Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
32 results about "HTTP tunnel" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
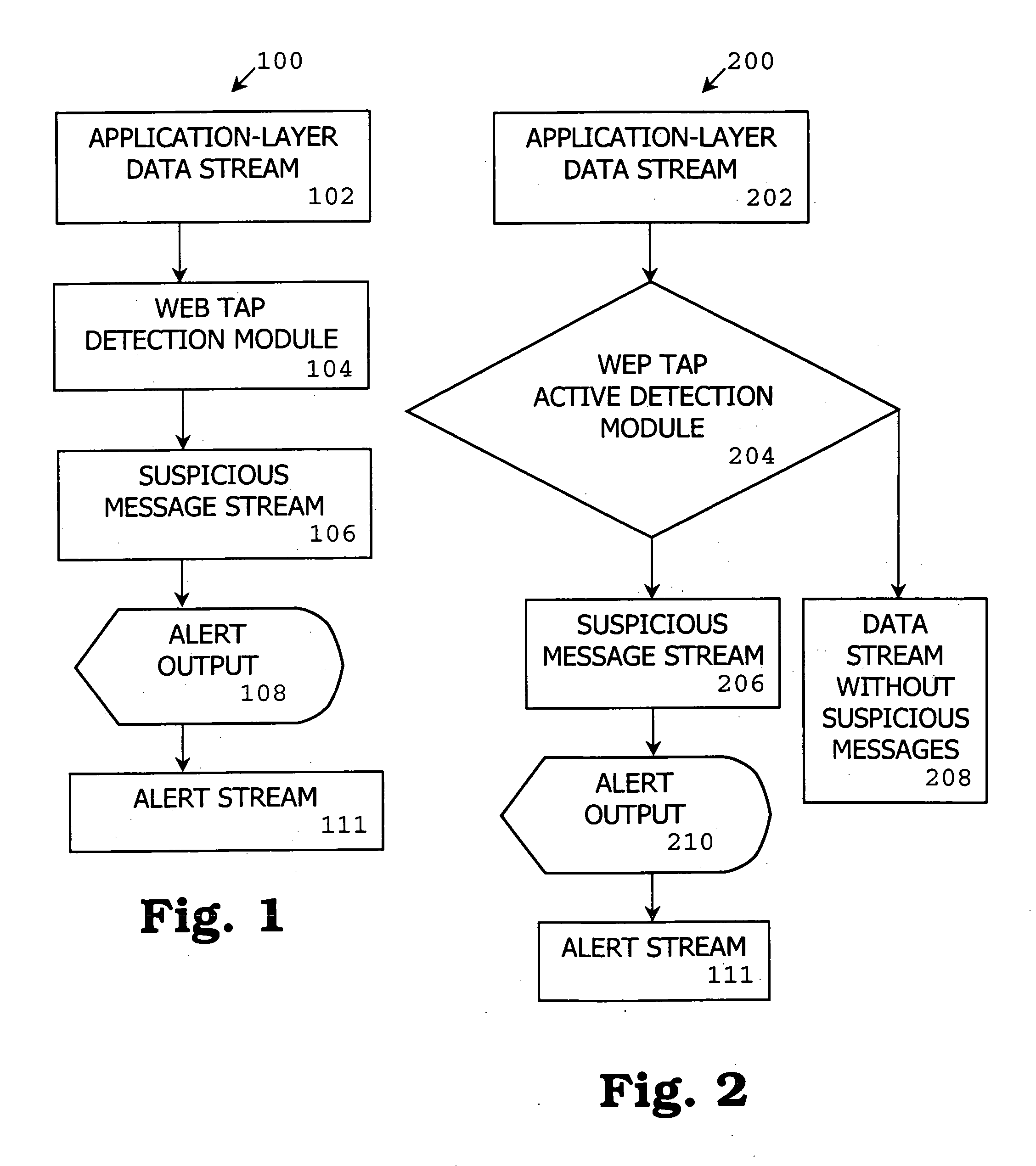
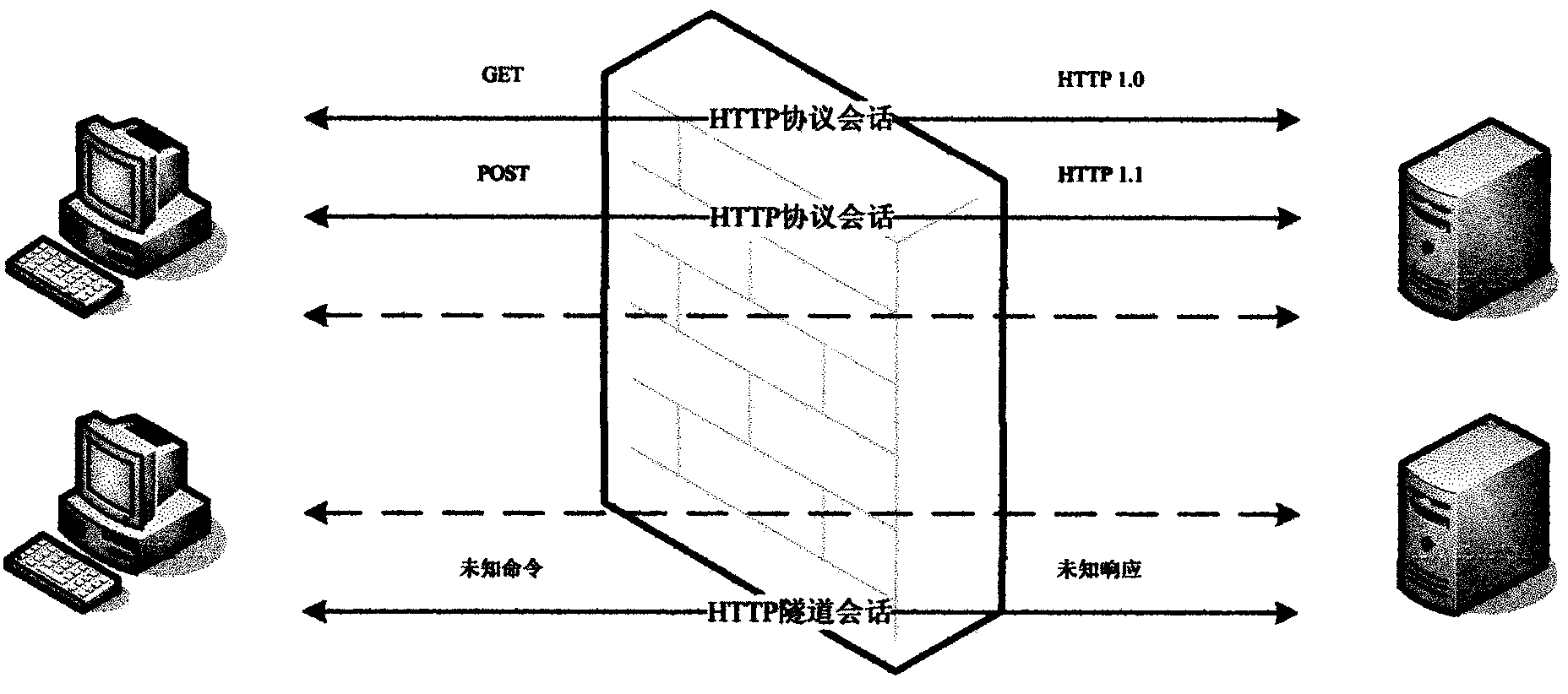
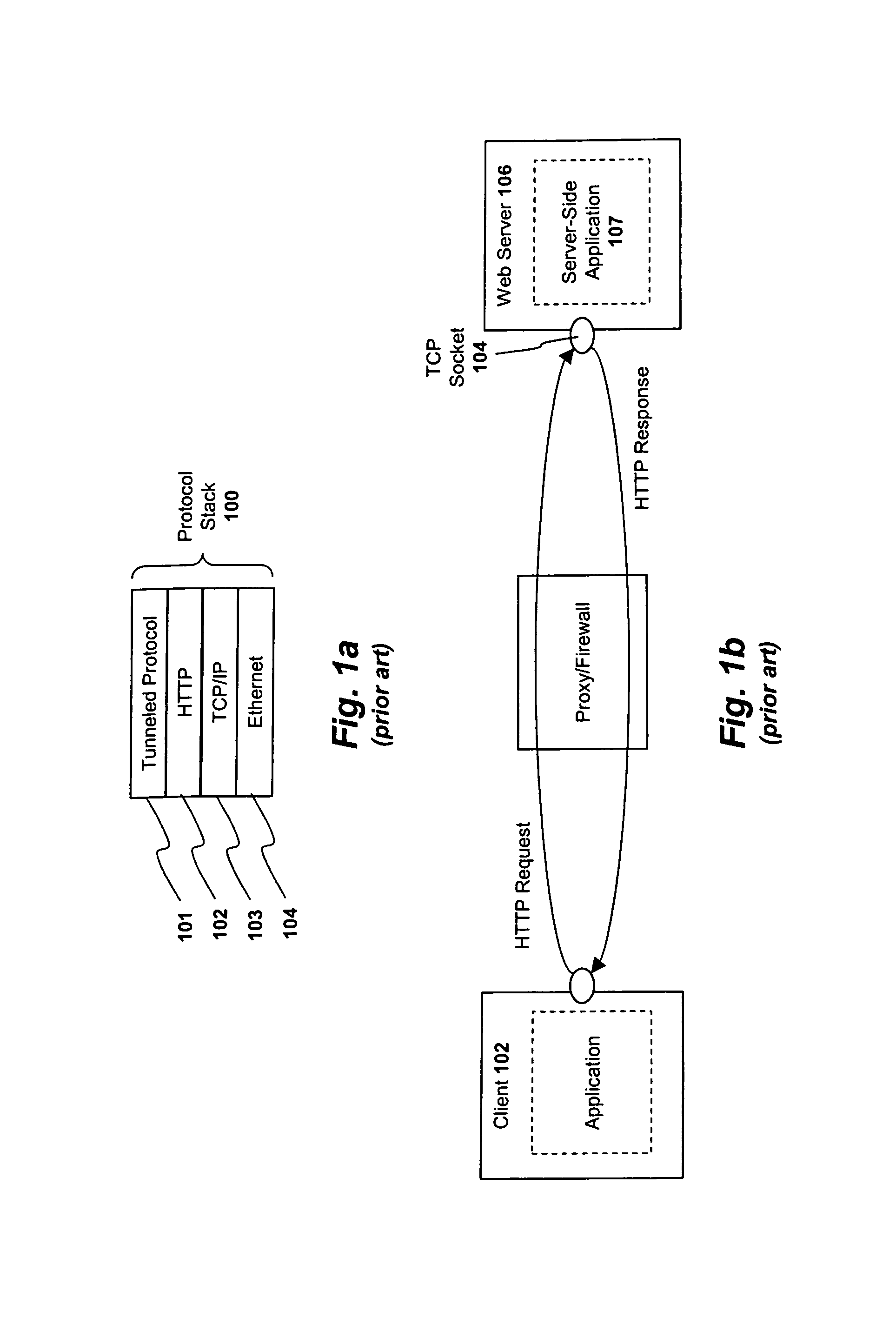
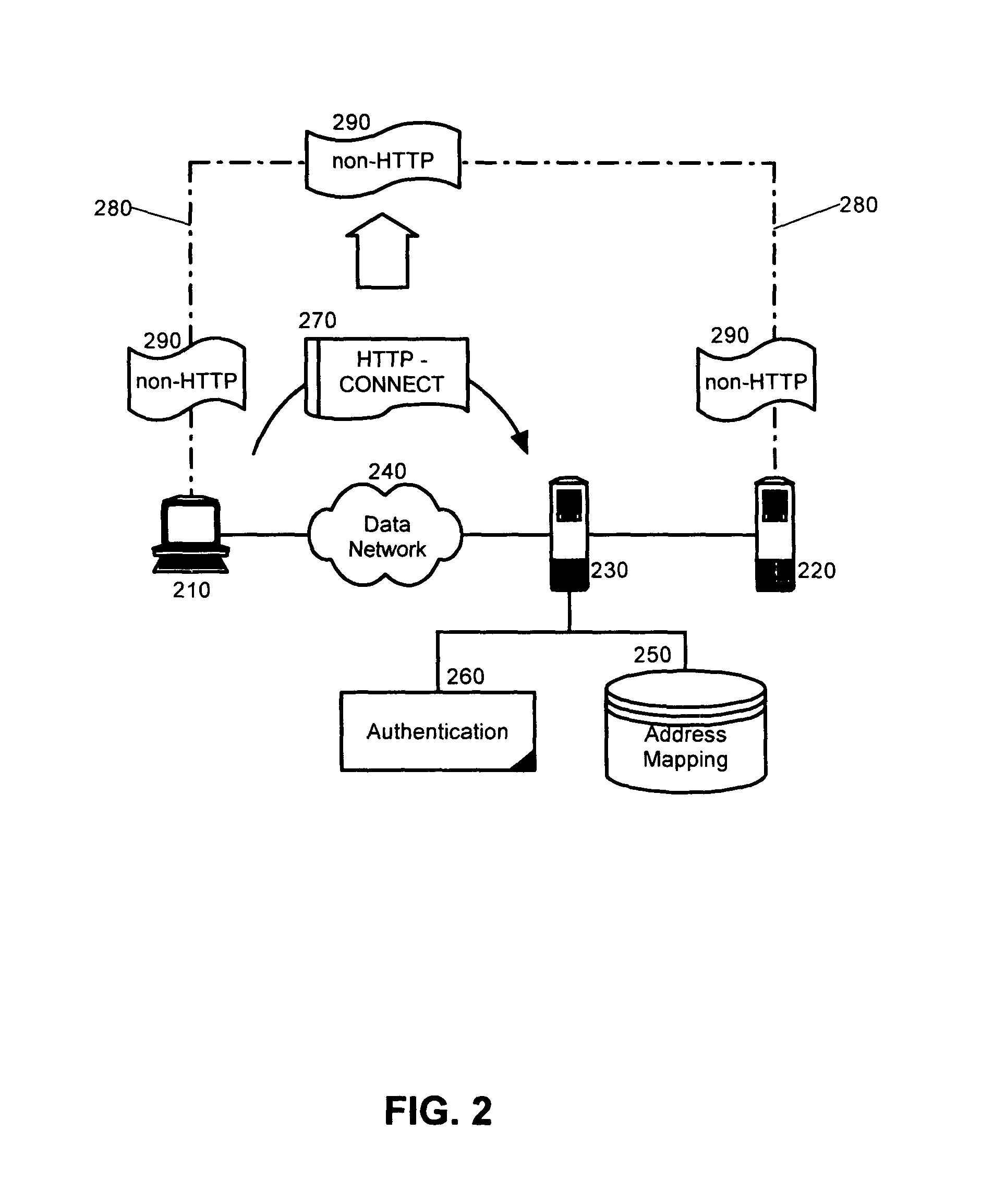
HTTP tunneling is used to create a network link between two computers in conditions of restricted network connectivity including firewalls, NATs and ACLs, among other restrictions. The tunnel is created by an intermediary called a proxy server which is usually located in a DMZ.
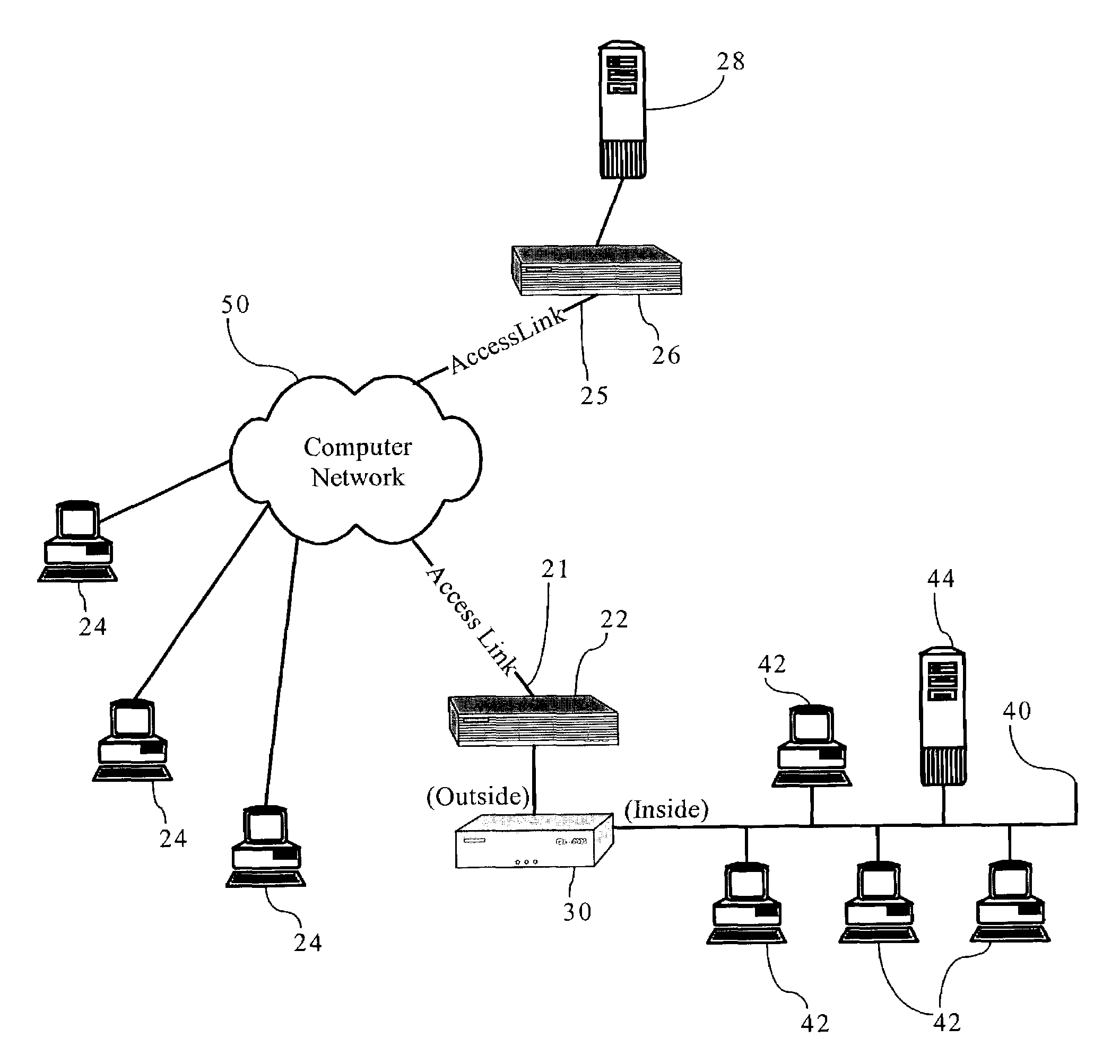
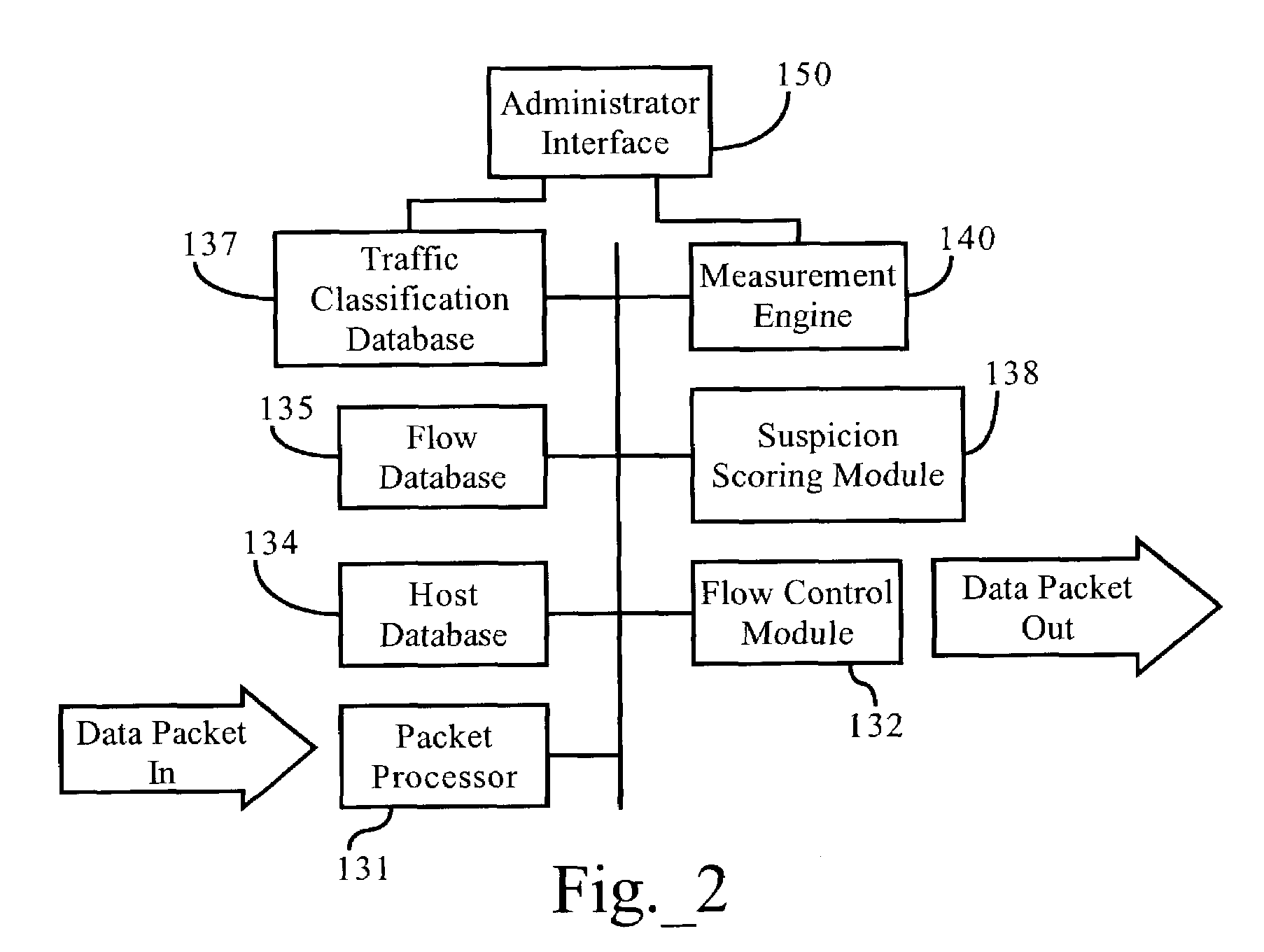
Methods, apparatuses, and systems allowing for bandwidth management schemes responsive to utilization characteristics associated with individual users
ActiveUS7296288B1Digital data processing detailsUnauthorized memory use protectionHTTP tunnelData stream
Methods, apparatuses and systems allowing for bandwidth management schemes responsive to utilization characteristics associated with individual users. In one embodiment, the present invention allows network administrators to penalize users who carry out specific questionable or suspicious activities, such as the use of proxy tunnels to disguise the true nature of the data flows in order to evade classification and control by bandwidth management devices. In one embodiment, each individual user may be accorded an initial suspicion score. Each time the user is associated with a questionable or suspicious activity (for example, detecting the set up of a connection to an outside HTTP tunnel, or peer-to-peer application flow), his or her suspicion score is downgraded. Data flows corresponding to users with sufficiently low suspicion scores, in one embodiment, can be treated in a different manner from data flows associated with other users. For example, different or more rigorous classification rules and policies can be applied to the data flows associated with suspicious users.
