Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
85results about How to "Protect users" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
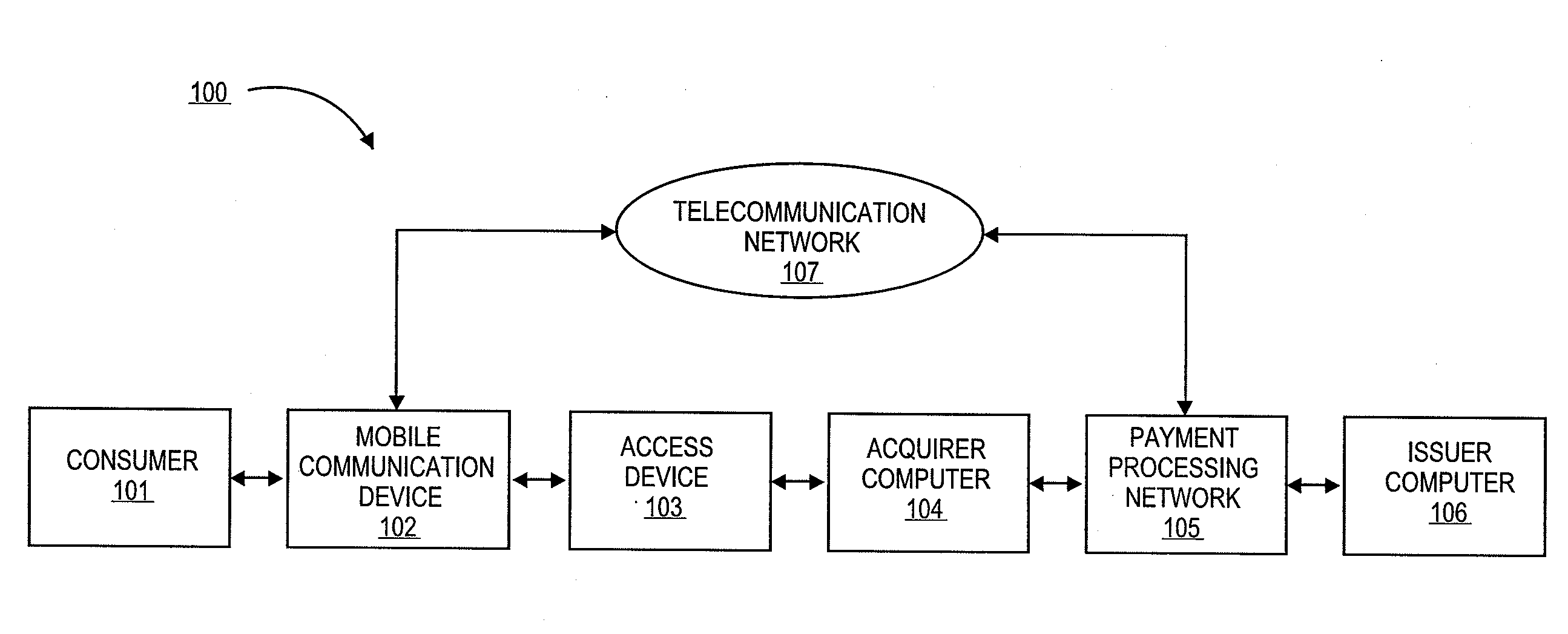
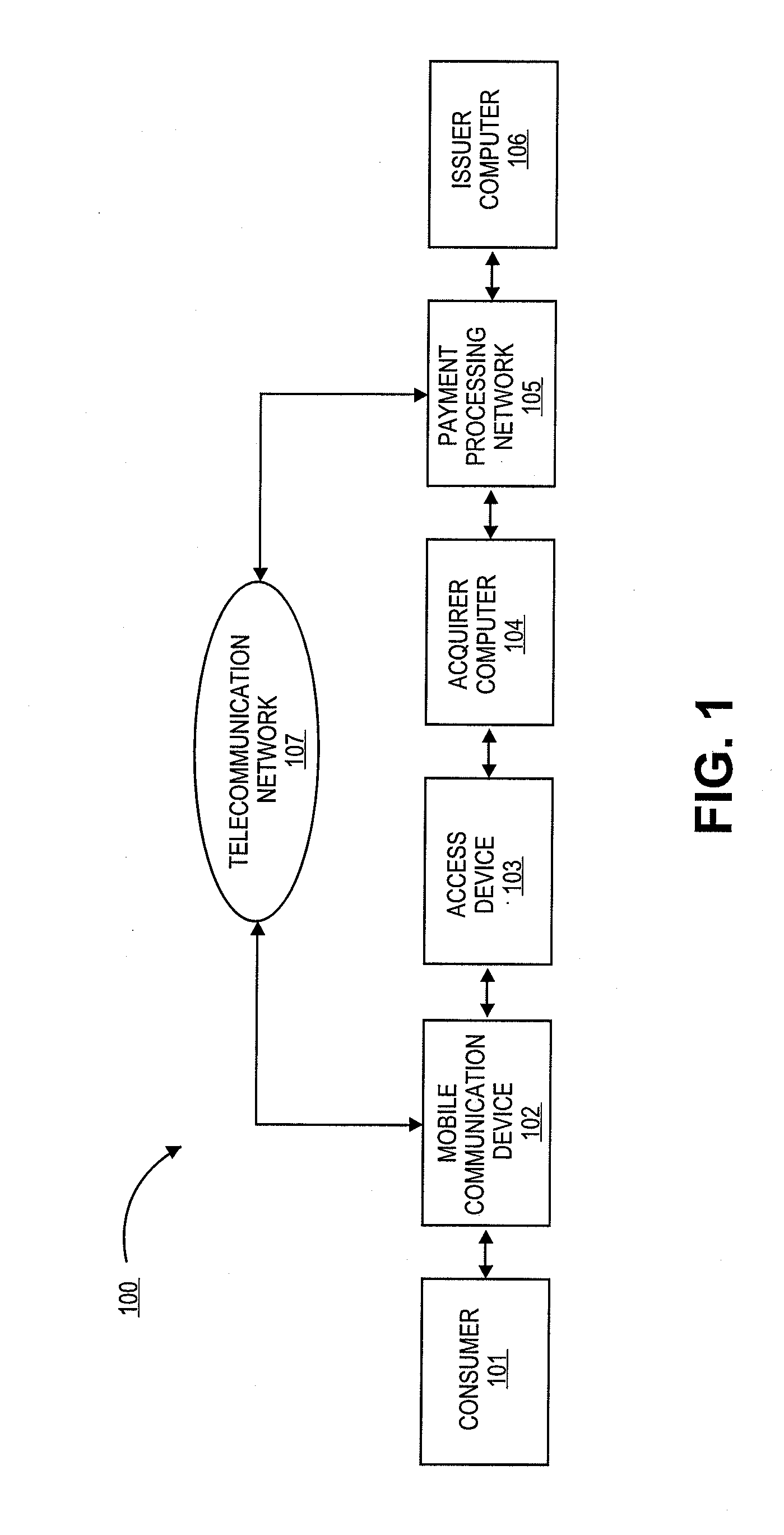
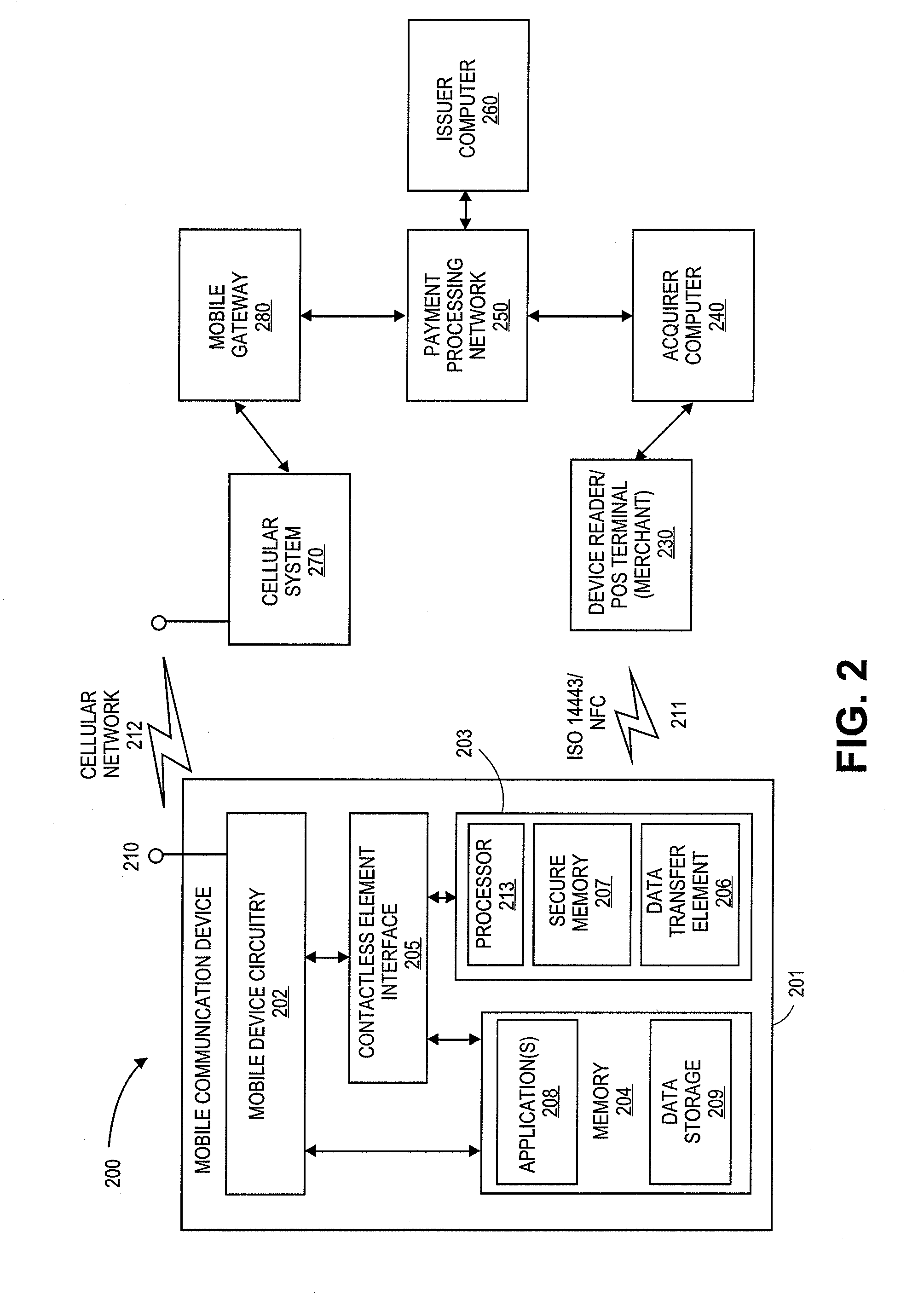
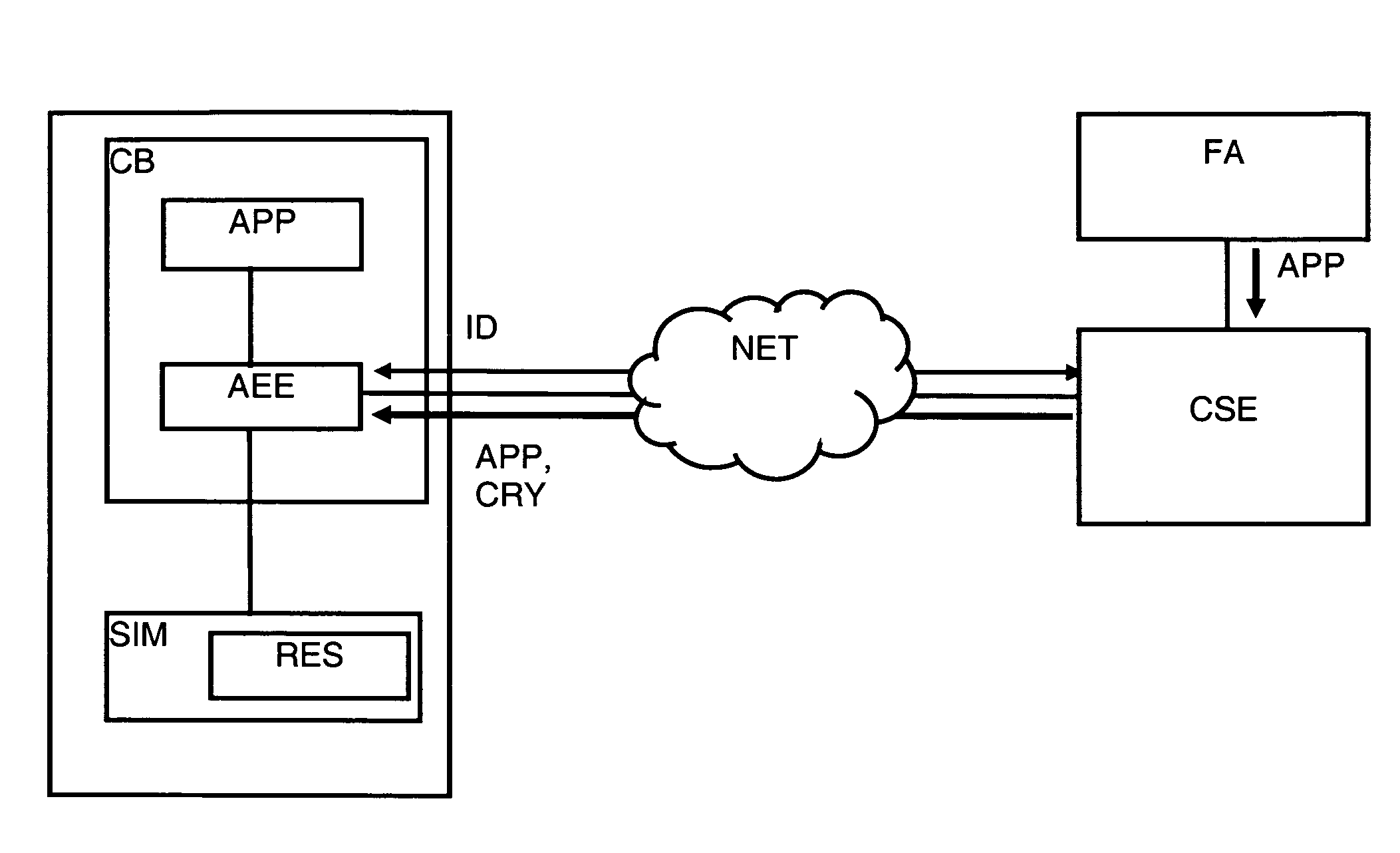
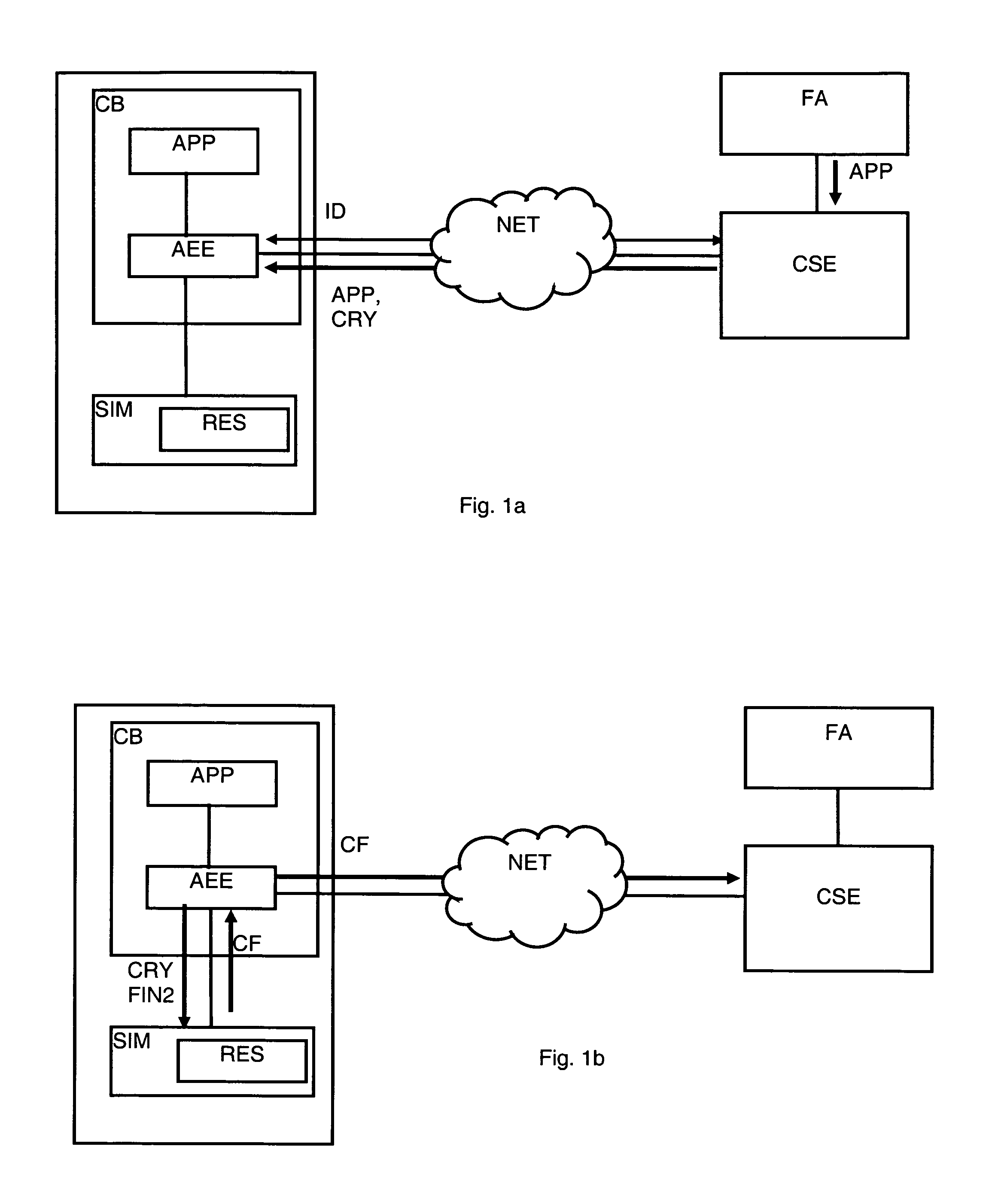
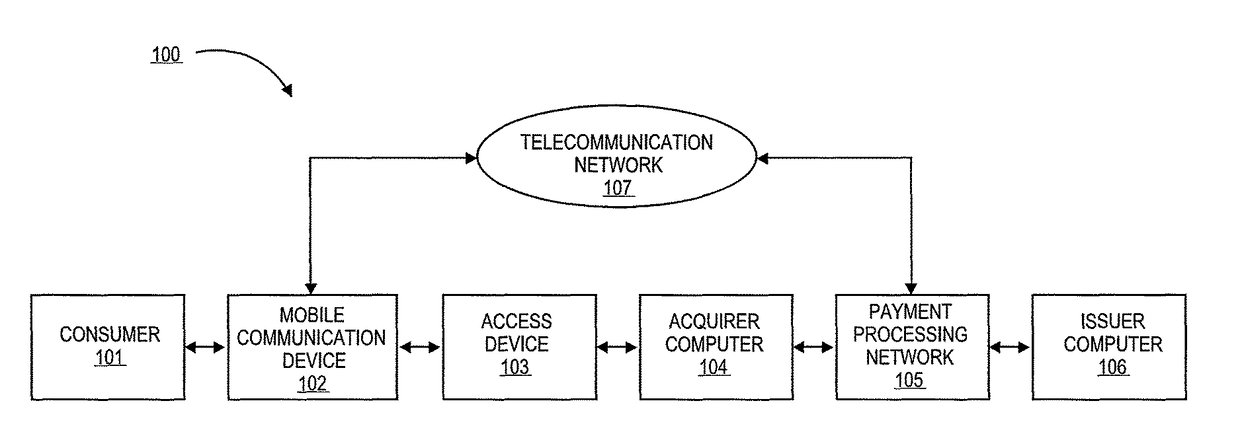
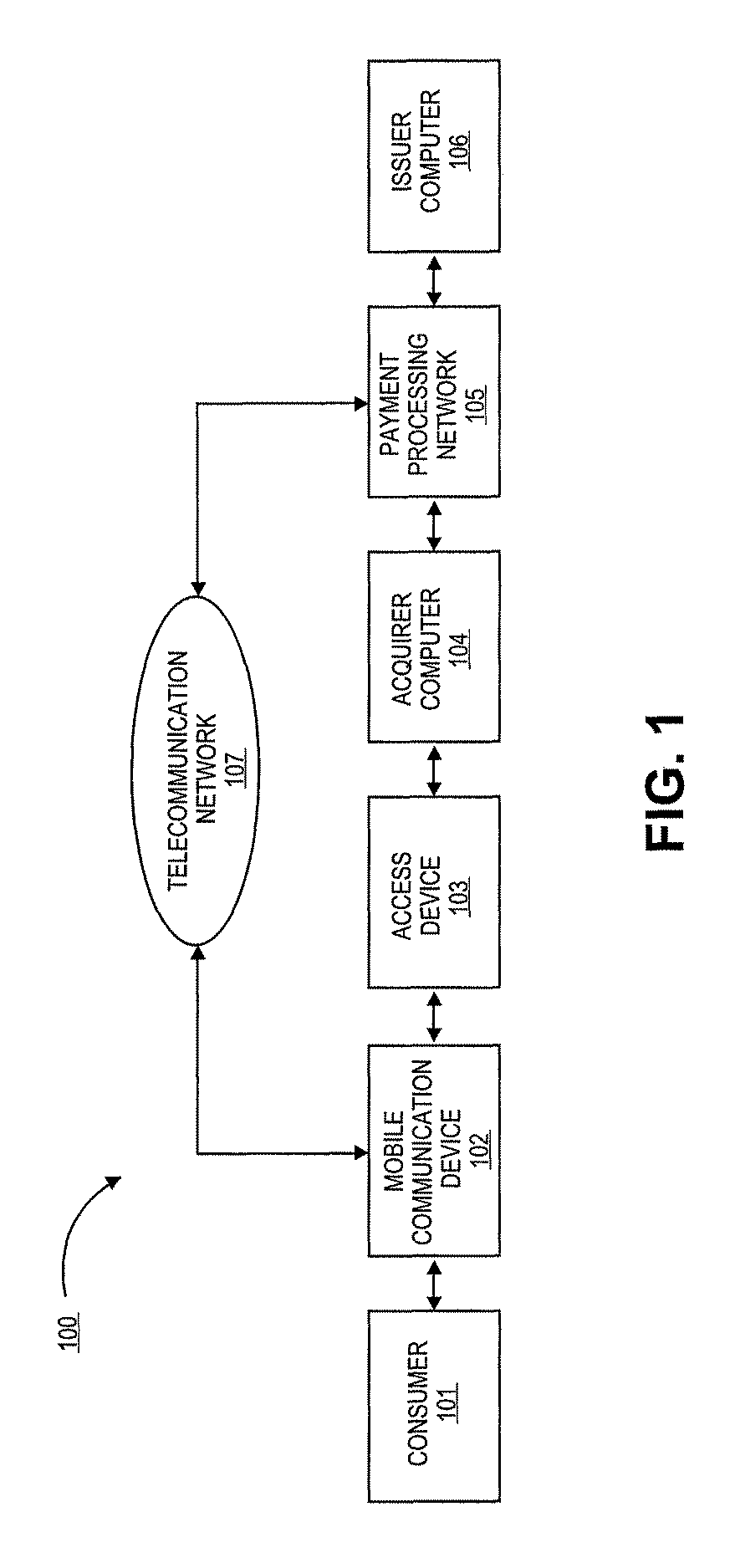
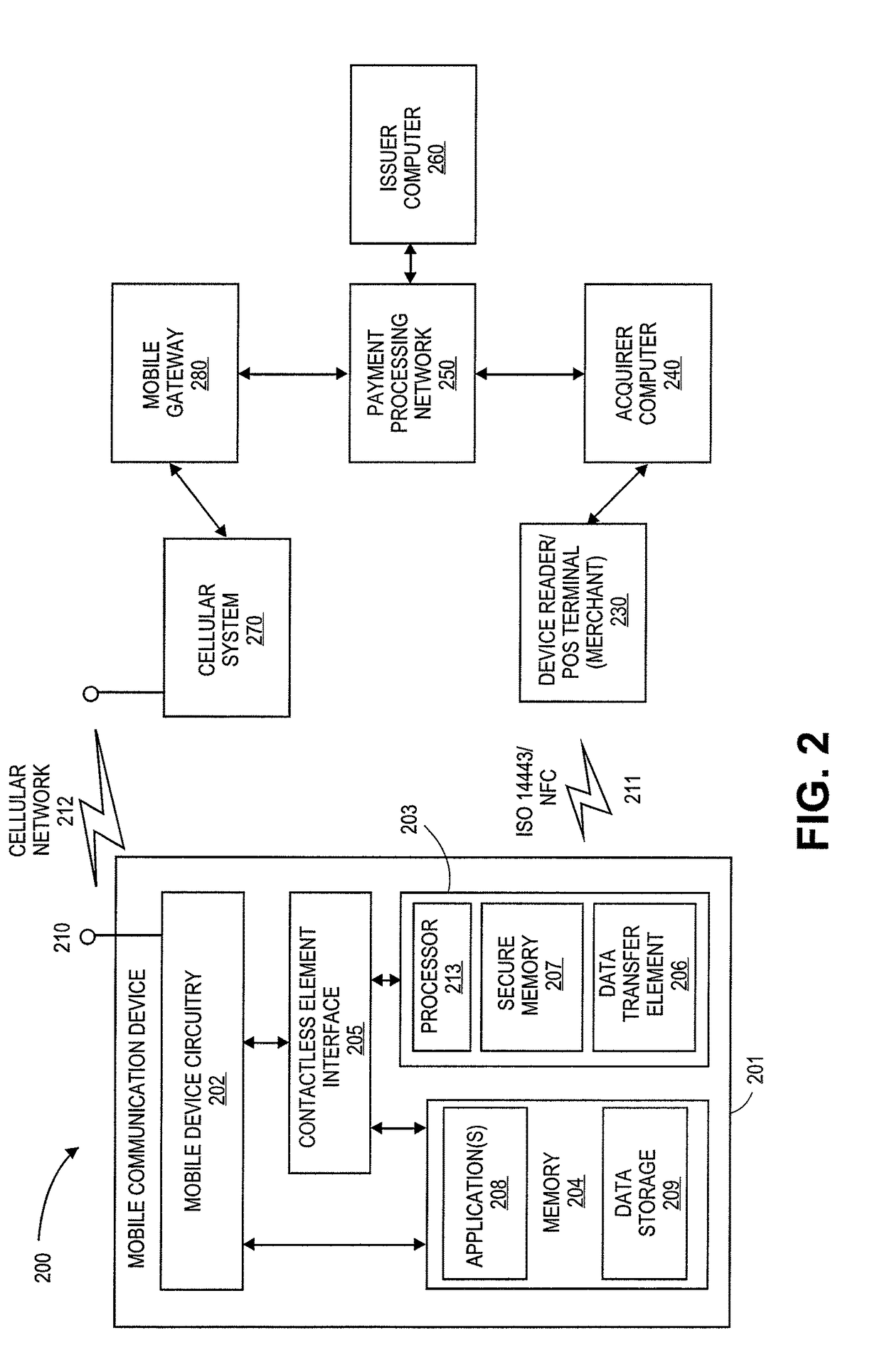
Authentication using application authentication element
ActiveUS20120246079A1Minimize riskImprove securityTransmissionSecurity arrangementUser authenticationNear field communication
Embodiments of the present invention can be directed to systems, apparatuses, and methods for performing transactions through mobile communication devices using telecommunications networks, systems, or proximity near-field communications systems. Embodiments may be directed to a mobile communication device displaying an application authentication element including a pre-selected authentication element. The application authentication element may include transaction data associated with a transaction conducted by a mobile communication device. The mobile communication device may obtain the pre-selected authentication element by either transmitting a request to a server computer or retrieving the pre-selected authentication element from a secure memory in the mobile communication device. A user authentication token may then be received by the mobile communication device from the user. The mobile communication device may then generate a secret token derived from the user authentication token, and if the secret token is correlated to a secret reference token, a transaction may be conducted.
