Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
150 results about "Risk characteristics" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
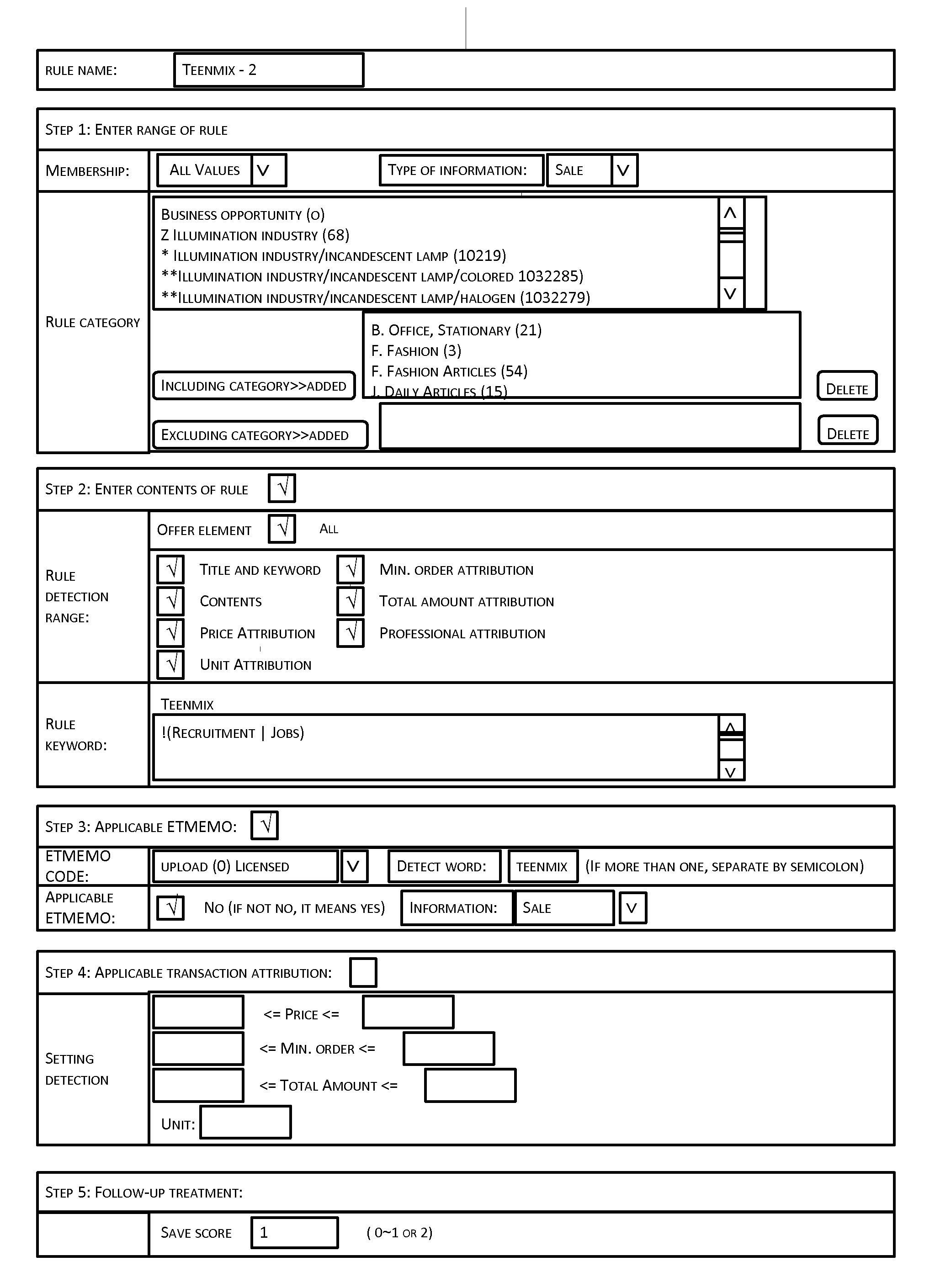
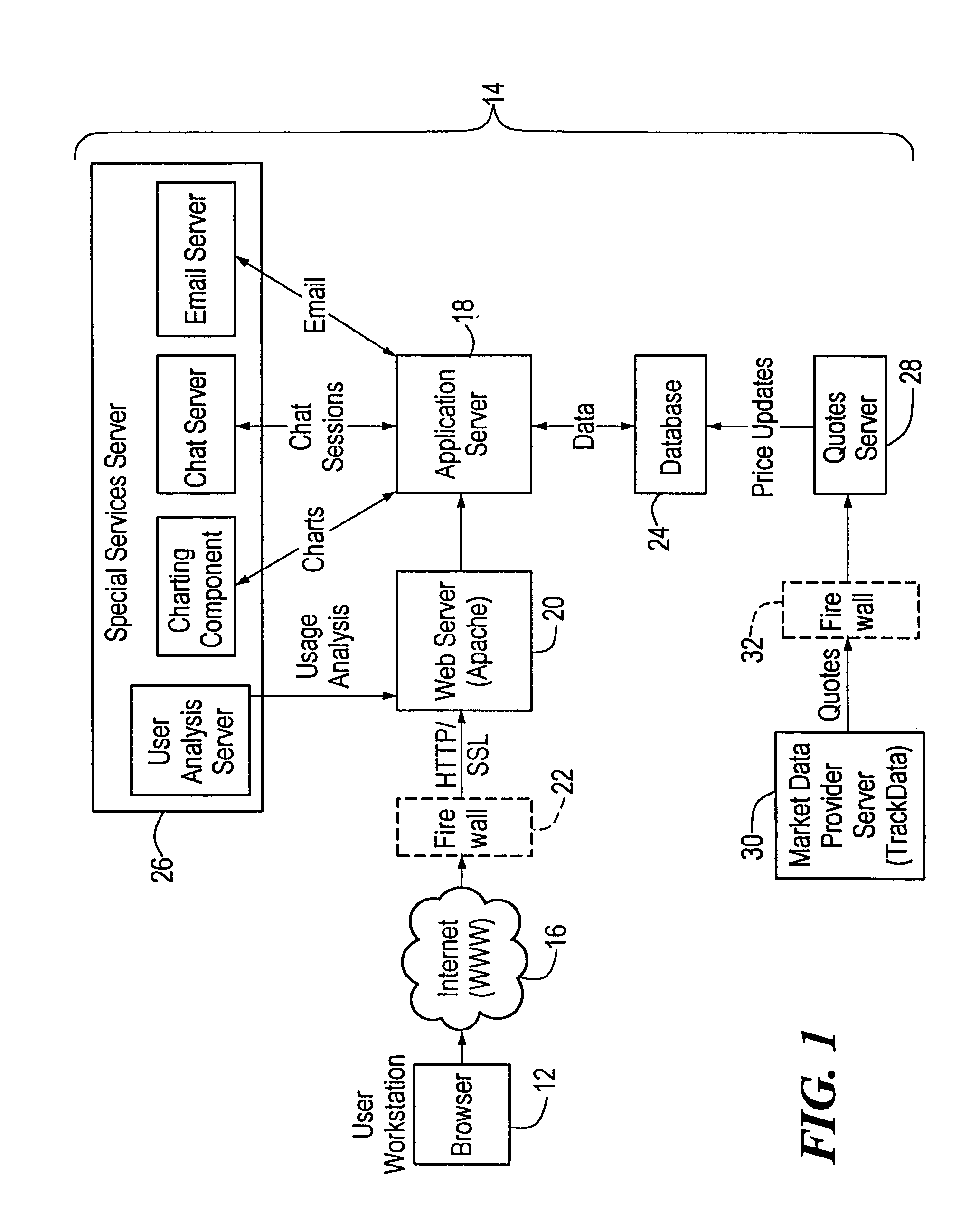
Method and System of Web Page Content Filtering
InactiveUS20120131438A1Low efficiencyAccurate contentComputer security arrangementsTransmissionE-commerceWeb page
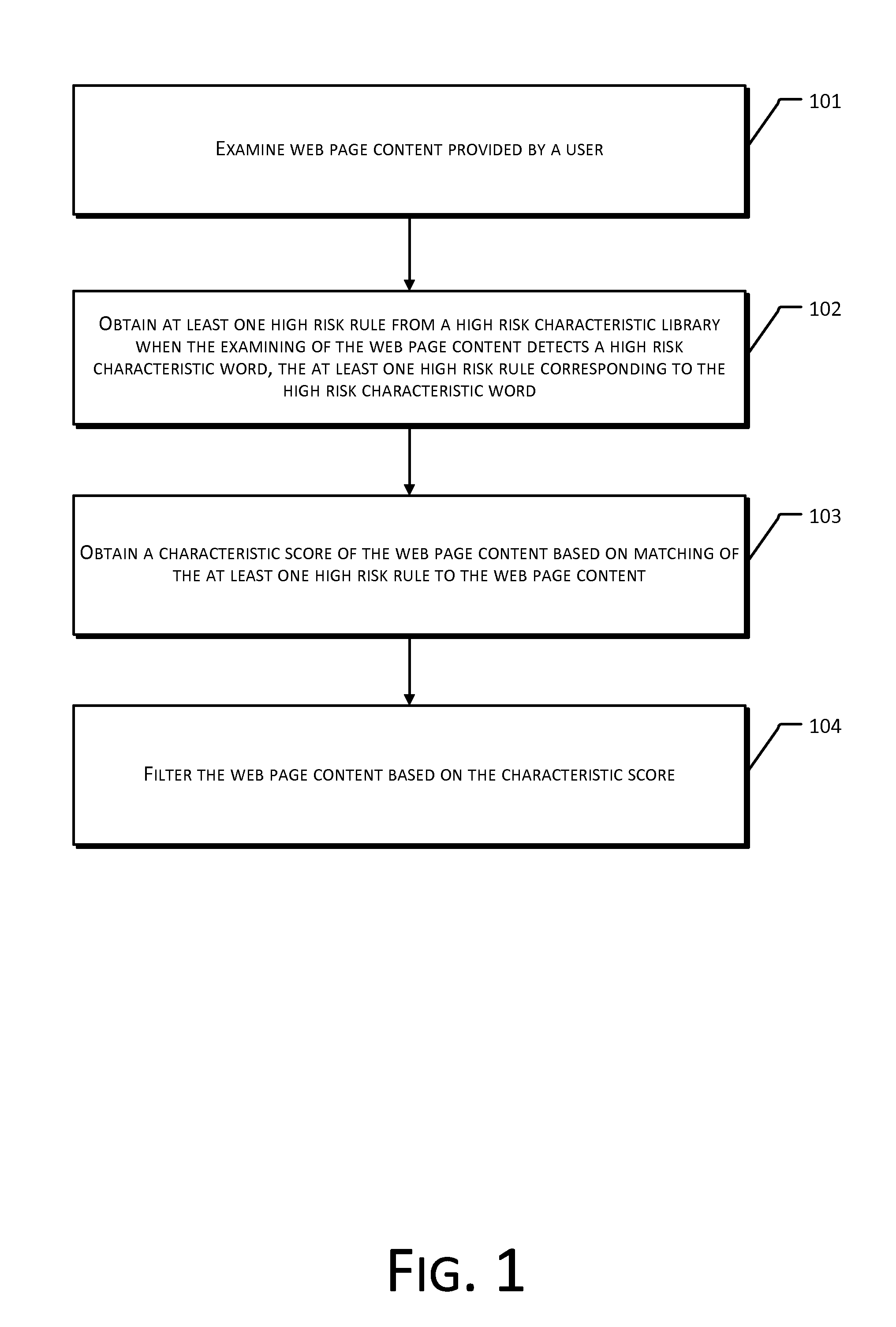
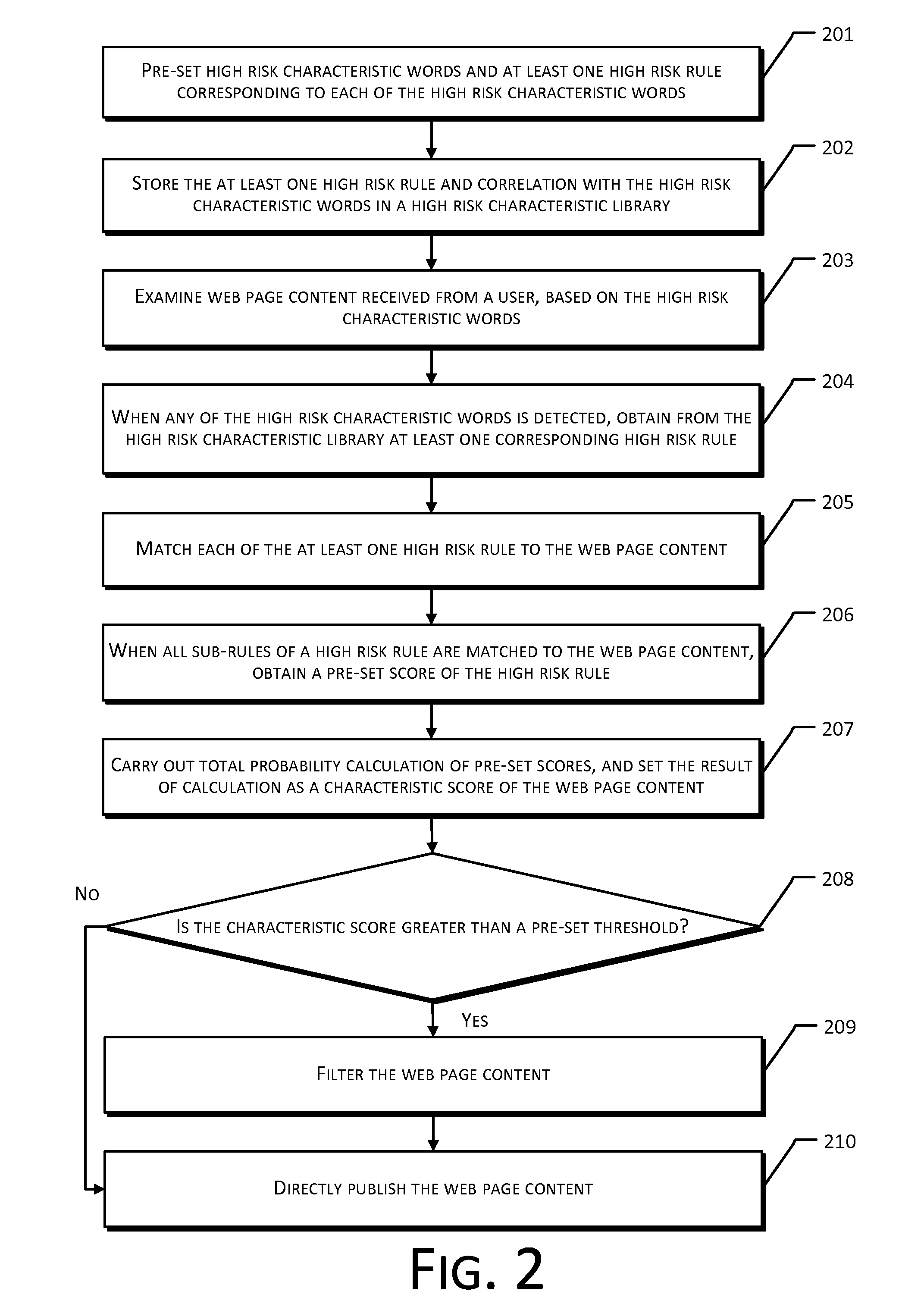
The present disclosure provides a method and system for web page content filtering. A method comprises: examining the web page content provided by a user; obtaining at least one high risk rule from a high risk characteristic library when the examining of the web page content detects a high risk characteristic word, the at least one high risk rule corresponding to the high risk characteristic word; obtaining a characteristic score of the web page content based on matching of the at least one high risk rule to the web page content; and filtering the web page content based on the characteristic score. The difference between the present disclosure and prior art techniques is that the disclosed embodiments can more precisely carry out web page content filtering to achieve better real-time safety and reliability of an e-commerce transaction.