Owner:CA TECH INC
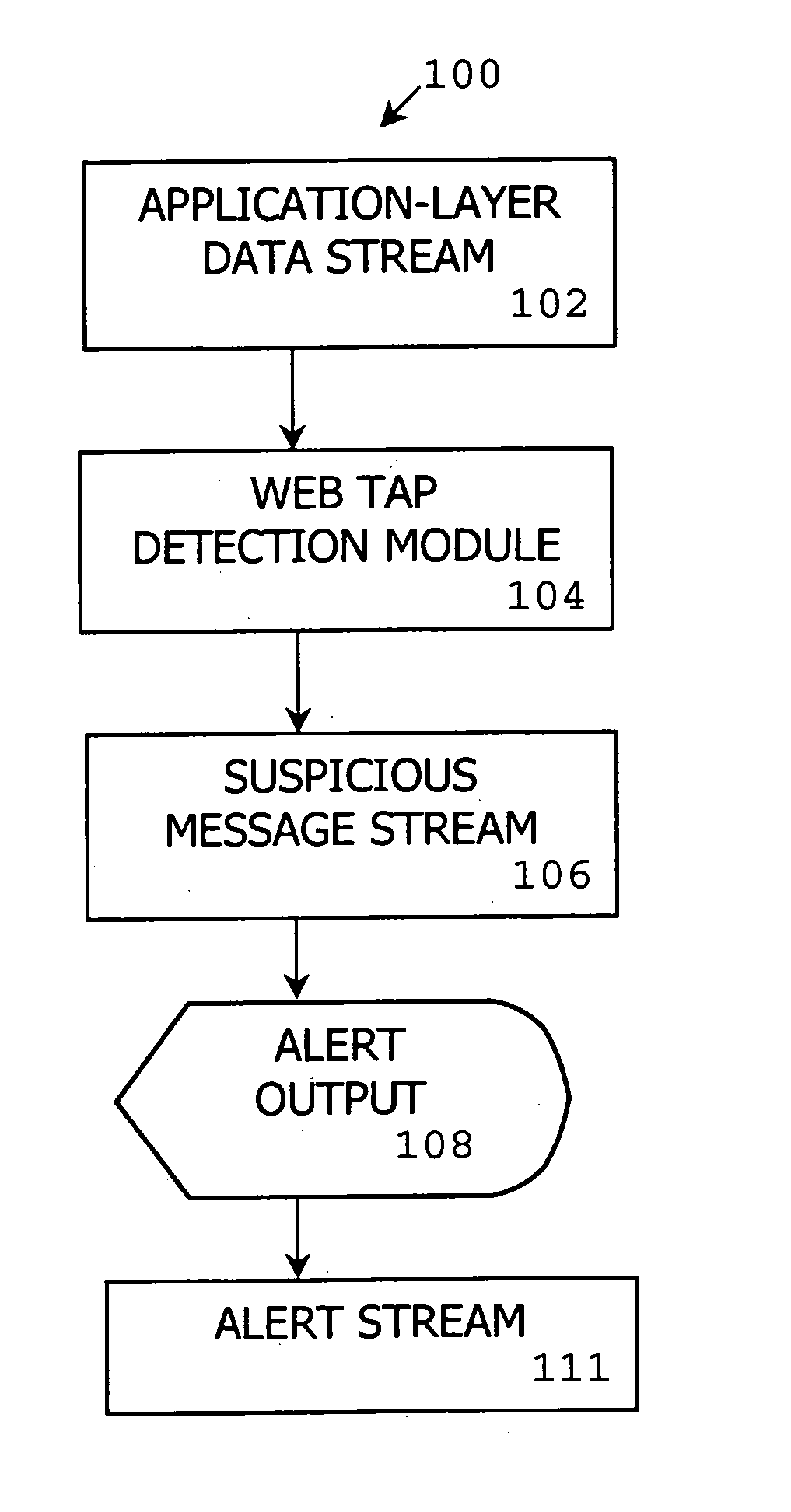
Method, system and computer program product for detecting security threats in a computer network
A method, system and computer program product detect attempts to send significant amounts of information out via HTTP tunnels to rogue Web servers from within an otherwise firewalled network. A related goal is to help detect spyware programs. Filters, based on the analysis of HTTP traffic over a training period, help detect anomalies in outbound HTTP traffic using metrics such as request regularity, bandwidth usage, inter-request delay time, and transaction size.
Owner:SYROWIK DAVID R +1
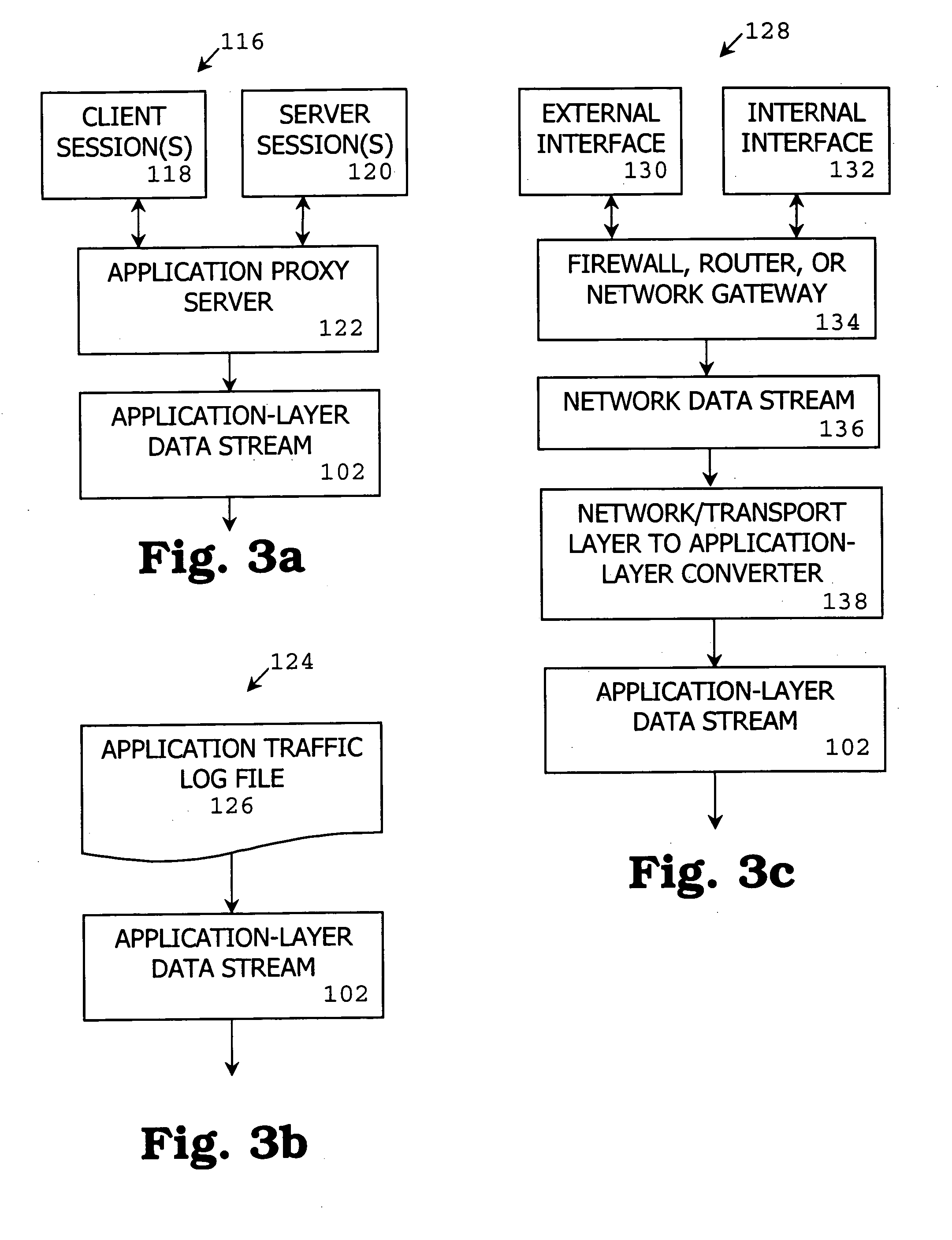
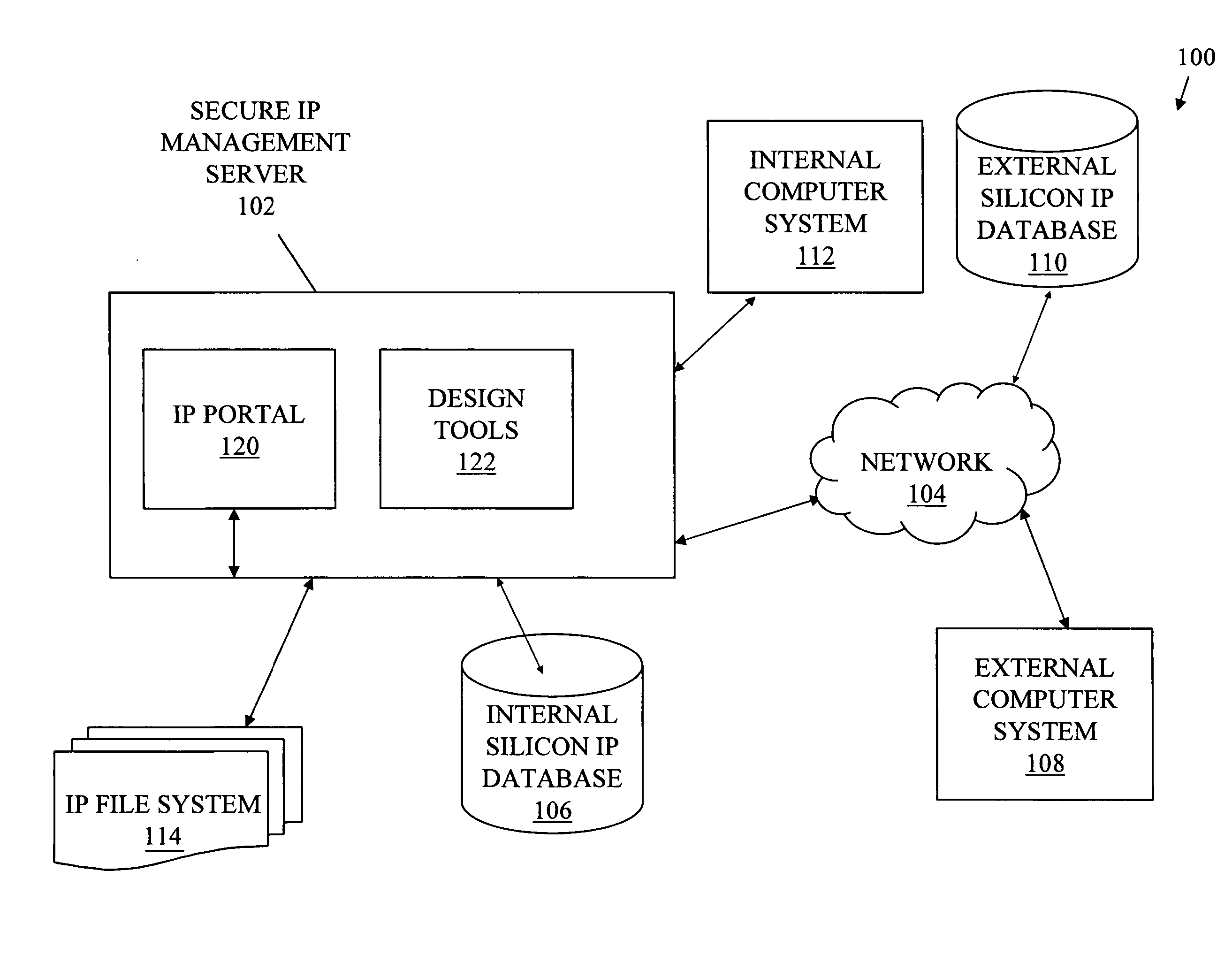
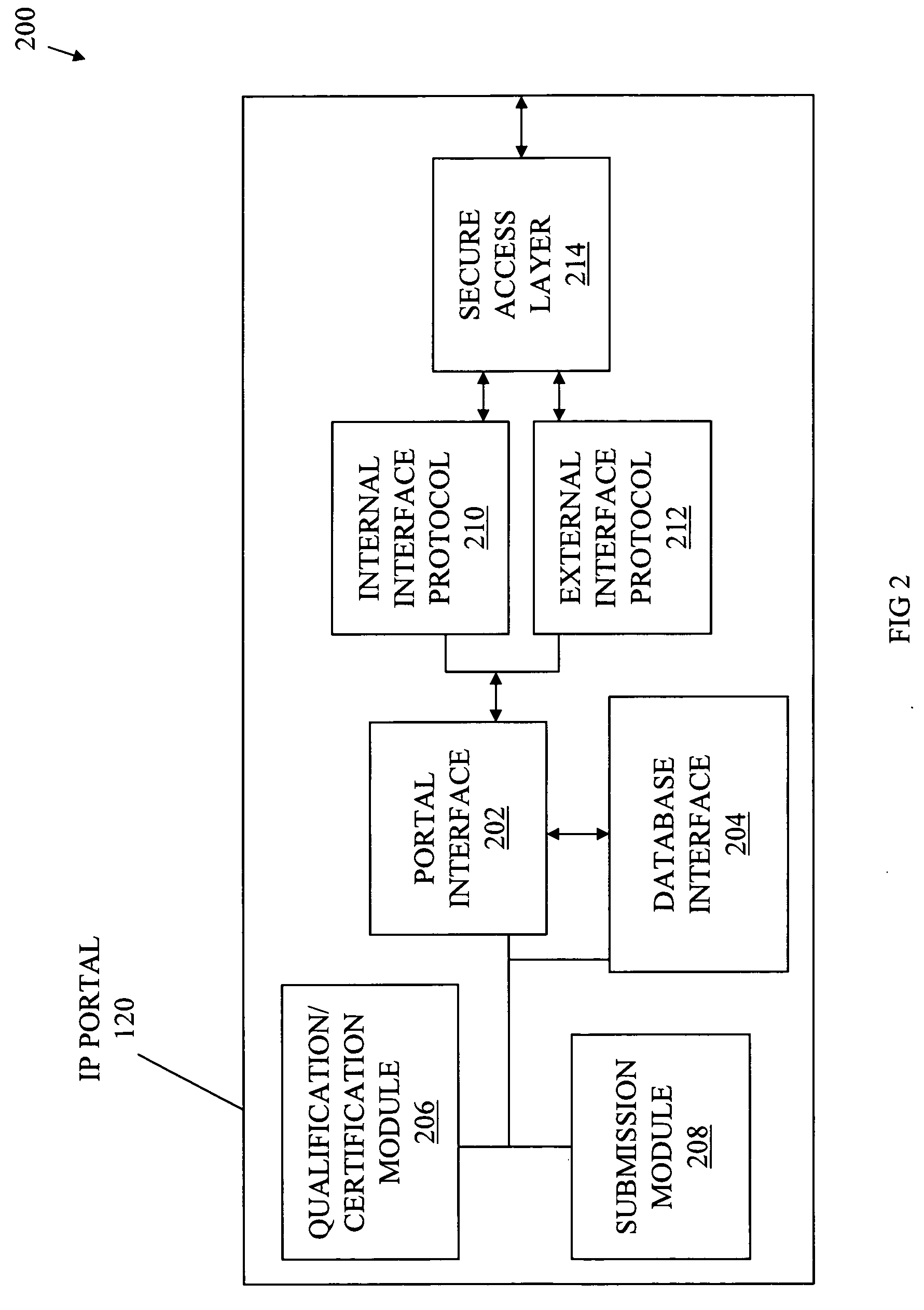
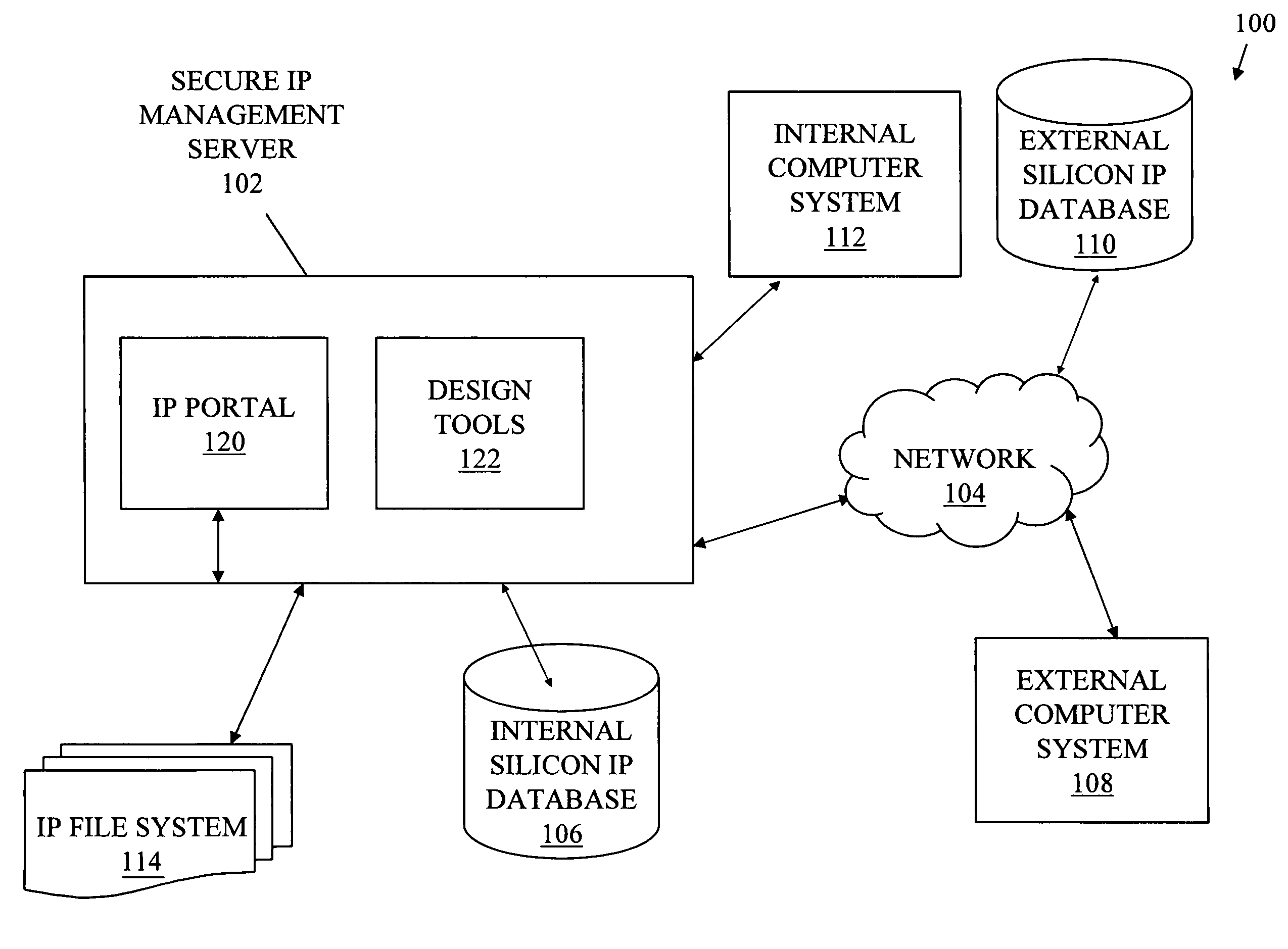
Schema-based portal architecture for assessment and integration of silicon IPs
InactiveUS20070201442A1Network connectionsSpecific program execution arrangementsDatabase interfaceHTTP tunnel
Systems, methods, and media for a schema-based portal for assessment and integration of silicon IPs are disclosed. Embodiments may generally include an IP portal system having a portal interface to receive inputs from users and to provide output to users and a database interface to transmit and receive information to and from a silicon IP database and an IP file system. Embodiments of the system may also include a secure access layer (HTTP tunnel, firewall, or proprietary secure access protocol) to securely communicate information and an internal interface protocol and an external interface protocol and the secure access layer. The internal interface protocol may authorize and encrypt communications to an internal user or design system and the external interface protocol may authorize and encrypt communications to an external user or design system. The portal interface may be a Web-based interface and schema-based in some embodiments.
Owner:IBM CORP
Method, system and computer program product for detecting security threats in a computer network
A method, system and computer program product detect attempts to send significant amounts of information out via HTTP tunnels to rogue Web servers from within an otherwise firewalled network. A related goal is to help detect spyware programs. Filters, based on the analysis of HTTP traffic over a training period, help detect anomalies in outbound HTTP traffic using metrics such as request regularity, bandwidth usage, inter-request delay time, and transaction size.
