Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
307 results about "Destination site" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
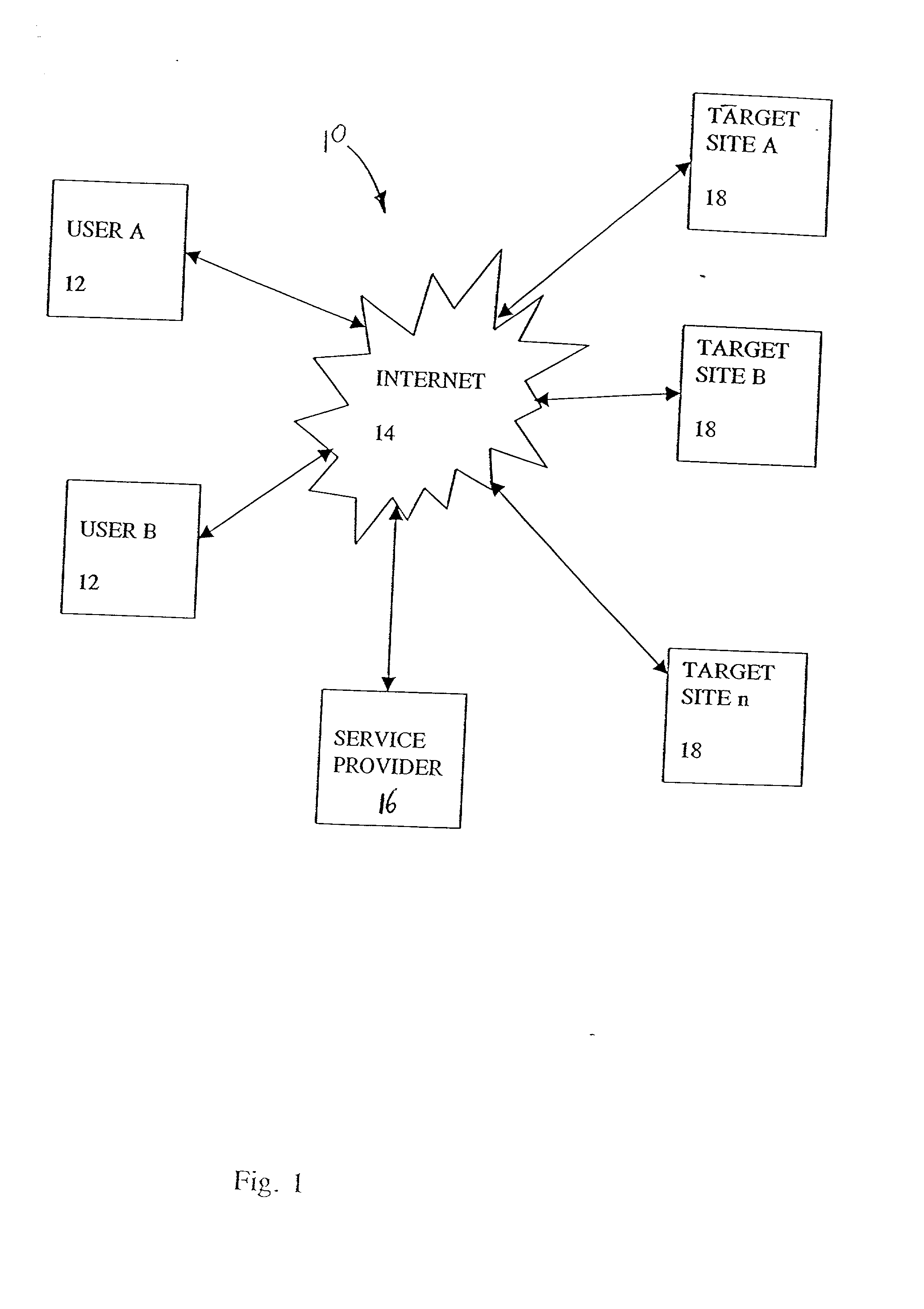
A destination site is a website with an assortment of content and jumping off points, intended to serve as a portal to the web for its users. Companies design such sites with the goal of making them the first stop for users interested in a particular topic or range of topics, and government agencies can use similar site designs.
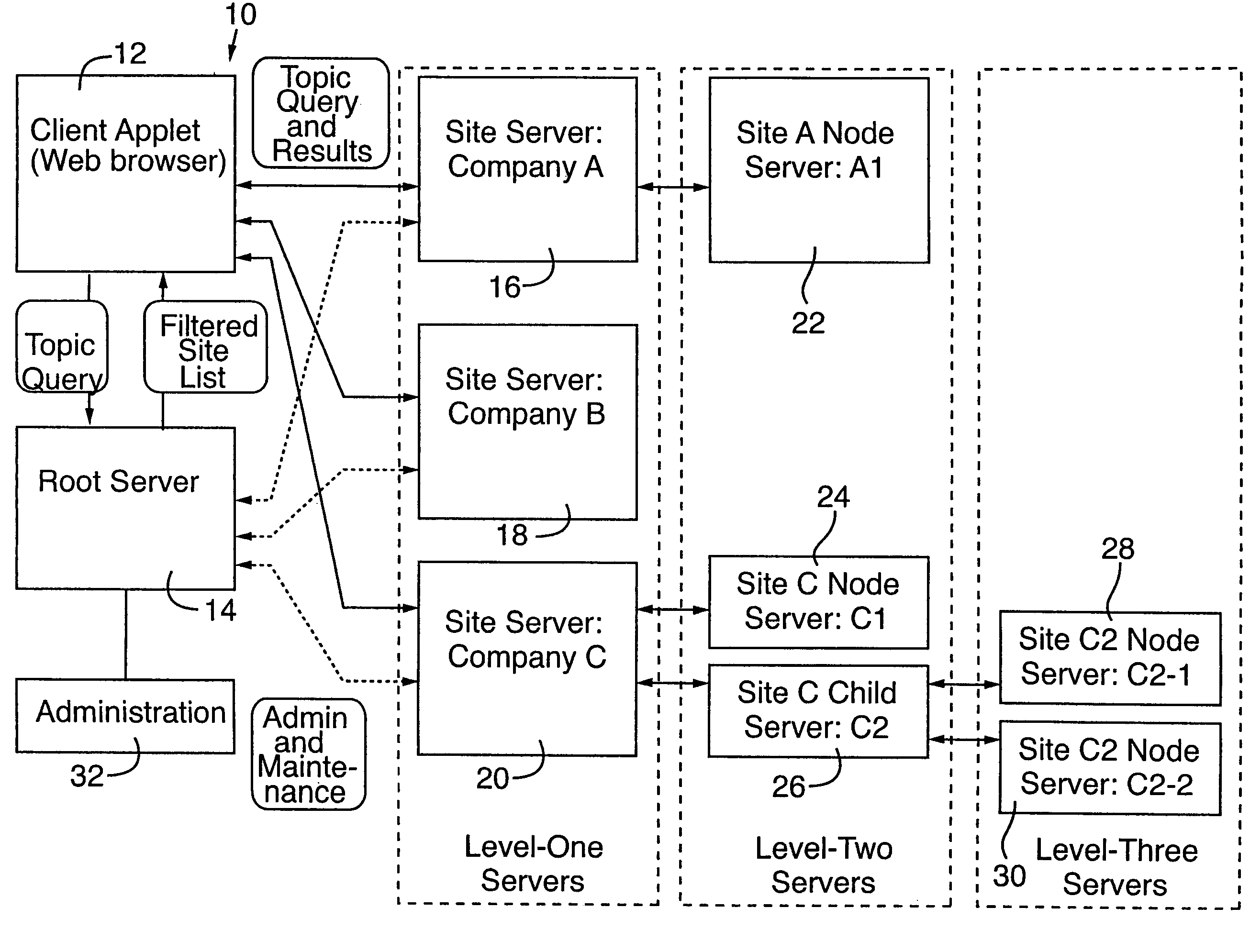
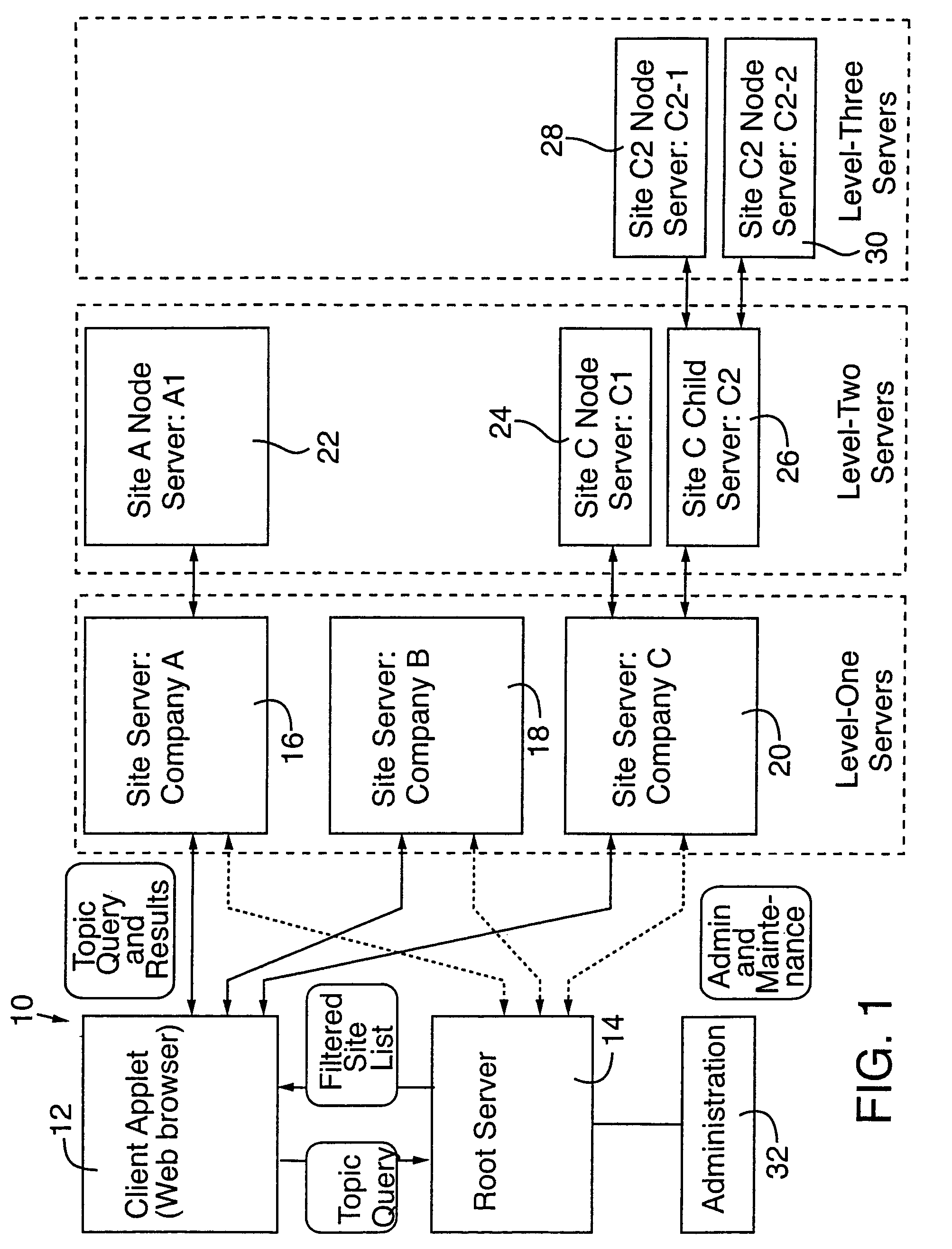
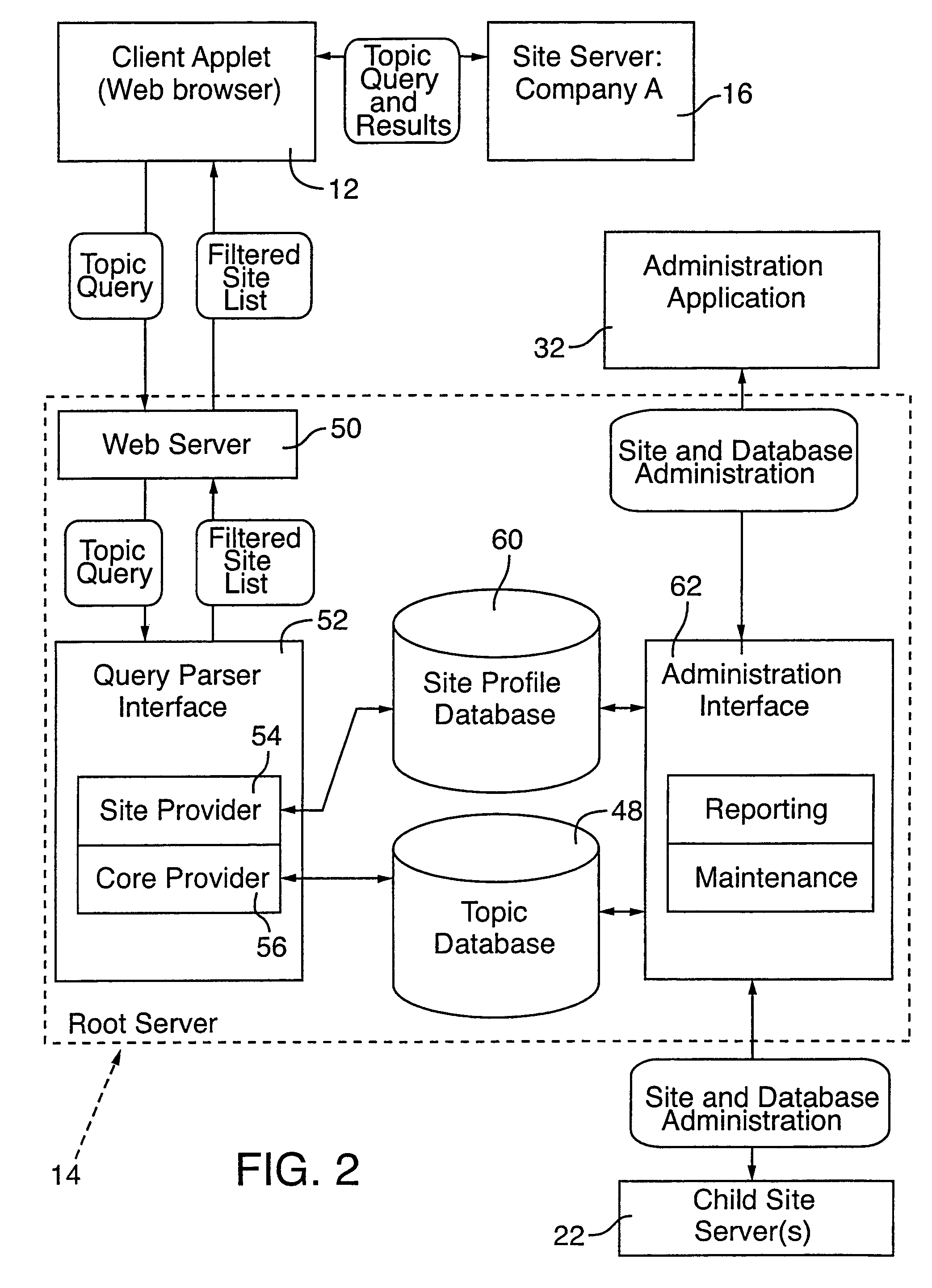
Distributed globally accessible information network
InactiveUS7430587B2Facilitate a trend of “de-centralizationCooperate effectivelyData processing applicationsWeb data indexingTelecommunications linkInformation networks
Owner:KOLOGIK LLC
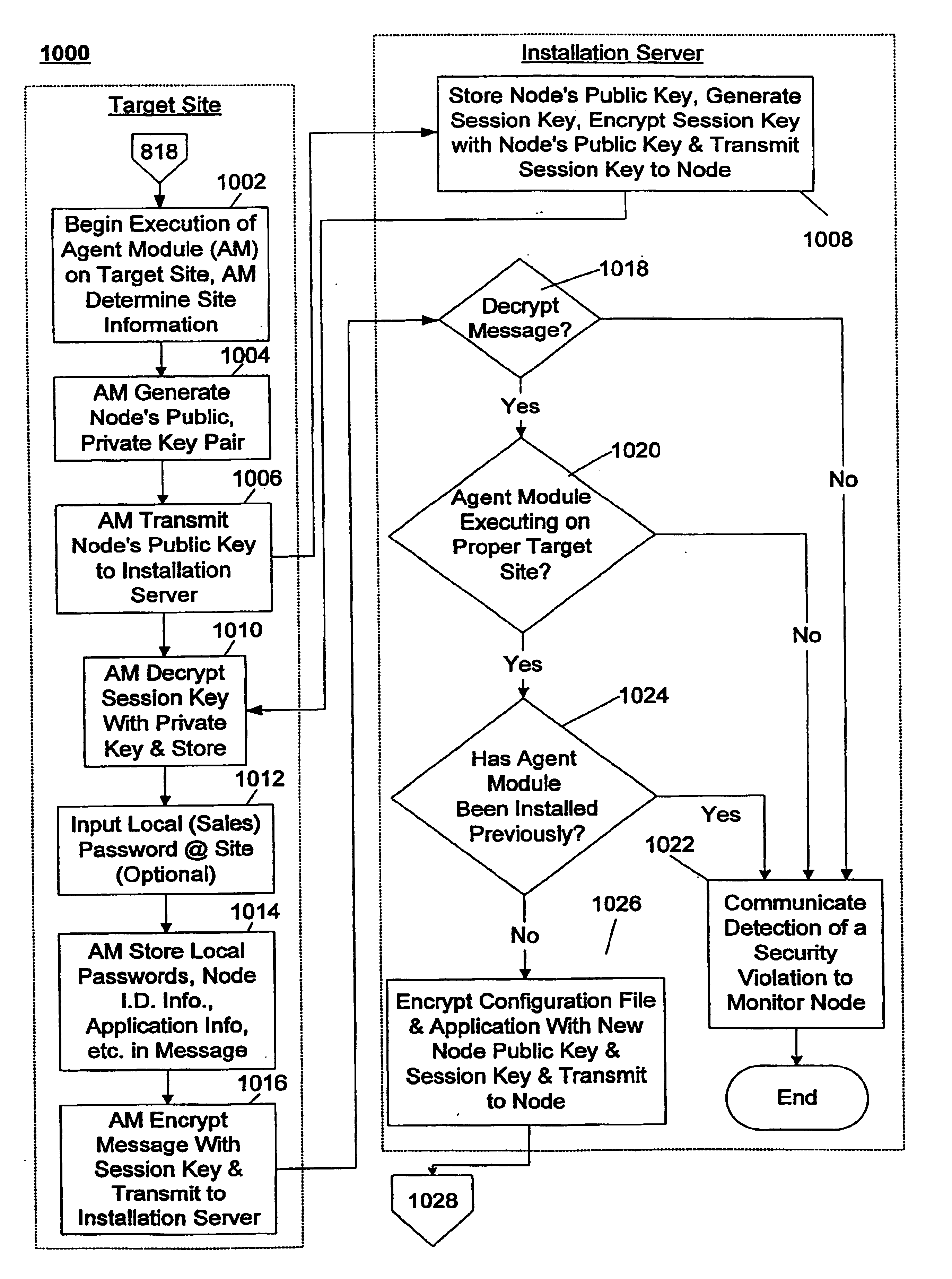
System and method for installing an auditable secure network
InactiveUS6918038B1Short timeImprove securityMemory loss protectionError detection/correctionStationPassword
A system and method for generating and remotely installing a private secure and auditable network is provided. Node identification, link, and application information is input into a template. A generator generates components using the information in the template and the components are remotely installed using an installation server. The components include agent modules which are each installed at predetermined target site and establish communication with the installation server to facilitate the download of other components, including application software and configuration files. Each node can only be installed once and is specific to a predetermined target site. For each link, a unique pair of keys is generated in a form which is not human readable, each key corresponds to a different direction of communication over the link. Data transmitted between nodes is encrypted using public-private key pairs. At least one monitor node manages the security of the network, strobes keys, and may take nodes out of the network in the event of a security violation. In such a case, one or more nodes, or the entire network, may be regenerated and installed anew. Throughout the generation and installation a plurality of verifications, authorizations, and password entries may be required by independent groups to arrive at the network. Preferably, the installation is audited by several groups, and the overall operation may be audited by a second monitor node to detect the presence of an interposed “pirate” node.
Owner:ANGEL SECURE NETWORKS
Identifying and providing targeted content to users having common interests
A computer process is disclosed for selecting items to present or recommend to users based on the referring sites accessed by such users. The process includes tracking referrals of users from referring sites to a target site, and recording the item selections of the referred users from an electronic catalog of the target site. The process may also include analyzing the recorded item selections of the users to identify, for a particular subset of the referring sites, a set of items that correspond to group preferences of users referred to the target site by the subset of referring sites. These identified items may thereafter be presented to users who access a site that is a member of the subset of referring sites.
