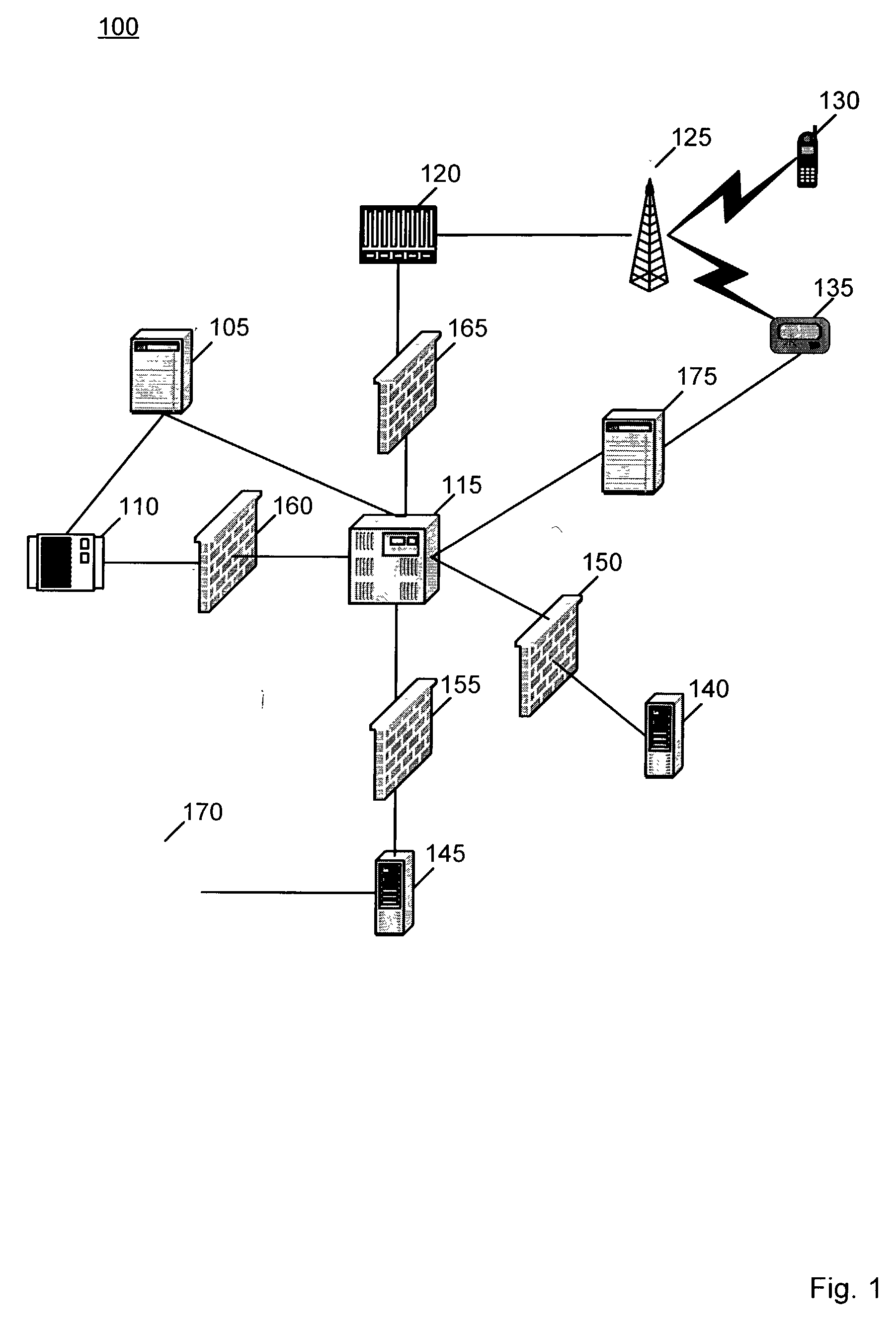
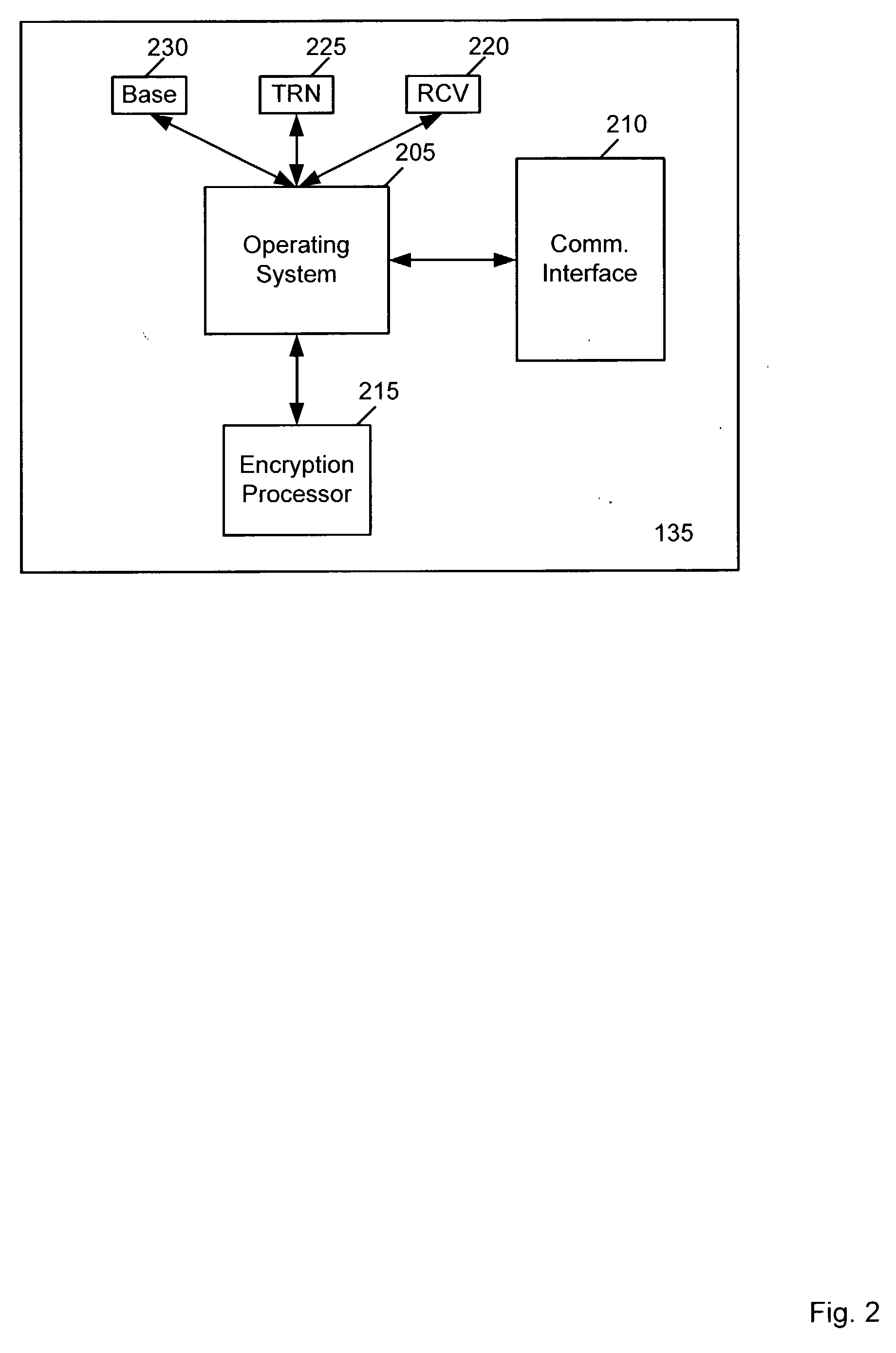
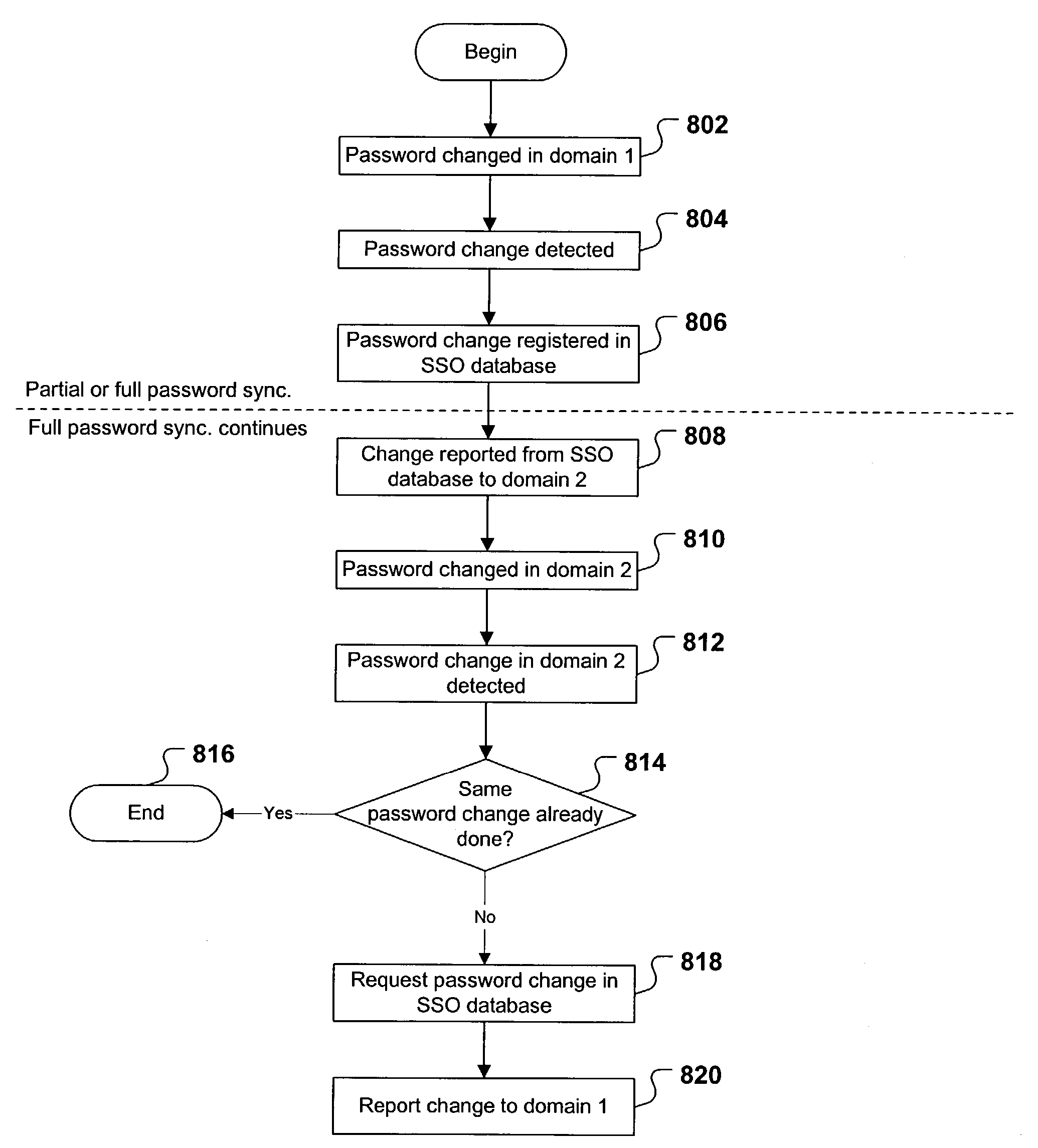
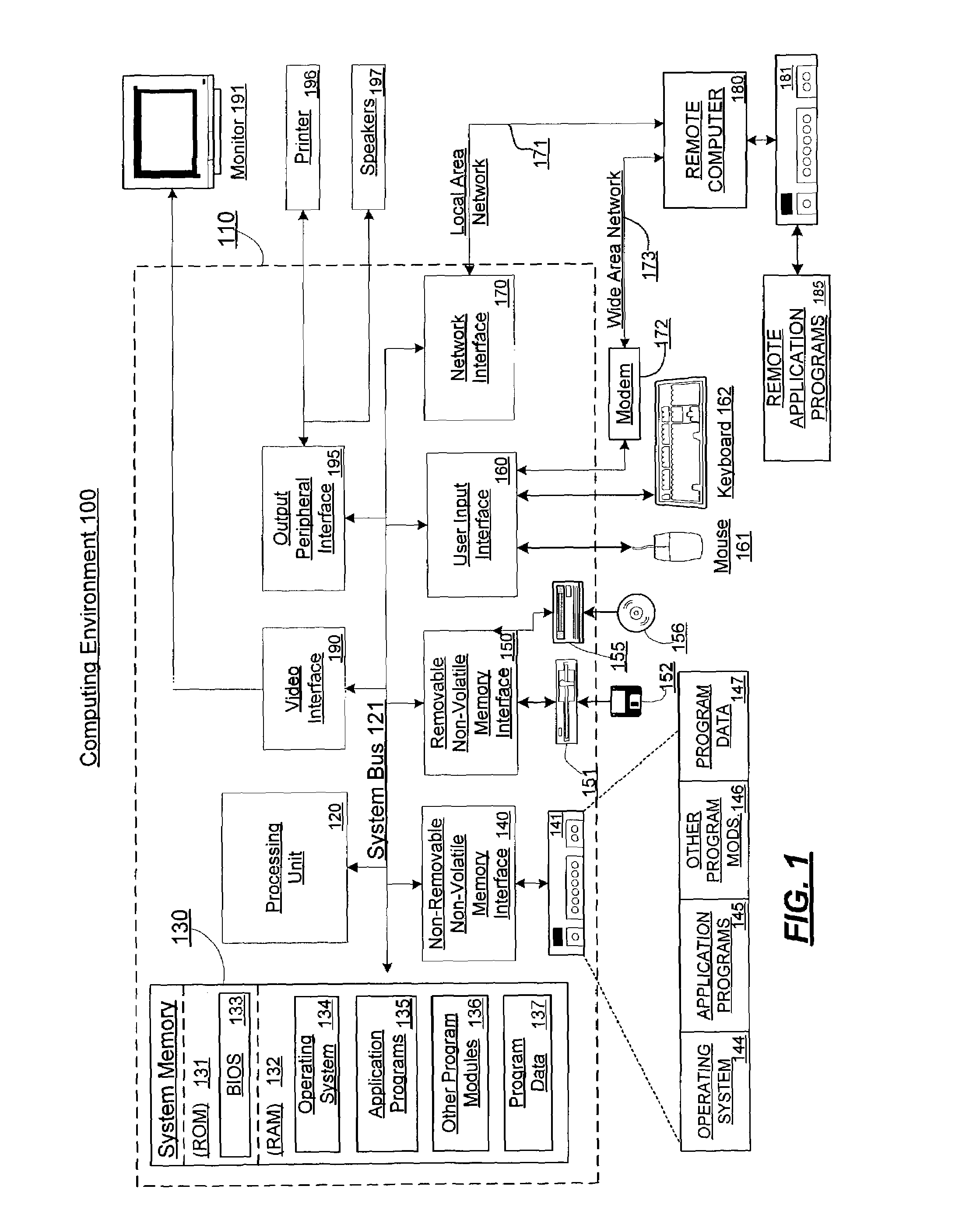
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
67 results about "Password synchronization" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
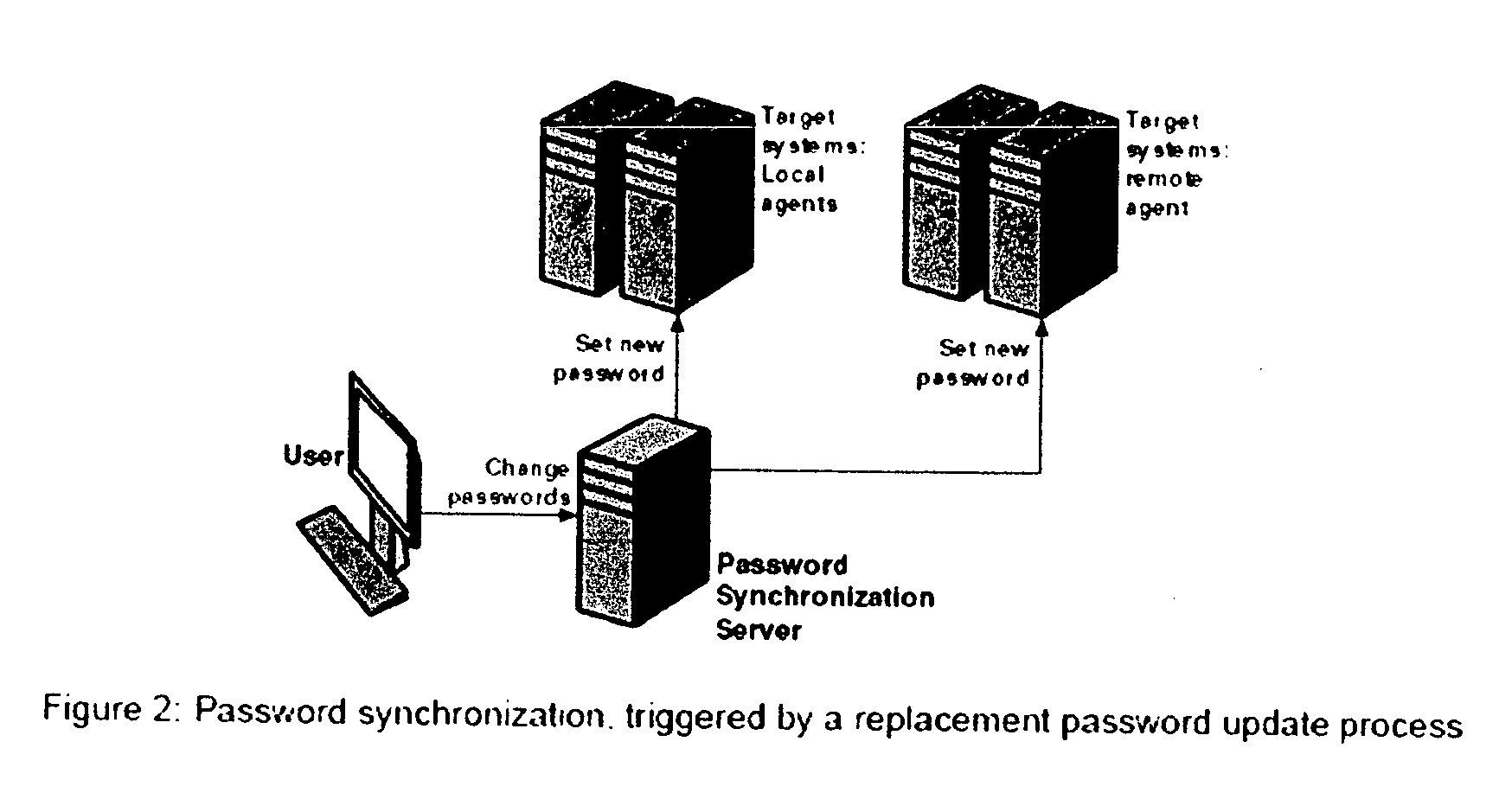
Password synchronization is a process, usually supported by software such as password managers, through which a user maintains a single password across multiple IT systems. Provided that all the systems enforce mutually-compatible password standards (e.g. concerning minimum and maximum password length, supported characters, etc.), the user can choose a new password at any time and deploy the same password on his or her own login accounts across multiple, linked systems.
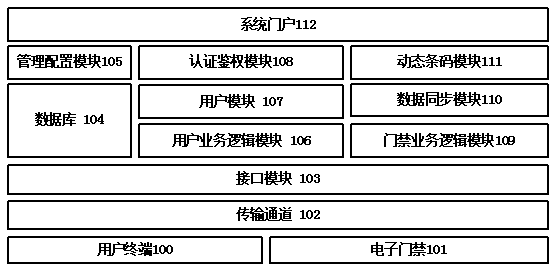
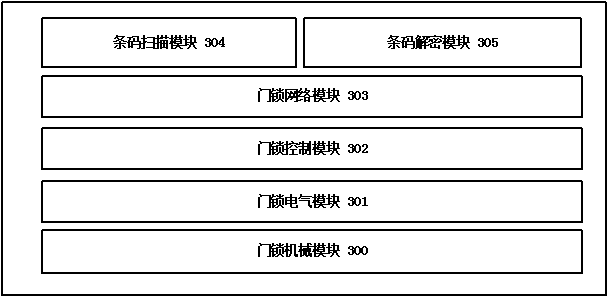
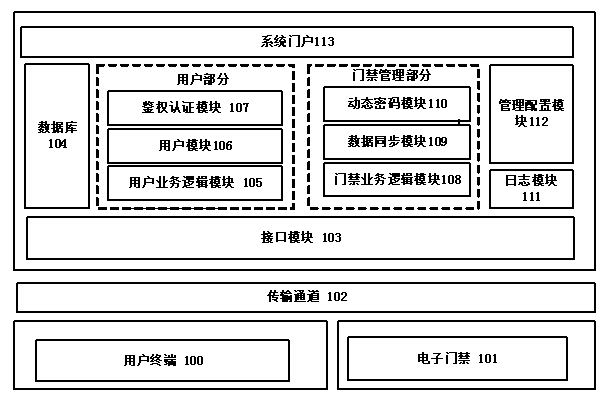
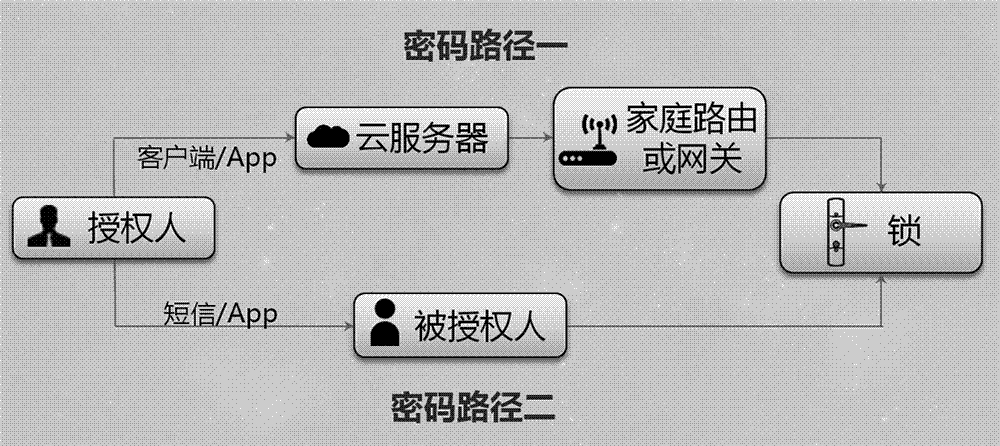
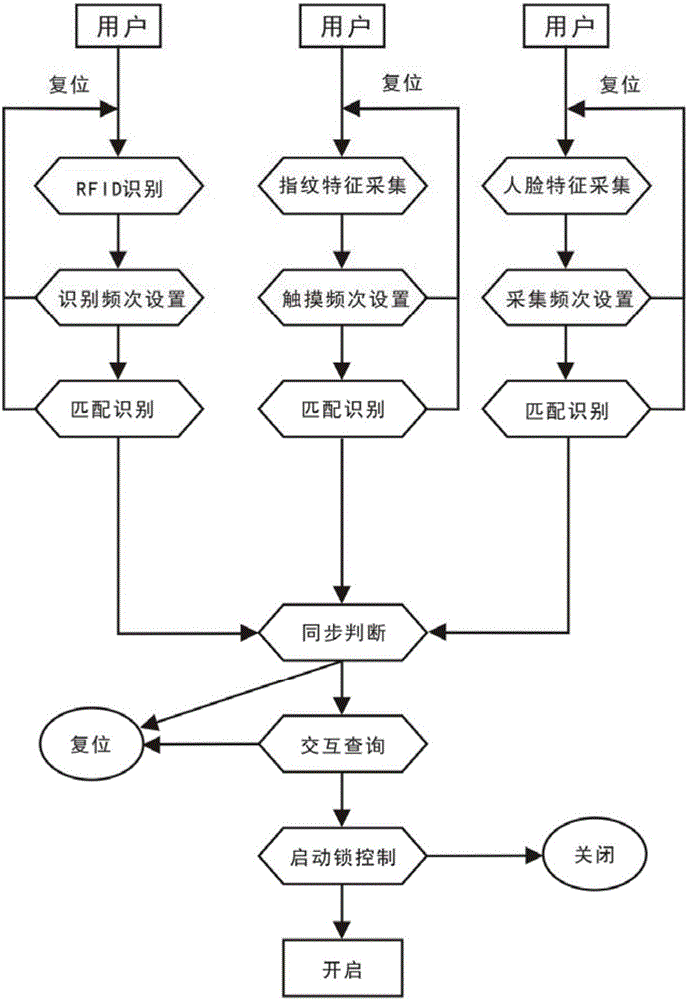
Electronic access control system of dynamic bar code
InactiveCN103544746AEasy to useFlexible controlIndividual entry/exit registersElectronic accessAccess method
The invention discloses an electronic access control system of a dynamic bar code. The electronic access control system comprises a mobile terminal, a service logic module, a bar code module and an access control module. According to the electronic access control system, a user registers and binds the terminal on a system, and when the user needs to access an entrance guard, the user applies for the permission of the entrance guard; the system generates a dynamic password, distributes the permission, and codes the dynamic password to the bar code after encrypting the dynamic password, pushes the dynamic password to a user terminal, and synchronizes the dynamic password to an access controller; the user scans the bar code on the access control system after acquiring the bar code, and the access control system scans the bar code to obtain the content included in the bar code and decrypts the content to obtain a password to judge whether a door is opened or not. The electronic access control system dynamically generates the bar code including password information and issues the bar code to the terminal user, thereby providing a convenient and rapid electronic entrance guard access method based on the dynamic bar code.
