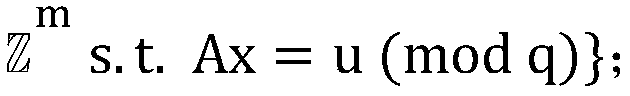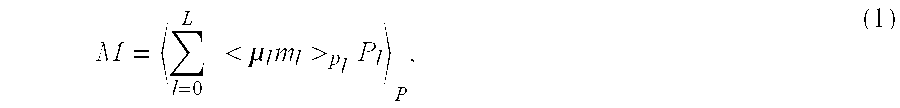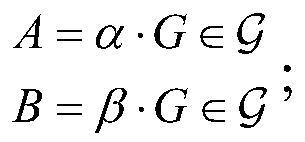Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
40 results about "Collision attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
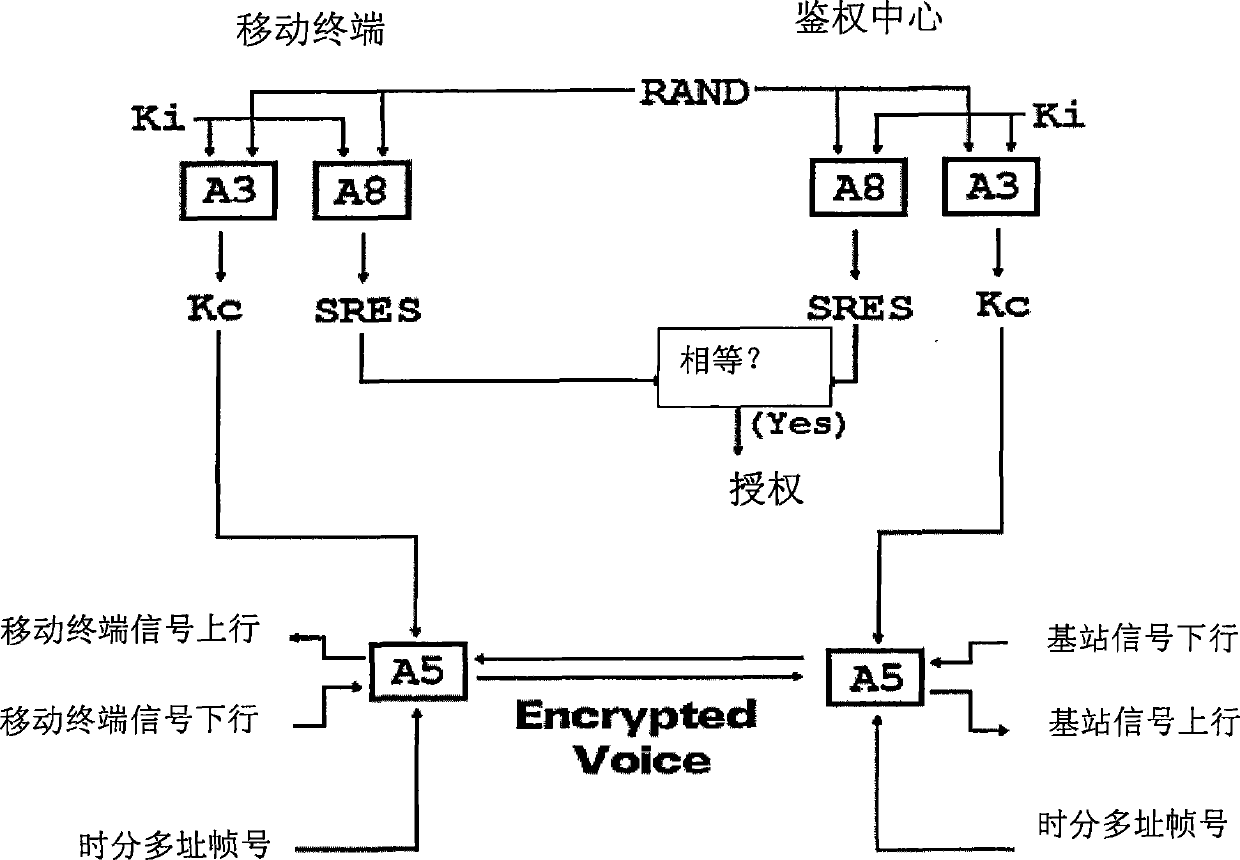
In cryptography, a collision attack on a cryptographic hash tries to find two inputs producing the same hash value, i.e. a hash collision. This is in contrast to a preimage attack where a specific target hash value is specified.
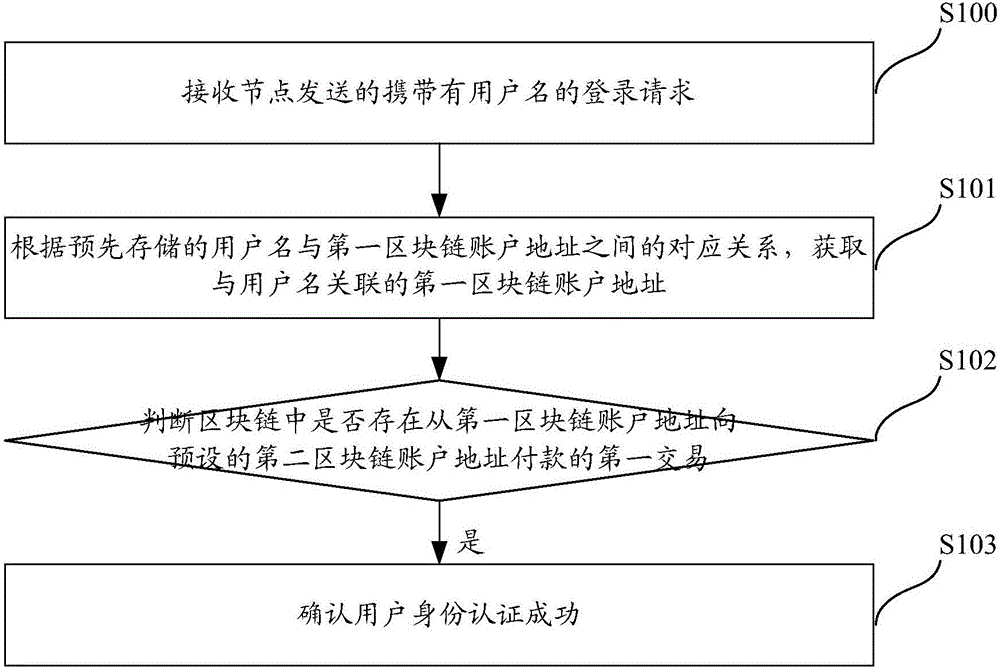
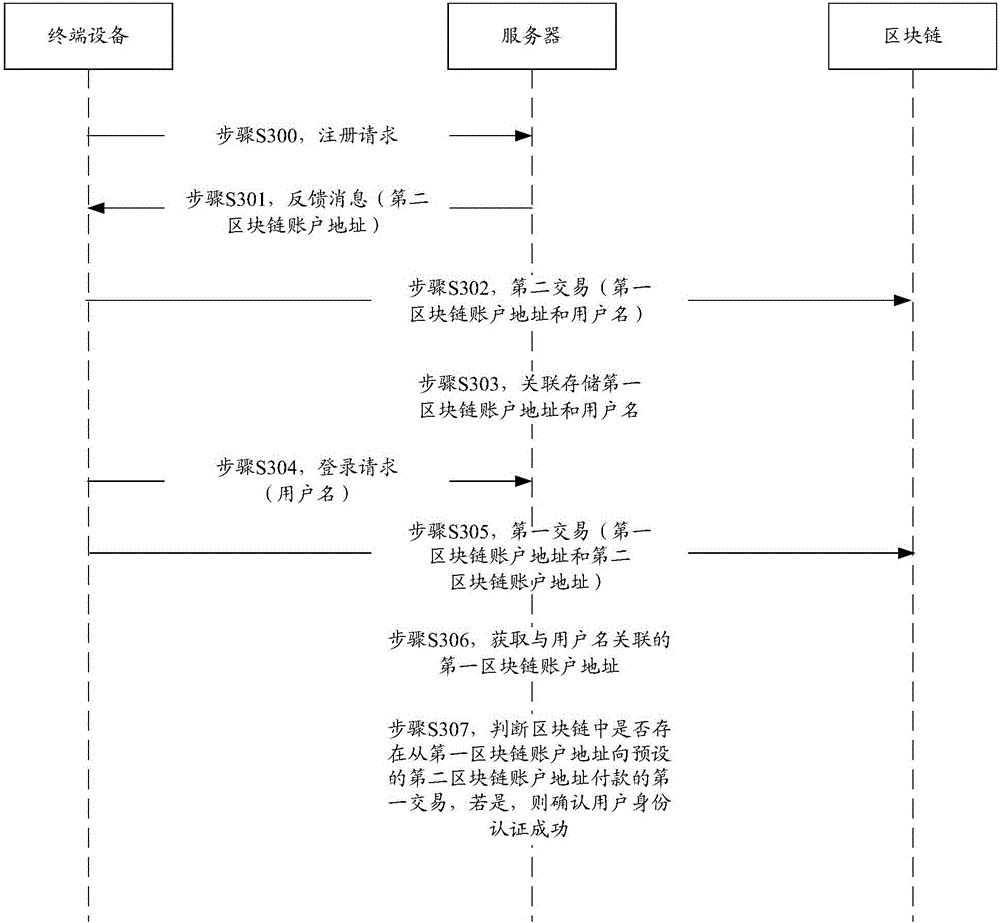
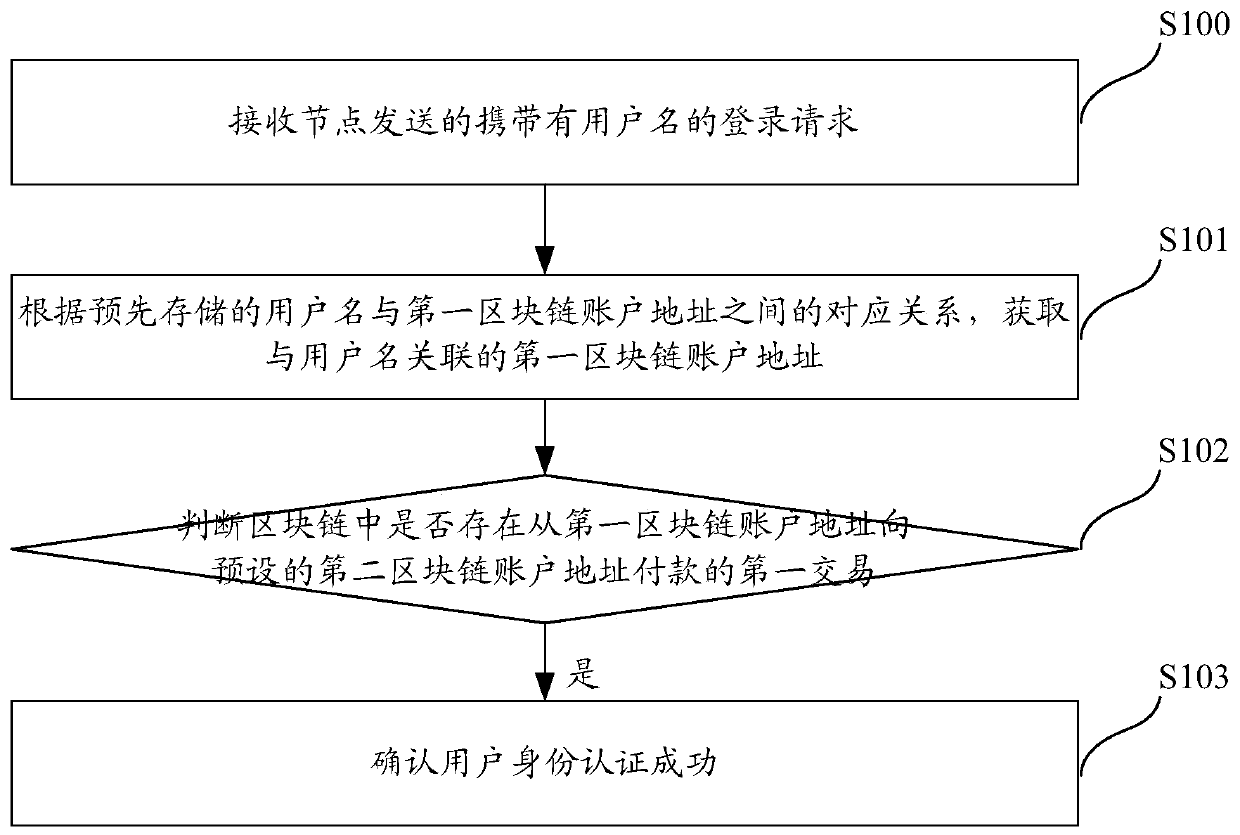
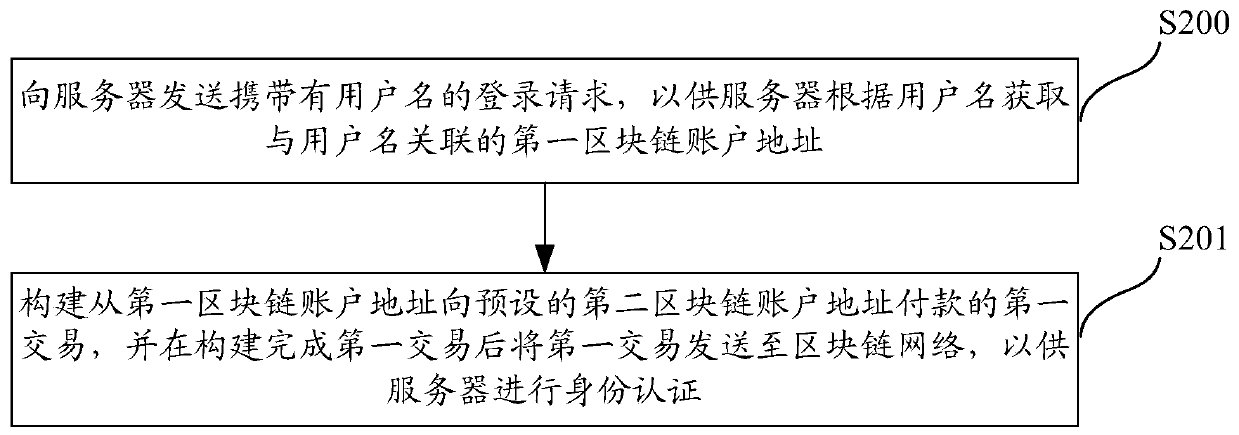
Method, system and server for authenticating identities on basis of block chain networks
The invention discloses a method, a system, a server and terminal equipment for authenticating identities on the basis of block chain networks. The method, the system, the server and the terminal equipment are used for authenticating the identities for nodes in the block chain networks. The method includes receiving login requests with user names; acquiring first block chain account addresses according to preliminarily stored corresponding relations between the user names and the first block chain account addresses; judging whether first transaction of payment from the first block chain account addresses to preset second block chain account addresses is available in block chains or not; determining that the identities of users are successfully authenticated if the first transaction is available in the block chains. The login requests are transmitted by the nodes. The first block chain account addresses are associated with the user names. The method, the system, the server and the terminal equipment have the advantages that transaction information stored in the block chains cannot be tampered and can be traced back and queried, and accordingly the authentication safety and the credibility of authentication procedures can be improved; the users do not need to input passwords during login and do not need to remember the passwords, accordingly, the convenience can be improved, and database collision attack due to the fact that other malicious personnel log in other websites by the aid of stolen user names and passwords can be prevented.