Owner:AMAZON TECH INC
Medical Device
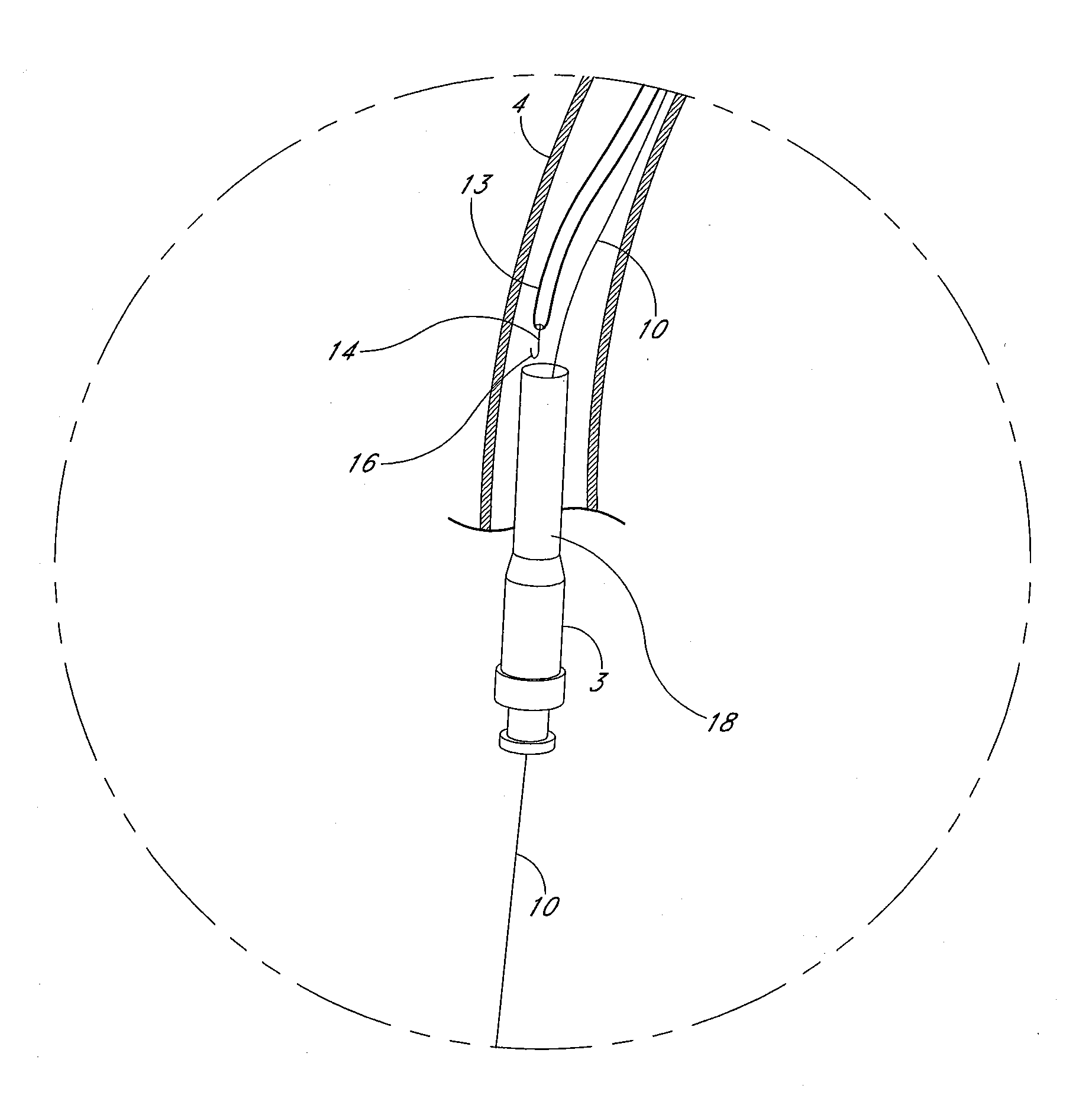
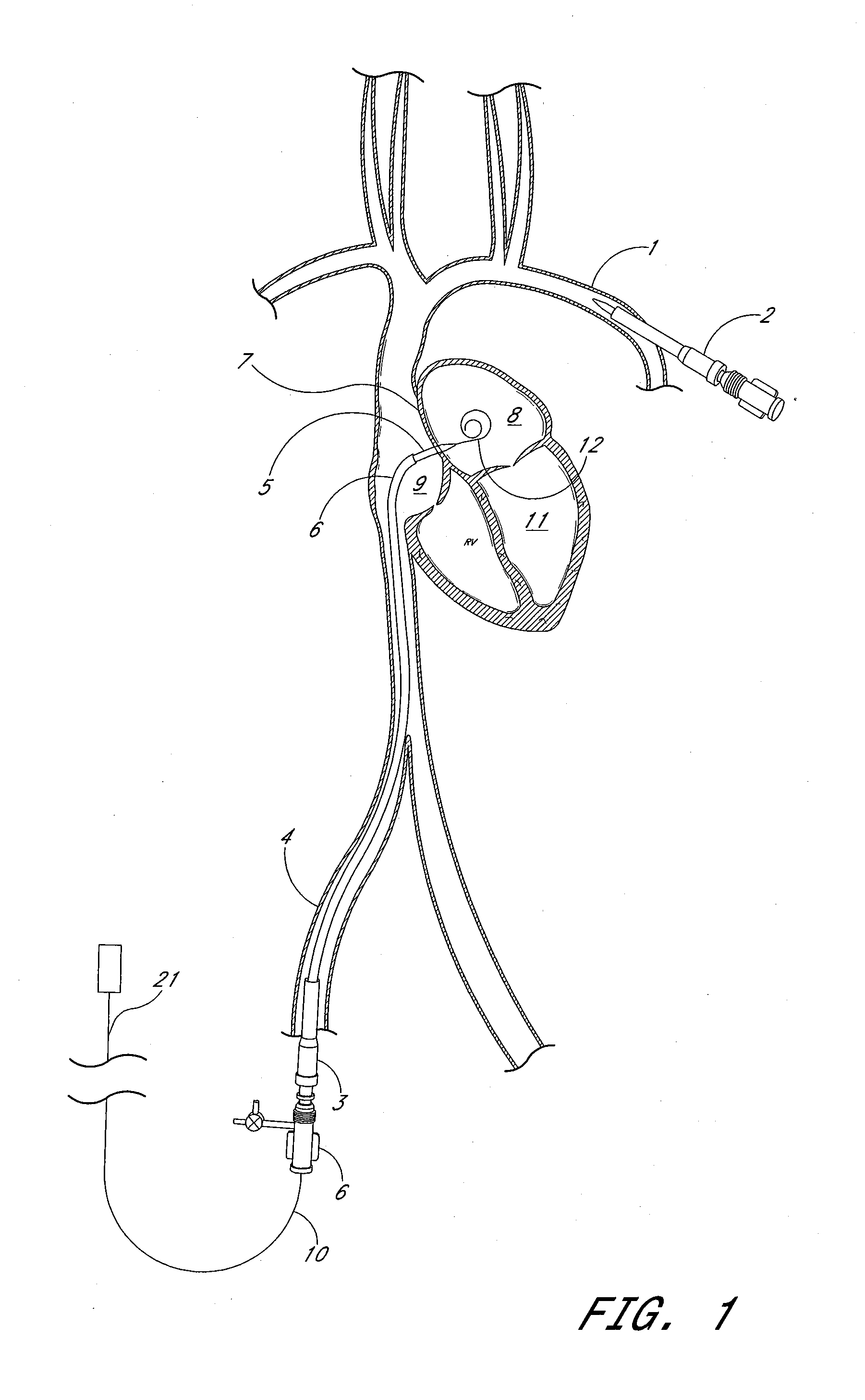
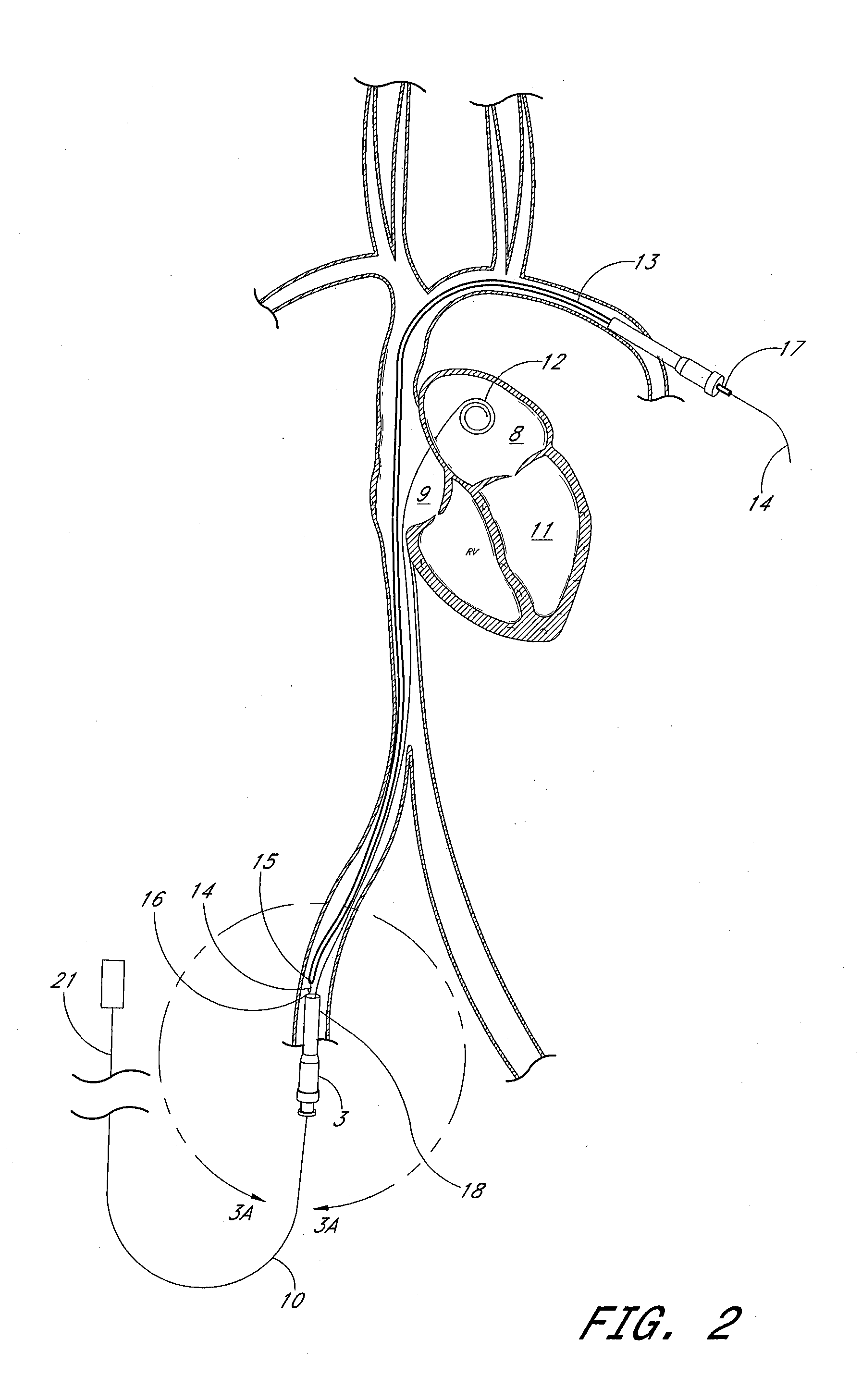
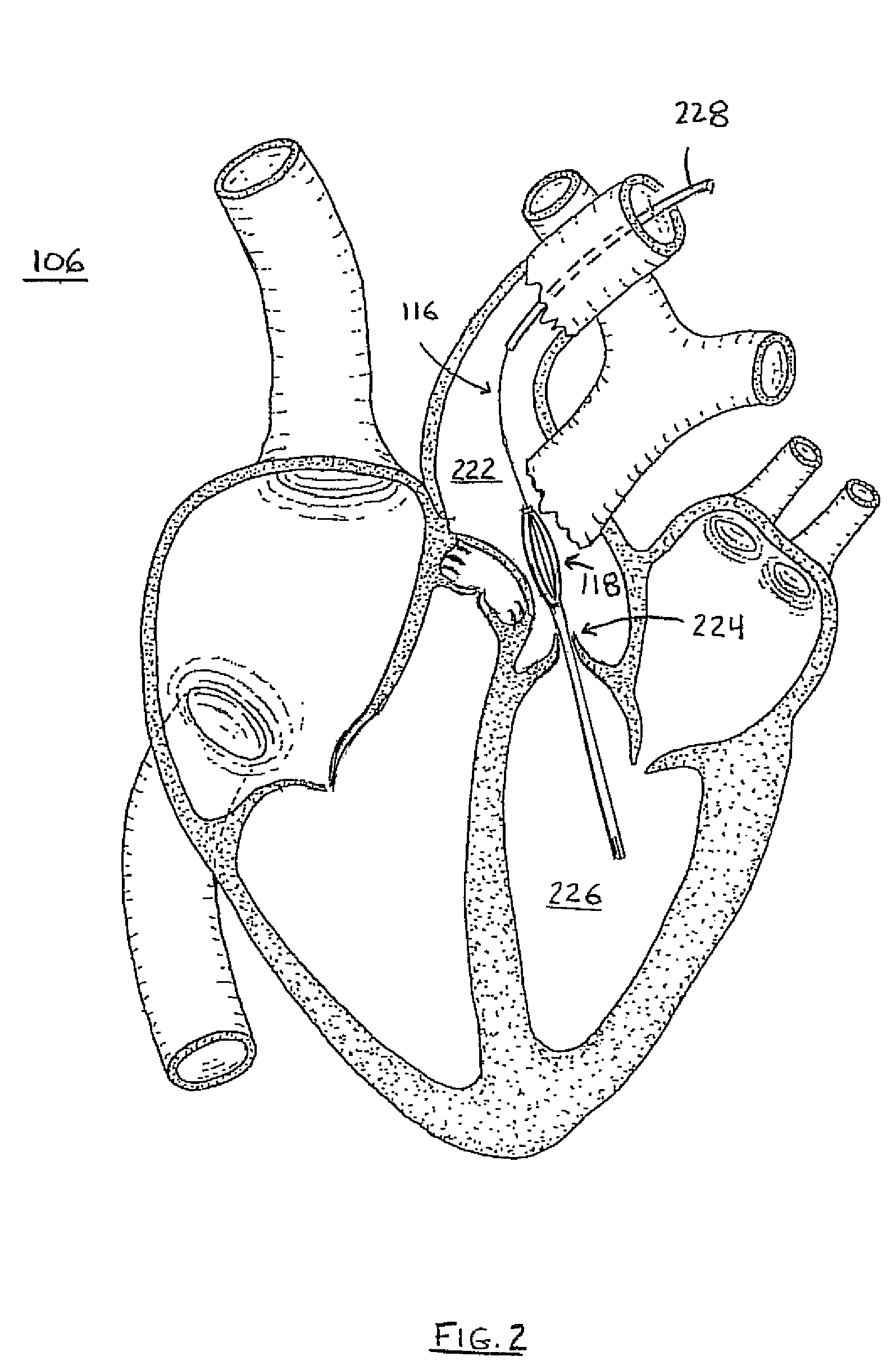
ActiveUS20080132747A1Reduce bending loadMinimizing contact pressureBlood pumpsIntravenous devicesAscending aortaImpeller
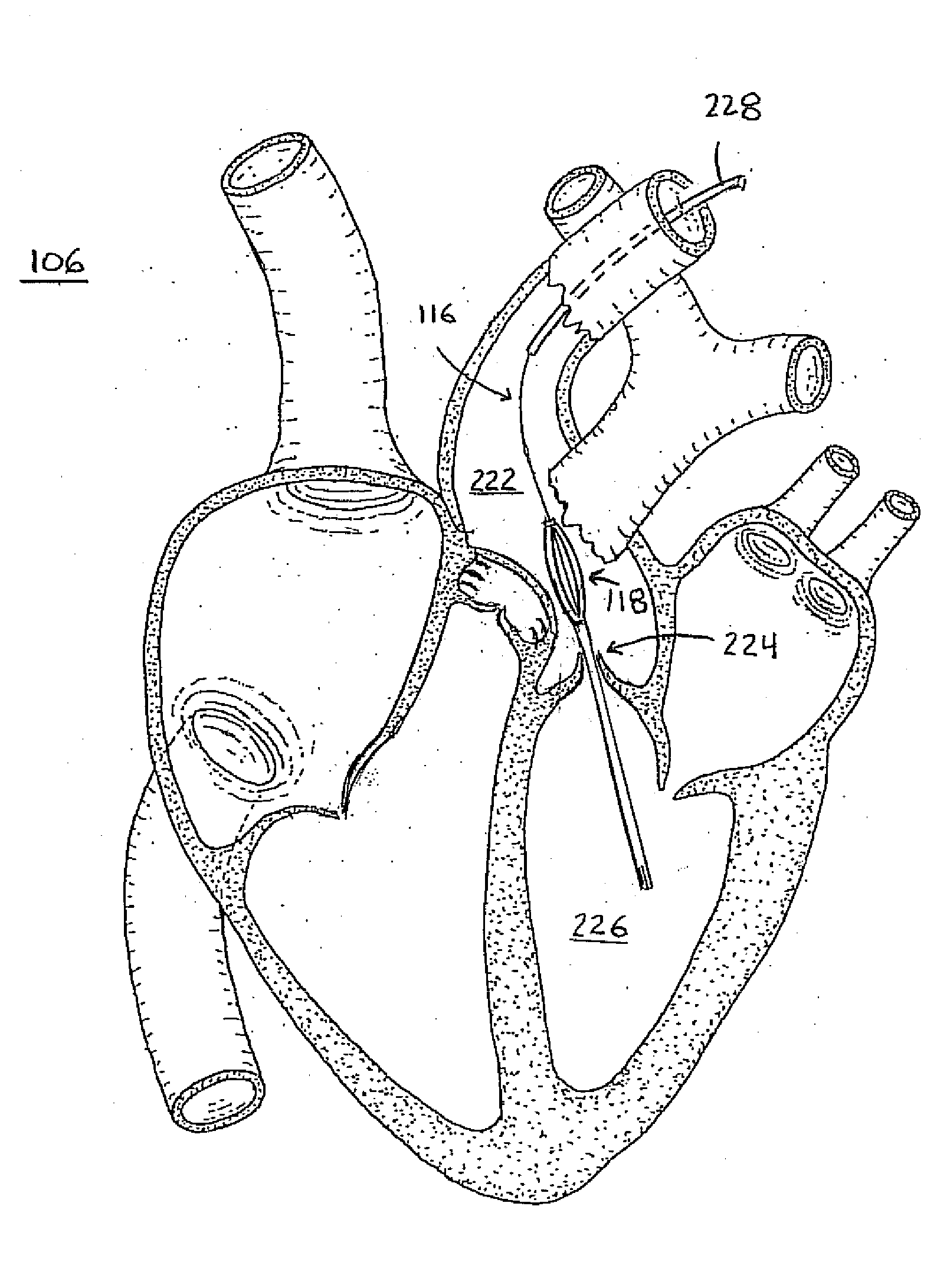
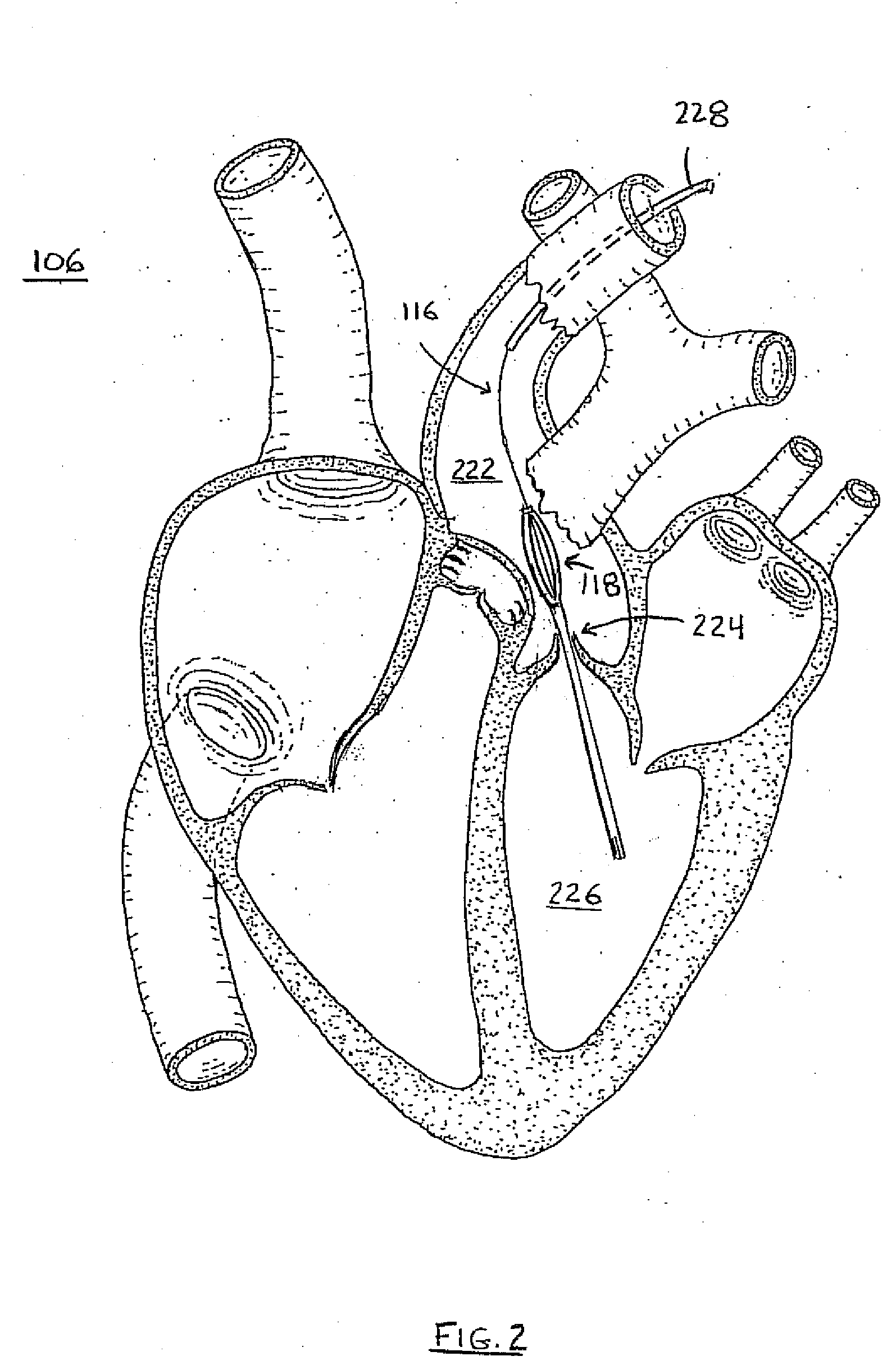
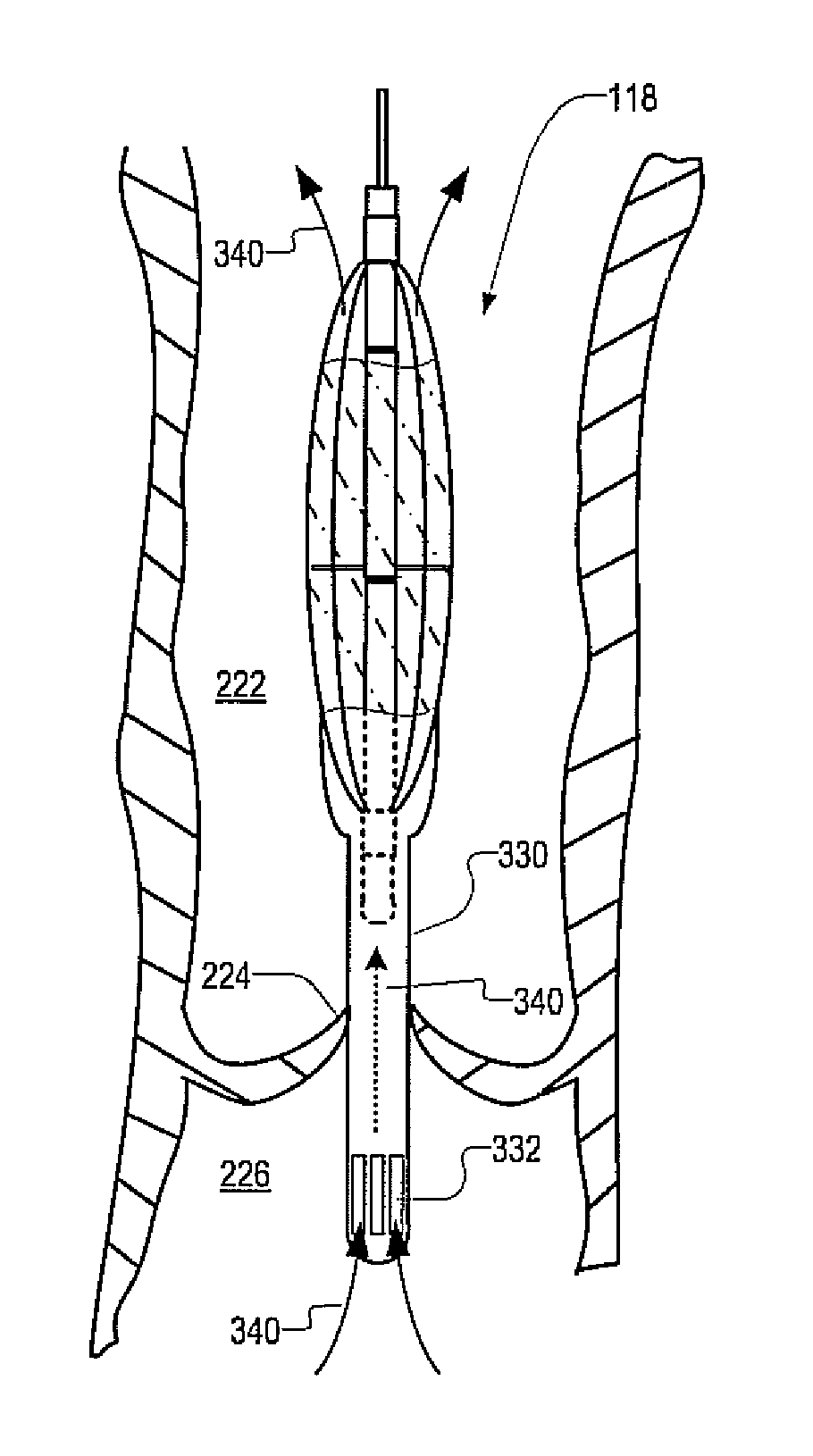
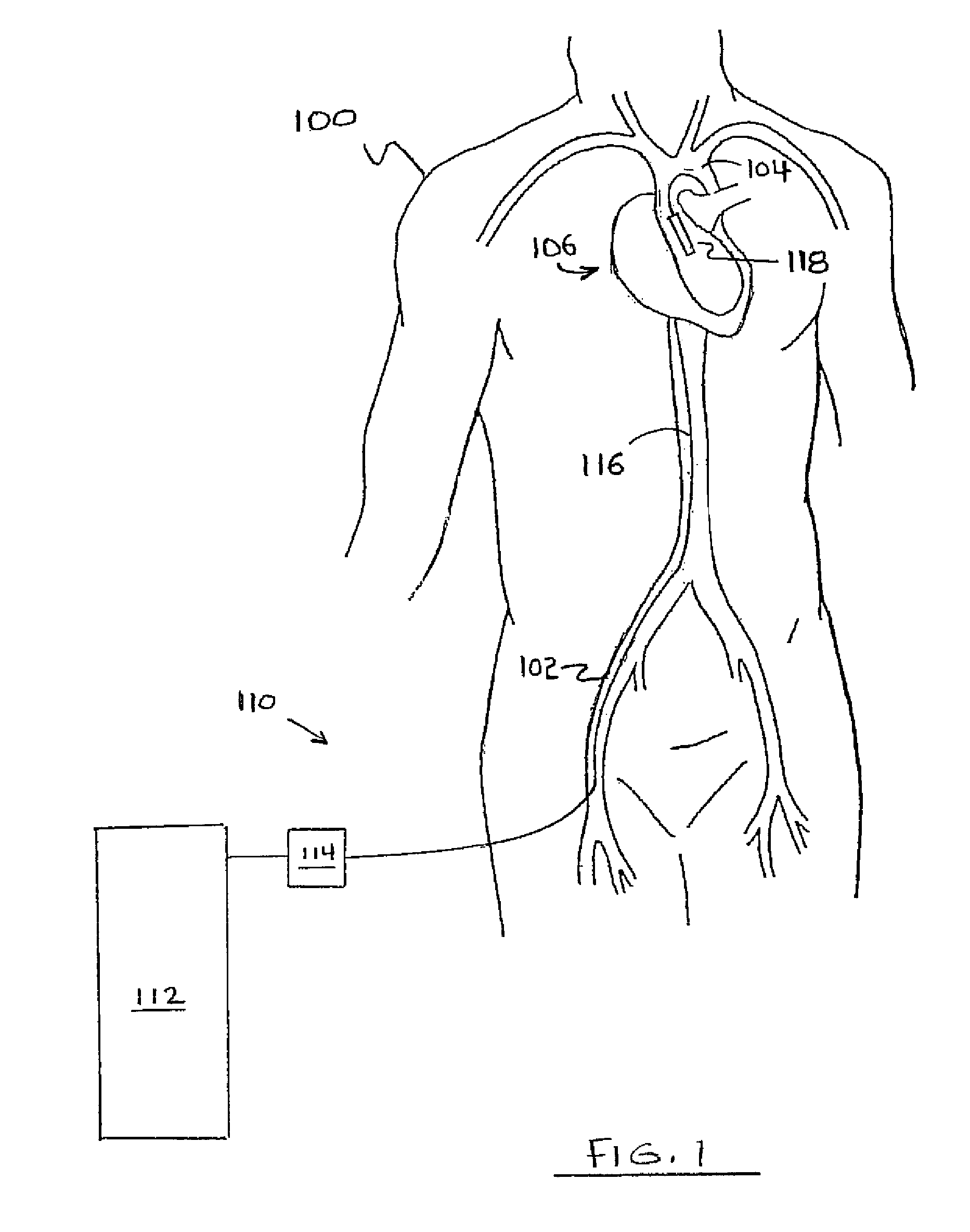
A temporary cardiac-assist device is disclosed. The device includes a pump assembly that is deployed in the ascending aorta or the heart. A torque transmission line couples the pump assembly to an external motor for driving impeller blades within the pump assembly. The pump assembly expands in size at its destination site for operation. In operation, neither the torque transmission line nor elements that support the impeller blades are under axial forces.
Owner:FBR MEDICAL INC
System for viewing content over a network and method therefor
InactiveUS20020029252A1Adding to appeal and desirabilityDiscounts/incentivesAdvertisementsWeb siteUser device
A system and method for viewing content over the Internet wherein a user accesses a service provider server to view a character icon provided by the service provider to a user interface device. The user will select web site addresses of subscriber target sites where the user can access enhancement content for the character icon to provide functionality to the character icon such as for animating the character icon on the user device. Addresses for such web sites may be provided to the user based on a particular character icon selection which may, in and of itself, signify interests and / or demographic information of the user. Access to enhancement content will be provided by accessing authorization codes present at the target sites. In a preferred embodiment, only certain enhancement content will be operable on certain character icons, thus requiring the user to locate enhancement content that is compatible with the user's character icon.
