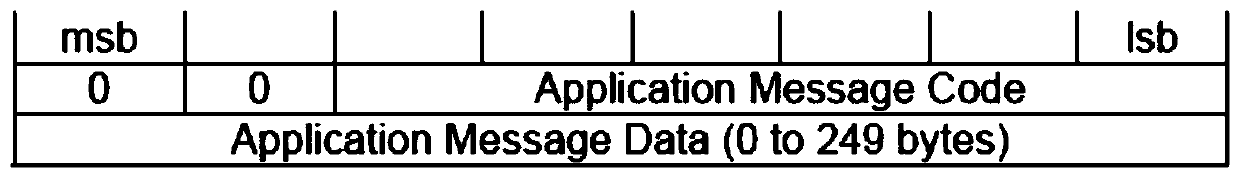
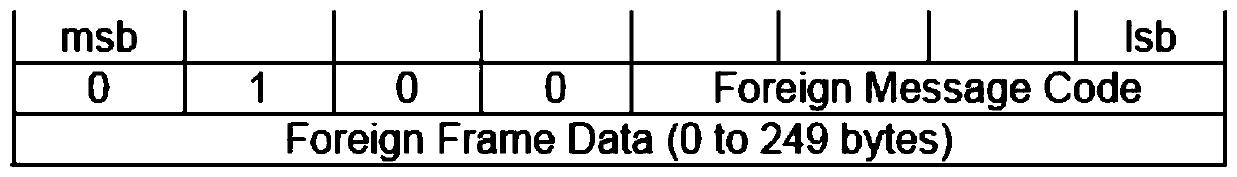
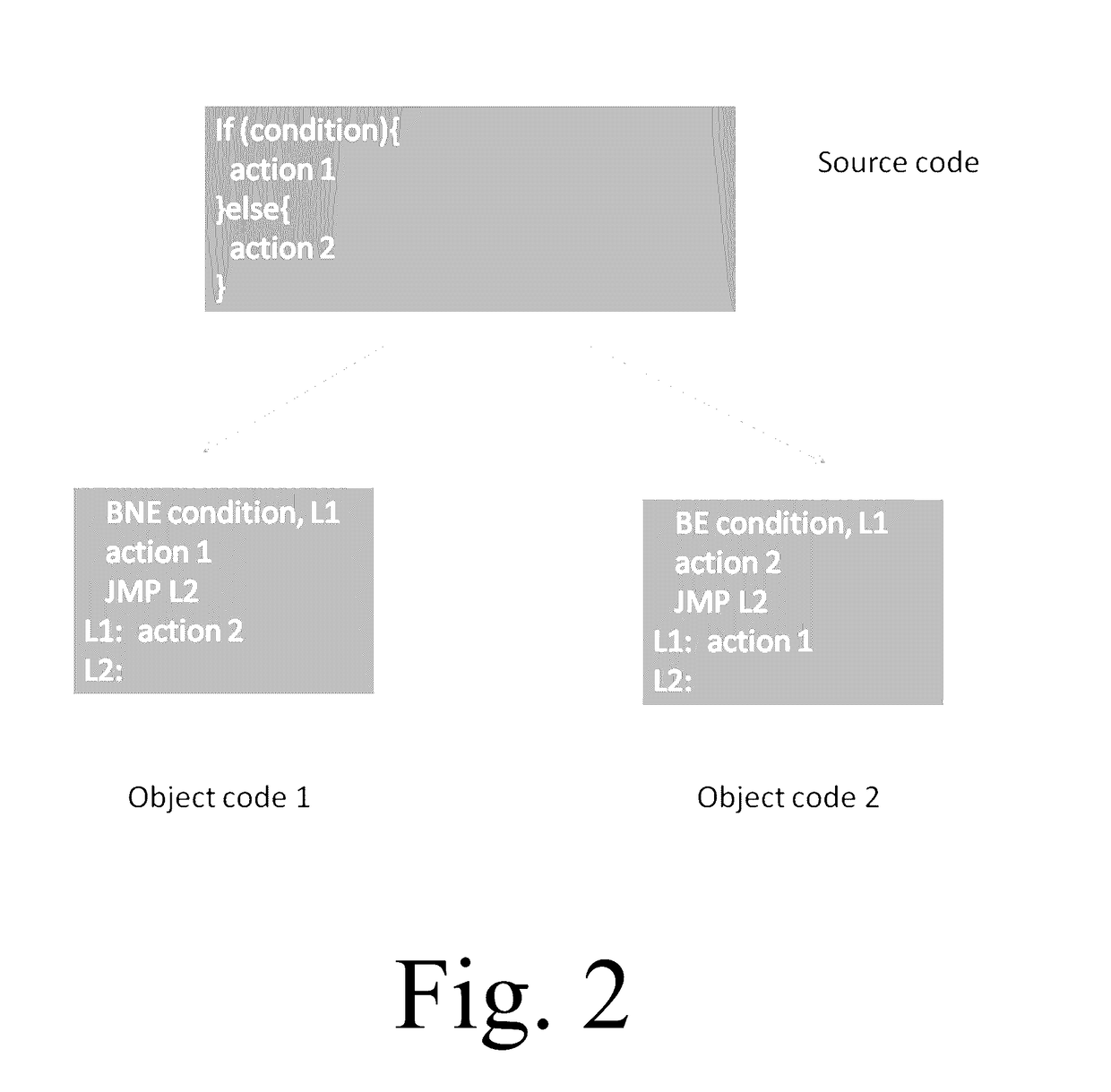
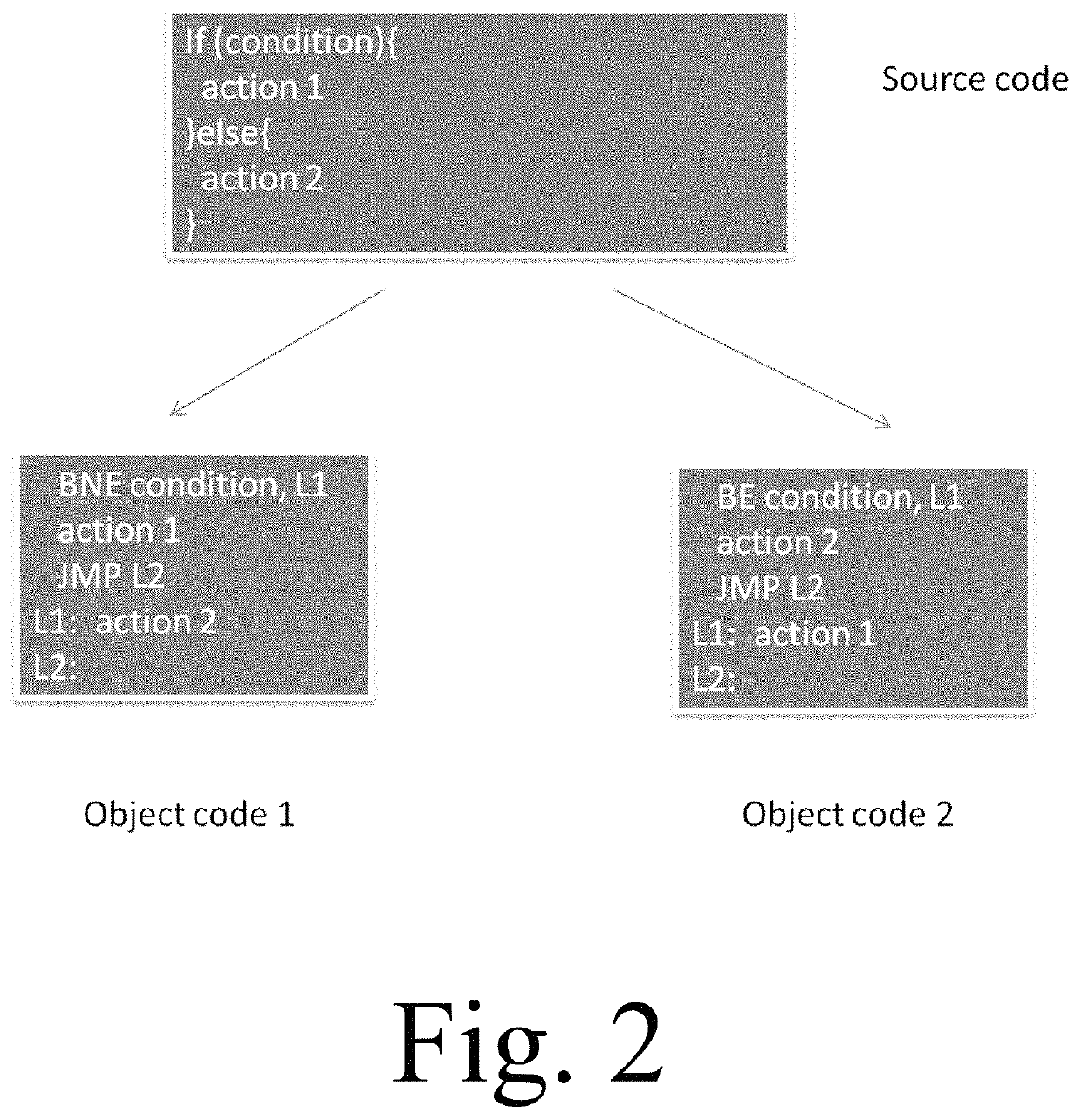
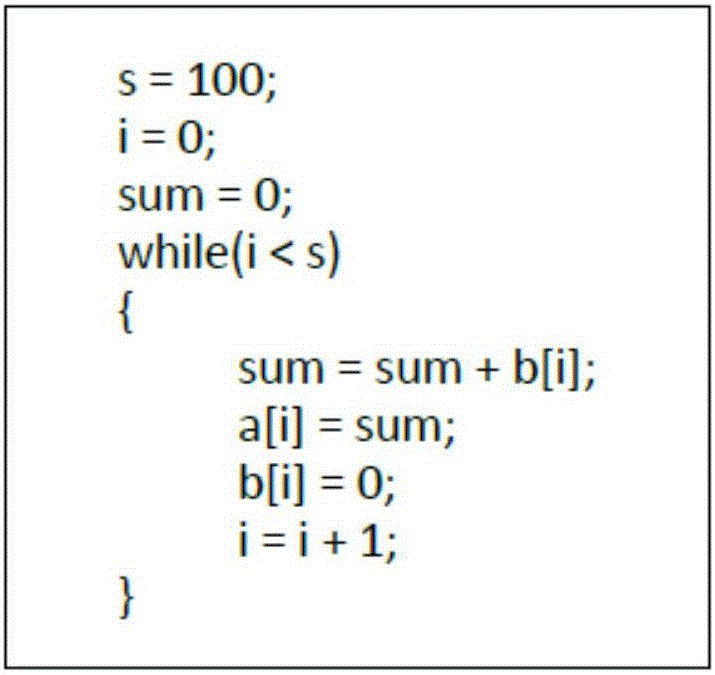
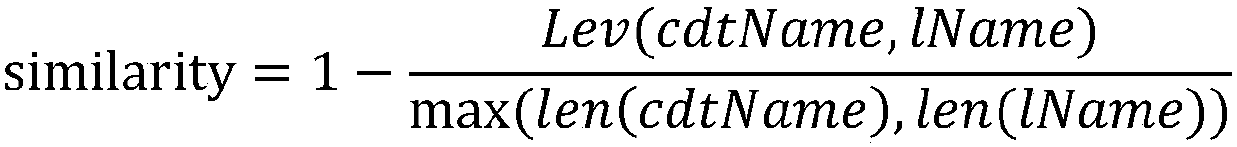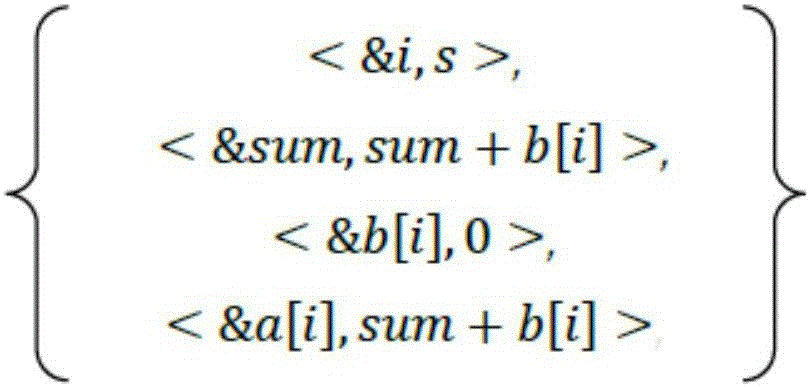Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
30 results about "Assignment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
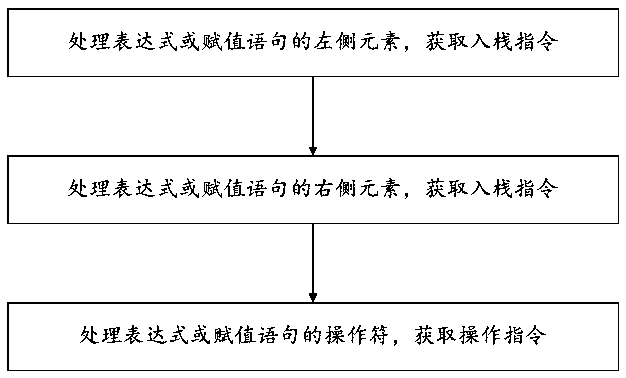
In computer programming, an assignment statement sets and/or re-sets the value stored in the storage location(s) denoted by a variable name; in other words, it copies a value into the variable. In most imperative programming languages, the assignment statement (or expression) is a fundamental construct.
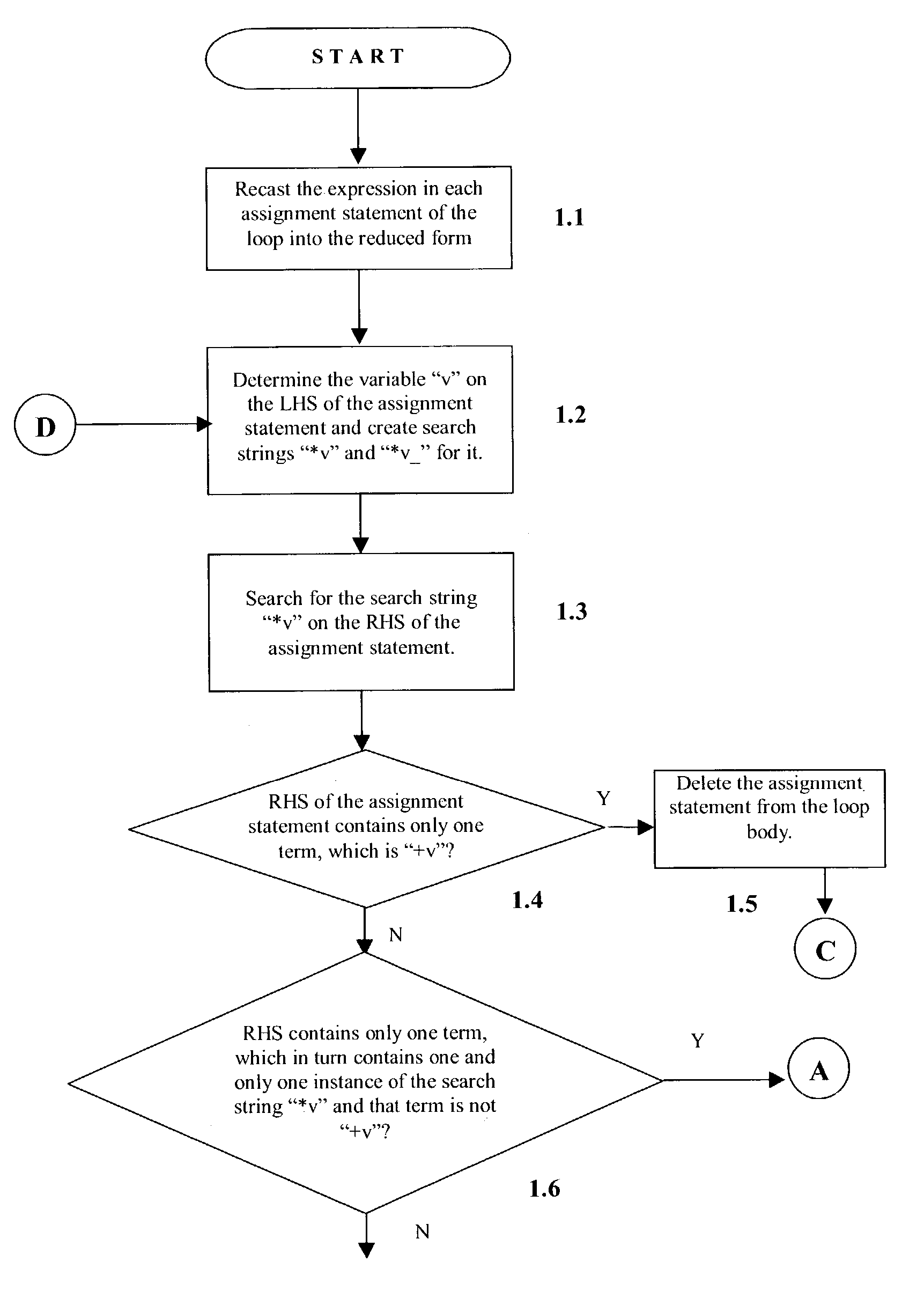
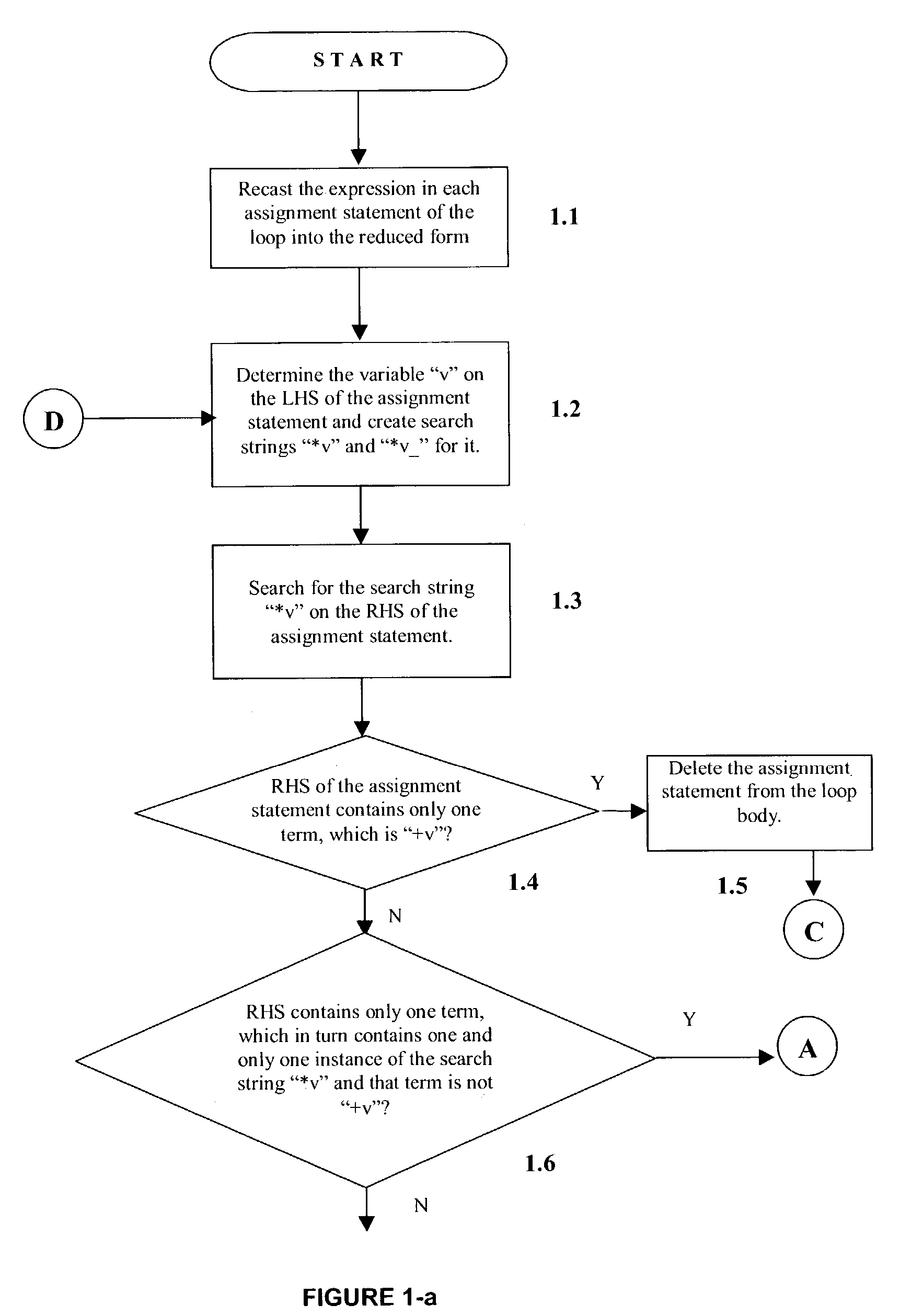
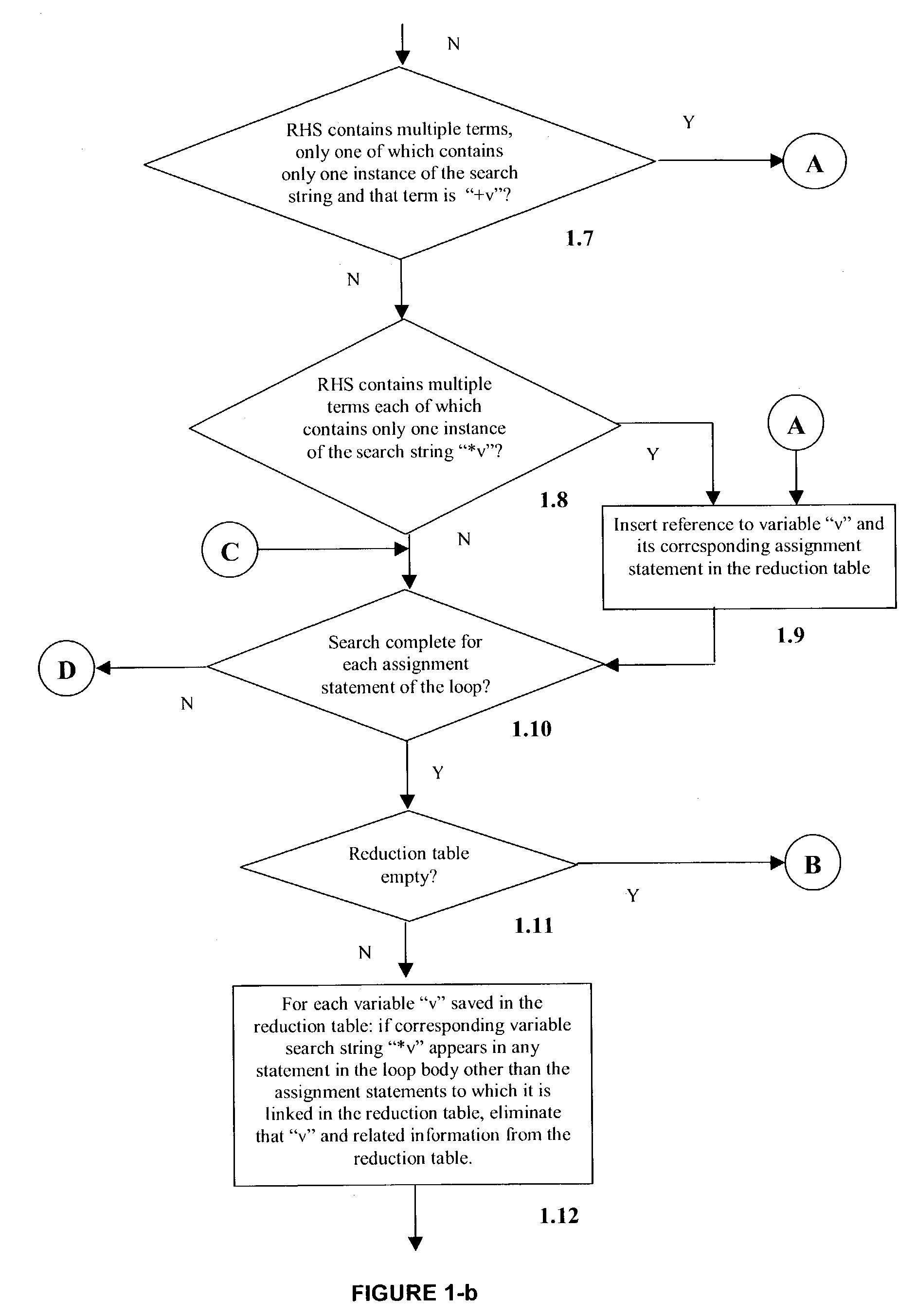
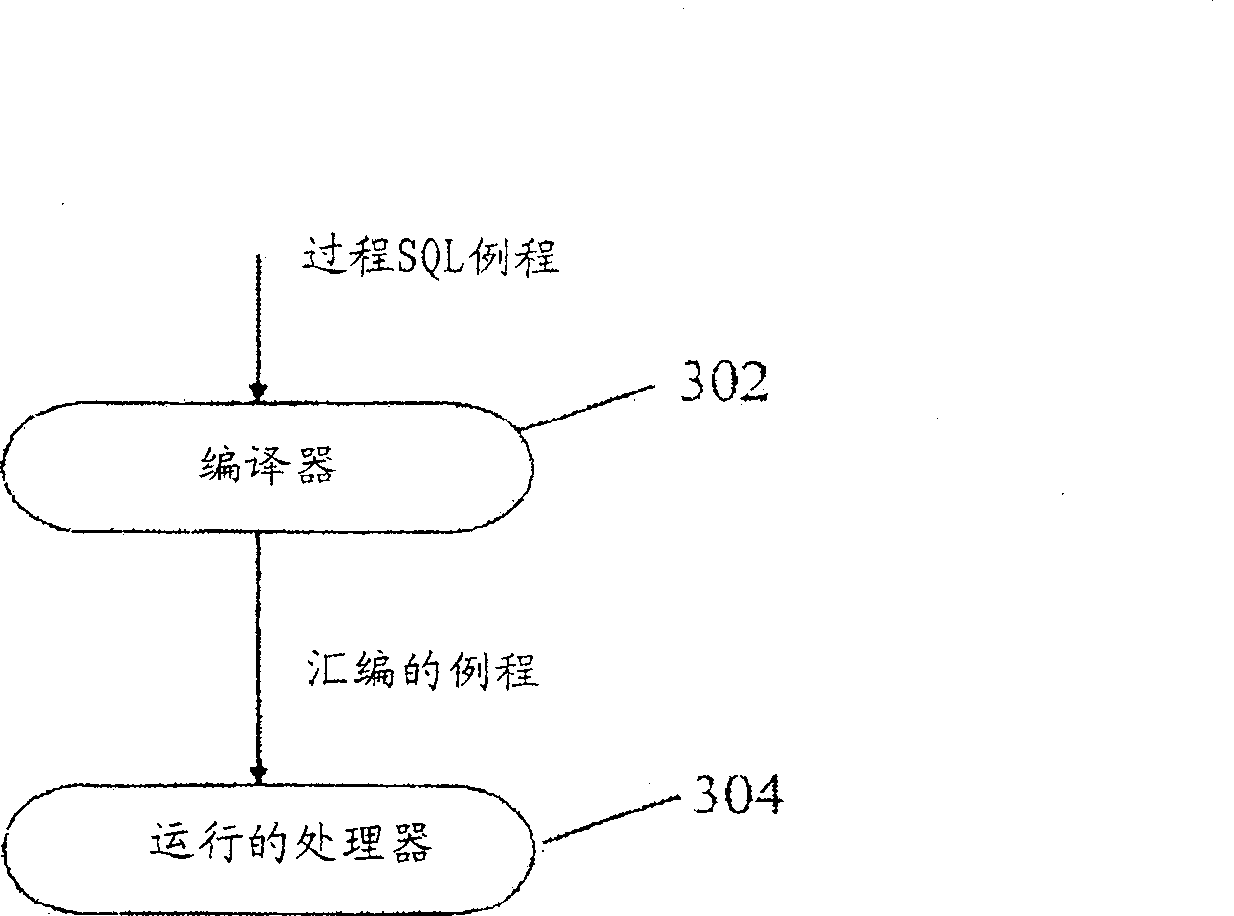
Detection of reduction variables in an assignment statement
This invention relates to a method, system and program product to detect reduction variables in assignment statements in the source code for enabling the parallel execution of program loops. The reduction variables found using the method herein described can be tagged to the respective loops and passed to a compiler through compiler directives for parallelizing the reduction operation, along with the information about each variable's respective associative operator.
Owner:IBM CORP
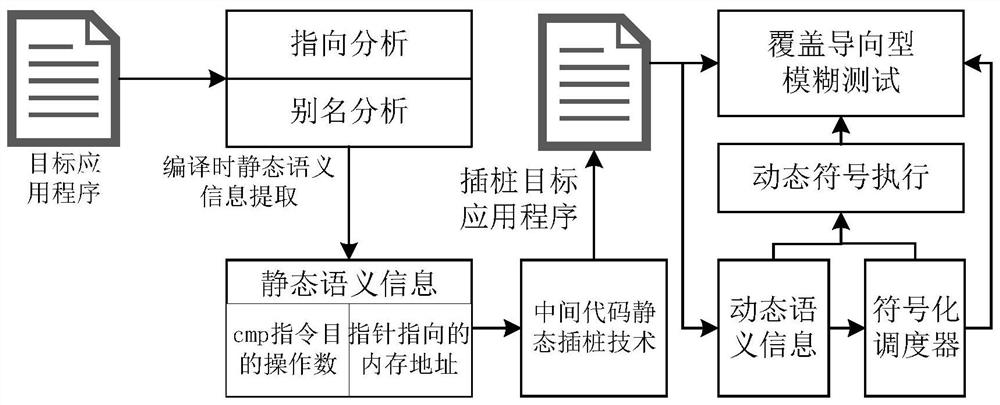
