Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
49 results about "Validation error" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A validation error occurs when you have Validation/Response Checking turned on for one of the questions and the respondent fails to answer the question correctly (numeric formatting , required response).
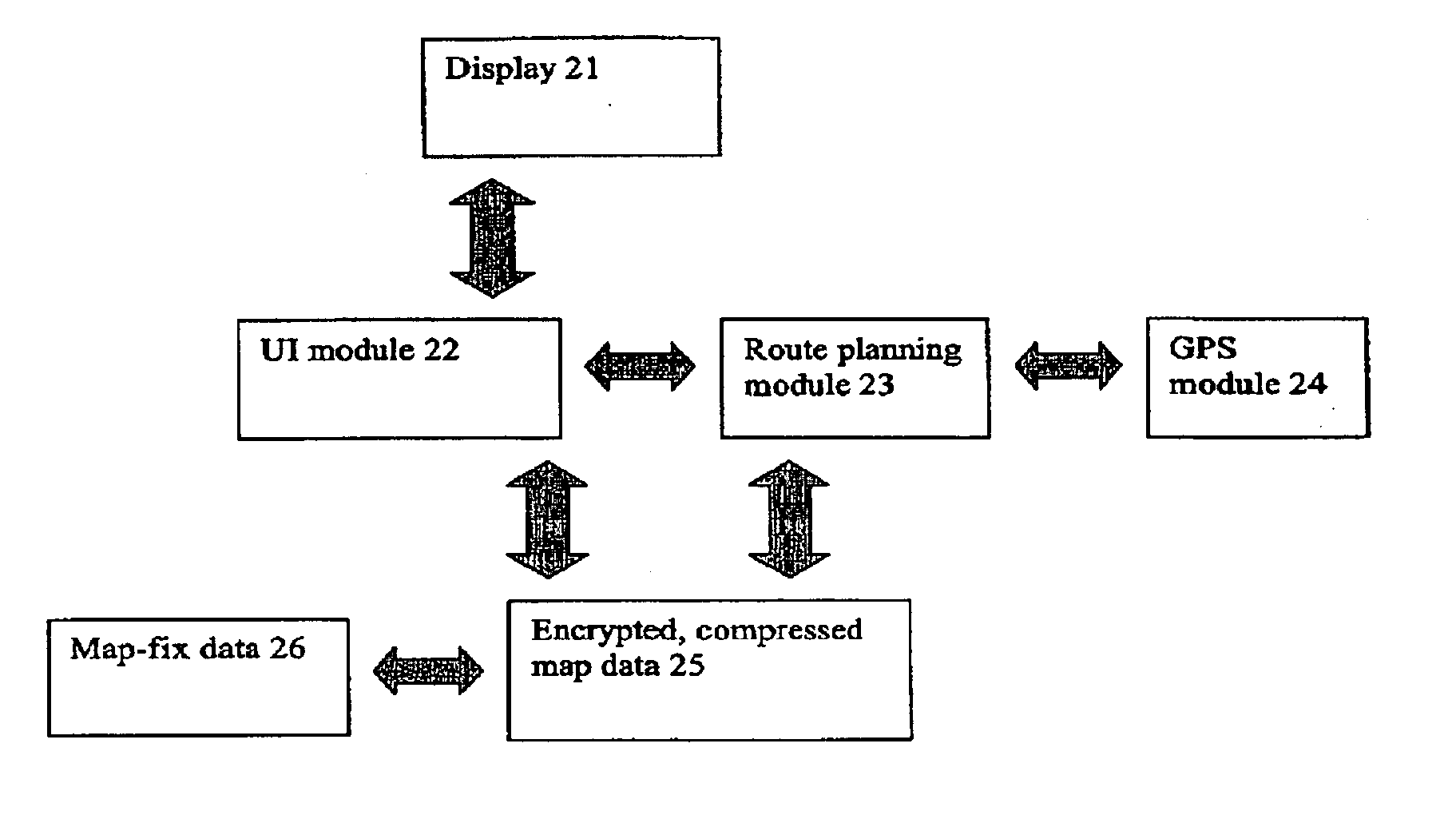
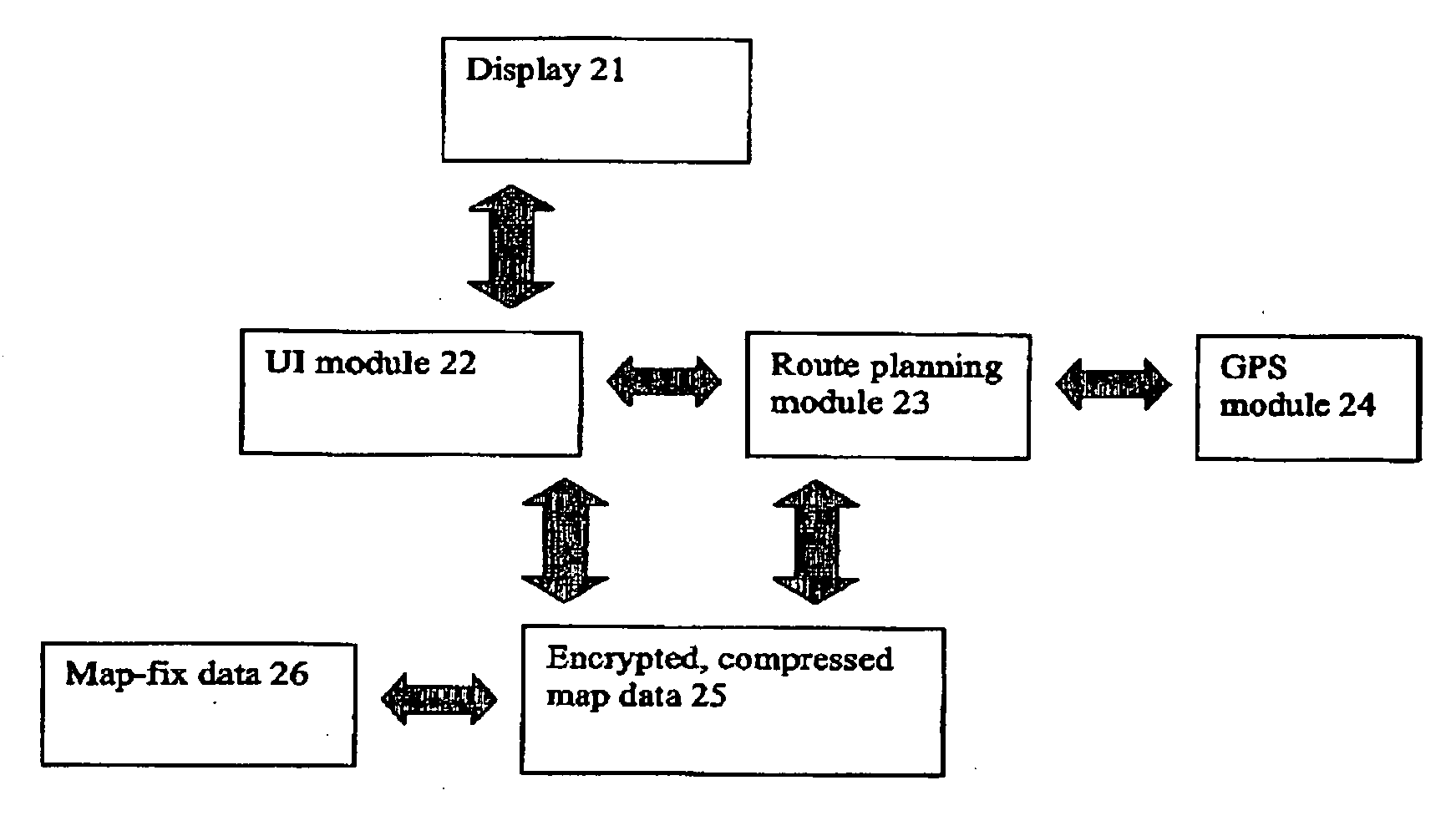
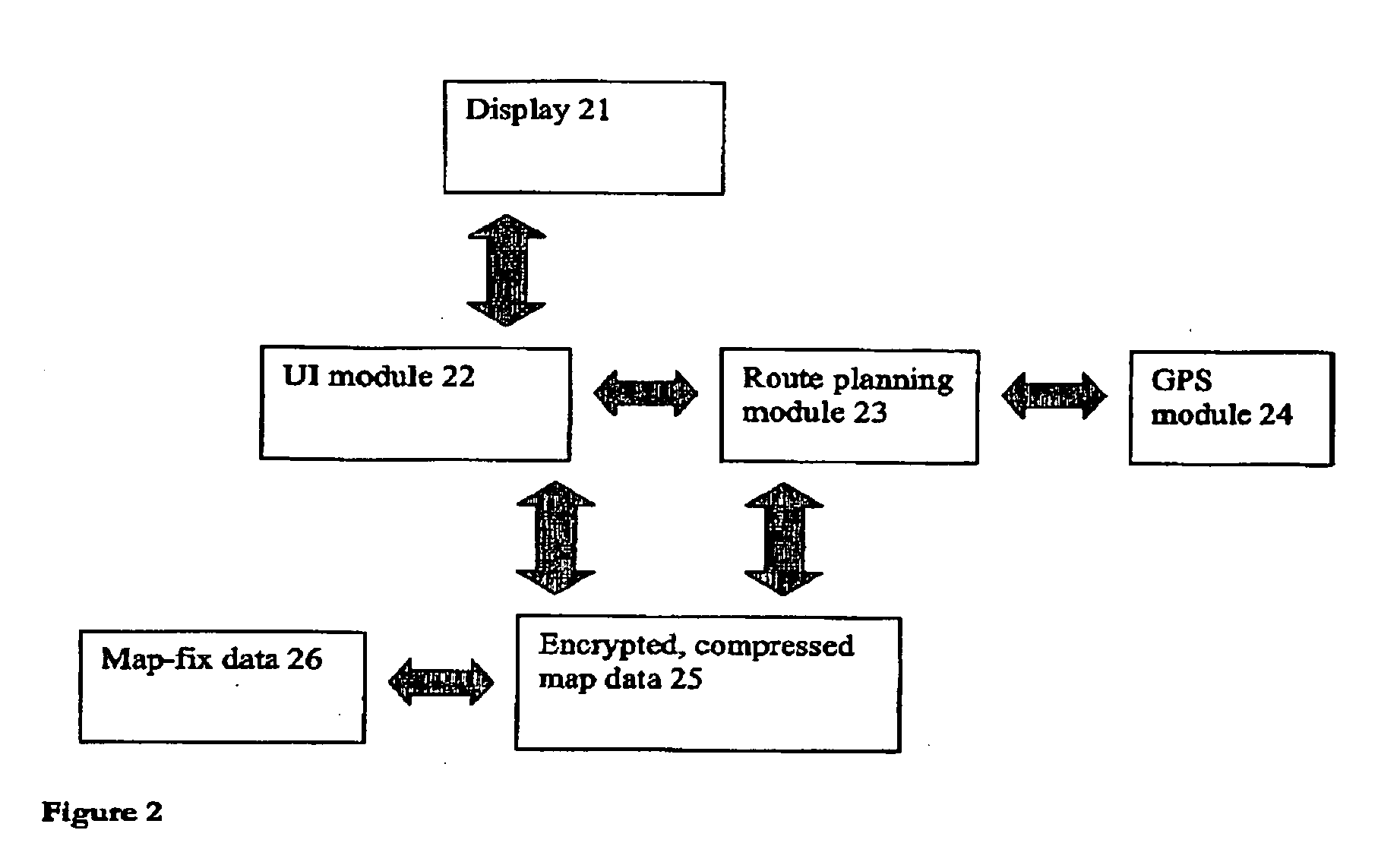
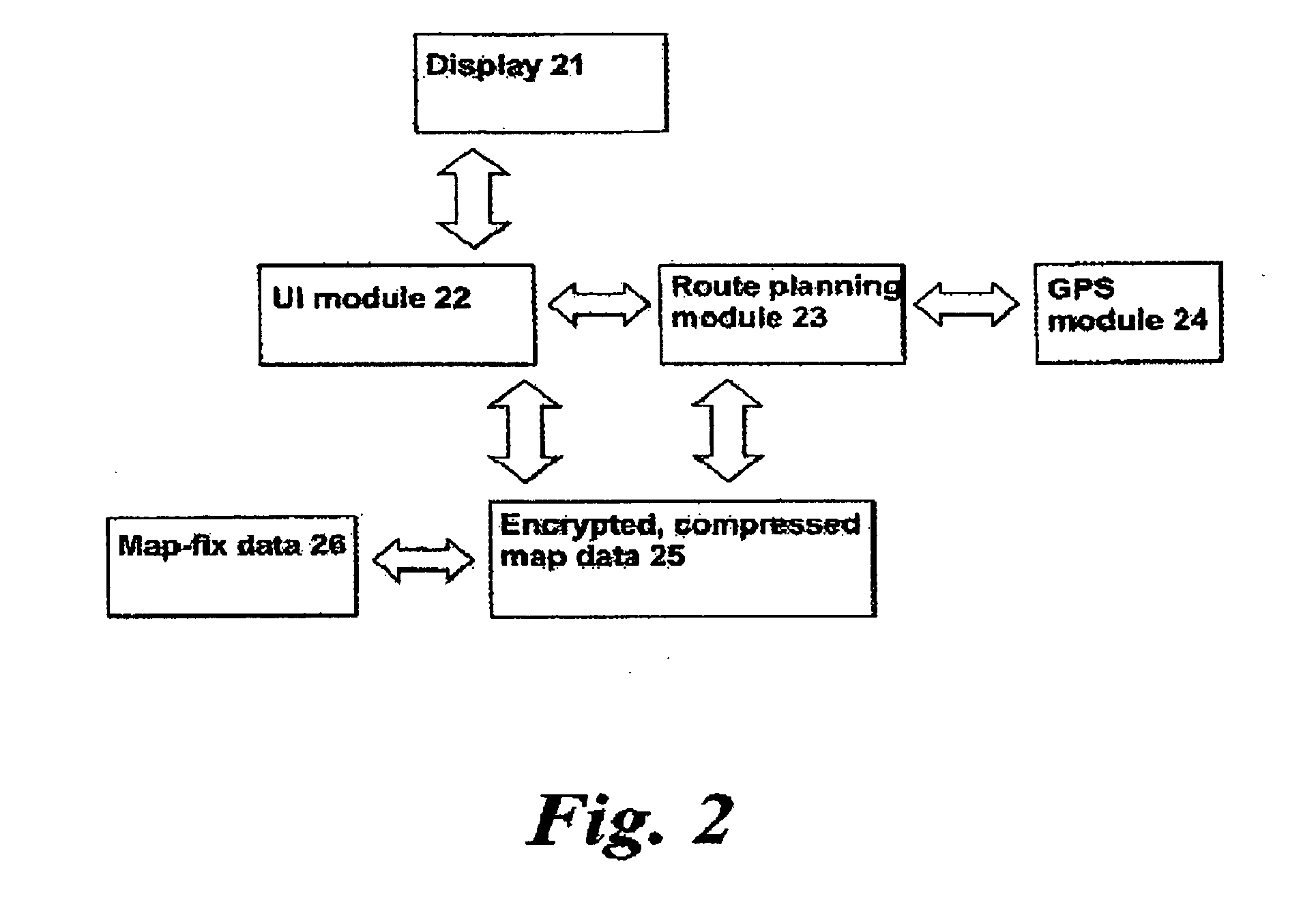
A method of reporting errors in map data used by navigation devices
InactiveUS20080082225A1Easy to accurately locateReduce license feeInstruments for road network navigationVehicle position/course/altitude controlComputer scienceEnd user
An end-user can input a map error report to a map error, directly on the device. The device stores the map error report and can send the report to a remote server for processing. Hence, it is no longer necessary for an end-user to simply report errors to the map vendor over a web link, then wait for that map vendor to verify the error, update its maps and finally supply the end-user with updates—a cycle that can take months and sometimes years to complete.
Owner:TOMTOM INT BV
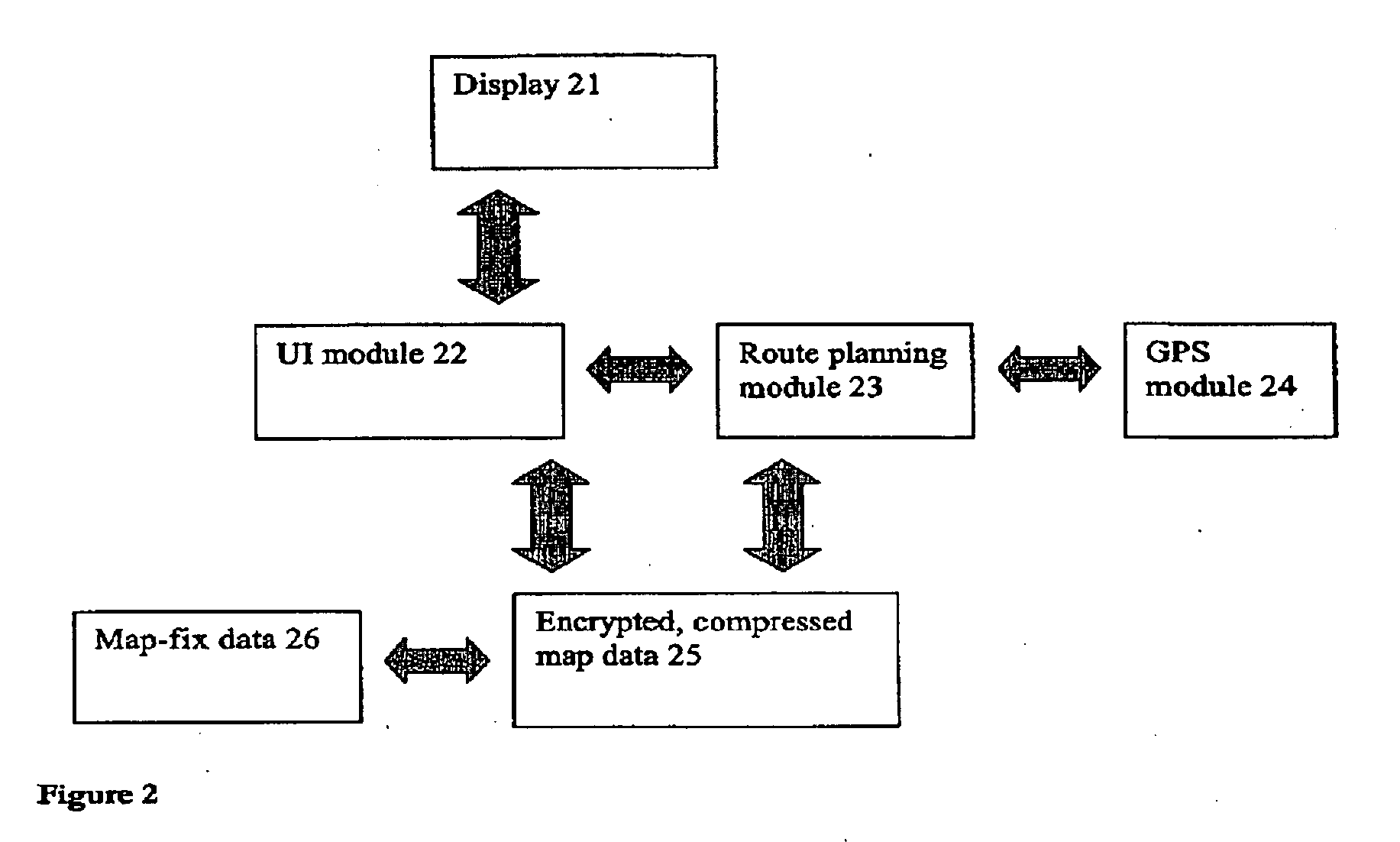
Method of generating improved map data for use in navigation devices
ActiveUS20080046274A1Instruments for road network navigationData processing applicationsReporting errorComputer science
An end-user can input a correction to a map error, directly on the device. The device is then able to use the correction without external processing of the correction. Hence, it is no longer necessary for an end-user to simply report errors to the map vendor over a web link then wait for that map vendor to verify the error, update its maps and finally supply the end-user with updates—a cycle that can take months and sometimes years to complete. Instead, the navigation device can use the correction immediately. End-users can also share corrections with other end-users and also with a shared remote server that aggregates, validates and distributes corrections.
