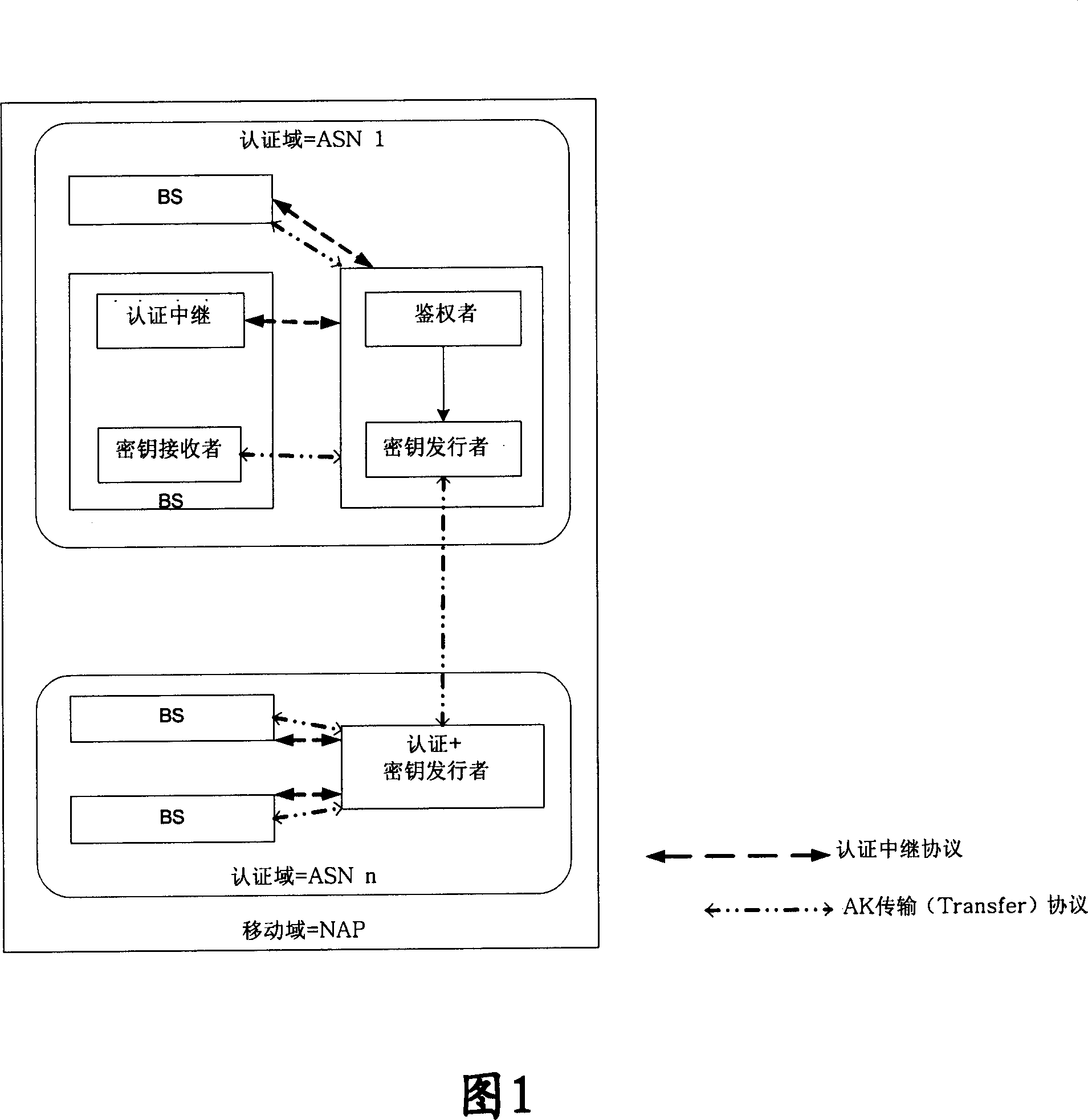
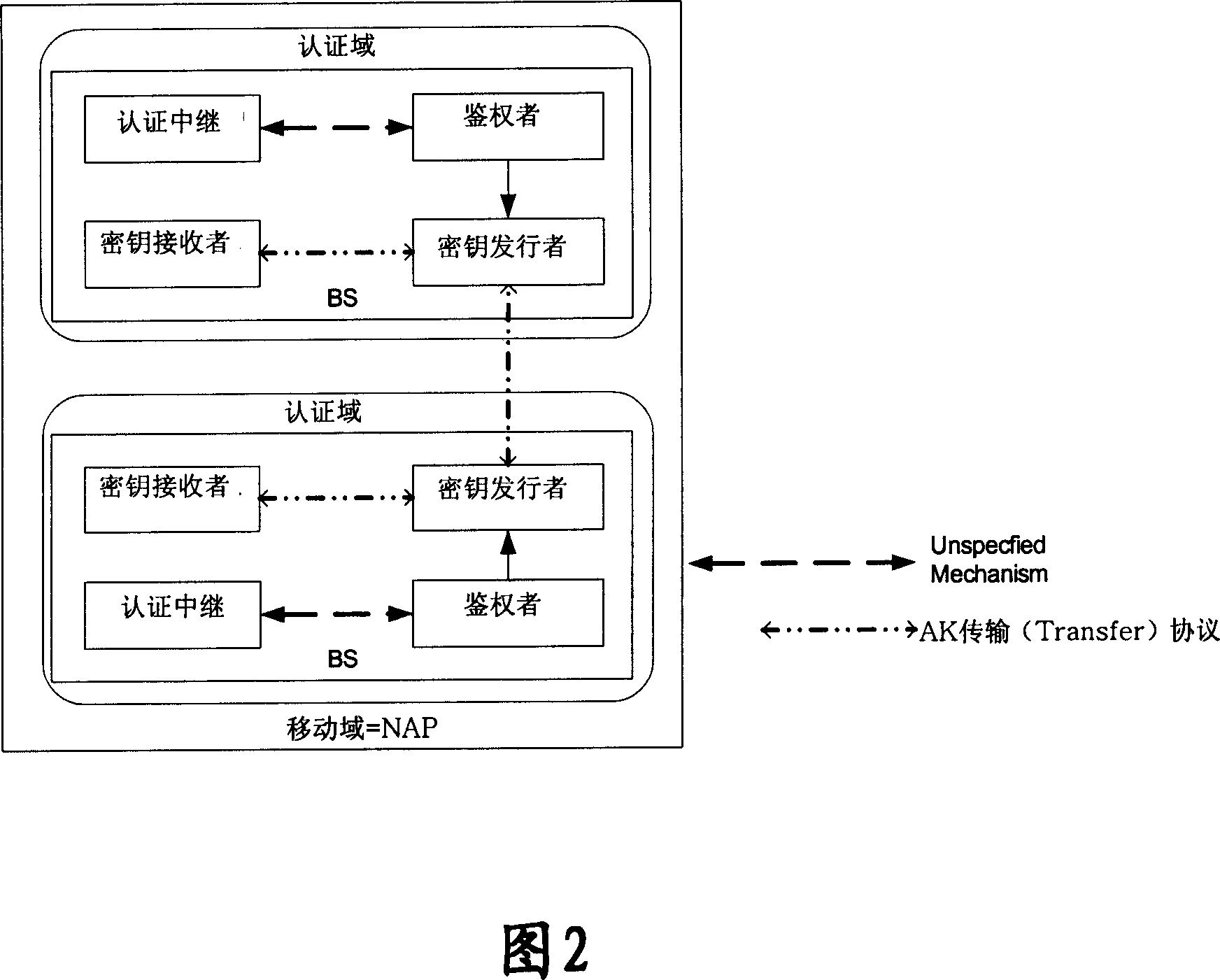
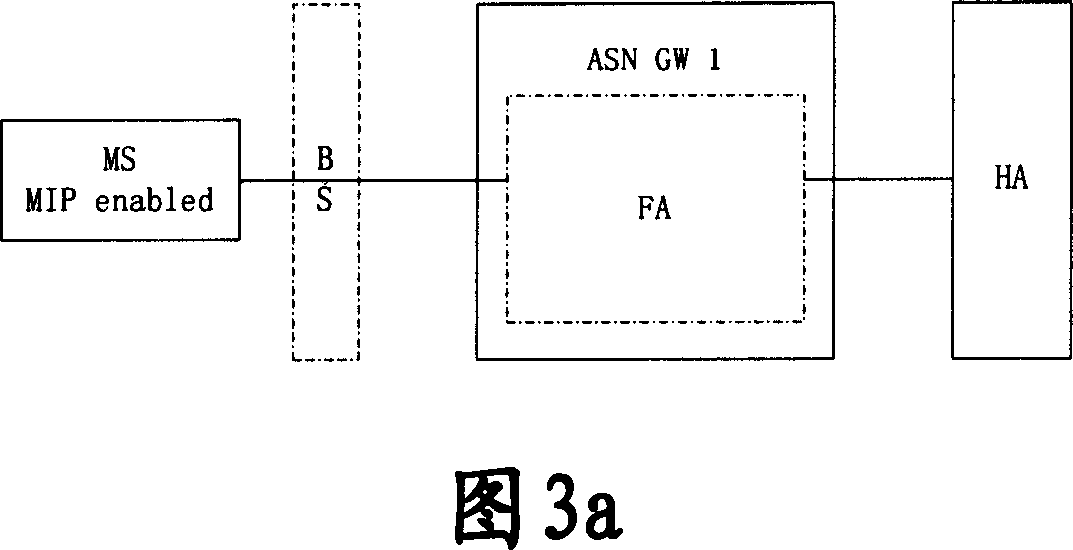
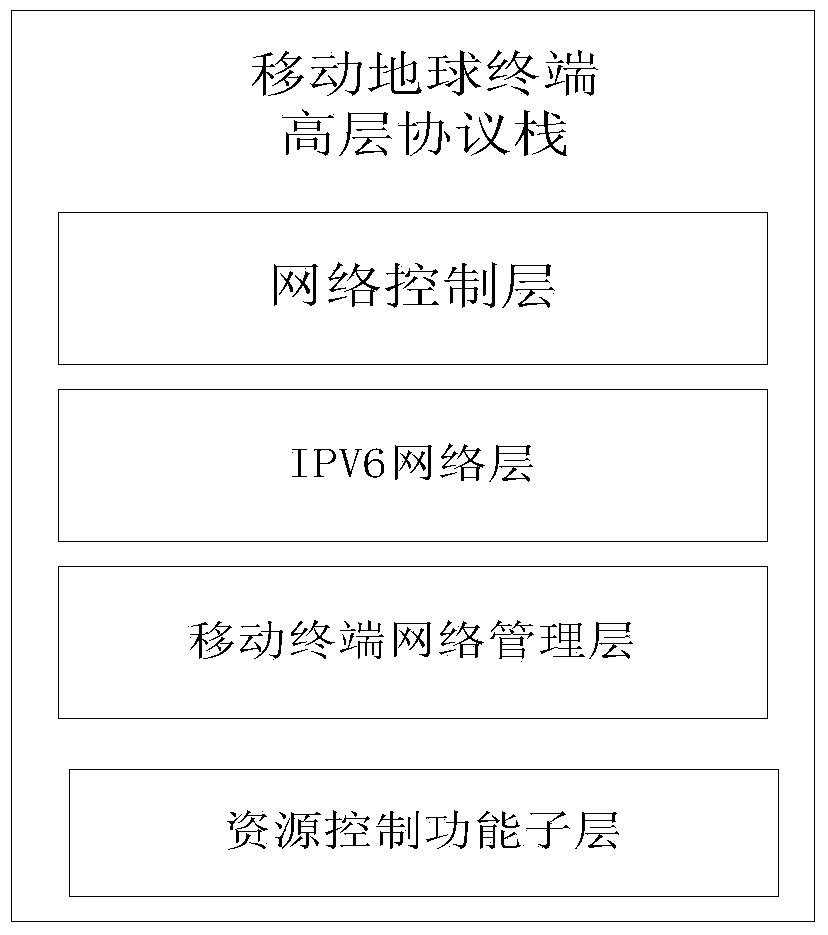
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
177 results about "Authentication authorization accounting" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Authentication, authorization, and accounting (AAA) Authentication, authorization, and accounting (AAA) is a term for a framework for intelligently controlling access to computer resources, enforcing policies, auditing usage, and providing the information necessary to bill for services.
