Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
41 results about "N-Hash" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In cryptography, N-Hash is a cryptographic hash function based on the FEAL round function, and is now considered insecure. It was proposed in 1990 by Miyaguchi et al.; weaknesses were published the following year.
System and method for caching hashes for co-located data in a deduplication data store
ActiveUS20130339319A1Digital data information retrievalError detection/correctionData memoryData storing
Systems and methods are provided for caching hashes for deduplicated data. A request to read data from the deduplication data store is received. A persist header stored in a deduplication data store is identified in a first hash structure that is not stored in memory of the computing device. The persist header comprises a set of hashes that includes a hash that is indicative of the data the computing device requested to read. Each hash in the set of hashes represents data stored in the deduplication data store after the persist header that is co-located with other data represented by the remaining hashes in the set of hashes. The set of hashes is cached in a second hash structure stored in the memory, whereby the computing device can identify the additional data using the second hash structure if the additional data is represented by the persist header.
Owner:GOOGLE LLC
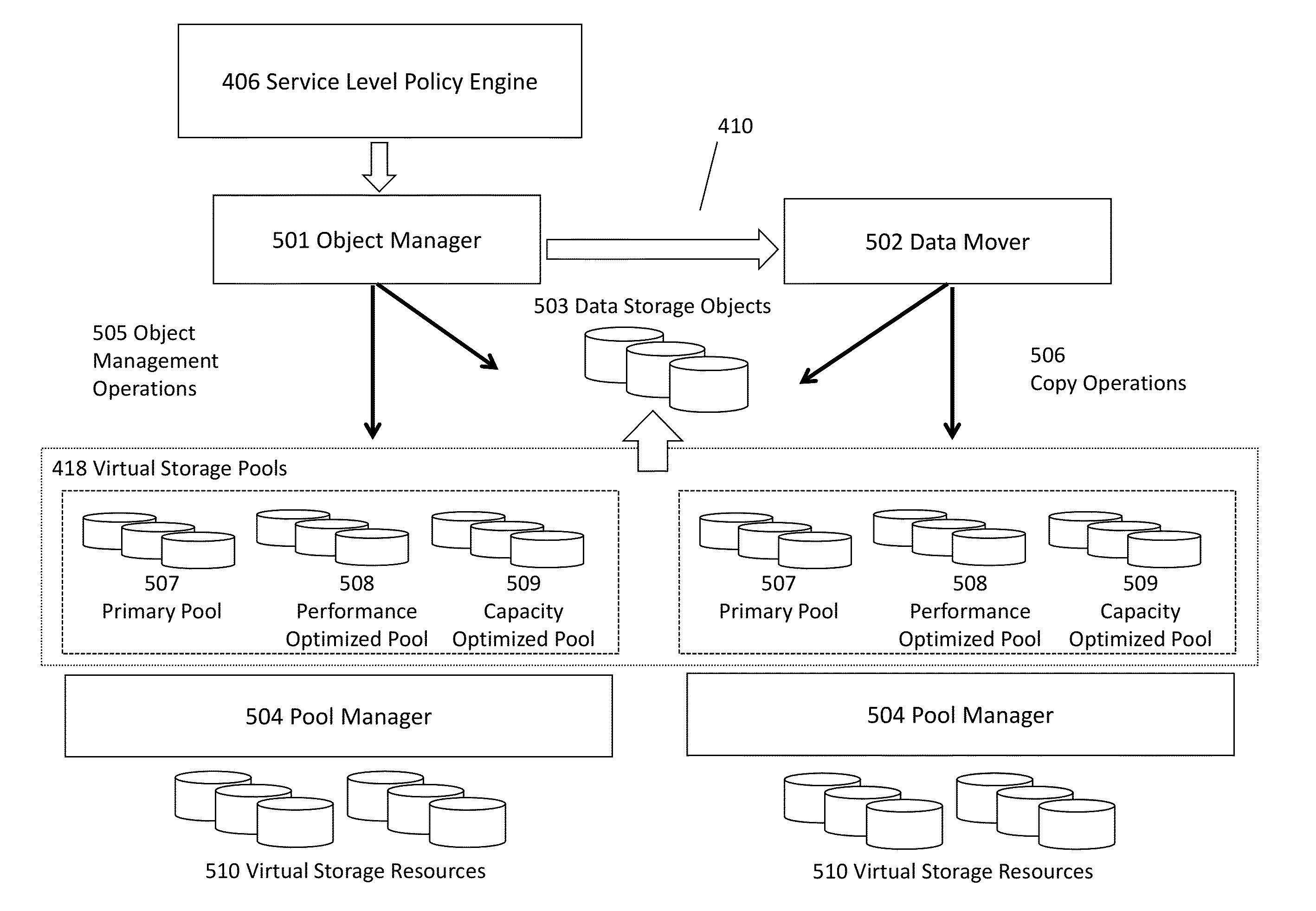
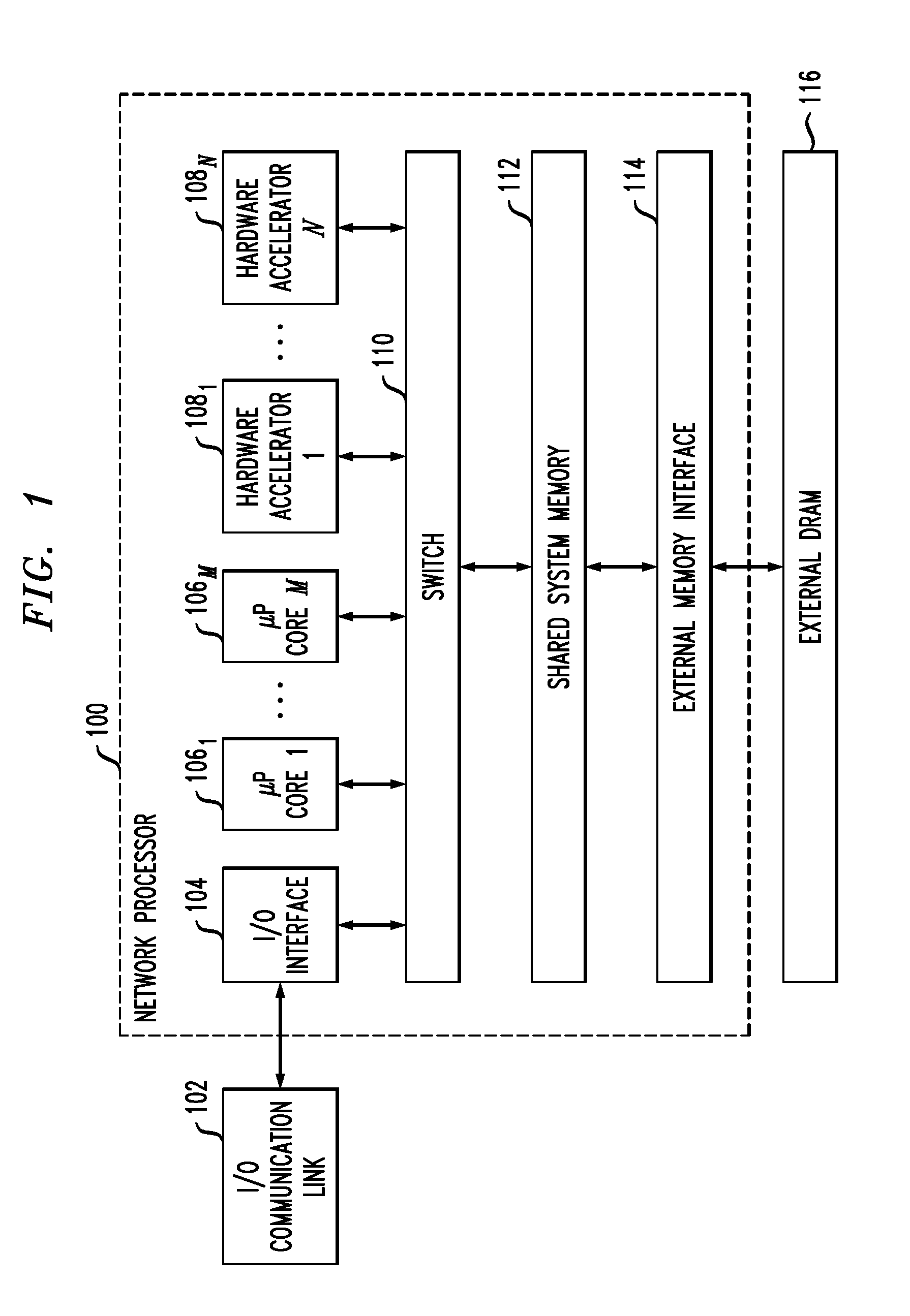
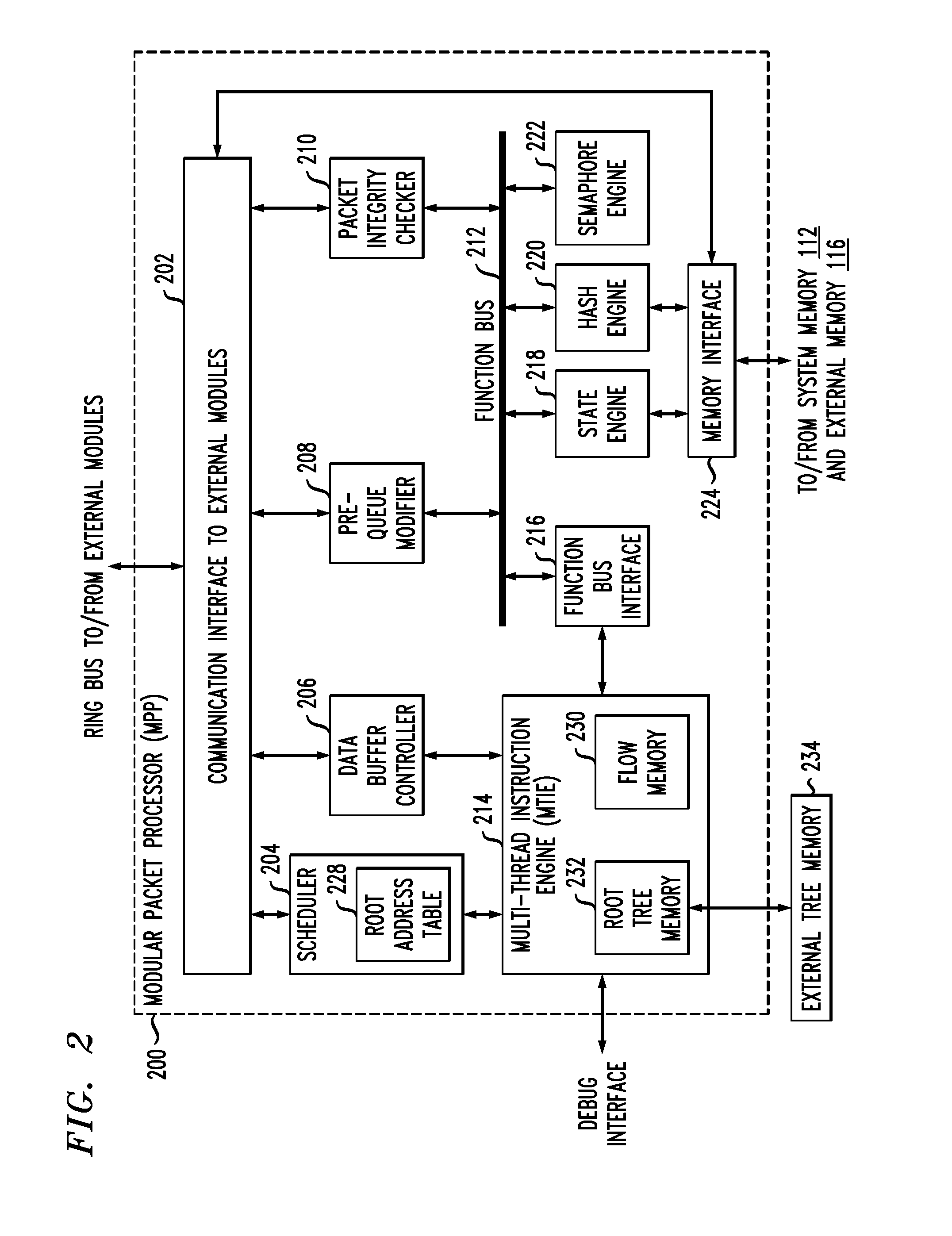
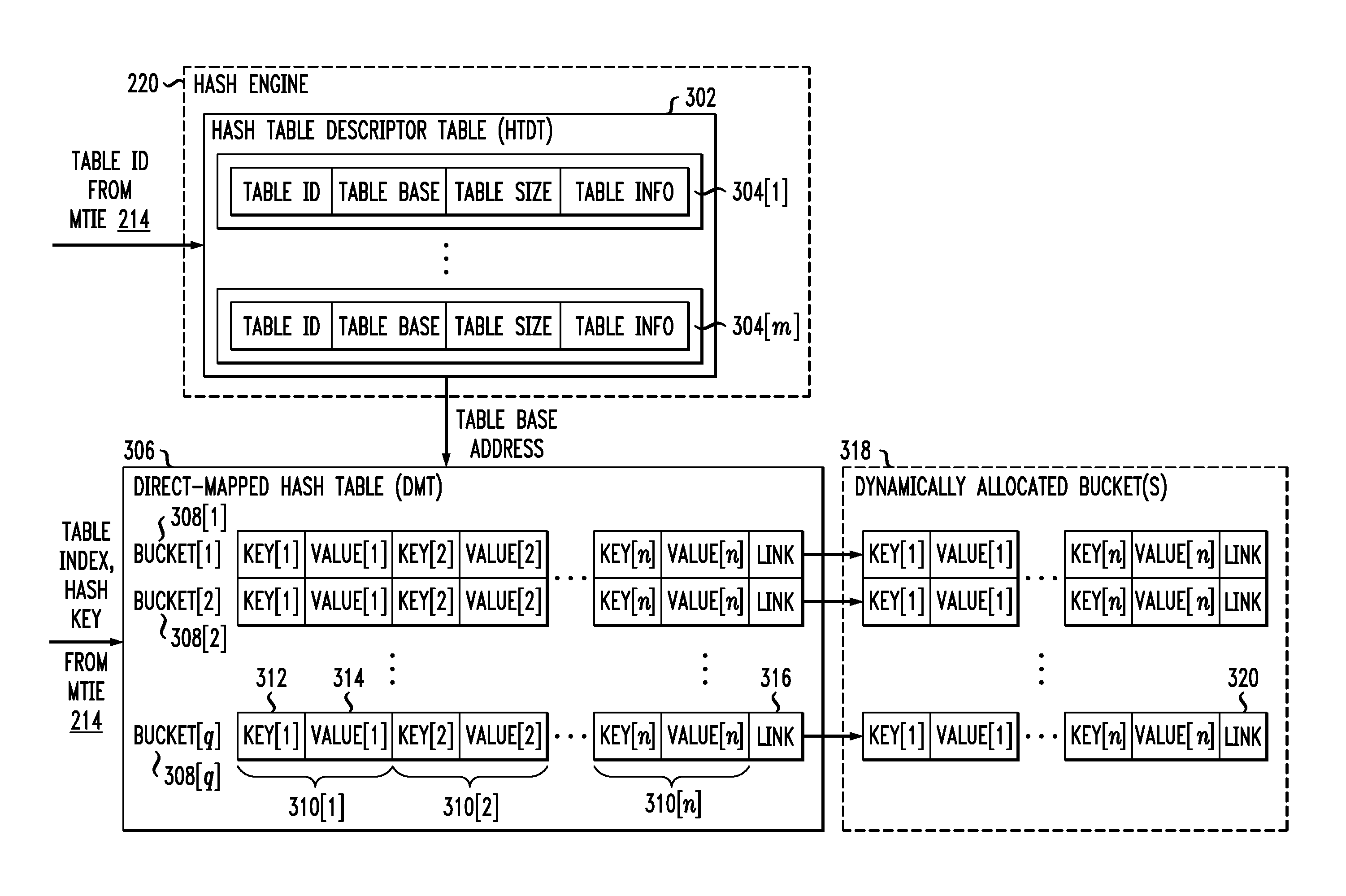
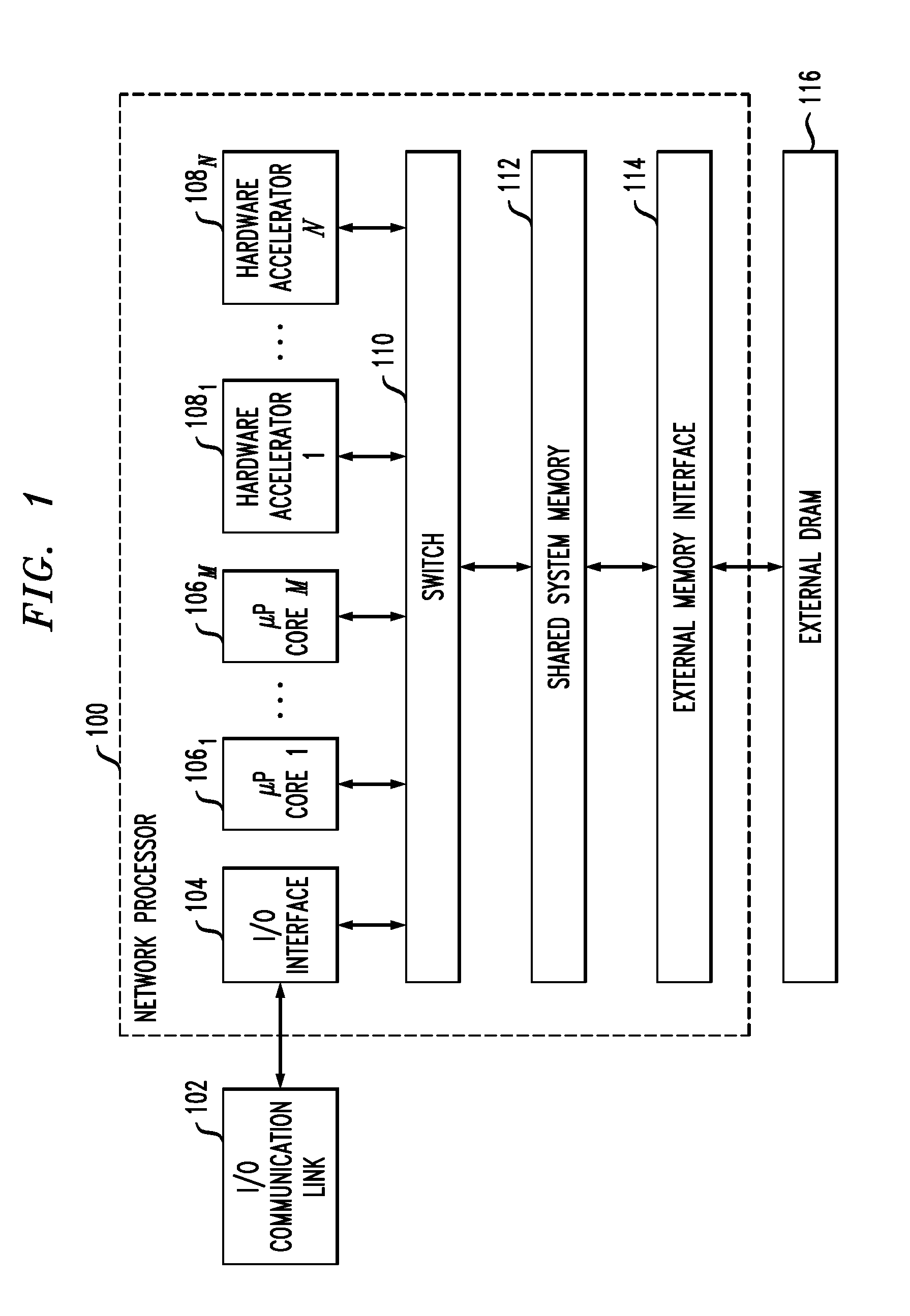
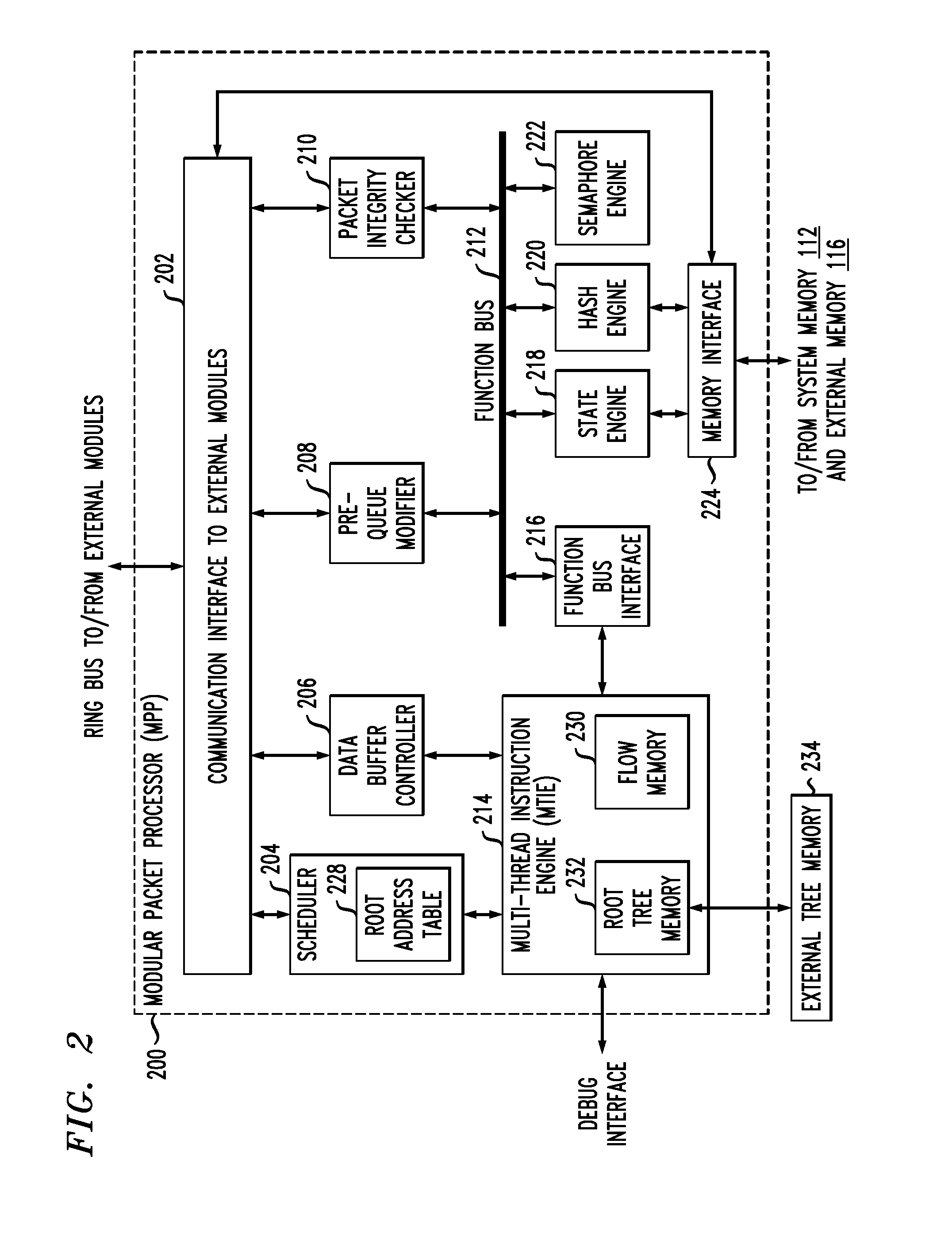
Hash processing in a network communications processor architecture
InactiveUS20110225391A1Well formedDigital data processing detailsMemory adressing/allocation/relocationNetwork communicationHash table
Described embodiments provide a hash processor for a system having multiple processing modules and a shared memory. The hash processor includes a descriptor table with N entries, each entry corresponding to a hash table of the hash processor. A direct mapped table in the shared memory includes at least one memory block including N hash buckets. The direct mapped table includes a predetermined number of hash buckets for each hash table. Each hash bucket includes one or more hash key and value pairs, and a link value. Memory blocks in the shared memory include dynamic hash buckets available for allocation to a hash table. A dynamic hash bucket is allocated to a hash table when the hash buckets in the direct mapped table are filled beyond a threshold. The link value in the hash bucket is set to the address of the dynamic hash bucket allocated to the hash table.
Owner:INTEL CORP
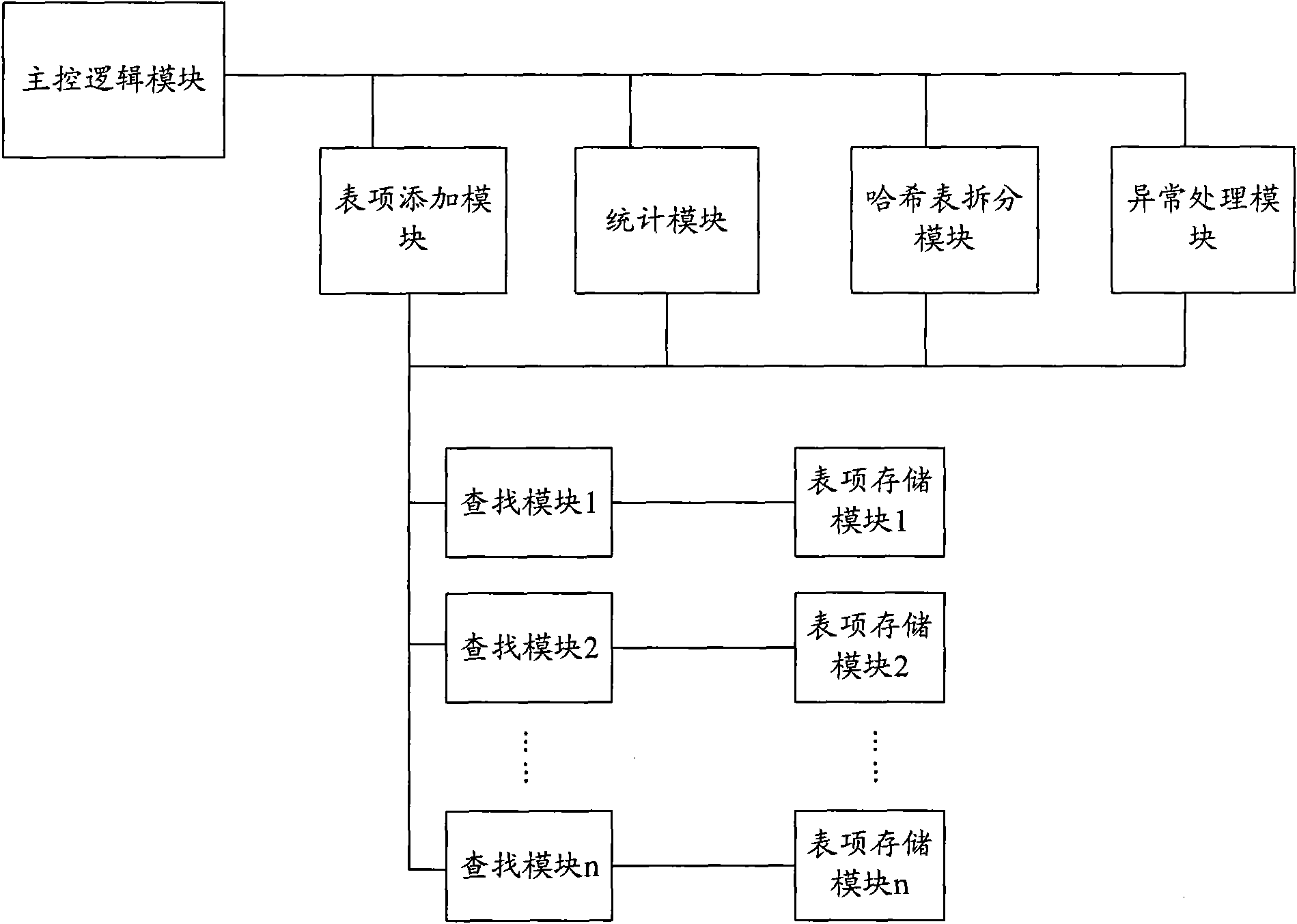
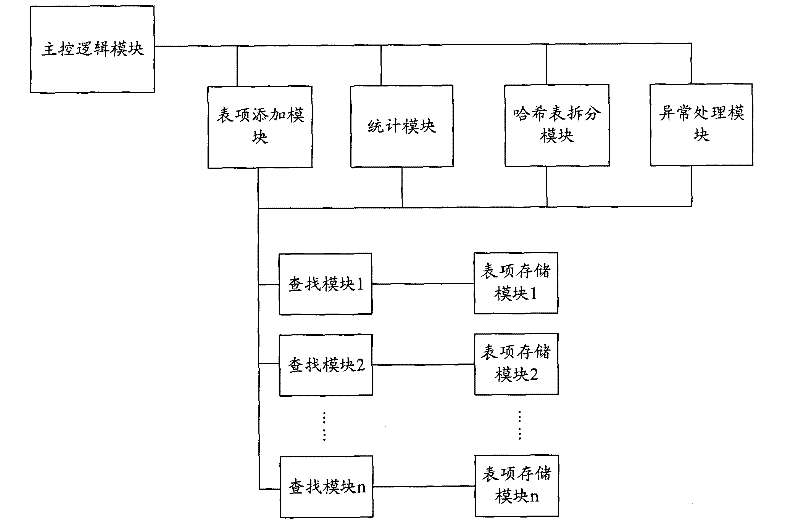
Apparatus and method for hash table storage, searching
ActiveCN101604337ASmall lookup time costHigh Tablespace UtilizationDigital data information retrievalSpecial data processing applicationsTheoretical computer scienceHash table
The invention discloses an apparatus and a method for hash table item storage, searching, which aim to solve the problem of hardness in balancing between time needed for table searching and table capacity in hash table storage structure in the prior art. According to the invention a large hash table storage space is divided into a plurality of hash sub-table storage spaces, each of which corresponds to N hash functions. When an item is stored, a hash value is computed using hash function corresponding to each hash sub-table sequentially, an empty position is found in the hash sub-table for storage of the item; when an item is searched, a search among all hash sub-tables is executed for enhancing speed of searching. The invention effectively solves the problem of hardness in balancing between time needed for table searching and table capacity in hash table storage structure in the prior art, implements storage of all items using ultimately low searching time and ultimately high table utilization without residual items.
