Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
50results about How to "Decryption implementation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
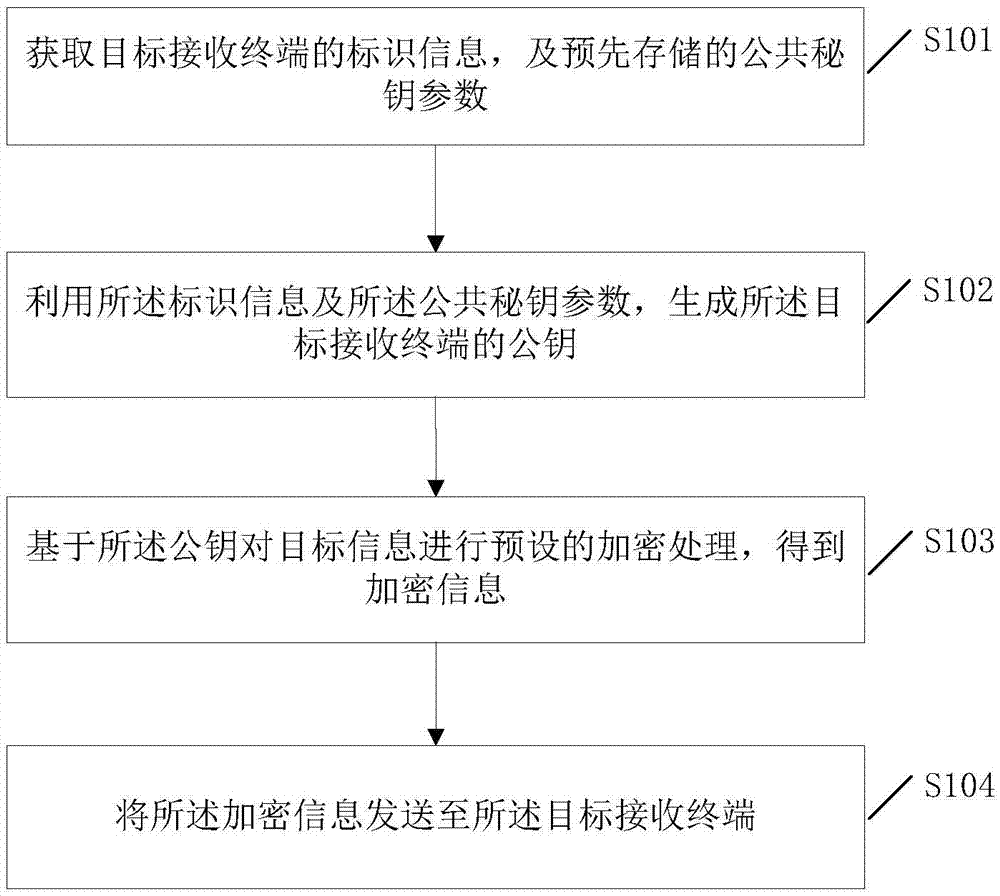
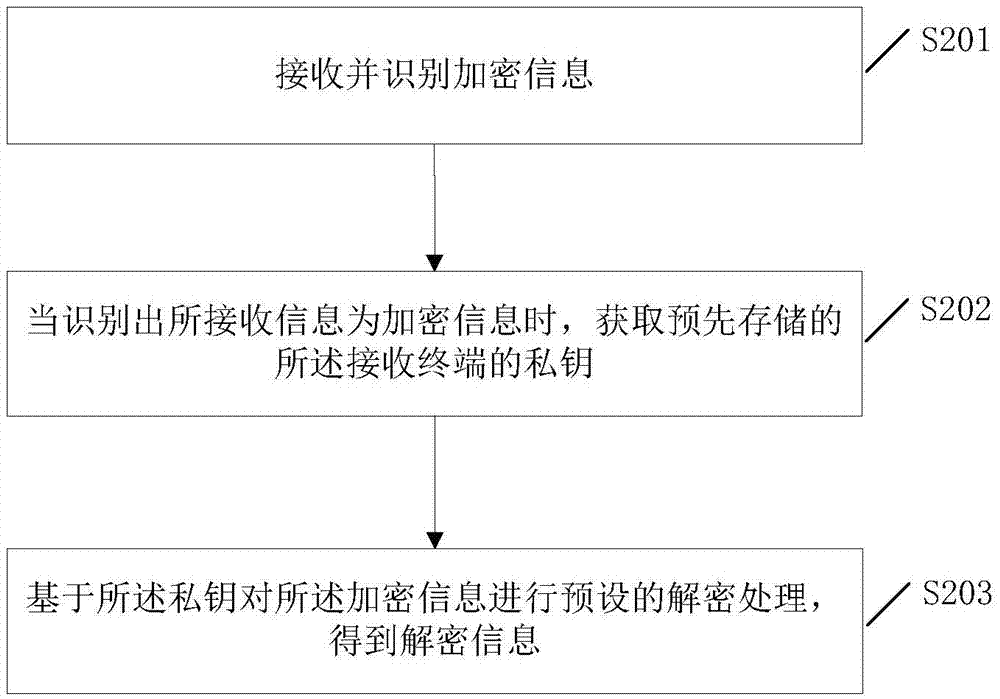
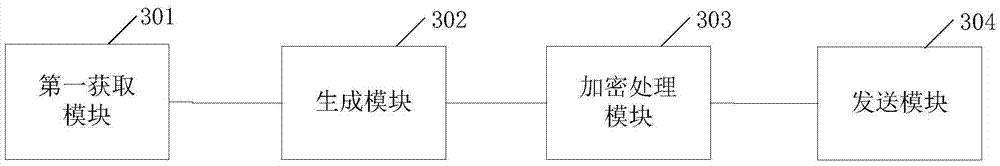
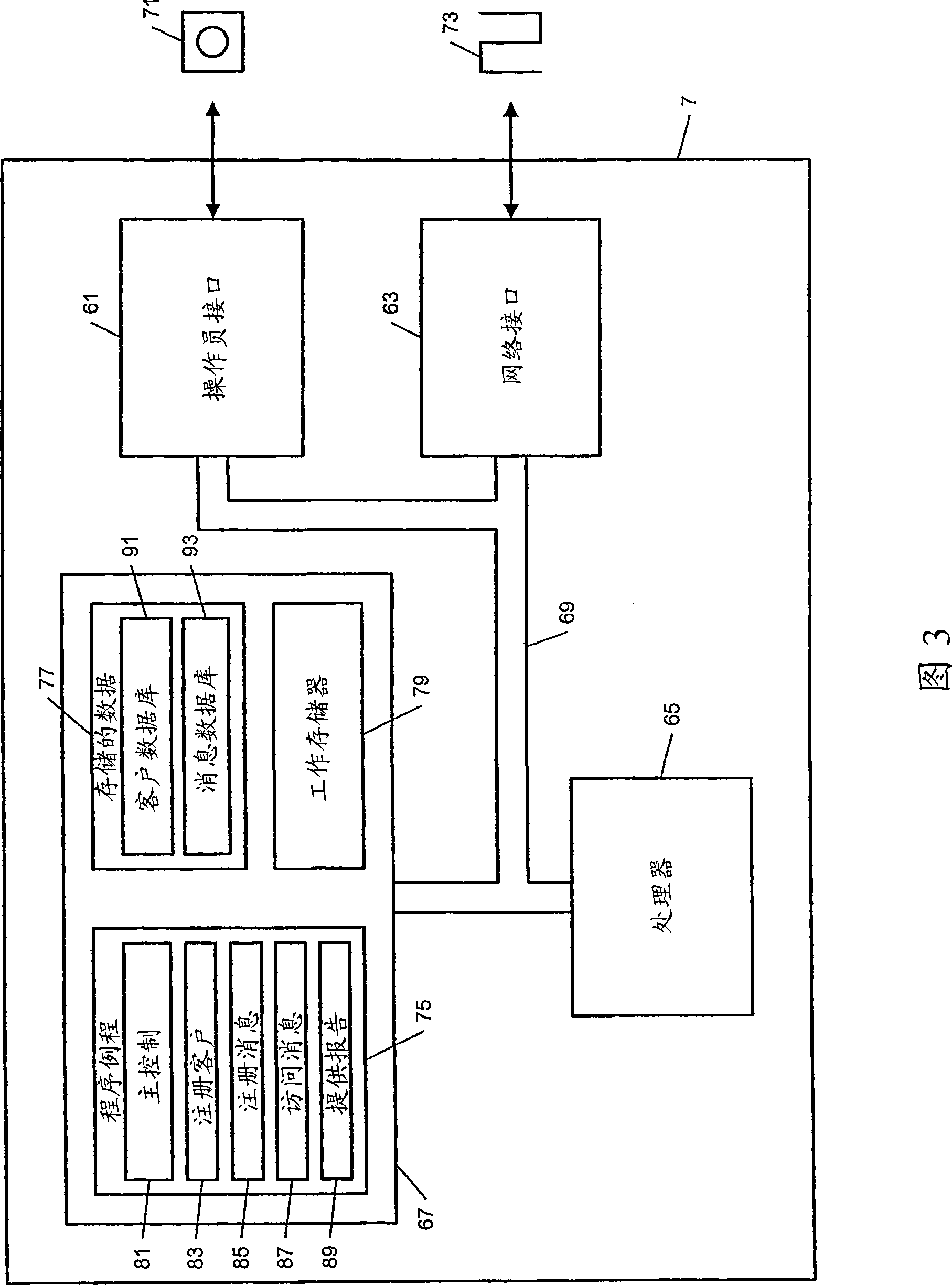
Information encryption and decryption processing method and system
InactiveCN105450395AImprove securityDecryption implementationKey distribution for secure communicationEnd-to-end encryptionThird party
The invention discloses an information encryption and decryption processing method, a sending terminal, a receiving terminal and an information encryption and decryption processing system. According to the method, a public key of a target receiving terminal is generated at the sending terminal based on identification information of the target receiving terminal, information to be sent is encrypted by the generated public key to improve the security of the information, the received encrypted information is decrypted by a particular private key of the terminal at the receiving terminal. Therefore, end-to-end encryption of the user information is realized by a "public key-private key" key based on the asymmetric encryption technology, any third party cannot obtain the information contents of a user, so information leakage of terminal information resulting from illegal interception and other reasons in a transmission process is avoided, and the security of the terminal information is further improved.
Owner:THUNDERSOFT
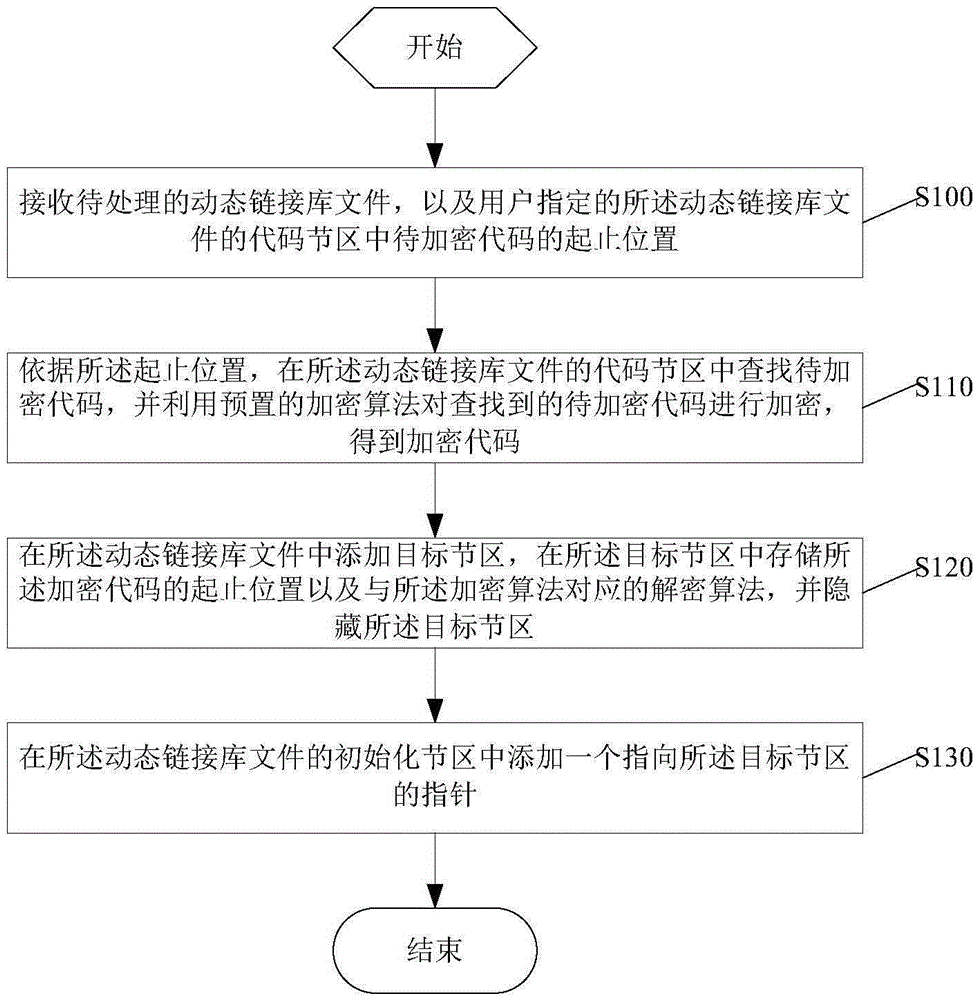
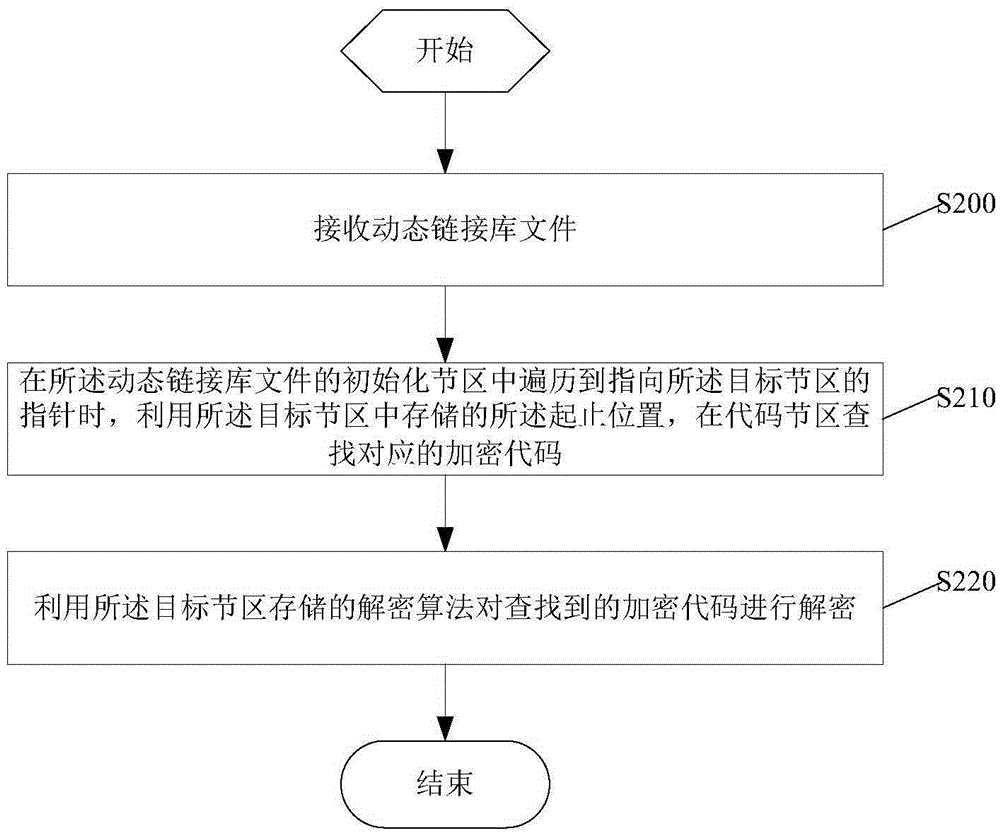
Dynamic-link library file encryption, decryption methods and devices
ActiveCN105426777ADecryption implementationIncrease the difficulty of decompilationDigital data protectionComputer hardwareEncryption
The application discloses dynamic-link library file encryption, decryption methods and devices. The encryption method comprises the following steps: receiving a dynamic-link library file to be processed as well as starting and stopping positions of a user-specified code to be encrypted in a code section of the dynamic-link library file; according to the starting and stopping positions, finding the code to be encrypted in the code section and encrypting the code to be encrypted by using a preset encryption algorithm so as to obtain an encrypted code; adding a target section in the dynamic-link library file, storing the starting and stopping positions of the encrypted code and a decryption algorithm corresponding to the encryption algorithm in the target section and hiding the target section; and adding a pointer pointing to the target section in an initialization section of the dynamic-link library file so as to carrying out the decryption algorithm of the target section through the pointer in an initialization process of the dynamic-link library file to decrypt the encrypted code. The encryption method provided by the application can encrypt the user-specified code and the encryption mode is more diversified.
Owner:中科创达(重庆)汽车科技有限公司
Electronic data communication system
InactiveCN101416458ADecryption implementationData switching networksSecuring communicationReceiptElectronic mail
Described is an electronic mail messaging system in which a plurality of user computers are connected to a mail registration server via the Internet. The mail registration server stores plural sets of decryption data, each set being required to decrypt a corresponding encrypted electronic mail message. Following receipt of an encrypted electronic mail message, a user computer communicates with the mailed registration server to effect decryption of the encrypted electronic mail message using the corresponding decryption data stored by the mail registration server. In this way, the accessing of the electronic mail message can be monitored by the mail registration server.
Owner:TREND MICRO INC
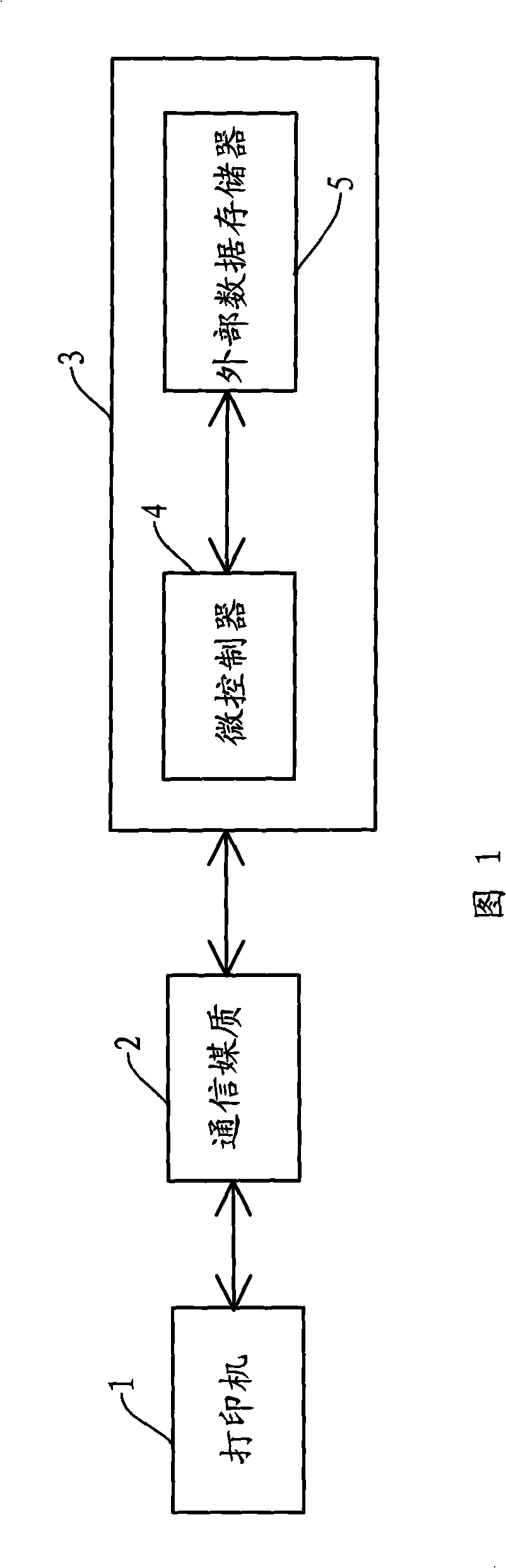
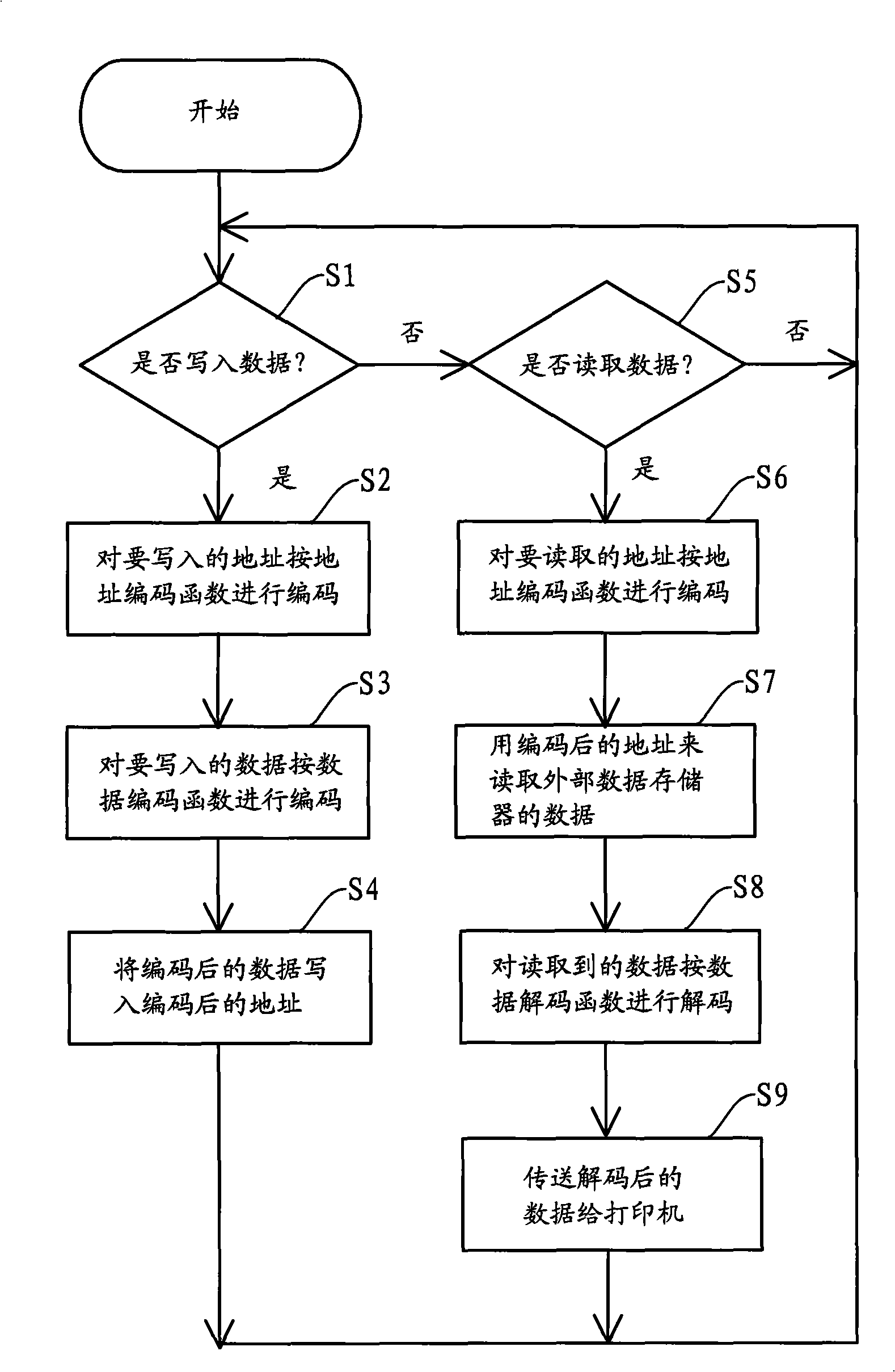
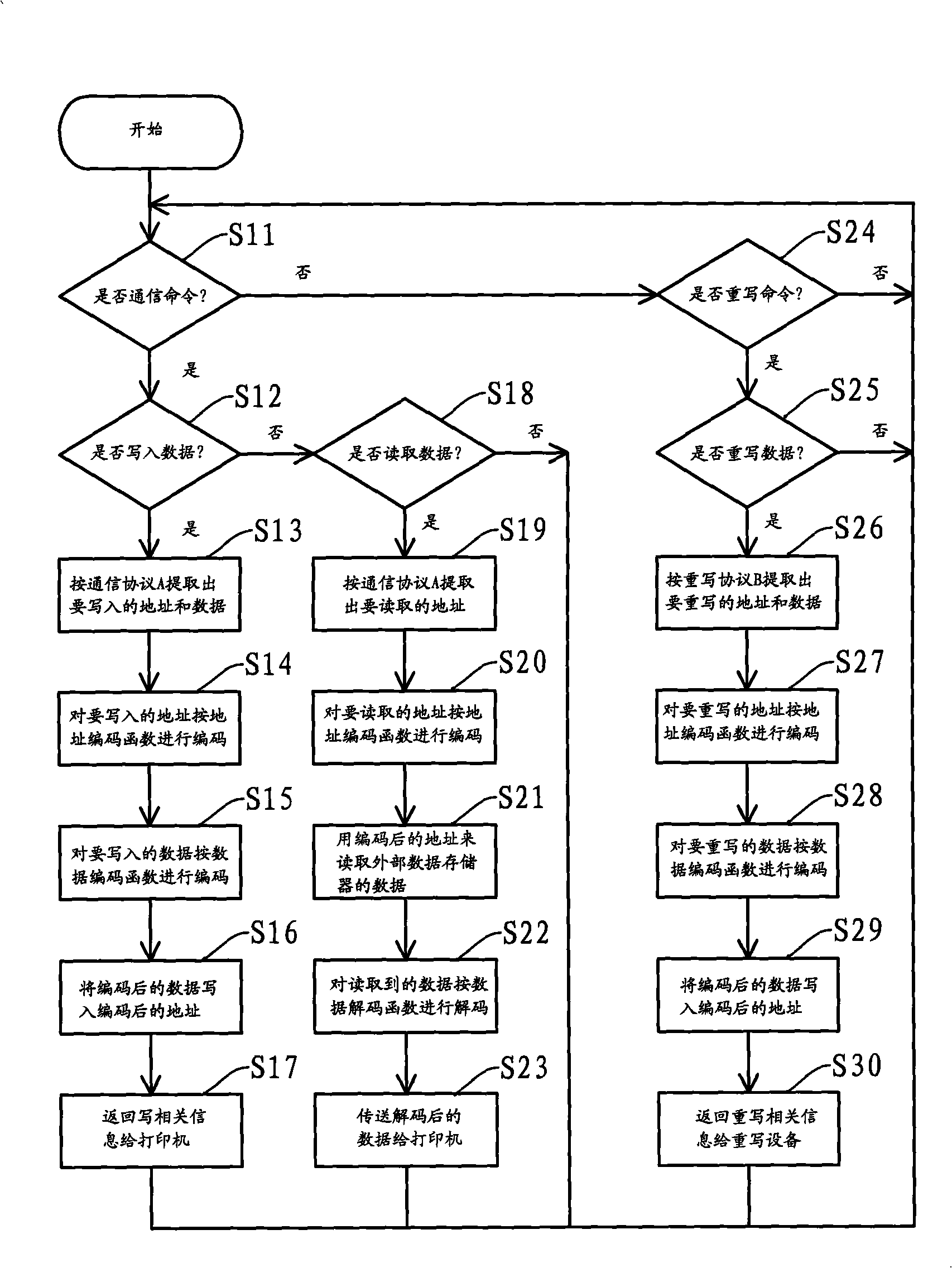
Method for ciphering, deciphering and rewriting external data memory
InactiveCN101276309AAvoid damageDecryption implementationUnauthorized memory use protectionOther printing apparatusDecoding methodsMicrocontroller
The present invention provides a method of encrypting, decoding and rewriting the external data memorizer, the encrypting method includes: a microcontroller processes code for the address and data to be written, writing the coded data in to the coded address; the decoding method includes the microcontroller coding the address needed to be read, reading data of the address according the coded address, and decoding the read data; the rewriting method includes the microcontroller extracting the address and data needed to be written according to the rewriting protocol, and coding the address and data, writing the coded data in the coded address. The encryption effectively prevents the data of the external data memorizer from incorrect rewrite, the encrypting method decodes the coded data, ensuring the printer recognize the data, the rewriting method effectively rewrites the external data memorizer, ensuring the chip setting with the external data memorizer circularly use.