Owner:SHANGHAI BOLU INFORMATION TECH
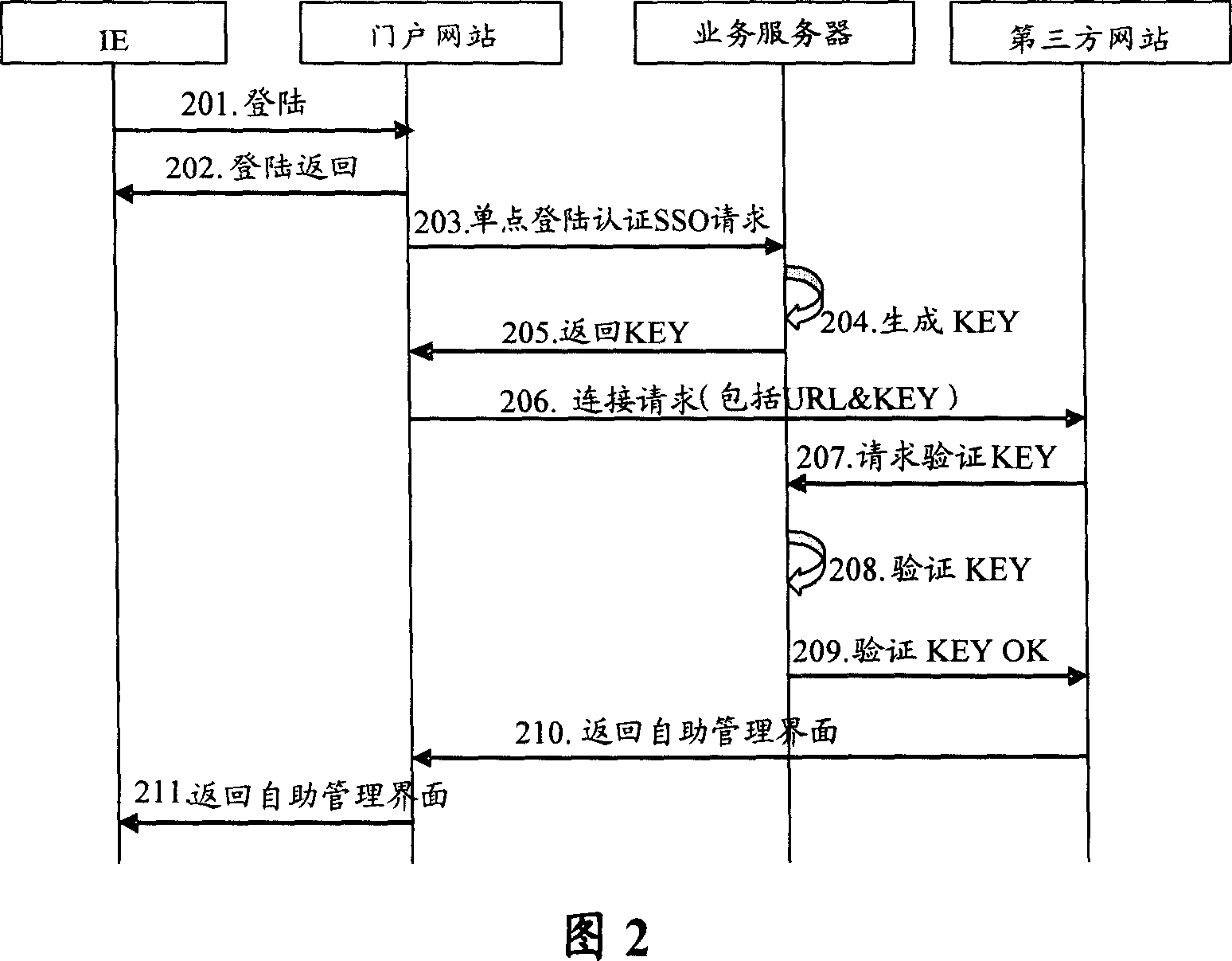
Method and system for switching third party landing and third party network and service server
ActiveCN1946022AAvoid transmissionGuaranteed absolute securityUser identity/authority verificationThird partyWeb service
This invention provides a method for transferring third party landing based on IP network including: a door network station carries a ciphered KEY generated randomly by a service server to send a link request to a third party network station so as to avoid transmission of user ciphered codes and ensure absolute security of user codes, besides, since the third party network station calls back the Web server by copying the ciphered KEY to verify the cryptographic key so as to secure the absolute safety of shaking hands, since the door network station does not transfer user ciphered codes with the third party network station, which is not necessary to synchronize with the door station about codes, thus the requirement of complicated maintenance to synchronization on ciphered codes to the third party is reduced. This invention also provides a system for authenticating the transfer of third party landing based on the IP network and the third party network station and service servers.
Owner:HUAWEI TECH CO LTD
Air-interface application layer security for wireless networks
ActiveUS20070101120A1Well formedSynchronising transmission/receiving encryption devicesWireless network protocolsAir interfaceProtocol Application
The present invention provides a method for encrypting data for transmission over a wireless link. The method includes encrypting at least one block of data, at an air-interface application layer, using an encryption algorithm that receives a cryptosynch as input. The value of the cryptosynch is based on an order of the at least one block of data relative to other blocks of data. The value of the cryptosynch is recoverable by a receiver based on the ordering of the ordering of the blocks of data. The at least one encrypted block of data is transmitted to a receiver that is operable to preserve the order of the at least one block of data relative to the other blocks of data.
Owner:ALCATEL LUCENT SAS
Method and apparatus for achieving crypto-syncronization in a packet data communication system
InactiveUS20060126844A1Reduce decreaseSynchronising transmission/receiving encryption devicesNetwork traffic/resource managementComputer hardwareCommunications system
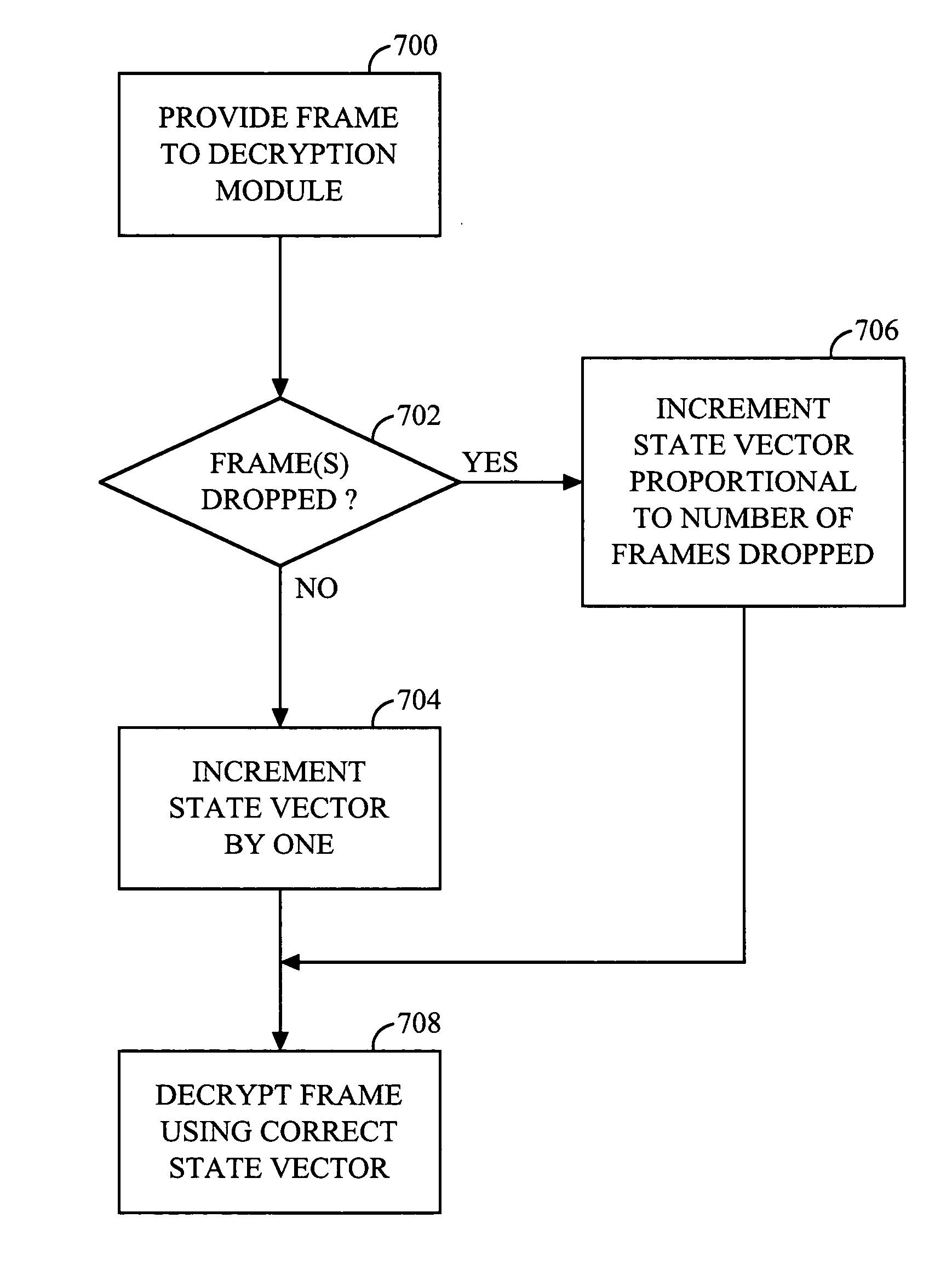
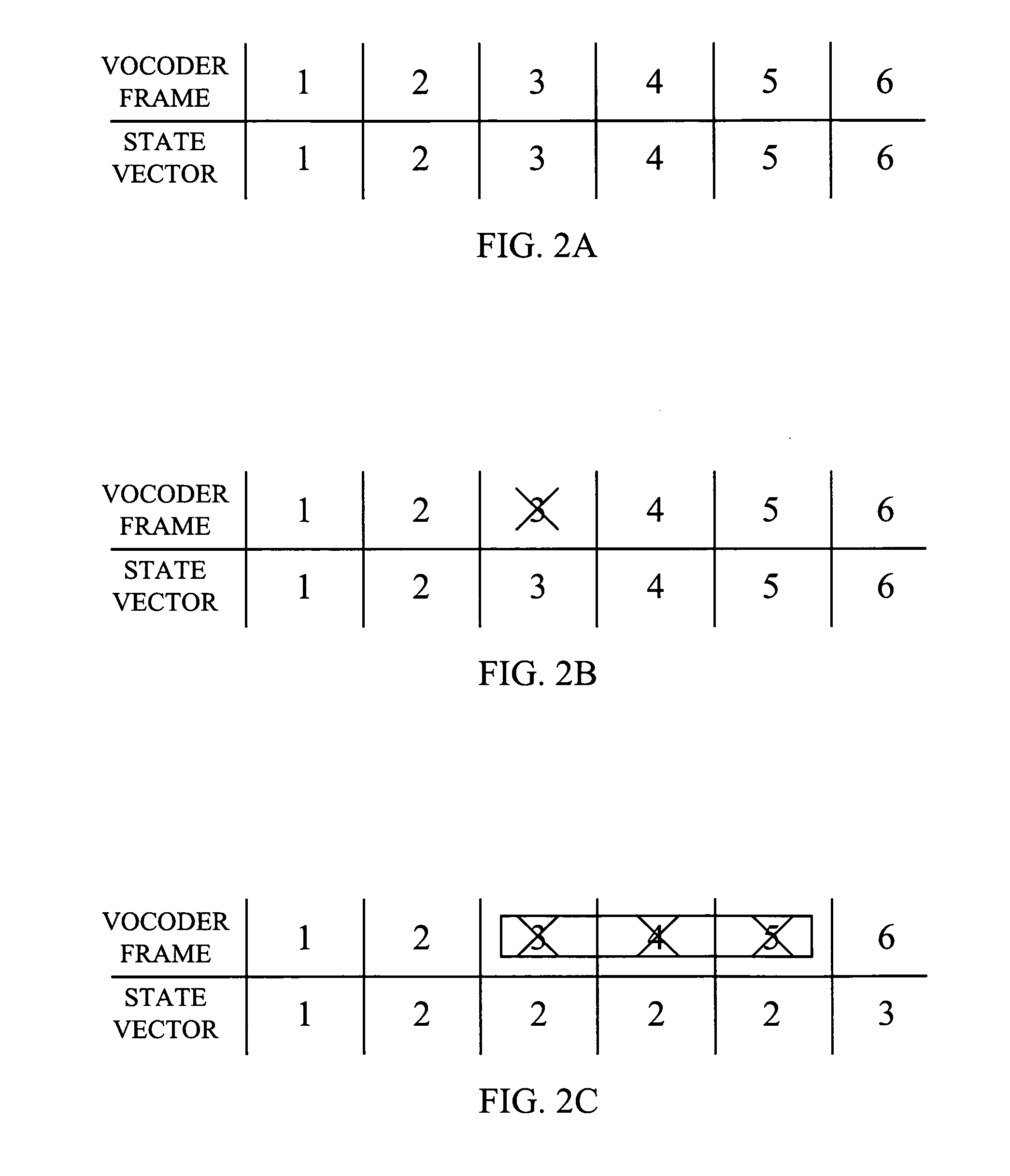
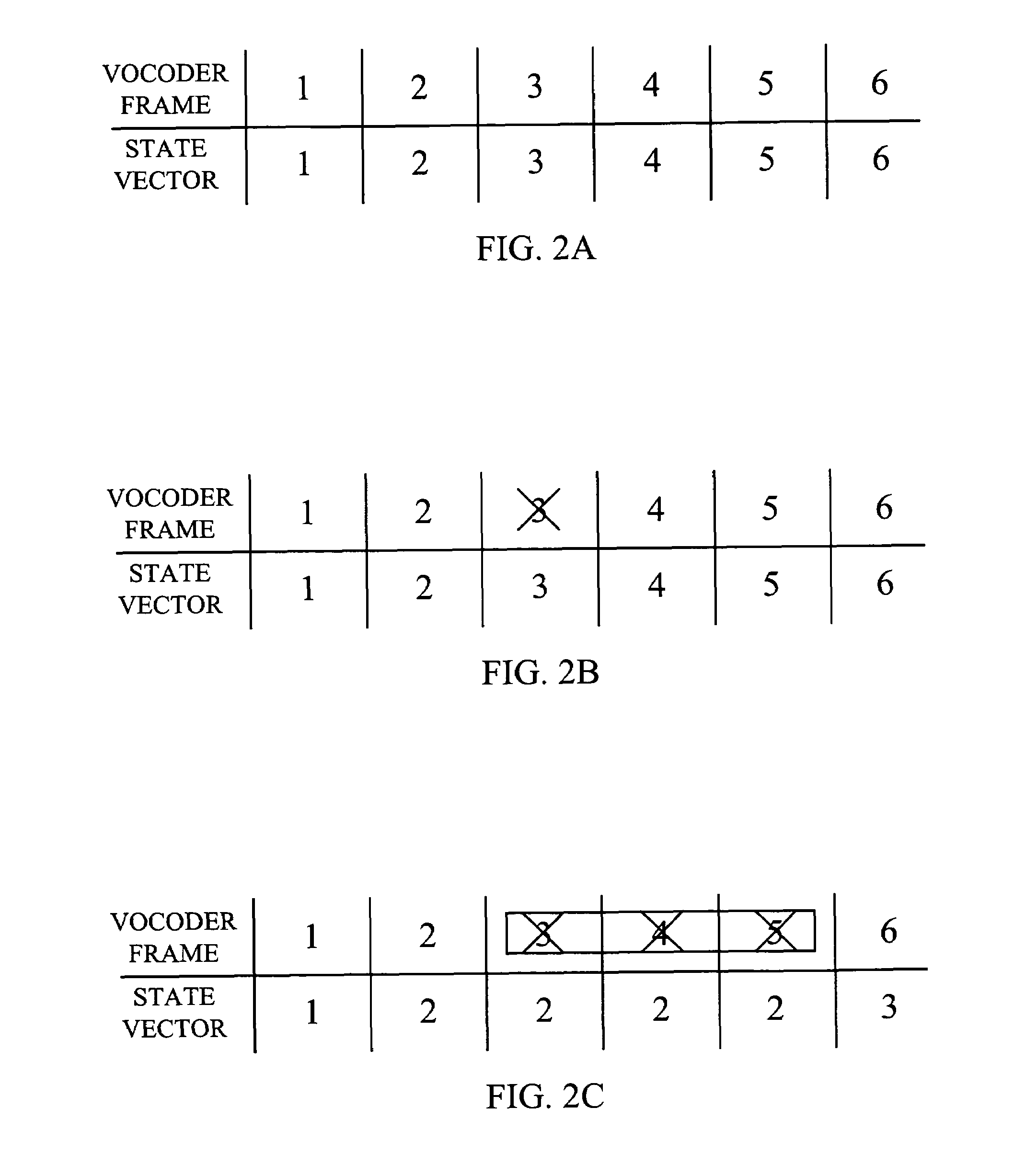
A method and apparatus for achieving crypto-syncronization in a packet data communication system employing cryptographic communications. In a transmitter, a state vector is incremented at a predetermined rate and is provided to an encryption module. The encryption module uses the state vector to sequentially encrypt the data frames. During periods of frame dropping prior to encryption, the state vector is disabled, thereby allowing for sequential encryption of the data frames. In a receiver, during a frame dropping condition, the state vector is advanced in proportion to the number of frames dropped. During an underflow condition at the receiver, the state vector is disabled for the duration of the underflow condition, and enabled once the underflow condition has passed.
Owner:QUALCOMM INC
Method for transmitting encrypted data, associated decrypting method, device for carrying out said methods and a mobile terminal for the incorporation thereof
ActiveUS7620184B2Avoid disadvantagesSynchronising transmission/receiving encryption devicesTime-division multiplexWireless transmissionNetwork packet
A process for transmitting encrypted data through a radio transmission channel having a frame structure such that a TDMA frame comprises at least time slots of a first type forming a traffic channel and at least one time slot of a second type forming an associated signaling channel, comprises steps according to which:a sequence of encrypted data packets is transmitted in the traffic channel on the basis of a determined time slot of the first type, whereas an associated cryptographic synchronization information cue is transmitted in the associated signaling channel inside a determined time slot of the second type, anda cryptographic synchronization delay information cue relating to the time gap between said determined time slot of the second type and said determined time slot of the first type, is also transmitted in the associated signaling channel.
Owner:CASSIDIAN SAS
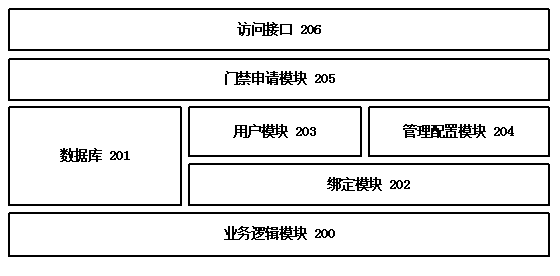
Electronic door control system with dynamic password
The invention discloses an electronic door control system with a dynamic password. The electronic door control system comprises a mobile terminal, a business logic module, a password module, and a door control module. A user performs registration and terminal binding on the system, when the user needs the door to open, the user applies for door control permission on the terminal, the system generates a dynamic password, assigns corresponding authority, synchronizes the password to a door control device, and sends the password to the user terminal through the ways of short messages and data transmission, the user obtains the dynamic password and types the password on the door control, and the door control system determines whether to open the door or not. Through dynamically generating passwords through the system and sending the passwords to a user and a terminal in real time, the electronic door control system provides a convenient electronic door control accessing method based on dynamic passwords for users.
Owner:SHANGHAI BOLU INFORMATION TECH
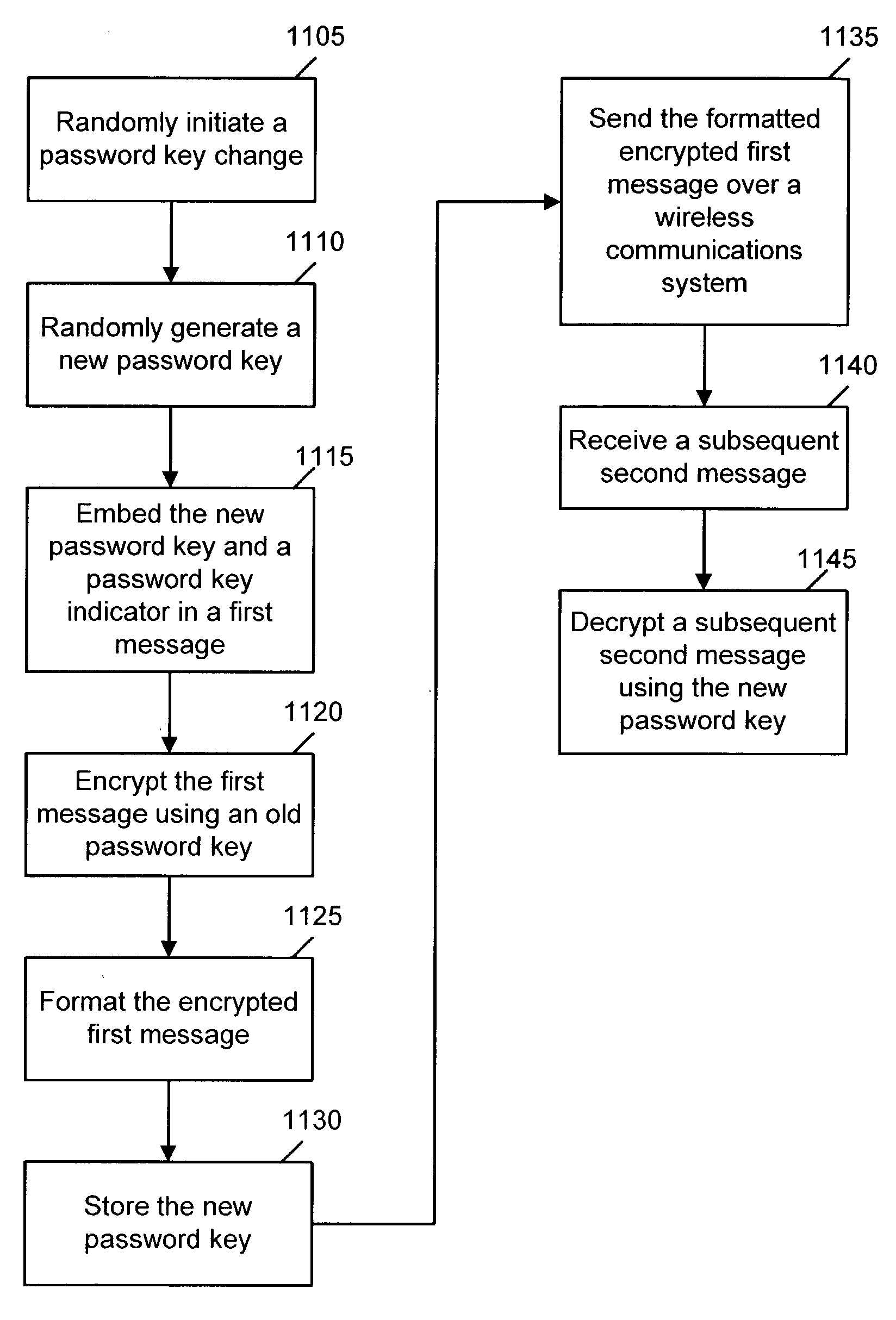
Password synchronization for wireless encryption system
InactiveUS20040081320A1Key distribution for secure communicationSynchronisation arrangementCommunications systemPassword
A method and system for dynamically changing password keys in a secured wireless communication system includes initiating a password key change, generating a new password key, embedding the new password key and a password key indicator in a first message, encrypting the first message using an old password key, storing the new password key, sending the formatted encrypted first message over a wireless communication system, receiving a subsequent second message, and decrypting the subsequent second message using the new password key.
