A risk identification method and device
A risk identification and risk technology, applied in character and pattern recognition, protocol authorization, data processing applications, etc., can solve problems such as low accuracy and inability to identify user risks, and achieve high accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
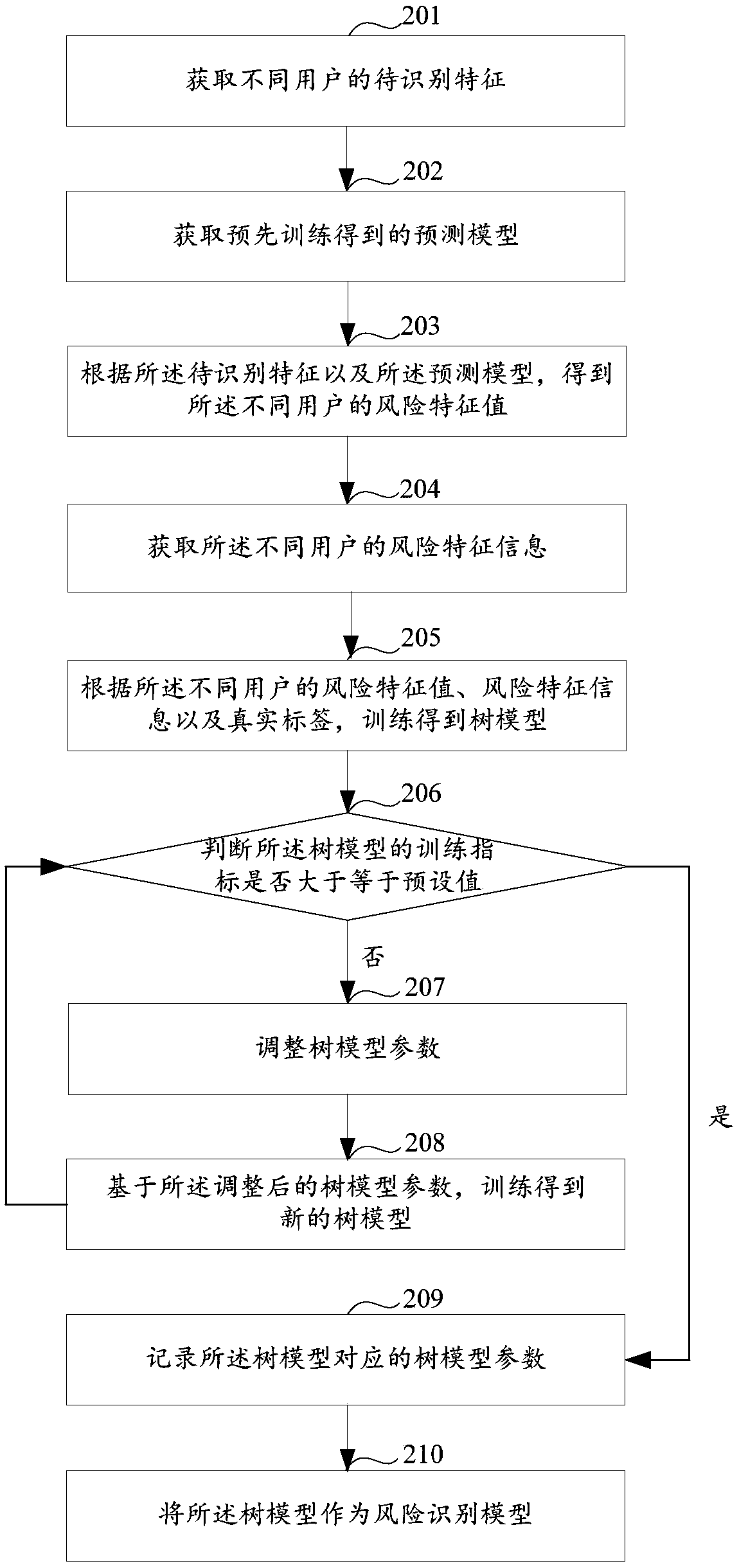
[0035] In risk identification, the probability that a user is a risk user can be obtained based on a prediction model, and then, whether the user is a risk user can be identified based on a pre-established risk identification strategy. Wherein, the risk identification strategy can be understood as a rule, which can determine whether a user is a risk user according to the probability that the user is a risk user.
[0036] For example, the risk identification strategy can be that when the probability that the user is a risk user (value range is 0 to 1) is greater than or equal to 0.9, the user is a risk user; then, when the probability that the user is a risk user is 0.8, it can be considered that the user does not belong to Risky users, when the probability that the user is a risky user is 0.9, it can be considered that the user is a risky user.
[0037] However, the existing risk identification strategies are usually formulated by decision makers based on experience, and the a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com