Owner:ZHUHAI TIANWEI TECH DEV CO LTD
Encryption and decryption method, device and system
ActiveCN107801187ADecryption implementationDecryption failedEncryption apparatus with shift registers/memoriesUser identity/authority verificationPlaintextCiphertext
The embodiment of the invention provides an encryption and decryption method, device and system, aiming to at least solve the problem that the verification between initiating end equipment and response end equipment cannot be performed under an existing AES-SIV mechanism in the case that the initiating end equipment does not know an MAC address of the response end equipment in advance. The methodincludes the following steps: enabling first equipment to acquire a first public key of second equipment; generating a first key and a first public key hash value at least according to the first public key of the second equipment; generating a first vector at least according to a preset MAC address and an MAC address of the first equipment; encrypting a first plaintext at least according to the first key and the first vector to generate a first ciphertext; sending a first message to the second equipment, or sending a second message to third equipment, and enabling the third equipment to send athird message to the second equipment, wherein the first message or the second message or the third message at least includes the first ciphertext, the first public key hash value and a first publickey of the first equipment; or, the scheme of the invention is applicable to the field of communication.
Owner:HONOR DEVICE CO LTD
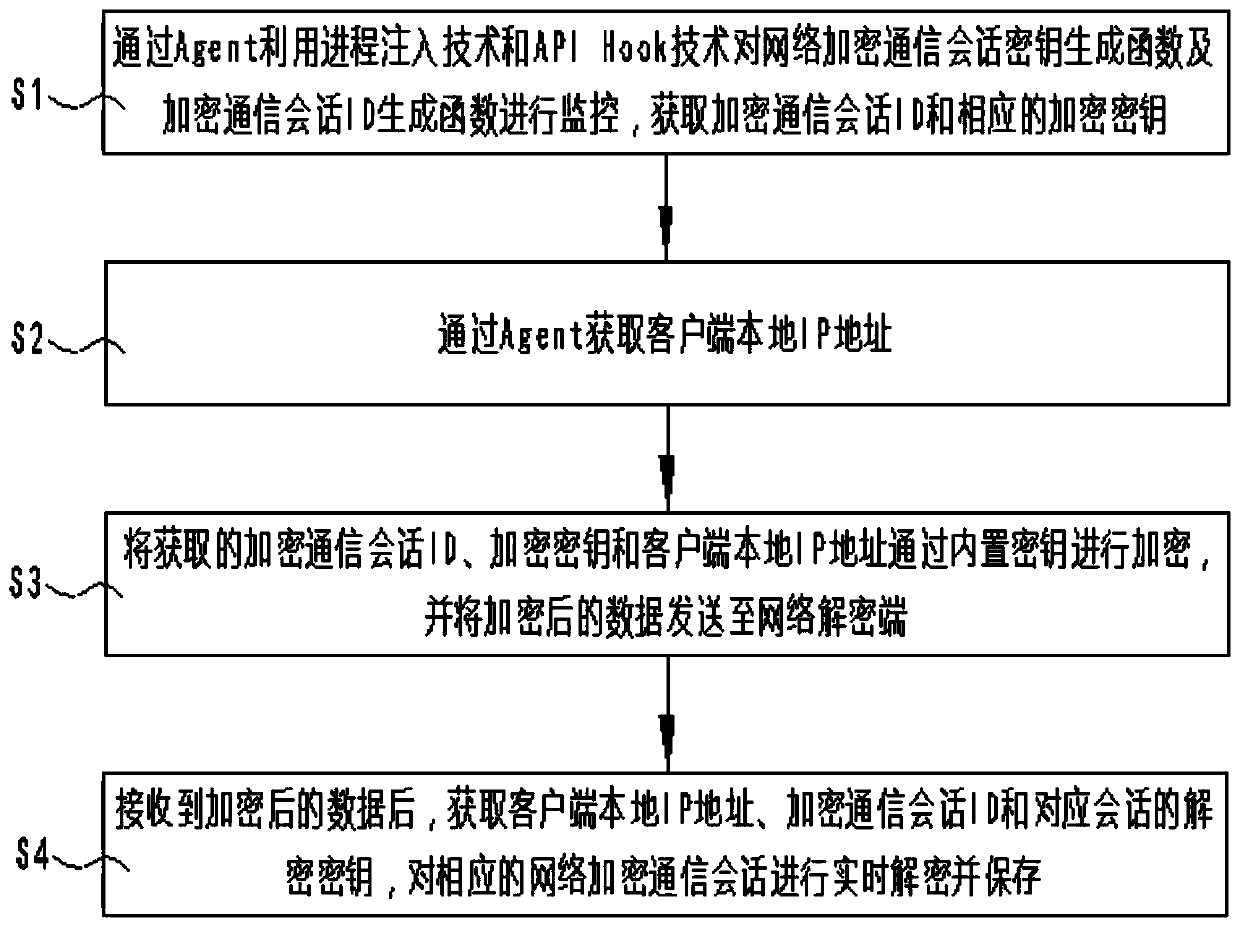
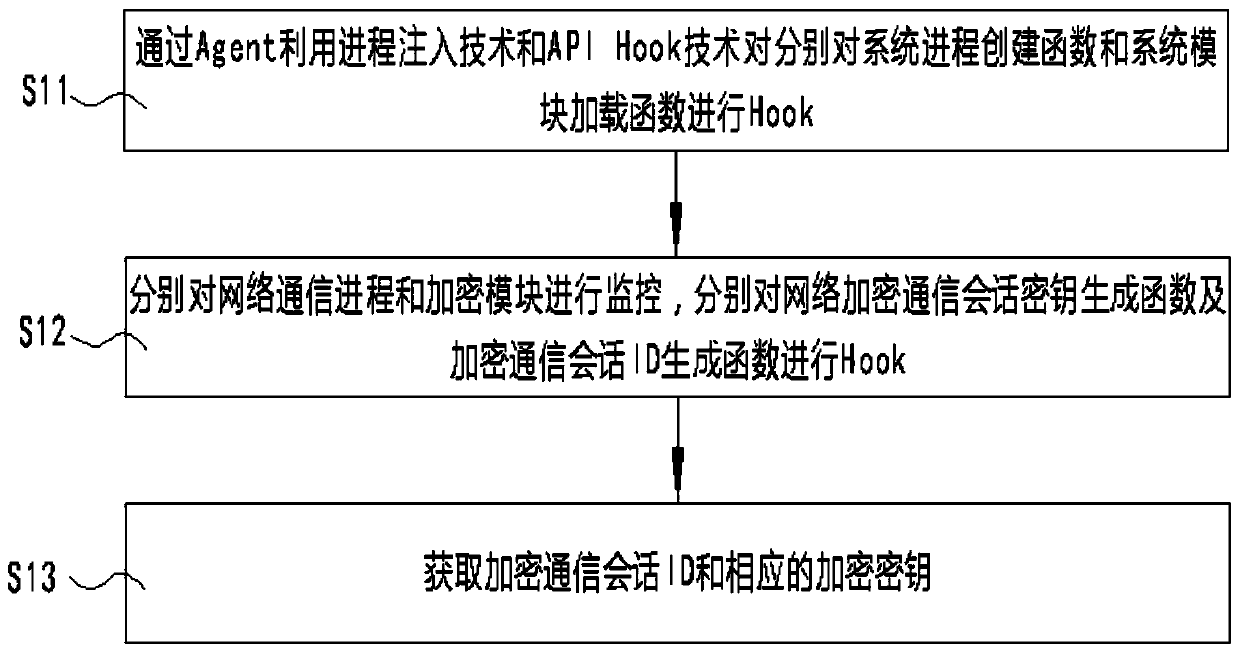
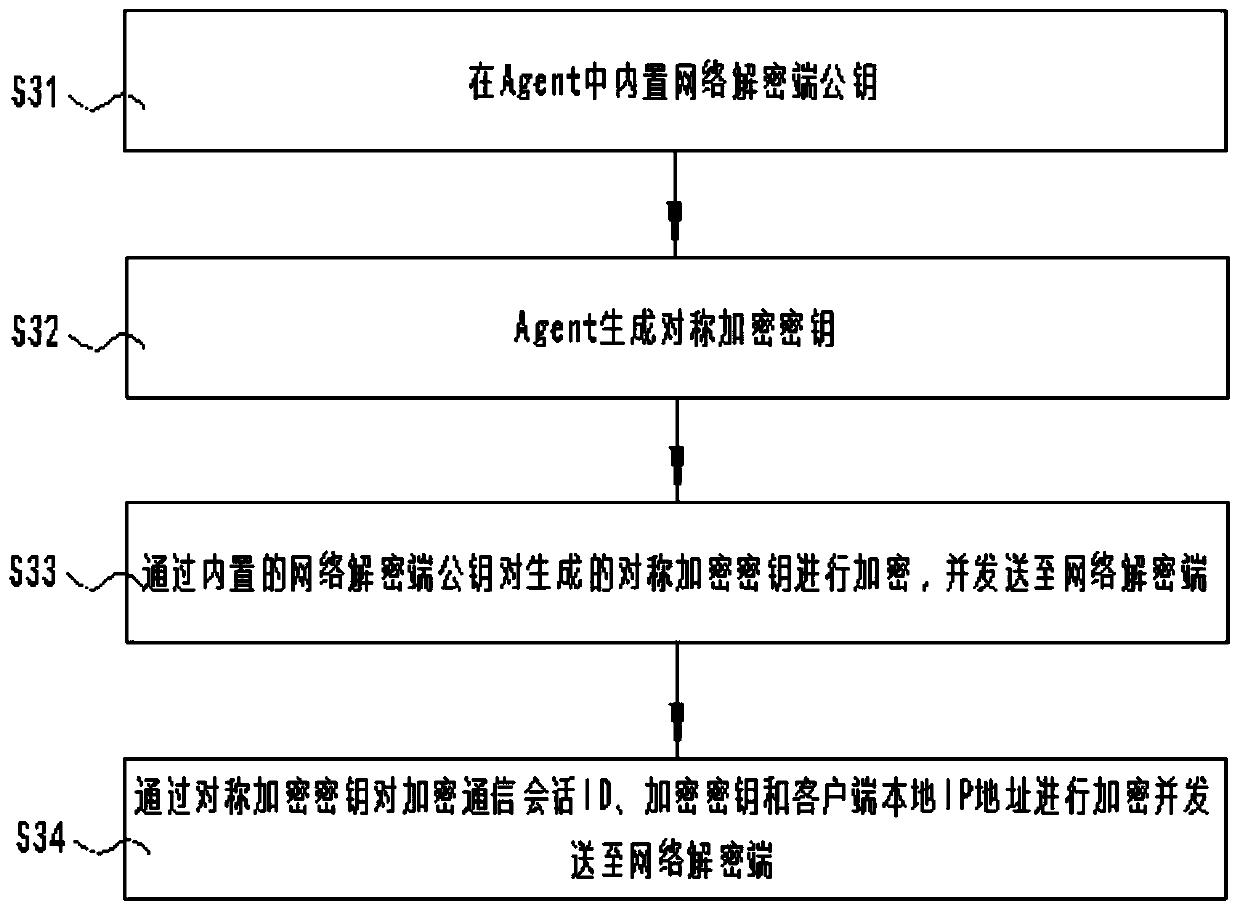
SSL/TLS network encryption communication information real-time decryption method based on memory analysis
The invention discloses an SSL / TLS network encryption communication information real-time decryption method based on memory analysis. The method comprises the following steps: monitoring a network encryption communication session key generation function and an encryption communication session ID generation function by using a process injection technology and an API Hook technology through an Agentto obtain an encryption communication session ID and a corresponding encryption key; obtaining a local IP address of the client through the Agent; encrypting the acquired encryption communication session ID, the network encryption communication session key and the local IP address of the client through a temporarily generated symmetric encryption key, and sending the encrypted data to a network decryption end; and after receiving the encrypted data, obtaining a local IP address of the client, the encryption communication session ID and a decryption key of the corresponding session, and decrypting and storing the corresponding network encryption communication session in real time. According to the invention, the extraction of the network communication encryption key and the real-time decryption of the network encryption communication content can be effectively realized, and the detection efficiency is improved.
Owner:成都安舟信息技术有限公司
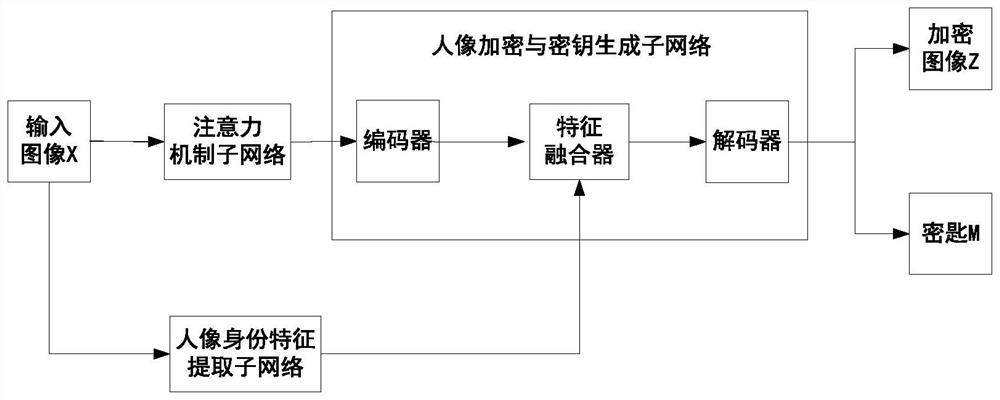
Portrait biological characteristic privacy protection and decryption method
ActiveCN111723395ADecryption implementationEnsure visual similarityCharacter and pattern recognitionDigital data protectionPrivacy protectionEngineering
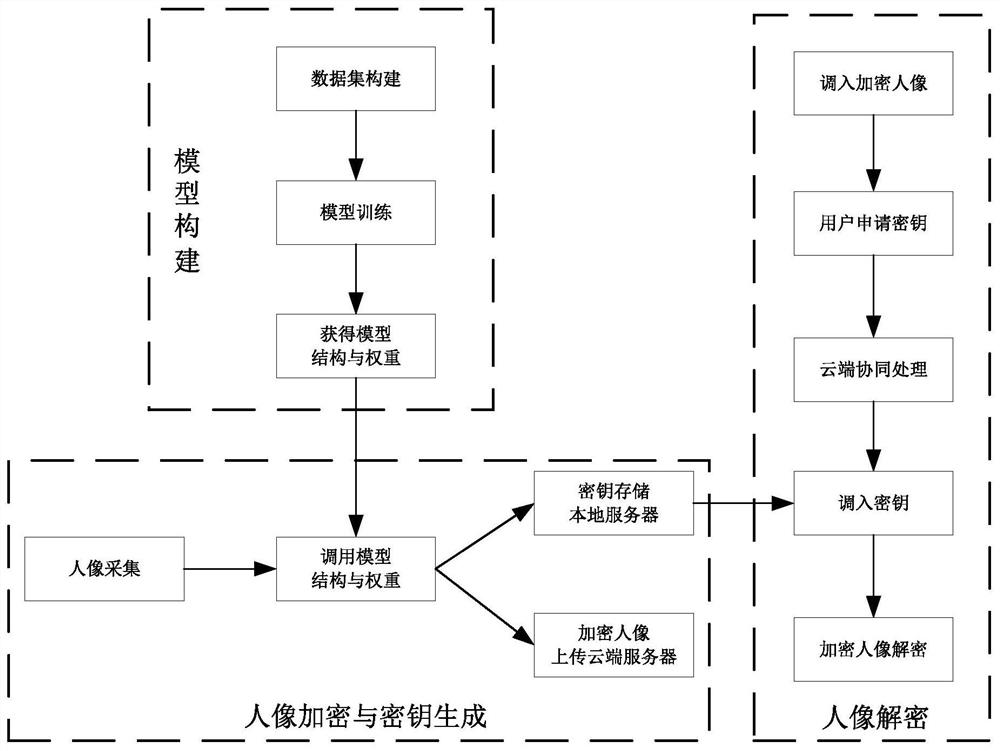
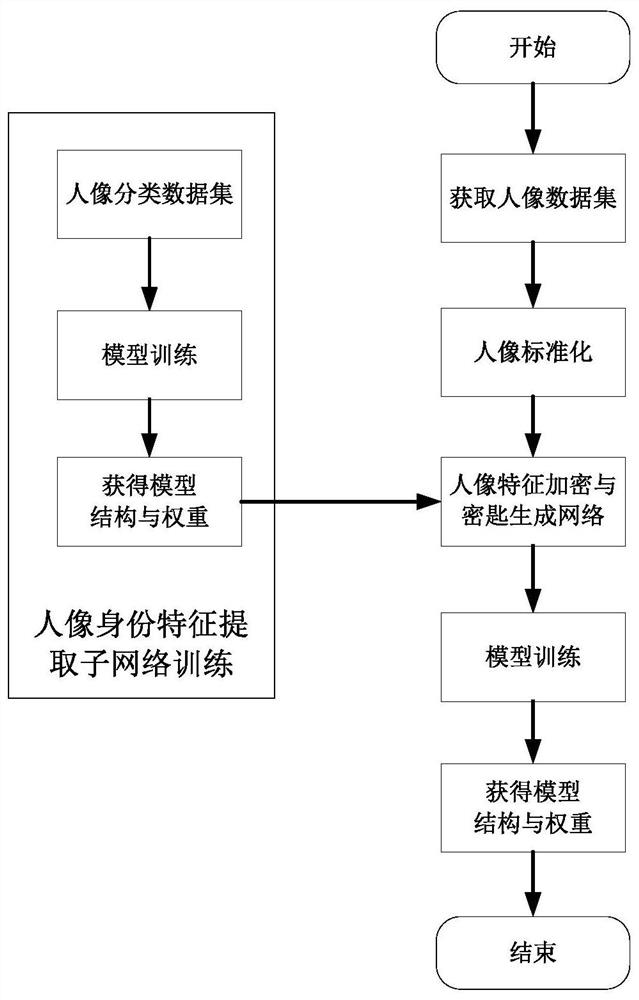
The invention discloses a portrait biological characteristic privacy protection and decryption method. The method comprises the following steps: constructing and training a portrait encryption and keygeneration network model, extracting portraits and corresponding identity information as input of the network model according to annotation information of a face database, and training a designed network by utilizing constructed data to finally obtain network model weights; actual portrait encryption and key storage: performing encryption and key generation on the actually acquired portrait by using the network model, and separately storing the encrypted portrait and the key; and decrypting the encrypted portrait, and cooperatively processing a decryption task of the user by the cloud serveraccording to a decryption demand of the user side. According to the method, a deep learning network technology is applied to portrait encryption to generate encrypted portraits with similar visual effects; the encrypted portrait and the secret key are stored separately, and the user is assisted to decode the portrait in a cloud cooperative processing mode, so that the possibility of information leakage can be reduced, and rapid decryption of the user is realized.
Owner:SOUTH CHINA UNIV OF TECH
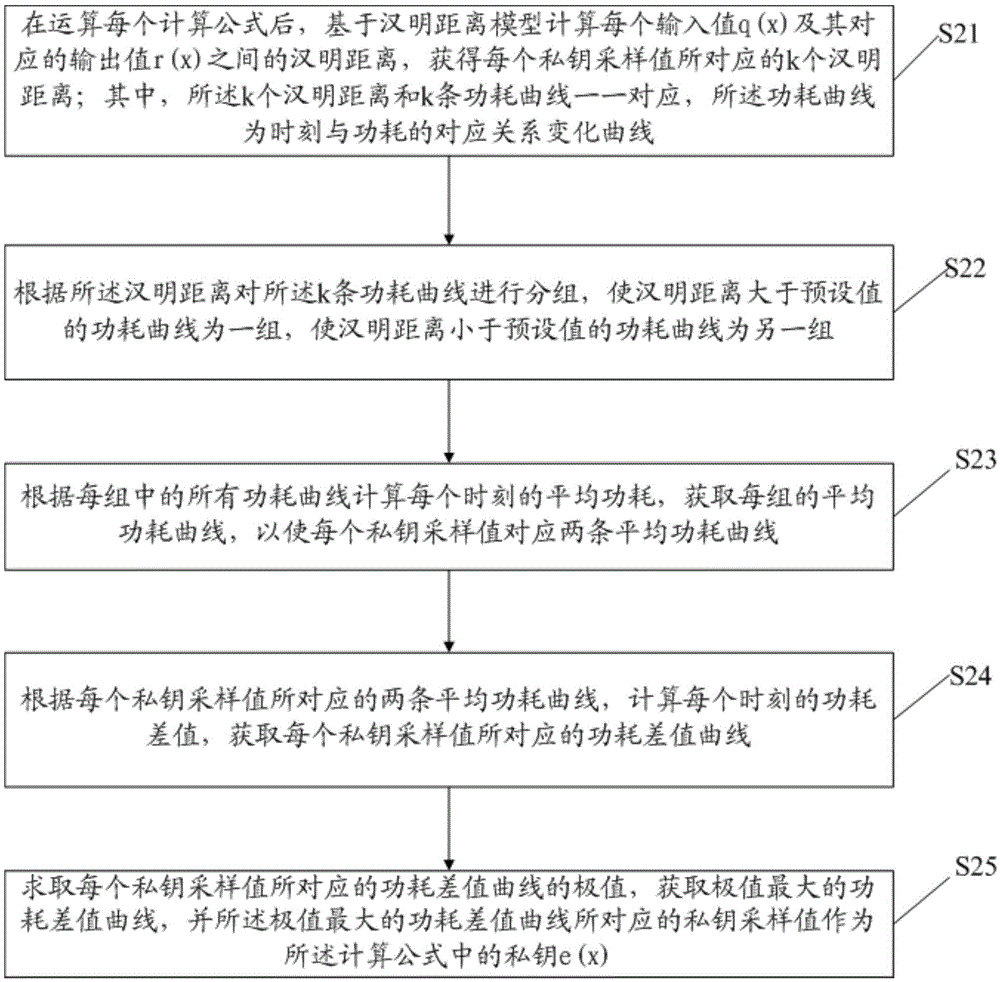
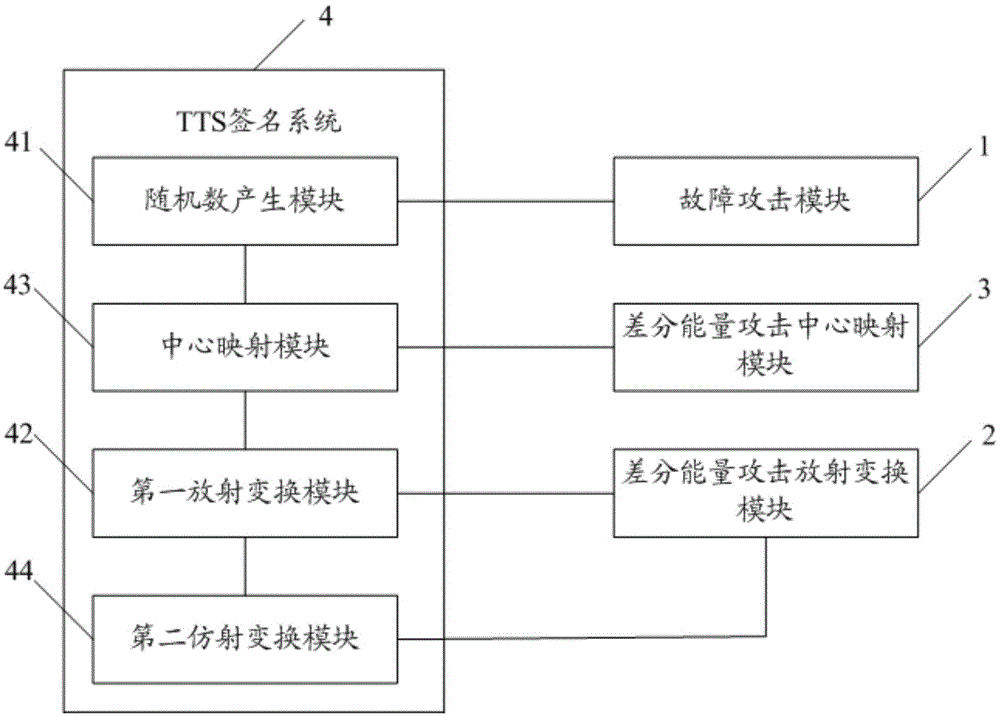
Decryption method for TTS signature
InactiveCN105530091ADecryption implementationImprove decryption efficiencyKey distribution for secure communicationTheoretical computer scienceHamming distance
The invention discloses a decryption method for a TTS signature, comprising steps of obtaining a calculation formula in the TTS signature algorithm, successively choosing numerical values in a set as private key sampling values in the calculation formula, successively choosing the numerical value from the set as an input value of the calculation formula to perform operation when each private key sampling value is chosen so as to obtain the power consumption curve generated during the operation process, wherein the set is ((00...0)2, (00...1)2, ...,(11...1)2), and adopting a differential energy attack method based on a Hamming distance model to perform analysis on the power consumption curve to obtain the private key in the TTS signature algorithm. The embodiment of the invention can improve the decryption efficiency of the TTS signature.