Owner:VISA INT SERVICE ASSOC
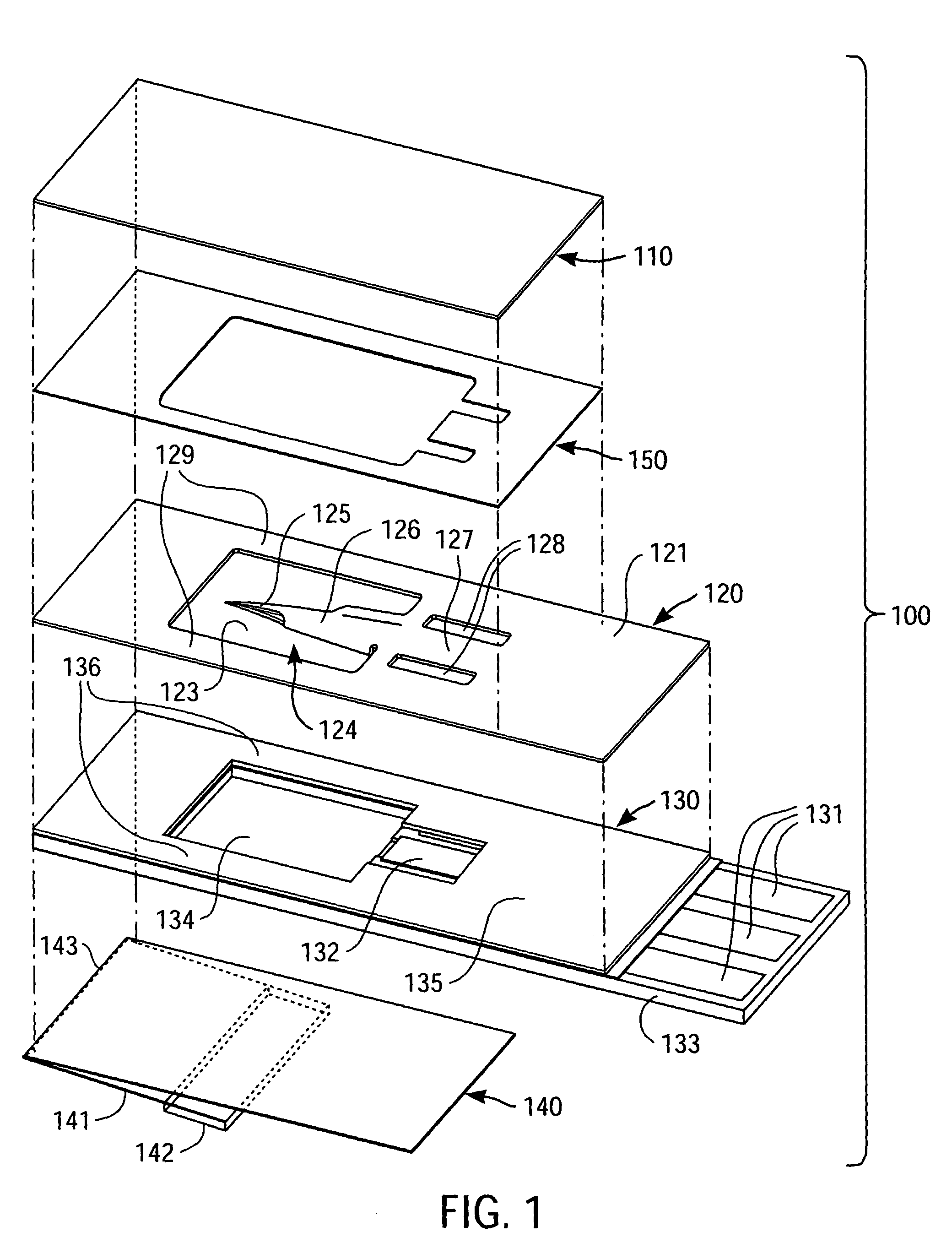
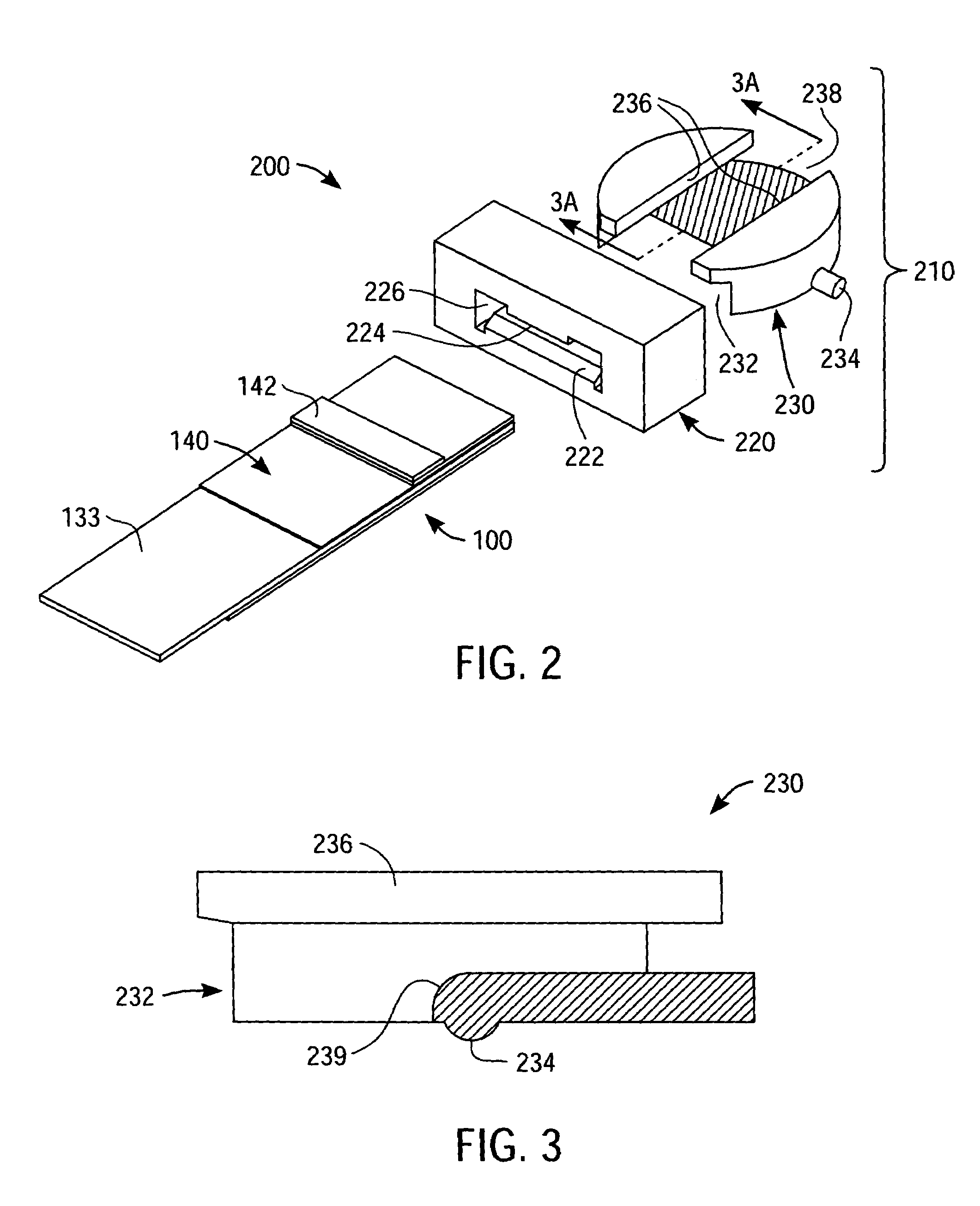
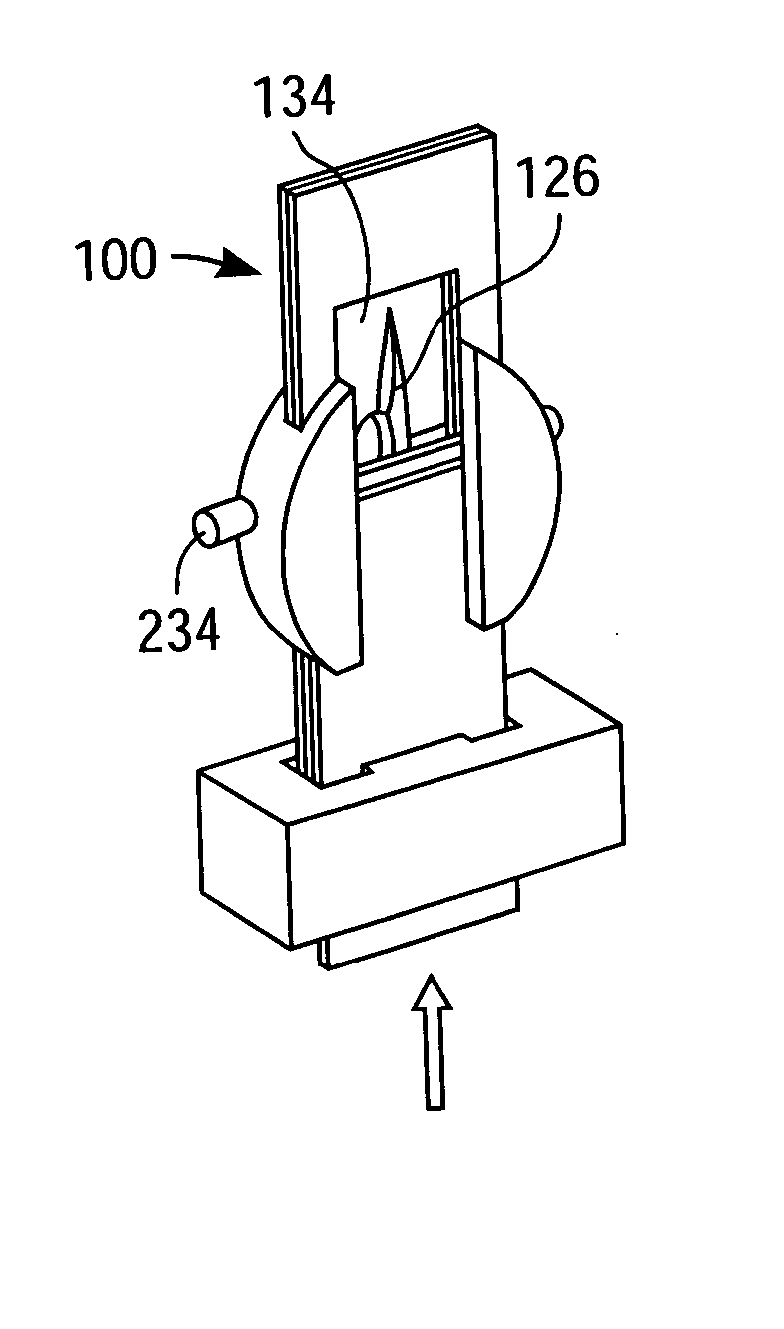
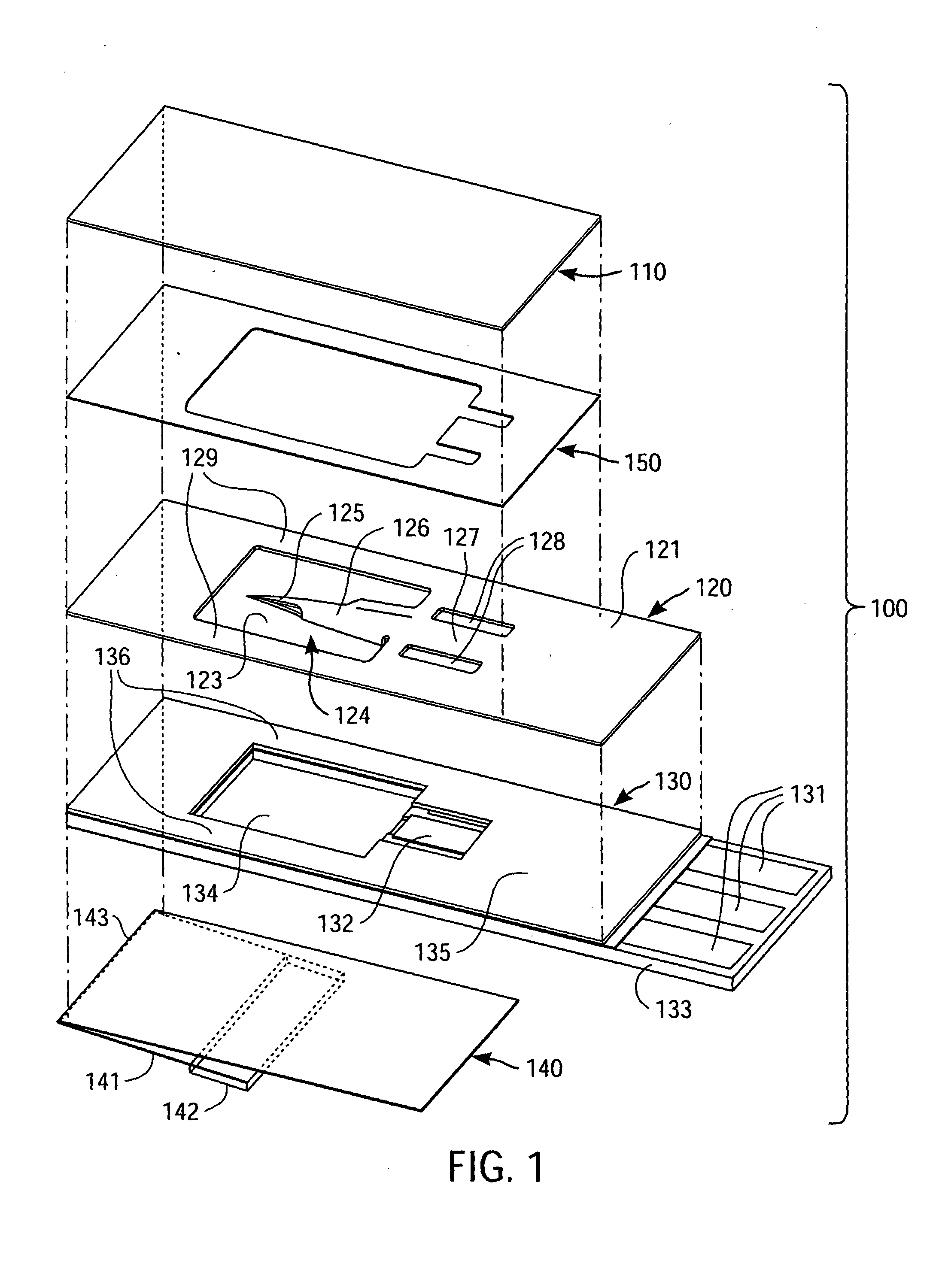
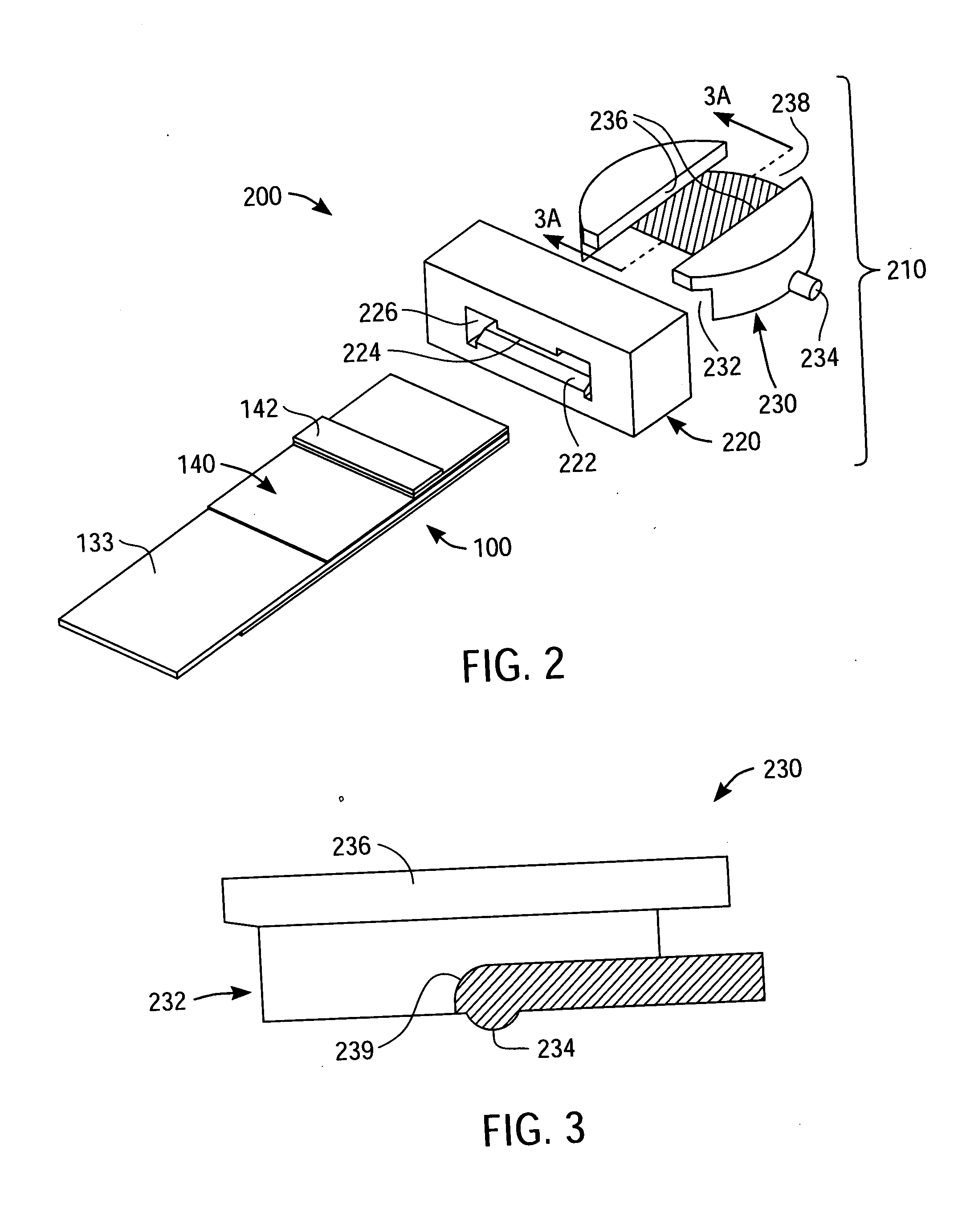
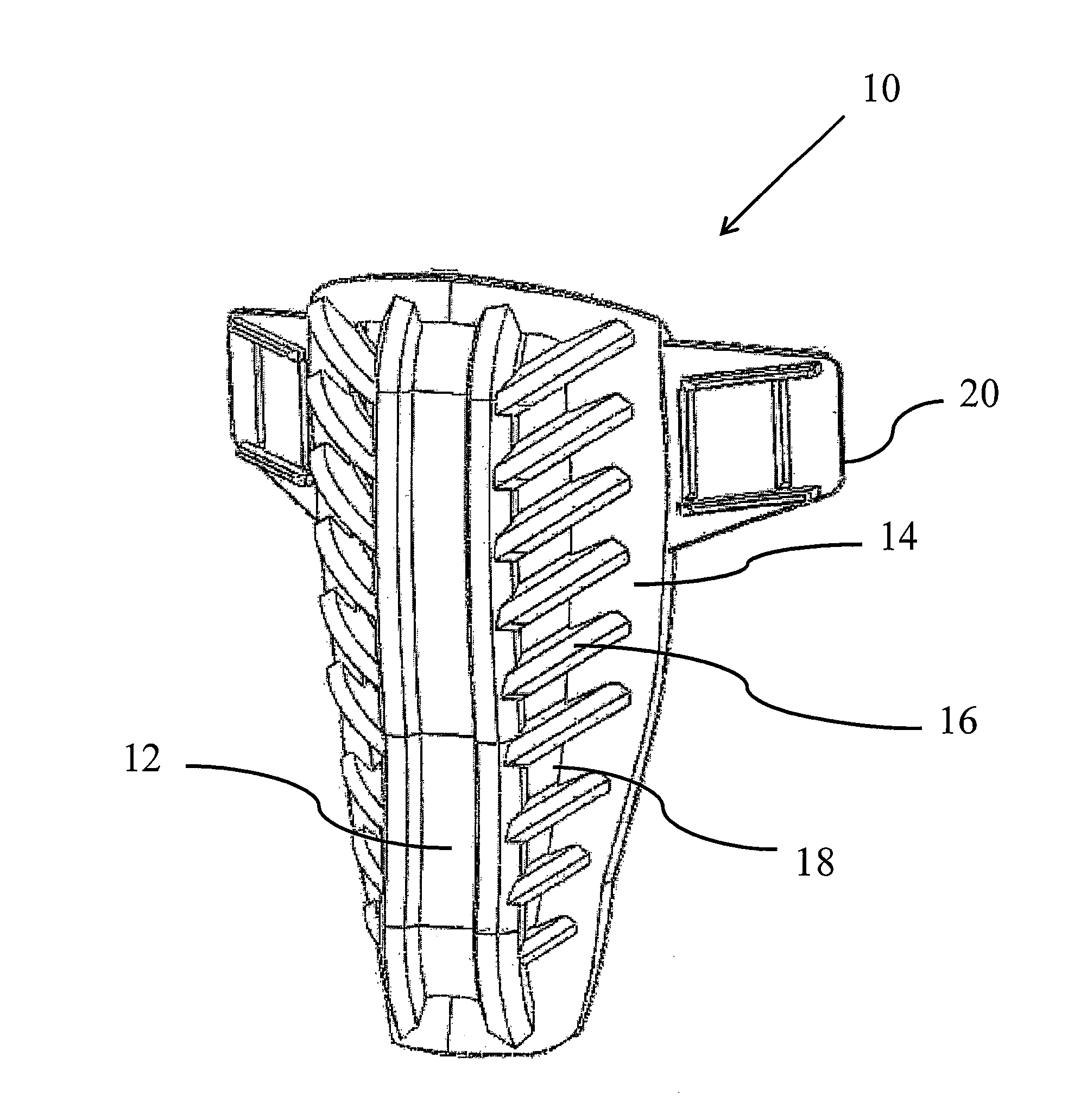
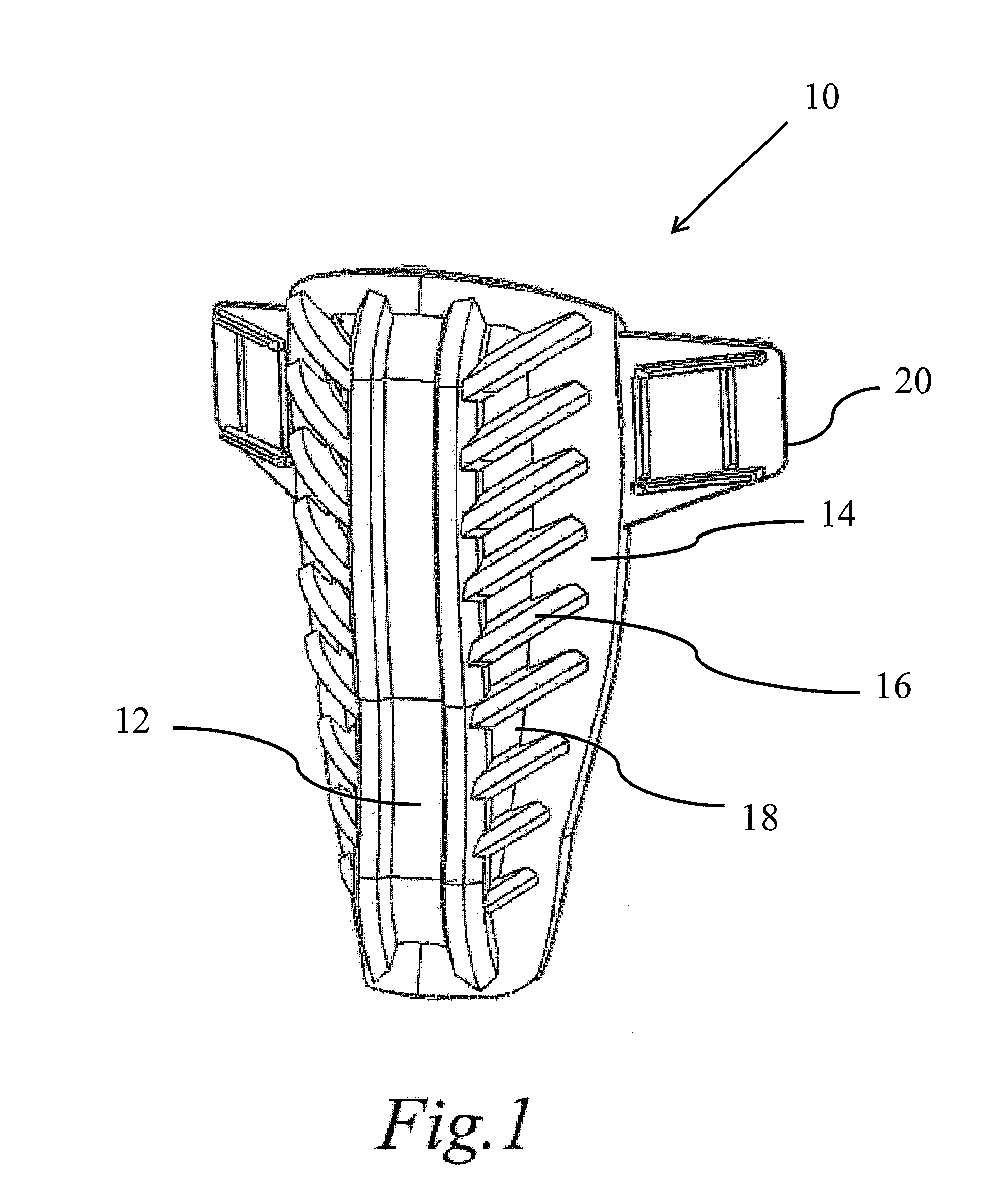
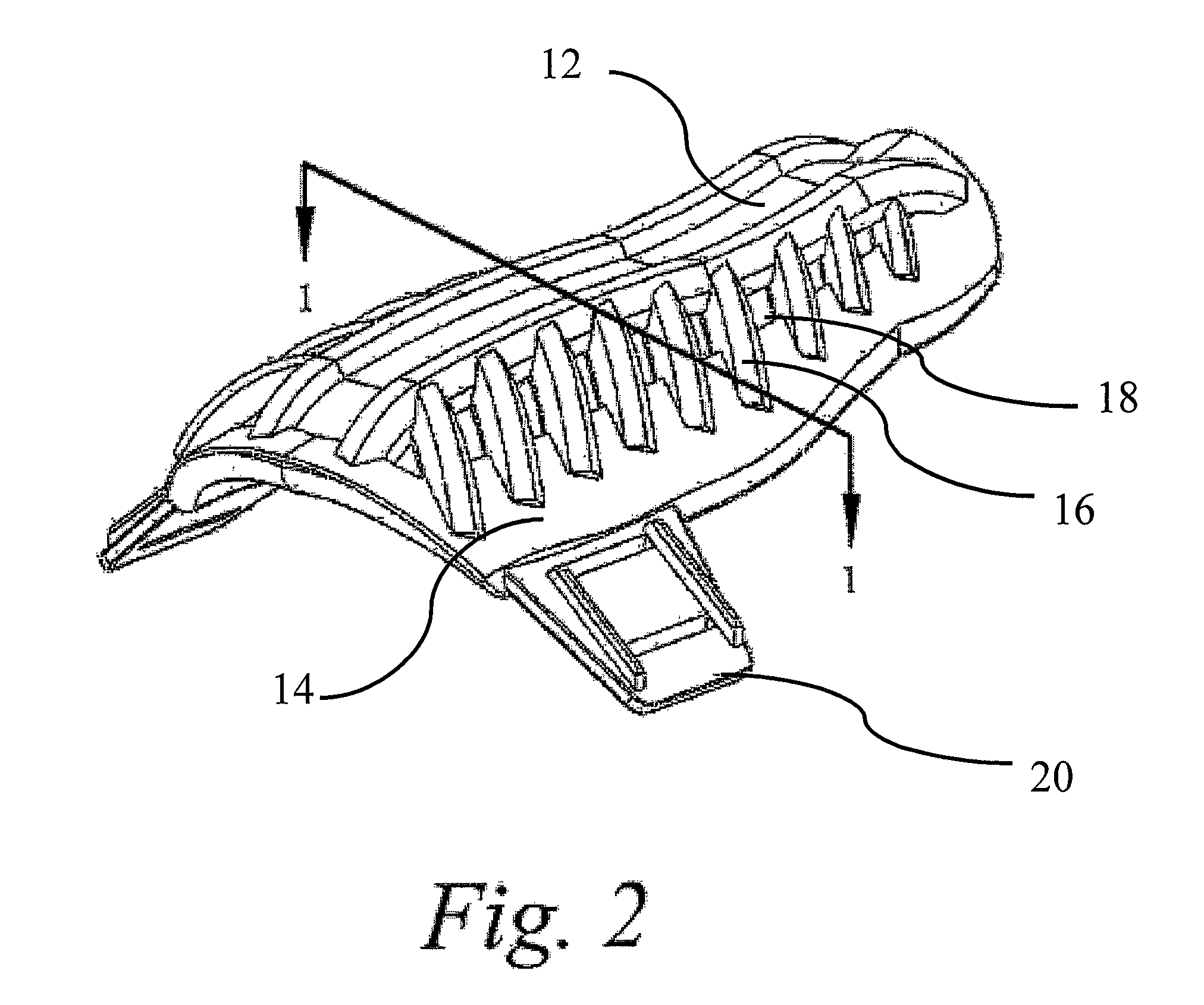
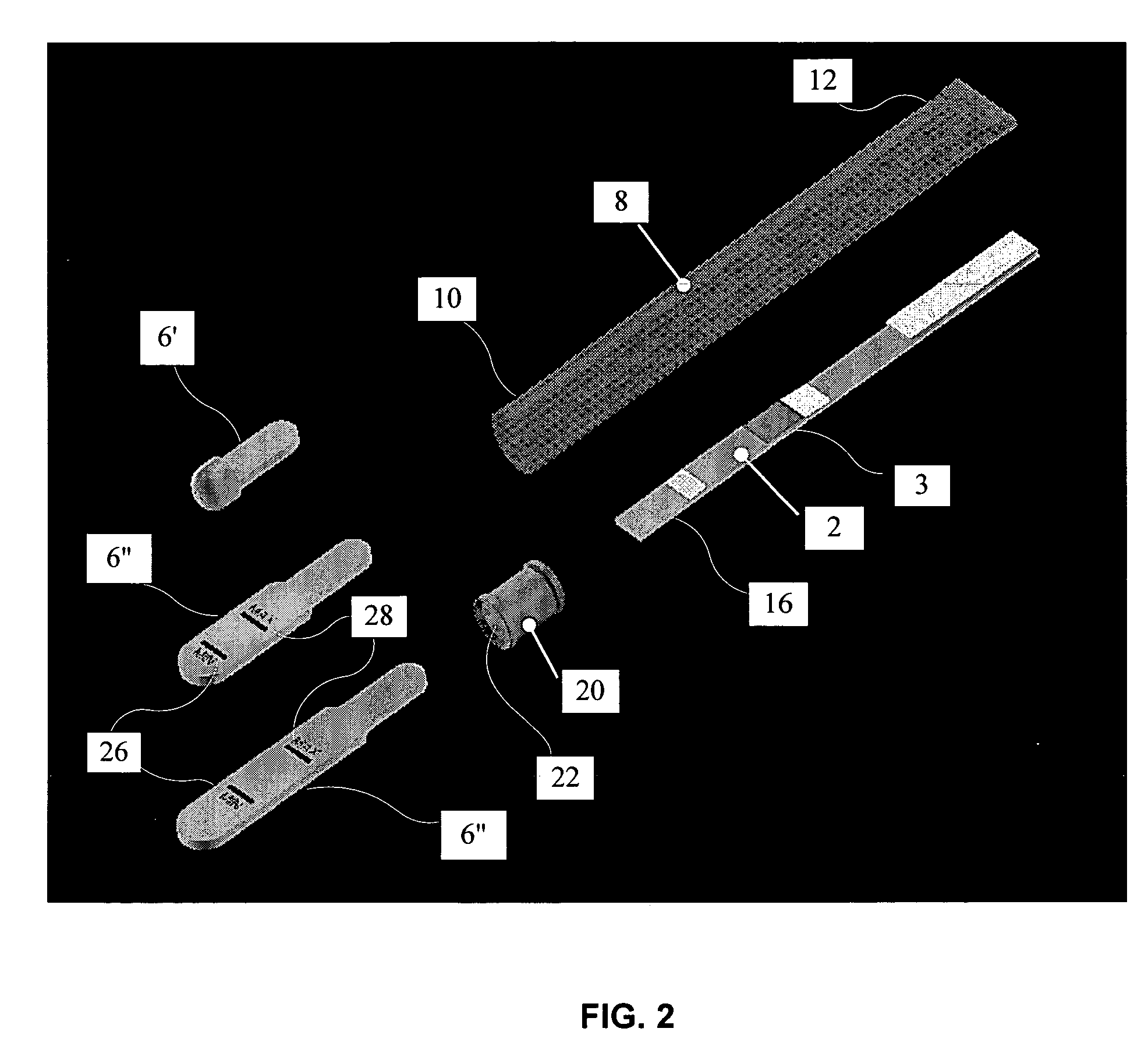
Packaged medical device with a deployable dermal tissue penetration member
A packaged medical device includes upper and lower flexible sheets, a lance body and a test strip. The lance body includes upper and lower surfaces, an opening that extends between the upper and lower surfaces and a dermal tissue penetration member that projects into the lance body opening. The test strip has an opening therethrough and is attached to the lance body lower surface such that the dermal tissue penetration member is operatively aligned with the test strip opening. The upper flexible sheet is attached to the lance body upper surface and covers the lance body opening, while the lower flexible sheet is detachably attached to the test strip and covers the test strip opening. The upper flexible sheet, lance body and test strip are configured such that, when the lower flexible sheet has been detached to uncover the test strip opening, the upper flexible sheet, lance body and test strip can be bent to deploy the dermal tissue penetration member from the lance body opening. A kit includes the packaged medical device described above and a deployment device for detaching the lower flexible sheet and bending the upper flexible sheet, lance body and test strip to deploy the dermal tissue penetration member. A method for deploying a dermal tissue penetration member of a packed medical device includes providing the packaged medical device described above, detaching the lower flexible sheet to uncover the test strip opening and bending the upper flexible sheet, lance body and test strip to deploy the dermal tissue penetration member.
Owner:LIFESCAN IP HLDG LLC
Packaged medical device with a deployable dermal tissue penetration member
A packaged medical device includes upper and lower flexible sheets, a lance body and a test strip. The lance body includes upper and lower surfaces, an opening that extends between the upper and lower surfaces and a dermal tissue penetration member that projects into the lance body opening. The test strip has an opening therethrough and is attached to the lance body lower surface such that the dermal tissue penetration member is operatively aligned with the test strip opening. The upper flexible sheet is attached to the lance body upper surface and covers the lance body opening, while the lower flexible sheet is detachably attached to the test strip and covers the test strip opening. The upper flexible sheet, lance body and test strip are configured such that, when the lower flexible sheet has been detached to uncover the test strip opening, the upper flexible sheet, lance body and test strip can be bent to deploy the dermal tissue penetration member from the lance body opening. A kit includes the packaged medical device described above and a deployment device for detaching the lower flexible sheet and bending the upper flexible sheet, lance body and test strip to deploy the dermal tissue penetration member. A method for deploying a dermal tissue penetration member of a packed medical device includes providing the packaged medical device described above, detaching the lower flexible sheet to uncover the test strip opening and bending the upper flexible sheet, lance body and test strip to deploy the dermal tissue penetration member.