Multi-level hybrid vulnerability automatic mining method
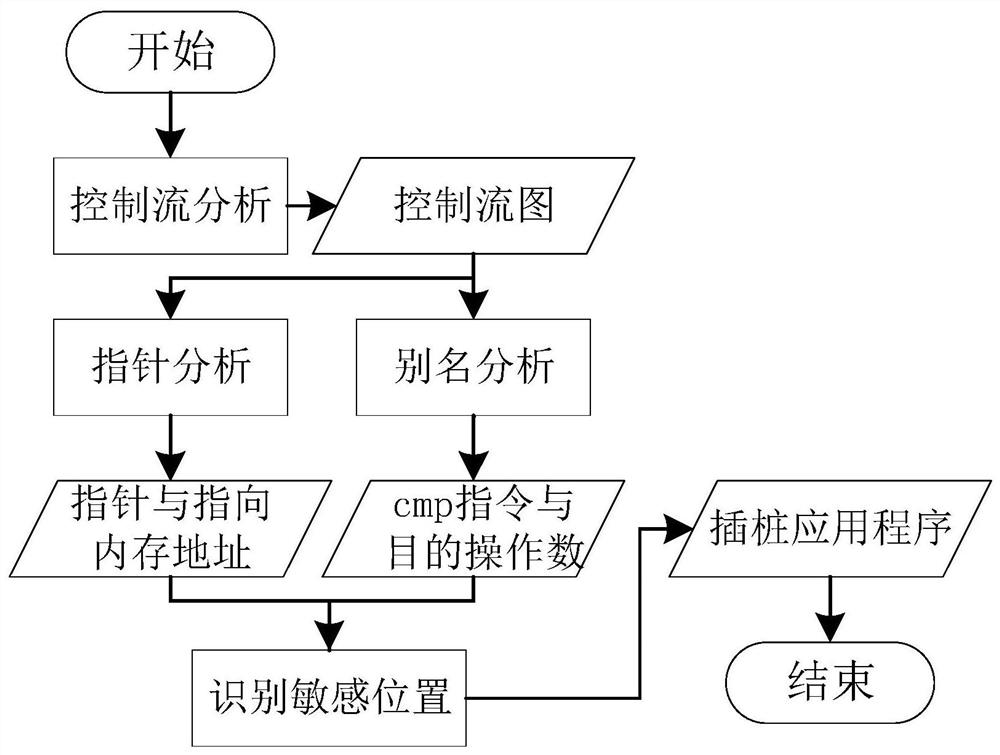
ActiveCN111859388ARich semantic informationImplement extractionSoftware testing/debuggingPlatform integrity maintainanceMemory addressRepresentation language
The invention belongs to the technical field of computers, and particularly relates to a multi-level hybrid vulnerability automatic mining method, which comprises the following steps: S1, obtaining pointer distribution and assignment processes in a program by utilizing pointer analysis through a static analysis technology, and recording memory address positions pointed by all pointers; obtaining adestination operand of the CMP type instruction by using an alias analysis technology so as to clarify a jump address of the target program; and S2, realizing instrumentation of the monitoring code to the key position of the target program through an intermediate code static instrumentation technology. According to the invention, the binary executable program is translated into the middle-layer representation language of the compiler, and compared with the binary executable program, the middle-layer representation language source code obtained through processing of the method has more semantic information; compared with C / C + + language analysis, the static analysis technology for the LLVM IR intermediate representation language can realize finer-grained static semantic information extraction during compiling.
