Method for acquiring operation log
A technique for running logs and obtaining methods, which is applied in the field of storage media containing the program, and can solve problems such as inability to process running log predictions, difficulty in obtaining running logs in software processing time order, and a large amount of manpower
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0047] In this embodiment, when a given module calls a function that exists in another module, the input function address or the virtual function address table (Virtual Address Table) is used as a mechanism to connect the function calls between modules and record them. In the operation log, the processing of the entire software is acquired as a processing operation log in chronological order without adjusting the modules themselves of the software. Specific instructions are given below.
[0048]
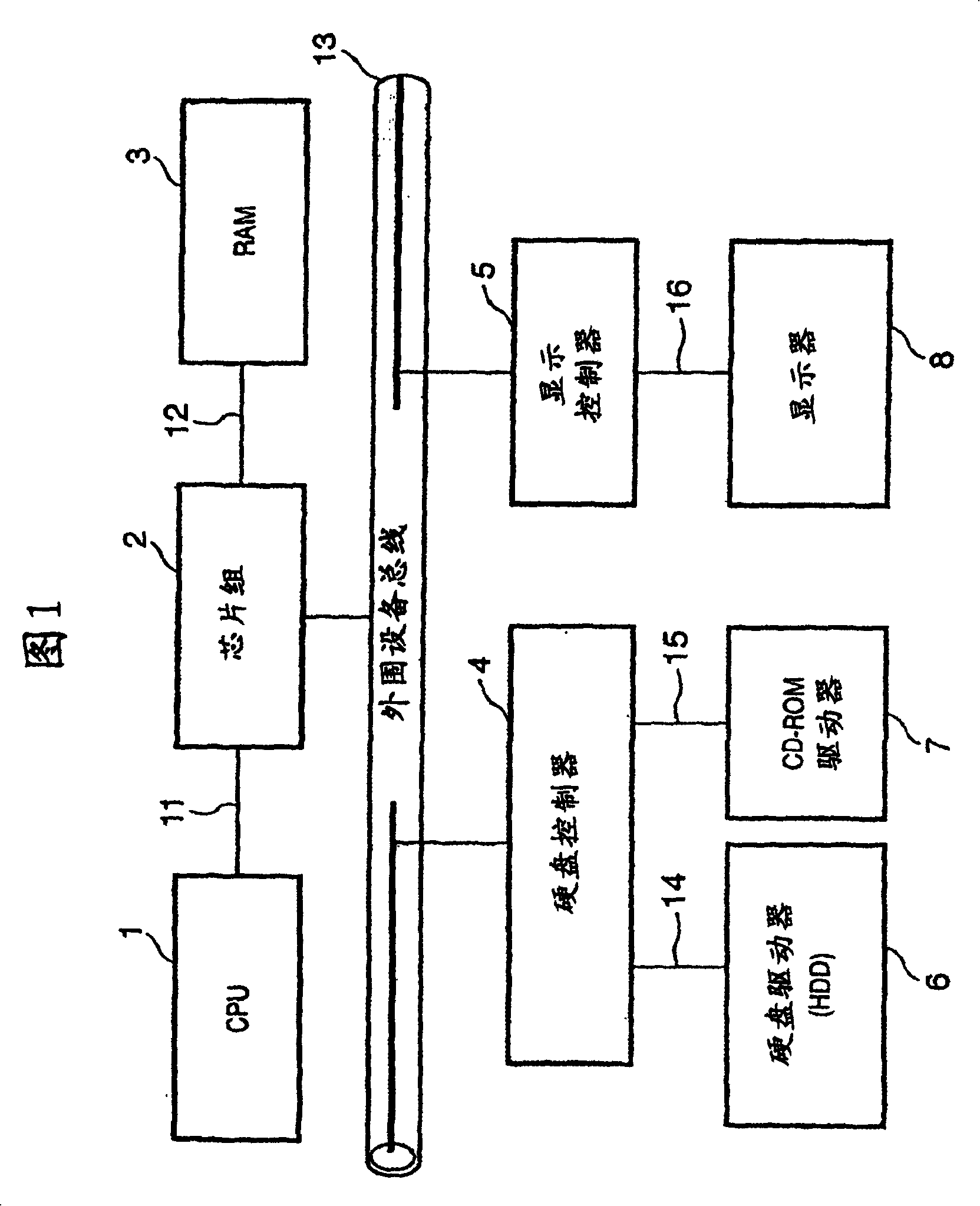
[0049] FIG. 1 is a block diagram of a configuration of a computer (software evaluation system) implementing an operation log acquisition method of a preferred embodiment of the present invention. To simplify the description, this software evaluation system is built inside a PC. However, the operation log acquisition method of the present invention is effective regardless of whether it is constructed inside a PC or in a network system constructed of a plurality of PCs.
[0050] Th...
