Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
30results about How to "Easy access management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Content Access Rights Management
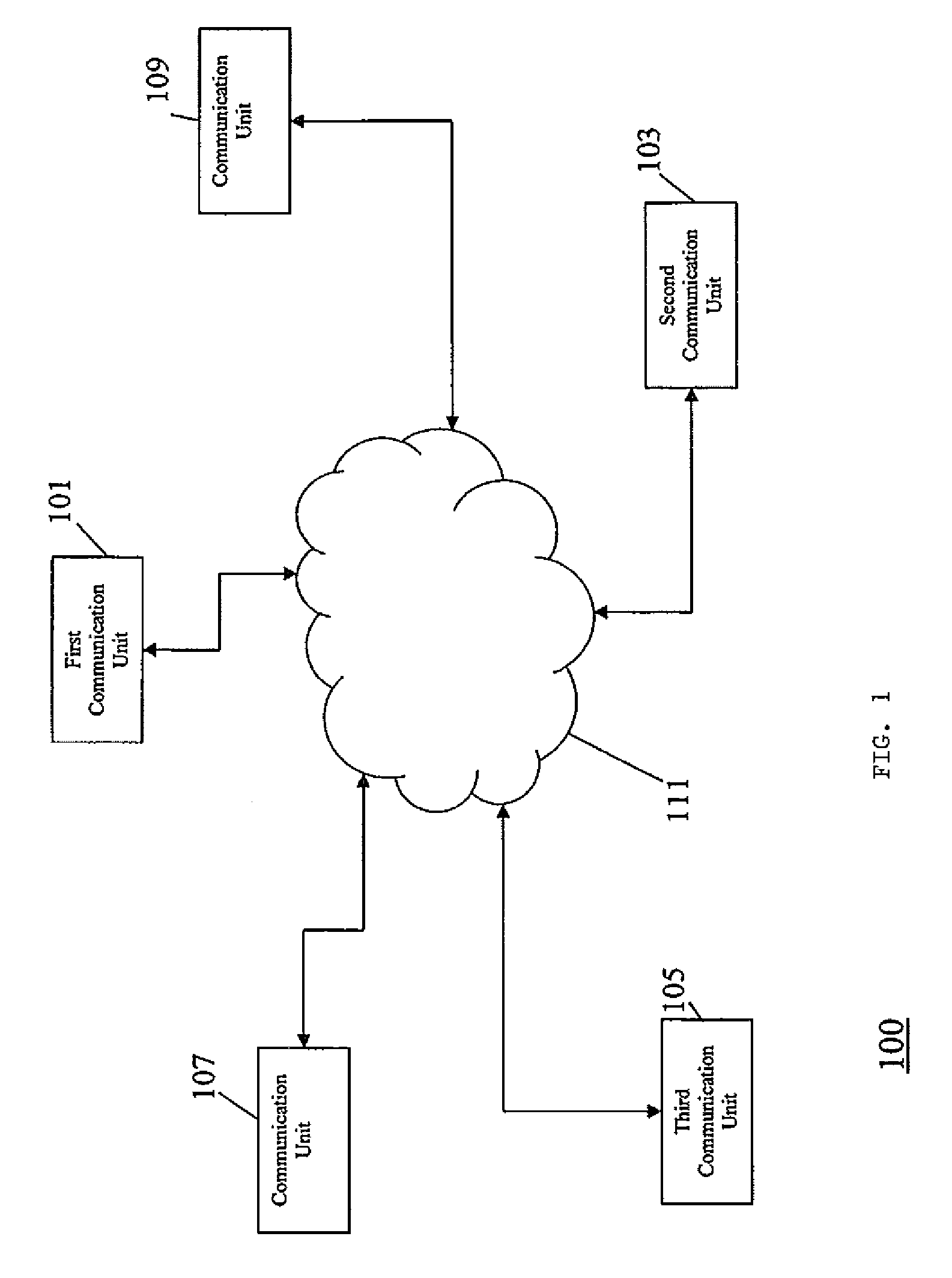
ActiveUS20080215509A1Easy to manageEasy access managementDigital data processing detailsDigital computer detailsDocument handlingRights management
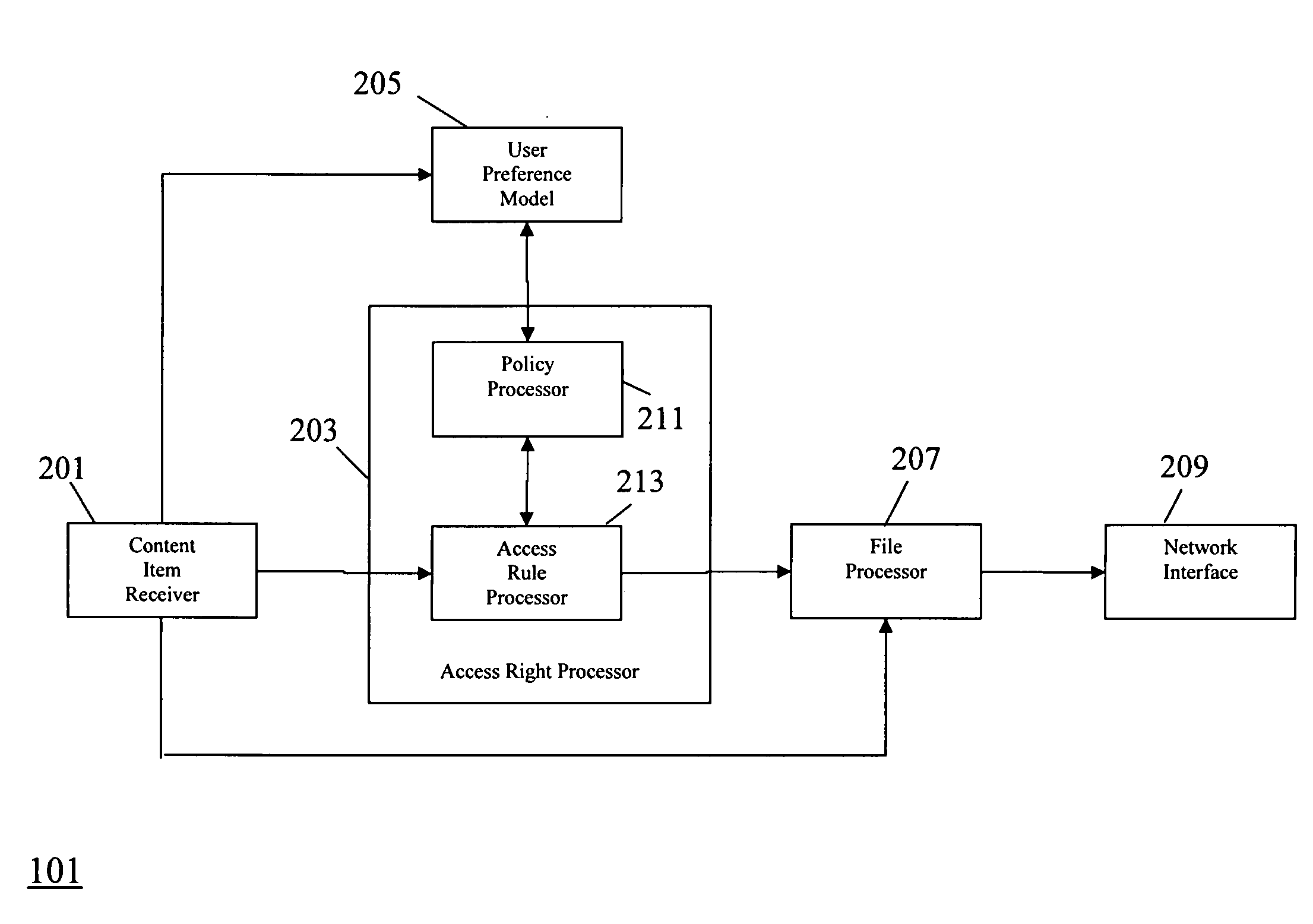
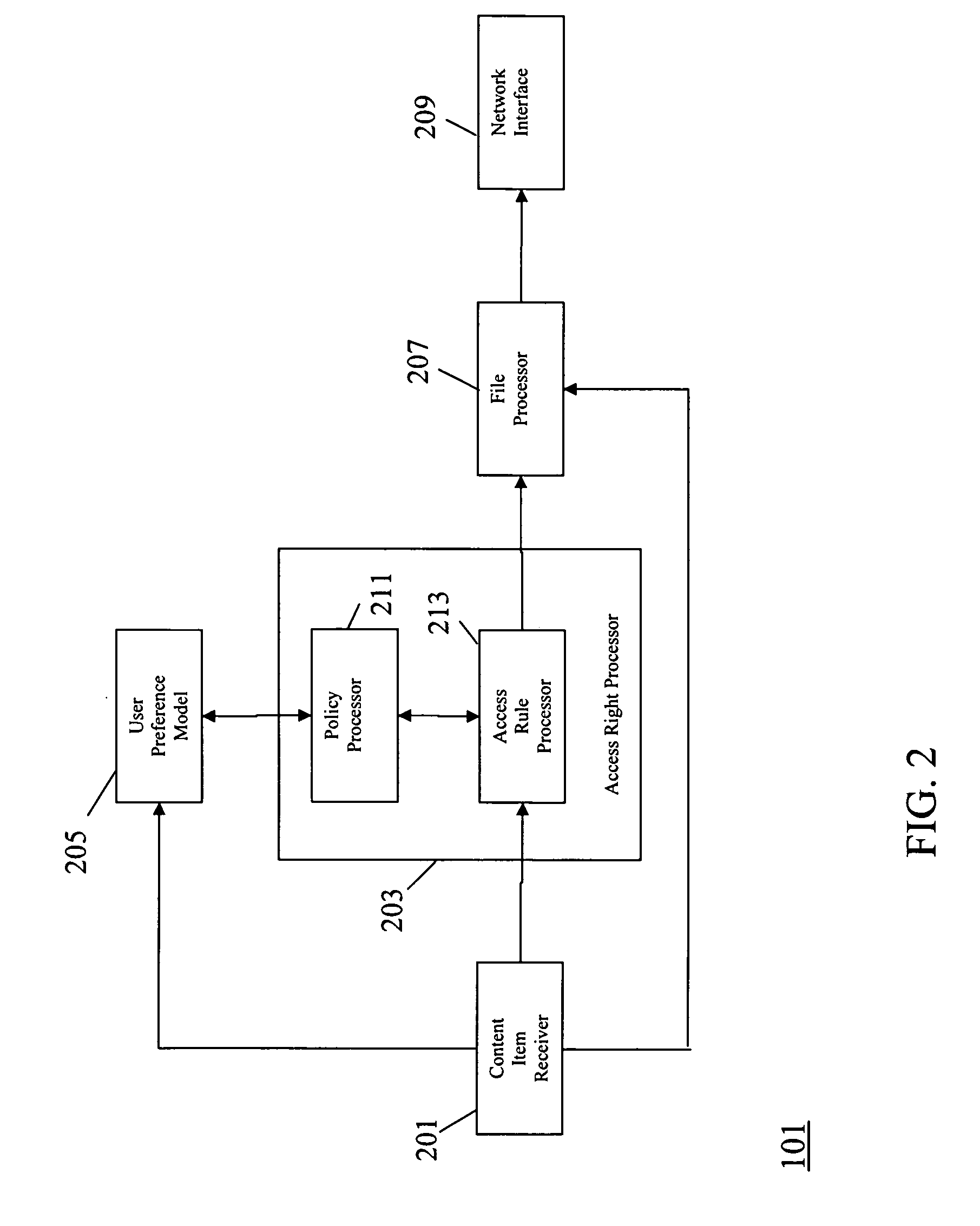
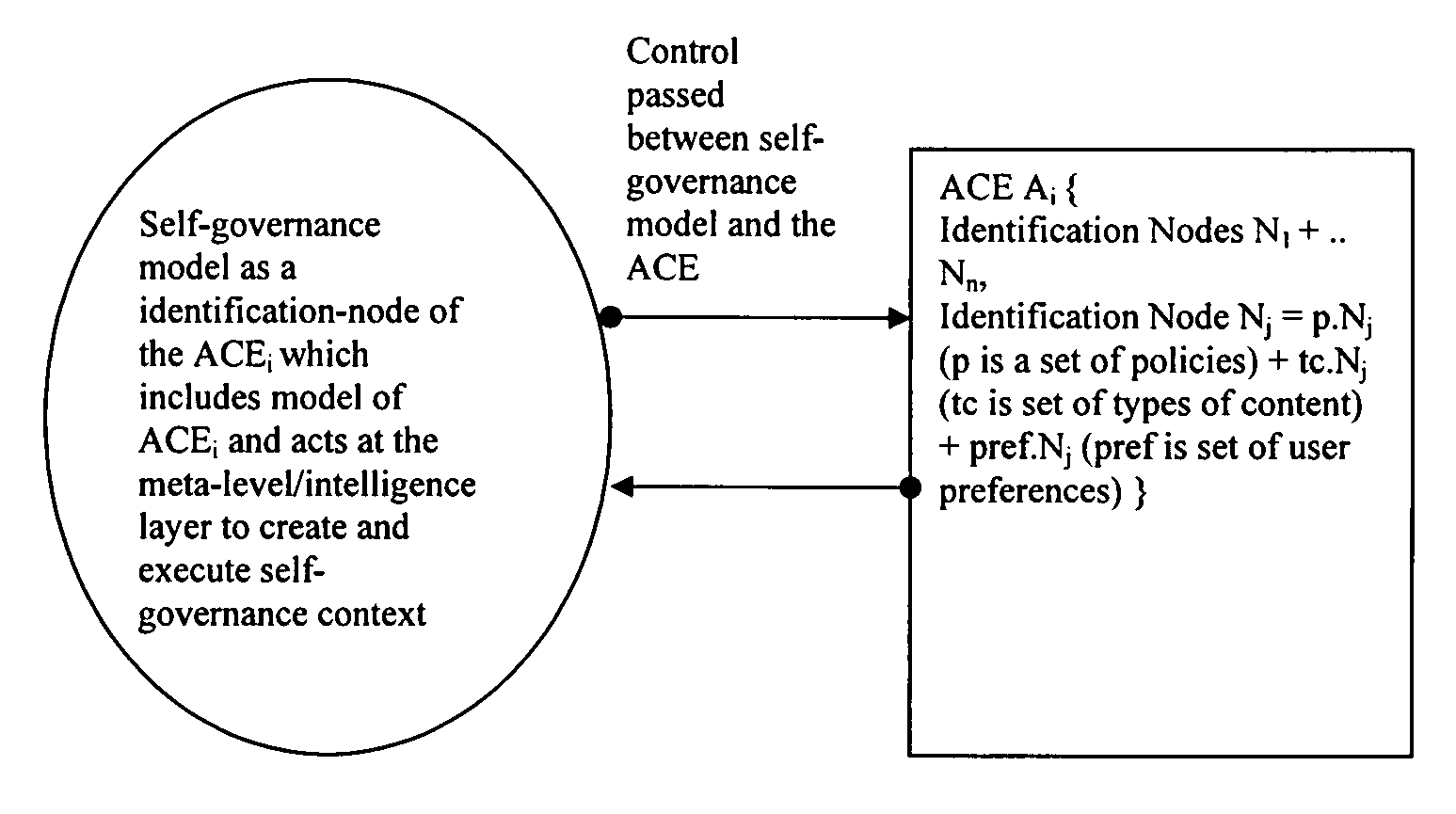
An apparatus (101) comprises a content item receiver (201) which receives a content item such as a digital photo or an audio or video clip. A user preference model (205) generates data indicative of user preferences for content item access. An access rule processor (203) determines a set of self-governance rules for the first content item in response to the user preference model. The self-governance rules are indicative of allowable actions for the first content item in other devices. A file processor (207) includes the set of self-governance rules with the content item and a network interface (209) transmits the content item to a second apparatus (103). The second apparatus (103) comprises functionality for restricting access to the content item in accordance with the set of self-governance rules. The invention may provide improved access rights management and in particular for personal content items.