Owner:TOMTOM GLOBAL CONTENT
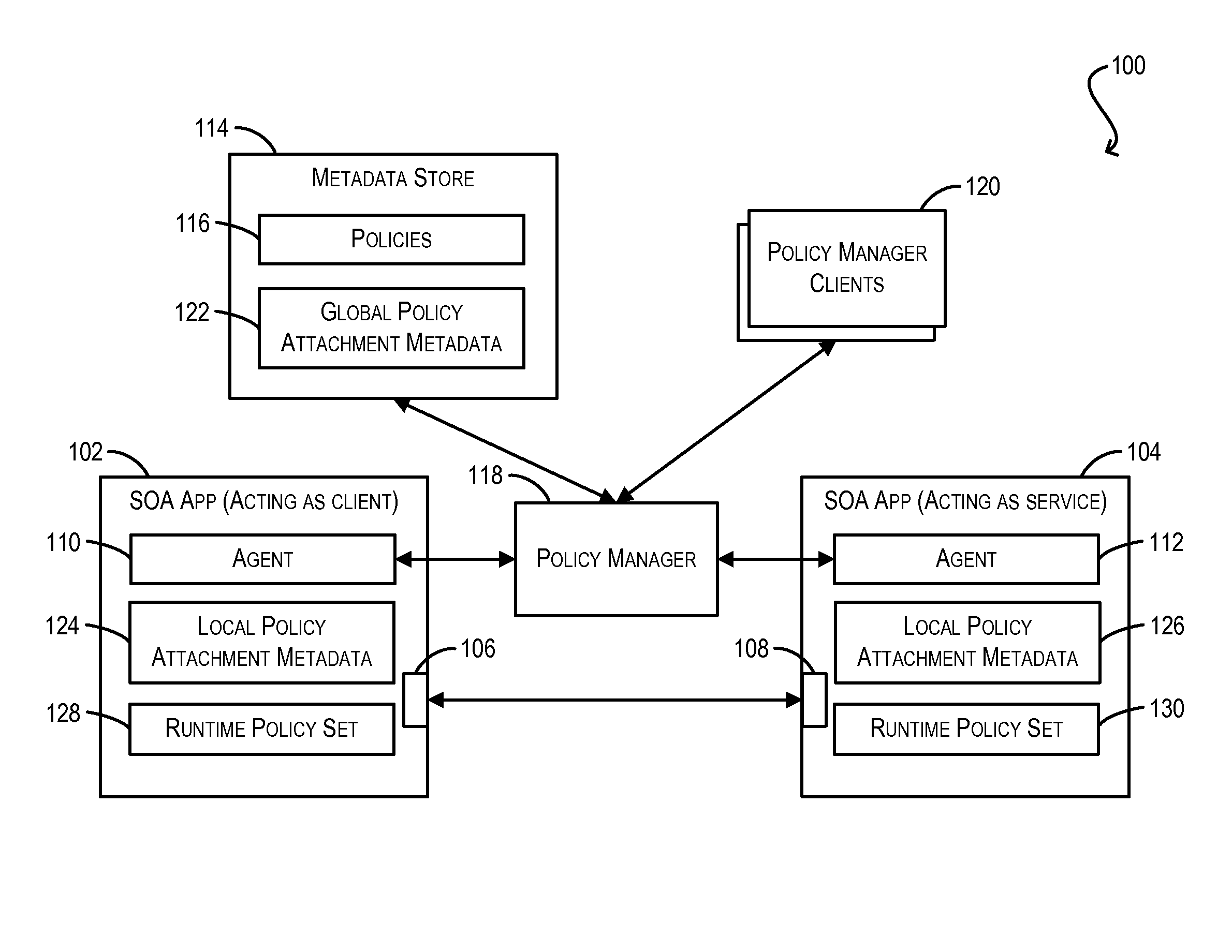
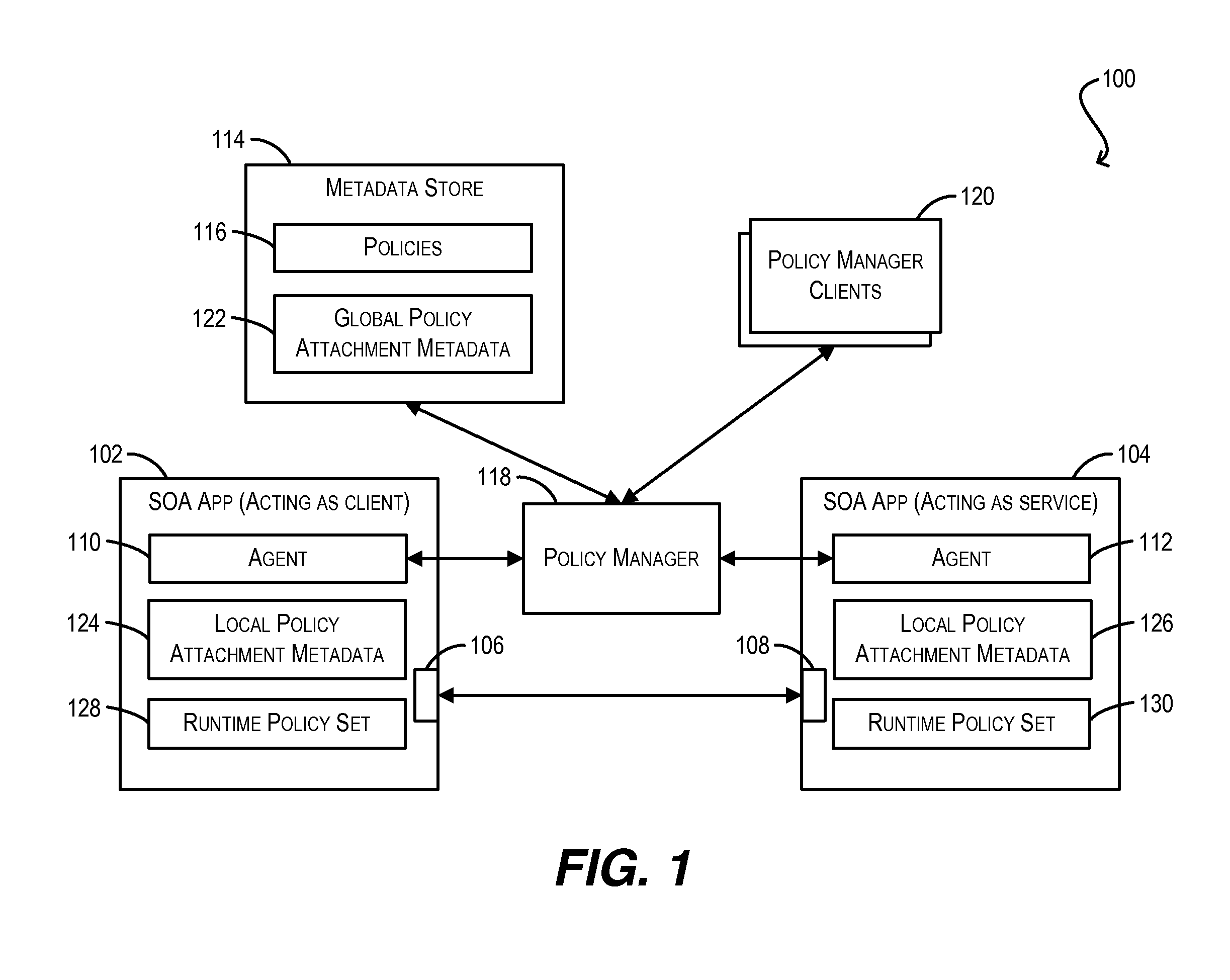
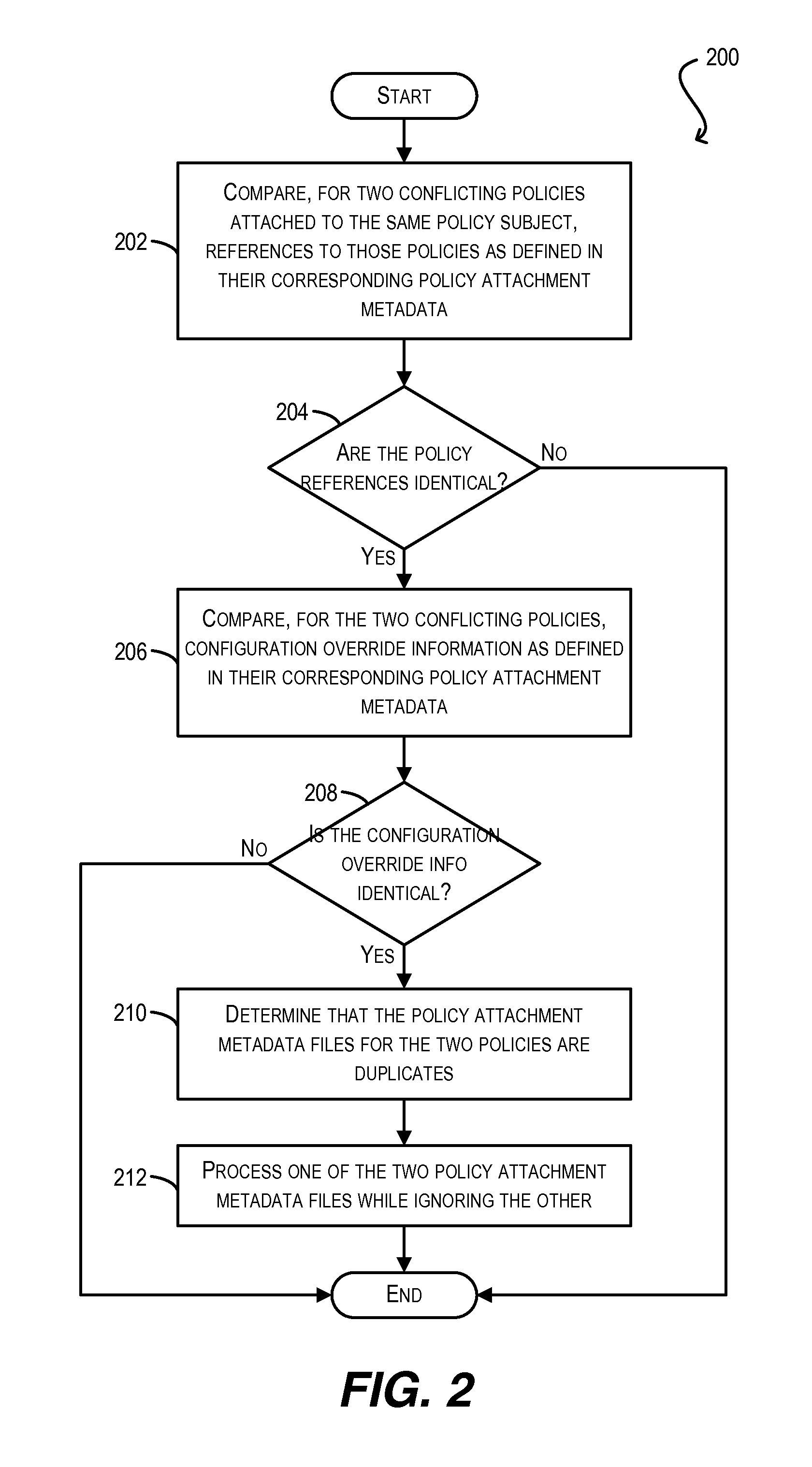
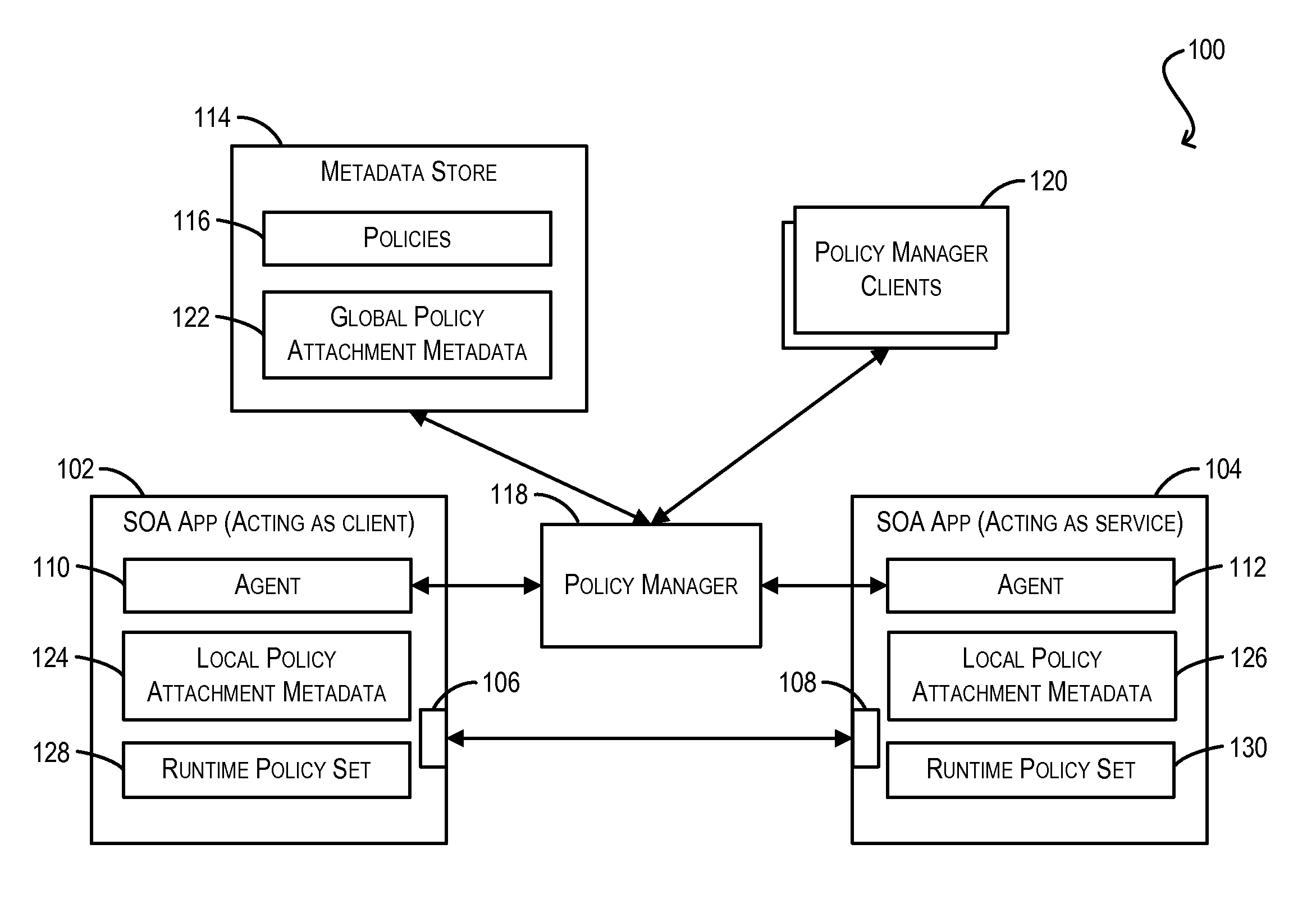
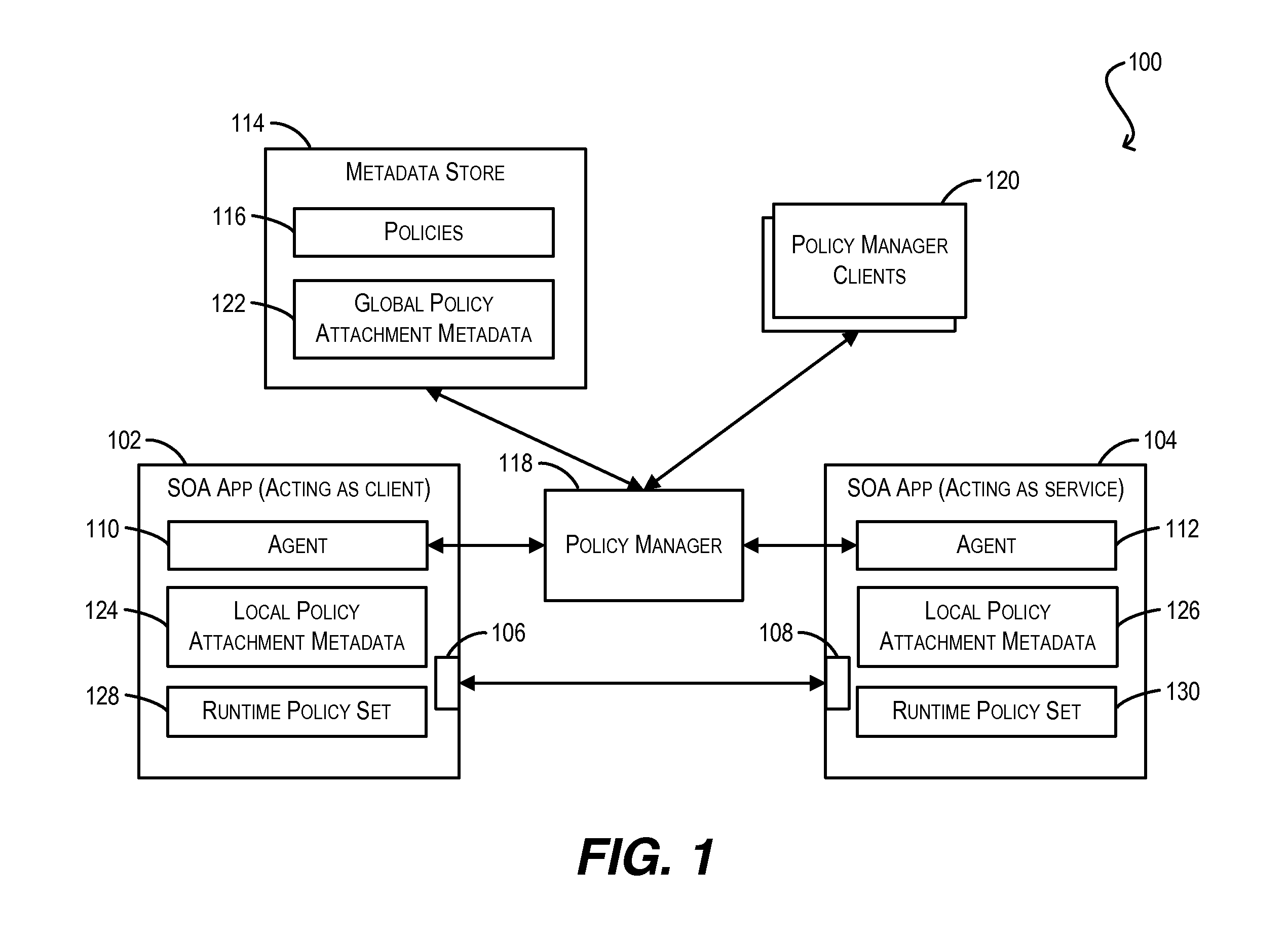
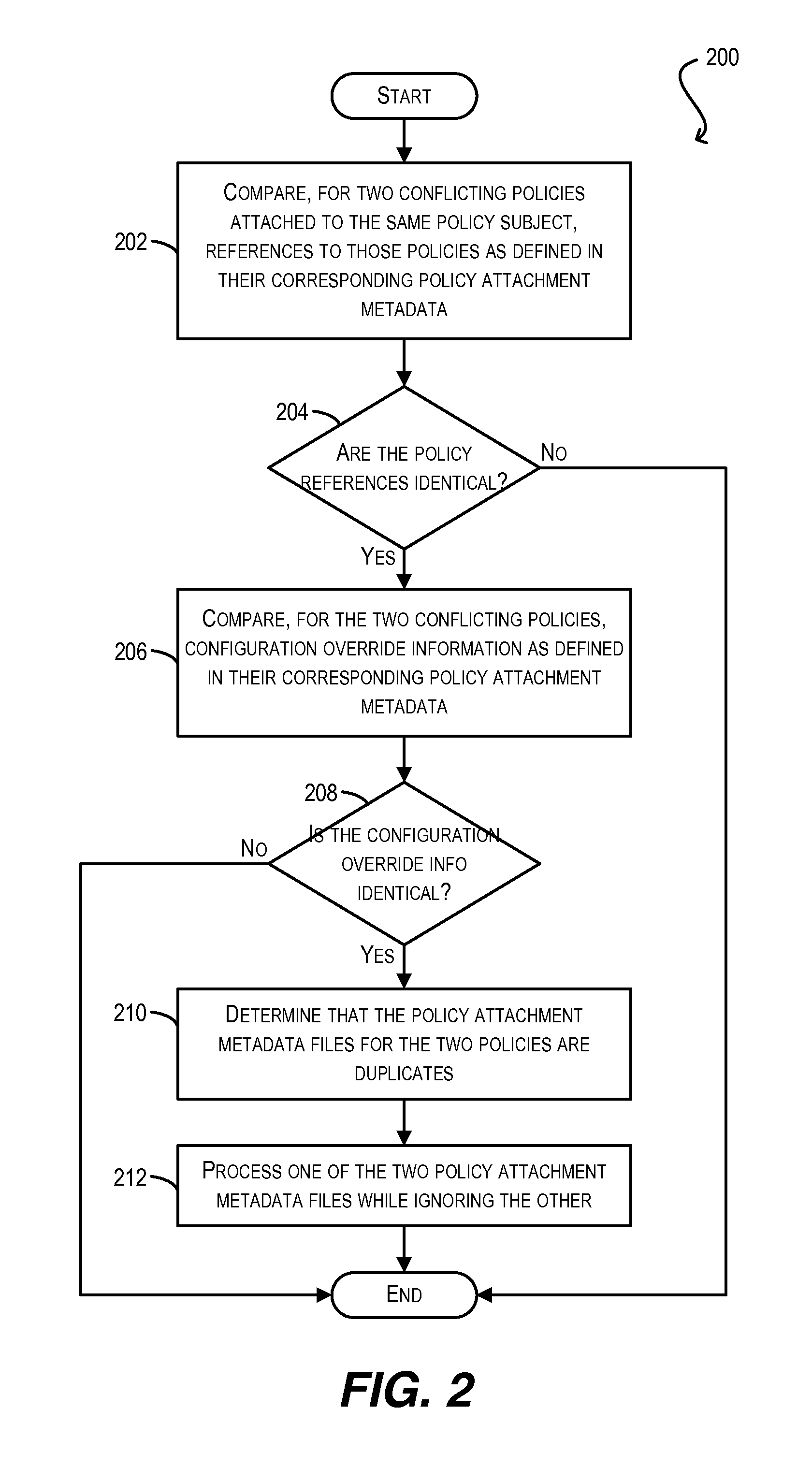
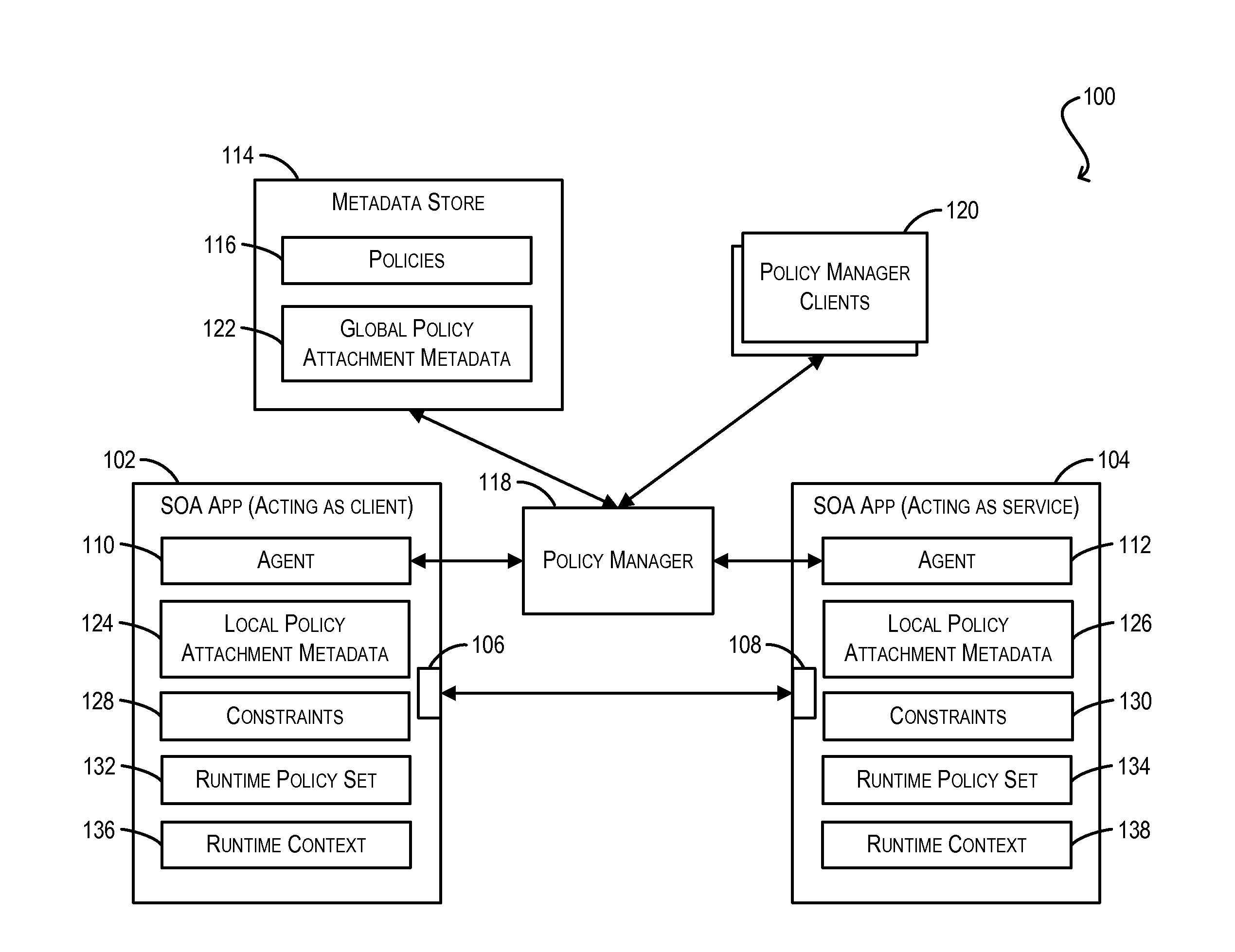
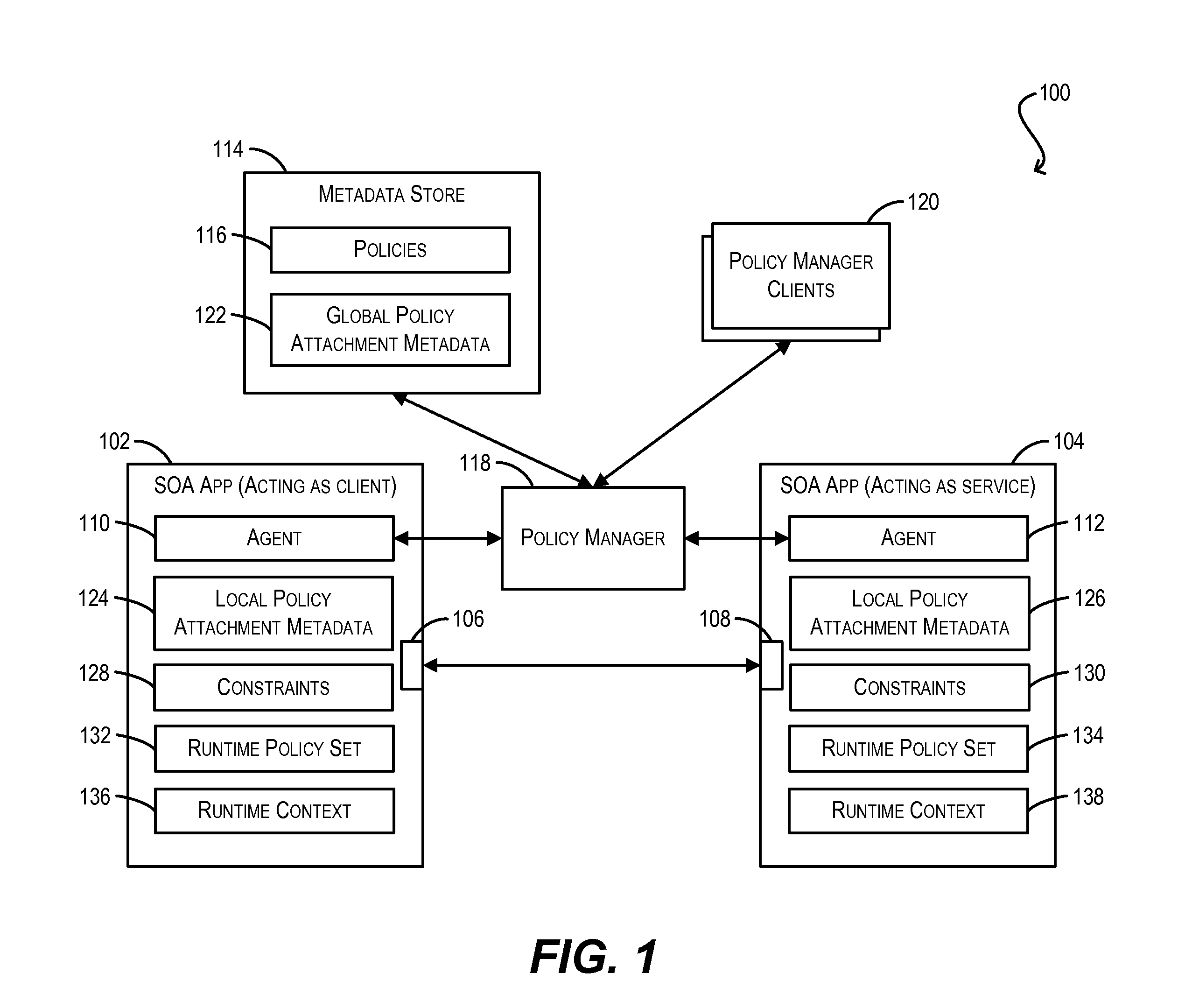
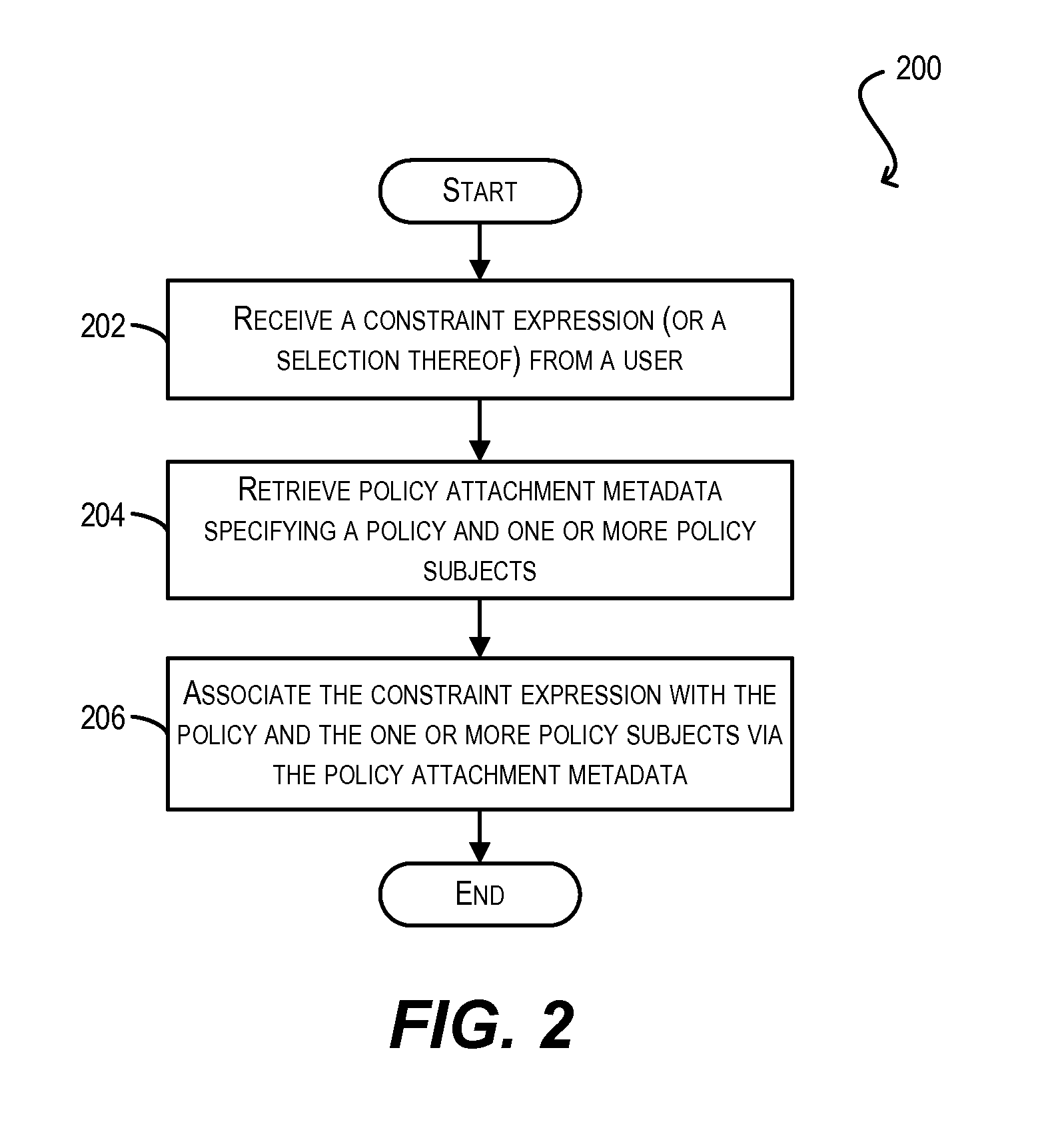
Conflict resolution when identical policies are attached to a single policy subject
ActiveUS8914843B2Digital computer detailsData switching networksWeb serviceUniform resource identifier
Techniques for resolving conflicts between web service policies that are attached (via LPA and / or GPA metadata) to a single policy subject (e.g., a WS client / service endpoint). In one set of embodiments, a determination can be made whether two conflicting policies that are attached to a single policy subject are identical. This determination can be based on, e.g., a Uniform Resource Identifier (URI) that is used to identify the policies in their respective policy attachment metadata files, as well as any policy configuration properties. If the two conflicting policies are determined to be identical, the policy attachment metadata for one of the policies can be considered valid, while the policy attachment metadata for the other, duplicate policy can be ignored. In this manner, validation errors arising from duplicate policy attachments can be avoided.
