Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
35 results about "Drive mapping" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
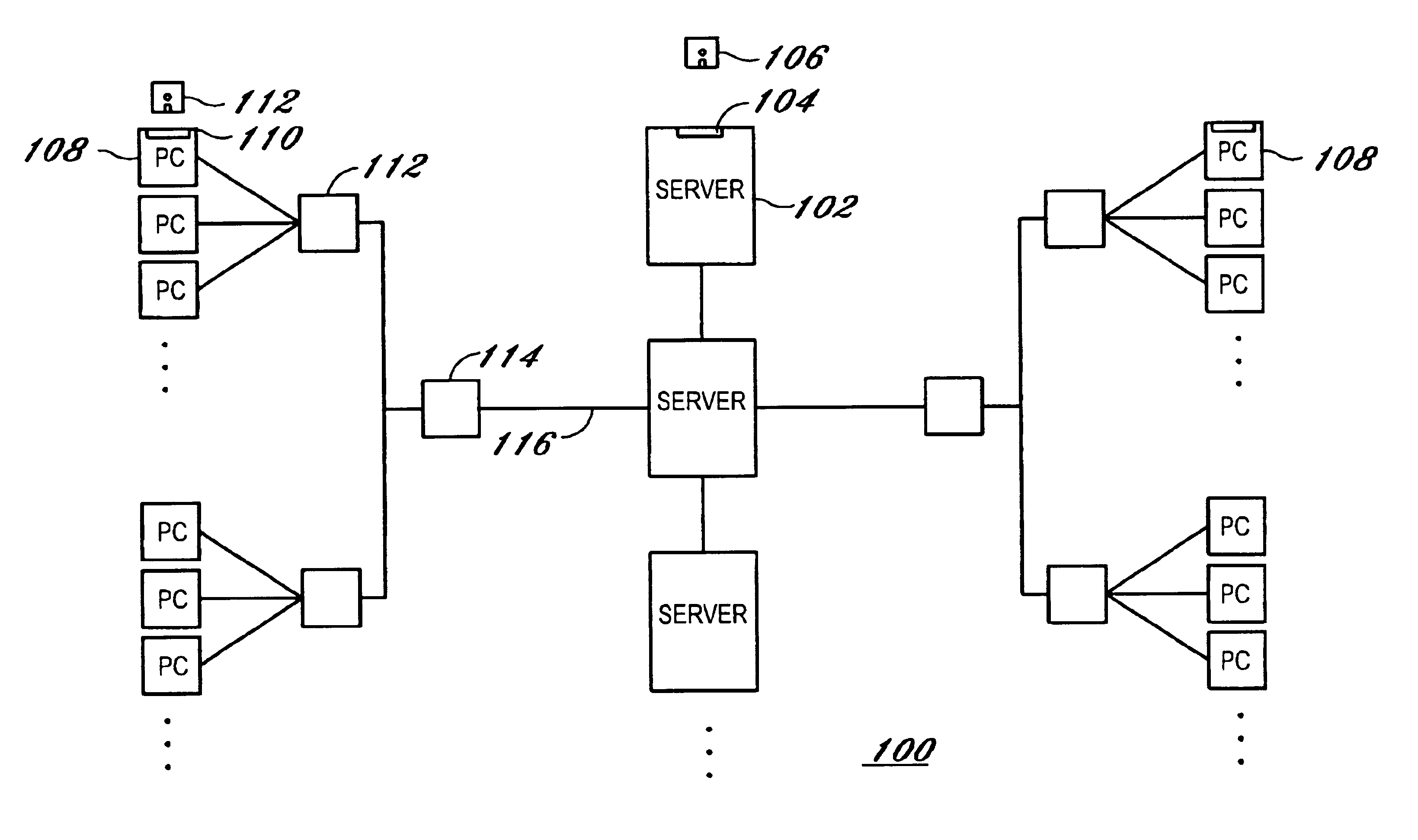
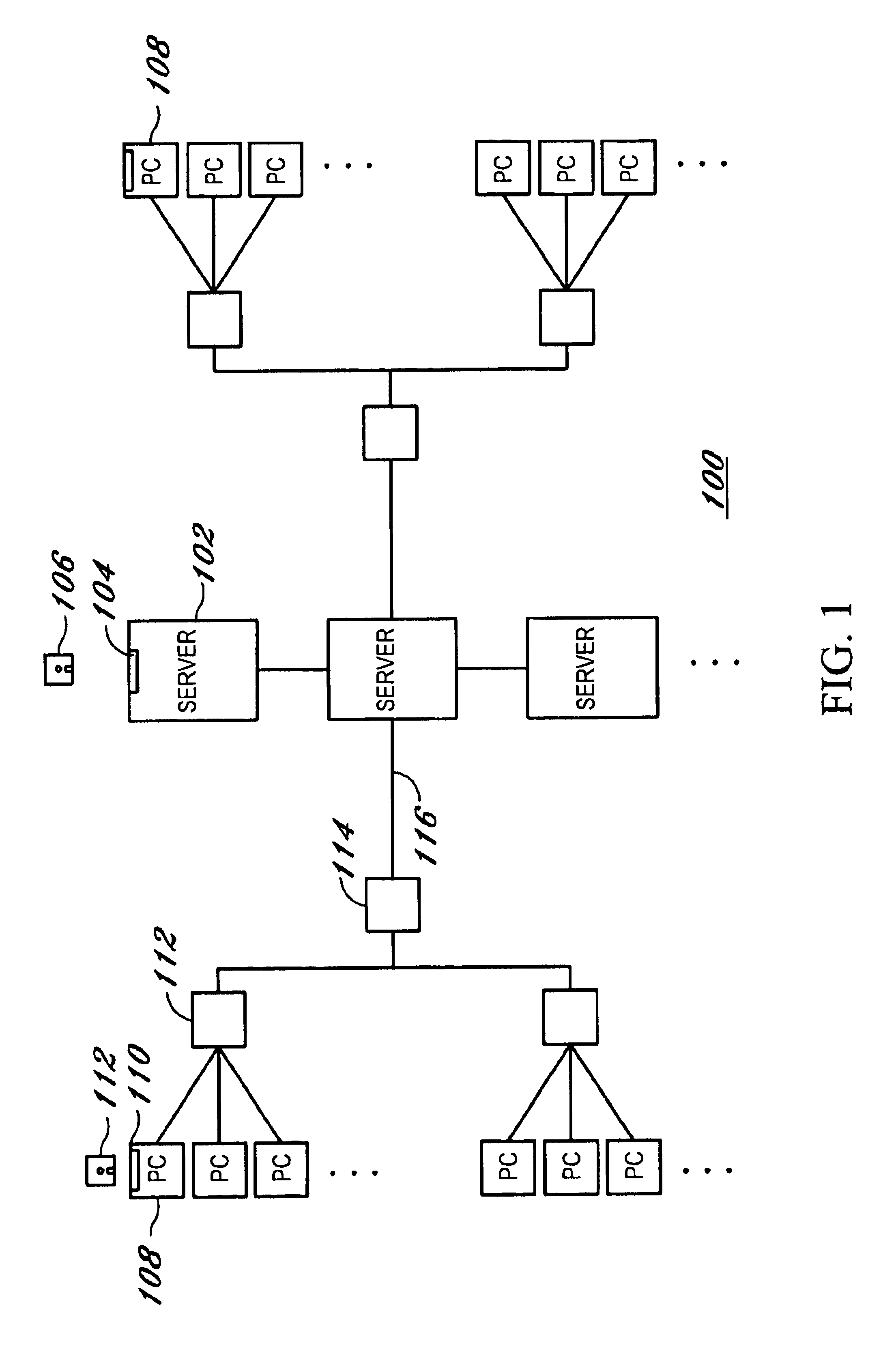
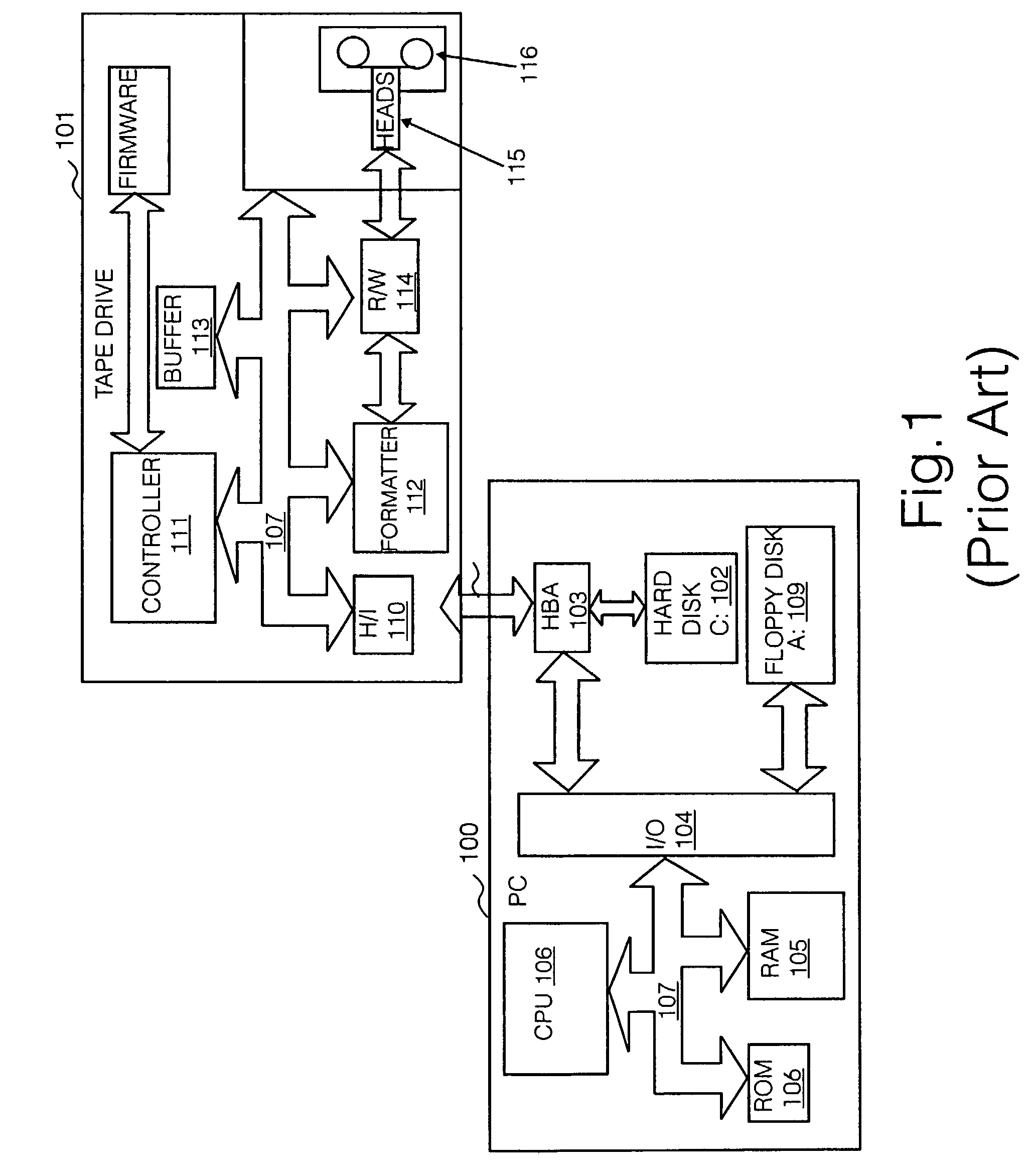
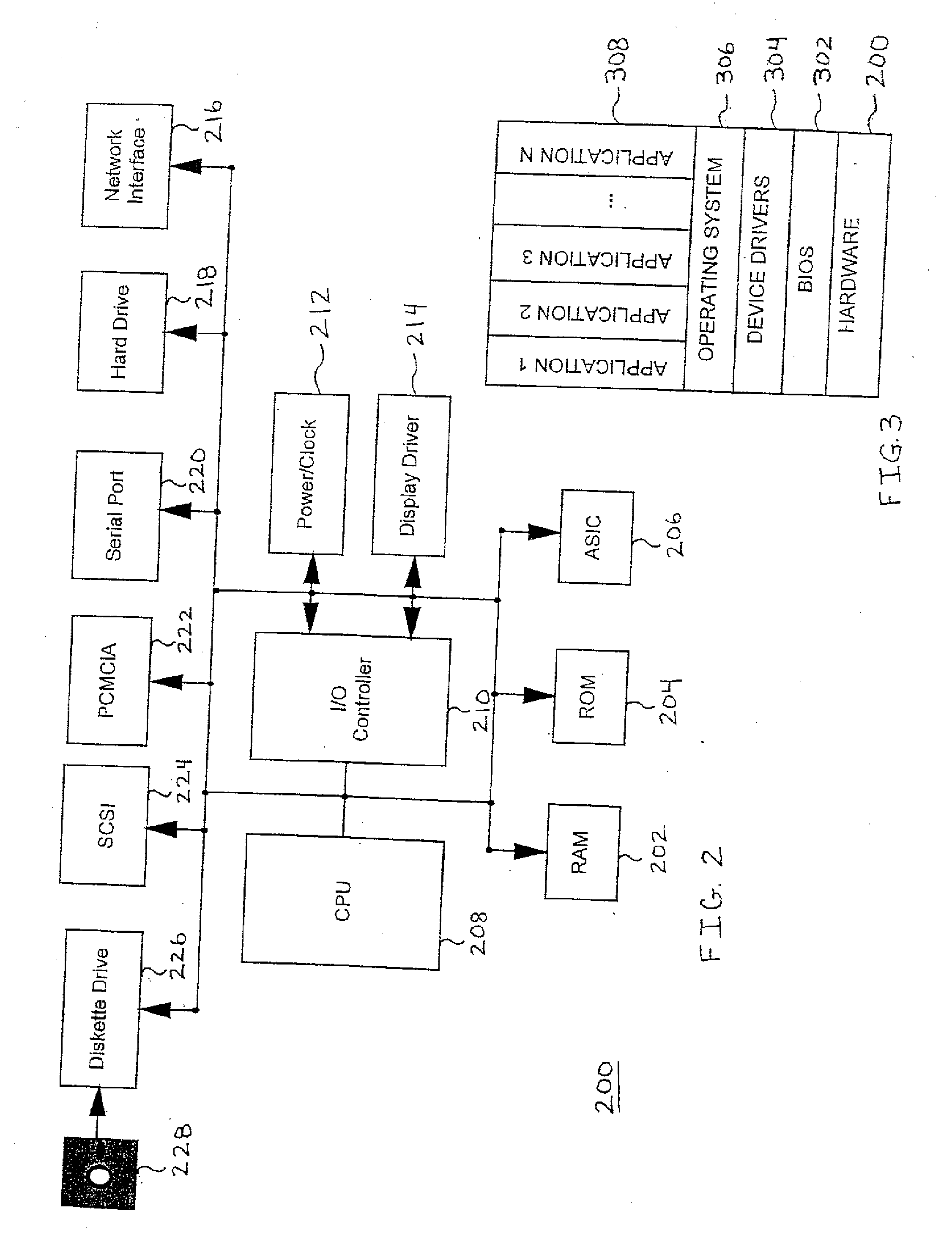
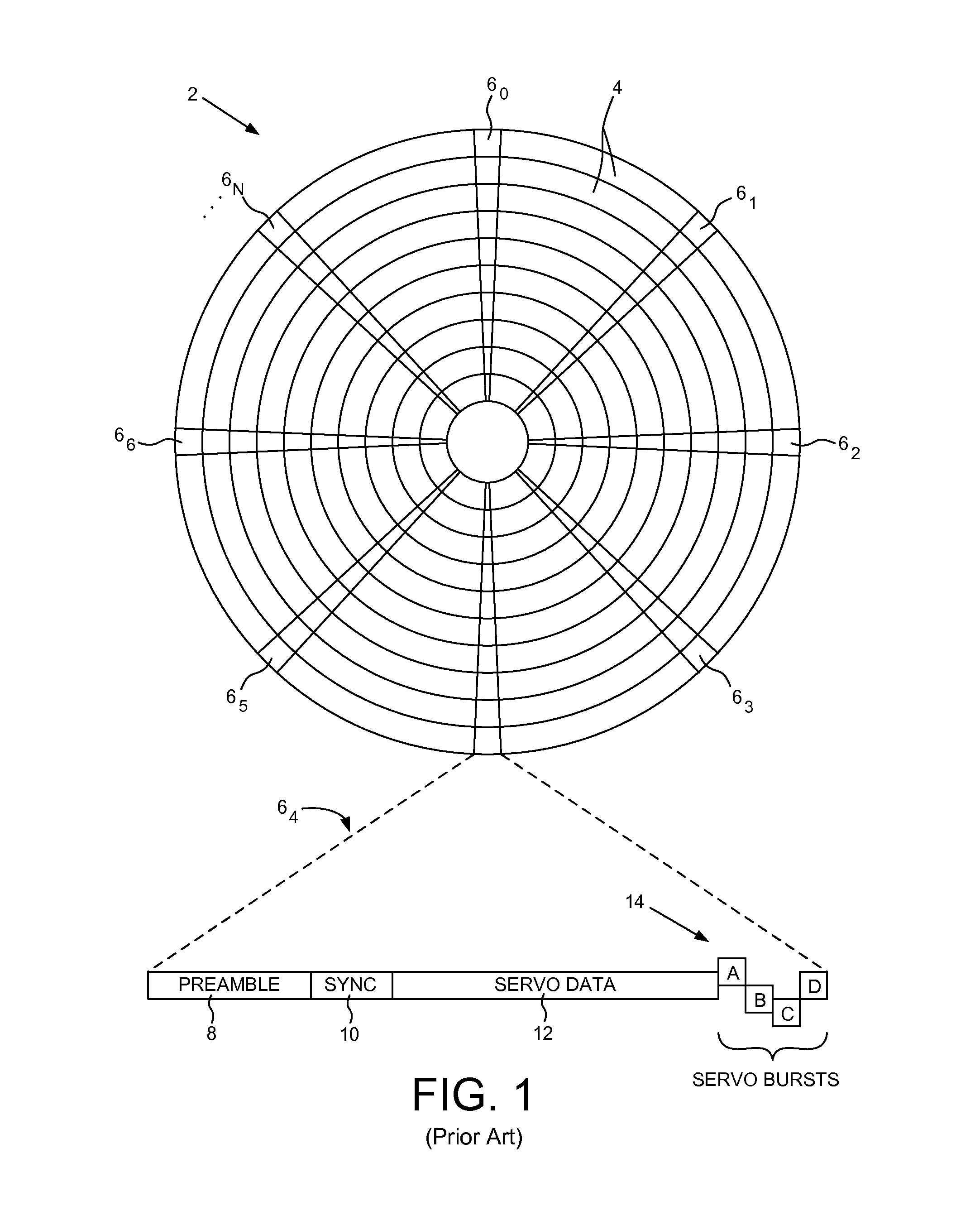
Drive mapping is how operating systems, such as Microsoft Windows, associate a local drive letter (A through Z) with a shared storage area to another computer (often referred as a File Server) over a network. After a drive has been mapped, a software application on a client's computer can read and write files from the shared storage area by accessing that drive, just as if that drive represented a local physical hard disk drive.
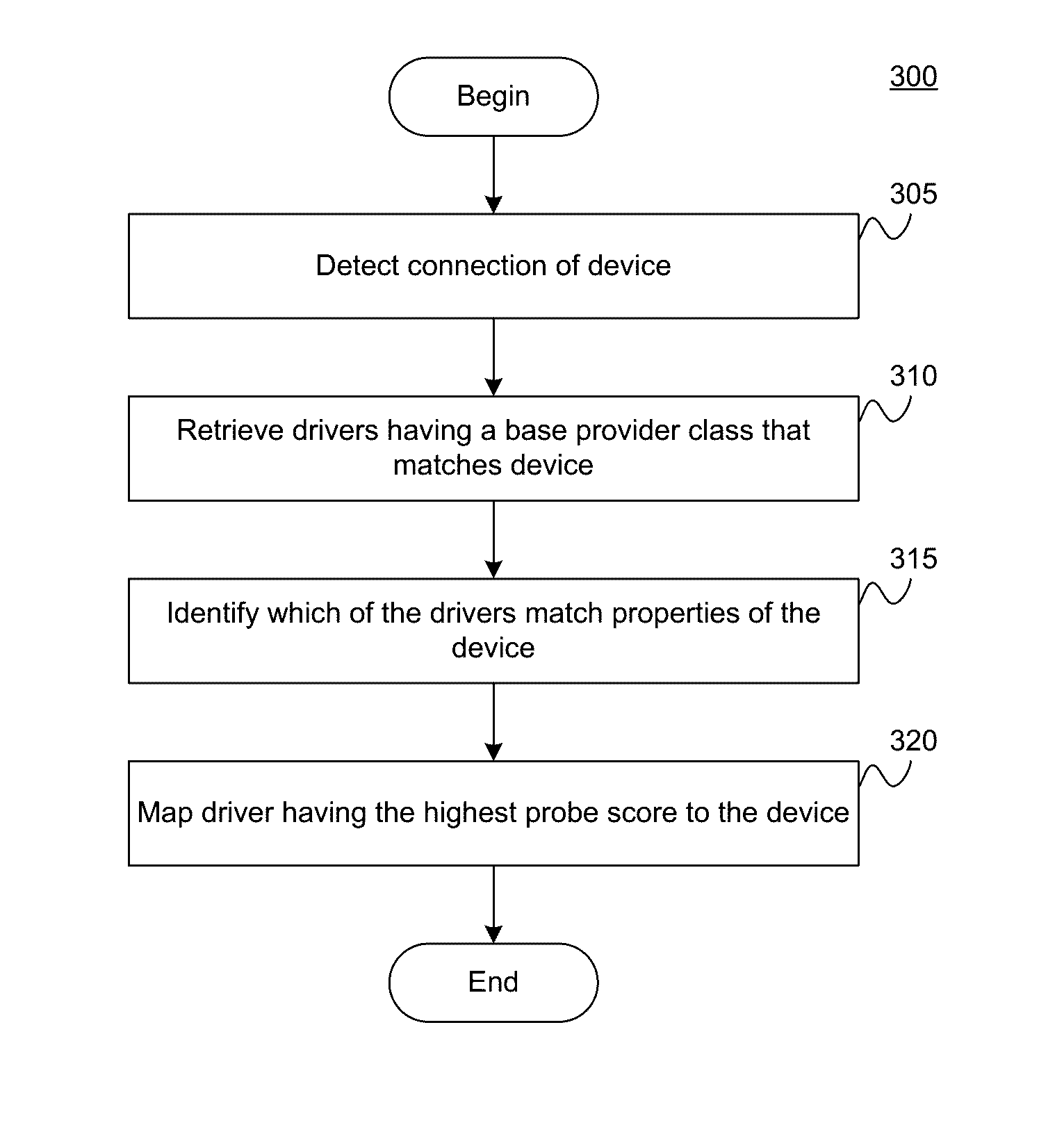
Method and apparatus to manage network client logon scripts using a graphical management and administration tool
A GUI (Graphical User Interface) Manager is used by a network administrator to fill-in predefined templates. The administrator does not need to compile, debug or write a single line of scripting code. The GUI manager has a “select the box” and “point and click” and “fill-in the blank” approach for selecting computer settings. The predefined configuration and / or template(s) are used by a logon script program on a client system to manage the configuration of resources on at least one client. There are three levels of resources that can be managed. The first type of resource is an operating system. The second type of resource is an application resource. And the third type of resource is to redirect a resource on the client to a resource on a network such as a drive letter mapping. Resources include configurations from the group of configuration settings consisting of drive mappings, shell folders, printer deployment, proxy server access, application paths, service packs, anti-virus updates, policies and automatic mail profile creation. In another embodiment, validation logic is used on the clients' system during the execution of an application program that takes the template and applies the defined configuration settings in the template to the clients' system so as to automatically configure at least one configuration setting for a user if the combination of one or more predefined conditions for a selected group, a selected operating system and a selected connection method are met. In still another embodiment, an interpretive engine is used on the client's system to permit the administration of client resources with a template while also allowing network administrators to build their own custom logon scripts.
