Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
41 results about "Calling convention" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
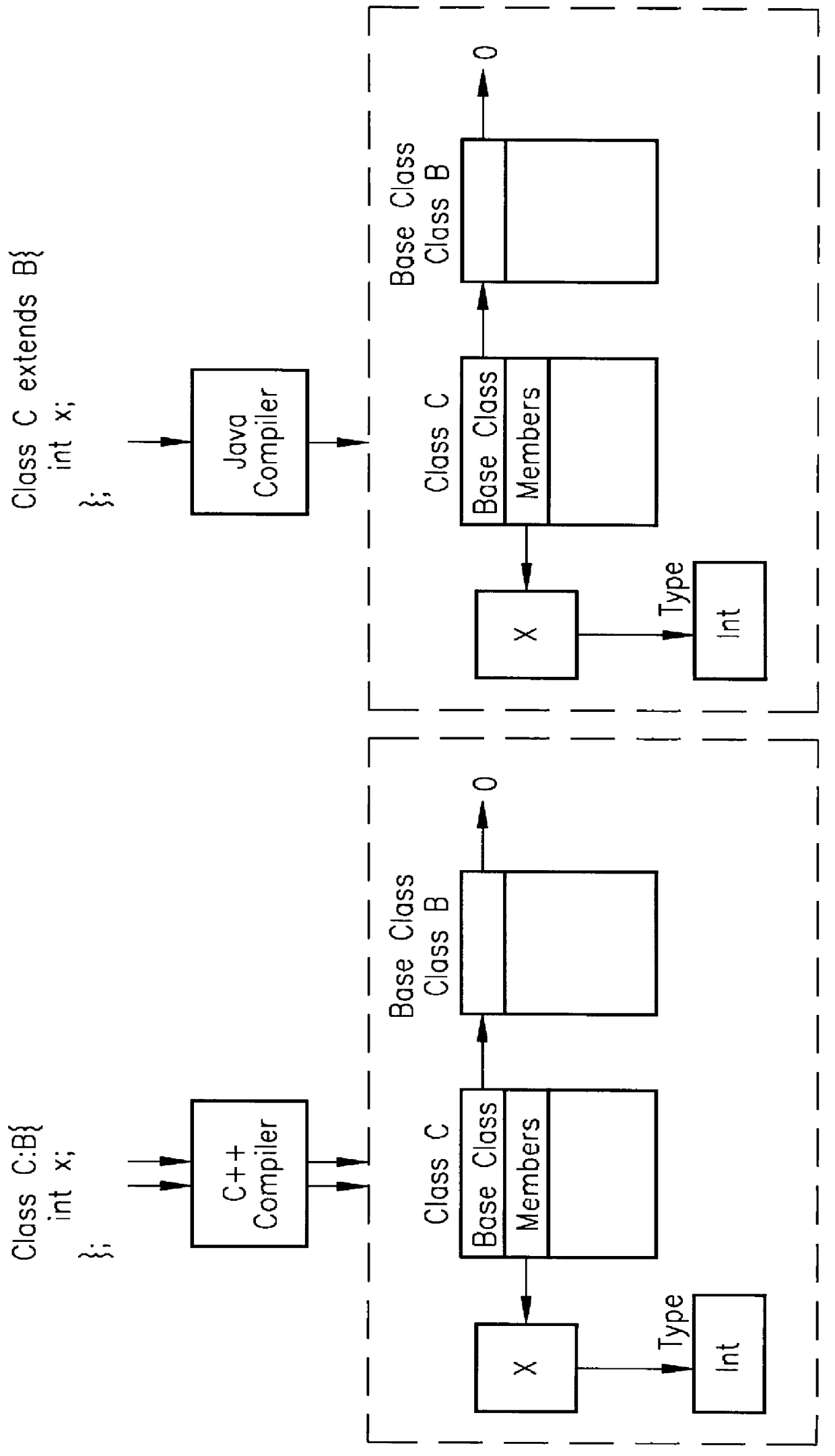
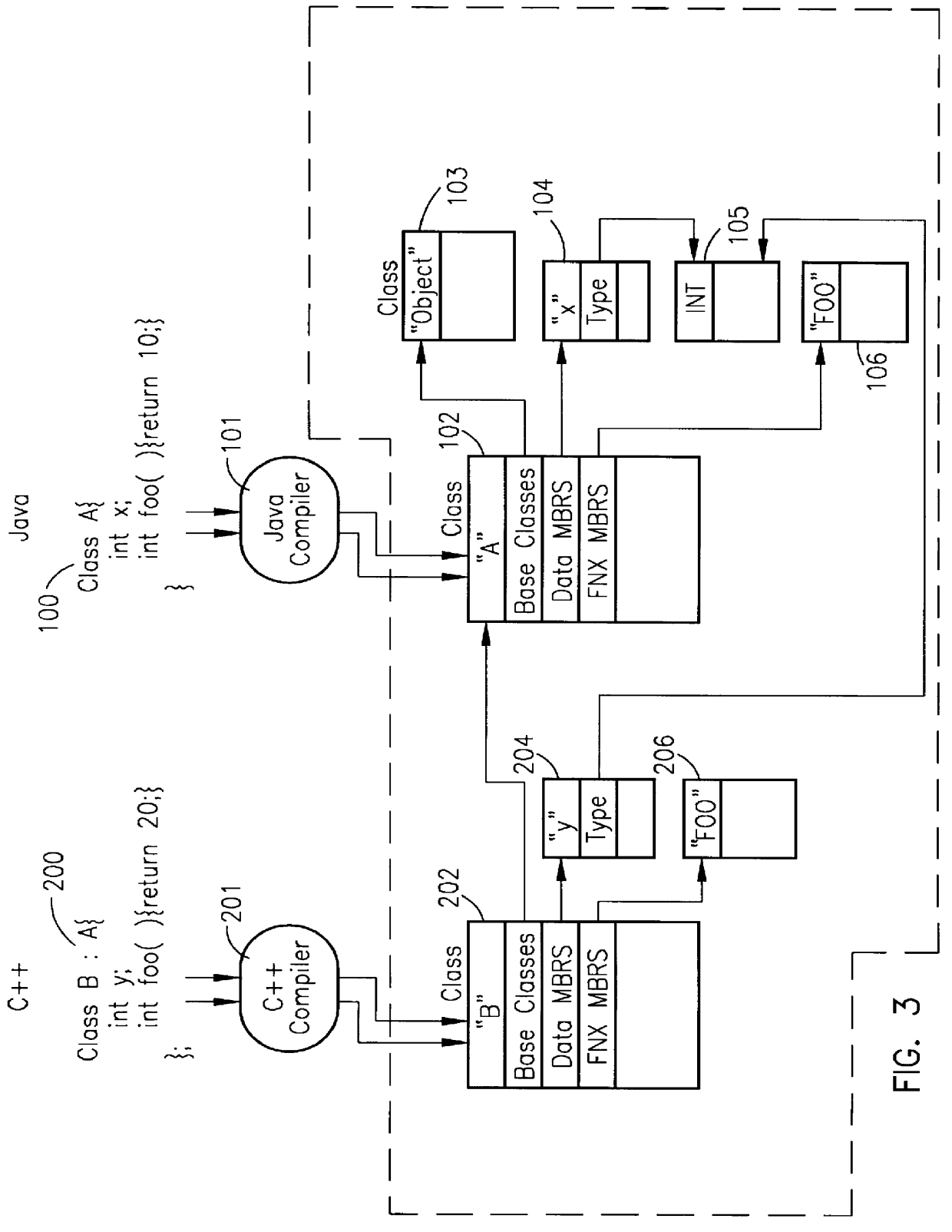
In computer science, a calling convention is an implementation-level (low-level) scheme for how subroutines receive parameters from their caller and how they return a result. Differences in various implementations include where parameters, return values, return addresses and scope links are placed (registers, stack or memory etc.), and how the tasks of preparing for a function call and restoring the environment afterward are divided between the caller and the callee.
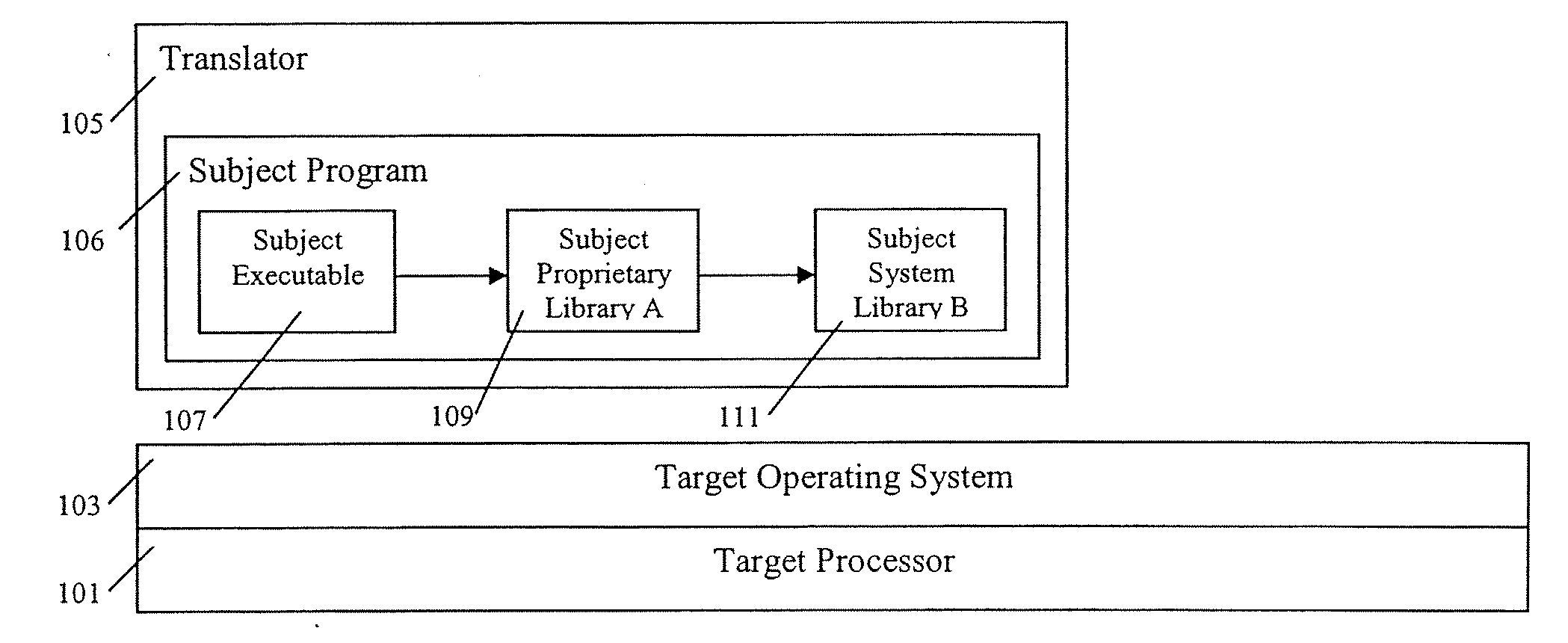
Dynamic native binding
ActiveUS20090100416A1Avoid overheadEfficient implementationBinary to binarySoftware simulation/interpretation/emulationObject codeFunction prototype
Owner:IBM CORP
Data representation for mixed-language program development
InactiveUS6067413AReduce the burden onRealized benefitsMultiprogramming arrangementsSoftware designType conversionShared object
Method for enabling the simultaneous use of a first and a second programming language within a computer program, and apparatus to practice the method. To enable this sharing of languages, the present invention first provides for a common runtime representation of the data between the several languages in a program as a shared object model. The shared object model includes the layout of complex data structures (e.g., classes), the creation of data, the calling conventions, the destruction of data, the runtime representation of type information, dynamic function call dispatch, and dynamic type conversions. The use of a shared object model enables the sharing of the several compilers' internal representation of data between the different languages as a persistent shared symbol table. This shared internal data representation enables the several compilers to define their respective internal data representations in terms common to each of the compilers.
Owner:OPEN INVENTION NEWTORK LLC
Systems and methods for hypervisor discovery and utilization
ActiveUS20060248528A1Software simulation/interpretation/emulationMemory systemsVirtual deviceComputer science
Systems and methods are provided, whereby partitions may become enlightened and discover the presence of a hypervisor. Several techniques of hypervisor discovery are discussed, such as detecting the presence of virtual processor registers (e.g. model specific registers or special-purpose registers) or the presence of virtual hardware devices. Upon discovery, information (code and / or data) may be injected in a partition by the hypervisor, whereby such injection allows the partition to call the hypervisor. Moreover, the hypervisor may present a versioning mechanism that allows the partition to match up the version of the hypervisor to its virtual devices. Next, once code and / or data is injected, calling conventions are established that allow the partition and the hypervisor to communicate, so that the hypervisor may perform some operations on behalf of the partition. Four exemplary calling conventions are considered: restartable instructions, a looping mechanism, shared memory transport, and synchronous or asynchronous processed packets. Last, cancellation mechanisms are considered, whereby partition requests may be cancelled.
Owner:MICROSOFT TECH LICENSING LLC
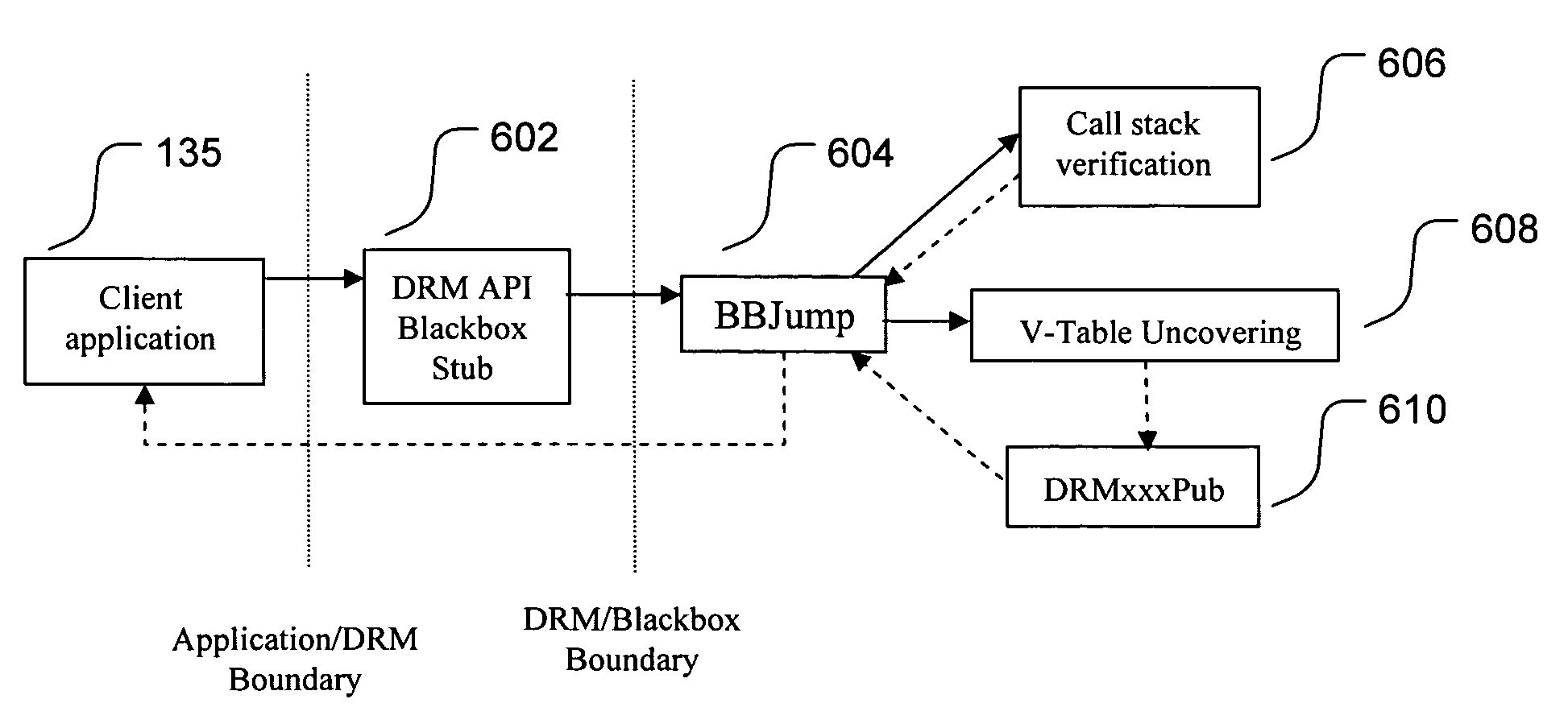
Run-time call stack verification
InactiveUS7546587B2Efficient identificationProgram/content distribution protectionSpecific program execution arrangementsCode moduleCall stack
Owner:MICROSOFT TECH LICENSING LLC
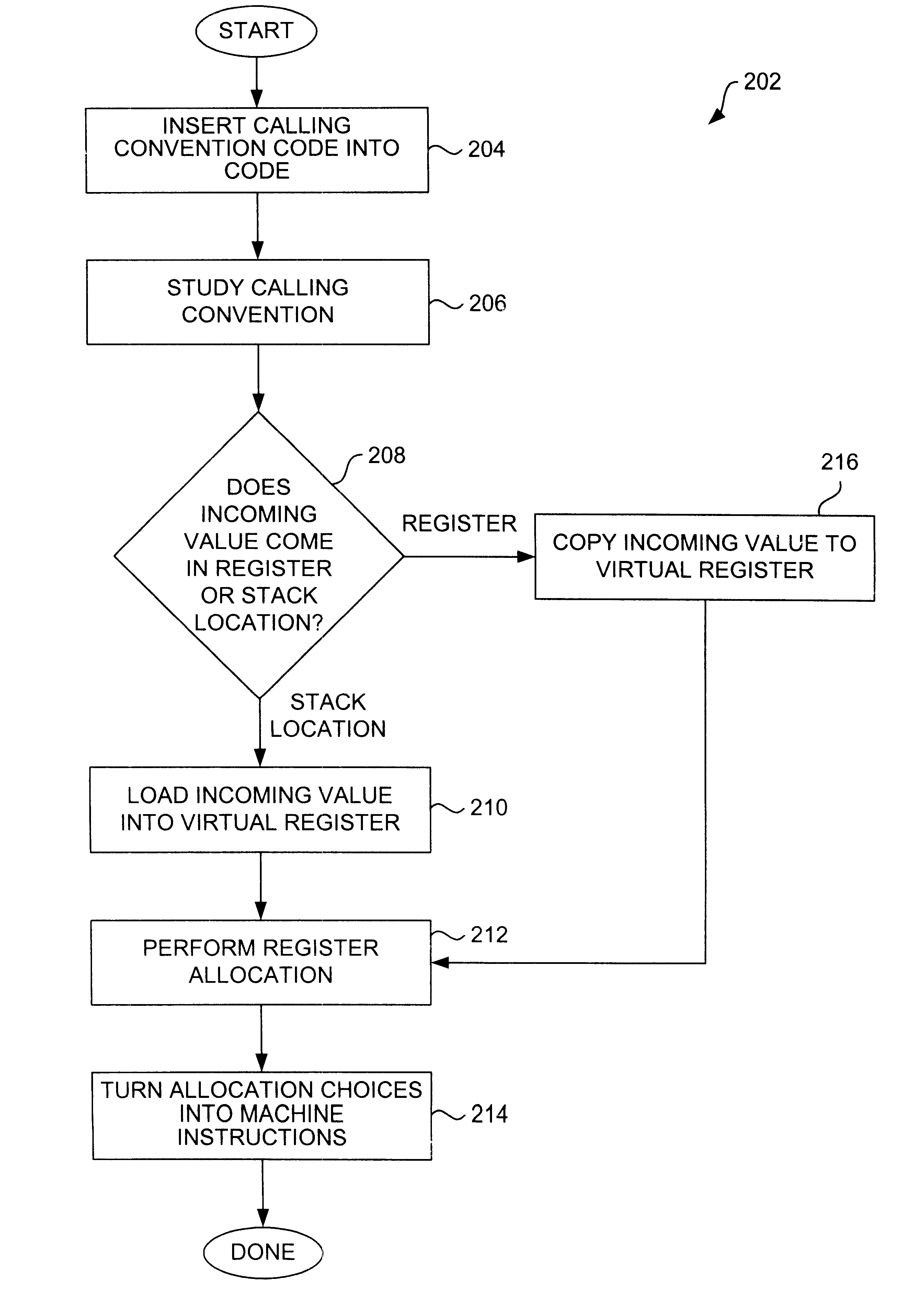
Method and apparatus for building calling convention prolog and epilog code using a register allocator
InactiveUS6408433B1Generate efficientlyEasy to transplantSoftware engineeringProgram controlRegister allocationProcessor register
Methods and apparatus for enabling a register allocator to build a calling convention are disclosed. According to one aspect of the present invention, a computer-implemented method for generating code associated with a calling convention includes obtaining compilable source code, and identifying at least one argument associated with the calling convention. The location of the argument with respect to memory space is described by a register mask. The method also includes performing a register allocation using a register allocator that is arranged to allocate registers. During the register allocation, code associated with the calling convention is produced automatically by the spill-code mechanism in the allocator without requiring the use of a specialized prolog or epilog code generator.
