Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
122results about How to "Accurate interception" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
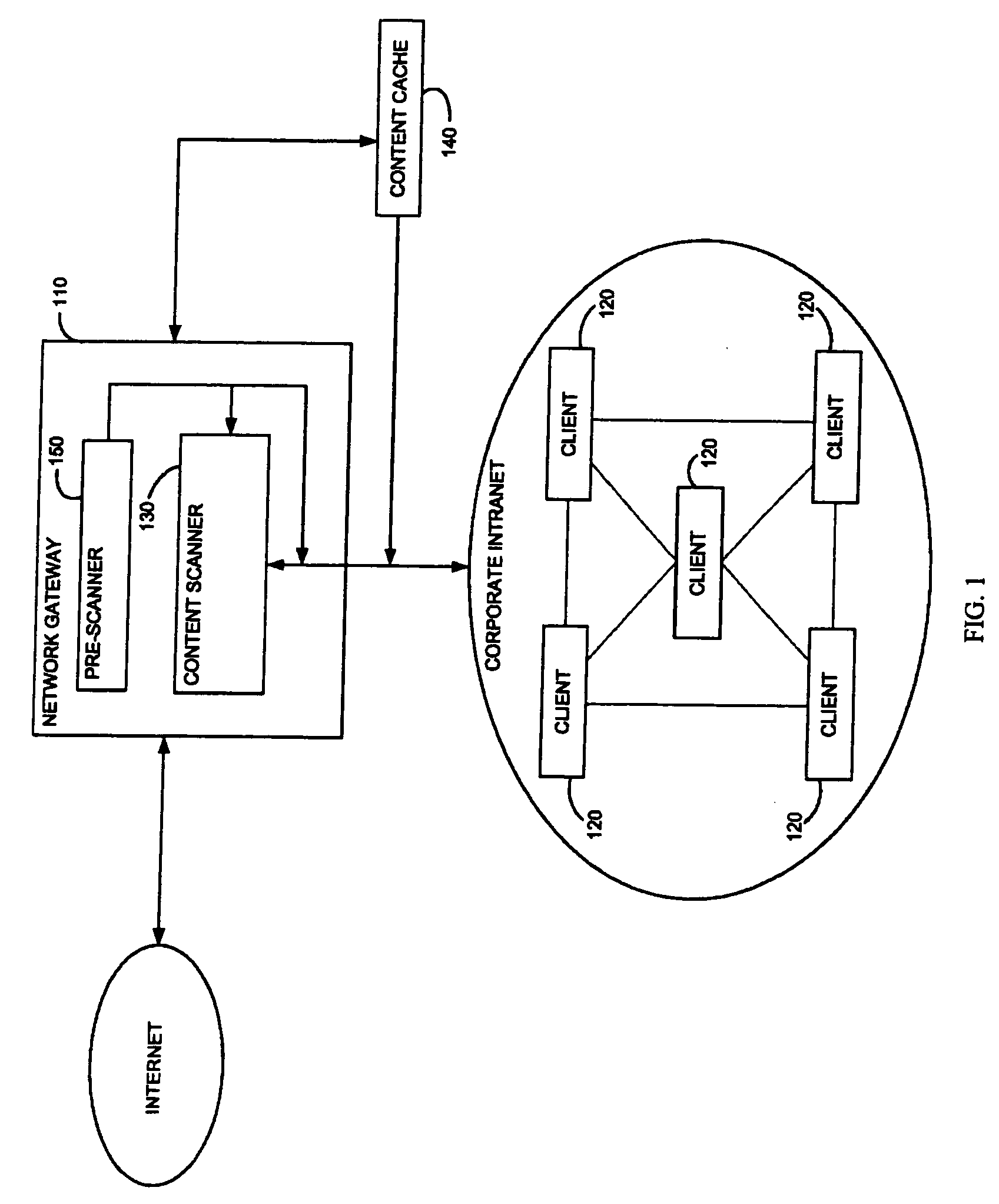
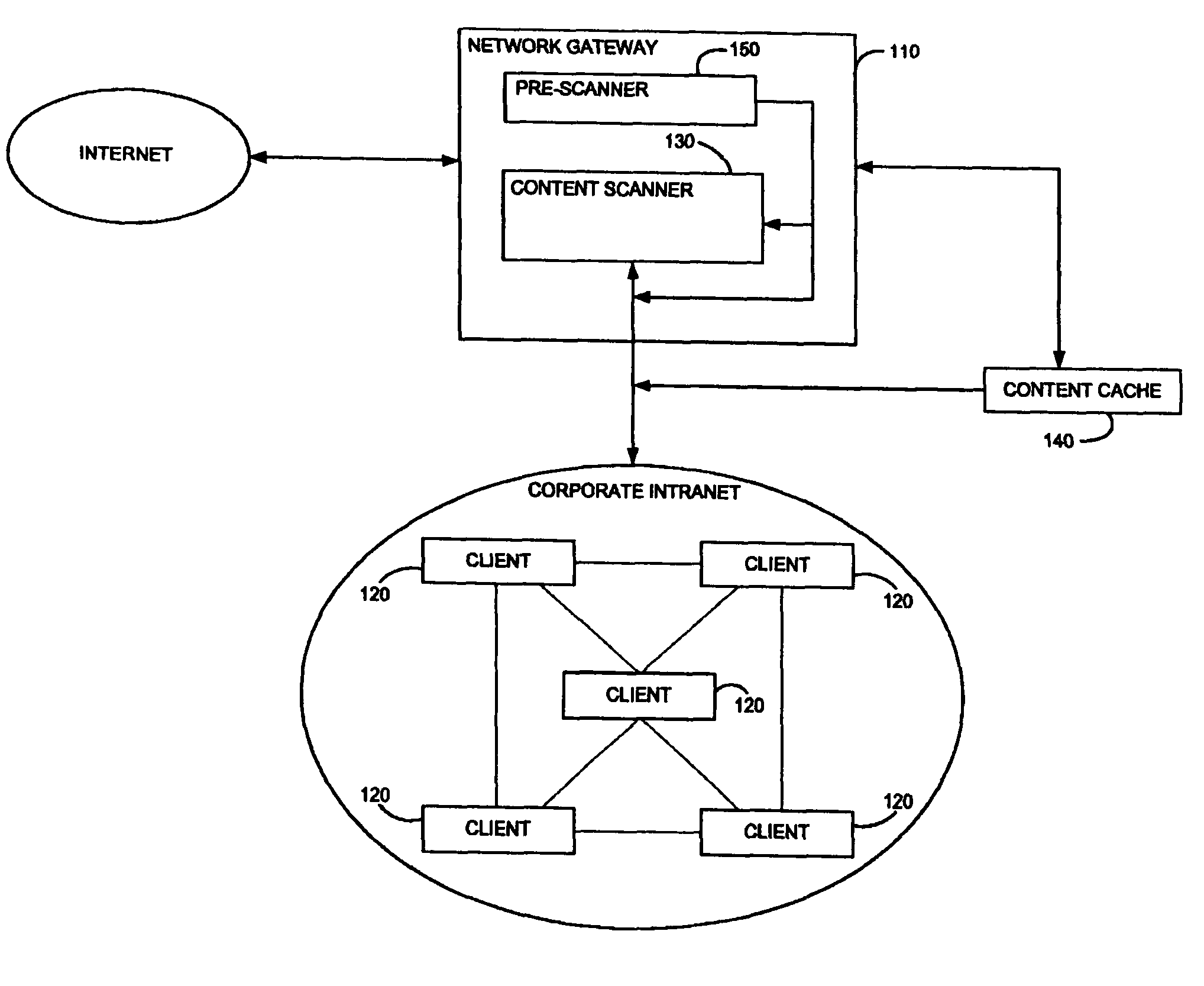
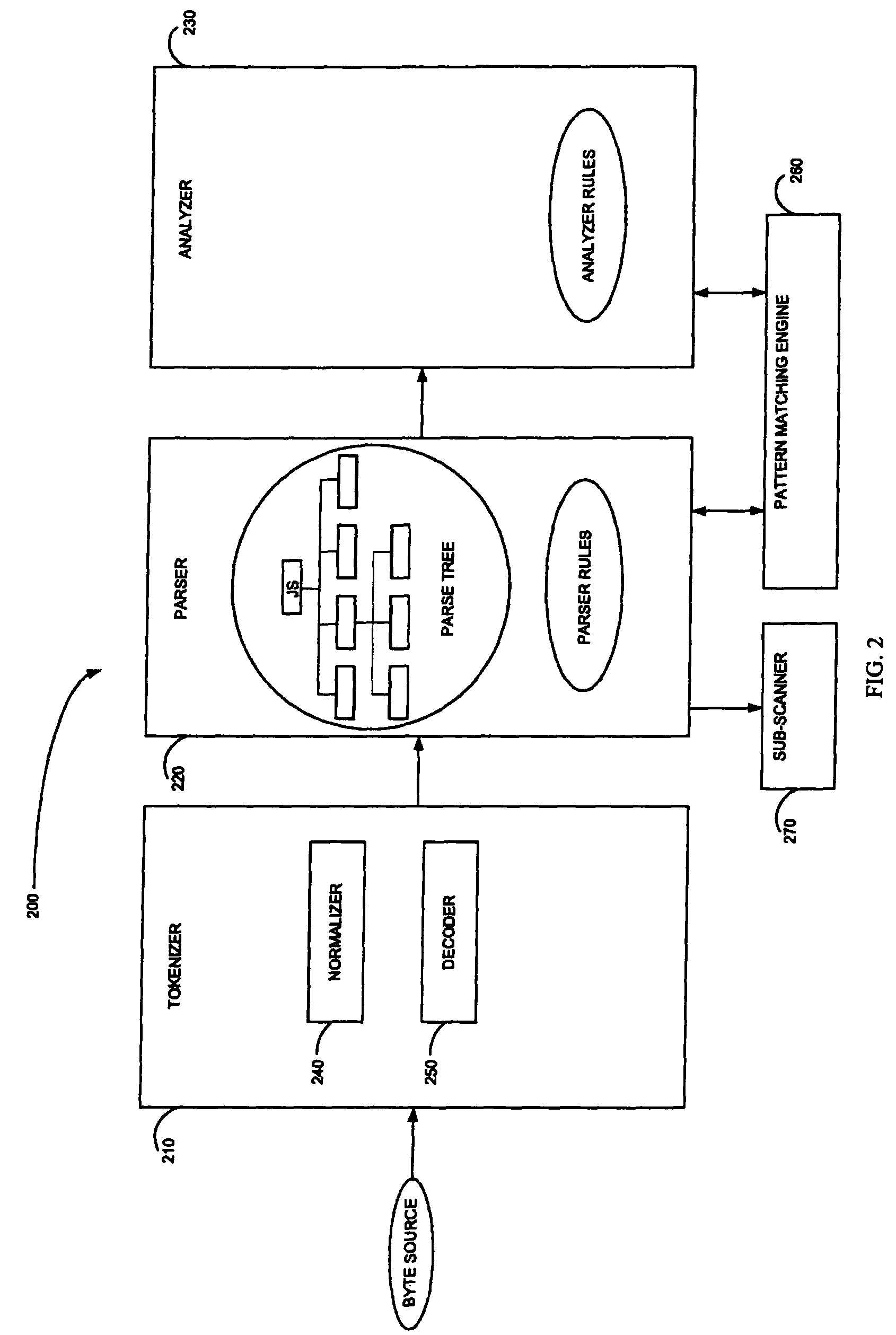
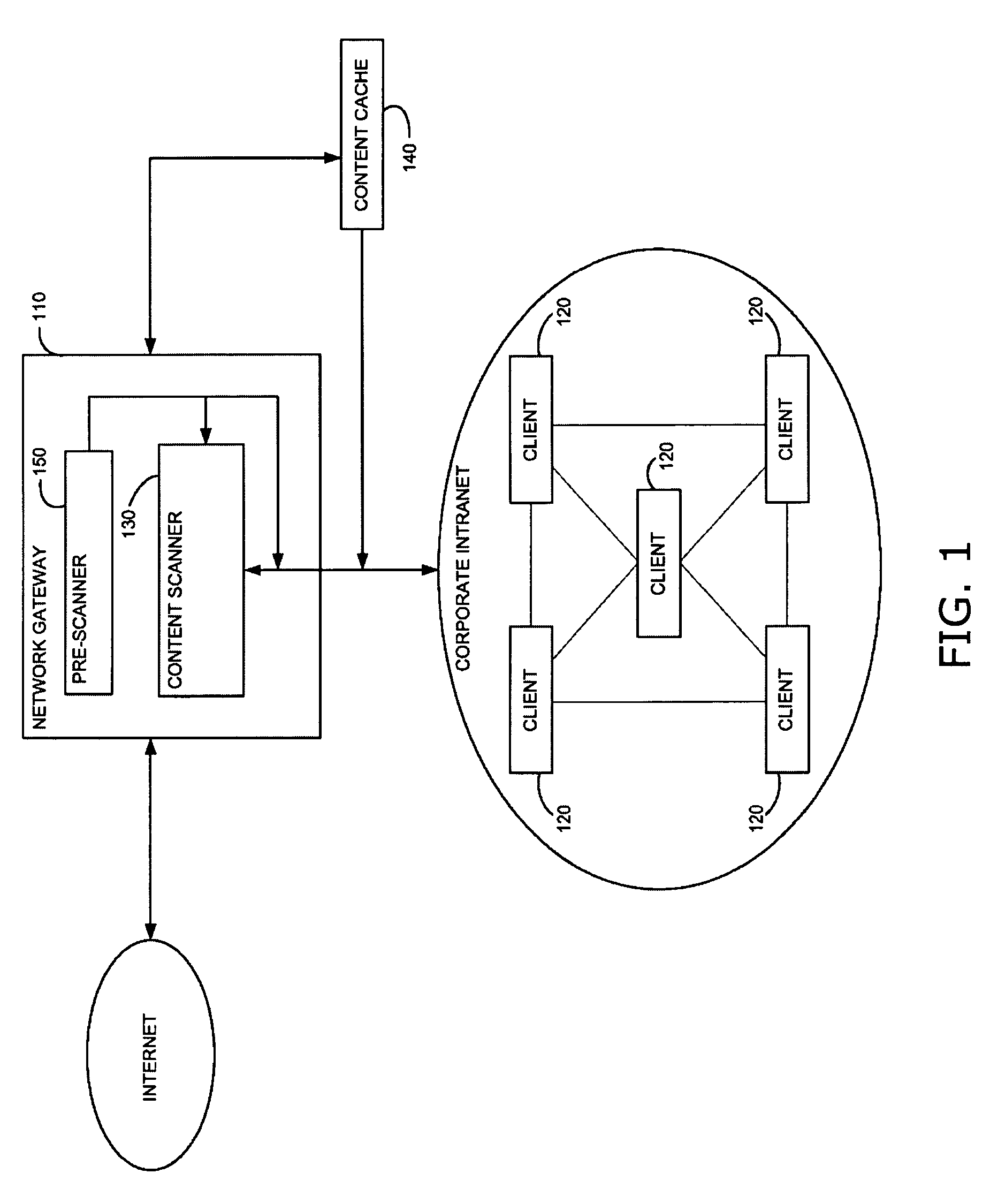
Method and system for adaptive rule-based content scanners for desktop computers
InactiveUS20050240999A1Efficiently describingAccurate interceptionMemory loss protectionUser identity/authority verificationInternet trafficSecurity system
A security system for scanning content within a computer, including a network interface, housed within a computer, for receiving content from the Internet on its destination to an Internet application running on the computer, a database of rules corresponding to computer exploits, stored within the computer, a rule-based content scanner that communicates with said database of rules, for scanning content to recognize the presence of potential exploits therewithin, a network traffic probe, operatively coupled to the network interface and to the rule-based content scanner, for selectively diverting content from its intended destination to the rule-based content scanner, and a rule update manager that communicates with said database of rules, for updating said database of rules periodically to incorporate new rules that are made available. A method and a computer readable storage medium are also described and claimed.