Owner:LIFESCAN IP HLDG LLC
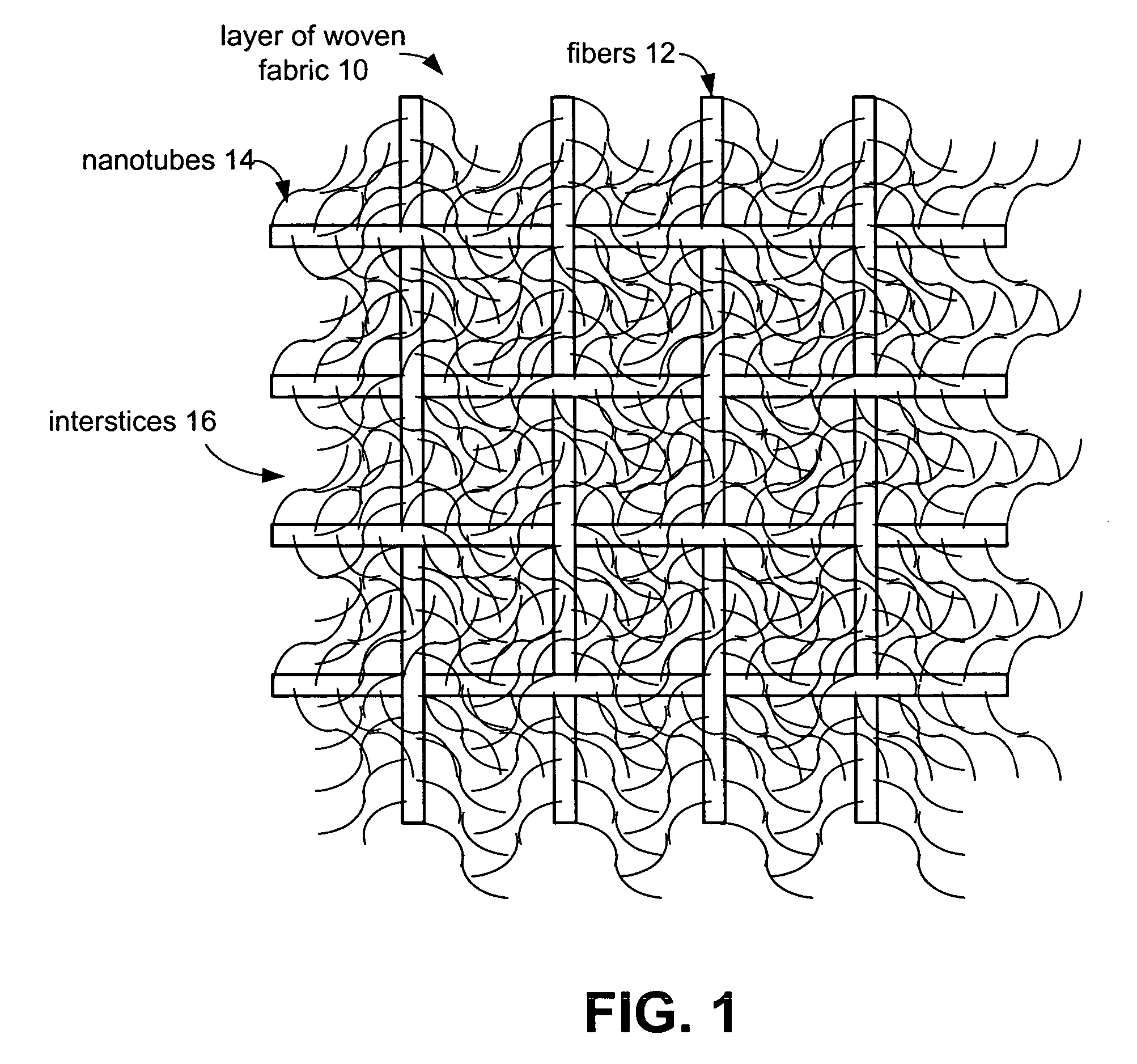
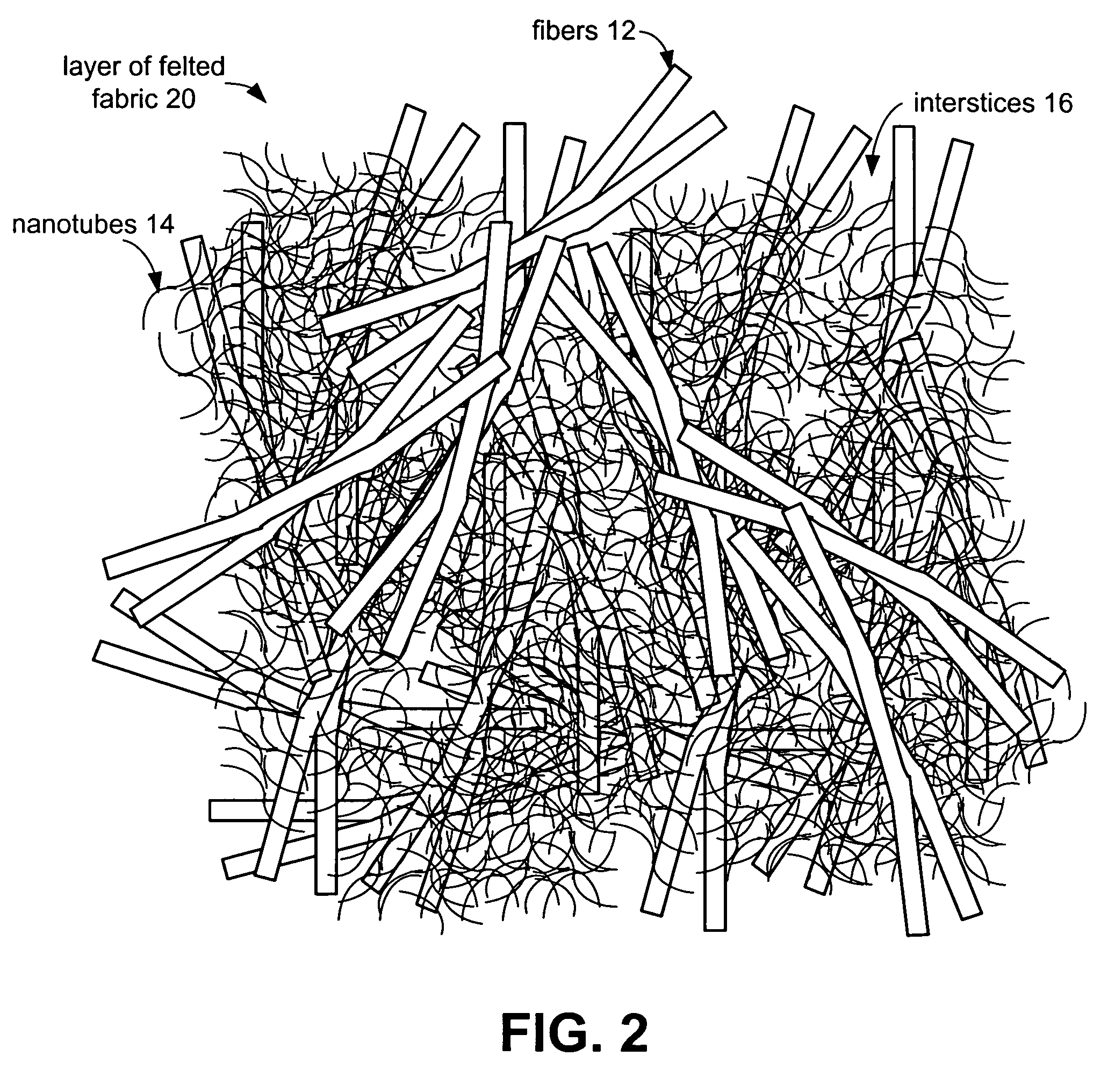
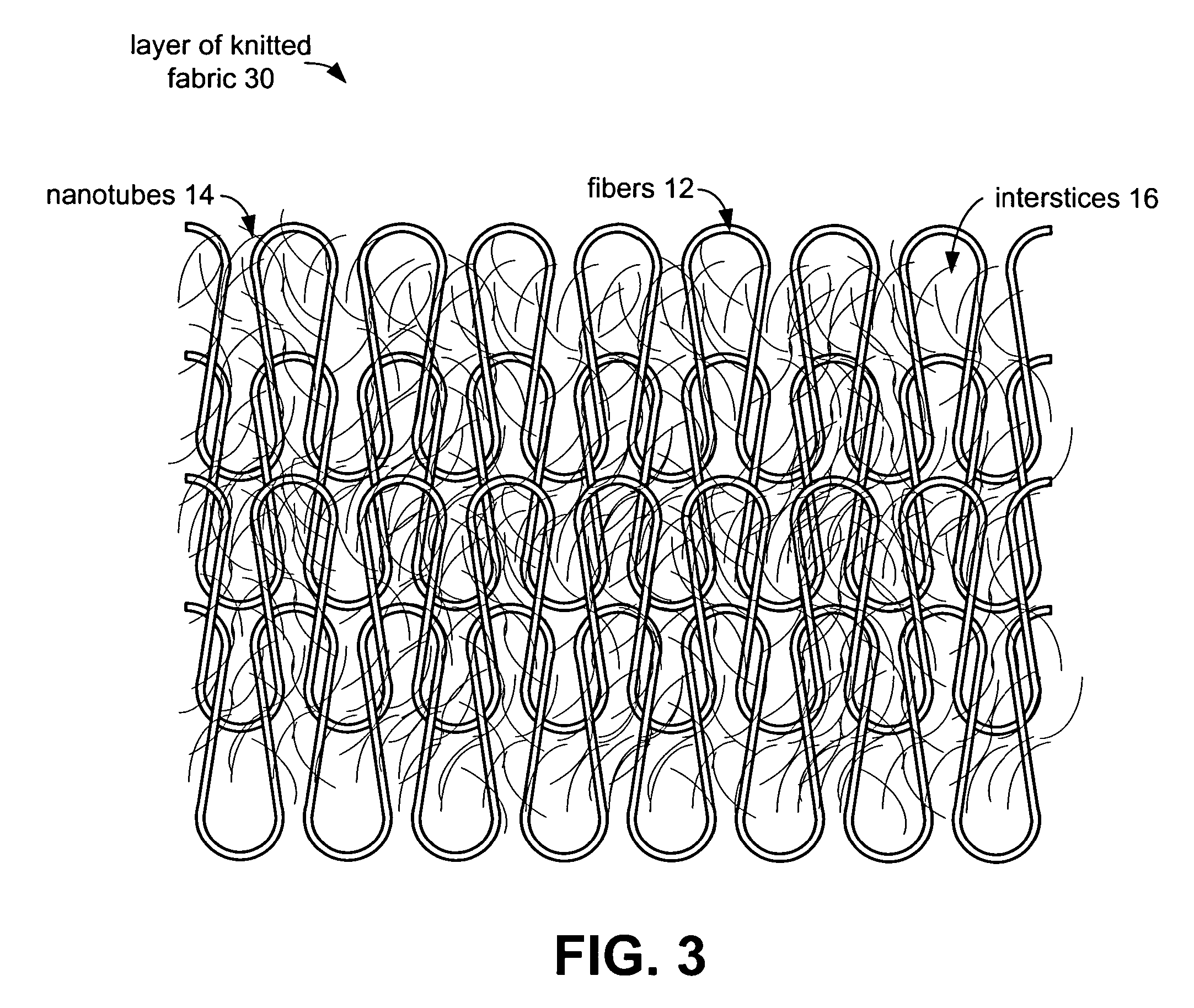
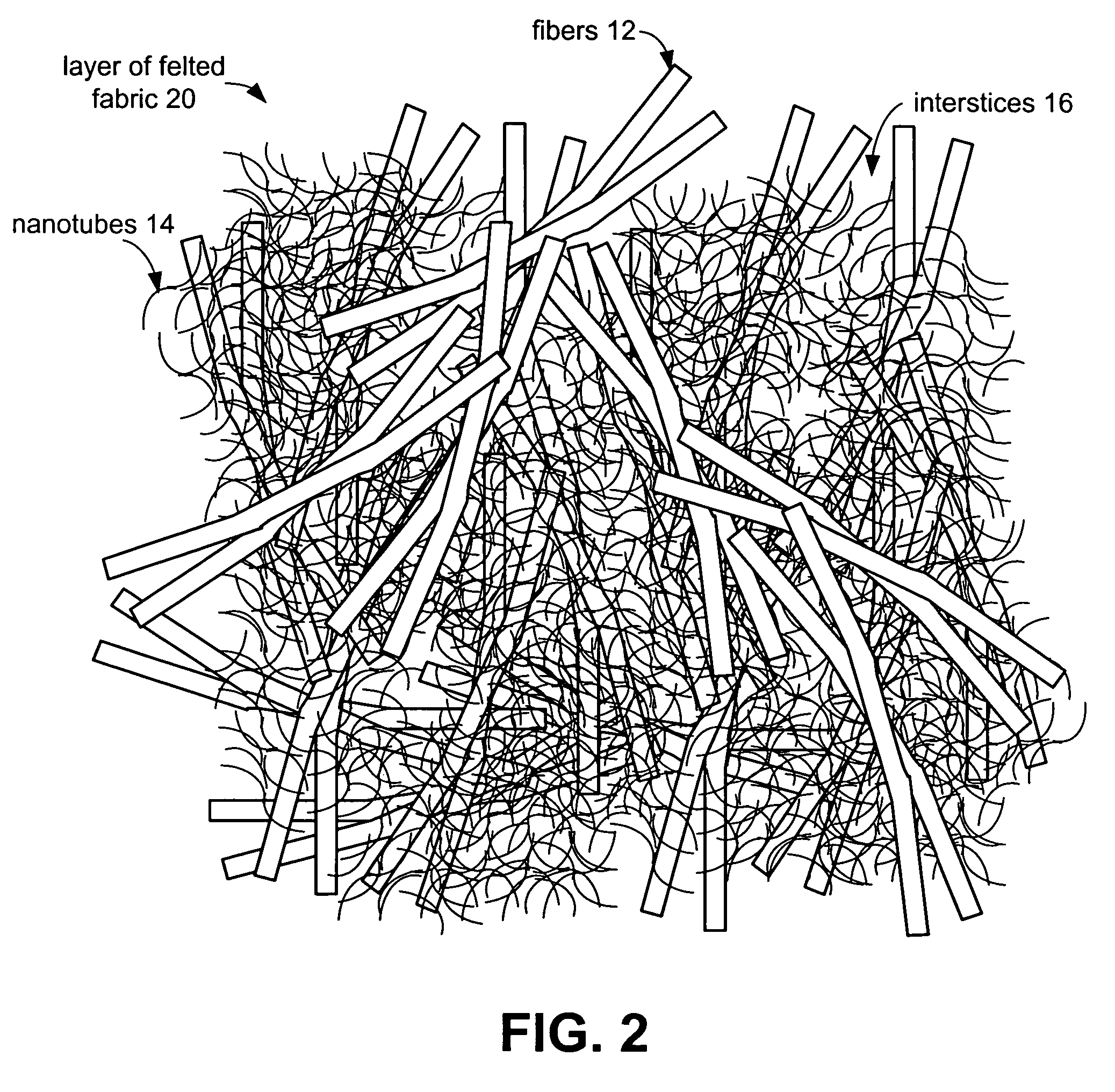
Ballistic fabrics with improved antiballistic properties
ActiveUS20060062944A1Good physical propertiesImprove propertiesMaterial nanotechnologyWarp knittingFiberYarn
The present invention provides fabrics that have unique mechanical, chemical, electrical, and thermal properties. The fabrics comprise layers of woven, knit or felted fibers, yarns or tow. Interstitially synthesized nanotubes, such as single-walled or multi-walled carbon nanotubes, enhance the fabric's antiballistic properties. These nanotubes may also insulate, semi-conduct or super-conduct electrical charges, or provide enhanced thermal properties of these fabrics which can be layered to form unique garments or structures.
Owner:LOCKHEED MARTIN CORP
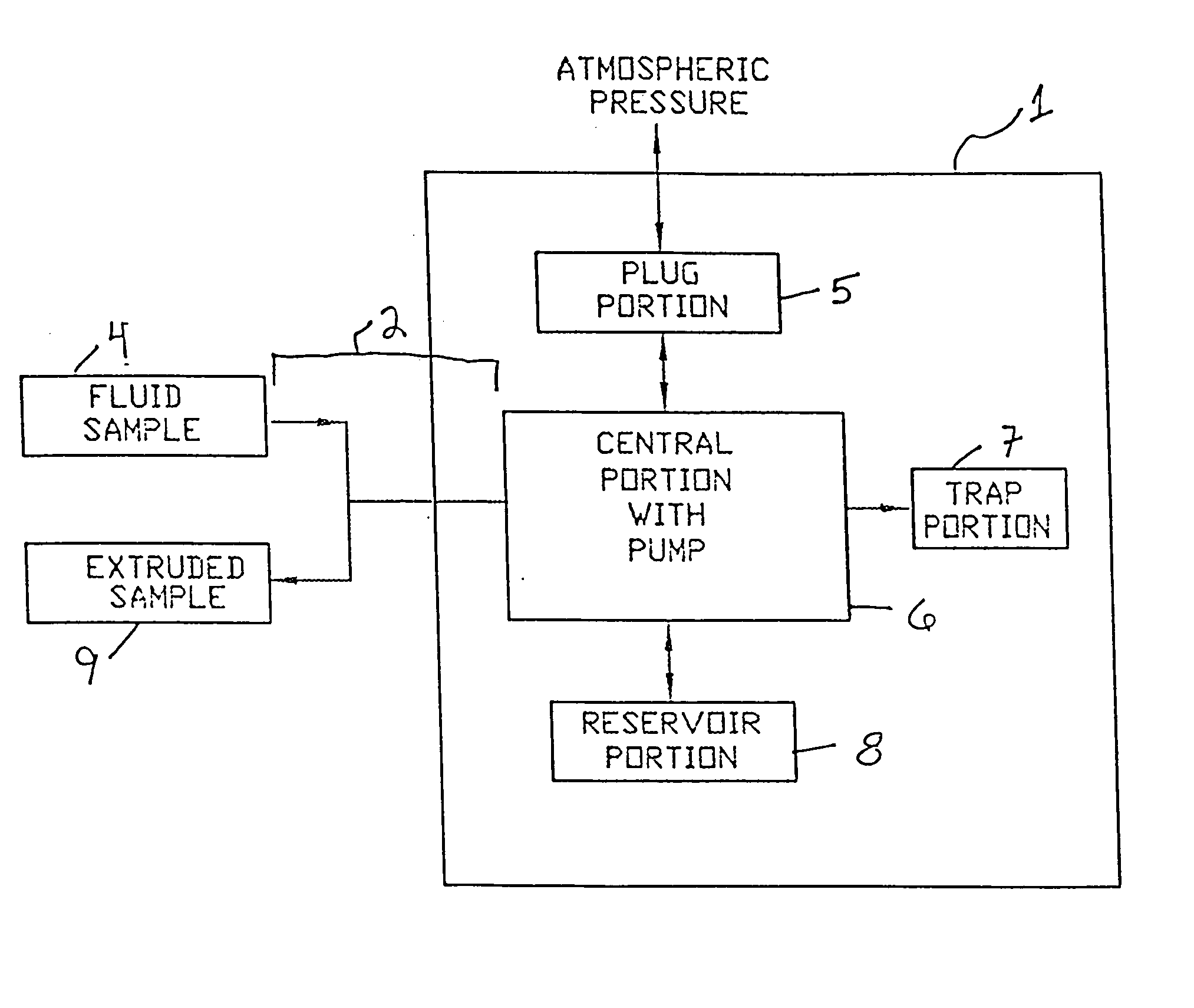
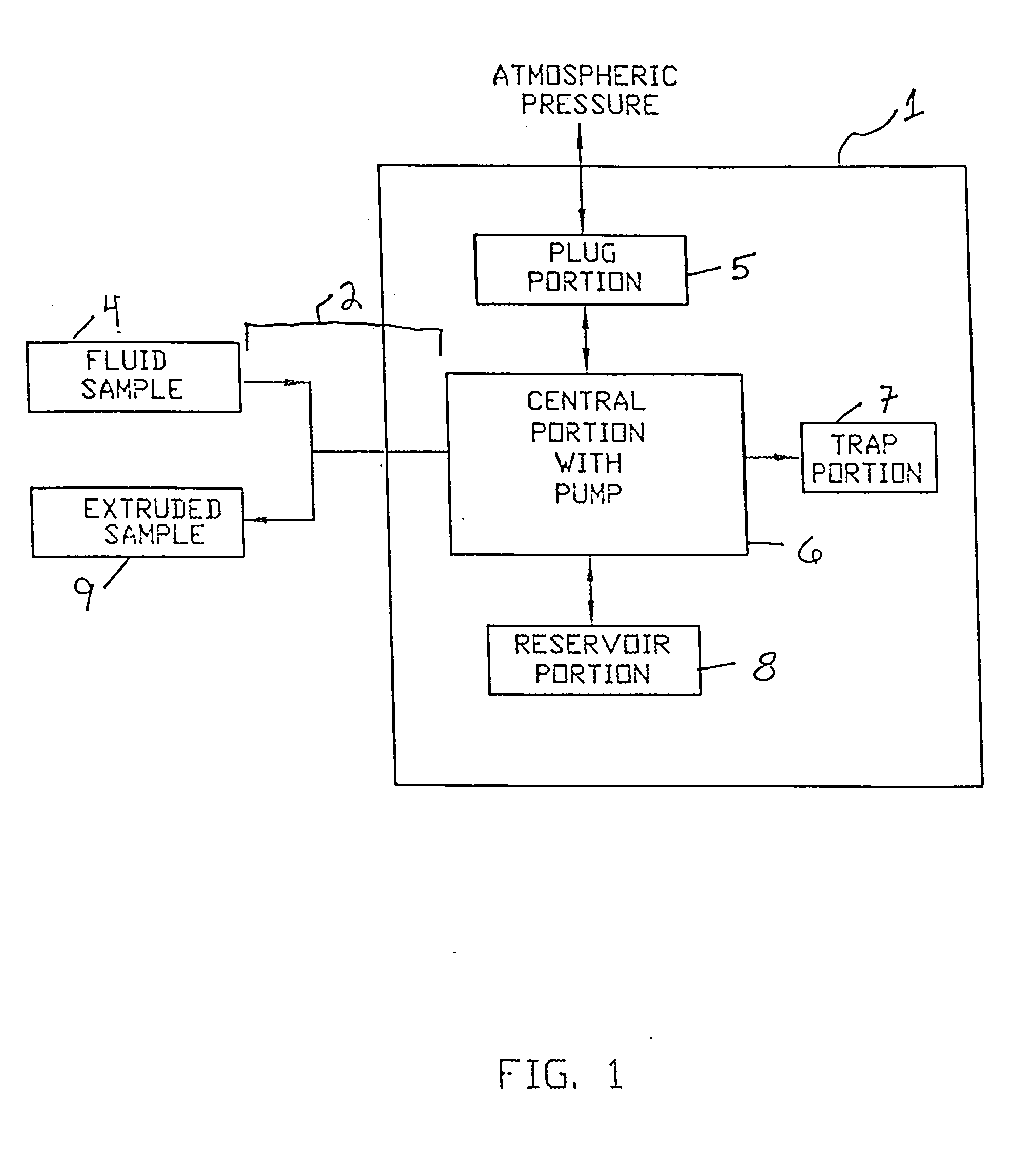
Micro-volume blood sampling device
InactiveUS20050178218A1Minimize transmissionEasy and rapid separationWithdrawing sample devicesLaboratory glasswaresAssayMicroDose
The invention features a single tool for collecting a known volume of a fluid biological sample from an animal, such as a human or small mammal, for mixing the sample with a predetermined amount of a reagent or a diluent, physically separate components of the sample, for storing the sample in a secure and stable fashion, and for then recovering some or all of the sample in a condition suitable for performing a diagnostic assay. The tool can be equipped with an optional means of recording or displaying information about the sample, such as a tag, a bar code, or a surface indicator that identifies, e.g., the date, animal number, and any additional information necessary. A second bar coded label to remove and attaché to the cage shall be provided. The cage / blood-sample can be correlated if needed at a later date.