Owner:GUANGZHOU UNIVERSITY
Object-based programming method and object-based programming system in C language programming
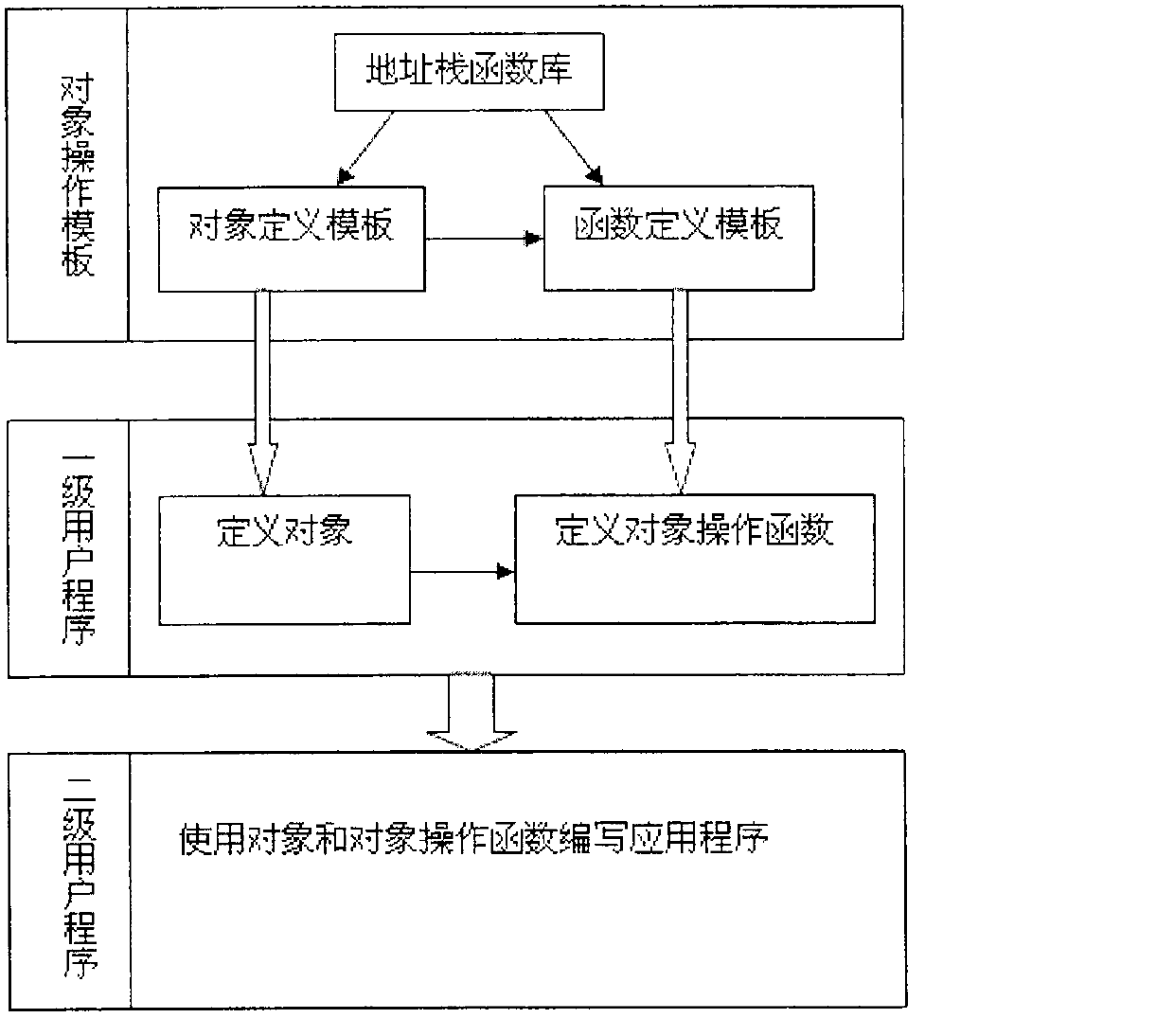
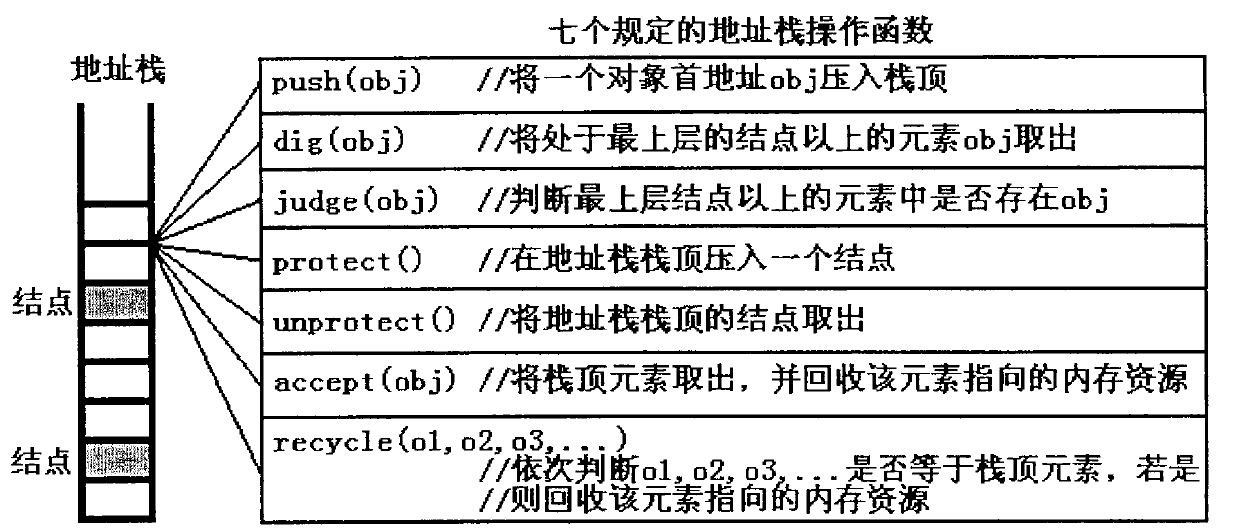
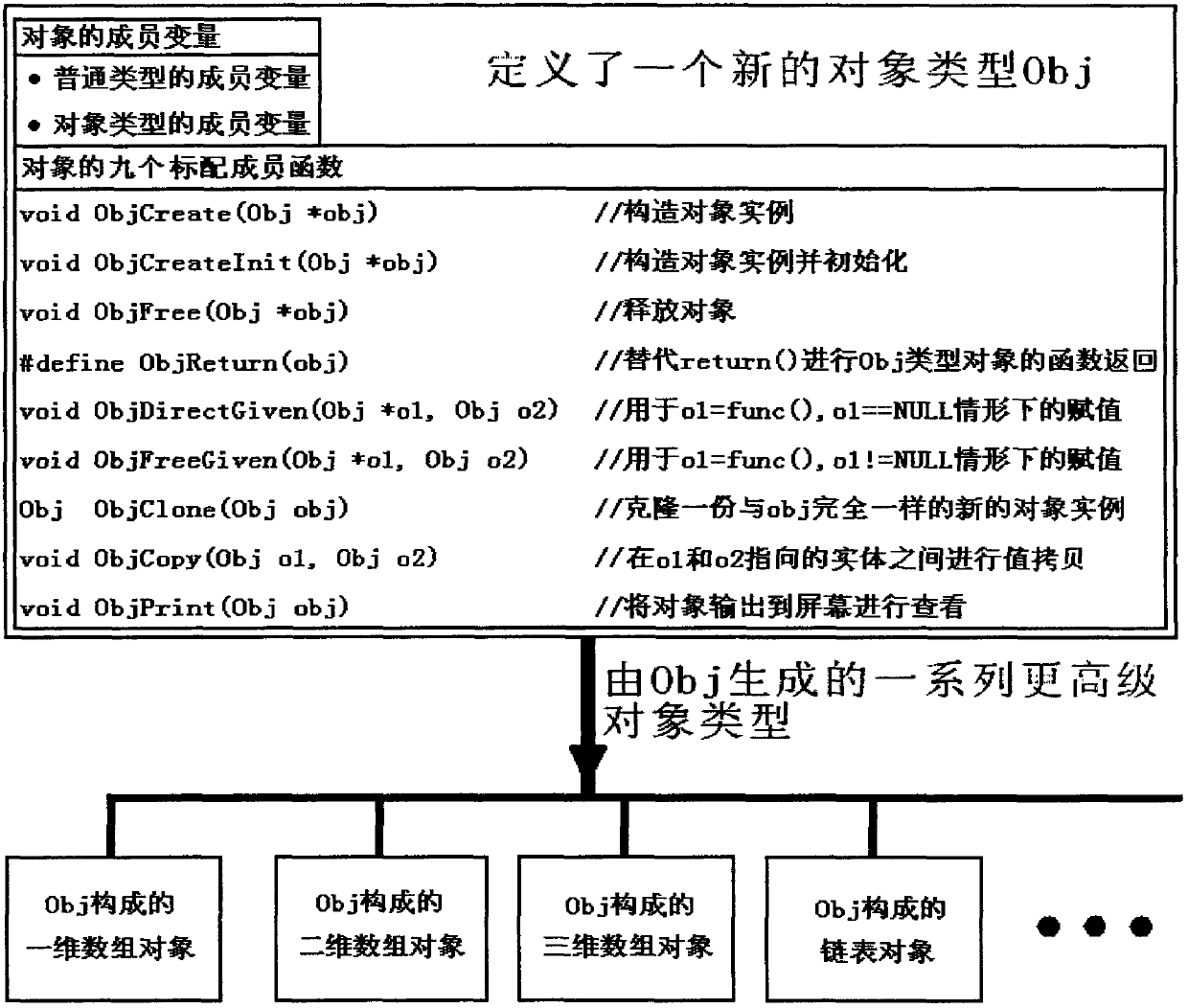
Certain currently popular programming languages (such as C++) are highly efficient but can easily bring about memory errors, and certain currently popular programming languages (such as Java) are safe in memories but lower in efficiency. The invention discloses an object-based programming method and an object-based programming system in C language programming, and the system is a convenient, safe and high-efficiency programming framework. The system utilizes the stack technique to efficiently judge the attribute of an 'object' (i.e. a non-generic type variable), also standardizes assignment and other operations on the object, and can release object resources and optimize the efficiency of object usage (or the efficiency of parameter transfer) simultaneously. The system provides defining templates for objects and object-operating functions, so that programmers can conveniently define the objects and the object-operating functions, the objects and functions defined by the defining templates can be conveniently subjected to recursionrecur and can be conveniently nested, invoked and operated in any other complex ways like generic type variables and functions, and the problems of memory safety and efficiency are automatically processed by the templates.
Owner:INST OF FLUID PHYSICS CHINA ACAD OF ENG PHYSICS
Condition compiling implementation method and device, equipment and storage medium
PendingCN113031963AIncrease flexibilitySmall limitationsCode compilationCreation/generation of source codeSoftware engineeringNon local
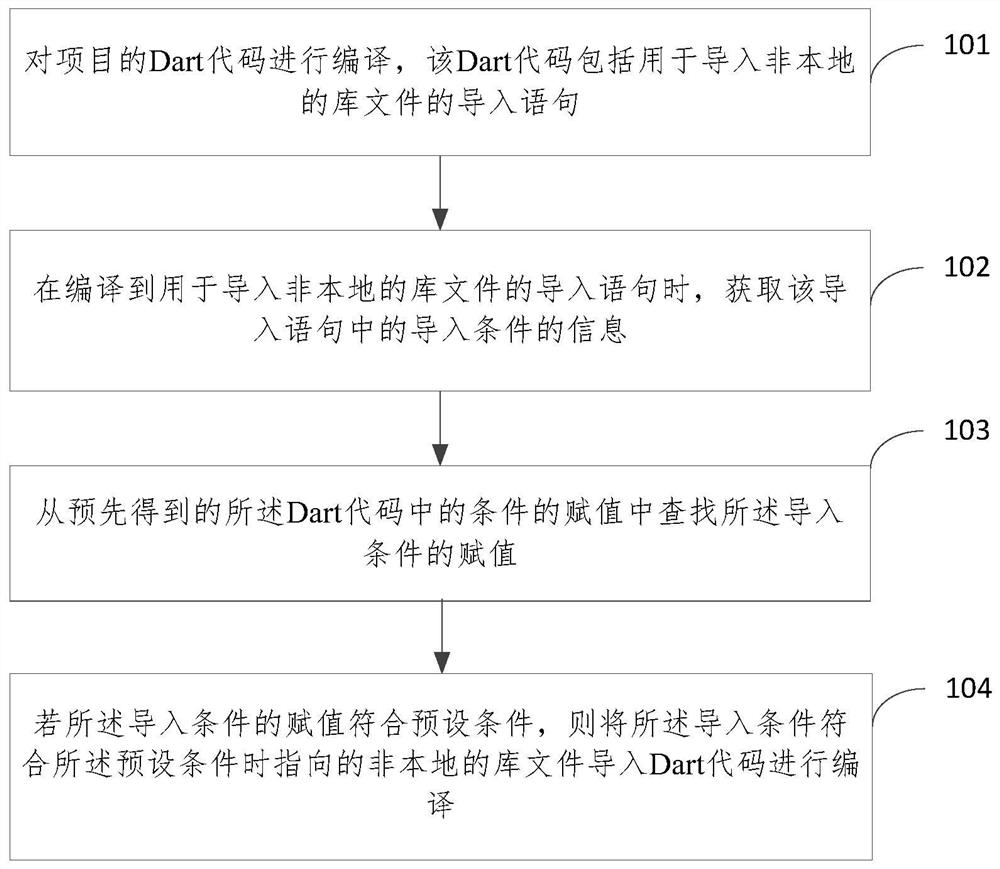
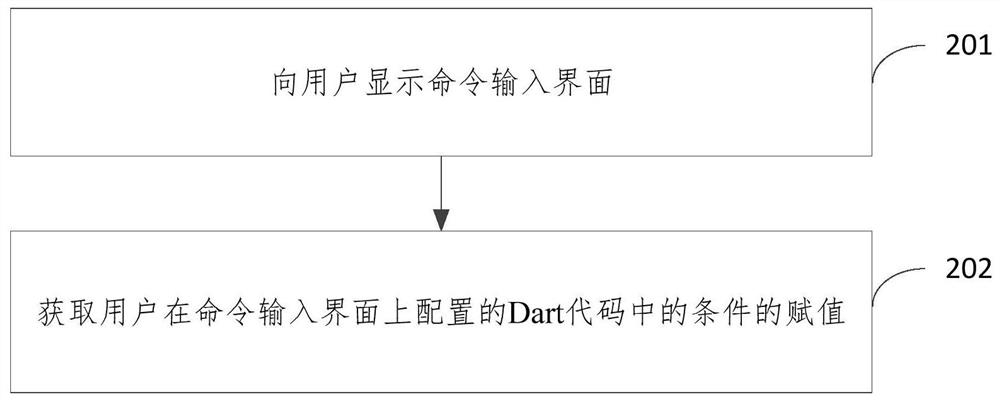
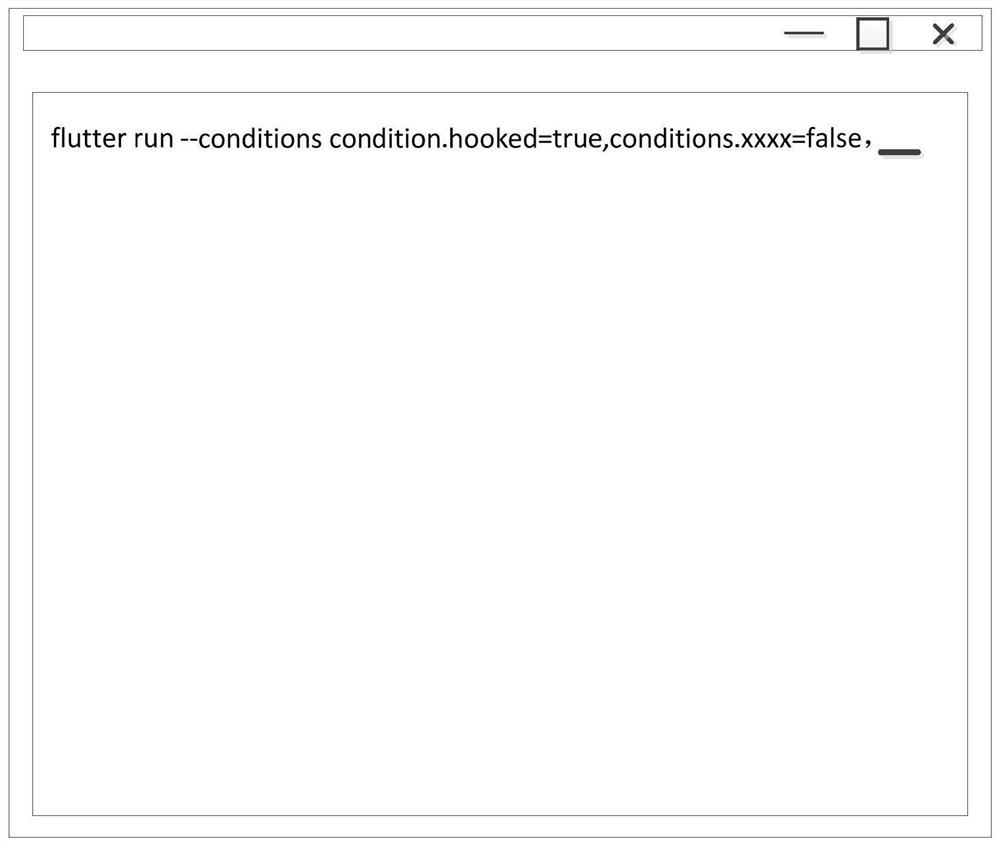
The embodiment of the invention relates to a condition compiling implementation method and device, equipment and a storage medium, and the method comprises the steps: compiling a Dart code of a project, obtaining the information of an import condition in an import statement when the import statement used for importing a non-local library file is compiled, and obtaining the information of the import condition in the import statement; searching the assignment of the import condition from the pre-obtained assignment of the condition in the Dart code, and when the assignment of the import condition meets the preset condition, importing the non-local library file pointed when the assignment of the import condition meets the preset condition into the Dart code for compiling, so that the condition compiling based on the Dart programming language is realized. According to the method, the non-local library file can be imported for compiling in Dart compiling, so that the flexibility of Dart programming is improved, and the limitation of Dart technology application is reduced.
Owner:BEIJING BYTEDANCE NETWORK TECH CO LTD
Interprocedural static slice extracting method based on idUCf quinary structure
ActiveCN104699599AReduce complexitySimplified Control Flow RelationshipsSoftware testing/debuggingComputational scienceAlgorithm
Owner:SHANGHAI PRECISION METROLOGY & TEST RES INST
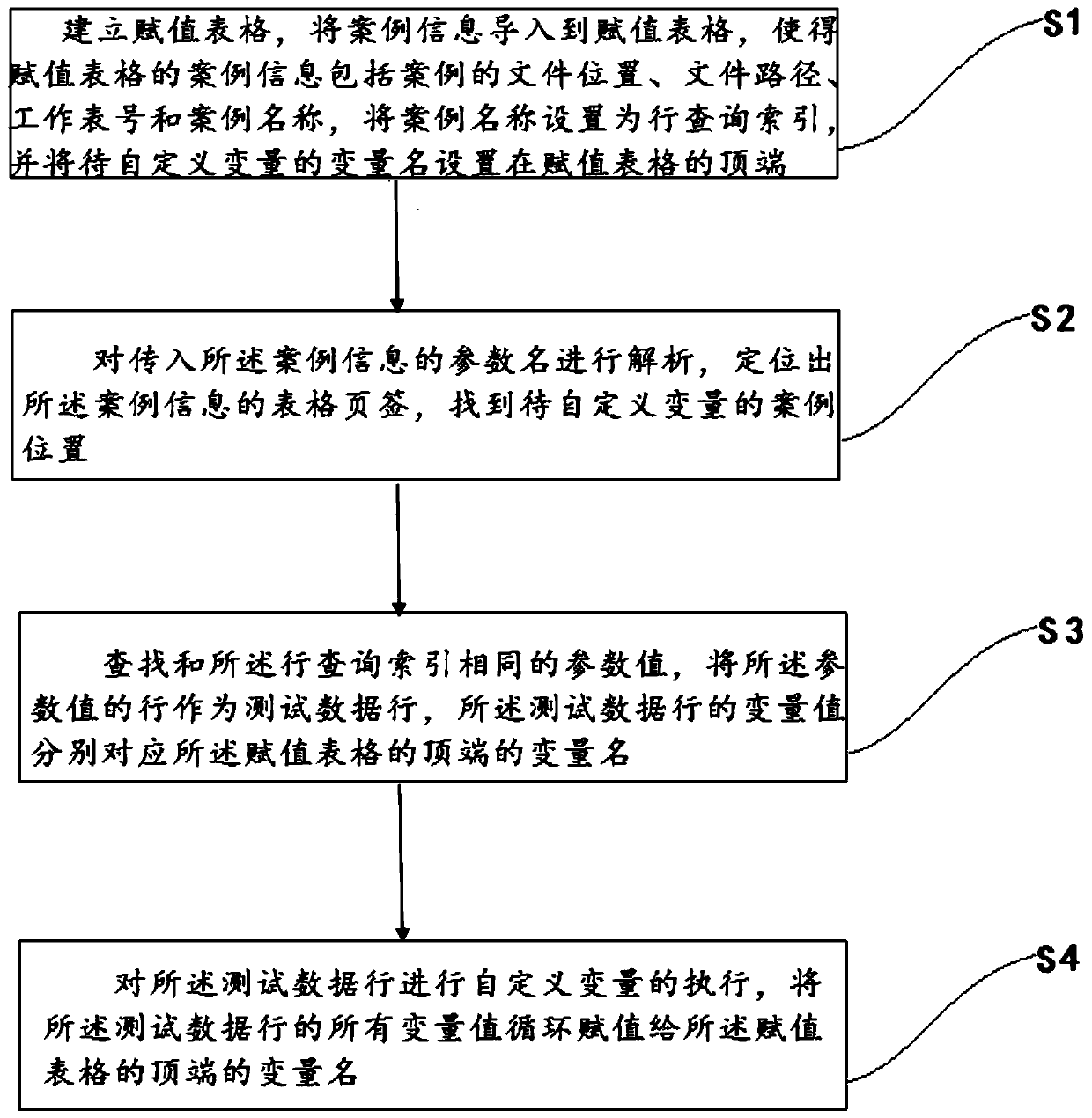
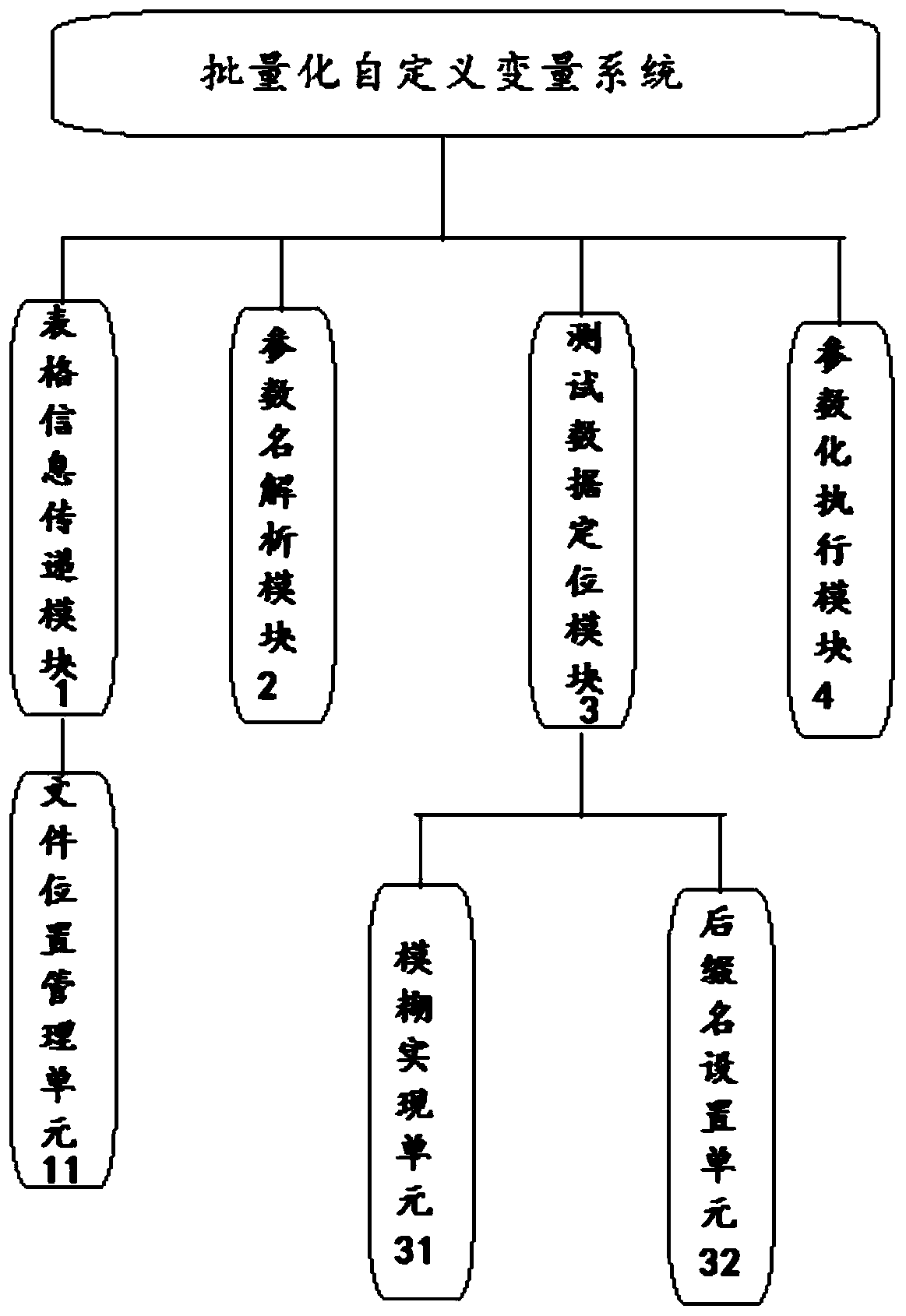
Method and system for customizing variables in batches
ActiveCN110968509AImprove efficiencyLower skill requirementsDatabase queryingSoftware testing/debuggingAlgorithmTheoretical computer science
The invention discloses a method and a system for customizing variables in batches. The method comprises the following steps: establishing an assignment table, importing case information into the assignment table, setting case names as line query indexes, and setting variable names of to-be-customized variables at the top end of the assignment table; analyzing the parameter names of the introducedcase information, positioning table tabs of the case information, and finding out case positions of to-be-customized variables; searching a parameter value which is the same as the line query index,taking a line of the parameter value as a test data line, and enabling variable values of the test data line to respectively correspond to variable names at the top end of the assignment table; and executing self-defined variables on the test data line, and circularly assigning all variable values of the test data line to variable names at the top end of the assignment table. According to the embodiment of the invention, the data separation of the test data and the automatic script is realized, the variable names can be quickly subjected to batch parameterized assignment, and the efficiency ofcustom variable assignment is remarkably improved.