Owner:ALIBABA GRP HLDG LTD
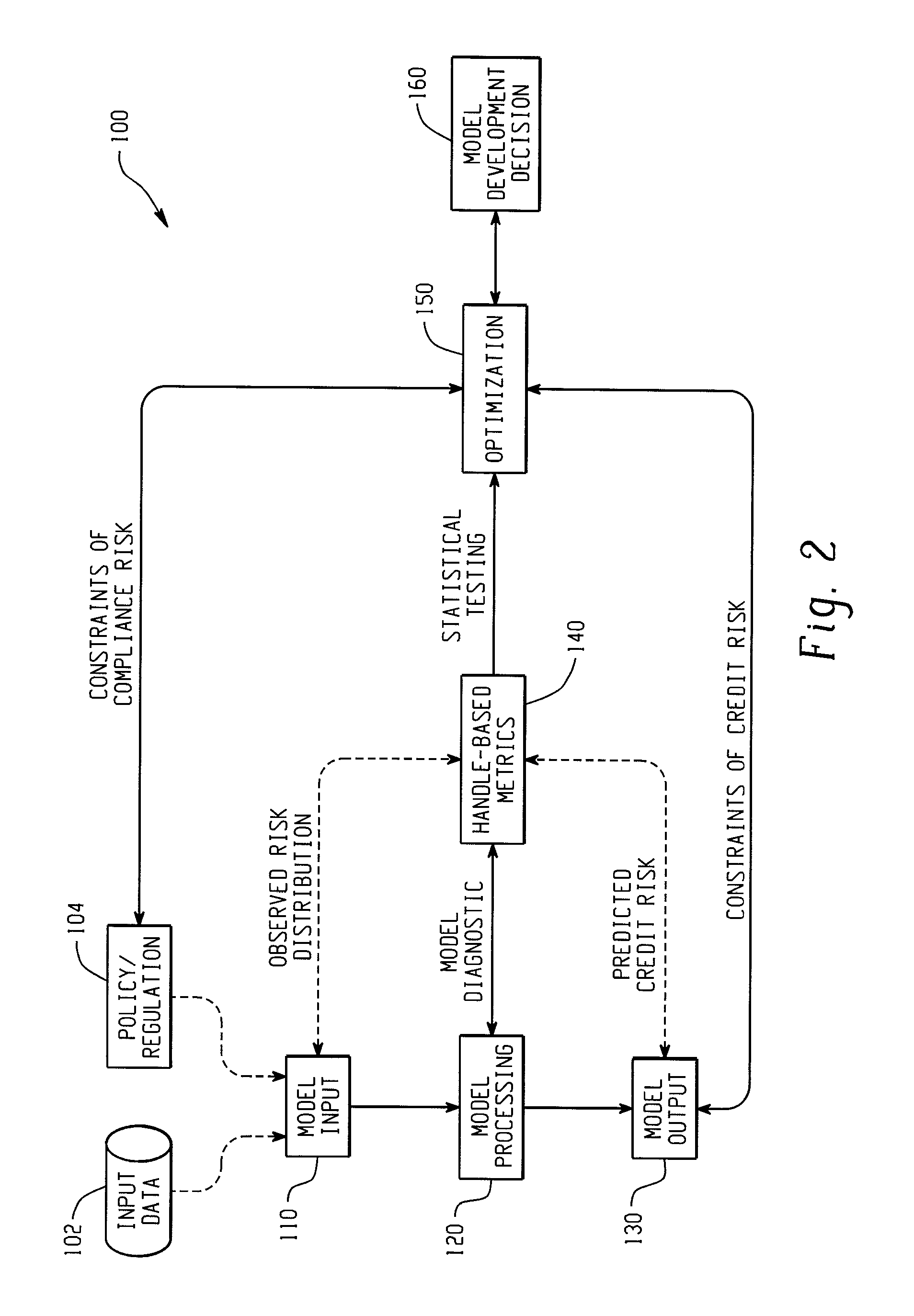
Computer-implemented systems and methods for integrated model validation for compliance and credit risk
ActiveUS8515862B2Accurate and explicit and testingMaximizing predictabilityFinanceFuzzy logic based systemsTheoretical computer scienceProcess validation
Computer-implemented systems and methods are provided for model validation of a model for compliance and credit risk. Model input, output, and processing validation areas are contained on a computer system. A handle data structure connects the model validation areas with handles that comprise a unified metric. A handle represents combinations of covariate patterns and describes the joint distribution of risk characteristics.
Owner:SAS INSTITUTE
Computer-Implemented Systems And Methods For Integrated Model Validation For Compliance And Credit Risk
ActiveUS20090299896A1Improve efficiencyImprove fairnessFinanceFuzzy logic based systemsTheoretical computer scienceComputerized system
Computer-implemented systems and methods are provided for model validation of a model for compliance and credit risk. Model input, output, and processing validation areas are contained on a computer system. A handle data structure connects the model validation areas with handles that comprise a unified metric. A handle represents combinations of covariate patterns and describes the joint distribution of risk characteristics.
Owner:SAS INSTITUTE
Systems and methods for quantifying flood risk
In various embodiments, a flood risk score may be determined for a property point that provides a comprehensive assessment of the property point's risk of flooding. Determining the flood risk score may include determining a flood risk characteristic for the property point and assigning a flood risk score that corresponds to the flood risk characteristic. In some embodiments, flood risk characteristics may include a difference in elevation between the elevation of the property point and an elevation of a calculated point (e.g., on a known flood risk zone boundary). Flood risk characteristics may also include a flood zone determination for the property point and / or proximity of the property point to a known flood risk zone boundary or a flood source. In some embodiments, flood risk scores may be provided on flood risk score reports.
Owner:CORELOGIC SOLUTIONS
Systems and methods for USA Patriot Act compliance
In preferred embodiments, the present invention includes computer-implemented methods and computer systems for know-your-customer risk assessment that assemble a plurality of data elements descriptive of the risk characteristics of a designated customer, wherein at least one data element is descriptive or risk characteristics determined by a government, weigh a selected plurality of the assembled data elements relative to the risk indicated by the determined data element values, and combine the weighted data elements into one or more indices representative of the know-your-customer risk of the designated customer. The present invention also includes computer readable media with computer code for performing these methods.
Owner:THE DUN & BRADSTREET CORPORATION
Analyzing investment data
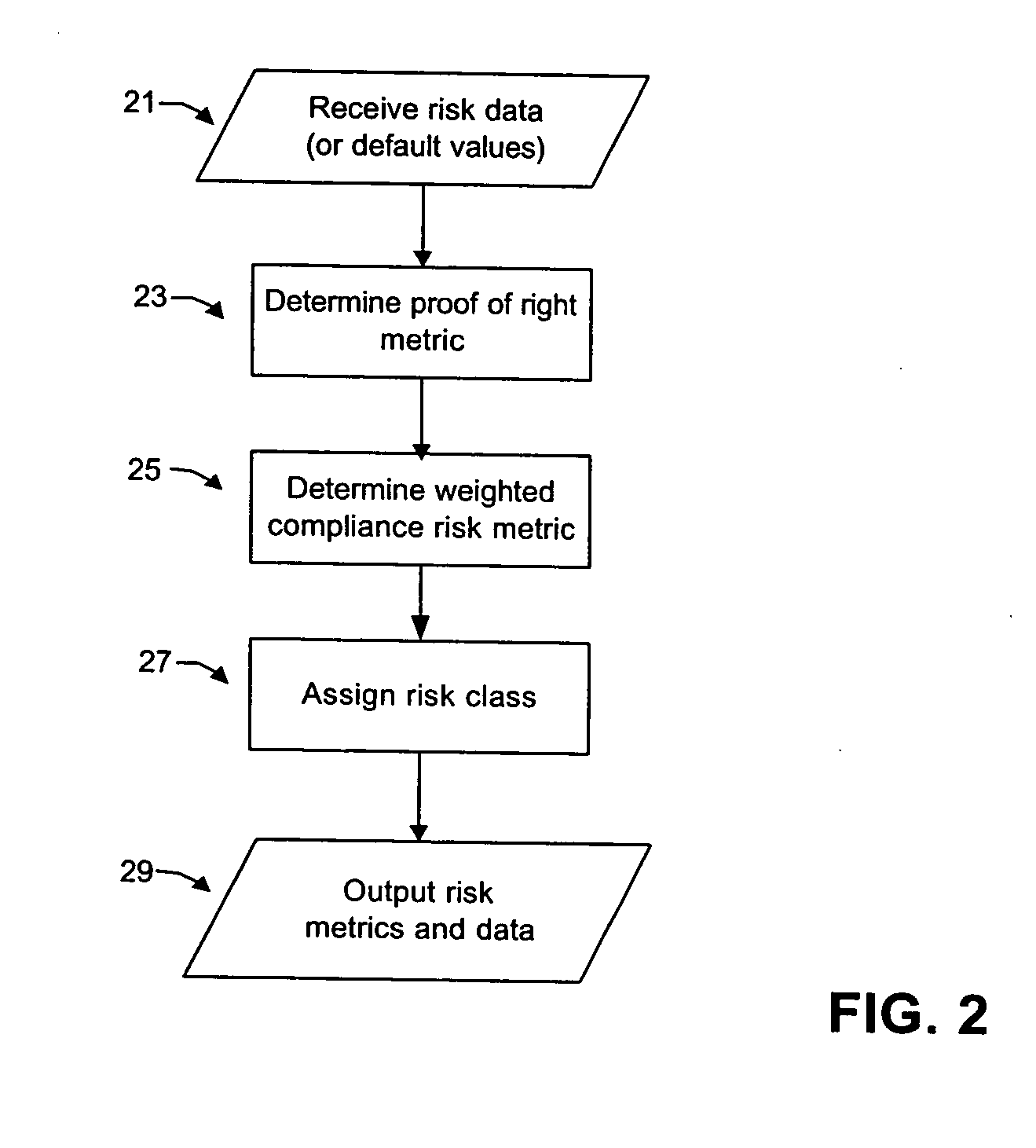
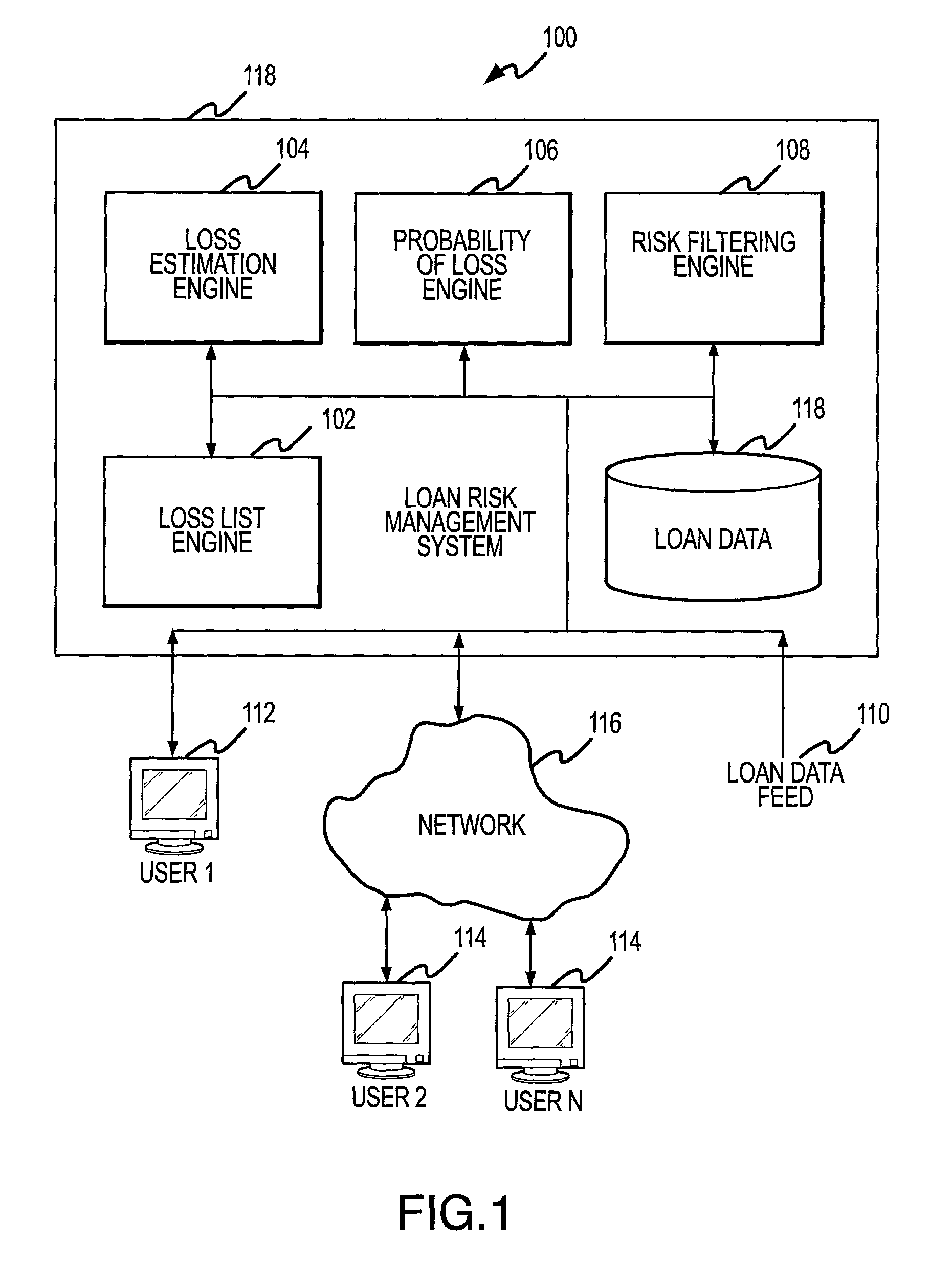
A system and method for analyzing loan data to identify risk. In a database, loan data is stored with one or more associated characteristics. The system includes a risk filtering engine is in communication with the database so that a user may apply one or more risk filters to the loan data to identify particular loans with particular risk characteristics. The system further includes a loss estimation engine for providing an estimated loss for each loan, a probability of loss engine for determining a probability of loss for each loan, and a loss list engine for generating a list of loans with heightened risk of loss.
