Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
57results about How to "Improve authentication capabilities" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
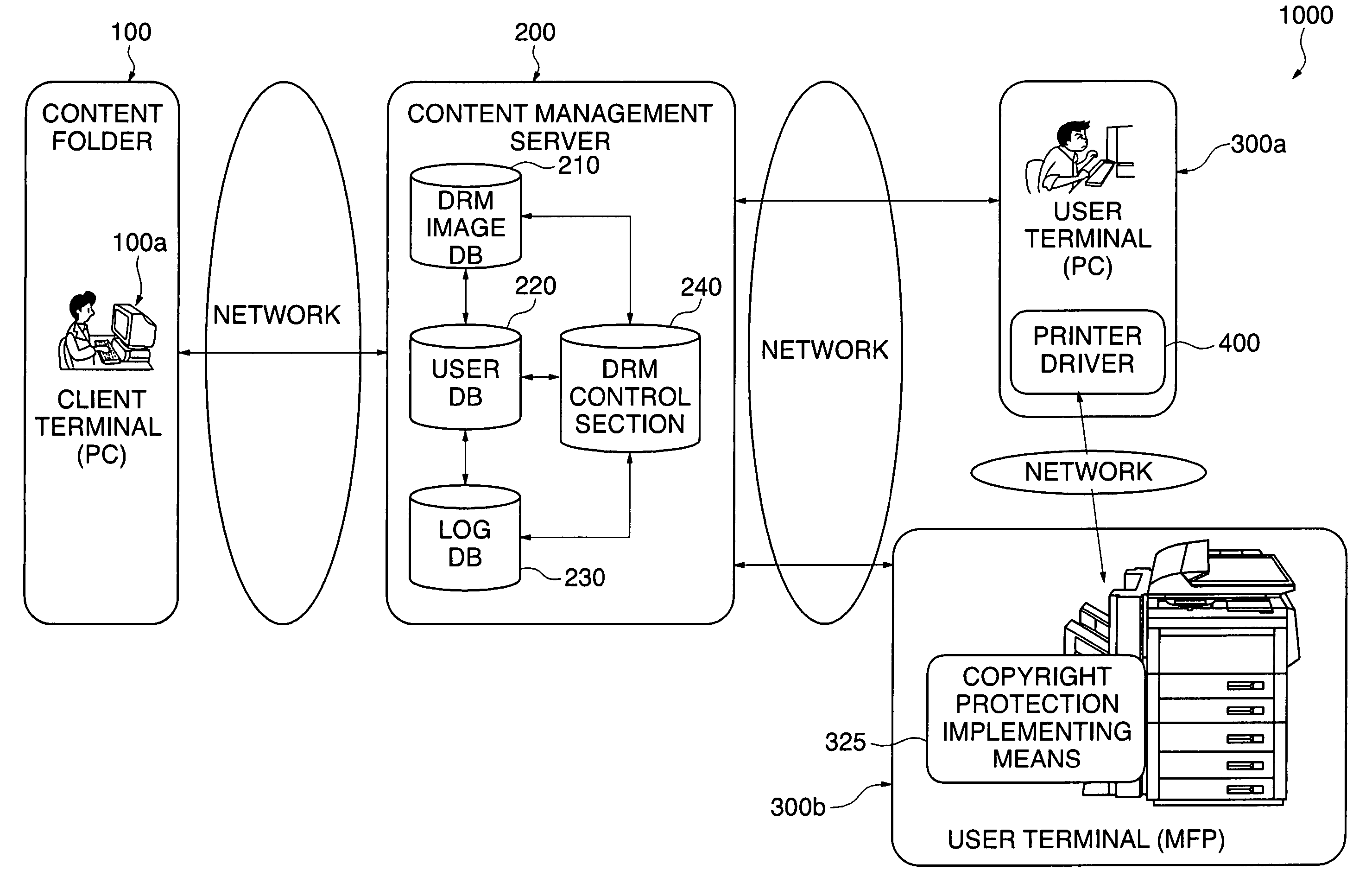
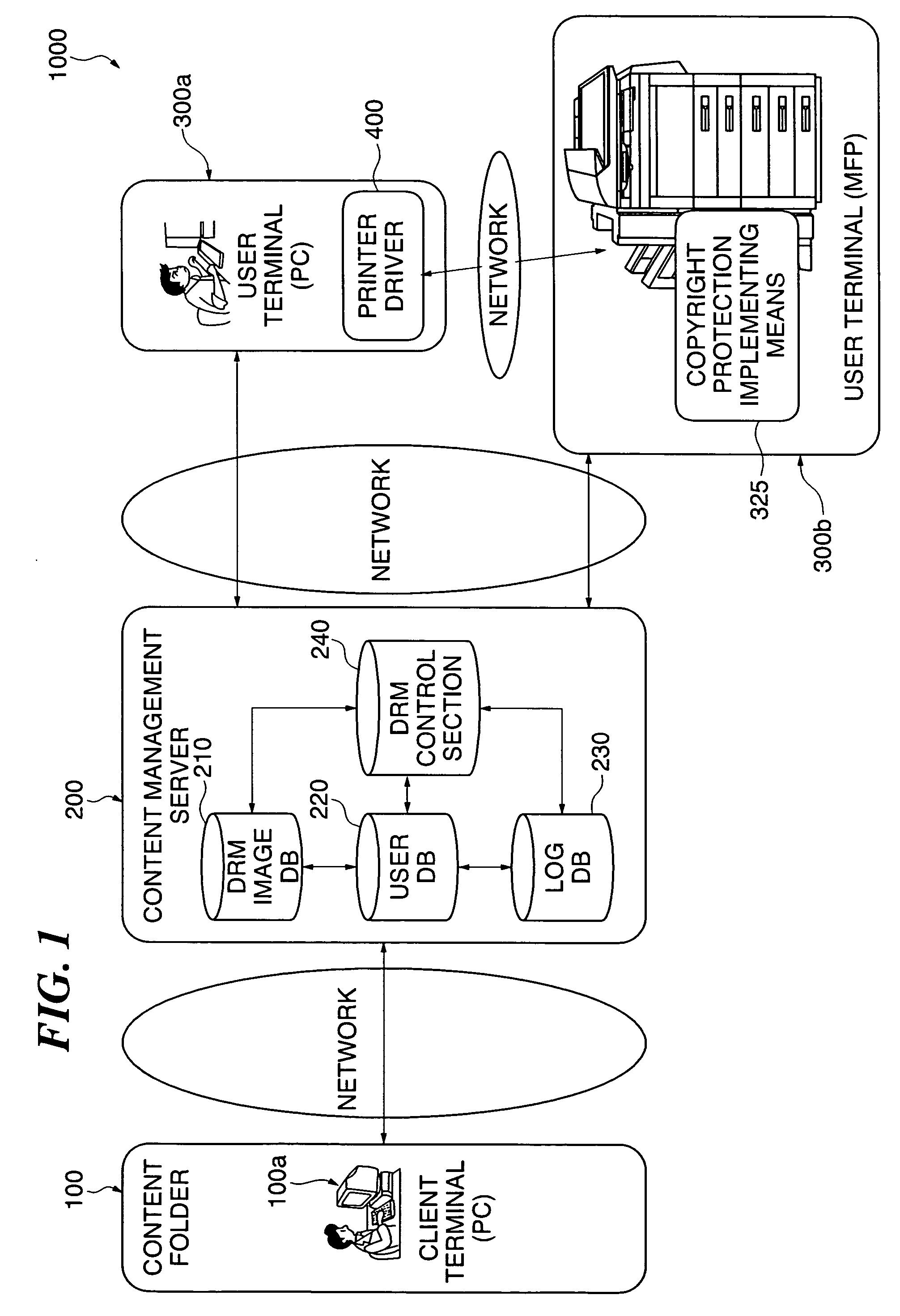
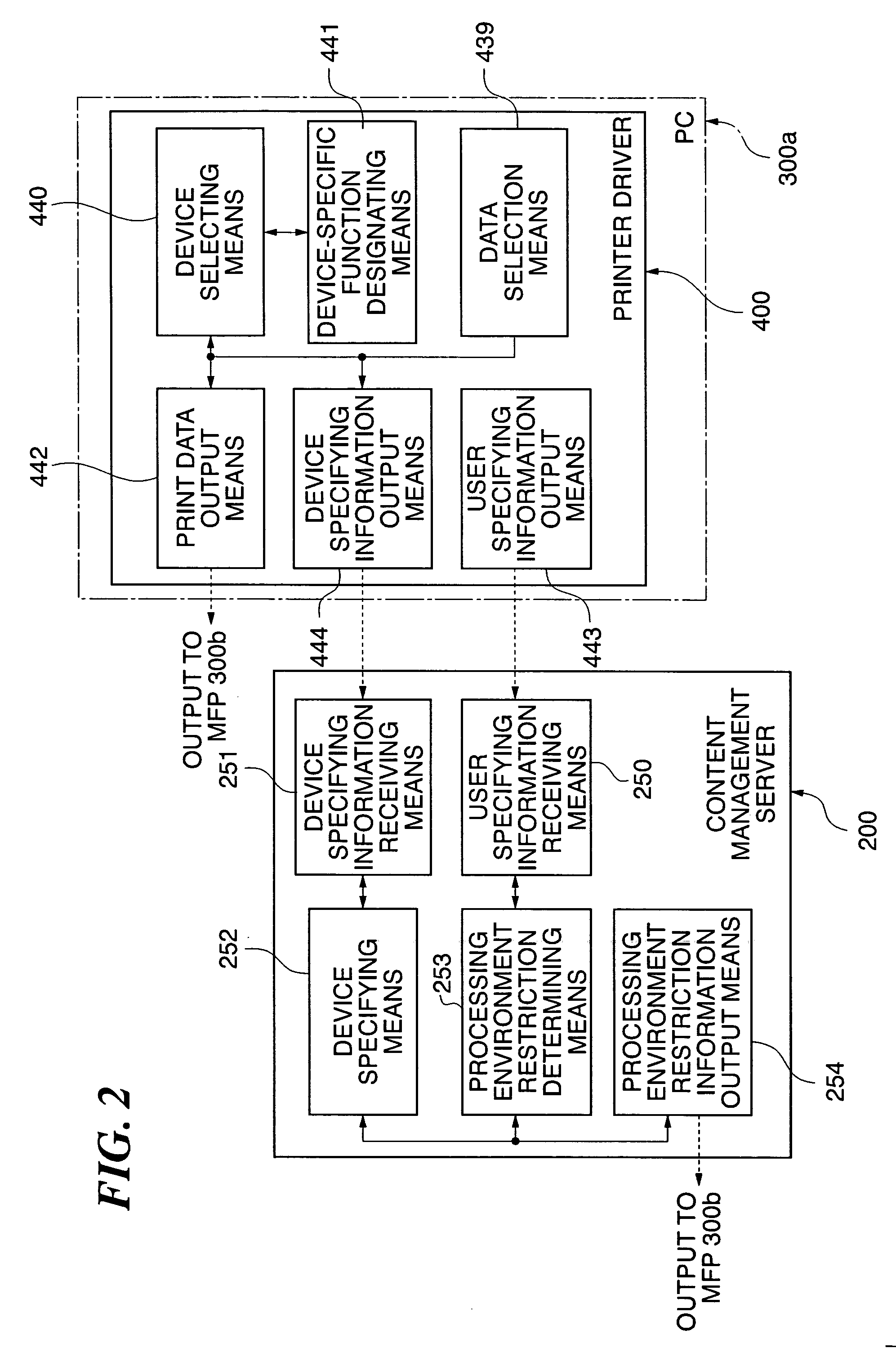
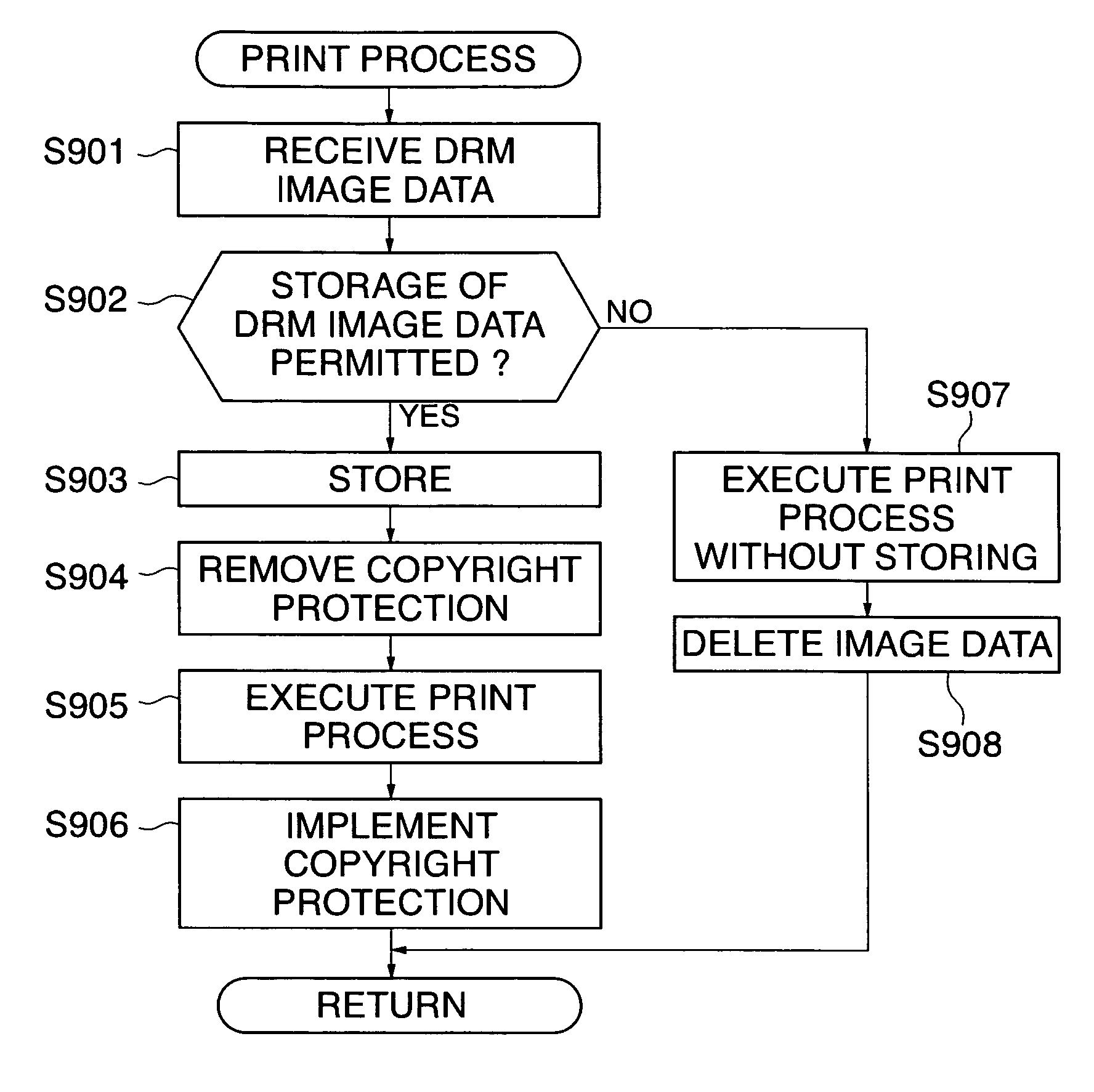
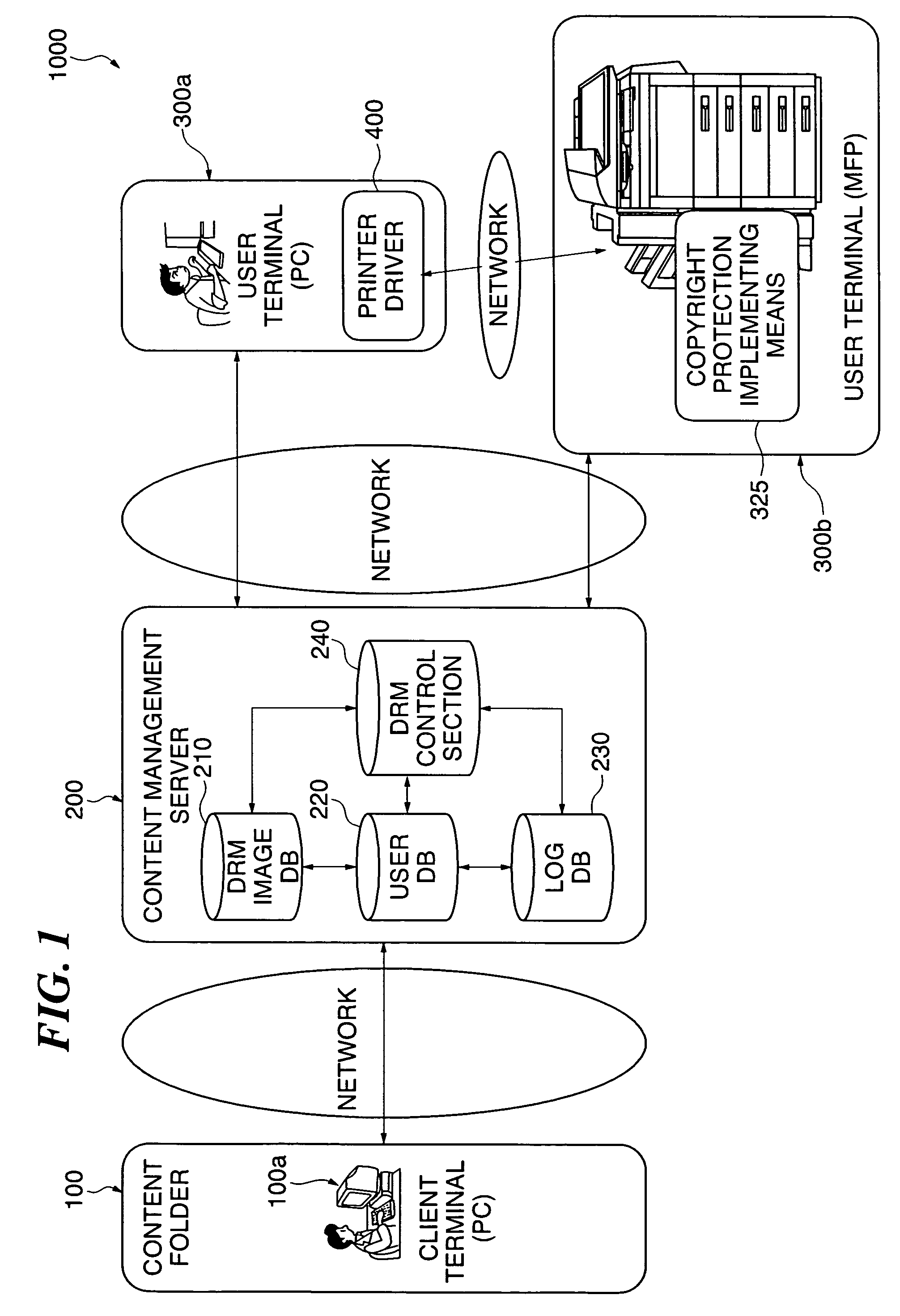
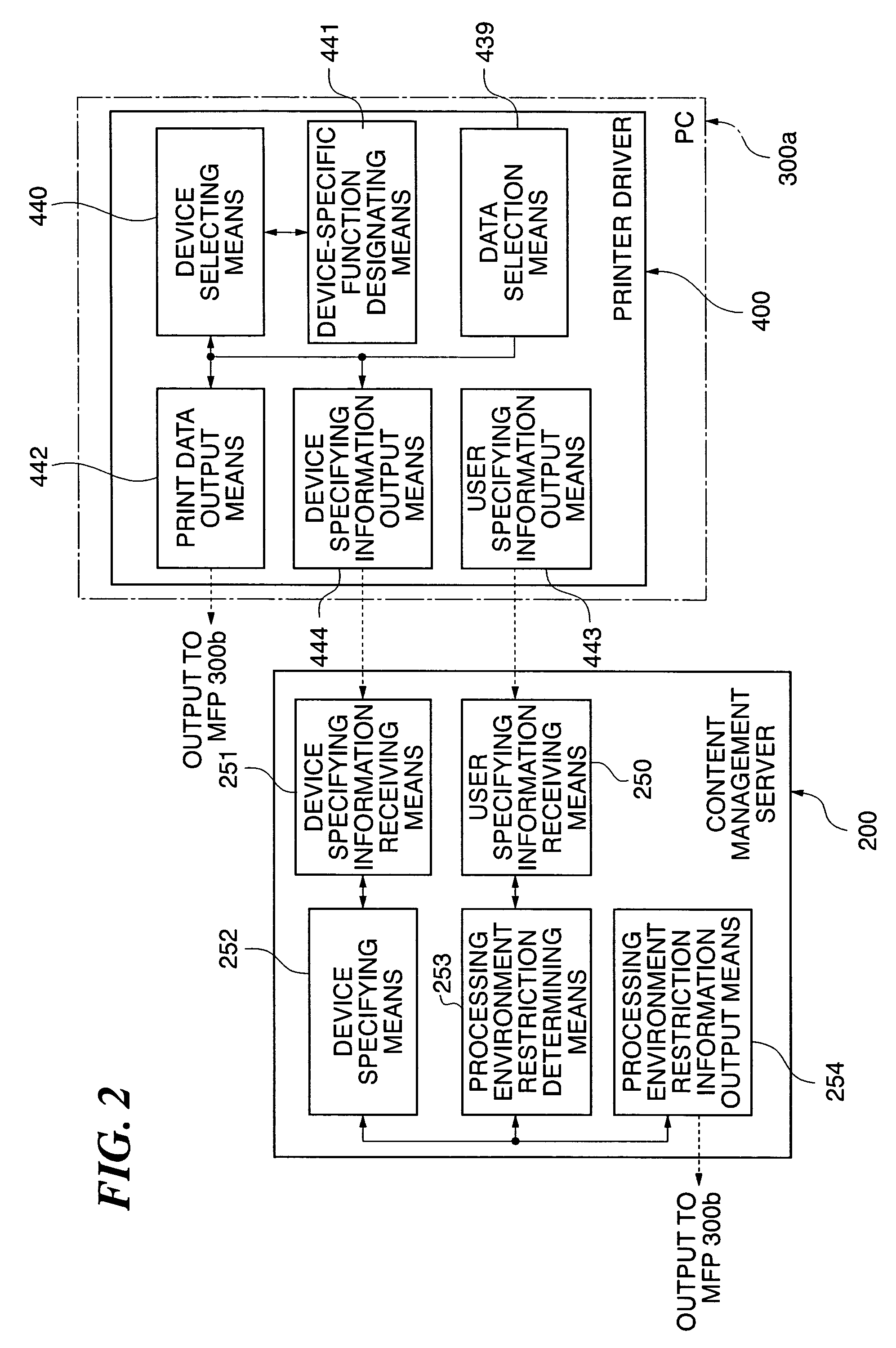
Communication system, image processing apparatus, image processing method, authentication server, image managing method, image managing program, and image processing system
InactiveUS20060015734A1Improve securityImprove authentication capabilitiesUser identity/authority verificationUnauthorized memory use protectionInformation processingImaging processing
A communication system which is capable of improving the security of a protected image. The protected image on which a predetermined protection process has been carried out and authentication information are transmitted from an information processing apparatus to an image processing apparatus and an authentication server, respectively. Permission information for permitting removal of the predetermined protection process is issued from the authentication server based on the authentication information, and is obtained by the image processing apparatus. When the protected image is subjected to predetermined image processing carried out by the image processing apparatus, the content of the predetermined image processing is regulated to within a predetermined range indicated by the permission information.
Owner:CANON KK
Image hiding and authentication method based on secret sharing
ActiveCN103761702AImprove securityDifferences in Statistical PropertiesImage data processing detailsPattern recognitionHash function
The invention discloses an image hiding and authentication method based on secret sharing, and belongs to the technical field of secret image sharing. The image hiding and authentication method is characterized by comprising the steps that firstly, difference Huffman encoding is conducted on a secret image, every three generated bit sequences are set to be one group to be converted into decimal numbers which are used as coefficients of a sharing polynomial in the Shamir (k, n) threshold scheme, the k and the n are positive integers, the k is smaller than or equal to the n, and n shadow images are generated; secondly, n significant carrier images are selected, the generated shadow images are embedded into the carrier images in a matrix encoding mode, authentication bits generated by the hash function are also embedded into the carrier images, and n disguise images are formed and are in the charge of n different participants respectively. The disguise images generated through the image hiding and authentication method has higher visual quality, existence of secret information cannot be perceived by attackers easily, and the safety of the secret information is ensured. Meanwhile, before the secret information is recovered, the disguise images provided by each participant need to be authenticated, only the disguise images passing through authentication can participate in recovery of the secret information, and the safety of the secret information is further strengthened.