Owner:SUNING CLOUD COMPUTING CO LTD
Method for realizing definite software operating time in single task operating environment
ActiveCN101957742AGuaranteed certaintySimple methodMachine execution arrangementsPathPingSoftware engineering
The invention discloses a method for realizing definite software operating time in a single task operating environment, which is characterized by comprising the following steps of: (1) programming a function meeting requirements by using a conventional programming method; (2) dividing external input, external output and algorithm of the function definitely; (3) establishing a local variable for the external output; (4) finding out all switch statements in the function; (5) establishing local variables for the external output of all the switch statements; (6) cutting the programs of all the switch statements out of the switch statements, and modifying the output of the switch statements into the local variables of the output of the switch statements; (7) in the switch statements, adding the local variables of the output of the switch statements to an assignment statement output by a switch statement operation result and an assignment statement for a global variable; (8) adding the switch statement operation result to follow-up program operation; (9) assigning the local variable of the external output to the external output; and finally (10) modifying functions called in the program. The invention can ensure that the operating time of the same function is definite without change when outputs and routes are different.
Owner:NANJING NRIET IND CORP
Inter-object conversion and assignment method and device
PendingCN110764770ALarge amount of overcomingOvercoming high couplingCode compilationCreation/generation of source codeTheoretical computer scienceComputers technology
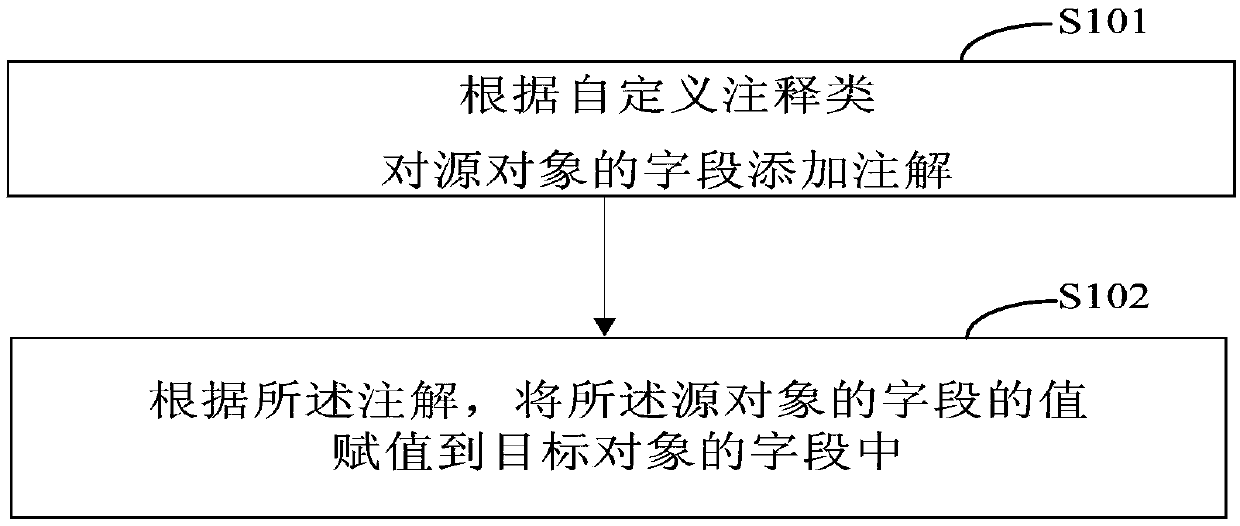
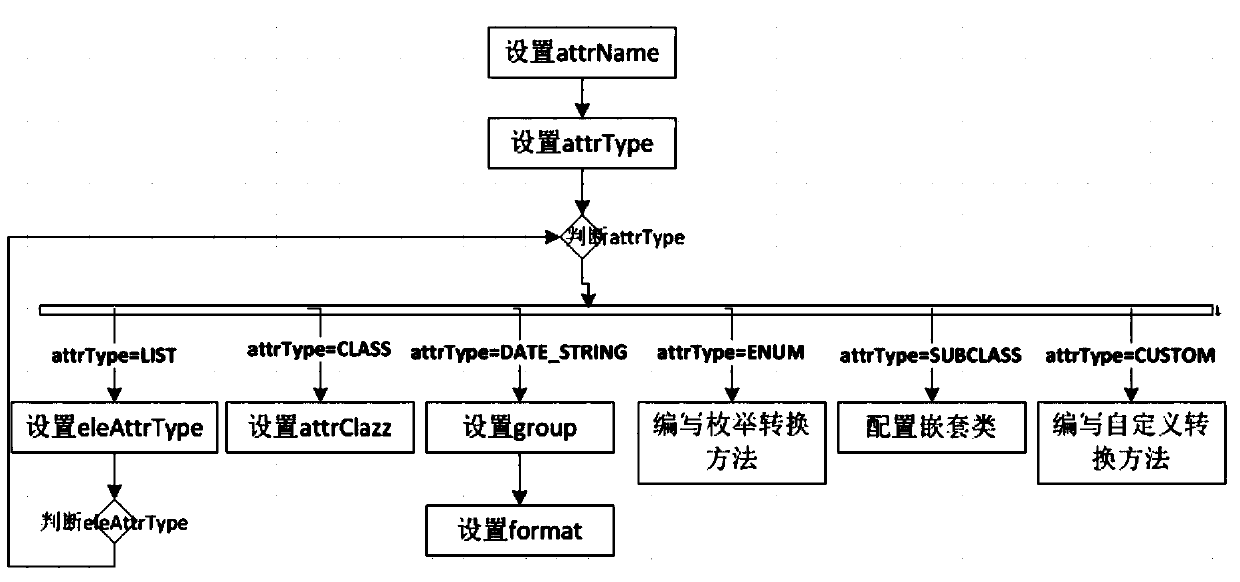
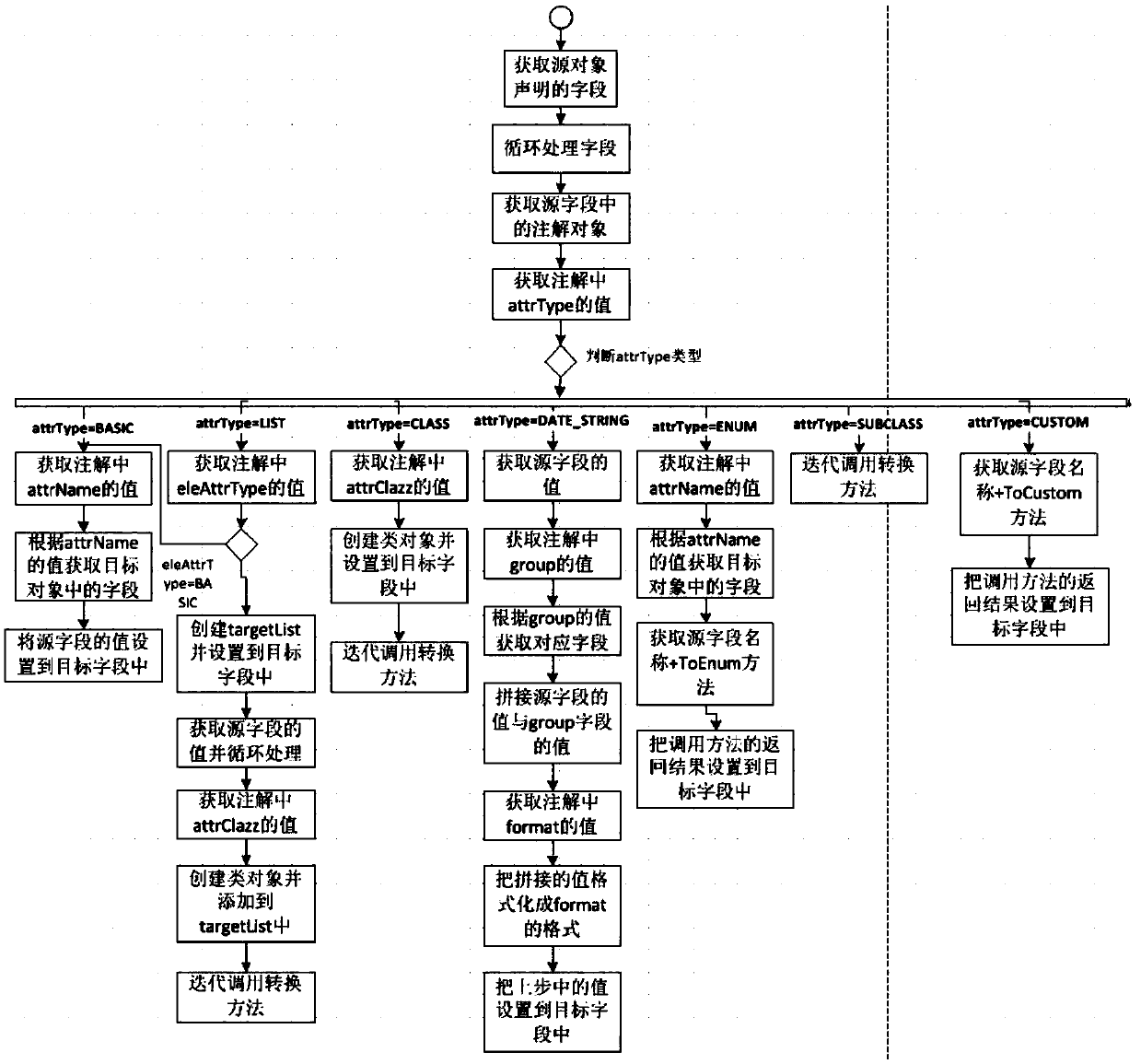
The invention discloses an inter-object conversion and assignment method and device, and relates to the technical field of computer technologies. A specific embodiment of the method comprises the steps of adding annotations to fields of a source object according to a user-defined annotation class; and according to the annotation, assigning the value of the field of the source object to the field of the target object. According to the embodiment, the technical problems that in the prior art, the code amount of conversion and assignment between objects is large, the coupling degree is high, anduniversality is not achieved are solved, and the technical effects that conversion and assignment between objects are more convenient, and the universality of conversion and assignment is greatly improved are achieved.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Multi-language intelligent contract compiling method based on blockchain
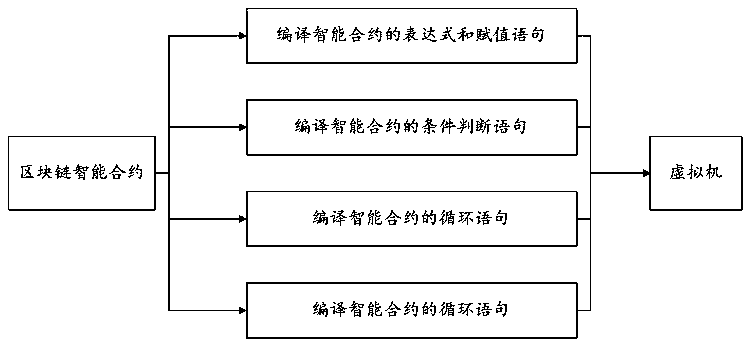
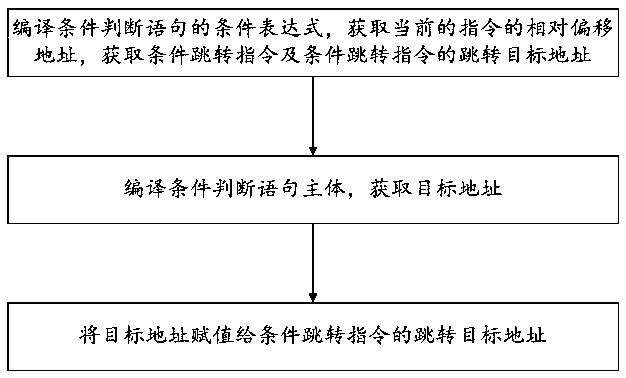
ActiveCN111399850ALower operating thresholdReduce learning costsProgramming languages/paradigmsEnergy efficient computingSoftware engineeringSmart contract
The invention discloses a multi-language intelligent contract compiling method based on blockchain. The method comprises the following steps: compiling an expression and an assignment statement of anintelligent contract; compiling a conditional judgment statement of the smart contract; compiling a loop statement of the intelligent contract; and compiling a function statement of the intelligent contract. During compiling, the method can be compatible with and support intelligent contracts compiled by multiple programming languages, the compiling efficiency is improved, the learning cost of different program languages is reduced, and the running threshold of the intelligent contracts is greatly reduced.
Owner:象链网络科技(上海)有限公司
Program running method and device and computing device
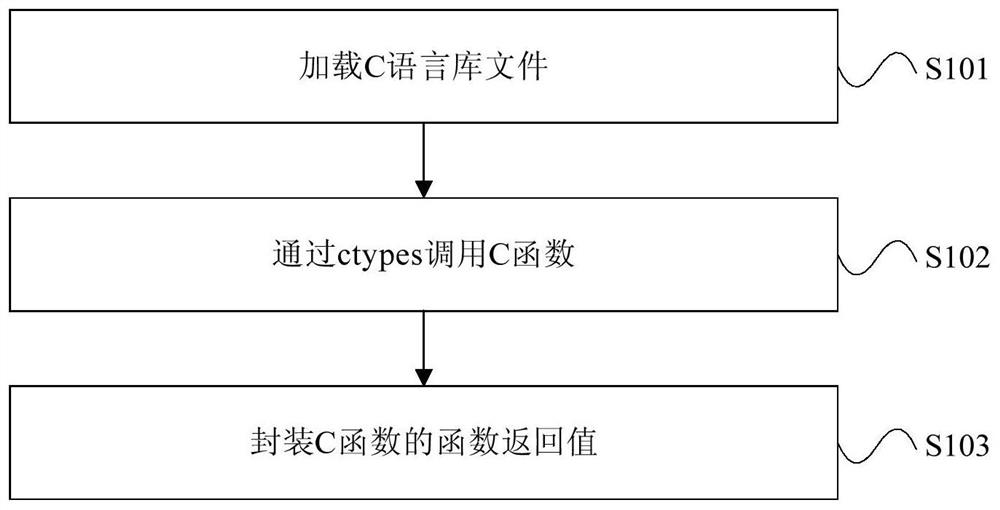
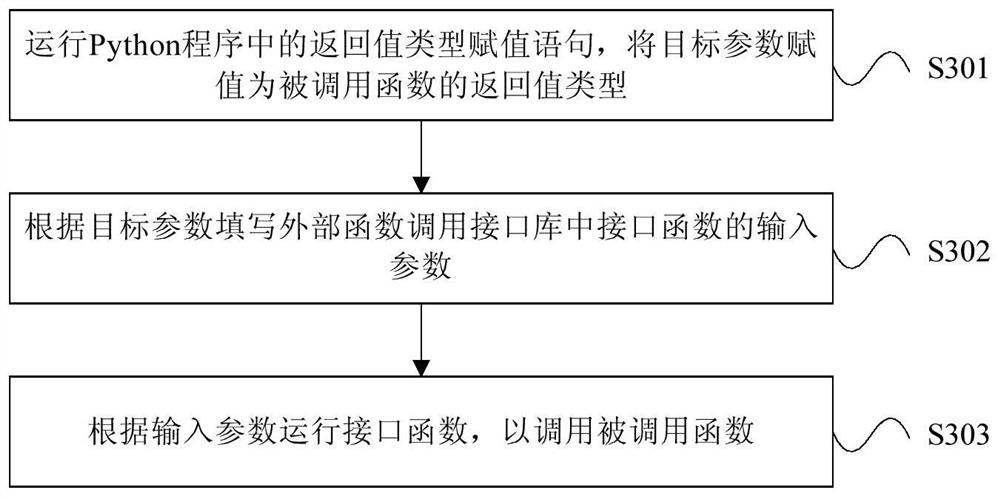
PendingCN111610966AImprove stabilityImprove acceleration performanceExecution paradigmsCreation/generation of source codePython languageExtensibility
The invention provides a program running method and device and a computing device. The program running method comprises the following steps: running a return value type assignment statement in a Python program, and assigning a target parameter as a return value type of a called function; wherein the programming language of the called function is different from the Python language; filling in inputparameters of an interface function in the external function call interface library according to the target parameters; wherein the input parameters comprise a function return value type and a function return value occupation length; and running the interface function according to the input parameter to call the called function. By running the return value type assignment statement in the Pythonprogram, the running instability and expandability of the Python program are improved.