Owner:ORACLE INT CORP
Method of generating improved map data for use in navigation devices
ActiveUS20080065325A1Instruments for road network navigationData processing applicationsReporting errorComputer science
An end-user can input a correction to a map error, directly on the device. The device is then able to use the correction without external processing of the correction. Hence, it is no longer necessary for an end-user to simply report errors to the map vendor over a web link then wait for that map vendor to verify the error, update its maps and finally supply the end-user with updates—a cycle that can take months and sometimes years to complete. Instead, the navigation device can use the correction immediately. End-users can also share corrections with other end-users and also with a shared remote server that aggregates, validates and distributes corrections.
Owner:TOMTOM GLOBAL CONTENT
Method of generating improved map data for use in navigation devices
InactiveUS20080177469A1Instruments for road network navigationData processing applicationsComputer scienceMarine navigation
An end-user can input a correction to a map error, directly on the device. The device is then able to use the correction without external processing of the correction. Hence, it is no longer necessary for an end-user to simply report errors to the map vendor over a web link then wait for that map vendor to verify the error, update its maps and finally supply the end-user with updates—a cycle that can take months and sometimes years to complete. Instead, the navigation device can use the correction immediately. End-users can also share corrections with other end-users and also with a shared remote server that aggregates, validates and distributes corrections.
Owner:TOMTOM INT BV
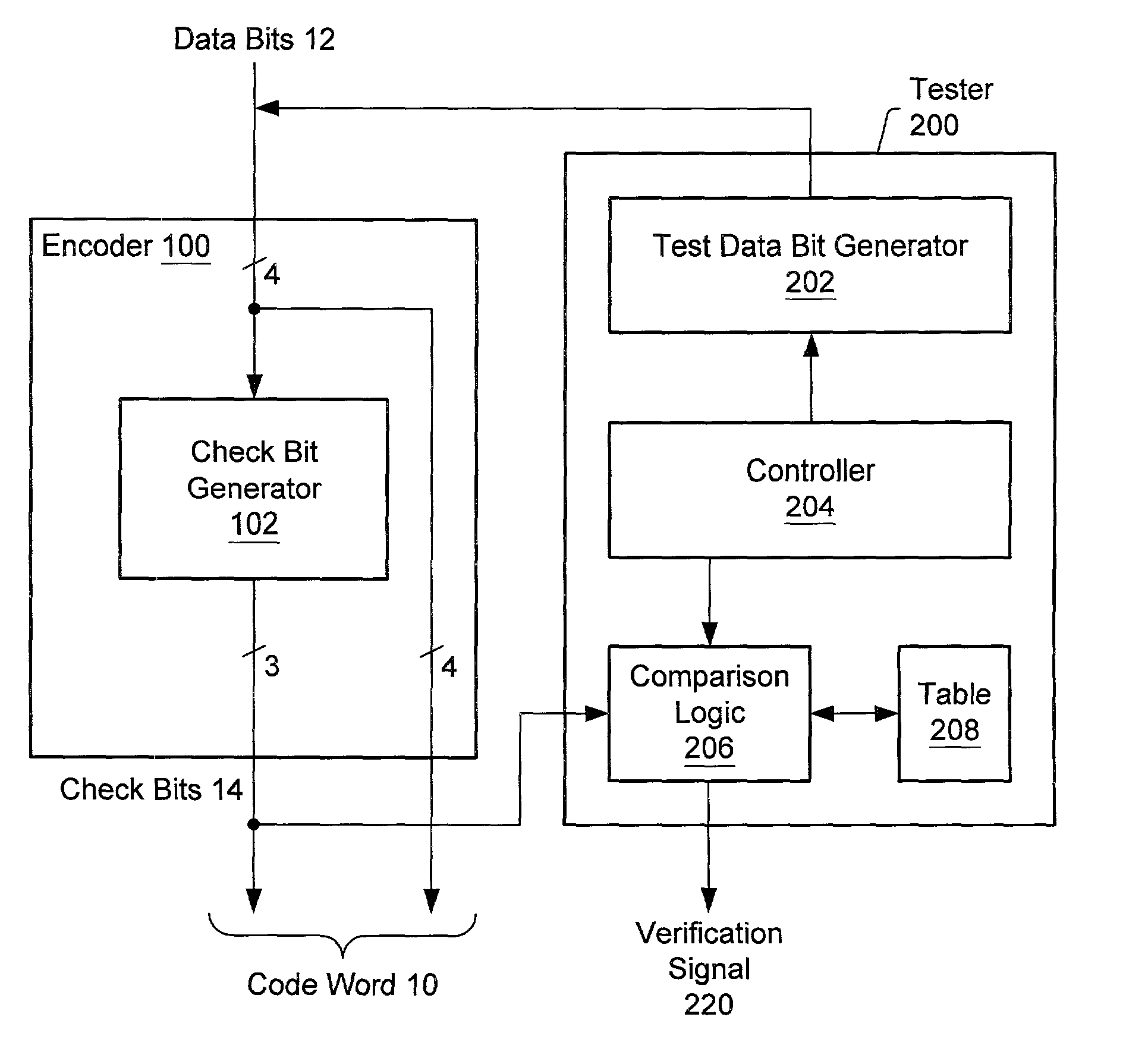
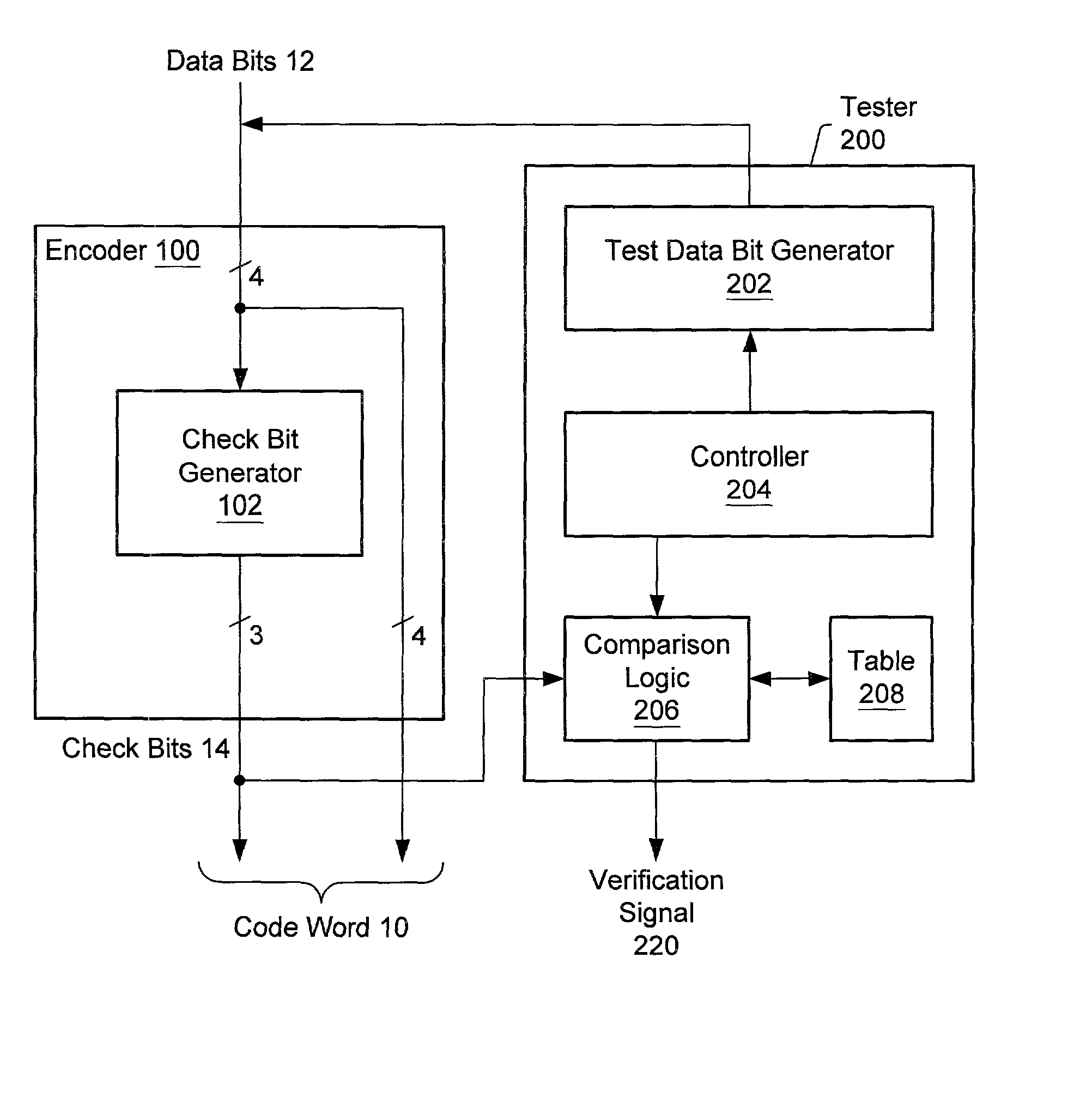
System and method for verifying error detection/correction logic
Owner:ORACLE INT CORP
System and method for verifying error detection/correction logic
A method of testing error correction / detection logic may involve providing each of a set of n data bit combinations to the error correction / detection logic. Each data bit combination has n bits, and the n data bit combinations may be created by creating an initial data bit combination whose data bits have the same logical value and then shifting a bit having the opposite value across the initial data bit combination. In response to being provided with the n data bit combinations, the error correction / detection logic generates a set of check bits for each of the n data bit combinations. The set of check bits generated by the error correction / detection logic for each of the n data bit combinations may then be verified.
Owner:ORACLE INT CORP
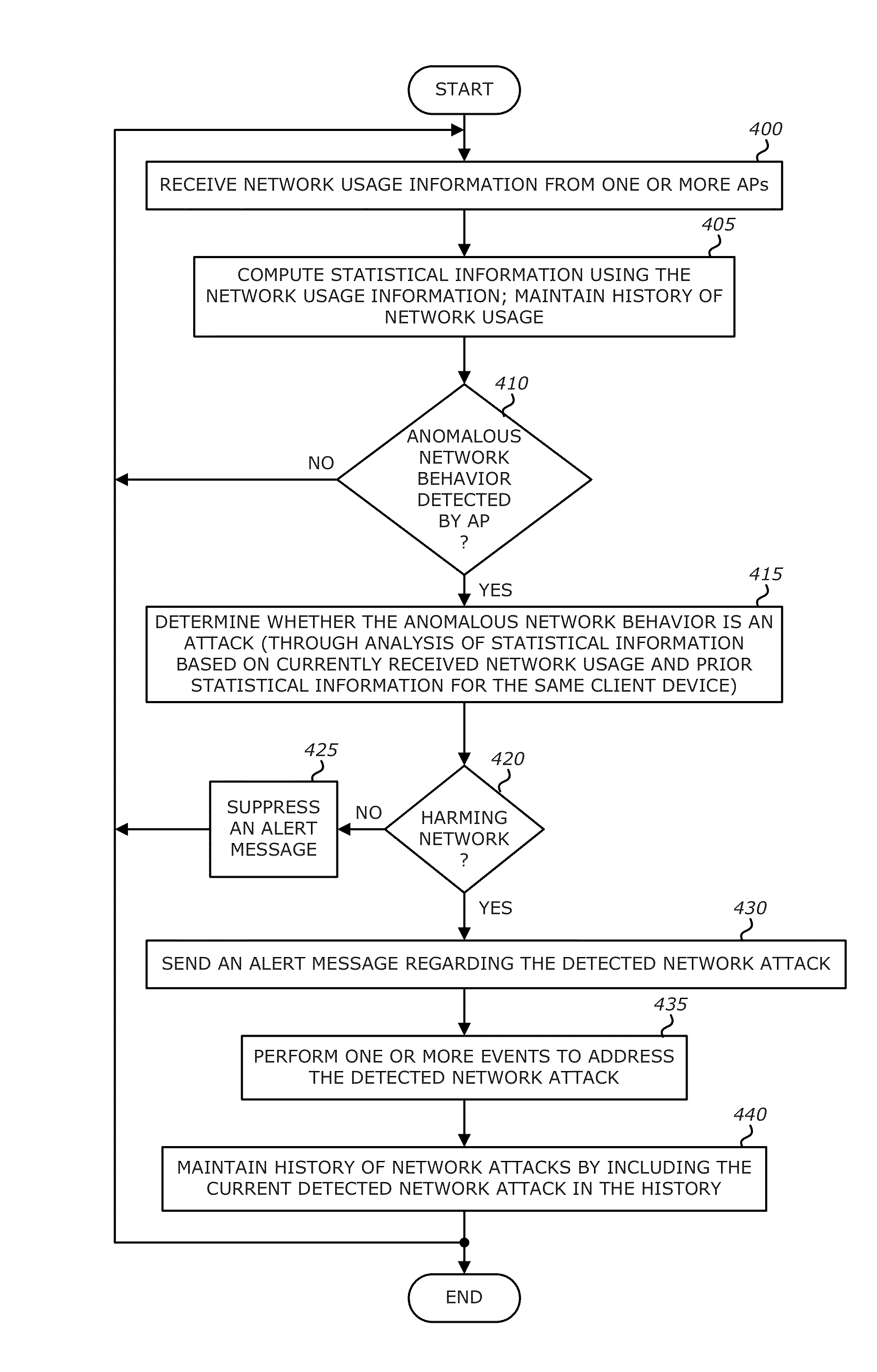
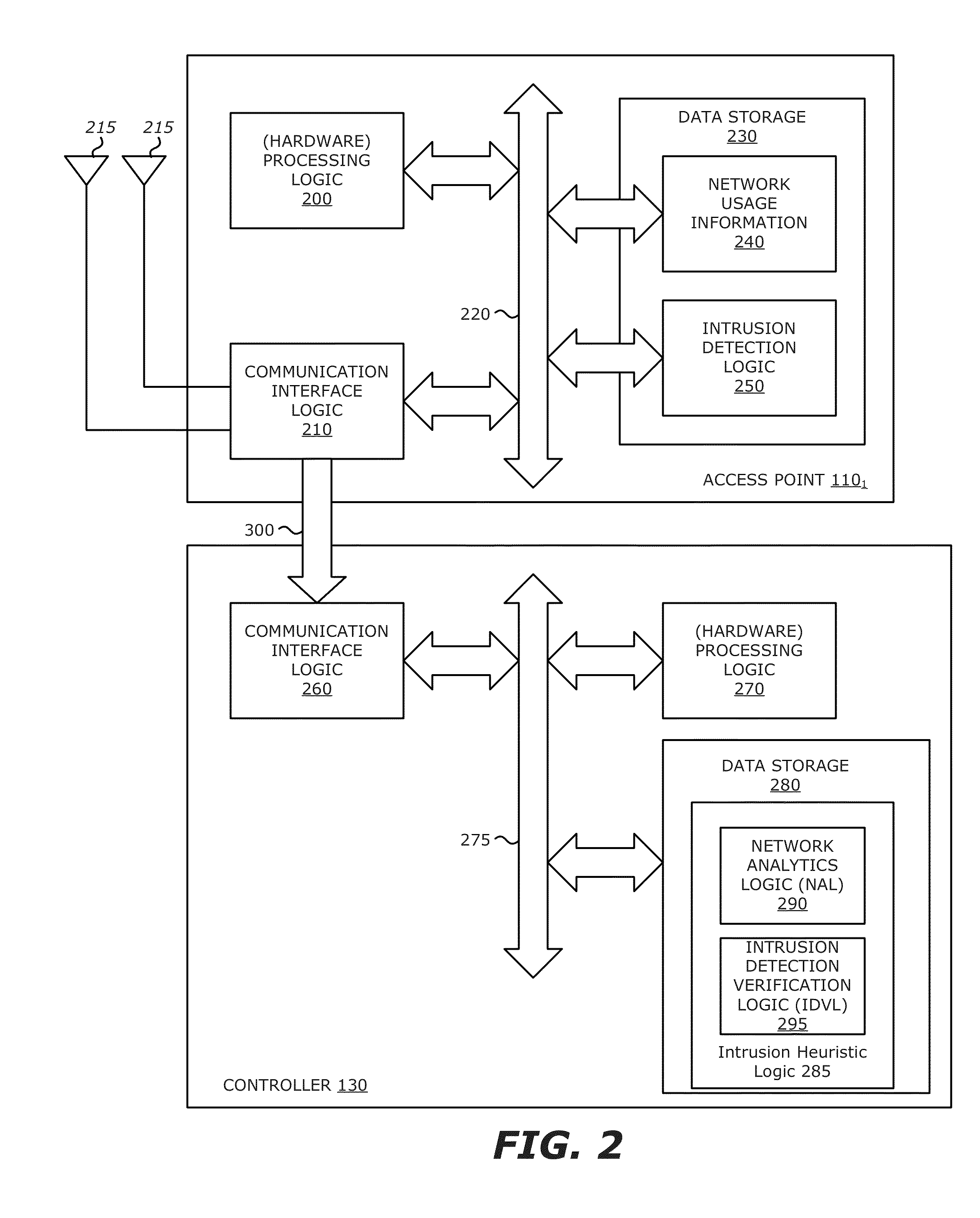
Apparatus, system and method for suppressing erroneous reporting of attacks on a wireless network
According to one embodiment, a method for suppressing erroneous alert messages for suspected network attacks comprises a first operation of determining an intrusion event. This may be conducted at a first network device. Then, the intrusion event is verified prior to transmission of the alert message. The verification may be conducted at a second network device. Thereafter, transmission of the alert message is suppressed in response to verifying that the intrusion event has been erroneously determined.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
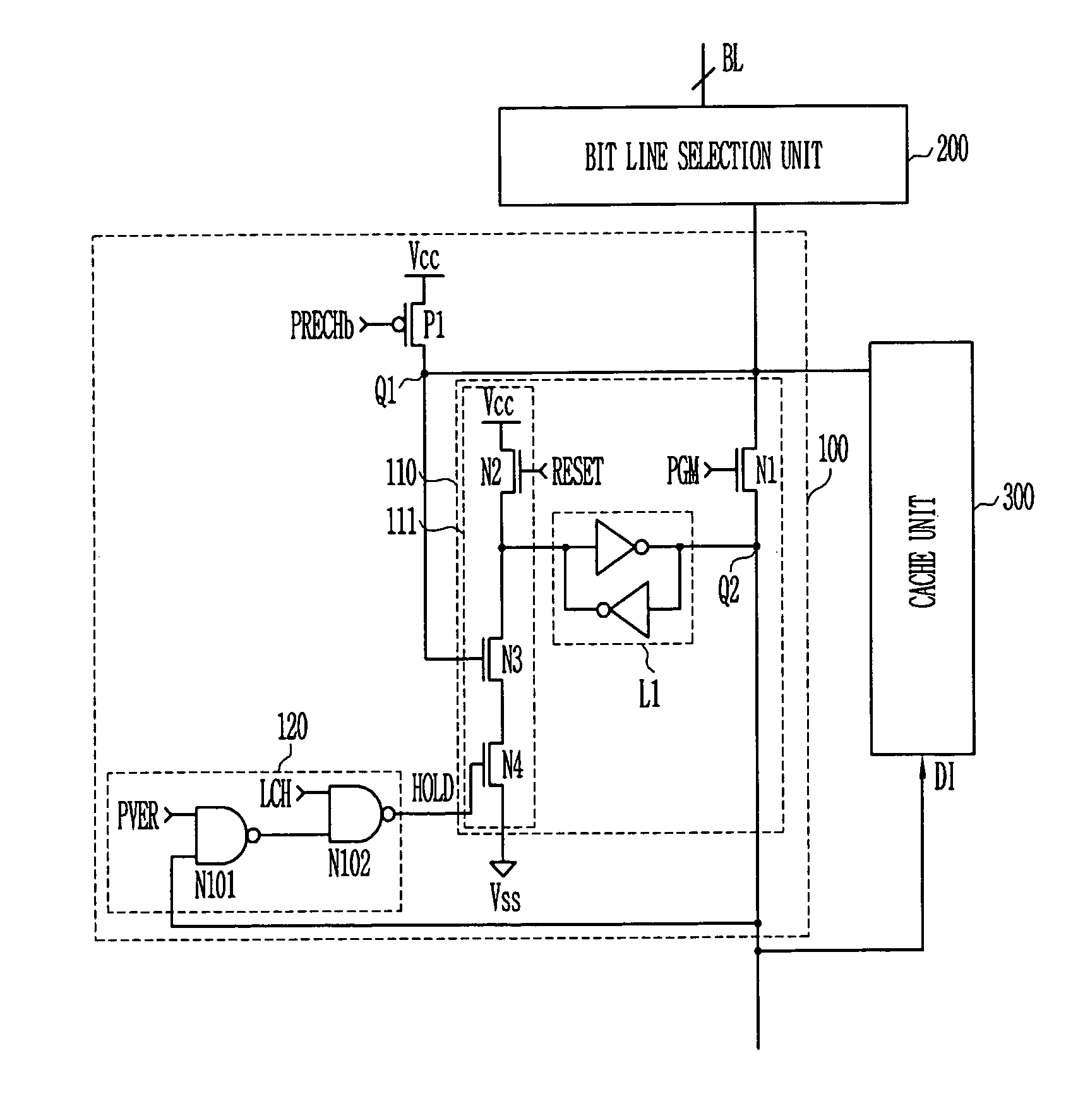
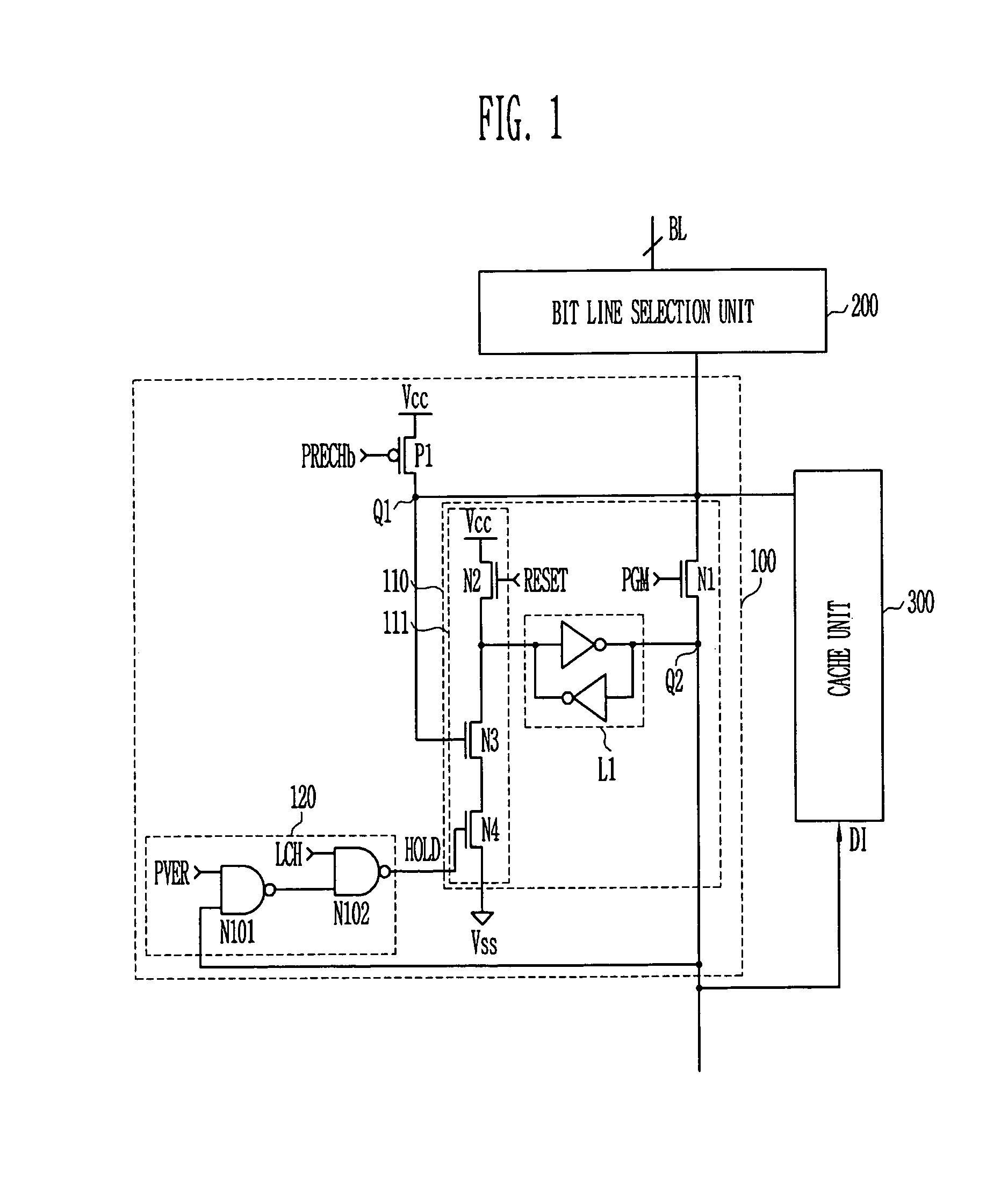
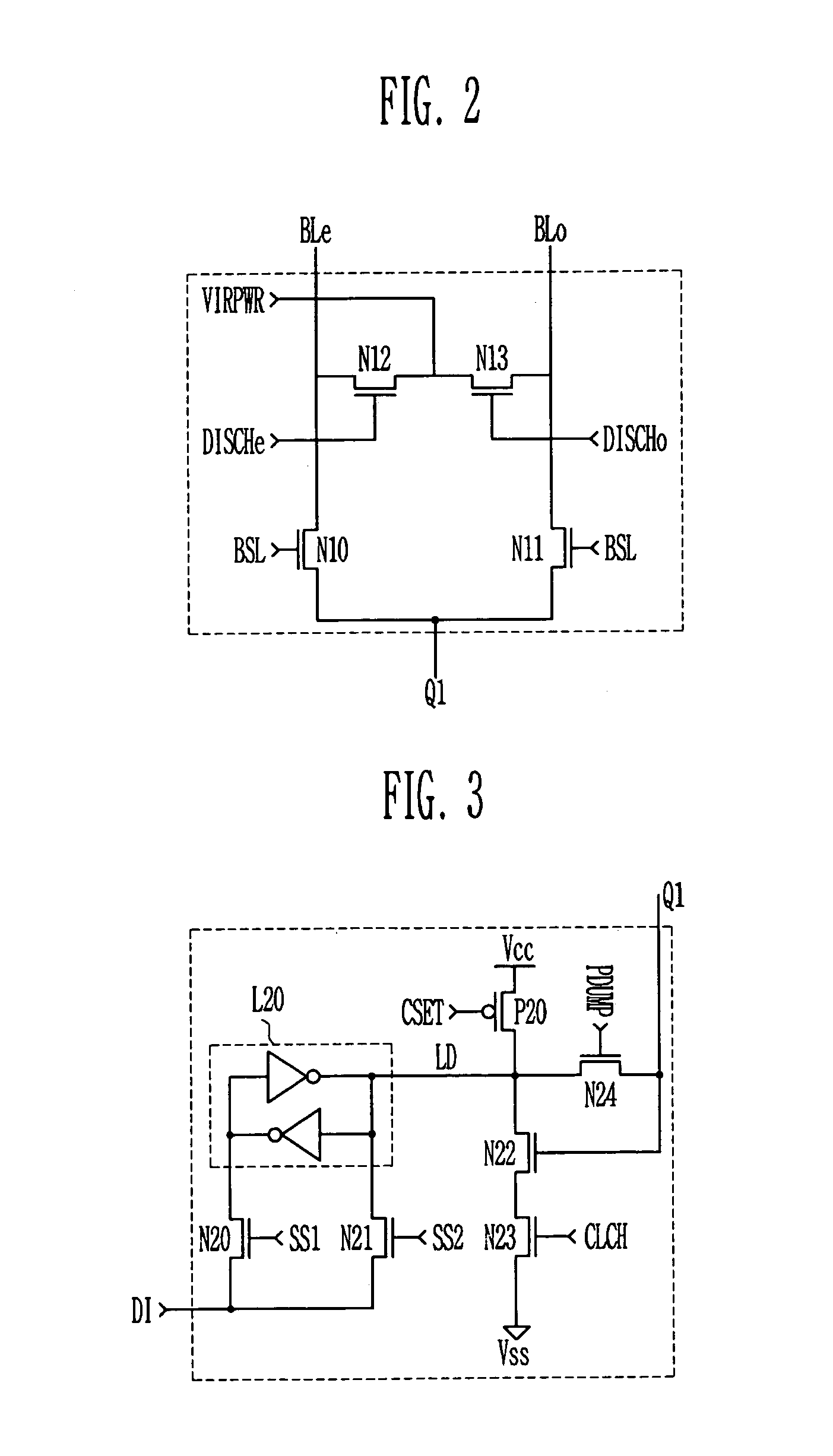
Page buffer for flash memory device
InactiveUS7099213B2Solve the real problemRead-only memoriesDigital storageComputer sciencePage buffers
The disclosed is a page buffer of a flash memory device. In accordance with the present invention, a latch is controlled through a program verification signal, a latch signal, and latch data in a page buffer during a program verification. As a result, there are many advantages. First, in the event that the program verification is performed after programming once more, a passed cell is not sensed again and maintains its value. Second, it is possible to prevent a problem caused by a sensing operation as well as a verification error due to an external factor. As a result, program operation errors can be prevented.
Owner:STMICROELECTRONICS SRL +1
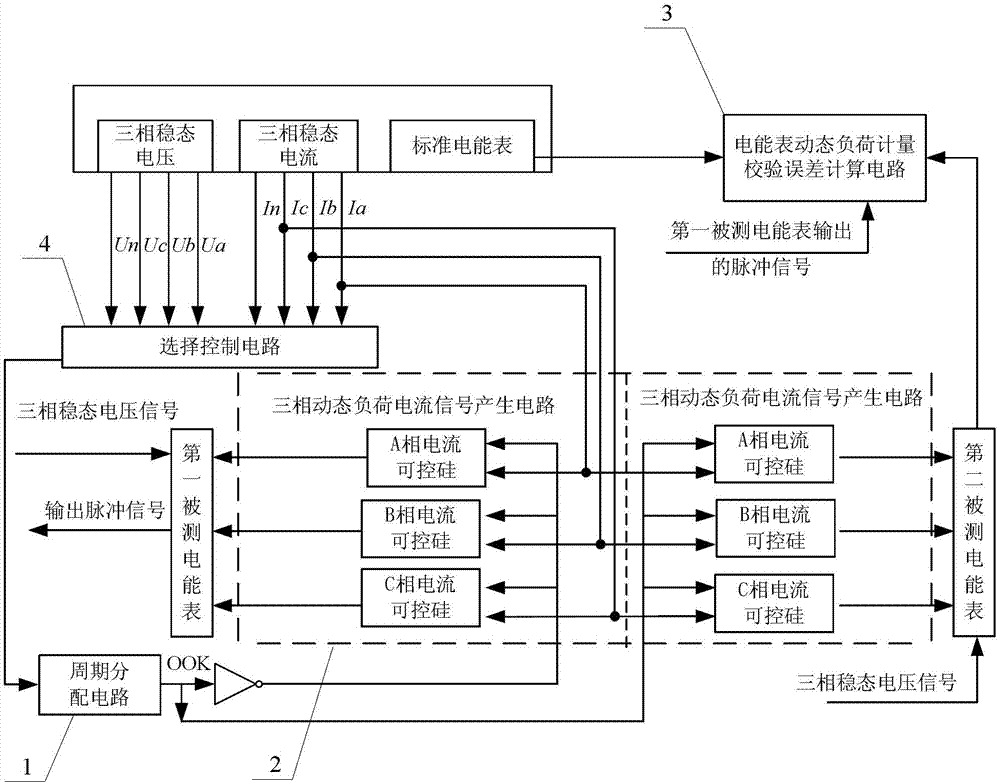