Owner:易海博
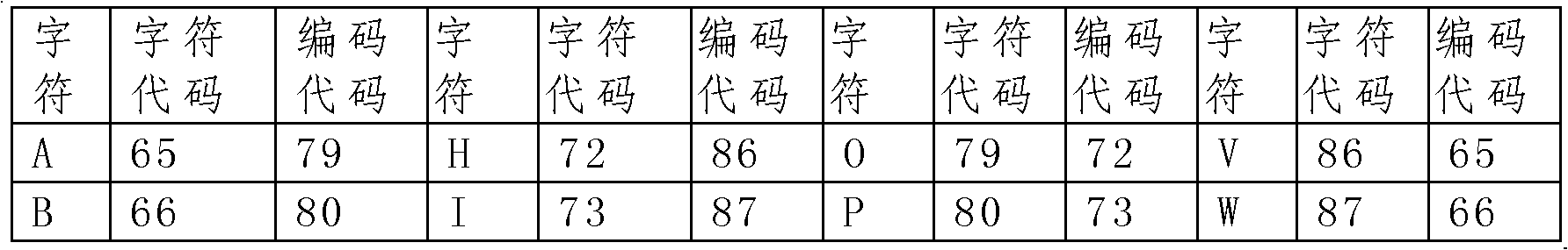
Electronic document security device
InactiveCN102096789AWithout compromising securityImprove confidentialityDigital data protectionCode generationElectronic document
The invention discloses an electronic document security device. The device comprises a code generation module, an encryption / decryption module, a code loading module, a code storage module, and a computer with an editing device, wherein the code storage module can store more than one encrypted code table; each encrypted code table is generated previously or immediately by the code generation module according to character codes in a universal code table; and the encrypted code table is irregular, i.e., the coding codes in the encrypted code table have no mathematical rule with the character codes. The electronic document security device has the advantages of extremely high security, safety, convenience and generality.
Owner:SHANGHAI DIAIBI CHEM TECH
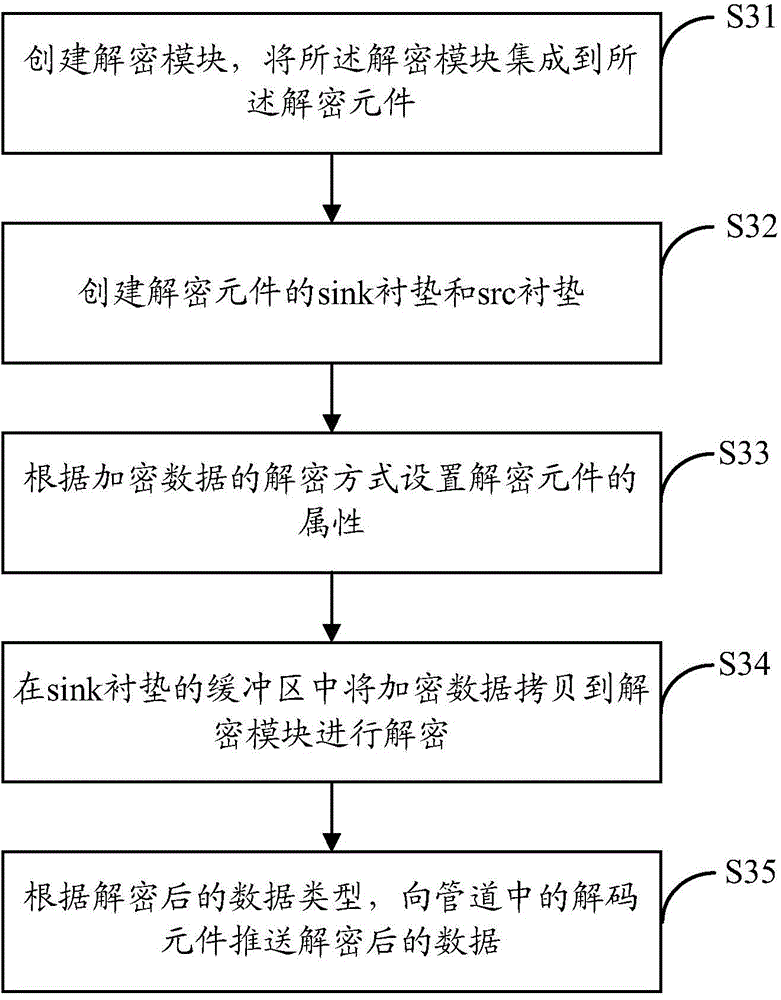
Method and device for decrypting and encrypting data by Gstreamer
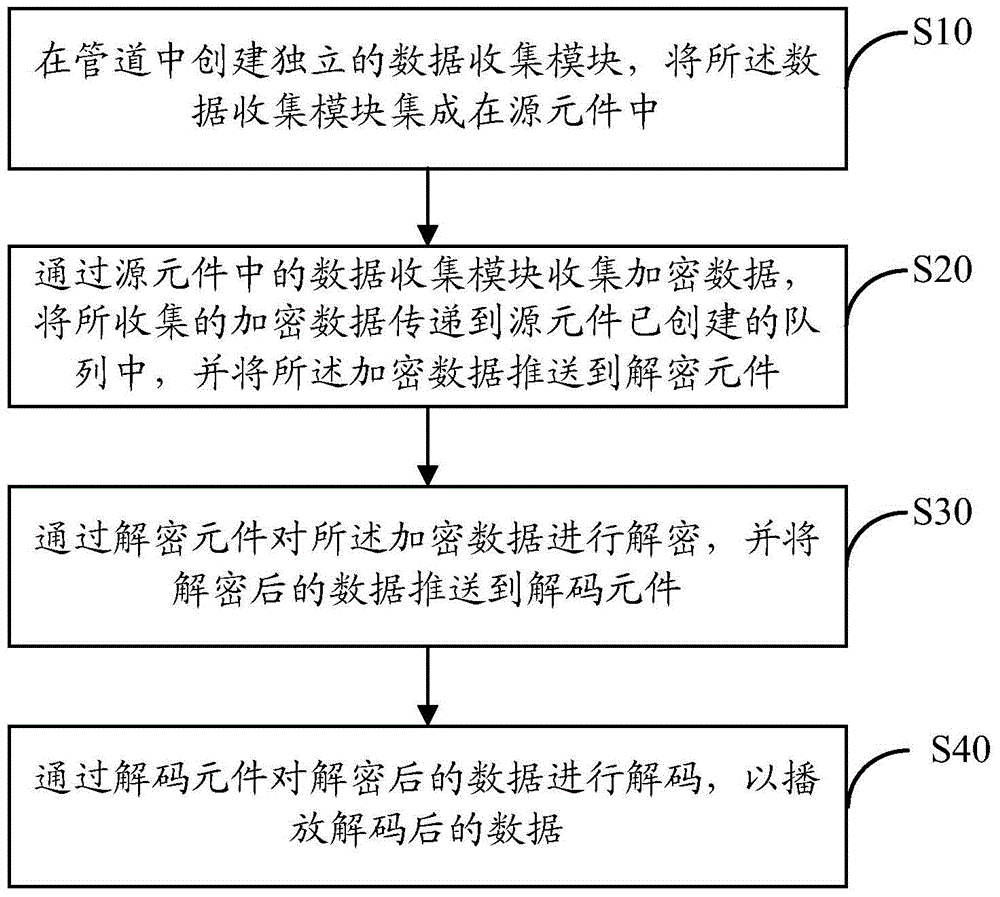
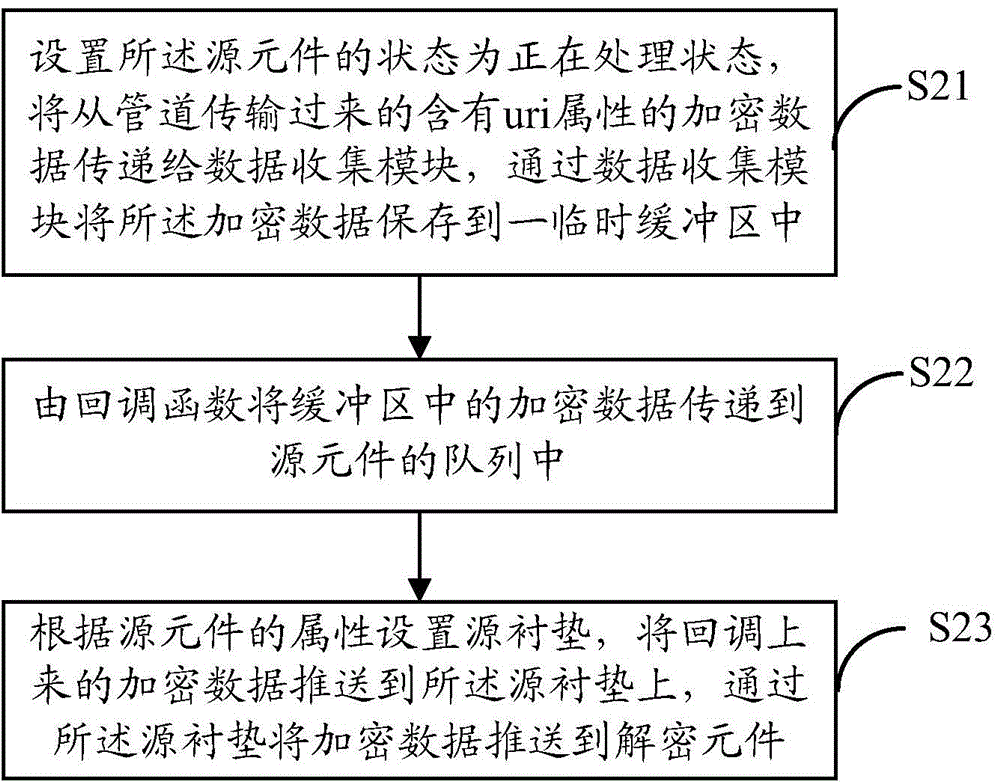
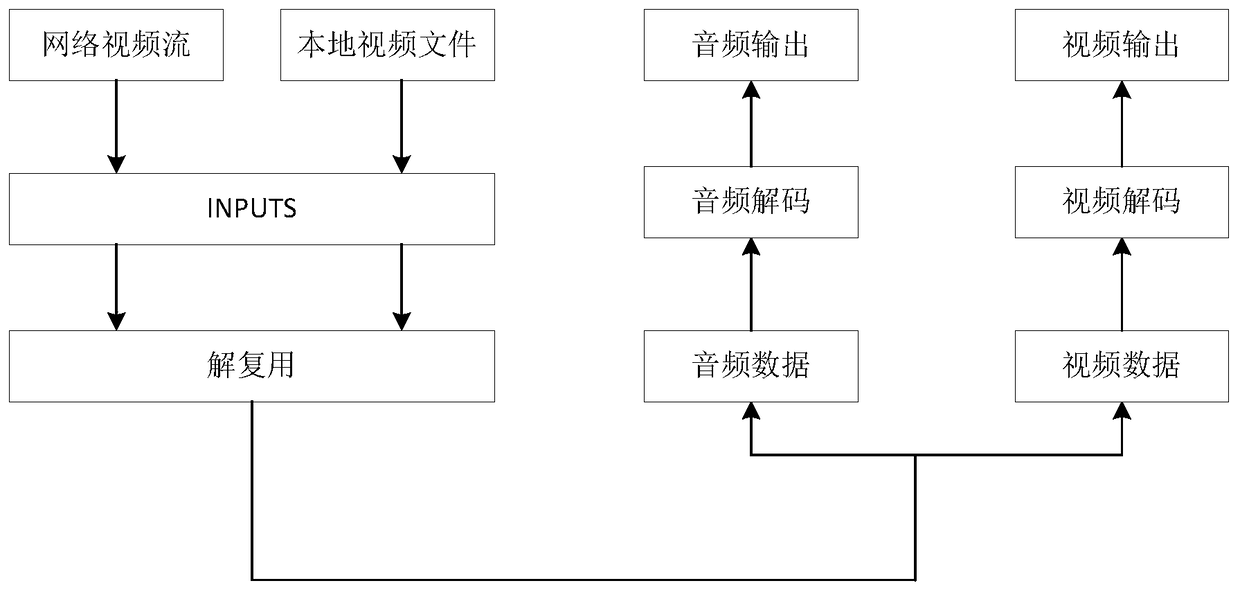
ActiveCN105763938ADecryption implementationNormal playSelective content distributionComputer hardwareData harvesting
The present invention discloses a method for decrypting and encrypting data by a Gstreamer. The method comprises a step of creating an independent data collection module in a pipeline, integrating the independent data collection module into a source element, collecting encrypted data through the data collection module, transmitting the collected encrypted data into the queue of the source element, and pushing the encrypted data to a decrypting element, a step of decrypting the encrypted data by the decrypting element, and pushing the decrypted data to a decoding element, and a step of decoding the decrypted data by the decoding element so as to play the decoded data. The invention also discloses a corresponding device for decrypting and encrypting data by a Gstreamer. According to the method and the device, the downloaded encrypted data can be normally played in the pipeline, the decryption of the encrypted data is realized, and the pipeline can normally play the encrypted data.
Owner:SHENZHEN TCL DIGITAL TECH CO LTD
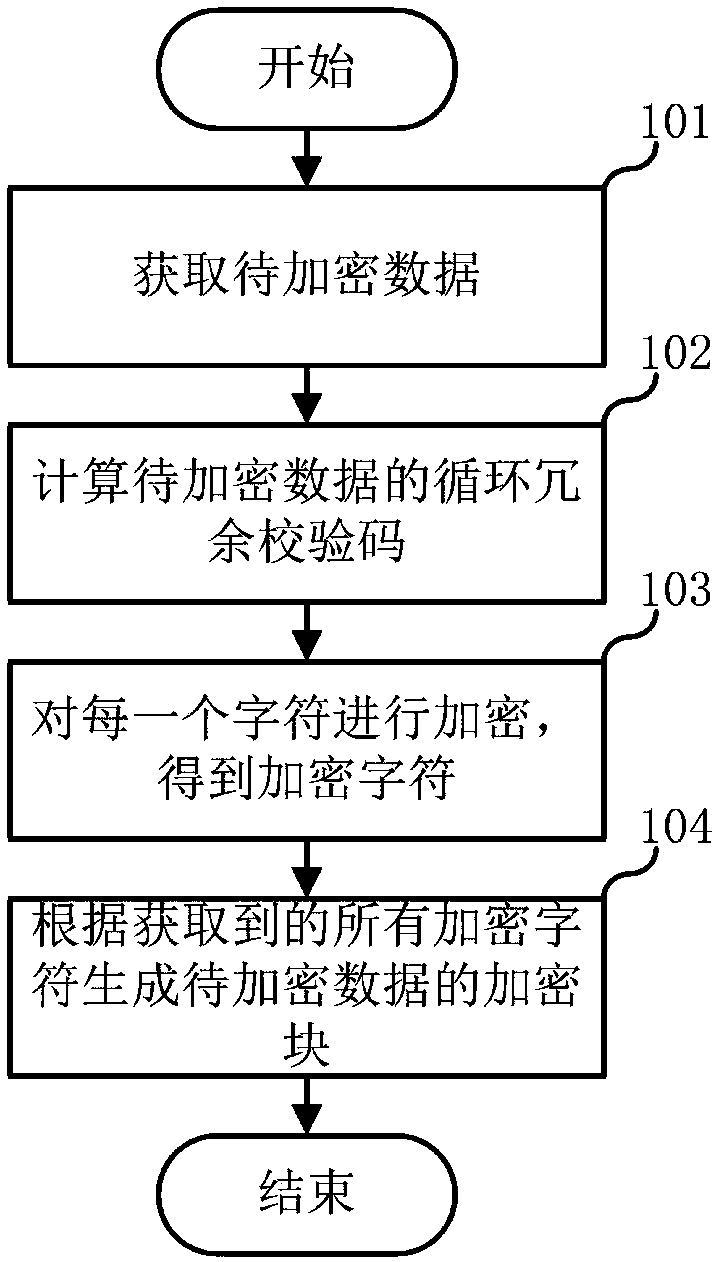
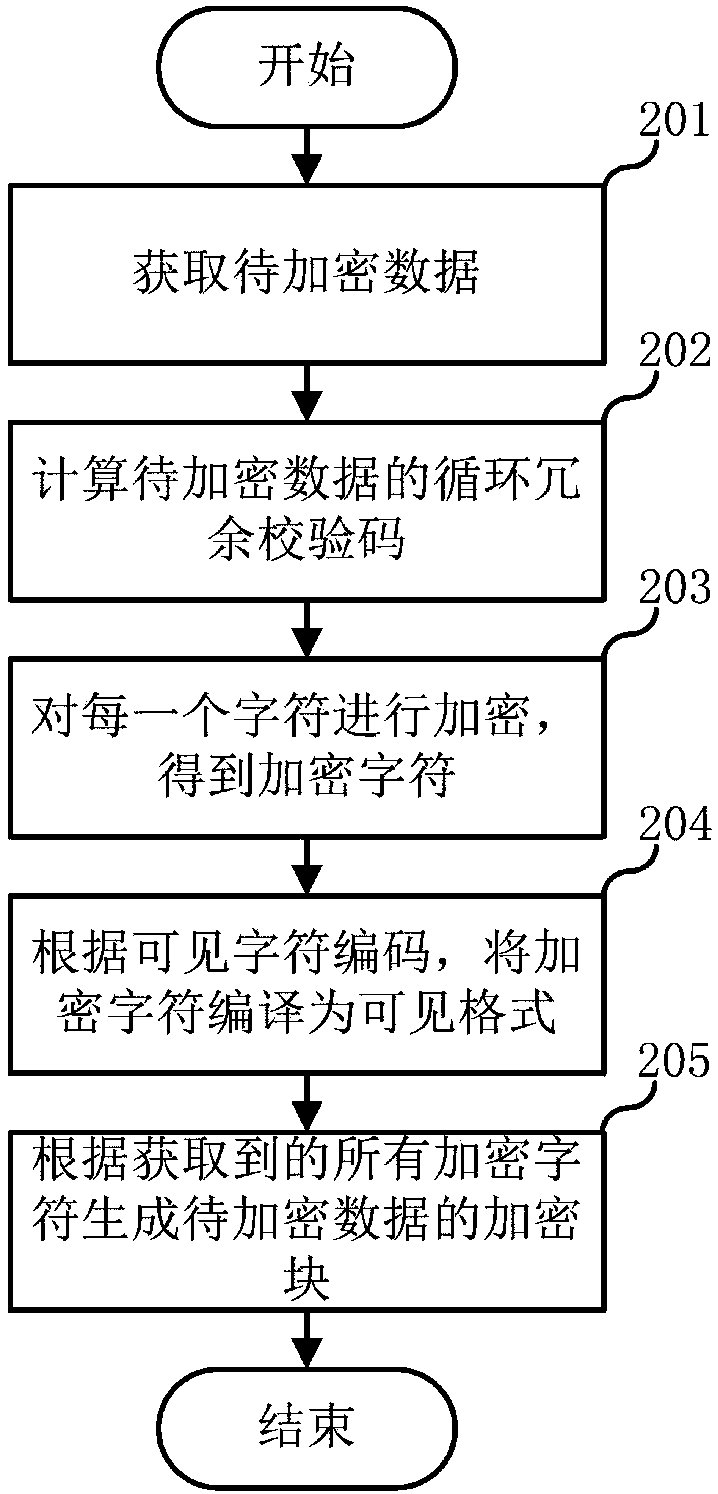
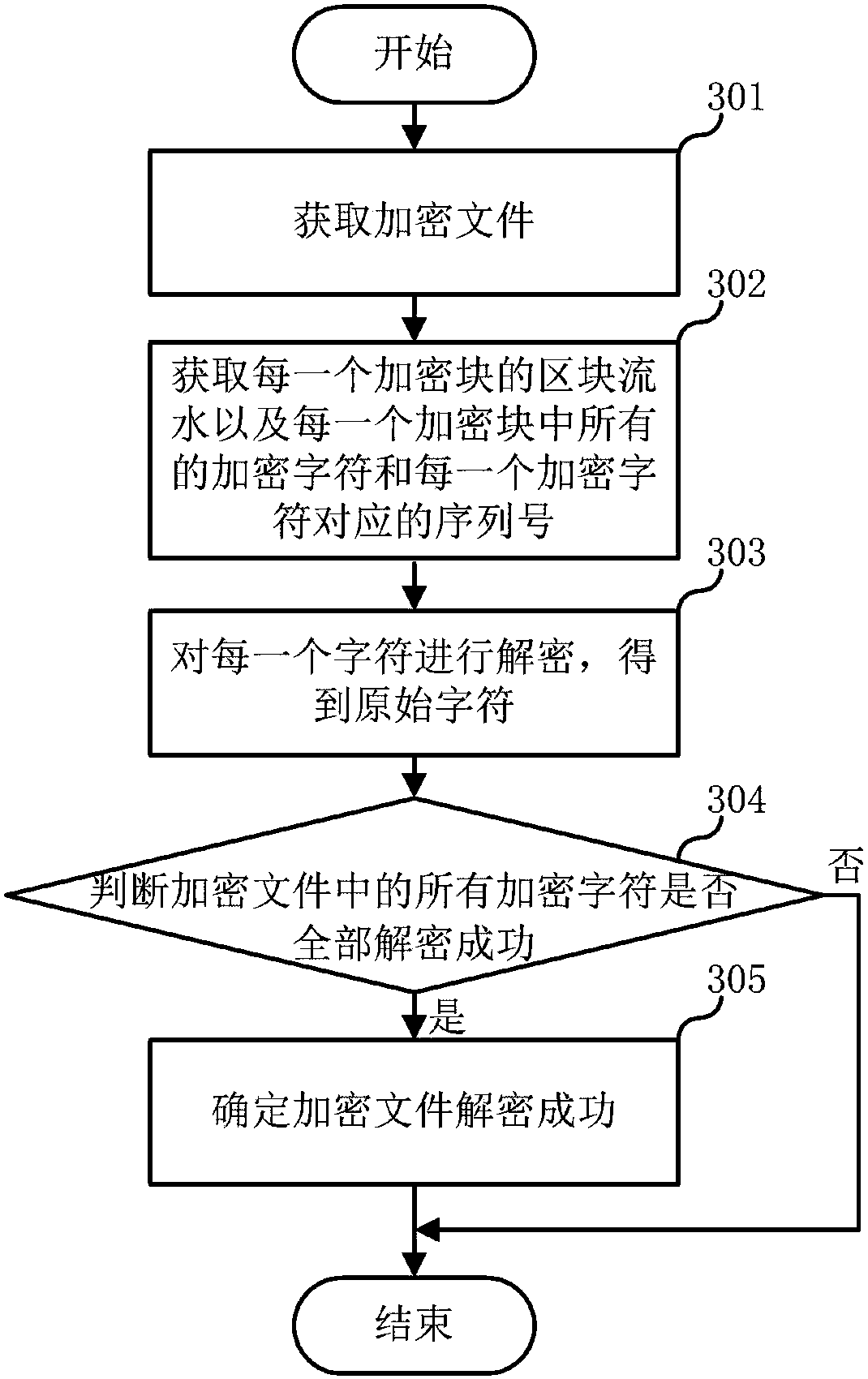
Data encryption method, data decryption method and related devices
ActiveCN108173885AAvoid destructionPrevent tamperingError preventionInformation processingRandom parameters
The invention relates to the technical field of information processing, and discloses a data encryption method, a data decryption method and related devices. The data encryption method comprises the steps that to-be-encrypted data is obtained, a block running number is assigned to the to-be-encrypted data, serial numbers are assigned to all characters in the to-be-encrypted data and a stray parameter is assigned to each character; a cyclic redundancy check code of the to-be-encrypted data is calculated, and the following operations are carried out on each character: based on a DES encryption algorithm, a fixed code corresponding to each character is calculated according to the cyclic redundancy check code, block running number, character, and serial number corresponding to the character ofthe to-be-encrypted data, and according to the fixed code and the stray parameter corresponding to the character, the character is encrypted to obtain an encryption character; each encryption character is obtained sequentially, and according to all encryption characters, an encryption block of the to-be-encrypted data is generated. The data encryption method and the data decryption method can effectively prevent leveling data from being damaged and tampered.