Owner:SEGAN
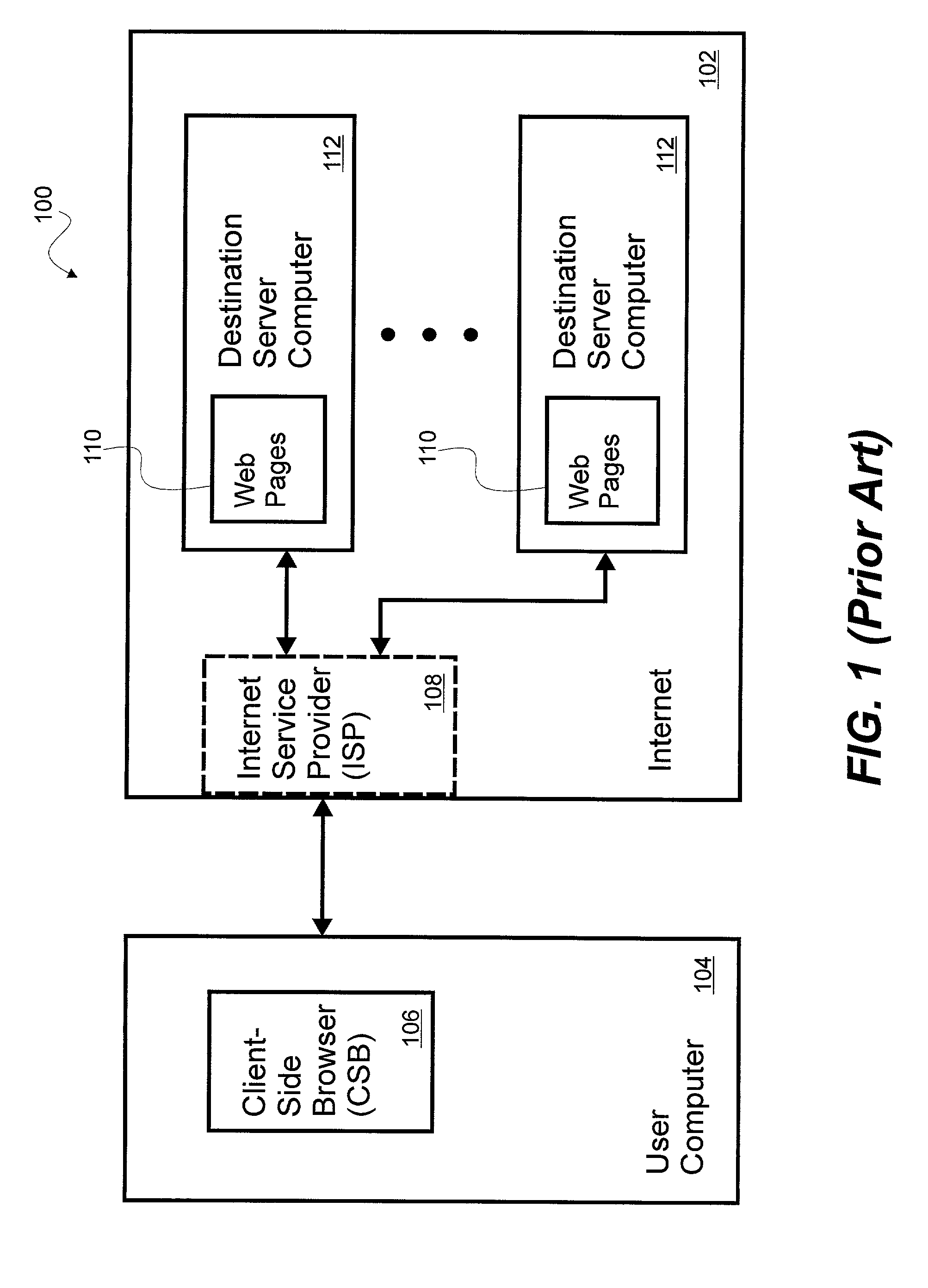
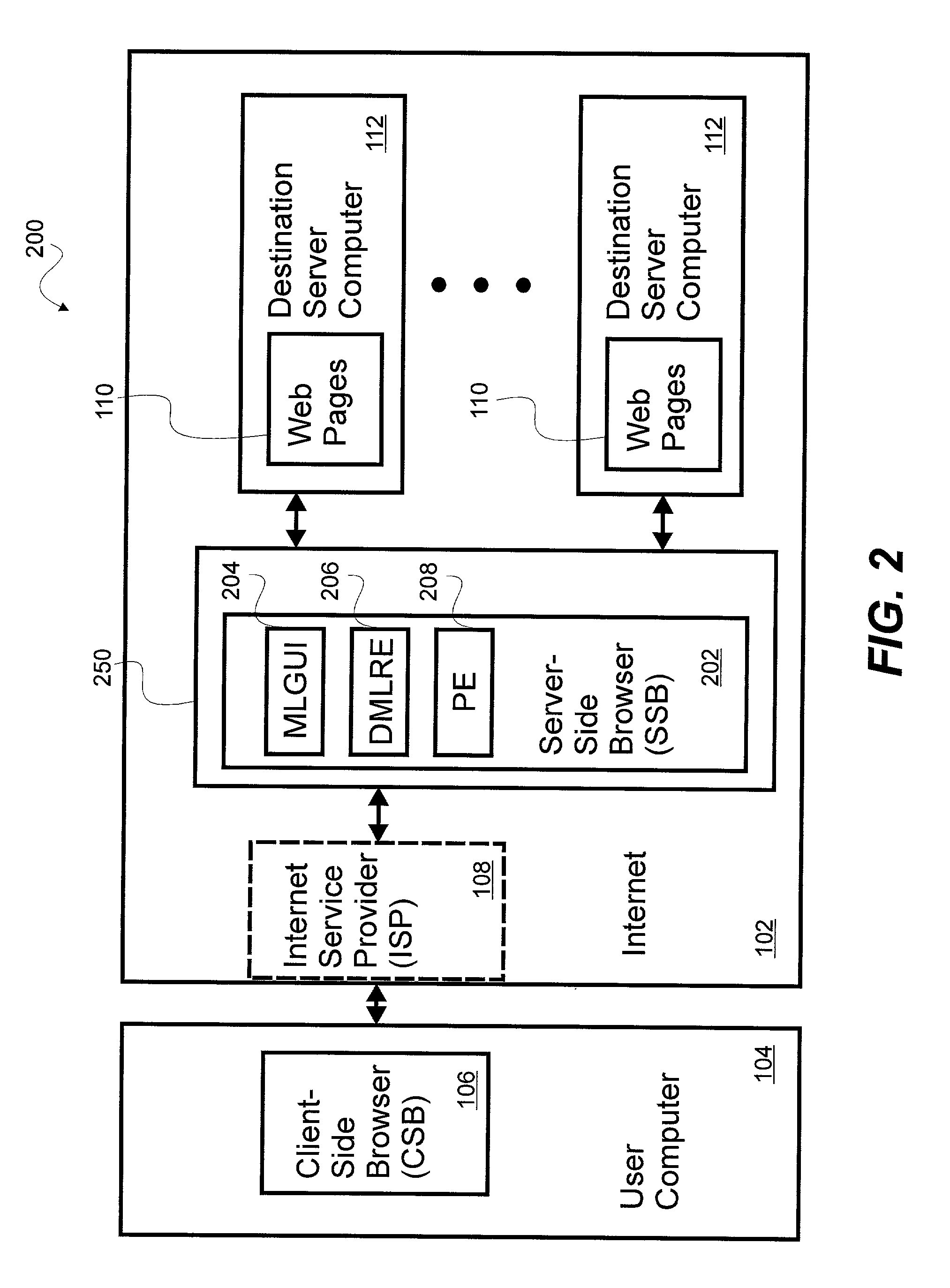
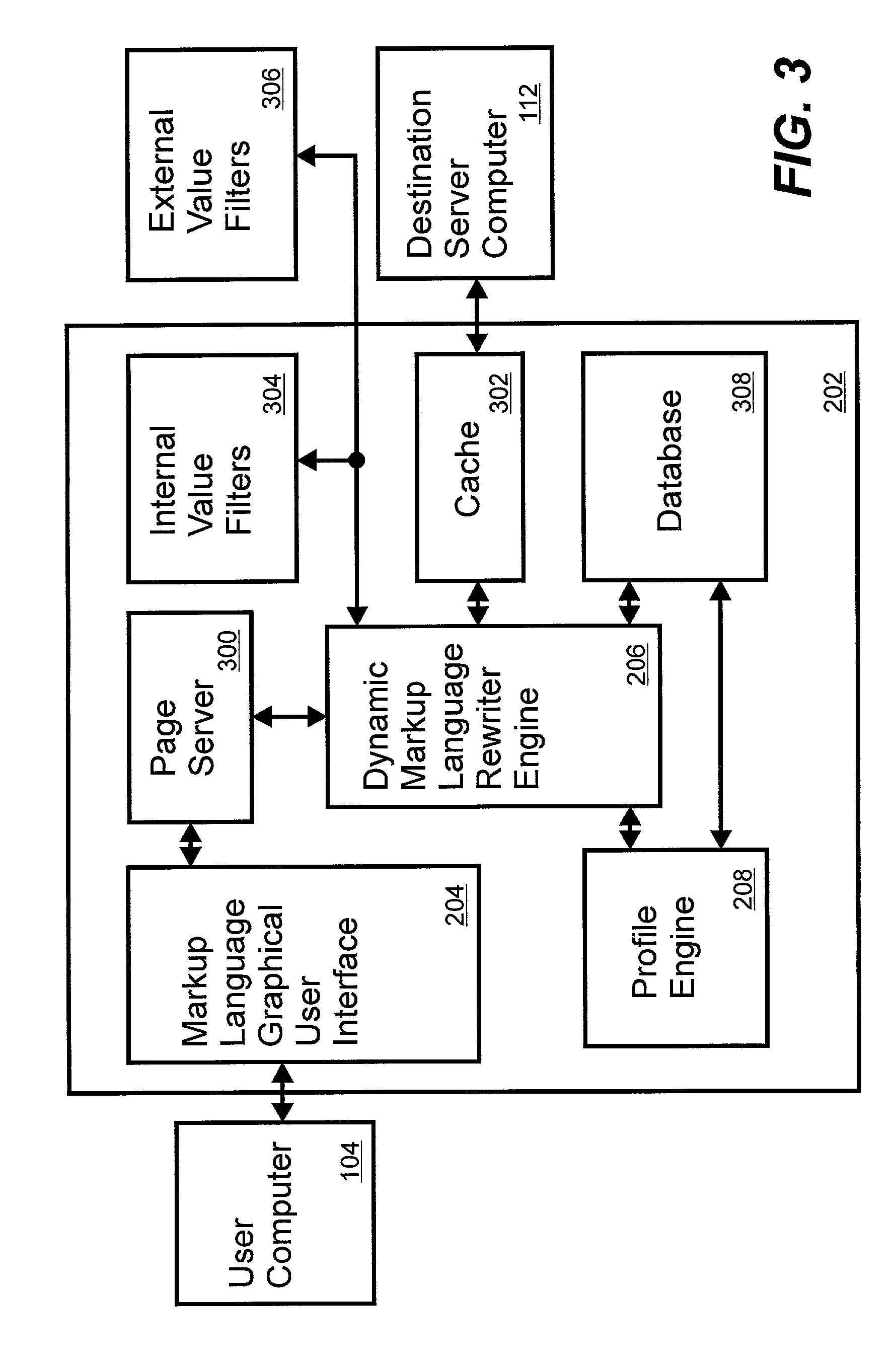
System and method for a server-side browser including markup language graphical user interface, dynamic markup language rewriter engine and profile engine
The invention is a system and method for customizing access and delivery of information distributed in a packet-based network. The system includes a user computer and a destination server computer separated by a server-side browser (SSB) server computer hosting a SSB. The SSB includes a markup language graphical user interface (MLGUI), a dynamic markup language rewriter engine (DMLRE) and a profiling engine (PE). The SSB may be configured as an intermediary infrastructure residing on the Internet providing customized information gathering for a user. The components of the SSB allow for controlling, brokering and distributing information more perfectly by controlling both browser functionality (on the client-side) and server functionality (on the destination site side) within a single point and without the necessity of incremental consents or integration of either side.
Owner:ORANGATANGO
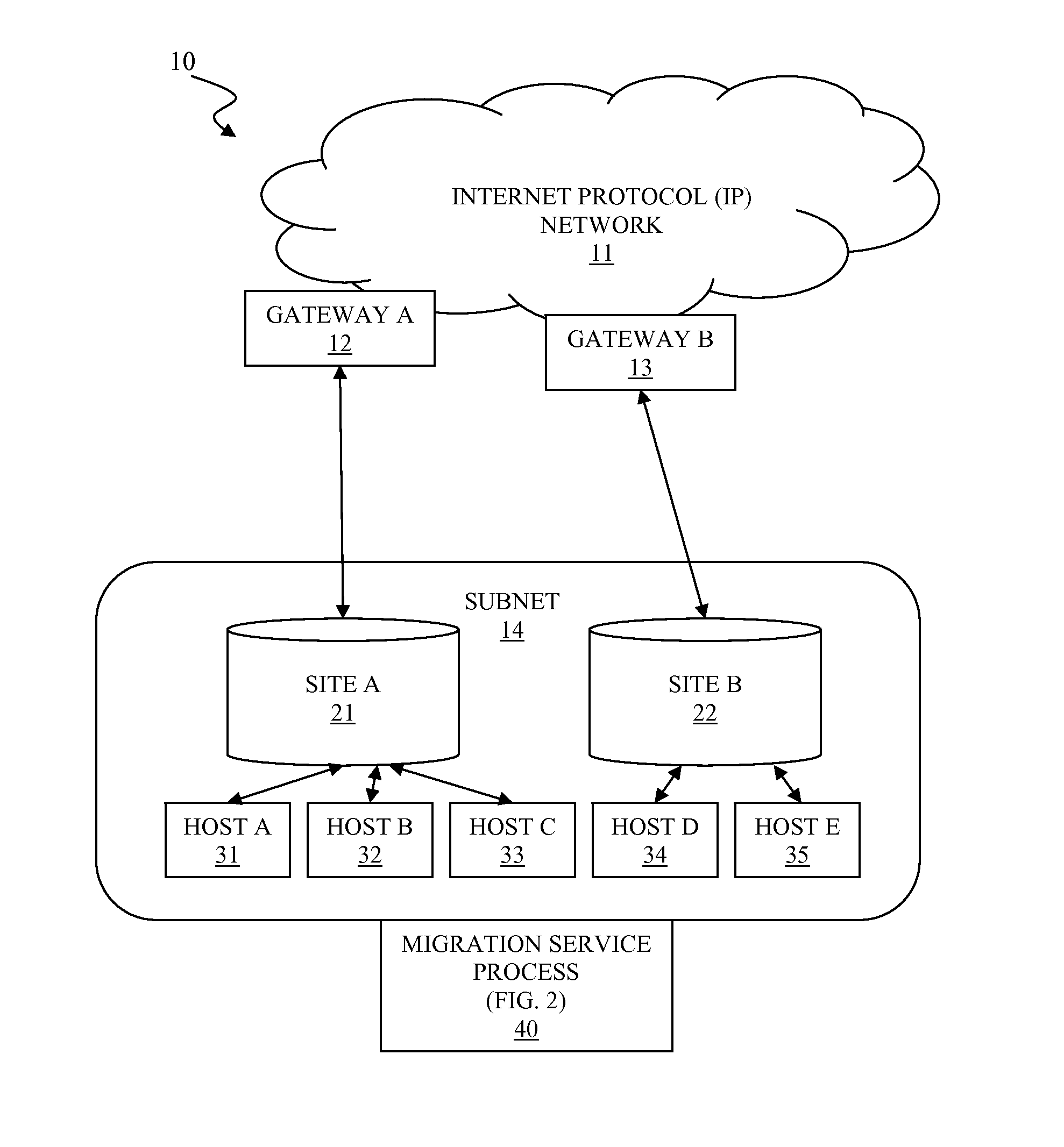
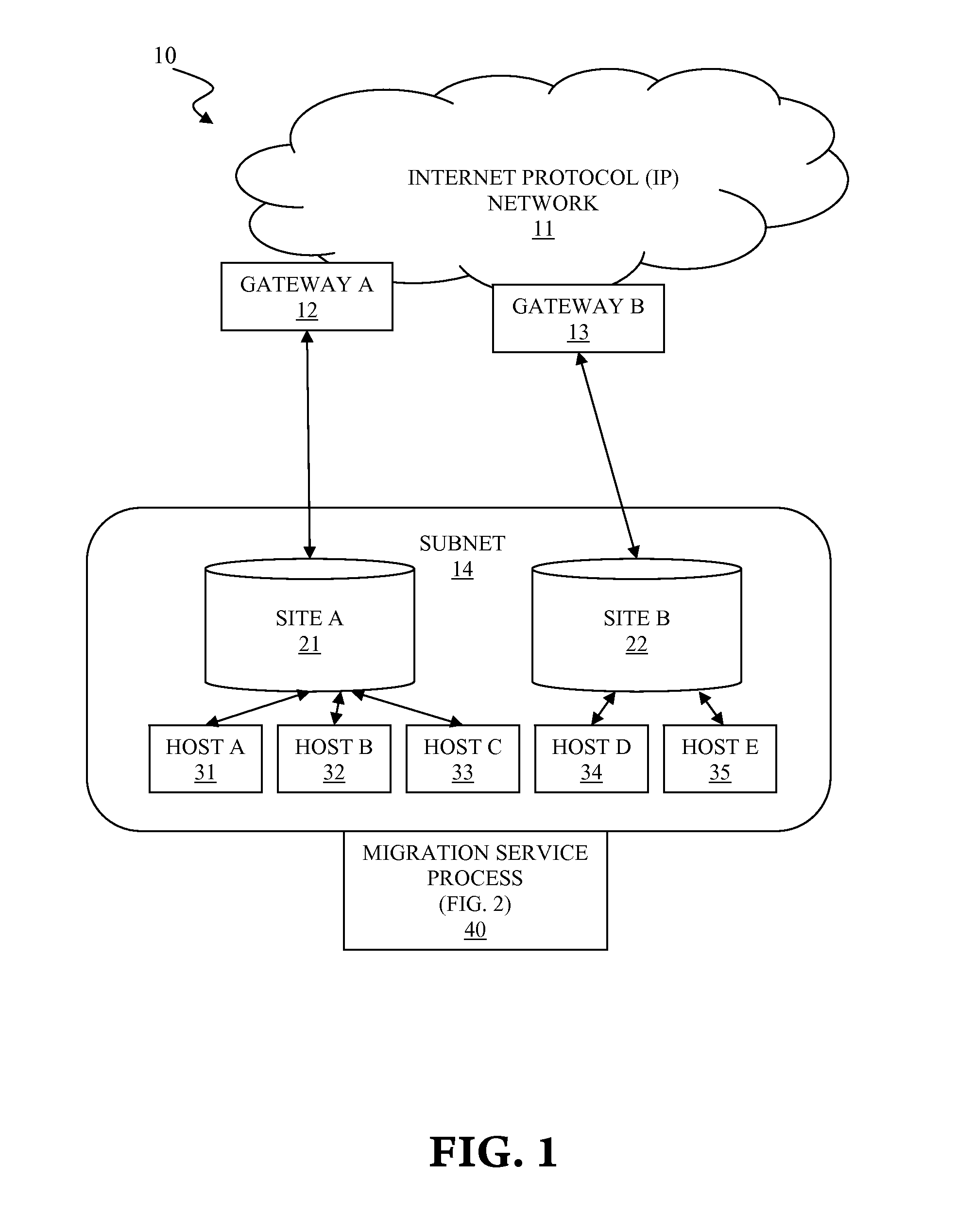
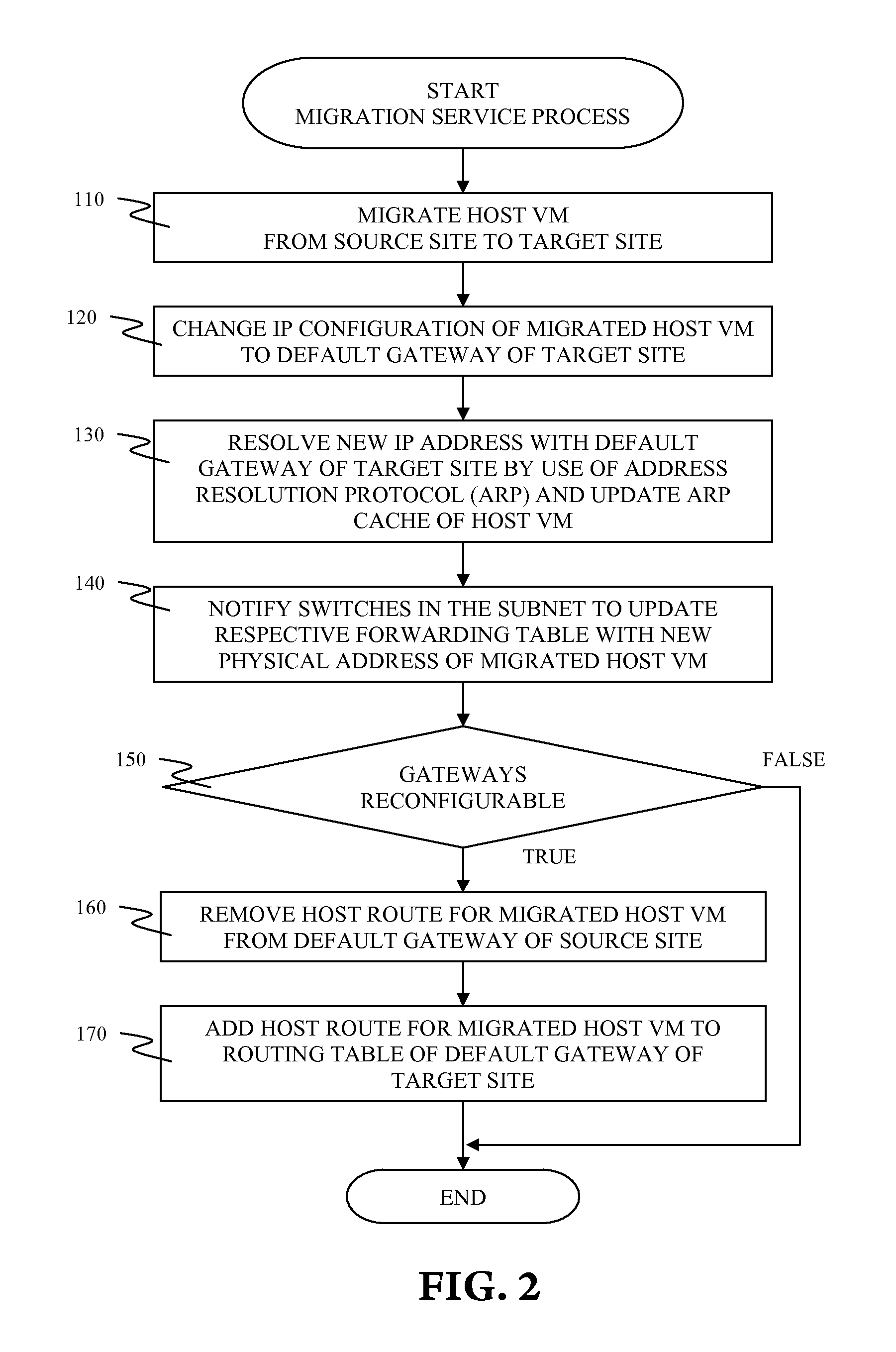
Routing optimization for virtual machine migration between geographically remote data centers
A system and associated method for optimizing routing of data traffic for a host virtual machine. The host virtual machine communicates with an Internet Protocol (IP) network via a default gateway of a source site prior to migration. A migration service process migrates the host virtual machine from the source site to a target site, which is geographically remote from the source site and consequently changes routing efficiency of the data traffic between the host virtual machine and the IP network. The migration service process reconfigures routing parameters of the migrated host virtual machine for data traffic going out to the IP network from the host virtual machine. The migration service process examines the IP network configurability and subsequently reconfigures the IP network for inbound data traffic coming into the migrated host virtual machine from the IP network when available.
Owner:IBM CORP
System and method for manipulating insertion pathways for accessing target sites
InactiveUS20120041422A1Increase flexibilityReduced flexibilityGuide needlesTransvascular endocardial electrodesCatheterInsertion site
A method for accessing a target site in the body by transferring a guidewire from an initial insertion site on the body to a different insertion site on the body is provided. In one aspect, a method for transferring a medical device or component, such as a sensor lead, from an initial insertion site to another insertion site is also provided. A guidewire of sufficient length, pliancy and deformability to perform a transfer from one insertion site to another insertion site is provided. In one aspect, the guidewire comprises a removable core mandrel to increase rigidity, facilitate insertion and / or improve steerability. A kit or system, comprising introducers, guidewires and catheters for performing a guidewire or device transfer is also provided.
Owner:PACESETTER INC
Methods of and systems for remote outbound control
InactiveUS20060072543A1Fast dataQuick updateData switching by path configurationData transmissionType of service
The present invention is directed to a system for and a method of selecting a combination of resources for transmitting data from a remote site to a destination site. The method comprises generating a list of combinations of resources at a regional site and transmitting the list to the remote site. Data is transmitted from the remote site to the regional site using each combination of resources and statistics for each transmission are stored. Metrics, based on the application at hand, are computed for each set of statistics corresponding to each transmission, and a preferred combination of resources is selected at the regional site based on the metrics. The regional site then transmits to the remote site information corresponding to the preferred combination of resources. The remote site is then configured to transmit data to the destination site using the selected combination of resources. Resources include links with a specified bandwidth, VPN and GRE tunnels, and routers configured to perform MPLS switching, type-of-service routing, and source routing.
Owner:AVAYA INC
Path planning method based on genetic algorithm
A path planning method based on the genetic algorithm includes the following steps: (1) establishing a path optimization mathematical model with a method, wherein the method specifically includes the steps of supposing that G is a path from the starting point 1 to the terminal point n, the path G does not include a repeated route or a round route, and the consumption of one route is the sum of weights on the route; (2) performing a path search process which specifically includes the following steps of starting from the starting point, searching for an optimized path within the range of the search radius with the genetic algorithm, moving along with a vehicle to the next node of a path obtained through the last search, taking the node as the starting point of the current search, searching out a path again on the basis of the node within the range of the search radius, and continuing to apply the method until the destination site is searched out. The path planning method based on the genetic algorithm is good in rapidity and stability and strong in applicability.
Owner:ENJOYOR COMPANY LIMITED
Available bandwidth control mechanism
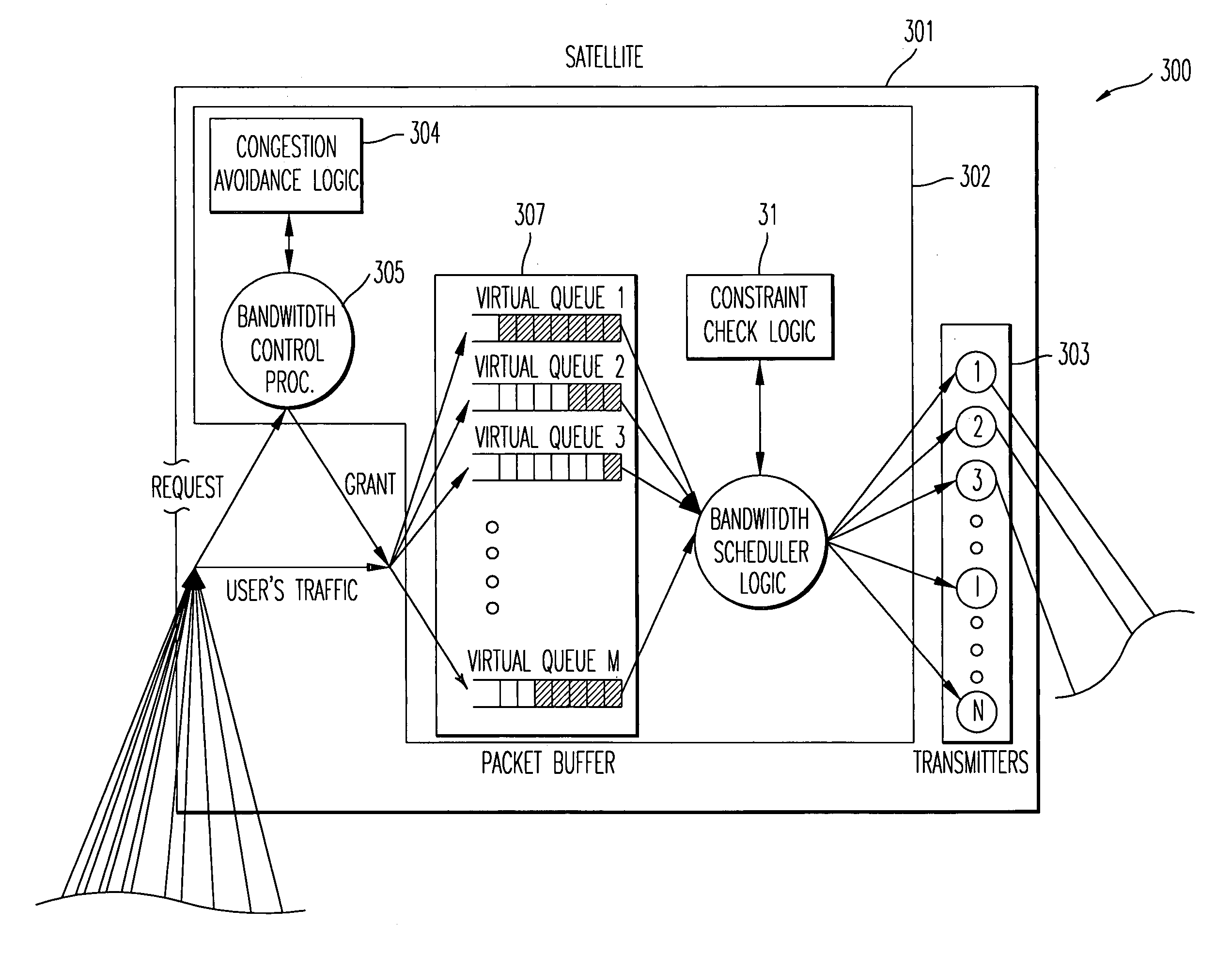
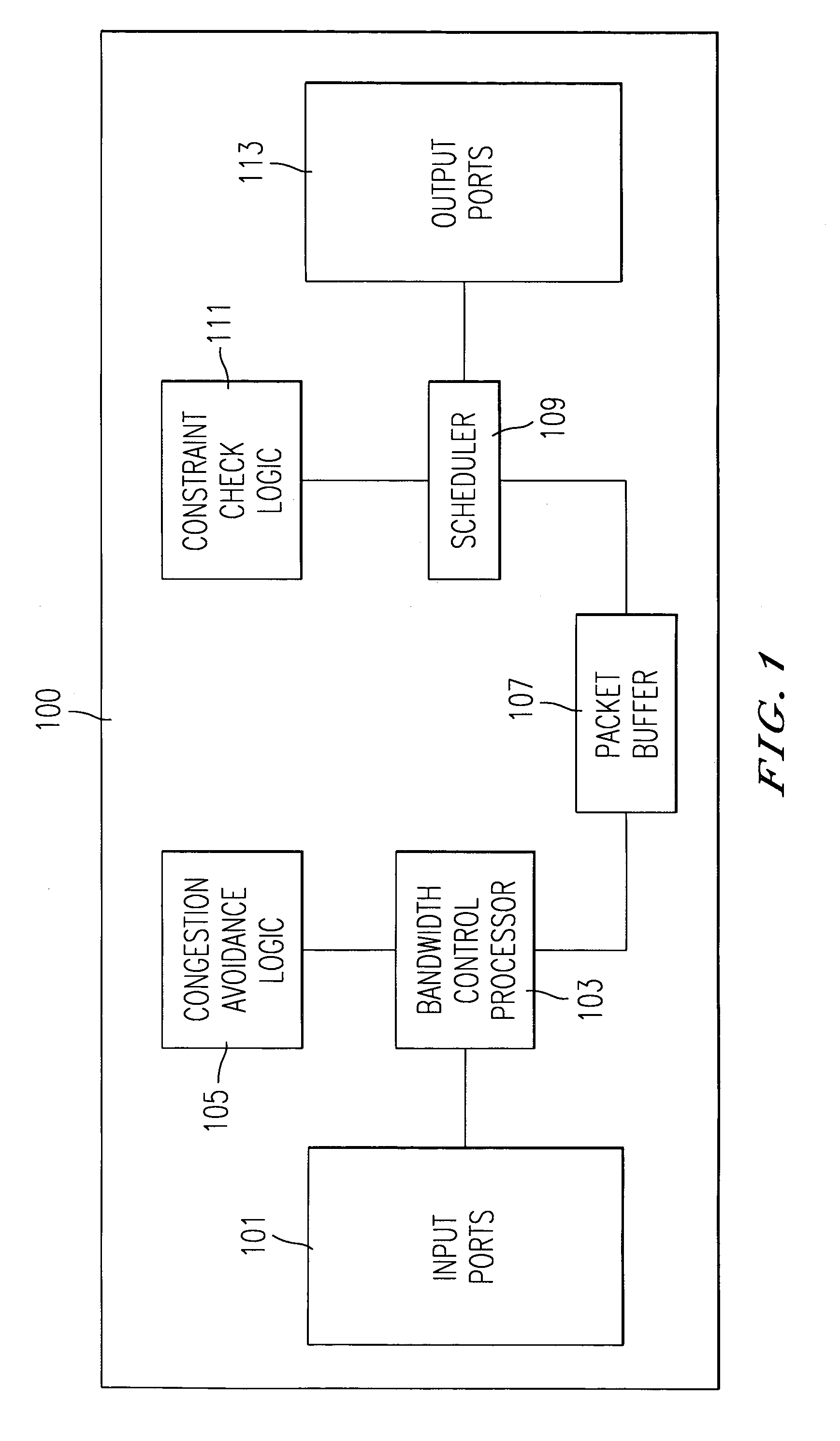
ActiveUS6947445B1Improve efficiencyImprove effective throughputError preventionTransmission systemsTraffic capacityReal-time computing
An approach for controlling bandwidth allocations for a switching system with transmission constraints is disclosed. A scheduler within a switching system generates bandwidth metrics for a destination site. A traffic control processing logic receives the bandwidth metrics. The traffic control processing logic includes a utilization module that determines utilization associated with the destination site based upon the received bandwidth metrics, and an error calculation module that computes the difference between the determined utilization and a target utilization. A gain and filtering module, which is also a part of the traffic control processing logic, computes a correction value based upon the difference between the determined utilization and the target utilization, in which the correction value being associated with the destination site. Further, the traffic control processing logic includes an adder that outputs a control value based upon a reference control value and the correction value. A bandwidth control processor assigns bandwidth allocation based upon the control value.