Owner:ZTE CORP
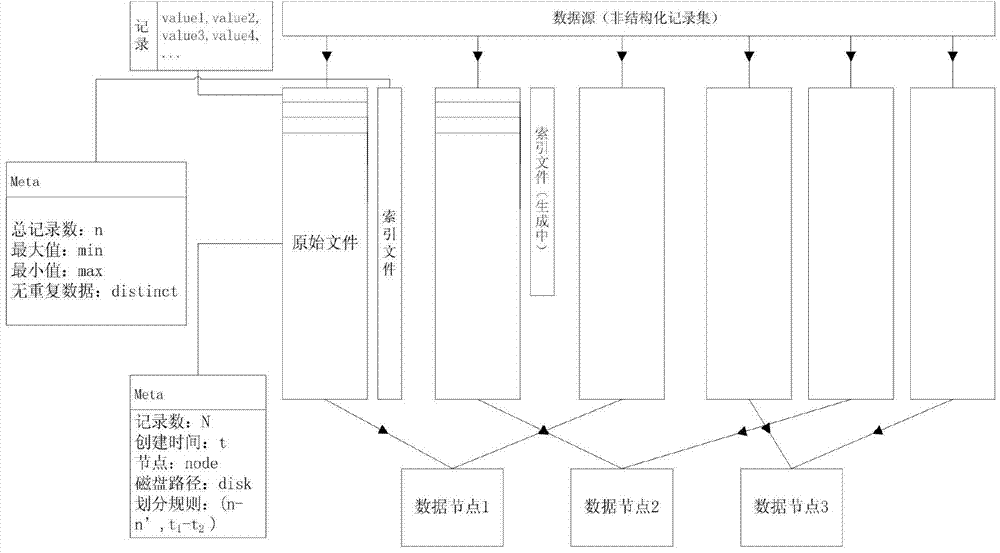
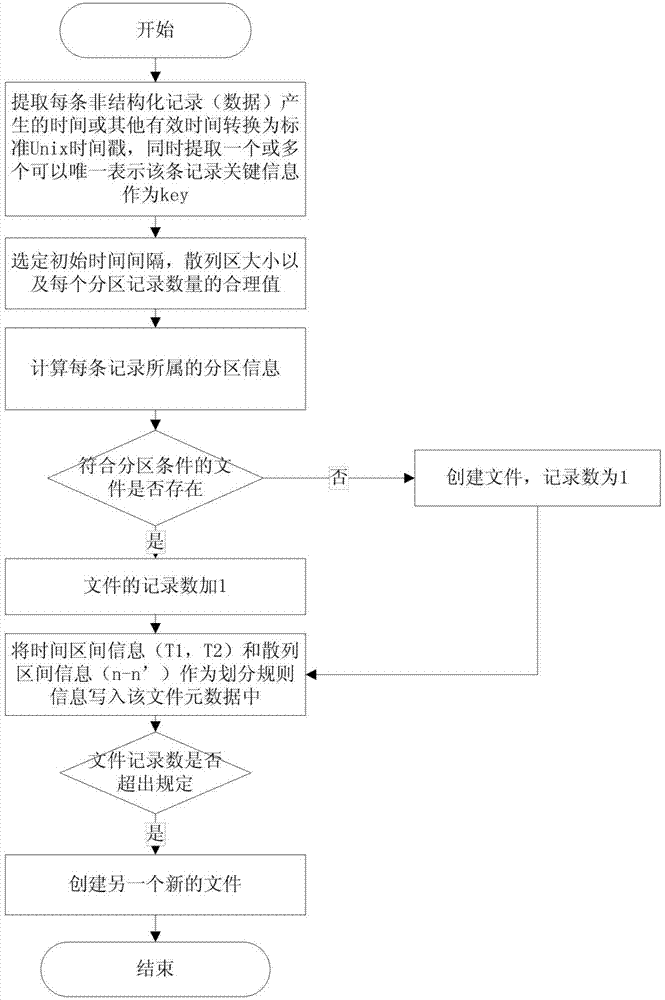
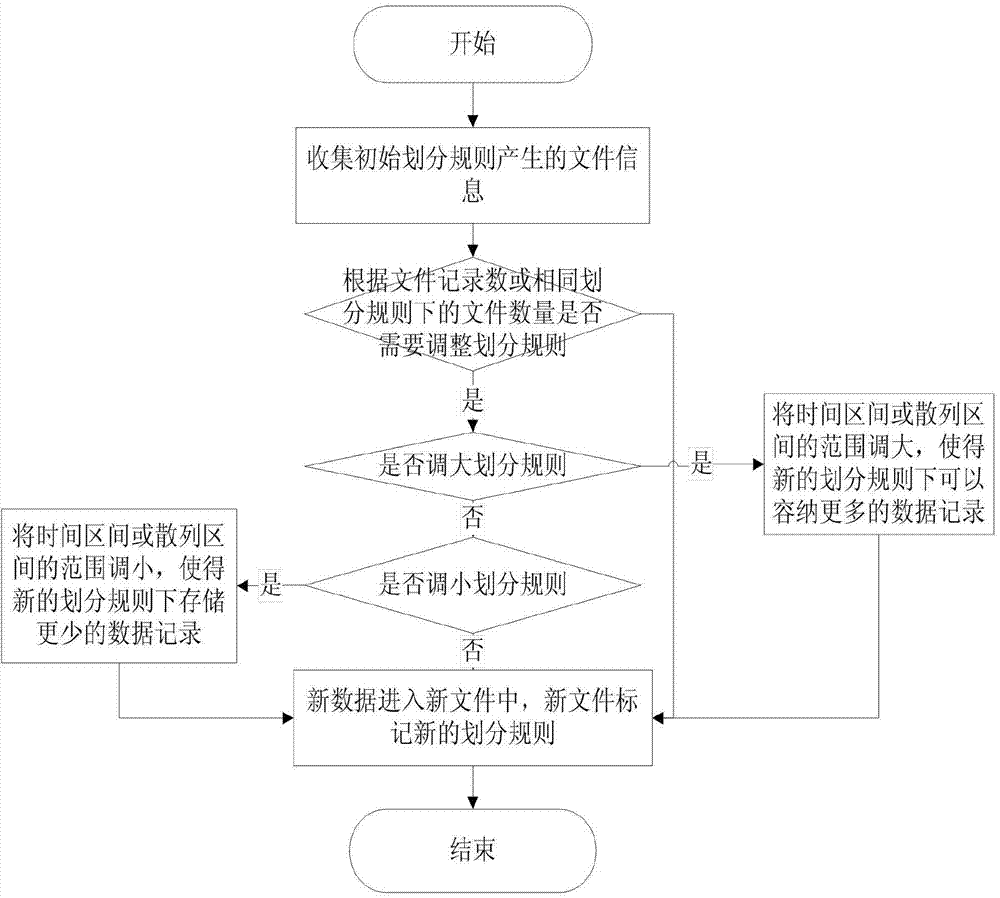
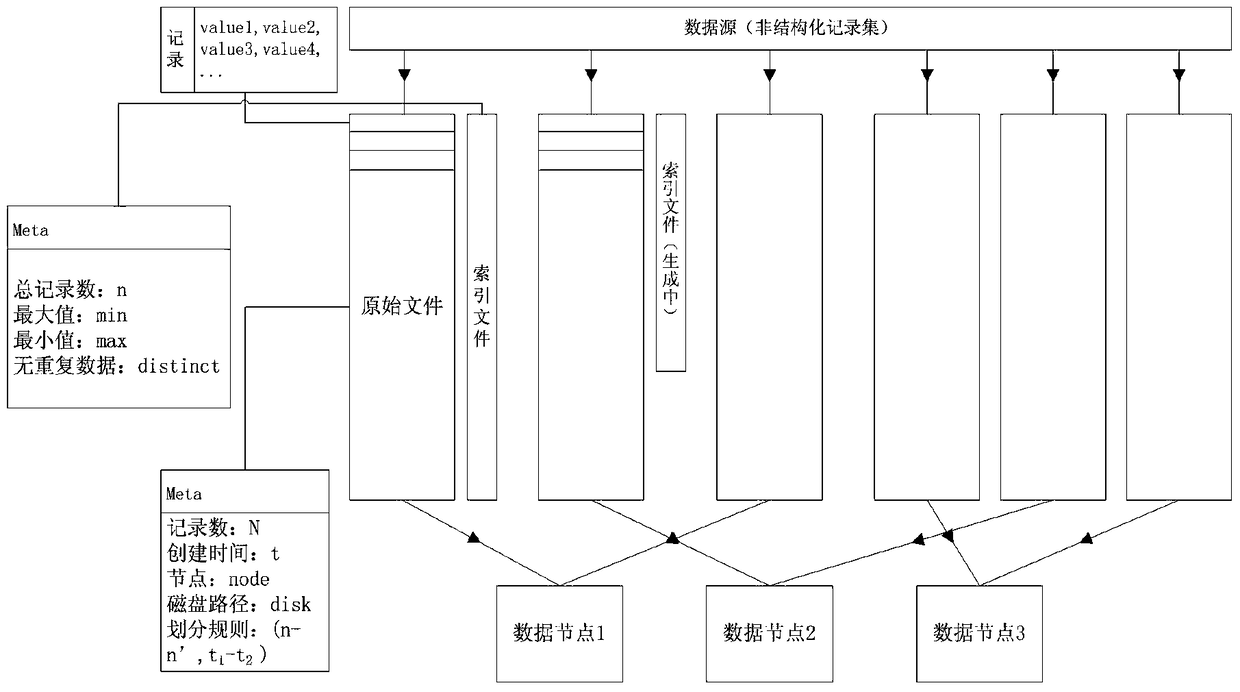
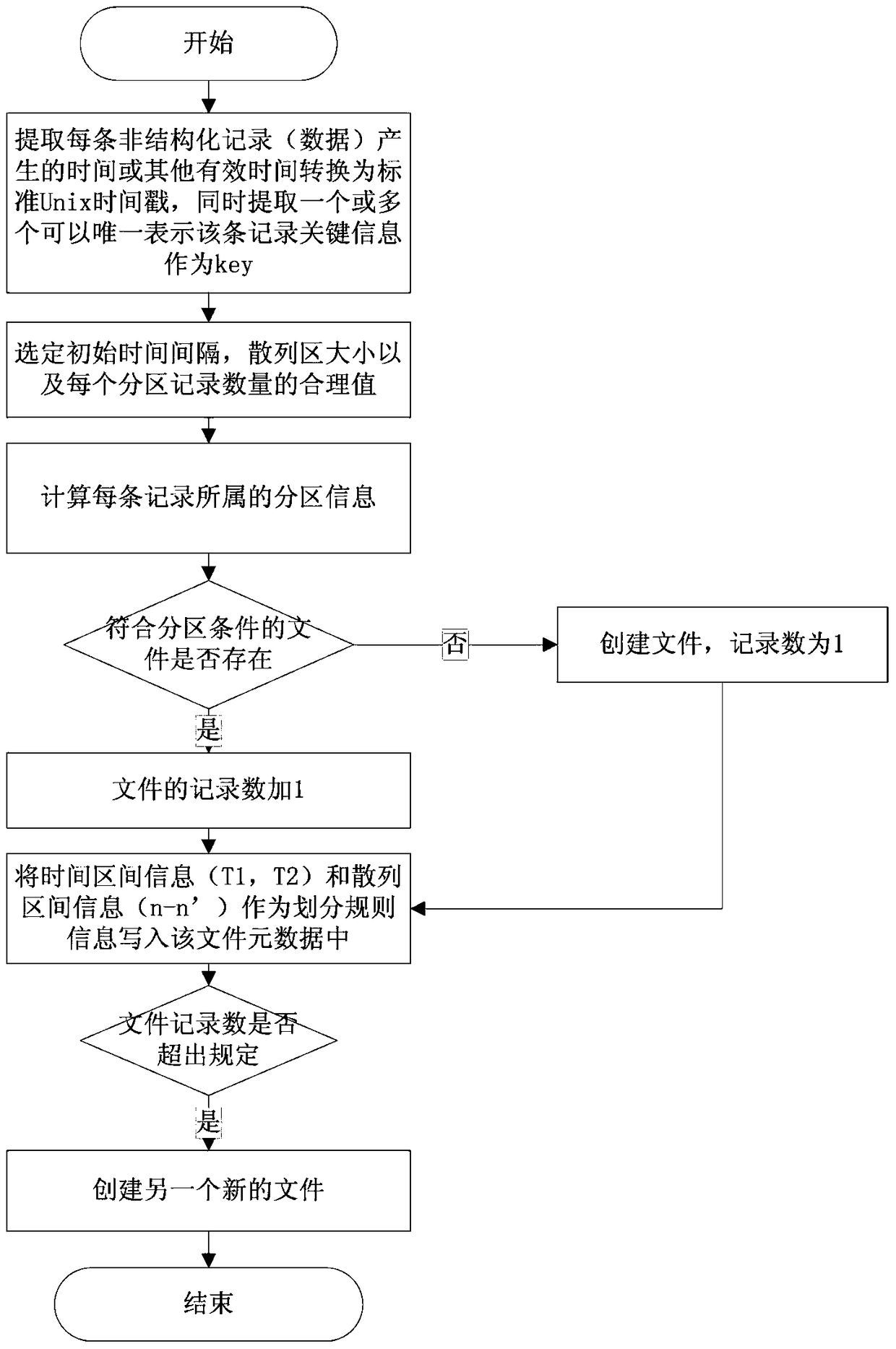
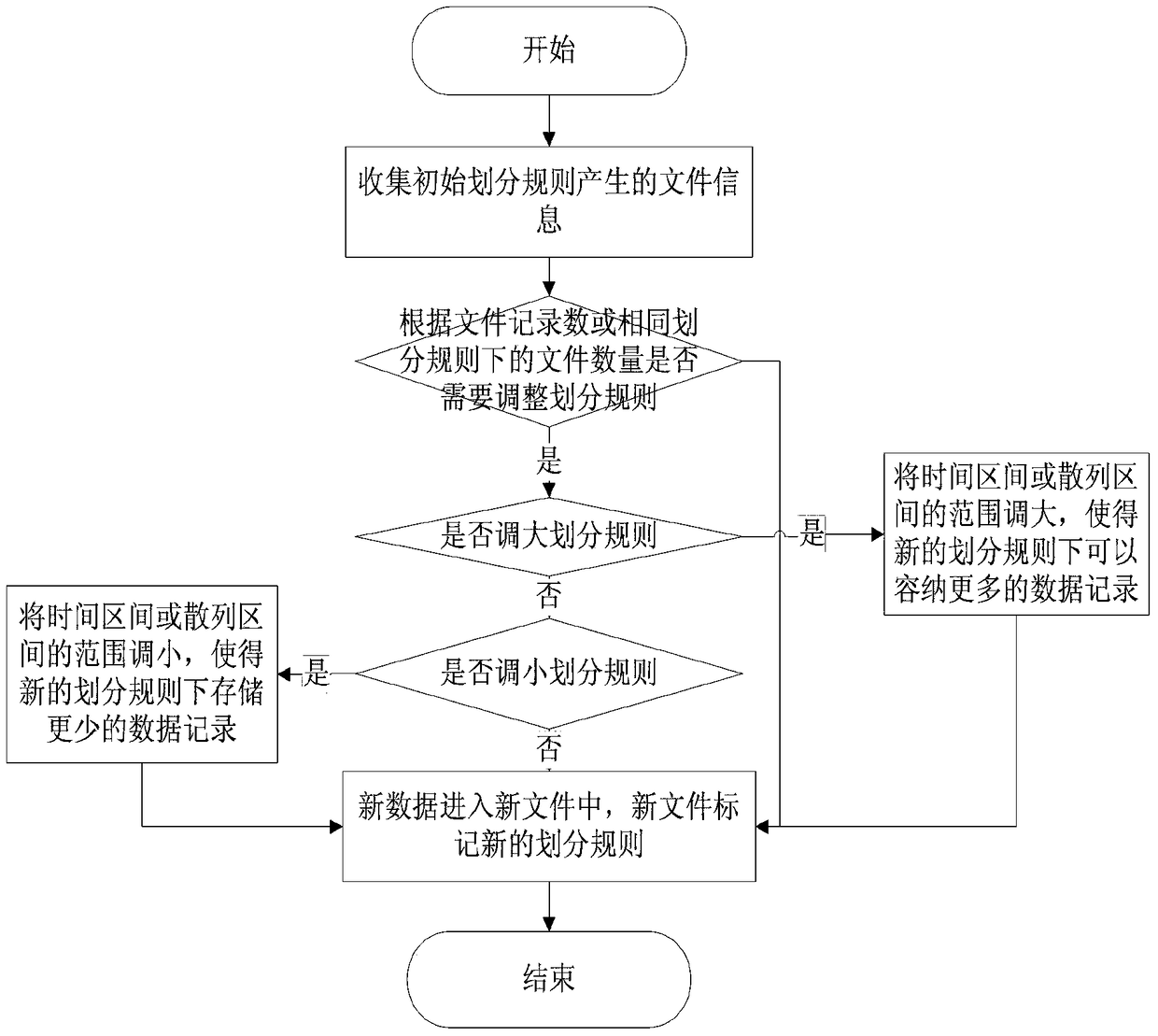
Data storage method for mass unstructured data
ActiveCN104731864AImprove retrieval efficiencySolve extraction puzzlesSpecial data processing applicationsData retrievalUnstructured data
The invention discloses a data storage method for mass unstructured data. The method comprises the steps that firstly, a time interval T is set, a data storage cluster is divided into a plurality of zones, records obtained at the same time interval T are stored in the same zone, and meanwhile each zone is divided into n hash zones; secondly, for each unstructured record, the generated time t of the unstructured record and one or more key information key solely expressing the unstructured record are extracted; thirdly, according to the time t of each record, the zone where the records are stored is determined, and the corresponding hash zone values of the records in the zones are calculated according to the key information of the record; fourthly, the records which are in the same time interval and are the same in hash zone value are written in the same file F according to the calculation result in the step three, the number of the records in the file F is counted, and if the number of the records is larger than the set threshold value K, another file is established in a current hash zone for storage. According to the storage method, the data retrieval efficiency can be greatly improved.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT +1
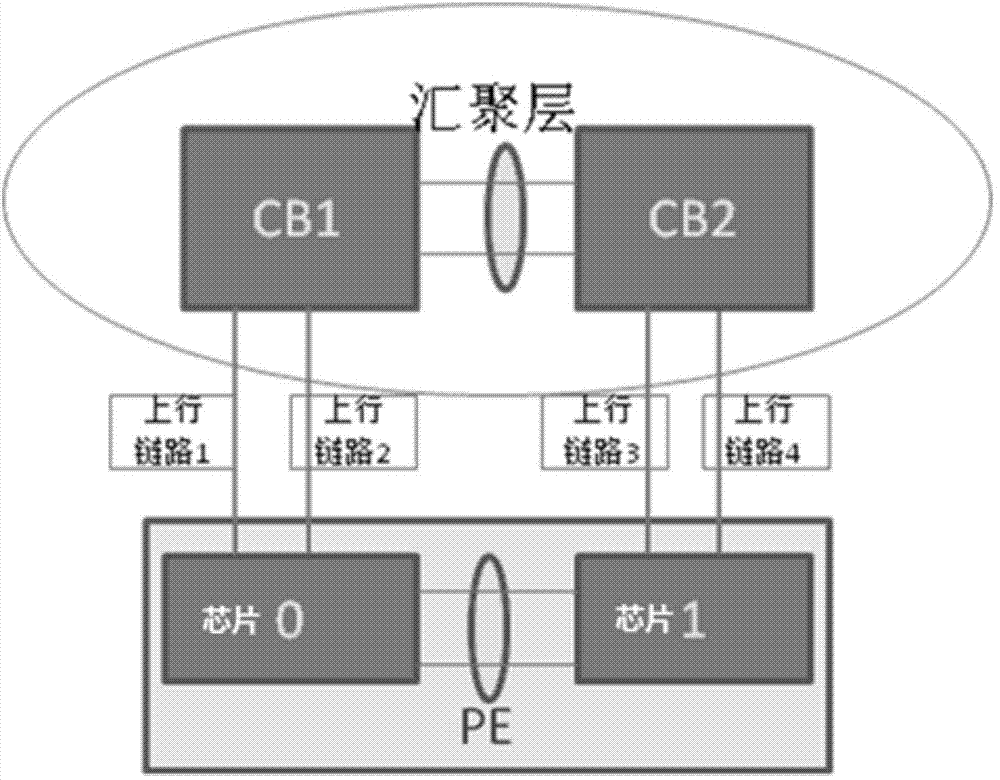
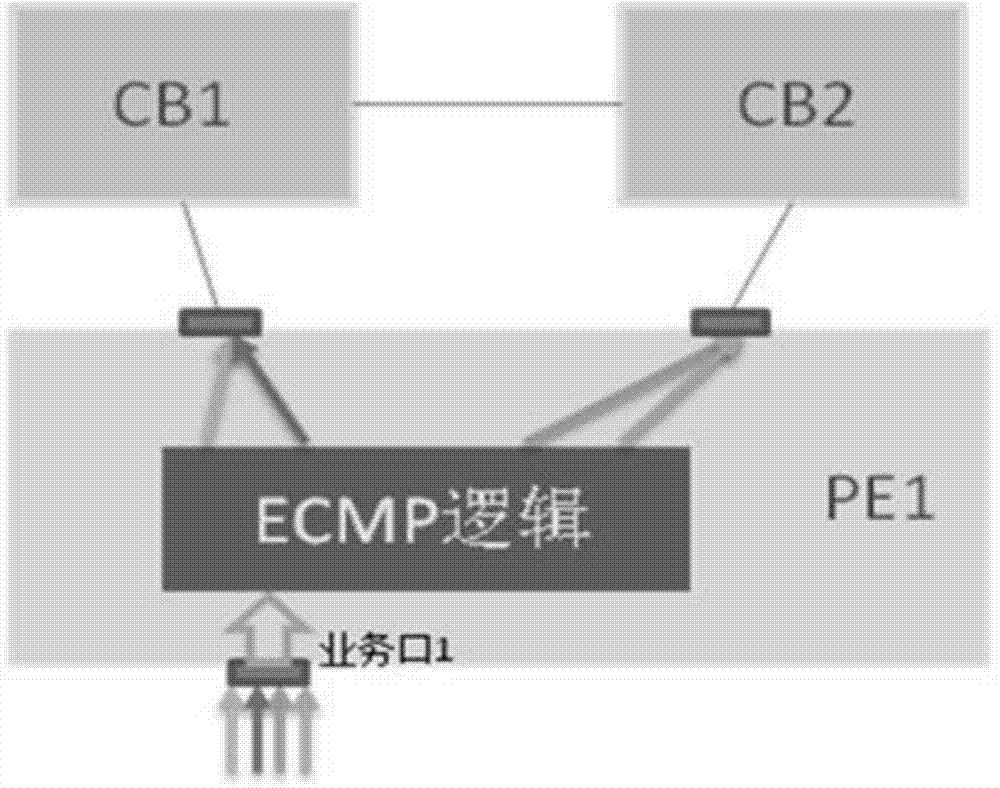
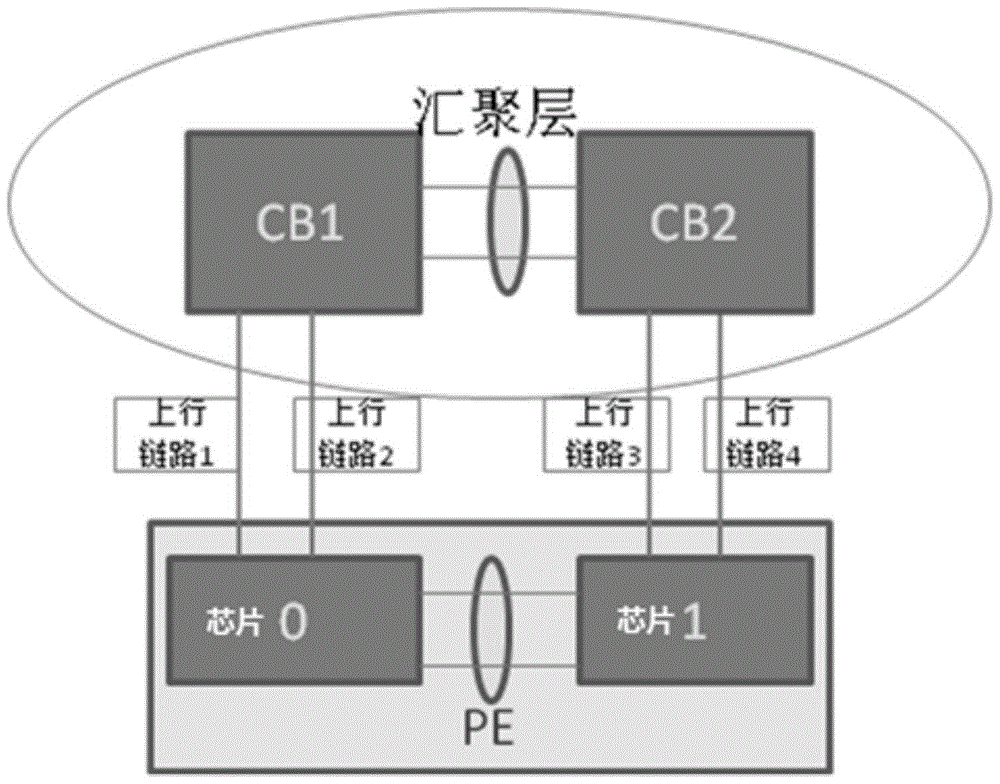
PE traffic scheduling method and device
The invention provides a PE traffic scheduling method and device which are applied to PE equipment of a VCF system. The method comprises the following steps that a Trunk a and a Trunk b are established for a first exchange chip, wherein the Trunk a comprises N Hash positions, and the N Hash positions are allocated to a port of G1 and a port of G2 respectively; the Trunk b comprises N Hash positions, and the N Hash positions are respectively allocated to the port of G2; the Trunk in the port of the G1 is marked as a, and the Trunk in the port of G2 is marked as b; a second exchange chip is processed in the same way; local forwarding items of uplink traffic on PE are issued to the first exchange chip and the second exchange chip, wherein outlets of the local forwarding items are uplink ports of the exchange chips; at least one Hash position in the corresponding Trunk is allocated again according to variation of the uplink state of an uplink port correspondingly. Compared with the prior art, uplink traffic can be more evenly distributed to all the uplinks of the two exchange chips.