Owner:AVANTRA BIOSCI CORP
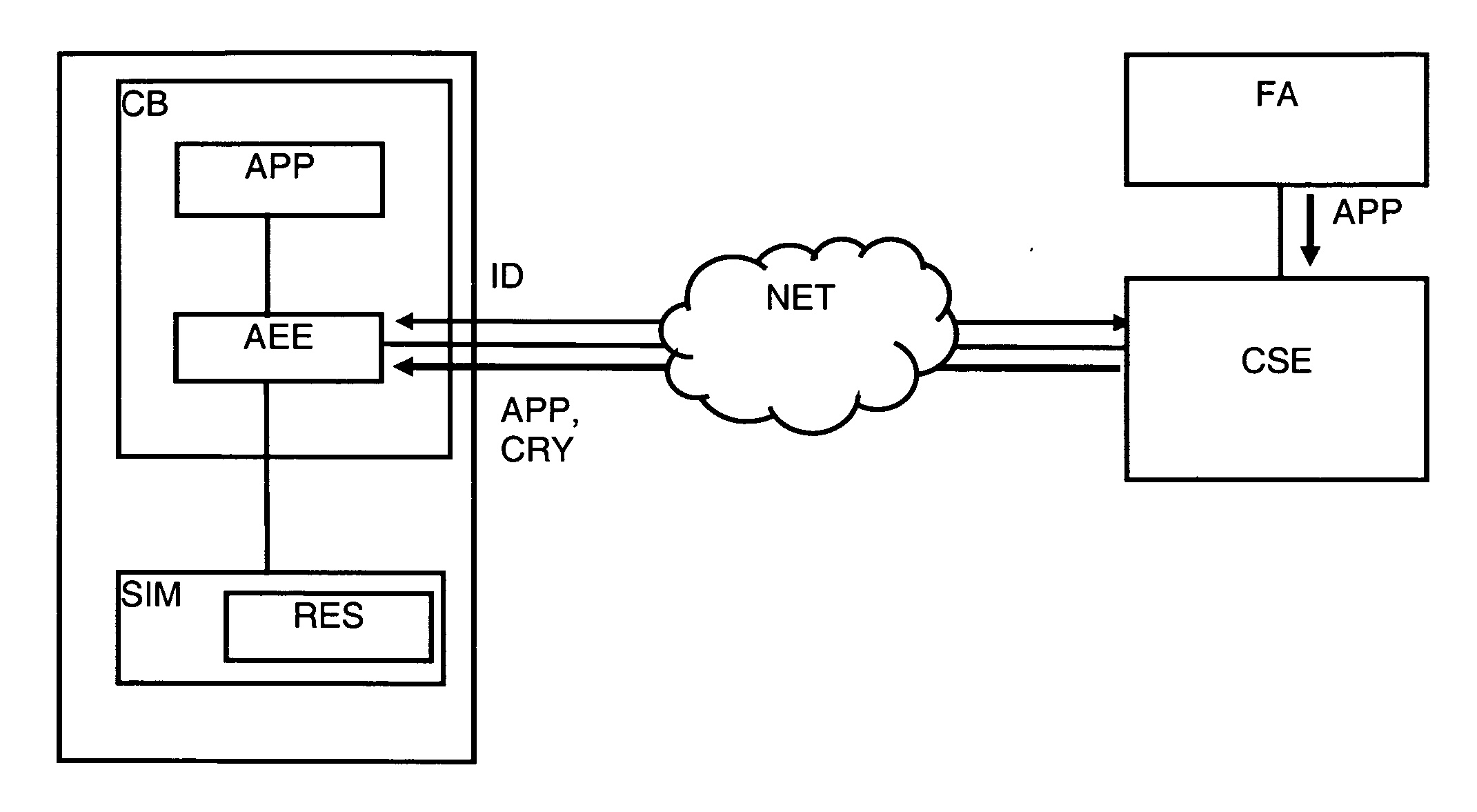
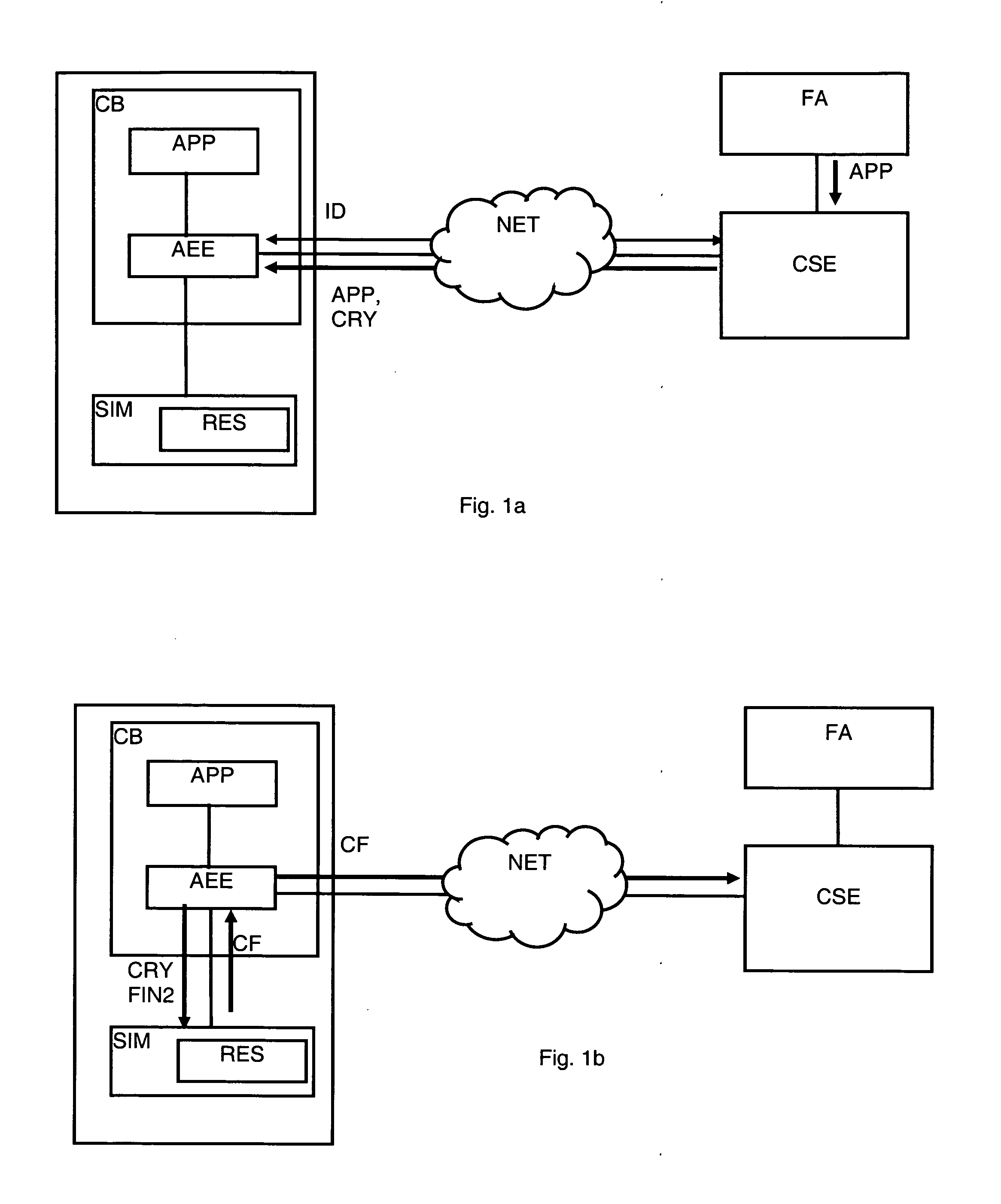
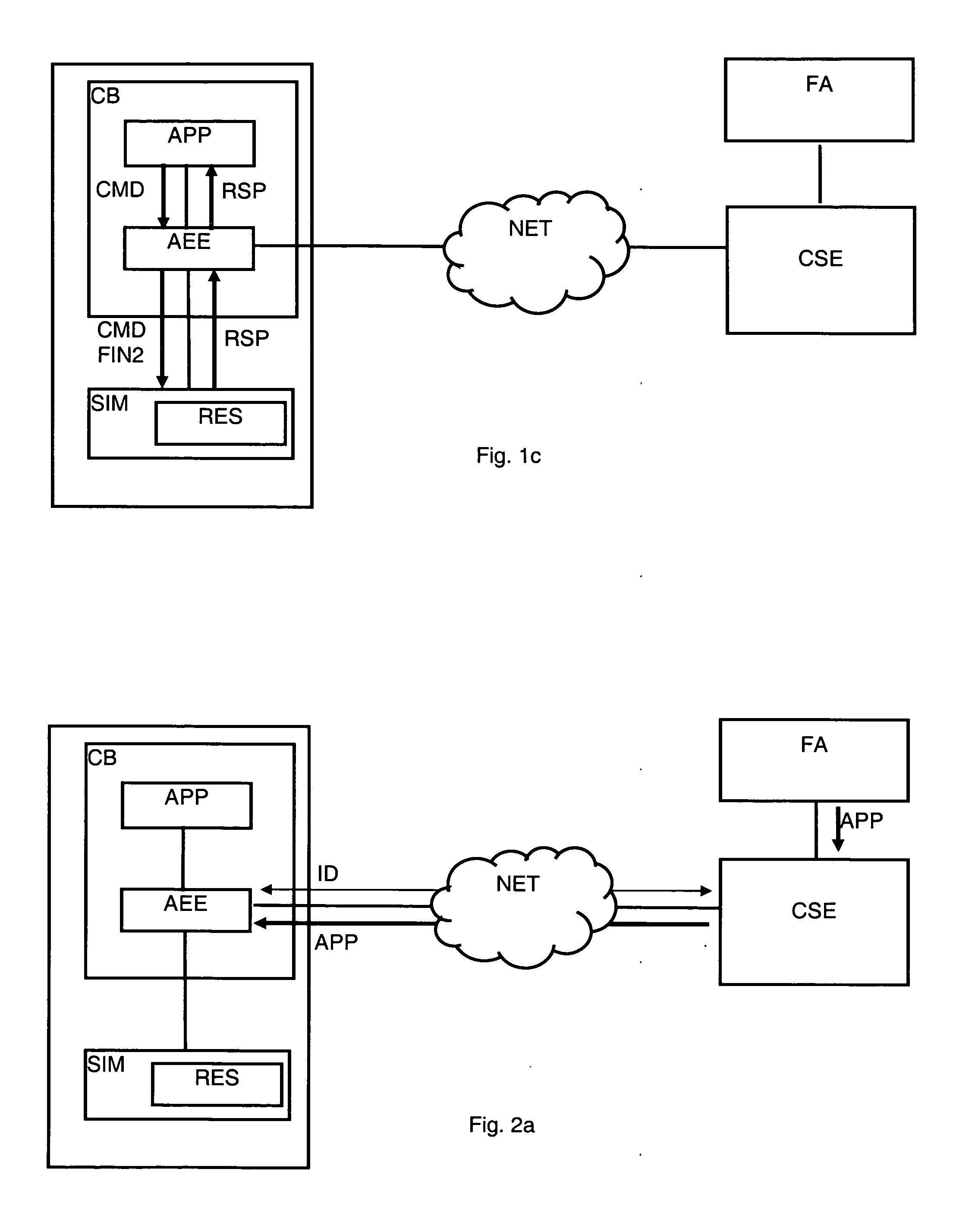
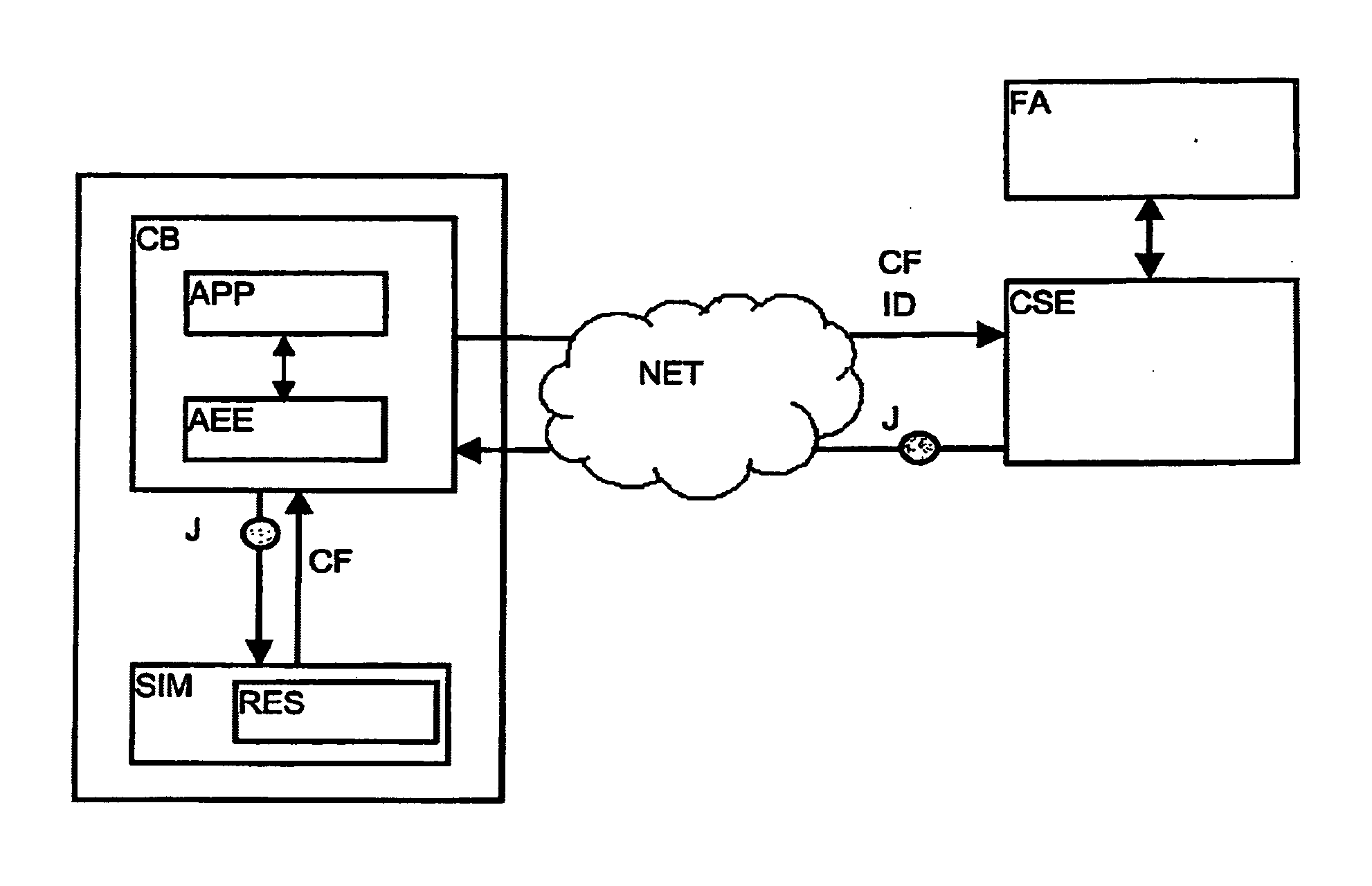
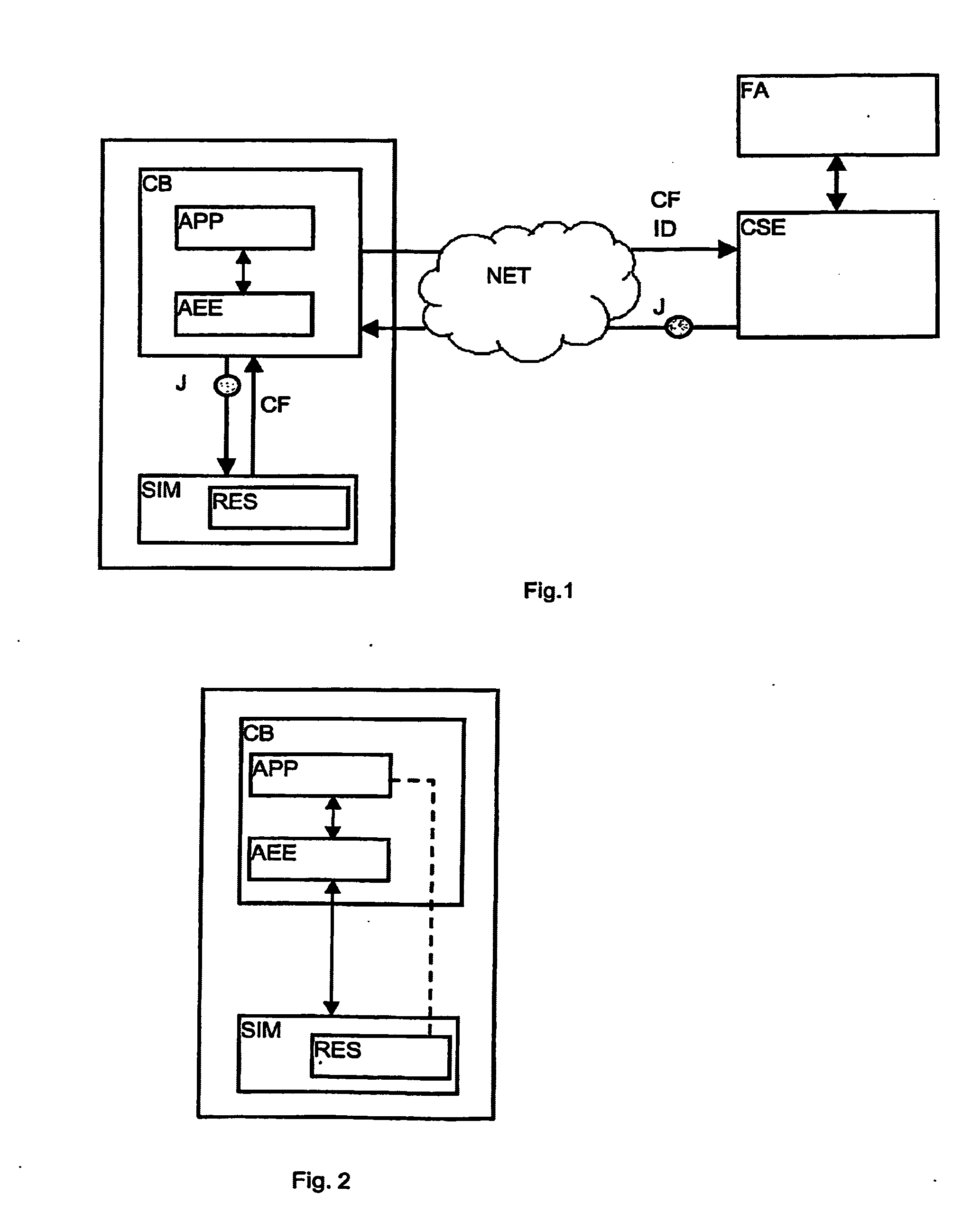
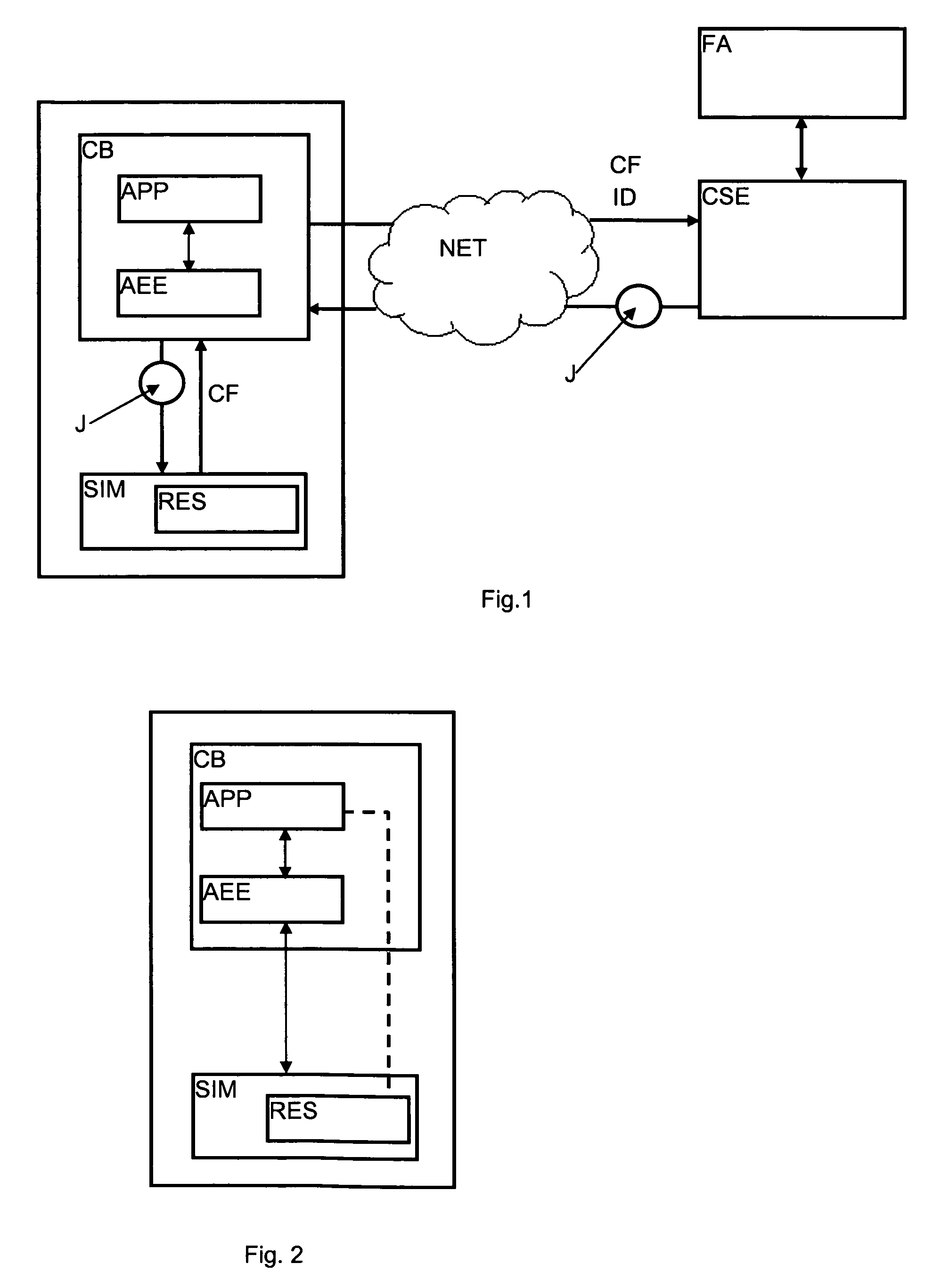
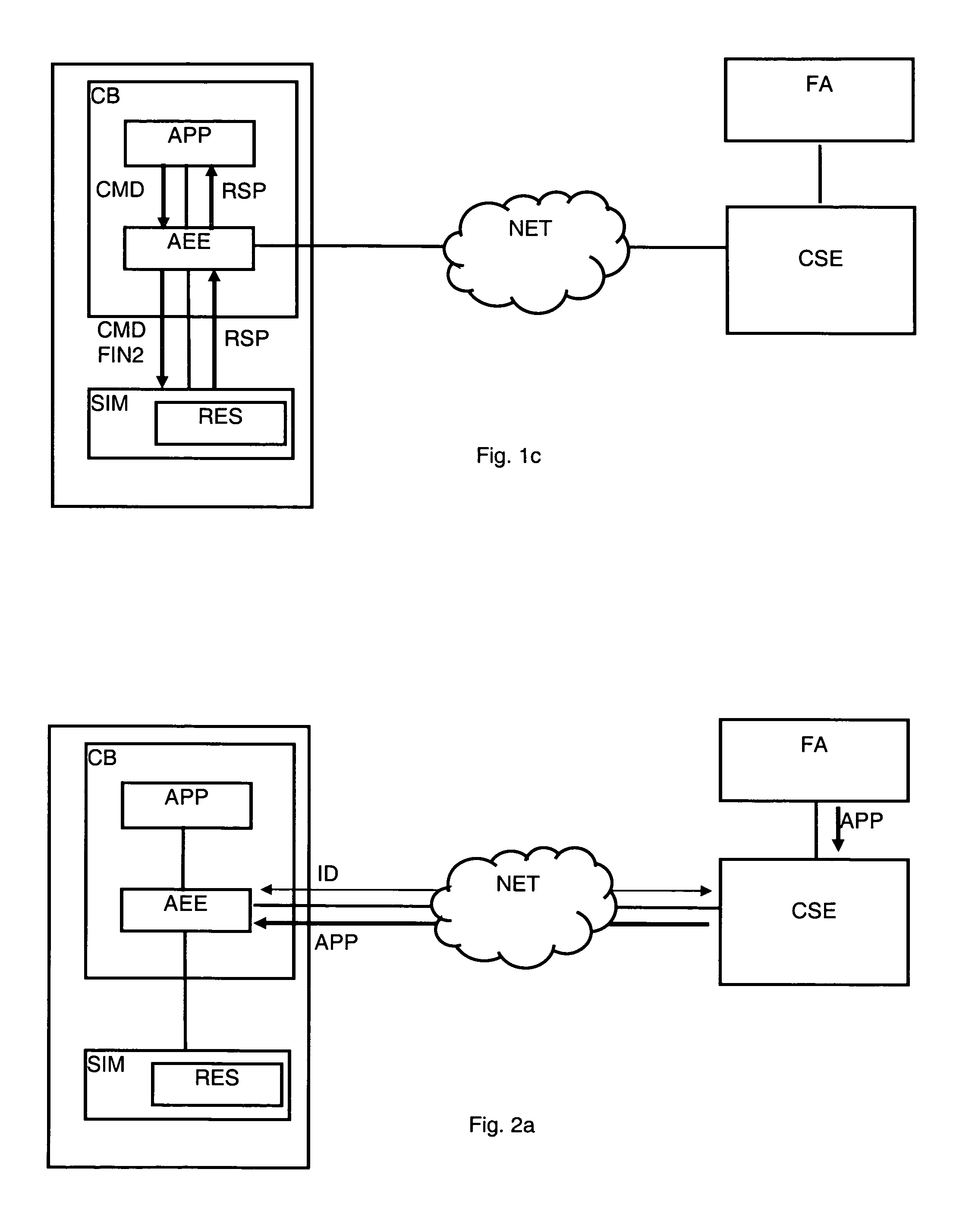
Method For The Authentication Of Applications
ActiveUS20070198834A1Controlling the riskProtect usersUnauthorised/fraudulent call preventionEavesdropping prevention circuitsNetwork connectionInit
A method is disclosed for the authentication of applications both at the time of their downloading, as well as at the time of their execution. At least one application works in an equipment connected by a network to a control server, the equipment being locally connected to a security module. The application is loaded and / or executed via an application execution environment of the equipment and uses resources stored in the security module. The authentication method includes reception by the control server, via the network, of data including at least the identifier of the equipment and the identifier of the security module, analysis and verification by the control server of the data; generation of a cryptogram including a digest of the application, data identifying the equipment and the security module and instructions intended for the module; transmission of the cryptogram, via the network and the equipment, to the security module; and verification of the application by comparing the digest extracted from the cryptogram received with a digest determined by the security module. Further, said method further comprising steps wherein, during the initialization and / or the activation of the application, the security module executes the instructions extracted from the cryptogram, to at least one of release and block the access to certain resources of the security module according to the result of the verification suited to this application carried out previously.
Owner:NAGRAVISION SA
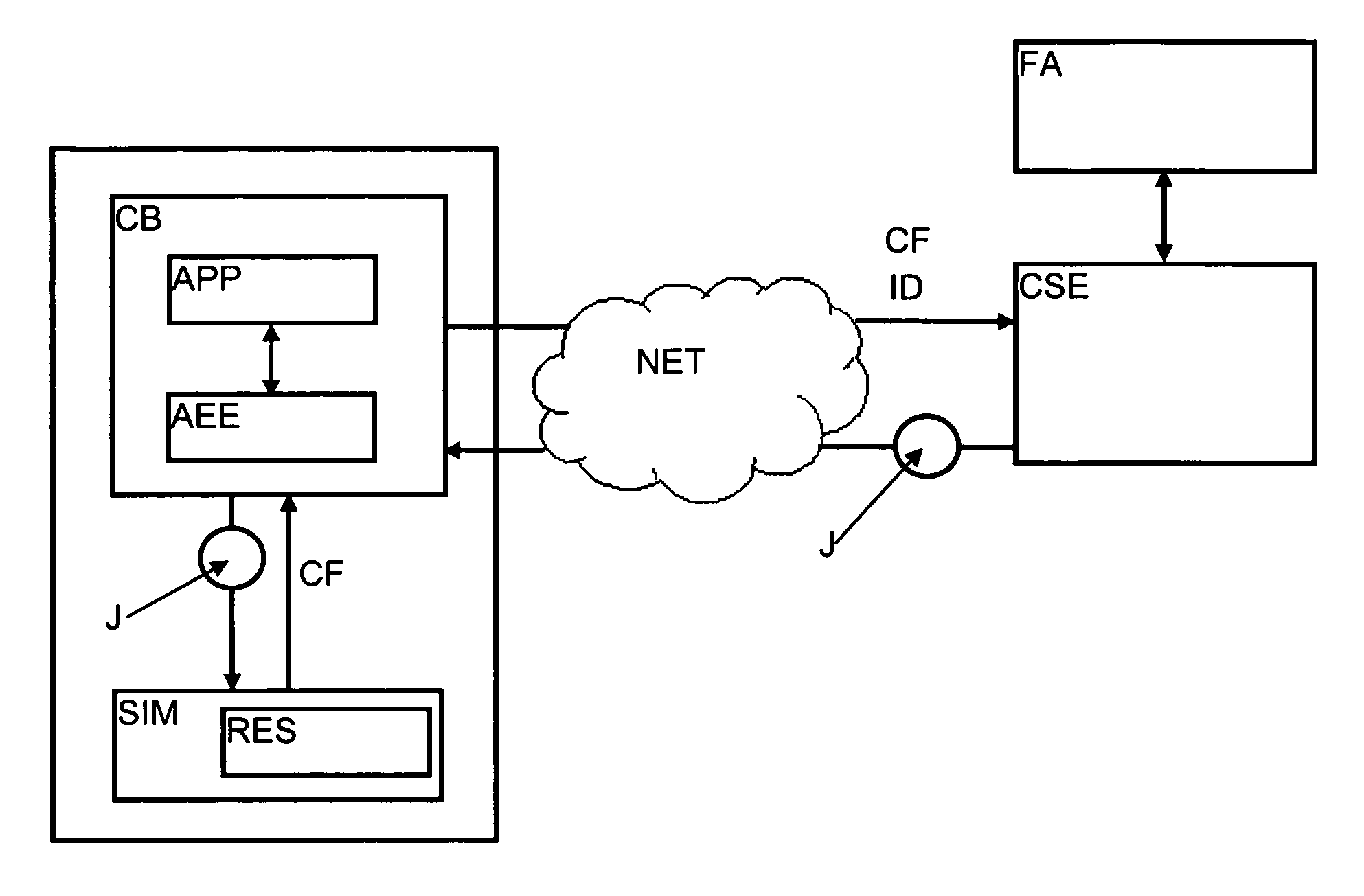
Method For Managing The Security Of Applications With A Security Module
ActiveUS20070274524A1Block and reduce functionControlling the riskDigital data processing detailsAnalogue secracy/subscription systemsCryptogramApplication security
The aim of this invention is to propose a method to manage the security of the set composed by an equipment, a security module and applications in order to limit the risk related to the fact that a security module could be fraudulently used by applications executed on a type of equipment and / or of software version that does not entirely fulfill the established security criteria. This aim is reached by a method for managing the security of applications with a security module functioning in an equipment connected to a network, said network being managed by a control server of an operator, said applications using resources as data or functions stored in a security module locally connected to said equipment, comprising the following preliminary steps: reception of data comprising at least the type and software version of the equipment and the identity of the security module, via the network, by the control server, analysis and verification by the control server of said data, generation of a cryptogram from the result of the verification of said data, and transmission of said cryptogram, via the network and the equipment, to the security module, said method further comprises steps wherein the security module analyses the received cryptogram and activates, respectively deactivates the resources as data or functions used by at least one application installed in the equipment, said cryptogram comprising the instructions conditioning the functioning of the application according to criteria established by the supplier of said application and / or the operator and / or the user of the equipment.