Owner:MOTOROLA SOLUTIONS INC
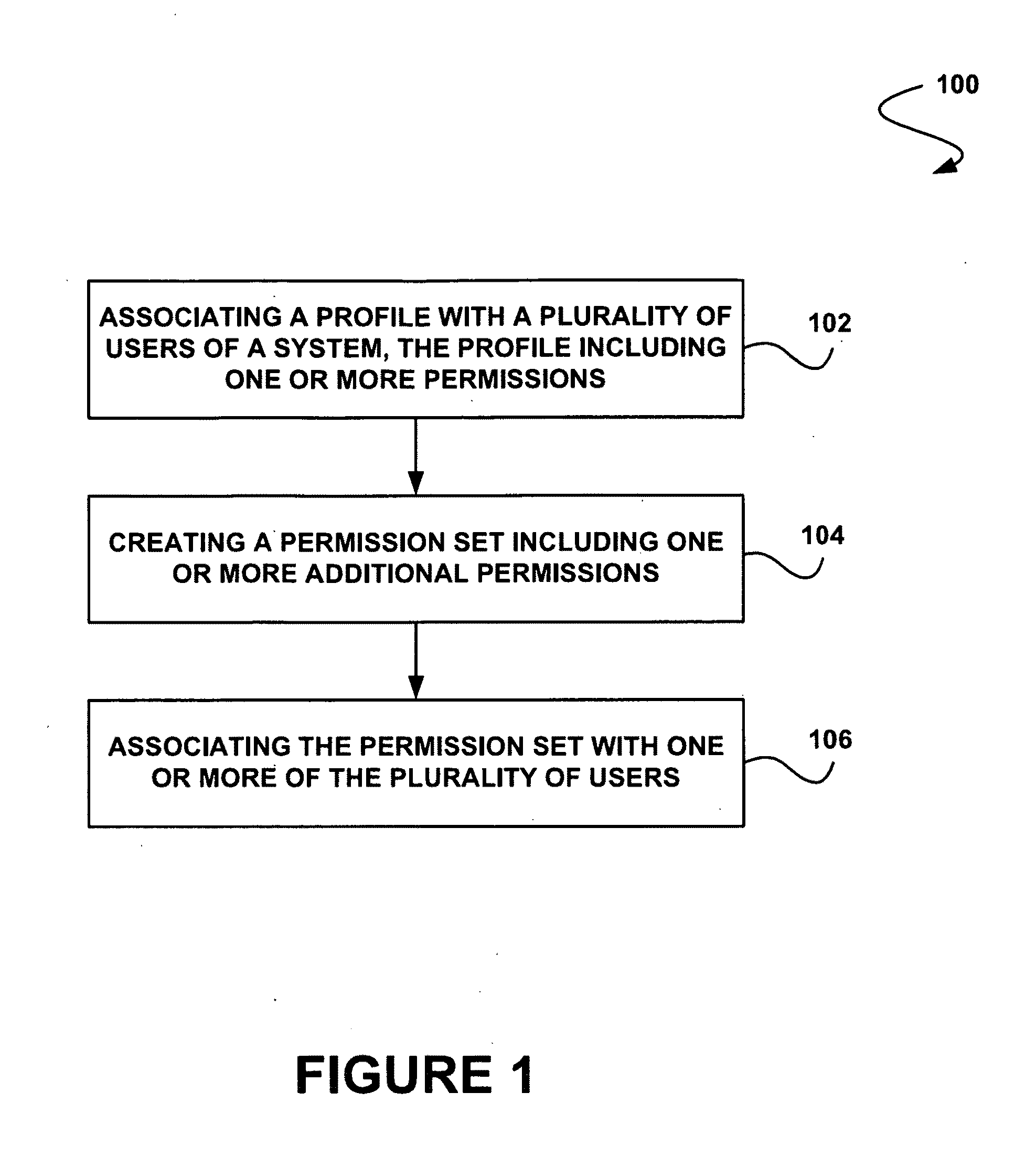
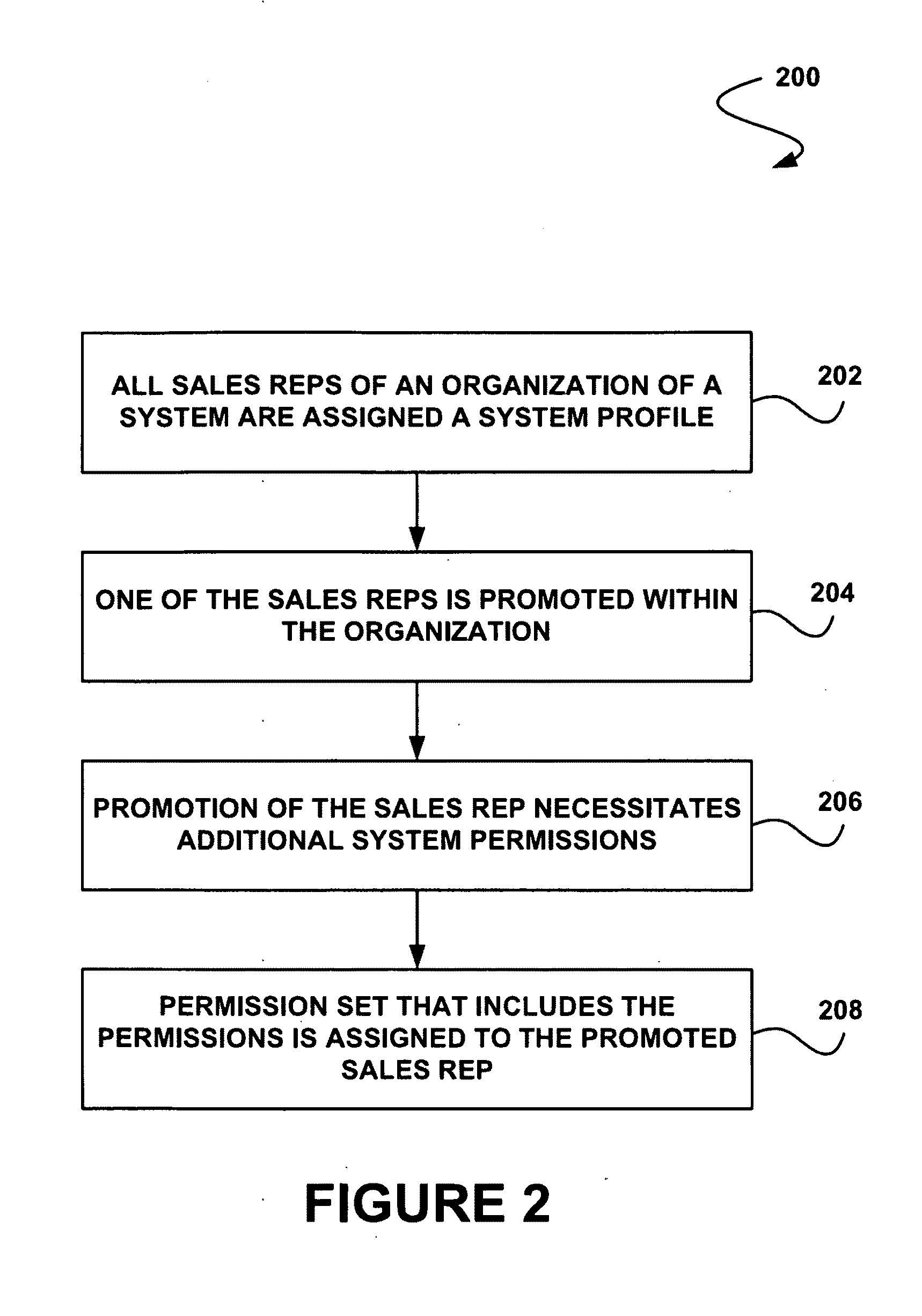
System, method and computer program product for associating a permission set with one or more users
InactiveUS20110246527A1Easy access managementImprove efficiencyDigital data processing detailsCryptography processingComputer programReduced risk
In accordance with embodiments, there are provided mechanisms and methods for associating a permission set with one or more users. These mechanisms and methods for associating a permission set with one or more users can enable improved access management, increased efficiency, enhanced security, reduced risk, greater governance, least privilege access, greater auditability, etc.
Owner:SALESFORCE COM INC
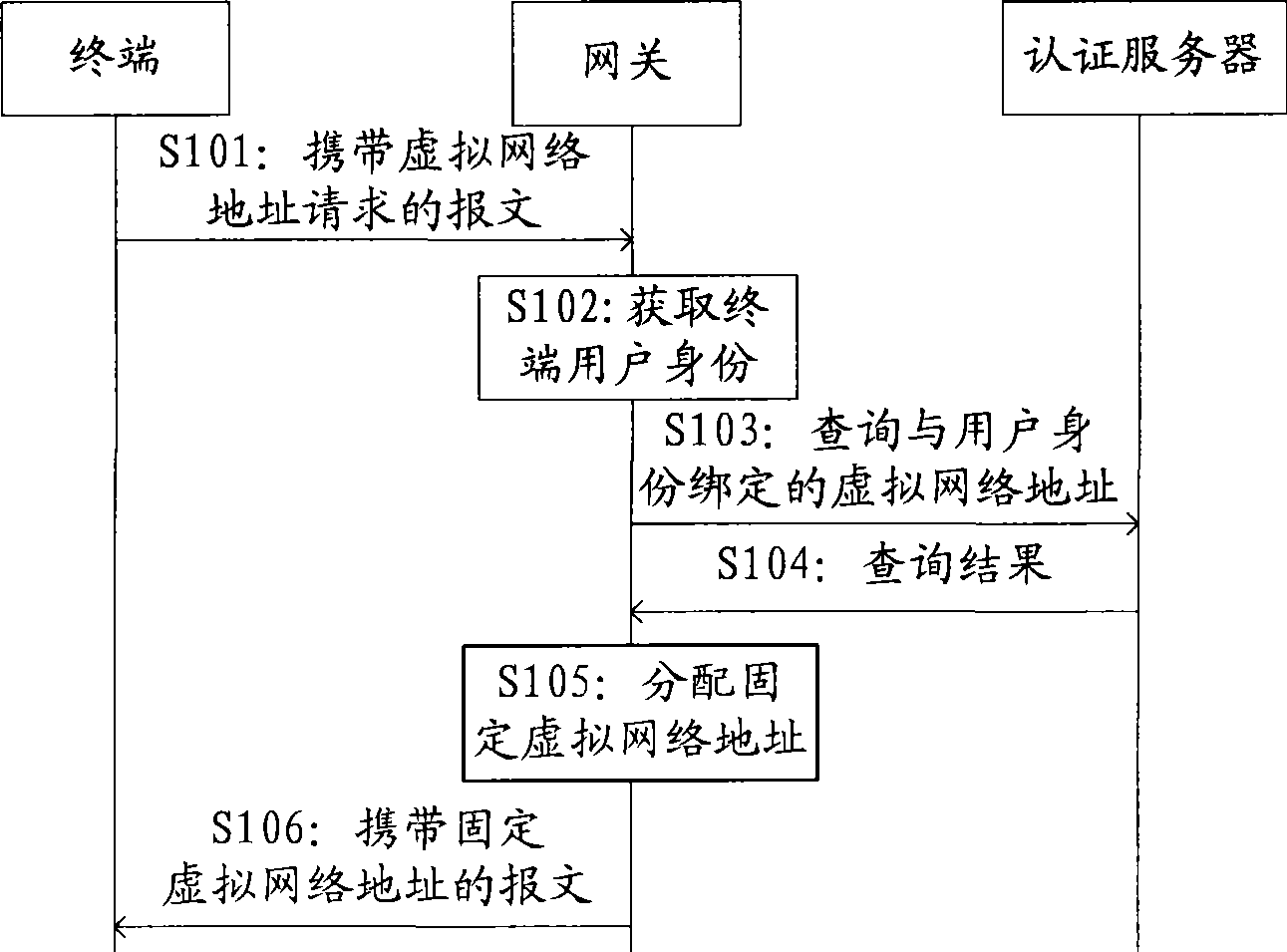
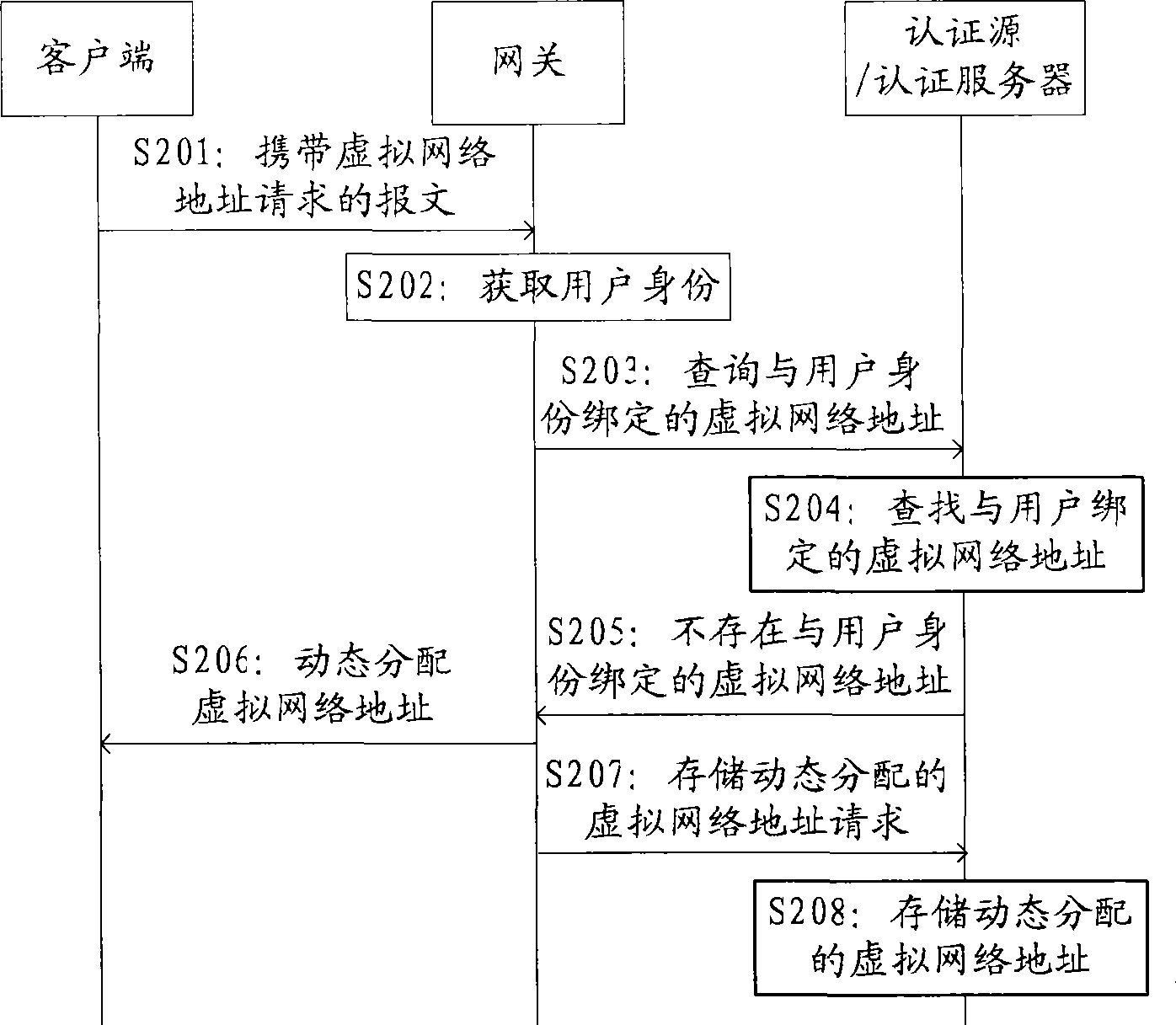
Method and gateway for distributing fixed virtual network address
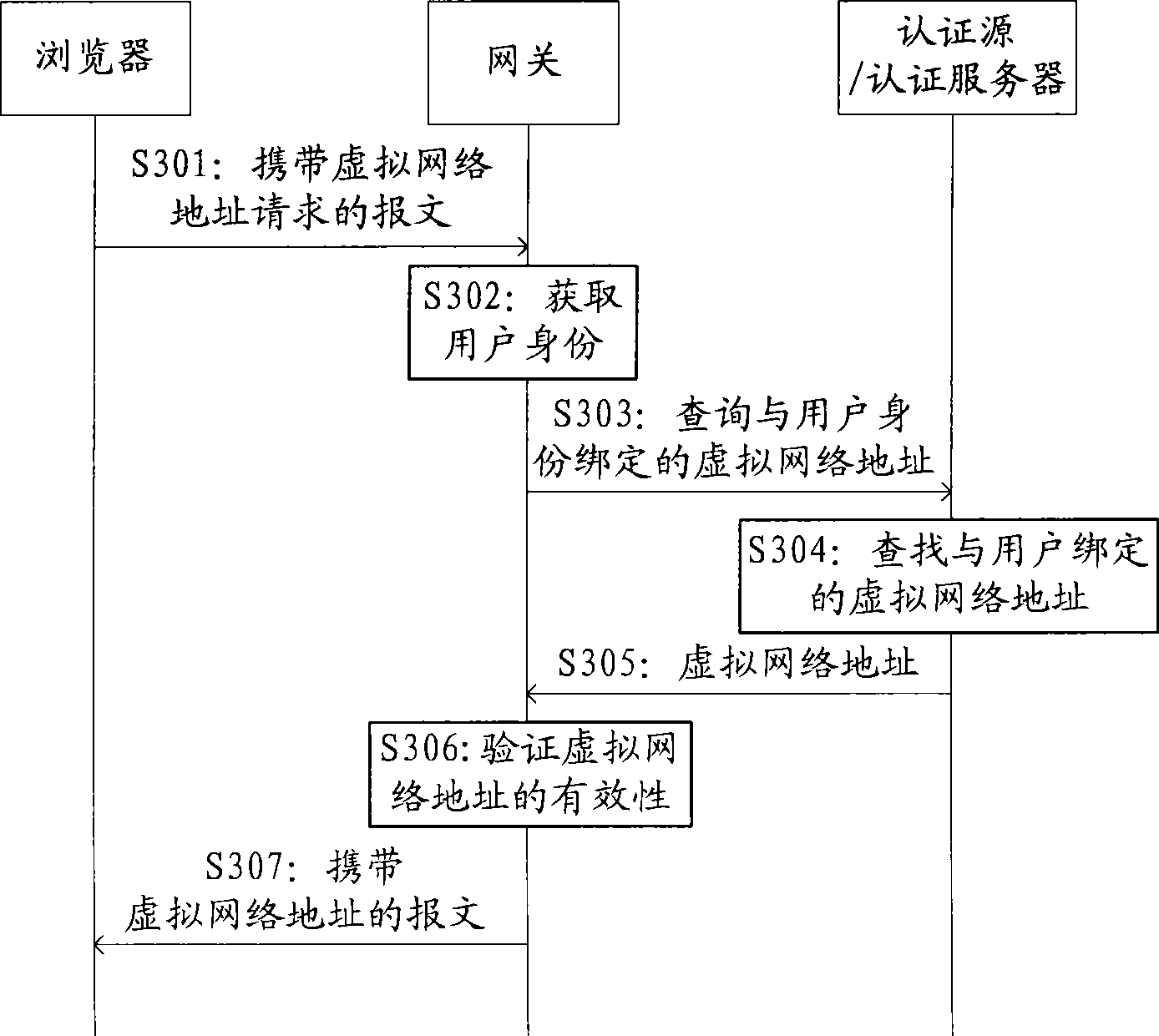
InactiveCN101442565AEasy access managementFacilitate behavior auditUser identity/authority verificationUser managementVirtual IP address
The embodiment of the invention belongs to the technical field of communication and provides a method for distributing a fixed virtual network address. The method comprises: receiving a message carrying a virtual network address request sent by a terminal; obtaining user identity of the terminal and according to the user identity, inquiring a virtual network address; according to an inquired result, distributing the fixed virtual network address for the terminal; and returning a response message carrying the fixed virtual network address to the terminal. The embodiment of the invention also provides a gateway. The embodiment can meet that a user can obtain the fixed virtual IP address at any moment and any place under the condition of higher requirement of mobility, and is convenient for user management, on-line control and user action audit.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
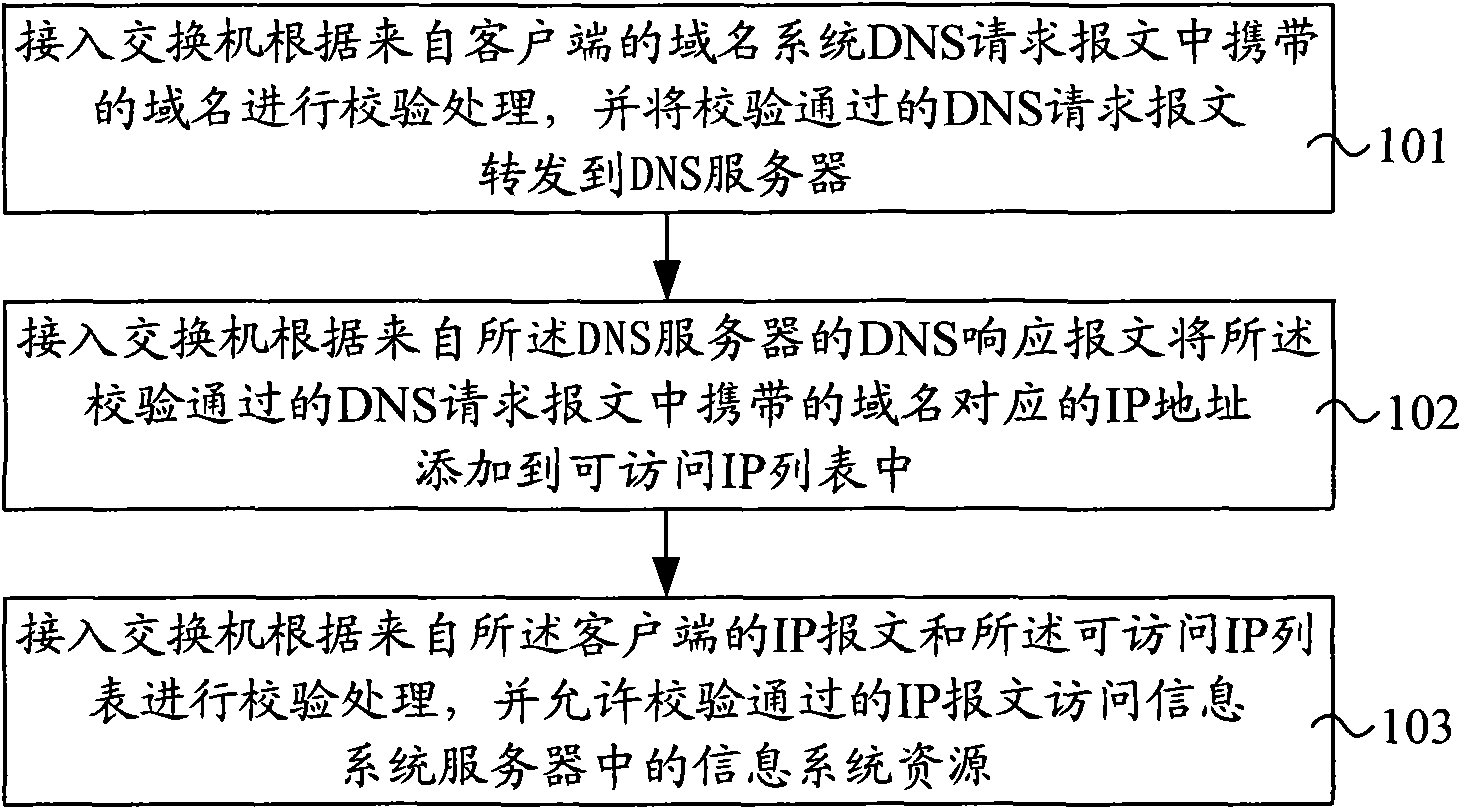
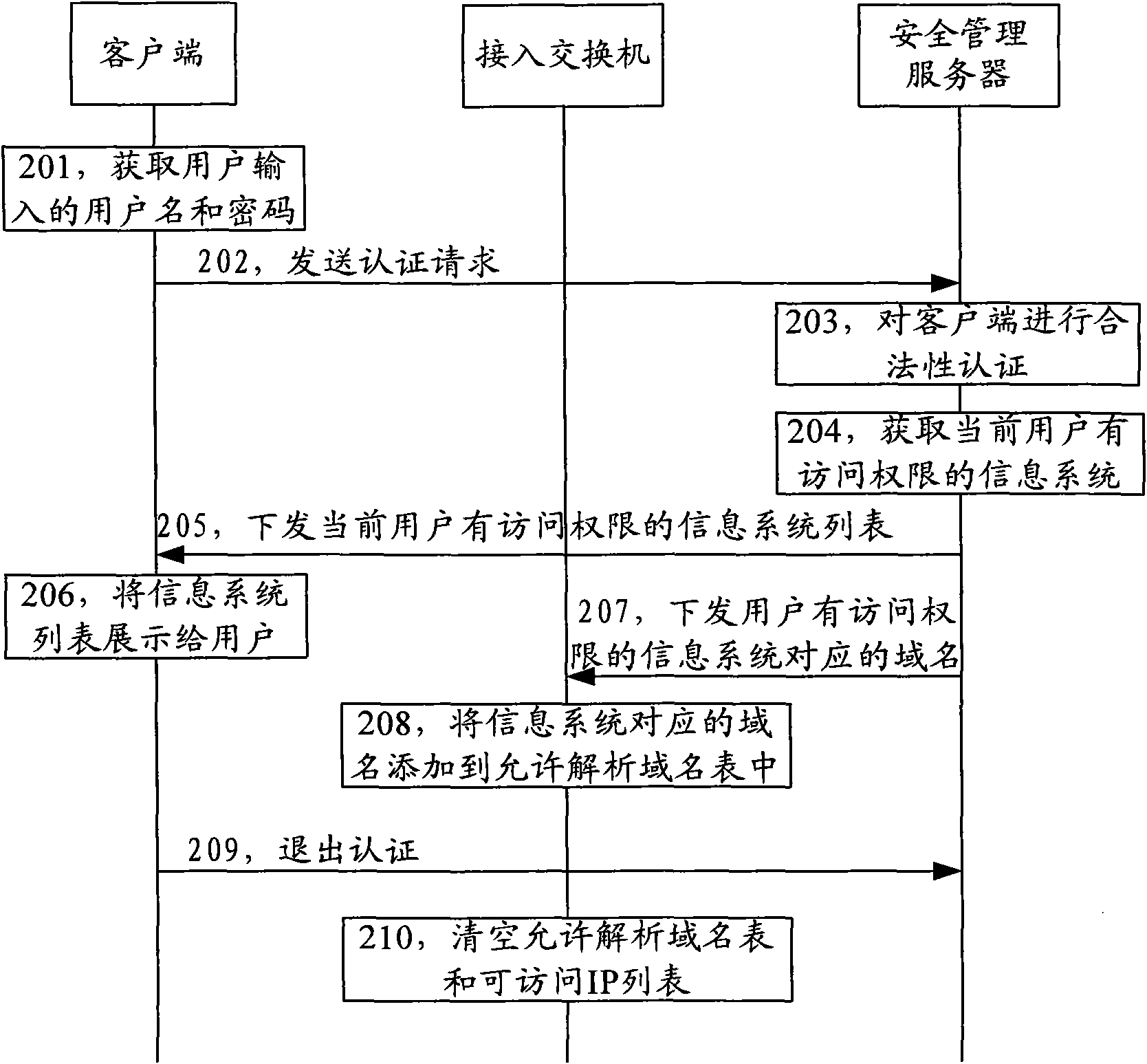
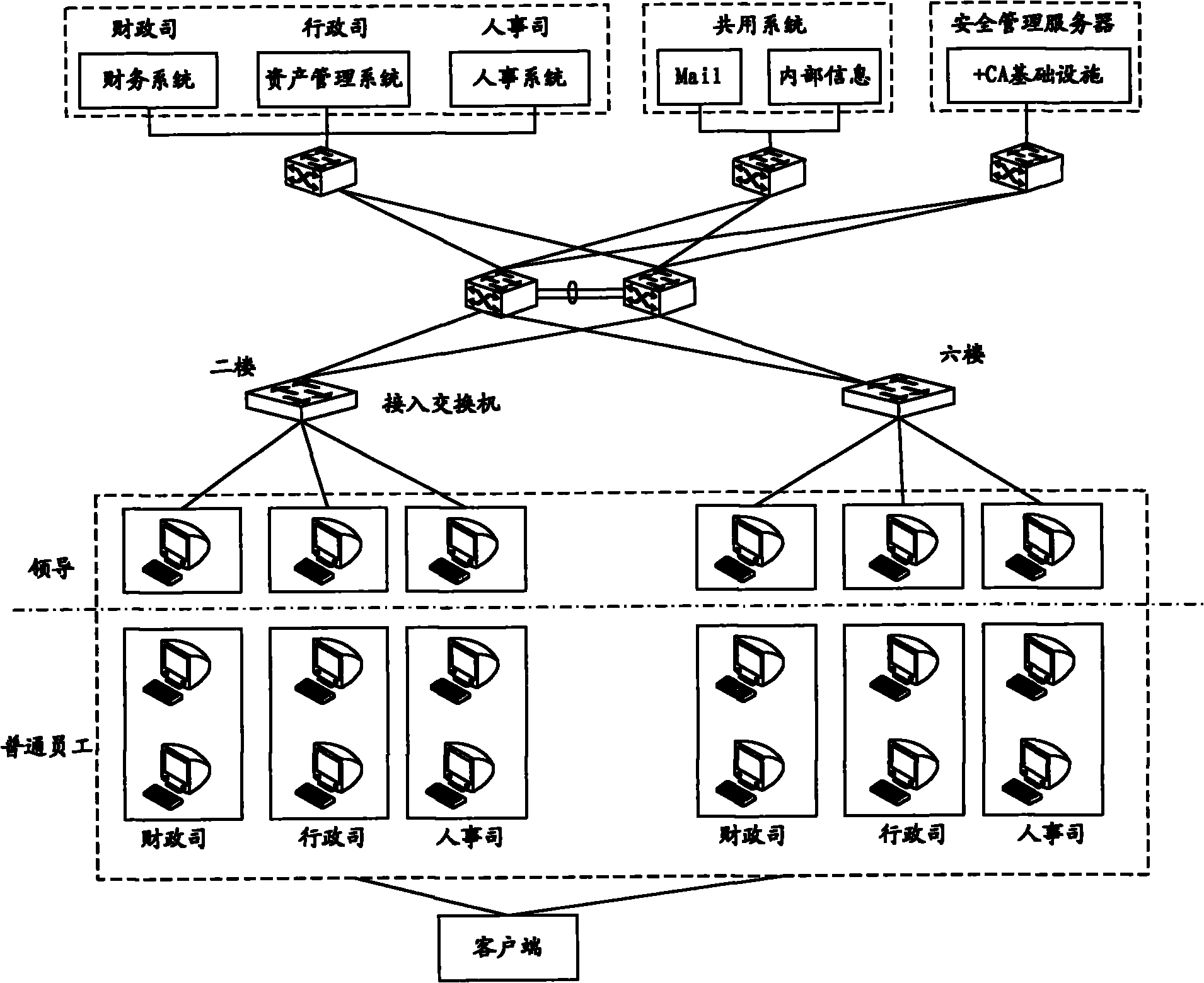
Access management method, device and system as well as access device for information system
The invention provides an access management method, a device and a system as well as an access device for an information system, wherein the method comprises: examining and handling according to a domain name carried in a domain name system DNS request massage from clients, and forwarding a DNS request massage passing the examination to a DNS server; adding an IP address corresponding to the domain name carried in the DNS request massage passing the examination according to a DNS response massage from the DNS server; and carrying out examining on the IP address according to an IP massage from the clients and an accessible IP list, and allowing the IP massage passing the examination to access the information system resources in the information system server. The device comprises a first examining module, a first appending module and a second examining module. The access device comprises an access management device of the information system. The invention also provides an access management system of the information system. The invention realizes a simple and convenient, and flexible access management.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