Electric energy meter dynamic measurement cycle power sequence proportional allocation calibration method
The electric energy meter dynamic measurement cycle power sequence proportional allocation calibration method belongs to the technical field of electric energy meter dynamic performance measurement. The electric energy meter dynamic measurement cycle power sequence proportional allocation calibration method solves the problem that a power signal source is adopted to produce dynamic load electric energy signals, and therefore measurement tracing error can not be given out in the existing dynamic performance measurement test of an electric energy meter. The electric energy meter dynamic measurement cycle power sequence proportional allocation calibration method adopts synchronous on-off keying (OOK) cycle on-off control signals generated from three-phase steady-state voltages or three-phase steady-state current signals to dynamically distribute the three-phase steady-state current signals, by using a power electronic component, such as controllable silicon, transient state, short time and long time three kinds of periodically-changed dynamic load current signals are controlled to be produced, and dynamic load power is input into the electric energy meter under test in a discrete electric energy sequence mode. Dynamic load measurement validation error of the electric energy meter under the test is calculated by collecting output impulse of a standard electric energy meter and the electric energy meter under the test, and dynamic load measurement test tracing of the electric energy meter under the test can be achieved. The electric energy meter dynamic measurement cycle power sequence proportional allocation calibration method is suitable for validation of electric energy meters.
Owner:STATE GRID CORP OF CHINA +1
Conflict resolution when identical policies are attached to a single policy subject
ActiveUS20130086627A1Avoid mistakesDigital computer detailsComputer security arrangementsWeb serviceData file
Techniques for resolving conflicts between web service policies that are attached (via LPA and / or GPA metadata) to a single policy subject (e.g., a WS client / service endpoint). In one set of embodiments, a determination can be made whether two conflicting policies that are attached to a single policy subject are identical. This determination can be based on, e.g., a Uniform Resource Identifier (URI) that is used to identify the policies in their respective policy attachment metadata files, as well as any policy configuration properties. If the two conflicting policies are determined to be identical, the policy attachment metadata for one of the policies can be considered valid, while the policy attachment metadata for the other, duplicate policy can be ignored. In this manner, validation errors arising from duplicate policy attachments can be avoided.
Owner:ORACLE INT CORP
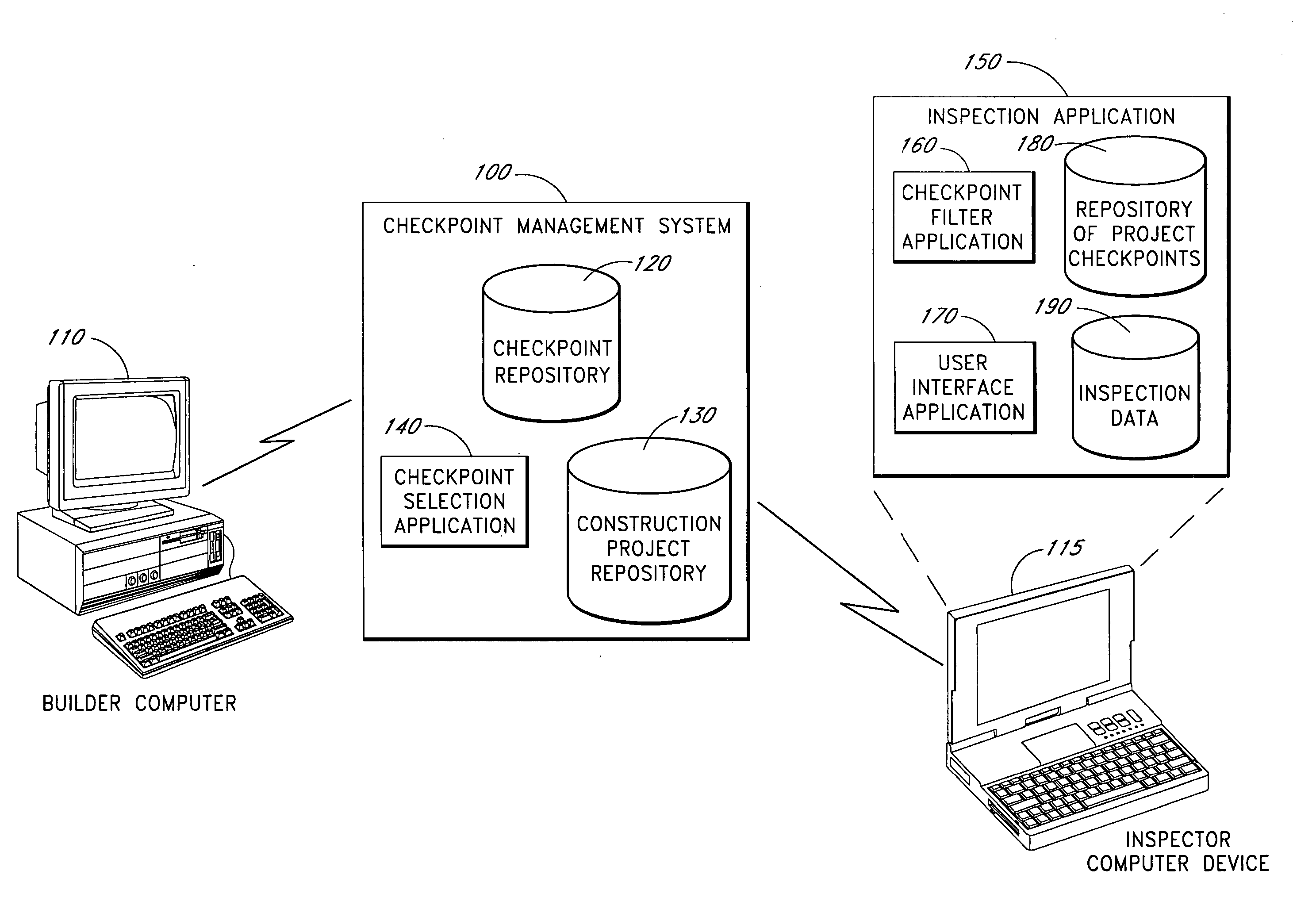
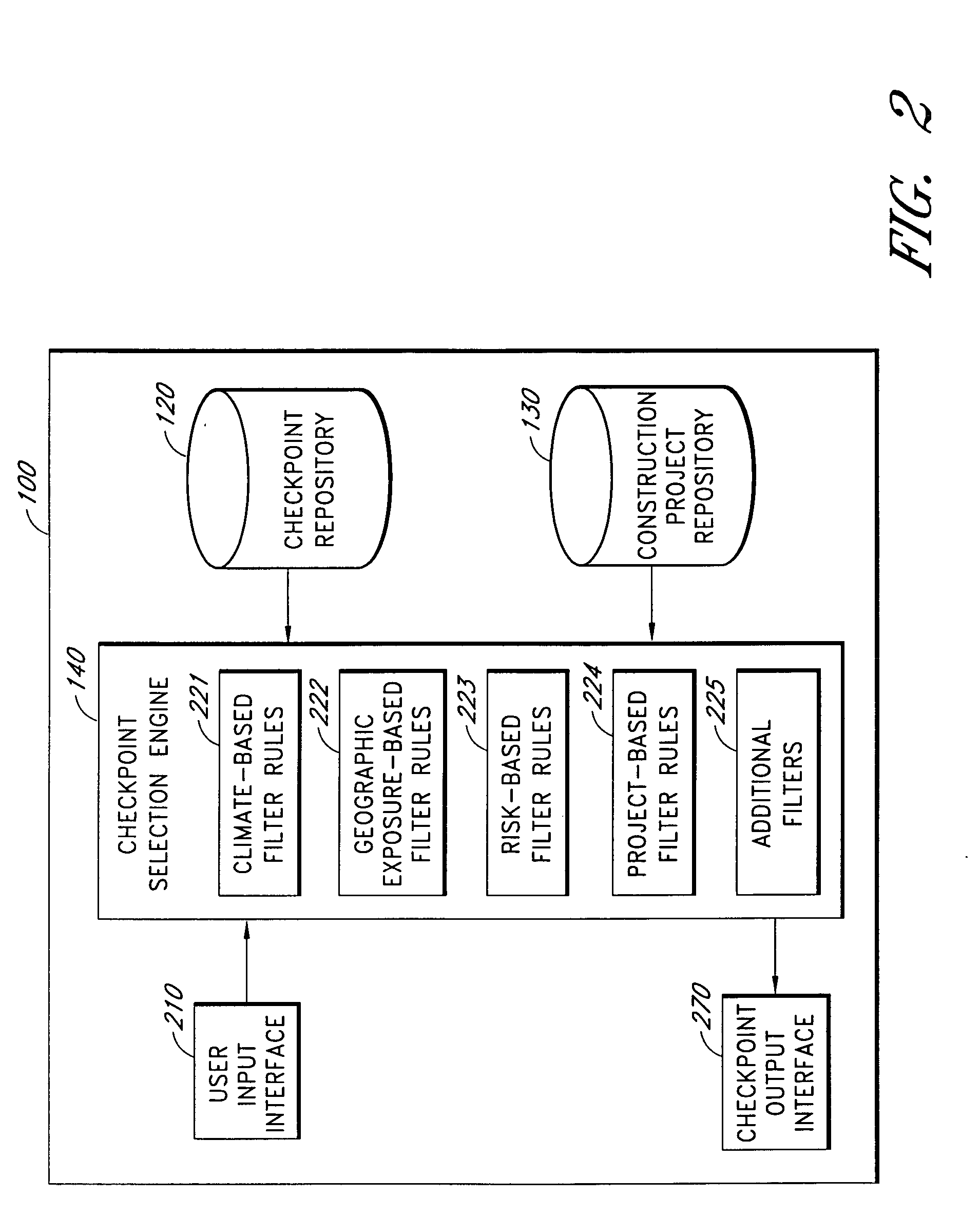
Systems and methods for selecting and prioritizing construction checkpoints
InactiveUS20060026009A1Reduce financial riskMinimizing financial riskCommerceValidation errorProject based
The computer-based system described herein accepts information about a building project and uses the information to select from a repository of construction checkpoints a subset of the checkpoints that are deemed to be relevant to improve a building's safety, durability and comfort and to reduce financial risk. The checkpoints may be selected and / or prioritized for viewing by an inspector inspecting the building project based on at least one of: project geographic location, project-specific exposure, type of structure, complexity of building components, product quality, builder's repeated deficiencies, and codes and specifications. The system may further be configured to receive information about a current stage of construction of the building project and to present checkpoints to the inspector that are relevant to the current stage of construction. The system may also be configured to prioritize presentation of selected checkpoints based at least in part on an assessment of financial risk posed by improper installation and / or construction of the selected checkpoints. In various embodiments, checkpoints that do not pass inspection may be tracked until repaired, and a record of the repair may be stored for later verifying that the error was repaired and not ignored.
