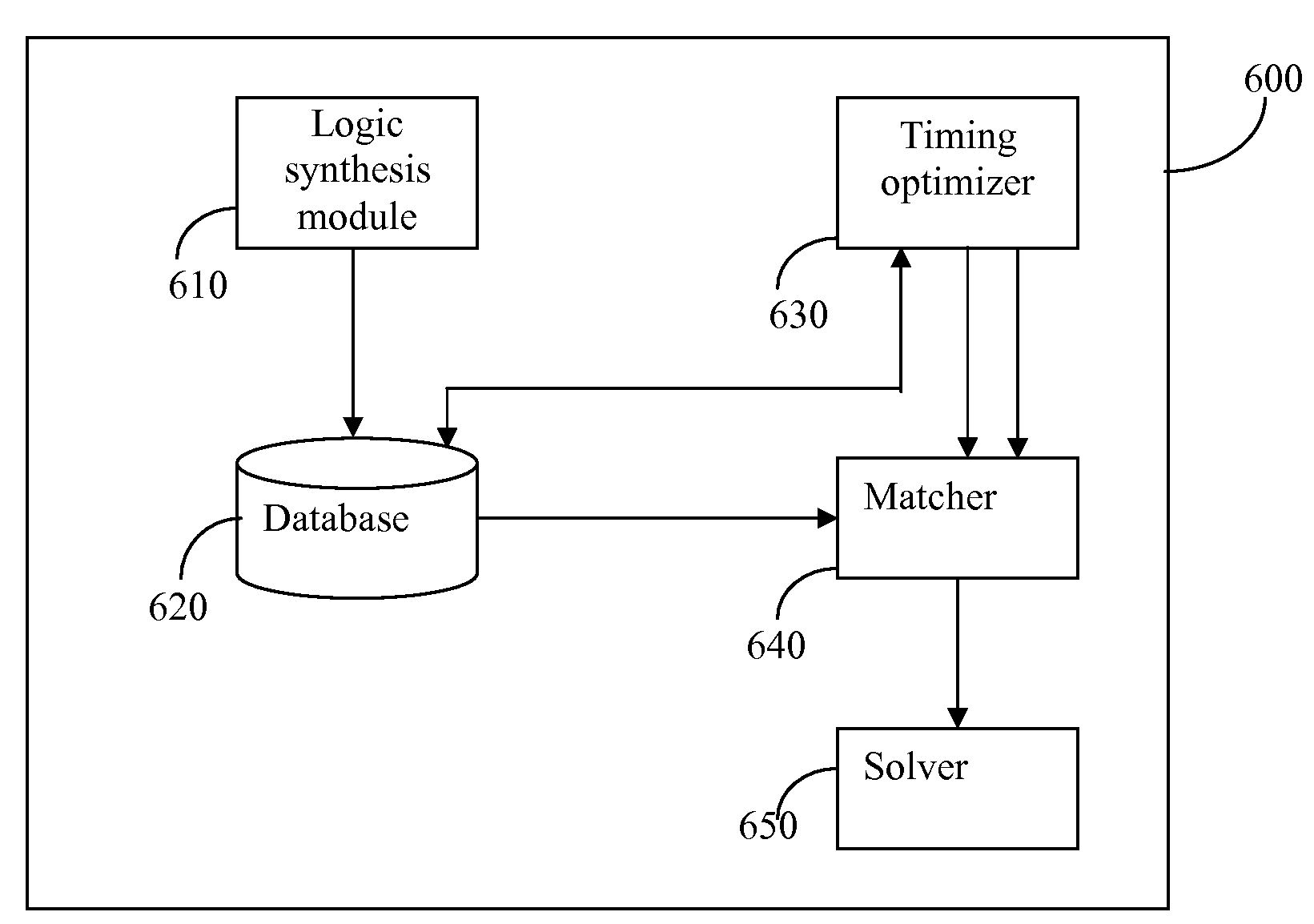
A method for generating timing exceptions for integrated circuit (IC) designs is disclosed. The method includes synthesizing an input RTL description into a gate-level netlist mapped to a technology library; detecting timing critical paths in the netlist; and determining for each detected timing critical path whether it induces timing exceptions. The timing exceptions generated by the disclosed method include, but are not limited to, multi-cycle paths, clock domain crossing false paths, asynchronous false paths, functional false paths, combinational false paths, sequential false paths, timing false paths, and the like.
Owner:ATRENTA
Methods for selectively pruning false paths in graphs that use high-precision state information
Methods are provided that allow a false path pruner to traverse a directed acyclic graph in conjunction with one or more checker programs that are analyzing a program for defects or other artifacts of interest. While the checkers may have ways of avoiding re-traversal of portions of the graph that have already been traversed, the false path pruner may override such decisions made by the checkers as a result of a false path in order to allow re-traversal during a future different traversal when that same defect or artifact may not lie along a false path, and therefore avoid missing a valid defect or artifact. Computer programs stored on tangible media are provided that implement the methods of the invention.
Owner:SYNOPSYS INC
Multi-path selecting method and receiver
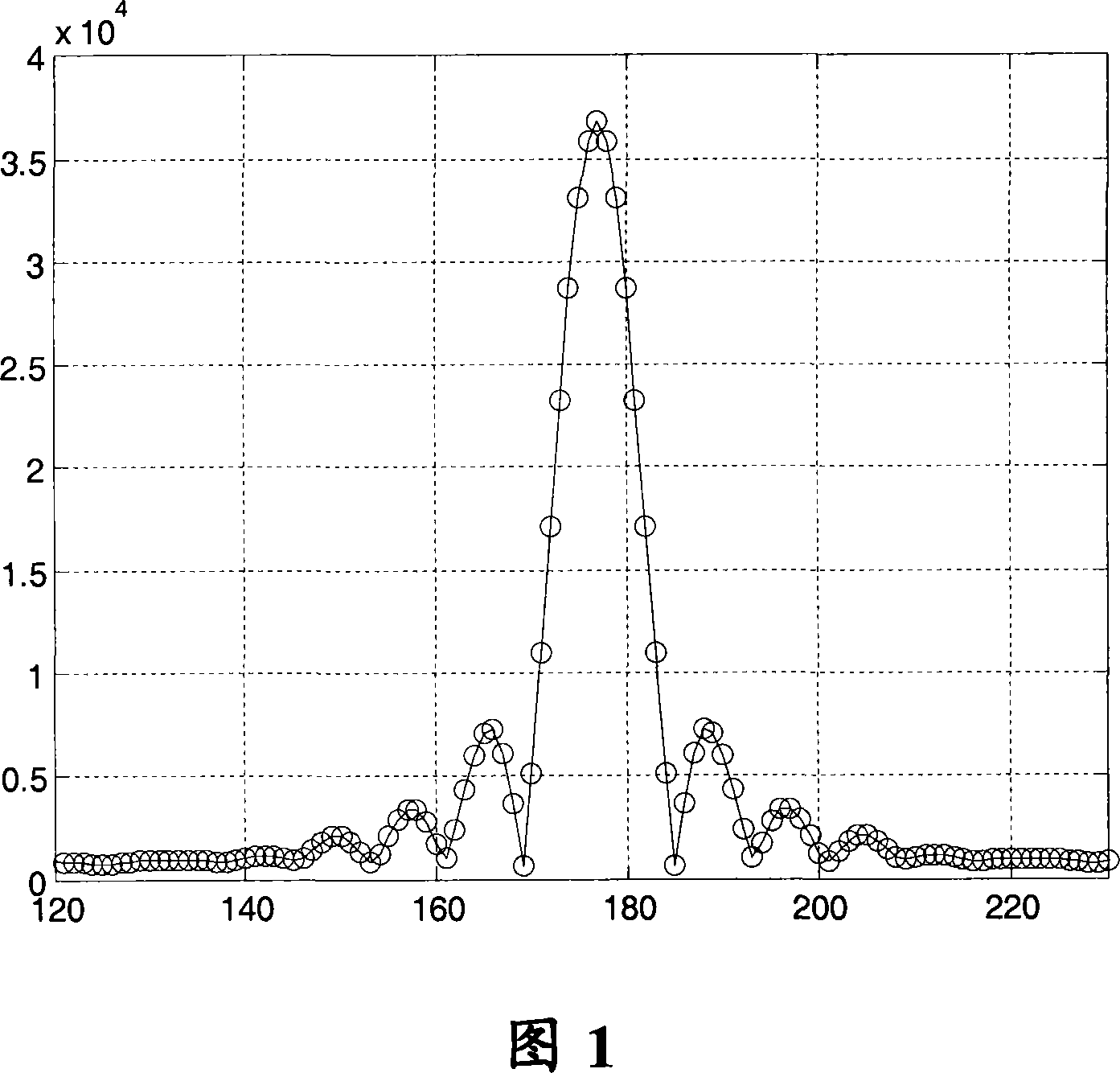
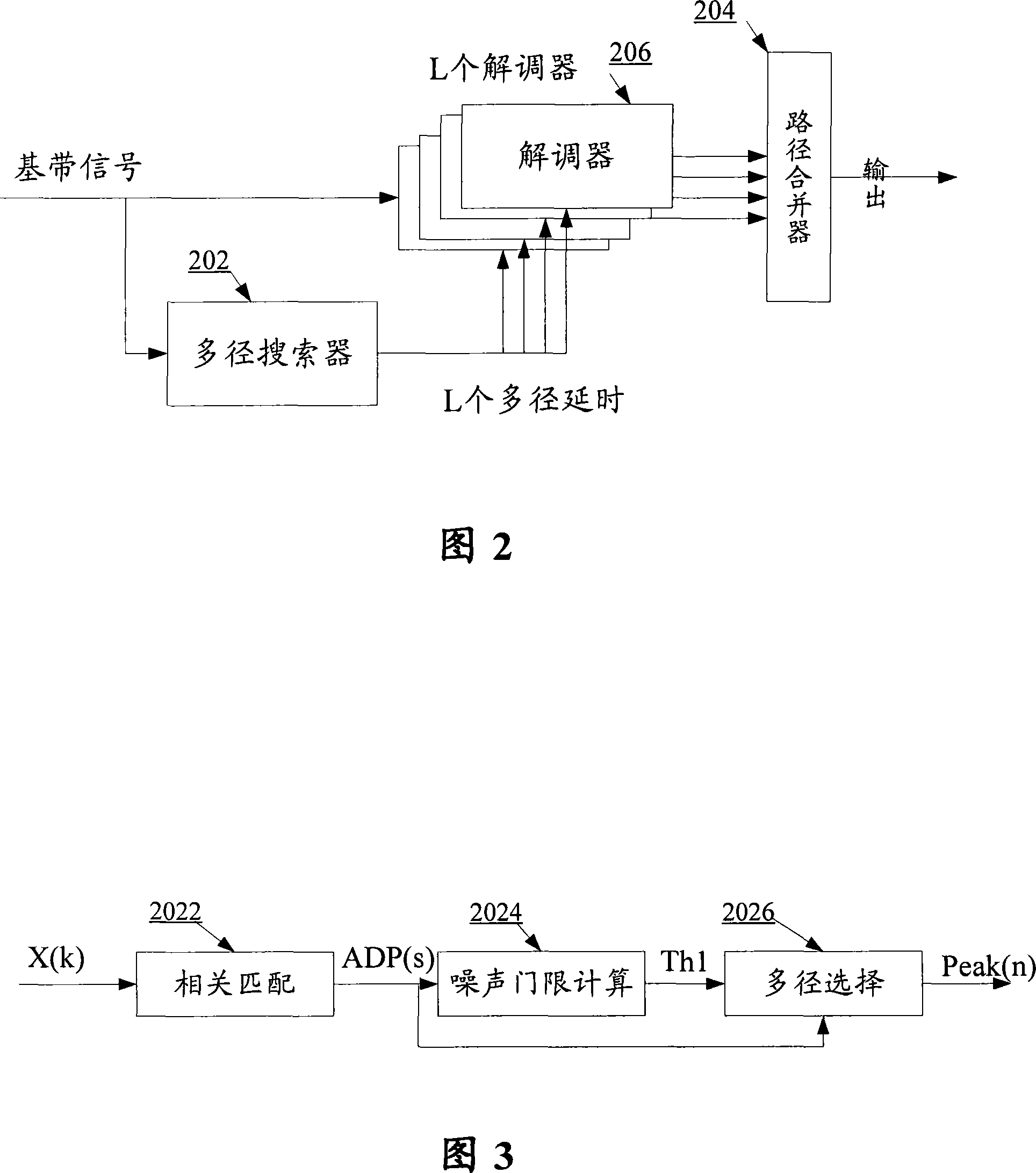
InactiveCN101072046AEfficient detectionAvoid capacity lossCode division multiplexTransmissionCapacity lossSignal-to-noise ratio (imaging)
The invention relates to a multi-path selection method and receiver thereof. The receiver comprises multi-path searcher for conducting different delay matching relative integration adopting local interference code and providing respectively each multi-path delay to at least a demodulator, at least a demodulator for conducting data demodulating according to the multi-path delay from the multi-path searcher and sending the modulation result to the path combiner, a path combiner for combining paths and out-putting the result. The invention can effectively shield false path resulted by peak side lobe so as to avoid capacity loss resulted by false path participating demodulation system.
Owner:ZTE CORP
Delay distribution calculation method, circuit evaluation method and false path extraction method
InactiveUS20070033554A1Delayed correctionAccurate calculationProgramme controlComputer controlRelevant informationFalse path
Delay distribution in an integrated circuit is calculated while taking into account a correlation of performance between interconnects or elements in the integrated circuit, thereby improving estimation accuracy. Circuit information, performance distribution information of the interconnects or elements in the integrated circuit, and correlation information of performance between the interconnects or elements are input. A vertex is selected for calculation, and a correlation between delay distribution at the selected vertex and delay distribution in a partial circuit including the selected vertex is calculated based on the performance distribution information and the correlation information.
Owner:PANASONIC CORP
Method and system for false path analysis
InactiveUS7958470B1Accurate identificationImprove the accuracy of RTL static timing estimationDetecting faulty computer hardwareComputer aided designTheoretical computer scienceFalse path
Disclosed are methods and systems for performing false path analysis. In one approach, the methods and systems identify a set of zero or more false paths based upon both implementation-specific design data and non-implementation-specific design data. In some approaches, disclosed are methods and systems for performing automated gate-level static timing false path analysis, identification, constraint generation, and / or verification using architectural information. Static timing paths at the gate-level can be linked to the architectural information via mapping techniques found in equivalence checking (EC). The gate level static timing paths can be analyzed in the context of the architectural information to identify false paths.
Owner:CADENCE DESIGN SYST INC
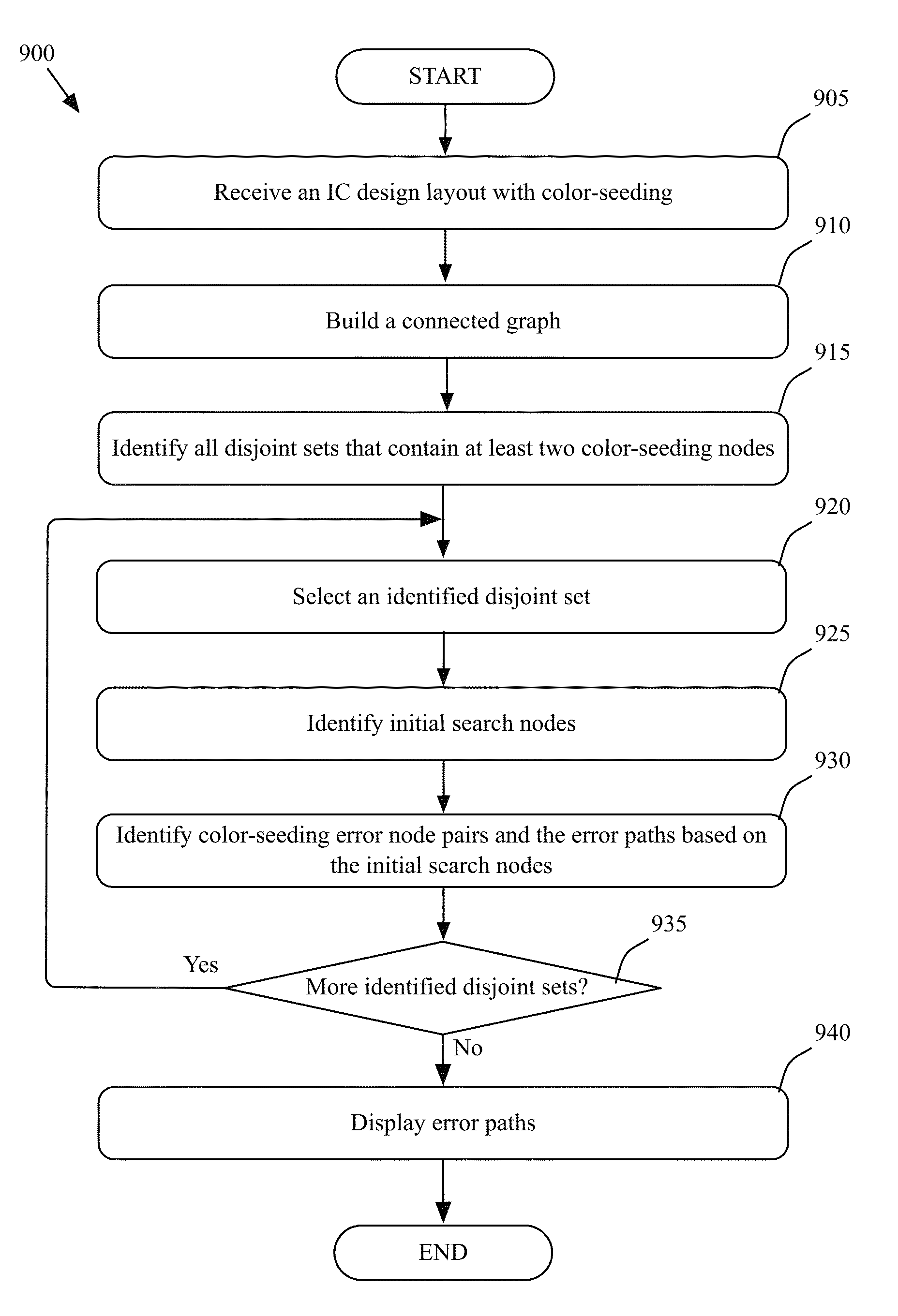
Method and apparatus for identifying double patterning color-seeding violations
ActiveUS9165104B1Originals for photomechanical treatmentComputer aided designGraphicsComputer architecture
A method for automatically performing a double patterning (DP) color-seeding check in order to discover color-seeding violations in an IC design layout. The method of some embodiments receives a layer of the IC design layout and performs an analysis on the layer of the design layout to determine several error paths. Each error path connects two color-seeding shapes that have a color-seeding violation. For each pair of shapes that has a color-seeding violation, the method of some embodiments displays a DP color-seeding violation marker on a graphical user interface (GUI) to visually assist a user to resolve the color-seeding violation.