Owner:AT&T MOBILITY II LLC
Password synchronization in a sign-on management system
InactiveUS7251732B2Digital data processing detailsUser identity/authority verificationPasswordUser identifier
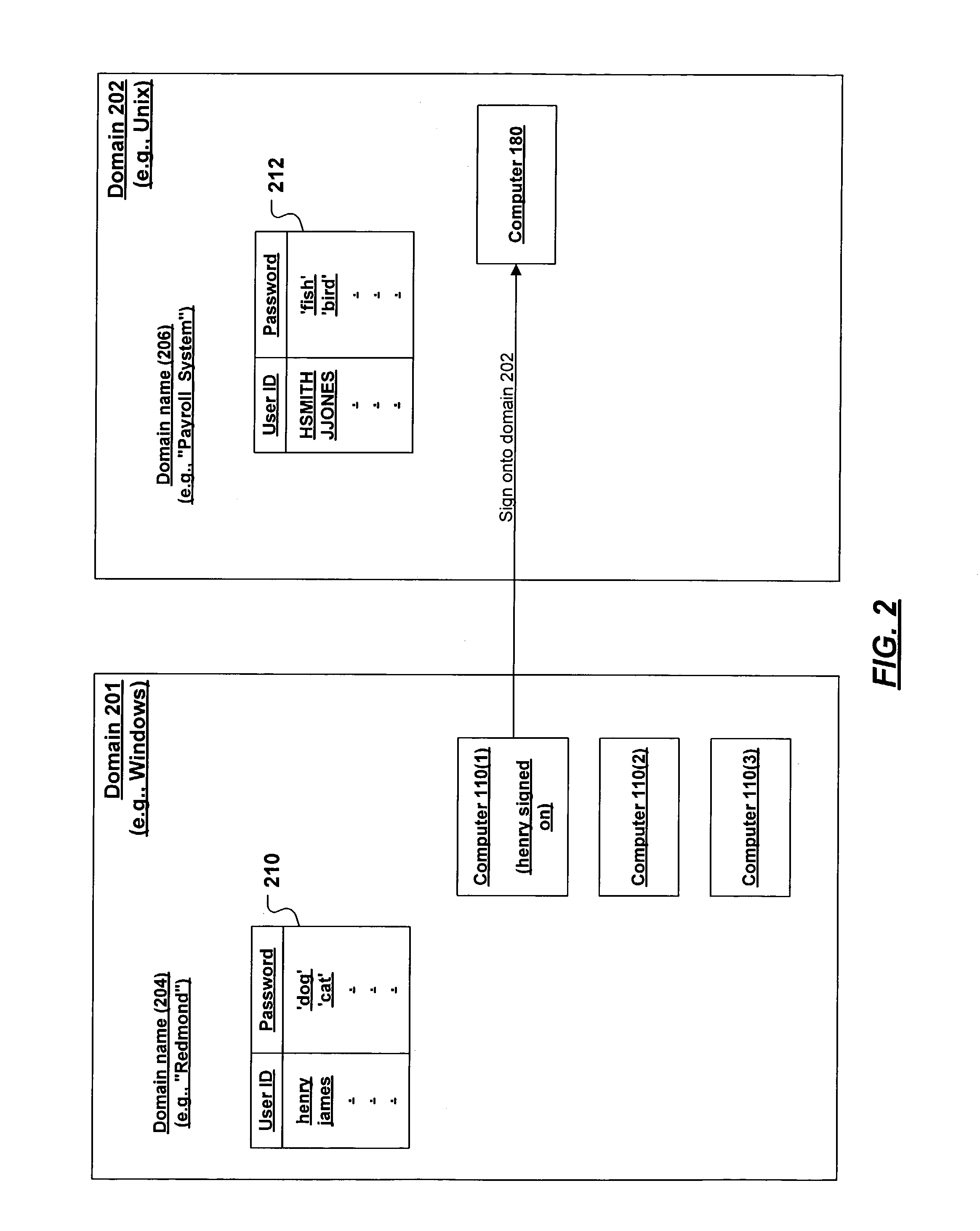
A mechanism that synchronizes passwords maintained for plural domains. A user maintains accounts in two domains. The first and second domains each maintain tables correlating userIDs with passwords, such that the same user's password can be different in the different domains. A database stores tables that correlate a given user's userID / password combination in the first domain with his corresponding userID / password combination in the second domain. The database is used to sign the user onto one domain when the user is working in the other domain. When the user changes his password in the first domain, the change is reported to the database, so that the database stores the current password. Optionally, the password change may be reported to the second domain, such that the user will have the same password in both domains.
Owner:MICROSOFT TECH LICENSING LLC
Controlled cryptoperiod timing to reduce decoder processing load
InactiveUS20090080648A1Synchronising transmission/receiving encryption devicesDigital data processing detailsReal-time computingPassword synchronization
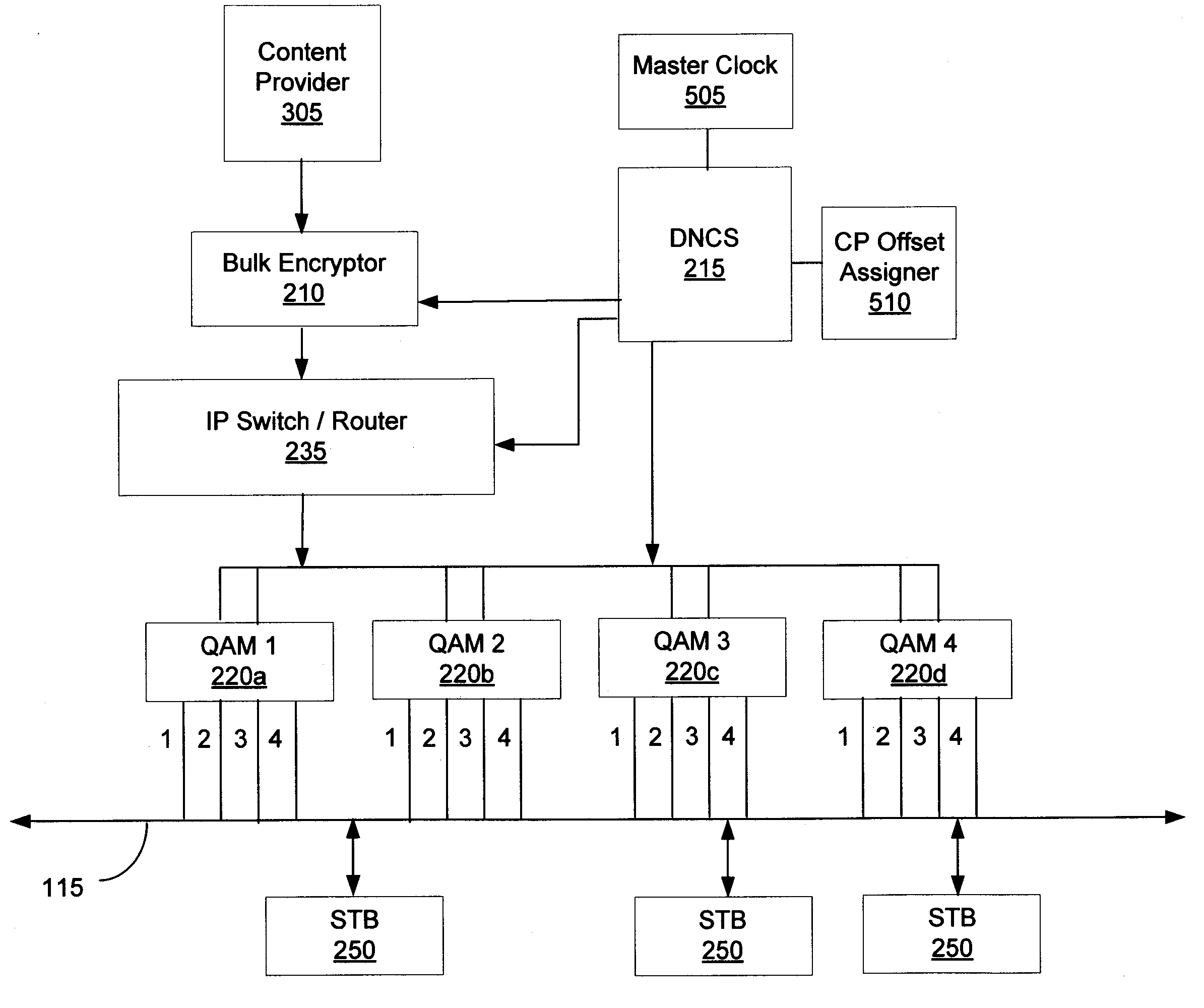
Systems and methods are disclosed for enabling encryptor devices to provide real-time messages having offset cryptoperiods according to an offset algorithm within common crypto-sync pulse boundaries. A master clock aligns the encryptor devices to a common crypto-sync pulse. Subsequently, a cryptoperiod offset aligner assigns a different offset value according to an algorithm to each encrypted service. The corresponding encryptor device then begins the cryptoperiod, during which real-time messages are transmitted, at the assigned offset value from the common crypto-sync pulse.