Owner:QUALITY BUILT
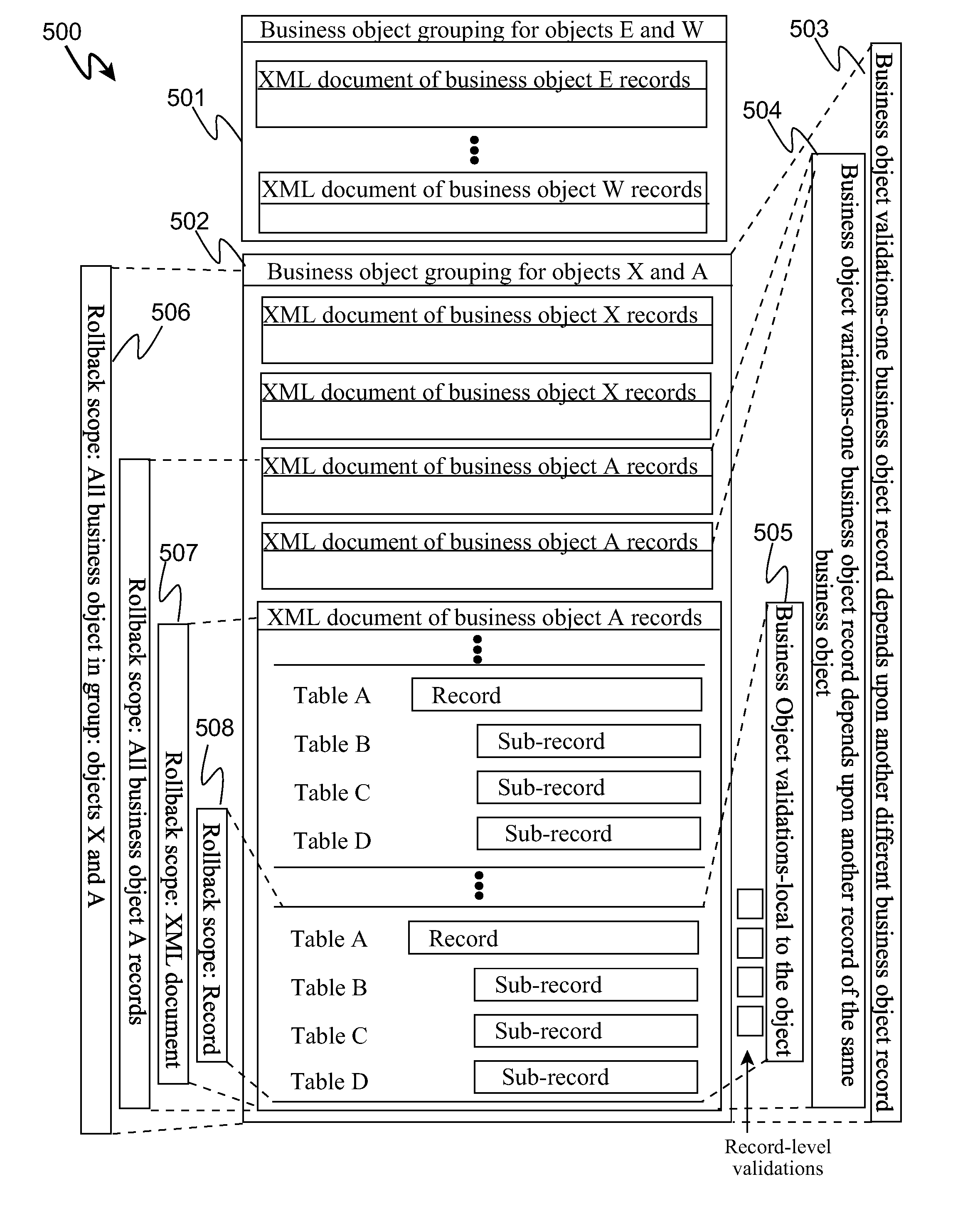
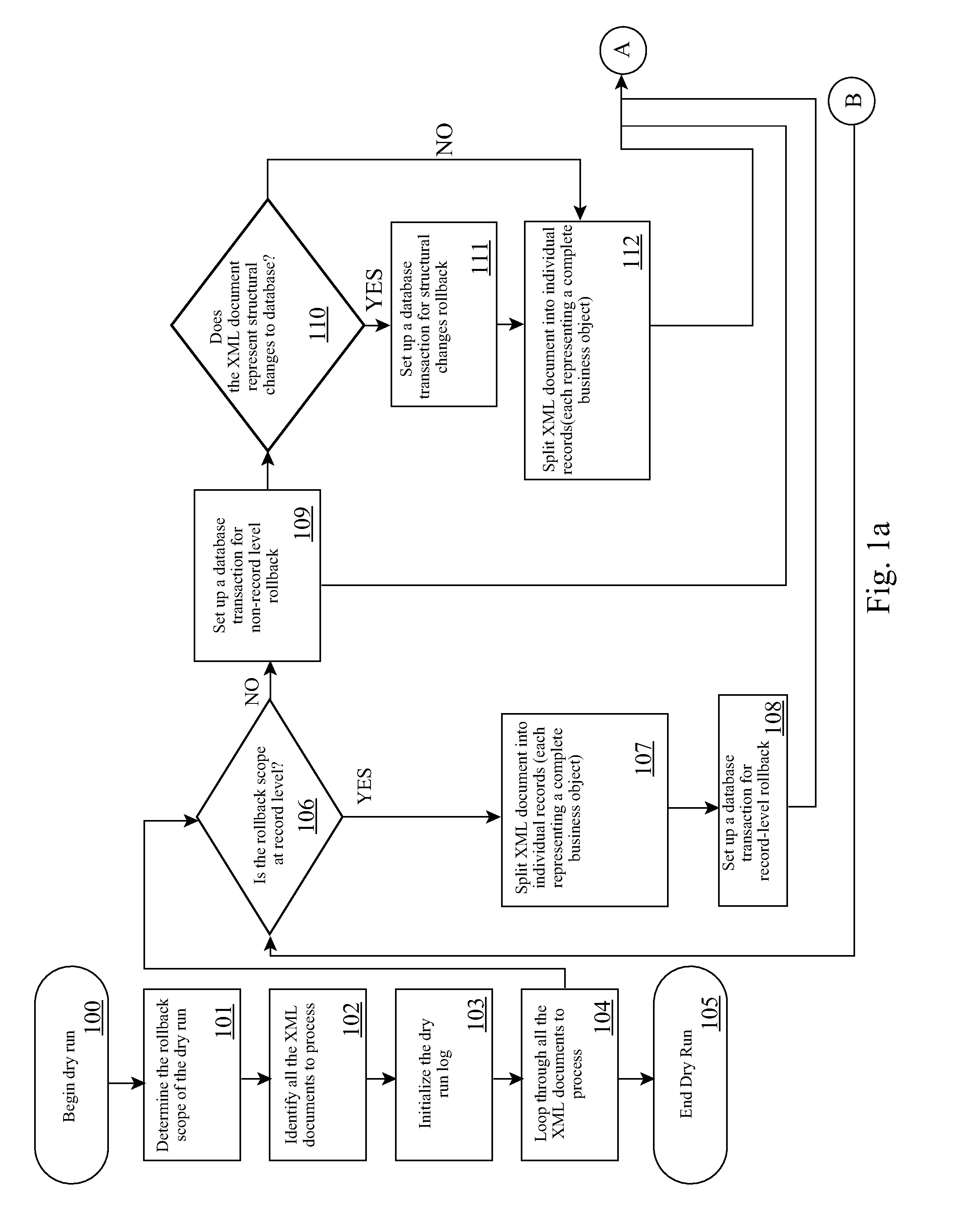
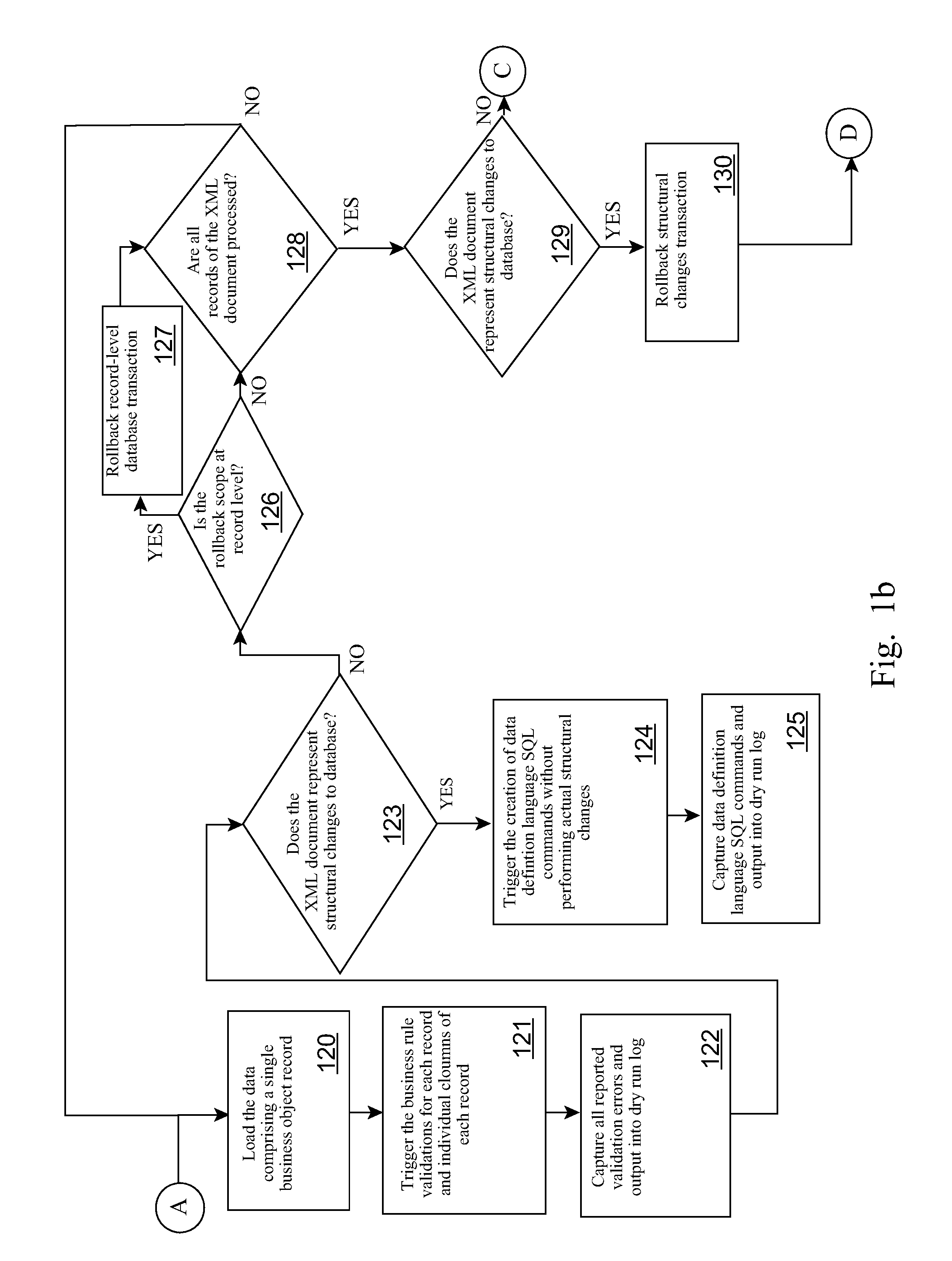
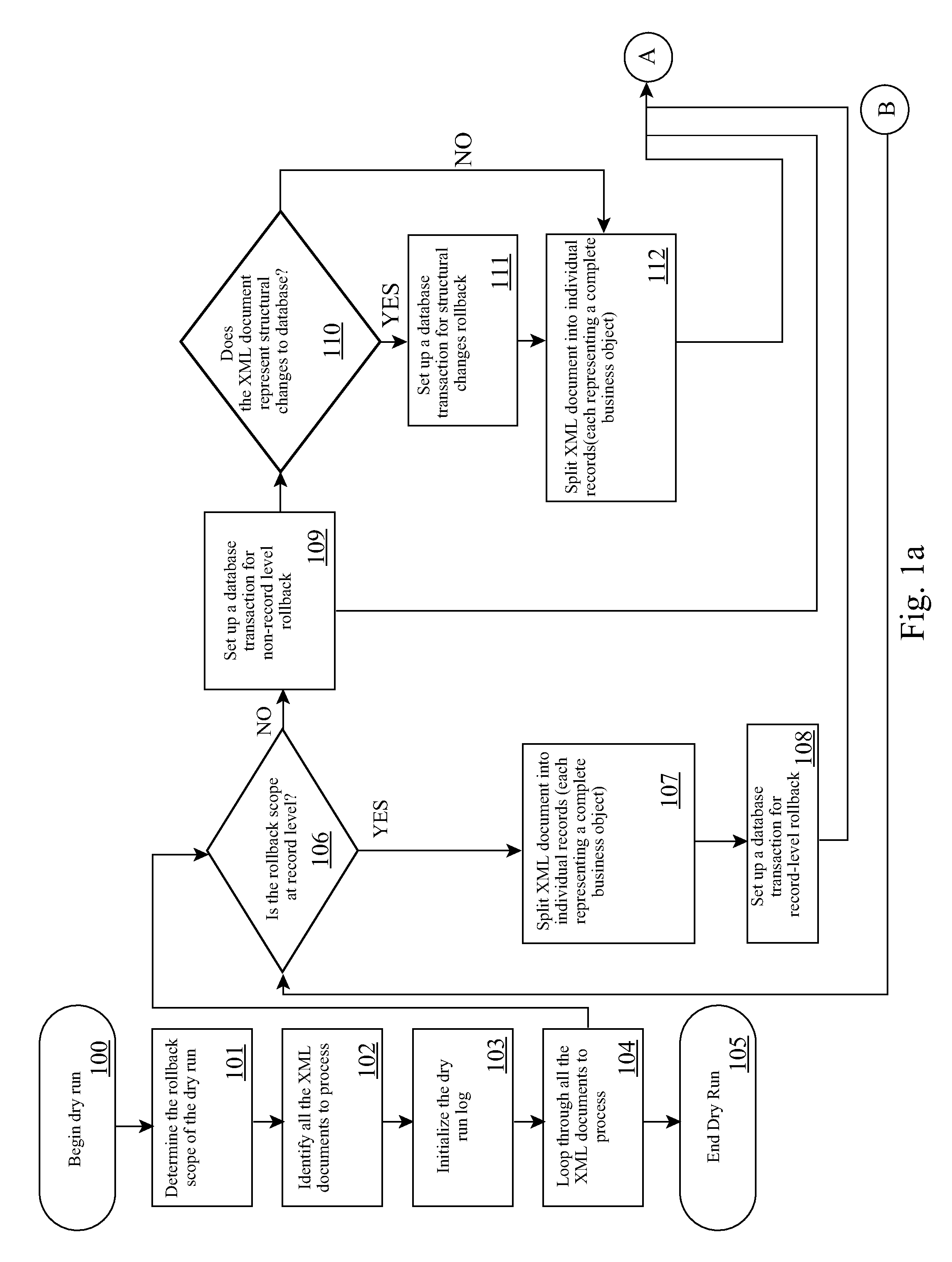
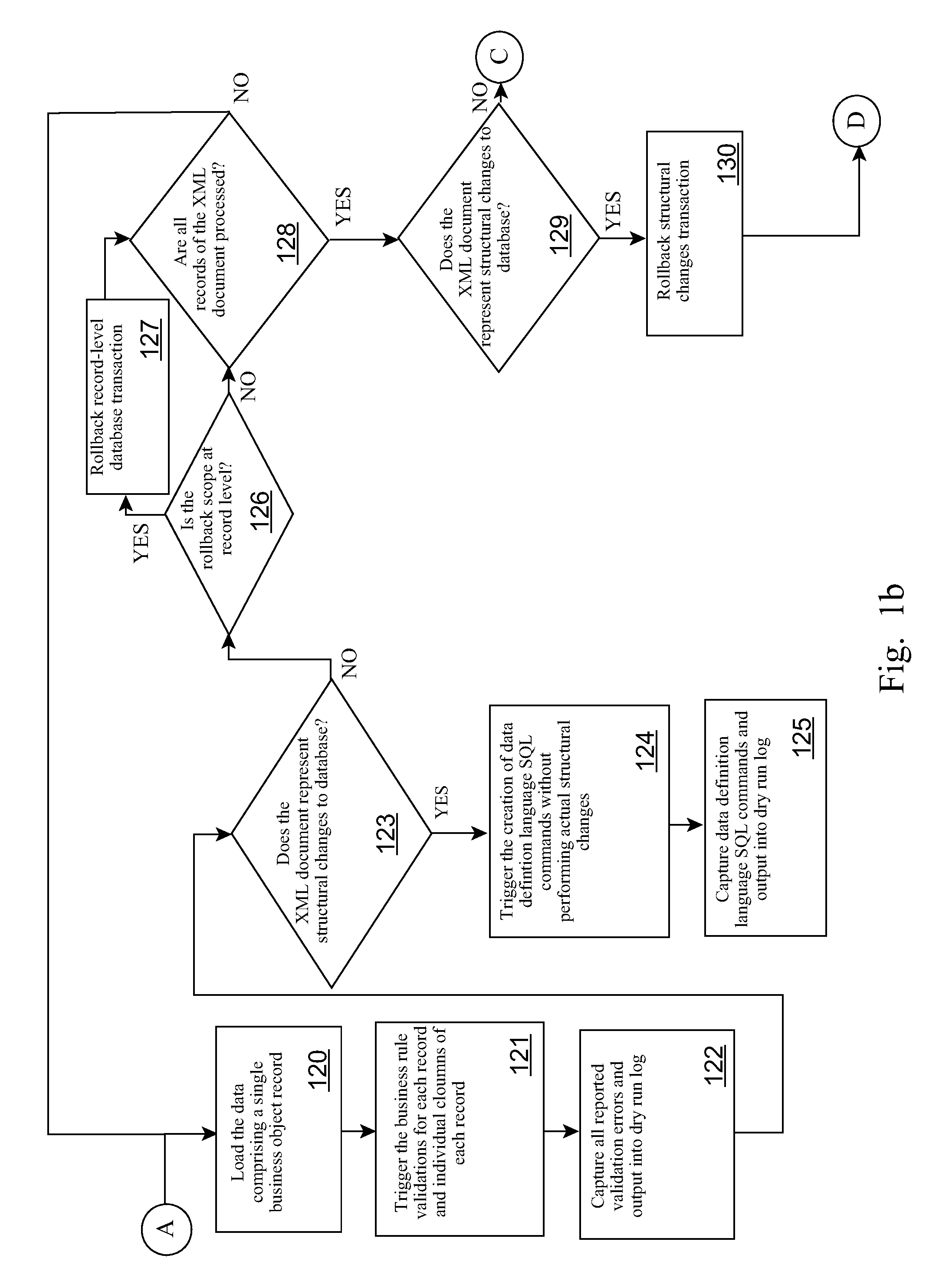
Non-Intrusive Measurement of Content Quality Using Dry Runs with Roll-back
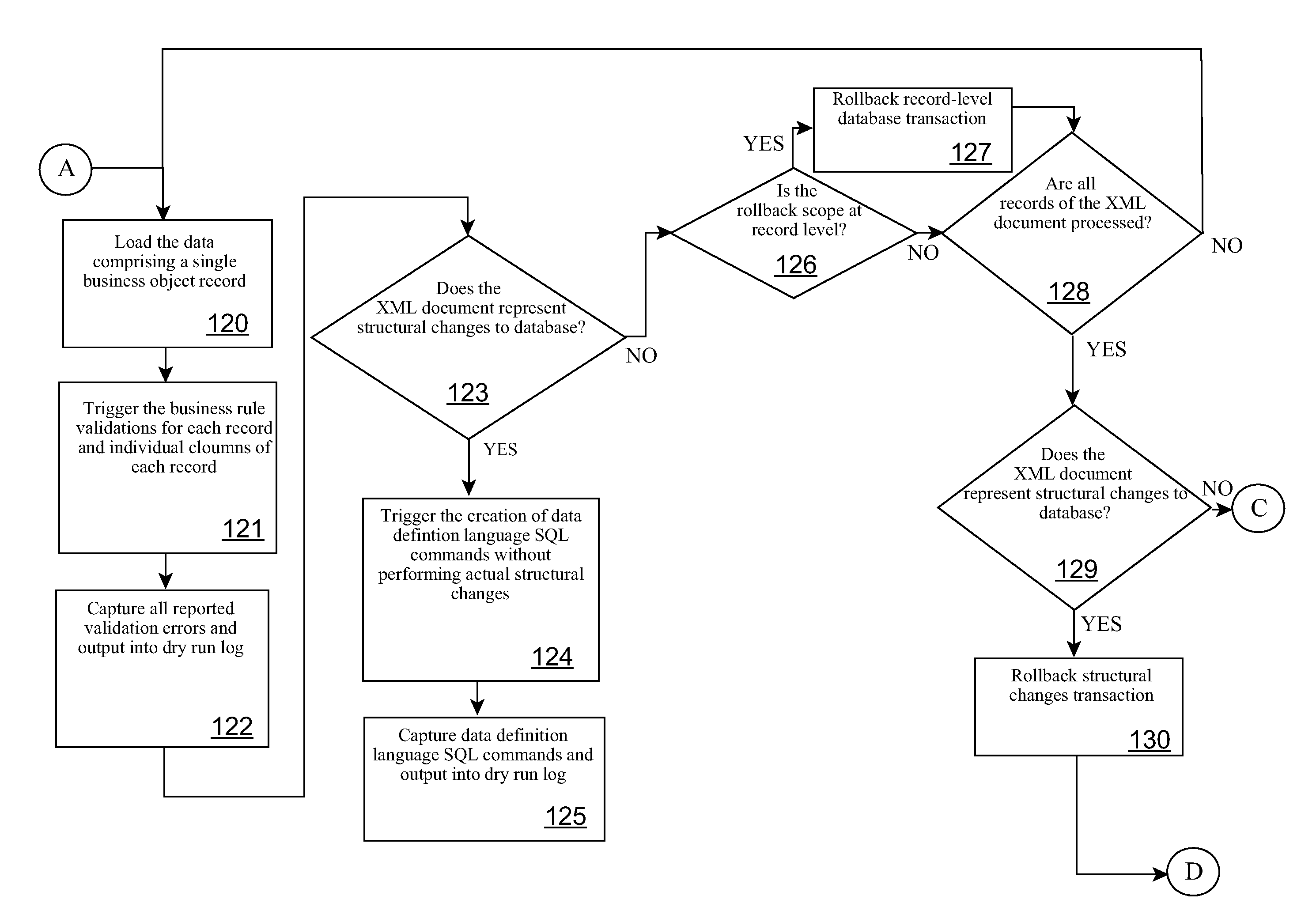
InactiveUS20110321012A1Reliability/availability analysisSpecific program execution arrangementsSoftware engineeringApplication software
Validation and determination of business application program content quality destined for loading on a target production computing environment is automated by receiving an application program into a controlled production computing environment, and, during a dry run test in the production computing environment, logging changes to content from an initial state as loaded by the application program; applying a business rule to the content during data loading to validate against business objects; capturing validation errors produced by the validation and structural change commands to the content into a log file; and automatically rolling back changes made to the content during the dry run test to the initial state thereby avoiding committing content changes to the production computing environment.
