Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
31 results about "Stack buffer overflow" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
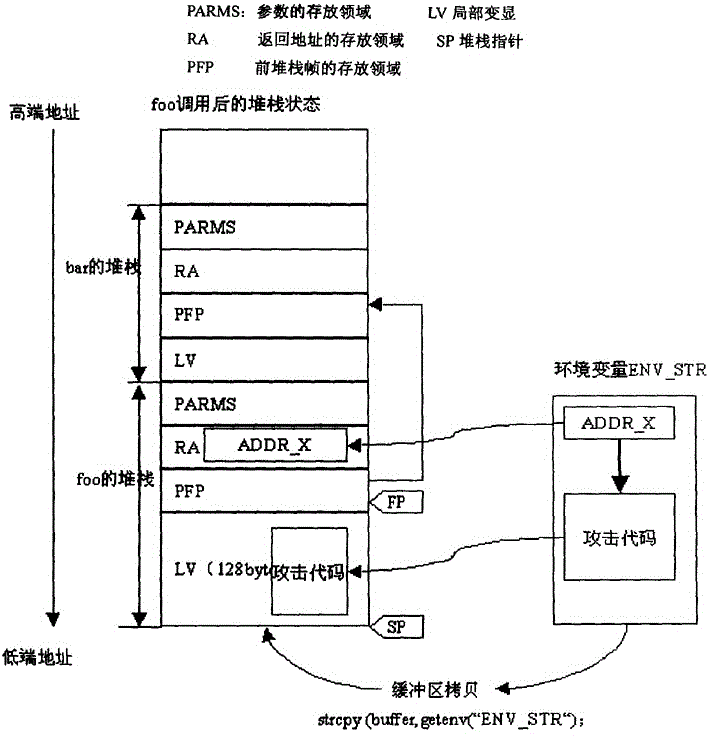
In software, a stack buffer overflow or stack buffer overrun occurs when a program writes to a memory address on the program's call stack outside of the intended data structure, which is usually a fixed-length buffer. Stack buffer overflow bugs are caused when a program writes more data to a buffer located on the stack than what is actually allocated for that buffer. This almost always results in corruption of adjacent data on the stack, and in cases where the overflow was triggered by mistake, will often cause the program to crash or operate incorrectly. Stack buffer overflow is a type of the more general programming malfunction known as buffer overflow (or buffer overrun). Overfilling a buffer on the stack is more likely to derail program execution than overfilling a buffer on the heap because the stack contains the return addresses for all active function calls.
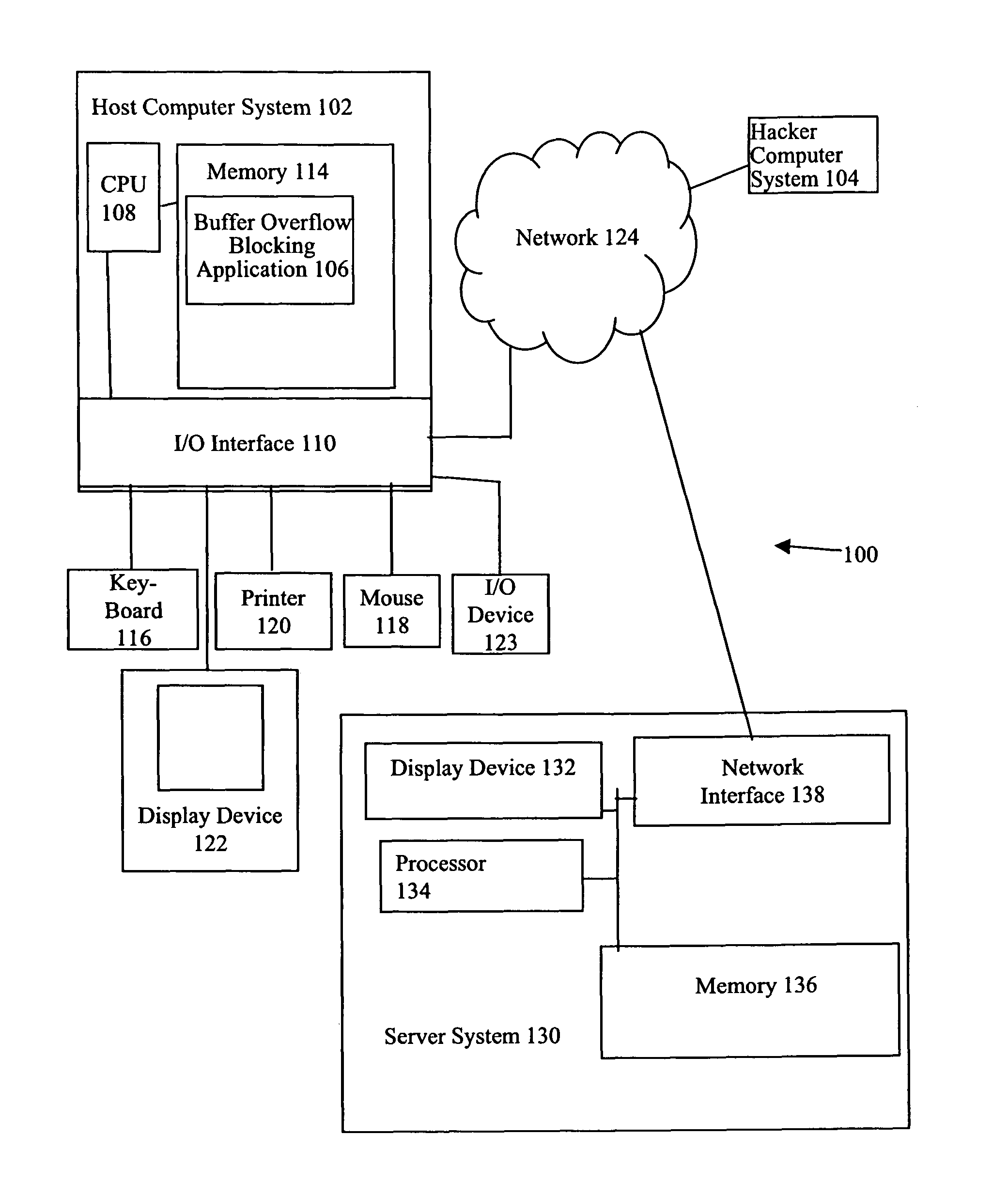
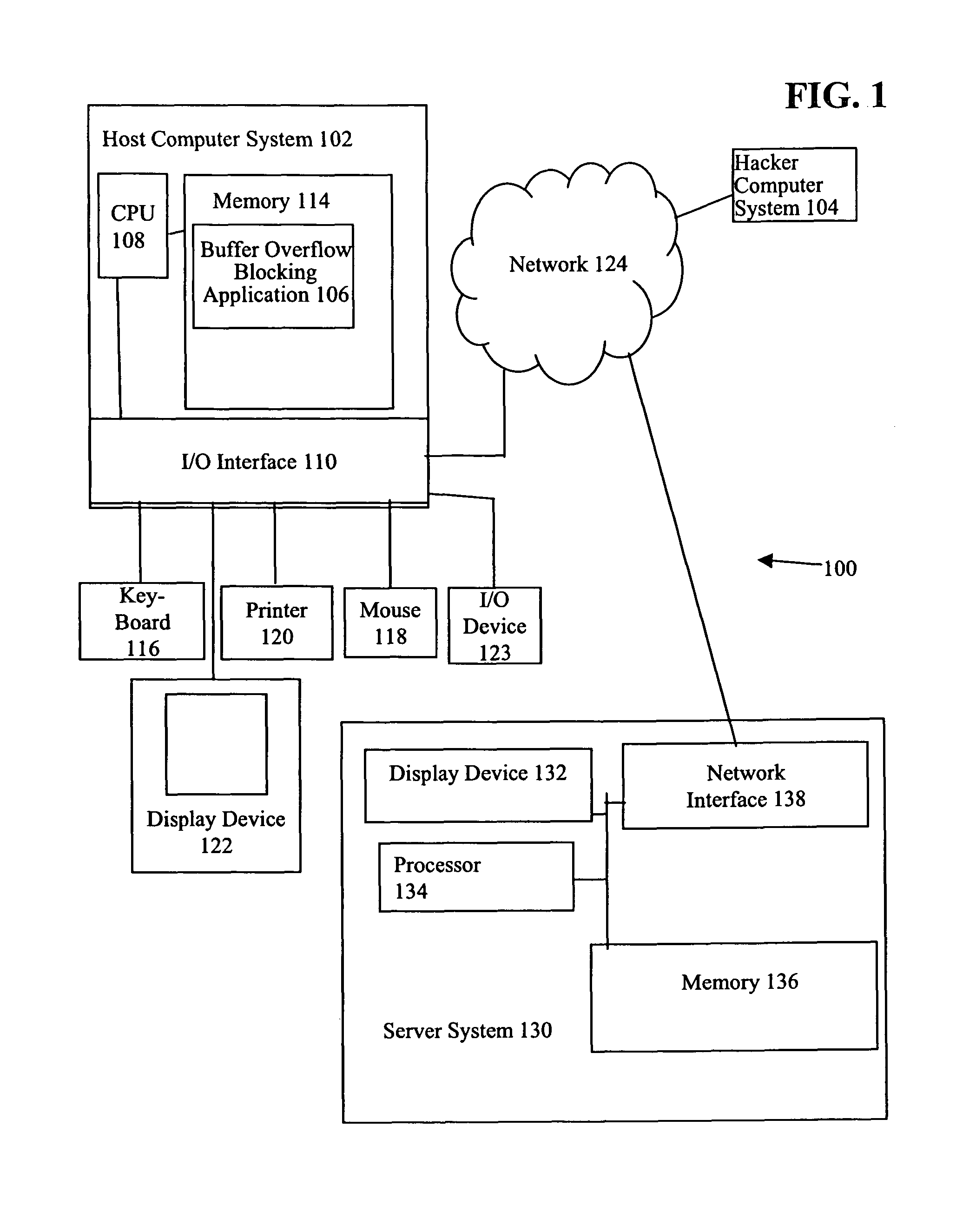
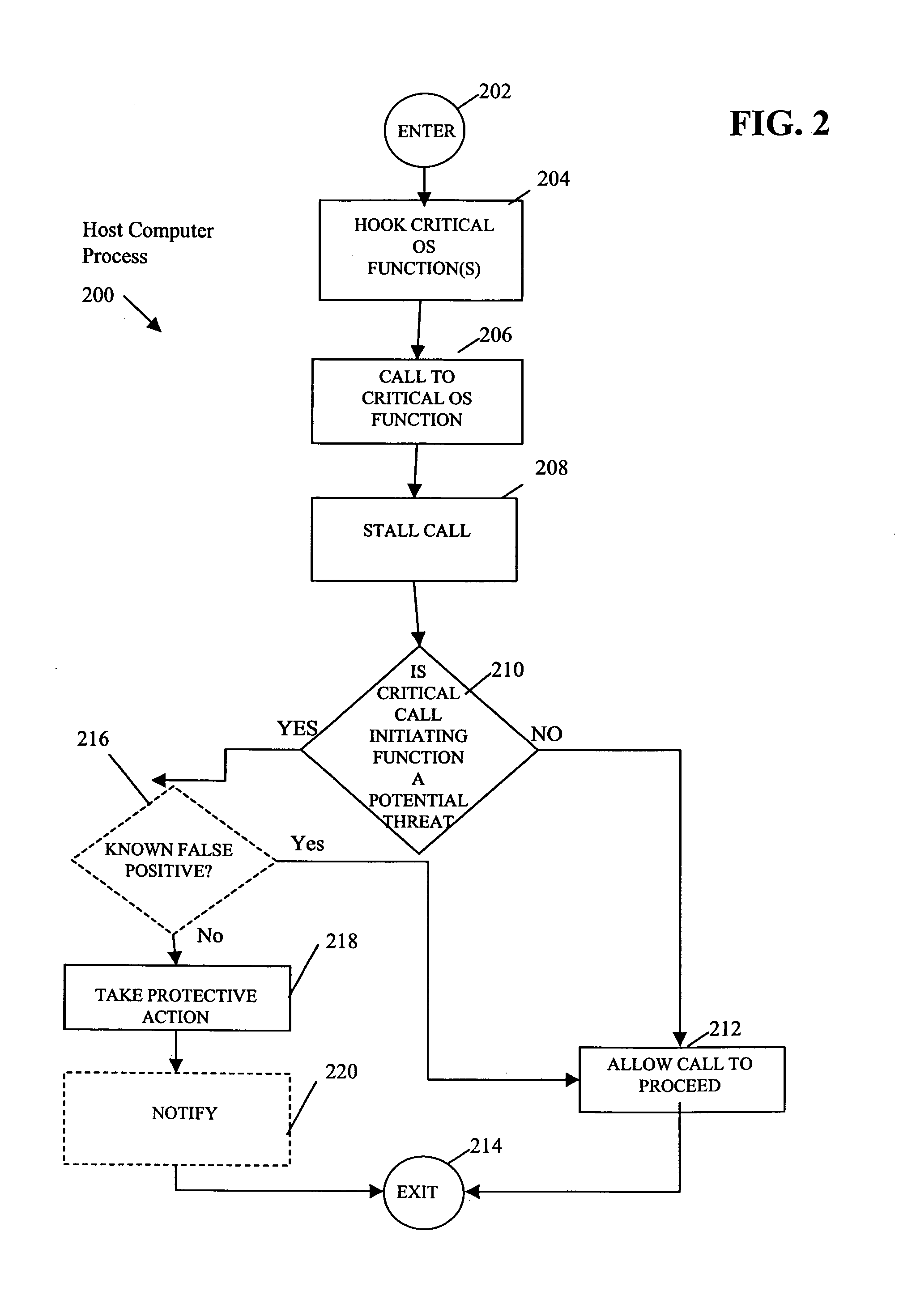
Method to identify buffer overflows and RLIBC attacks
ActiveUS7945953B1Lookup is very fastMemory loss protectionError detection/correctionStack buffer overflowFunction point
A method and system detect buffer overflows and RLIBC attacks by determining if a critical call initiating function is a “potential threat”. In one embodiment, a critical call initiating function is considered a potential threat if the value of the return address of the critical call initiating function points to a location in memory between the location of the highest Thread Environment Block (TEB) or Process Environment Block (PEB) and the location of the lowest Thread Environment Block (TEB) or PEB. In another embodiment, a critical call initiating function making a call to a predefined critical operating system function is considered a potential threat if the value of the return address of the critical call initiating function points to the beginning of a new function with a zero offset.