Owner:QUEST SOFTWARE INC
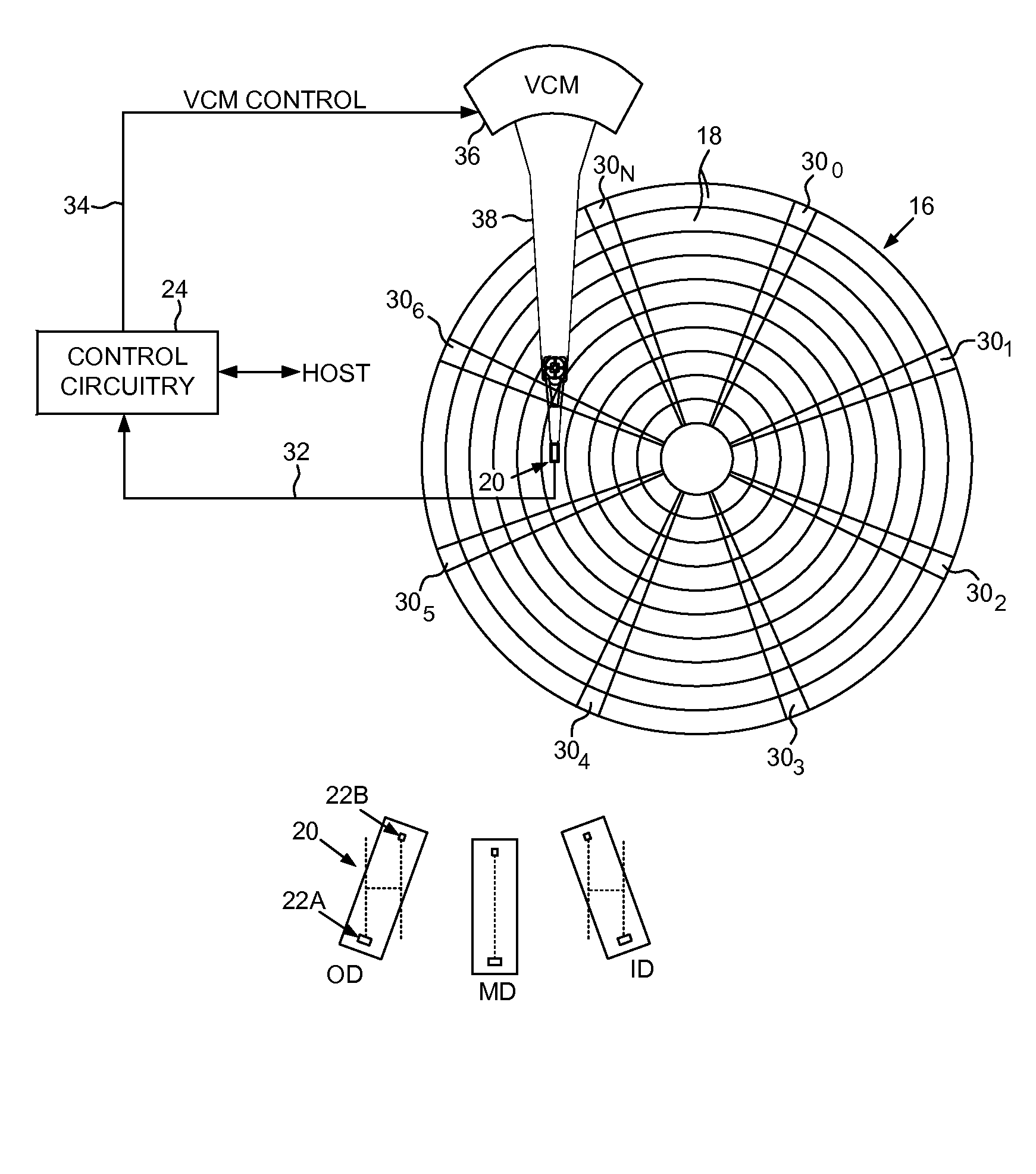
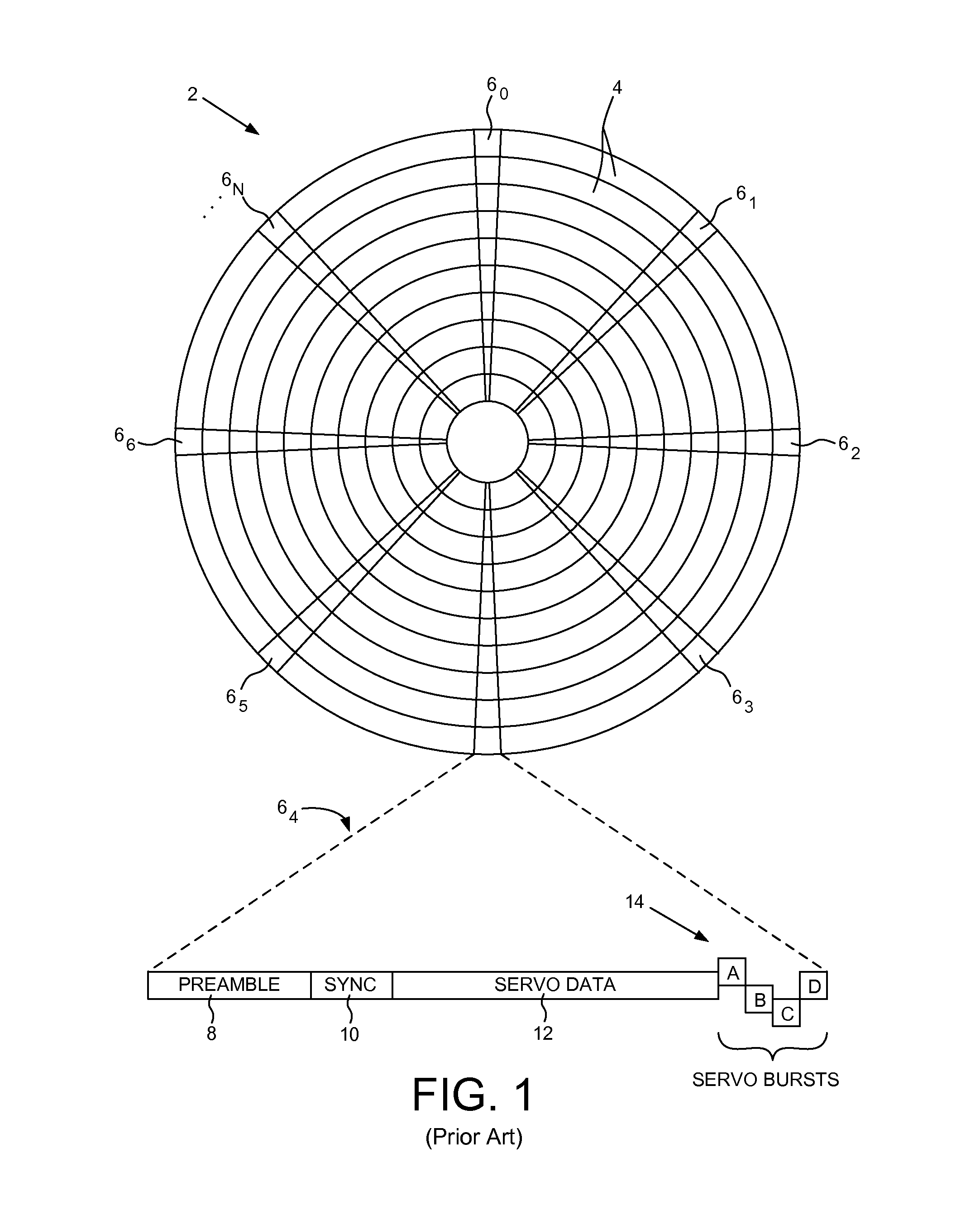
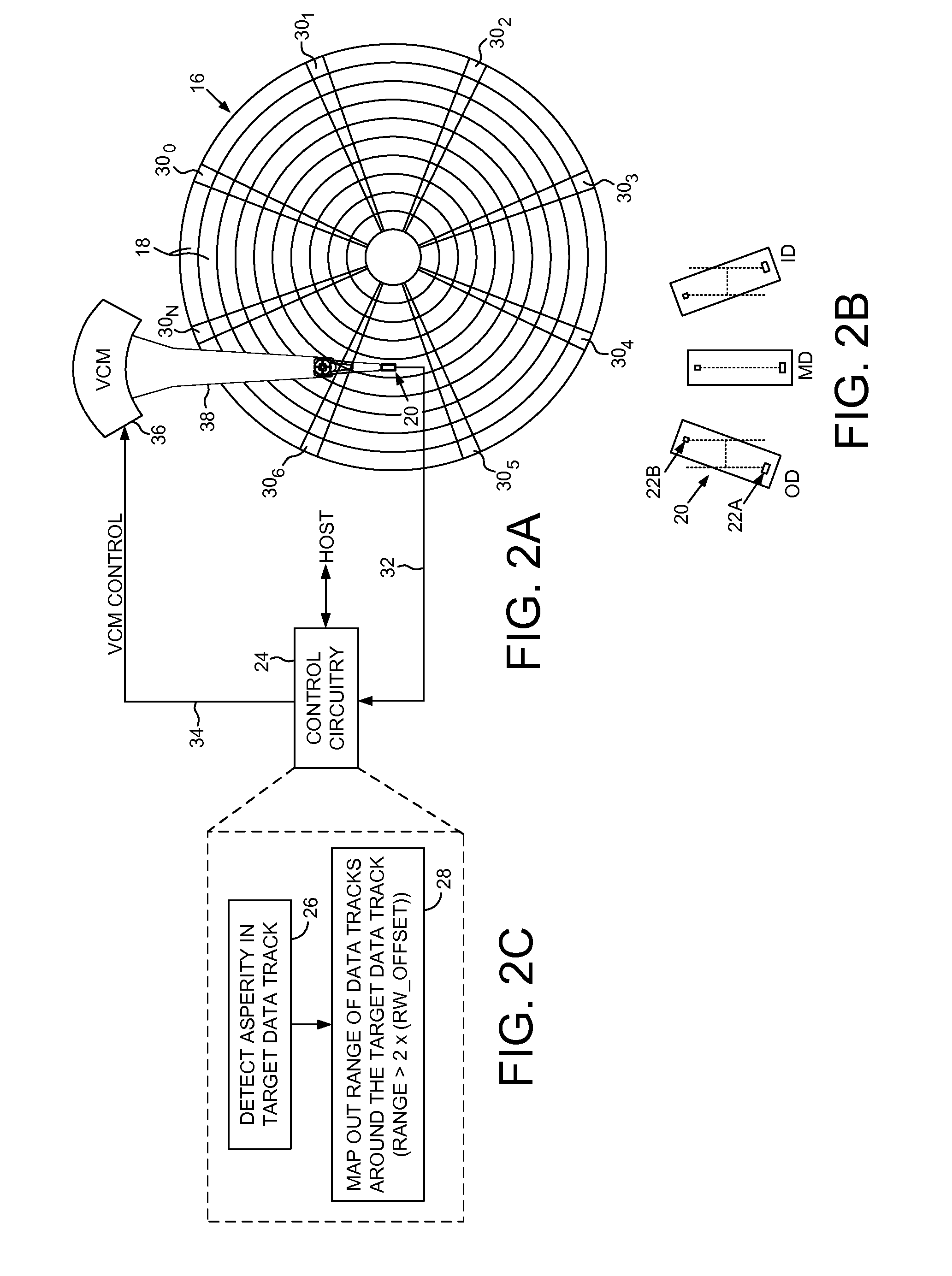
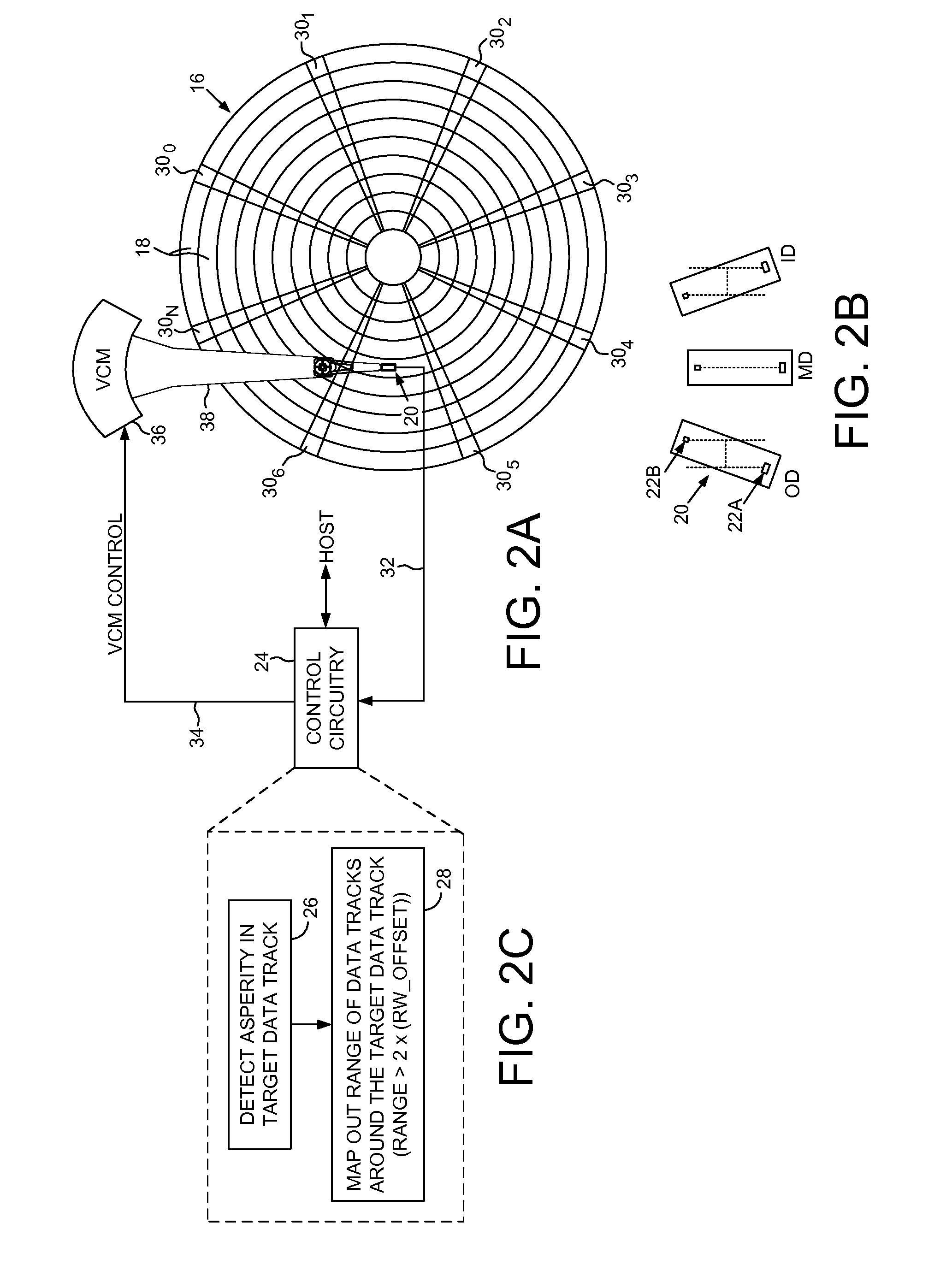
Disk drive mapping out data tracks to avoid thermal asperities
ActiveUS8687313B2Driving/moving recording headsRecord information storageDrive mappingComputer science
A disk drive is disclosed comprising a head actuated over a disk comprising a plurality of data tracks, wherein the head comprises a write element and a read element. An asperity in a target data track is detected, and a range of data tracks proximate the target data track is mapped out, wherein the range of data tracks spans at least twice a radial offset between the read element and the write element at the radial location of the target data track.
Owner:WESTERN DIGITAL TECH INC
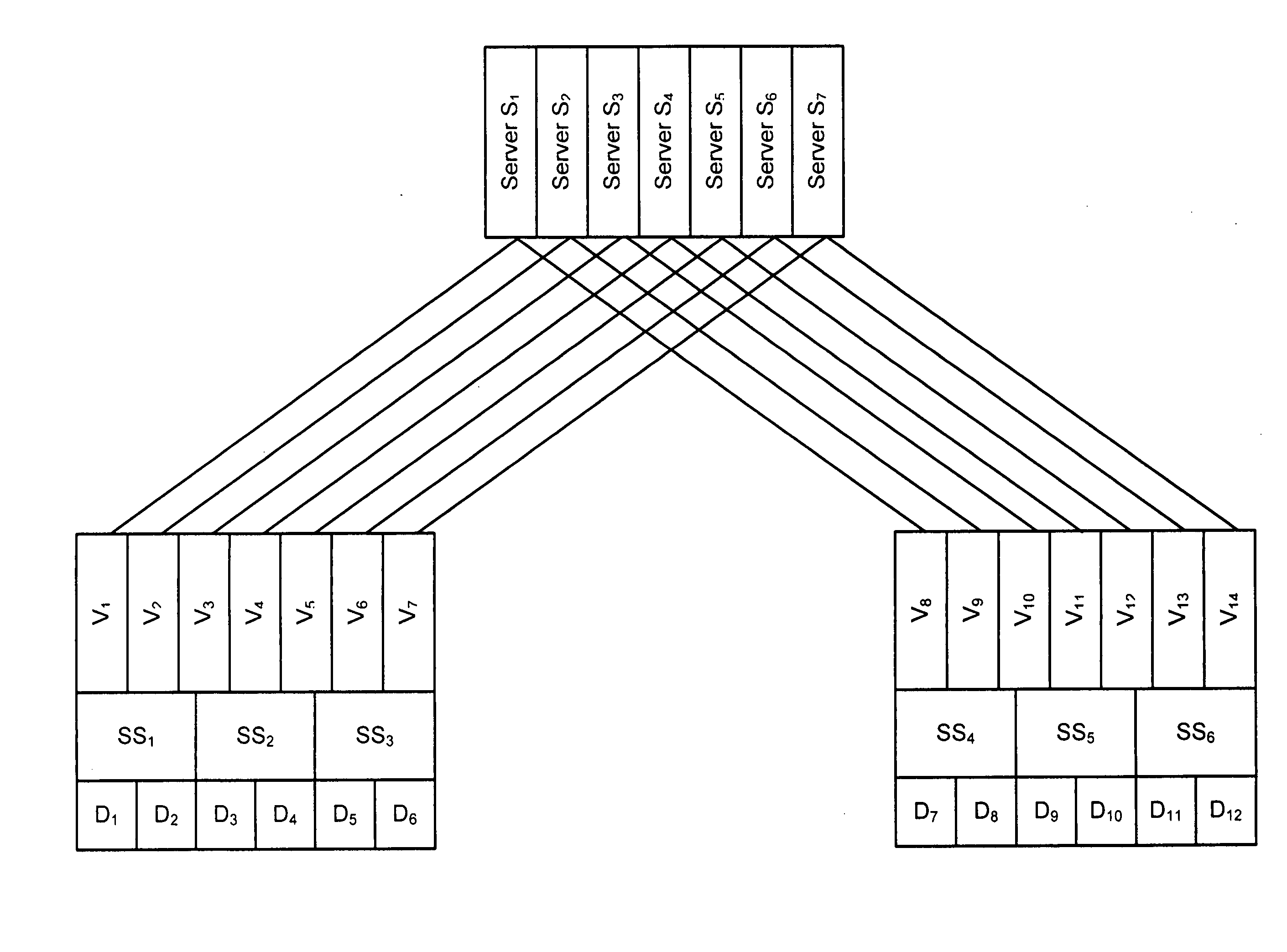
Virtual drive mapping
InactiveUS20080140930A1Low costSave powerMemory systemsInput/output processes for data processingDrive mappingComputer science
The automatic mapping of a set of physical drives to virtual drives is disclosed. Given a maximum set of n physical servers, S1-Sn, and a maximum set of m physical drives, D1-Dm, a mapping of a set of virtual drives, V1-Vn, to the physical drives D1-Dm, is created, assuming n and m are fixed and known, and one virtual drive is created per server. Physical drives of size Dsize are organized into a maximum of p “Stripe Sets” SS1-SSp, each Stripe Set containing an equal number of physical drives. Each virtual drive will have a size, Vsize=(m*Dsize) / n (rounded down to the nearest integer). Virtual drives are mapped sequentially to Stripe Sets, starting with V1 mapped to SS1. Successive virtual drives are mapped to Stripe Sets until all virtual drives have been mapped to a Stripe Set.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
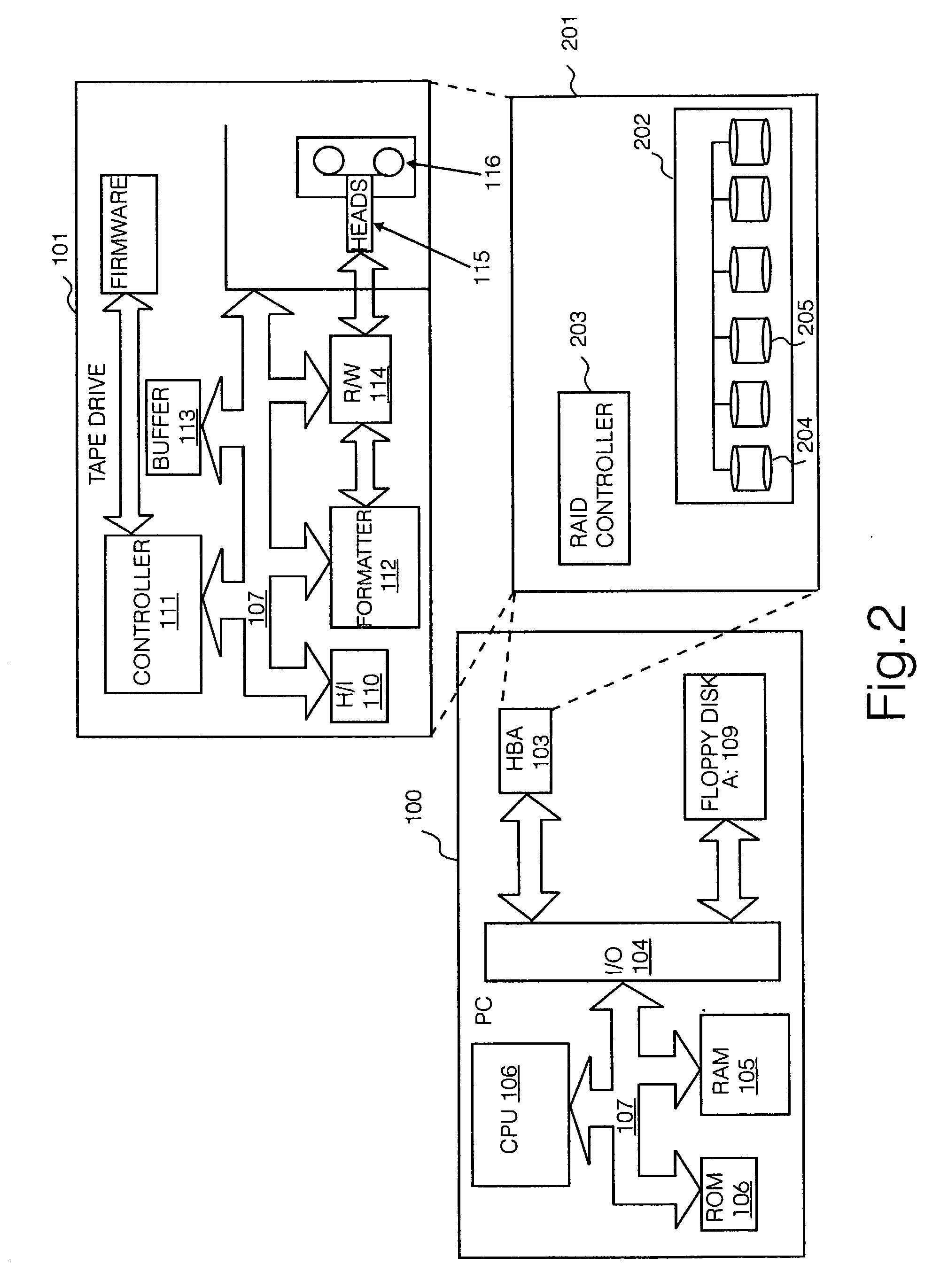
Method, disaster recovery record, back-up apparatus and RAID array controller for use in restoring a configuration of a RAID device
InactiveUS20020194528A1Wide rangeRedundant data error correctionRedundant operation error correctionOperational systemRecovery record
A computer system has (1) an array of data storage devices, (2) an operating system stored on a RAID device and (3) a RAID controller. In response to detection of a computer system failure, the RAID device configuration is automatically restored. A system back-up memory stores a recovery record of physical drive to logical drive mapping for the RAID device. The RAID controller enables the recovery record to be processed in response to detection of a system failure. In response to computer system failure detection, the recovery record information restores the RAID array configuration. Following system failure, a computer system manager instigates the procedure by pressing a button.
Owner:HEWLETT PACKARD DEV CO LP
Managing client configuration settings in a network environment
InactiveUS20070118888A1Digital data processing detailsUser identity/authority verificationThree levelAnti virus
A GUI (Graphical User Interface) Manager is used by a network administrator to fill-in predefined templates. The administrator does not need to compile, debug or write a single line of scripting code. The GUI manager has a “select the box” and “point and click” and “fill-in the blank” approach for selecting computer settings. The predefined configuration and / or template(s) are used by a logon script program on a client system to manage the configuration of resources on at least one client. There are three levels of resources that can be managed. The first type of resource is an operating system. The second type of resource is an application resource. And the third type of resource is to redirect a resource on the client to a resource on a network such as a drive letter mapping. Resources include configurations from the group of configuration settings consisting of drive mappings, shell folders, printer deployment, proxy server access, application paths, service packs, anti-virus updates, policies and automatic mail profile creation. In another embodiment, validation logic is used on the clients' system during the execution of an application program that takes the template and applies the defined configuration settings in the template to the clients' system so as to automatically configure at least one configuration setting for a user if the combination of one or more predefined conditions for a selected group, a selected operating system and a selected connection method are met. In still another embodiment, an interpretive engine is used on the client's system to permit the administration of client resources with a template while also allowing network administrators to build their own custom logon scripts.