Owner:NEW H3C TECH CO LTD
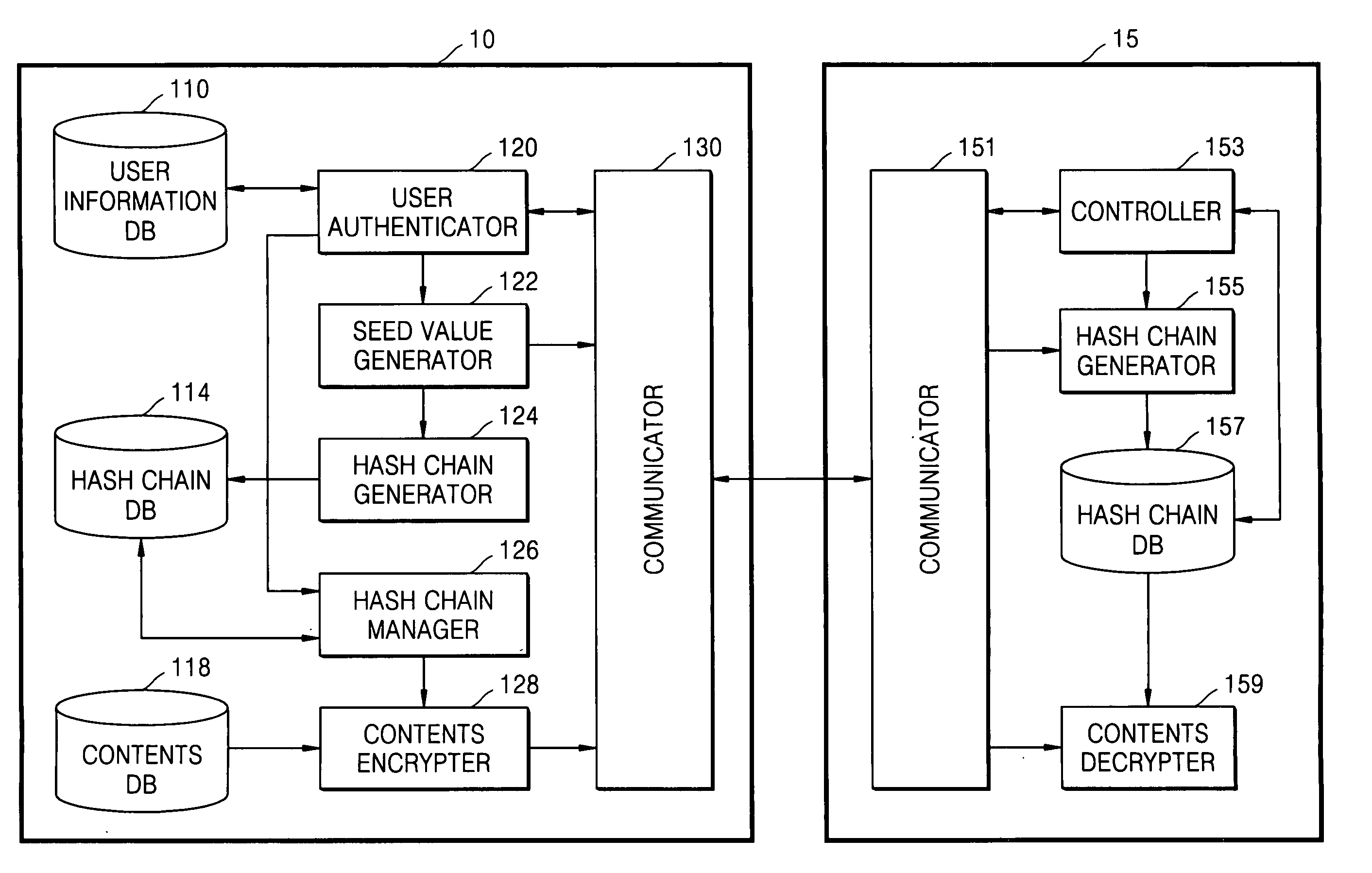
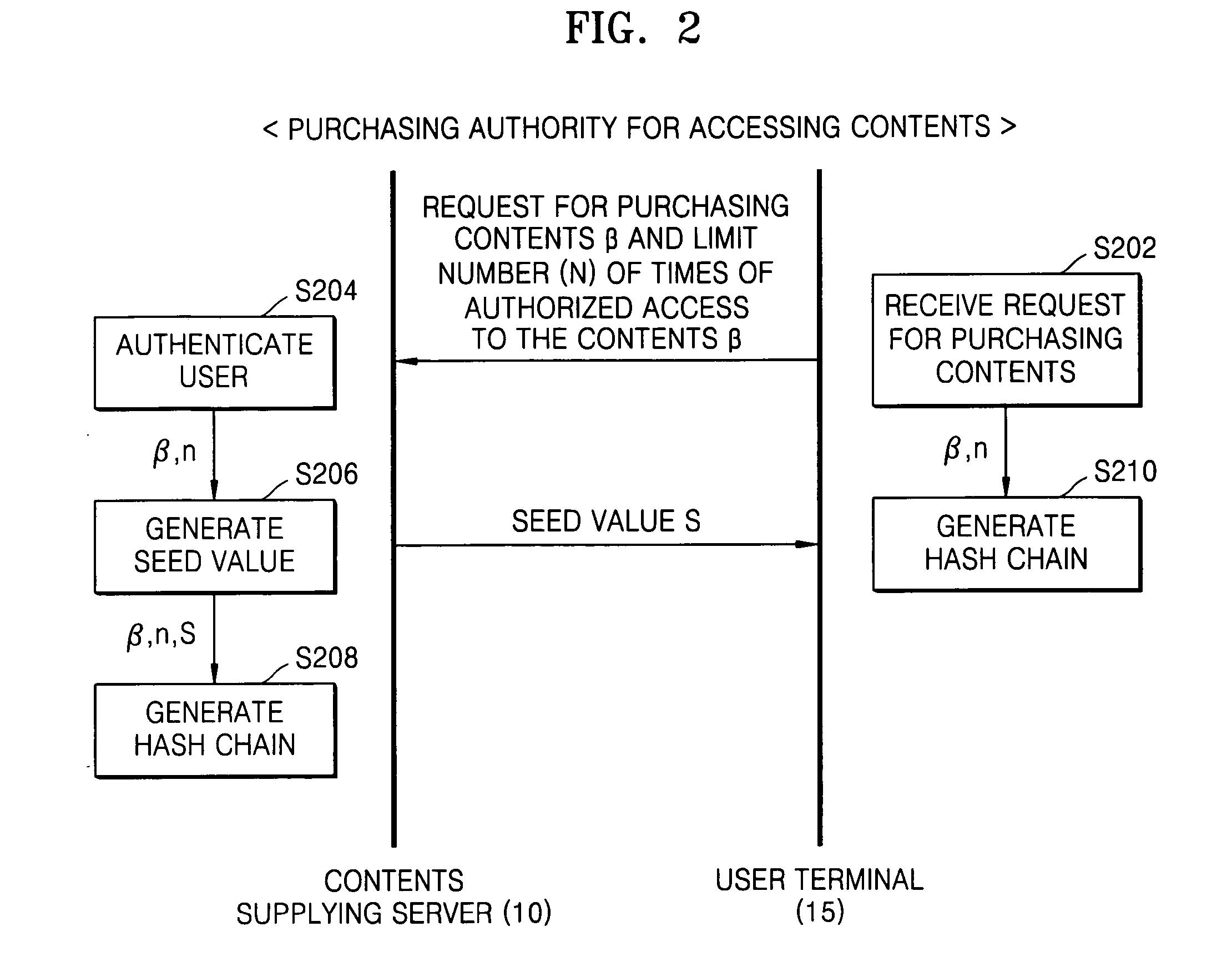
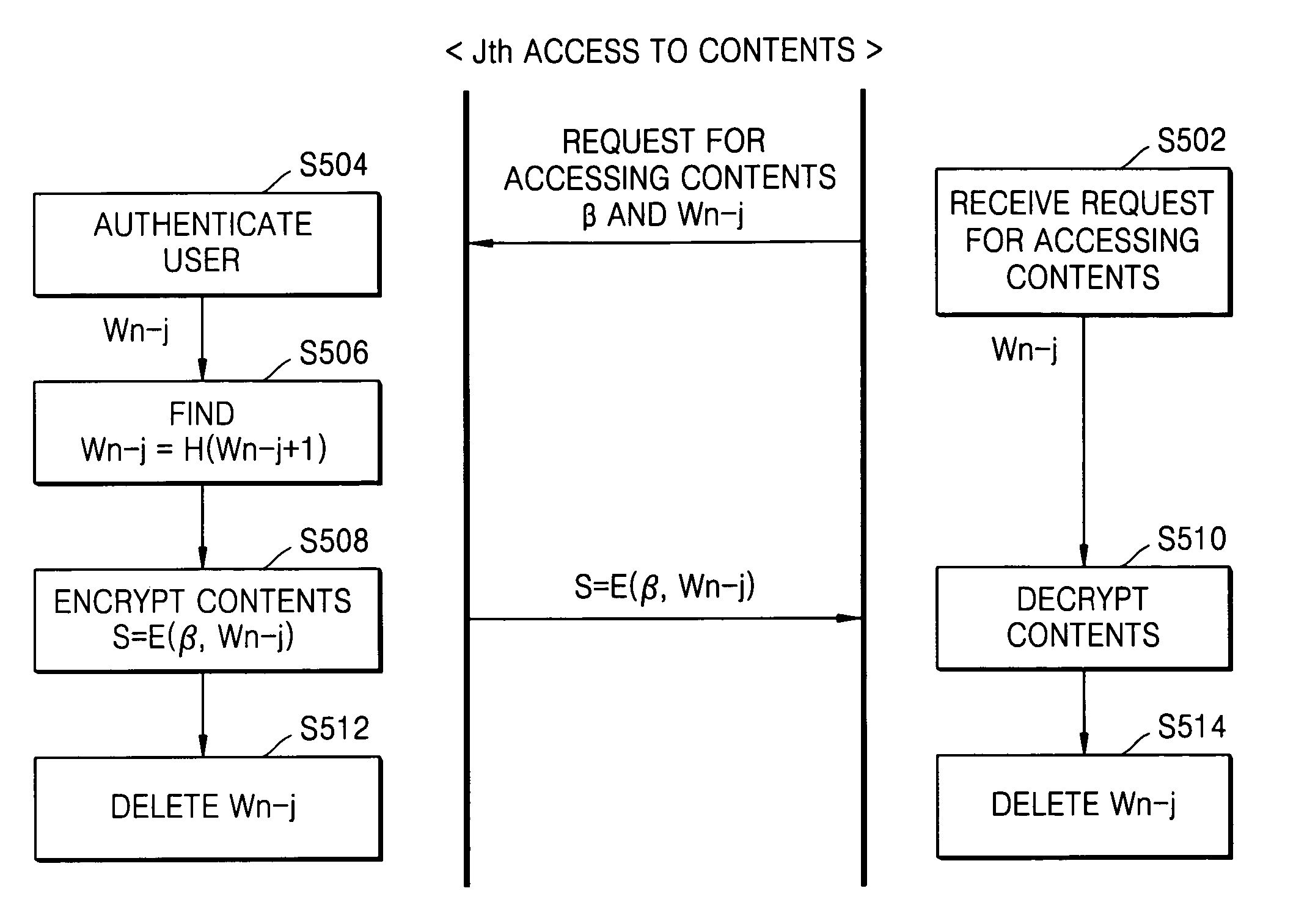
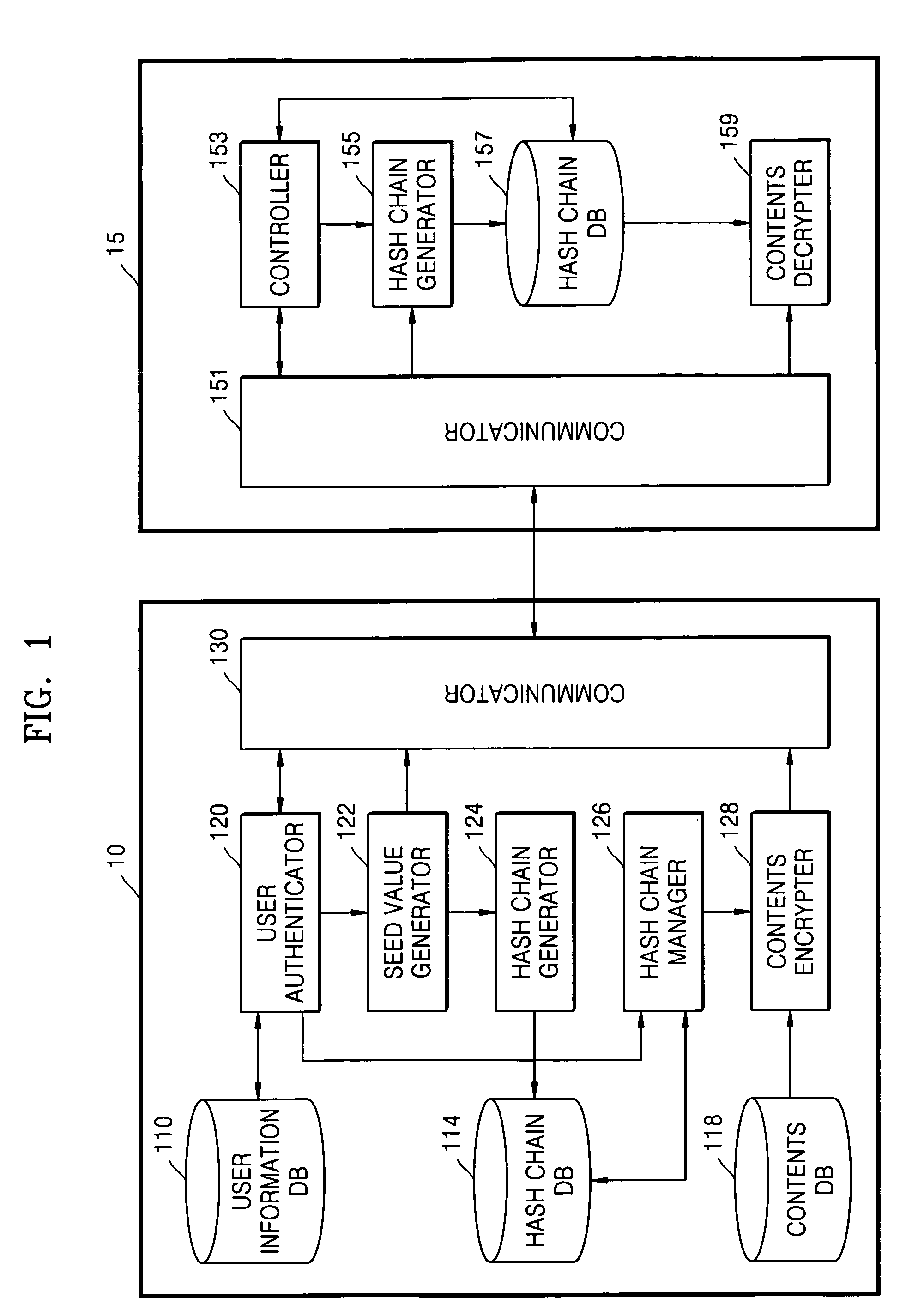
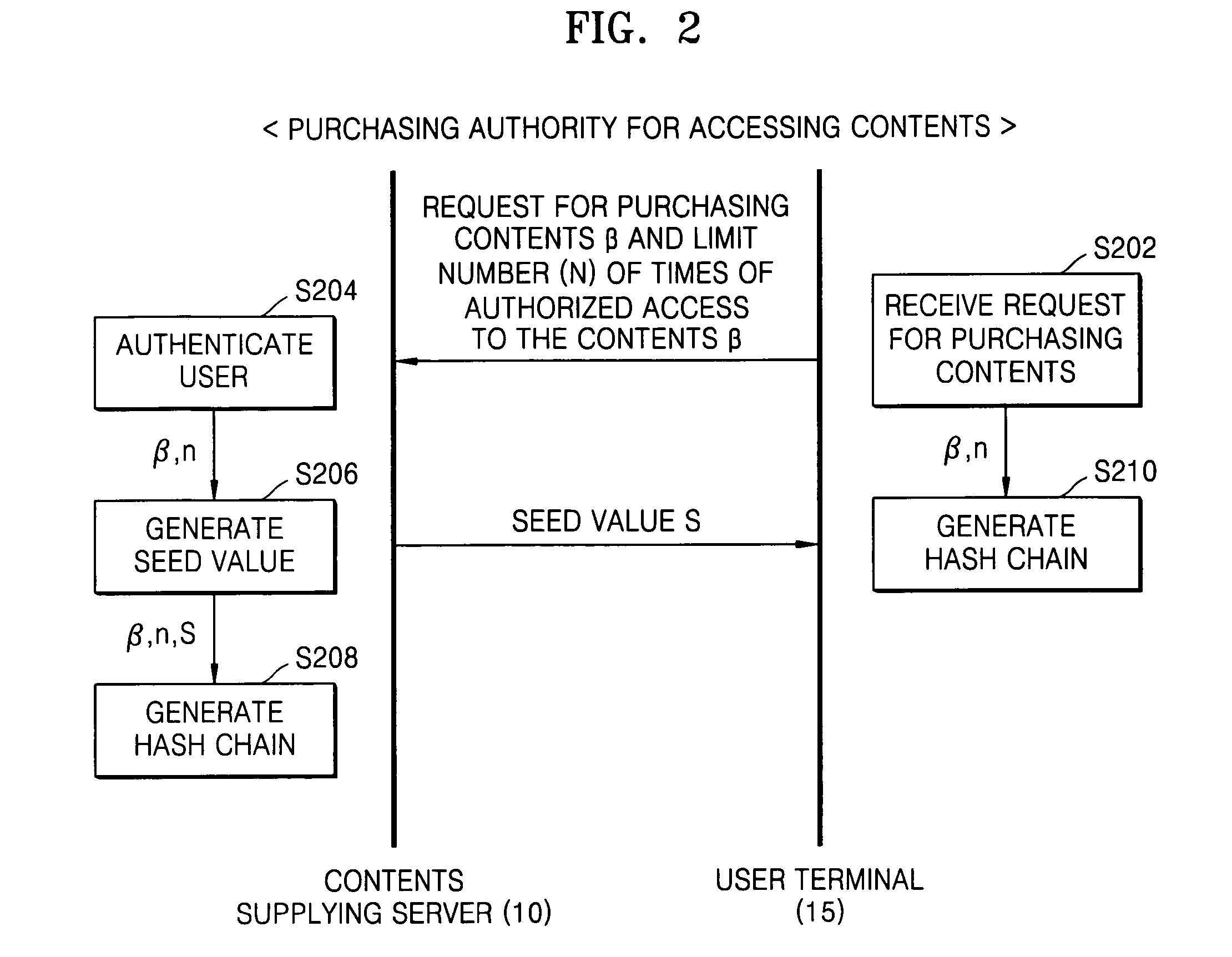
Method and apparatus for limiting number of times contents can be accessed using hash chain
ActiveUS20050256910A1Effectively managing copyrightSimply and securely limitingKey distribution for secure communicationDigital data processing detailsComputer networkHash chain
A method and apparatus are provided for simply and securely limiting a number of times that contents can be accessed using a hash chain. The apparatus limiting a number of times contents are accessed by a user terminal includes a hash chain generator receiving information indicating selected contents by the user terminal and information indicating how many times (n) the user terminal has authority to access the selected contents and generating a hash chain including n hash values derived from a seed value, and a contents access manager deleting the hash values one by one from the hash chain whenever the user terminal accesses the selected contents such that the number of times the contents can be accessed by the user terminal is decreased by the number of deleted hash values.
Owner:SAMSUNG ELECTRONICS CO LTD
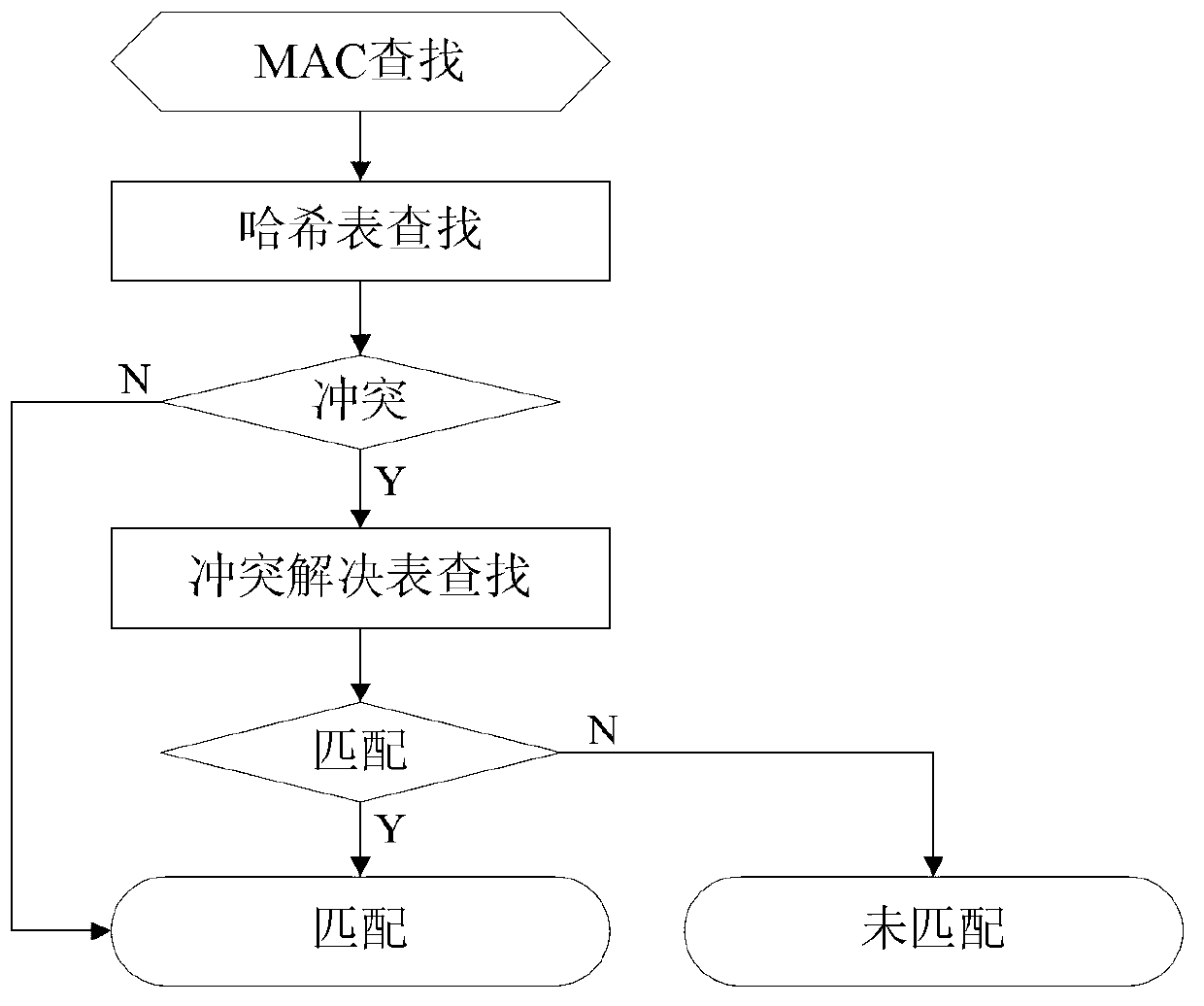
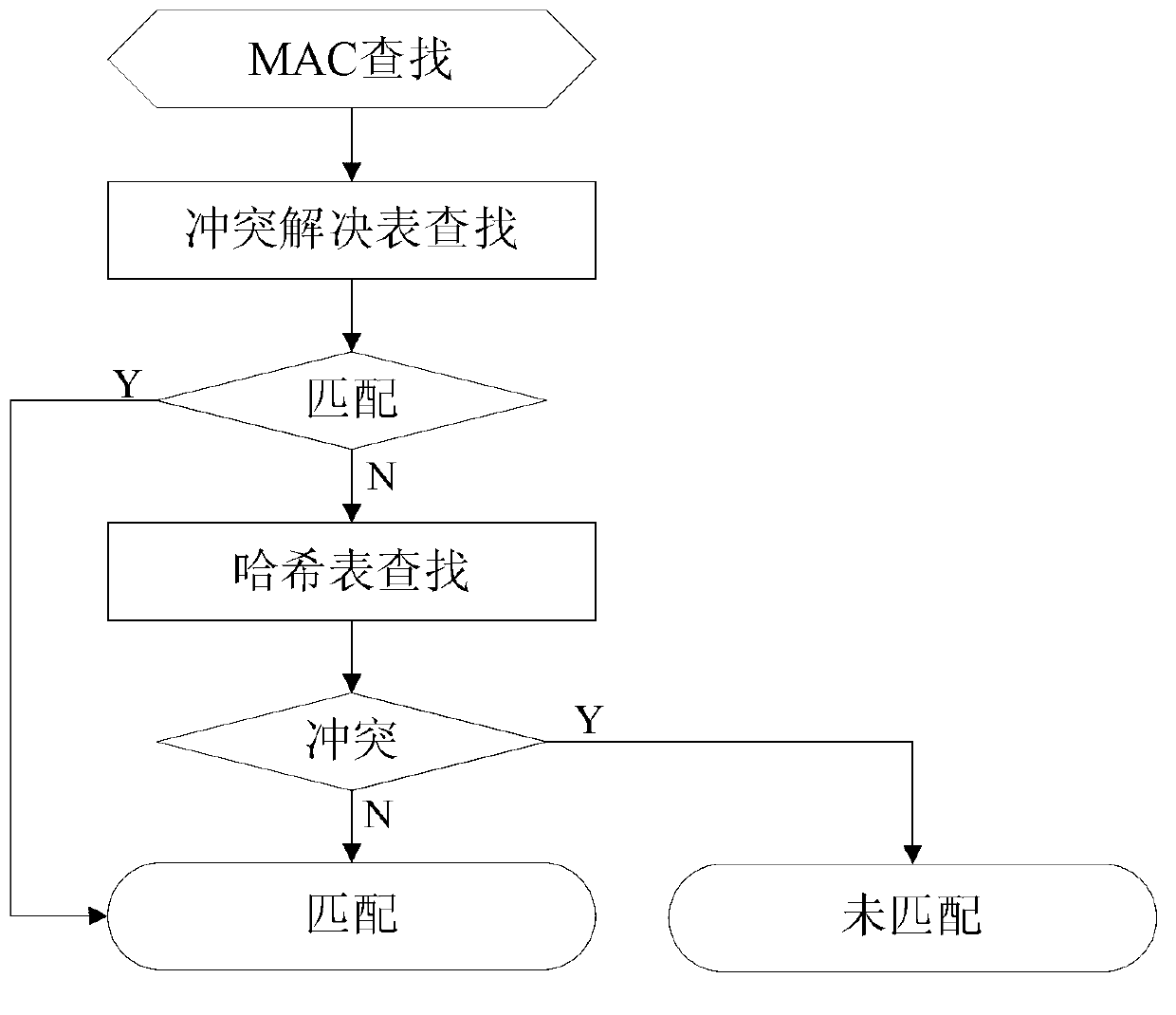
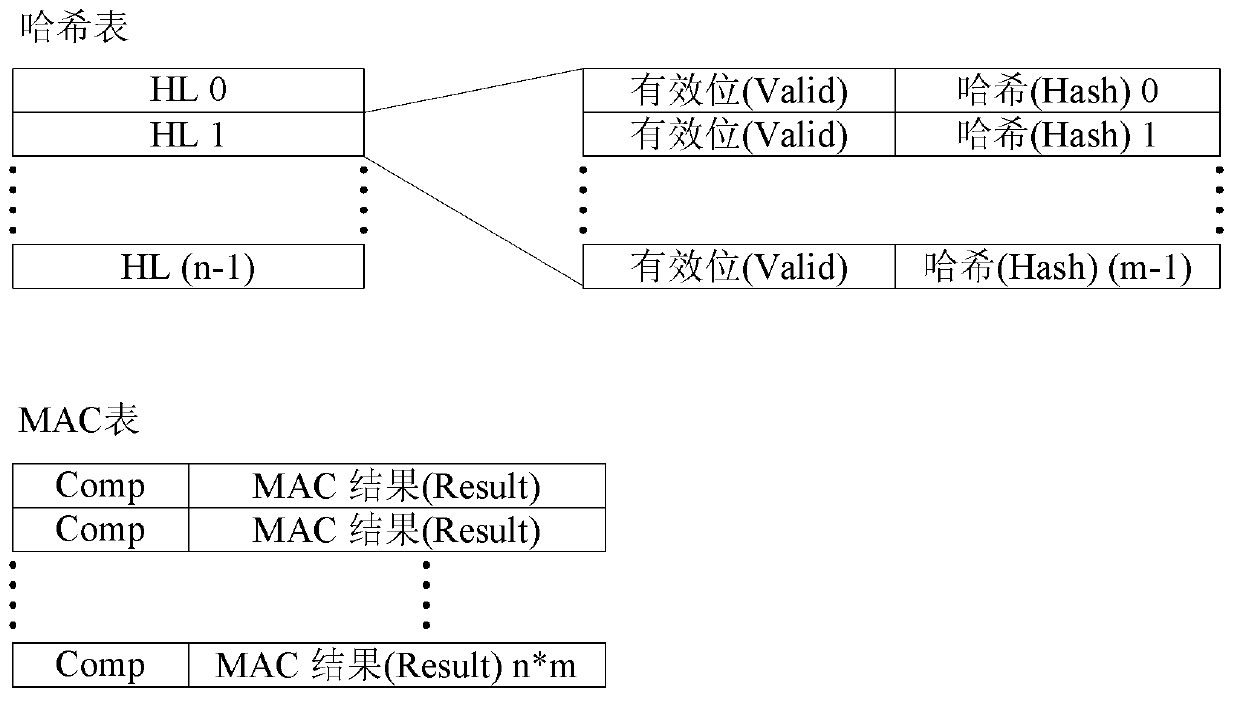
Determination method and device for media access control (MAC) address Hash collision
ActiveCN103001878AReduce occupancyReduce hash collisionsData switching networksComputer hardwareMedia access control
The invention provides a determination method and device for media access control (MAC) address Hash collision. The method comprises performing N-order Hash on key values, obtaining N Hash values, enabling N to be an integer larger than 2; respectively using M Hash values to search M Hash tables in a one-to-one correspondence mode, obtaining M Hash table items, and enabling M to be smaller than N; using (N-M) Hash values in the N Hash values except the M Hash values to undergo ergodic comparison with the Hash values in the M Hash table items, and searching and / or studying MAC addresses where Hash collision exists. According to an embodiment, by performing multiple-order Hash on the key values, the probability of the Hash collision is effectively reduced, and accordingly occupation of a ternary content addressable memory (TCAM) space is greatly reduced.
