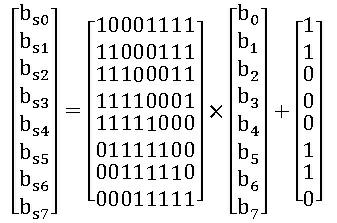Method for constructing reinforced hash function based on compression function
A construction method and function technology, applied in the field of information security, can solve problems such as collision attack, preimage attack and second preimage attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0007] The following is an example, taking strengthening SHA-1 as an example.
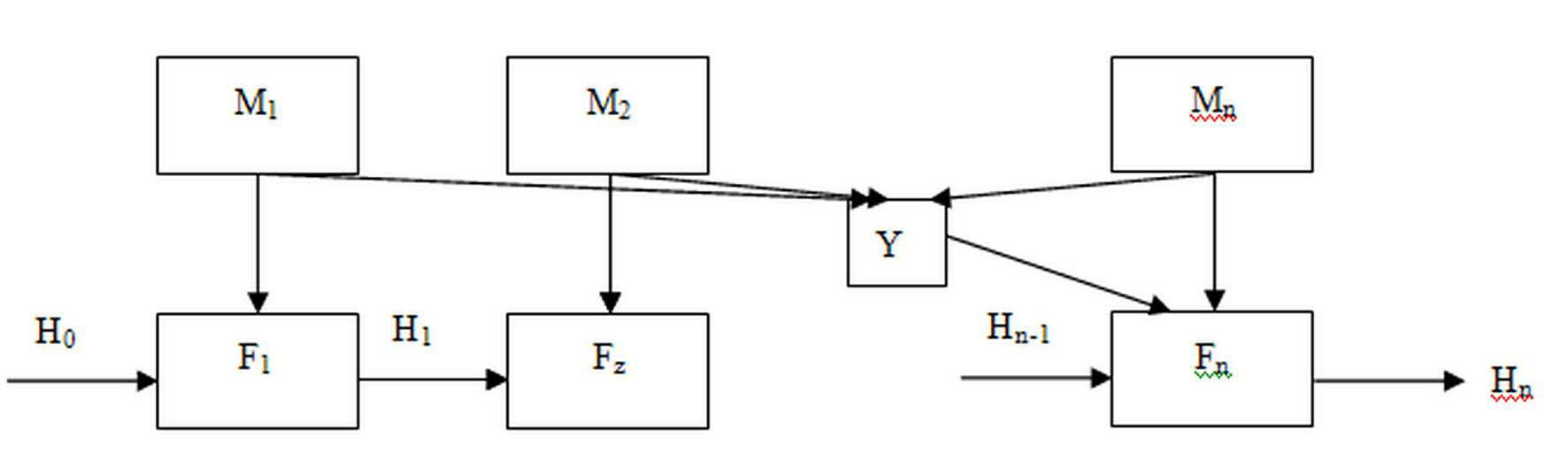
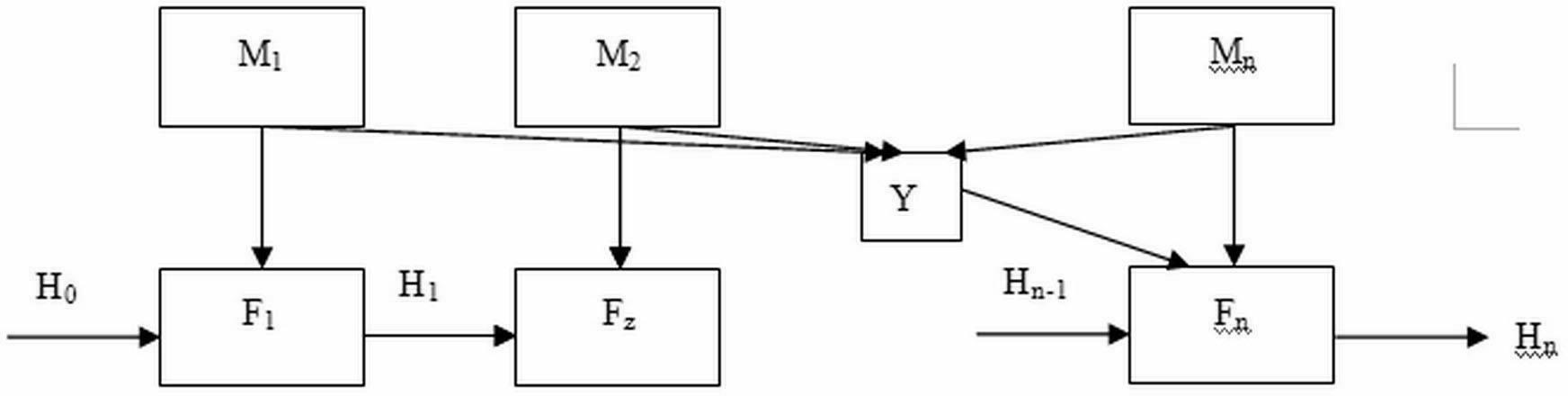
[0008] The intermediate packet still uses the less secure SHA-1 compression function F z , since this function is already very clear, it will not be described in detail here. The first group and the last group use different reinforced functions F 1 and F n . The hardened algorithm is based on the compression function like SHA-1. It has a buffer to store the 160bit intermediate result of the operation and the final hash result H i , i is the order of the packets, and its input is the 512bit plaintext packet M i and the intermediate result H of the previous grouping i-1 , the last grouping adds an input Y. The iterative process of Hash can be expressed as follows: H 1 =F 1 (M 1 , H 0 ), where H 0 is the initial value of the buffer, H i =F i (M i , H i-1 ), where i is greater than 1 and less than n, H n =F n (Y, M n , H n-1 ), n is the number of groups.
[0009] The first packet c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com