Owner:ORACLE INT CORP
Method and apparatus for performing native binding
ActiveUS20050015781A1Avoid overheadEfficient implementationTransformation of program codeSoftware simulation/interpretation/emulationObject codeFunction prototype
Owner:IBM CORP
Run-time call stack verification
InactiveUS20050198645A1Reduce usageEfficient identificationProgram/content distribution protectionSpecific program execution arrangementsCode moduleCall stack
Run-time call stack verification is used to determine that a code module has been called by a legitimate caller. A return address on the stack indicates where execution is to return upon execution of the next return instruction, and this return address is indicative of where the code module was called from. The code module may determine that the call is allowed, or disallowed, based on the location of the return address. A calling convention is provided that allows the code module to be called through an intermediary, while also preserving the original return address that was in effect at the time the intermediary was called and also resisting modification to the call stack during the time that the original return address is being verified.
Owner:MICROSOFT TECH LICENSING LLC
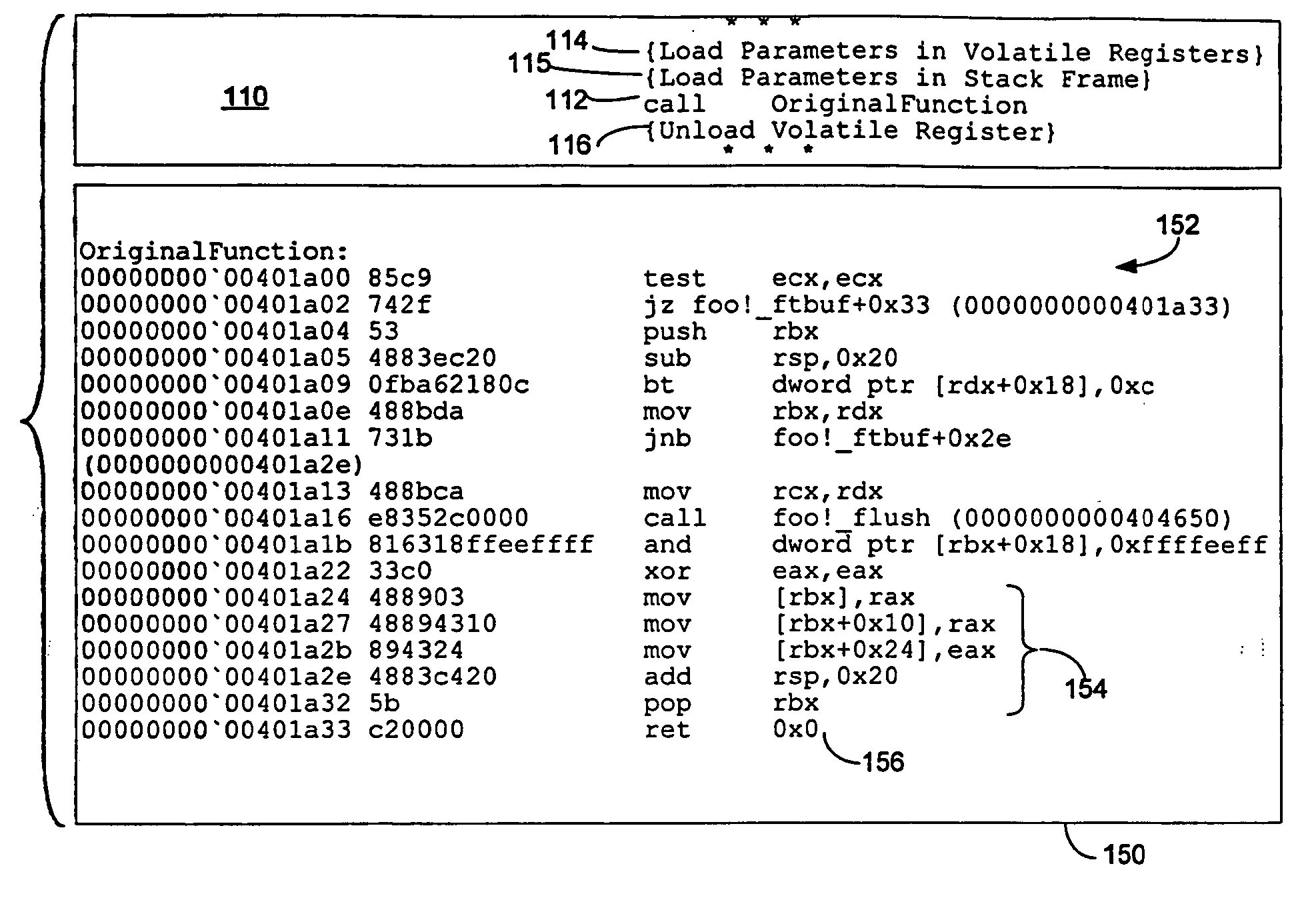
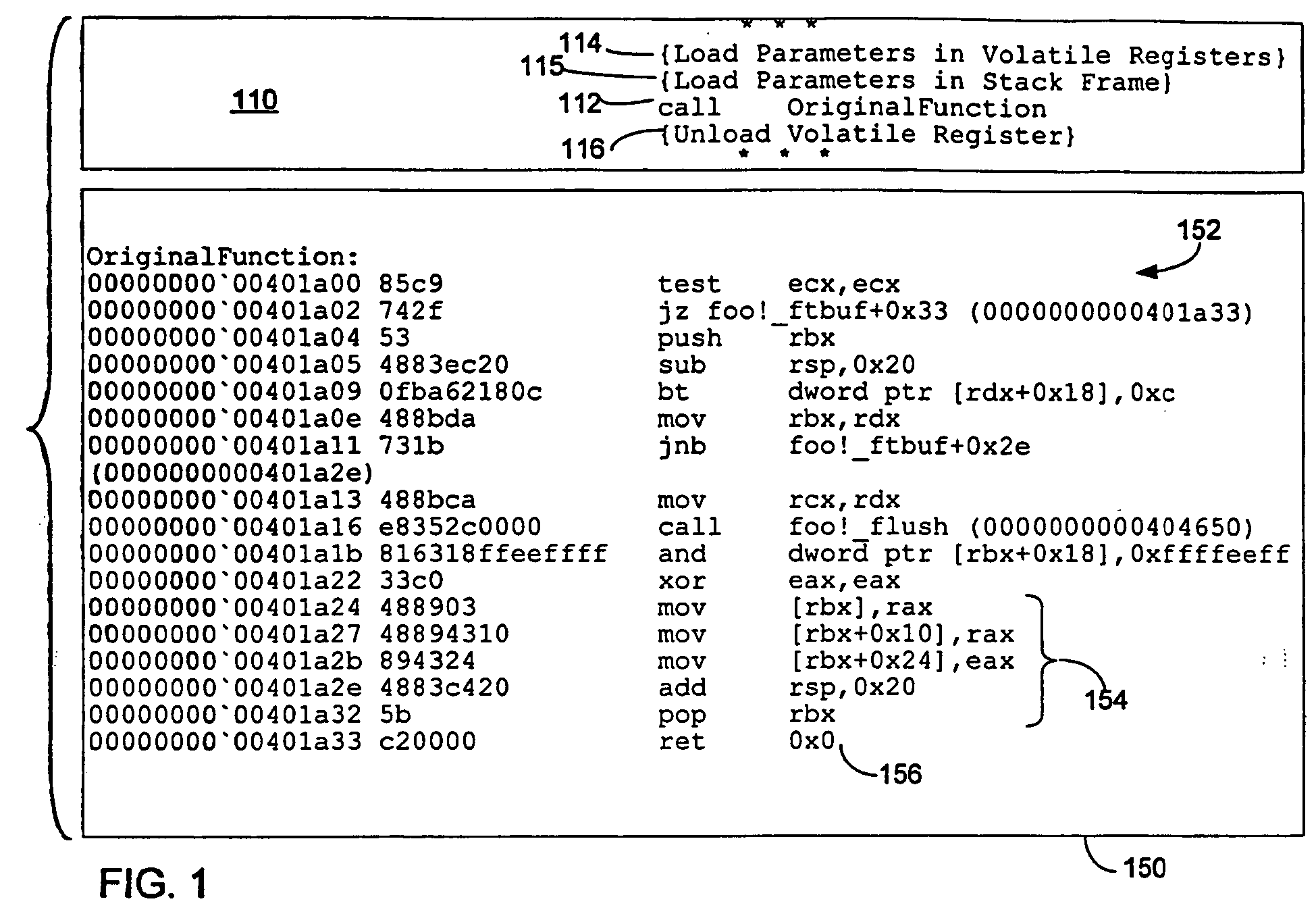
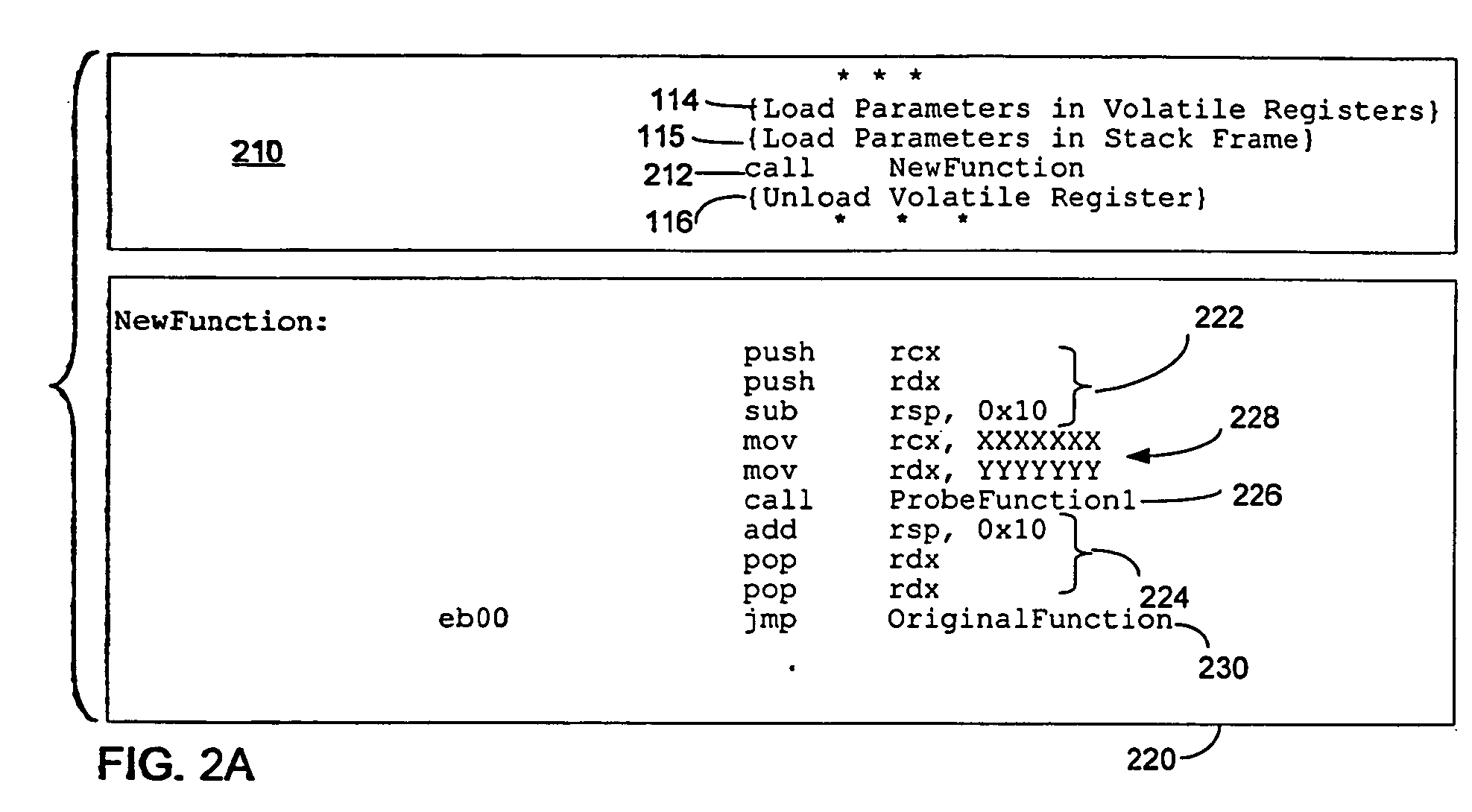
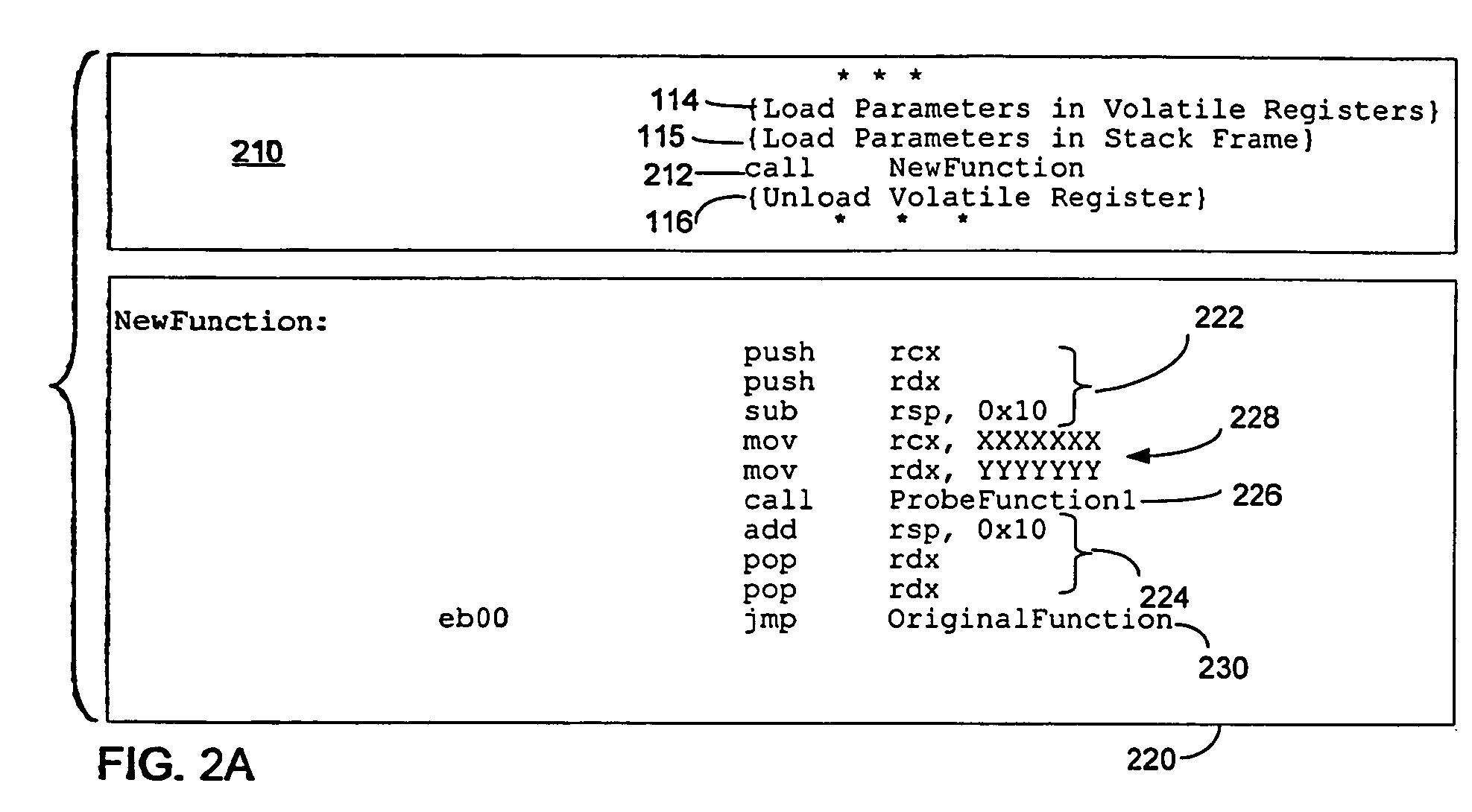
Method of instrumenting code having restrictive calling conventions
ActiveUS20060218537A1Software engineeringError detection/correctionWrapper functionException handling
A development environment for computer programs in which programs under test may be instrumented with probe functions. The probe functions are called through a wrapper function structured to comply with restrictive calling conventions of the platform for which the computer program is developed. By complying with the calling convention, proper operation of the computer program is achieved during testing even if an exception handler, or other program element that relies on compliance with the calling convention, is invoked. Once instrumented, the computer program may be tested to determine whether it executes desired logic function to determine the performance of the program or for other test functions.