Owner:QUEST SOFTWARE INC
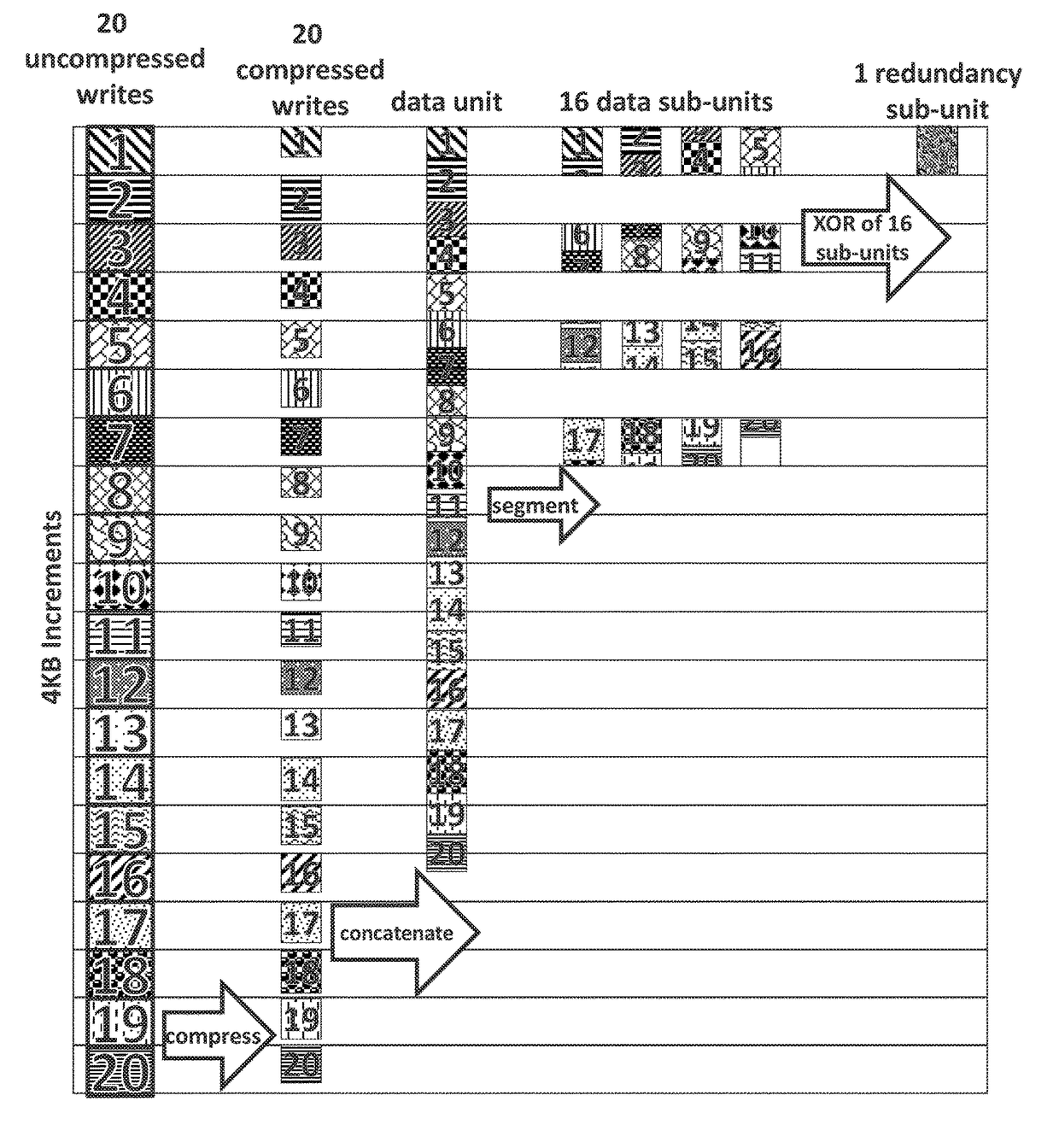
Method and apparatus for storing information using an intelligent block storage controller
ActiveUS9665303B1Low failure rateReduce Warranty CostsMemory architecture accessing/allocationInput/output to record carriersDrive mappingControl store
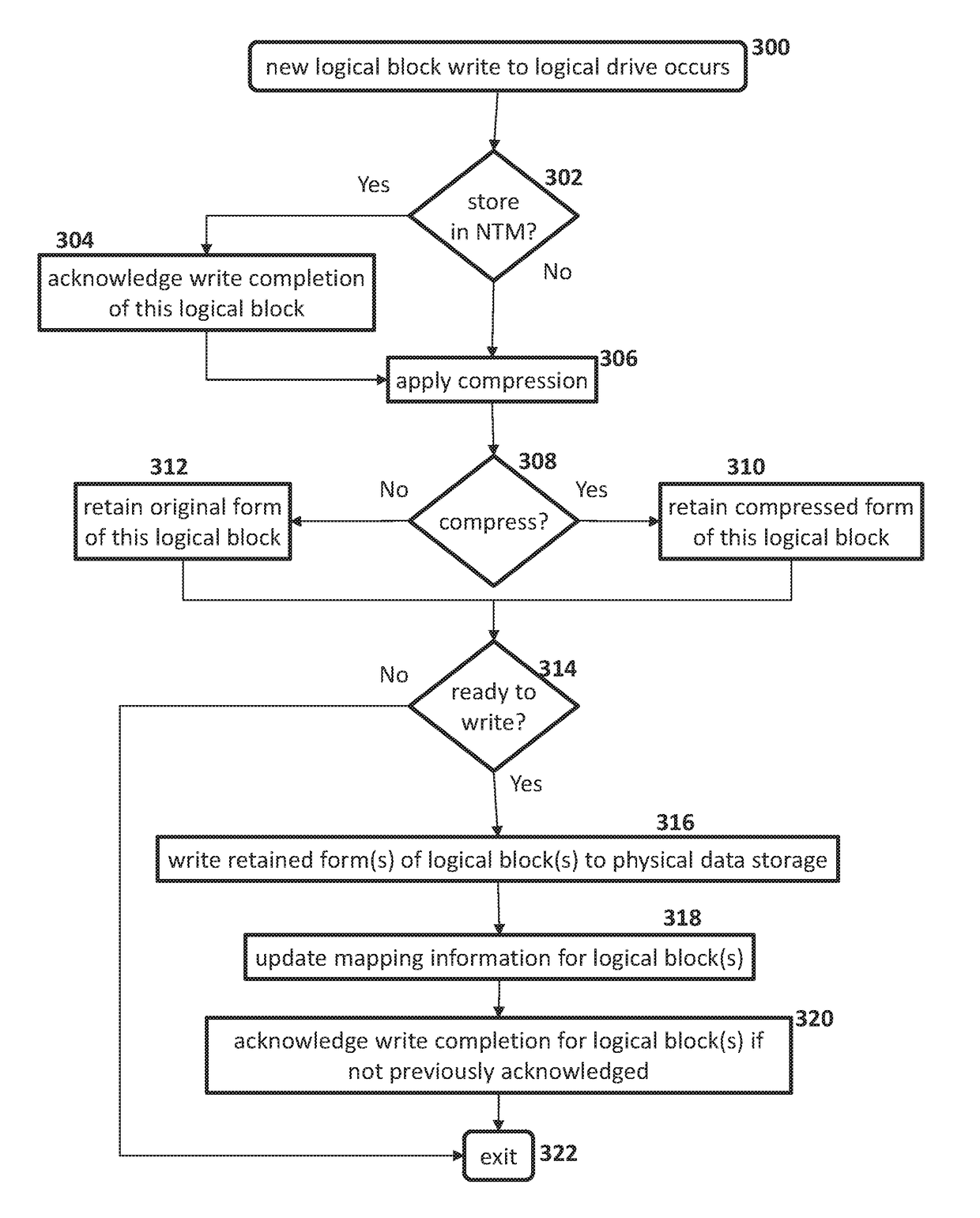
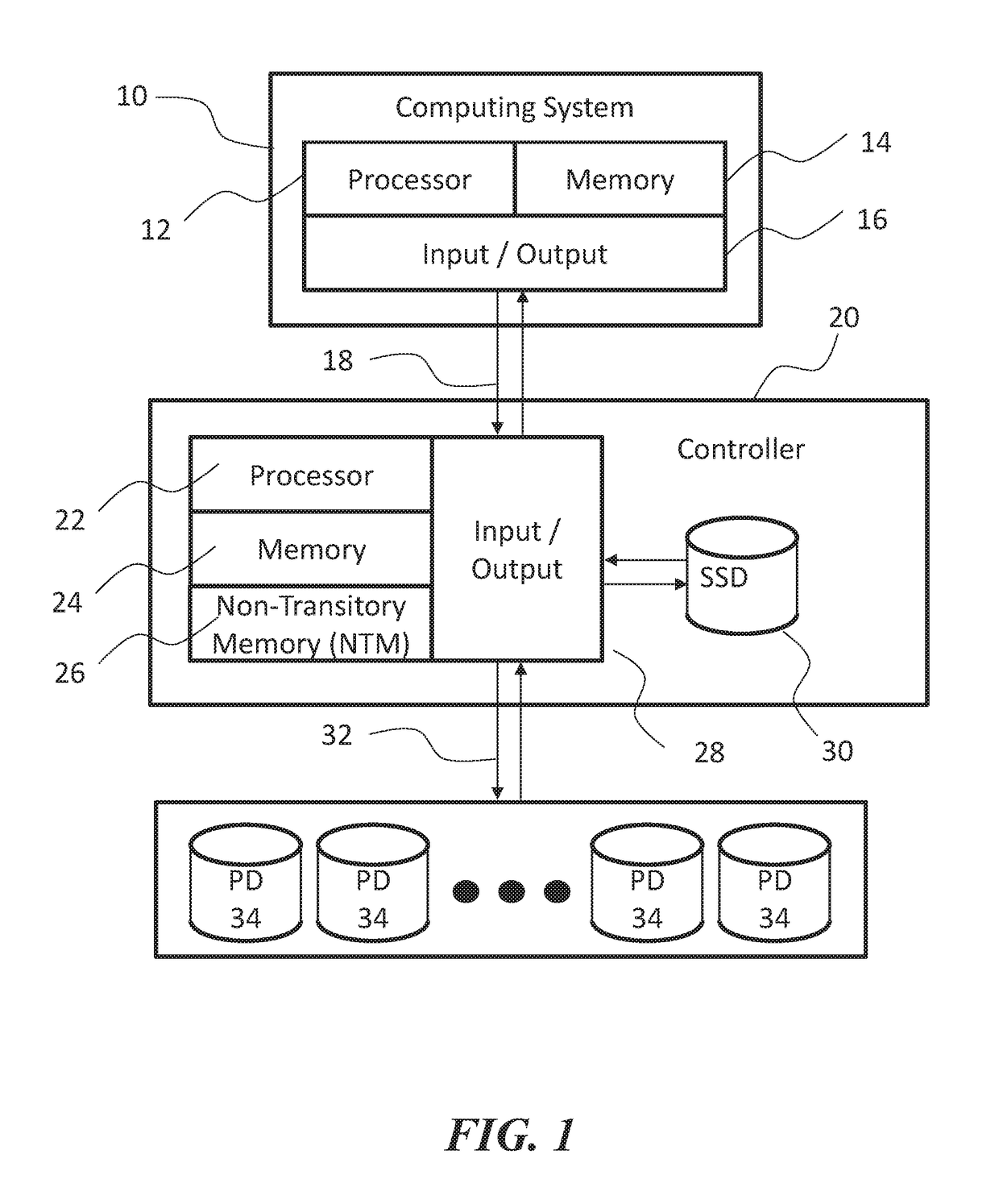
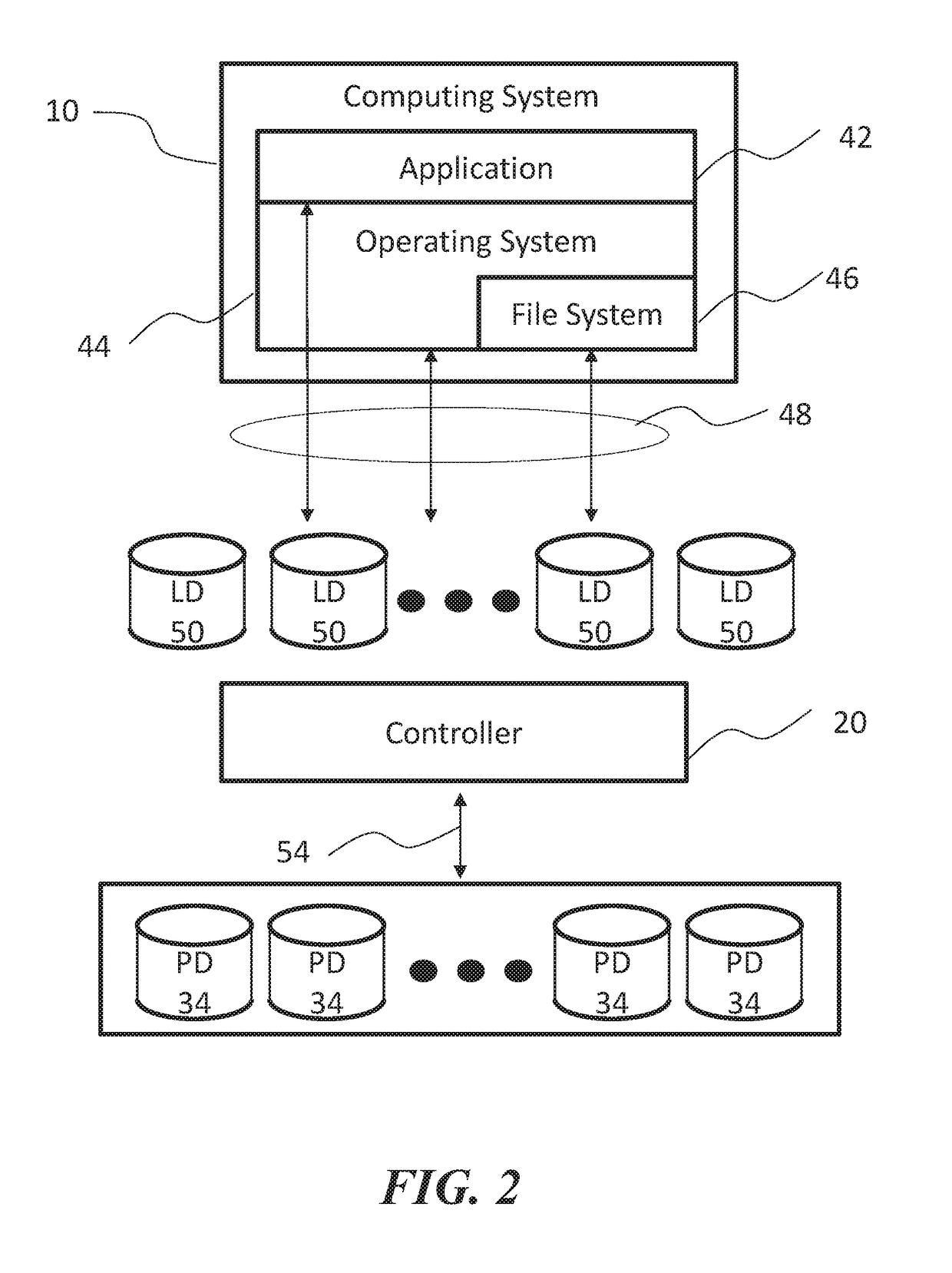
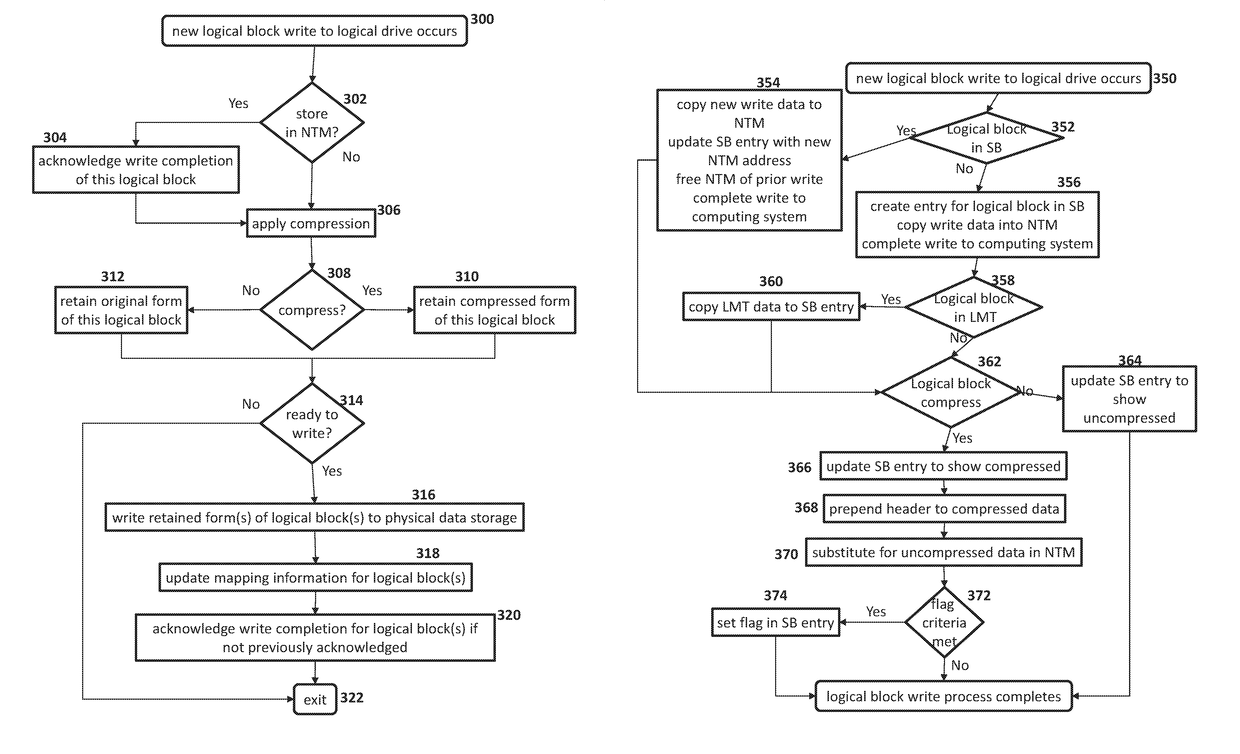
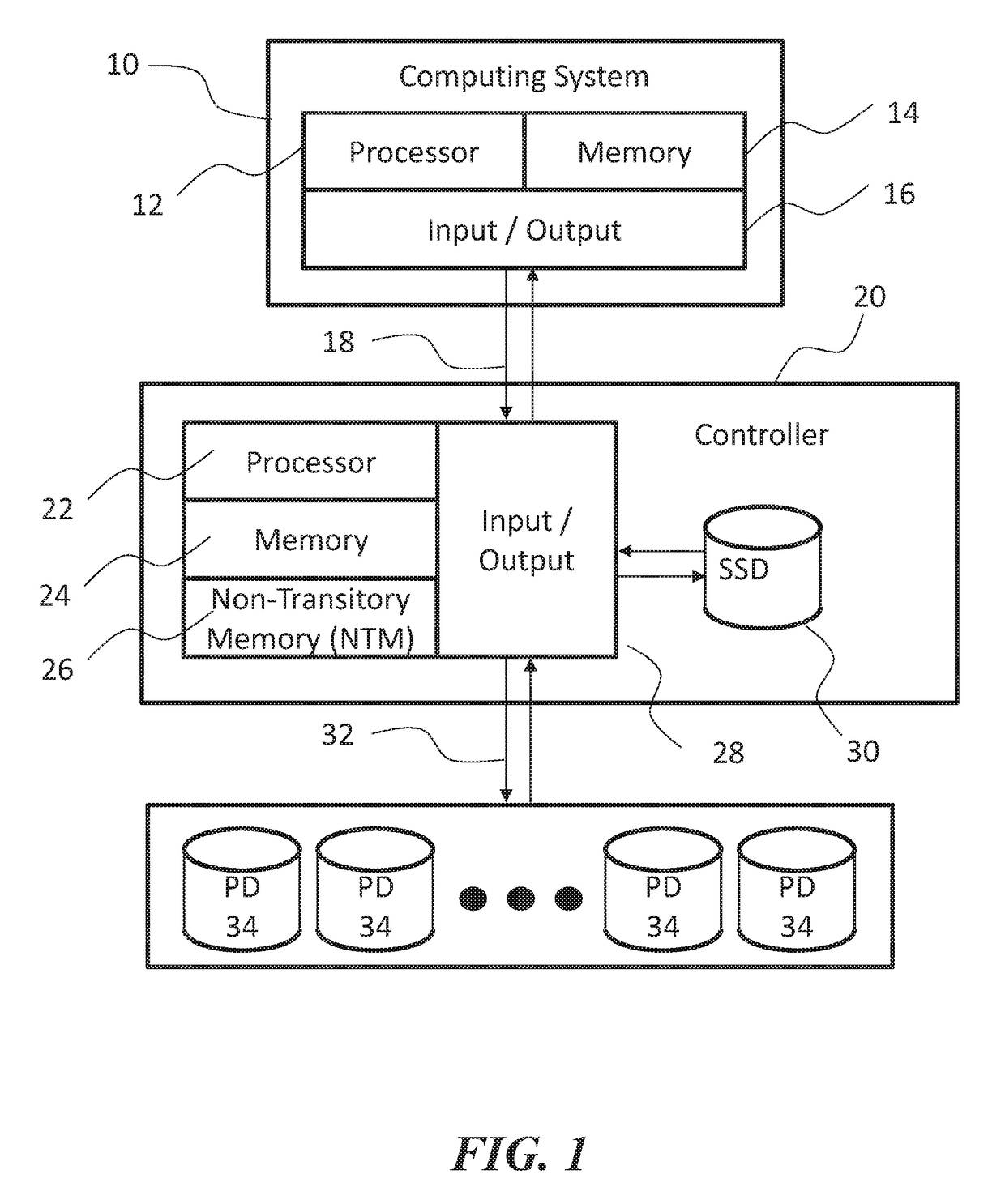
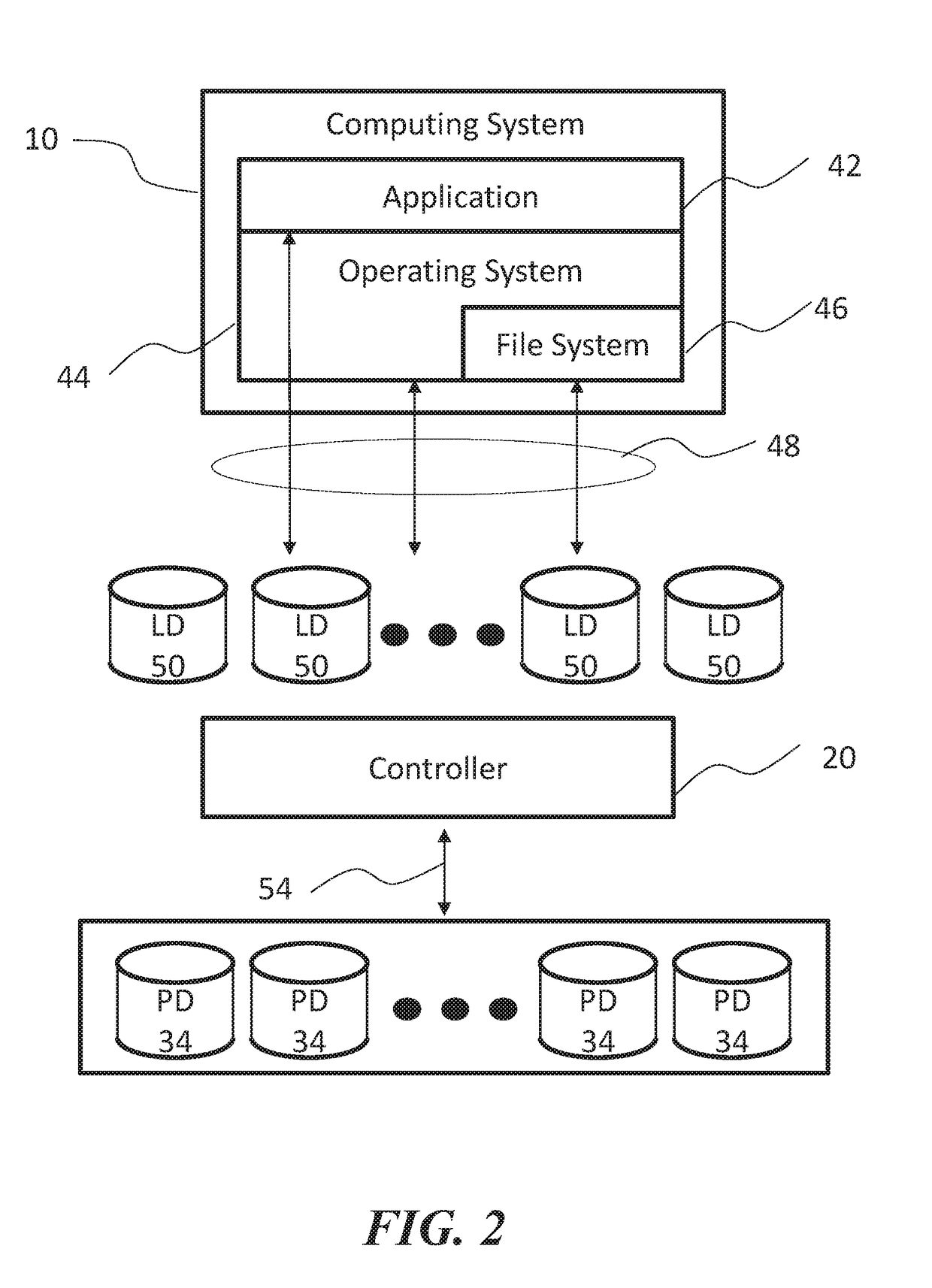
Methods, devices, and media for improving data storage reliability and efficiency comprising: creating at least one logical storage drive comprising a plurality of logical blocks; mapping the at least one logical storage drive to at least one physical storage drive based on many-to-one mapping or one-to-many mapping, wherein the at least one physical storage drive comprises a plurality of physical blocks; and applying a compression algorithm to data held in one or more logical blocks, aggregating units of the data, and storing the units of the data into one or more physical blocks.
Owner:DIVERGENT STORAGE SYST INC
Universal and integrated wafer testing real-time monitoring software system and its open system architecture
InactiveUS20060036394A1Shorten cycle timeRisk minimizationElectrical testingStructural/machines measurementProduction lineDrive mapping
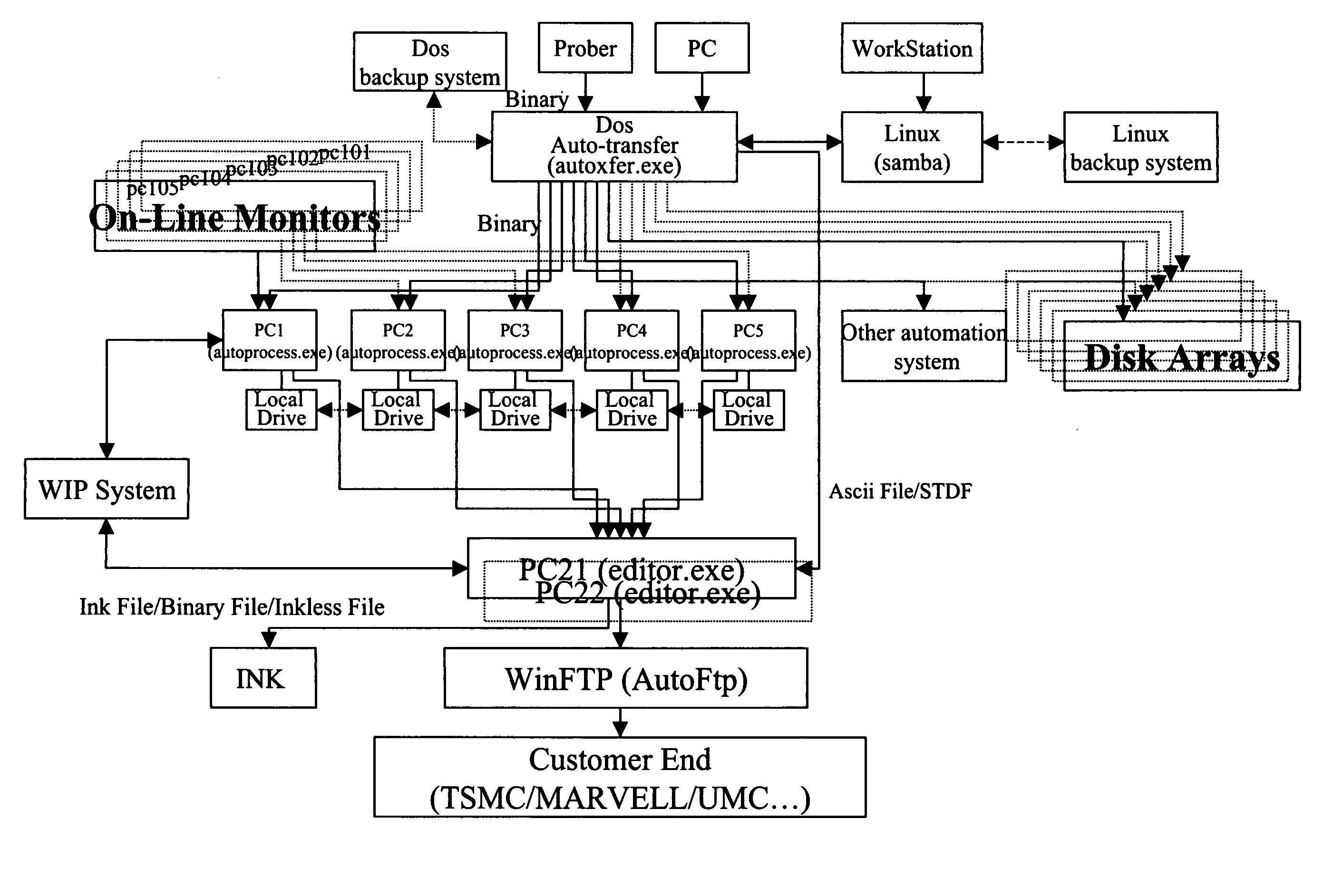
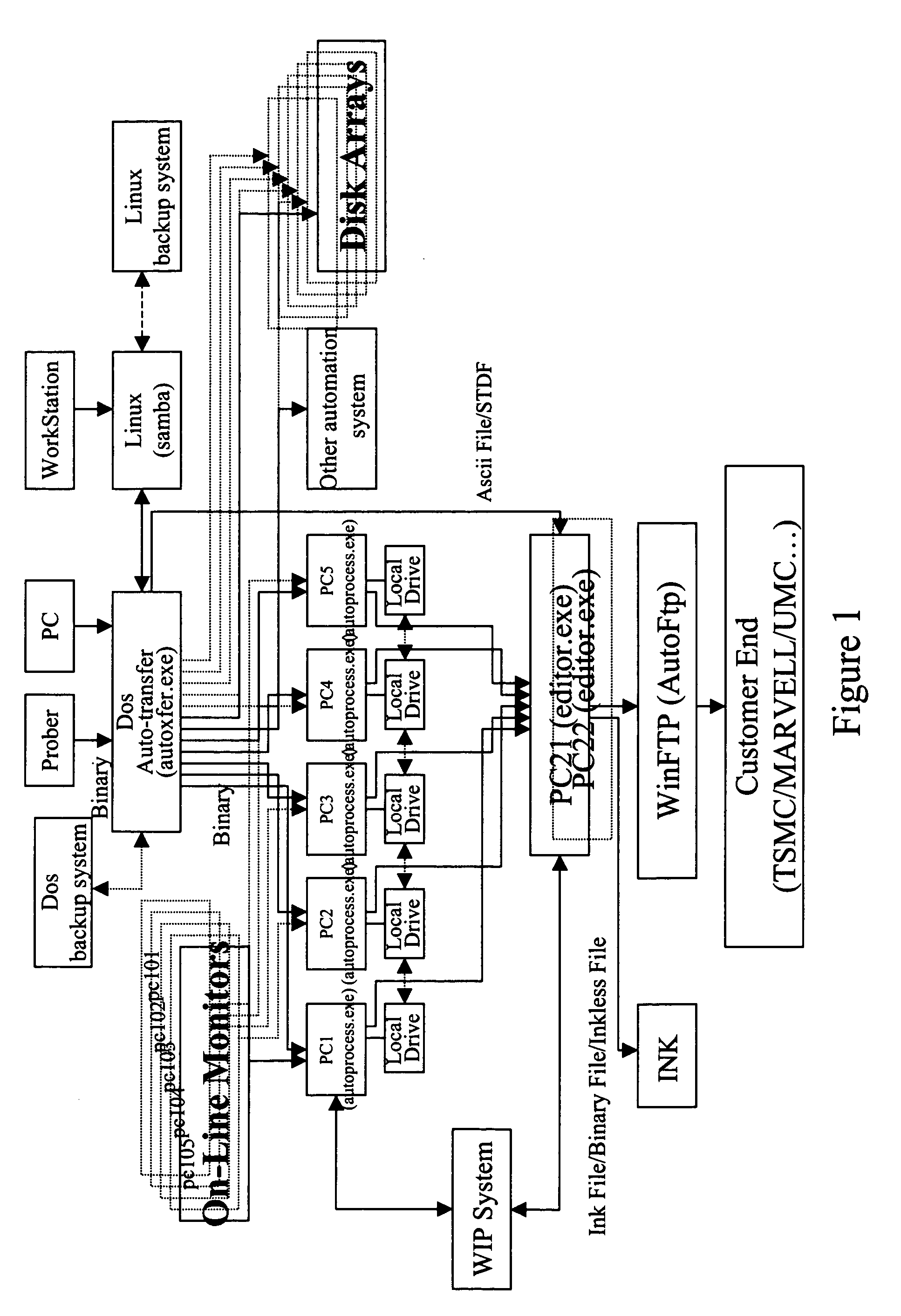
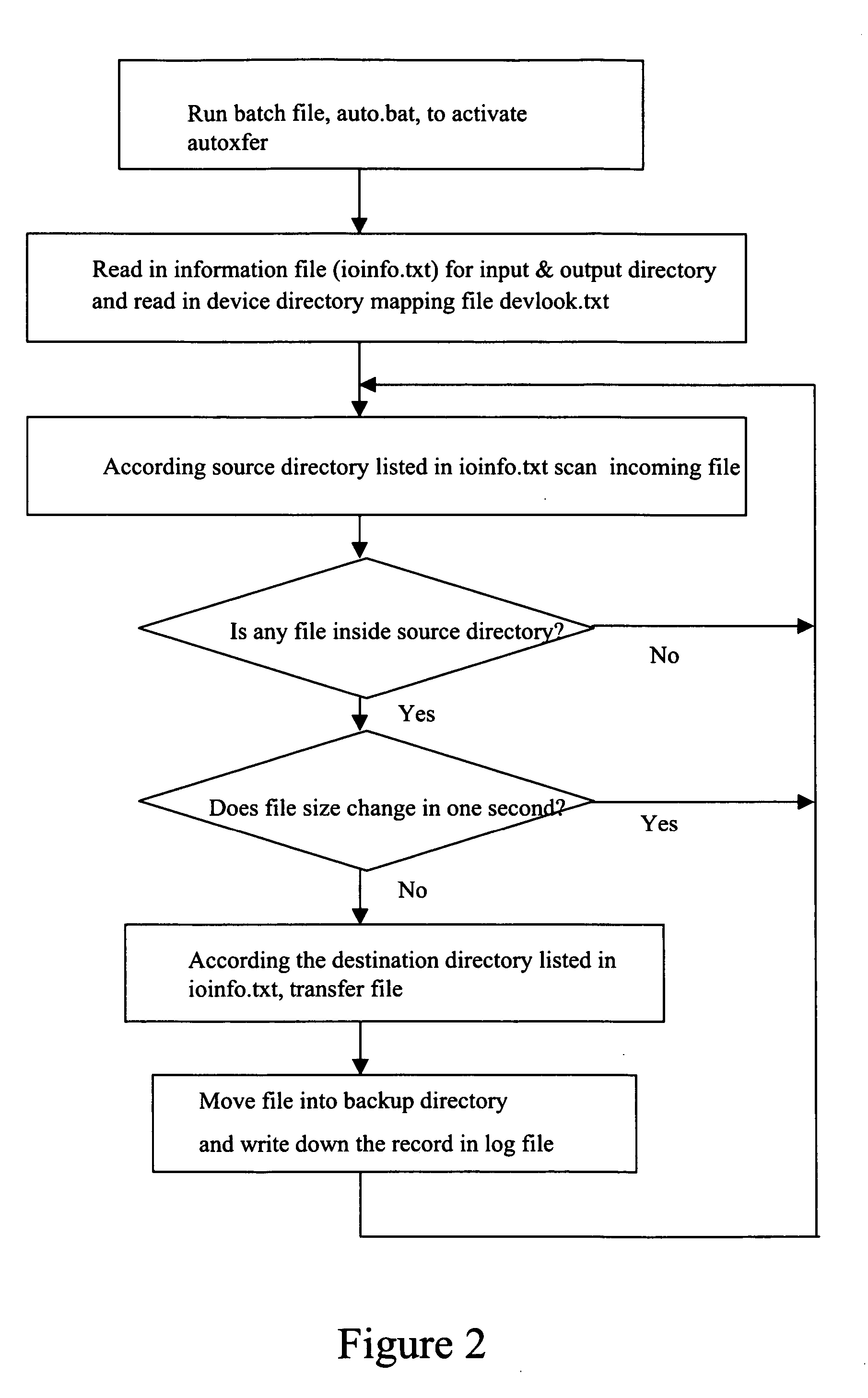
A wafer testing real-time monitoring software system and its unique open software architecture which achieves real-time monitoring of wafer test results and on-line changing of externally hooked software to satisfy customer needs without changing its main program. The software structure receives and processes binary files from different probers and converts these into readable ASCII files. The system consists of four software programs that can operate independently. These programs are an automatic transfer program, a program which converts wafer test results from a binary file to an ASCII file, a program which receives the ASCII files and performs wafer map editing, and an auto-ftp program which automatically scans data and sends data to remote locations. Additionally, multiple workstations can process data from probers simultaneously. The on-line monitor on a production line can see production results from multiple major workstations through the network drive and drive mapping functions.