Owner:CADENCE DESIGN SYST INC
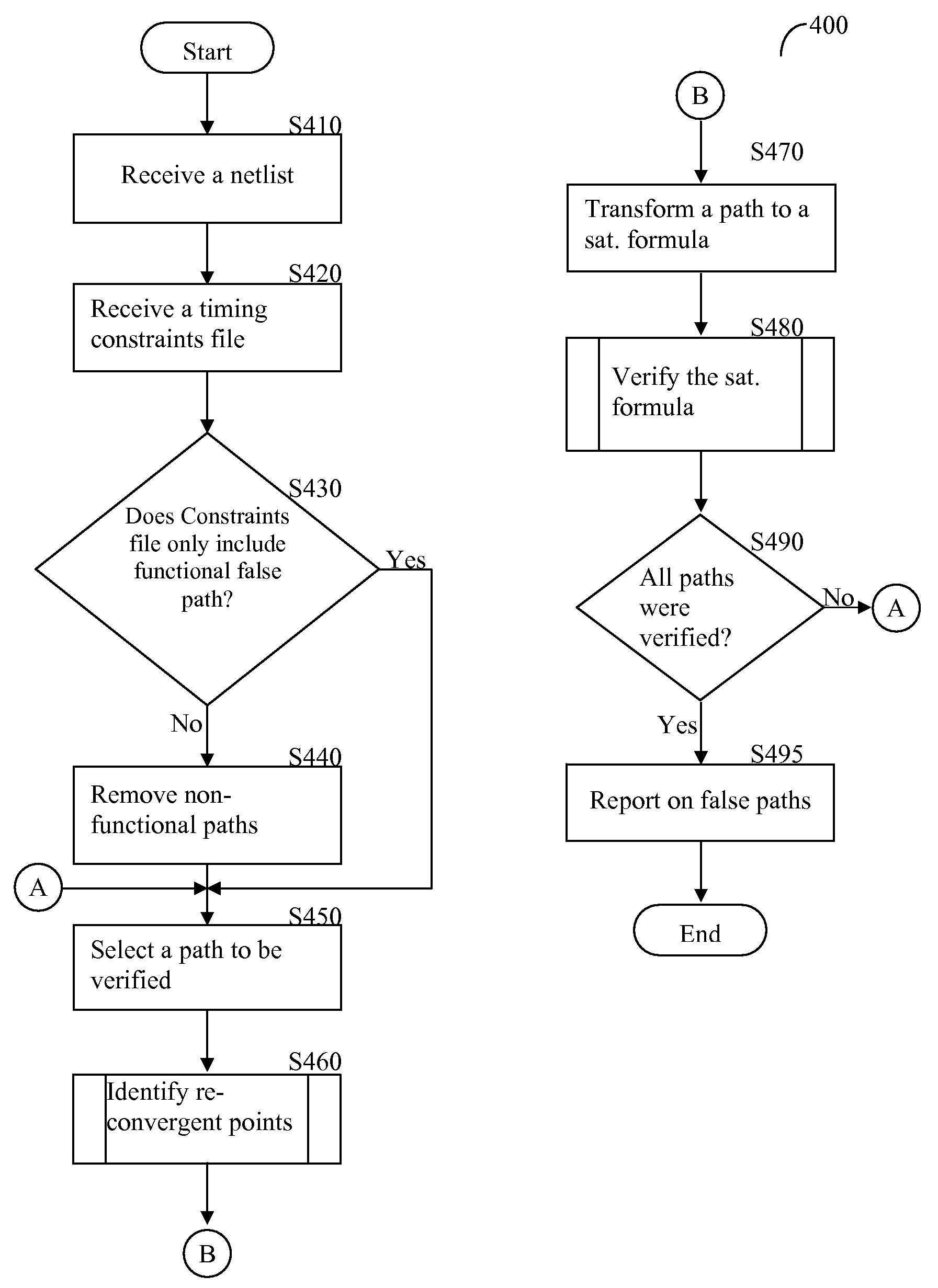
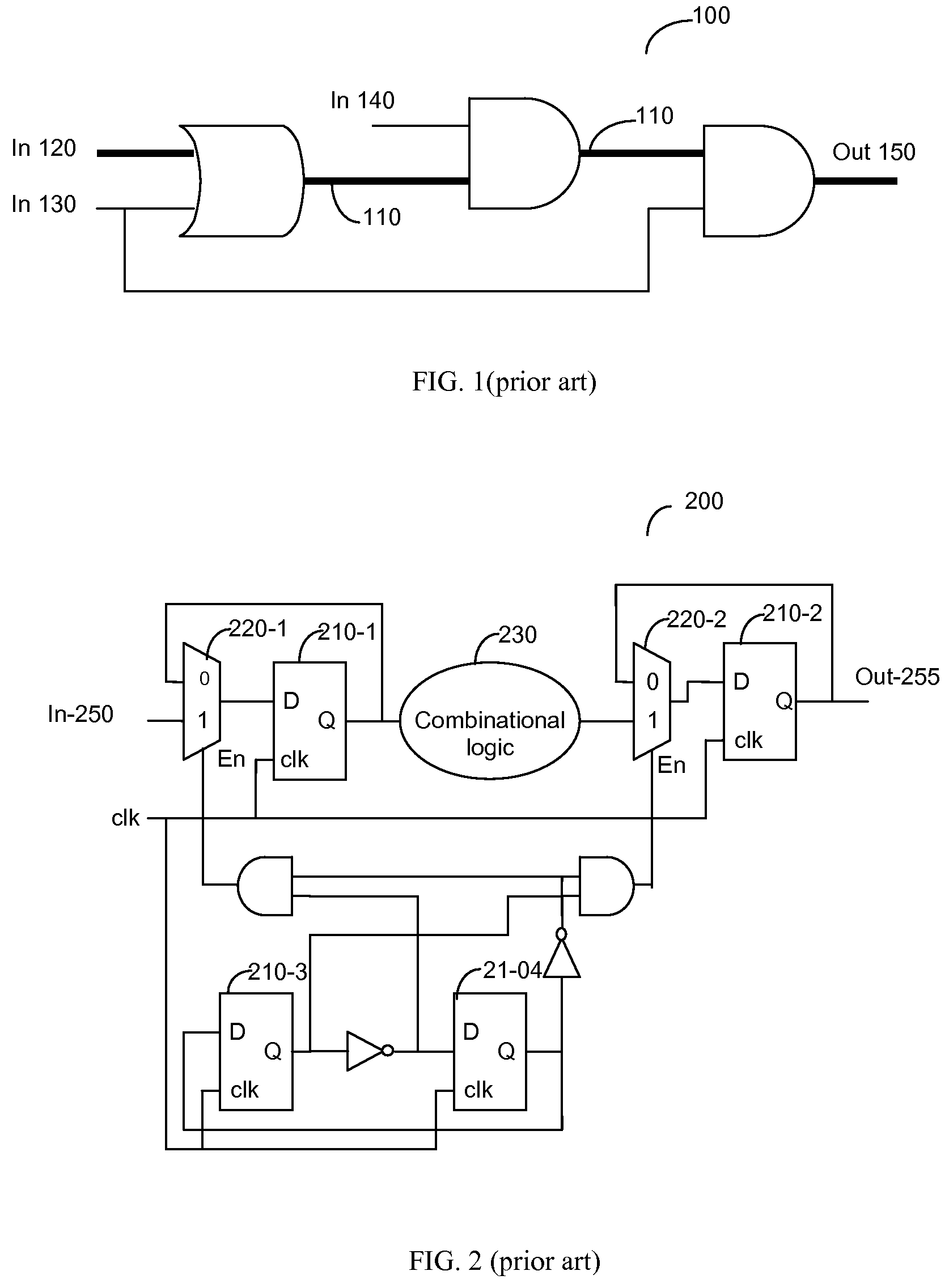
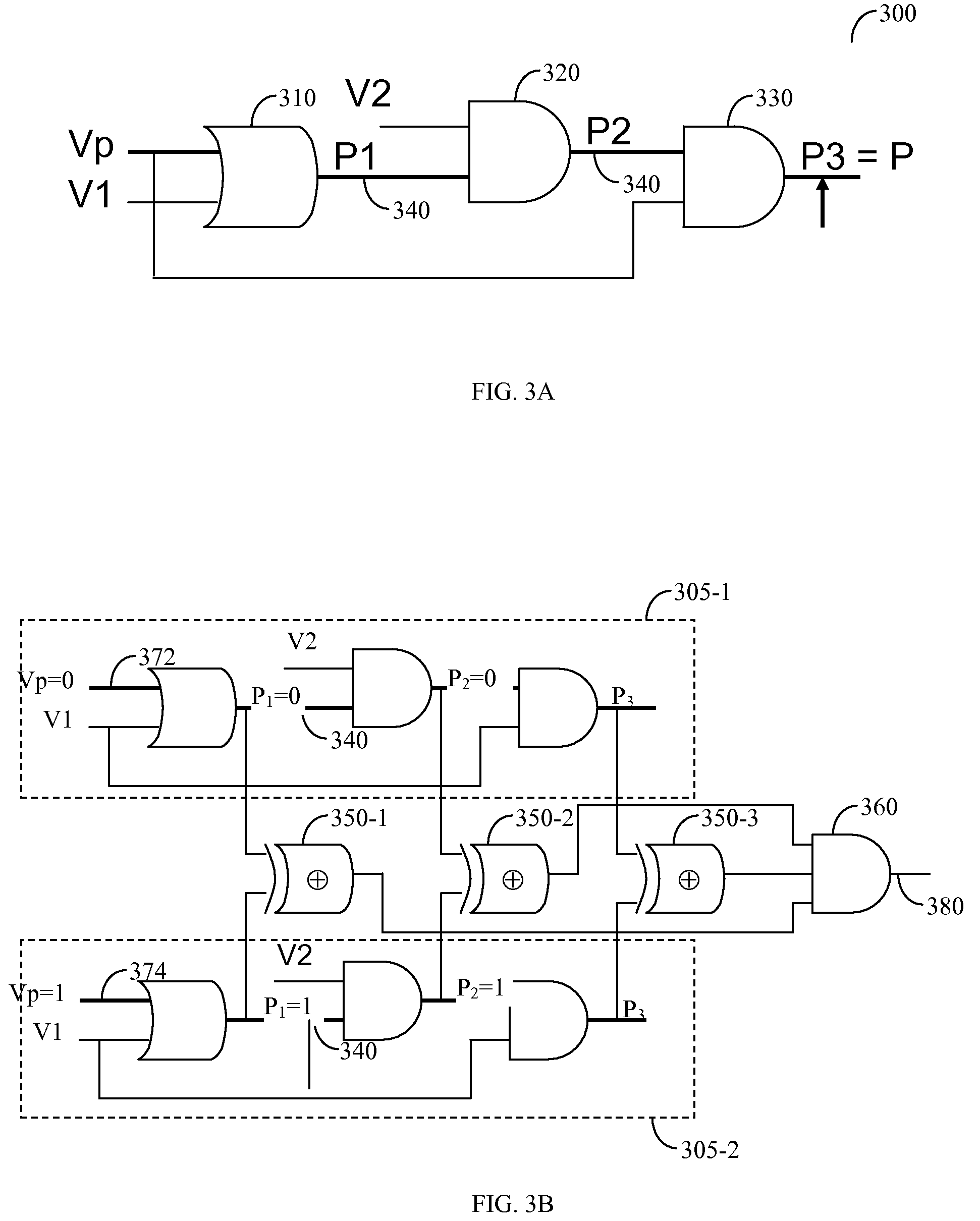
Method for modeling and verifying timing exceptions
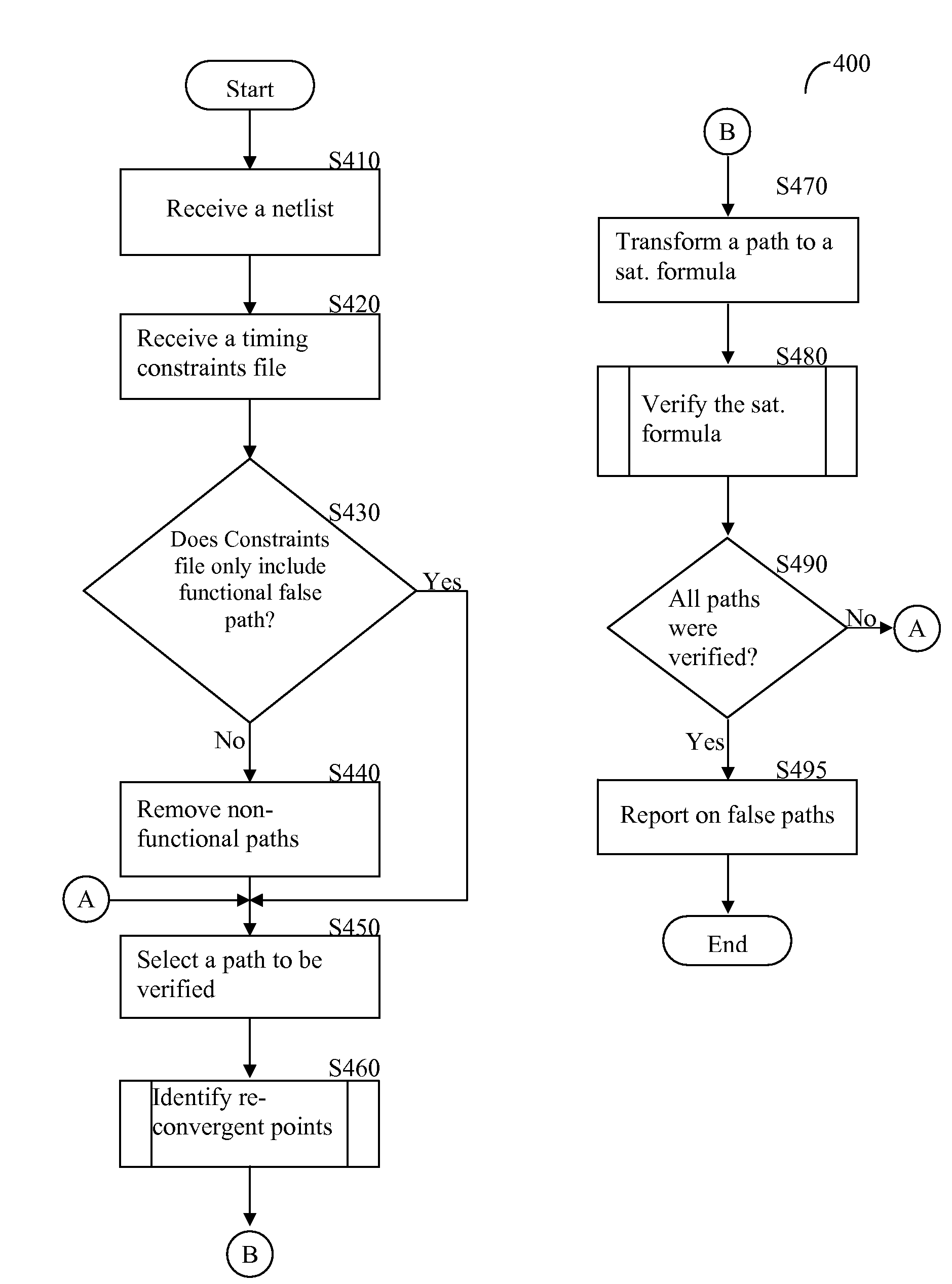
ActiveUS7650581B2Computer aided designSoftware simulation/interpretation/emulationComputer architectureFalse path
A method and system for timing exception verification in integrated circuit (IC) designs included verification of functional false paths as well as multi-cycle paths (MCPs). A false path or a MCP is modeled to a satisfiability formula and the formula is validated using a Boolean satisfiability solver. Time required for timing exception verification can be significantly reduced.