Owner:MICROSOFT TECH LICENSING LLC
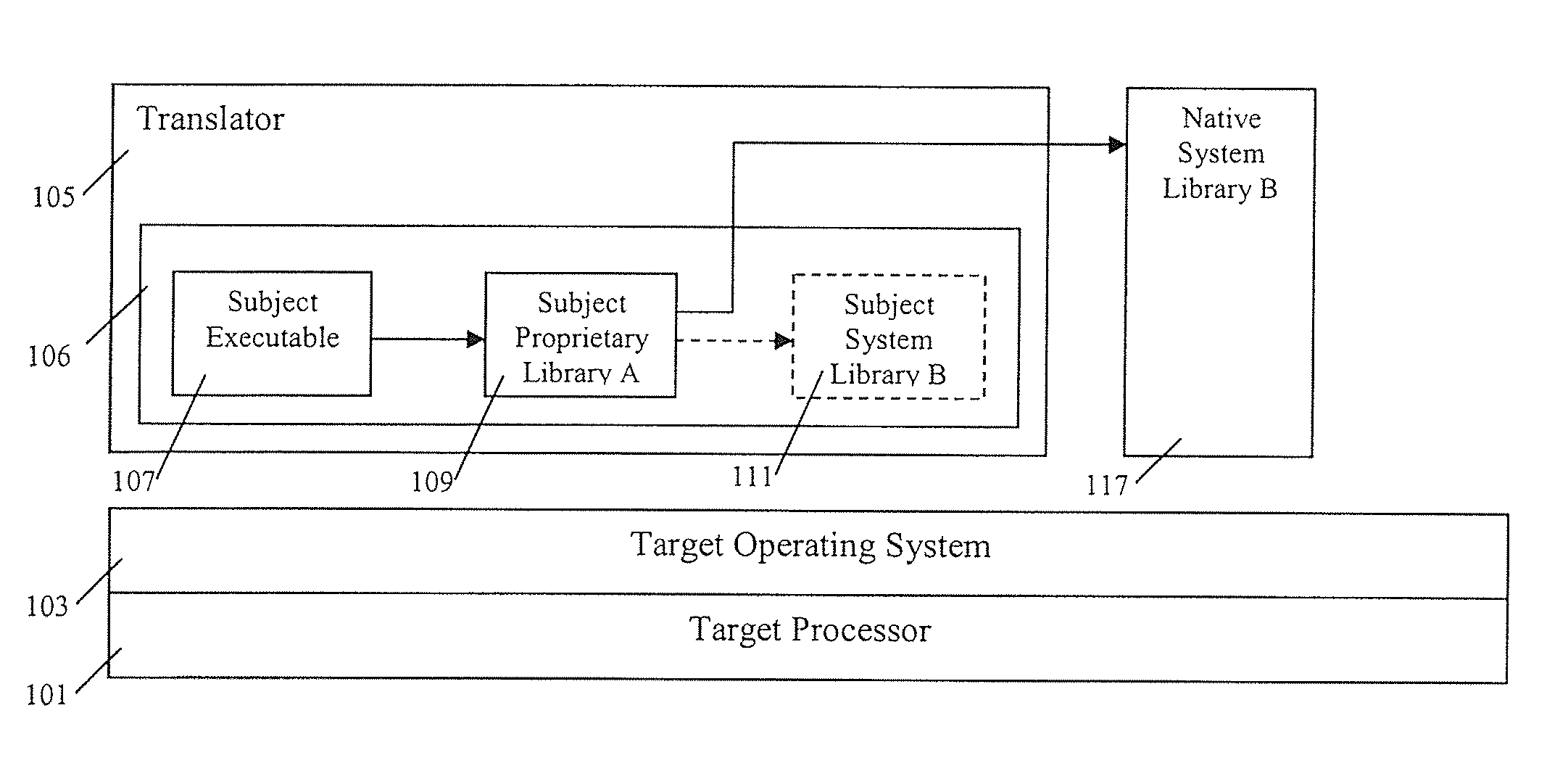
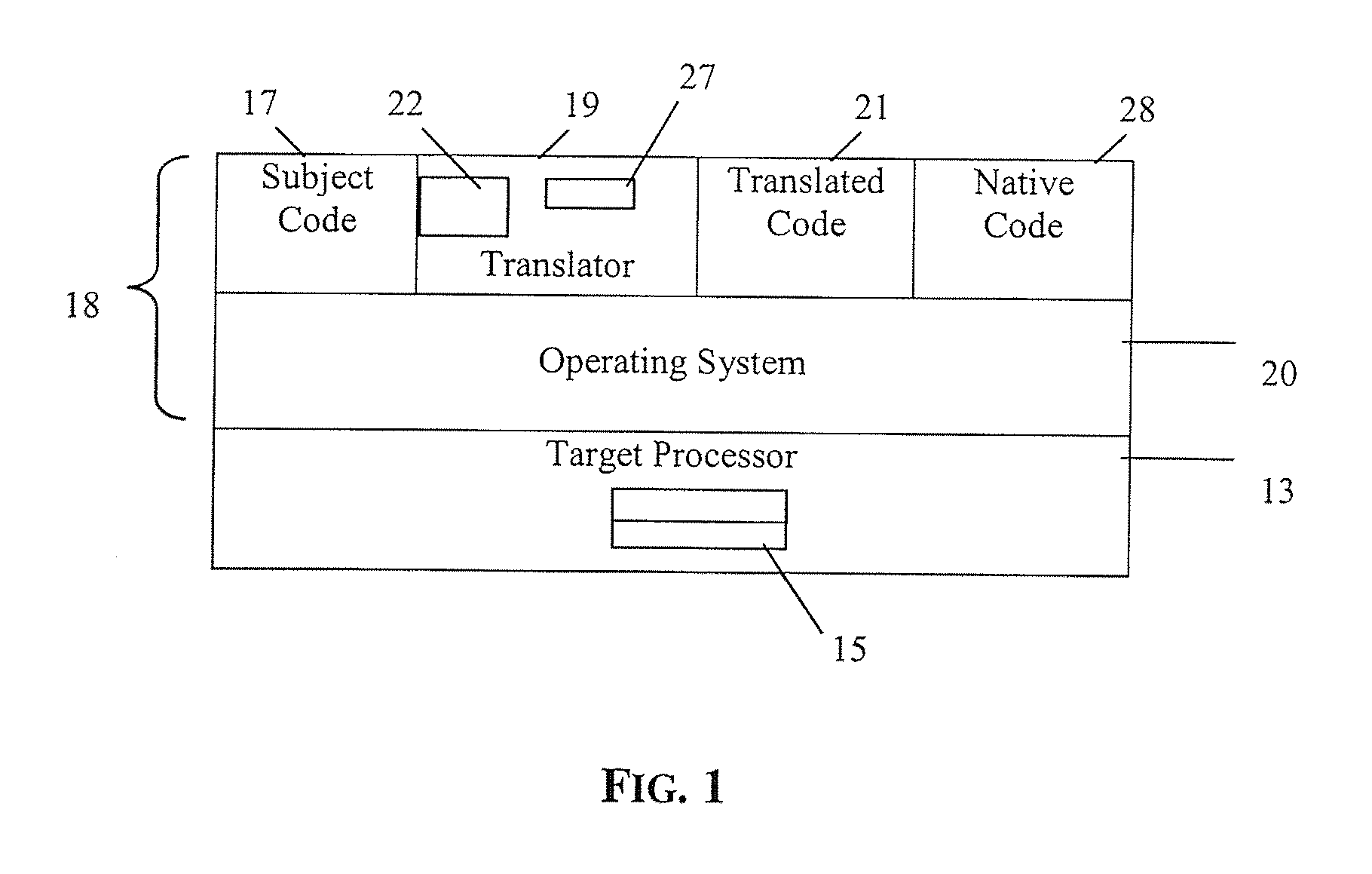
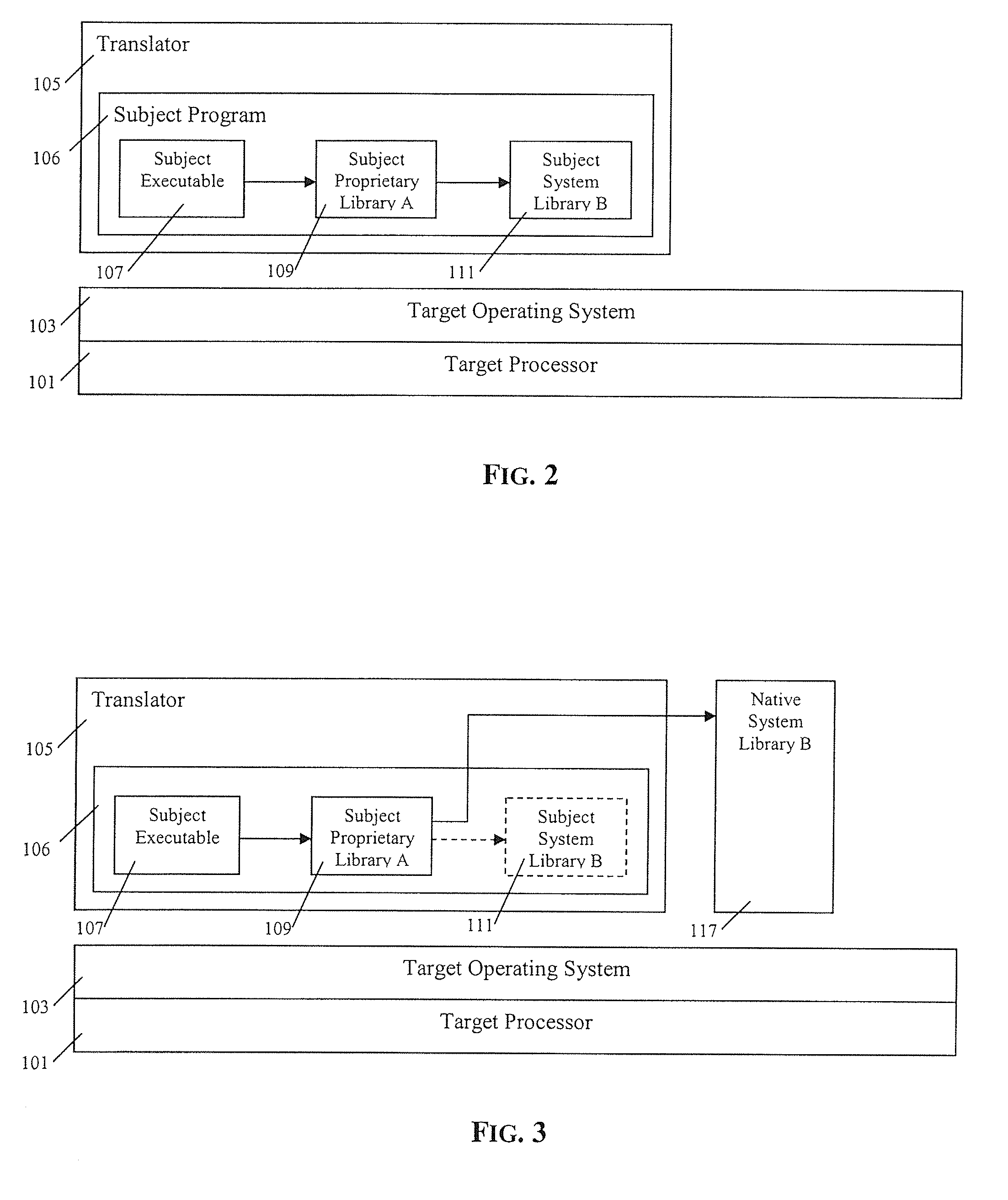
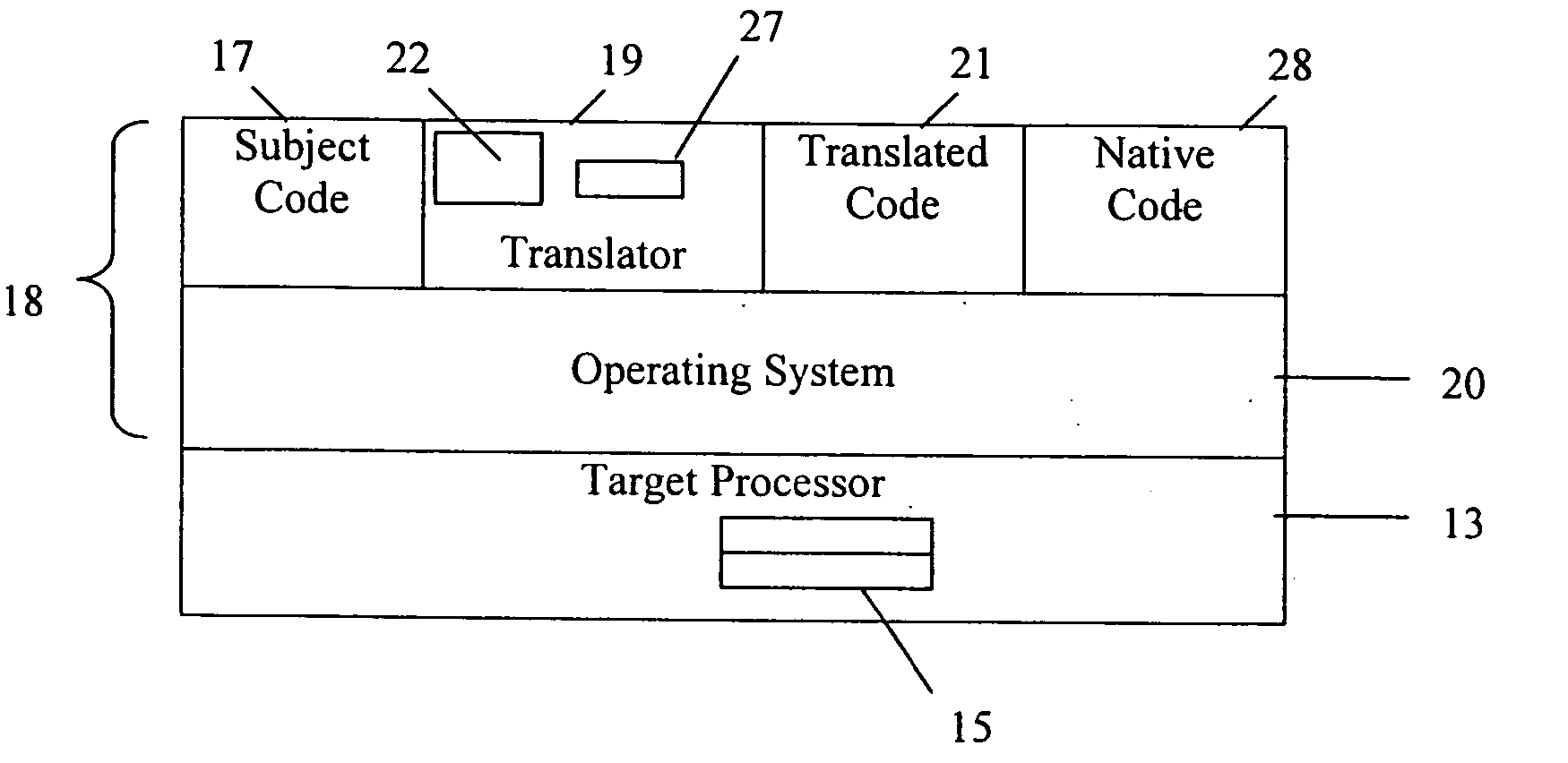
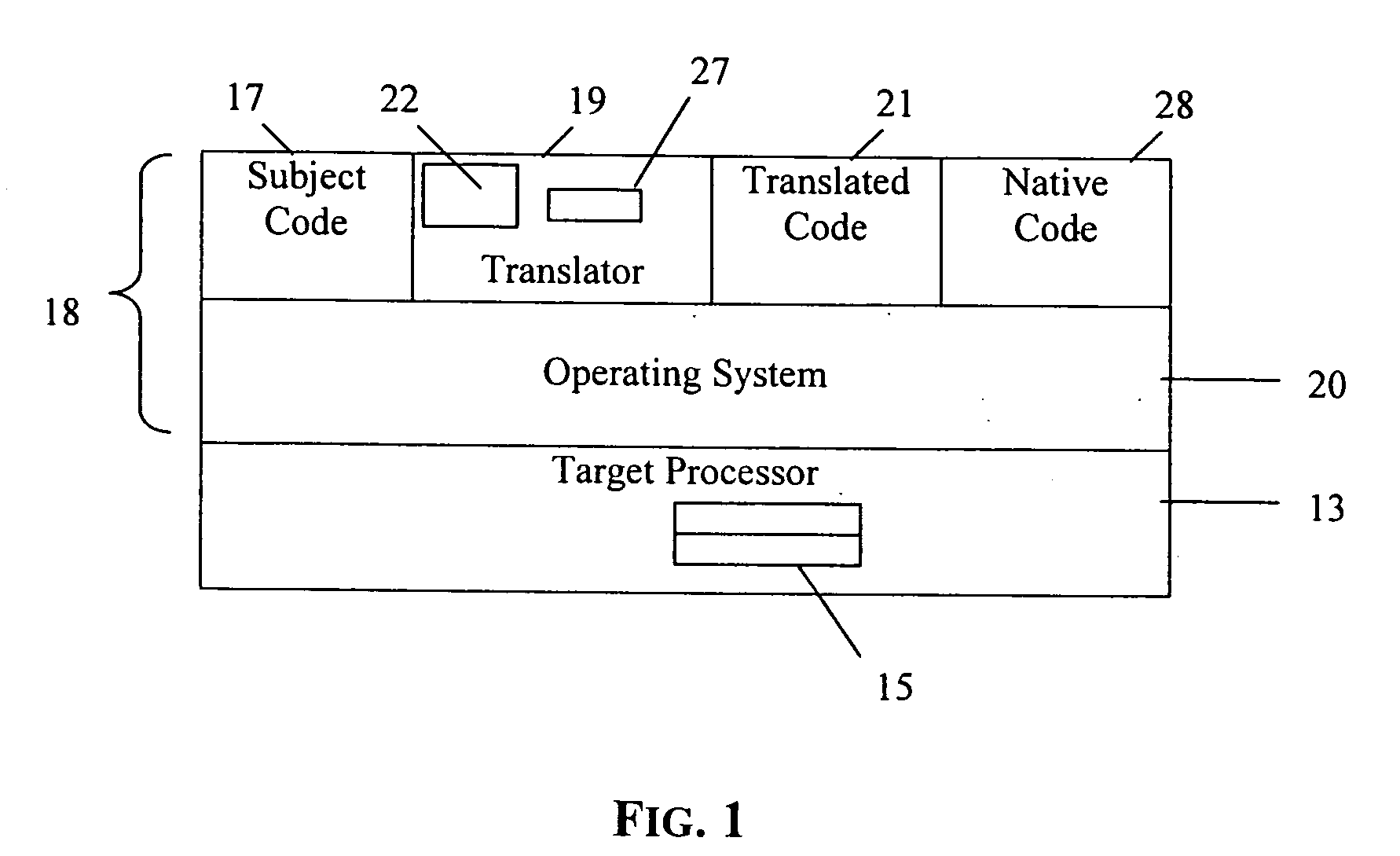
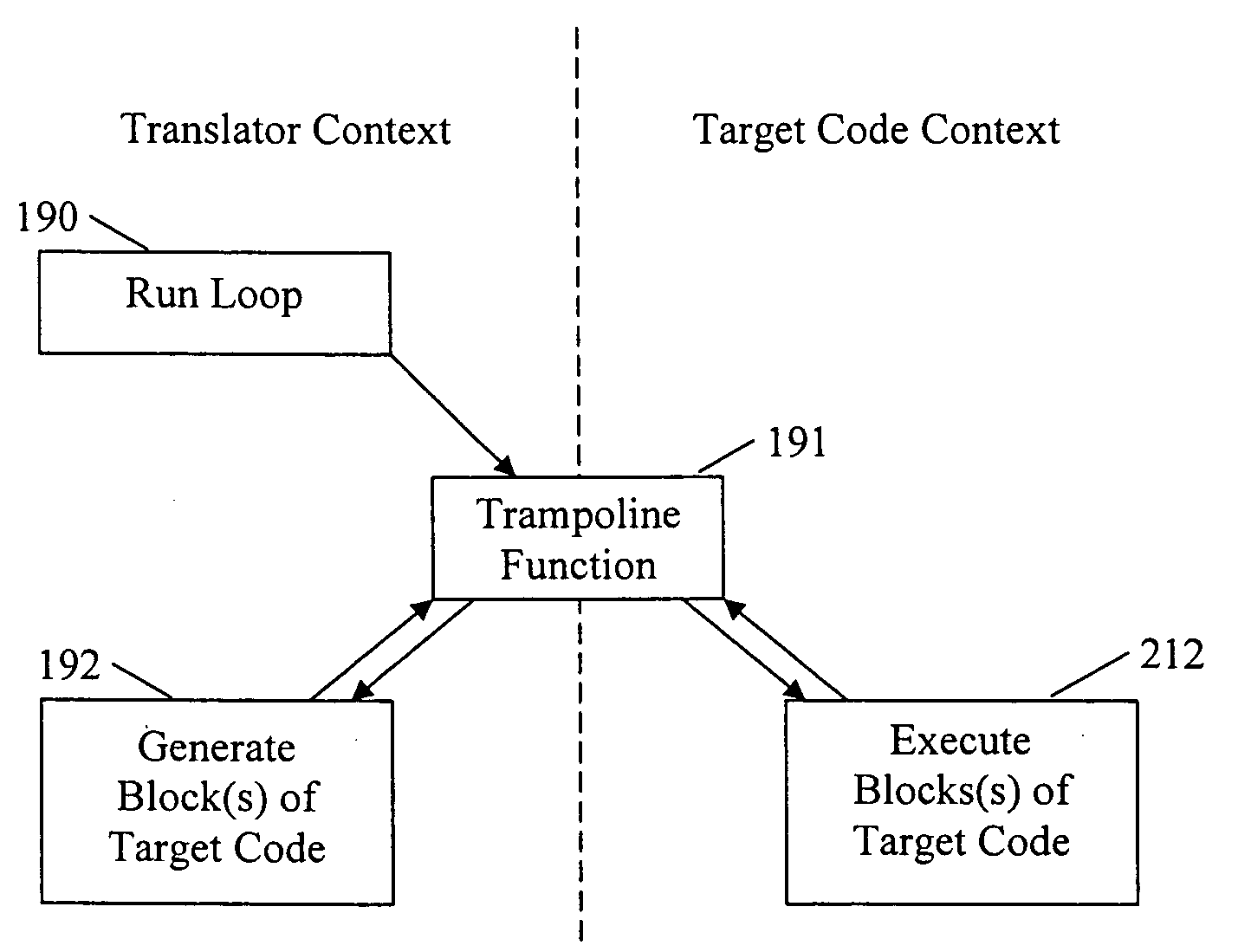
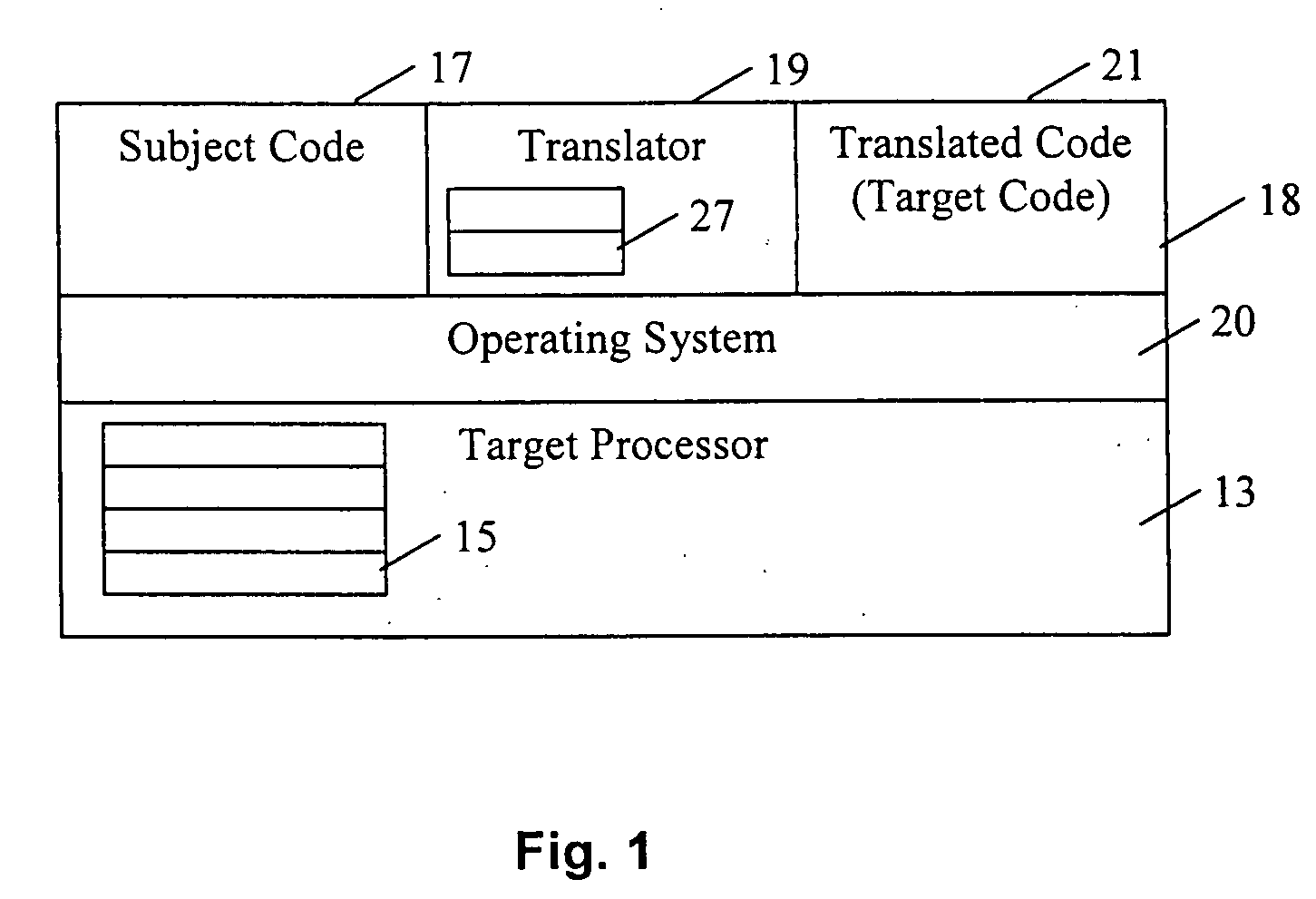
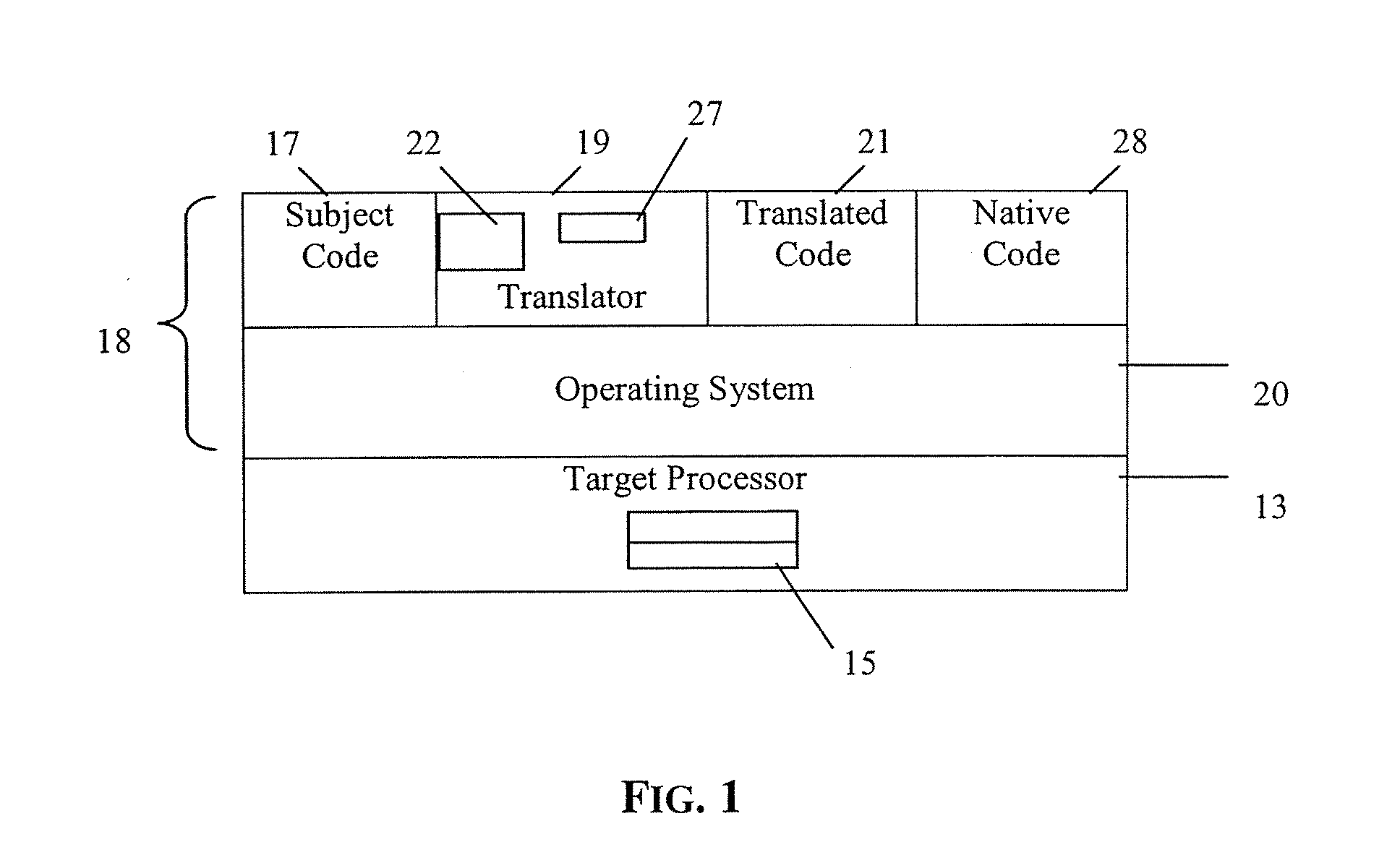
Execution control during program code conversion
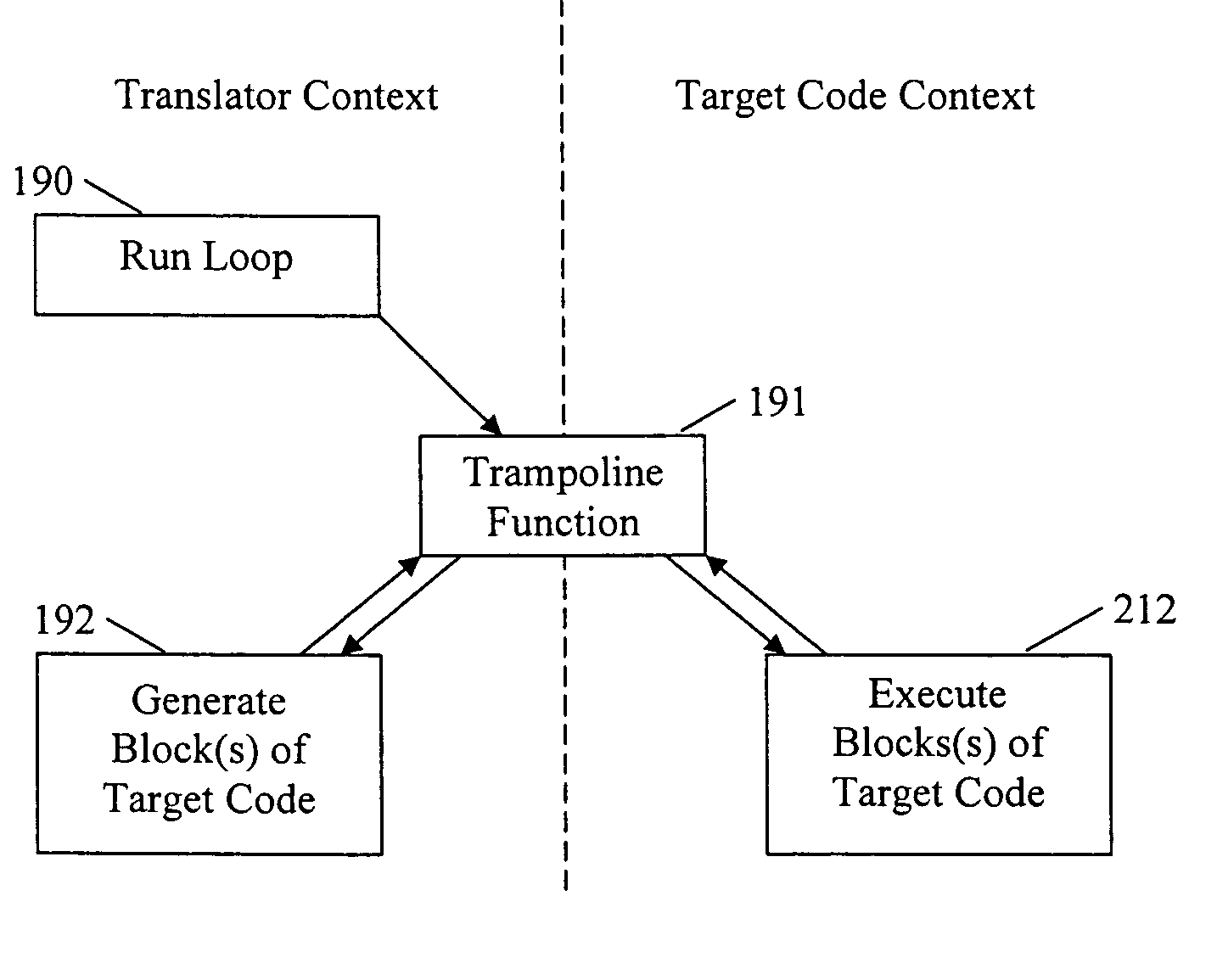
ActiveUS20060206880A1Reduce overheadImprove performanceSoftware engineeringProgram controlProgramming languageCoding block
An execution control method is described for use in a translator (19) which converts subject code (17) into target code (21). The translator (19) includes a translator trampoline function (191) which is called from a translator run loop (190) and which in turn calls either to a translator code generator (192) to generate target code, or else calls previously generated target code (212) for execution. Control then returns to the translator trampoline function (191) to make a new call, or returns to the translator run loop (190). Other aspects include making context switches through the trampoline function (191) and setting first and second calling conventions either side of the trampoline function (191). Jumping directly or indirectly between target code blocks (212) during execution is also described.