Owner:FINJAN LLC
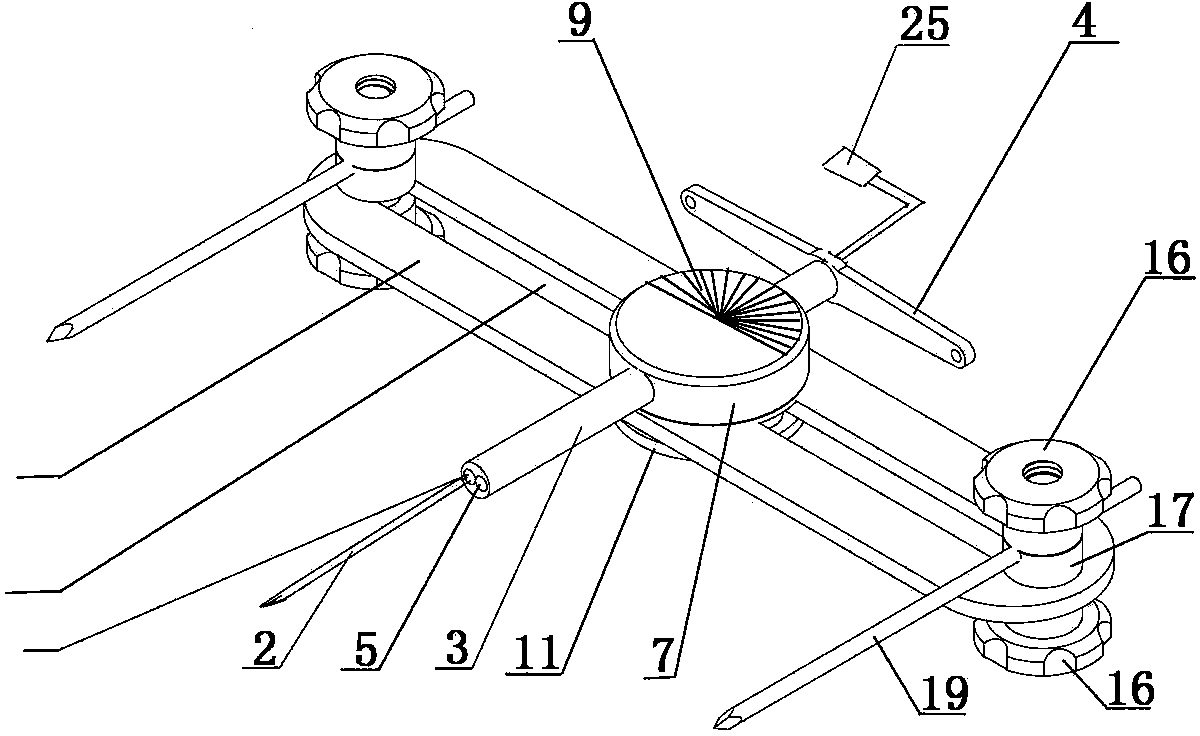
Longitudinal minimal-invasion bone cutter for tubular bones
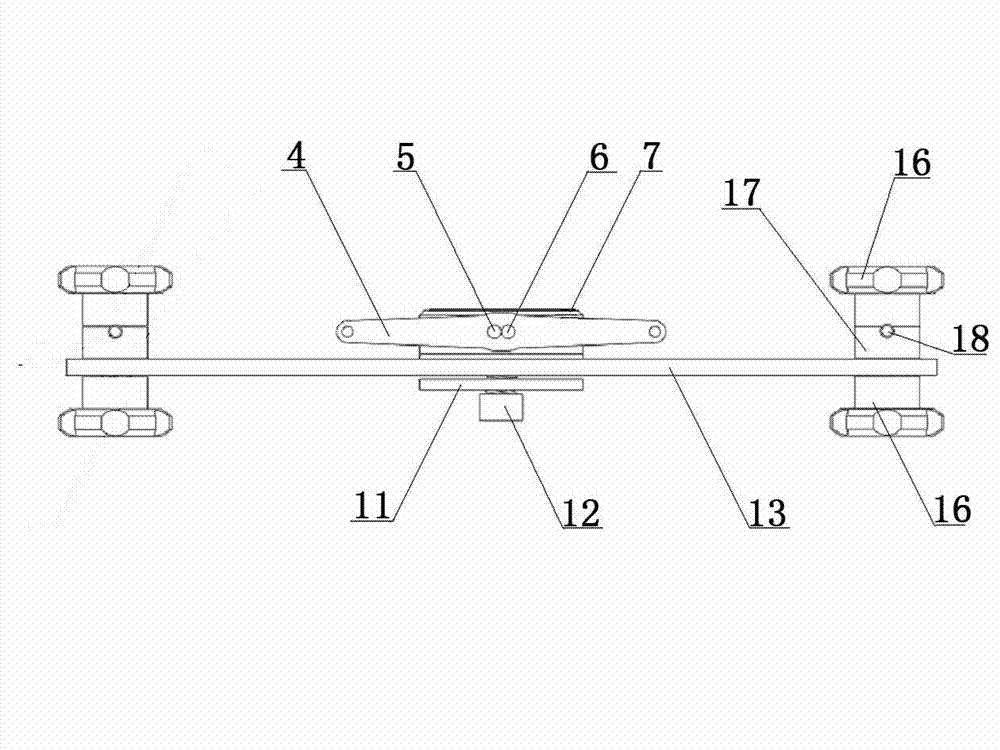
InactiveCN102860860AFor lateral tractionFacilitates longitudinal osteotomySurgeryTraction TreatmentPeriosteum
A longitudinal minimal-invasion bone cutter for tubular bones comprises a bone cutting end bone cutting device and far end positioning devices. The bone cutting end bone cutting device is slidingly sleeved on a positioning adjusting guide rail which is in a long-strip shape, a sliding groove is arranged in the middle of the positioning adjusting guide rail along the length direction, and scales of the positioning adjusting guide rail are arranged along the sliding groove. The far end positioning devices are symmetrically sleeved at two ends of the positioning adjusting guide rail slidingly. By means of the longitudinal minimal-invasion bone cutter, medical workers can perform longitudinal bone cutting operations on the tubular bones according to treatment needs, and the longitudinal minimal-invasion bone cutter is convenient to operate. When the operations are performed, the longitudinal minimal-invasion bone cutter provides convenience for transverse traction of bone blocks and meets needs of angiitis treatment. The bone cutting operations performed by the aid of the longitudinal minimal-invasion bone cutter belong to minimal-invasion operations, do not damage nerves, blood vessels, soft tissues and periostea, have small invasion, facilitate reconstruction and union of bones, and meet needs of longitudinal traction treatment of the tubular bones. By means of the longitudinal minimal-invasion bone cutter, safety and accuracy of the longitudinal bone cutting operations of the tubular bones are improved, medical workers can conveniently perform the operations, and the operation effect is guaranteed.
Owner:JIANGSU GUANGJI MEDICAL TECH
Method and system for adaptive rule-based content scanners for desktop computers
InactiveUS7975305B2Efficiently describingAccurate interceptionMemory loss protectionUser identity/authority verificationTraffic capacityThe Internet
A security system for scanning content within a computer, including a network interface, housed within a computer, for receiving content from the Internet on its destination to an Internet application running on the computer, a database of rules corresponding to computer exploits, stored within the computer, a rule-based content scanner that communicates with said database of rules, for scanning content to recognize the presence of potential exploits therewithin, a network traffic probe, operatively coupled to the network interface and to the rule-based content scanner, for selectively diverting content from its intended destination to the rule-based content scanner, and a rule update manager that communicates with said database of rules, for updating said database of rules periodically to incorporate new rules that are made available. A method and a computer readable storage medium are also described and claimed.
Owner:FINJAN LLC
Vehicle-mounted anti-unmanned-aerial-vehicle net bullet interception system
ActiveCN107054678AAccurate interceptionImprove interception efficiencyDefence devicesArresting gearIn vehicleRadar
A vehicle-mounted anti-unmanned-aerial-vehicle net bullet interception system comprises a searching cradle head, an early warning detector, a launch canister and bullet ammunition, wherein the early warning detector and the launch canister are arranged on the searching cradle head, and the bullet ammunition is arranged in the launch canister. According to the vehicle-mounted anti-unmanned-aerial-vehicle net bullet interception system, the technical problem that an interception method provided by the prior art only applies to propeller-type unmanned aerial vehicles made from metal, is difficult to apply to high-speed maneuverable unmanned aerial vehicle targets and is prone to causing secondary damage to ground surface personnel or other targets are solved. According to the vehicle-mounted anti-unmanned-aerial-vehicle net bullet interception system, unmanned aerial vehicle distance and speed information is obtained through a millimeter wave one-emitting-and-double-receiving early warning frequency-modulated radar, the unmanned aerial vehicles are searched, traced and automatically targeted through the searching cradle head, and a net bullet is launched; the net bullet is equipped with a close sensing fuse, timely ignition is conducted with the miss distance serving as the base point, small rockets are launched so as to enable the net bullet to obtain best cooperating of the net setting speed and the flight speed, and the time for approaching the targets are shortened to the greatest extent; and interception and capturing efficiency of the net bullet interception system are improved, and the vehicle-mounted anti-unmanned-aerial-vehicle net bullet interception system is suitable for accurate interception and capturing of the high-speed maneuverable unmanned aerial vehicles.
Owner:芜湖博高光电科技股份有限公司
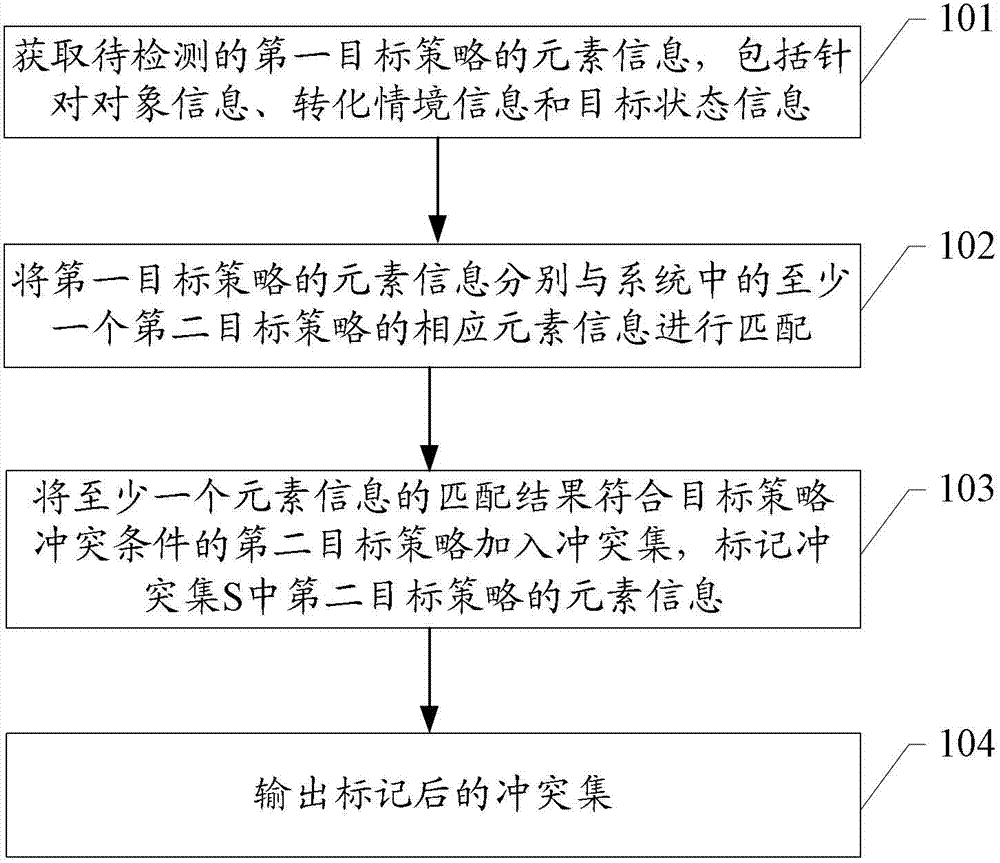
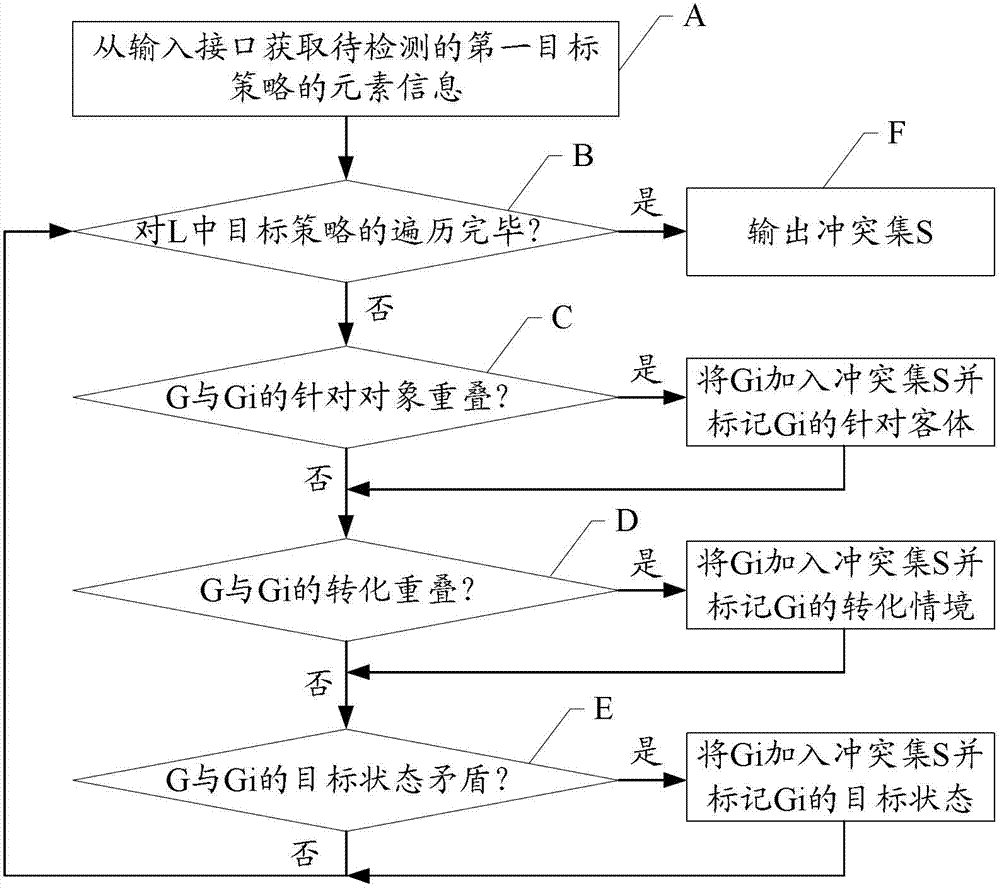
Policy conflict processing method for system and policy conflict processing system
InactiveCN102760076AAccurate interceptionReduce conflict detection burdenMultiprogramming arrangementsInformation processingPotential conflict
The embodiment of the invention discloses a policy conflict processing method for a system and a policy conflict processing system, and is applied to the technical field of information processing. In the embodiment of the invention, element information of a first target policy to be detected can be obtained; the element information of the first target policy is matched with corresponding element information of at least one second target policy in the system respectively; at least one second target policy, the element information matching result of which accords with target policy conflict conditions, is added in a conflict set, so that the target policies possible to potentially conflict with the first target policy in the system to be detected can be known; element information of the second target policy with the matching result according with the target policy conflict conditions in the conflict set is marked, and the elements that can concretely conflict with the first target policy potentially in the second target policy can be known; and finally, the marked conflict set is output, so that potential conflicts can be intercepted in the elaboration phases of the target policies more conveniently and more accurately.