Owner:HUGHES NETWORK SYST
Method for Inter-Site Data Stream Transfer in a Cooperative Data Stream Processing
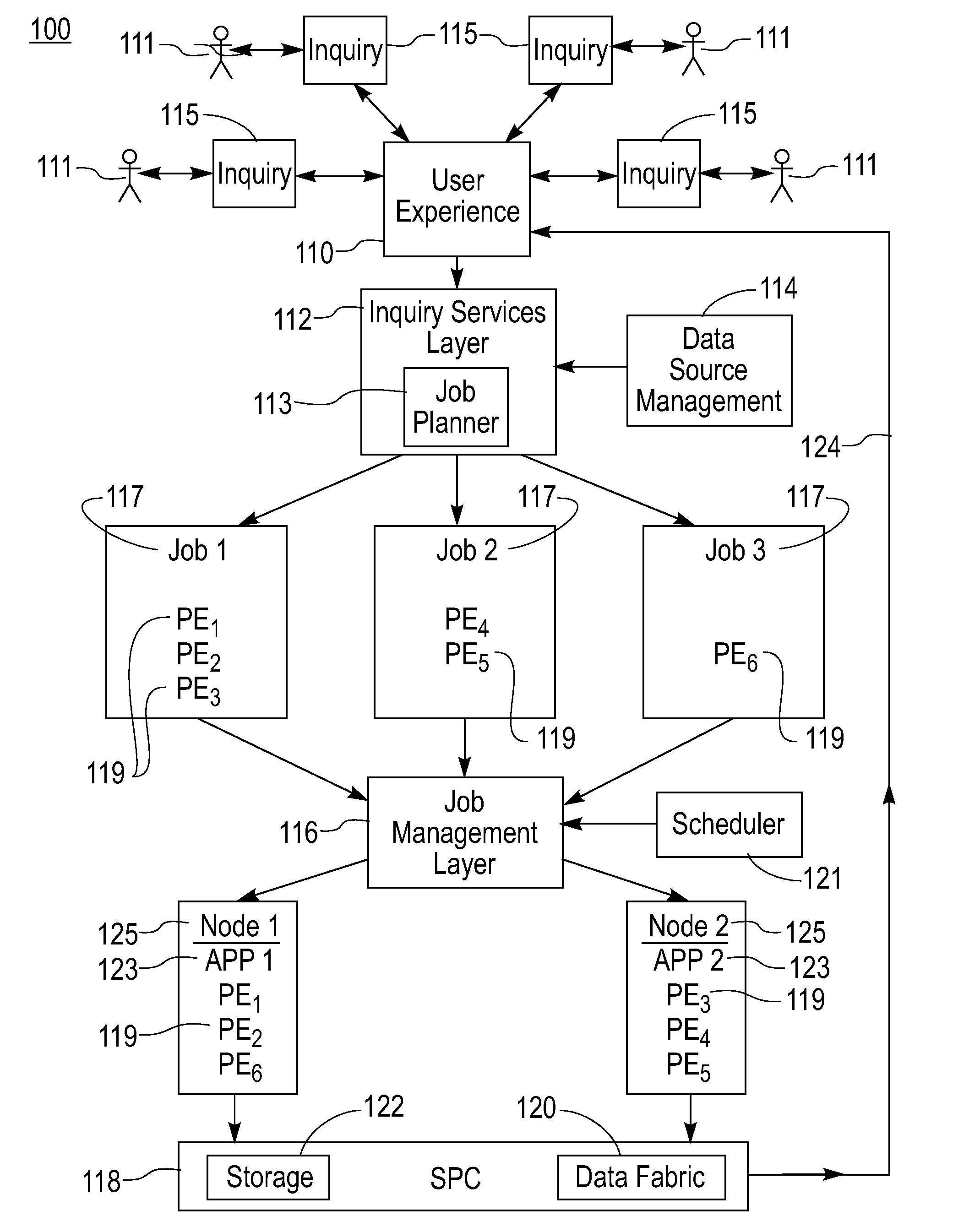
InactiveUS20080256166A1Easy to shareEasy to receiveMultiple digital computer combinationsData switching networksNetwork connectionProgram planning
A cooperative data stream processing system is provided that utilizes a plurality of independent, autonomous and potentially heterogeneous sites in a cooperative arrangement to process user-defined inquiries over dynamic, continuous streams of data. The system derives jobs from the inquiries and these jobs are executed on the various distributed sites by executing applications containing processing elements on these sites. Therefore, components of a given job can be executed simultaneously and in parallel on a plurality of sites within in the system. The sites associated with a given job execution have the need to share data, both primal and derived. A tunnel mechanism is provided that establishes tunnels between pairs of sites within the system. Each tunnel includes either a sink processing element on an originating site and a source processing element on a destination site or a gateway processing element on each site and a network connection between the sink and source processing elements. The sink and source processing elements are in communication with application processing elements on their respective sites and facilitate the exchange of data between these application processing elements. Tunnels can be establish on demand or in accordance with a prescribed plan and can be job specific of generic to any job executing on a given pair of sites.
Owner:IBM CORP
Schema evolution in replication
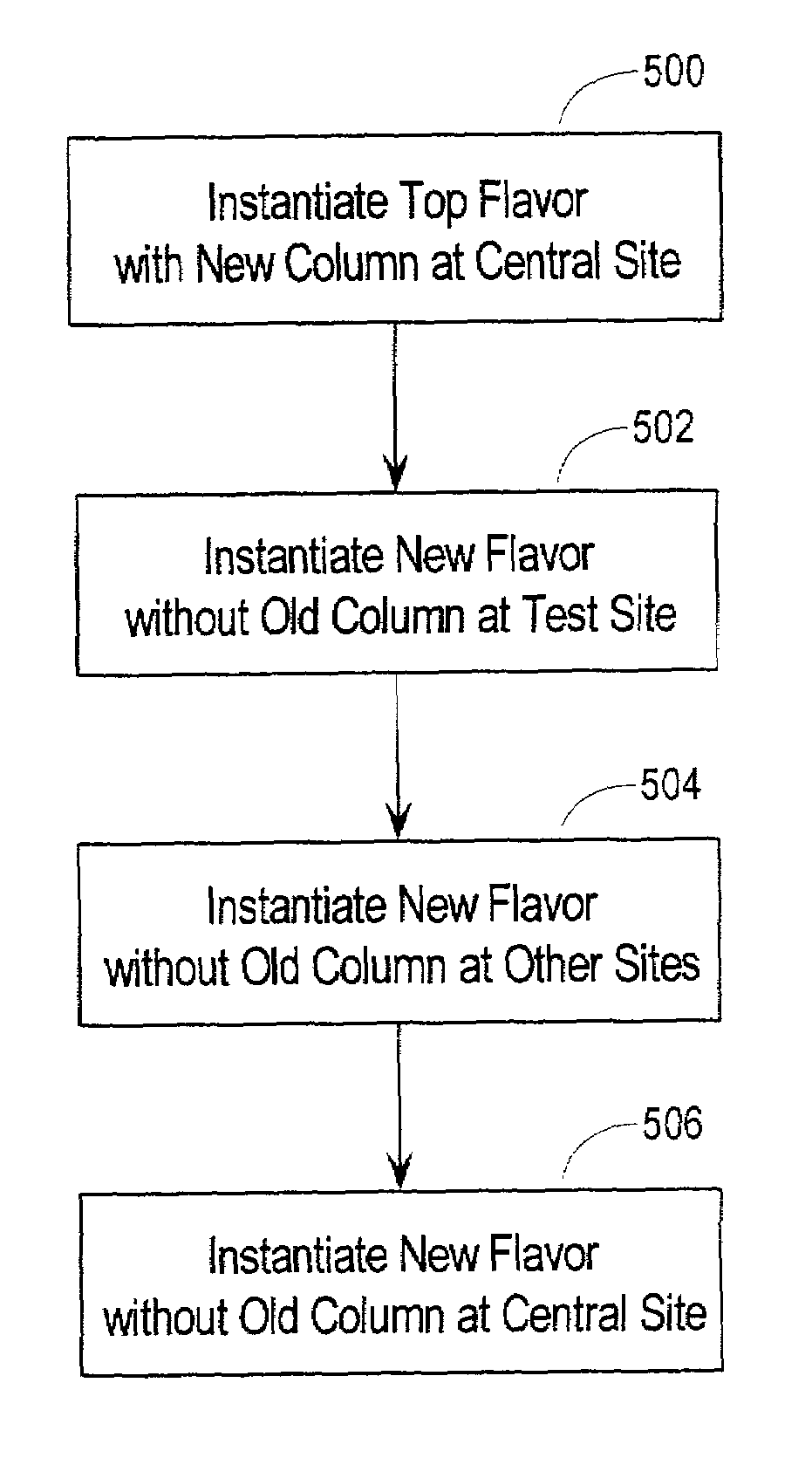
InactiveUS7162689B2Digital data information retrievalData processing applicationsFlavorDistributed database
Schema evolution involves defining flavored object groups. Specifically, related collections of replicated tables and other database objects, which are defined as belonging to an object group, are given different “flavors.” A flavor describes different subsets of the objects and even different subsets of the columns in the master tables. In one embodiment, when one site in a distributed database system propagates changes to a replicated database object, the current flavor for the site is also transmitted, so that the destination site can make the necessary adjustments in the uploaded changes by dropping the values for obsolete columns and using default values for new columns.
Owner:ORACLE INT CORP
Secure network computing
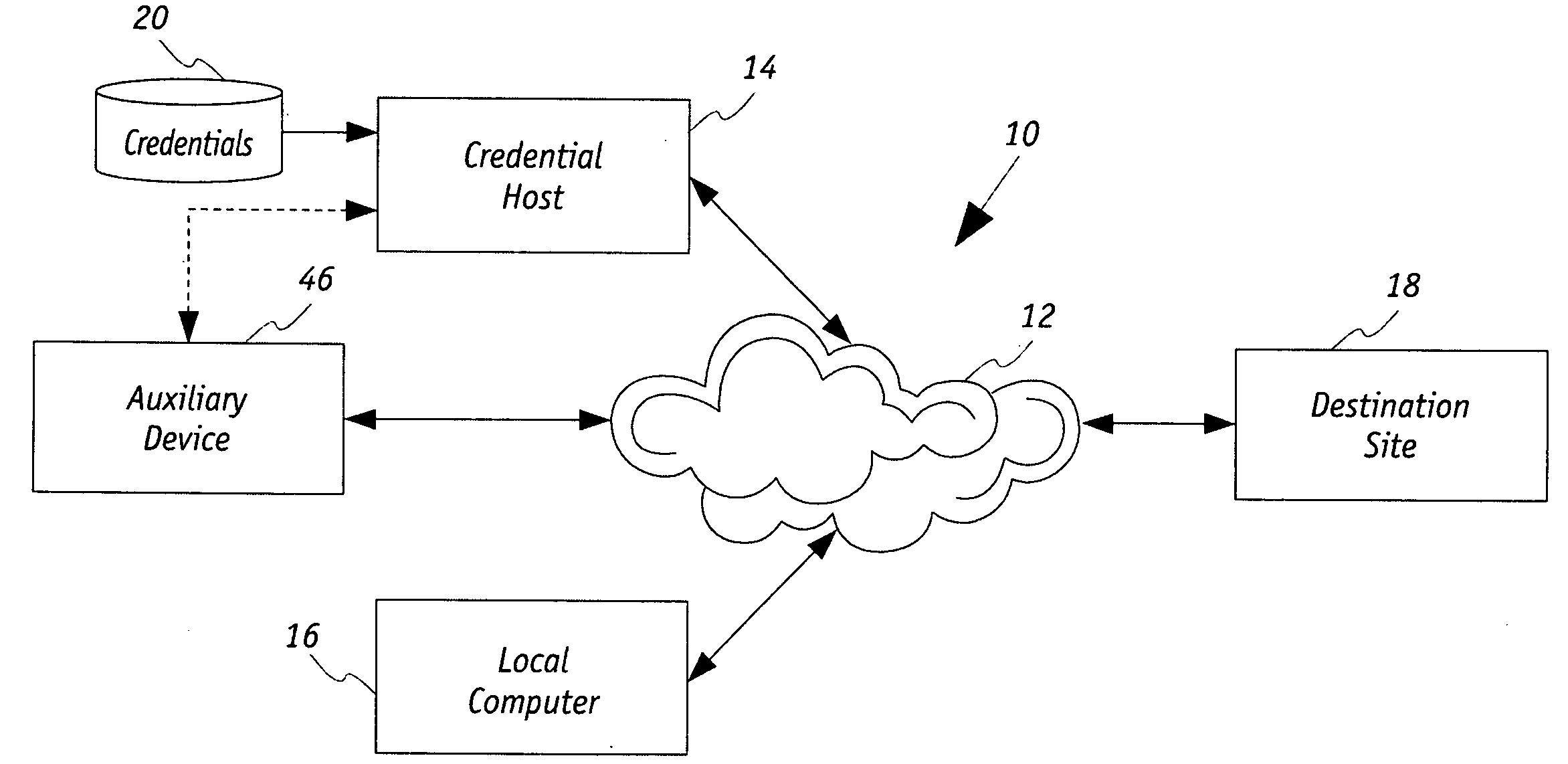
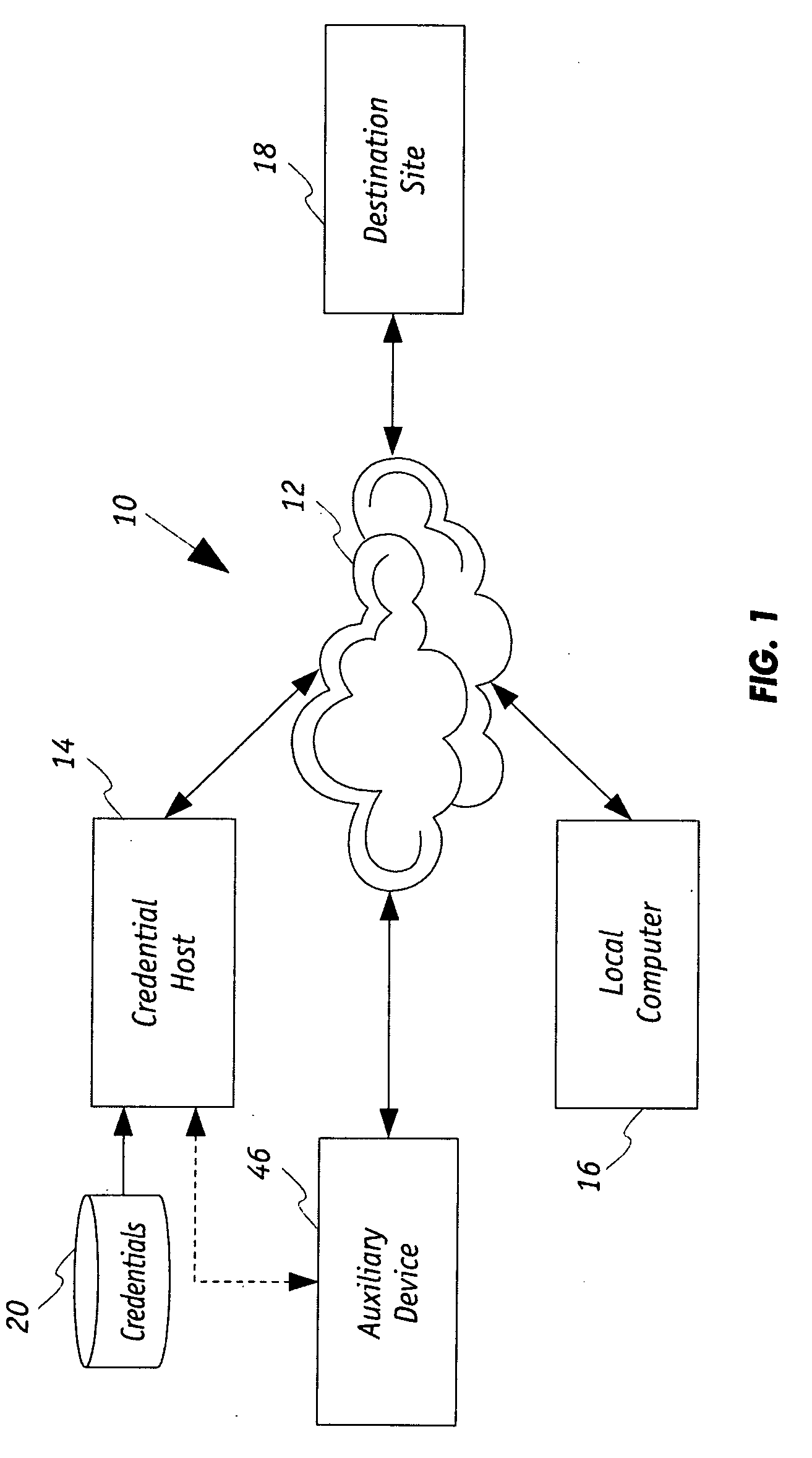
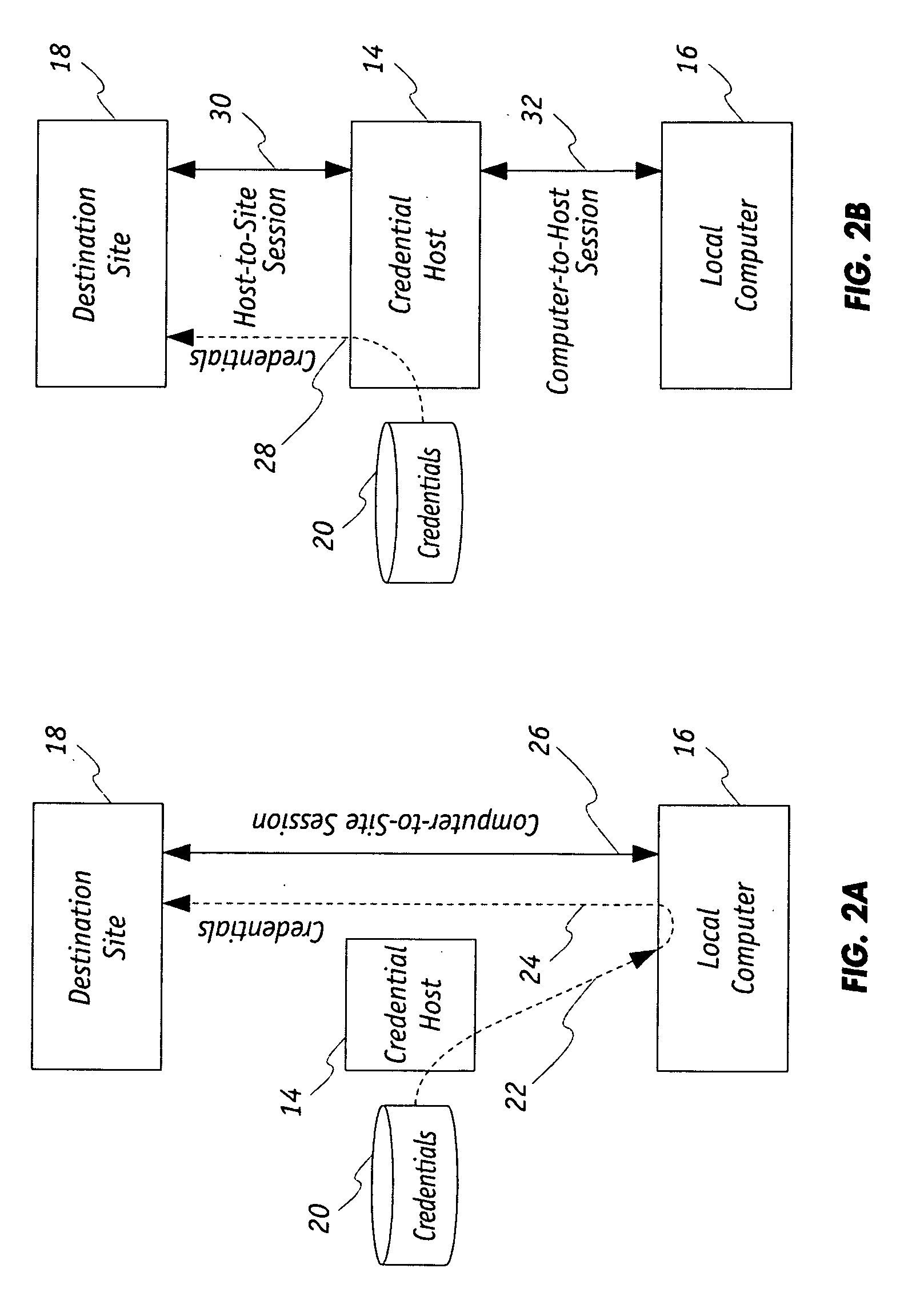
ActiveUS20100100928A1Minimize the possibilityImprove securityDigital data processing detailsMultiple digital computer combinationsComputer scienceAuthentication
A host based security system for a computer network includes in communication with the network a credential host that is operative in concert with a local computer and a destination site. The destination site has a credential authentication policy under which credentials associated with the local computer upon being authenticated authorizes data to be communicated between each of the destination site and the local computer during a communication session over the network. The credential host stores the credentials to be used by the destination and is operative to transmit the credentials onto the network in response to a request received from the local computer. The destination site upon the credentials being received and authenticated thereat is operative to transmit session information onto the network. In turn, the local computer is then operative to commence the communication session upon receipt of said the information.