Owner:NAGRAVISION SA
Ballistic fabrics with improved antiballistic properties
ActiveUS8080487B2Good physical propertiesImprove propertiesMaterial nanotechnologyWarp knittingFiberYarn
Owner:LOCKHEED MARTIN CORP
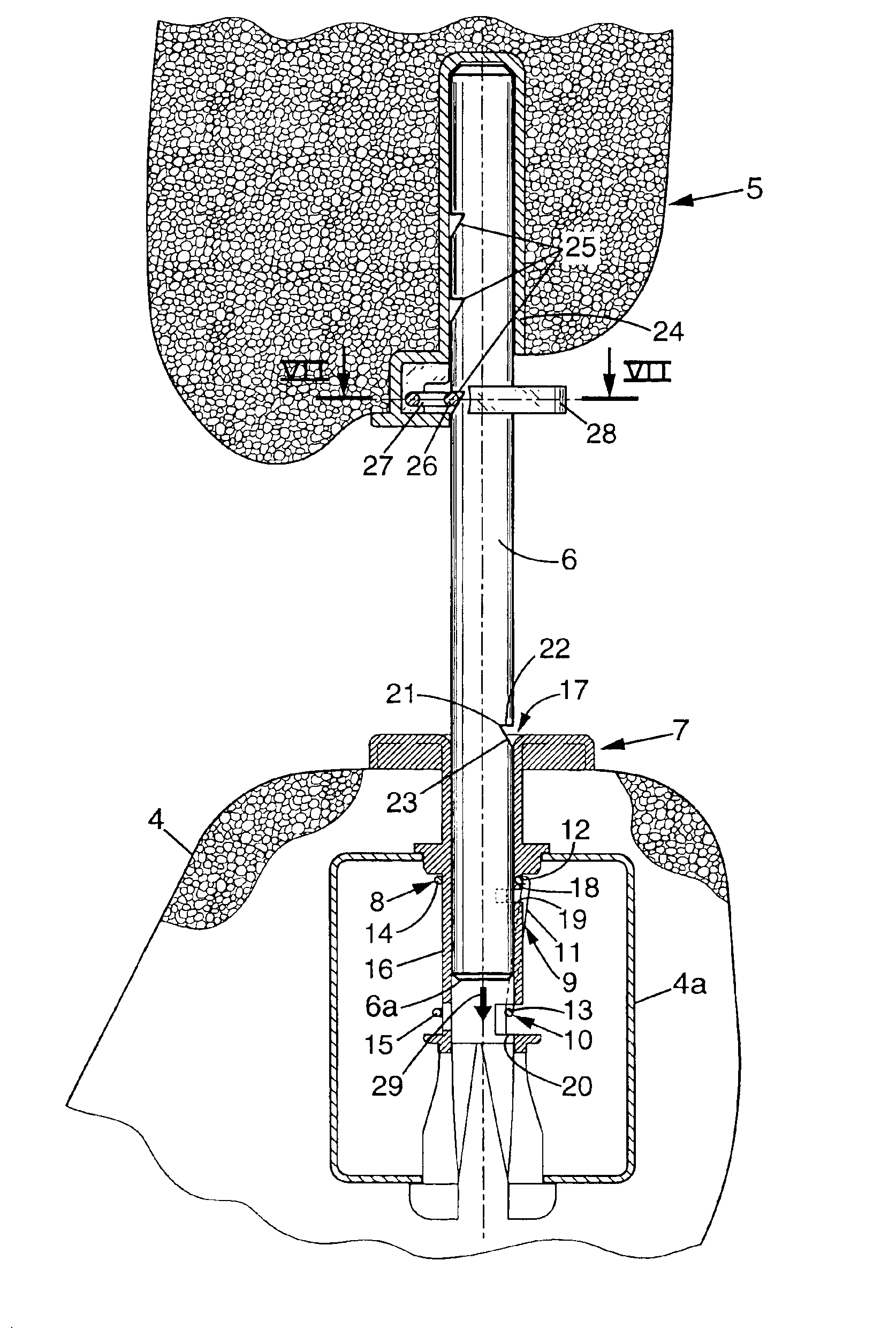
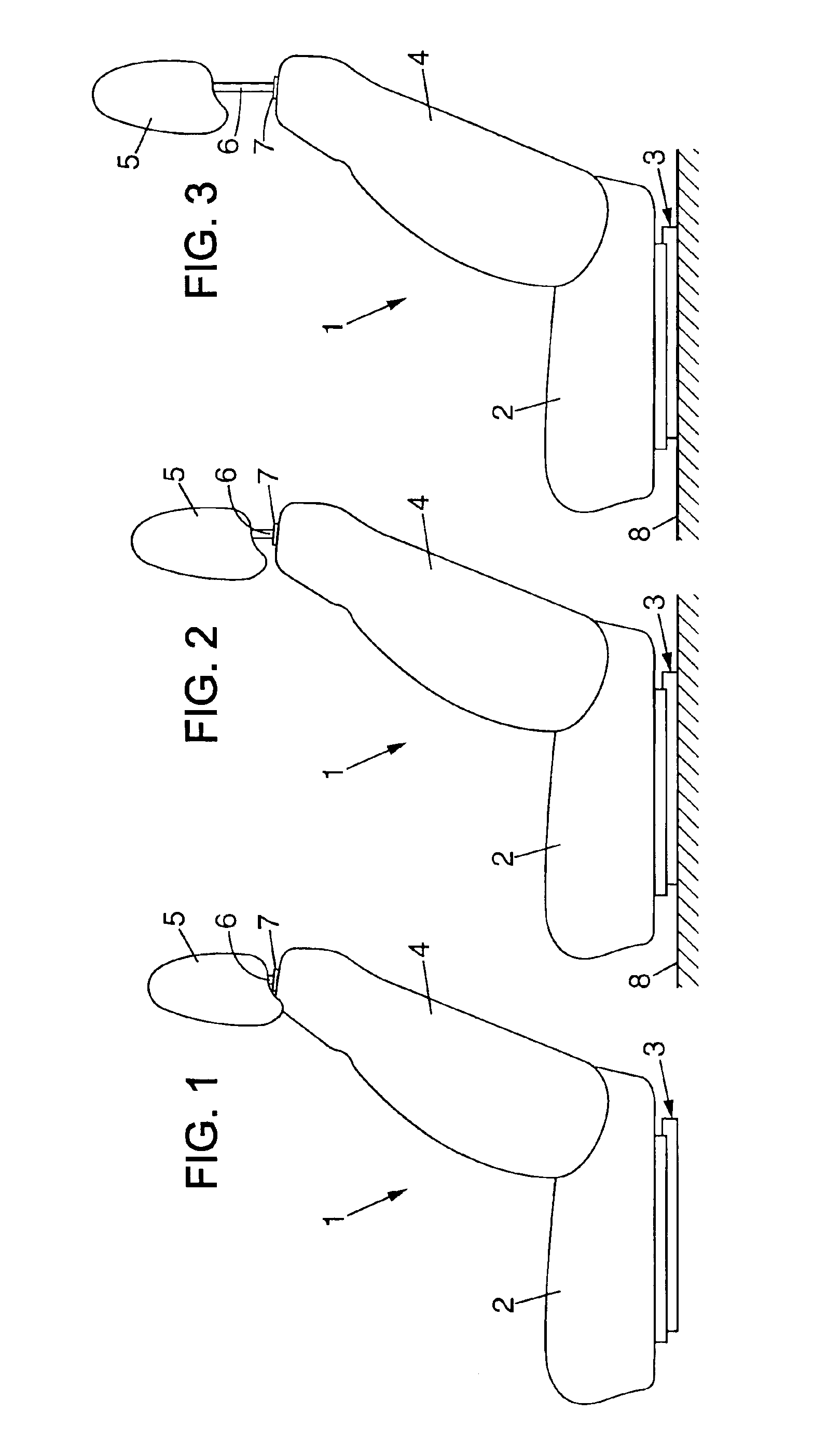
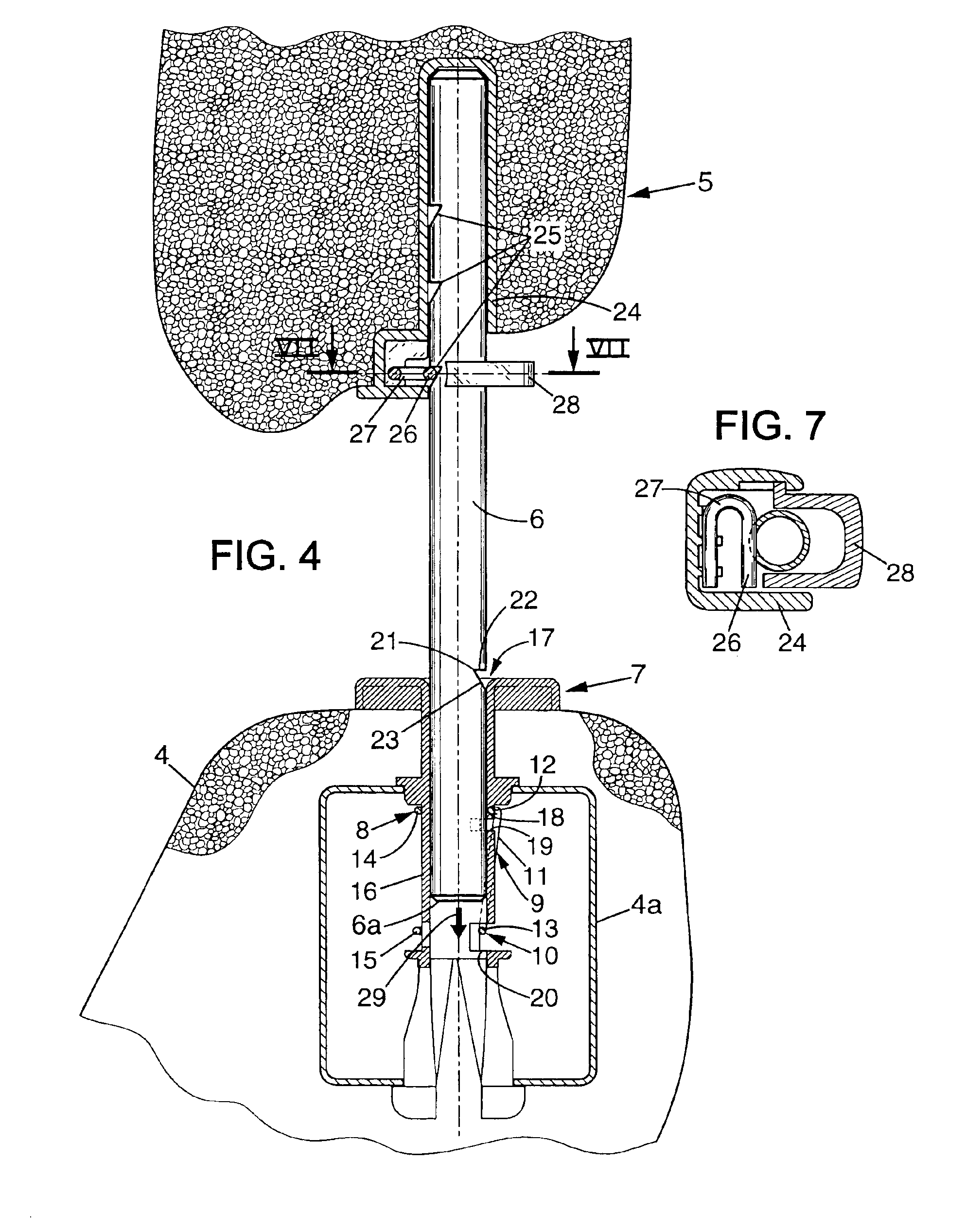
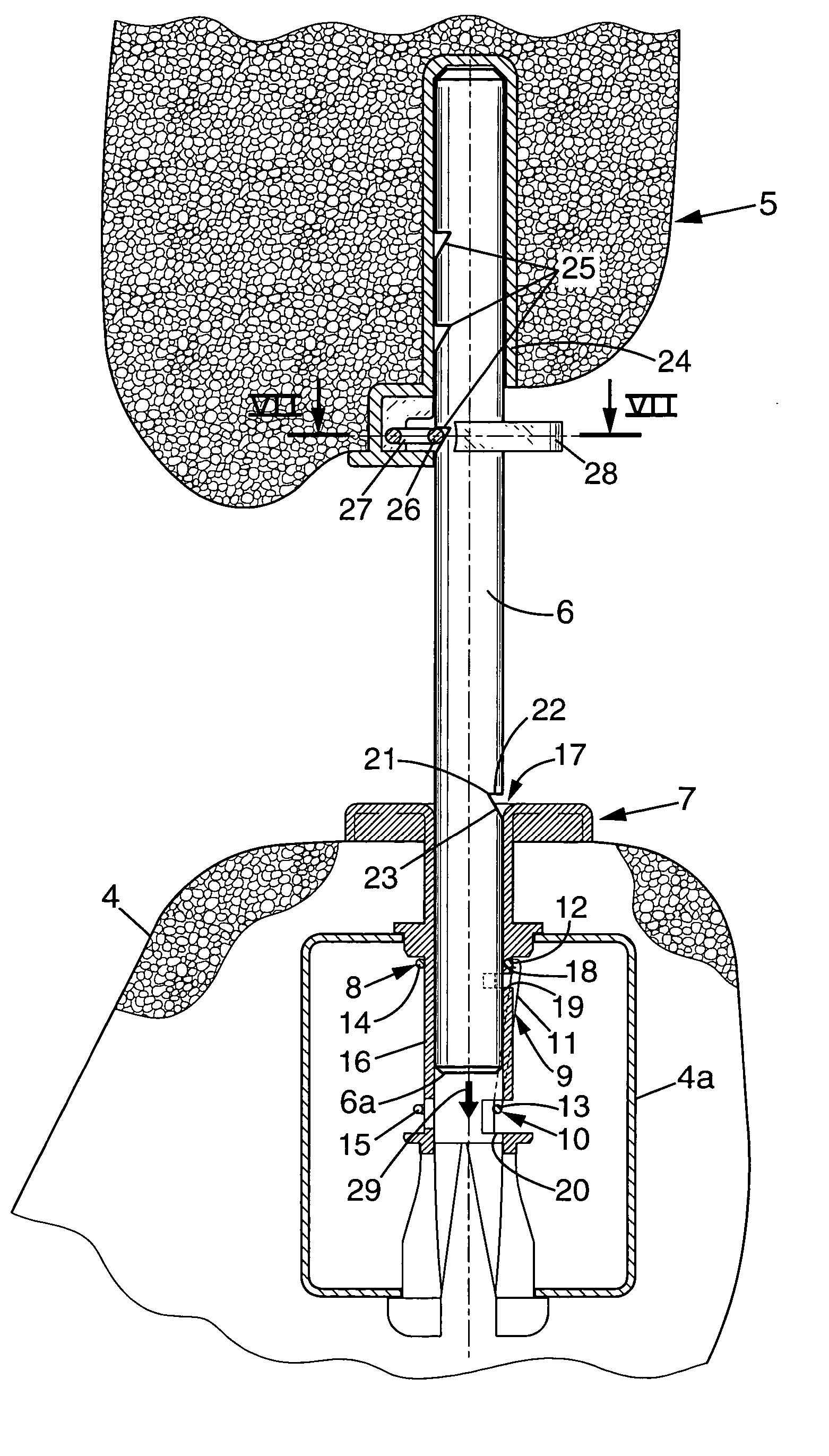
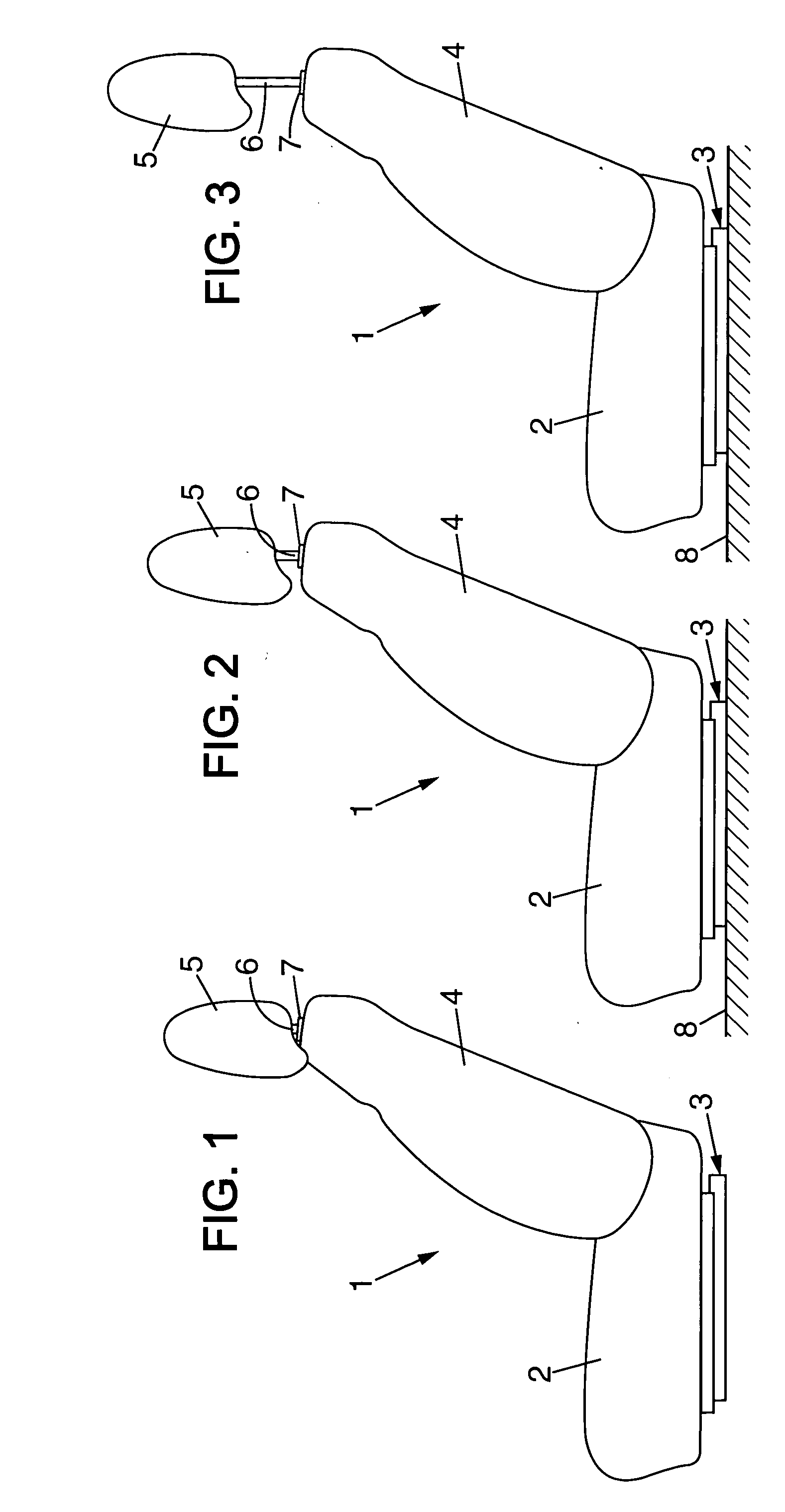
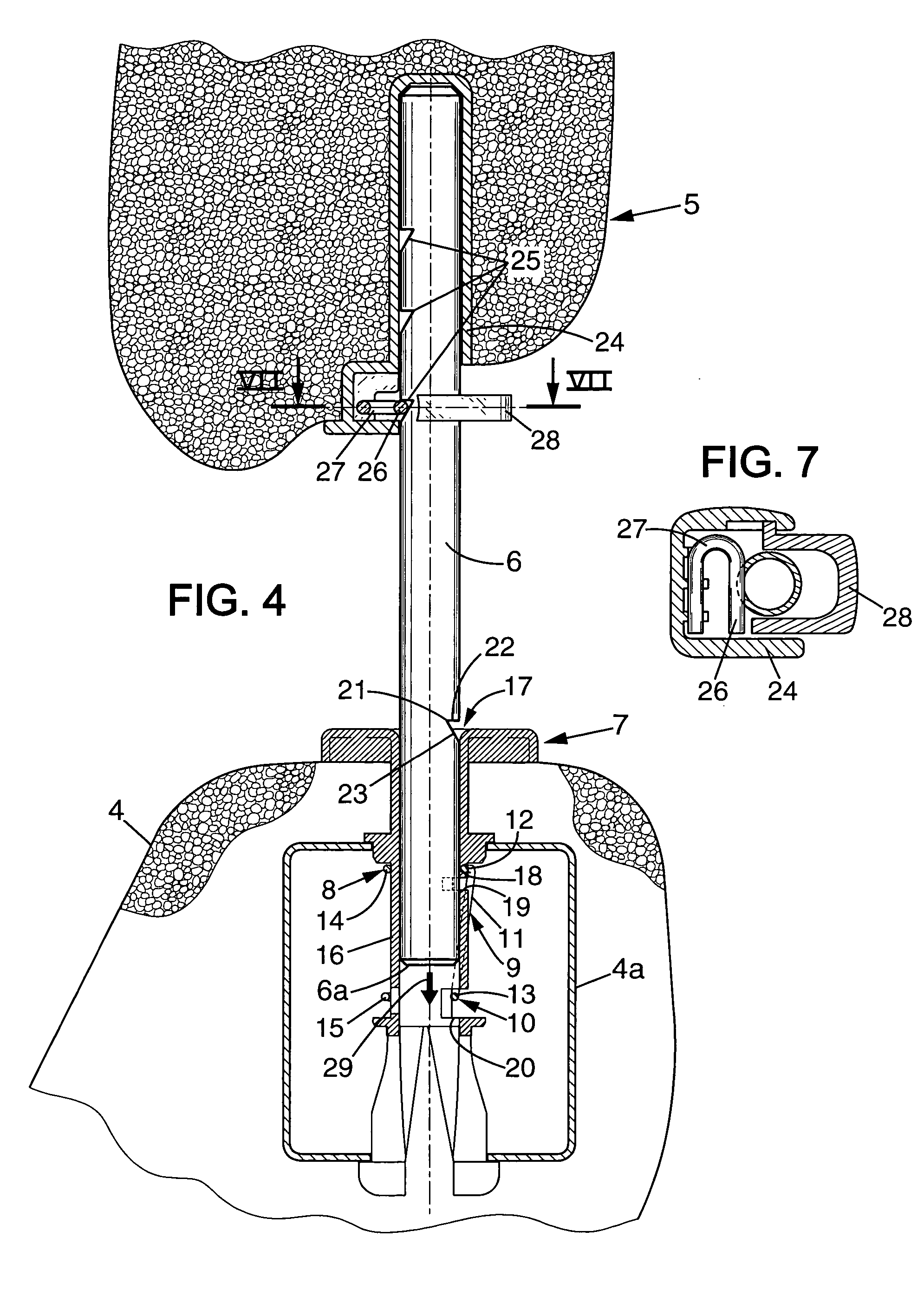
Headrest device for a vehicle seat, and a vehicle seat including such a device
InactiveUS6874854B2Easy to installEasy to transportVehicle seatsOperating chairsStops deviceActuator
A headrest device for a vehicle seat, the headrest device including a stop device that is mounted to move between an active position adapted to prevent the headrest from being moved downwards beyond a low abutment position, and an inactive position adapted to enable the headrest to be moved downwards beyond its low abutment position into a retracted position. An actuator device is adapted to move the stop device from its inactive position to its active position while the headrest is being moved into its retracted position.
Owner:FAURECIA
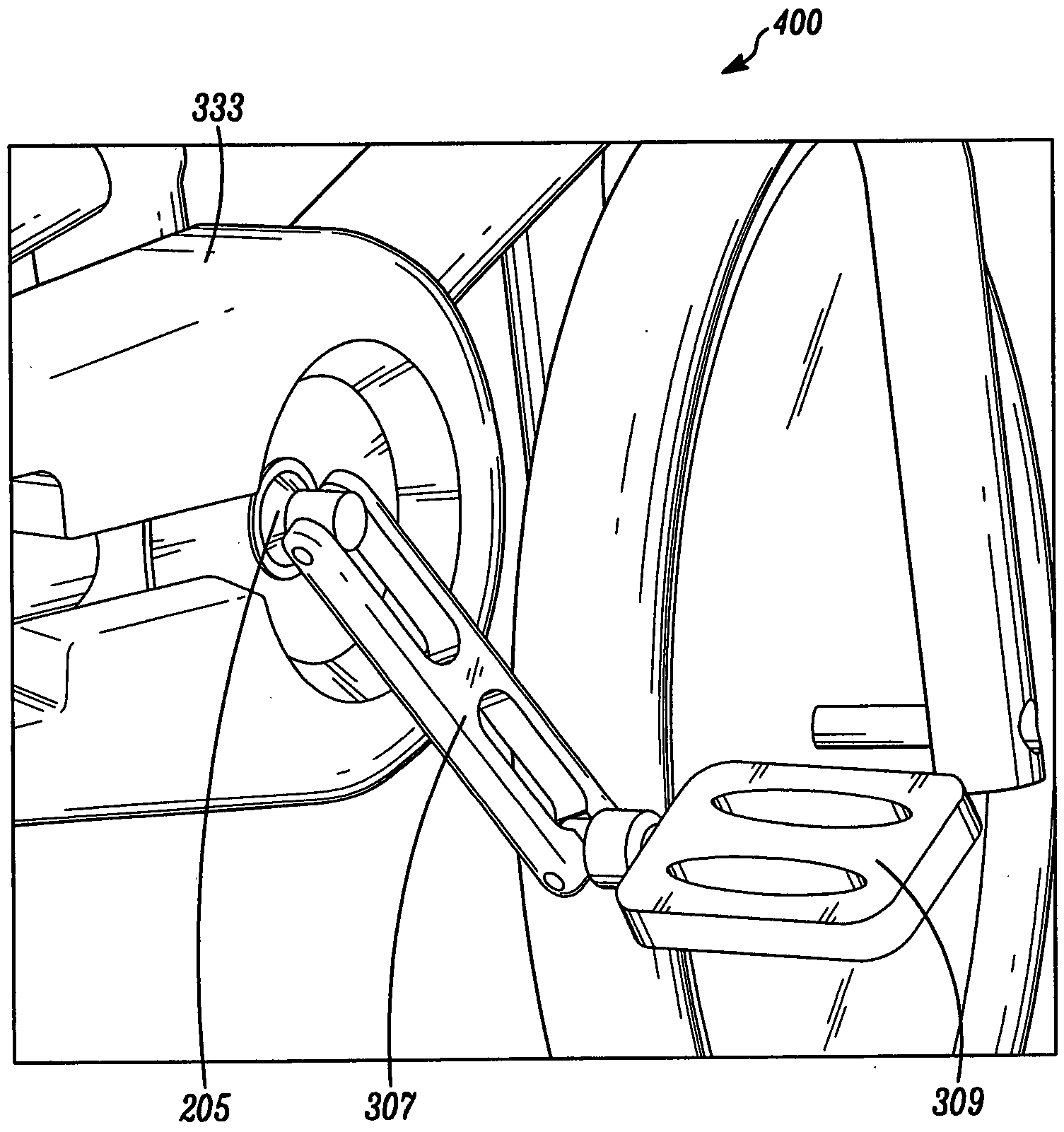
Device and methods for detecting an analyte in a sample
InactiveUS20070054414A1Protect usersEasy to manufactureEnzymologyLaboratory glasswaresAnalyteEngineering
Disclosed is a device, for detecting an analyte in a sample, comprising a sample pad for collecting the sample, a test strip coupled to the sample pad, and a housing enclosing and allowing visualization of the test strip. The sample pad can include one or more markings for determining the amount of sample collected. The device can also include a run fluid container that fits over the sample pad and forms an air-tight seal around the housing. Further, the device can include a second sample pad / test strip combination for detection of a second analyte. Also disclosed are methods for detecting an analyte in a sample using the device.
Owner:RAPID MEDICAL DIAGNOSTICS CORP
Shade cutter
InactiveUS20070277657A1No risk of injuryVibration minimizationMetal sawing devicesMetal working apparatusEngineeringKnife blades
Owner:HILGENDORF DENNIS J +2
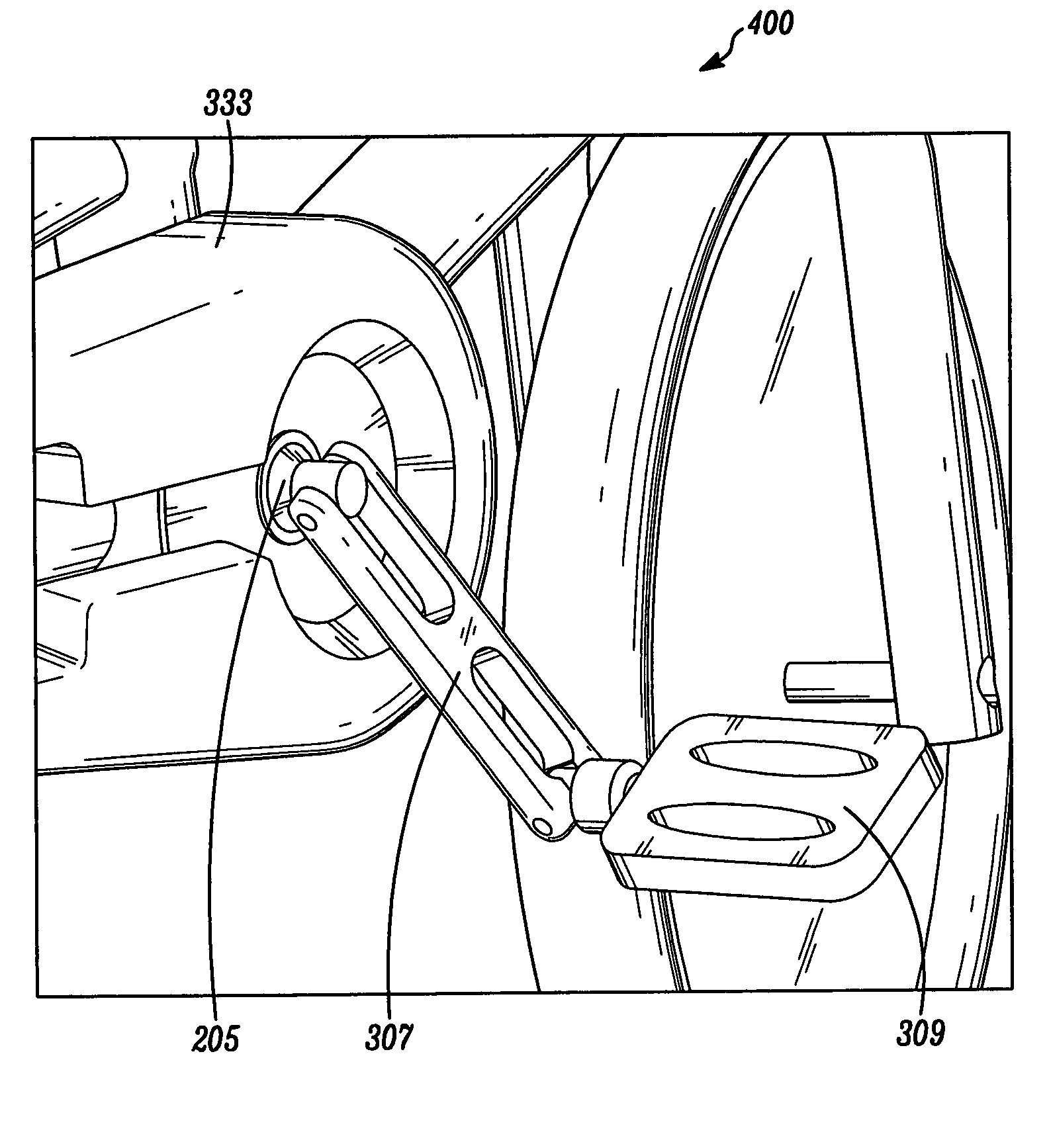
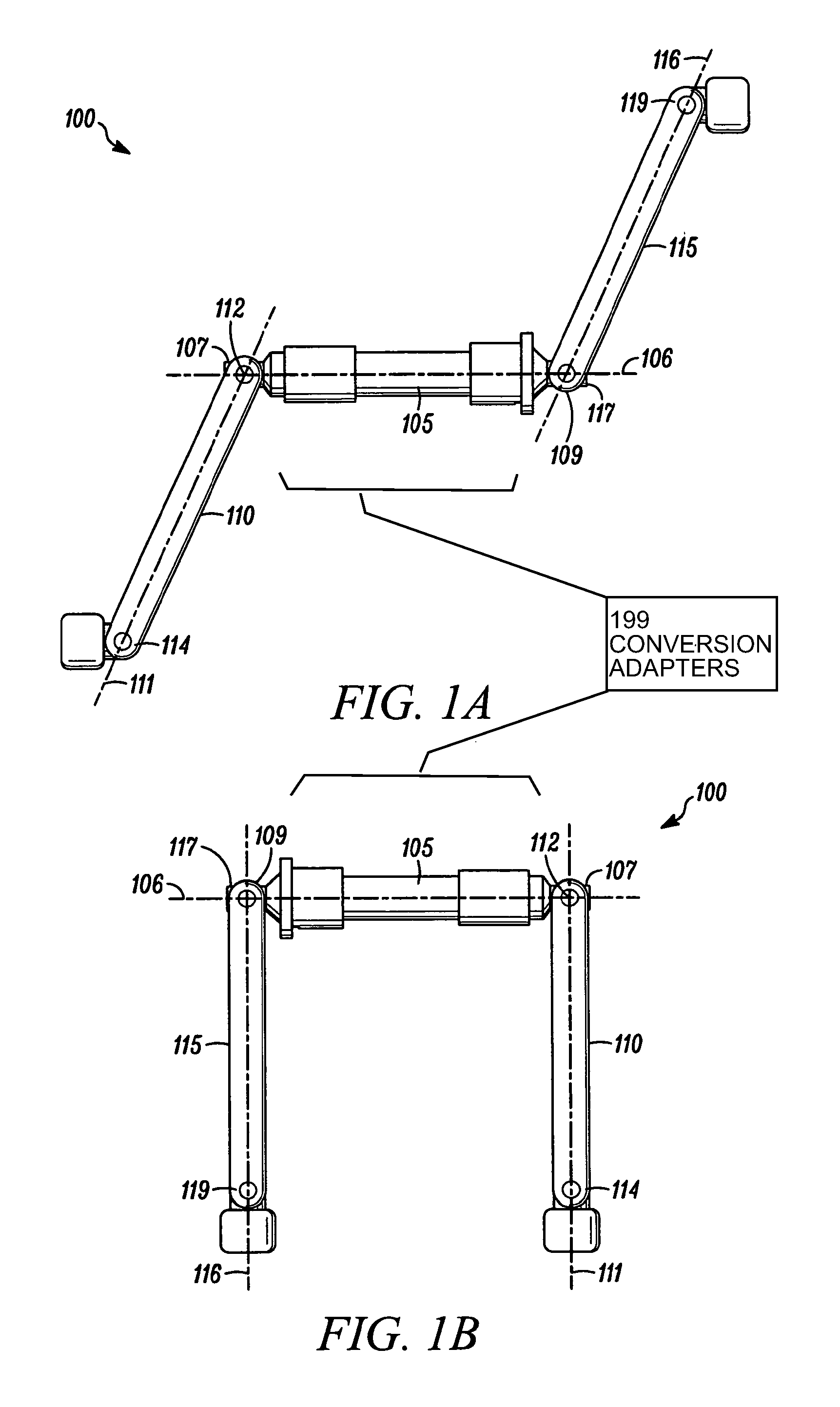
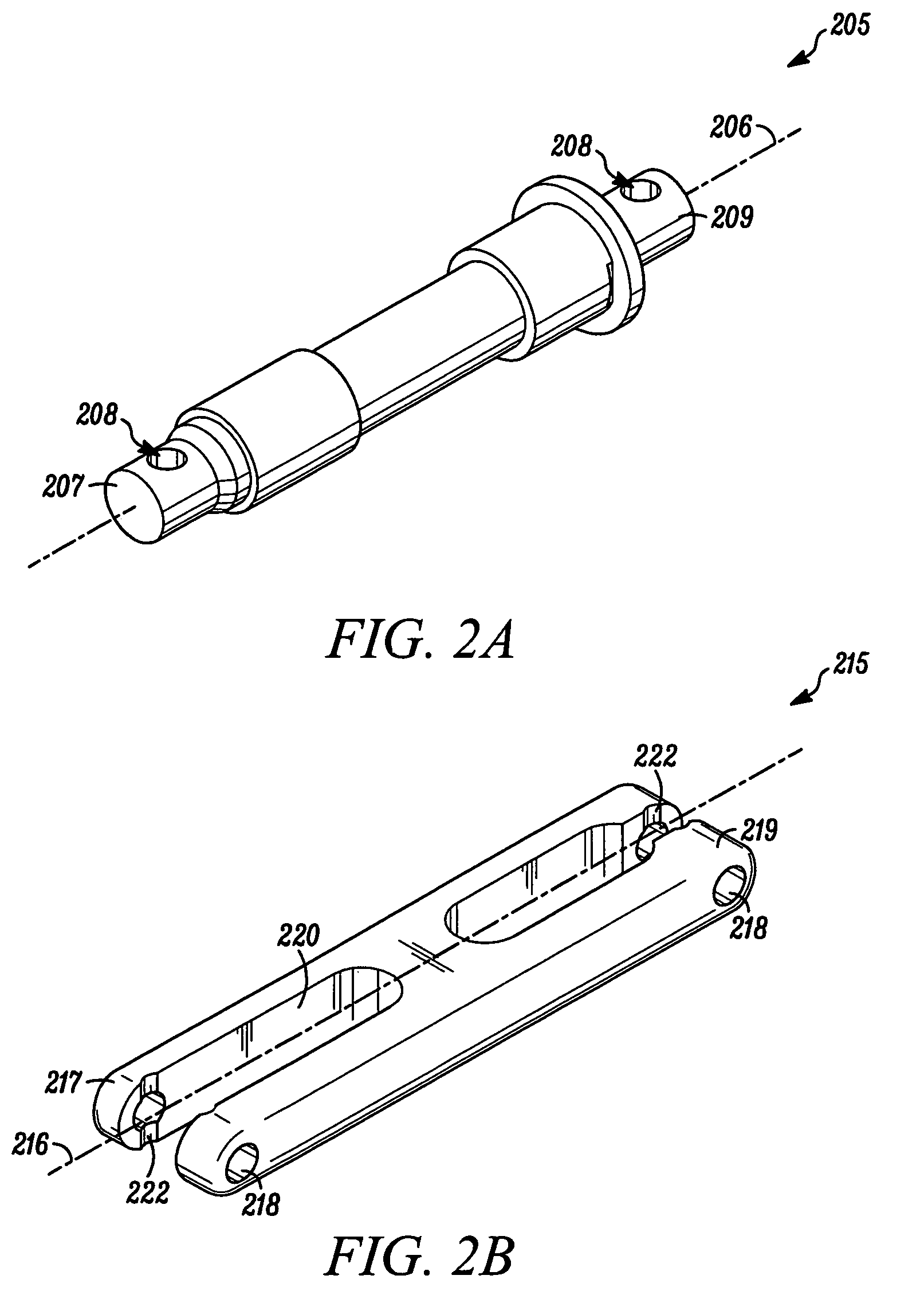
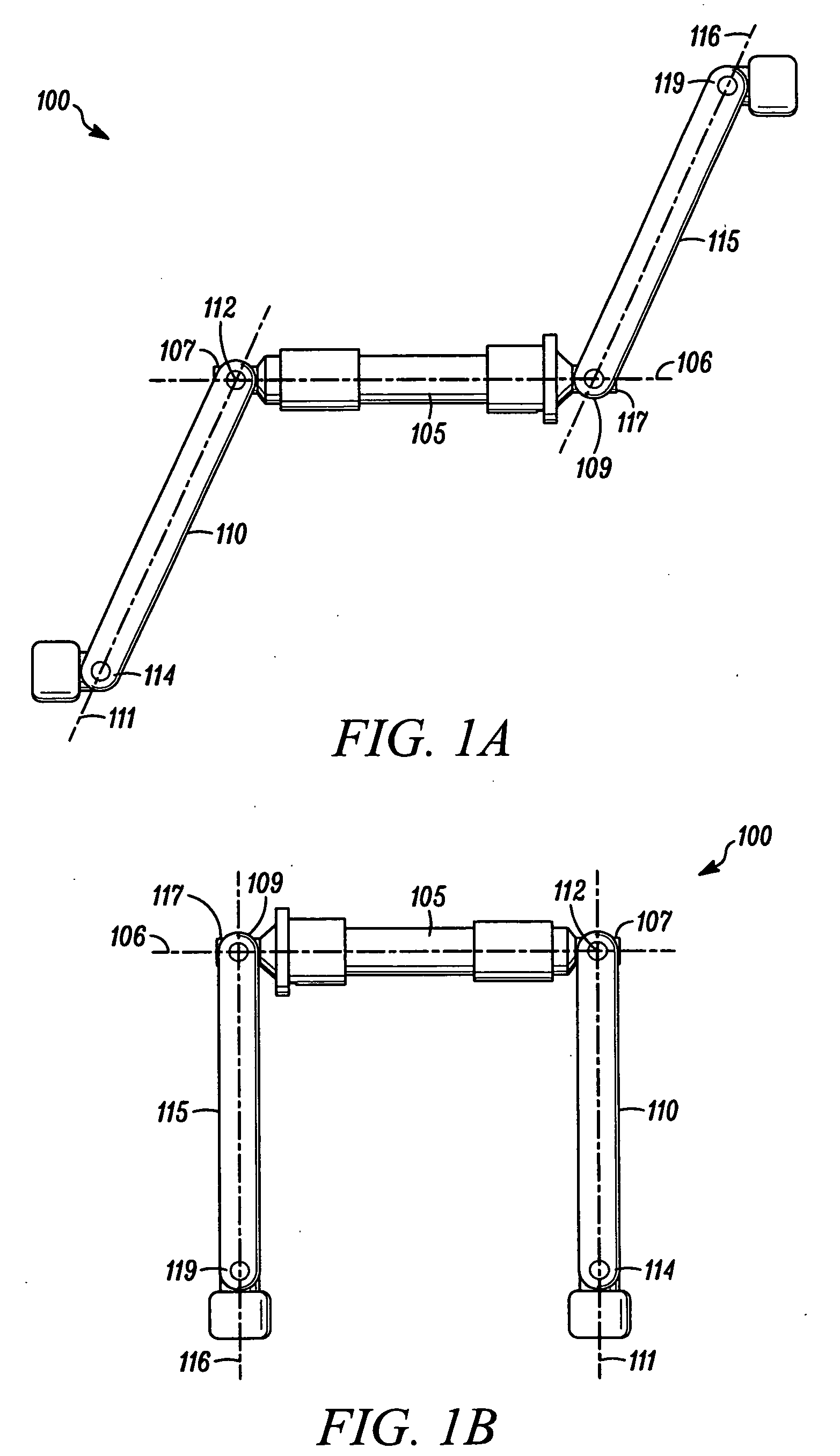
Convertible, push-bicycle for a child
An articulable crankset for converting a pedal-powered vehicle into a push-powered vehicle is provided. The articulable crankset can be in a retracted position to provide at least less of an obstruction to a user's legs during use of the push-powered vehicle than a non-retractable crankset. The vehicle can be a bicycle, and the articulable crankset can be a component of a production bicycle or a component of a conversion kit that will convert a bicycle from a pedal-powered bicycle to a convertible bicycle that can also function as a push-powered bicycle.