Owner:ZTE CORP
Task scheduling mechanism and system based on consistent hash algorithm
ActiveCN106250226AAchieve random assignmentFlexible matchingProgram initiation/switchingExecution unitHash table
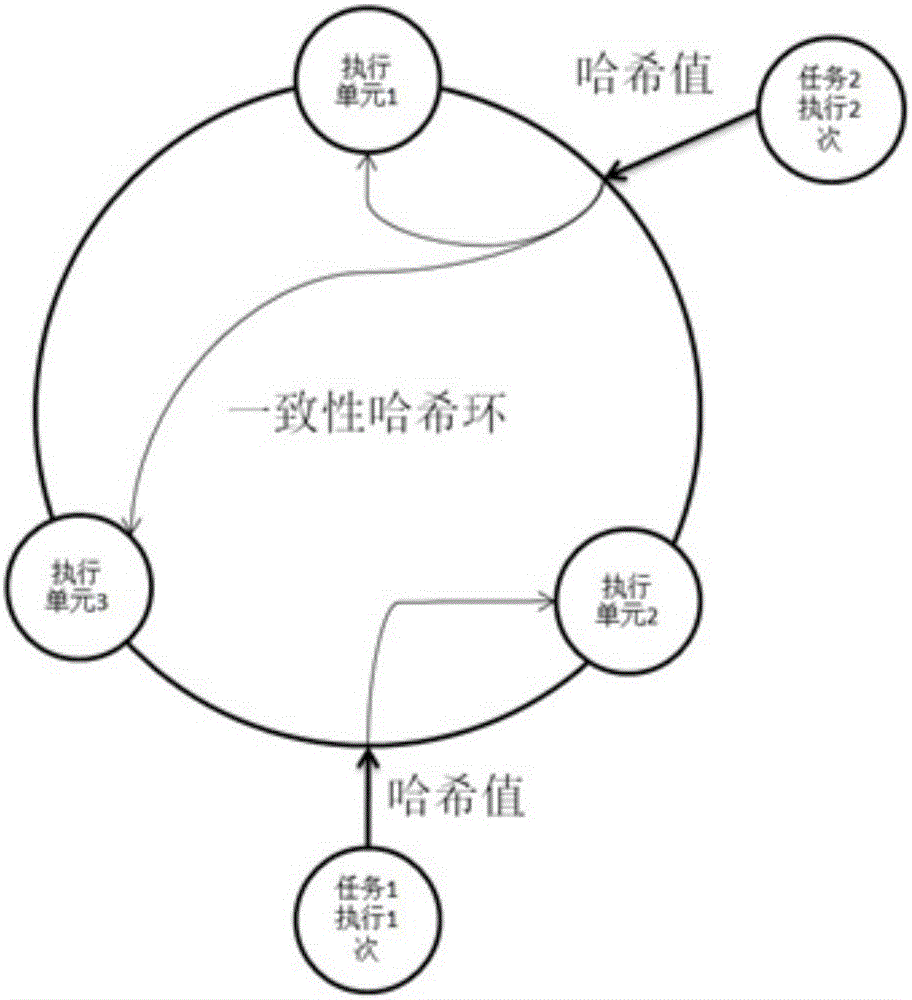
The invention provides a task scheduling mechanism and system based on a consistent hash algorithm. The method comprises the steps of obtaining a hash value of an available execution unit and a hash value of a task to be executed; distributing the hash value of the execution unit and the hash value of the task to a consistent hash ring; obtaining the execution times of the task; choosing a search direction; searching for n hash values of corresponding execution units closest to the position of the hash value of the task on the consistent hash ring according the search direction; enabling the value of the n is equal to the value of the execution times; obtaining n execution units corresponding to the hash values of the n corresponding execution units; establishing a mapping relation between the task and the n execution units; establishing a mapping table from the execution units to the task according to the mapping relation. According to the task scheduling mechanism, the consistent hash algorithm is applied to a task scheduling technology, the task and the execution units can be flexibly matched, and the scheduling requirement of periodical tasks can be met.
Owner:福建省华渔教育科技有限公司
Video stream address authentication method and apparatus
ActiveCN107465660AImprove securityIncreased complexityEncryption apparatus with shift registers/memoriesUser identity/authority verificationComputer hardwareClient-side
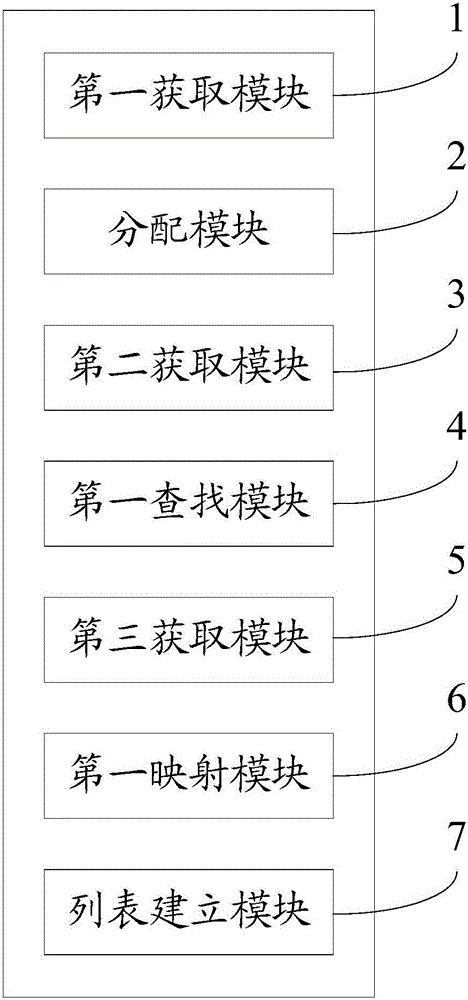
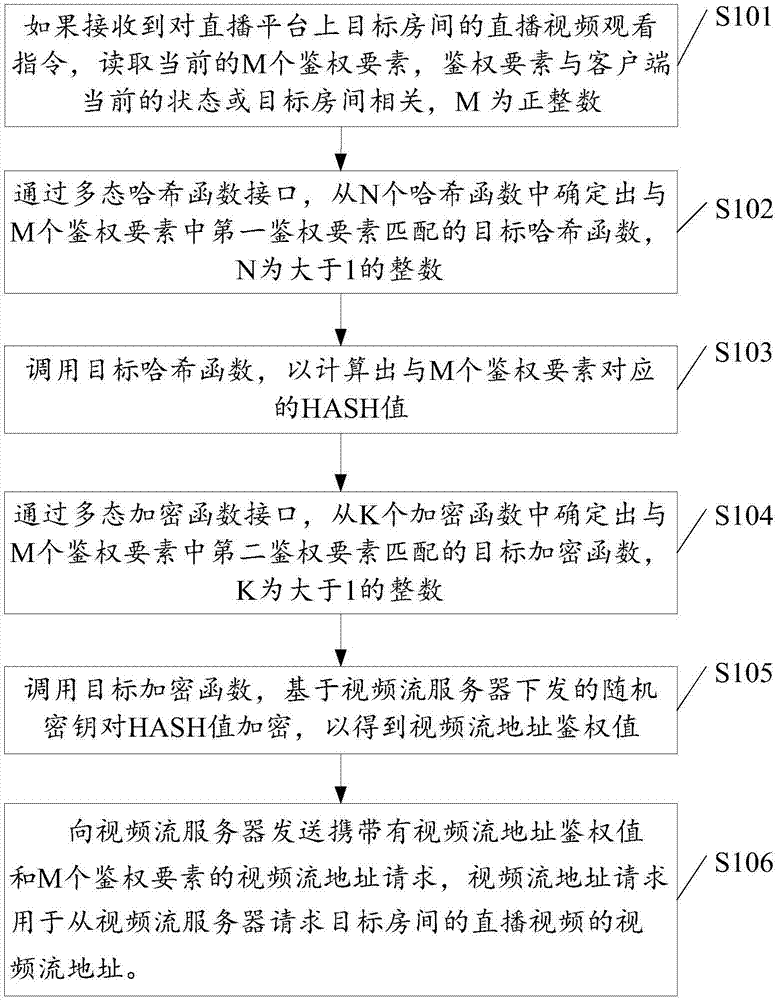
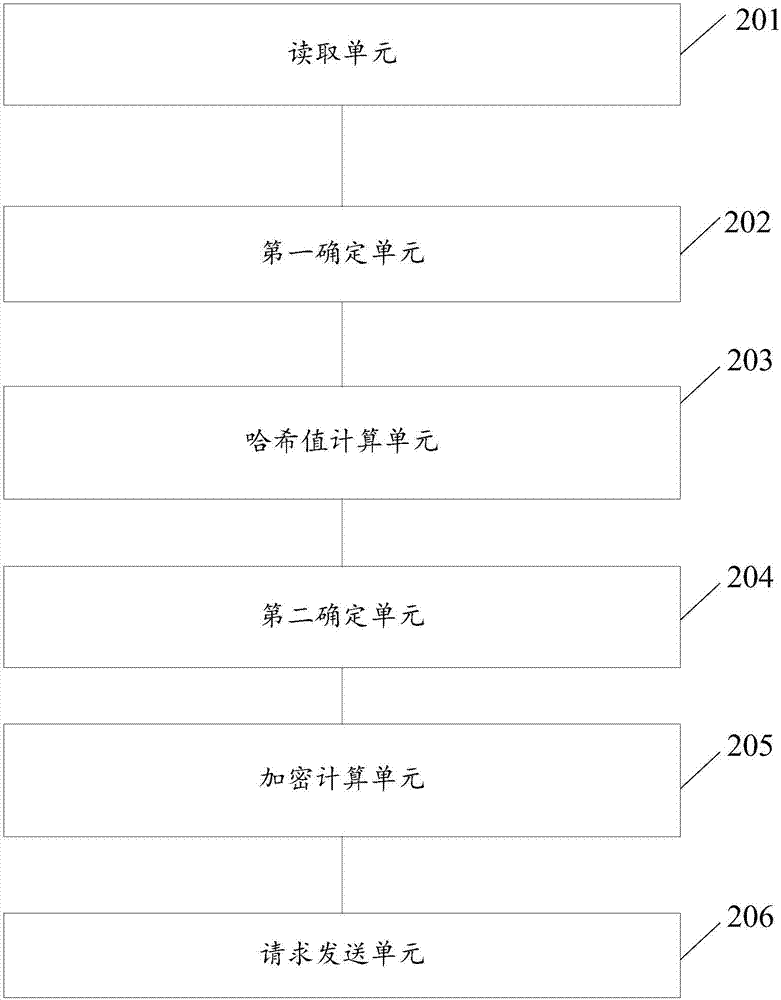
The invention discloses a video stream address authentication method. The method comprises the following steps: if a live video viewing instruction of a target room on a live broadcast platform is received, obtaining M authentication elements, wherein the authentication elements are related to the current state of a client or the target room; determining a target hash function matched with a first authentication element in the M authentication elements from N hash functions through a multi-state hash function interface; calling the target hash function to calculate hash values of the M authentication elements; determining a target encryption function matched with a second authentication element in the M authentication elements from K encryption functions through a multi-state encryption function interface; calling the target encryption function to encrypt the hash values of the M authentication elements based on a random key released by a video stream server so as to obtain a video stream address authentication value; and sending a request carrying the address authentication value to the video stream server. By adoption of the video stream address authentication method disclosed by the invention, the technical problem of relatively low security of video stream address authentication is solved.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
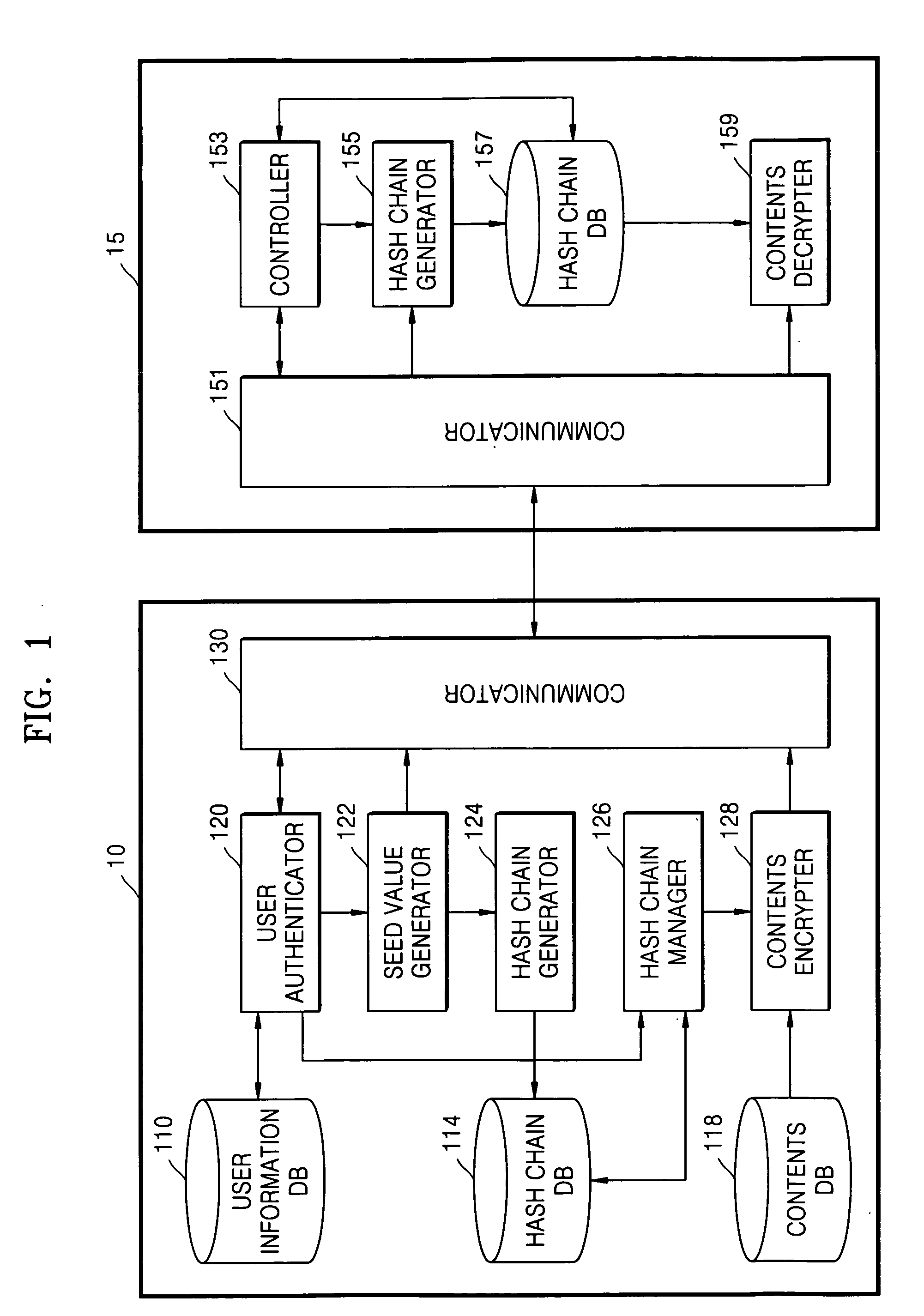
Method and apparatus for limiting number of times contents can be accessed using hash chain
ActiveUS7788728B2Simply and securely limitingEffectively managing copyrightKey distribution for secure communicationDigital data processing detailsHash chainComputer terminal
A method and apparatus are provided for simply and securely limiting a number of times that contents can be accessed using a hash chain. The apparatus limiting a number of times contents are accessed by a user terminal includes a hash chain generator receiving information indicating selected contents by the user terminal and information indicating how many times (n) the user terminal has authority to access the selected contents and generating a hash chain including n hash values derived from a seed value, and a contents access manager deleting the hash values one by one from the hash chain whenever the user terminal accesses the selected contents such that the number of times the contents can be accessed by the user terminal is decreased by the number of deleted hash values.
Owner:SAMSUNG ELECTRONICS CO LTD
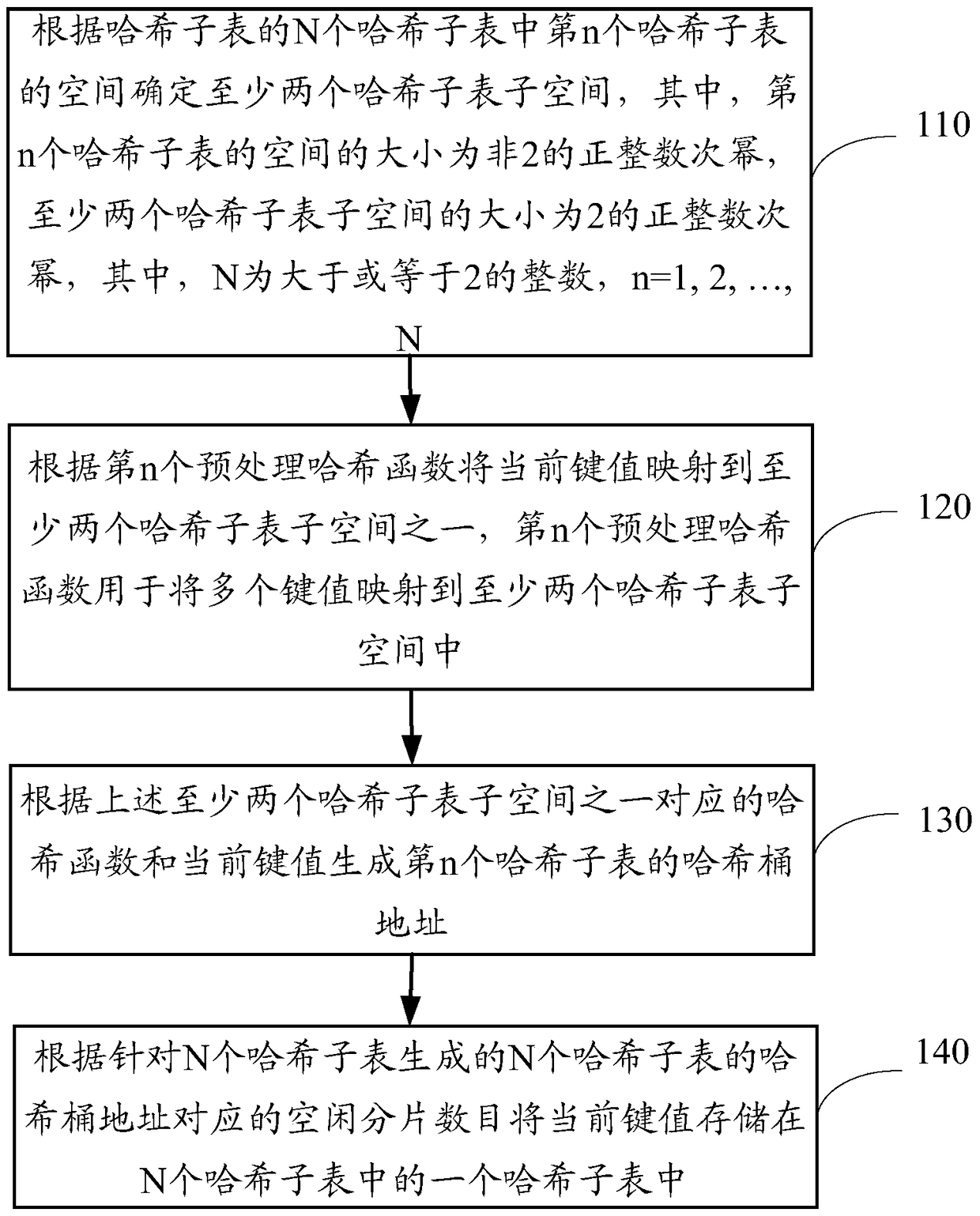
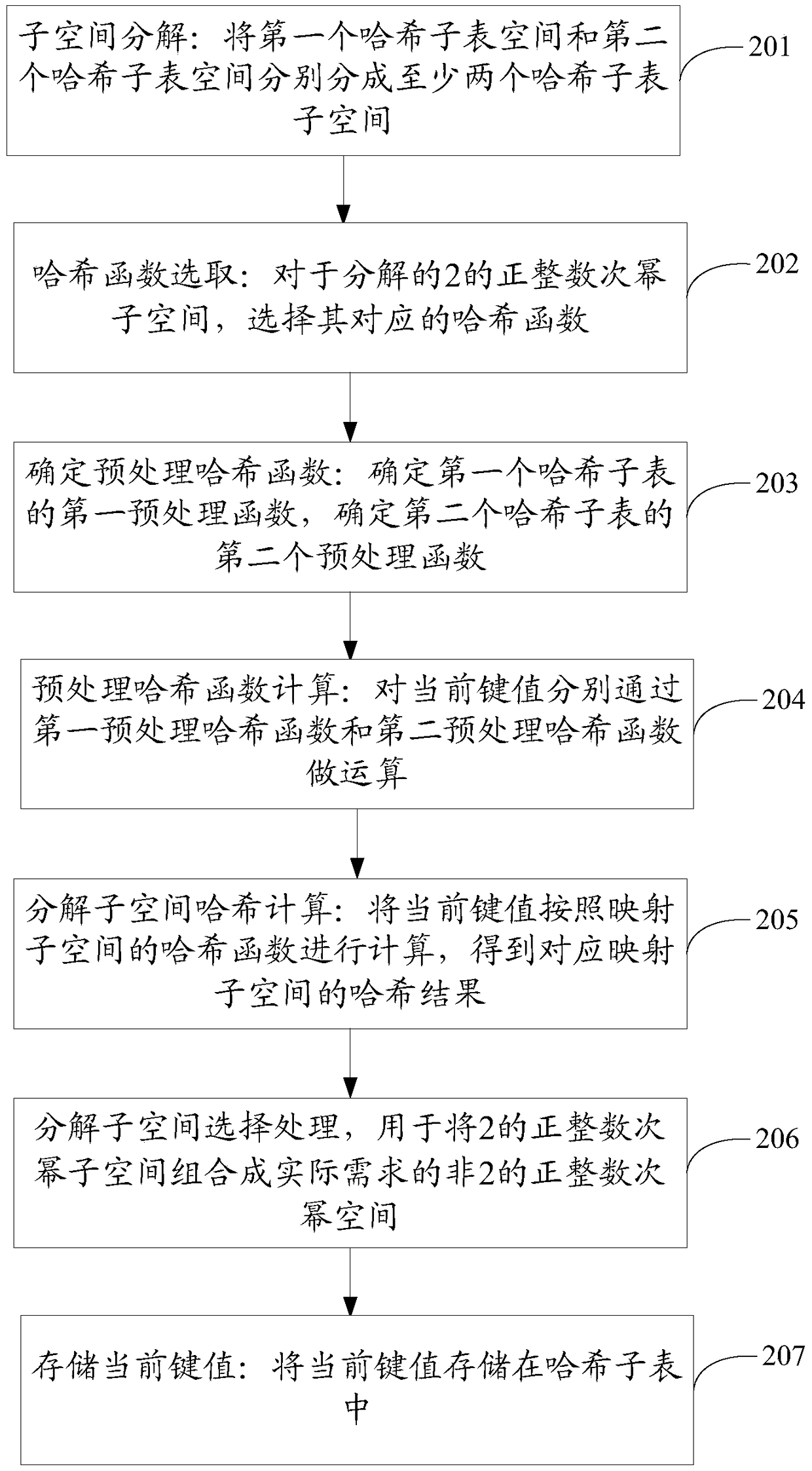
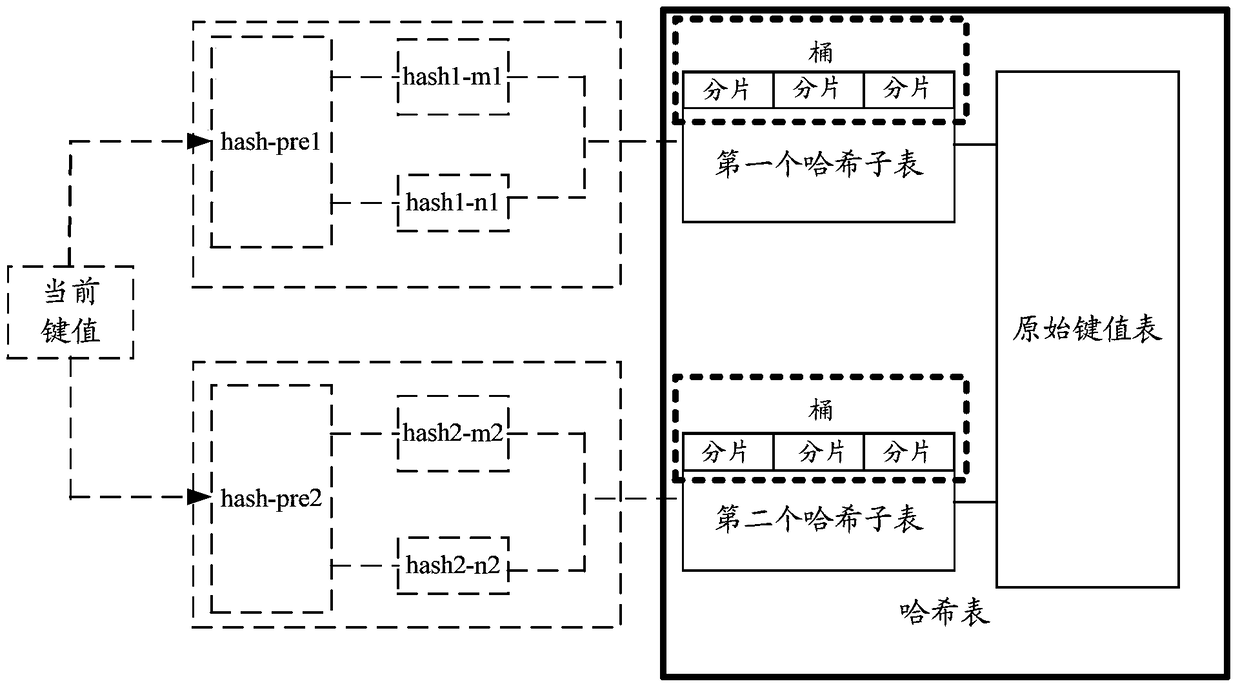
Method and equipment for creating hash table
ActiveCN105095212AMatch the requirements of the table item wellCutting costsSpecial data processing applicationsComputer hardwareHash table
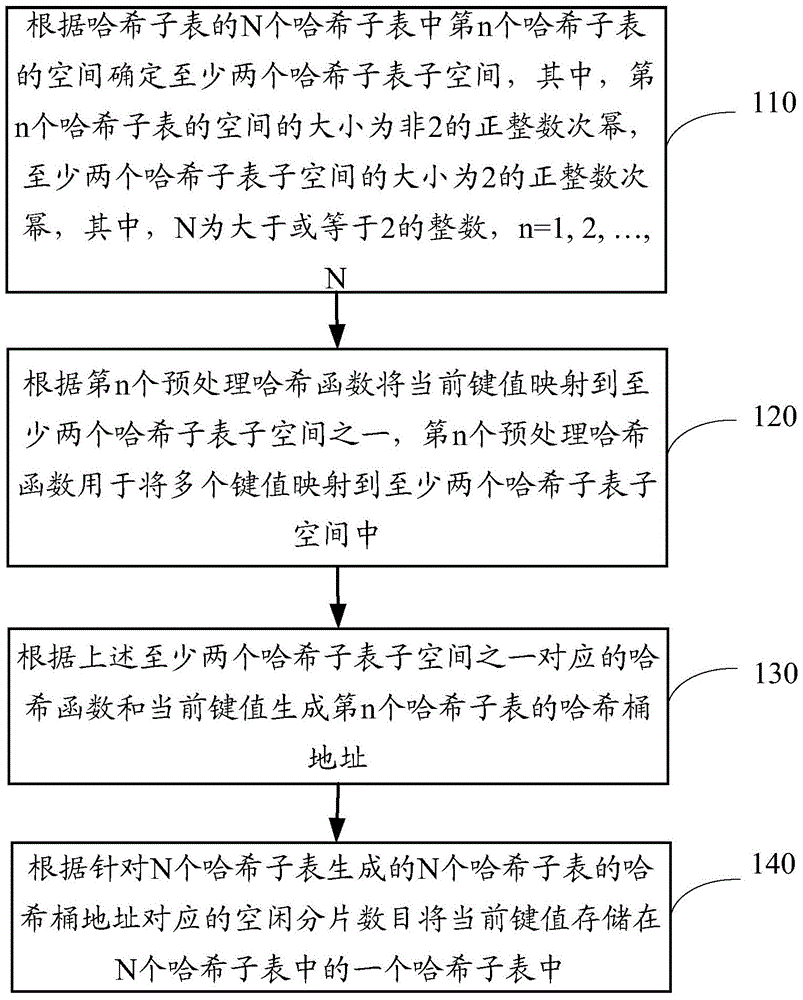
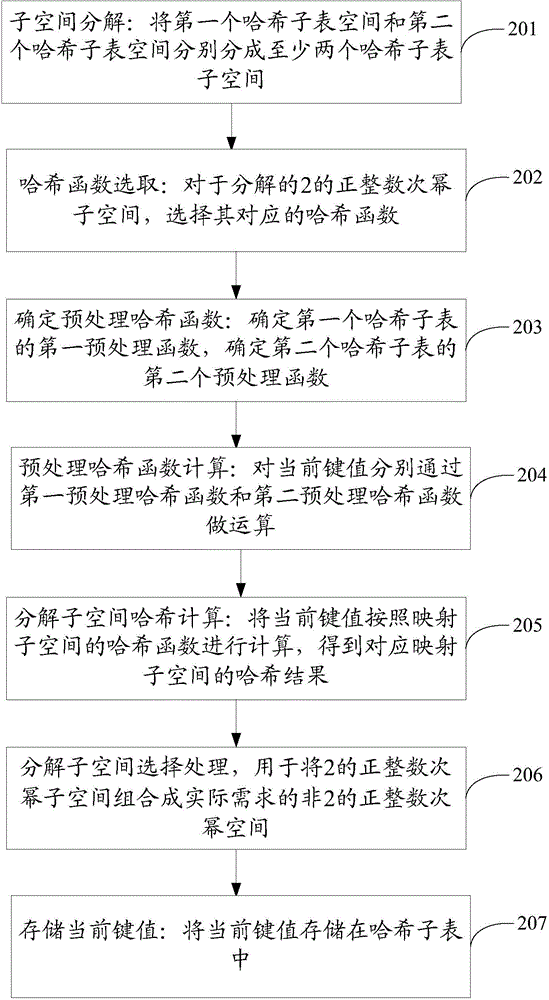
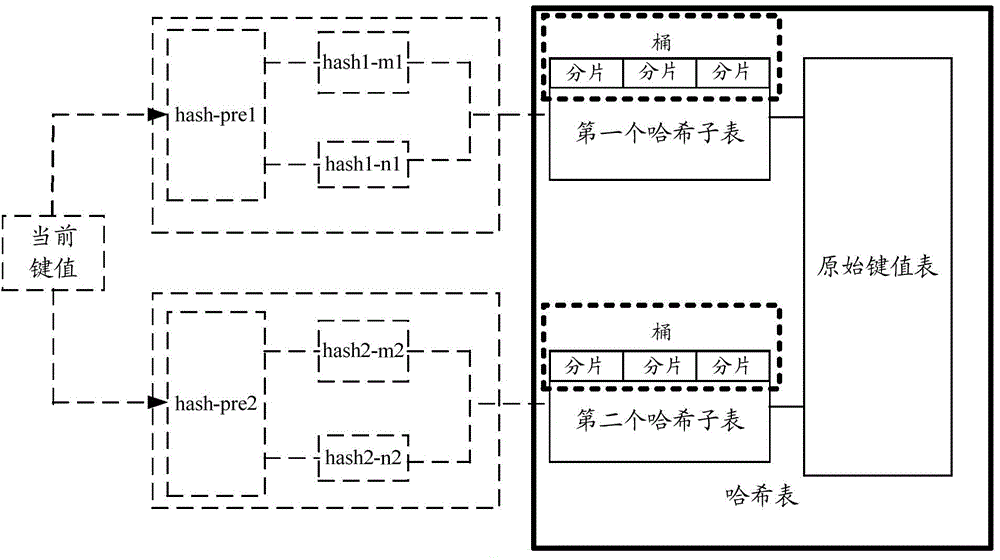