Owner:JIANGSU PAYEGIS TECH CO LTD
Base collision attack detecting method and system
ActiveCN104811449AImprove securityAvoid bad consequencesUser identity/authority verificationCollision attackComputer security
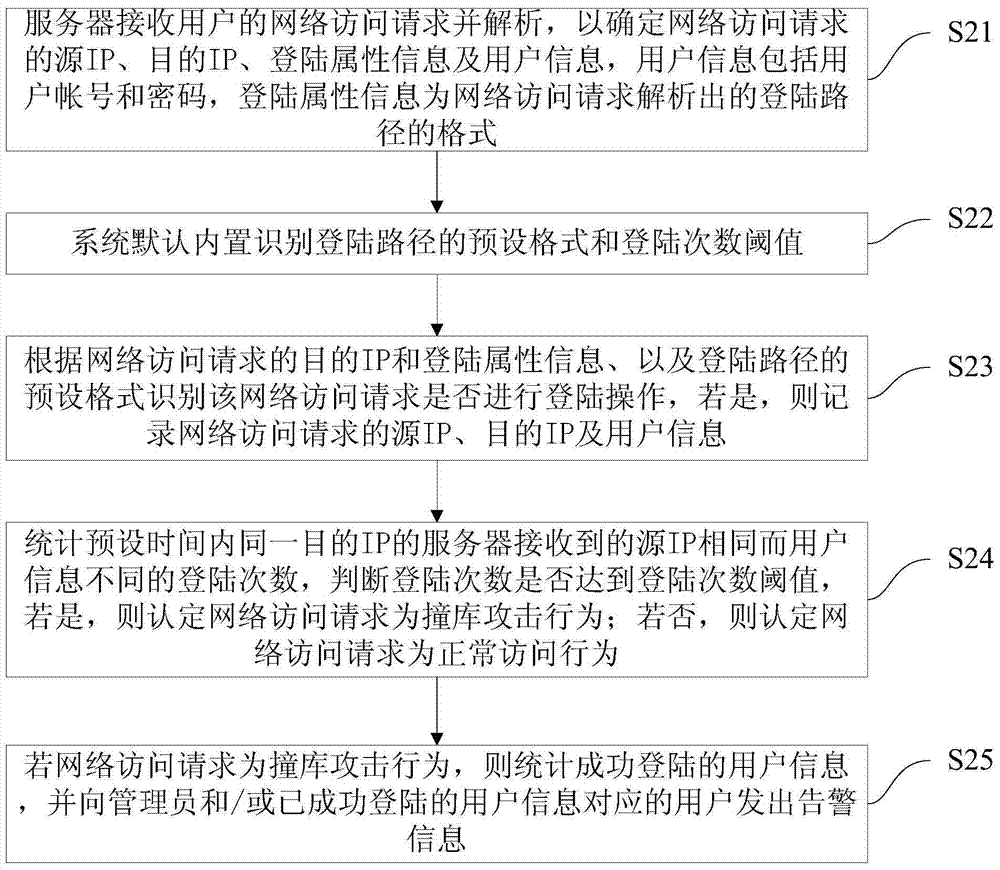
The invention discloses a base collision attack detecting method and system. The method includes the following steps: receiving a network access request of a user and analyzing the network access request to determine an source IP, a target IP, login attribute information and user information; configuring a preset login route and a login times threshold or preset format and a login times threshold of a system default built-in login route; conducting identification to determine whether to conduct login operation according to the target IP, the login attribute information and the preset format of the preset login route or the login route, on yes judgment, recording the source IP, the target IP and user information; recording the times of login that servers of the same target IP receives identical source IP but different user information in the preset time, judging if the times of login reach the login times threshold, on yes judgment, assuming the base collision attack behavior, on no judgment, assuming normal access behavior. The method and system can monitor the base collision attack behavior to improve user information safety and avoid poor result caused by user information leakage.
Owner:SANGFOR TECH INC
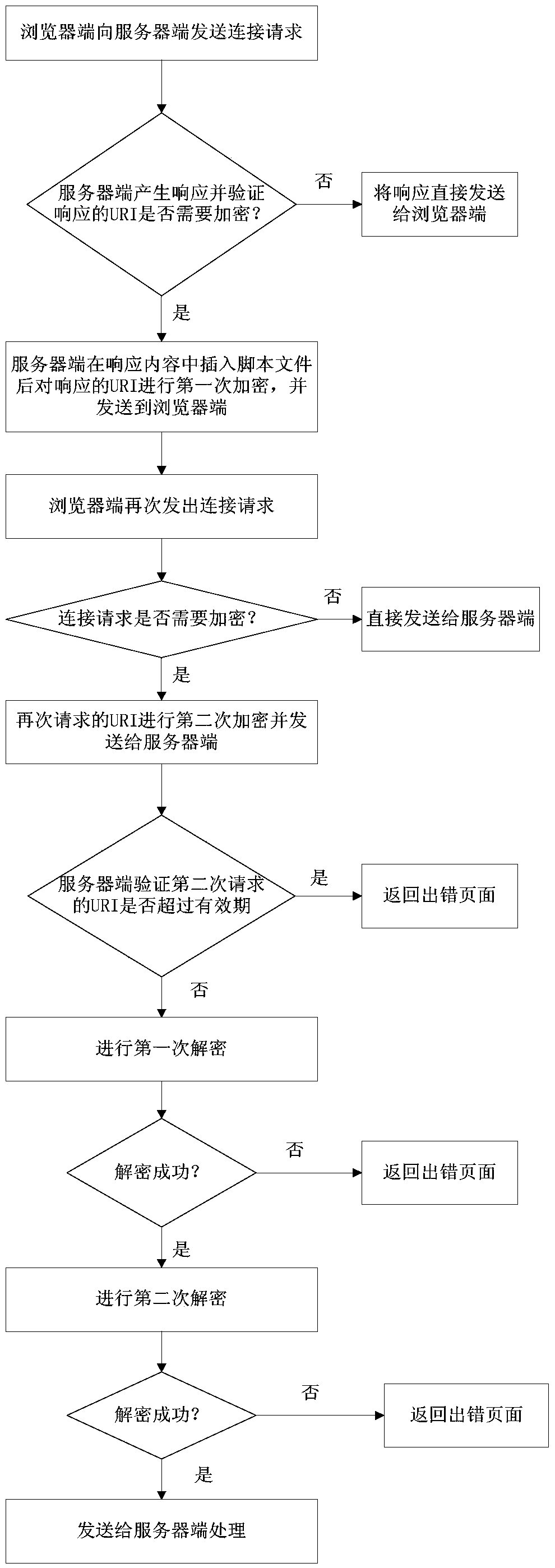
WEB site link dynamic hiding method and device capable of effectively preventing network attacks
ActiveCN105516208ACredential stuffing attack protectionProtection against hazardsTransmissionWeb siteCollision attack
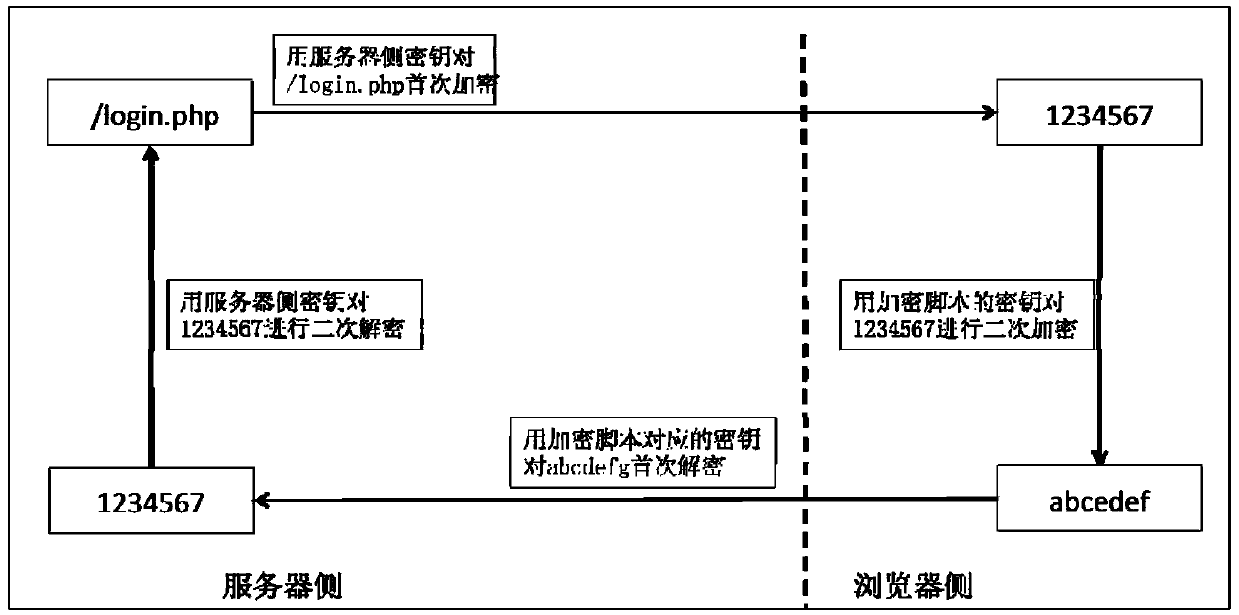
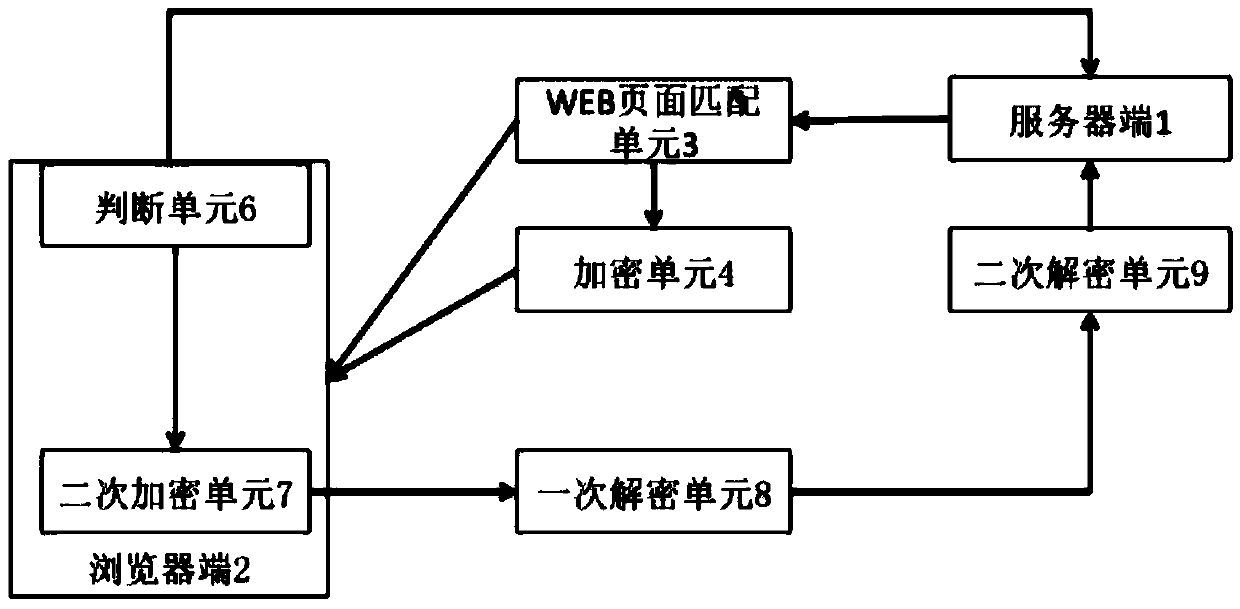
The invention discloses a WEB link dynamic hiding method capable of effectively preventing network attacks. The method comprises the following steps that firstly, a browser side sends a connecting request to a server side; secondly, the server side verifies whether it is needed to encrypt a responsive URI or not, the URI needing to be encrypted is encrypted for the first time, and the encrypted URI and a script file used for encrypting the browser side are sent to the browser side together; thirdly, after connection is established, the URI requested for revisiting is encrypted for the second time through the scrip file in the browser side, and the URI encrypted for the second time is sent, or the URI is sent directly; fourthly, the server side verifies the URI requested by the browser side again and carries out first-time decryption and second-time decryption after the URI passes the verification, and an error webpage is returned if the URI does not pass the verification or decryption fails. By means of the method, the safety of a WEB site can be improved, and various attacks such as library collision attacks and network crawlers can be defended. The invention further discloses a device applied to the method.