Owner:SYNOPSYS INC
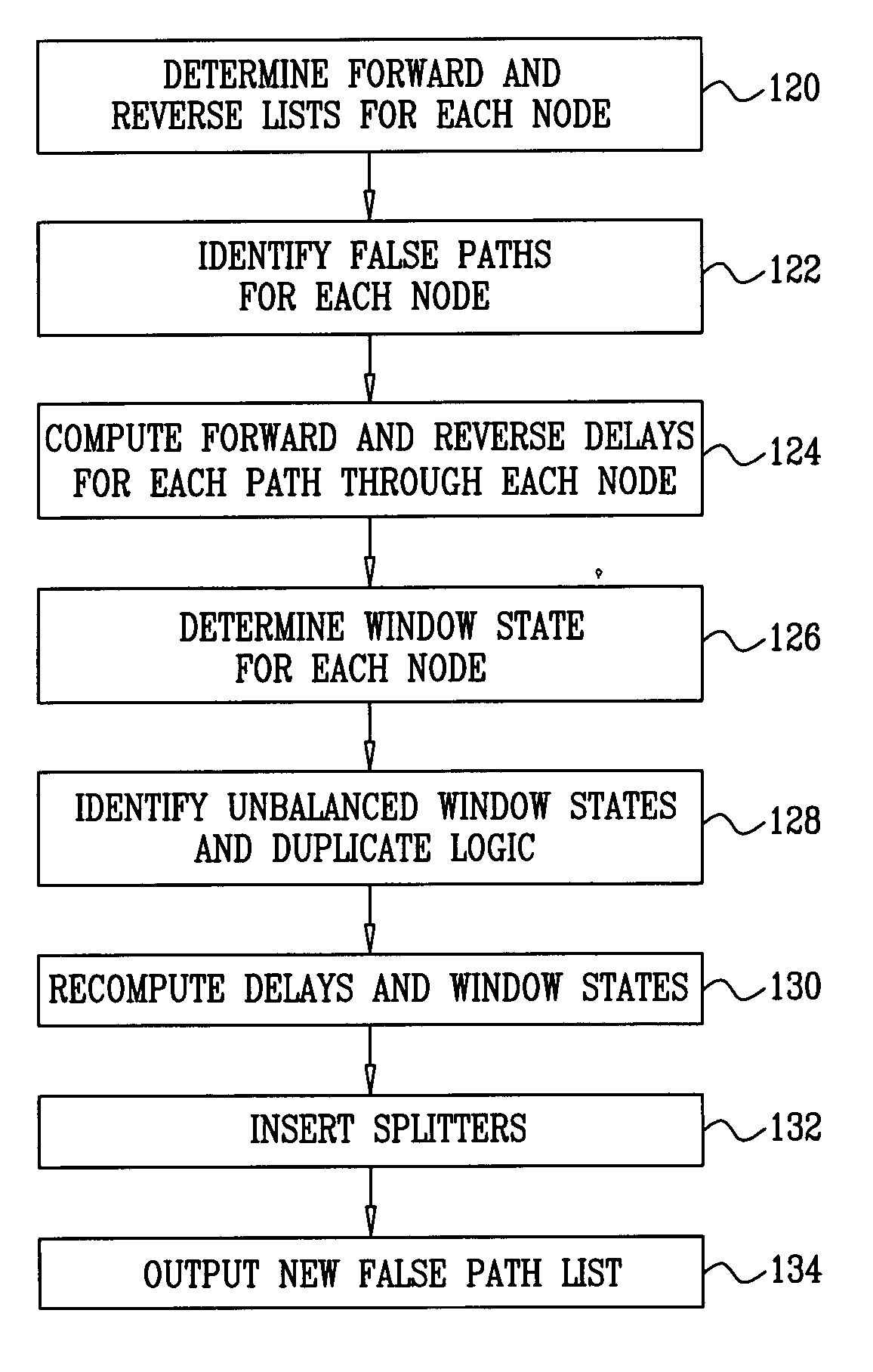
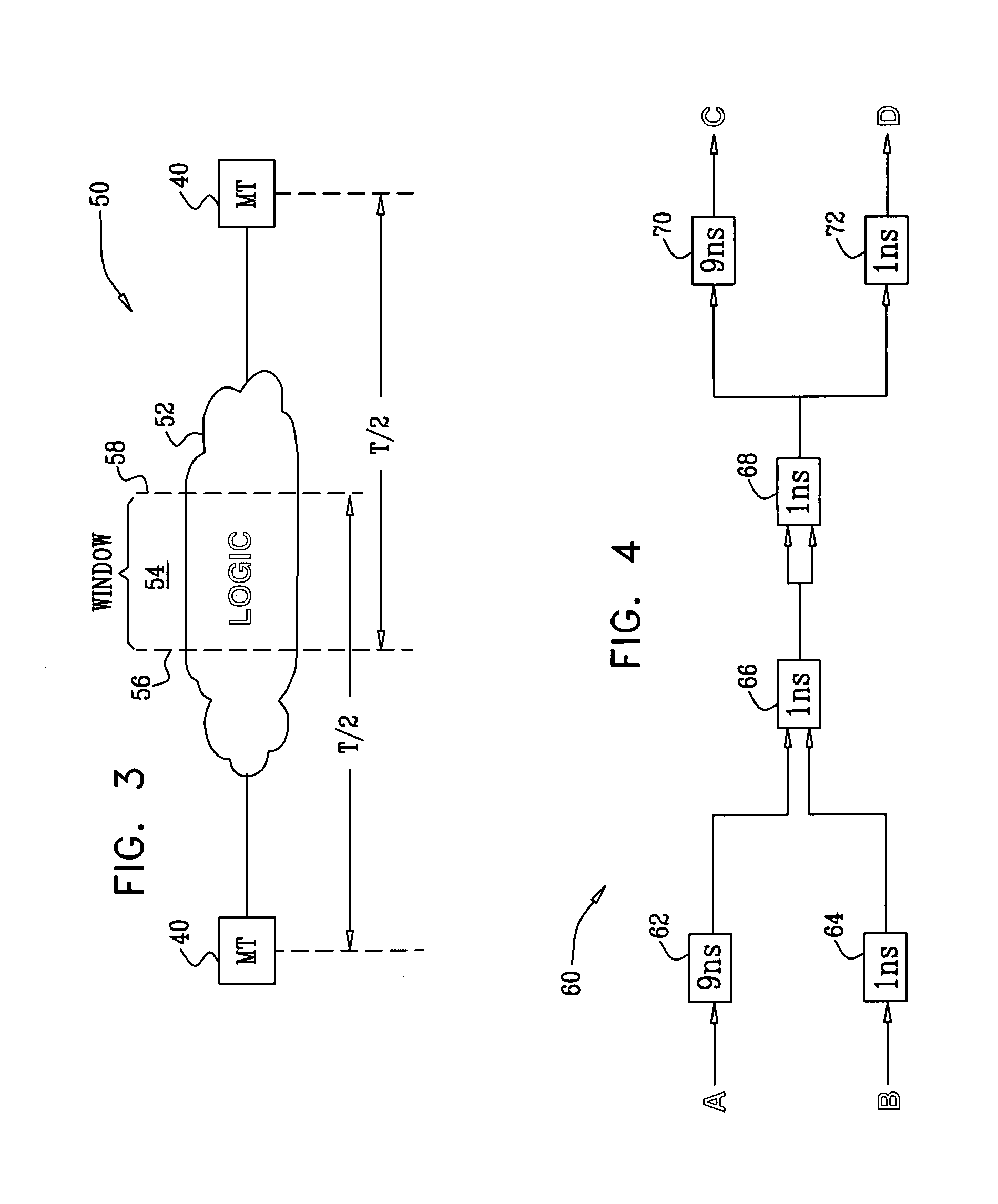
False path handling
InactiveUS20090044159A1Increase the number ofAdd depthComputer aided designSoftware simulation/interpretation/emulationFalse pathCircuit design
A method for circuit design includes performing a timing analysis of a design of a processing stage in an integrated electronic circuit. The processing stage has inputs and outputs and includes circuit components arranged so as to define multiple logical paths between the inputs and the outputs. A timing constraint to be applied in splitting the processing stage into multiple sub-stages is specified. At least one of the logical paths is identified as a false path, to which the timing constraint is not to apply. The design is modified responsively to the timing analysis, to the timing constraint, and to identification of the false path, so as to split the processing stage into the sub-stages.
Owner:MPLICITY
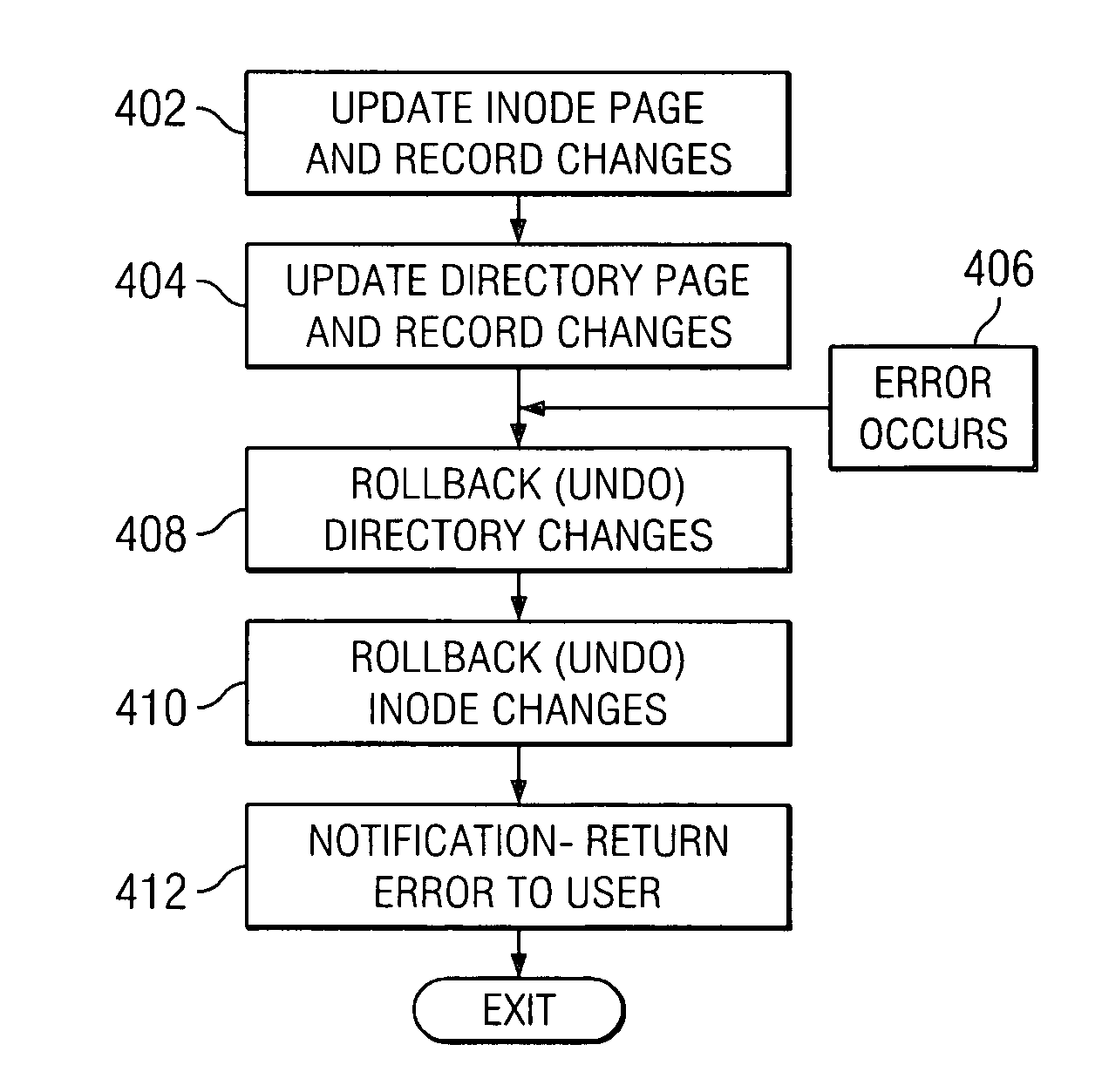
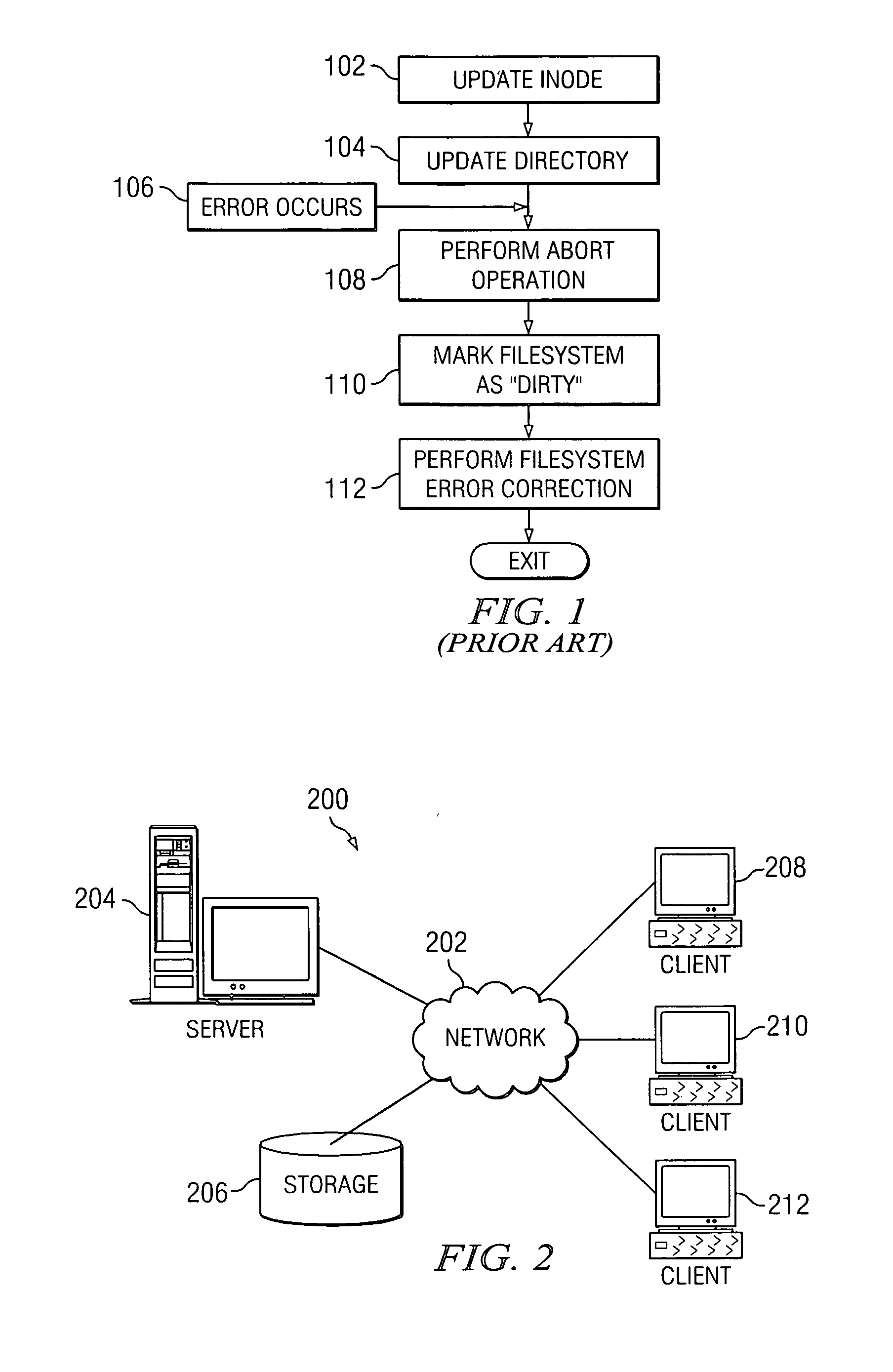
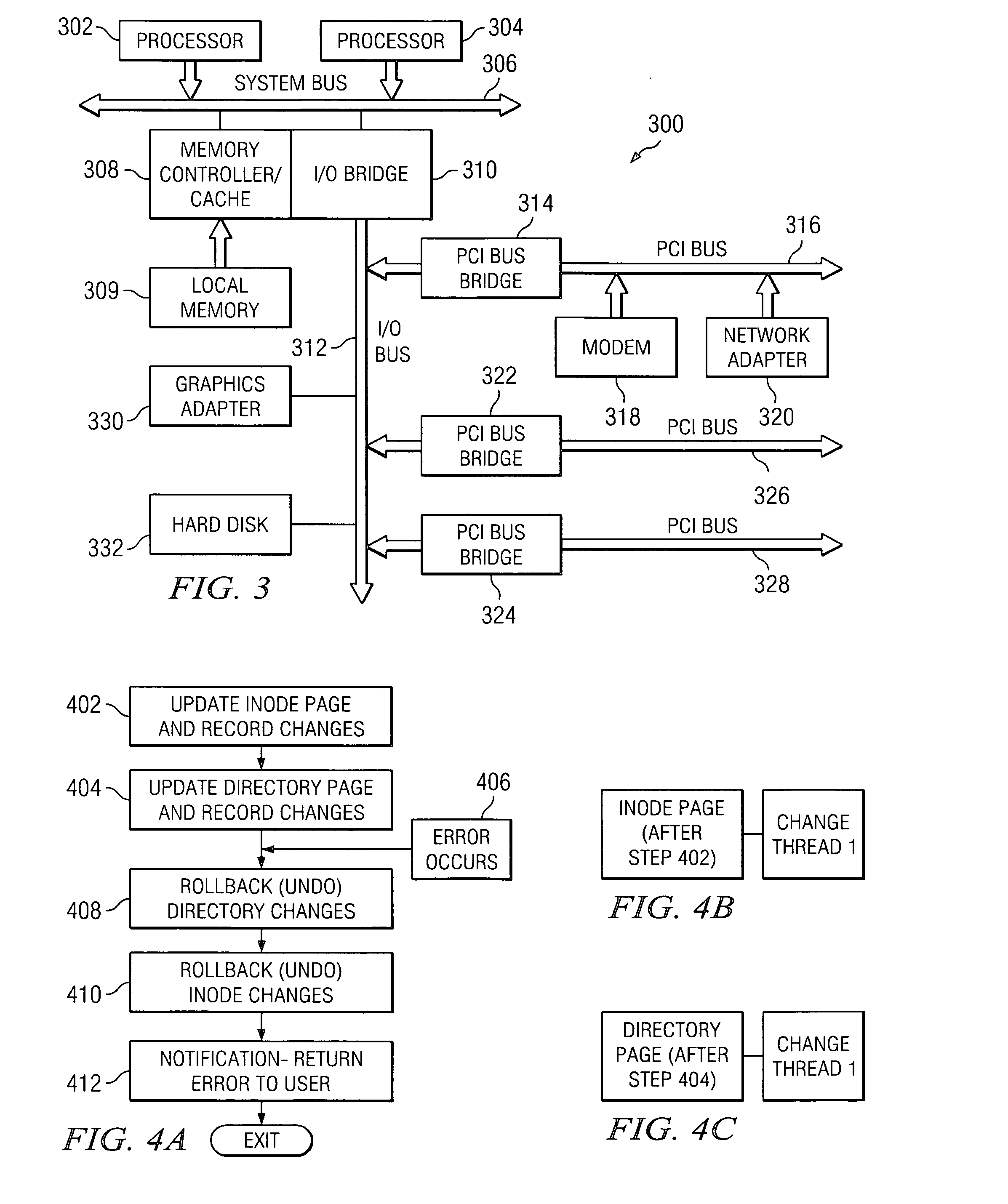
Autonomic and fully recovering filesystem operations
A filesystem operation binds “undo” information to given filesystem resources, in order for the filesystem operation to reverse or rollback changes made to the resources, and thereby return a filesystem affected by a failed or incomplete operation from an inconsistent state to a previous, consistent state. Changes can be undone, to return the filesystem to a consistent state, as long as any further changes can also be undone successfully. Latter changes can be undone by making sure that no operation is fully successful until the preceding operations that changed the same metadata are successful. In an error path, the operation can go through every resource modified to determine if other threads have modified data beyond the initial modification. A failing thread can notify later threads that an operation has failed and all changes are to be undone. Each thread can then run through and undo all pertinent metadata changes that were made.