Owner:GEN DIGITAL INC
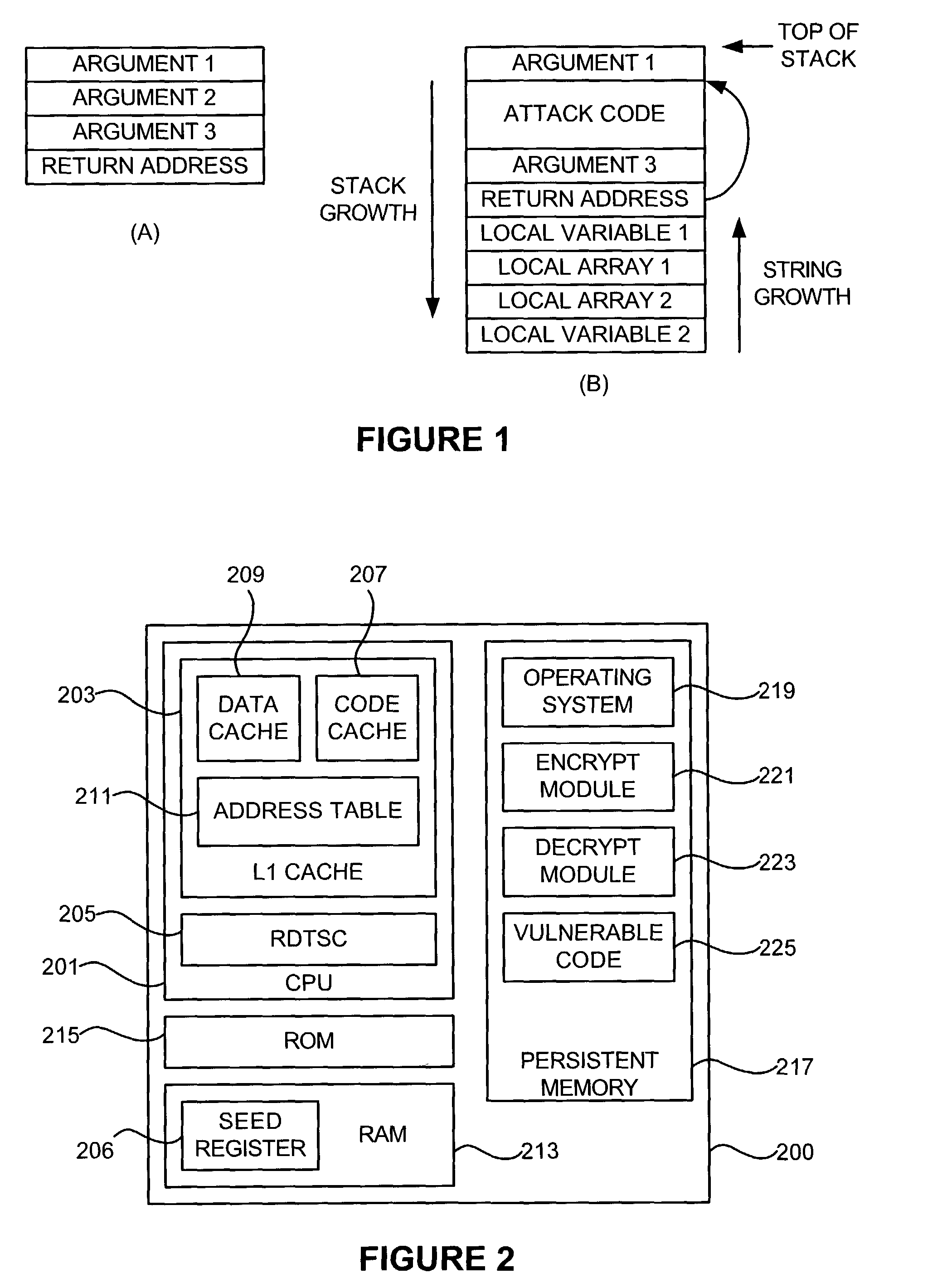
Preventing stack buffer overflow attacks
ActiveUS7086088B2Preventing stack buffer overflow attackDetecting faulty hardware by power-on testMemory loss protectionComputer hardwareStack buffer overflow
A method and system for preventing stack buffer overflow attacks in a computer system are disclosed. A computer system can prevent stack buffer overflow attacks by encrypting return addresses prior to pushing them onto the runtime stack. When an encrypted return address is popped off the runtime stack, the computer system decrypts the encrypted return address to determine the actual return address. A random encryption key can be used, which can be generated from the CPU's clock cycle counter. Multitasking environments can add a seed register to the task state so that each task can use a unique seed to encrypt the return addresses.
Owner:NOKIA INC
Method and device for detecting buffer overflow and code instrumentation method and device
InactiveCN101630350AReduce false alarm rateImprove targetingPlatform integrity maintainanceStack buffer overflowParallel computing
The invention discloses a device and a method for detecting buffer overflow, a code instrumentation device and a code instrumentation method. The detection method comprises the following steps: identifying a code related with a buffer from a program source code, and inserting a buffer length information code corresponding to the code related with the buffer in the program source code; and performing model check on the program code inserted with the buffer length information code, judging whether the buffer overflow exists in the program code according to the buffer length information code, and reporting a code executing track causing the buffer overflow when the buffer overflow exists. The technical scheme disclosed by the invention can detect actually existing buffer overflow.
Owner:SIEMENS CHINA
Data retransmission control method for mobile communication system
InactiveCN1496157AAvoid lossAvoid processing delaysError prevention/detection by using return channelNetwork traffic/resource managementStack buffer overflowTime delays
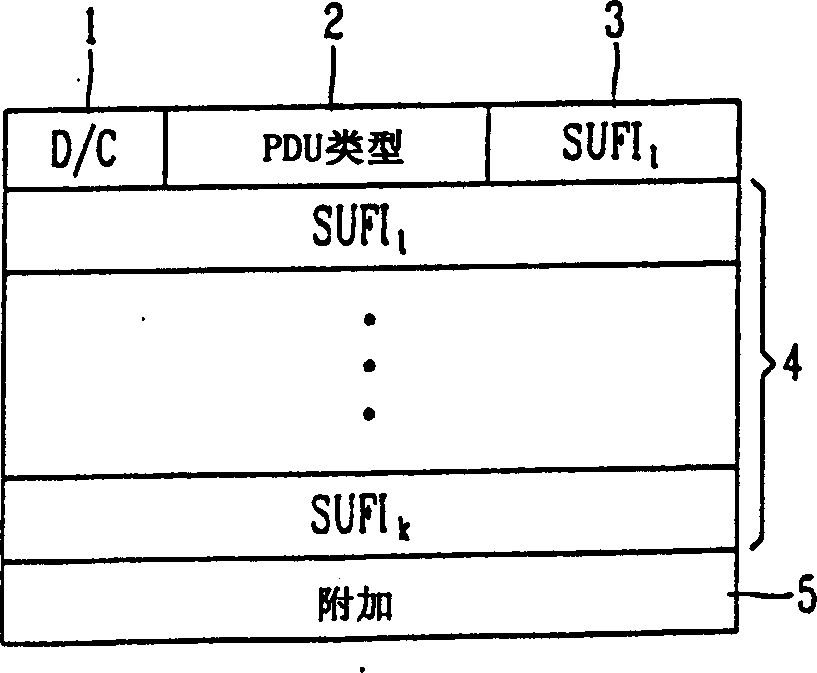
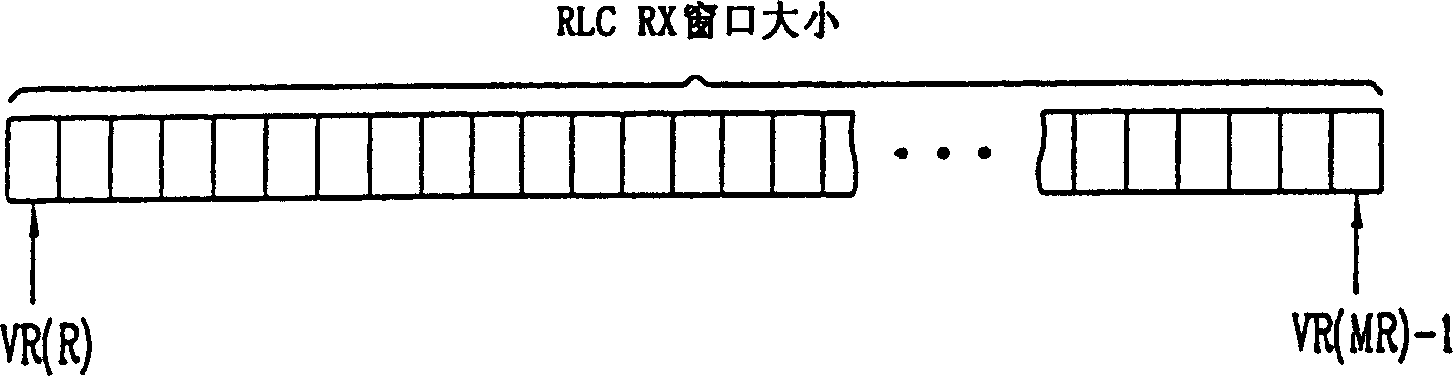
A data transfer controlling method in a mobile communication system, in which a window size SUFI (super-field) is controlled and thus a receiving buffer for a transfer of next data is controlled, thereby preventing a damage such as a data loss. For a reception of a protocol data unit (PDU) of a radio link control (RLC) layer, the window size SUFI and the receiving buffer are properly controlled, thereby preventing a data loss according to a buffer overflow, a time delay, and a waste of a radio resource. Also, the present invention can provide affirmative effects on the 3GPP communication standard by disclosing a positive utilization method of the window size SUFI only of which form has been defined.