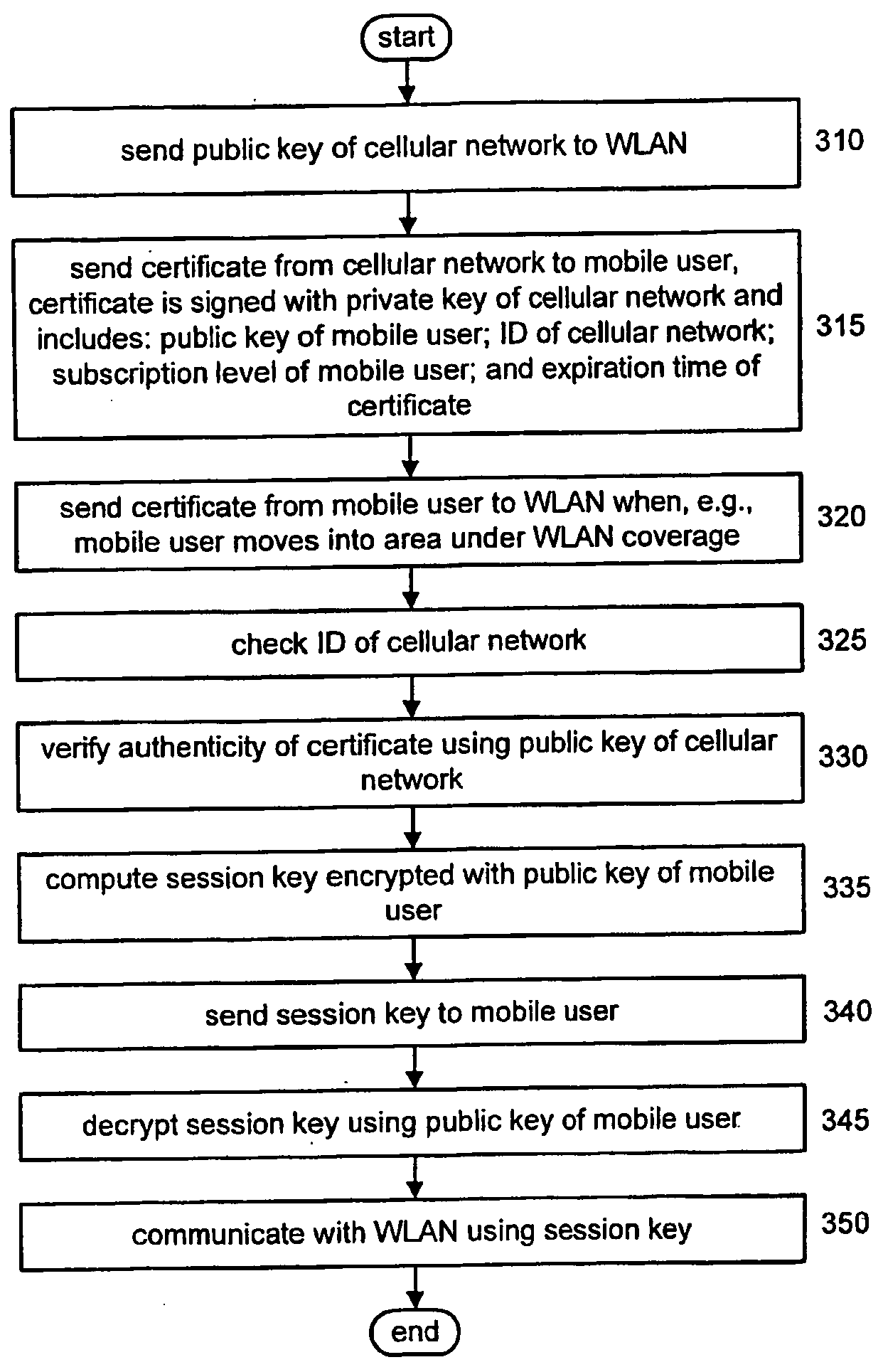
Certificate based authentication authorization accounting scheme for loose coupling interworking
InactiveUS20050154909A1Key distribution for secure communicationUnauthorised/fraudulent call preventionFinancial transactionLoose coupling
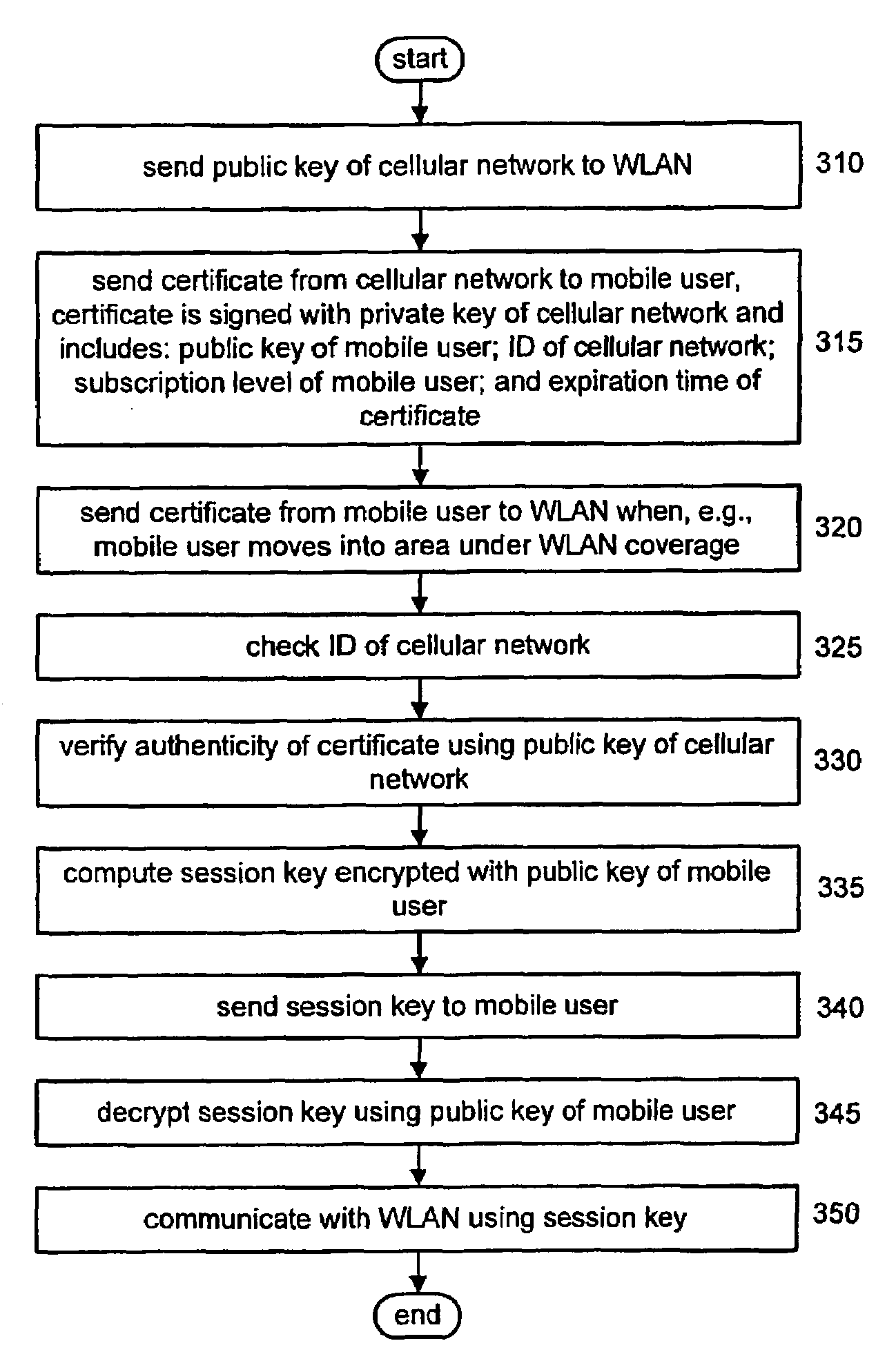
A method of Authentication Authorization and Accounting (AAA) in an interworking between first and second networks that do not belong in the same asministrative domain, using certificate based transactions. In the method according to the invention, the second network sends a public key to the first network, and a certificate to a mobile device. The certificate includes information regarding the subscription level of the mobile device and is signed with a private key of the second network. Upon detection of the first network the mobile device transmits the certificate and the first network authenticates the certificate using the public and private keys of the second network, and authorizes access to the network in response. The first network then sends a session key encrypted with a public key of the mobile device. The mobile device decrypts the session key with a private key and access the first network using the session key. In this manner, interworking is implemented without requiring the deployment of a special interworking function to bridge between the two different types of networks.
Owner:THOMSON LICENSING SA
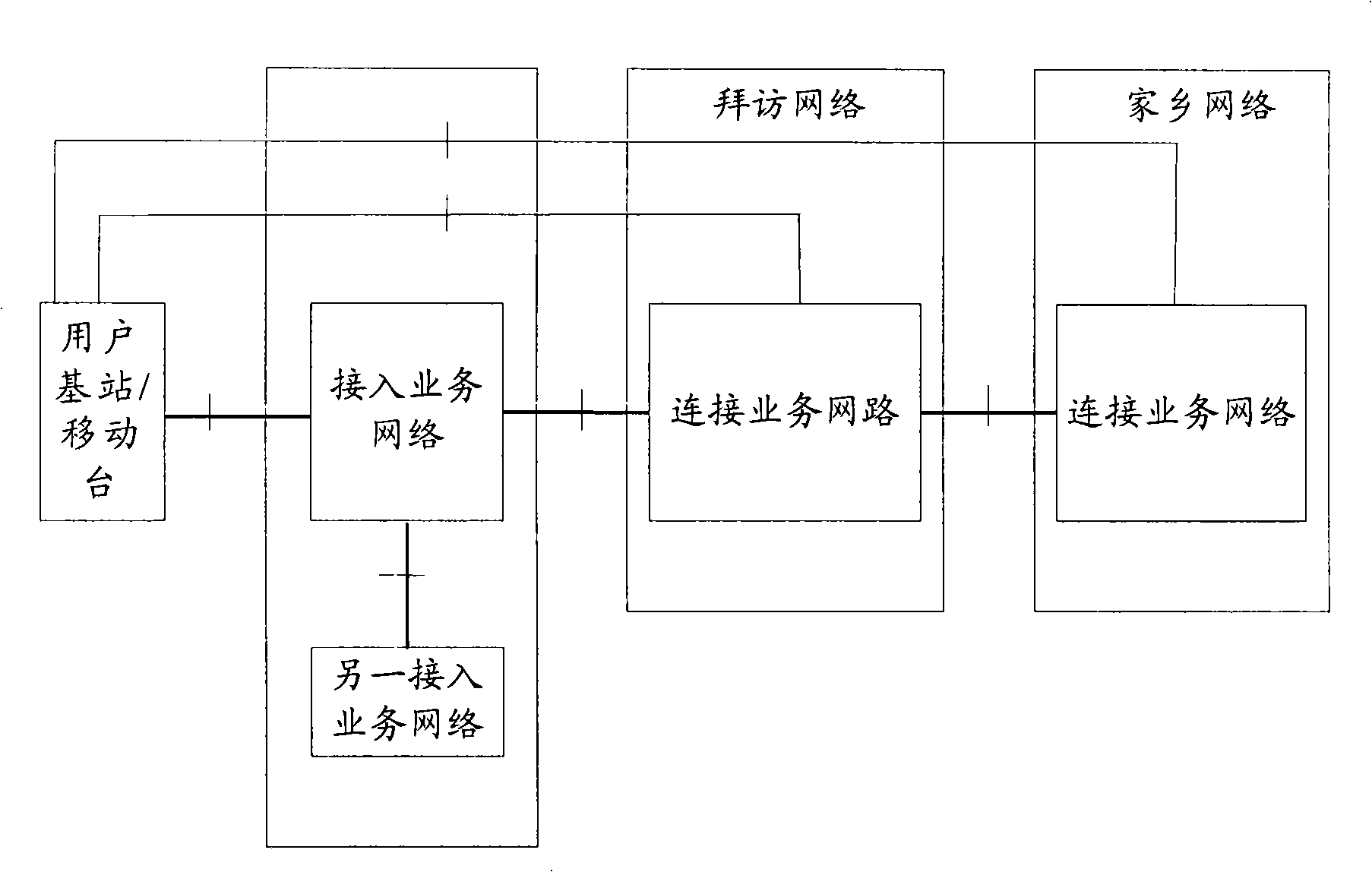
Method and system for providing roaming service in mobile communication system
InactiveUS20070025298A1Accounting/billing servicesNetwork traffic/resource managementPacket data serving nodeTelecommunications
A method and system for a roaming service in a mobile communication system are provided. The system includes an access terminal for transmitting an NAI (network access identifier) to a packet data serving node of the visited network and an AAA (authentication authorization accounting) of the home network, for transmitting subscriber profile information of the access terminal to the visited network. The packet data serving node of the visited network determines whether or not the access terminal subscribes to the roaming service on the basis of the NAI, and, when it is determined that the access terminal subscribes to the roaming service, sends a request for transmitting the subscriber profile information of the access terminal to the AAA of the home network. The packet data serving node of the visited network also provides at least one data service that the home network has provided to the subscriber, using the subscriber profile information.