Owner:广州安锐信息技术有限公司
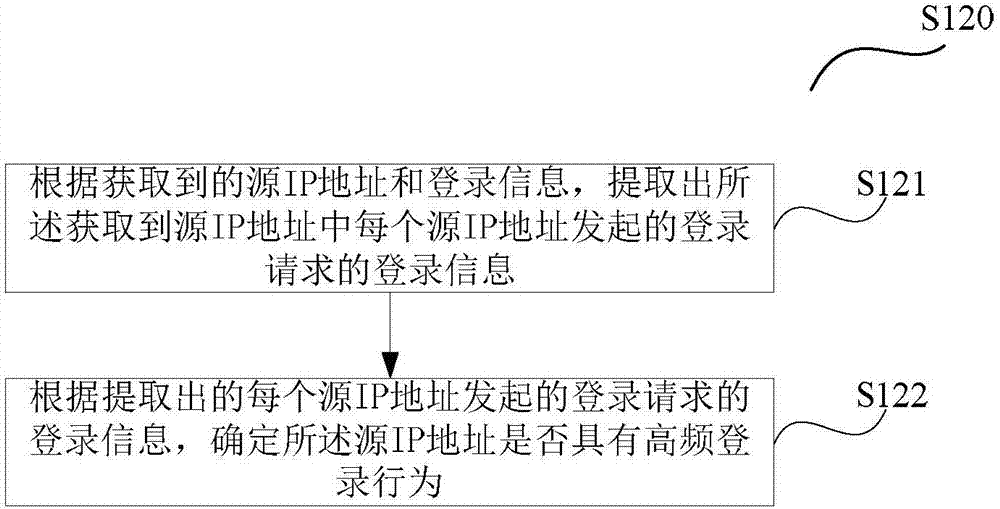
Method and device for detecting database collision attack
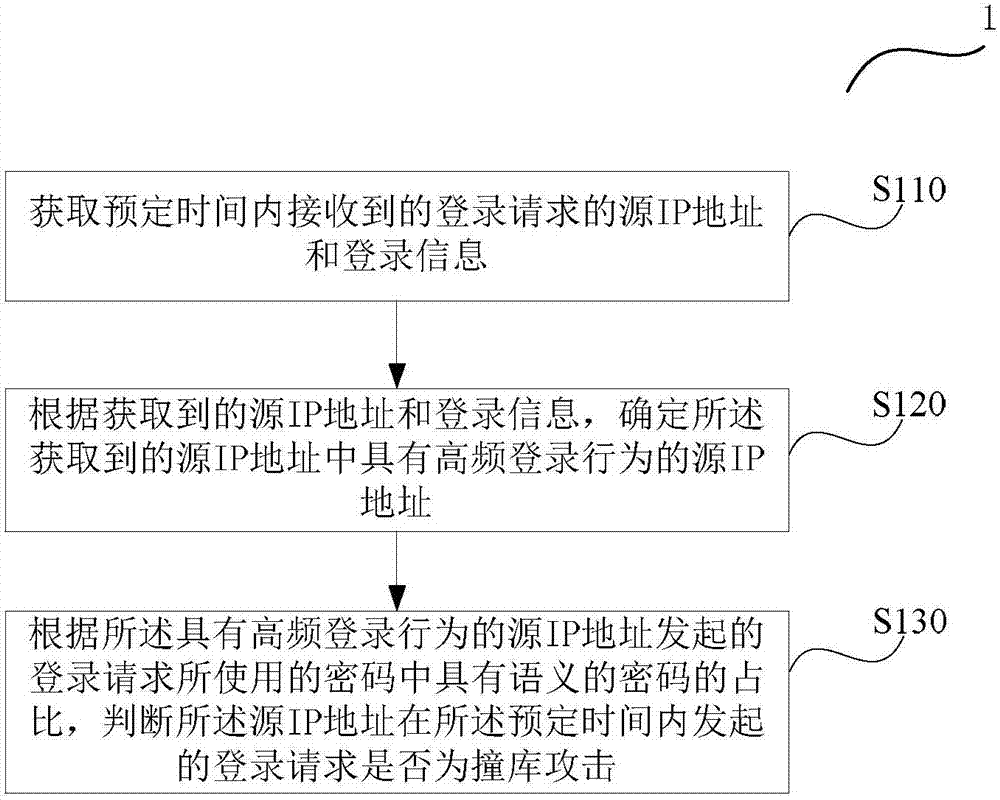
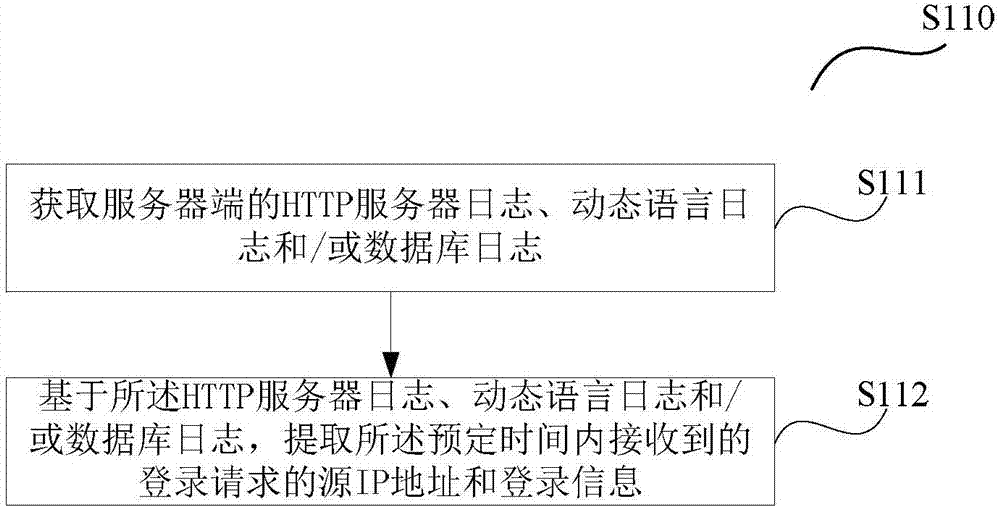
The invention provides a method and a device for detecting a database collision attack. The method comprises the steps of: acquiring source IP addresses and login information of login requests received within a predetermined time; determining a source IP address having high-frequency login behavior among the acquired source IP addresses according to the acquired source IP addresses and login information; and judging whether the login request initiated by the source IP address having high-frequency login behavior within the predetermined time is a database collision attack according to a proportion of passwords with semantic meanings in passwords used by the login request initiated by the source IP address, wherein the passwords with semantic meanings are passwords with the probability that the passwords have semantic meanings exceeding a predetermined probability threshold value. The method and the device provided by the invention improve the precision of database collision attack detection.
Owner:ALIBABA GRP HLDG LTD
Defense method for database dragging and collision attack on database layer
InactiveCN107563197AEnsure safetyActive miningDigital data protectionPlatform integrity maintainanceCollision attackSQL
The invention relates to a defense method for database dragging and collision attack on a database layer. The method includes the steps that a backstage defense module for enticing attack is allocatedin a database, an SQL request is input, and the backstage defense module conducts judgement according to a feedback value of the SQL request; if an attack condition is satisfied, blockage is carriedout; otherwise, the the access is normal, the request is completed and data is returned back to finish the whole process. According to the method, by means of the backstage defense module for enticingthe attack, during actual operation, the input SQL request is responded, whether or not the current SQL is aggressive can be judged, the aggressive SQL is blocked, and data is returned back to normalaccess. According to the method, by setting a backdoor structure on the database directly, the database dragging and collision behaviors of an attacker can be dug out and found out more proactively,intelligently and efficiently to ensure safety of the database.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Multi-factor identity authentication method for preventing library collision attacks
ActiveCN105187382AAvoid Credential Stuffing AttacksImprove verification capabilitiesTransmissionBrute forcePassword
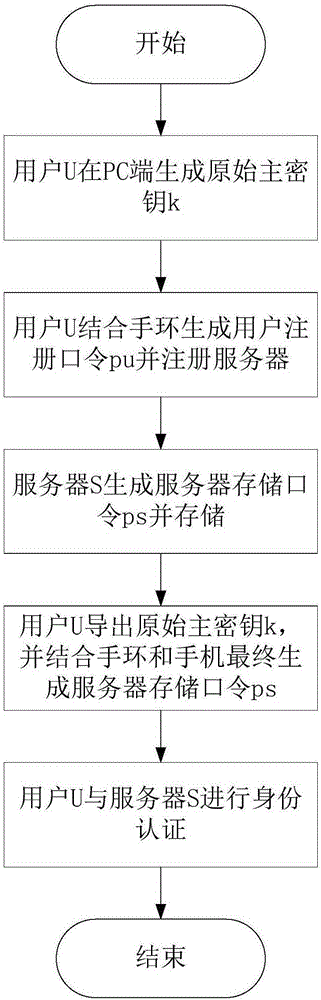
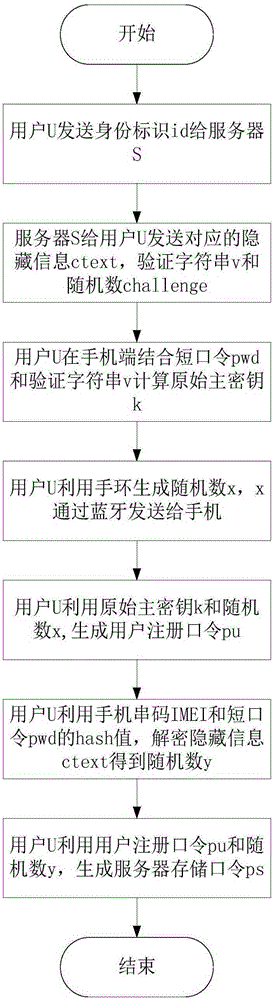
The invention discloses a multi-factor identity authentication method for preventing library collision attacks, which is mainly used for solving the problem that user passwords in the existing website login systems are vulnerable to brute force attacks and library collision attacks. The multiple factors in the multi-factor identity authentication method disclosed by the invention comprises a user password, a mobile phone and a bracelet, which are indispensable to complete the security authentication of user identity. The multi-factor identity authentication method comprises the steps of: (1) a user uses a short password to generate an original master key through a termination key derivation function and processes the original master key for twice in combination with two random numbers related to the bracelet and the mobile phone respectively to generate a server storage password, and stores the server storage password in a server; (2) the user successively derives the original master key and two different random numbers in combination with the bracelet and the mobile phone factors to generate the server storage password; and (3) the user uses the server storage password to carry out mutual authentication with the server. The multiple factors in the multi-factor identity authentication method disclosed by the invention is used for generating different original master keys for different websites and providing security protection to effectively avoid the risk that a single password is vulnerable to embezzlement for identity camouflage.
Owner:XIDIAN UNIV
HDFS-based safe storage system
InactiveCN106549963AEncryption apparatus with shift registers/memoriesSource Data VerificationConfidentiality
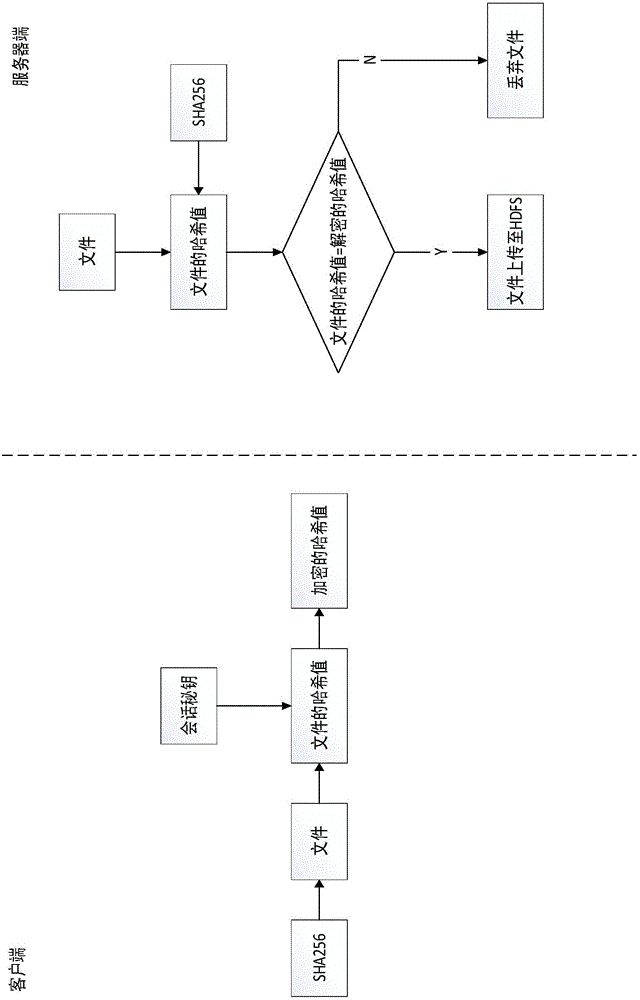
An HDFS-based safe storage system belongs to the technical field of cloud storage. Continuous development of network construction leads to explosive growth of data; currently network attack means emerge one after another; based on the above situation, how to store the data efficiently and safely is a problem that needs immediate solution. According to the HDFS-based safe storage system, an SHA256 algorithm is used for replacing CRC32 for data verification, and success rates of collision attacks can be greatly lowered; HDFS takes no measures regarding data safety; as for the issue of network data safety, the invention puts forward a method based on an AES algorithm and an RSA algorithm to ensure data confidentiality, the AES algorithm is used for enciphering the data, the RSA algorithm is used for enciphering secret keys of the AES algorithm, and therefore data safety is improved while enciphering operation does not take too much time. Experiment results show that safe transmission and storage of the data can be realized effectively via the method.
