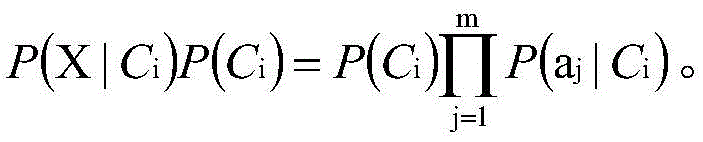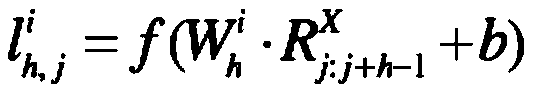Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
75 results about "Software classification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
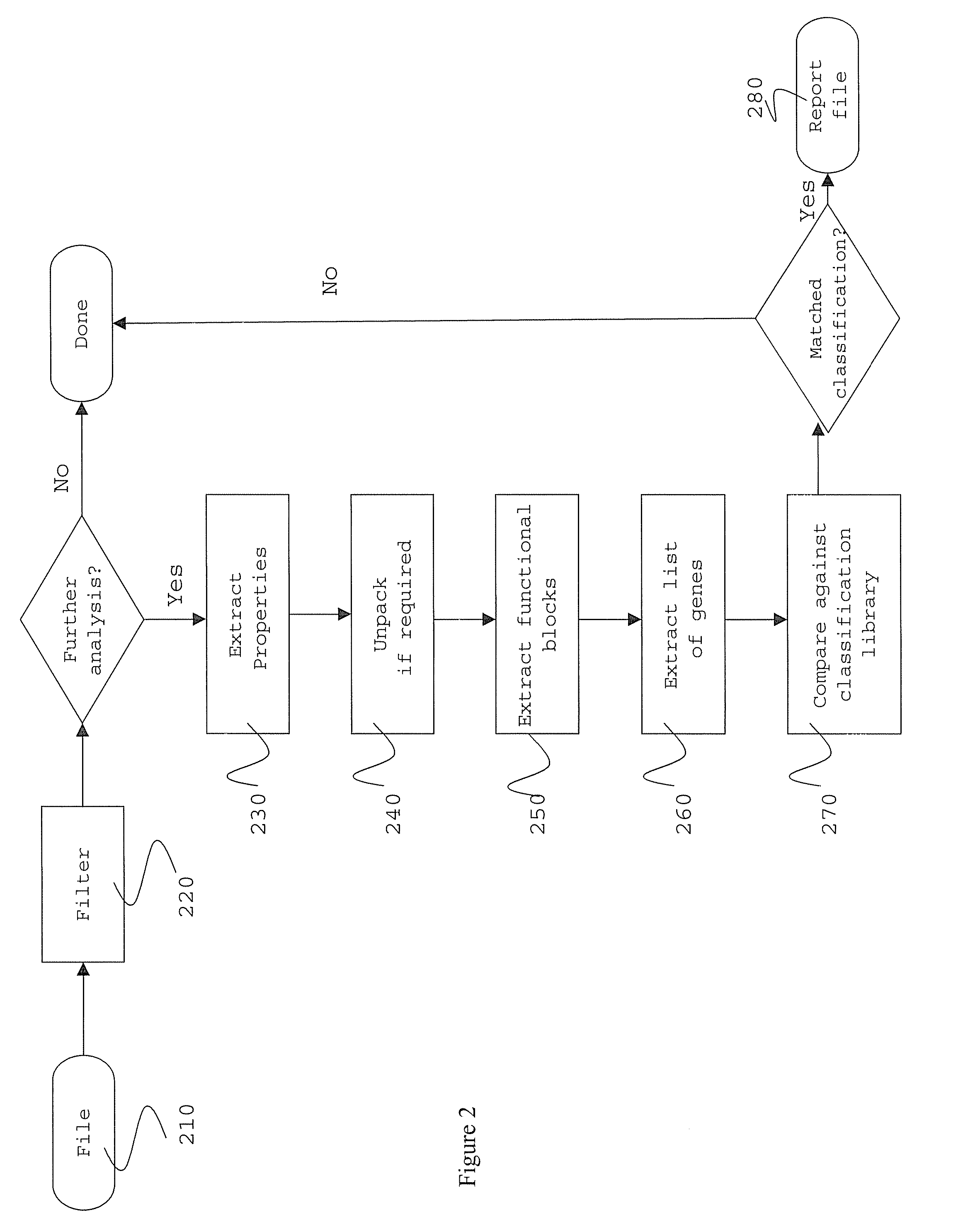
There are three broad classifications: Application software is the general designation of computer programs for performing tasks. Application software may be general purpose (word processing, web browsers, etc.) or have a specific purpose (accounting, truck scheduling, etc.).
Classification of software on networked systems
InactiveUS7856661B1Memory loss protectionUser identity/authority verificationNetworked systemComputerized system
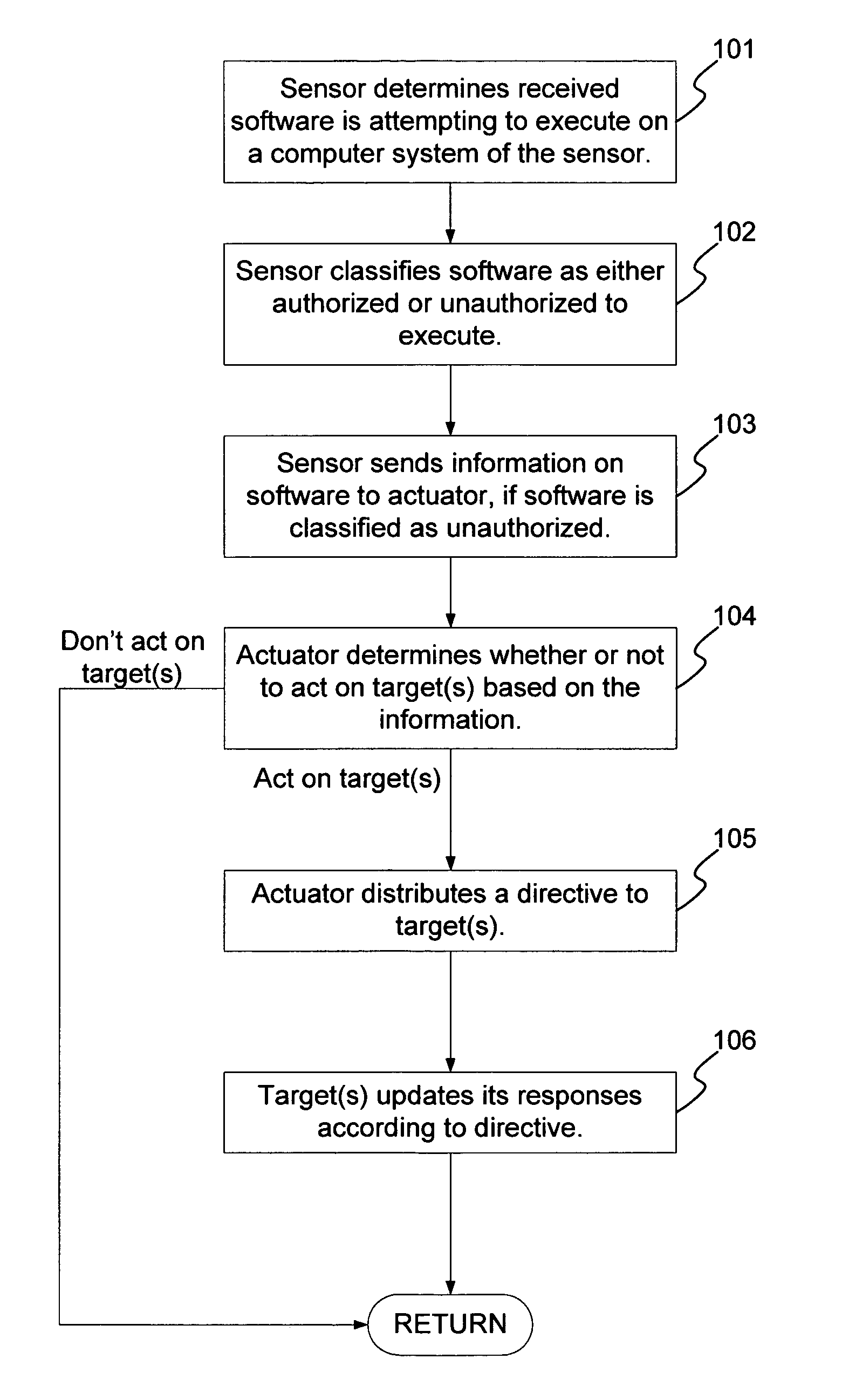
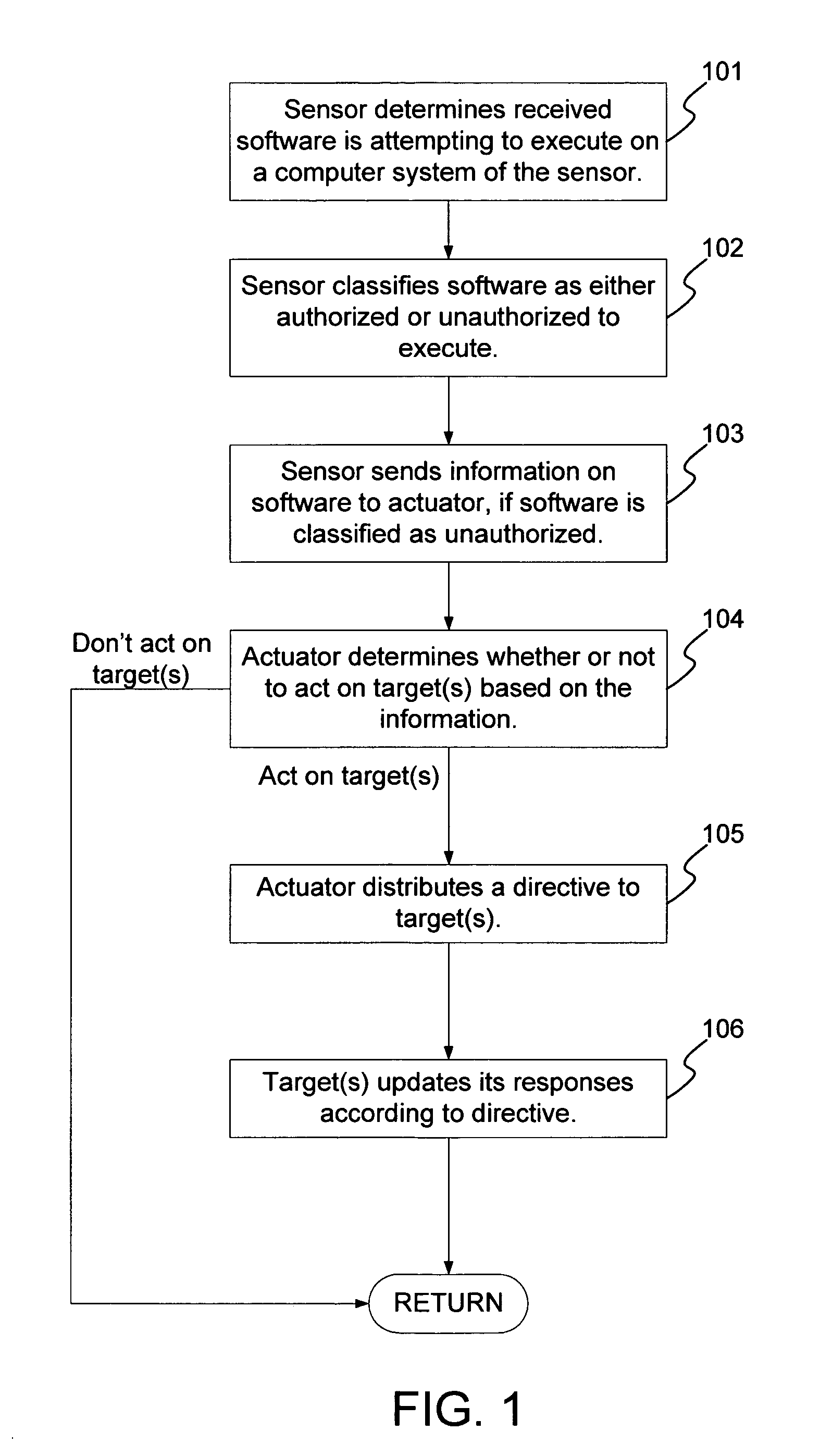
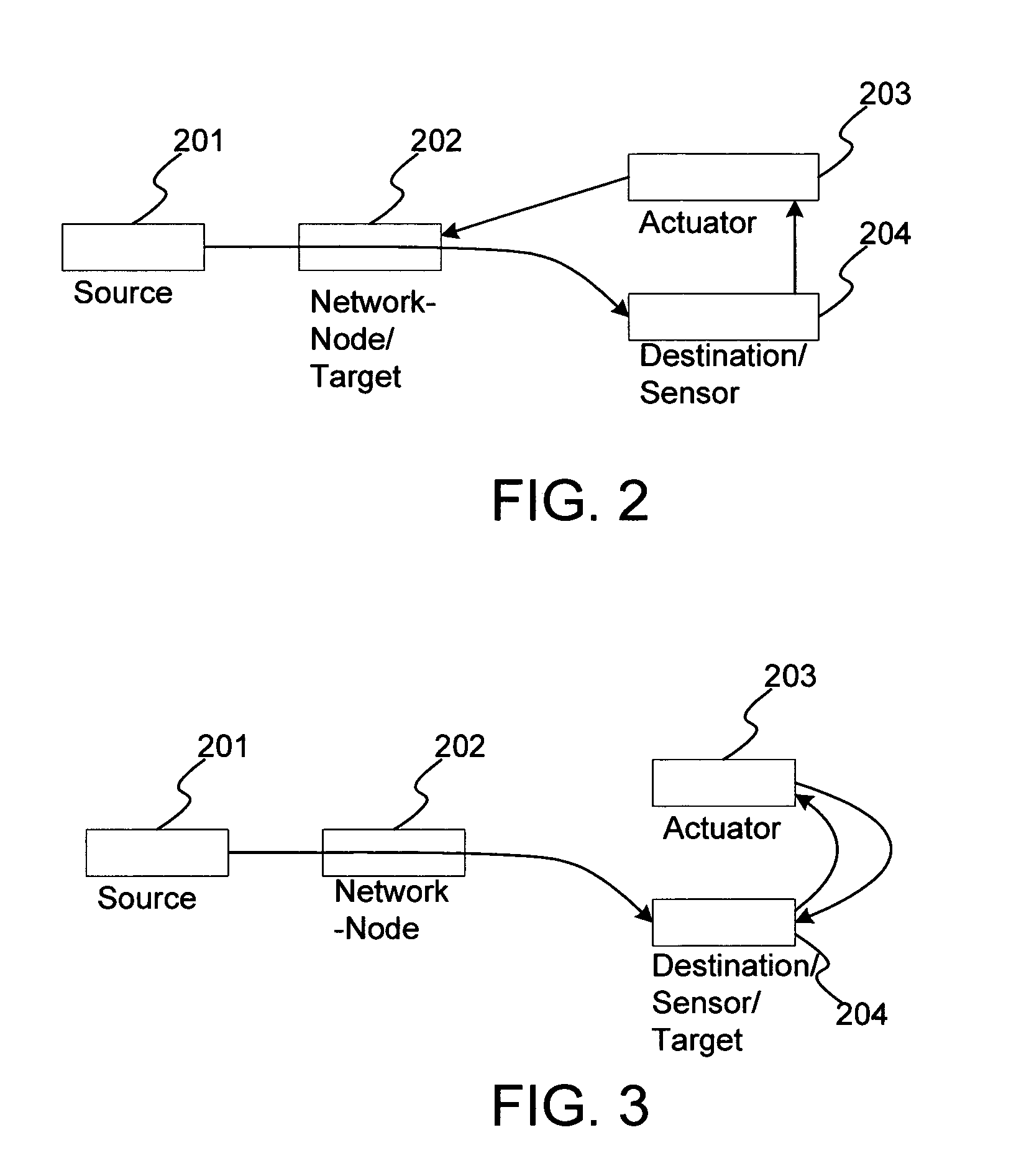
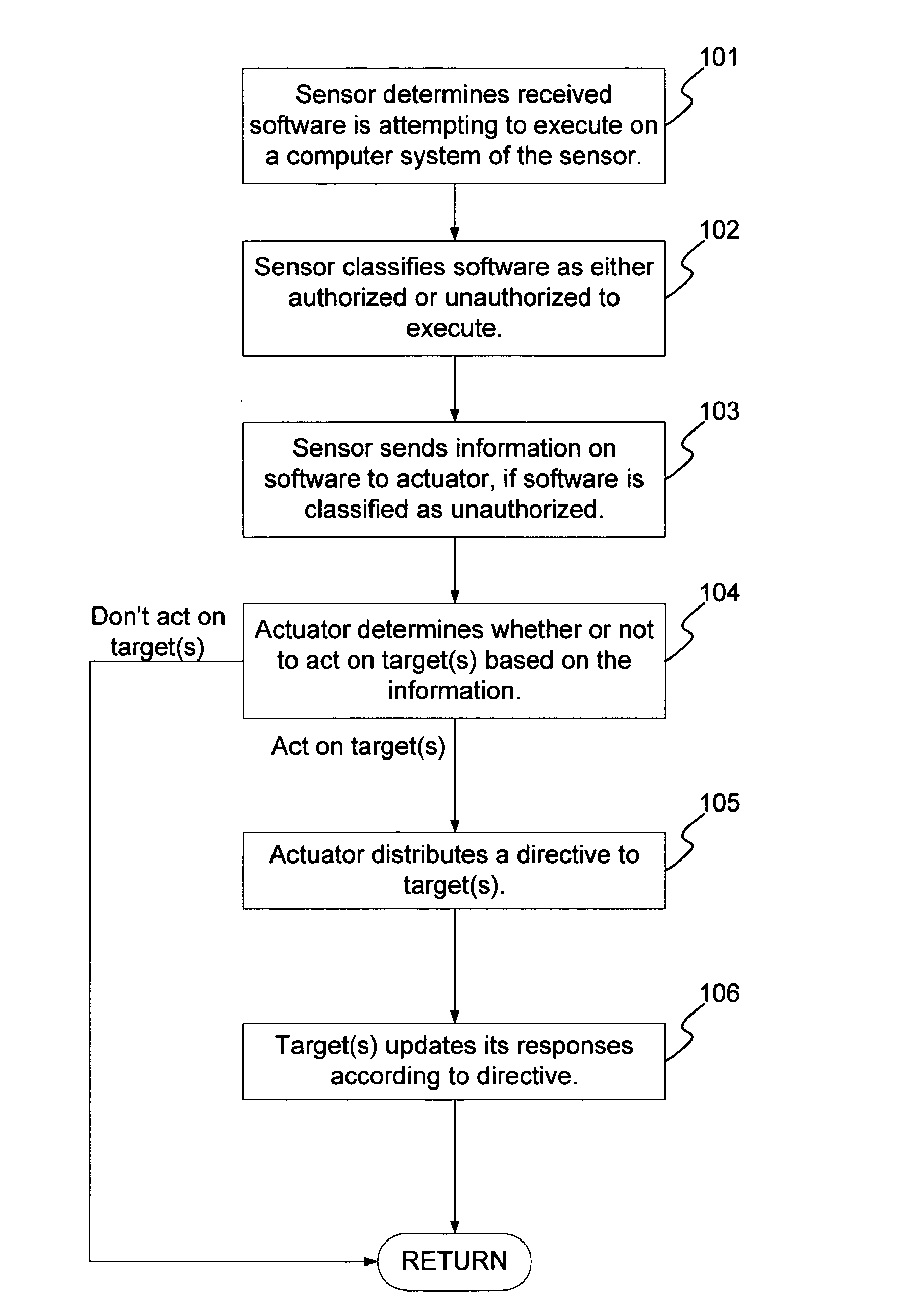
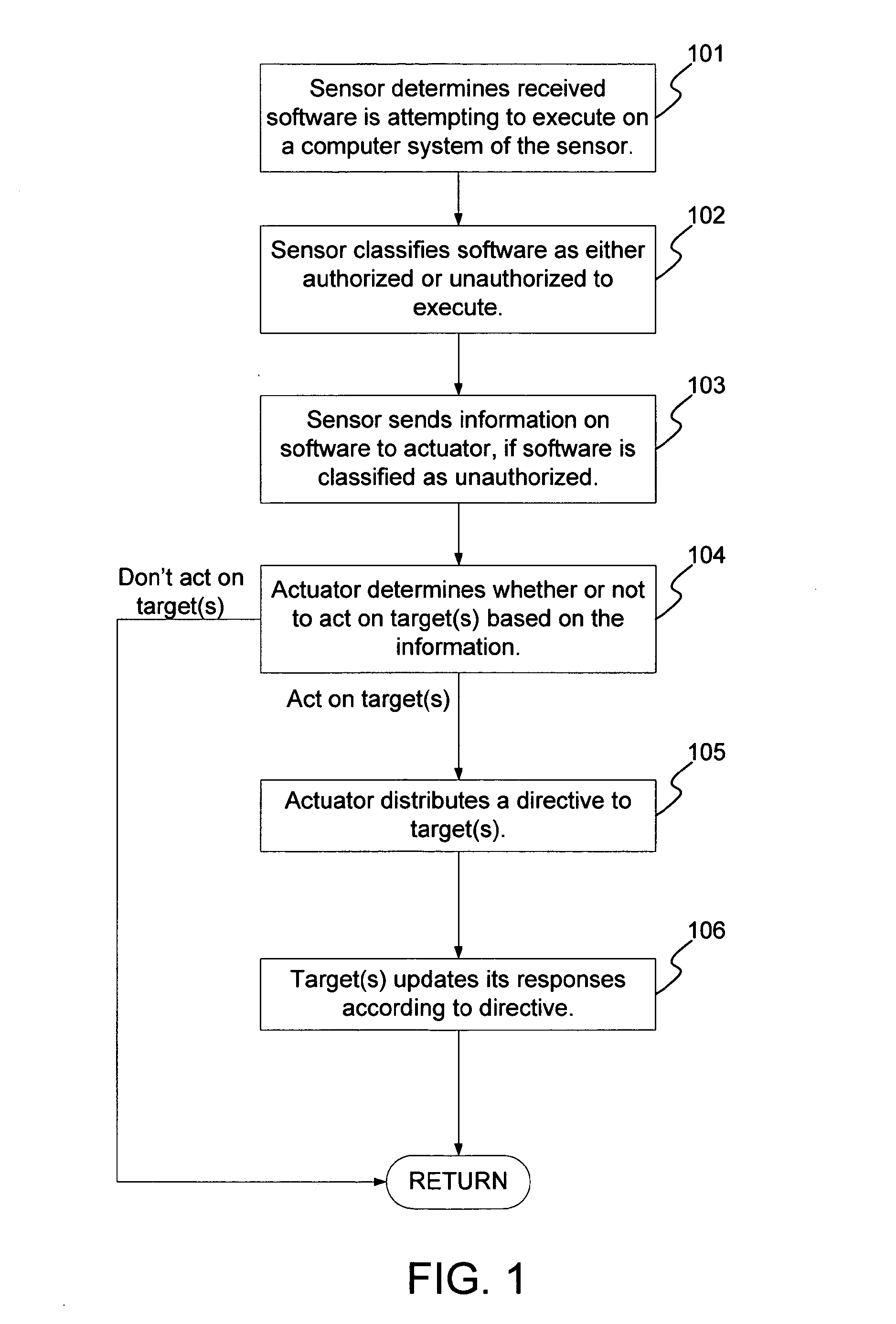
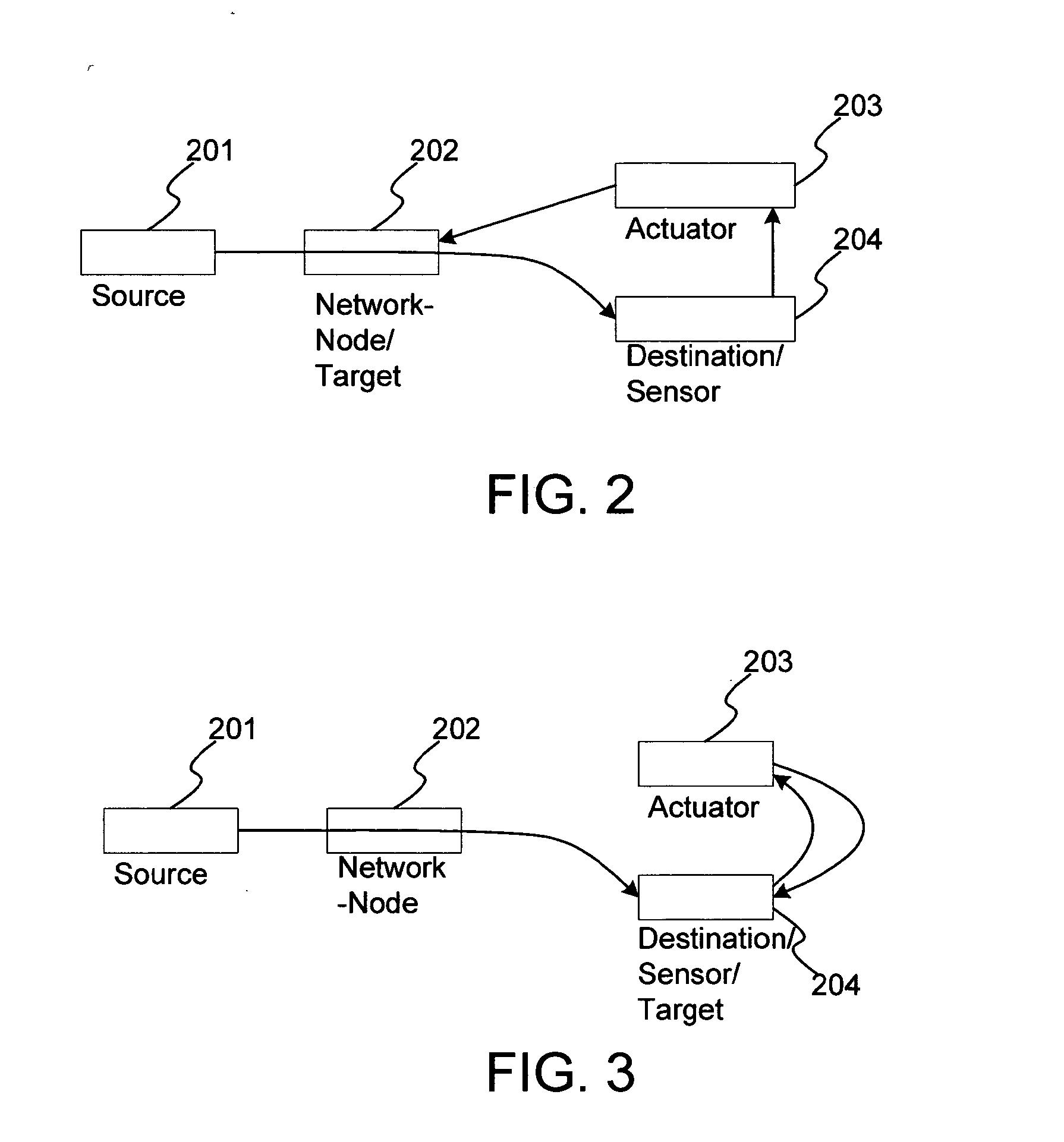
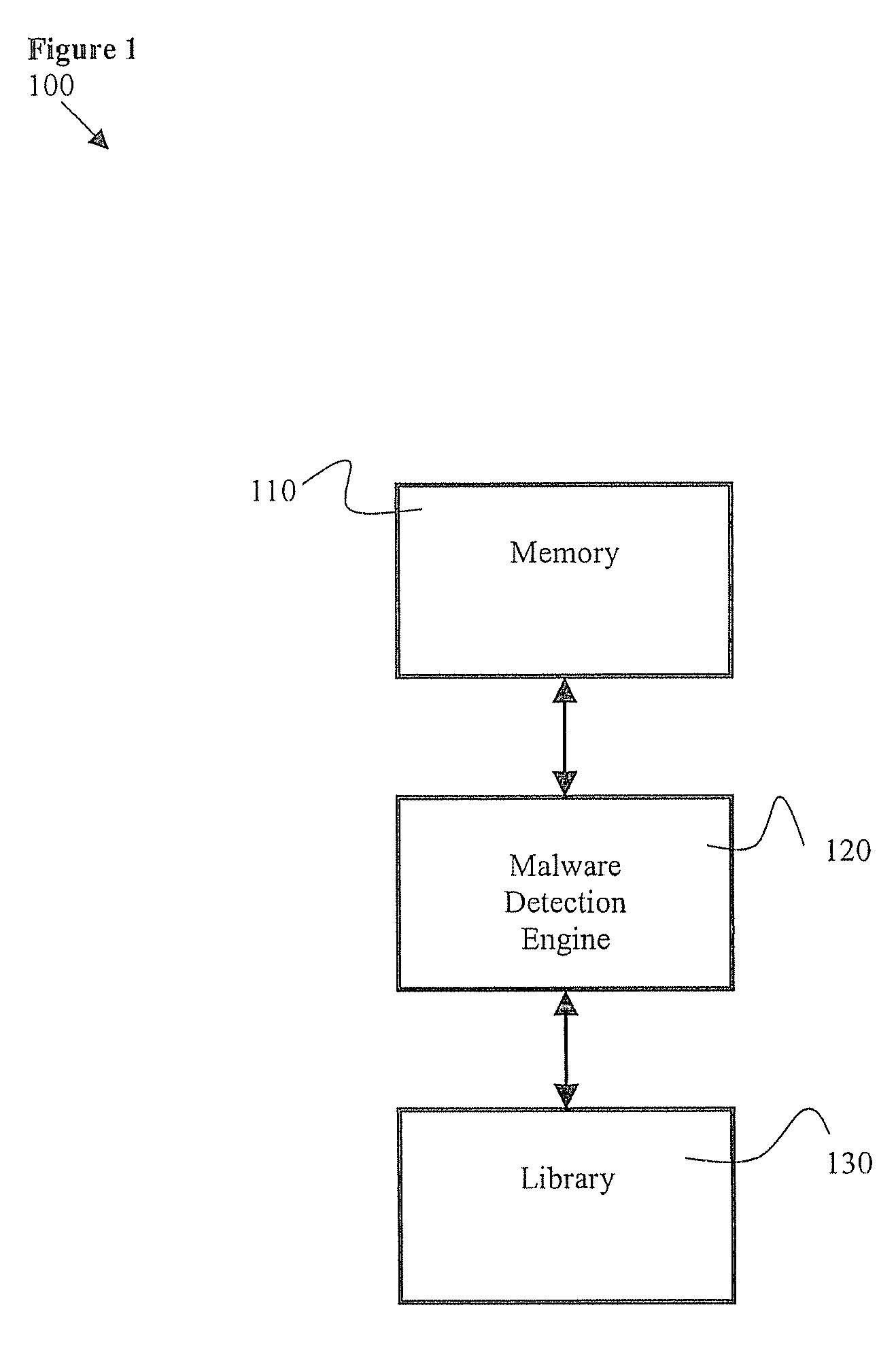
A method and system for the classification of software in networked systems, includes: determining a software received by a sensor is attempting to execute on a computer system of the sensor; classifying the software as authorized or unauthorized to execute, and gathering information on the software by the sensor if the software is classified as unauthorized to execute. The sensor sends the information on the software to one or more actuators, which determine whether or not to act on one or more targets based on the information. If so, then the actuator sends a directive to the target(s). The target(s) updates its responses according to the directive. The classification of the software is definitive and is not based on heuristics or rules or policies and without any need to rely on any a priori information about the software.