Owner:CHEN WEN LING +1
Intelligent household equipment control method, device and equipment, and readable storage medium
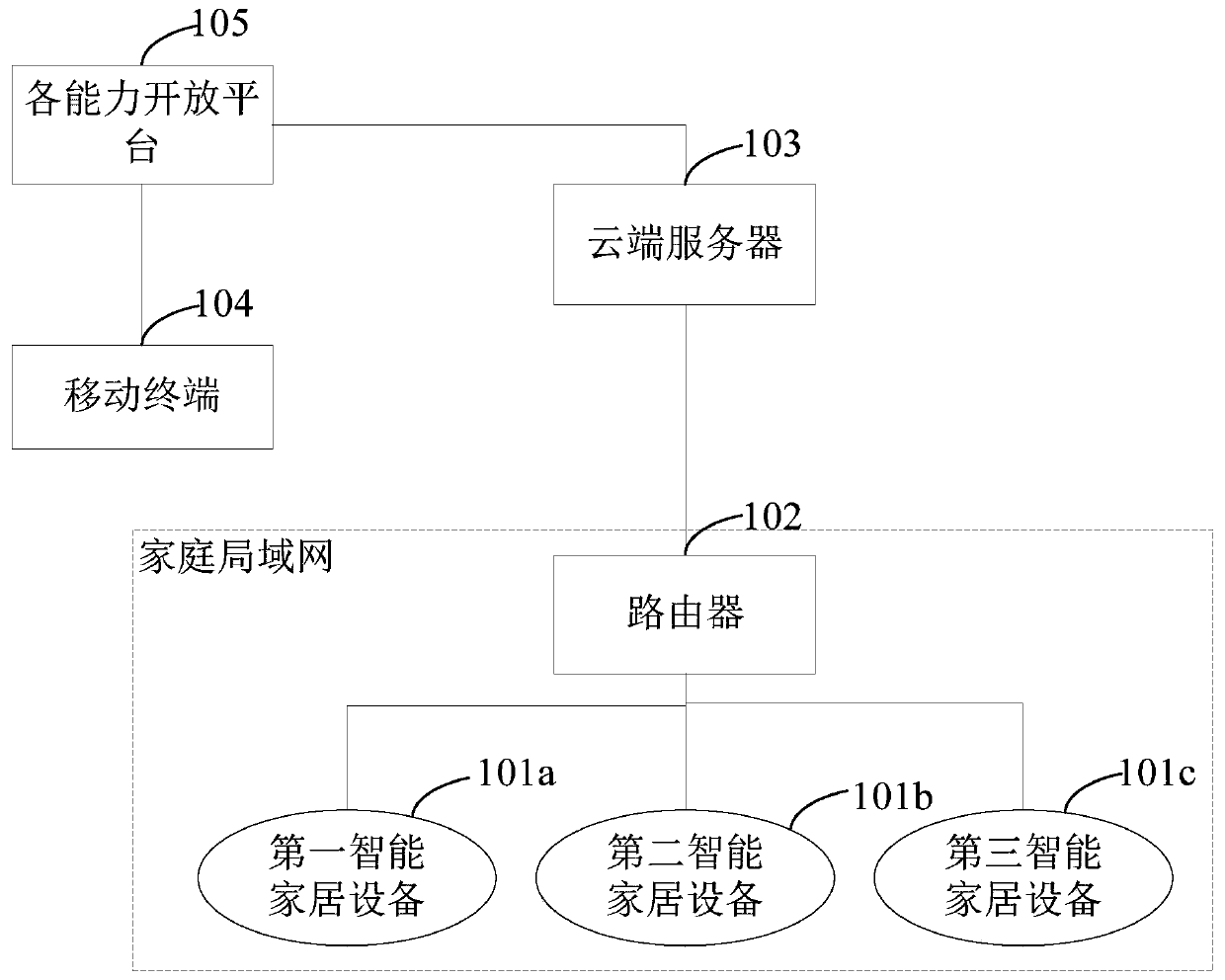
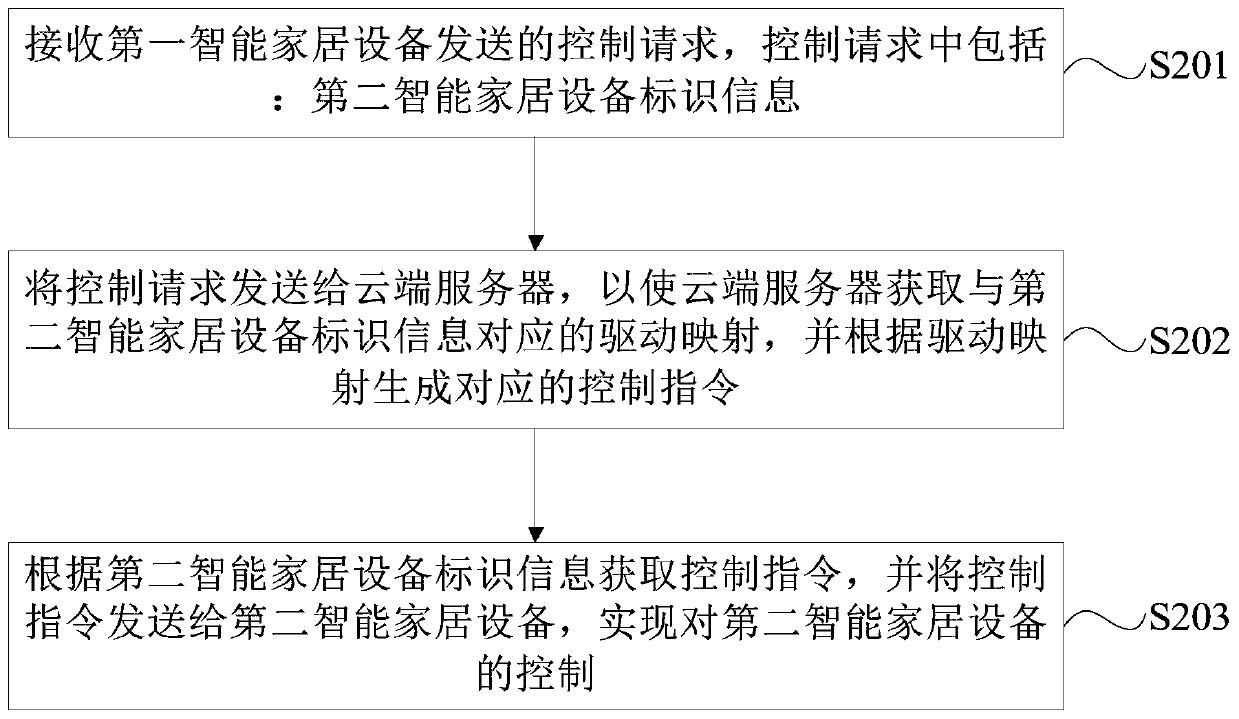
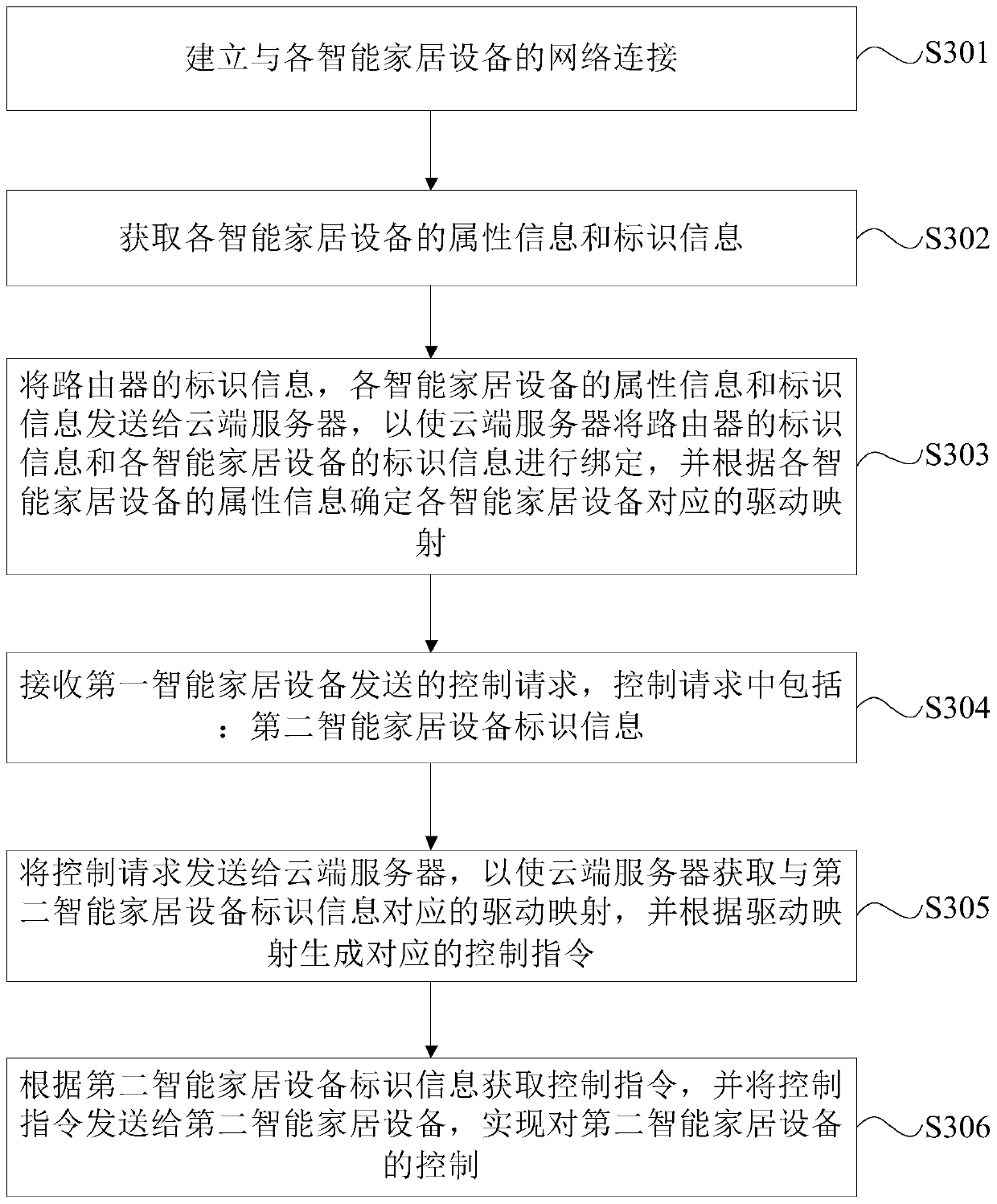
The embodiments of the invention provide an intelligent household equipment control method, device and equipment, and a readable storage medium. The method comprises the following steps of receiving acontrol request sent by a first intelligent household device, where the control request includes second intelligent household device identification information; sending the control request to a cloudserver so that the cloud server obtains driving mapping corresponding to the second intelligent household device identification information, and generates a corresponding control instruction according to the driving mapping; and acquiring the control instruction according to the second intelligent household device identification information, and sending the control instruction to a second intelligent household device to implement control of the second intelligent household device. The intelligent household devices of all manufacturers in a family can be uniformly controlled, which is labor-saving and time-saving, and the intelligent household devices of various manufacturers and various models can be applied in one household local area network so that an application range of each intelligent household device is greatly enlarged.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD +1
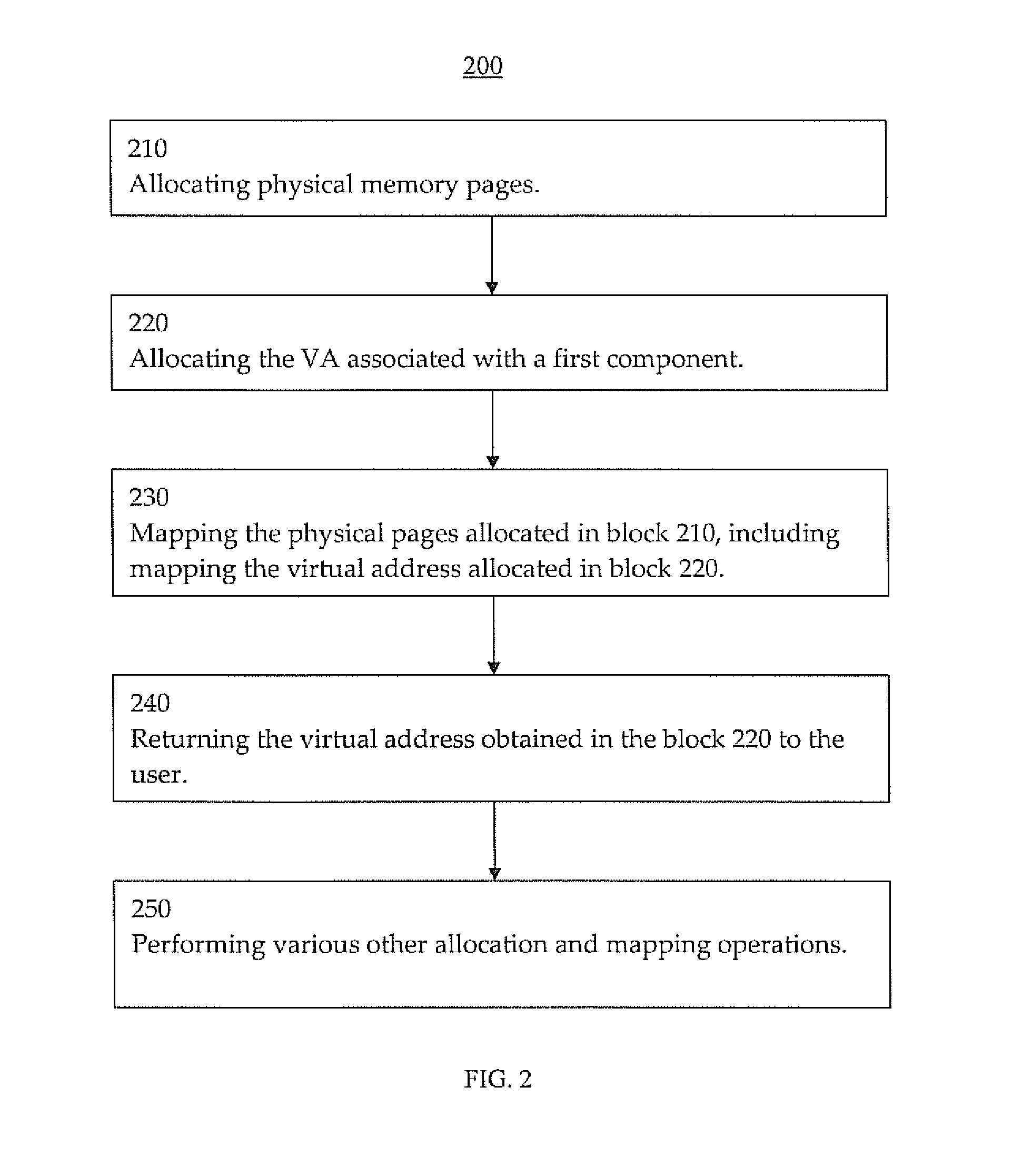
Unified memory systems and methods
ActiveUS20150206277A1Improve utilizationMemory adressing/allocation/relocationImage memory managementGraphicsDrive mapping
The present invention facilitates efficient and effective utilization of unified virtual addresses across multiple components. In one embodiment, the presented new approach or solution uses Operating System (OS) allocation on the central processing unit (CPU) combined with graphics processing unit (GPU) driver mappings to provide a unified virtual address (VA) across both GPU and CPU. The new approach helps ensure that a GPU VA pointer does not collide with a CPU pointer provided by OS CPU allocation (e.g., like one returned by “malloc” C runtime API, etc.).
Owner:NVIDIA CORP
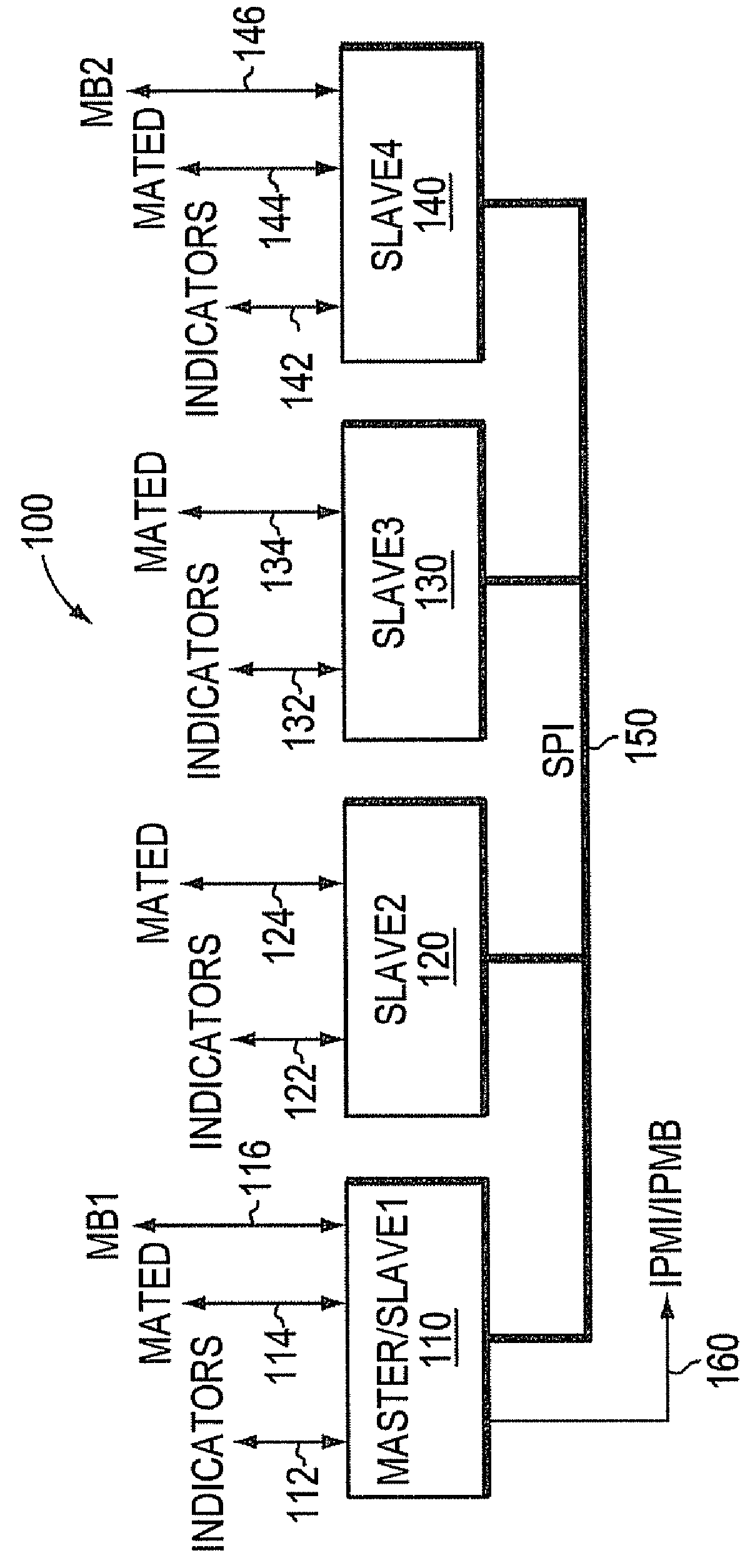
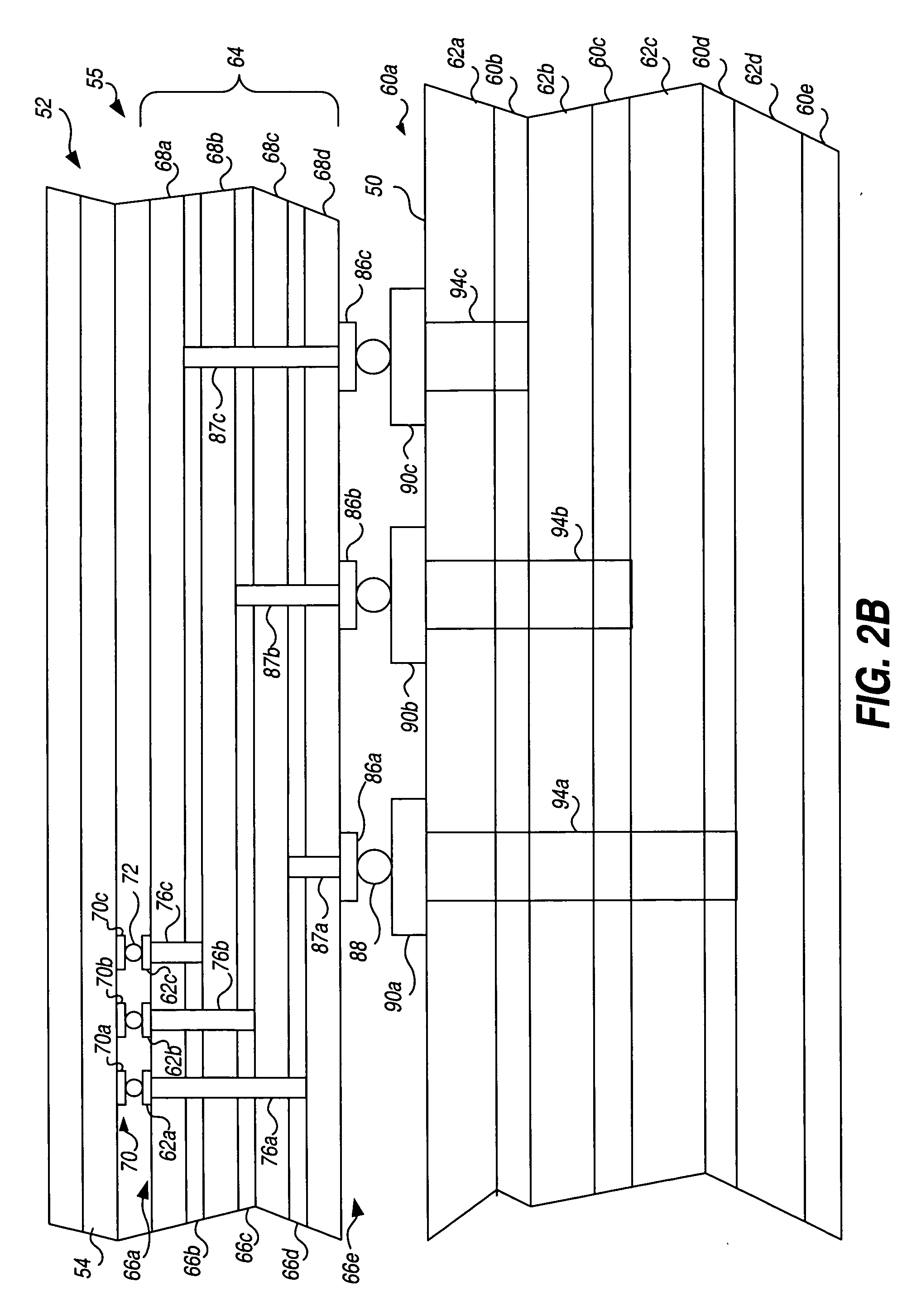
Drive mapping using a plurality of connected enclosure management controllers
According to one aspect, a computing system having a plurality of enclosure management controllers (EMCs) is disclosed. In one embodiment, the EMCs are communicatively coupled to each other and each EMC is operatively connected to a corresponding plurality of drive slots and at least one of a plurality of drive slot status indicators. Each EMC is operative to receive enclosure management data, detect an operational status of the drive slots, and generate drive slot status data. One of the EMCs is configured to function at least partly as a master EMC to receive drive slot status data and, based on received enclosure management data and received drive slot status data, generate mapped data for each one of the EMCs for selectively activating at least one of the drive slot status indicators to indicate corresponding operational status.
Owner:AMERICAN MEGATRENDS
Method and apparatus for storing information using an intelligent block storage controller
ActiveUS9665302B1Low failure rateReduce Warranty CostsMemory architecture accessing/allocationInput/output to record carriersDrive mappingControl store
Methods, devices, and media for improving data storage reliability and efficiency comprising: creating at least one logical storage drive comprising a plurality of logical blocks; mapping the at least one logical storage drive to at least one physical storage drive based on many-to-one mapping or one-to-many mapping, wherein the at least one physical storage drive comprises a plurality of physical blocks; and applying a compression algorithm to data held in one or more logical blocks, aggregating units of the data, and storing the units of the data into one or more physical blocks.