Optical transmission system and optical node
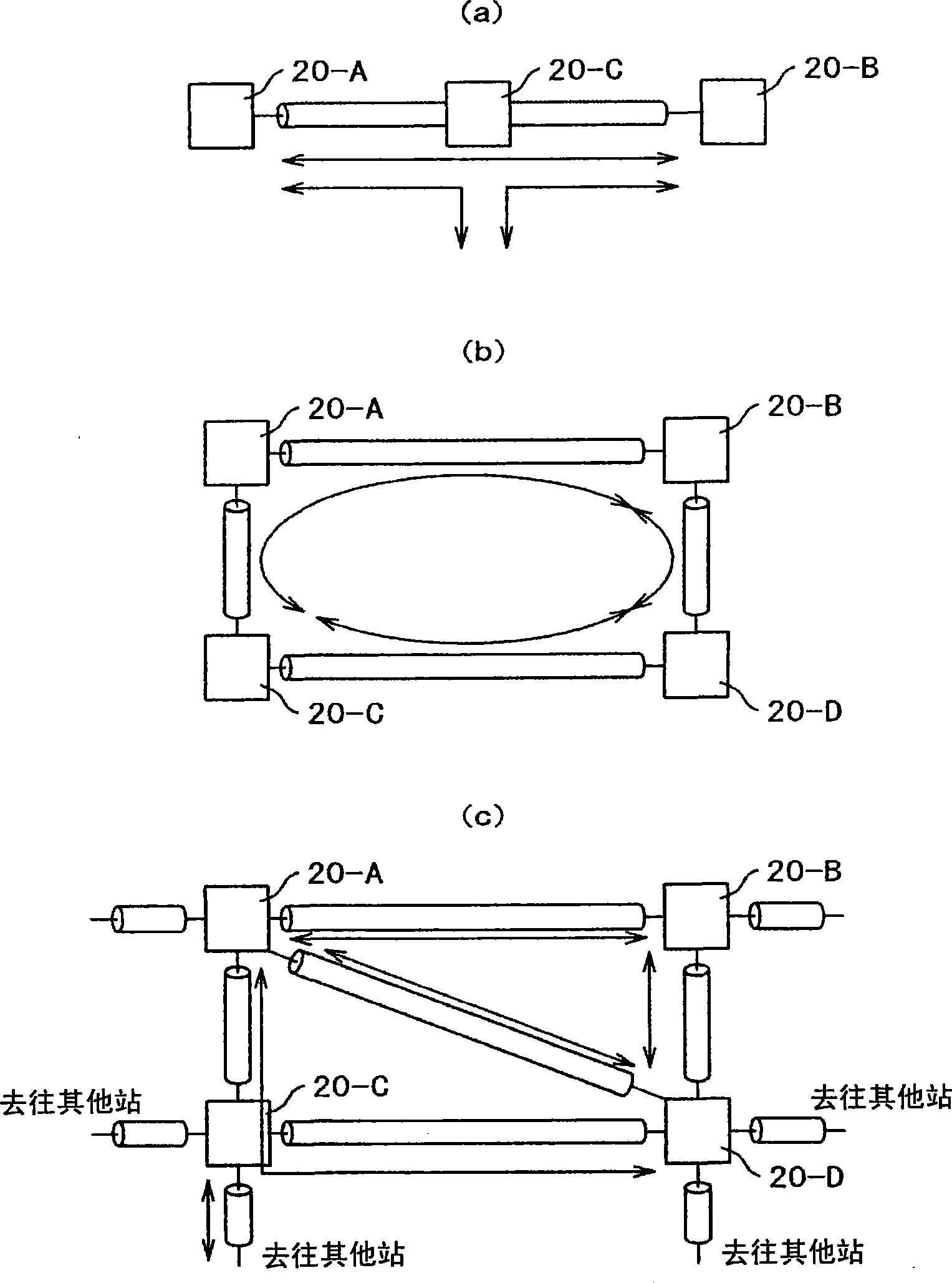
InactiveCN101442376AEasy access managementBus-type electromagnetic networksWavelength-division multiplex systemsIntegrated monitoringTransceiver
The invention provides an optical transmission system and optical node. On condition of a pair of 1 type gateways and a pair of N type gateways which are mixed, unexpected alarms will not be produced, and gateway management can be carried out as now. The optical transmission system comprises an integrated monitoring and controlling unit which is to control an optical add-drop unit so as to cause transmit signals from the optical transceiver of a first optical node to be received by the optical transceivers of plural different optical nodes, the purpose can be achieved by an optical transmission system provided with an alarm inhibiting device that can inhibit the optical transceiver, which is a source of transmission, from issuing any unexpected alarm.
Owner:HITACHI LTD
Access control method and device based on GPRS network and integrated identification network
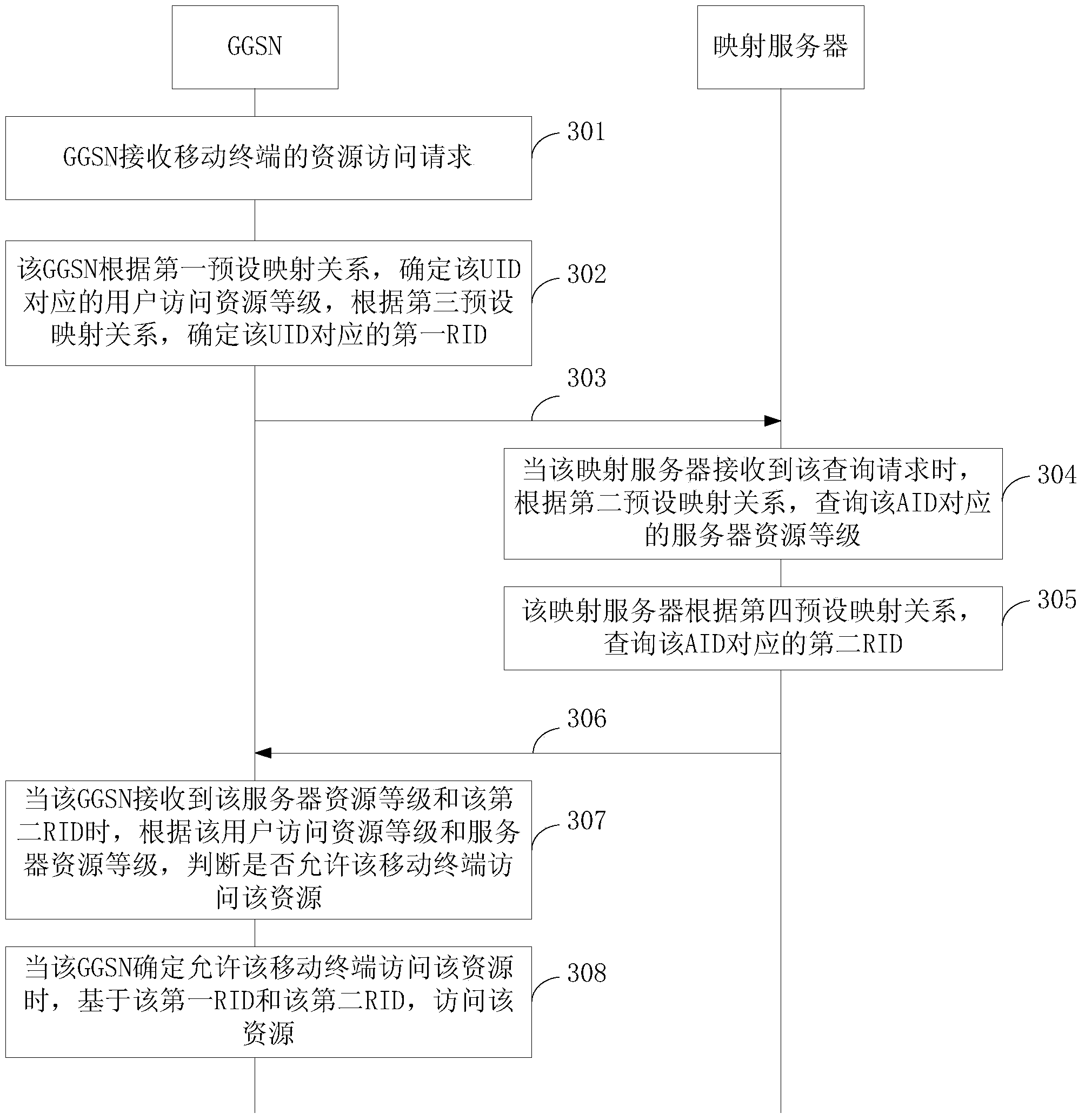
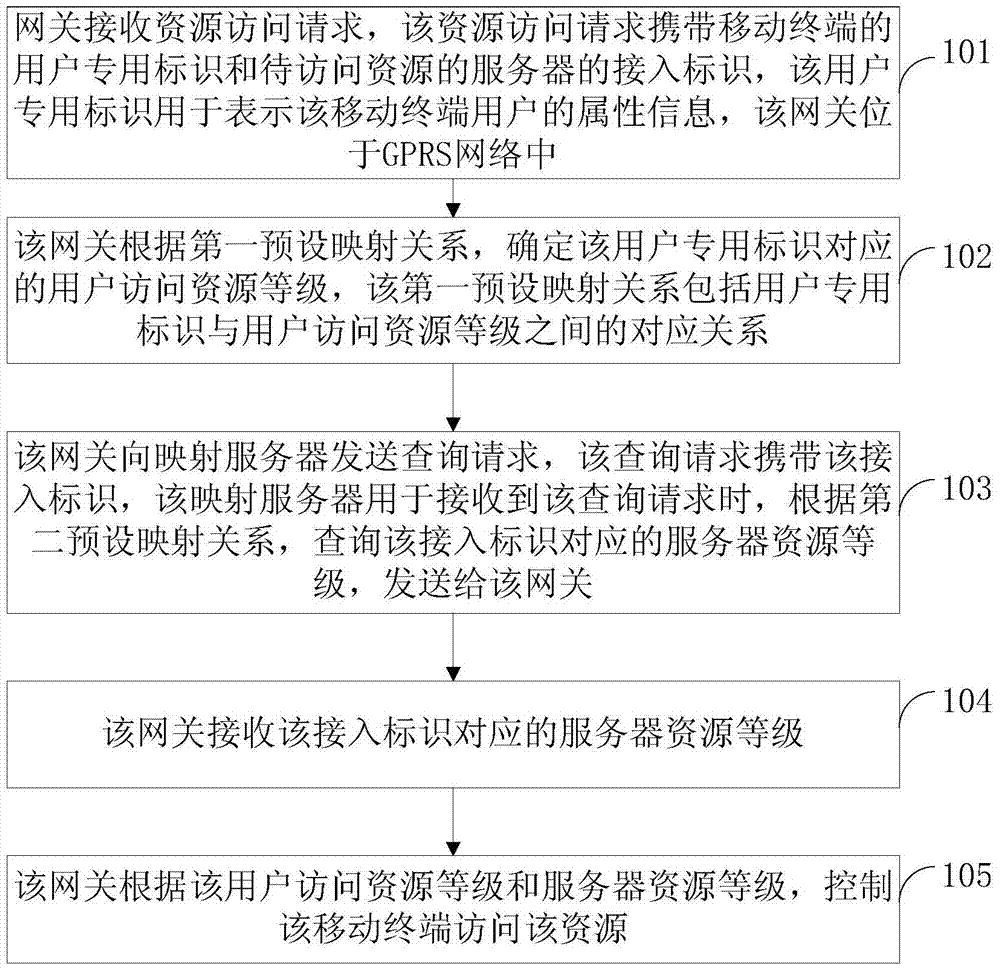
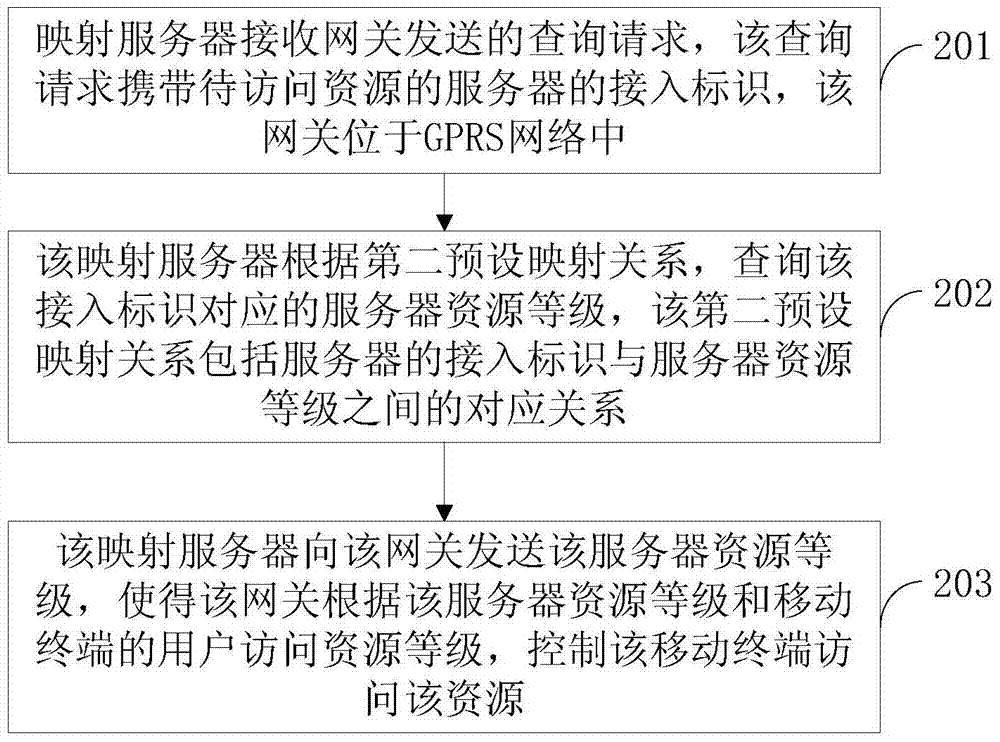
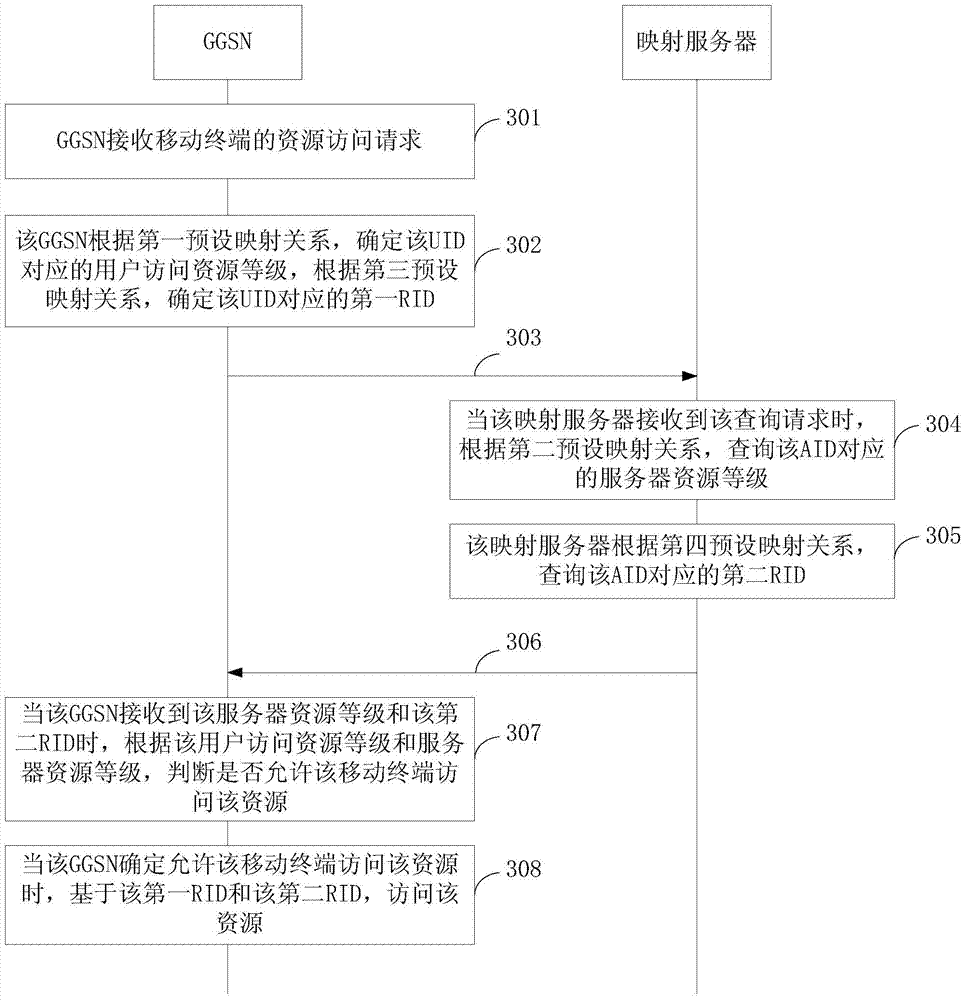
InactiveCN104168165AEasy to controlEasy access managementData switching by path configurationSecurity arrangementWeb technologyAccess control
The invention discloses an access control method and a device based on a GPRS network and an integrated identification network, belonging to the network technology field. The method comprises: a gateway receives resource access requests, wherein the resource access request carries a user exclusive identifier and an access identifier and the user exclusive identifier is used for expressing attribute information of a mobile terminal user; the gateway determines the level of the user access resource according to a first preset mapping relation; the gateway transmits inquiry requests to the mapping server, wherein the inquiry request carries an accessing identifiers; the gateway receives a server resource level corresponding to the access identifier; the gateway controls the access resource of the mobile terminal according to the user access resource level and the server resource level. The invention introduces the user exclusive identifiers in the GPRS network, performs distinguishing on various terminal users according to the user exclusive identifiers, realizes the control of various user access resources and is convenient to access and manage the server resource.
Owner:BEIJING JIAOTONG UNIV
Implementation method of communication middleware by adopting HTTP proxy database protocol
ActiveCN111818166AStrong penetrating powerEasy to develop and testDigital data information retrievalEncryption apparatus with shift registers/memoriesConnection poolEngineering