Owner:IBM CORP
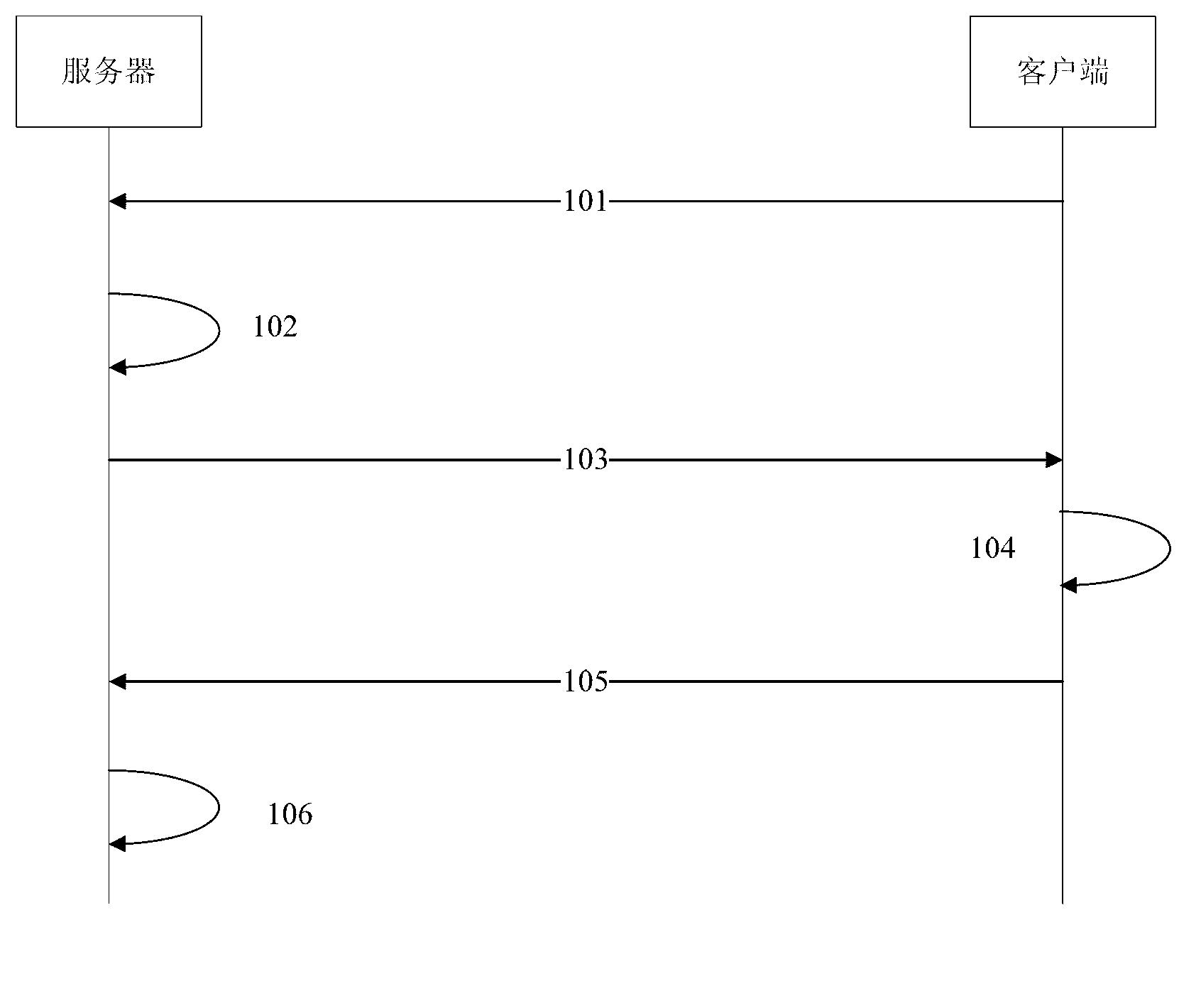
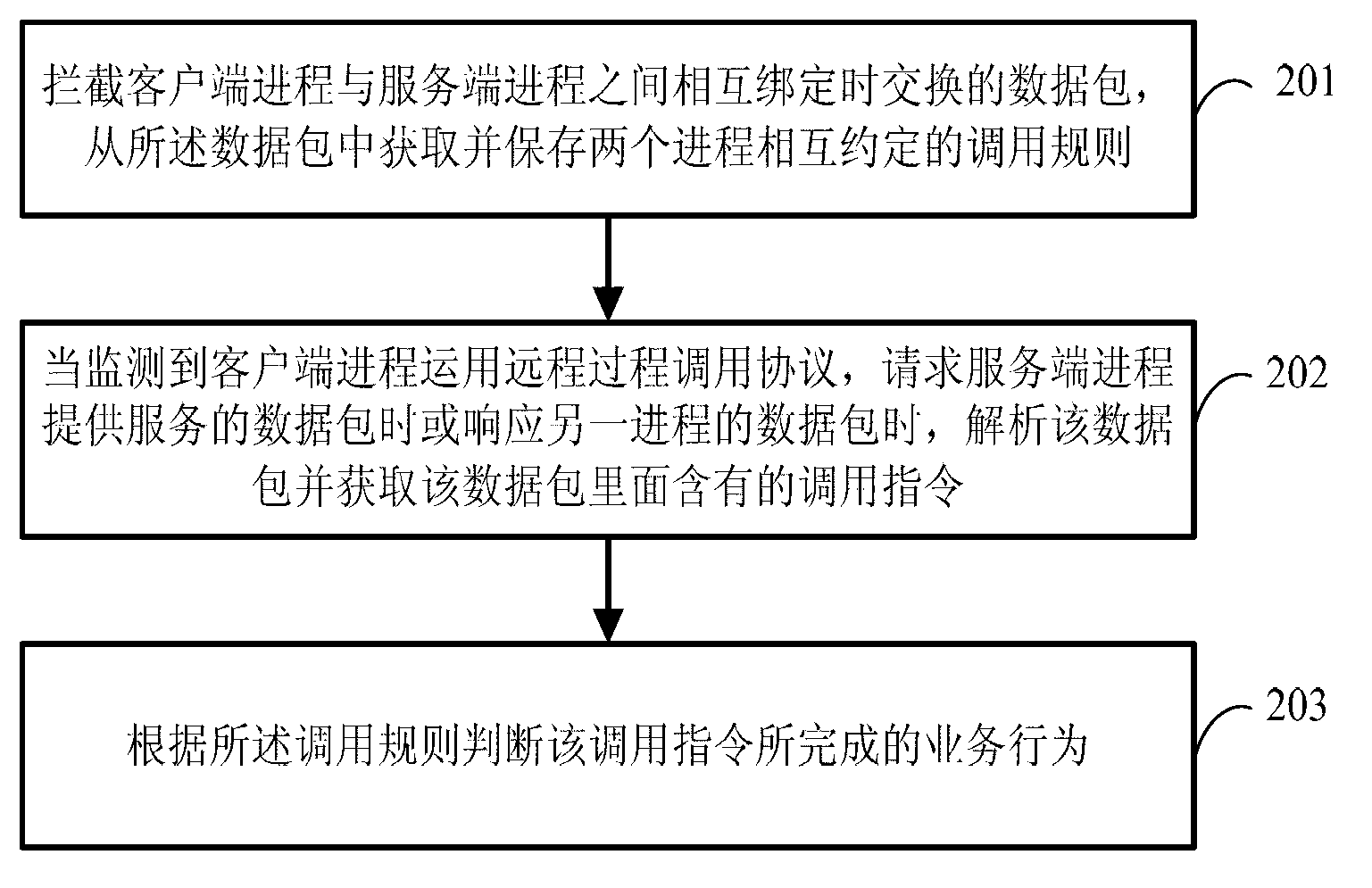
Method and system aiming at remote procedure calling conventions to perform status tracking
ActiveCN103023906AAvoid attackEffective defensive operationsTransmissionNetwork packetBusiness activities
The invention discloses a method and system aiming at remote procedure calling conventions to perform status tracking. The method comprises: intercepting exchanged data packages when a client-side progress and a server-side progress are mutually bound, and acquiring and storing calling conventions mutually protocoled by the two progress from the data packages; when monitoring that the client-side progress applies the remote procedure calling conventions, requests service data packages provided by the server-side progress or responds to data packages of another progress, analyzing and data packages and acquiring calling commands contained in the data packages; and judging business activities completed by the calling commands according to the calling conventions. The method and system aiming at remote procedure calling conventions to perform status tracking solve the problem of acquiring accurate meaning of called interfaces and function numbers during remote position control (RPC) calling between existing client-sides and servers.