Owner:KROOZN
Roll dispenser
InactiveUS6929213B1Protect usersFilament handlingDomestic applicationsMechanical engineeringEngineering
Owner:CONTRERAS EMILIANO
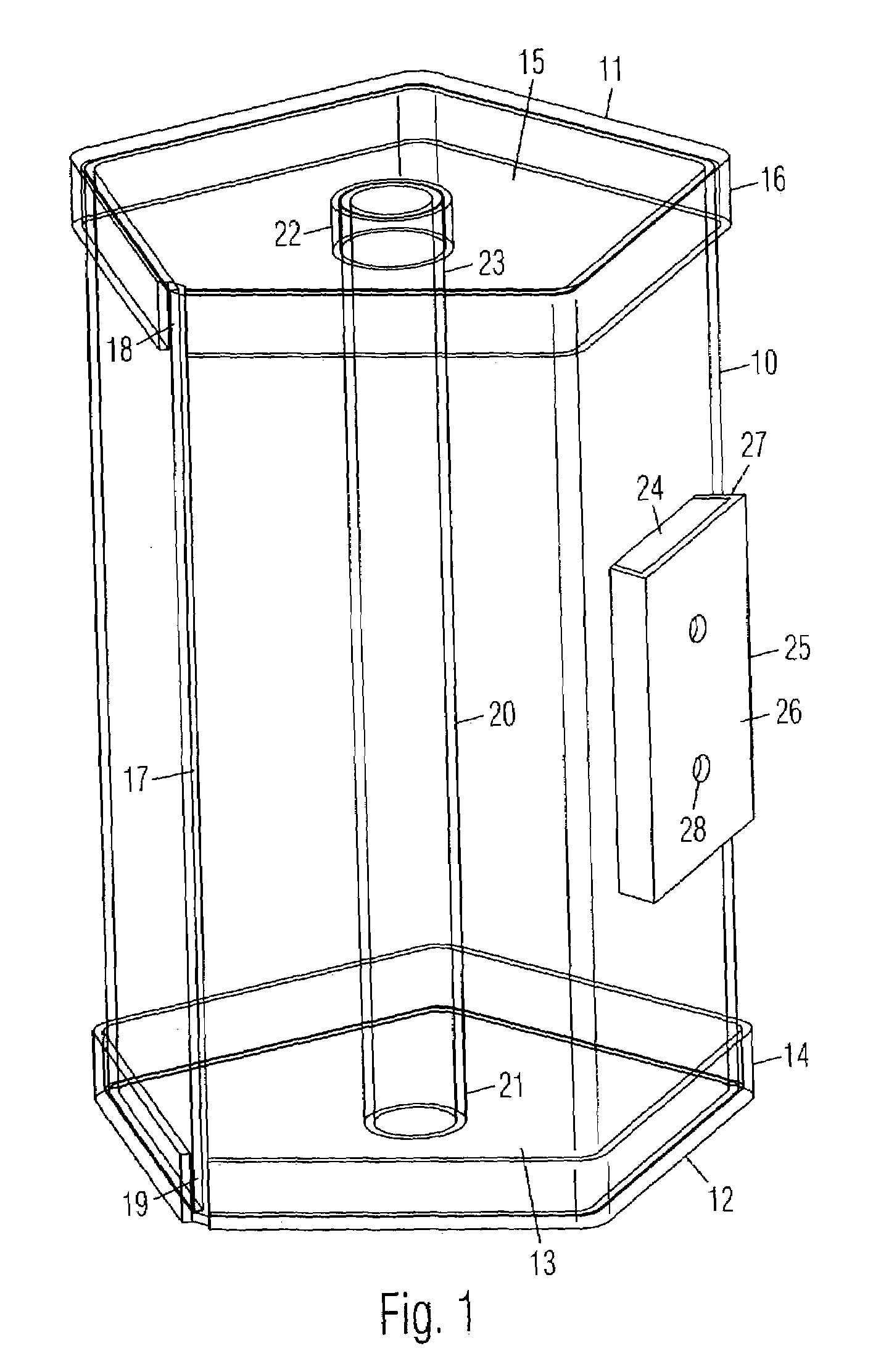
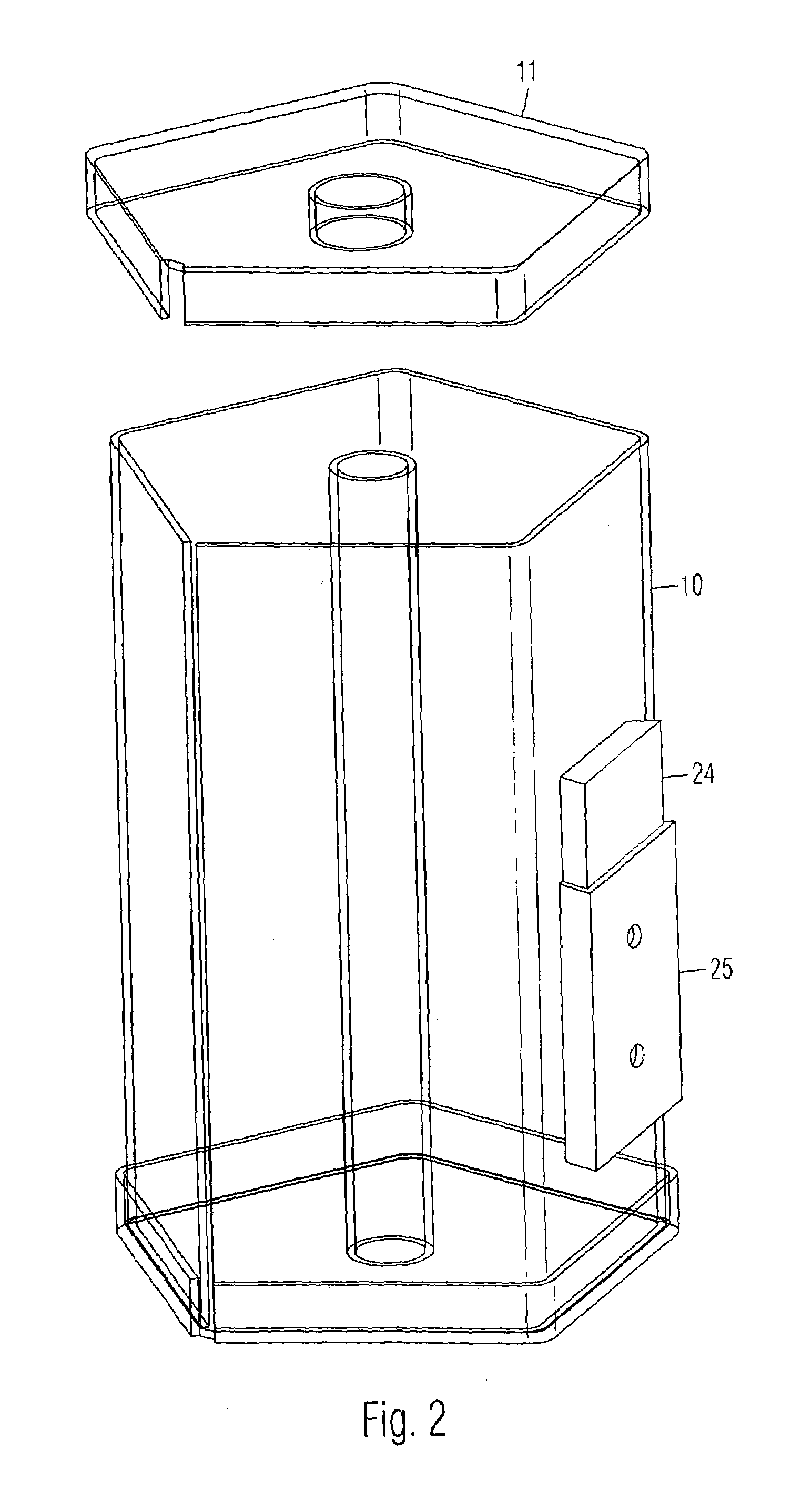
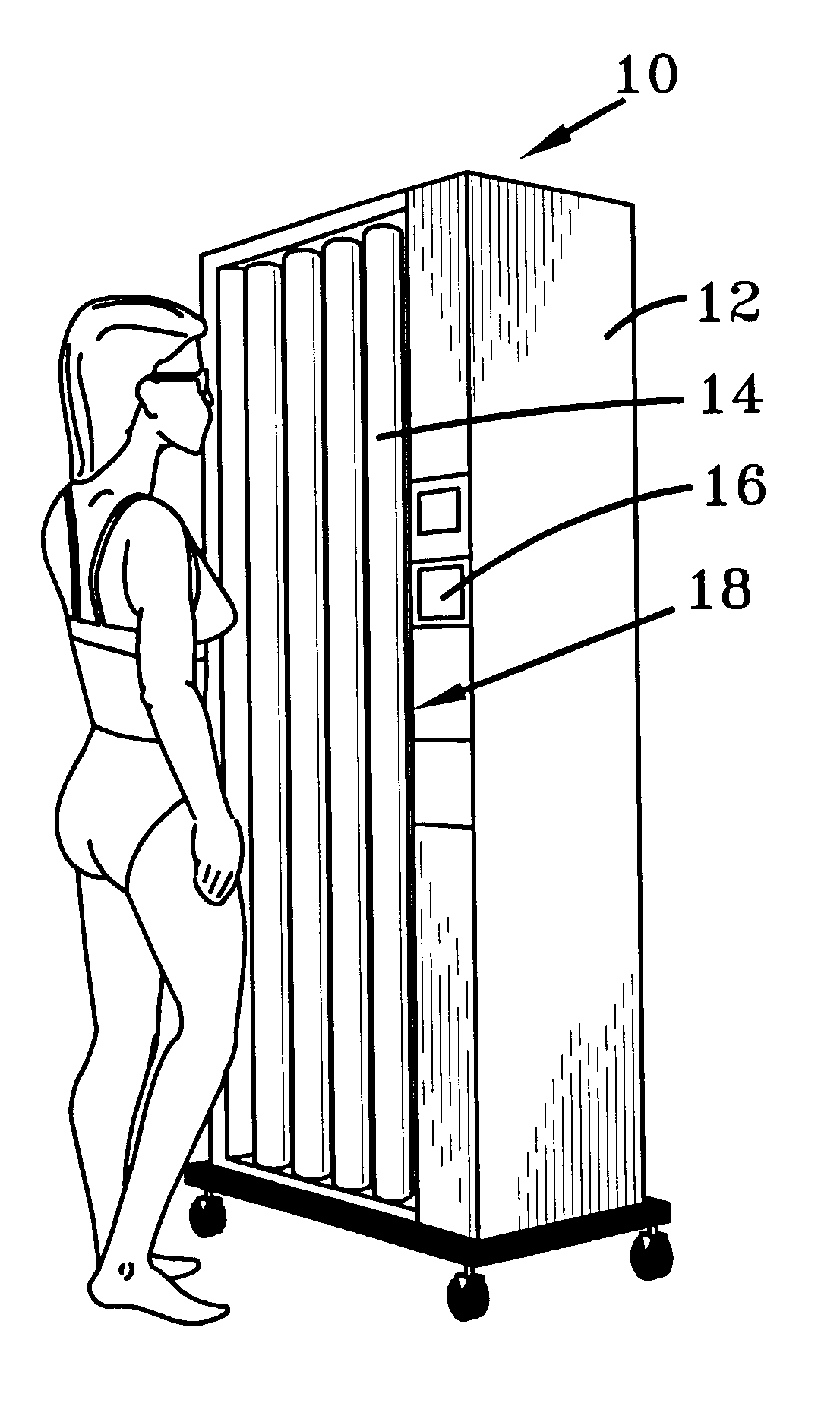
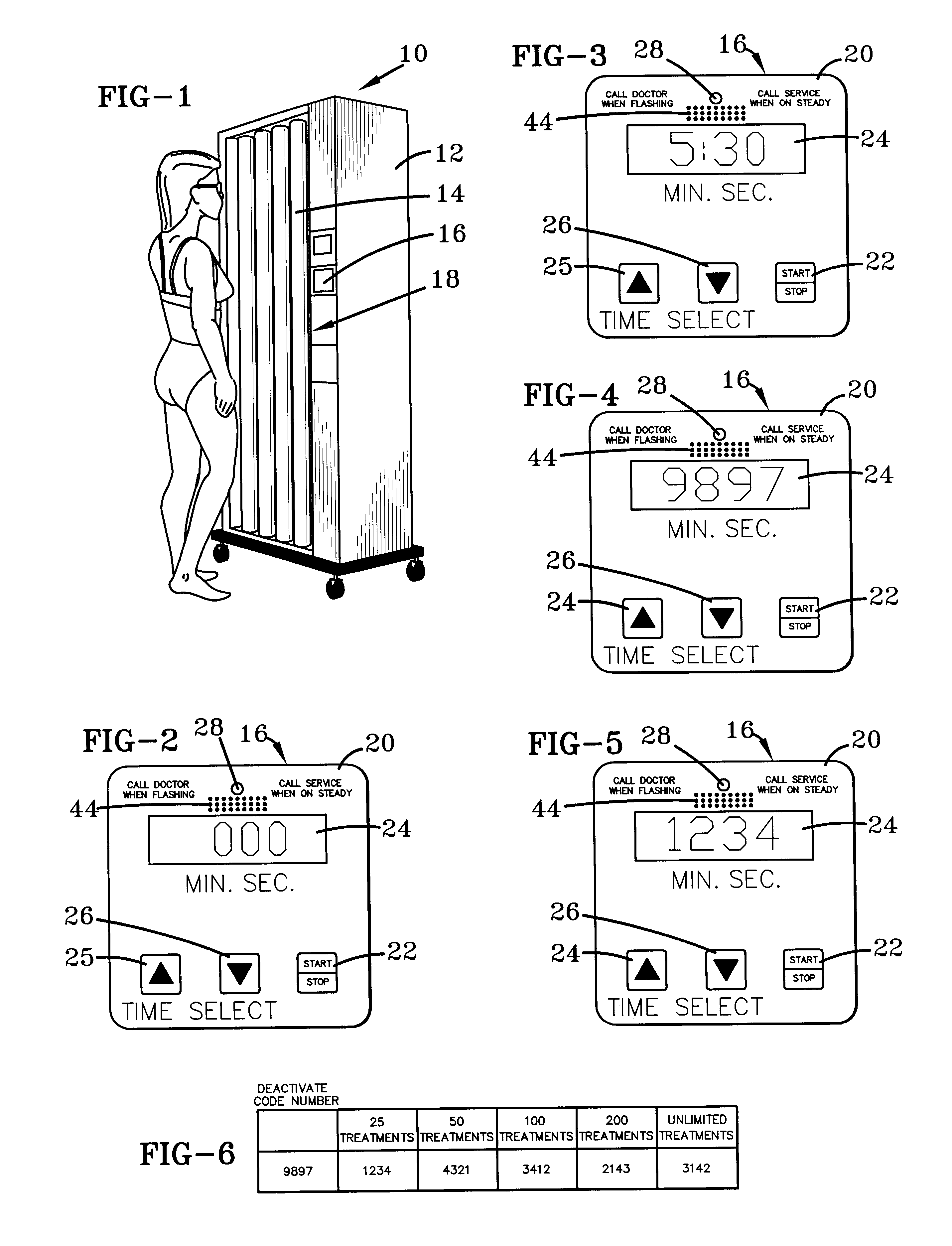
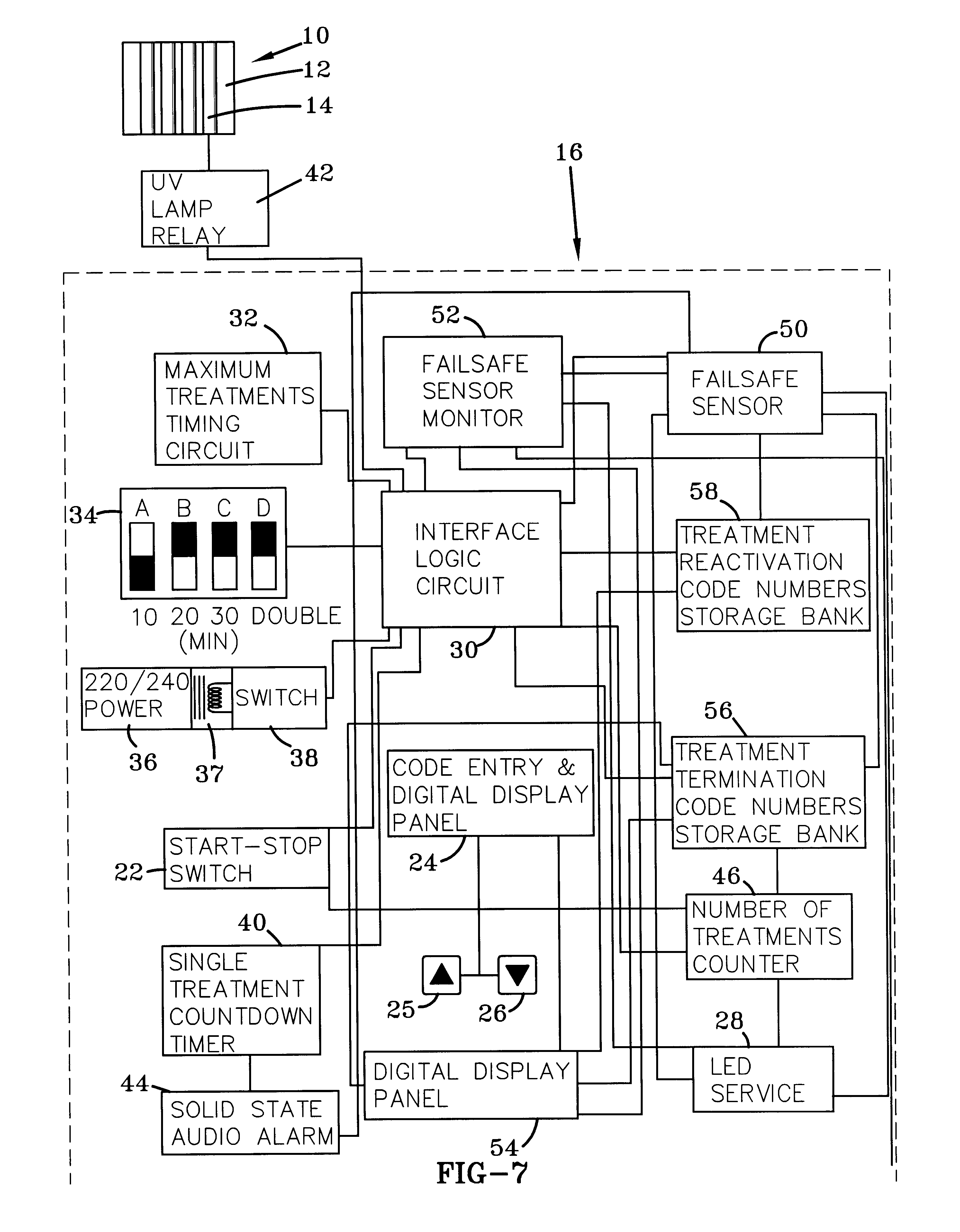
Phototherapeutic device and method
InactiveUS6345215B1Avoid failureLimit its operationMechanical power/torque controlElectrotherapyLight treatmentEngineering
A microprocessor to control and to prevent failure in mechanisms, particularly those that perform timed intervals of work. The microprocessor controls the length of each interval of work, and limits the mechanism to perform only a predetermined number of work intervals, after which it deactivates the device, allowing the mechanism to reactivate only after entry of a coded number or operation of a key switch. The microprocessor monitors all functions of the mechanism and includes a first failsafe circuit that shuts down the mechanism in the event of malfunction. A second failsafe circuit monitors the first failsafe circuit, and bypasses it to shut down the mechanism in the event of malfunction in the first failsafe circuit.
Owner:NAT BIOLOGICAL & SYST CORP +1
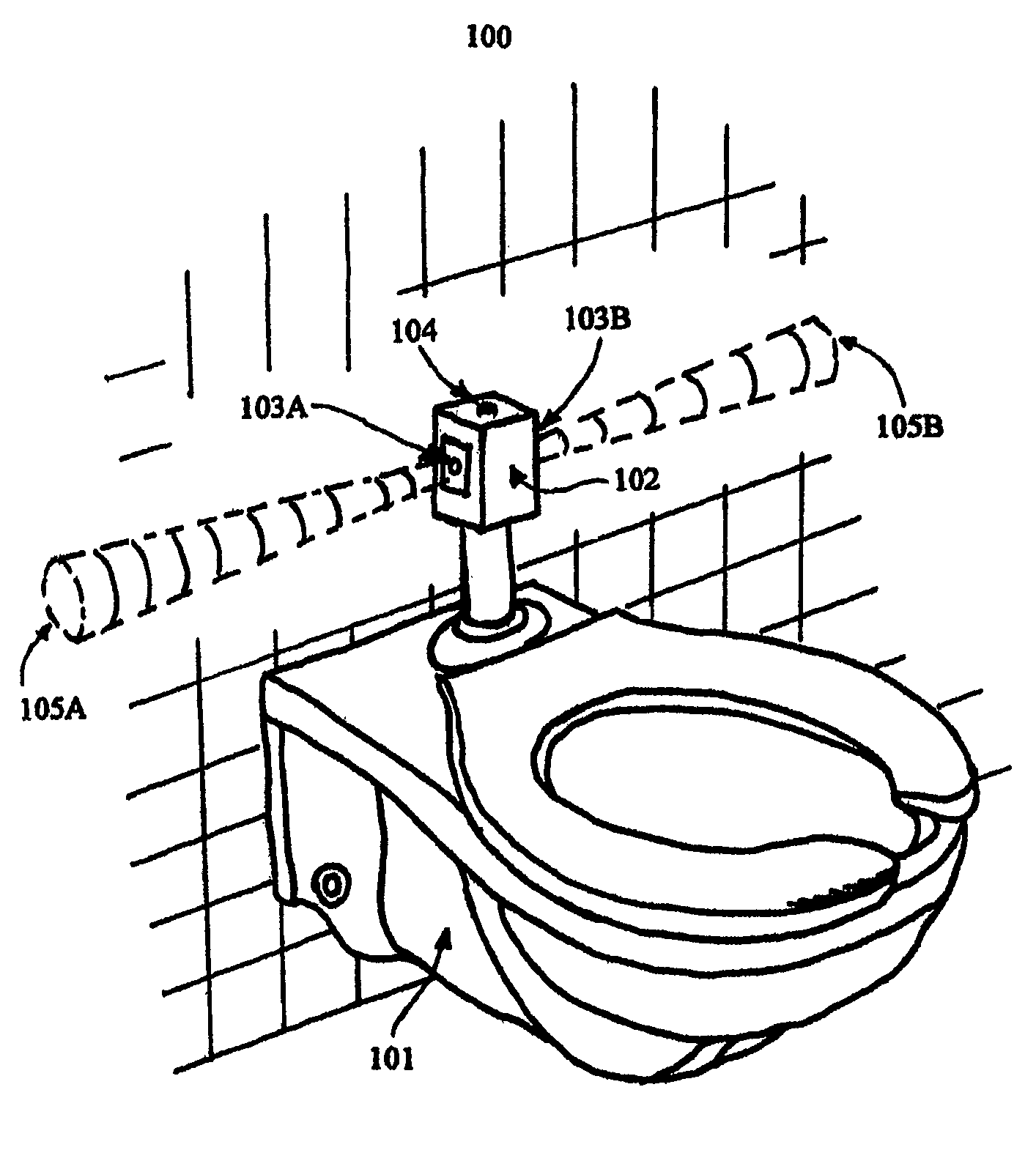
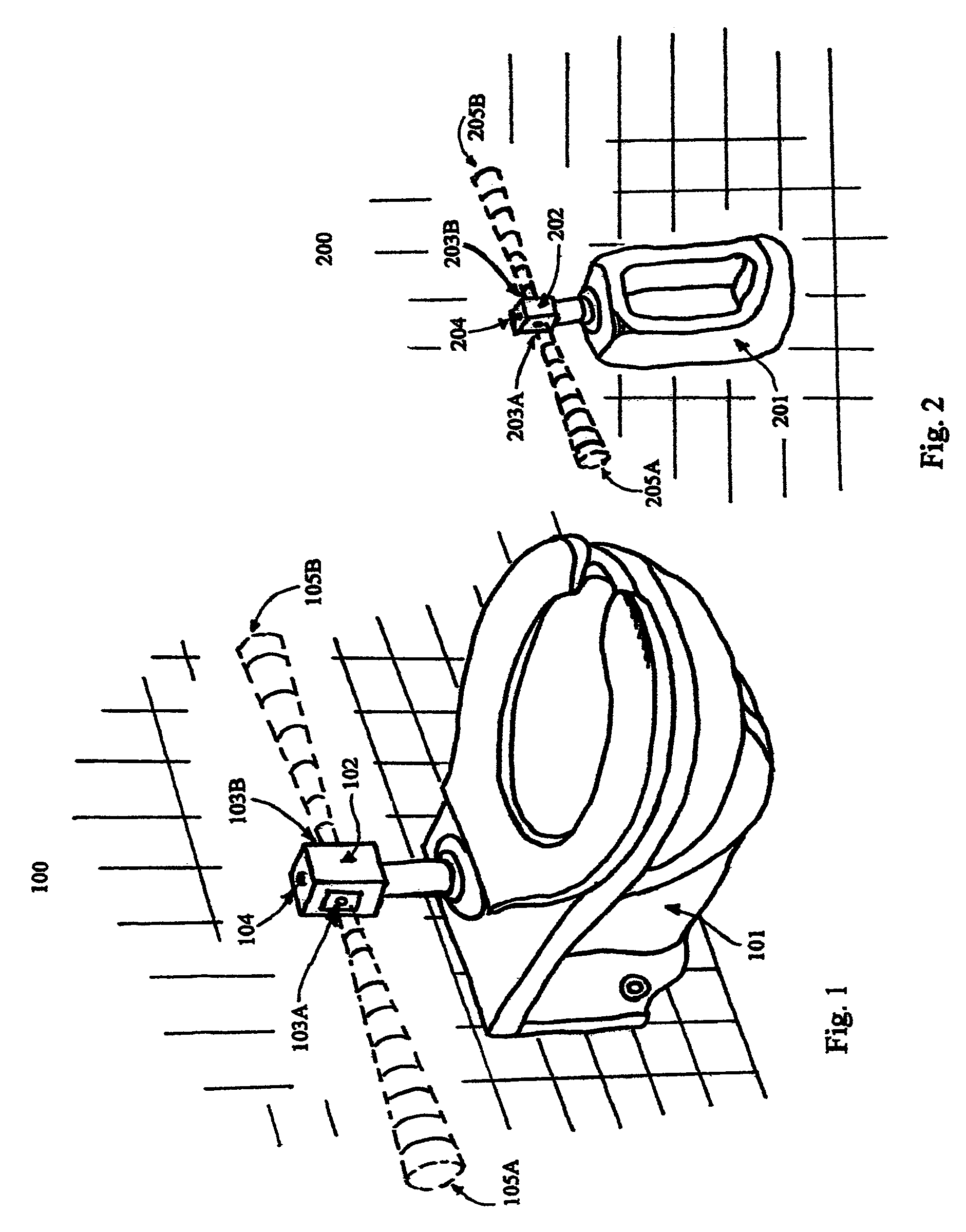
Sanitary, user activated, water saving, motion sensing flushing method and device
A flushing system with a sensing module, having at least one sensor and a controller circuit having a sensor detection and trigger sub-circuit operatively coupled to the at least one sensor, and a flushing mechanism operatively coupled to the motion sensing module.