Owner:CISCO TECH INC
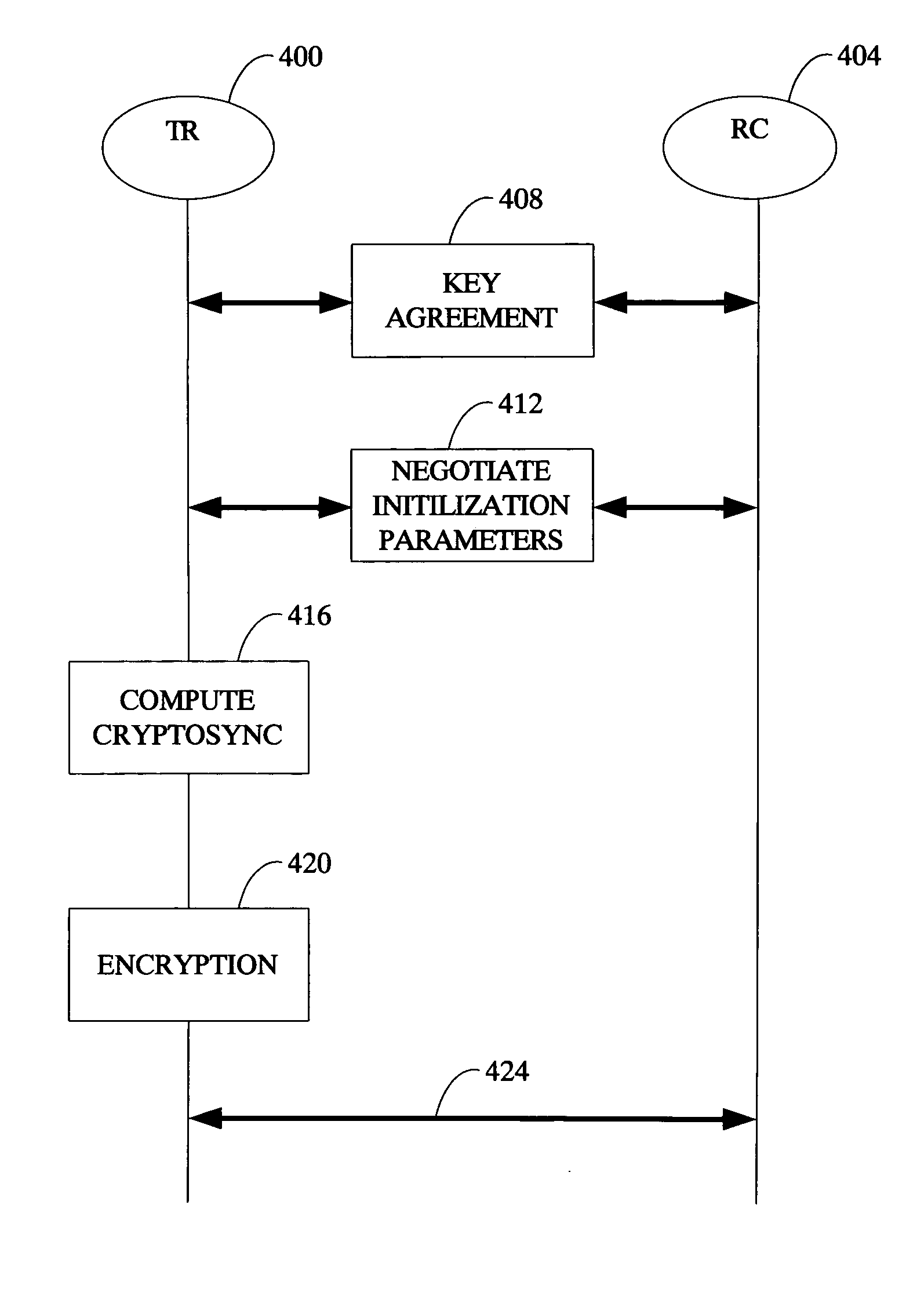
Method and apparatus for fast secure session establishment on half-duplex point-to-point voice cellular network channels
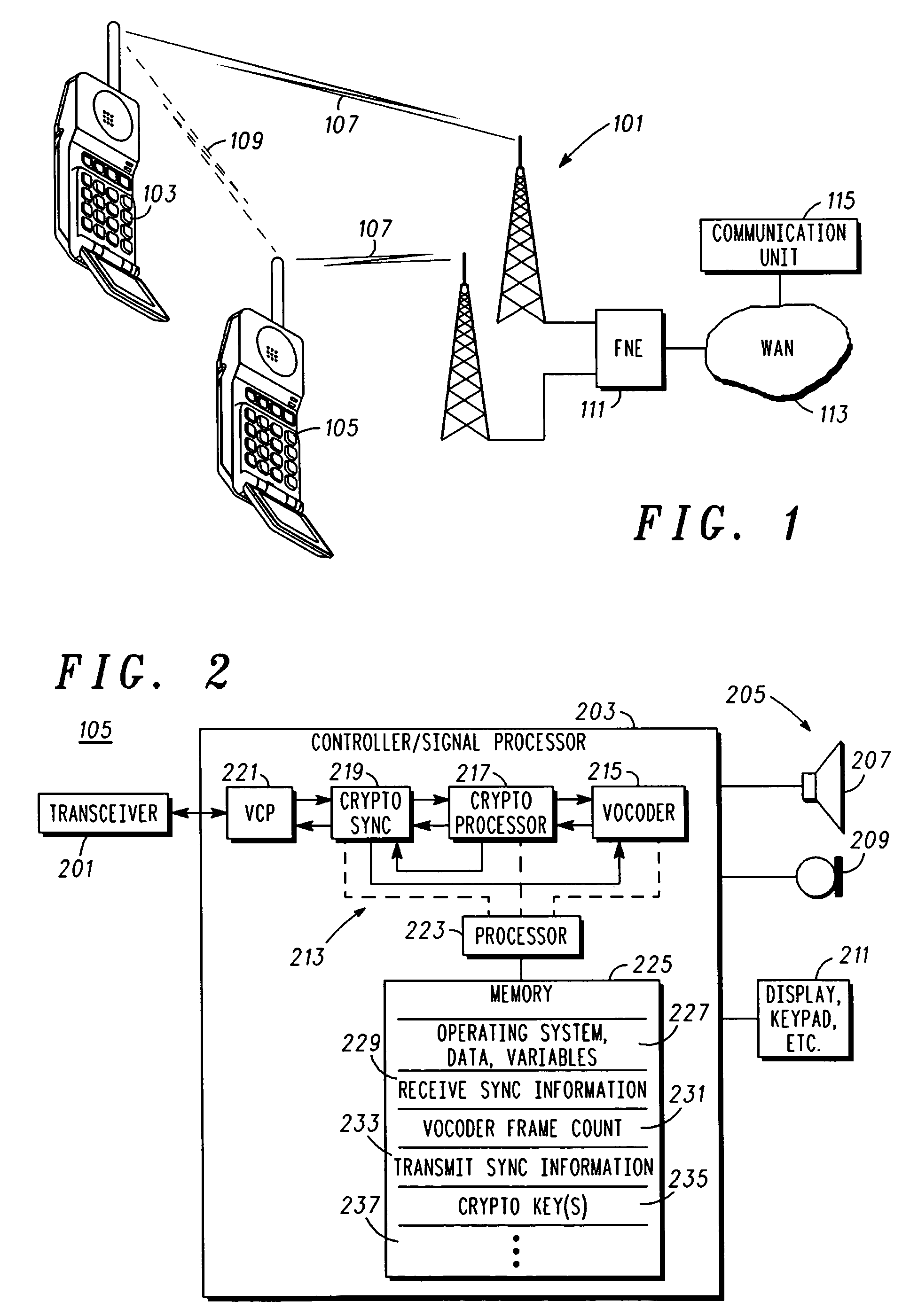
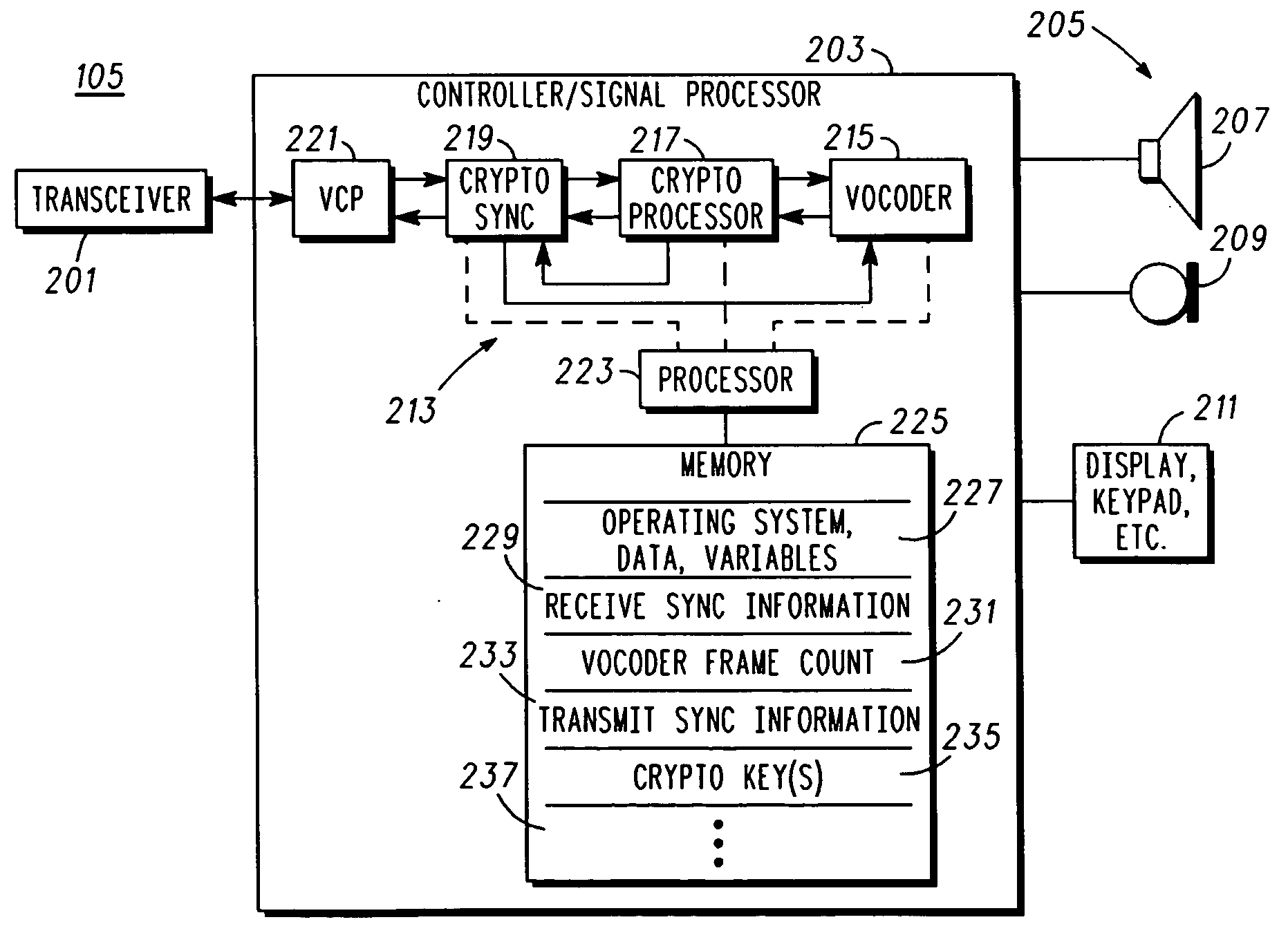
ActiveUS20060269065A1Public key for secure communicationSecret communicationComputer hardwareCommunication unit
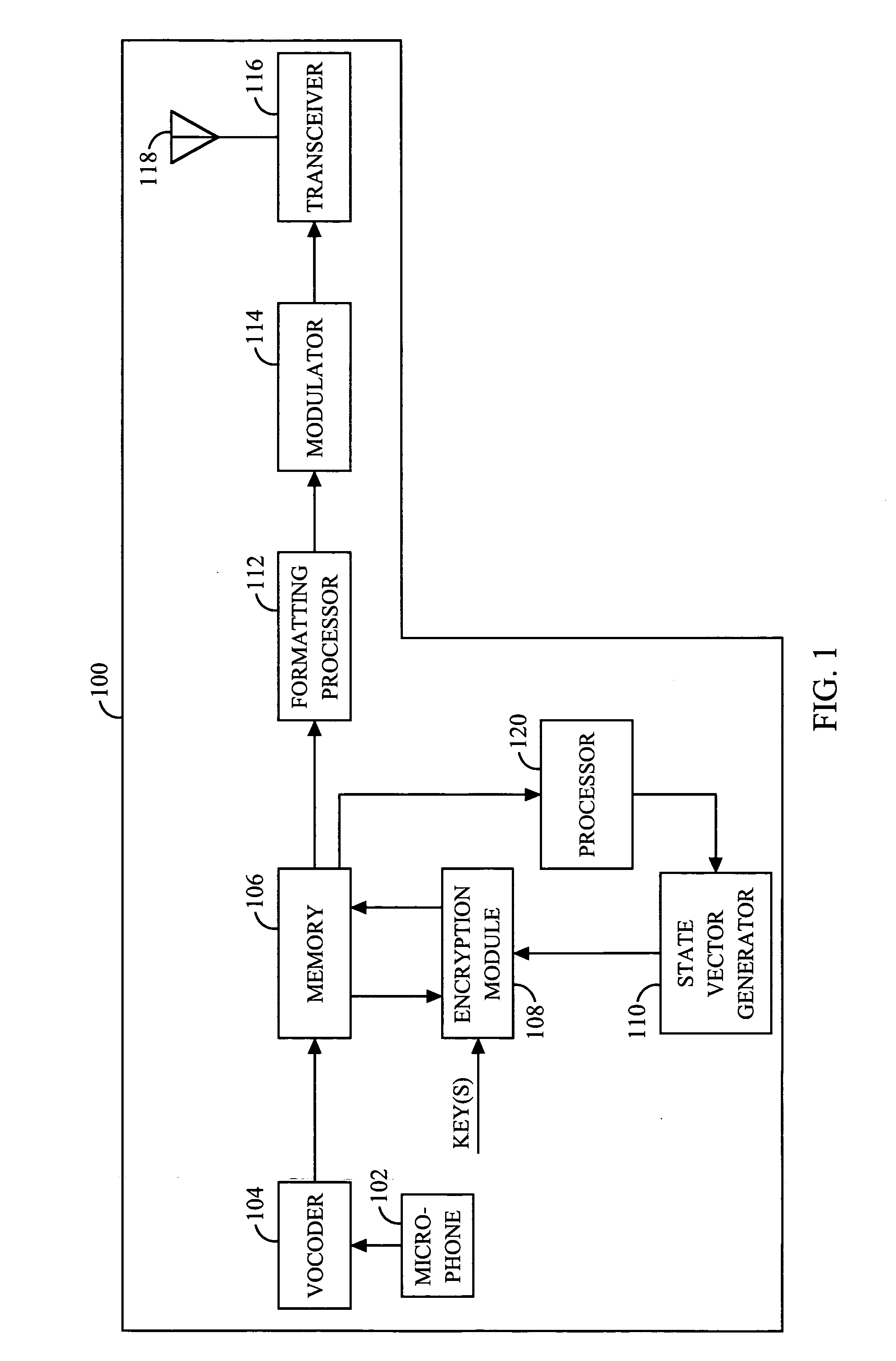
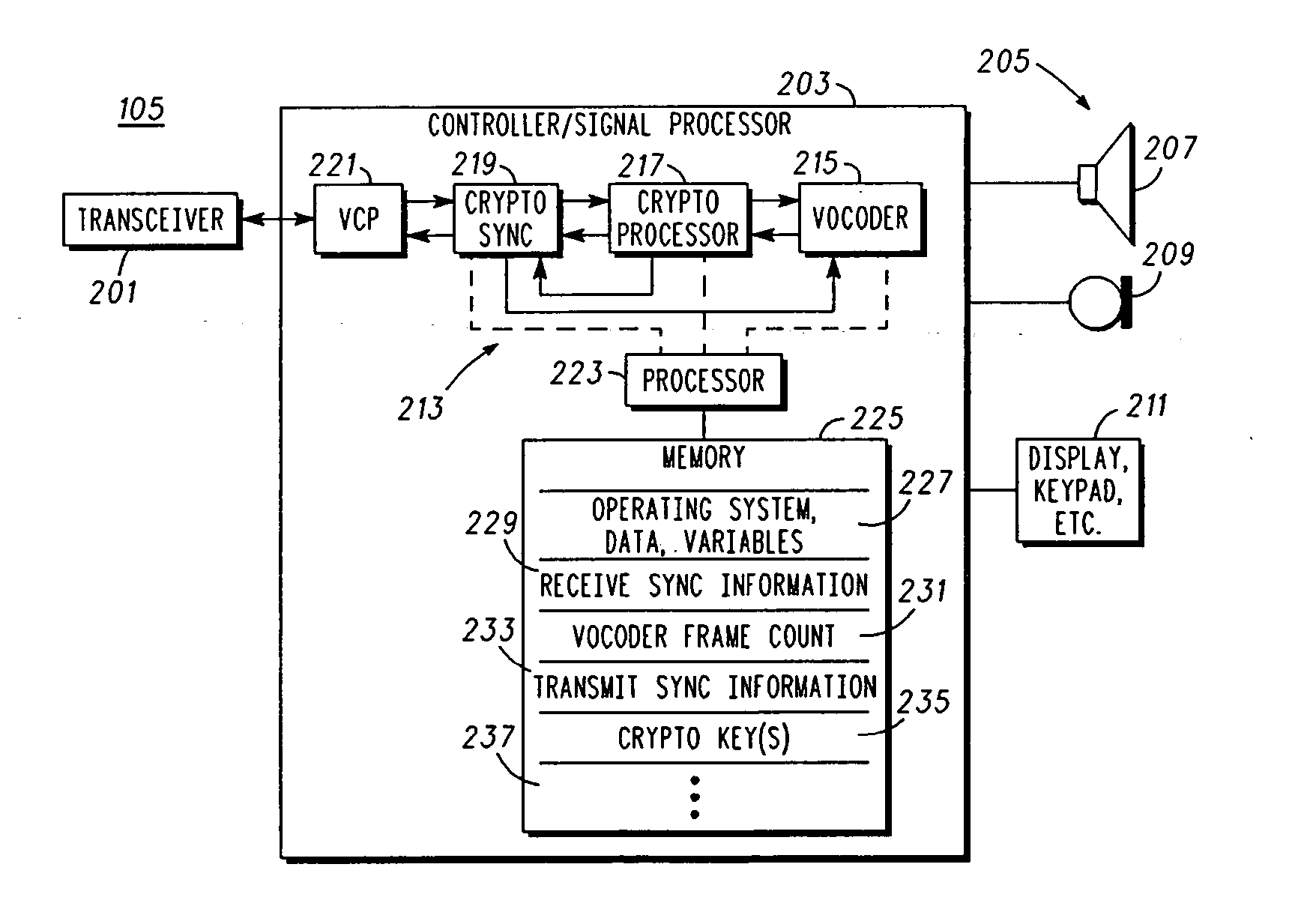
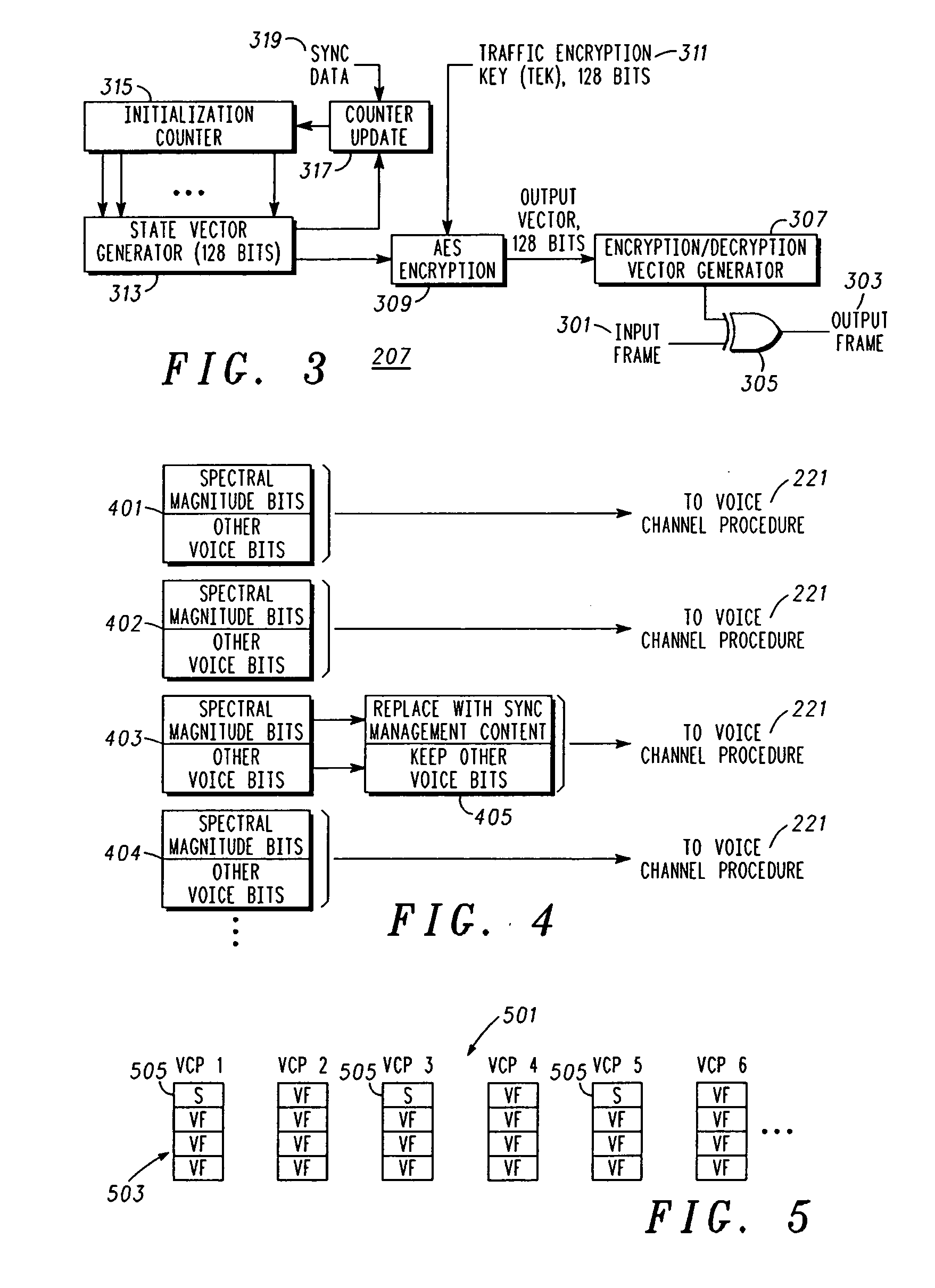
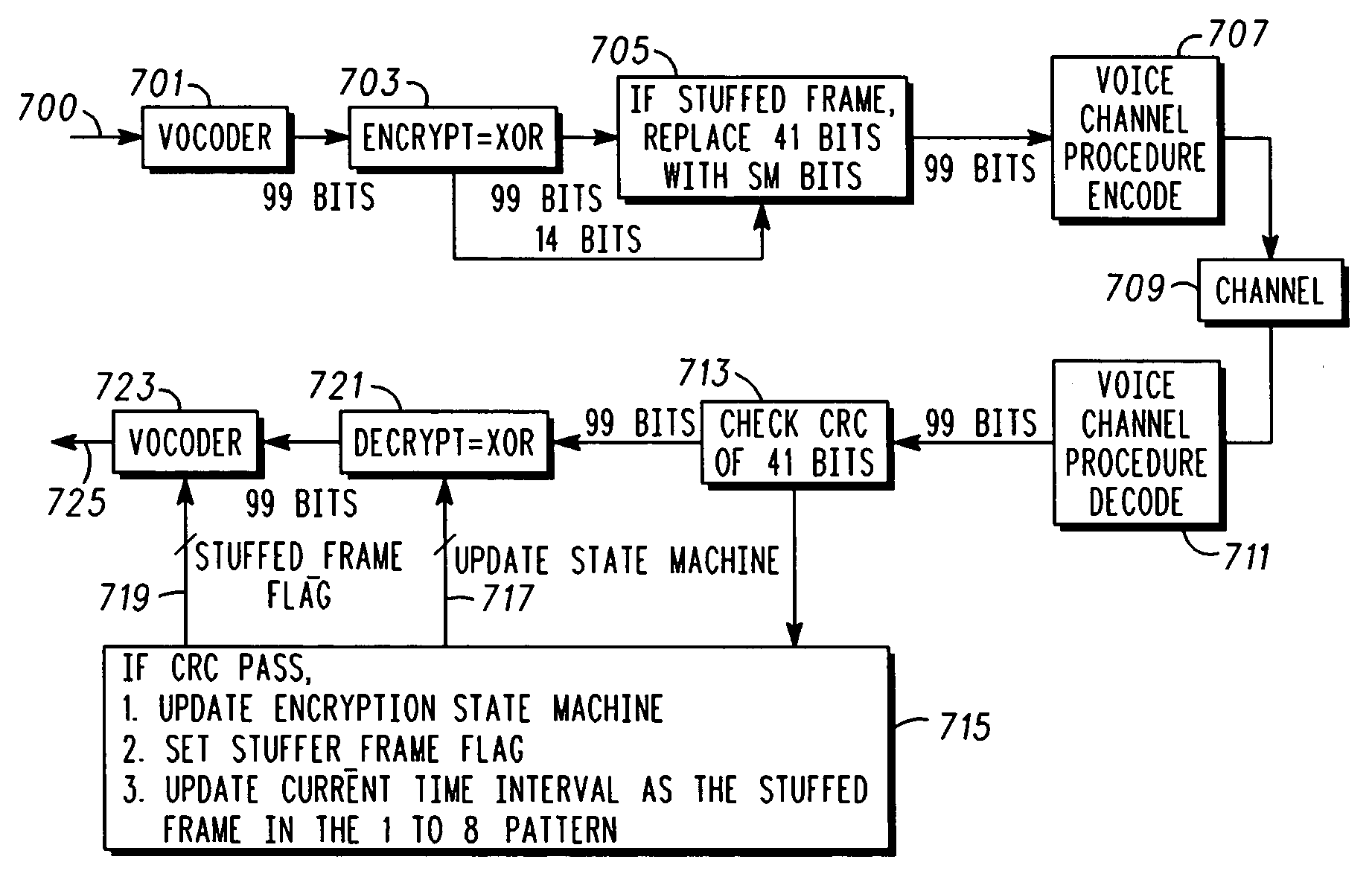
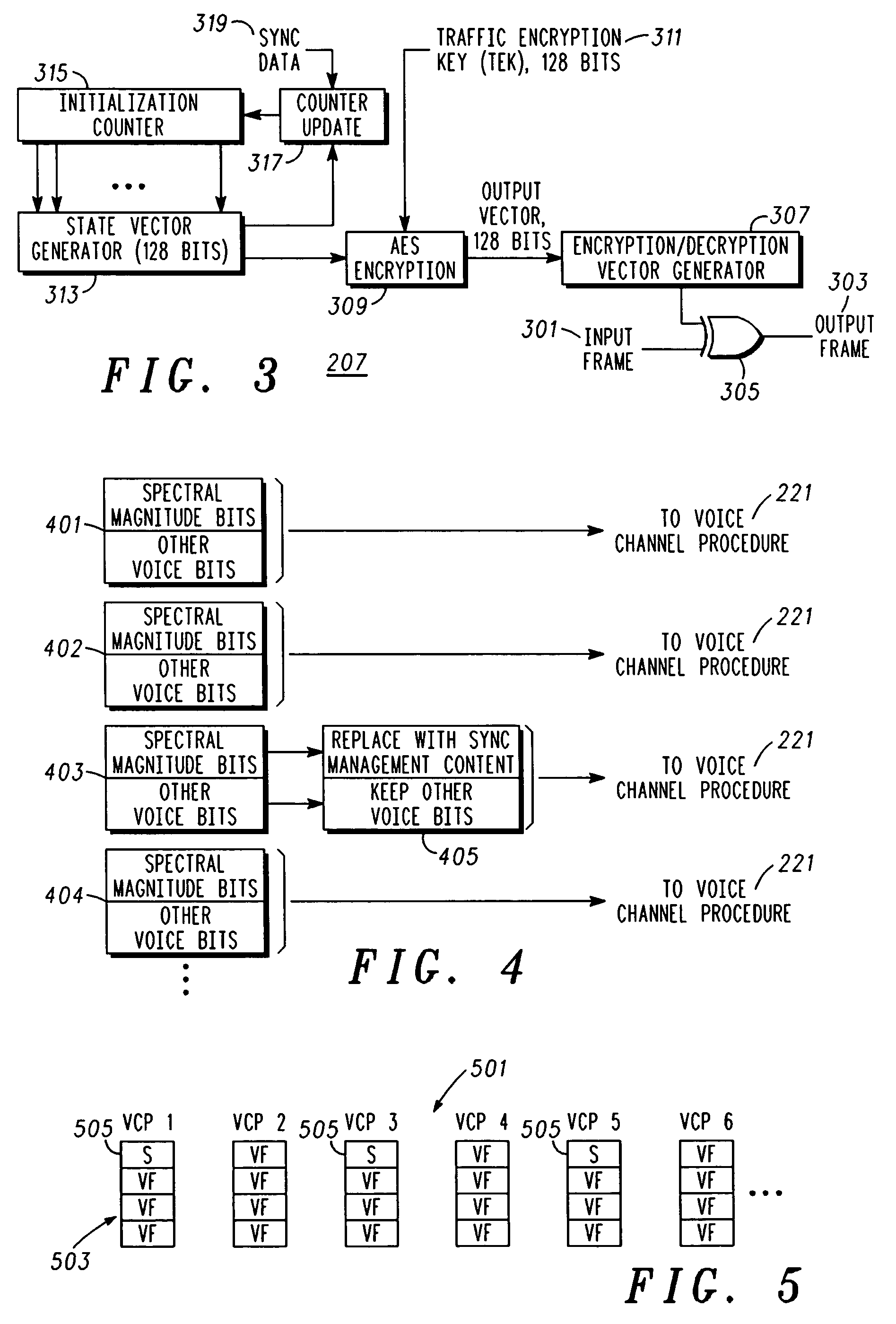
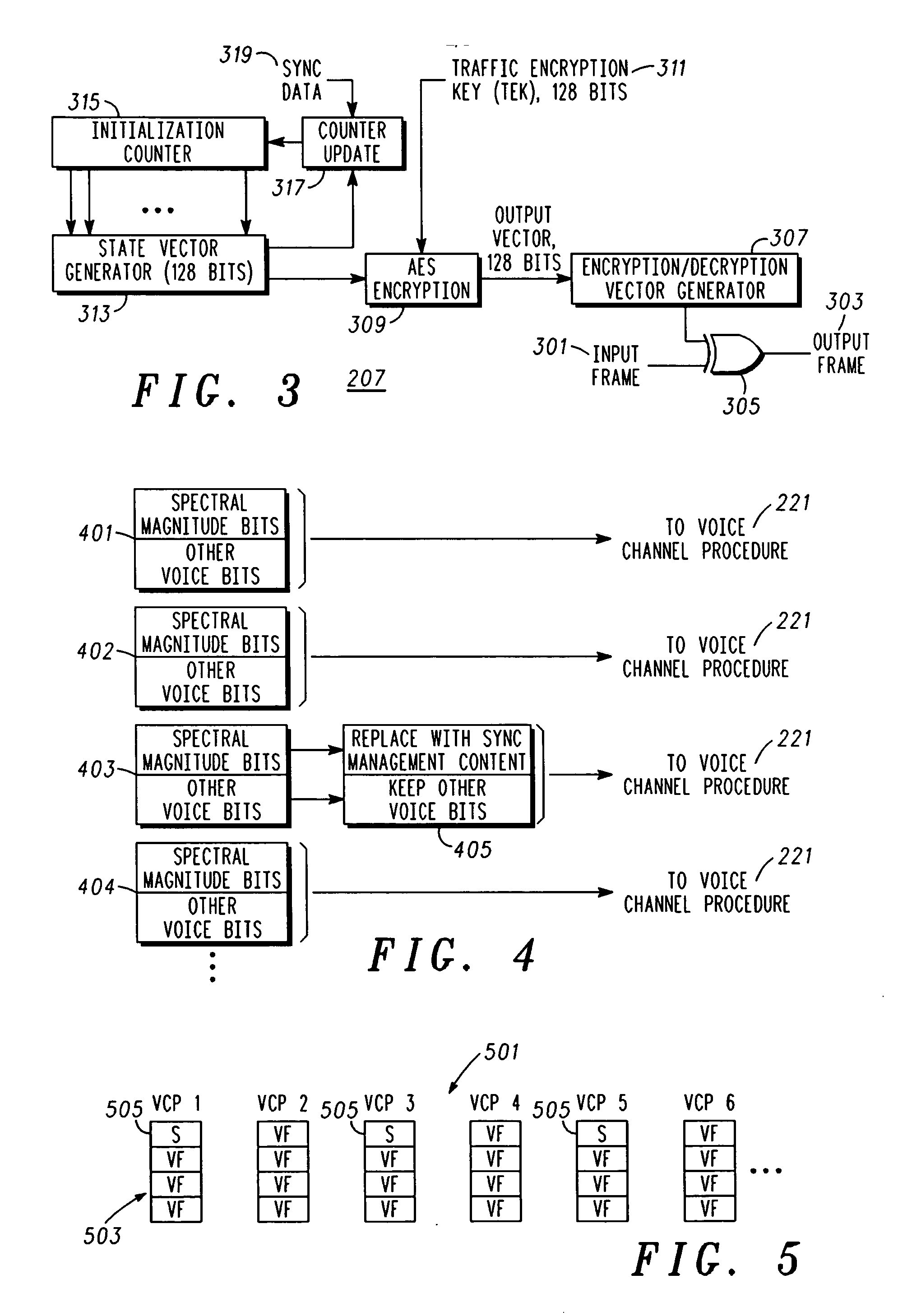
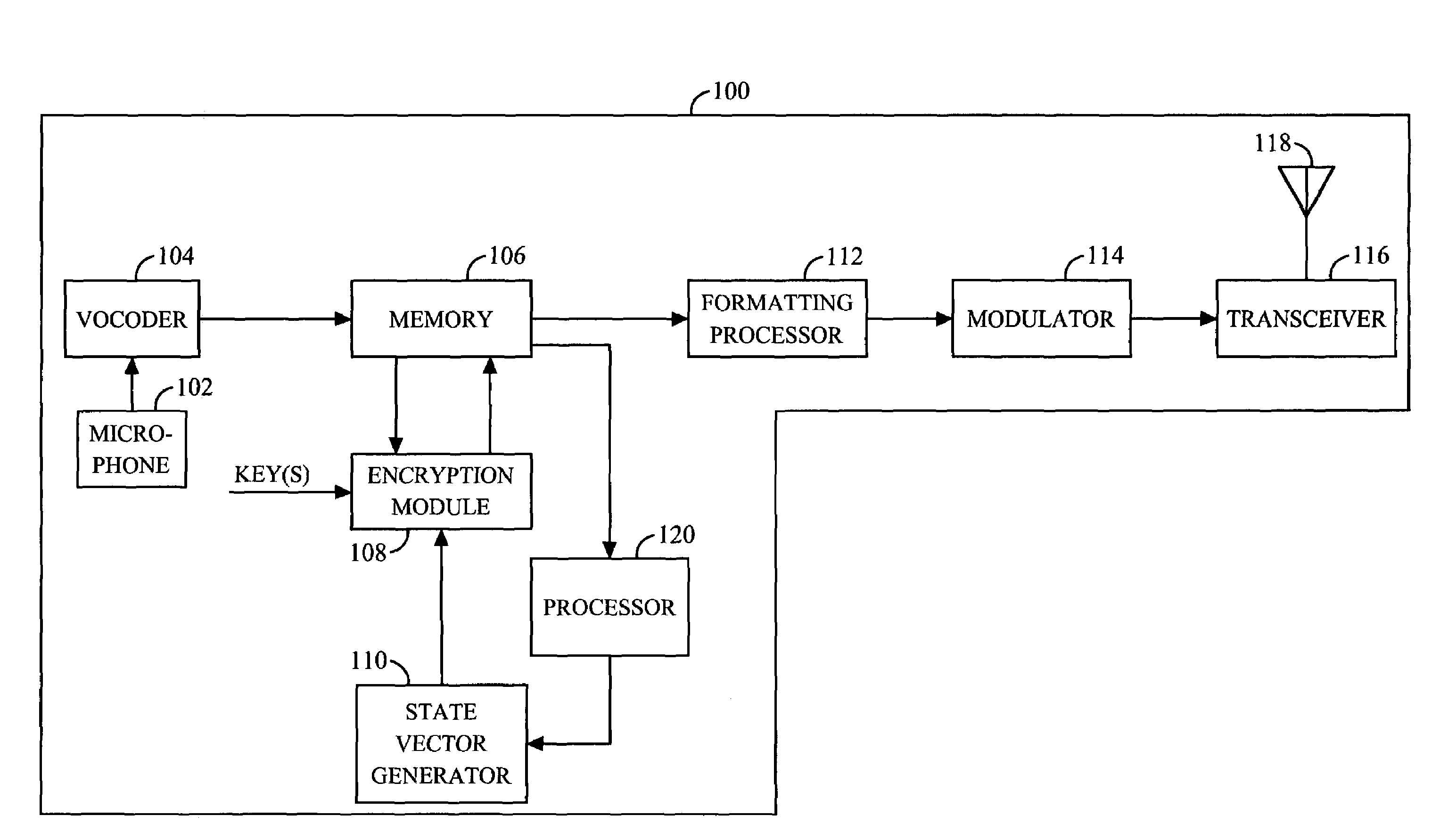
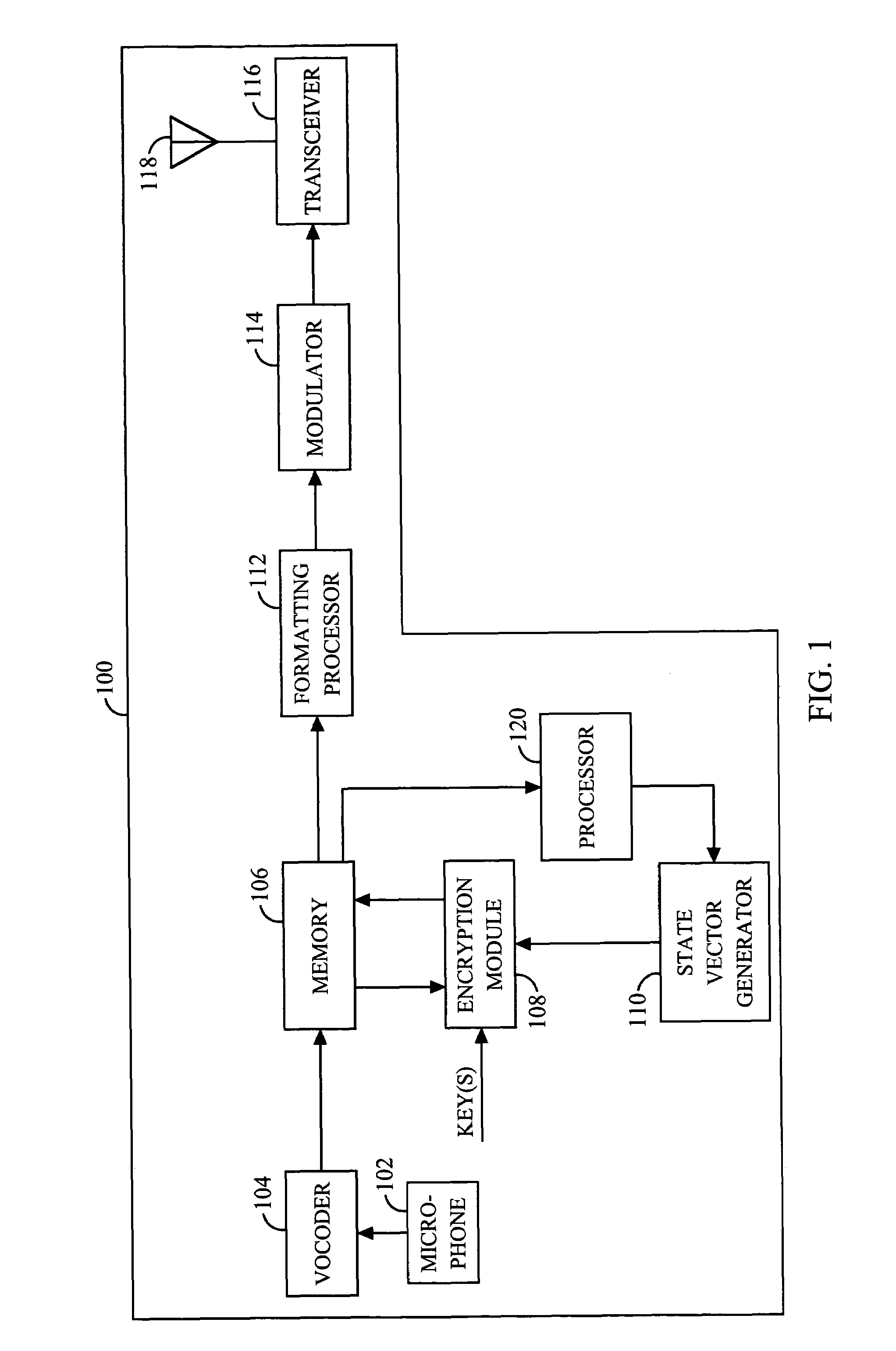
An apparatus (213) and corresponding methods (FIG. 7) to facilitate maintaining crypto synchronization while processing communication signals in a communication unit includes a vocoder (215) configured to convert input audio band signals to vocoder output frames; a crypto processor (217) configured to encrypt the vocoder output frames to provide encrypted output frames; and a synchronizer (219) configured to substitute in a predetermined manner synchronization information corresponding to an encryption state of the crypto processor for a portion of the encrypted data in a portion of the encrypted output frames to provide resultant output synchronization frames suitable for synchronizing a decryption process at a target communication unit.