Owner:BEIJING QIHOO TECH CO LTD
Method and apparatus for performing native binding
ActiveUS20090094586A1Avoid overheadEfficient implementationBinary to binarySoftware simulation/interpretation/emulationObject codeCalling convention
Owner:IBM CORP
System and method providing inlined stub
InactiveUS6980997B1Facilitates communication and execution performanceReduce copyData processing applicationsSpecific program execution arrangementsRemote function callExtensibility
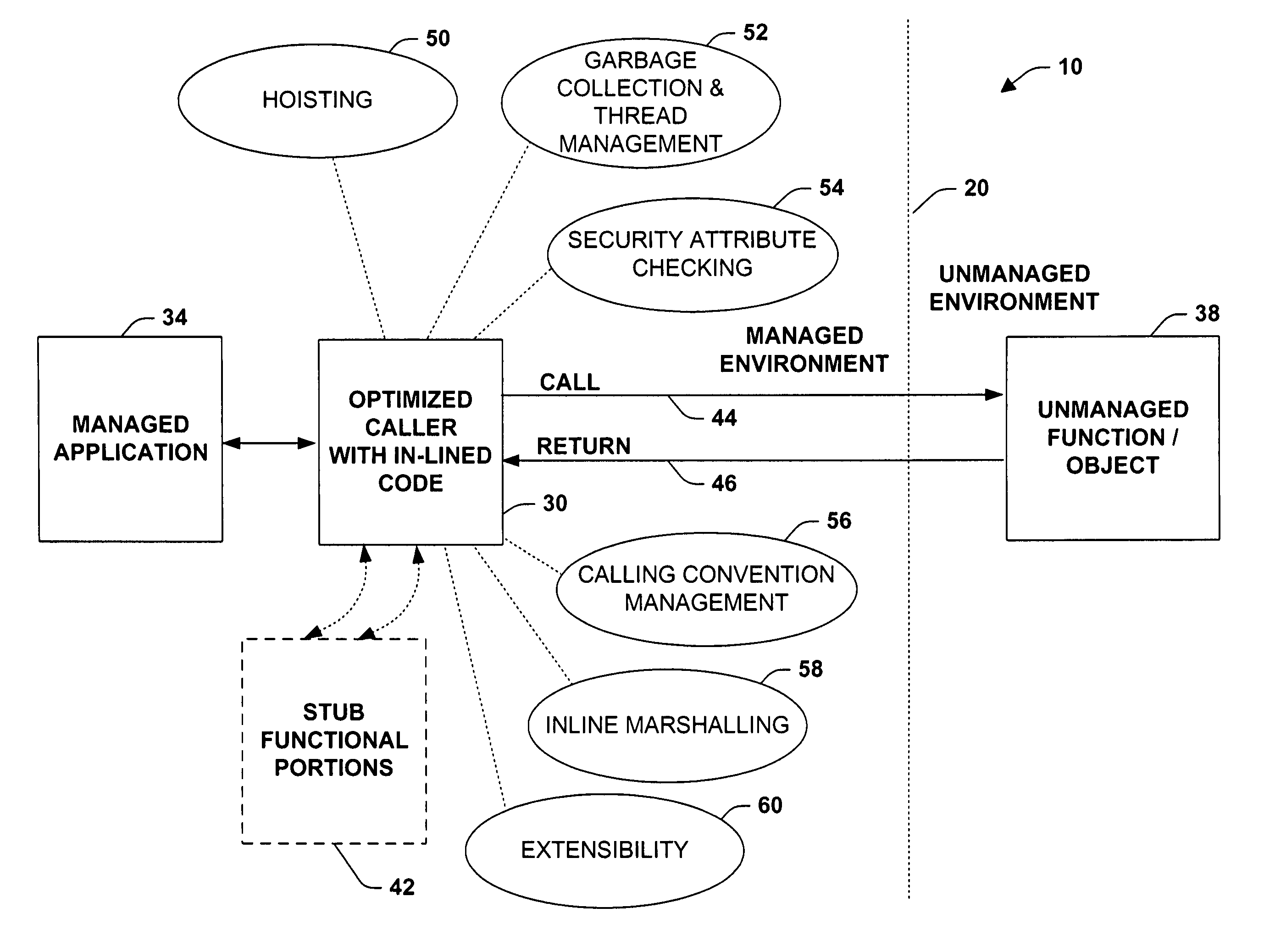
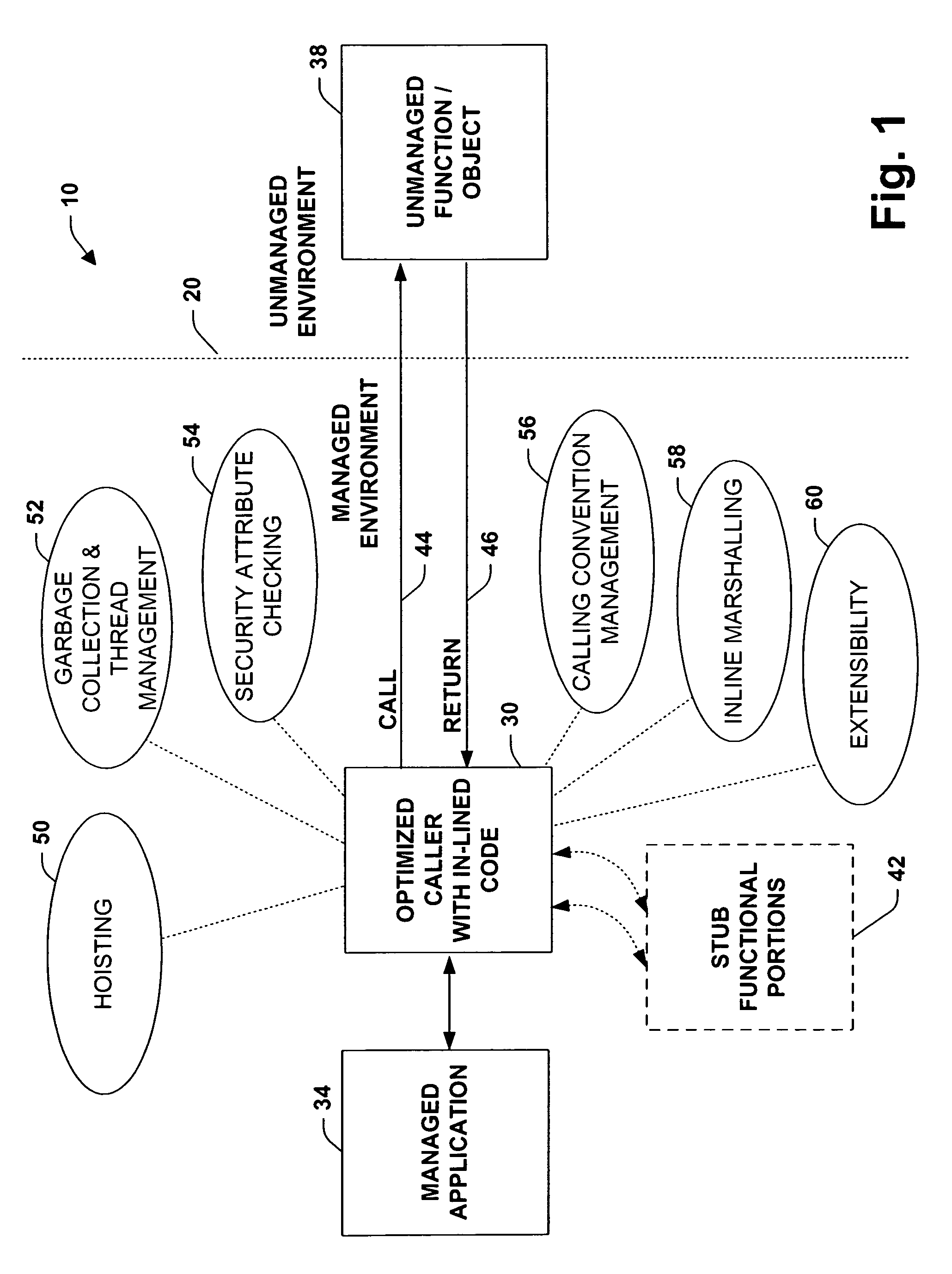
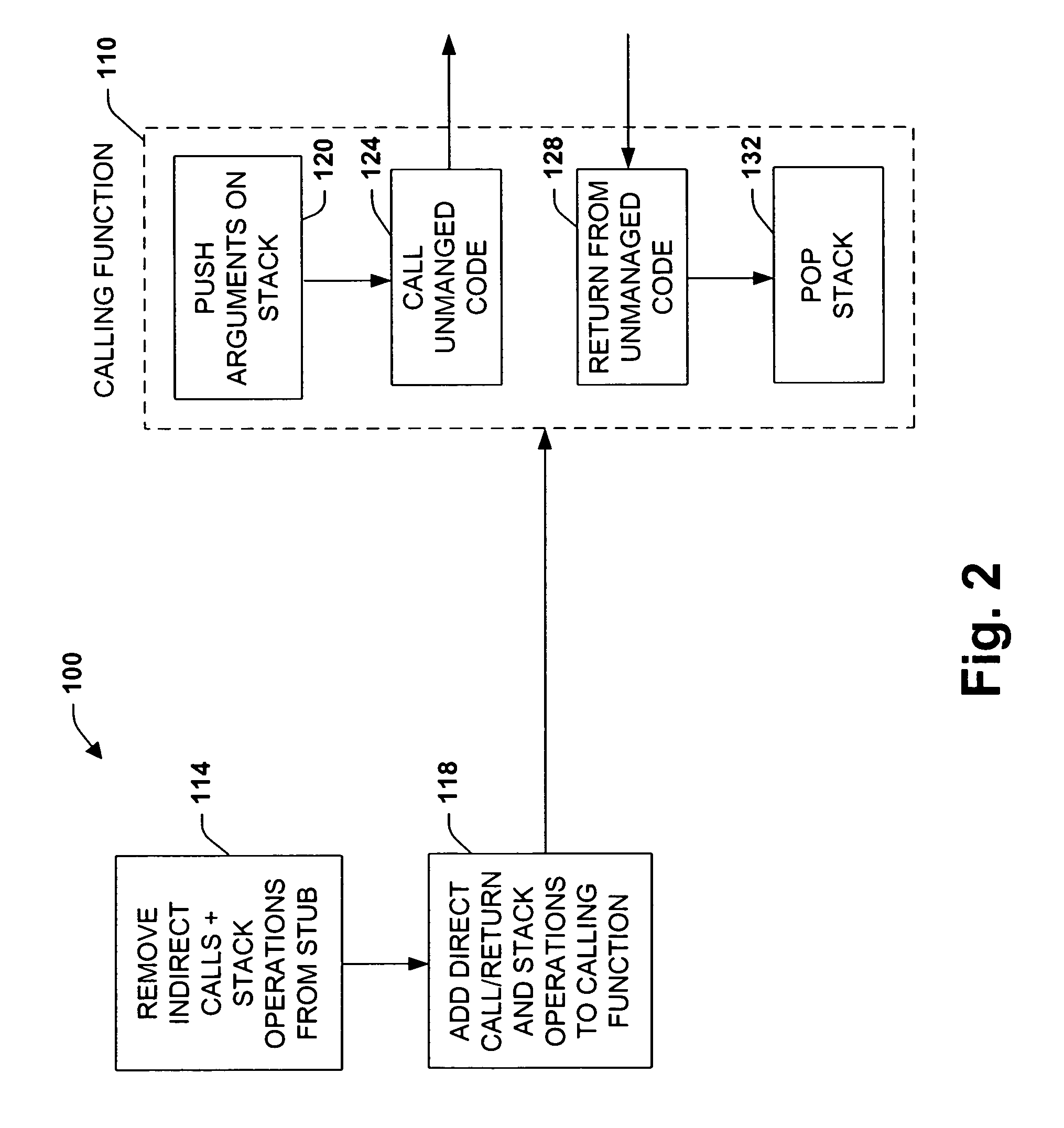
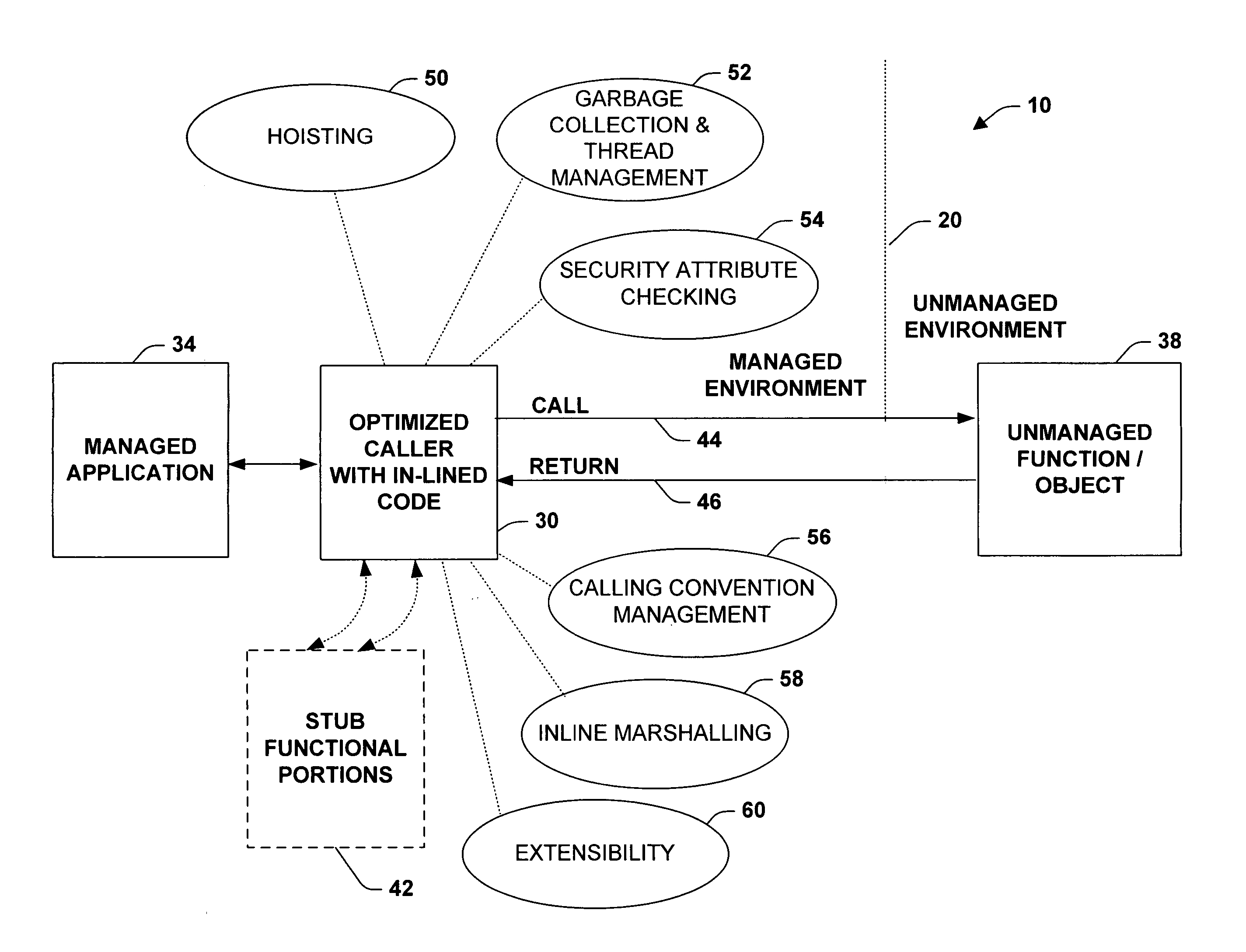
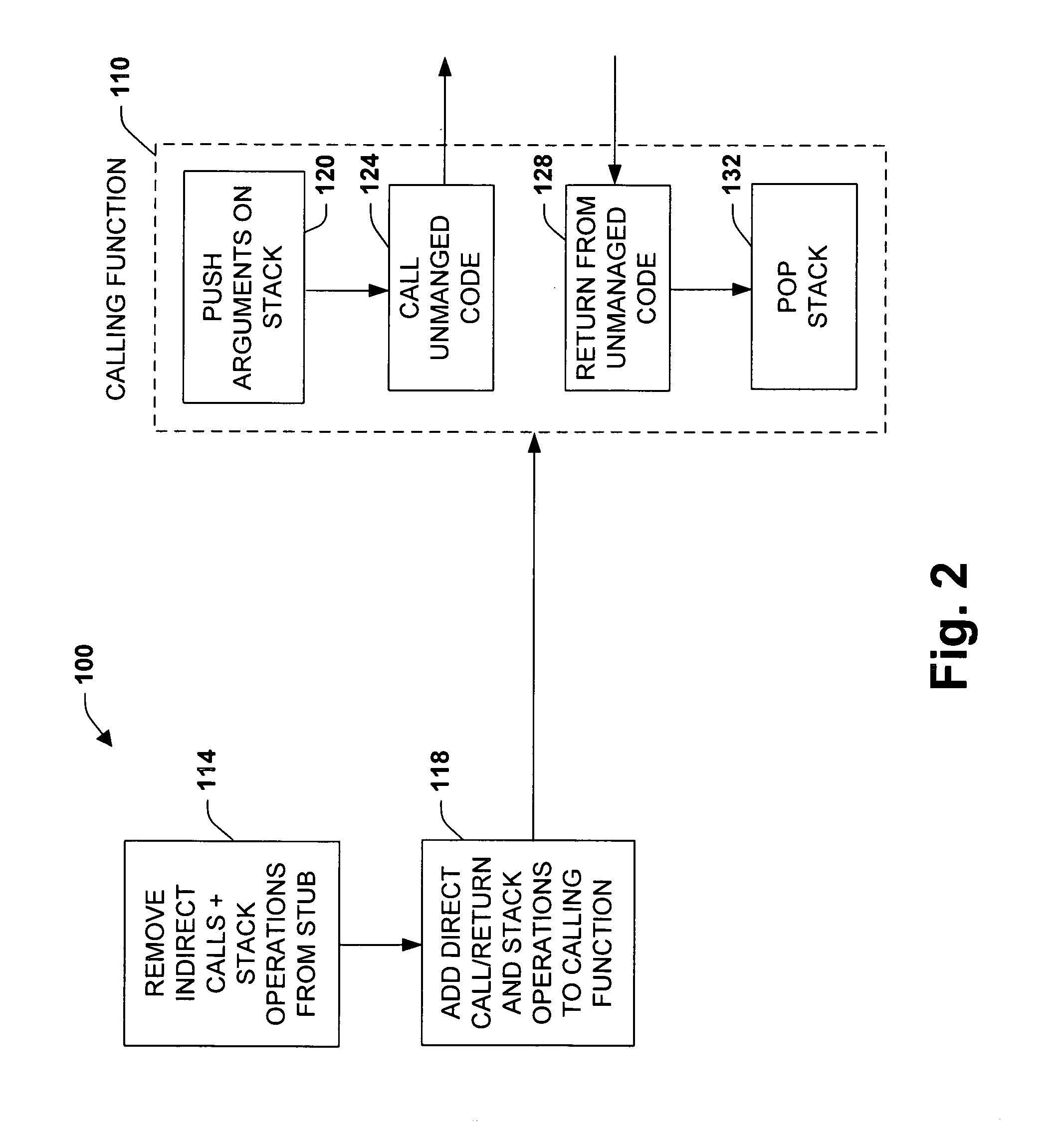
A system and method is provided to facilitate communications between object systems. A caller is provided having optimized in-lined functionality when initiating a remote function call between managed and unmanaged object systems, for example. The in-lined functionality includes utilizing direct calls and returns within a calling function. In this manner, pushing additional arguments onto an execution stack because of an external stub reference is mitigated. In addition, one or more code loops can be analyzed to enable stack markers to be “hoisted” and thus pushed a single time instead of each time the calling function executes. Other aspects of the optimized caller provide garbage collection and thread management, security attribute checking on outgoing calls, calling convention considerations, wherein arguments and return values are organized according to the convention utilized by the remote object system, and in-lined marshalling to provide enhanced performance over external stub code references. Code extensibility options can be included enabling functions to be generalized thereby insulating object systems from implementation details of the called functions.
Owner:MICROSOFT TECH LICENSING LLC
System and method providing inlined stub
InactiveUS20060085460A1Facilitates communication and execution performanceReduce copyData processing applicationsDigital data processing detailsExtensibilityRemote function call
A system and method is provided to facilitate communications between object systems. A caller is provided having optimized in-lined functionality when initiating a remote function call between managed and unmanaged object systems, for example. The in-lined functionality includes utilizing direct calls and returns within a calling function. In this manner, pushing additional arguments onto an execution stack because of an external stub reference is mitigated. In addition, one or more code loops can be analyzed to enable stack markers to be “hoisted” and thus pushed a single time instead of each time the calling function executes. Other aspects of the optimized caller provide garbage collection and thread management, security attribute checking on outgoing calls, calling convention considerations, wherein arguments and return values are organized according to the convention utilized by the remote object system, and in-lined marshalling to provide enhanced performance over external stub code references. Code extensibility options can be included enabling functions to be generalized thereby insulating object systems from implementation details of the called functions.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for performing native binding to execute native code
ActiveUS7434209B2Avoid overheadEfficient implementationTransformation of program codeSoftware simulation/interpretation/emulationObject codeCalling convention
Owner:INT BUSINESS MASCH CORP
System and method for efficiently generating native code calls from byte code in virtual machines
Owner:ORACLE INT CORP
Method for applying plug-in technology to data filtering of information distribution software
ActiveCN103176795ARealization of process conditionsRealize the filtering functionSpecial data processing applicationsSpecific program execution arrangementsExtensibilityInformation type
The invention discloses a method for applying plug-in technology to data filtering of information distribution software. The method includes the following steps: defining type identifiers of all types of information in a system, and pointing out the information type of data when an information source side sends the data and a user side subscribes for the data; defining identifiers of all types of subscription conditions in the system, and pointing out the subscription conditions in a subscription request of the user side; defining data structures of the subscription conditions; developing plug-in boards; and integrating the software and calling procedures. According to the method, the plug-in technology is adopted, reasonable plug-in interfaces and calling conventions are designed, plug-in dynamic loading and calling mechanisms are adopted, and then the condition matching and filtering functions of the information distribution software are achieved. When new information types are added into the system, a host program of the information distribution software does not need to be changed, the coupling degree between software modules can be improved beneficially, flexibility and expansibility of the information distribution software can be improved, and therefore applicability of the information distribution software can be improved.