The invention provides a method and equipment for creating a hash table. The method comprises following steps: determining subspace of at least two hash sub-tables according to space of the nth hash sub-table in N hash sub-tables of the hash table, wherein the size of the nth hash sub-table is non-positive integral power of 2 and sizes of subspace of at least two hash sub-tables are positive integral power of 2; mapping the current key value to one of sub-space of at least two hash sub-tables based on the nth pre-processed hash function used for mapping multiple key values to at least two sub-space of at least two hash sub-tables; generating an address of a hash bucket for the nth hash sub-table according to a hash function corresponding to one of subspace of the at least two hash sub-tables and the current key value; and storing the current key value into a hash sub-table of N hash sub-tables according to the number of free wafers corresponding to addresses of hash buckets for the N hash sub-tables generated by the N hash sub-tables. The method and equipment for creating the hash table have the capacities of reducing waste of space and decreasing cost of realization.
Owner:上海在赢端智能科技有限公司
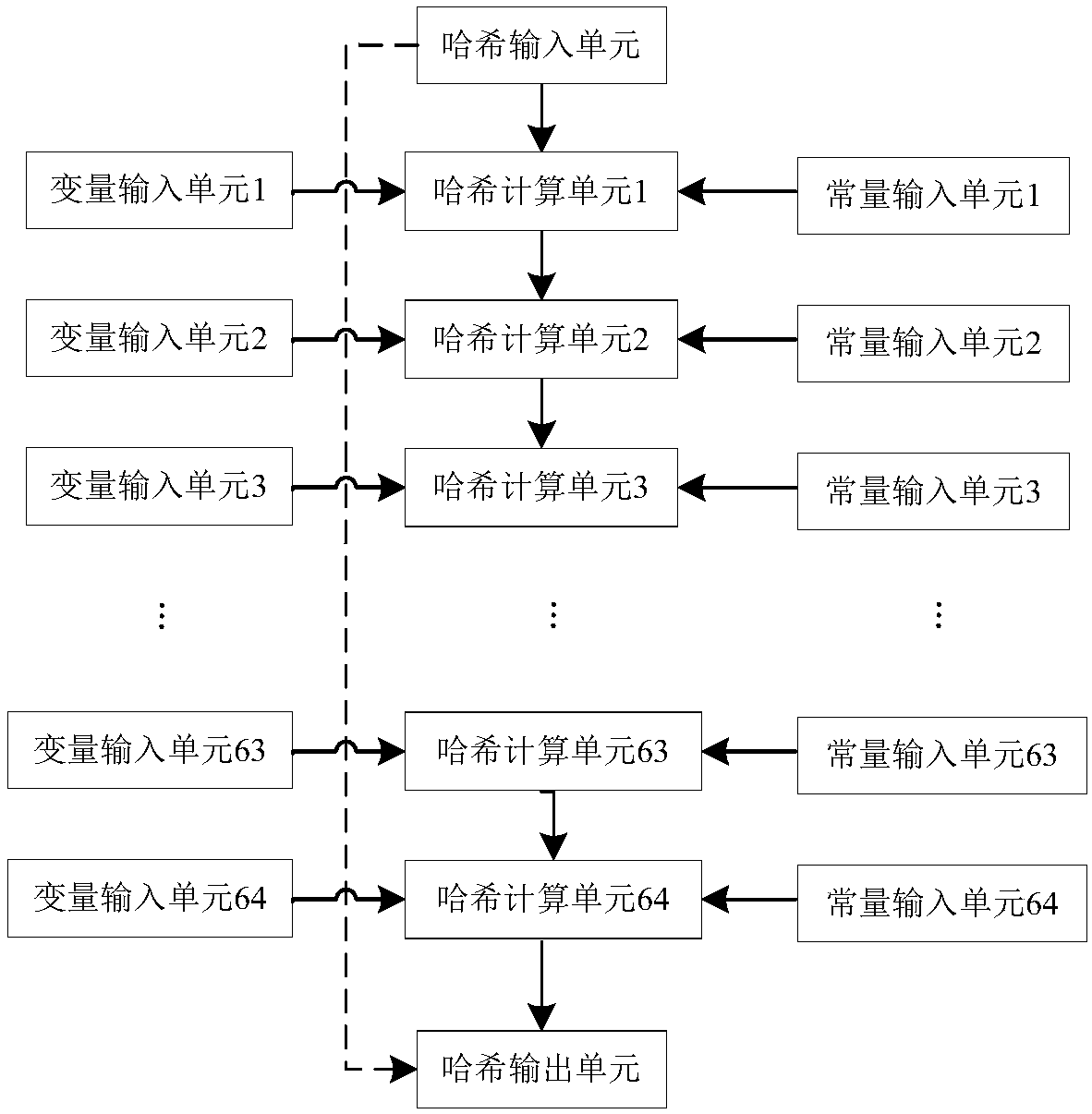
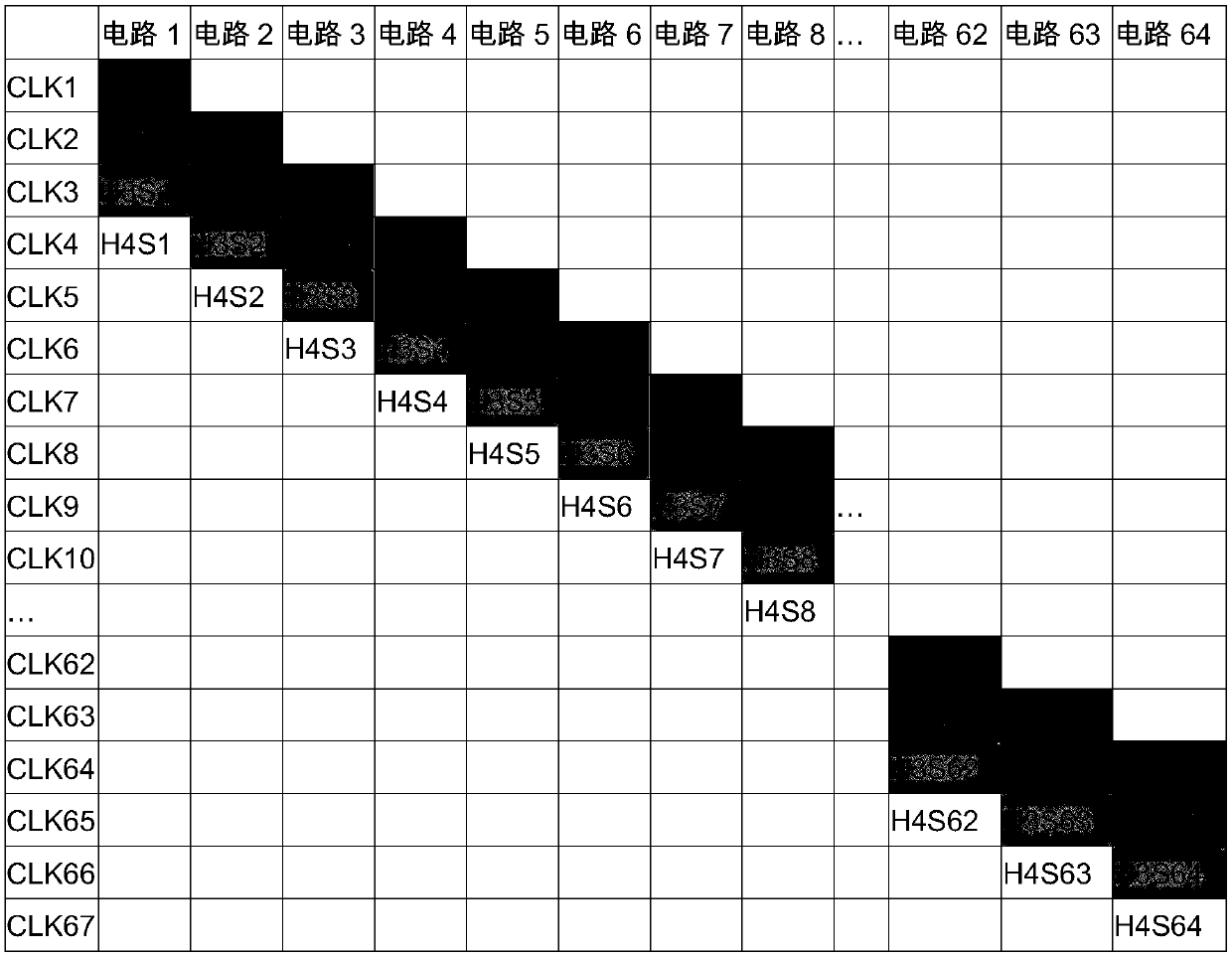
special computing circuit for realizing Hash operation
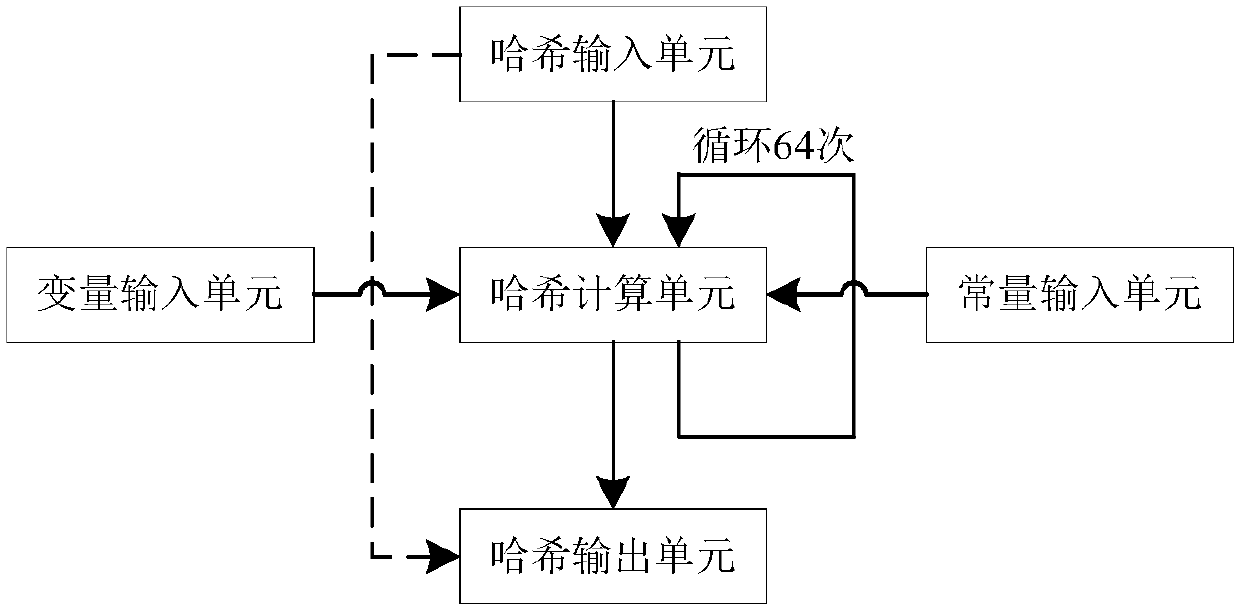
ActiveCN109905228AReduce power consumptionLow costEncryption apparatus with shift registers/memoriesUser identity/authority verificationTheoretical computer scienceN-Hash
The invention discloses a special computing circuit for realizing Hash operation. The special computing circuit comprises at least one Hash computing module, The device specifically comprises a variable, a constant input unit, a Hash input unit, a Hash output unit and a Hash calculation unit. Wherein the number of times of iterative operation of the Hash operation is N, and each calculation modulecompletes N times of iterative operation by using N Hash calculation units; Wherein the N hash calculation units are connected through a hardware connecting line, a group of new input data is initially input to the hash calculation unit through the hash input unit in the clock period A of each calculation, and the hash input value of the next hash calculation unit is the hash output value of theprevious hash calculation unit; The number of the N variable input units and the number of the constant input units are correspondingly connected with the N Hash calculation units respectively and used for inputting corresponding variable values and constant values. And a result is output by the Hash output unit after the primary Hash operation is finished. By utilizing the special computing circuit, the power consumption and the cost of the computing circuit can be reduced during Hash operation.
Owner:北京智云芯科技有限公司
Hash processing in a network communications processor architecture
InactiveUS8539199B2Digital data processing detailsMemory adressing/allocation/relocationComputer architectureEngineering
Described embodiments provide a hash processor for a system having multiple processing modules and a shared memory. The hash processor includes a descriptor table with N entries, each entry corresponding to a hash table of the hash processor. A direct mapped table in the shared memory includes at least one memory block including N hash buckets. The direct mapped table includes a predetermined number of hash buckets for each hash table. Each hash bucket includes one or more hash key and value pairs, and a link value. Memory blocks in the shared memory include dynamic hash buckets available for allocation to a hash table. A dynamic hash bucket is allocated to a hash table when the hash buckets in the direct mapped table are filled beyond a threshold. The link value in the hash bucket is set to the address of the dynamic hash bucket allocated to the hash table.
Owner:INTEL CORP
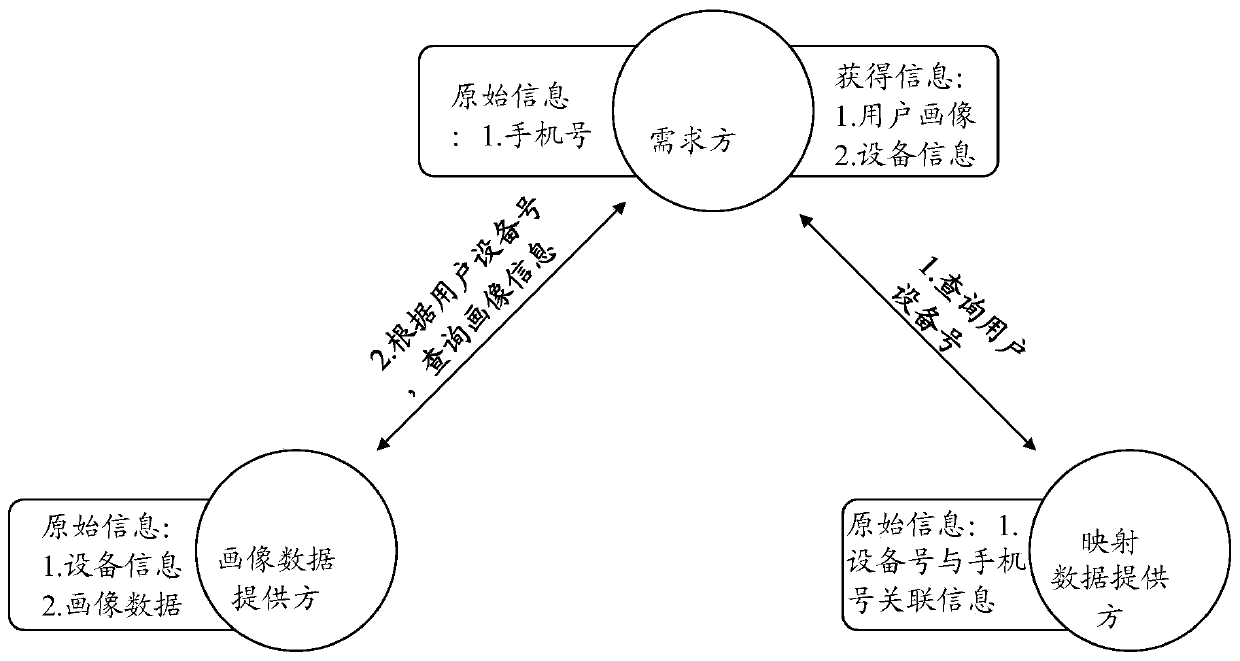
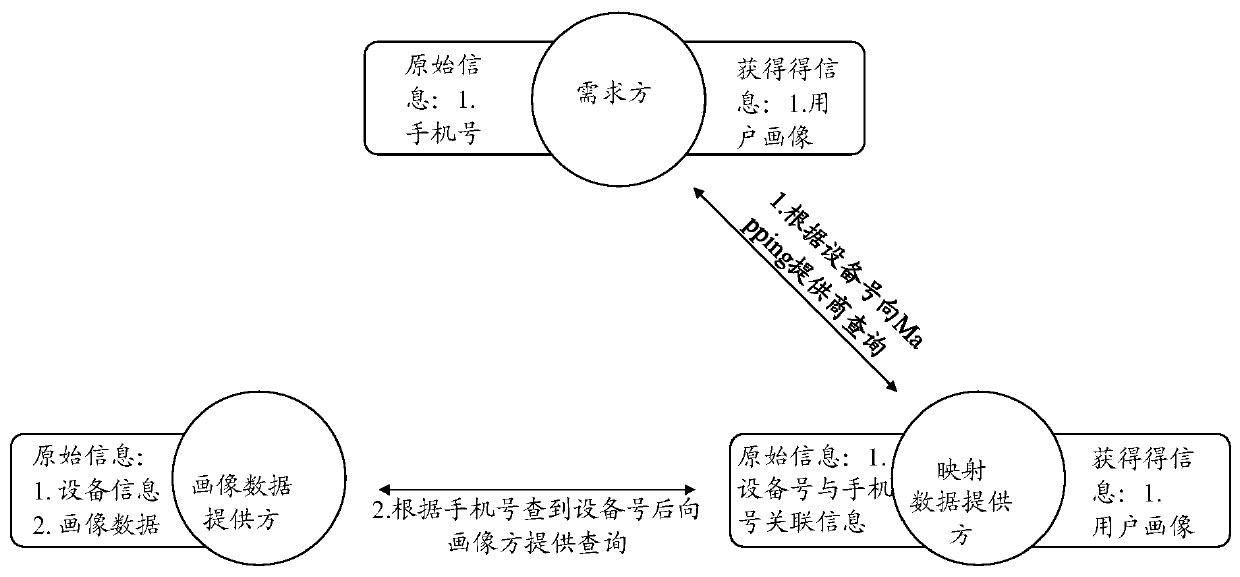
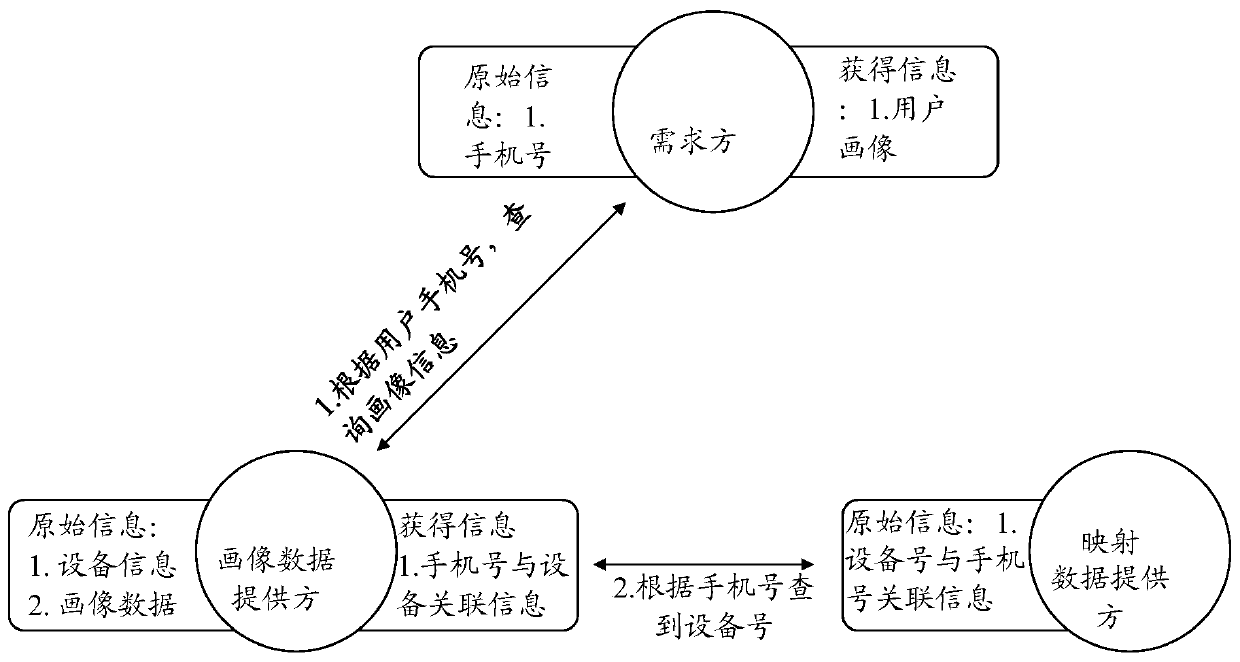
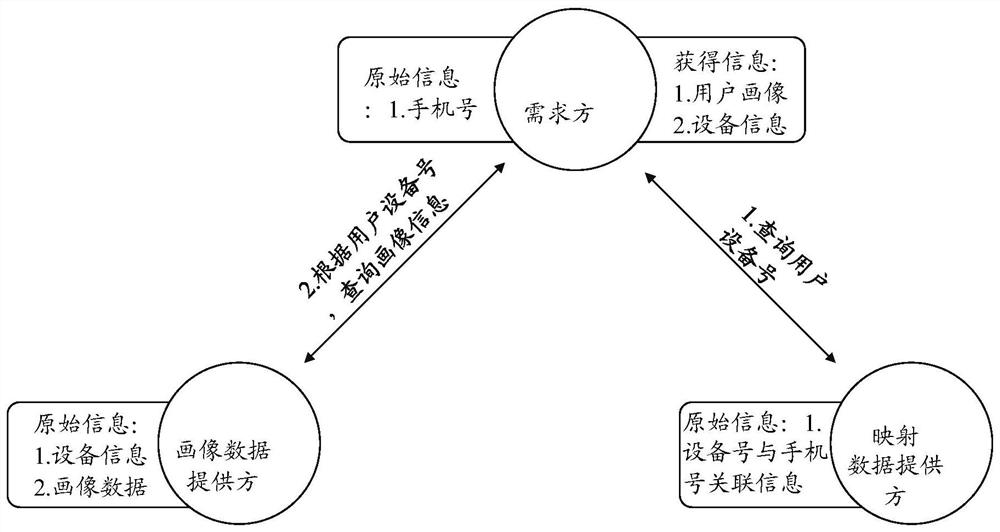
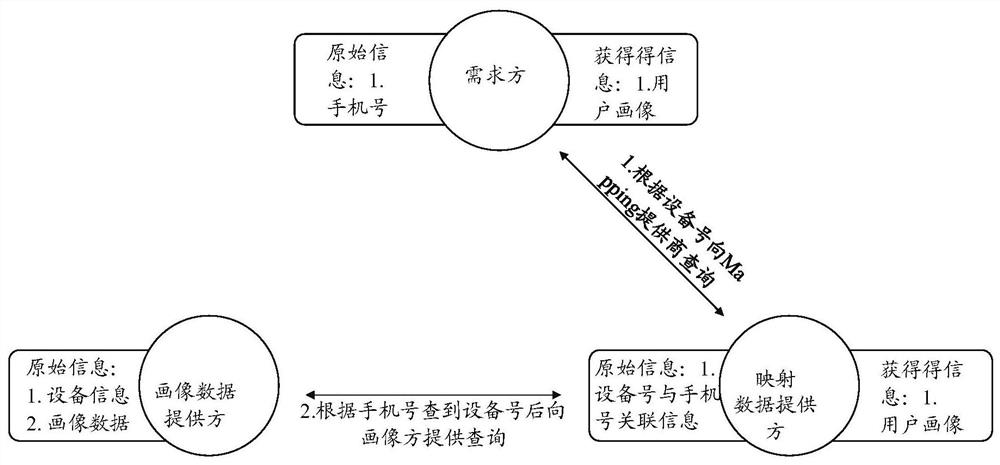
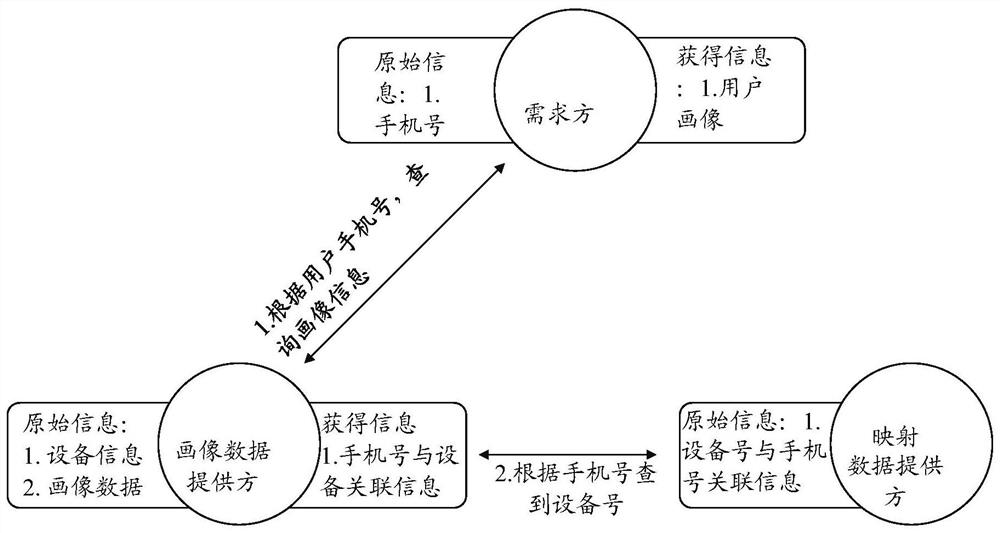
Method for realizing data fusion and data privacy protection based on Hash algorithm and session control
ActiveCN110263575AGuarantee privacy and securityGuarantee data securityAdvertisementsDigital data protectionData privacy protectionSession control
The invention relates to a method for realizing data fusion and data privacy protection based on a Hash algorithm and the session control. The method comprises the following steps that a demand module sends a query request after Hash calculation to a mapping data providing module; the mapping data providing module inquires whether the data exists or not; a demand module queries the provider data from the portrait data providing module; a portrait data providing module inquires the previous n hash value lists; the mapping data providing module returns the hit information to the portrait data providing module; and the portrait data providing module queries the data. By the adoption of the method for realizing data fusion and data privacy protection based on the Hash algorithm and the session control, the leakage of the high-sensitivity information caused by query of low-sensitivity information is avoided, and the data derogatory caused by the data diffusion is also avoided. According to the implementation scheme, the user privacy information of three parties cannot be leaked except the user portrait information, so that the data privacy and the data security of the individual users and the enterprise users are guaranteed.