Owner:HUAWEI TECH CO LTD +1
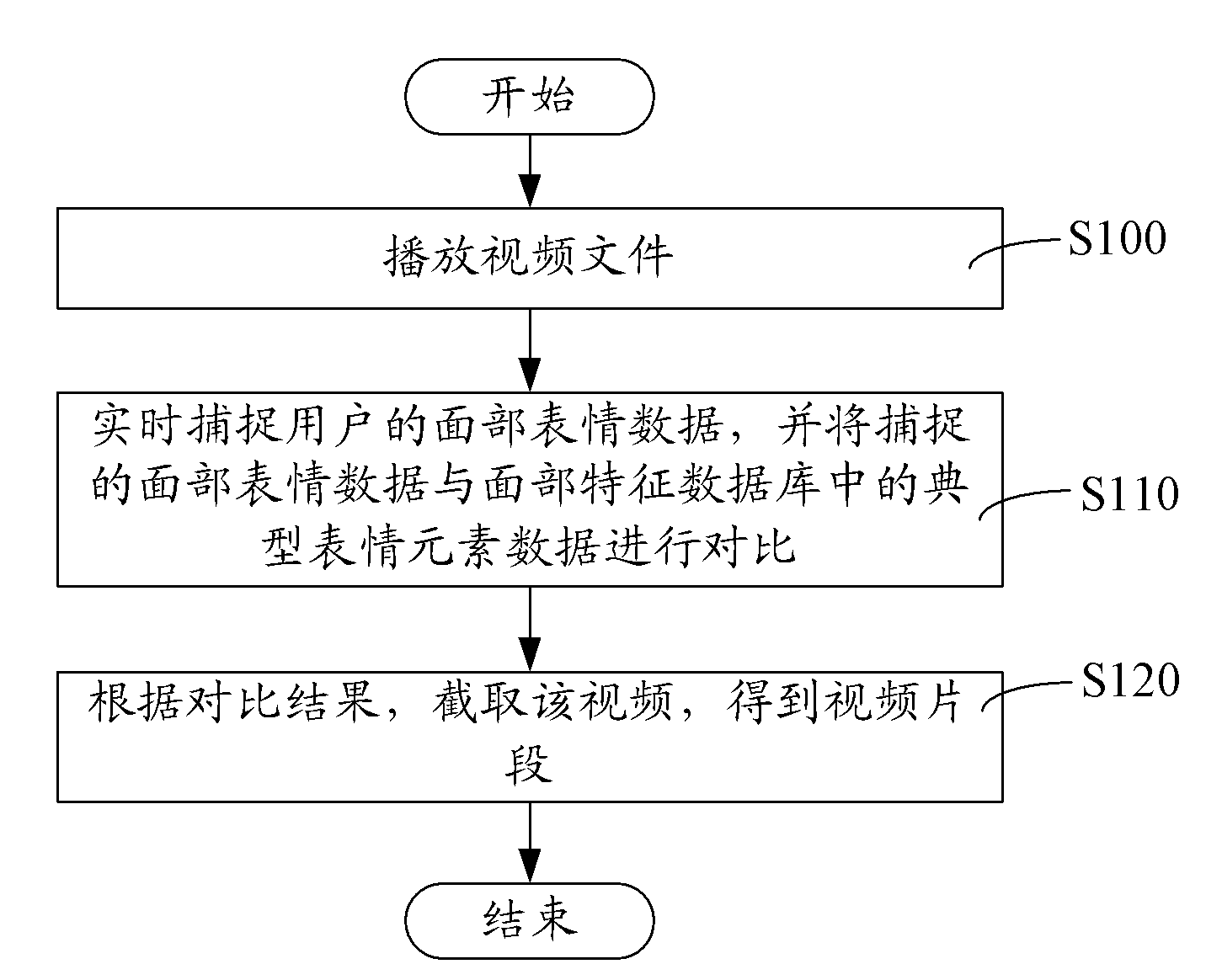
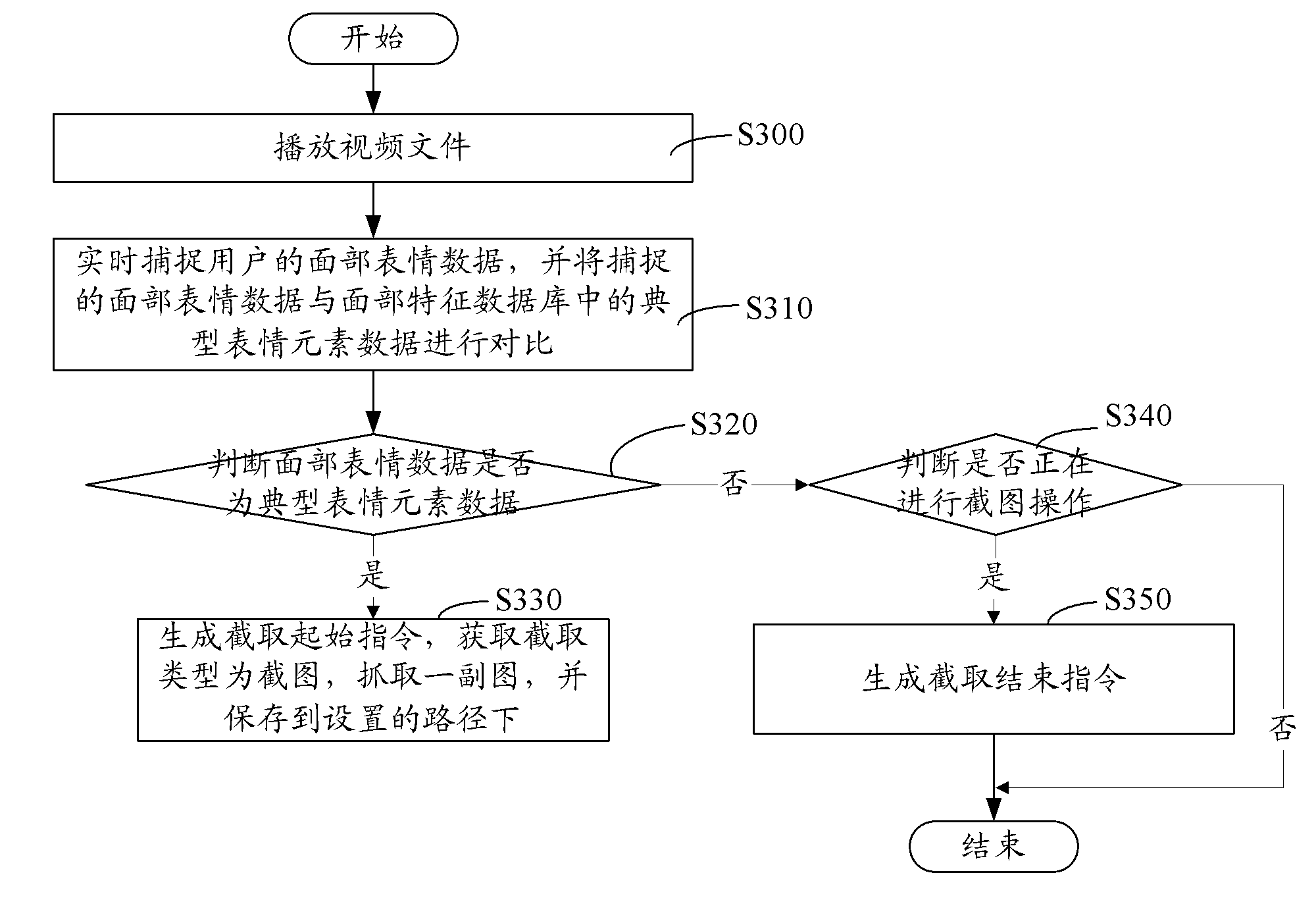
Method and system for video clip generation
InactiveCN102693739AAccurate interceptionDoes not affect the playback effectCarrier indexing/addressing/timing/synchronisingPattern recognitionFacial expression
The invention relates to a method and system for video clip generation. The method comprises the following steps: playing a video file; capturing facial expression data of a user in real time and comparing the captured facial expression data with typical expression element data in a facial feature database; and intercepting the video according to the comparison result to obtain a video clip. According to the method and system for video clip generation, when the video file is played, facial expression data of a user are collected in real time; the collected facial expression data are compared with the typical expression element data in the facial feature database; and according to the comparison result, the video is intercepted to obtain the video clip that corresponds to the typical expression element data. Therefore, a needed video clip can be intercepted accurately and a playing effect is not influenced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Longitudinal minimal-invasion bone cutter for tubular bones
InactiveCN102860860BFor lateral tractionFacilitates longitudinal osteotomySurgeryLess invasive surgeryEngineering
A longitudinal minimal-invasion bone cutter for tubular bones comprises a bone cutting end bone cutting device and far end positioning devices. The bone cutting end bone cutting device is slidingly sleeved on a positioning adjusting guide rail which is in a long-strip shape, a sliding groove is arranged in the middle of the positioning adjusting guide rail along the length direction, and scales of the positioning adjusting guide rail are arranged along the sliding groove. The far end positioning devices are symmetrically sleeved at two ends of the positioning adjusting guide rail slidingly. By means of the longitudinal minimal-invasion bone cutter, medical workers can perform longitudinal bone cutting operations on the tubular bones according to treatment needs, and the longitudinal minimal-invasion bone cutter is convenient to operate. When the operations are performed, the longitudinal minimal-invasion bone cutter provides convenience for transverse traction of bone blocks and meets needs of angiitis treatment. The bone cutting operations performed by the aid of the longitudinal minimal-invasion bone cutter belong to minimal-invasion operations, do not damage nerves, blood vessels, soft tissues and periostea, have small invasion, facilitate reconstruction and union of bones, and meet needs of longitudinal traction treatment of the tubular bones. By means of the longitudinal minimal-invasion bone cutter, safety and accuracy of the longitudinal bone cutting operations of the tubular bones are improved, medical workers can conveniently perform the operations, and the operation effect is guaranteed.
Owner:JIANGSU GUANGJI MEDICAL TECH
Audio generating method and device
ActiveCN106547797AAccurate interceptionEasy to operateElectrophonic musical instrumentsSpeech analysisSpeech recognition
The present invention relates to an audio generating method. The method comprises the following steps: performing theme extraction on comparison audio to obtain a comparison note sequence, wherein the comparison note sequence comprises a comparison note position, a comparison note pitch and a comparison note duration; obtaining original audio matched with the comparison audio by audio retrieval, and obtaining an original note sequence corresponding to the original audio, wherein the original note sequence is obtained by performing theme extraction on the original audio and comprises an original note position, an original note pitch and an original note duration; calculating a theme distance between segments of the comparison audio and the original audio according to the comparison note sequence and the original note sequence; and intercepting the segments of the original audio with the minimum theme distance as the generated audio. The segments of the original audio require no manual pickup, a user only needs to upload the comparison audio, so that the operation is convenient, and the intercepted segments are accurate. In addition, the invention further provides an audio generating device.
