Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
100results about How to "Achieve experience" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
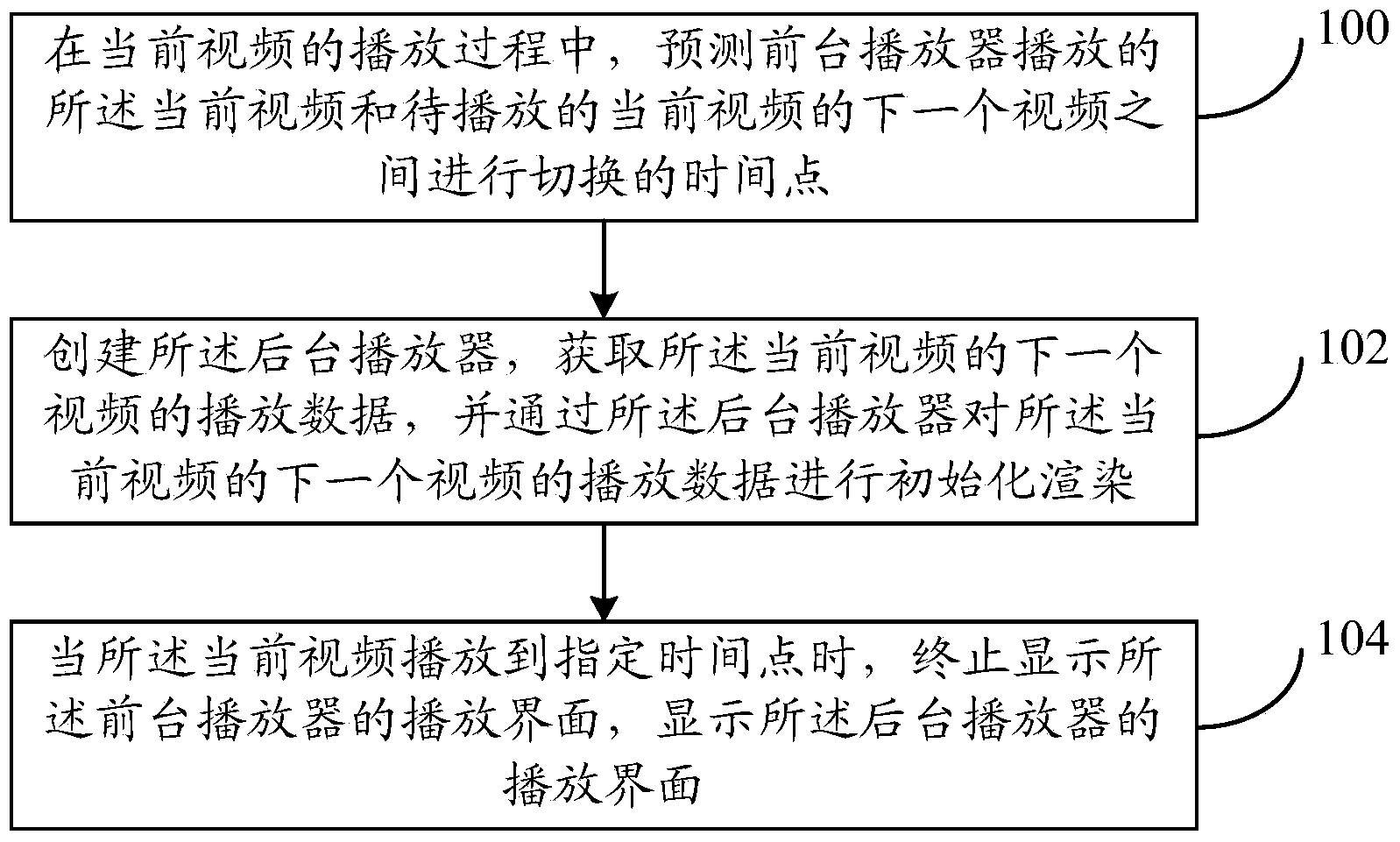
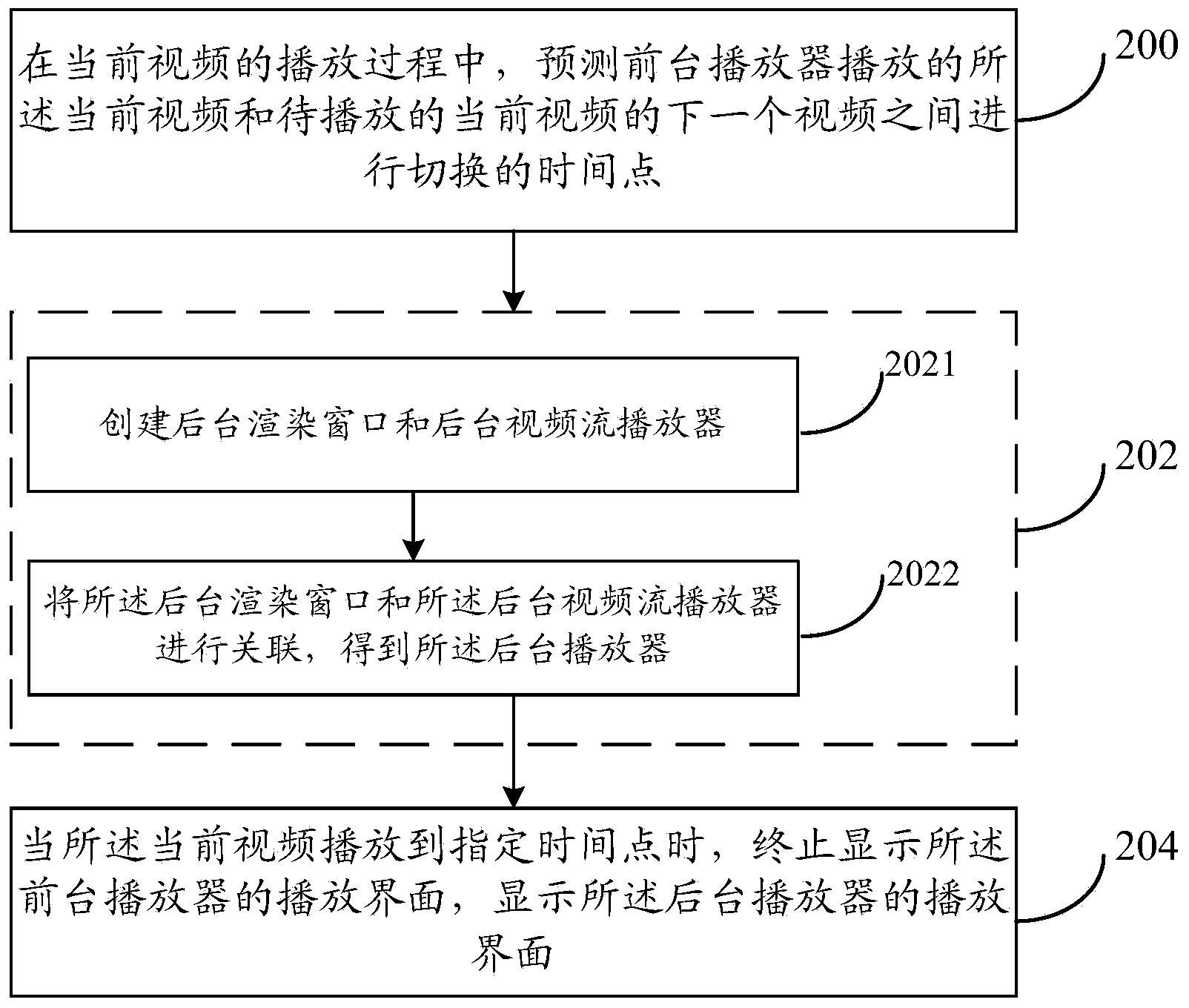
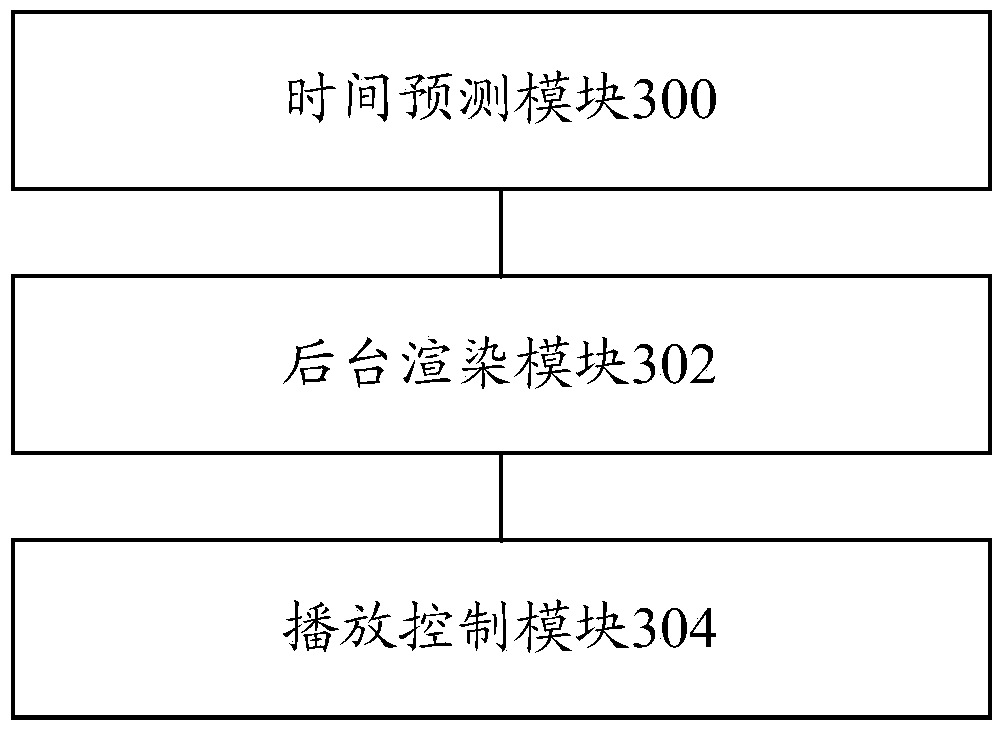
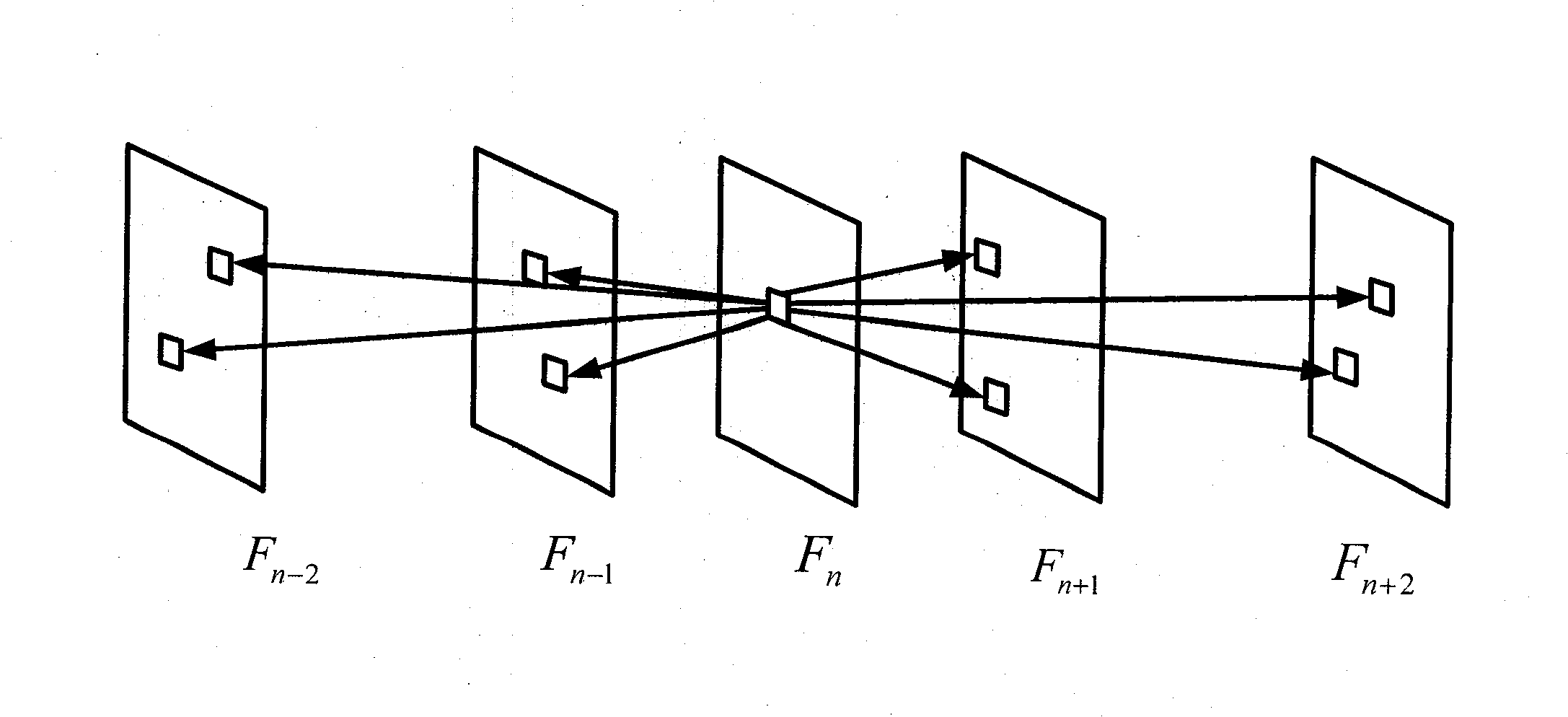
Video switching method and video switching device
The invention provides a video switching method and a video switching device. The video switching method includes: during the playing process of a current video, forecasting a time point between the current video played by a foreground player and a next video of a current video to be played, wherein the foreground player is used for playing the current video, and the next video of the current video is played through a background player to be established; when the next video of the current video is a video, different in code stream, of the current video or a video different from the current video, establishing the background player, acquiring play data of the next video of the current video and subjecting the play data of the next video of the current video to initial rendering; when the current video is played to a designated time point, stopping displaying the play interface of the foreground player displaying the play interface of the background player; designating the time point as the time point for switching or the time point for the end of the current video. Therefore, user experience in seamless viewing is realized.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
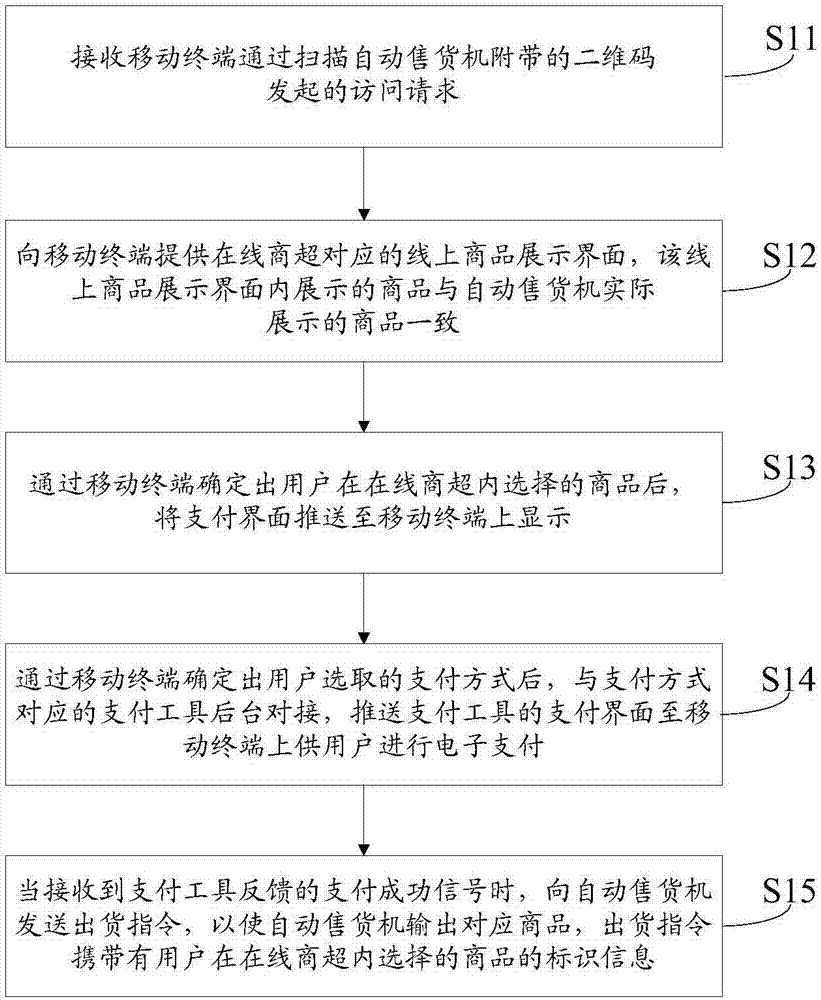
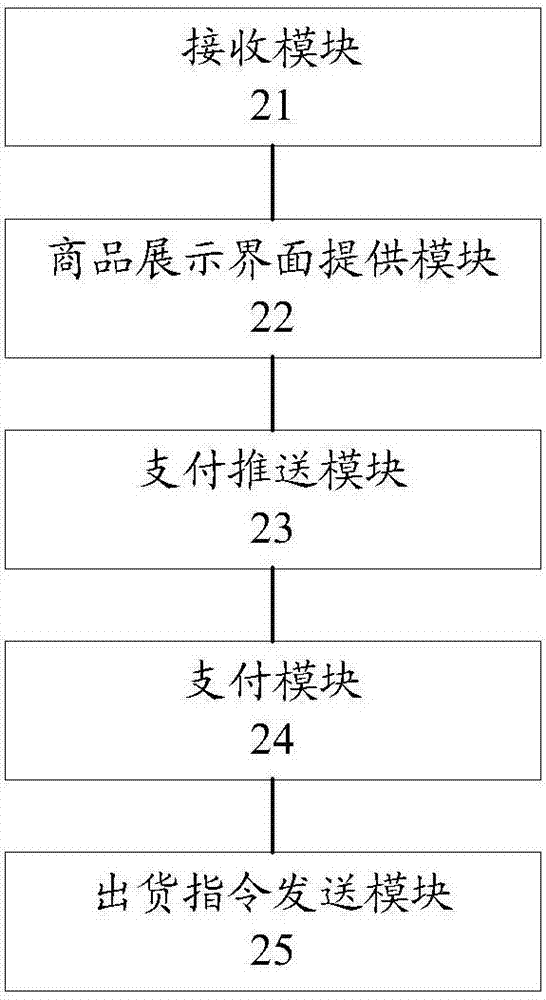
Vending machine and control method and device thereof and system
InactiveCN107016788ALow costImprove consumer satisfactionCoin-freed apparatus detailsPayment architecturePaymentButt joint
The invention provides a vending machine and a control method and device thereof and a system and relates to the technical field of vending. The method includes the steps that an access request issued when a mobile terminal scans a two-dimensional code attached to the vending machine is received; a commodity display interface corresponding to an online commodity supermarket is provided for the mobile terminal, and commodities displayed in the commodity display interface correspond to commodities displayed in the vending machine; after commodities selected by the user in the online commodity supermarket are confirmed through the mobile terminal, a payment interface is pushed to the mobile terminal to be displayed; after a payment mode selected by the user is confirmed through the mobile terminal, the mobile terminal is in butt joint with a payment tool background corresponding to the payment mode, and a payment interface of a payment tool is pushed to the mobile terminal for electronic payment for the user; when a payment success signal fed back by the payment tool is received, a delivery instruction is transmitted to the vending machine, and the vending machine outputs the corresponding commodities. The cost of the vending machine is greatly reduced, and the satisfaction of the user is improved.