Owner:PERSONAL CAPITAL TECH COPORATION
Installation for harvesting ocean currents (IHOC) and methods and means for its delivery, installation and servicing
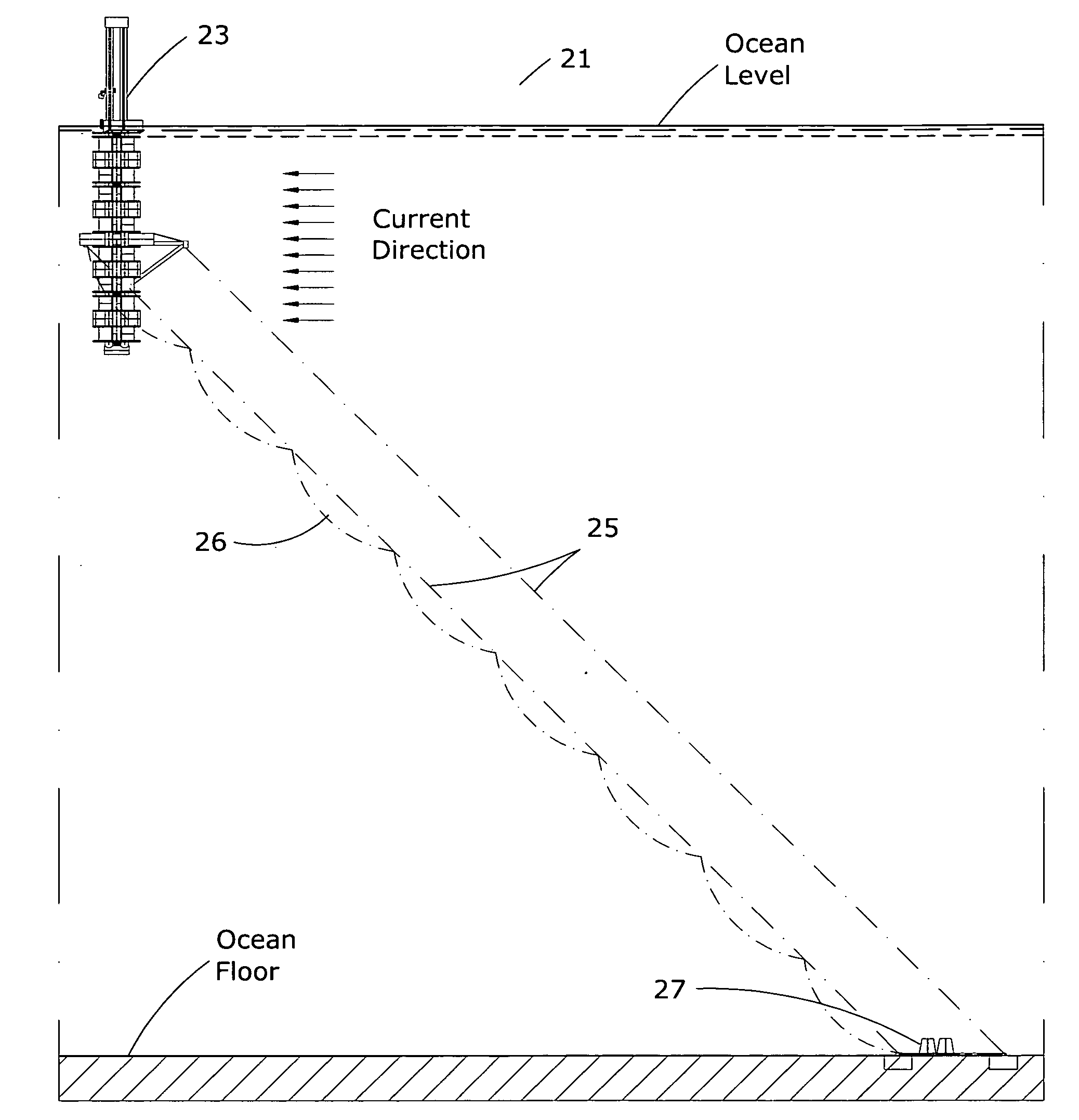
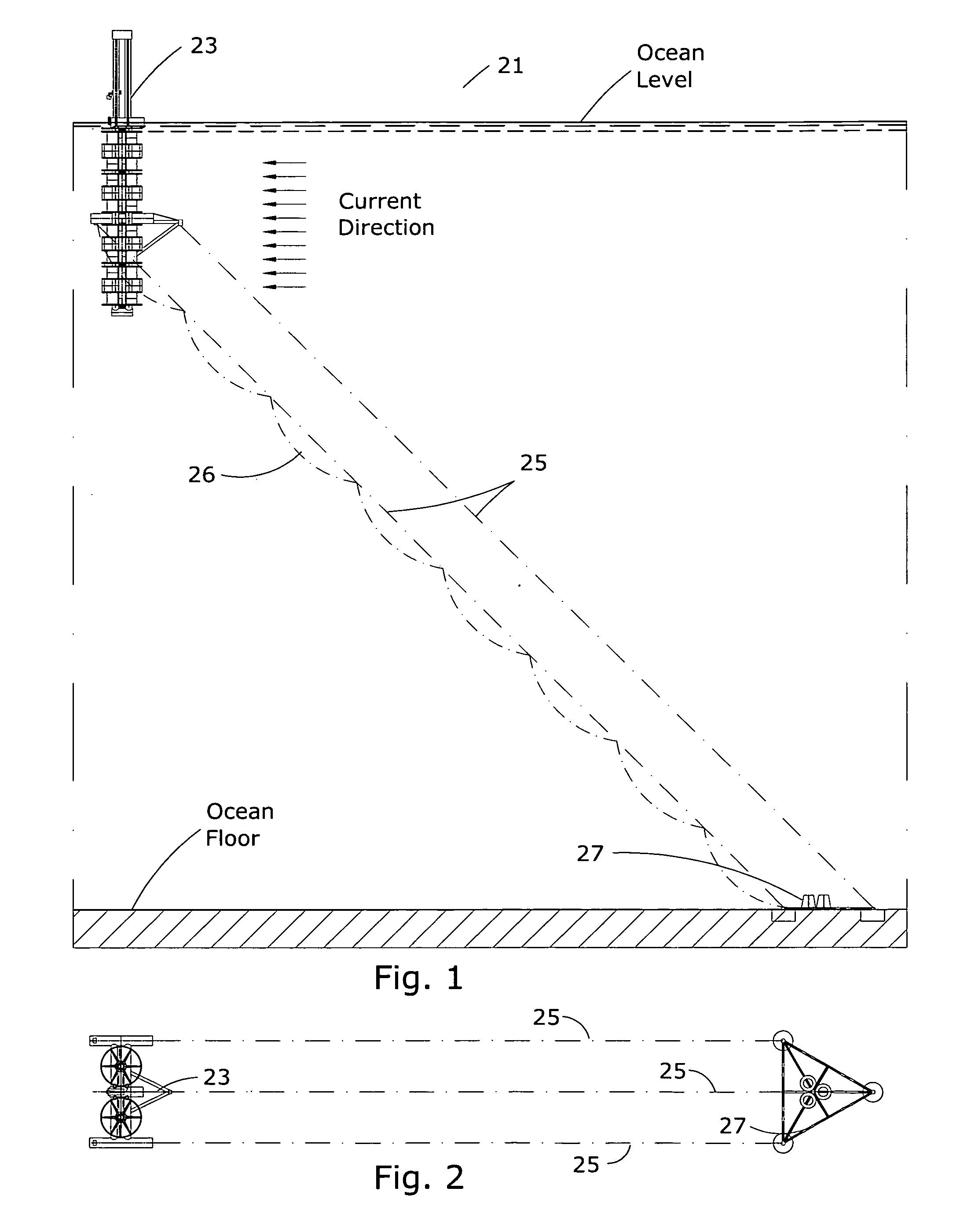
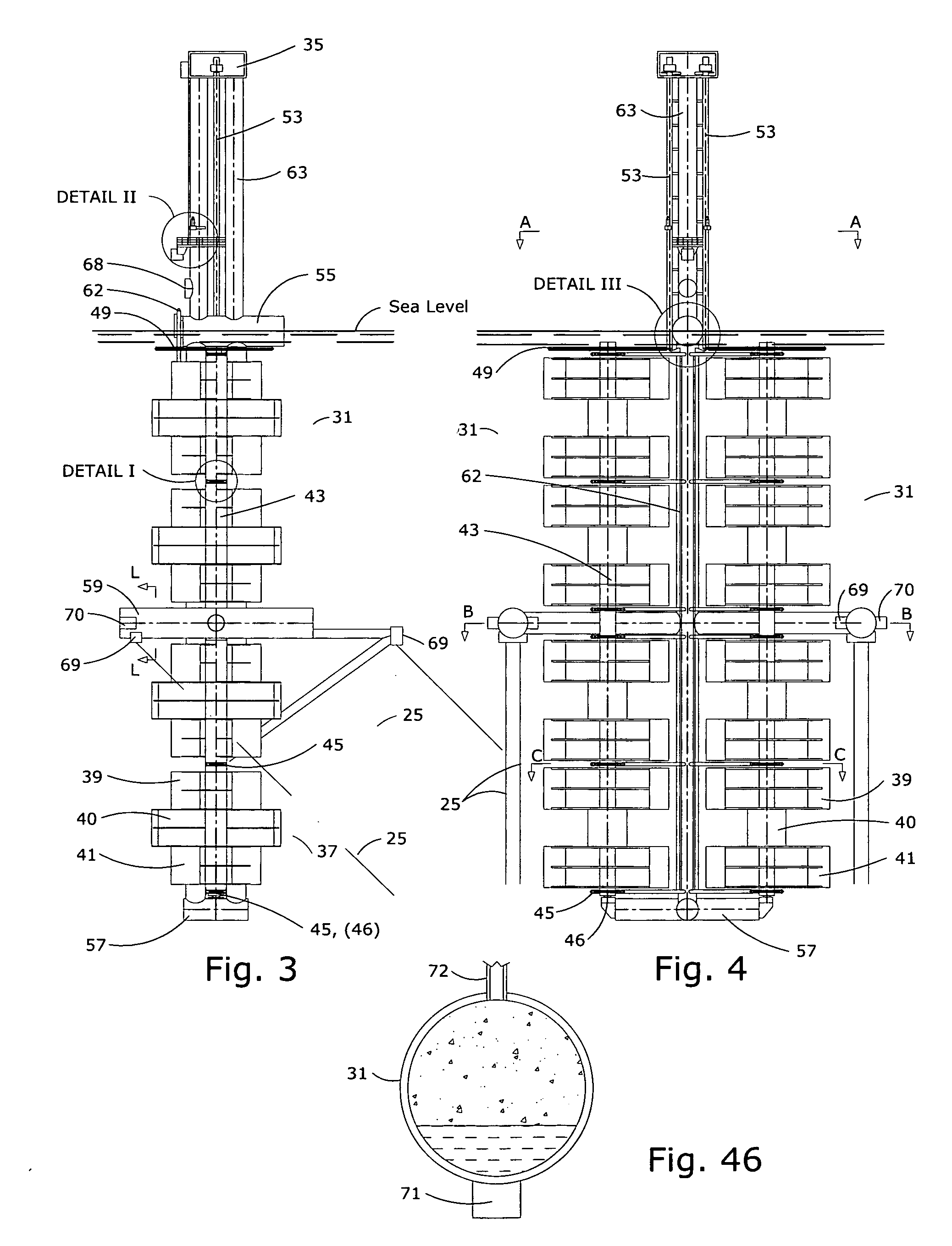
InactiveUS20100164230A1Increasing and lowering pressureLittle strengthEngine fuctionsMachines/enginesElectric power transmissionEngineering
Installation for harvesting energy of ocean currents (IHOC) in deepwaters is based on utilization of a semisubmersible platform and the multiple of vertically oriented Darrieus type hydraulic turbines. The turbines are located as close as possible to ocean surface, where speed of current is usually at its maximum. Since speed of current fluctuate during the seasons a system controlling buoyancy force of that keeps IHOC floating near surface is employed. The mooring system consists of three tethers, which prevent transferring of overturning moment applied to IHOC to anchoring base. The electric power generators are located in a machinery room on a structure well above sea level and would transmit electric power to the shore utilizing flexible cable. During hurricane it will be lowered to the depth preventing turbines from being affected by wave actions, at the same time it would keep machinery room above wave action. For the purpose of delivery assembled on shore Turbine Housing to destination site and installing it there a special convoy is formed consisting of Catamaran Delivery Barge and Stabilizing Platform.The second Embodiment of this invention is designed to harvest energy of tides in deepwaters.
Owner:BELINSKY SIDNEY IRVING +1
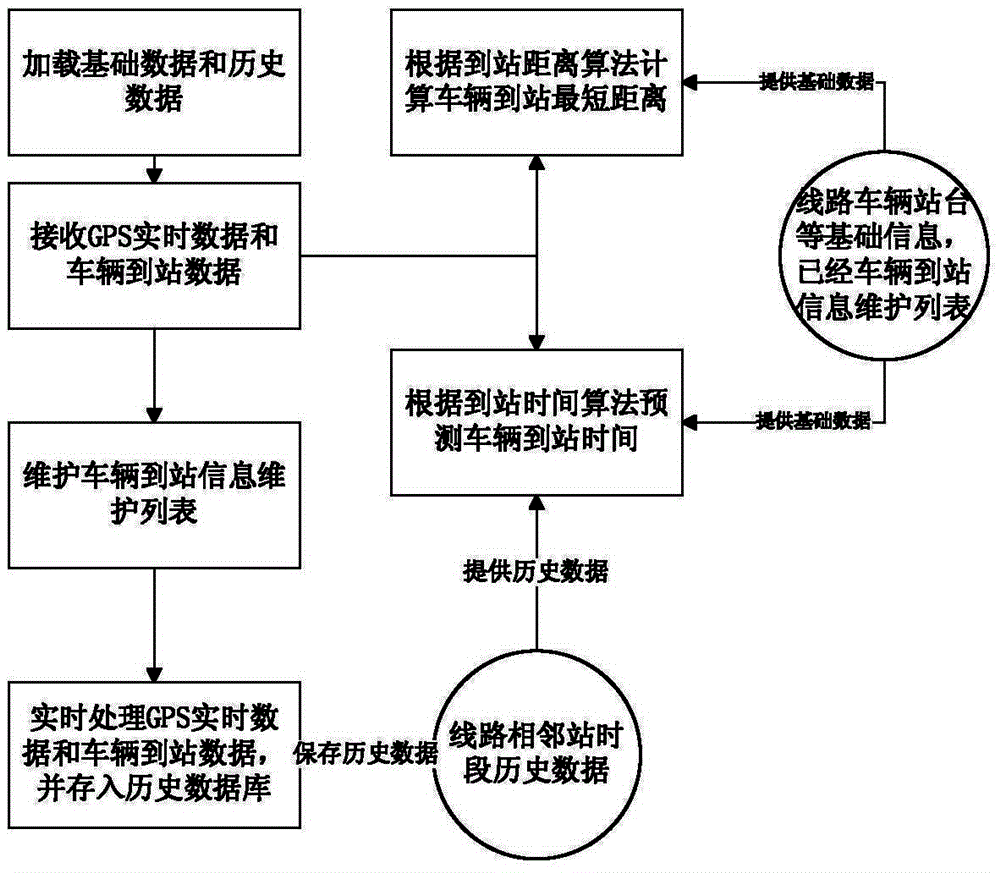
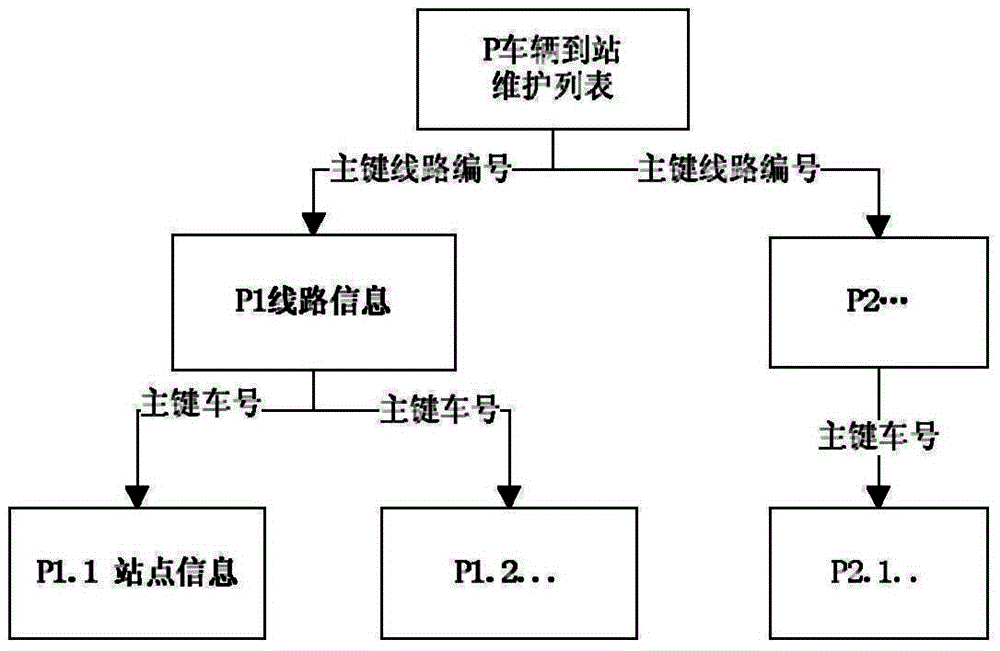
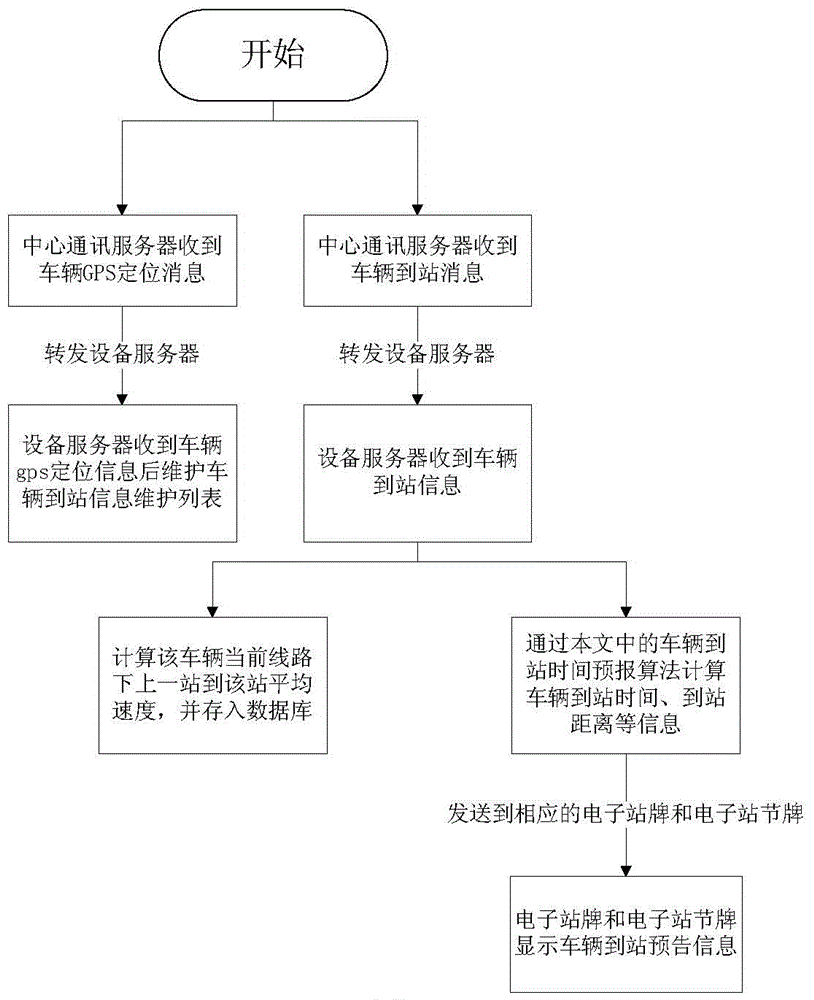
Public transport vehicle arrival time prediction method based on history data
ActiveCN104064024AOvercome the problem of not being able to locate long distancesAccurate acquisition in real timeRoad vehicles traffic controlInformation dataPublic transport
A public transport vehicle arrival time prediction method based on history data comprises the following steps: a)receiving GPS real-time data uploaded by a GPS device on a public transport vehicle and vehicle arrival information data in real time; b) processing the GPS real-time data after the GPS real-time data of the vehicle is obtained successfully; and c) after the vehicle arrival information is obtained successfully, searching station devices to send information from on-line station devices according to the line serial number and the running direction in the vehicle arrival information and obtaining the closet vehicle distance of a target station; and through obtaining the history data and today's data of the running speed of a vehicle between adjacent stations on the line at set time running period, by utilizing a weighted average method to estimate the average running speed of the vehicle between the adjacent stations on the current line and at the current time period, and on the basis of the bypassed inter-station distances and inter-station average running speed of the vehicle running to the station, each inter-station running time of the vehicle can be estimated, and the vehicle arrival time can be predicted jointly. With the method, the prediction distance is long, the real-time performance is good and the accuracy is good.
Owner:ENJOYOR COMPANY LIMITED
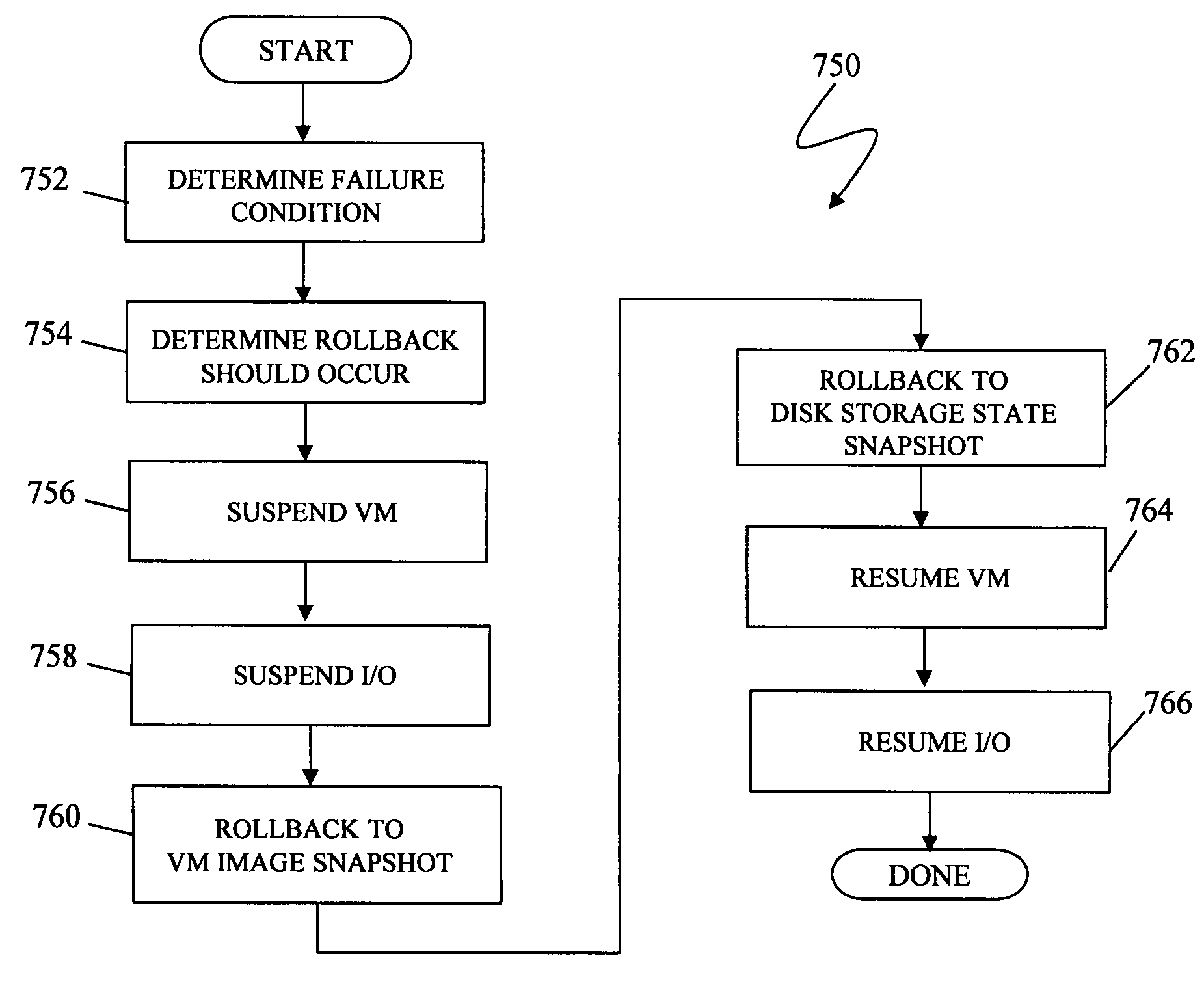
Active/active storage and virtual machine mobility over asynchronous distances
ActiveUS8667490B1Resource allocationSoftware simulation/interpretation/emulationActive storageActive systems
A system for providing mobility of a virtual machine between a first site and a second site of an active / active system is disclosed. For a virtual machine operating on the first site, it may be determined that the second site is a destination site between the first site and the second site. While the virtual machine is operating on the first site, storage data may be transferred from the first site to the second site. Operation of the virtual machine may be suspended on the first site. Operation of the virtual machine may be resumed on the second site. In the event of link failure between the first site and the second site, operation of the virtual machine may be maintained on the second site.
Owner:EMC IP HLDG CO LLC
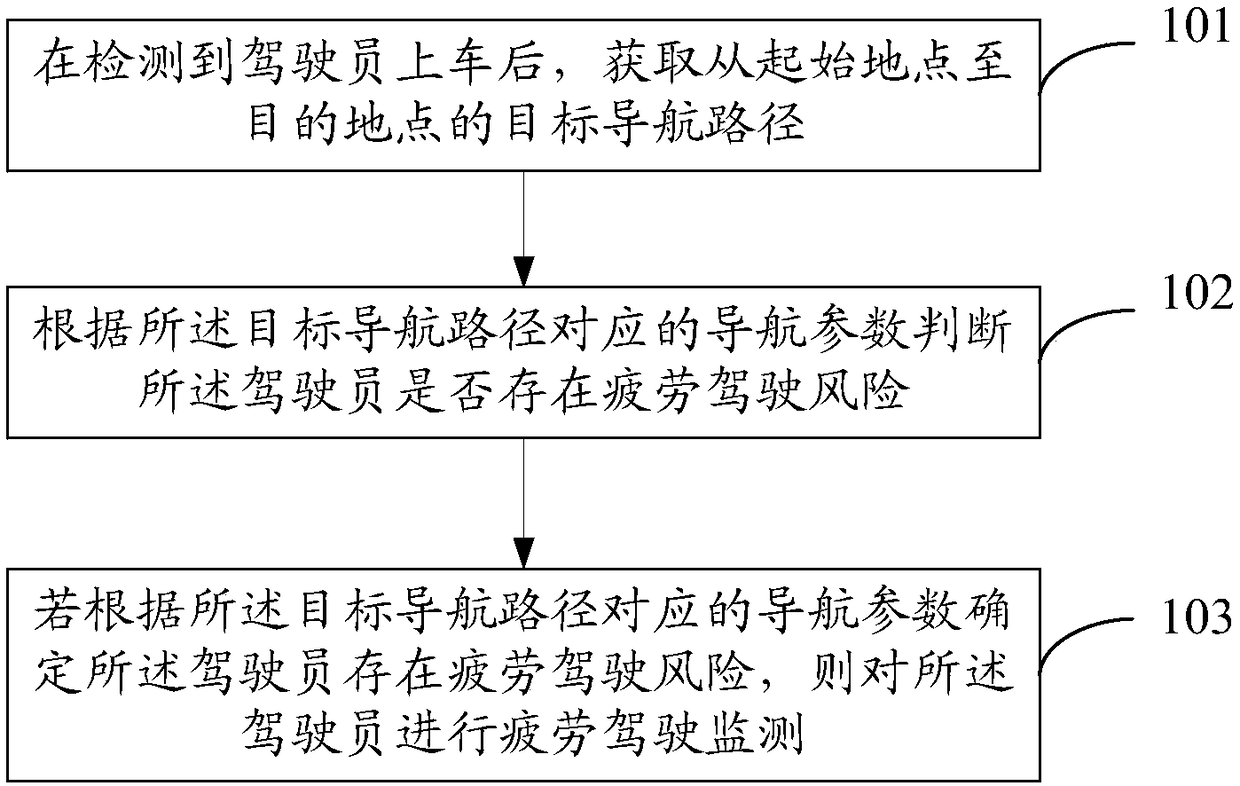
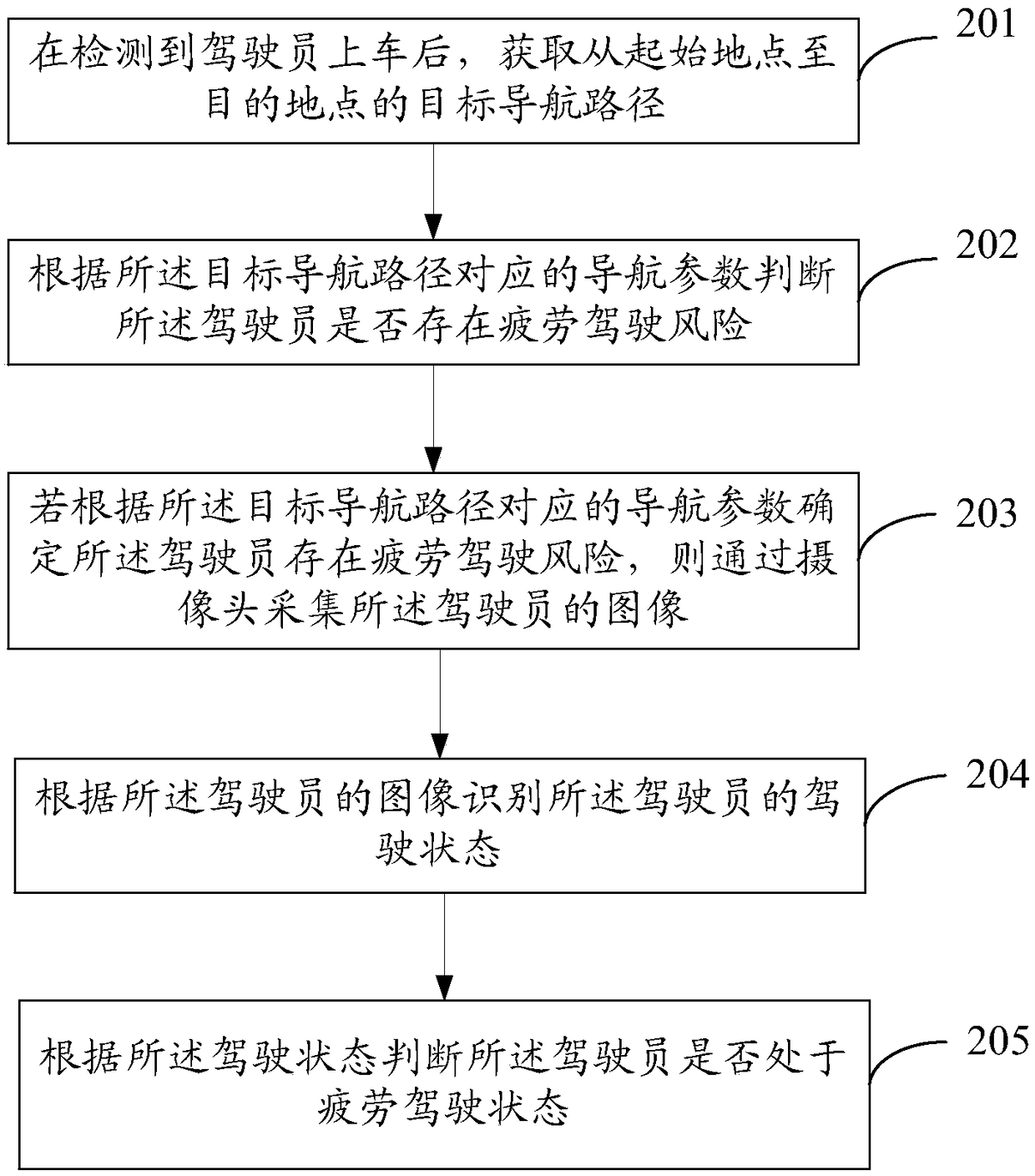
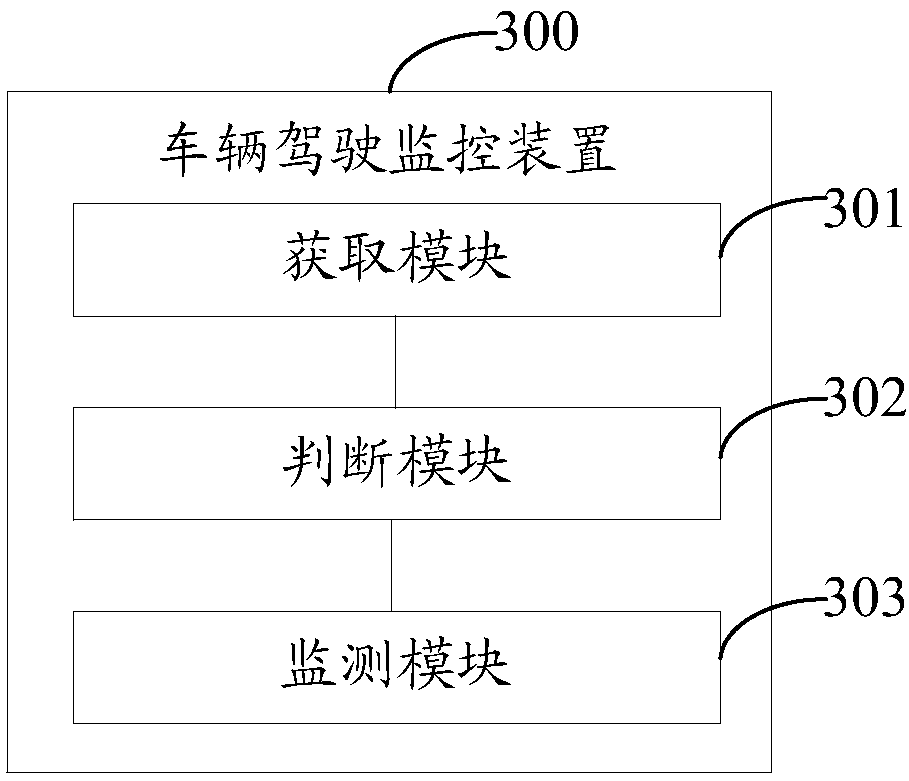
Vehicle driving monitoring method and device and vehicle
InactiveCN108238053ATimely judgment of fatigue drivingTimely judgment of fatigue driving riskInstruments for road network navigationTractorsDriver/operatorDriving risk
The invention provides a vehicle driving monitoring method and device and a vehicle. The method includes the steps that when it is detected that a driver gets on the vehicle, a target navigation routefrom a start site to a destination site is obtained; whether the driver is in a fatigue driving risk or not is judged according to navigation parameters corresponding to the target navigation route,wherein the navigation parameters comprise navigation time and / or the navigation distance; and if it is confirmed that the driver is in the fatigue driving risk according to the navigation parameterscorresponding to the target navigation route, fatigue driving monitoring is conducted on the driver. By the adoption of the provided vehicle driving monitoring method, whether the driver is in the fatigue driving risk or not can be judged in advance according to the navigation parameters, fatigue driving monitoring is conducted on the driver when it is confirmed that the driver is in the fatigue driving risk, whether the driver is in fatigue driving or not can be judged in time, and the vehicle driving safety is improved.