Owner:TENCENT TECH (SHENZHEN) CO LTD
GPS-based steering needle instrument
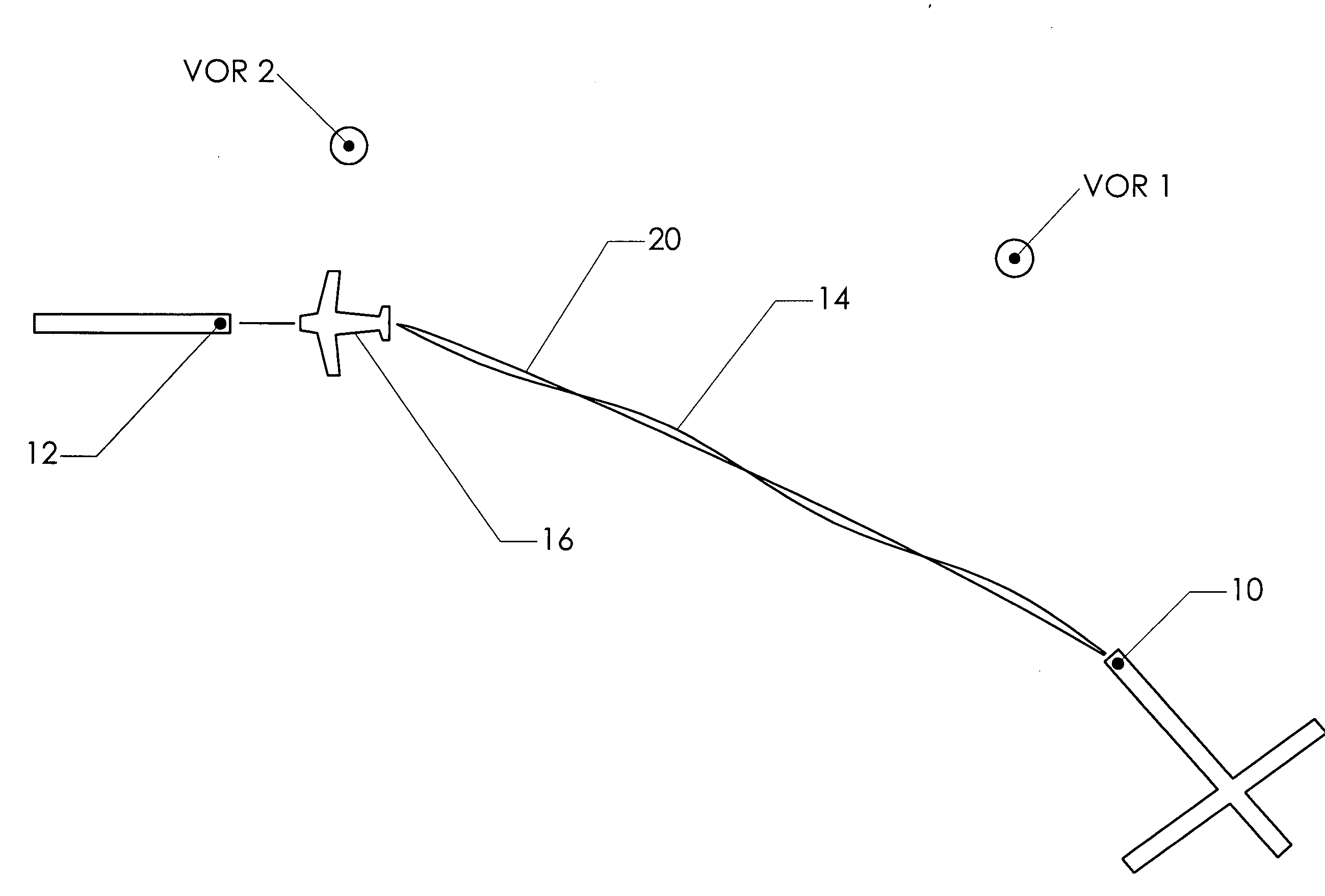
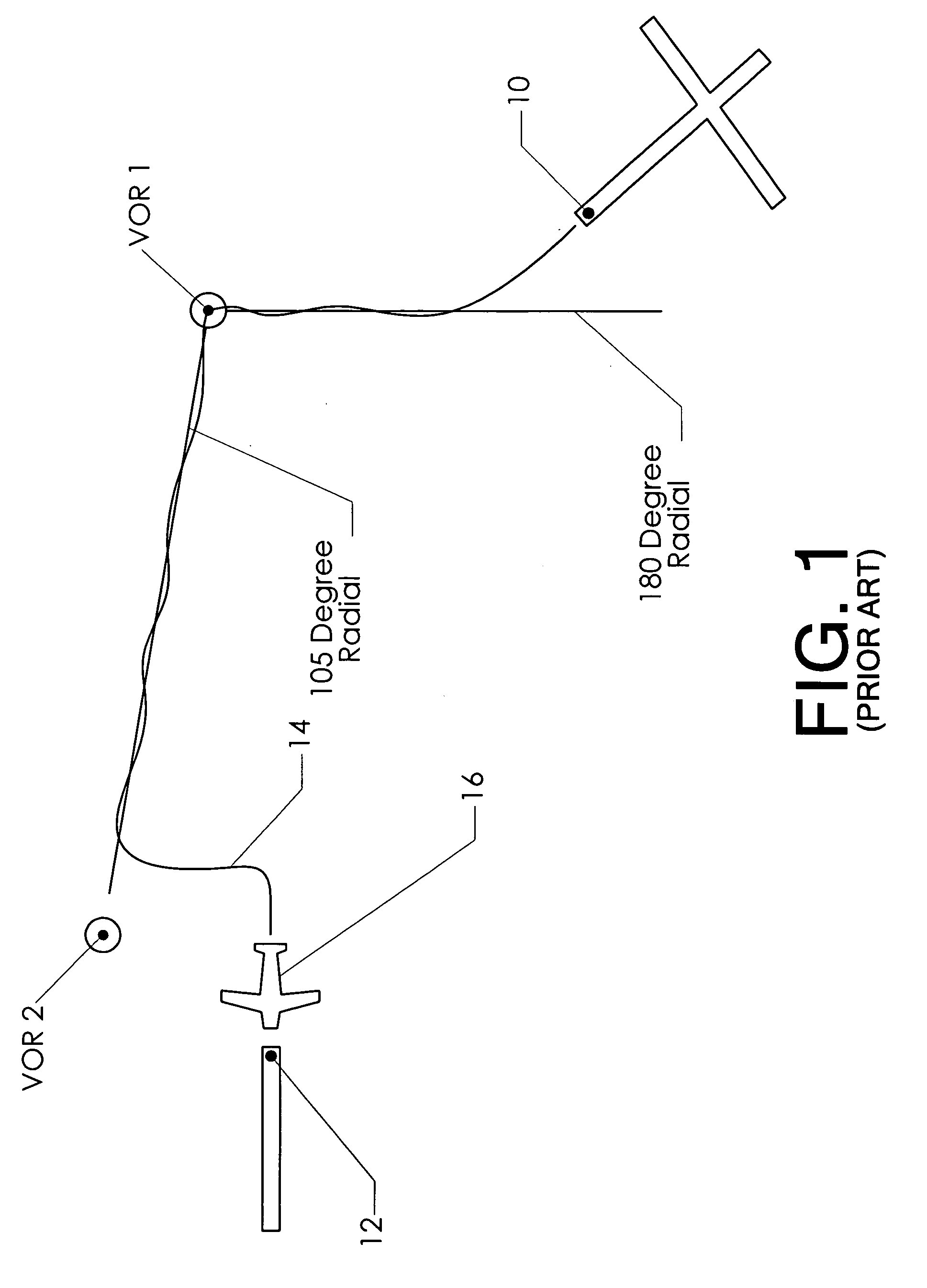
InactiveUS20060161336A1Accurate interceptionImproves inventionAnalogue computers for vehiclesInstruments for road network navigationTrackwayVisual perception
A a flight instrument enabling a pilot to intercept and precisely follow a predefined GPS track. The instrument—known as a GPS steering indicator—provides a visual display which is similar in appearance to other aircraft instruments (and therefore instantly recognizable to nearly all pilots). However, the instrument is preferably differentiated somewhat in its visual appearance to convey to the pilot the fact that it displays steering commands rather than cross track error. An indicator needle deflects to instruct the pilot which way to turn and how much to turn in order to intercept and fly along a predefined GPS track. By centering the indicator needle, the pilot maintains the desired instantaneous track.
Owner:EMBRY RIDDLE AERONAUTICAL UNIV
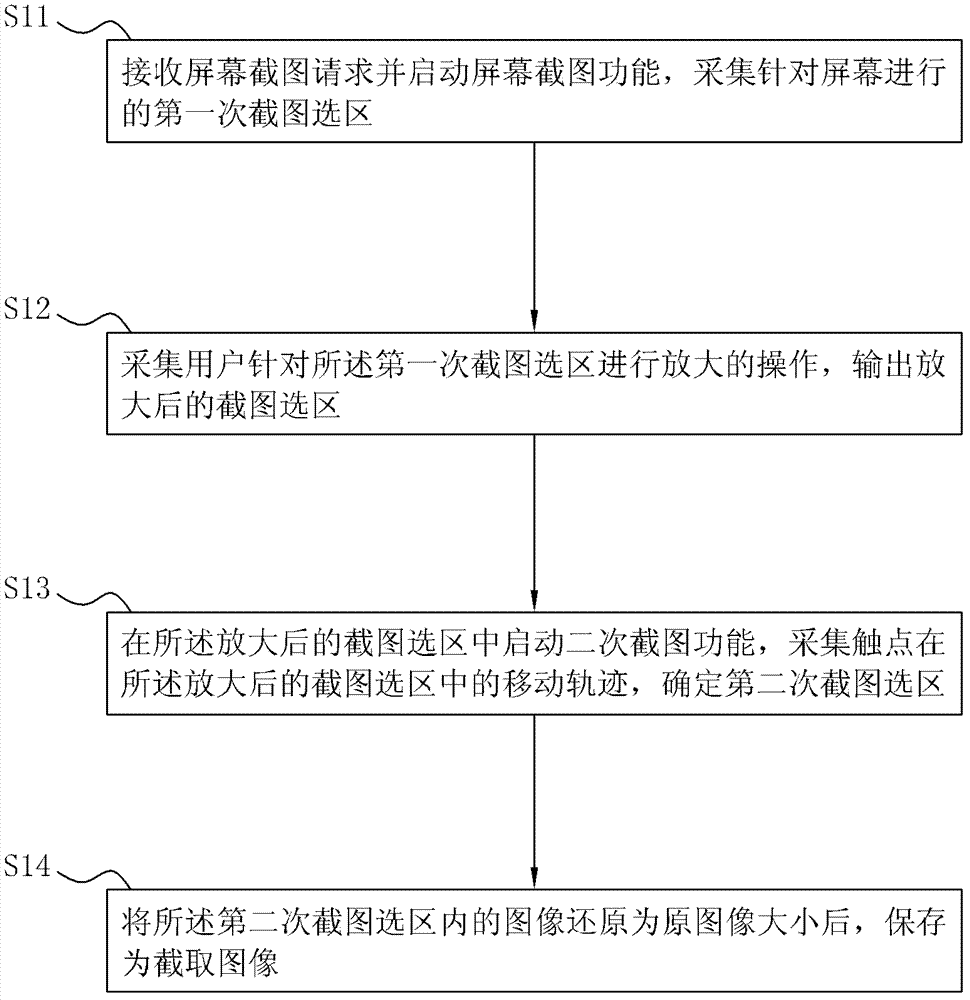
Method for obtaining image through twice-screenshot and client
ActiveCN102708539AAccurate interceptionMeet higher level needsGeometric image transformationAlgorithmComputer graphics (images)
The invention provides a method for obtaining an image through twice-screenshot and a client, belonging to the technical field of computers and software. The method comprises the following steps of: receiving a screenshot request, starting a screenshot function, and collecting a first screenshot selecting zone for the a screen; collecting the amplifying operation of a user on the first screenshot selecting zone, and outputting the amplified screenshot selecting zone; starting a second screenshot function in the amplified screenshot selecting zone, collecting the moving track of a contact point in the amplified screenshot selecting zone, and confirming the second screenshot selecting zone; and restoring the image in the second screenshot selecting zone to the original image size, and then storing the image to be a shot image. By using the invention, when the user performs the screenshot operation, and a target image in the screen is smaller, the user can shot the smaller target image roughly at first; after the shot image is amplified, the second screenshot is carried out, so that the user can more accurately shoot the target image to meet higher demands of the user.
Owner:SHANGHAI LIANGMING TECH DEV
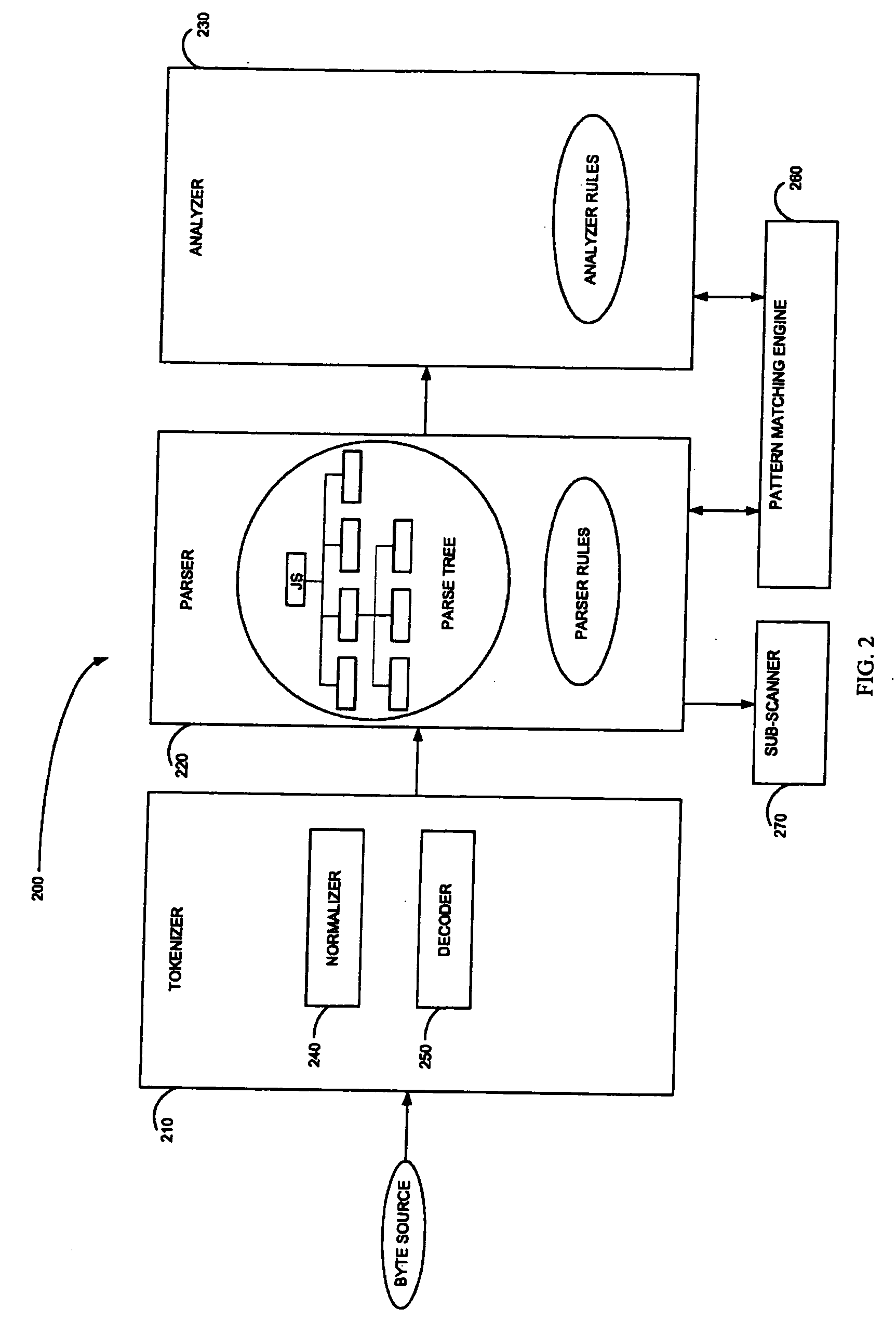
Method and system for adaptive rule-based content scanners
InactiveUS8225408B2Efficiently describingAccurate interceptionMemory loss protectionSoftware engineeringPattern generationByte
Owner:FINJAN LLC
Video screenshot method and video screenshot device
InactiveCN106412708AAccurate interceptionSolve the problem that the video picture cannot be accurately capturedSelective content distributionTimestampUser input
The embodiment of the invention discloses a video screenshot method and a video screenshot device. The video screenshot method comprises the steps of acquiring a video screenshot operation which is inputted by a user in allusion to a currently played video file; when the video screenshot operation is matched with a set screenshot operation, acquiring a timestamp corresponding to a starting moment of the video screenshot operation in the video file; determining a video clip according to the timestamp corresponding to the starting moment of the video screenshot operation and the video screenshot operation, performing a framing operation by taking the video clip as an operation object, stopping the framing operation for the video clip when the end of the video screenshot operation is detected, and acquiring at least one screenshot image of the video file. Through the technical scheme disclosed by the invention, accurate interception for a user expected image in the video can be realized.