Owner:LOONGSON TECH CORP
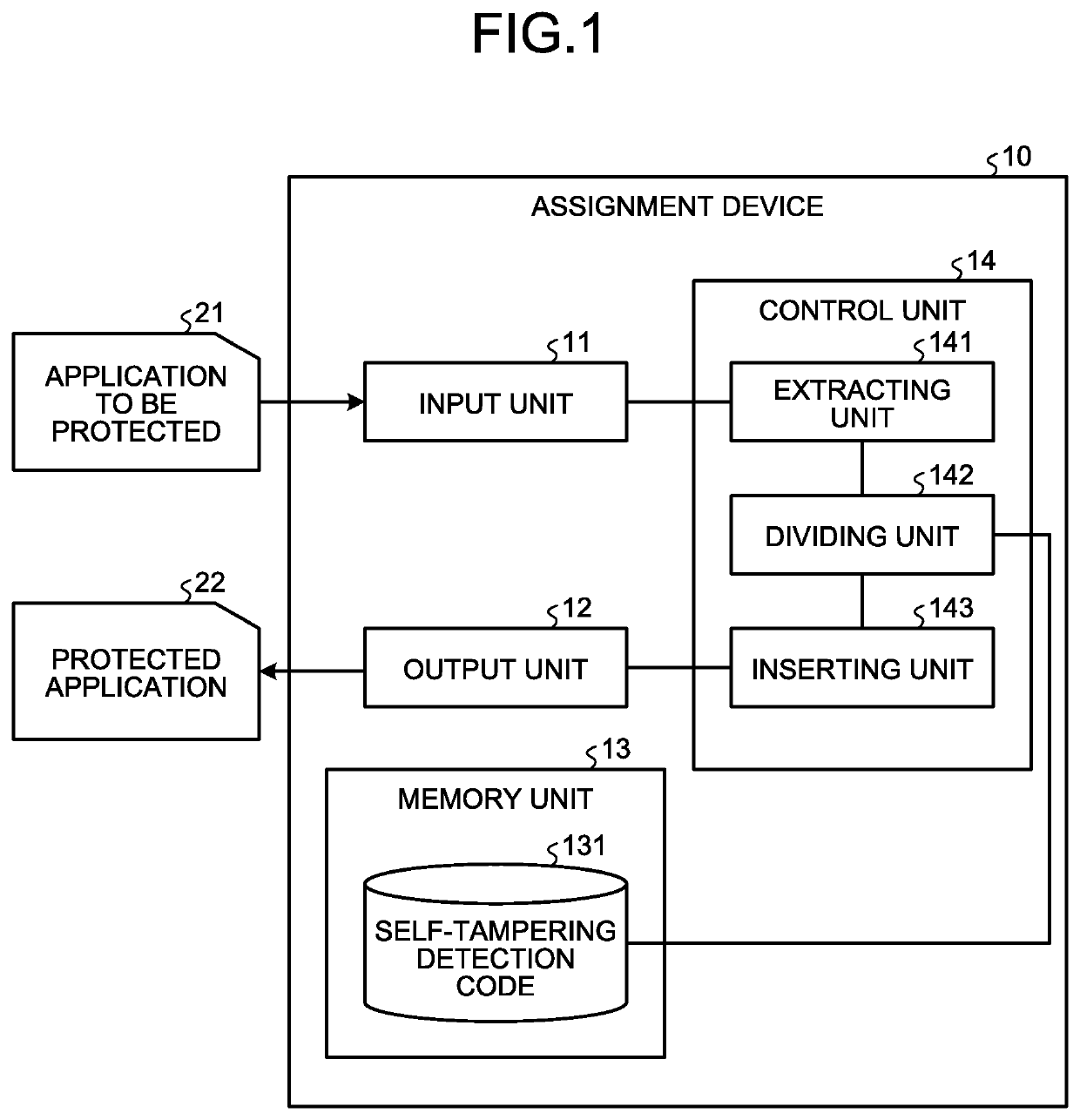
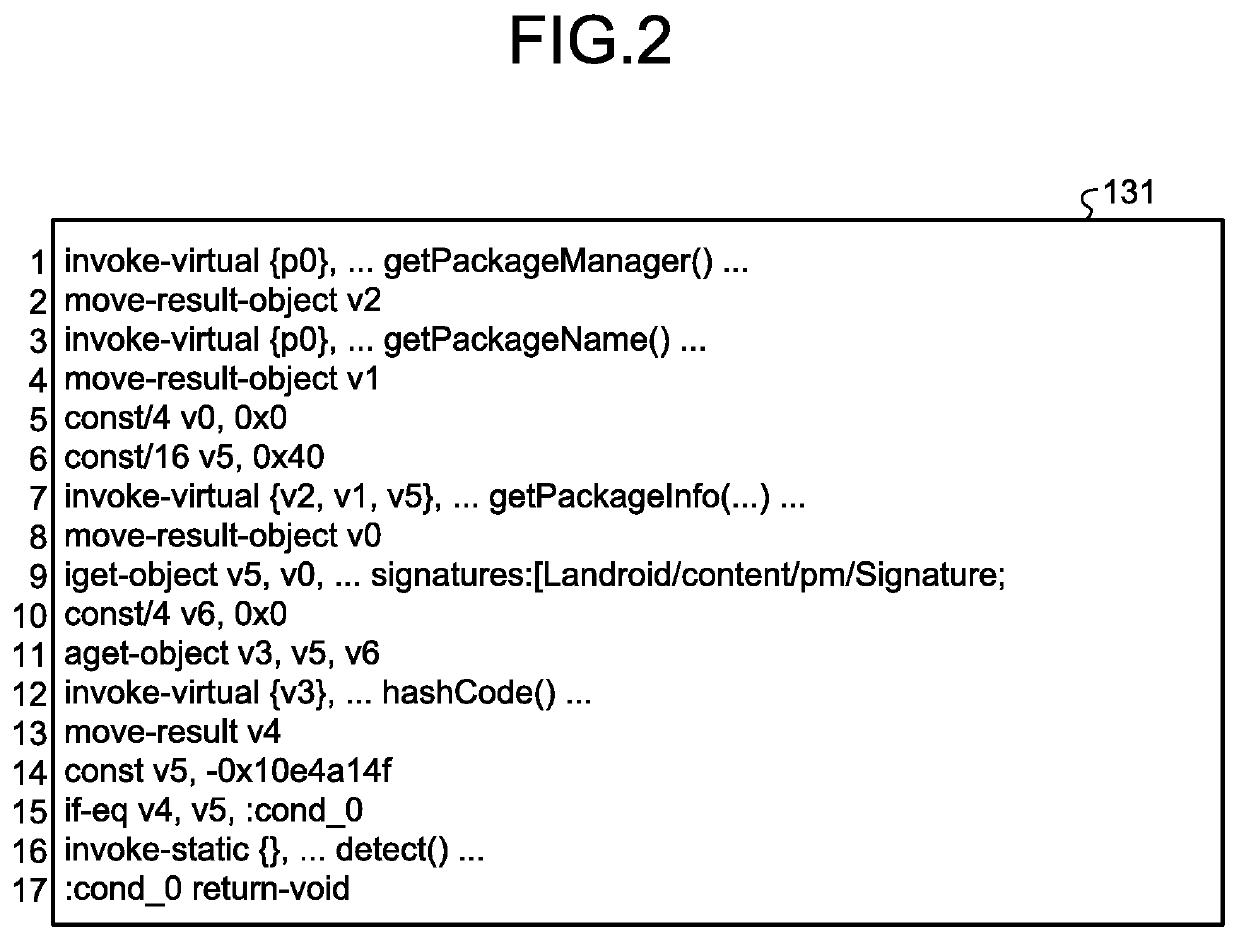
Assignment device, assignment method, and assignment program
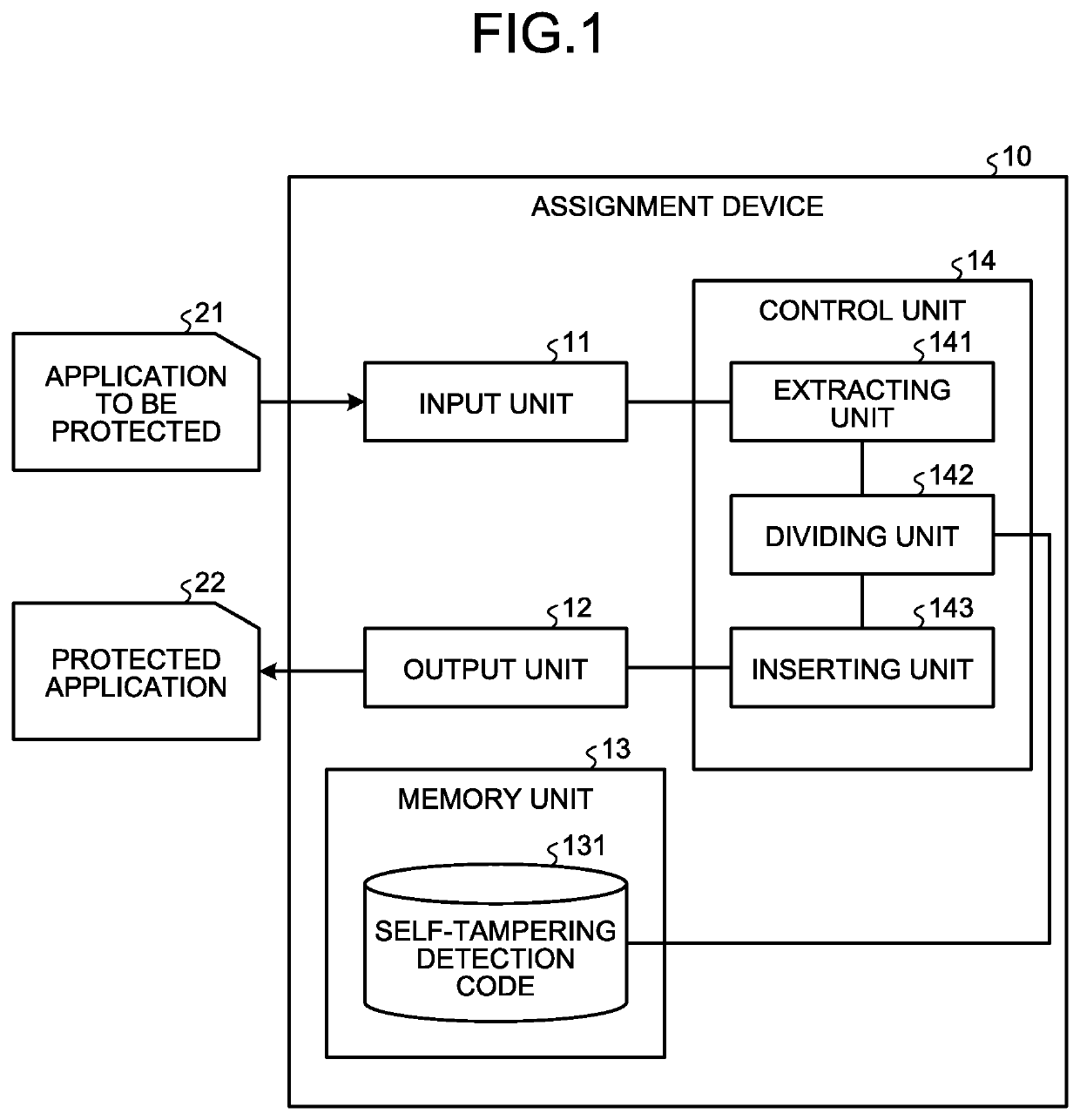
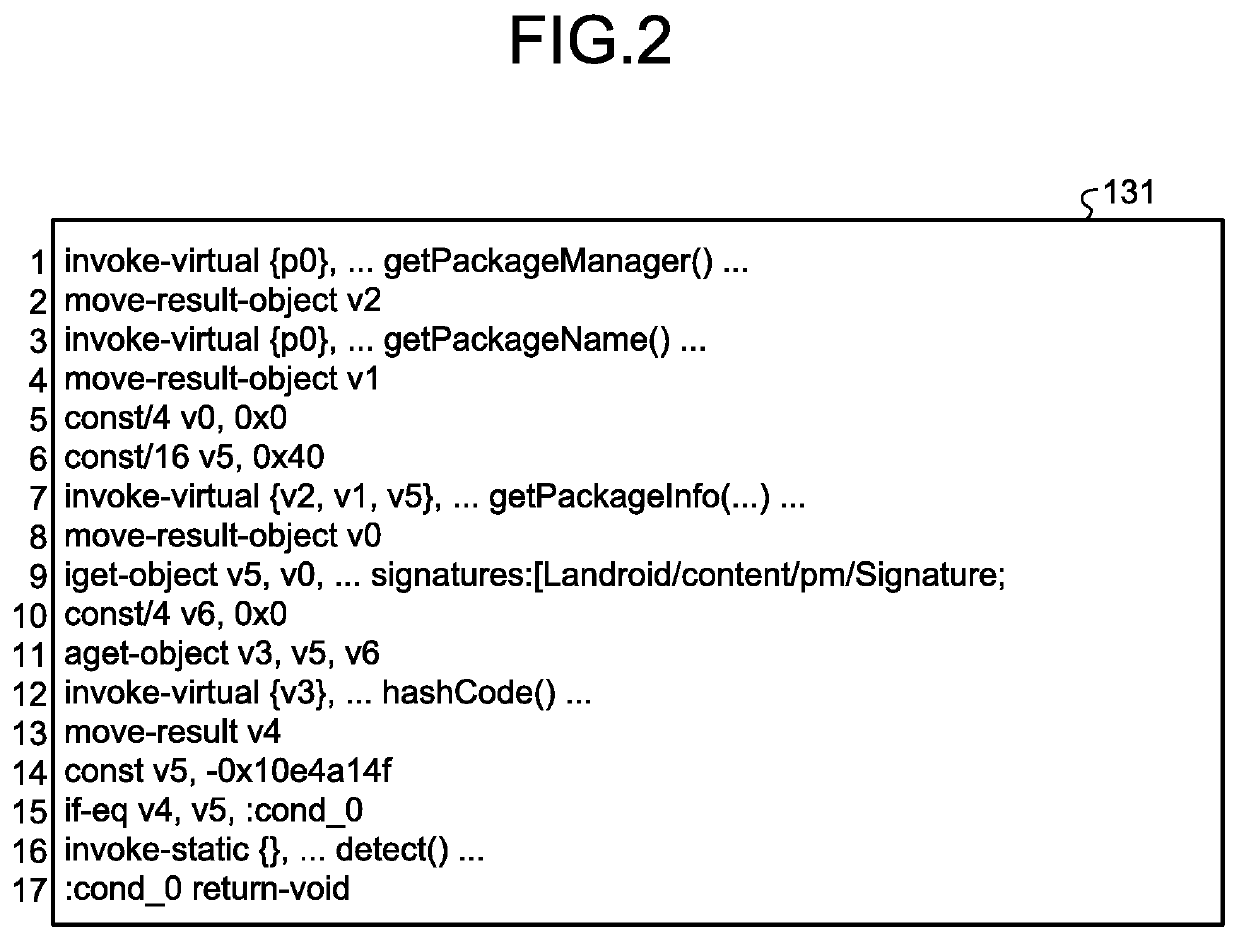
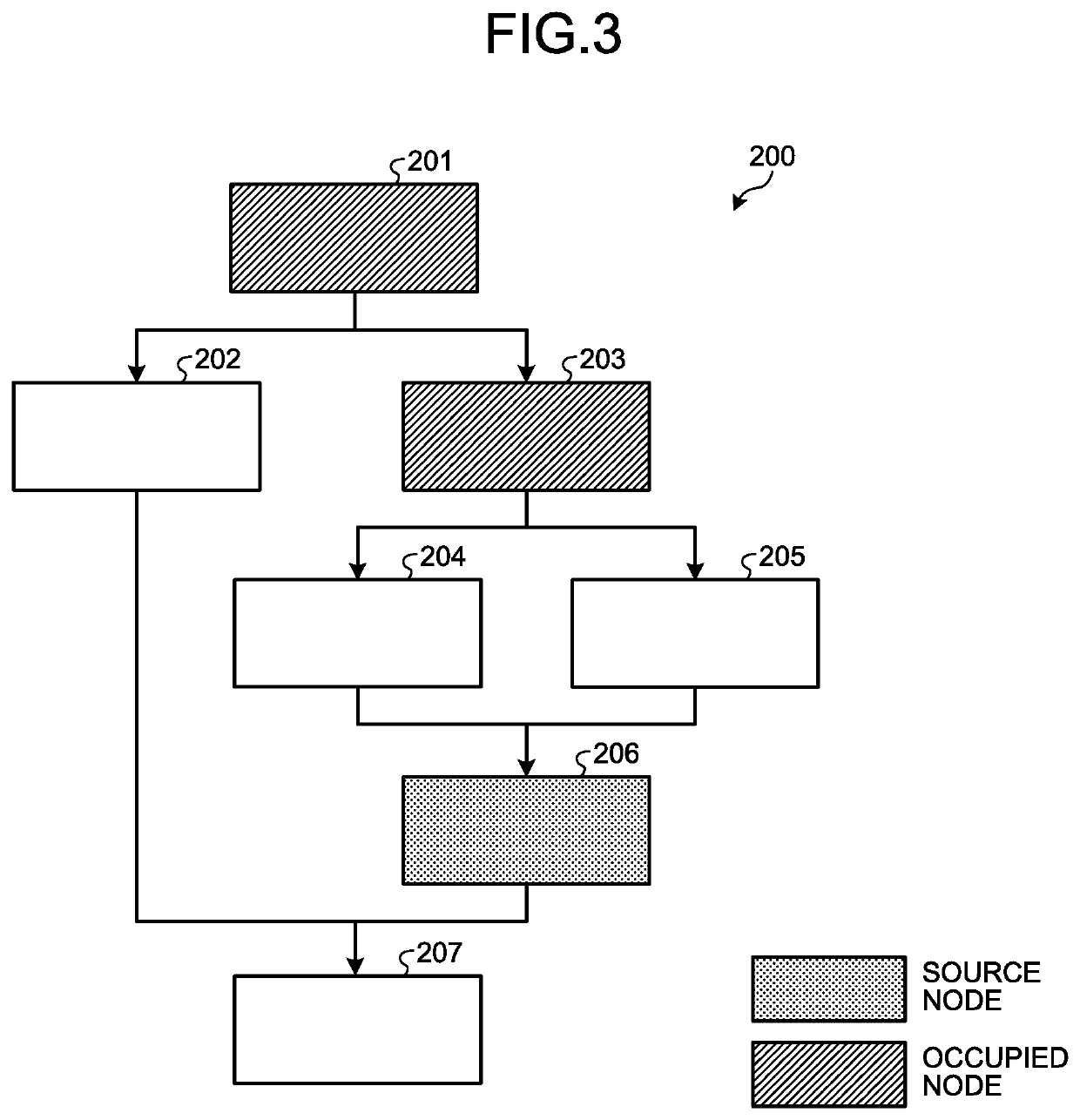
ActiveUS20200042695A1Easy to findDigital data protectionPlatform integrity maintainanceParallel computingEngineering
An extracting unit randomly extracts a block from among the blocks of instruction strings constituting the byte code of a first program and, at the time of execution of the first program, extracts the blocks which are invariably executed before the randomly-extracted block. A dividing unit randomly divides, into a plurality of blocks, the instruction strings constituting the byte code of a second program which enables detection of tampering of the first program. An inserting unit inserts the plurality of blocks, which are obtained by division by the dividing unit, at different positions in the block extracted by the extracting unit, while maintaining the execution sequence written in the second program.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
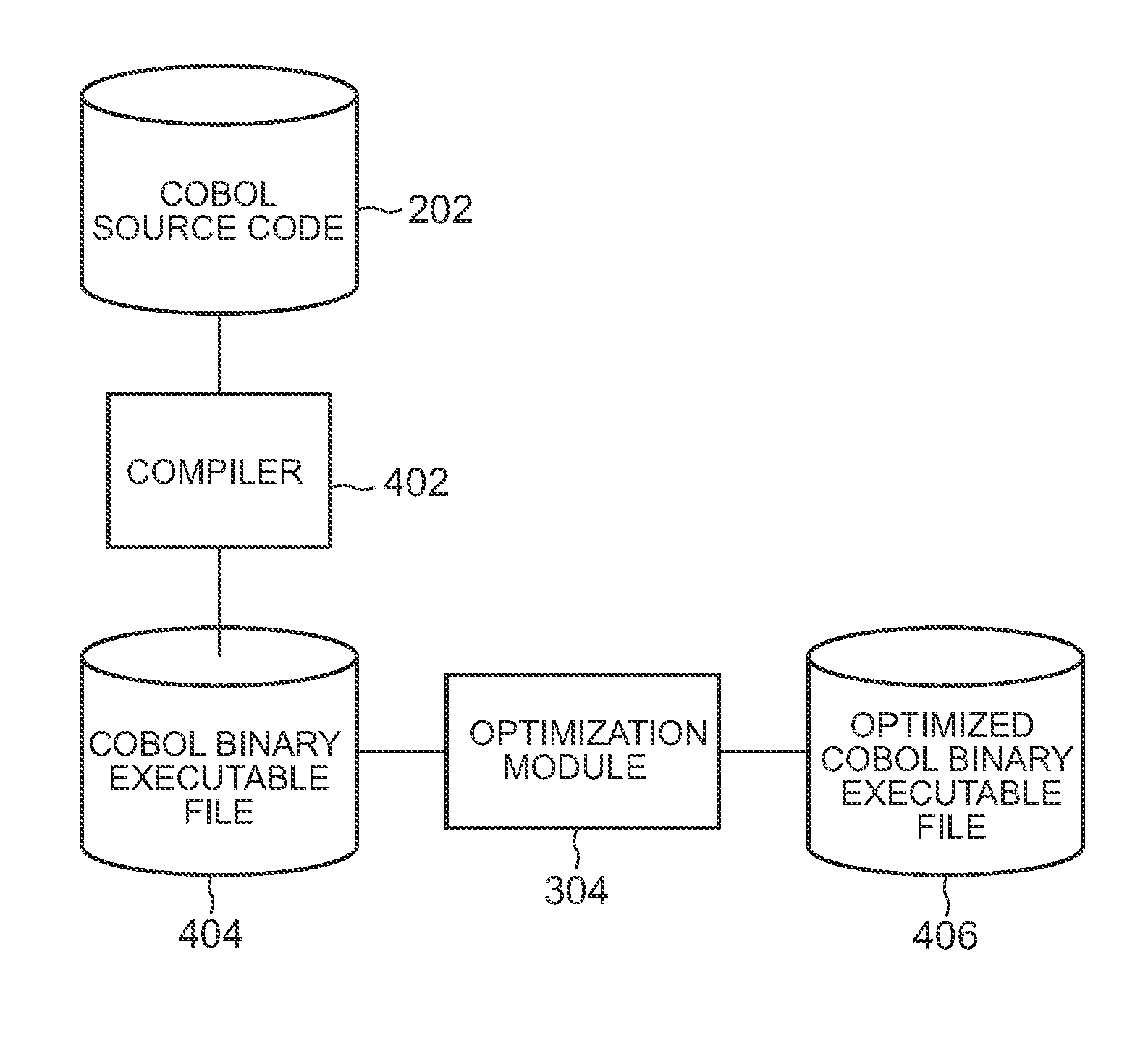
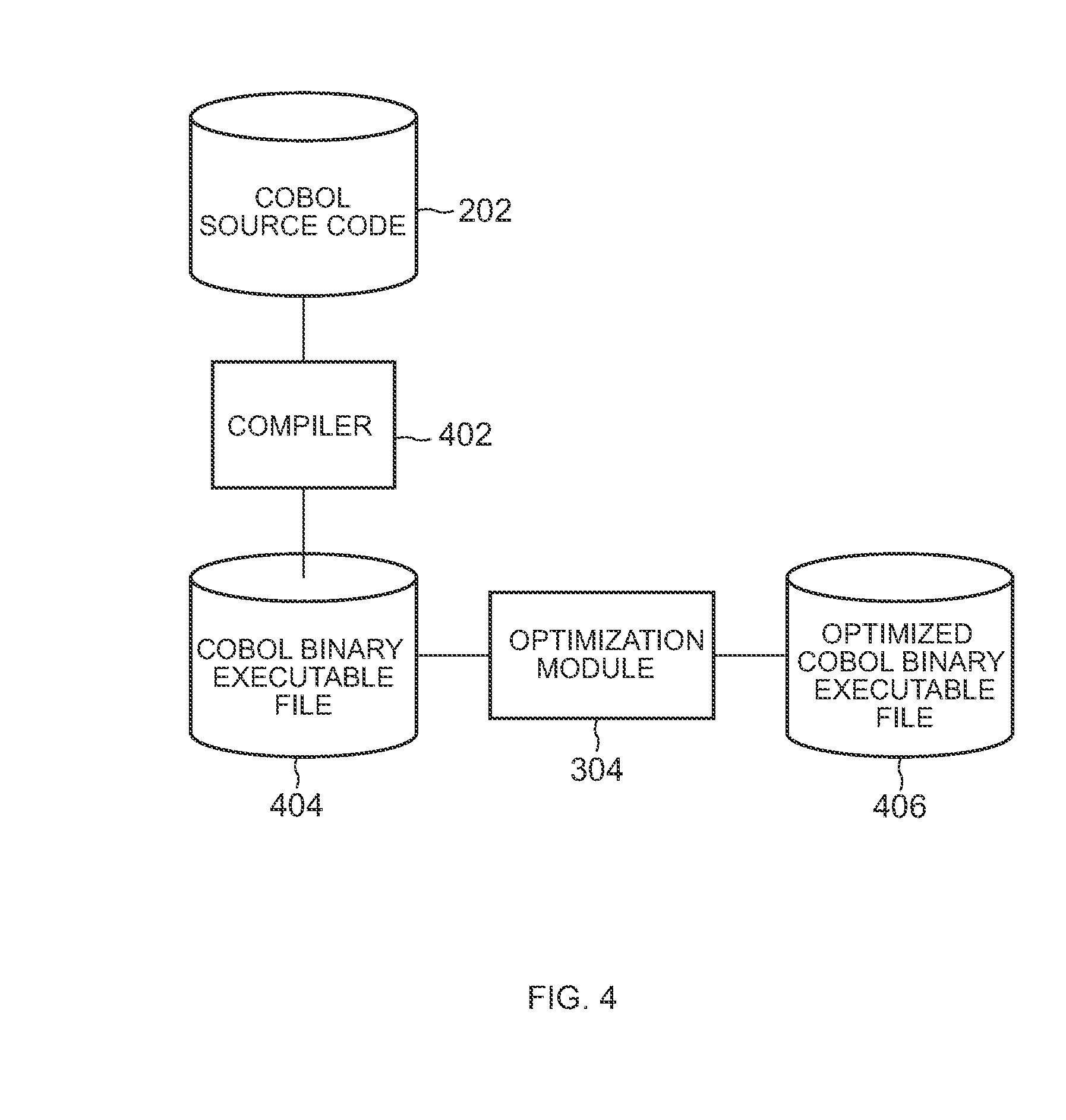
Method, program, and system for code optimization
Method, program and system for code optimization. The method includes detecting a sign assignment instruction having an input operand and an output operand identical in size to each other. Analyzing and determining whether a value of the input operand results from an add or subtract operation and if the value is greater than the value prior to the operation. If so then removing the sign assignment instruction on the condition that the input operand and the output operand of the sign assignment instruction have their addresses identical to each other and replacing the sign assignment instruction with a copy instruction for copying the value of the input operand of the sign assignment instruction to a value of the output operand on the condition that the addresses of the input operand and the output operand of the sign assignment instruction are not identical and do not overlap each other.
Owner:IBM CORP
A programming method of can-lonworks protocol conversion logic
ActiveCN107247678BElectric digital data processingTheoretical computer scienceProtocol (object-oriented programming)
The invention relates to a programming method for CAN-LonWorks protocol conversion logic, comprising the following steps: defining operators and defining the priority of each operator; defining unique digital codes corresponding to protocol variables; according to CAN-LonWorks protocol conversion requirements, using Operands and operators, and formulate the explicit assignment expressions of each protocol variable through operator rules; compress and convert the explicit assignment expressions, so as to encode the explicit assignment expressions into implicit assignment expressions; The assignment expression is checked, if the parsing is correct, the check is passed and a line of end mark "END" is appended at the end of the assignment expression. The programming method of the CAN-LonWorks protocol conversion logic provided by the present invention performs on-demand programming on the conversion logic to adapt to different application occasions.
Owner:NINGBO CRRC TIMES TRANSDUCER TECH CO LTD
Method to reduce the number of copies of values in procedural language and system therefor