Owner:MCAFEE LLC
Classification of software on networked systems
ActiveUS20110119760A1Multiplex system selection arrangementsMemory loss protectionHeuristicComputerized system
A method and system for the classification of software in networked systems, includes: determining a software received by a sensor is attempting to execute on a computer system of the sensor; classifying the software as authorized or unauthorized to execute, and gathering information on the software by the sensor if the software is classified as unauthorized to execute. The sensor sends the information on the software to one or more actuators, which determine whether or not to act on one or more targets based on the information. If so, then the actuator sends a directive to the target(s). The target(s) updates its responses according to the directive. The classification of the software is definitive and is not based on heuristics or rules or policies and without any need to rely on any a priori information about the software.
Owner:MCAFEE LLC
Method and system for classification of software using characteristics and combinations of such characteristics
ActiveUS20080005796A1Memory loss protectionUnauthorized memory use protectionMalwareComputer science
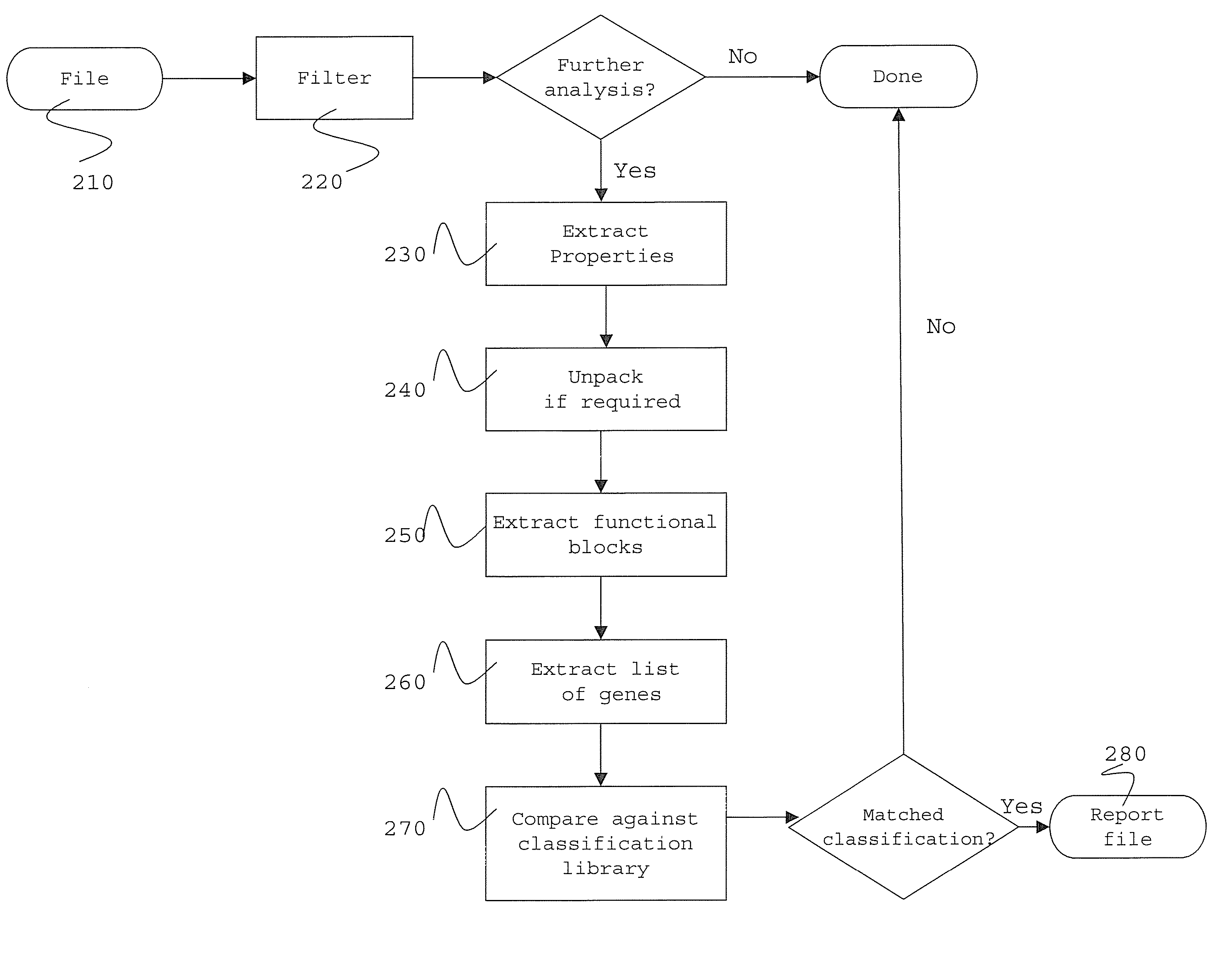
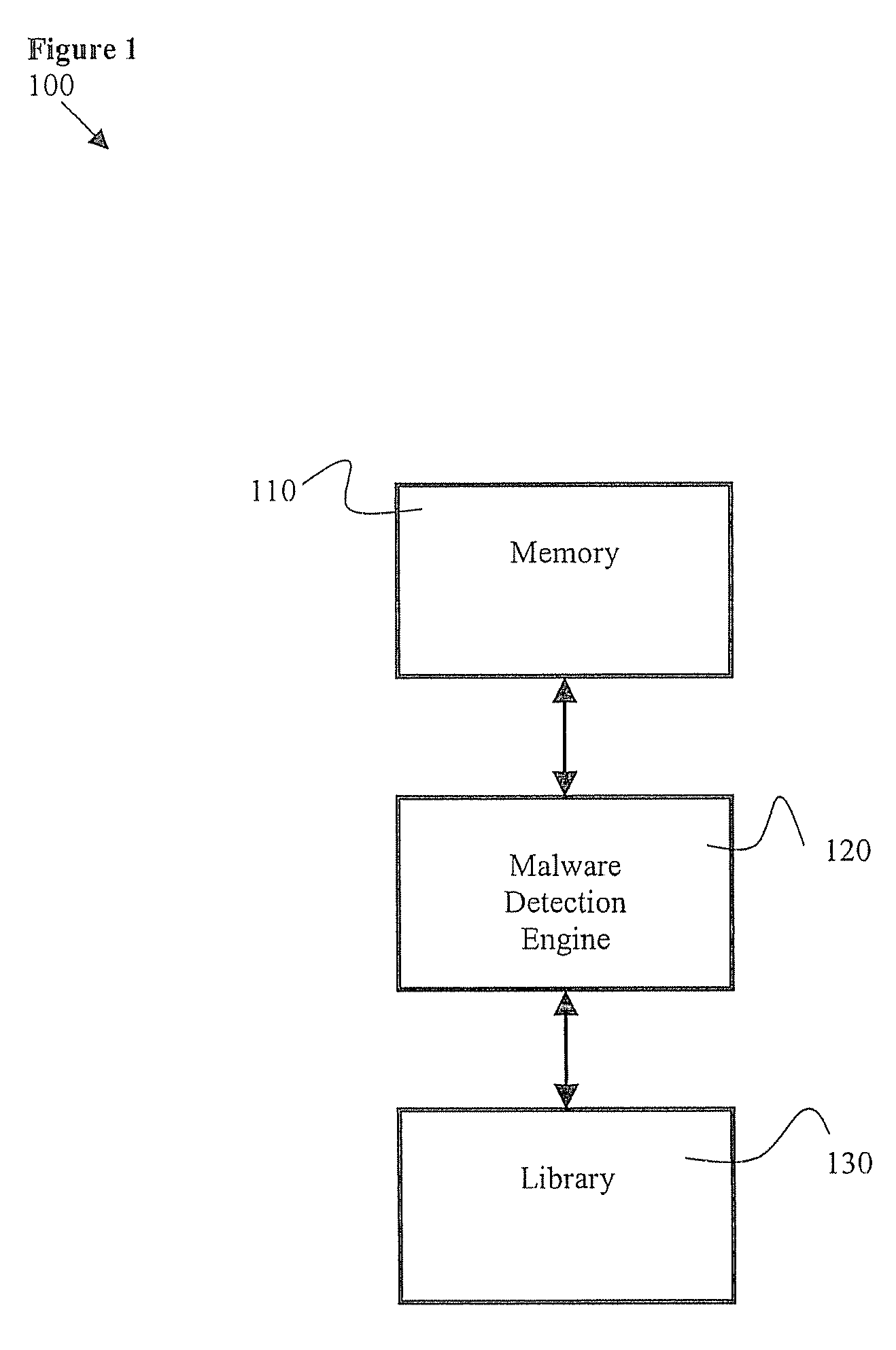
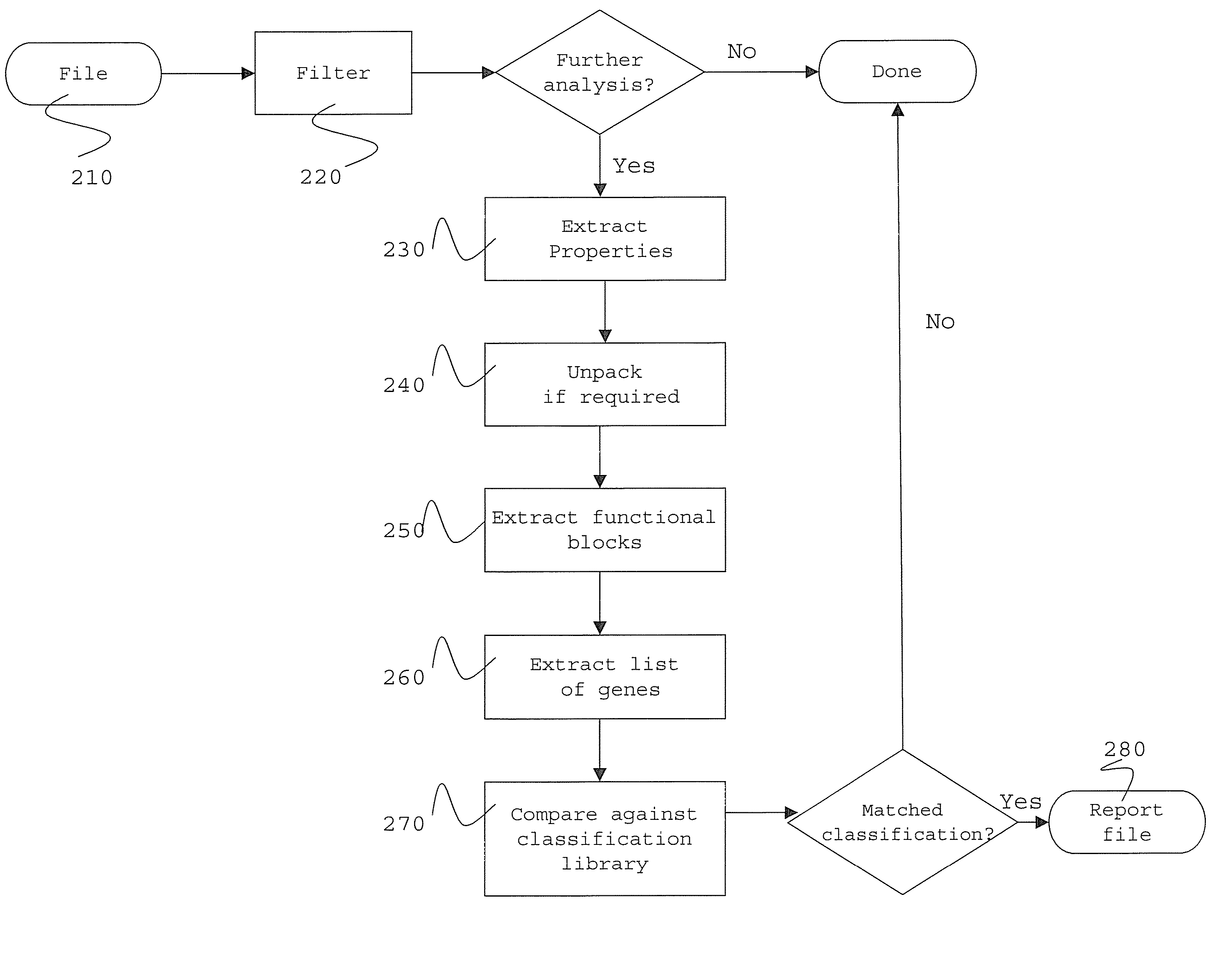
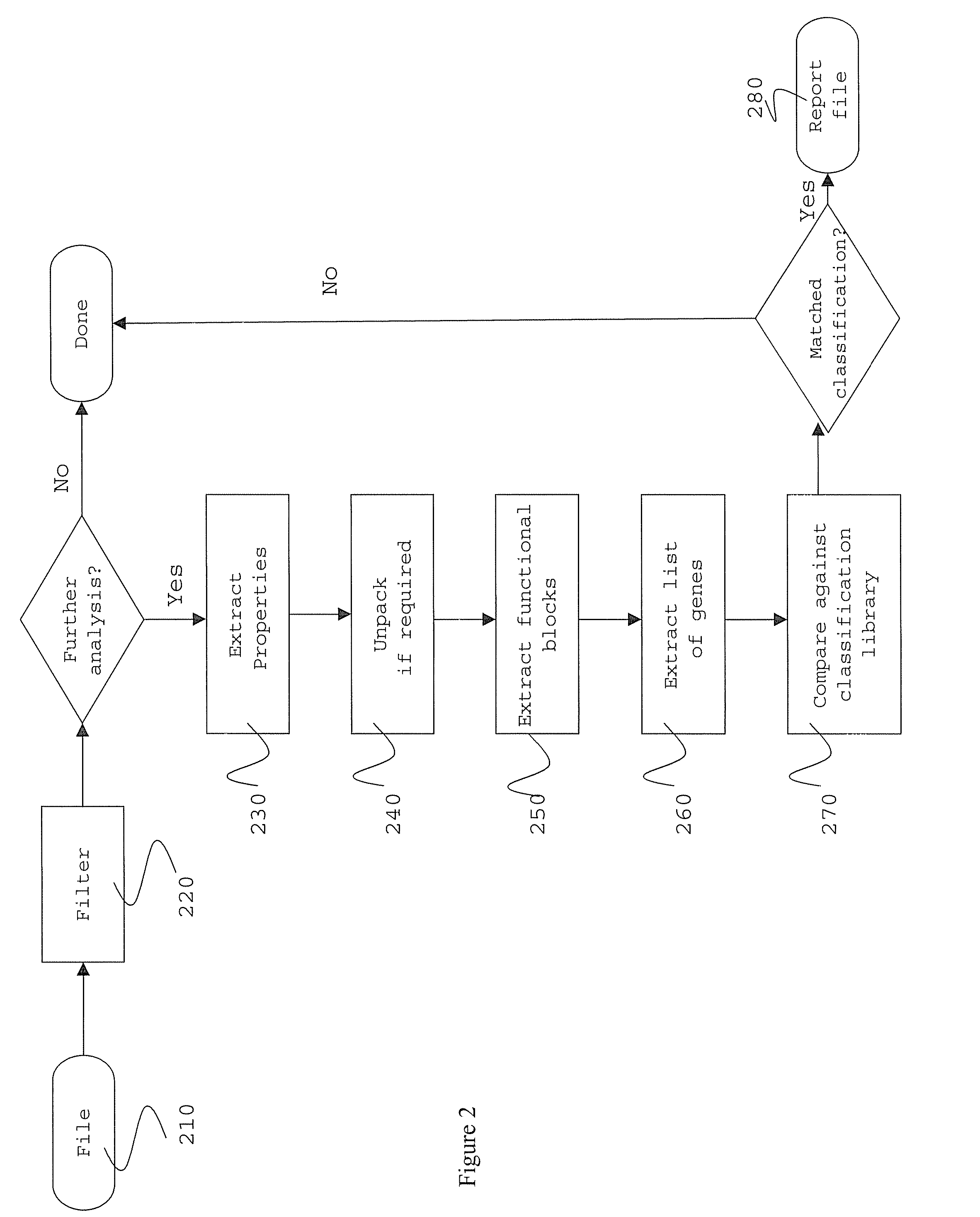
Certain embodiments of the present invention provide methods and systems for software classification. Certain embodiments provide a method for identification of malware. Certain embodiments provide a method for identification of unwanted software. The method includes identifying one or more functional blocks and / or properties of software. The method further includes identifying genes in the functional blocks and / or properties. The method also includes matching the resulting list of genes against one or more combinations of classifications of groupings of genes. Additionally, the method includes classifying the software. Certain embodiments provide a method for generating classifications. The method includes identifying functional blocks and / or properties. Furthermore, the method includes combining a plurality of genes to form a classification.