Owner:SHANGHAI YUDE INFORMATION TECH CO LTD
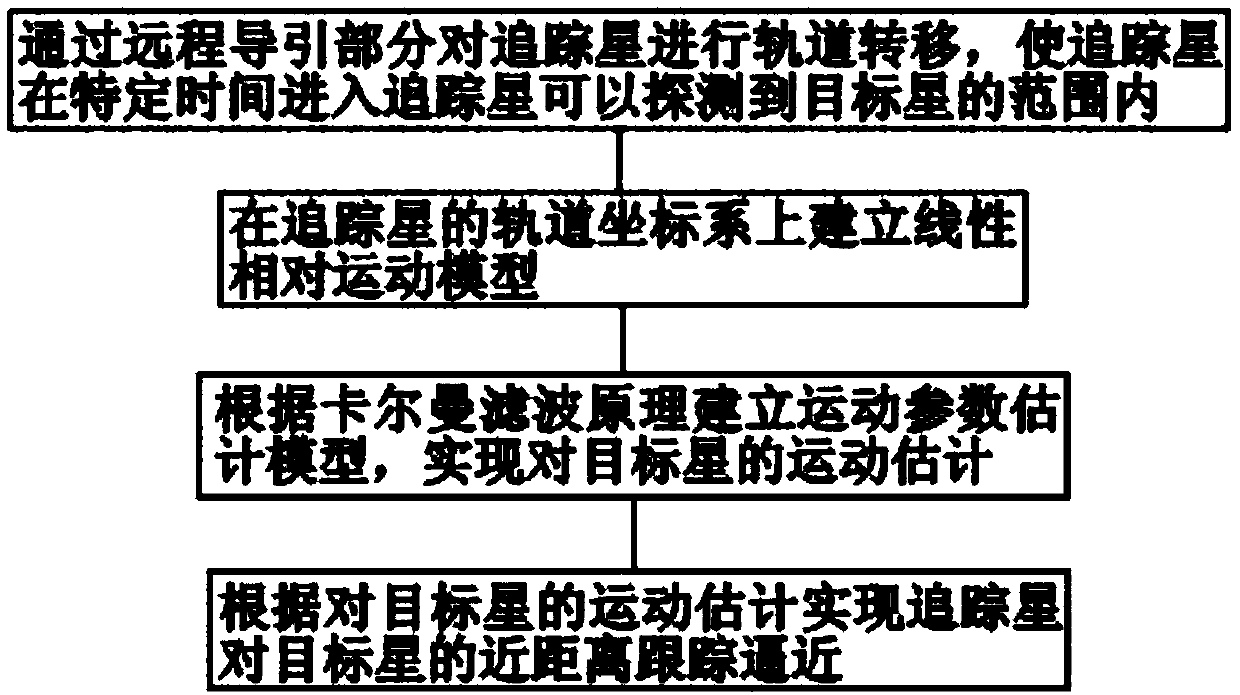
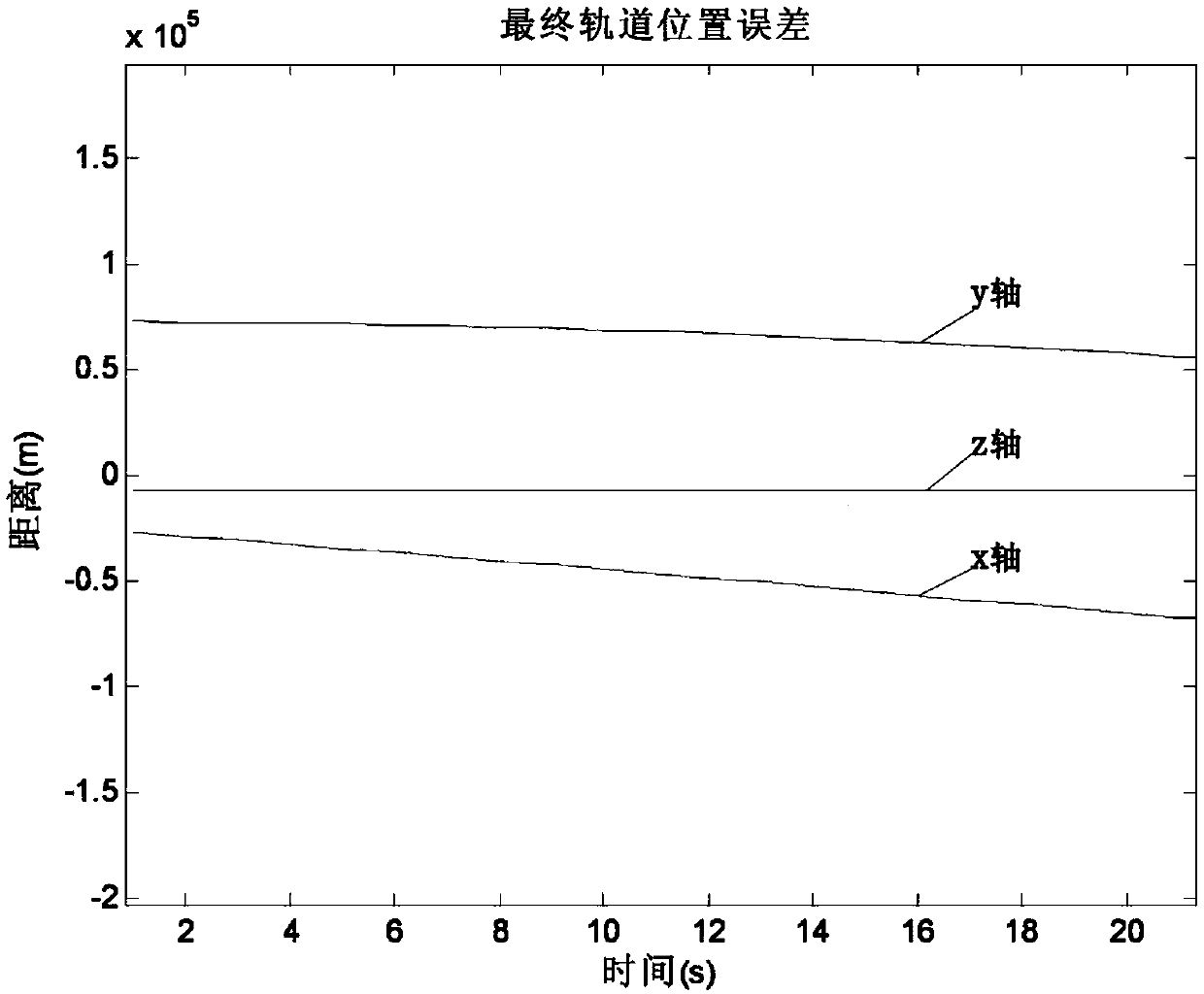
Track control method applied to non-cooperative maneuvering target interception
InactiveCN108279703AAccurate interceptionShorten the timeTarget-seeking controlPosition/course control in three dimensionsOptimal controlRelative motion
The invention discloses a track control method applied to non-cooperative maneuvering target interception. The method presents an interception concept taking a target motion estimation as basis and aclose distance approached terminal control as the interception concept; the method presents two-impulse optimal track changing method on the basis of track changing fuel optimization model in a remoteguiding stage; at the close distance tracking and approaching stage, a relative motion model is built up by considering that the target has maneuvering uncertainty, and the target motion estimation method is presented; finally, for achieving accurate interception, the method of applying the optimal controlled optimal tracking method to approach the target before the target is not maneuvered and then applying a slide mode control method after the target is maneuvered can be presented to carry out the final interception.
Owner:HENAN INST OF ENG
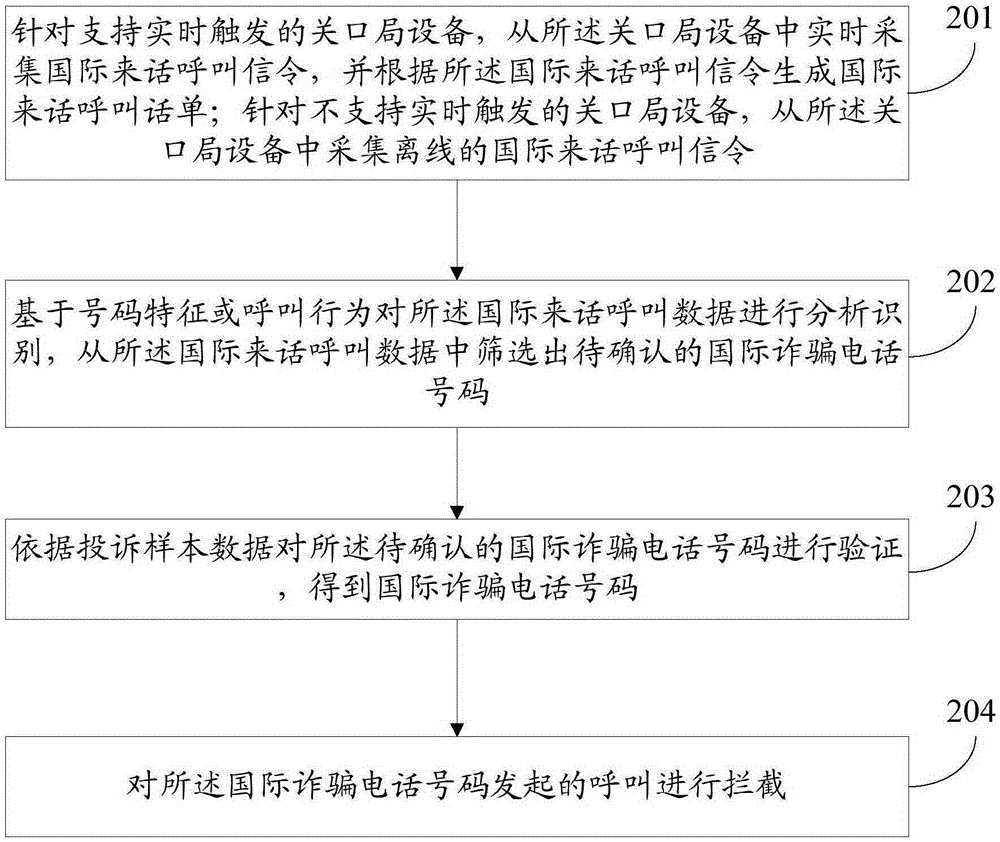
Method for preventing and controlling international fraud call and apparatus thereof
The invention discloses a method for preventing and controlling an international fraud call and an apparatus thereof. The method comprises the following steps of collecting international incoming call data; based on a calling characteristic, analyzing and identifying the international incoming call data, and screening an international fraud telephone number to be confirmed from the international incoming call data; based on complaint sample data, verifying the international fraud telephone number to be confirmed and acquiring the international fraud telephone number; and intercepting an international fraud telephone number call.
Owner:CHINA MOBILE COMM GRP CO LTD
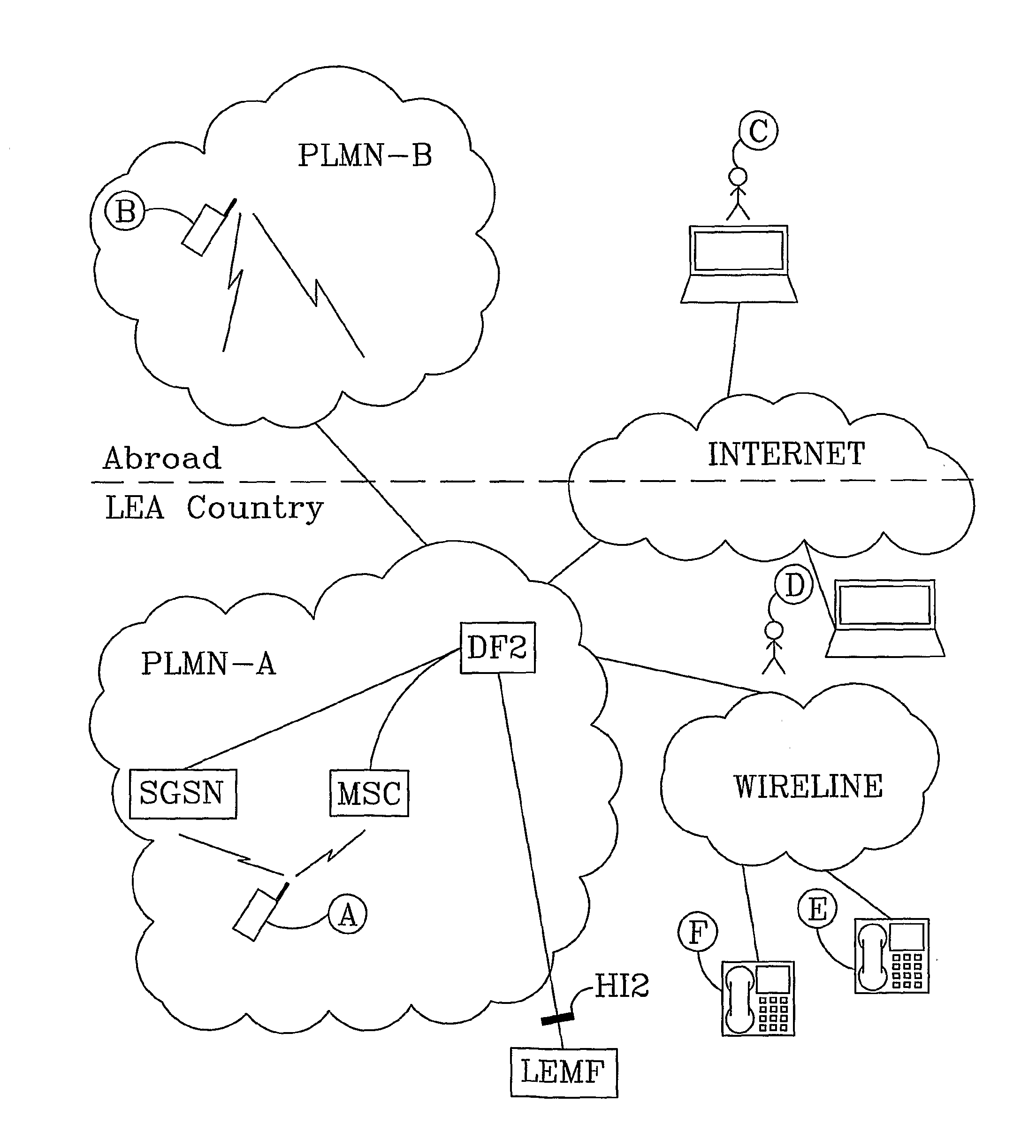
Advanced Lawful Interception of Sms
InactiveUS20080102866A1Accurate interceptionLess administrative workRadio/inductive link selection arrangementsAutomatic exchangesTelenetShort message service center
The present invention relates to methods and arrangements to intercept Short Message Services (SMS) in a telecommunication system (TS). The telecommunication system comprises a telecommunication Network (PLMN-A) that comprises a Short Message Service Centre (SMSC; ICE, IAP) responsible for relaying Short Messages (SMs) to / from all subscribers belonging to the telecommunication network. The method comprises the following steps: Receiving in the Short Message Service Centre (SMSC), a request to monitor Short Messages (SMs) related to a subscriber (A, Al, B, C, D, E, F) in the telecommunication system (TS). Registering in the Short Message Service Centre (SMSC) a Short Message (SM) related to the monitored subscriber (A, Al, B, C, D, E, F). Delivering from the Short Message Service Centre (SMSC), information related to the registered Short Message.