Owner:HANGZHOU ZONGS INTELLIGENT TECH CO LTD
Wireless lock control system based on intelligent terminal and method
InactiveCN106600757AWith on-site alarm functionWith remote alarm functionIndividual entry/exit registersTransmissionKey pressing32-bit
The invention provides a wireless lock control system of an electronic lock based on an intelligent terminal and a method, the wireless lock control system is used in a U type glass door lock / bicycle lock, the wireless lock control system comprises a main control CPU, a wireless module, a fingerprint module, a touch key module, a distribution network button, a LED display circuit, a buzzer module, an alarm circuit, an EEPROM memory, a power supply circuit module and a motor driver circuit module which are connected with the main control CPU, the power supply circuit module includes a rechargeable device; wireless transmission is encrypted by an AES encryption mode, the touch key module can add a 6 to 12 bit password, and a 32 bit virtual password is set; the fingerprint module adopts a semiconductor fingerprint sensor, and can add 100 pieces of user passwords, and a door can be opened by direct pressing of a user fingerprint; the electronic door lock is connected with the wireless main control CPU to realize the real-time monitoring and remote control of a door lock device so as to achieve full intelligent user experience.
Owner:SHENZHEN KAADAS INTELLIGENT TECH CO LTD
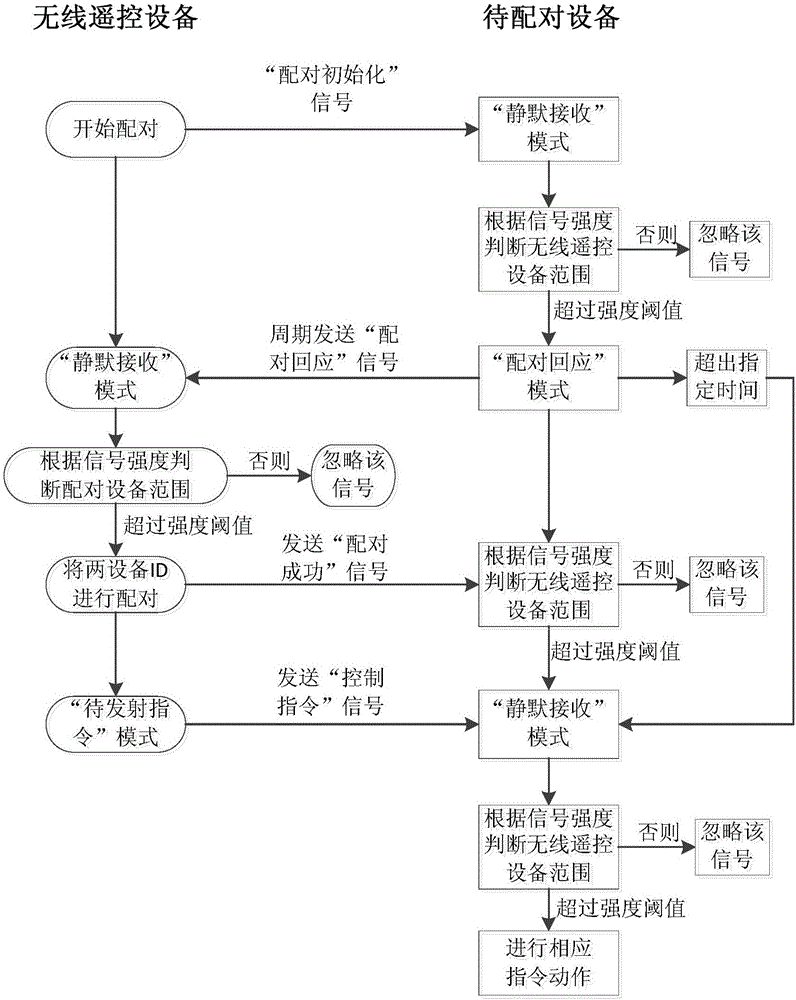
Automatic equipment pairing method based on wireless signal intensity
InactiveCN105101467AAvoid tedious and complicated pairing processEasy to implementConnection managementRemote controlCommunications security
The invention provides an automatic equipment pairing method based on wireless signal intensity. The automatic equipment pairing method comprises: wireless remote control equipment broadcasts a pairing initialization signal to equipment to be paired; after the equipment to be paired receives the pairing initialization signal, detecting the intensity of the signal; if the intensity of the signal is higher than a first preset intensity threshold, sending a pairing response signal to the wireless remote control equipment; when the wireless remote control equipment receives the pairing response signal within a preset time, detecting the intensity of the pairing response signal; if the intensity is higher than a second preset intensity threshold, the wireless remote control equipment pairs the network ID identifier thereof with the network ID identifier of the equipment to be paired, and sends a pairing success signal to the equipment to be paired in the case of pairing success; and the equipment to be paired stops sending the pairing response signal after receiving the pairing success signal. The method provided by the invention can be used for automatically completing equipment pairing and ensuring the pairing and communication security of the equipment, moreover, the method is easy to achieve, and the user experience is improved.
Owner:TSINGHUA UNIV
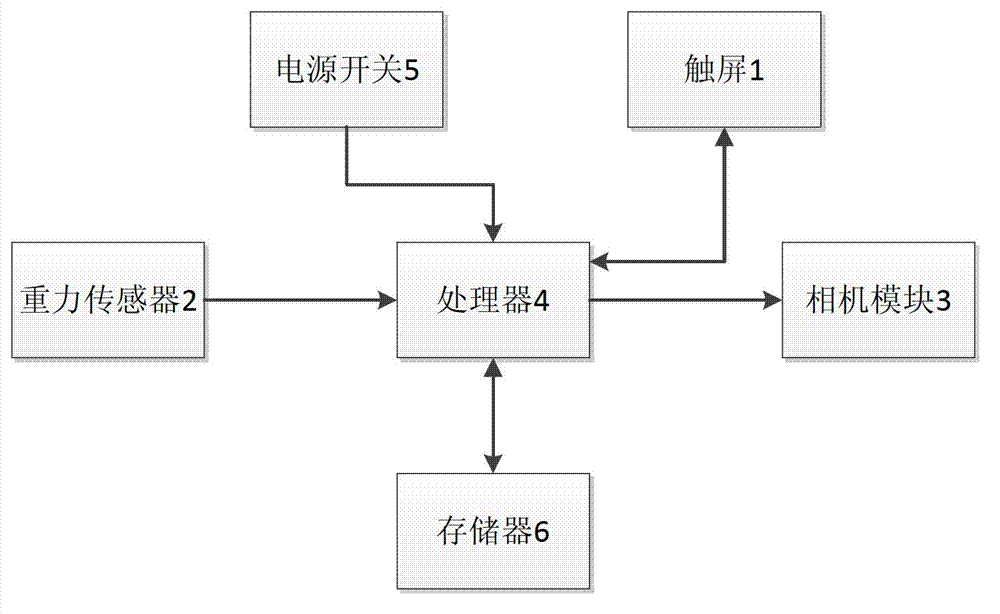
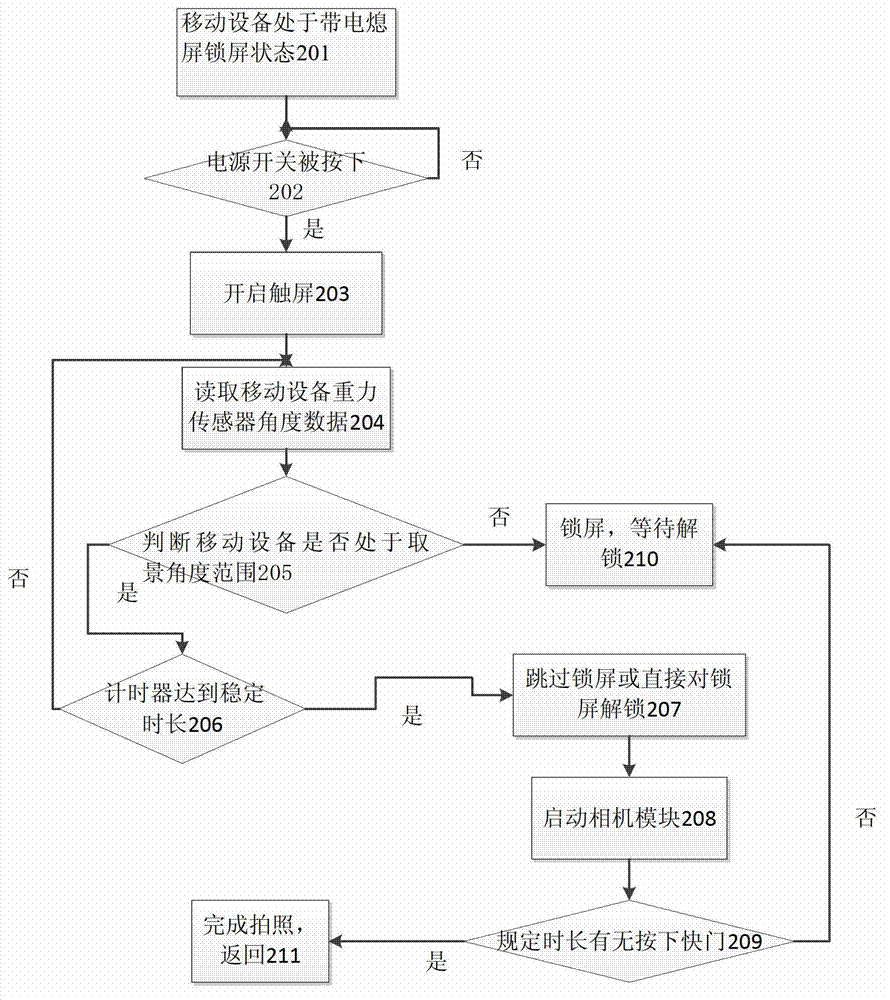
Method of starting camera by mobile device
ActiveCN103037103ASimple to extreme design styleWill not affect operating proceduresSubstation equipmentCamera moduleSmart technology
The invention relates to the mobile device technology, in particular to a method of starting a camera by a mobile device. When a key of the mobile device is pressed down, the method includes a first step of opening a touch screen (1) to transfer into a bright screen, a second step of reading angle data of the mobile device in a gravity sensor (2) of the mobile device and a third step of starting a camera module (3) when the angle data of a device body of the mobile device are in the range of viewing angle and predetermined stable length of time is kept. The method of starting the camera by the mobile device has the advantages of reducing operating steps required by a user who uses the mobile device to the minimum when a photographed function is started, and not influencing other operating procedures when the user uses other functions of the mobile device and initially guaranteeing photographing effect of tacking pictures due to the design of a function of straightening movement starting the camera. The method of starting the camera by the mobile device adopts humanized intellectual technology and enables the user to experience the simplest design style of the mobile device.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
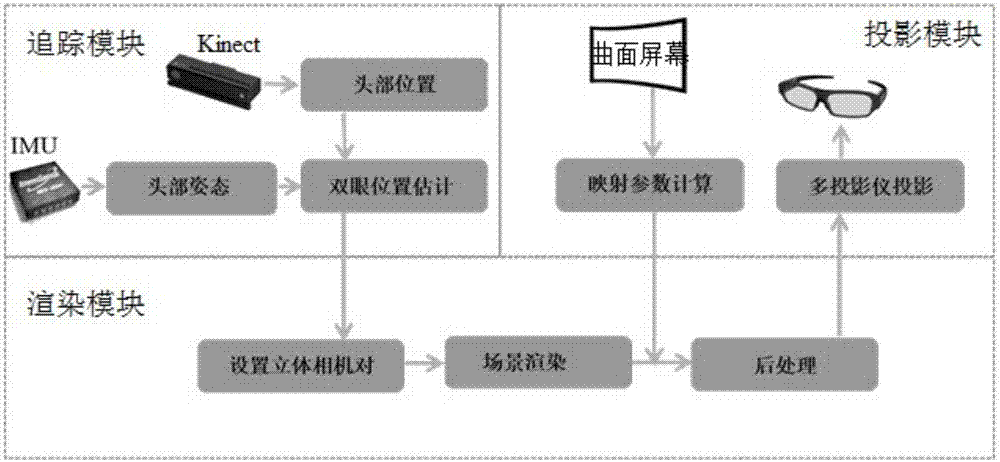
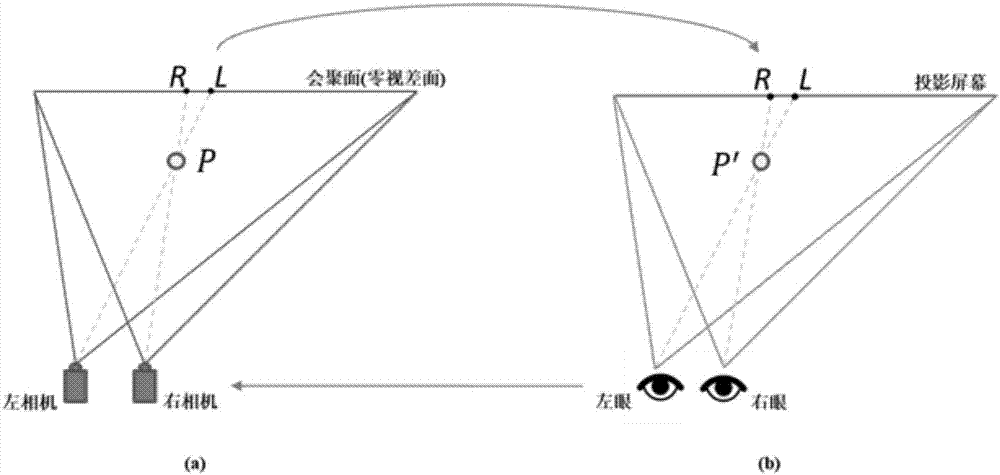
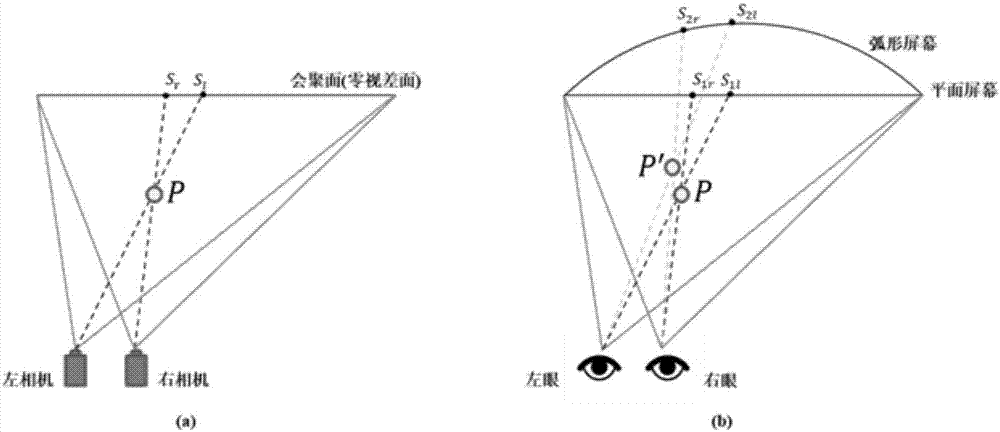
Immersive three-dimensional rendering projection system and method for moving view point on curved screen
ActiveCN107333121AHigh resolutionRender in real timeInput/output for user-computer interactionGraph readingUser perceptionStereo cameras
The invention relates to an immersive three-dimensional rendering projection system and method for a moving view point on a curved screen. The method is based on an immersive three-dimensional rendering projection system for a moving view point on a curved screen. The method comprises the following steps: acquiring user information: tracking user's head position and posture information, and estimating user's binocular positions and sight direction; setting three-dimensional rendering parameters: according to the estimated user's binocular positions and sight direction, adjusting a three-dimensional camera in real time to perform three-dimensional rendering of the moving view point on the parameters; performing dynamic parallax adjustment: performing post processing on the parallax of the rendered three-dimensional image according to the relative position relation between the user and the screen and the geometric shape information of the projection screen, so that the user views comfortable and correct three-dimensional images at his position; optimizing user perception: for user's head posture and eyeball movement, further optimizing the image respectively after the dynamic parallax adjustment; and projecting a three-dimensional scene: watching a virtual roaming three-dimensional scene by the user wearing a pair of three-dimensional glasses.