Owner:GOOGLE TECH HLDG LLC +1
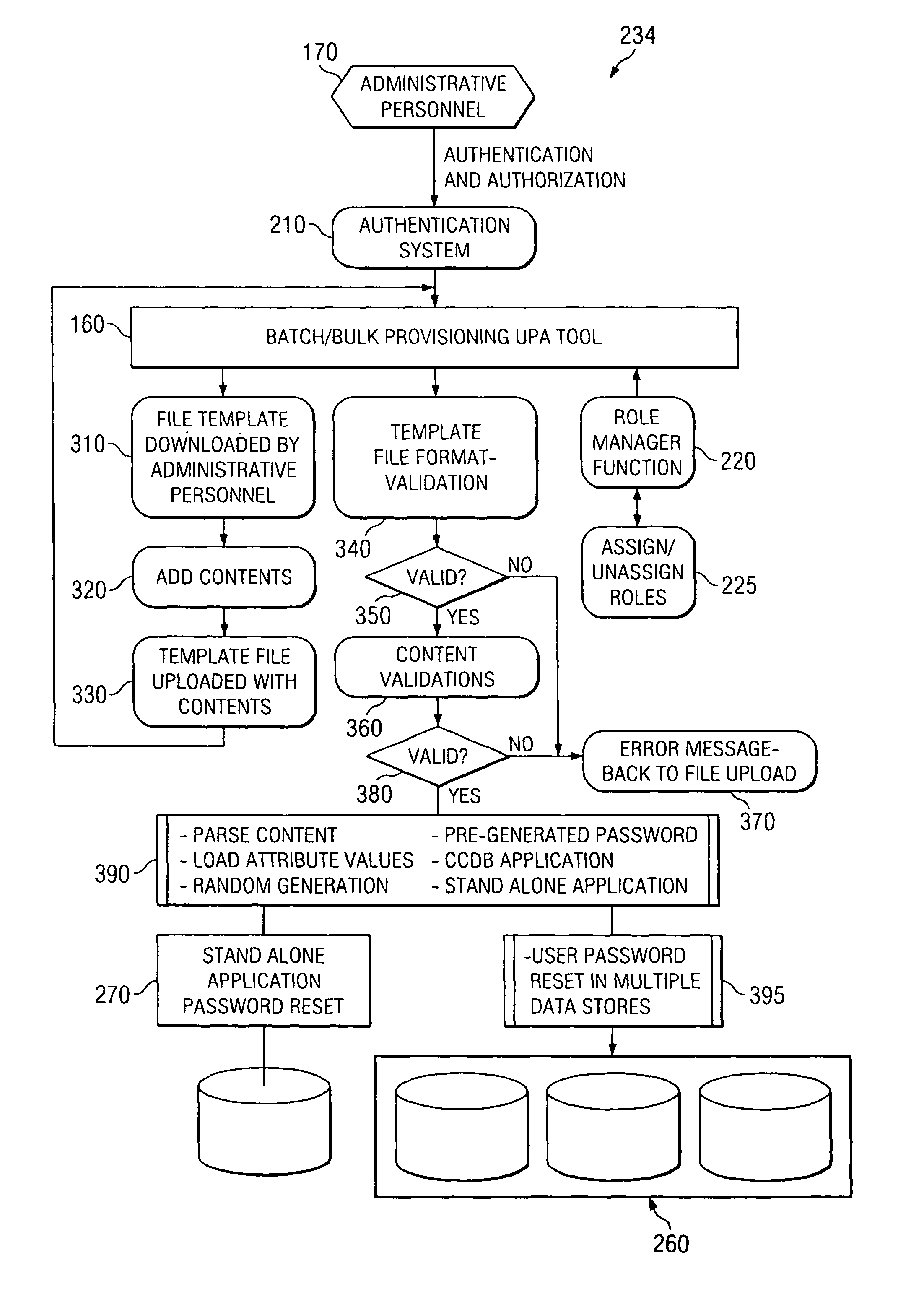
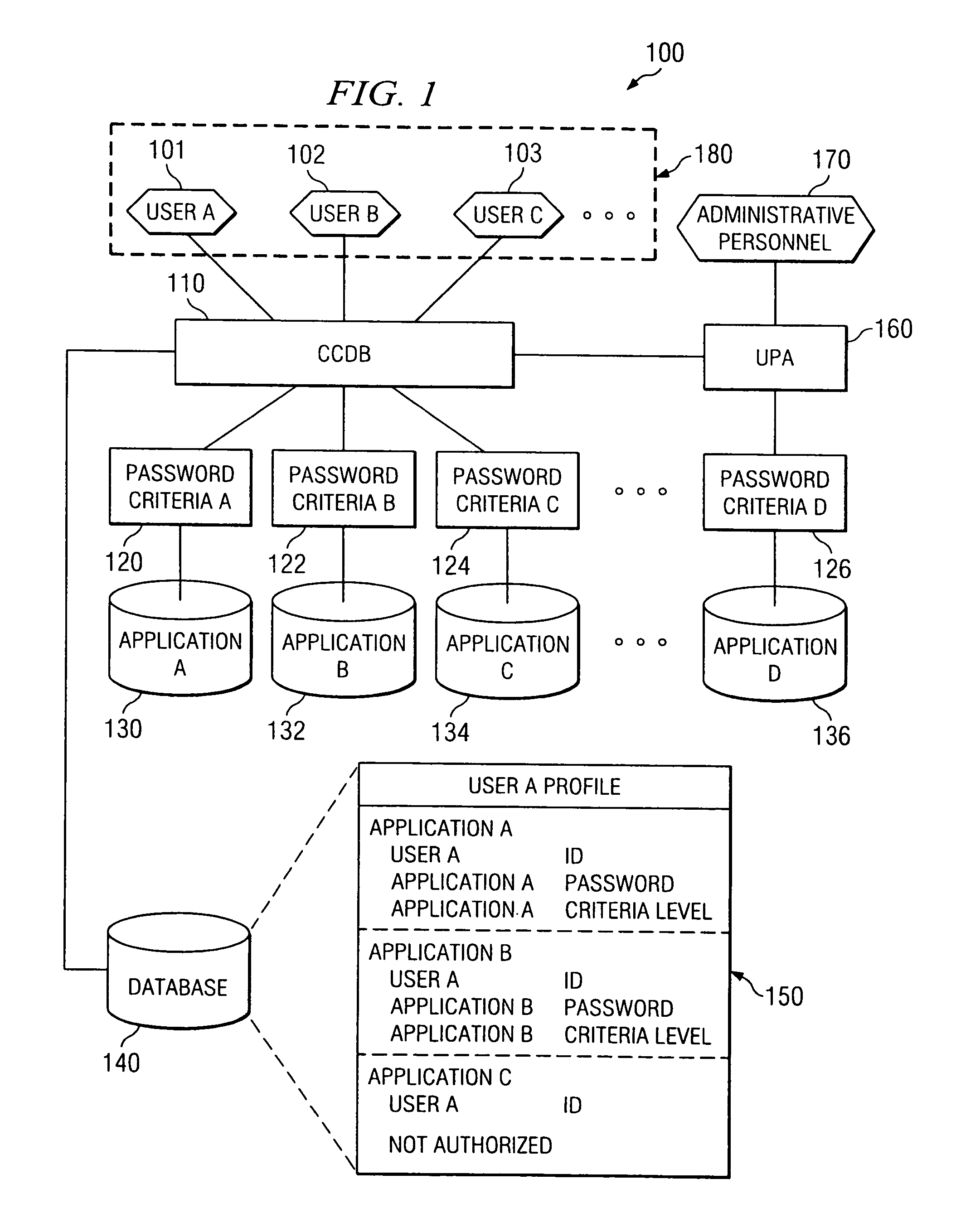
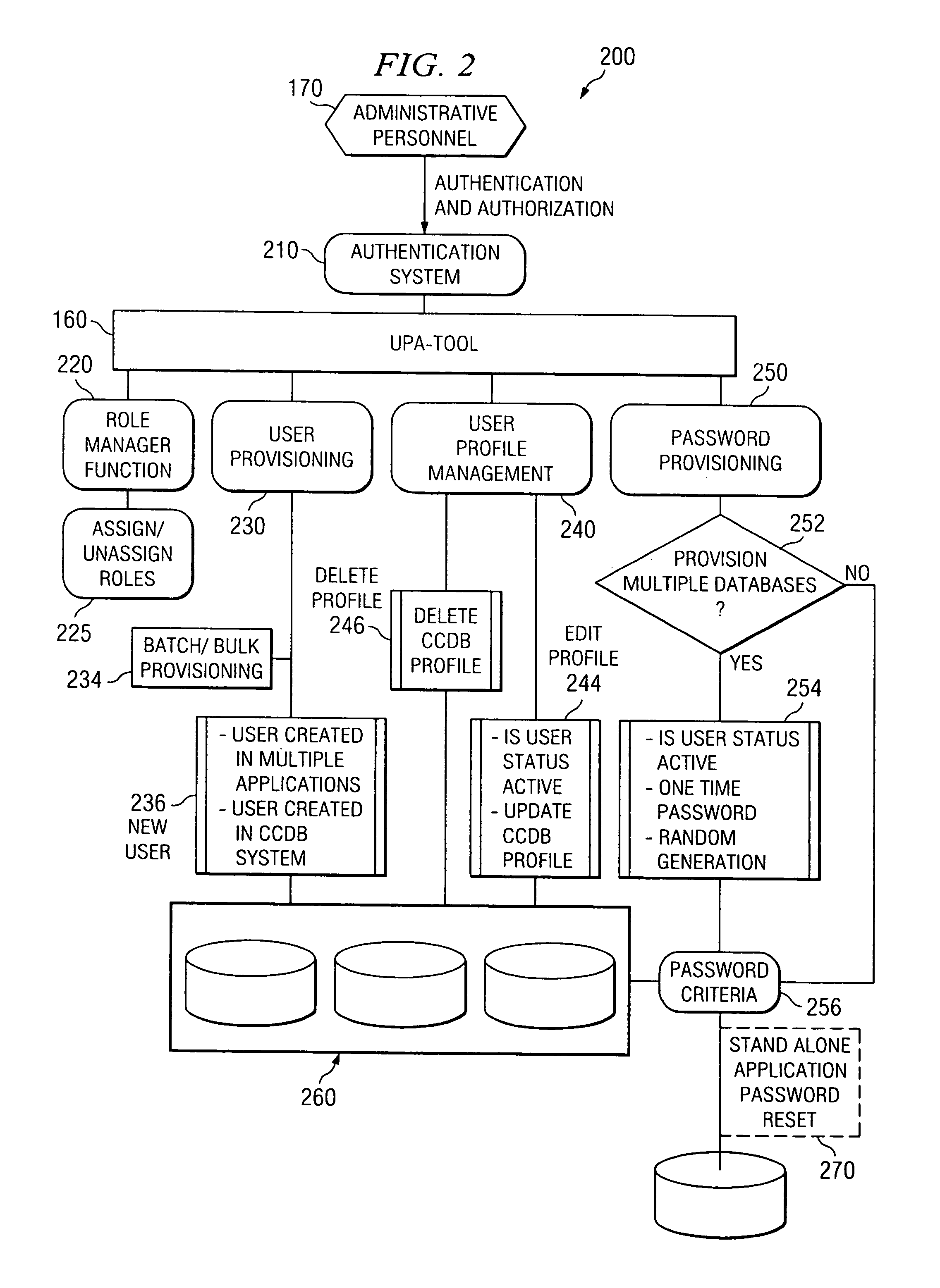
Integrated user profile administration tool
A computer system is provided including a single sign-on system with applications and a data store storing user profiles, each including a user ID, wherein each of the user profiles has a corresponding application password for one or more of the applications, and a user profile administration tool. The user profile administration tool includes a password provisioning section where an administrator selects a user profile and further selects an application type. The application type includes an application type wherein the administrator resets the password for one or more of the applications. The application type also includes a stand-alone application type wherein the administrator resets a password for a stand-alone application. The user profile administration tool further includes a password synchronizing section wherein the user profile administration tool automatically synchronizes the application passwords with each of the corresponding user profiles.
Owner:T MOBILE INNOVATIONS LLC
Method and apparatus for providing encryption and integrity key set-up
InactiveUS20060205386A1Synchronising transmission/receiving encryption devicesUnauthorised/fraudulent call preventionComputer hardwareCommunications system
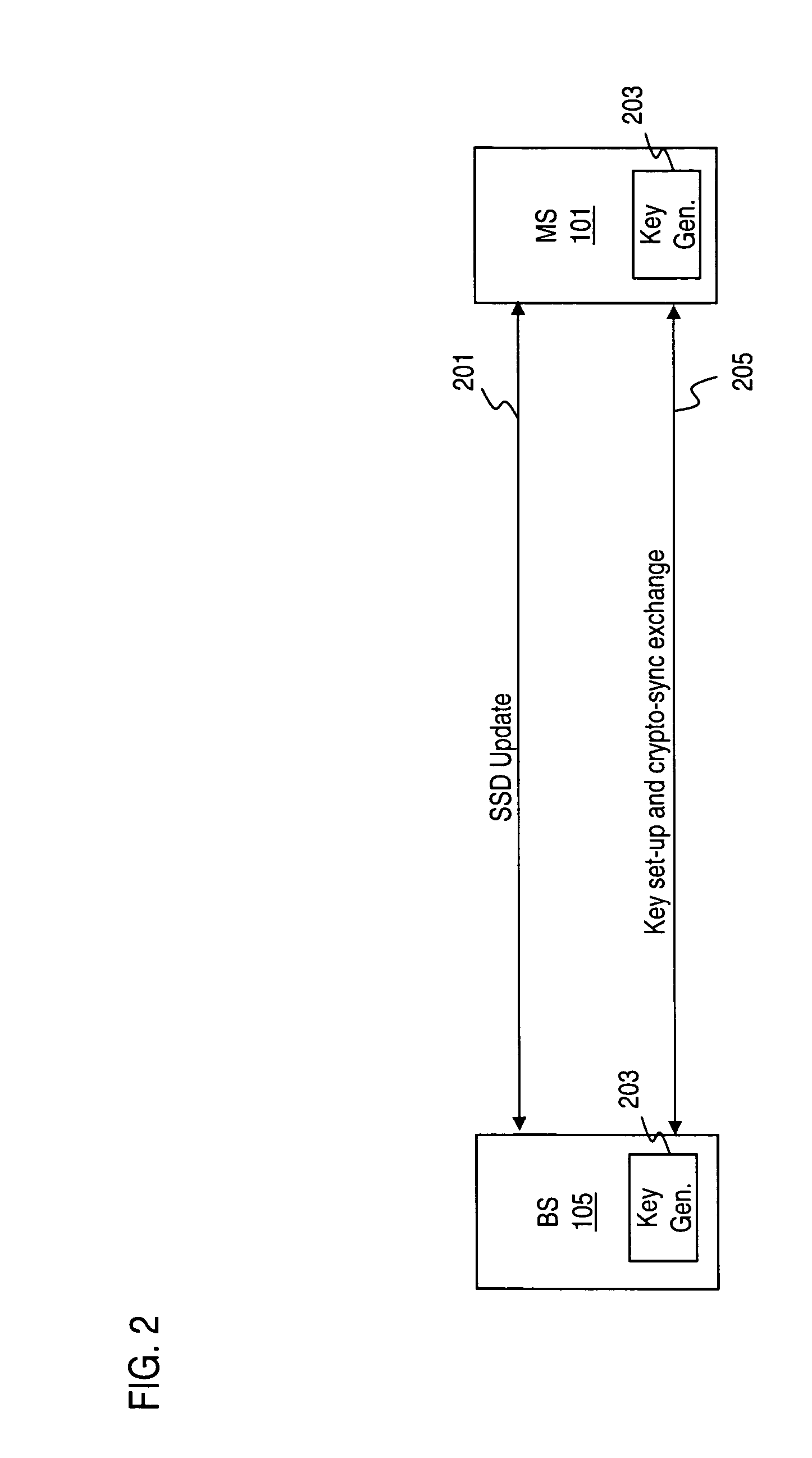
An approach is provided for communication signaling. Update of shared secret data is initiated with a mobile station. A random value associated with authentication of the mobile station is received. A key is generated based on the updated shared secret data and the random value. Set-up of the key and crypto-sync exchange is then executed with the mobile station. The above process is particularly suitable for deployment in radio communication systems, such as a cellular system.
Owner:NOKIA CORP
Crypto-synchronization for secure communication
InactiveUS7715559B2Synchronising transmission/receiving encryption devicesError preventionComputer hardwareSecure communication
An apparatus (213) and corresponding methods (FIG. 7) to facilitate maintaining crypto synchronization while processing communication signals in a communication unit includes a vocoder (215) configured to convert input audio band signals to vocoder output frames; a crypto processor (217) configured to encrypt the vocoder output frames to provide encrypted output frames; and a synchronizer (219) configured to substitute in a predetermined manner synchronization information corresponding to an encryption state of the crypto processor for a portion of the encrypted data in a portion of the encrypted output frames to provide resultant output synchronization frames suitable for synchronizing a decryption process at a target communication unit.