Owner:SAMSUNG ELECTRONICS CO LTD
Transitive authentication authorization accounting in the interworking between access networks
InactiveUS20050154895A1Digital data processing detailsUser identity/authority verificationAccess networkTrust relationship
A method and a system for allowing a user device that has already been authenticated by a first communications network to gain access to a second communications network without undergoing authentication by the second communications network. The first communications network and the second communications network have a pre-established trust relationship there between. A packet is received from the user device that includes a user device public key, by the second network via the first network. A session key is sent from the second network to the user device, via the first network, when a source Internet Protocol (IP) address associated with the packet falls into a range allocated to the first network. The session key is encrypted with the user device public key. The user device decrypts the session key using a private key and uses the session key thereafter to access the second network. Further a mapping is generated to correlate the identity of the user device with the session key such that usage data relate to user device is generated by the second communications network and transmitted to the first communications network, which generates accounting information indicative of user device access of the second communications network.
Owner:INTERDIGITAL CE PATENT HLDG
Address distributing method for broadband wireless access system
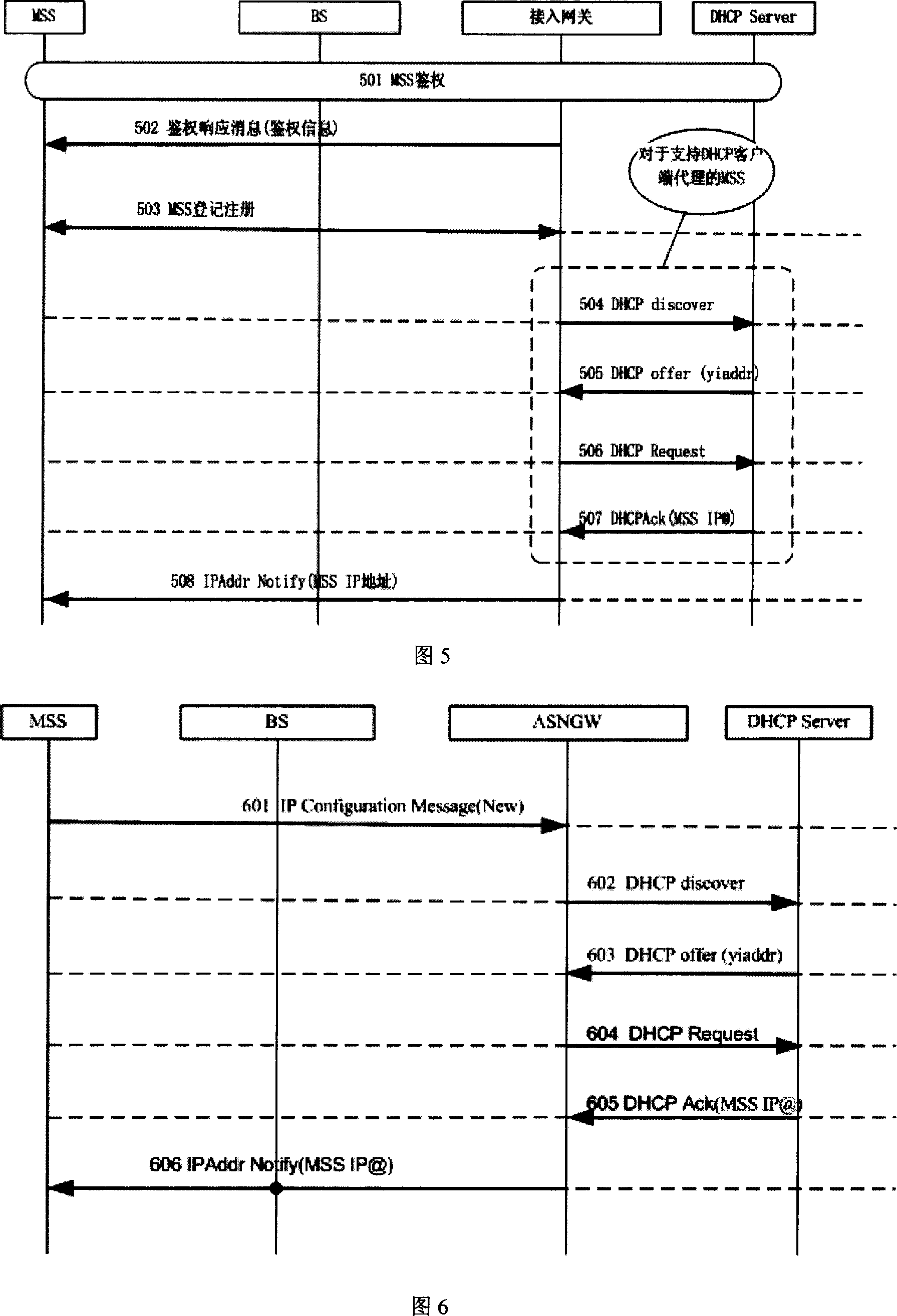
The invention provides an address allocating method for wideband wireless access system, comprising the steps of: when connecting to network, mobile terminal sends user / equipment authentication request to AAA (Authentication,Authorization and Accounting) server; after the authorization succeeds, the mobile terminal sends registering request to access gateway; the mobile terminal completes registering, the access gateway obtains mobile terminal-supported IP address allocating mode according to the user configuration information returned after the authorization succeeds; the access gateway replaces the mobile terminal as DHCP Client to send IP address allocating request to DHCP server or does not request IP address but waits for the mobile terminal to actively request IP address; the DHCP server allocates IP address to corresponding MAC address, the access gateway transfers the allocated IP address to the mobile terminal and the mobile terminal completes local address binding. And it reduces implementing difficulty and cost, reduces system overhead and speeds up switching.
Owner:ZTE CORP
A system and method for oriented and customized distribution of the network contents
InactiveCN101056187APossess the ability to release customized information in a targeted mannerSpecial service provision for substationIp addressGeolocation
The invention discloses a system and method for issuing the network contents in the fixed position, orientation and customized mode, this system framework consists of user terminal equipment, network access point equipment, intelligent network boundary system, network information application server, user authentication accounting and positioning system and contents management system. The intelligent network boundary system has the contents index matching subsystem, contents buffer memory subsystem, contents reading subsystem and contents issuing subsystem; the contents management system shall save and manage the information issued to the network users by the network operator or network owner; the user authentication accounting and positioning system has the system user name / IP address / user access point equipment / geographic position database. With the network contents issuing system and method in fixed position, orientation and customized mode, the network operator may issue the network contents to all network clients in the fixed position, orientation and customized mode.
Owner:王伟珣
Certificate based authentication authorization accounting scheme for loose coupling interworking
InactiveUS7735126B2Key distribution for secure communicationUnauthorised/fraudulent call preventionAdministrative domainLoose coupling
A method of Authentication Authorization and Accounting (AAA) in an interworking between first and second networks that do not belong in the same administrative domain, using certificate based transactions. In the method according to the invention, the second network sends a public key to the first network, and a certificate to a mobile device. The certificate includes information regarding the subscription level of the mobile device and is signed with a private key of the second network. Upon detection of the first network the mobile device transmits the certificate and the first network authenticates the certificate using the public and private keys of the second network, and authorizes access to the network in response. The first network then sends a session key encrypted with a public key of the mobile device. The mobile device decrypts the session key with a private key and access the first network using the session key. In this manner, interworking is implemented without requiring the deployment of a special interworking function to bridge between the two different types of networks.
Owner:THOMSON LICENSING SA
Broadband access method and device
The invention provides a broadband access method and device. The method comprises the steps that an address application broadcast message of VXLAN packaging carrying QinQ information is received through a VXLAN tunnel; VXLAN packaging is relieved, and the address application broadcast message is transmitted to an authentication authorization billing server; when the address application broadcast message is ensured to be authenticated, the address application broadcast message is converted into an address application unicast message; the address application unicast message carries the QinQ information used for IP address allocation and the identifier of the VXLAN tunnel; the converted address application unicast message is transmitted to an address server; an address response message which is transmitted by the address server and carries the allocated IP address is received; and VXLAN packaging is performed on the address response message according to the VXLAN tunnel, and the address response message of VXLAN packaging is transmitted through the VXLAN tunnel. The cost of the broadband access business can be reduced by the broadband access method and device.