Owner:上海富数科技有限公司
Hash algorithm hardware realization device based on FPGA
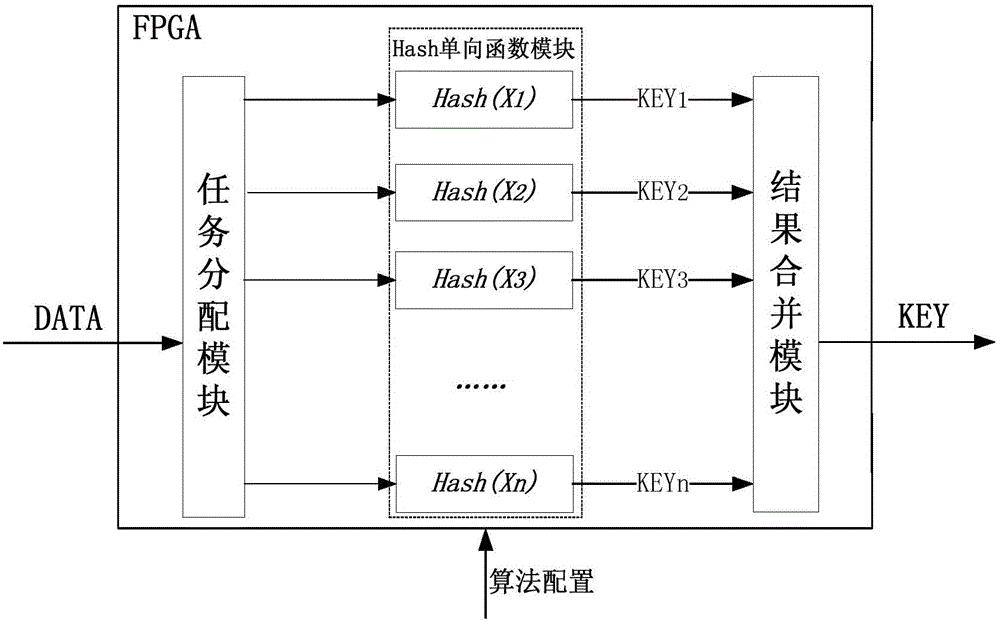
InactiveCN105827394AQuick searchFast encryptionEncryption apparatus with shift registers/memoriesAlgorithmOne-way function
The invention discloses an FPGA-based Hash algorithm hardware realization device. At present, the HASH algorithm in the industry is basically based on pure software implementation, resulting in low Hash performance, especially in the case of long table entries, high-speed table lookup with large table entries or large data volumes that require encryption, relying on pure software implementation Hardly realistic. The present invention comprises a task distribution module, a Hash one-way function module and a result merging module, and is characterized in that: the input DATA data is disassembled into n small pieces by the task distribution module, which are respectively X1, X2...Xn, and then the Hash single Compute to the n Hash one-way functions in the function module to obtain n KEY values, and then perform the result merging calculation by the result merging module, and finally obtain the KEY value of the DATA data. The invention is mainly based on the FPGA to realize the Hash algorithm, and executes operations concurrently in slices, and the speed is dozens of times faster than that of pure software.
Owner:ZHEJIANG EBANG COMM
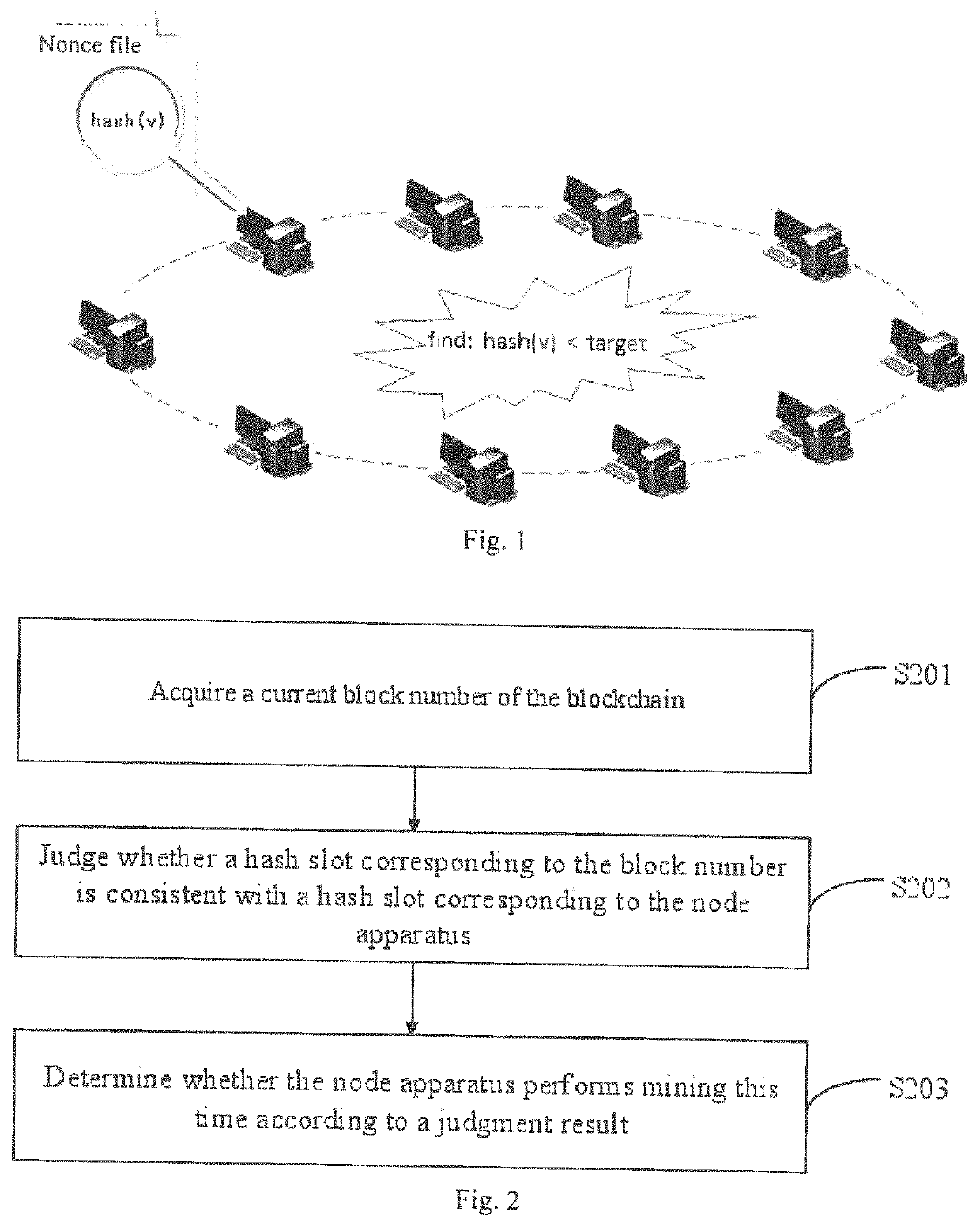
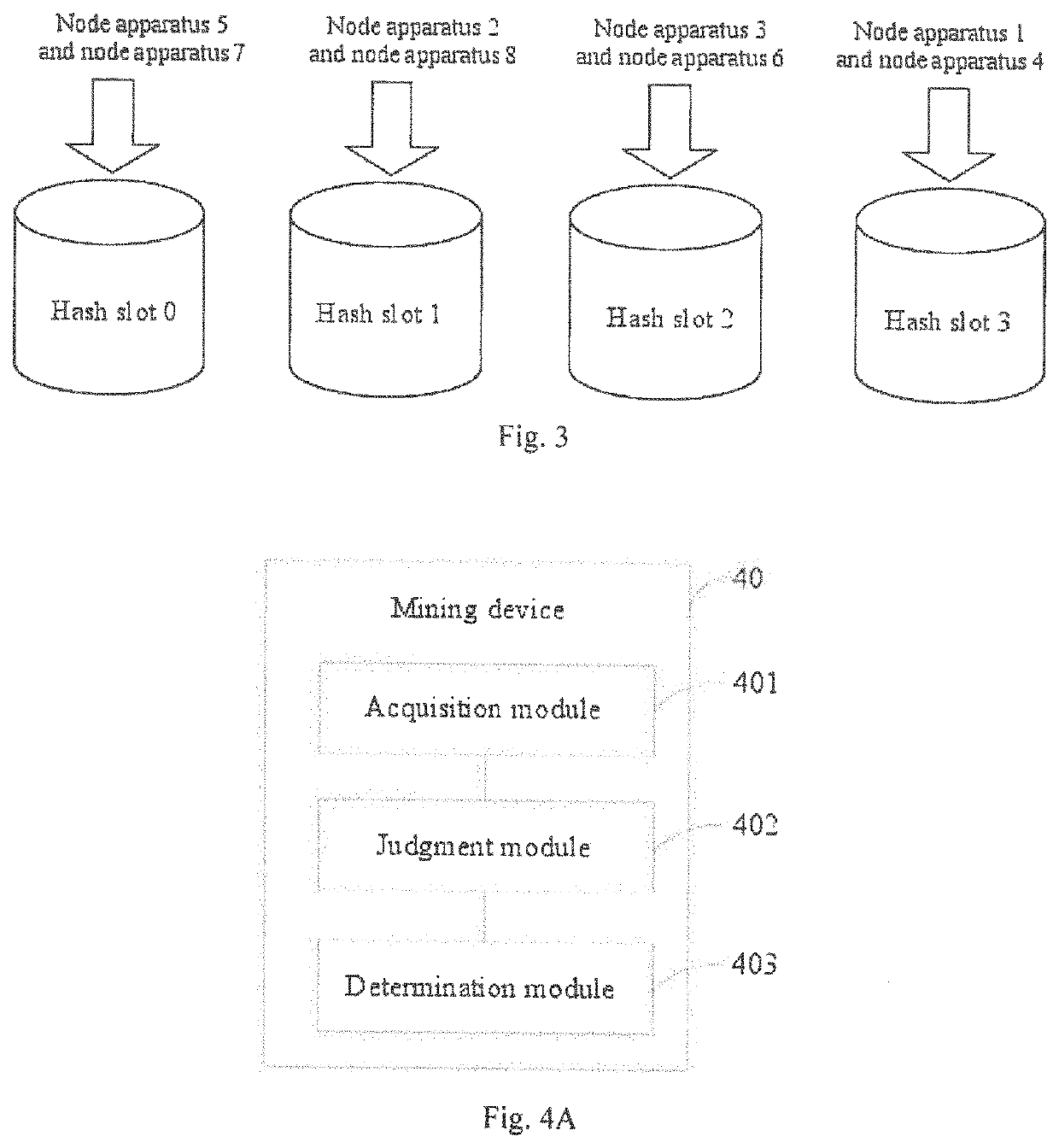
Block chain mining method, device, and node apparatus
ActiveUS10664485B2Mining probability of a node apparatusStrong computing powerDatabase updatingKey distribution for secure communicationAlgorithmTheoretical computer science
A blockchain mining method, device, and a node apparatus are used to solve the technical problem of unequal distribution of mining opportunities for node apparatuses in a blockchain network. The method comprises: acquiring a current block number of the blockchain; judging whether a hash slot corresponding to the block number is consistent with a hash slot corresponding to the node apparatus, wherein the node apparatuses in the blockchain network are distributed in N hash slots by means of a hash algorithm, and N is a positive integer greater than or equal to 2; and determining whether the node apparatus performs mining this time according to a judgment result.
Owner:CLOUDMINDS SHANGHAI ROBOTICS CO LTD
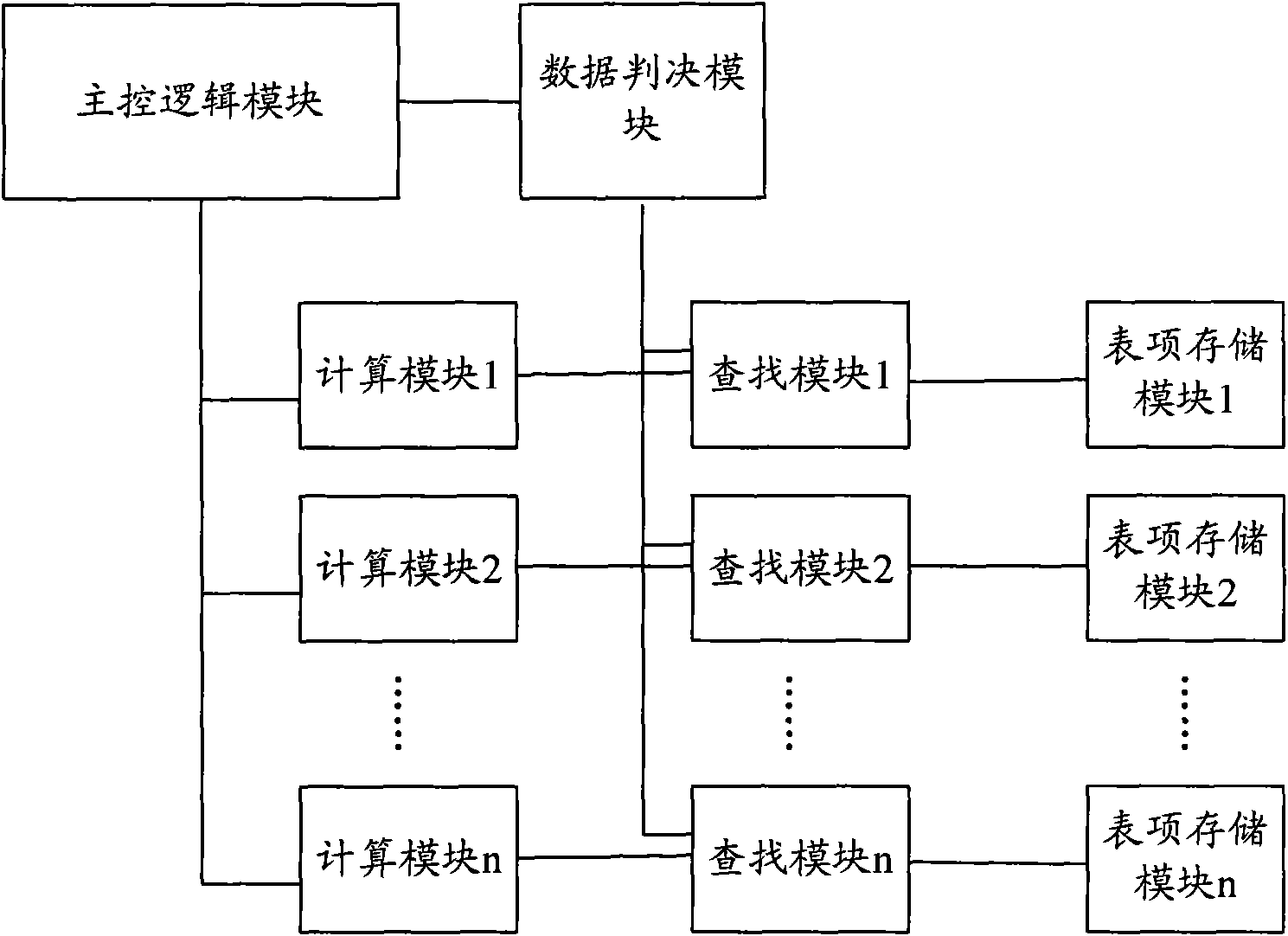
A parallel Hash lookup table architecture and method
InactiveCN109189792AGuaranteed randomnessGuaranteed independenceSpecial data processing applicationsDatabase indexingComputer hardwareLookup table
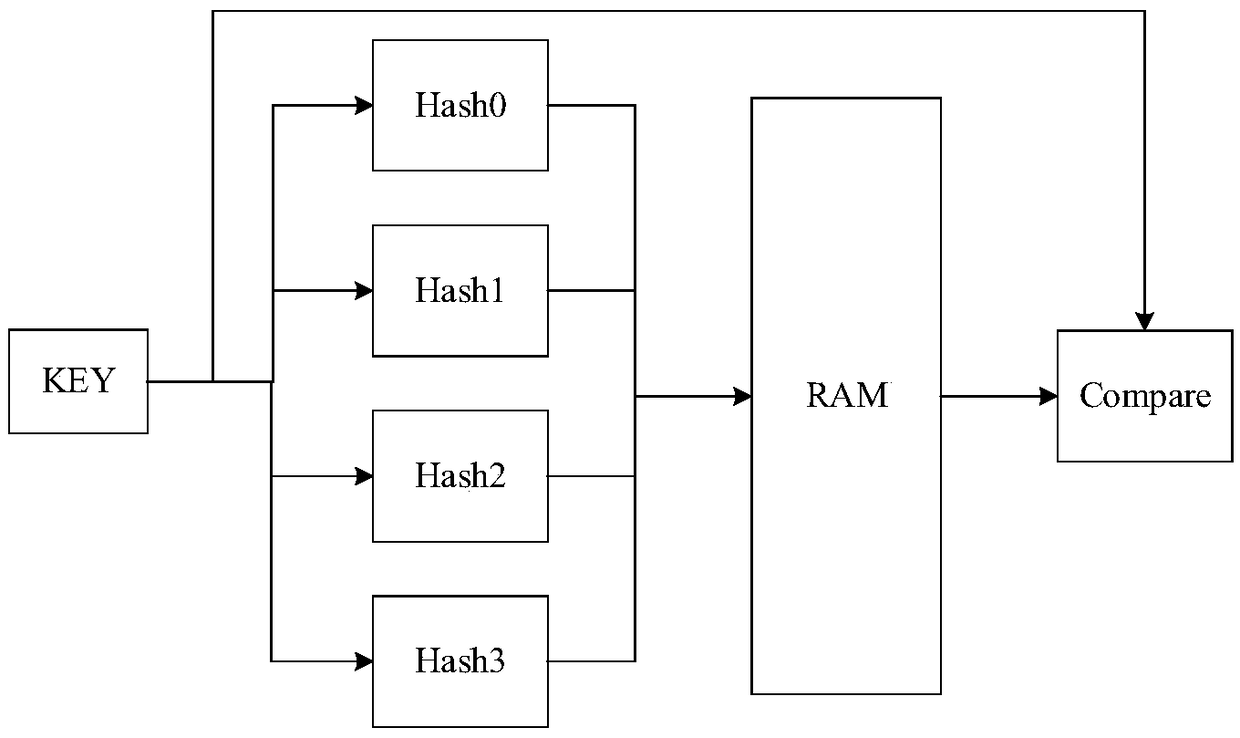
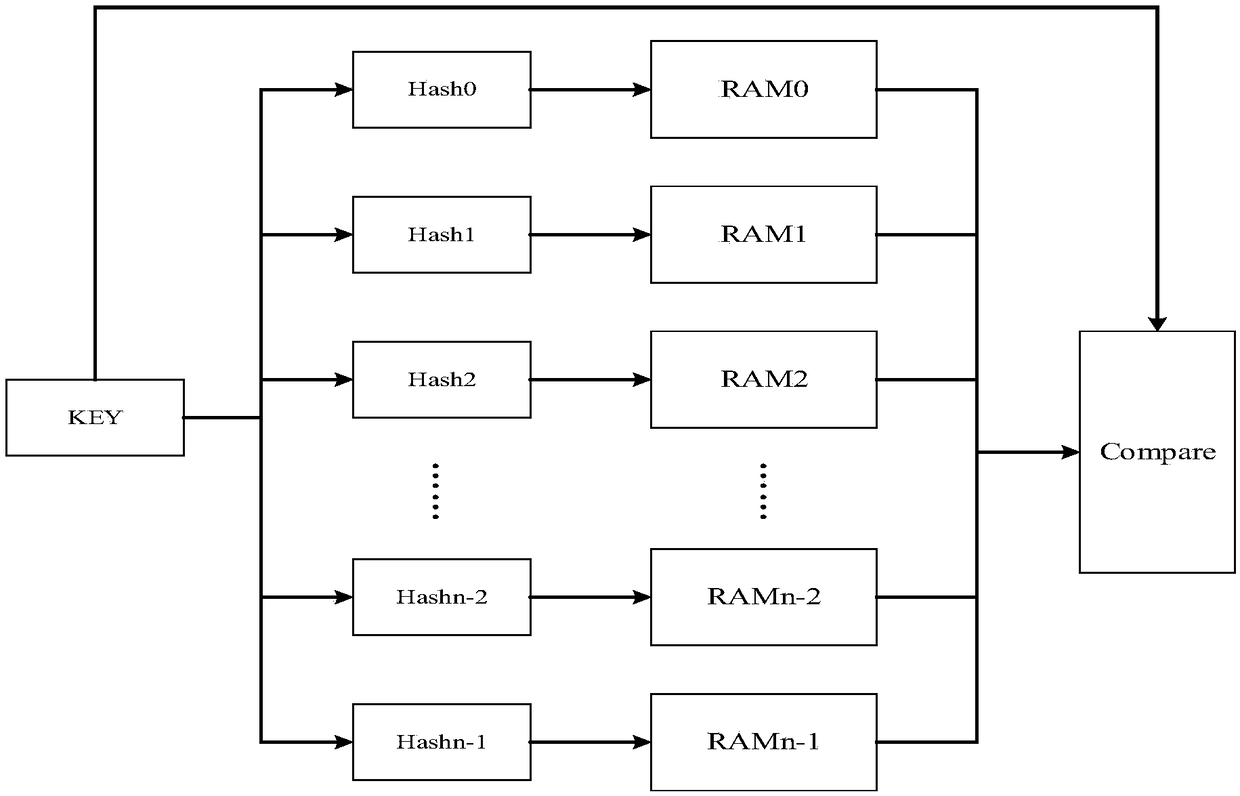
The invention provides a parallel Hash lookup table structure and method. The architecture comprises: a lookup Hash key value KEY determining a bit width according to requirements; n Hash functions, each choosing a different expression; n rams, independent of each other, corresponding to the Hash functions one by one; a Compare module, completing the comparison of n ram lookup results and the lookup key value KEY, and getting the correct look-up table content according to the comparison result, wherein each Hash function corresponds to a ram of different depths. The invention can effectively solve the problem of poor searching performance in the prior art and no longer needs multiple cyclic comparisons and hash calculations, and there is no need to read RAM space for multiple times, thereby greatly compressing the time of looking up table, and improving the efficiency of hash searching.