Owner:CLAYTON FIXED INCOME SERVICES
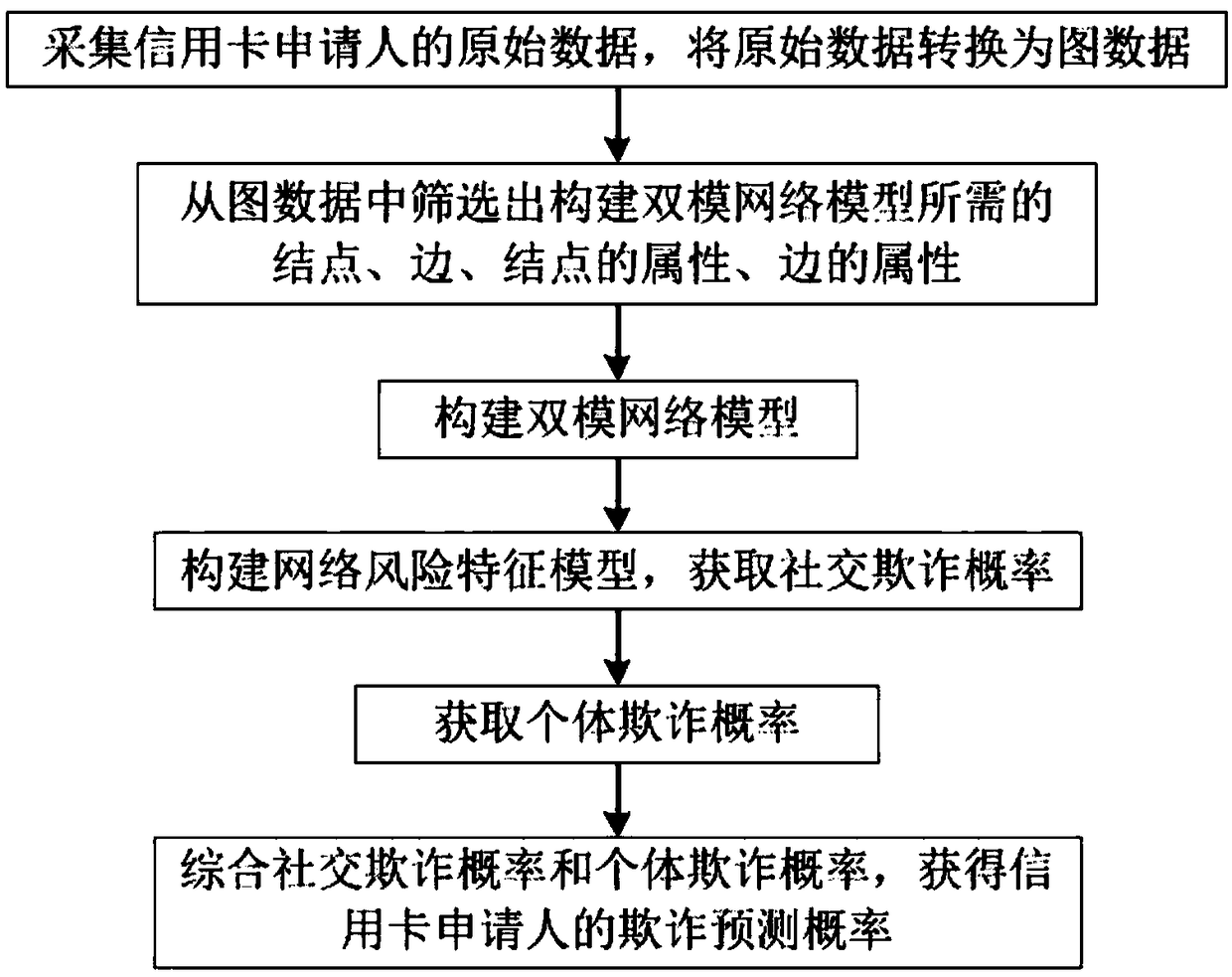
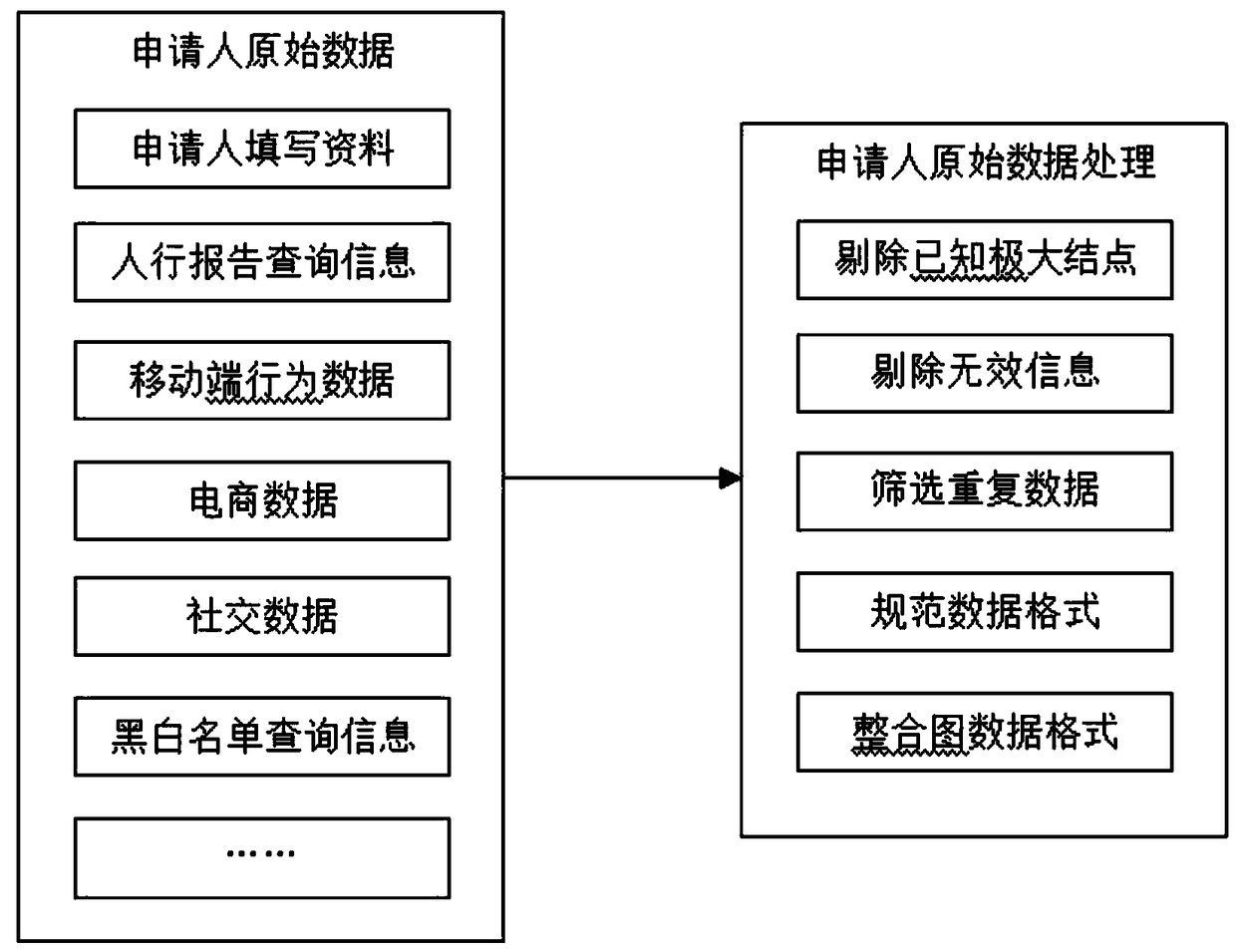
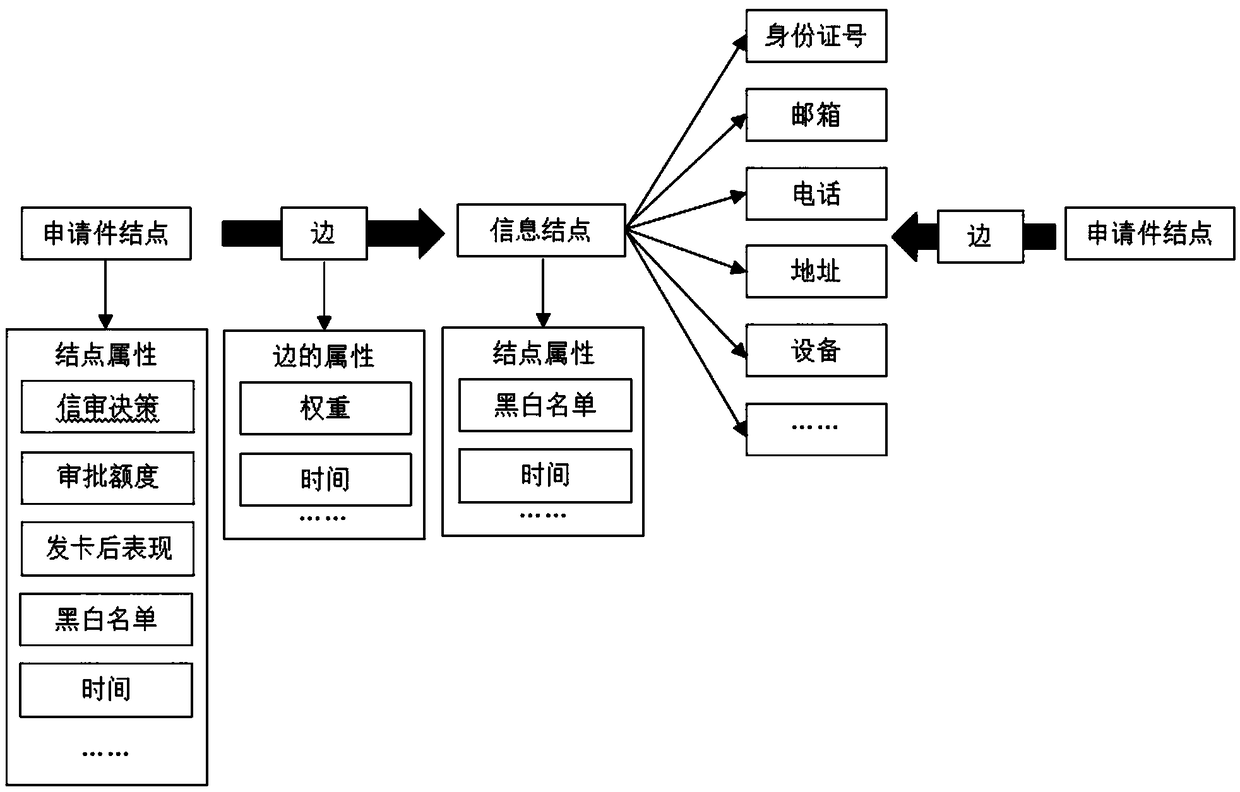
Credit card anti-fraud prediction method based on dual-mode network diagram mining algorithm
InactiveCN108492173AReal-time computingSolve the problem of risk identificationFinanceComputing modelsCredit cardRisk Control
The invention discloses a credit card anti-fraud prediction method based on a dual-mode network diagram mining algorithm. The method concretely comprises the following steps that the original data ofthe credit card applicant is acquired and the original data are converted into the diagram data; the nodes, the edges, the attributes of the nodes and the attributes of the edges required for constructing a dual-mode network model are selected out of the diagram data through screening; the dual-mode network model is constructed; a network risk characteristic model is constructed and the probability of network fraud is acquired; the probability of personal fraud is acquired; and the probability of network fraud and the probability of personal fraud are integrated so as to obtain the fraud prediction probability of the credit card applicant. The multidimensional data information related to the applicant is collected, the credit card application field data knowledge map is constructed, the dual-mode network model capable of reflecting the correlation between the clients is acquired and the influence of the individual and group risk on the applicant fraud probability can be accurately integrated so that the risk of identity forgery, group fraud and group attack can be effectively reduced, and the financial anti-fraud risk control capacity can be enhanced.
Owner:上海氪信信息技术有限公司 +1
Systems and methods for USA Patriot Act compliance
In preferred embodiments, the present invention includes computer-implemented methods and computer systems for know-your-customer risk assessment that assemble a plurality of data elements descriptive of the risk characteristics of a designated customer, wherein at least one data element is descriptive or risk characteristics determined by a government, weigh a selected plurality of the assembled data elements relative to the risk indicated by the determined data element values, and combine the weighted data elements into one or more indices representative of the know-your-customer risk of the designated customer. The present invention also includes computer readable media with computer code for performing these methods.
Owner:THE DUN & BRADSTREET CORPORATION
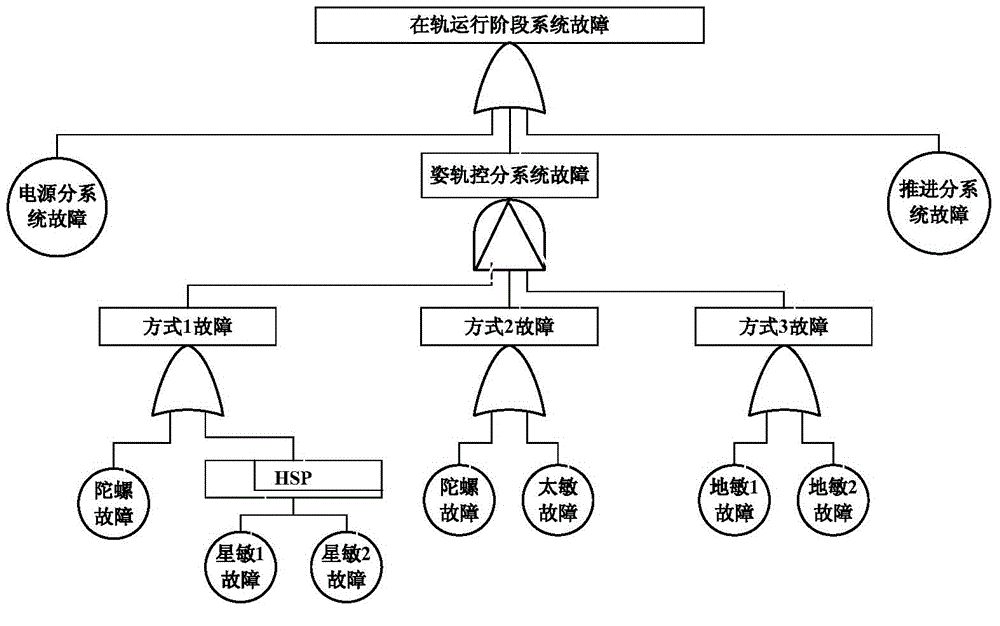
Multi-stage task spacecraft reliability improving method based on risks
ActiveCN104317990AAccurately describe routine failuresAccurately characterize failure riskSpecial data processing applicationsModelling analysisImproved method
The invention relates to a multi-stage task spacecraft reliability improving method based on risks. The multi-stage task spacecraft reliability improving method based on the risks comprises the following steps of (1) determining the conversion relation of a key task stage and a task result state and between the task result states, (2) the key task stage risk characteristic is analyzed, a fault tree, a dynamic fault tree and a Bayes network method are used, a risk characteristic model is built, and relative data are collected to determine the key task failure occurring possibility and main risk factors, and (3) a spacecraft task process event tree model is built, the different task result state possibility is obtained by solving the model, the main risk factors are combined, and reliability improving measures are made. The multi-stage task spacecraft reliability improving method can realize the multi-stage task spacecraft conventional invalidity, redundancy backup invalidity and relative invalidity modeling analysis, the task result state possibility and the main risk factors are obtained, and the multi-stage task spacecraft reliability improving method based on the risks can provide technical support for the spacecraft reliability improving.