Owner:SOPHOS
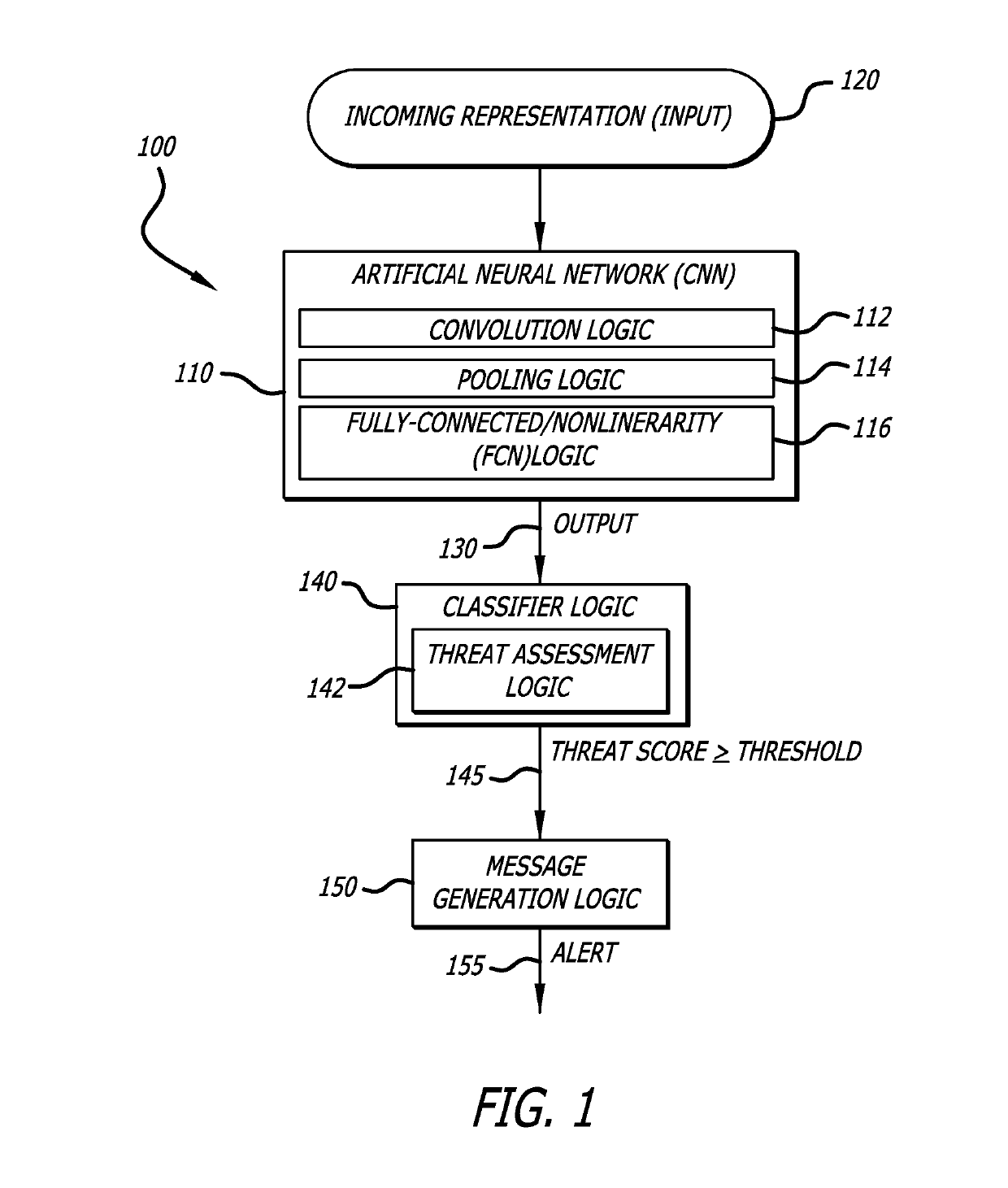
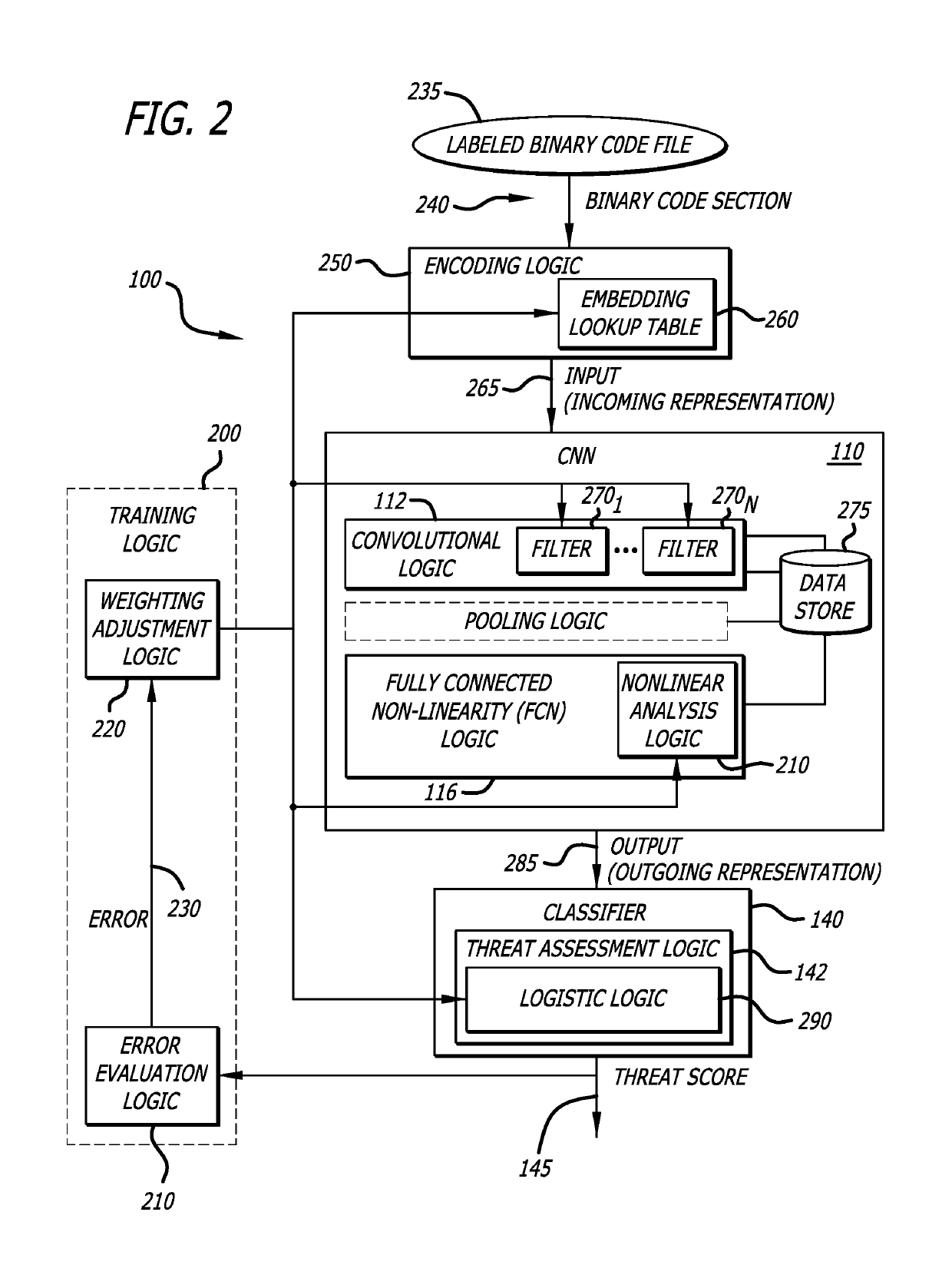
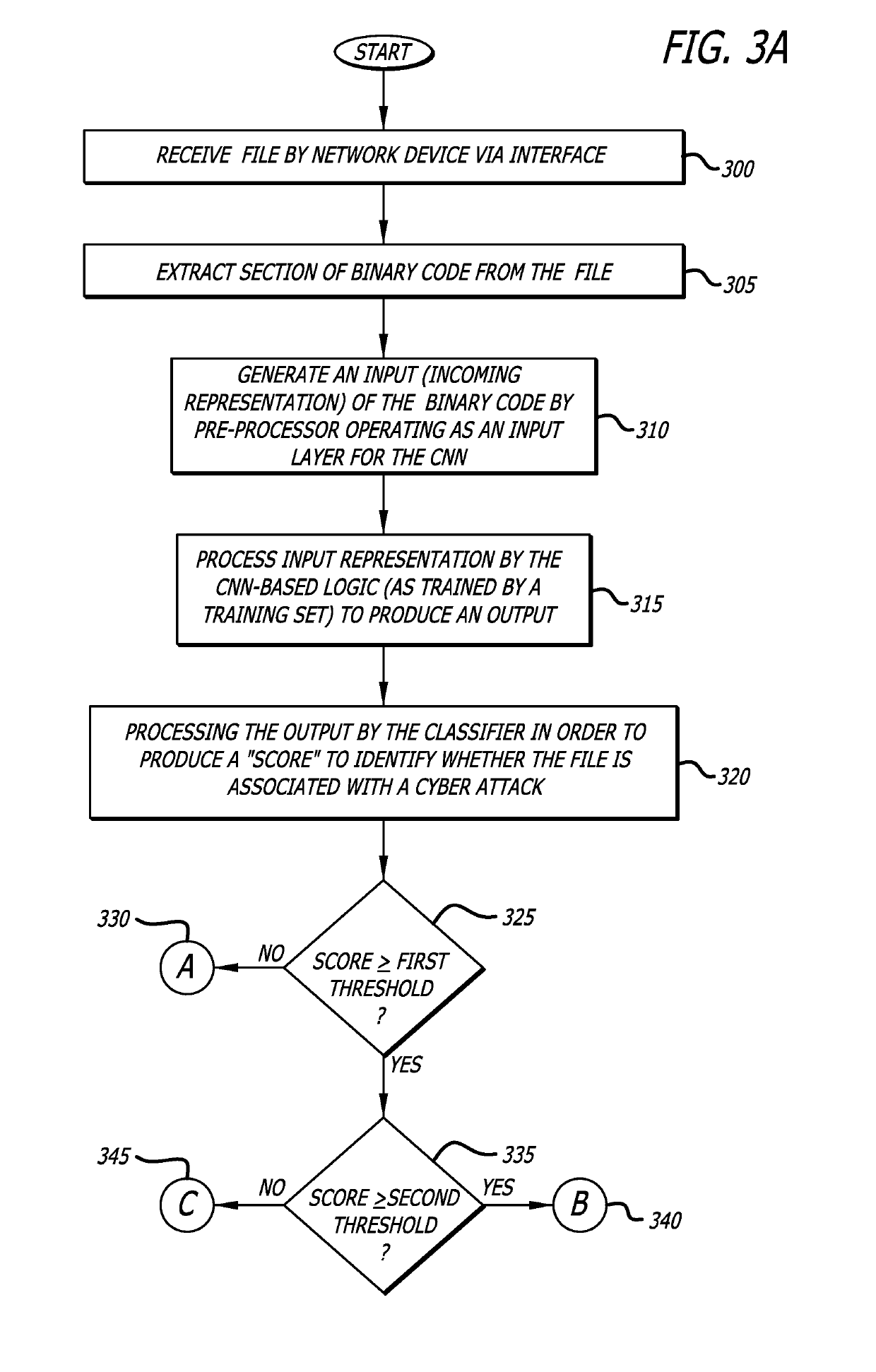
System and method for analyzing binary code for malware classification using artificial neural network techniques
A system for detecting whether a file including content s associated with a cyber-attack is described. The content may include an executable file for example. The system includes an intelligence-driven analysis subsystem and a computation analysis subsystem. The intelligence-driven analysis subsystem is configured to (i) receive the file, (ii) inspect and compute features of the file for indicators associated with a cyber-attack, and (iii) produce a first output representing the detected indicators. The computational analysis subsystem includes an artificial neural network to (i) receive a network input being a first representation of at least one section of binary code from the file as input, and (ii) process the first representation of the section to produce a second output. The first output and the second output are used in determination a classification assigned to the file.
Owner:GOOGLE LLC
Computer malicious software detection novel method based on software control flow features
ActiveCN103177215AOptimize detection resultsImprove stabilityPlatform integrity maintainanceSpecial data processing applicationsControl flowFeature set
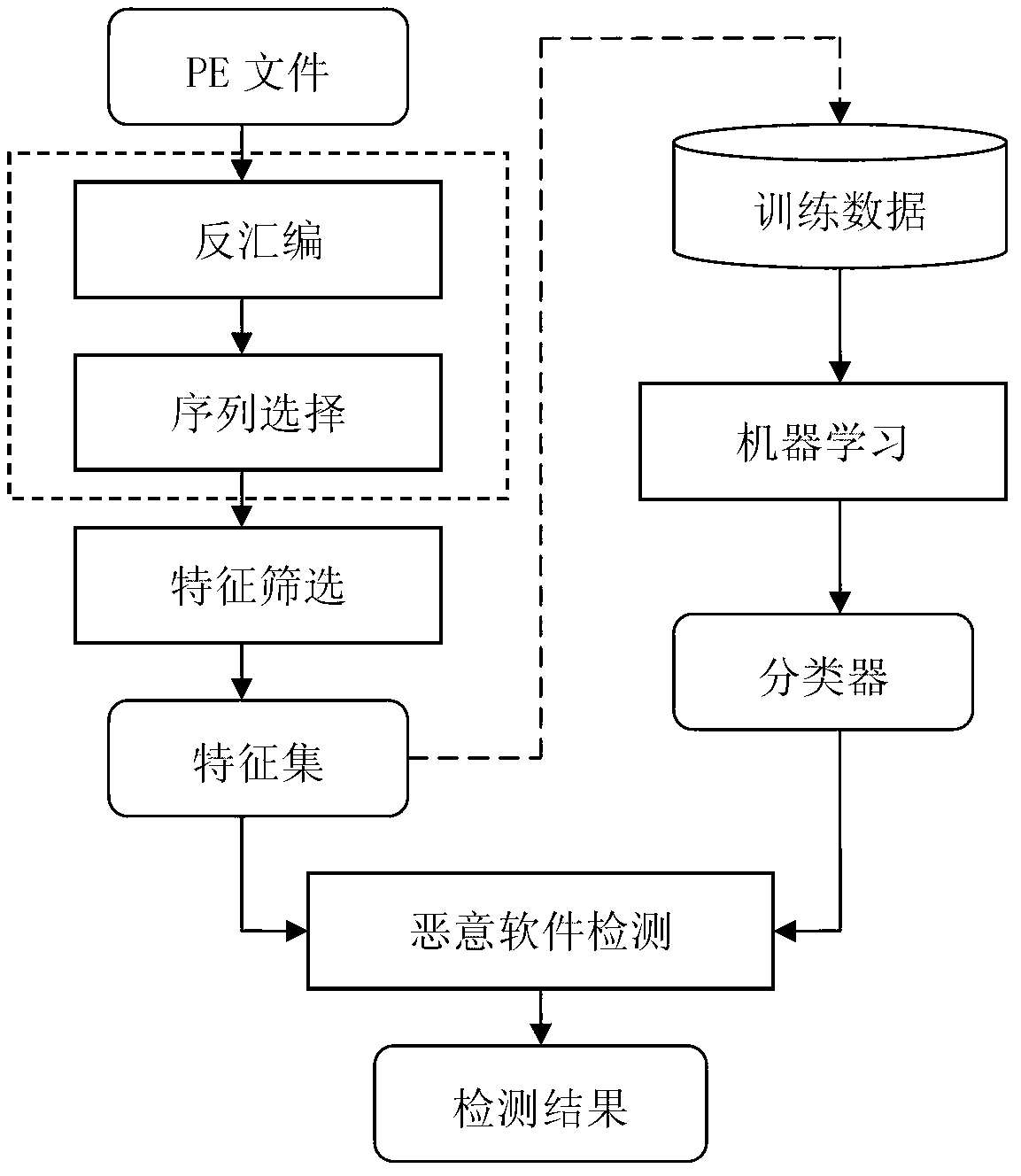
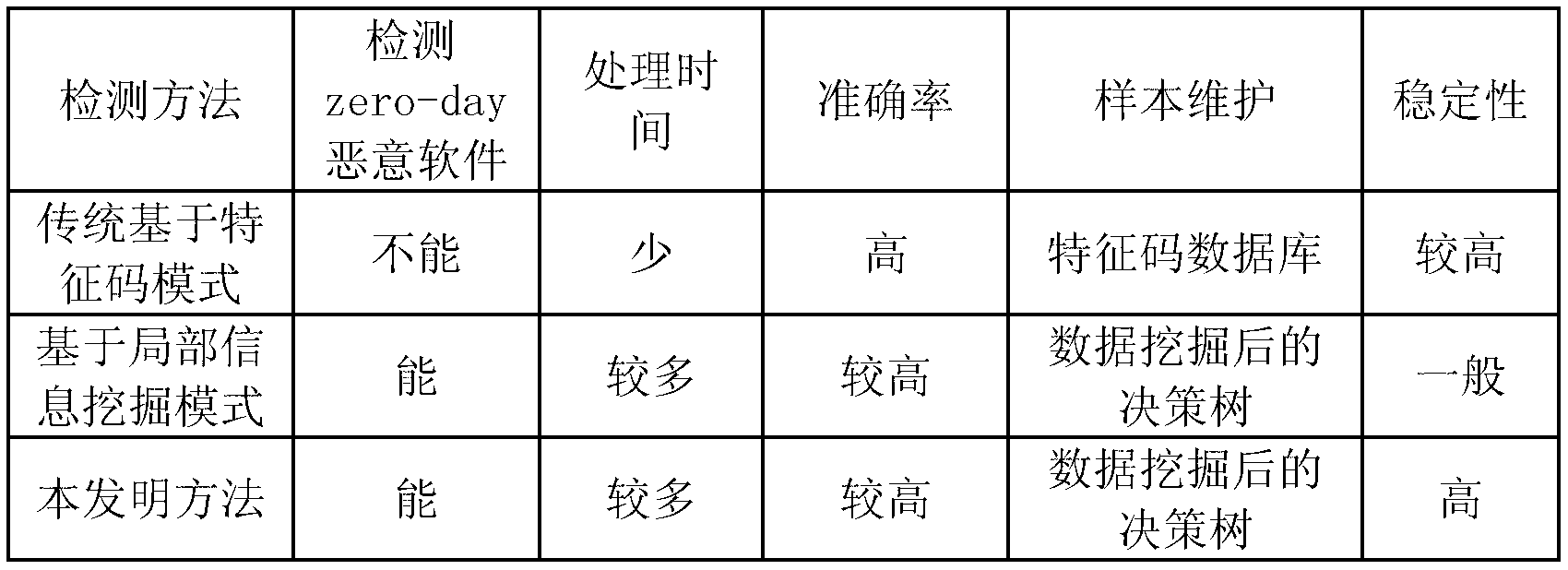
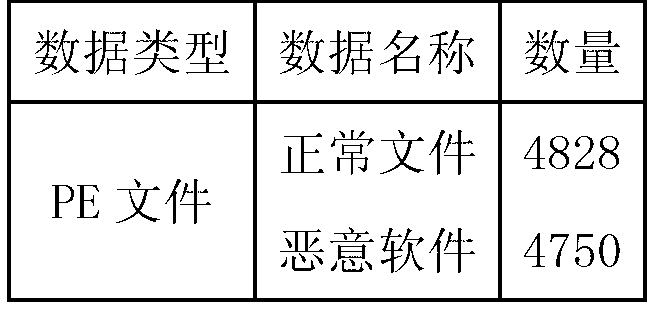
Provided is a computer malicious software detection novel method based on software control flow features. Static analysis is conducted on a control flow structure of a binary file, an operation code sequence is extracted automatically, a spatial vector model is utilized to convert the sequence to structuralized information, the structuralized information acts as a feature set of a file after being screened, a software classification rule is found from volume feature sets by using a data mining method, and the software classification rule is used for detecting malicious software. The computer malicious software detection novel method based on the software control flow features can not only effectively detect common zero-day malicious software, but also have a good detection result for malicious software utilizing a vague and polymorphic technology, and maintain good stability for calculated attack.
Owner:STATE GRID SICHUAN ELECTRIC POWER CORP ELECTRIC POWER RES INST +1
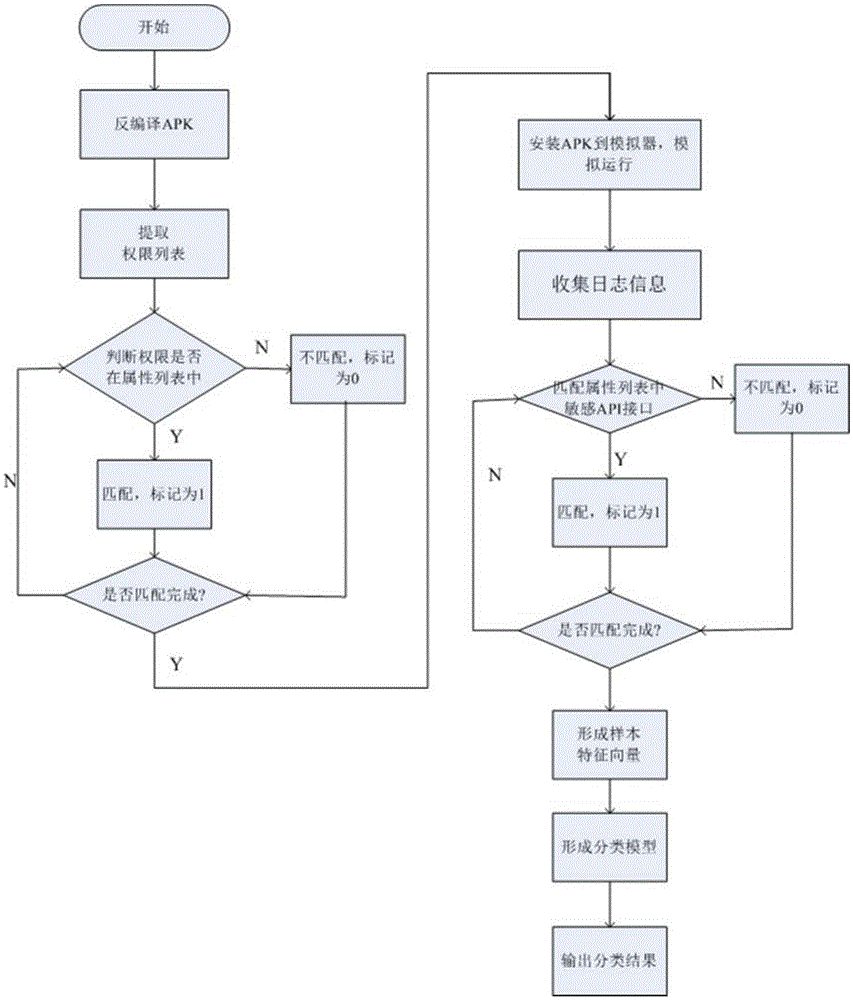
Method and device for Android malicious software classification based on Naive Bayes
InactiveCN105468977APlatform integrity maintainanceApplication programming interfaceMachine learning
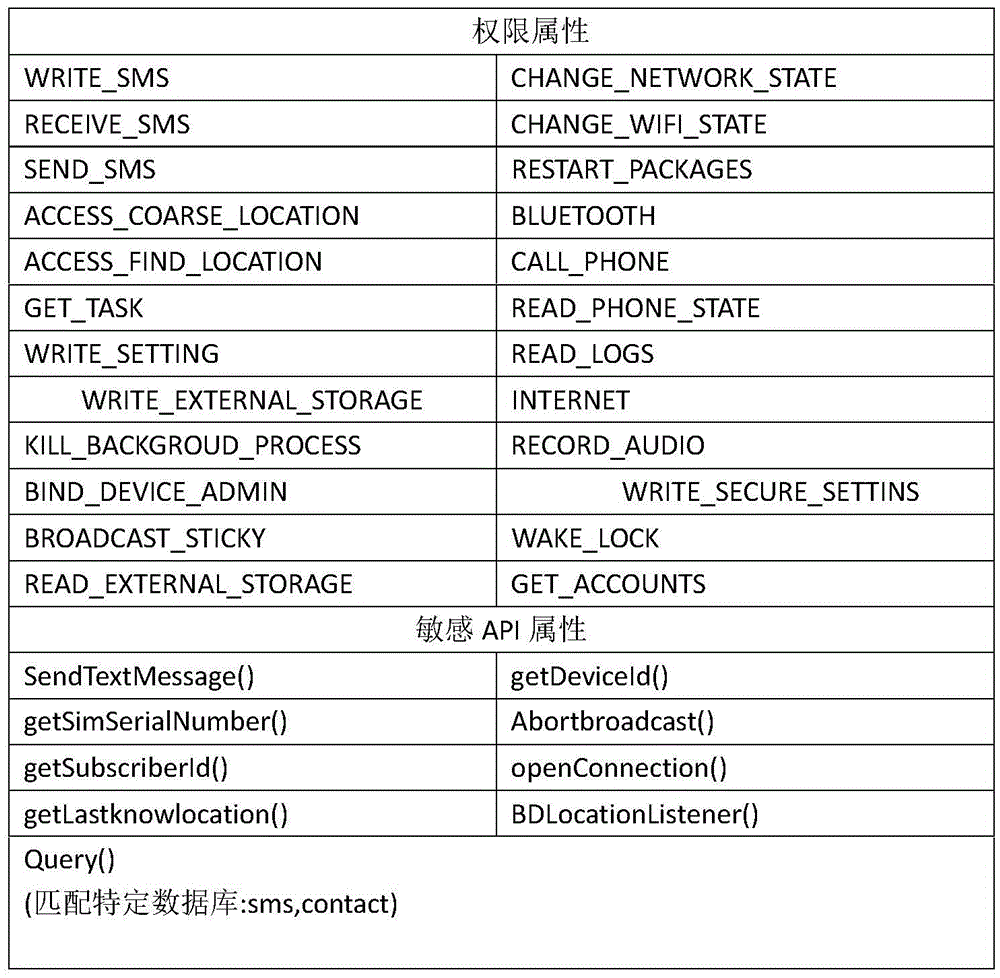
The invention discloses a method and a device for Android malicious software classification based on Naive Bayes, wherein the method is used for extracting authority attribute characteristics and sensitive API (Application Programming Interface) attribute characteristics of malicious software mainly through a dynamic and static combination method, and performing classification through a Naive Bayes algorithm; and the device comprises a characteristic attribute set module, an authority characteristic attribute module, a sensitive API characteristic attribute module, a Naive Bayes classification model module, an output module and an updating module. The algorithm has firm mathematical foundation and steady classification efficiency, and needs relatively less parameters; the algorithm is simple; and malicious applications can be classified quickly and accurately, and thus, classification efficiency is improved.
Owner:XIAMEN ANSCEN NETWORK TECH CO LTD
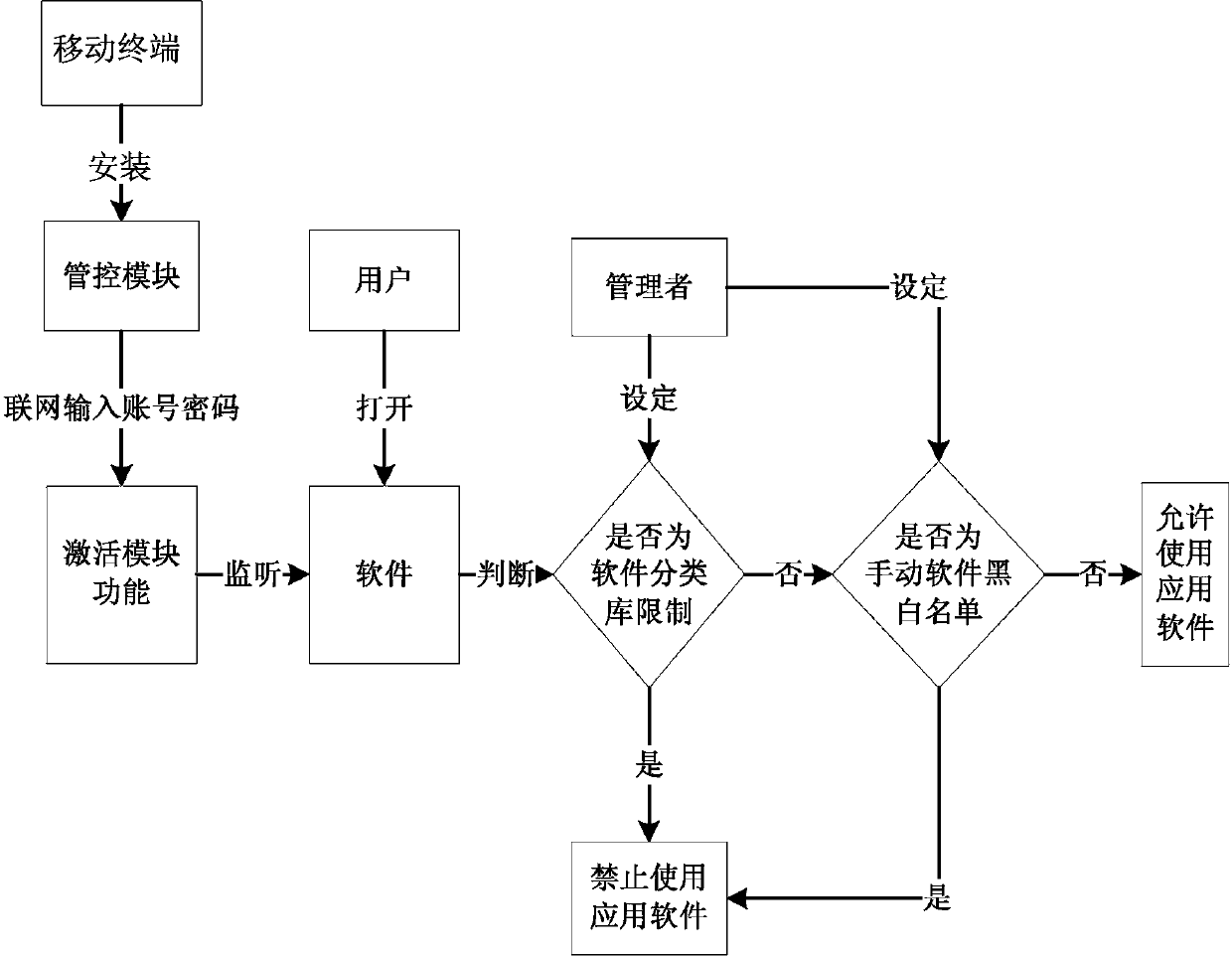
Method for controlling application software based on mobile terminal
InactiveCN104202323AAvoid contactPrevent addictionComputer security arrangementsTransmissionSoftware engineeringComputer terminal
The invention provides a method for controlling application software based on a mobile terminal. The method mainly comprises the steps of mounting a control application on the mobile terminal by a manager, and restricting whether a user can use the application software on the mobile terminal by setting an application software control strategy. The method for controlling the application software based on the mobile terminal has the advantages that even application software which has not been installed on the mobile terminal also can be added into a forbidden list through an application software classification library set by the manager, accordingly youngsters are prevented from being excessively addicted to software such as games and chart communication, and the youngsters are also prevented from contacting poor application software.