Owner:LG ELECTRONICS INC
Method for protecting against ROP attacking and stack overflow based on simulated stacks and thread injecting
ActiveCN107229862ATo achieve the purpose of detecting ROP attacksNo need to change the overflow protection mechanismPlatform integrity maintainanceStack buffer overflowProtection mechanism
The invention discloses a method for protecting against ROP attacking and stack overflow based on simulated stacks and thread injecting, and relates to the technical field of protection of ROP attacking. According to the technical scheme, the technical problems are solved in the prior art that ROP vicious codes without commands can bypass stack-overflow protection since a program loading position is fixed and the stack overflow occurs when remote threads utilized in using the simulated stacks to monitor a target progress are injected. The method comprises the steps of using the threads to inject the threads into the target progress (the progress which needs to be protected), opening up a simulated stack space, monitoring a command procedure which simulates the target progress, conducting execution on the simulated stacks by obtaining effective code strings among call commands and ret commands attached by ROP, and then achieving the purpose of detecting ROP attacking by using a traditional overflow protection mechanism.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
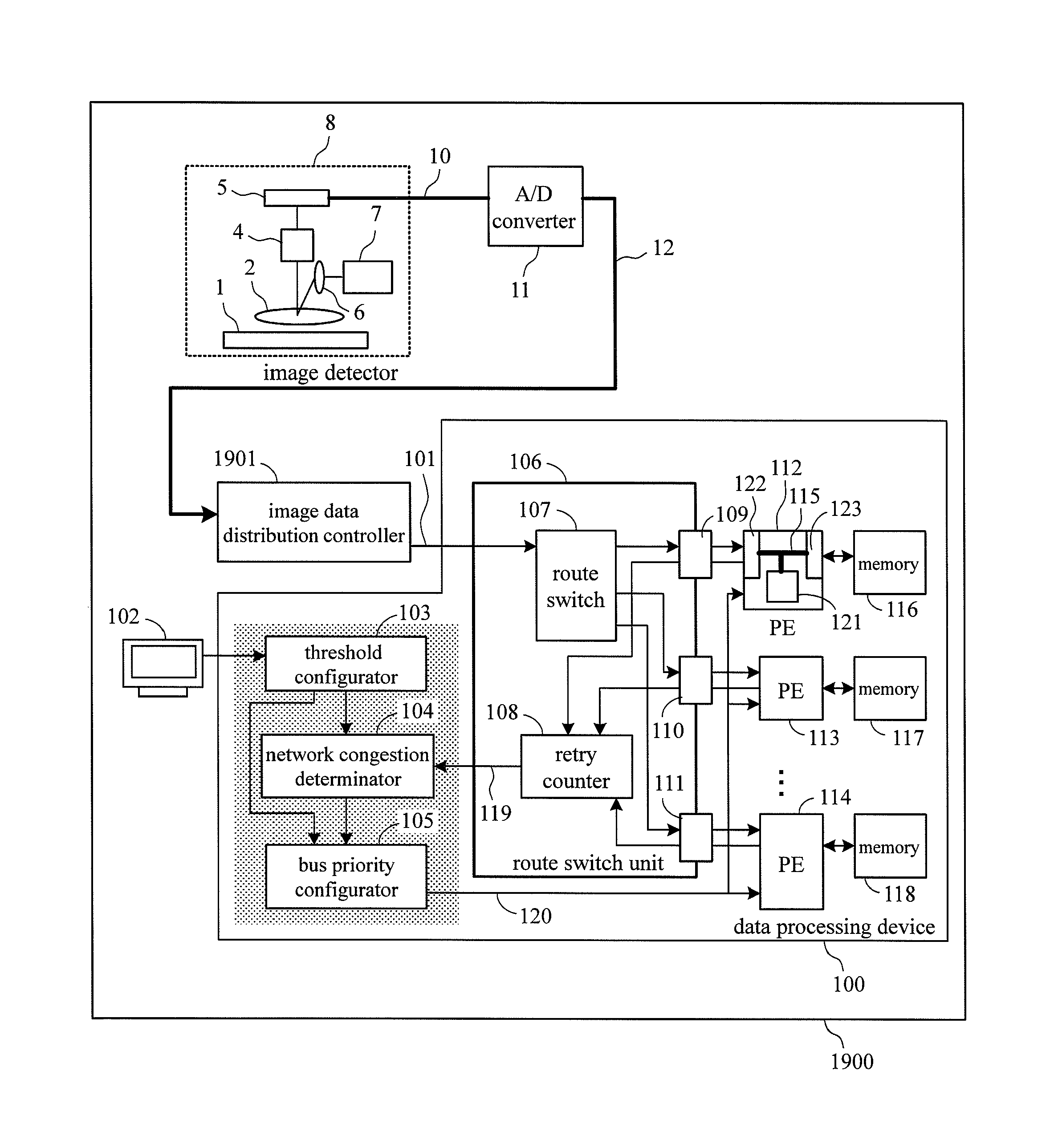
Data processing device, semiconductor external view inspection device, and data volume increase alleviation method
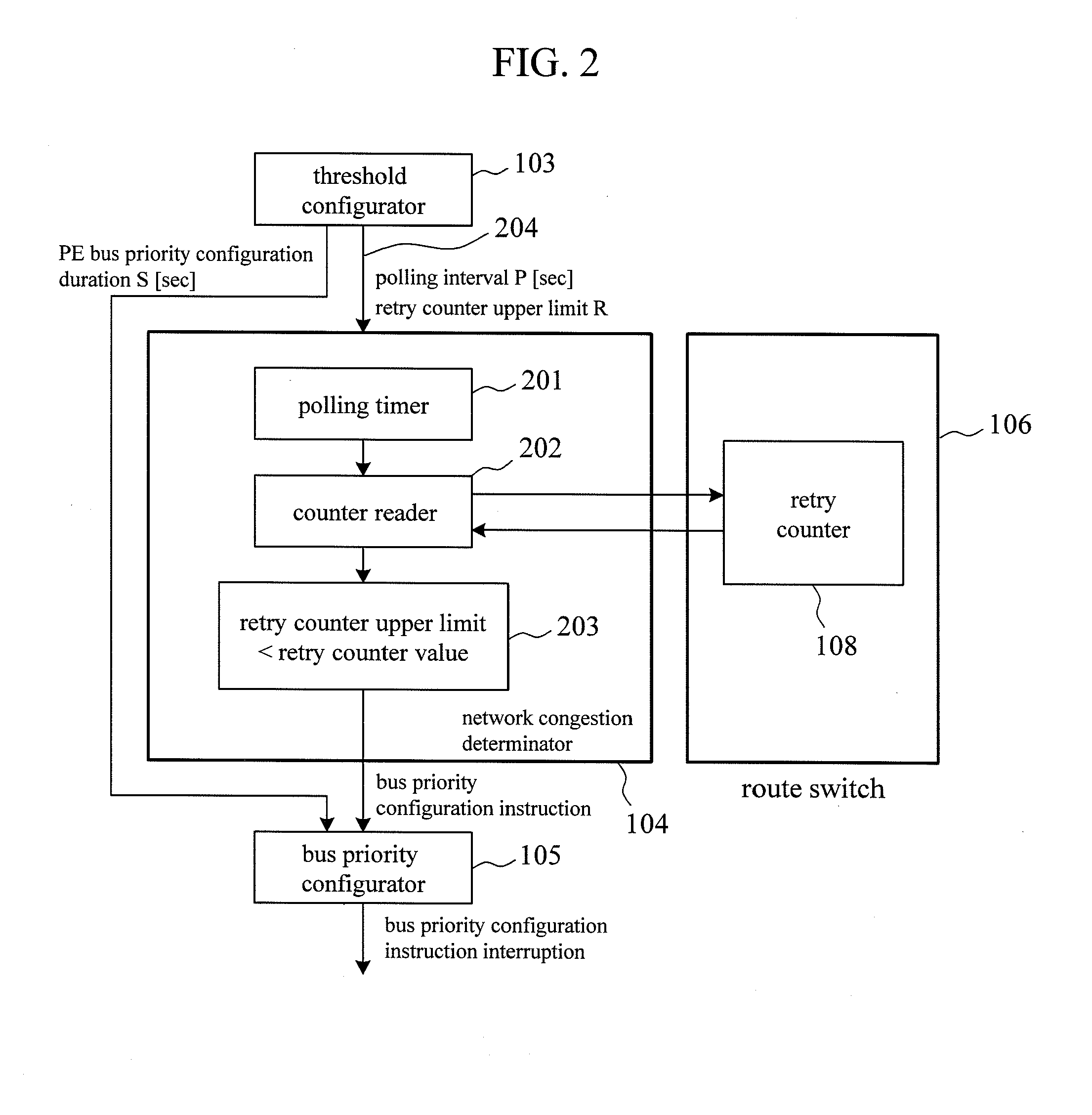
ActiveUS20140372656A1Suppressing buffer over flowSuppress overflowProcessor architectures/configurationElectric digital data processingStack buffer overflowProcessor element
Provided is a data processing device with which, when a temporary network congestion occurs, it is possible to avoid a buffer overflow and sustain a process. When a request for retransmission of the same data with respect to a processor element from a buffer occurs continuously a prescribed number of iterations, a data processing device according to the present invention determines that it is possible that a buffer overflow occurs, and suppresses an increase in the volume of data which is accumulated in the buffer (see FIG. 1).
Owner:HITACHI HIGH-TECH CORP
Dynamic stack memory management method
PendingCN105468965AAvoid attackPrevent overflowPlatform integrity maintainanceNormal conditionsStack buffer overflow
The invention discloses a dynamic stack memory management method. The method is characterized in that when a computer program is executed, a sub-process is called each time and a stack space of a current process is allocated, a calling parameter is stored like a normal condition and an address is returned; but when a frame pointer is stored and a local variable is allocated, an extra memory space is allocated between the frame pointer and a starting address of the local variable or an extra memory space is allocated between a return address and the frame pointer, and the size of the extra space is randomly determined when the program is executed, so that the relative position of the return address and the local variable in a stack memory cannot be obtained by analyzing a source program or a compiled target program. According to the method, whether a currently executed program is being attacked or not can be detected and the program can be prevented from being attacked, so that an attacker is effectively prevented from using stack buffer overflow to perform attack.