Owner:CHINA ACAD OF LAUNCH VEHICLE TECH
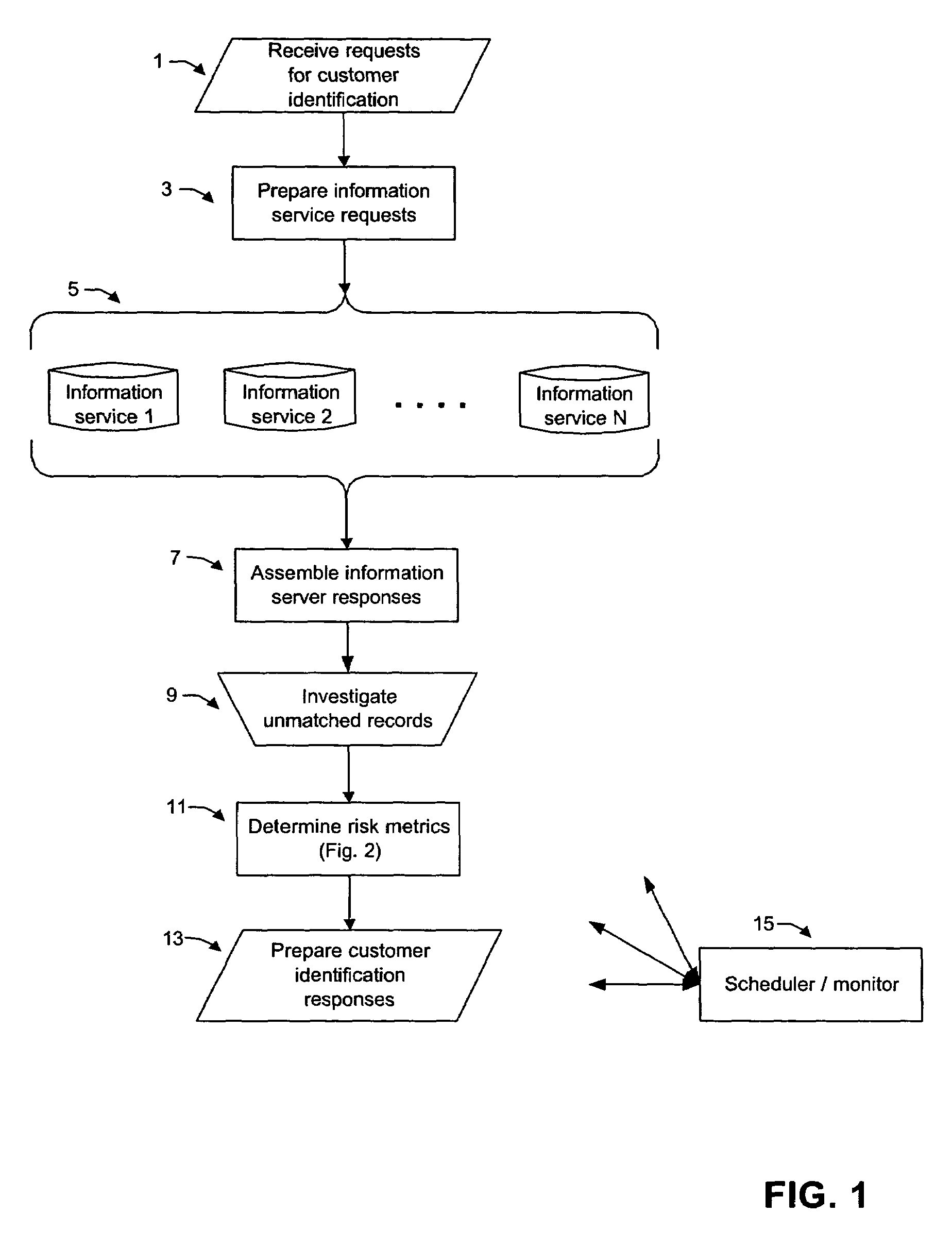
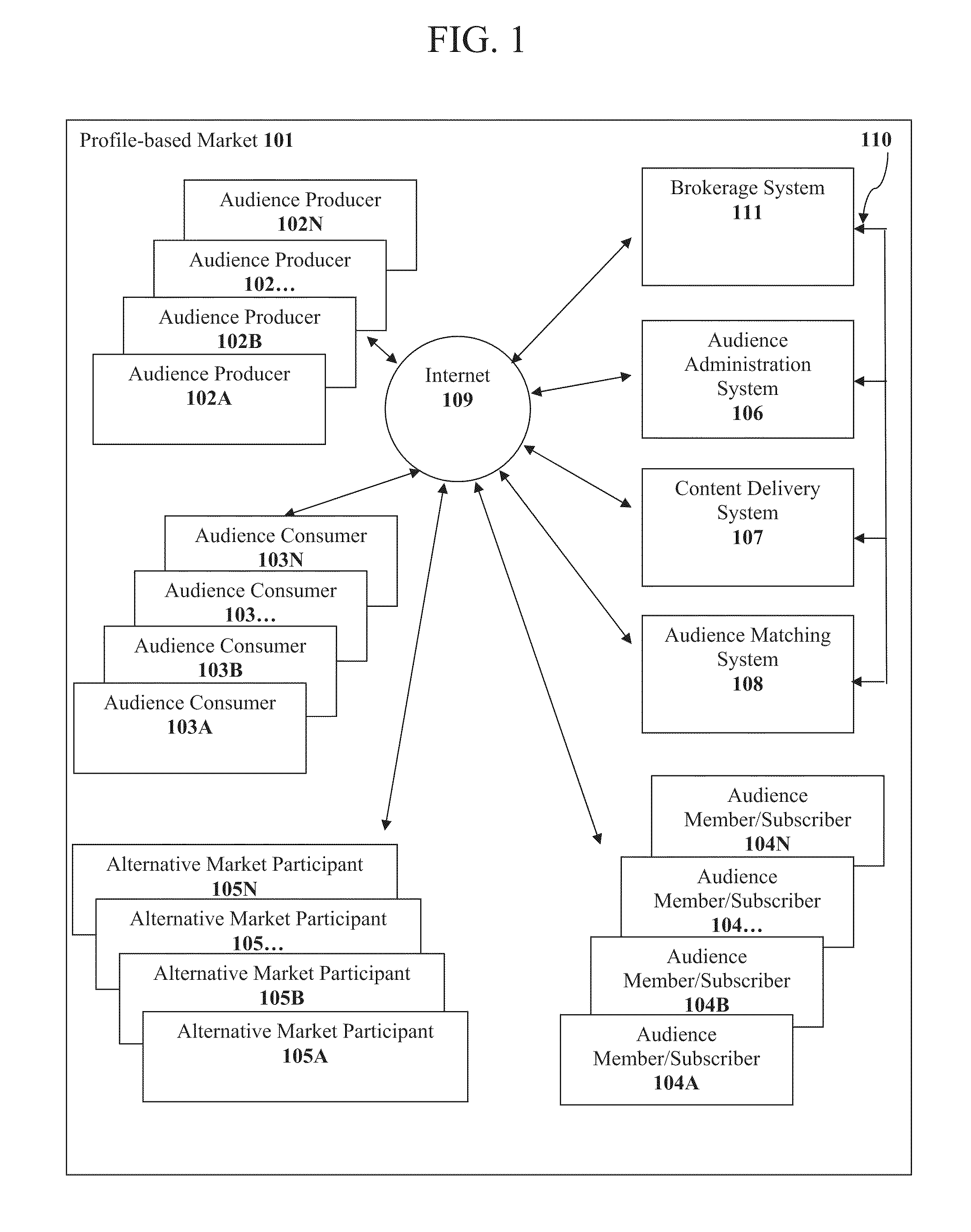
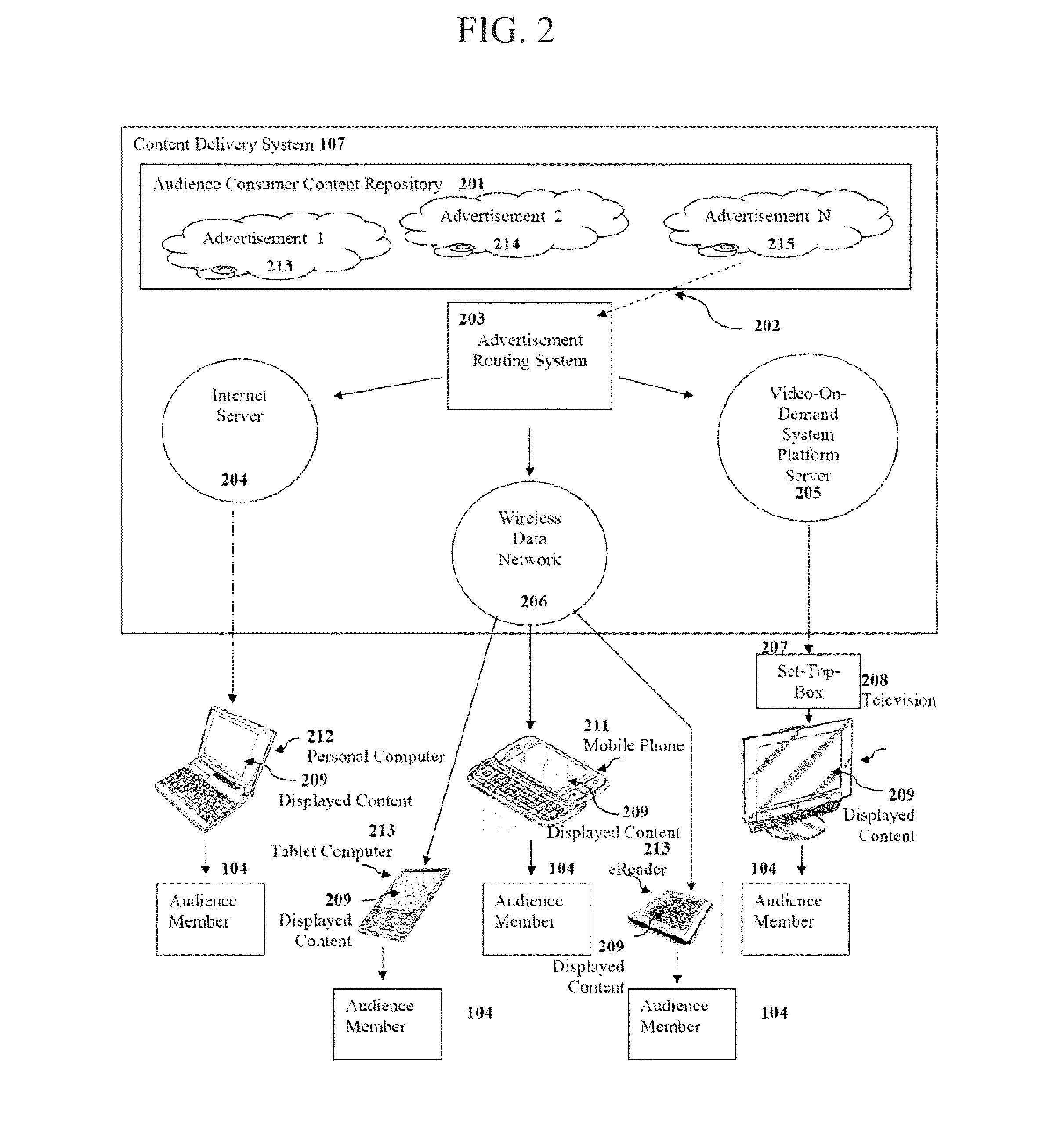
Methods, Systems, and Computer Program Products For Managing Organized Binary Advertising Asset Markets
Binary advertising markets are developed where personalized media such as digital and even analog advertising is delivered to and accessed by audience members enabling advertisers to buy advertising for broadcast to televisions, smartphones and other types of digital devices. The market is designed to provide participants a new way to have their orders entered, matched, executed, and settled, to manage and monitor risk characteristics of their content placement or advertising placement transactions, and any rights and positions that result from those transactions. Standardized units of exchange represented by profile access rights and display space access rights appropriately designed for their respective markets are used in both primary direct and secondary alternative markets. Processes are also implemented where an audience member receives economic benefit in exchange for confirming view of or rating an advertisement, or viewing advertisements while logged in.
Owner:MANAGED AUDIENCE SHARE SOLUTIONS
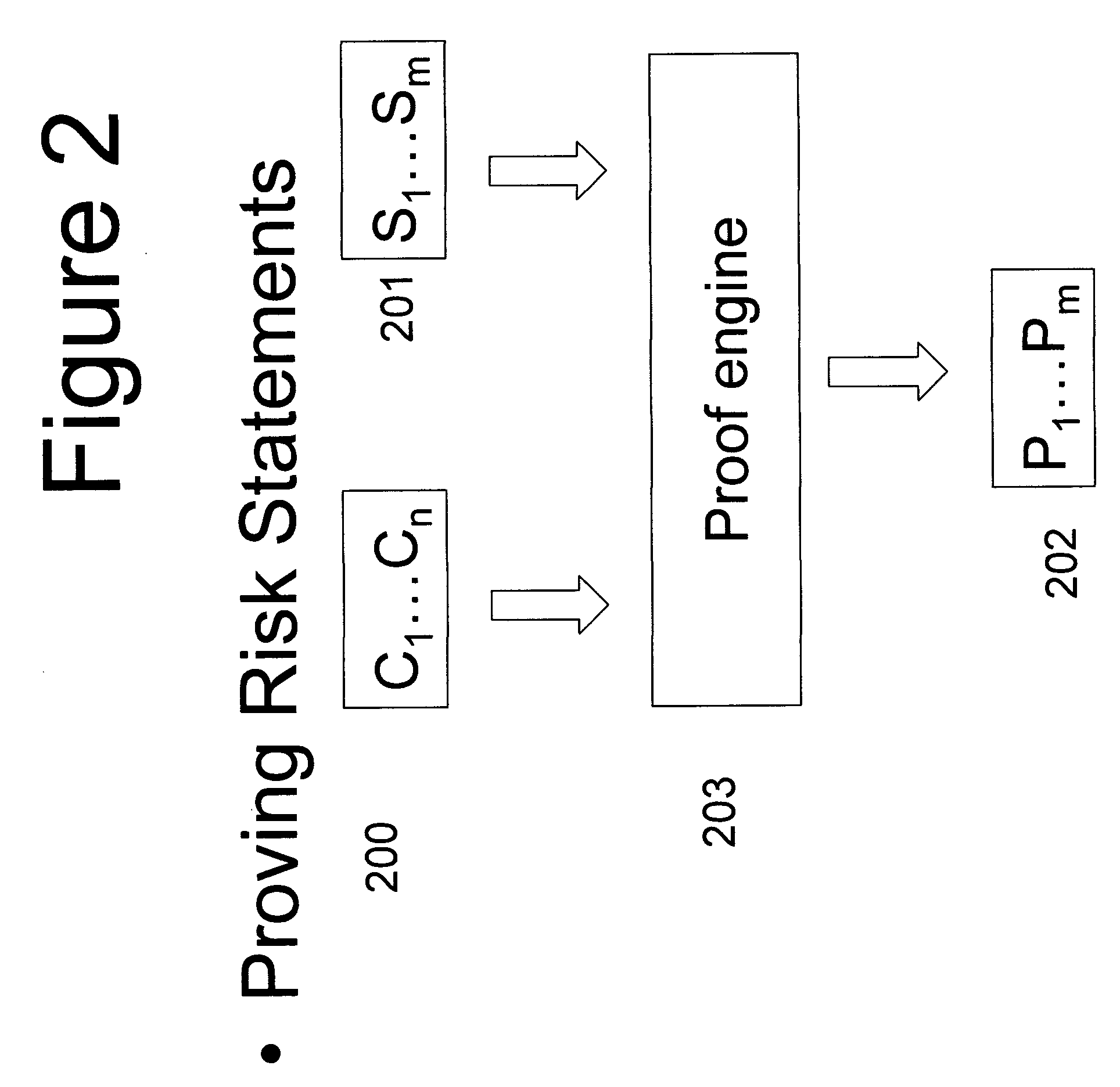
Process for verifiably communicating risk characteristics of an investment portfolio
In accordance with a preferred embodiment of the invention, there is disclosed a process for verifiably communicating risk characteristics of an investment portfolio to an investor without disclosing the exact composition of the portfolio comprising: A procedure for the investment manager to describe acceptable characteristics of an investment portfolio within the portfolio's prospectus, An algorithm and procedure for the investment manager to cryptographically commit to portfolio contents without disclosing the exact composition, An algorithm and procedure to calculate the risk statistics concerning the limitations specified in the prospectus concerning the acceptable configurations of assets holdings without disclosing the exact composition, An algorithm and procedure employing cryptographic means to prove that each such statistic is within the numerical range specified in the prospectus, An algorithm and procedure to check the validity of proofs claiming that each statistic is within a particular range, and A set of procedures involving one or more third parties to provide assistence, including sending the commitments for portfolio contents to a court or to a regulatory body in case of dispute.