The invention discloses an implementation method of communication middleware by adopting an HTTP proxy database protocol. Database protocols realized by different manufacturers themselves are adoptedin the database middleware to connect different databases, different manufacturers need to add different JDBC drive packages in advance, and the JDBC drive packages are packaged into HTTP protocols for proxy communication. The HTTP protocol can penetrate through the gateway layer more easily, the influence of the network layer is reduced, and development testing and formal deployment are facilitated. The Client only needs one access address, so that multiple types of databases can be conveniently accessed and managed at the same time. The number of connection pools of the database layer can beobviously reduced after service growth. Rich sql execution conditions and runtime monitoring information can be increased. The flexible database access control, such as access permission and requestfrequency, can be self-defined.
Owner:杭州隐捷适生物科技有限公司
Content access rights management system which embeds restricted metadata into a picture
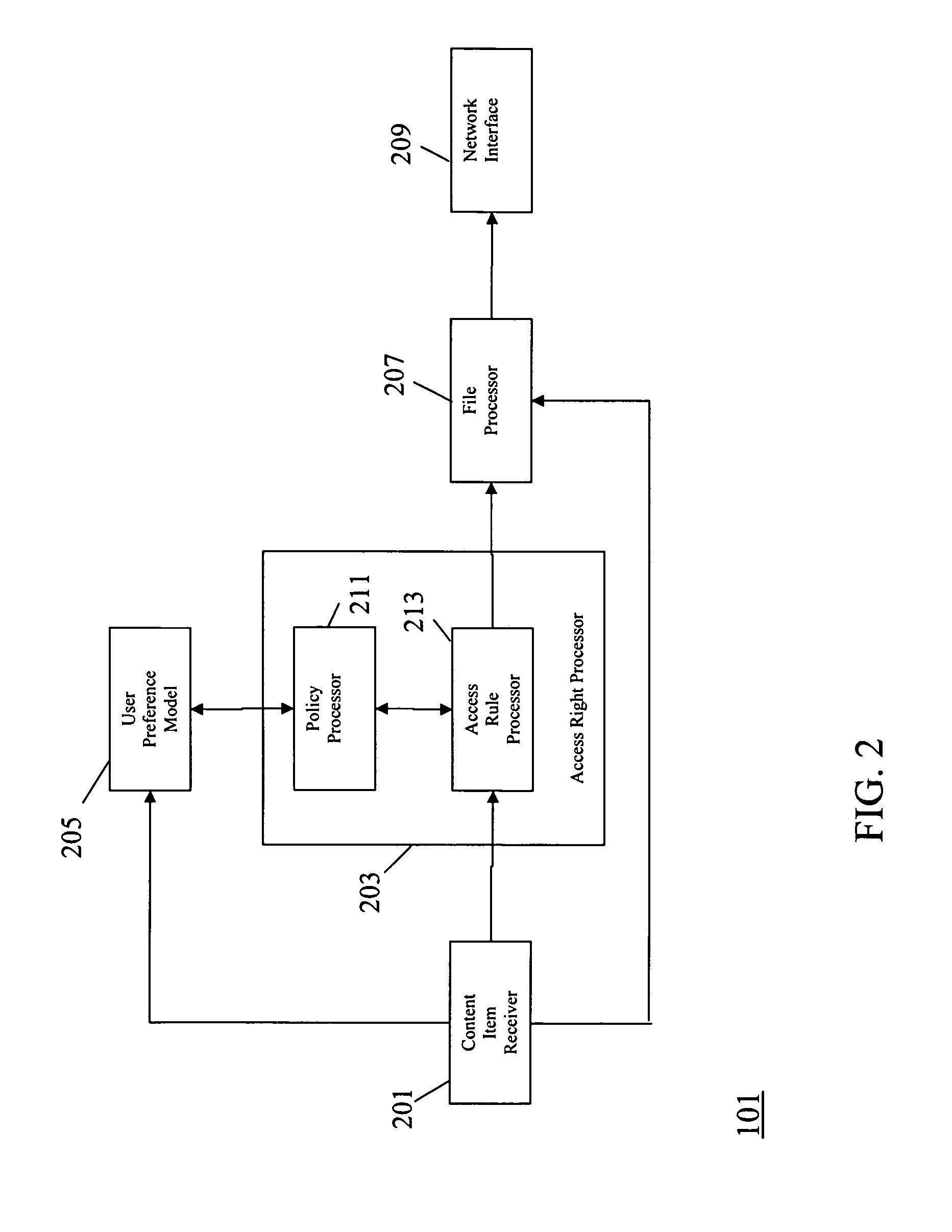
ActiveUS8141166B2Easy to manageEasy access managementDigital data processing detailsDigital computer detailsDocument handlingRights management
An apparatus comprises a content item receiver which receives a content item such as a digital photo or an audio or video clip. A user preference model generates data indicative of user preferences for content item access. An access rule processor determines a set of self-governance rules for the first content item in response to the user preference model. The self-governance rules are indicative of allowable actions for the first content item in other devices. A file processor includes the set of self-governance rules with the content item and a network interface transmits the content item to a second apparatus . The second apparatus comprises functionality for restricting access to the content item in accordance with the set of self-governance rules. The invention may provide improved access rights management and in particular for personal content items.
Owner:MOTOROLA SOLUTIONS INC
Image creation apparatus and method, and computer program
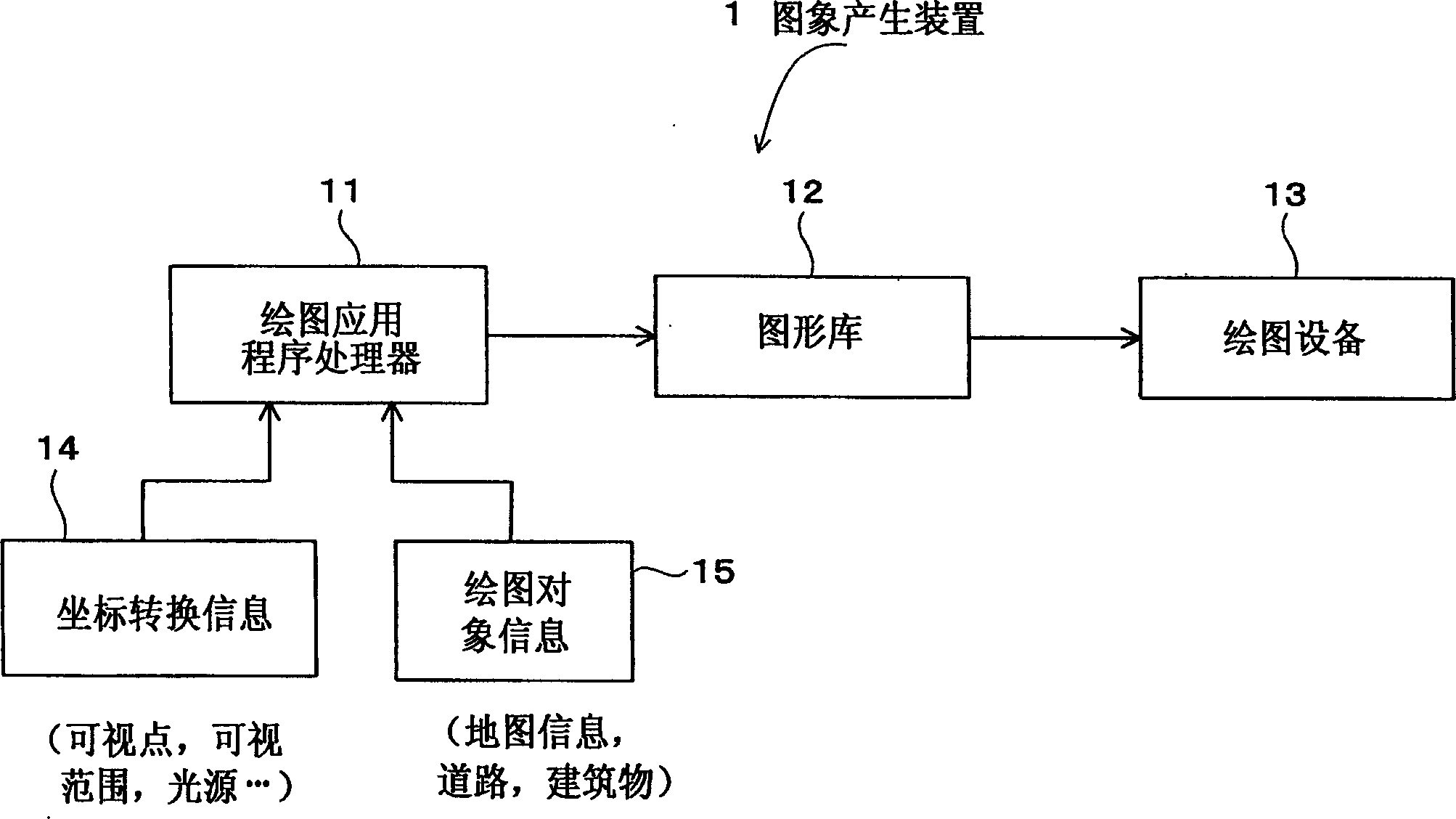
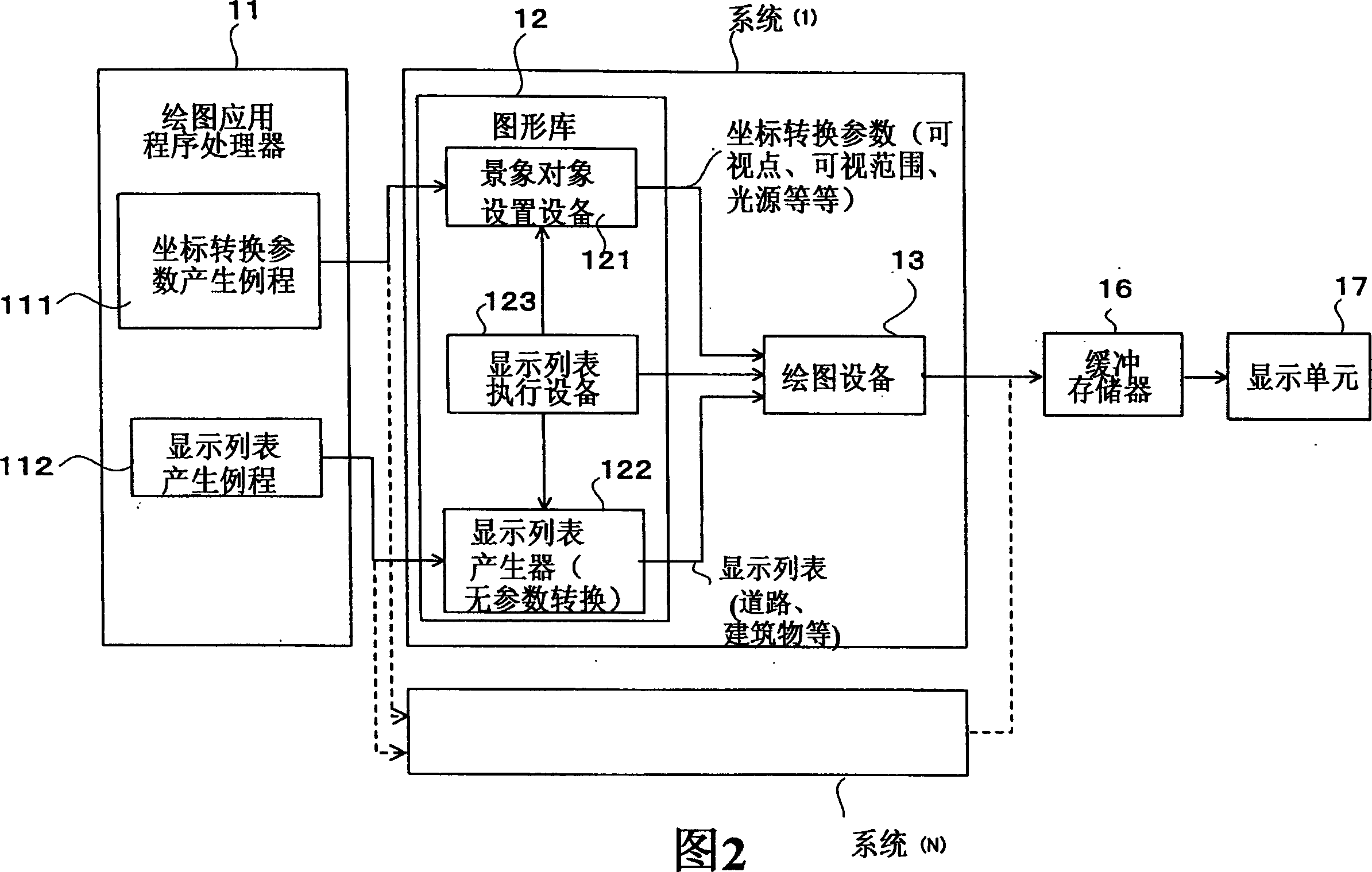
InactiveCN1559056AAvoid effects related to exclusive controlEasy to manageIndoor gamesRoad vehicles traffic controlComputer graphics (images)Engineering
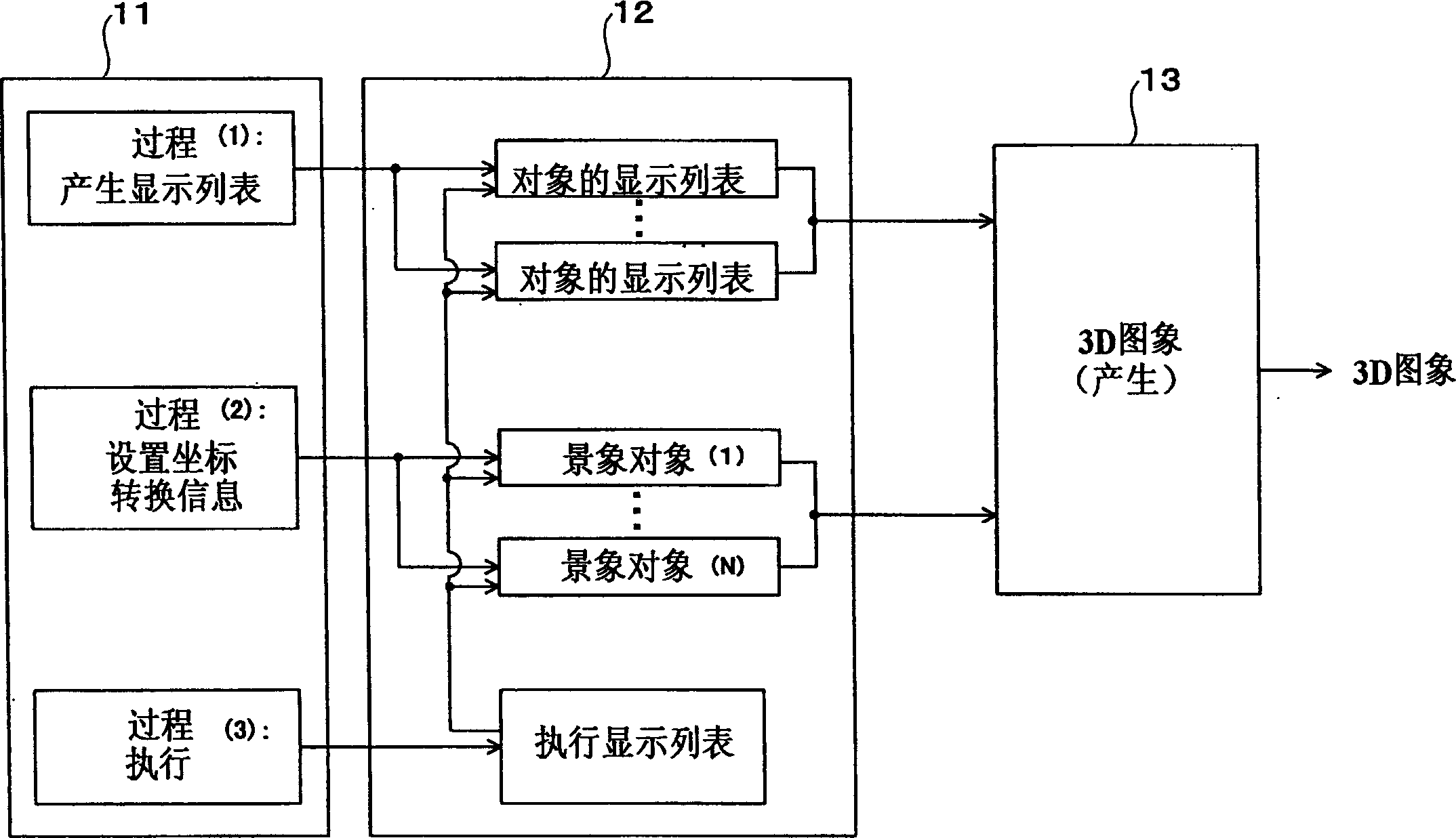
An image generating apparatus (1) is provided with a drawing application processor (11) and a graphics library (12) that allow a drawing device (13) to generate a three-dimensional image. The drawing application processor (11) separately includes: a coordinate transformation information generating device for generating coordinate transformation information to generate an image; and a drawing object information generating device for generating drawing object information. The drawing device (13) generates the three-dimensional image by incorporating the coordinate transformation information with the drawing object information. The coordinate transformation information is managed by the identifier. The drawing device incorporates the coordinate transformation information, which is identified by the identifier for a drawing execution, into the drawing object information, to generate the three-dimensional image.