Owner:TIANJIN CHIP SEA INNOVATION TECH CO LTD +1
Object processing method and device, electronic equipment and storage medium
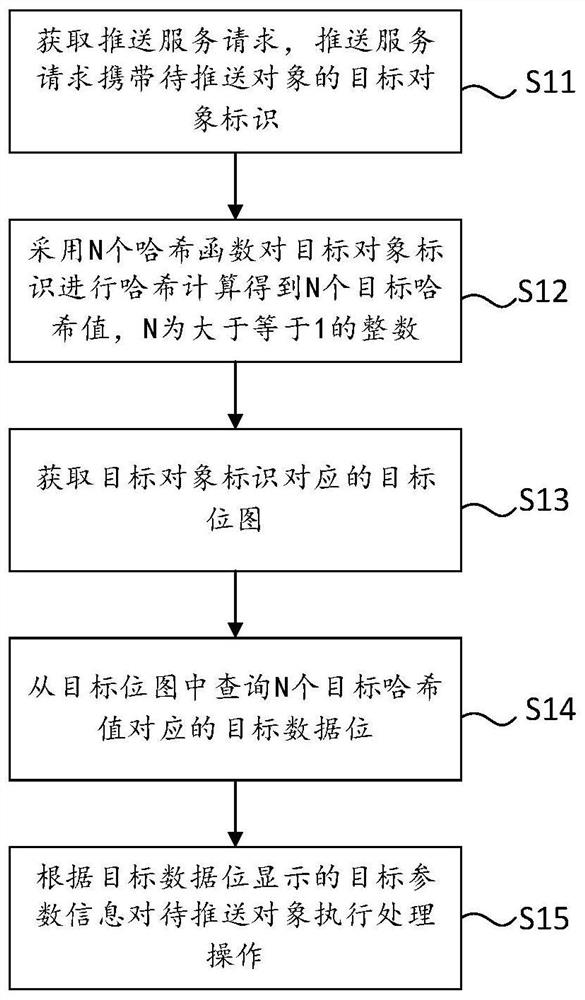
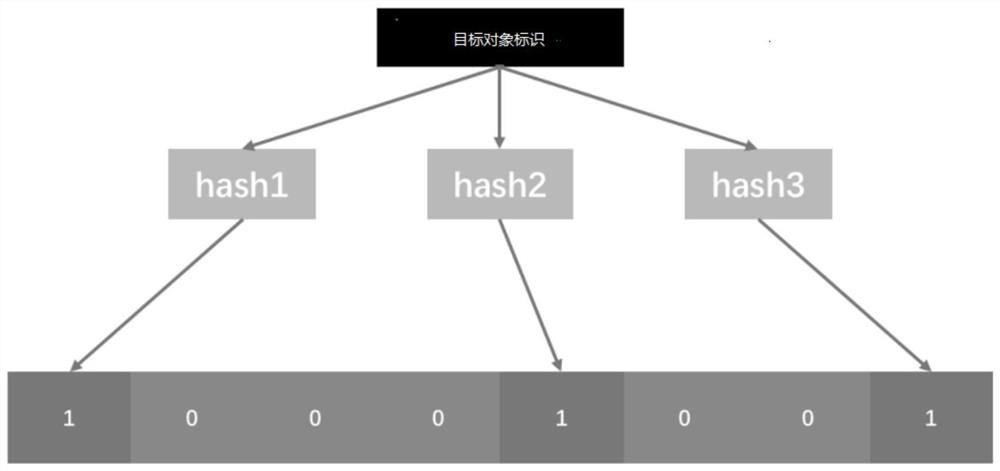
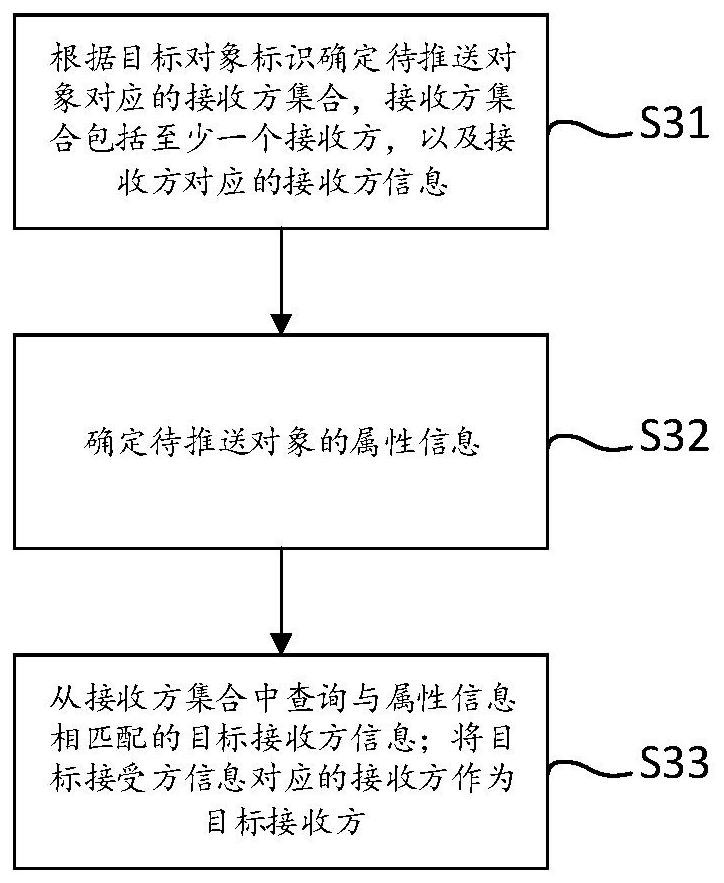
PendingCN112330398AConfigurableEasy to operateBuying/selling/leasing transactionsWeb data queryingAlgorithmEngineering
The invention discloses an object processing method and device, electronic equipment and a storage medium. The method comprises the steps that a push service request is acquired, and the push servicerequest carries a target object identifier of a to-be-pushed object; performing hash calculation on the target object identifier by adopting N hash functions to obtain N target hash values, wherein Nis an integer greater than or equal to 1; obtaining a target bitmap corresponding to the target object identifier; querying target data bits corresponding to the N target hash values from the target bitmap; and executing a processing operation on the to-be-pushed object according to the target parameter information displayed by the target data bit. According to the method, the parameters displayedby the data bits in the target bitmap are obtained through the hash value obtained by calculating the target object identifier, whether the to-be-pushed object is pushed or not can be quickly determined according to the parameters, the method is simple in operation, the algorithm has configurability, and the processing efficiency is higher when the data volume of the object is huge.
Owner:JINGDONG TECH HLDG CO LTD
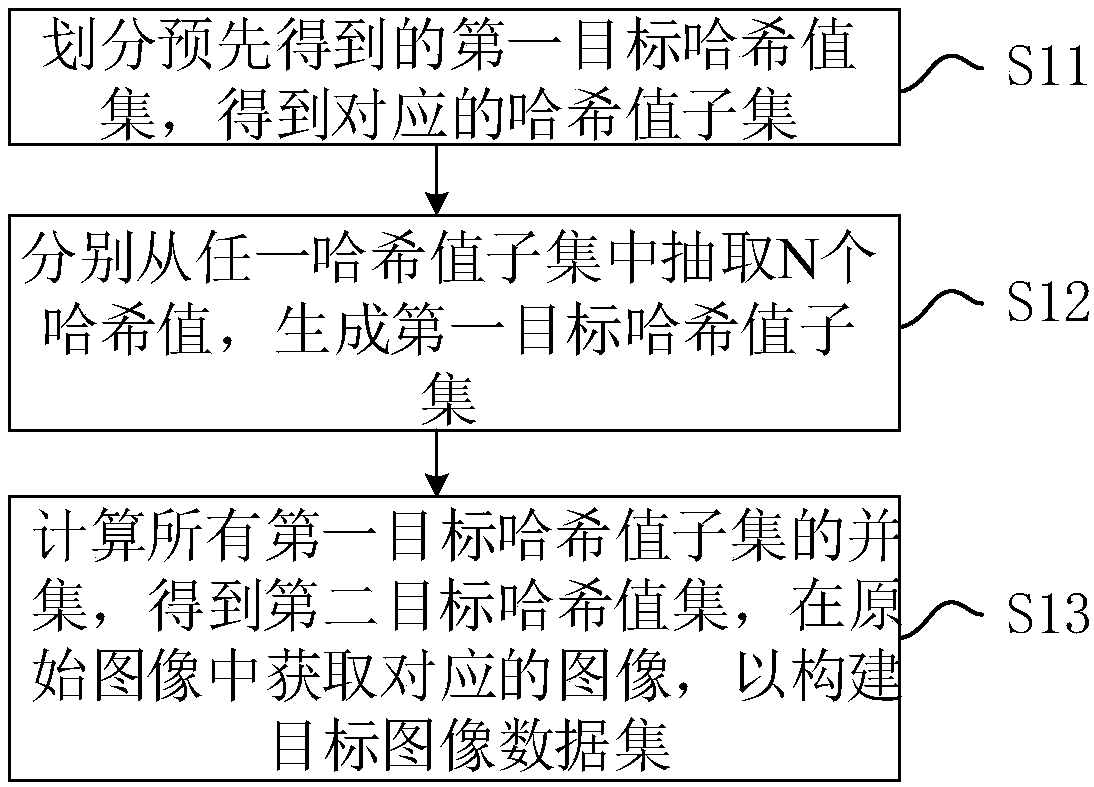
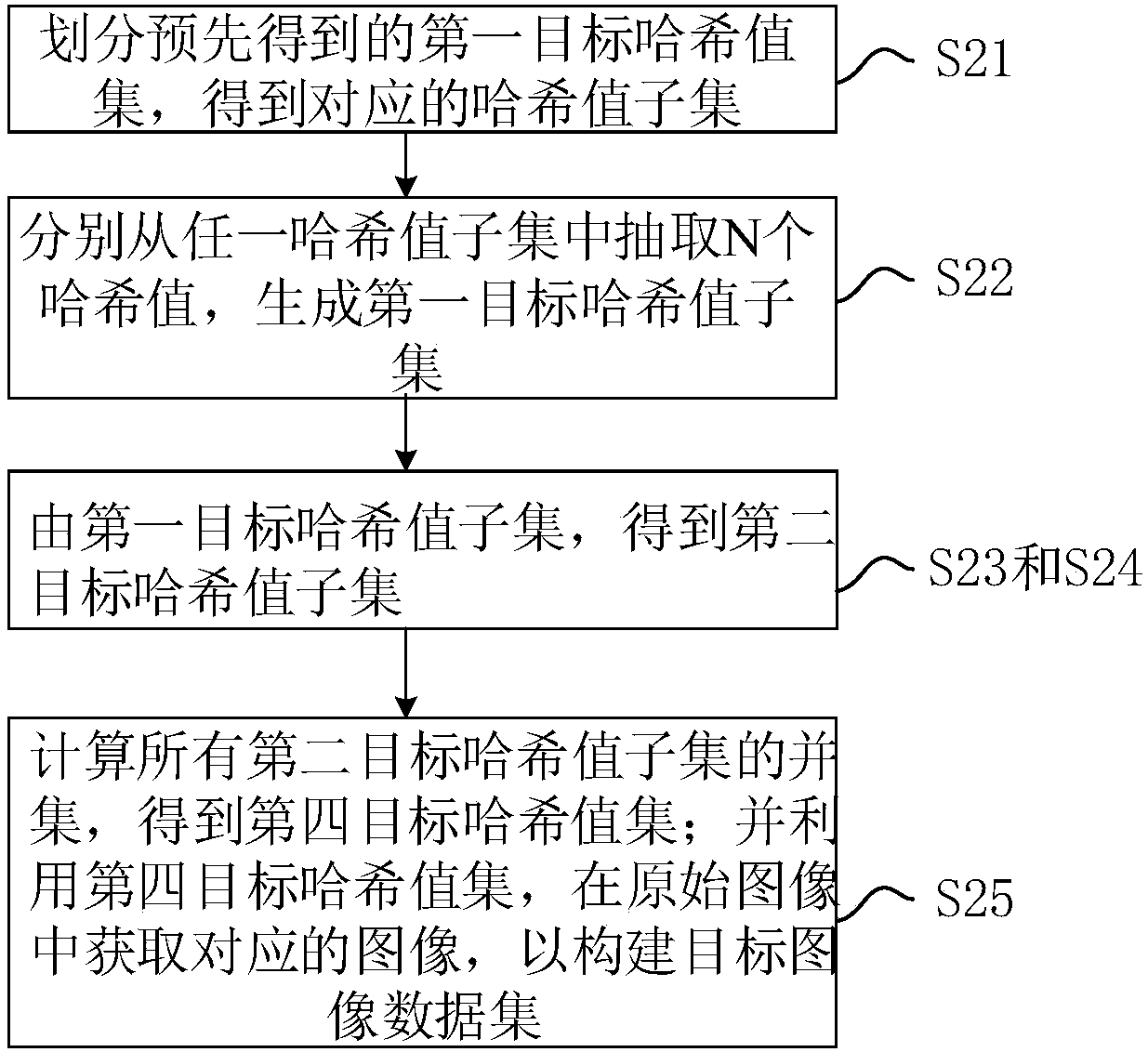
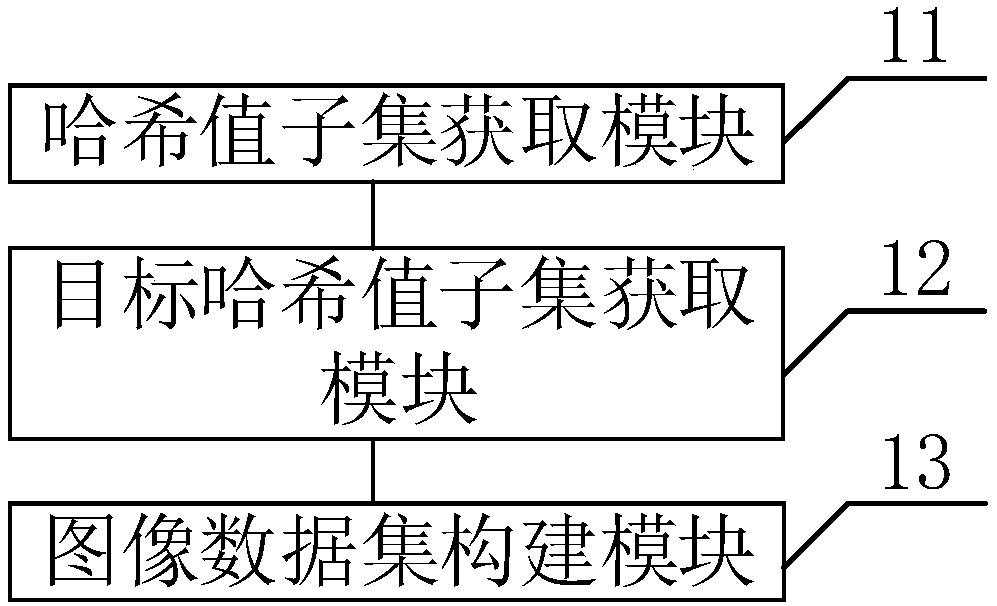
Image data set construction method and system and computer readable storage medium
ActiveCN107798389AImprove training effectCharacter and pattern recognitionMachine learningValue setData set
The invention discloses an image data set construction method and system and a computer readable storage medium. The method comprises the steps of dividing a first target hash value set which is obtained in advance to obtain corresponding hash value subsets having m hash values, with m being an integer larger than or equal to 1; extracting N hash values from any hash value subset respectively, andgenerating a first target hash value subset, wherein n is a positive integer smaller than or equal to m; calculating a union set of all the first target hash value subsets to obtain a second target hash value set, using a second target hash value set, and obtaining a corresponding image in the original image so as to construct a target image data set. The process of obtaining the first target hash value set includes obtaining an original image data set to obtain a corresponding original image, calculating a hash value of the original image, removing the repeated hash value according to the hash value obtained through calculation to obtain the first target hash value set. An image data set which is differentiated is constructed.
Owner:STATE GRID CHONGQING ELECTRIC POWER CO ELECTRIC POWER RES INST +2
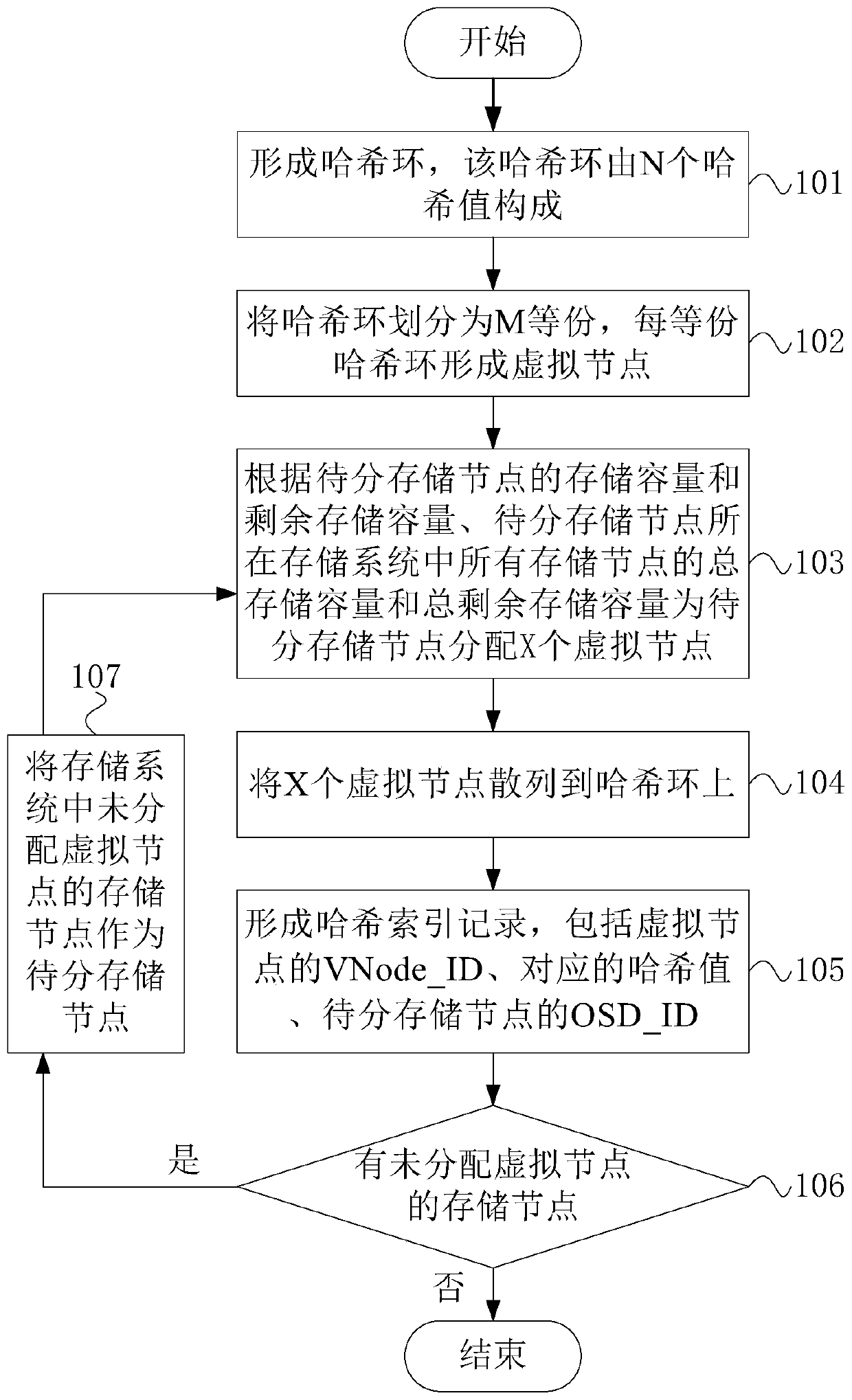
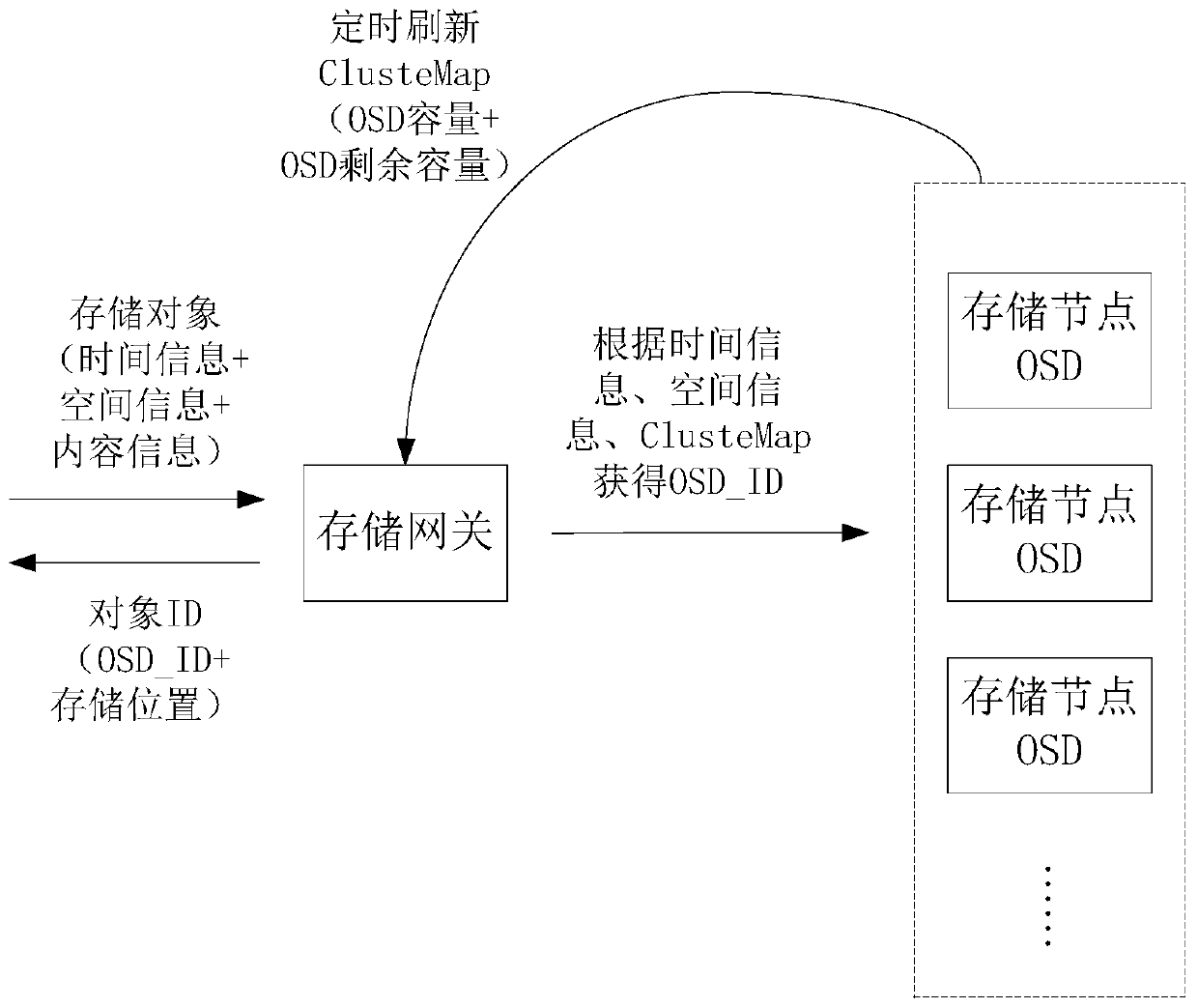
Storage capacity balancing method and device and object storage method and device
ActiveCN110633053ACapacity balanceConvenient queryInput/output to record carriersObject storageOperating system
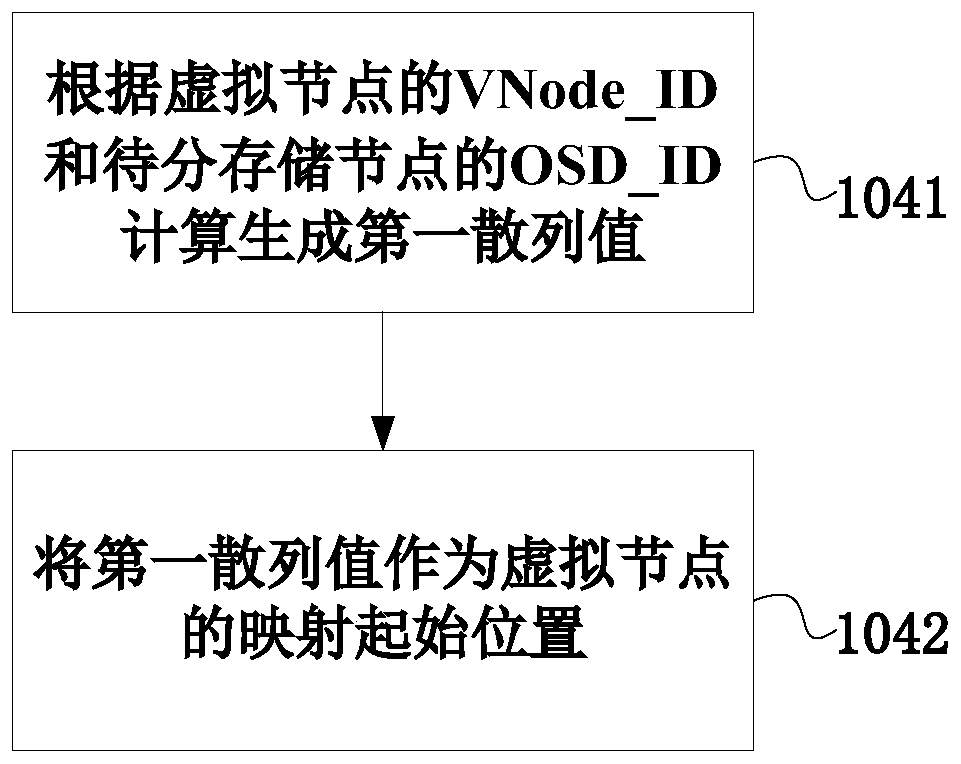
The invention discloses a storage capacity balancing method and device and an object storage method and device. The storage capacity balancing method comprises the steps of forming a hash ring, wherein the hash ring is composed of N hash values; dividing the hash ring into M equal parts, wherein each equal part of the hash ring forms a virtual node; allocating X virtual nodes to the to-be-distributed storage nodes according to the real-time capacity information of the storage nodes; hashing the X virtual nodes onto a hash ring; forming a hash index record, wherein the Hash index record comprises VNode _ ID of virtual nodes, corresponding Hash values and OSD _ IDs of the to-be-distributed storage nodes; and repeatedly distributing the virtual nodes to all the storage nodes in the storage system, hashing the virtual nodes and forming a hash index record. When the virtual nodes are allocated to the storage nodes, the real-time capacity information of the storage nodes and all the storagenodes in the storage system is referred to, the write-in amount of each storage node is automatically balanced, and the capacity balance of each storage node is ensured to the maximum extent.