Owner:SZYDLO MICHAEL GREGORY
Enterprise operation risk prediction method and system
ActiveCN110889556AImprove forecast accuracyImprove accuracyWeb data indexingForecastingBusiness enterpriseKnowledge graph
The invention relates to an enterprise operation risk prediction method. The method includes collecting the information data inside and outside an enterprise, and performing the data fusion processingon the collected information data; constructing and drawing a knowledge graph by utilizing the processed information data; extracting operation risk characteristic information data of an enterprise needing risk prediction from the knowledge graph by using a graph embedding method, and constructing an operation risk model by using the operation risk characteristic information data; and inputting the enterprise information data of which the risk needs to be predicted into the operation risk model, so that the development risk of the enterprise can be predicted and judged, correct decision on risk management of the enterprise of which the risk needs to be predicted is facilitated, and the asset safety of the enterprise of which the risk needs to be predicted is protected.
Owner:FUJIAN YIRONG INFORMATION TECH +4
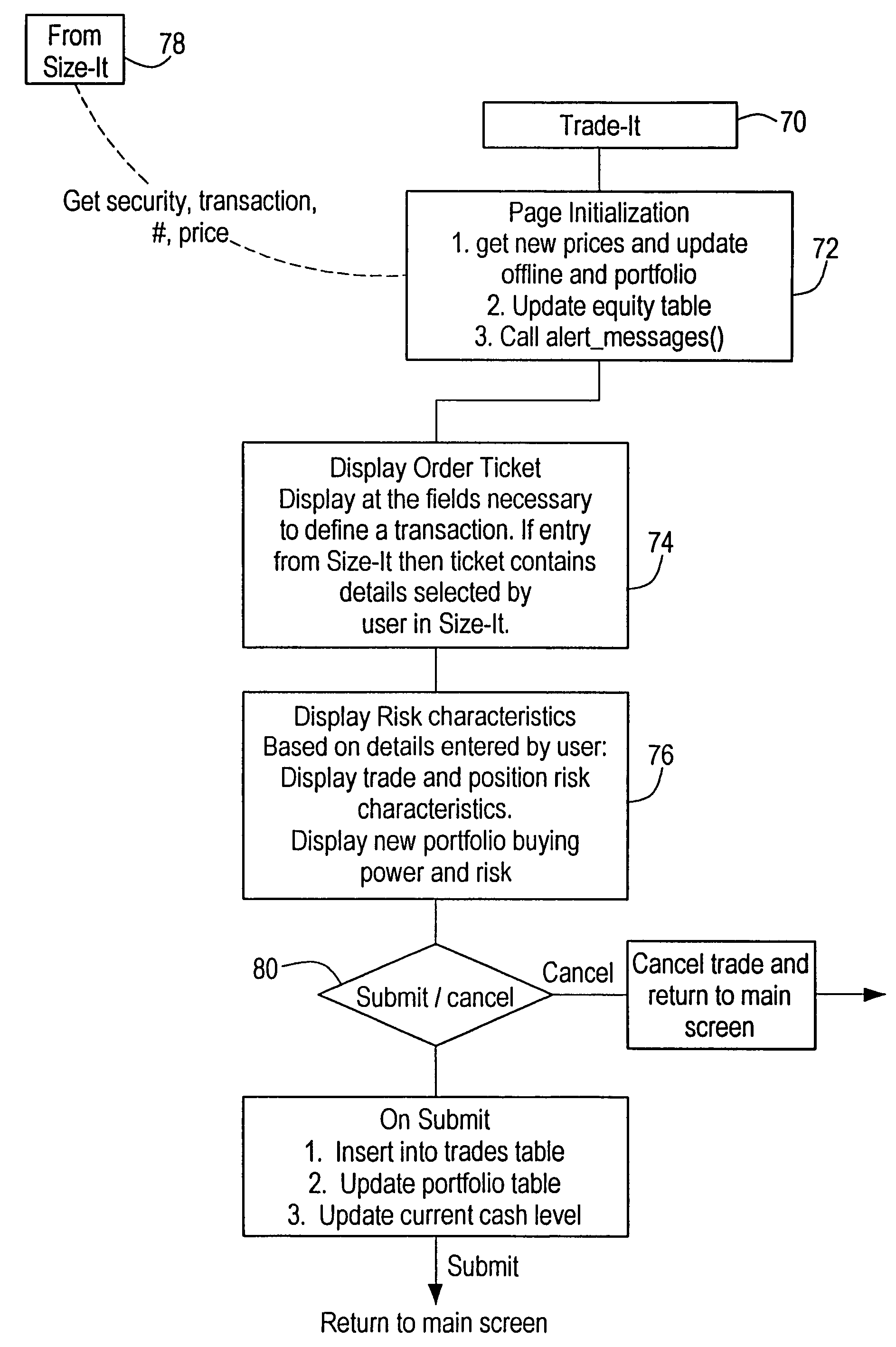
Portfolio accounting and risk management system
A method and system for managing investment portfolio risk on a computer system. A plurality of parameters, including an identifier, a market price, a stop-loss price, a commission, a skid, and a number of shares or contracts all associated with an investment instrument, are stored on a computer-readable medium, along with an equity value associated with a user's portfolio. A point risk value is determined for a potential investment. The point risk value is an intermediate value multiplied by the number of shares or contracts, the intermediate value comprising the market price minus the stop-loss price plus the commission plus the skid (for long transactions). A plurality of risk scenarios are displayed showing proposed numbers of shares or contracts associated with the point risk value for a plurality of selected size risk values. Other risk characteristics may also be determined and displayed.
Owner:BARON TRUST
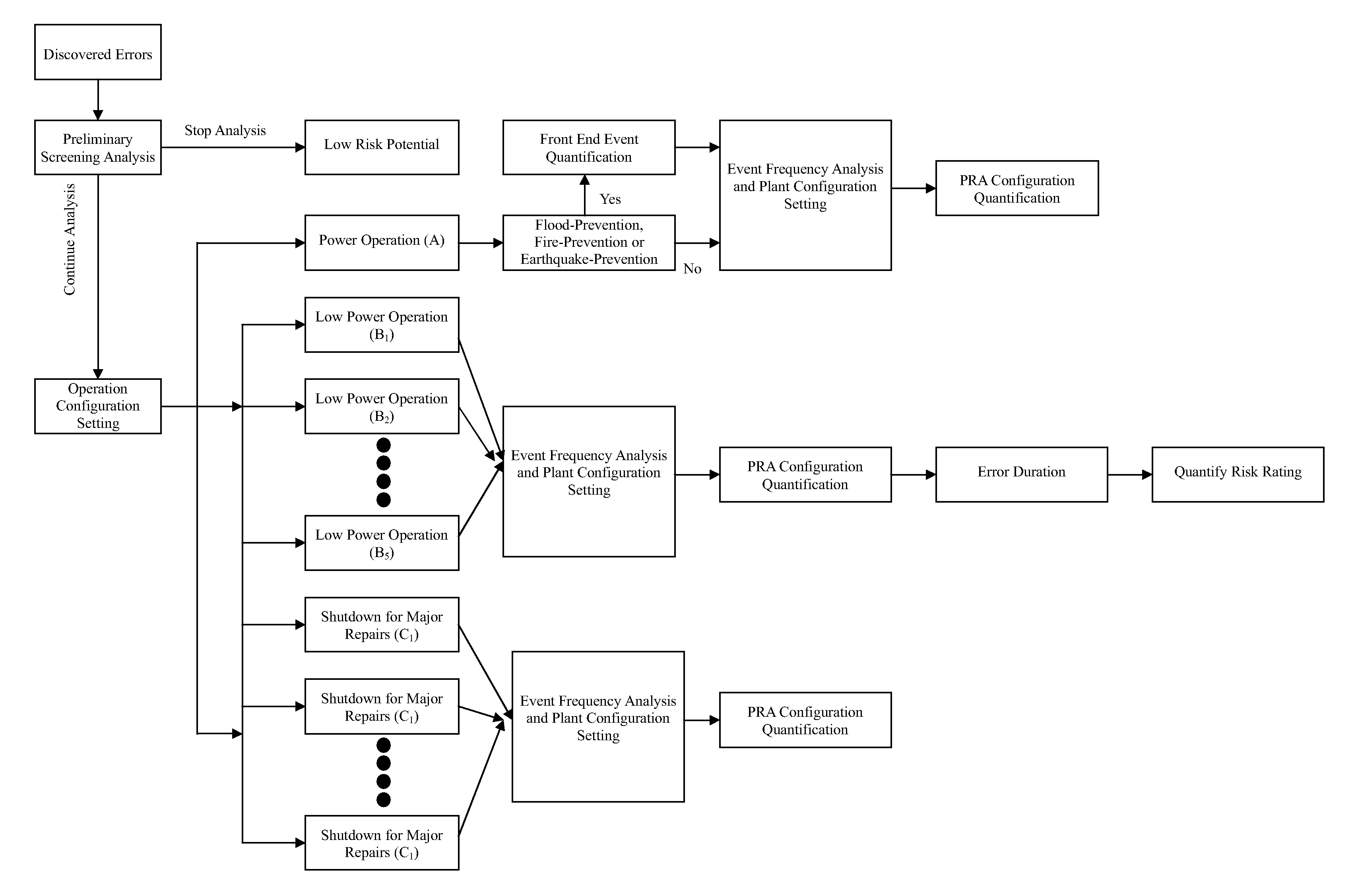
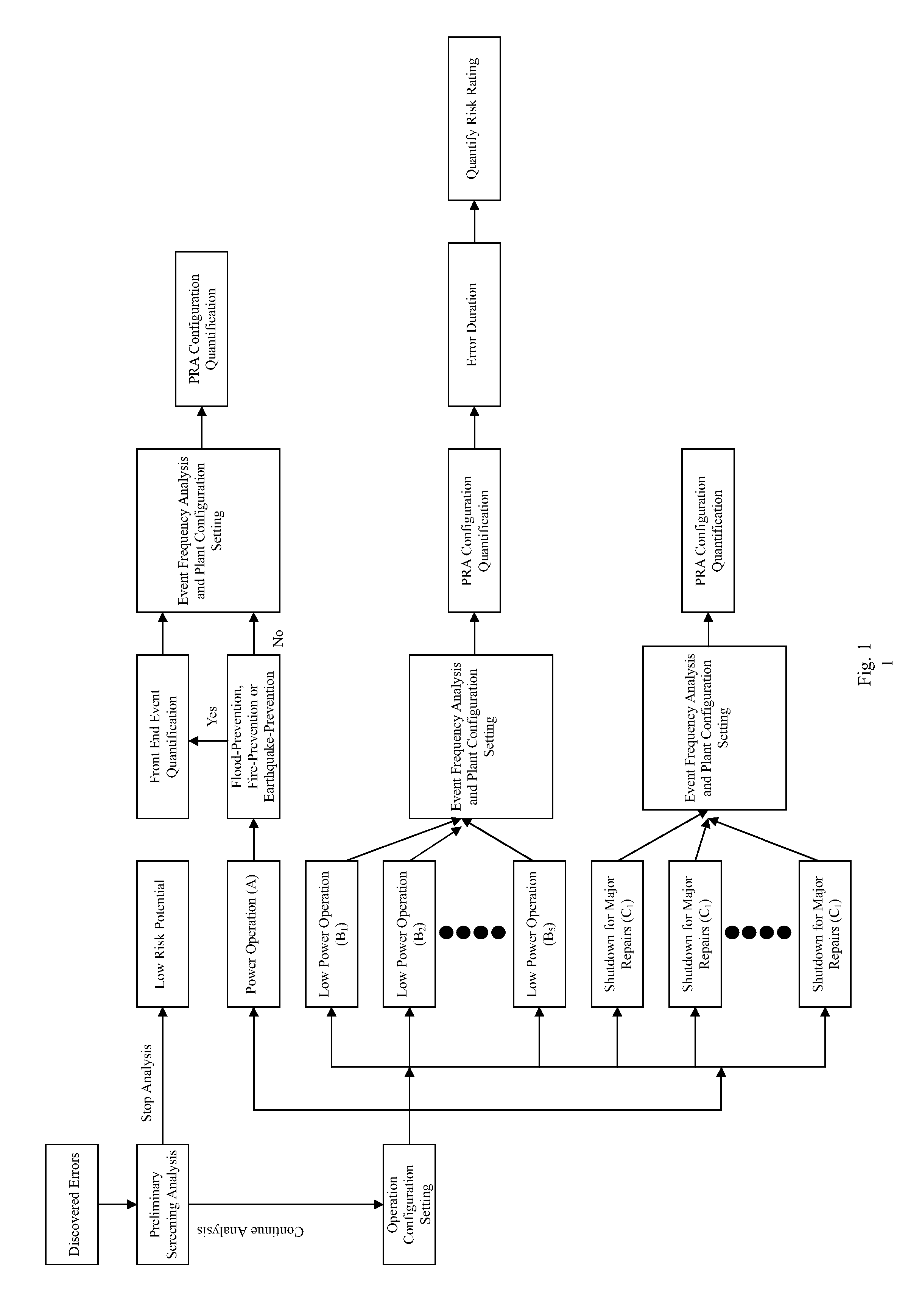
All aspect quantification system for the risk rating of operating errors for an advanced boiling water reactor
InactiveUS20100138253A1Improve consistencyFail to accuratelyFinanceClimate change adaptationProbabilistic risk assessmentRisk effect
Based on the discovered operating errors under all basic operating mode s for advanced boiling water reactor, a suitable quantification analytical model is employed to fast assess the risk situation for the discovered operating errors and quantified results are used to differentiate the risk rating for the operating errors. This is used to determine the necessity and urgency for the corrective measures to respond to the errors. The adopted quantification analytical model is the safety assessment (Probabilistic Risk Assessment, PRA) model for all basic operating mode s for advanced boiling water reactor, including power operation, low power operation and shutdown for major repairs. For the discovered operating error during power operation period, the invention uses the specifically developed safety assessment model for plant event, earthquake, flood and fire to determine risk effect for the discovered operating error on different event to manifest the risk characteristics for the discovered operating error and match the quantification results to existing plant design, operation and maintenance conditions.