Owner:THE 28TH RES INST OF CHINA ELECTRONICS TECH GROUP CORP
Method of instrumenting code having restrictive calling conventions
A development environment for computer programs in which programs under test may be instrumented with probe functions. The probe functions are called through a wrapper function structured to comply with restrictive calling conventions of the platform for which the computer program is developed. By complying with the calling convention, proper operation of the computer program is achieved during testing even if an exception handler, or other program element that relies on compliance with the calling convention, is invoked. Once instrumented, the computer program may be tested to determine whether it executes desired logic function to determine the performance of the program or for other test functions.
Owner:MICROSOFT TECH LICENSING LLC
Method for acquiring operation log
The invention relates to a running log acquisition method, which is used for acquiring running logs of programs including a function which executes predefined process and a step changing the address of the loaded function which executes predefined process into the address of the function to acquire the running log; wherein the function to acquire the running log comprises the following steps: analyzing the traced function name firstly; if the function name is not in the form of C++ decoration name, the running log of the function is acquired in the normal mode; if the function name is C++ decoration name, the decoration is removed from the decoration name according to a compiler rule and the information after removing the decoration is acquired; the information after removing the decoration comprises the function name and function parameter information such as function parameter type, calling convention and function return type, etc.; the acquired information after removing the decoration is used as a function definition file to acquire the running log and displays the running log in the form after removing the decoration.
Owner:CANON KK
Method and system for supporting dual conventions for methods that return structures
InactiveUS6199200B1Software engineeringSpecific program execution arrangementsCombined useClient-side
A technique for providing support for multiple calling conventions for methods and procedures that return structures is provided. A source code of a client program may be compiled by either of two compilers, wherein one compiler employs a calling convention that is different from the first one. A binary library containing a procedure and a converter for each procedure returning a structure to a client program, is provided to support two calling conventions. If the client program is compiled by a compiler using a first calling convention, the program is compiled such that it calls the procedure directly and receives a result, a structure, via the first calling convention. Compiling the client program with a compiler using the second conventions results in calls to the procedure being routed to the converter, which calls the associated procedure, using the first calling convention. The converter receives the result from the procedure and returns the result to the client program using the second calling convention. A special modification to the signature of the procedure as it appears in the library source code, combined with the use of macros to generate a companion converter, permit a binary library to be built by a single compiler, such that the library supports the calling conventions for returning structures appropriate to two different compilers.
Owner:IBM CORP
Method and device for calling function
InactiveCN103853532AAvoid problems caused by inconsistent calling conventionsSpecific program execution arrangementsCode compilationCode moduleEmbedded system
The invention discloses a method and a device for calling a function. The method comprises the steps of: obtaining a plurality of alternate code modules for executing function call in response to the detected function call in program, wherein the plurality of alternate code modules respectively accord with a plurality of call conventions; obtaining the special call convention adopted by the called function; selecting the code module according with the special call convention from the plurality of alternate code modules to execute the function call according to the obtained special call convention. The device is corresponding to the method. According to the method and the device provided by the invention, the matching of the call conventions of a calling party and a called party of the function can be ensured, and problems caused by the inconsistent call conventions can be avoided.
Owner:IBM CORP
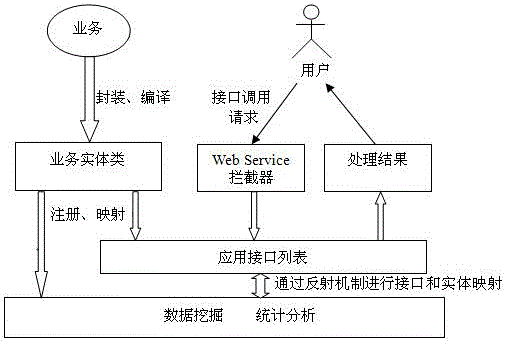
Data-mining-oriented cloud implementation method
InactiveCN105843927AComputationally efficientCutting costsSpecial data processing applicationsStatistical analysisBusiness data
The invention discloses a data-mining-oriented cloud implementation method, which belongs to the technical field of business data analysis. The data-mining-oriented cloud implementation method comprises the following steps: S1: packaging all business service functions into an interface entity class, compiling the interface entity class, adding the information, which includes the name, the calling convention, the function description and the like, of the entity class into an application interface list by a DMaaS platform, and realizing mapping between the interface and the business entity class; S2: after a user uses the interface, sending a WebService request to a platform, and searching the corresponding interface and entity class in the interface list after a WebService interceptor intercepts the request; and S3: obtaining an entity object through a refection technology to carry out business processing, and finally, returning a processing result to the user to realize the functions of data mining and data statistical analysis. The data-mining-oriented cloud implementation method is simple in operation, can realize the efficient calculation of mass data, can effectively reduce the expenditure of an enterprise and has a good popularization and application value.
Owner:INSPUR QILU SOFTWARE IND
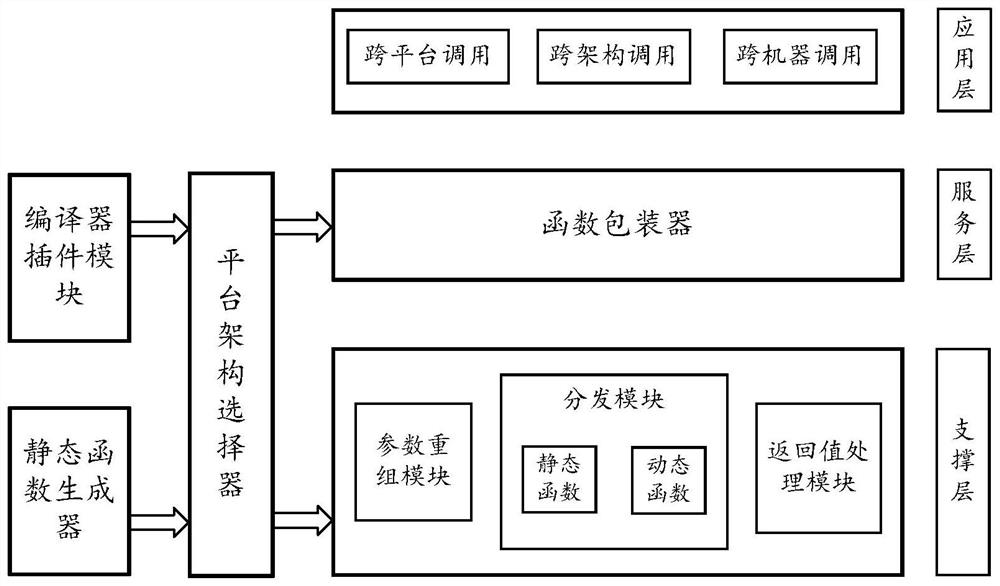
Function calling method, computing device and storage medium
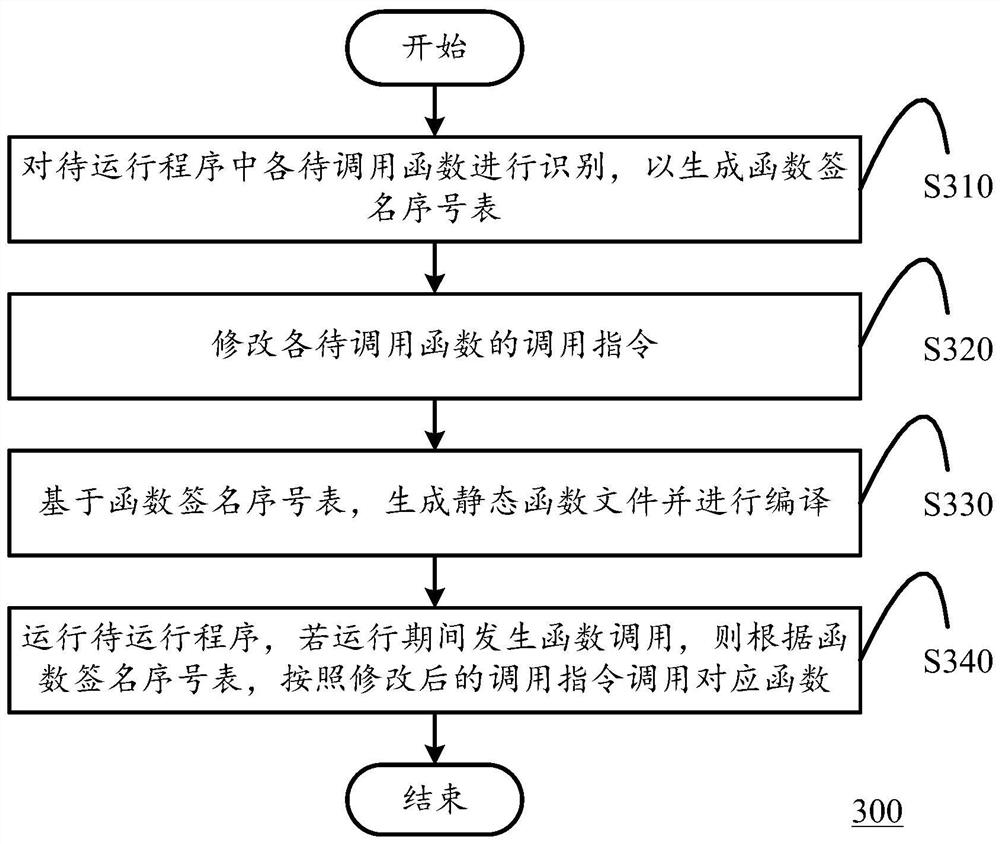
PendingCN114217886ASave human effortReduce error rateLink editingProgram loading/initiatingProgramming languageParallel computing
The invention discloses a function calling method, computing equipment and a storage medium, and the method comprises the steps: identifying each to-be-called function in a to-be-run program to generate a function signature sequence number table; modifying a calling instruction of each function to be called; generating a static function file based on the function signature sequence number table and compiling the static function file; and running the to-be-run program, and if function calling occurs during running, calling a corresponding function according to the function signature sequence number table and the modified calling instruction. According to the technical scheme, call agreement conversion between different architectures and platforms is completed through automatic construction and static function call, and function call with high efficiency and low overhead is achieved.
Owner:UNIONTECH SOFTWARE TECH CO LTD
Systems and methods for hypervisor discovery and utilization
ActiveUS8635612B2Software simulation/interpretation/emulationMemory systemsProcessor registerVirtual device
Systems and methods are provided, whereby partitions may become enlightened and discover the presence of a hypervisor. Several techniques of hypervisor discovery are discussed, such as detecting the presence of virtual processor registers (e.g. model specific registers or special-purpose registers) or the presence of virtual hardware devices. Upon discovery, information (code and / or data) may be injected in a partition by the hypervisor, whereby such injection allows the partition to call the hypervisor. Moreover, the hypervisor may present a versioning mechanism that allows the partition to match up the version of the hypervisor to its virtual devices. Next, once code and / or data is injected, calling conventions are established that allow the partition and the hypervisor to communicate, so that the hypervisor may perform some operations on behalf of the partition. Four exemplary calling conventions are considered: restartable instructions, a looping mechanism, shared memory transport, and synchronous or asynchronous processed packets. Last, cancellation mechanisms are considered, whereby partition requests may be cancelled.
Owner:MICROSOFT TECH LICENSING LLC
Processor arrangement and method for operation thereof
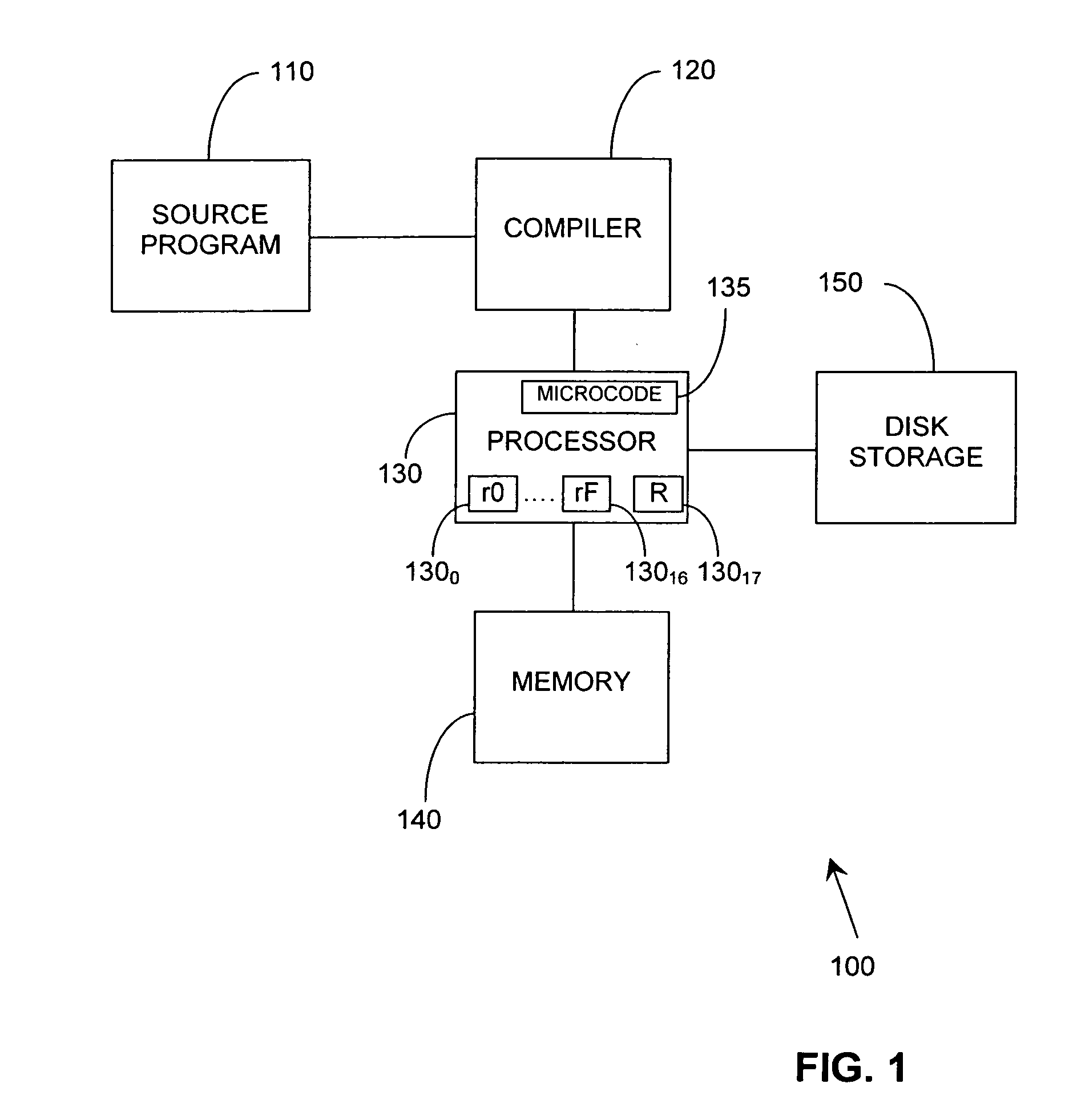
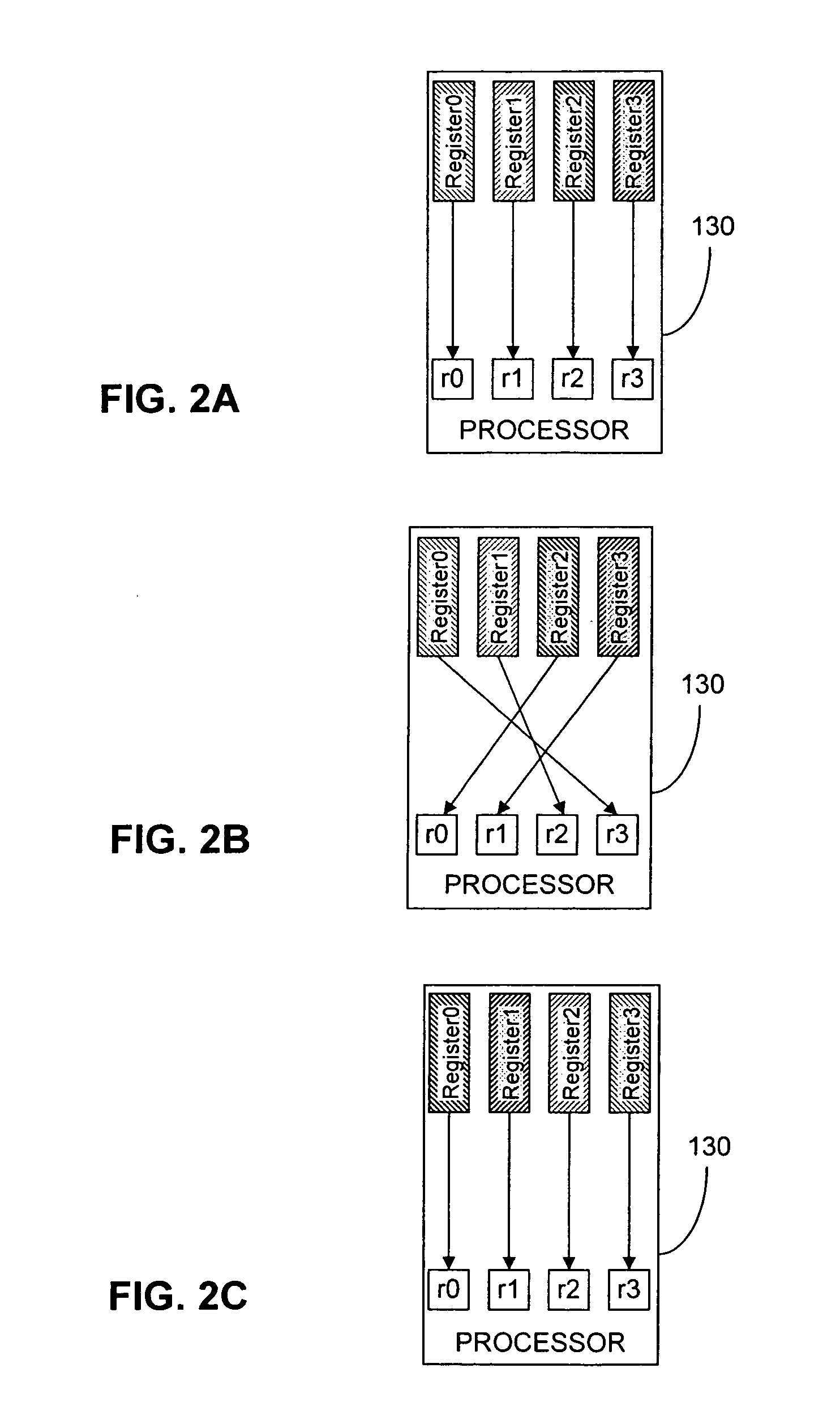
InactiveUS20060037010A1The process is simple and fastThe testing process is simpleSoftware engineeringMemory systemsRegister allocationParallel computing
A method and arrangement (100) for remapping of registers (1300-13017) of a processor (130) to improve runtime performance of dynamically linked applications or to simplify the code for a wide class of iterative refinement algorithms is based on providing a CPU instruction to remap registers en masse. The advantage of this is that it is simpler and faster than recompiling things at runtime and it obviates use of a calling convention, so that the parameter ordering in registers is the same for all calls regardless of what the optimum layout might be, allowing more efficient code. Compilers would also be simpler to write and test, and code would compile far quicker than it does at present, since it would eliminate many previous constraints on register allocation, making optimisation far simpler.
