Determination method and device for media access control (MAC) address Hash collision
A MAC address and hash collision technology, which is applied in the field of determination of media access control address hash collision, can solve the problems of high cost, high TCAM resource occupation, TCAM capacity and TCAM power consumption, etc., to reduce occupation and hash The effect of the probability of conflict
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] In order to make the purpose, technical solution and advantages of the present invention more clear, the embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings. It should be noted that, in the case of no conflict, the embodiments in the present application and the features in the embodiments can be combined arbitrarily with each other.
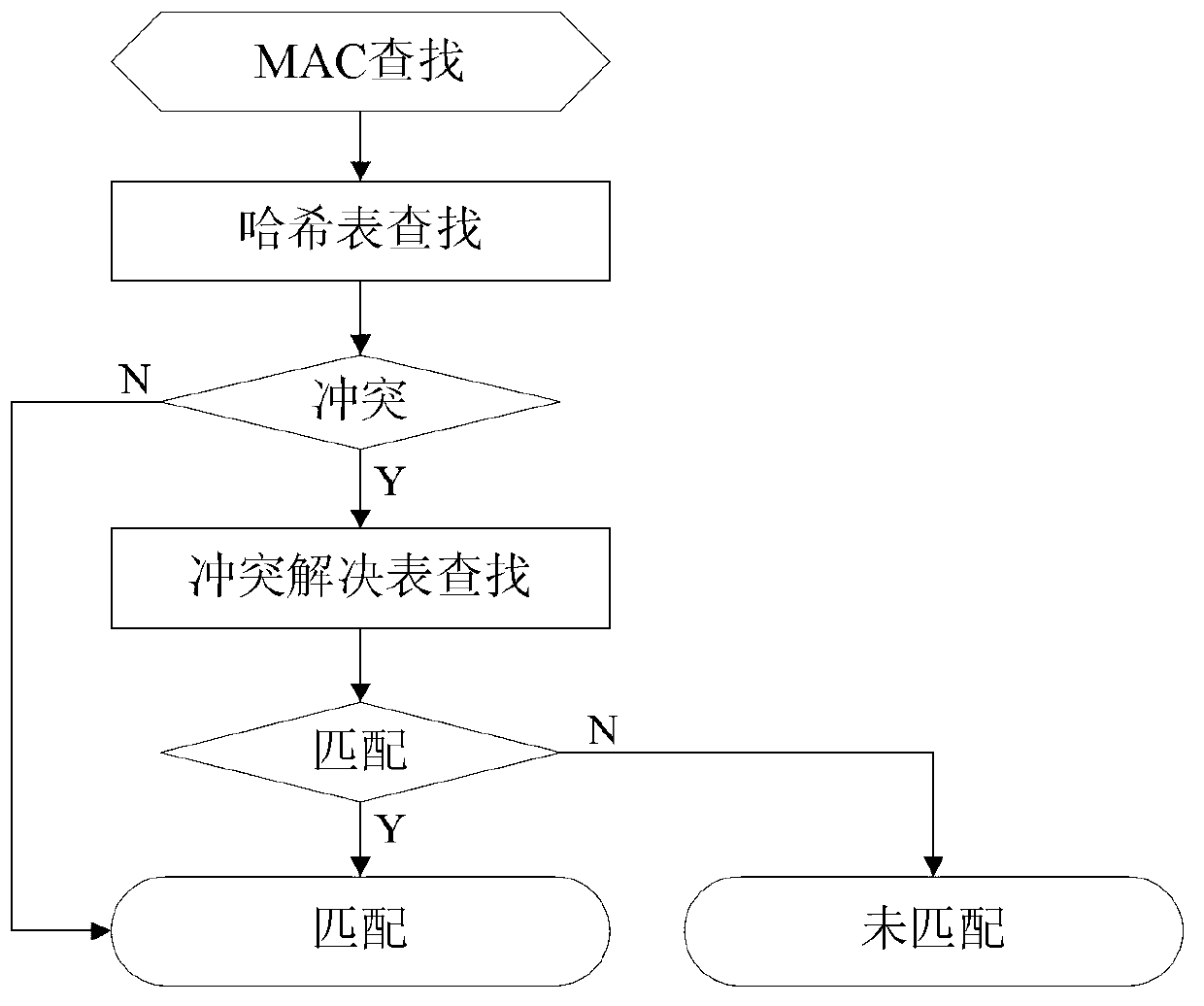
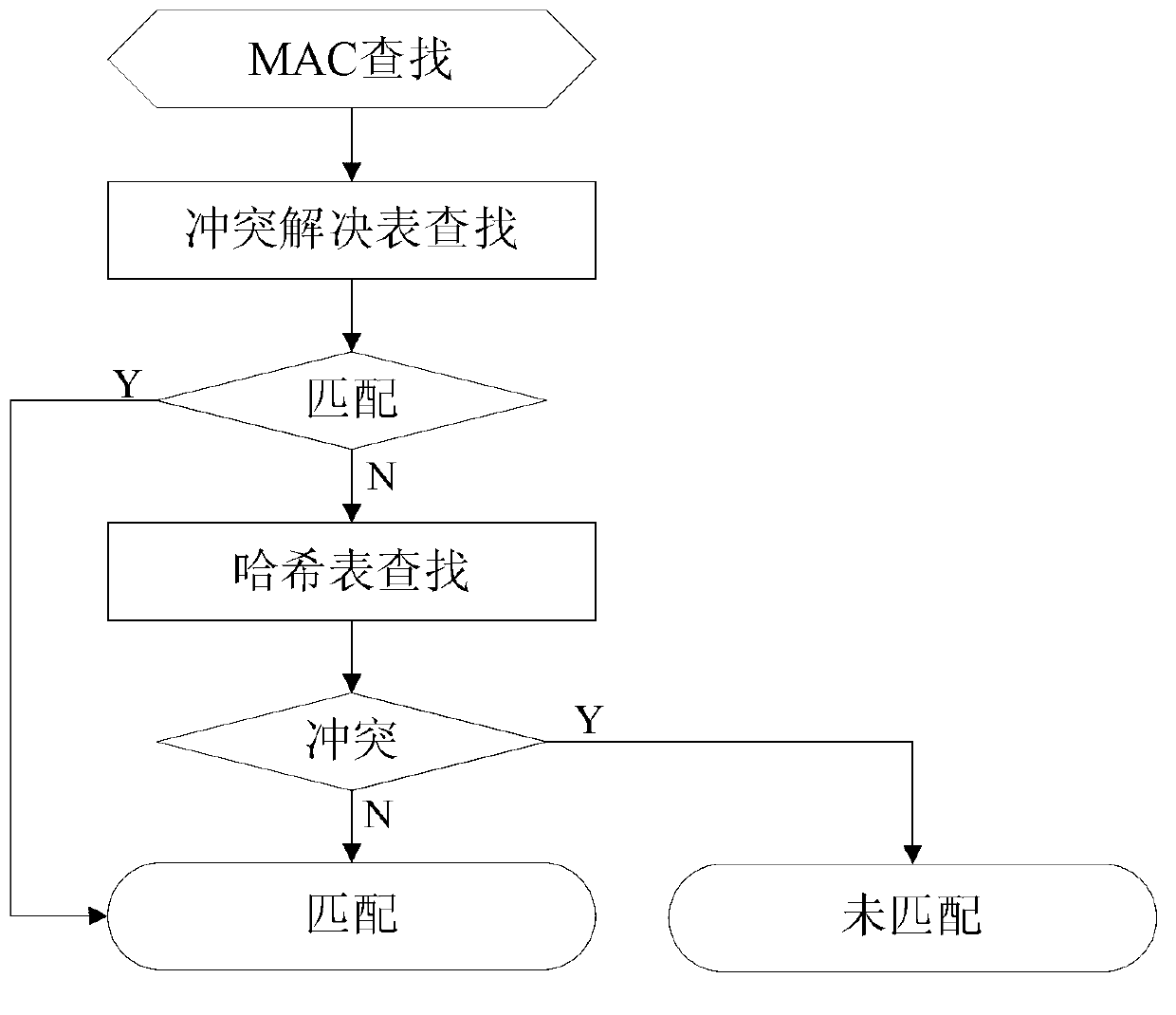
[0042] The hash conflict in the embodiment of the present invention mainly exists in the following two situations:
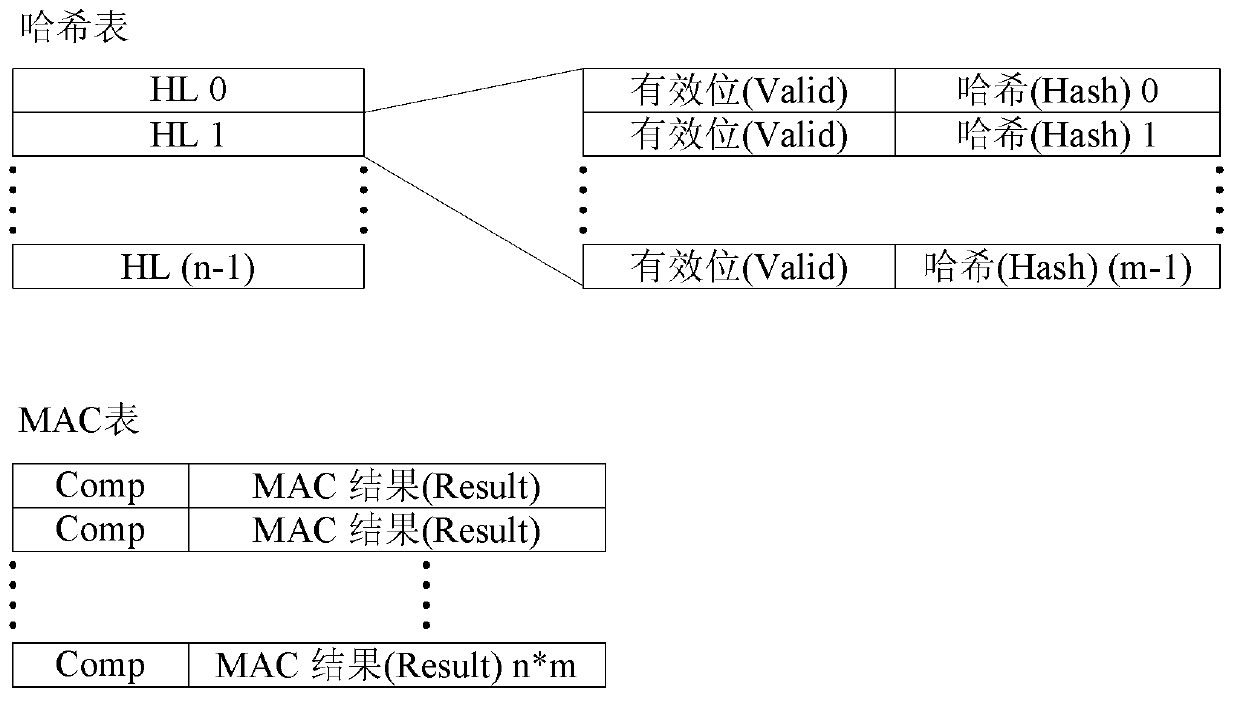
[0043] 1) When MAC is searched, the search key value has not been learned into the entry, but has a hash conflict with the key value that has been learned into the entry, and the same MAC table entry is found. At this time, it is necessary to use the search key value and Compare the Compare field in the table result to determine whether it is the entry corresponding to the search key value;
[0044] 2) Hash collision during MAC learning.
[0045] For the abov...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com