Owner:TELEFON AB LM ERICSSON (PUBL)
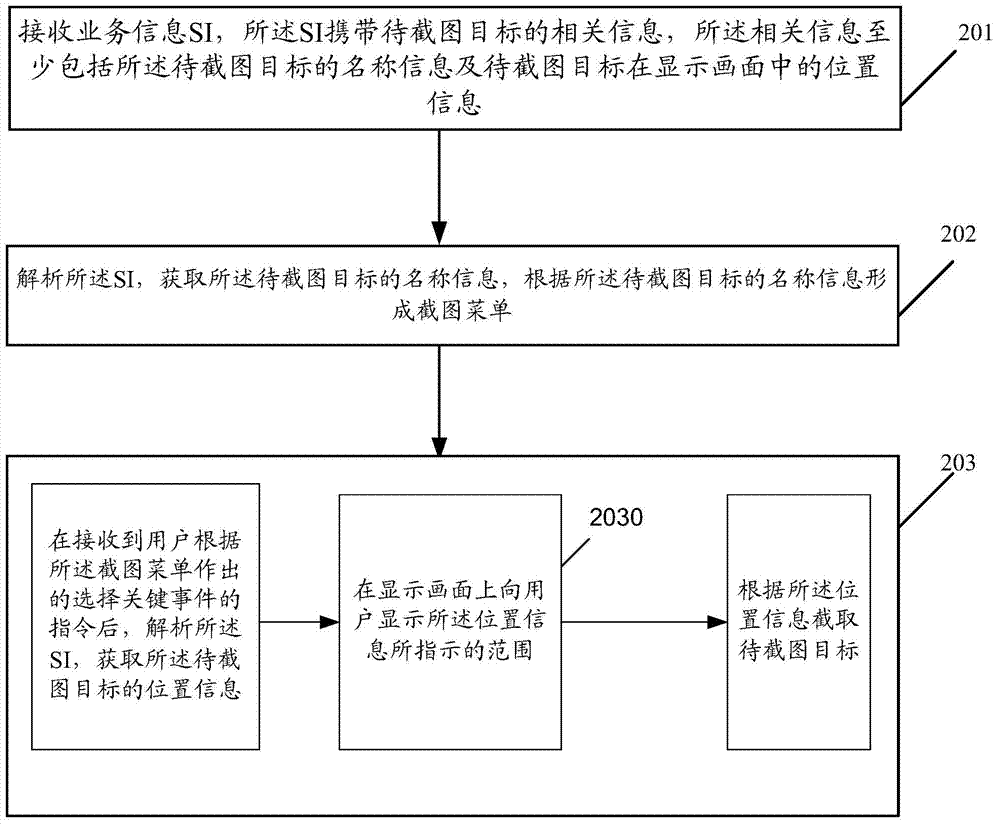
Method for grabbing picture, set top box and television equipment
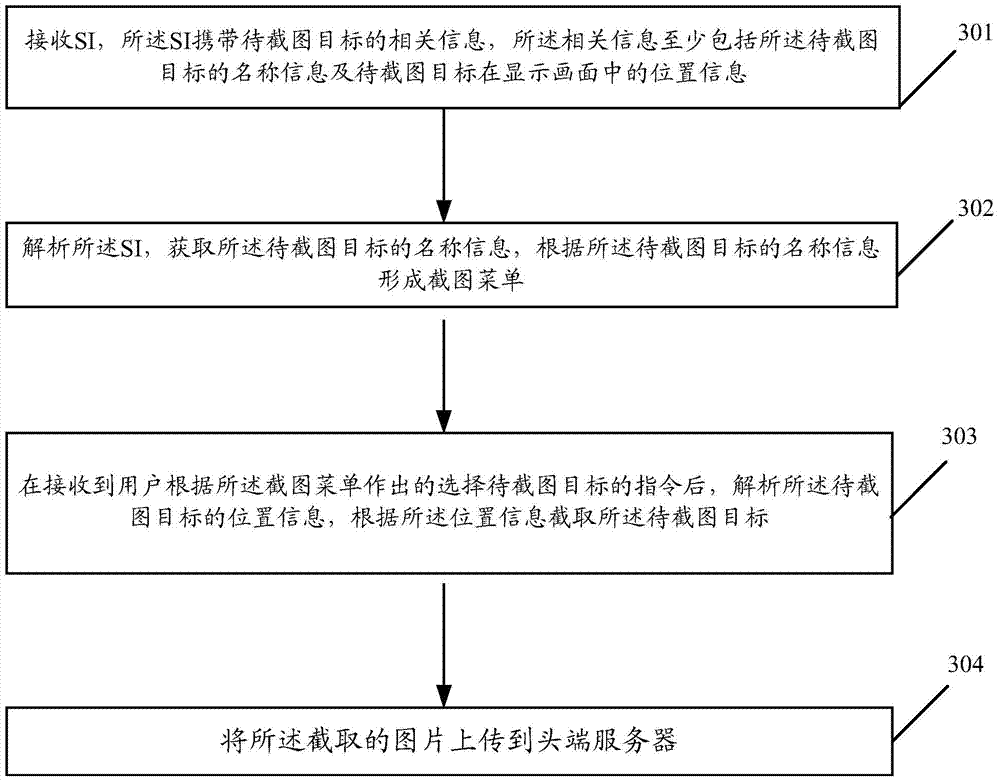
ActiveCN103491446AAccurate interceptionSelective content distributionInput/output processes for data processingEvent information tableTelevision equipment
The invention provides a method for grabbing a picture. The method comprises the steps that an event information table SI is received in real time, the SI carries position information of a target to be grabbed in a display frame, the SI is analyzed, the position information of the target to be grabbed in the display frame is obtained, a dynamic tracking menu picture-grabbing menu is formed according to the position information of the target to be grabbed, and after the instruction that the target to be grabbed is selected is received, the target to be grabbed, selected by a user, is displayed in a picture-grabbing following mode, wherein the instruction is made by the user according to the picture-grabbing menu. In the method for grabbing the picture, the user can grab the picture which the user wants more accurately.
Owner:GLOBAL INNOVATION AGGREGATORS LLC
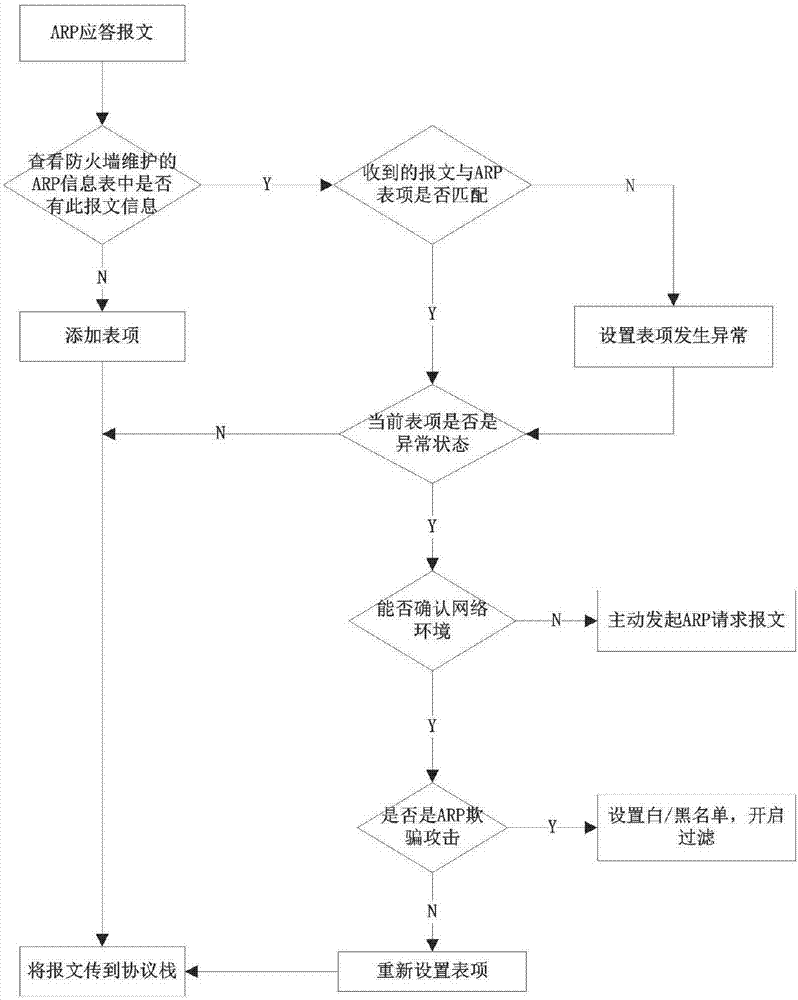
Device and method for data interception and time sequence drifting detection of interface of synchronous dynamic random access memory
InactiveCN101989466AAccurate interceptionSolve the problem that the correct data cannot be interceptedDigital storageDifferential signalingSynchronous dynamic random-access memory
The invention discloses a device and a method for the data interception and the time sequence drifting detection of an interface of a synchronous dynamic random access memory. The device comprises a differential signal to single-ended signal converting circuit, a first phase delay circuit and a data interception circuit, wherein the differential signal to single-ended signal converting circuit isconnected to a synchronous transmission interface to receive a differential data interception signal transmitted by the synchronous transmission interface and convert the differential data interception signal into a single-ended data interception signal; the first phase delay circuit is connected to the differential signal to single-ended signal converting circuit and regulates the phase of the single-ended data interception signal to generate a single-ended data interception signal subjected to phase delay; and the data interception circuit is connected to the first phase delay circuit to intercept synchronous data transmitted by the synchronous transmission interface according to the single-ended data interception signal subjected to the phase delay.
Owner:SUNPLUS TECH CO LTD
False link interception method, device and system
InactiveCN105959330AAccurate interceptionImprove recognition efficiencyTransmissionDomain nameClient-side
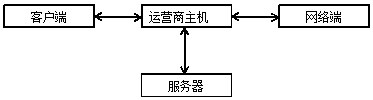
The invention relates to the technical field of network safety and especially relates to a false link interception method and system. The false link interception method is characterized by carrying out identification on a webpage access request initiated by a user client and obtaining a mirror image link; actively analyzing domain name information of the link and safety of the specific webpage content information; and intercepting a false link access request, thereby providing a more accurate and higher-recognition efficiency false link interception method for users. The false link interception method can be realized by establishing function modules, combining the function modules into a function module framework, and implementing the function module framework through computer programs stored in a computer readable storage medium. The false link interception system is established based on the false link interception method. The system comprises a client, an operator host, a network end and a server. The server of the false link interception system has the function module framework, and the system can enter the computer programs for implementing the function module framework, so that false link interception is realized.
Owner:广东世纪网通信设备股份有限公司
Method and device for intercepting page elements
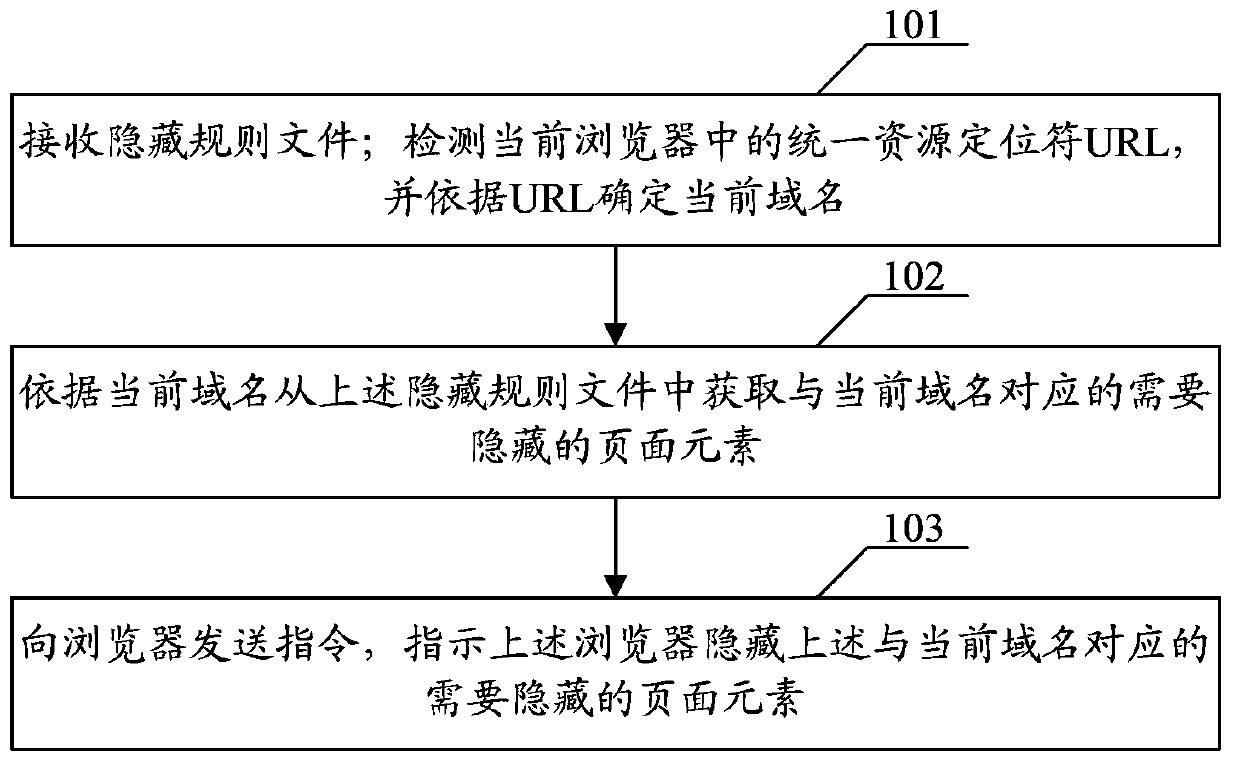
InactiveCN104216929AComprehensive and accurate interceptionAchieve hiddenWeb data indexingSpecial data processing applicationsDomain nameIntercept method
The embodiment of the invention discloses a method and device for intercepting page elements. The method comprises the steps that a hidden rule file is received; a uniform resource locator (URL) in a current browser is detected, and a current domain name is determined according to the URL; the page elements corresponding to the current domain name and needing to be hidden are obtained from the hidden rule file according to the current domain name; an instruction is sent to the browser, and the browser is indicated to hide the page elements corresponding to the current domain name and needing to be hidden. The page elements needing to be hidden are carried in the hidden rule file, and the page elements corresponding to the current domain name and needing to be hidden are obtained from the hidden rule file by determining the current domain name and according to the current domain name; the page elements need to be hidden are then hidden, and thus the effect that the page elements irrelevant to text are comprehensively and accurately intercepted is achieved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Traffic roads charging station charge-escape prevention intercepting system
InactiveCN101114389AImprove recognition rateShielding from external signal interferenceTicket-issuing apparatusAnalytical controlCharging station
The invention discloses an interception system preventing from fee evasion for traffic toll collection stations. The system comprises a photoelectric detecting system used for detecting vehicle passing, an analysis and control system connected with the photoelectric detecting system which transfers collection information to the analysis and control system, and an interceptor connected with the analysis and control system which transfers control information to the interceptor. The system has intelligence, high recognition rate compared with the present brain judgment and hand control; rapidity: once the vehicles of fee evasion act rashly passes the card, the system only spends one to two second in analyzing the situation and ejecting the interceptor so that the vehicles of fee evasion cannot pass the card; and reliability: the system adopts an advanced infrared photoelectric vehicle separator, which can discriminate accurately whether the vehicles are those of fee evasion or not, and shield effectively the interference from external signals by light transmitting. The system is a comparatively ideal and rapid interception system preventing from fee evasion.