Owner:NEW H3C TECH CO LTD
Real-time identifying method of interaction type network television user
InactiveCN1893638AImprove concurrent processing performanceEnsure safetyMetering/charging/biilling arrangementsTwo-way working systemsInteraction typeAuthentication authorization accounting
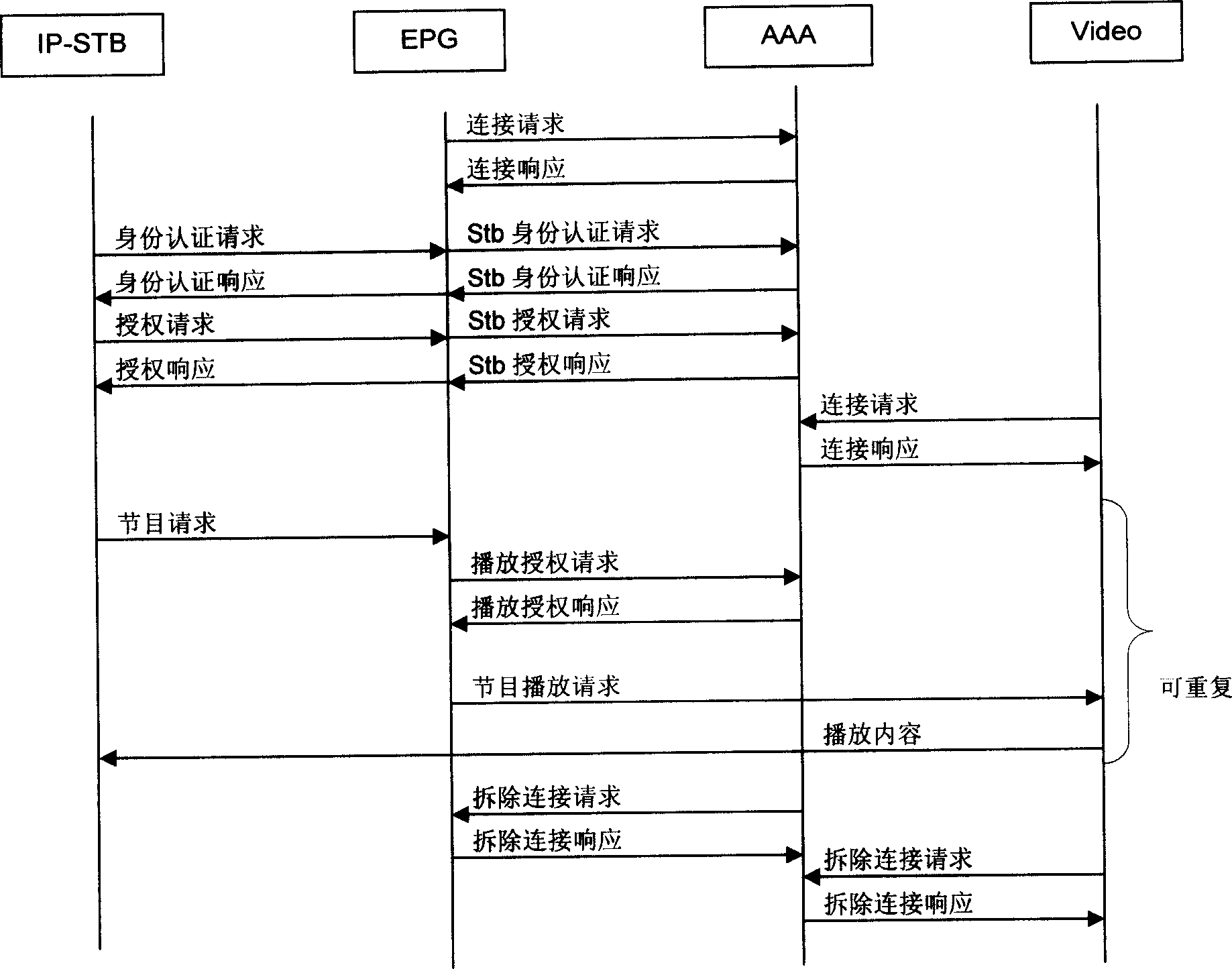
The method includes authentication procedure of turning on TV set, and content service procedure. The authentication procedure of turning on TV set includes steps: building connection between electronic navigation guide server and authentication authorization charging server; network set-top box (STB) sends a request of authenticating device ID to the charging server; after authentication of device ID, STB sends a request of authorizing user to the charging server; the charging server sends response of authorizing user to carry out authorization; building connection between the charging server and video server; sending request of authorized playing to the charging server; content service procedure includes steps: STB sends out program request; after obtaining playing authorization, user sends request for playing content. The invention can carry out authentication in realtime. Authentication for both parties, and MD5 cryptographic algorithm are adopted to guarantee security of system.
Owner:沈阳鼎通科技有限公司
Access processing method, base station and terminal
The embodiment of the invention provides an access processing method, a base station and a terminal. The method comprises the following steps of: receiving an access request message, transmitted by the terminal, by the base station; transmitting an access control message to the terminal by the base station if access failure frequency of the terminal reaches a preset threshold value so as not to transmit the access request message to the base station any longer by the terminal in a period of time; or transmitting the access control message to the terminal so as not to transmit the access request message to the base station any loner by the terminal. According to the technical scheme provided by the embodiment of the invention, the access of the terminal with multiple continuous access fails and due and temporarily-defaulting account or other illegal terminals during interaction between the terminal and the base station can be controlled, so that reaccess of the illegal terminals is prevented or interval time of adjacent access requests of the terminal is prolonged; and waste of an air interface and ground link bandwidth in an interactive authentication process between an abnormal user terminal and AAA (Authentication Authorization Accounting) can be reduced, so that uplink bandwidth resources of a normal Wimax (Worldwide Interoperability for Microwave Access) user can be guaranteed.
Owner:HUAWEI TECH CO LTD
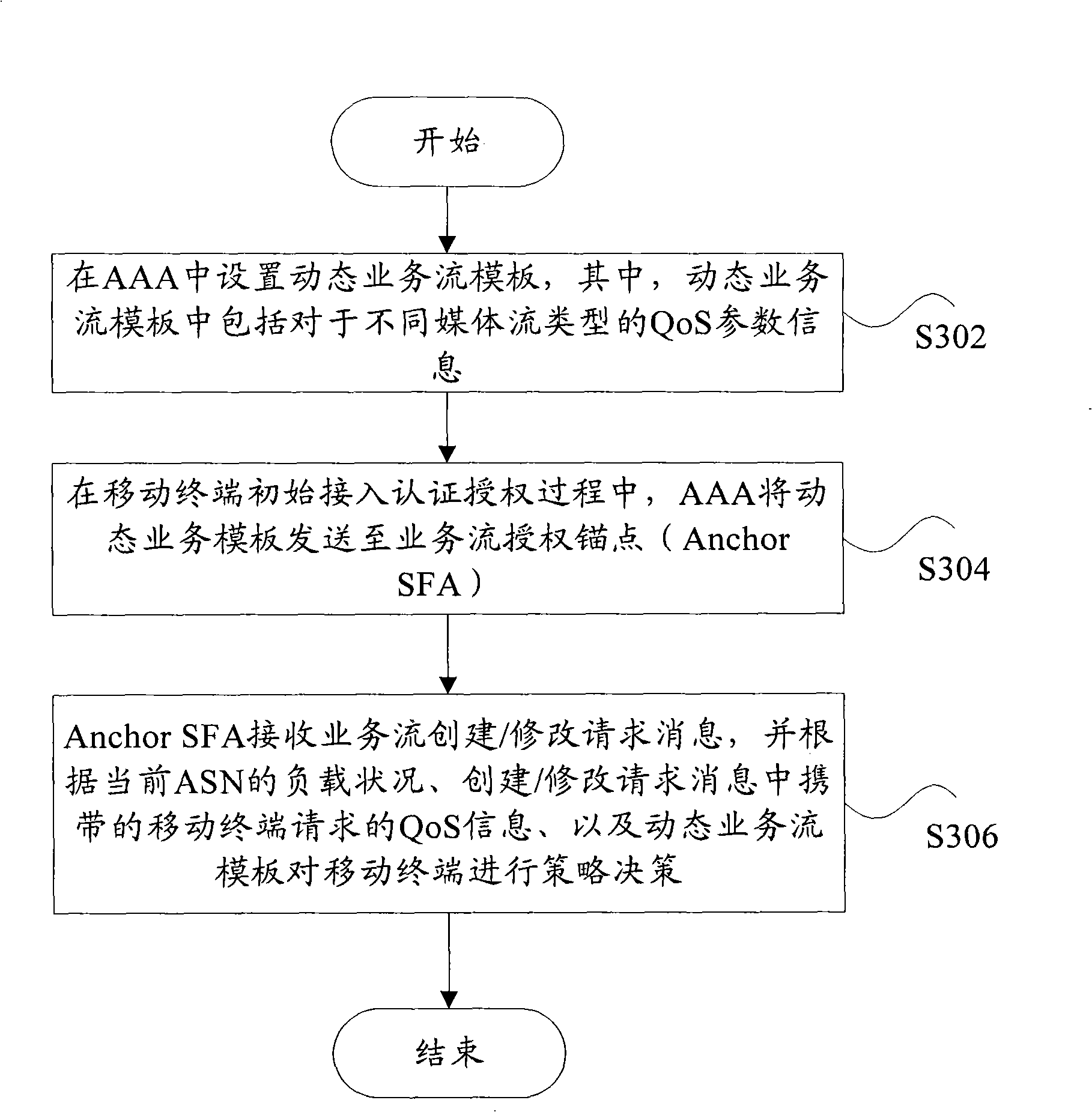
QoS guarantee method and system of dynamic business, AAA and Anchor SFA
The invention provides a QoS ensuring method of a dynamic service, a system and AAA and Anchor SFA, comprising: arranging a dynamic service flow module in an authentication authorization charging functional entity, wherein the dynamic service flow module includes service quantity parameter information corresponding to different medium flow types; transmitting the dynamic service flow module to a service flow authorization anchor point by the authentication authorization charging functional entity when a mobile terminal is initially accessed to the authentication authorization; receiving theservice flow building / modifying request information by the service flow authorization anchor point, and performing strategy decision-making according to load accessed to the service network, service quality information requested by the mobile terminal carried in the service flow building / modifying request information. According to the process, QoS of the dynamic service is ensured under network environment of non-strategy charging control.
Owner:ZTE CORP
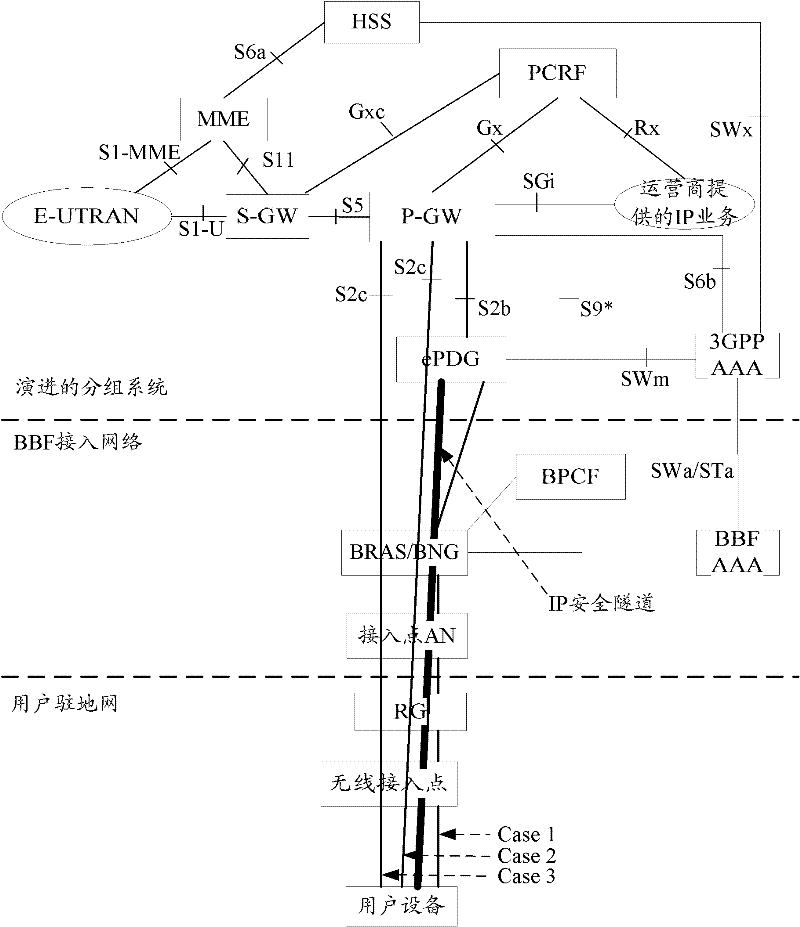
Fixed network perception user access method and system thereof
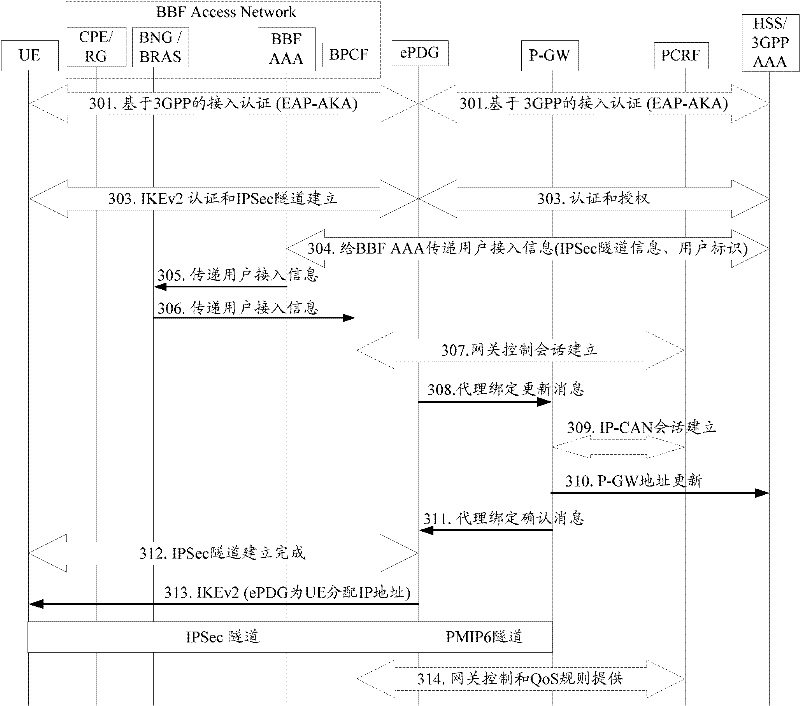
ActiveCN102457847ASupport for the implementation of admission controlSupport admission controlAssess restrictionConnection managementAccess methodBroadband
The invention discloses a fixed network perception user access method and a system thereof. The method is characterized in that: based on an authentication process phase of a mobile network to user equipment, authentication authorization and accounting (AAA) of a 3rd generation partnership project (3GPP) acquires user access information and further transmits to the AAA of a broadband forum (BBF); the AAA of the BBF provides the user access information to a broadband policy control function (BPCF); the BPCF discovers a policy and charging rules function (PCRF) which are served for the user according to the received user access information and initiates session establishment to the PCRF. By using the method and the system of the invention, fixed network equipment can identify user access according to the user access information so as to support and implement admission control to the service which is developed for the user.