Owner:SYROWIK DAVID R +1
HTTP tunnel detection method based on decision tree classification algorithm
ActiveCN102035698ASimplify the training processReduce consumptionData switching networksHTTP tunnelData stream
The invention discloses a HTTP (Hyper Text Transport Protocol) tunnel detection method based on decision tree classification algorithm, used for solving the technical problem of poor stability of a conventional tunnel detection method based on the transport layer packet statistic characteristic analysis. In the technical scheme of the invention, an HTTP data stream and a tunnel data stream are used to train a decision tree classification model, with lower requirement on quantity of training sets than a statistic fingerprint method; secondly, compared with the statistic fingerprint method in which only two flow characteristics can be utilized, the decision tree classification method can use more characteristics to train the model, therefore, obtained classification rules are more precise and stable; the process to train the model is relatively simple, does not involve image fingerprint consumes less internal storage; finally, the judgment of the decision tree classification method is made according to attributes on a plurality of branch nodes without depending on one specific critical value, which achieving better stability.
Owner:JIANGSU ZHONGWEI HEAVY IND MACHINERY +1
Tunneling apparatus and method for client-server communication
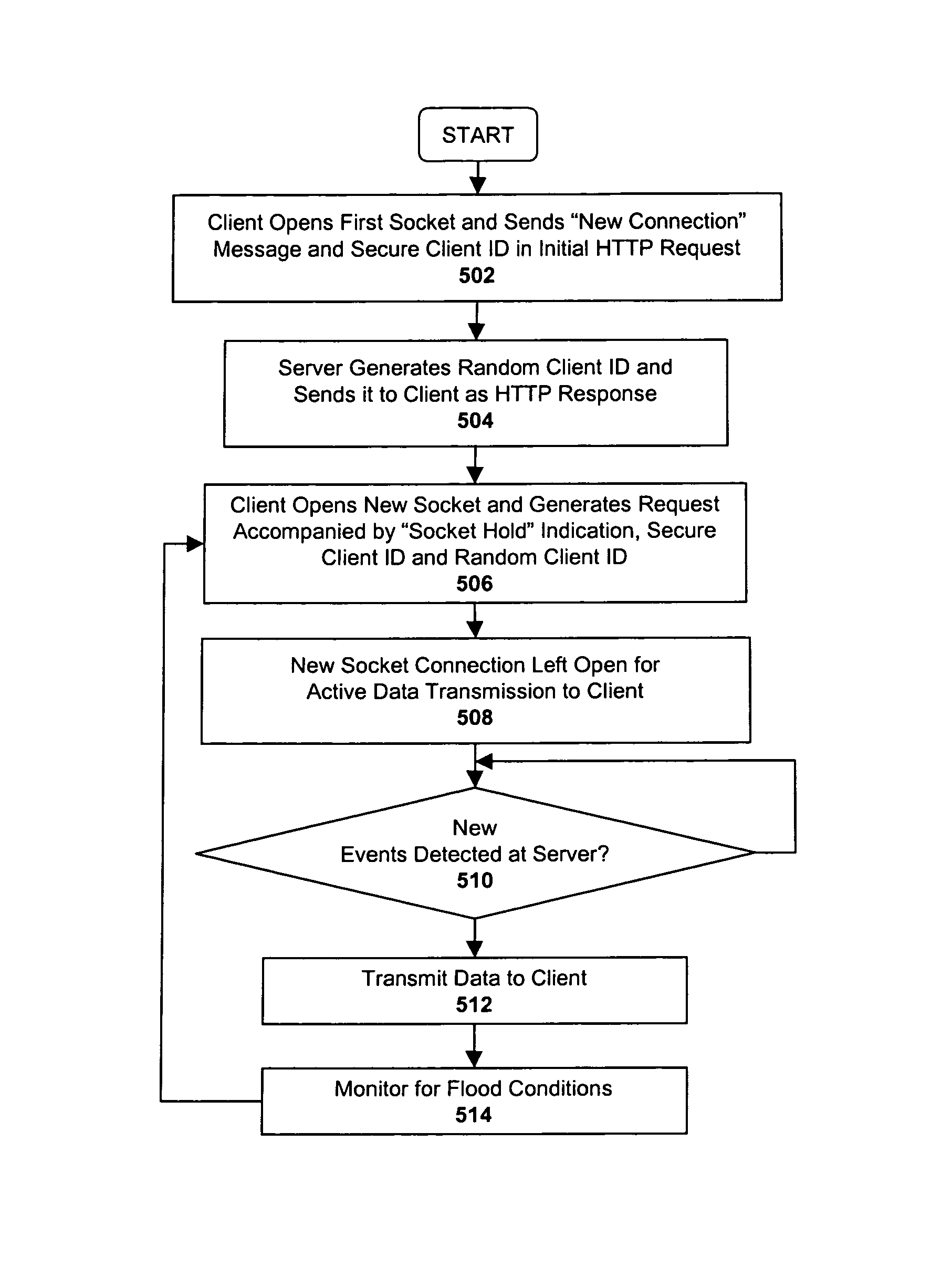
An HTTP tunneling service is described for creating a tunneled path between a client and a server (e.g., over a firewall or other data / protocol filtering device). According to one embodiment of the invention the client sends the server an initial request to open a preliminary socket connection which includes a secure client ID previously assigned to the client. The server opens the preliminary socket connection, generates a random client ID and transmits the random client ID to the client. The preliminary socket connection is then closed. The client then sends a second request to open a second socket connection using both the unique ID and the secure client ID for authentication purposes.
Owner:SAP AG
Network intrusion detection method and system
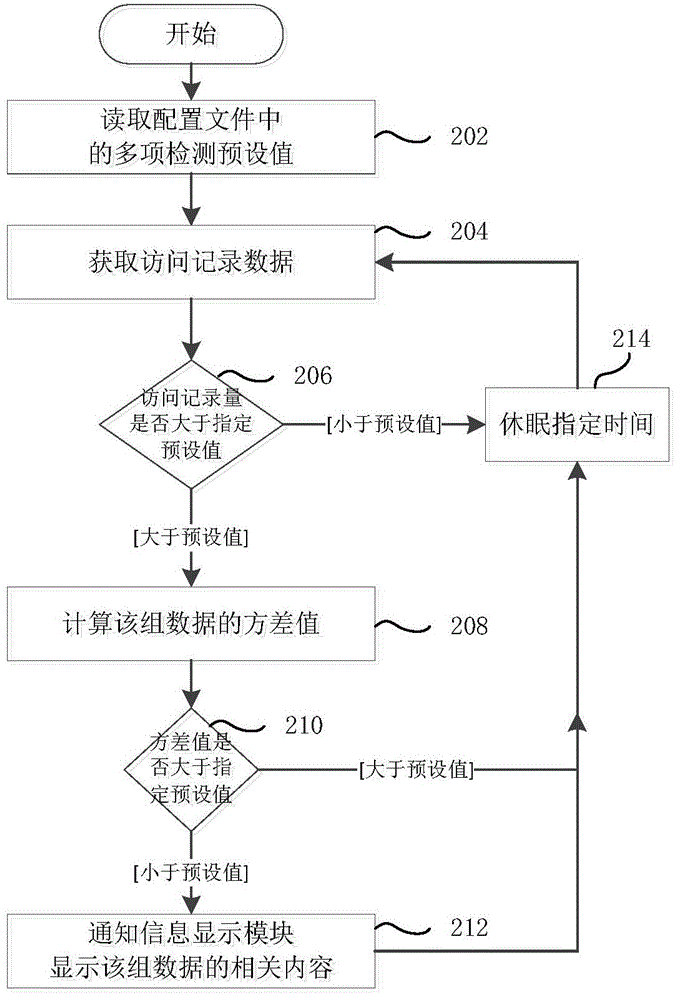
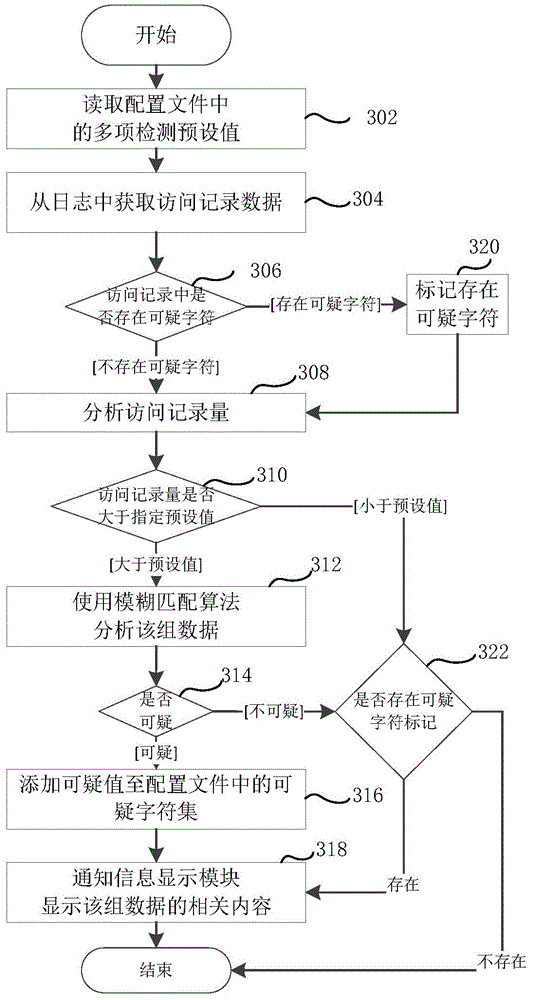
The invention provides a network intrusion detection method and system. The network intrusion detection method comprises the following steps that access data within a preset time period are obtained; access data feature information is extracted from the access data; whether suspicious access exists or not is judged according to the access parameter feature information. According to the network intrusion detection method and system, a remote program adopting the HTTP tunnel penetrating technology can be efficiently detected out, and the system safety can be improved; in addition, the network intrusion detection system does not need to be additionally arranged behind a firewall, and therefore system cost is reduced.
Owner:SUZHOU CODYY NETWORK SCI & TECH
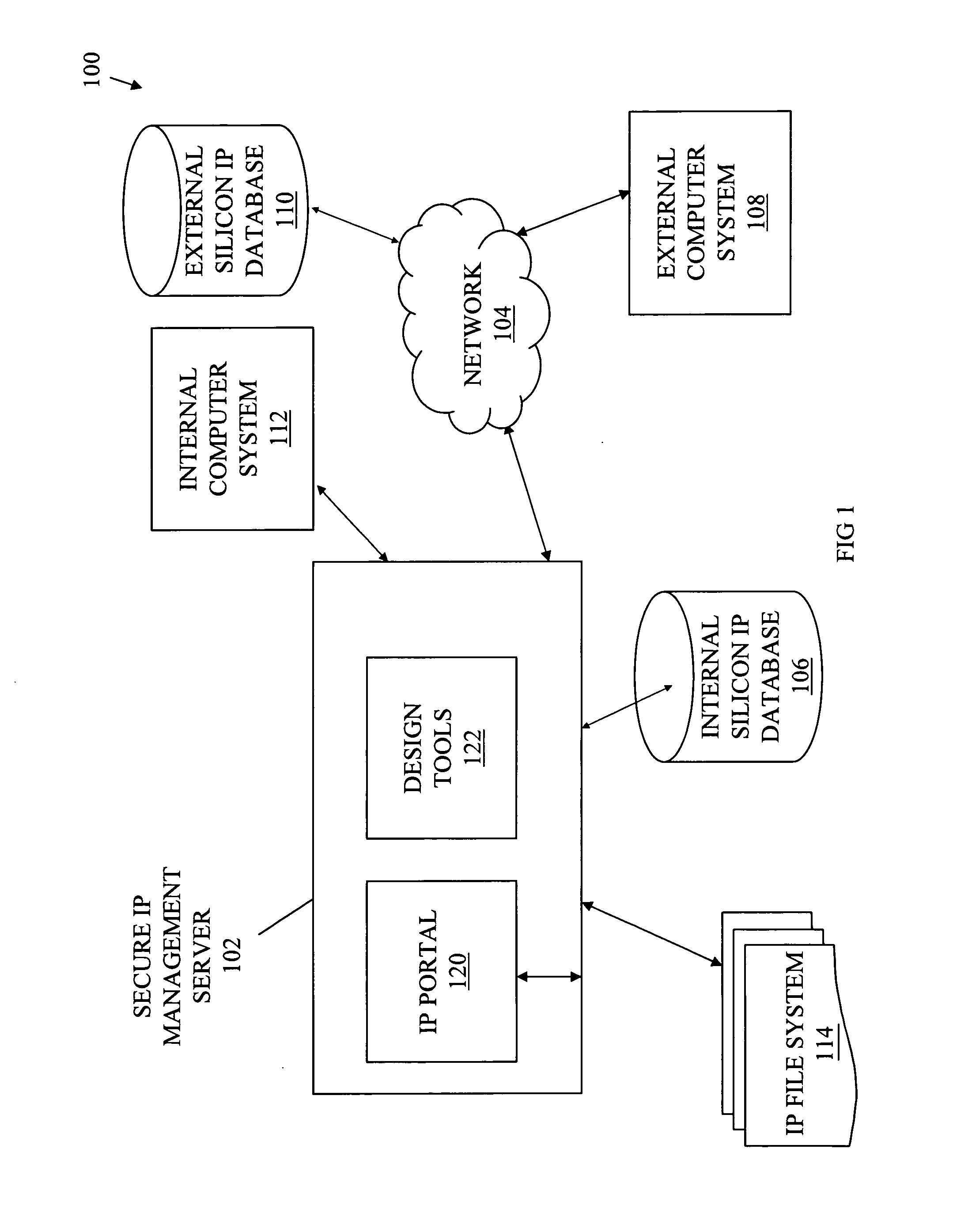
Schema-based portal architecture for assessment and integration of silicon IPs
InactiveUS7870381B2Network connectionsSpecific program execution arrangementsDatabase interfaceHTTP tunnel
Systems, methods, and media for a schema-based portal for assessment and integration of silicon IPs are disclosed. Embodiments may generally include an IP portal system having a portal interface to receive inputs from users and to provide output to users and a database interface to transmit and receive information to and from a silicon IP database and an IP file system. Embodiments of the system may also include a secure access layer (HTTP tunnel, firewall, or proprietary secure access protocol) to securely communicate information and an internal interface protocol and an external interface protocol and the secure access layer. The internal interface protocol may authorize and encrypt communications to an internal user or design system and the external interface protocol may authorize and encrypt communications to an external user or design system. The portal interface may be a Web-based interface and schema-based in some embodiments.
Owner:INT BUSINESS MASCH CORP
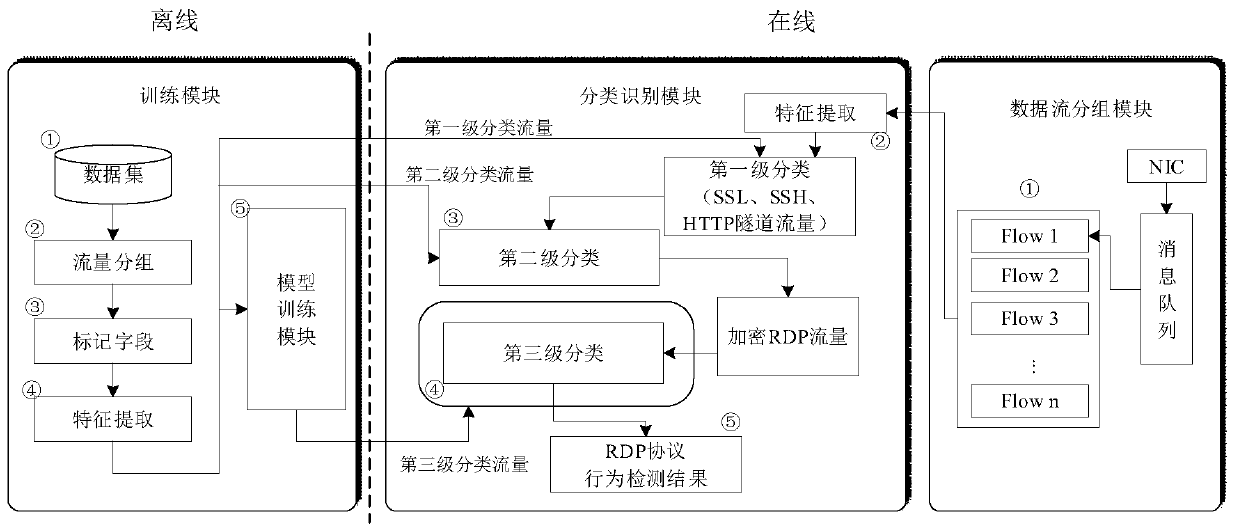
Multistage classification detection method for remote desktop protocol traffic behaviors
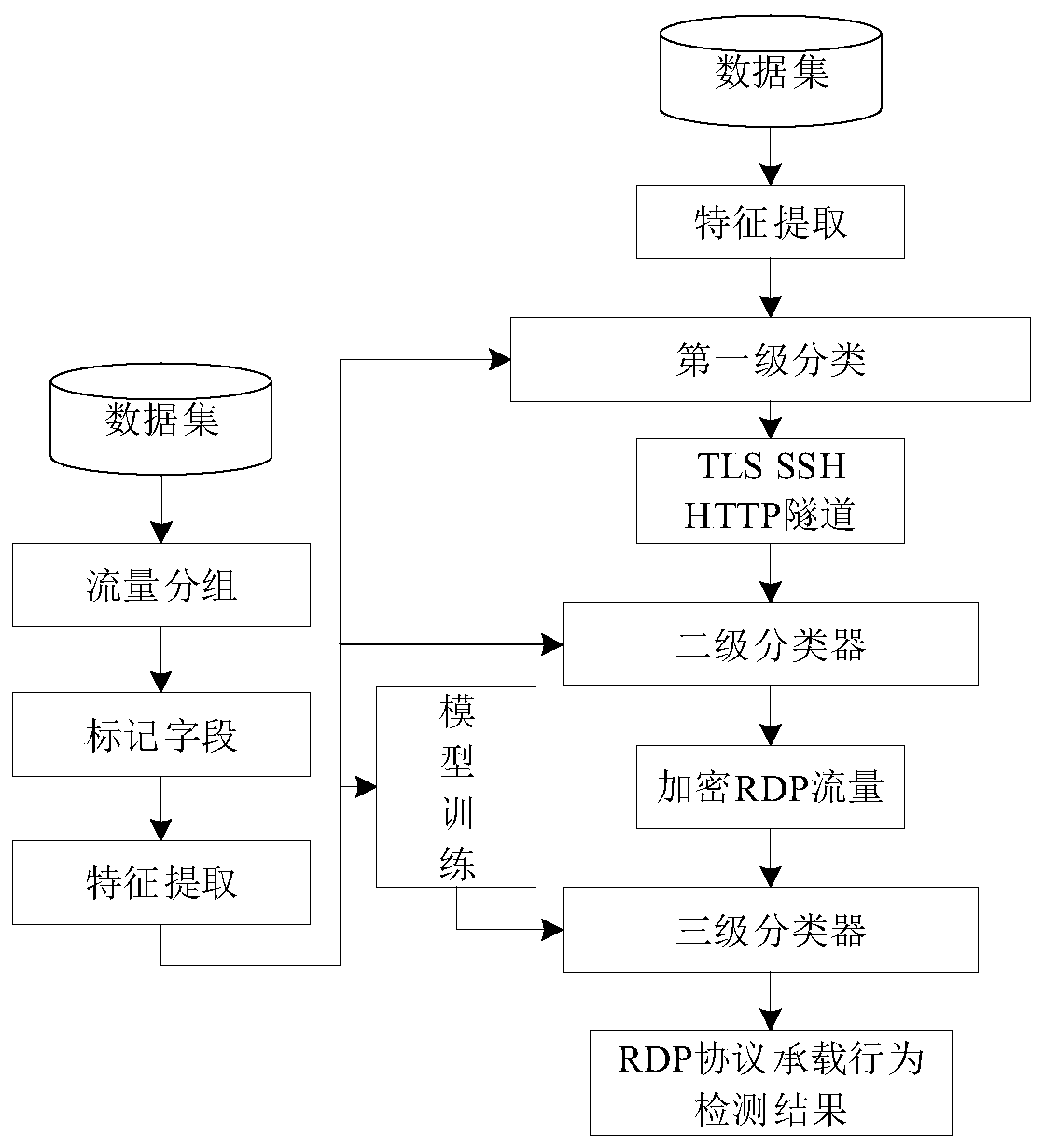
ActiveCN111147394AThe classification result is accurateImprove portabilityData switching networksHTTP tunnelRemote desktop
The invention discloses a multistage classification detection method for remote desktop protocol traffic behaviors, and the method comprises the steps: firstly screening out encrypted RDP protocol traffic which comprises the recognition of a TLS protocol, an SSH protocol and HTTP tunnel traffic; then, identifying the encrypted RDP flow according to the message length sequence characteristics of the RDP protocol in the connection establishment stage; and finally, for behaviors contained in the encrypted RDP protocol traffic, extracting features from three levels of traffic length, load randomness and interactivity, and classifying by using a machine learning method to realize identification of internal fine grit of the RDP protocol traffic, i.e., identification of RDP protocol traffic behaviors. On the premise of ensuring privacy, RDP protocol flow identification and classification of specific operation behaviors generated when a user remotely controls a server can be effectively realized through multi-stage classification processing of flow.