Owner:NAT GEOMATICS CENT OF CHINA
Data encryption method and device, and terminal
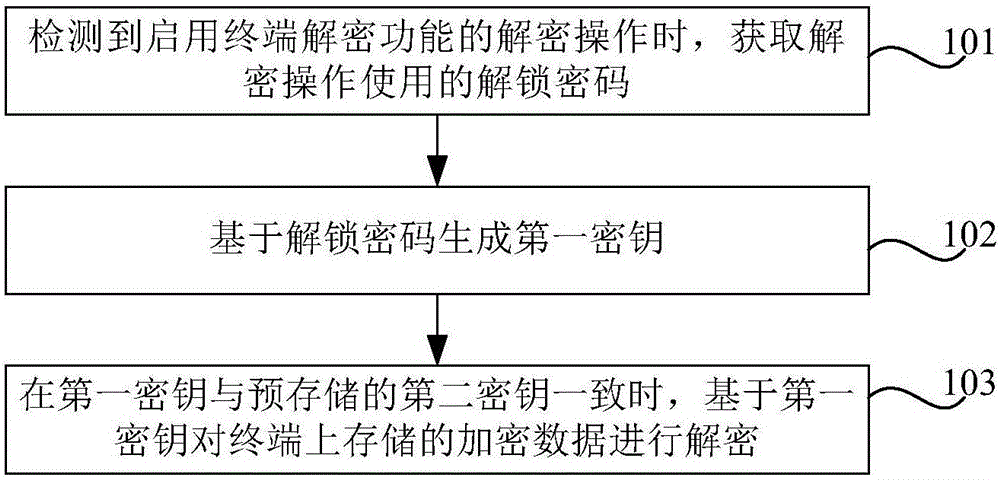
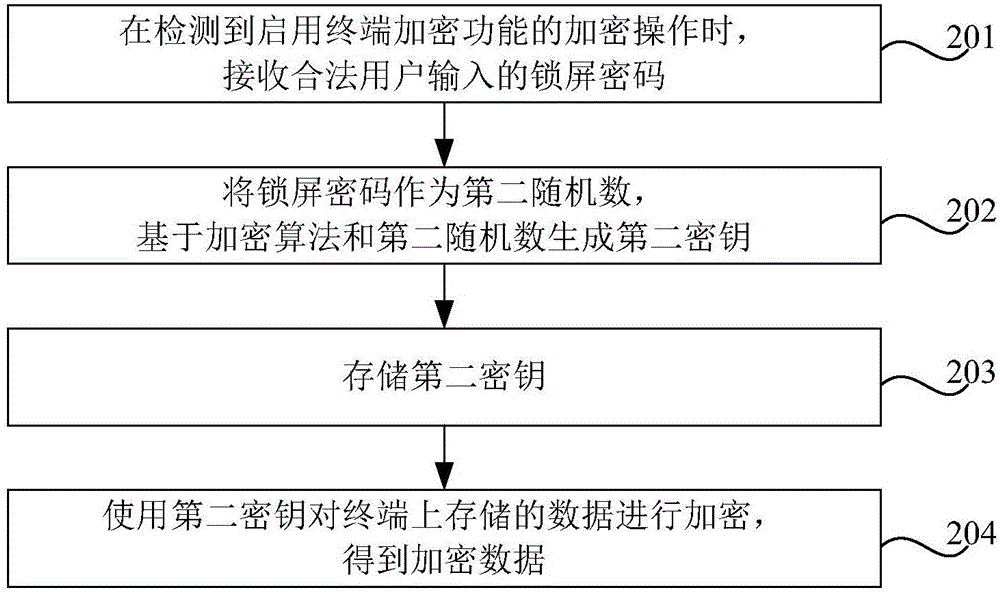
InactiveCN106789070AImprove data securityImprove user experienceKey distribution for secure communicationUser identity/authority verificationData securityLock screen
The invention provides a data encryption method and device, and a terminal. The method can comprise the following steps: when a decryption operation of enabling a terminal decryption function is detected, obtaining an unlocking password used by the decryption operation; generating a first key based on the unlocking password; and when the first key is consistent with a pre-stored second key, decrypting encrypted data stored on the terminal based on the first key, wherein the second key is generated based on a lock screen password set by a legal user. By application of the data encryption method and device provided by the embodiment of the invention, the encrypted data on the terminal are decrypted without losing any data, therefore the data security of the terminal is improved, convenience is provided for the user and the user experience is optimized.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
Method and device and system for encrypting and decrypting media content
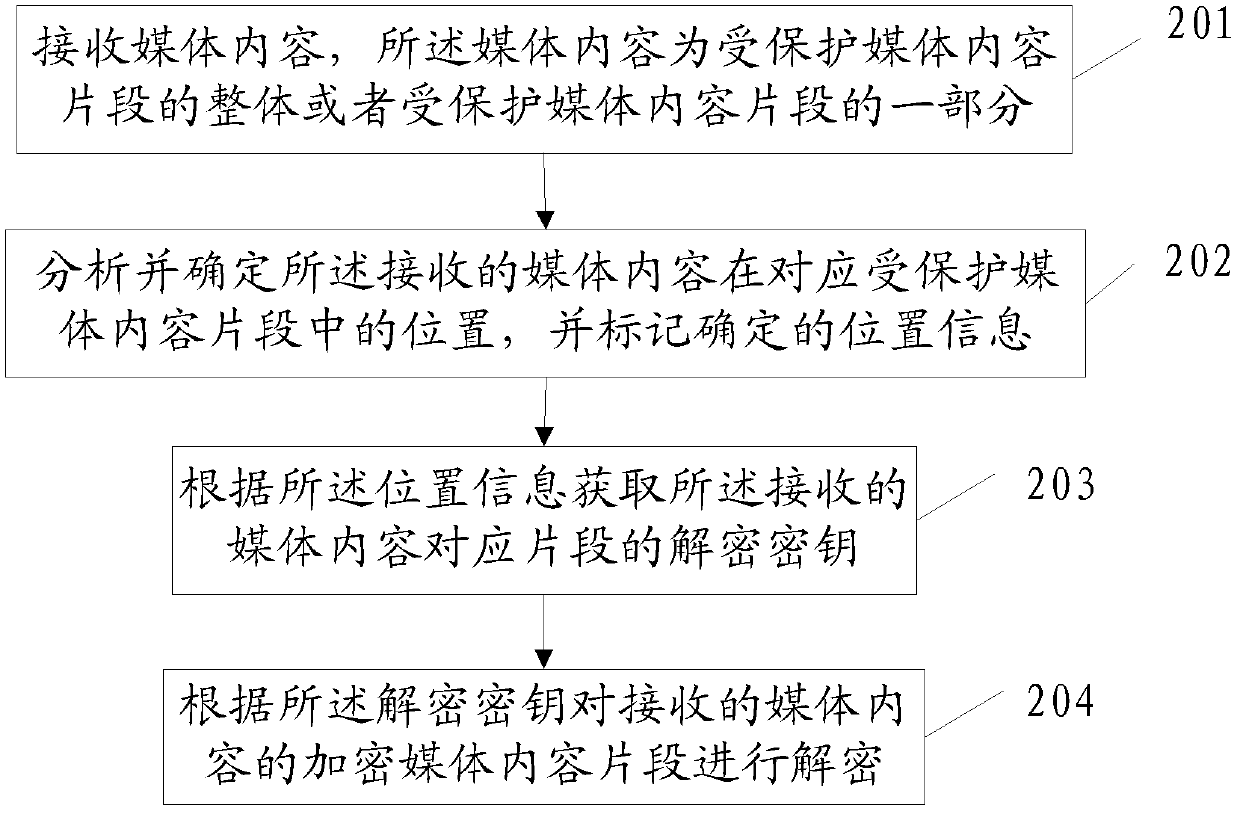
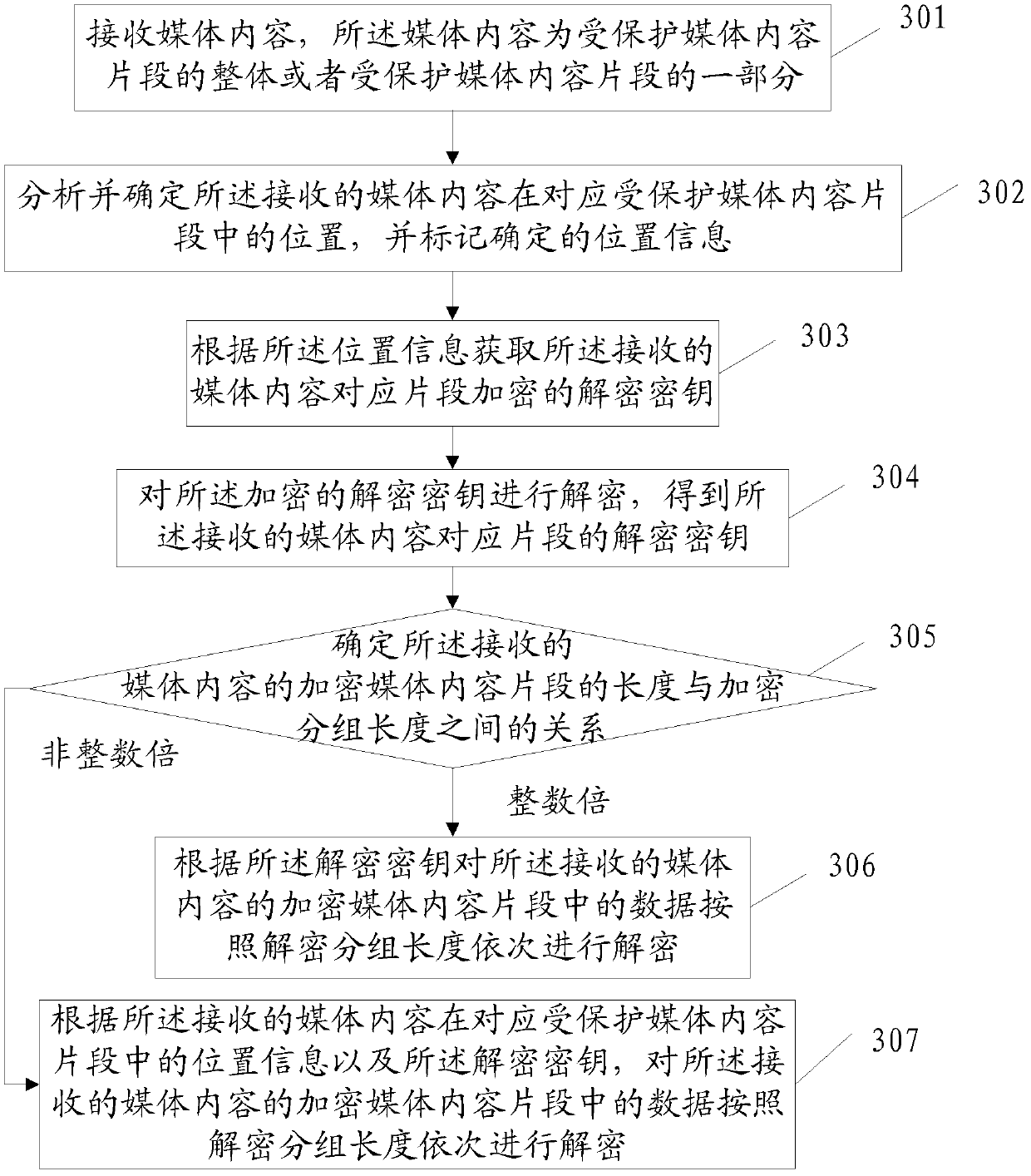
InactiveCN103297809ADecryption implementationMeet the needs of encryption operationsSelective content distributionEncryption decryptionMedia content
The invention discloses a method and device and system for encrypting and decrypting media content, and relates to the field of data encrypting and decrypting operation. The requirement for encrypting and decrypting operation with a segment as a unit can be met. The encrypting and decrypting method includes the steps that in the encrypting process, the media content is encrypted with the segment as the unit, an encryption key of the encrypted segment is stored in the head portion added for the media content segment, and the encryption key and the encrypted media content segment are sent out together. When a decryption end receives part of media content of the whole or segmental protected media content formed by the encrypted media content segment and the head portion, the position of the received media content in the corresponding protected media content segment is analyzed and determined, a decryption key of the corresponding received media content segment is obtained according to position information, and the encrypted media content segment of the received media content is decrypted according to the decryption key. The method and device and system for encrypting and decrypting the media content is mainly applied to encrypting and decrypting process of the media content with the segment as the unit.
Owner:HUAWEI TECH CO LTD
Information encryption algorithm, information encryption device, information decryption algorithm, information decryption device and communication method
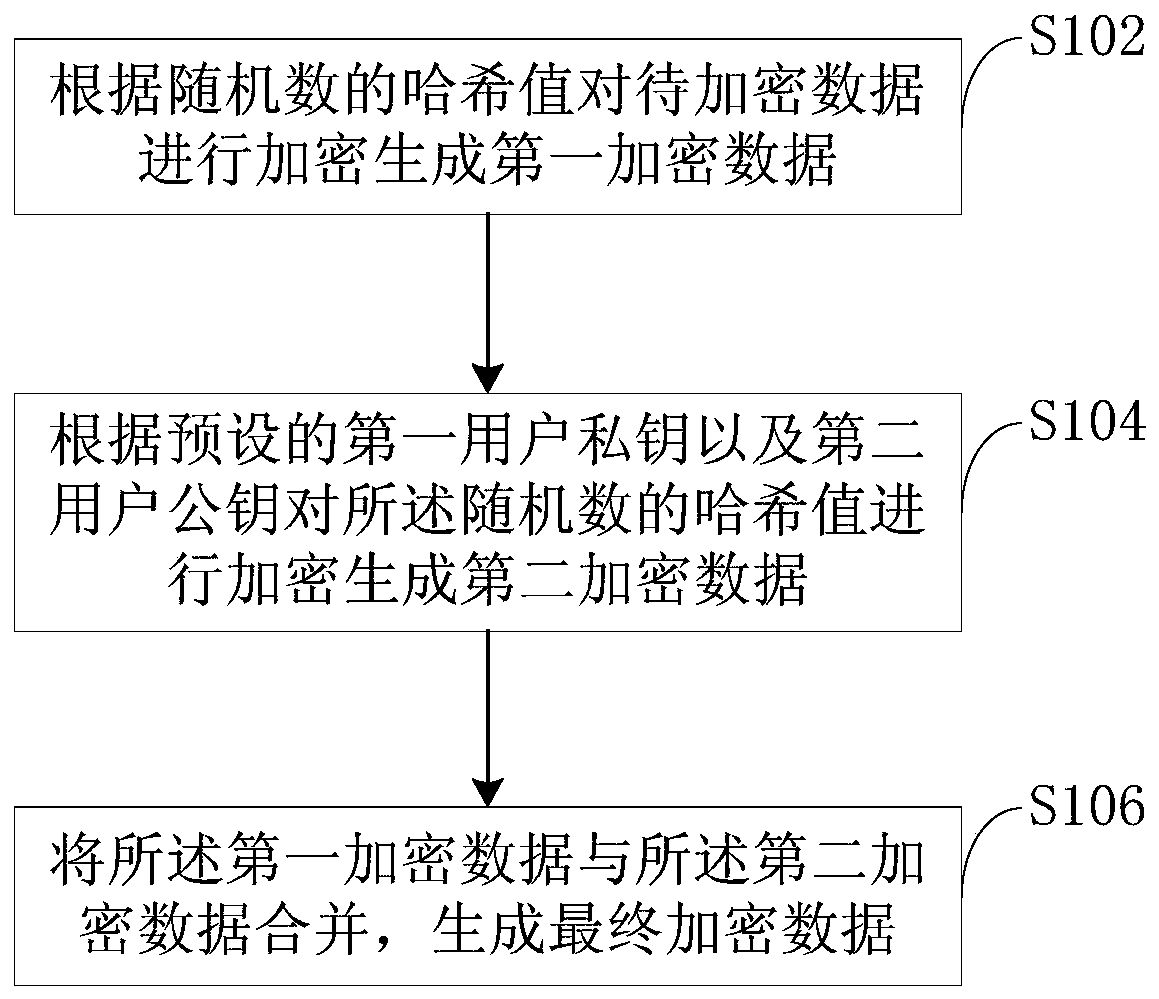
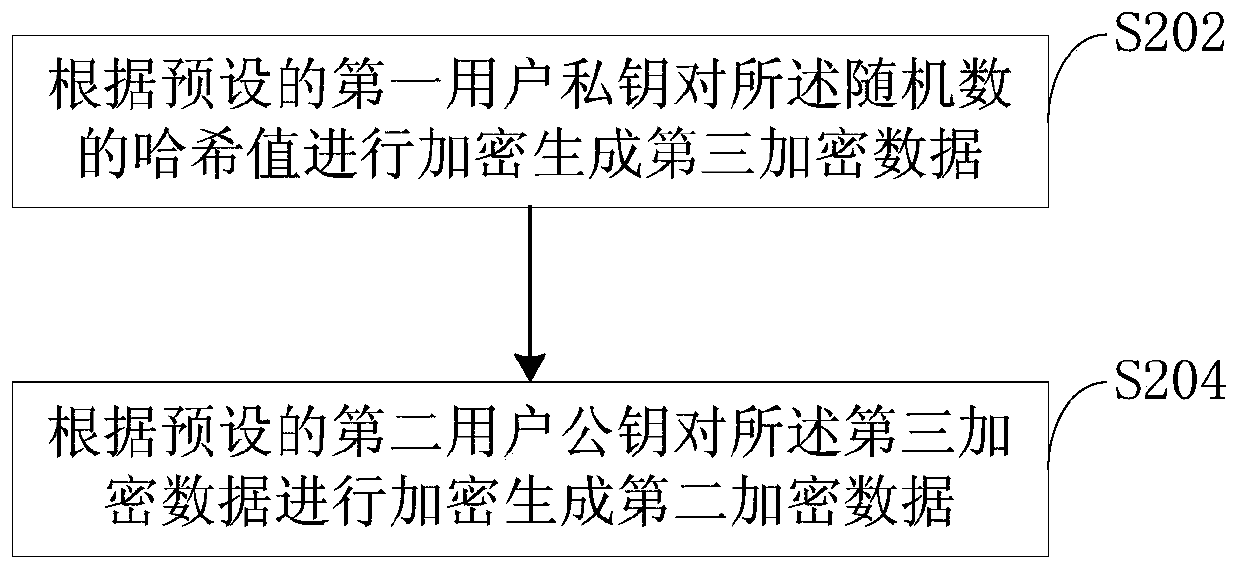
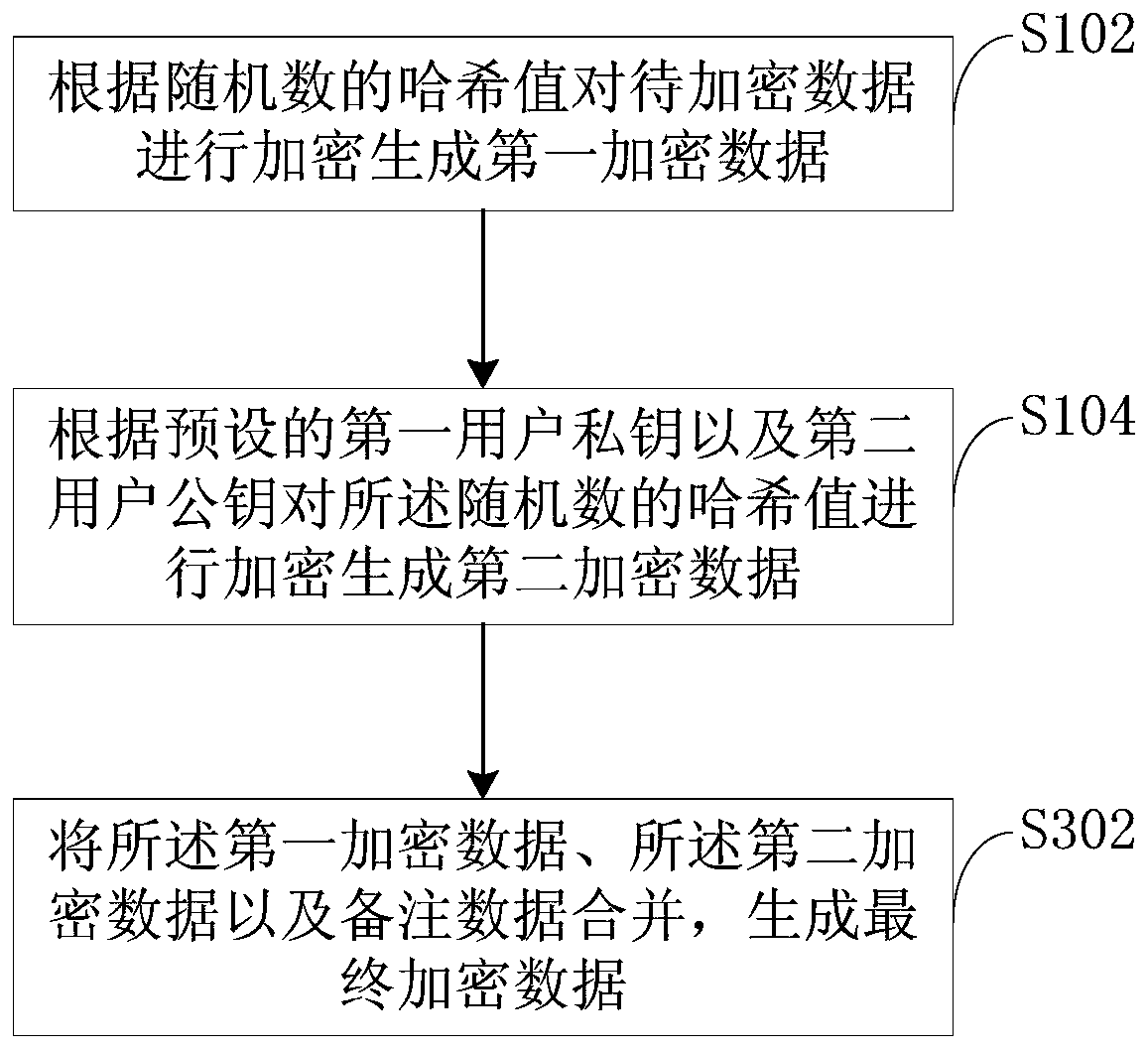
PendingCN111510282ADecryption implementationEnsure safetyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesAlgorithmTheoretical computer science
The invention is applicable to the technical field of blockchains, and relates to an information encryption algorithm, an information encryption device, an information decryption algorithm, an information decryption device, and a communication method. The information encryption algorithm comprises the following steps of: encrypting to-be-encrypted data according to a hash value of a random numberto generate first encrypted data; encrypting the hash value of the random number according to a preset first user private key and a preset second user public key to generate second encrypted data; andcombining the first encrypted data with the second encrypted data to generate final encrypted data. According to the information encryption algorithm provided by the invention, only a first user public key and a second user private key can be used for decrypting the second encrypted data and acquiring the hash value of the random number for decrypting the to-be-encrypted data, thereby realizing decryption of the encrypted data; and the second user private key is only owned by a second user serving as an information receiving end, so that the security of communication information is effectively ensured.
Owner:刘佳
Encryption method, decryption method, server and storage medium
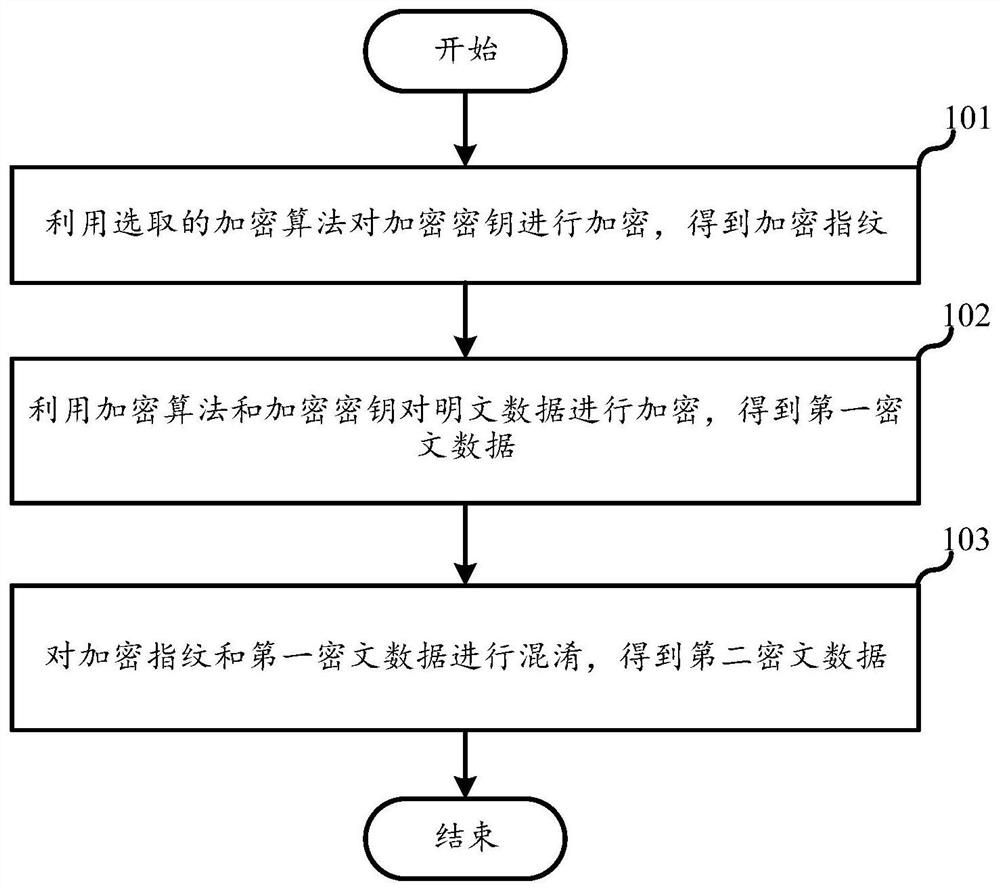
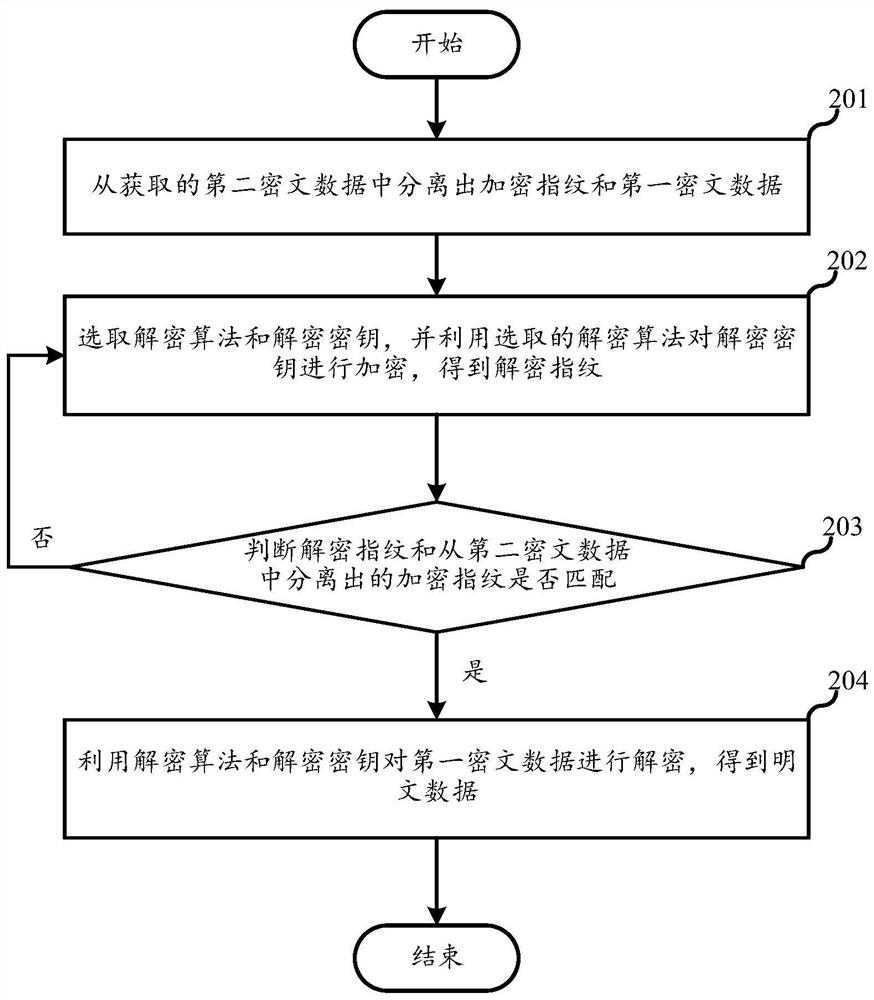
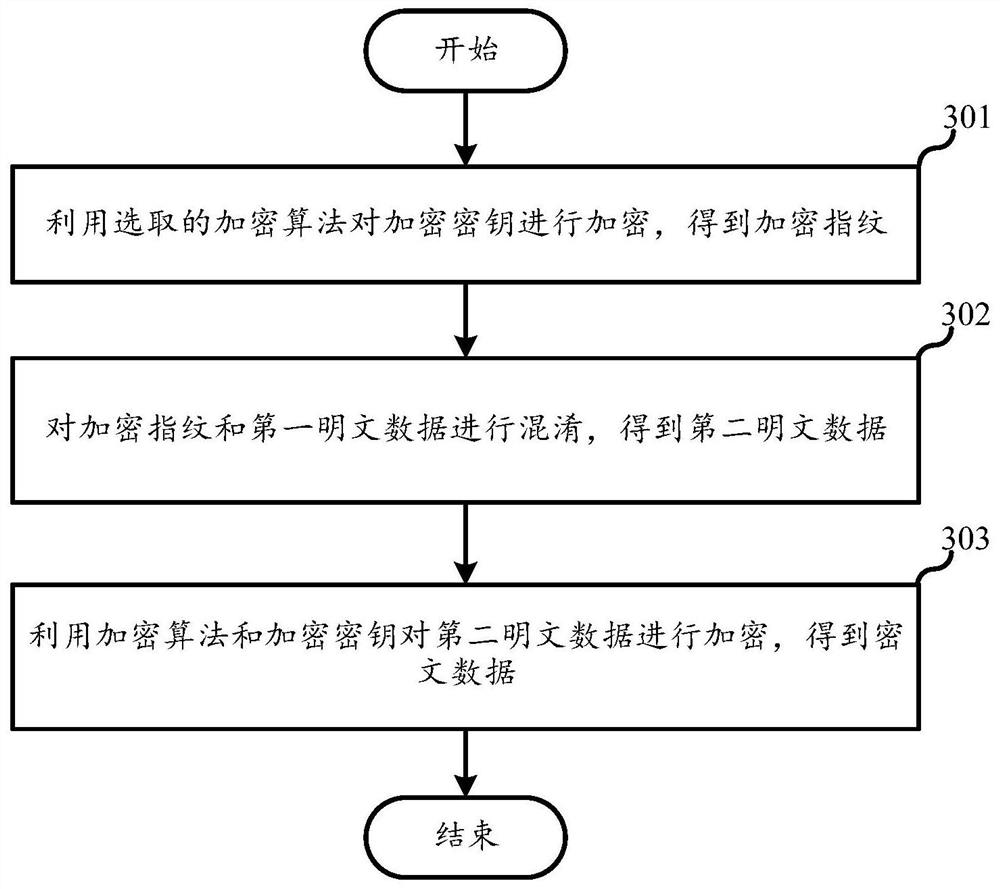
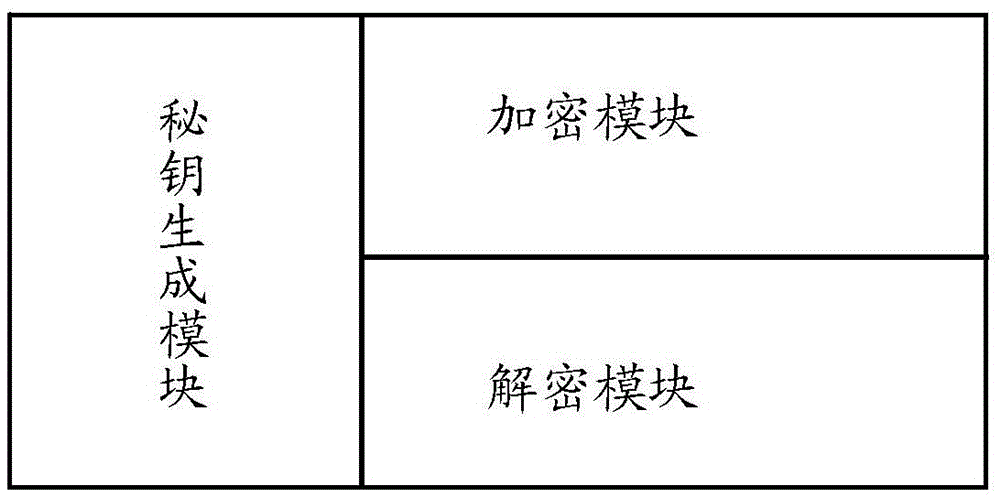
PendingCN113839780AImprove securityAvoid security issuesKey distribution for secure communicationMultiple keys/algorithms usageCiphertextTheoretical computer science
The embodiment of the invention discloses an encryption method, a decryption method, a server and a storage medium, and belongs to the field of communication. The encryption method comprises the following steps: encrypting an encryption key by using a selected encryption algorithm to obtain an encrypted fingerprint; encrypting plaintext data by using the encryption algorithm and the encryption key to obtain first ciphertext data; and mixing the encrypted fingerprint and the first ciphertext data to obtain second ciphertext data. The encryption key is encrypted by using the encryption algorithm, so the encryption key is difficult to crack, the security of the encryption key is improved, the first ciphertext data obtained by encrypting the plaintext data by using the encryption algorithm and the encryption key is difficult to crack, and the security of the data is improved; after the first ciphertext data is obtained, the encrypted fingerprint and the first ciphertext data are mixed to obtain the second ciphertext data, so the data security is improved.