Owner:DIVERGENT STORAGE SYST INC
Computer system having a network access point
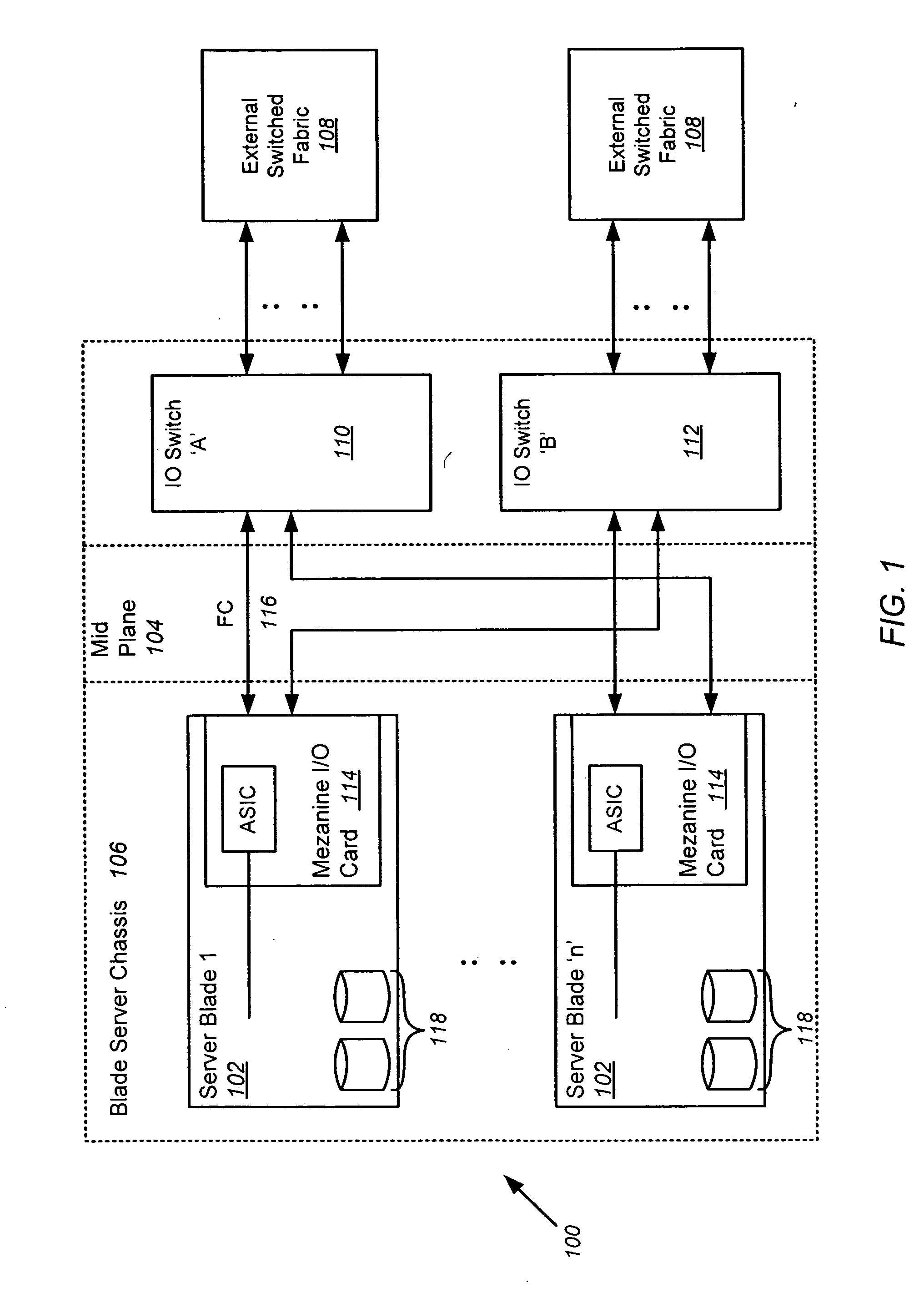
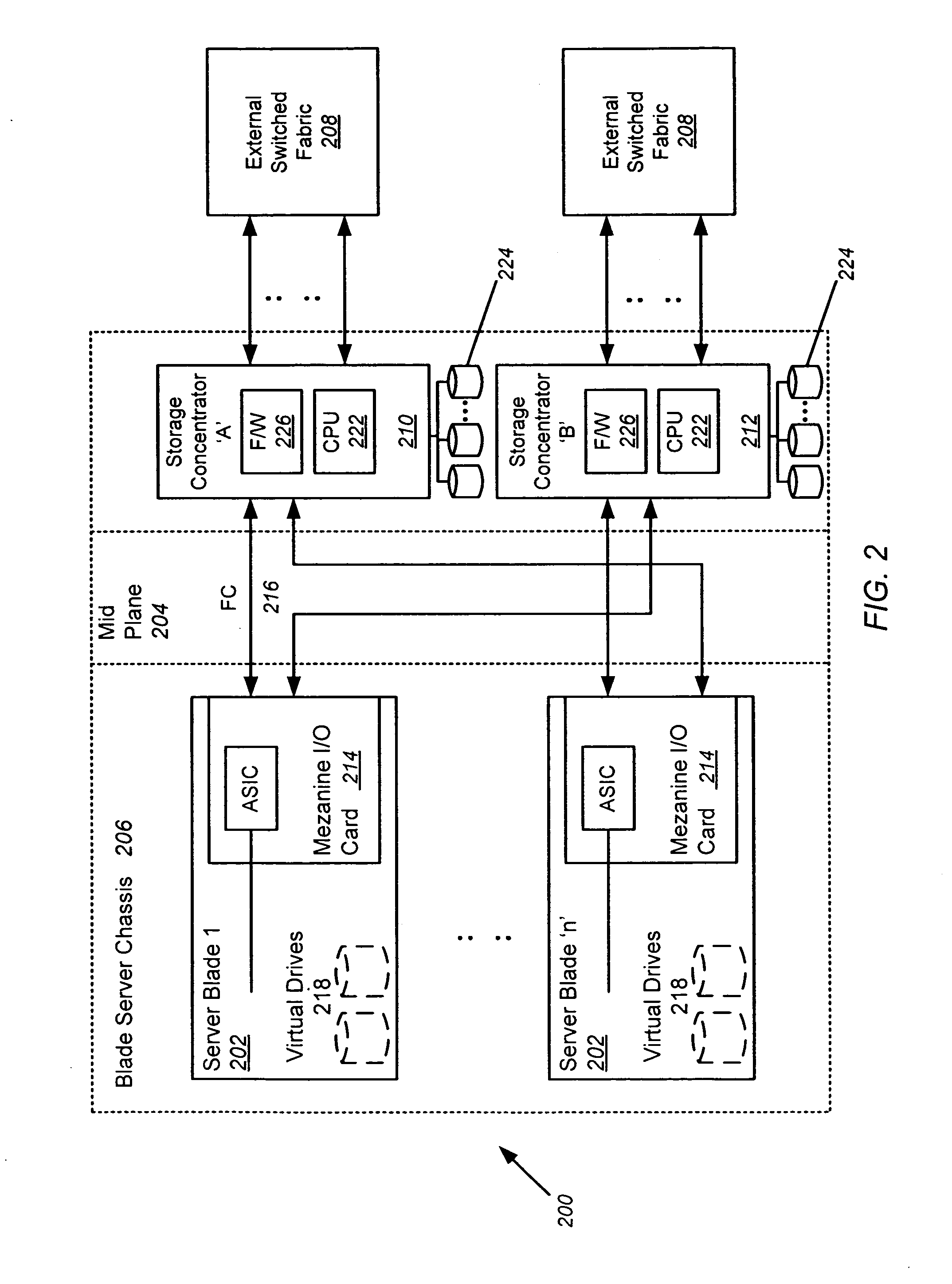
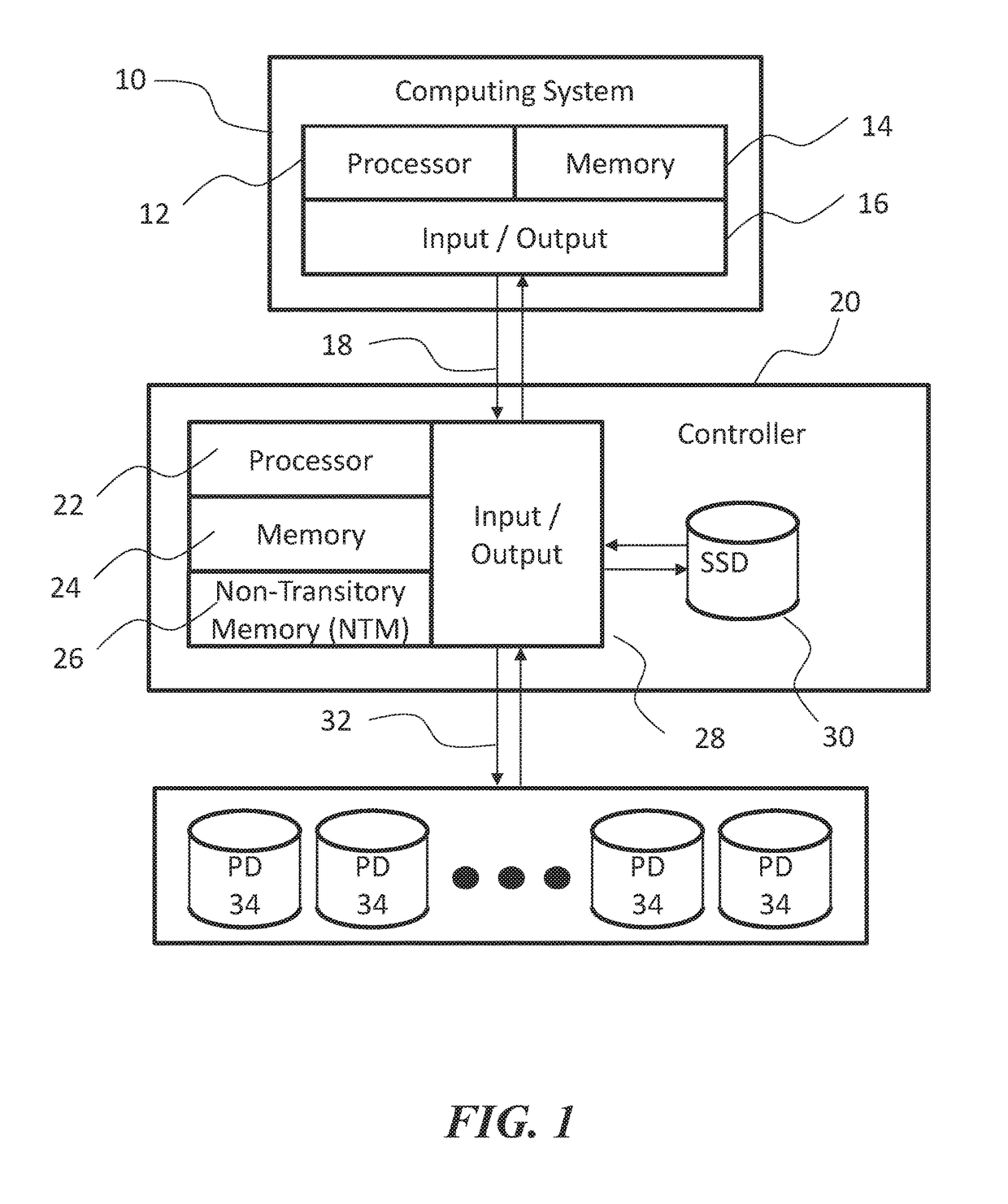
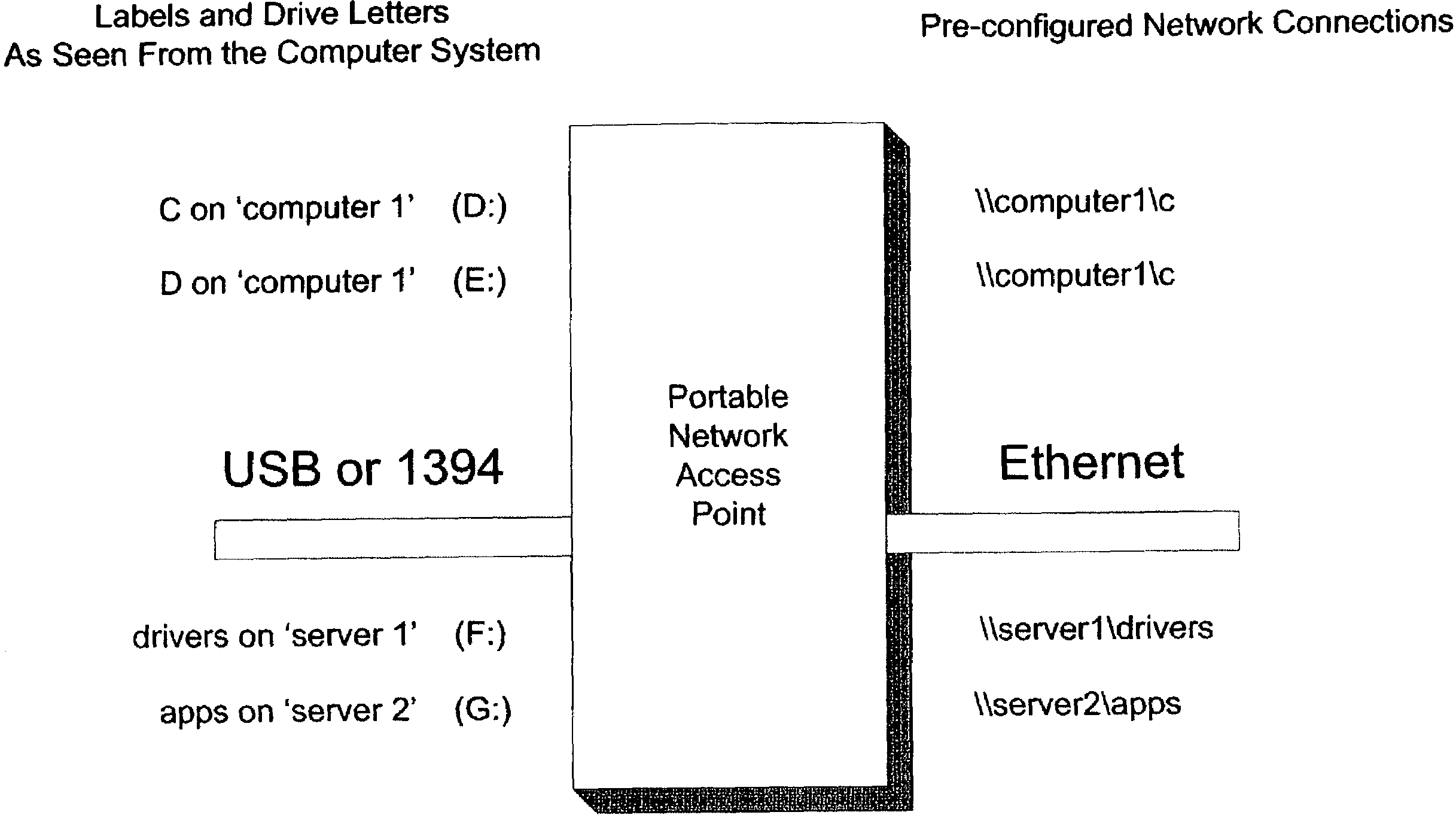
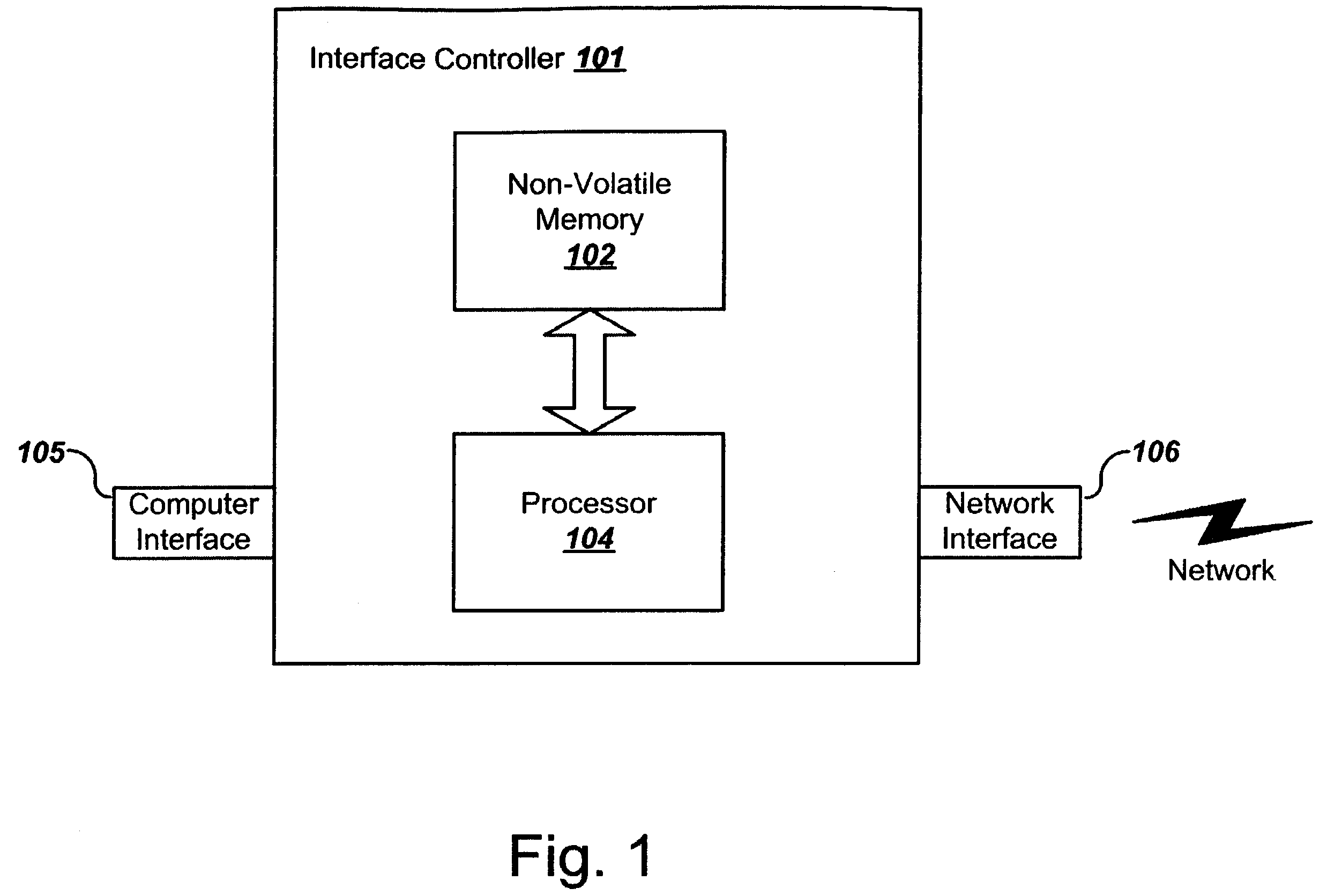
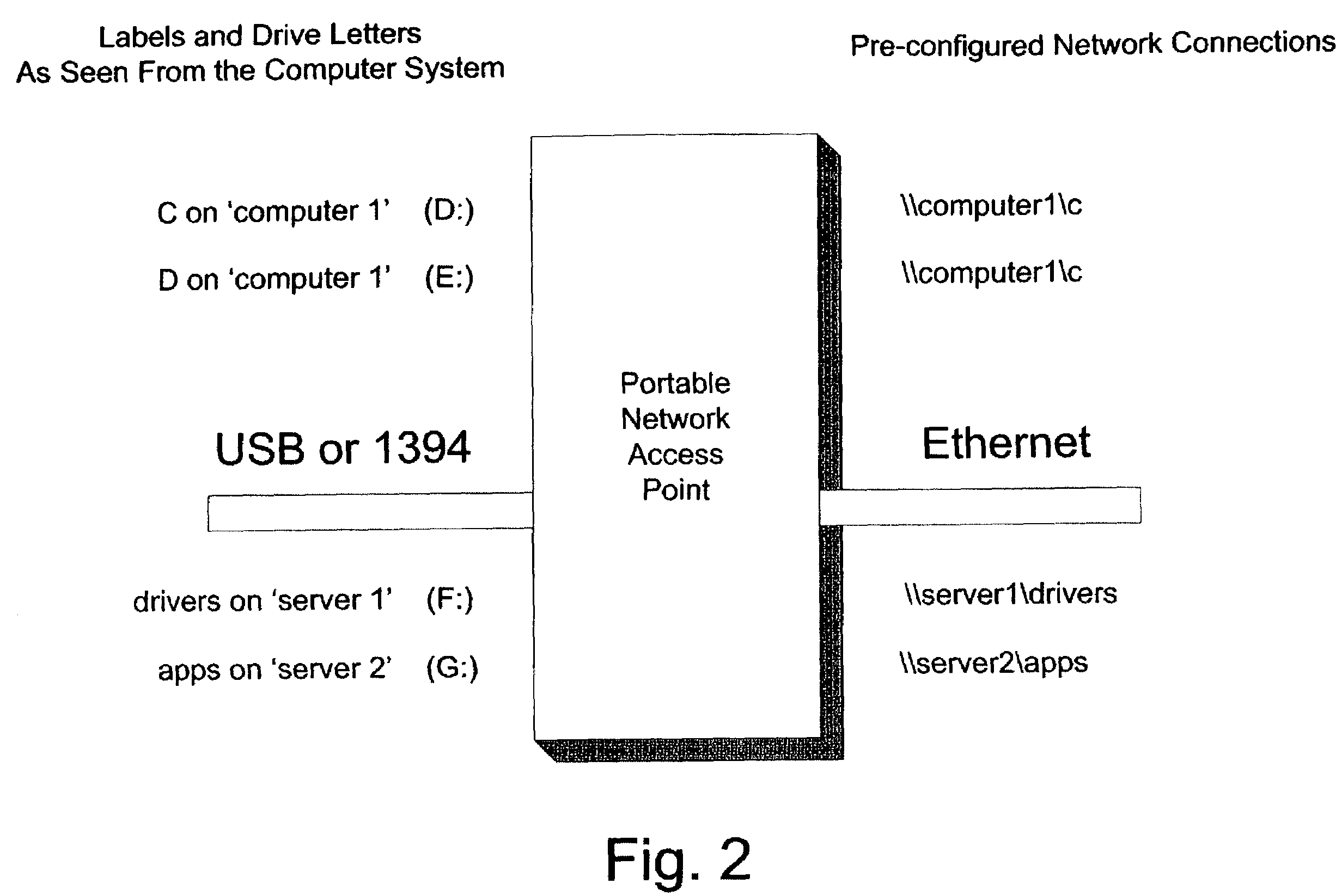
ActiveUS7231449B2Input/output to record carriersMultiple digital computer combinationsDrive mappingComputerized system
A computing system incorporating a portable network access point device is disclosed allowing access to mapped network drives through FireWire (1394) or USB. The device contains all the necessary functions to access a network and shared network drives. The hardware has ethernet on one end and USB or FireWire on the other. When connected to a network, this device will attempt to connect to all shared network drives for which it has been programmed. When connected to a computer via USB / FireWire, the computer loads the drivers and maps the listed drives. The computer need not load the entire network stack to access these drives. After a onetime configuration, the technician would be able to access shared drives from any computer without reconfiguring the computer's network settings or drive mappings. The computer system accessing the device through the USB / FireWire port sees a storage device. As seen from the network, however, the device looks like a network card attached to the network.
Owner:LENOVO PC INT
Light beam and light spot controllable illuminating device
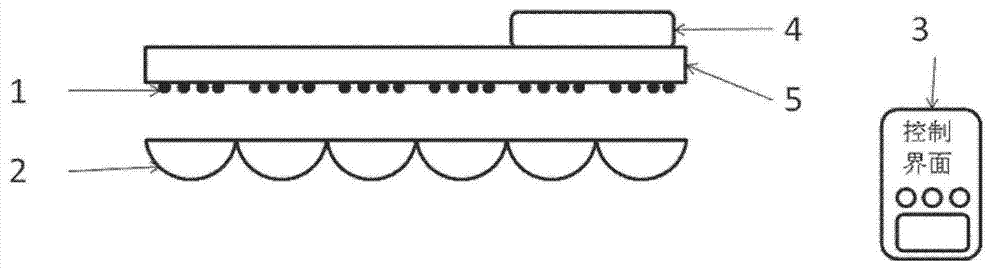
InactiveCN102927473AEasy to controlLow costPoint-like light sourceElectric lightingDrive mappingLight spot
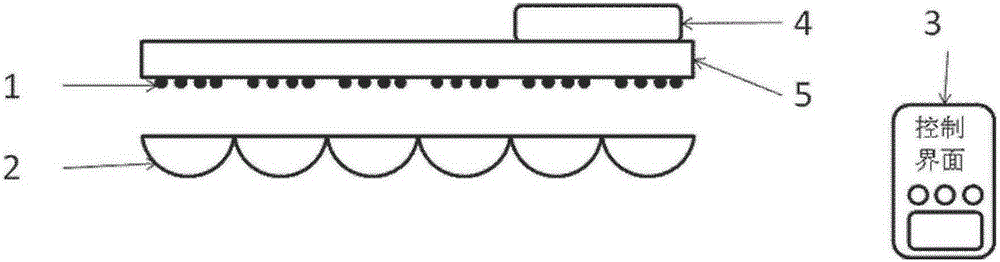
The invention discloses a light beam and light spot controllable illuminating device which comprises an array light source unit (1), an integrated lens unit (2), a target illuminating effect input device (3), an illuminating effect and light source drive mapping transfer device (4) and an array light source driving device (5). The integrated lens unit (2) is arranged on one side of the array light source unit (1). The target illuminating effect input device (3) is used for receiving control signals input by the outside, and the controls signals are transmitted to the illuminating effect and light source drive mapping transfer device (4). The illuminating effect and light source drive mapping transfer device (4) converts the control signals to array light source driving signals according to the relation between the control signals and the illuminating effect, and the array light source driving signals are transmitted to the array light source driving device (5). The light beam and light spot controllable illuminating device has the advantages of being simple in structure and stable in performance.