Owner:IBM CORP
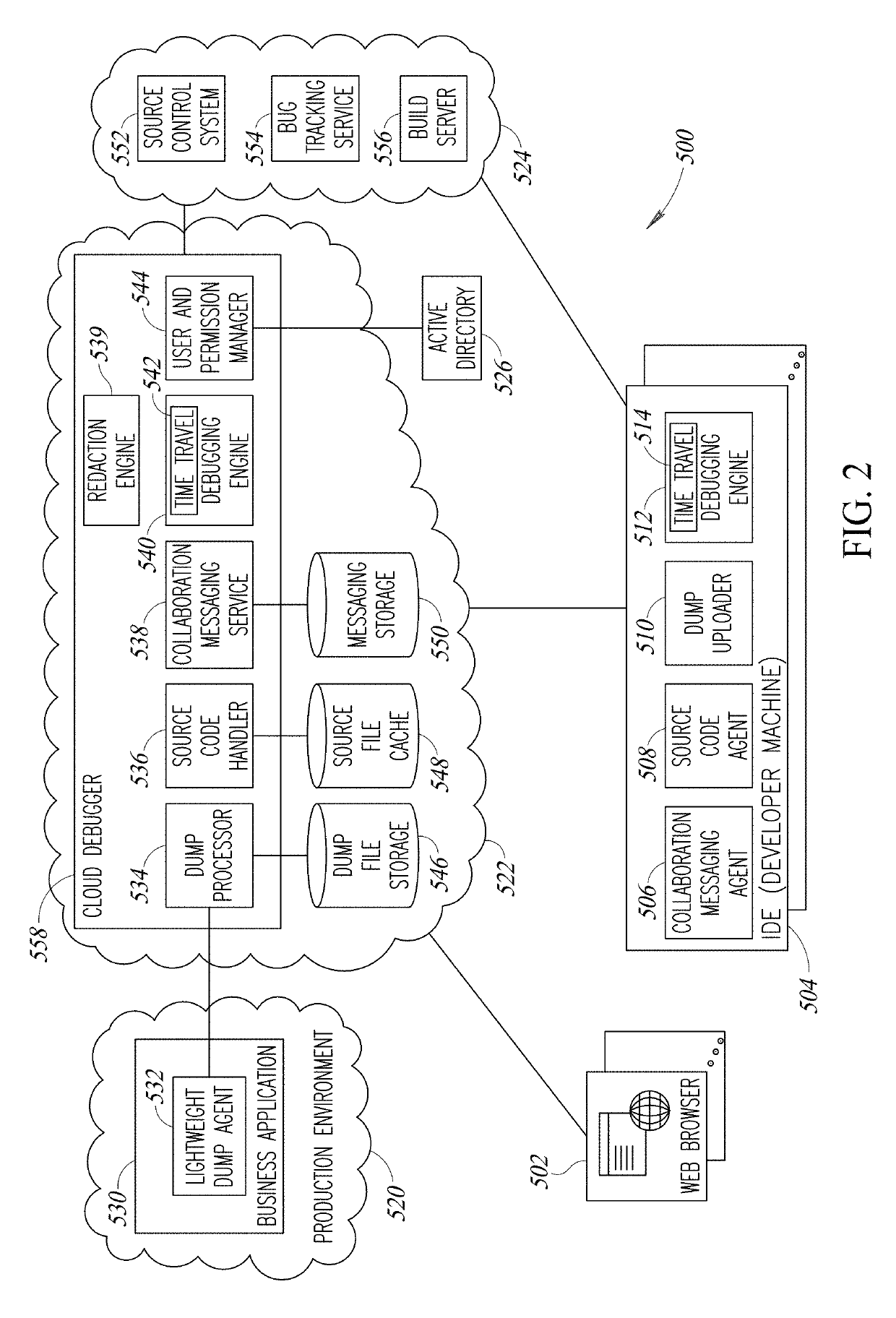
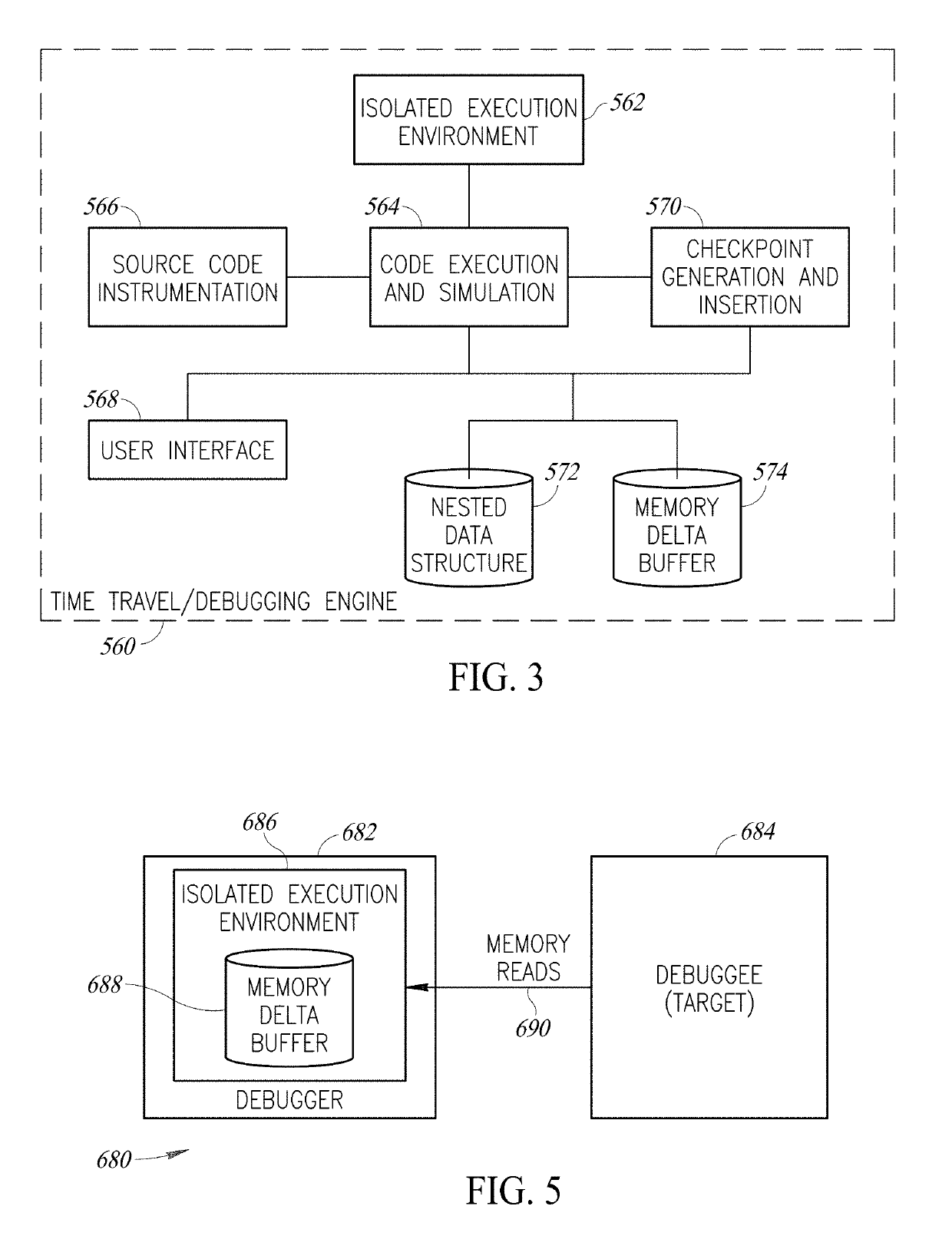
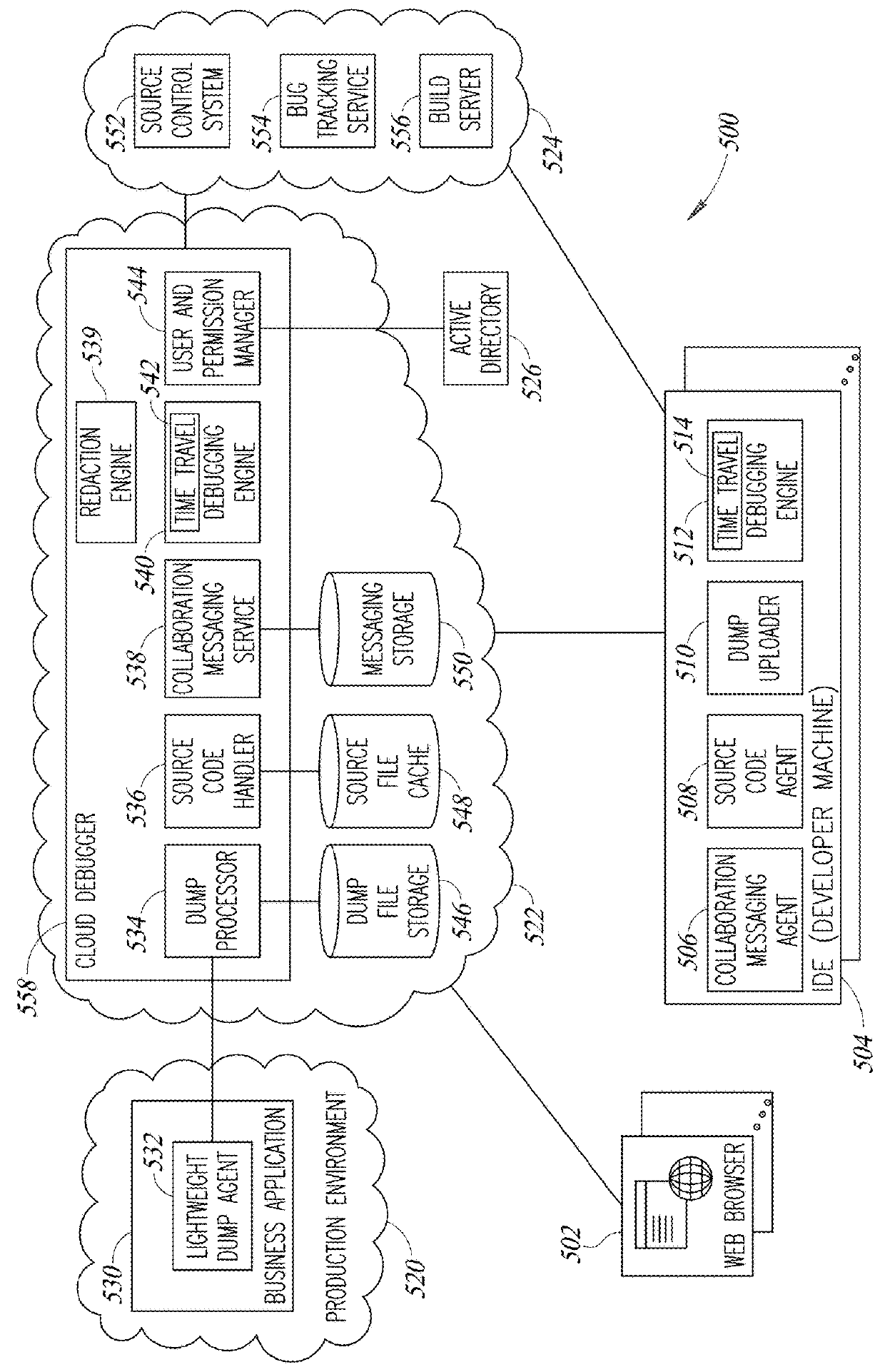
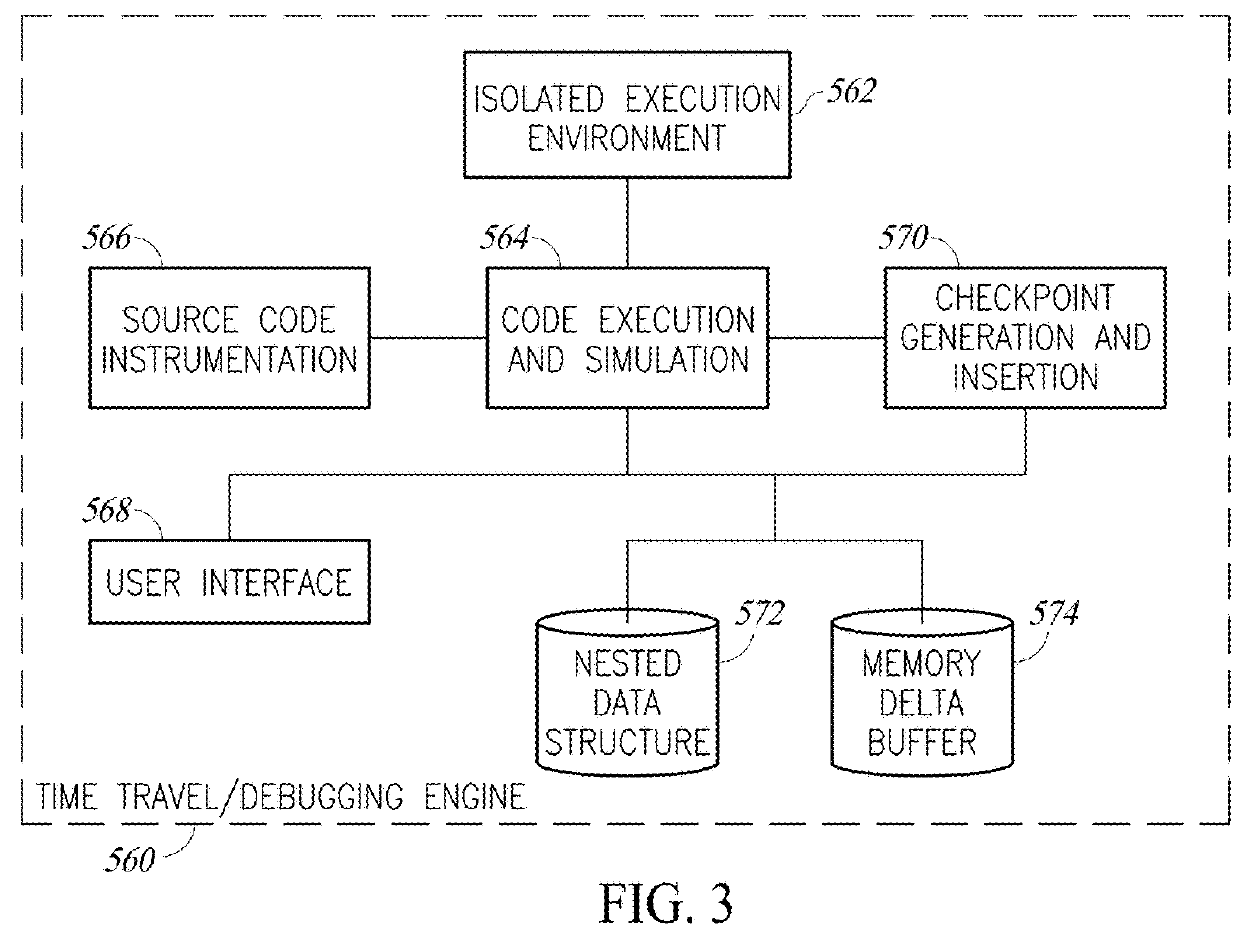
Time Travel Source Code Debugger Incorporating Redaction Of Sensitive Information
ActiveUS20190213355A1Easy to changeSpeed up the debugging processDecompilation/disassemblyDigital data protectionHead-up displaySource code
A novel and useful system and method of time traveling source code debugging including several advanced capabilities that significantly improve the source code debugging process. Upon hitting a breakpoint or opening a dump file, the debugger travels to the future which can be altered by a user by modifying code on the fly (live coding) and receiving immediate feedback to validate bug fixes. Visual annotations including values of variables and expressions are provided as a heads up display effectively flattening time and space. A pivoting capability allows a user to switch the execution context of the code at any time. Point in time links that store the state of the debugging session can be created and activated. An asynchronous collaboration and messaging system enables multiple participants to share a debugging session. An optional redaction capability is also provided for obscuring or replacing sensitive private information.
Owner:OZCODE LTD
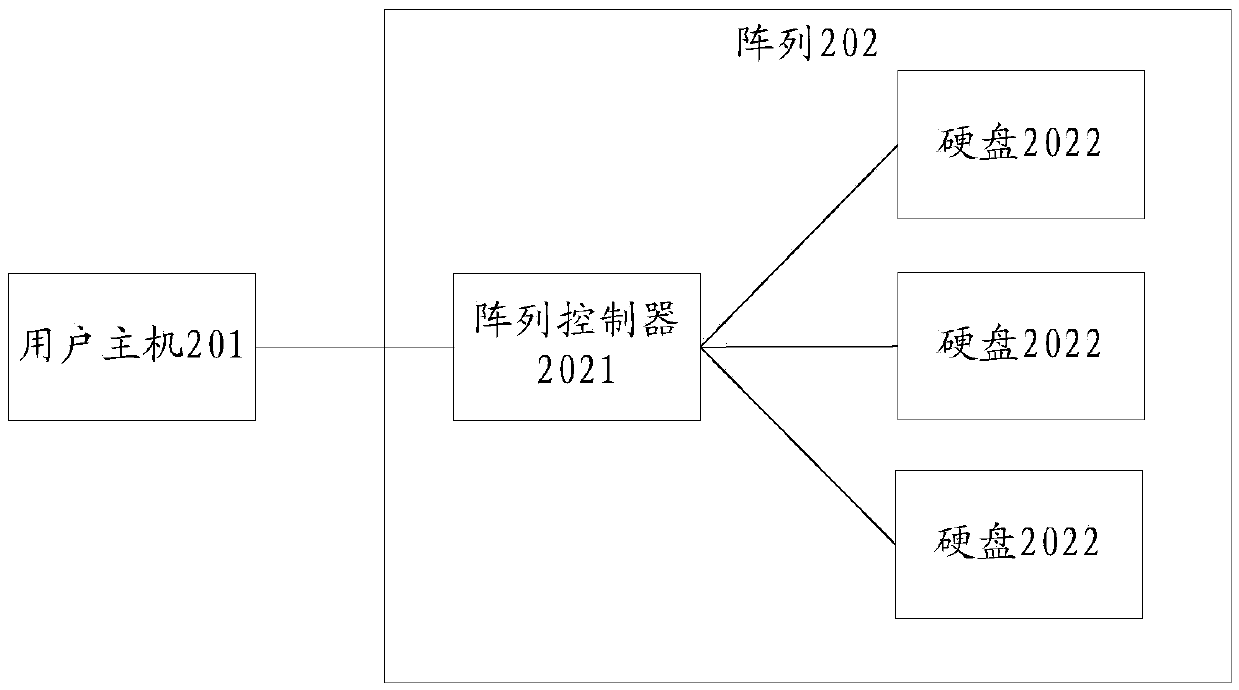
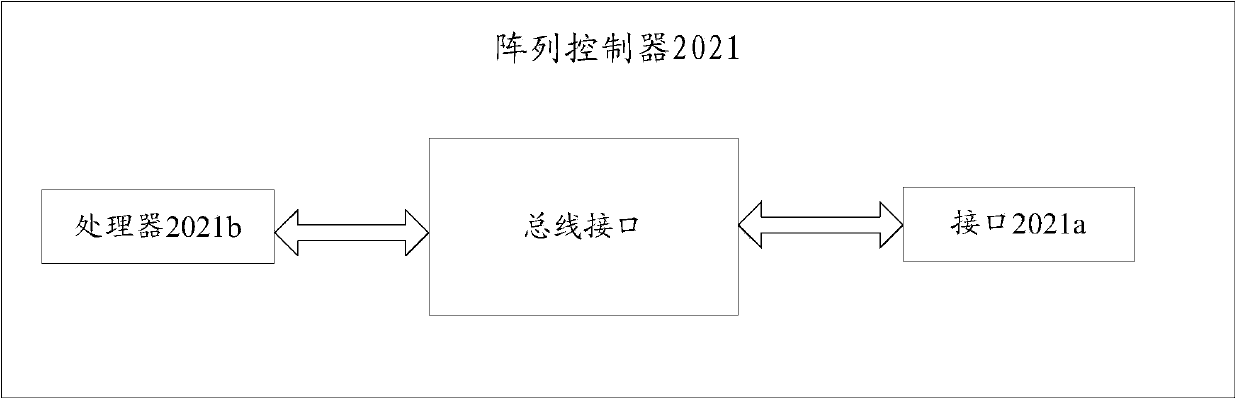
Array control unit, array and data processing method
ActiveCN104182701AAvoid writingReduce time overheadMemory adressing/allocation/relocationDigital data protectionLogical block addressingComputer access
An embodiment of the invention relates to the technical field of data processing, in particular to an array control unit, an array and a data processing method with an aim to solve the problems about additional write-in of IO and large expenditure of time due to the fact that for an existing array adopting a thick LUN (logical unit number) technology, residual data are removed through additional data writing in order to avoid occurrence of errors when a subscriber's host computer accesses to an unwritten data area if a data integrity field (DIF) technology is adopted. The array control unit comprises interfaces and a processor, the interfaces are used for receiving data reading demands sent by the subscriber's host computer, and the processing is used for reading data from the thick LUN. If validation errors of logical block addressing (LBA) occur, and second identification of the thick LUN stored in the array control unit is not recorded in the thick LUN, information fields corresponding data are read, read data are determined to be the residual data, and additional write-in of the data is accordingly avoided.
Owner:HUAWEI TECH CO LTD
System and methods for handling verification errors
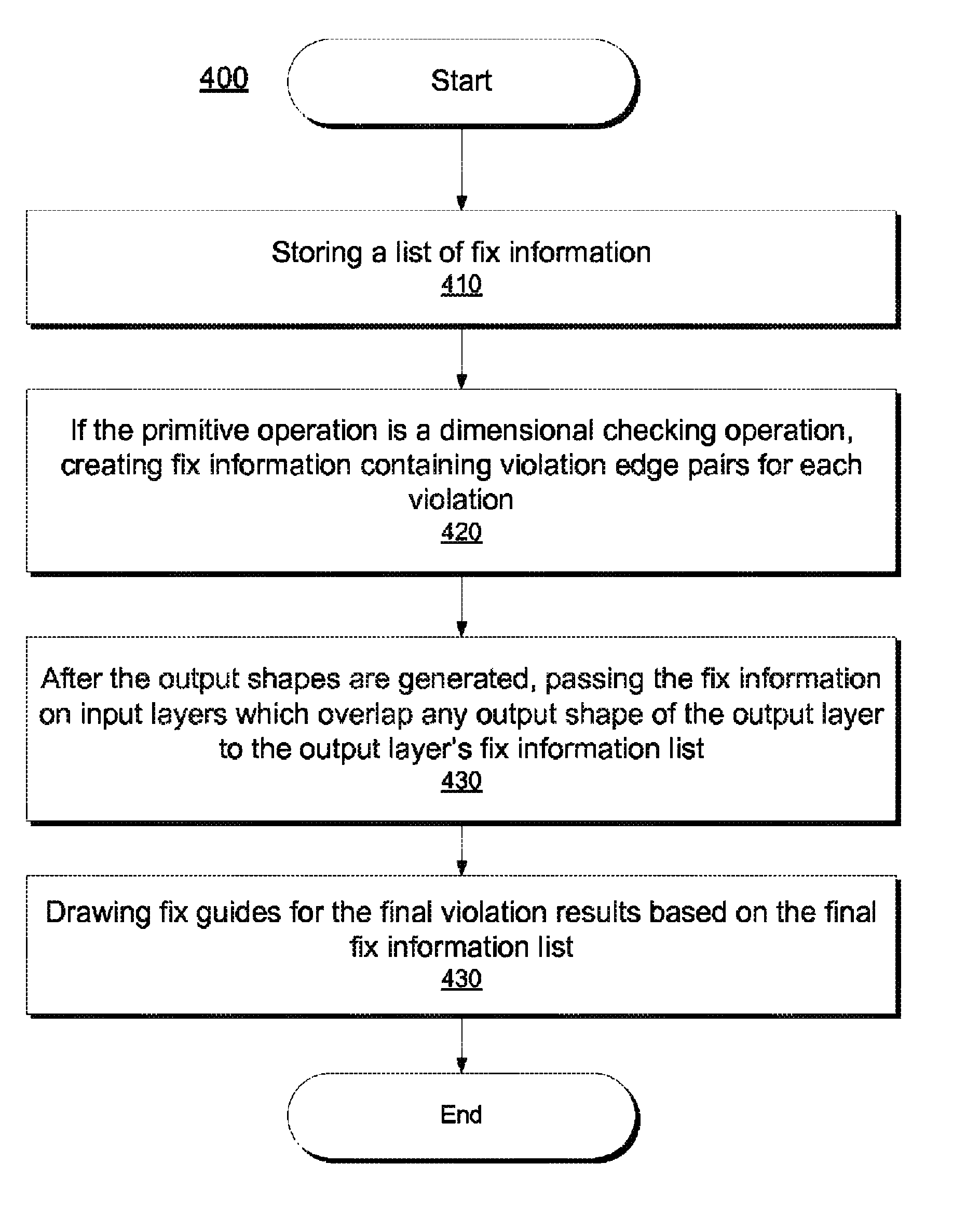
ActiveUS20130254727A1Well formedCAD circuit designSpecial data processing applicationsComputer architecturePrimitive operation
Systems, apparatus and methods for handling verification violations are disclosed. In one aspect, a method stores a list of fix information in addition to geometric shapes for each layer during verification, such as design rule checking For each primitive operation step performed during verification, two tasks are performed. First, if the primitive operation is a dimensional checking operation (i.e., width, spacing or enclosure), then for each violation, the first task creates fix information containing violation edge pairs and adds the created fix information to the fix information list on the output layer. Second, for all operations and after the output shapes on the output layer are generated, a second task passes the fix information on input layers which overlap any output shape of the output layer to the output layer's fix information list. Finally, fix guides for the final violation results are generated and drawn based on the final fix information list.
Owner:SYNOPSYS INC
Time Travel Source Code Debugger Incorporating Pivoting Ability
ActiveUS20190213101A1Easy to changeSpeed up the debugging processDecompilation/disassemblyPlatform integrity maintainanceHead-up displayRotation function
A novel and useful system and method of time traveling source code debugging including several advanced capabilities that significantly improve the source code debugging process. Upon hitting a breakpoint or opening a dump file, the debugger travels to the future which can be altered by a user by modifying code on the fly (live coding) and receiving immediate feedback to validate bug fixes. Visual annotations including values of variables and expressions are provided as a heads up display effectively flattening time and space. A pivoting capability allows a user to switch the execution context of the code at any time. Point in time links that store the state of the debugging session can be created and activated. An asynchronous collaboration and messaging system enables multiple participants to share a debugging session. An optional redaction capability is also provided for obscuring or replacing sensitive private information.