Owner:GREEN NET WORLD FUJIAN NETWORK TECH
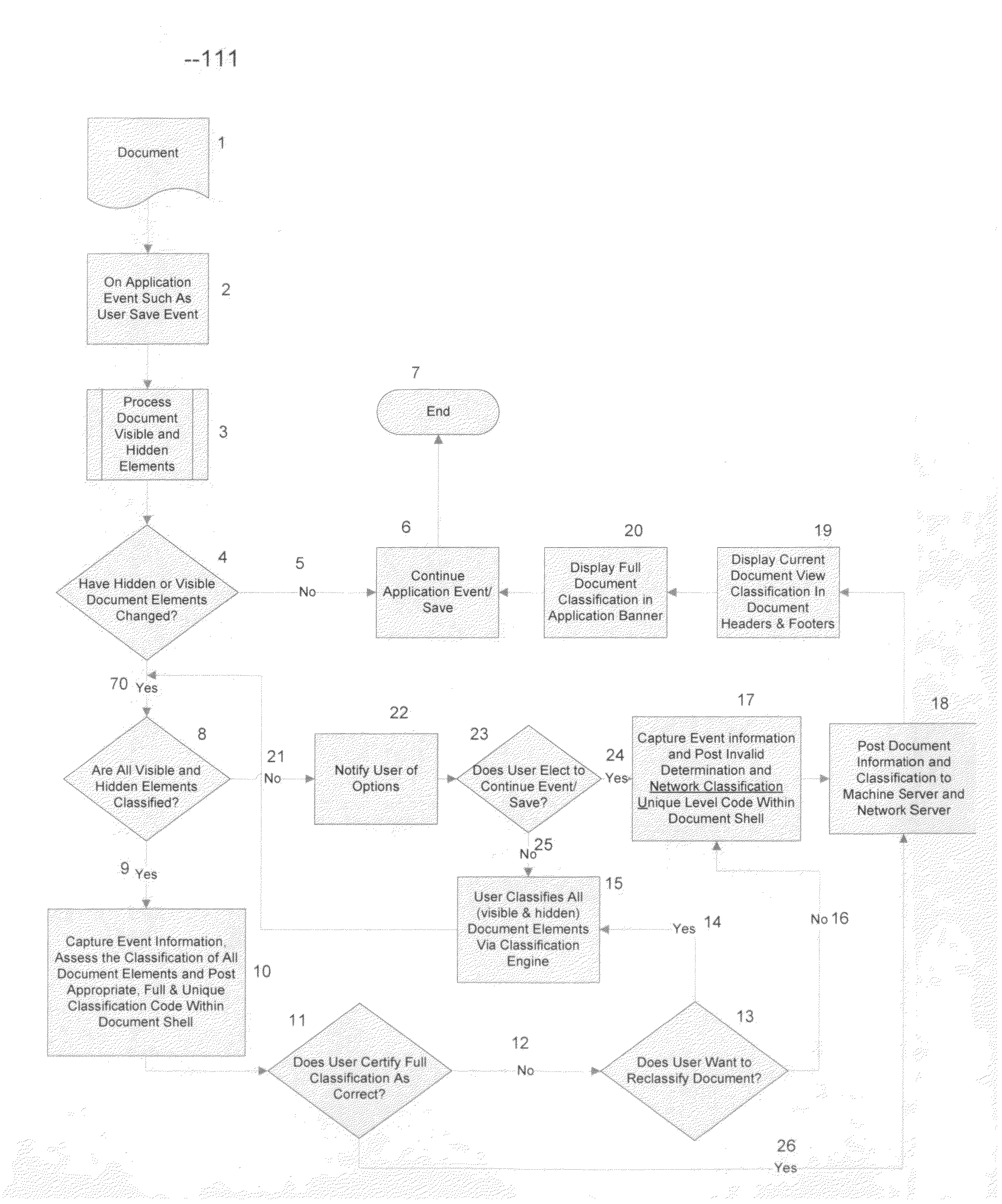
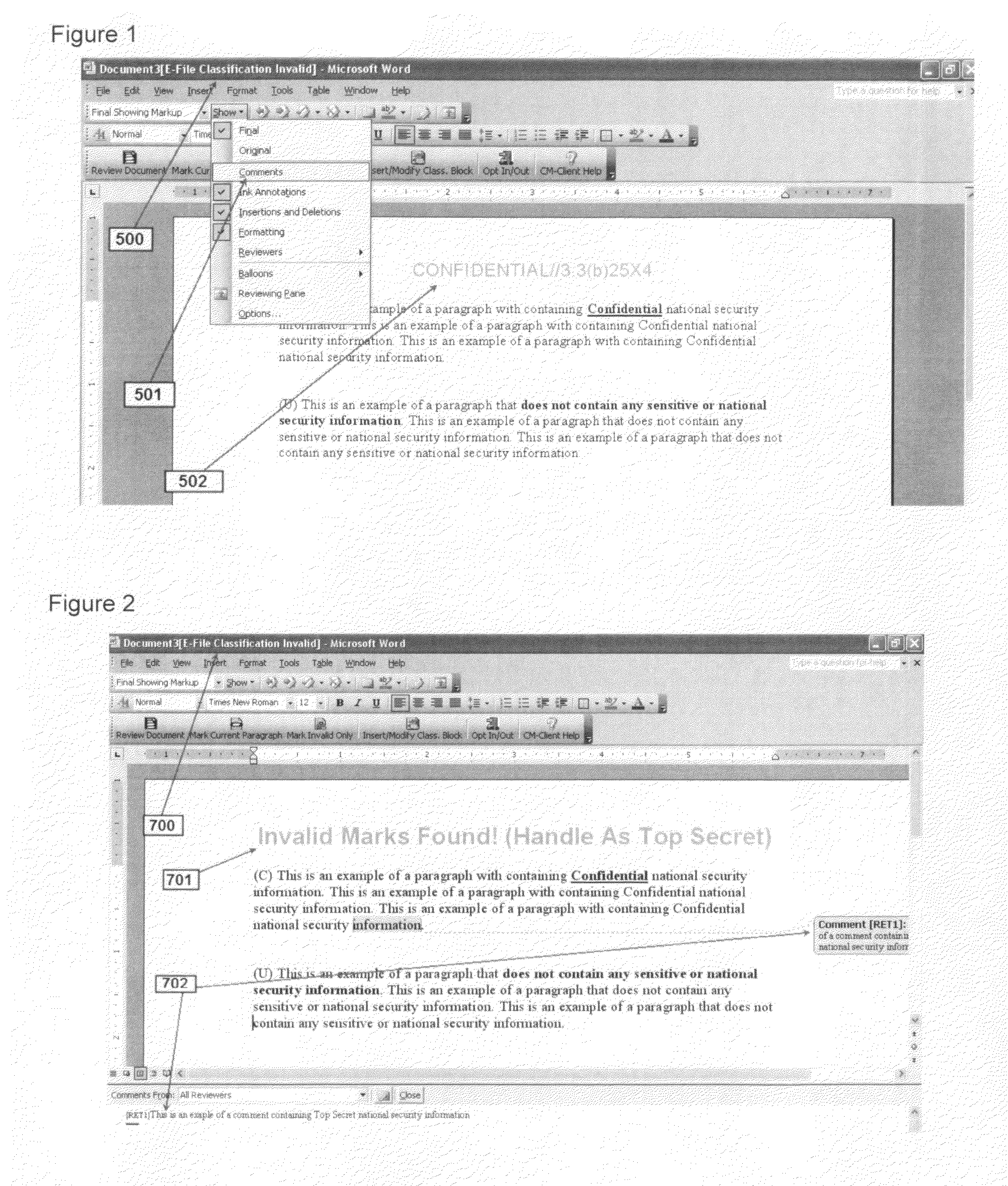
Methods to dynamically establish overall national security or sensitivity classification for information contained in electronic documents; to provide control for electronic document/information access and cross domain document movement; to establish virtual security perimeters within or among computer networks for electronic documents/information; to enforce physical security perimeters for electronic documents between or among networks by means of a perimeter breach alert system
InactiveUS20100186091A1Simple methodReliable classificationDigital data processing detailsAnalogue secracy/subscription systemsPhysical securityDocumentation procedure
The invention is an a document classification and marking engine / method that functions in a real-time compatible mode with off-the-shelf word processors, e-mail programs and presentation or other document development software applications. The software engine is used for the security classification of sensitive or national security classified information in electronic format and is enhanced by methods and processes that ensure that the software classification engine considers all document informational elements regardless of attributes assigned to the text that may hide text from the user. The software engine provides a complete and reliable document classification determination interface method based on user selections and uniquely codes the full text classification determination in a persistent manner within the electronic shell of the document in real-time and dynamically displays the text based full classification determination in the banner of the host document development application. The unique codes of the full classification embedded in the electronic shell of the document enable effective and reliable software processes and methods that establish controls for access, movement, storage etc. for electronic documents, as well as virtual electronic security perimeters, on a computer, networks of computers and / or among computer networks and domains of networks. The full or complete and persistent classification codes embedded in the document shell also enables reliable software processes and methods that immediately warn or alert security personnel of a beach of a physical security perimeter between or among computers networks or domains of networks established to protect the information contained in electronic document format.
Owner:TURNER JAMES LUKE +1
Application software classification system, application software classification method and server
InactiveCN105956083AGuaranteed accuracyReduce workloadNatural language data processingSpecial data processing applicationsFeature vectorClassification methods
The embodiment of the invention provides an application software classification system, an application software classification method and a server. Firstly, a word segmentation result is obtained by carrying out word segmentation processing on text information for describing application software; then after the word segmentation result is processed, a feature vector of each piece of application software is obtained; and finally, by the feature vectors, clustering the application software. When the application software is pre-classified by the method, workload of operating personnel of a software application store can be reduced and efficiency of classifying the application software is improved. By adopting the method, accuracy of classifying the application software also can be improved, and user experience is improved.
Owner:GUANGZHOU UC NETWORK TECH CO LTD
Malware classification method for optimizing feature extraction
ActiveCN109829306AImprove accuracyImprove F1 scorePlatform integrity maintainanceClassification methodsMalware
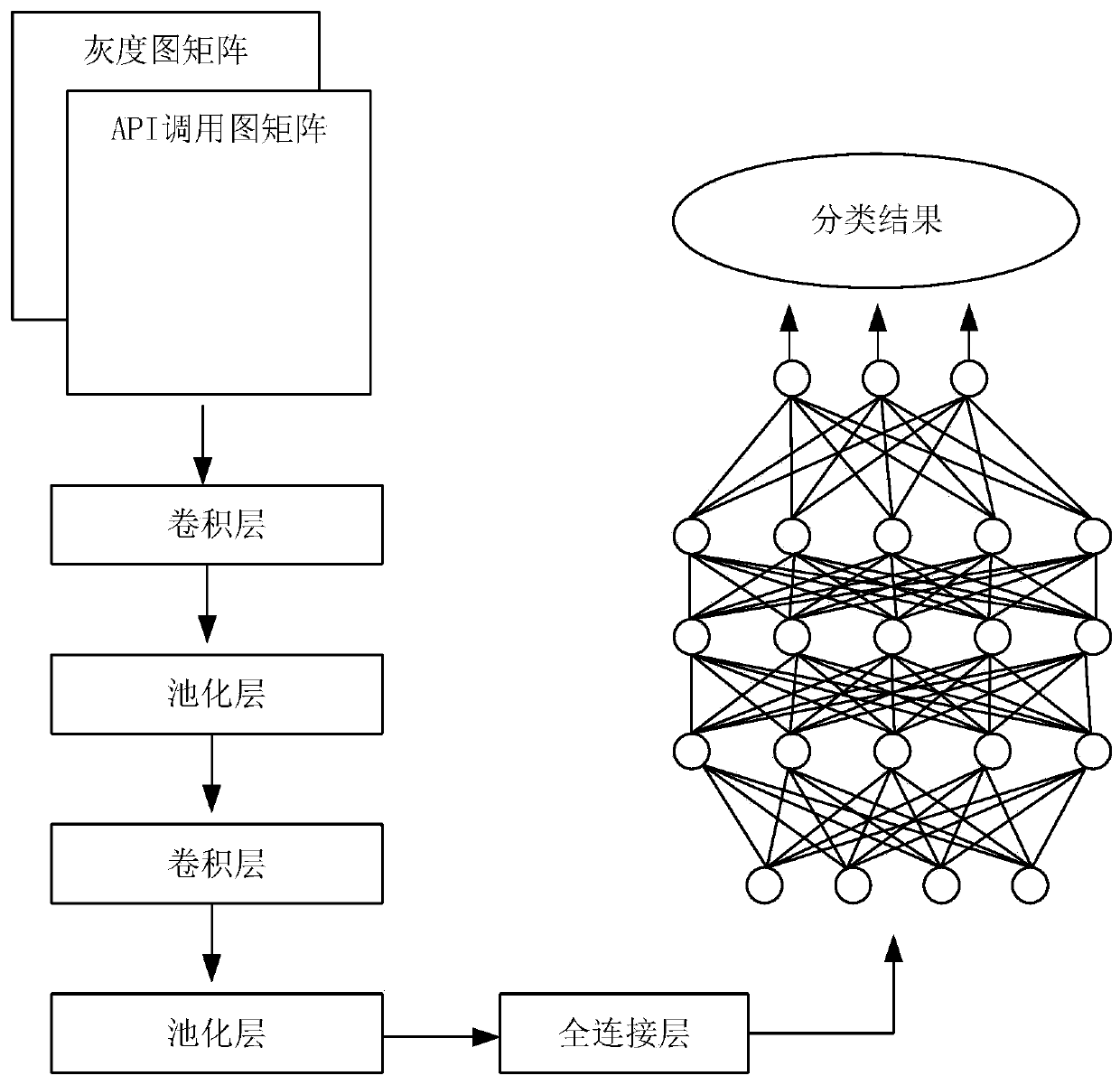
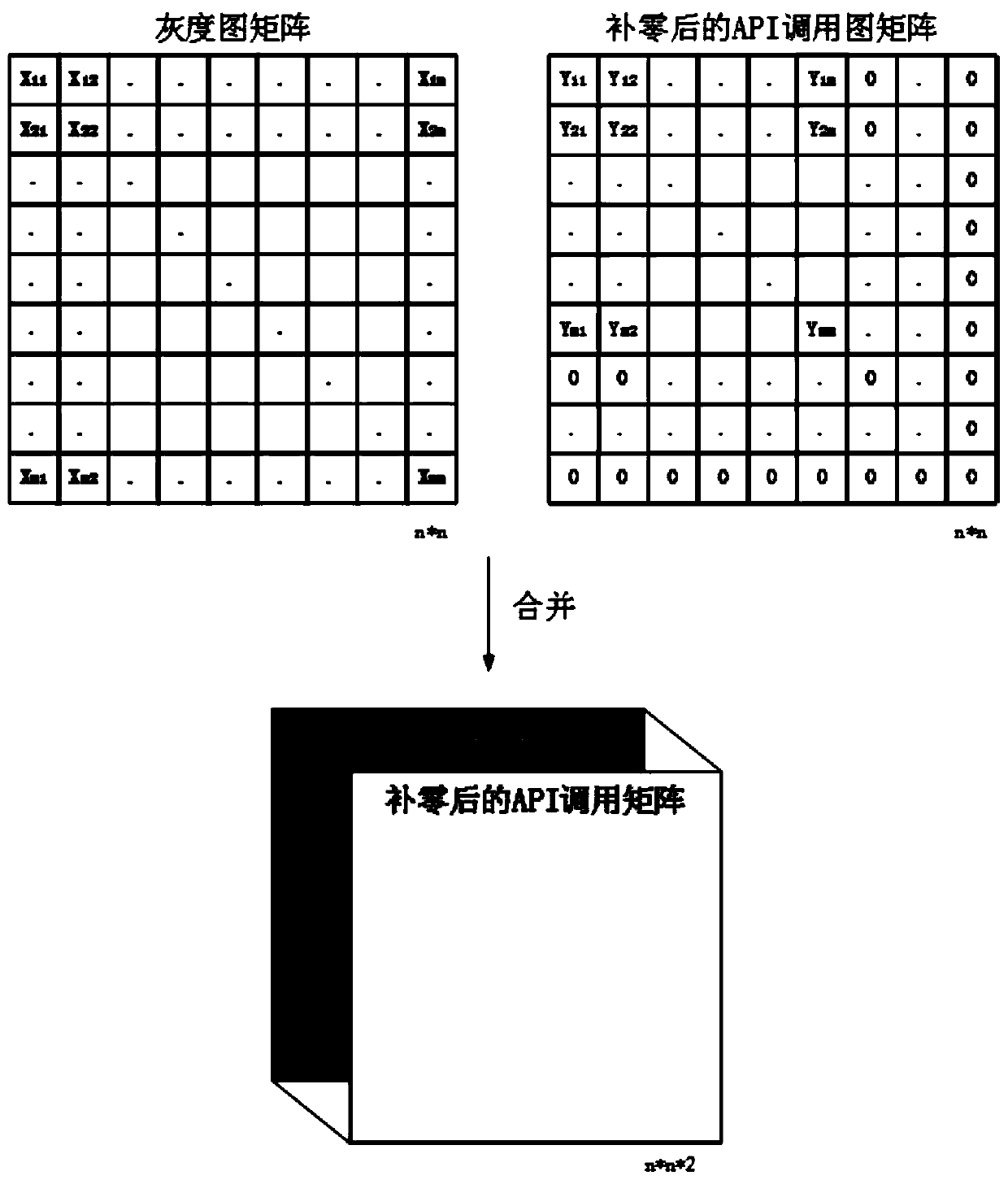
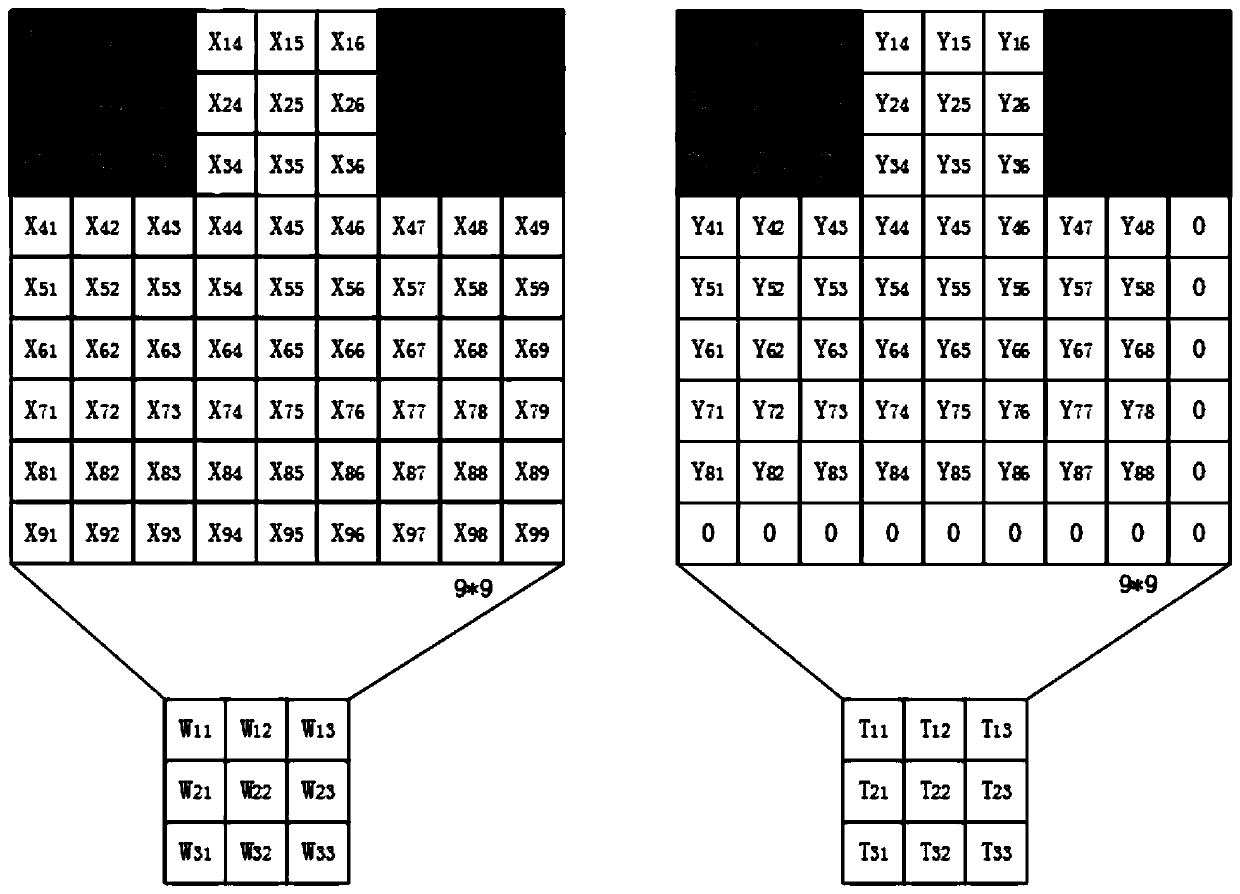
The invention belongs to the field of information security, and particularly relates to a malicious software classification method for optimizing feature extraction. According to the method, the extraction mode of malicious software is optimized, and the convolutional neural network in deep learning is used as a main classifier. The single static feature cannot reflect the feature of the malware comprehensively, for example, the grayscale image can only represent the overall contour of the malware, and the API call image can only represent the control structure of the malware. Aiming at the problems, the method extracts the two features, and combines the two features into a dual-channel picture feature matrix to serve as the input of the convolutional neural network, so that the overall contour of the malicious software can be expressed, and the process which can be executed by the malicious software can be completely expressed. According to the method, the problem that malicious software cannot be completely embodied during sample feature extraction is effectively solved, and a good classification effect is achieved.