Owner:PIONEER CORP
Shielding hood device
InactiveCN103600643AFacilitate masking servicesEmission reductionRemovable external protective coveringsShielding blockMechanical engineering
The invention discloses an article shielding hood device, and particularly provides the shielding hood device for an automobile. The shielding hood device comprises a hood body assembly composed of a front hood body, a rear hood body, a left hood body, a right hood body, an upper hood body and fixing ropes. Extensible bodies used for adjusting the covering area of the hood bodies, liners capable of enabling the hood bodies to be flat and shielding blocks are arranged on the hood body assembly, wherein the shielding blocks can be flexibly mounted and connected according to requirements and can also be conveniently dismounted and replaced. A storage assembly is arranged outside the hood body assembly. The shielding hood device has the advantages that the shielding hood device is universal for shielding various automobile types attractively and conveniently at a public parking lot so that the automobiles can be stored and managed, various advertisement carriers can be arranged according to different requirements, and the advertising resources of public parking lots can be fully used; the components can be replaced according to different requirements of season changing and different requirements of vision, so that the shielding hood device can better meet requirements, and cost is lowered.
Owner:何剑
Method, system and method for controlling access of host computer
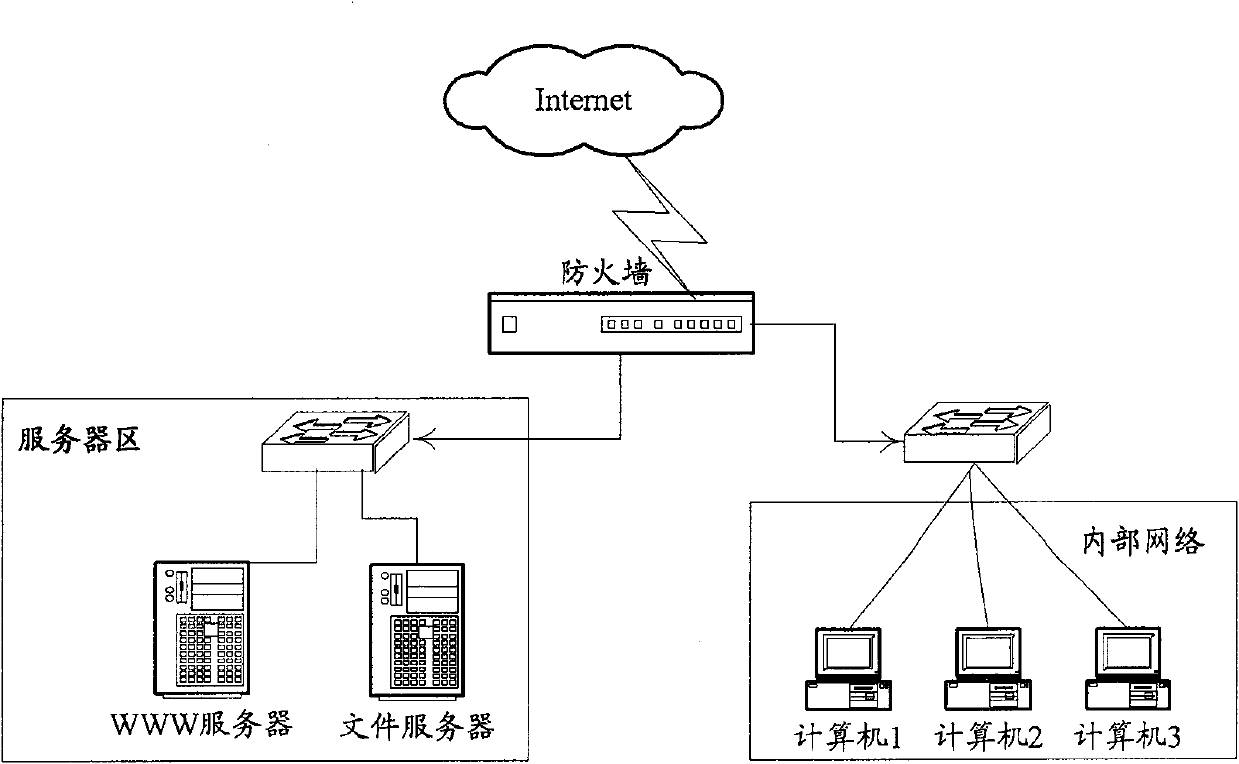
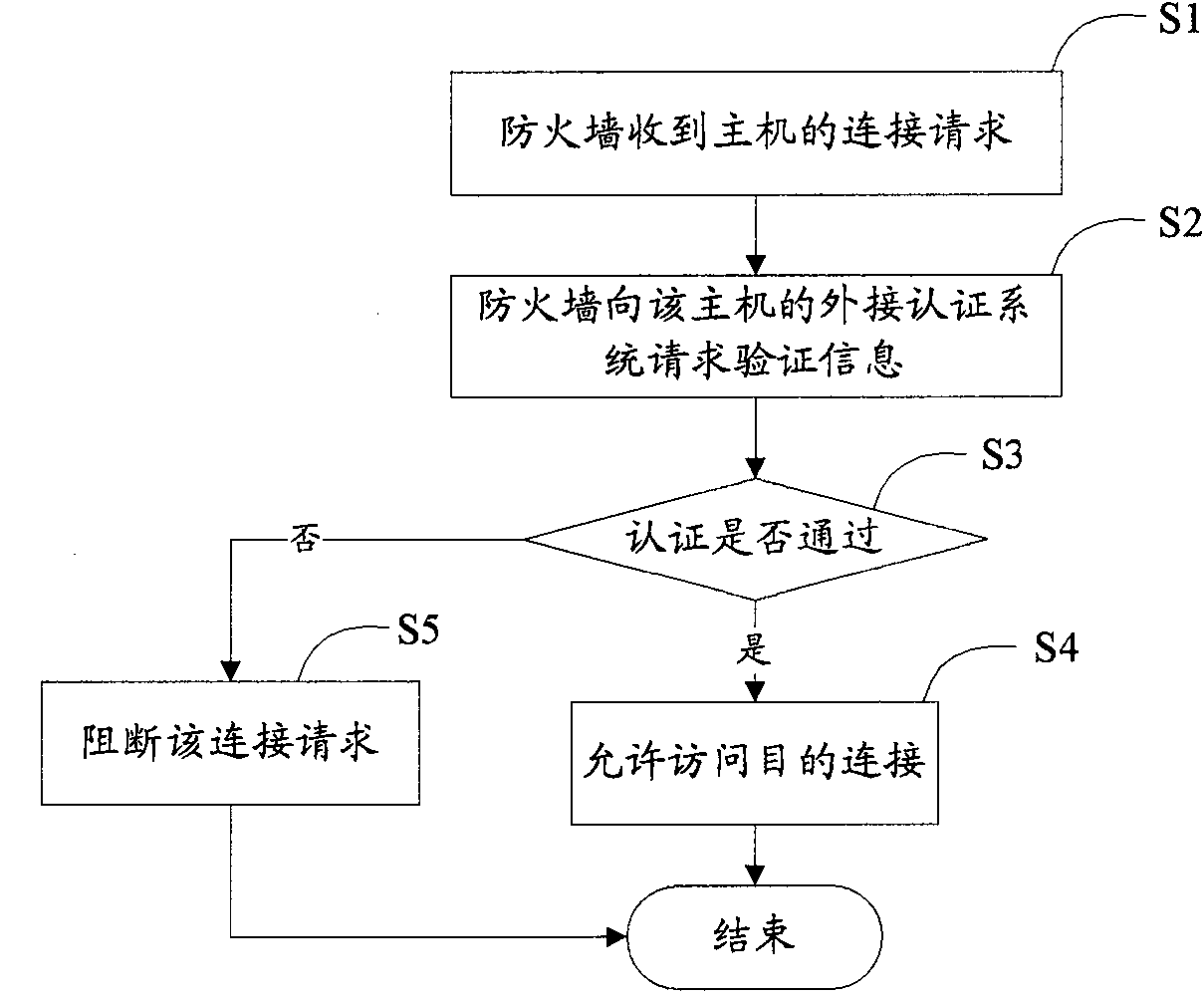
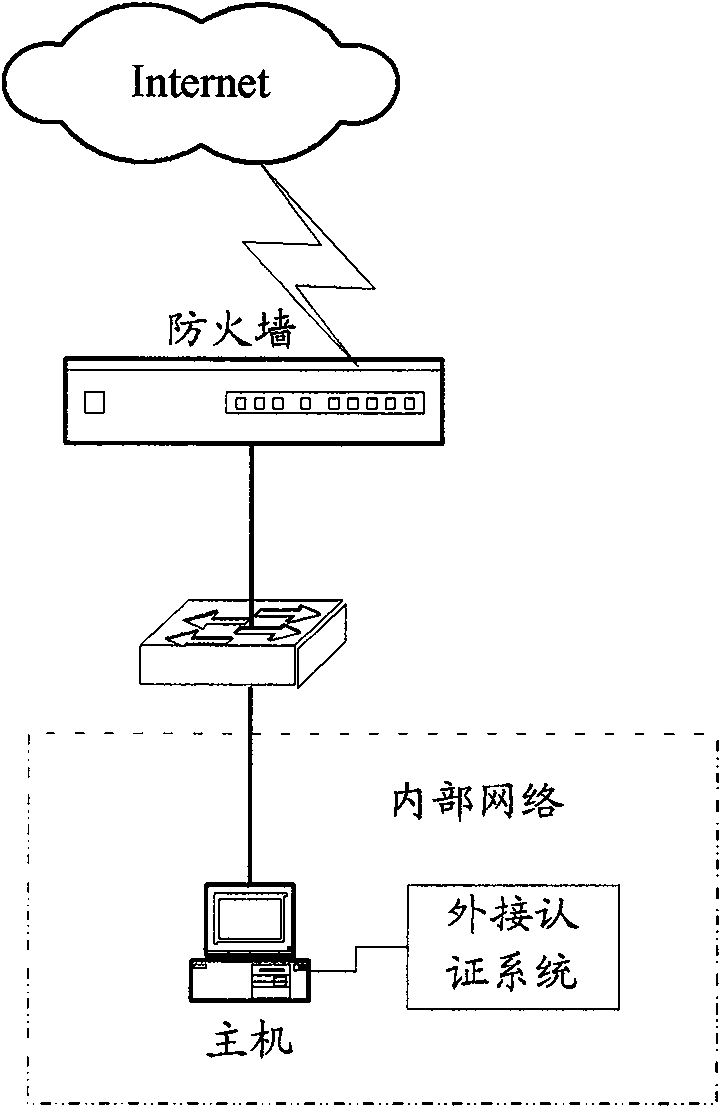
InactiveCN102088453AControl accessEasy access managementSecuring communicationIp addressMedia access control
The invention discloses a method, system and device for controlling access of a host computer, which relate to the field of network security and are used for solving the problem that the access of the host computer cannot be effectively controlled in the prior art. The method comprises the following steps of: receiving a connection request from the host computer and requesting for verification information from an external authentication system of the host computer by a firewall; authenticating the obtained verification information through an access strategy by the firewall; if the authentication passes, allowing access of destination connection; and if the authentication fails, blocking the connection request. The system comprises the host computer, the external authentication system and the firewall, wherein the external authentication system is connected with the host computer; and the firewall is arranged between the host computer and the Internet and comprises a verification managing module, a connection tracking module and a blocking module. In a technology disclosed by the invention, the verification information is acquired according to the external authentication system of the host computer independent of an access request, an Internet protocol (IP) address, a media access control (MAC) address and the like, so that access of the host computer can be effectively controlled.