Owner:ZTE CORP
Method and processor for encryption and decryption
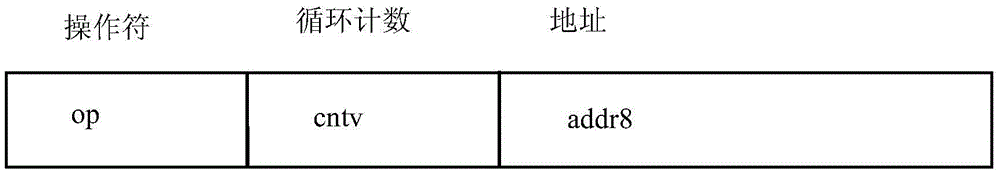
ActiveCN106888082ASimple structureDecryption implementationEncryption apparatus with shift registers/memoriesIndex registerCounting Number
The invention discloses a method and processor for encryption and decryption, relates to the encryption and decryption technology and effectively reduces the logic unit number occupied by ARS during FPGA realization. According to the method, input data is stored in an input data register, and a data storage address addr=addr1+addr8 is updated; if a reading of a cycle counter is smaller than a cycle counting number in an instruction, an index register and the cycle counter are respectively plus one, transfer to an instruction address designed by addr8 is then carried out, zero setting of the cycle counter is carried out, and cycle operation in a 0-15 scope is realized; original data of the register is stored to another register when register writing operation is simultaneously carried out, reading operation from a storage device to the register and writing operation from the register to another register is combined to one same instruction, a 16-times cycle program block is realized through six instructions, and the method is for encryption and decryption.
Owner:北京京航计算通讯研究所
Program stream decryption method, device and terminal
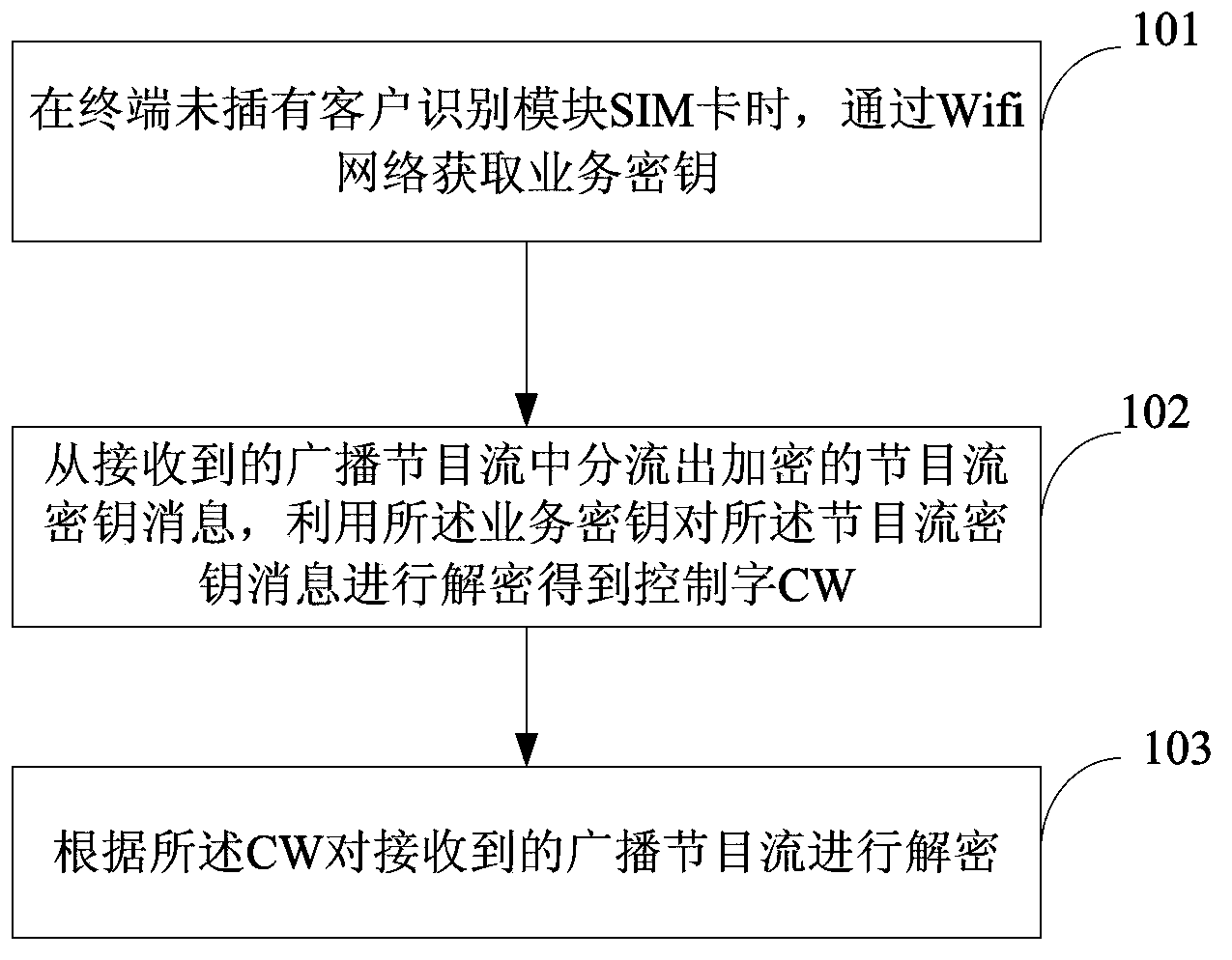
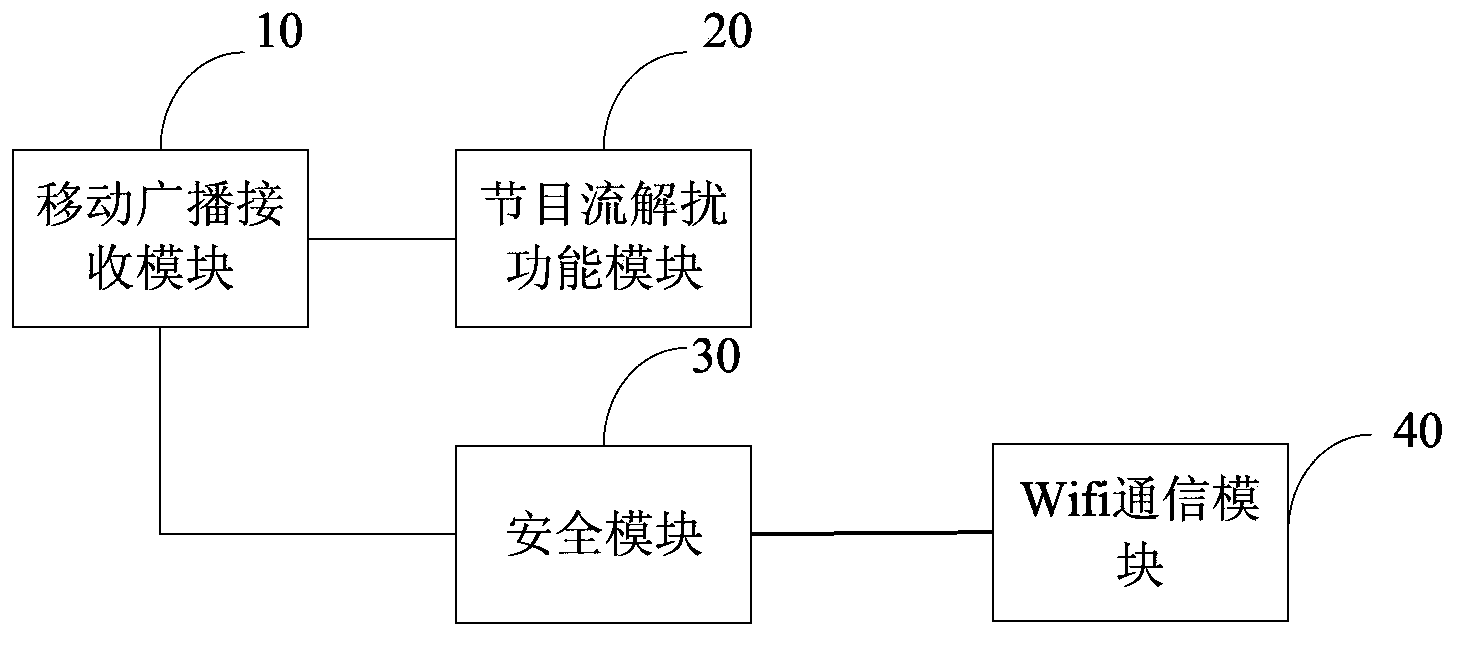
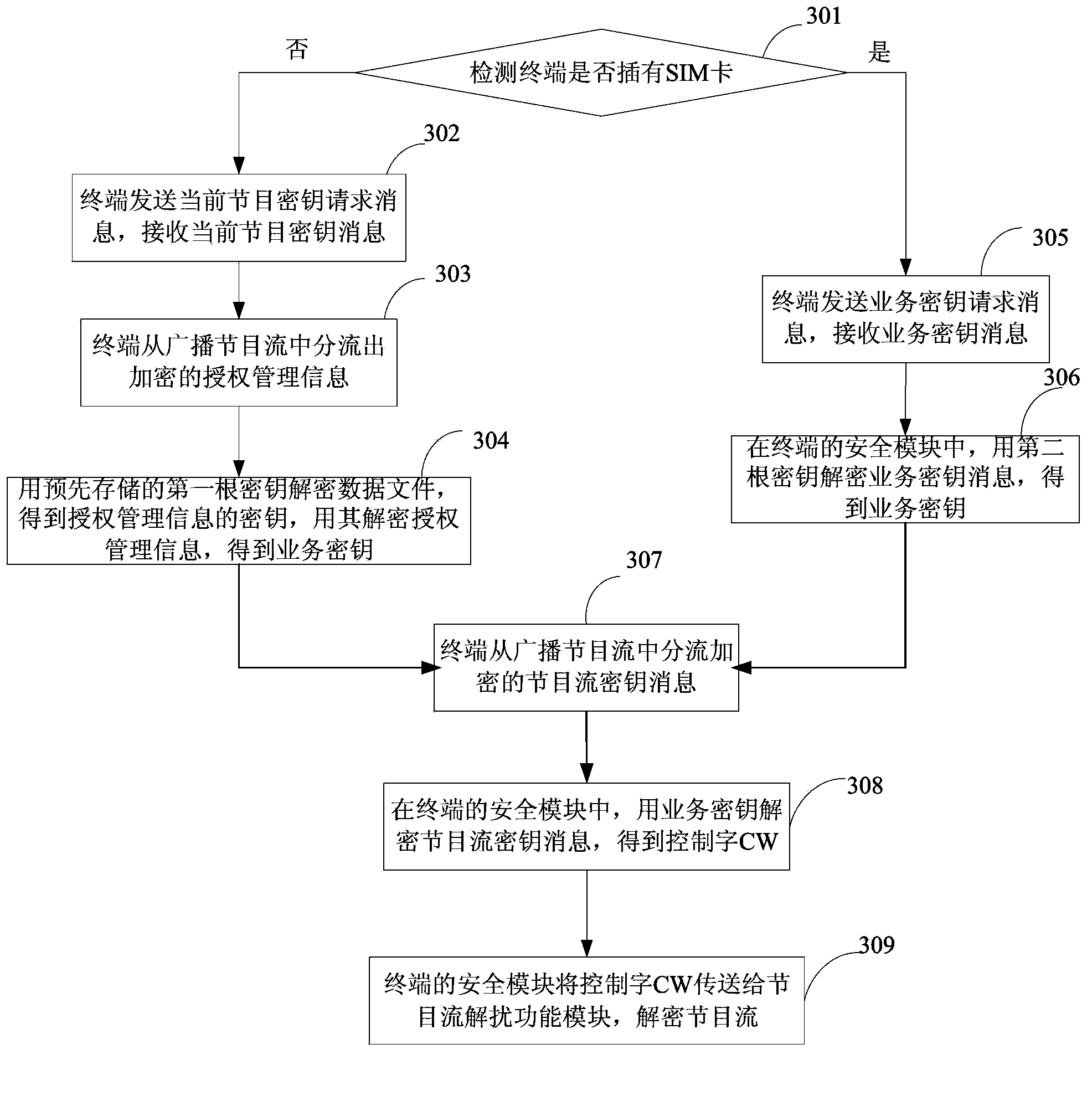
InactiveCN104104996ADecryption implementationLow retrofit costSelective content distributionWifi networkRadio program
The invention provides a program stream decryption method, a device and a terminal, belonging to the mobile broadcasting television field. The program stream decryption method comprises steps of obtaining business through Wifi network when a client identification module SIM card is not inserted in the terminal, separating the encrypted program stream secret key information from the received broadcasting program stream, utilizing the business secret key to perform decryption on the program stream secret key information to obtain a control word CW, and performing decryption on the received broadcasting programs stream according to the CW. The technical scheme of the invention enables the terminal usage not to be limited by the operator to achieve decryption of the program stream secret key and watching broadcasting programs on the premise that the terminal cost and the network device alternation cost are not increased.
Owner:CHINA MOBILE COMM GRP CO LTD
File encryption method and device and file decryption method and device
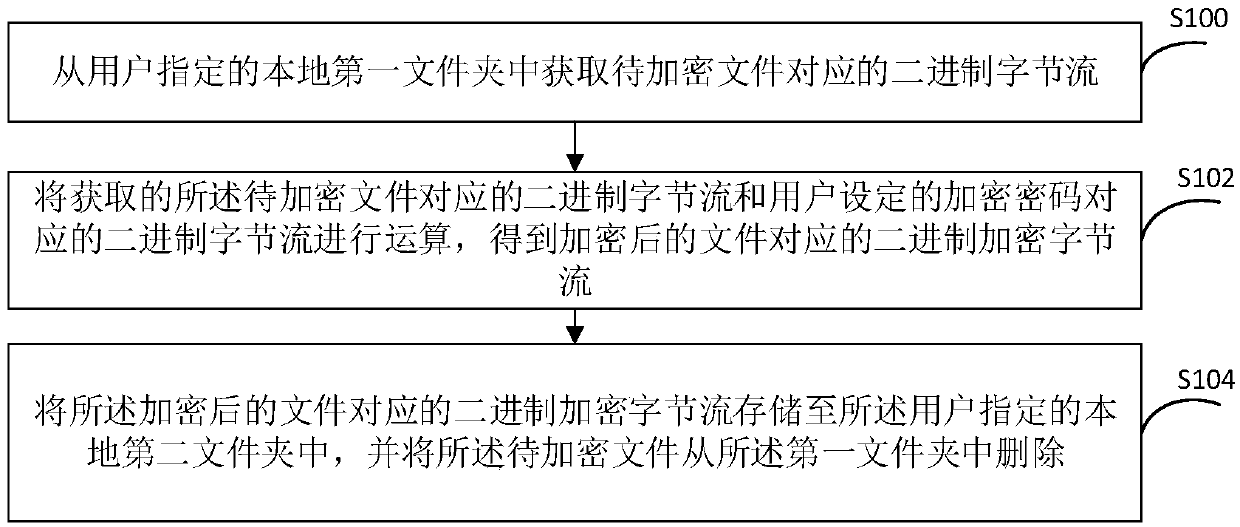
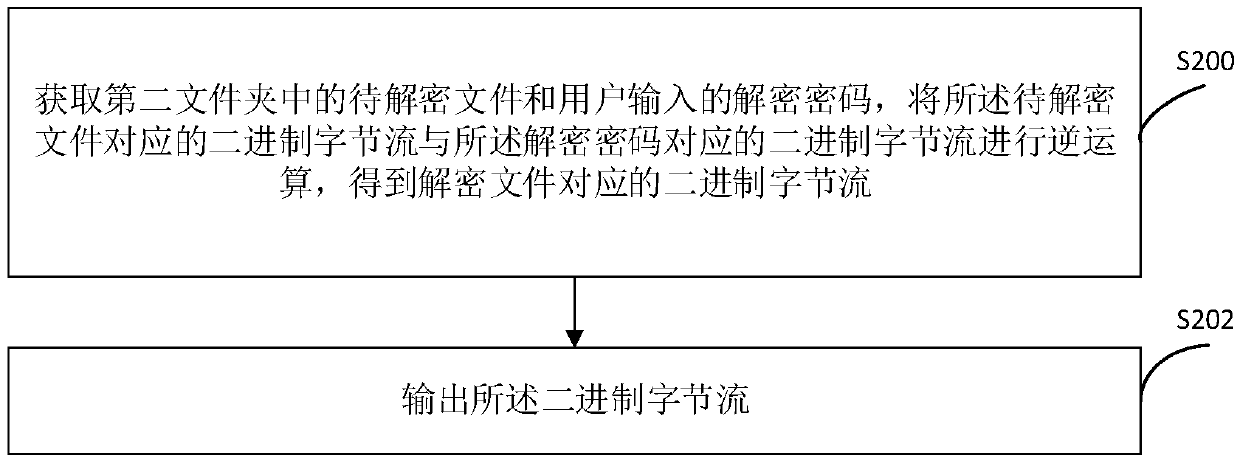
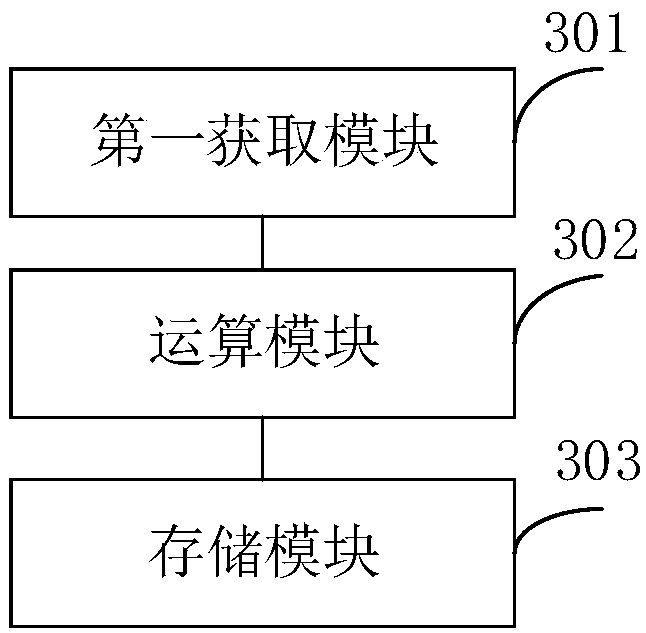
InactiveCN109670323AGood encryptionDecryption implementationKey distribution for secure communicationDigital data protectionPasswordByte
The invention provides a file encryption method and device and a file decryption method and device. The encryption method comprises the following steps of obtaining a binary byte stream correspondingto a to-be-encrypted file from a local first folder appointed by a user; performing operation on the obtained binary byte stream corresponding to the to-be-encrypted file and the binary byte stream corresponding to the encryption password set by the user to obtain a binary encryption byte stream corresponding to the encrypted file; and storing the encrypted file in a local second folder specifiedby the user, and deleting the to-be-encrypted file from the first folder. Therefore, the file can be encrypted efficiently and conveniently.