Owner:BEIJING UNIV OF TECH
Database collision attack monitoring method, device and system and computer storage medium
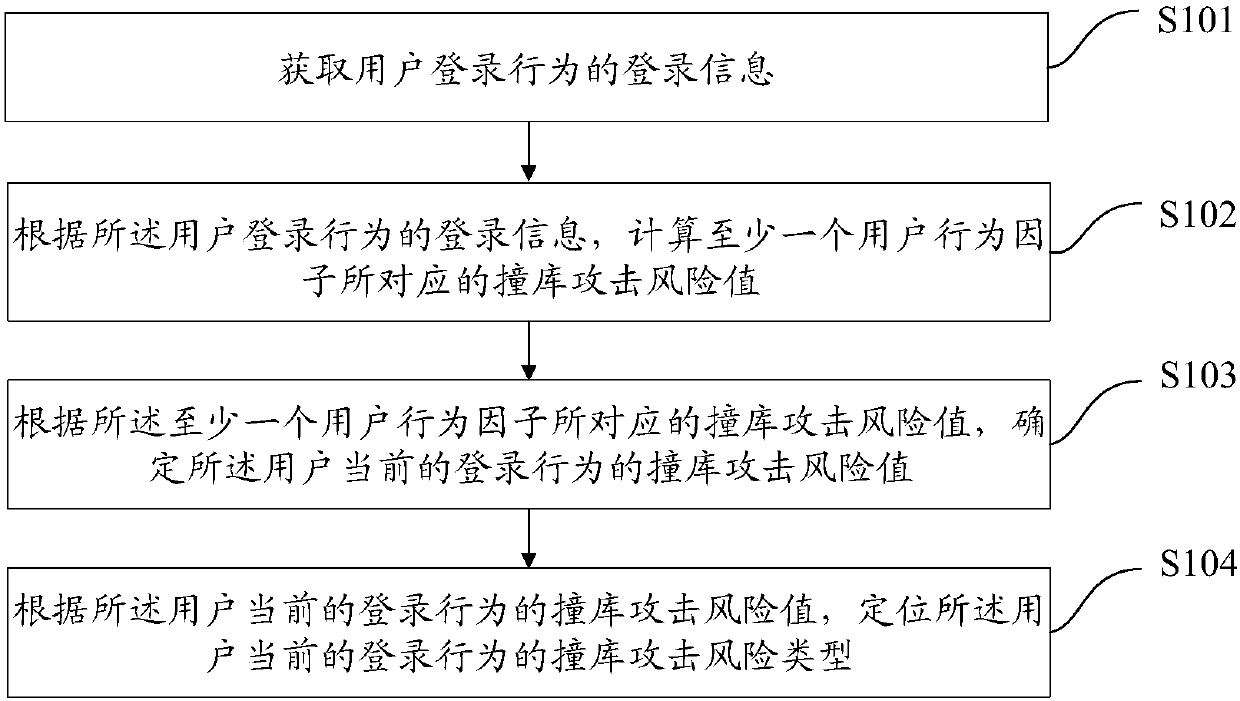
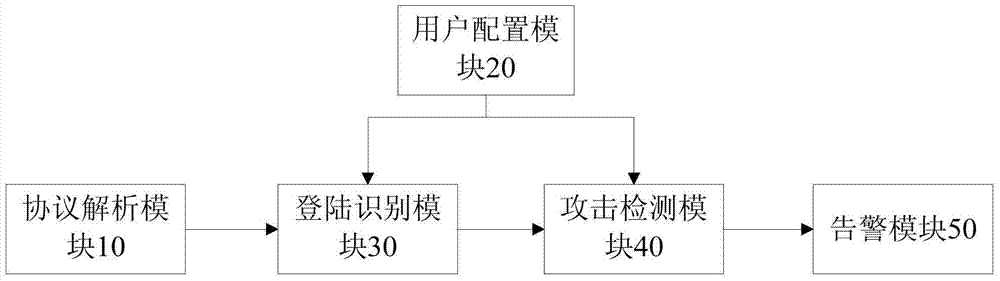
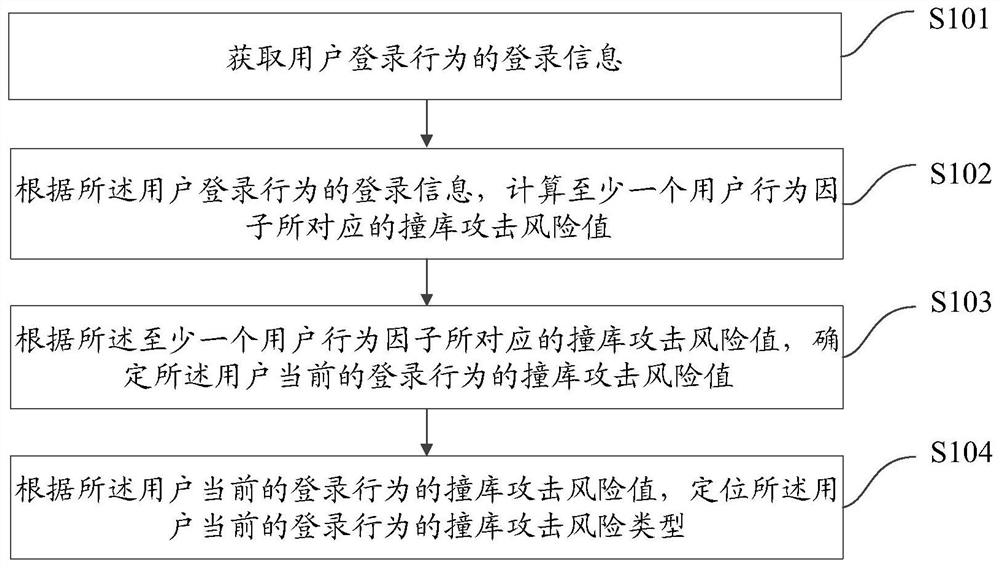
The embodiment of the invention discloses a database collision attack monitoring method. The method comprises the steps of obtaining login information of a user login behavior; calculating a databasecollision attack risk value corresponding to at least one user behavior factor according to the login information of the user login behavior; determining a database collision attack risk value of thecurrent login behavior of the user according to the database collision attack risk value corresponding to the at least one user behavior factor; and positioning a database collision attack risk type of the current login behavior of the user according to the database collision attack risk value of the current login behavior of the user. The embodiment of the invention further discloses a database collision attack monitoring device and system and a computer storage medium.
Owner:CHINA MOBILE COMM GRP CO LTD
Message authentication code with blind factorization and randomization
InactiveUS20100169657A1Improve securityMinimizes attackUser identity/authority verificationPlaintextComputer hardware
The message authentication code with blind factorization and randomization is a computational method for improving the security of existing Message Authentication Code (MAC) methods through the use of blind integer factorization. Further, blind randomization is used as a countermeasure to minimize collision attacks where different plaintexts produce the same MAC.
Owner:KING FAHD UNIV OF PETROLEUM & MINERALS RES & INNOVATION SUPPORT OFFICE
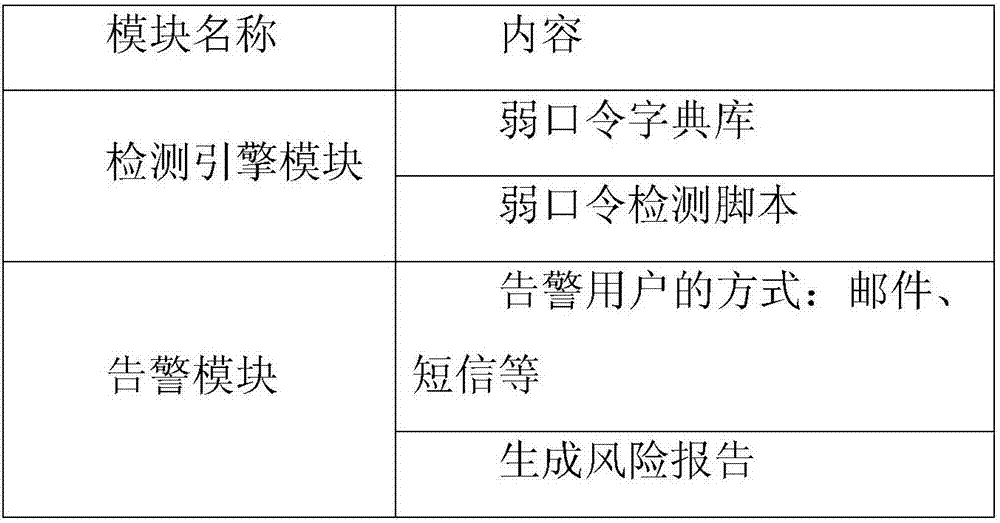
Weak command detection system and realization method and WEB platform
InactiveCN107426203ATimely detection of weak password risksTimely detection of risksDigital data authenticationTransmissionBrute forcePassword
The invention discloses a weak command detection system, and a realization method and a WEB platform. The method comprises the following steps: acquiring user information; judging whether the acquired user information is encrypted; if the user information is unencrypted, regarding that the detected target has the weak command risk; if the user information is encrypted, judging an encryption way of the user information, and blasting the password of the user according to the encryption way, if the password of the user is successfully blasted by brute force, regarding that the detected target has the weak command risk; if the password of the user cannot be blasted by the brute force, enabling a detection engine module to call a collision attack module to perform the collision attack; regarding that the detected target has the weak command risk under the situation that the attack is successful. By using the method disclosed by the invention, the user can immediately find the weak command risk of the detected target and the brought potential hazard, thereby evading and solving the risk.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
Method for constructing reinforced hash function based on compression function
ActiveCN102638344ASafe by designMature designUser identity/authority verificationPlaintextHash function
The invention belongs to the field of information safety, in particular to the cryptology field, and relates to a method for reinforcing a hash function based on a compression function. The method is used for reinforcing key loops of the hash function, namely reinforcing a first group of the compression function and a final group of the compression function, and increasing the operations of multiple bits or utilizing a present safety group code algorithm by aiming at a majority of operations of a present hash function based on a single bit. The method comprises the following steps of: reinforcing by taking a method of resisting a current differential code analysis and the like as the principal method, also considering about some other attacks, such as a second preimage attack, further adding an input variable in the input of the final group of the compression function, namely a simple compression manner of all group information. The reinforcing method disclosed by the invention has the advantages that when key groups are reinforced, the increase of calculated amount is not large along with the increase of the length of a plaintext; and the decoding obstacle is configured through the most key position, the preimage attack, collision attack, the second preimage attack and the like can be effectively resisted.
Owner:GUILIN UNIV OF ELECTRONIC TECH
Construction method of strong anti-collision chameleon hash function
ActiveCN109600216AImprove securityResist attackKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCollision attackSecurity parameter
The invention discloses a construction method of a strong anti-collision chameleon hash function, which comprises the following steps of S1, inputting a security parameter n, and generating public andprivate key pairs (PK, SK) by a system, the public key PK being capable of specifying a message space M, a random space R and a chameleon hash function range Y; and S2, inputting the public key PK generated by the KGen and a message m Epsilon M, Hash algorithm outputting Hash y Epsilon Y and random r Epsilon R; and S3, inputting a public key PK, and outputting b belongs to {0, 1} through a Hash Epsilon Y of the message m Epsilon M and a random vector r Epsilon R check algorithm, if b = 1, then (y, r) is a valid hash of the message m, otherwise is invalid; and S4, inputting a private key SK, amessage m Epsilon M and a corresponding Hash random pair (y, r), and a new message m' Epsilon M to output a random vector r' satisfying HCheck (PK, m', y, r ') = 1. The invention also discloses a verification method of the strong anti-collision chameleon hash function. The method can resist strong anti-collision attacks and can be well applied to the scene of a high-security chameleon hash function.