InactiveCN100487653CReduce the number of copiesDigital data information retrievalProgram controlTheoretical computer scienceSemantics
Owner:INT BUSINESS MASCH CORP
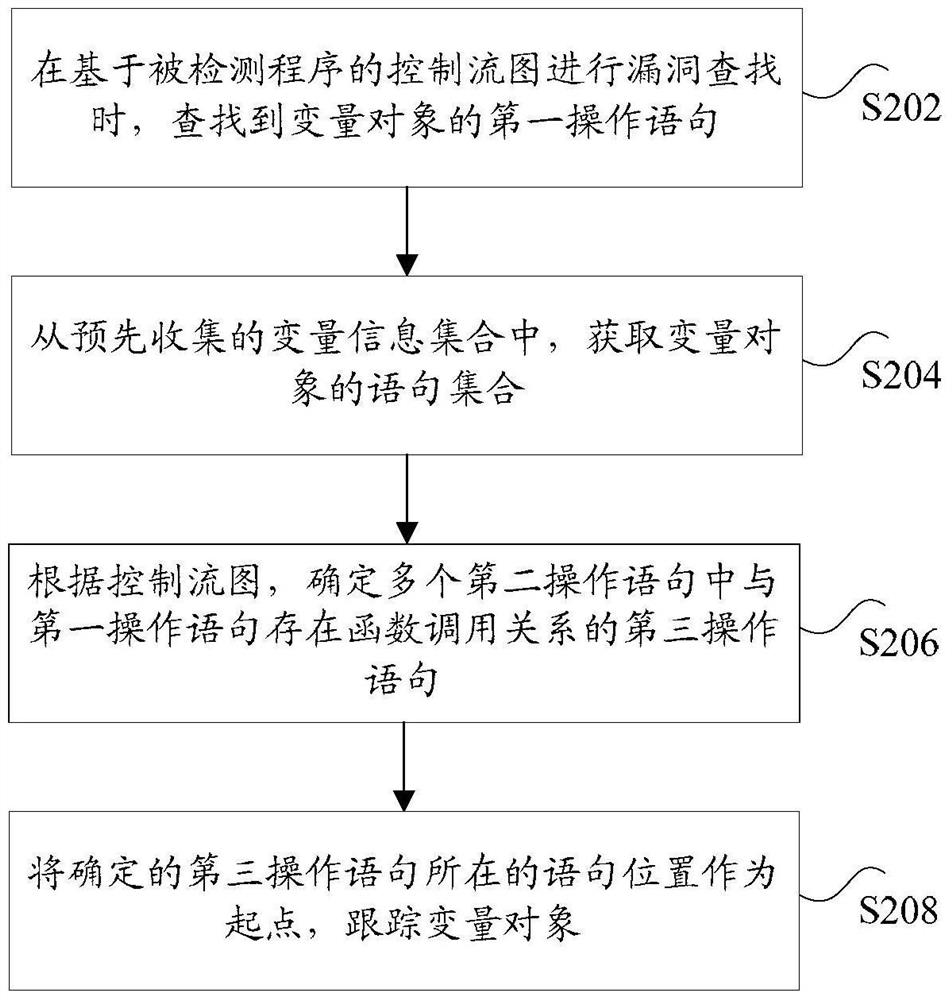
Method and device for tracking variable objects
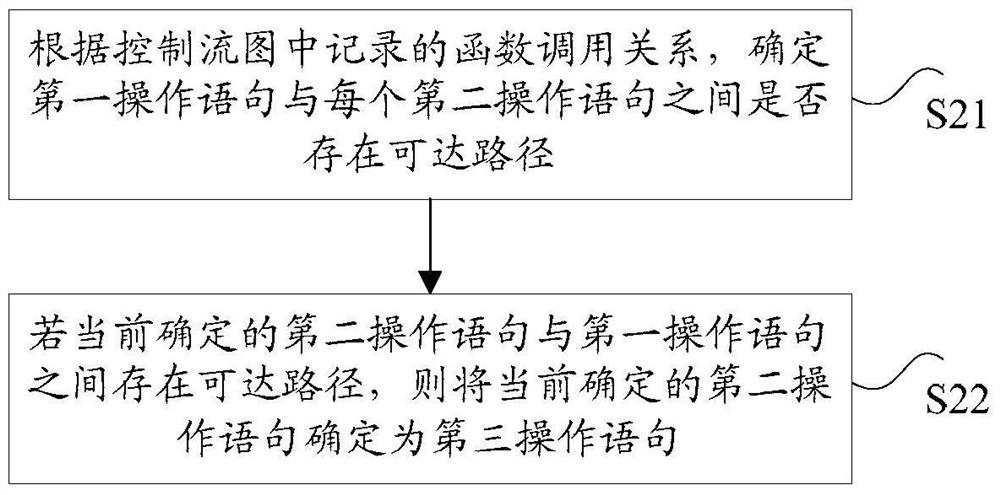
ActiveCN106940772BImprove scanning accuracyExact searchPlatform integrity maintainanceControl flowBug Search
The invention discloses a tracking method and device of a variable object. The method comprises the following steps: when carrying out bug search on a control flow diagram based on a detected program, finding out a first manipulation language of the variable object, wherein the first manipulation statement is used for indicating to carry out assignment operation and valuing operation on the variable object; obtaining a statement set of the variable object from a pre-collected variable information set, wherein the statement set comprises a plurality of second manipulation statements, and manipulation which is indicated by the second manipulation statements and is carried out on the variable object is opposite to manipulation which is indicated by the first manipulation statement and is carried out on the variable object; determining a third manipulation statement, having function calling relation with the first manipulation statement, in the plurality of second manipulation statements according to the control flow diagram; by taking a statement position of the determined third manipulation statement as a starting point, tracking the variable object. By adopting the tracking method and device of the variable object, the technical problem that missed reports of bugs are caused by the fact that the variable object cannot be tracked in a bug scanning process is solved.
Owner:ALIBABA GRP HLDG LTD
Method for realizing definite software operating time in single task operating environment
ActiveCN101957742BGuaranteed certaintySimple methodMachine execution arrangementsPathPingSoftware engineering
Owner:NANJING NRIET IND CORP
Assignment device, assignment method, and assignment program
ActiveUS11403388B2Easy to findMemory loss protectionError detection/correctionParallel computingByte
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
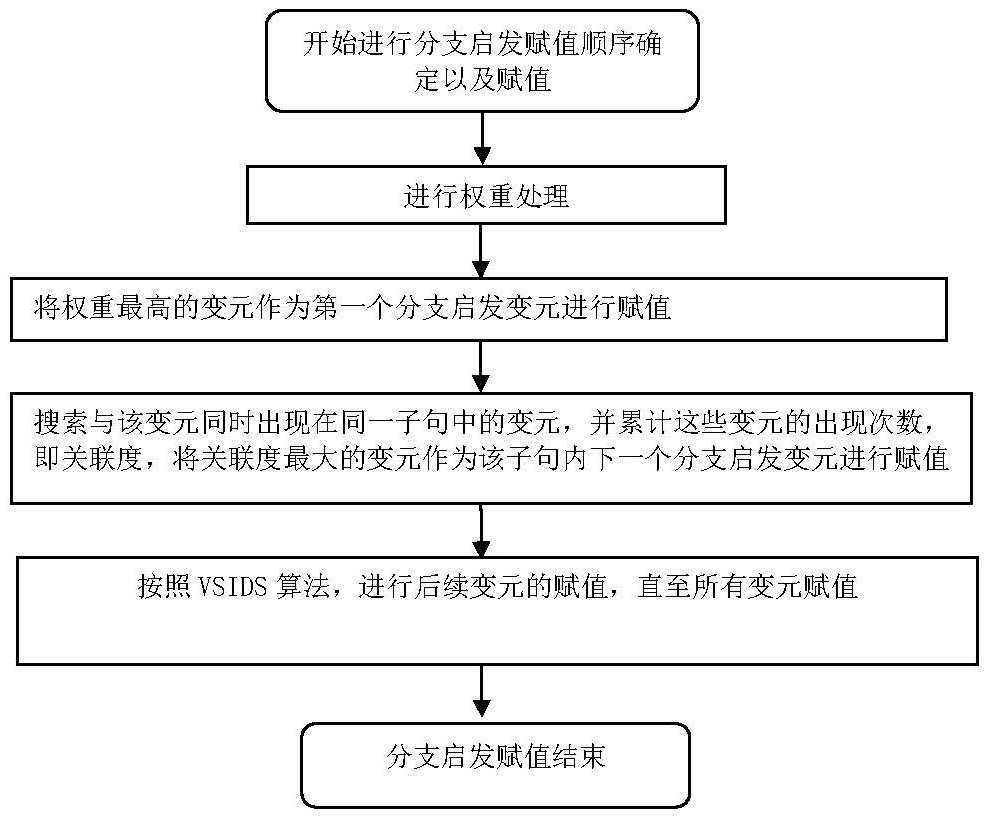
Variable element assignment sequence, assignment optimization algorithm and Boolean satisfiability verification algorithm
PendingCN112733350AAssignment optimizationSoftware testing/debuggingDesign optimisation/simulationAssignmentSatisfiability
The invention discloses a variable element assignment sequence and assignment optimization algorithm and a Boolean satisfiability verification algorithm. According to the assignment sequence optimization algorithm for the branch heuristic variables, at least one variable determines an assignment sequence by adopting the following steps: taking a current variable to be assigned as a current variable; searching for associated variables appearing in the same clause with the current variable at the same time; accumulating the number of times that the associated variable and the current variable appear in the same clause at the same time; and selecting the associated variable with the least number of times as a to-be-assigned variable after the current variable. According to the invention, the calculation time of the branch heuristic algorithm can be shortened.