Owner:XIAN HUIZE INTPROP OPERATIONS MANAGEMENT CO LTD
Detection method and system for buffer overflow
InactiveCN103559439AEfficient detectionPlatform integrity maintainanceStack buffer overflowApplication programming interface
The invention provides a detection method for buffer overflow, and belongs to the field of information safety. The method comprises the steps as follows: when buffer overflow happens, a malicious code calls a system API (application program interface) function; a return address of the system API function is checked according to the system API function called by the HOOK malicious code; and whether overflow of a buffer region happens is judged according to the feedback address. According to the technical scheme of the detection method and system, effective detection of buffer overflow is realized.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
Fault-tolerant method of software stack buffer overflow
InactiveCN102521079AGuaranteed correctnessDo not overwrite each otherProgram controlRedundant operation error correctionFault toleranceStack buffer overflow
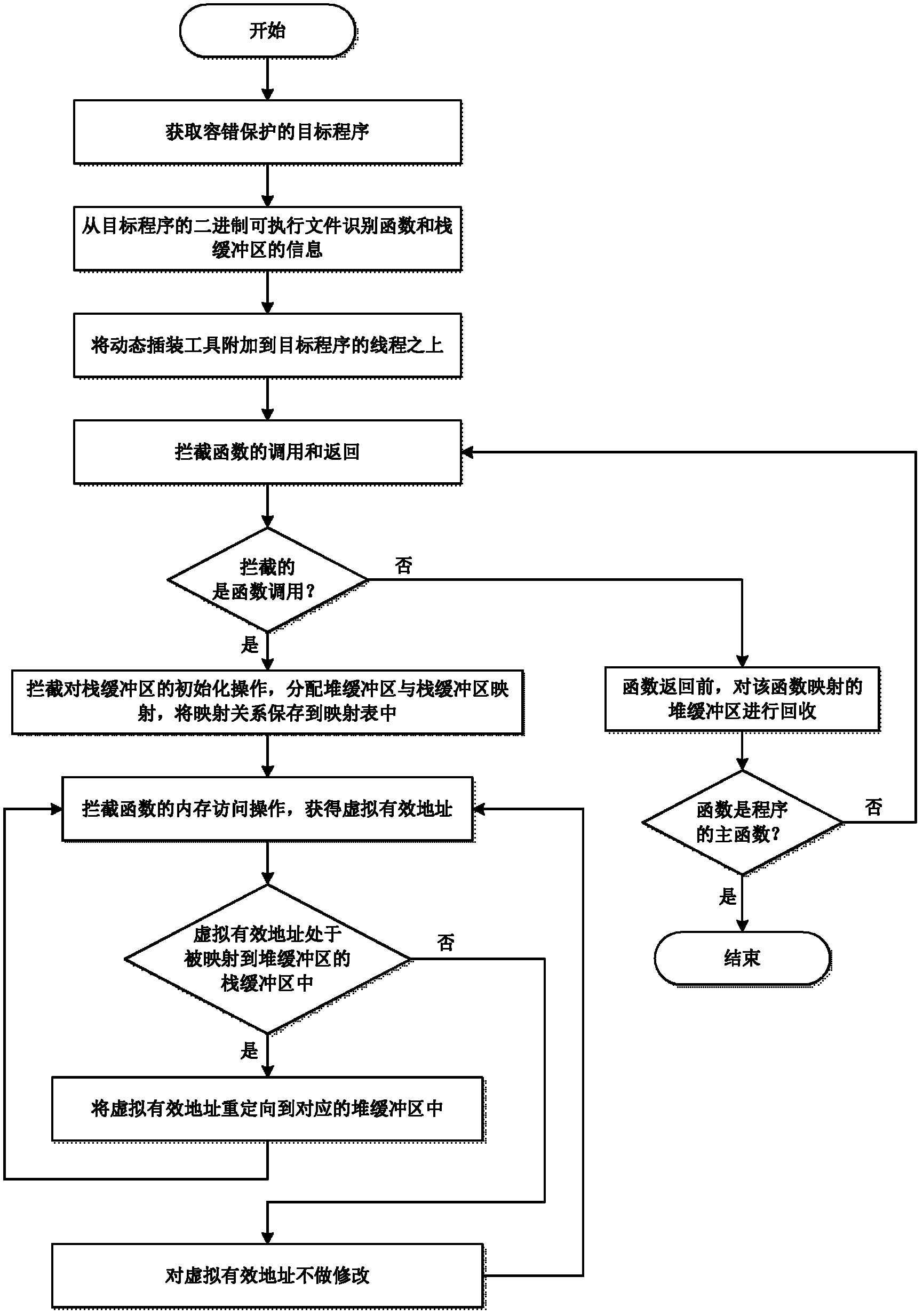
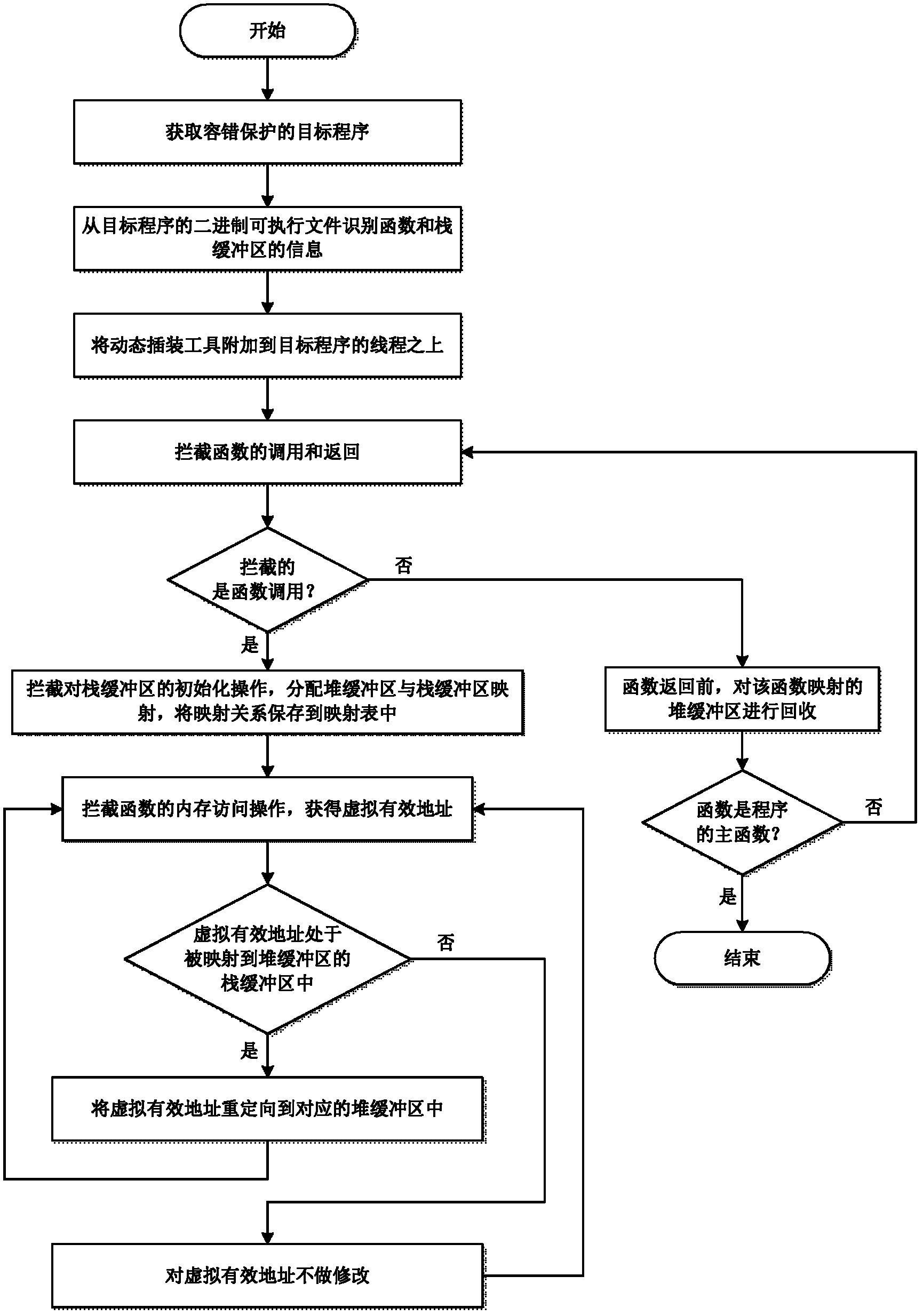
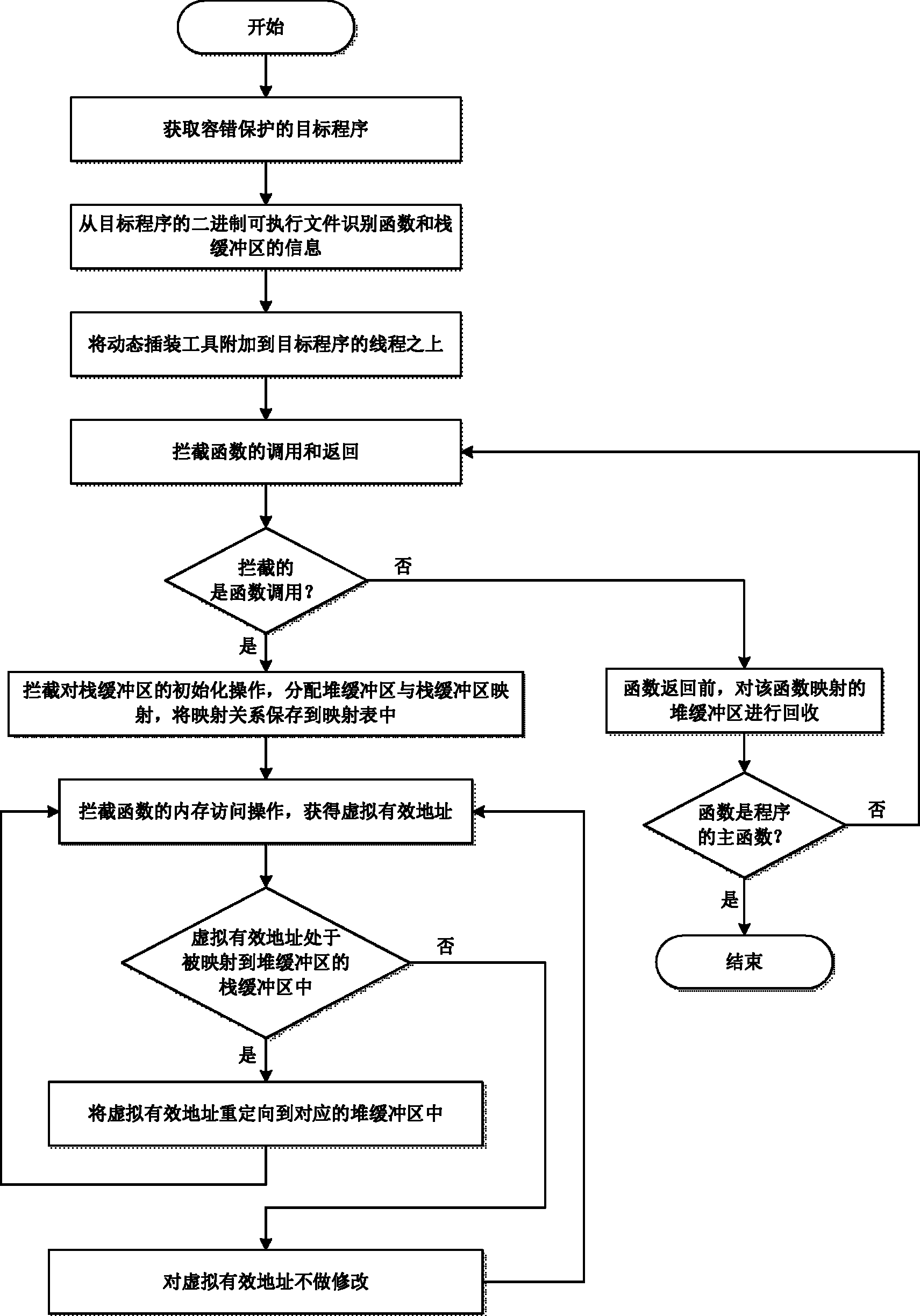
The invention provides a fault-tolerant method of software stack buffer overflow, which comprises the following steps of: obtaining a fault-tolerant-protection target program; parsing a binary executable file of the target program so as to identify functions in the target program and information of the stack buffer in the functions; attaching a dynamic instrumentation tool to all threads of the target program; using the dynamic instrumentation tool to intercept function call and function return; determining whether the intercept results are the function call of the target program or not, if so, using the dynamic instrumentation tool to intercept the initialization operation of the stack buffer, allocating a heap buffer in the heap space of the target program, so that the heap buffer is mapped with the stack buffer; saving a mapping relationship between the stack buffer and the heap buffer in a mapping table, and the mapping relationship comprising stack buffer information and heap buffer information; and using the dynamic instrumentation tool to intercept all memory access operations in order to obtain the virtual effective addresses of the memory access operation. The method realizes the fault tolerance of the stack buffer overflow.