Owner:ANHUI UNIVERSITY
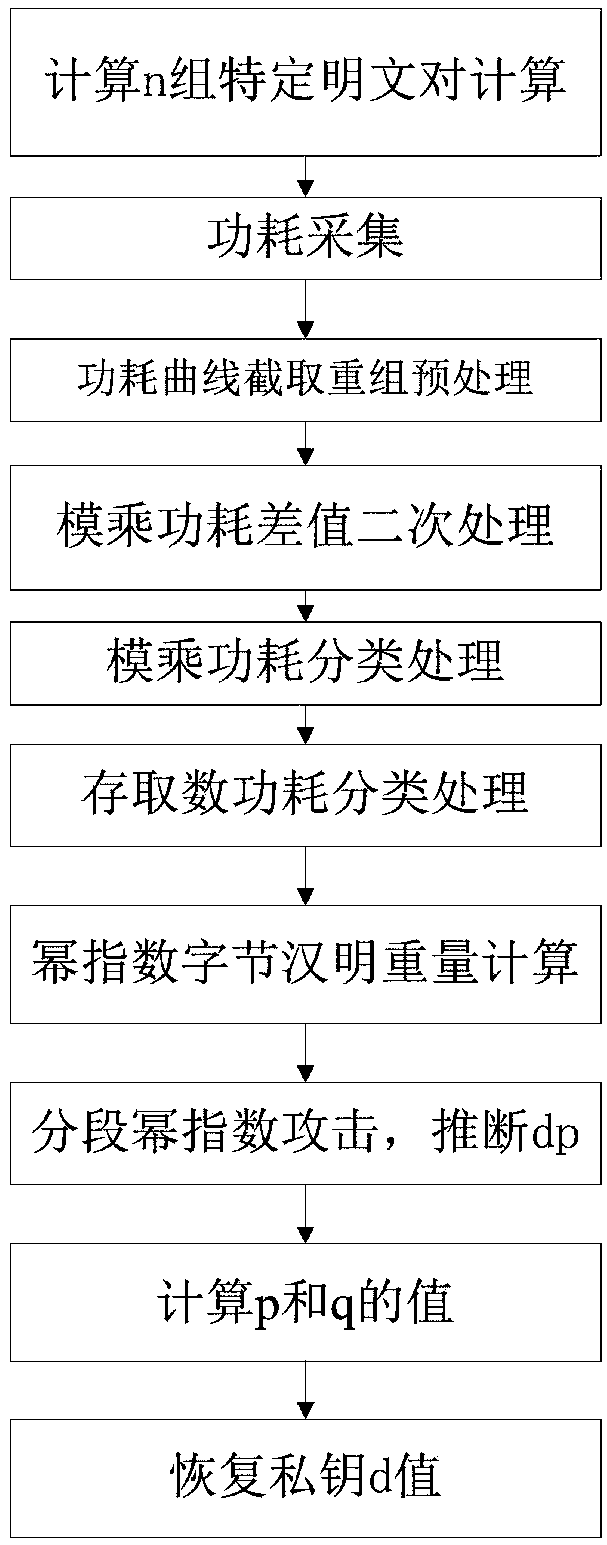
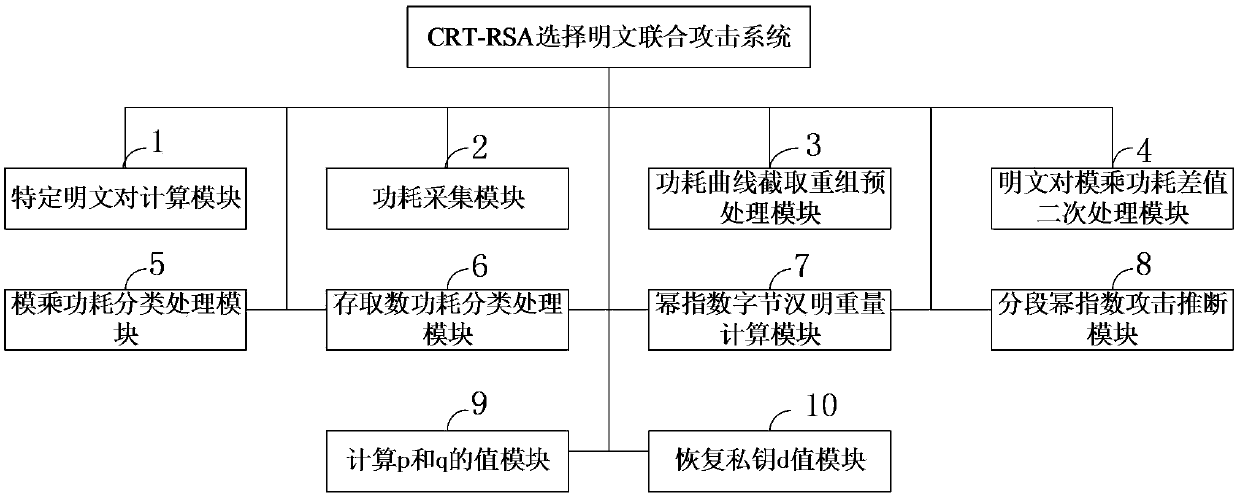
New method and system for selecting plaintext combined attack by CRT-RSA
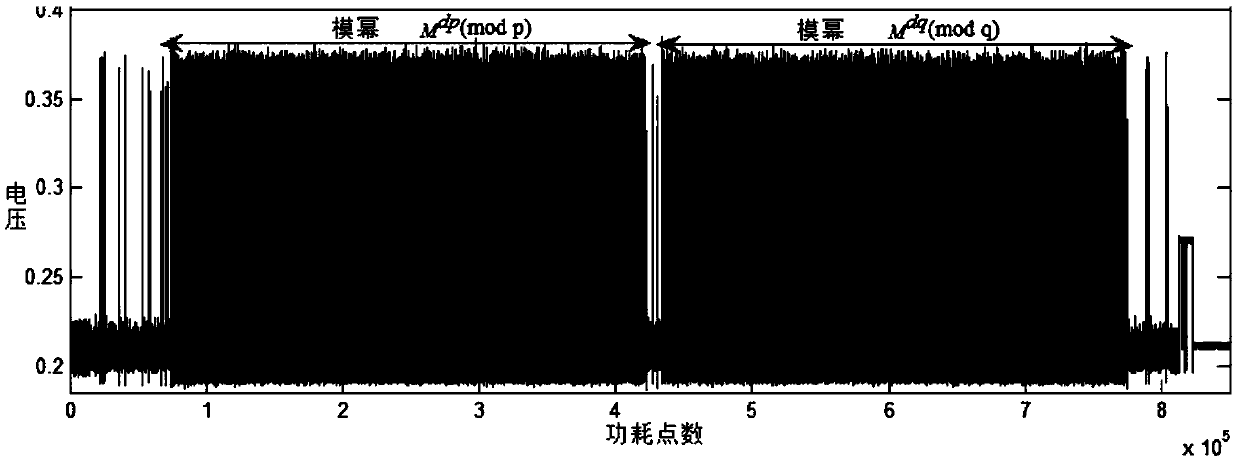
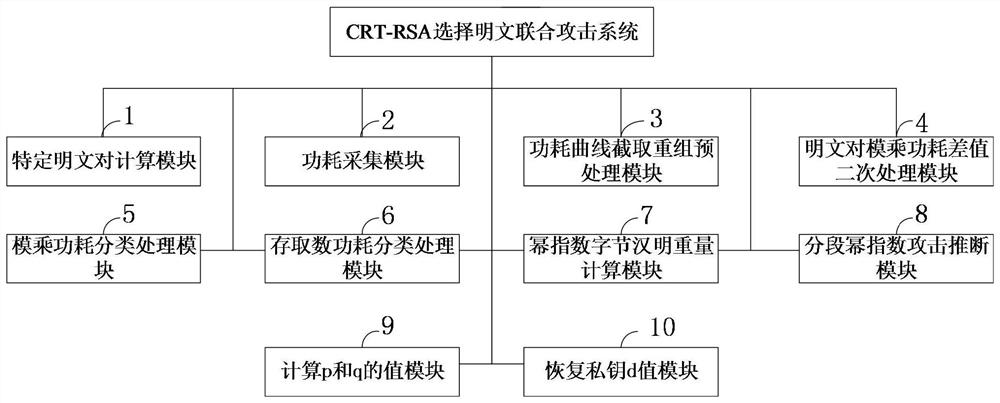
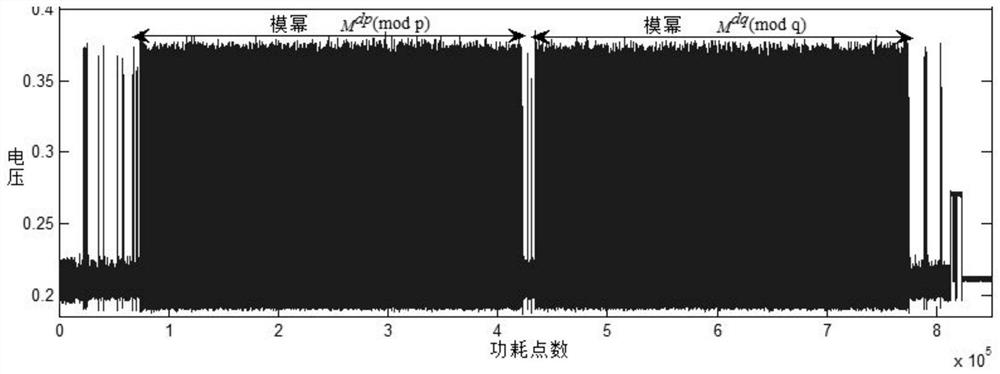
ActiveCN108833120AImprove accuracyReduce the impact of noisePublic key for secure communicationUser identity/authority verificationPlaintextCollision attack
The invention belongs to the field of information security, and discloses a new method and system for selecting a plaintext combined attack by CRT-RSA. In the attack process, the dp and dq of the CRT-RSA algorithm are used as targets, and then the private key parameters p, q are derived; during the plaintext collision attack process, multiple sets of plaintext pairs are selected and superimposed,and the modular multiplication power consumption difference is subjected to secondary treatment as the collision classification set; in the attack process, combined with the access number power consumption power exponent Hamming weight information leakage in the CRT-RSA modular power exponentiation process, the modular multiplication power segmentation is performed, and the plaintext collision attack is selected by segments. The invention combines other information leakage in the process of CRT-RSA modular exponentiation (such as access number power consumption power exponent Hamming weight information leakage), performs modular multiplication power segmentation, implements segmented selection of plaintext collision attacks, and can avoid local collision attack errors, which improves the attack accuracy. Finally, the private key parameters p, q are derived, and the private key d value is restored.
Owner:CHENGDU UNIV OF INFORMATION TECH
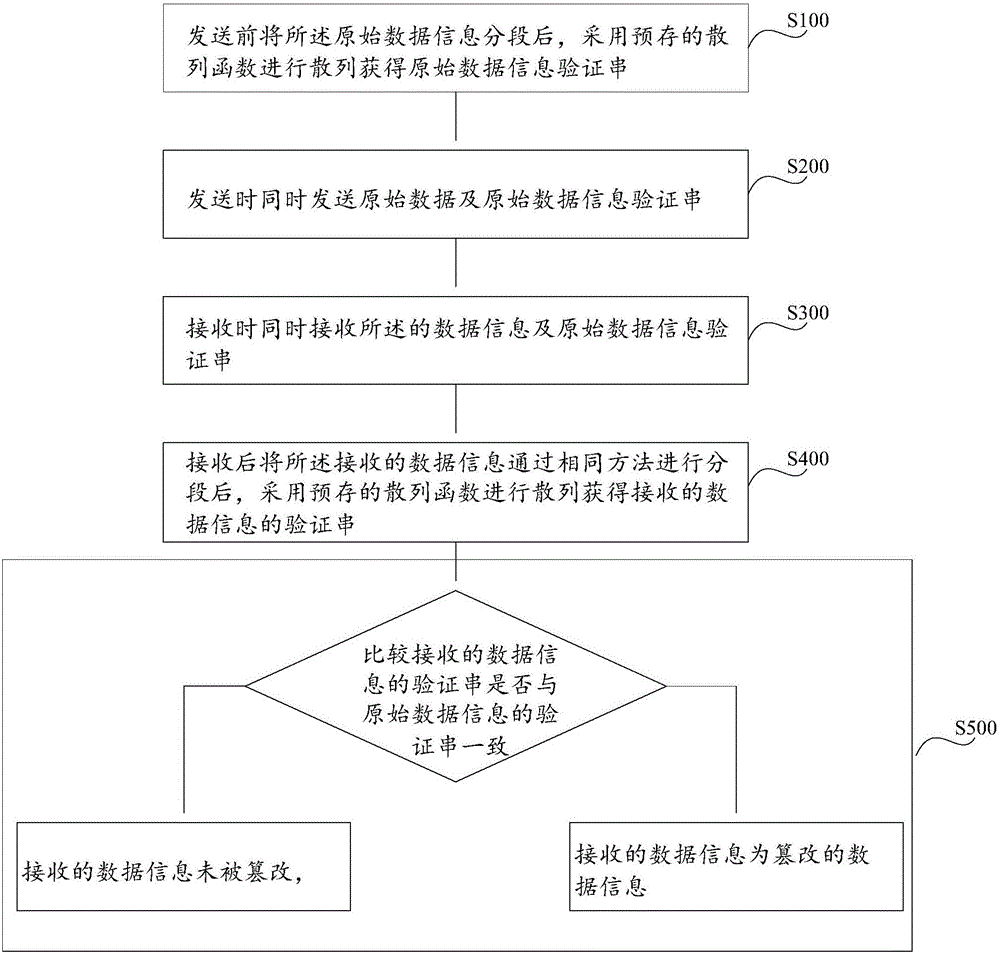
Data tamper-proofing method and system
InactiveCN106570423APrevent Collision AttacksStop falsified dataDigital data protectionTamper resistanceThird party
The invention discloses a data tamper-proofing method comprising the following steps of after original data information is segmented before sending, hashing the segmented information by using a pre-stored hash function to acquire an original data information verification string; synchronously sending the original data and the original data information verification string when in sending, synchronously receiving the sent data information and original data information verification string when in receiving; after the data information and the original data information verification string are received, segmenting the received data information, and then hashing the segmented information by using the pre-stored hash function to acquire a received data information verification string; and judging whether the received data information verification string is accordant with the original data information verification string by comparison, if yes, determining that the received data information is not tampered, and otherwise, determining that the received data information is tampered. The invention also provides a data tamper-proofing system. According to the method and the system provided by the invention, the difficulty of tampering the data by a third party is greatly increased, a collision attack from the third party with the aid of a rainbow table is effectively prevented, data falsification of a user is prevented, and data transmission security is ensured.
Owner:PHICOMM (SHANGHAI) CO LTD
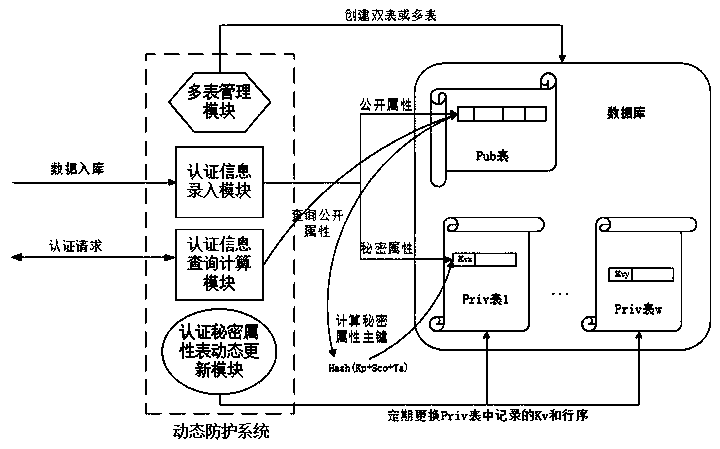
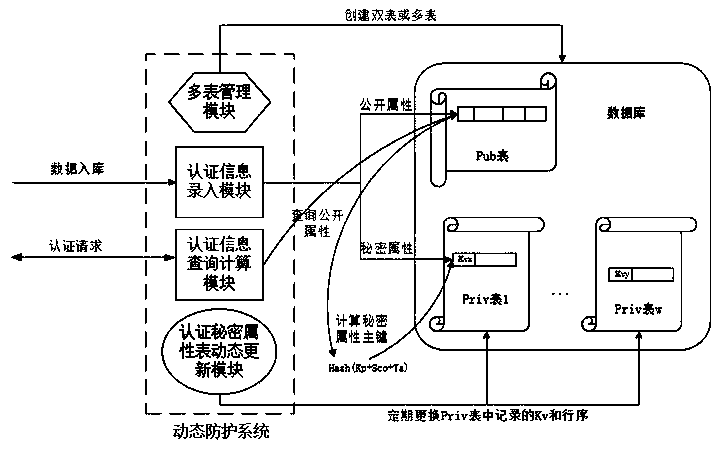
Dynamic data protection method and device for preventing database collision attacks
ActiveCN110032862AReduce the possibilityImprove defenseDigital data authenticationSpecial data processing applicationsCollision attackDatabase storage structures
The invention relates to a dynamic data protection method and device for preventing database collision attack. The method comprises the steps of changing a database storage structure for storing authentication information into double tables from a single table; isolating and obfuscating the public attribute and the authentication secret attribute of the authentication entity, wherein the authentication entity public attribute table does not contain any field associated with the authentication secret attribute table, and a main key of the authentication secret attribute table is a dynamic hashvalue; inquiring the database double tables when an application system carries out authentication, and calculating an authentication entity public attribute hash value corresponding to the authentication entity public attribute dynamically. The safety protection device based on the method is deployed at the front end of a database and maintains the updating and calculation query of double tables.According to the present invention, the traditional mode of strong association and static binding of authentication public attributes and authentication secret attributes is changed, a data protectiontechnology of sensitive attribute separation and dynamic updating is provided, the authentication record information of a database is differentiated, the influence of database leakage on database collision attack is reduced to the maximum extent, and the safety of a website and an authentication system is guaranteed.