Owner:SHENZHEN STATE MICRO TECH CO LTD
a sat solver
ActiveCN109146077BImprove solution efficiencySolving SAT QuestionsCAD circuit designSpecial data processing applicationsTheoretical computer scienceProcessing
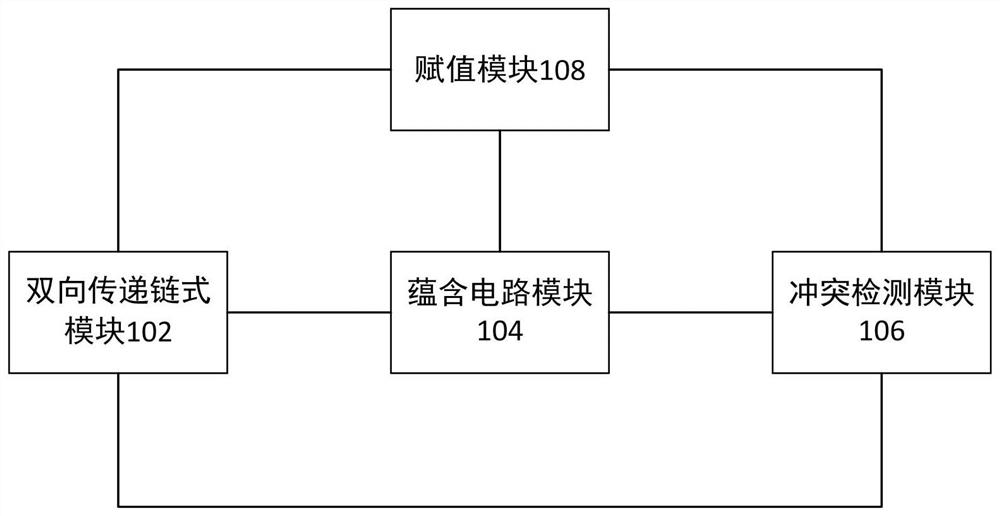
The invention discloses a SAT solver, comprising: a two-way transmission chain module (102), used for two-way transmission of variables to be solved; an implication circuit module (104), used for providing implied values for the variables to be solved; conflict detection Module (106), for detecting whether the current assignment of the assignment module (108) will cause conflict; assignment module (108), for assigning a value to the variable to be solved, and its output value is determined by the state machine of the variable to be solved The current state of and the input signal of the assignment input are jointly determined. The solution of the present invention can solve the problem of low processing efficiency of the SAT solver based on software in the prior art, and achieve the effect of improving the processing efficiency.
Owner:何安平 +2
Method and device for improving bytecode reverse engineering effect of smart contract
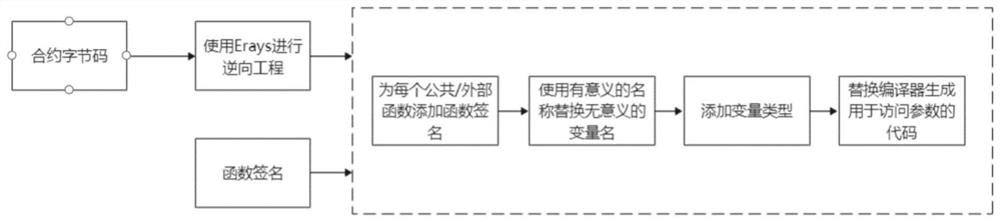
ActiveCN113504940ASolve the problem of poor readability of output resultsConducive to public reviewReverse engineeringEnergy efficient computingSoftware engineeringParameter
The invention relates to the technical field of block chain smart contracts, and provides a method and a device for improving a bytecode reverse engineering effect of a smart contract. According to the method, under the condition that a function signature is known, a compiler can be better improved, and the readability of the reverse engineering result of the smart contract is improved. According to a main scheme in the invention, the method comprises the following steps: S1, conducting reverse engineering on a contract bytecode through Erays so as to obtain a reversed code; S2, according to the known function signature in the contract bytecode, adding a function id and a parameter type to each common / external function of the code obtained after reverse engineering, and generating a parameter list; S3, for each function in the contract bytecode in the step S1, replacing a meaningless variable name with a meaningful parameter name; S4, for an assignment statement, if the parameter of the corresponding function is assigned to a variable, adding the type of the corresponding parameter to the variable; and S5, replacing the code, which is generated by the compiler and is used for accessing the parameter, with a simple assignment statement.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
A software patch detection method and device based on data flow analysis
ActiveCN111177733BEliminate hard-to-recognize puzzlesImprove detection efficiencyPlatform integrity maintainanceData streamAlgorithm
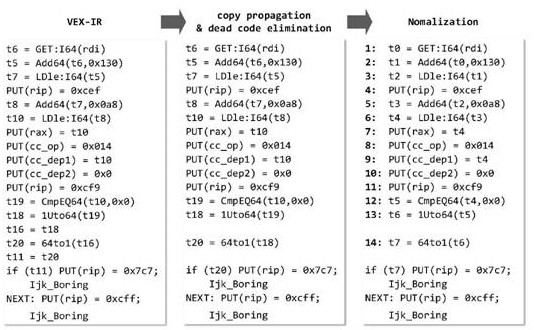
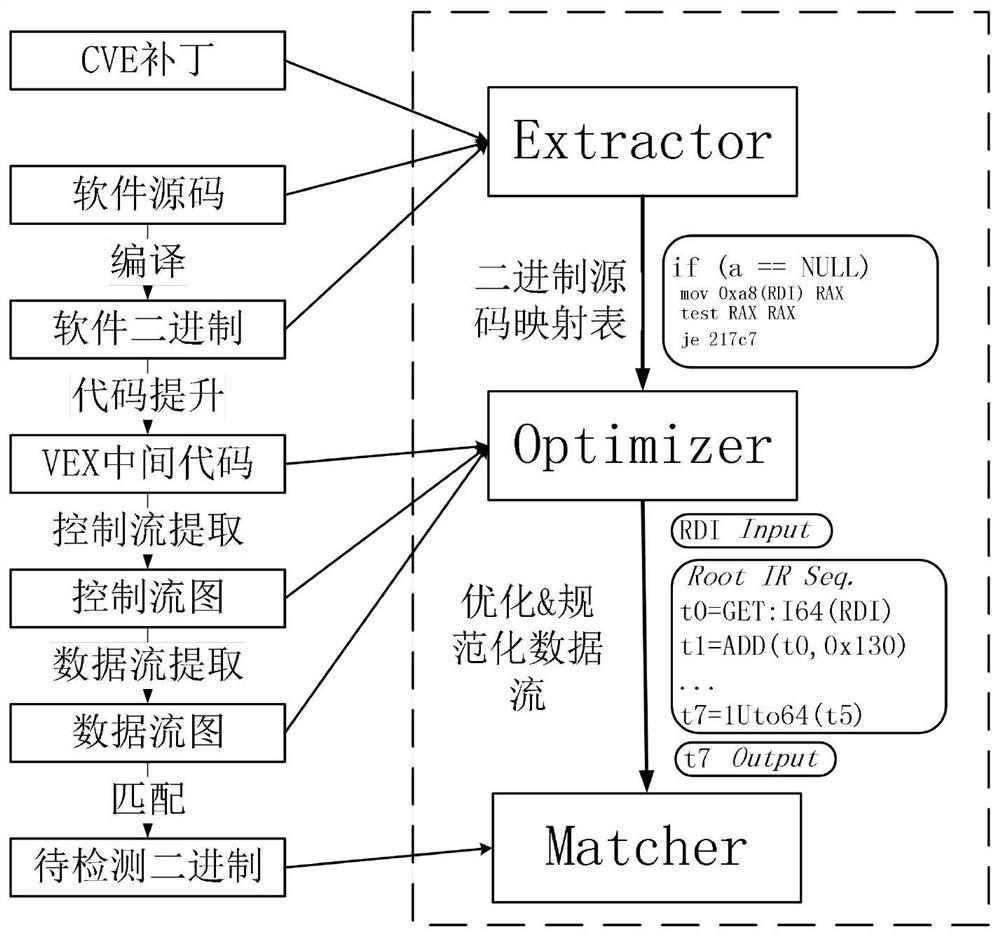
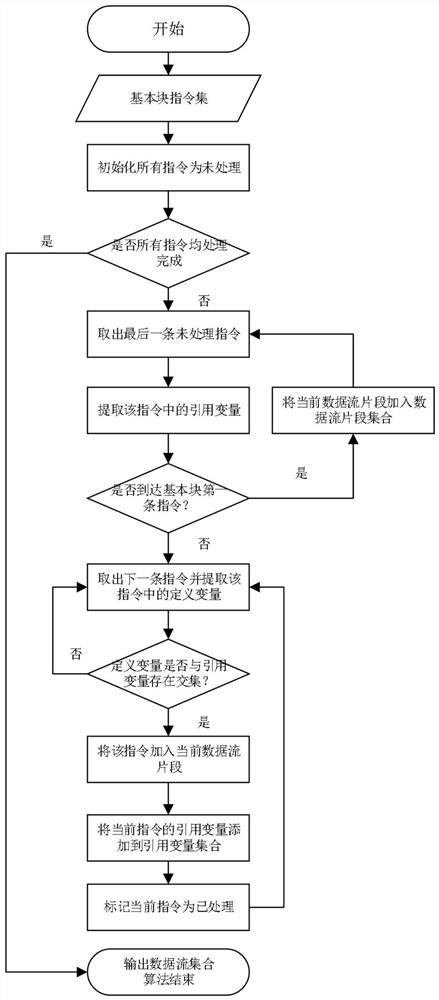
A software patch detection method based on data flow analysis, using Extractor to analyze the patch code, and sequentially select and detect the modification semantics of assignment statements and conditional statements, function call statements, type-related statements, and other types of statements in the patch code. It is the feature of the patch to be detected; the mapping relationship between the binary code and the source code is established; VEX‑IR is selected as the intermediate code of the binary code promotion of the device firmware in the Internet of Things environment, and the binary code is analyzed using the open source Angr to extract the Control flow, the control flow takes functions as units, each of the functions includes nodes as basic blocks, and the control flow of program jump semantics as edges; the data flow in the basic block is analyzed, and the basic block The code is reversely analyzed one by one, and the use chain of variables in each statement is extracted; the data flow across the basic block is analyzed; the extracted data flow is optimized; the patch feature is obtained from the basic block, and it is multi-stage match.
Owner:BEIHANG UNIV
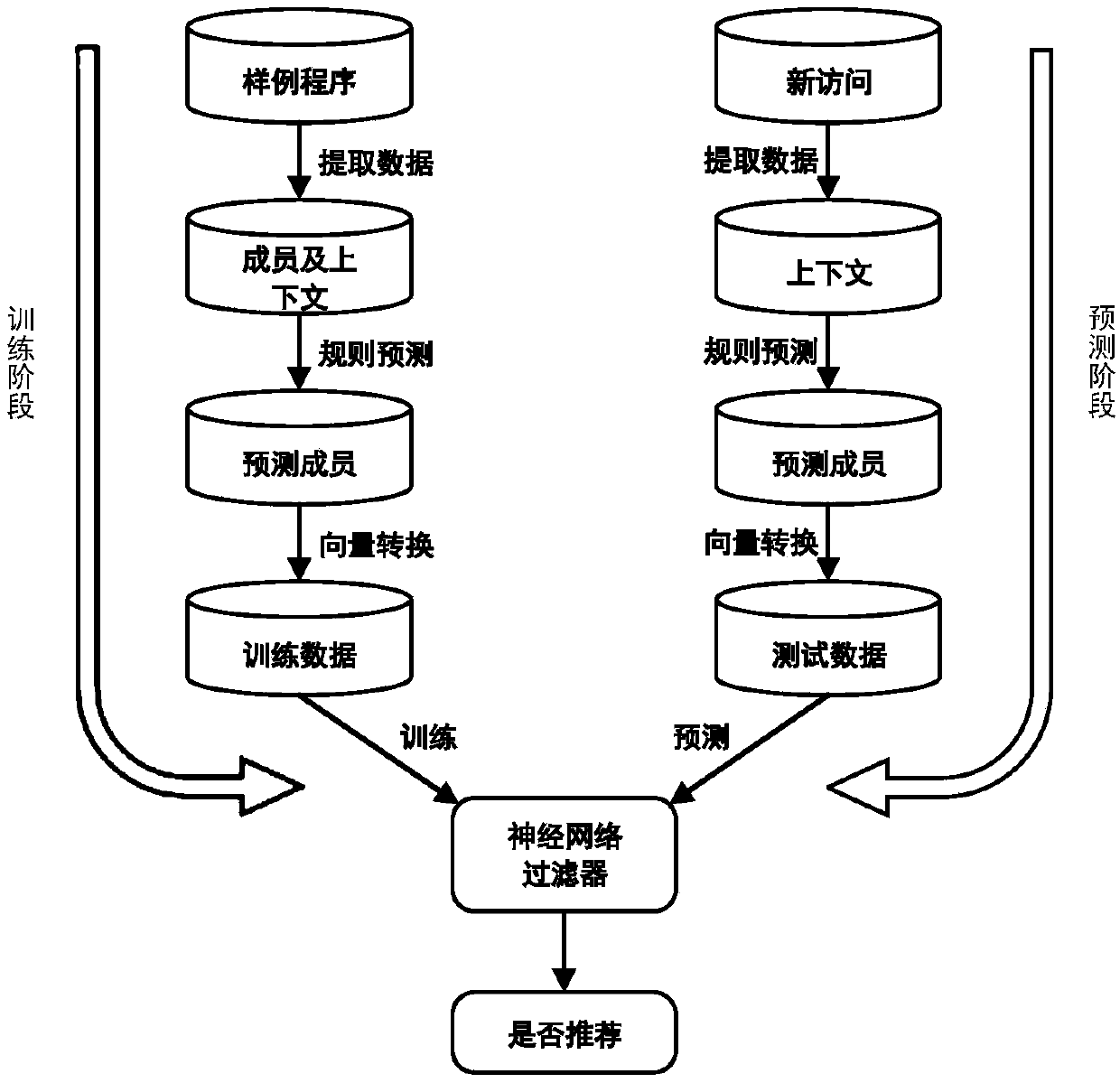
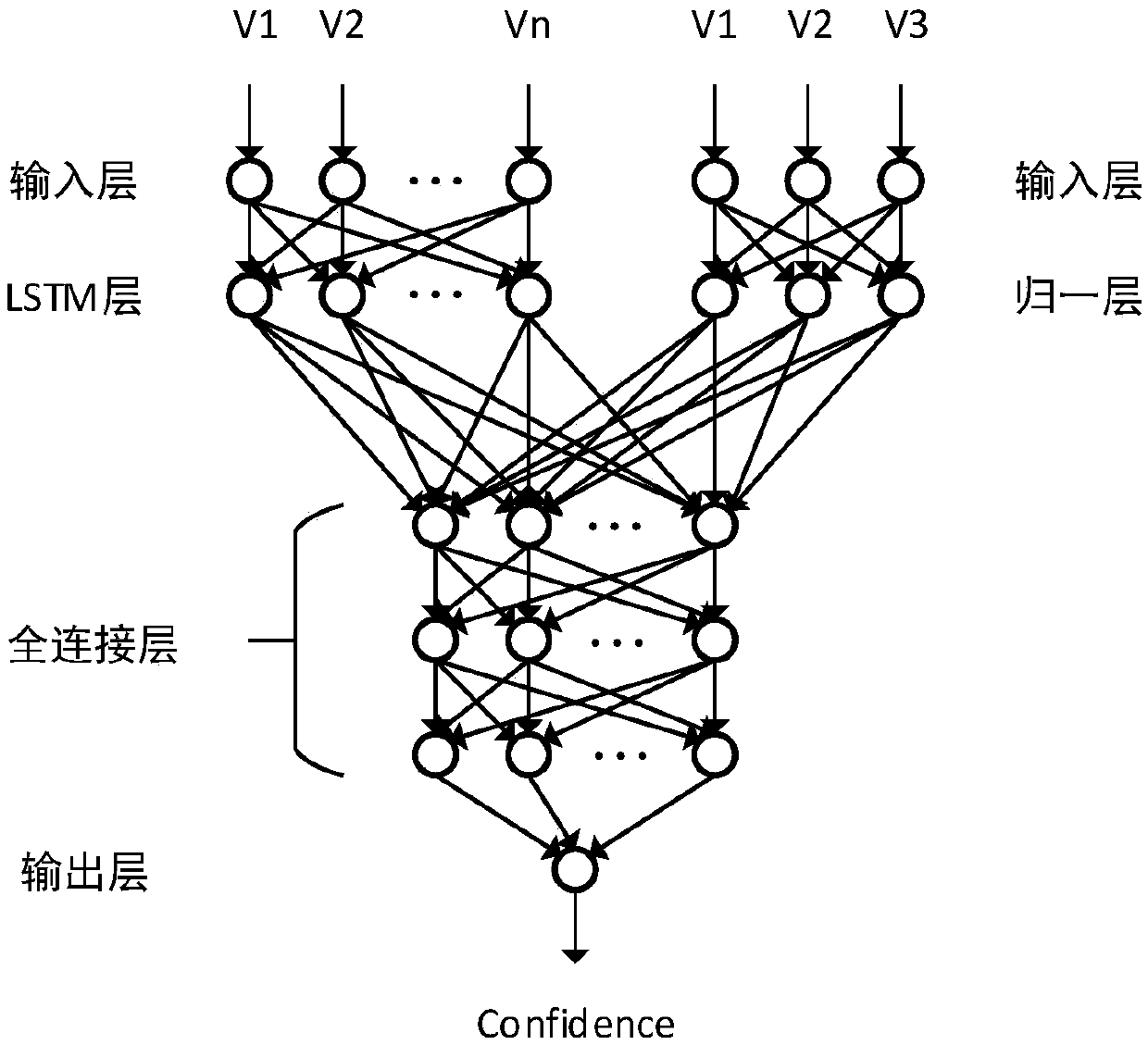
A non-api member recommendation method based on heuristics and neural networks
The invention relates to a non-API object recommendation method based on heuristics and neural networks, and belongs to the technical field of code completion and code recommendation. According to themethod, all members included in a non-API object declaration type are collected according to non-API member accessing sample sample on the right side of an assignment statement in open source software, the members comprise members obtained by inheritance, then inaccessible members are eliminated according to the relationship between the class where the assignment statement is located and the non-API object declaration type, and the remaining accessible members are all taken as candidates and put into an initial candidate list cdtList for the use of subsequent use. Prediction is conducted on the sample in step one based on three kinds of specific heuristic rules. The neural networks are trained by using information to obtain a filter capable of filtering low-reliability prediction results.When a programmer enters '.' in a non-API sample object on the right side of the assignment statement, non-API members which might access are predicted. According to the method, the probability thatthe number of recommended members under the same data set is correct is obviously higher than existing methods and tools.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Project code automatic optimization method and device, equipment and medium
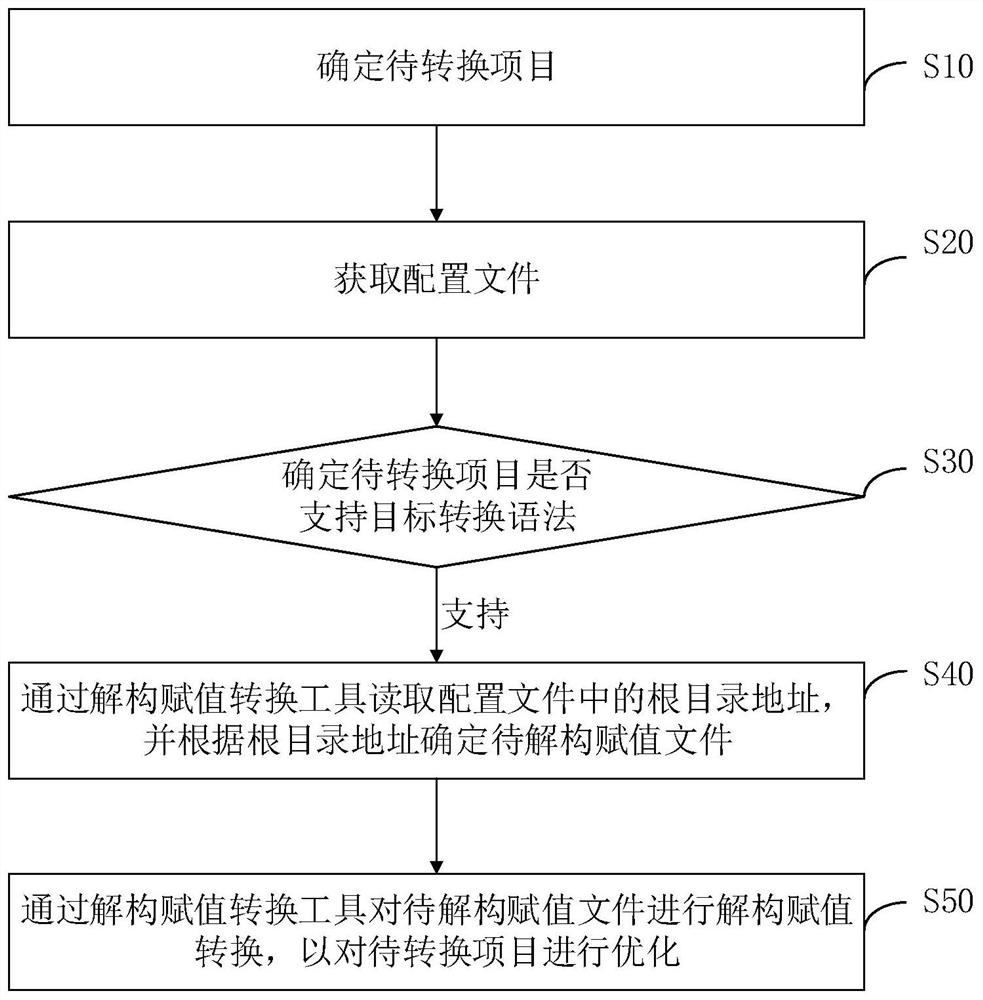
PendingCN112527314AAutomatic optimization nowReduce learning costsDatabase distribution/replicationSpecial data processing applicationsSoftware engineeringAssignment
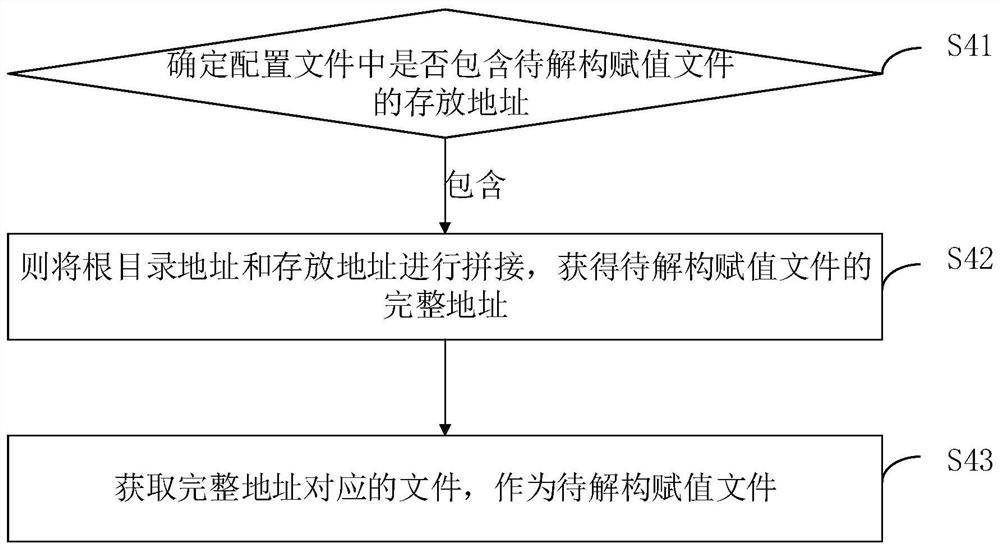
The invention is applied to the field of artificial intelligence, relates to the field of block chains, and discloses a project code automatic optimization method and device, computer equipment and astorage medium. The method comprises the steps of determining a to-be-converted project, wherein a deconstruction assignment conversion tool is installed in the to-be-converted project, and obtaininga configuration file, wherein the configuration file comprises a root directory address of the to-be-converted project, determining whether the to-be-converted project supports a target optimization grammar, if the to-be-converted project supports the target optimization grammar, reading the root directory address in the configuration file through a deconstruction assignment conversion tool, and determining a to-be-deconstructed assignment file according to the root directory address, performing deconstruction assignment conversion on the to-be-deconstructed assignment file through a deconstruction assignment conversion tool so as to optimize the to-be-converted project. According to the method, a user can convert the to-be-deconstructed assignment file through the deconstruction assignment conversion tool without knowing the deconstruction assignment grammar of the ES6, so that automatic optimization of project codes is realized, and the project optimization efficiency is improved.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
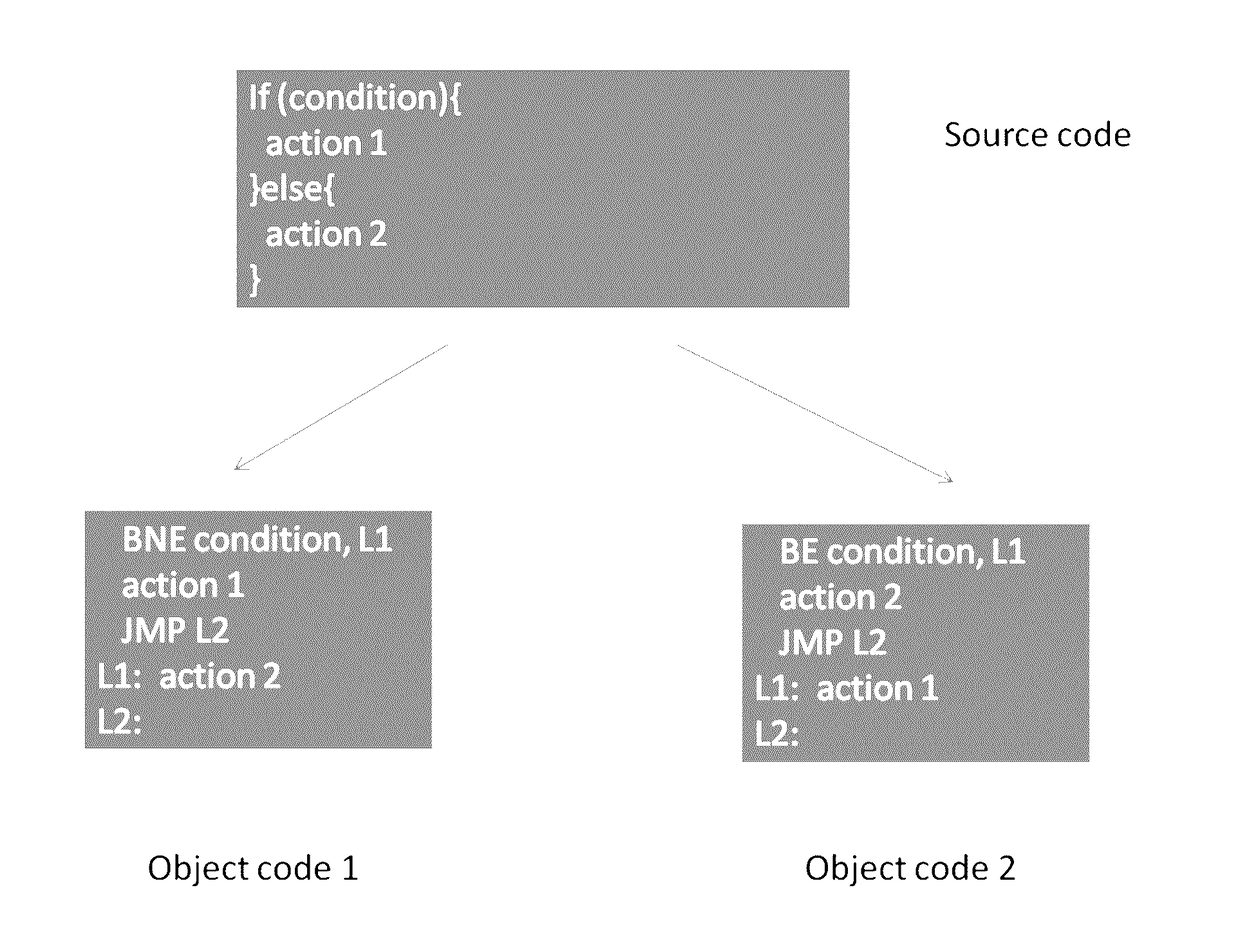
System and Method for Protecting Software from Buffer Overruns