Owner:HUAZHONG UNIV OF SCI & TECH
Method and apparatus for controlling buffer overflow in a communication system
ActiveUS7412004B2Promote recoveryGreat dangerColor television with pulse code modulationColor television with bandwidth reductionStack buffer overflowControl communications
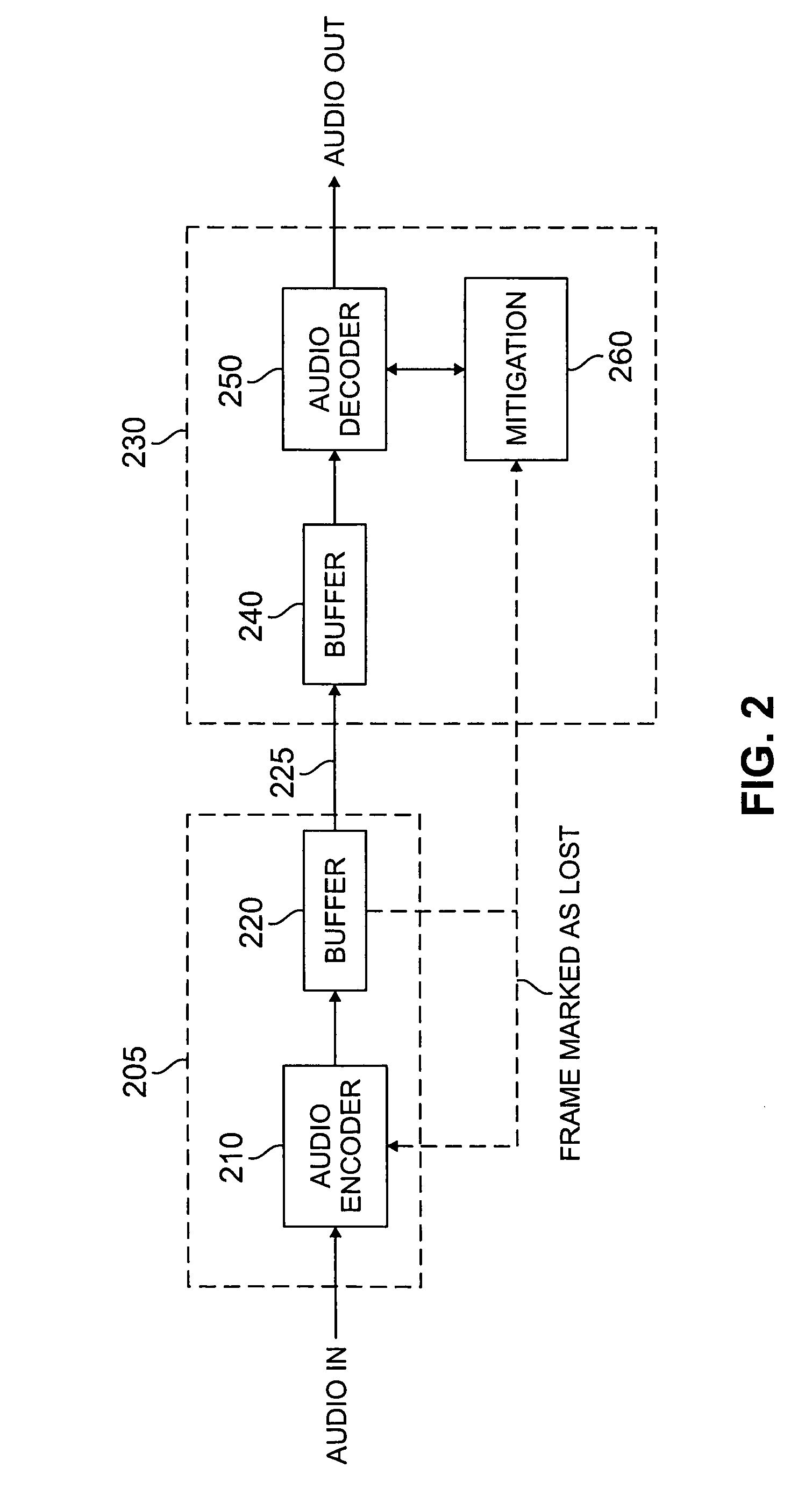
A method and apparatus are disclosed for controlling a buffer in a digital audio broadcasting (DAB) communication system. An audio encoder marks a frame as “dropped” whenever a buffer overflow might occur. Only a small number of bits are utilized to process a lost frame, thereby preventing the buffer from overflowing and allowing the encoder buffer-level to quickly recover from the potential overflow condition. The audio encoder optionally sets a flag that provides an indication to the receivers that a frame has been lost. If a “frame lost” condition is detected by a receiver, the receiver can optionally employ mitigation techniques to reduce the impact of the lost frame(s).
Owner:AVAGO TECH INT SALES PTE LTD
Home network system with transmission error recovery
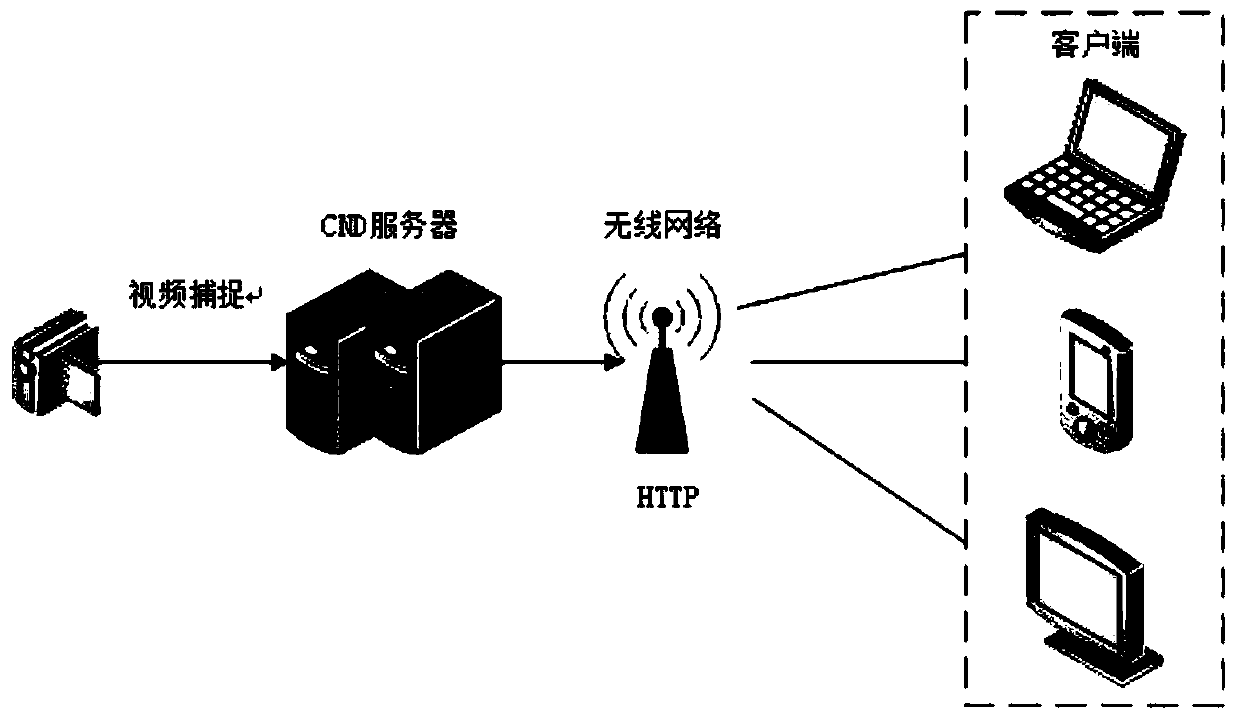
ActiveUS20130205353A1Increase ratingsEnergy efficient ICTMultiple digital computer combinationsStack buffer overflowClient-side
A client TV in a home entertainment network receives and buffers an audio / video stream from a server, before playing the stream. In the case of buffer underflow, the client TV requests the server to raise the transmission rate. If this causes an ensuing buffer overflow, the client TV requests the server to reset the transmission rate or stop transmitting altogether for a short time.