Owner:OZCODE LTD
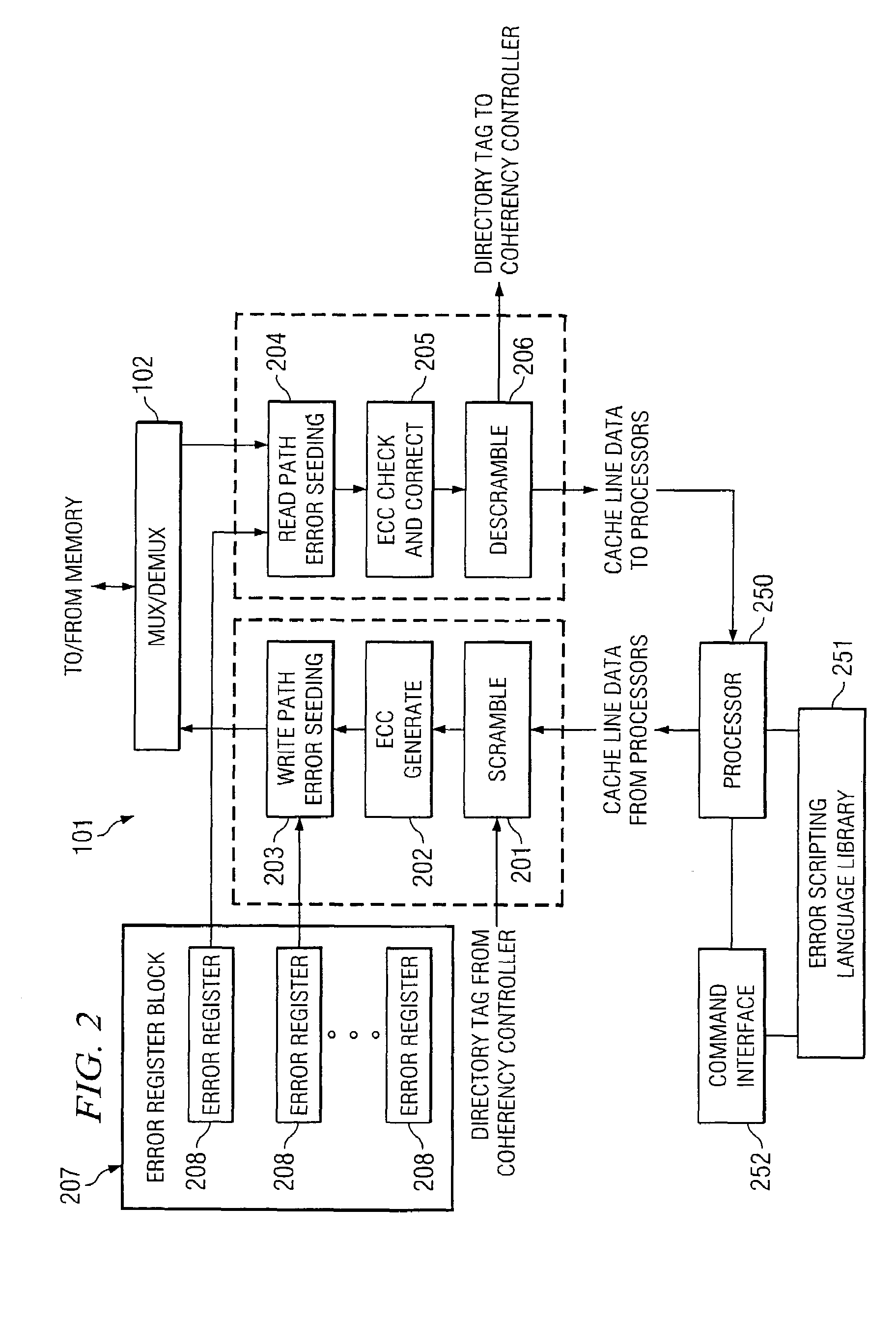
Systems and methods for scripting data errors to facilitate verification of error detection or correction code functionality
InactiveUS7401269B2Convenient verificationCorrect operation testingError detection/correctionBit fieldData error
In one embodiment, the present invention is directed to a method for inserting errors into data to facilitate validation of an error detection algorithm. The method comprises: receiving a data corruption command for a plurality of bits; determining, from the data corruption command, a plurality of bit fields within the plurality of bits for data corruption; determining a minimum and maximum number of errors for each of the plurality of bit fields; determining a total number of errors to be inserted; inserting the minimum number of errors into each of the plurality of bit fields at random locations; and randomly inserting additional errors into the plurality of bit fields subject to the maximum number of errors until the total number of errors are inserted.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
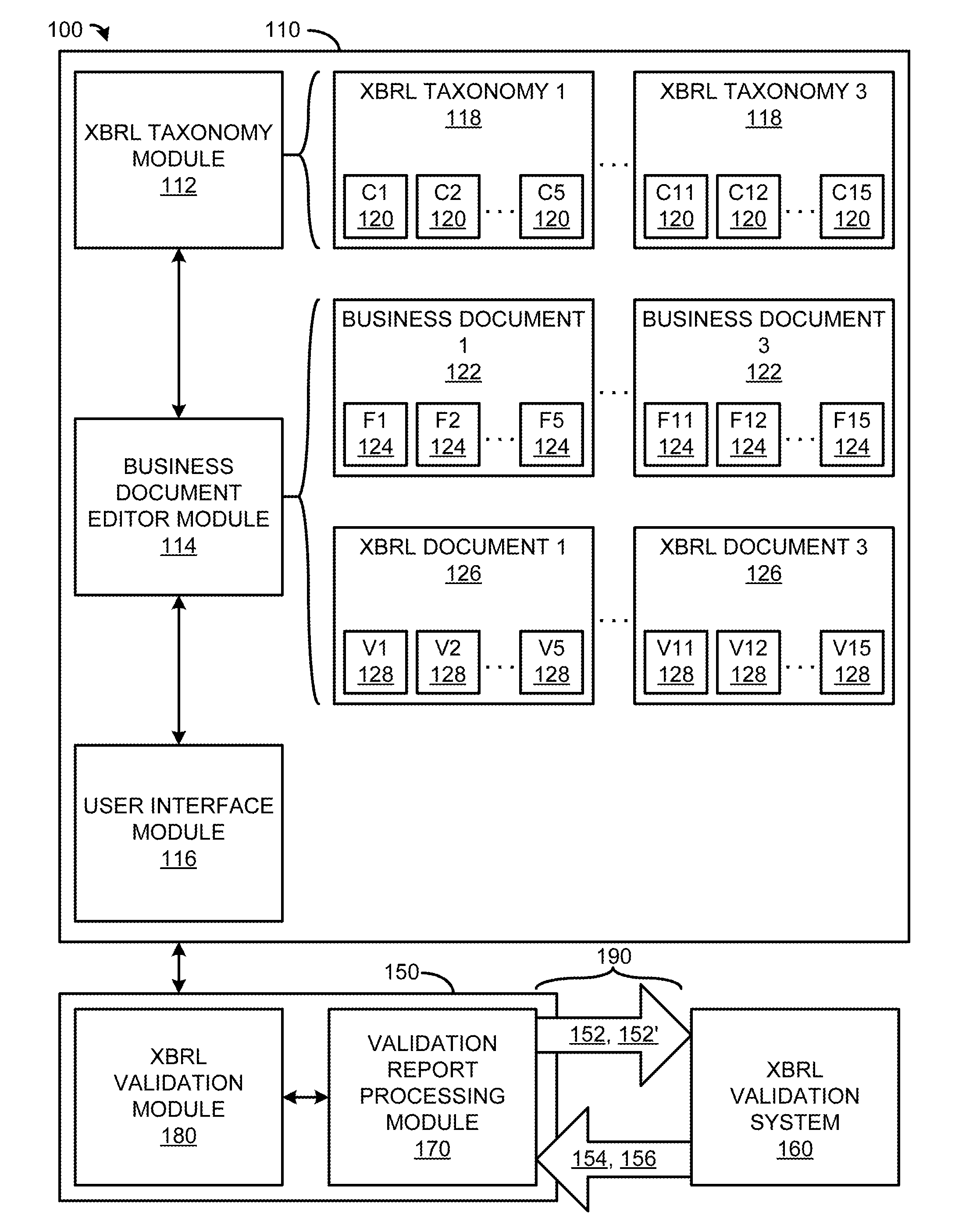
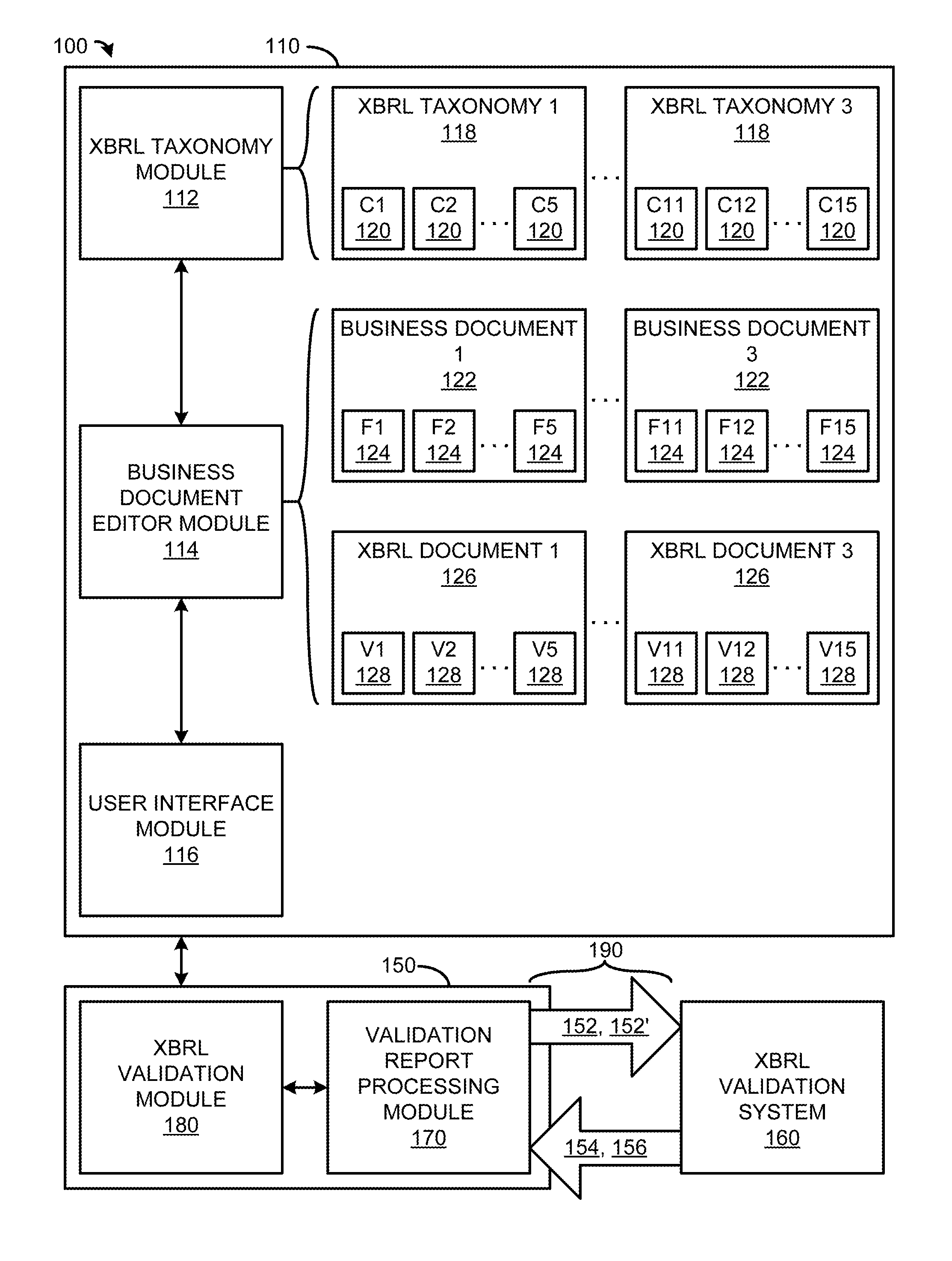
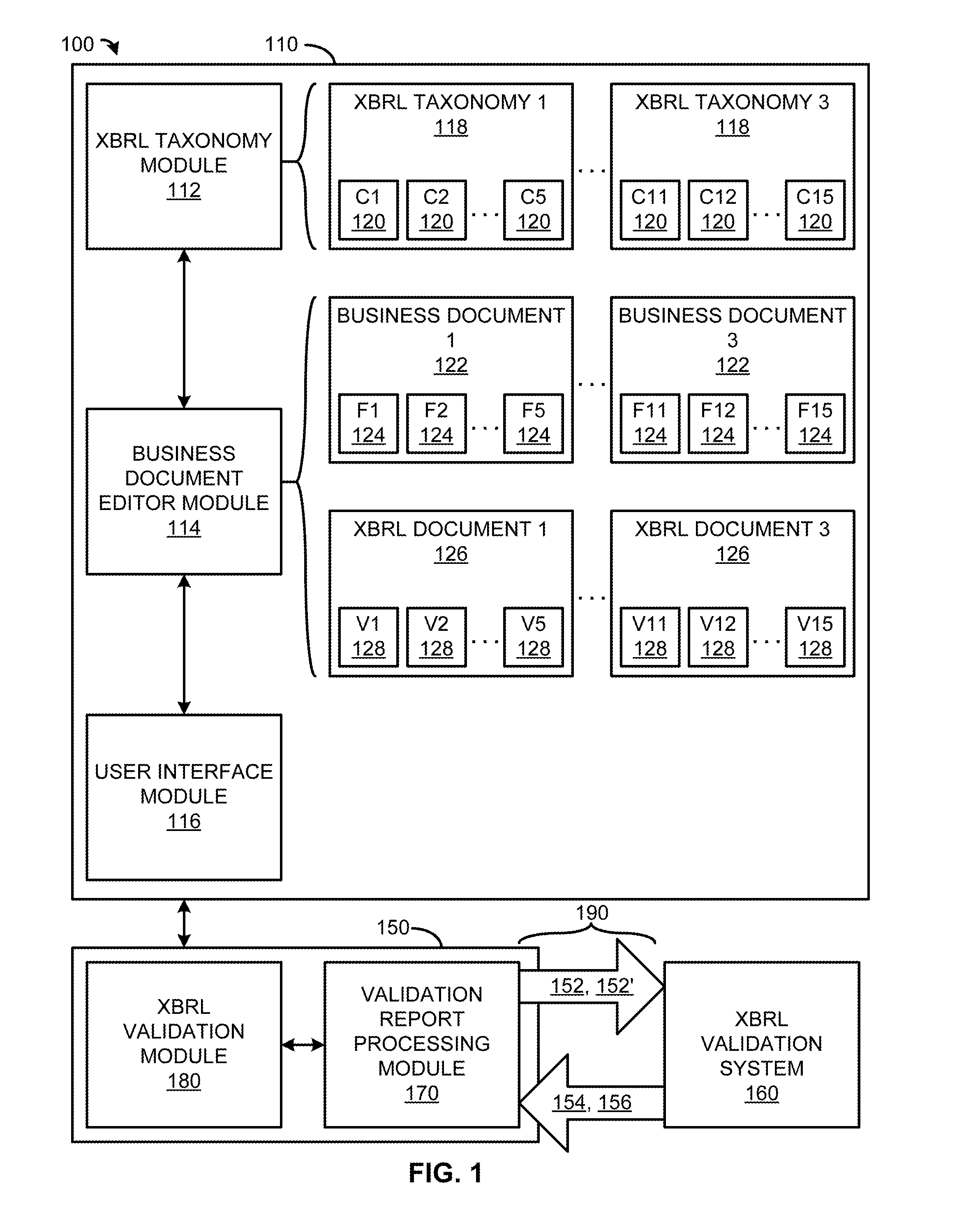
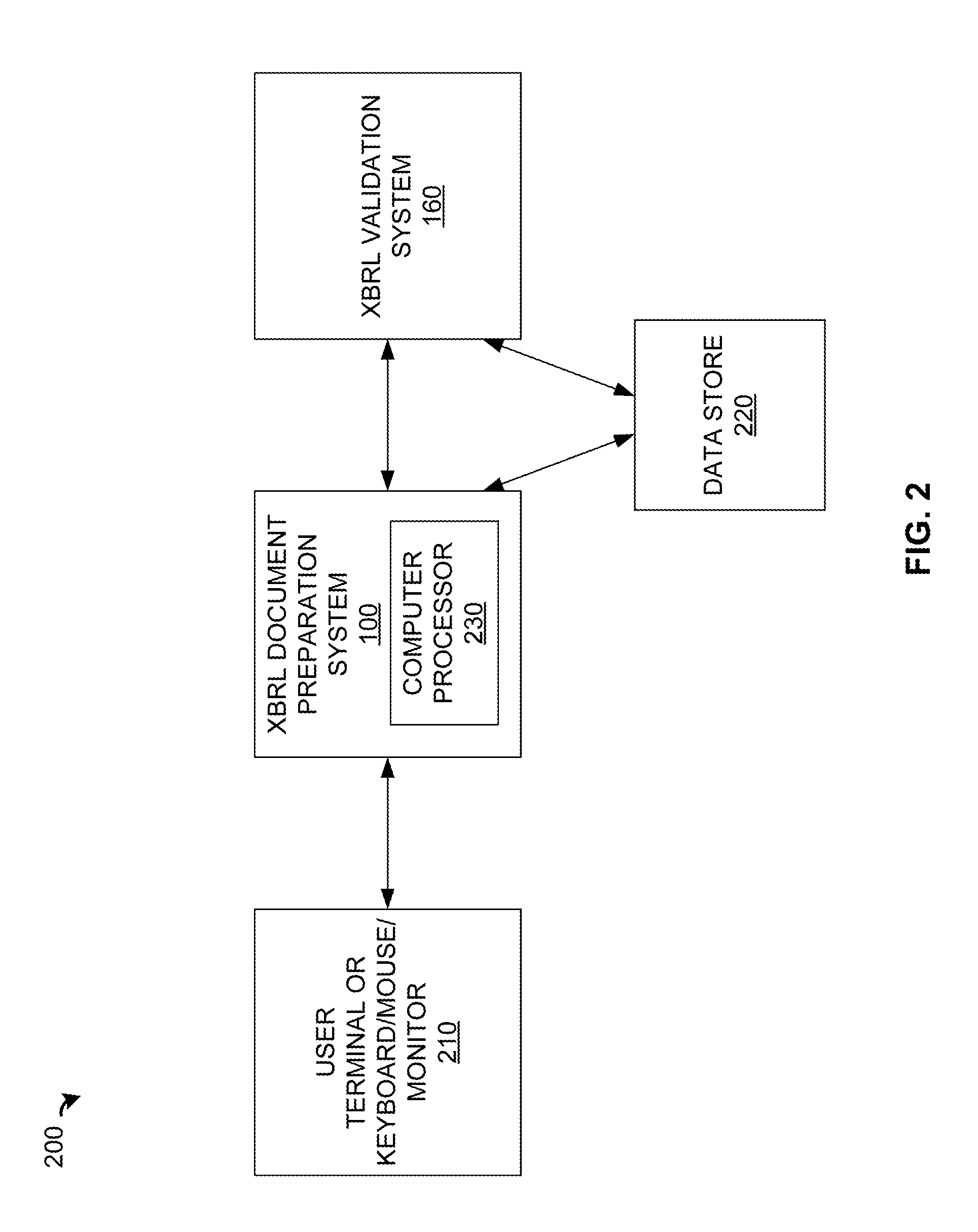
Systems and Methods for Navigating to Errors in an XBRL Document Using Metadata
ActiveUS20130262981A1Easy to navigateEasy to markNatural language data processingSpecial data processing applicationsProcess moduleDocumentation
An XBRL document preparation system comprises an XBRL taxonomy module including one or more XBRL taxonomies having one or more XBRL concepts; a business document editor module that facilitates tagging of one or more entries of a business document with one or more XBRL tags based on the XBRL concepts, and generating an XBRL document including XBRL code corresponding to the tagged entries of the business document; an XBRL document validation system that validates the generated XBRL document and generates at least one of validation errors and warnings corresponding to the XBRL code; an XBRL validation report processing module that associates at least one of the generated validation errors and warnings with a specific source among the tagged entries of the business document; and a user interface module that identifies and facilitates editing the specific source among the tagged entries of the business document.
Owner:WORKIVA
Validation of conditional policy attachments
Framework for conditionally attaching web service policies to a policy subject (e.g., a web service client or service endpoint) at subject runtime. In one set of embodiments, a validation process can be performed at a policy subject during an initialization phase to ensure that there are no validation errors with respect to the web service policies that may be conditionally attached to the subject. This validation process can include grouping the policies that have been associated with the policy subject (via policy attachment metadata) by their corresponding constraint expressions, and determining which groups can potentially overlap (i.e., be simultaneously attached to the policy subject) at runtime. Each set of overlapping groups can then be validated using a predefined set of validation rules to identify potential errors pertaining to the policies in the set.
Owner:ORACLE INT CORP
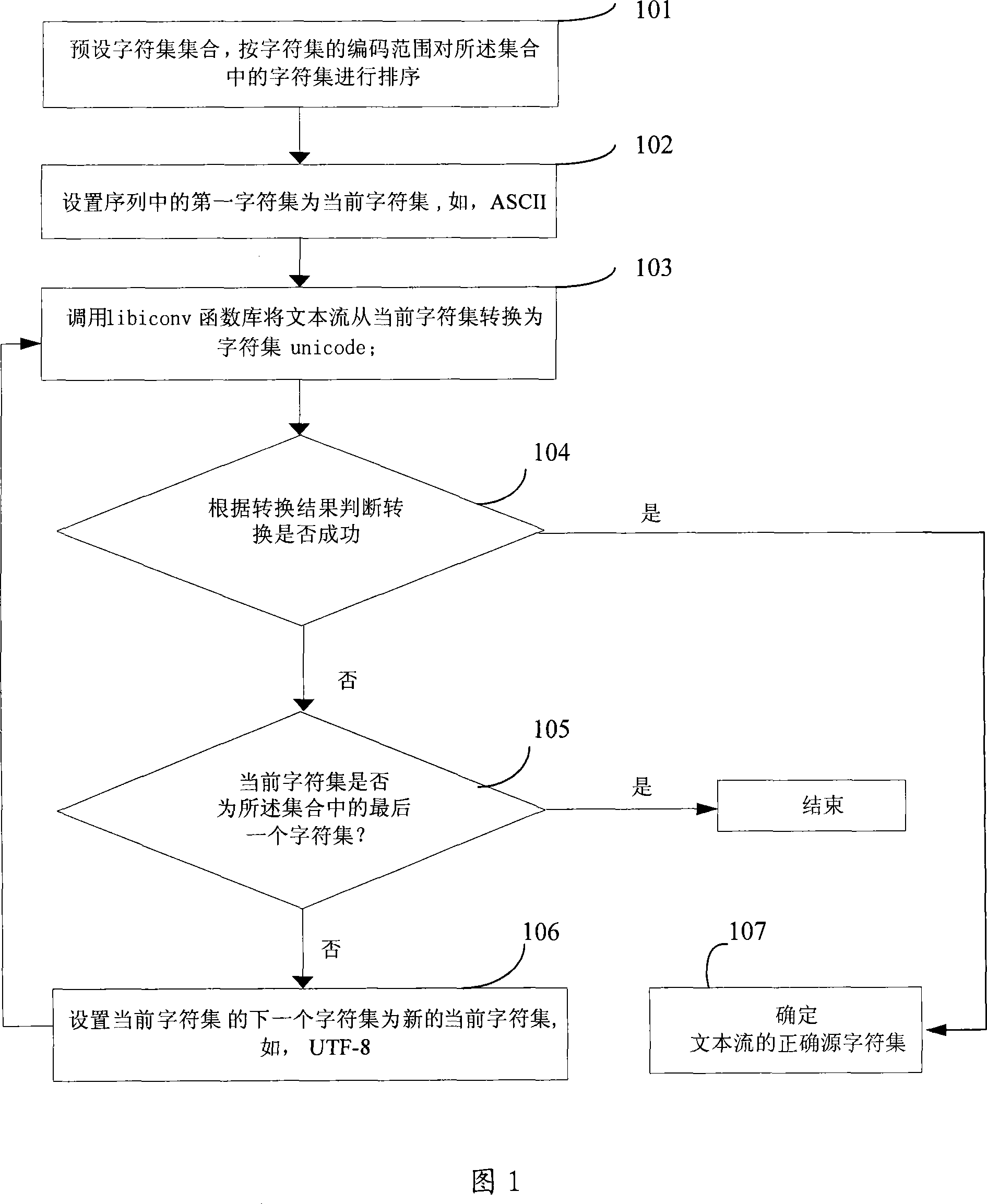
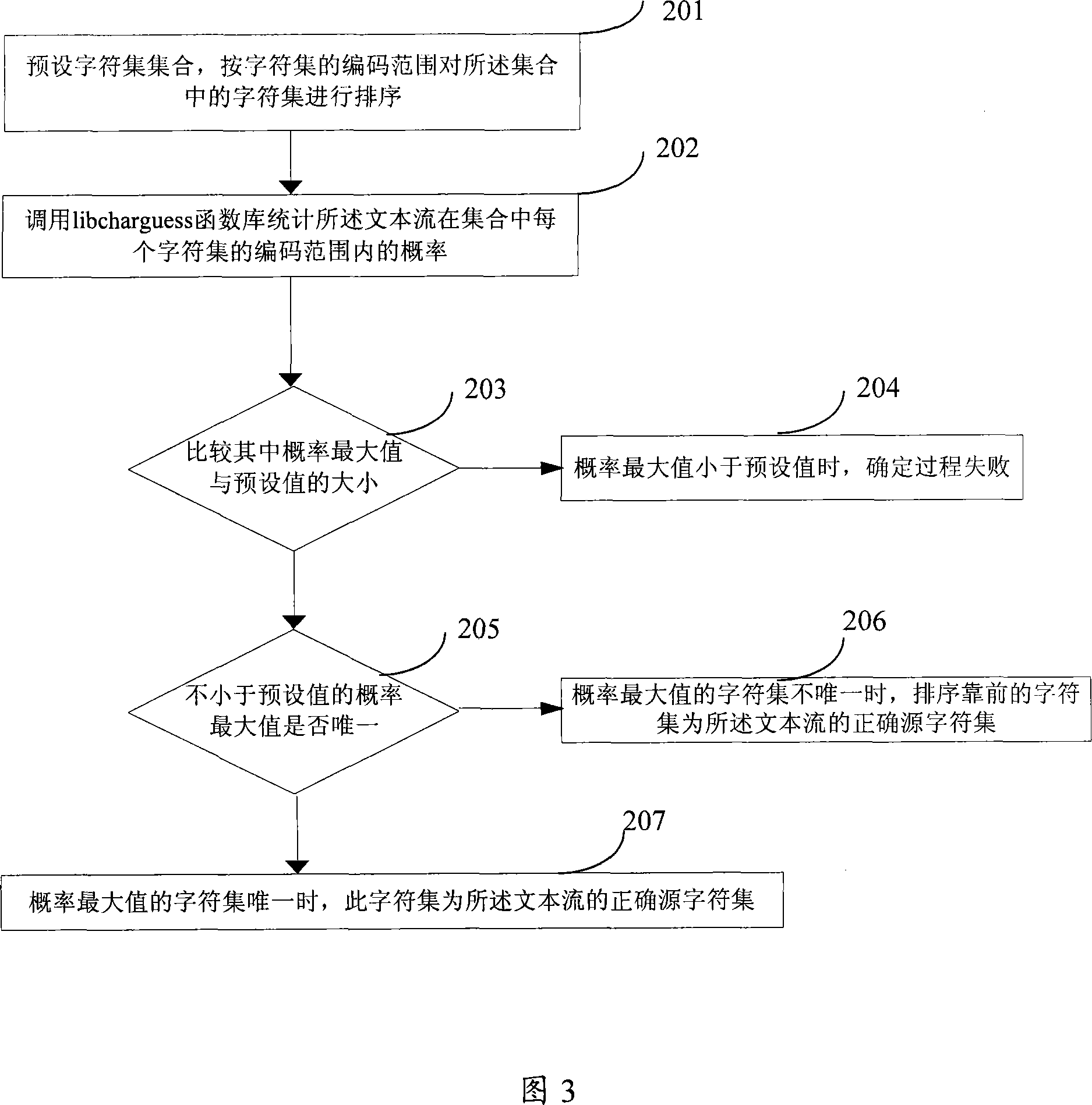
Method and apparatus for confirming text stream character set
InactiveCN101034391AThe result is accurateSpecial data processing applicationsAlgorithmTheoretical computer science
The invention provides a method determining a character set in the text flow, including: default characters in the set, according to the encoding scope of the character set arranging the character set in rank in the pool; Set up the first set of characters in the sequence described for the current character set; convert the above text flow to the character set, if successful conversion, the current characters regarded as the correct source character set in the text flow referred; If the conversion failed, the next step is implemented; judging whether the present character set is the last character set in the sets referred, if not, in the current set up a new character set next to the current set as a new current set, implementing the above step. The present invention also provides a device determining a set of characters in the text flow. Use of methods and devices of this invention providing, can quickly determine a copy of the source of characters in the flow received, at the same time is able to recognize the character sets in the secondary with possible confusion and avoid validation error.
