Fixed network perception user access method and system thereof
A technology that perceives users and fixed networks, applied in the field of communication, can solve problems such as non-support, lower user satisfaction, and unfavorable smooth progress of user services
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
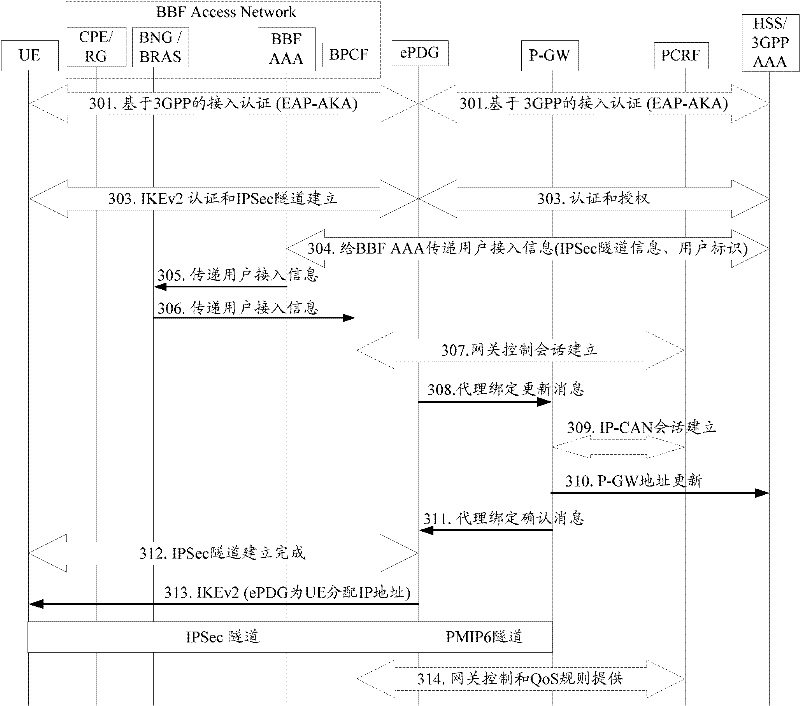
[0097] The UE accesses through the fixed network WLAN, and the mobile operator regards the fixed network access as untrustworthy access, and deploys ePDG in the mobile network to ensure the security of data transmission. When the UE establishes an IP-Sec tunnel to the ePDG, the ePDG authenticates to the 3GPP AAA. After passing the authentication, the 3GPP AAA establishes a session with the BBF AAA to notify the BBF AAA of user access. The message used for notification carries user access information, and the message may also indicate that the UE has passed authentication in the mobile network. BBF AAA sends user access information to BPCF through BRAS / BNG. BPCF discovers PCRF according to the user ID, and establishes S9 with PCRF * session. The specific implementation process is as image 3 Shown:
[0098] 301. The UE accesses the EPC network through the untrusted BBF network. The 3GPP-based Extensible Authentication Protocol-Authentication and Key Agreement (EAP-AKA) acc...
Embodiment 2
[0113] The UE access scenario in the second embodiment is the same as that in the first embodiment, the main difference is that after the access authentication is completed, the ePDG provides the user access information to the 3GPP AAA through the P-GW. The specific implementation process is as Figure 4 Shown:
[0114] 401. For the process of UE accessing the network, performing access authentication, and allocating an IP address for the UE, refer to steps 301 to 302 of Embodiment 1.
[0115] 402. The UE starts the IKEv2 authentication process, and performs an authentication procedure between the ePDG and the 3GPP AAA. After passing the authentication, an IP-Sec tunnel is established between the UE and the ePDG.
[0116] 403. The ePDG sends a Proxy Binding Update message to the P-GW to request PMIP registration. The message also includes user access information, and the user access information includes user identifiers (such as IMSI / NAI), IP-Sec tunnel information, and the...
Embodiment 3
[0125] The UE accesses through the fixed network WLAN, and the mobile operator regards the fixed network access as trusted access. The UE and the P-GW establish a DSMIP tunnel, the P-GW transmits user access information to the 3GPP AAA, the 3GPP AAA establishes a session with the BBF AAA, and notifies the BBF AAA of user access. The message used for notification carries user access information, and the message may also indicate that the UE has passed authentication in the mobile network. BBFAAA uses the session established between the user and the BRAS / BNG during the fixed network authentication phase to pass the user access information to the BRAS / BNG. The BRAS / BNG further discovers the BPCF according to the IP address and the configuration relationship, and transmits the user access information to the BPCF. BPCF discovers PCRF according to the user ID, and establishes S9 with PCRF * session. The specific implementation process is as Figure 5 Shown:
[0126] 501. The UE...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com