Owner:TAIYUAN UNIVERSITY OF SCIENCE AND TECHNOLOGY
Identity authentication method based on face and authentication apparatus thereof
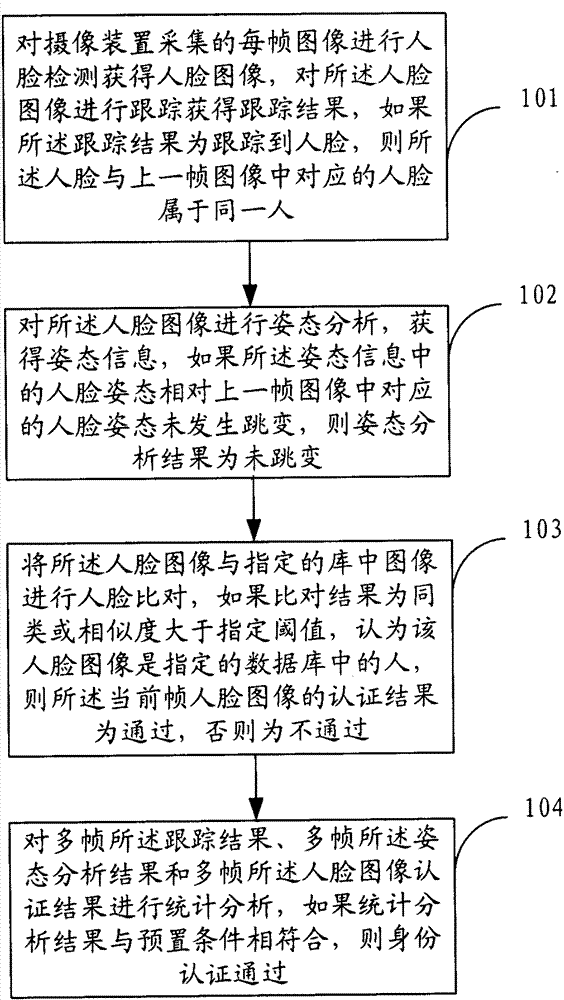
ActiveCN102375970AAvoid the authentication processImprove authentication capabilitiesCharacter and pattern recognitionFace detectionStatistical analysis
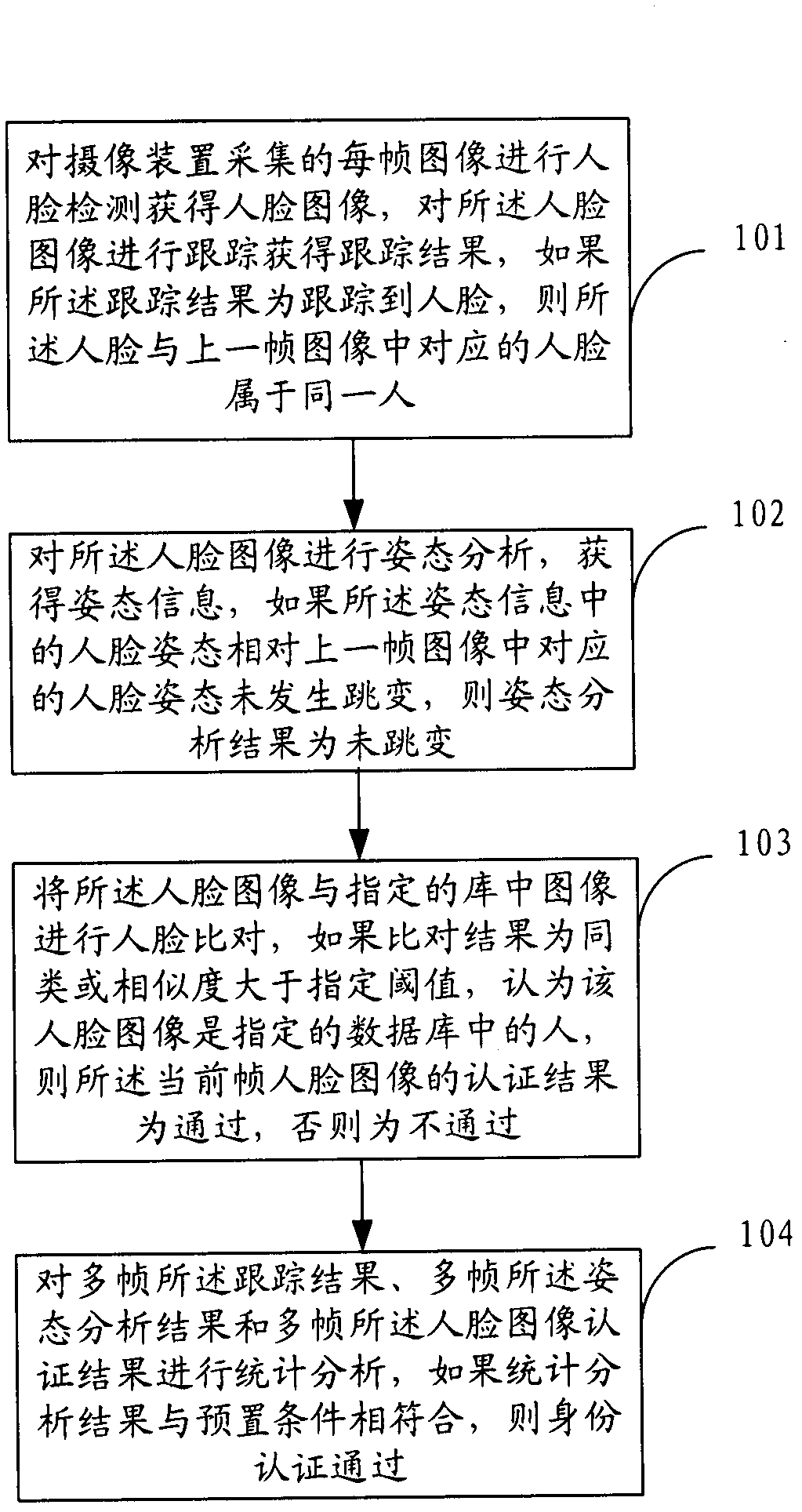
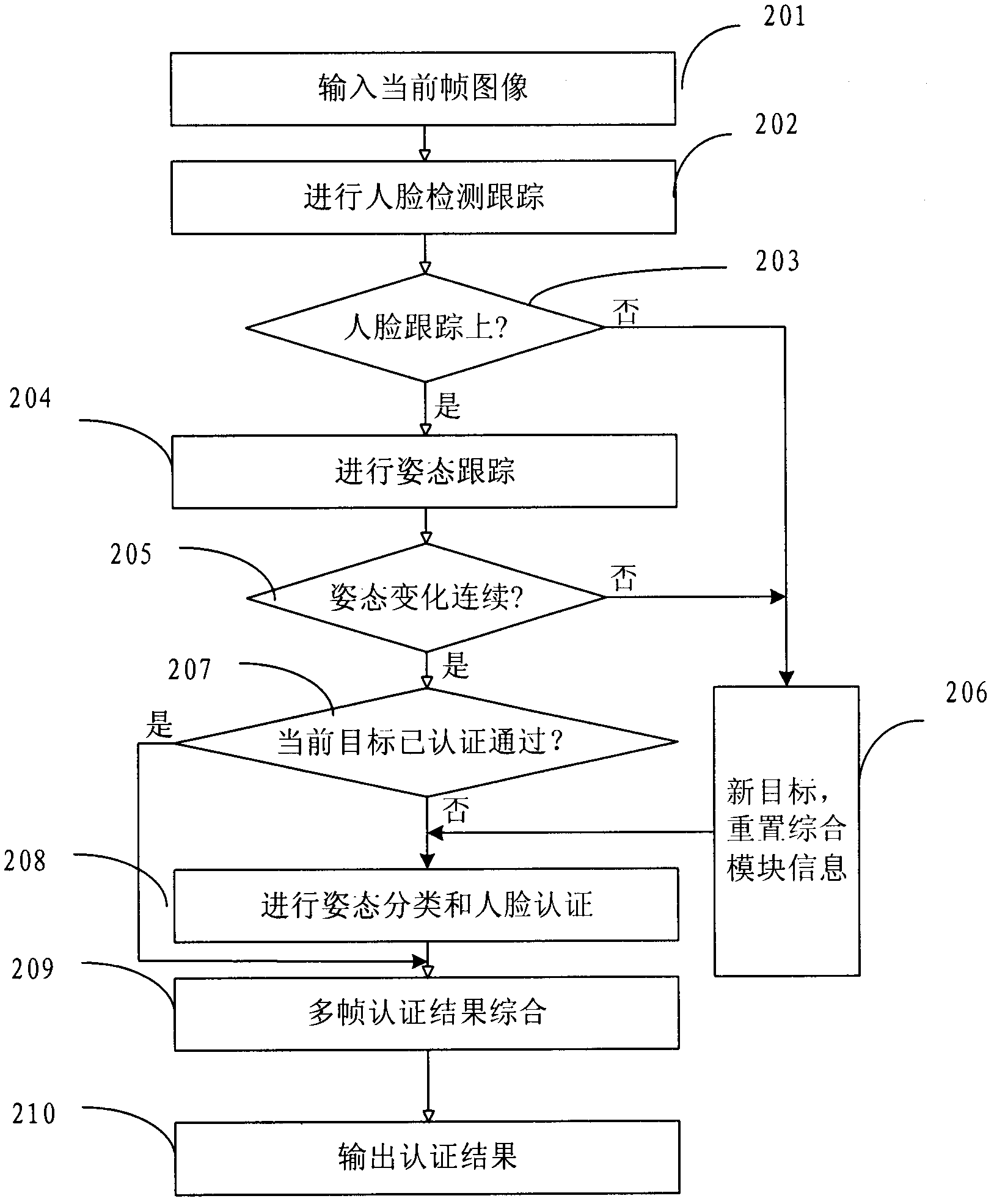
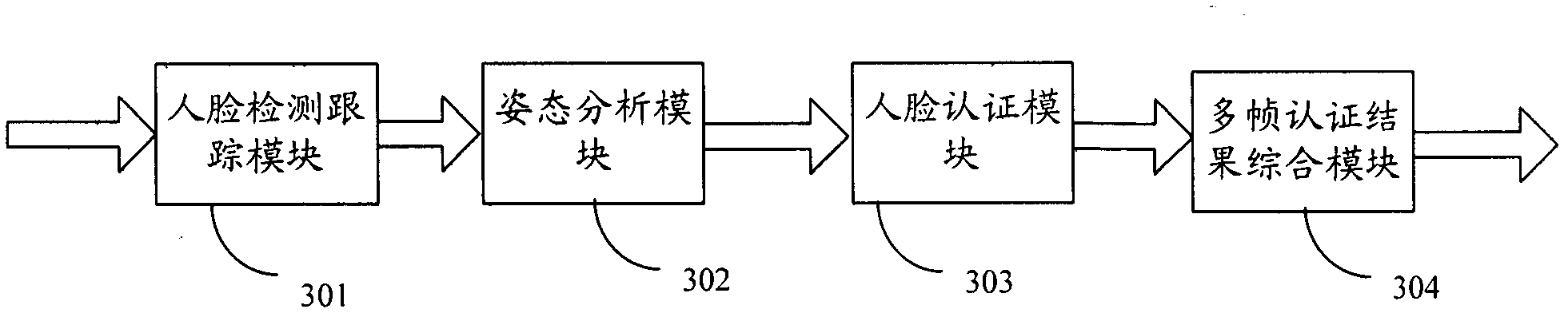
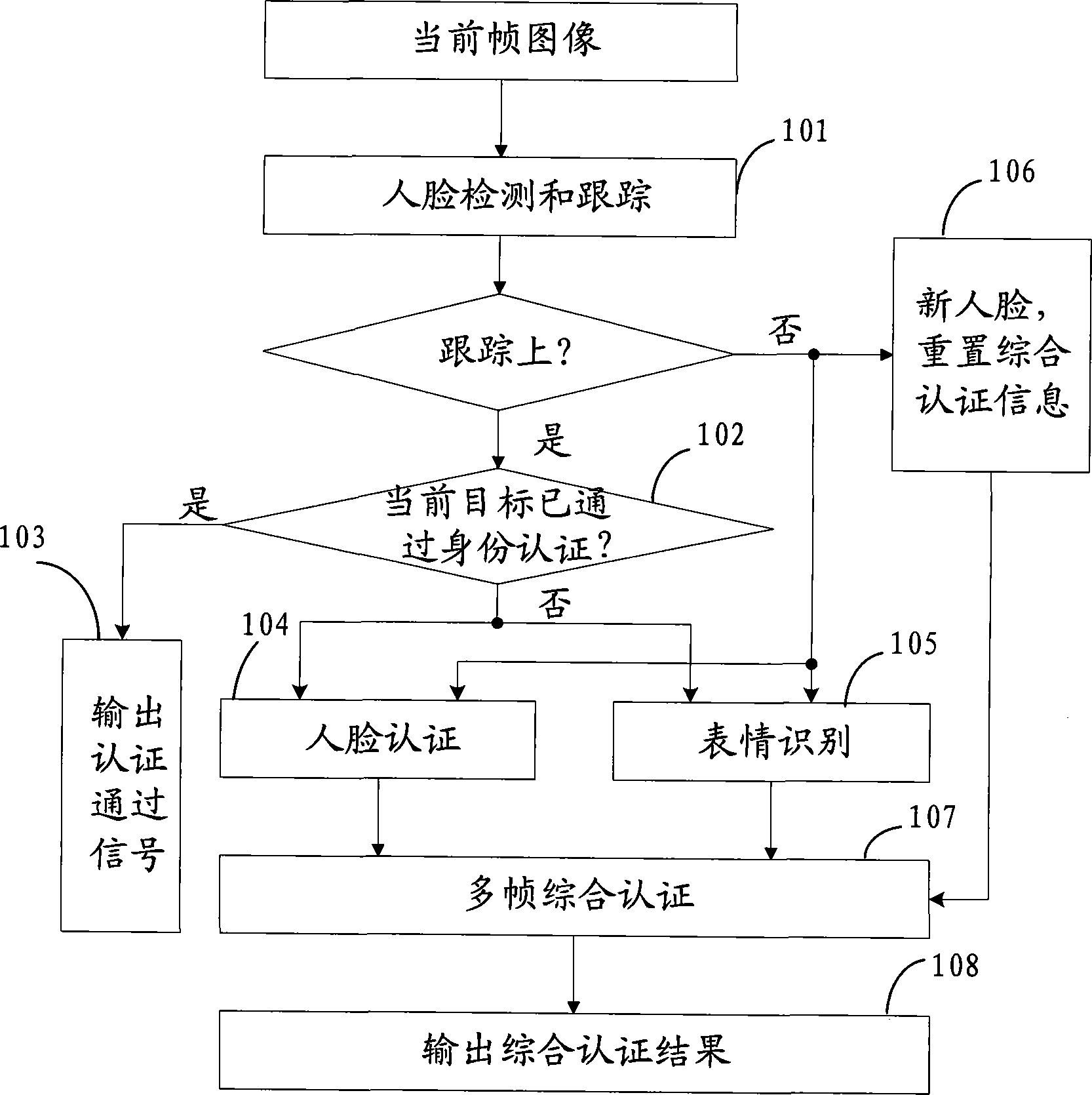
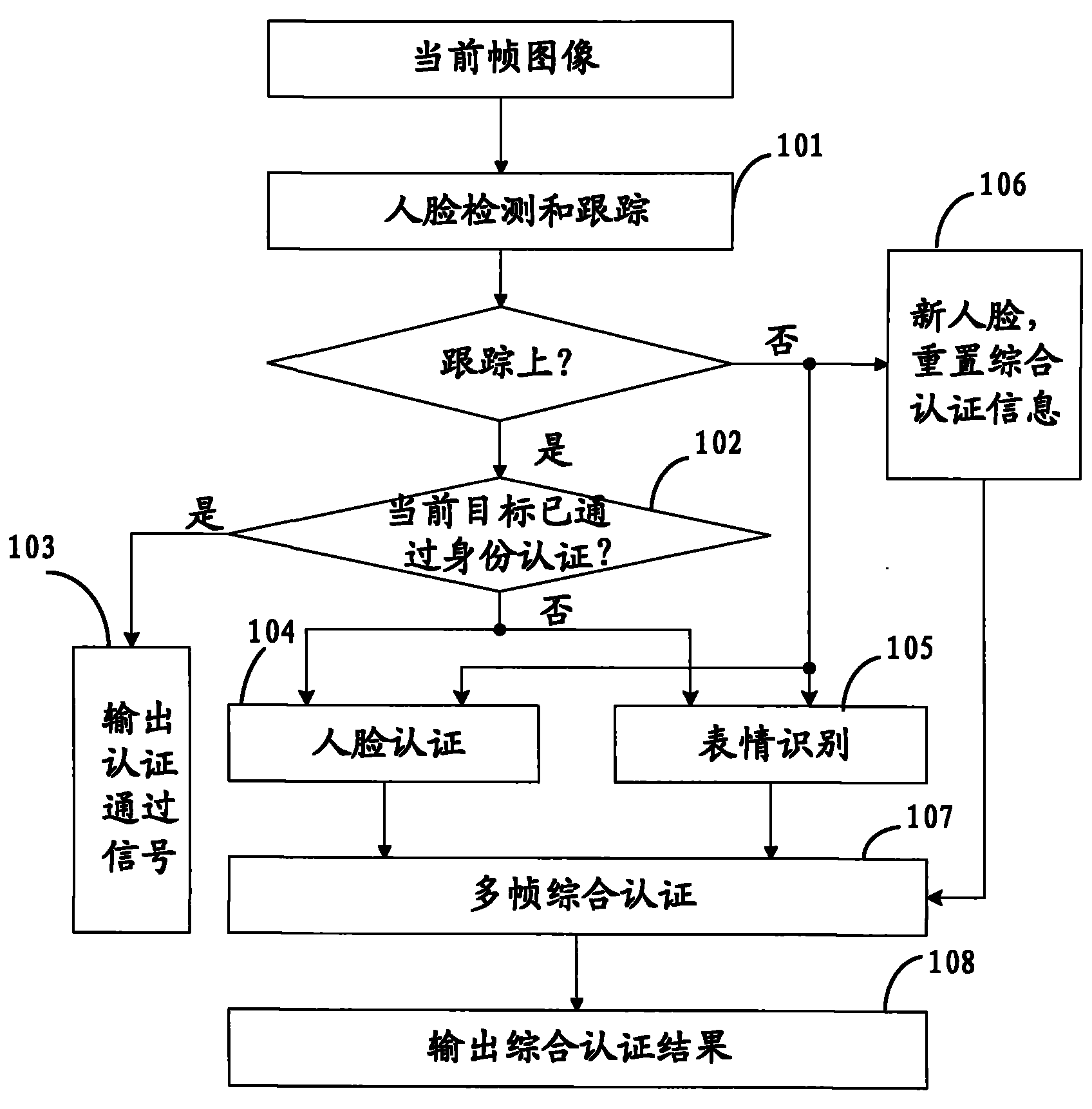
The invention provides an identity authentication method based on a face and an authentication apparatus thereof. The method comprises the following steps: carrying out face detection on each frame of image acquired by a camera device to obtain a face image, and tracking the face image to obtain a tracking result; carrying out an attitude analysis, wherein if a face attitude in obtained attitude information is not jumped relative to a face attitude corresponding to a prior frame of image, an attitude analysis result is not jumped; carrying out face comparison; carrying out statistics analysis on a plurality of frames of tracking results, a plurality of frames of attitude analysis results and a plurality of frames of face image authentication results, wherein if a statistics analysis result is in accordance with a preset condition, identity authentication is passed. According to the method and the apparatus thereof in the invention, a two-dimensional flat picture is utilized to distinguish a photograph from a human, in the prior art utilizing three-dimensional information and carrying out photograph identification cause that a system identification speed is substantially decreased and an application requirement can not satisfied, and the above technical problem is solved in the invention.
Owner:GUANGDONG VIMICRO
Fingerprint authentication using touch sensor data
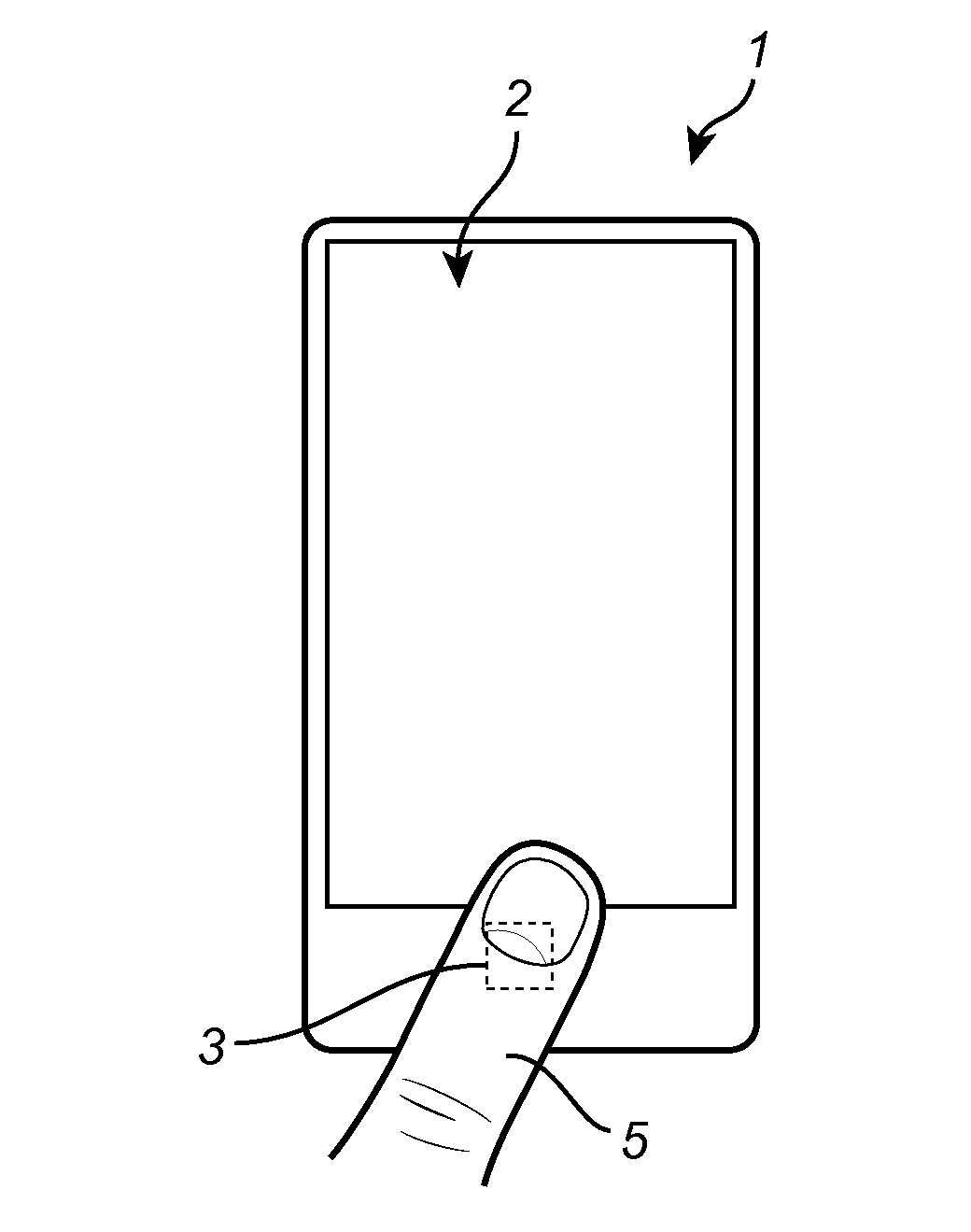
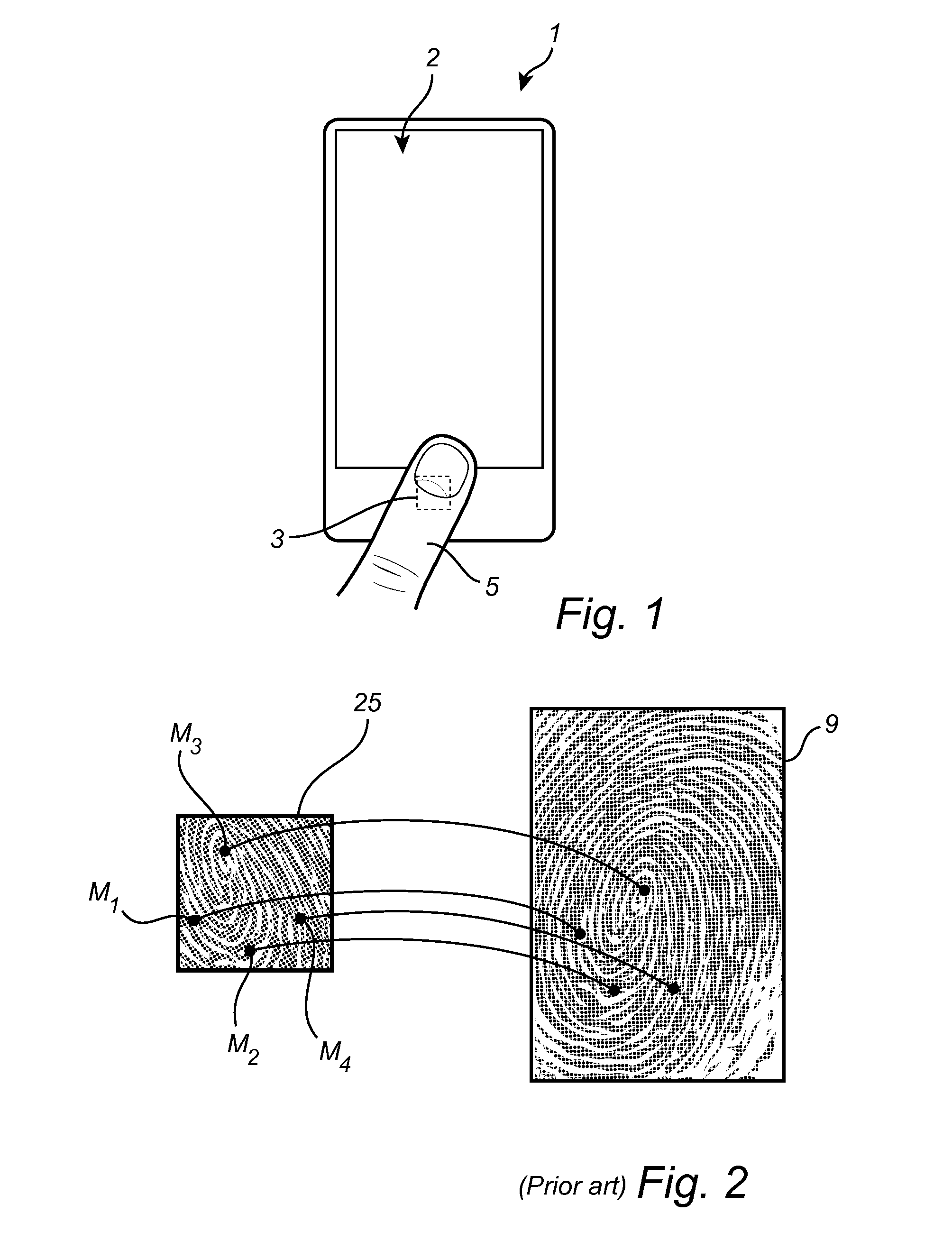
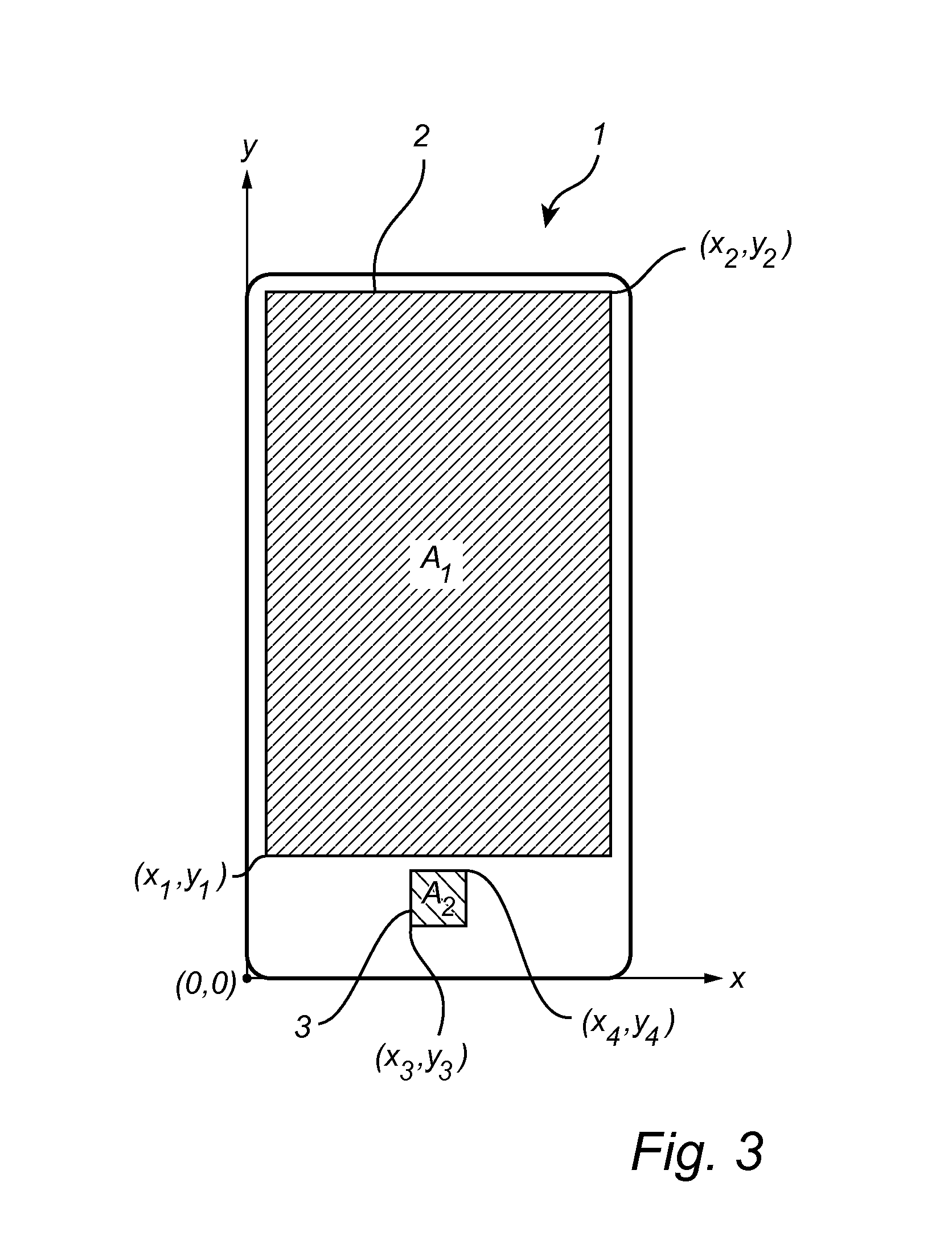
ActiveUS20160180146A1Resolution be lowerReduce timeDigital data processing detailsDigital data authenticationComputer visionFingerprint
A method of authenticating a candidate fingerprint by means of an electronic device comprising a touch sensor; and a fingerprint sensor. The method comprises the steps of: acquiring at least one touch sensor signal indicative of a sub-area of the touch sensor being touched by the candidate finger; acquiring at least one fingerprint image of the candidate fingerprint; retrieving a stored enrollment representation of the enrolled fingerprint of the enrolled finger; determining an authentication representation of the candidate fingerprint based on the fingerprint image; and determining an authentication result based on the authentication representation, the stored enrollment representation, and the at least one touch sensor signal.