Owner:ZTE CORP
AAA server, P-GW, PCRF, obtaining method and system for customer equipment identification
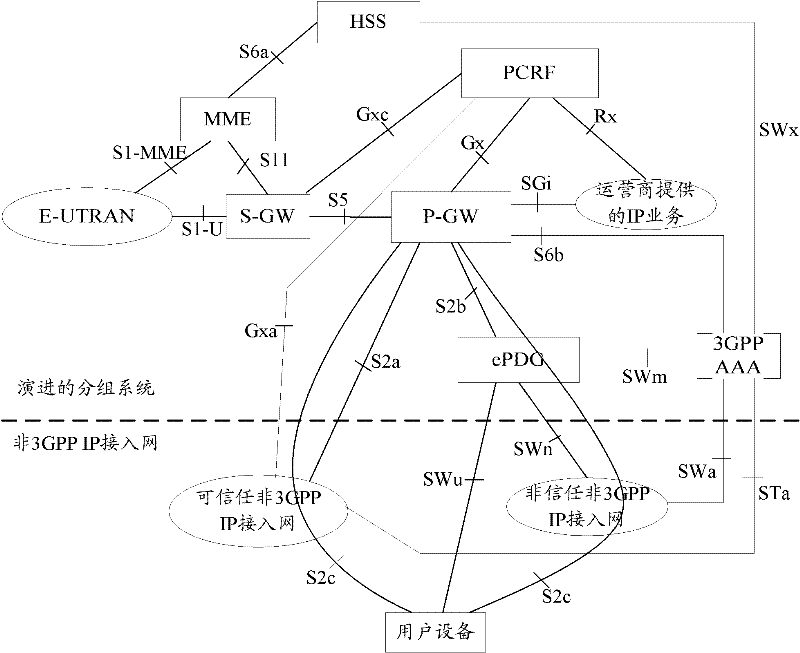
InactiveCN101459904AEasy accessAccounting/billing servicesData switching networksAccess networkUser device
The invention discloses an acquisition method for an AAA server, P-GW, PCRF and a user device mark and a system thereof, wherein the acquisition method of the user device mark comprises conducting the access authorization for an authorization accounting server and a user device, sending the access receiving information for an external agent of a non 3GPP access network by the authorization accounting server, and then carrying the true mark of the user device in the access receiving information, and sending the true mark of the user device to a grouping data network gateway by the authorization accounting server after verifying that the user device mark is a false mark of the user device in the authorization process of the authorization accounting server and the grouping data network gateway. The invention further provides an authorization accounting server, a grouping data network gateway, a strategic accounting control functional entity, an acquisition method of a user device mark and a system thereof. A non 3GPP terminal can be assured to directly access into an EPC network through the invention.
Owner:ZTE CORP
Packet data web gateway identification saving method and system in multi-access scene
InactiveCN101730072AGuaranteed uptimeAssess restrictionConnection managementAccess networkNetwork connection
The invention discloses a packet data web gateway identification saving method and system in multi-access scene. The method includes that: when user equipment simultaneously accesses a packet data network by two access networks, namely a first access network and a second access network, and the identical packet data network connection is established, an affiliation user or authentication charging server saves the identification of the packet data web network; the first access network is a third generation partner plan 3GPP access network, and the second access network is a non-3GPP access network; or the first access network is a non-3GPP access network, and the second access network is a 3GPP access network; when releasing the access of one access network of the two access networks, the affiliation user or authentication charging server saves the identification of the packet data web gateway. The method can reasonably notify HSS / AAA, P-GW identification can be correctly stored or deleted, and the system is ensured to normally operate in related P-GW identification operation in multi-access scene.
Owner:ZTE CORP
Control method and device for network address translation service
InactiveCN101150519AIncrease flexibilityReduce complexityData switching networksPersonalizationNetwork addressing
The invention provides an operation control method for Network Address Transformation (NAT), which includes the following steps: the description information of NAT service corresponding to the user is firstly established in an Authentication, Authorization, Accounting (AAA) server, when the user gets online and passes the authentication and authorization, the description information of NAT service can be obtained from the AAA server, and the NAT gateway can control the NAT operation of the user according to the description information. The invention also provides a control device for NAT operation. By using the technical proposal of the invention, the flexibility of the NAT operation control can be enhanced and the individualized NAT service for the users can be realized.
Owner:NEW H3C TECH CO LTD
Network architecture of backward compatible authentication, authorization and accounting system and implementation method
InactiveCN1809072AImprove scalabilityEmphasize compatibilityMetering/charging/biilling arrangementsUser identity/authority verificationNetwork access serverTelecommunications network
This invention relates to one back compatible identification charging system network structure, which comprises network interface servo translation agent, local servo translating agent, relay agent, and trustee agent, network interface servo and local identification charging servo, wherein, the network structure is divided into service area A, B, and C according to each local identification servo and connecting internet according to management areas of I, II and agent.
Owner:SOUTHEAST UNIV
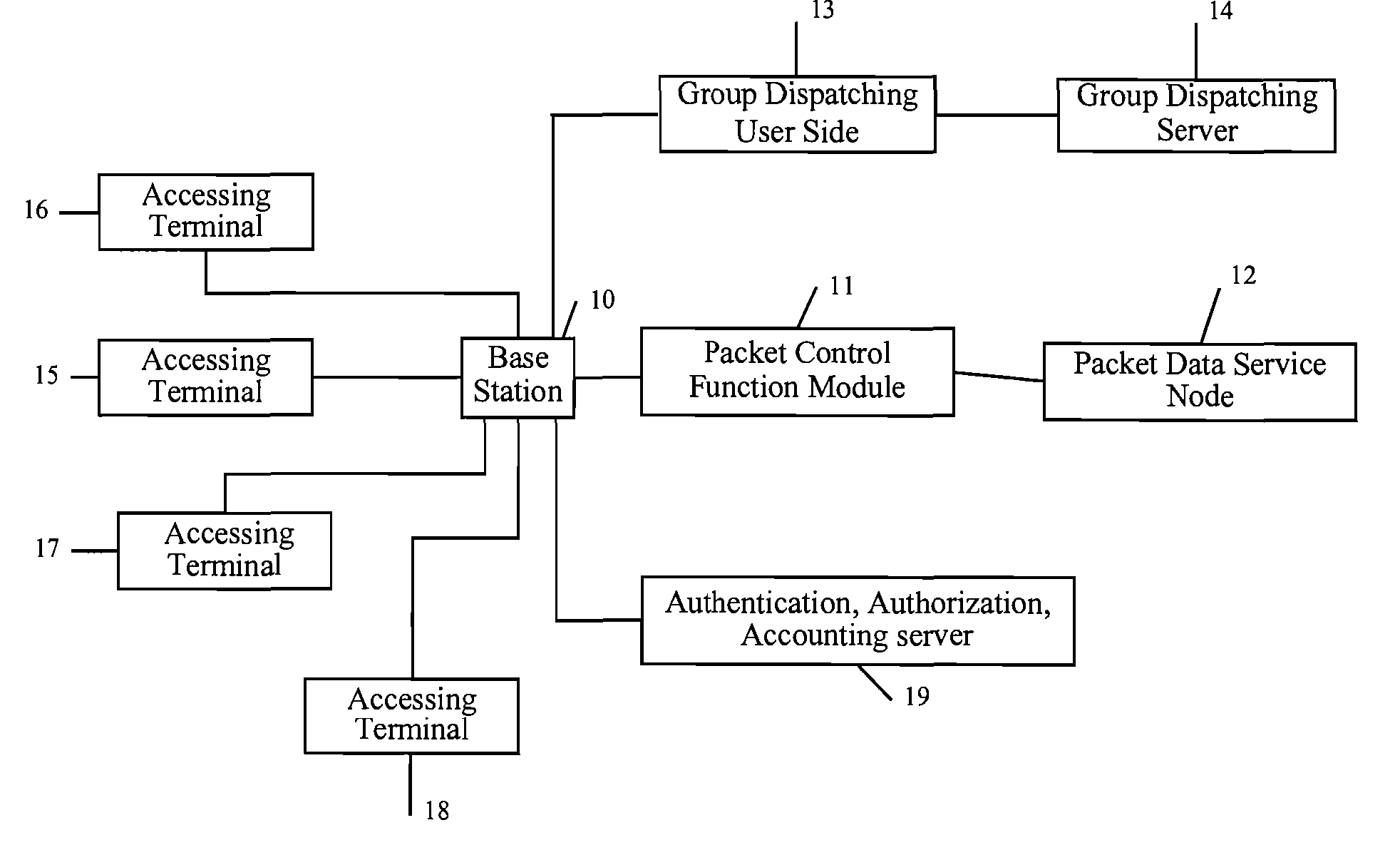
System of Group Communication and a Method of Group Call Processing Based on Cdma 2000 High-Speed Packet Data Network
InactiveUS20070225024A1Overcomes shortcomingSpecial service for subscribersConnection managementHigh rateGroup communication systems
The present invention discloses a system of group communication and a method of group call processing based on CDMA2000 high-rate packet data network. The group communication system based on CDMA2000 high-rate packet data network includes: base station, packet control function module, packet data service node and AAA (authentication, authorization, accounting) server. The system further includes: multiple accessing terminals for making or responding the service request of group talk; group dispatching server for providing centralized control of group talk service, implementing the entire group talk service procedure from group user authentication to transmission of voice service package; group dispatch user side, which is an accessing gateway of group communication system, for providing signaling and service link between the base station and the group dispatching server. The present invention realizes the group communication system in the current high-rate packet data network, so that the group communication system satisfies the requirements of third generation communication, and adapts the development of the communication system.