Embodiment approach
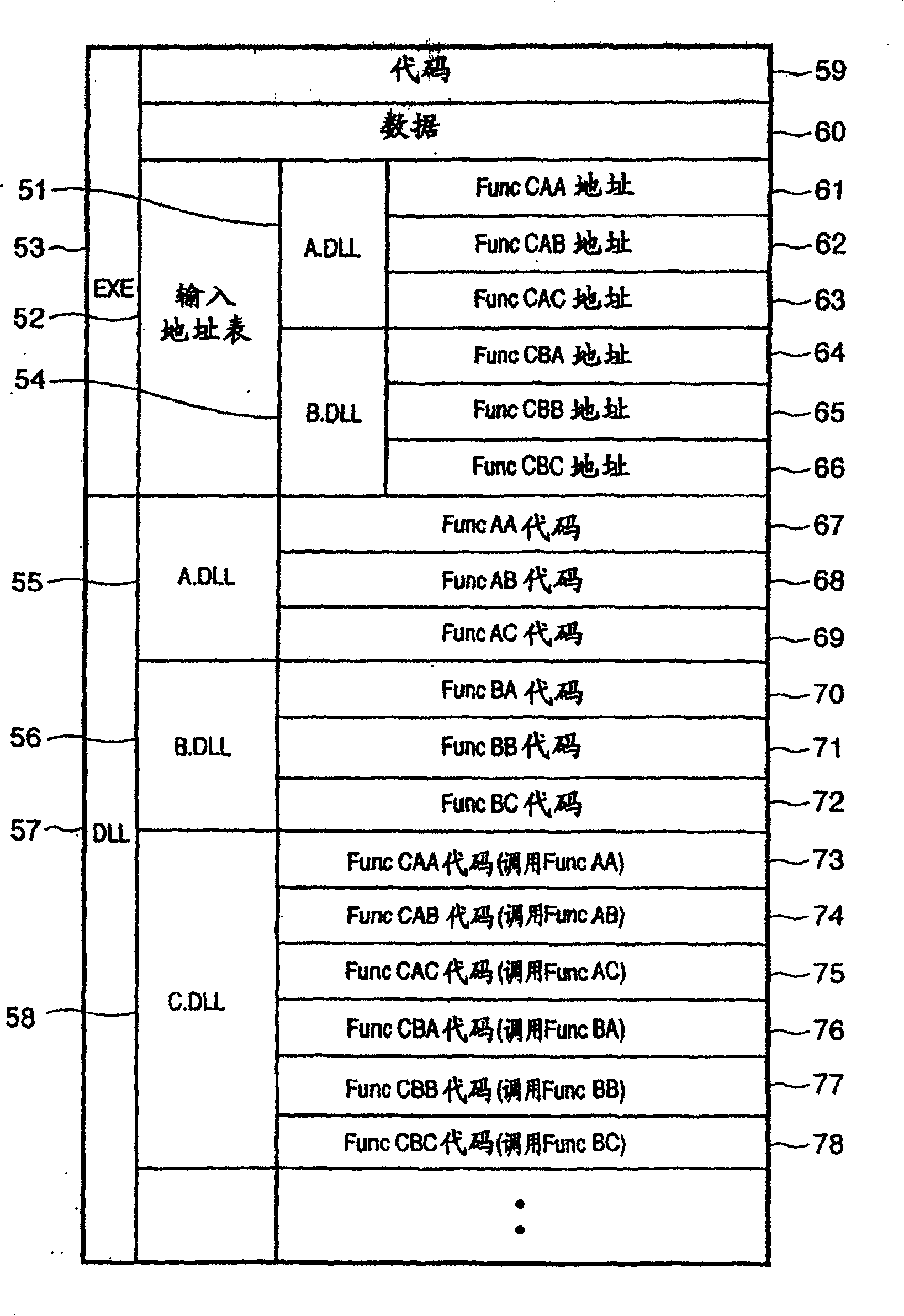
[0070] Figure 10 An example of a function definition file instructing the software evaluation system of the parameter and return value format of each function and method is shown. This file describes the DLL / interface name and function / method name ("function / method" refers to "function or method", which is also applicable to the description below), and the parameters and return value types corresponding to these functions / methods. The software evaluation system according to the operation log acquisition method of this embodiment determines the parameters / return values of each function / method according to the content instructed by the function definition file, and obtains the content as an operation log.
[0071] Figure 11 show using Figure 10 The function definition file shown is an example of the obtained operation log of the software evaluation system implementing the operation log acquisition method according to the first embodiment of the present invention. Generat...
no. 2 example
[0074] The following second embodiment is directed to a method of acquiring operation logs designed to acquire functions whose function definition information has been specified in its C++ modified name, and in particular relates to directly creating a C++ function without additional user-defined function definition files. The operation log acquisition method for obtaining the operation log, thereby reducing the processing load needed to analyze the cause of the software failure.
[0075] According to this embodiment, the method first analyzes the tracked function name; if the function name is not in the form of a decorated name (decorated), then obtain the running log of the function in a normal manner; if the function name is a decorated name, then according to the compiled The decorator rule removes the modification to the modified name, and obtains the information (symbol) after the modification, and the information after the modification includes the function name and func...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com