Owner:FINGERPRINT CARDS ANACATUM IP AB
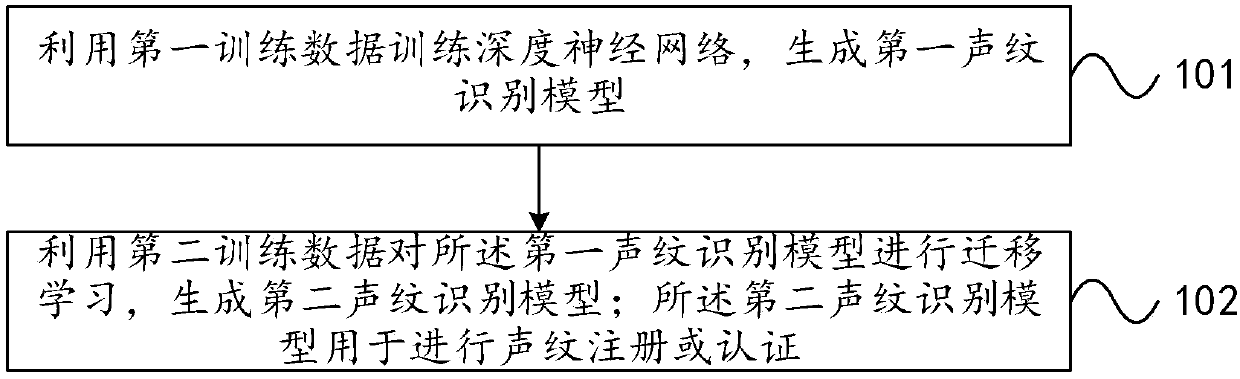
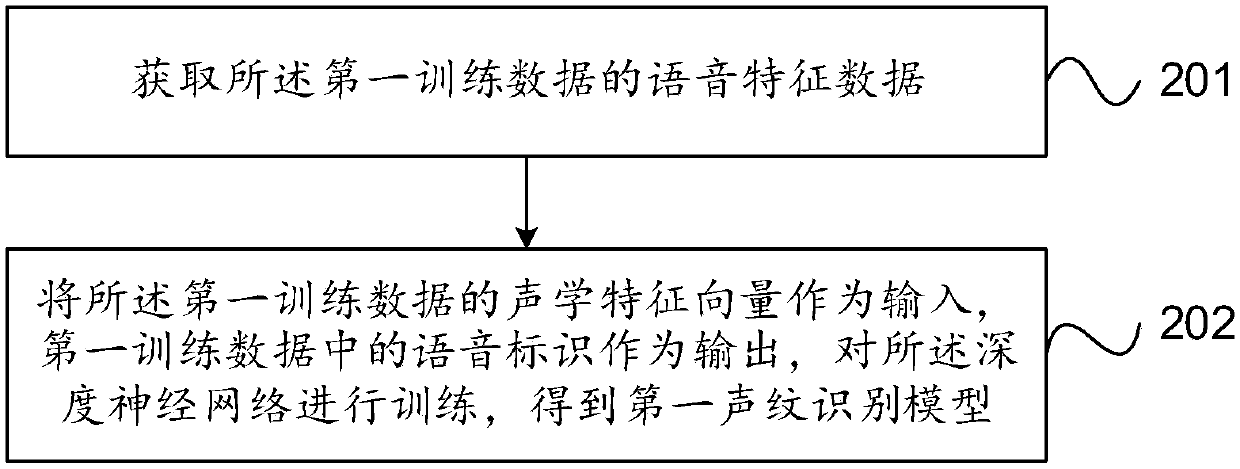
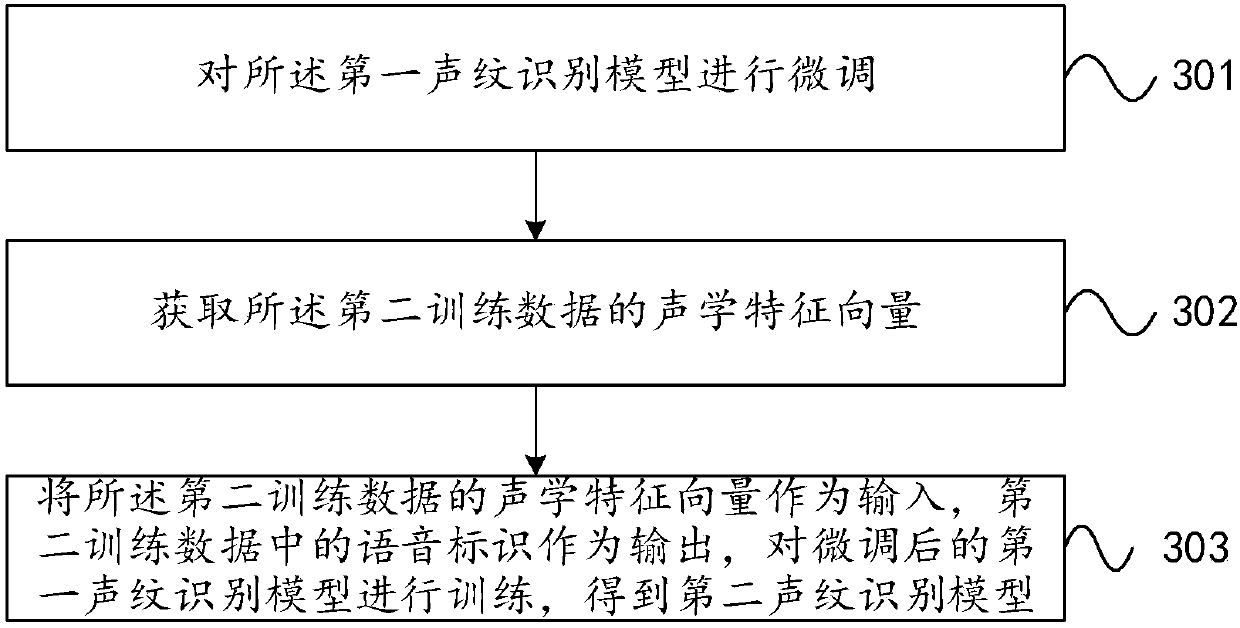
Method and system for training voiceprint recognition model
ActiveCN107610709AGuaranteed performanceEasy to identifySpeech analysisNeural learning methodsPattern recognitionData needs
The invention provides a method and system for training a voiceprint recognition model, and the method comprises the steps: training a depth neural network through first training data, and generatinga first voiceprint recognition model; carrying out the transfer learning of the first voiceprint recognition model through second training data, and generating a second voiceprint recognition model, wherein the second voiceprint recognition model is used for voiceprint registration or authentication. The method can solve a problem in the prior art that a large amount of time cost and economic costis needed for guaranteeing the performances of an algorithm because a large amount of data needs to be recorded for the end-to-end voiceprint authentication algorithm in order to develop the voiceprint authentication algorithm and a product for a characteristic scene. The method can make the most of the whole training data, and improves the voiceprint recognition and authentication performances of the specific data through the transfer learning.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
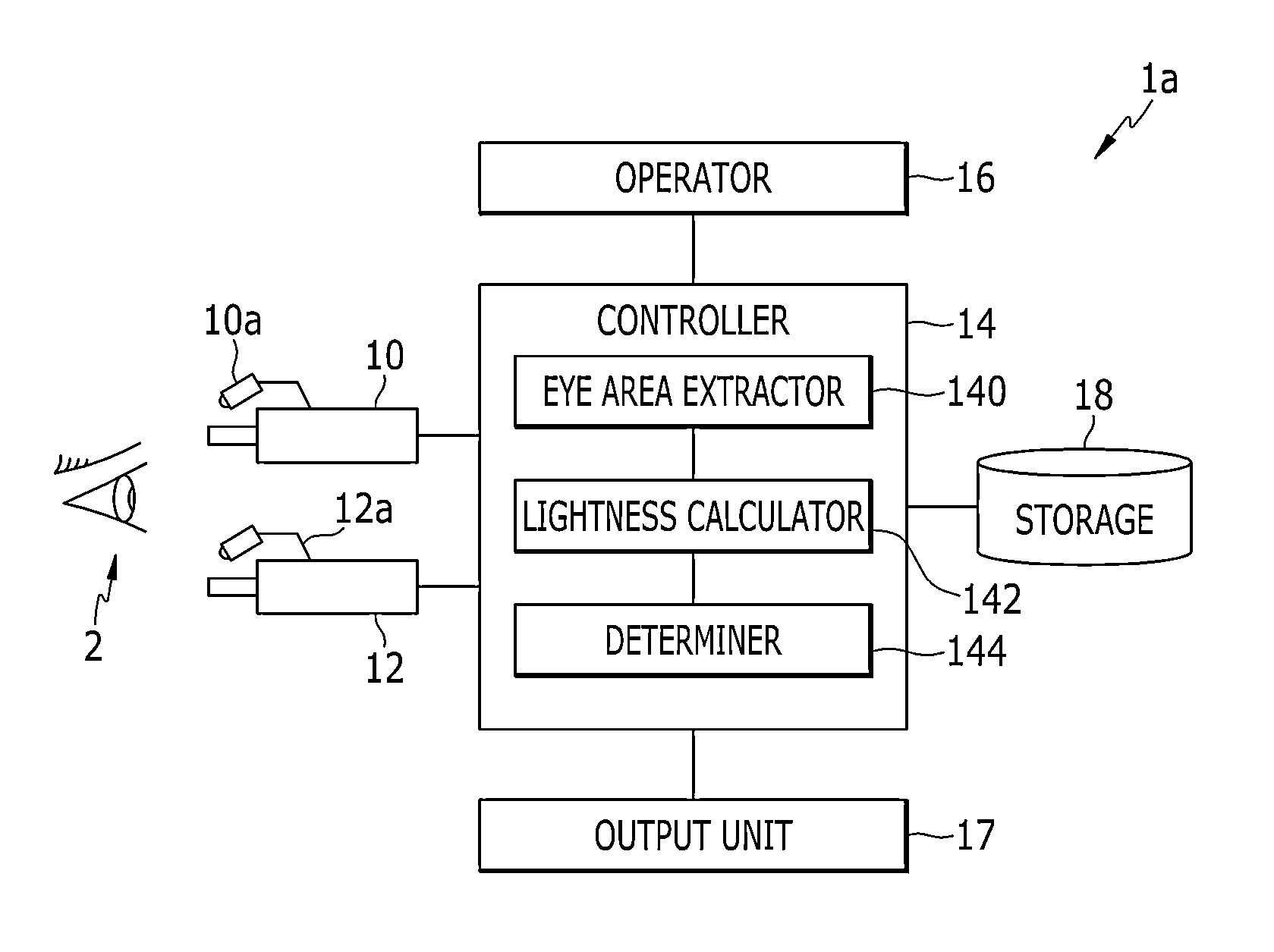
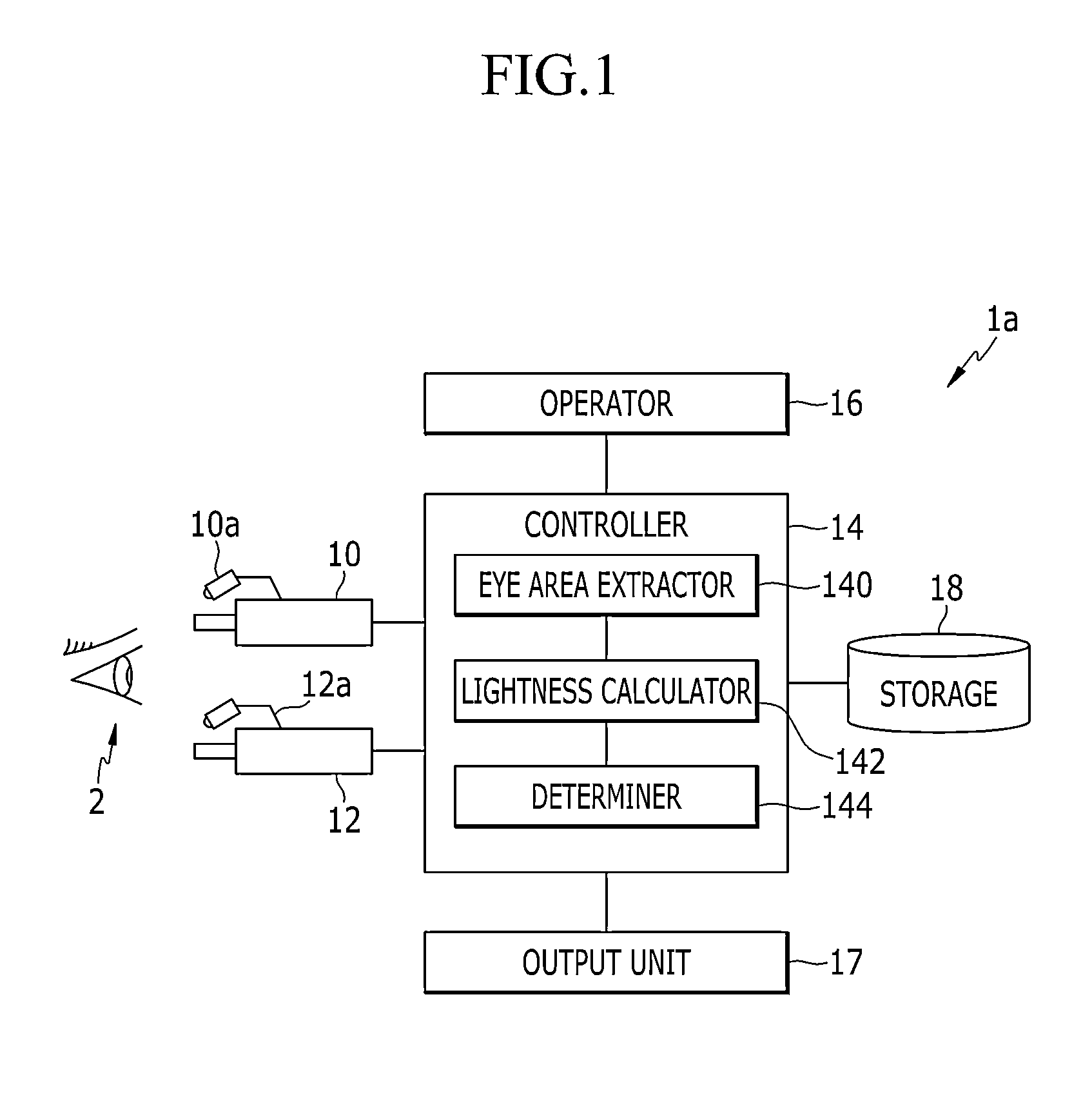
Apparatus and method for identifying fake face
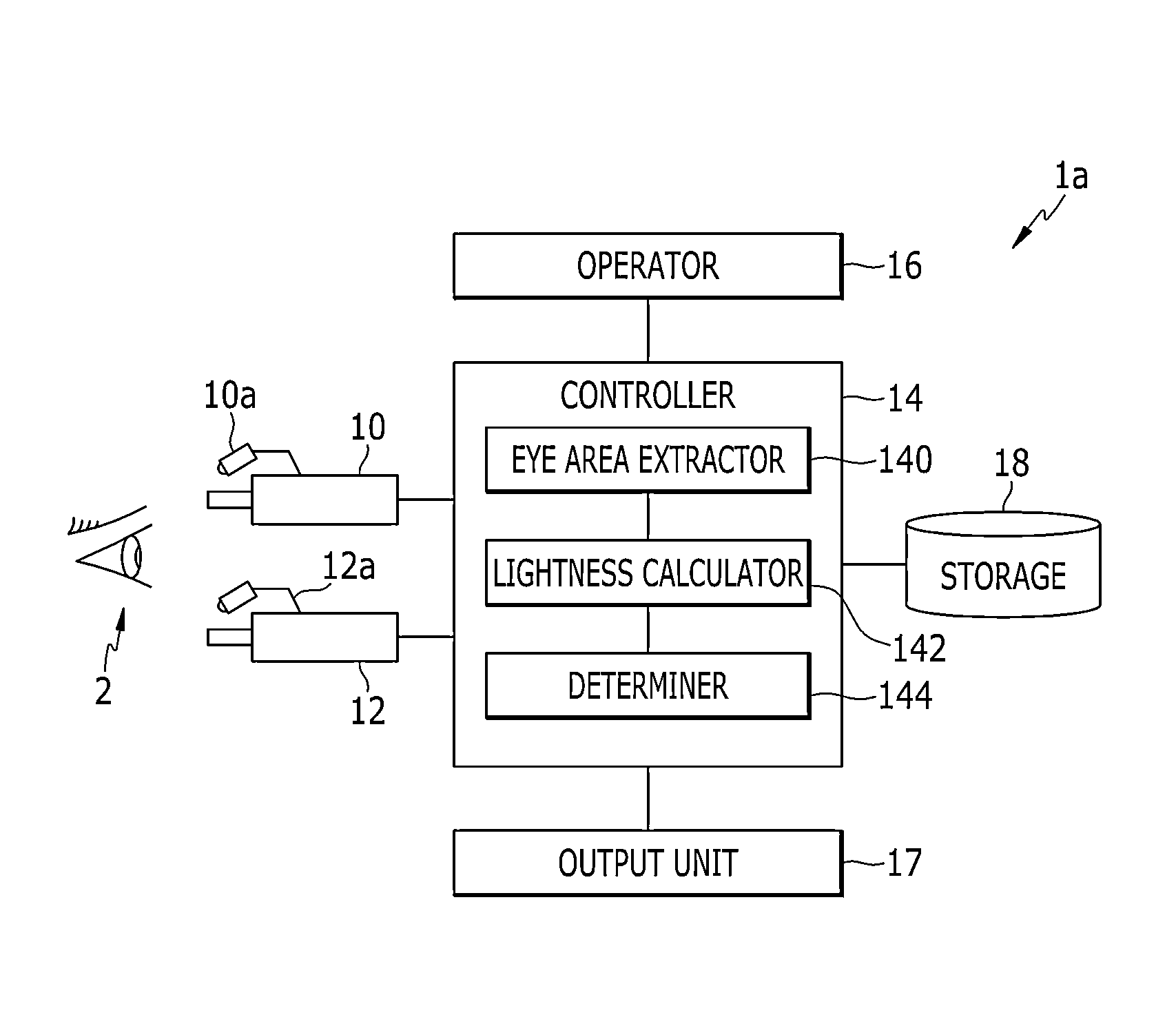
An apparatus for identifying a fake face is provided. A first eye image acquirer acquires a first eye image by taking a picture of a subject while radiating a first ray having a first wavelength. A second eye image acquirer acquires a second eye image by taking a picture of the subject while radiating a second ray having a second wavelength that is shorter than the first wavelength. A controller extracts a first area and a second area having brighter lightness than the first area from each of the first and second eye images, calculates a lightness of the first area and a lightness of the second area in the first eye image, and a lightness of the first area and a lightness of the second area in the second eye image, and determines whether the subject uses a fake face based on the calculated lightness.
Owner:SUPREMA INC
Identity authentication method and identity authentication system based on human face
ActiveCN102385703AImprove authentication capabilitiesQuick distinctionCharacter and pattern recognitionPattern recognitionAuthentication system
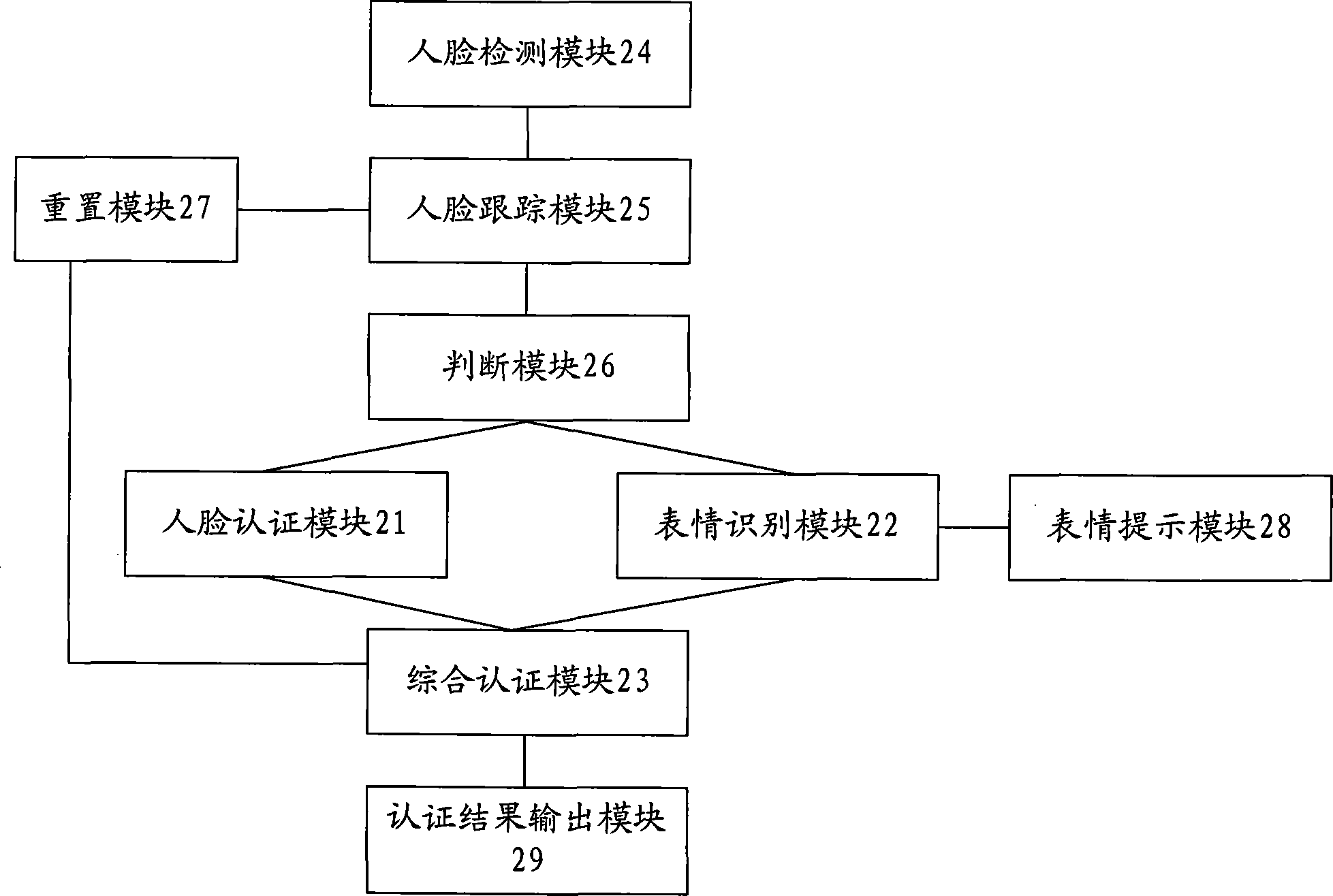
The invention provides an identity authentication method and an identity authentication system based on a human face, which are used for solving the problem of distinguishing real persons from photos in the authentication process of the human face. The identity authentication method comprises the following steps of: carrying out human face authentication and facial expression recognition on a current frame image; carrying out comprehensive authentication on a human face authentication result and a facial expression recognition result of a continuous multiframe according to a preset strategy; and if the comprehensive authentication result is human face authentication pass and at least comprises two expressions, passing the identity authentication of the human face. According to the identity authentication method and the identity authentication system provided by the invention, by combining the expression recognition with human face recognition, the authentication performance is improved and the phenomenon that a jactitator passes the authentication by using a photo is avoided.