Owner:OZENICK DEBRA LYNN
Headrest device for a vehicle seat, and a vehicle seat including such a device
InactiveUS20040145228A1Mitigate such drawbackEasy to installVehicle seatsOperating chairsStops deviceEngineering
A headrest device for a vehicle seat, the headrest device including a stop device that is mounted to move between an active position adapted to prevent the headrest from being moved downwards beyond a low abutment position, and an inactive position adapted to enable the headrest to be moved downwards beyond its low abutment position into a retracted position. An actuator device is adapted to move the stop device from its inactive position to its active position while the headrest is being moved into its retracted position.
Owner:FAURECIA
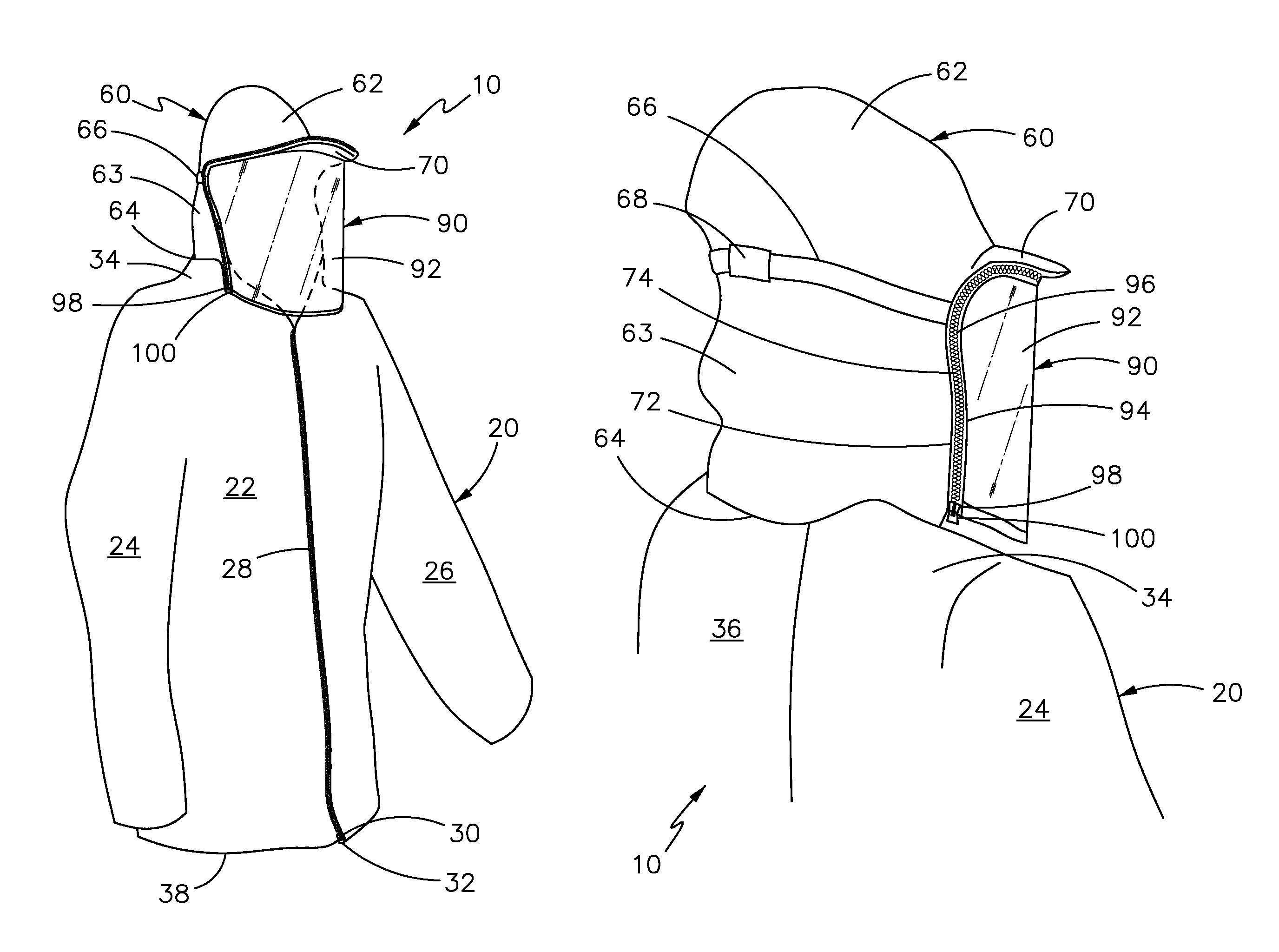
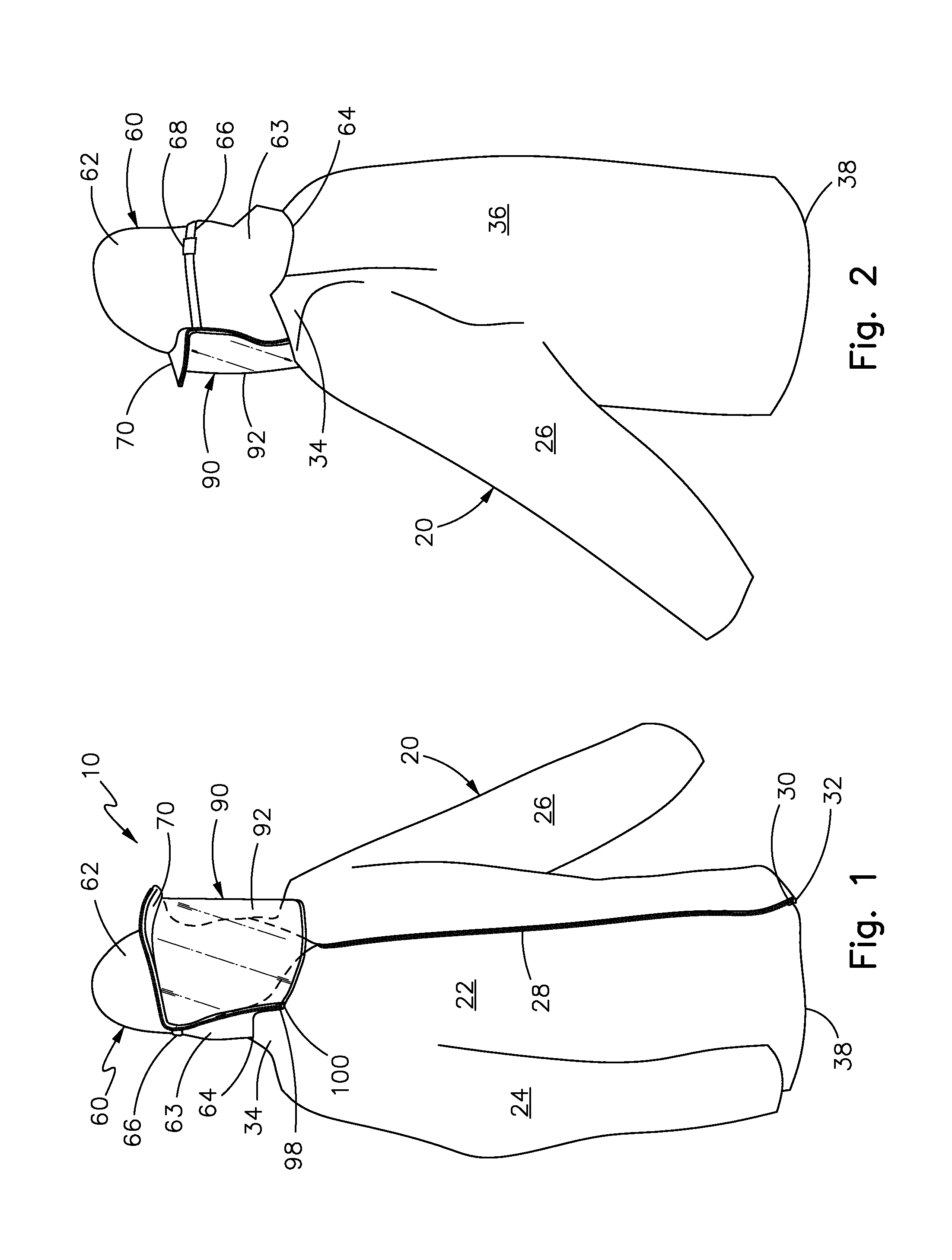
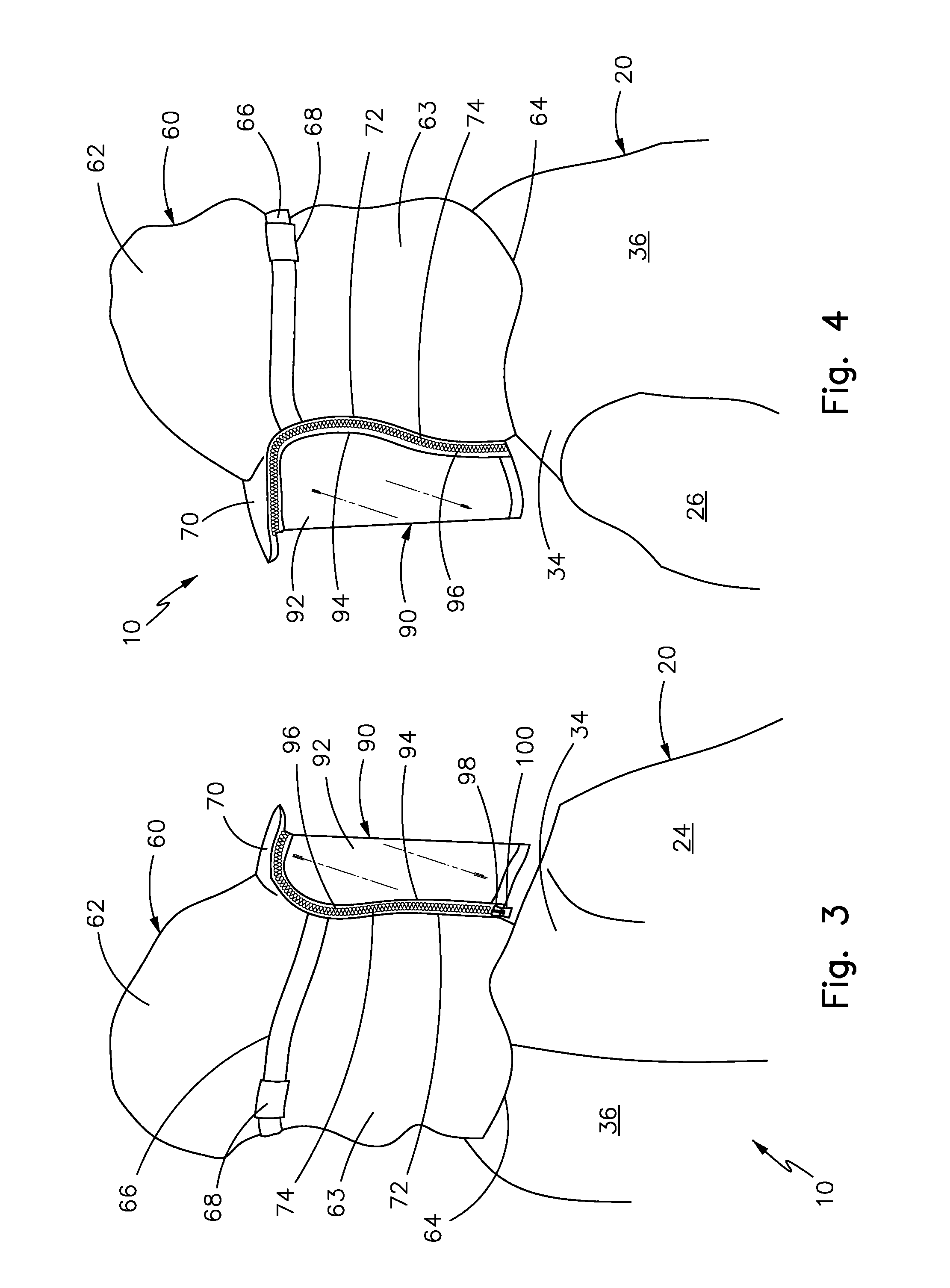
Article of clothing
An article of clothing, comprising a coat assembly having a front side, a backside, and first and second sleeves. The front side and the backside define a shoulder area where they meet above the first and second sleeves. A hood assembly has a crown. Extending from the crown is a flap that terminates at an end. Also extending from the crown at a predetermined angle is a visor. The visor extends from the crown a first predetermined distance. The hood assembly comprises a first zipper tape. The first zipper tape comprises first zipper teeth. A shield assembly comprises a shield. The shield has a second zipper tape. The second zipper tape comprises second zipper teeth. The second zipper teeth have means to engage the first zipper teeth.
Owner:MOLINA JUAN CARLOS
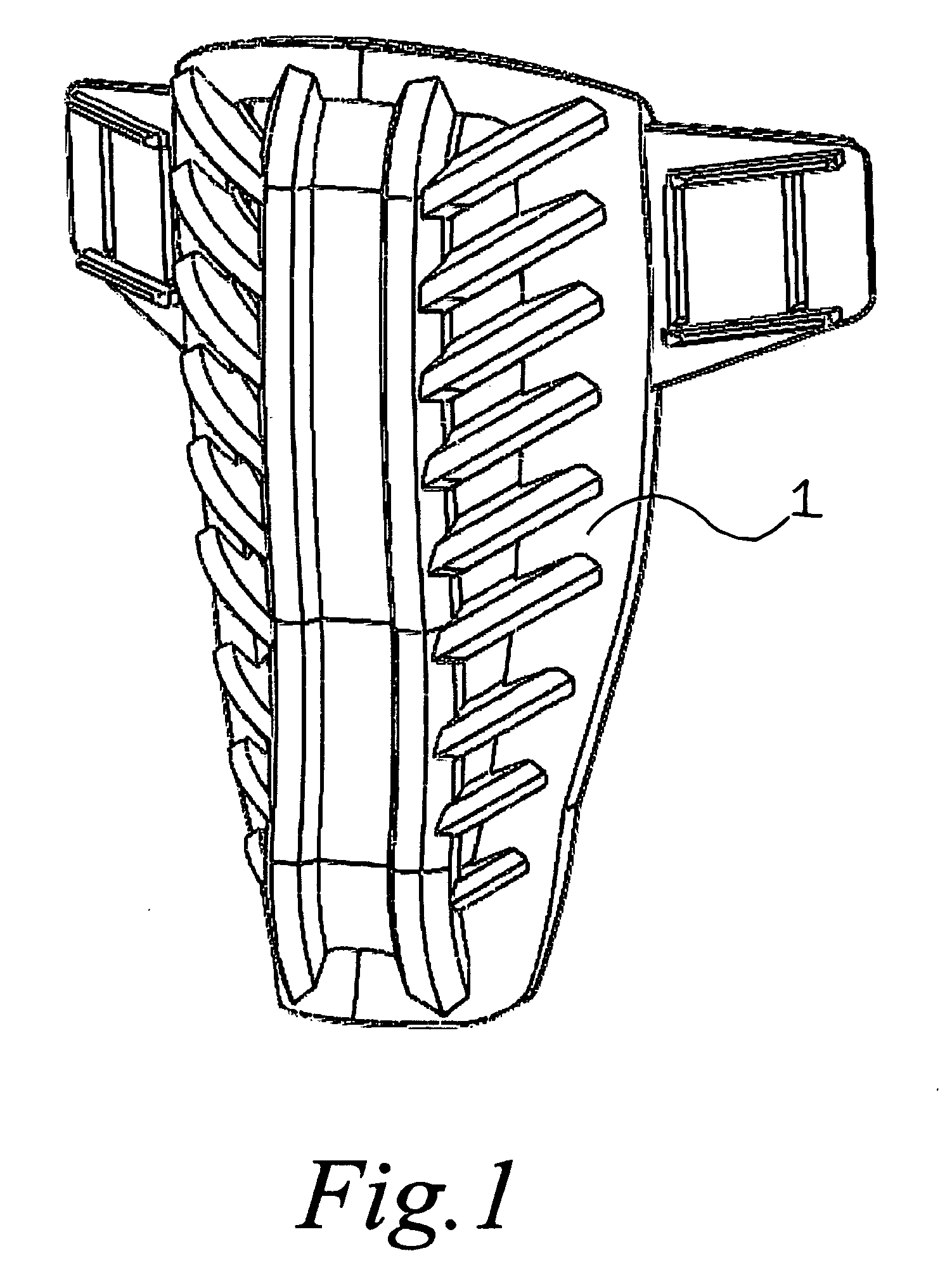
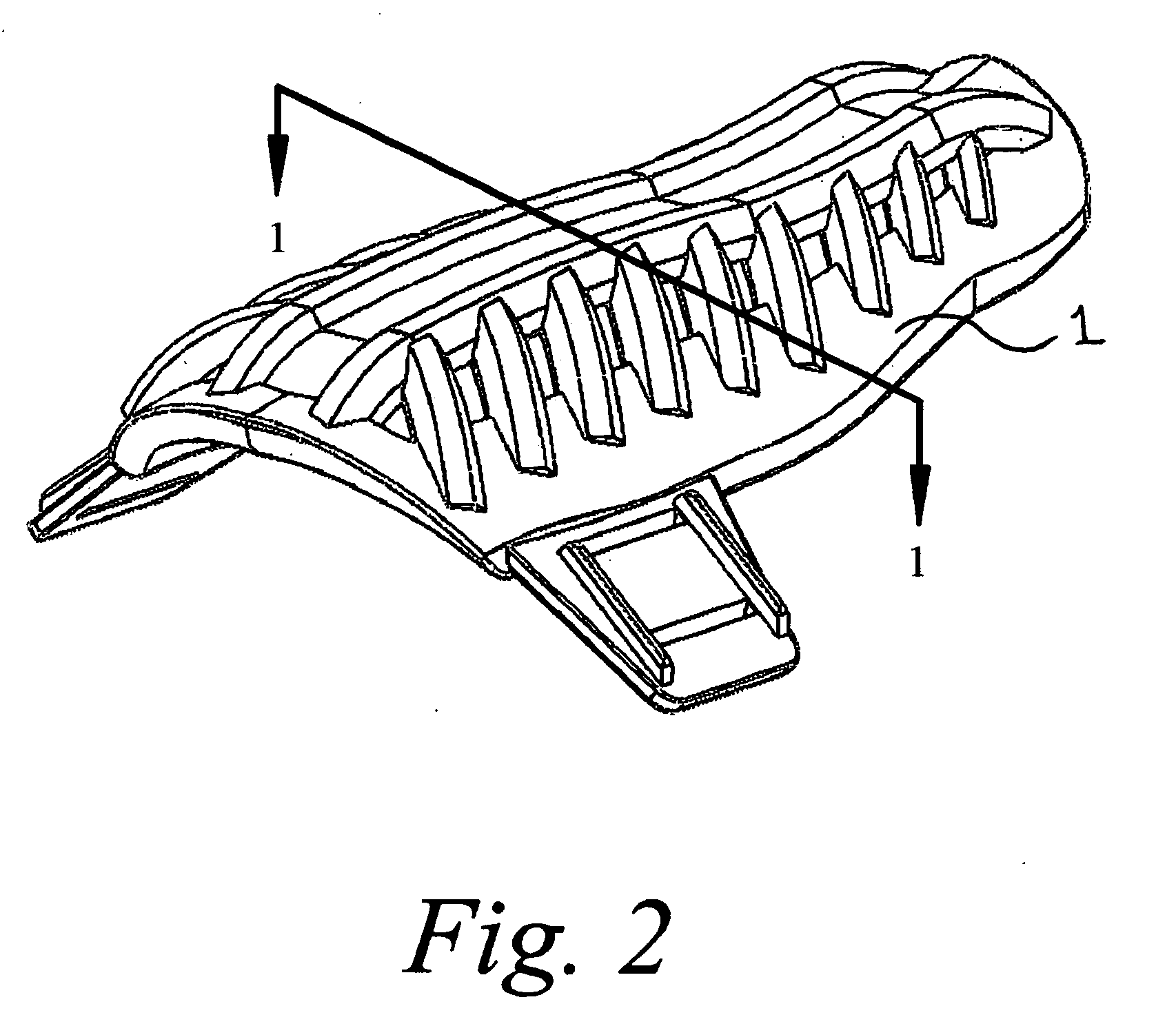
Energy absorbing and displacing structure for athletic protective equipment
InactiveUS7917971B2Protect usersReduce weightChemical protectionHeat protectionBand shapeEnergy absorption
An energy absorbing and displacing structure for athletic protective equipment, such as an athletic shin-guard, is provided using a flexible web-shaped body to hold a rigid band-shaped member in place.The inner rigid band-shaped member follows the contour of the desired area to protect. The outer flexible web-shaped body is made of a softer rubber like material and works as a locator and supporter keeping the inner, rigid band-shaped member, in proper location.
Owner:SUPREME ATHLETIC WEAR
Method for managing the security of applications with a security module
ActiveUS8001615B2Controlling the riskProtect usersDigital data processing detailsAnalogue secracy/subscription systemsComputer networkCryptogram
A method for managing the security of applications with a security module associated to an equipment connected to a network managed by a control server of an operator. The applications use resources as data or functions stored in the security module locally connected to the equipment. The method may include steps of receiving, analyzing and verifying, by the control server, identification data from the equipment and the security module, generating a cryptogram from the result of the verification of the identification data, transmitting the cryptogram to the security module of the equipment, and selectively activating or selectively deactivating by the security module at least one resource as data or functions of the security module by executing instructions included in the cryptogram and conditioning the functioning of an application according to criteria established by a supplier of the application or the operator or a user of the equipment.
Owner:NAGRAVISION SA
Method for the authentication of applications
ActiveUS8261365B2Controlling the riskProtect usersDigital data processing detailsAnalogue secracy/subscription systemsApplication softwareAuthentication
Owner:NAGRAVISION SA
Articulable crankset for converting a pedal-powered vehicle into a push-powered vehicle
InactiveUS20100192722A1Protect usersPassenger cyclesWheel based transmissionTreadleAutomotive engineering
The teachings provided herein relate to an articulable crankset for converting a pedal-powered vehicle into a push-powered vehicle having the articulable crankset in a retracted position to provide at least less of an obstruction to a user's legs during use of the push-powered vehicle than a non-retractable crankset. The vehicle can be a bicycle, and the articulable crankset can be a component of a production bicycle or a component of a conversion kit that will convert a bicycle from a pedal-powered bicycle to a convertible bicycle that can also function as a push-powered bicycle.
Owner:KROOZN
Cordless Soldering Iron
ActiveUS20190134730A1Protect usersSoldering ironSoldering auxillary devicesTemperature controlHand held
A cordless, hand held soldering iron operable with a control station providing wireless temperature control functionality and a charging station.
Owner:HAKKO CO LTD
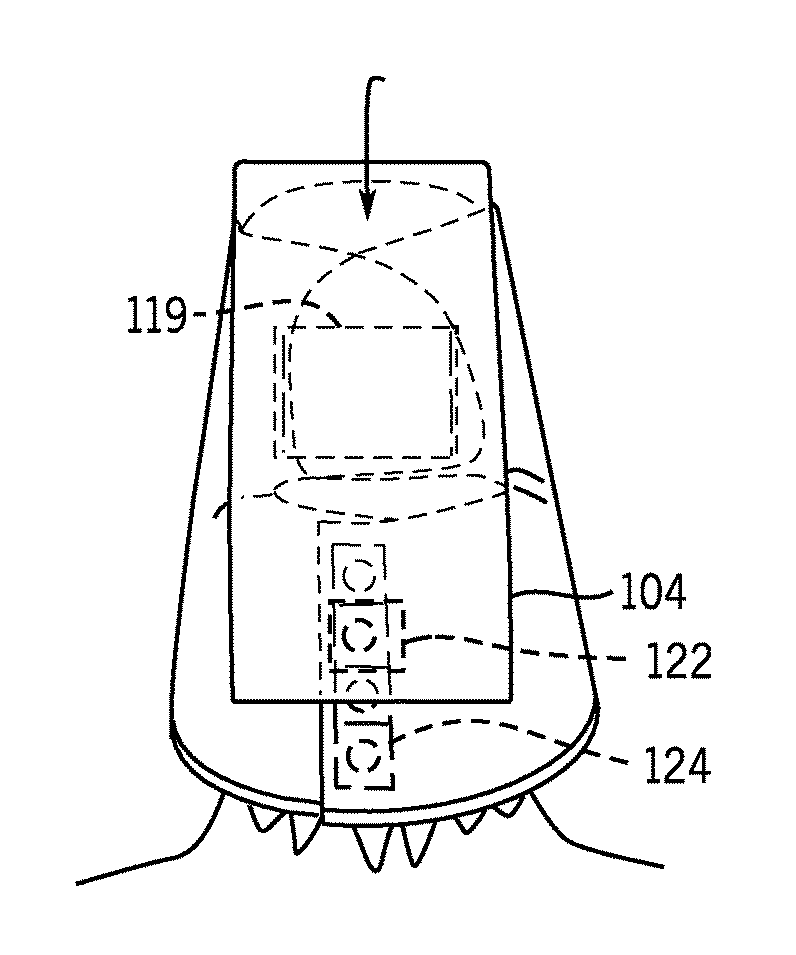
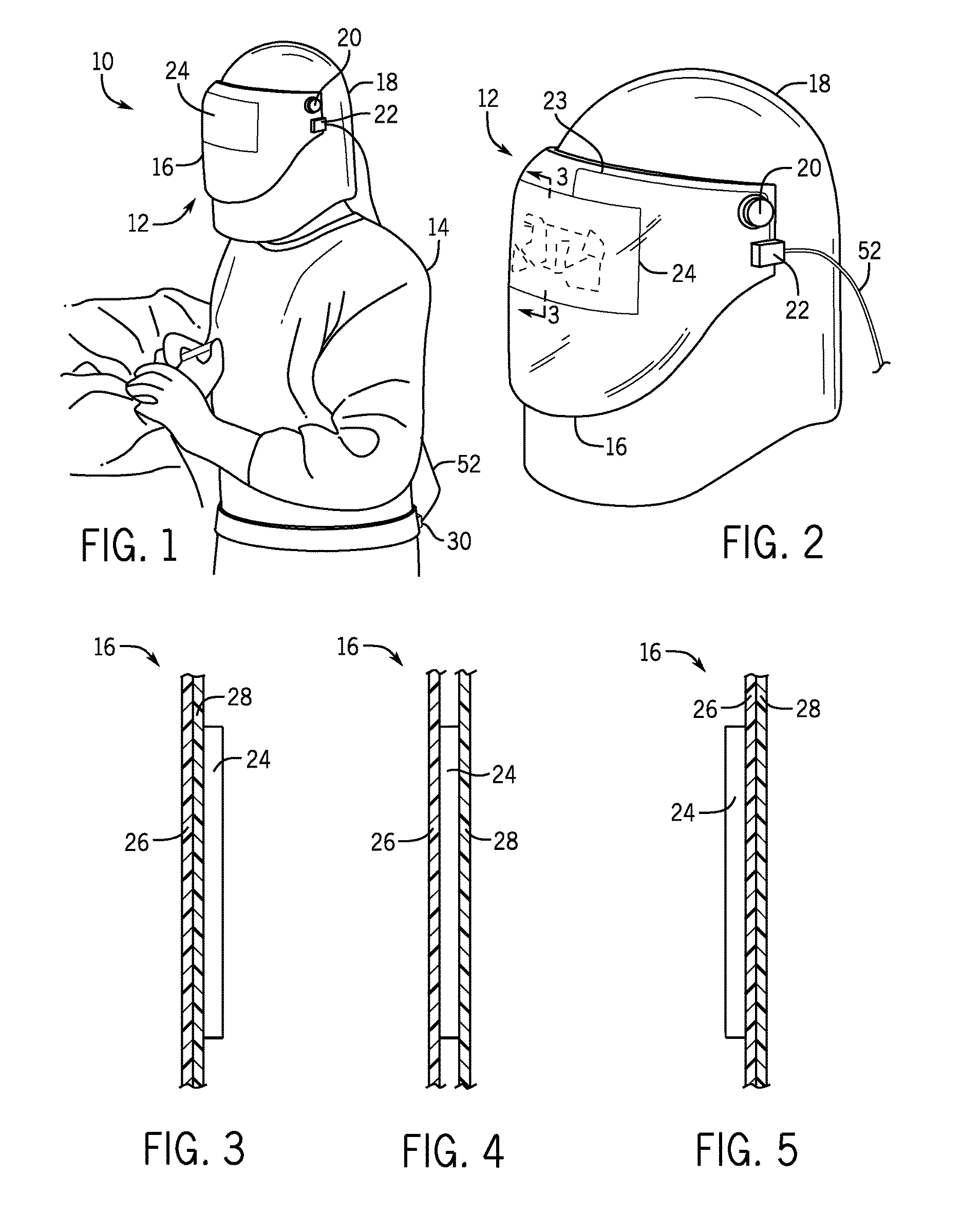
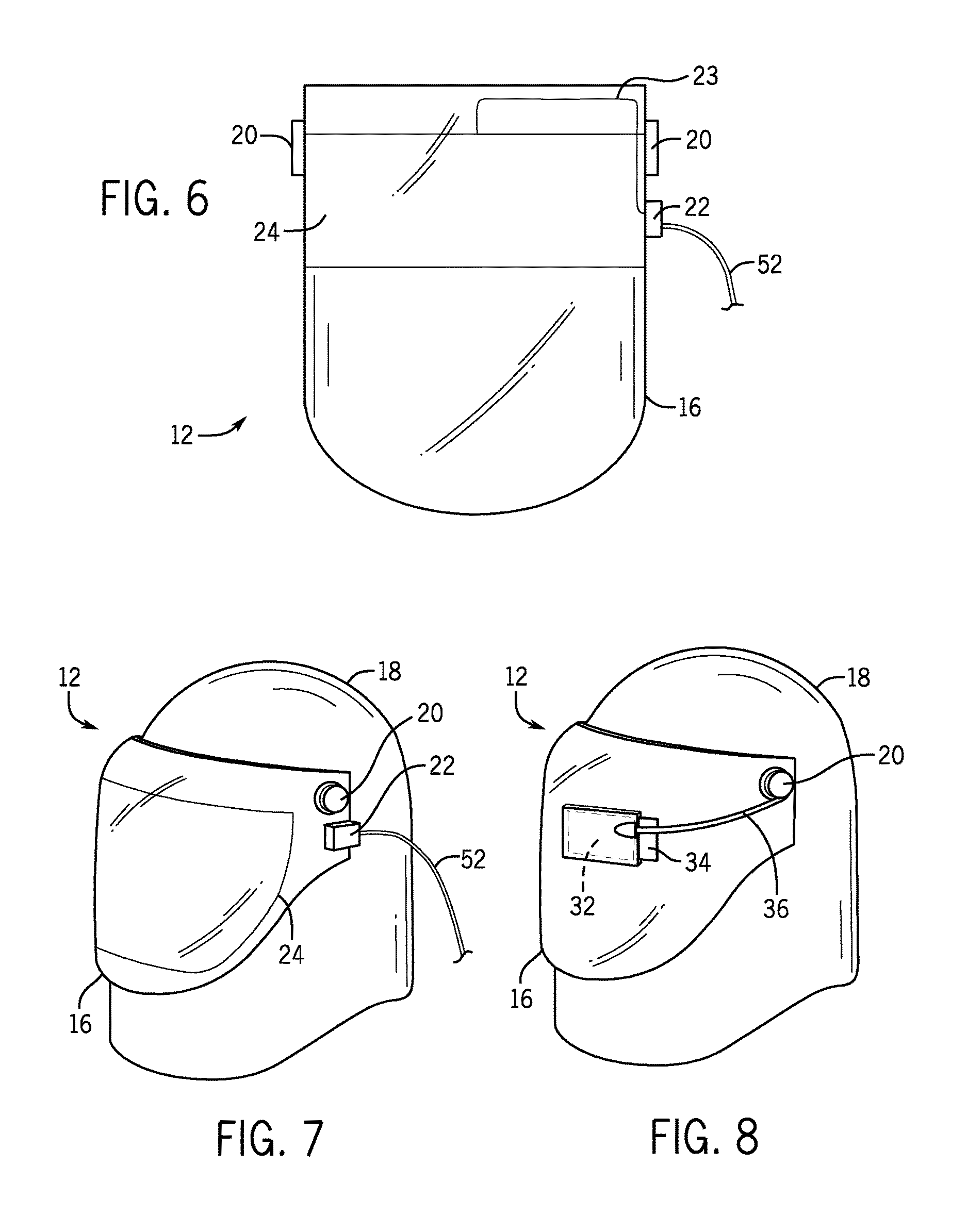
Shield for protecting a user from radiation emitted during x-ray imaging
ActiveUS20170004895A1Reduce decreaseProtect usersChemical protectionHeat protectionEngineeringRadiation
A shield is disclosed for protecting a user from radiation emitted during X-ray imaging. The shield includes a lead layer for absorbing the radiation. The shield comprises first and second opposing flaps configured to position a first portion of the shield around an upper part of the user's head in a deployed configuration, whereby the portion, a component having first and second ends that are attached to the first and second opposing flaps, respectively, wherein the component is adapted to expand to enable the first portion of the shield to adjust to fit around the upper part of the user's head, and third and fourth opposing flaps configured to position a second portion of the shield around a lower part of the user's head.