Owner:BLUEDON INFORMATION SECURITY TECH CO LTD
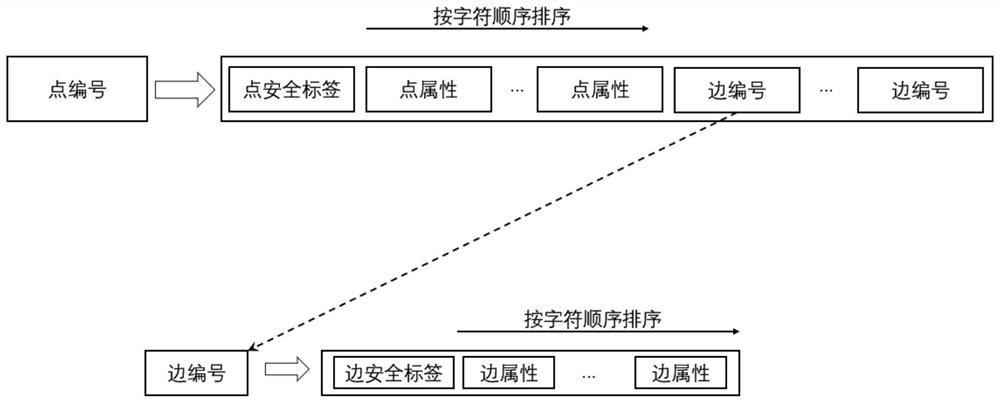
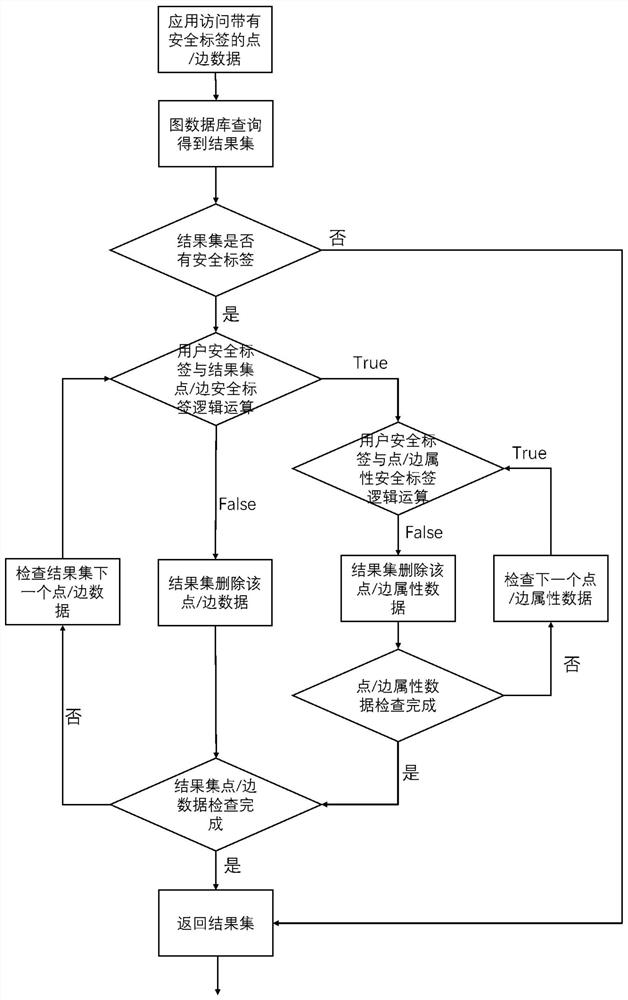
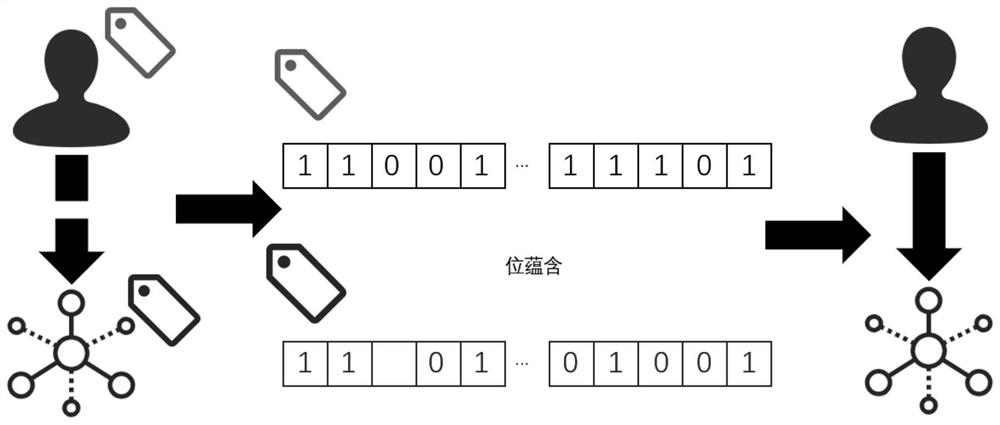
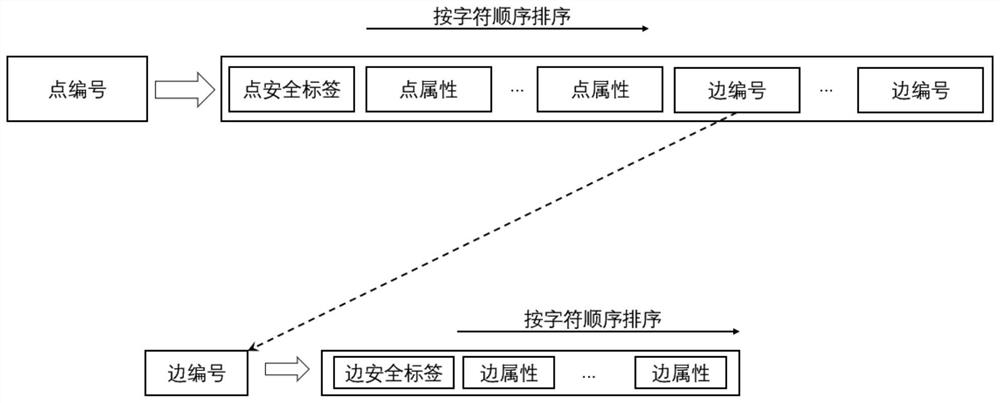
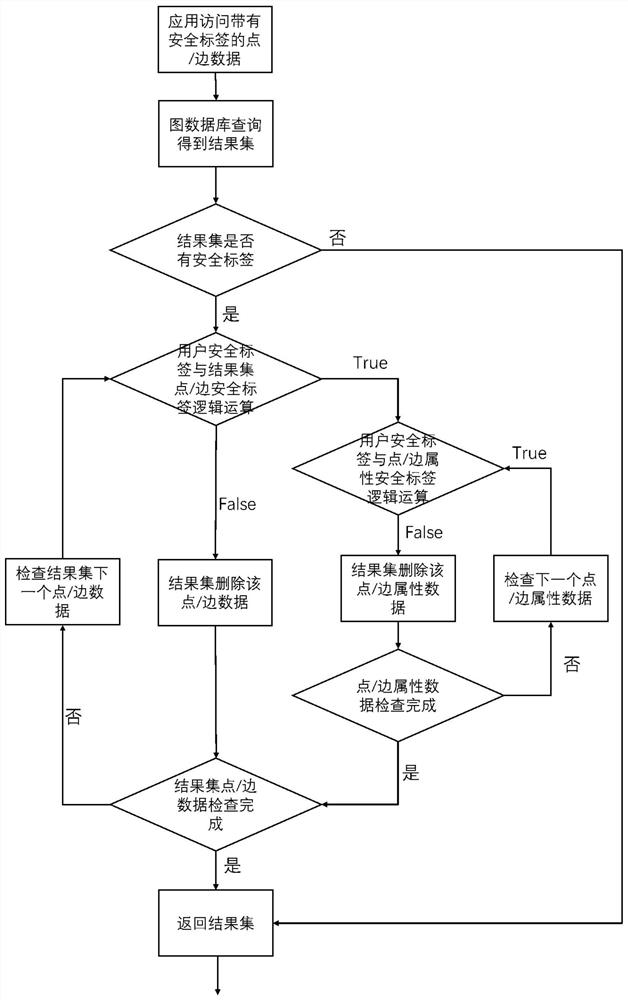
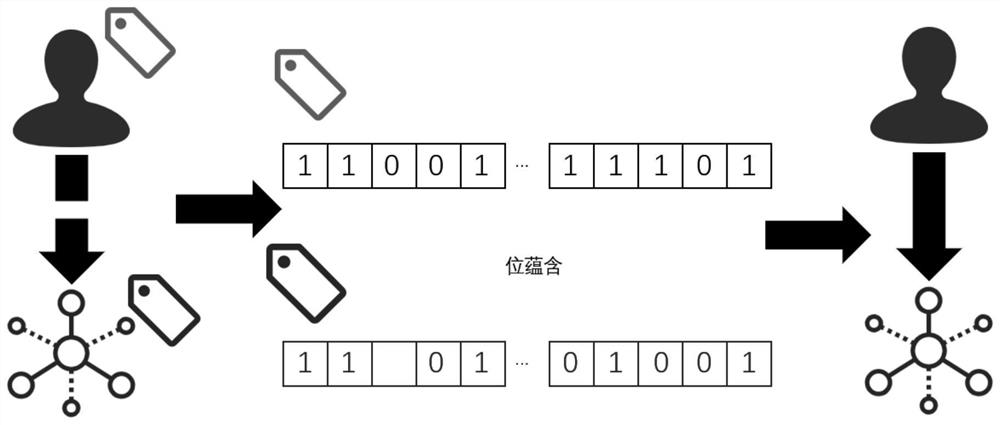
Mass graph data fine-grained access control method based on security tags
ActiveCN112699410AWithout sacrificing access performanceImprove securityStill image data indexingDigital data protectionTheoretical computer scienceData access
The invention provides a mass graph data fine-grained access control method based on security tags, and belongs to the field of mass data processing. The method comprises the steps that a security label is added in a point / edge / attribute storage structure of graph data and user information and used for determining security requirements needed by access, the security label does not need to be defined in advance, and the security label is set after data generation or security design is completed; and when graph data query is carried out, the user security label is compared with the security label of the point / edge / attribute data to judge whether the user has permission to access the data or not. The security tag supports logic expression representation, and security access control of different granularities is realized by adopting a point, edge and attribute three-level granularity security tag; according to the invention, bit operation is adopted to accelerate security label logic calculation and filtering calculation of point / edge / attribute data. According to the method, the security of mass graph data access is greatly improved while the graph data access performance is not sacrificed.
Owner:BEIJING SCISTOR TECH
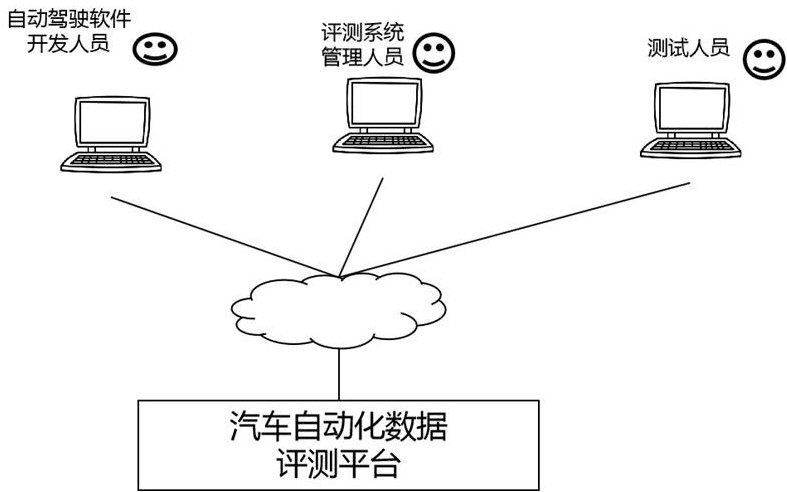
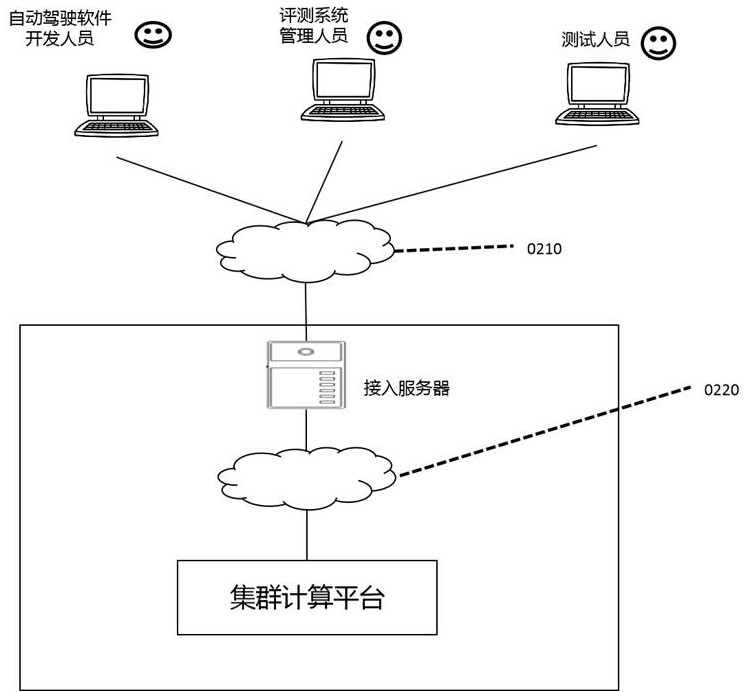
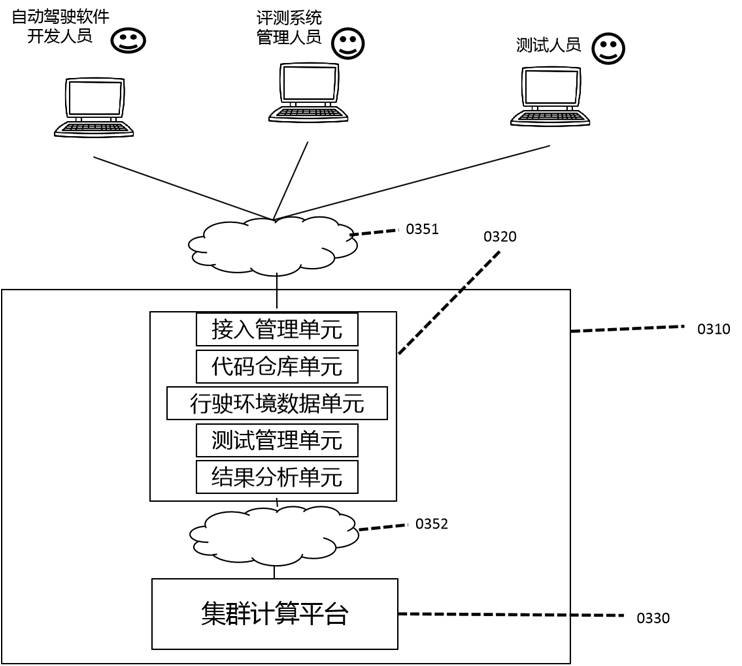
Automatic driving software evaluation system
An automatic driving software evaluation system is used for testing automatic driving software or modules and comprises an access server and a cluster computing platform. The system further comprises an access management unit, a code warehouse unit, a driving environment data unit and a test management unit. The driving environment data unit comprises driving environment data, and the driving environment data is obtained by 3D modeling after acquisition of a real vehicle on an actual road; the tested automatic driving software or module is uploaded to the code warehouse unit through the network 1; the driving environment data is uploaded to the driving environment data unit through the network 1; the test management unit drives the code warehouse unit to distribute test automatic driving software or modules to the cluster computing platform according to the test plan; the test management unit drives the driving environment data unit to distribute the driving environment data to the cluster computing platform according to the test plan; and the automatic driving software or module virtually executes automatic driving operation according to the driving environment data and outputs automobile automatic driving control output data.
Owner:ZHIJI AUTOMOTIVE TECH CO LTD
A bill storage device based on financial management
ActiveCN111688383BEasy access managementGood for classification and storageFiling appliancesAnimal repellantsTicketEngineering
The invention discloses a bill storage device based on financial management, which comprises a bottom plate, a carrier plate and a tubular frame. Frame, the outer side of the upper end of the tubular frame is fixedly connected with a mounting plate by bolts, and the inner side of the tubular frame is slidingly connected with a movable column, the left and right ends of the outer side of the movable column are welded with limiting plates, and the upper end of the movable column It is connected with the middle part of the upper side wall of the protective cover. The outer side of the protective cover is covered with a movable cover, and the inner sides of the left and right ends of the protective cover are slidingly connected with the first movable block, and the first movable block is connected with the inner side of the movable cover. Wall snap connection. The bill storage device based on financial management facilitates the access management of bills, facilitates the classification and storage of bills, makes it easier to search for subsequent bills, and also has the function of preventing insects and improving practicability.
Owner:PEOPLES HOSPITAL OF HENAN PROV
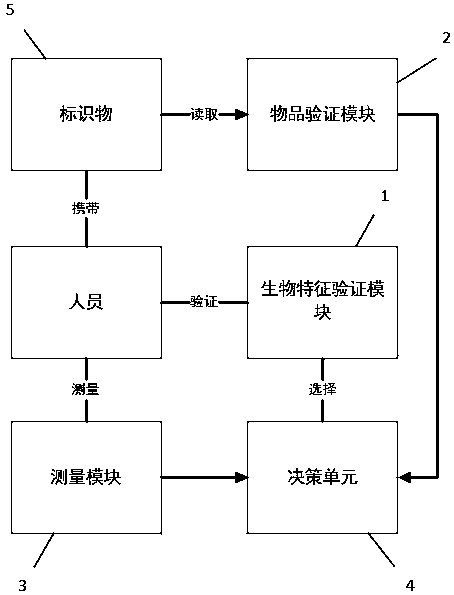
Underground mine personnel access recognition system and method
ActiveCN111259731AEasy access managementImprove reliabilityIndividual entry/exit registersMultiple biometrics useComputer scienceIndustrial engineering
The invention discloses an underground mine personnel access recognition system and method. The system comprises the steps: enabling personnel to carry a marker when entering, reading the code of themarker through a verification unit, and measuring the height and weight; the decision-making unit selects a corresponding biological characteristic verification module according to the height and / or weight value, and the result and the code are stored together; if verification is passed, releasing, If verification is not passed, prompting; when the person leaves, the verification unit reads the marker code and measures the height and the weight; the decision-making unit selects a corresponding biological characteristic verification module according to the height and / or weight value, and the result and the code are checked and verified; if verification is passed, releasing, If verification is not passed, prompting. The method has the substantive effects that through combination of a traditional mode and a new mode, the biological characteristics of personnel are fully utilized, the verification reliability is improved on the premise that the verification process is not complex and time-consuming, and in-out management of the personnel is facilitated.
Owner:中铝智能科技发展有限公司
After-loading transfer bed for gynecological tumor radiotherapy
InactiveCN114767399AMeet fixed needsGuaranteed repeatabilityStretcherX-ray/gamma-ray/particle-irradiation therapyRatchetAir spring
A lifting device is arranged between a bed board and a bottom frame, the lifting device comprises a bearing plate, a supporting mechanism and a safety lock, the supporting mechanism comprises vertical frames, air springs and connecting rod assemblies which are symmetrically arranged, the two connecting rod assemblies are connected through carrier rollers, the carrier rollers make contact with the bottom face of the bearing plate, and the safety lock is arranged on the supporting plate. One end of each air spring is rotationally connected to the corresponding vertical frame, the other end of each air spring acts on the corresponding connecting rod assembly, the two vertical frames are fixed to the bottom frame, one end of the bearing plate is connected with the synchronous plate, the two sides of the synchronous plate are connected with the wing plates respectively, and the roller sets arranged on the synchronous plate and the wing plates can slide along the vertical frames; the safety locks are symmetrically arranged on the two sides of the bearing plate, each safety lock comprises a ratchet strip and a bidirectional pawl mechanism, the ratchet strips are fixed to the corresponding vertical frames, the bidirectional pawl mechanisms are rotationally arranged on the corresponding wing plates, brake cables used for controlling bidirectional pawls are connected to the brake handles, and the brake handles are connected to the control plate. The transfer bed is stable and comfortable in transfer and safe and reliable in locking.
Owner:AFFILIATED CANCER HOSPITAL OF SHANDONG FIRST MEDICAL UNIV SHANDONG CANCER INST (SHANDONG CANCER HOSPITAL)
Access control method and device based on gprs network and integrated identification network
InactiveCN104168165BEasy to controlEasy access managementData switching by path configurationSecurity arrangementUser identifierAccess management
The invention discloses an access control method and device based on a GPRS network and an integrated identification network, belonging to the field of network technology. The method includes: the gateway receives a resource access request, the resource access request carries a user-specific identifier and an access identifier, and the user-specific identifier is used to represent the attribute information of the mobile terminal user; the gateway determines the user access resource level according to the first preset mapping relationship; The gateway sends a query request to the mapping server, and the query request carries an access ID; the gateway receives the server resource level corresponding to the access ID; the gateway controls the mobile terminal to access resources according to the user access resource level and the server resource level. The invention introduces user-specific identifiers into the GPRS network, distinguishes different mobile terminal users according to the user-specific identifiers, realizes the control of different users' access to resources, and facilitates the access management of server resources.
Owner:BEIJING JIAOTONG UNIV
Outdoor smart playground
ActiveCN107939089BAchieve maintenanceReduce humidityPaving gutters/kerbsGround pavingsControl systemSimulation
The invention relates to an outdoor intelligent sports field, which includes a sports field and a central control system for intelligent management. The sports field is a closed field with a field boundary isolation body surrounding it, and the sports field is equipped with Enclosed sports area, the sports field and the entrance and exit passages of the closed sports area are provided with an access control device for the site, and the open ground can be a permeable ground. The access control device includes an access control identifier and a passage blocking device. The central control system is based on the The legal access control identification information collected by the access control recognizer or the relevant opening command input from the outside sends an instruction to unblock the control circuit of the corresponding channel blocking device, and controls the corresponding channel blocking device to release the blocking state. The invention is beneficial to improve the automatic management level of the site, reduce the labor cost and reduce the ground water.