Owner:NANJING UNIV OF SCI & TECH
System for accessing data of cloud database using transparent technology
ActiveUS20150074794A1Improve operating convenience and using satisfactionEnsure network securityMultiple digital computer combinationsProgram controlHTTP tunnelThe Internet
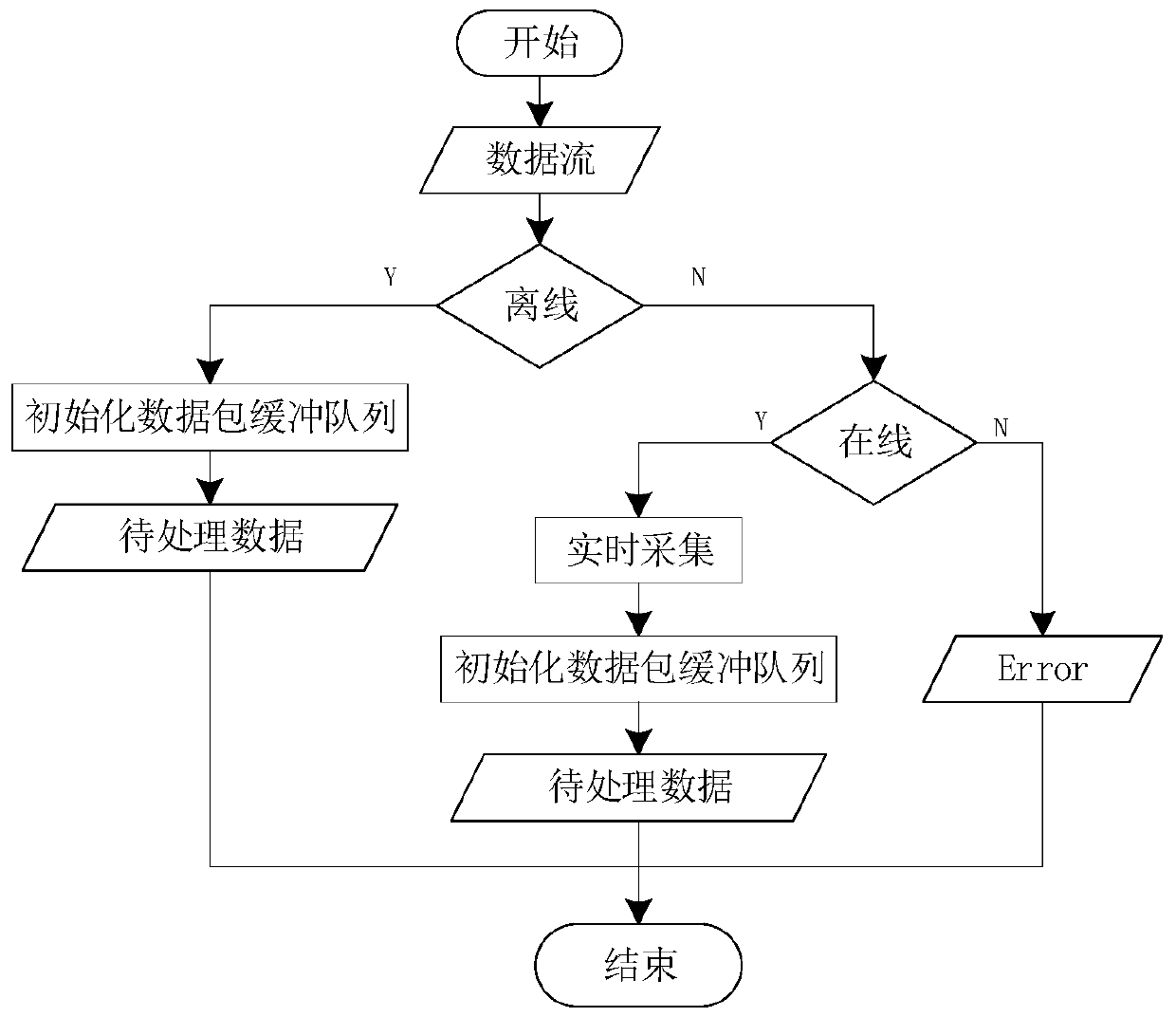
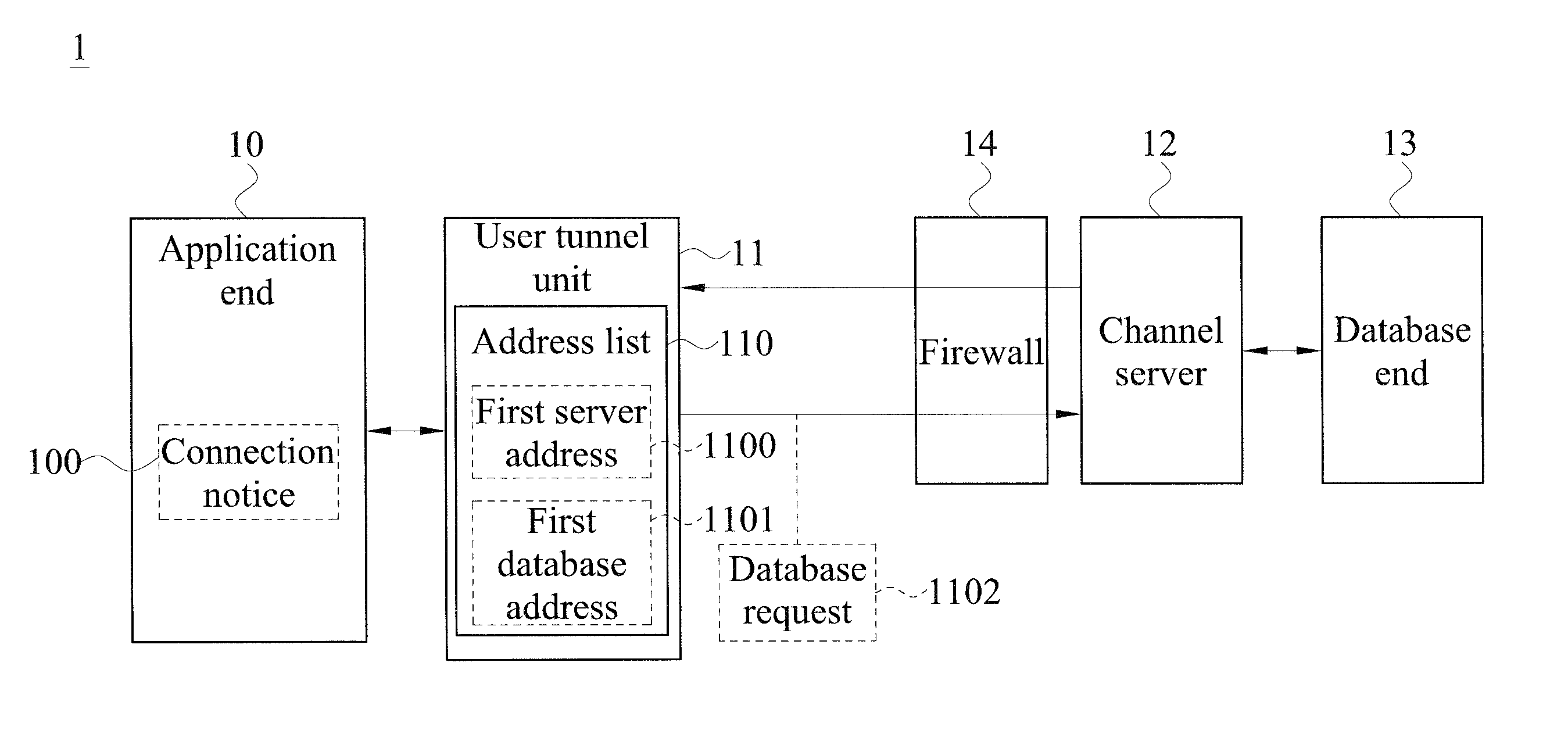
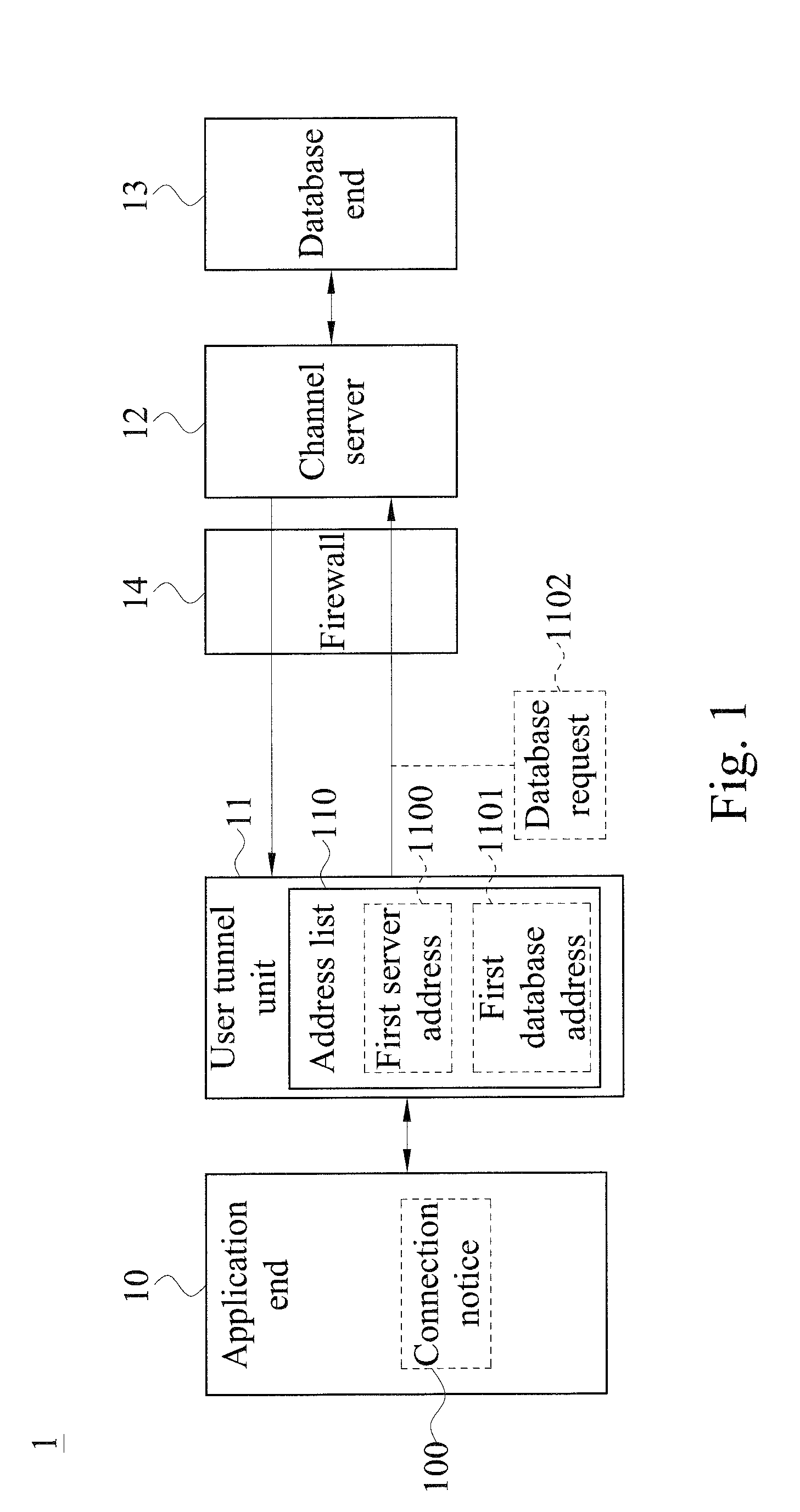
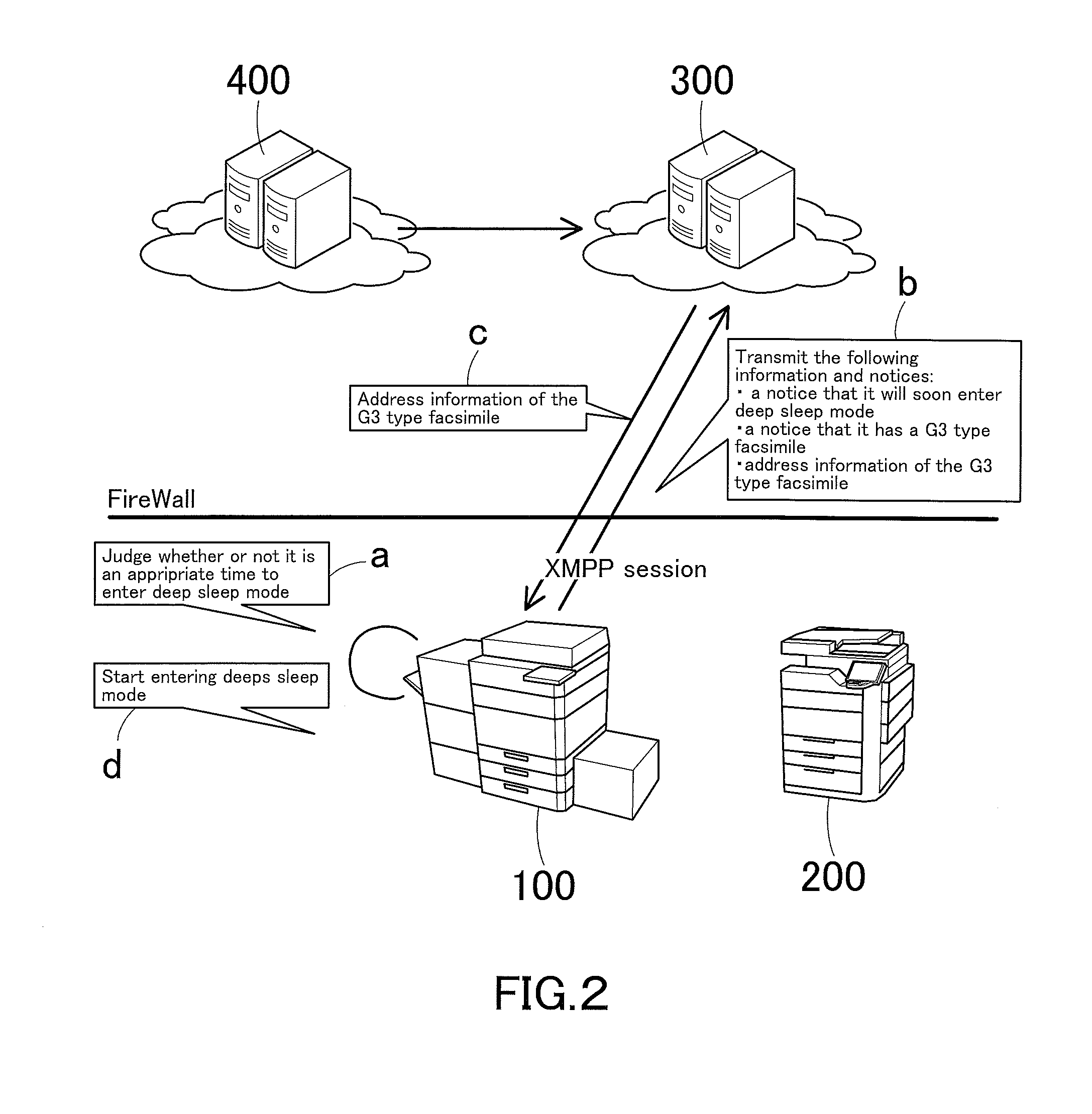
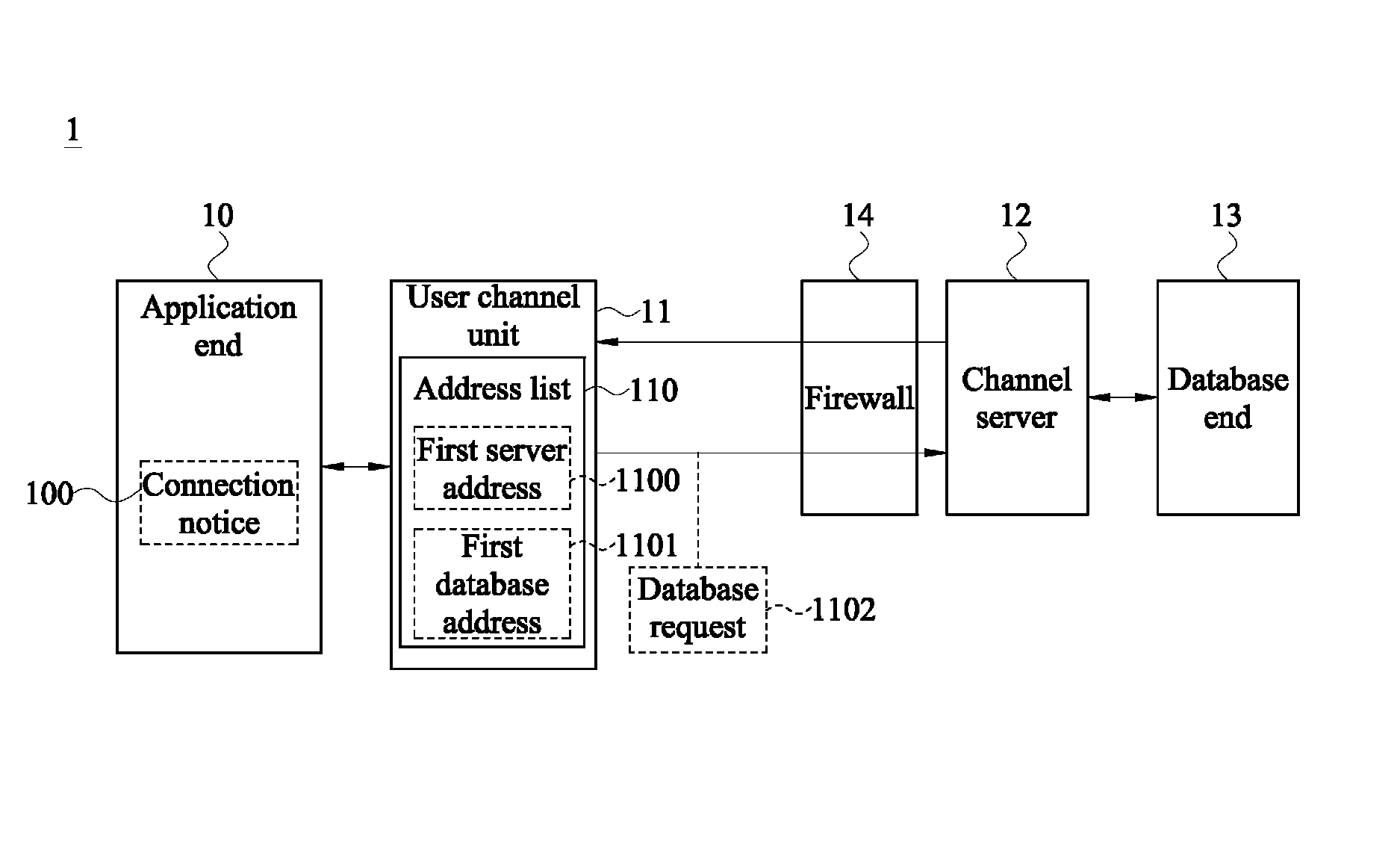
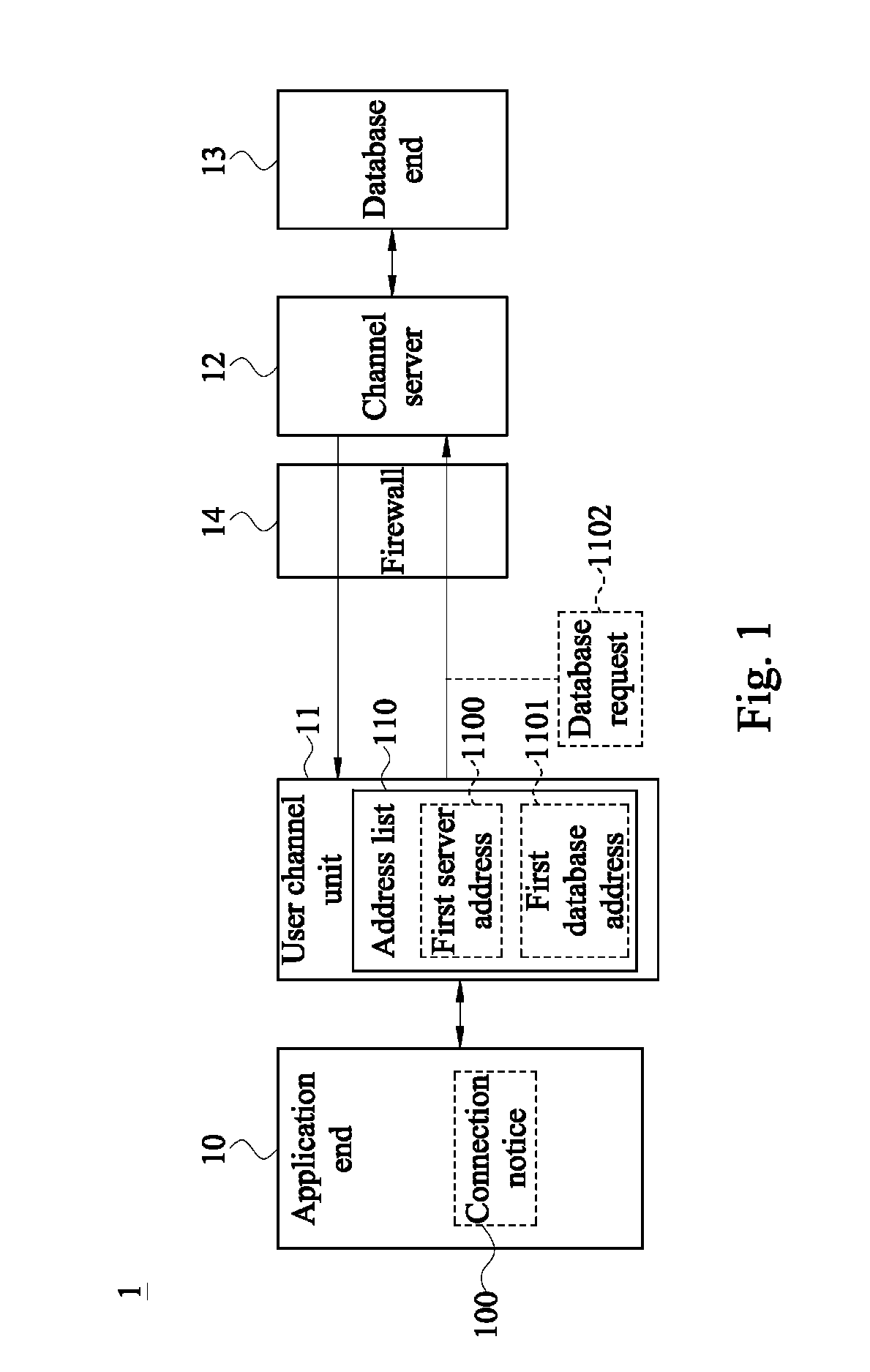
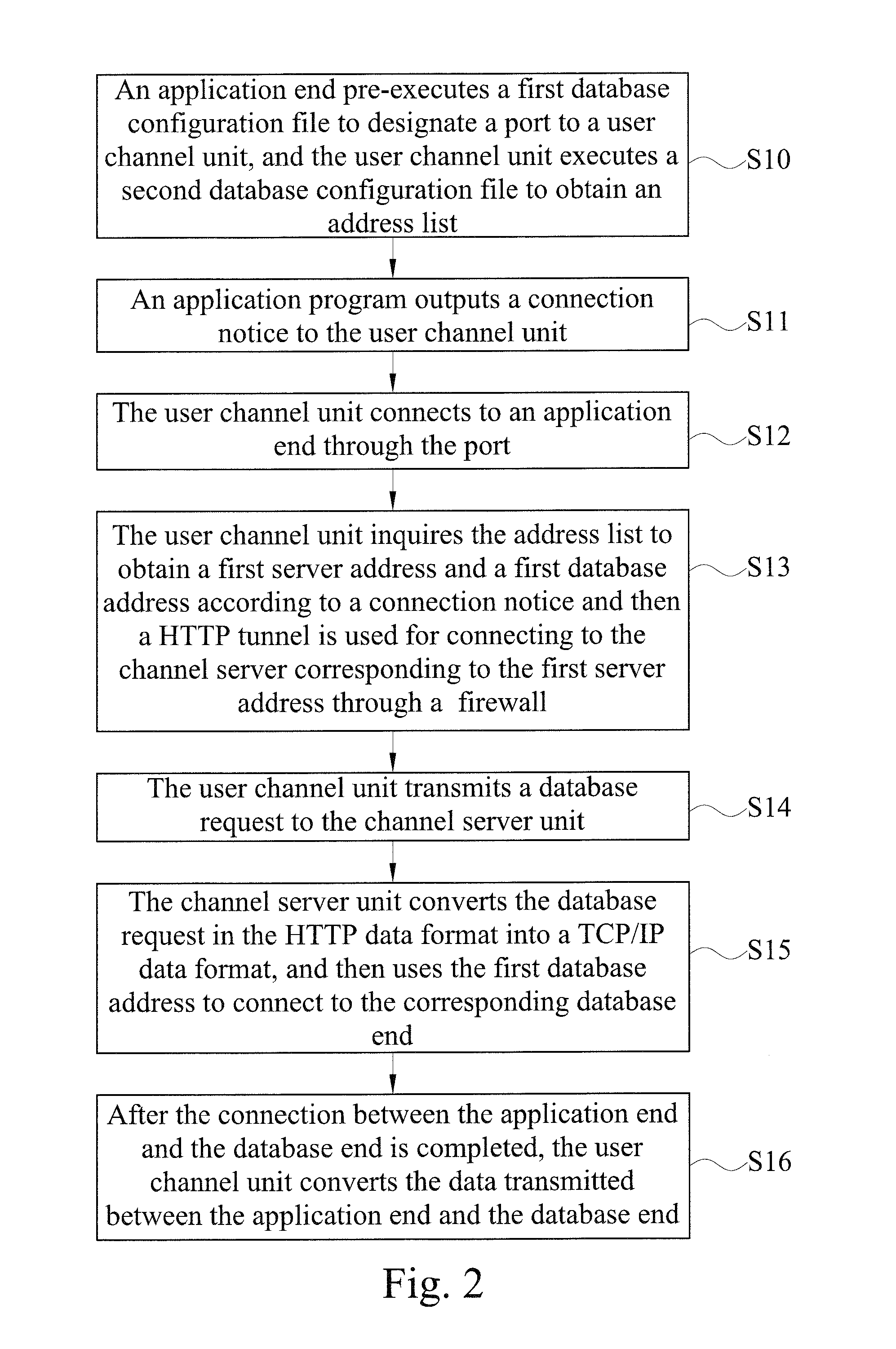
Disclosed is a system for accessing data of a cloud database via transparent technology, and the system includes at least one channel server and at least one cloud database end. When a connection notice is outputted from an application end, the user channel unit detects a first server address and a first database address in a HTTP data format, and connects to a corresponding channel server via the HTTP tunnel to send a database request, so that the channel server can convert the first database address in the HTTP data format into a TCP / IP data format and then connect to a corresponding database end. Therefore, the application end can access data from the database behind the firewall via the Internet without modifying any program code.