Owner:CHAO CHUN CHANG +1
Systems and methods for quantifying flood risk
In various embodiments, a flood risk score may be determined for a property point that provides a comprehensive assessment of the property point's risk of flooding. Determining the flood risk score may include determining a flood risk characteristic for the property point and assigning a flood risk score that corresponds to the flood risk characteristic. In some embodiments, flood risk characteristics may include a difference in elevation between the elevation of the property point and an elevation of a calculated point (e.g., on a known flood risk zone boundary). Flood risk characteristics may also include a flood zone determination for the property point and / or proximity of the property point to a known flood risk zone boundary or a flood source. In some embodiments, flood risk scores may be provided on flood risk score reports.
Owner:CORELOGIC SOLUTIONS
Risk control method, device, server and readable storage medium
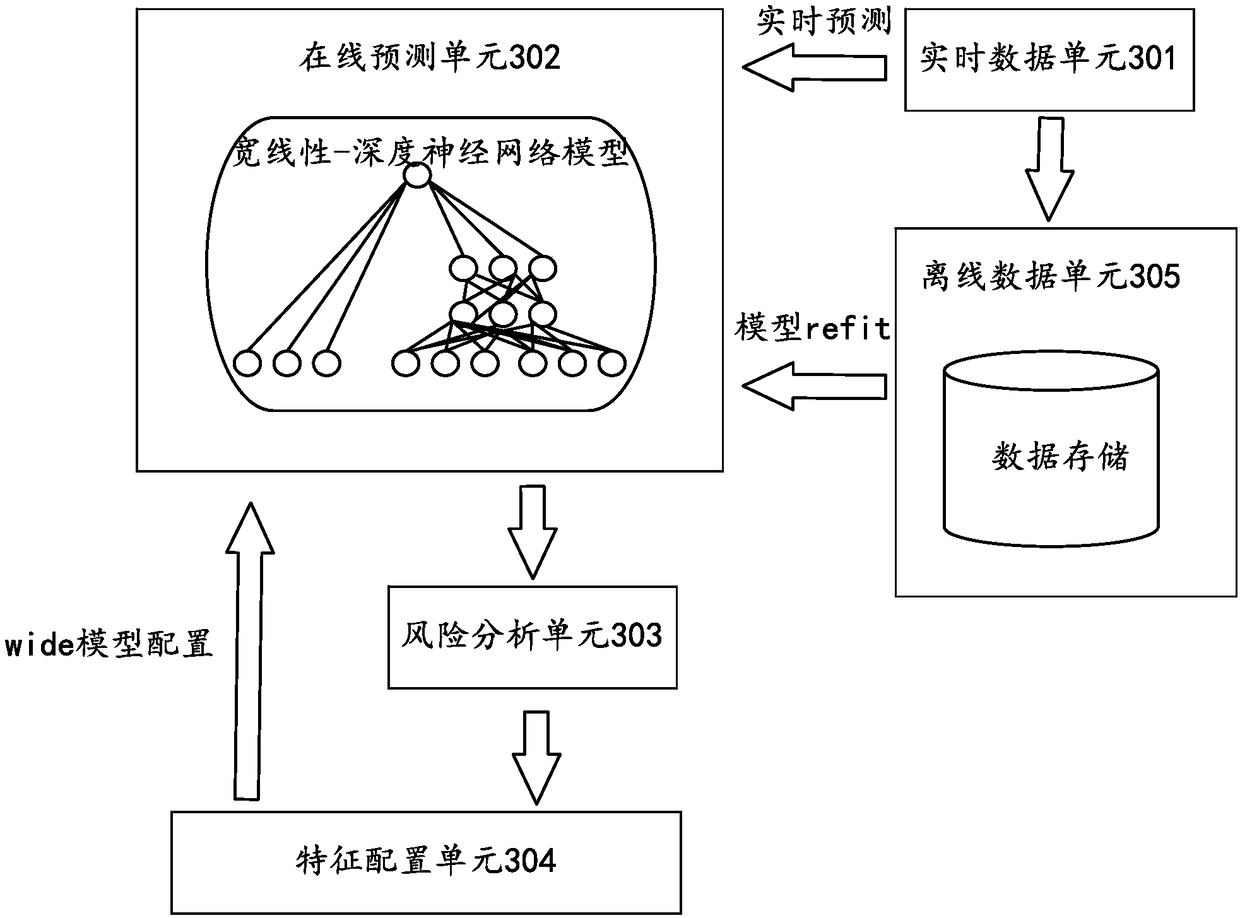
The embodiment of the invention provides a risk control method which comprises the steps of entering a risk characteristic into a preset widely linear-deep neural network model for risk predication, and obtaining a risk score of transaction data. The widely linear-deep neural network model adopted by the method integrates the advantages of a wide linearity model and a deep neural network model, and a risk transaction can be effectively identified.
Owner:ADVANCED NEW TECH CO LTD
Method and system for monitoring safety of oil and gas pipeline based on unmanned aerial vehicle line patrol, and software storage device
ActiveCN107808133AReduce security management costsImprove Security Monitoring EfficiencyImage enhancementImage analysisMaintenance managementSpatial analysis
The invention discloses a method and a system for monitoring safety of an oil and gas pipeline based on unmanned aerial vehicle line patrol and a software storage device. The method comprises the steps of S1, acquiring multi-source data generated by safety monitoring of the oil and gas pipeline with an unmanned aerial vehicle; S2, carrying out risk identification on a mono-temporal image accordingto a characteristic library obtained by historical risk characteristic training, carrying out the risk identification on a multi-temporal image by use of a saturation-based change detection method toidentify change regions between different time phases, calculating and combining mono-temporal and multi-temporal risk identification results; S3, reappearing an inspection process of the unmanned aerial vehicle for the oil and gas pipeline in a three-dimensional platform; S4, carrying out route planning of the unmanned aerial vehicle inspection and analysis of a water-flooded space of the pipeline; and S5, outputting a pipeline hidden danger report which includes a risk identification report and a spatial analysis report, and making a decision according to the pipeline hidden danger report.According to the method and the system for monitoring the safety of the oil and gas pipeline based on unmanned aerial vehicle line patrol and the software storage device, the safety management cost ofthe oil and gas pipeline is effectively reduced, the safety monitoring efficiency is improved and the operation and maintenance management level of a pipe network is enhanced.
Owner:中石化石油工程地球物理有限公司
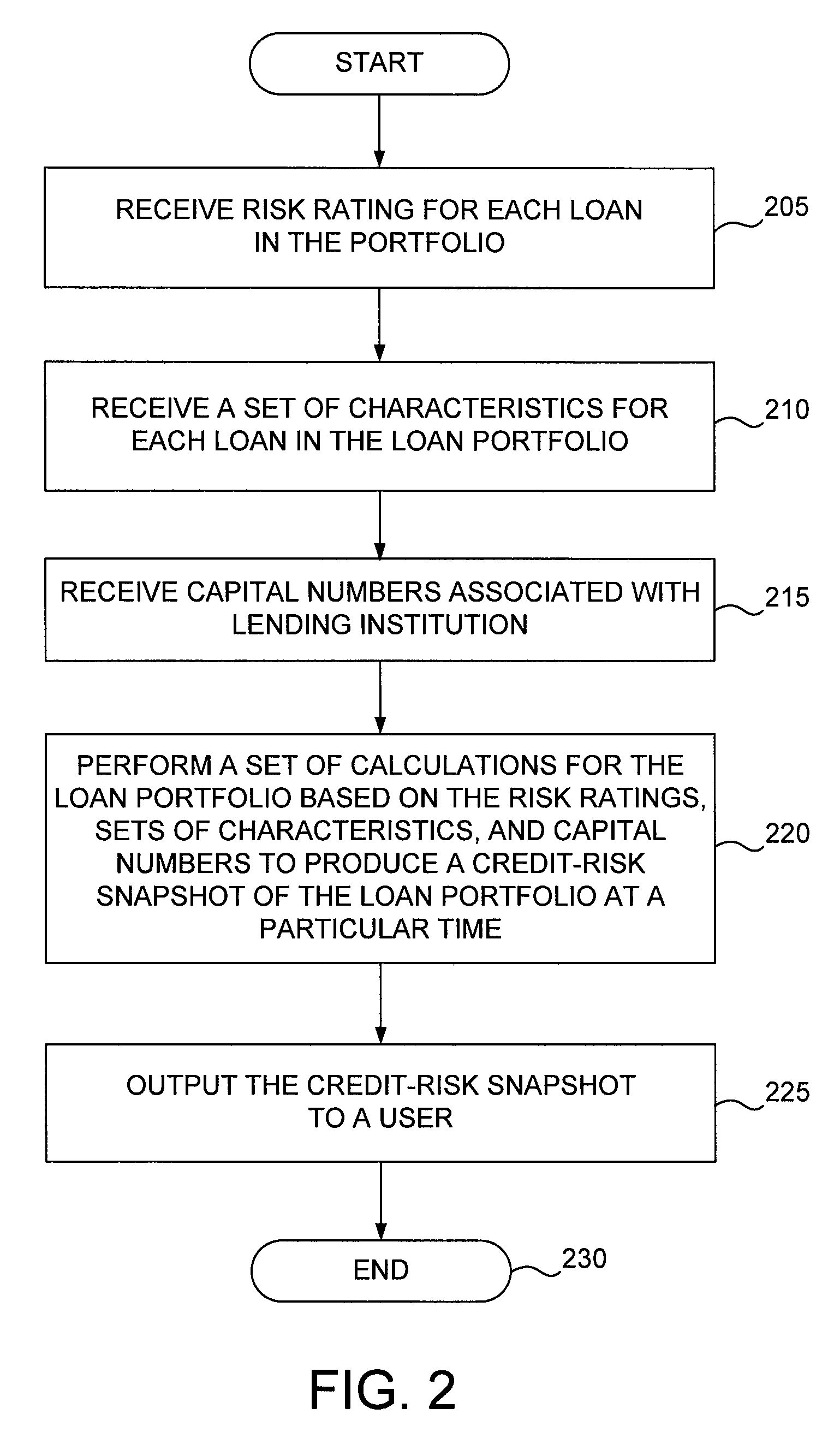
Method and system for assessing credit risk in a loan portfolio
A method and system for assessing credit risk in a loan portfolio of a lending institution is described. One embodiment receives a risk rating for each loan in the loan portfolio, the risk rating having been assigned based on a set of risk characteristics associated with the loan's concentration segment in accordance with a bifurcated model; receives a set of characteristics for each loan in the loan portfolio; receives capital numbers associated with the lending institution; performs a set of calculations for the loan portfolio to produce a credit-risk snapshot of the loan portfolio at a particular time, the set of calculations including at least one of expected loss, unexpected loss, economic capital, value at risk, and shareholder value added; and outputs the credit-risk snapshot of the loan portfolio to a user. Some embodiments also produce a trend analysis based on a plurality of credit-risk snapshots.
Owner:STURM FINANCIAL GRP
A risk identification method and device
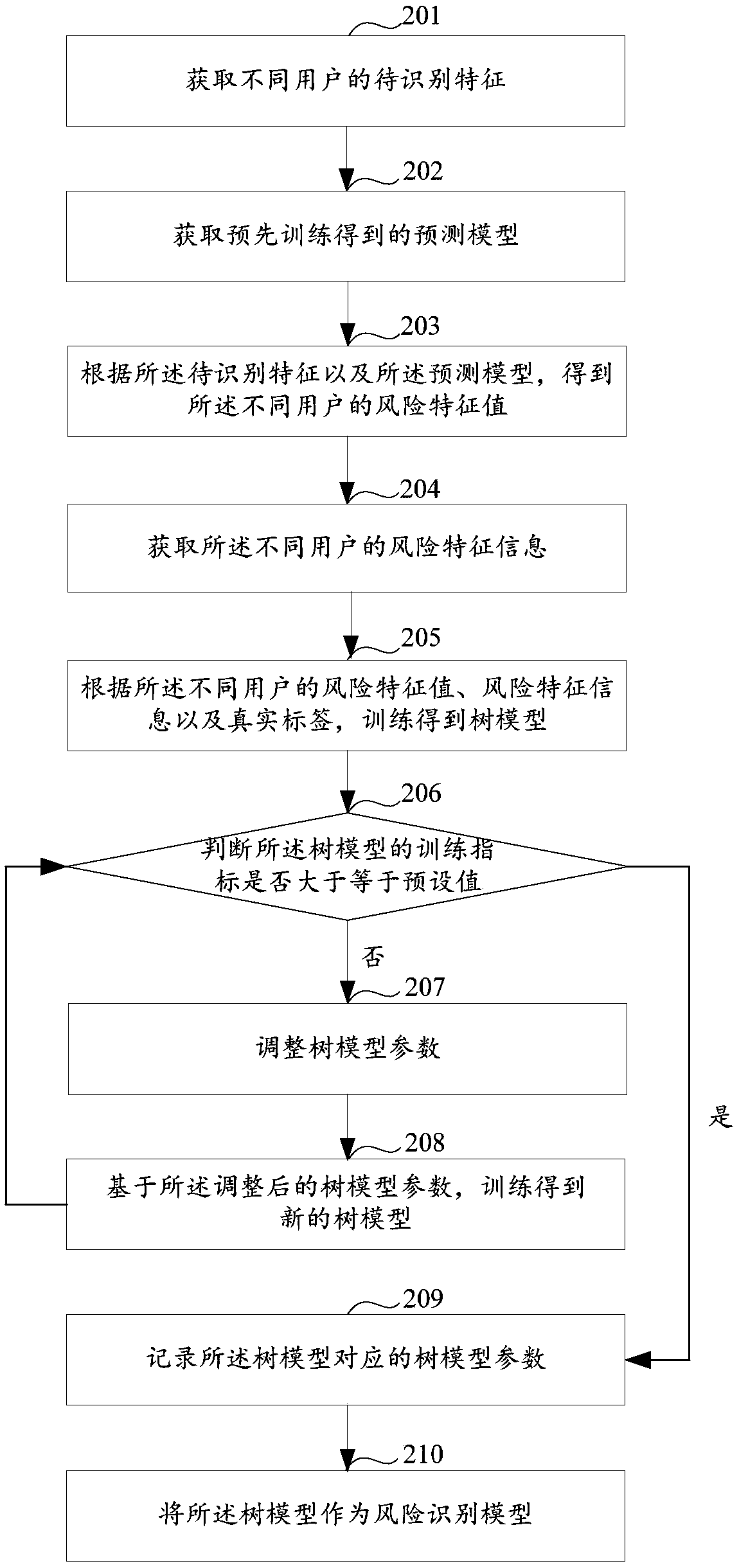
ActiveCN109544166AImprove accuracyCharacter and pattern recognitionProtocol authorisationRisk identificationData mining
The invention discloses a risk identification method and device. The method comprises the following steps: obtaining a risk characteristic value of a user to be identified, wherein the risk characteristic value is used for characterizing the probability that the user to be identified belongs to a risk user; acquiring risk characteristic information of the user to be identified, wherein the risk characteristic information is used to characterize the information related to the risk in the information of the user to be identified; acquiring a pre-trained risk identification model, wherein the risk identification model is obtained based on risk eigenvalues of different users, risk characteristic information and real label training; identifying whether the user to be identified belongs to a risk user according to the risk characteristic value, the risk characteristic information and the risk identification model of the user to be identified.