Owner:JINGUAZI TECH DEV CO LTD
Communication method and conference system for multi-party conference
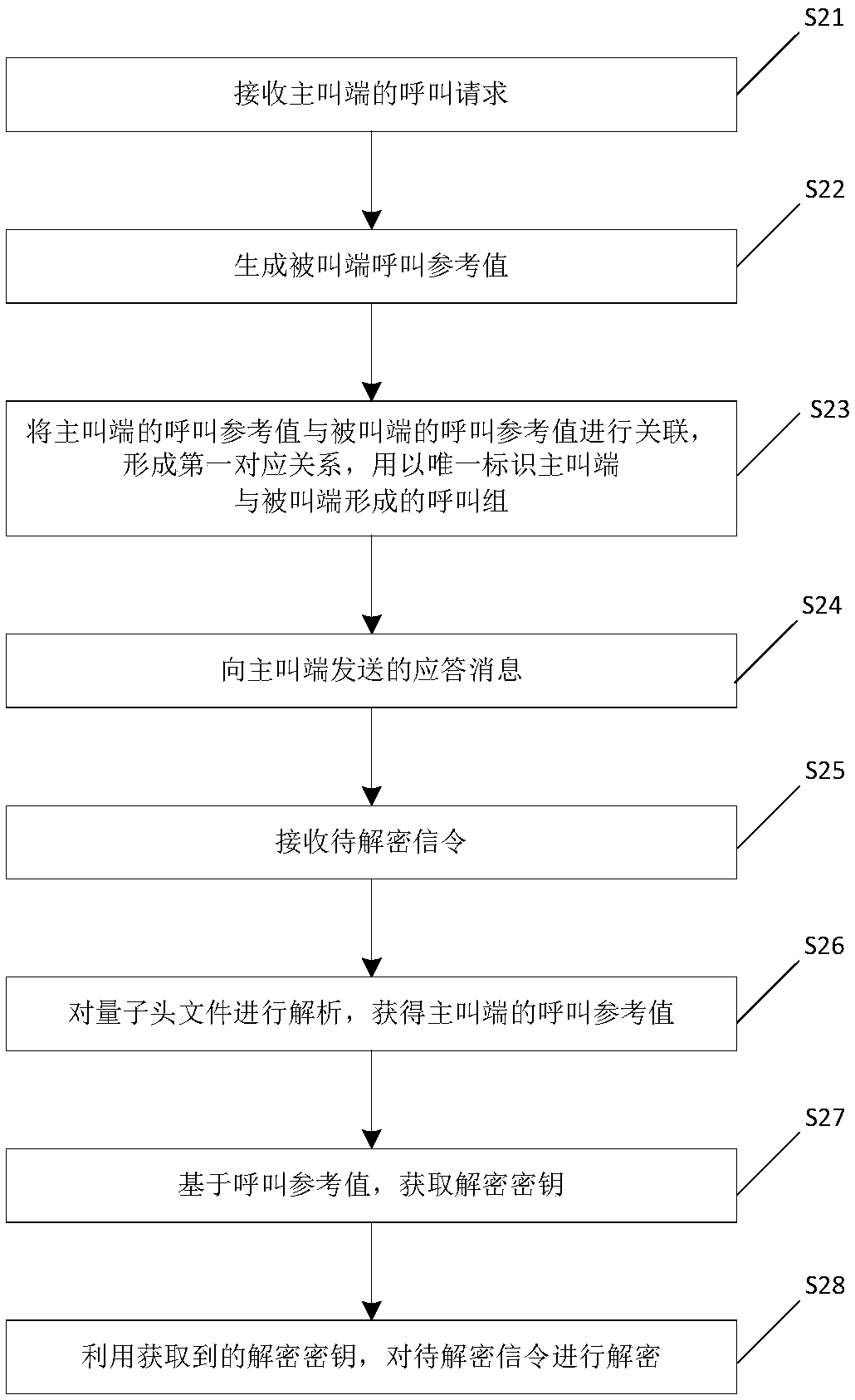
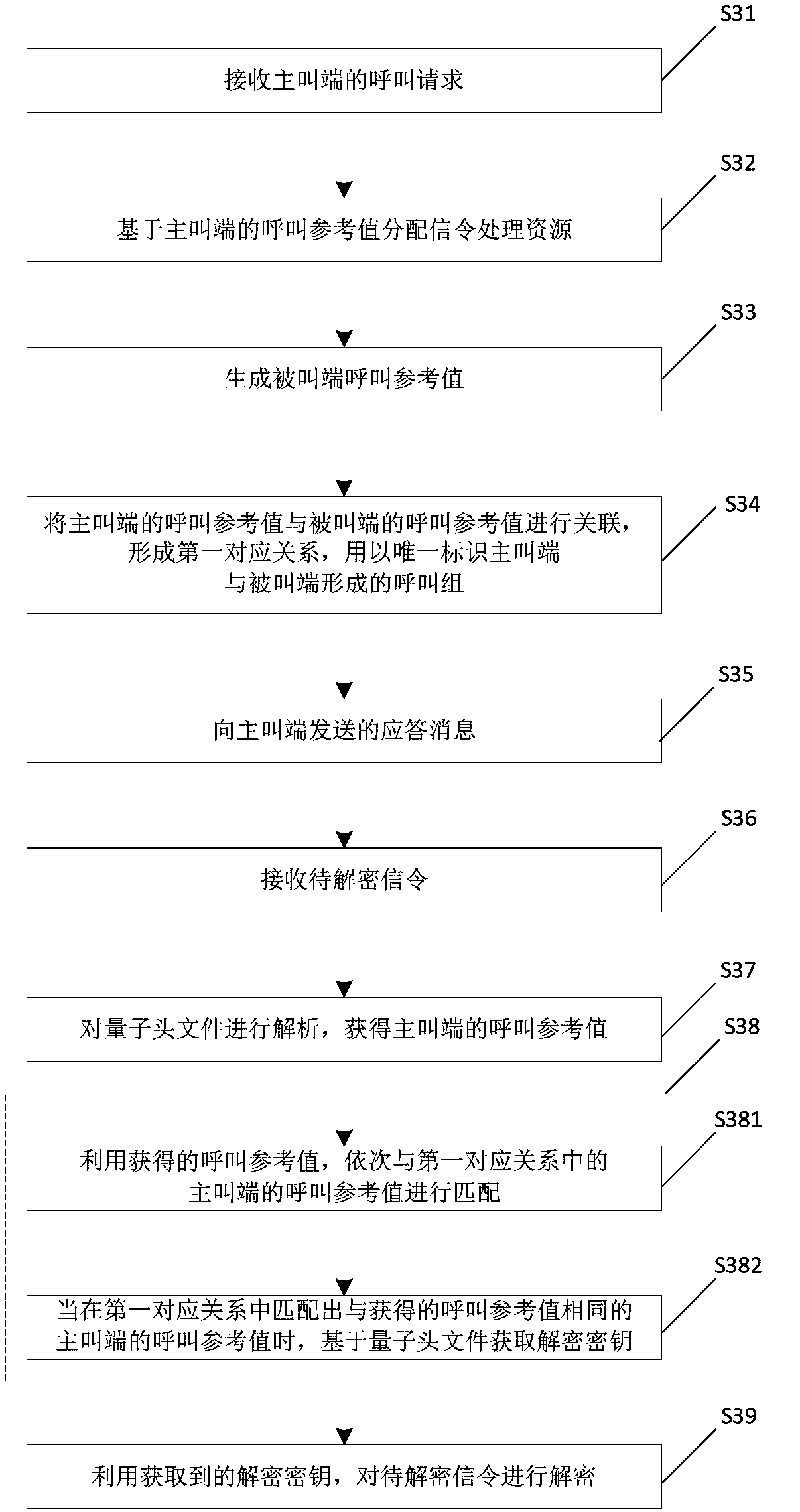
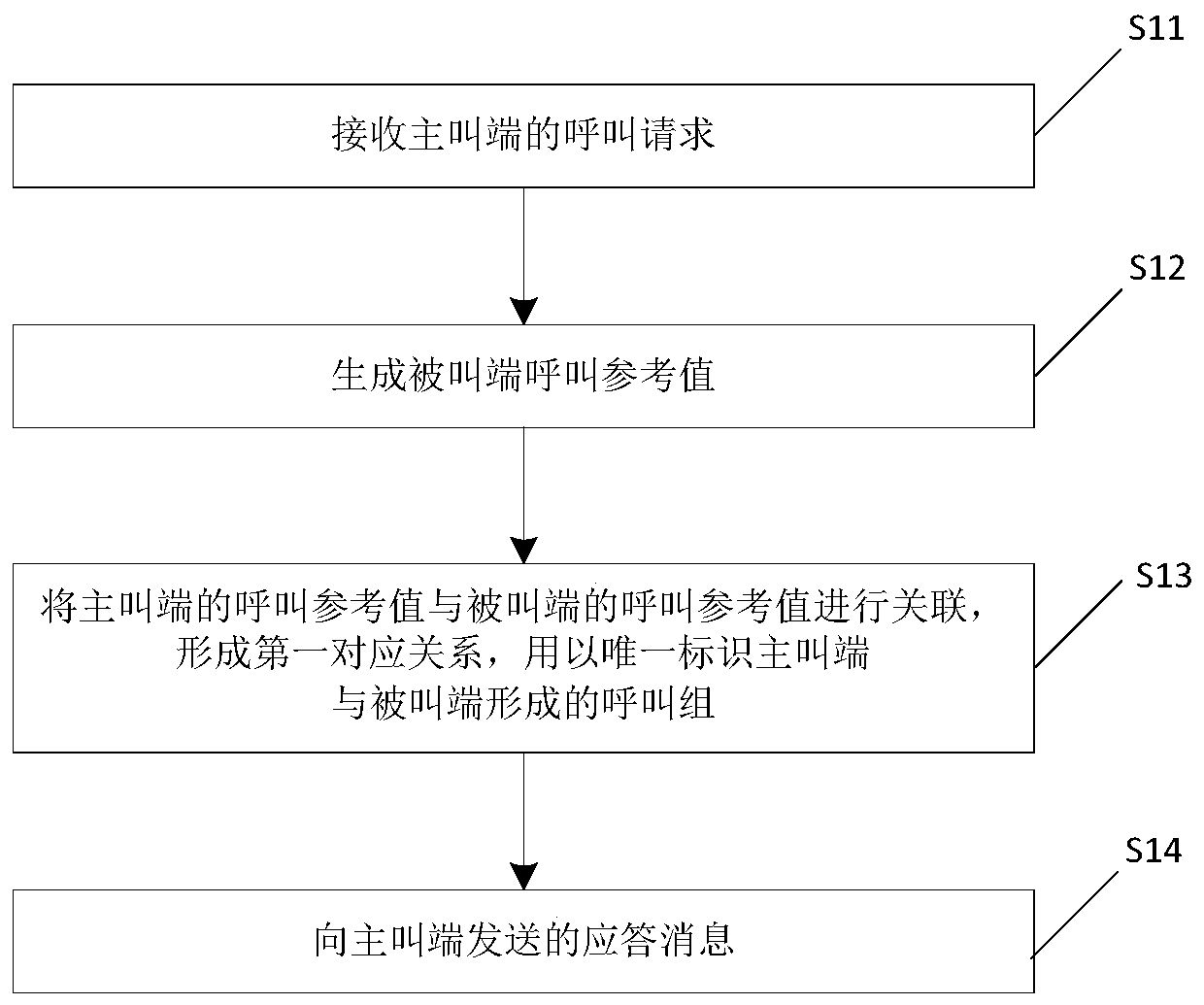
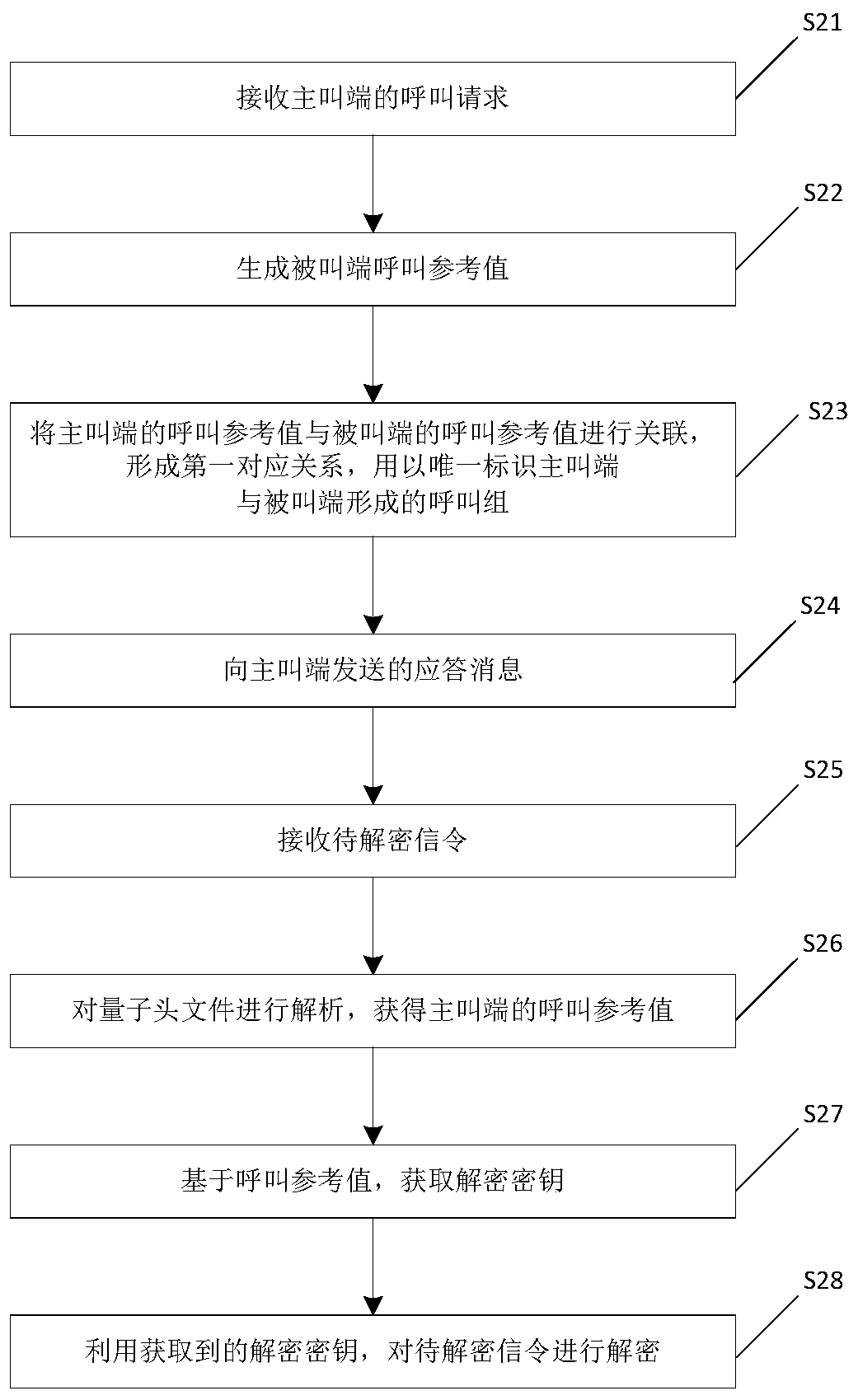
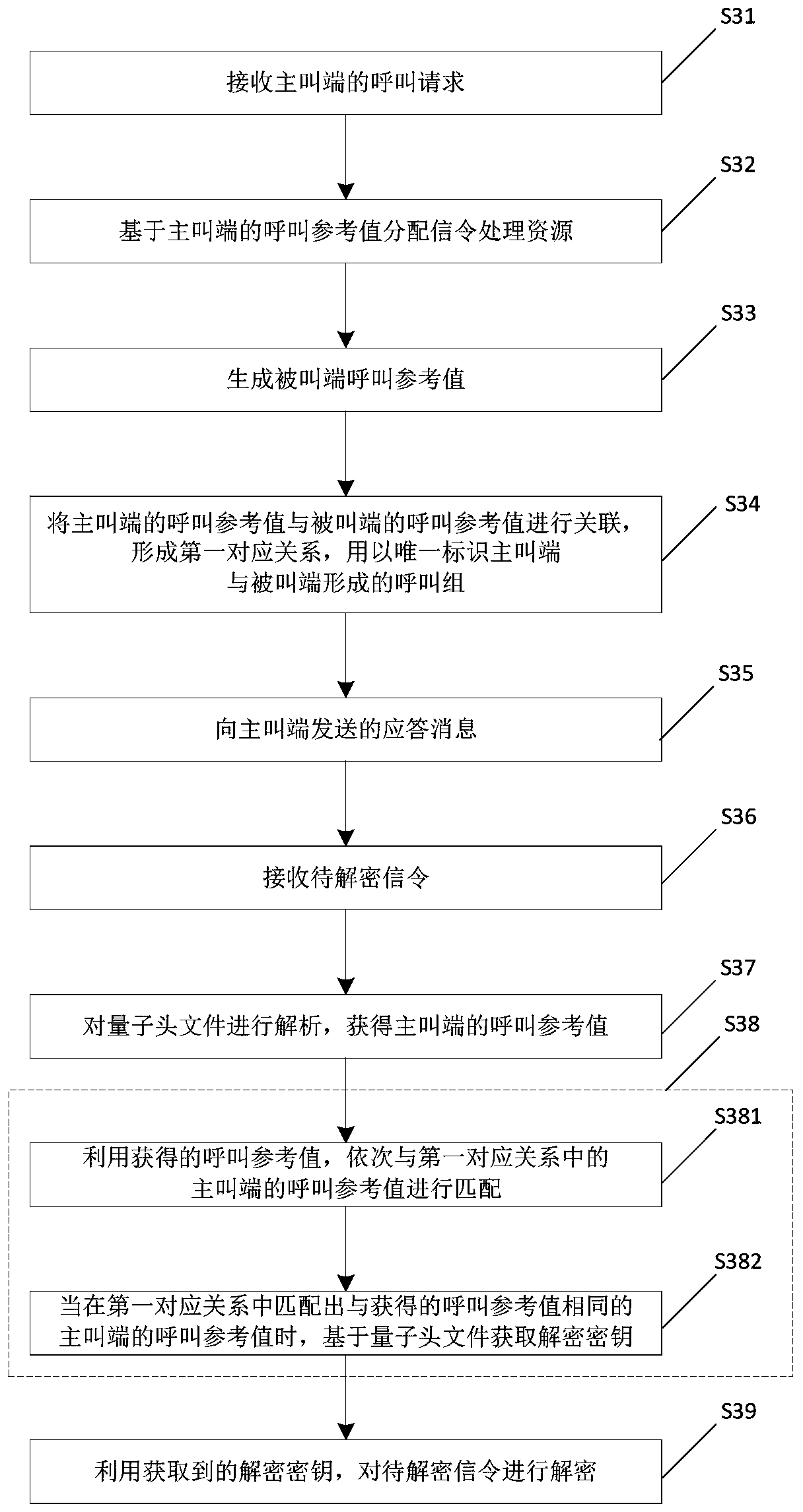
ActiveCN109246385AGet call referenceImprove securityTelevision conference systemsTwo-way working systemsConference call
The invention relates to the technical field of video conference communication, in particular to a communication method and a conference system for a multi-party conference. The method comprises the following steps of: receiving a call request of a calling party, wherein the call request carries a call reference value of the calling party, and the call reference value of the calling end is generated by the calling end, and is used for uniquely identifying the current conference call of the calling end; generating a callee call reference value; associating a call reference value of the callingterminal with a call reference value of the called terminal to form a first corresponding relationship; sending an answer message the calling terminal, the answer message carrying a call reference value of the called terminal. The calling end and the called end corresponding to each call group in the invention store the call reference values of the local end and the opposite end. In the process of conference communication, the subsequent calling end and the called end can uniquely determine the corresponding opposite end by using the stored call reference values, so that the accurate controlof the conference can be realized.
Owner:SUZHOU KEDA TECH
Data crawling method and device, storage medium and terminal
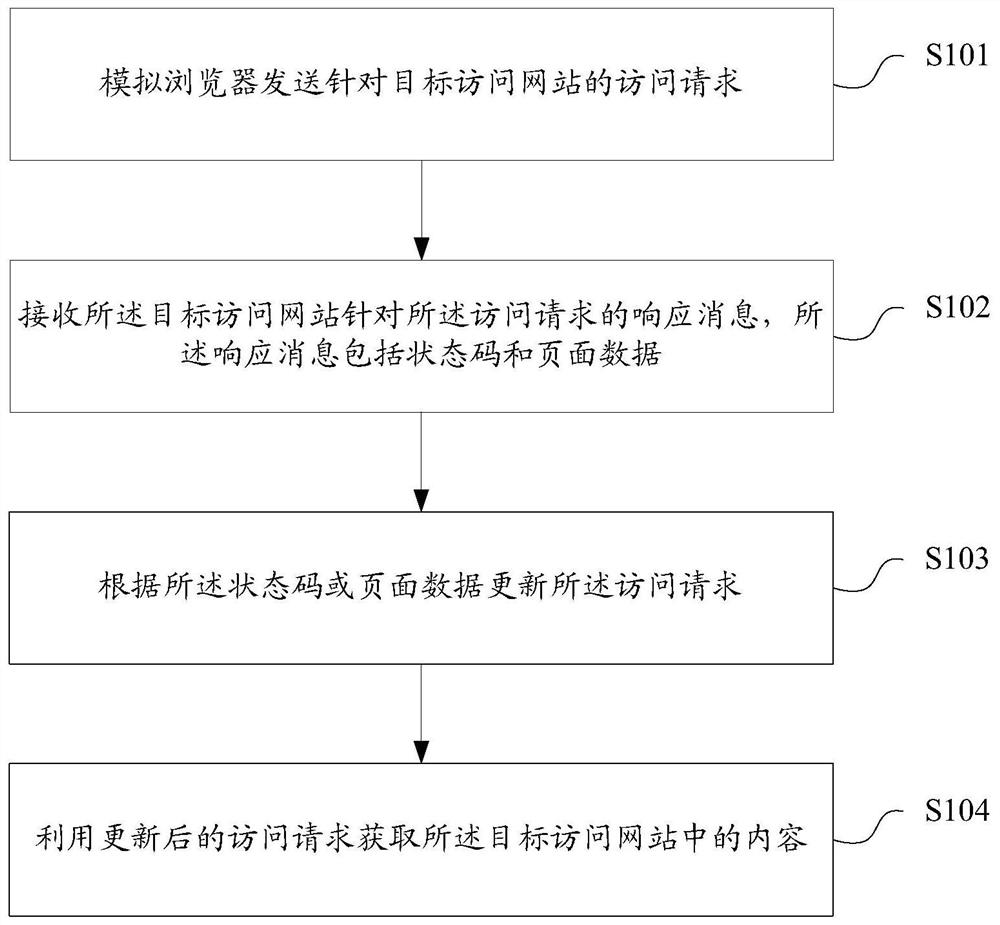
InactiveCN111666465AImprove automatic resilienceImprove the efficiency of crawling dataWeb data indexingWeb siteWeb crawler
The invention discloses a data crawling method and device, a storage medium and a terminal. The data crawling method comprises the steps of simulating a browser to send an access request for a targetaccess website; receiving a response message of the target access website for the access request, wherein the response message comprises a state code and page data; updating the access request according to the state code or the page data; and obtaining the content in the target access website by utilizing the updated access request. According to the technical scheme, the data crawling efficiency of the web crawler can be improved.
Owner:JINGZAN ADVERTISING SHANGHAI CO LTD
Dynamic multi-party signature encryption and decryption method and system
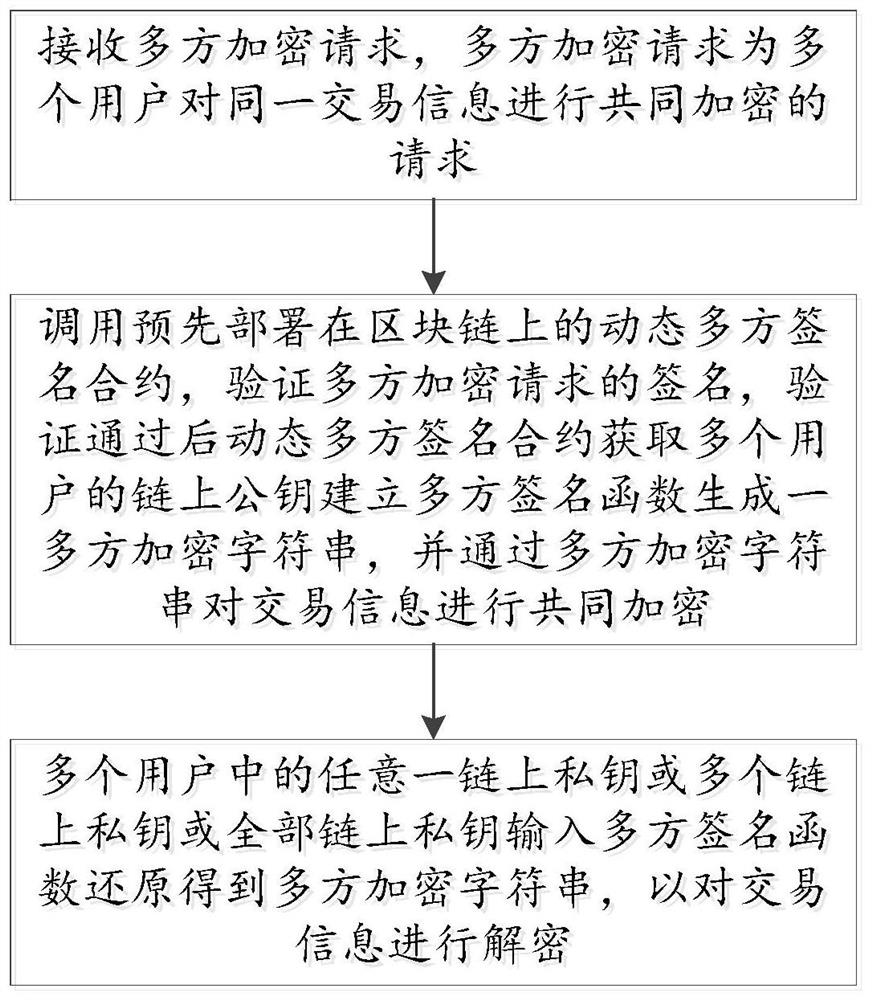
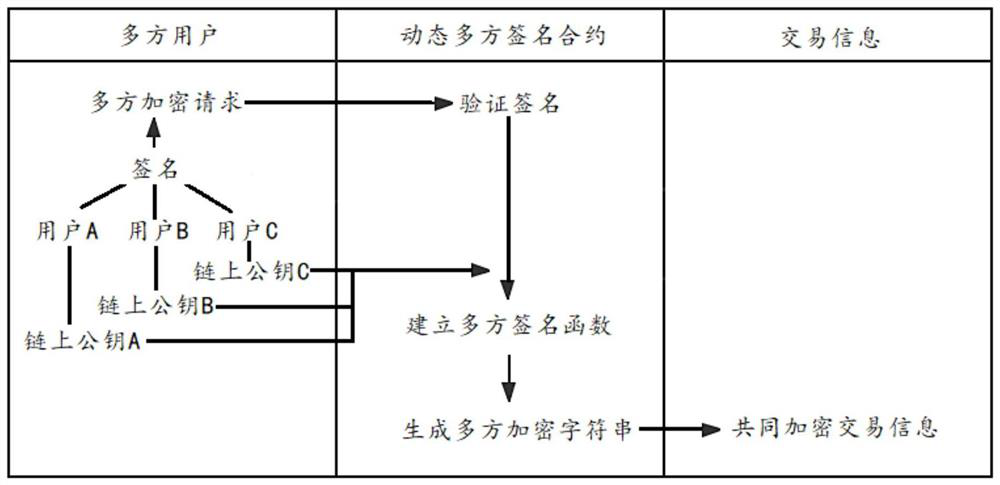
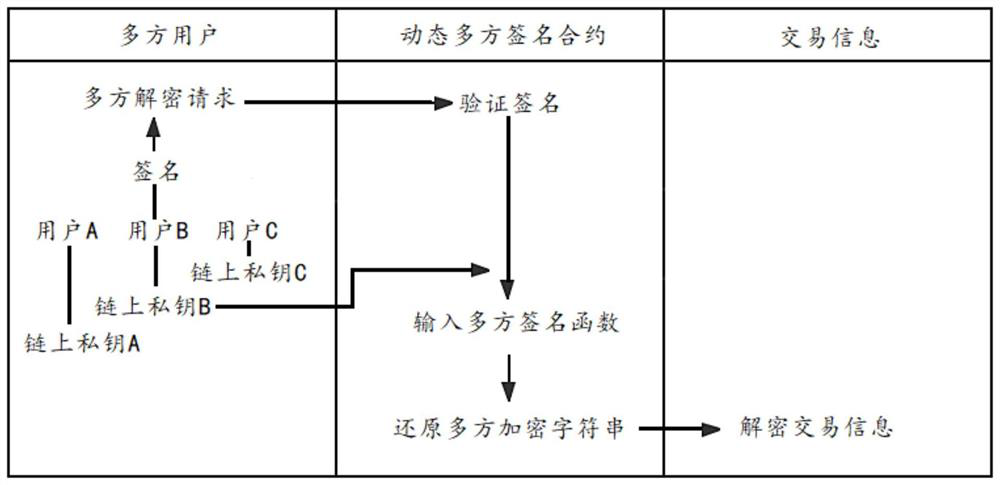
PendingCN112906041AFlexible privacy protectionDecryption implementationDigital data protectionEngineeringFinancial transaction
The invention discloses a dynamic multi-party signature encryption and decryption method and system, and the method comprises the following steps: receiving a multi-party encryption request which is a request that a plurality of users carry out the common encryption of the same transaction information; and calling a dynamic multi-party signature contract pre-deployed on the block chain, verifying a signature of the multi-party encryption request, after verification is passed, obtaining on-chain public keys of a plurality of users by the dynamic multi-party signature contract, establishing a multi-party signature function to generate a multi-party encryption character string, and performing common encryption on the transaction information through the multi-party encryption character string, wherein any one on-chain private key or multiple on-chain private keys or all on-chain private keys in the multiple users are input into the multi-party signature function to be restored to obtain a multi-party encrypted character string so as to decrypt the transaction information. The technical problem that transaction information encryption and decryption are inflexible and limited is solved, and the method has the technical characteristics of multi-user encryption and decryption, dynamic and adjustable encryption and decryption, wide application scene, convenience in auditing, safety and reliability.