Owner:SHANDONG UNIV
Mobile terminal and operating method thereof
ActiveCN102830926AImproved handling and agilityRealize the user experienceInput/output processes for data processingHuman–computer interactionComputer terminal
The invention discloses a mobile terminal. The mobile terminal comprises a first touch module, a second touch module and a touch screen controller. The first touch module is disposed in a first touch area of the mobile terminal. The second touch module is disposed in a second touch area of the mobile terminal. The second touch area and the first touch area are located at different positions of the mobile terminal. The touch controller is connected with the first touch module and the second touch module respectively and capable of processing input signals from the two touch modules simultaneously, so that the mobile terminal can be operated by any touch area or the two touch areas in cooperation. Operating performance and flexibility of the mobile terminal can be improved, and high-level user experience is improved.
Owner:BEIJING SAMSUNG TELECOM R&D CENT +1
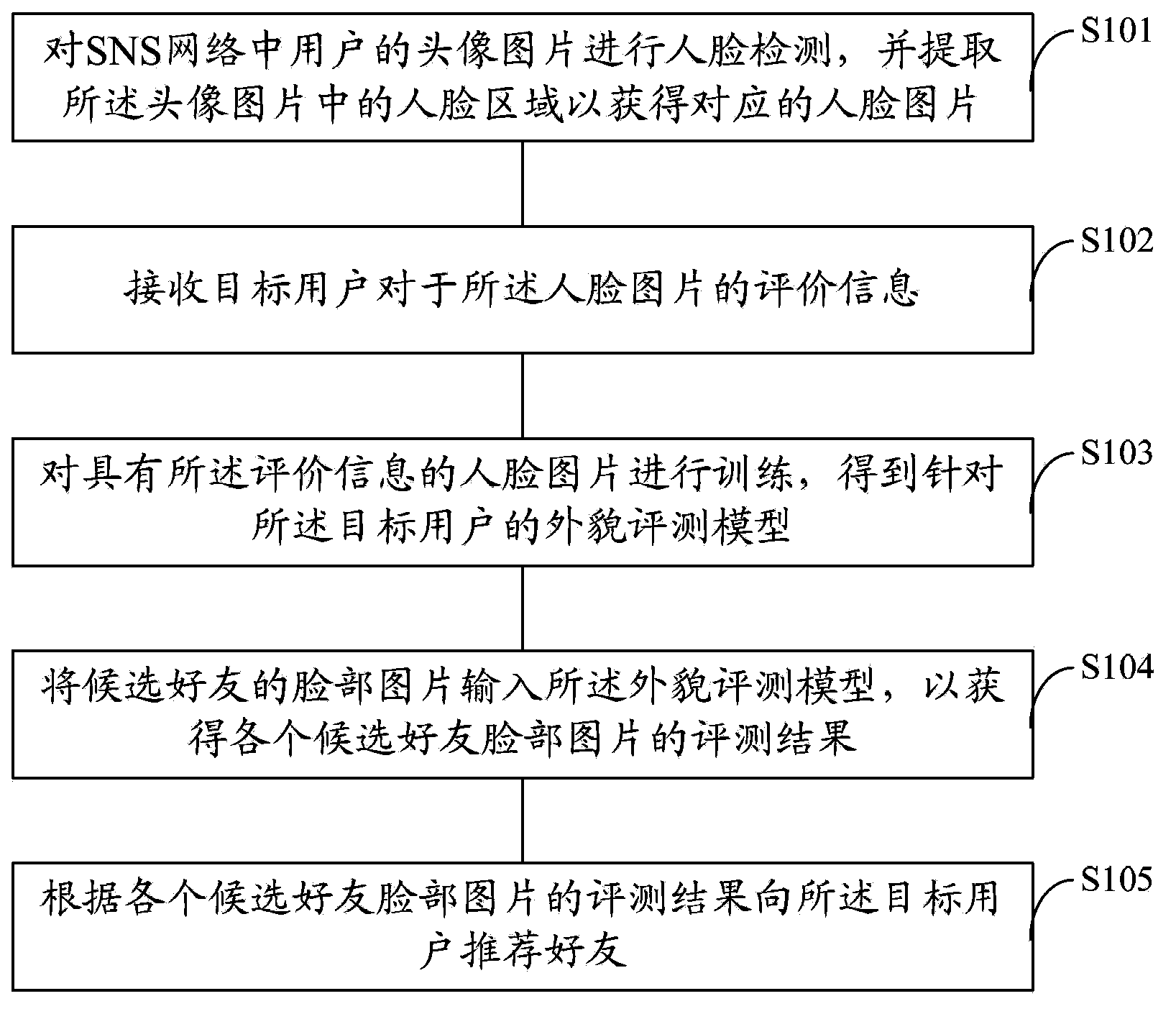
Friend recommendation method and system in SNS network
InactiveCN103678323AAchieve experienceAchieve recommendationCharacter and pattern recognitionSpecial data processing applicationsEvaluation resultFace detection
The invention provides a friend recommendation method and system in the SNS network. The friend recommendation method in the SNS network comprises the steps that face detection is carried out on head pictures of users in the SNS network, and face areas in the head pictures are extracted to obtain corresponding face pictures; evaluation information of the face pictures is received from a target user; the face pictures with the evaluation information are trained, and an appearance evaluating model with respect to the target user is obtained; the face pictures of candidate friends are input into the appearance evaluating model to obtain the evaluation result of the face picture of each candidate friend; friends are recommended to the target user according to the valuation result of the face picture of each candidate friend. By means of the technical scheme, the friend recommendation method and system in the SNS network can realize the function of friend recommendation in the SNS network on the basis of accurately meeting the preference for the appearances of friends for the target user.
Owner:云汉芯城(上海)互联网科技股份有限公司
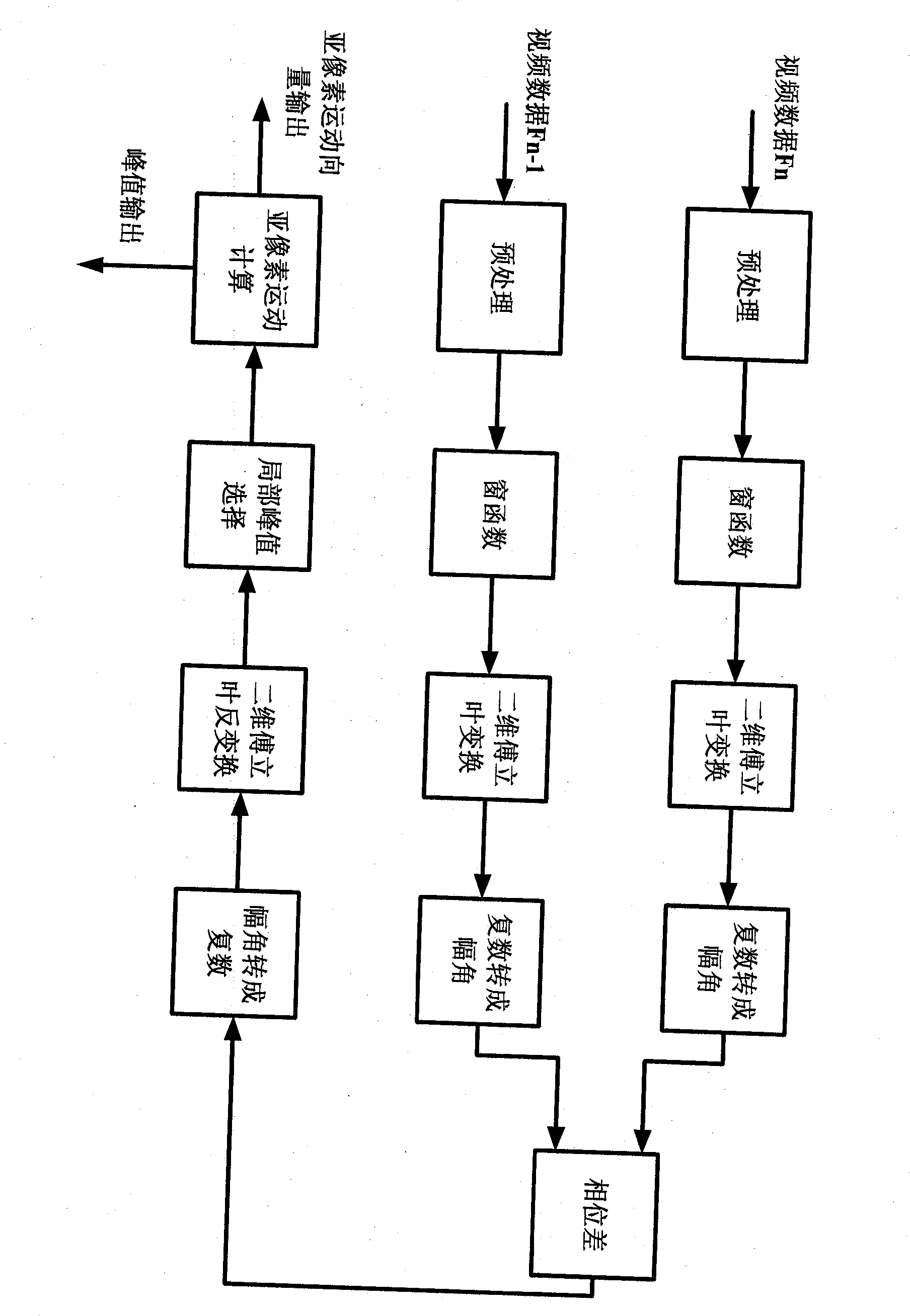
Super-resolution reconfiguration method based on multiframe motion estimation and merging
InactiveCN102236889AAchieve experienceAccurate acquisitionImage enhancementTelevision system detailsPhase correlationImage resolution
The invention relates to a super-resolution reconfiguration method based on multiframe motion estimation and merging. In the method, a phase relevant plane is solved from every two adjacent frames in a multiframe image, and multiframe sub-pixel motion estimation is realized on the basis of a parabolic model on the separated two-dimensional phase relevant plane; and a motion vector of a decimal part and a motion vector of an integer part of the sub-pixel motion estimation are applied to a low-resolution image and a high-resolution image respectively, and the current frame image and a plurality of adjacent reference frame images are merged to reconfigure the high-definition image corresponding to the current frame image and provide the reconfigured high-definition image for users, so the ornamental user experience of the users on high-definition video data by network transmission is realized.
Owner:王洪剑
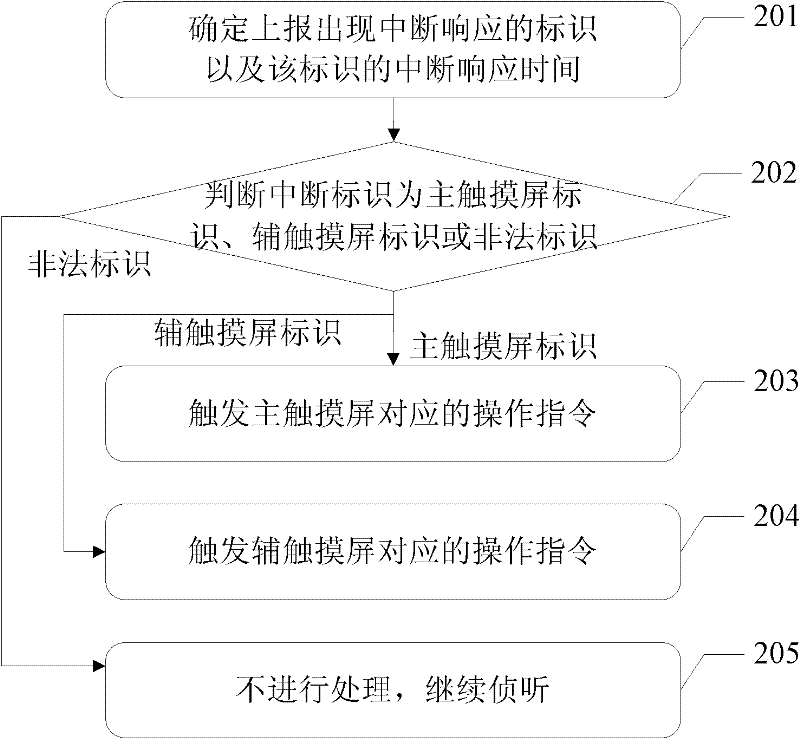
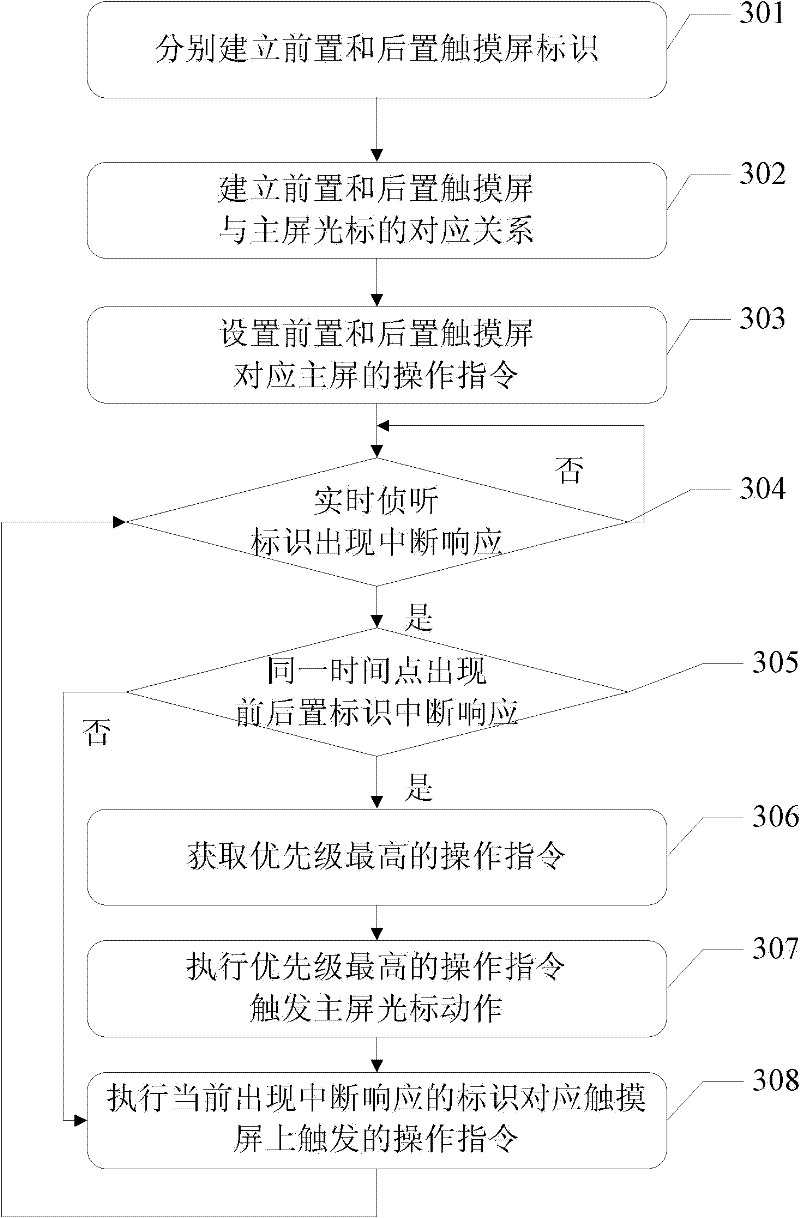
Electronic equipment input method, device and electronic equipment based on device
ActiveCN102681710ASmooth information inputNo intermittent information inputInput/output processes for data processingTouchscreenTouch function
The invention discloses an electronic equipment input method, a device and electronic equipment based on the device. The method comprises the following steps of: additionally arranging a plurality of touch screens (such as a front main touch screen, a back auxiliary touch screen and the like) with multi-point touch functions on the electronic equipment; performing operations such as real-time interception, concurrent interruption arbitration and the like by establishing identifications which correspond to the touch screens; and making a main screen of the electronic equipment respond to parallel operation of a plurality of touch screens by a user. The user can perform electronic equipment input operation smoothly without intermittency in an unobstructed way by using an auxiliary touch screen arranged on the electronic equipment through the method disclosed by the invention; and meanwhile, a main touch screen and the auxiliary touch screen on the electronic equipment are controlled to perform parallel work, so that the main screen of the electronic equipment can be used for receiving commands of the plurality of touch screens simultaneously, and new user experience of parallel work of the plurality of touch screens can be realized.