Owner:YARNTON TECH LLC
Method and device for accessing terminal of fixed or nomadic user to network
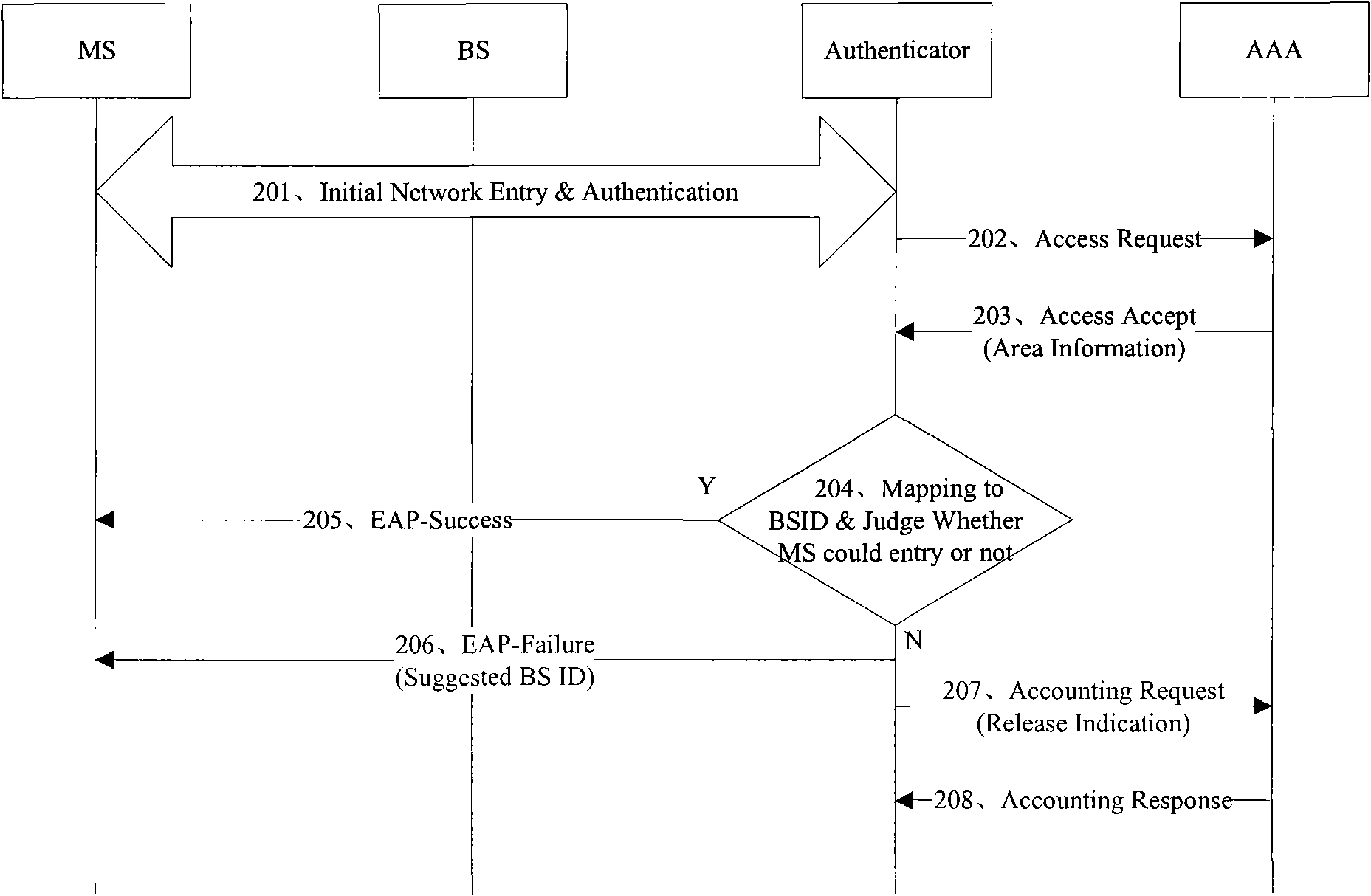
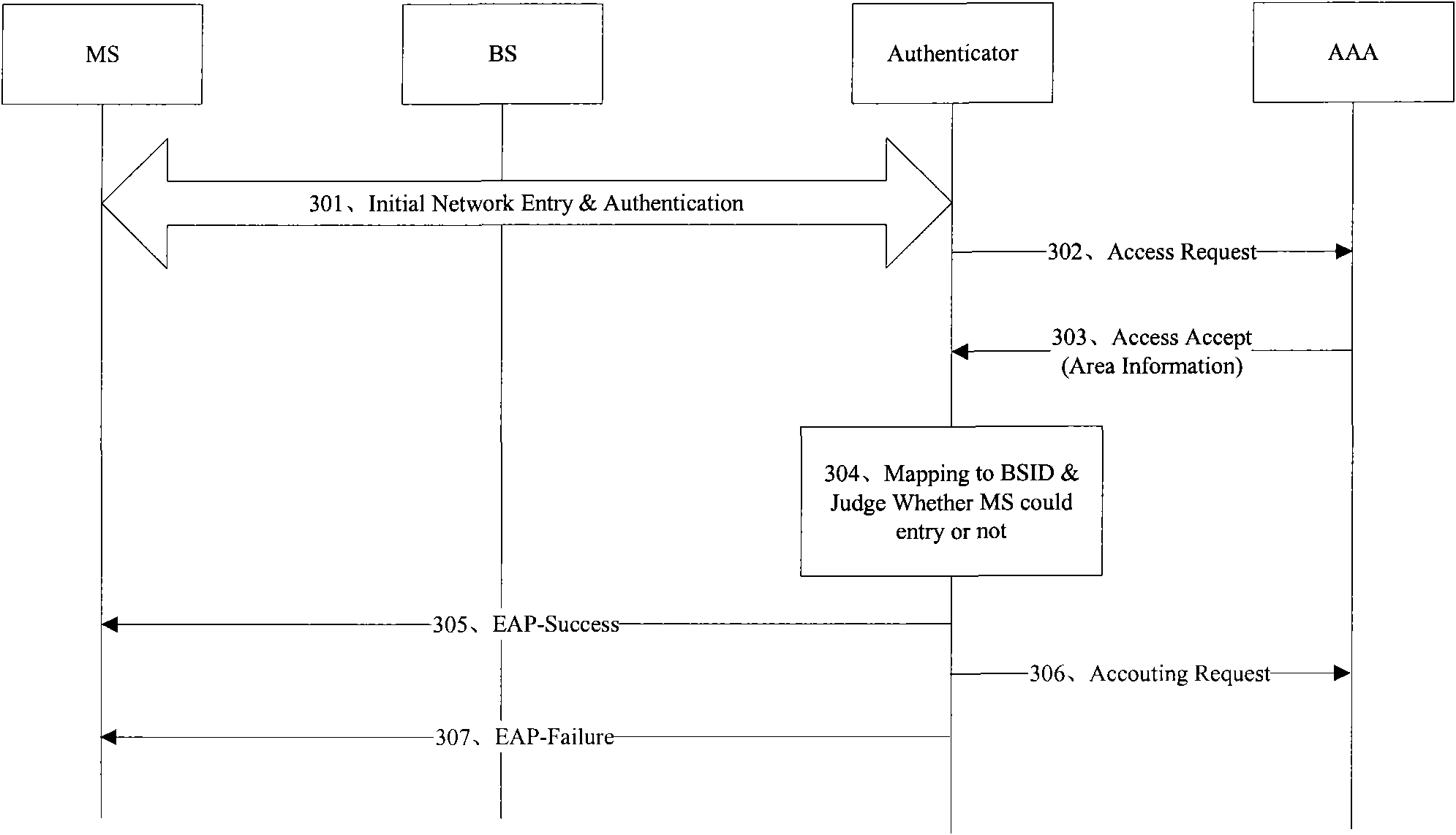
ActiveCN101640889AGeographically restrictedAssess restrictionTransmissionFixed serviceAuthentication authorization accounting
The embodiment of the invention discloses a method for accessing a terminal of a fixed or nomadic user to a network. The method is characterized by comprising the following steps: transmitting an access request message to an authentication, authorization and accounting server AAA; receiving an access granted message from the AAA, wherein the access granted message carries area information which is granted to access the terminal; converting the area information into a base station identification BS ID list which is granted to access the base station; and transmitting an authentication succeeded message to the terminal if the BS ID of the terminal accessed to the base station currently is in a range of the BS ID list so as to ensure that the terminal can carry out a subsequent network accessing process. The method and a device for accessing the terminal of the fixed or nomadic user to the network ensure that the terminal of the fixed or nomadic user can be correctly accessed in an area which is granted to access so as to restrict the area range of the terminal of the fixed or nomadic user accessing to the network.