Owner:GUANGDONG VIMICRO
IP (Internet Protocol) address management method and system as well as DHCP (Dynamic Host Configuration Protocol) server
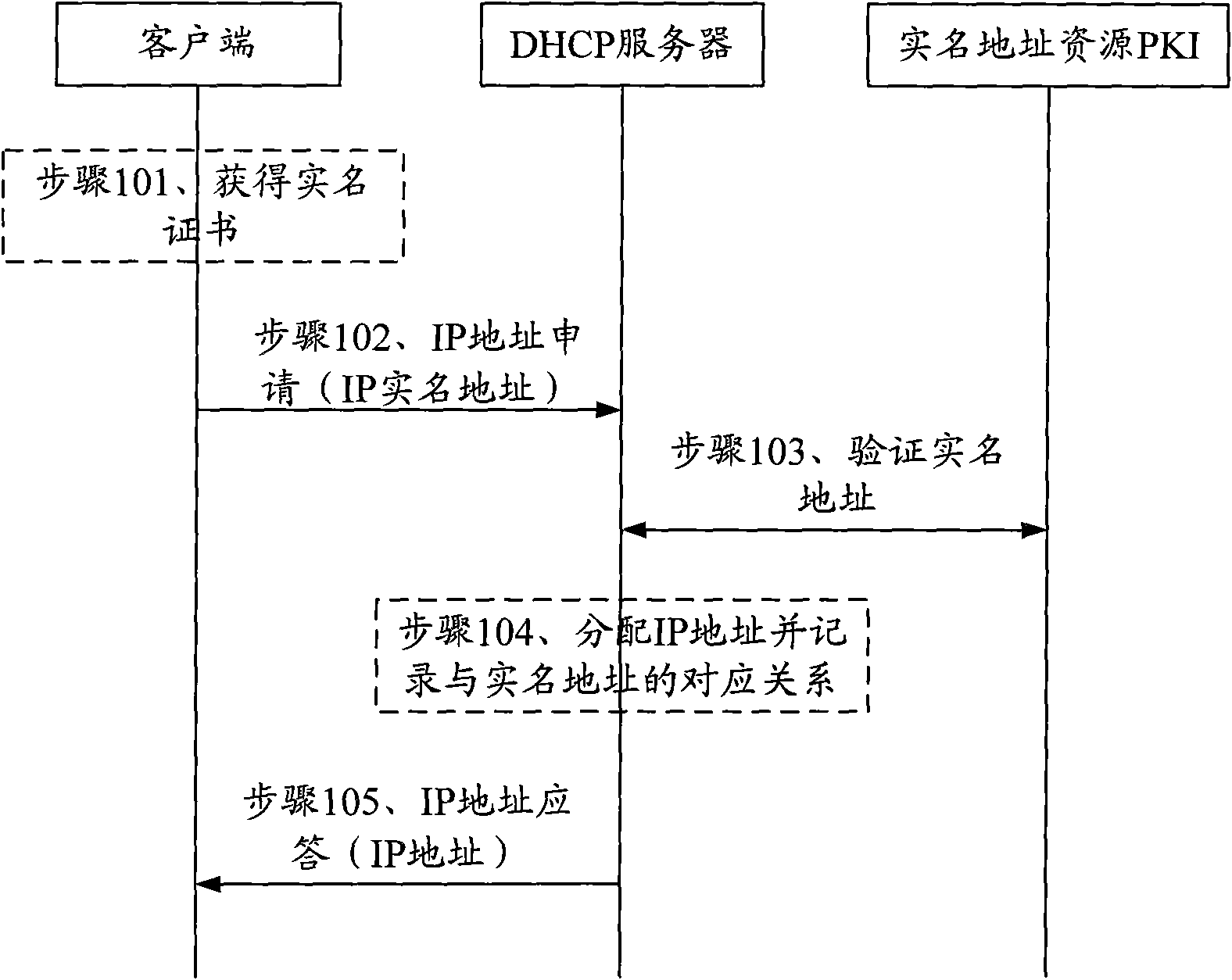
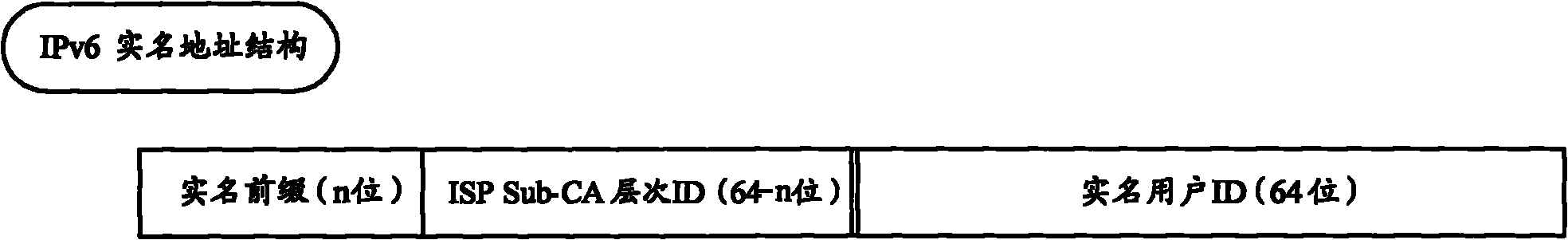
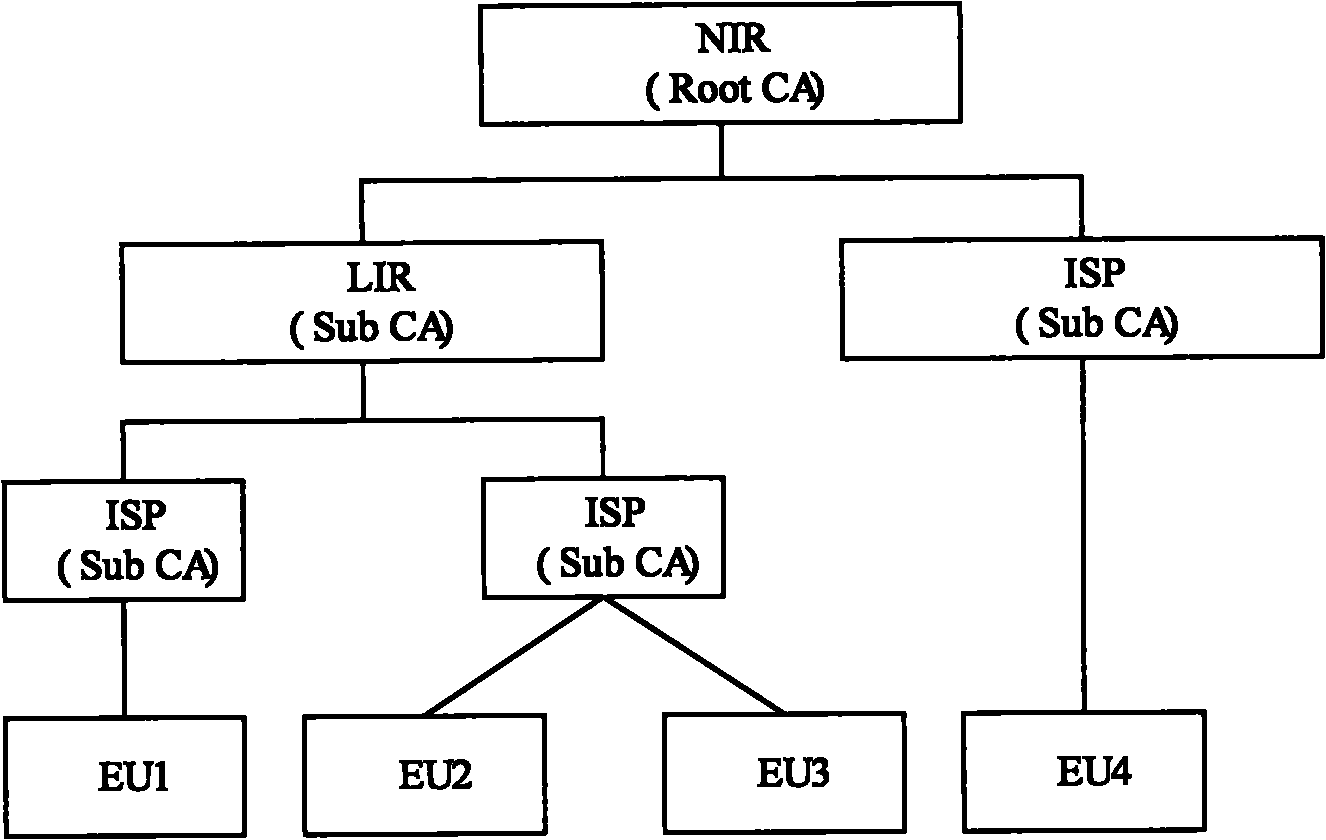
The invention provides IP (Internet Protocol) address management method and system as well as DHCP (Dynamic Host Configuration Protocol) server, wherein the method comprises the following steps of: receiving an IP address application message sent by a client, wherein the IP address application message carries a real name IP address for identifying the user identity of the client; allocating an IPaddress for the client and recording the corresponding relation of the IP address and the real name IP address into a database; and returning an IP address response message to the client, wherein theIP address response message carries the allocated IP address. The invention enhances the client authentication capacity of a DHCP protocol through introducing an IPv6 real name address and a resourcePKI (Public Key Infrastructure) thereof by combining an expanded DNS (Domain Name Server) protocol.
Owner:CHINA INTERNET NETWORK INFORMATION CENTER
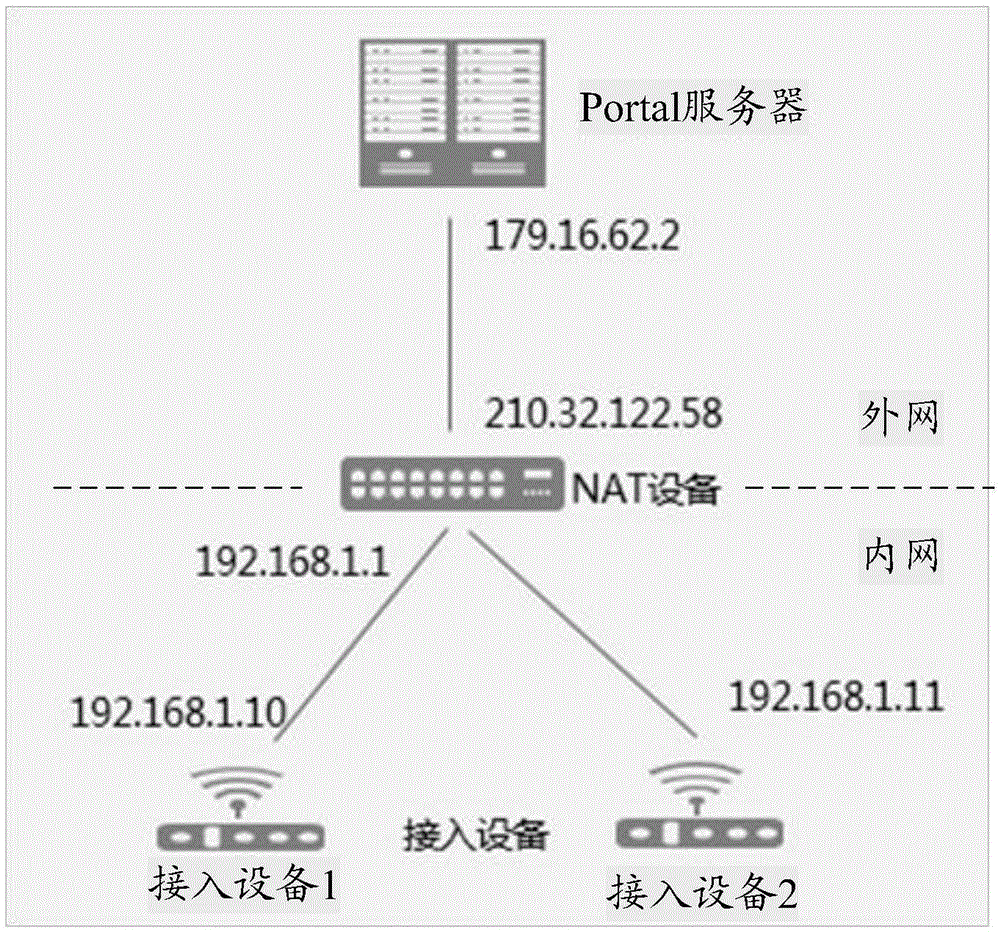
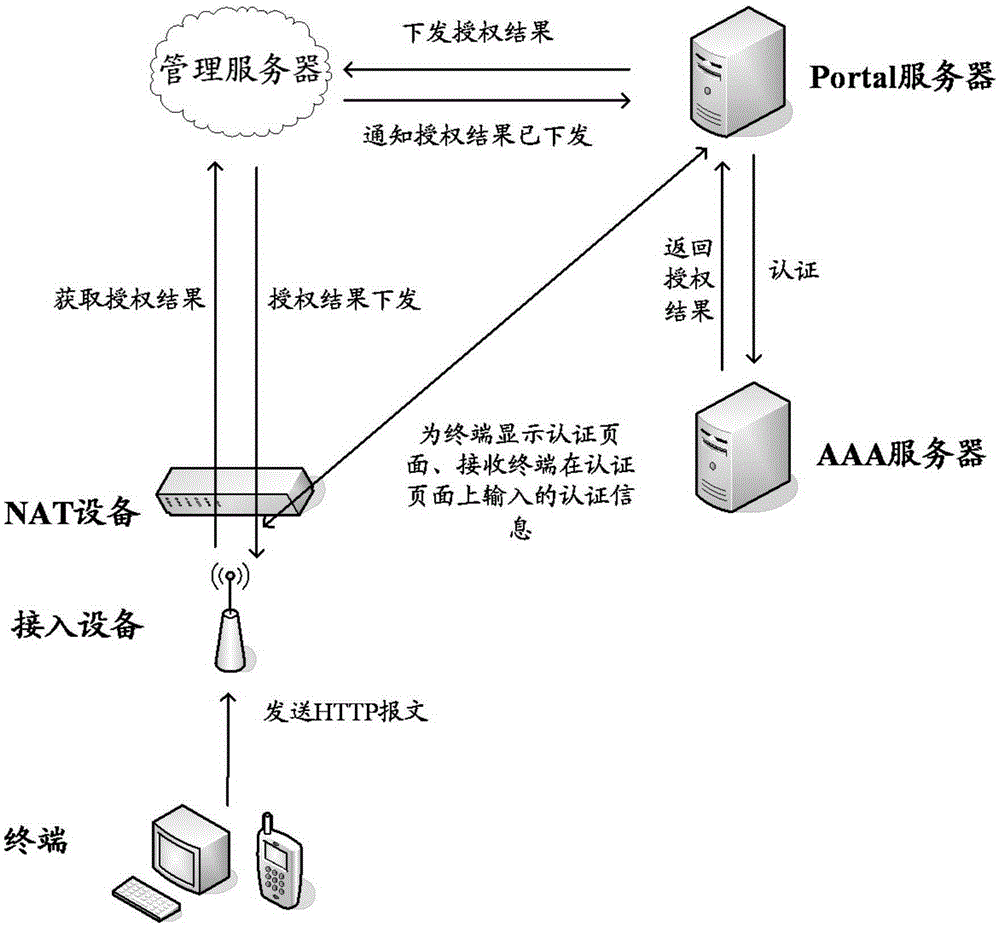
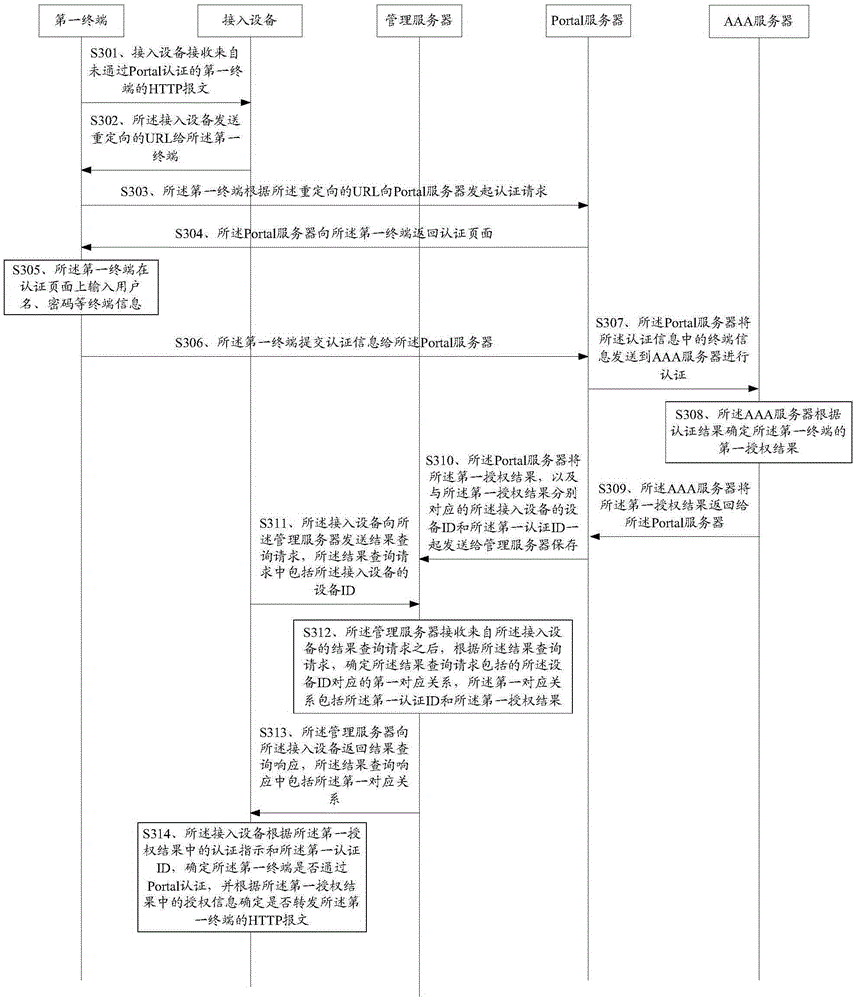
Portal authentication method, access device and management server
ActiveCN106656911AImprove authentication efficiencyReduce the number of interactionsTransmissionAuthorizationDatabase
The invention discloses a Portal authentication method, an access device, a management server, and a Portal server. An access device sends a result query request to a management server and receives a first corresponding relation returned by the management server in response to the result query request, wherein the first corresponding relation comprises first authentication ID and a first authorization result, and the first corresponding relation is provided by a Portal server for the management server; and the access device, according to authentication indication in the first authorization result and the first authentication ID, determines whether a first terminal succeeds in Portal authentication, and according to authorization information in the first authorization result, determines whether to forward a hyper text transfer protocol (HTTP) message of the first terminal such that Portal authentication can be completed under the condition that an NAT device exists between the first terminal and the Portal server.
Owner:HUAWEI TECH CO LTD
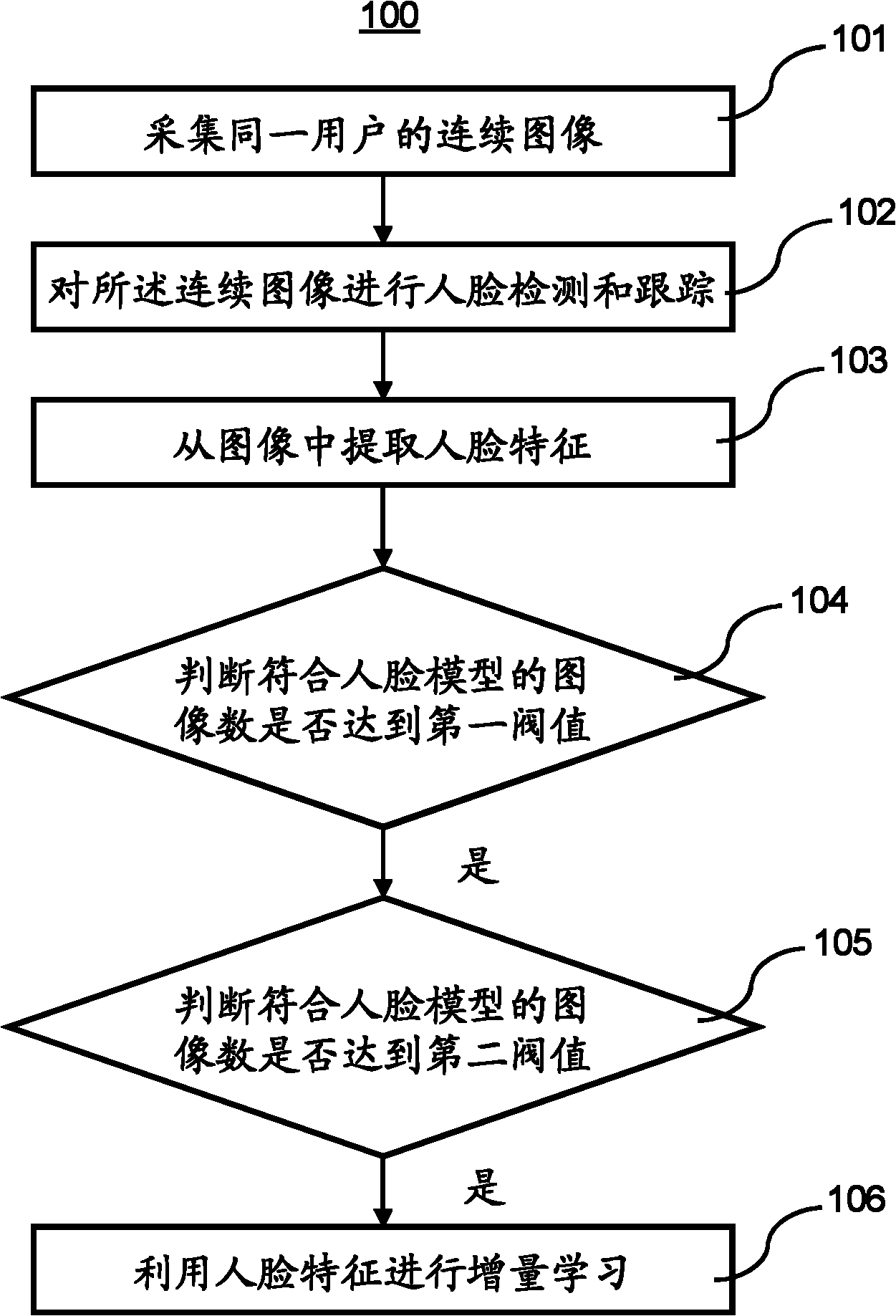
Human face authentication method and device
InactiveCN102004905AImprove authentication capabilitiesAchieve self-maintenanceCharacter and pattern recognitionSelf maintenanceUser authentication
The invention discloses a human face authentication method, which comprises the following steps of: extracting human face characteristics from a plurality of frame images; judging whether the human face characteristics in the plurality of frame images accord with a preset human face model or not, and when the number of images according with the preset human face model exceeds a first threshold value, considering that user authentication corresponding to the human face characteristics in the plurality of frame images is successful; when the number of images according with the preset human face model exceeds a second threshold value, extracting all human face characteristics in the plurality of frame images as sample characteristics; and performing increment training on the preset human face model by utilizing the sample characteristics, wherein the second threshold value is not less than the first threshold value. In the method, more approximate sample images are used for training the human face model in the continual using process of users, so that the authentication capacity of the human face model is enhanced, and the self-maintenance is realized.