Owner:HARBIN ENG UNIV
Software sorting method and device
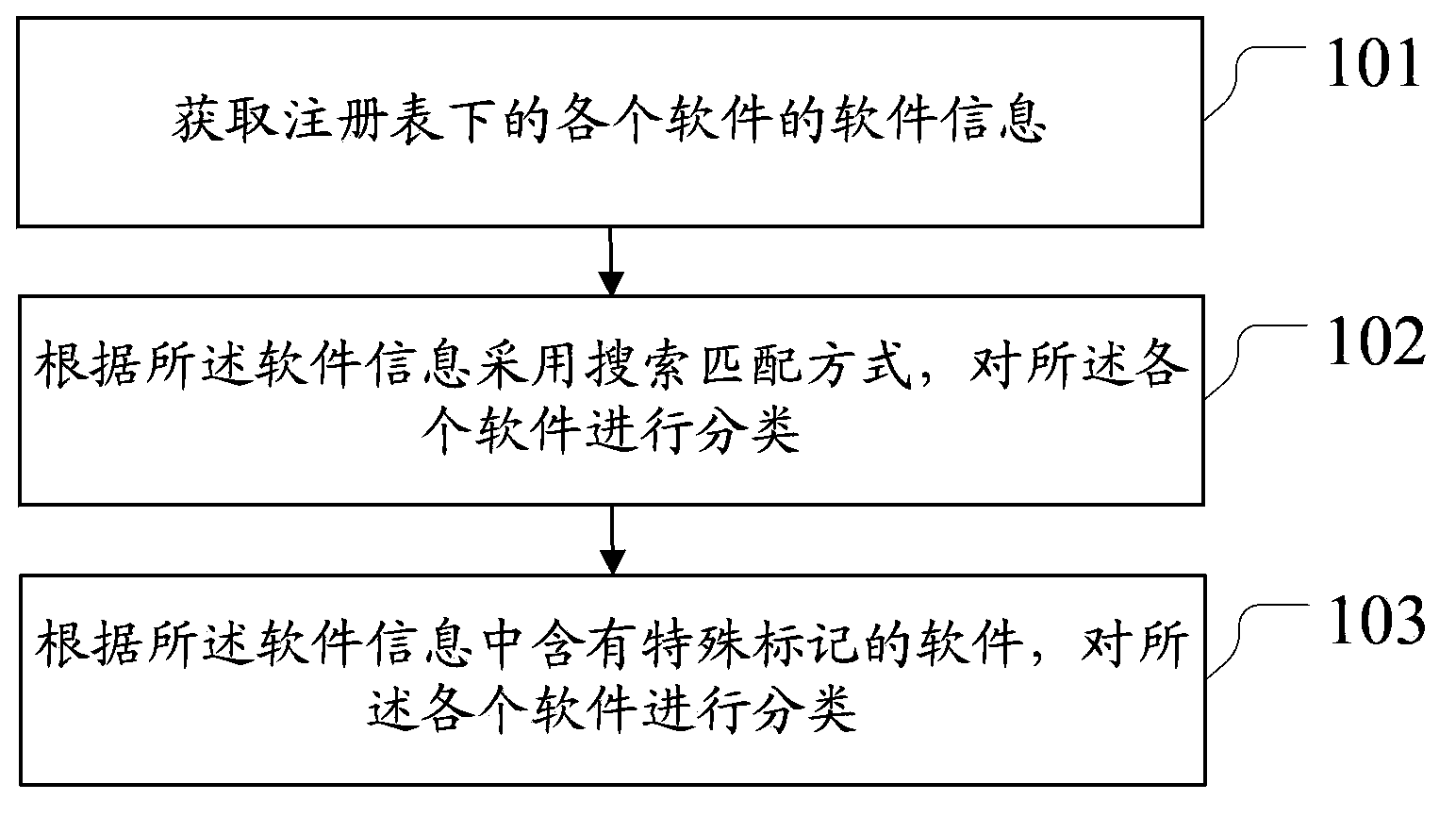
ActiveCN103577252AReduced manual operation workloadMultiprogramming arrangementsSoftware engineeringWorkload
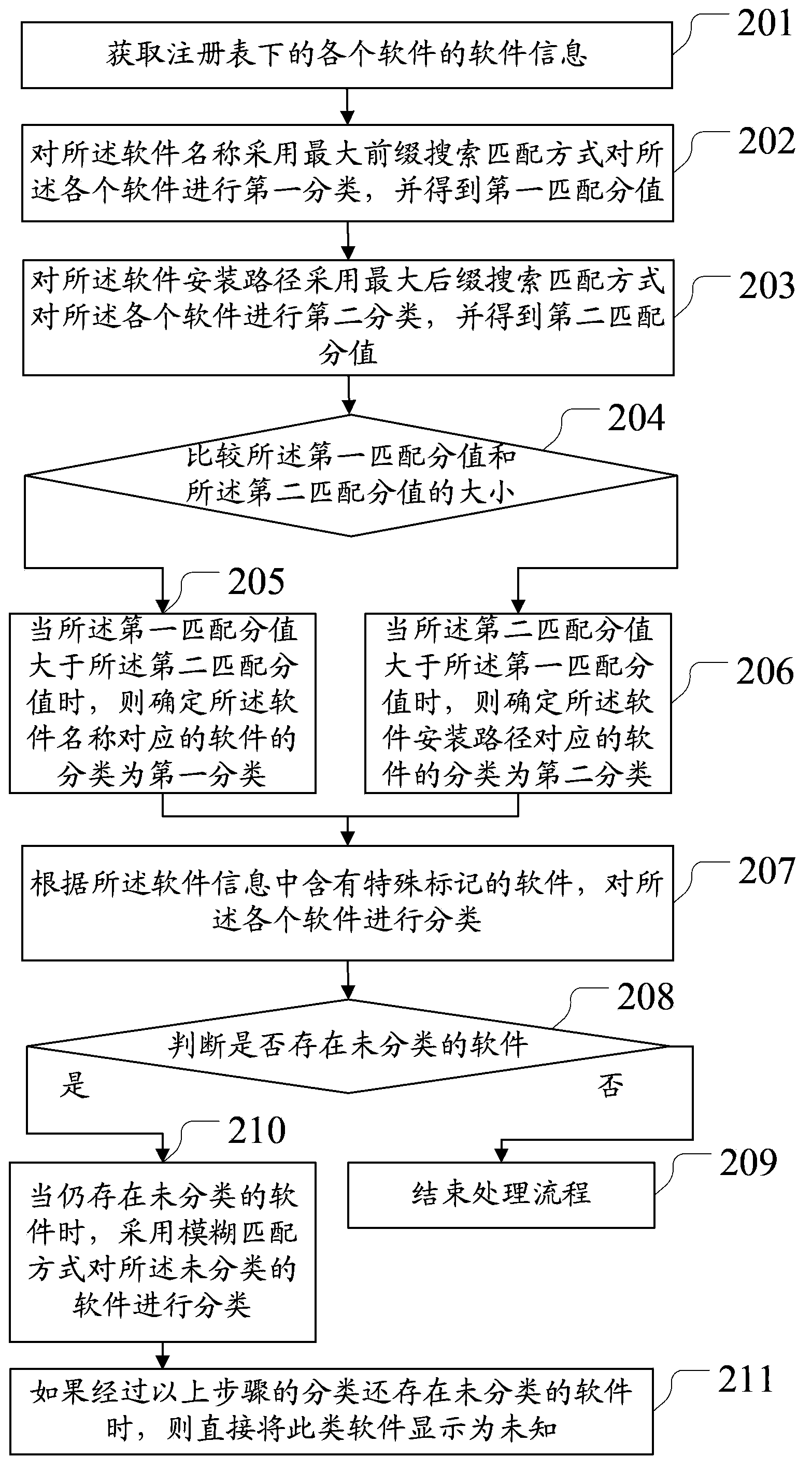
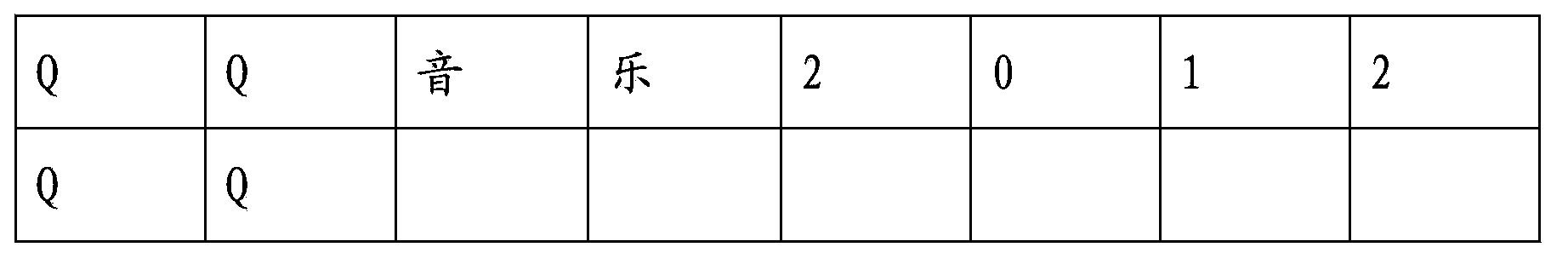
The invention discloses a software sorting method and device and relates to the technical field of software sorting. According to a scheme of an embodiment of the software sorting method and device, information of software in a registry is obtained; the software is sorted through a search matching way according to the software information; the software is sorted according to special mark contained software in the software information. The scheme of the embodiment of the software sorting method and device is suitable for software sorting. The software sorting method and device have the advantages of accurately identifying types of the software, sorting the software and reducing workloads of artificial operation.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Target pushing object pushing method and apparatus and server
InactiveCN106202195AAttract interestIncrease incomeSpecial data processing applicationsSoftware engineeringComputer terminal
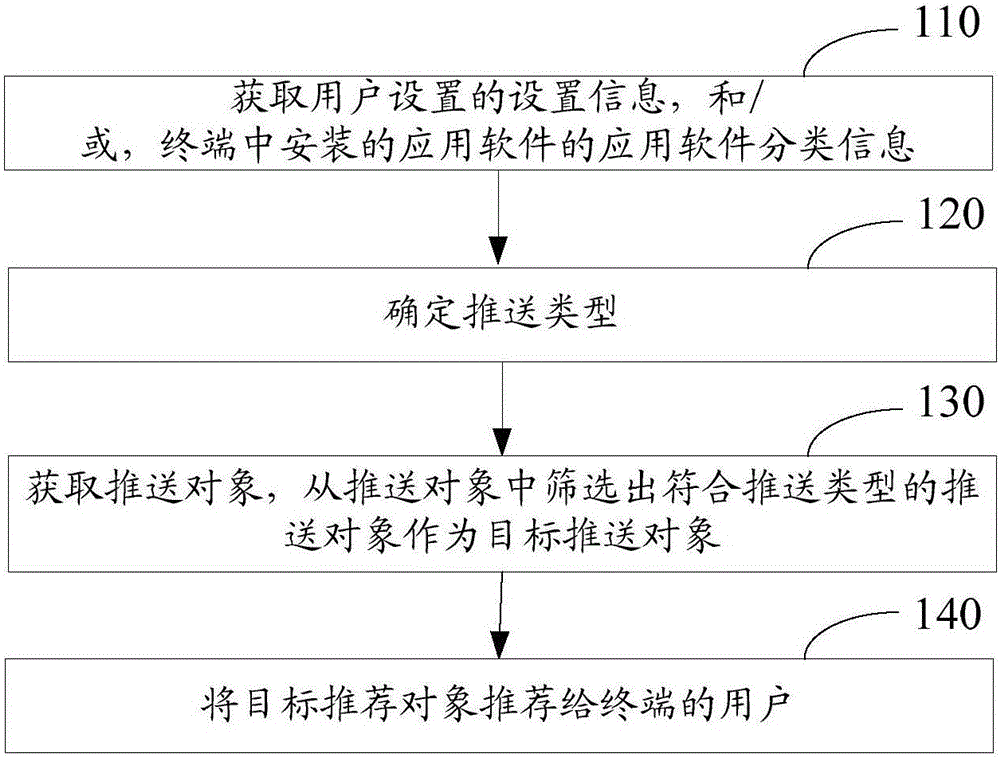
The invention discloses a target pushing object pushing method and apparatus. The method comprises the steps of obtaining setting information of user settings, and / or, application software classification information of application software installed in a terminal; determining a pushing type according to the setting information of a user setting application, and / or, the application software classification information of the application software installed in the terminal; obtaining pushing objects, and screening out the pushing object of the pushing type from the pushing objects to serve as a target pushing object; and pushing the target pushing object to the user of the terminal so as to display the target pushing object on the terminal. According to the method, contents can be pushed to users according to user preferences, so that user interests are attracted and earnings are achieved.
Owner:BEIJING KINGSOFT INTERNET SECURITY SOFTWARE CO LTD
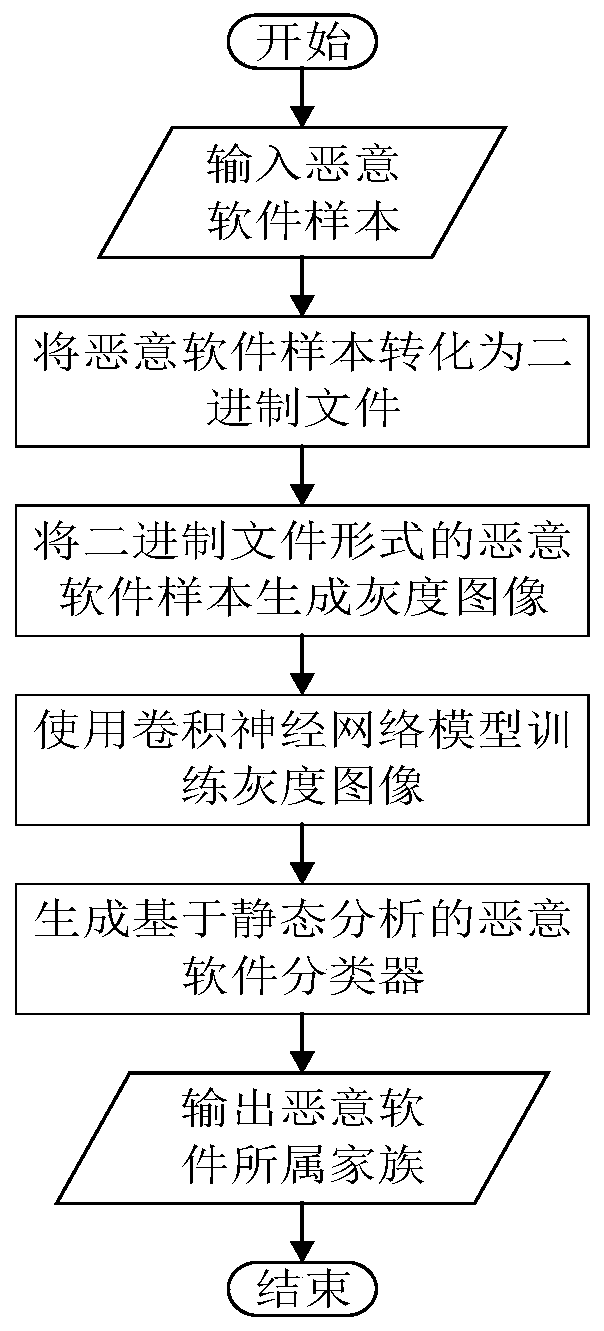
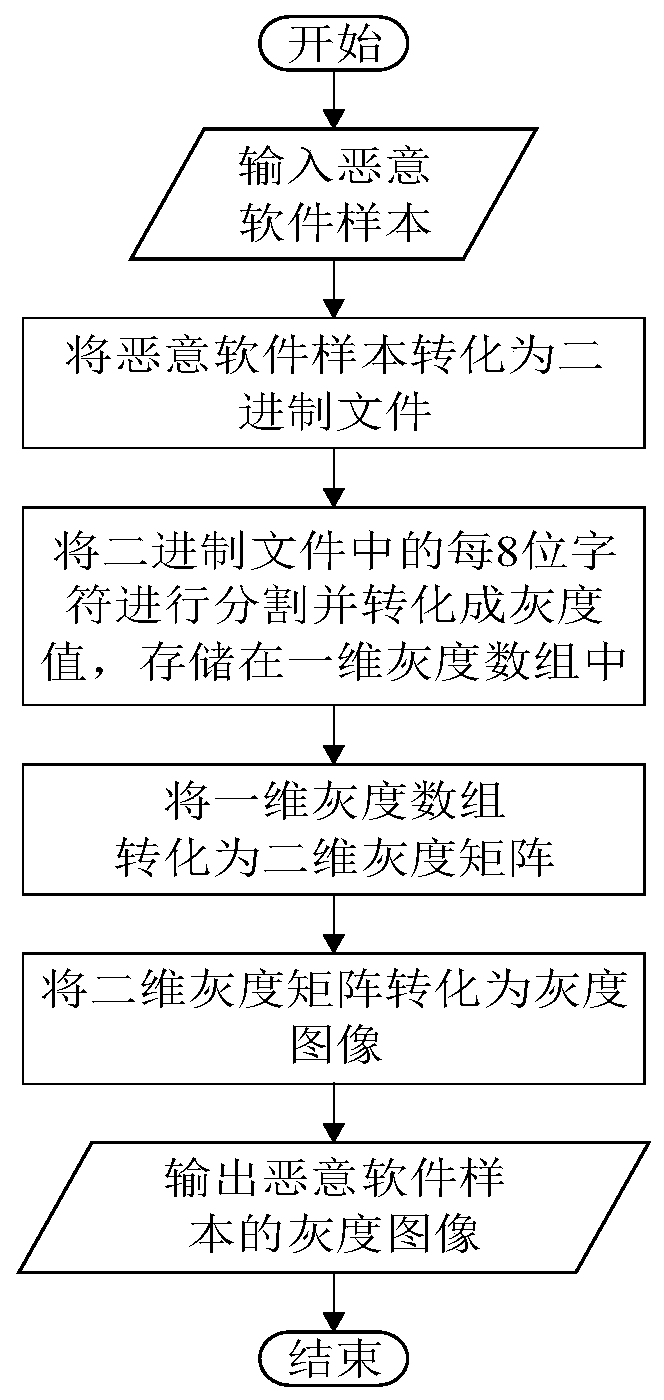
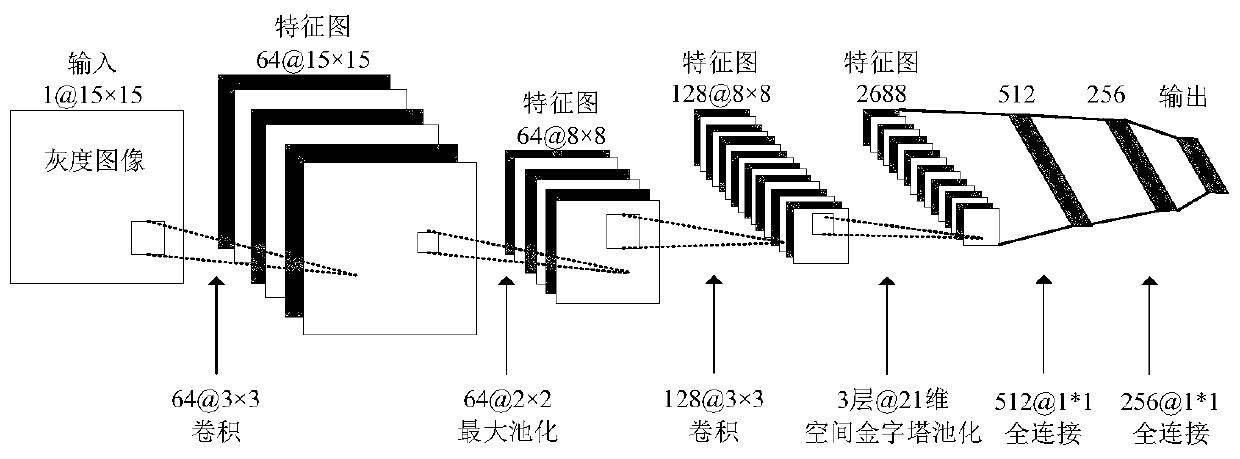
Malicious software classification method based on static analysis
InactiveCN111552964AReduce lossesSave time and costCharacter and pattern recognitionPlatform integrity maintainanceEngineeringComputer vision
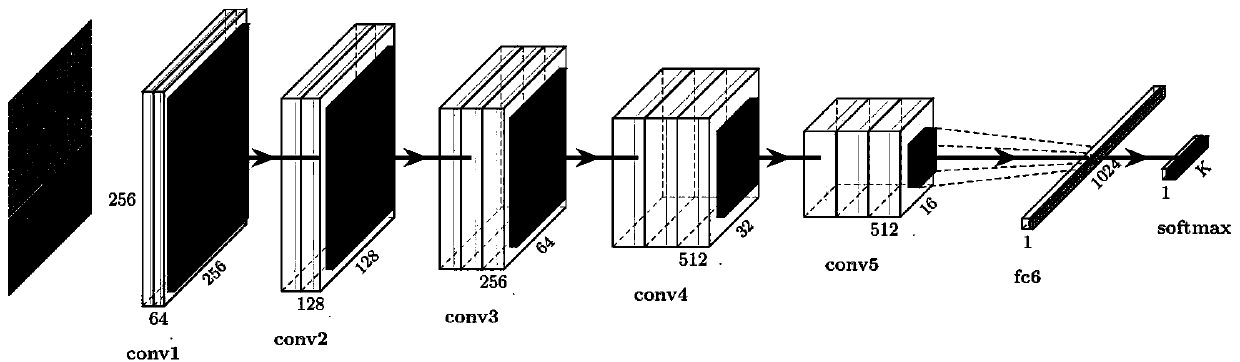
The invention belongs to the technical field of computer security, and particularly relates to a malicious software classification method based on static analysis. The malicious software classification method comprises the following steps: converting malicious software into a binary file, generating a grayscale image, training the grayscale image by adopting a convolutional neural network model with a spatial pyramid pooling layer so as to obtain a static classifier, and carrying out family classification on malicious software samples through the static classifier. According to the malicious software classification method, the grayscale image can be used as a feature to classify malicious software, so that information loss caused in an image preprocessing stage is effectively reduced. According to the malicious software classification method, the malicious software is classified by analyzing the contour features of the malicious software, so that professionals can be helped to reduce the cost of identifying the malicious software.
Owner:HARBIN ENG UNIV
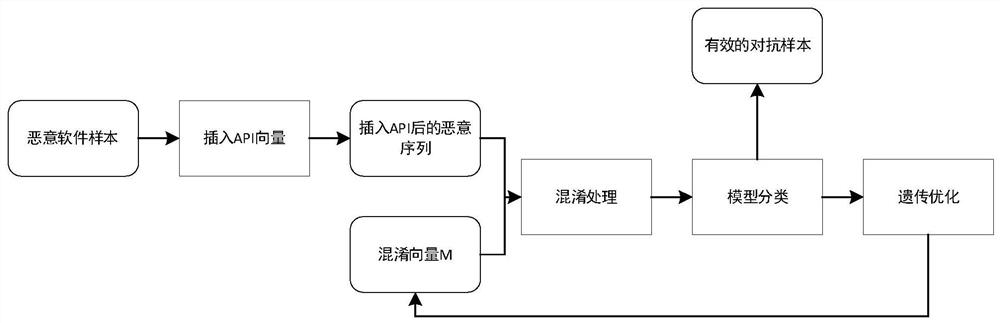
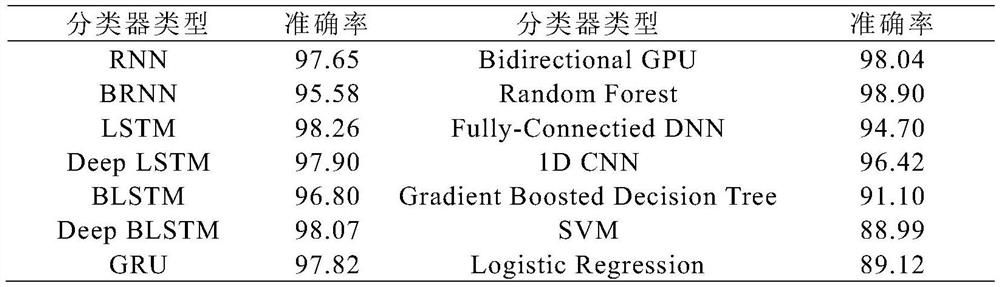
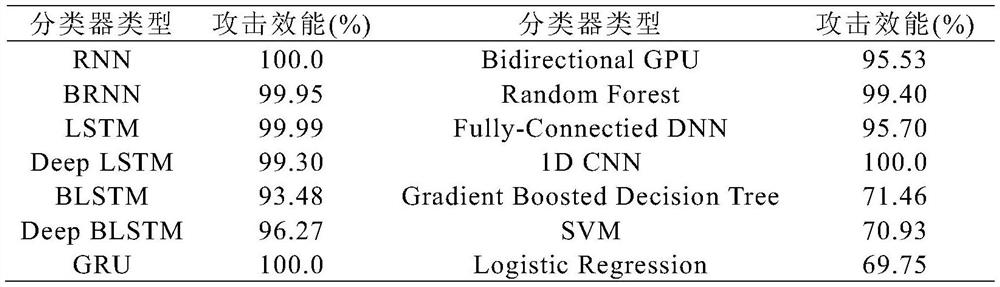
Malicious software confrontation sample generation method combined with API fuzzy processing technology
ActiveCN112231703AIncrease success rateFunction increasePlatform integrity maintainanceGenetic algorithmsAlgorithmGenetics algorithms
The invention relates to a malicious software confrontation sample generation method combined with an API fuzzy processing technology, and belongs to the technical field of computers and information science. The method comprises the following steps: firstly, inserting irrelevant API vectors into an original API calling sequence to preliminarily realize obfuscation of malicious software feature functions; then performing confusion operation of function call redirection on the sample, and hiding function functions of an API; and finally, feeding the modified sample to a malware classifier, checking whether the malware classifier realizes error classification or not, and solving an optimization problem by utilizing a genetic algorithm. The invention has higher practicability and better meetsthe actual requirements; compared with a black-box-oriented adversarial sample generation method, the invention has the advantages that original functions of malicious software are not damaged, the success rate is high when the malware classifier is cheated, and the problems that the success rate of cheating adversarial samples is low and the functions of the malicious software are damaged are greatly solved.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
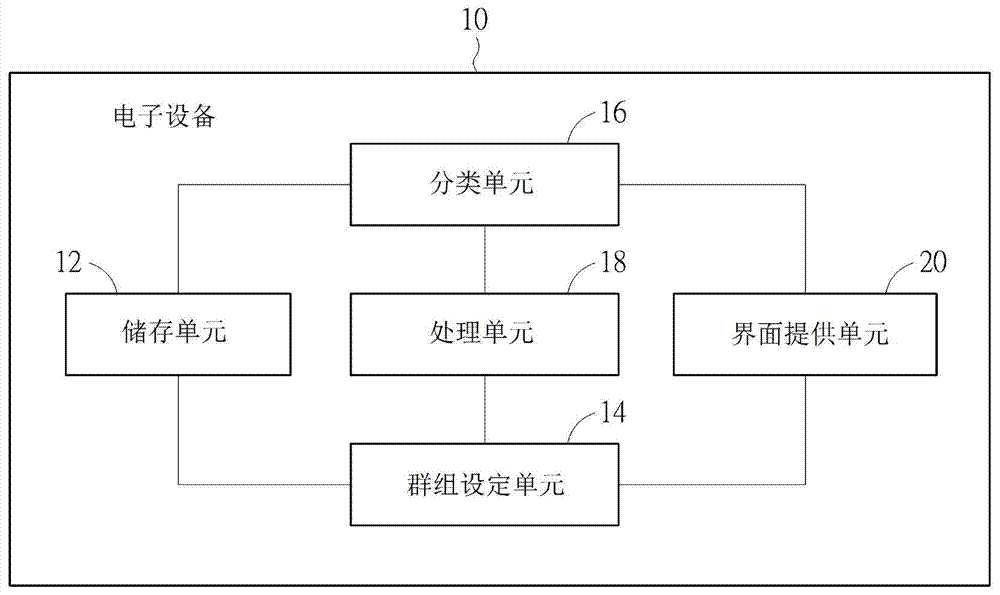
Software classification method and electronic device with software classification function
InactiveCN103778197AImprove ease of useProgram controlSpecial data processing applicationsSoftware engineeringElectronic equipment
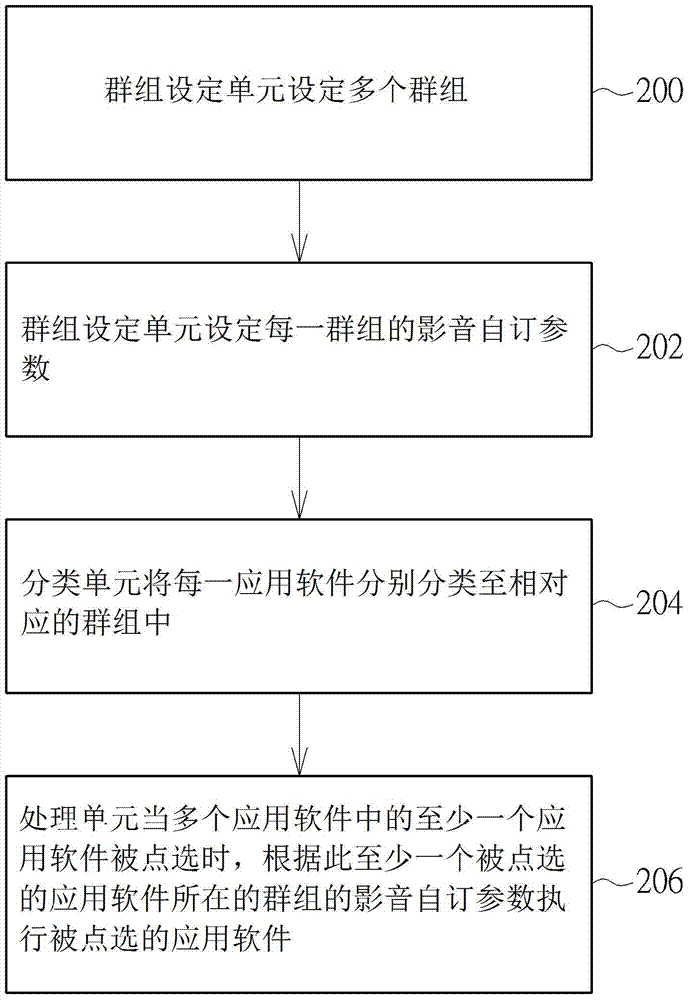
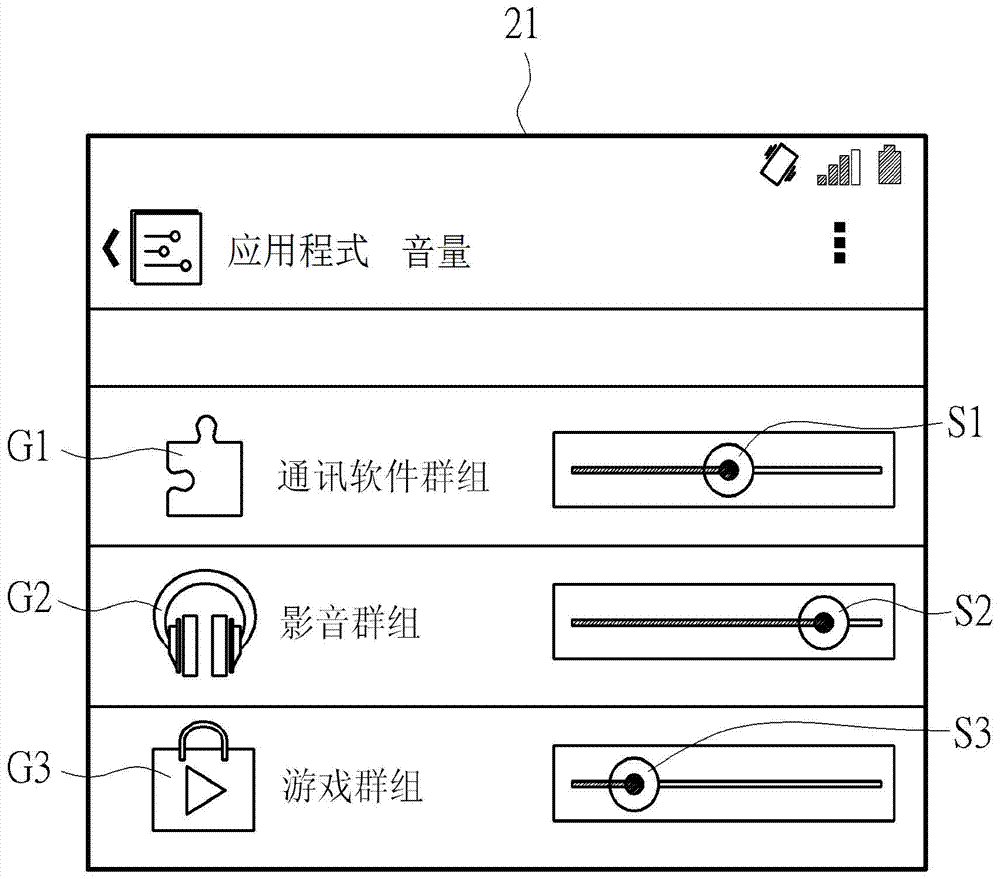
The invention provides a software classification method which is applied to an electronic device with a plurality of software applications. The software classification method comprises the following steps: setting a plurality of groups; setting a video and audio custom parameter for each of the groups; respectively classifying each of the software applications to the corresponding group; when at least one of the software applications is clicked, executing at least one software application according to the video and audio custom parameters of the groups where at least one software is located.