Owner:MOTOROLA SOLUTIONS INC
Methods for secure and bandwidth efficient cryptographic synchronization
ActiveUS20070113085A1Efficient use of bandwidthEasy to useSynchronising transmission/receiving encryption devicesMultiple keys/algorithms usageTransmission protocolSecure Real-time Transport Protocol
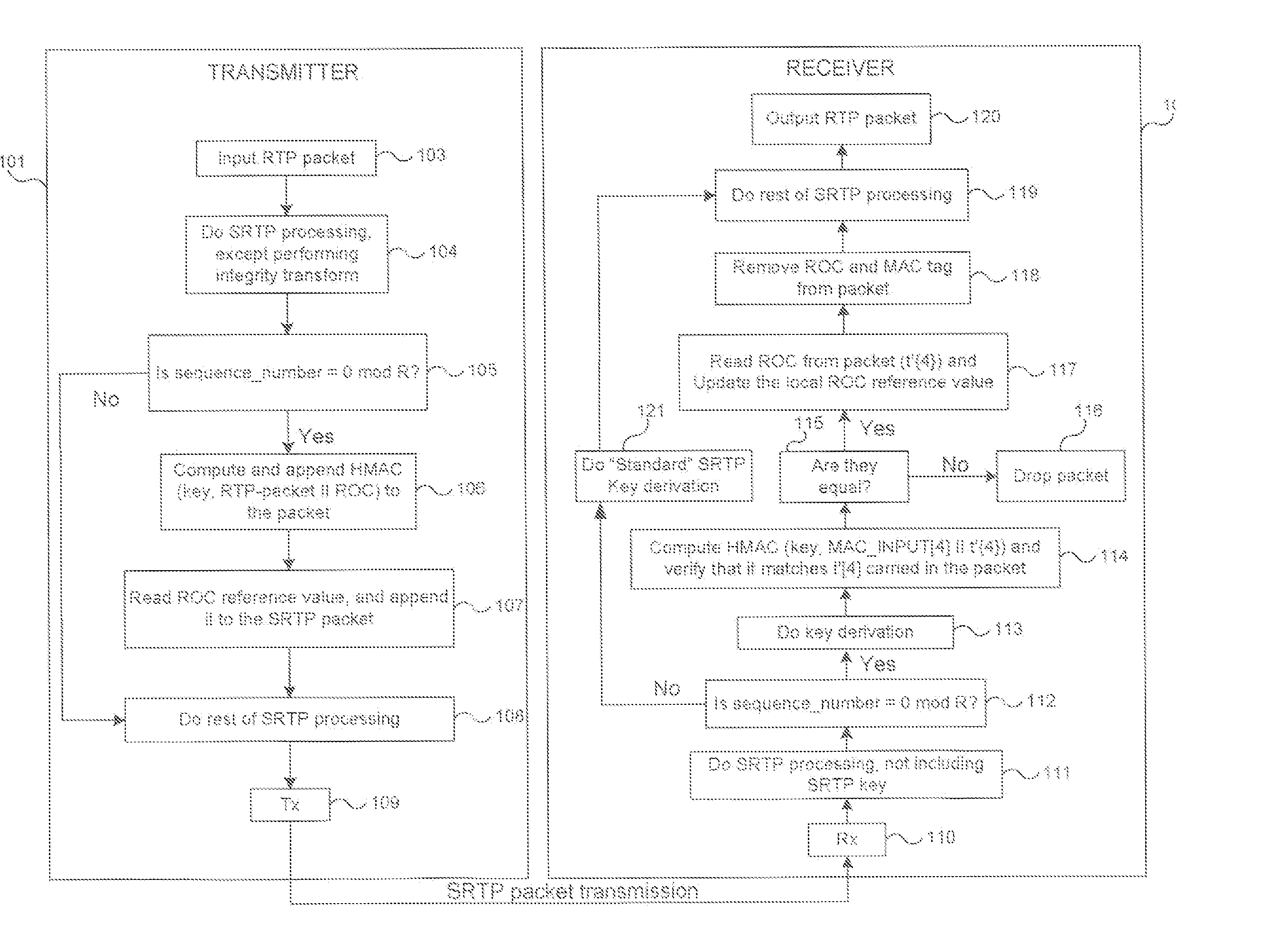
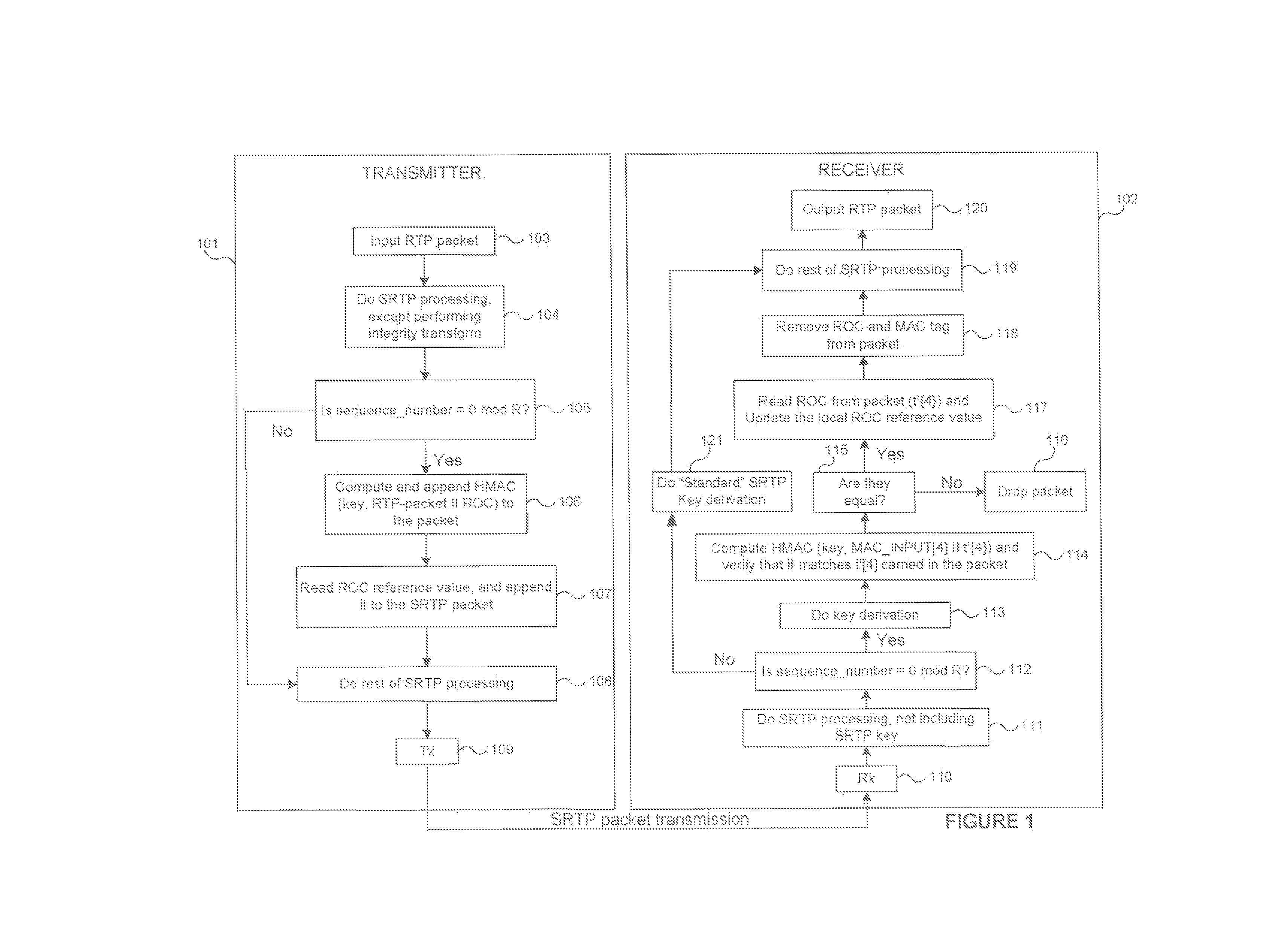
Methods for cryptographic synchronization of data packets. A roll-over counter (ROC) value is periodically appended to and transmitted with a data packet when a function of the packet sequence number equals a predetermined value. The ROC effectively synchronizes the cryptographic transformation of the data packets. Although the disclosed methods are generally applicable to many transmission protocols, they are particularly adaptable for use in systems wherein the data packets are transmitted to a receiver using the Secure Real-Time Transport Protocol (SRTP) as defined in Internet Engineering Task Force (IETF) Request for Comments (RFC) 3711.
Owner:TELEFON AB LM ERICSSON (PUBL)
Crypto-synchronization for secure communication
InactiveUS20060045136A1Synchronising transmission/receiving encryption devicesError preventionComputer hardwareSecure communication
An apparatus (213) and corresponding methods (FIG. 7) to facilitate maintaining crypto synchronization while processing communication signals in a communication unit includes a vocoder (215) configured to convert input audio band signals to vocoder output frames; a crypto processor (217) configured to encrypt the vocoder output frames to provide encrypted output frames; and a synchronizer (219) configured to substitute in a predetermined manner synchronization information corresponding to an encryption state of the crypto processor for a portion of the encrypted data in a portion of the encrypted output frames to provide resultant output synchronization frames suitable for synchronizing a decryption process at a target communication unit.
Owner:MOTOROLA SOLUTIONS INC
Method of cryptographic synchronization
InactiveUS7752441B2Synchronising transmission/receiving encryption devicesUnauthorised/fraudulent call preventionComputer hardwarePassword synchronization
Owner:ALCATEL-LUCENT USA INC
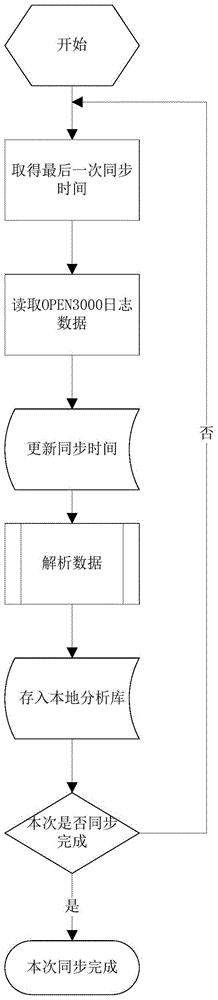
User behavior counting method for power scheduling automatic system based on log
ActiveCN104572978ARealize unified collectionThe result is accurate and reliableData processing applicationsSpecial data processing applicationsPasswordKeyword analysis
The invention discloses a user behavior counting method for a power scheduling automatic system based on a log. The user behavior counting method comprises the following steps: triggering a synchronous procedure at a special moment or a time interval, visiting data in a database list of the power scheduling automatic system according to a time field, storing the data into a local log analysis table, connecting the local log analysis table to a work station of the power scheduling automatic system through a remote logging interface, comparing and analyzing a file edition and content according to a work station address, a user name, a password, a synchronous interval and the like to form an operation log; trimming and extracting the user operation log, returning the file operation log to the server through a ftp protocol, storing the file operation log to a local log analysis table, adopting a Lucene engine to establish full-text index for the database and the file log, performing keyword analysis through a Chinese word segmentation algorithm, and providing user operation behavior counting and application using condition analysis. The user behavior counting method has the advantages of realizing collecting, extracting, recording and analyzing of user operation log for electric scheduling automation.
Owner:STATE GRID CORP OF CHINA +1
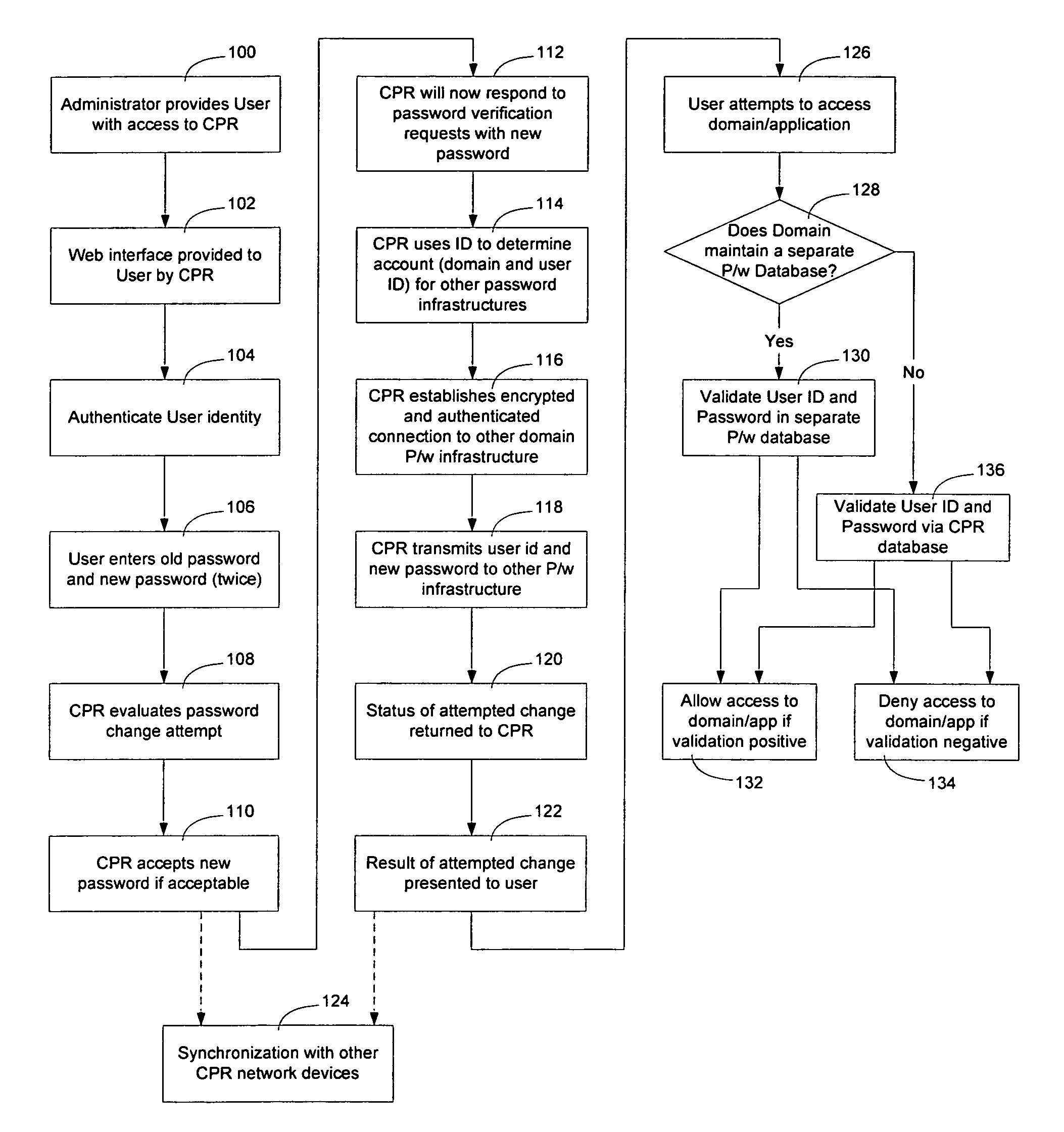
Method and apparatus for securely synchronizing password systems
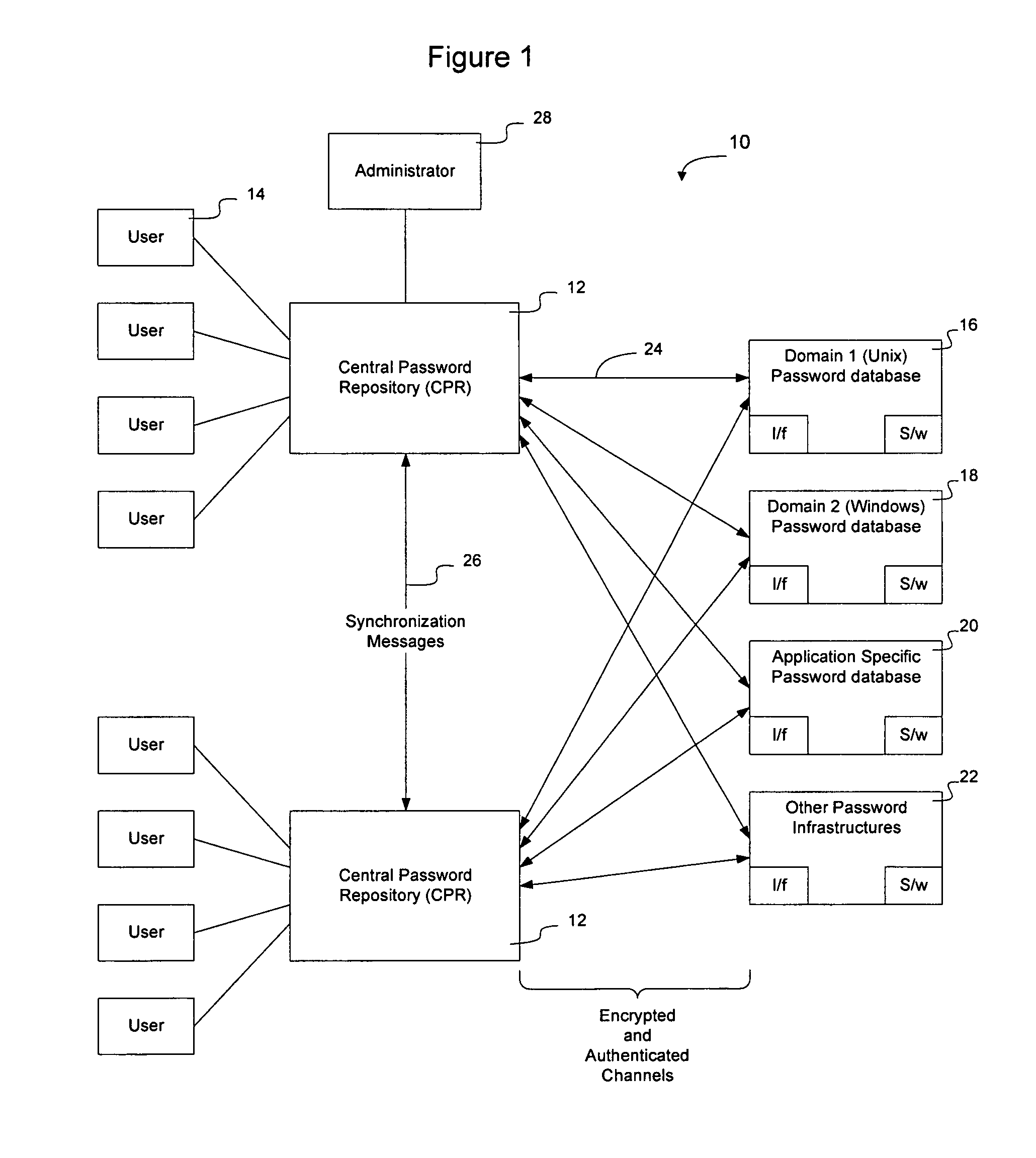
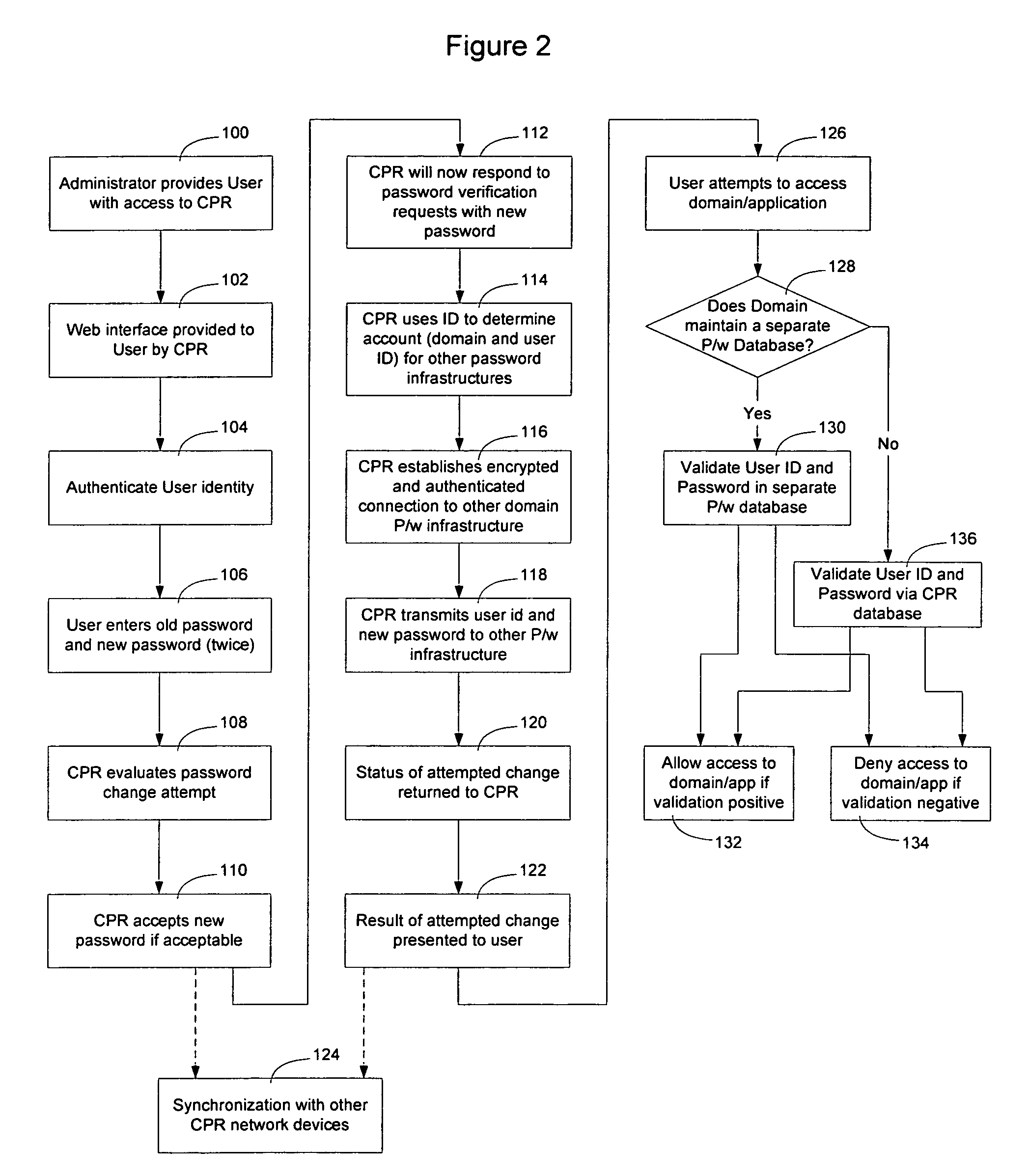
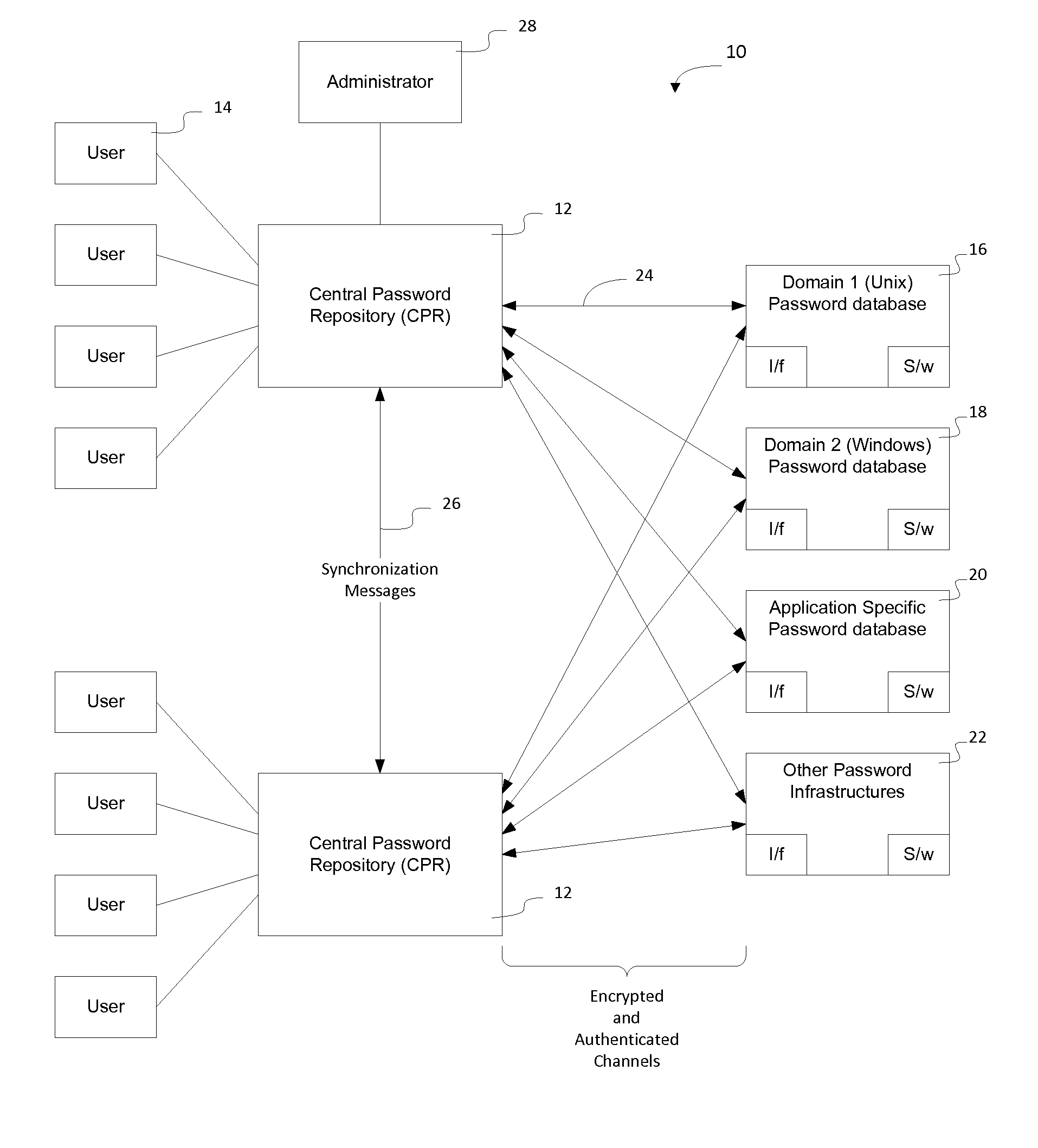
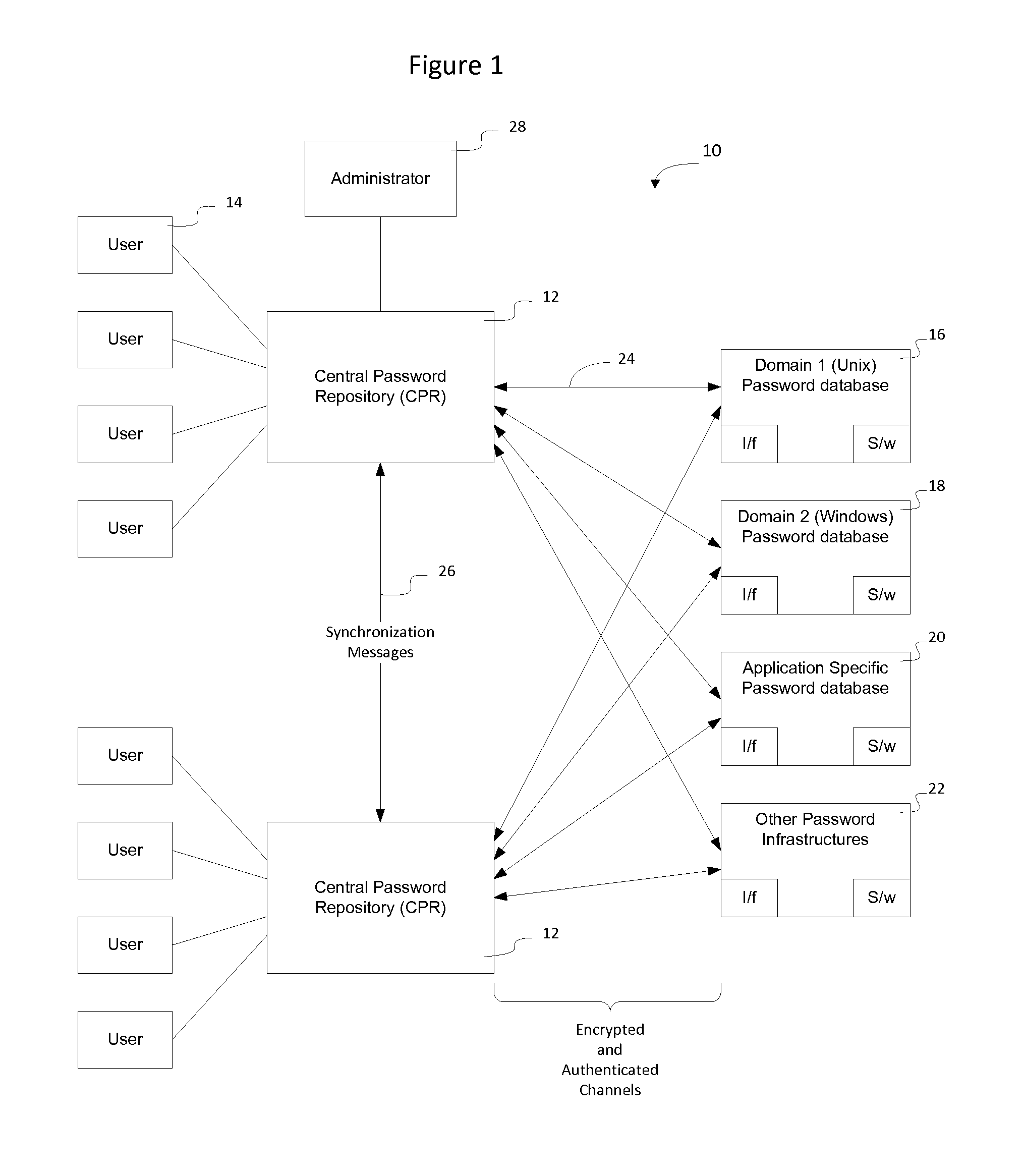
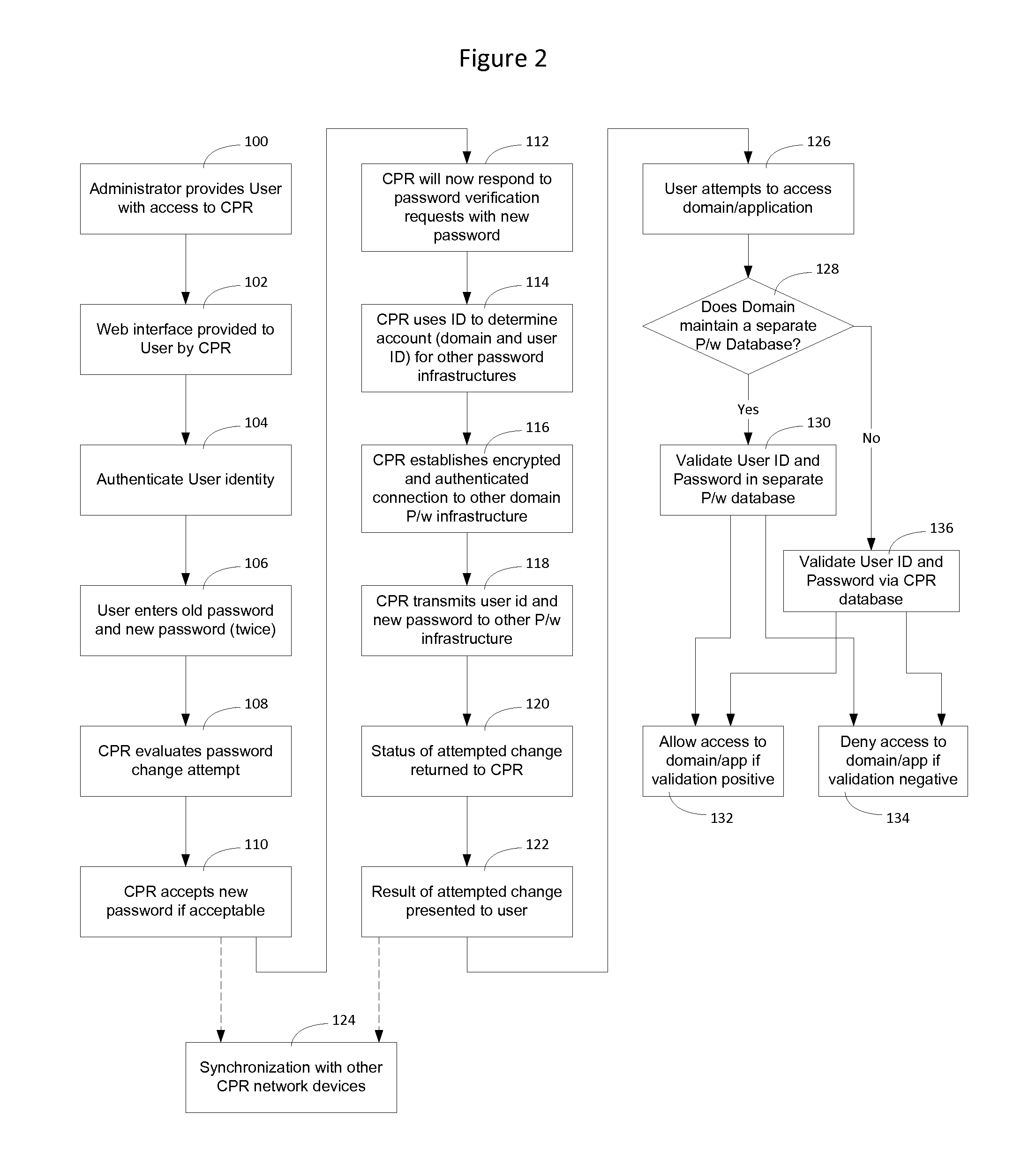
A centralized password repository (CPR) provides network users with a password portal through which the user can manage password access to domains and applications on the network. A subset of the domains and applications on the network may be required, by design, to maintain a separate password infrastructure. For these systems, the CPR establishes a secure and authenticated communication channel and software on the system interfaces with the password infrastructure to synchronize the password in the system password infrastructure with the password in the CPR. For other systems not required to maintain a separate password infrastructure, the CPR performs password services by responding to requests from those systems seeking to validate user IDs and passwords. The CPR enables an administrator to modify network privileges and enables a user to alter passwords on the network through a single interface.
Owner:RPX CLEARINGHOUSE
Safety communication method suitable for remote control with limited capability at controlled end
InactiveCN101931623AImprove confidentialityLimited number of solutionsError prevention/detection by using return channelSecure communicationTelecommunications link