Owner:BEIJING CHJ AUTOMOTIVE TECH CO LTD
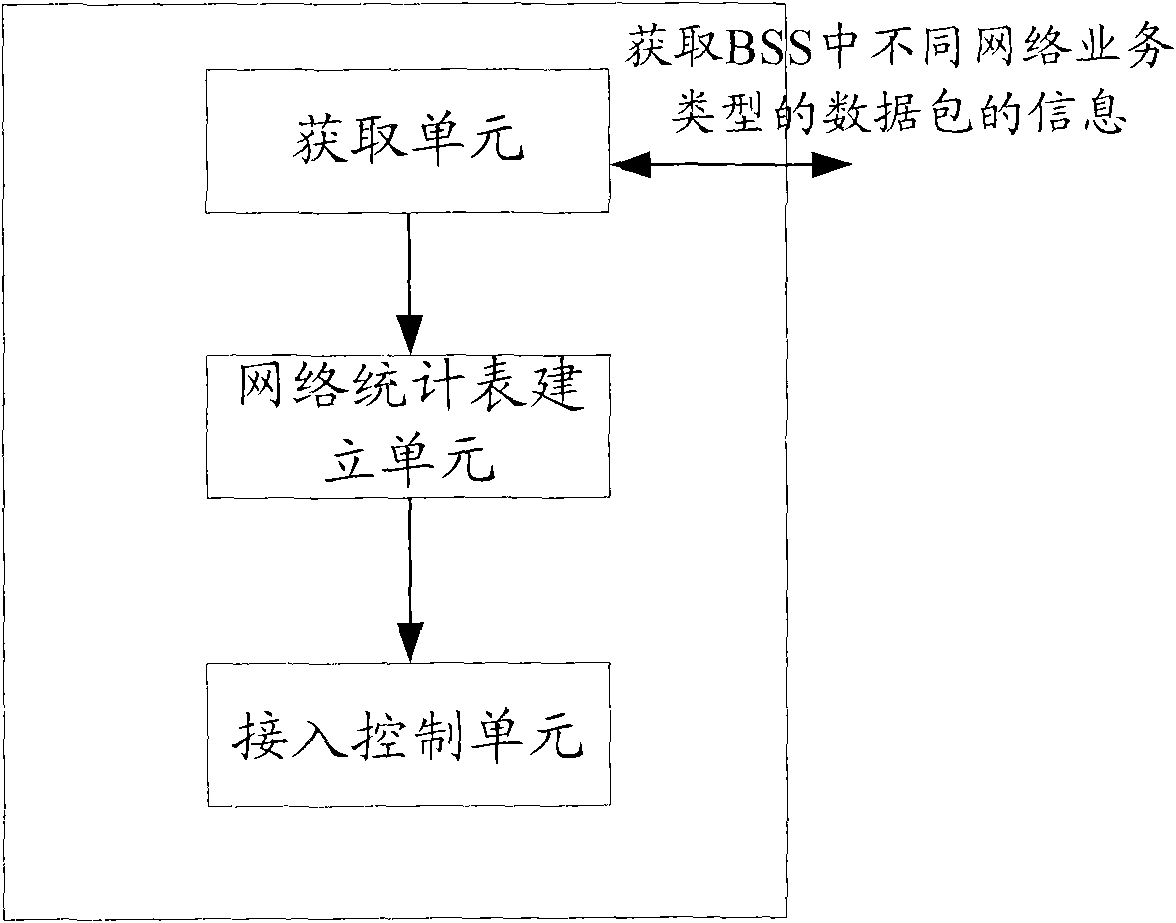
Network access behavior-based access control method and system for wireless local area network
InactiveCN102088754AMaintain validityMaintain continuityAssess restrictionNetwork serviceNetwork service header
The invention discloses a network access behavior-based access control method and system for a wireless local area network. The method comprises the following steps: a network side acquires information of data packets of different network service types in a BSS (Base Station Subsystem) according to a network service type; the network side establishes information of a network flow statistical table of the BSS according to the acquired information of the data packets of different network service types, wherein the information of the network flow statistical table comprises source sites, destination sites, service types, network access behavior durations and network access behavior occurring time of the data packets; and the network side generates information of the relation among the network service type, corresponding time and corresponding network data flow of each site in the BSS according to the established information of the network statistical table of the BSS, and performs access control according to the generated information of the relation among the sites in the BSS. By applying the method and the system, the problem of effective distribution of network resources in the wireless local area network is solved.
Owner:THE PLA INFORMATION ENG UNIV
System and method for improving online search engine results
InactiveUS20060167852A1Improving online search engine resultPromote resultsData processing applicationsWeb data indexingRelevant informationApplication programming interface
System and method for improving online search engine results. In one embodiment, a search system queries one or more servers of a destination site to obtain detailed and relevant information. In one embodiment, this query is in the form of an application programming interface call. Based on the content received in response to the aforementioned queries, a plurality of content pages may then be used to build one or more search databases against which user searches may be made during some future time period.
Owner:R2 SOLUTIONS
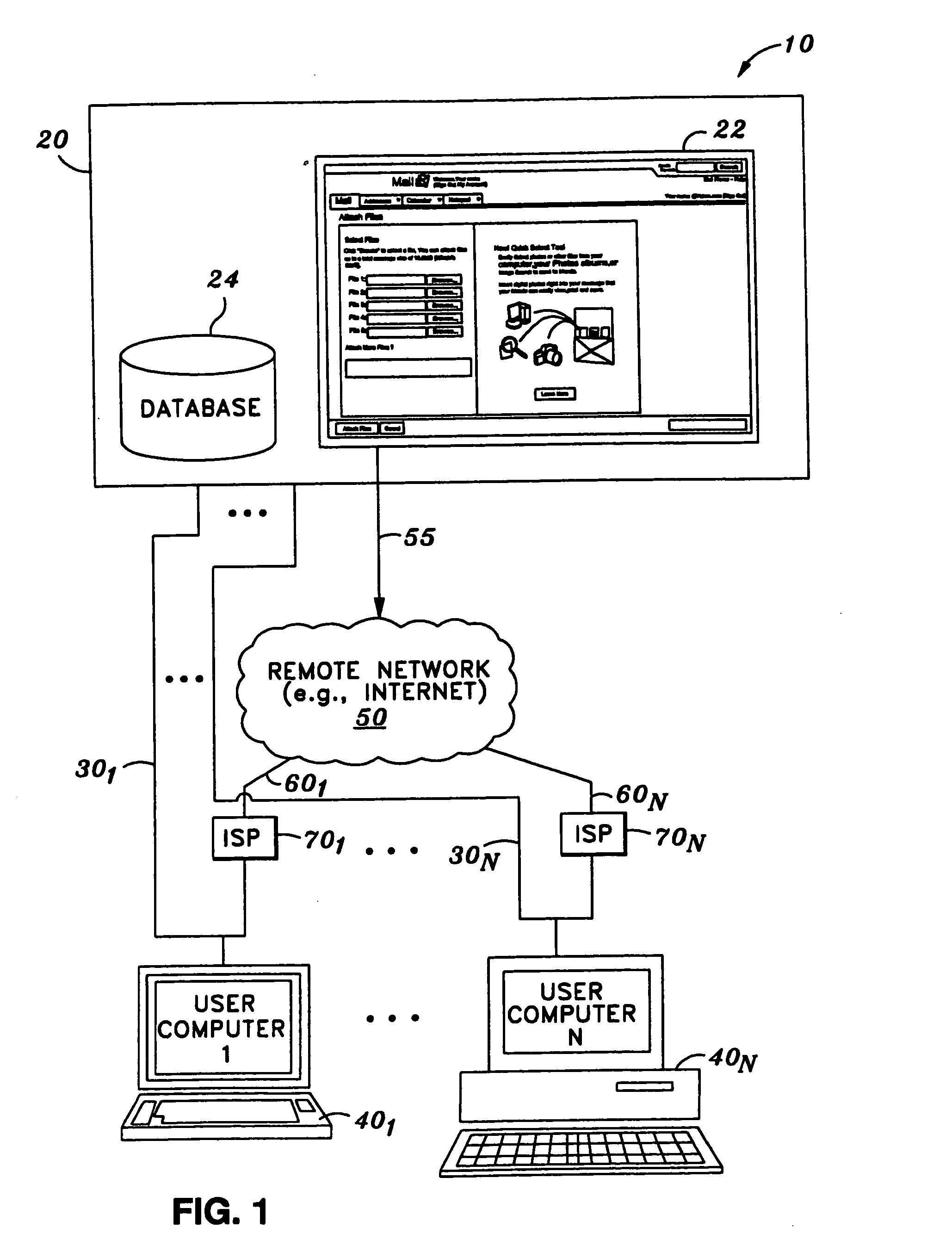
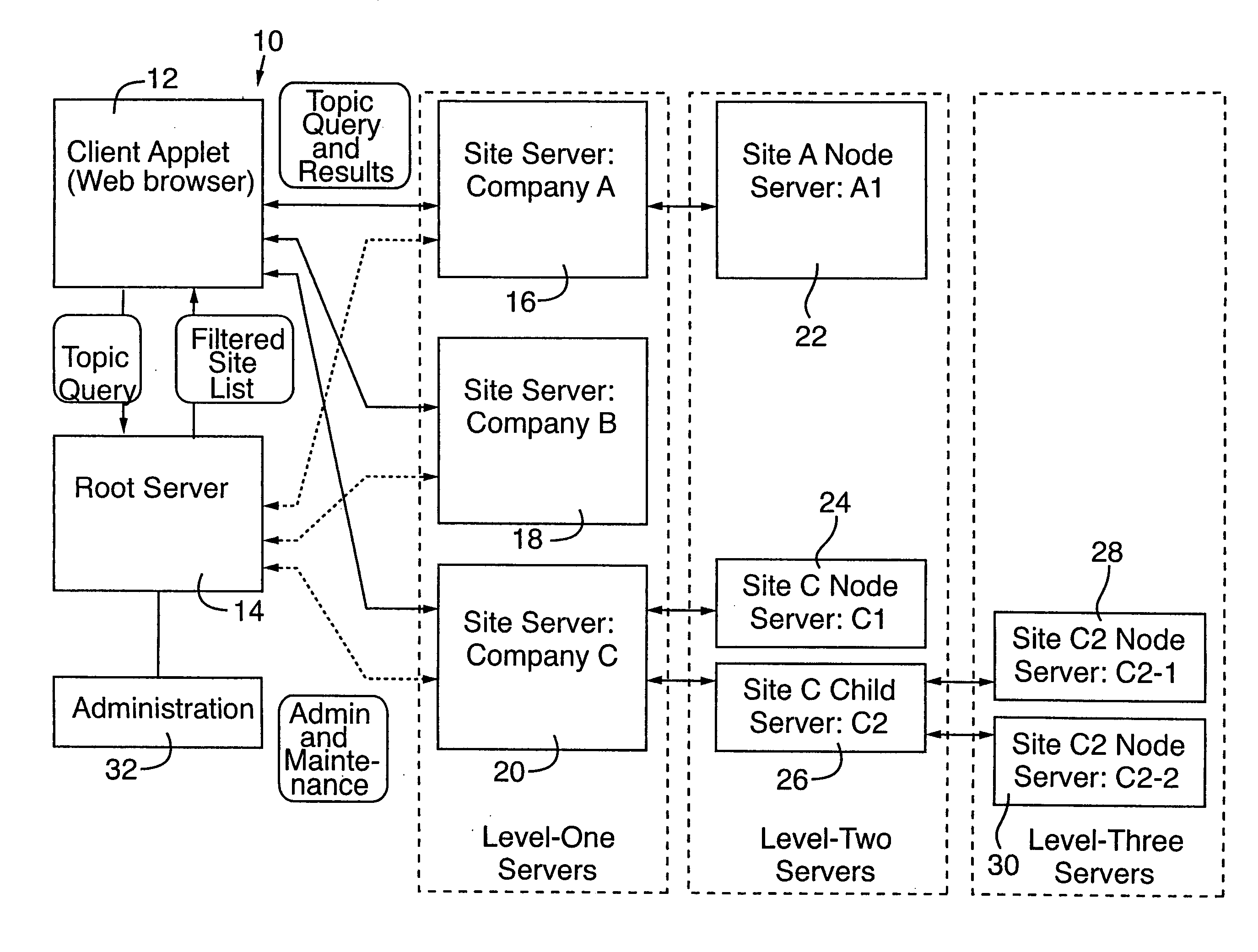
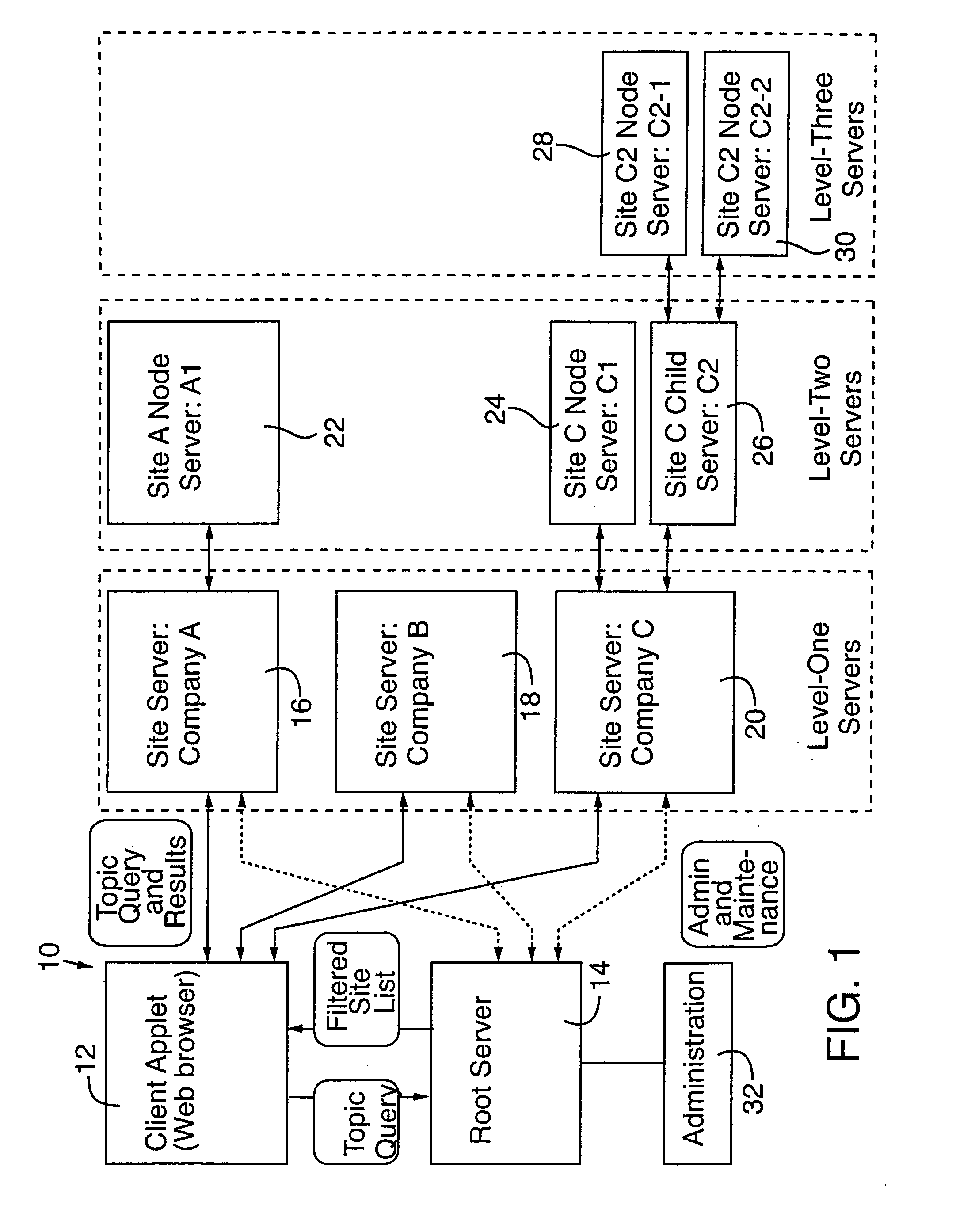
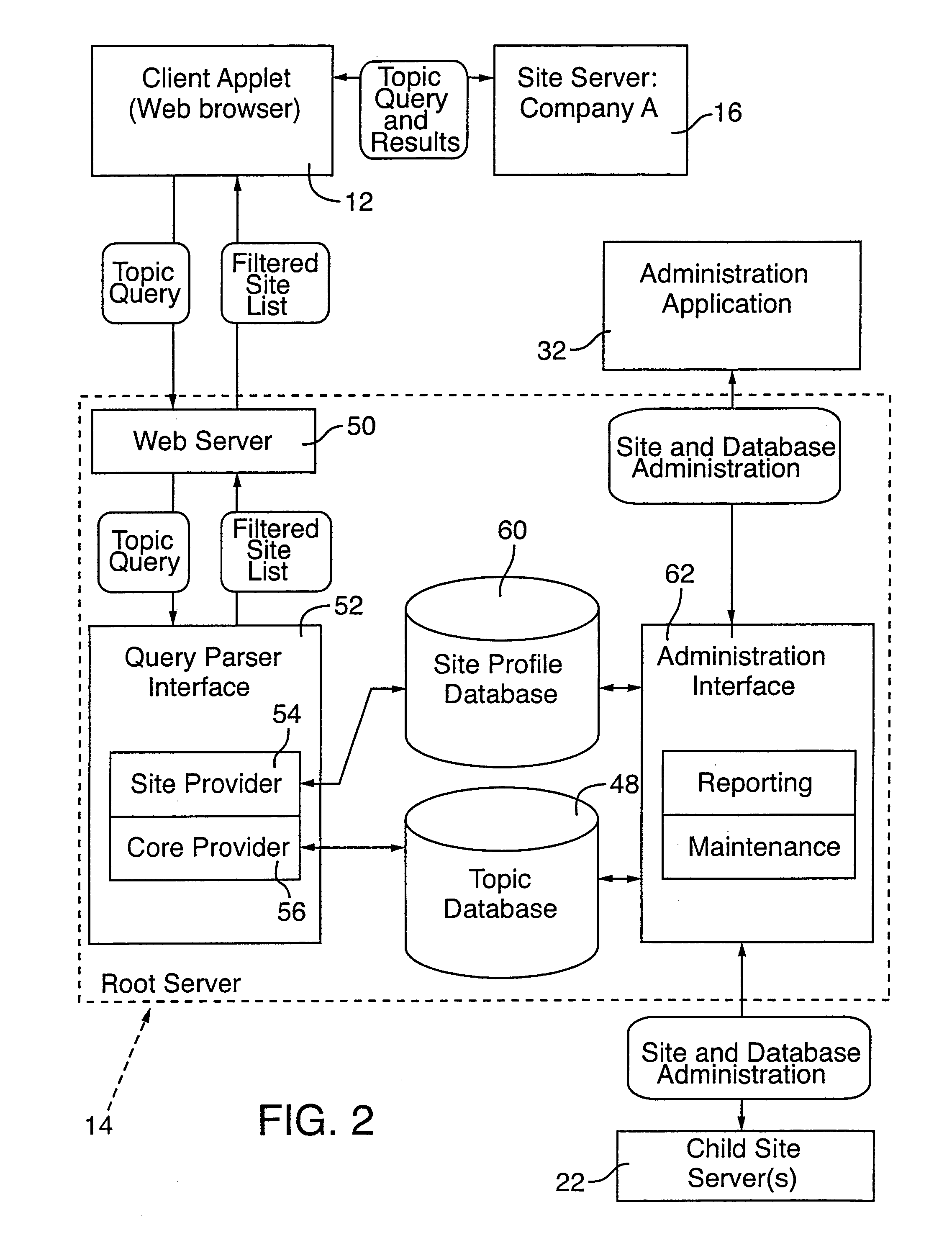
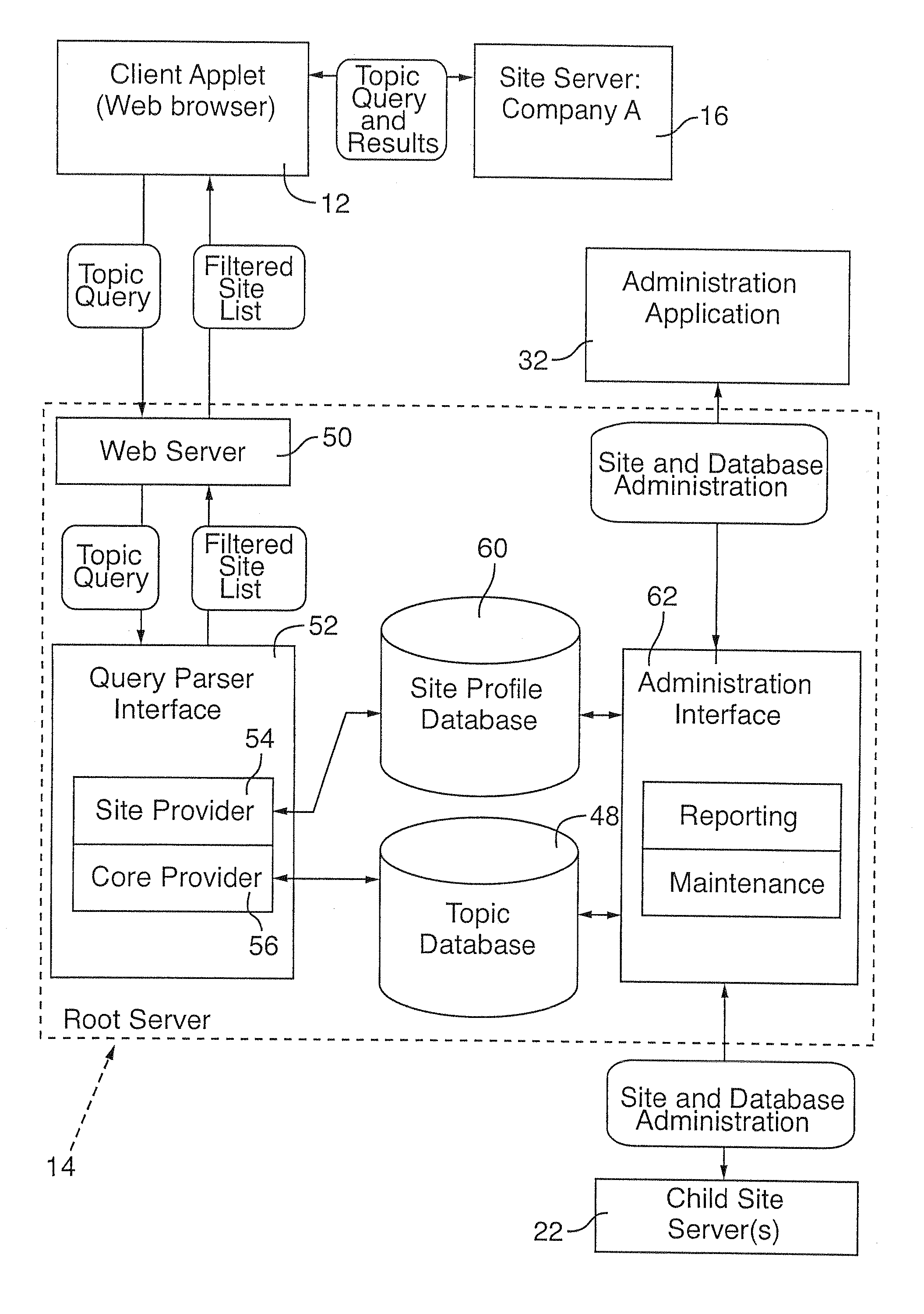
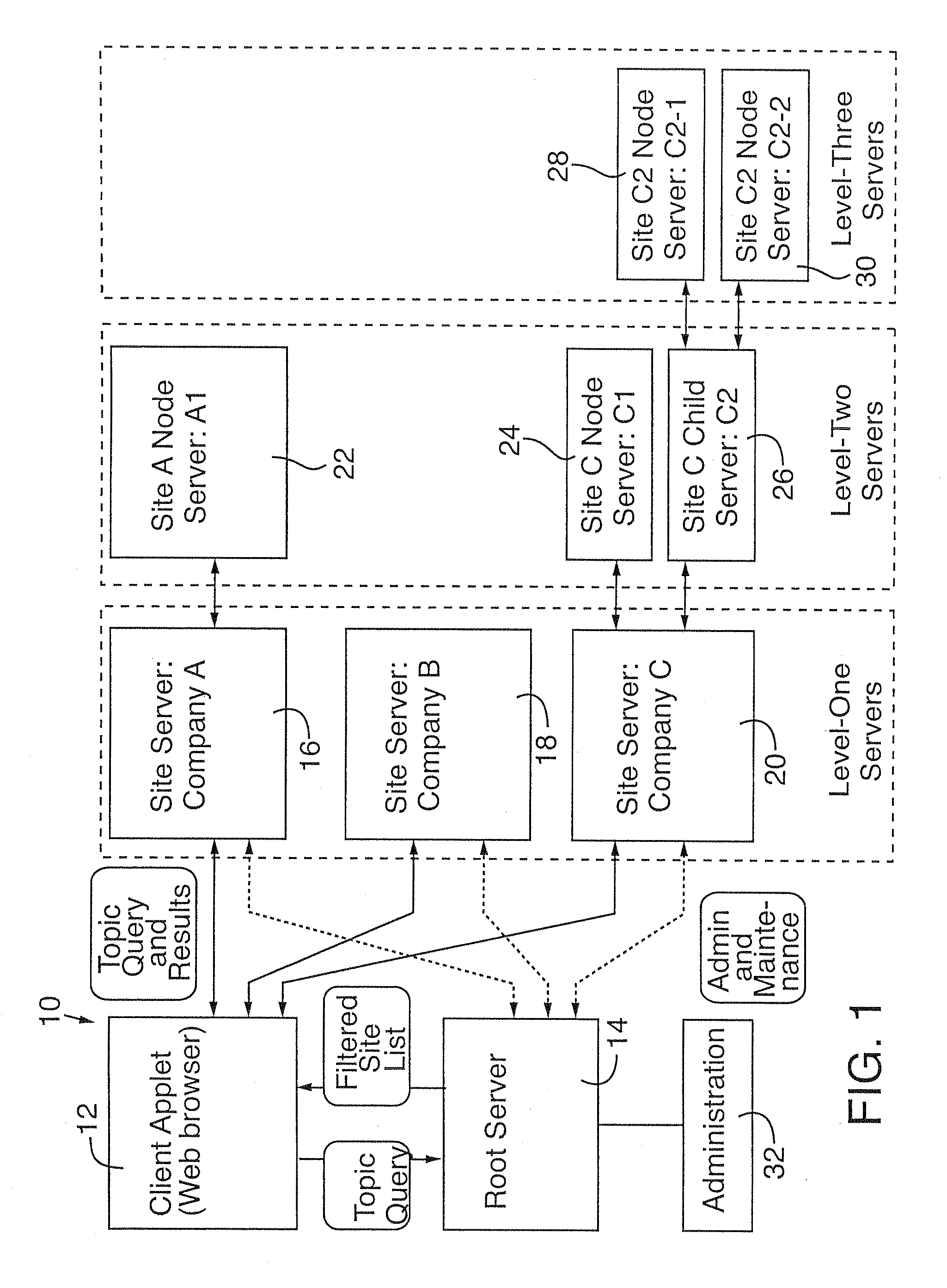
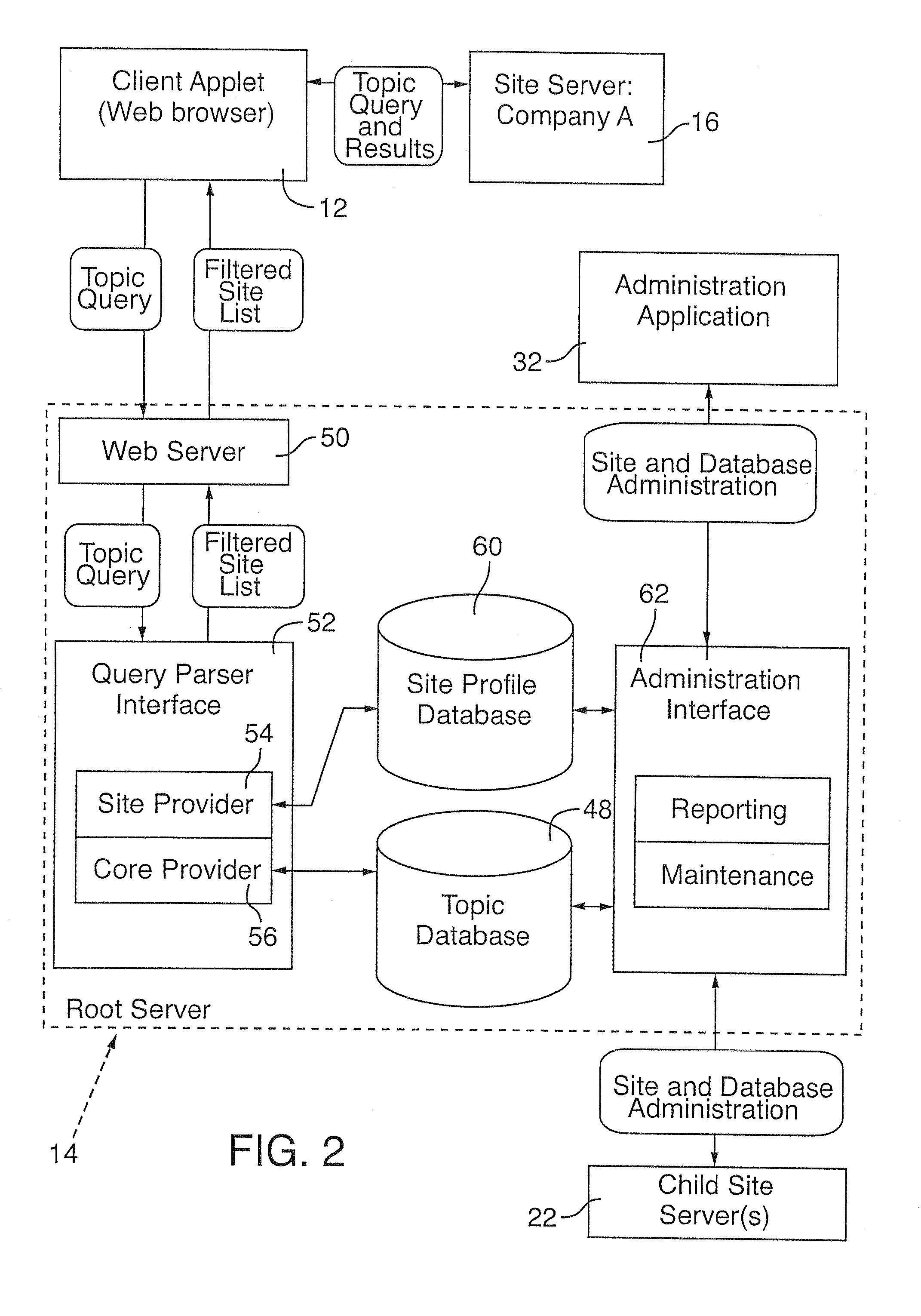
Distributed globally accessible information network
InactiveUS20050172010A1Facilitate a trend of “de-centralizationCooperate effectivelyWeb data indexingMultiple digital computer combinationsConfigfsThe Internet
A distributed information network is constructed for gathering information from sites distributed across a globally accessible computer network, i.e., the Internet. The distributed information network preferably includes a root server that stores a list of multiple distributed sites each represented by metadata. A network browser delivers an information search request to the root server, which in response develops a profiled information search request. The information provider of each of the distributed sites stores metadata corresponding to information content that is retrievable in response to the profiled information search request for search results derivable from the information content to which the metadata correspond. A profiled information communication link between the root server and each of the multiple distribution sites enables formation of a path for delivery of the search results to a destination site, from a site or sites represented by the metadata of the profiled information search request.