Owner:LEADCORE TECH
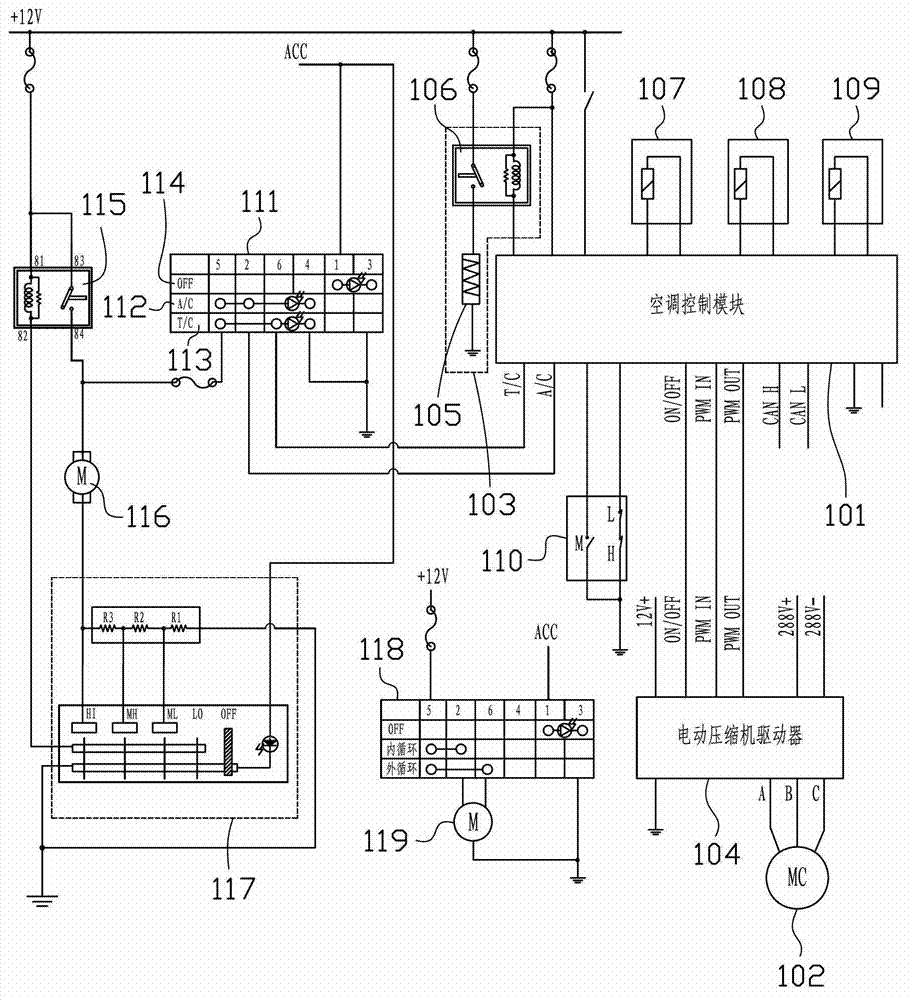
Air conditioning system for hybrid power vehicle
InactiveCN103158495AEnergy saving and fuel saving rateImprove fuel economyAir-treating devicesVehicle heating/cooling devicesIn vehicleEvaporator
The invention provides an air conditioning system for a hybrid power vehicle. The air conditioning system for the hybrid power vehicle comprises a motor compressor, a condenser, a receiver-drier, an expansion device, an evaporator, a heater, a blower, an air conditioning control module, an in-vehicle temperature sensor and an air conditioning switch, wherein the air conditioning control module is connected with a field bus, and used for controlling working states of the motor compressor and the heater; the in-vehicle temperature sensor is connected with the air conditioning control module and used for measuring in-vehicle temperature and supplying the measured temperature to the air conditioning control module; the air conditioning switch comprises a refrigeration switch and a heating switch, both the refrigeration switch and the heating switch are electrically connected with the air conditioning control module and respectively used for sending refrigeration and heating request signals after being triggered, and then the air conditioning module at least combines in-vehicle temperature to determine the working state of the motor compressor and the heater. The air conditioning system for the hybrid power vehicle has the advantages that a constant temperature function which is not possessed by a traditional vehicle manual air conditioning system is achieved, frequency conversion performance is possessed, energy is saved, and fuel saving ratio is improved.
Owner:HANGZHOU BRANCH ZHEJIANG GEELY AUTOMOBILE RES INST +2
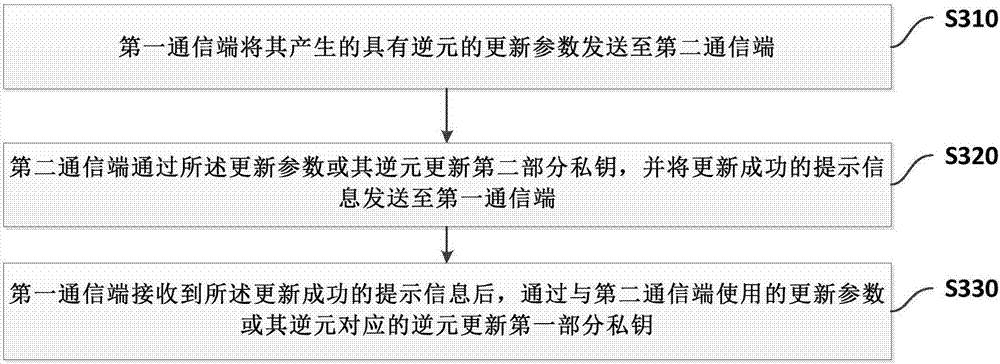
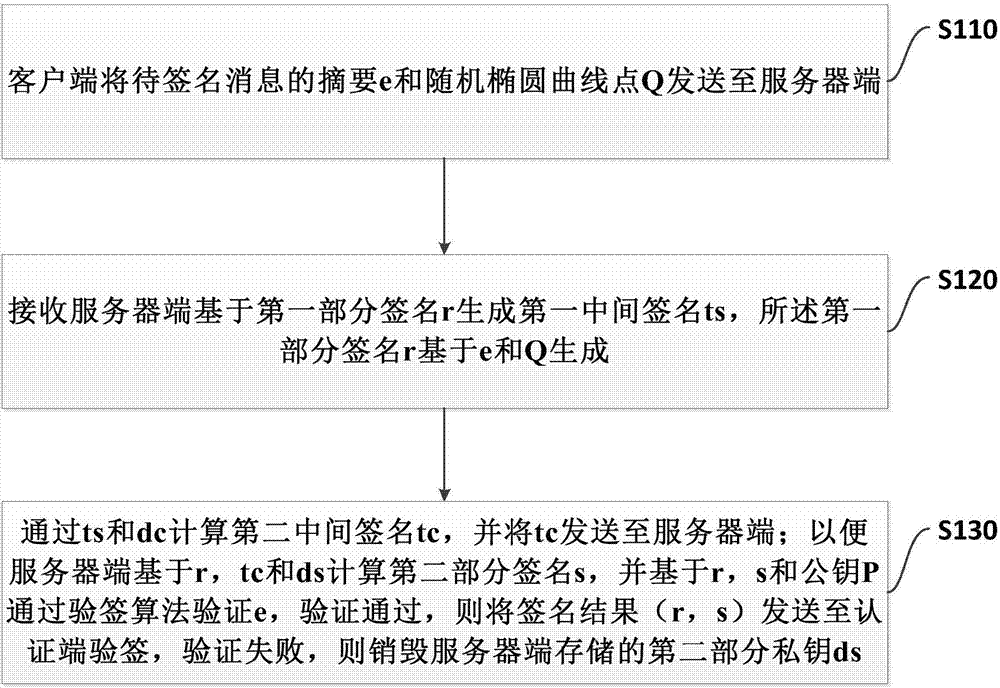
Private key protection method, system and device based on key updating
ActiveCN107302438AReliable digital signatureAvoid Offline AttacksKey distribution for secure communicationPublic key for secure communicationSystems designDigital signature
The invention provides a private key protection method, system and device based on key updating. The first part of private keys are stored at a first communication end, the second part of private keys are stored at a second communication end, and electronic signatures are generated after cooperative operation of the first part of private keys and the second part of private keys. The method comprises the following steps: sending generated updating parameters with inverse elements to the second communication end by the first communication end; after the first communication end receives successfully updated prompt messages fed back at the second communication end through the updating parameters or the second part of private keys updated by the inverse elements, updating the first part of private keys through the updating parameters used at the second communication end or the inverse elements corresponding to the updating parameters. Through the key system design that the private keys are stored at the two communication ends respectively, the technological means of dynamic key updating is combined, the attacks, such as bucket effect and exhaustive trial and error, of Hackers for single-point attack of the client are avoided, the business risk that digital signatures are counterfeited by a server is avoided, and the using convenience is promoted.
Owner:吕文华
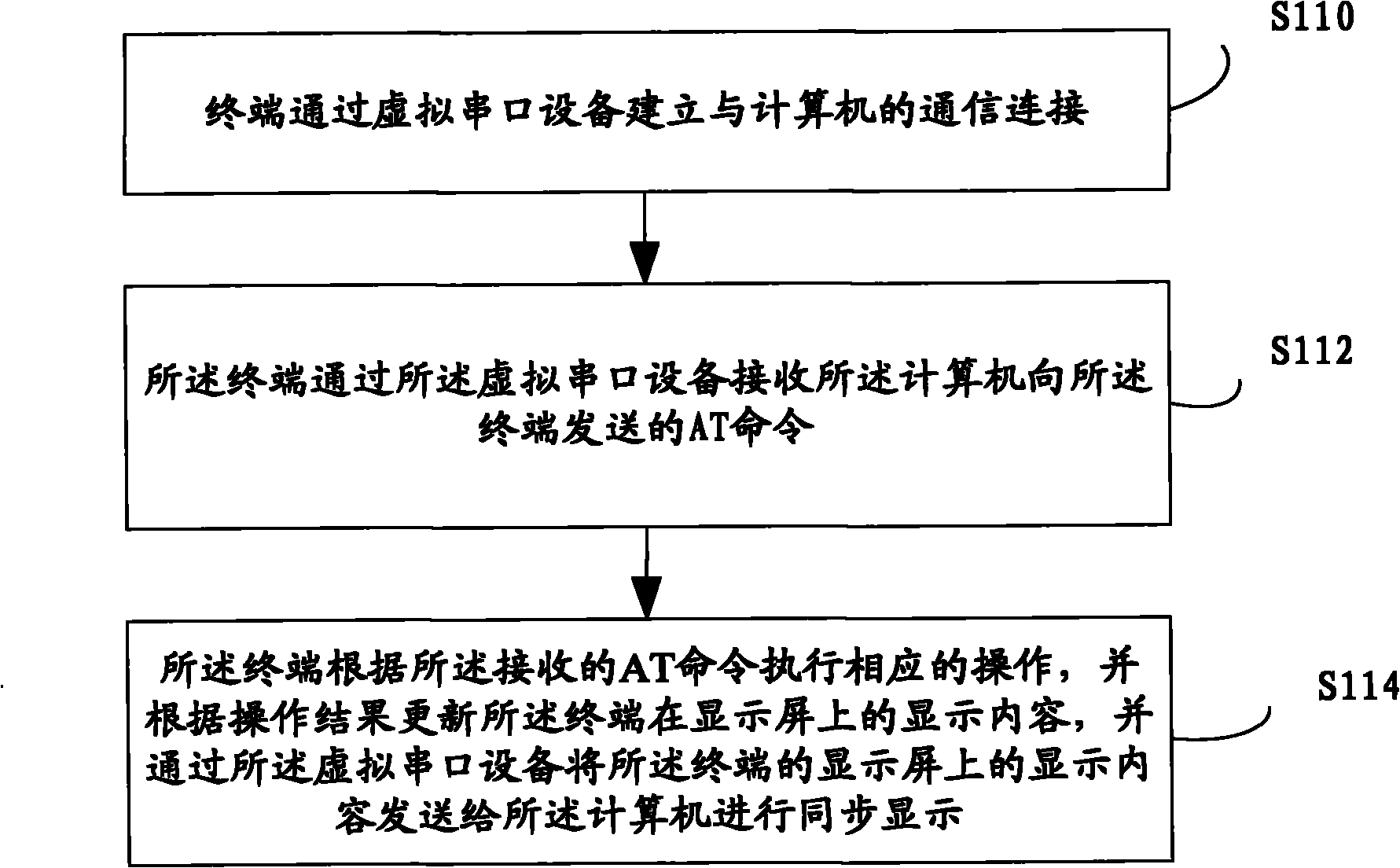
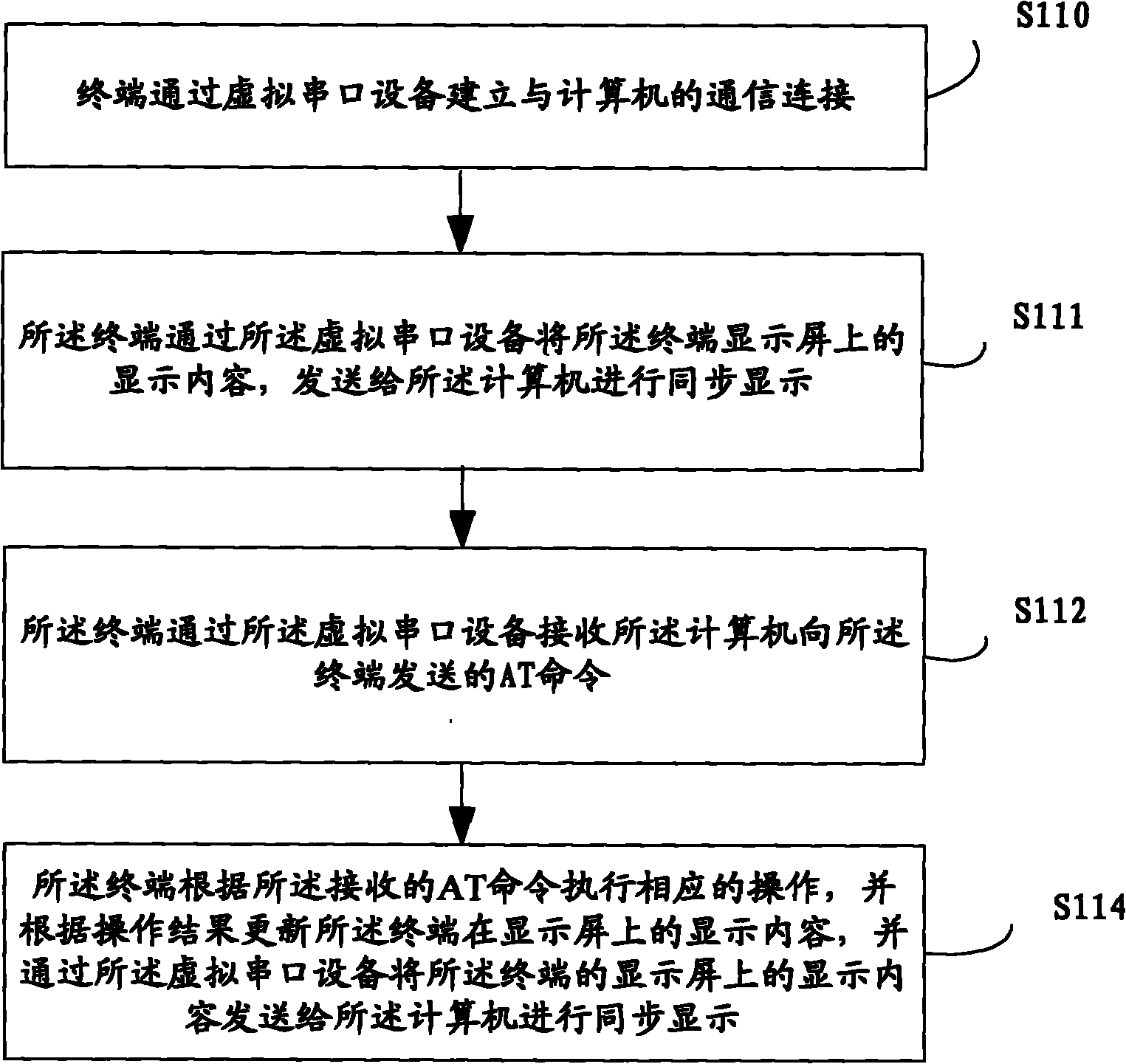
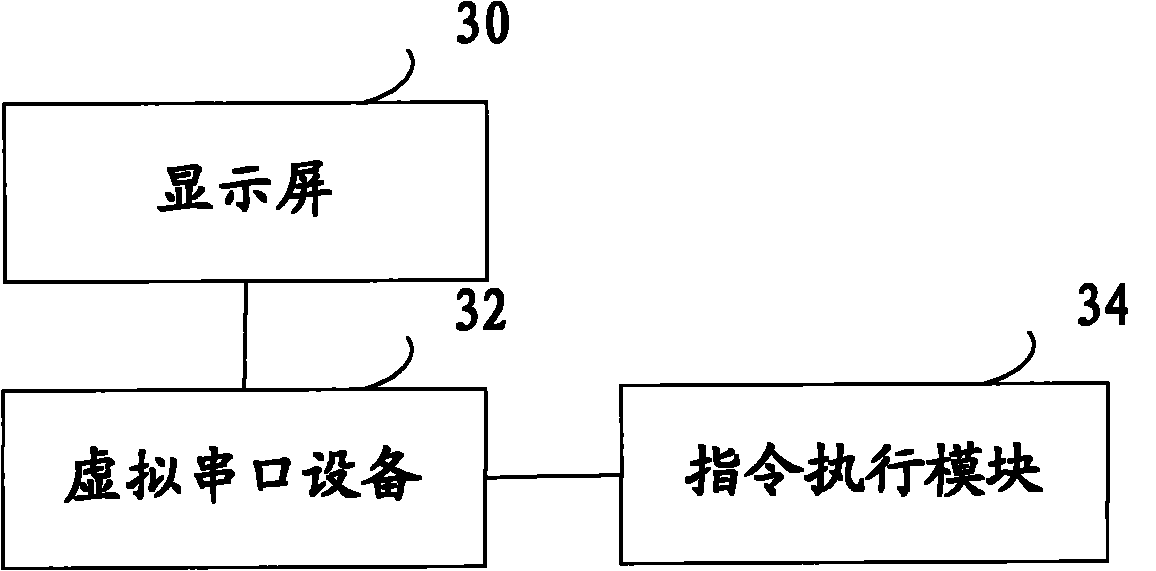
Terminal control method, terminal and computer
InactiveCN102033838AAchieve experienceRealize remote displayElectric digital data processingComputer terminalComputer engineering
The embodiment of the invention provides a terminal control method, a terminal and a computer. The terminal control method comprises the following steps of: establishing a communication connection with the computer through a virtual serial port device by the terminal; receiving an AT (Attention) command sent by the computer to the terminal through the virtual serial port device by the terminal, wherein the AT command is used for indicating the terminal to perform specific operations; and executing corresponding operations according to the received AT command, updating a display content of the terminal on a display screen according to an operation result and sending the display content of the terminal on the display screen to the computer for synchronous display through the virtual serial port device, by the terminal. By implementing the invention, a user can obtain the experience for operating the terminal, without contact with the terminal, and the experience of the user is enhanced.