Owner:北京绿茵天地体育运营管理有限公司
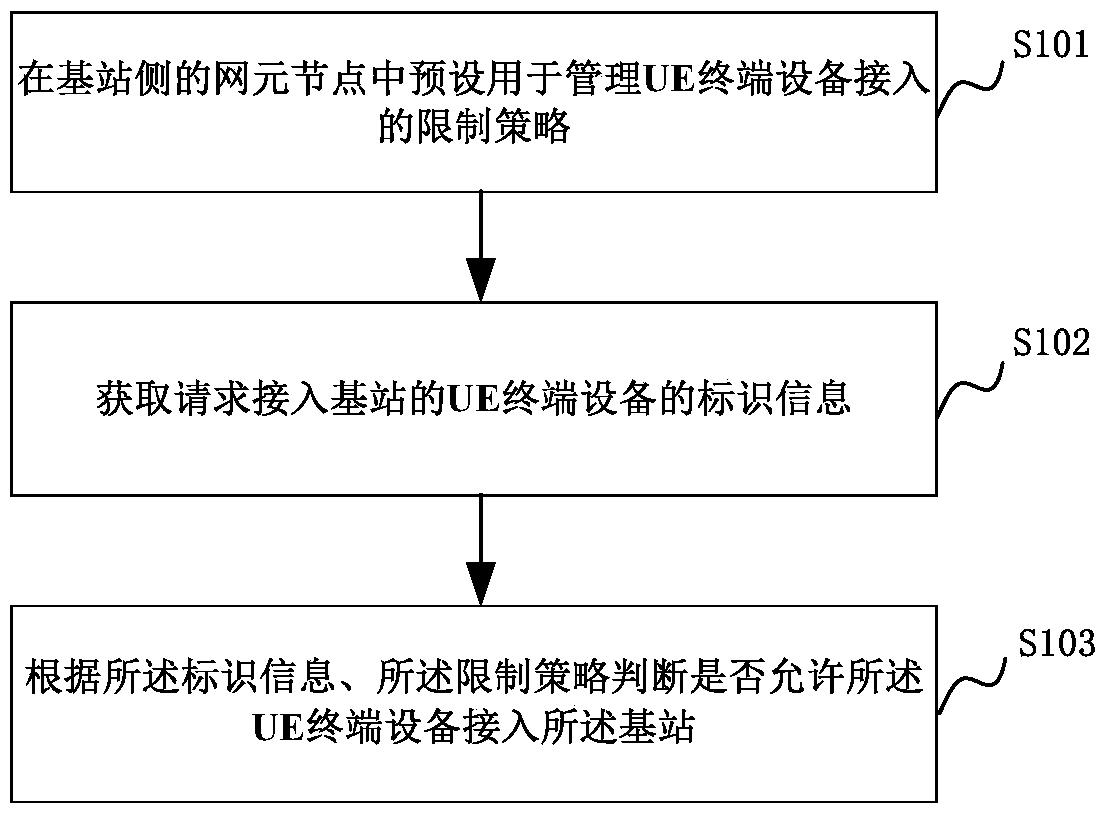
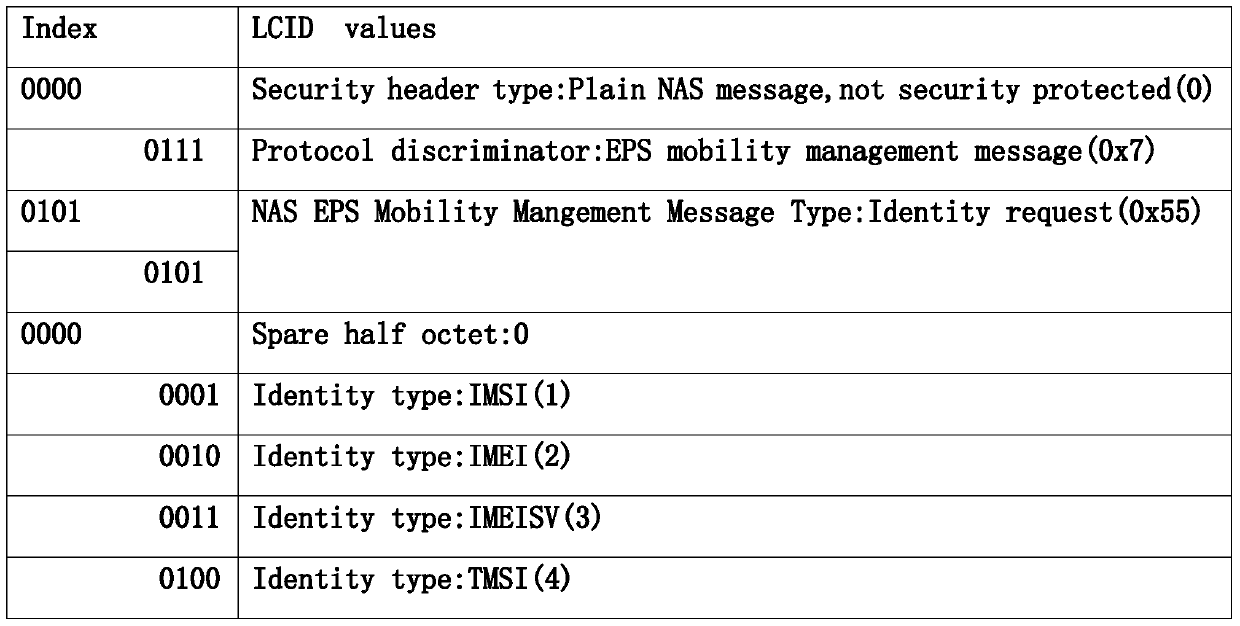
Access control method and system for ue terminal equipment
The invention relates to an access control method and system for UE (User Equipment) terminal equipment. The method comprises: presetting a restriction strategy for managing the access of the UE terminal equipment in a network element node of a base station; acquiring identification information of the UE terminal equipment requesting to access the base station; and according to the identification information and the restriction strategy of the network element node, judging whether the UE terminal equipment is permitted to access the base station or not. By adopting the method and the system, the access of the UE terminal equipment can be controlled at the base station, so that convenience is provided for managing and controlling the UE terminal equipment within the coverage of the base station.
Owner:COMBA TELECOM SYST CHINA LTD
A fine-grained access control method for massive graph data based on security labels
ActiveCN112699410BWithout sacrificing access performanceImprove securityStill image data indexingDigital data protectionTheoretical computer scienceData access
The invention provides a fine-grained access control method for massive image data based on a security label, which belongs to the field of massive data processing. The method of the present invention includes: adding a security label to the point / edge / attribute storage structure and user information of the graph data to determine the security requirements required for access. The security label does not need to be defined in advance and is set after data generation or security design is completed ; When querying graph data, compare the user security label with the security label of the vertex / edge / attribute data to determine whether the user has permission to access the data. The security label of the present invention supports logical expression representation, adopts point, edge, and attribute three-level granularity security labels, and realizes security access control of different granularities; the present invention also uses bit operations to accelerate security label logic calculation and point / edge / attribute data filter calculation. The method of the invention greatly improves the security of mass image data access without sacrificing the graph data access performance.
Owner:BEIJING SCISTOR TECH
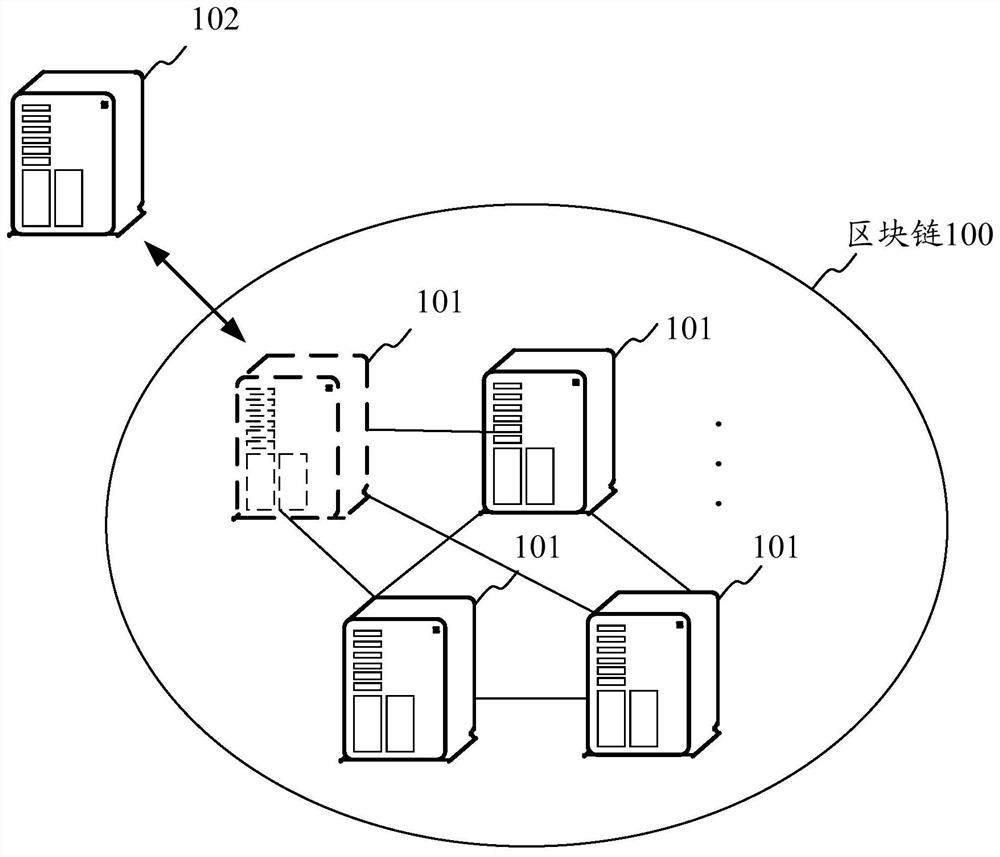
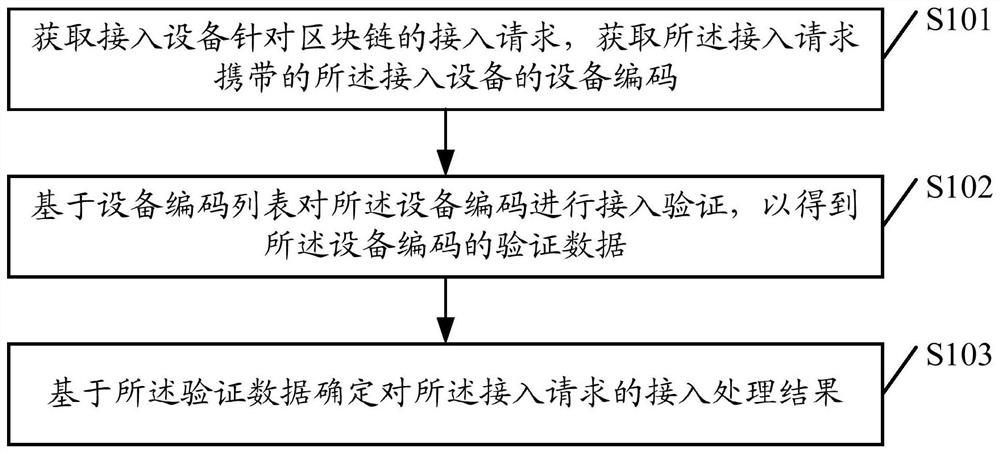
Device access processing method, device and storage medium
ActiveCN111327602BGuaranteed normal operationReduce duplicate accessSecuring communicationTimestampingSerial code
The invention discloses a device access processing method, device and storage medium, wherein the method includes: obtaining an access request of an access device for a blockchain, obtaining a device code of the access device carried in the access request, The device code is a device serial number generated according to the service timestamp of the access device; access verification is performed on the device code based on the device code list to obtain verification data of the device code; based on the verification data An access processing result for the access request is determined. By adopting the present invention, the device access management in the block chain network can be optimized, the repeated access of single block node devices with multiple identities can be reduced, and the normal operation of the block chain network can be guaranteed.
Owner:TENCENT TECH (SHENZHEN) CO LTD
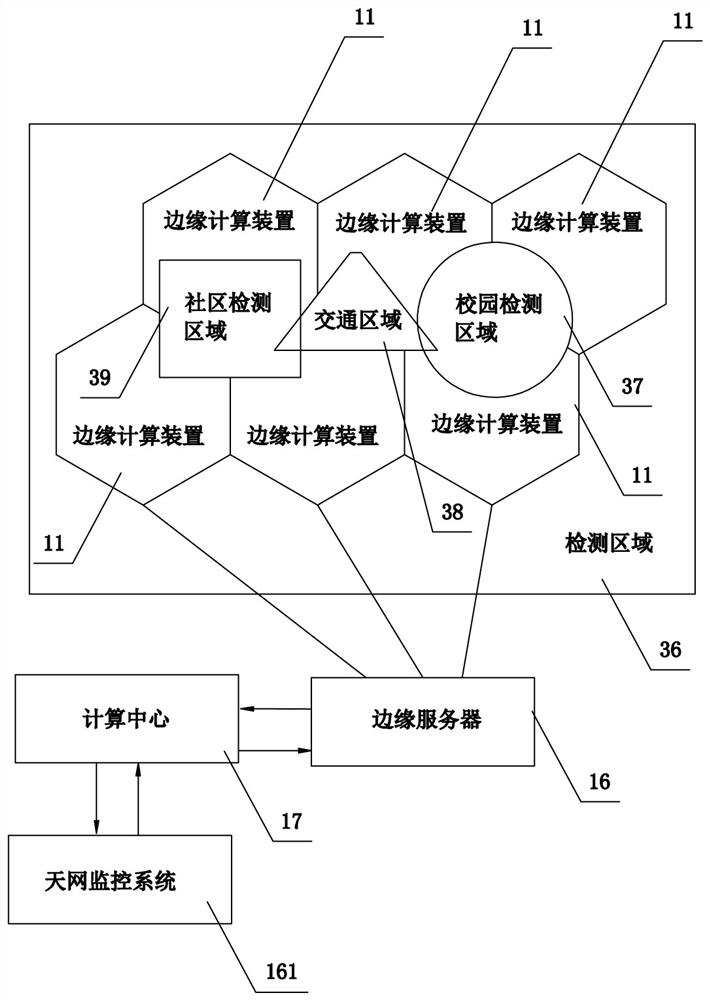
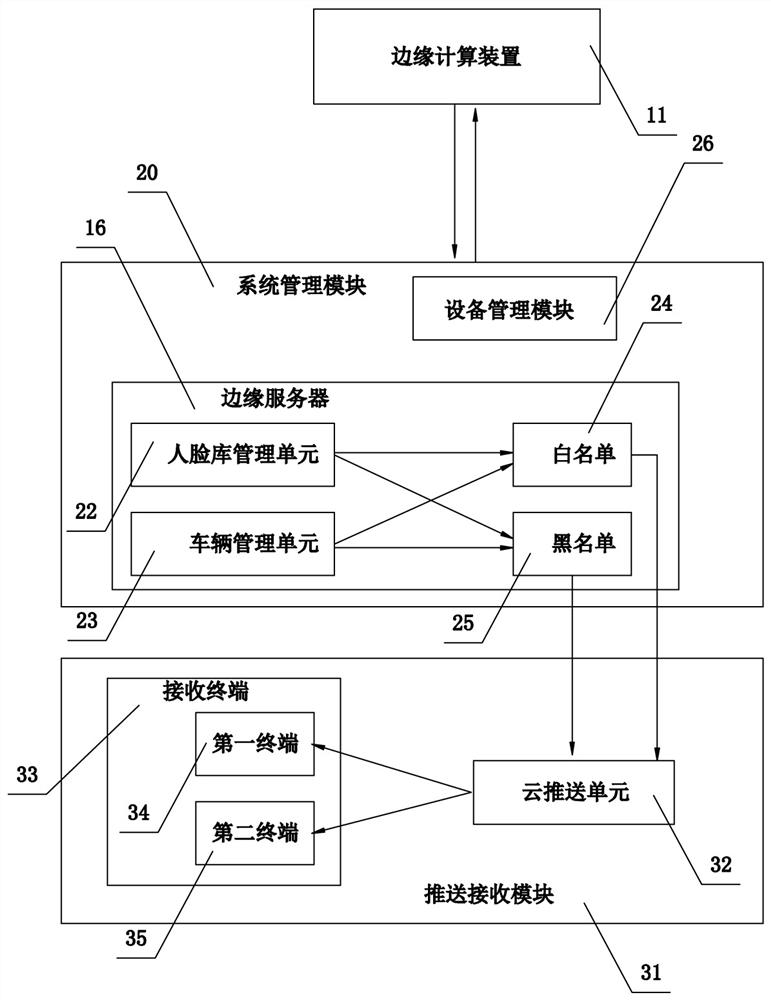
Campus access management system and edge computing device applicable to same
PendingCN113361327AAvoid mixingEasy access managementTelevision system detailsData processing applicationsEdge computingSystems management
The invention discloses a campus access management system and an edge computing device suitable for the same. The campus access management system includes a plurality of edge computing devices used for identifying and acquiring portrait feature information, at least one system management module used for receiving data transmitted by the edge computing devices, and at least one pushing and receiving module used for receiving identification signals of the system management module and pushing information. The edge computing devices are connected through a communication network to form a detection and recognition area. According to the invention, the edge computing devices are arranged to identify the school arrival information of students, card swiping is not needed, people not in the school are easy to distinguish, strangers are effectively prevented from being mixed into the campus, the campus access management is more convenient, and the campus access management efficiency is improved.
Owner:福建榕融芯微电子科技有限公司
Semi-automatic spiral type lifting device
The invention discloses a semi-automatic spiral type lifting device. The semi-automatic spiral type lifting device comprises a mounting box arranged in a concrete road layer; three lifting bodies arearranged in the mounting box; three driving arms are arranged in the mounting box; three first rotating shafts are arranged in the middle of the adjacent two lifting bodies; a driving gear is fixedlyarranged on each first rotating shaft; and the tooth number of the driving gear is as same as that of a driven gear. The parts are centralized together through the mounting box and the mounting box isembedded in the concrete road layer, so that the unstable problem in dispersed mounting is avoided; meanwhile, the lifting bodies adopt a triangular distribution mode, so on one hand, vehicle passageis obstructed, and on the other hand, through cooperation with the three driving arms, synchronous lifting of three lifting columns, synchronous lifting of two lifting columns and single lifting of single lifting column are realized and the lifting mode of the lifting columns is expanded.