Owner:HUAWEI TECH CO LTD
Network access method and system
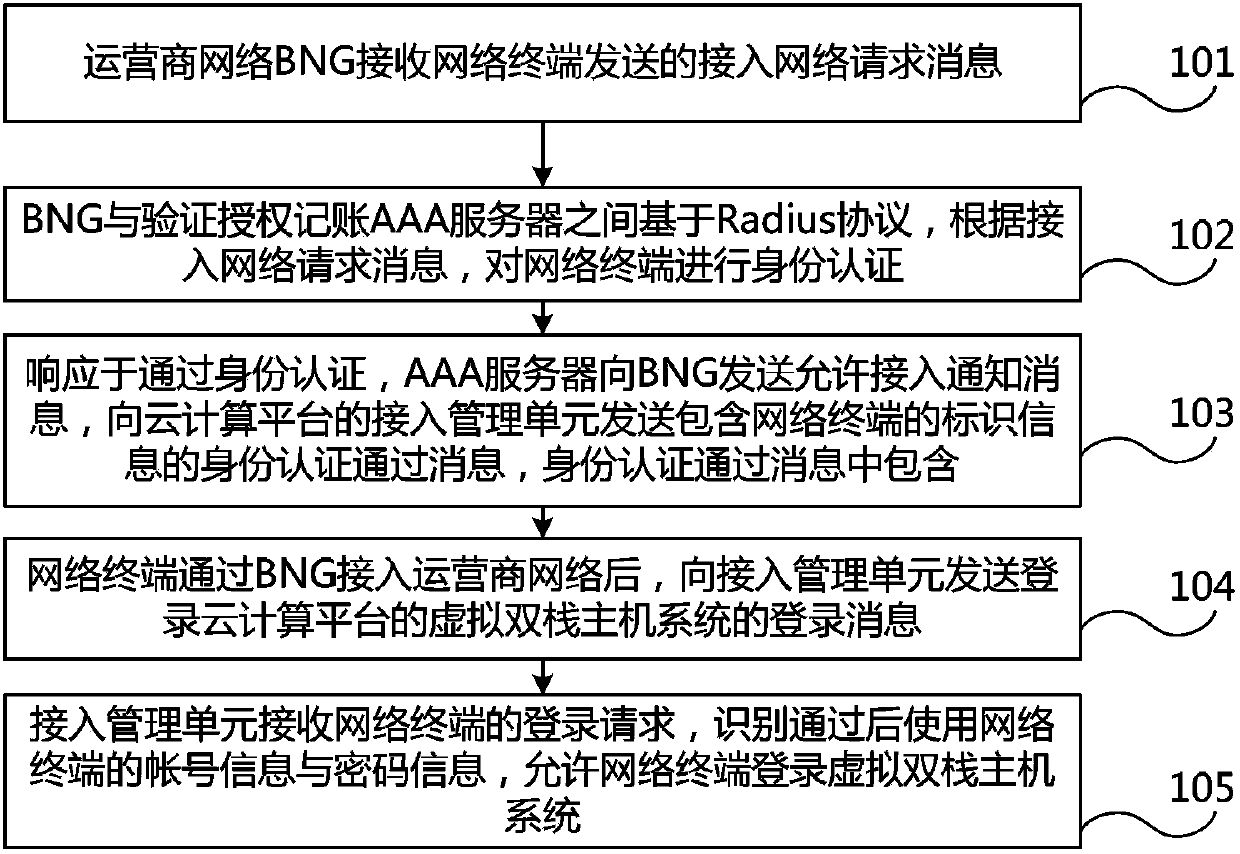
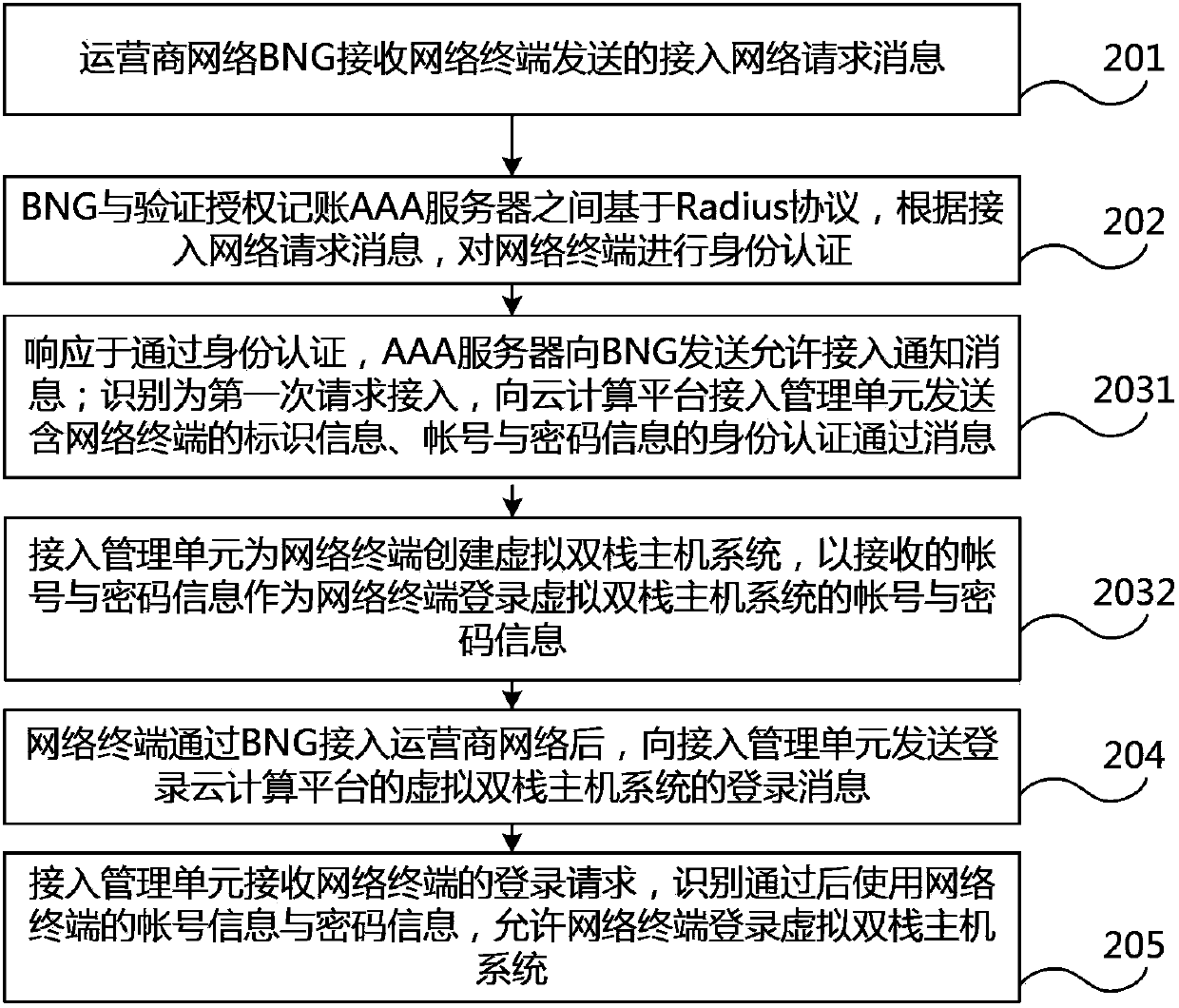
ActiveCN103873449AAvoid secondary authenticationSimplify the certification processNetworks interconnectionNetwork terminationThe Internet
The invention discloses a network access method and a network access system. The network access method comprises the following steps: performing identity authentication on a network terminal based on a Radius protocol through an operator network BNG (broadband network gateway) and an AAA (authentication authorization accounting) server; in response to passing of the identity authentication, sending an identity authentication passing message for the network terminal to an access management unit of a cloud computing platform by the AAA server, so that when the network terminal logs in a virtual dual-stack host system of the cloud computing platform, the access management unit of the cloud computing platform can directly identify the network terminal according to the identity authentication passing message sent by the AAA server, and allows the network terminal to log in the virtual dual-stack host system. According to the technical scheme provided by the invention, secondary authentication on the network terminal caused by isolation between the BNG equipment of a network layer and the cloud computing platform of an application layer is avoided, the authentication flow of a user is simplified, and meanwhile, the user can conveniently access the internet through the virtual dual-stack host system provided by the cloud computing platform.
Owner:CHINA TELECOM CORP LTD
Method and system for authentication processing, 3GPP authentication authorization accounting server and user device
The invention relates to a method and a system for authentication processing, a 3GPP authentication authorization accounting server and a user device. The method for authentication processing of the embodiment of the invention comprises the following steps: receiving authentication request messages carrying authentication method instruction information; determining the authentication method according to the authentication method instruction information; and carrying out the corresponding authentication processing according to the authentication method. The system for authentication processing comprises a 3GPP authentication authorization accounting server and a network device through which the user device is connected with the 3GPP authentication authorization accounting server. The authentication request messages sent by the user device carry the authentication method instruction information with different parameters, so that the 3GPP authentication authorization accounting server can distinguish between different authentication methods, and carry out the corresponding authentication processing in accordance with the authentication methods determined by the 3GPP authentication authorization accounting server.
Owner:HUAWEI TECH CO LTD
Transitive authentication authorization accounting in the interworking between access networks
InactiveUS7721106B2Digital data processing detailsUser identity/authority verificationAccess networkWeb authentication
A method and a system for allowing a user device that has already been authenticated by a first communications network to gain access to a second communications network without undergoing authentication by the second communications network. The first communications network and the second communications network have a pre-established trust relationship there between. A packet is received from the user device that includes a user device public key, by the second network via the first network. A session key is sent from the second network to the user device, via the first network, when a source Internet Protocol (IP) address associated with the packet falls into a range allocated to the first network. The session key is encrypted with the user device public key. The user device decrypts the session key using a private key and uses the session key thereafter to access the second network. Further a mapping is generated to correlate the identity of the user device with the session key such that usage data relate to user device is generated by the second communications network and transmitted to the first communications network, which generates accounting information indicative of user device access of the second communications network.
Owner:INTERDIGITAL CE PATENT HLDG
Terminal shift management system and method thereof
InactiveUS20090132635A1Digital data processing detailsMultiple digital computer combinationsComputer networkControl system
The present invention relates to a terminal control system, and more particularly, to a system and a method which allows a user to shift an IP service from a terminal to which the service is currently provided to a user's other terminal, thereby enabling the user to continuously using the IP service without disconnection. The system comprises: an authentication authorization accounting (AAA) interface unit which receives unique information having fixed properties with respect to a terminal authenticated by a subscriber terminal authentication system and a user of the authenticated terminal; a terminal interface unit which receives status information having variable properties with respect to the authorized terminal and a currently used service; a unique information managing unit which stores and manages the unique information; a status information managing unit which stores and manages the status information; and a terminal shift management control unit which provides information regarding terminals available for the current service with reference to the unique information and the status information, when there is a terminal shift request, generates service session information which is required when the currently used service is sent to a terminal selected from the information and sends the generated service session information to the selected terminal to which the service is to be shifted. Accordingly, the user of the terminal can conveniently change the terminal to continuously use the IP service without disconnection while using the IP service.
Owner:ELECTRONICS & TELECOMM RES INST
Method for generating and distributing movable IP Key
InactiveCN101075870AGuaranteed normal executionUser identity/authority verificationBroadcastingMobile IP
The method comprises: during authentication process, the authentication, authorization and accounting (AAA) server sends the key information to the anchor authenticator; according to said key information, the authenticator gets the key between the mobile node and the external agent and the key between the external agent and the home agent; when receiving a broadcast message from the external agent, according to the address of the external agent, the terminal figures out the key between the mobile node and the external agent, and triggers the mobile IP registration request; the home agent processes the registration request, and after success of registration, returns the request confirmation; according to ht e received registration confirmation, said terminal gets the address of the home agent, and figures out the key between the mobile node and the home agent.
Owner:HUAWEI TECH CO LTD
Gateway identifier reporting method and system thereof
InactiveCN102348193AEasy to operateSecurity arrangementNetwork data managementHome subscriber serverAuthentication authorization accounting
The invention discloses a gateway identifier reporting method. A packet data network gateway (P-GW) identifier is reported to a home subscriber server (HSS) / authentication, authorization and accounting server (AAA) by an evolutionary packet data gateway (ePDG). The invention additionally discloses a gateway identifier reporting system, which comprises a reporting unit used for the ePDG to report the P-GW identifier to the HSS / AAA. By adopting the method and the system disclosed by the invention, the operational process can be unified and the operation can be simplified in different scenes of 3rd generation partnership project (3GPP) access and non-3GPP access.
Owner:ZTE CORP
A network system, policy management control server and policy management control method
InactiveCN101150853AImprove reliabilityAssess restrictionConnection managementNetwork access serverNetworked system
The embodiment of the invention discloses a network system, comprising a network access server, an authentication charging server and a service server, also comprising: a strategy manage control server for acquiring user service using state information to generate strategy control information according to the service server and / or the authentication charging server, the strategy control information is used for directing the network access server to manage and control the conversation of users, and sending the generated strategy control information to the network access server; the network access server manages and controls the conversation of users according to the strategy control information. The embodiment of the invention also discloses a strategy manage control server, a service server and an authentication charging server. The invention can improves user conversation reliability of a NAS device during using the service.
Owner:HUAWEI TECH CO LTD
Satellite communication integrated QoS (Quality of Service) safeguard system
ActiveCN103648132AHigh trafficImprove experienceNetwork traffic/resource managementNetwork topologiesQuality of serviceAccess route
The invention provides a satellite communication integrated QoS (Quality of Service) safeguard system which comprises a QoS safeguard structure of a ground station system and a QoS safeguard structure of a mobile earth terminal. The QoS safeguard structure of the ground station system comprises a wireless gateway module of the ground station, a certificate authority charging module, an access route module of the ground station, and a beam QoS proxy module. The QoS safeguard structure of the mobile earth terminal comprises a terminal side higher layer protocol stack module and a terminal side hollow interface protocol stack module. The satellite communication integrated QoS safeguard system provided by the invention can provide distinguished services for different types services such as voice or video phone service, real-time stream service, interactive services and background services, thereby ensuring the quality of service of services in various types, optimizing the flow of the network and enhancing the user experience.