Owner:DONGGUAN YULONG COMM TECH +1
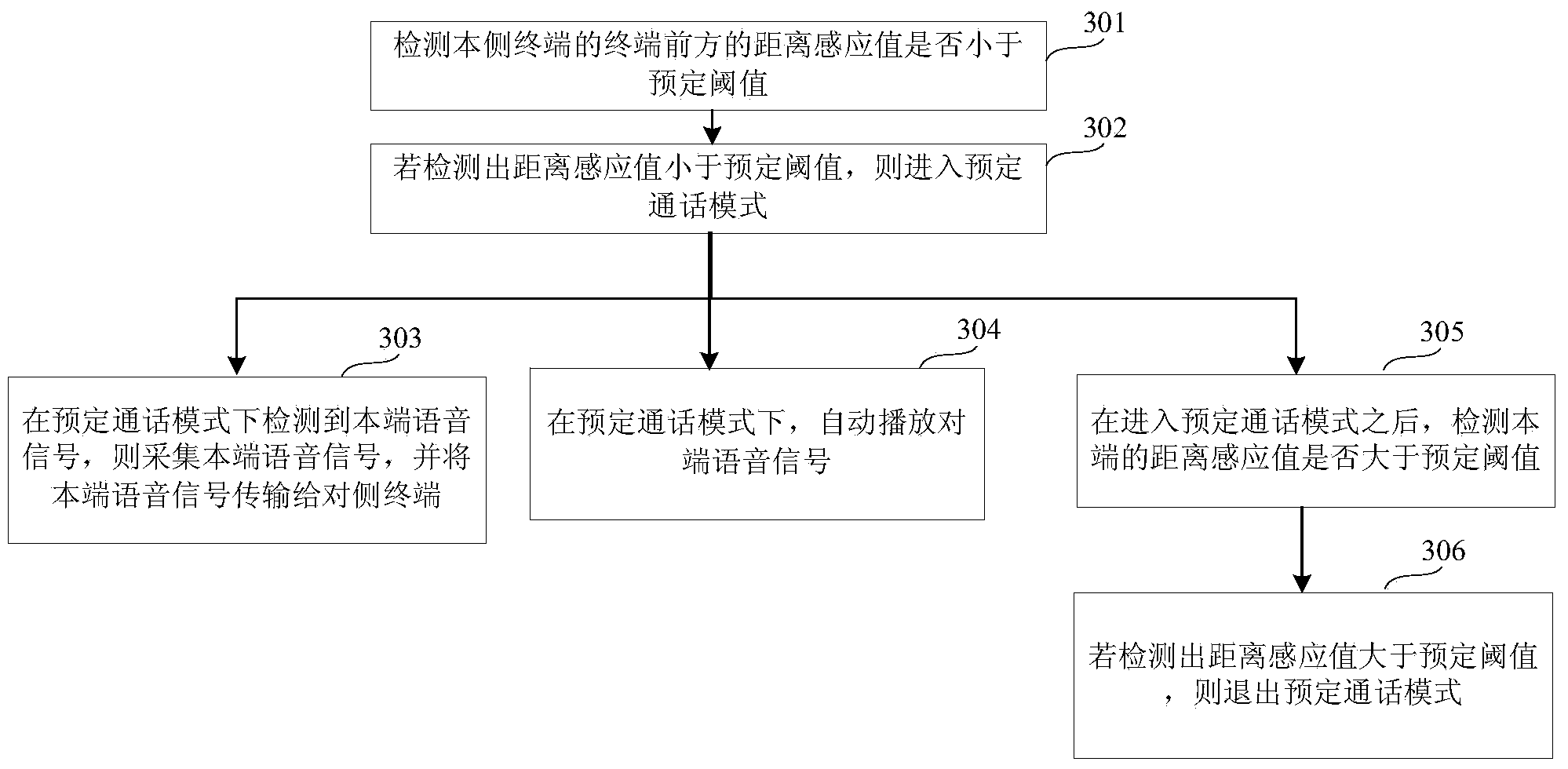
Voice communication method, voice playing method and devices
ActiveCN103973544ASolve the problem that the network walkie-talkie cannot be used smoothlyAchieve experienceSubstation equipmentAutomatic exchangesVoice communicationComputer science
The invention discloses a voice communication method, a voice playing method and devices, and belongs to the field of communication. The voice communication method includes detecting a distance sensing value of a local end and determining whether the distance sensing value is smaller than a preset threshold value or not; entering a preset communication mode if the detected distance sensing value is smaller than the preset threshold value; automatically playing voice signals of an opposite end in the preset communication mode; acquiring voice signals of the local end when the voice signals of the local end are detected in the preset communication mode, and transmitting the voice signals of the local end to the opposite end. The voice communication method, the voice playing method and the devices have the advantages that the problem that network interphones cannot be smoothly utilized when users cannot conveniently carry out press operation or click operation on terminals at present is solved; an effect that network interphones can be automatically triggered to play and acquire voice and can be utilized without other operation as long as users attach terminals to the ears is realized.
Owner:XIAOMI INC
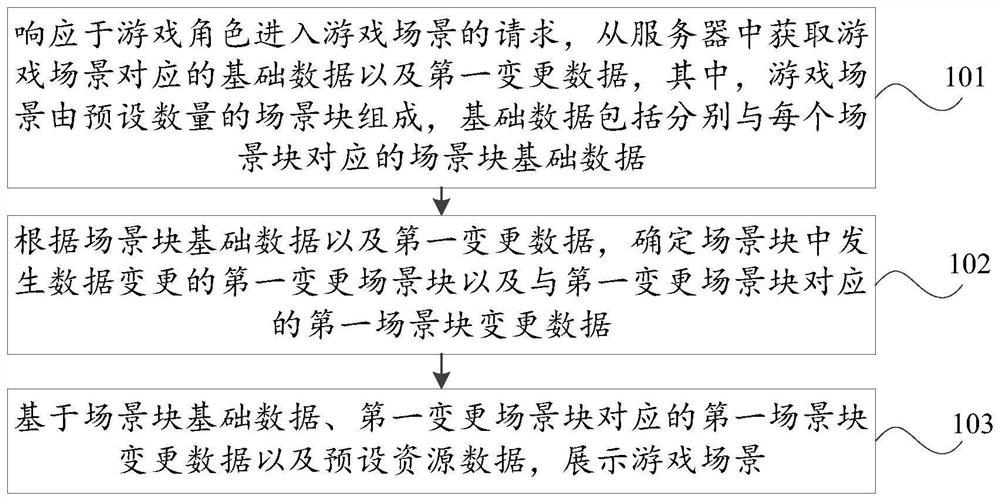
Game scene data processing method and device, storage medium and computer equipment
ActiveCN112023399AModification is smallIncrease creation speedVideo gamesComputer visionComputer equipment
The invention discloses a game scene data processing method and device, a storage medium and computer equipment, wherein the method comprises the steps: obtaining basic data and first change data corresponding to a game scene from a server in response to a request that a game role enters the game scene, and enabling the game scene to be composed of a preset number of scene blocks, wherein the basic data comprises scene block basic data corresponding to each scene block, and the first change data comprises modification data of a player for resources in the game scene; according to the scene block basic data and the first change data, determining a first change scene block with data change in the scene blocks and first scene block change data corresponding to the first change scene block; and displaying the game scene based on the scene block basic data, the first scene block change data corresponding to the first change scene block and preset resource data.
Owner:SHANGHAI PERFECT WORLD SOFTWARE CO LTD
Device and method for quickly starting or awakening intelligentized television
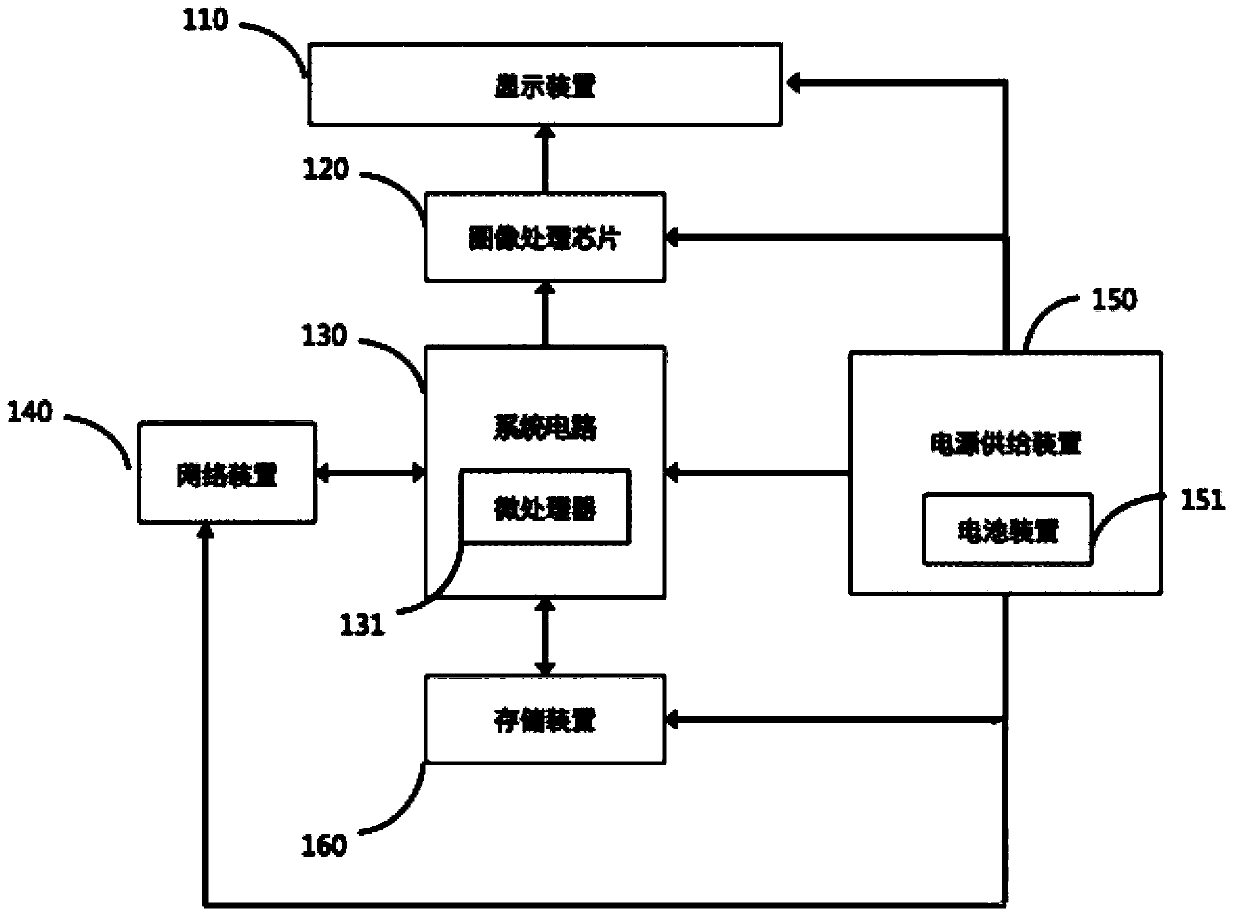
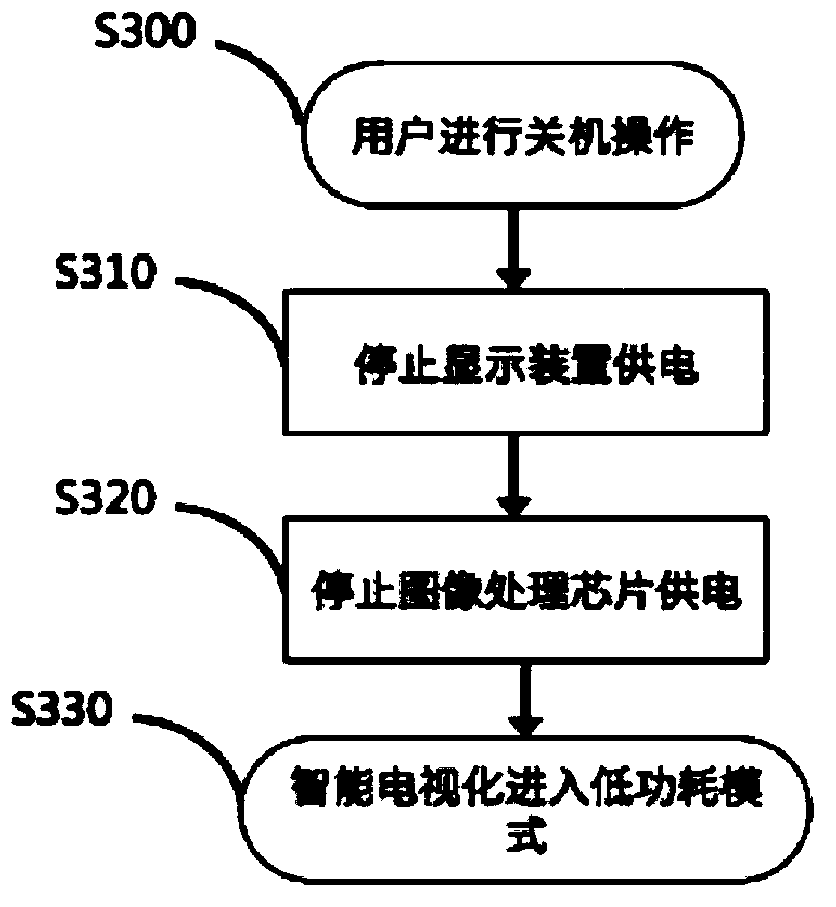
InactiveCN103428561ARealize the user experienceFast bootTelevision system detailsColor television detailsDisplay deviceImaging processing
The invention discloses a device for quickly starting or awakening an intelligentized television. The device comprises a display device for image displaying, an image processing chip connected with the display device and used for image processing, a system circuit connected with the image processing chip, a memory device for memorizing data and a network device for regularly updating the network data, wherein the system circuit is provided with a microprocessor and connected with the network device, the image processing chip and the memory device respectively. The device further comprises a power supply device, wherein the power supply device is connected with the display device, the image processing chip, the system circuit, the network device and the memory device respectively. The device for quickly starting or awakening the intelligentized television can achieve quick starting or awakening by setting a low power consumption mode.