Owner:QISDA SUZHOU +1
Scenario simulation teaching and practical training system
The invention discloses a scenario simulation teaching and practical training system, and particularly relates to a real-time recording and playback audio and video system. The characteristics lie in that image acquisition signals are connected to a scenario simulation teaching and practical training commenting platform; real-time image recording is carried out through the platform; virtual dotting and cutting are carried out on a recorded image so as to form mini thumbnail mark points; a file, which not only can be used for whole process playback but also can be used for segmental playback, is formed through hardware acquisition and software classification. The scenario simulation teaching and practical training system utilizes a splitting technology very conveniently, and different split segments are made into a catalogue at the same time so as to be provided for consumers to use. The technology does not occupy physical partition, and only the catalogue is made in form, thereby being simple and convenient.
Owner:SHANGHAI FENGHAO ELECTRONICS TECH CO LTD
Mobile terminal and application software classification-based power-saving method thereof
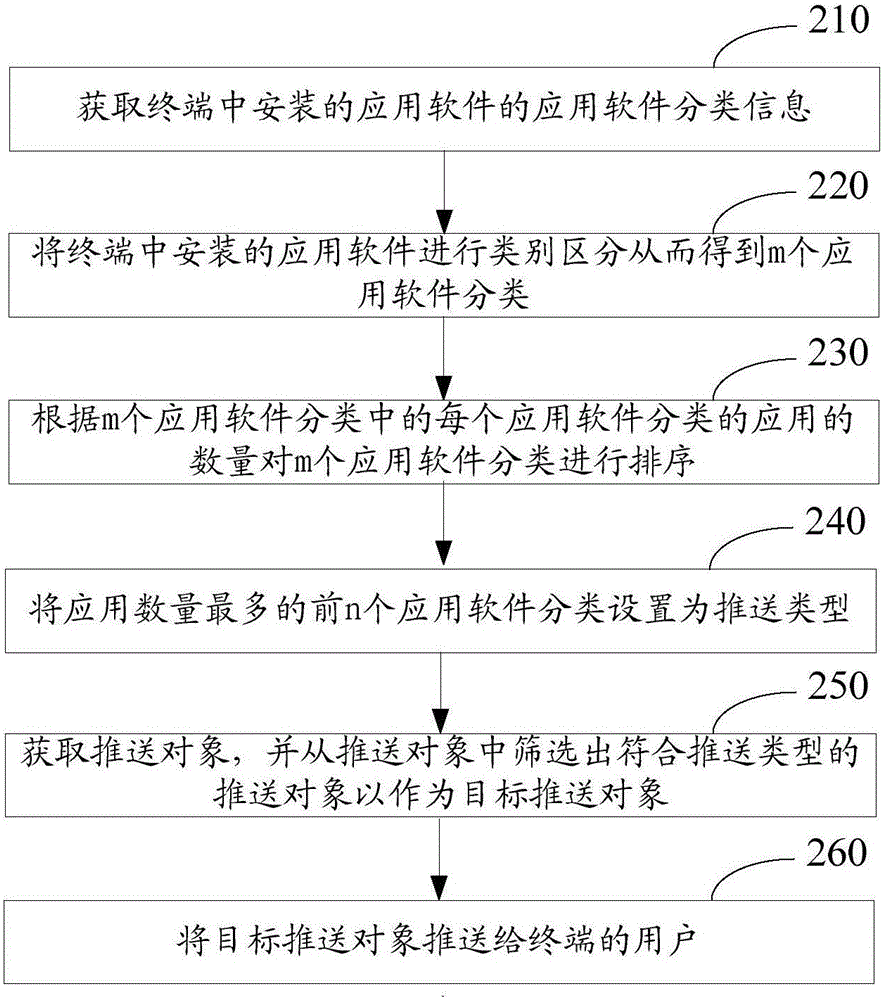
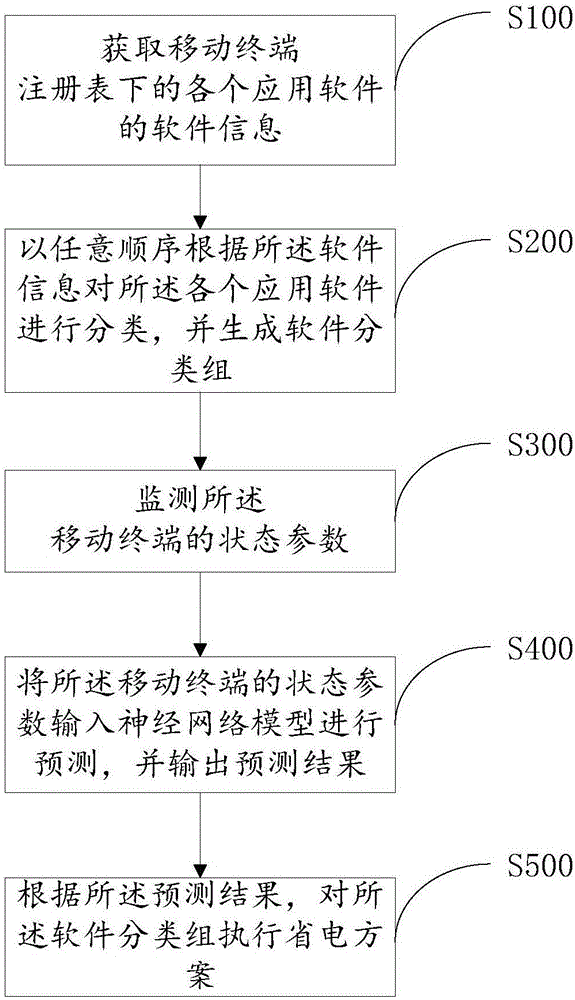
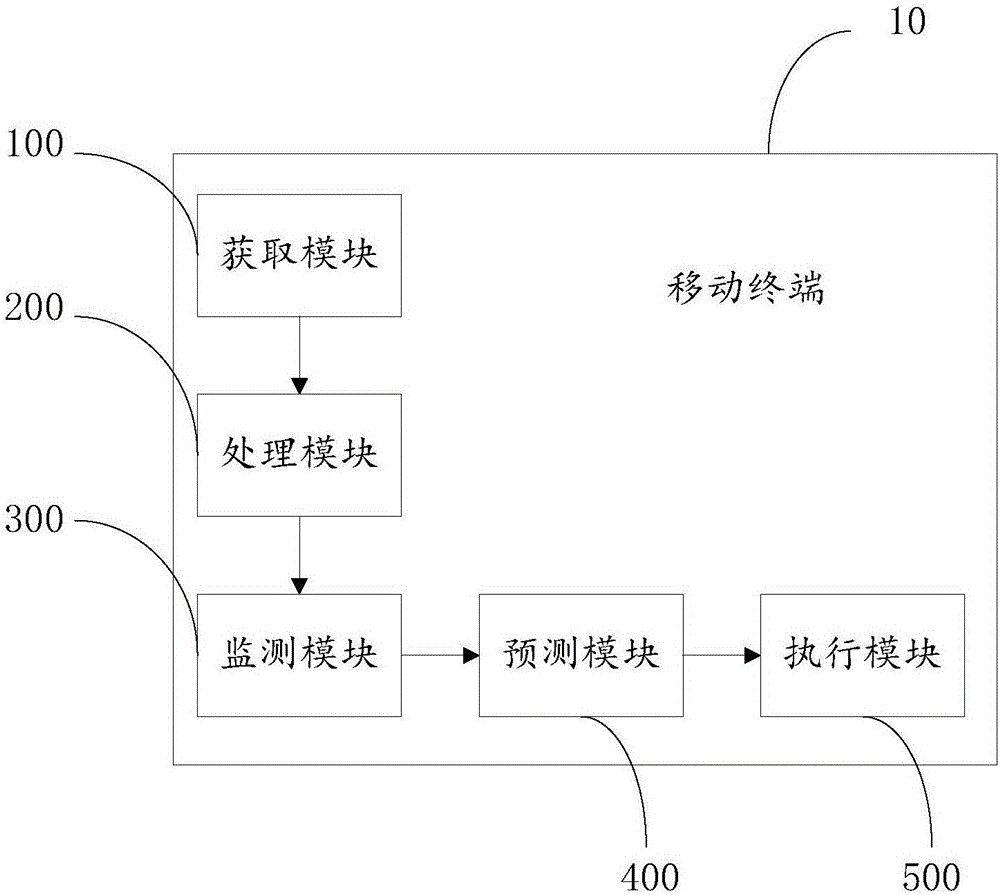
The invention discloses a mobile terminal and an application software classification-based power-saving method thereof, and belongs to the field of mobile communications. A neural network-based power-saving method of the mobile terminal comprises the steps of obtaining software information of application software in registries of the mobile terminal; classifying the application software according to the software information in any sequence, and generating software classification groups; monitoring state parameters of the mobile terminal; inputting the state parameters of the mobile terminal to a neural network model for performing prediction, and outputting a prediction result; and executing power-saving schemes on the software classification groups according to the prediction result. The invention furthermore discloses the mobile terminal. According to the mobile terminal and the method, the application software of the mobile terminal is classified, the application software same in type forms the application software classification groups, and the power-saving schemes are intensively executed according to the groups, so that the power of the mobile terminal is saved more efficiently and systematically.
Owner:SHANGHAI GREEN ORANGE IND
Method and system for classification of software using characteristics and combinations of such characteristics
Certain embodiments of the present invention provide methods and systems for software classification. Certain embodiments provide a method for identification of malware. Certain embodiments provide a method for identification of unwanted software. The method includes identifying one or more functional blocks and / or properties of software. The method further includes identifying genes in the functional blocks and / or properties. The method also includes matching the resulting list of genes against one or more combinations of classifications of groupings of genes. Additionally, the method includes classifying the software. Certain embodiments provide a method for generating classifications. The method includes identifying functional blocks and / or properties. Furthermore, the method includes combining a plurality of genes to form a classification.
Owner:SOPHOS
Client software classification method based on human needs
InactiveCN102855130AClear logicPlatform integrity maintainanceSpecific program execution arrangementsSoftware systemClassification methods
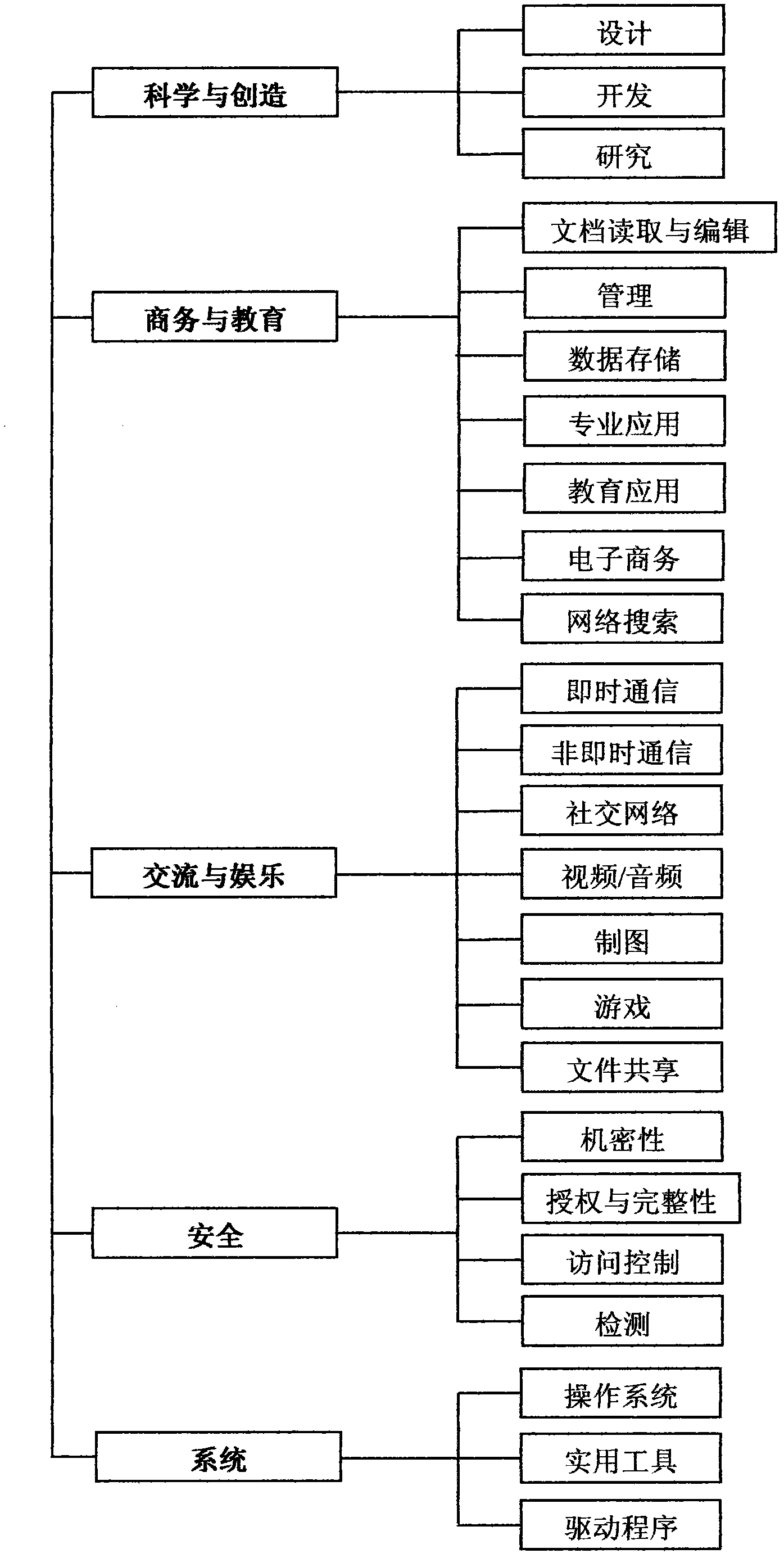
The invention relates to a client software classification method based on human needs. The method includes first classifying various client software into five layers (system, safety, communication and entertainment, business and education, and science and creation) according to the human demand analysis theory of American psychologist Maslow, then determining the corresponding layers according to functions of the client software, conducting classification, and finally conducting classification again on contained software in each layer according to difference of application fields and specific characteristics of the software. The method grasps core essence of the client software, is comprehensive in range, clear in logic and capable of being applied in expanding mode, and is favorable for conducting integral safety evaluation and change trend prediction of a computer software system.
Owner:袁艺
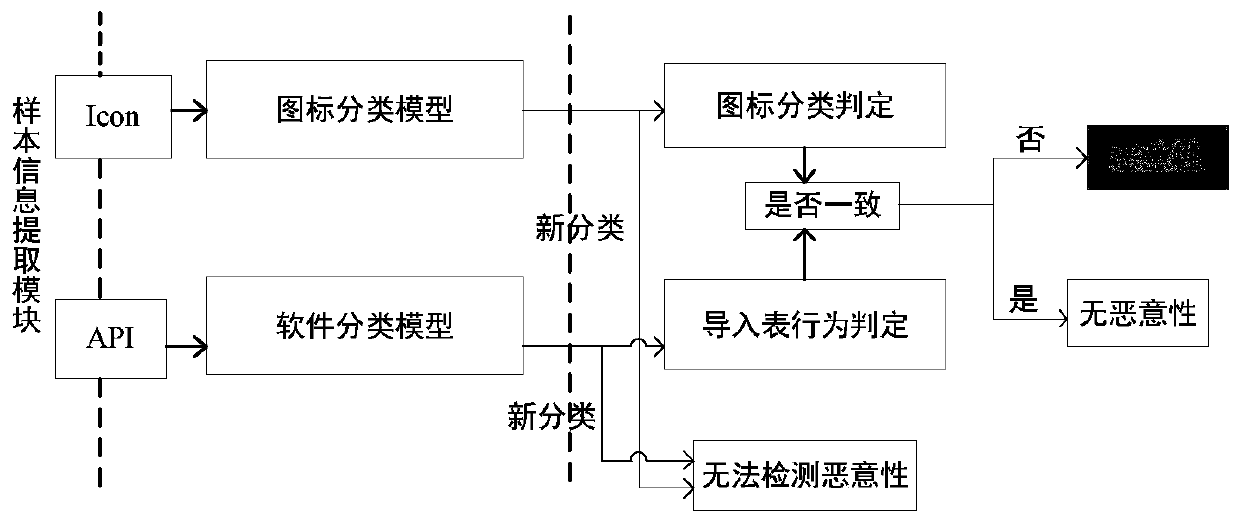
Malicious program recognition method and device based on icon representation and software behavior consistency analysis
InactiveCN109871686ASolve efficiency problemsSolve costly problemsPlatform integrity maintainanceNeural architecturesInformation repositoryStructure analysis
The invention belongs to the technical field of network security. The invention particularly relates to a malicious program recognition method and device based on icon representation and software behavior consistency analysis. The method comprises the following steps of: obtaining a sample; collecting known classification normal software data; extracting known normal software icon resource data and import table API data, constructing a CNN deep learning model, respectively training icons and import table API information, establishing an icon classification model and a software classification model, and obtaining a software program routine information base according to icon classification and software behavior classification information; Performing structure analysis on the sample to be tested, extracting icon resource data and import table API function data, testing through a CNN deep learning model, and obtaining icon classification and software behavior classification information ofthe sample to be tested; And judging the behavior consistency of the classification of the to-be-tested sample icons and the software behavior classification according to the test result. Automatic and batched malicious program rapid detection is achieved, and malicious program codes disguised through software similar icons and the like are effectively recognized.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
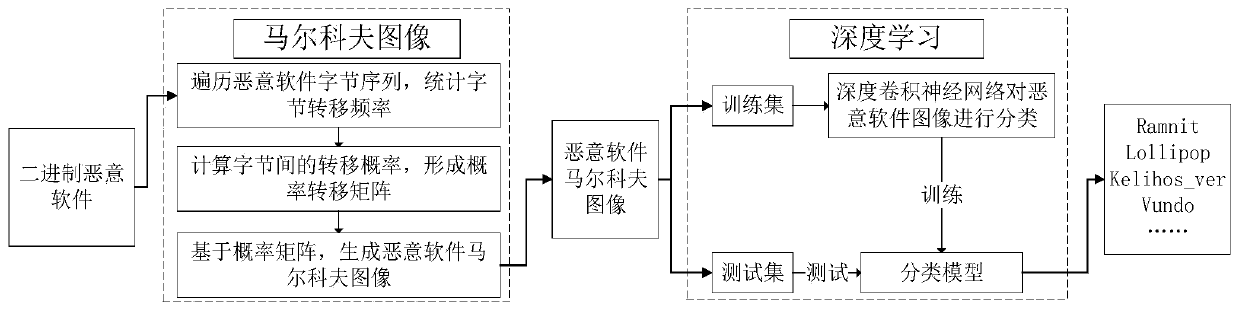
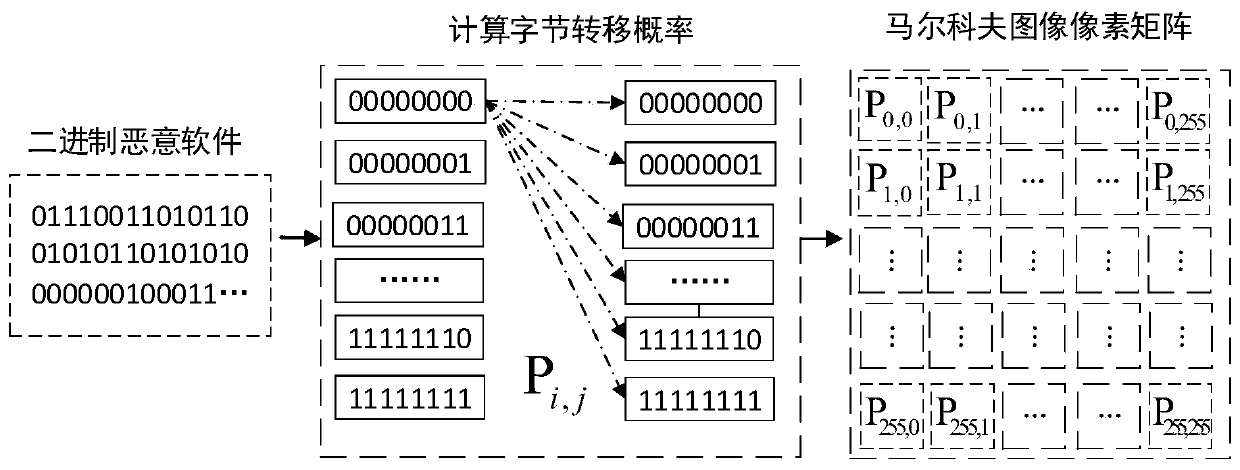
Malicious software classification method based on Markov graph and deep learning
ActiveCN111259397AReduce redundancyImprove classification accuracyCharacter and pattern recognitionPlatform integrity maintainanceMalwareByte
The invention discloses a malicious software classification method based on a Markov graph and deep learning, and the method comprises the steps: firstly carrying out the statistics of the byte transfer frequency of malicious software, converting the byte transfer frequency into a Markov image, and completing the classification of the malicious software through a deep convolution neural network, wherein the designed deep convolutional neural network structure is redesigned on the basis of VGG16, the depths of convolutional layers and pooling layers of the deep convolutional neural network structure are the same as those of the VGG16, and the deep convolutional neural network structure comprises 13 convolutional layers and 5 pooling layers in total. Different from the VGG16, the deep convolutional neural network designed by the invention only has one full connection layer, and the output dimension of the deep convolutional neural network is 1024. The method is wide in applicability, andredundancy of byte information can be effectively reduced; and the method does not depend on a pre-trained model, and has higher classification accuracy.