A compiler transforms the source code into object code, but it will postpone the assignment of all of the machine language jumps until installed time. This can be performed by labeling the jumps during compiled time, similarly to how variables are labeled for later indexing by the debugger. At installation time, given a random key, the installer will take the jump labels and assign random ordering of the code and data using the key as a seed. The final effect is that the same source code can potentially generate an infinite number of object codes, with the exact same functionality of execution. The main difference, however, is that as more jump labels are included, less fixed offsets between buffers are available to the black hat.
Owner:ROBOTIC RES OPCO LLC
System and method for protecting software from buffer overruns
A compiler transforms the source code into object code, but it will postpone the assignment of all of the machine language jumps until installed time. This can be performed by labeling the jumps during compiled time, similarly to how variables are labeled for later indexing by the debugger. At installation time, given a random key, the installer will take the jump labels and assign random ordering of the code and data using the key as a seed. The final effect is that the same source code can potentially generate an infinite number of object codes, with the exact same functionality of execution. The main difference, however, is that as more jump labels are included, less fixed offsets between buffers are available to the black hat.
Owner:ROBOTIC RES OPCO LLC
Method for automatically synthesizing commonly-used cyclic abstracts and generating program specifications
InactiveCN106681786ADoes not cause precision problemsHigh degree of automationProgram controlMemory systemsTheoretical computer scienceAbstract syntax tree
The invention discloses a method for automatically synthesizing commonly-used cyclic abstracts and generating program specifications. The method comprises the steps of 1, generating an abstract syntax tree of a program to be verified; 2, analyzing the abstract syntax tree generated in the step 1 to generate an abstract of program statements; 3, analyzing the abstract generated in the step 2 to generate specifications of the program statements; 4, performing verification on the specifications generated in the step 3, and therefore proving the characters of the program to be verified in an assistant mode. Cyclic statements of the operation commonly-used data structure are converted into a series of abstract assignment statements, the cyclic statements are effectively extracted, and the cyclic statements can be analyzed by means of an assignment language analysis method. The program characters, particularly the relationship between the program states before and after program execution, are effectively described according to the program specifications generated by the statement abstract, the specifications effectively assist the program verification process, the automatic degree and efficiency of program verification are improved, and burdens of verification workers are relieved.
Owner:NANJING UNIV
A Method of Instruction Optimization
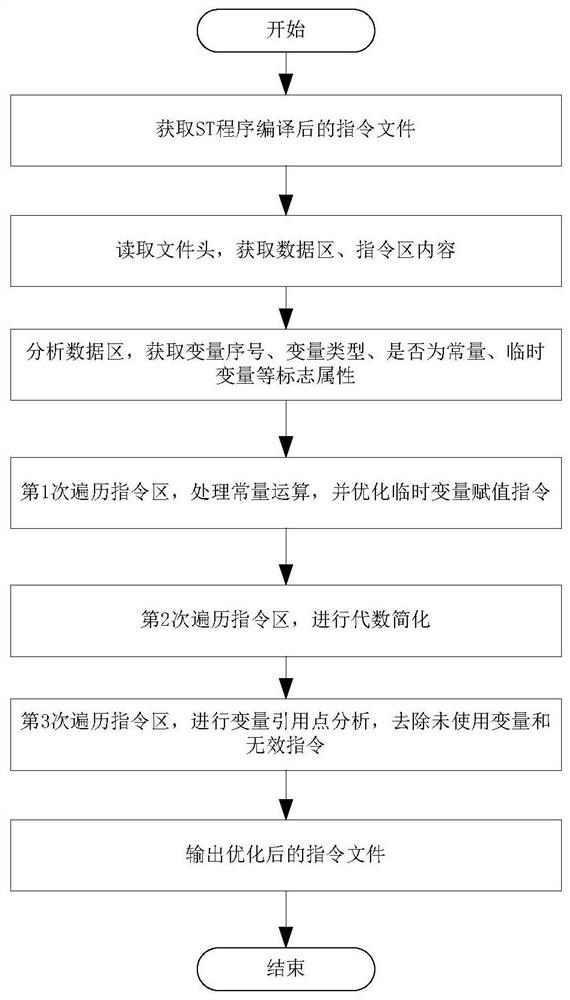
ActiveCN108733410BImprove efficiencyRun fastMachine execution arrangementsFast optimizationProcessing
The invention discloses an instruction optimization method, which comprises the following steps: step 1, obtaining the instruction file compiled by the structured text program, obtaining the contents of the data area and the instruction area; step 2, analyzing the data area, and extracting variable information; step 3, dividing Traversing the instruction area three times, sequentially adopting optimization methods of assignment optimization, algebraic simplification, and reference point processing to merge, delete, and adjust instructions; step 4, store optimized data and instruction information as files. This optimization method can perform reliable and fast optimization of instructions by analyzing instruction files of a predetermined format after ST program compilation, and improve program operating efficiency.
Owner:NR ELECTRIC CO LTD +1
A java program dynamic analysis method, device and storage medium
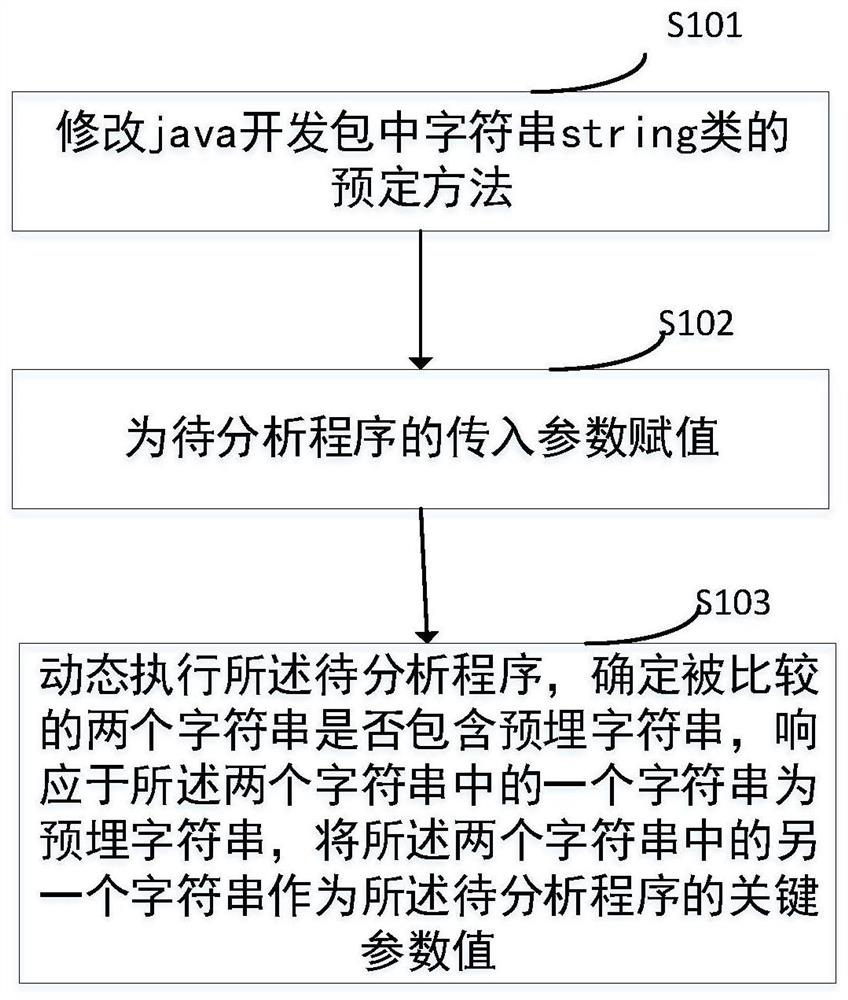
The application provides a java program dynamic analysis method, comprising: modifying the predetermined method of the character string class in the java development kit; assigning values to the incoming parameters of the program to be analyzed, the assignment including pre-embedded strings; dynamically executing the pending method an analysis program that determines whether the two character strings being compared contain a pre-embedded character string, responsive to one of the two character strings being a pre-embedded character string, converting the other of the two character strings to As the key parameter value of the program to be analyzed. The method provided by this application can directly perform dynamic analysis of programs without performing syntax and semantic analysis.
Owner:CHINA CONSTRUCTION BANK
Programming method of CAN-LonWorks protocol conversion logic
The invention relates to a programming method of CAN-LonWorks protocol conversion logic. The method includes: defining operators and the priority of each operator; defining the only digital code corresponding to each protocol variable; using operation number and the operators to compile the explicit assignment expression of each protocol variable according to CAN-LonWorks protocol conversion requirements and through operator rules; performing compression conversion on the explicit assignment expressions to encode the explicit assignment expressions into implicit assignment expressions; inspecting the implicit assignment expressions, determining that the inspection is passed if the implicit assignment expressions are correctly analyzed, and adding ending tags 'END' to the tails of the assignment expressions. The programming method programs the conversion logic according to needs to adapt to different application occasions.
Owner:NINGBO CRRC TIMES TRANSDUCER TECH CO LTD
Incomplete division method and device for maximum cardinal subset of ontology library
PendingCN113157815ARelational databasesSpecial data processing applicationsAlgorithmTheoretical computer science
The invention provides an incomplete division method and device for a maximum cardinal subset of an ontology library. Comprising the following steps: according to an ontology library containing logic conflicts and a limited coordination cluster number k, obtaining a minimum uncoordinated subset set and a problem formula set, and building a model decision variable set X and model auxiliary decision variable sets Q and Y; constructing a quadratic integer programming constraint C according to k, X, Q, Y and the minimum discordant subset; enabling the sum of X to form a quadratic integer programming objective function Z, solving the minimum value of Z under the condition that C is met, obtaining a variable assignment set, obtaining different clusters through different integer values corresponding to each formula in the problem formula set in the variable assignment set, and dividing the clusters into limited coordination clusters which keep the maximum cardinal subset of the input ontology library; constructing a quadratic integer programming model by using the minimum incongruous subset, and finally solving the model to incompletely divide the ontology library into limited coordination clusters and enable the limited coordination clusters to retain the maximum cardinal subset in the ontology library.
Owner:HUZHOU TEACHERS COLLEGE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com