Owner:中科天御(苏州)科技有限公司
Message authentication code with blind factorization and randomization
InactiveUS8190892B2Improve securityMinimizes attackUser identity/authority verificationComputer hardwarePlaintext
Owner:KING FAHD UNIV OF PETROLEUM & MINERALS RES & INNOVATION SUPPORT OFFICE
Information dispersion method and system based on distributed object storage system security
InactiveCN112486412AImprove data confidentialityIncrease the lengthInput/output to record carriersRedundant data error correctionHash functionAlgorithm
The invention is applicable to the field of data information distribution technology improvement, and provides an information dispersion method based on distributed object storage system security, which comprises the following steps: S1, calculating a data block hash value in a salting manner to resist collision attack of a hash function and improve the confidentiality of data; S2, improving the calculation efficiency by using an SHA2512 hash algorithm, and replacing the random key with the hash value of the original data; S3, inputting the data with the same content, and encoding the data through an AONTNZZD algorithm to generate data blocks with the same content so as to realize data deduplication. According to the AONTNZZD algorithm, the length of a data block is additionally selected as a salt value of hash operation when the hash value of the data block is calculated, and therefore an attacker can be prevented from carrying out hash function attack. According to the AONTNZZD algorithm, an NZZD code based on binary shift and exclusive-OR operation is adopted, and the relatively good encoding and decoding rate is achieved.
Owner:FOSHAN SAISICHAN TECH CO LTD +1
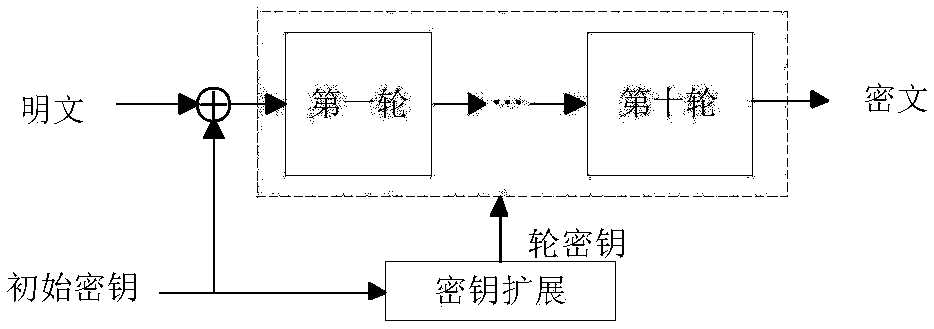
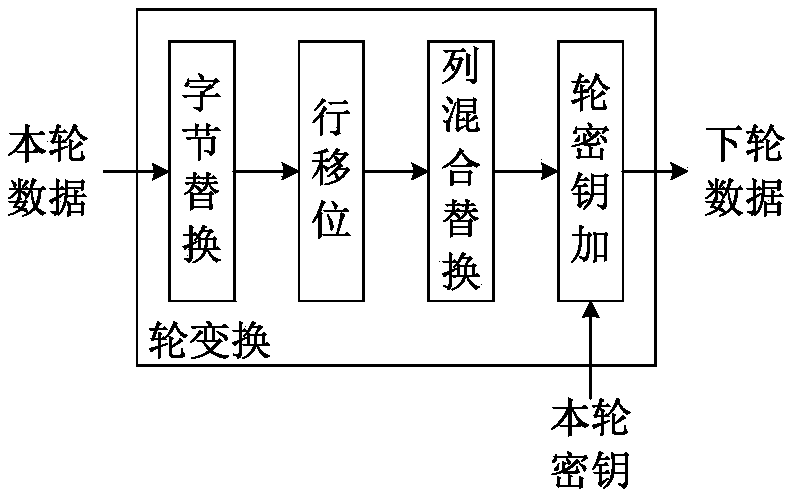
Random delay S-box-based high-speed AES encryption circuit capable of defending collision attack
ActiveCN109347621AReduce areaEncryption apparatus with shift registers/memoriesS-boxCollision attack
The invention provides a random delay S-box-based high-speed AES encryption circuit capable of defending a collision attack. An AES encryption circuit is a fully-unfolded structure and consists of 10turns of round transformation units; circuit throughput rate is improved through a pipeline technique, and the circuit processing speed is accelerated, wherein a byte substituting unit in a round transformation unit is based on a parallel S-box structure; a random delay is respectively added to an input end and an output end of each S-box, thereby damaging the collision attach detecting conditionand achieving the purpose of defending the collision attack. Compared with the traditional collision attack defensive measure, the circuit in the invention can greatly reduce the circuit area.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
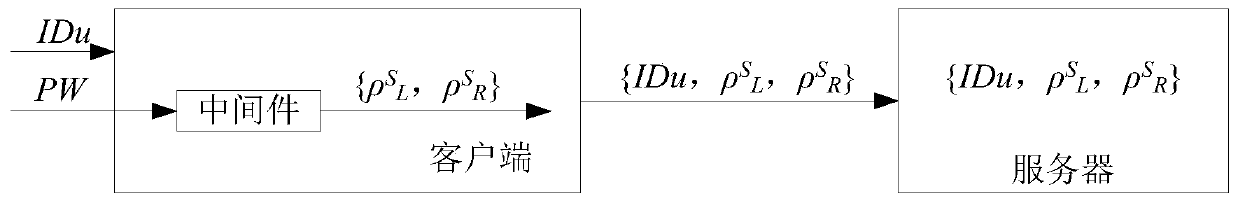
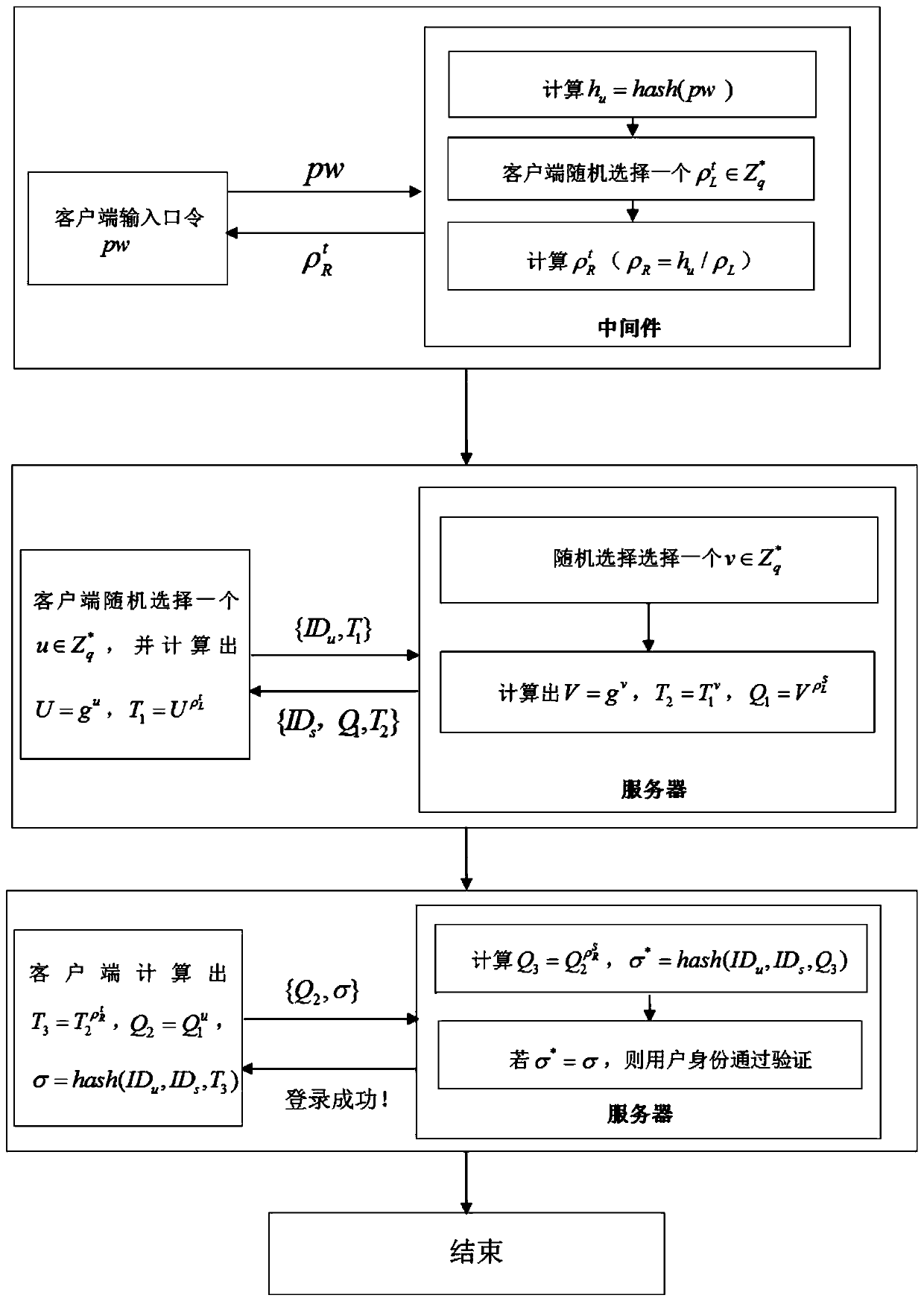
Password verification method and system for preventing library collision attack, middleware and storage medium
InactiveCN110086621AReduce the risk of credential stuffing attacksSave the trouble of preventing credential stuffing attacksKey distribution for secure communicationPublic key for secure communicationApplication serverValidation methods
The invention relates to a password verification method and system for preventing library collision attack, a middleware and a storage medium. The password verification method comprises the followingsteps of decomposing a user password PW into two mutually associated login random factors, and carrying out password verification on the two login random factors and the user registration informationgenerated by registration in combination with a user identity identifier IDu, wherein the user registration information comprises the user identity identifier IDu and two mutually associated registration random factors decomposed from the user password PW. The basic design idea of the password verification method is that a password inputted by a user is decomposed into two random factors, and thetwo random factors and the server are subjected to password verification, so that the risk that a user uses the same password on different application servers to suffer from library collision attacksis reduced, the trouble that the user uses different passwords to prevent library collision attacks is omitted, and therefore the method is more convenient, practical and safer.