Owner:LENOVO (SINGAPORE) PTE LTD
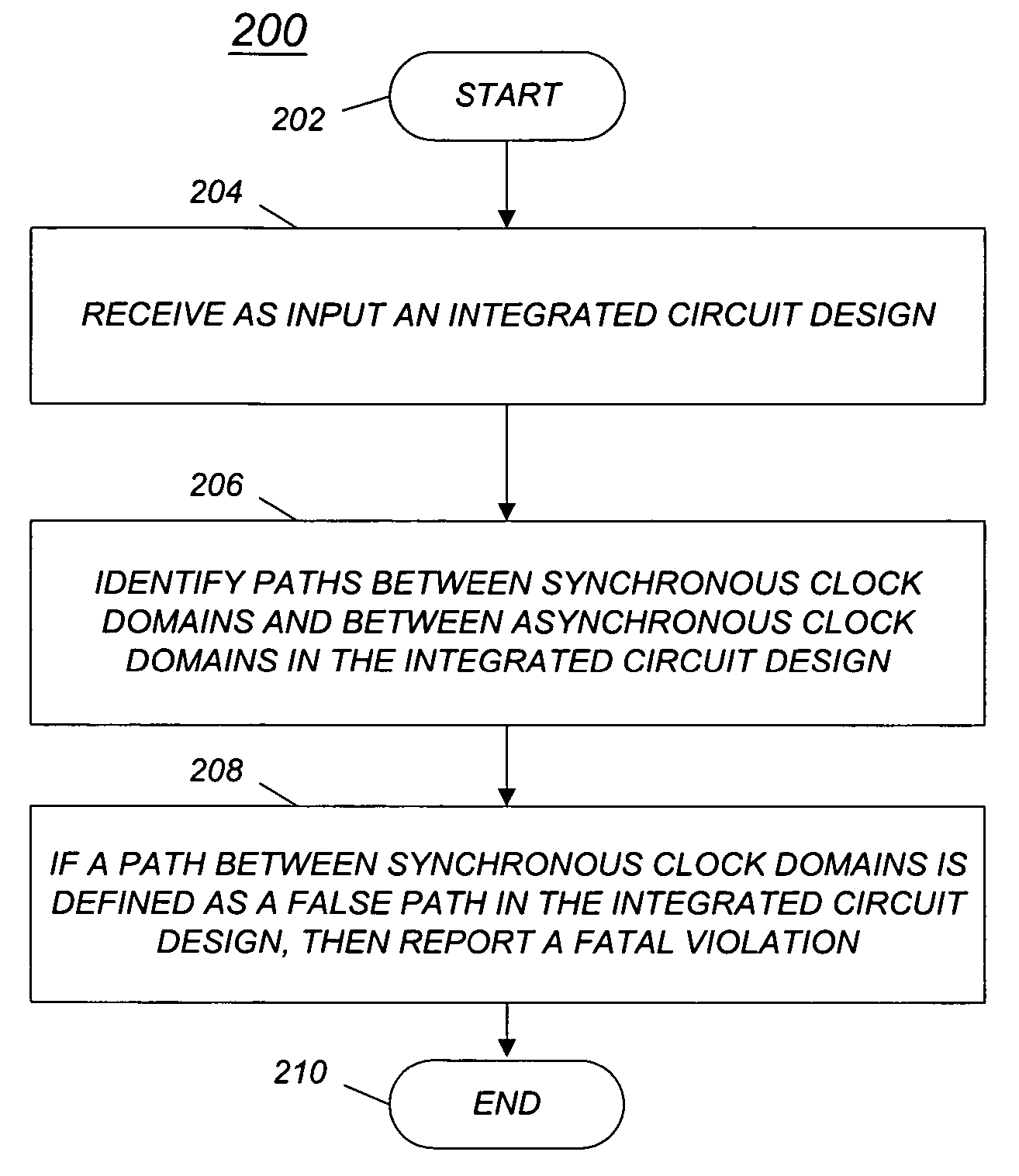
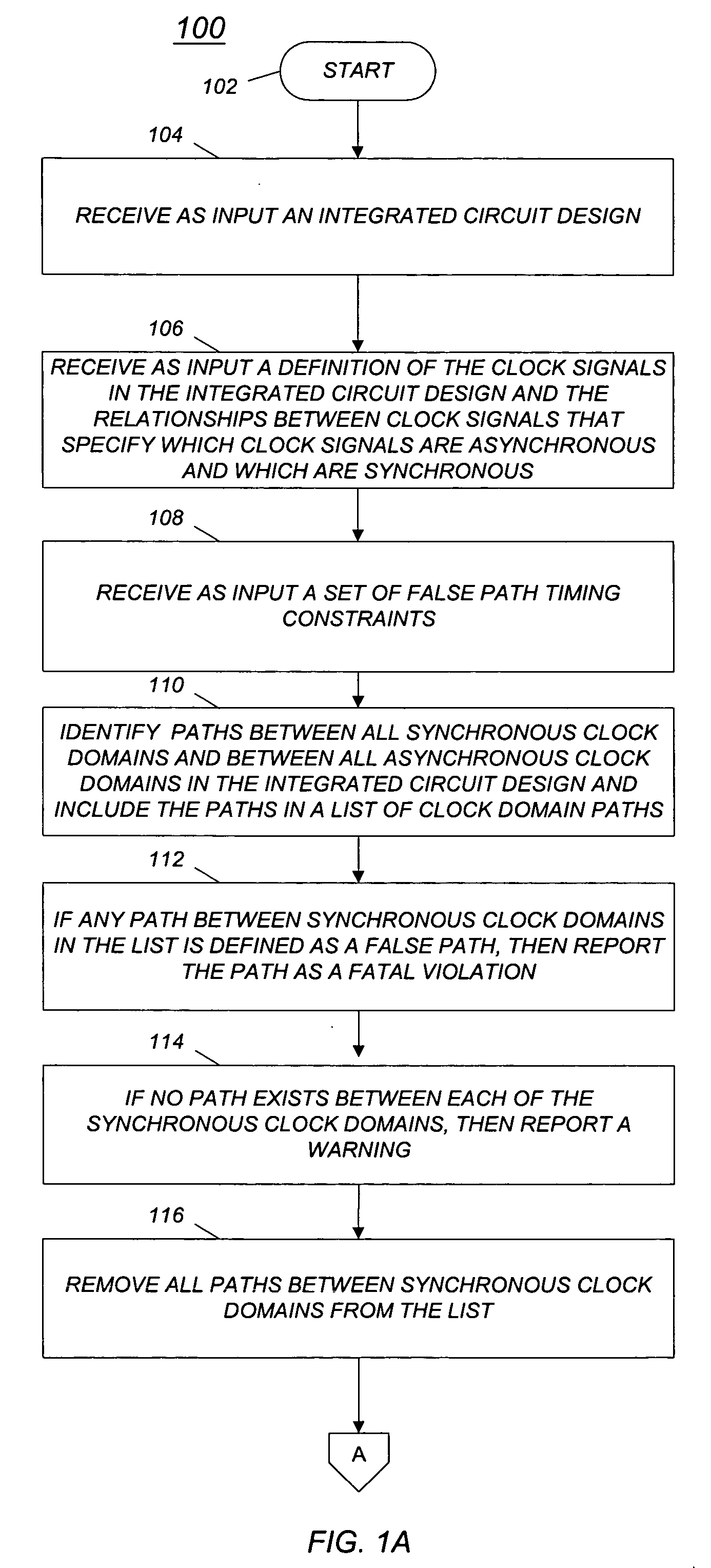
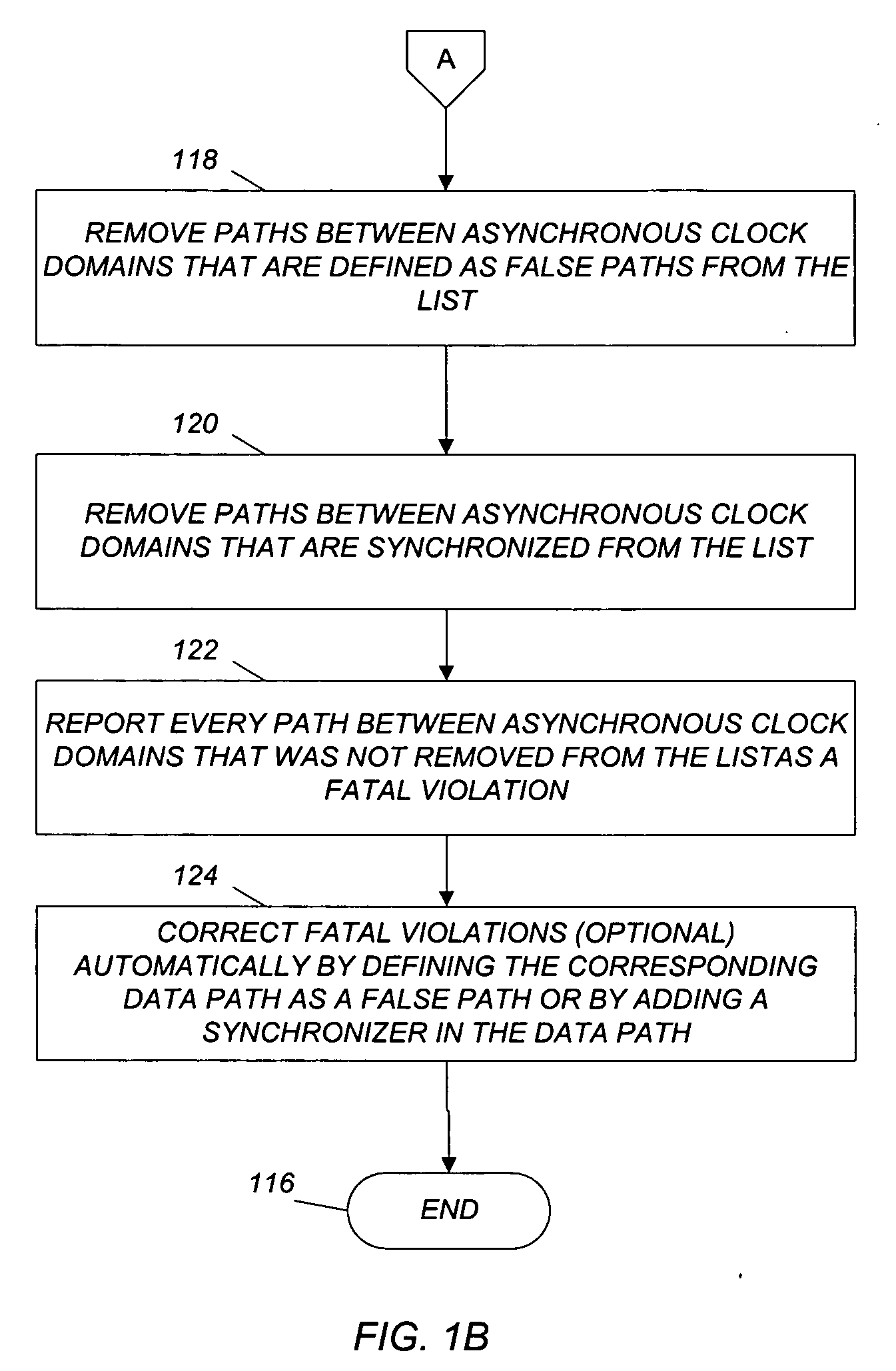
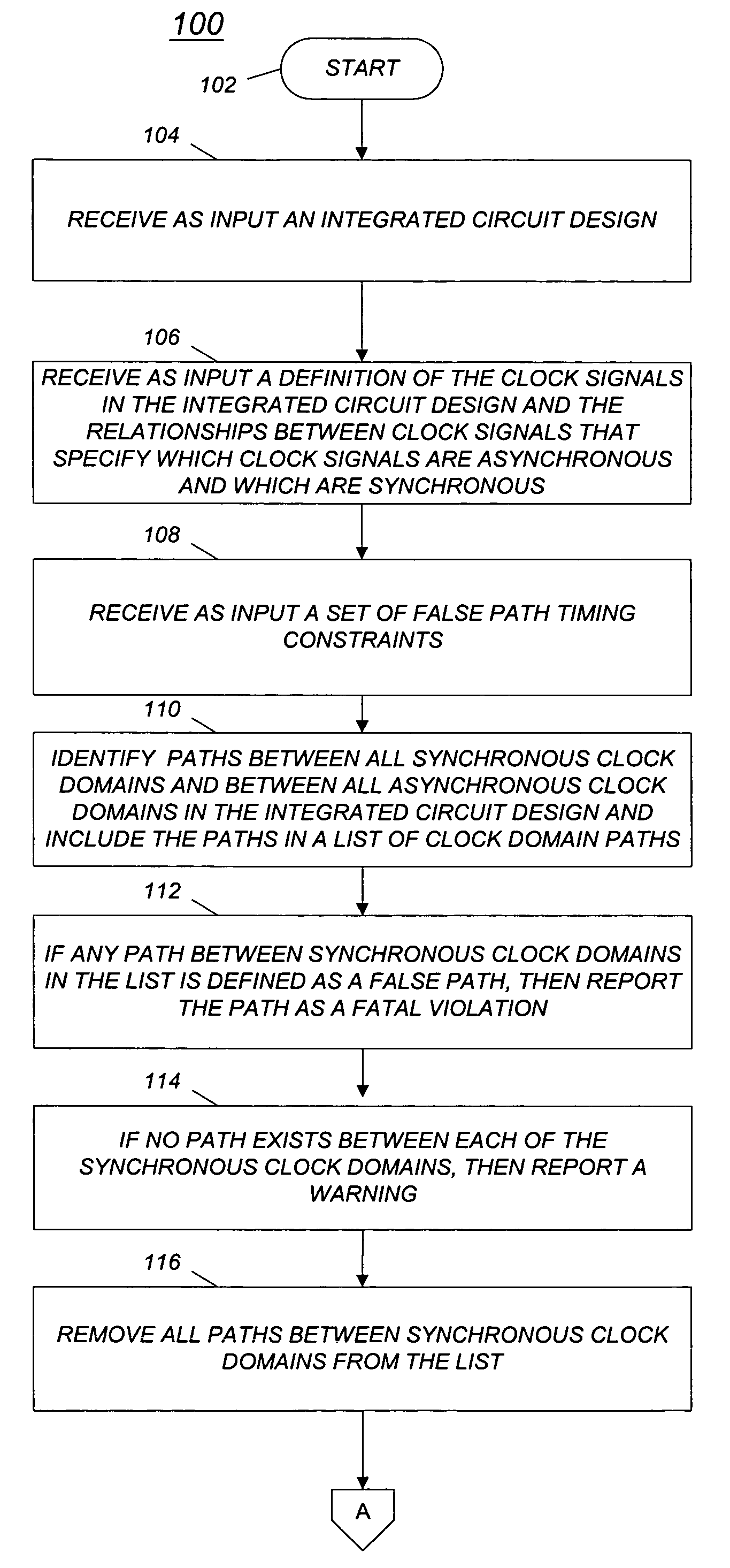
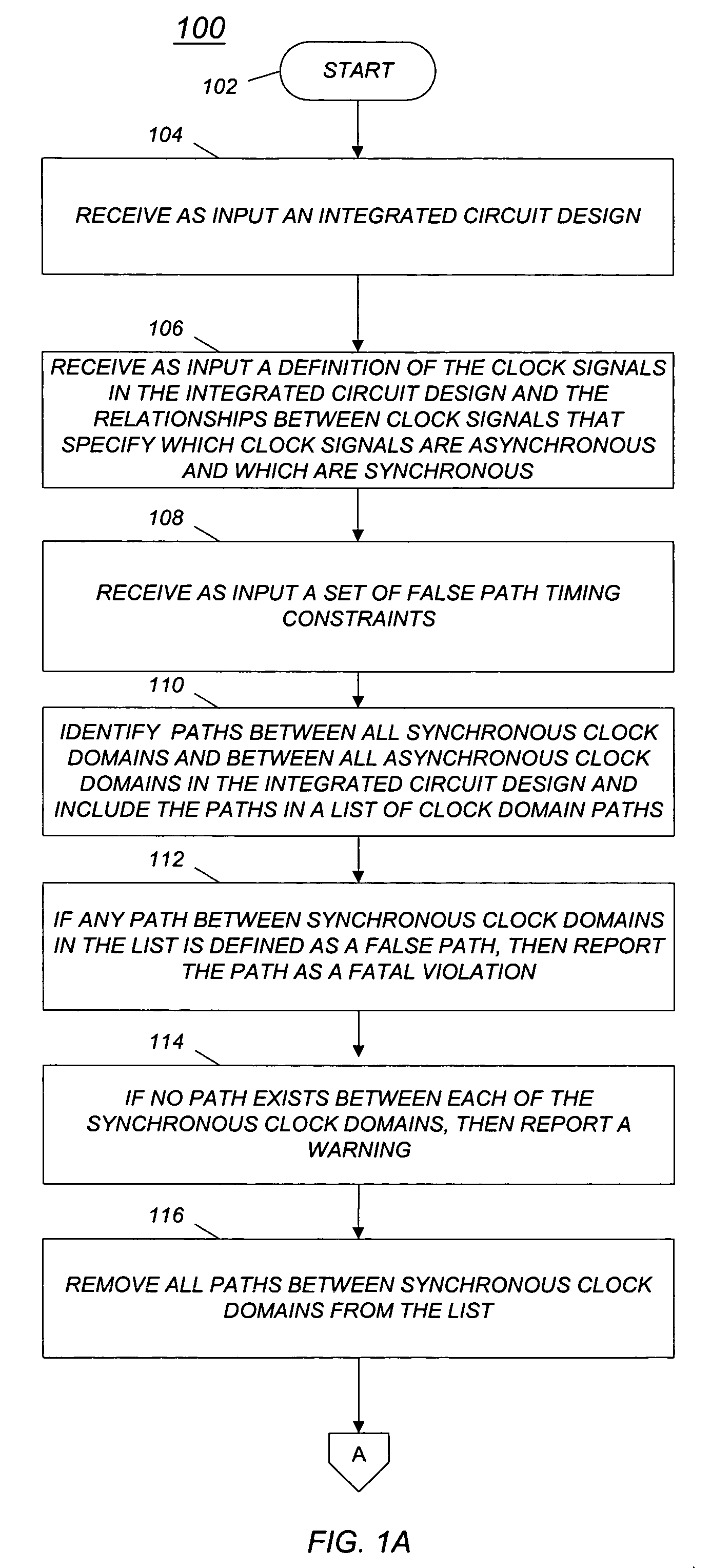
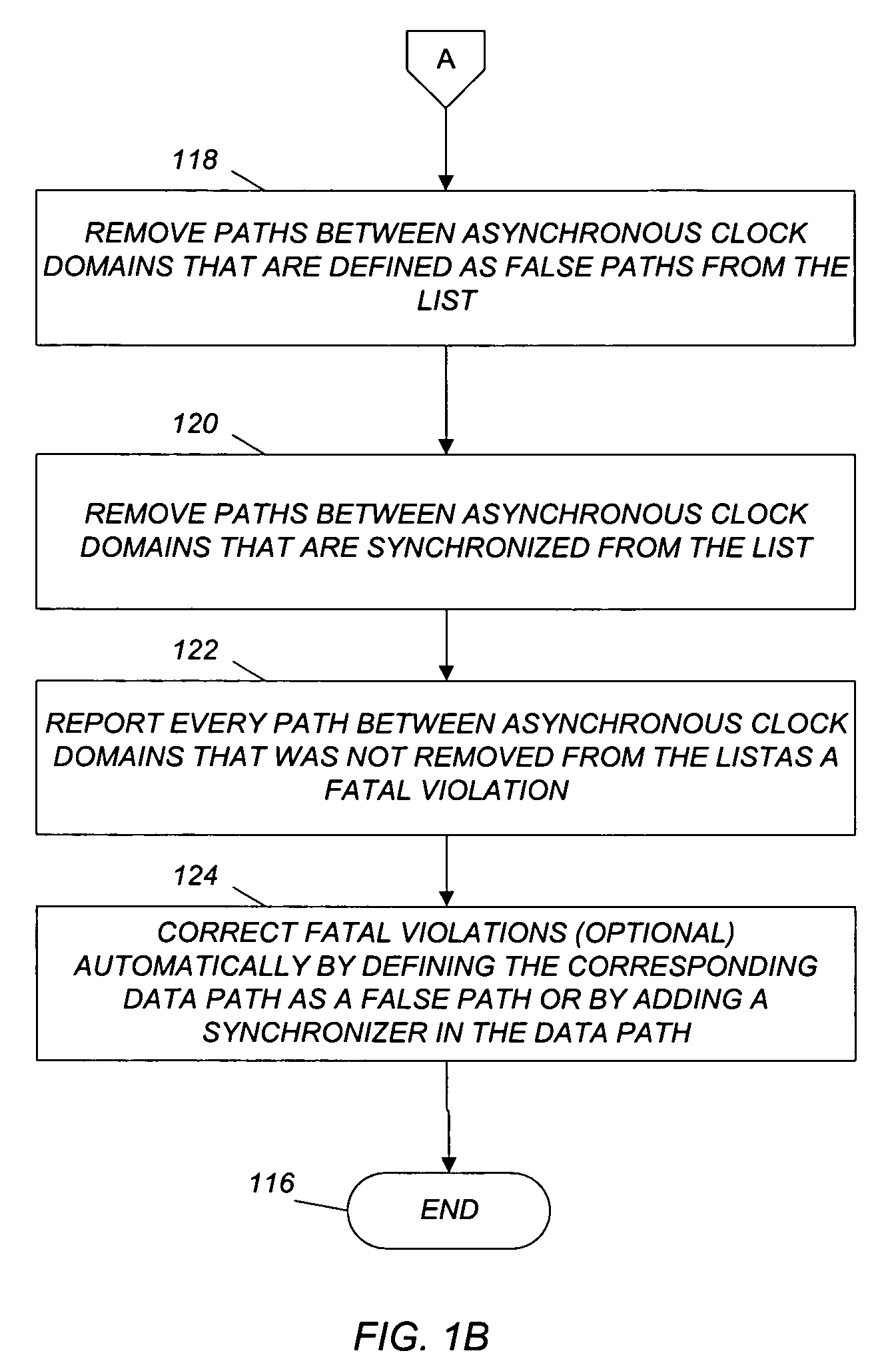
Method and computer program for management of synchronous and asynchronous clock domain crossing in integrated circuit design
A method and computer program are disclosed for managing synchronous and asynchronous clock domain crossings that include steps of: (a) receiving as input an integrated circuit design; (b) identifying paths between synchronous clock domains and paths between asynchronous clock domains in the integrated circuit design; and (c) if a path between synchronous clock domains is defined as a false path in the integrated circuit design, then reporting a fatal violation.
Owner:BELL SEMICON LLC
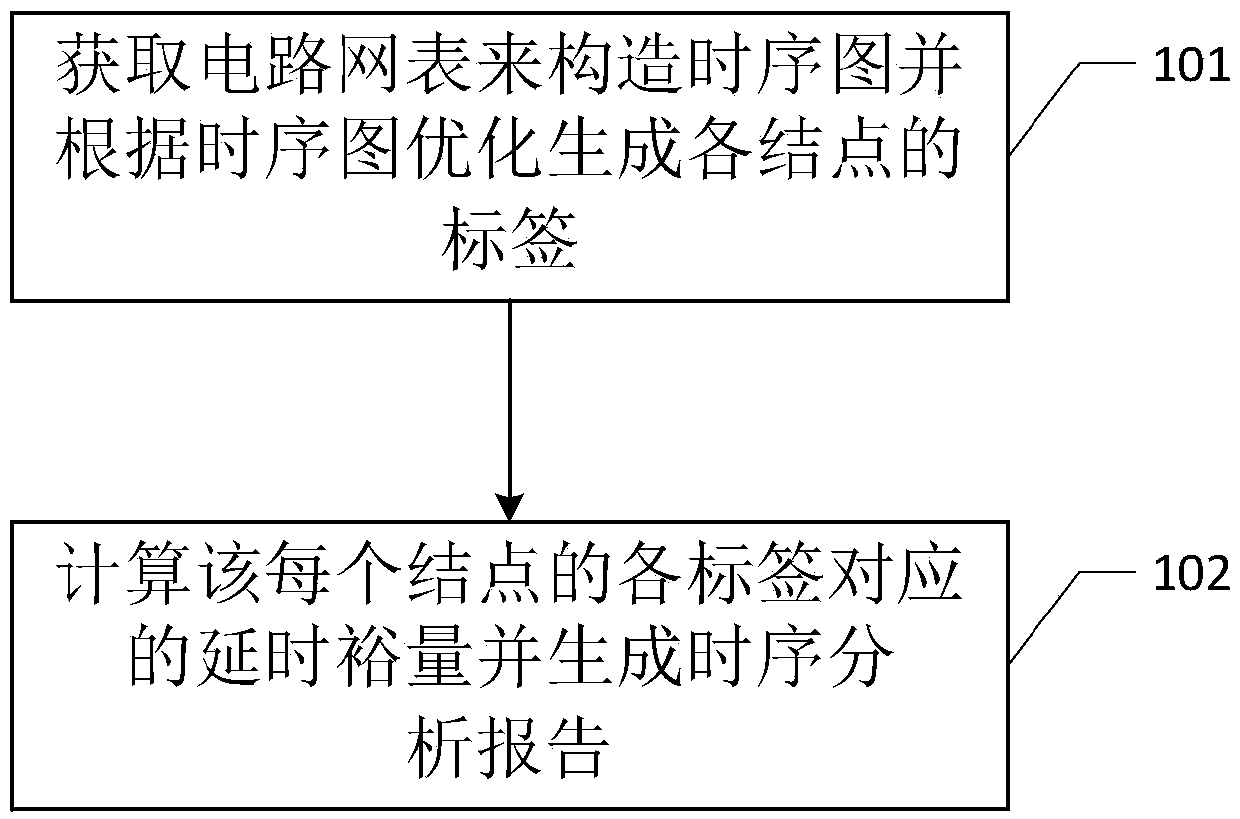
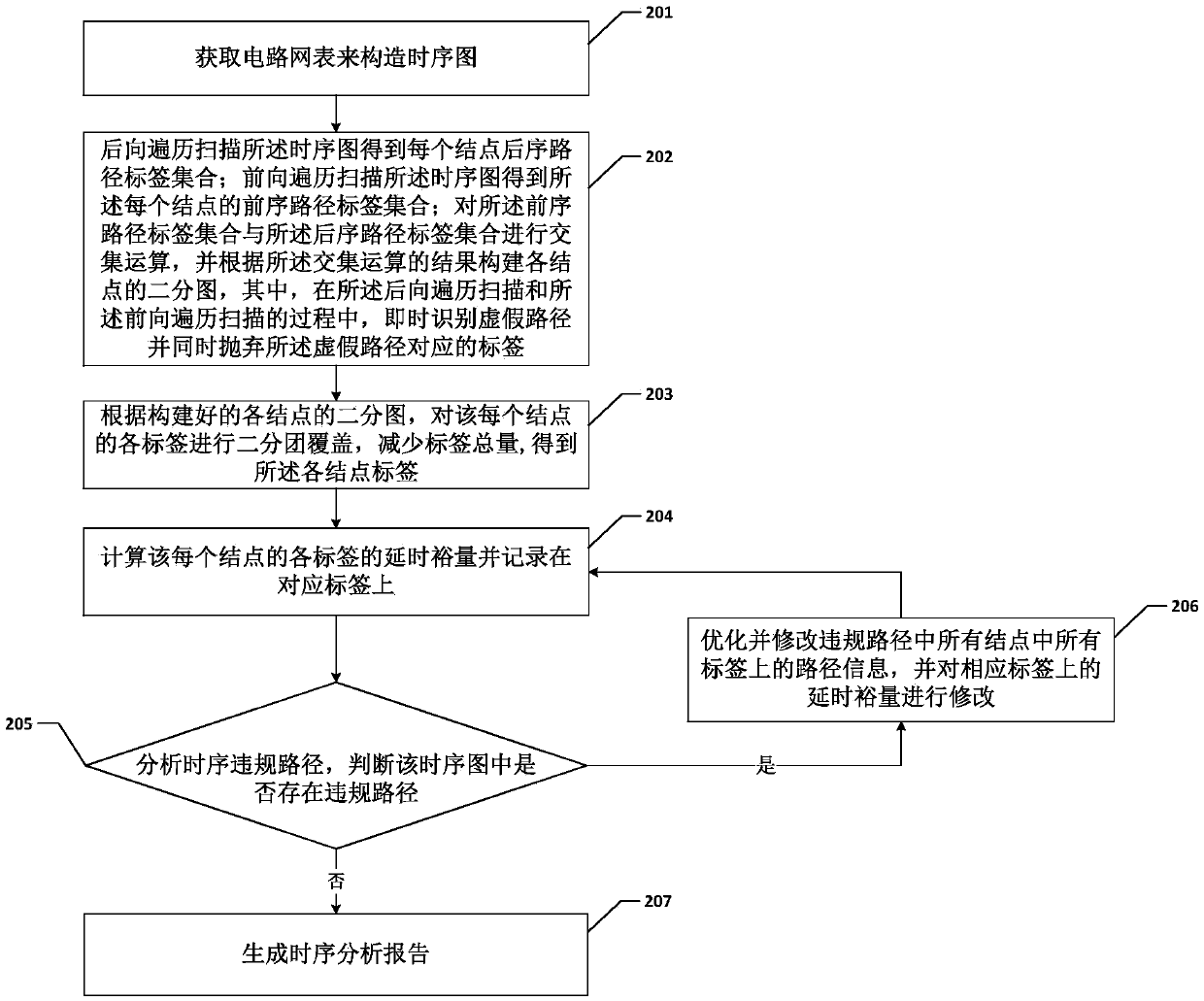
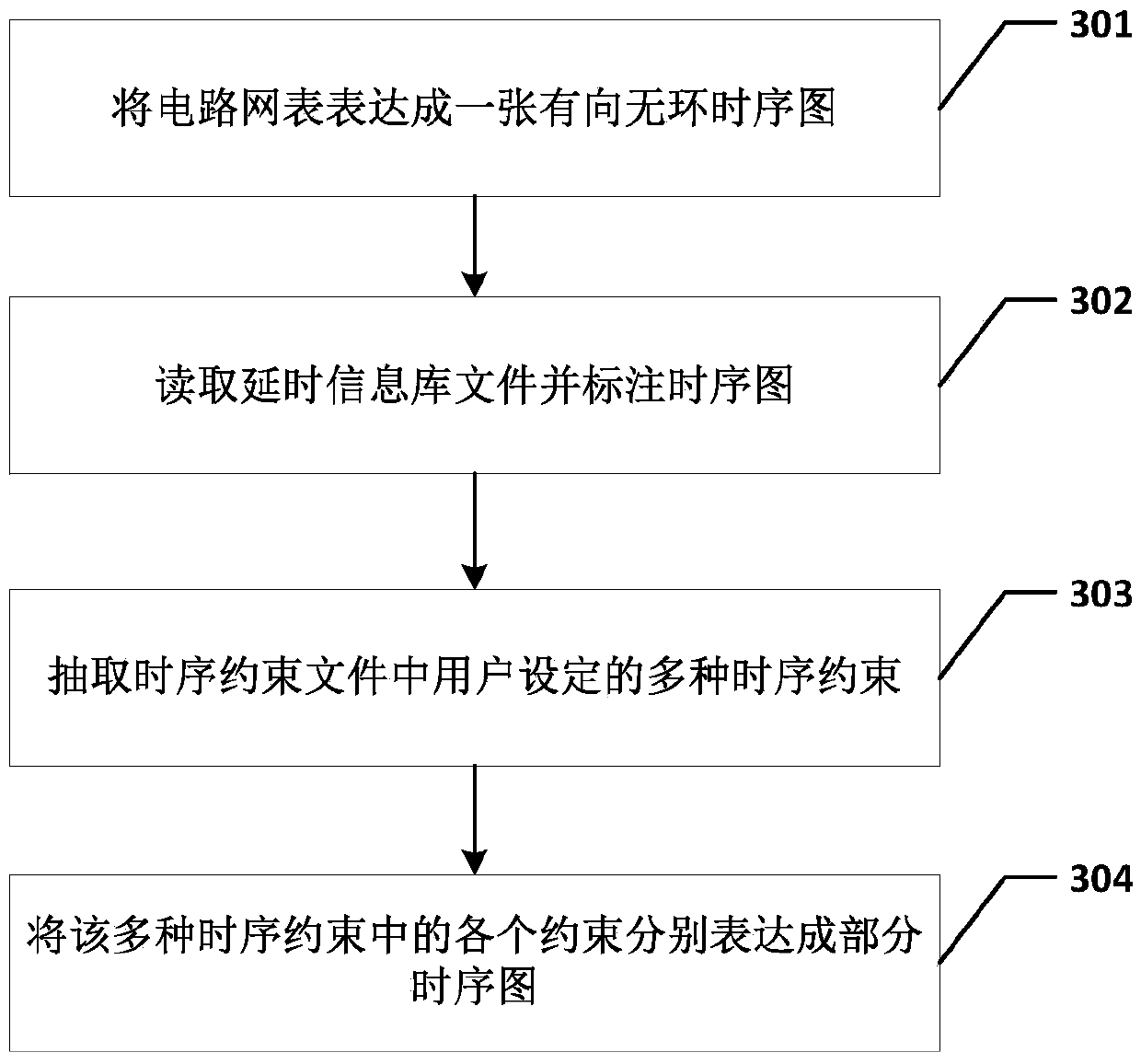
A memory optimization type static time sequence analysis method and system
ActiveCN109710998AIncrease space overheadReduced analysis efficiencySpecial data processing applicationsFalse pathAnalysis method
The invention relates to a digital circuit, and discloses a memory optimization type static time sequence analysis method and system. According to the method, on the premise that the subgraphs are notexpanded, in the traversing and scanning process, false paths are identified and discarded in real time, the influence of the false paths on downstream nodes is reduced, redundant calculation is reduced, meanwhile, multiple time sequence constraints on each node are dynamically and differentially processed in the traversing process, dichotomy coverage is correspondingly carried out, and the number of labels on each node is reduced. According to the application, occupation of system memory space can be greatly reduced, the system operation efficiency is improved, and the system performance isimproved.
