Drive mapping method based on user identity authentication
A technology of user identity authentication and mapping method, which is applied in the field of drive letter mapping based on user identity authentication, and can solve the problem of not being able to guarantee the security of user data as a whole.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] The specific implementation manners of the present invention will be described below in conjunction with the accompanying drawings.
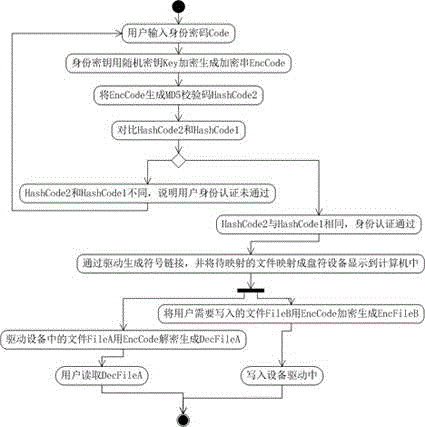
[0017] Such as figure 1 Shown is the method flowchart of the technical solution of the present invention, as can be seen from the figure, the present invention specifically comprises the following steps:
[0018] Step 101: When the user needs to map the drive letter, the user enters the identity password, and the machine reads the user identity information;
[0019] Step 102: use the encryption mode encryption defined in EncMode to encrypt the user identity data with the random key Key in the file header to generate the encrypted string EncCode;
[0020] Step 103: Perform MD5 verification on the encrypted string EncCode to generate an identity verification value to generate user HashCode2;
[0021] Step 104: compare the user HashCode2 with the HashCode1 stored in the file header, if HashCode1=HashCode2, the identity authentication is pa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com