Owner:KOLOGIK LLC
Via Site for Managing Network Bandwidth
A system for using one or more via sites to manage network bandwidth, according to one embodiment of the present invention comprises a first call manager at a source site receiving an offer message to connect a call. The offer message includes an endpoint media settings list. The first call manager determines a first filtered media preferences list based on a source media settings list and the endpoint media settings list. The first call manager and transmits an invite message to a second call manager at a first via site. The invite message includes the first filtered media preferences list. The first call manager receives from the second call manager a call settings list that includes a description of the call settings negotiated between the source site, the first via site and a destination site.
Owner:MITEL NETWORKS INC +1
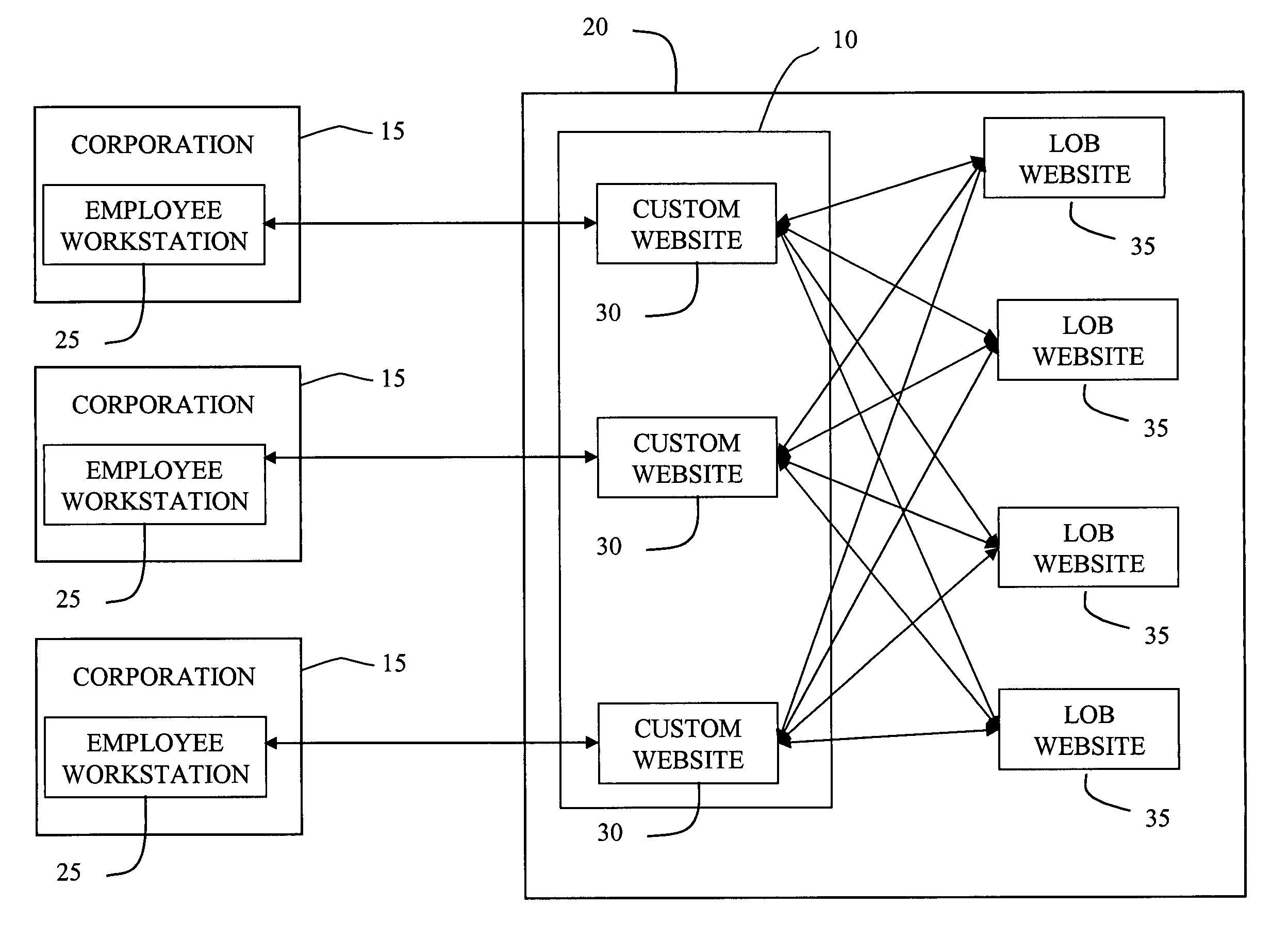
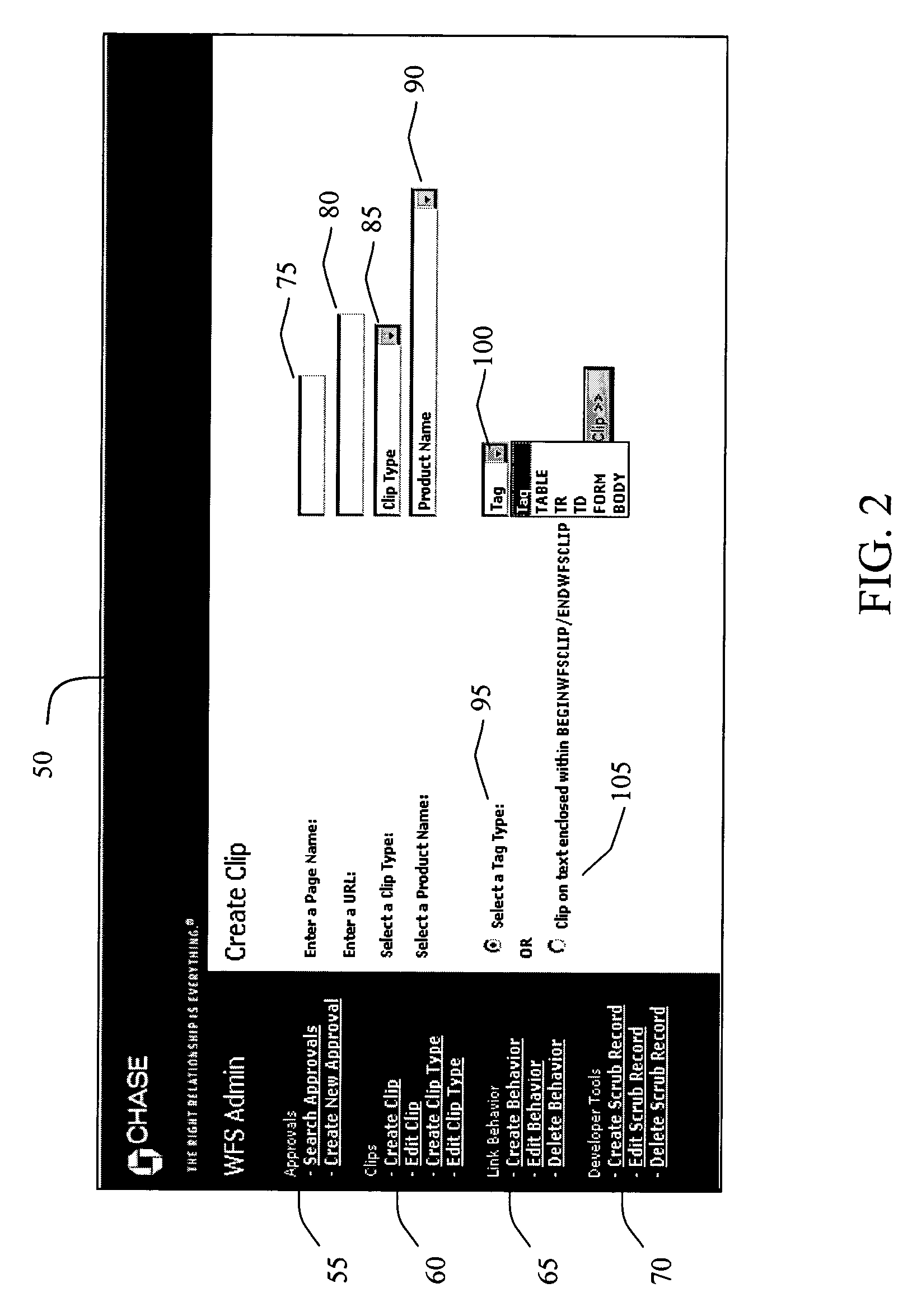
System and method for customizing a portal environment
ActiveUS7536433B2Not effectiveMultiple digital computer combinationsWebsite content managementWeb siteLook and feel
A system and method for creating a customized portal environment website that retrieves content from external websites and presents this content with a consistent and controlled look and feel. Three features of this invention that enable the consistent look and feel are clipping, scrubbing and link behavior tools. The clipping tool identifies the structure of clipped pages. The structure of the clipped content is stored in a database in the system. As the system dynamically retrieves clipped pages from the target site, the system compares the structure of the retrieved clip to the anticipated, stored structure of the clip. If the two structures match, the clipped page is rendered in the look and feel of the custom website. If the structures do not match, the dynamically clipped page is displayed in a new separate window. The scrubbing feature of the present invention allows the designer of the website to define a global structure for all pages that are retrieved from a particular domain. If a requested page does not conform to the defined structure, the system opens a new window for the page. The link behavior tool of the present invention traps a request for the embedded link upon it's execution and redirecting the request to a page that has already been approved and clipped or by opening a new window for the embedded link.
Owner:JPMORGAN CHASE BANK NA
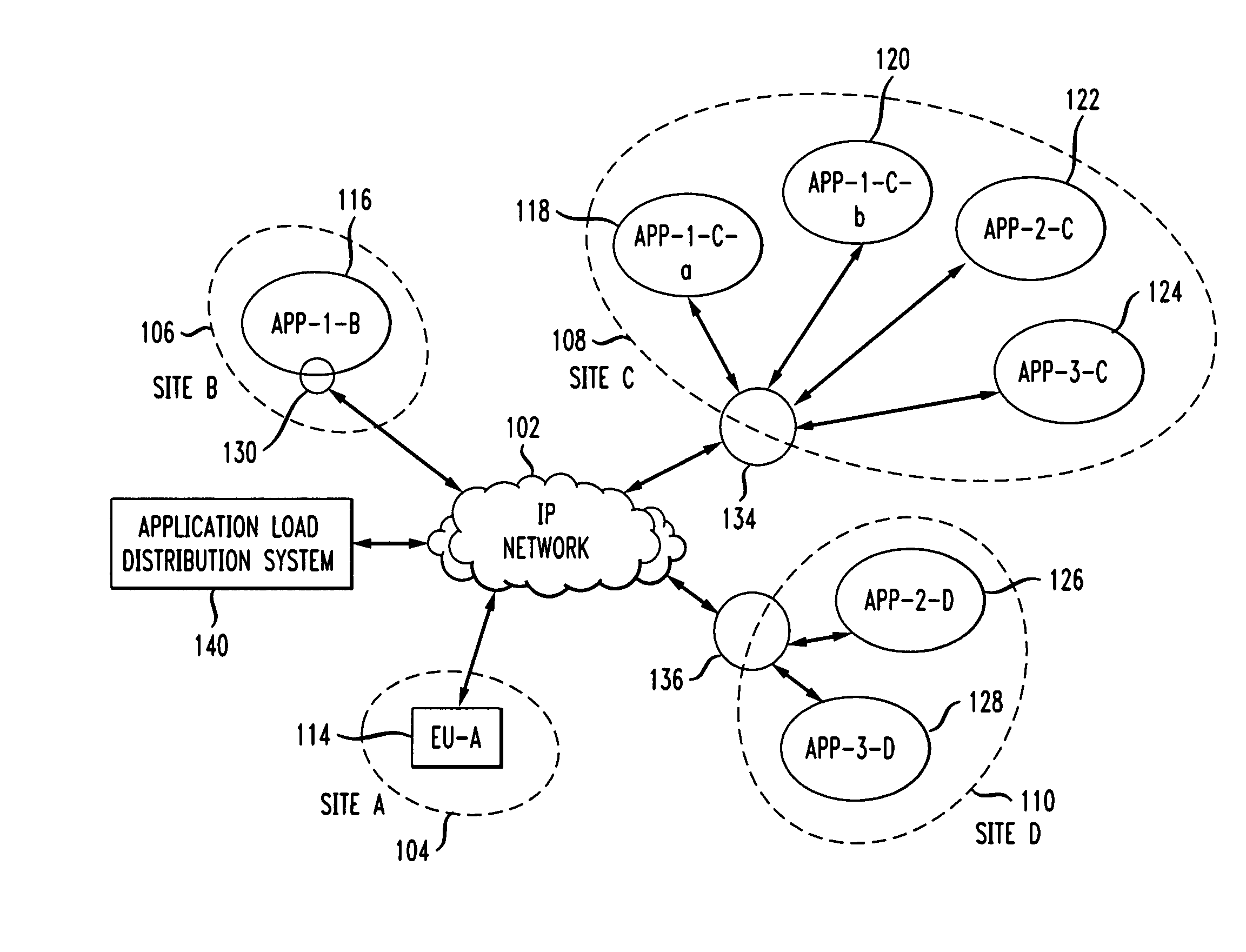
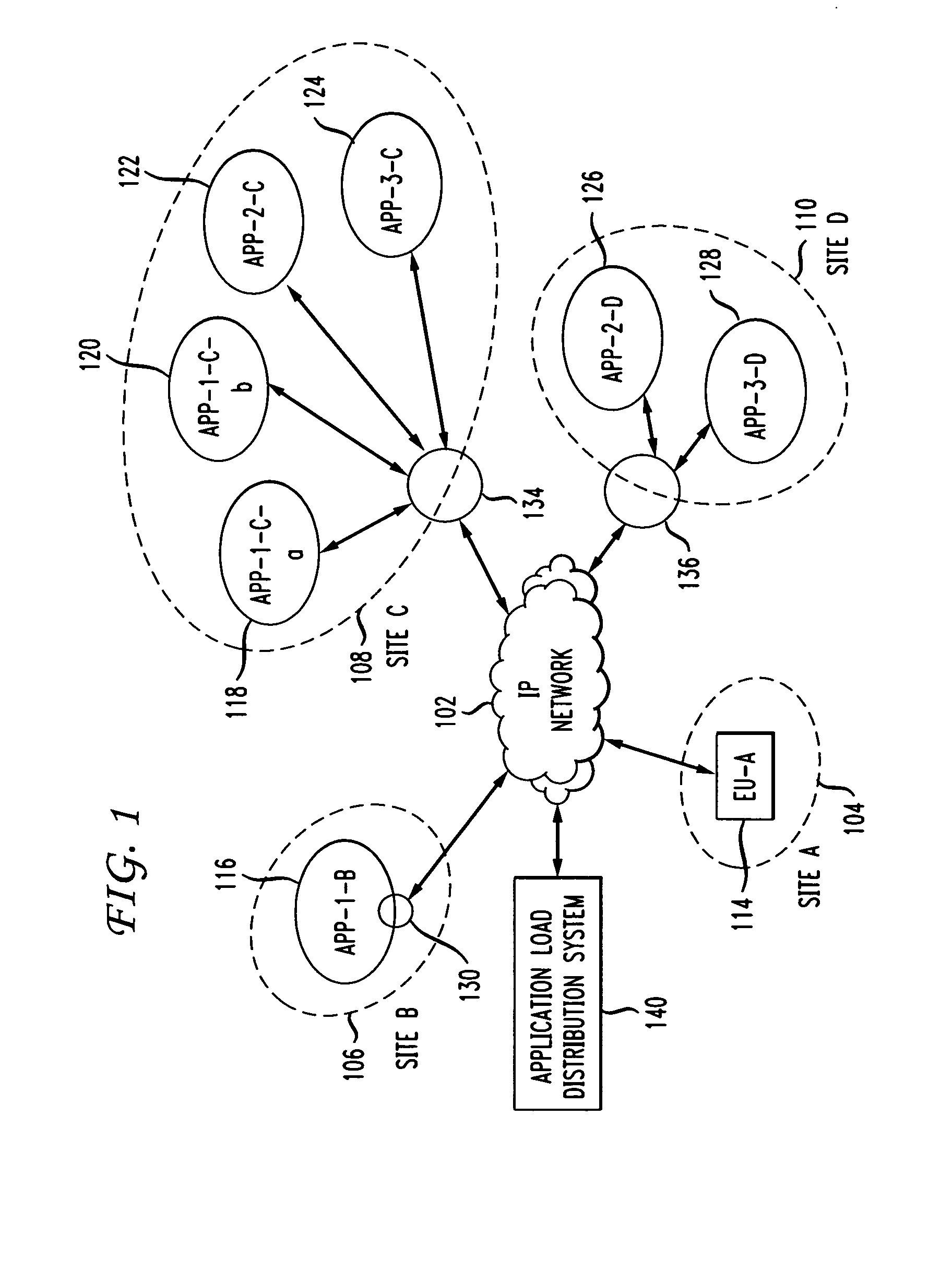
Application load distribution system in packet data networks
InactiveUS20090259768A1Digital computer detailsTransmissionApplication lifecycle managementSession Initiation Protocol
The present invention routes an application request to at least one of a plurality of sites in a packet data network. Session Initiation Protocol (SIP) messages that establish initial dialogs and SIP messages that are stand-alone requests are sent from a call session control function system to a SIP application load distribution system. The SIP application load distribution system routes a SIP message to at least one destination site, based at least in part on user-defined local state data and a user-defined application load distribution policy. Local state data is sent from a plurality of sites to an application management and health checking system. Local state data may be sent autonomously from the plurality of sites. Local state data may also be sent from the plurality of sites in response to a request issued by the application management and health checking system.
Owner:AT&T LABS
Method and device for preserving pacing information across a transport medium
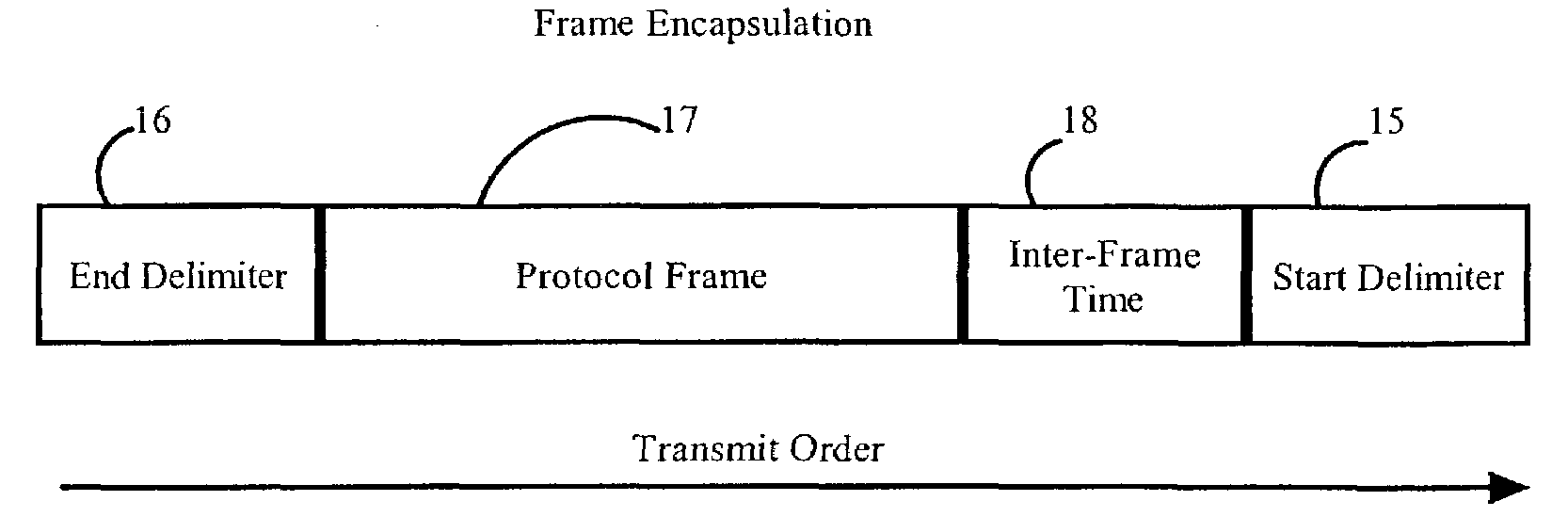
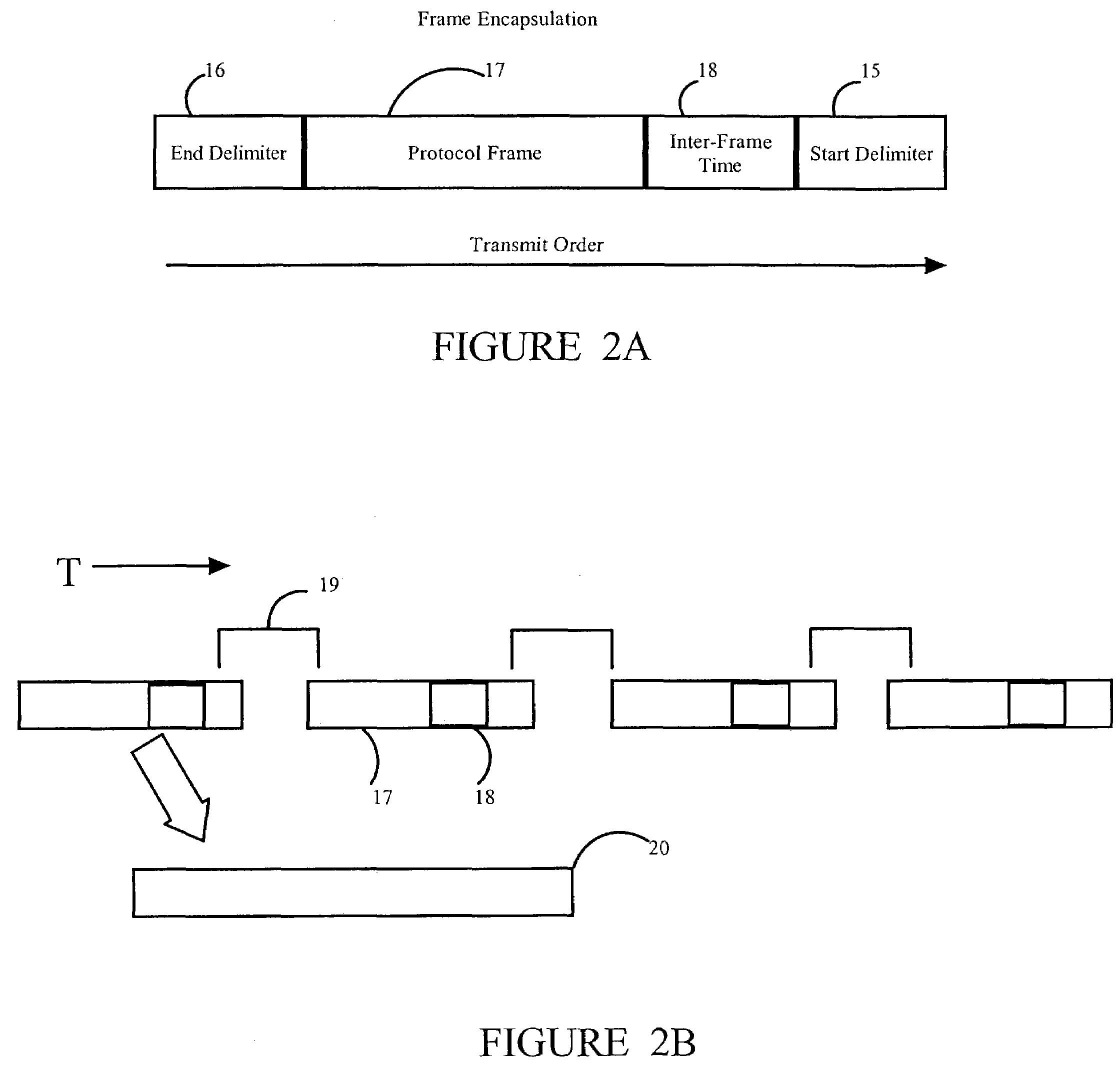
ActiveUS7539209B2Low costImprove reliabilityTransmission control/equlisationFrequency-division multiplex detailsFrame timeTransport medium
The invention relates to data communications, more particularly to a protocol encapsulation technique which captures the time between frames at a transmitting site for comparison with an idle counter at a receiving site. At the originating site, the time between successive frames in the native protocol is encoded in an interframe time field associated with each respective frame, before the time encoded frame is mapped into the protocol associated with the transport medium. At the destination site, the framing associated with the transport medium is removed to reveal the interframe time field. The value contained in this field is compared with the value of an idle counter running at the native protocol rate. When the idle count is greater than or equal to the encoded inter-frame time, the data contained in the frame is then delivered to the client.