Owner:ADVANCED NEW TECH CO LTD
Integrated risk assessment method for calculating operation uncertainty of electric transmission line
ActiveCN103914792AEffective Evaluation AnalysisThe comprehensive risk weight is scientific and reasonableData processing applicationsRisk levelDecision taking
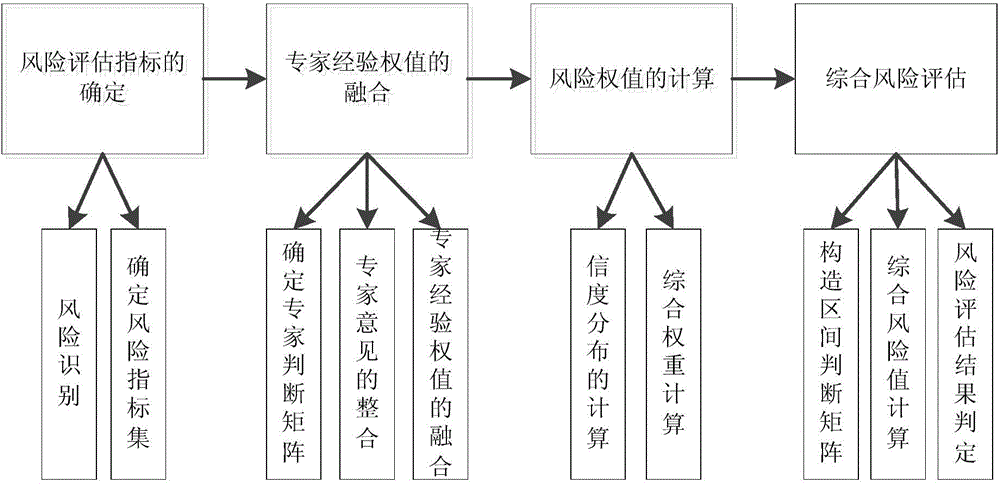
The invention discloses an integrated risk assessment method for calculating the operation uncertainty of an electric transmission line. The integrated risk assessment method includes the following steps: (1) identifying and collecting characteristic factors for causing operation risks of the electric transmission line, determining risk characteristic indexes, and building an operation risk assessment index set of the electric transmission line, (2) fusing expert advice weights with a fusion theory, (3) using uncertain rational numbers to calculate reliability distribution to determine risk weights, and combining the risk weights and the fused expert advice weights in the step (2) to calculate integrated risk weights of the risk assessment index set, and (4) calculating a final integrated risk value in cooperation with section judgment matrixes, processing results, and judging risk levels. By means of the integrated risk assessment method, a subjective and objective analytical method is used in a combined mode, powerful supports are provided for finding potential operation risks as soon as possible, reducing the possible risks of line operation and reducing risk operation losses, and the integrated risk assessment method is the premise and the guarantee of scientifically and reasonably managing the risks and making decisions.
Owner:EXAMING & EXPERIMENTAL CENT OF ULTRAHIGH VOLTAGE POWER TRANSMISSION COMPANY CHINA SOUTHEN POWER GRID +1
A method and a system for identifying abnormal transactions based on a fund transaction network
ActiveCN109461078AAccurate and fully determinedAccurate identificationFinanceRisk modelTransaction data
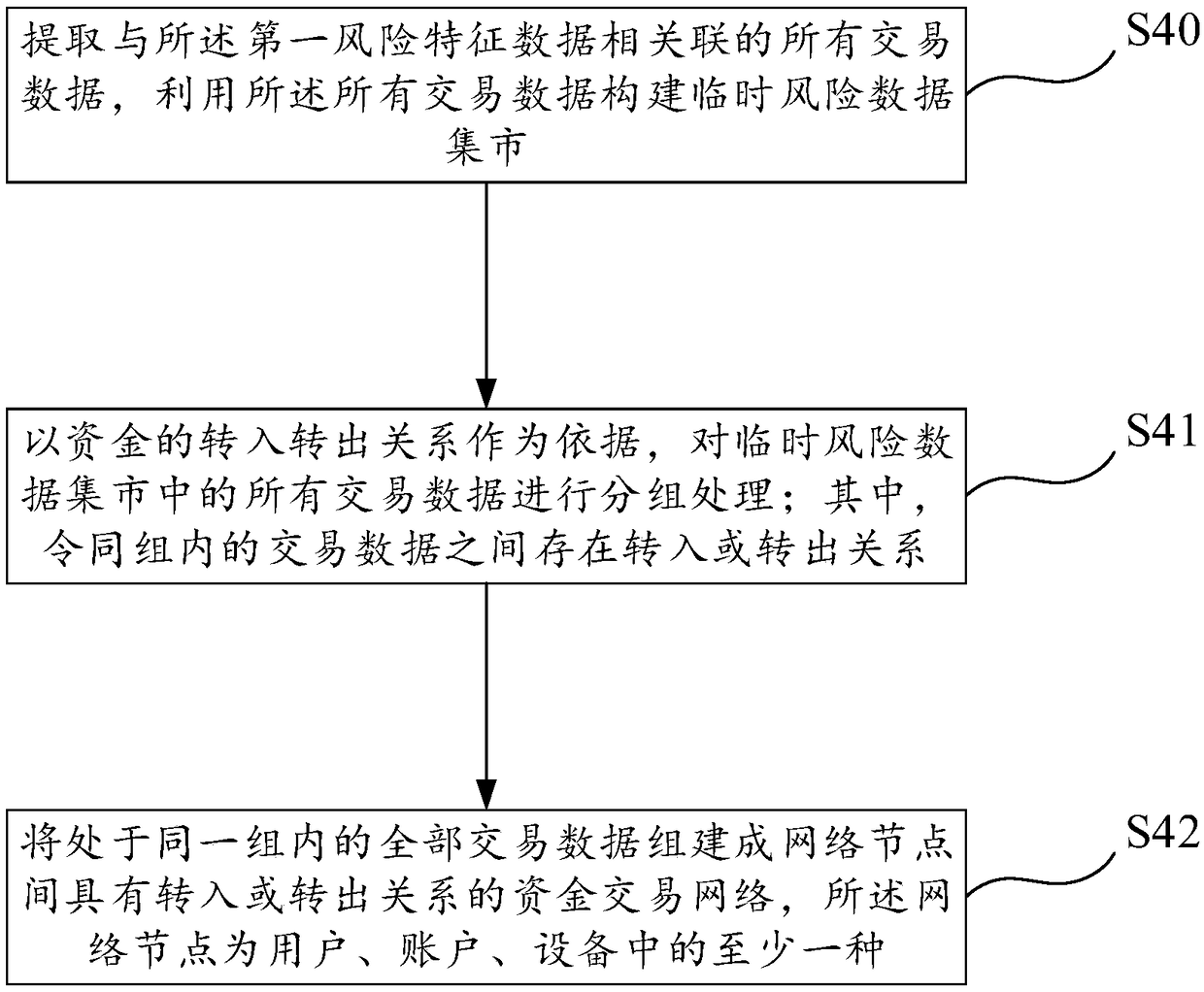
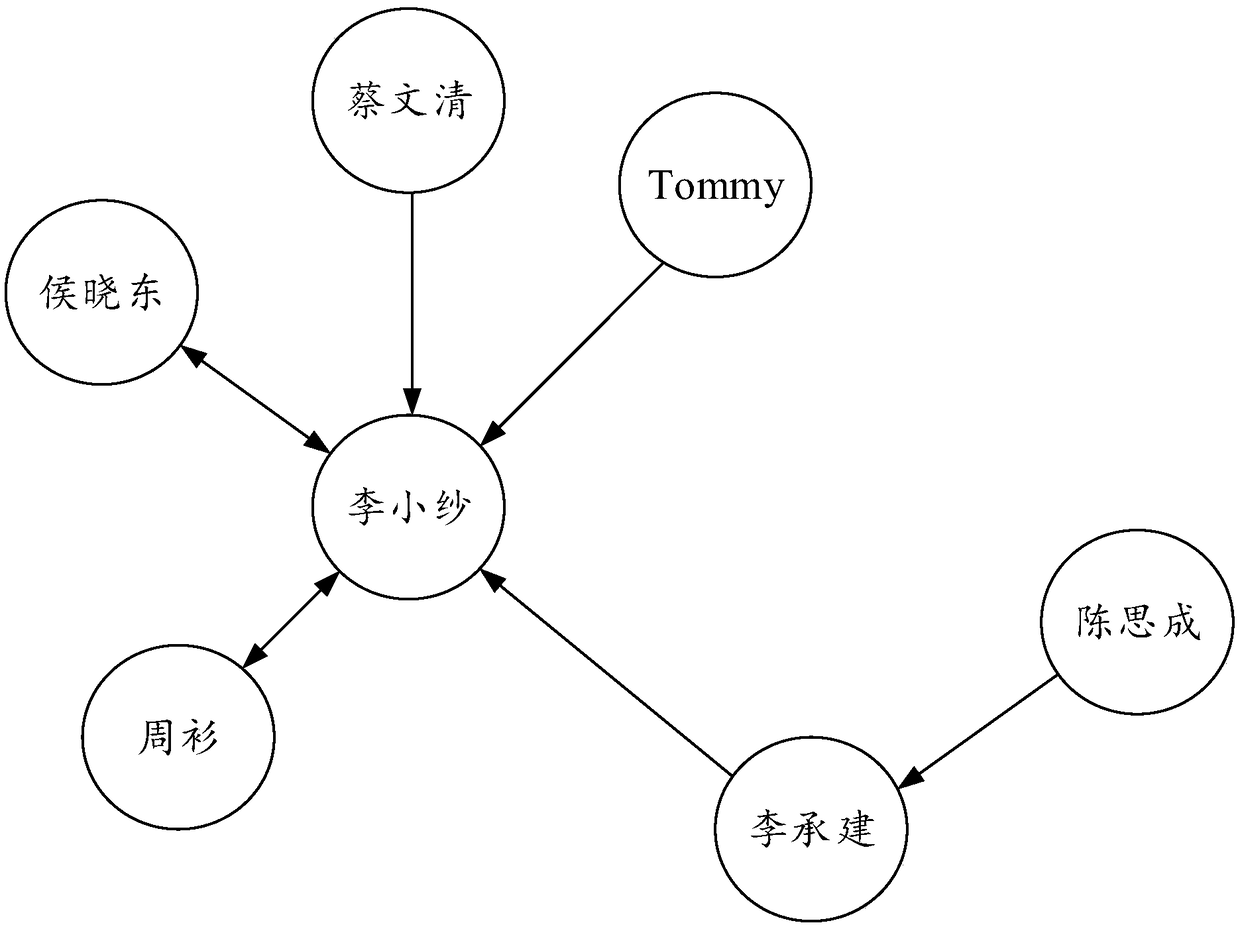
The invention discloses a method and a system for identifying abnormal transactions based on a fund transaction network, The abnormal transaction identification method comprises the following steps: the step of constructing a data mart through multi-subject data, the step of determining the basic index data, the step of generating the first risk characteristic data, the step of forming a pluralityof fund transaction networks based on the transaction data, the step of generating suspicious cases of abnormal transactions and the step of generating suspicious screening reports; The abnormal transaction identification system includes: data mart building module, basic index mining module, risk characteristics generation module, transaction network building module, suspicious case generation module and screening report generation module. Based on the established fund transaction network and transaction risk model, the invention can completely restore the money laundering process and the money laundering scene, and provides strong support and assistance for the money laundering behavior investigation. The invention also has the prominent advantages of high precision, good comprehensiveness, strong objectivity and the like.
Owner:北京领雁科技股份有限公司
City gas pipeline risk rank quantitative assessment method and application thereof
InactiveCN102799766ARun accuratelyRun fastData processing applicationsSpecial data processing applicationsThird partyAlgorithm
The invention discloses a city gas pipeline risk rank quantitative assessment method and application thereof. According to the method, a calculation model and a mathematic function for gas pipeline risk rank assessment are determined by selecting tool functions such as a correlation function, a matter element matrix with same characteristics and the like for the gas pipeline risk characteristics, namely a third-party damage and corrosion factor, a design factor and an operation management factor by introducing a matter element and an extension set theory, and defining and calculating a gas pipeline risk rank. In order to simplify a calculation process, a Visual Basic program for the gas pipeline risk rank calculation is programmed on the basis above, so that a manual calculation result is validated and the applicability of the gas pipeline risk rank assessment method based on the matter element and the extension theory set in practice is improved to a great extent; and therefore, the objectivity and the accuracy of the risk rank assessment are embodied and simultaneously the method has a certain practical value. The method is an effective method for enhancing gas pipeline risk management.
Owner:CHANGZHOU UNIV
Risk characteristic screening and describing message generation method and device and electronic equipment
The embodiment of the invention discloses a risk characteristic screening and describing message generation method and device and electronic equipment. The method comprises the steps: screening the risk characteristics according to the characteristic weights of a plurality of risk characteristics and a predetermined condition for the restraint of the length of a message generated according to therisk characteristics, and generating a description message for a to-be-described event through the screened risk characteristics.
Owner:ADVANCED NEW TECH CO LTD
Risk identification and business processing method and device
ActiveCN106682906AImprove accuracySolve the problem of not identifying potentially risky accountsDiscounts/incentivesTransmissionRisk identificationData mining
The invention discloses a risk identification and business processing method and a device, comprising: obtaining the relationship data of a target account wherein the relationship data of the target account contains a first account that establishes a social relationship with the target account; determining the risk characteristic value of the first account and the risk spreading probability value of the first account wherein the risk spreading probability value is used to represent the probability of the first account to spread the risk to the target account; utilizing the risk characteristic value of the first account and the risk spreading probability value of the first account to calculate the risk characteristic value of the target account; and according to the risk characteristic value of the target account, identifying whether the target account belongs to a risk account or not. According to the invention, through the obtaining of the relationship data of the target account and under the assistance of a label spreading algorithm, the risk characteristic value of the target account could be predicted and obtained from the risk characteristic value of other accounts through the use of the established social relationship with the target account so as to further determine the risk condition of the target account and to effectively resolve the problem in the prior art that the potential risk account could not be identified.