Owner:刘惠斌
Method and device for processing webpage so as to display on handheld equipment
ActiveCN102023998AAchieve experienceSave traffic resourcesSpecial data processing applicationsWeb pageComputer science
The invention provides a novel webpage processing method and a webpage processing device. The novel webpage processing method comprises the following steps of: filtering a markup language code of a webpage and confirming a first position in a filtered text block on the basis of a keyword so as to carry out treatment before display on at least one text paragraph behind the first position and provide the text paragraph to the handheld equipment used by a user, wherein the area of a display screen of the handheld equipment is limited by the size of the handheld equipment. By adopting the invention, the simplified webpage content is more close to the content which is expected to view by the user, and redundancy is eliminated to the greatest extend, therefore, the handheld equipment used by the user can display the content which is expected to display by the user as more accurate as possible, and the user experience of demand during viewing is realized.
Owner:CREATIVE TECH CORP
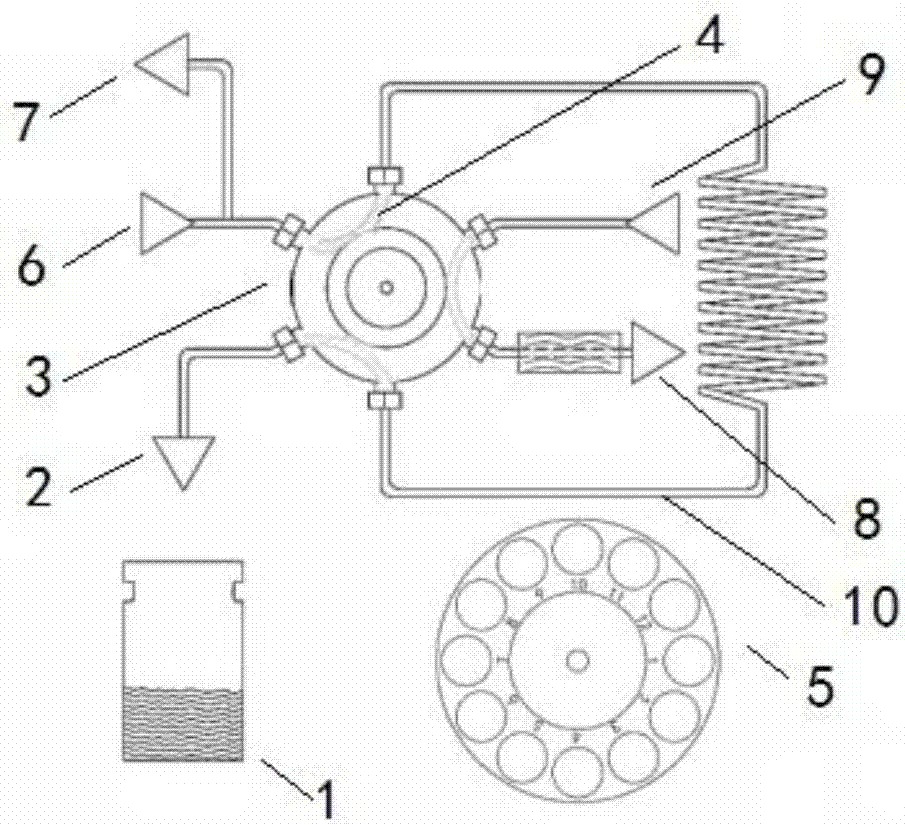
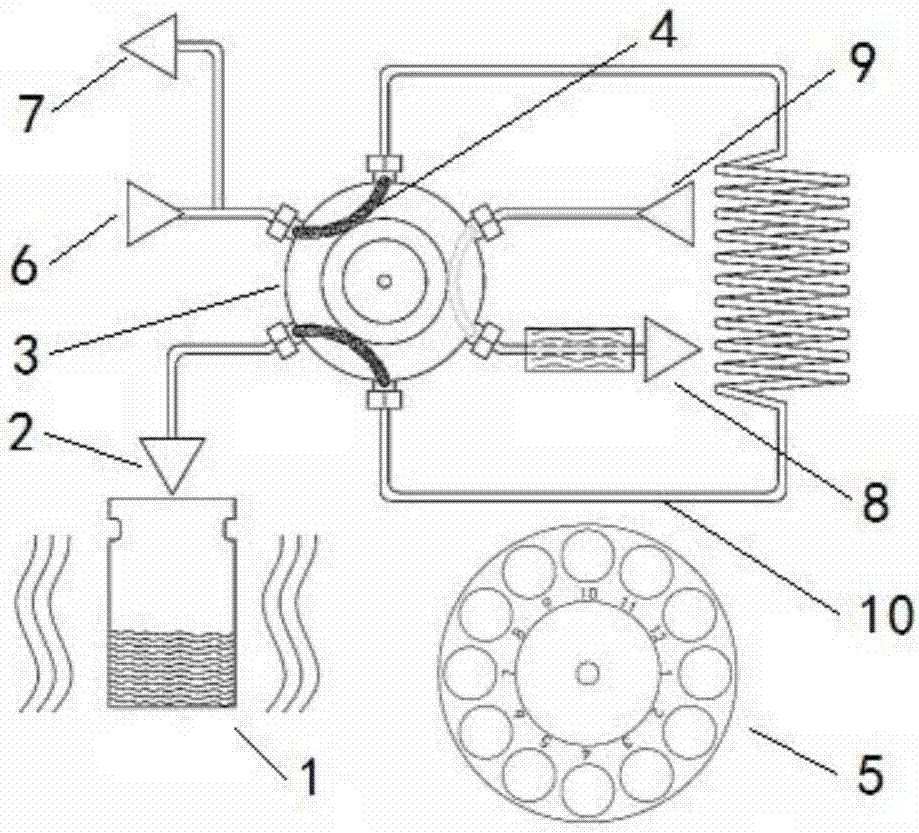
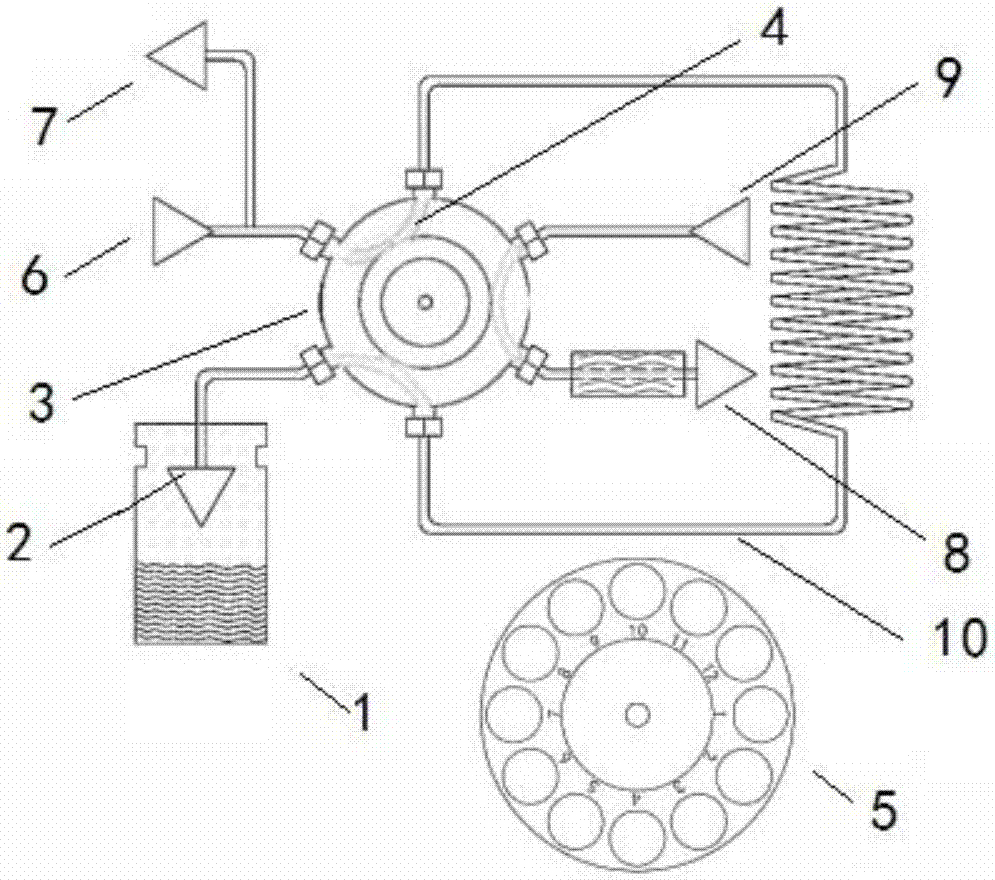
Full-automatic headspace sampling device
The invention discloses a full-automatic headspace sampling device which comprises a sampling needle, a heating furnace, a sample bottle lifting mechanism, a six-way valve, a gas quantifying cup, a pressurizing control valve, a release control valve, a gas phase carrying interface, a gas chromatograph interface and a controller, wherein the sample bottle lifting mechanism is used for driving a sample bottle to move to be in a waiting position, a heating position or a sampling position; the six-way valve has six connection interfaces and can be rotated; and the controller is used for controlling the sample bottle lifting mechanism to drive the sample bottle to move to the heating position from the waiting position after sampling action is completed, used for driving the sample bottle to move to the sampling position from the heating position after heating is completed, or used for driving the sample bottle to the waiting position from the sampling position after sample feeding action is completed. The full-automatic headspace sampling device provided by the invention can completely meet daily analysis requirements of laboratories of common medicine monitoring, environment protection and the like, and is an ideal tool for directly and efficiently extracting volatile organic compounds from any non-volatile organic matters and for feeding samples to gas chromatography analysis.
Owner:BCTTECH
Experience air conditioner, experience machine and scene movement system of experience machine
PendingCN109489124AIncrease interest in sportsRelaxMechanical apparatusSpace heating and ventilation safety systemsAir volumeControl signal
The invention discloses an experience air conditioner, an experience machine and a scene movement system of the experience machine. An existing air conditioner only has an indoor temperature functionas a household electrical appliance. The experience air conditioner comprises an air conditioning system (1), the air conditioning system is provided with a scene experience control module (2), the scene control module comprises a controller (3) and an odor releaser (4) connected with the controller (3) as well as a signal receptor (5) connected with sports equipment (19), the sports equipment signal receptor (5) is used for transmitting a signal to the controller (3), the controller is used for outputting a control signal to a display and the air conditioning system (1), the playing speed ofthe display and the air supply mode, the temperature adjustment and odor release of the air conditioning system (1) are controlled through the signal, and the air supply mode comprises the control ofthe air outlet temperature, the air outlet angle, the air speed and the air volume of the of the air conditioner as well as the room humidity. According to the experience air conditioner, the experience machine and the scene movement system of the experience machine, the movement system and a VR scene system are arranged, so that the air conditioner is used as an air conditioner for body buildingand oxygen supply, an indoor exercise auxiliary instrument and a part of an entertainment tool.
Owner:王冠红
Management method, apparatus and system for remotely destroying private key
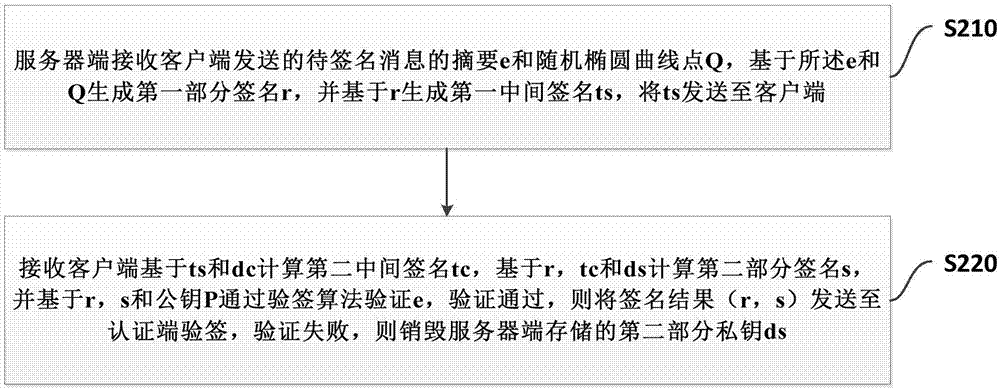
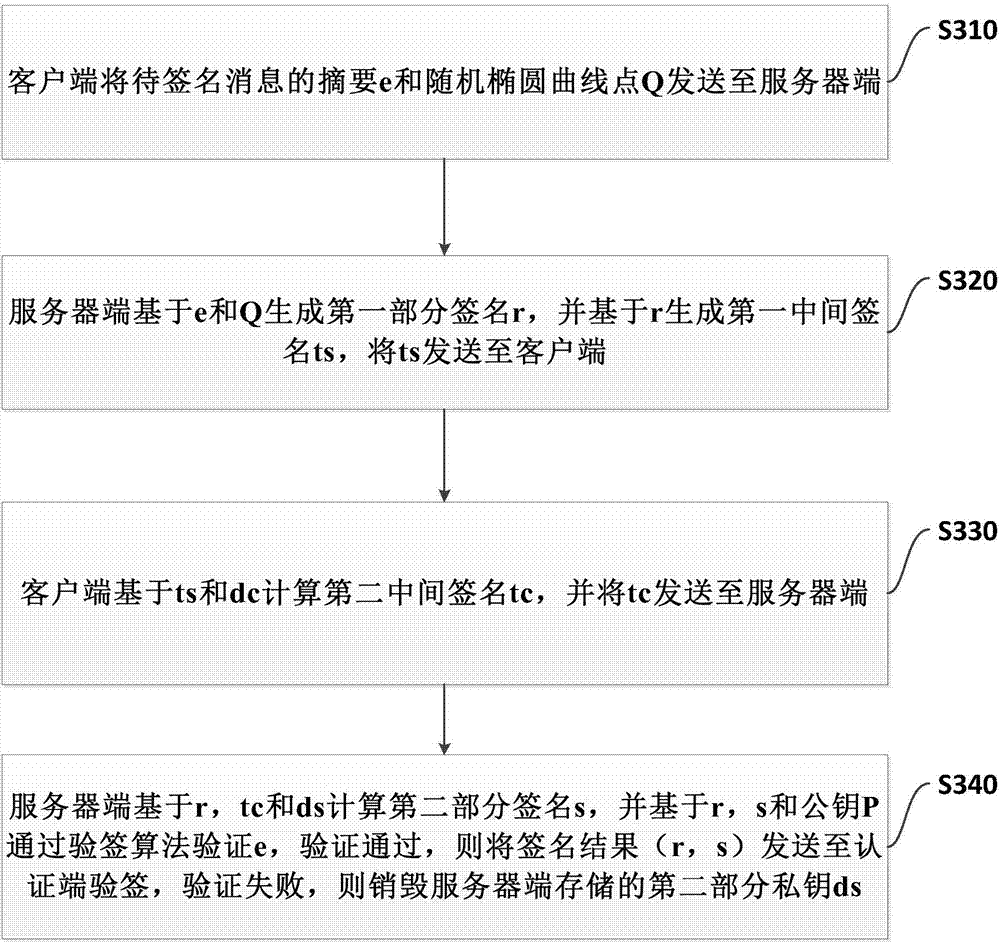
ActiveCN107370599AReliable digital signatureAvoid Offline AttacksKey distribution for secure communicationPublic key for secure communicationClient-sideTrial and error
The invention provides a management method, apparatus and system for remotely destroying a private key. A client stores a first part of the private key dc, a server side stores a second part of the private key ds, and an electronic signature is generated after cooperative calculation on the first part of the private key and the second part of the private key. The method comprises the following steps: sending a digest e and a random elliptic curve point Q by the client to the server side; receiving a first intermediate signature ts of the server side; and calculating a second intermediate signature tc through the ts and the dc, and sending the tc to the server side so that the server side can calculate a second part of the signature s and verify the e, if verification succeeds, a signature result (r, s) is sent to an authentication end for verification, and if the verification fails, the second part of the private key ds stored at the server side is destroyed. According to the invention, through the design of a key system for storing partial private keys respectively by using a client and a trusted central server and through combination with the technical means of dynamic key destruction,hacker attacks such as client-side single-point attacks, exhaustive trial and error attacks and the like are avoided.