Owner:RADTEC MEDICAL DEVICES
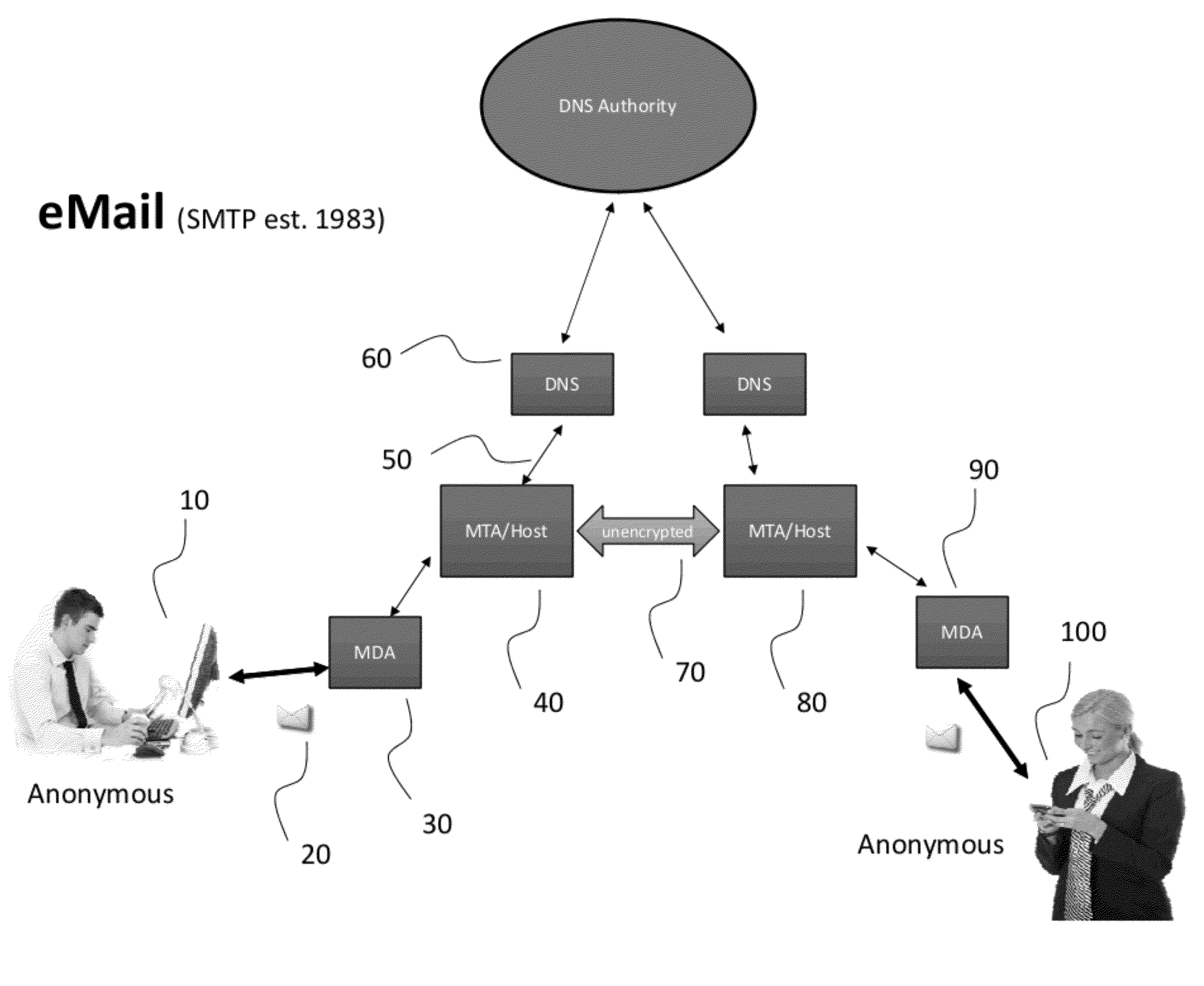
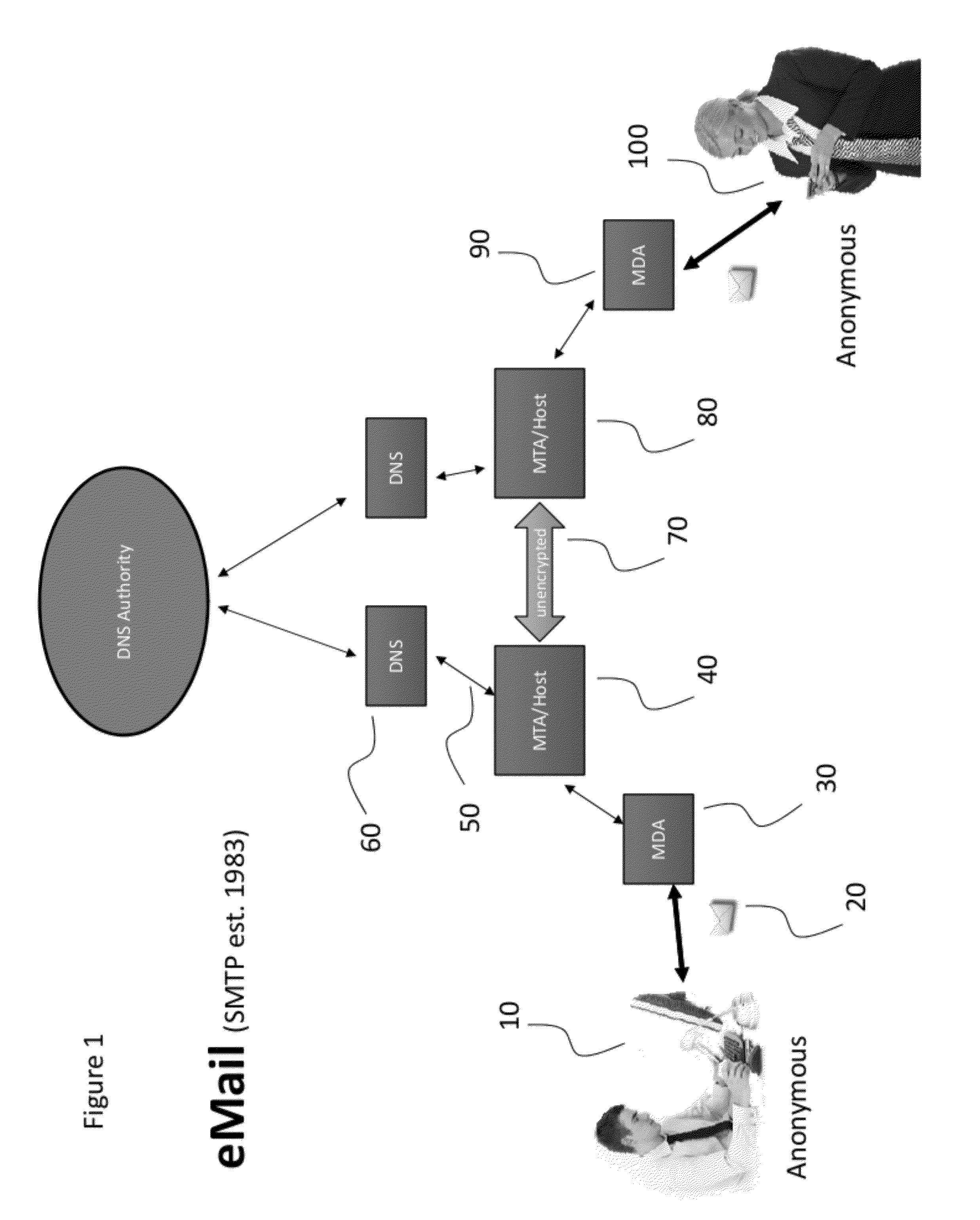
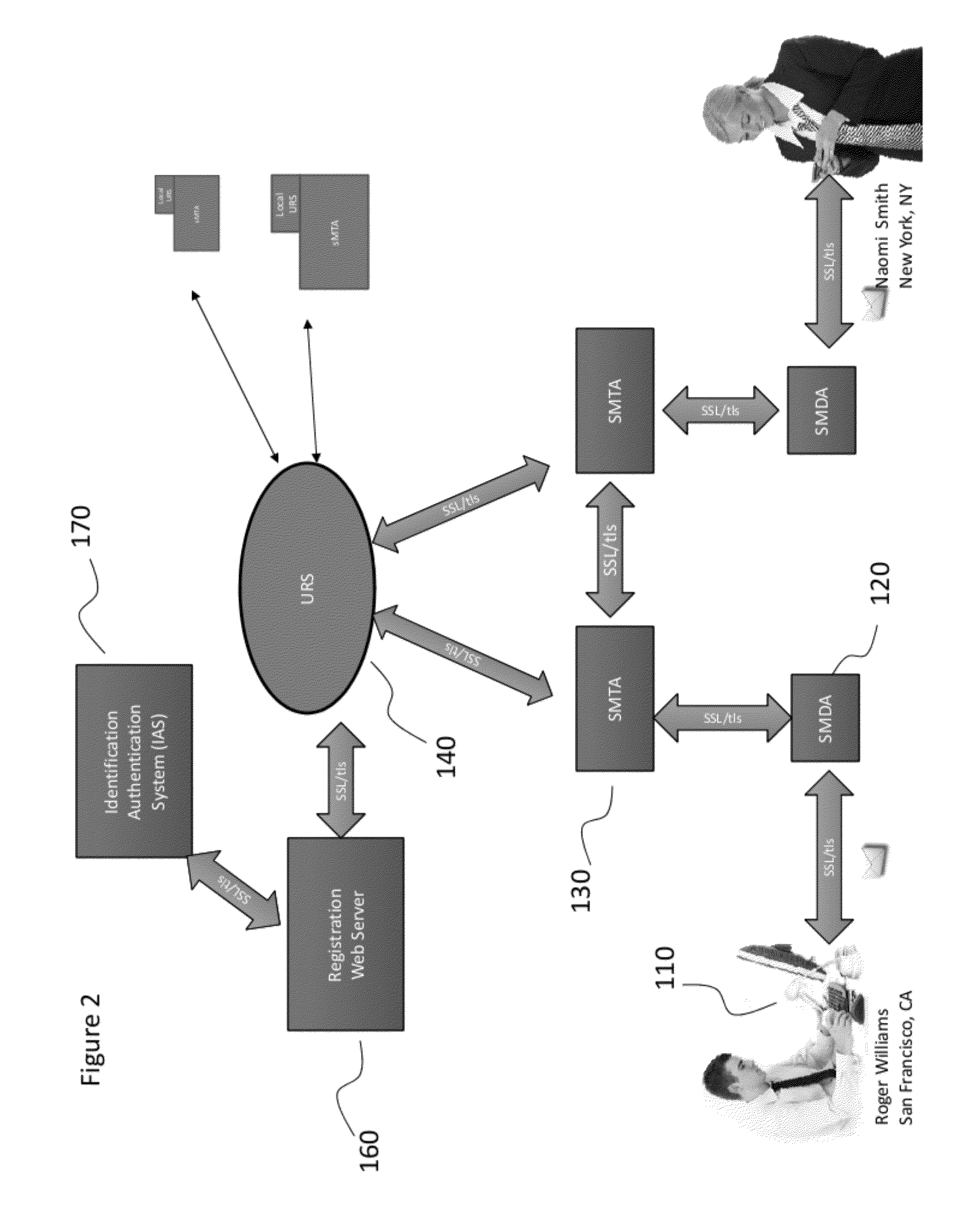
Publicly available protected electronic mail system
InactiveUS20120304261A1Positive environmental impactEfficient deploymentDigital data processing detailsComputer security arrangementsInternet privacyElectronic mail
Owner:JUSTICE JAMES
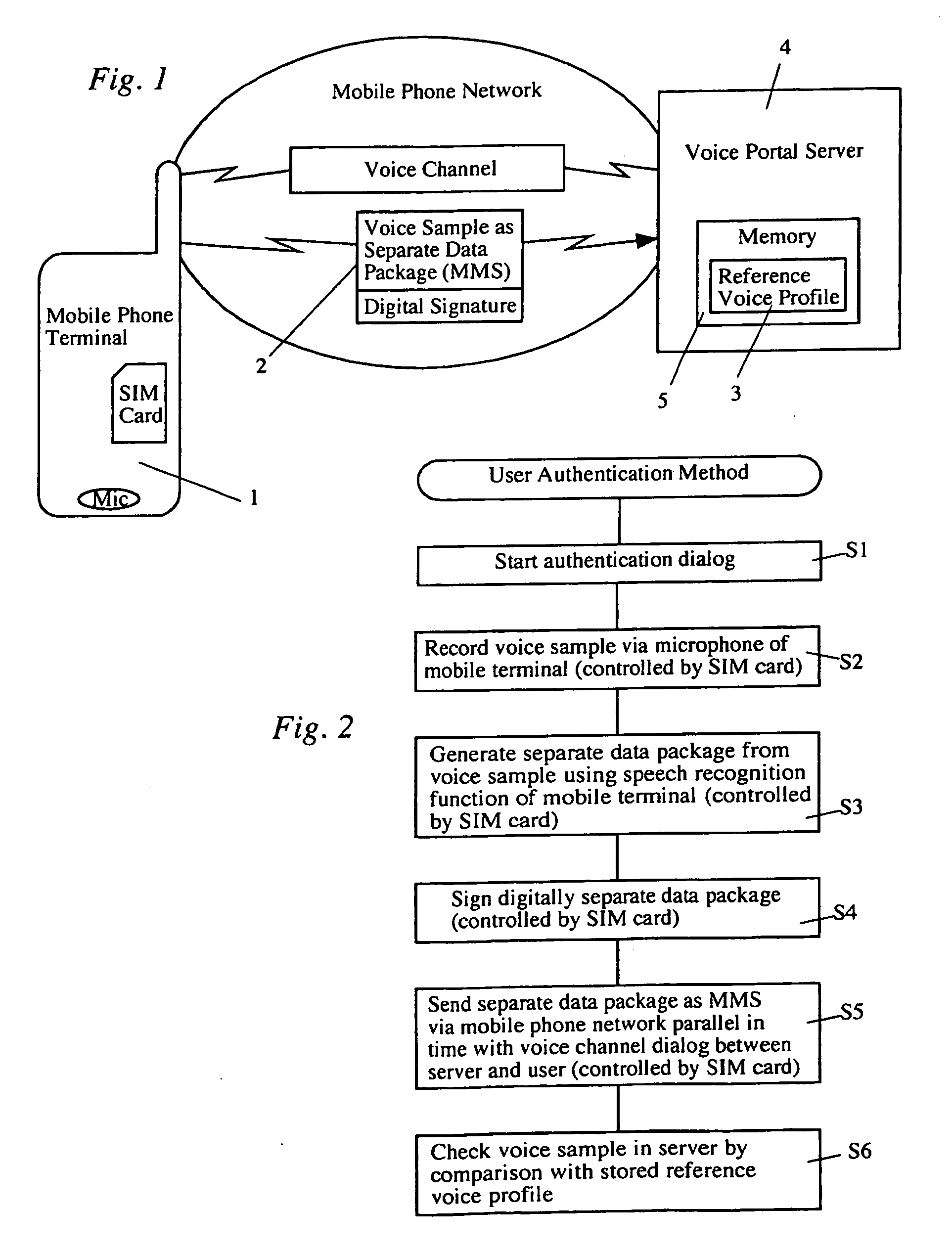
Method for authentication of a user on the basis of his/her voice profile
ActiveUS20100291901A1Low implementation costImprove reliabilityUnauthorised/fraudulent call preventionEavesdropping prevention circuitsData packUser authentication
Voice recording used for authentication is transmitted to the voice portal of the service provider not by way of the voice channel, but rather by way of a data channel. In this connection, the voice recording is sent not synchronous to speech and subject to loss, but rather asynchronously and loss-free, in an extra data package (for example advantageously as a Multimedia Messaging Service (MMS) data package). For this purpose, the resources that are available as standard items in most mobile phone terminals, such as digital voice recording and MMS transmission, can be utilized. Preferably, the subscriber's identification module or SIM card in the mobile phone terminal can store and implement the corresponding control program.
Owner:AI SOFTWARE LLC
Energy absorbing and displacing structure for athletic protective equipment
InactiveUS20100205724A1Protect usersReduce weightChemical protectionHeat protectionEnergy absorptionBand shape
An energy absorbing and displacing structure for athletic protective equipment, such as an athletic shin-guard, is provided using a flexible web-shaped body to hold a rigid band-shaped member in place.The inner rigid band-shaped member follows the contour of the desired area to protect. The outer flexible web-shaped body is made of a softer rubber like material and works as a locator and supporter keeping the inner, rigid band-shaped member, in proper location.
Owner:SUPREME ATHLETIC WEAR
Device and methods for detecting an analyte in a sample
InactiveUS7749771B2Protect usersEasy to manufactureBioreactor/fermenter combinationsBiological substance pretreatmentsAnalyteHermetic seal
Owner:RAPID MEDICAL DIAGNOSTICS CORP
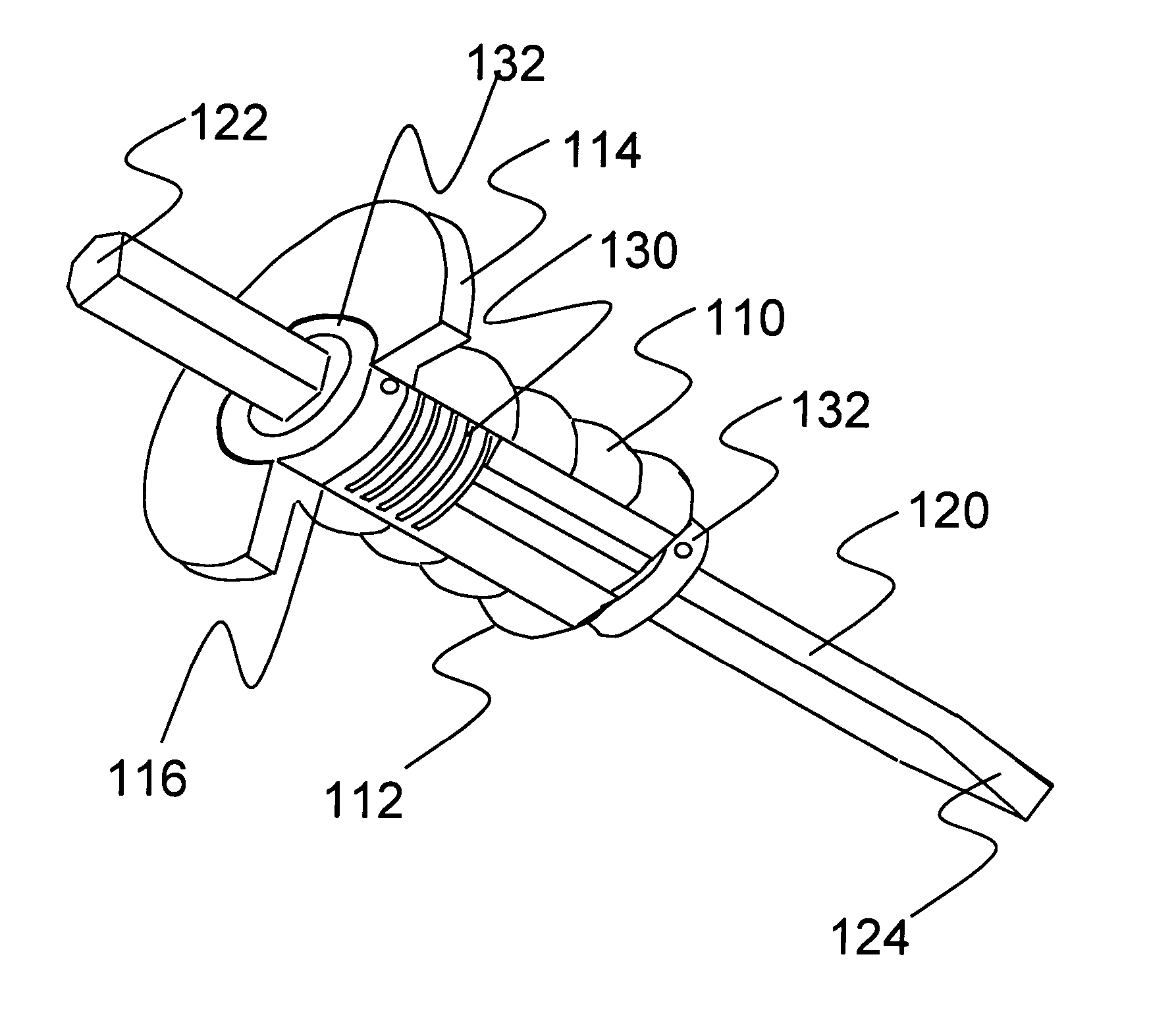
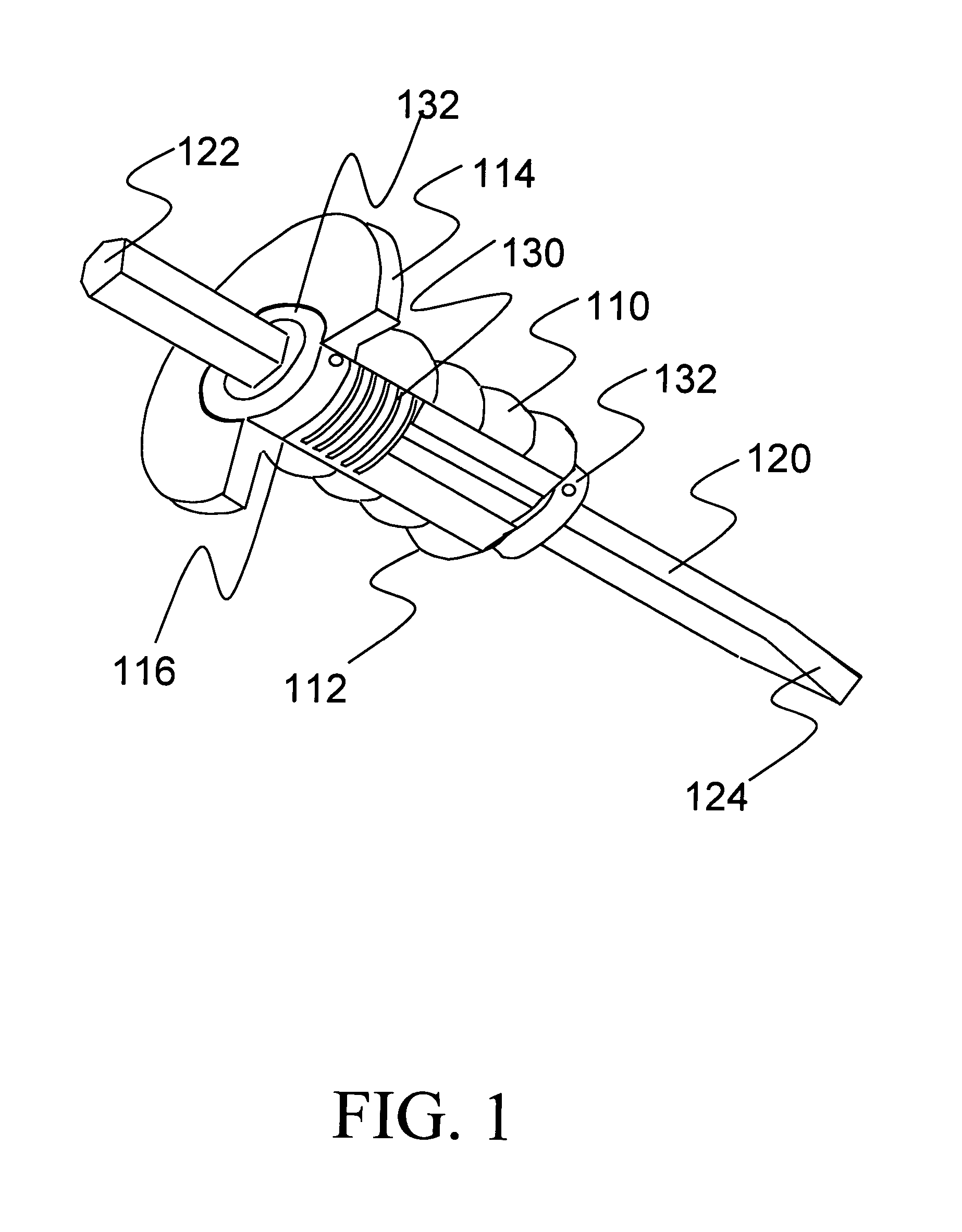
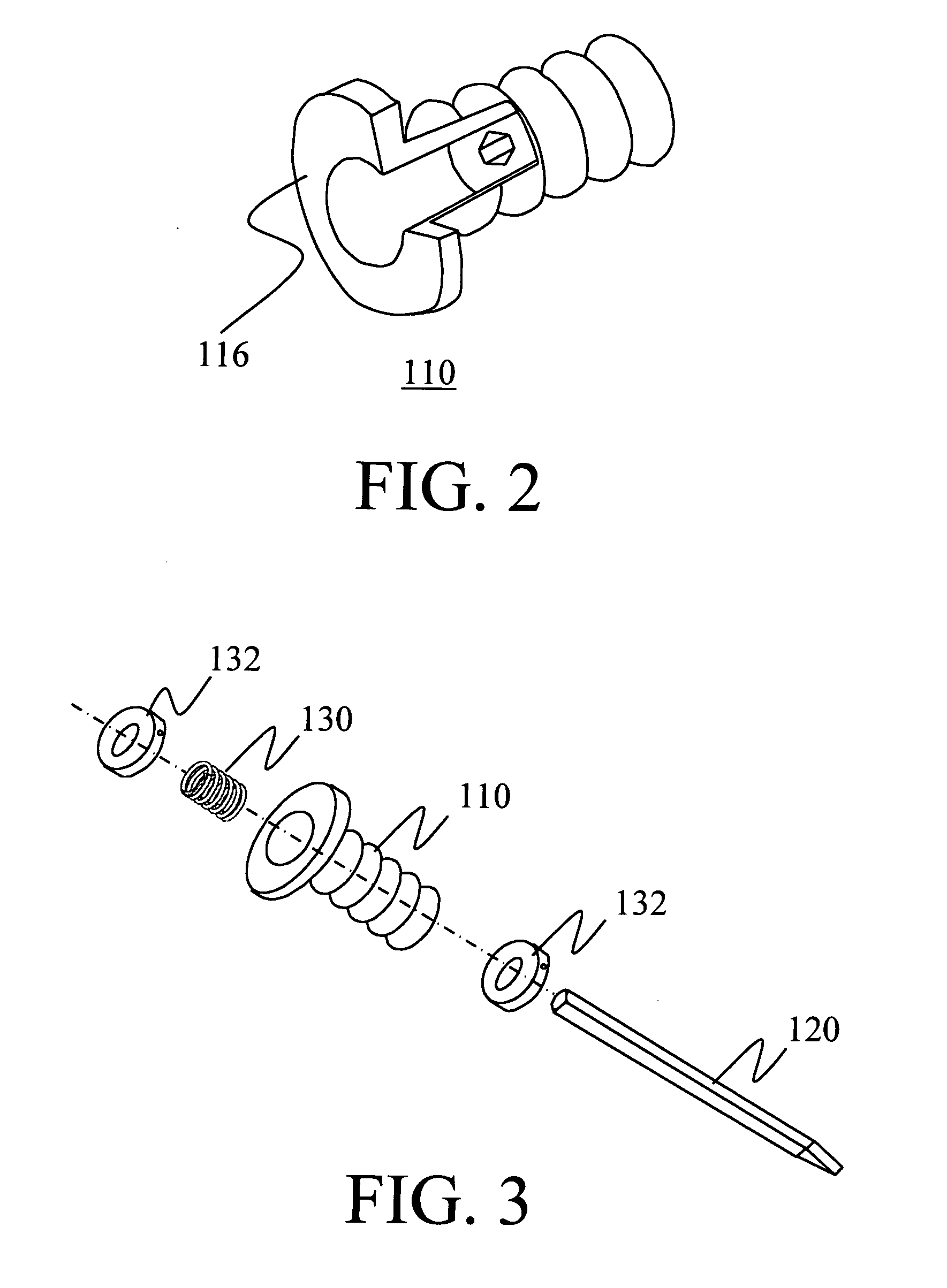
Shock-absorbing handle for impact tool
InactiveUS20050097708A1Easy and economical to manufactureEasy and economical to and assembleTravelling carriersHoldersEngineeringFlange
The present invention is a shock-absorbing apparatus that dampens the impact between a hand and an impact tool 120. The apparatus includes a handle 110 that can be gripped in the hand and allow the impact tool 120 movement within the handle 110. A shock-absorbing means 130 provides a shock-absorbing function to the handle 110. A stopping means 132 limits the movement of one end of the impact tool 120. The handle 110 may include a flange extending from the upper region of the handle 110 to provide protection from hand injury, and a gripping surface on the exterior of the handle 110 that cushions and enhances the grip and control of the impact tool 120.
Owner:CRAWFORD BRUCE ALLAN
Method for authentication of a user on the basis of his/her voice profile
ActiveUS20050107070A1High error rateUniform and loss-free voice transmissionElectric signal transmission systemsUnauthorised/fraudulent call preventionService provisionNetwork packet
Voice recording used for authentication is transmitted to the voice portal of the service provider not by way of the voice channel, but rather by way of a data channel. In this connection, the voice recording is sent not synchronous to speech and subject to loss, but rather asynchronously and loss-free, in an extra data package (for example advantageously as a Multimedia Messaging Service (MMS) data package). For this purpose, the resources that are available as standard items in most mobile phone terminals, such as digital voice recording and MMS transmission, can be utilized. Preferably, the subscriber's identification module or SIM card in the mobile phone terminal can store and implement the corresponding control program.
Owner:AI SOFTWARE LLC
Authentication using application authentication element
ActiveUS9883387B2Improve securityHarder to fool the userTransmissionProtocols using social networksTelecommunications networkCommunications system
Embodiments of the present invention can be directed to systems, apparatuses, and methods for performing transactions through mobile communication devices using either telecommunications networks or proximity near-field communications systems. Embodiments may be directed to a mobile communication device displaying an application authentication element. The application authentication element may include a pre-selected authentication element and transaction data associated with a transaction conducted by a mobile communication device. The mobile communication device may obtain the pre-selected authentication element by either transmitting a request to a server computer or retrieving the pre-selected authentication element from a secure memory in the mobile communication device. A user authentication token may be received by the mobile communication device from the user. The mobile communication device may generate a secret token that is derived from the user authentication token. If the secret token is correlated to a secret reference token, then a transaction may be conducted.
Owner:VISA INT SERVICE ASSOC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com