Owner:江苏博悦物联网技术有限公司
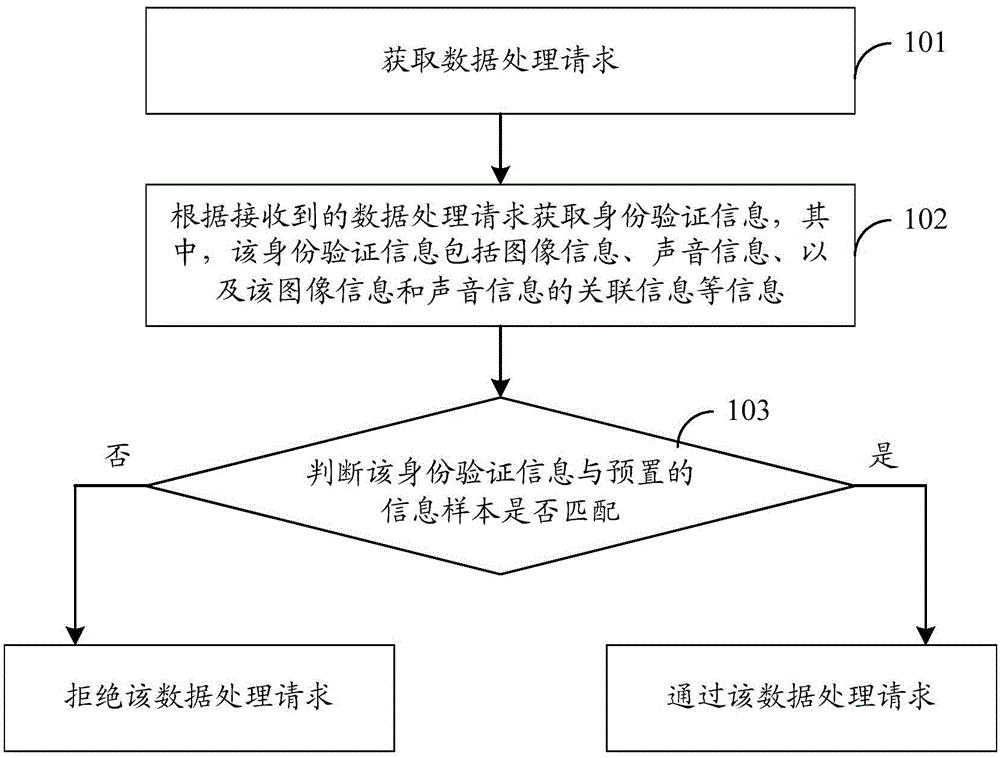
Identity verification method, apparatus and system
ActiveCN104967593AIncreased complexityIncrease the difficultyUser identity/authority verificationInformation securityData mining
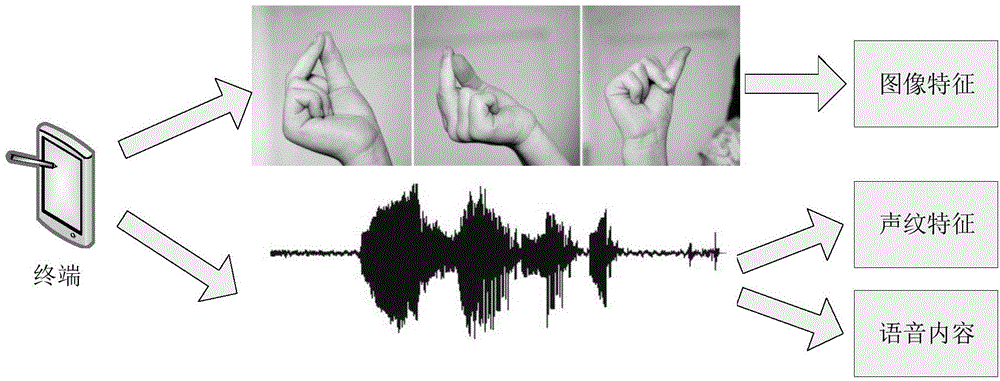
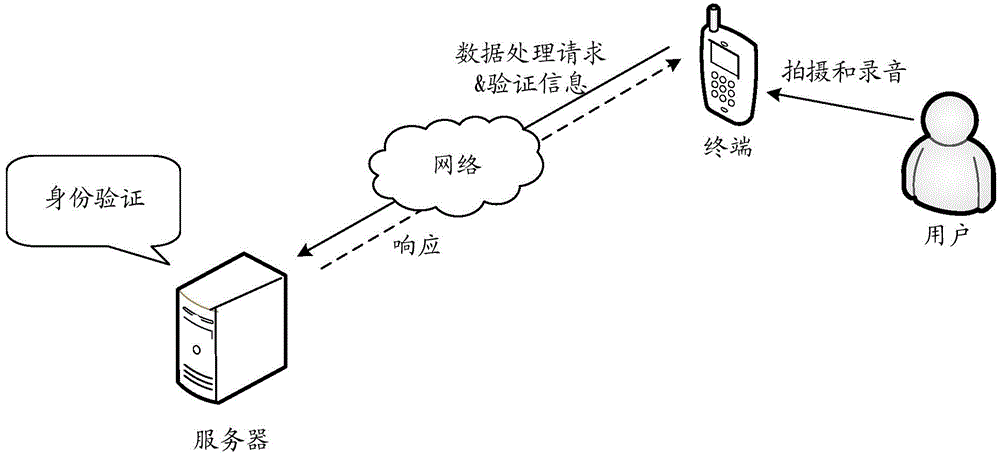
The embodiments of the invention disclose an identity verification method, apparatus and system. The method provided by one embodiment of the invention comprises obtaining a data processing request and obtaining identity verification information according to the data processing request, wherein the identify verification information comprises image information, sound information, and association information of the image information and the sound information; determining whether the identify verification information matches a preset information sample, in case of a match, approving the data processing request, and otherwise, in case of a mismatch, rejecting the data processing request. The scheme provided by the invention can enhance the identify verification effect and greatly improves the information security.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
Apparatus and method for identifying fake face
An apparatus for identifying a fake face is provided. A first eye image acquirer acquires a first eye image by taking a picture of a subject while radiating a first ray having a first wavelength. A second eye image acquirer acquires a second eye image by taking a picture of the subject while radiating a second ray having a second wavelength that is shorter than the first wavelength. A controller extracts a first area and a second area having brighter lightness than the first area from each of the first and second eye images, calculates a lightness of the first area and a lightness of the second area in the first eye image, and a lightness of the first area and a lightness of the second area in the second eye image, and determines whether the subject uses a fake face based on the calculated lightness.
Owner:SUPREMA INC
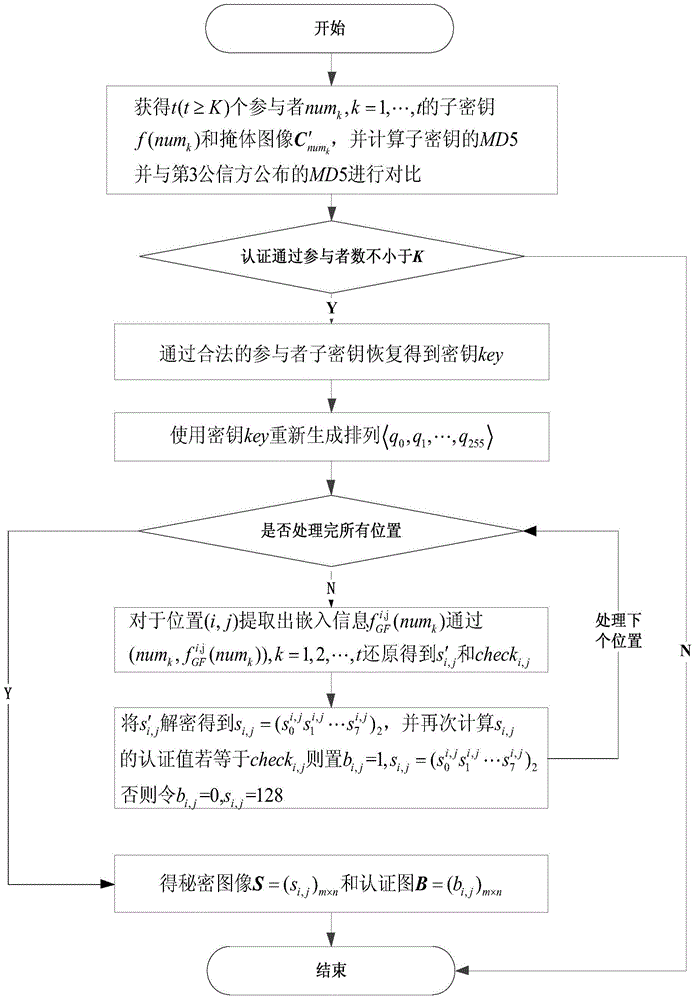
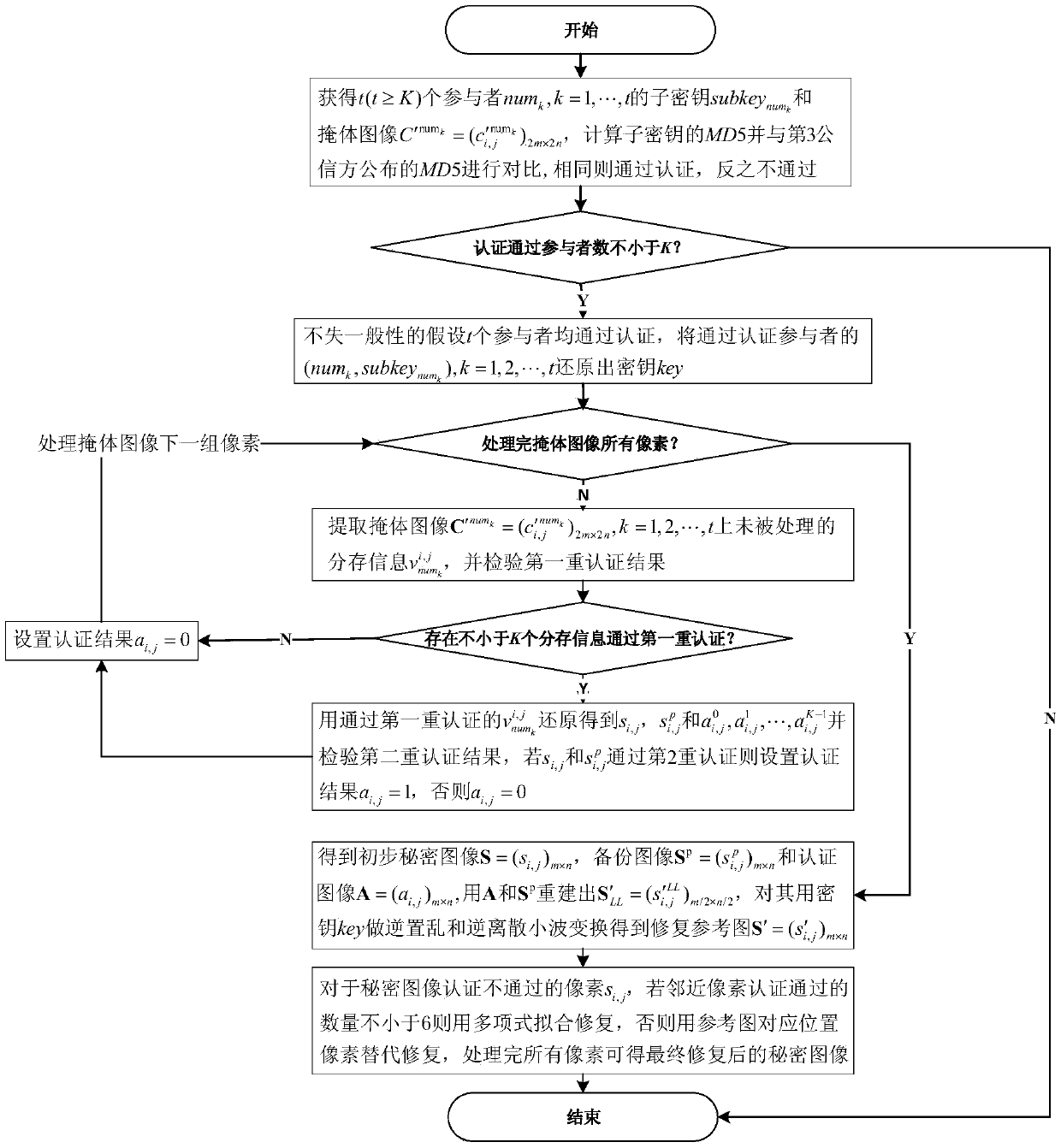
(K,N) meaningful non-expansion image divide-storage and reconstruction method based on GF(23)
ActiveCN104881838AIncrease transfer loadImprove visual qualityDigital data protectionImage data processing detailsThird partyReconstruction method
The invention provides a (K,N) meaningful non-expansion image divide-storage and reconstruction method based on GF(23); the method comprises the following steps: firstly generating an encryption mapping table and encrypting secret pixels through using secret pixel positional information; carrying out (K, N) divide-storage for secret pixel authentication information and the encrypted pixels under a GF (23) Galois field, and embedding the information into corresponding pixels of a mask image; finally carrying out (K,N) divide-storage for a mapping table generation secret key, calculating a MD5 value of each subkey, and publishing the MD5 values to a third party trusted party so as to prevent cheating of a subkey holder. Compared with a conventional method, the (K,N) meaningful non-expansion image divide-storage and reconstruction method can accurately identify a secret image attack zone without any pixel expansion; the mask image is equal in size with the secret image, and the mask image with embedded divide-storage information has excellent visual sense quality.
Owner:SHAANXI NORMAL UNIV
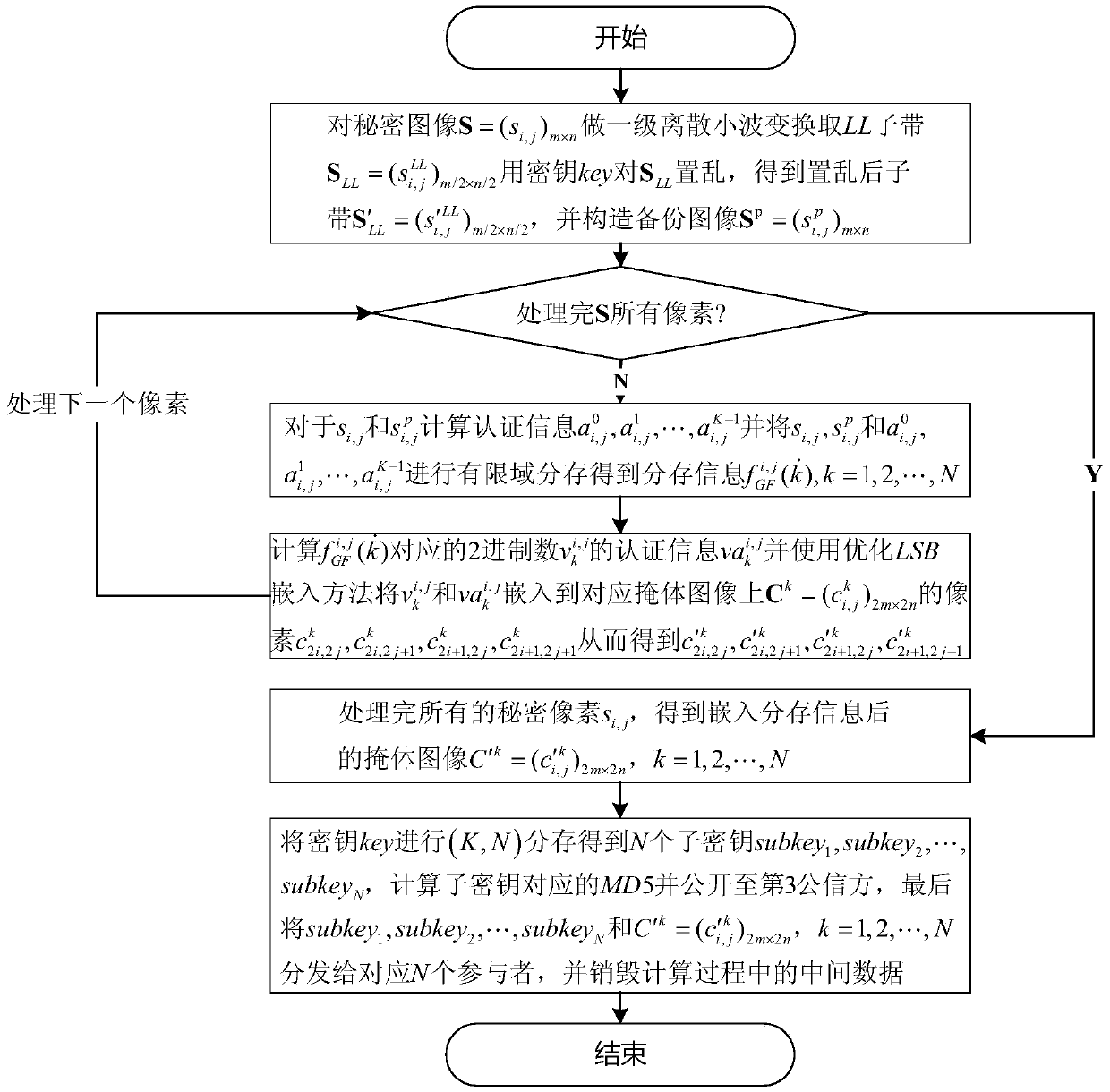
GF (27) finite field and dual authentication-based meaningful (K, N) image sharing and reconstructing method
ActiveCN105590297AThe certification process is reliableImprove visual qualityGeometric image transformationComputer hardwareBunker
The invention provides a GF (27) finite field and dual authentication-based meaningful (K, N) image sharing and reconstructing method. Ring the sharing period, the sub-band of a secret image LL is scrambled, and the coefficients of bits are backed up by different numbers according to the degrees of importance thereof. Finally, a backup image of the same size with the secret image is formed. After that, secret pixels, backup pixels and the corresponding dual-authentication information are shared in the form of (K, N) in the GF (27) finite field. Based on the optimized LSB method, the shared information and primary authentication bits are embedded into the lower-order bits of a bunker block to maximally ensure the visual quality of distributed bunker images. During the reconstruction process, the shared information for recovery is screened through the primary authentication step. After that, the reliability of recovered secret pixels and the reliability of recovered backup pixels are verified through the secondary authentication step, so that an authentication image, a backup image and a preliminary secret image are formed. In combination with the secret image, a recovered reference image and the authentication image, the non-pass pixels of the secret image during the authentication process are subjected to polynomial fitting repair and alternative repair, so that the repair quality after the attack is better.
Owner:SHAANXI NORMAL UNIV
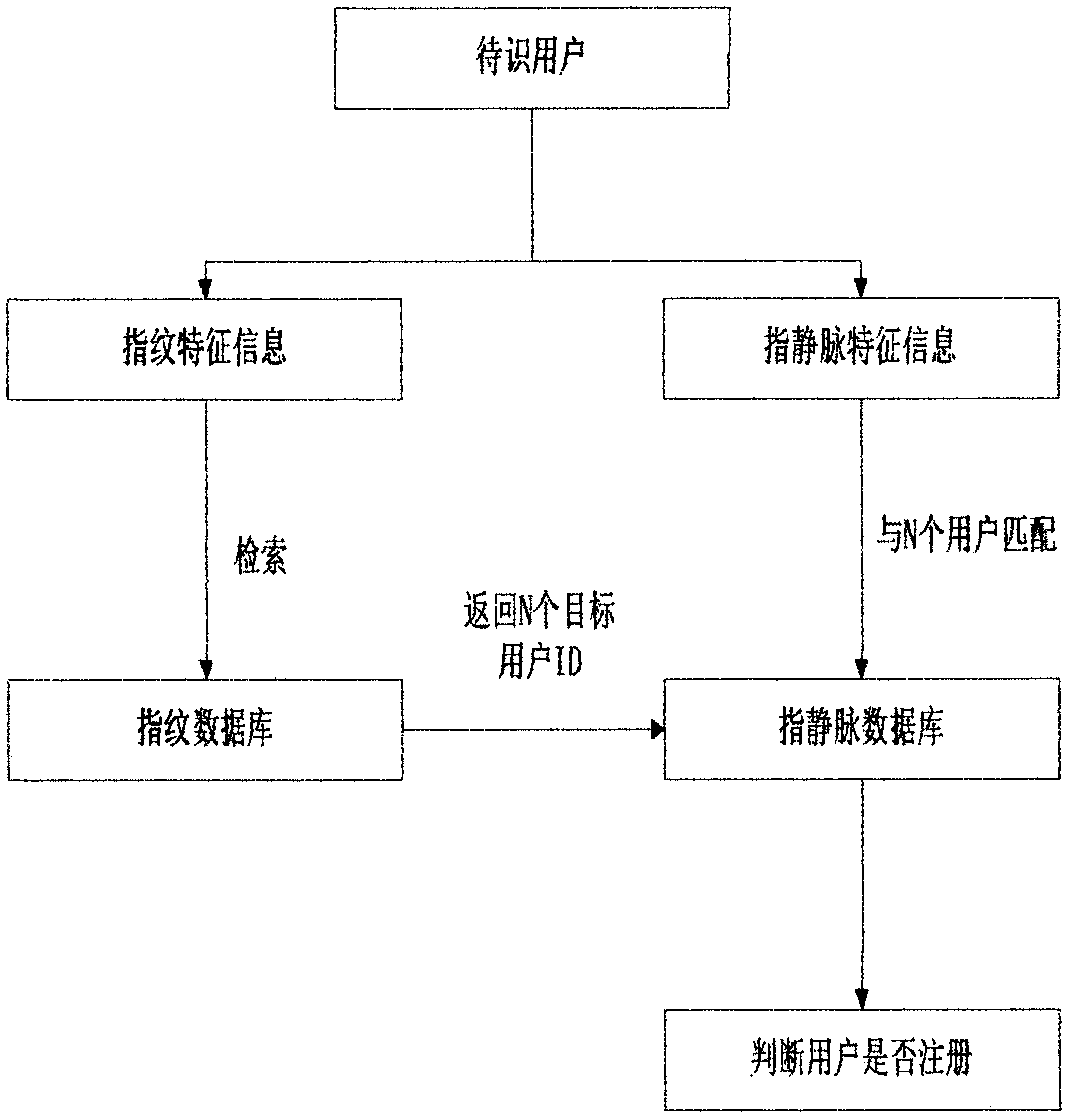
Fingerprint and finger vein combined recognition algorithm
InactiveCN109583279AThe recognition result is reliableImprove security levelSubcutaneous biometric featuresAcquiring/reconising fingerprints/palmprintsVeinFinger vein recognition
The invention discloses a fingerprint and finger vein combined recognition algorithm, which comprises the following steps of: firstly, retrieving N candidate users by utilizing a fingerprint feature point-based local surrounding point relative position and direction field similarity algorithm, and carrying out matching by using a finger vein recognition method based on combination of feature points and binary images; Experiments show that based on a fingerprint feature point local surrounding point relative position direction field similarity algorithm, the algorithm is good in stability, highin anti-interference capability and high in retrieval speed. The finger vein recognition algorithm based on the combination of the feature points and the binary image is stable. Under the condition that the false recognition rate is certain, the recognition performance of the fingerprint and finger vein combined recognition algorithm is obviously higher than that of a traditional fingerprint andfinger vein single-mode recognition algorithm; And the identification efficiency is also obviously improved.