Owner:北京马赫谷科技有限公司
Method and device for sending digital television signal data based on alternative text combination
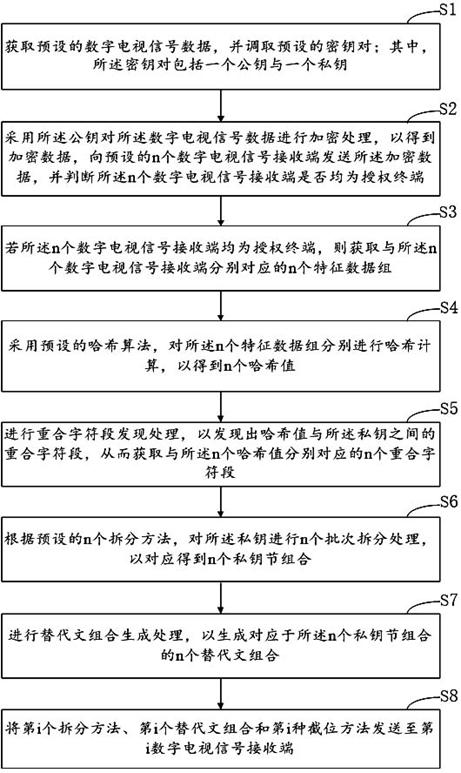
ActiveCN113518244AImprove securityImprove information securityEncryption apparatus with shift registers/memoriesSelective content distributionTelecommunicationsFeature data
The invention discloses a method and a device for sending digital television signal data based on alternative text combination. The method comprises the steps: acquiring preset digital television signal data, and calling a preset key pair; performing encryption processing to obtain encrypted data, and sending the encrypted data; if signal receiving ends are all authorized terminals, acquiring n feature data sets; respectively carrying out Hash calculation to obtain n Hash values; performing discovery processing on coincident character fields to obtain n coincident character fields corresponding to the n hash values respectively; performing n-batch splitting processing on the private key to correspondingly obtain n private key section combinations; performing alternative text combination generation processing to generate n alternative text combinations corresponding to the n private key section combinations; and sending the ith splitting method, the ith alternative text combination and the ith interception method to the ith digital television signal receiving end, thereby improving the security of the secret key and the information security and realizing the fine control of the authority.
Owner:深圳佳力拓科技有限公司
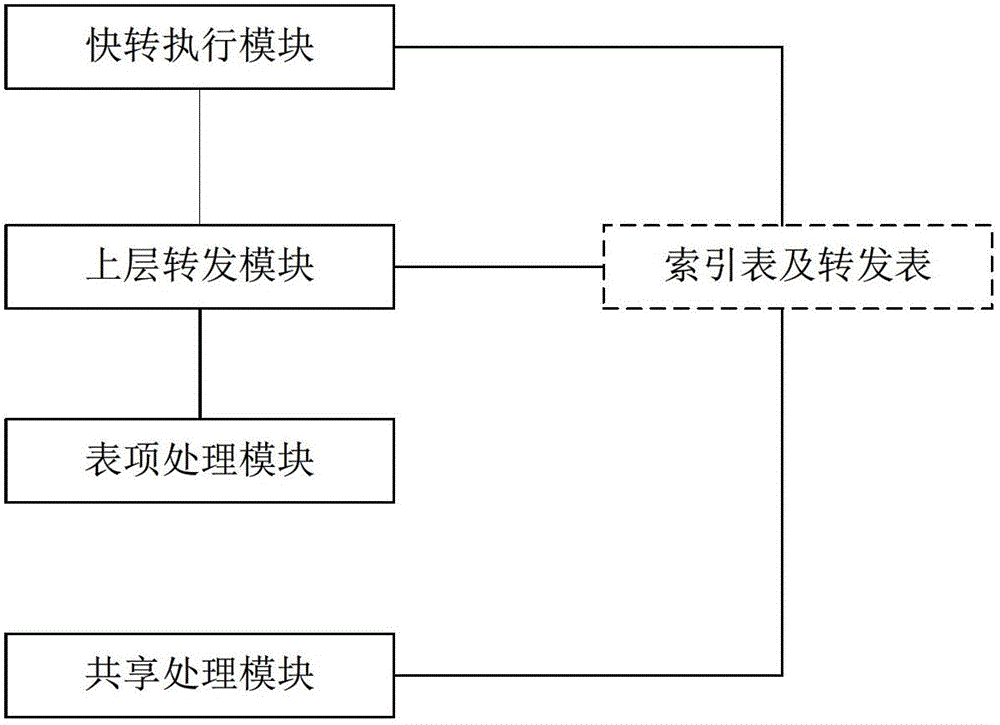
Method and device for fast message forwarding
The present invention provides a fast forwarding method and a corresponding device. The method includes: calculating a Hash value according to the session characteristics of the message, and determining the corresponding Hash bucket in the index table according to the Hash value; wherein the index table includes N Hash buckets ; Wherein each index entry holds a forwarding pointer pointing to a forwarding entry in the forwarding table; traverse the Hash bucket, and perform fast forwarding when the forwarding entry corresponding to the session feature is found, but the corresponding one is not found during the traversal process Submit the upper-layer forwarding module for processing when forwarding the table item; save the processing result information of the upper-layer forwarding module in the forwarding table item, calculate the Hash value according to the session characteristics and determine the corresponding Hash bucket, and save the forwarding pointer pointing to the forwarding table item in In the hash bucket. The invention adopts a new table item structure and a query design method, can calmly deal with the problem of Hash conflicts, and provides an expansion mechanism to deal with severe Hash conflicts.
Owner:杭州迪普信息技术有限公司
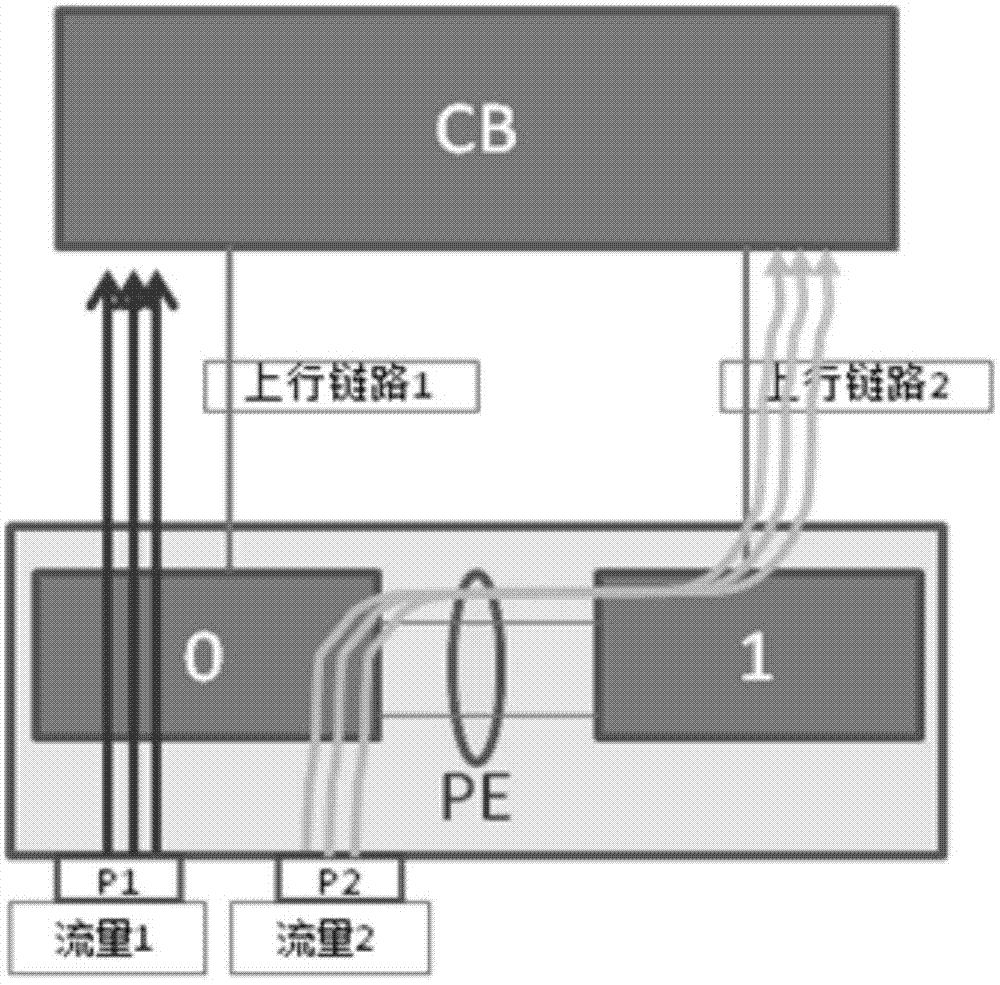
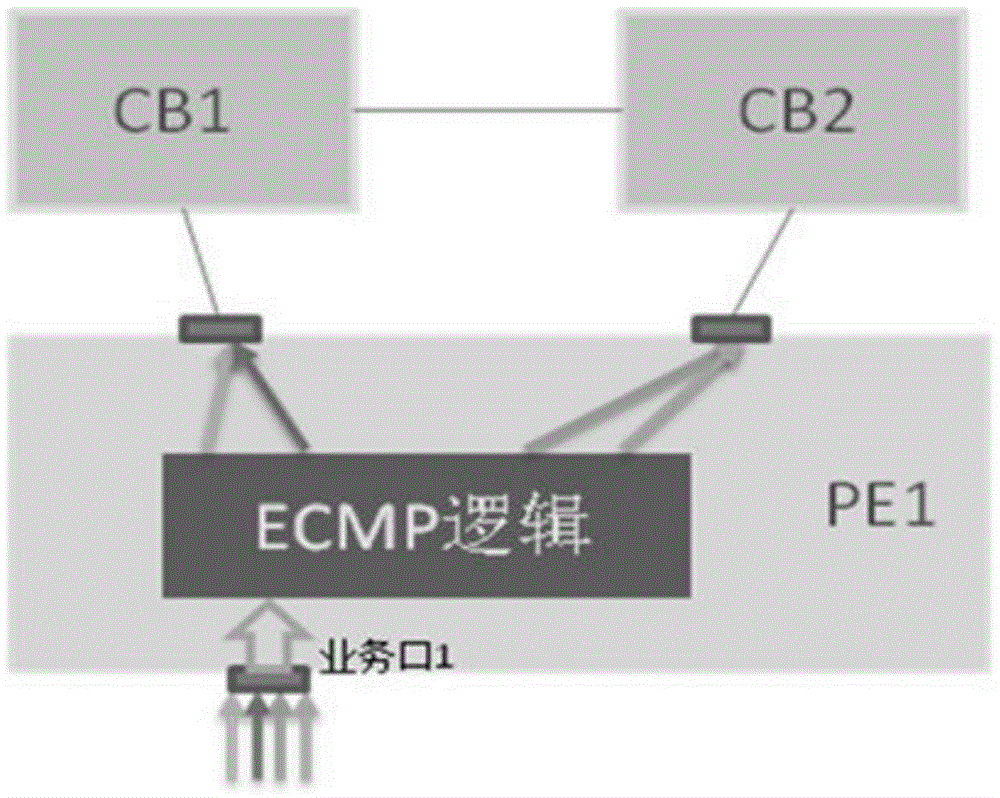
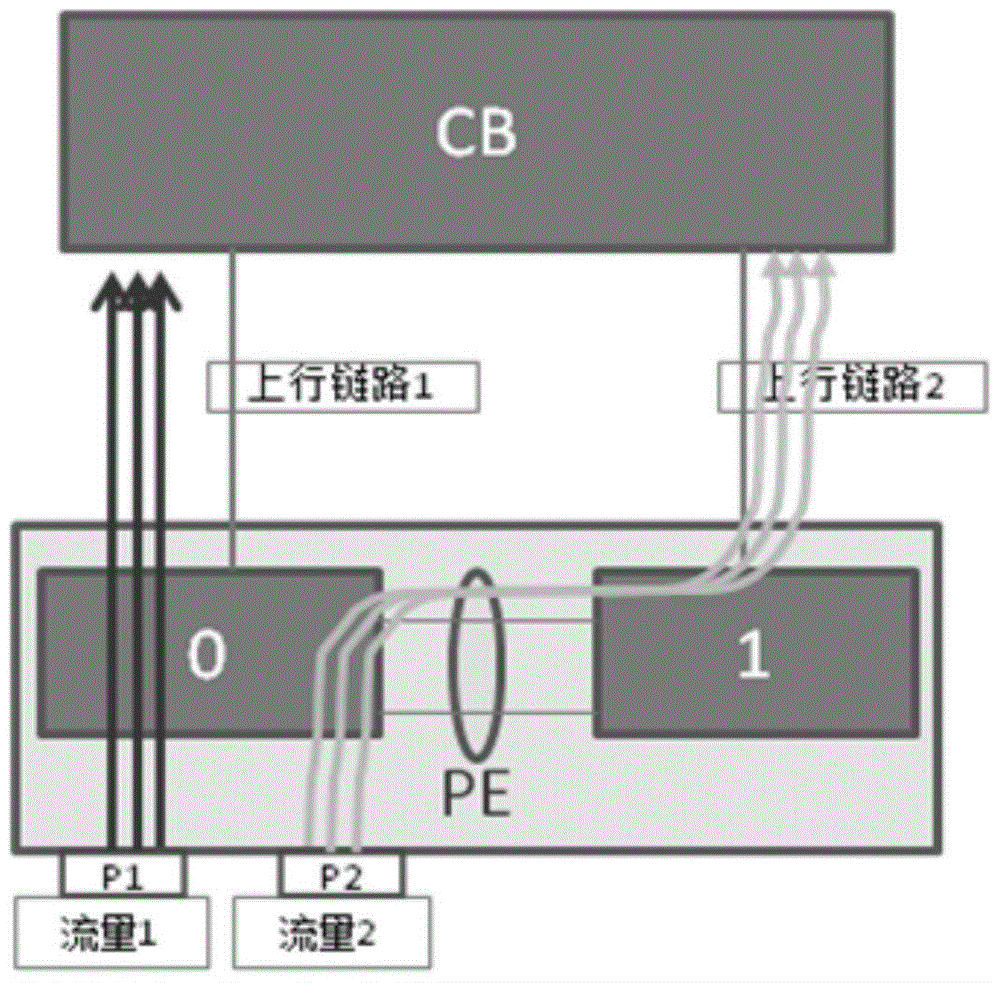
A flow scheduling method and device for PE equipment
ActiveCN103763135BSolve the problem of load sharingData switching networksComputer scienceReal-time computing
Owner:NEW H3C TECH CO LTD
Apparatus and method for hash table storage, searching
ActiveCN101604337BSmall lookup time costHigh Tablespace UtilizationDigital data information retrievalSpecial data processing applicationsTheoretical computer scienceHash table
The invention discloses an apparatus and a method for hash table item storage, searching, which aim to solve the problem of hardness in balancing between time needed for table searching and table capacity in hash table storage structure in the prior art. According to the invention a large hash table storage space is divided into a plurality of hash sub-table storage spaces, each of which corresponds to N hash functions. When an item is stored, a hash value is computed using hash function corresponding to each hash sub-table sequentially, an empty position is found in the hash sub-table for storage of the item; when an item is searched, a search among all hash sub-tables is executed for enhancing speed of searching. The invention effectively solves the problem of hardness in balancing between time needed for table searching and table capacity in hash table storage structure in the prior art, implements storage of all items using ultimately low searching time and ultimately high table utilization without residual items.
Owner:ZTE CORP
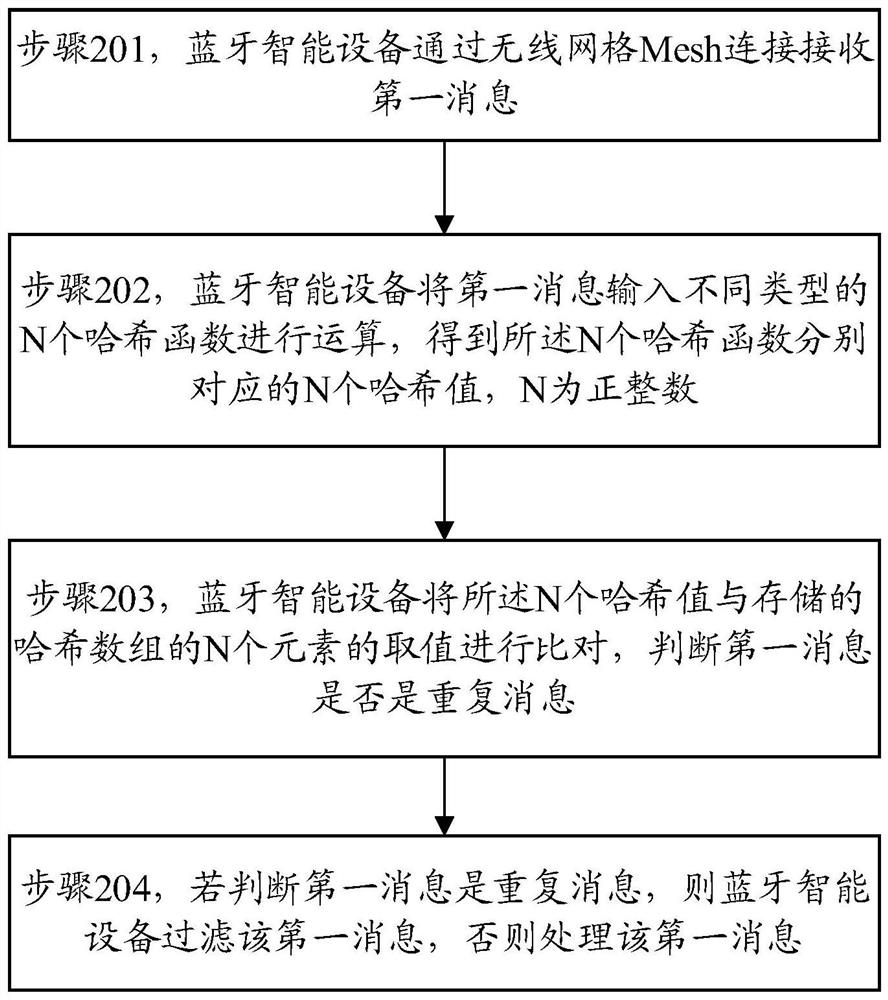
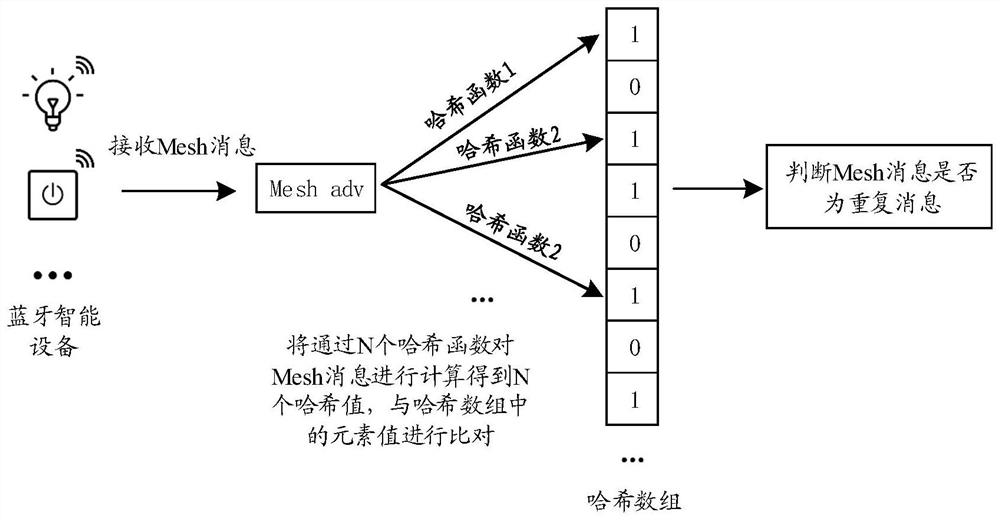
Message filtering method and device in Bluetooth wireless mesh network
PendingCN114786141ANetwork topologiesMessaging/mailboxes/announcementsWireless mesh networkMessage handling
The invention provides a message filtering method and device in a Bluetooth wireless grid network, and the method comprises the steps: receiving a first message through Bluetooth wireless grid connection by Bluetooth intelligent equipment, inputting the first message into N hash functions of different types for operation, obtaining N hash values corresponding to the N hash functions, and then comparing the N hash values with values of N elements of a stored hash array to judge whether the first message is a repeated message, if the first message is judged to be a repeated message, filtering the first message, and otherwise, processing the first message. According to the method, the memory and processing resource consumption of the equipment can be reduced in a resource limited scene, and the message processing efficiency is improved.
Owner:BESTECHNIC SHANGHAI CO LTD
A method for data fusion and data privacy protection based on hash algorithm and session control
ActiveCN110263575BGuarantee privacy and securityGuarantee data securityAdvertisementsDigital data protectionData privacy protectionSession control
The invention relates to a method for realizing data fusion and data privacy protection based on a Hash algorithm and the session control. The method comprises the following steps that a demand module sends a query request after Hash calculation to a mapping data providing module; the mapping data providing module inquires whether the data exists or not; a demand module queries the provider data from the portrait data providing module; a portrait data providing module inquires the previous n hash value lists; the mapping data providing module returns the hit information to the portrait data providing module; and the portrait data providing module queries the data. By the adoption of the method for realizing data fusion and data privacy protection based on the Hash algorithm and the session control, the leakage of the high-sensitivity information caused by query of low-sensitivity information is avoided, and the data derogatory caused by the data diffusion is also avoided. According to the implementation scheme, the user privacy information of three parties cannot be leaked except the user portrait information, so that the data privacy and the data security of the individual users and the enterprise users are guaranteed.
Owner:上海富数科技有限公司
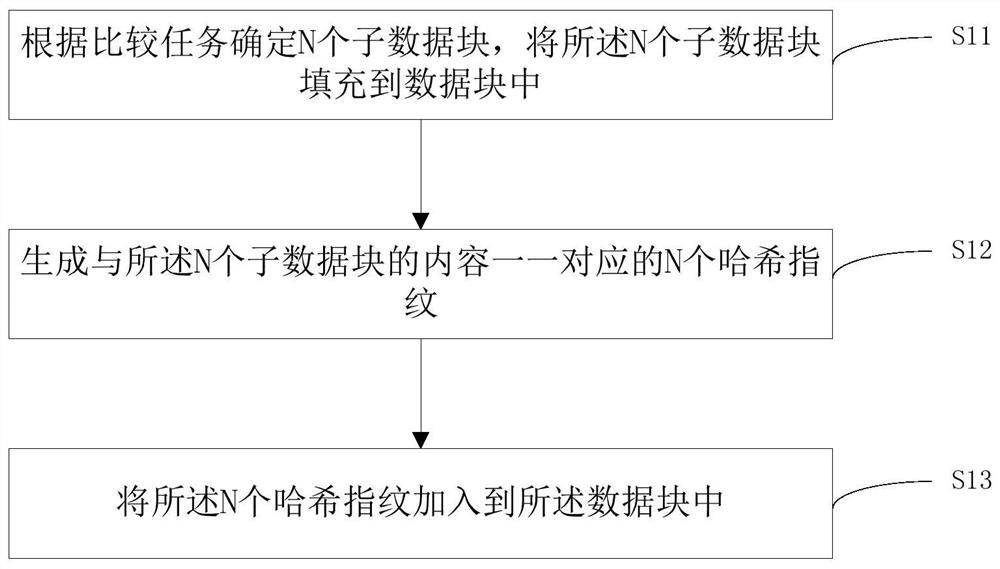
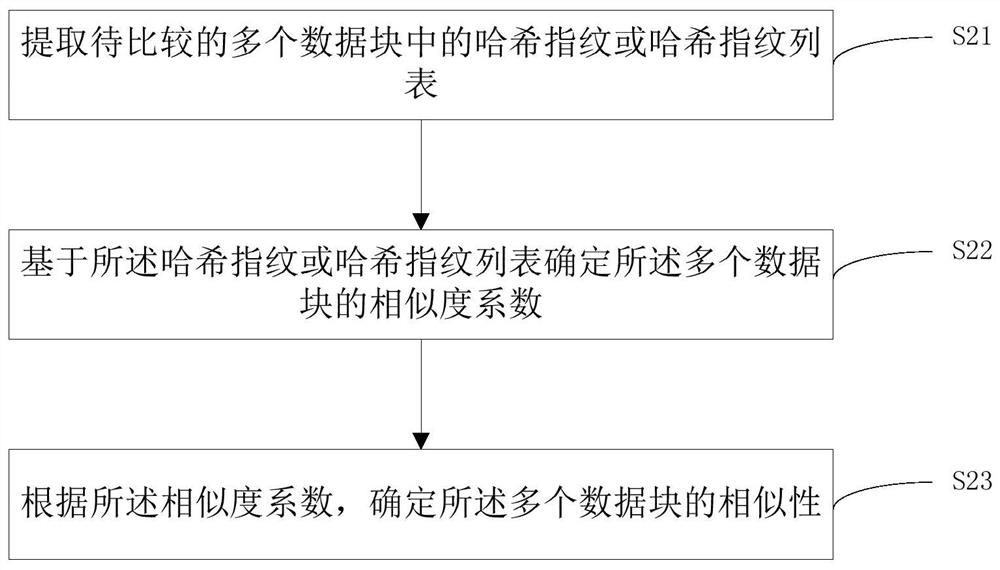
Data block construction and comparison method and device, medium and equipment
PendingCN112667144AQuick extractionInput/output to record carriersDatabase indexingAlgorithmEngineering
The invention relates to a data block construction and comparison method and device, a medium and equipment. The method comprises the steps of determining N sub-data blocks according to a comparison task, and filling the data blocks with the N sub-data blocks; generating N hash fingerprints in one-to-one correspondence with the contents of the N sub-data blocks; and adding the N hash fingerprints into the data blocks. When data block similarity comparison is carried out, hash fingerprints or hash fingerprint lists in a plurality of to-be-compared data blocks are directly extracted, and similarity coefficients of the plurality of data blocks are determined based on the hash fingerprints or hash fingerprint lists, so that the process of segmenting big data and calculating the hash fingerprints is avoided, the calculation time is saved, and the efficiency is improved.
Owner:BEIJING BAISHANCLOUD TECH CO LTD
A Time Stamp Generation Method Based on Blockchain Digital Signature
ActiveCN110830260BSolve the problem of single point of failureUser identity/authority verificationAlgorithmDigital signature
The invention discloses a block chain-based digital signature time stamp generation method, which mainly includes three stages: a system parameter establishment stage, a signature stage, and a verification stage. Among them, in the signing phase, the signer obtains the hash values of the n latest confirmed blocks in the blockchain, and binds these n hash values with the message M to be signed as M', and for M 'Sign to get the signature T, the signer calculates the hash value h of M'||T, and uploads h to the blockchain through the transaction Tx. After the verifier completes the verification of the signature T, the time range after the generation time of the block where the nth hash value is located and before the generation time of the block where the transaction Tx is located is taken as the timestamp of the signature T, which is a decentralized An accurate method for timestamping digital signatures.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
A data storage method for massive unstructured data
ActiveCN104731864BSolve extraction puzzlesFlexible size adjustmentSpecial data processing applicationsData retrievalUnstructured data
The invention discloses a data storage method for mass unstructured data. The method comprises the steps that firstly, a time interval T is set, a data storage cluster is divided into a plurality of zones, records obtained at the same time interval T are stored in the same zone, and meanwhile each zone is divided into n hash zones; secondly, for each unstructured record, the generated time t of the unstructured record and one or more key information key solely expressing the unstructured record are extracted; thirdly, according to the time t of each record, the zone where the records are stored is determined, and the corresponding hash zone values of the records in the zones are calculated according to the key information of the record; fourthly, the records which are in the same time interval and are the same in hash zone value are written in the same file F according to the calculation result in the step three, the number of the records in the file F is counted, and if the number of the records is larger than the set threshold value K, another file is established in a current hash zone for storage. According to the storage method, the data retrieval efficiency can be greatly improved.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT +1
Method and device for creating a hash table
ActiveCN105095212BMatch the requirements of the table item wellCutting costsSpecial data processing applicationsComputer hardwareHash table
The invention provides a method and equipment for creating a hash table. The method comprises following steps: determining subspace of at least two hash sub-tables according to space of the nth hash sub-table in N hash sub-tables of the hash table, wherein the size of the nth hash sub-table is non-positive integral power of 2 and sizes of subspace of at least two hash sub-tables are positive integral power of 2; mapping the current key value to one of sub-space of at least two hash sub-tables based on the nth pre-processed hash function used for mapping multiple key values to at least two sub-space of at least two hash sub-tables; generating an address of a hash bucket for the nth hash sub-table according to a hash function corresponding to one of subspace of the at least two hash sub-tables and the current key value; and storing the current key value into a hash sub-table of N hash sub-tables according to the number of free wafers corresponding to addresses of hash buckets for the N hash sub-tables generated by the N hash sub-tables. The method and equipment for creating the hash table have the capacities of reducing waste of space and decreasing cost of realization.
Owner:上海在赢端智能科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com