Owner:苏州希恒建筑工程有限公司
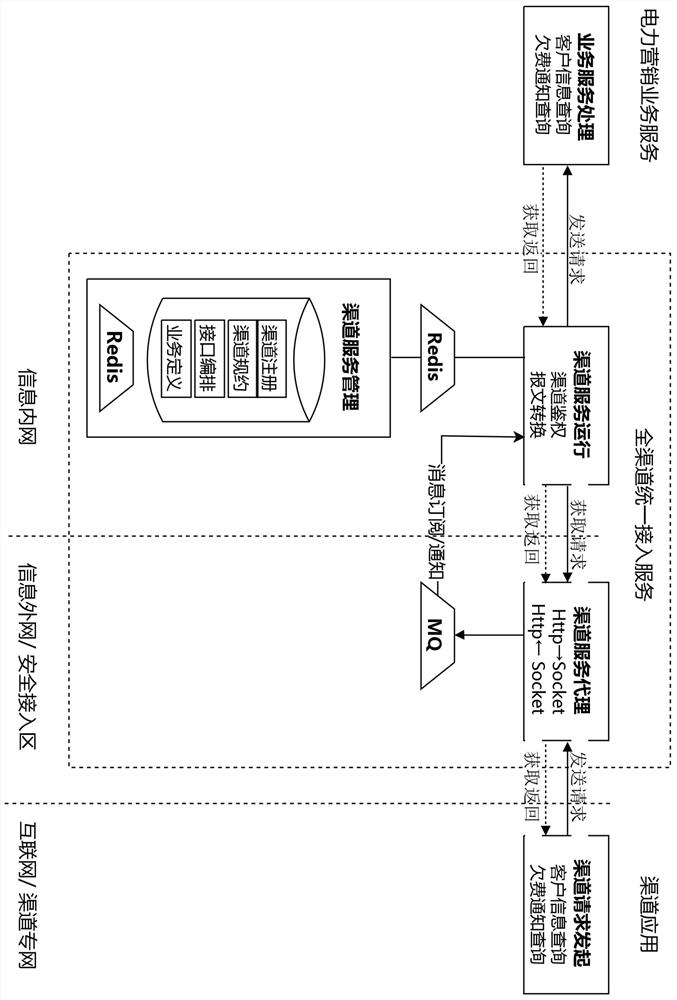
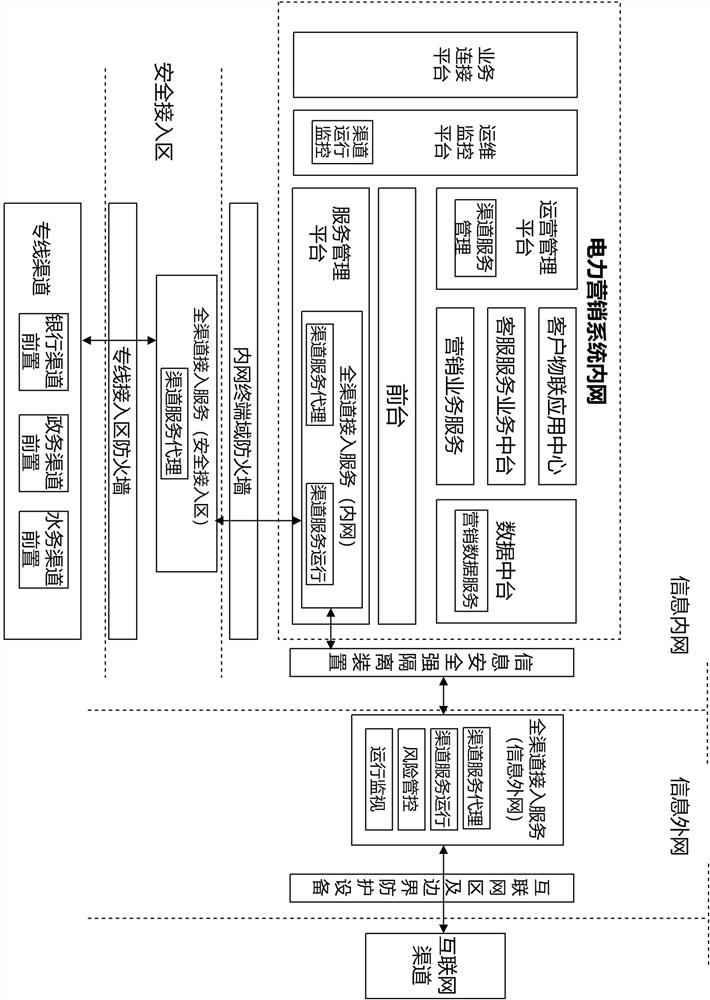
An omni-channel unified access platform and method for a power marketing system
ActiveCN113642939BStandardized Access StandardsEasy access managementResourcesEngineeringDedicated line
Owner:STATE GRID JIANGSU ELECTRIC POWER CO LTD MARKETING SERVICE CENT +3
Intelligent door lock, rental house management system and rental house management method
InactiveCN111294392AConvenient statisticsImprove the level of public security prevention and controlNon-mechanical controlsIndividual entry/exit registersGear wheelElectric machine
The invention provides an intelligent door lock, a rental house management system and a rental house management method. The intelligent door lock comprises a box body, a motor, a transmission gear, asector gear, a spring bolt and a control module; the box body is provided with a containing space, and a lock hole is formed in one side of the box body; the motor is arranged in the accommodating space of the box body; the transmission gear is arranged in the accommodating space of the box body and is in driving connection with the power output end of the motor; a fan-shaped gear is arranged in the accommodating space of the box body and is meshed with the transmission gear; the spring bolt is matched with the fan-shaped gear so as to extend out or retract along the lock hole under the driving of the fan-shaped gear; and the control module is arranged in the accommodating space of the box body and is connected with the motor. Compared with the prior art, the method can help a landlord tobetter count building management, and a set of practical population management mechanism is formed; an intelligent rental community is created, and the public security prevention and control level ofthe community is improved.
Owner:深圳市风行达电子有限公司
Household appliance maintenance public service box applied to community
InactiveCN113561147AEasy access managementConvenient display of readiness for repairApparatus for meter-controlled dispensingWork tools storageIndustrial engineeringManufacturing engineering
The invention discloses a household appliance maintenance public service box applied to a community. The household appliance maintenance public service box comprises a maintenance tool box, a service machine arranged on one side of the maintenance tool box and a household appliance storage box arranged on the other side of the maintenance tool box, a plurality of storage chambers are arranged in the maintenance tool box, tool boxes are arranged in the storage chambers, and cover plates are hinged to the tops of the tool boxes; a sterilization component and a communicating pipe are arranged at the bottom of the cover plate; a return detection device is arranged on the outer wall of the maintenance tool box and comprises a C-shaped support plate, a tool detection component and a sterilizing agent spraying component, wherein the tool detection component and the sterilizing agent spraying component are arranged on the inner wall of the C-shaped support plate; and a plurality of storage chambers are arranged in the household appliance storage box, movable partition plate components and weighing detection components are arranged in the storage chambers, and intelligent multi-rotating-shaft sealing plate components and a self-storage maintenance platform device are arranged on the side wall of the household appliance storage box. According to the public service box, access management, sterilization and disinfection can be conveniently carried out on maintenance tools, a maintenance platform can be conveniently provided, and the to-be-maintained preparation conditions of the to-be-maintained household appliances can be conveniently displayed.
Owner:安庆市电匠院网络科技有限公司
Buffer management method based on signaling protocol
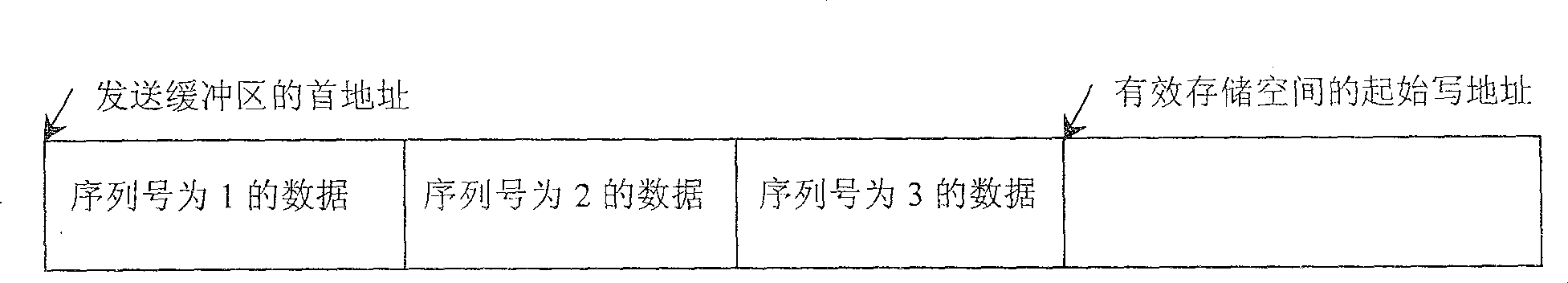
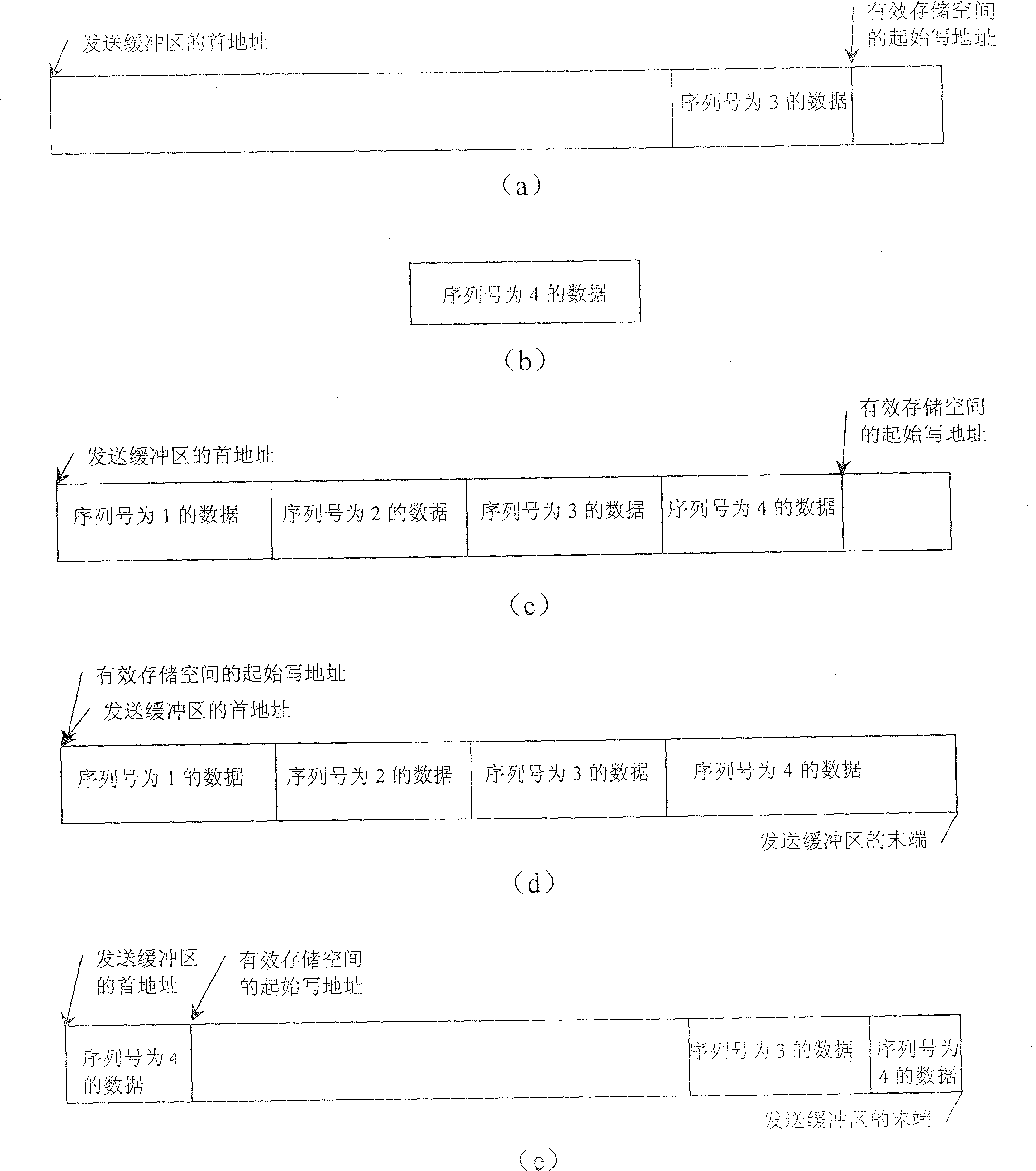
InactiveCN100474840CIncrease profitEasy access managementData switching networksData accessSignaling protocol
A method for buffer management based on signaling protocol sets up buffer area with preset storage space based on signaling protocol and carries out data access management for said buffer area by form of cyclic queue read / write data.
Owner:任秀花
A semi-automatic spiral lifting device
The invention discloses a semi-automatic spiral type lifting device. The semi-automatic spiral type lifting device comprises a mounting box arranged in a concrete road layer; three lifting bodies arearranged in the mounting box; three driving arms are arranged in the mounting box; three first rotating shafts are arranged in the middle of the adjacent two lifting bodies; a driving gear is fixedlyarranged on each first rotating shaft; and the tooth number of the driving gear is as same as that of a driven gear. The parts are centralized together through the mounting box and the mounting box isembedded in the concrete road layer, so that the unstable problem in dispersed mounting is avoided; meanwhile, the lifting bodies adopt a triangular distribution mode, so on one hand, vehicle passageis obstructed, and on the other hand, through cooperation with the three driving arms, synchronous lifting of three lifting columns, synchronous lifting of two lifting columns and single lifting of single lifting column are realized and the lifting mode of the lifting columns is expanded.
Owner:苏州希恒建筑工程有限公司
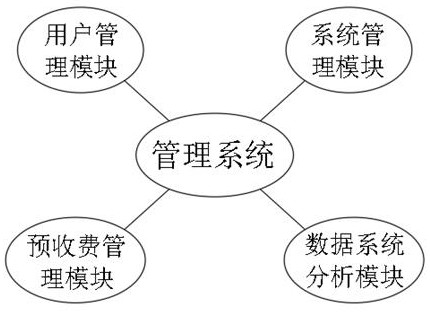
Water resource intelligent conveying control management system
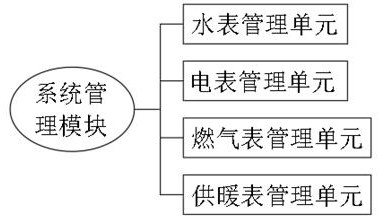
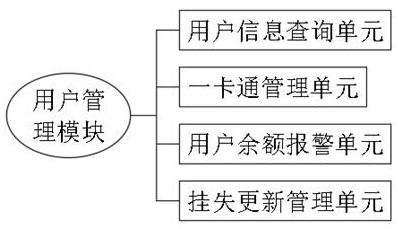
InactiveCN113947844AImprove work efficiencyMeet purchase needsUtility meters data arrangementsApparatus for hiring articlesSystems managementCard reader
The invention provides a water resource intelligent conveying control management system, and relates to the technical field of water resource control management. The water resource intelligent conveying control management system comprises a system management module, a user management module, a pre-charging management module and a data system analysis module. The system management module comprises a water meter management unit, an electricity meter management unit, a gas meter management unit and a heating meter management unit; the user management module comprises a user information query unit, a one-card management unit, a user balance alarm unit and a loss report updating management unit; the pre-charging management module comprises a pre-receiving management unit, a balance query unit and a short message information reminding unit; and the data system analysis module comprises a user data recording unit. By designing special management software and a card reader-writer, data can be recorded, counted, analyzed and inquired, and the problems that meter reading and charging are difficult in water, electricity, gas and heating management are solved.
Owner:沈阳和同科技有限公司
Rights management method and system
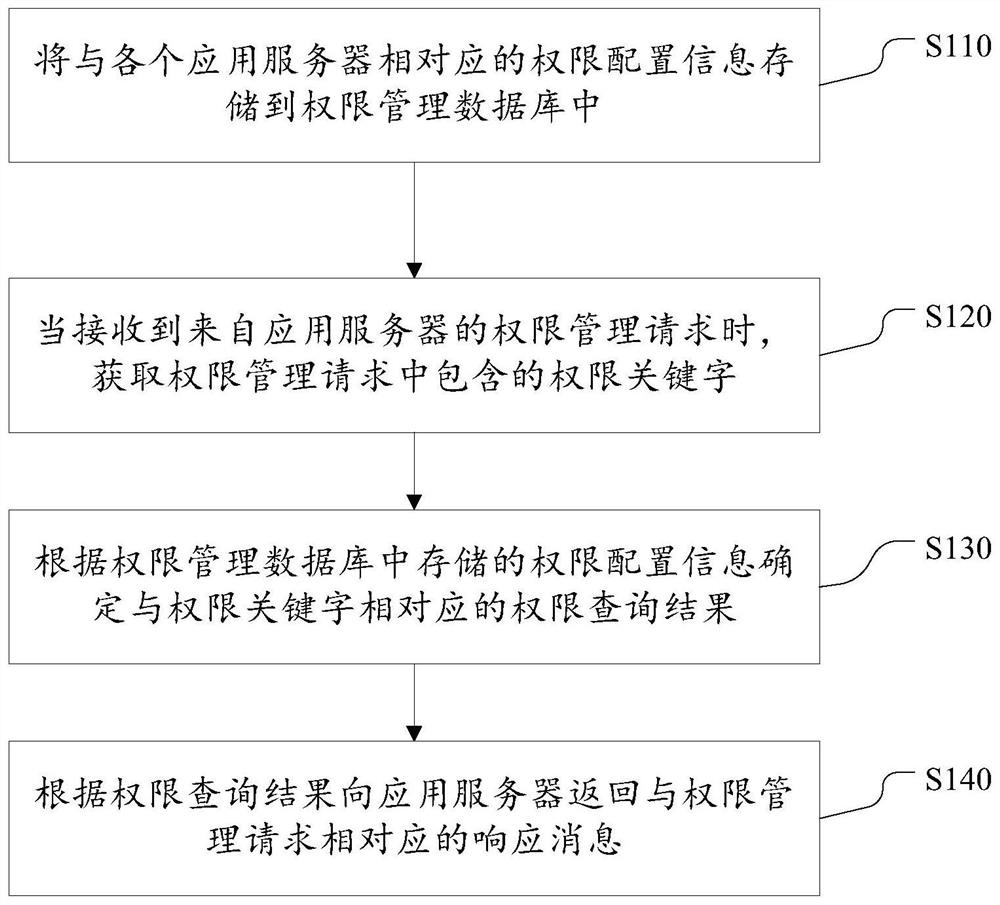
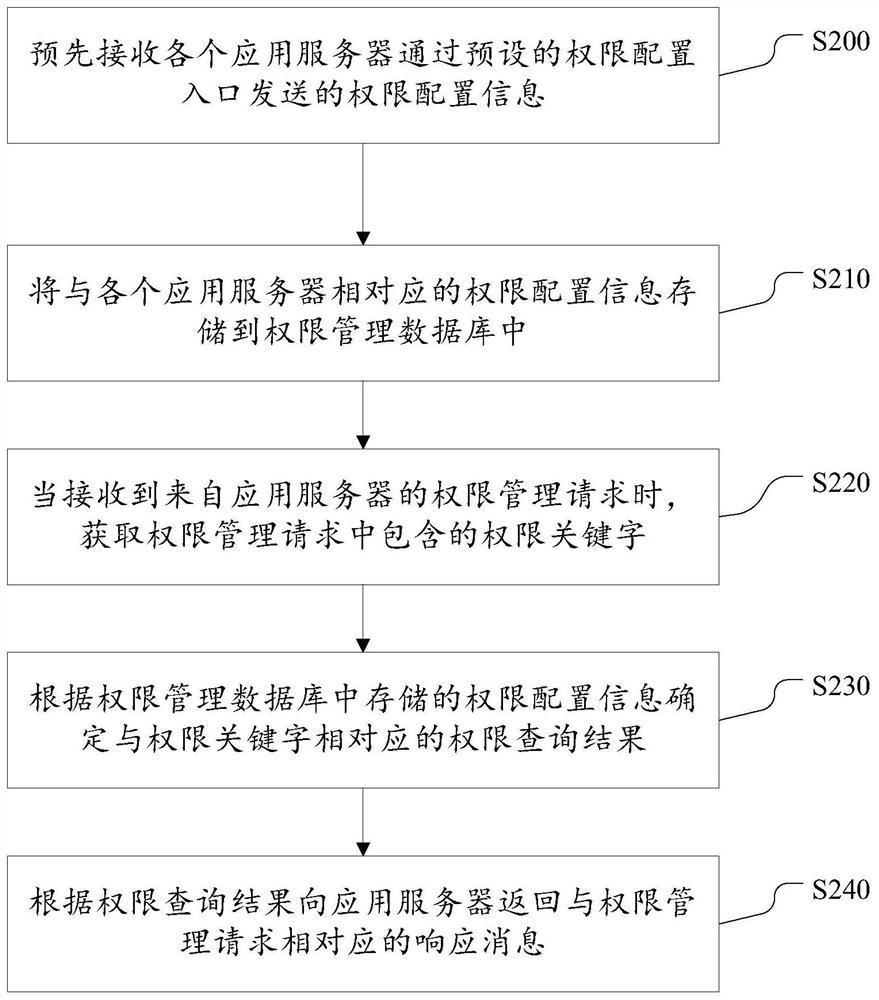
ActiveCN108173839BReduce overheadImprove business operation efficiencyTransmissionApplication serverRights management
The invention discloses a rights management method and system. Wherein, the method includes: storing the authority configuration information corresponding to each application server in the authority management database; when receiving the authority management request from the application server, obtaining the authority keyword contained in the authority management request; according to the authority management The permission configuration information stored in the database determines the permission query result corresponding to the permission keyword; returns a response message corresponding to the permission management request to the application server according to the permission query result. It can be seen that, by adopting this solution, the permission information of multiple application systems can be managed and queried in a unified manner, without the need for each application system to maintain the permission management information by itself, which saves the overhead of each application system and improves the business operation efficiency of the application system. Provides convenience for rights management operations.
Owner:BEIJING QIHOO TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com