Owner:TOP GLORY TECH INC CO LTD
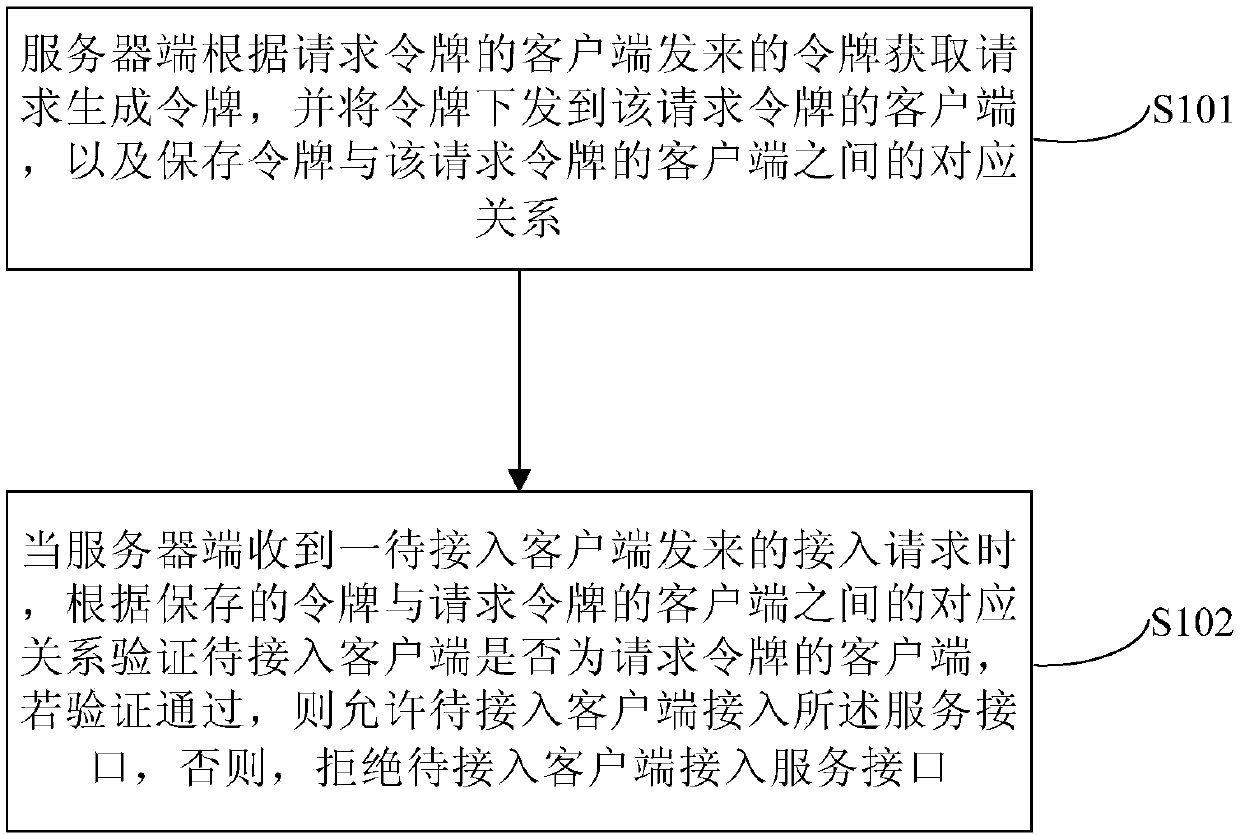
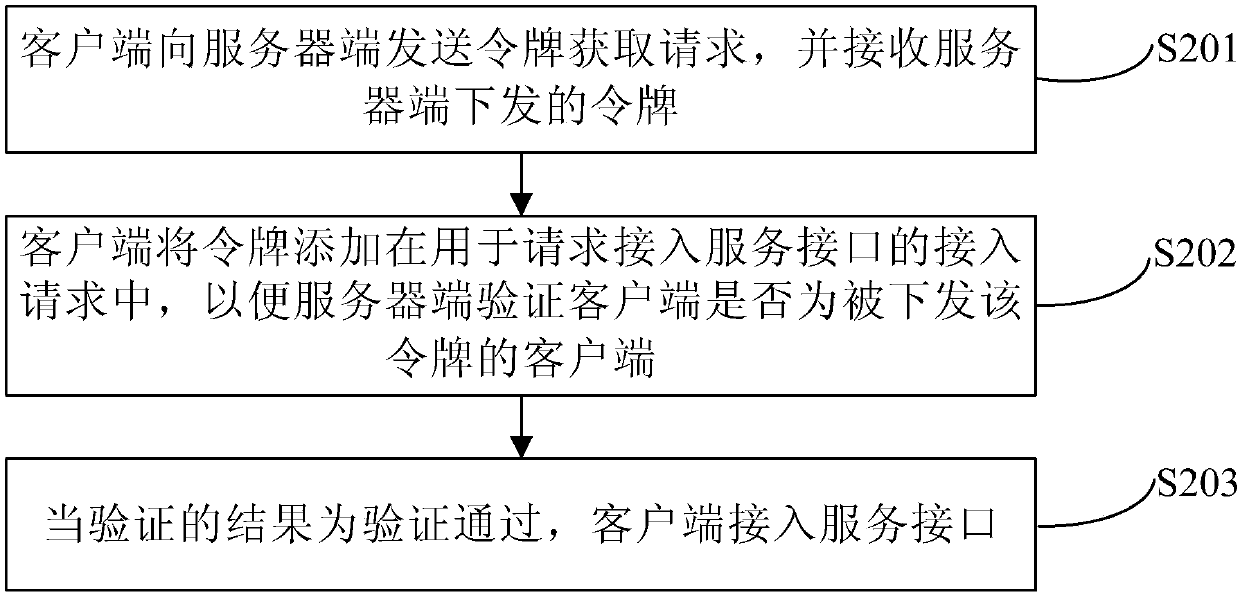
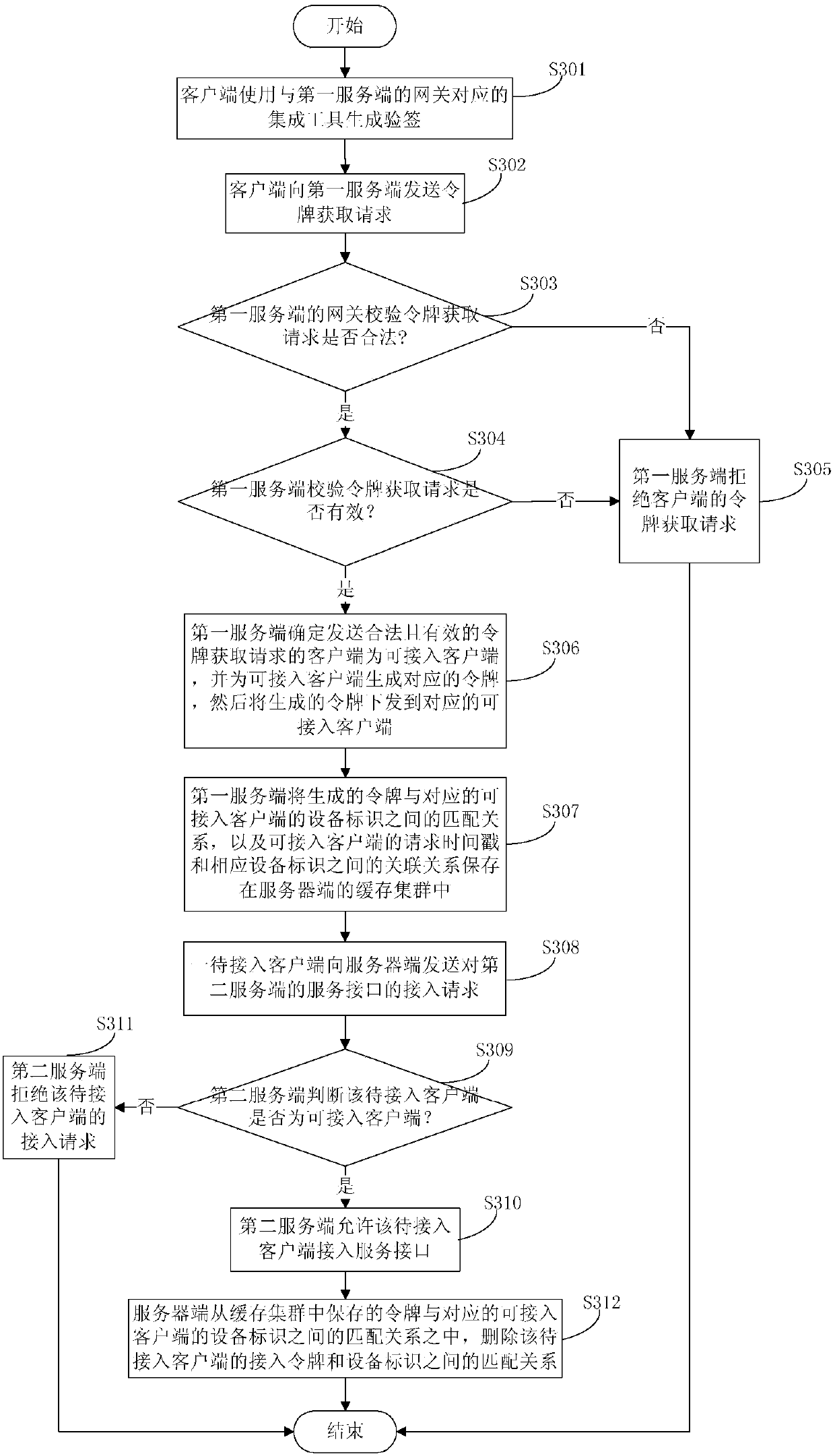
Secure access method and device for a service interface
ActiveCN109756337AImprove authentication capabilitiesImprove data integrityUser identity/authority verificationClient-sideServer-side
The invention discloses a secure access method and device for a service interface, and relates to the technical field of computers. A specific embodiment of the method comprises the following steps: aserver generates a token according to a token acquisition request sent by a client requesting the token, sends the token to the client requesting the token, and stores a corresponding relationship between the token and the client requesting the token; When the server side receives an access request sent by a client side to be accessed, the server side sends the access request to the client side;and verifying whether the to-be-accessed client is the client of the request token according to the stored corresponding relationship, if the verification is passed, allowing the to-be-accessed clientto access the service interface, and otherwise, refusing the to-be-accessed client to access the service interface. According to the embodiment, the identity verification capability, the data integrity and the anti-brushing capability of the background server side are enhanced under the condition that the cost is allowed.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
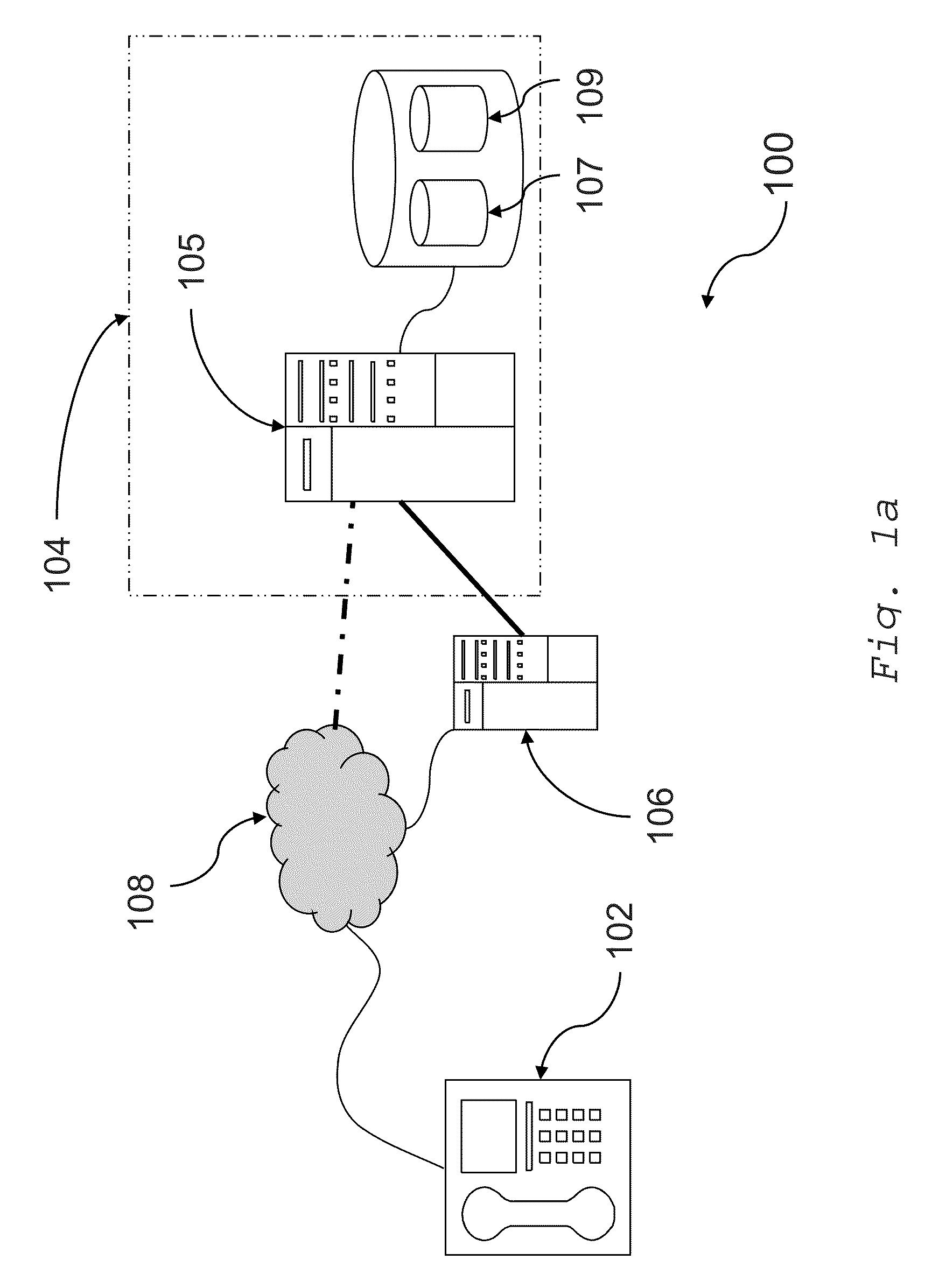
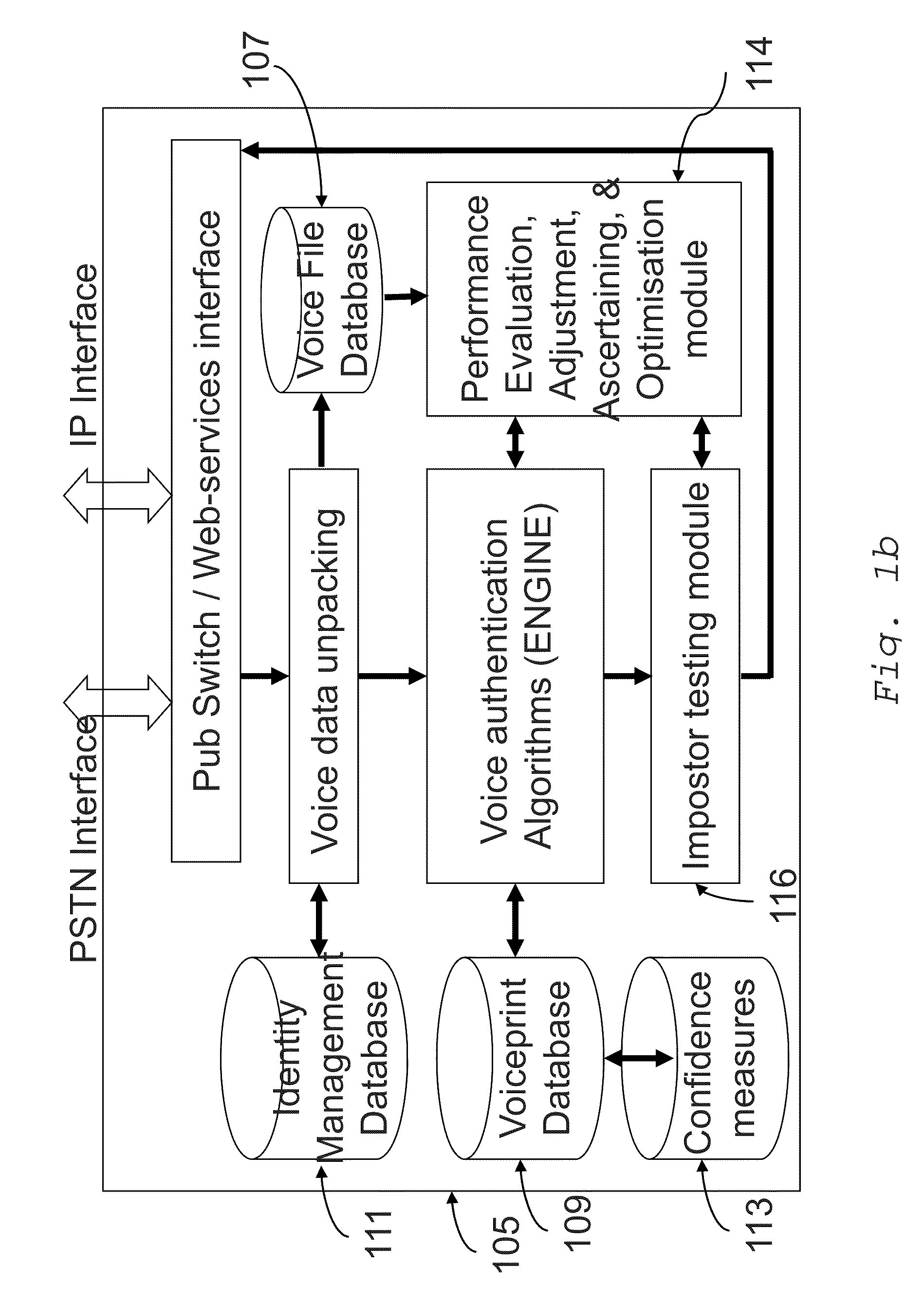
Voice authentication system and methods
ActiveUS8775187B2Easily brokenImprove authentication capabilitiesDigital data authenticationSpeech recognitionComputer hardwareAuthentication system
A method for configuring a voice authentication system comprises ascertaining a measure of confidence associated with a voice sample enrolled with the authentication system. The measure of confidence is derived through simulated impostor testing carried out on the enrolled sample.
Owner:AURAYA
Key generation, certification and data transmission method based on physiological features
ActiveCN103944725ALower listeningReduced chance of stealingEncryption apparatus with shift registers/memoriesUser identity/authority verificationHuman bodyNODAL
The invention relates to a key generation, certification and data transmission method based on physiological features. The method comprises the following steps that a, physiological sensors which collect the physiological features synchronously are arranged on a human body, and one of the physiological sensors is set to be a coordinator; b, the physiological sensors extract the physiological features to obtain a first key; c, the coordinator extracts the physiological features to obtain a second key; d, the sensors carry out logical operation on the physiological feature data to be transmitted and personal codes to be transmitted and the first key and then carry out encoding, and encoded and enciphered data are obtained; e, the encoded and enciphered data are obtained and the first key are forwarded to the coordinator through relay nodes in a certain frequency or are directly transmitted to the coordinator; f, the coordinator obtains a third key according to the matched relation between the second key and the first key; g, the coordinator decodes the encoded and enciphered data through the third key and the personal codes, and finally physiological data collected by the physiological sensors are obtained. The method is easy and effective to implement, and can improve the safety of transmission of the human body physiological feature data.
Owner:JIANGSU R & D CENTER FOR INTERNET OF THINGS
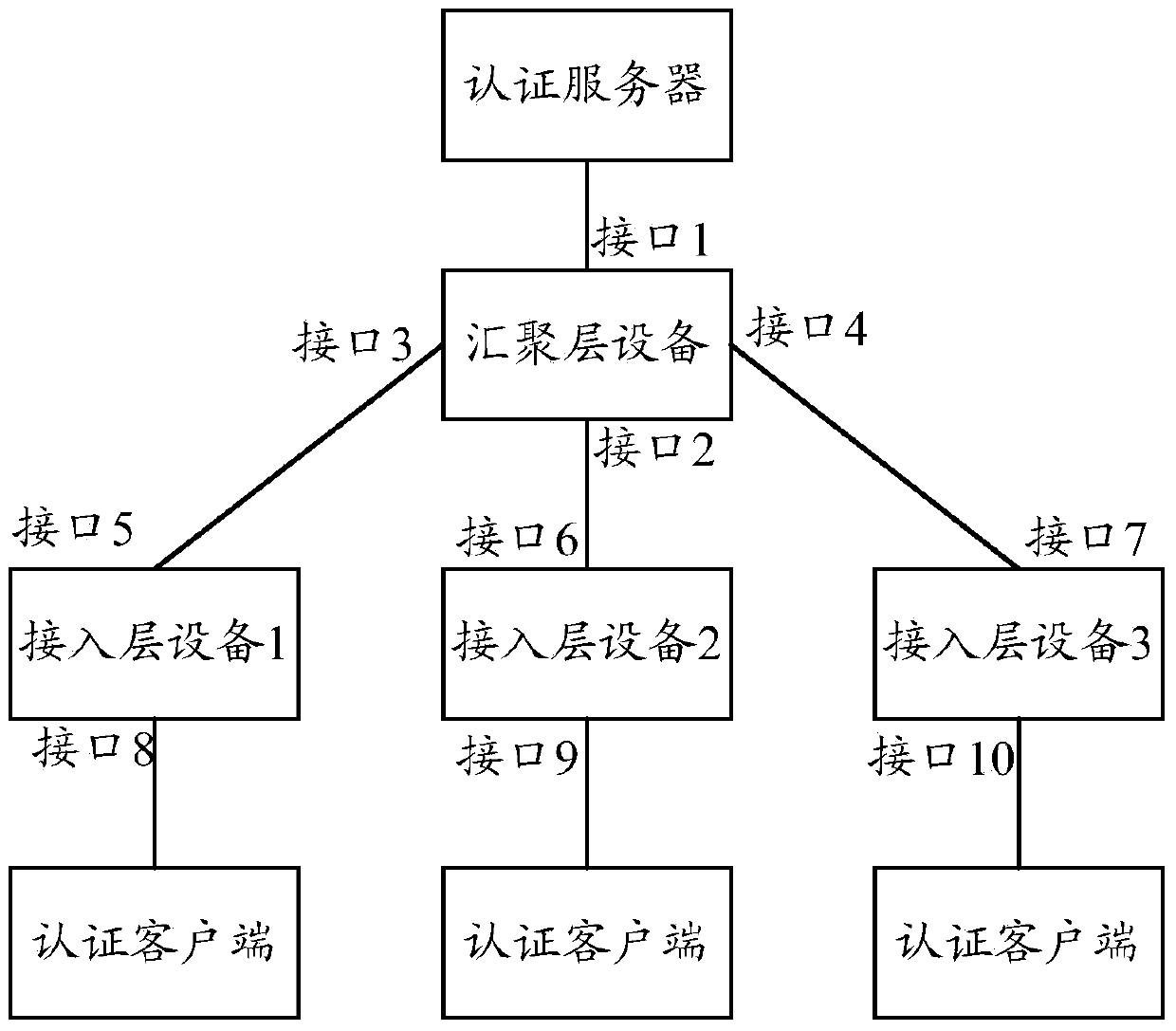
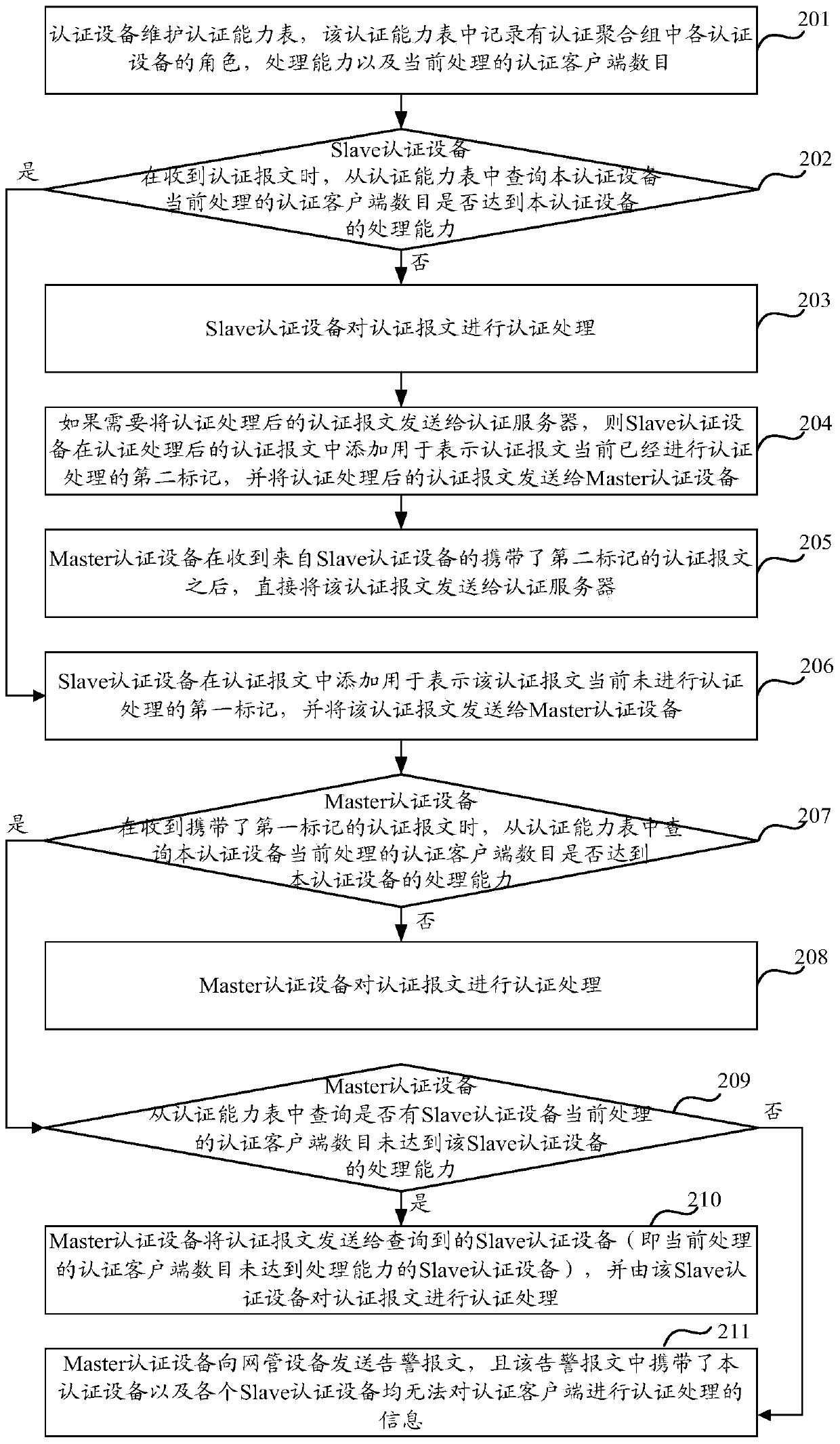
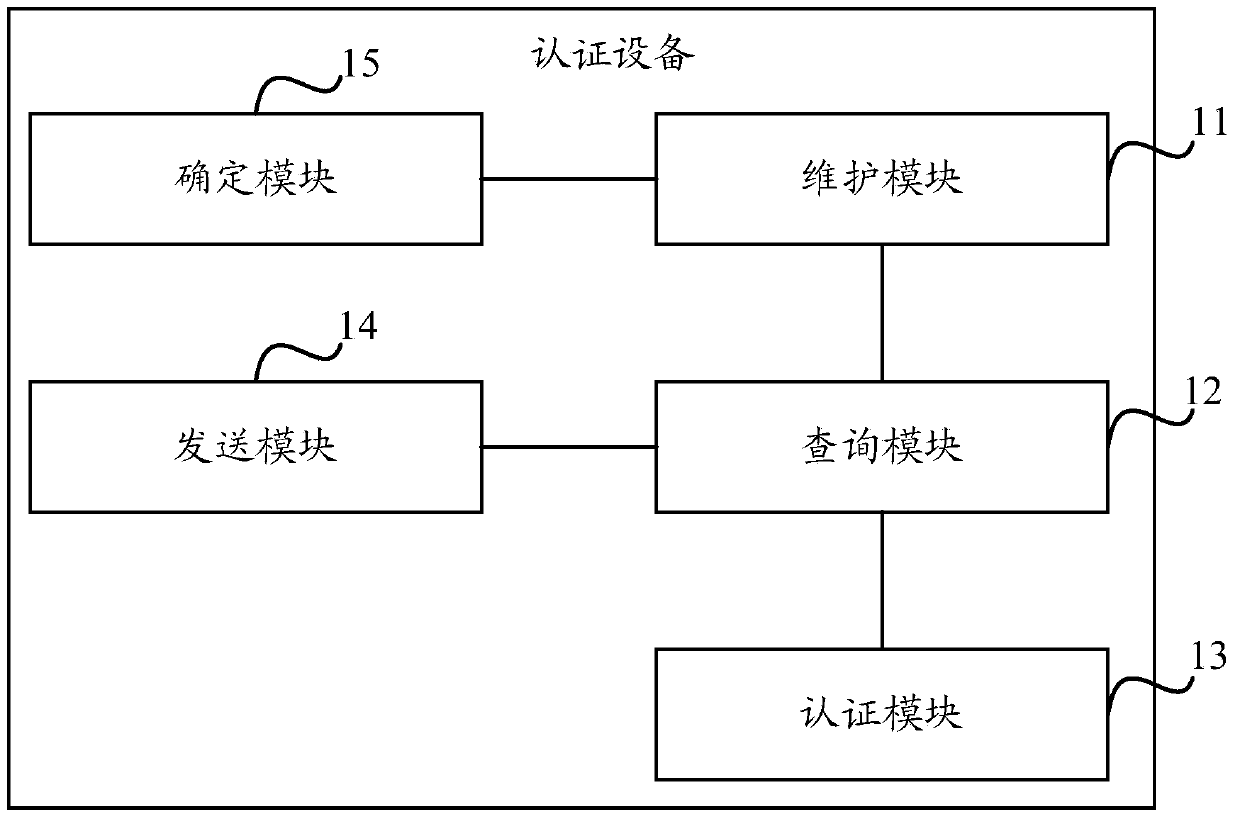
Authentication method and device
The invention discloses an authentication method and device. The authentication method includes the steps that a first authentication device is used for maintaining an authentication capability list; if the first authentication device is a Slave authentication device, whether the number of authentication client sides which are processed by the authentication device at present reaches the processing capability of the authentication device or not is inquired from the authentication capability list when an authentication message is received; if not, the authentication message is authenticated; if yes, a first mark is added into the authentication message, and then the authentication message is sent to a Master authentication device; if the first authentication device is the Master authentication device, when the authentication message which carries the first mark is received, the authentication message is authenticated if the number of authentication client sides which are processed at present by the authentication device does not reach the processing capability of the authentication device through the inquiry from the authentication capability list. In the embodiment of the authentication method and device, the processing loads of a convergence layer device can be reduced, and the bottleneck of network authentication is avoided.