Owner:SICHUAN UNIV
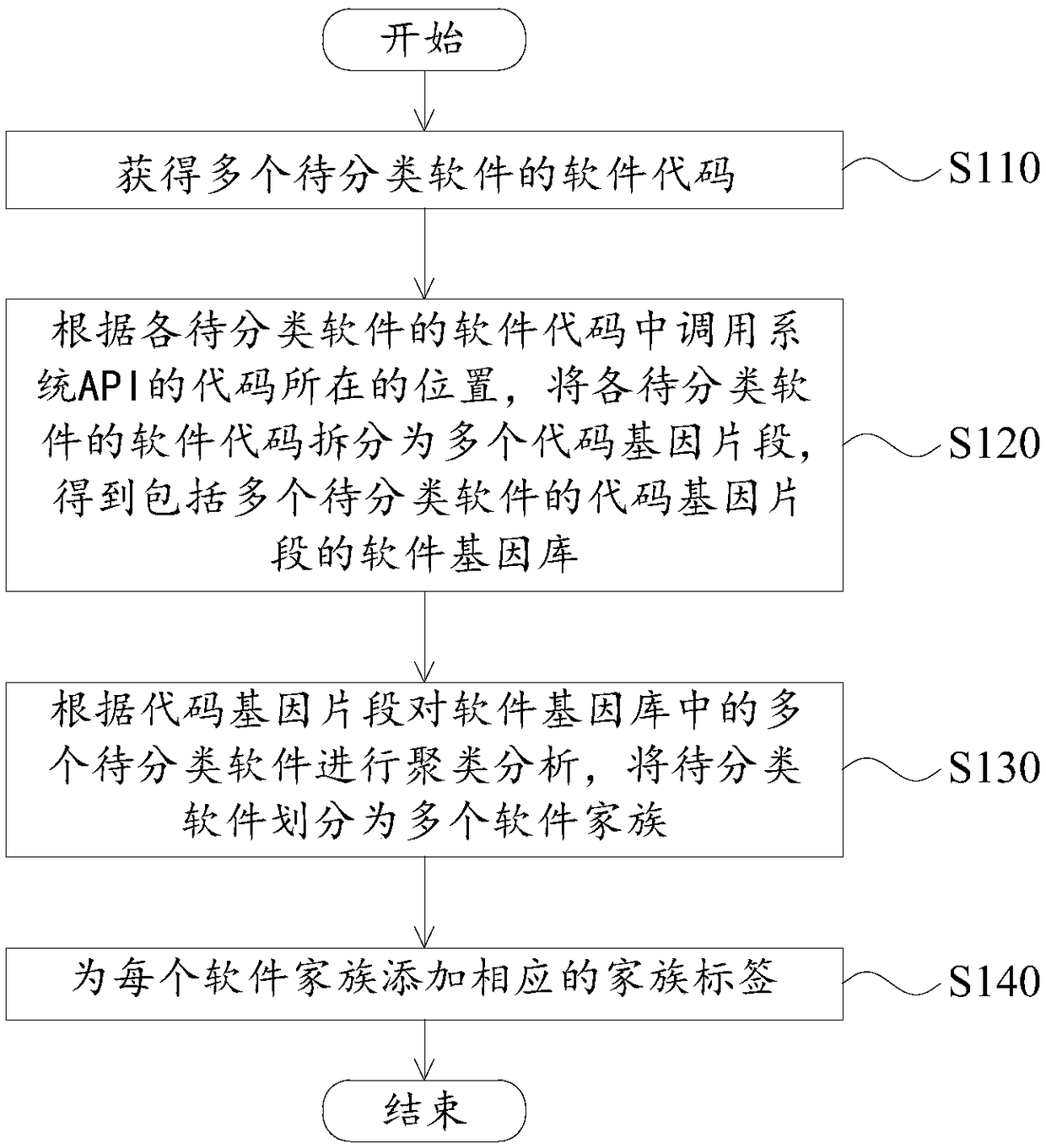
Software classification method and apparatus
InactiveCN108734215AThe classification information is accurateCannot be forgedDecompilation/disassemblyCharacter and pattern recognitionSoftware engineeringGene
The present application provides a software classification method and apparatus. The method comprises: obtaining software codes of a lot of to-be-classified software; according to the location of thecode for calling the system API in the software code of each to-be-classified software, splitting the software code of each to-be-classified software into a plurality of code gene segments to obtain asoftware gene library including the code gene segments of a lot of to-be-classified software; performing clustering analysis on a lot of to-be-classified software in the software gene library according to the plurality of code gene segments, and dividing a lot of to-be-classified software into a plurality of software families; and adding a corresponding family tag for each of the software families. Thus, according to the technical scheme of the present application, the software can be classified according to the software code itself, so that the classification information of the software is more accurate and the classification information cannot be forged.
Owner:上海戎磐网络科技有限公司
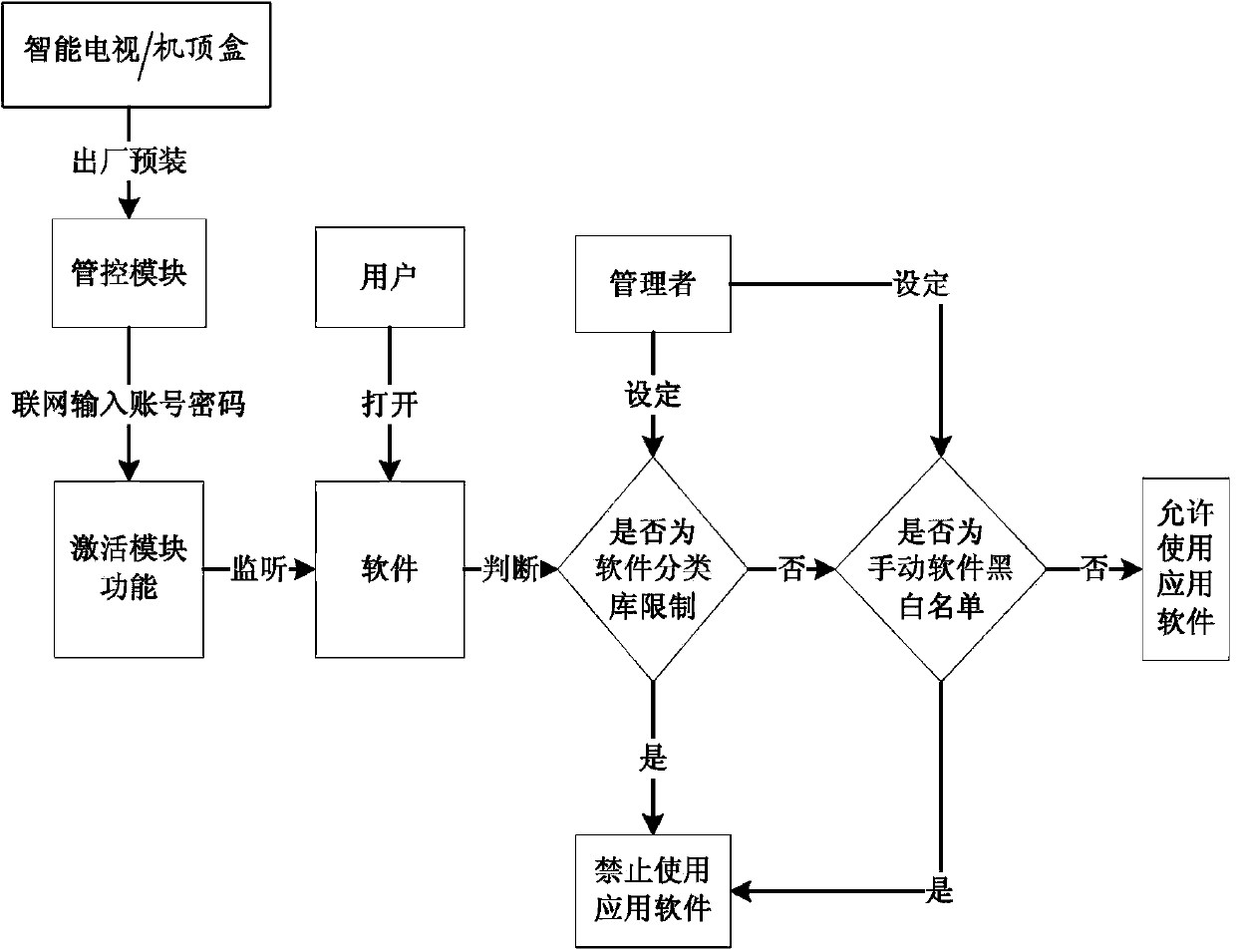
Smart television/set-top box application software based control method
InactiveCN104202666AEasy to controlPrevent addictionSelective content distributionSpecific program execution arrangementsSoftware engineeringApplication software
The invention provides a smart television / set-top box application software based control method. The smart television / set-top box application software based control method mainly comprises the steps of: mounting a control application on a smart television / set-top box by a manager; restricting whether a user can use application software on the smart television / set-top box by setting an application software control strategy. The smart television / set-top box application software based control method has the advantages that even application software which has not been installed on the smart television / set-top box also can be added into a forbidden list firstly through an application software classification library set by the manager, accordingly youngsters are prevented from being excessively addicted to software such as games and chart communication, and the youngsters are also prevented from contacting poor application software.
Owner:GREEN NET WORLD FUJIAN NETWORK TECH
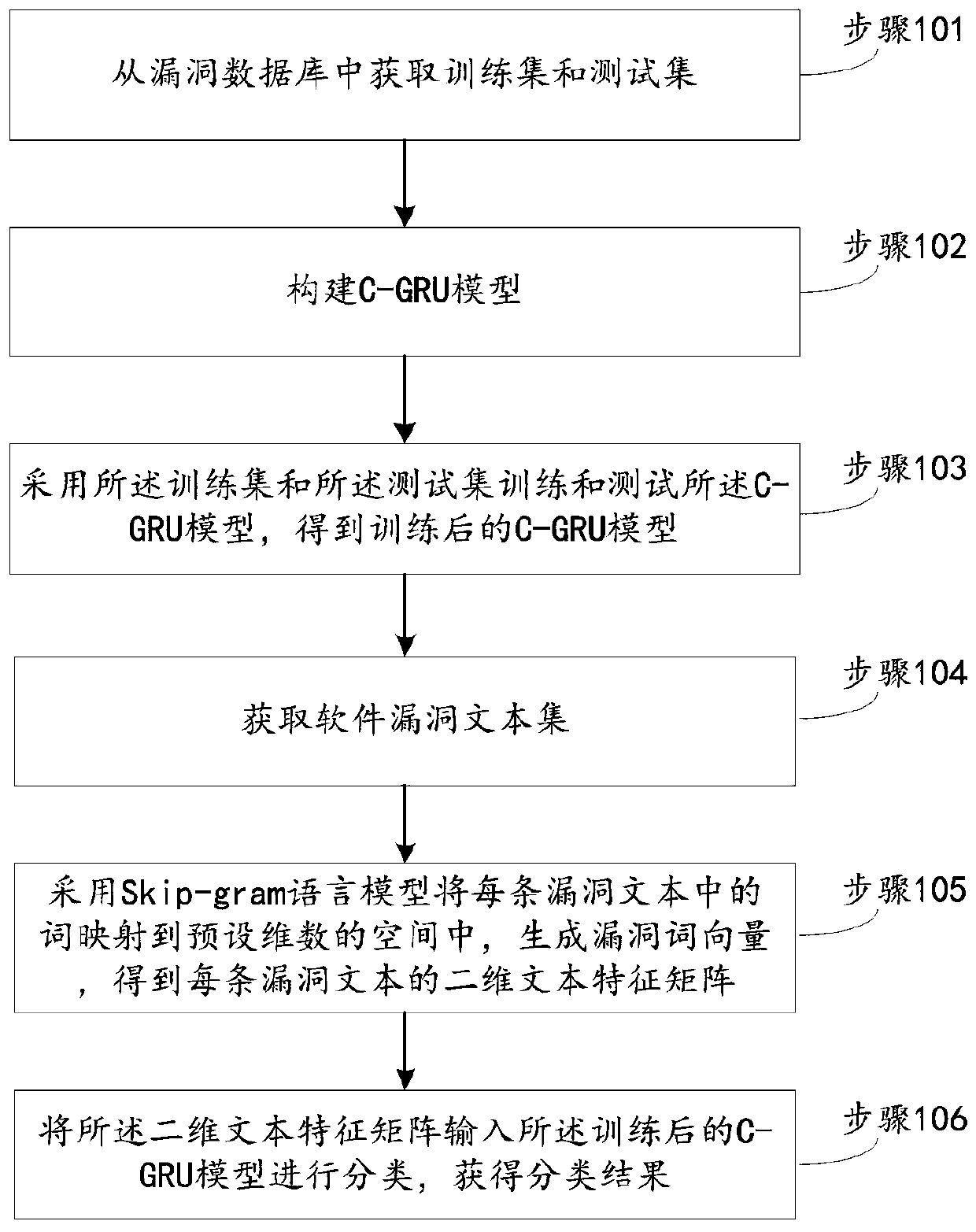
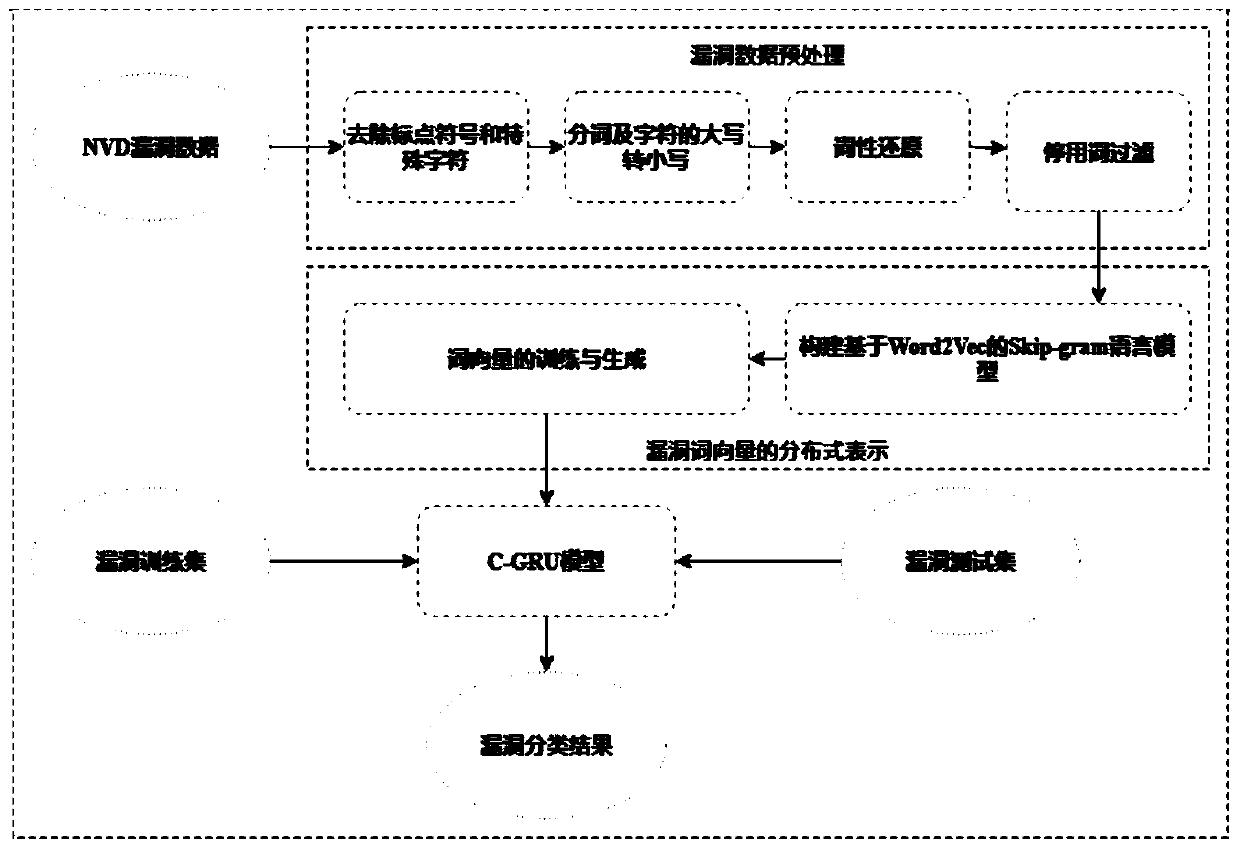
Software vulnerability classification method and system
ActiveCN110348227AImprove classification accuracyReduce sparsityCharacter and pattern recognitionPlatform integrity maintainanceClassification methodsNetwork model
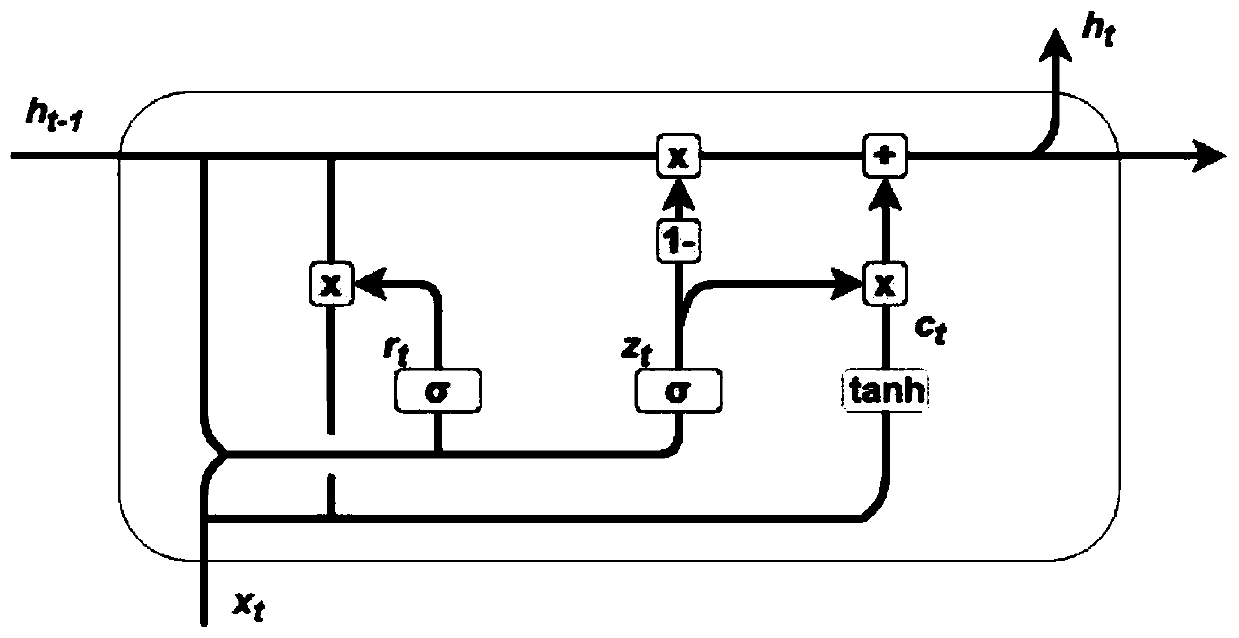
The invention provides a software vulnerability classification method and system. Skip-is used in the classification method. The classification method comprises the following steps: training and generating vulnerability word vectors by using a Skip-gram language model; mapping words in each vulnerability text into a space with a limited dimension, to represent semantic information, thereby reducing the sparsity of the word vector; then, fully using the advantages of feature extraction and semantic information representation of the convolutional neural network and the recurrent neural network;constructing a C-GRU neural network model, using a convolutional neural network to extract local features of text vectors, using a GRU to extract global features related to text contexts, and fusing the features extracted by the two complementary models. According to the method, the technical defects that an automatic vulnerability classification method based on a machine learning algorithm is poor in effect of processing high-dimensional and sparse problems, text features and representation semantic information cannot be well extracted, and specific vulnerability information is ignored are overcome, and the software classification accuracy is improved.
Owner:YANSHAN UNIV
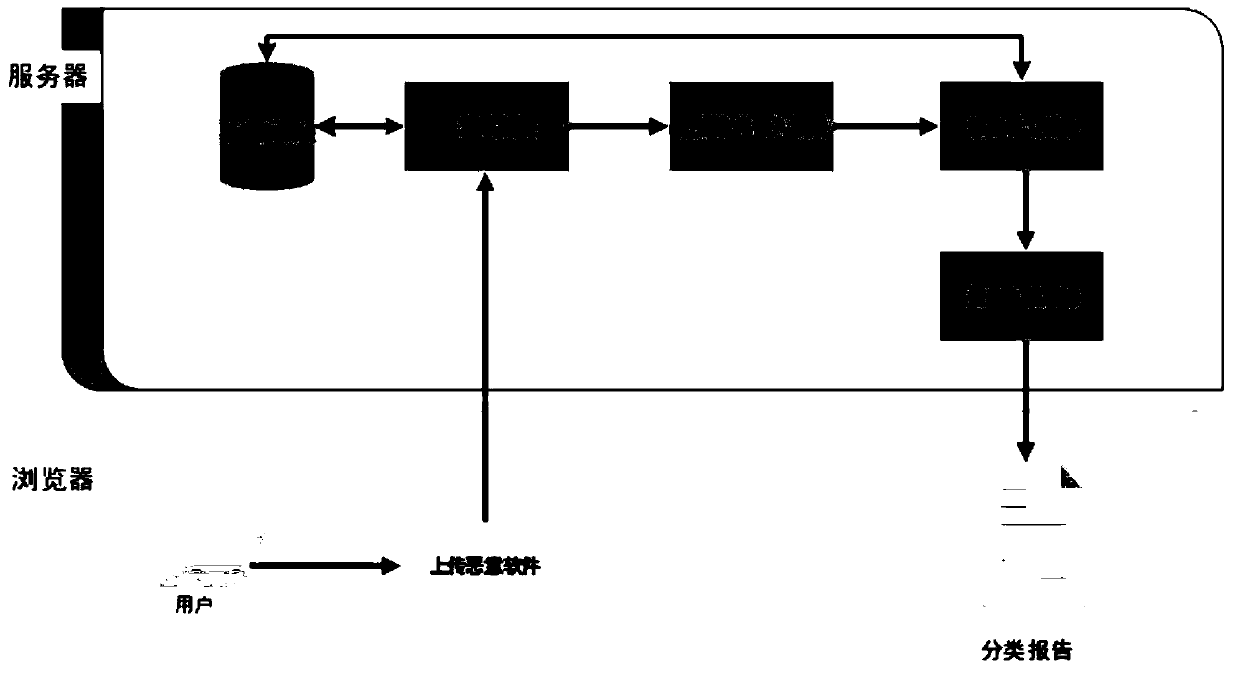
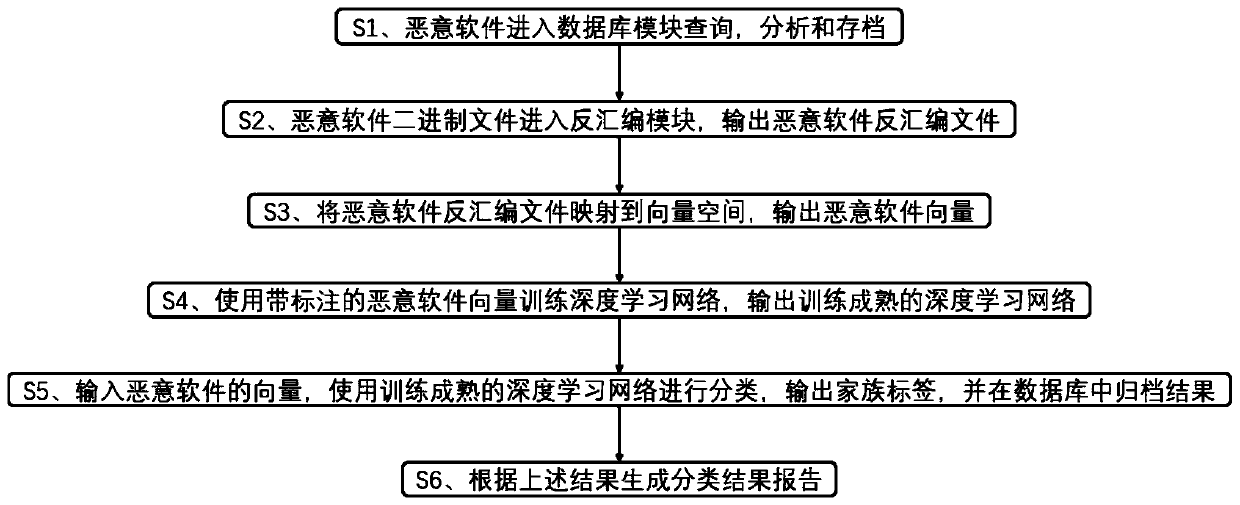
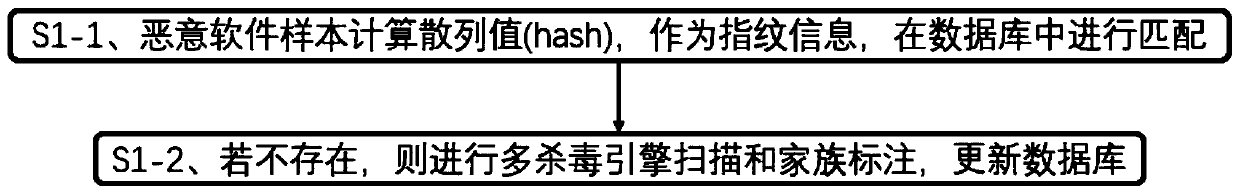
Large-scale malicious software classification system and method based on deep learning
ActiveCN110968869AGuaranteed periodic updatesImprove robustnessDecompilation/disassemblyCharacter and pattern recognitionEngineeringMalware
The invention discloses a large-scale malicious software classification system and method based on deep learning, and relates to the technical field of computer information security. The large-scale malicious software classification system comprises a database module, a disassembling module, a malicious software embedding module and a deep learning module, and the database module is configured toperiodically and automatically collect malicious software information from a network space, especially each large open-source malicious software platform; the disassembling module performs disassembling analysis on the malicious software; the malicious software embedding module comprises a malicious software embedding method, maps a malicious software disassembling file to a vector space and outputs a malicious software vector; the deep learning module is used for learning on the supervised malicious software sample set to obtain a mature model in a training stage; in the detection stage, vectors of the malicious software are input into the mature model, family information of the malicious software is output, a classification result is obtained. Through implementation of the scheme, the classification efficiency and robustness of the large-scale malicious software are improved.