Owner:SHANGHAI ANLOGIC INFOTECH CO LTD
Method for modeling and verifying timing exceptions
ActiveUS20080288904A1Computer aided designSoftware simulation/interpretation/emulationComputer architectureFalse path
A method and system for timing exception verification in integrated circuit (IC) designs included verification of functional false paths as well as multi-cycle paths (MCPs). A false path or a MCP is modeled to a satisfiability formula and the formula is validated using a Boolean satisfiability solver. Time required for timing exception verification can be significantly reduced.
Owner:SYNOPSYS INC
Method and computer program for management of synchronous and asynchronous clock domain crossing in integrated circuit design
A method and computer program are disclosed for managing synchronous and asynchronous clock domain crossings that include steps of: (a) receiving as input an integrated circuit design; (b) identifying paths between synchronous clock domains and paths between asynchronous clock domains in the integrated circuit design; and (c) if a path between synchronous clock domains is defined as a false path in the integrated circuit design, then reporting a fatal violation.
Owner:BELL SEMICON LLC
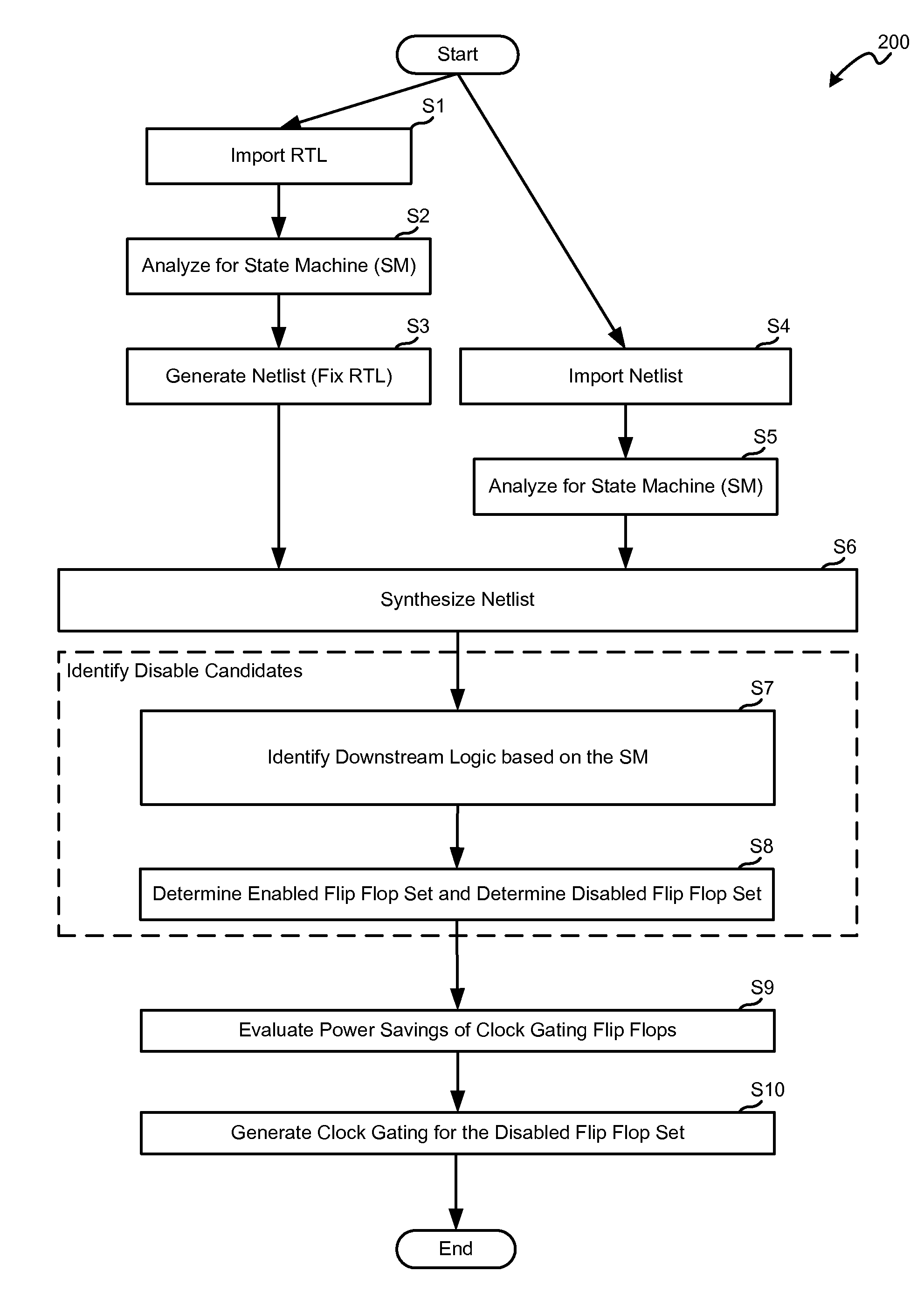
Method for multi-cycle path and false path clock gating
ActiveUS7958476B1Reduce Switching Power ConsumptionConsumes less powerVolume/mass flow measurementPower supply for data processingEngineeringFalse path
A power optimization method of deriving gated circuitry in an integrated circuit (IC) is provided. A design description of the IC is received and analyzed. A state machine is identified based on the analysis. One or more candidate blocks are determined to be capable of being disabled. At least one of the candidate blocks is selected based on one or more states of the state machine. A gating circuit is inserted for gating the selected candidate block(s). In another embodiment of power optimization, one or more state machines are identified and a synthesized netlist is generated. One or more candidate blocks in the synthesized netlist are determined to be capable of being disabled. At least one of the candidate blocks is selected based on one or more states in the state machine, and a gating circuit is inserted for gating the selected candidate block(s).
Owner:SYNOPSYS INC
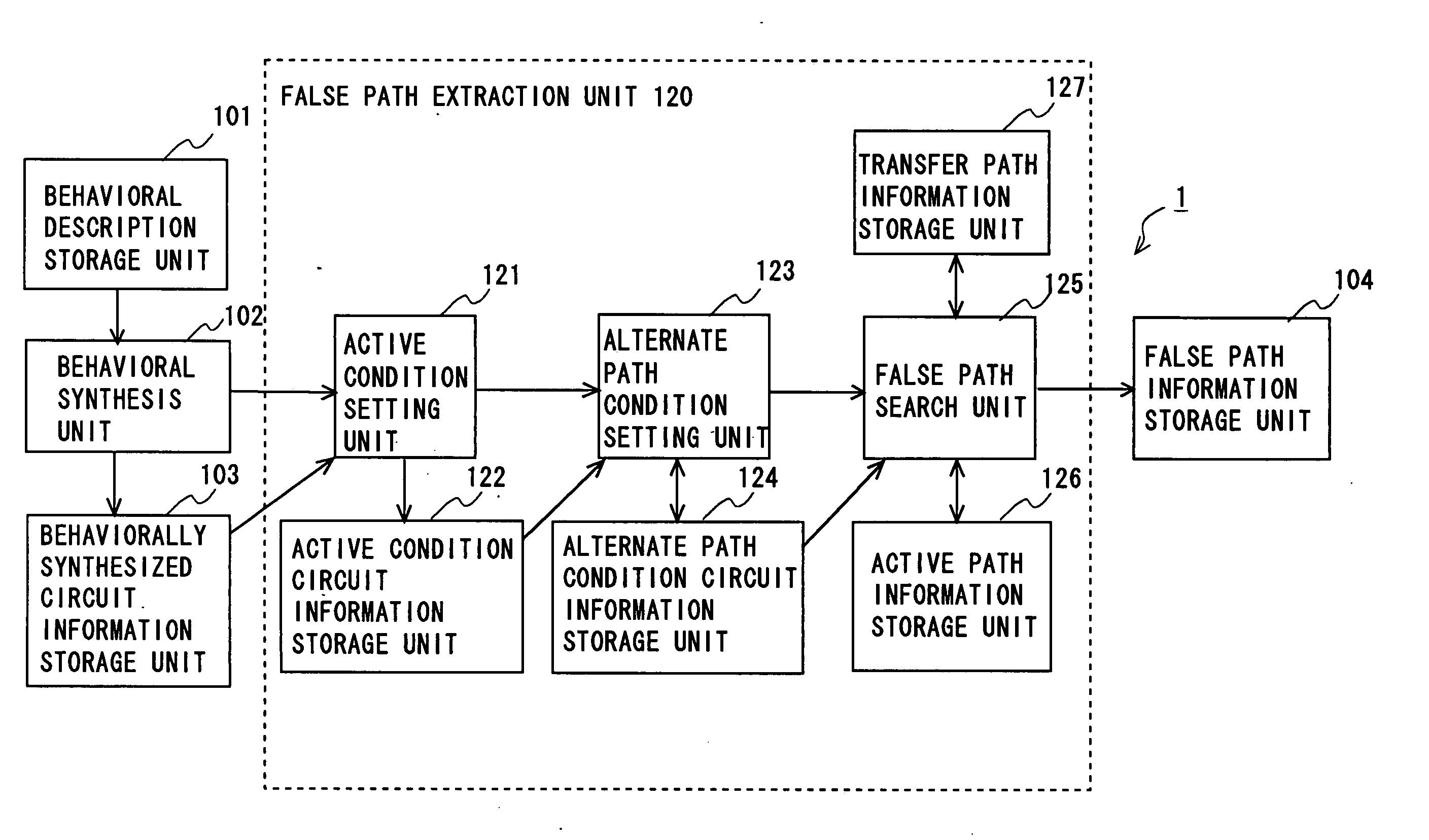
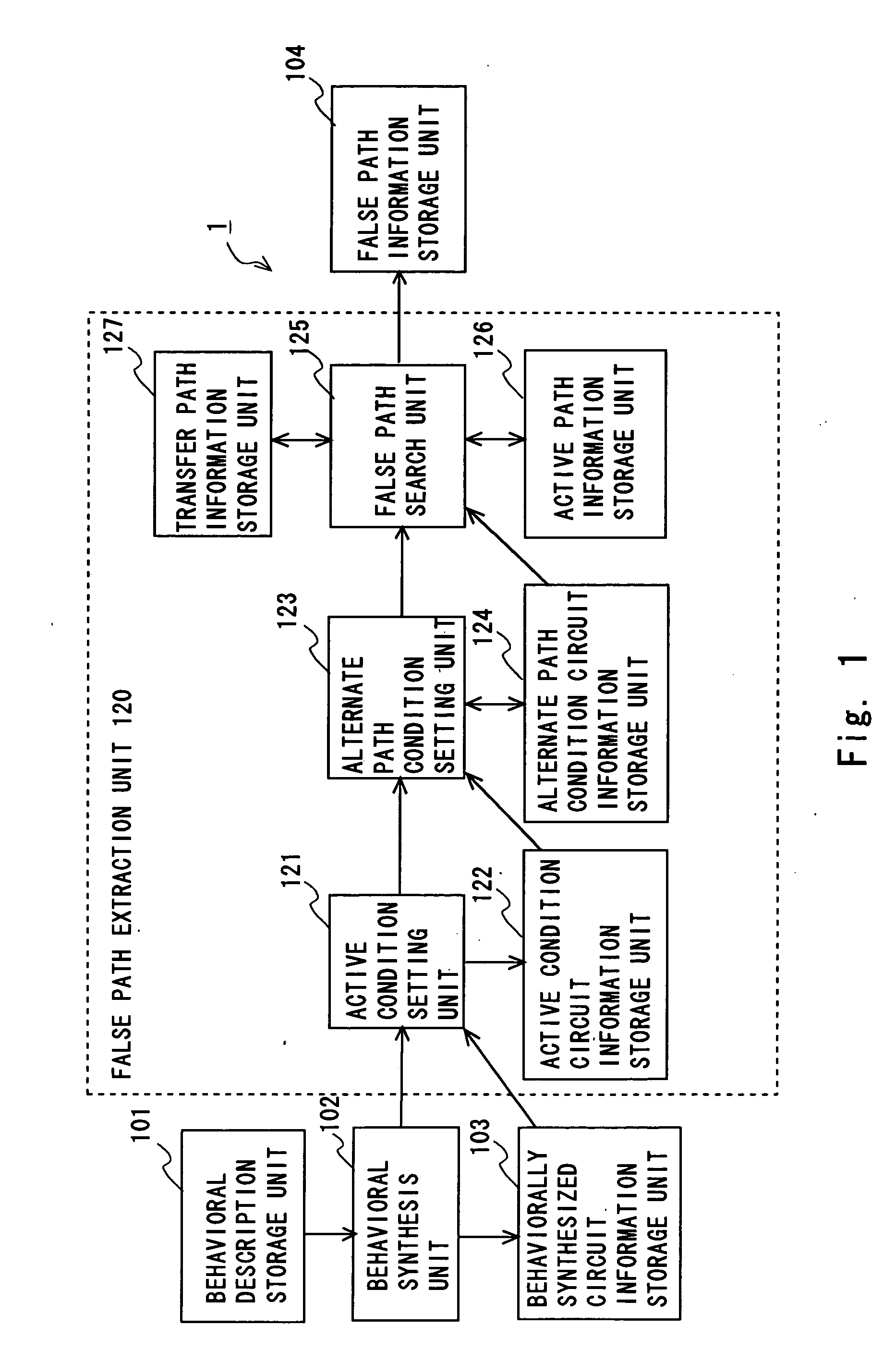
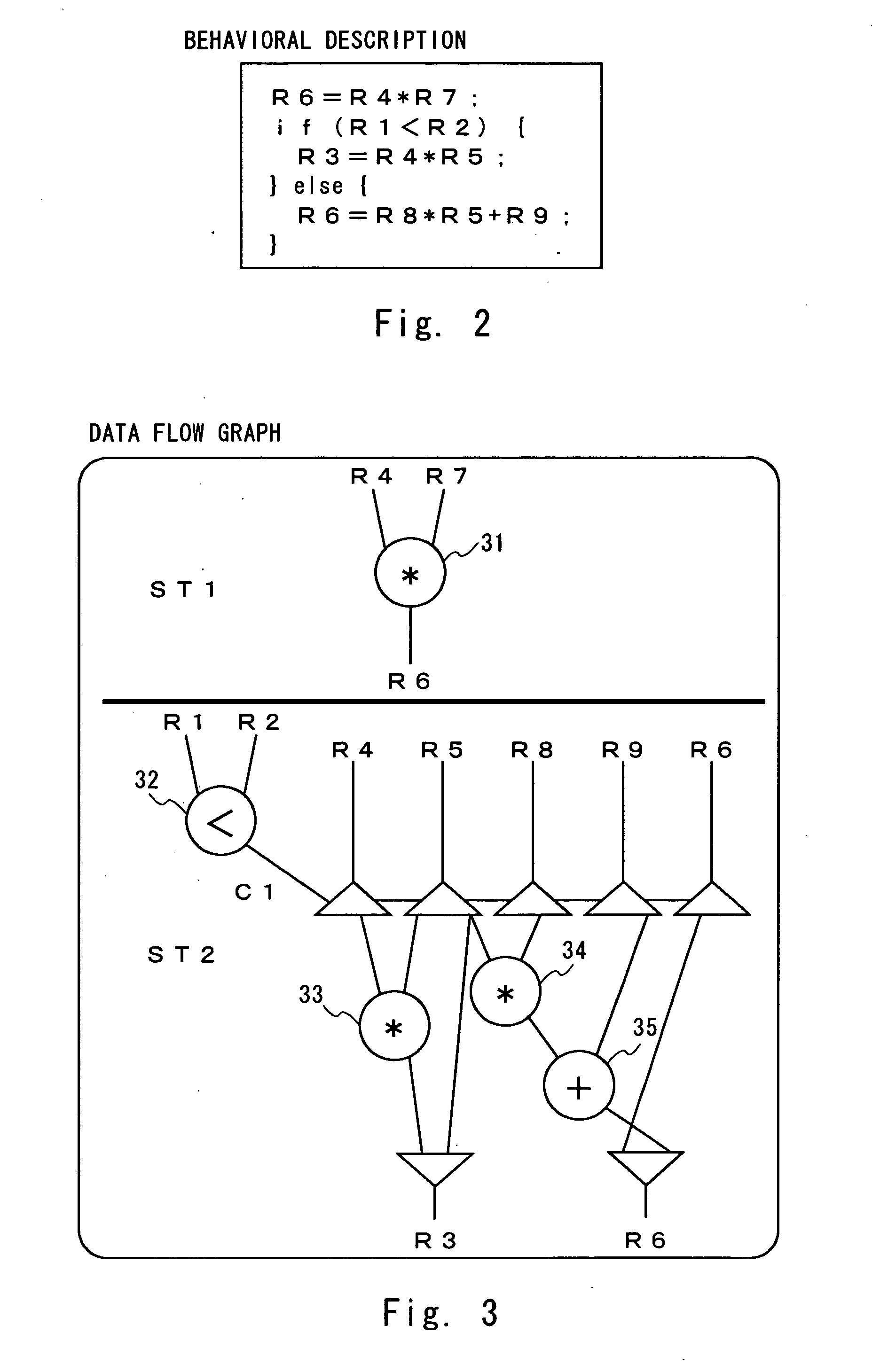
Circuit design assistant system, circuit design method, and program product for circuit design
InactiveUS20050223345A1Accurate detectionGenerate accuratelyCAD circuit designSoftware simulation/interpretation/emulationFalse pathDatapath
The computer program product according to an embodiment of the invention causes a computer to execute the process including acquiring circuit information generated by behavioral synthesis, determining an active condition of a net, determining an active condition of an alternate path, determining an active condition of an alternate data path, determining an active condition of each path, and detecting a false path.