Owner:SPACE STAR TECH CO LTD
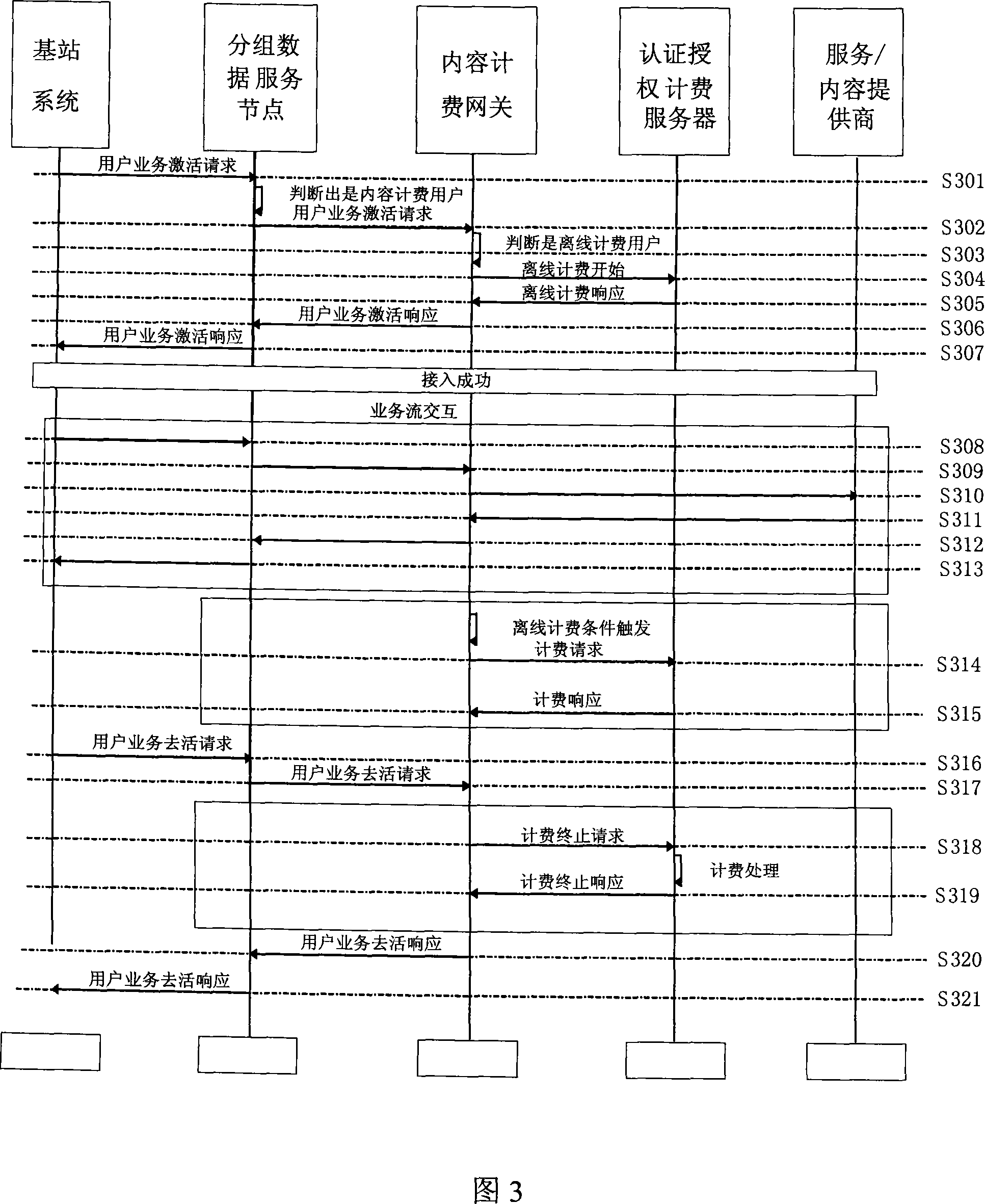
Off-line accounting system and method
InactiveCN101222342ARealize content billing functionImplement regular billingMetering/charging/biilling arrangementsAccounting/billing servicesPacket data serving nodeComputer science
The invention discloses a off line charging system and a method thereof; the method includes the following contents that: a grouped data network is additionally provided with a content charging gateway; a grouped data service node analyzes an off line charging user and routes messages of the off line charging user to the content charging gateway; the content charging gateway analyzes the message of the off line charging user and charges analyzed service types according to corresponding charging rules, and the acquired charging information is reported to a certification authorization charging server; the certification authorization charging server generates the off line charging bill according to the information reported by the content charging gateway. The invention adopting the method has the advantages of easily realizing the difference of the non-content charging and the content charging messages and realizing the off line charging of the content charging message.
Owner:ZTE CORP
Method, system and server for prompting the cause for user terminal authentication failure
InactiveCN1968094ASimple requirementsUser identity/authority verificationWeb pageAuthentication authorization accounting
The invention relates to a method for prompting user terminal about the identification failure reason via net page, wherein it comprises that: when user terminal fail to identify on the identification charge server, the server based on failure reason sends one page address; user terminal connects said address and displays the reason. The invention also provides relative system and charge server.
Owner:HUAWEI TECH CO LTD
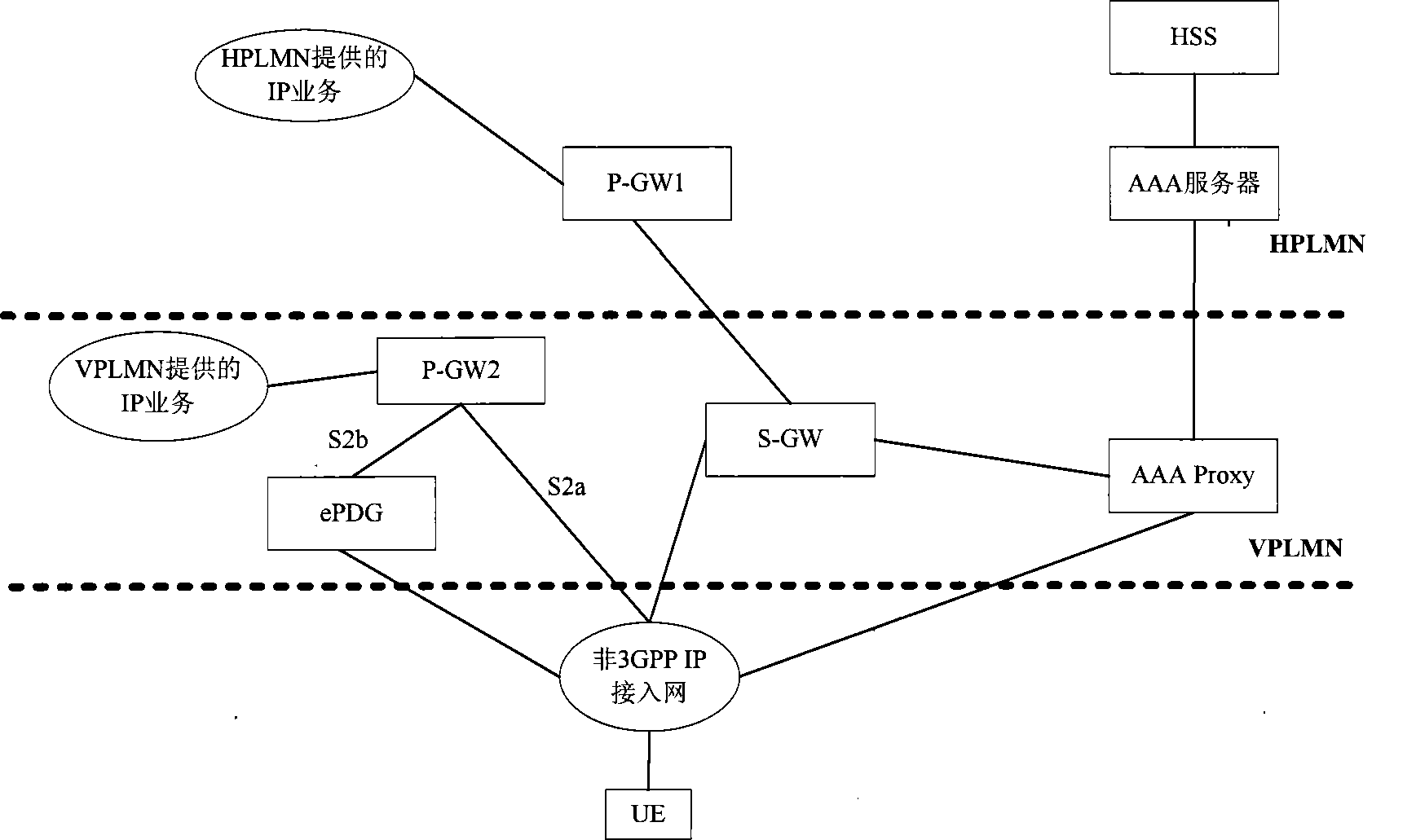
Method for implementing access network
The invention aims to provide a method for realizing the access to a network. The method comprises the following steps: step 1, the authentication, authorization & accounting server (AAA Server) of an HPLMN (home public land mobile network) sends a notice of the distrust relation between the HPLMN and a non-3GPP access network to the authentication, authorization & accounting proxy (AAA Proxy) of a VPLMN (virtual public land mobile network) when UE authenticates and authorizes; and step 2, the AAA Proxy obtains no trust relation between the HPLMN and the non-3GPP access network and judges a trust relation between the VPLMN and the non-3GPP access network, then the AAA Proxy determines to adopt a chain type access mode to access to the UE to the IP service provided by the HPLMN through the non-3GPP access network. The invention can solve the problem that how of the UE is accessed to the P-GW1 (PDN-GW1: Public Data Network-Gateway1) through the non-3GPP access network when the relation between the HPLMN and the non-3GPP access network is distrusted, the relation between the UPLMN and the Non 3GPP Accesss is trusted, and the VPLMN is not provided with an ePDG (evolved Packet Data Gateway).
Owner:福建省永阳国有资本投资集团有限公司
Method and system for wireless local area network user to access fixed broadband network
InactiveUS20150295929A1Synchronisation arrangementAccounting/billing servicesAuthentication authorization accountingBroadband network gateway
A method and system for a wireless local area network user accessing a fixed broadband network, the method includes: a broadband network gateway (BNG) device initiating an identity authenticating process to an authentication authorization accounting (AAA) server for a wireless local area network (WLAN) user; after the AAA server successfully authenticates the WLAN user, the BNG device acquiring a mobility identifier of the WLAN user from the AAA server; after receiving the mobility identifier of the WLAN user, the BNG device allowing the mobility access of the WLAN user.
Owner:ZTE CORP
Configuration method and system of Linux virtual server
ActiveCN101908967AImprove securityImprove maintenance convenienceUser identity/authority verificationData switching networksNetworked systemClient-side
The invention relates to configuration method and system of a Linux virtual server, wherein the configuration system of the Linux virtual server comprises an LVS (Linux Virtual Server), a user interface module, an AAA (Authentication Authorization Accounting) client and an instruction translating module, wherein the user interface module is used for transmitting received configuration instruction information to the AAA client and then transmitting successfully authorized configuration instruction information to the instruction translation module when receiving an authorization result returned by the AAA client, wherein the authorization result represents that the configuration instruction information is successfully authorized; the AAA client is used for transmitting the configuration instruction information to an AAA server and then transmitting the authorization result returned by the AAA server to the user interface module; and the instruction translating module is used for translating a successfully authorized configuration instruction into an operation instruction supported by the LVS and executing or notifying the LVS to execute configuration operation corresponding to the operation instruction. The invention improves the convenience for users to maintain network systems containing the LVS.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com