Plaintext selection related collision attack method based on mask SM4 cryptographic algorithm
A technology of choosing plaintext and collision attack, which is applied to the usage of multiple keys/algorithms, countermeasures for attacking encryption mechanisms, encryption devices with shift registers/memory, etc. It can solve the problems that collision attacks are difficult to work, and achieve effective attacks Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0062] The present invention will be further described below in conjunction with the accompanying drawings.
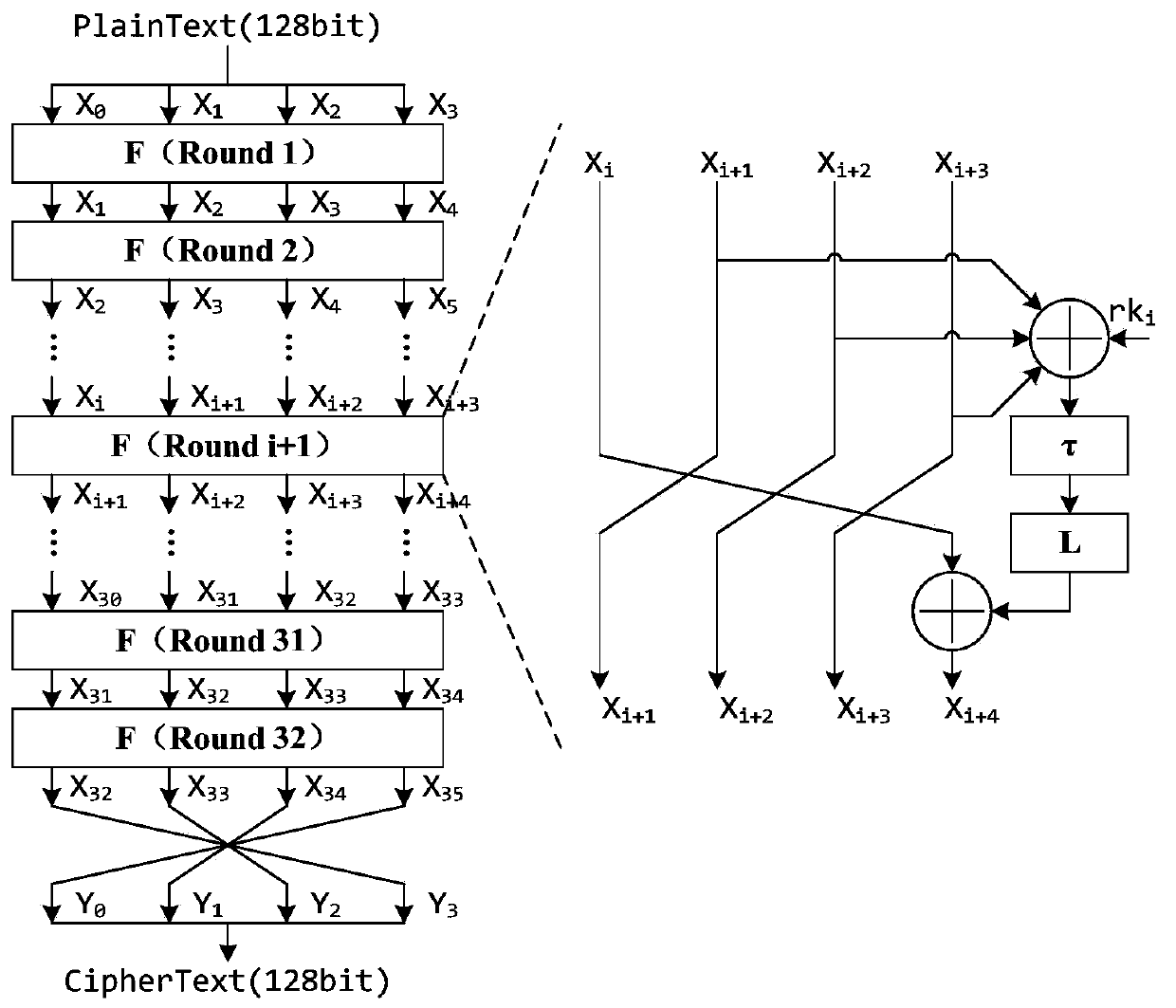
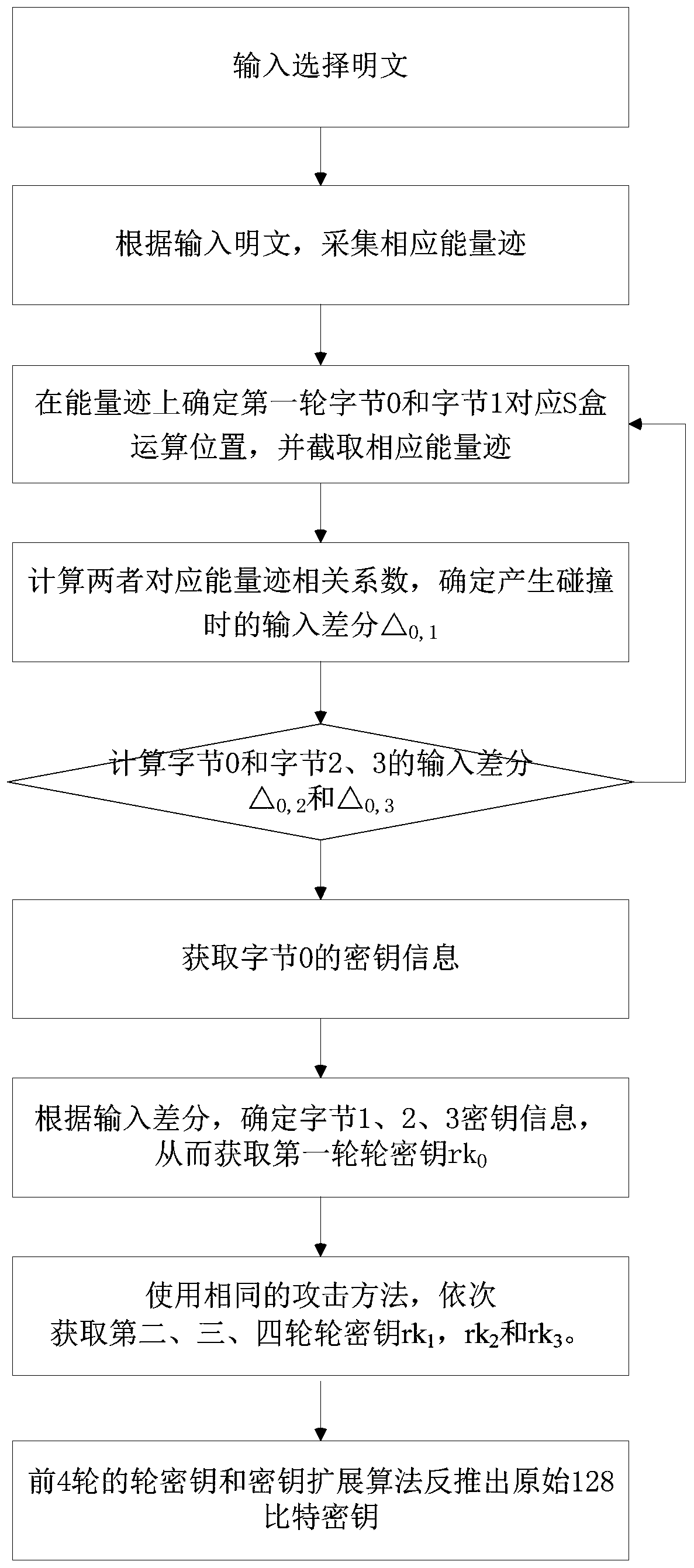
[0063] Such as image 3 As shown, a chosen plaintext correlation collision attack method based on the masked SM4 cipher algorithm includes the following content.
[0064] 1. Measurement stage
[0065] In the measurement phase, the attacker chooses to enter the plaintext of the SM4 cryptographic algorithm, encrypts the cryptographic device to be attacked, and records and collects the corresponding energy traces for use in the collision detection phase.
[0066] Let SM4 password algorithm input plaintext be in (i=0,1,2,3); the round key of the first round is Choose input plaintext, fixed x i0 = 0, and let x i1 =x i2 =x i3 , its value is traversed from 0 to 255 in turn, each value is encrypted for N times, and the corresponding N energy traces are recorded and collected. Each energy trace contains T sampling points, which is recorded as Where 0≤n≤N-1, 0≤α≤255...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com