The invention discloses a safety communication method suitable for remote control with a limited capability at a controlled end. The method comprises the following steps of: setting password sets at a control end and the controlled end and generating a password set according to an input initialization password by an irreversible method, wherein the password set comprises an index number and the password per se and encryption and decryption are performed by using the password corresponding to the recorded index number in a normal communication process; when the password is asynchronous, transmitting the index number by encrypting to perform password synchronization; and when a password set updating condition is met, negotiating about the update of the password set by transmitting a selected index number. A password set generating device for calculating the password set and communicating with the controlled end only when the password set is needed to be generated is arranged at the controlled end. Various attacks are resisted effectively by using a dynamic password and operation of real-time password calculation needed by the transmission of each data packet is avoided. Simultaneously, the password per se does not need to be transmitted on a communication link in password synchronizing and password set updating processes, so that simpleness and safety are realized.
Owner:SOUTH CHINA UNIV OF TECH
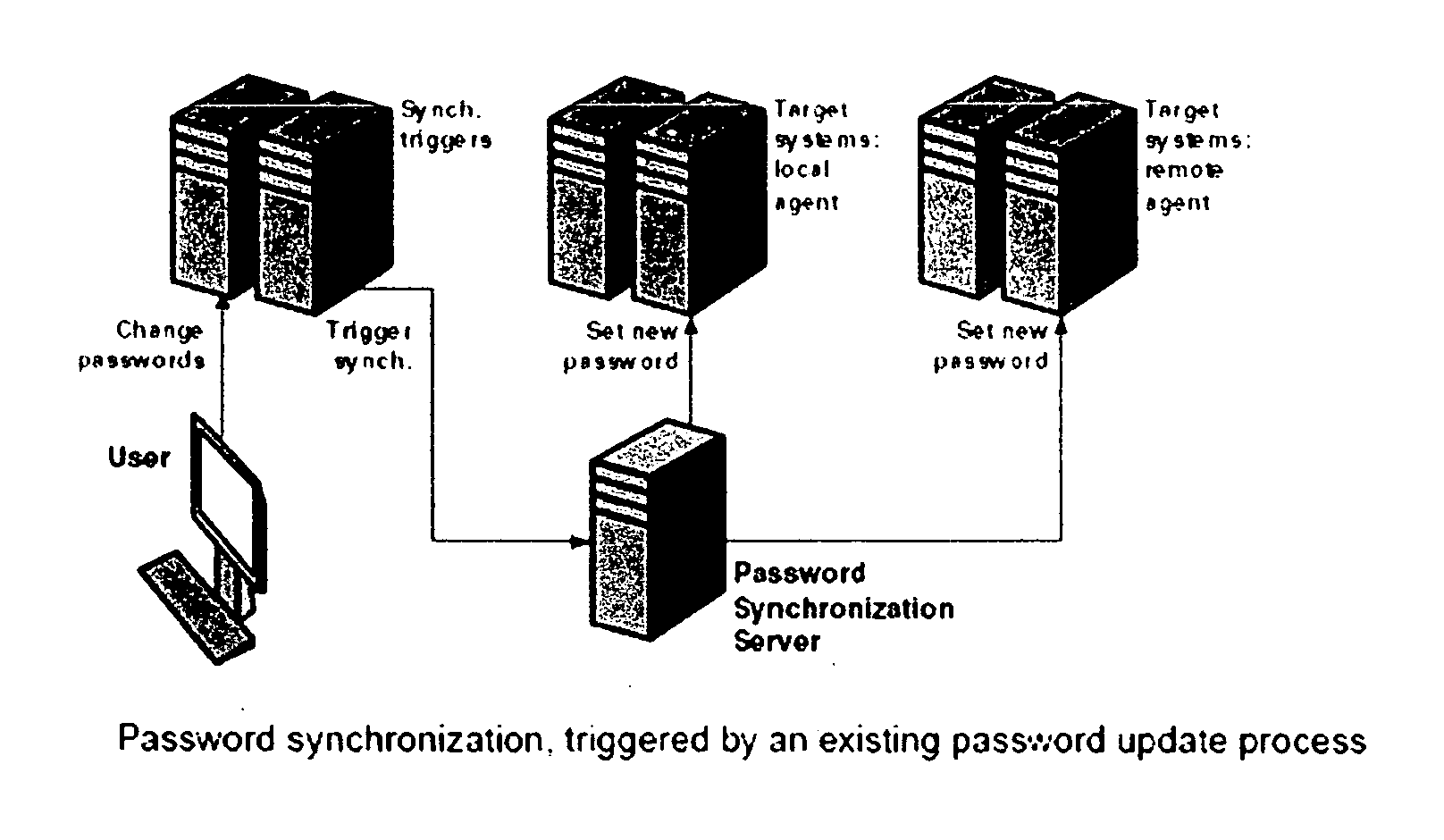
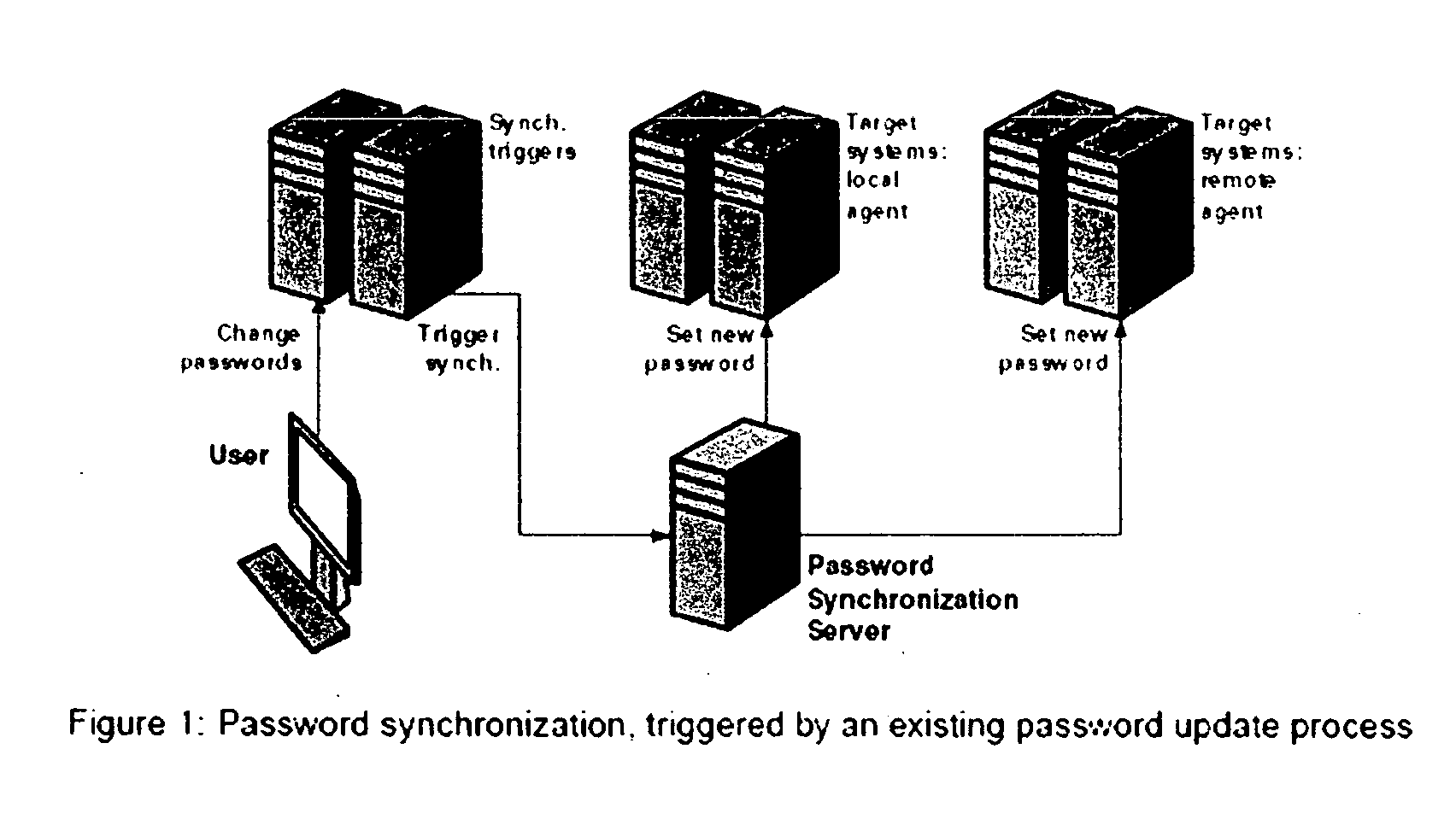
Method for reduced signon, using password synchronization instead of a credential database and scripts
InactiveUS20060031926A1Improve availabilityReduce in quantityDigital data processing detailsMultiple digital computer combinationsOperational systemDisplay device
A method for reducing the number of times that a user must type his own login ID or password into various systems that require authentication is disclosed. The method comprises the steps of: 1. A user signs into his workstation, using a standard login ID and current network password. 2. A plugin program, inserted into the workstation operating system's login subsystem, captures the user's login ID and password. 3. In environments where this is either not technically possible or where insertion of such a plugin program is infeasible, once the user has completed the initial workstation login, a secondary login prompt is displayed, asking the user to re-enter his current network password. 4. A second operating system plugin program is launched, which monitors all user interface activity—keystrokes and pointer events representing user input, processes that are executed, and windows and data fields activated on the workstation's display(s). 5. The monitor plugin compares the values entered by the user into data fields to the login ID and password captured in step 2 or 3. Where a new match is found, identifying characteristics of the data field, such as window ID, window title, field ID, field name, field position within the window and process ID, are stored in a data file, an operating system configuration database, or some other database. 6. The monitor plugin compares the data fields displayed on the workstation to a list of already known data fields in storage. If a data field is displayed that matches one whose characteristics have already been captured in storage, the login ID or password that were intercepted in step 2 or step 3 are automatically inserted into that data field, as appropriate. The present invention provides a method for reduced signon, whereby the number of separate instances where a user must provide his own login credentials is reduced, possibly to a single set of ID / password per workstation login session. This method improves the level of service offered by an IT organization to its users, as it saves time and effort for those users.
Owner:M TECH INFORMATION TECH
Method and apparatus for achieving crypto-syncronization in a packet data communication system
InactiveUS7474749B2Reduce decreaseSynchronising transmission/receiving encryption devicesNetwork traffic/resource managementComputer hardwareCommunications system
A method and apparatus for achieving crypto-syncronization in a packet data communication system employing cryptographic communications. In a transmitter, a state vector is incremented at a predetermined rate and is provided to an encryption module. The encryption module uses the state vector to sequentially encrypt the data frames. During periods of frame dropping prior to encryption, the state vector is disabled, thereby allowing for sequential encryption of the data frames. In a receiver, during a frame dropping condition, the state vector is advanced in proportion to the number of frames dropped. During an underflow condition at the receiver, the state vector is disabled for the duration of the underflow condition, and enabled once the underflow condition has passed.
Owner:QUALCOMM INC
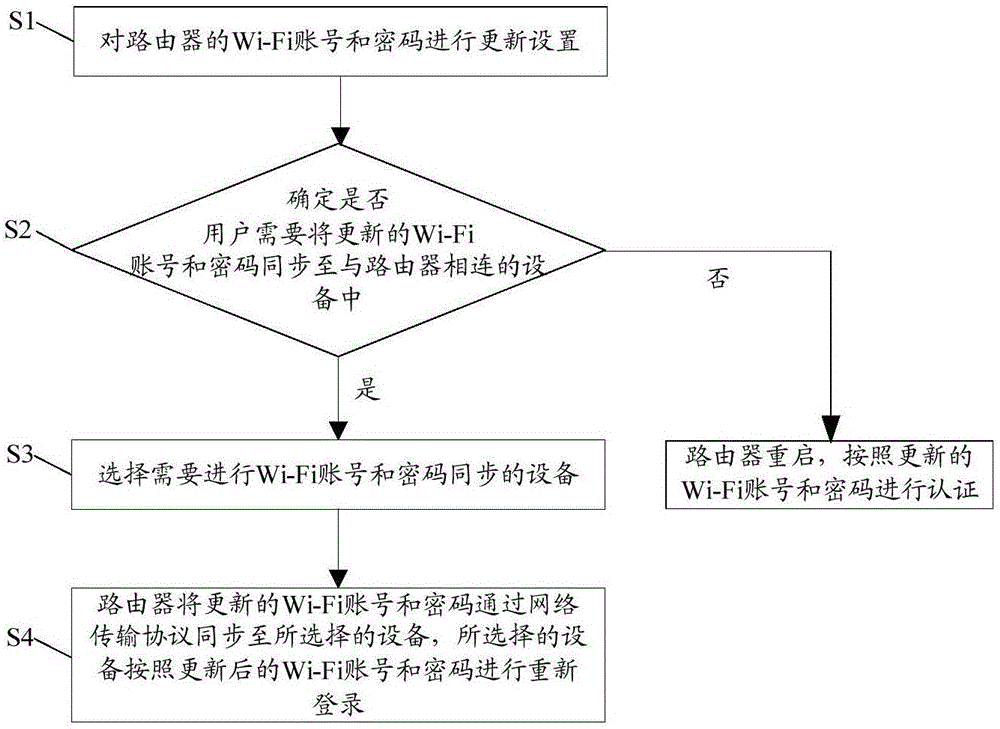
Control method for realizing Wi-Fi (Wireless-Fidelity) network configuration
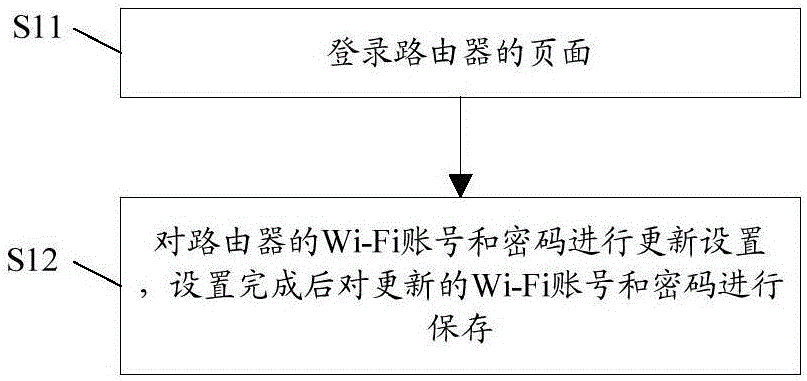
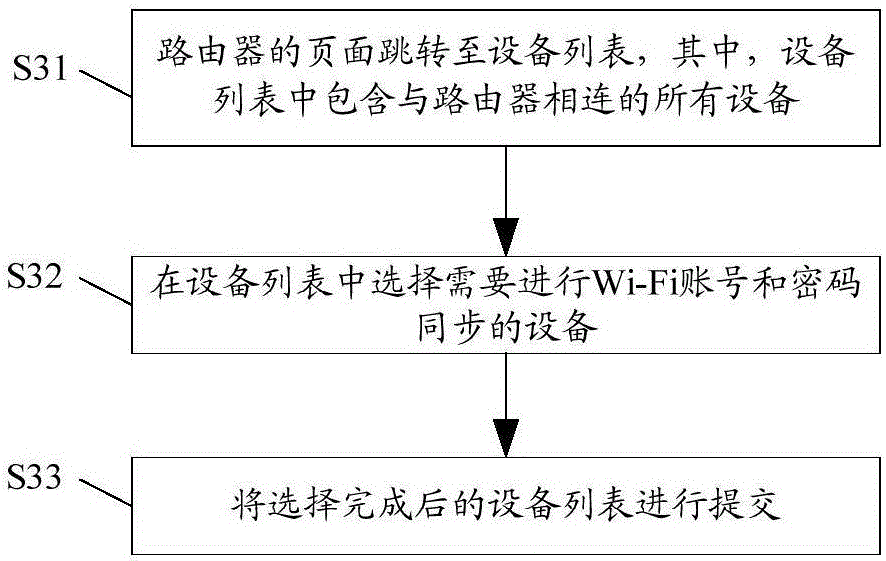
The invention provides a control method for realizing Wi-Fi (Wireless-Fidelity) network configuration, which relates to the technical field of wireless network access, and can reduce the tediousness and the complexity of equipment for performing network configuration again after a Wi-Fi account and a password of a router are updated. The control method comprises the steps of S1, updating a Wi-Fi account and a password of a router; S2, determining whether a user needs to synchronize the updated Wi-Fi account and the updated password to equipment connected with the router or not; if so, turning to a step S3, and if not, restarting the router, and performing authentication according to the updated Wi-Fi account and the updated password; S3, selecting equipment which requires to perform Wi-Fi account and password synchronization; and S4, synchronizing the updated Wi-Fi account and the updated password, by the router, to the selected equipment through a network transmission protocol, wherein the selected equipment logs in again according to the updated Wi-Fi account and the updated password. The control method provided by the invention is used for realizing Wi-Fi network configuration.