Owner:NEC ELECTRONIS CORP
Delay distribution calculation method, circuit evaluation method and false path extraction method
InactiveUS7131082B2Delayed correctionAccurate calculationProgramme controlComputer controlRelevant informationFalse path
Delay distribution in an integrated circuit is calculated while taking into account a correlation of performance between interconnects or elements in the integrated circuit, thereby improving estimation accuracy. Circuit information, performance distribution information of the interconnects or elements in the integrated circuit, and correlation information of performance between the interconnects or elements are input. A vertex is selected for calculation, and a correlation between delay distribution at the selected vertex and delay distribution in a partial circuit including the selected vertex is calculated based on the performance distribution information and the correlation information.
Owner:SOCIONEXT INC
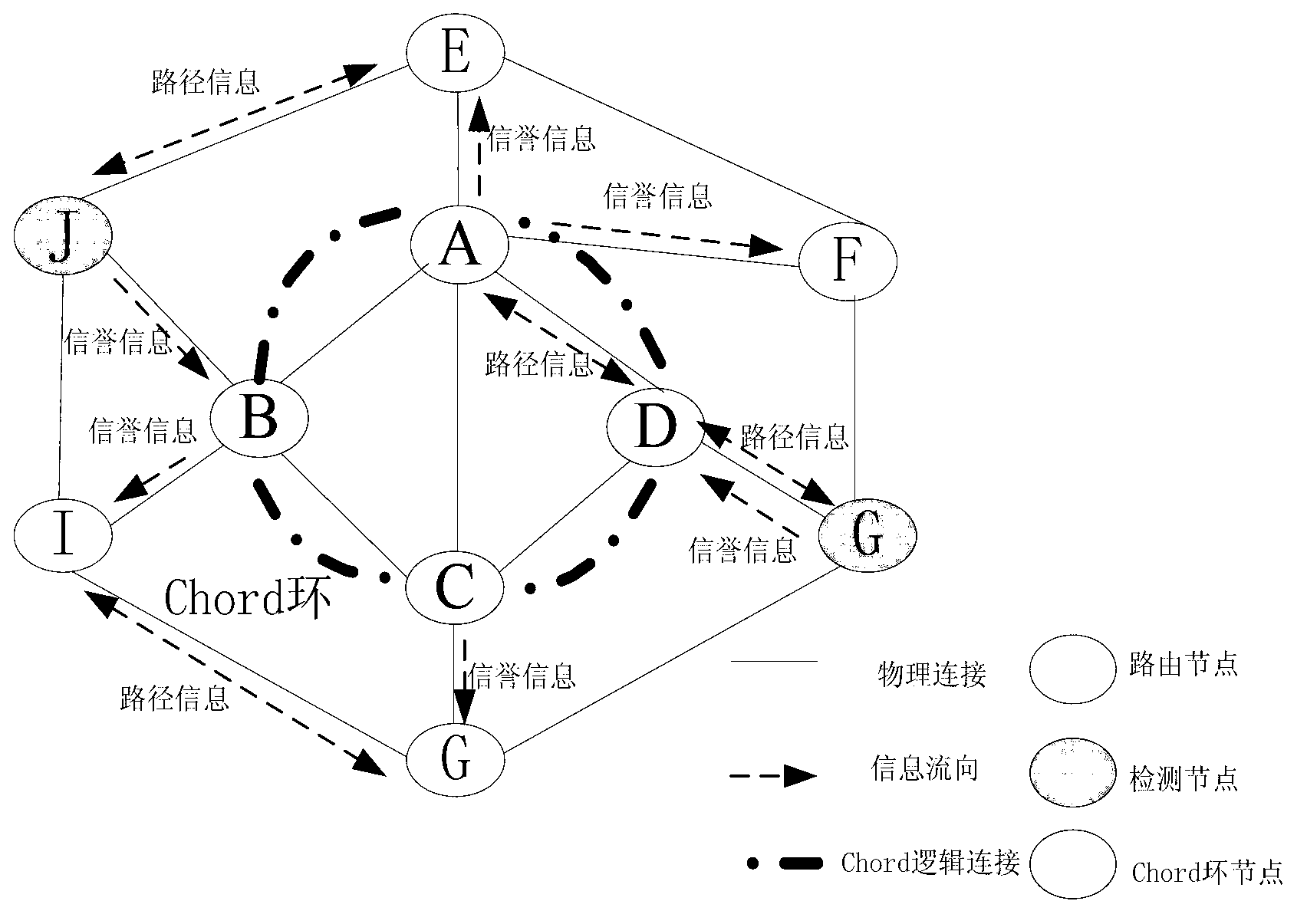
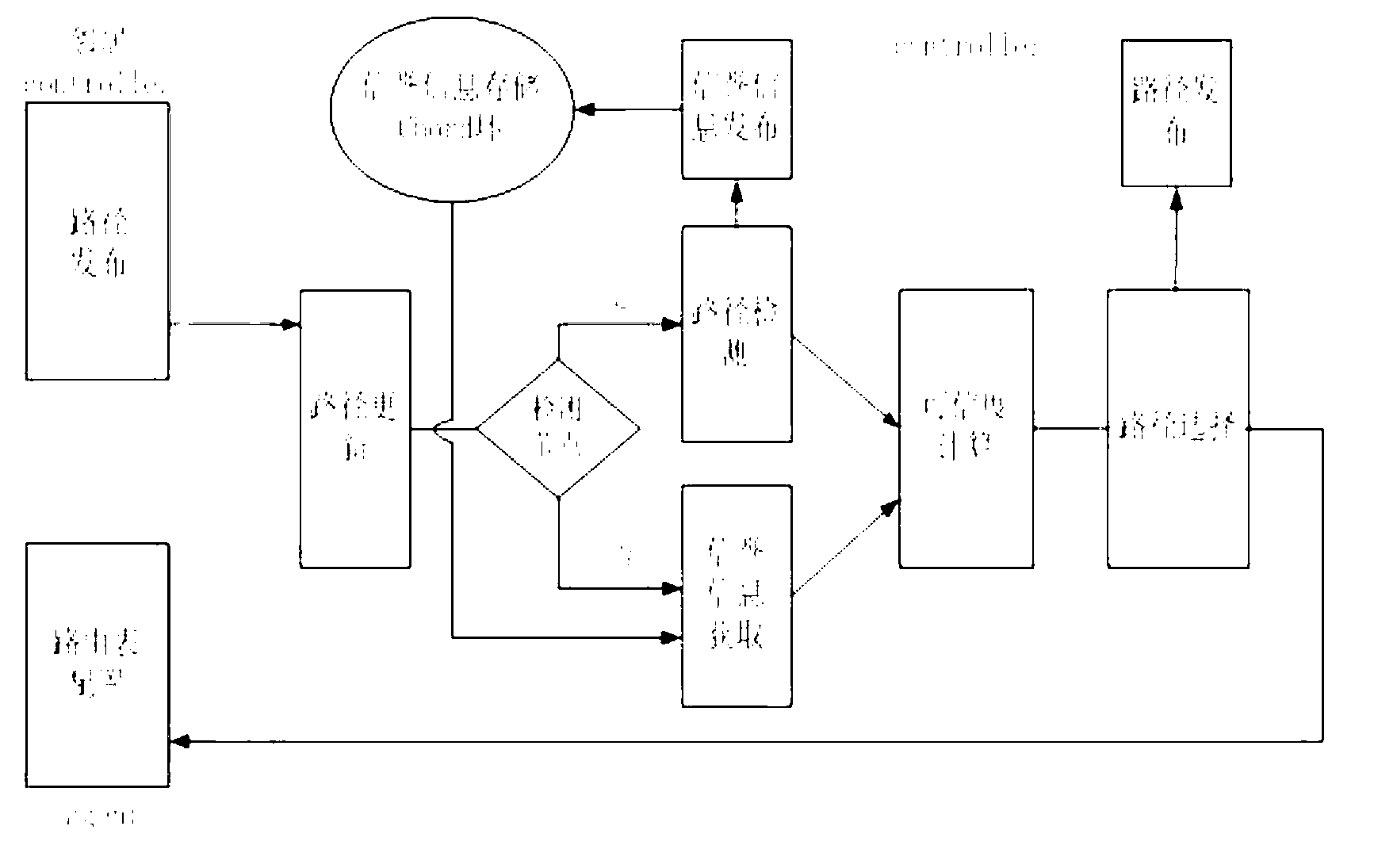
Credible inter-domain route selection method
InactiveCN103200103AIncrease credibilityImprove good performanceData switching networksRouting decisionNODAL
The invention discloses a credible inter-domain route selection method. According to the credible inter-domain route selection method, false path detection is carried out by a partial detection node, the credibility of nodes in a network is calculated according to detection results, and the credibility is released to an inter-domain chord ring after the calculation is completed; and when other nodes which are not subjected to false path detection mechanism deployment are subjected to route selection, the credibility of nodes on candidate paths is obtained from the chord ring, the credibility of the paths is calculated, and finally, true and credible paths are selected for release. The method comprises the steps of: (1) selecting credible information sources when the false path detection is carried out by the partial detection node; and (2) selecting partial nodes from the Internet so as to construct the chord ring. According to the credible inter-domain route selection method, a credibility mechanism is introduced into inter-domain route decision, inter-domain route information is subjected to credibility evaluation, and the true and credible paths are selected for release.
Owner:SOUTHEAST UNIV
Method and device for extracting false paths in gate-level network lists, and terminal equipment
ActiveCN107784185AQuick extractionImprove the efficiency of research and developmentSpecial data processing applicationsFalse pathPhases of clinical research
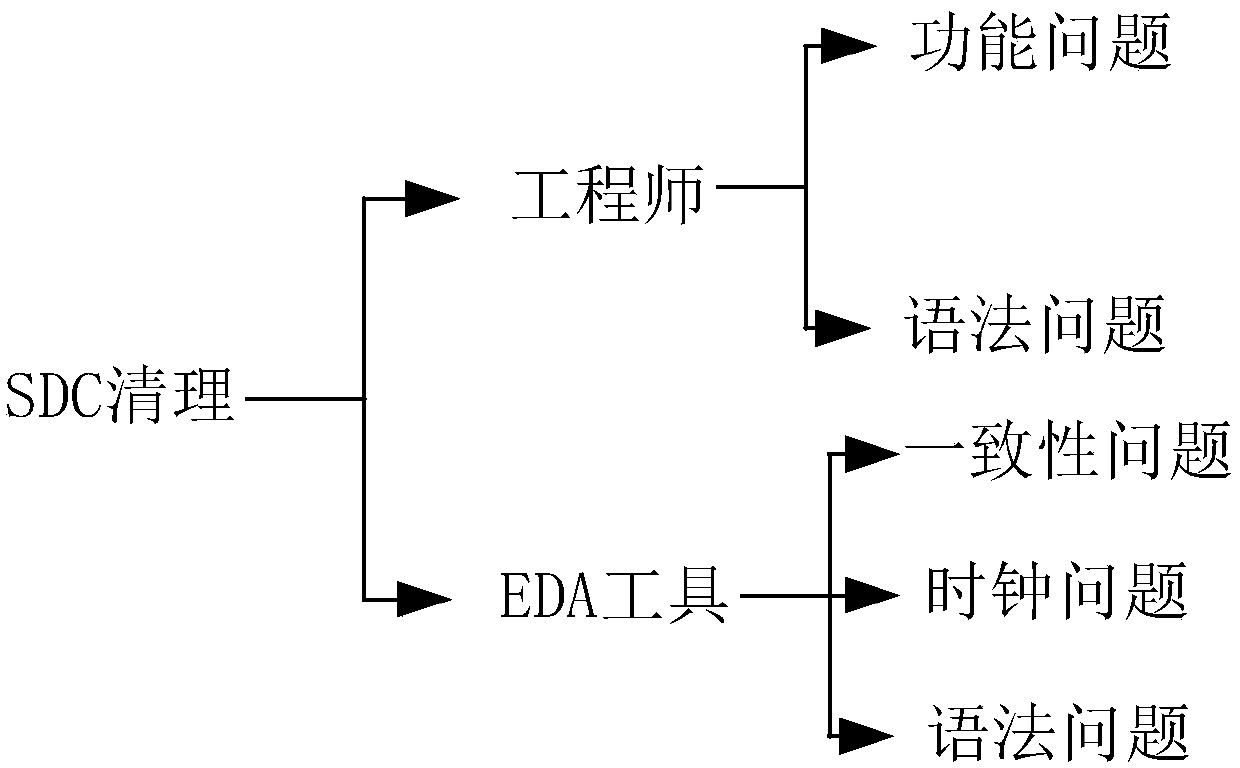
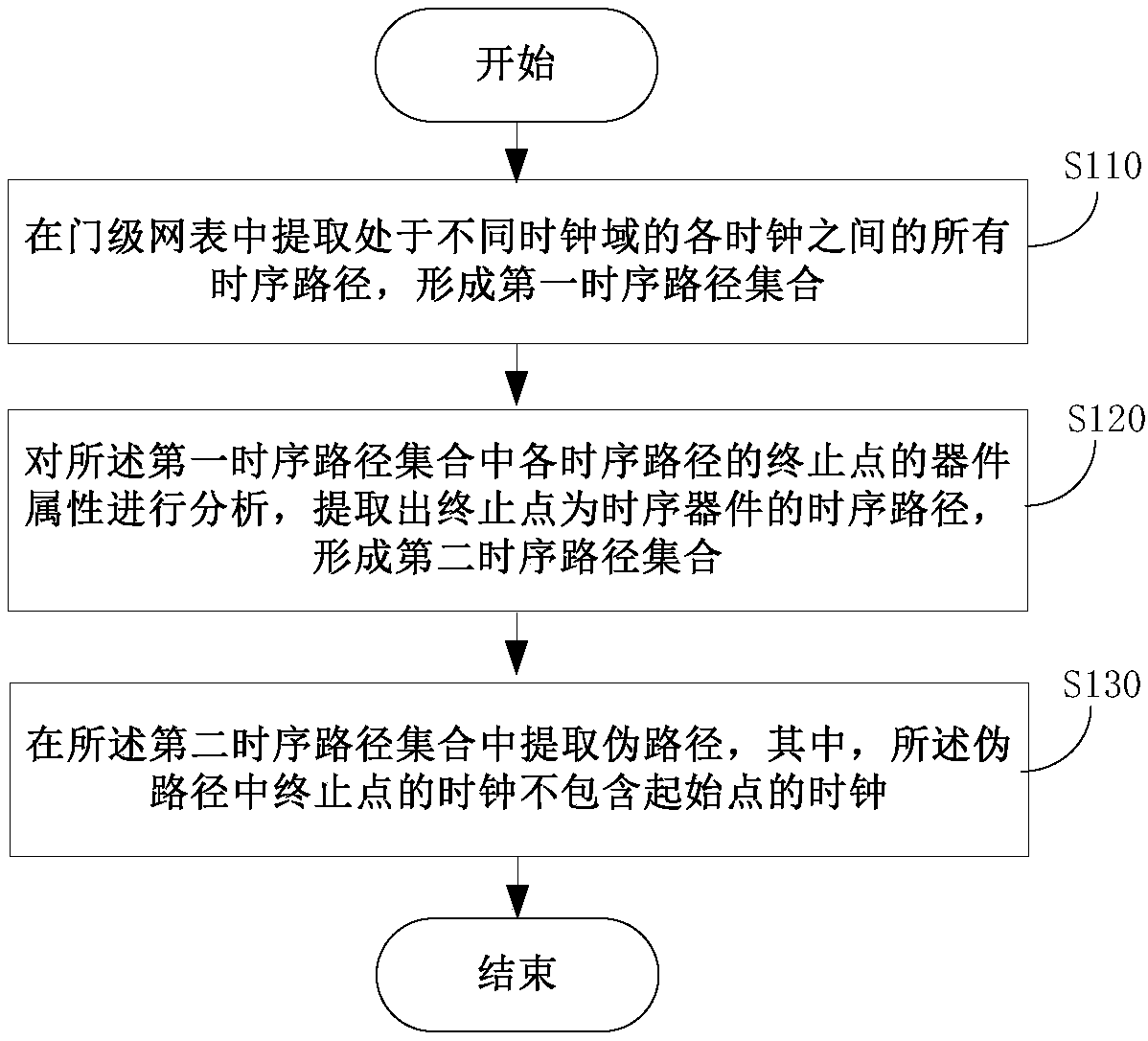
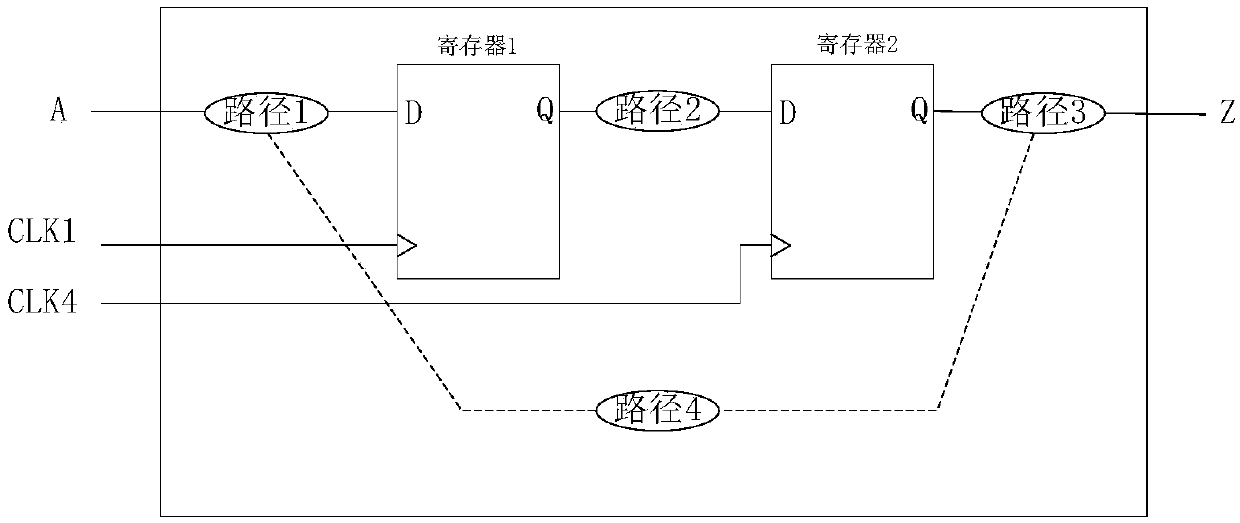
The invention discloses a method and a device for extracting false paths in gate-level network lists, and terminal equipment. The method includes extracting all time sequence paths positioned among various clocks of different clock domains from the gate-level network lists; sorting and filtering the extracted time sequence paths according to screening conditions to obtain the false paths in the gate-level network lists. The screening conditions include that termination points of paths are time sequence devices, and clocks of the termination points do not include clocks of start points. The method, the device and the terminal equipment have the advantages that the false paths in the gate-level network lists can be quickly extracted by the aid of the method, accordingly, inspection and simulation verification can be carried out on the extracted false paths in SDC (Synopsys design constraint) cleaning phases, deficiency of SOC (system on a chip) designs can be checked, problems of the SOCdesigns further can be discovered at early phases, and the chip development efficiency can be greatly improved.