Owner:SOUTHEAST UNIV
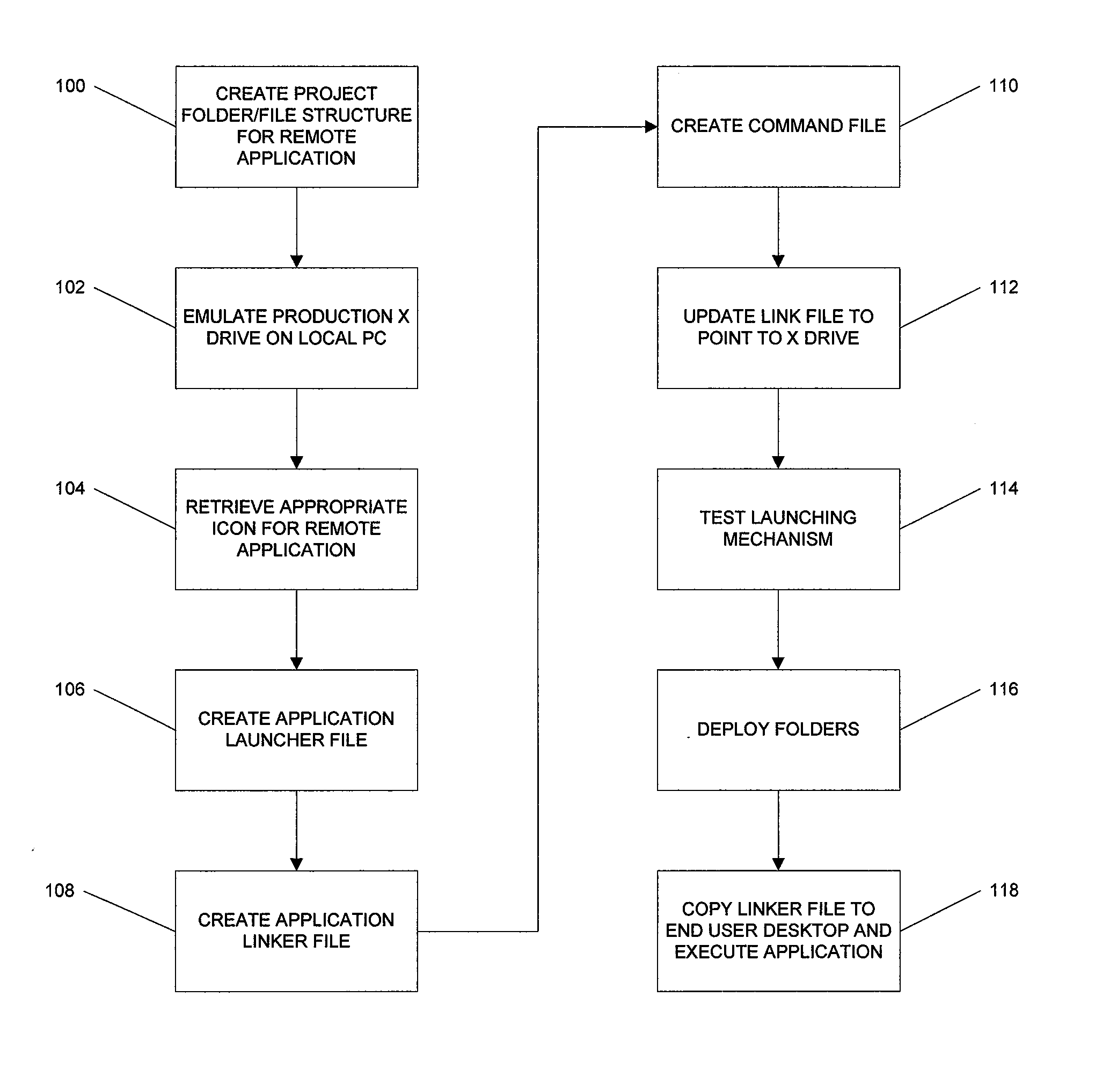
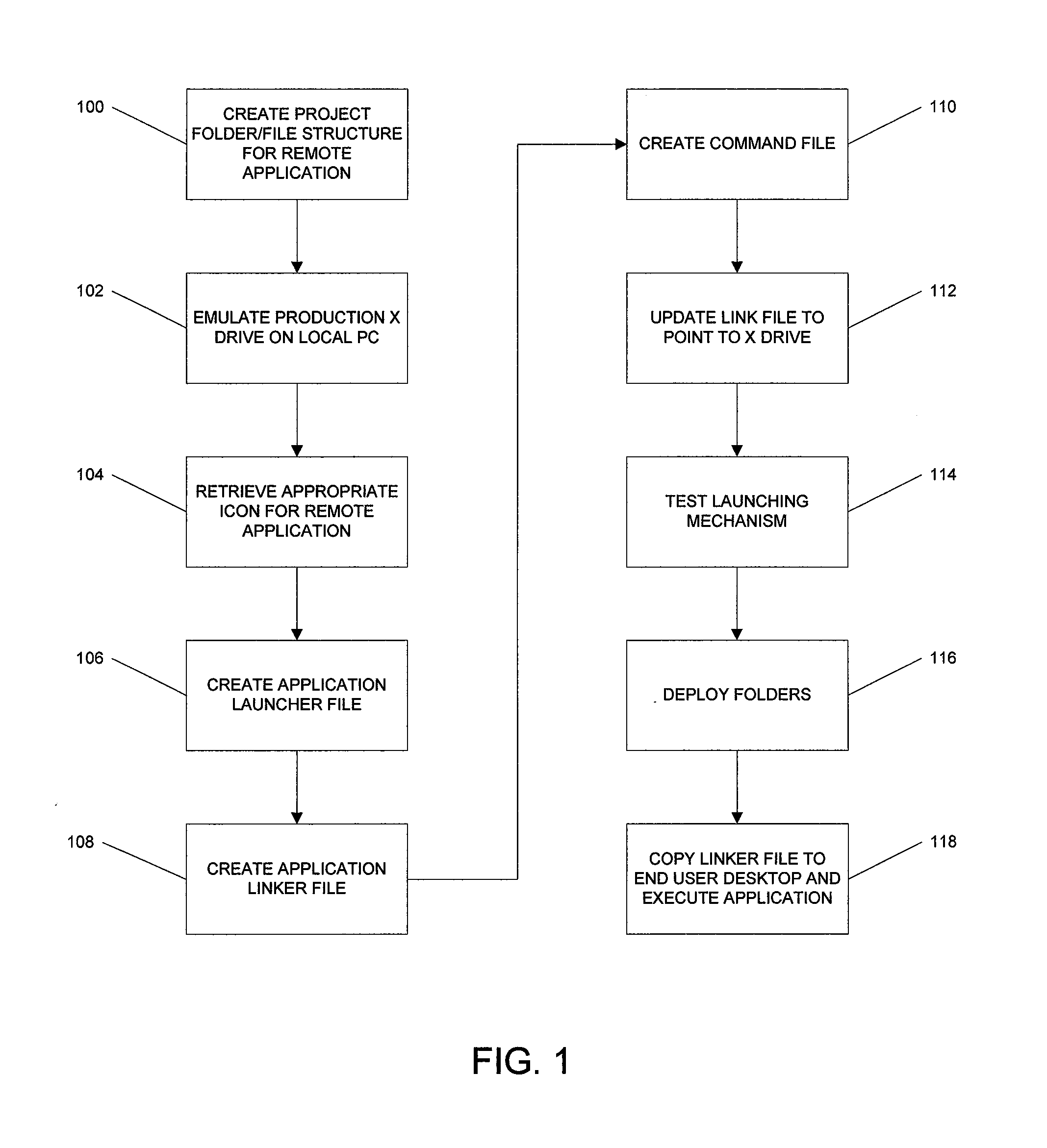
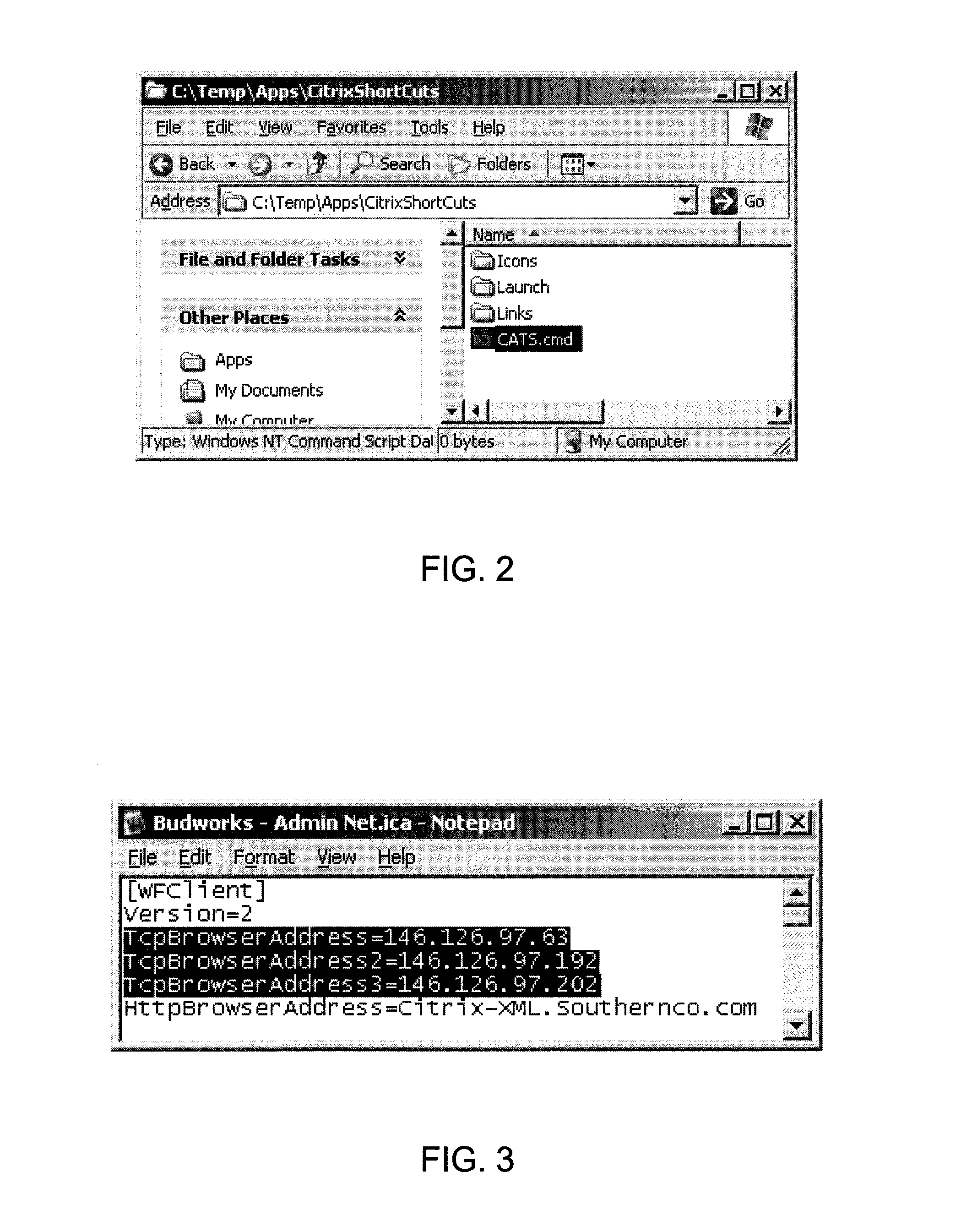
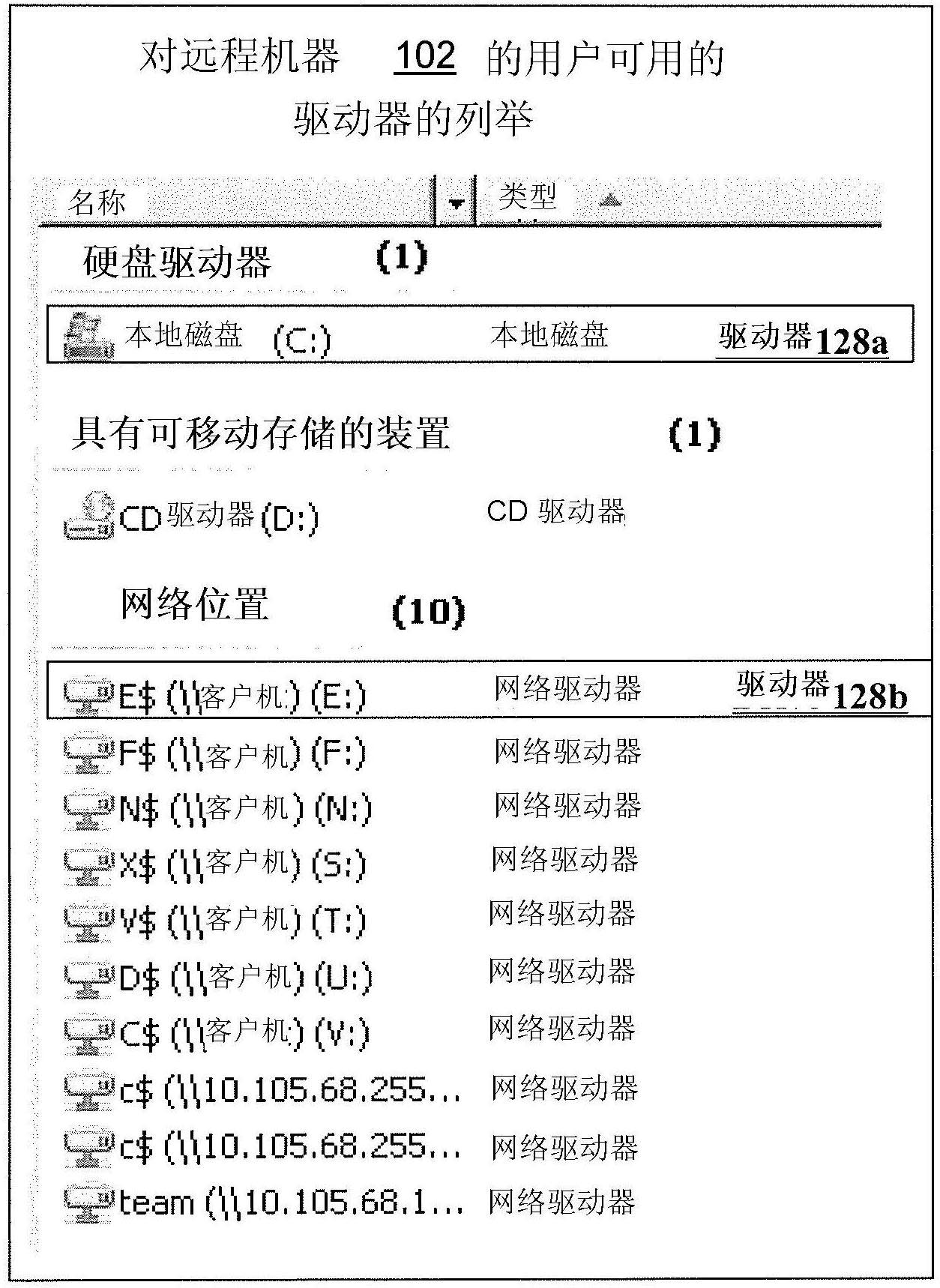
Remote application linking infrastructure
ActiveUS8117240B1Simpler to implement and support and scaleEasy to identifyDigital data processing detailsProgram controlDrive mappingFile server
A method, system, and computer readable medium for controlling user access from a segmented network to shared remote applications stored on a remote server. The method begins by generating a folder / file structure for a remote application that is to be shared on the segmented network. A file server drive mapping to a linking infrastructure data is generated for the remote application and an icon associated with the remote application is retrieved. An application launcher file is generated for the remote application. Then, an application linker file associated with the application launcher file for the remote application is generated. A command file is generated for copying the application linker file to a user's desktop. The linker file is updated to point to the file server drive. A folder for user access to the remote application is then deployed that includes the remote application icon, the application linker file, the application launcher file, and the command file.
Owner:SOUTHERN COMPANY SERVICES
Methods and systems for displaying, on a first machine, data associated with a drive of a second machine, without mapping the drive
ActiveCN102656578AInterprogram communicationMultiple digital computer combinationsClient agentDrive mapping
Methods and systems for displaying data associated with a client drive of a client computing device in a virtualized desktop executing on a remote computing device without explicitly mapping the client drive onto the remote computing device are described. A first client agent executing on a client computing device establishes a user session with a remote computing device. The first client agent transmits data identifying the client drive of the client computing device to a second client agent executing on the remote computing device. The second client agent receives data associated with the client drive and generates a shell link using the received data associated with the client drive in the context of the user session. The second client agent displays the data associated with the client drive of the client computing device in a virtualized desktop executing on the remote computing device.
Owner:CITRIX SYST INC
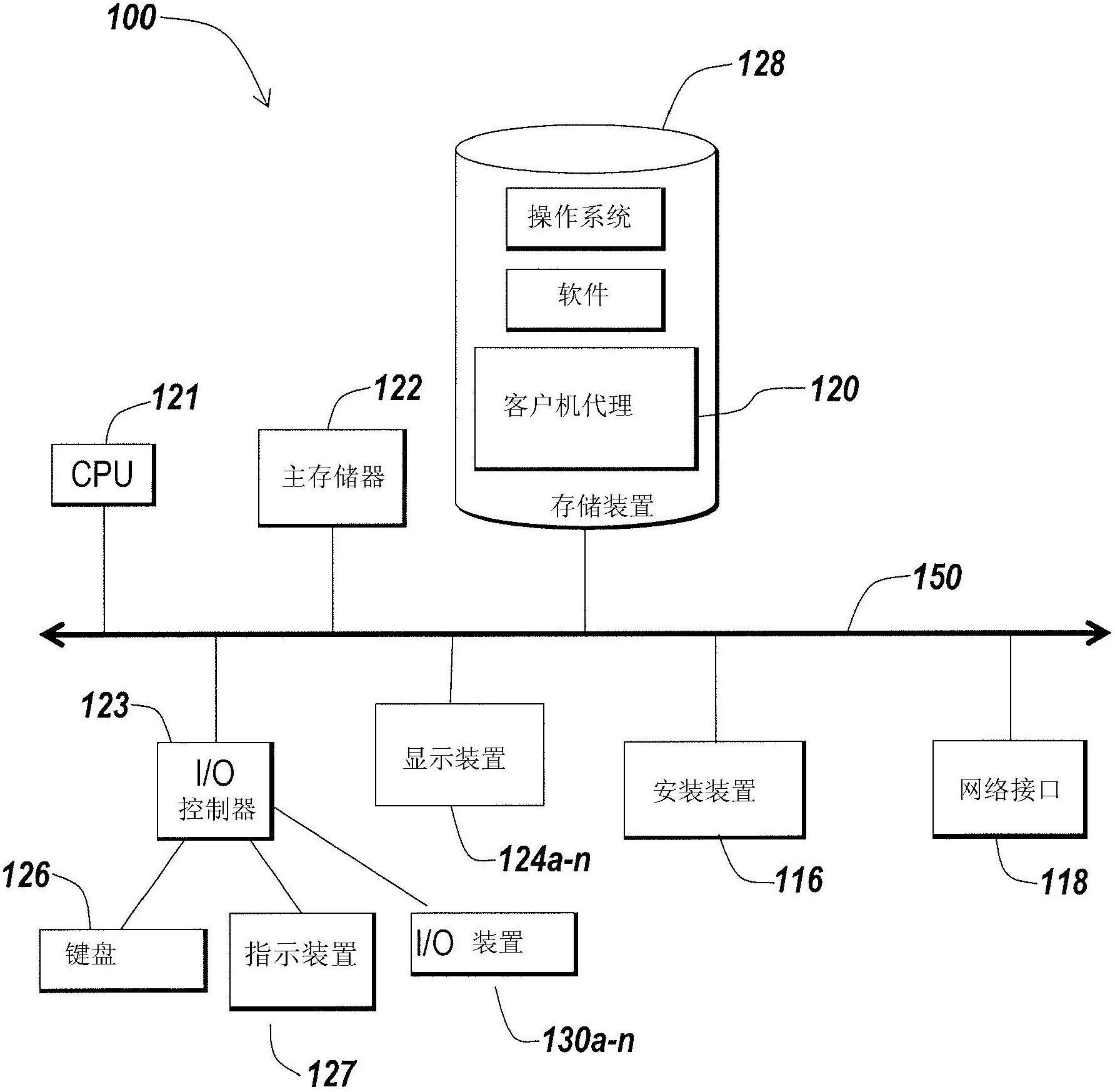
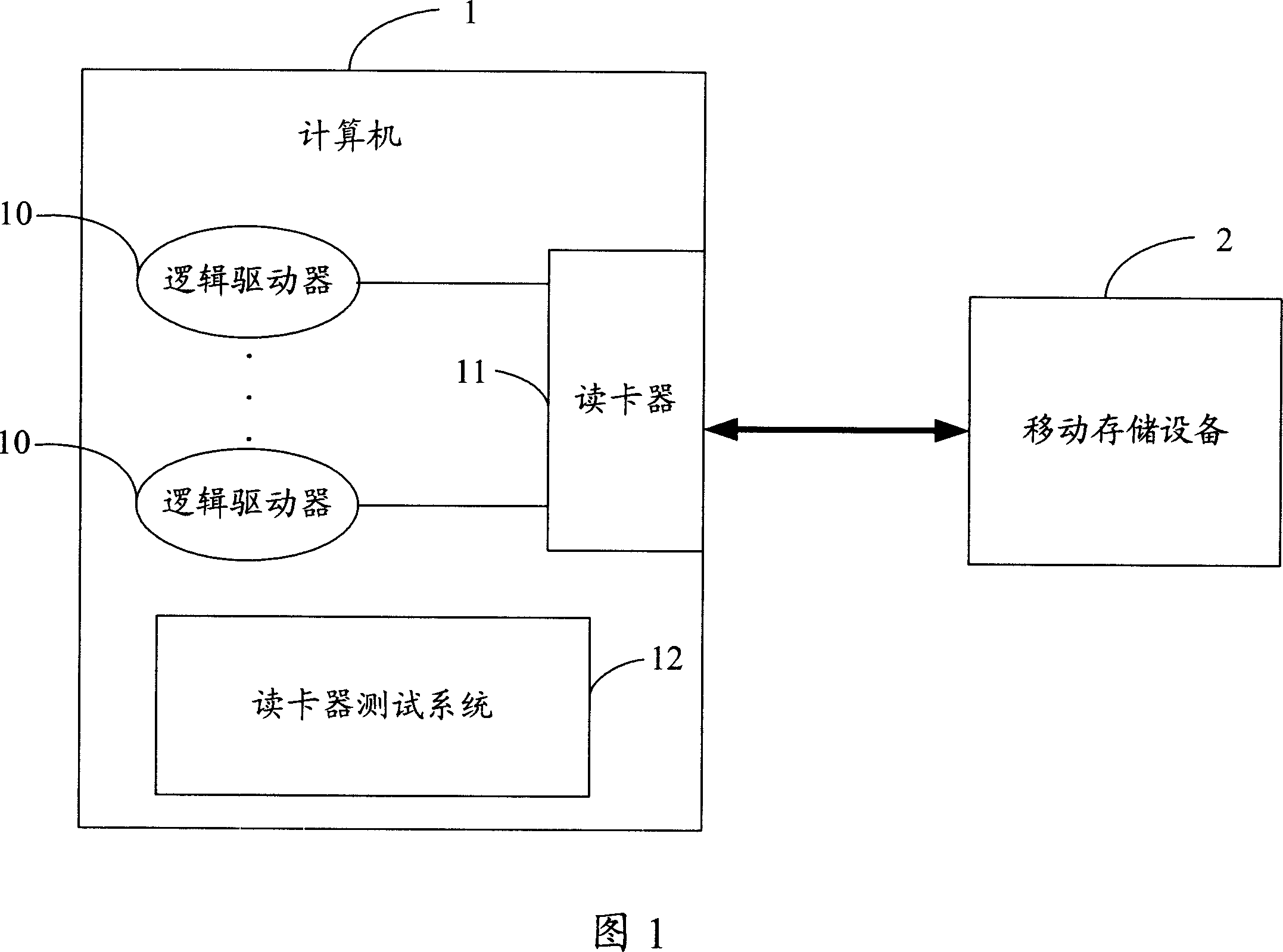
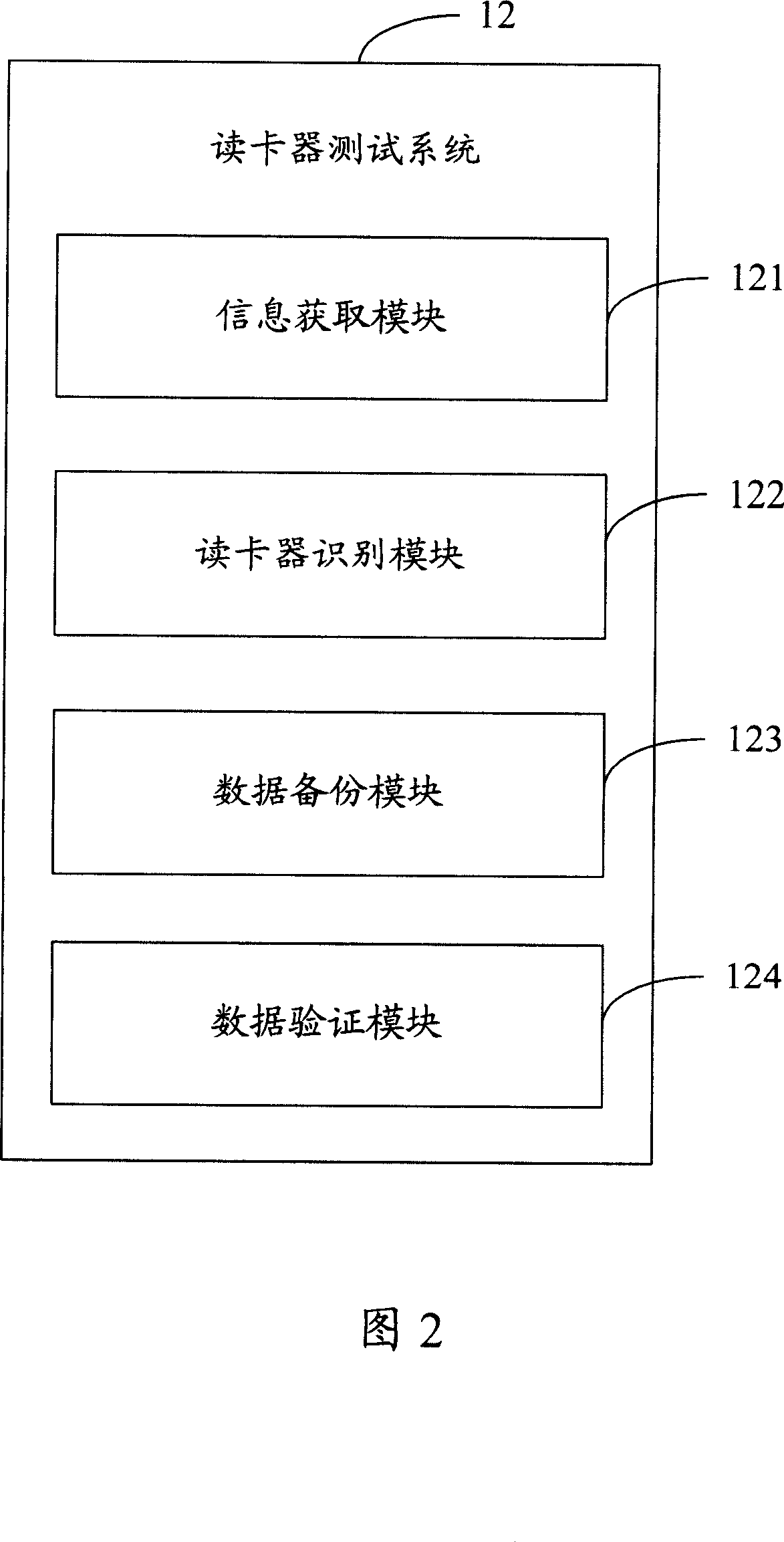
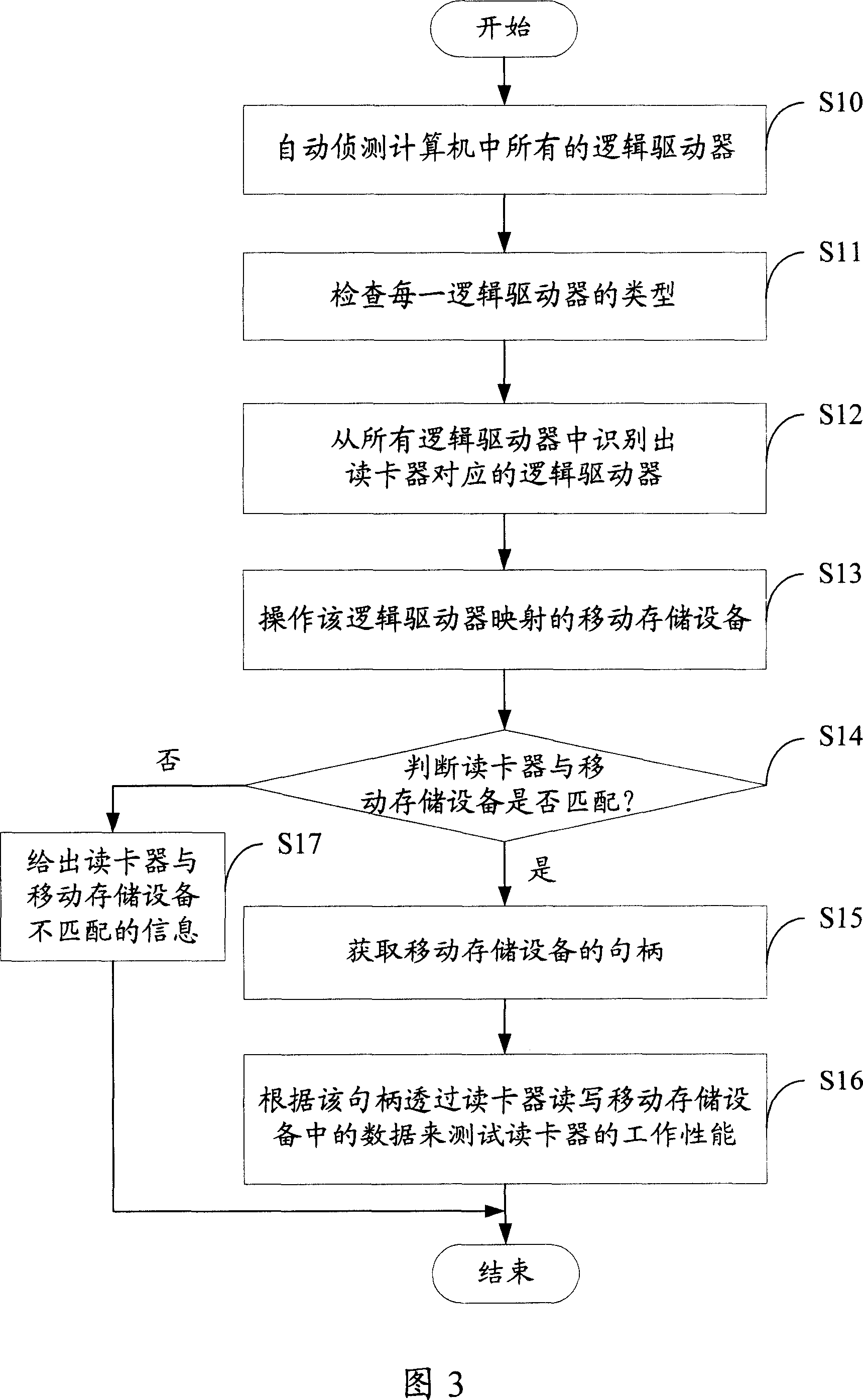
Card reader testing system and method
InactiveCN1932775AHigh precisionShorten the timeError detection/correctionDrive mappingRemovable media
A testing system and method for card reader tests its work capability to dispose data, according to the correctness of data to removal storage equipment corresponding read-write logical drive of the card reader. Identify the logical drive corresponding to the card reader and operate removal storage equipment mapping with the logical drive to judge whether they are matching. If they don't match, give the non-matching information and if they do, capture the handle of the removal storage equipment. According the data of handle read removal storage equipment, test the work capability to dispose data of the reader. It replaces manpower and enhances precision to analyze the reader's function.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
Dynamic address mapping of a fibre channel loop ID
InactiveUS7945702B1Change is minimalAlkali orthophosphate fertiliserAmmonium orthophosphate fertilisersFiberDrive mapping
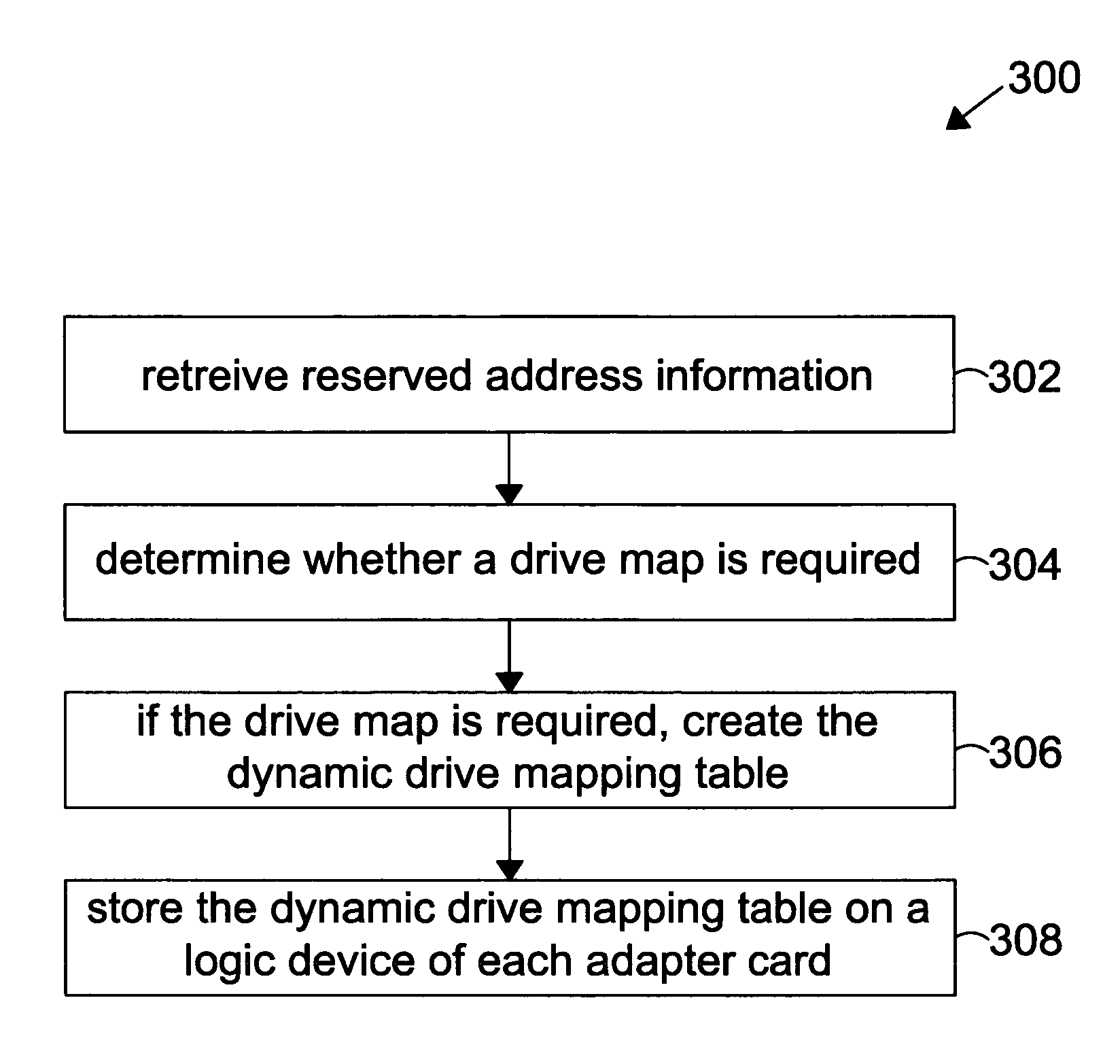
The present invention is a method and a system for dynamic mapping of a fiber channel loop ID in an ALPA loop. Based on reserved address information for the fiber channel system and a number of select ID bits for a slot ID, a dynamic drive mapping table is created. A unique address may be assigned to each drive and each controller in the ALPA loop. The created drive mapping table may be stored on logic decoding circuitry of an adaptor card coupled to each disk drive in the ALPA loop. When fiber channel loop ID signals are sent from a backplane, the fiber channel loop ID signals are translated into seven bits within an ALPA address range based on the dynamic drive mapping table. The converted signals may be sent to the disk drive coupled the adaptor card at boot up time.