Owner:中科赛诺(北京)科技有限公司
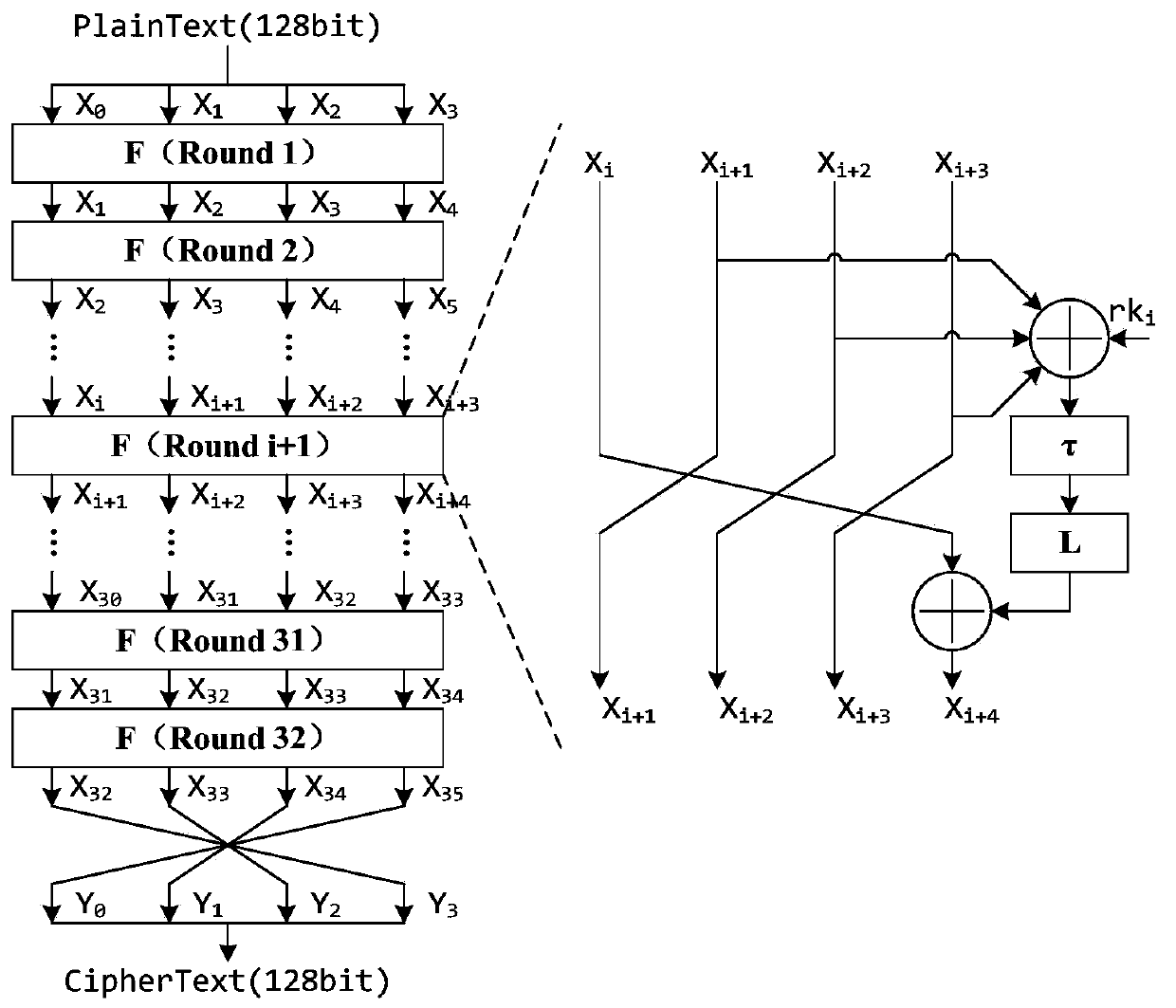
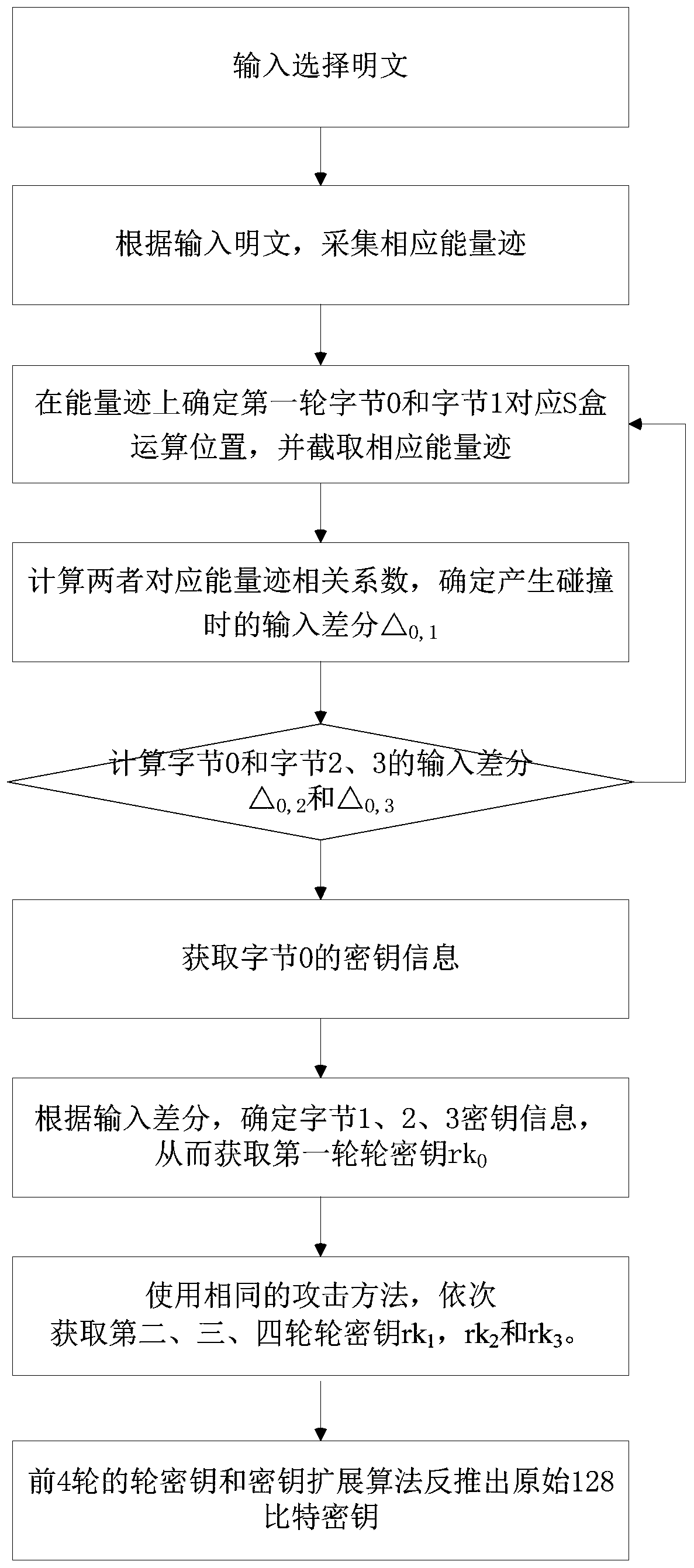
Plaintext selection related collision attack method based on mask SM4 cryptographic algorithm
PendingCN111030820AReduce encryption timesThe minimum number of encryption times is reducedMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesPlaintextAlgorithm
The invention relates to the field of side channel attacks, and discloses a plaintext selection related collision attack method based on a mask SM4 cryptographic algorithm. The method comprises a measurement stage and a collision detection stage; in the measurement stage, an attacker performs encryption operation on cryptographic equipment by selecting an input plaintext, records and collects a corresponding energy trace for use in the collision detection stage; in the collision detection stage, the attacker performs correlation calculation according to the collected energy traces and based onthe energy traces corresponding to the two collision bytes, so that the input difference of the collision bytes is determined; four round secret keys are obtained after obtaining the input differenceamong the four bytes, namely the round secret key information of the first round; and then the attack method is repeatedly performed, and round keys of the second round, the third round and the fourth round are sequentially solved; and finally an original 128-bit key is reversely deduced through a key expansion algorithm. According to the method, the encryption frequency required by collision isreduced, and the algorithm attack on the mask SM4 is realized.
Owner:成都三零嘉微电子有限公司
RNS-based cryptographic system and method
InactiveUS8462939B2Blind factorization even morePublic key for secure communicationUser identity/authority verificationCiphertextCollision attack
The RNS-based cryptographic system and method uses a symmetric residue number system (RNS) for encryption and decryption of messages, i.e., the sender and receiver agree upon a set of relatively prime numbers, referred to as the basis, whose product is an integer, and both the RNS and the integer are kept secret. To break the cipher, an attacker must factor the secret integer, which is unknown to the attacker, given only the upper bound of the unknown integer, a problem referred to as blind factorization of the unknown integer, which is a computationally hard problem. The method may be combined with a discrete logarithm problem, and the ciphertext may be padded with random values to hide the upper bound of the unknown integer. When the ciphertext requires multiple blocks, subsets of the basis and / or the random number padding may be used to prevent collision attacks.
Owner:KING FAHD UNIVERSITY OF PETROLEUM AND MINERALS
Method and system for detecting credential stuffing attacks
ActiveCN104811449BImprove securityAvoid bad consequencesUser identity/authority verificationIp addressCollision attack
The invention discloses a method and system for detecting credential stuffing attacks. The method includes the following steps: receiving and analyzing a user's network access request to determine its source IP, destination IP, login attribute information and user information; configuring a preset login path and The threshold of login times, or the preset format and login times threshold of the system's default built-in identification of the login path; according to the destination IP and login attribute information, the preset login path or the preset format of the login path to identify whether to perform a login operation, and if so, record it Source IP, destination IP, and user information; count the number of logins received by the server with the same destination IP within the preset time with the same source IP but different user information, and determine whether the number of logins reaches the threshold of login times, and if so, it is considered a credential library Attack behavior; if not, it is considered as a normal access behavior. The invention can realize the monitoring of credential stuffing attack behavior, so as to improve the security of user information and avoid adverse consequences caused by leakage of user information.
Owner:SANGFOR TECH INC
A crt-rsa chosen plaintext joint attack method and system
ActiveCN108833120BImprove accuracyReduce the impact of noisePublic key for secure communicationUser identity/authority verificationPlaintextAlgorithm
The invention belongs to the field of information security, and discloses a CRT-RSA selected plaintext joint attack method and system. During the attack process, the d p and d q As the attack target, then derive the private key parameters p, q; in the plaintext collision attack process, select multiple sets of plaintext pairs, superimpose them, and do secondary processing on the power consumption difference of the model multiplication as a collision classification set; in the attack process, Combined with the disclosure of the Hamming weight information of the access number power consumption exponent during the CRT-RSA modular exponentiation operation, the modular multiplication power consumption is segmented, and the segmented plaintext collision attack is implemented. The present invention combines the problems of other information leaks (such as access number power consumption exponent Hamming weight information leak) in the CRT-RSA modular exponentiation process, performs modular multiplication power consumption segmentation, and implements segmentation selection plaintext collision attacks, which can avoid partial The collision attack is wrong, thereby improving the attack accuracy, and finally deriving the private key parameters p, q, and recovering the private key d value.
Owner:CHENGDU UNIV OF INFORMATION TECH
Digital signature method and system with security only depending on discrete logarithms
ActiveCN111654369AResistance to collision attacksReduce computational complexityKey distribution for secure communicationUser identity/authority verificationAlgorithmDigital signature
The invention relates to a digital signature method and system with security only depending on discrete logarithms. The method comprises the following steps: acquiring system parameters of a digital signature system; selecting random numbers alpha and beta to obtain a private key SK = (alpha, beta); generating a public key according to the private key; selecting a message m and a random number k,wherein m belongs to Zn, Zn is an integer set composed of 0-n-1, and R represents random selection; generating a signature in a discrete logarithm signature mode according to the message m and the random number k; and performing consistency verification on the signature. Collision attacks can be resisted, and the safety performance of the digital signature system is improved.
Owner:麦希科技(北京)有限公司
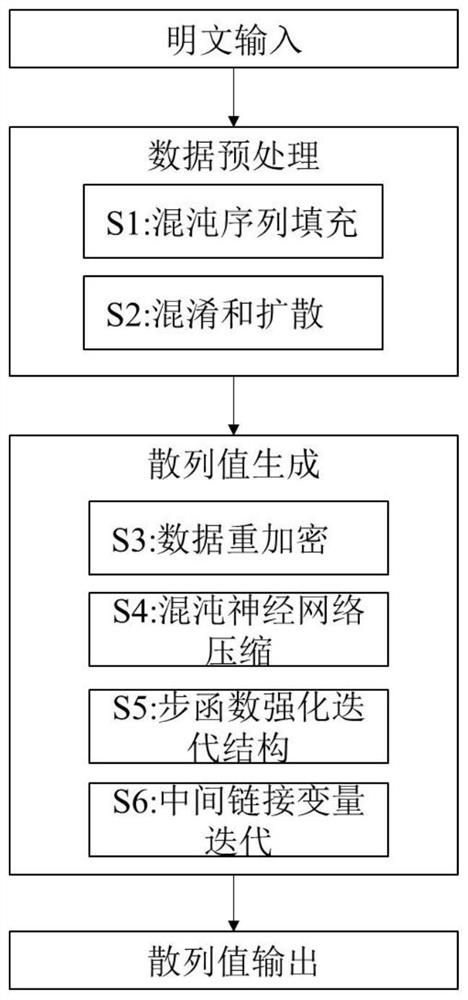
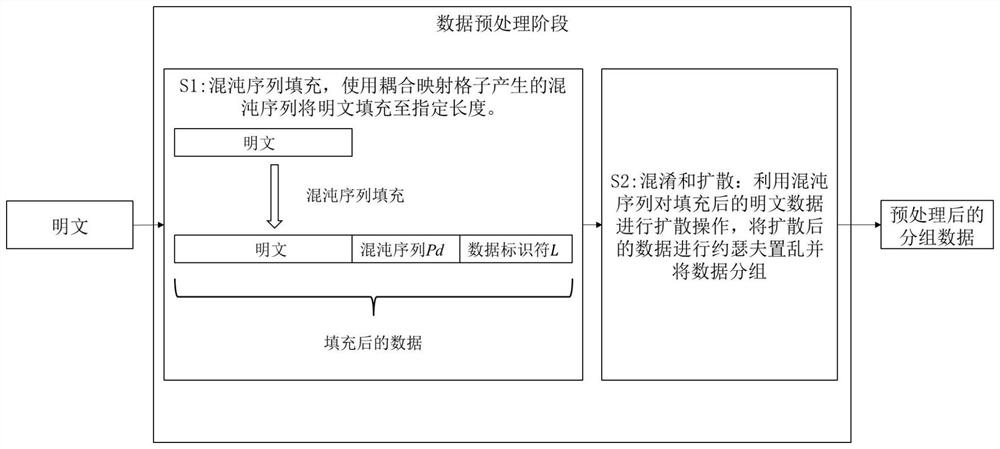
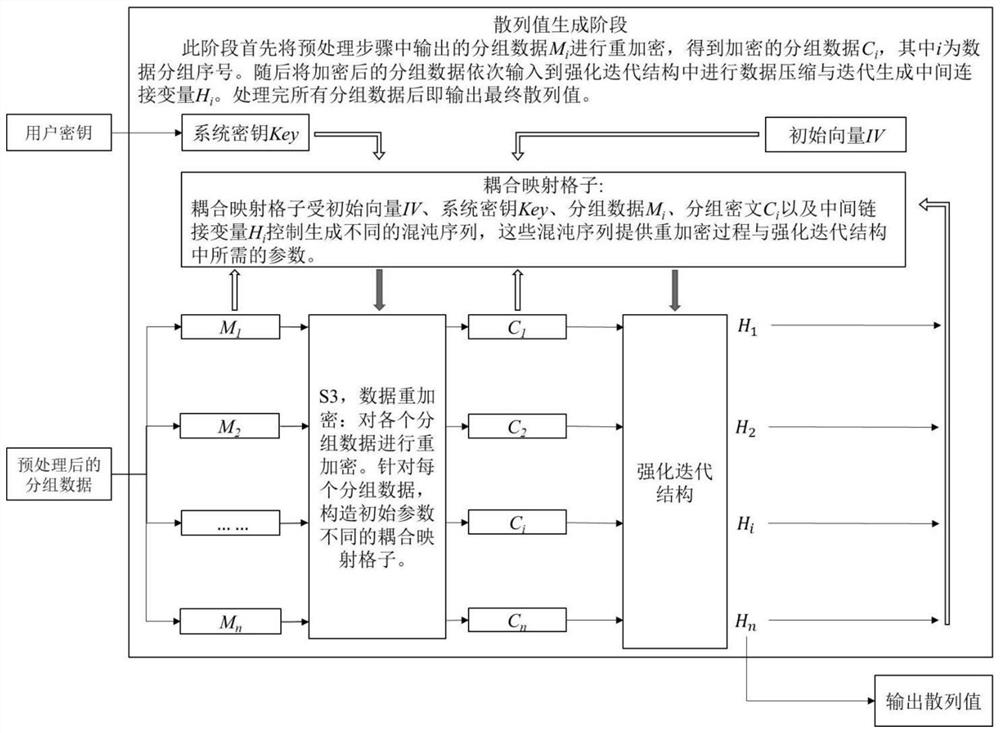
Method for constructing hash function with secret key based on chaotic neural network and enhanced iterative structure
PendingCN114418066AIncreased resistance to length extension attacksGuaranteed collision resistanceSecuring communication by chaotic signalsNeural architecturesPlaintextHash function
The invention discloses a method for constructing a hash function with a secret key based on a chaotic neural network and an enhanced iterative structure. The method comprises the following steps of: coupling mapping grids to generate a chaotic sequence to fill a plaintext; the chaotic neural network serves as a compression function to process grouped data; the enhanced iterative structure processes each packet data to generate a hash value. The method has the beneficial effects that the capabilities of resisting intermediate meeting attacks, multi-collision attacks, length extension attacks and second primary image attacks aiming at long information of the hash function can be improved, so that the hash function has better collision resistance and mapping uniformity; the method can be applied to the password fields of digital signatures, key generation, hash-based message authentication codes, deterministic random bit generators and the like.