Owner:SHANGHAI JIAO TONG UNIV
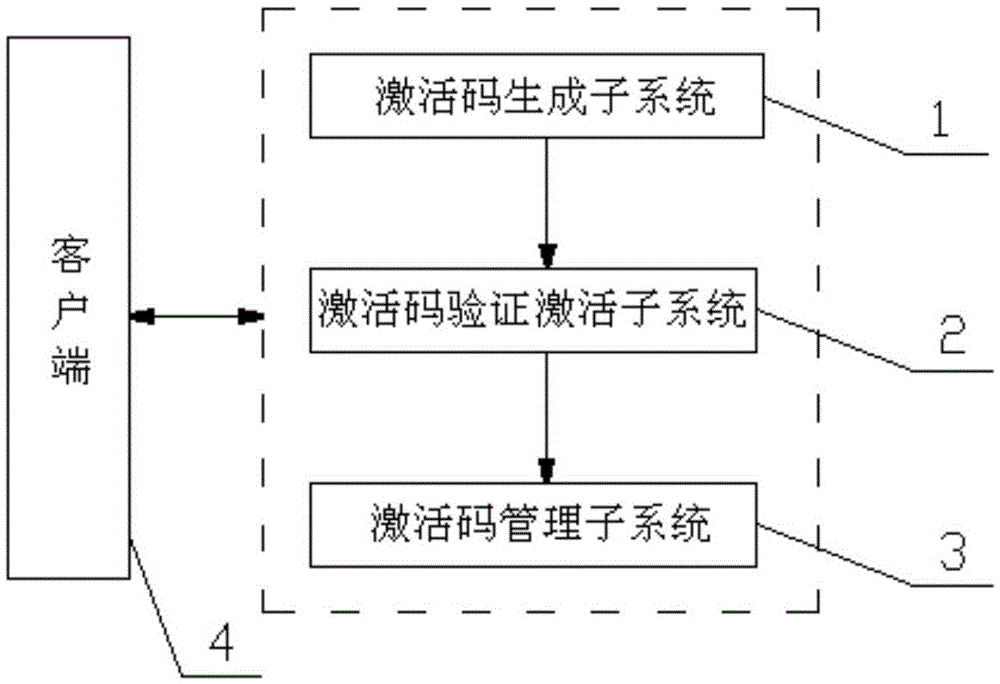
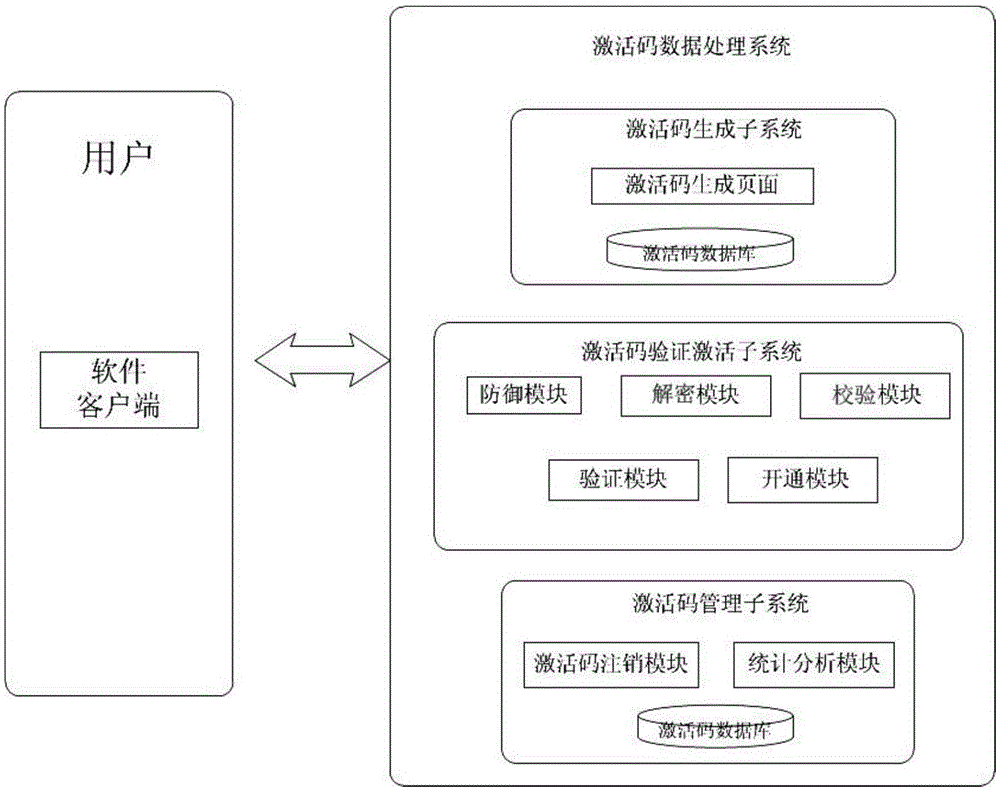
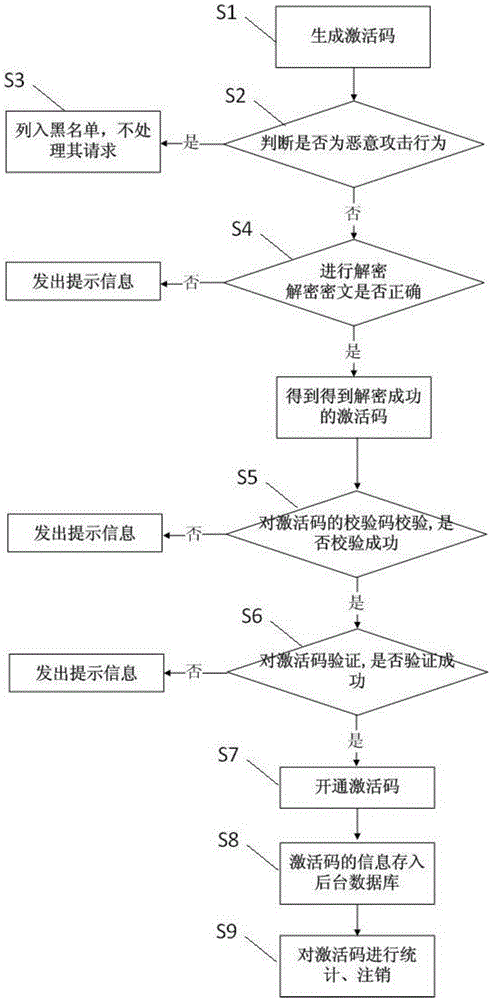
Multi-dimensional information based activation code data processing system and method
ActiveCN105656898AInformativePrevent brute force crackingTransmissionData processing systemStatistical analysis
The present invention provides a multi-dimensional information based activation code data processing system and method. The system comprises an activation code generation sub-system for generating an activation code, an activation code verification activation sub-system for implementing security defense, activation code verification and activation code provisioning, and an activation code management sub-system for statistic management of the activation code. The system has the following advantages of being convenient for statistics and analysis, that is, the activation code has a large amount of information, and static analysis can be performed on the information conveniently according to marketing channels and software classification; being convenient for management and maintenance, that is, activated service logic verification is carried out at a service side, and when the activated service logic verification needs to be adjusted, the service side only needs to be modified and a client side is not modified, thereby facilitating maintenance and management; and being safer, that is, the activation code verification activation sub-system is added, thereby effectively preventing malicious attack, and preventing the activation code from being cracked violently.
Owner:GUANGXI YINGTENG EDUCATION & TECHNOLOGY CO LTD
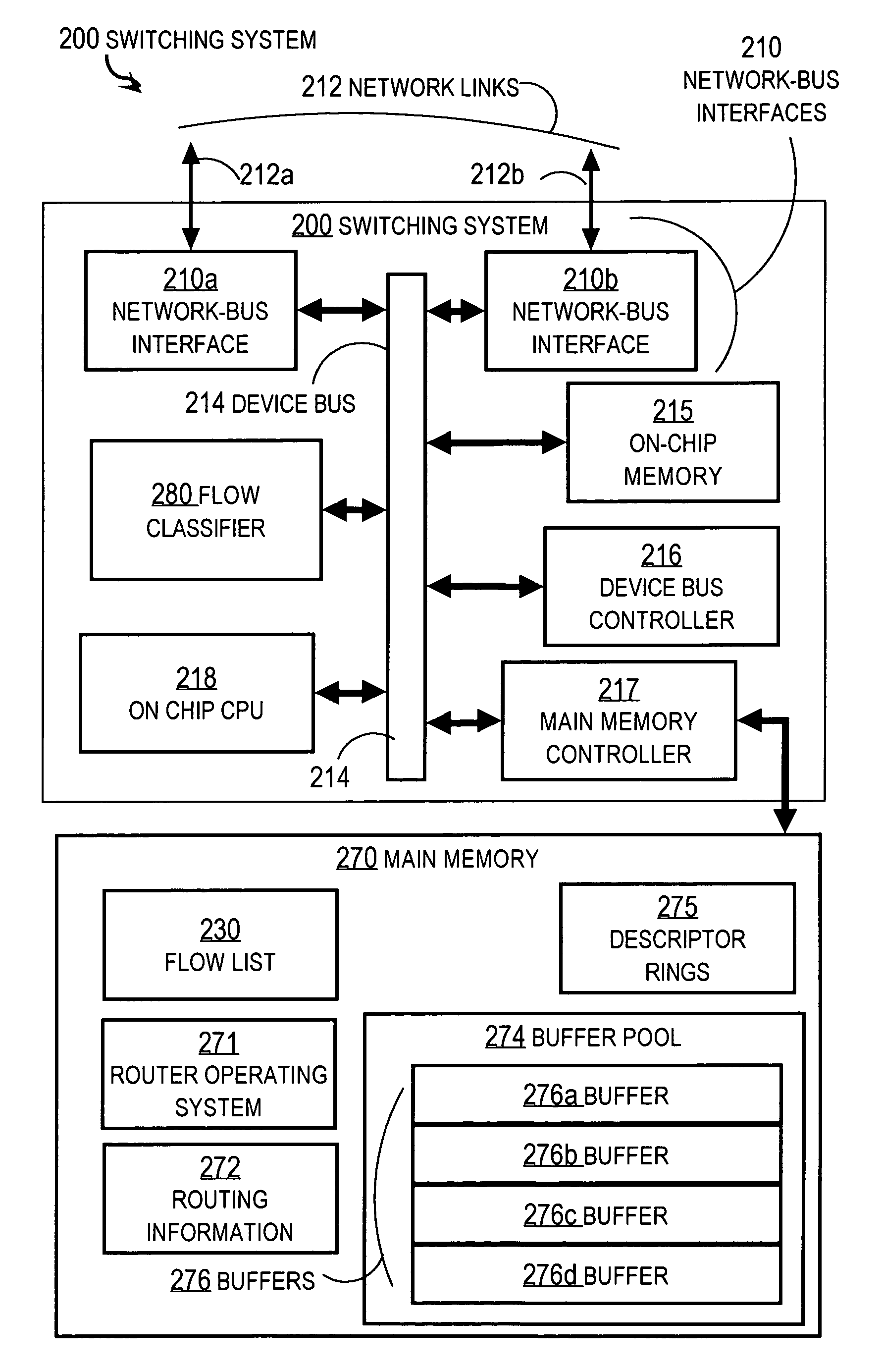
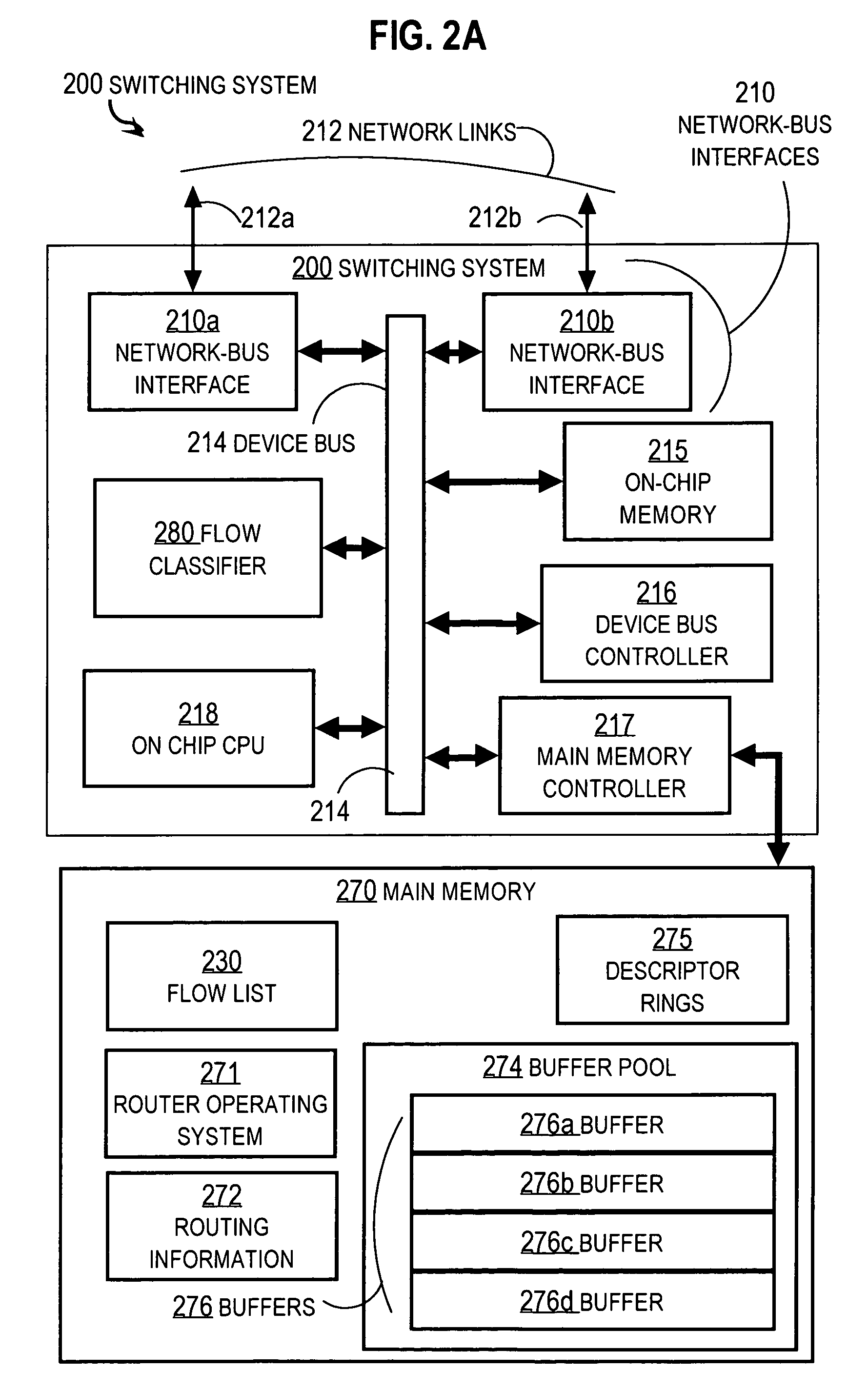
Apparatus for hardware-software classification of data packet flows
ActiveUS8228908B2Time-division multiplexData switching by path configurationGeneral purposeMissing data
An apparatus for routing data packets includes a network interface, a memory, a general purpose processor and a flow classifier. The memory stores a flow structure. Every packet in one flow has identical values for a set of data fields in the packet. The memory stores instruction that cause the processor to receive missing flow data and to add the missing flow to the flow structure. The apparatus forwards a packet based on the flow. The flow classifier determines a particular flow and whether it is already stored in the flow structure. If not, then the classifier determines whether that flow has already been sent to the processor as missing data. If not, then the classifier stores into a different data structure data that indicates the flow has been sent to the processor but is not yet included in the flow data structure, and sends missing data to the processor.
Owner:CISCO TECH INC
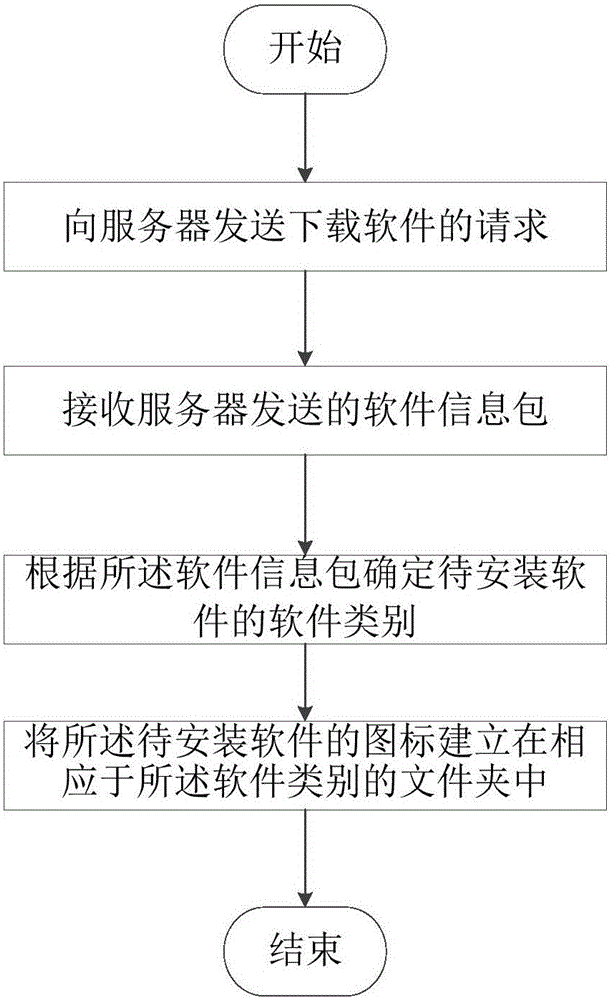
Terminal, server and software classification method
InactiveCN105893470ANo need for manual classificationMetadata still image retrievalSpecial data processing applicationsSoftware engineeringComputer science
The invention relates to the field of terminals, and discloses a terminal, a server and a software classification method. The software classification method comprises the following steps: sending a software downloading request to a server; receiving a software information package sent by the server according to the software downloading request; determining a software category of to-be-installed software according to the software information package; and establishing an icon of the to-be-installed software in a folder corresponding to the software category according to the software category. According to the software classification method, the software icon of the to-be-installed software can be automatically installed in the folder corresponding to the software category without carrying out manual classification by a user.
Owner:LETV HLDG BEIJING CO LTD +1
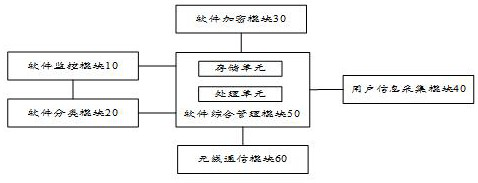
Computer software protection system
PendingCN112307441AImprove securityEase of use guaranteedDigital data protectionDigital data authenticationSoftware engineeringSoftware protection
The invention provides a computer software protection system. The system comprises a software monitoring module, a software classification module, a software encryption module, a user information acquisition module and a software comprehensive management and control module; the software monitoring module is used for detecting the software category, downloading time and use frequency of softwares in a computer; the software classification module is used for performing classification processing on the softwares according to the software category, downloading time and use frequency of the softwares and distributing classification results to the software comprehensive management and control module; the software encryption module is used for calling a classification result from the software comprehensive management and control module to classify and encrypt software; the user information acquisition module is used for acquiring login information and fingerprint information of a user and sending the login information and the fingerprint information to the software comprehensive management and control module; and the software comprehensive management and control module is used for confirming the use permission of the user to the software according to the login information and the fingerprint information of the user and decrypting the softwares in the use permission range.
Owner:LUOYANG INST OF SCI & TECH
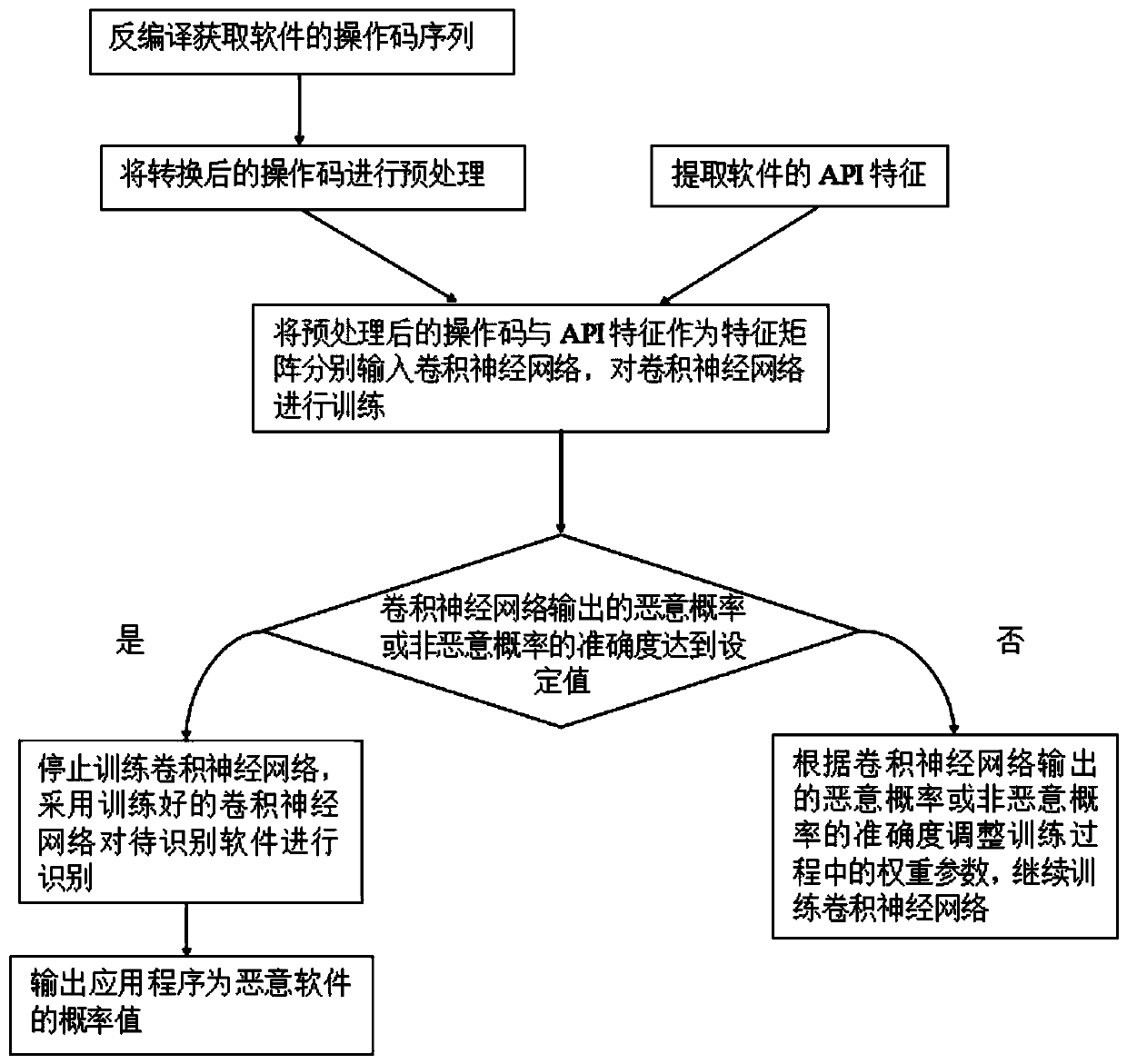
Malicious software classification method and system based on dual-channel convolutional neural network
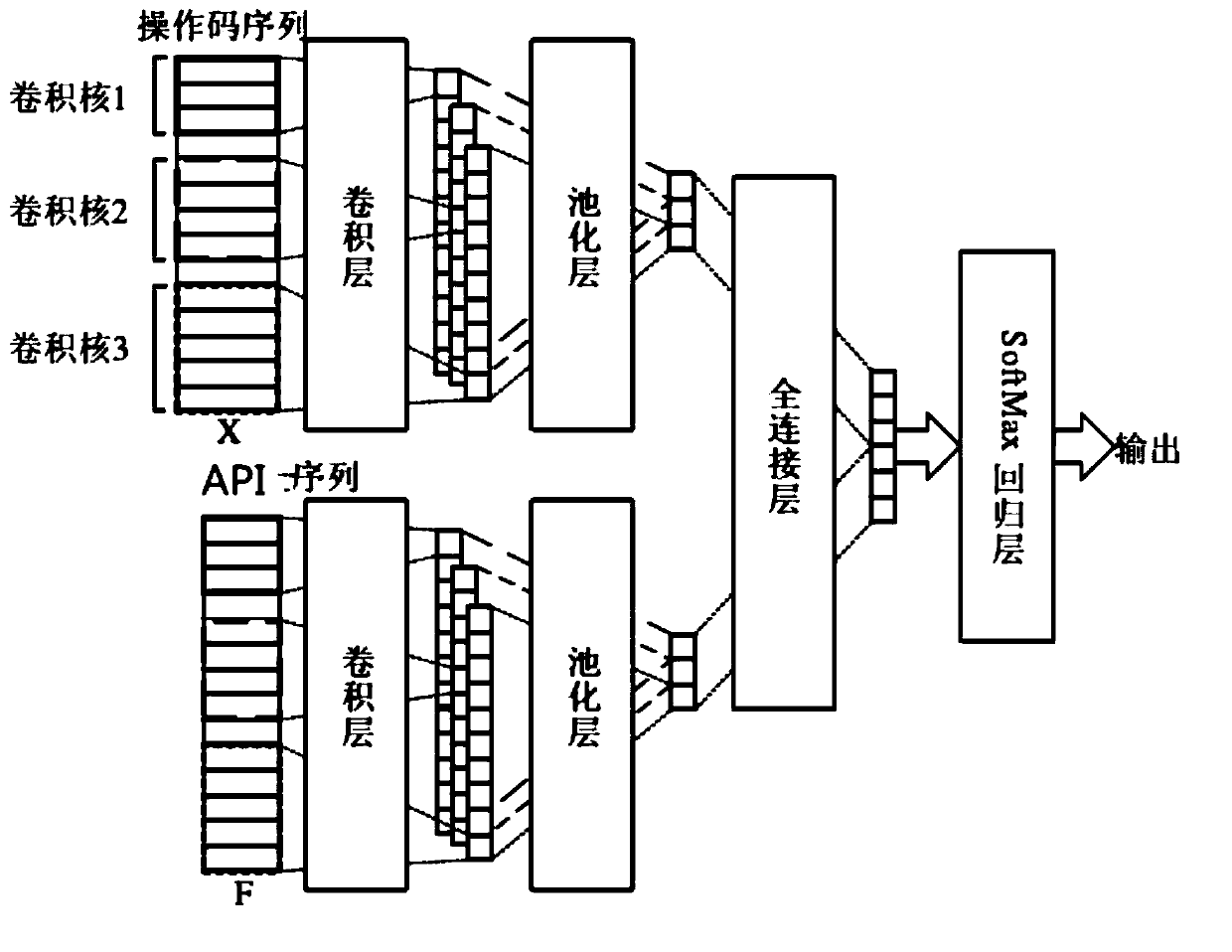
InactiveCN110458239AImprove persuasivenessFrequent instruction associationCharacter and pattern recognitionPlatform integrity maintainanceFeature extractionApplication software
The invention discloses a malicious software classification method and system based on a dual-channel convolutional neural network, and the system comprises: a training sample processing module and anoperation code extraction module which are used for decompiling a training sample, and obtaining an operation code sequence of an application program; an API feature extraction module which is used for obtaining sensitive API features of the training sample; a dual-channel convolutional neural network training module which is used for training by using the operation code sequence and the sensitive API feature sequence and obtaining a dual-channel convolutional neural network of which the output is accurate; an accuracy judgment module and a detection module which are used for judging whetherthe accuracy output by the dual-channel convolutional neural network reaches a set value or not, and detecting the to-be-identified software when the accuracy reaches the set value; and a probabilityoutput module which is used for outputting a probability value that the to-be-identified software is malicious software. According to the method, the advantages of the operation code sequence of the application program and the sensitive API feature detection are combined, and the accuracy and the data processing are greatly improved.
Owner:东北大学秦皇岛分校
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com