Owner:HISENSE VISUAL TECH CO LTD
Multi-phase models for timing closure of integrated circuit designs
ActiveUS9152742B1Computer aided designSoftware simulation/interpretation/emulationTiming closureHierarchical design
In one embodiment, a method of designing an integrated circuit is disclosed, including receiving a first partition block for a top level of a hierarchical design of an integrated circuit; analyzing each pin of the first partition block for an attribute associated with the pin indicating a timing exception; and if a timing exception other than false path is indicated then generating an internal timing pin in a first timing graph model of the first partition block for each timing exception, and adding a timing arc and a dummy arc coupled to the internal timing pin in the first timing graph model of the first partition block. The internal timing pin adds a timing exception constraint for each timing exception. Timing of the top level may then be analyzed with the first timing graph model to determine if timing constraints, including the added timing exception constraints, are met.
Owner:CADENCE DESIGN SYST INC
Methods for selectively pruning false paths in graphs that use high-precision state information
Methods are provided that allow a false path pruner to traverse a directed acyclic graph in conjunction with one or more checker programs that are analyzing a program for defects or other artifacts of interest. While the checkers may have ways of avoiding re-traversal of portions of the graph that have already been traversed, the false path pruner may override such decisions made by the checkers as a result of a false path in order to allow re-traversal during a future different traversal when that same defect or artifact may not lie along a false path, and therefore avoid missing a valid defect or artifact. Computer programs stored on tangible media are provided that implement the methods of the invention.
Owner:SOFTWARE INTEGRITY GRP INC
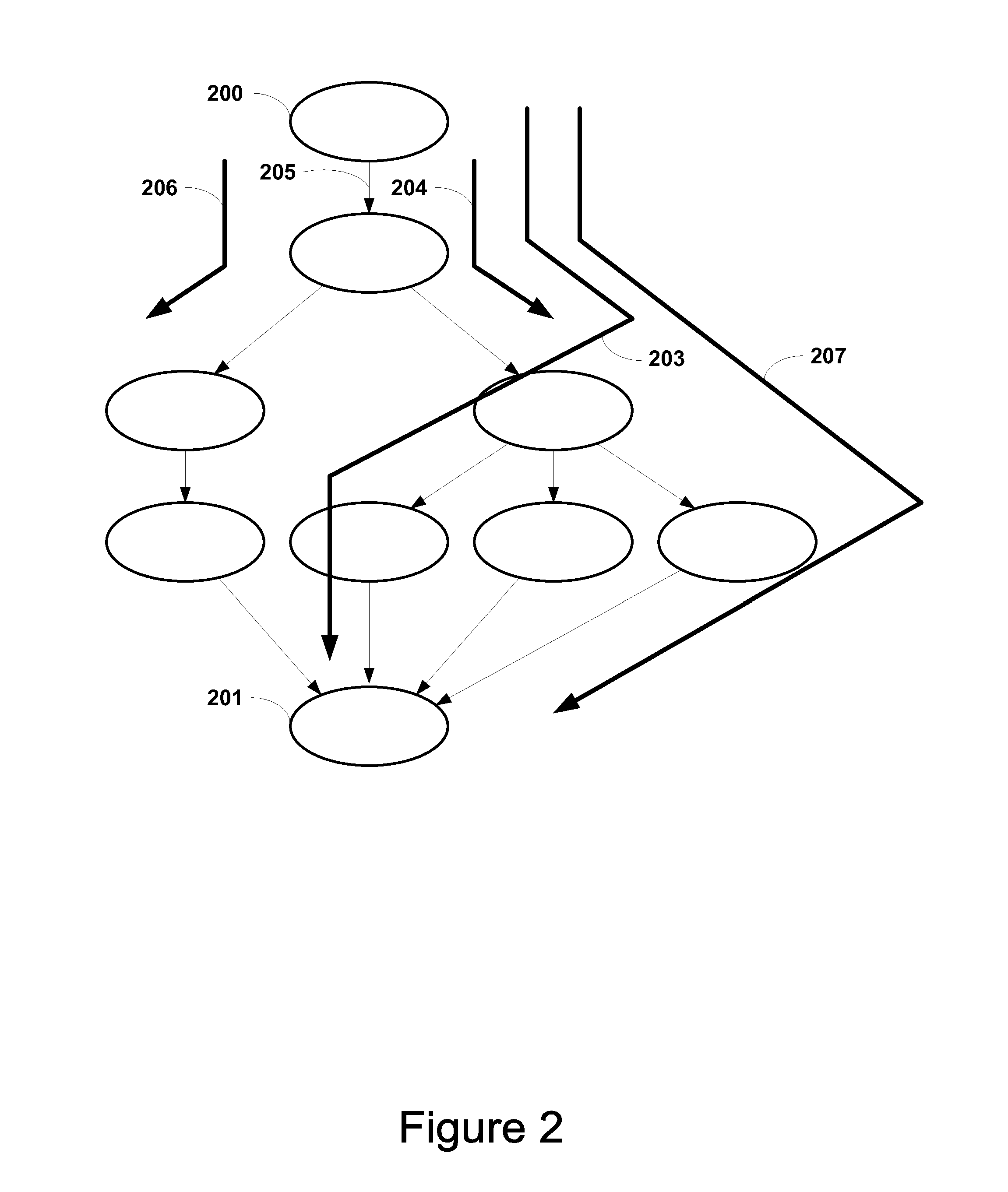
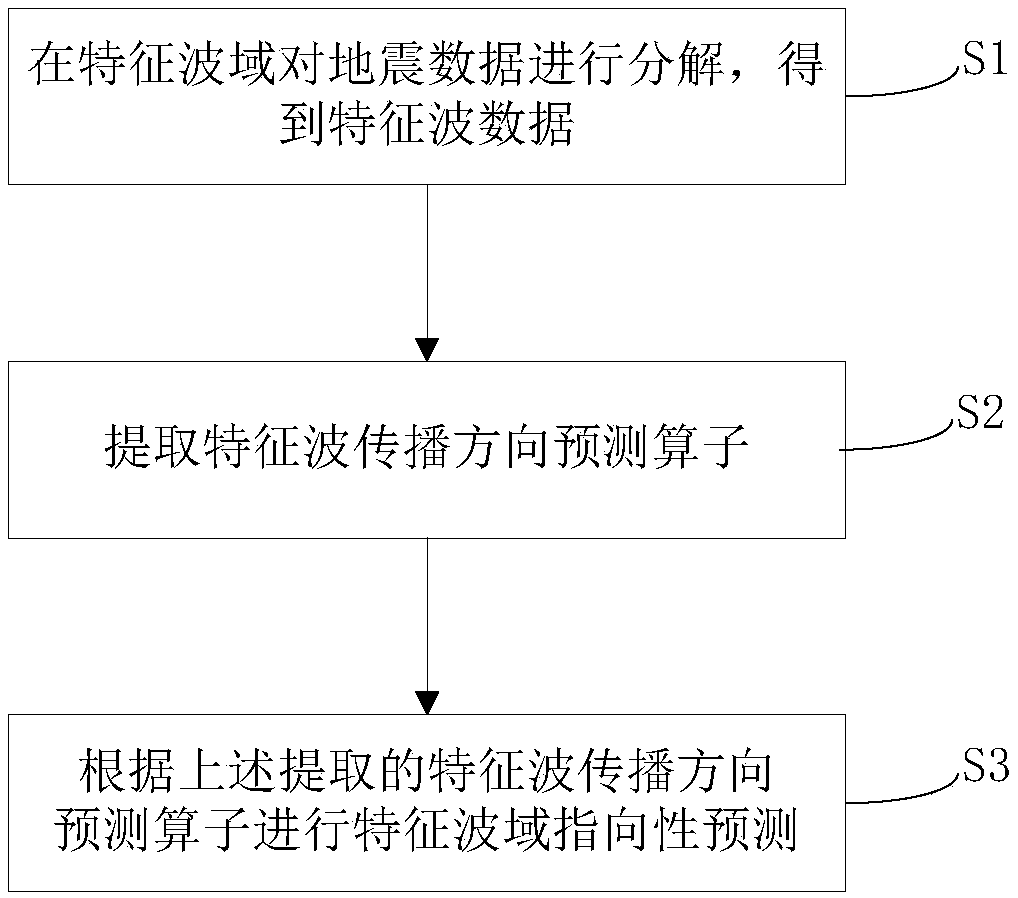
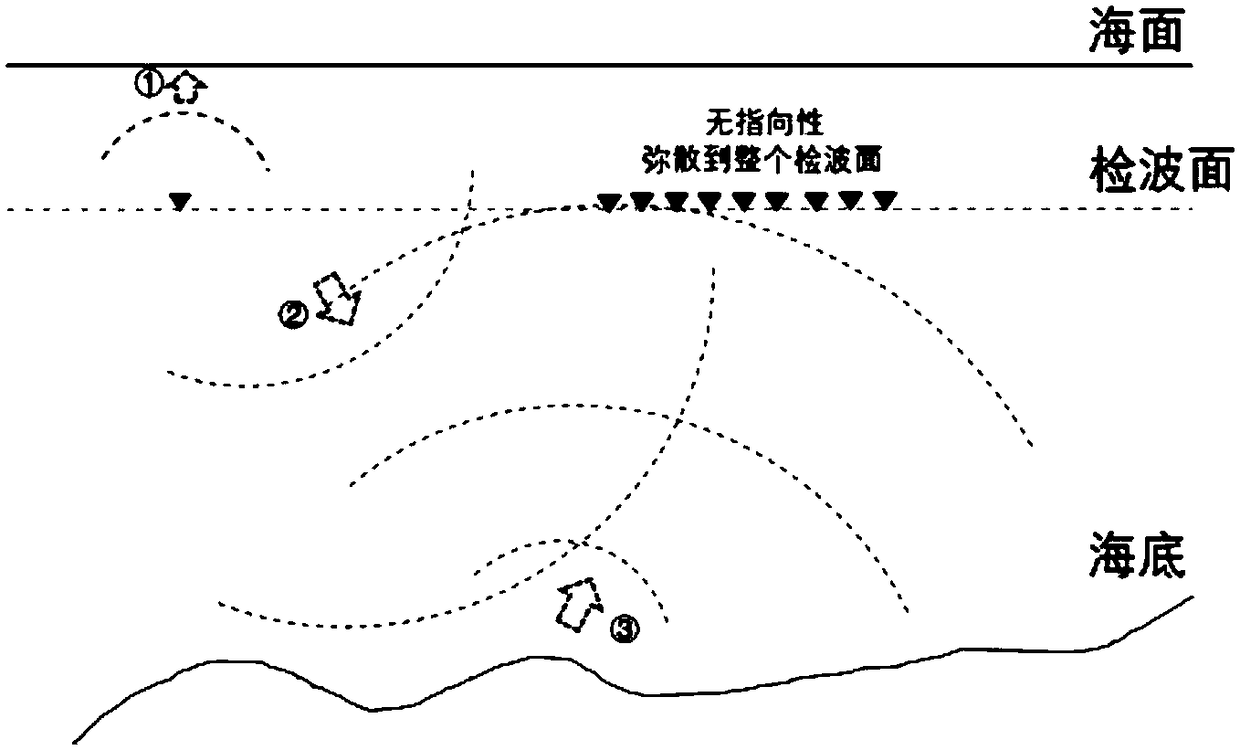
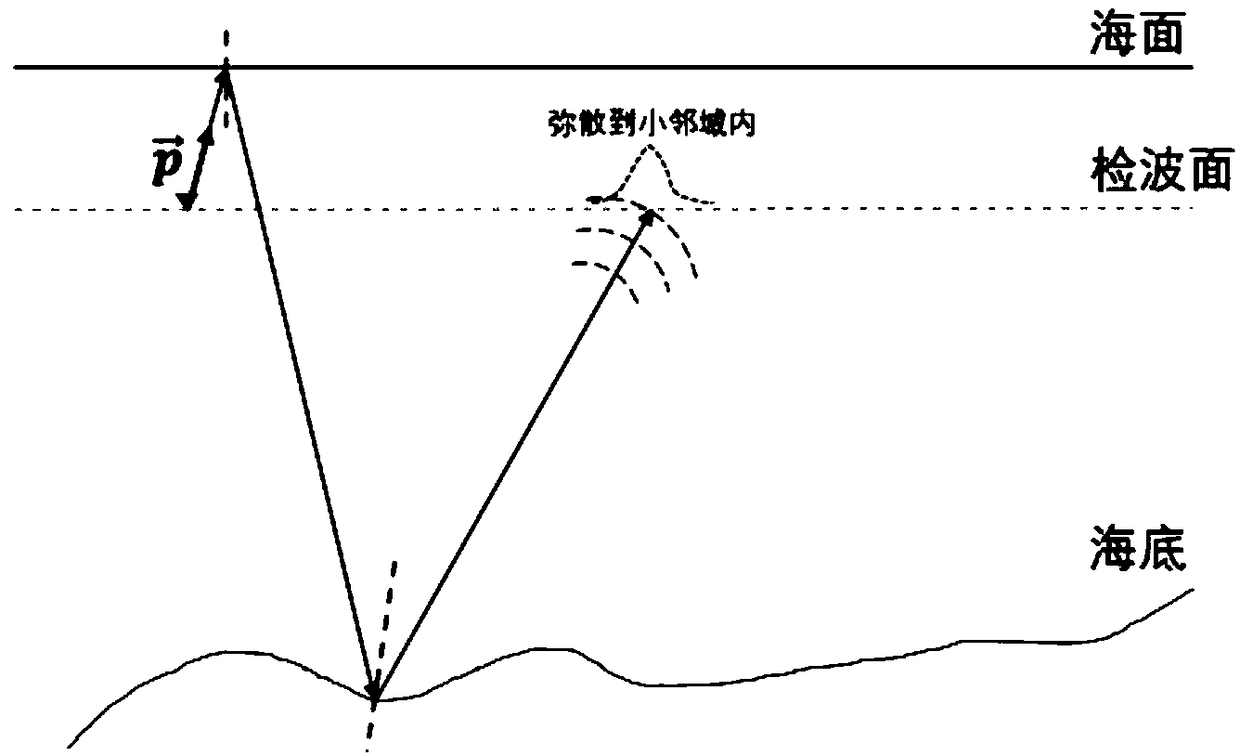
Shallow water multi-wave model directivity prediction method of characteristic wave domain,
ActiveCN109239772AReduce distractionsImprove signal-to-noise ratioSeismic signal processingDecompositionWave model
The invention relates to a shallow water multi-wave model directivity prediction method of a characteristic wave domain, belongs to the technical field of geophysical exploration, and solves the problem that a prediction result of an existing shallow water multiple-wave prediction method has artifact interference. The method comprises the following steps of decomposing seismic data in a characteristic wave domain to obtain characteristic wave data; extracting a characteristic wave propagation direction prediction operator; performing characteristic wave domain directivity prediction accordingto the extracted characteristic wave propagation direction prediction operator. According to the method, characteristic wave decomposition and synthesis are introduced, and the direction information of the seismic data is utilized, so that false paths can be avoided during multi-wave prediction, the false noise interference is reduced, and the prediction precision is improved; meanwhile, the predicted shallow water multi-wave forms and the amplitudes confirm to the actual conditions, so that the signal-to-noise ratio and the resolution ratio of the seismic data of the target area are effectively improved; and in addition, the method can be applied to the suppression of three-dimensional seismic data shallow water multi-wave, so that the data processing effect of oil and gas exploration inthe shallow water area is greatly improved.
Owner:ZHANJIANG BRANCH OF CHINA NATIONAL OFFSHORE OIL CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com