Owner:上海简苏网络科技有限公司
Secret sharing method and system based on visual effect
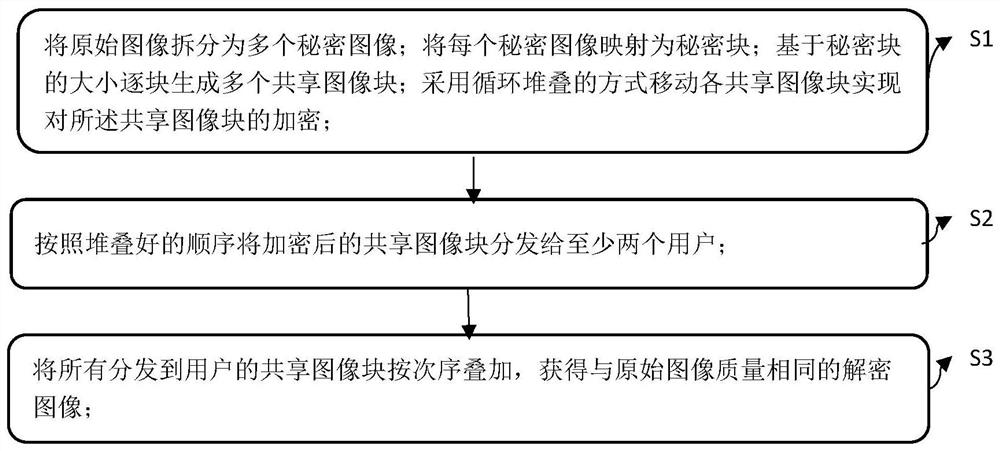
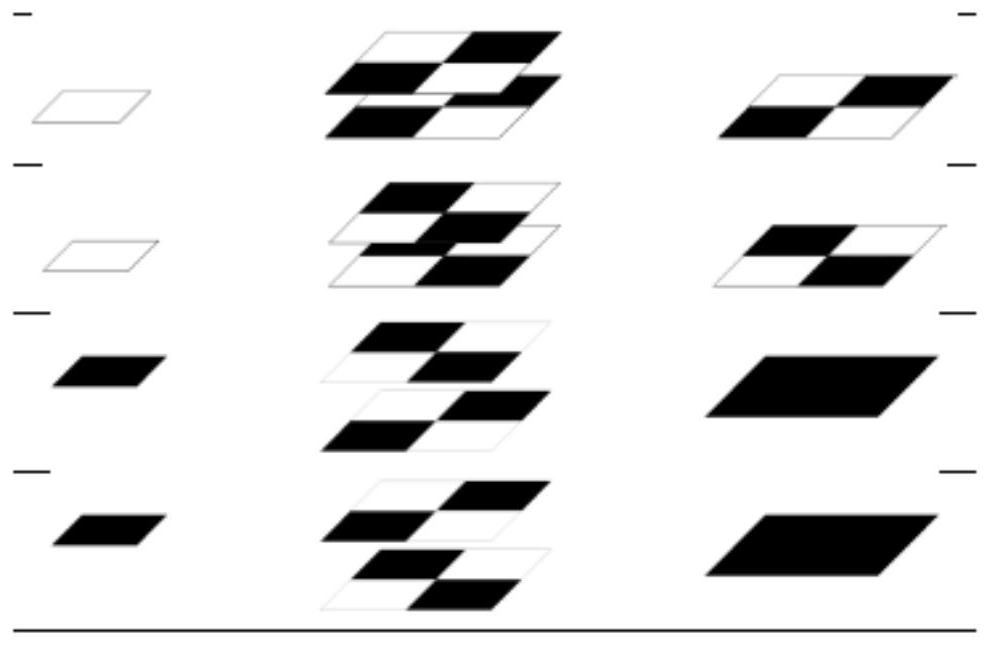
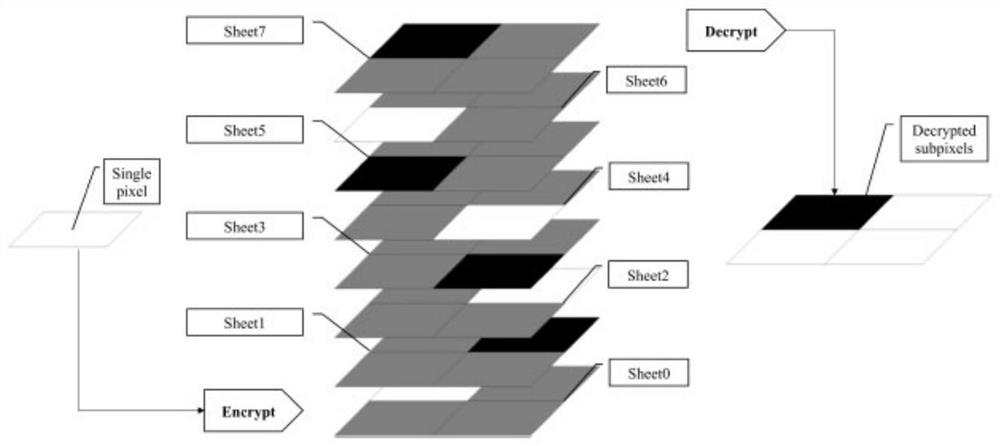
ActiveCN112422767AEliminate extensionsImprove performancePictoral communicationComputer graphics (images)Engineering
The invention provides a secret sharing method and system based on a visual effect. The secret sharing method comprises the following steps: splitting an original image into a plurality of secret images; mapping each secret image into a secret block; generating a plurality of shared image blocks one by one based on the size of the secret block; moving the shared image blocks in a cyclic stacking mode to achieve encryption of the shared image blocks; superposing all the shared image blocks in sequence during decryption to obtain a decrypted image with the same quality as the original image, wherein the secret block is provided with a plurality of pixels. The size of the shared image is the same as that of the secret image by encrypting the image block one by one, so that pixel expansion iseliminated, the image recovery performance is improved, and almost lossless visual encryption is realized; by processing the mapping relation of the pixel blocks before and after encryption, higher contrast is obtained, meanwhile, electronic equipment does not need to be used in the traditional encryption and decryption process, and the shared image blocks can be directly printed on paper to be decrypted by vertically arranging multiple pieces of paper.
Owner:国家电网有限公司大数据中心
File encryption and decryption method, device and equipment
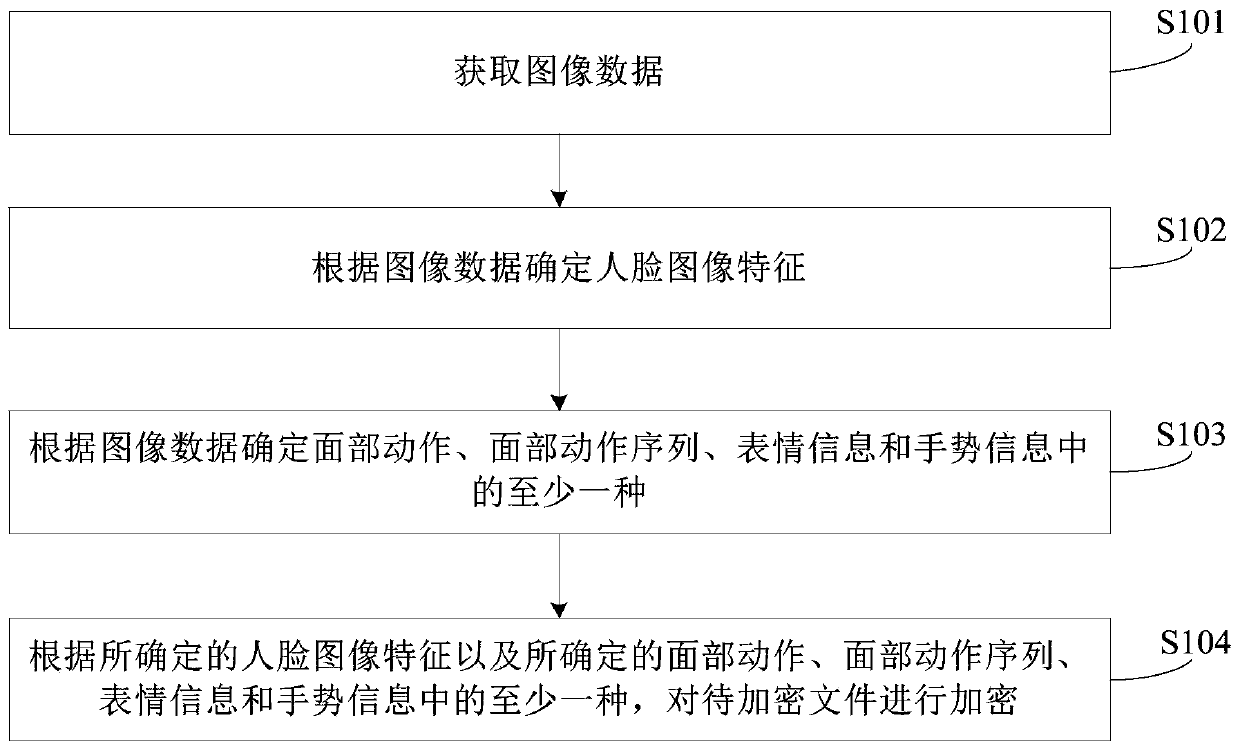
PendingCN111414639ASimple and efficient operationImprove user experienceDigital data protectionDigital data authenticationComputer visionImaging Feature
The embodiment of the invention provides a file encryption and decryption method, device and equipment. The method comprises: acquiring image data; determining face image features according to the image data; determining at least one of a facial action, a facial action sequence, expression information and gesture information according to the image data; and encrypting the to-be-encrypted file according to the determined face image features and the determined at least one of the face action, the face action sequence, the expression information and the gesture information. The method provided bythe embodiment of the invention is simple and convenient to operate and high in safety.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
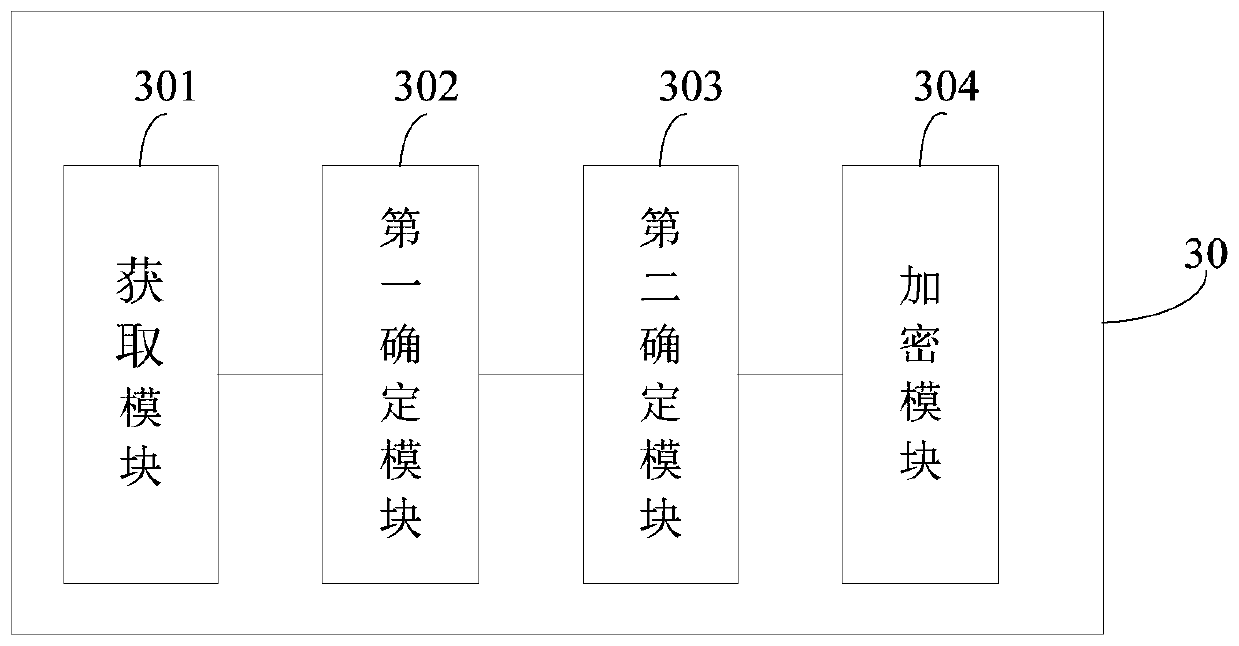
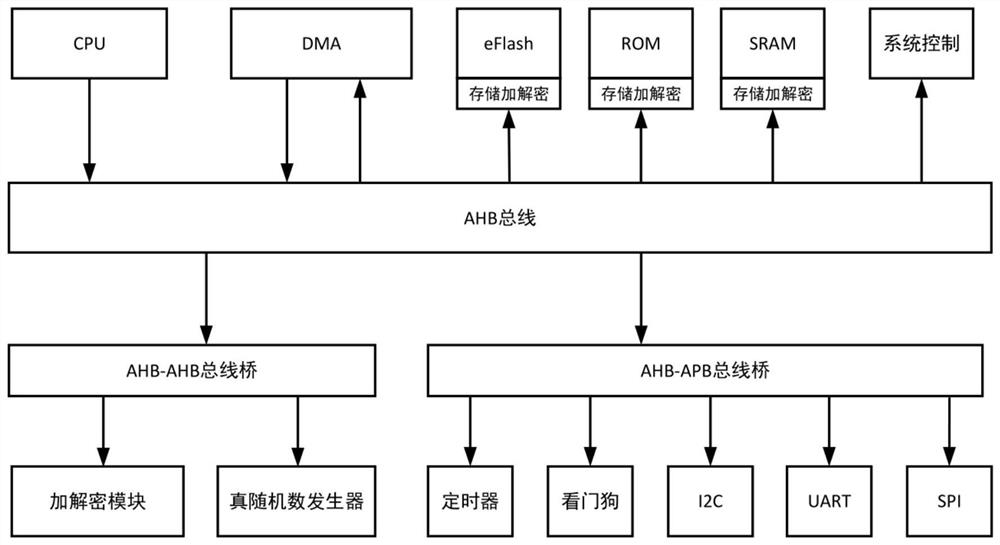
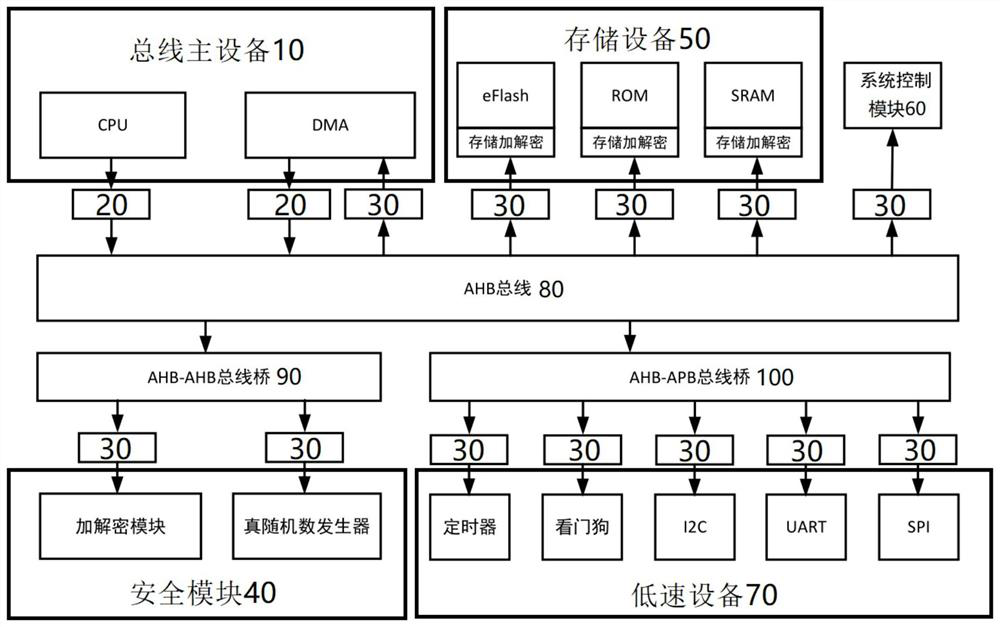
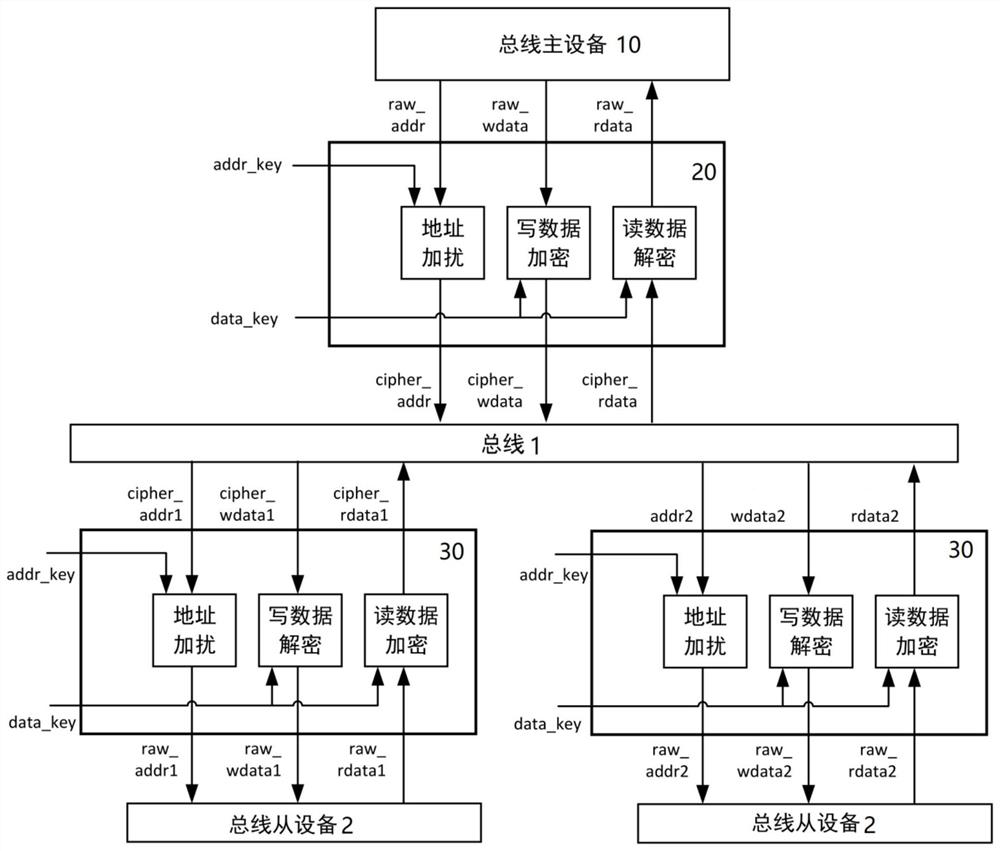
Chip structure and operation method thereof
PendingCN113177210ADecryption implementationImprove securityDigital data protectionInternal/peripheral component protectionComputer hardwareEngineering
The invention provides a chip structure and an operation method thereof. The operation method comprises the following steps: at least one bus master device initiates a read command and / or a write command, provides the read command and / or the write command to a bus, and receives write data and / or read data; the at least one bus transmits the read command and / or the write command to the bus slave device and transmits the write data and / or the read data to the bus master device; the at least one bus slave device receives the read command and / or the write command, generates write data and / or read data according to the read command and / or the write command, and provides the write data and / or the read data to the bus; at least one first encryption and decryption module is connected between any bus master device and any bus, and is used for encrypting and / or decrypting commands and data transmitted between the bus master device and the bus; at least one second encryption and decryption module is connected between any bus slave device and any bus, and encrypts and / or decrypts commands and data transmitted between the bus slave device and the bus.
Owner:青芯半导体科技(上海)有限公司
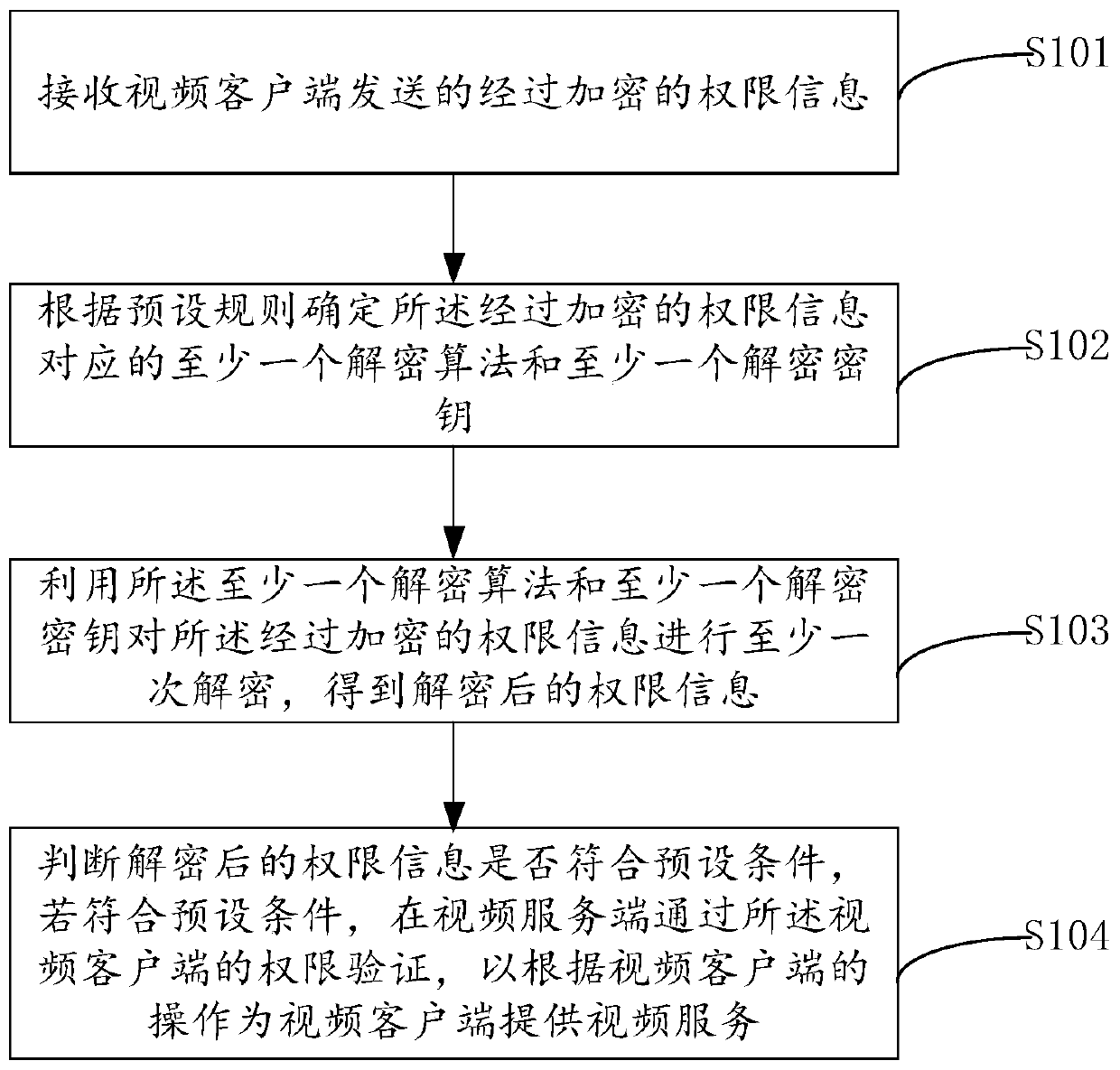
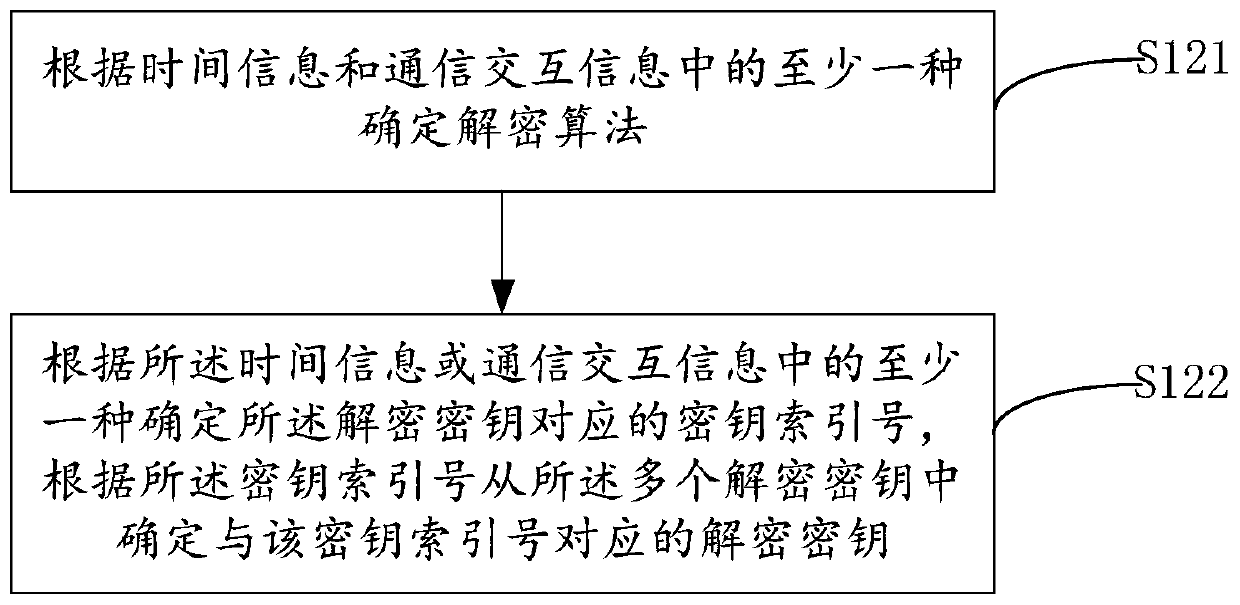
Authority authentication method, encryption method, device and system for network video access
The invention provides a network video access permission identification method, apparatus and system, and a permission encryption method and apparatus, and relates to the technical field of internet video information. Permission information sent by a video client is identified, a corresponding decryption algorithm and a decryption key are determined through predetermined rules, and thus the permission information is decrypted. When the decrypted permission information conforms to predetermined conditions, it is determined that permission identification succeeds. In the permission identification process, a user does not have to register an account in advance by use of the video client, and user experience is improved. At the same time, decryption of the permission information requires use of a correct decryption algorithm and a correct decryption key at the same time, and otherwise, correct permission information cannot be obtained, such that the risk of being captured, analyzed and cracked during the communication process is avoided. In addition, the decryption algorithm and the decryption key are independent of each other so that even if one of the two is cracked, the system security can be ensured through the protection strategy of the other.