Owner:SONY ELECTRONICS INC +1
Adaptive transmission algorithm based on PI control streaming media
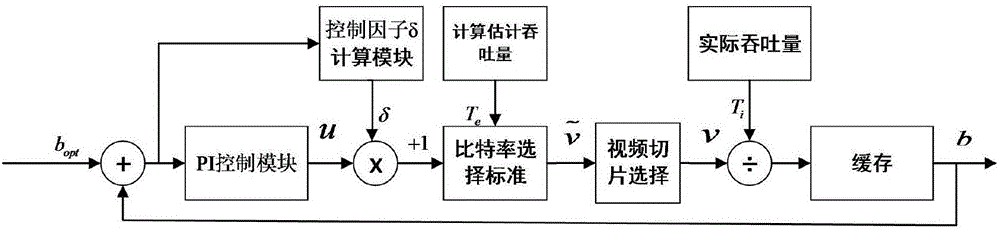
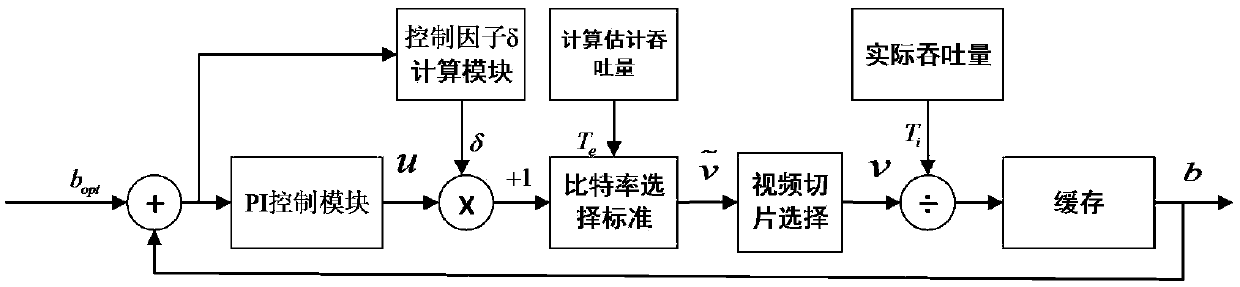
ActiveCN106453270APrevent playback from freezingAvoid utilizationTransmissionSelective content distributionStack buffer overflowSelf adaptive
The invention relates to an adaptive transmission algorithm based on PI control streaming media, comprising the following steps: the estimated throughput is calculated; the video allowance in a buffer is calculated; at the initial stage of video playing, the method enters a stage of quick start when the buffer is smaller than a target buffer and enters a stage of adaptive transmission when the buffer reaches the target buffer; in the stage of quick start, an adaptive algorithm based on real-time throughput is adopted; and in the stage of adaptive transmission, an adaptive transmission framework based on PI control is adopted, the offset of the buffer relative to the target buffer is used as error feedback information, and a dynamic control factor is introduced to combine a PI controller and an ITB controller nonlinearly. According to the invention, the PI controller and the ITB controller are combined nonlinearly by introducing the dynamic control factor and dynamically controlling the degree of control of the PI controller and the ITB controller, which can prevent problems caused by buffer overflow, such as video playing stagnation or low bandwidth utilization rate.
Owner:深圳云天畅想信息科技有限公司
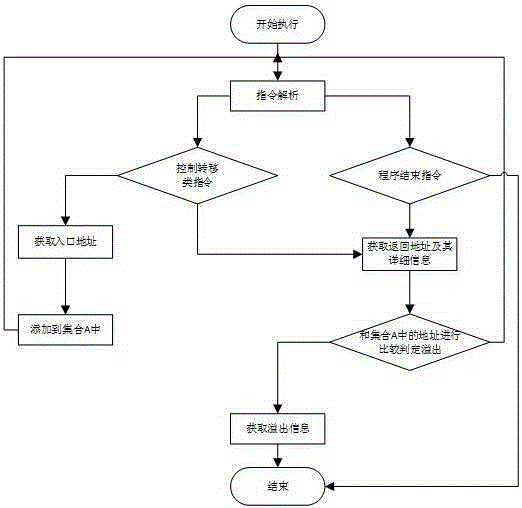
Stack overflow position detection method
ActiveCN105117332AImprove adaptabilityThe decision logic is simpleSoftware testing/debuggingPlatform integrity maintainanceStack buffer overflowCommercial software
The invention provides a stack overflow position detection method and relates to the technical field of software detection. The method is used for quickly detecting a stack overflow position to help software analysis. The method comprises: defining a set A and executing test software by utilizing program instrumentation; when executing a call instruction, obtaining an in-stack address and storing the in-stack address in the set A; and when executing a ret instruction, judging whether a return address is in the set A or not, and if so, judging that stack overflow does not occur to a function, or otherwise, judging that stack overflow occurs to the function. The technical scheme of the invention is mainly used for software analysis, a module with stack overflow can be quickly and accurately positioned, and a specific position causing stack overflow can be accurately positioned through further analysis. According to the method, commercial software can be processed without the need for a source code of tested software, all function types such as various complicated nested functions can be detected, and better adaptability is achieved.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
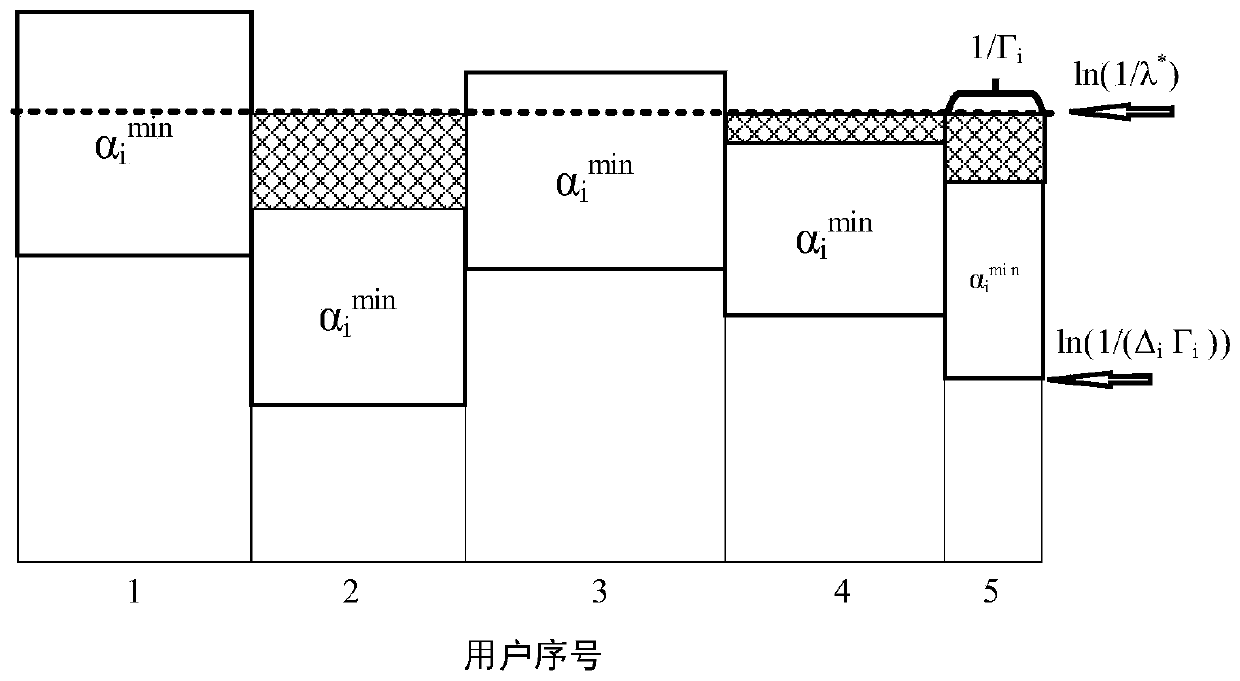
Optimal buffer resource allocation method based on yoke theory in wireless content distribution network
ActiveCN110049507AImprove distribution performanceSpillover Probability MinimizationWireless communicationContent distributionStack buffer overflow
The invention provides an optimal buffer resource allocation method based on yoke theory in a wireless content distribution network. First, a relationship between a backlog length, a buffer capacity,a data arrival rate, and a service rate in a buffer is determined. A buffer overflow probability expression is determined by applying a martingale theory. The maximum buffer overflow probability tolerable by each service user is given, and the minimum buffer capacity required by each service user is determined. According to the relation between the buffer capacity contributed by the intermediate node and the minimum buffer capacity required by the user who serves the intermediate node, the connection relation between the user and the edge equipment is determined, so that the optimization problem of minimizing the buffer overflow probability sum is constructed, and an optimal buffer resource allocation scheme is determined by using a water injection method. The probability of buffer overflow of the intermediate node is reduced, the content distribution efficiency is improved, and the distribution performance of the wireless content distribution network is further improved.
Owner:NANJING INST OF TECH
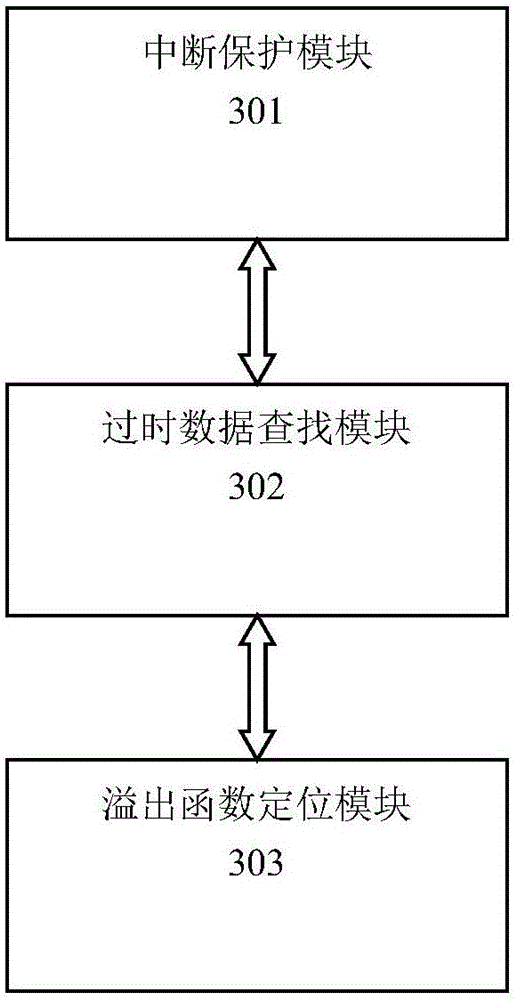
Method and apparatus for locating buffer overflow vulnerability
ActiveCN106228065ASolve the damageRapid positioningPlatform integrity maintainanceStack buffer overflowData information
The invention relates to a method and an apparatus for locating buffer overflow vulnerability. According to the method and the apparatus, outdated data information on a stack can be used to reestablish a function calling relation chain in the case that buffer overflow at the stack covers a stack frame address and a function return address, and an overflow function can be further directly located by virtue of the reestablished function calling relation chain. The method comprises the following steps: when the buffer overflow occurs, allowing a current program to be interrupted by an error so as to avoid the execution of a malicious code; taking an address indicated by a current ESP register as a starting point, and successively finding and determining an outdated stack frame pointer and an outdated return address from outdated data on the stack, wherein a value of the outdated return address is the return address of a last sub-function called by the overflow function, and a function corresponding to the return address is the overflow function. According to the method and the apparatus, a novel way of directly locating the overflow function rather than the way of adopting a stack calling function for successively backtrackeing is used, a vulnerability function is located by using the outdated data on the stack, different situations are classified to be processed, so that the outdated data can be reused, and the overflow function and the overflow address can be rapidly located.