Owner:IBM CORP
Execution control during program code conversion
ActiveUS8615749B2Improve performanceReduce overheadSoftware engineeringProgram controlProgramming languageCoding block
Owner:INT BUSINESS MASCH CORP
Register allocation method and device, electronic equipment and computer storage medium
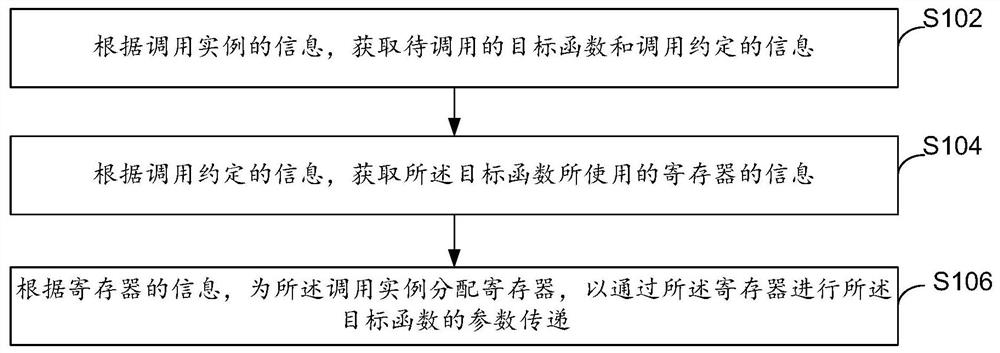
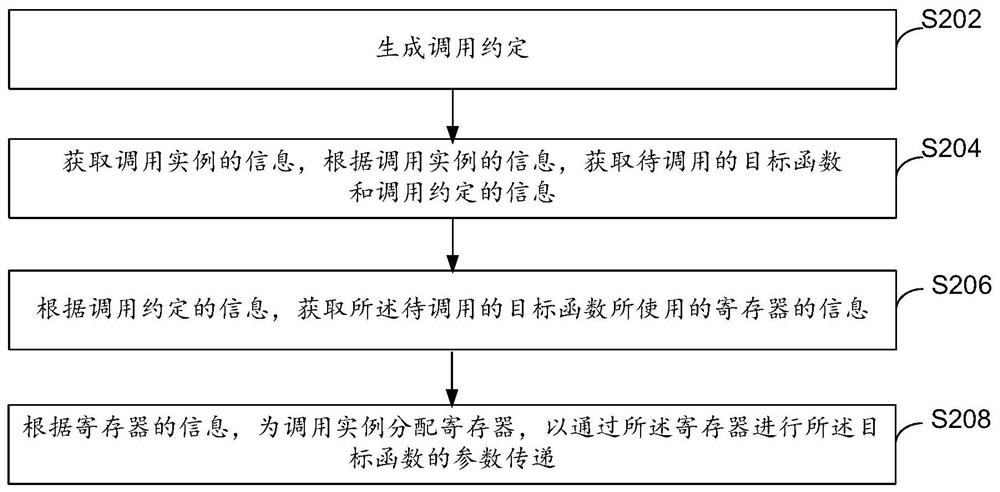
PendingCN111857816AReduce delivery costsImprove compilation efficiencyRegister arrangementsComputer hardwareRegister allocation
The embodiment of the invention provides a register allocation method and device, electronic equipment and a computer storage medium. The register allocation method comprises the steps: according to information of a calling instance, obtaining a to-be-called target function and calling agreement information, wherein the calling agreement comprises definition information of all available registersin current equipment; acquiring information of a register used by the target function according to the called and appointed information; and according to the information of the register, allocating the register to the calling instance so as to carry out parameter transmission of the target function through the register. Through the embodiment of the invention, the transmission cost of register parameters is effectively reduced, and the code compiling efficiency is improved.
Owner:ALIBABA GRP HLDG LTD
Inter-process communication method and device
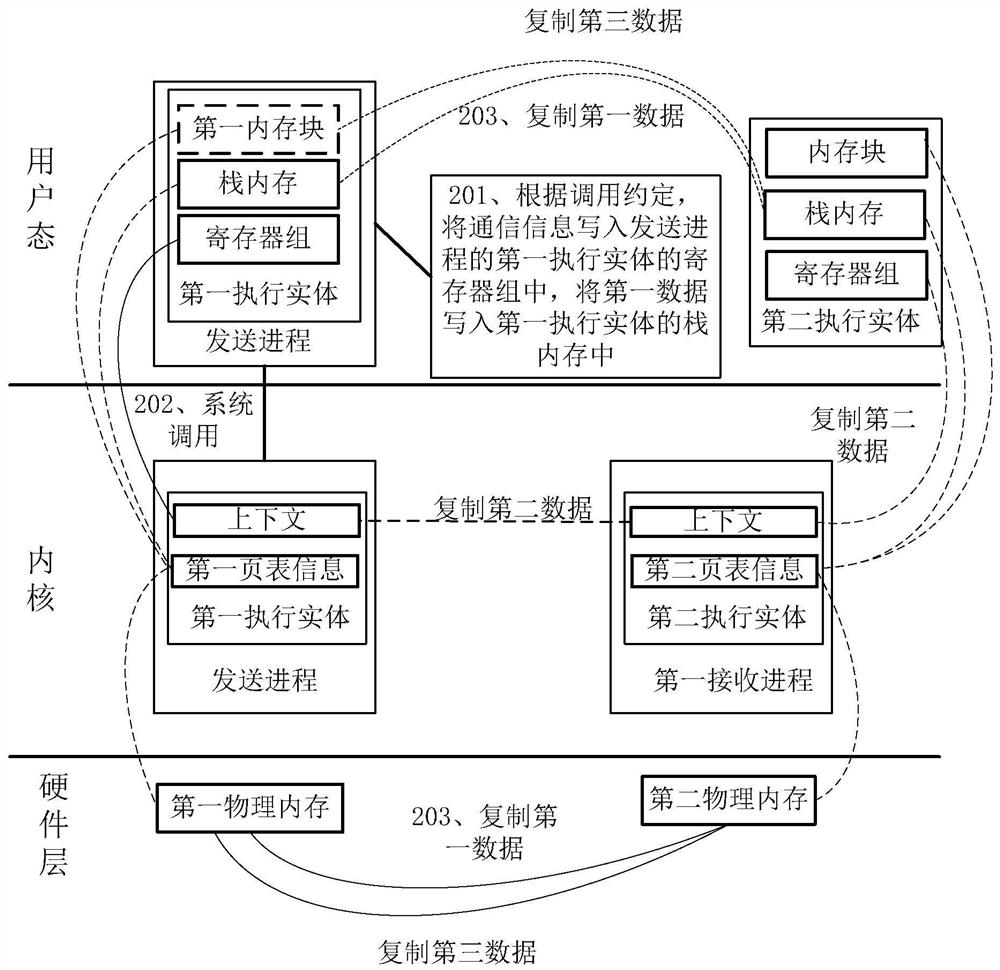
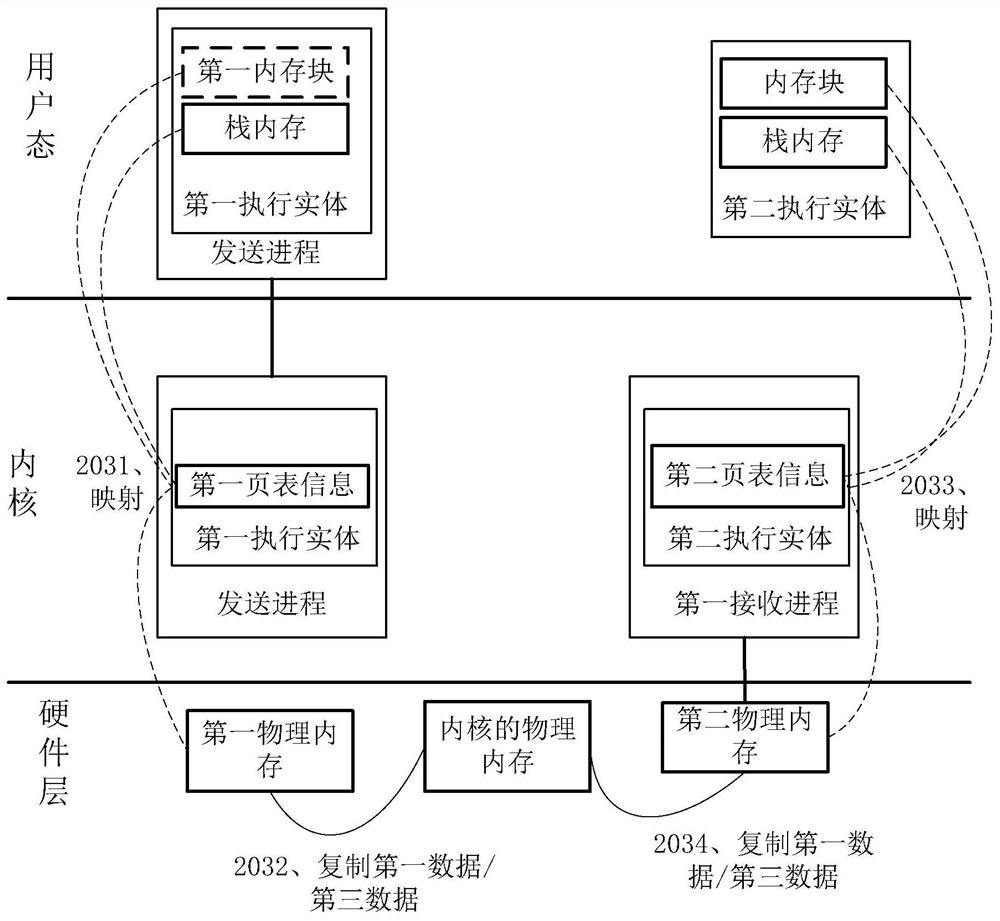
PendingCN114064302AReduce overheadReduce performance overheadInterprogram communicationInput/output processes for data processingTerm memoryInter-process communication
The invention discloses an inter-process communication method. The method is applied to a computer system. The method comprises the following steps: writing data to be transmitted between a sending process and a receiving process into a register block and a stack memory of a first execution entity of the sending process according to a calling agreement; writing the address of the stack memory and a first value representing the data volume of the data in the stack memory into a register group; and copying the data to be transmitted from the stack memory of the first execution entity to the stack memory of the second execution entity through the second execution entity receiving the process according to the address of the stack memory and the corresponding first value. Data are transmitted through the register block and the stack memory, the communication performance of the IPC is improved, in addition, the invention further provides an inter-process communication scheme of the multi-stage IPC sequence, the intermediate process of the multi-stage IPC sequence only needs to forward the address and the data length of the memory block, cross-process copying can be achieved, and the communication performance of the multi-stage IPC is improved.
Owner:HUAWEI TECH CO LTD
Use of Name Mangling Techniques To Encode Cross Procedure Register Assignment
InactiveUS20100169872A1Software engineeringProgram controlProcessor registerTheoretical computer science
Optimizing a program having a plurality of functions. The program is optimized using an optimization technique that requires breaking a calling convention. The first function of the plurality of functions is modified as a result of optimizing. A name of the first function is mangled to form a unique first mangled name. Mangling comprises changing the name. The unique first mangled name includes, as a result of mangling, first information conveying at least in part how the first function was modified. A second function of the plurality of functions, being a caller of the first function, is also modified to correctly invoke first function using the unique first mangled name to apply the optimization technique. A compilation tool can, after optimizing, use the first information to take a first action with respect to the first procedure, wherein the compilation tool otherwise would require the calling convention to remain unbroken in order to take the first action.
Owner:IBM CORP
Method for sterilization and algae killing by ultrasonic treatment of ballast water and system device
InactiveCN102627369ANo pollutionMeeting the technical requirements of the ConventionAuxillariesWater/sewage treatment with mechanical oscillationsUltrasonic cavitationWater discharge
The invention relates to an ultrasonic sea chest cavitation sterilization machine and an ultrasonic ballast water cavitation sterilization machine for a ship sea chest, a method for killing and inhibiting marine organisms by ballast water, and a system device, which are researched and developed for cross-sea propagation of harmful microorganisms, funguses and pathogens caused by injecting and discharging the harmful microorganisms, the funguses and the pathogens in the water at different places along with a ship, and cross contamination of a sea area caused by non-control discharge of the ballast water when the goods are loaded and unloaded and the seawater (or fresh water) are injected and discharged in running, anchoring and mooring processes of the ship; the intrusion of the foreign species can cause hazard to marine ecology, and the hazard is listed as one of four marine hazards by International Environment Fund (CEF). According to the invention, ultrasonic wave is made to a device to be connected to an inlet of the ship sea chest and a pipeline of the ballast water in series, and ultrasonic cavitation cell crushing can be carried out on the harmful microorganisms, the funguses and the pathogens in the seawater (or fresh water) by utilizing a function of ultrasonic wave for crushing the cells, so that the inactivating and sterilizing treatment effects can be realized, and the method can play the following roles that: 1, cavitation sterilization is carried out on the water entering into the sea chest through the ultrasonic sea chest cavitation sterilization machine, so that the cells are crushed, algae and shellfish microorganisms in a coarse filter of the sea chest are killed, and the possibility of blockage of the coarse filter of the sea chest and a water inlet pipeline can be reduced, thus the algae and shellfish microorganisms cannot produced and survived in a ballast water pipeline, a water discharge pipeline, a water pump and a filter and the pipeline is kept unblocked; and 2, ballast and discharge pipelines are internally connected with the ultrasonic ballast water cavitation sterilization machine in series, ultrasonic cavitation is carried out on the seawater (fresh water) entering into a ballast tank, so that the cells are crushed, and the residual algae and shellfish microorganism pathogens are inactivated and killed, thus the bacterium in the seawater (fresh water) into the ballast tank reach requirements of international maritime organization (IMO) International Ship Ballast Water and Sediment Control and Management Convention (latter called convention), and one of four marine hazards, that is to say, the intrusion problem of the foreign specifies, can be solved and eliminated. The invention provides guarantee of technical equipment for equipping ballast water equipments of all ocean going vessels before 2017 according to the requirement of the international maritime organization (IMO) convection.
Owner:刘利华
Use of name mangling techniques to encode cross procedure register assignment
InactiveUS8468511B2Software engineeringProgram controlTheoretical computer scienceRegister assignment
Owner:INT BUSINESS MASCH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com