Owner:北京立通无限科技有限公司
Methods and systems for reservoir history matching for improved estimation of reservoir performance
InactiveCN105122153ADesign optimisation/simulationSpecial data processing applicationsPresent methodErrors and residuals
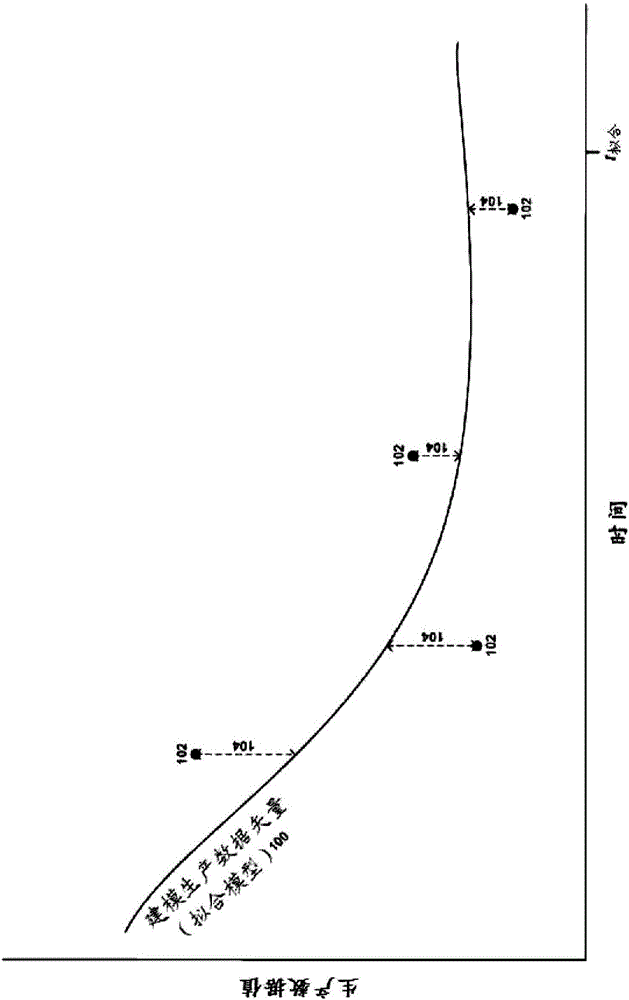
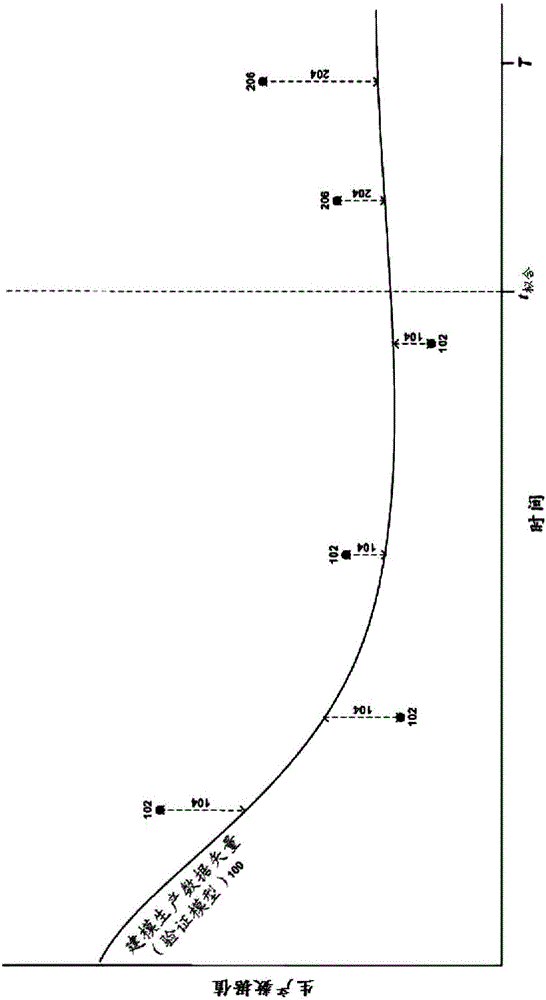
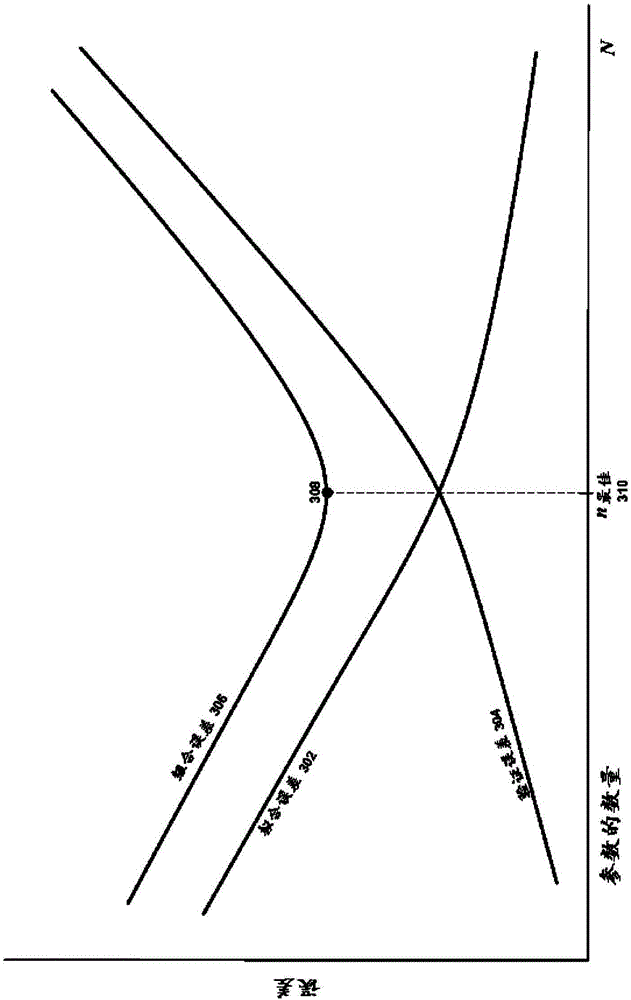
The present disclosure presents methods and apparatuses for forecasting geological formation production data. For example, some example methods include identifying an array of parameter sets, determining a fitting error between a first set of the historical production data and modeled production data, wherein the modeled production data is obtained through execution of a simulation model based on each parameter set of the array, determining a validation error between a second set of the historical production data and extrapolated production data for each parameter set of the array, determining a combined error for each parameter set of the array based on the fitting error and the validation error, and identifying an optimal parameter set size for modeling the target geological region, wherein the optimal parameter set size is determined in reference to a minimum combined error of the combined errors determined for each parameter set of the array.
Owner:HALLIBURTON ENERGY SERVICES INC
Method and apparatus for implementing persistence and refreshing of validation error messages based upon hierarchical refresh levels
A method, apparatus and computer program product are provided for implementing persistence and refreshing of validation error messages based upon hierarchical refresh levels. A validation level is identified when a validation completes. Error messages stored in a message repository with a refresh tag level less than or equal to the validation level are removed. Then new error messages with a refresh tag level less than or equal to the validation level are collected and added to the message repository. The validation level indicates a type of validation stage that potentially updates the status of a particular error condition and message. Multiple validation levels may be represented by predefined numeric values, with larger values representing higher levels in a hierarchy.
Owner:IBM CORP
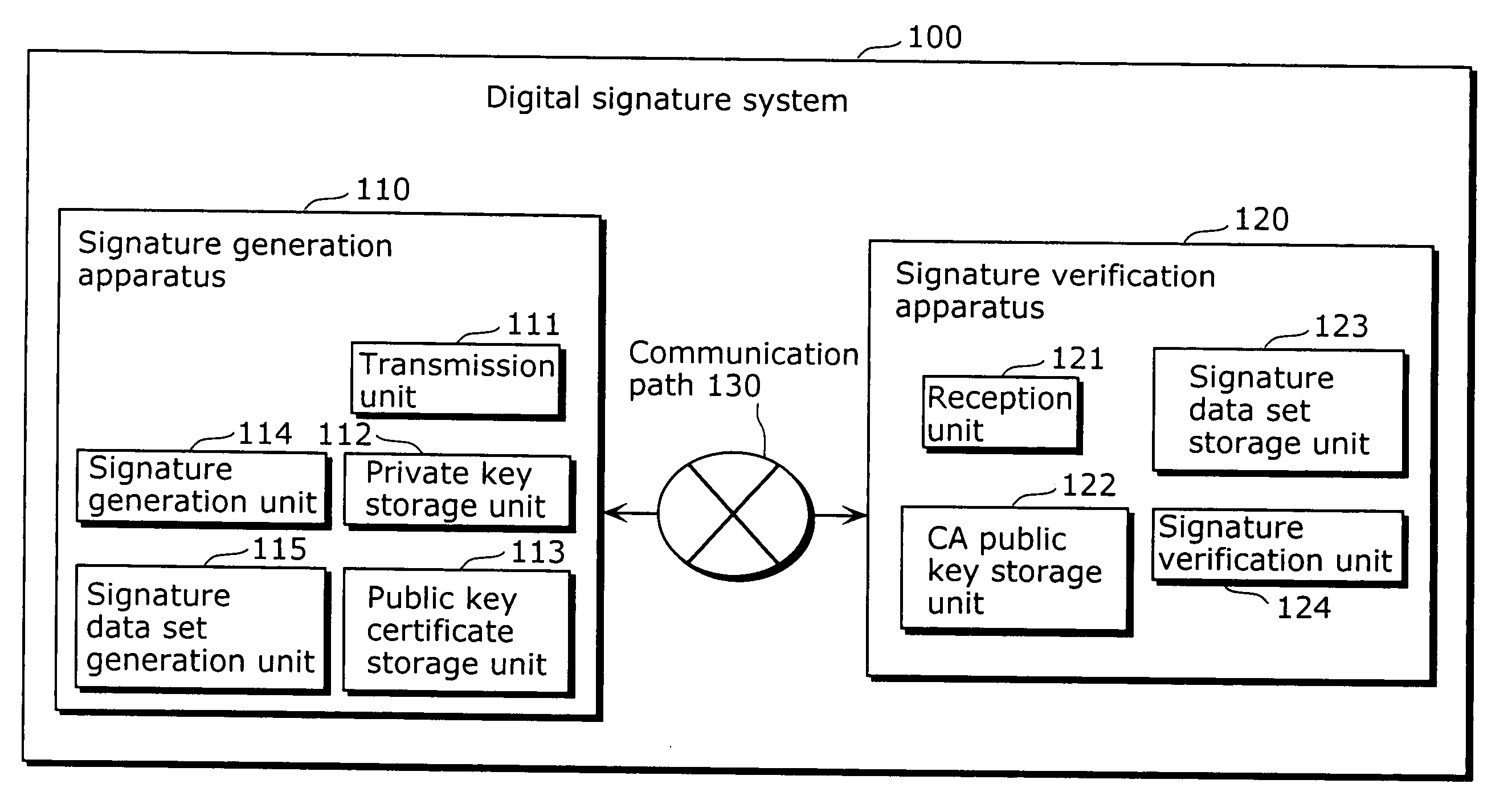
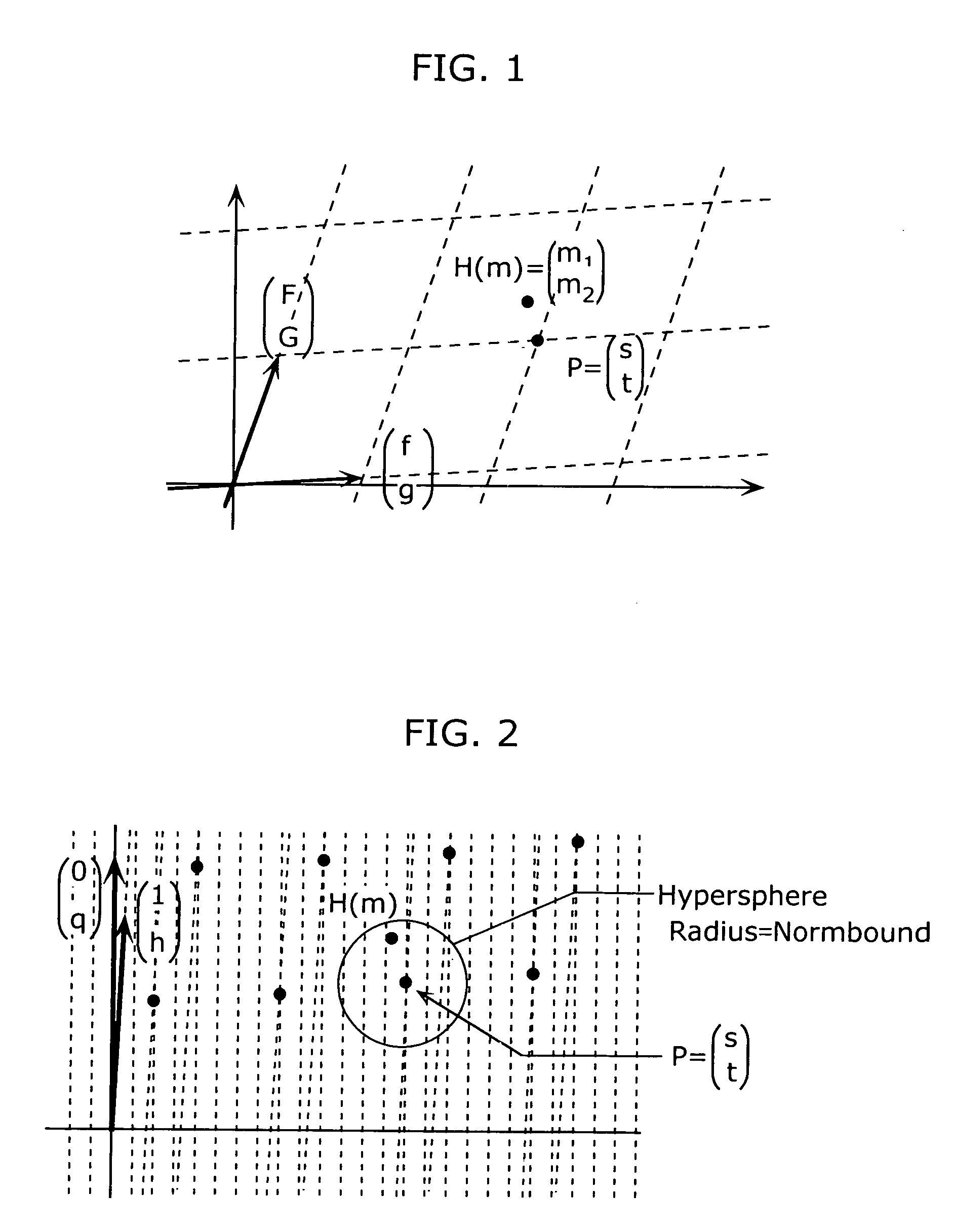
Signature generation apparatus and signature verification apparatus
ActiveUS20090235078A1Increase valueAvoid it happening againKey distribution for secure communicationMultiple keys/algorithms usageComputer scienceSignature vector
A signature generation apparatus and a signature verification which can surely prevent occurrence of inappropriate signature verification error are providedA signature generation apparatus (110) includes a signature generation unit (114) which calculates a signature vector (s, t) for a message m using a private key, and generates signature data S indicating polynomials sl and sh that can specify the polynomial s and a polynomial th which is a quotient when the polynomial t is divided by q.
Owner:PANASONIC CORP
Systems and methods for navigating to errors in an XBRL document using metadata
ActiveUS8739025B2Easy to markEasy to editNatural language data processingSpecial data processing applicationsDocumentation procedureProcess module
Owner:WORKIVA
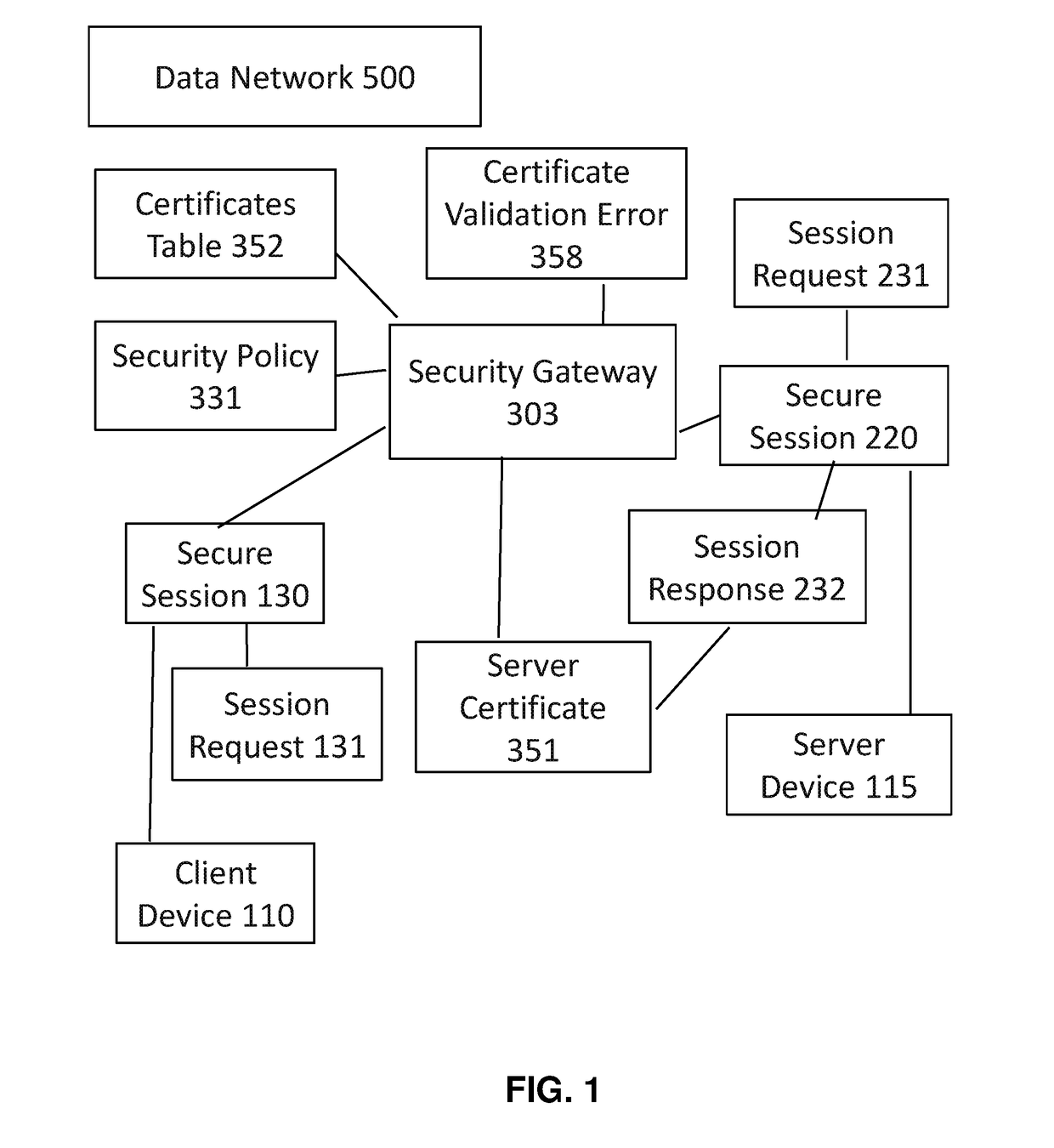
Processing a Security Policy for Certificate Validation Error
ActiveUS20180262348A1Well formedUser identity/authority verificationMultiple keys/algorithms usageNetwork dataSecurity policy
Disclosed herein are systems and methods for a security gateway to process secure network sessions where there is a server certificate validation error. In various embodiments, varying security policies can be applied to the secure network sessions, including intercepting of network data, bypass of the security gateway, or termination of the secure sessions.
Owner:A10 NETWORKS
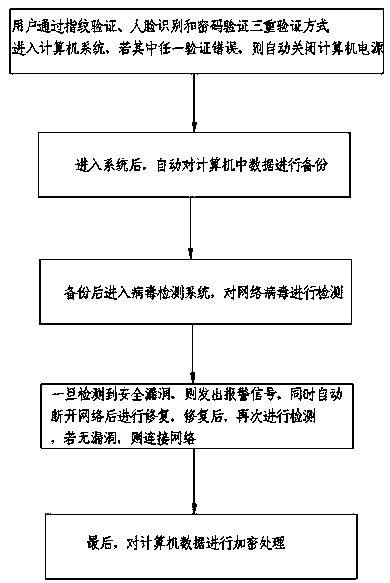
Computer network protection method and system
InactiveCN108710793AEasy to operateImprove securityDigital data protectionDigital data authenticationPasswordComputerized system
The invention discloses a computer network protection method and system. The protection method comprises the following steps: A, a user enters a computer system through triple verification modes of fingerprint verification, face recognition and password verification, and if any of the verification goes wrong, the computer power is automatically turned off; B, after entering the system, the data inthe computer are automatically backed up; C, after the data are backed up, a virus detection system is entered to detect network virus; D, once a security hole is detected, an alarm signal is issued,meanwhile, the network is automatically disconnected and repaired; after the repair, the detection is performed again; if there is no loophole, the network is connected; E, finally, the computer dataare encrypted. The protection method adopted by the invention is simple in operation and high in security performance, effectively protects the data in the computer and ensures data safety.
Owner:MAANSHAN RUNQI NEW MATERIAL SCI & TECH
System and methods for handling verification errors
ActiveUS8732631B2CAD circuit designSpecial data processing applicationsComputer architecturePrimitive operation
Systems, apparatus and methods for handling verification violations are disclosed. In one aspect, a method stores a list of fix information in addition to geometric shapes for each layer during verification, such as design rule checking For each primitive operation step performed during verification, two tasks are performed. First, if the primitive operation is a dimensional checking operation (i.e., width, spacing or enclosure), then for each violation, the first task creates fix information containing violation edge pairs and adds the created fix information to the fix information list on the output layer. Second, for all operations and after the output shapes on the output layer are generated, a second task passes the fix information on input layers which overlap any output shape of the output layer to the output layer's fix information list. Finally, fix guides for the final violation results are generated and drawn based on the final fix information list.
Owner:SYNOPSYS INC
Non-intrusive measurement of content quality using dry runs with roll-back
InactiveUS9092576B2Hardware monitoringReliability/availability analysisSoftware engineeringApplication software
Validation and determination of business application program content quality destined for loading on a target production computing environment is automated by receiving an application program into a controlled production computing environment, and, during a dry run test in the production computing environment, logging changes to content from an initial state as loaded by the application program; applying a business rule to the content during data loading to validate against business objects; capturing validation errors produced by the validation and structural change commands to the content into a log file; and automatically rolling back changes made to the content during the dry run test to the initial state thereby avoiding committing content changes to the production computing environment.
Owner:INT BUSINESS MASCH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com