Owner:NEW H3C TECH CO LTD
A Method of Image Hiding and Authentication Based on Secret Sharing
ActiveCN103761702BImprove securityDifferences in Statistical PropertiesImage data processing detailsHash functionInformation recovery
The invention discloses an image hiding and authentication method based on secret sharing, and belongs to the technical field of secret image sharing. The image hiding and authentication method is characterized by comprising the steps that firstly, difference Huffman encoding is conducted on a secret image, every three generated bit sequences are set to be one group to be converted into decimal numbers which are used as coefficients of a sharing polynomial in the Shamir (k, n) threshold scheme, the k and the n are positive integers, the k is smaller than or equal to the n, and n shadow images are generated; secondly, n significant carrier images are selected, the generated shadow images are embedded into the carrier images in a matrix encoding mode, authentication bits generated by the hash function are also embedded into the carrier images, and n disguise images are formed and are in the charge of n different participants respectively. The disguise images generated through the image hiding and authentication method has higher visual quality, existence of secret information cannot be perceived by attackers easily, and the safety of the secret information is ensured. Meanwhile, before the secret information is recovered, the disguise images provided by each participant need to be authenticated, only the disguise images passing through authentication can participate in recovery of the secret information, and the safety of the secret information is further strengthened.
Owner:TAIYUAN UNIVERSITY OF SCIENCE AND TECHNOLOGY
Communication system, image processing apparatus, image processing method, authentication server, image managing method, image managing program, and image processing system
InactiveUS8314958B2Improve securityImprove authentication capabilitiesUser identity/authority verificationUnauthorized memory use protectionInformation processingCommunications system
A communication system which is capable of improving the security of a protected image. The protected image on which a predetermined protection process has been carried out and authentication information are transmitted from an information processing apparatus to an image processing apparatus and an authentication server, respectively. Permission information for permitting removal of the predetermined protection process is issued from the authentication server based on the authentication information, and is obtained by the image processing apparatus. When the protected image is subjected to predetermined image processing carried out by the image processing apparatus, the content of the predetermined image processing is regulated to within a predetermined range indicated by the permission information.
Owner:CANON KK
Automatic monitoring method for mobile terminal traffic
ActiveCN108199919AImprove experienceMeet personalized access needsSubstation equipmentData switching networksData connectionTime segment
The invention relates to an automatic monitoring method for mobile terminal traffic. The method comprises the following steps: setting a preset monitoring time period, extracting keywords with a frequency of occurrence up to 40% in a network content accessed by a user, and establishing an interest network content tag database of legitimate users; obtaining a data traffic fusion value of each started software within the preset monitoring time period respectively by a mobile terminal according to a corresponding duty index, a user favorite index, a data flow consumption index, a data traffic consumption weight, an attitude change index and a data traffic adaptive alcohol influence factor of each started software within the preset monitoring time period; and after the mobile terminal successfully identifies the legal identity of a current operator, when judging that the traffic fusion value corresponding to the started software exceeds a corresponding data traffic monitoring threshold bythe mobile terminal, and the total data traffic consumed by all started software within the preset monitoring time period exceeds a data traffic total limit value, closing a current data connection mode by the mobile terminal to implement the monitoring processing for data traffic.
Owner:NINGBO UNIV
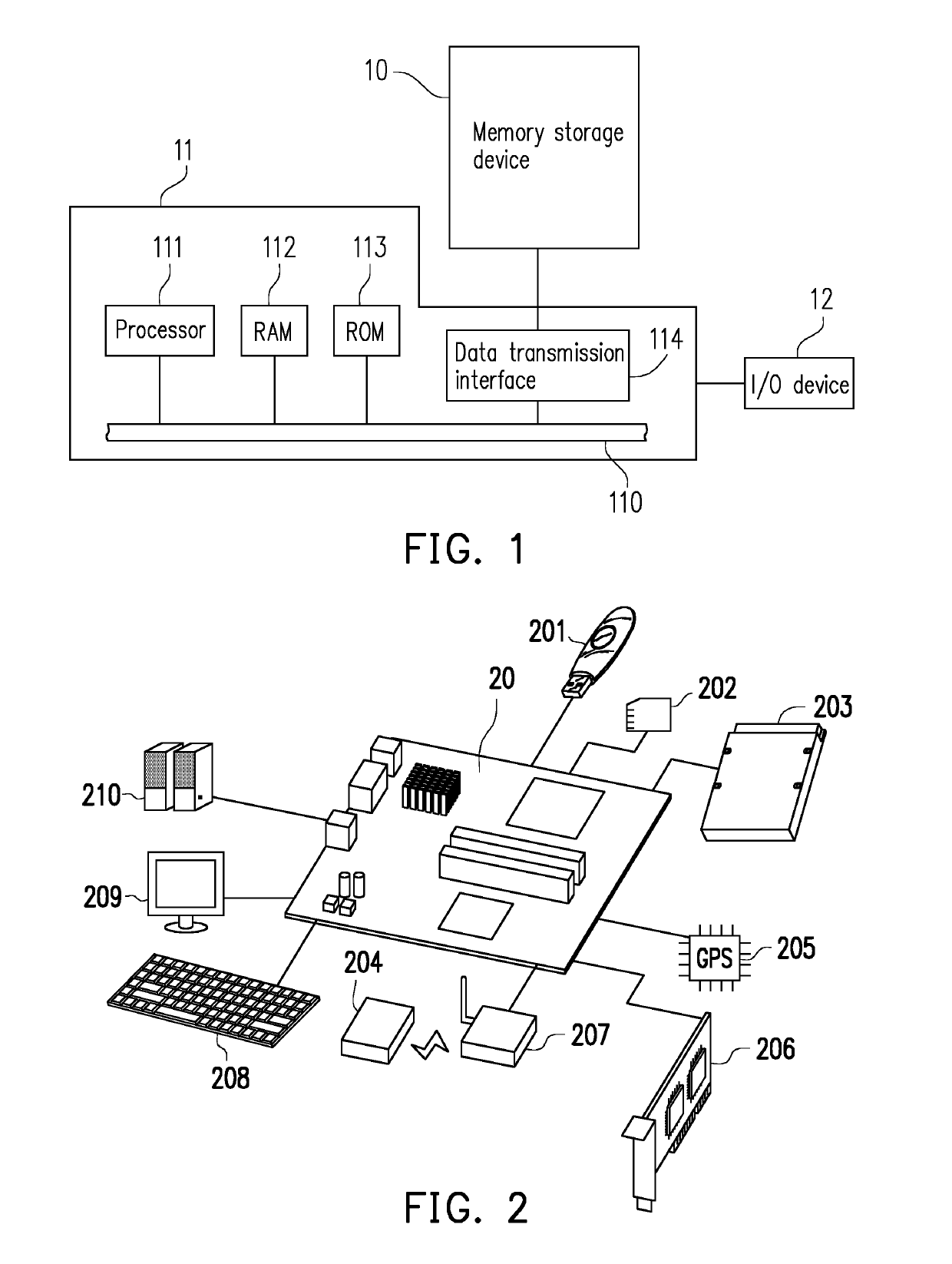
Memory storage system, host system authentication method and memory storage device
ActiveUS20190222427A1Improve abilitiesImprove authentication capabilitiesKey distribution for secure communicationUser identity/authority verificationComputer hardwareAuthentication information
A memory storage system is provided according to an exemplary embodiment of the disclosure. The memory storage system includes a host system and a memory storage device. In a first handshake operation, the memory storage device transmits first encrypted information corresponding to first authentication information to the host system, and the host system transmits second encrypted information corresponding to the first authentication information to the memory storage device. In a second handshake operation, the memory storage device transmits third encrypted information corresponding to second authentication information to the host system, and the host system transmits fourth encrypted information corresponding to third authentication information to the memory storage device based on the third encrypted information. The third authentication information is configured to encrypt data transmitted between the host system and the memory storage device in a developer command transmission stage.
Owner:PHISON ELECTRONICS
Generalized signcryption method based on coding
ActiveCN110932863AImprove securityReduce key storageKey distribution for secure communicationError preventionQuantum computerKey storage
The invention discloses a generalized signcryption method based on coding. The generalized signcryption method comprises the following steps: 1) setting public parameters; 2) generating a public key and a private key for a registered user; 3) defining a distinguishing function, and judging the existence condition of the public key of the user; (4) carrying out signcryption operation on the transmission information, that is, the public key of the receiver is firstly used for encryption, and then the private key of the sender is used for signature; 5) carrying out unsigncryption operation on thesigncryption text, that is to say, decryption is performed by using a private key of a receiver, signature verification is carried out by using the public key of the sender to complete code-based generalized signcryption. According to the method, the conversion among encryption, signature and signcryption functions can be realized according to the existence of the public key by the users of the transmitting party and the receiving party, so that the generalized signcryption function of quantum computing resistance is realized, meanwhile, the key storage amount can be reduced, and the securityis relatively high.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
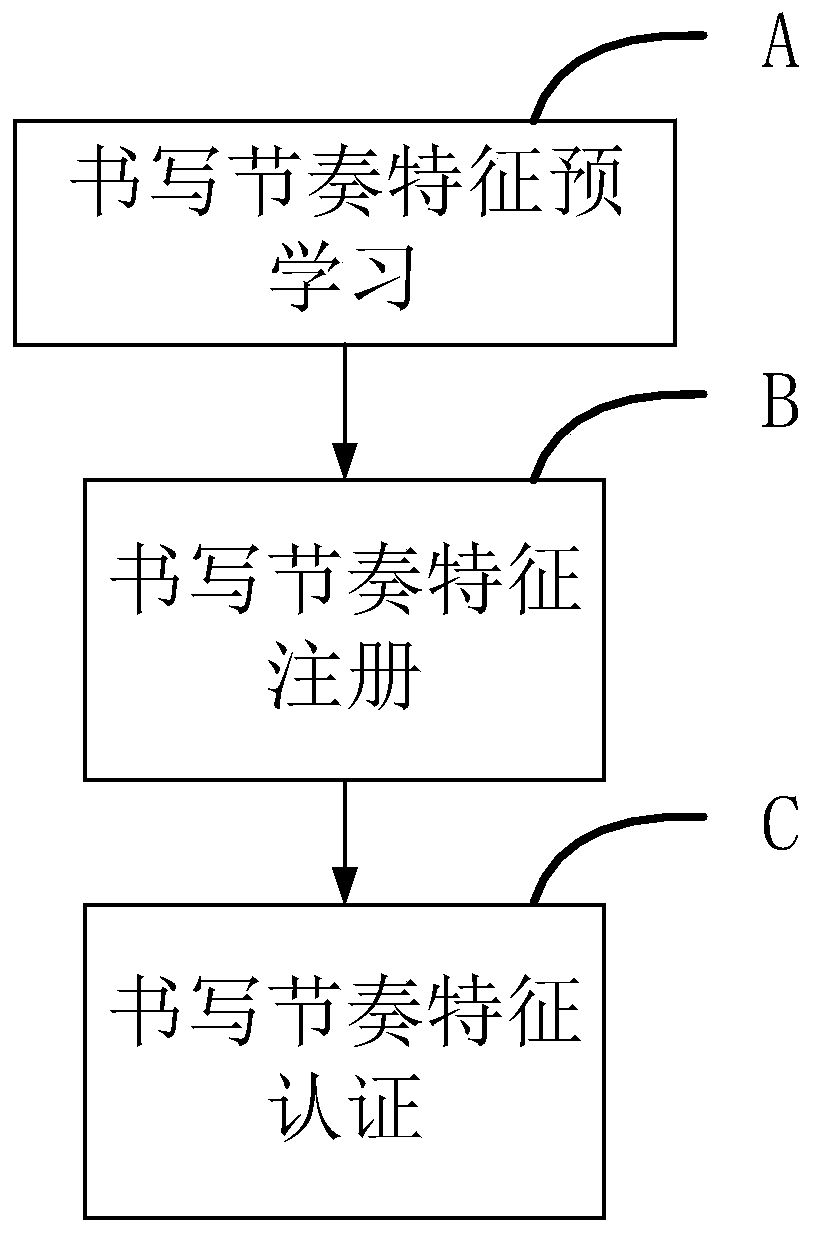
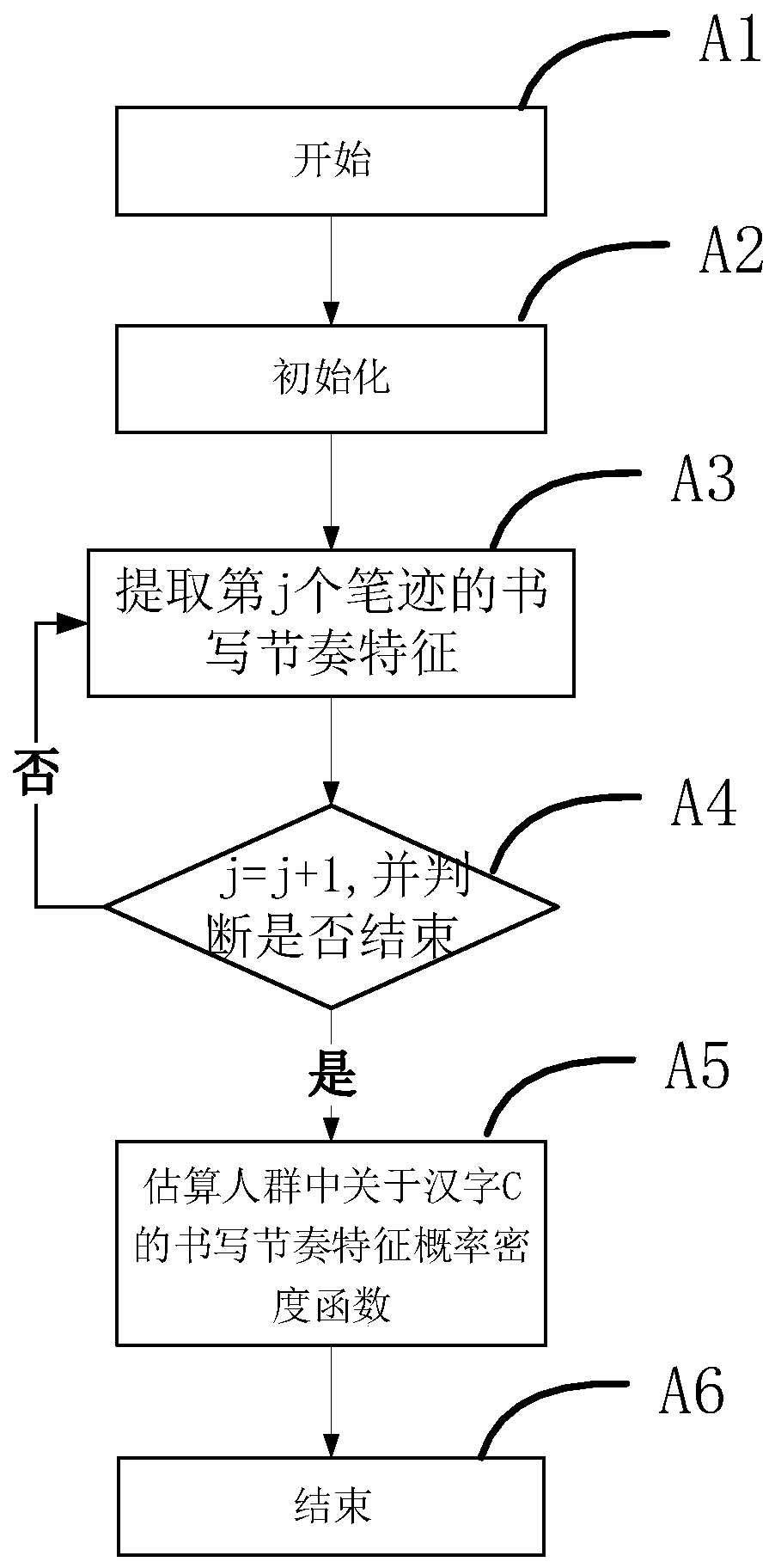
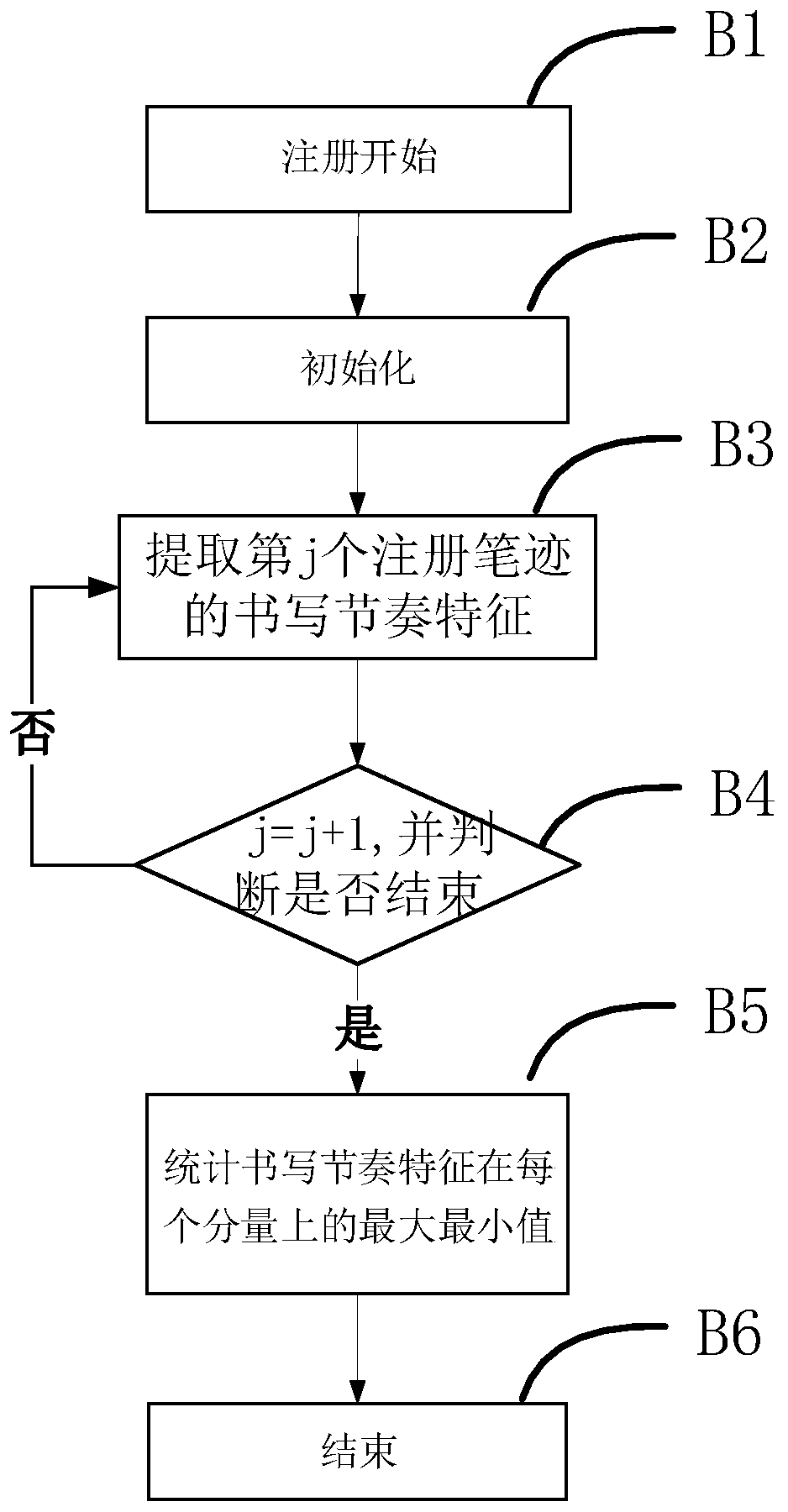
Writing rhythm feature extraction and authentication method in online handwriting authentication
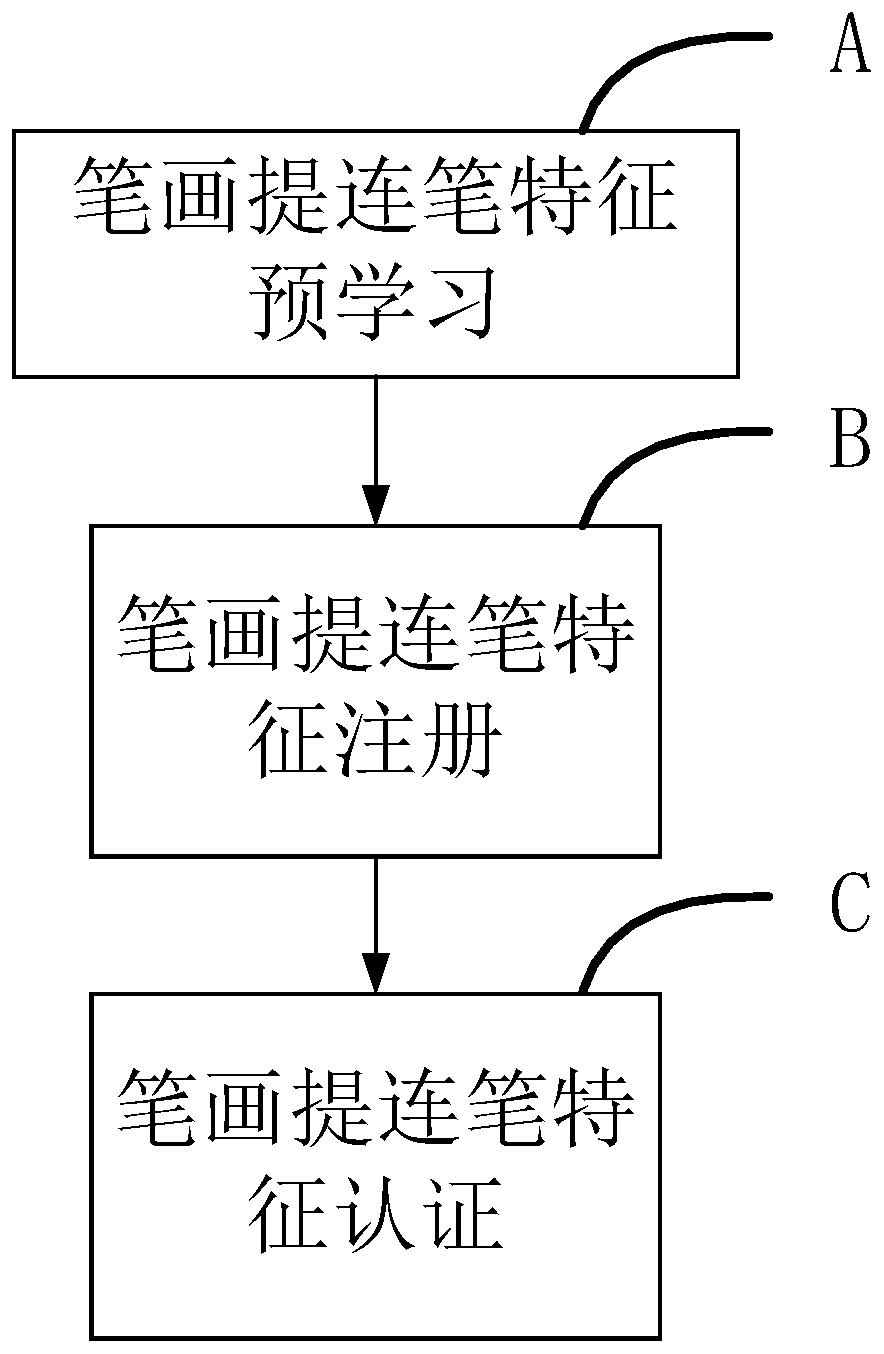
PendingCN111310546AIncrease the difficultyImprove authentication capabilitiesCharacter and pattern recognitionComplex mathematical operationsHandwritingSpeech recognition
The invention relates to the field of information security, and discloses a writing rhythm feature extraction and authentication method in online handwriting authentication. The method comprises the following steps: writing rhythm feature pre-learning, obtaining a writing rhythm characteristic probability density function; writing rhythm feature registration, calculating the maximum value and theminimum value of the registered handwriting sample on each component of the writing rhythm characteristics, authenticating the writing rhythm characteristics, calculating the probability of observingall stable and consistent writing rhythm characteristic components of the tested handwriting sample and the registered handwriting sample, and taking the probability value as a basis for further judgment. The invention discloses a method for extracting and authenticating writing rhythm characteristics in online handwriting authentication. Writing rhythm characteristics are effectively extracted, the probability of occurrence of the stable and consistent writing rhythm characteristics in crowds is estimated, and the attack difficulty and attack cost of a facsimile are greatly increased by effectively identifying a writing mode which is not easy to perceive, so that the handwriting authentication performance is improved.