Owner:BANKEYS TECH
Tourism landscape realization system based on virtual reality technology
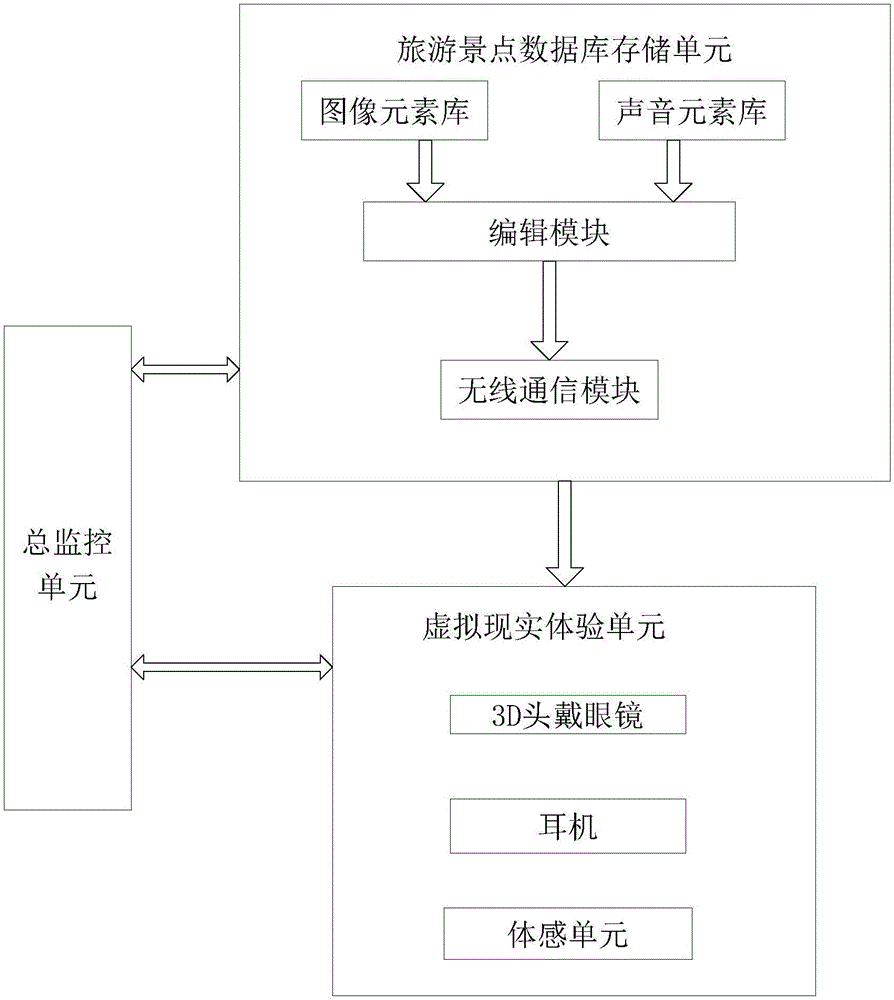
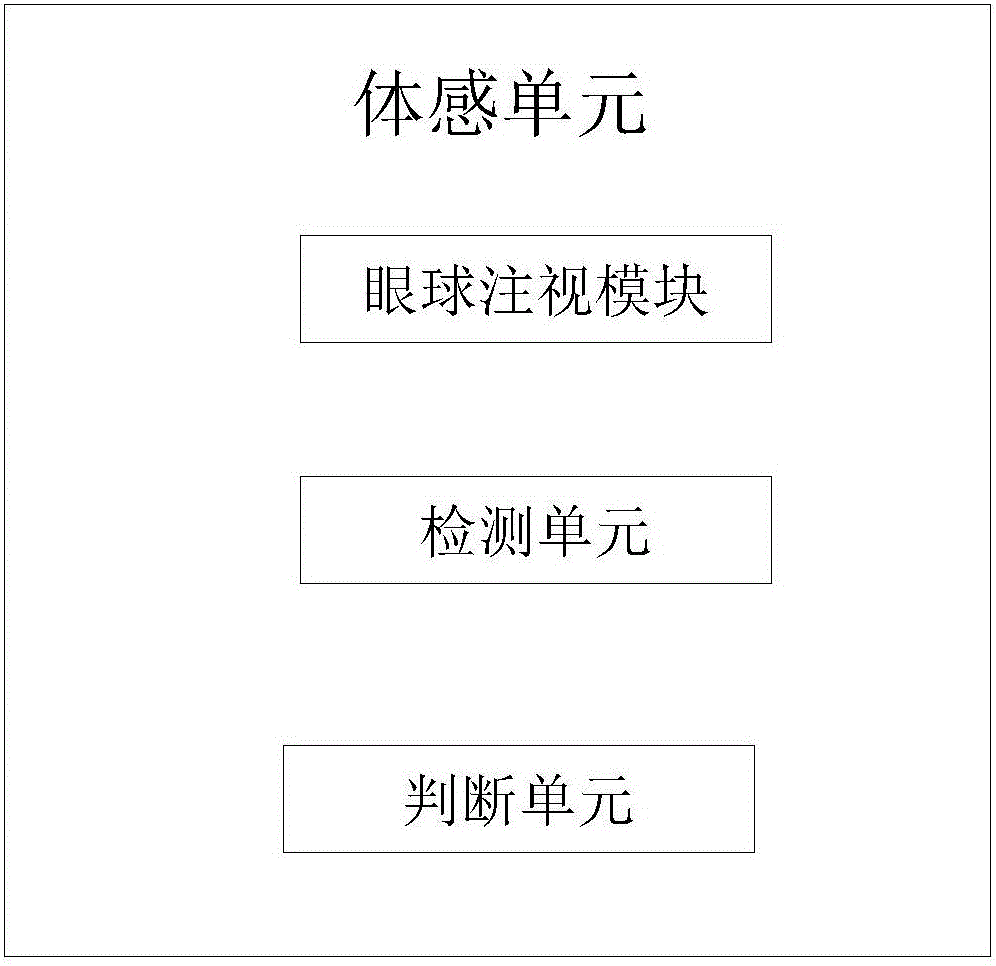
InactiveCN106445444AAchieve experienceRealize intelligent controlData processing applicationsDigital output to display deviceData informationVisual perception
The invention discloses a tourism landscape realization system based on virtual reality technology. The tourism landscape realization system comprises a tourism attraction database storing unit and a virtual reality experience unit, the tourism attraction database storing unit is arranged in a tourism attraction and stores landscape information of the tourism attraction, the landscape information includes an image element library, a voice element library, an editing module and a wireless communication module, and the editing module calls data information in the image element library and the voice element library for scene editing in virtual environment and transmits edited information to the wireless communication module; the wireless communication module transmits received information to the virtual reality experience unit which comprises 3D head-mounted glasses, an earphone and a somatosensory unit. 3D sceneries are edited through the tourism attraction database storing unit, and whether voice needs to be added or not is taken into account in the process of editing, so that due to the voice element library, a user can acquire more vivid visual and auditory experience, and vivid effect in the process of viewing is realized.
Owner:DALIAN VINCENT SOFTWARE TECH
Game scene picture adjusting method and device, mobile terminal and storage medium
ActiveCN109499061AReduce dependenceAchieve experienceVideo gamesVirtual controlGraphical user interface
The embodiment of the invention provides a game scene picture adjusting method and device, a mobile terminal and a storage medium. The game scene picture adjusting method and device are applied to themobile terminal capable of displaying a graphical user interface. The contents displayed by the graphical user interface include game scene pictures. The method comprises the steps that a target display area is provided to display part of game scene pictures; mobile information of the mobile terminal is monitored and contains, at least, the moving direction of the mobile terminal; if the includedangle formed by the moving direction and a first reset direction is in a preset included angle rang, the game scene pictures in the target display area are zoomed in or out according to the mobile information. In the embodiment, virtual controls for zooming in and out can be decreased, accordingly the occupied display area can be decreased, immersive user experience is achieved, view fields of virtual scenes are adjusted without the finger occupation of a user, it can be ensured that the fingers are used for other operations, conflict of different operations is avoided, and operation consistency is kept.
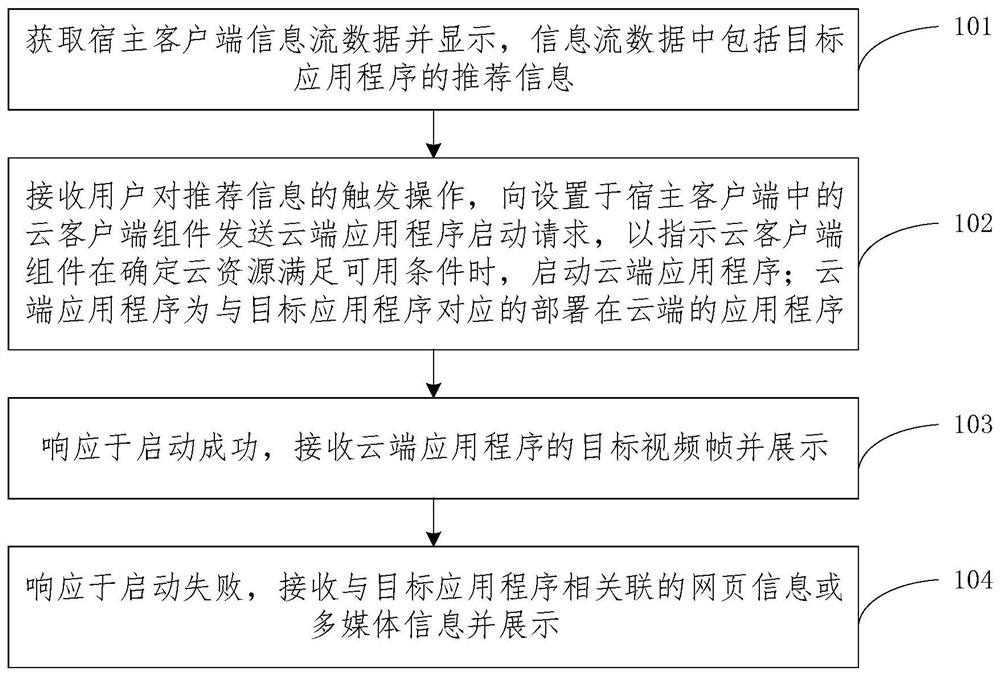
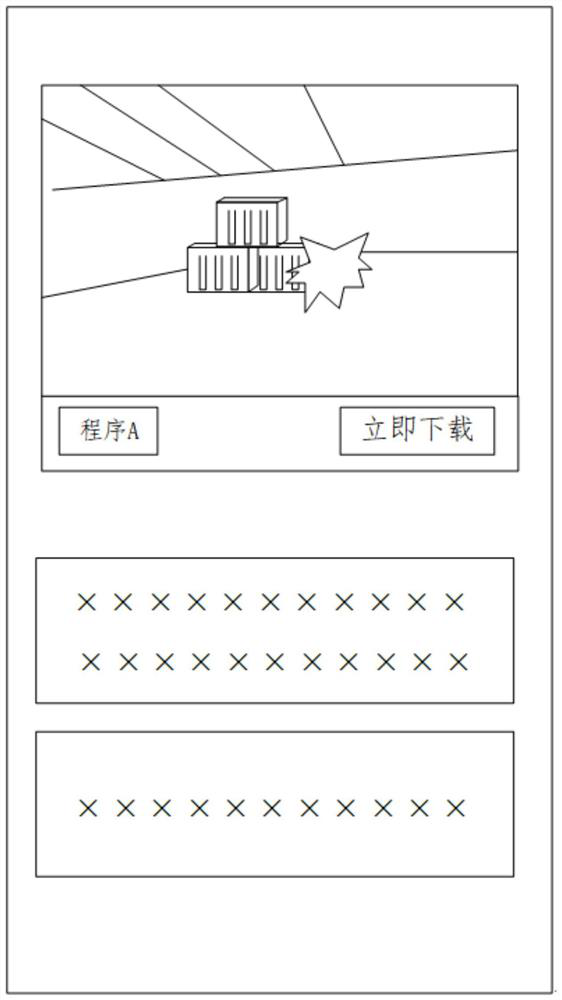
Owner:NETEASE HANGZHOU NETWORK
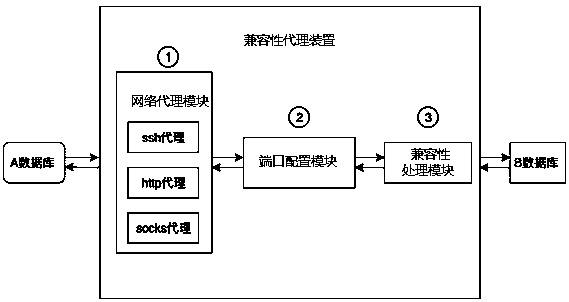
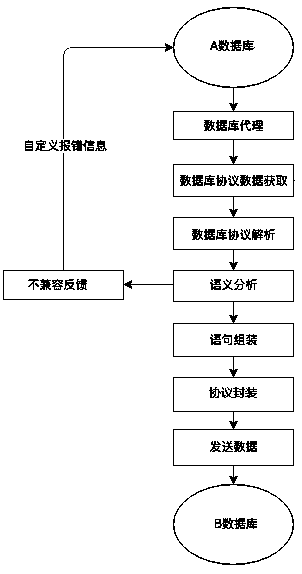
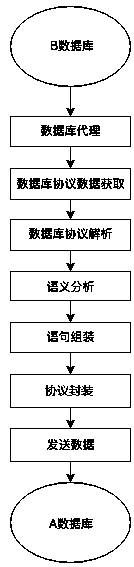
Database compatibility method based on protocol analysis and compatibility proxy device thereof
PendingCN111125218AImprove efficiencyImprove compatibilityDatabase management systemsSpecial data processing applicationsOn-ProtocolEngineering
The invention relates to the technical field of databases, and discloses a database compatibility method based on protocol analysis, which comprises the following steps: a compatibility proxy device is set between a client requesting a database and a server of a target database; the compatibility agent device receives the request of the client and the protocol packet of the request database, analyzes and assembles the request and the protocol packet, and sends the request and the protocol packet to the server; the compatibility agent device receives return data and a database protocol packet of a server of a target database, analyzes and assembles the return data and the database protocol packet, and returns the return data and the database protocol packet to a client requesting the database; the invention further discloses a compatibility agent device which comprises a network agent module, a port monitoring module and a compatibility processing module.
Owner:CHENGDU DBAPP SECURITY
Novel network-based mathematics learning system
According to the invention, on the basis of fusion of all editions of teaching materials in the country, scientific mathematics exercises are compiled according to the teaching material content and are presented to the user by a web way. Meanwhile, according to the system analysis, the network learning content and the classroom teaching process are synchronized, so that students can be helped to realize knowledge consolidation. Because the mathematics learning and the network game are combined and elements like updating completion, transcript team fight and the like of the network game can be absorbs, the mathematics learning interests of the students are simulated and the boring mathematics learning process can be improved, so that the students can learn mathematics during game playing and master the mathematics in happiness.
Owner:ZHENJIANG RUNXIN TECH INFORMATION
Dielectric-free floated projection virtual frame and reality interaction technology
ActiveCN108646578AAchieve interactionAchieve experienceComputer controlTotal factory controlDielectricSimultaneous localization and mapping
The invention discloses a dielectric-free floated projection virtual frame and reality interaction technology. Based on a motion sensing or speech recognition technology and a dielectric-free floatedprojection technology, the dielectric-free floated projection virtual frame and reality interaction technology implements dielectric-free floated projection virtual frame and reality interaction, andimplements matching of the virtual world position and the real position. In the specific implementation process, an SLAM (simultaneous localization and mapping) technology, a preset technology or a real-time correction technology are also used. The interaction technology uses a position decision device to determine the consistency of the virtual and real positions, and then triggers different applications based on the relationship between the virtual and real positions. The dielectric-free floated projection virtual frame and reality interaction technology realizes the function of connecting and interacting with the virtual frame and the object in reality by taking the dielectric-free air imaging as the basis and by combining the software with the hardware. The dielectric-free floated projection virtual frame and reality interaction technology belongs to a wholly new smart home control system and provides a new interaction experience and mode.
Owner:FEIXIANG TECH CO LTD
Application interaction method and device, equipment and medium
PendingCN112817781AAchieve experienceImprove experienceResource allocationInterprogram communicationStreaming dataSoftware engineering
Owner:BEIJING BYTEDANCE NETWORK TECH CO LTD
Method for automatically configuring a power utilization end based on house type household appliances and soft installation arrangement in decoration software
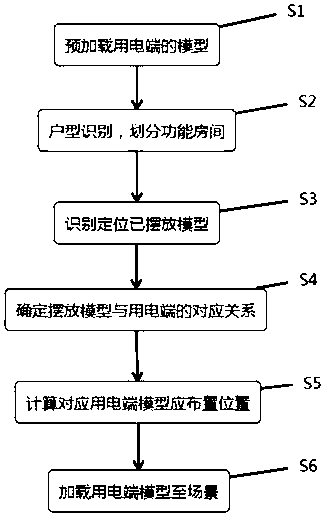
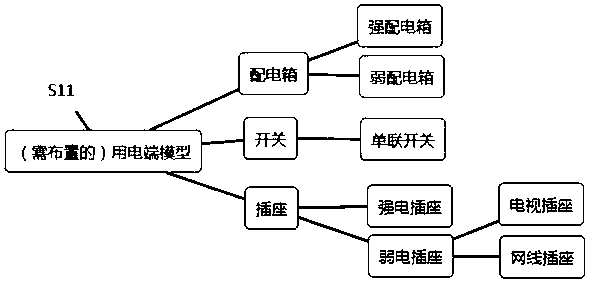
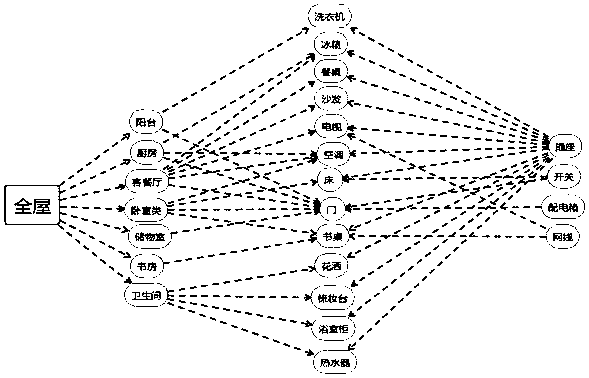
PendingCN109583010AAutomatic configuration is easy to operateLabor savingDesign optimisation/simulationSpecial data processing applicationsRoombaNational standard
The invention discloses a method for automatically configuring a power utilization end based on house type household appliances and soft installation arrangement in decoration software, and the methodcomprises the following steps: (1) preloading a model of the power utilization end, and obtaining the parameter information of a model entity; (2) obtaining all rooms in all house types, and dividingthe types according to the space; (3) traversing the objects in each room, and identifying all the objects needing to be configured with the power utilization ends; (4) carrying out article matchingaccording to national standards and user habits, and constructing a corresponding relation; (5) carrying out article matching according to national standards and user habits, and determining positiondata; And (6) loading the corresponding power utilization end model to a corresponding position. According to the method, the automatic configuration power utilization end is selected as a research target, the automatic configuration operation is relatively simple, the labor is saved, the method is suitable for multi-space automatic adaptation, and the experience of configuration one-key operationis realized.