Owner:WUHAN GREENET INFORMATION SERVICE
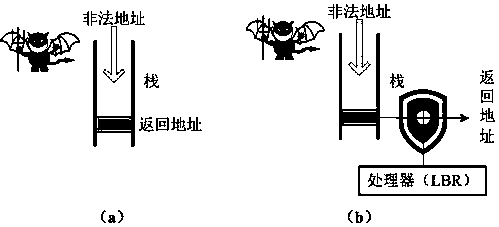
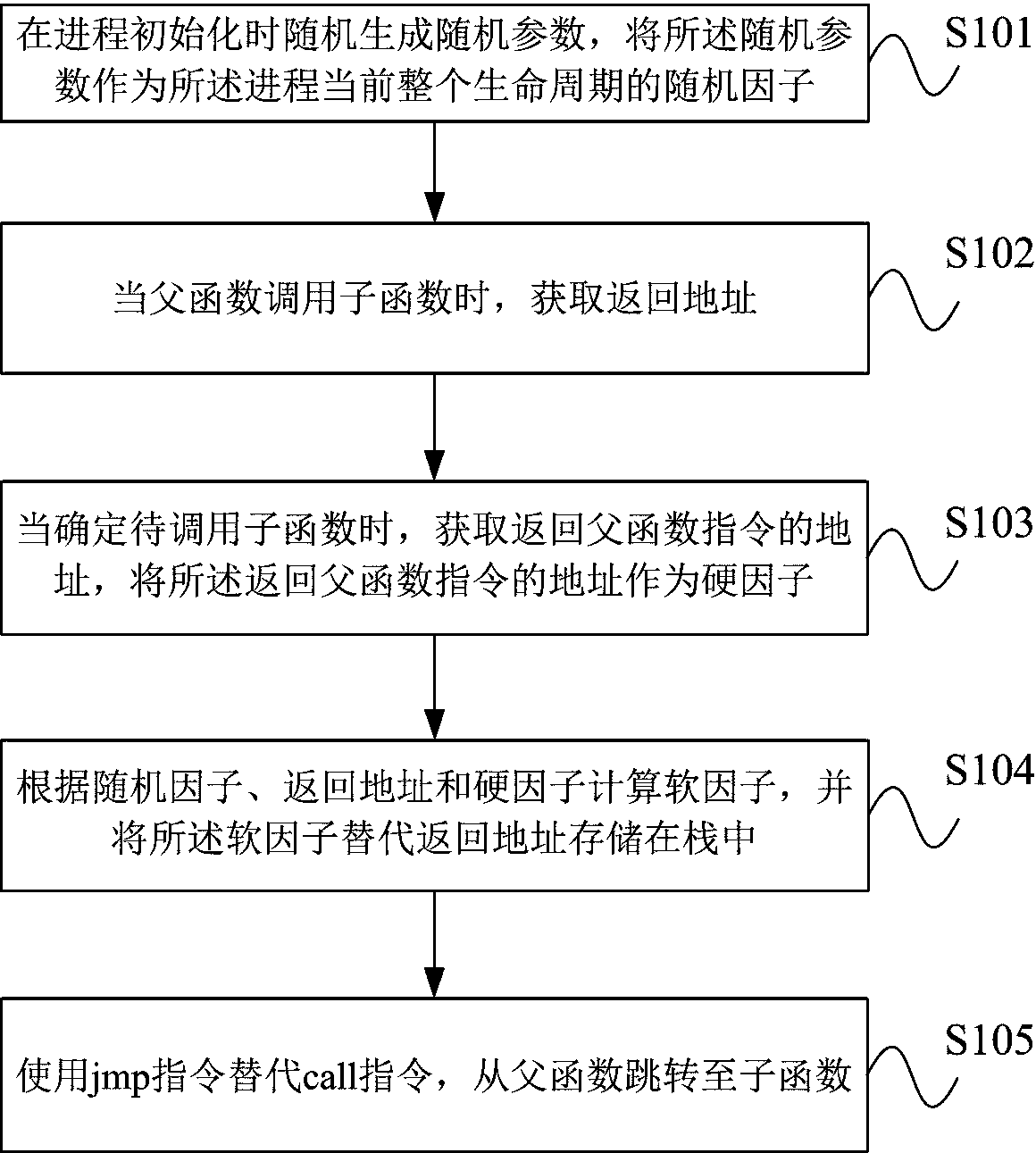
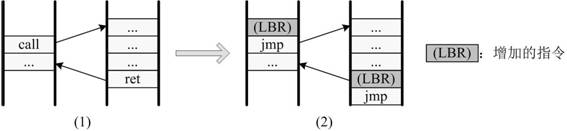
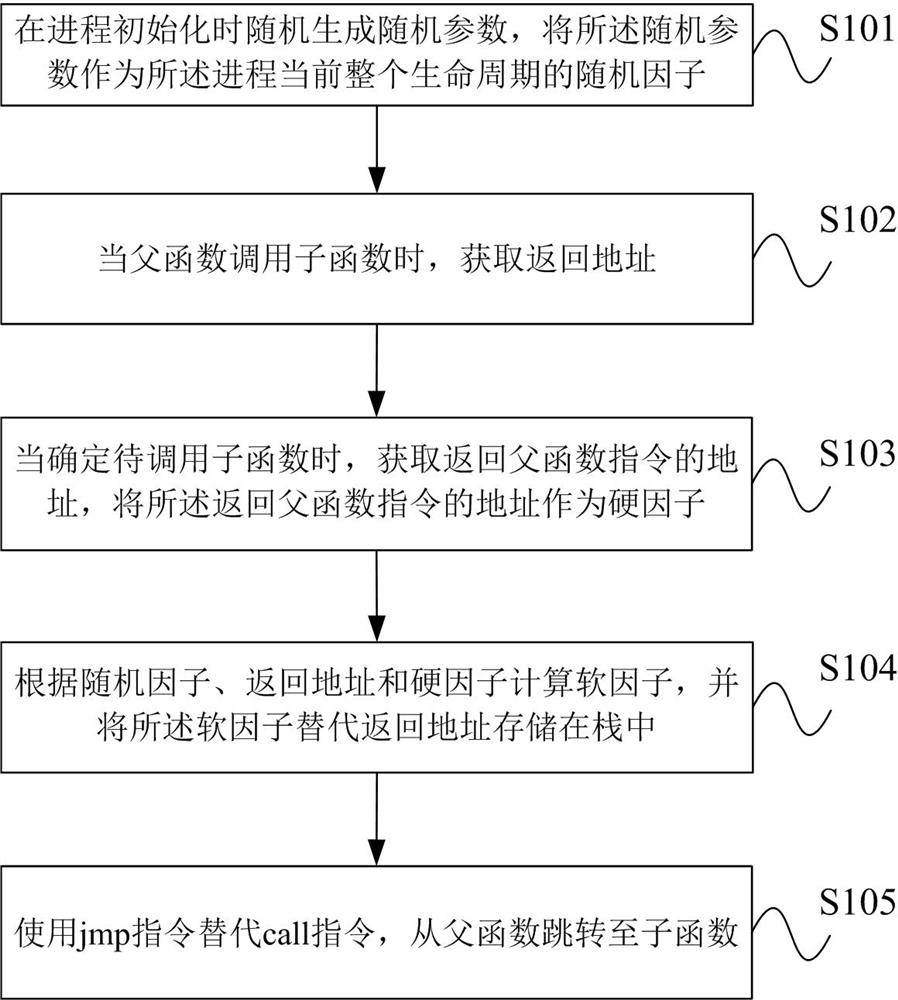
Stack buffer overflow attack defense method based on LBR
ActiveCN109858253AGuaranteed operating efficiencyPlatform integrity maintainanceComputer hardwareStack buffer overflow
The invention provides a stack buffer overflow attack defense method based on an LBR. An original call instruction and a let instruction are replaced by using a set instruction set. Hardware factors are introduced into protection of the return address in the stack, the 'address' stored in the stack is actually a software factor for generating a real return address, and the real return address canbe obtained only after the software factor is combined with the hardware factor provided by the processor LBR, so that an attacker directly attacks data in the stack to fail. Due to the fact that an attacker does not have the capability of directly attacking a physical system, it can be reasonably assumed that hard factors cannot be attacked and tampered. Based on the credibility of the hard factor, the stack data protection scheme provided by the invention is effective by combining the design of preventing replay of the random factor. Different from a shadow stack or an address returning encryption method, the method does not depend on too much computational complexity and redundant space, only a plurality of instructions are added, and the operation efficiency is guaranteed.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
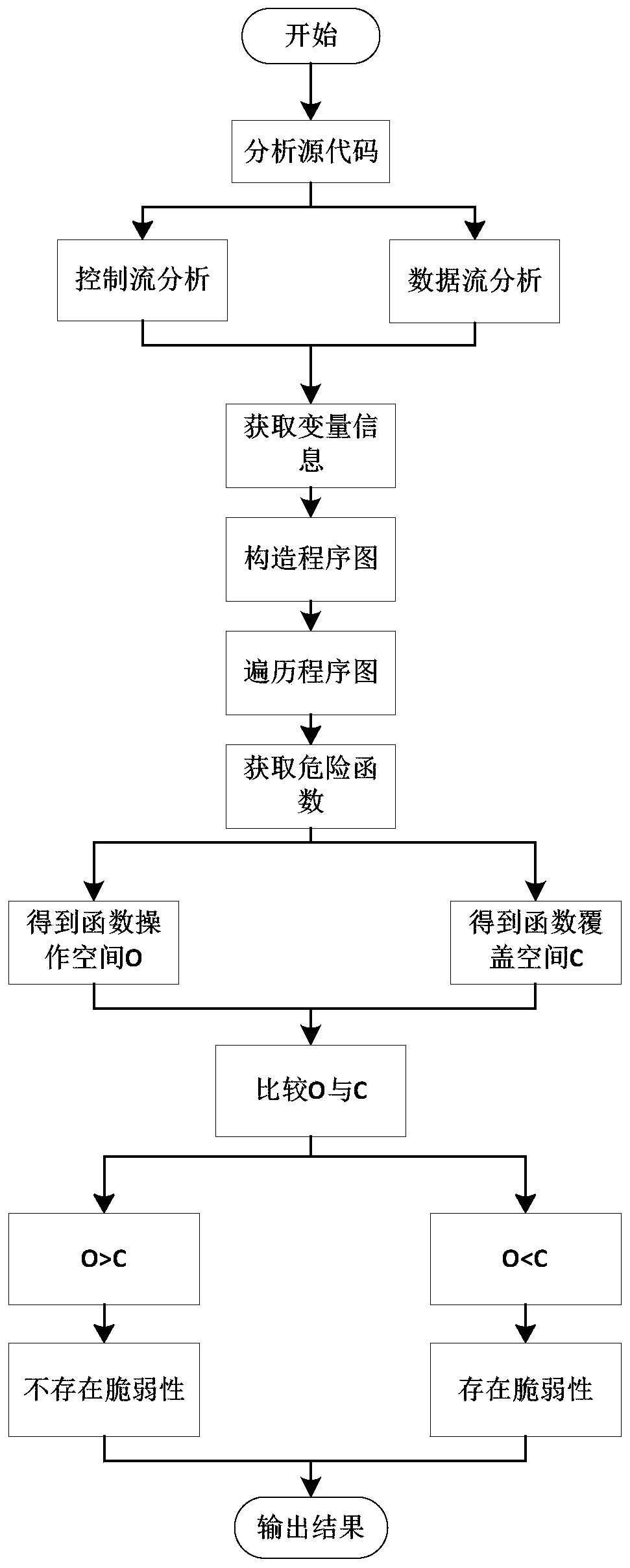
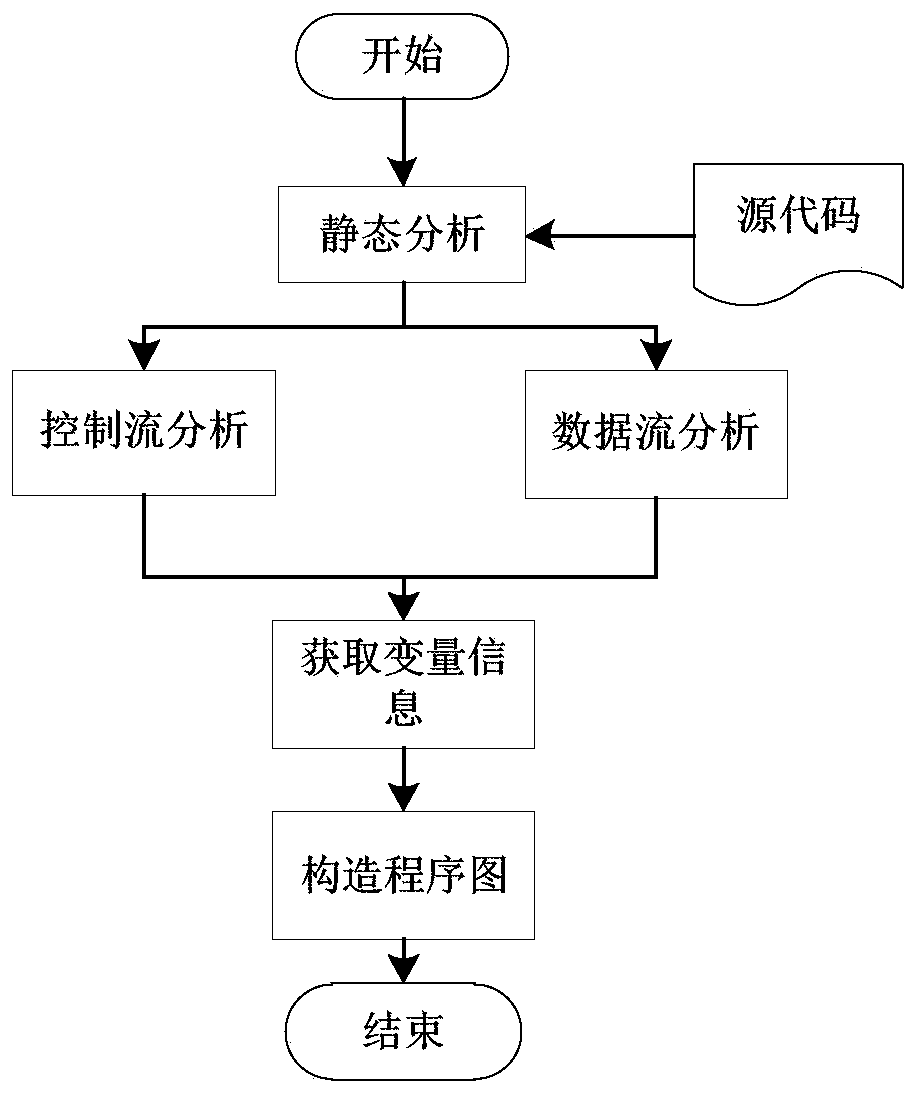
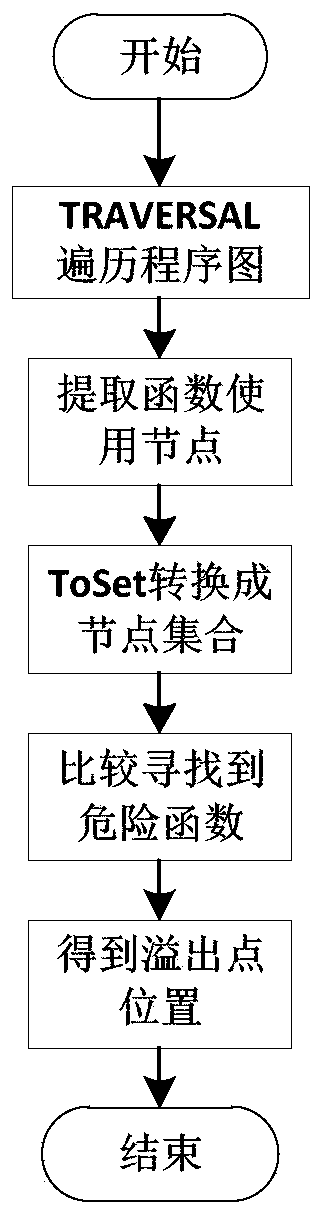
A stack buffer overflow vulnerability detection method based on a program diagram
PendingCN109784048AVulnerability detection appliesImprove detection efficiencyPlatform integrity maintainanceStack buffer overflowParallel computing
The invention discloses a stack buffer overflow vulnerability detection method based on a program diagram. The method comprises the steps that 1, after source codes are statically analyzed, constructing a corresponding program diagram; 2, traversing the program chart to find a danger function to obtain an overflow point position; 3, calculating the address offset between the buffer space operatedby the overflow point comparison function and the size of the space to be covered; And 4, judging whether address offset occurs or not to obtain a vulnerability detection result, Wherein the danger function mainly aims at three danger functions of Strncpy (), Memcpy () and Gets (); for the Strncpy () and Memcpy () functions, buffer area space O and coverage space C of function operation are obtained, and for the Gets () function, only buffer area space O of the function needs to be obtained; For a Strncpy function, if the replication length n<O, there is no vulnerability, if the replication length n>O and O<C, there is vulnerability; For the Memcpy function, if the copy length n <O, there is no vulnerability, if n<O and O<C, then there is vulnerability; for the Gets function, if O = [0, infinite], then there is vulnerability..
Owner:JIANGSU UNIV