Owner:BULL GRP CO LTD
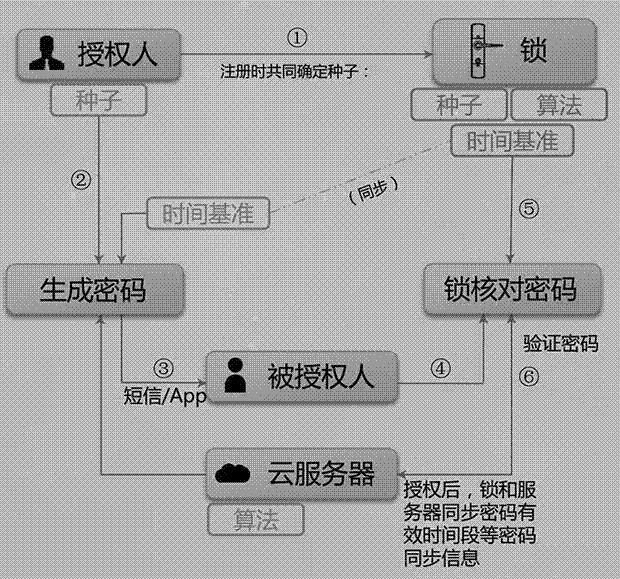
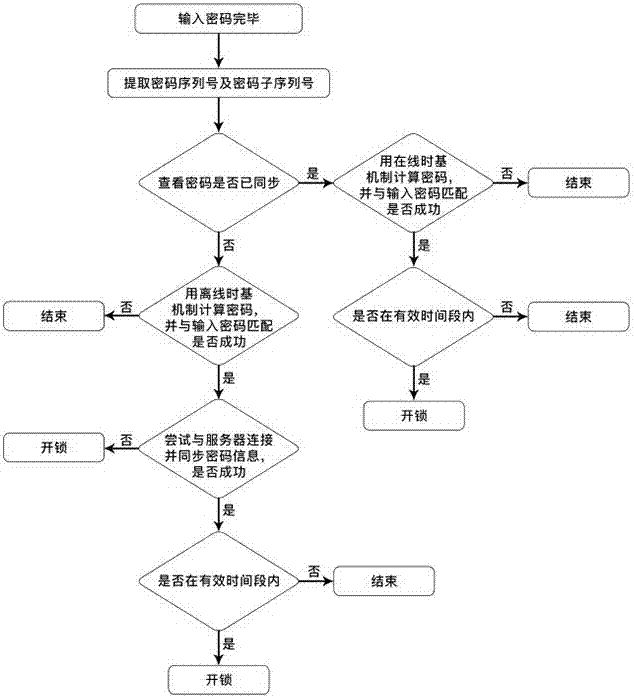
Password management method for intelligent lock
InactiveCN107221061AGet rid of excessive dependenceChange the effective time period at willIndividual entry/exit registersBuying/selling/leasing transactionsEffective timeWireless network
The invention relates to a password management method. Passwords are generated by computing seeds and a time reference through a password generation algorithm; a server records an effective time period of each password; the password management method comprises a password verification step; the password verification step comprises judgment within the effective time period, if an intelligent lock locally contains password synchronization information, whether the input password is within the effective time period or not is judged according to effective time period information of the password synchronization information; and if the intelligent lock does not locally contain the password synchronization information, whether the input password is within the effective time period or not is judged according to a preset treaty rule. According to the password management method, on one hand, excessive dependence on a network is avoided, and on the other hand, the server cannot directly modify the password or set the password. The potential safety hazard is avoided; password management is safe, reliable and flexible in use, and the dependence on a wireless network is reduced.
Owner:北京摇光智能科技有限公司
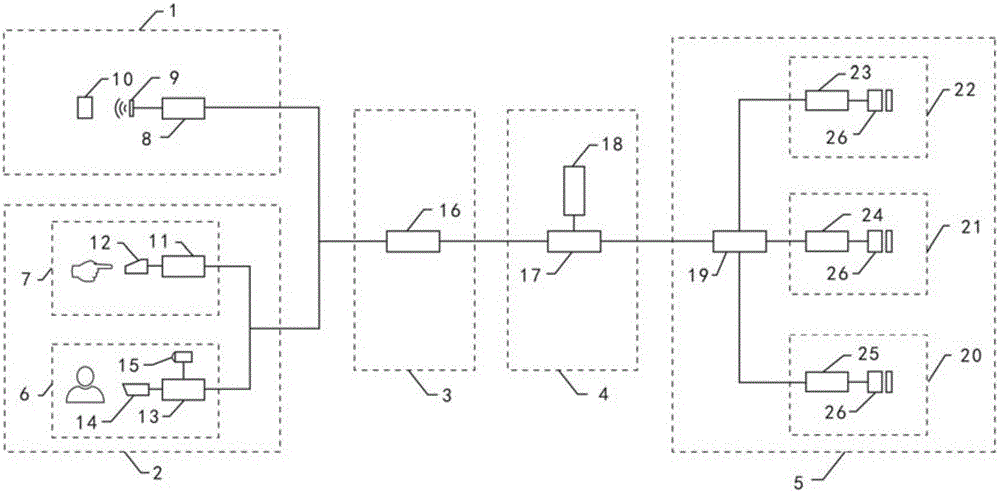
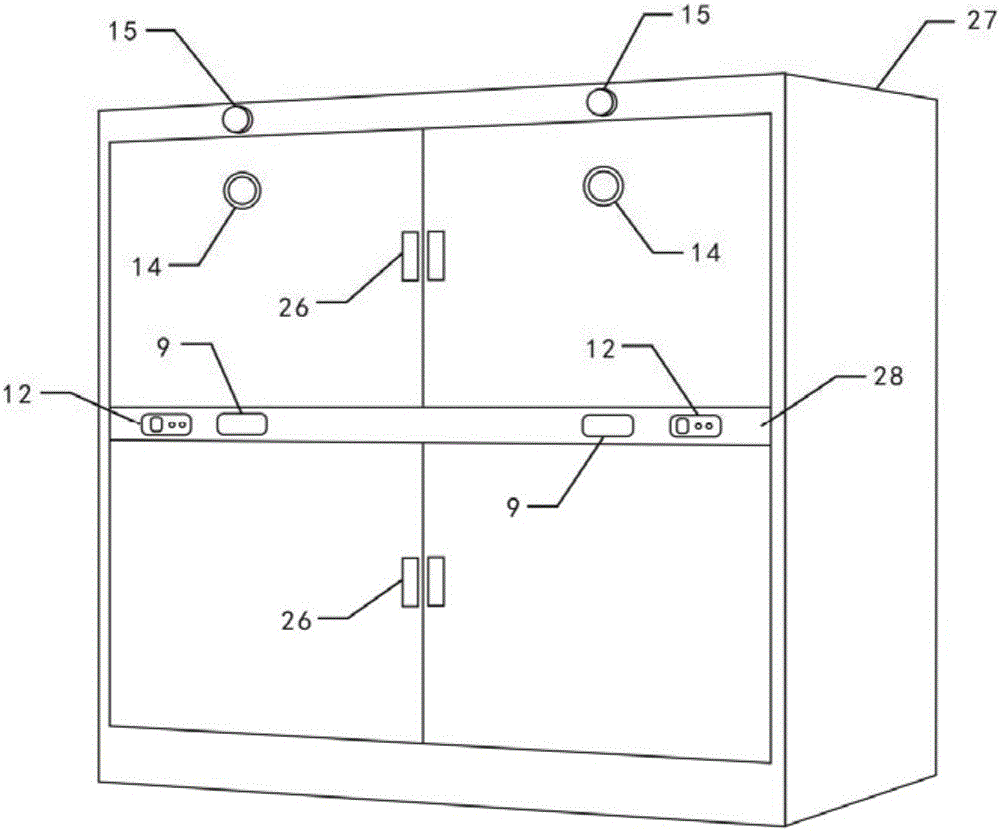
Examination paper secrecy system capable of synchronously controlling physical identification password and biological characteristic identification password and method thereof
InactiveCN105069340AIncrease the difficulty of being crackedIncrease the difficulty of crackingDigital data authenticationPasswordComputer science
The invention discloses an examination paper secrecy system capable of synchronously controlling a physical identification password and a biological characteristic identification password. The system is mainly composed of a physical identification password sampling module, a biological characteristic identification password sampling module, a synchronization identification processing module, a password data processing centre and a multi-mode dominant synchronization identification coded lock module. The system of the invention greatly increases the difficulty that the password is broken by using a united mode of physical recognition and biometric feature recognition, and a manner that one person simultaneously recognizes the password. Simultaneously, the system enables an illegal person who does not know and is not similar the operation program hard or not to open a secrecy cabinet by synchronizing the control program; then a leading synchronization recognition mode enable three leading passwords to disorder the original password after being matched with a reference code so as to improve the difficulty of breaking the password, and the password is carried by a user so as to used on site, so the password is hard to forge or to be stolen so as to enable the secret password of a examination paper secrecy cabinet to have stability and anti-falsification.
Owner:YULIN NORMAL UNIVERSITY
Method and apparatus for generating a cryptosync
InactiveCN101785272ASynchronising transmission/receiving encryption devicesSecurity arrangementComputer hardwareSegmentation and Reassembly
A method and apparatus for generating a cryptosync is disclosed that generates a cryptosync with the desired variability without the overhead in complexity and size of prior cryptosyncs. The cryptosync is generated from a combination of fields including fields relating to the segmentation and reassembly of the data packets at a transmitting terminal and a receiving terminal. The resultant cryptosync does not repeat during the use of a particular security key.
Owner:QUALCOMM INC
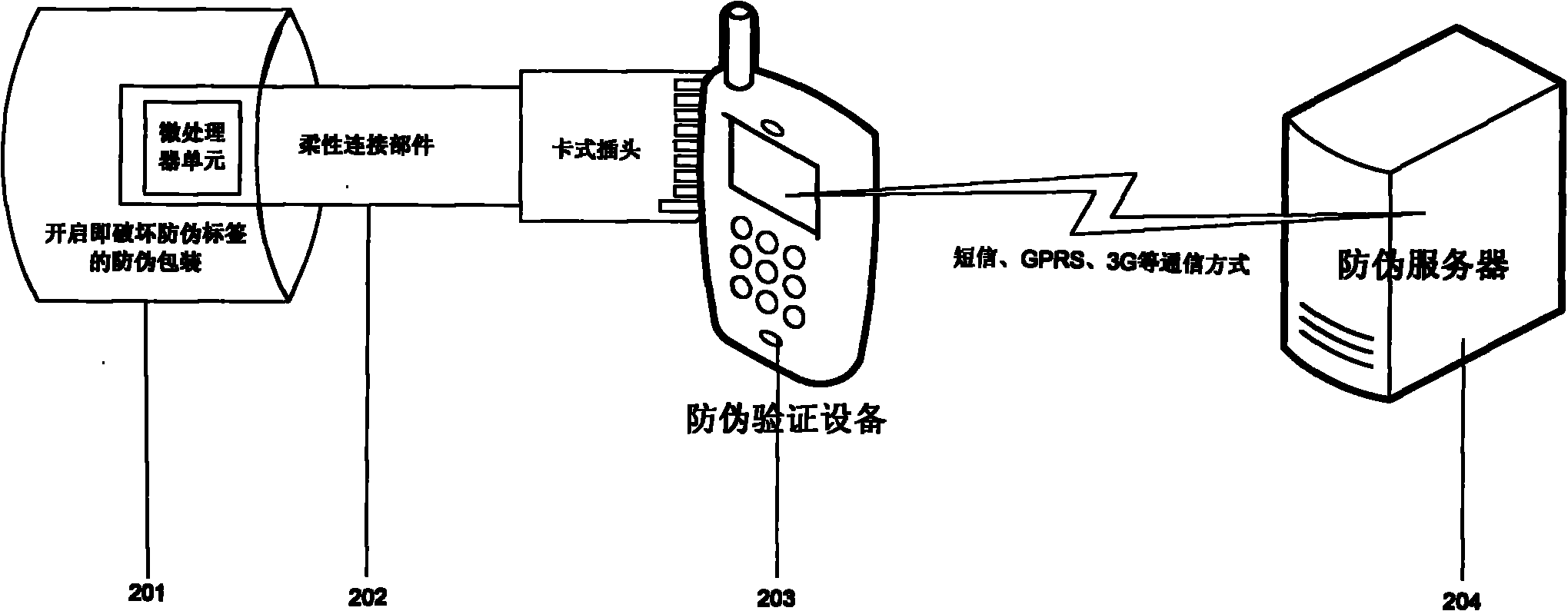
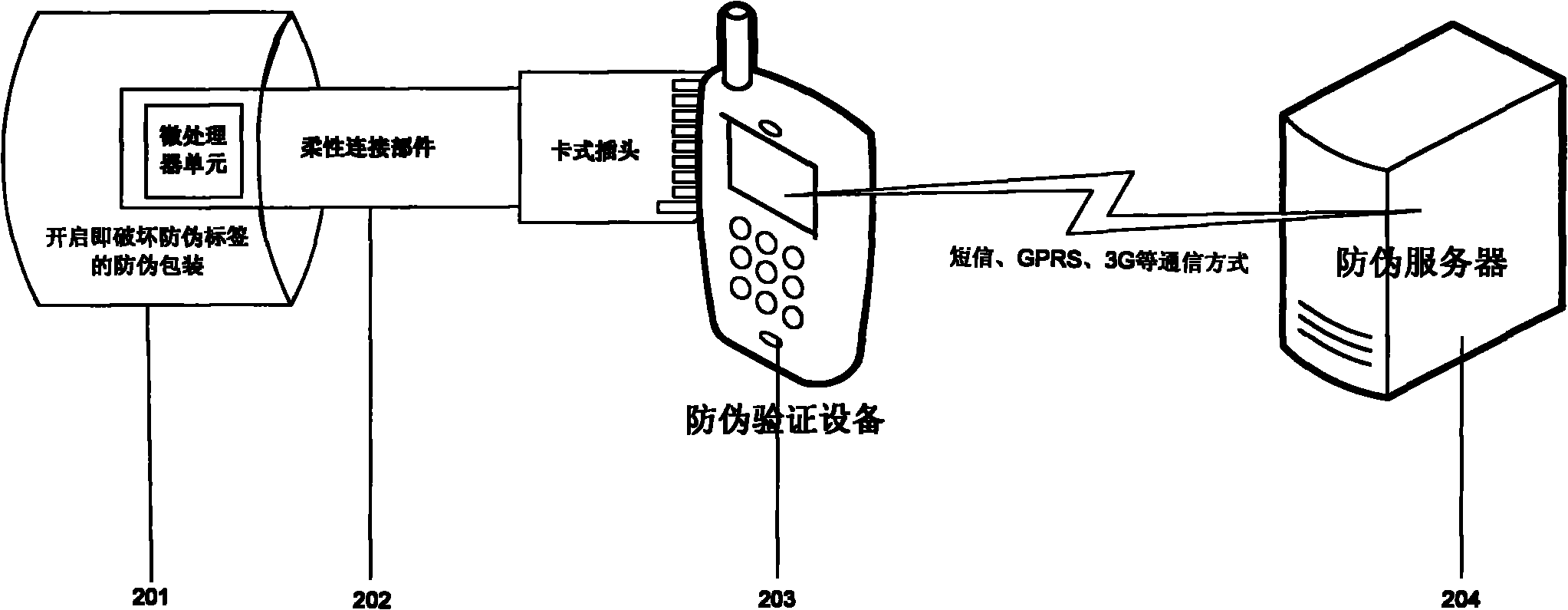
Interactive anti-counterfeiting authentication method and intelligent anti-counterfeiting label
InactiveCN102185832ALow costRealize verificationTransmissionRecord carriers used with machinesValidation methodsPassword
The invention discloses an interactive anti-counterfeiting authentication method which comprises an anti-counterfeiting label, anti-counterfeiting authentication equipment and an anti-counterfeiting server, wherein the anti-counterfeiting label comprises a microprocessor unit which can execute an anti-counterfeiting authentication logic; and the anti-counterfeiting label and the anti-counterfeiting server conduct interactive authentication based on passwords and a one-way encryption algorithm with the help of the anti-counterfeiting authentication equipment, and synchronize and update the passwords simultaneously. An intelligent anti-counterfeiting label which is applicable to the interactive anti-counterfeiting authentication method comprises the microprocessor unit, and the intelligent anti-counterfeiting label includes an anti-counterfeiting logic and adopts an easily destroyed package, is connected with a cassette plug which meets the standard of a storage card interface, defined by the SD (Secure Digital) association, through a flexible connecting part, is connected with the anti-counterfeiting authentication equipment through the cassette plug, is powered by the anti-counterfeiting authentication equipment, and interacts with the anti-counterfeiting authentication equipment through an analog expanded memory card or SDIO (secure digital input / output) equipment. The interactive anti-counterfeiting authentication method is applicable to the anti-counterfeiting identification field, has a reasonable cost compared with an anti-counterfeiting subject matter with certain value, has the advantages of usability, accuracy and safety, and supports multiple authentications.
Owner:赵晓宇
Double-password car alarm
The invention discloses a double-password car alarm which comprises a processor, a control signal receiver connected with the processor, and an alarm connected with the processor, wherein the double-password car alarm further comprises an eye mask recognizer and a dynamic password input device; the eye mask recognizer and the dynamic password input device are connected with the processor; the double-password car alarm also comprises a dynamic password generator connected with the processor and a dynamic password transmitter connected with the processor and used for transmitting a password to a mobile terminal; a synchronous driver is arranged between the eye mask recognizer and the dynamic password generator; the double-password car alarm further comprises an eye mask / dynamic password synchronization verifier connected with the processor and an image capturing device connected with the processor. The double-password car alarm is simple in structure and convenient to use, can effectively improve the use stability by adopting double alarm of eye mask and dynamic password, greatly improves the use safety, can effectively prevent artificial cracking, and improves the applicability and practicability.
Owner:张彬彬
Cluster group call security encryption synchronization method
InactiveCN103686616AImprove securityIncrease the duration of safe callsBroadcast service distributionSecurity arrangementPasswordSecret code
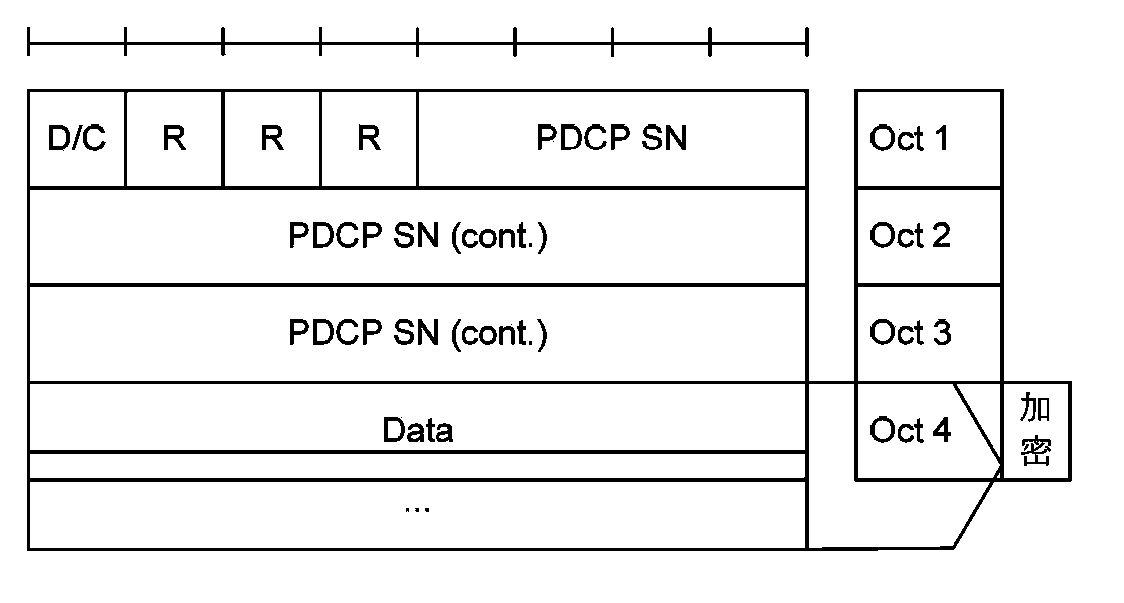
Provided is a cluster group call security encryption synchronization method. The method comprises that: an N is confirmed via cluster group call communication limit time; length of an SN is extended for N bits in a packet data convergence protocol PDCP layer protocol data unit PDU transmitting cluster group call information; and password synchronization is performed in encryption and / or decryption by a synchronization code COUNT comprising the extended SN via adopting a stream password algorithm. After application of the embodiment of the invention, security communication limit time is increased and security of a cluster group call is further enhanced.
Owner:POTEVIO INFORMATION TECH
Dynamic password synchronization method
InactiveCN103605579AAutomatically sync common passwordsProgram synchronisationPasswordElectronic communication
The invention provides a dynamic password synchronization method which is applied amongst multiple electronic communication devices to synchronize a common password possessed by each electronic communication device. Each two electronic communication devices share at least one communication network which is mutually communicated. The method includes: setting a synchronization sequence of all electronic communication devices; when one the password of one of the electronic communication devices changes, transmitting the password sequentially through the communication network of each two electronic communication devices according to the synchronization sequence, and synchronously updating the password of each electronic communication device. The method allows common passwords in multiple personal electronic devices to be automatically synchronized.
Owner:INVENTECSHANGHAI TECH +2
Method and Apparatus for Securely Synchronizing Password Systems
InactiveUS20120072977A1Digital data processing detailsMultiple digital computer combinationsPasswordNetizen
Owner:RPX CLEARINGHOUSE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com