Owner:SYSCOM COMP ENG
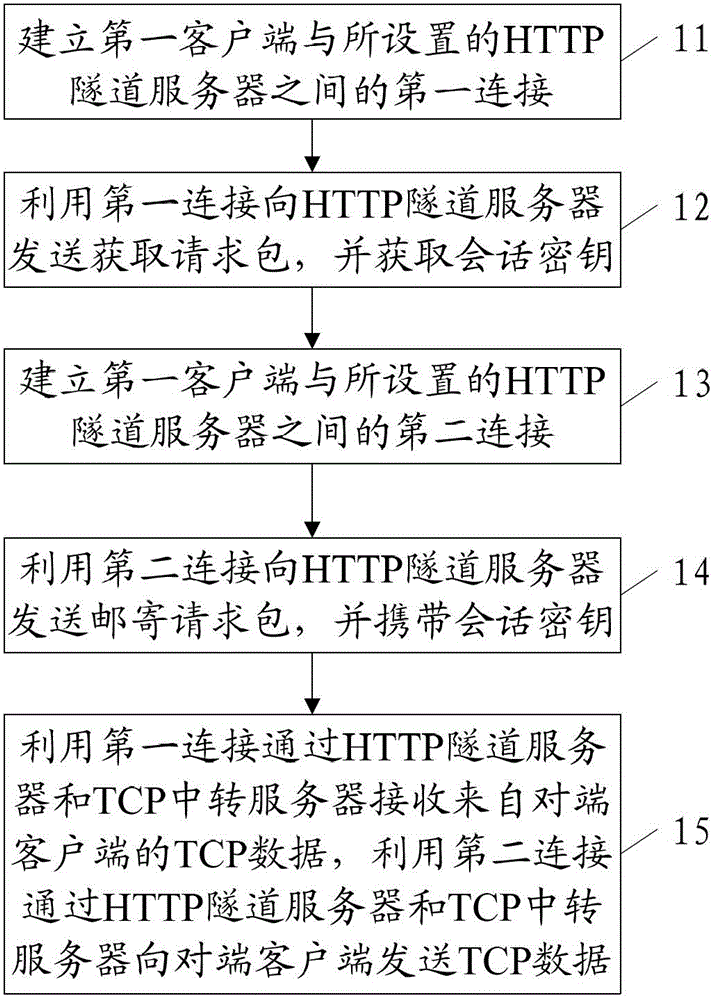
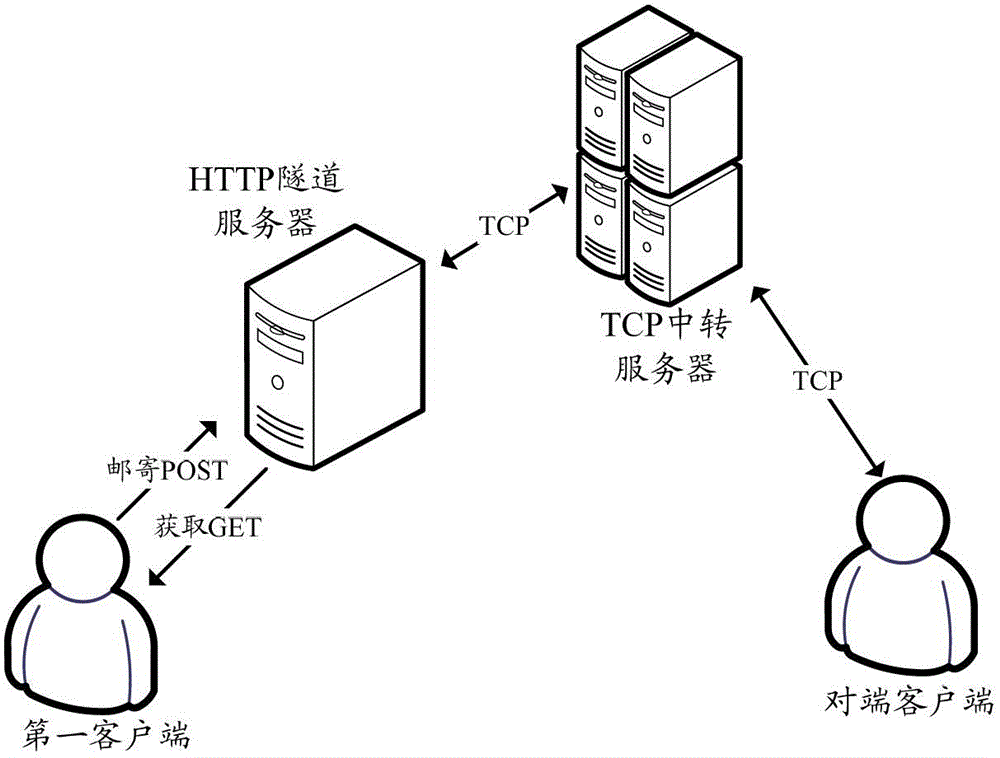
Data transmission method among client terminals in restricted network and client terminals
ActiveCN103516573AGuaranteed reliabilityIntegrity guaranteedNetworks interconnectionHTTP tunnelClient-side
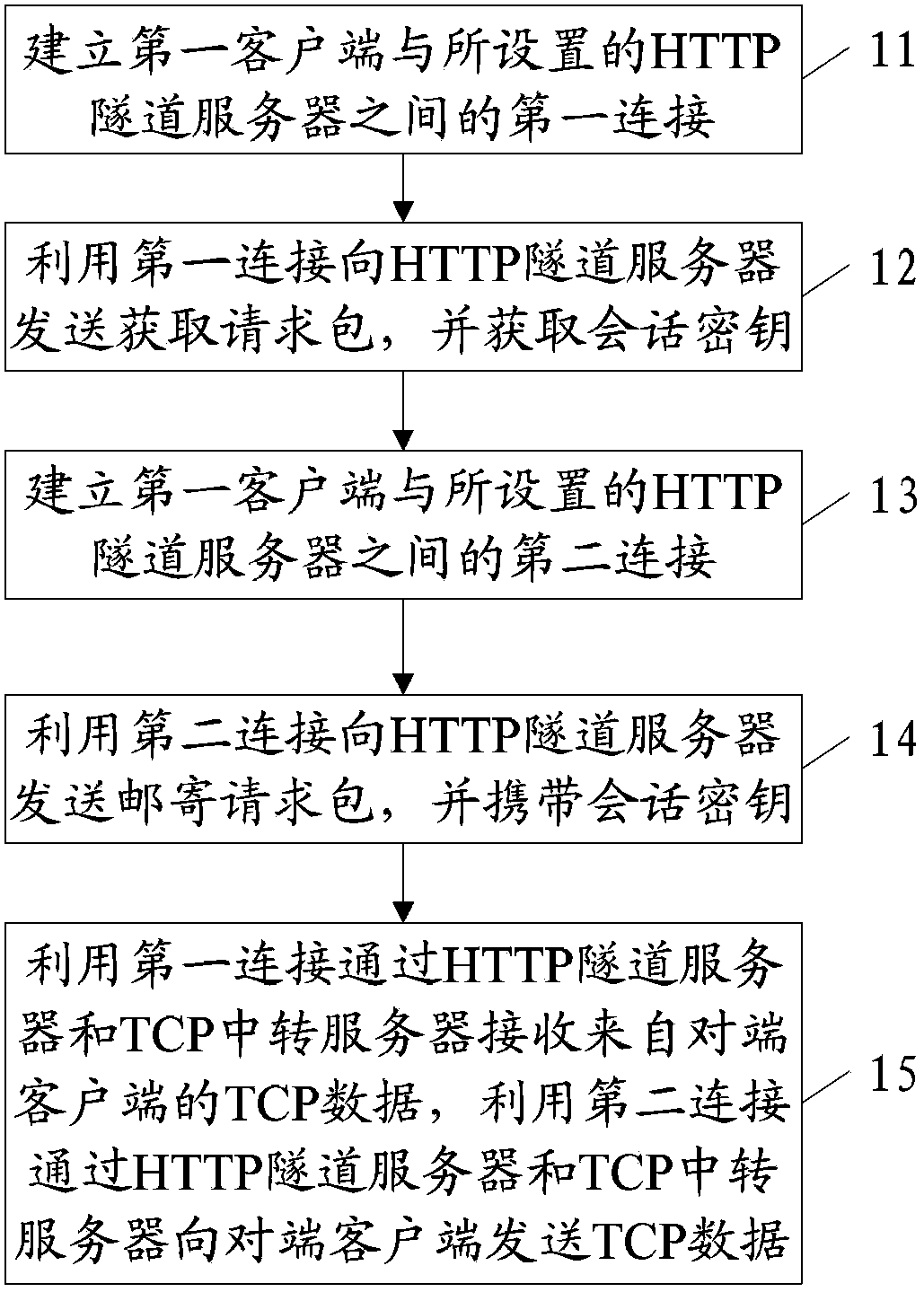
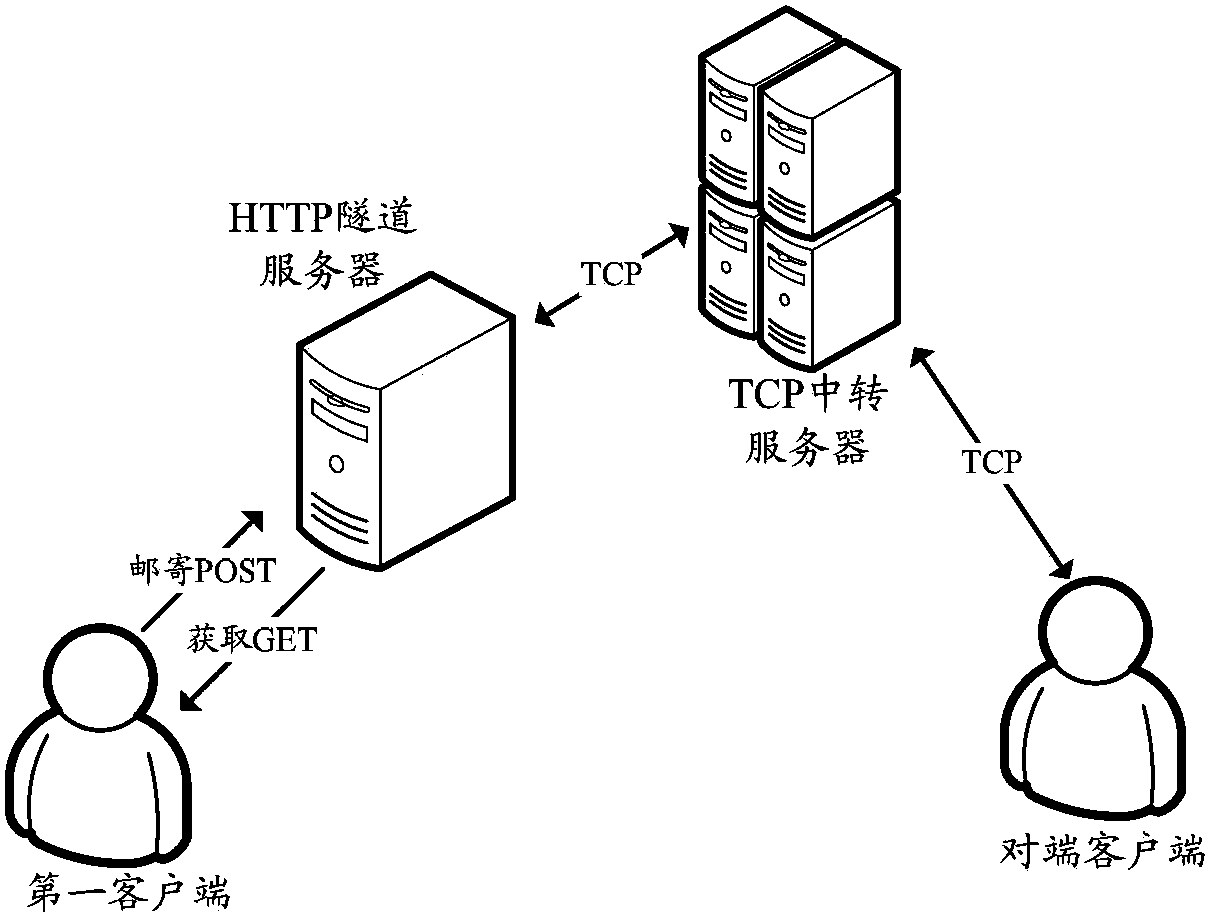
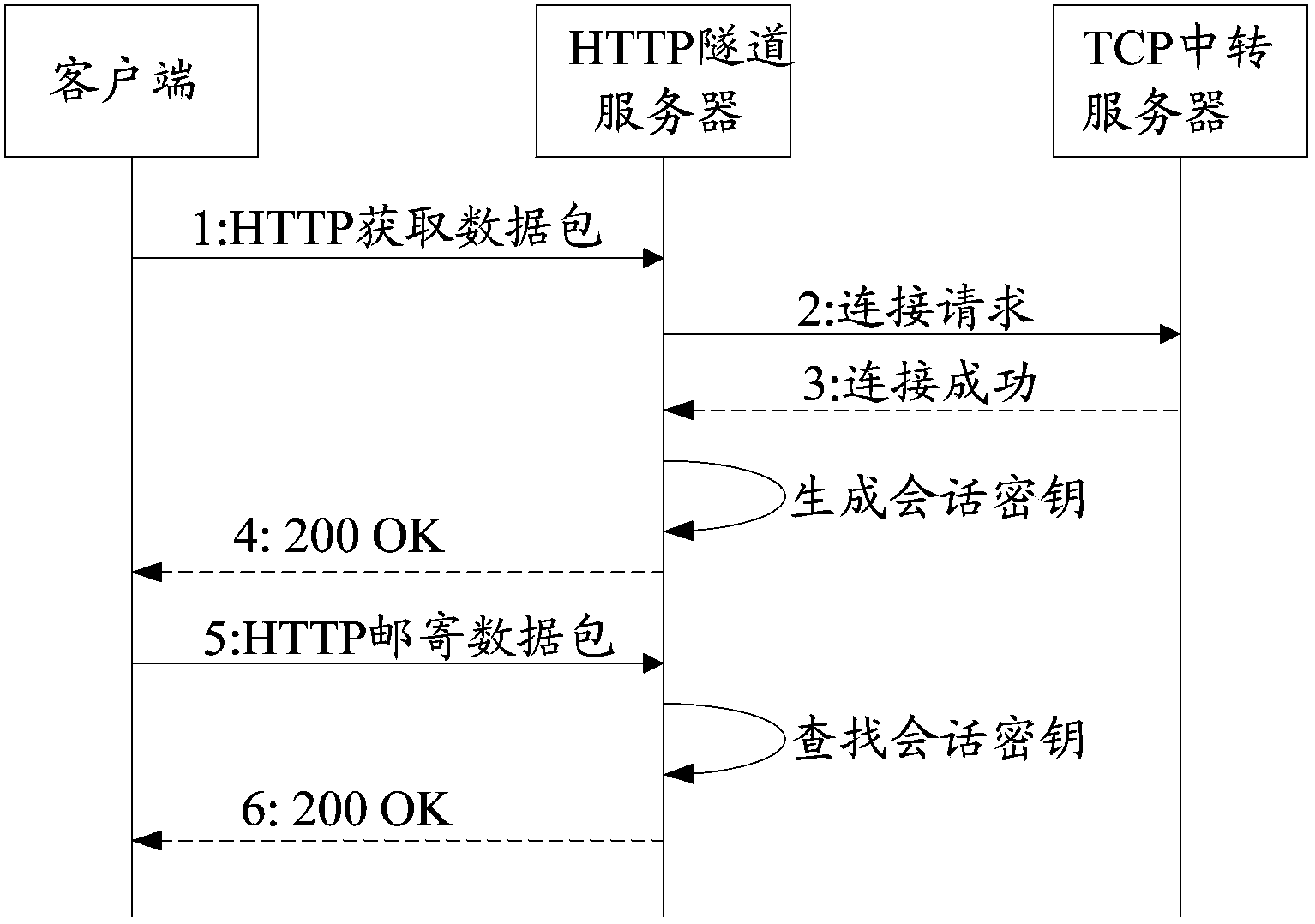
The invention discloses a data transmission method among client terminals in a restricted network and the client terminals in order to achieve data transmission among different client terminals in the restricted network in which only HTTP transmission is permitted. The data transmission method among the client terminals in the restricted network includes the steps that first connection between a first client terminal and an HTTP tunnel server is established; an acquiring request packet is sent to the HTTP tunnel server through the first connection, and a session key is further acquired; second connection between the first client terminal and the HTTP tunnel server is established; a mailing request packet is sent to the HTTP tunnel server through the second connection, and a session key is carried in a packet header; TCP data from an opposite end client terminal are received through the HTTP tunnel server and a TCP transit server by the aid of the first connection, and TCP data are sent to the opposite end client terminal through the HTTP tunnel server and the TCP transit server by the aid of the second connection.
Owner:BEIJING FEINNO COMM TECH
Information processing unit, information processing method, remote server, and information processing system
InactiveUS20090240819A1Multiple digital computer combinationsData switching networksInformation processingHTTP tunnel
There is provided an information processing unit including an application execution section to execute an application to request establishment of an HTTP tunneling connection with a connection target unit, a connection establishment section to set a maximum content length settable with the connection target unit, establish an HTTP tunneling connection with the specified content length with the connection target unit via a connected proxy server and update the HTTP tunneling connection with the specified content length a plurality of times upon closure of the established connection, and a connection management section to manage connection status of each of a plurality of HTTP tunneling connections and make the application execution section recognize the plurality of HTTP tunneling connections as one virtual HTTP tunneling connection.