Owner:ADVANCED NEW TECH CO LTD
Supplier Risk Dashboard
InactiveUS20130041713A1Disadvantages and reduced eliminatedRisk reduced eliminatedFinanceDashboardData source
A system and method for a supplier risk dashboard is disclosed. A method for determining comprehensive supplier risk includes receiving a first supplier data from a first data source, the first supplier data indicating a plurality of suppliers and one or more risk characteristics associated with each of the plurality of suppliers to an organization. The method further includes receiving a second supplier data from a second data source, the second supplier data indicating a plurality of suppliers and one or more risk characteristics associated with each of the plurality of suppliers to the organization. The method also includes for one or more of the suppliers indicated in the first supplier data, associating one or more risk characteristics indicated in the first supplier data with one or more risk characteristics indicated in the second supplier data.
Owner:BANK OF AMERICA CORP
Training of risk control model, risk control method, device and equipment for identifying embezzlement of secondary release account
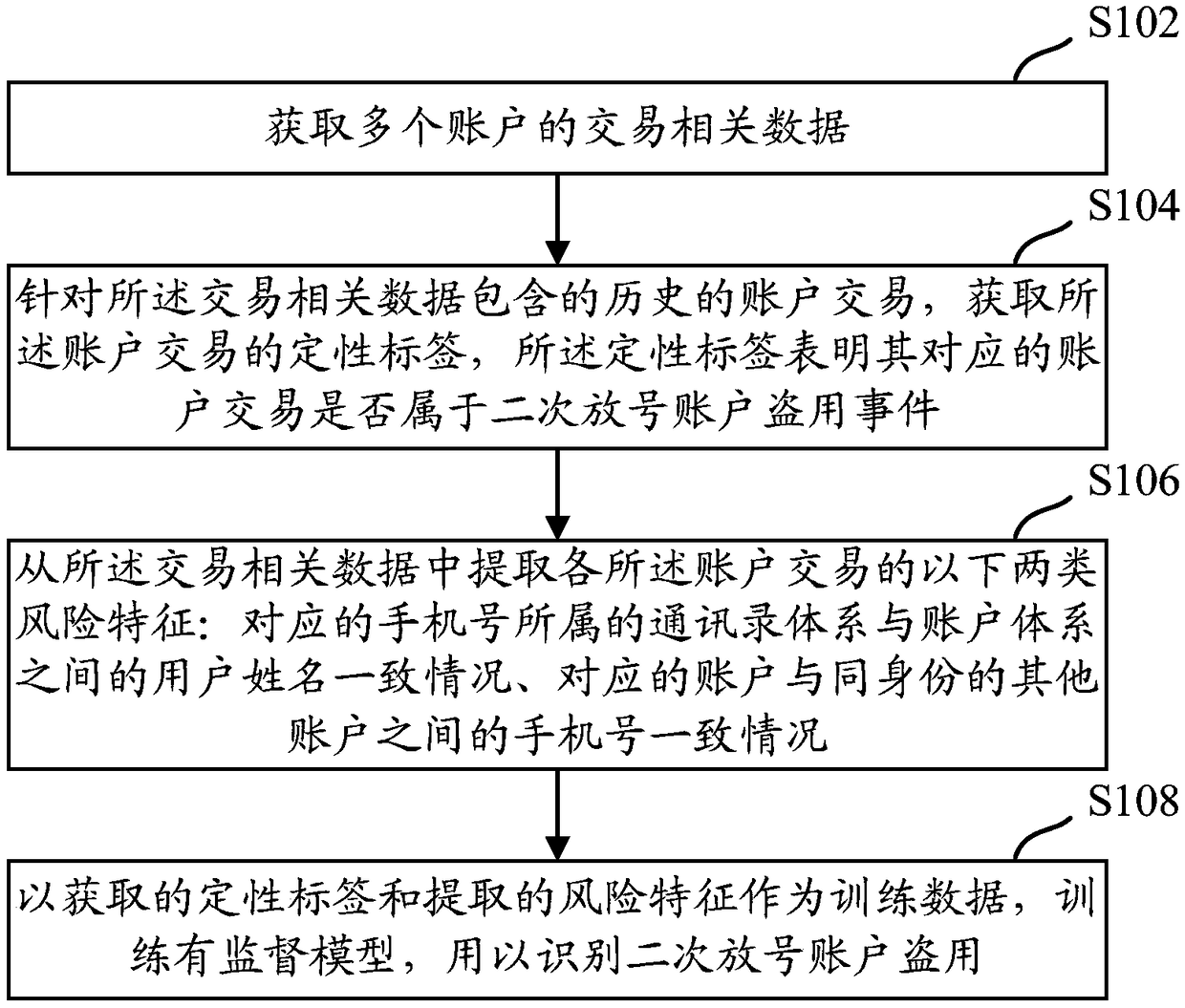
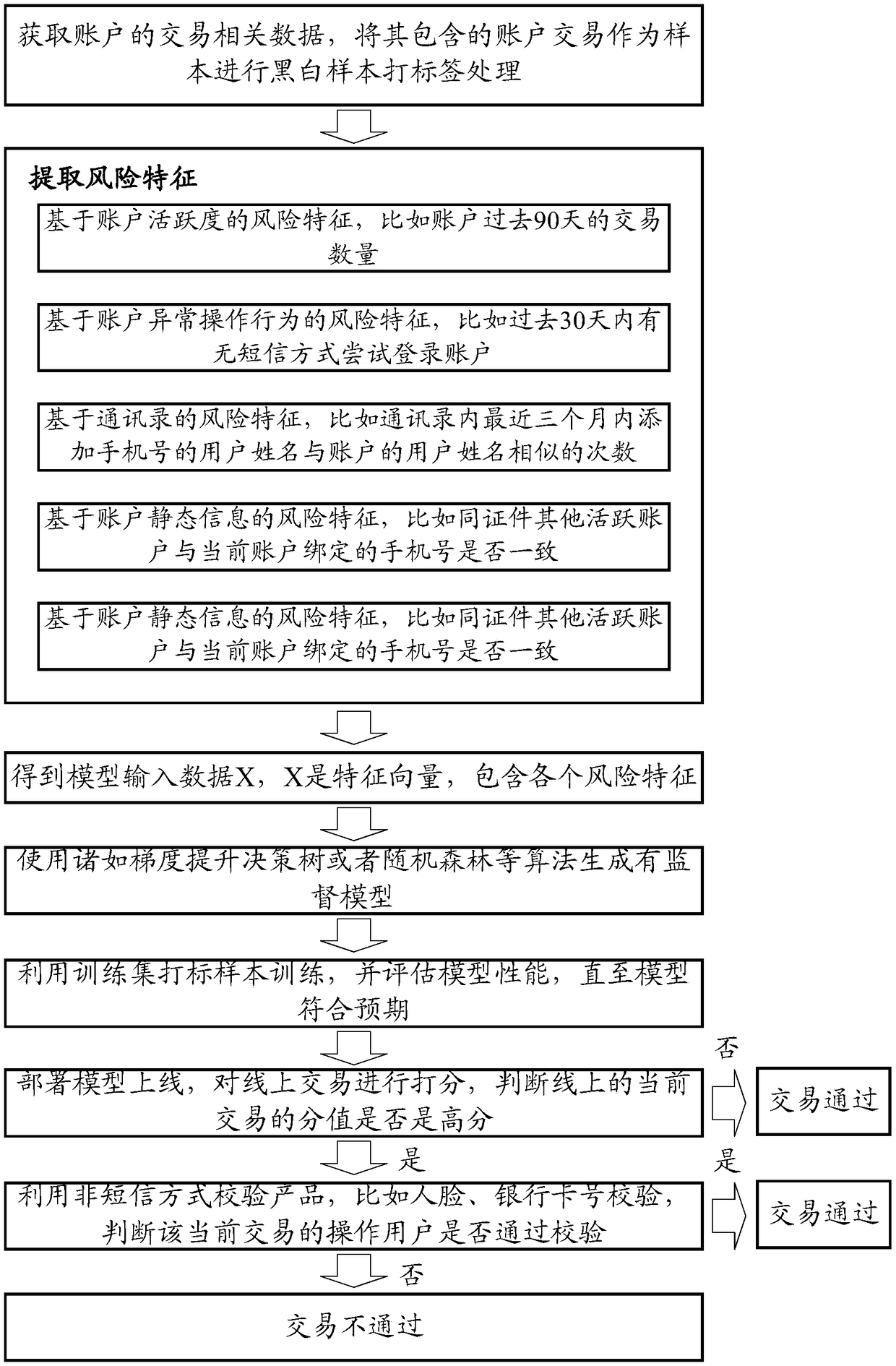
ActiveCN109087106AMisappropriation identificationCommerceProtocol authorisationRisk ControlAddress book
The embodiment of the specification disclose risk control model training, a risk control method, a device and equipment for identifying the embezzlement of a secondary release account. The scheme includes: acquiring transaction-related data of multiple accounts; obtaining a qualitative tag of the account transaction according to the historical account transaction included in the transaction related data, wherein the qualitative tag indicates whether the corresponding account transaction belongs to a secondary loosening account embezzlement event; extracting the following two types of risk characteristics of each account transaction from the transaction related data: the corresponding mobile phone number belongs to the address book system and the user name between the account system is identical, and the corresponding account is identical with the mobile phone number between other accounts with the same identity; using the obtained qualitative labels and extracted risk characteristics as training data, a supervised model being trained to identify the embezzlement of the secondary release account. The trained supervised model is used to identify the embezzlement of the secondary release account.
Owner:ADVANCED NEW TECH CO LTD
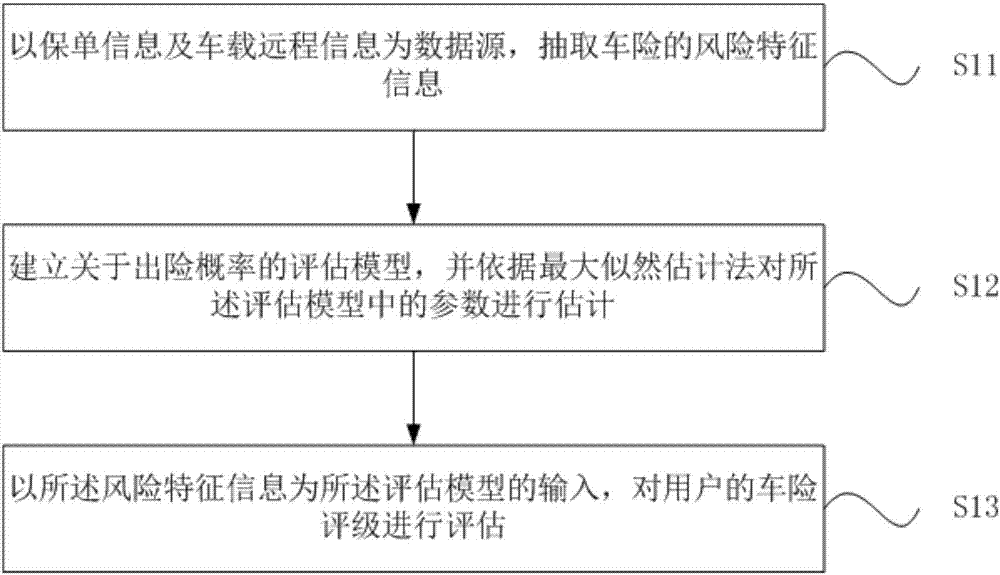
Classified estimation method and device for vehicle insurance
InactiveCN107203945AAvoid Evaluation ErrorsEffective assessmentFinanceRisk rankingMathematical model
The invention relates to a classified estimation method and device for vehicle insurance and belongs to the technical field of intelligent vehicles. The method comprises the following steps: risk characteristic extraction is performed firstly, risk characteristics of a driver and a driving vehicle are obtained, and then 8-dimensional risk characteristics describing driving behaviors of the driver are defined by combining with vehicle-mounted remote information; then a mathematical model for the risk characteristics and loss is established through logistic regression, model parameters are estimated on the basis of historical data with a maximum likelihood method, and value-at-risk thresholds of different risk ranking groups are determined after the model parameters are obtained; finally, risk characteristics and risk values of a to-be-estimated customer are calculated, and risk ranking is performed according to a risk rank table. According to the method, vehicle risks can be ranked through effective combination of driver information, driving vehicle information and driving behavior characteristics, artificial participation is not needed in the whole process, dependence on personal experience is avoided, and the method is direct, effective and convenient to use.
Owner:清华大学苏州汽车研究院(吴江)
Large-scale bridge engineering risk assessment method
The invention discloses a large-scale bridge engineering risk assessment method. In the implementation of the method, a work-risk decomposition structure WBS-RBS is adopted to carry out bidirectionaldecomposition on a construction project according to a construction process and risk types, a risk decomposition matrix RBM is constructed, opinion investigation is carried out through a plurality ofexperts in the industry to know risk characteristics, and an initial risk value r is calculated through quantitative classification of risk probability and loss; when the correction weight omega of the risk source is determined, performing risk relative importance judgment and opinion consistency inspection by adopting the FAHP, and performing weighted correction on the risk value; summarizing thesurvey data of the plurality of experts and calculating to obtain a comprehensive risk value; and determining the risk severity level according to the magnitude of the multi-level comparison comprehensive risk value and a risk evaluation index threshold value, so that the evaluation result conforms to the engineering practice. The method can accurately, objectively and systematically identify andevaluate the risk, and can lay a foundation for the safety and high quality of large-scale bridge construction.
Owner:SOUTHWEST JIAOTONG UNIV +1
AI driving risk analysis method based on multi-dimensional data, server and storage medium
PendingCN110069988AAvoid one-sided influenceImprove accuracyCharacter and pattern recognitionResourcesRisk profilingDriving risk
The invention relates to the artificial intelligence technology, and discloses an AI driving risk analysis method based on multi-dimensional data, and the method comprises the steps: enabling an analysis server to obtain a to-be-analyzed image, sent by a terminal, of a target user; calling one or more pre-trained face recognition models to recognize the to-be-analyzed picture so as to recognize face risk characteristics of a preset type; extracting user data corresponding to a target user from a predetermined database, and extracting structural feature data of the preset type from the user data; and splicing the preset type of face risk features and the preset type of structural feature data into a multi-dimensional comprehensive risk feature, and inputting the comprehensive risk feature into a pre-trained driving risk analysis model to output a comprehensive risk analysis value. The invention further discloses an analysis server and a computer storage medium. According to the invention, the accuracy and objectivity of driving risk analysis can be improved.
Owner:CHINA PING AN PROPERTY INSURANCE CO LTD
An optimization method and apparatus for policy configuration
ActiveCN109255486AShorten the optimization cycleExamples cannot be limitedForecastingPayment protocolsData miningRisk characteristics
An optimization method and apparatus for policy configuration are disclosed. The method comprises: determining a policy configuration to be optimized in an initial policy; obtaining a prediction result outputted from the preset test data by using the current policy configuration in the policy, and performing statistics on the prediction result to obtain at least one index value, wherein the indexvalue is used for judging whether the current business index meets the preset requirements; If the current business indicator does not meet the preset requirements, optimizing the policy configuration, wherein the optimizing process comprises adjusting a combination mode of risk characteristics contained in the policy configuration, adjusting a numeric symbol used for representing the relationshipbetween the risk characteristics and the eigenvalue, or adjusting an eigenvalue corresponding to the risk characteristics contained in the policy configuration; After optimization, if the current business indicator meets the preset requirements, determining that the policy configuration in the current policy is available policy configuration.
Owner:ADVANCED NEW TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com