Owner:NETWORK APPLIANCE INC
Disk drive mapping out data tracks to avoid thermal asperities
ActiveUS20120327533A1Record information storageAlignment for track following on disksDrive mappingComputer science
A disk drive is disclosed comprising a head actuated over a disk comprising a plurality of data tracks, wherein the head comprises a write element and a read element. An asperity in a target data track is detected, and a range of data tracks proximate the target data track is mapped out, wherein the range of data tracks spans at least twice a radial offset between the read element and the write element at the radial location of the target data track.
Owner:WESTERN DIGITAL TECH INC
Digital auendant console
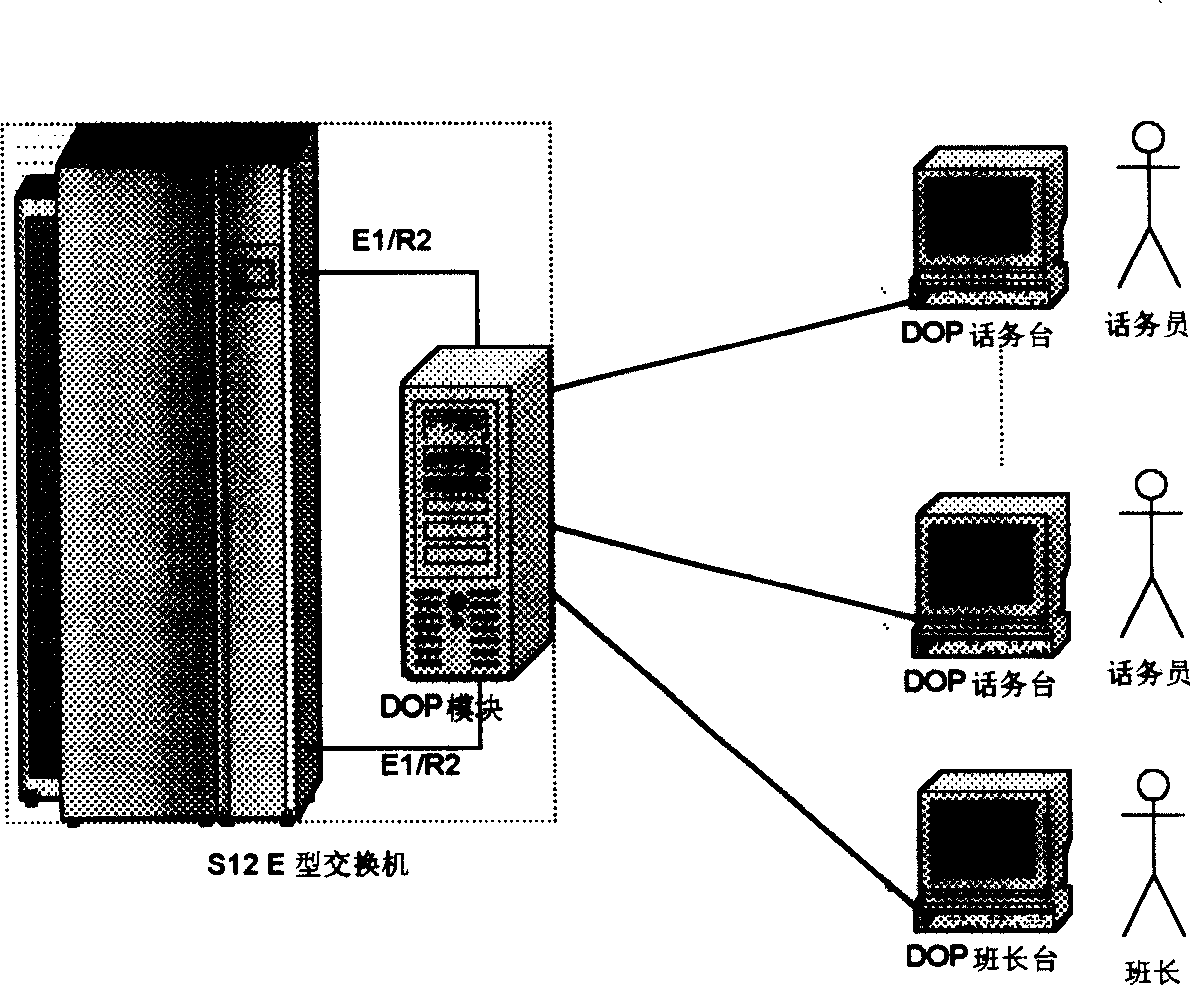
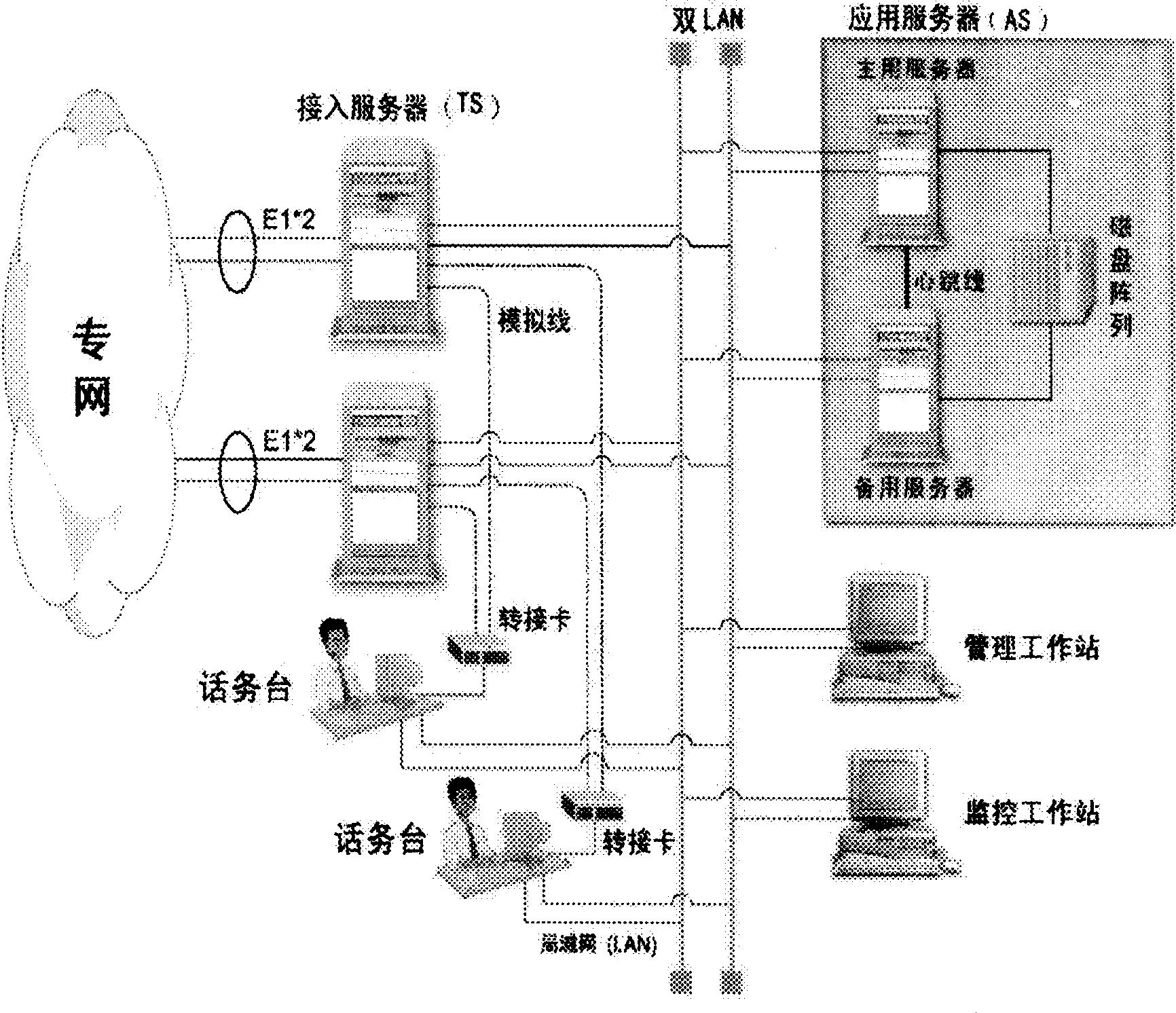
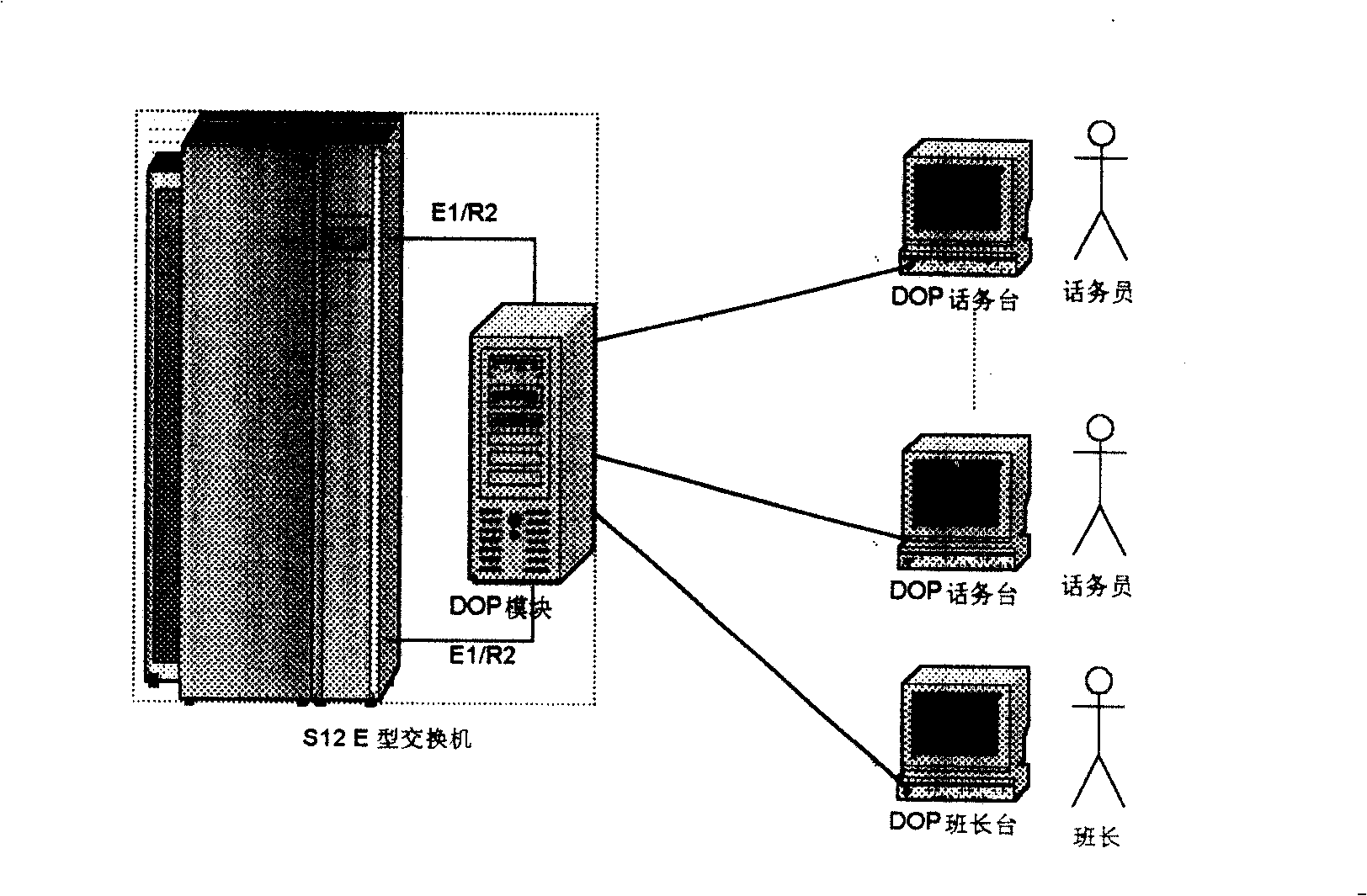
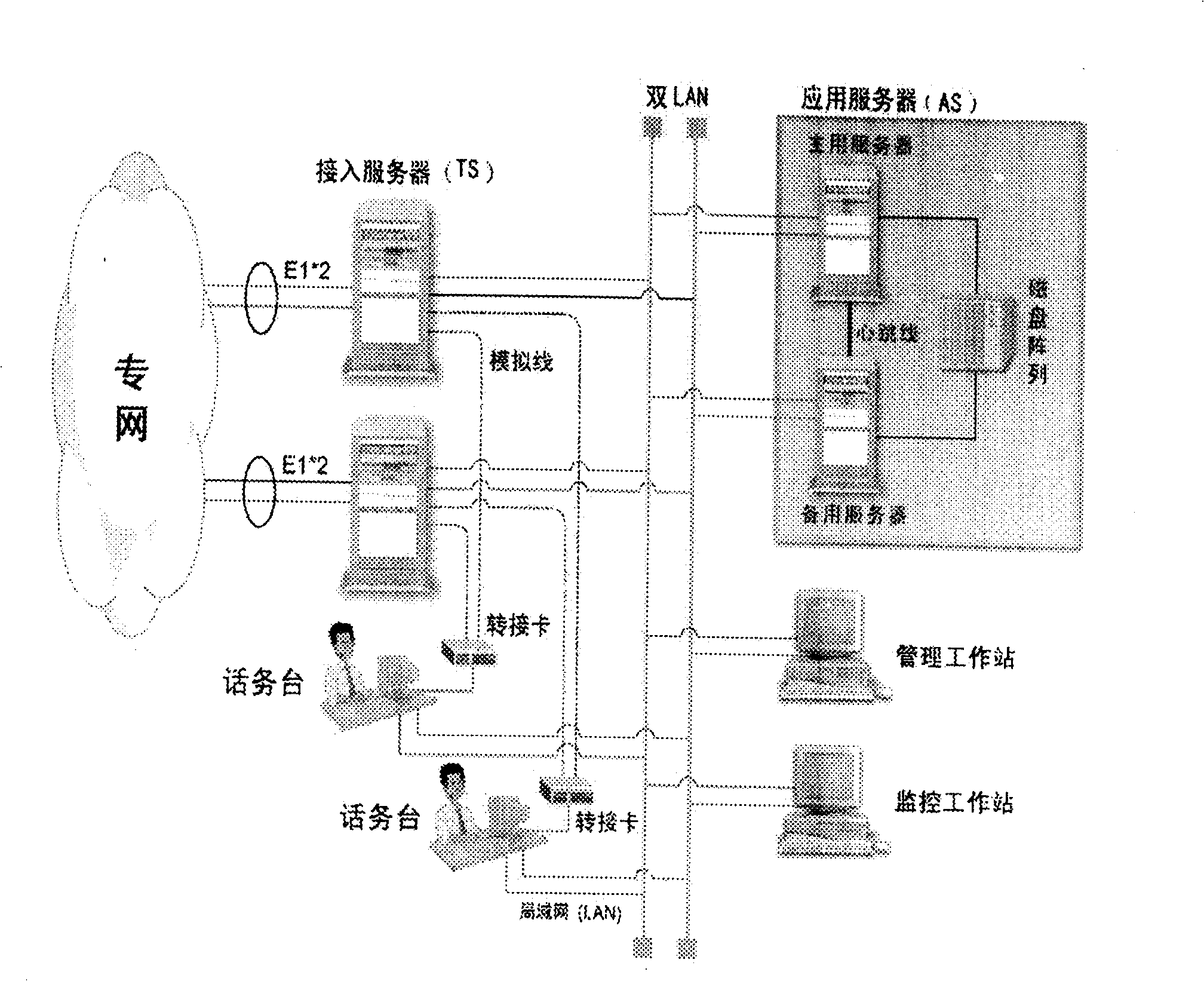
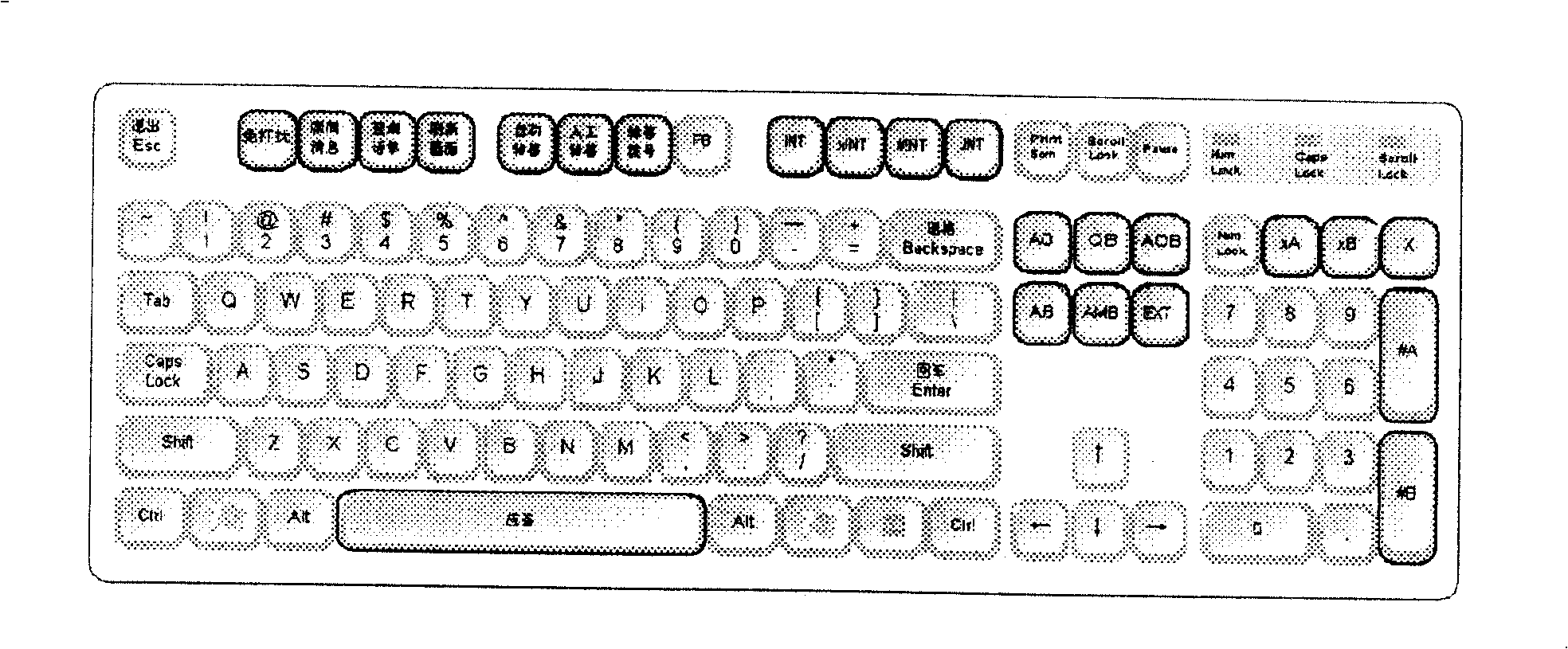
A digital telephone station including several telephone stations, the two computer backup of the connect server, the two computer backup of the applied server, the two network backup and the two electrical source backup. The two network backup is that insert two network cards on each equipment, tie the two network cards together in the interleaving way through software, assign one network IP address, other equipments call on the computer by the IP as the identification. When a passage can't work, it automatically switches onto the other passage. The two computer backup of the connect server uses two independent connect servers, besides it adds the system state monitor module. The two computer backup of the applied server uses the hardware to collocate the disk array, and has the information exchange communications through the software isochronous module. The connect server adopts the SS7 information order to connect in. It uses the DOP keyboard driving mapping technology, and catches the burst signal of the DOP special disk, then maps it onto the standard 101 keyboard. This invention mainly solves the technology problem that the present telephone station can only adapted to the S1240E series hub and can't work after the hub is upgraded.
Owner:SHANGHAI SUSR TELECOM TECH
Subscriber's line information managing system for telecommunication service platform
InactiveCN1658633AReasonable and fast business processing abilitySpecial service for subscribersDrive mappingIp address
A digital telephone station including several telephone stations, the two computer backup of the connect server, the two computer backup of the applied server, the two network backup and the two electrical source backup. The two network backup is that insert two network cards on each equipment, tie the two network cards together in the interleaving way through software, assign one network IP address, other equipments call on the computer by the IP as the identification. When a passage can't work, it automatically switches onto the other passage. The two computer backup of the connect server uses two independent connect servers, besides it adds the system state monitor module. The two computer backup of the applied server uses the hardware to collocate the disk array, and has the information exchange communications through the software isochronous module. The connect server adopts the SS7 information order to connect in. It uses the DOP keyboard driving mapping technology, and catches the burst signal of the DOP special disk, then maps it onto the standard 101 keyboard. This invention mainly solves the technology problem that the present telephone station can only adapted to the S1240E series hub and can't work after the hub is upgraded.
Owner:上海阿尔卡特网络支援系统有限公司
Method and apparatus for storing information using an intelligent block storage controller
ActiveUS20180101331A1Reduce in quantityIncrease capacityMemory architecture accessing/allocationInput/output to record carriersDrive mappingControl store
Methods, devices, and media for improving data storage reliability and efficiency comprising: creating at least one logical storage drive comprising a plurality of logical blocks; mapping the at least one logical storage drive to at least one physical storage drive based on many-to-one mapping or one-to-many mapping, wherein the at least one physical storage drive comprises a plurality of physical blocks; and applying a compression algorithm to data held in one or more logical blocks, aggregating units of the data, and storing the units of the data into one or more physical blocks.
Owner:DIVERGENT STORAGE SYST INC
Policy-driven device control in operating systems
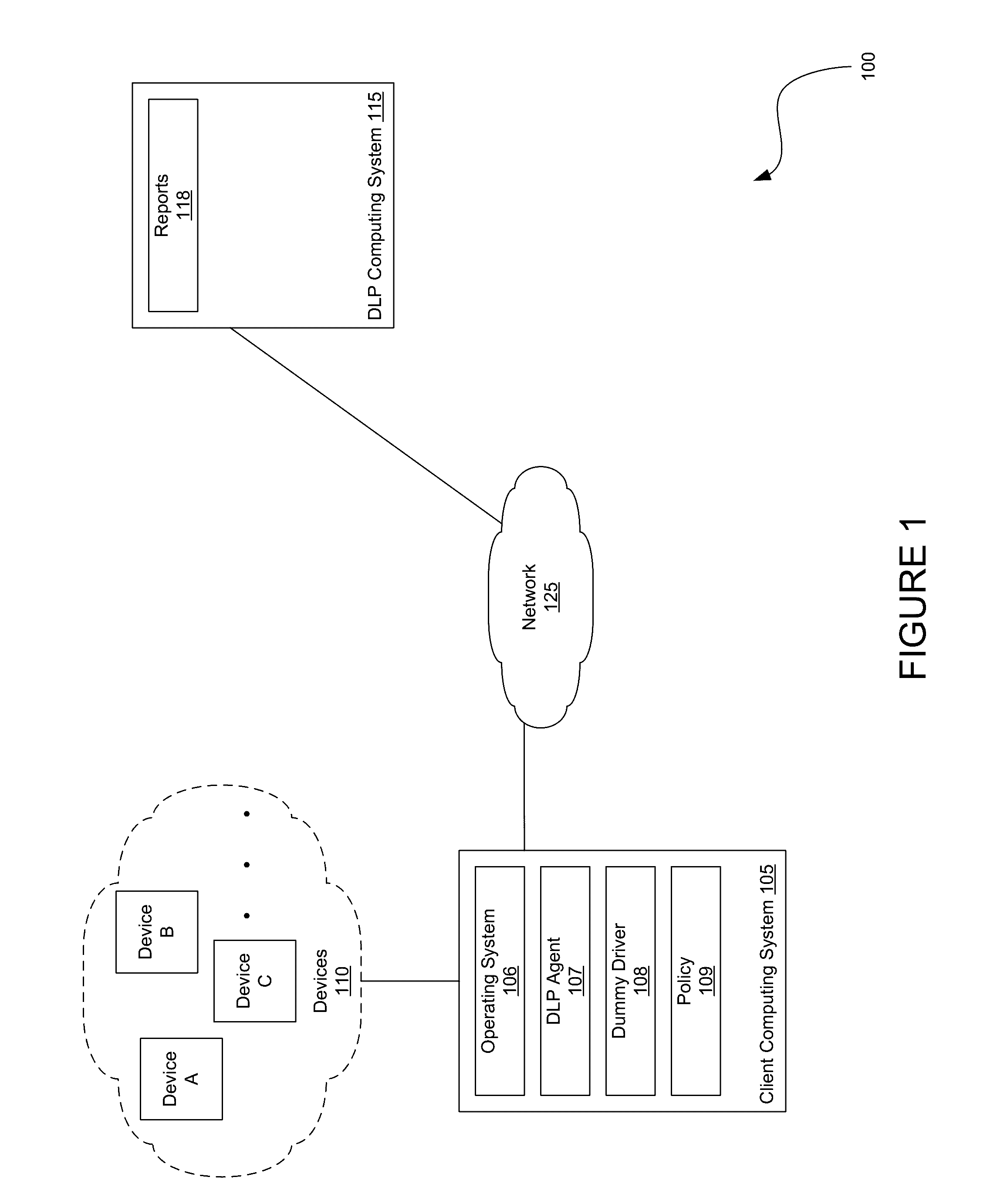
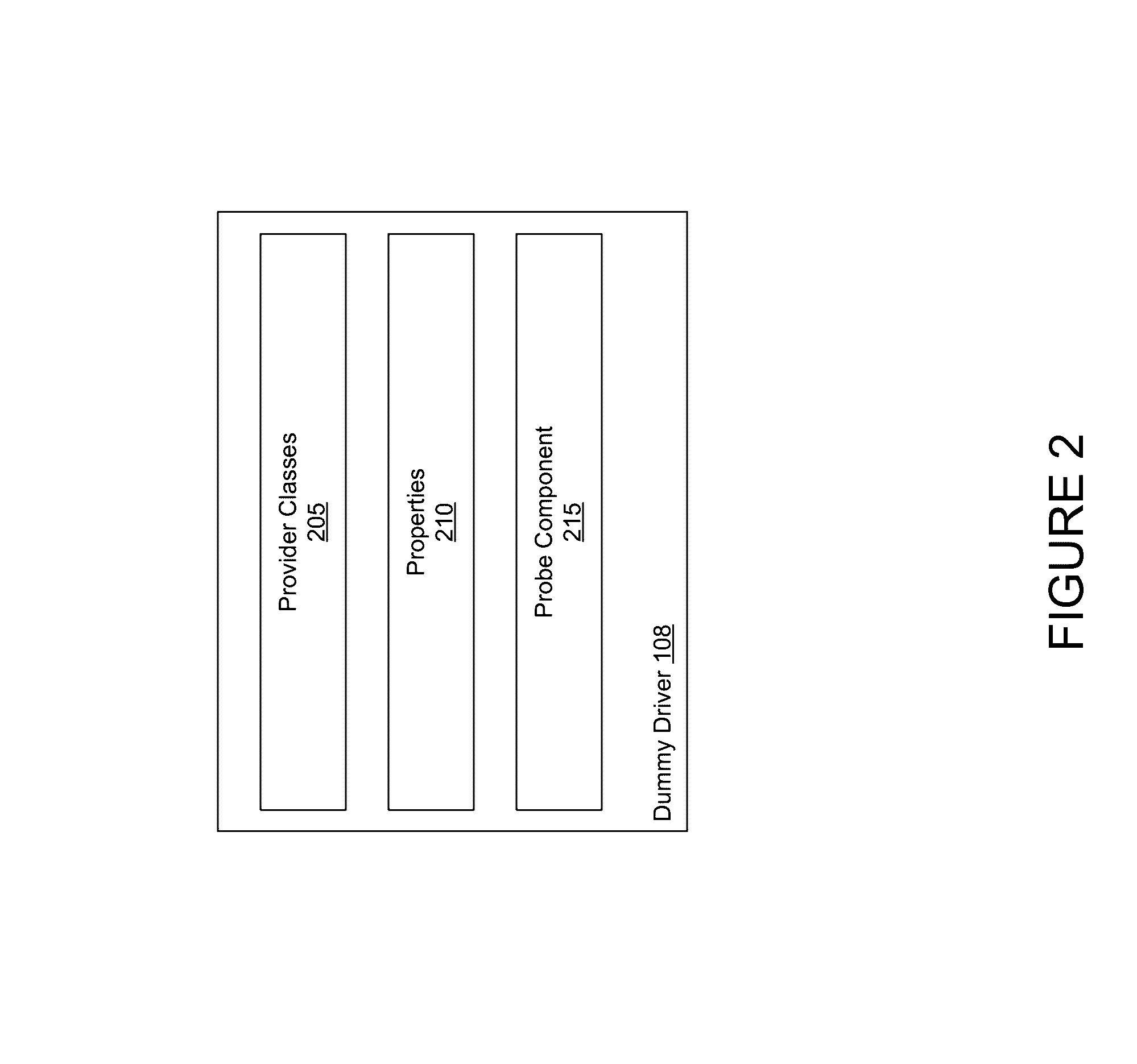
InactiveUS20160292462A1Avoid accessInternal/peripheral component protectionOperational systemDrive mapping
Techniques describe a policy-driven approach to controlling device access. A dummy driver is mapped to the device. The dummy driver receives a request by an operating system to access services provided by the device. The dummy driver determines, based on a policy, whether to block access to the device. If so, the dummy driver prevents services from being accessed via the operating system.