Owner:SONY CORP
Http tunnel active detection method, terminal device and storage medium
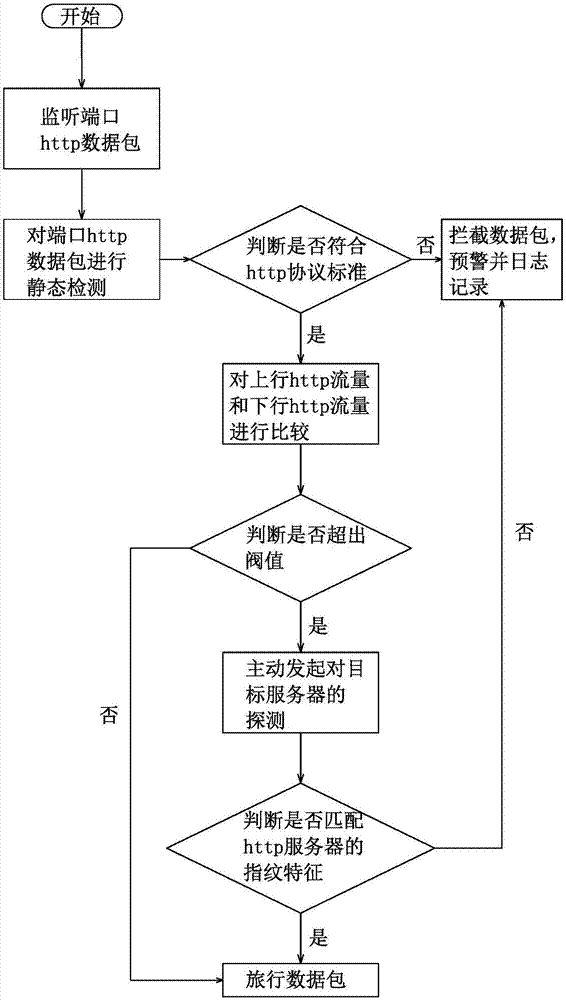
The invention discloses an http tunnel active detection method. The http tunnel active detection method includes the following steps: S1, continuously monitoring an http data packet which is connected to the network through a port until the http data packet can be monitored, and then entering the step S2; S2, performing static detection on the monitored http data packet, determining whether the http data packet accords with the http protocol standard, if so, entering the step S3, and if not, entering the step S6; S3, comparing the uplink flow of the connection and the downlink flow of the connection to determine whether the difference of the flows is greater than the threshold, if so, entering the step S4, and if not, entering the step S5; S4, actively initiating detection of the target server of the data packet of the connection to determine whether the target server matches the fingerprint characteristic of the http server, if so, entering the step S5, and if not, entering the step S6; S5, releasing the data packet of the connection; and S6, intercepting the data packet of the connection, performing early warning, and carrying out log recording.
Owner:XIAMEN ANSCEN NETWORK TECH CO LTD
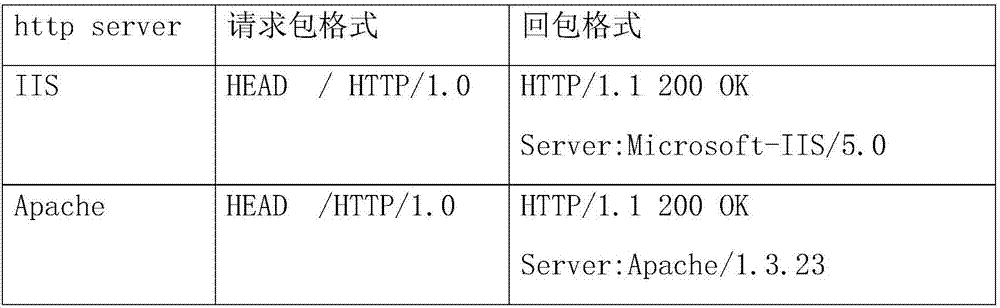
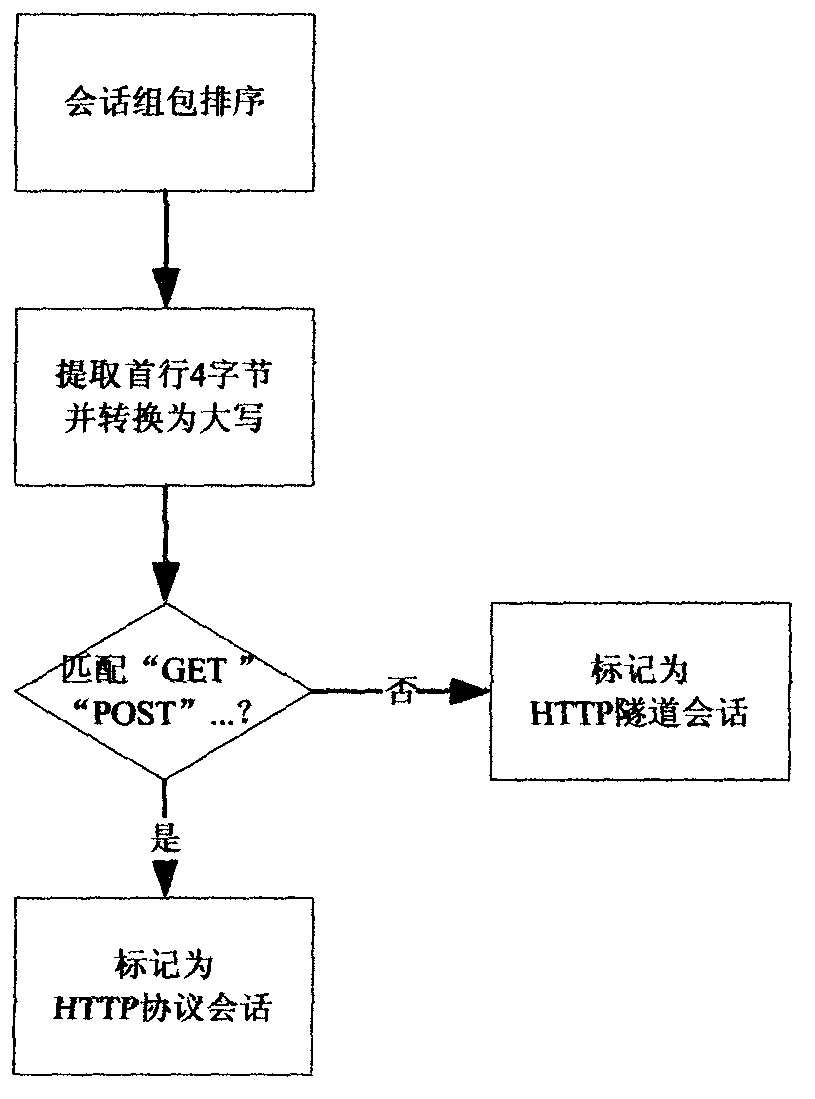
Method for detecting HTTP tunnel data based on conversation and HTTP protocol standard
InactiveCN104243228APrevent penetrationData switching networksHTTP tunnelComputer network technology
The invention belongs to the technical field of computer networks, and provides a method for detecting HTTP tunnel data based on a conversation and the HTTP protocol standard. A system captures a data packet of an HTTP port and establishes a conversation linked list according to the IP address and the port. When the data packet arrives at a detection system, firstly, the system examines and maintains the conversation linked list, a record is added if not record exists, and the record is deleted from the conversation linked list if the RST data packet or the FIN data packet exists; secondly, the system examines the content of the data packet and judges whether the conversation connection meets the standard HTTP protocol, such as a client-side command GET, a client-side command POST, a server-side response HTTP / 1.0 and a server-side response HTTP / 1.1, or not, if the conversation connection meets the standard HTTP protocol, the conversation is marked as HTTP protocol data, and if the conversation connection does not meet the standard HTTP protocol, the conversation is marked as HTTP tunnel data. By means of the method, the HTTP tunnel data can be recognized, differential service can be conducted on the HTTP tunnel data, or data which are not the HTTP protocol data can be prevented from penetrating through the HTTP port.
Owner:金琥
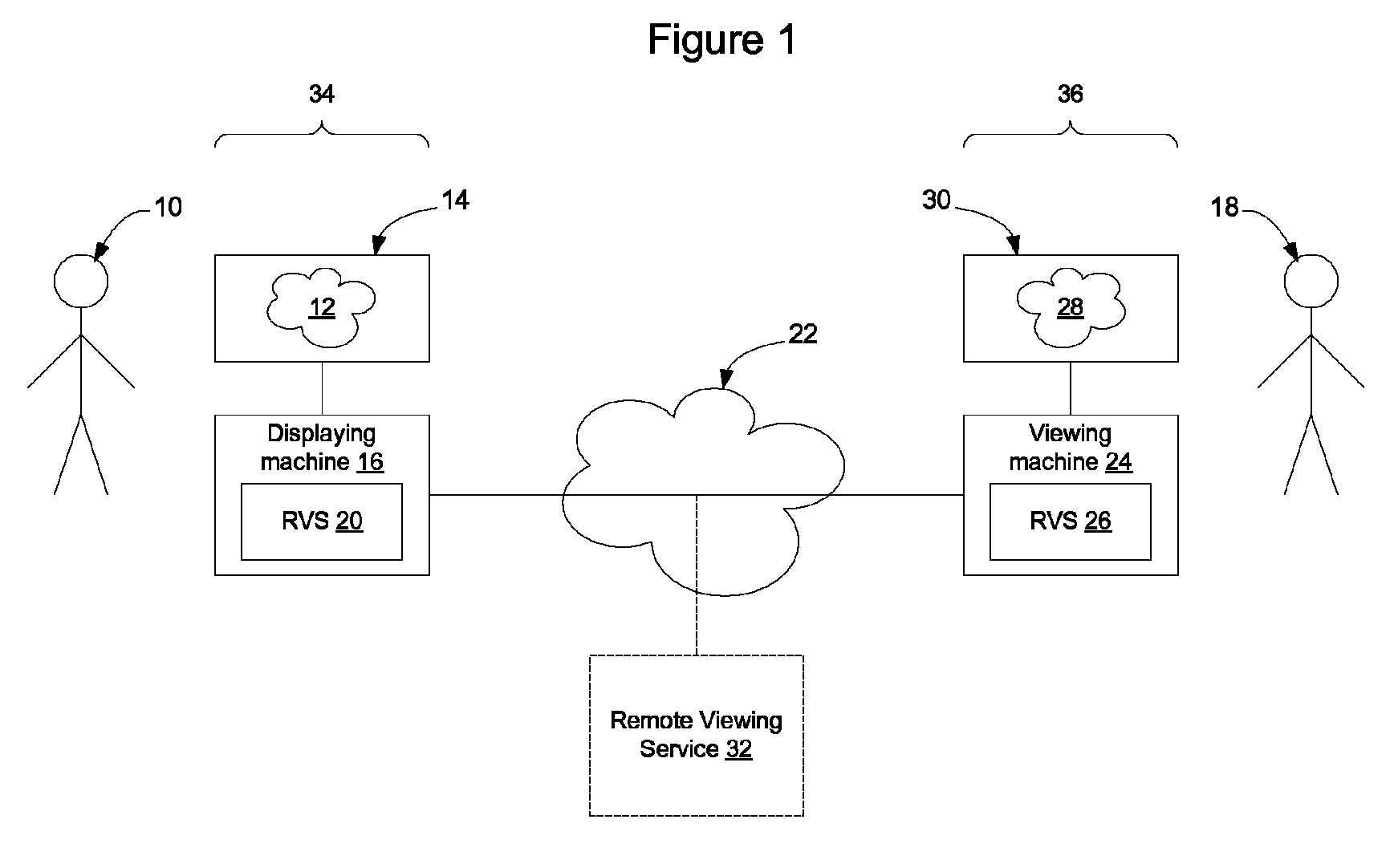
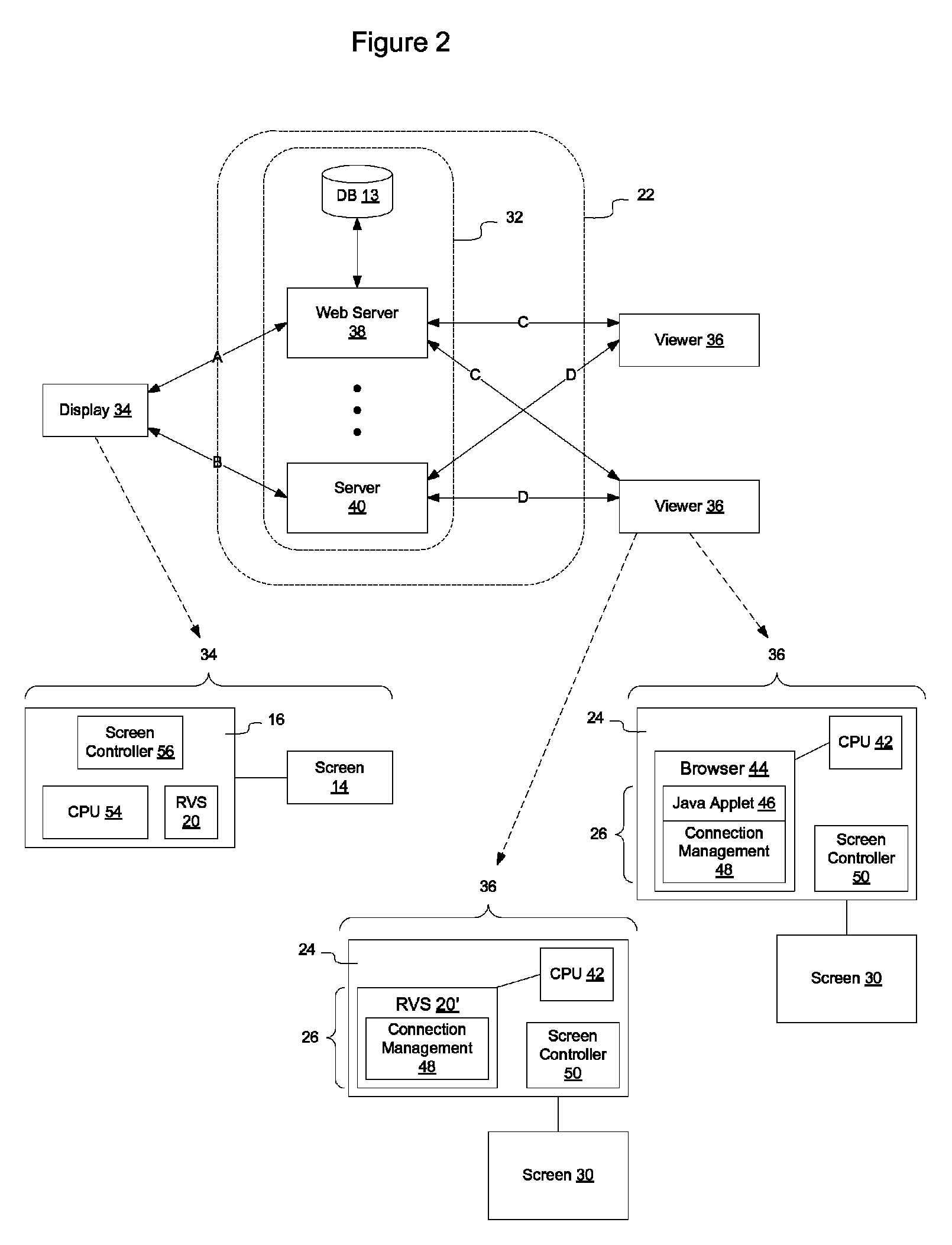
Method and apparatus for reconnecting to a remote viewing session
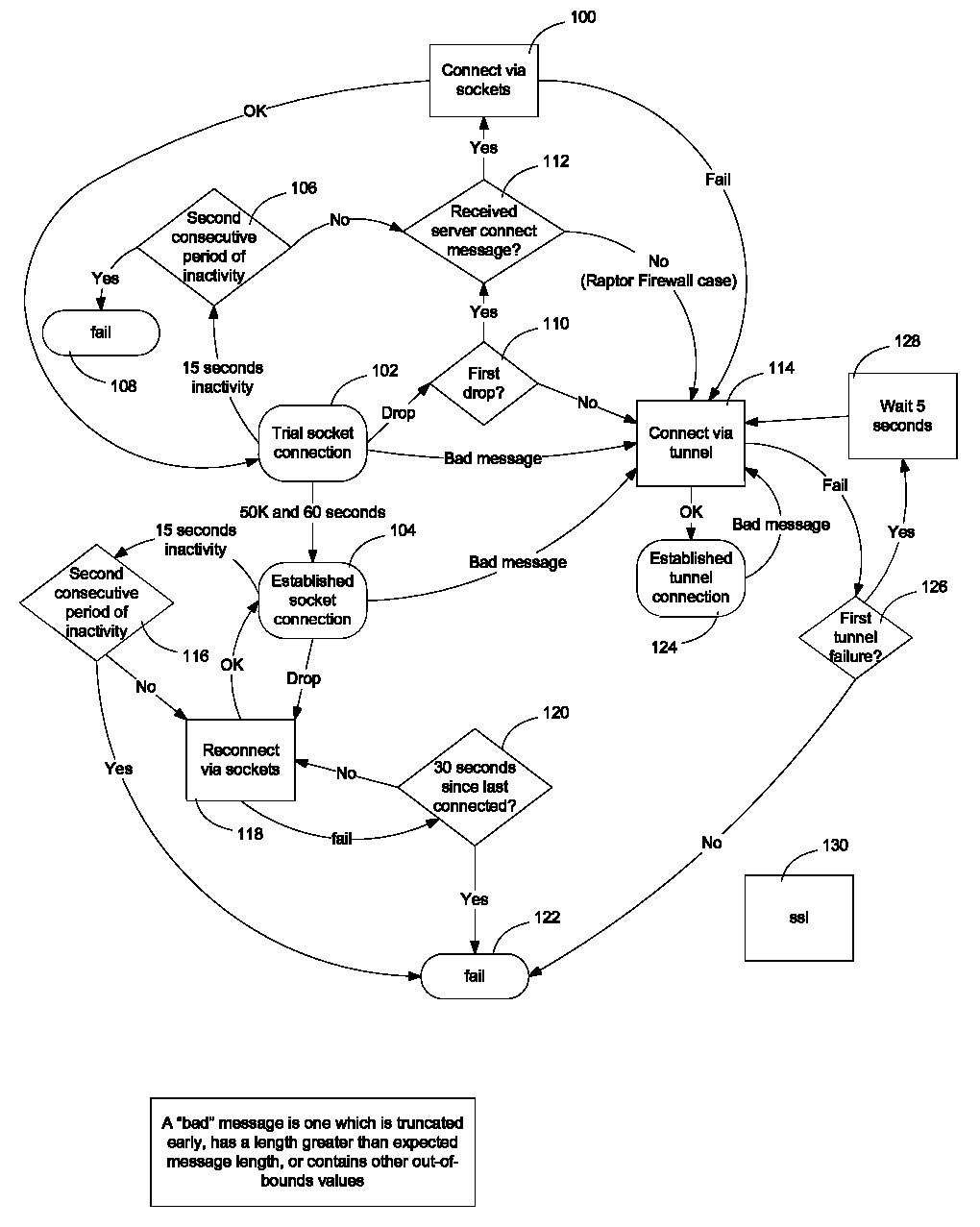
Remote viewing software at a display may contain control logic to enable it to manage the connection associated with a session. The connection management process may preferentially elect to establish a socket connection and, if that is unavailable or unreliable, may use HTTP tunneling. The connection management process may also automatically reconnect the display to the session so that the display is not required to manually re-join an ongoing session. The connection management process also manages the termination of the session to ensure that both the server and the client process at the display end the session correctly.