Owner:GUANGDONG SANWEIJIA INFORMATION TECH CO LTD
Ship cabin experience system construction method based on virtual reality
PendingCN109992902AEasy to moveAchieve experienceGeometric CADDesign optimisation/simulationQuality by DesignSimulation
The invention discloses a ship cabin experience system construction method based on virtual reality. The method is characterized in that a three-dimensional immersion type ship cabin experience systemis constructed by adopting a VR technology; a computer is imported into a preset cabin model, a cabin three-dimensional scene is generated, an experiencer observes the cabin three-dimensional scene at any angle through head-mounted three-dimensional display equipment, an operation handle is used for interacting with the cabin scene, scene replacement, material replacement and object movement arecarried out, and changes of air flow, temperature, light and sound are felt. Compared with the prior art, the method has the advantages that an immersion effect is generated, approximately real experience is created in the aspects of vision, mood and feeling. A cabin design scheme is completed by a user through interactive selection in the virtual cabin. Design quality is improved, a design periodis shortened, and the design cost is saved.
Owner:ZHONGCHUAN NO 9 DESIGN & RES INST
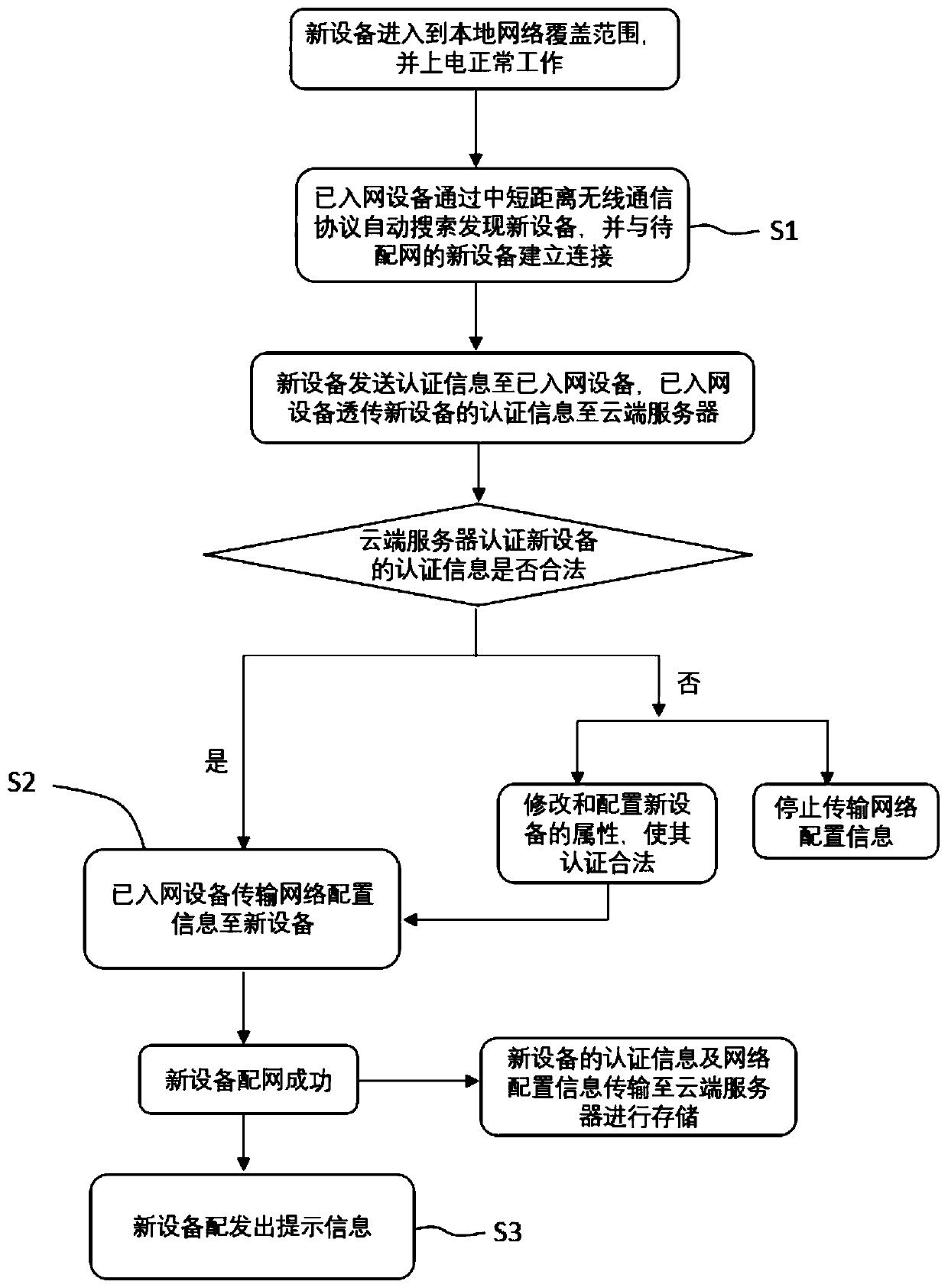
Automatic network distribution method for intelligent equipment and intelligent equipment
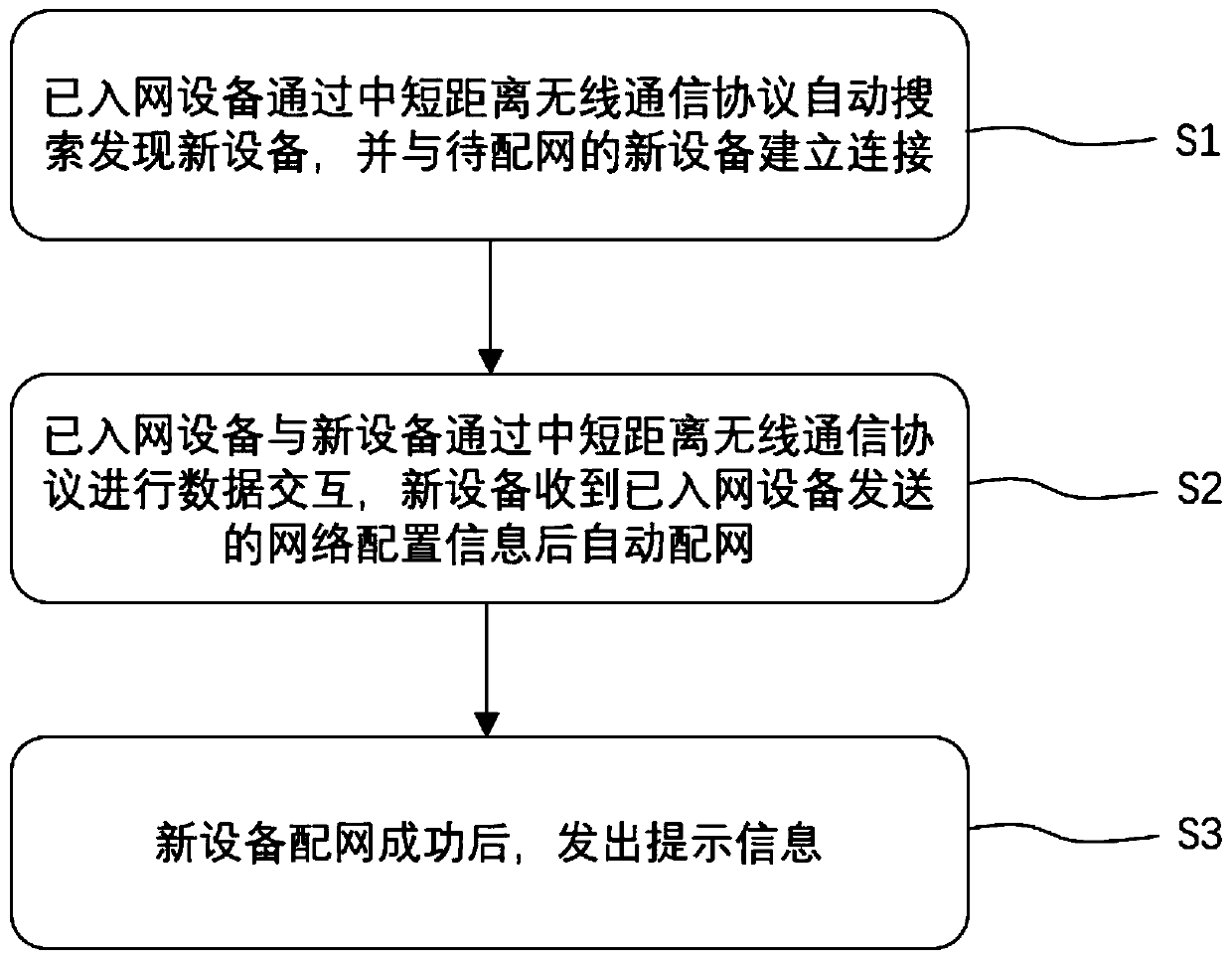
PendingCN111586105AStable and efficient transmissionImprove securityConnection managementTransmissionWireless communication protocolEngineering
The invention provides an automatic network distribution method for an intelligent device and the intelligent device, and the method is used for the network access configuration of a new device to besubjected to network distribution, and comprises the following steps: S1, enabling a network-accessed device to automatically search and find the new device through a medium-short distance wireless communication protocol, and building a connection with the new device to be subjected to network distribution; S2, performing data interaction between the networked equipment and the new equipment through a medium-short distance wireless communication protocol, and automatically distributing the network by the new equipment after receiving the network configuration information sent by the networkedequipment. Meanwhile, the invention provides the intelligent equipment for automatic network distribution by adopting the method. The whole network distribution process of the new equipment is automatically completed by the networked equipment and the new equipment, manual intervention and operation are not needed in the period, and the experience of non-inductive network distribution is achieved.Moreover, data interaction is carried out by adopting a medium-short distance wireless communication protocol, efficient and stable transmission of data can be realized in a family range, and the data security is also greatly improved.
Owner:VATTI CORP LTD
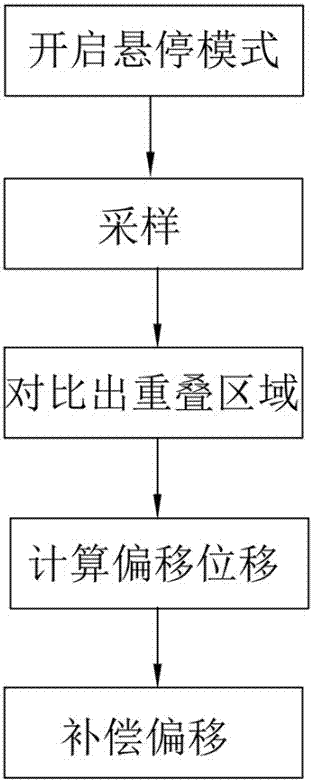
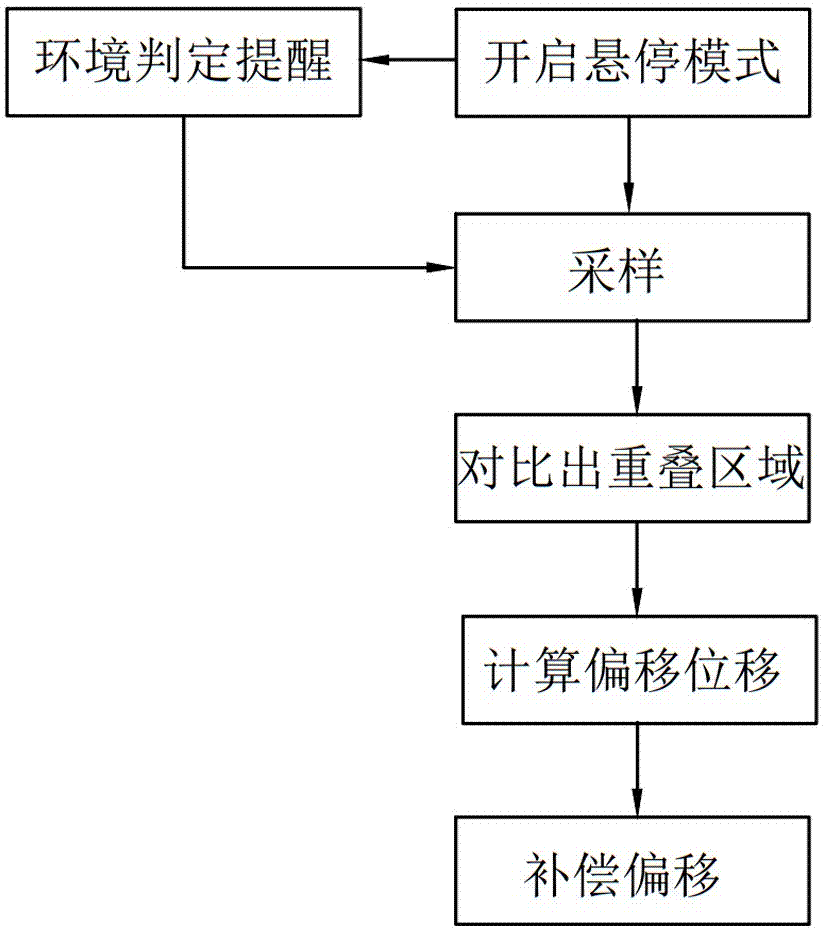
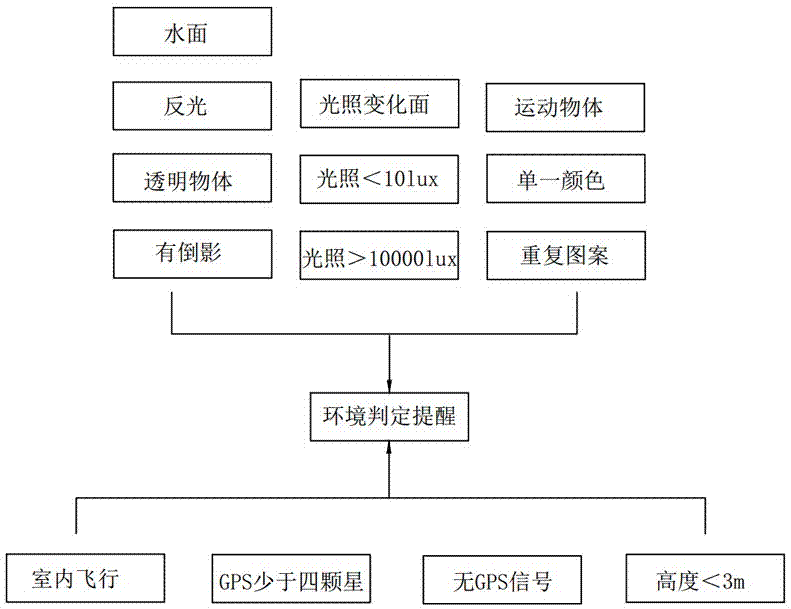
Automatic hovering method of unmanned aerial vehicle (UAV)
PendingCN107977014AEasy to useCause damageAttitude controlPosition/course control in three dimensionsUncrewed vehicleOptical flow
The invention relates to an automatic hovering method of a UAV. A UAV body and an optical flow positioning device arranged on the UAV are included. The automatic hovering method of the UAV comprises the following steps that S1) a hovering mode is started, and an initial hovering image is recorded; S2) sampling is started; S3) an image sampled in the step 2) is compared with the initial image to obtain an overlapped area therebetween; S4) according the overlapped area in the step S3), displacement which needs offset is calculated; and S5) according to a calculation result in the step S4), the UAV is controlled to compensate the offset. The method is simple in steps, time from start to realization of hovering is very short, optical flow positioning hovering instead of an optical flow positioner is used, the total cost of the UAV is reduced, the AUV is lighter and saves more energy, and accurate positioning can be realized. The whole calculation process is convenient and rapid, and the UAV can be corrected rapidly in the hovering process and returns to the original position.
Owner:GUANGZHOU WALKERA TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com