Owner:CIENA
Distributed globally accessible information network implemented to maintain universal accessibility
InactiveUS20090094205A1Increase currentEasy to integrateWeb data indexingDigital data processing detailsTelecommunications linkThe Internet
A distributed information network is constructed for gathering information from sites distributed across a globally accessible computer network, i.e., the Internet. The distributed information network preferably includes a root server that stores a list of multiple distributed sites each represented by metadata. A network browser delivers an information search request to the root server, which in response develops a profiled information search request. The information provider of each of the distributed sites stores metadata corresponding to information content that is retrievable in response to the profiled information search request for search results derivable from the information content to which the metadata correspond. A profiled information communication link between the root server and each of the multiple distribution sites enables formation of a path for delivery of the search results to a destination site, from a site or sites represented by the metadata of the profiled information search request.
Owner:KOLOGIK LLC
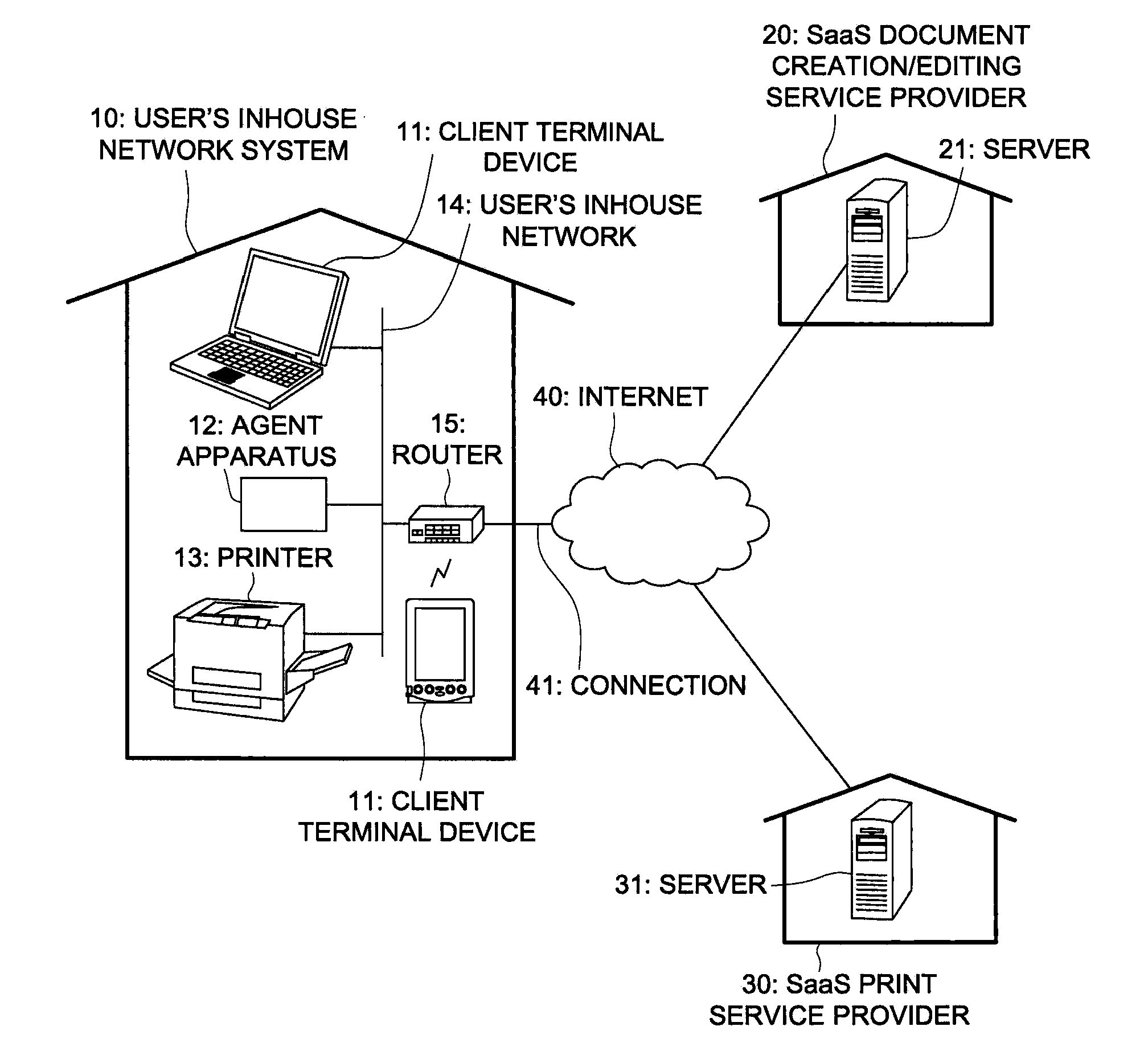
Print support apparatus, printing system and print support program
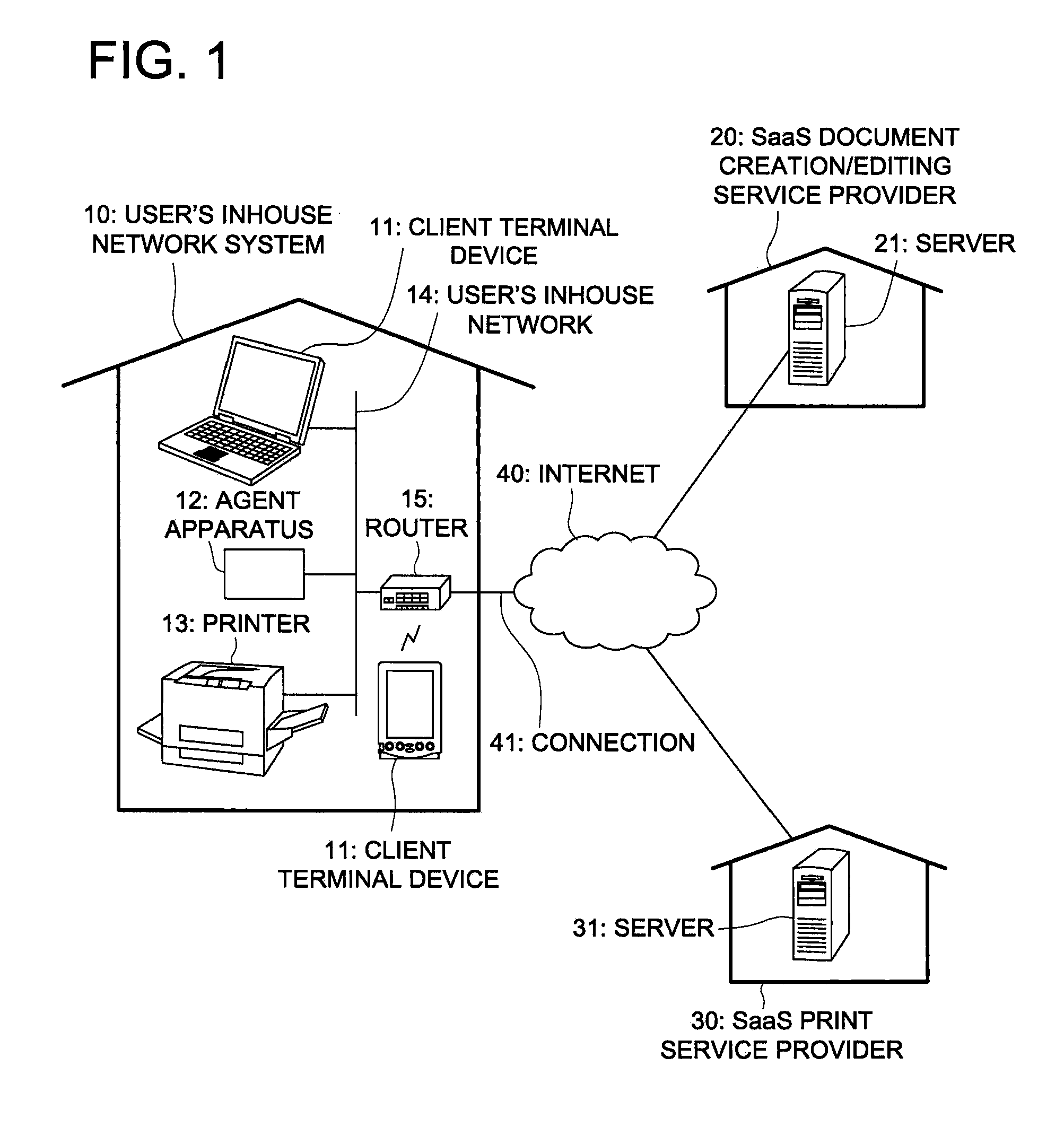
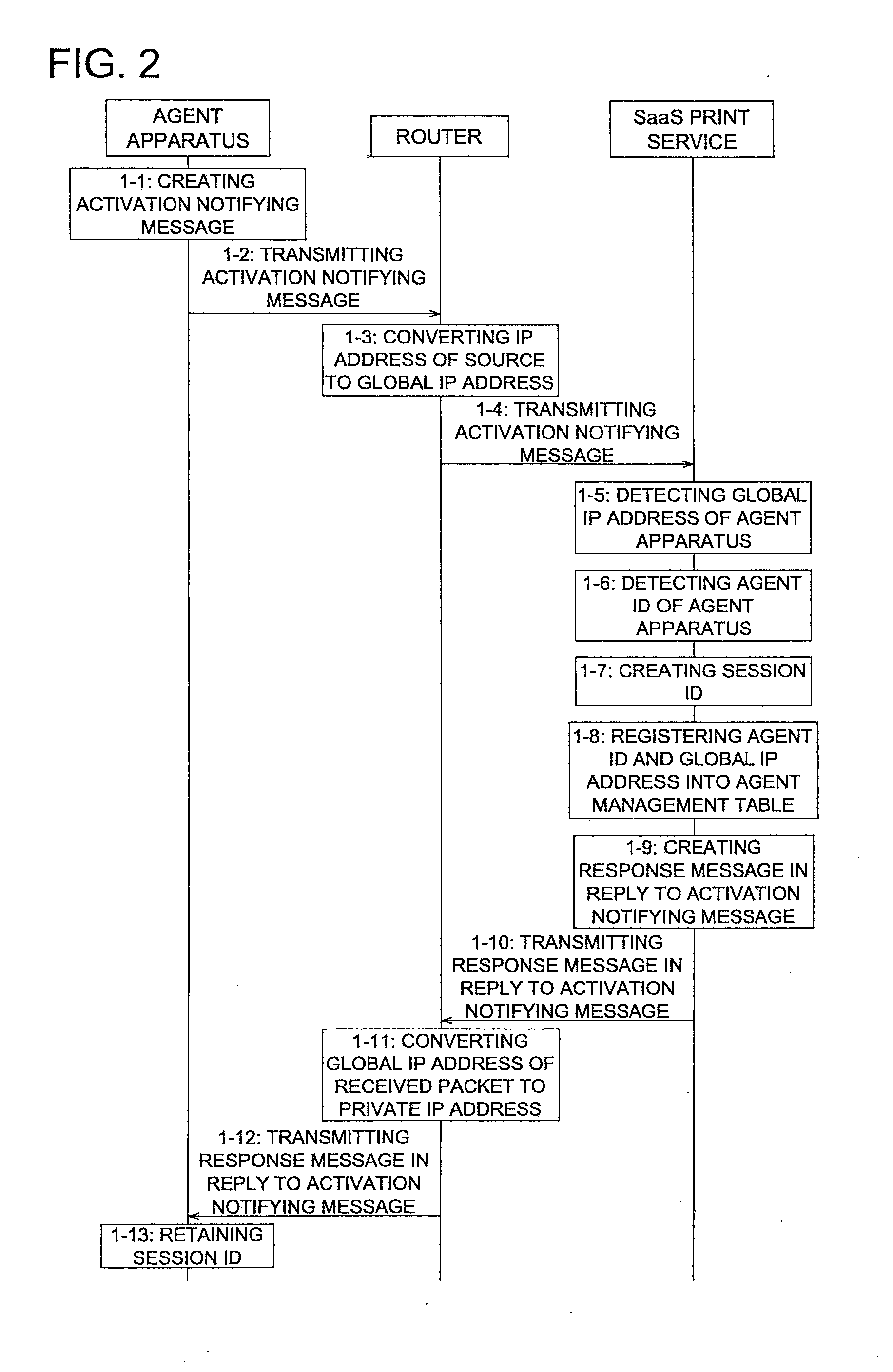
InactiveUS20120182573A1Easy to implementEasy to operateDigital output to print unitsComputer printingThe Internet
Disclosed is a print support apparatus that makes it possible even for a client, who has no document creation / editing application program and no printer driver, to implement a printing operation easily and safely by employing the SaaS. The print support apparatus, which is to be installed in a user's inhouse network being connectable to the Internet, includes: a detecting section to detect a printer coupled to the user's inhouse network; a notifying section to notify a print service server of information for specifying the printer above-detected; an acquiring section that accesses a predetermined storing destination site, in which print data created from document data by the print service server by executing a printer driver corresponding to the printer above-detected, is stored, so as to acquire the print data from the predetermined storing destination site concerned; and a data transferring section to transfer the print data to the printer above-detected.
Owner:KONICA MINOLTA BUSINESS TECH INC
Medical device
ActiveUS9028392B2Delay deploymentImprove stabilityBlood pumpsIntravenous devicesAscending aortaImpeller
A temporary cardiac-assist device is disclosed. The device includes a pump assembly that is deployed in the ascending aorta or the heart. A torque transmission line couples the pump assembly to an external motor for driving impeller blades within the pump assembly. The pump assembly expands in size at its destination site for operation. In operation, neither the torque transmission line nor elements that support the impeller blades are under axial forces.
Owner:FBR MEDICAL INC
Concealed communication method
The invention discloses a concealed communication method. The method comprises the following steps that encryption is performed on first original data on a sending end and a receiving end so as to form concealed information and generate a binary sequence of the concealed information, and the binary sequence is recorded as a sending-end original cipher; the binary sequence of the concealed information is converted into a sending-end Chinese character sequence and is sent to the receiving end; the receiving end receives the concealed information and carries out decryption. Through the above mode, by using the concealed communication method provided in the invention, a Chinese character coding is used to embed the concealed communication into a Chinese character; through analyzing the concealed information which needs to be transmitted, the concealed information is converted into English letters in a split-up mode and then are converted into a Chinese character; then the Chinese character is transmitted to a target site through forms of a mail, a webpage and a picture so that a purpose of transmitting the concealed information is reached. A concealed channel established by using the method possesses advantages of a high capacity and high concealed performance. In the method, the concealed information is packed and transmitted in a data portion of an IP data packet.
Owner:SUZHOU INST FOR ADVANCED STUDY USTC
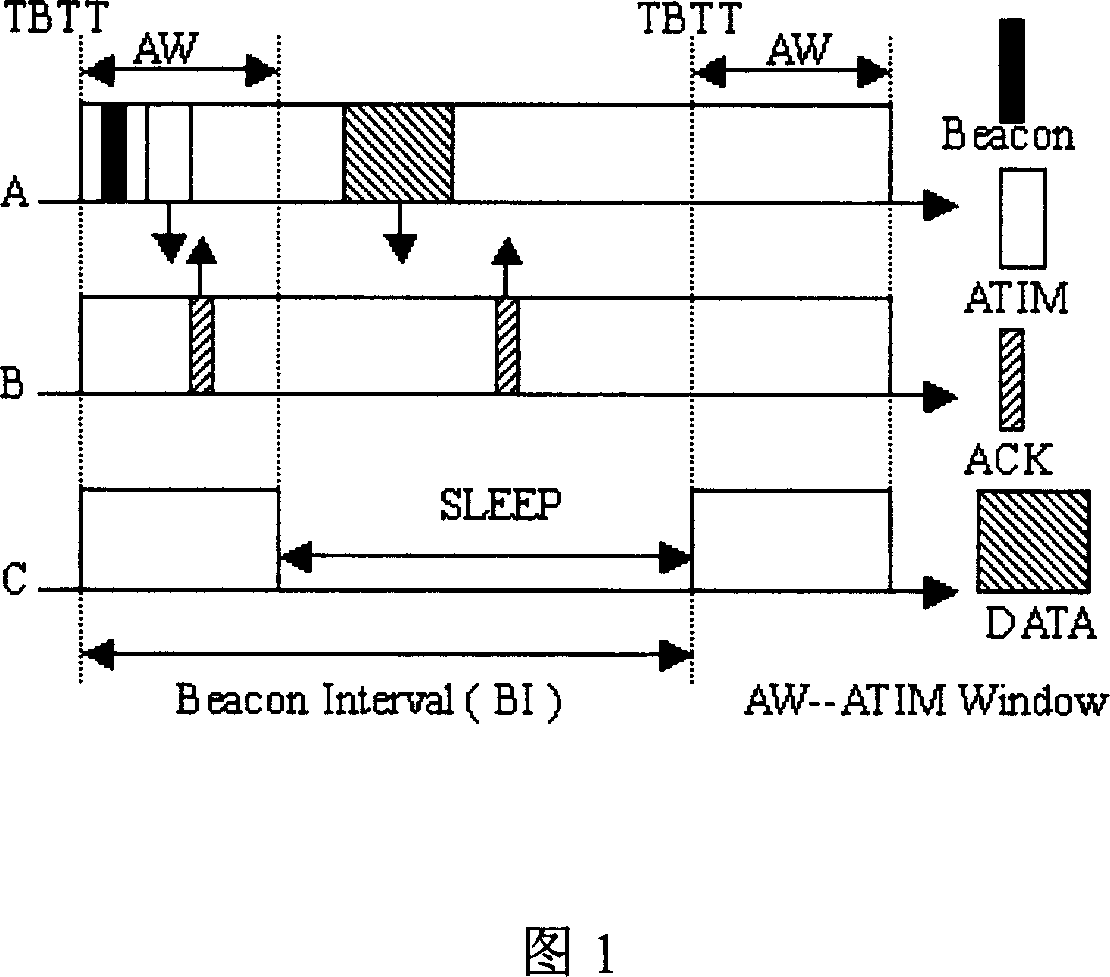
A method for improving the WLAN energy-saving efficiency
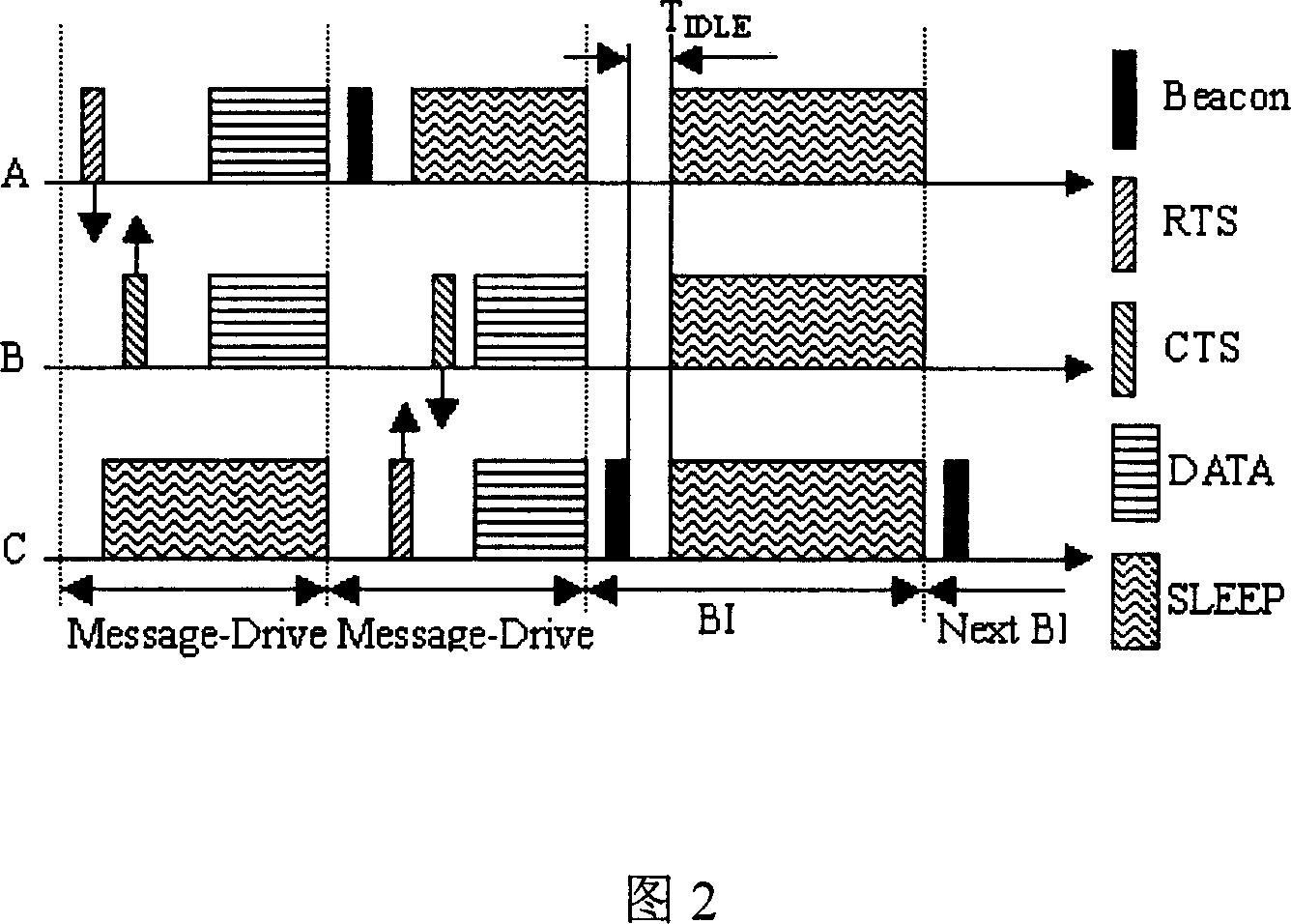
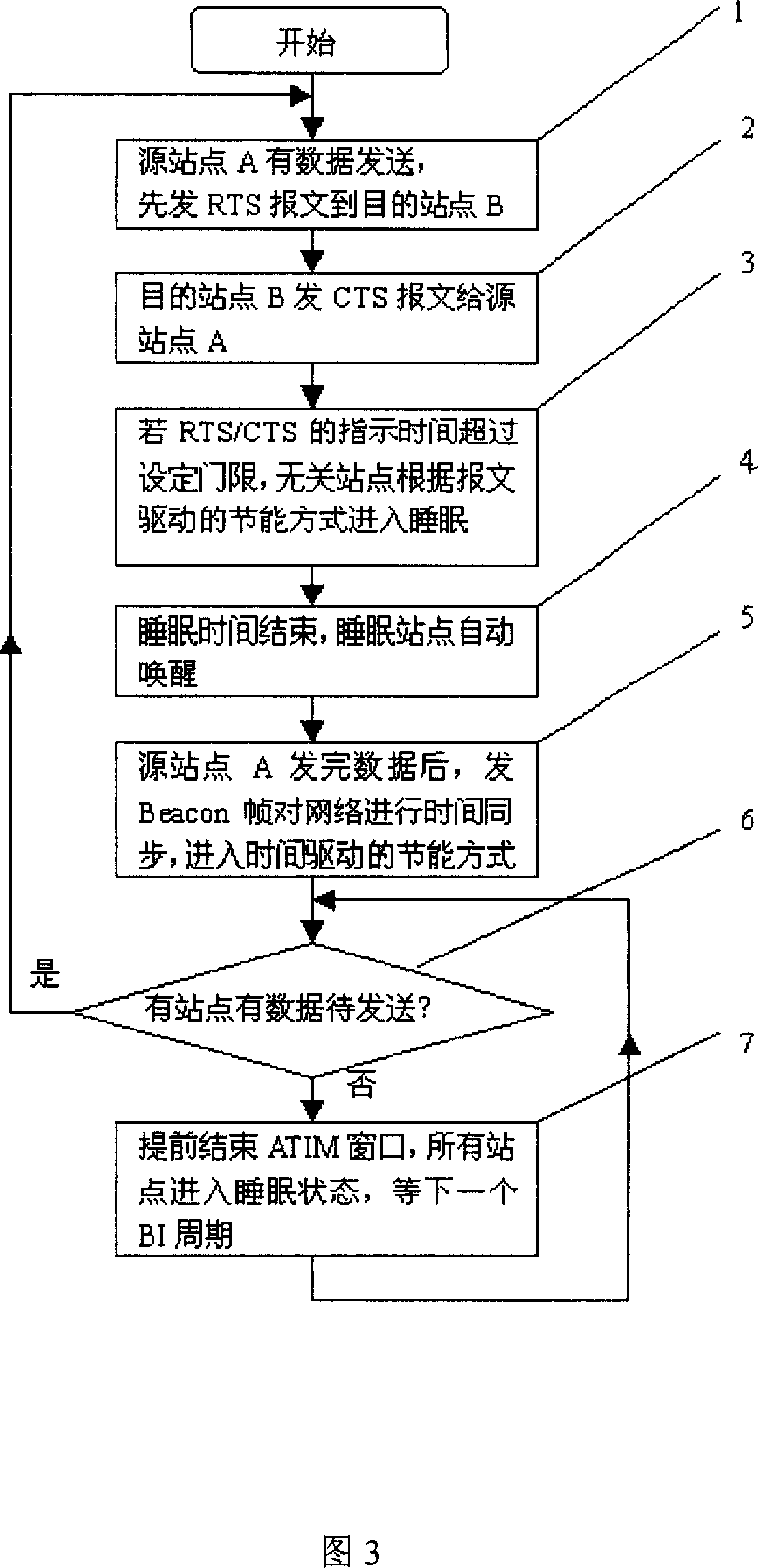
The invention relates to the wireless LAN technical field, a method for improving the wireless LAN energy-saving efficiency, including: time drive and message drive combination based energy-saving mode. When the active website wants to send the data, firstly send the RTS message to the destination site, after the destination site received the RTS message, send the CTS message to the source site, in which, both the RTS and CTS have the time required for the subsequent data exchanging; according to the message drive energy-saving mode, other sites may be entered into the sleep status according to the transmission time specified by the RTS / CTS message mentioned above; after the data exchanging completed, the sleep site is awaken; if the medium is idle within the specified time TIDLE, indicates that all websites have no data for sending, then close the ATIM window in advance, all sites entered into the sleep status to wait for the next BI period for awaking. The TIDLE value equals to the DIFS value specified in IEEE 802.11.
Owner:INST OF SEMICONDUCTORS - CHINESE ACAD OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com