Owner:SOUTHEAST UNIV
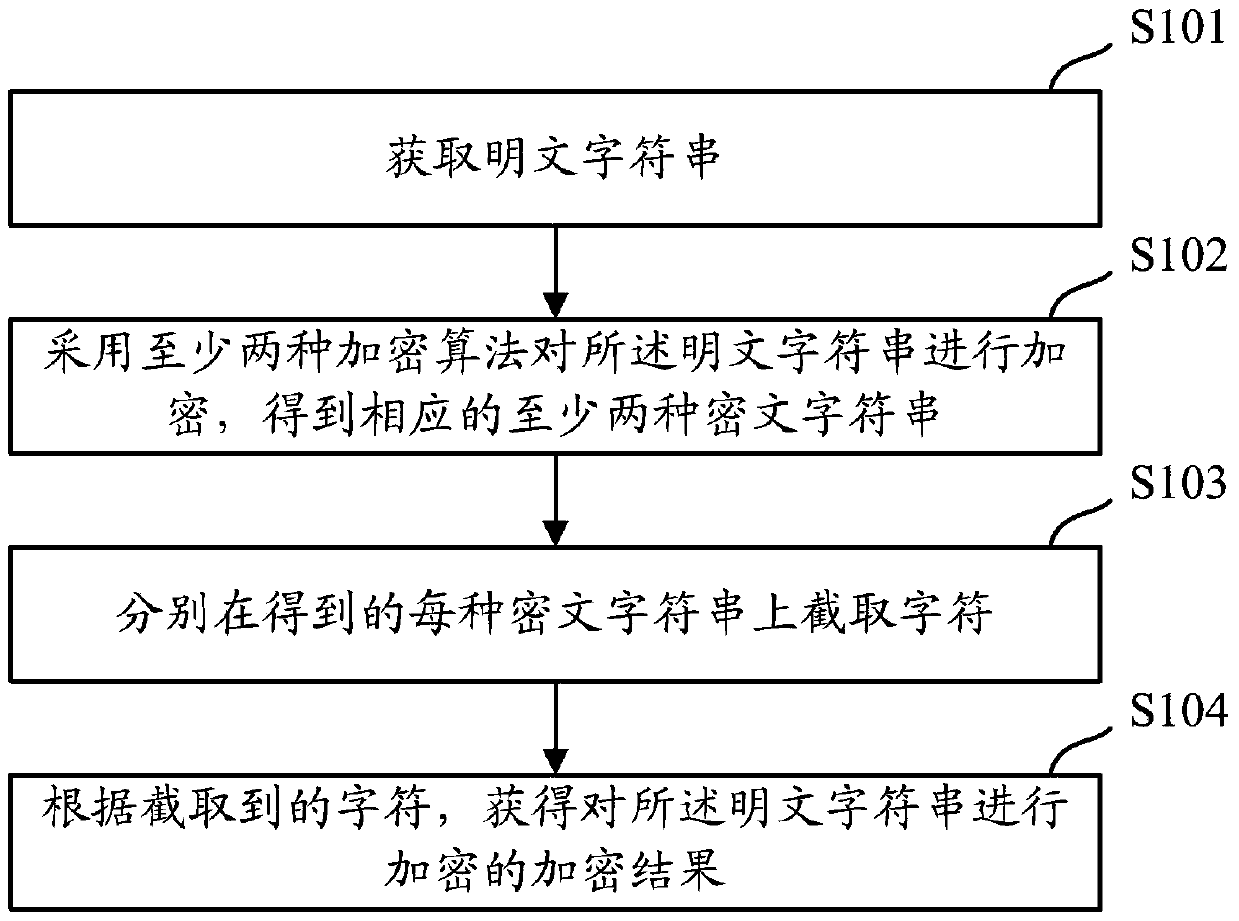
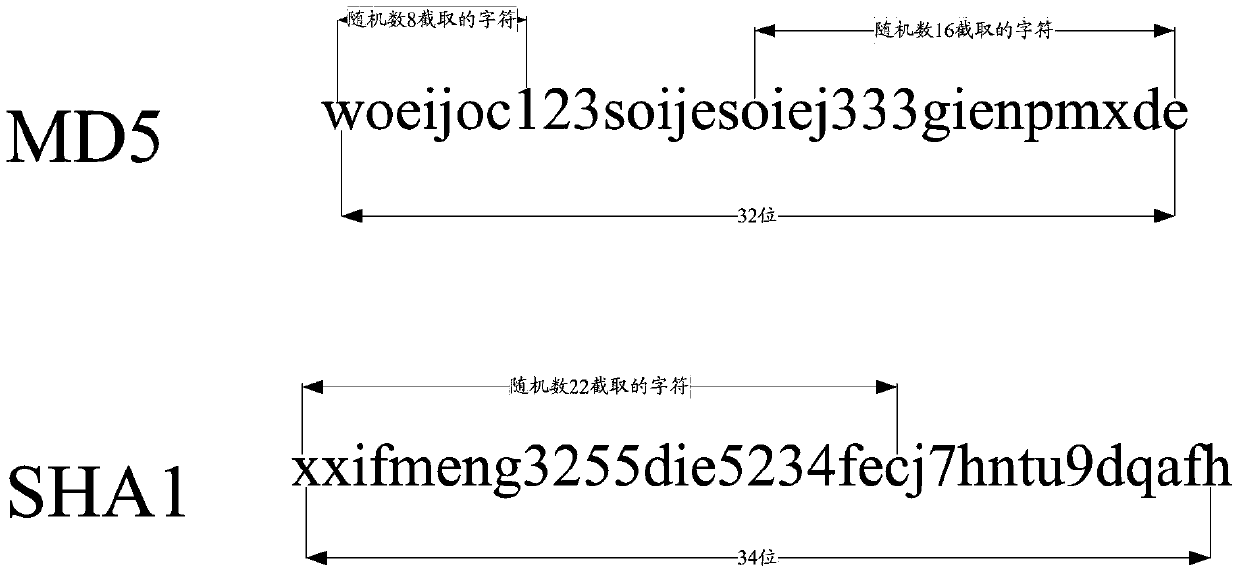
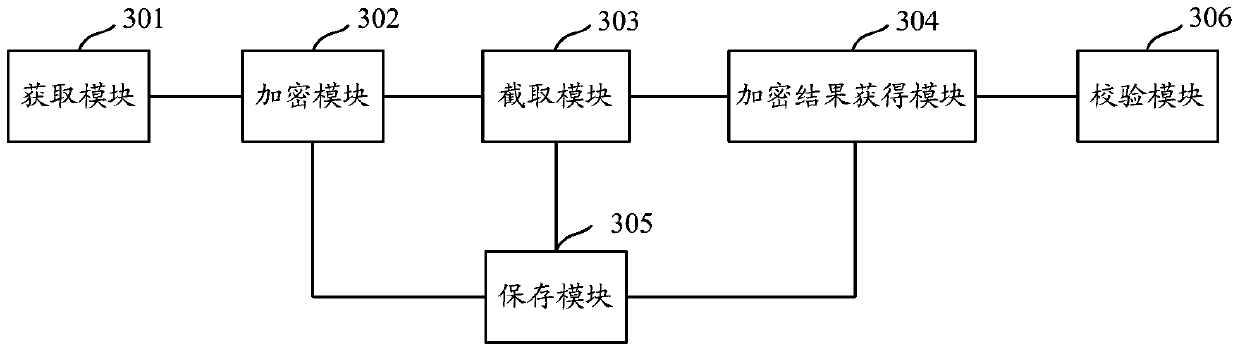
An encryption method and device
ActiveCN106549756BAvoid crackingImprove securityMultiple keys/algorithms usageComputer hardwarePlaintext
The present invention provides an encryption method and apparatus. The objective of the invention is to solve the problem that an encryption mode in the prior art may reduce the security of stored standard passwords. The method includes the following steps that: a plaintext character string is acquired; the acquired plaintext character string is encrypted through adopting at least two kinds of encryption algorithms, so that at least two corresponding ciphertext character strings can be obtained; characters are intercepted from each kind of obtained ciphertext character strings; and the encryption result of encryption performed on the plaintext character string can be obtained according to the intercepted characters. The encryption result obtained by using the above method contains the ciphertext character strings obtained after the encryption is performed with the different encryption algorithms, and the ciphertext character strings contained in the encryption result are not complete ciphertext character strings, but the incomplete intercepted character strings, and therefore, the encryption method can assist in effectively preventing the encryption result from being subjected to collision attack, violent attack or rainbow table comparison attack compared with an encryption method according to which a single encryption algorithm is adopted to perform encryption to obtain complete ciphertext character strings, and therefore, the security of the encryption result can be improved.
Owner:ADVANCED NEW TECH CO LTD
A credential stuffing attack monitoring method, device, system and computer storage medium
The embodiment of the present invention discloses a credential stuffing attack monitoring method, including: obtaining the login information of the user's login behavior; calculating a credible stuffing attack risk value corresponding to at least one user behavior factor according to the login information of the user's login behavior; The credential stuffing attack risk value corresponding to the at least one user behavior factor determines the credential stuffing attack risk value of the user's current login behavior; according to the credential stuffing attack risk value of the user's current login behavior, locates the user The credential stuffing attack risk type of the current login behavior. The embodiment of the invention also discloses a credential stuffing attack monitoring device, system and computer storage medium.
Owner:CHINA MOBILE COMM GRP CO LTD
Login behavior detection method and device, storage equipment and electronic equipment
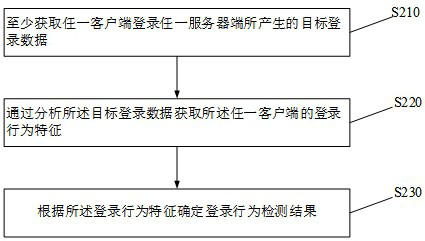
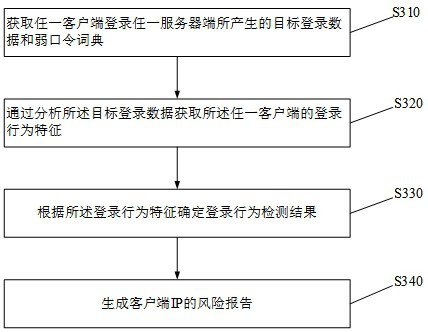
ActiveCN114640546AAccurately determine the type of attack behaviorEnsuring secure login requirementsUser identity/authority verificationAttackPassword
Embodiments of the invention provide a login behavior detection method and apparatus, a storage device and an electronic device. The method comprises the steps of at least obtaining target login data generated when any client logs in any server; by analyzing the target login data, login behavior characteristics of the any client are obtained, and the login behavior characteristics are at least used for representing the relation between all user names and all login passwords in the multiple login processes; a login behavior detection result is determined according to the login behavior characteristics, and the login behavior detection result is used for representing that any client has a blasting attack behavior, a spraying attack behavior, a library collision attack behavior or a weak password login risk behavior. According to the method provided by the embodiment of the invention, the security detection of the login behavior can be realized, and the universality is relatively high.
Owner:北京微步在线科技有限公司
Attack test method and device
InactiveCN101588578BReduce capacity requirementsHigh speedPublic key for secure communicationData switching networksChosen-plaintext attackCollision attack
The invention provides a collision attack test method and a device. The invention provides the collision attack test method aiming to solve chosen-plaintext attack of a key in an encryption algorithm of the prior art. The method comprises the following steps: receiving a plaintext; storing at least one part of the plaintext; judging whether the analogical number of the stored at least one part of the plaintext and other stored at least one part of the plaintext is more than or equal to a first threshold value; outputting a signal with an attack mode in the current plaintext if the analogical number is more thanor equal to the first threshold value, otherwise, outputting a normal signal; and repeating the steps before the next plaintext comes. The method and the device have the advantages that the method and the device can test the inputting plaintext with obvious attack mode and avoid the chosen-plaintext attack on the key.
Owner:GIESECKE & DEVRIENT (CHINA) INFORMATION TECH CO LTD
Identity authentication method, system and server based on blockchain network
The invention discloses a method, a system, a server and terminal equipment for authenticating identities on the basis of block chain networks. The method, the system, the server and the terminal equipment are used for authenticating the identities for nodes in the block chain networks. The method includes receiving login requests with user names; acquiring first block chain account addresses according to preliminarily stored corresponding relations between the user names and the first block chain account addresses; judging whether first transaction of payment from the first block chain account addresses to preset second block chain account addresses is available in block chains or not; determining that the identities of users are successfully authenticated if the first transaction is available in the block chains. The login requests are transmitted by the nodes. The first block chain account addresses are associated with the user names. The method, the system, the server and the terminal equipment have the advantages that transaction information stored in the block chains cannot be tampered and can be traced back and queried, and accordingly the authentication safety and the credibility of authentication procedures can be improved; the users do not need to input passwords during login and do not need to remember the passwords, accordingly, the convenience can be improved, and database collision attack due to the fact that other malicious personnel log in other websites by the aid of stolen user names and passwords can be prevented.
Owner:JIANGSU PAYEGIS TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com