Owner:GLANCE NETWORK
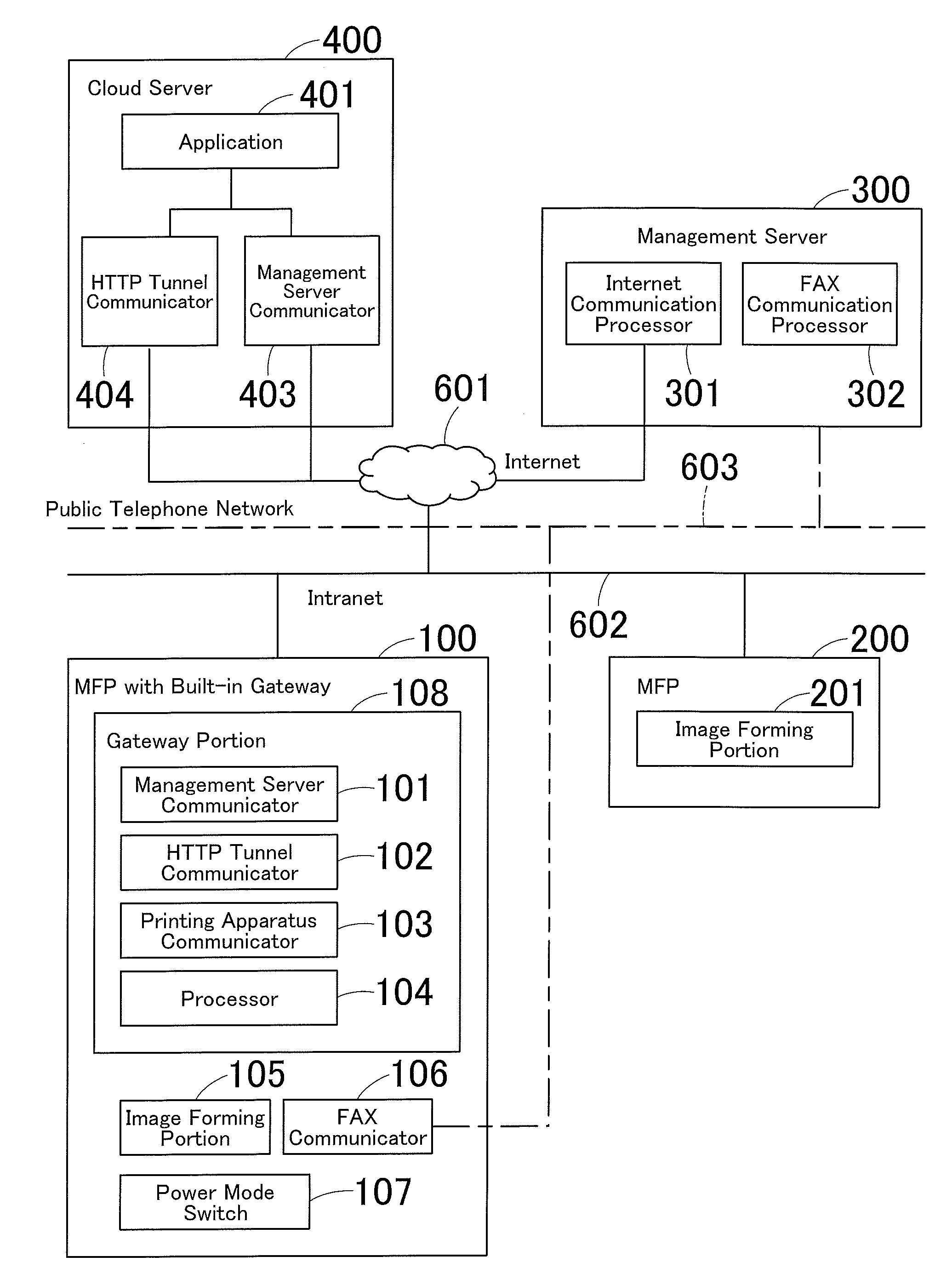
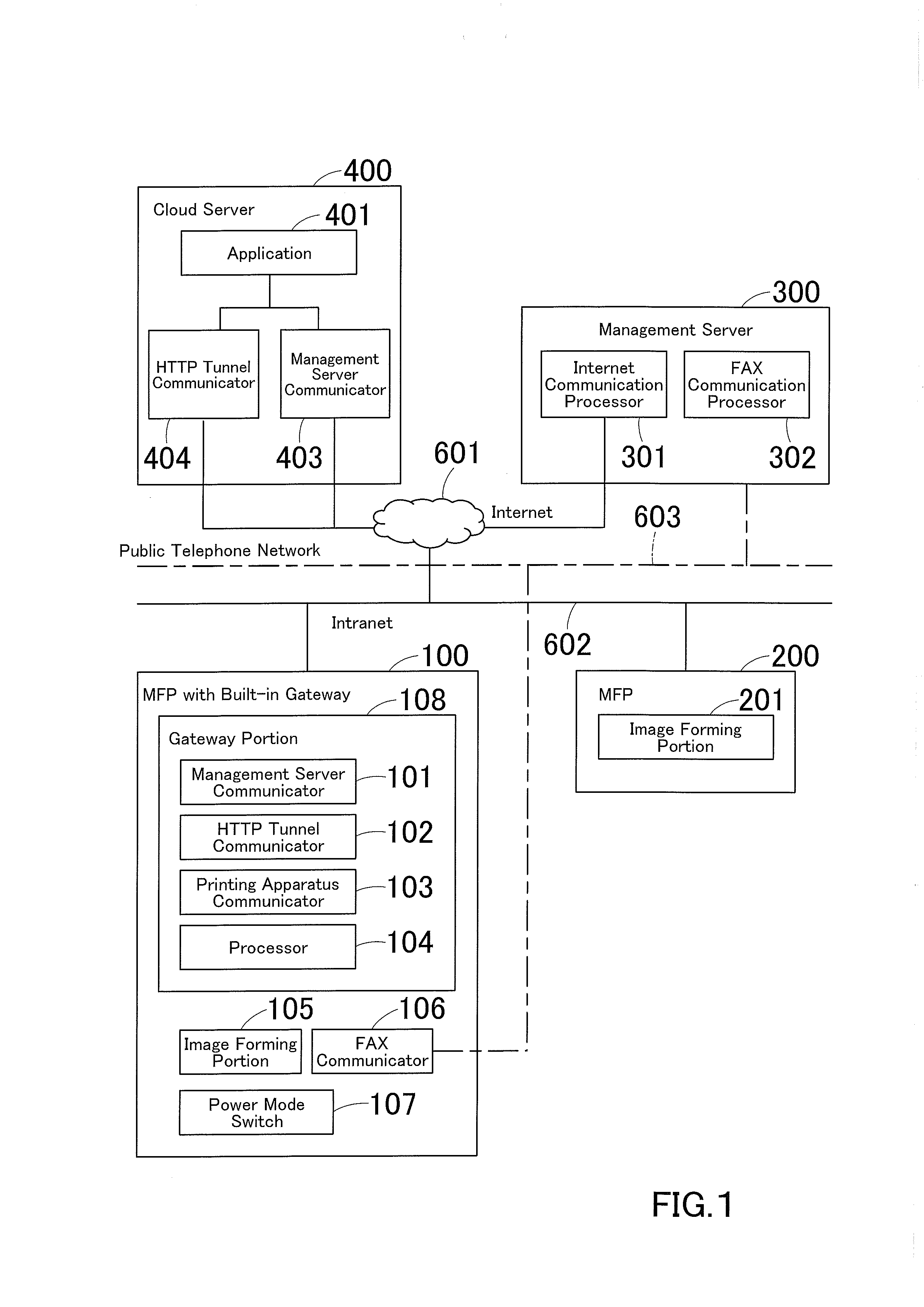
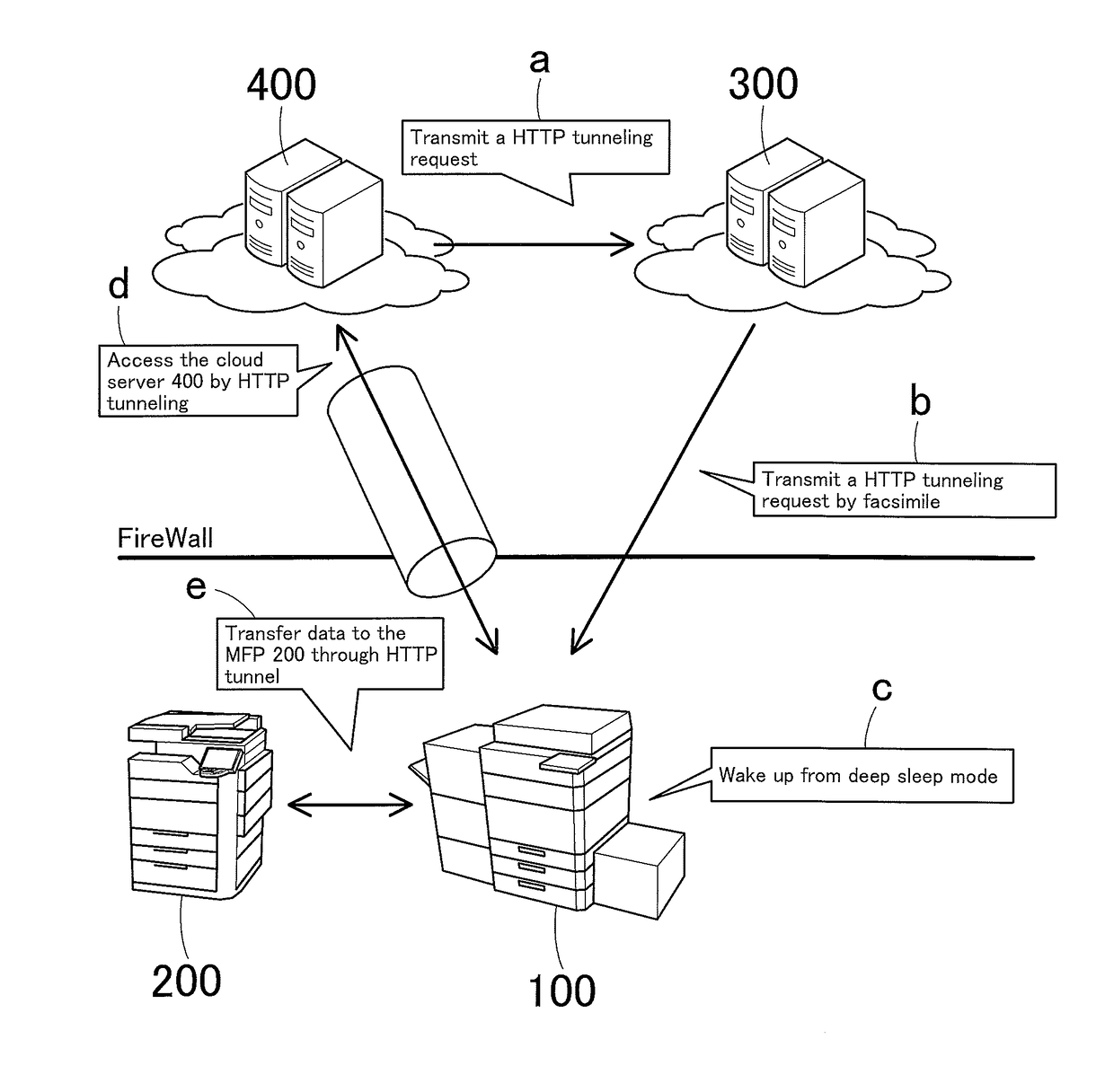
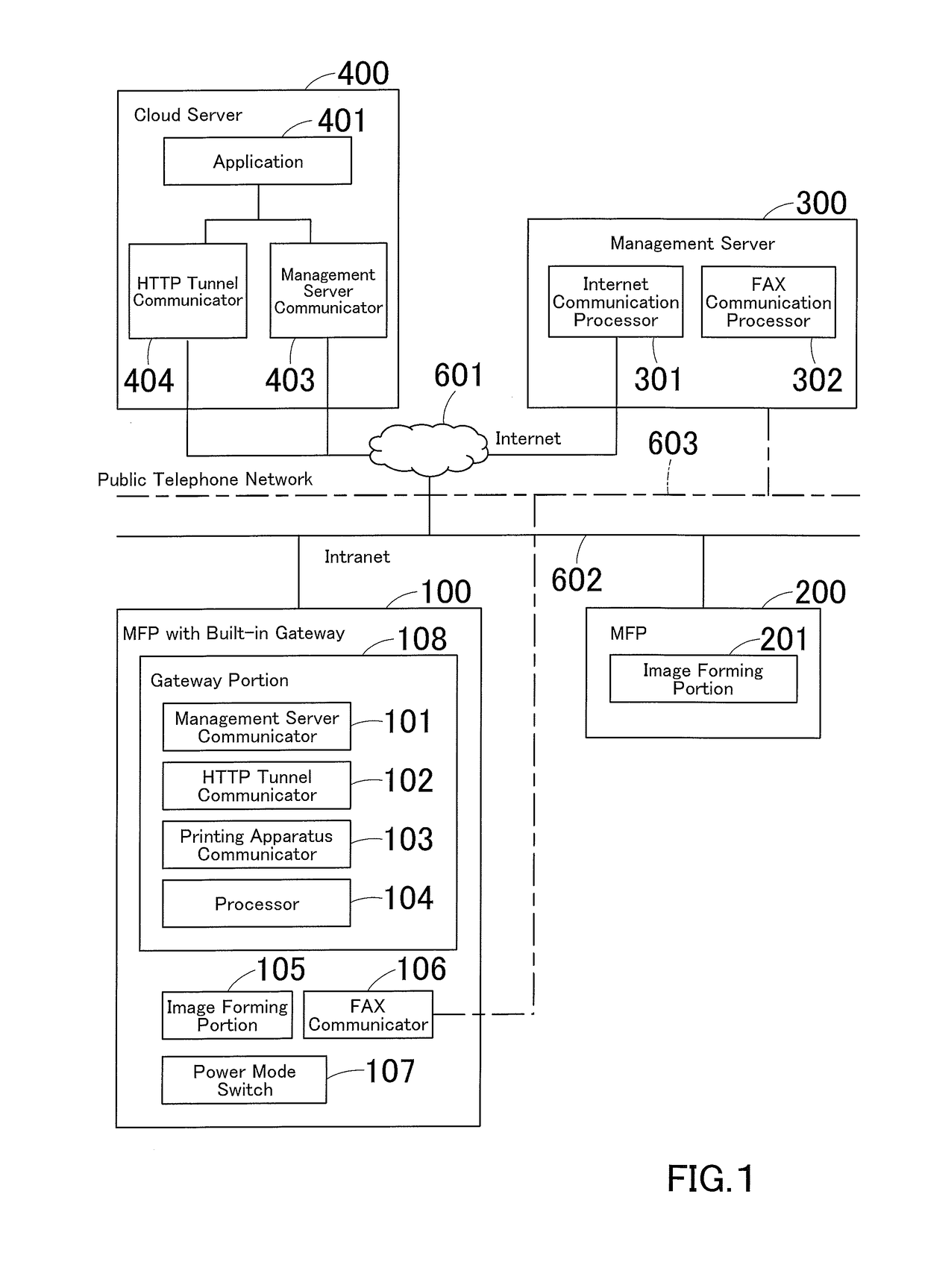
Communication system and communication method
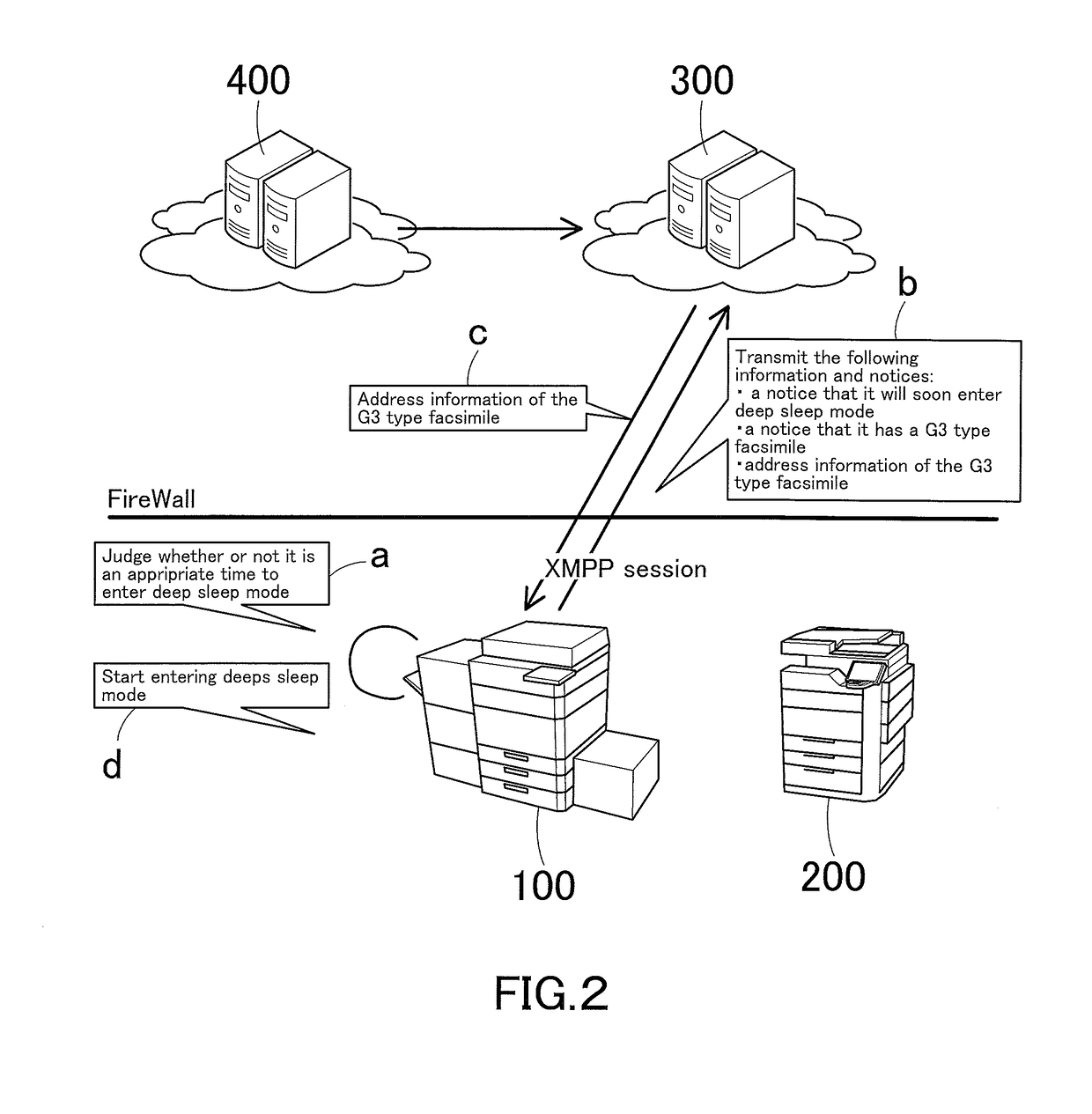
ActiveUS20160150112A1Networks interconnectionEnergy efficient computingCommunications systemHTTP tunnel
A communication system includes a cloud server, a management server, a gateway-enabled device, and a printing apparatus, and these are connected to each other. The gateway-enabled device includes a mode switch that wakes up the device from power saving mode when a HTTP tunneling request is received from the cloud server via a second requesting portion of the management server, a tunneling portion that accesses the cloud server by HTTP tunneling if the request is received via a first requesting portion of the management server during normal operation mode or that does the same after back to normal operation mode if the request is received via the second requesting portion by a method allowing waking up from power saving mode, a receiver that receives a print job from the cloud server having being accessed by HTTP tunneling, and a transfer portion that transfers the print job to the printing apparatus.
Owner:KONICA MINOLTA INC
System for accessing data of cloud database using transparent technology
ActiveUS9148404B2Improve operating convenience and using satisfactionEnsure network securityUser identity/authority verificationNetworks interconnectionHTTP tunnelThe Internet
Disclosed is a system for accessing data of a cloud database via transparent technology, and the system includes at least one channel server and at least one cloud database end. When a connection notice is outputted from an application end, the user channel unit detects a first server address and a first database address in a HTTP data format, and connects to a corresponding channel server via the HTTP tunnel to send a database request, so that the channel server can convert the first database address in the HTTP data format into a TCP / IP data format and then connect to a corresponding database end. Therefore, the application end can access data from the database behind the firewall via the Internet without modifying any program code.
Owner:SYSCOM COMP ENG
HTTP tunnel Trojan horse detection method based on deep learning
InactiveCN109600394AStrong distinguishabilityEfficient detectionNeural architecturesTransmissionHTTP tunnelNetwork communication
The invention relates to the technical field of HTTP tunnel Trojan horse detection based on communication flow analysis, in particular to an HTTP tunnel Trojan horse detection method based on deep learning. The method comprises the steps: classifying the captured data packets according to a quintuple to form a TCP session linked list; extracting a load byte of each TCP package in the TCP session linked list, and converting the first 1024 bytes into an image as the input of a deep learning model; training a model and detecting suspected Trojan horses. According to the Trojan horse detection method, the deep learning model is established, and the network communication traffic generated by the HTTP tunnel Trojan and the normal application program is learned; the characteristics of the HTTP tunnel Trojan traffic are automatically extracted, and the effective detection of the HTTP tunnel Trojan traffic in the network is realized, so that the HTTP tunnel Trojan traffic hidden in a local areanetwork can be timely detected, and the safety of the local area network is protected.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Program, information processing method and device, and data structure
InactiveUS7840593B2Firmly connectedProgram control using stored programsDigital data processing detailsInformation processingTelecommunications
The present invention relates to a program, an information processing method and apparatus, and a data structure with which connection can be formed reliably between apparatuses having different capabilities. A service that can be provided to another party is represented by five dimensional parameters, namely, Access Method, Link Speed, X scale, Y scale, and Audio Codec. The values of the parameters are all represented by integer values. Access Method is represented by number 1 in the case of RTSP / TCP+RTP / UDP, and by number 2 in the case of HTTP tunnelling. Link Speed is normalized by kbps as a base unit, and X scale and Y scale are normalized by 16 pixels as a base unit. Audio Codec supports predetermined methods represented by numbers 0 to 6. The present invention can be applied to a personal computer.
Owner:SONY CORP
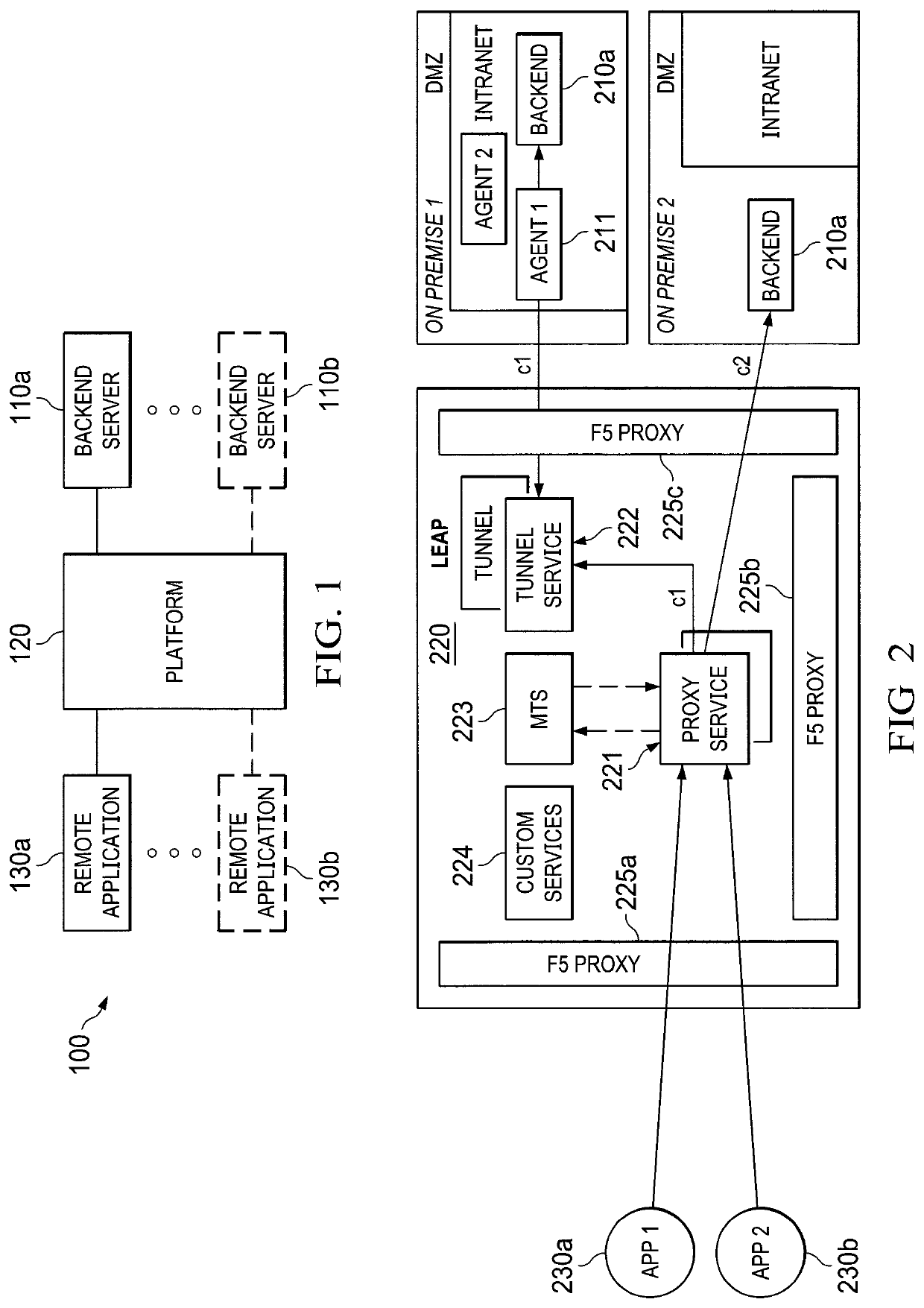
Systems and methods for providing communications between on-premises servers and remote devices
ActiveUS10873567B2Improve securityEasy to handleNetworks interconnectionHTTP tunnelTelecommunications
A system having an off-premises proxy server residing in a cloud computing environment and backend servers residing in an enterprise computing environment are provided. Requests received by the off-premises proxy server for access to a first, non-publicly accessible backend server are routed to a tunnel server which stores the request and waits to be polled by a tunnel agent connected to the first backend server. When the tunnel server is polled, the request is forwarded through an HTTP tunnel to the tunnel agent, which forwards it to the backend server for processing. Responsive information is returned to the tunnel agent, which forwards it through the HTTP tunnel to the tunnel server and returned through the off-premises proxy server to the remote application. Requests for access to a first, publicly accessible backend server are routed by the off-premises proxy server directly to the backend server for processing and return of responsive information.
