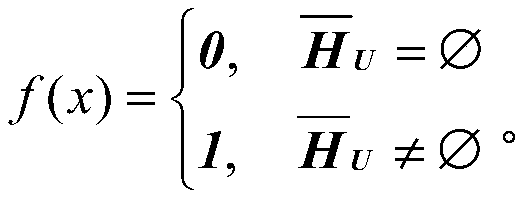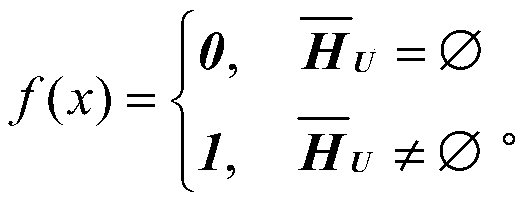Generalized signcryption method based on coding
A generalized encoding technology, applied to key distribution, can solve the problems of no longer safe security methods and no longer safe and reliable public key cryptography methods, and achieve the effects of high security, reduced key storage, and improved use efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
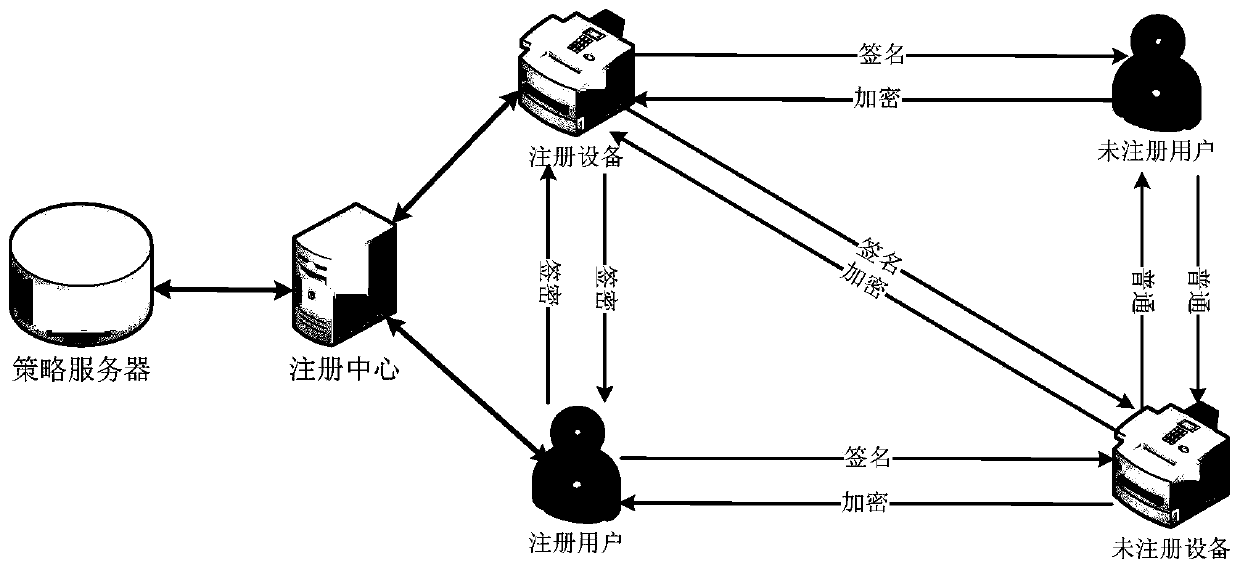
[0041] The present invention is described in further detail below in conjunction with accompanying drawing:
[0042] refer to figure 1 , the encoding-based generalized signcryption method of the present invention comprises the following steps:
[0043] 1) Set public parameters;
[0044] The concrete operation of step 1) is:
[0045]The public parameters are set through a unified policy server, and then broadcast to all users. Among them, the system parameters that need to be set include the security parameter k, the prime number q with a length of k bits, and the finite field GF q and two Hash functions h 1 and h 2 ,in, * represents that the lengths of 0-bit strings and 1-bit strings are arbitrary, and n and n-k are the lengths of 0-bit strings and 1-bit strings.
[0046] 2) Generate public and private keys for registered users;
[0047] The concrete operation of step 2) is:
[0048] Randomly select (n,k,d)-dimensional QC-LDPC codes on the finite field GFq, n=2 a , d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com