Owner:SYMANTEC CORP
Redistribution metal for output driver slew rate control
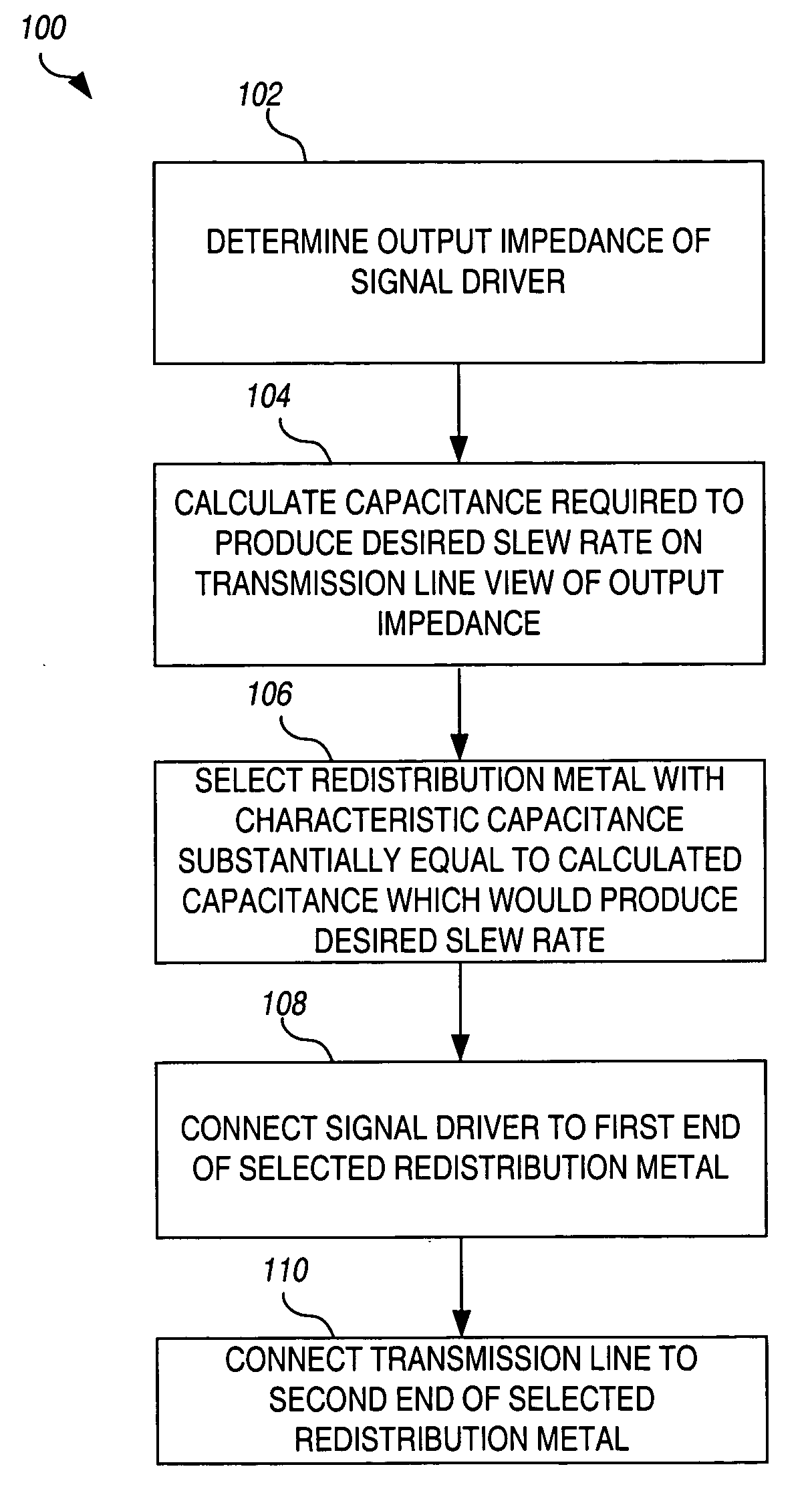
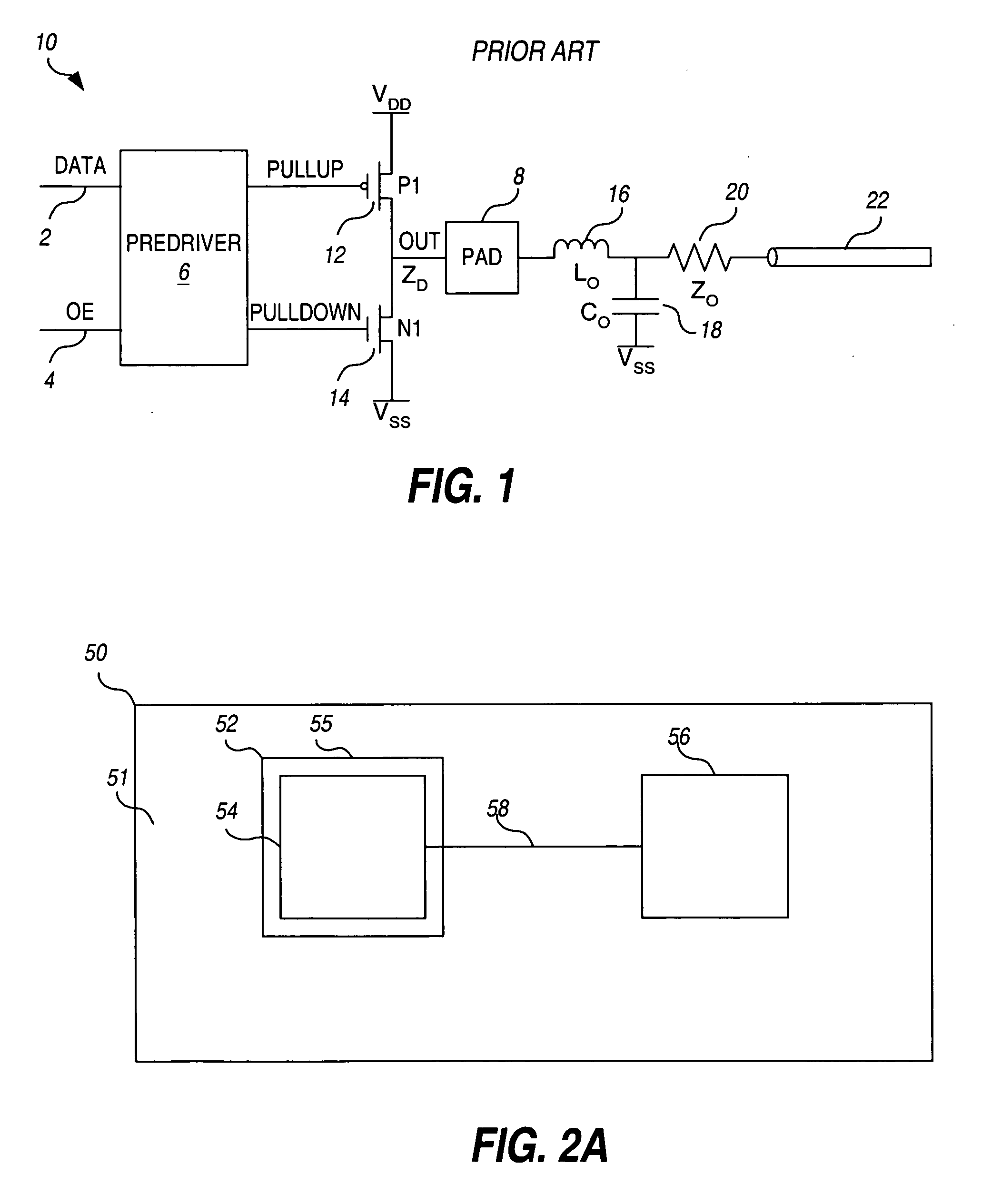
InactiveUS20050060677A1Eliminates circuit complexityRemoval costComputer aided designSoftware simulation/interpretation/emulationCapacitanceDrive mapping
A novel method is presented for mapping a signal driver of an integrated circuit to one of a plurality of interconnect pads. The output impedance of the signal driver and desired slew rate for a signal generated by the signal driver is used to calculate a desired characteristic capacitance to provide a resulting characteristic time constant required to achieve the desired slew rate on a transmission line connected to receive the signal. The characteristic capacitance associated with each at least one possible interconnection path between the driver and pad is estimated, and one of the interconnection paths whose associated characteristic capacitance is substantially equal to the desired characteristic capacitance is selected, and the output driver is then mapped to the pad associated with the selected interconnection path.
Owner:BROADCOM INT PTE LTD
Method and apparatus for storing information using an intelligent block storage controller
ActiveUS20180101332A1Reduce in quantityIncrease capacityMemory architecture accessing/allocationInput/output to record carriersDrive mappingControl store
Methods, devices, and media for improving data storage reliability and efficiency comprising: creating at least one logical storage drive comprising a plurality of logical blocks; mapping the at least one logical storage drive to at least one physical storage drive based on many-to-one mapping or one-to-many mapping, wherein the at least one physical storage drive comprises a plurality of physical blocks; and applying a compression algorithm to data held in one or more logical blocks, aggregating units of the data, and storing the units of the data into one or more physical blocks.
Owner:DIVERGENT STORAGE SYST INC
Drive mapping method based on user identity authentication
ActiveCN104794072AUser identity/authority verificationUnauthorized memory use protectionUser needsDrive mapping
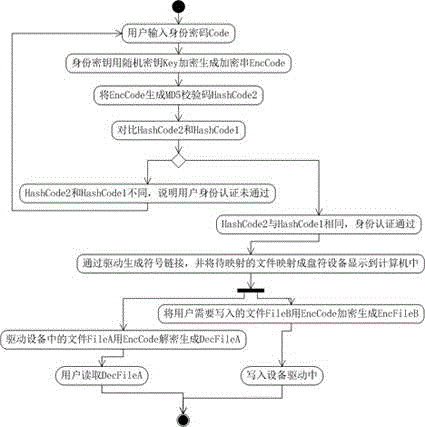
The invention relates to a drive mapping method based on user identity authentication. When a user needs to map a drive, the user inputs an identity password, and an identity secret key is generated into an encrypted string EncCode through a random secret key Key; MD5 verification is carried out on the encrypted string EncCode to generate an identity verification value HashCode2; HashCode2 is compared with HashCode1, and if HashCode1= HashCode2, identity authentication passes; a symbolic link is generated through a drive, and mapped into drive equipment; when the user reads a file, specified file data in the equipment are decrypted through the encrypted string EncCode to be read and operated by the user; when the user needs to write the file in, the file is encrypted through the encrypted string EncCode and stored in a file body. The data safety of the user is high, and the method conforms to the use habit of the user better.
Owner:BEIJING VRV SOFTWARE CO LTD
Lighting device with controllable beam spot
InactiveCN102927473BEasy to controlLow costElectric lightingElectric light circuit arrangementDrive mappingControl signal
The invention discloses a light beam and light spot controllable illuminating device which comprises an array light source unit (1), an integrated lens unit (2), a target illuminating effect input device (3), an illuminating effect and light source drive mapping transfer device (4) and an array light source driving device (5). The integrated lens unit (2) is arranged on one side of the array light source unit (1). The target illuminating effect input device (3) is used for receiving control signals input by the outside, and the controls signals are transmitted to the illuminating effect and light source drive mapping transfer device (4). The illuminating effect and light source drive mapping transfer device (4) converts the control signals to array light source driving signals according to the relation between the control signals and the illuminating effect, and the array light source driving signals are transmitted to the array light source driving device (5). The light beam and light spot controllable illuminating device has the advantages of being simple in structure and stable in performance.
Owner:SOUTHEAST UNIV
Digital auendant console
ActiveCN100452673CFulfilling transfer requirementsMeet the requirements of HASpecial service for subscribersManual exchangesDrive mappingIp address
A digital telephone station including several telephone stations, the two computer backup of the connect server, the two computer backup of the applied server, the two network backup and the two electrical source backup. The two network backup is that insert two network cards on each equipment, tie the two network cards together in the interleaving way through software, assign one network IP address, other equipments call on the computer by the IP as the identification. When a passage can't work, it automatically switches onto the other passage. The two computer backup of the connect server uses two independent connect servers, besides it adds the system state monitor module. The two computer backup of the applied server uses the hardware to collocate the disk array, and has the information exchange communications through the software isochronous module. The connect server adopts the SS7 information order to connect in. It uses the DOP keyboard driving mapping technology, and catches the burst signal of the DOP special disk, then maps it onto the standard 101 keyboard. This invention mainly solves the technology problem that the present telephone station can only adapted to the S1240E series hub and can't work after the hub is upgraded.
Owner:SHANGHAI SUSR TELECOM TECH
General continuous data protection method, device and electronic equipment
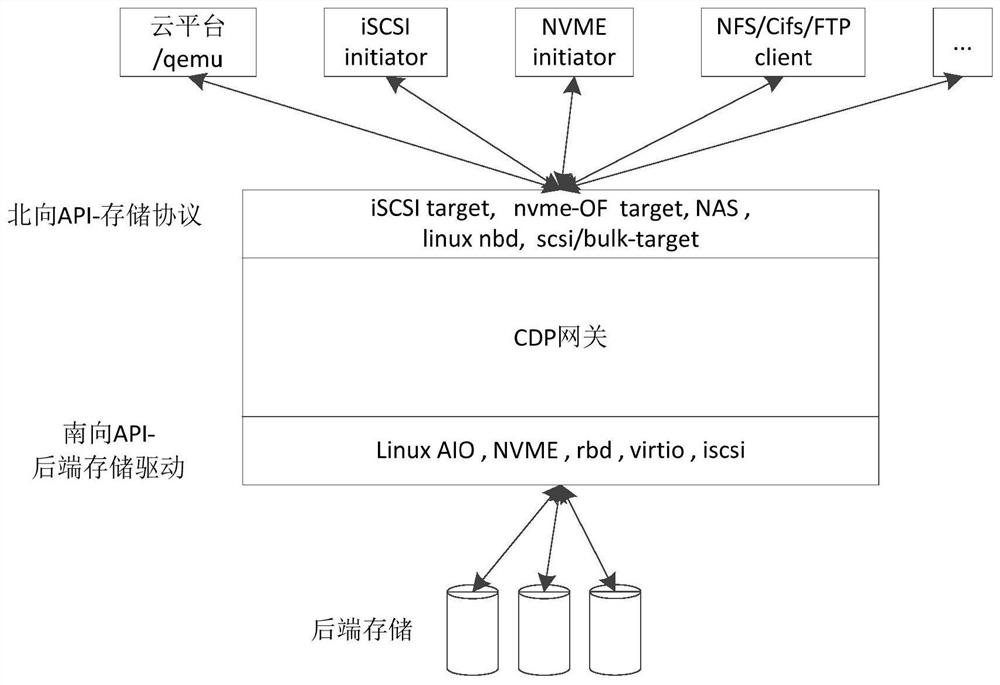
ActiveCN112540872BCompatible with reading and writing requirementsRead and write needs are metInput/output to record carriersRedundant operation error correctionDrive mappingEngineering
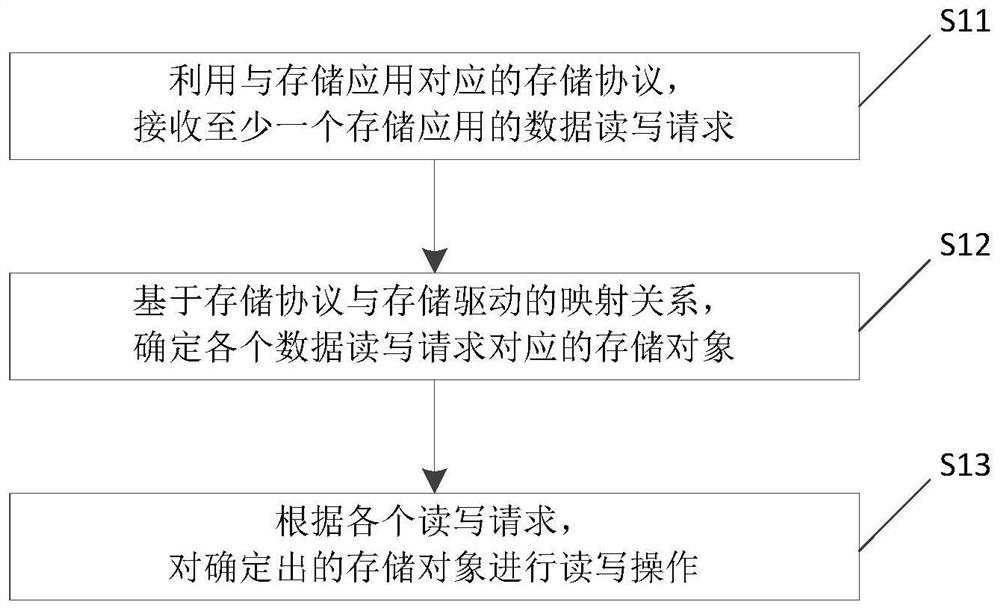
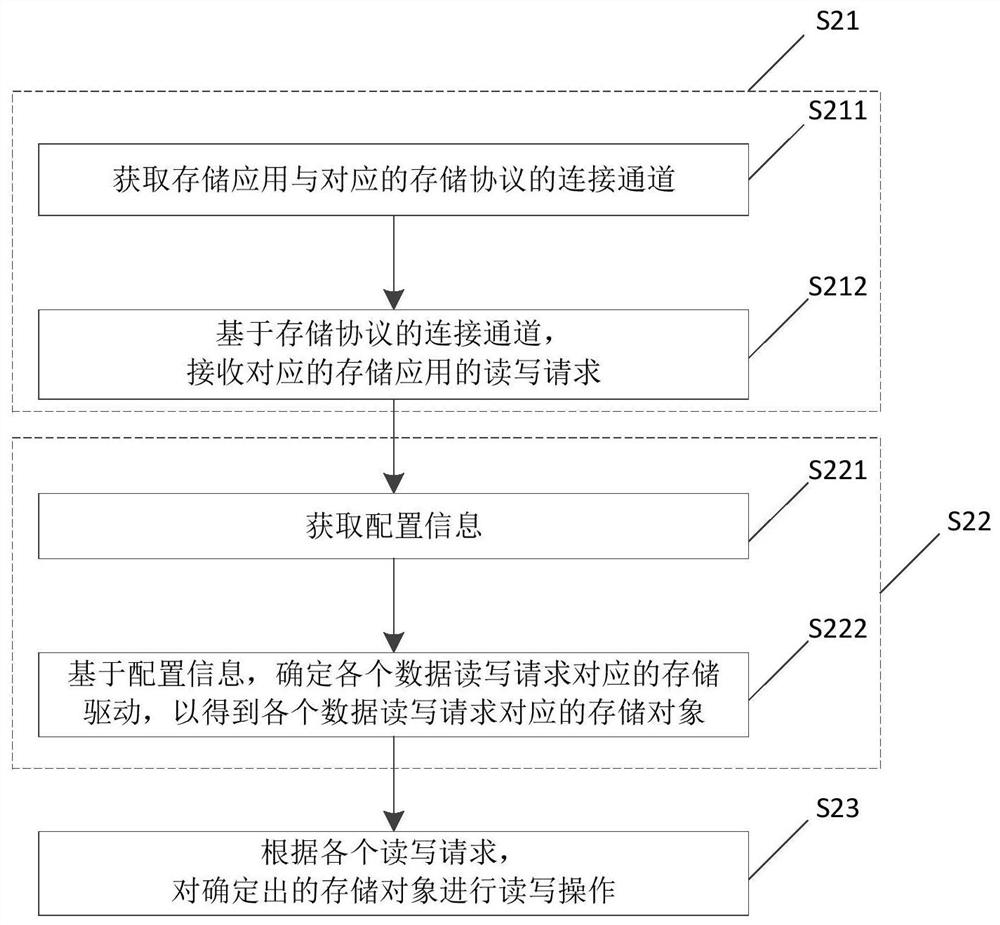
The present invention relates to the technical field of data backup, in particular to a general continuous data protection method, device and electronic equipment, the method includes receiving at least one data read and write request of the storage application by using a storage protocol corresponding to the storage application; based on the storage protocol The mapping relationship with the storage driver determines the storage object corresponding to each of the data read and write requests, and the storage object corresponds to the storage driver; according to each of the read and write requests, perform read and write operations on the determined storage object. Locally integrates at least one storage protocol corresponding to a storage application. Using the correspondence between storage applications and storage protocols, it can be compatible with the read and write requirements of various storage applications; and also integrates the mapping relationship between storage protocols and storage drivers. Using the mapping relationship, at least one storage driver for storing objects can be locally integrated, so that the storage requirements of at least one storage application can be met without additional deployment of continuous data protection.
Owner:WUXI CHINAC DATA TECH SERVICE
Methods and systems for displaying, on a first machine, data associated with a drive of a second machine, without mapping the drive
ActiveCN102656578BInterprogram communicationMultiple digital computer combinationsClient agentDrive mapping
Methods and systems for displaying data associated with a client drive of a client computing device in a virtualized desktop executing on a remote computing device without explicitly mapping the client drive onto the remote computing device are described. A first client agent executing on a client computing device establishes a user session with a remote computing device. The first client agent transmits data identifying the client drive of the client computing device to a second client agent executing on the remote computing device. The second client agent receives data associated with the client drive and generates a shell link using the received data associated with the client drive in the context of the user session. The second client agent displays the data associated with the client drive of the client computing device in a virtualized desktop executing on the remote computing device.
Owner:CITRIX SYST INC
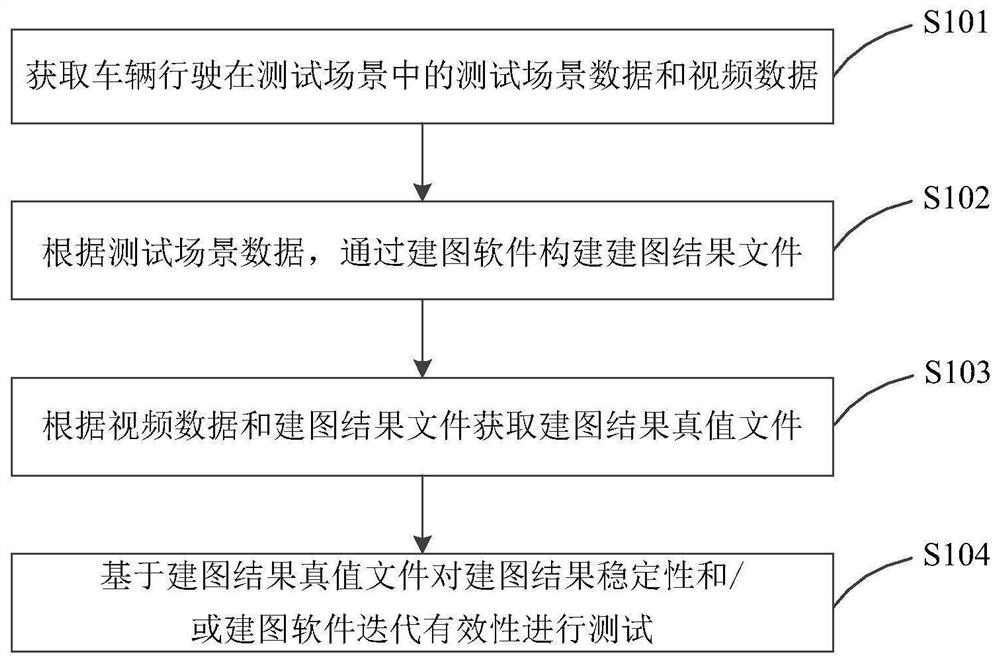
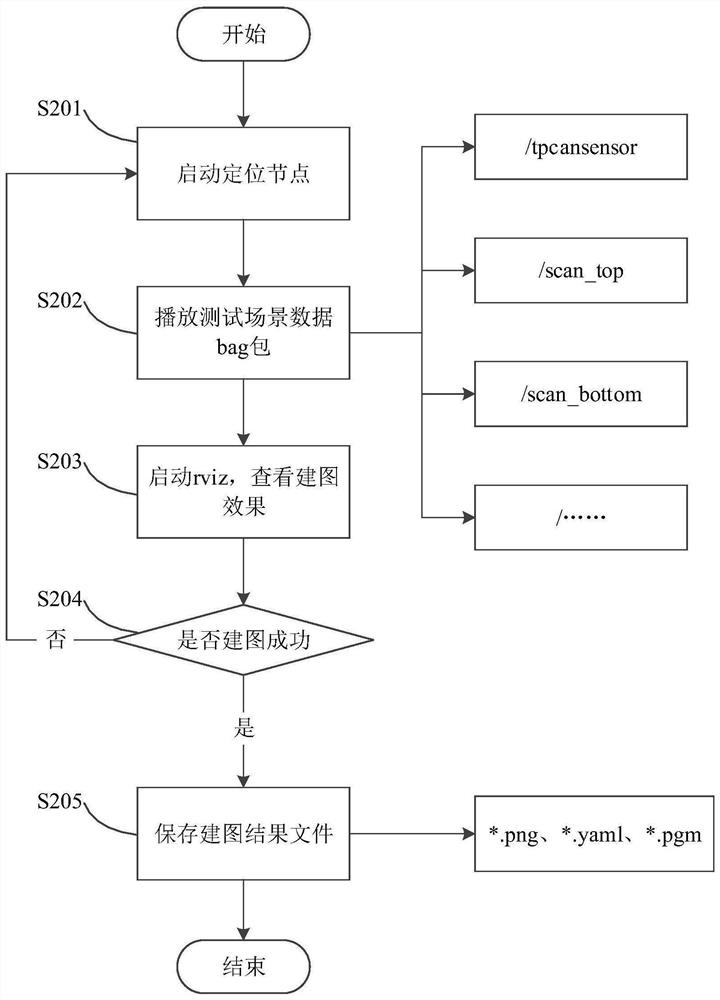
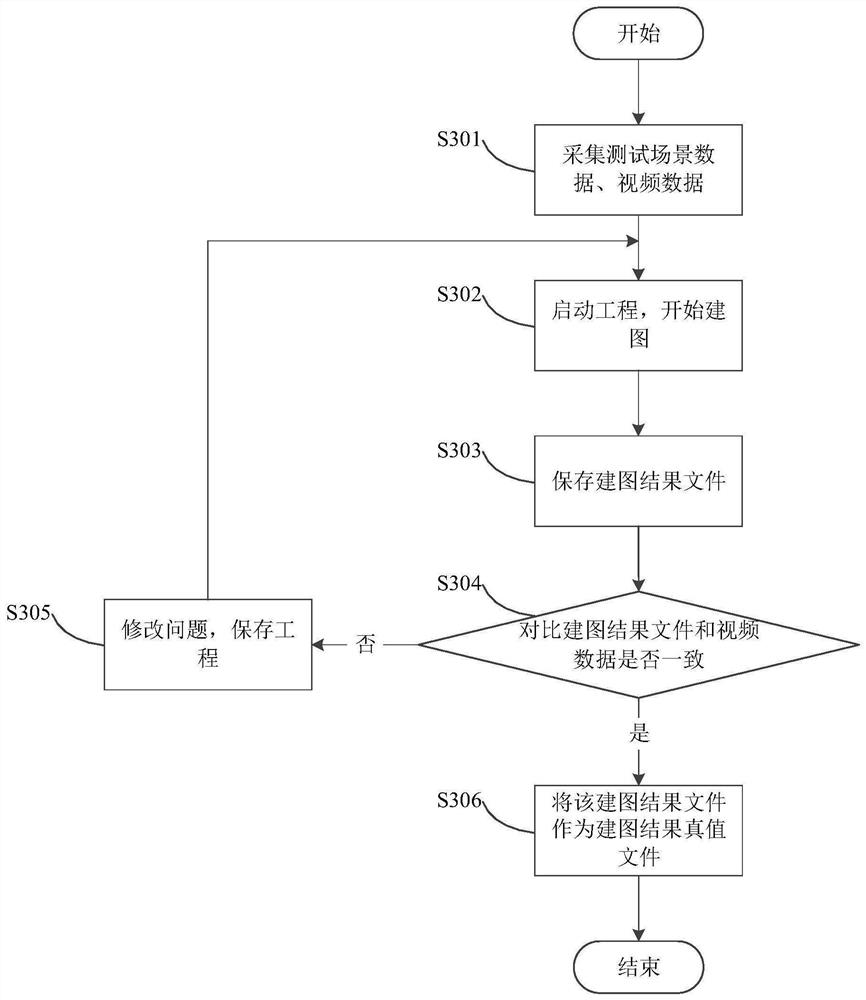
Method and device for testing automatic driving mapping result and computer equipment
The invention discloses a method and device for testing an automatic driving mapping result and computer equipment. The method comprises the following steps of: acquiring test scene data and video data of a vehicle driving in a test scene; according to the test scene data, constructing a mapping result file through mapping software; obtaining a mapping result true value file according to the video data and the mapping result file; and testing the stability of the mapping result and / or the iteration effectiveness of the mapping software based on the mapping result true value file. Therefore, the mapping result test can be independently carried out from two aspects, namely, the stability of the mapping result and effectiveness of iteration of the mapping software, so that the mapping problem can be found as early as possible.
Owner:BEIJING AUTOMOBILE RES GENERAL INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com