Owner:OPEN TEXT CORPORATION
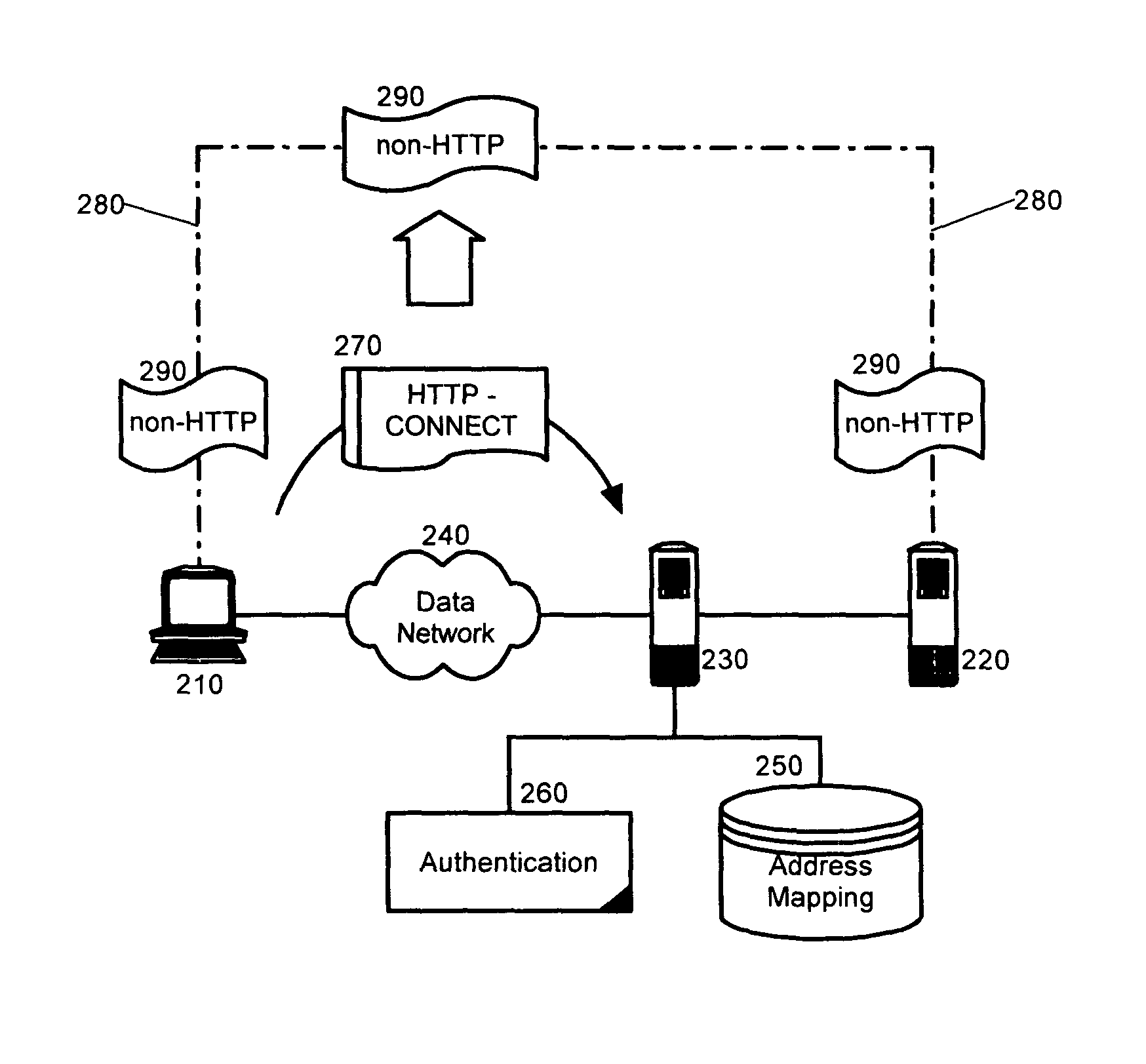
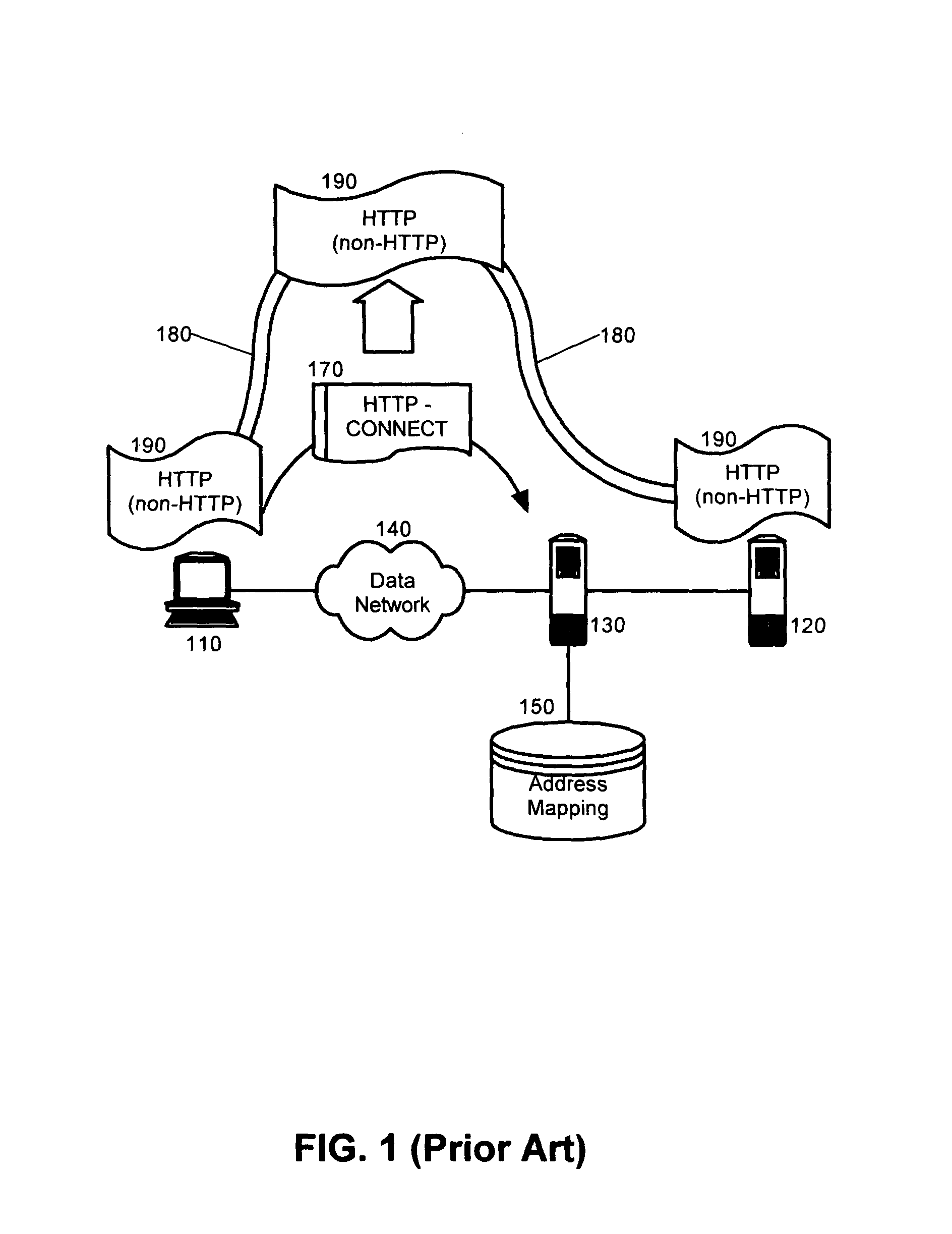
Tunneling non-HTTP traffic through a reverse proxy
A method, system and apparatus for tunneling non-hypertext transfer protocol (HTTP) data streams through a reverse proxy. The method can include soliciting a connection with a reverse proxy protecting a back-end server computing device. A connection can be established with the back-end server computing device via the reverse proxy through the solicitation. Responsive to establishing the connection, the connection can be maintained in order to exchange non-HTTP data over the secured connection. Significantly, and unlike prior art HTTP tunneling implementations, in the present invention, the non-HTTP data can be exchanged over the connection without encapsulating the non-HTTP data within HTTP messages.
Owner:INT BUSINESS MASCH CORP
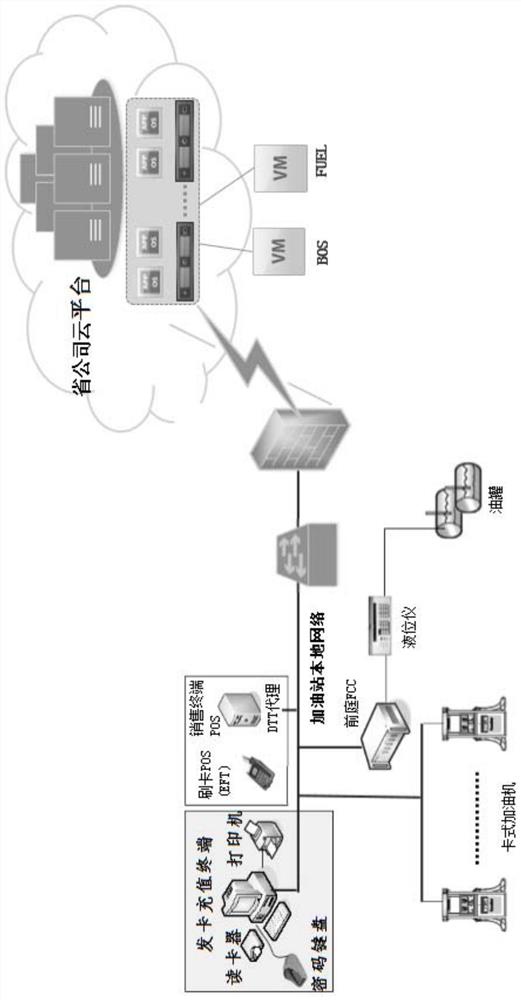
Cloud management method for gas station system
The invention discloses a cloud management method for a gas station system, and the method comprises the steps: building a private cloud platform, deploying a background management server (BOS) virtual machine and an oil product server (FUEL) virtual machine in the cloud platform, building an HTTP tunnel between a gas station and the cloud platform, and achieving the data transmission. According to the method disclosed by the invention, mutual communication and data transmission between station-level equipment are realized on the premise of ensuring that the existing IP address is not changedand the existing application software architecture, program and network architecture are not changed; meanwhile, after the gas station system is managed through the method, operation and maintenance personnel can be reduced, the management cost is reduced, BOS and FUEL are managed in a centralized mode at the cloud end, the station-level maintenance difficulty is reduced, meanwhile, no BOS or FUELexists at the station level, and station-level machine room management is reduced.
Owner:北京东晨联创科技股份有限公司
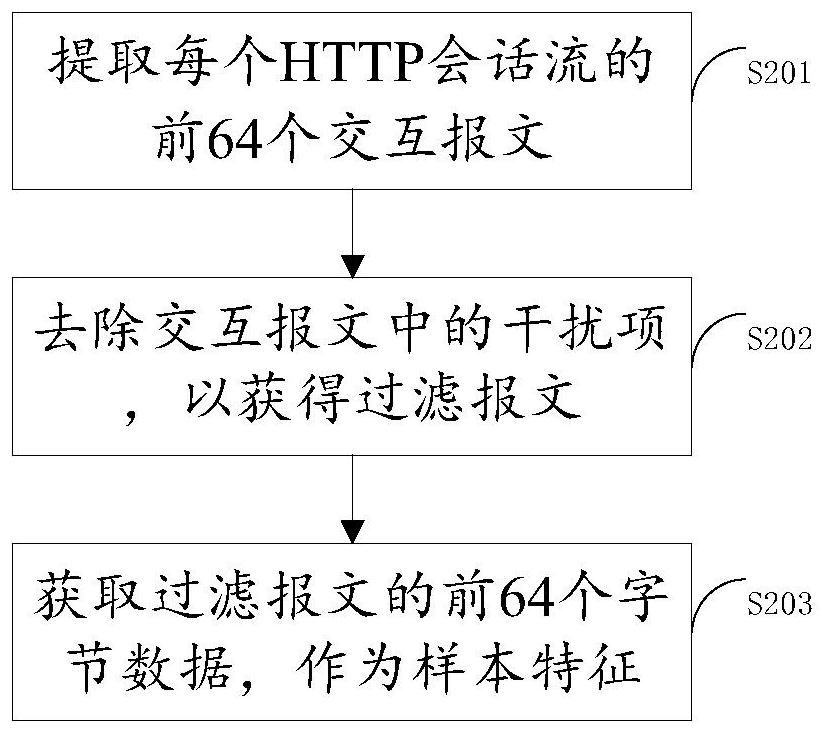
HTTP tunnel detection method and device, electronic equipment and storage medium
PendingCN114254704AImprove detection rateSolve the low detection rateCharacter and pattern recognitionNeural architecturesHTTP tunnelFeature extraction
The embodiment of the invention provides an HTTP (Hyper Text Transport Protocol) tunnel detection method and device, electronic equipment and a storage medium, and relates to the technical field of traffic security detection. The method comprises the following steps: preprocessing a to-be-detected sample to obtain an HTTP session stream; performing feature extraction on the HTTP session stream and generating a grey-scale map; and inputting the grey-scale map into a preset neural network model for detection so as to obtain a probability value that the to-be-detected sample is an HTTP tunnel, performing feature extraction on the HTTP session flow, and enabling the extracted features to more fully reflect session flow features, thereby improving the detection rate and solving the problem of low detection rate of an existing method.
Owner:BEIJING TOPSEC NETWORK SECURITY TECH +2
Using hyper-text transfer protocol tunneling to transition a computer from a low power mode to a normal power mode
A communication system includes a cloud server, a management server, a gateway-enabled device, and a printing apparatus, and these are connected to each other. The gateway-enabled device includes a mode switch that wakes up the device from power saving mode when a HTTP tunneling request is received from the cloud server via a second requesting portion of the management server, a tunneling portion that accesses the cloud server by HTTP tunneling if the request is received via a first requesting portion of the management server during normal operation mode or that does the same after back to normal operation mode if the request is received via the second requesting portion by a method allowing waking up from power saving mode, a receiver that receives a print job from the cloud server having being accessed by HTTP tunneling, and a transfer portion that transfers the print job to the printing apparatus.
Owner:KONICA MINOLTA INC
HTTP tunnel detection method based on decision tree classification algorithm
ActiveCN102035698BSimplify the training processReduce consumptionData switching networksHTTP tunnelData stream
The invention discloses a HTTP (Hyper Text Transport Protocol) tunnel detection method based on decision tree classification algorithm, used for solving the technical problem of poor stability of a conventional tunnel detection method based on the transport layer packet statistic characteristic analysis. In the technical scheme of the invention, an HTTP data stream and a tunnel data stream are used to train a decision tree classification model, with lower requirement on quantity of training sets than a statistic fingerprint method; secondly, compared with the statistic fingerprint method in which only two flow characteristics can be utilized, the decision tree classification method can use more characteristics to train the model, therefore, obtained classification rules are more precise and stable; the process to train the model is relatively simple, does not involve image fingerprint consumes less internal storage; finally, the judgment of the decision tree classification method is made according to attributes on a plurality of branch nodes without depending on one specific critical value, which achieving better stability.
Owner:JIANGSU ZHONGWEI HEAVY IND MACHINERY +1
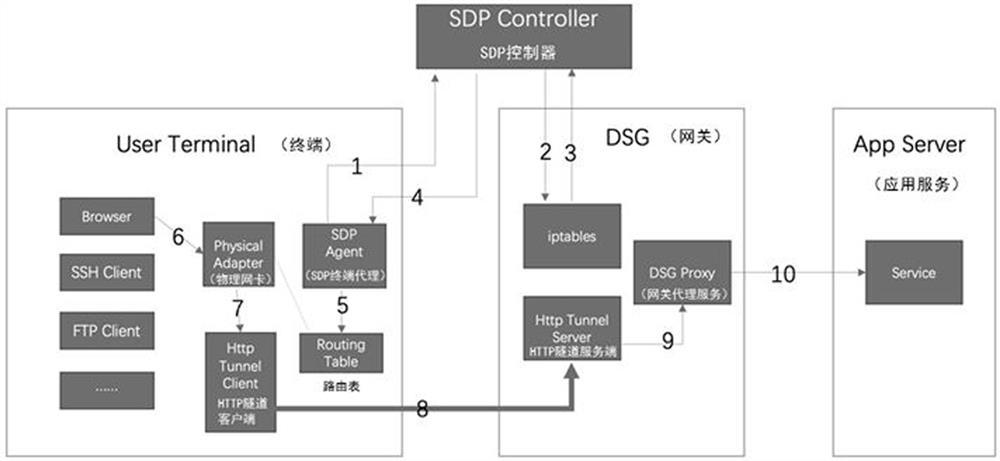
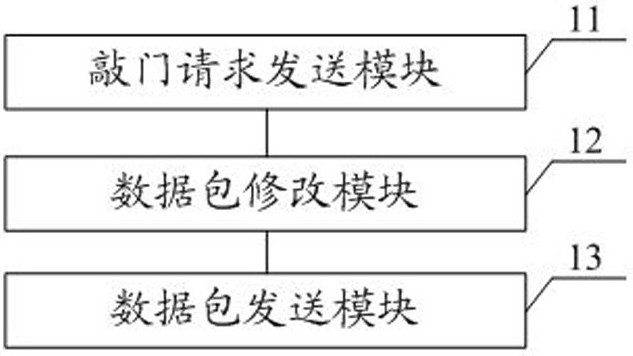
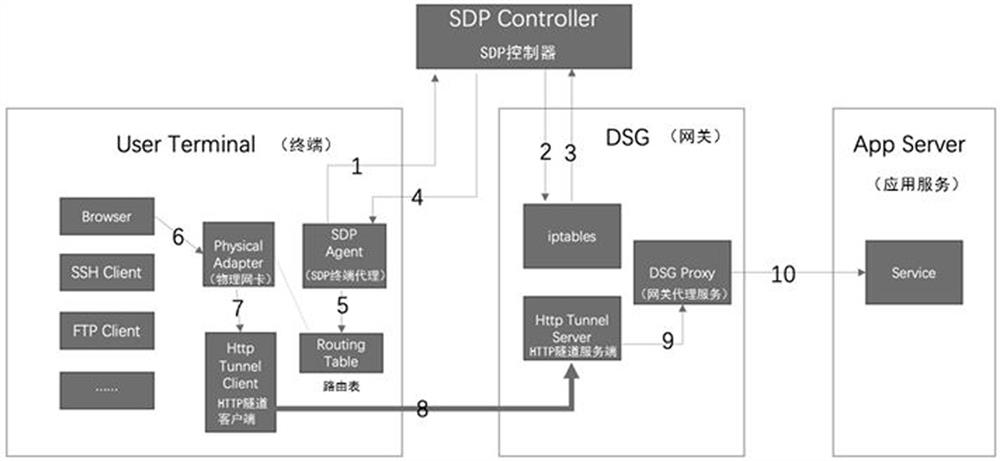
SDP terminal traffic proxy method and device, equipment and storage medium
ActiveCN113852697AImplement authentication controlImprove securityTransmissionHTTP tunnelEngineering
The invention discloses an SDP terminal traffic proxy method and device, equipment and a storage medium. The method comprises the following steps: sending a knock request to an SDP controller through an SDP terminal proxy, receiving a knock result obtained after the SDP controller accesses a target gateway according to the knock request, and then configuring a routing table of a terminal according to the knock result; acquiring an application access request of a user for a target application through a physical network card, and sending the application access request to an HTTP tunnel client according to the routing table, so that a data packet corresponding to the application access request is modified through the HTTP tunnel client, and the modified data packet contains equipment identification information corresponding to a local terminal; and sending the modified data packet to an HTTP tunnel server of the target gateway through the HTTP tunnel client, so that the target gateway performs authority control on the user according to the equipment identification information in the modified data packet. The authentication management and control of the four-layer traffic can be realized.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Network-based data processing method and electronic device
InactiveCN110311850AImprove securityEasy to handleNetworks interconnectionHTTP tunnelComputer science
Owner:BEIJING TOPSEC NETWORK SECURITY TECH +2
A kind of SDP terminal traffic agent method, device, equipment and storage medium
ActiveCN113852697BImplement authentication controlImprove securitySecuring communicationData packHTTP tunnel
The present application discloses an SDP terminal traffic proxy method, device, equipment and storage medium. The method includes: sending a knock request to the SDP controller through the SDP terminal agent, and receiving the knock result obtained after the SDP controller accesses the target gateway according to the knock request, and then configuring the terminal according to the knock result Routing table: Obtain the user's application access request for the target application through the physical network card, and send the application access request to the HTTP tunnel client according to the routing table, so as to modify the corresponding application access request through the HTTP tunnel client data packet, so that the modified data packet contains the device identification information corresponding to the local terminal; the modified data packet is sent to the HTTP tunnel server end of the target gateway through the HTTP tunnel client, so that the target gateway Perform permission control on the user according to the device identification information in the modified data packet. It can realize the authentication and control of the four-layer traffic.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Data transfer method between clients in restricted network and clients
ActiveCN103516573BGuaranteed reliabilityIntegrity guaranteedNetworks interconnectionHTTP tunnelClient-side
Owner:BEIJING FEINNO COMM TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com