Owner:POWERINFO
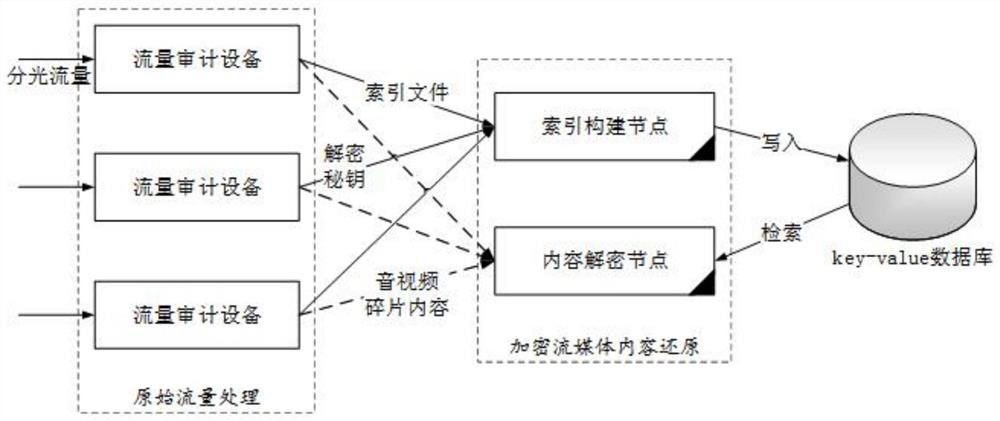
A kind of decryption method and device for encrypted streaming media network traffic
ActiveCN113014590BDecryption implementationStrong real-timeSecuring communicationInternet trafficMediaFLO
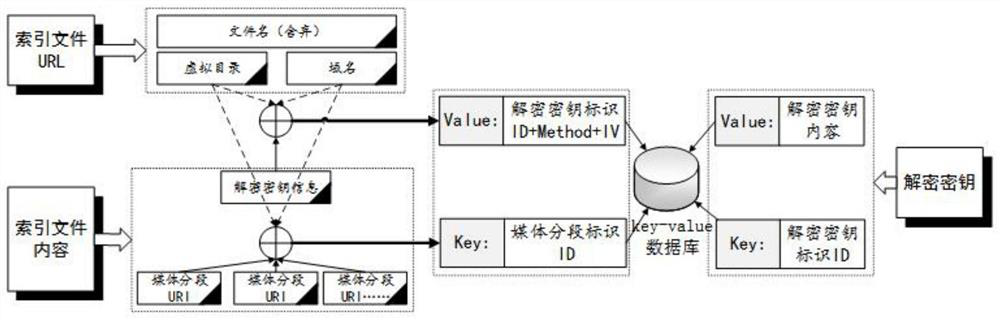
The invention discloses a decryption method for encrypted streaming media network traffic, which includes the following steps: Step S1: audio and video media index file identification and information return, decryption key identification and information return, audio and video media segment content identification and return Information return; Step S2: Receive the index file information returned by the traffic auditing device, and extract the path identifier of each media segment in the index file, which involves in-depth analysis of high-speed network traffic-audio and video streaming media restoration-encrypted streaming media content restoration technology field. The decryption method for encrypted streaming media network traffic This solution is oriented to the network traffic audit requirements in the form of bypass deployment, and has strong real-time performance. It can build an index, query an index in real time, and realize content decryption, so as to detect harmful network traffic in time. information, hidden dangers of leakage, etc., so that users can take corresponding measures in a timely manner.
Owner:积至(海南)信息技术有限公司
Video encryption method and decryption method based on multi-projector splicing and fusion
ActiveCN108307203BImplement encryptionEncryption and decryption implementationPicture reproducers using projection devicesSelective content distributionComputer hardwarePassword
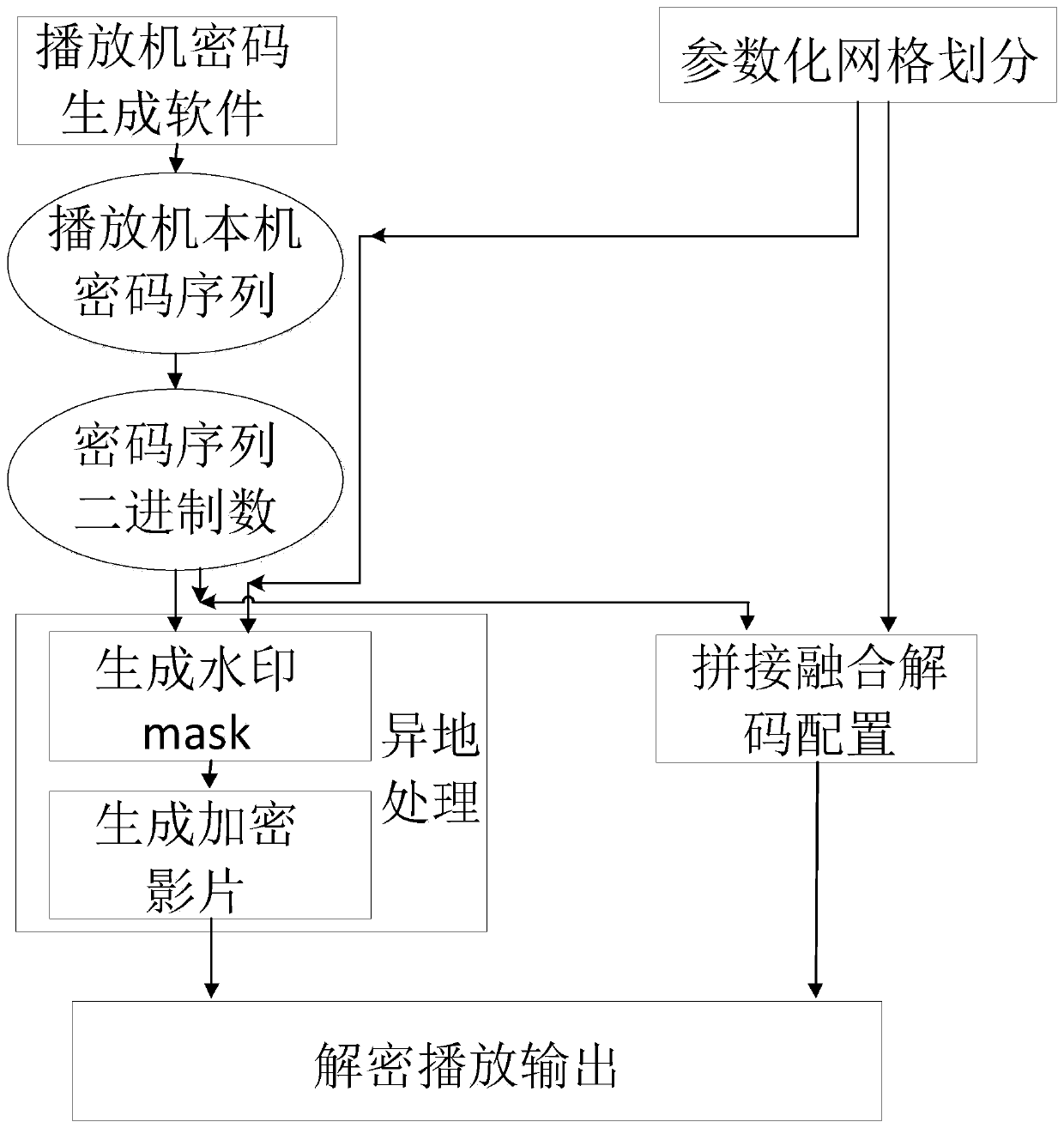
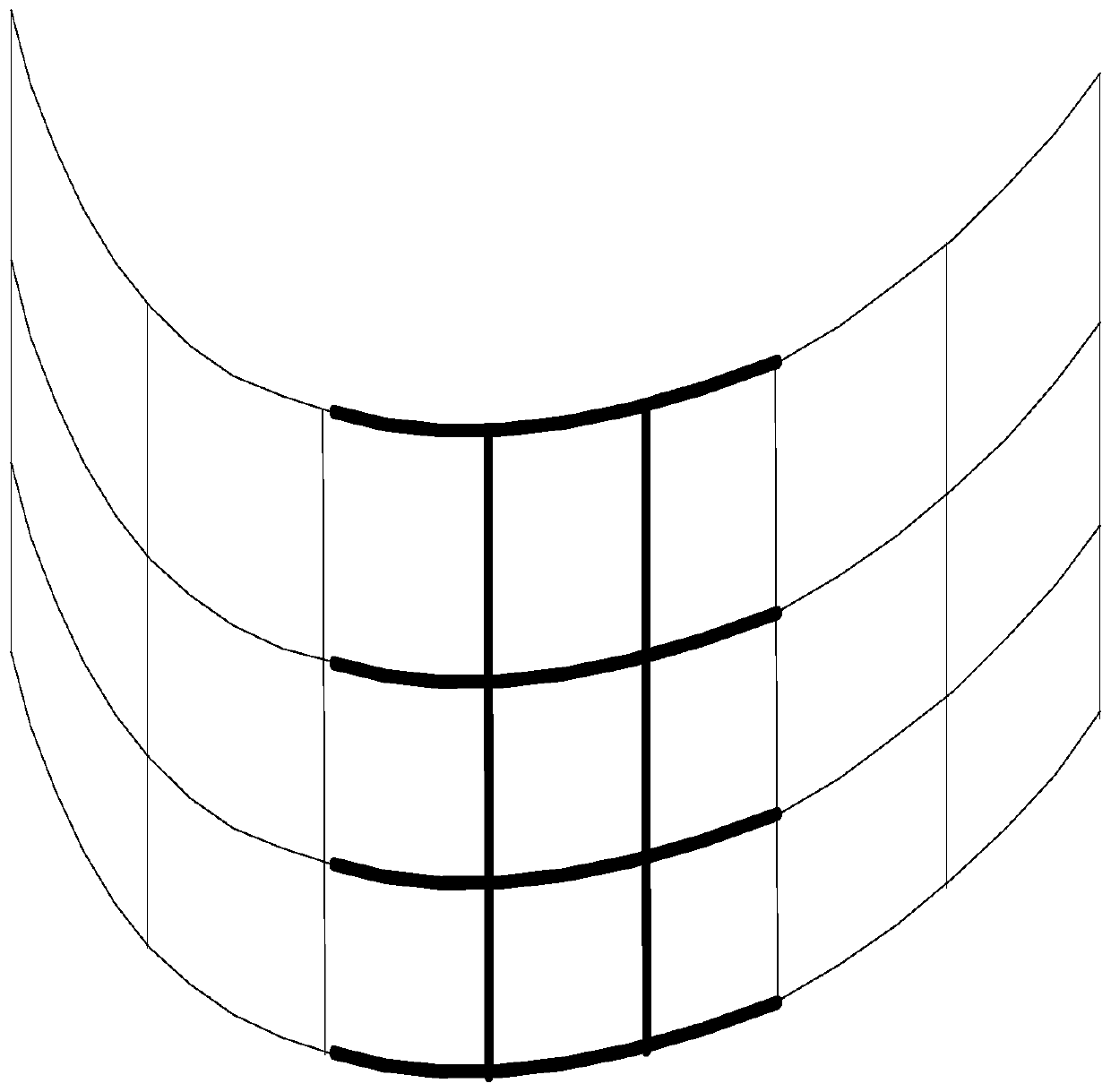
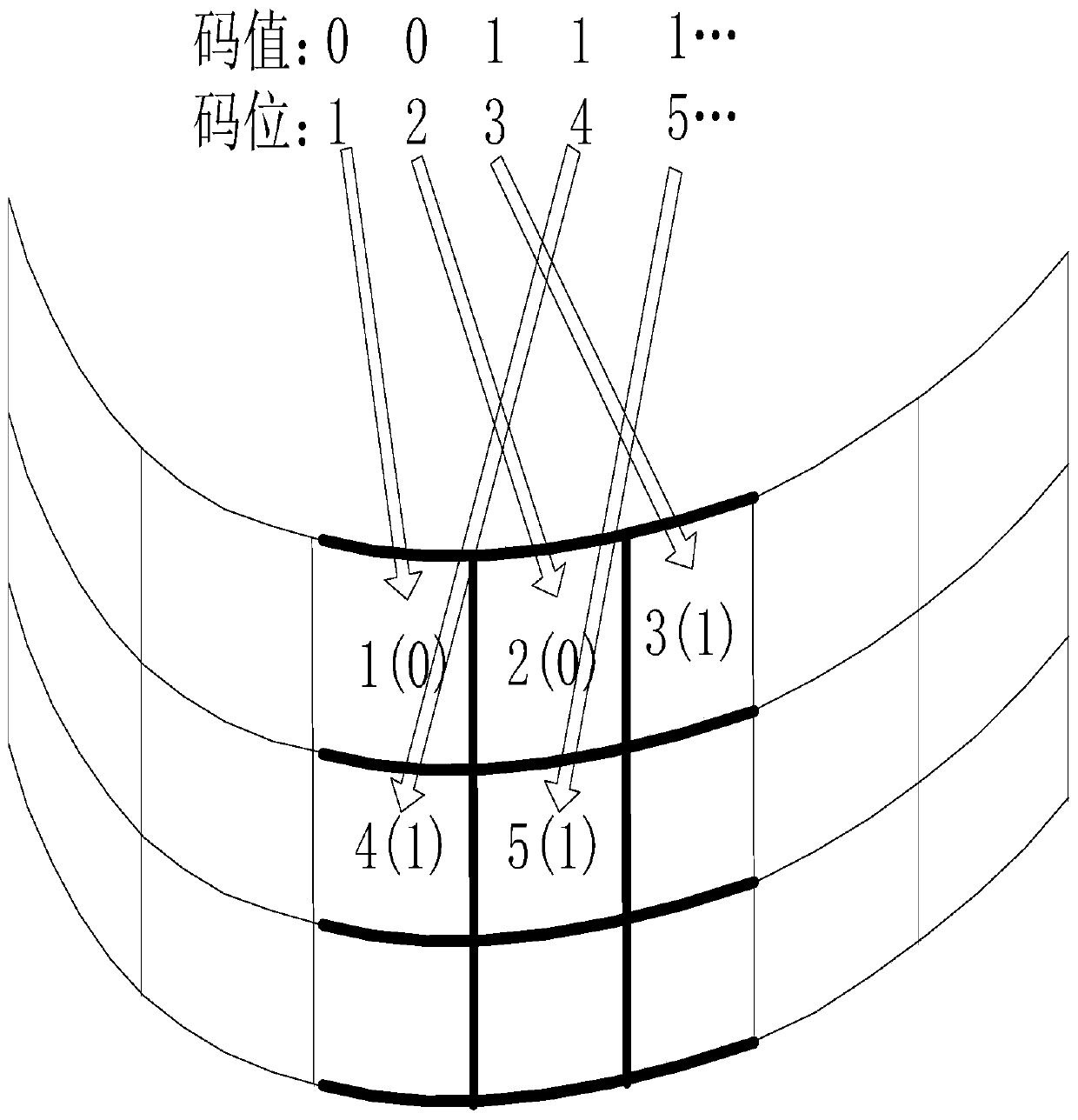
The invention belongs to the field of video encryption, particularly relates to a film encryption method and a film decryption method based on multi-projector splicing fusion, and aims at providing afilm source encryption and decryption technology for solving a problem of movie copyright protection. The method comprises the following steps of (1) carrying out parameterized division on a projection curtain, and selecting an encryption area; (2) generating a password on a target machine by using encryption software; (3) converting the password into a binary number, and selecting the front n bits of the binary number to generate a film encryption mask; (4) overlapping a watermark mask to generate an encrypted film in a process of rendering the generated film; (5) during a playing step, calling the same encryption program, generating a password which is the same as the encryption, converting the password into a binary array, and generating a splicing fusion decryption configuration parameter; and (6) calling the decryption configuration parameter by splicing fusion software and playing the encrypted film source in order to realize decrypted playing. According to the film encryption method and the film decryption method based on the multi-projector splicing fusion, an encryption technology for a multi-projector special curtain splicing fusion film is realized.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI +1
Ciphertext video player and playback method
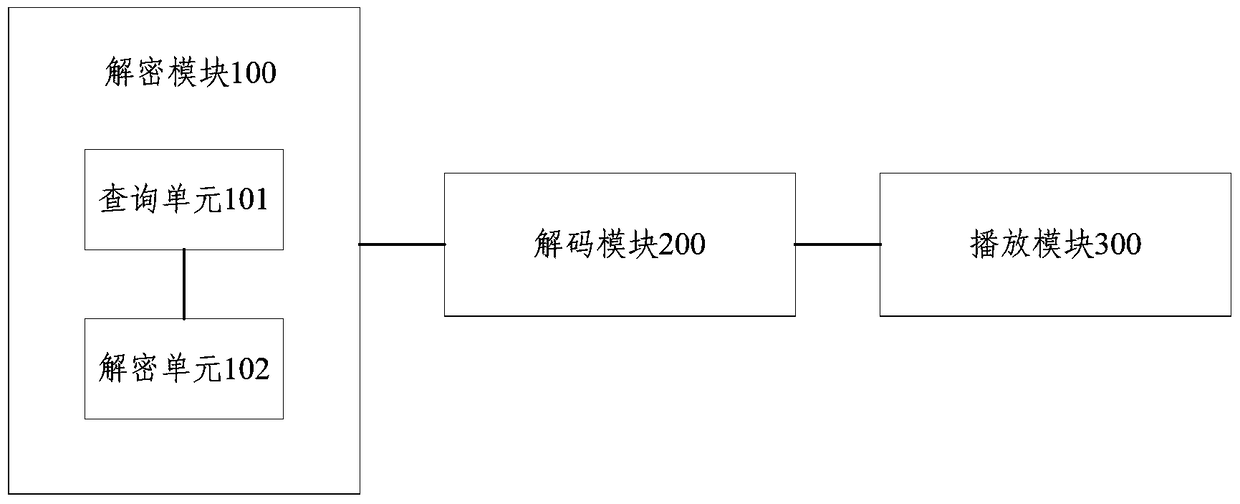
InactiveCN105187912BDecryption function extensionDecryption implementationSelective content distributionComputer hardwareVideo player
The present invention provides a ciphertext video player and a playing method. The ciphertext video player comprises a decryption module, a decoding module and a playing module. The decryption module is used for calling the video decryption algorithm in a preset video decryption dynamic link library and decrypting a ciphertext video to be played. The decoding module is used for decoding the decrypted video data after the decryption module completes decryption. The playing module is used for playing the decoded video data. According to the ciphertext video player and the playing method, the decryption and playing of an encrypted video can be realized.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Communication method and conference system for multi-party conference
ActiveCN109246385BGet call referenceImprove securityTelevision conference systemsTwo-way working systemsConference callData science
The invention relates to the technical field of video conference communication, in particular to a communication method and a conference system for a multi-party conference. The method comprises the following steps of: receiving a call request of a calling party, wherein the call request carries a call reference value of the calling party, and the call reference value of the calling end is generated by the calling end, and is used for uniquely identifying the current conference call of the calling end; generating a callee call reference value; associating a call reference value of the callingterminal with a call reference value of the called terminal to form a first corresponding relationship; sending an answer message the calling terminal, the answer message carrying a call reference value of the called terminal. The calling end and the called end corresponding to each call group in the invention store the call reference values of the local end and the opposite end. In the process of conference communication, the subsequent calling end and the called end can uniquely determine the corresponding opposite end by using the stored call reference values, so that the accurate controlof the conference can be realized.
Owner:SUZHOU KEDA TECH
Steganography and decryption method based on LIBS technology
InactiveCN113447472AIncrease the difficultyLow costInksAnalysis by thermal excitationElement analysisEngineering
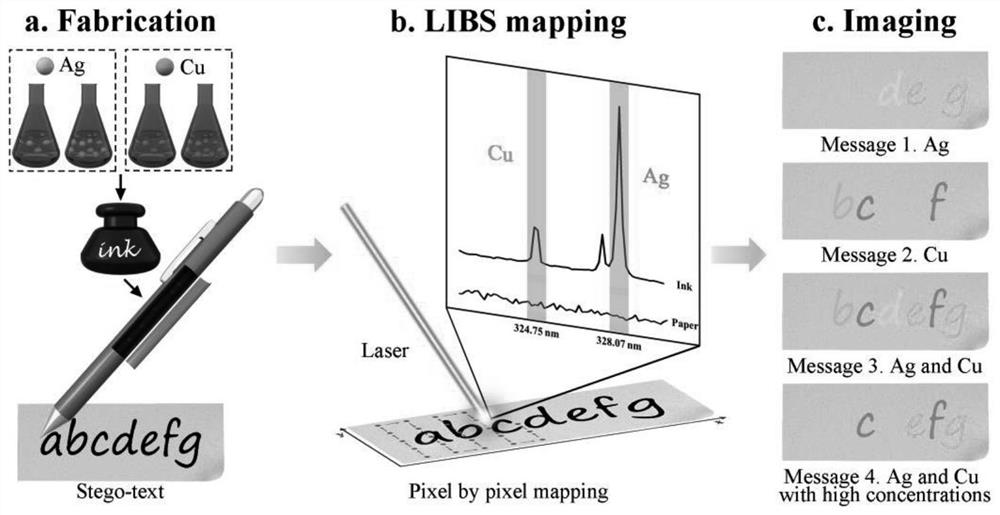
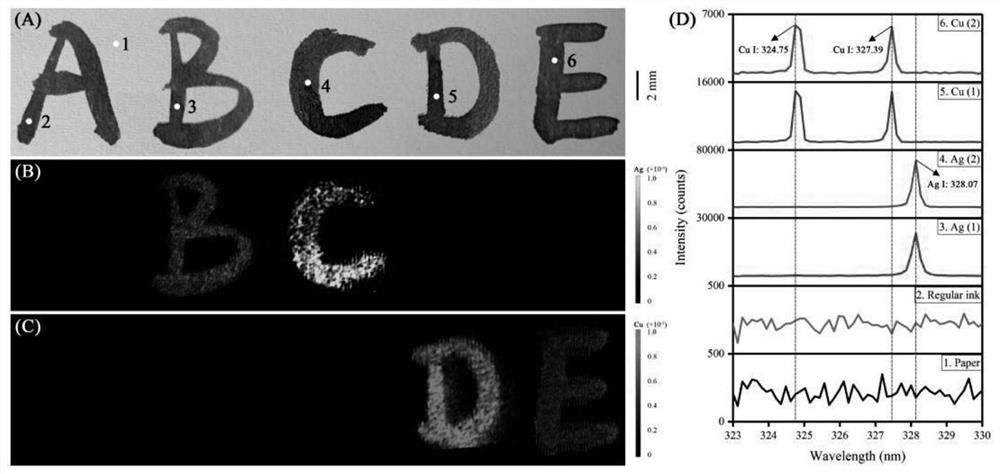
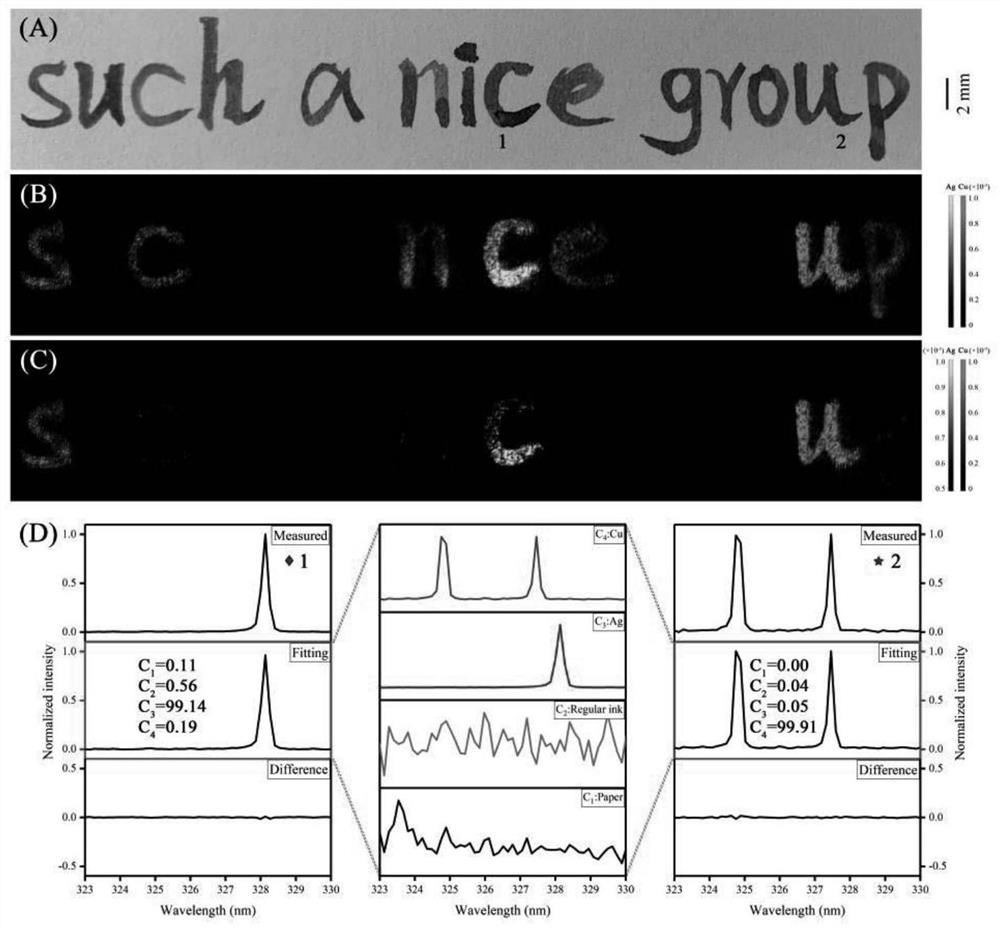
The invention provides an application of a laser-induced breakdown spectroscopy (LIBS) technology in information decryption, and provides an information steganography and decryption method based on an LIBS technology, which uses solutions containing different concentrations and different elements as ink to write an encrypted text, and performs element analysis and imaging on the encrypted text through the LIBS technology so as to realize decryption. The steganography and decryption method is low in cost, high in stability and high in safety, and has a good application prospect in the technical field of information encryption.
Owner:SICHUAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com