Owner:JIANGNAN UNIV
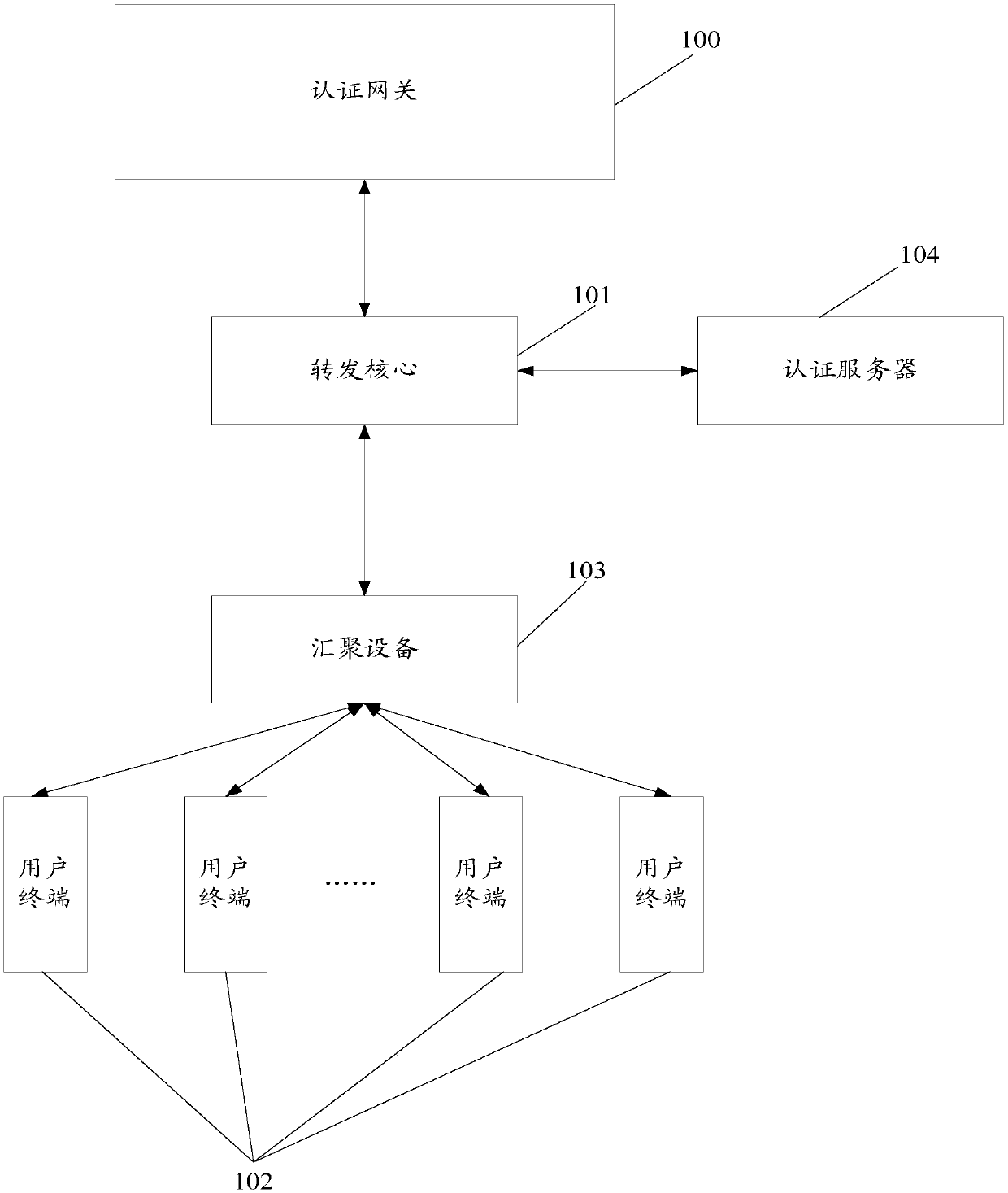
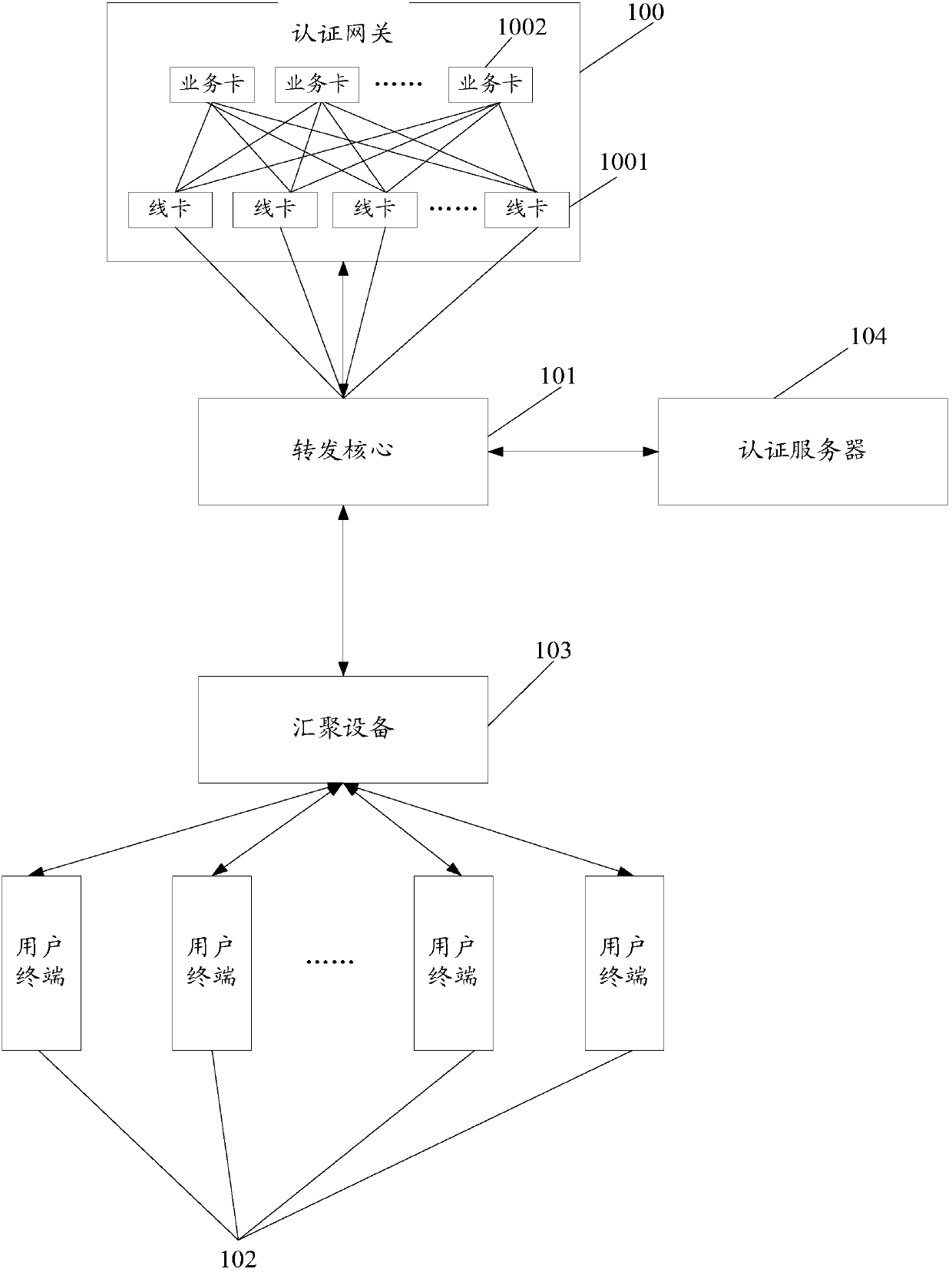
Authentication method and device
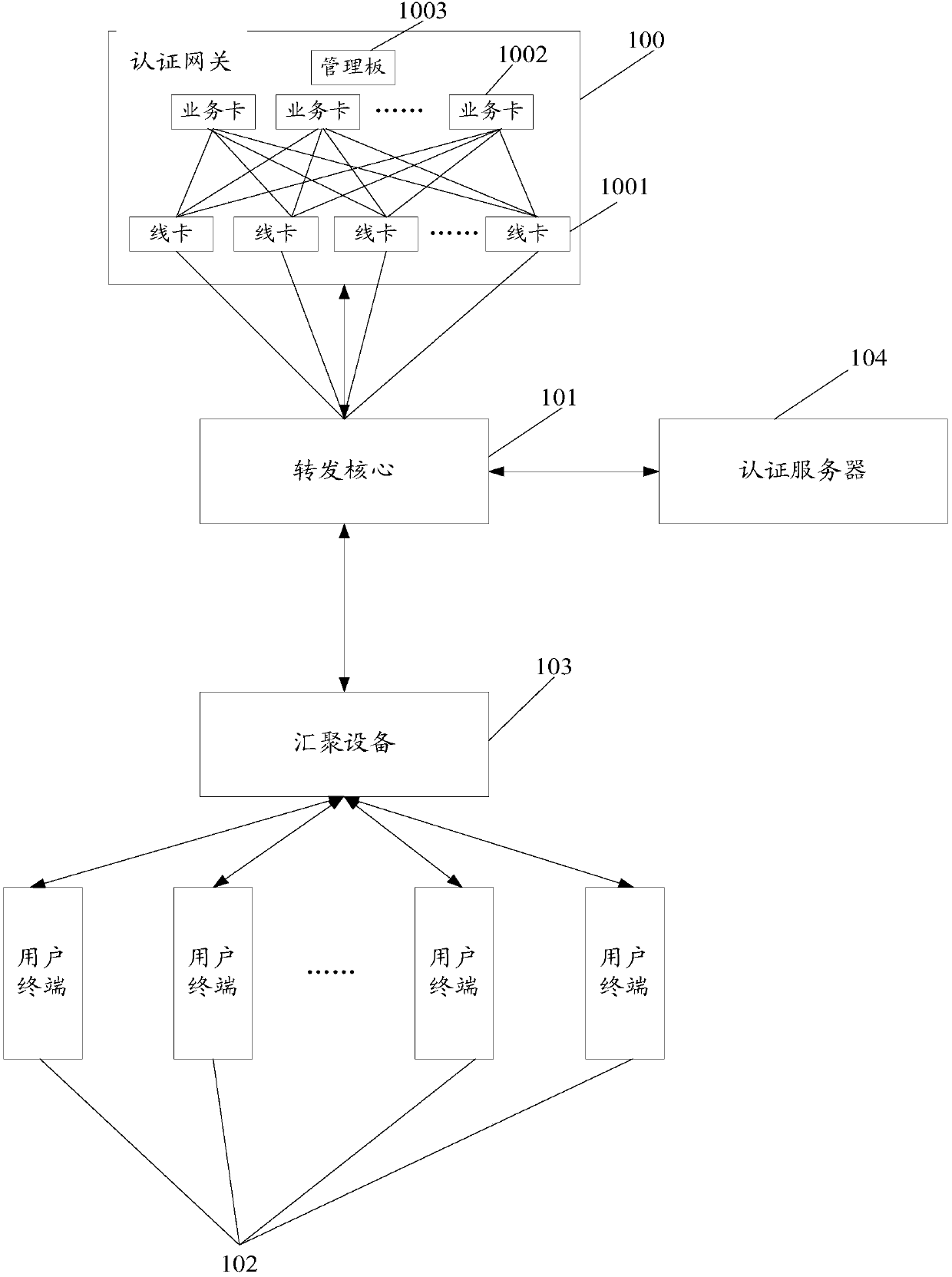
ActiveCN107659578AIncrease authentication capacityImprove authentication capabilitiesTransmissionBusiness cardComputer terminal
The invention provides an authentication method and device. The method comprises the following steps: a first line card receives an authentication message for a user terminal sent by a forwarding kernel, wherein the authentication message comprises a first line card address corresponding to the user terminal, and the first line card is determined by the forwarding kernel according to the first line card address; the first line card sends the authentication message to a first business card, wherein the first business card is used for determining a redirection link according to the authentication message and sending the redirection link to the user terminal through the forwarding kernel, and the redirection link points to an authentication server; and the first line card receives an authentication attribute message through the forwarding kernel and sends the authentication attribute message to the authentication server, and the authentication server authenticates the user terminal according to the authentication attribute message, wherein the authentication attribute message is determined by the user terminal according to the redirection link. The authentication method and device provided by the invention has the advantages that the authentication capacity and the authentication performance of an authentication system are improved, and the equipment maintenance cost and the laborcost are reduced.
Owner:RUIJIE NETWORKS CO LTD
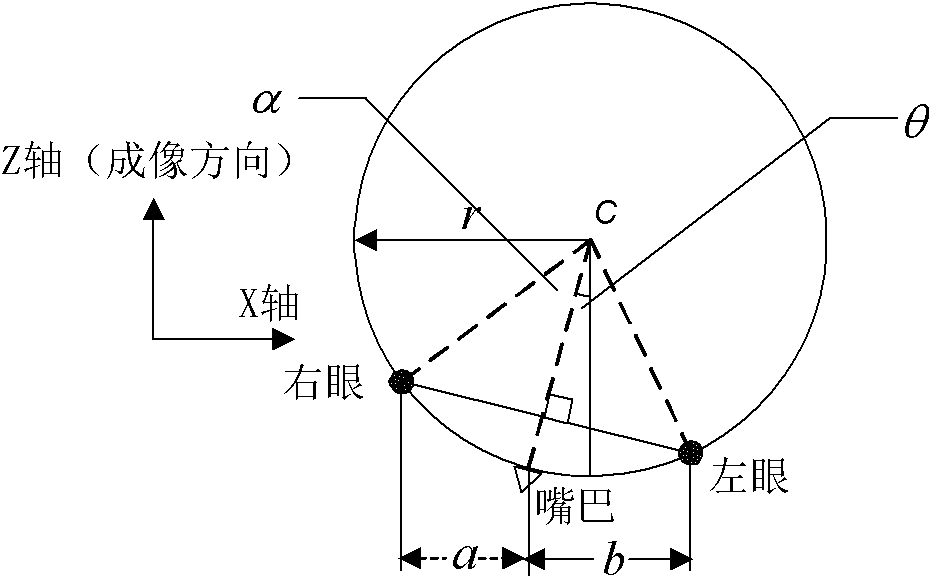
A face-based identity authentication method and authentication device
ActiveCN102375970BAvoid the authentication processImprove authentication capabilitiesCharacter and pattern recognitionFace detectionPattern recognition
The invention provides an identity authentication method based on a face and an authentication apparatus thereof. The method comprises the following steps: carrying out face detection on each frame of image acquired by a camera device to obtain a face image, and tracking the face image to obtain a tracking result; carrying out an attitude analysis, wherein if a face attitude in obtained attitude information is not jumped relative to a face attitude corresponding to a prior frame of image, an attitude analysis result is not jumped; carrying out face comparison; carrying out statistics analysis on a plurality of frames of tracking results, a plurality of frames of attitude analysis results and a plurality of frames of face image authentication results, wherein if a statistics analysis result is in accordance with a preset condition, identity authentication is passed. According to the method and the apparatus thereof in the invention, a two-dimensional flat picture is utilized to distinguish a photograph from a human, in the prior art utilizing three-dimensional information and carrying out photograph identification cause that a system identification speed is substantially decreased and an application requirement can not satisfied, and the above technical problem is solved in the invention.
Owner:GUANGDONG VIMICRO
End-to-end verification method and system for telecommunication service unauthorized access prevention
ActiveCN111625803AImprove access efficiencyImprove security authentication access capabilitiesData processing applicationsDigital data protectionAccess to informationAuthentication
The invention discloses an end-to-end verification method and system for telecommunication service unauthorized access prevention, and relates to the field of telecommunication services. The method comprises the steps: when a salesman opens a preset module, triggering a public authentication verification interface; calling a corresponding verification service from multiple types of verification services contained in the public authentication verification interface for verification; generating a token of the user through the unified authentication service according to a preset authentication rule; and verifying the validity of the token of the user after submitting a telecommunication service handling order. According to the invention, the end-to-end security of sensitive information access, sensitive service scenes and complex service handling of users in the telecommunication industry can be improved, and user information acquisition and illegal service handling caused by unauthorizedaccess of the users are avoided; through an end-to-end token authentication mechanism, the problem of business personnel and user-level authentication capability is solved, and the user experience, security control and operation analysis control level are improved on the premise of not sacrificing the basic business capability.
Owner:北京思特奇信息技术股份有限公司
Data processing method and device, computer readable storage medium and computer equipment
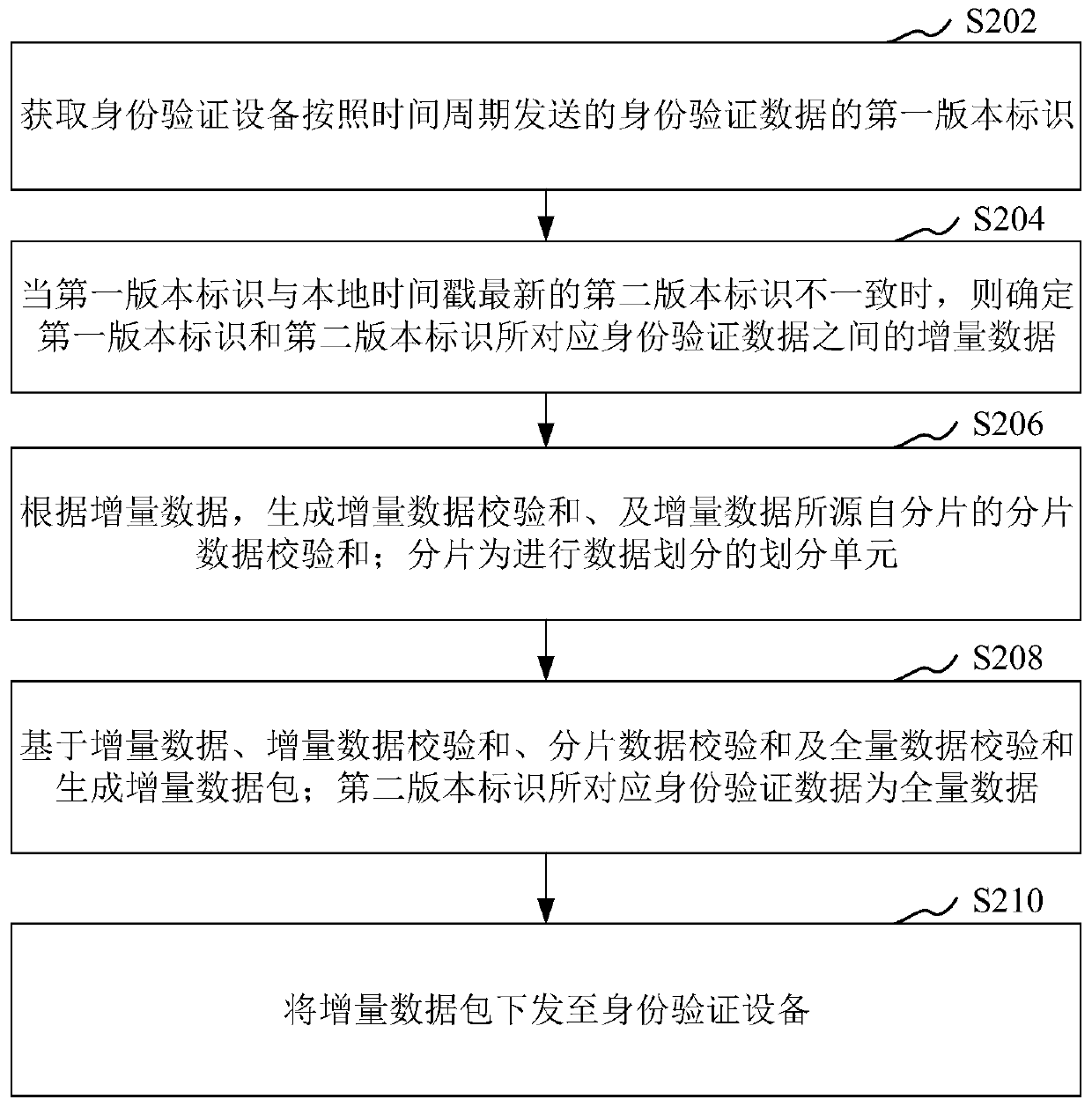
ActiveCN111368279AGuaranteed validityImprove authentication capabilitiesDigital data authenticationData switching networksData packProgramming language
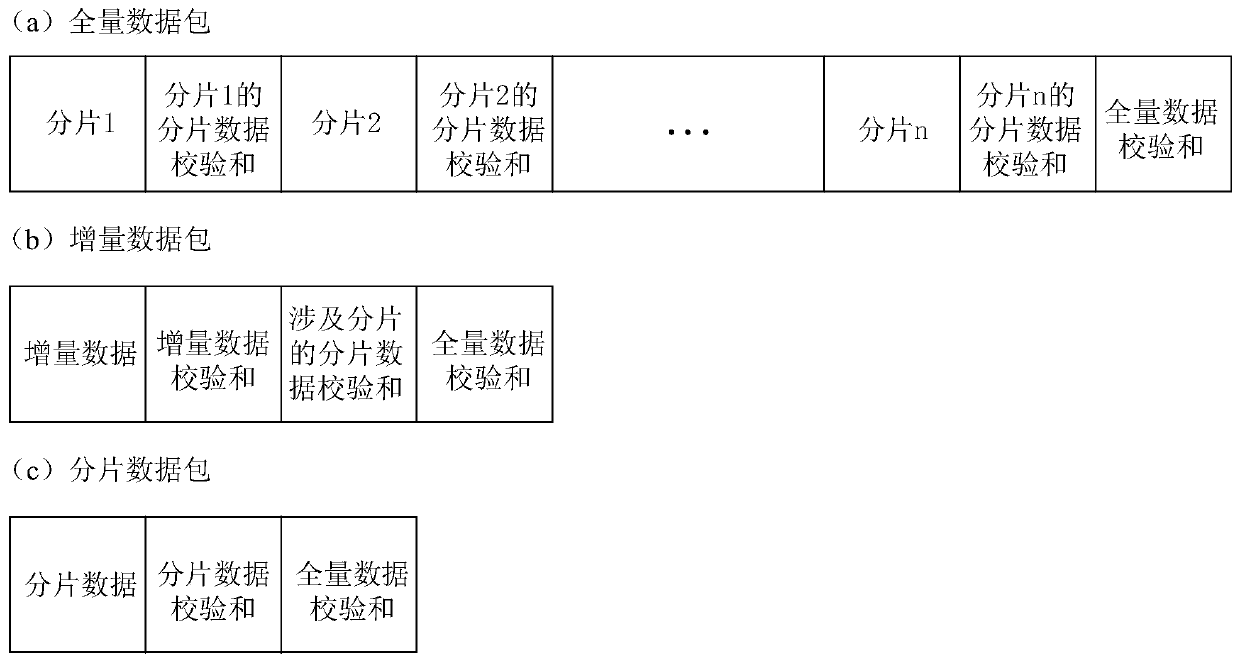
The invention relates to a data processing method and device, a computer readable storage medium and computer equipment. The method comprises the steps of obtaining a first version identifier of identity verification data sent by an identity verification device according to a time period; when the first version identifier is inconsistent with a latest second version identifier of a local timestamp, determining incremental data between identity verification data corresponding to the first version identifier and the second version identifier; according to the incremental data, generating an incremental data checksum and a fragment data checksum of fragments from which the incremental data comes; wherein the fragments are division units for data division; generating an incremental data packetbased on the incremental data, the incremental data checksum, the fragmented data checksum and the full data checksum; wherein the identity verification data corresponding to the second version identifier is full data; and issuing the incremental data packet to the identity authentication device. According to the scheme provided by the invention, the identity verification effect can be improved.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
Method for extracting and authenticating stroke extraction and connection characteristics in online handwriting authentication
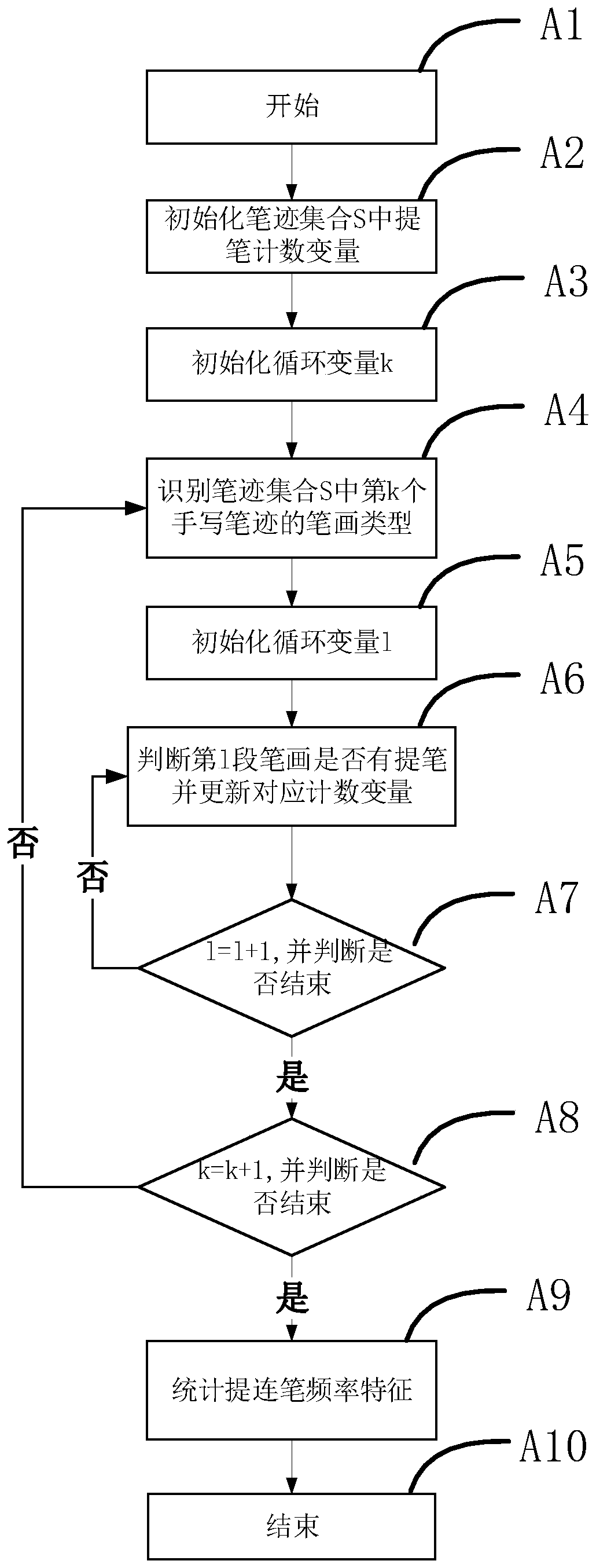
ActiveCN111310543AEfficient extractionImprove authentication capabilitiesDigital data authenticationDigital ink recognitionPattern recognitionHandwriting
The invention relates to the field of information security, and discloses a method for extracting and authenticating stroke extraction and connection characteristics in online handwriting authentication. The method comprises the following steps: carrying out stroke extraction and pen feature pre-learning; obtaining the probability of occurrence of the false extraction and continuous extraction features in the crowd; registering stroke extraction and connection stroke characteristics, counting the occurrence frequency of stroke virtual extraction and connection stroke characteristics of a registered user, finding out stable virtual extraction and connection stroke according to the occurrence frequency, authenticating the stroke extraction and connection stroke characteristics, calculating the occurrence probability of stable and consistent combination of the virtual extraction stroke and the connection stroke in the crowd, and taking the probability as a basis for further judgment. Theinvention discloses a method for extracting and authenticating stroke extraction and connection characteristics in online handwriting authentication. According to the method, the characteristics of the virtual extraction pen or the continuous extraction pen in the local strokes can be effectively extracted, the occurrence probability of the stable and consistent combination of the virtual extraction pen and the continuous extraction pen in the crowd is estimated, a writing mode which violates writing standards and is stable can be recognized, and the handwriting authentication performance is improved.
Owner:HUBEI UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com