Owner:中誉通信有限公司
Method and system for realizing filtering of malicious calls through real-time algorithm
ActiveCN106506769ARelieve the stress of analyzing interceptsHigh efficiency in filtering malicious callsSubstation equipmentAutomatic exchangesReal time algorithmReal time analysis
The invention belongs to the technical field of mobile telephone communication, and particularly relates to a method for realizing filtering of malicious calls through a real-time algorithm. The method comprises the following steps that: a calling number initiates a call to a called number already applying for malicious call protection; the calling number and the called number are transmitted to a real-time malicious call analyzing and filtering platform; the real-time malicious call analyzing and filtering platform matches the calling number and the called number with a number library, and judges whether to intercept the calling number or not by using the real-time algorithm; and if the calling number is not intercepted, the calling number is put through. The invention also discloses a malicious call filtering system. The malicious call filtering system comprises a malicious call intercepting assembly module, a support platform module, an algorithm model module and an external connection interface module. In the method, the malicious call protection is applied through the called number, the calling number and the called number are transmitted to the real-time malicious call analyzing and filtering platform, the calling number and the called number are matched with the number library for interception, and whether to intercept the non-intercepted calling number or not is judged by the real-time algorithm, so that filtering of the malicious calls is realized, and the trouble of a called user is avoided.
Owner:ZHEJIANG PONSHINE INFORMATION TECH CO LTD
Unscented Kalman filter algorithm-based method for predicting residual life of bearing
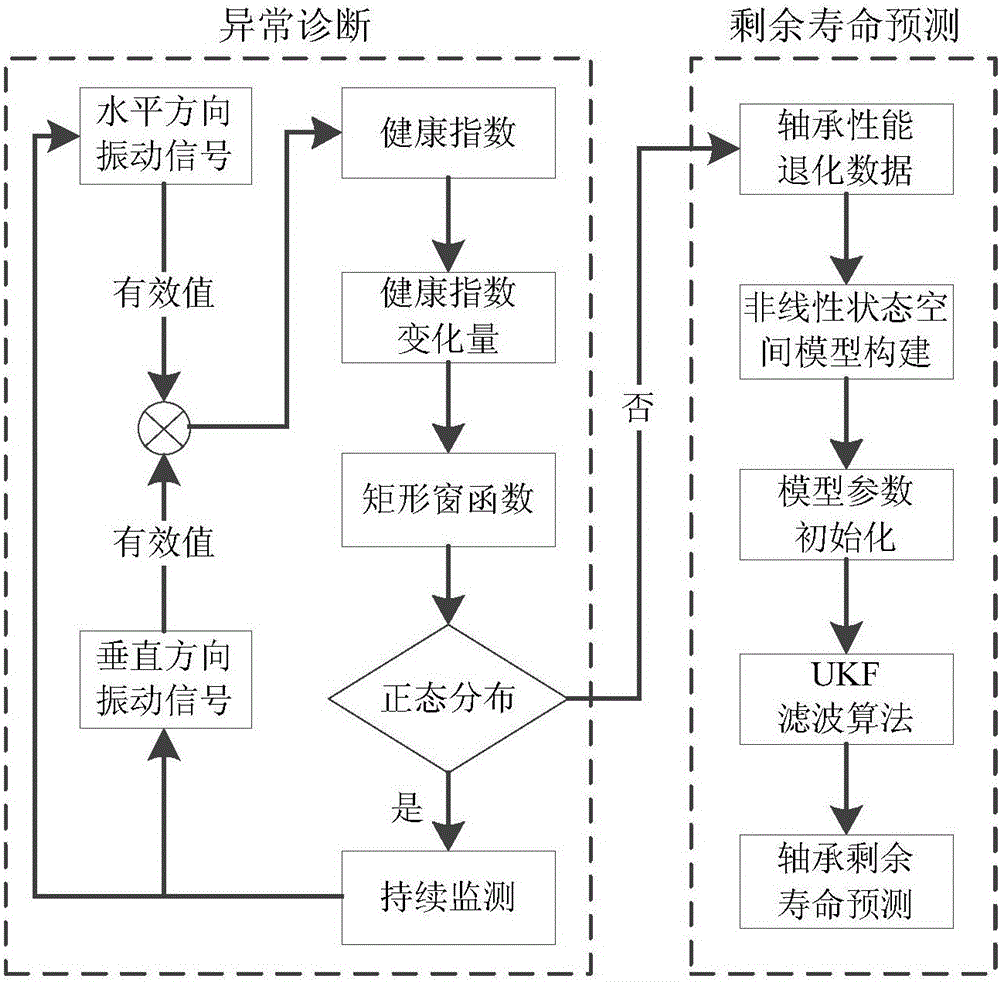
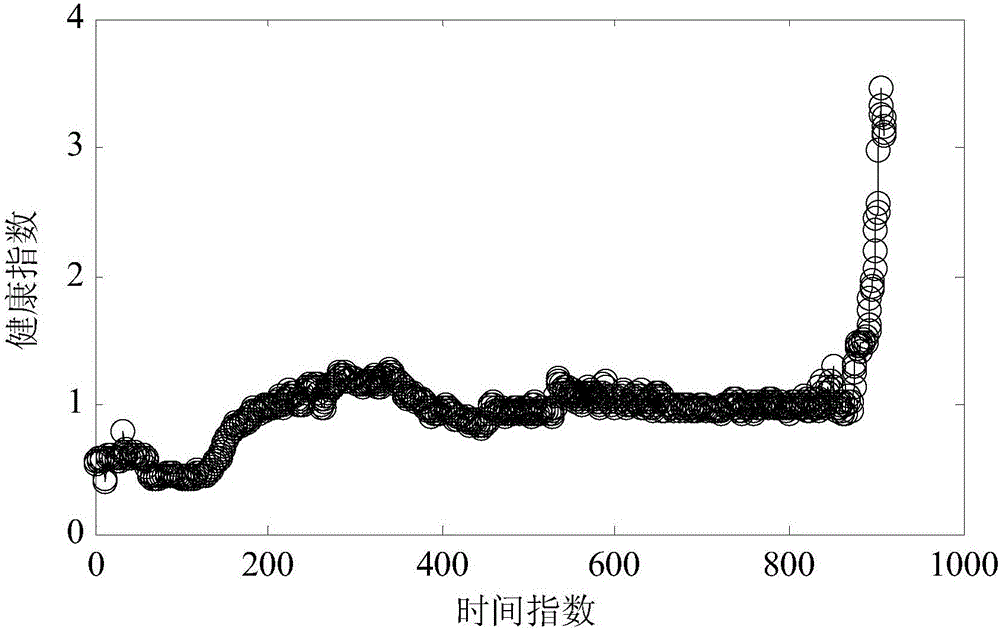
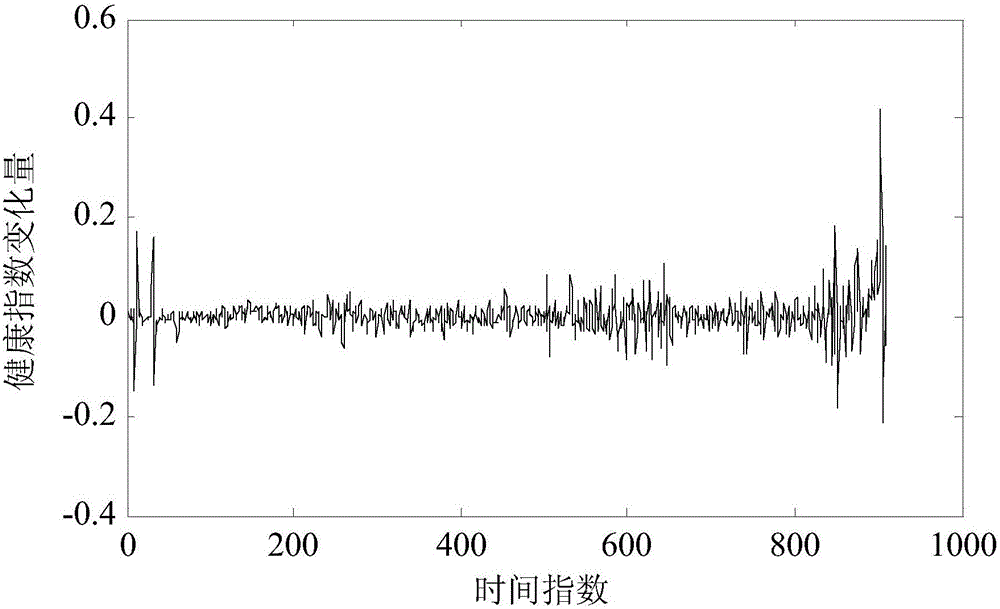
InactiveCN106021719AAccurate interceptionImprove forecast accuracyDesign optimisation/simulationSpecial data processing applicationsHealth indexState space
The invention discloses an unscented Kalman filter algorithm-based method for predicting the residual life of a bearing. The method comprises the following steps of 1) acquiring a full-life periodic vibration signal of the bearing; 2) calculating an effective value by utilizing the vibration signal and constructing an index that reflects a health state of the bearing based on the effective value; 3) calculating a health index change quantity at each moment and intercepting health index data in a bearing wear period by utilizing a rectangular window function and a K-S test; and 4) performing fitting analysis on the health index data in the wear period, constructing a state space model that represents a bearing degradation process, updating model parameters by utilizing the health index data obtained by observation currently and an unscented Kalman filter algorithm, and predicting the residual life of the bearing. The unscented Kalman filter algorithm-based method for predicting the residual life of the bearing, provided by the invention, is relatively high in prediction precision.
Owner:ZHEJIANG UNIV OF TECH
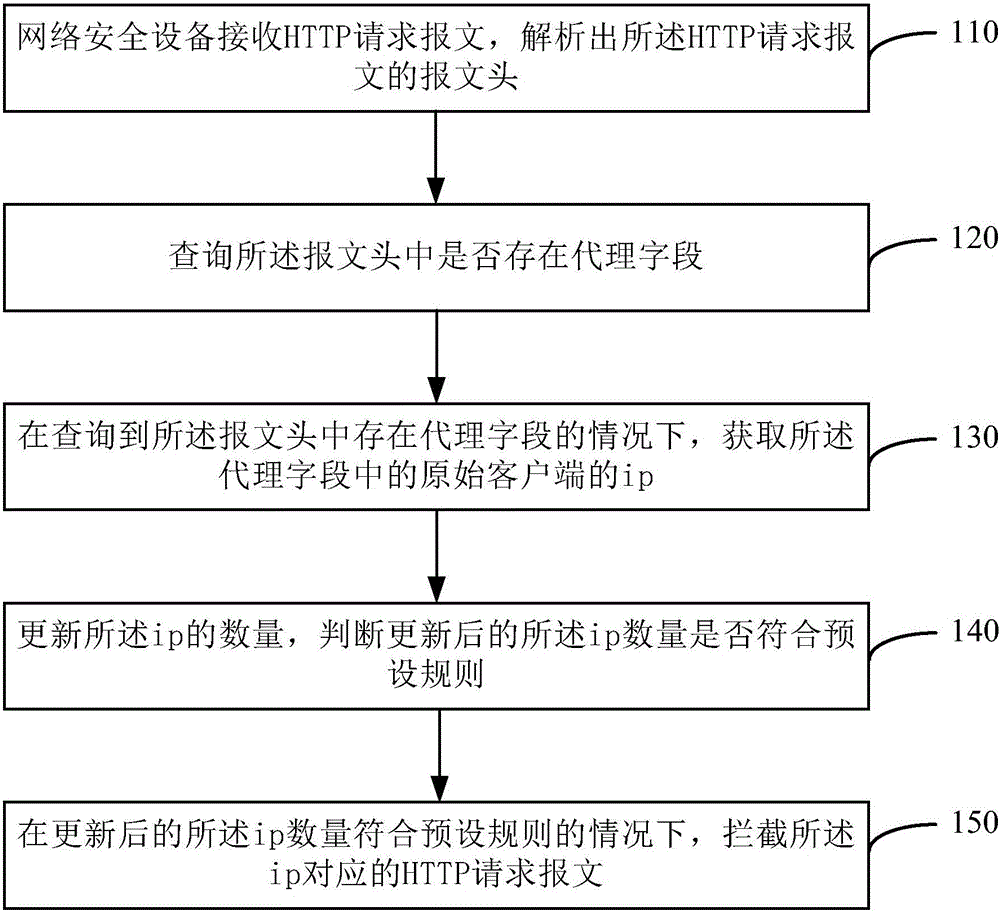
Method and device for preventing HTTP proxy attack
InactiveCN105959313APreventing HTTP Proxy AttacksAccurate interceptionTransmissionClient-sideDistributed computing
A method and device for preventing HTTP proxy attacks provided by the present application, the method is applied to a network security device, and the method includes: the network security device receives an HTTP request message, and parses out the message of the HTTP request message header; inquire whether there is a proxy field in the message header; if there is a proxy field in the message header, obtain the ip of the original client in the proxy field; update the quantity of the ip, and judge Whether the updated ip number conforms to the preset rule; if the updated ip number meets the preset rule, intercept the message corresponding to the ip. By applying the embodiment of the present application, the real attacker can be identified, so as to accurately intercept the HTTP request message sent by the attacker.
Owner:HANGZHOU DPTECH TECH
Method and device for intercepting resource requests
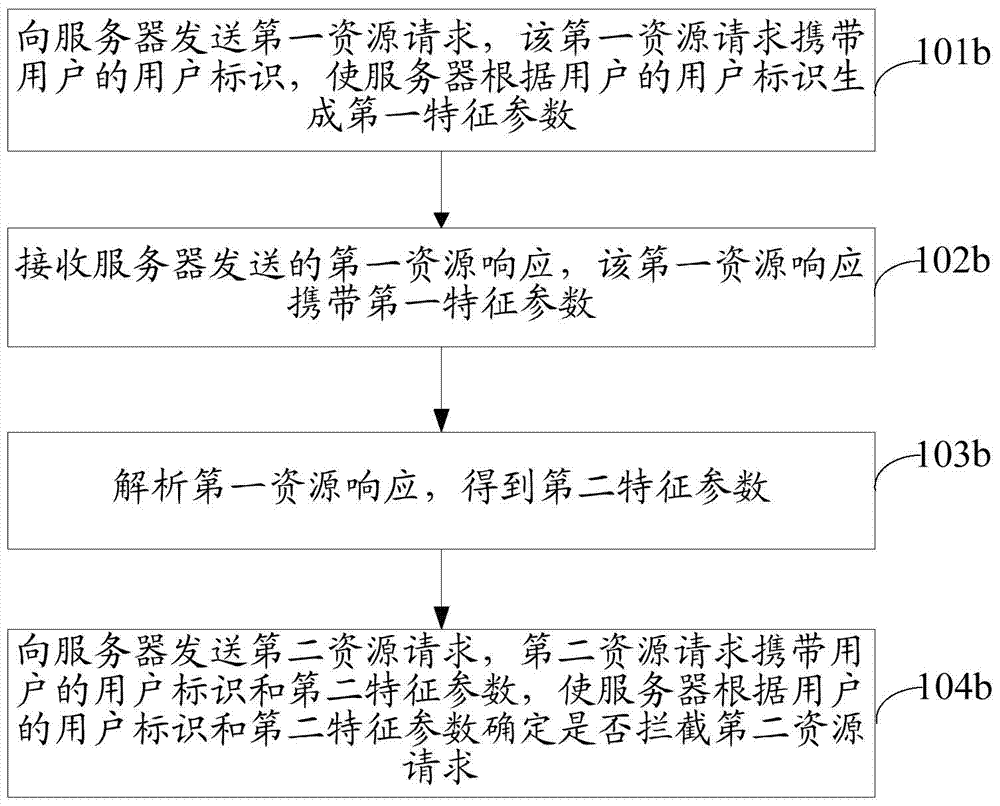
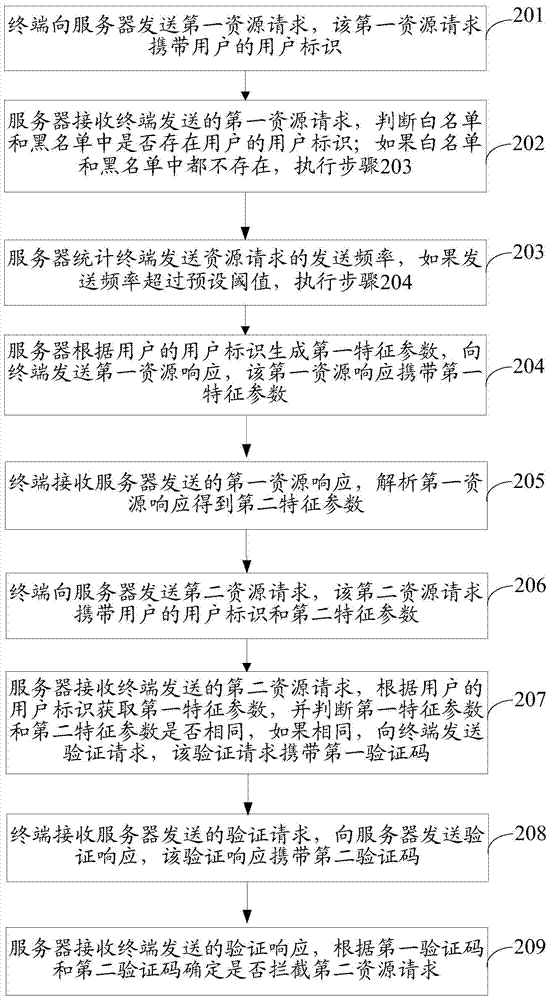
InactiveCN104519069AAccurate interceptionImprove accuracyTransmissionComputer terminalFeature parameter
The invention discloses a method and device for intercepting resource requests, and belongs to the field of safety of computers. The method comprises the steps that a first resource request sent by a terminal is received, and the first resource request carries user identification of a user; a first feature parameter is generated according to the user identification of the user and current time, and a first resource response which carries the user identification of the user and the first feature parameter is sent to the terminal; a second resource request which is sent by the terminal and carries a second feature parameter is received, and the second feature parameter is obtained when the terminal analyzes the first resource response; whether the second resource request is to be intercepted or not is determined according to the user identification of the user and the second feature parameter. The device comprises a first receiving module, a generation module, a second receiving module and a determination module. The resource requests of program simulation can be accurately intercepted by the device with the method, and the interception accuracy is improved.
Owner:GUANGZHOU HUADUO NETWORK TECH
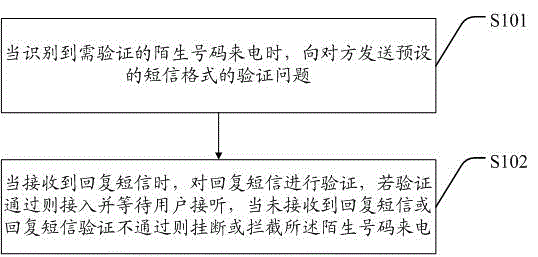
Telephone verification method and system
ActiveCN105187605AAccurate interceptionSubstation equipmentMessaging/mailboxes/announcementsText messageTelephony
The invention discloses a telephone verification method and a system. The method comprises steps that, A, when an incoming call of a strange number needing verification is identified, a verification question in a preset short message format is sent to an opposite side; B, when a reply short message is received, verification on the reply short message is carried out, if passes, access to a user is carried out, and the incoming call waits a user to answer, if no reply short message is received or verification does not pass, the incoming call of the strange number is hang up or stopped. According to the method and the system, when the incoming call of the strange number occurs, the verification question is automatically sent to the opposite side, when the question is wrongly answered or is not answered, the incoming call is hang up or stopped, when the verification question is correctly answered by the opposite side, whether the incoming call is answered is determined by the user, and thereby crank calls can be more accurately stopped.
Owner:东营市东凯空港产业园有限公司
Active network defense system for embedded equipment and defense method thereof
ActiveCN107360182AEasy to use and flexibleImprove accuracyTransmissionProactive cyber defenceNetworking protocol
An active network defense system for embedded equipment includes a network protocol stack module and an active network defense module. The active network defense module comprises a firewall upper-layer module and a firewall bottom-layer module. The firewall upper-layer module includes a message detection module and an exception handling module. A system defense method includes: 1, installing an active network defense system; 2, enabling the message detection module to analyzes a received network message to determine whether the message has a problem, directly transmitting the message to a protocol stack if not, or going to the next step if so; 3, enabling an exception handling unit to determine whether an exception message is an attack message, going to the next step if so, or sending a request message to query the real environment of the network and returning to step 2 if not; 4, discarding the current message, setting a white / black list, and opening a bottom-layer filter. The active network defense system for embedded equipment has characteristics of active identification and defense, and can prevent common embedded network attacks suffered by embedded equipment, thereby protecting the network security of the embedded equipment.
Owner:NANJING ACOINFO TECH CO LTD
Method, system and device for positioning and identifying specific plate of invoice picture
ActiveCN109426814AAutomate the processPrecise positioningCharacter and pattern recognitionRecognition algorithmInvoice
The invention relates to a method, a system and a device for positioning and identifying a specific plate of an invoice picture. The method for positioning and identifying a specific plate of an invoice picture comprise the following steps of: obtaining an invoice picture; determining invoice information to be identified; according to the information of the invoice to be recognized, positioning and dividing the area of the invoice picture in which the invoice is located to obtain the information picture of the invoice to be recognized; identifying text content of the picture of the invoice information to be recognized, and acquiring the invoice information to be recognized. Because the target is located and cut directly before recognition, the invoice information corresponding to each recognition content is clearly and creatively realized to automatically recognize each invoice, which fills in the blank of the technical field and has a broad application prospect. It fundamentally solves the drawback that the existing image recognition algorithm can only recognize every character in the invoice picture without distinction, but can not distinguish the required invoice information. Therefore, the acquisition of invoice information is truly automated.
Owner:SF TECH
Video data processing method and device, computer equipment and storage medium
PendingCN111626123AQuick captureAccurate interceptionBiometric pattern recognitionHuman bodyData set
The invention relates to artificial intelligence, and provides a video data processing method and device, computer equipment and a storage medium, and the method comprises the steps: obtaining a target data set and a to-be-processed video set; extracting at least two video frame images from each original video; enabling the image recognition model to perform image binarization processing, edge detection processing and contour tracking processing on the video image; obtaining a license plate area, a human face area and a human body feature area, extracting text features of the license plate area through a character segmentation algorithm, obtaining a license plate number result, extracting human face features of the human face area through a YOLO algorithm, obtaining a human face result, extracting human body posture features of the human body feature area through a chain code curvature algorithm, and obtaining a human body feature result; determining an identification result; extracting a matching fragment; and performing splicing to obtain a video synthesis fragment, and performing sorting to obtain a target video. In addition, the invention also relates to a blockchain technology, and the target data set can be stored in the blockchain node.
Owner:PINGAN INT SMART CITY TECH CO LTD
User request intercepting method and device
ActiveCN107241300AComprehensive interceptionAccurate interceptionTransmissionIp addressIntercept method
The invention discloses a user request intercepting method and device. One specific implementation manner of the method comprises the steps of acquiring an activity ID of a user request, and determining whether a cache server has data corresponding to the activity ID; if the cache server does not have data corresponding to the activity ID, determining whether a user IP address of the user request is included in a preset IP address set; if the user IP address is included in the IP address set, marking the user request; if the user IP address is not included in the IP address set, determining whether the value of the activity ID is greater than a preset maximum activity ID value stored in the cache server; recording user requests with activity ID value greater than the maximum activity ID value; and intercepting the marked user requests. Through adoption of the user request intercepting method and device, illegal user requests are intercepted accurately and comprehensively.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Sizing intercepting rock core drilling tool
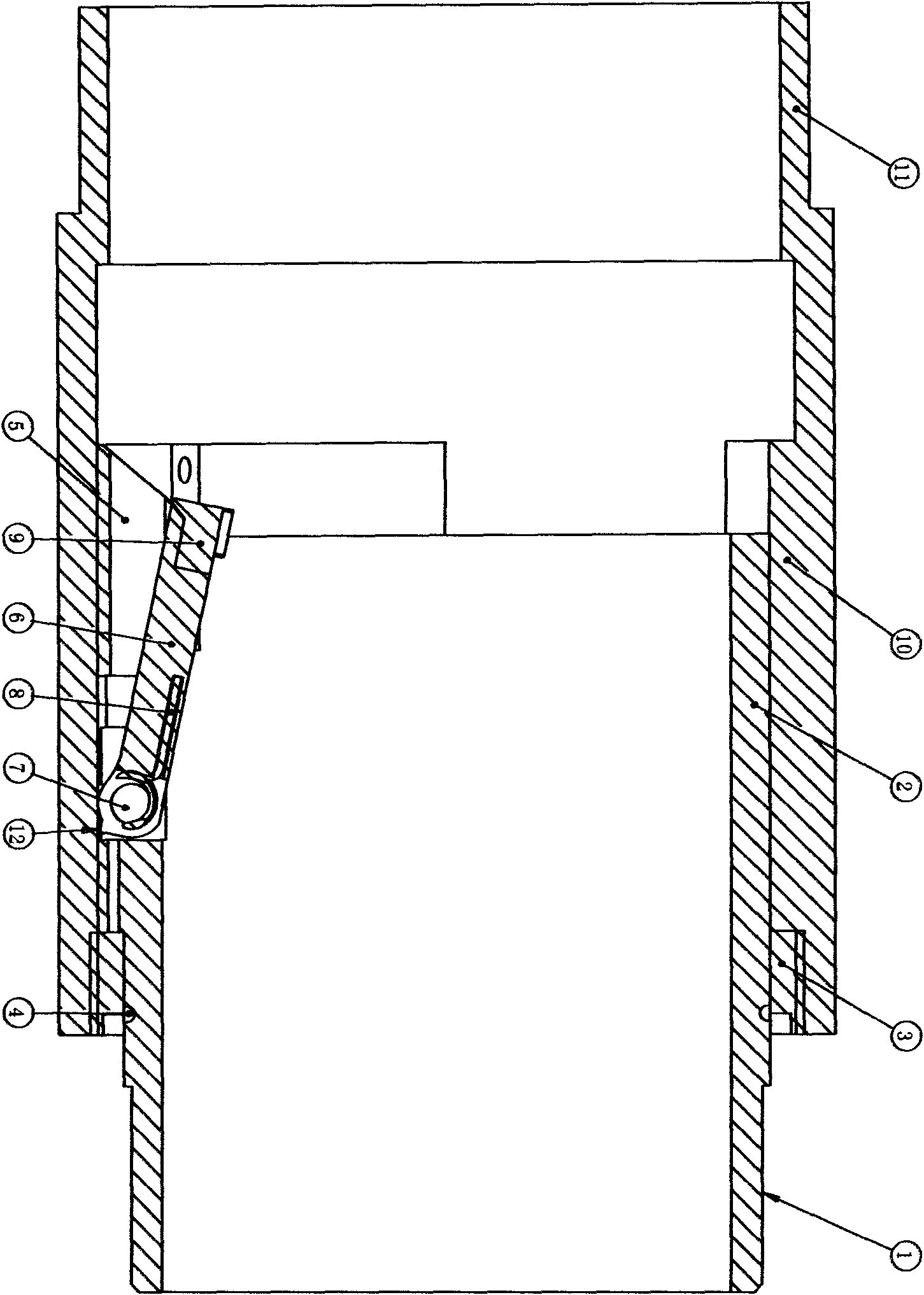
The invention discloses a sizing intercepting rock core drilling tool, which belongs to the field of drilling, boring and manufacturing circular stone pillars. An inner core screw thread of a drilling tool key slot is connected with a screw thread at the upper part of a drill bit; a drilling tool upper sleeve screw thread is connected with a long core tube; a small section of long core tube is equivalently added in drilling; and the drilling tool is lifted within a set size, an embedded tool bit is enabled to act through the conversion of the resistance force, the friction force and the elastic force so as to transversely cut a rock core so as to extract the rock core. The drilling tool can be made into an independent part, a key slot inner core is connected with an upper sleeve spline, the lower plane of the upper sleeve is overlapped with the upper plane of the drill bit, and the drilling pressure and the torsion are transferred to implement the drilling. A retainer ring and the upper sleeve screw thread are connected with each other to lock a longitudinal gap, top cutter bodies are overlapped and rotated inside an insert, and the transverse cutting depth of the tool bit can be controlled. The drill bit is lifted, and precipitated sand and stone resist the drill bit, so that the spline slides, the insert and the top cutter bodies slide, two overlapped oblique surfaces are staggered so as to push the tool bit to transversely cut the rock core, and when the tool bit is continuously lifted, the broken rock core is lifted out of the ground.
Owner:禹畅
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com