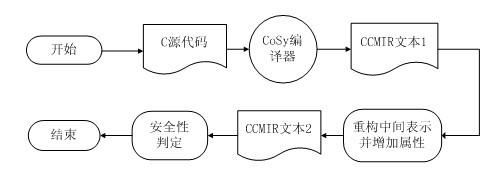
Detection method for buffer overflow of reconstructed CoSy intermediate representation
ActiveCN102662834AImprove versatilityReduce complexitySoftware testing/debuggingProgram controlStack buffer overflowLocal variable
The invention aims at providing a detection method for buffer overflow of reconstructed CoSy intermediate representation, namely a method for analyzing a source code and detecting the buffer overflow. The method comprises the steps of: (1) analyzing and scanning a source program by a CoSy compiler to generate intermediate representation CCMIR (common CoSy medium-level intermediate representation); (2) reconstructing a CCMIR text and increasing a safety attribution to a non-static-state local variable, so as to judge the buffer overflow; and (3) judging the buffer overflow of the final intermediate representation CCMIR. By the adoption of the method, the code can be rapidly reconstructed, and the reconstruction process is simple and feasible and has excellent versatility; and rapid and high-efficiency detection on the potential errors, which cause the buffer overflow, in the program can be realized after reconstruction.
Owner:58TH RES INST OF CETC
Communication device
InactiveCN103081419APrevent overflowPrevent the connection from being forcibly cut offData switching networksTransmission throughputStack buffer overflow
In a relay device for relaying a LAN-side and a WAN-side TCP communication (two TCP communications), buffer overflow in a LAN-side receiving buffer and a WAN-side transmission buffer of the relay device is prevented even if the WAN-side line bandwidth is smaller than the LAN-side line bandwidth, and, further, the connection is prevented from being forcibly cut. The value of the receiving window size (rwnd) contained in an ACK packet which is sent back to the LAN-side transmission terminal is controlled on the basis of the RTT, the discard rate and the transmission throughput measured in the WAN-side TCP communication, and on the basis of the total value of the unaligned data size of the receiving buffer, the aligned data size, the untransmitted data size of the WAN-side transmission buffer, and the ACK waiting data size. Further, when rwnd falls below a pre-set threshold value and then exceeds said value again, an ACK packet containing the value of the receiving window size (rwnd) is immediately transmitted to the LAN-side transmission terminal.
Owner:HITACHI LTD
Reducing buffer overflow
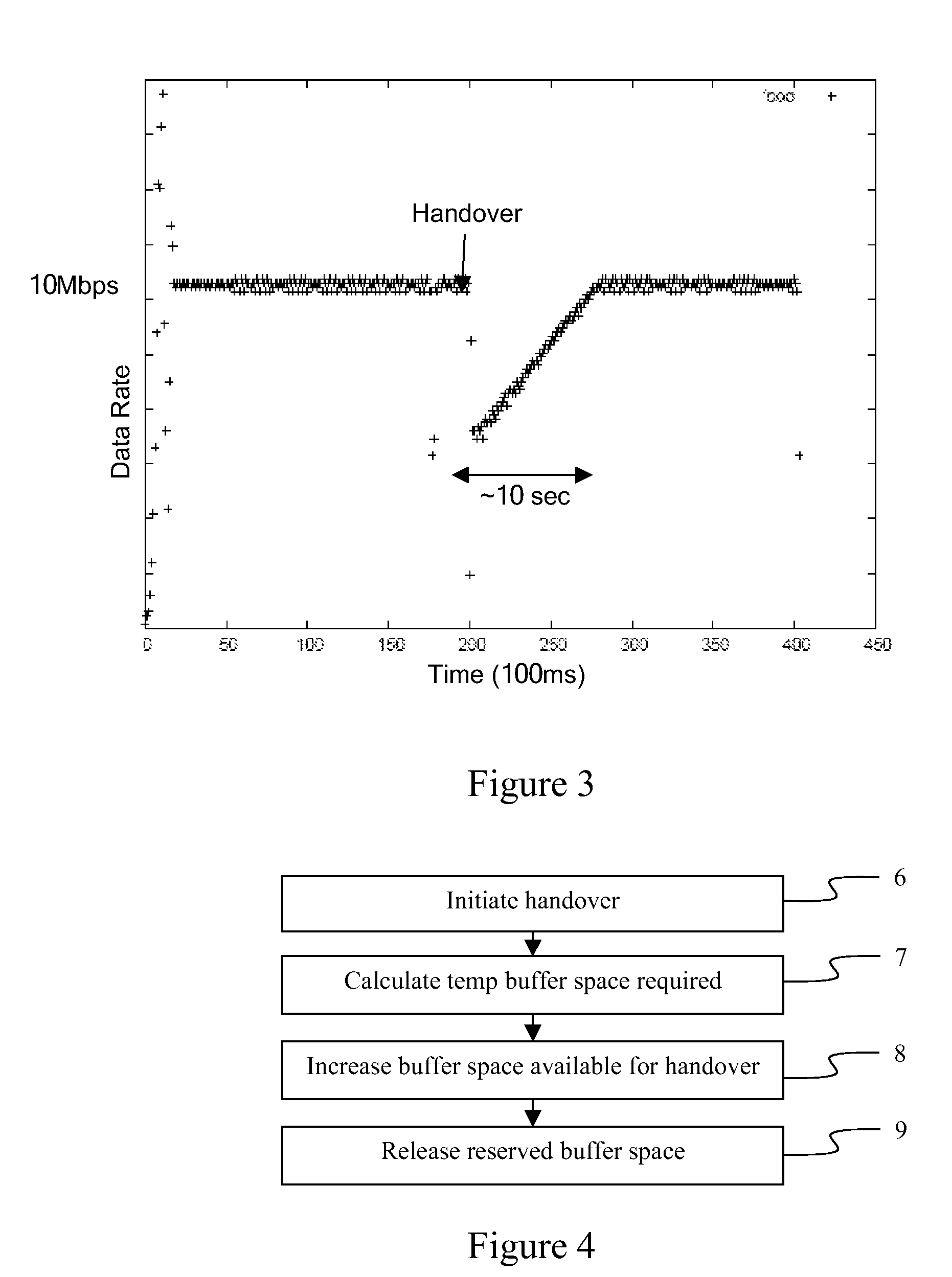
InactiveUS8170557B2Low costSmall round-trip timeError preventionNetwork traffic/resource managementStack buffer overflowCellular radio
A method of reducing buffer overflow in a cellular radio network caused by a transfer of data from a buffer in a first cell to a buffer in a second cell when a handover of mobile equipment from said first cell to said second cell occurs. The method comprises temporarily increasing an amount of temporary buffer space required to handle data transferred from the buffer of the first cell to the buffer of the second cell. In one embodiment of the method, prior to increasing the amount of temporary buffer space, the amount of temporary buffer space required is calculated.
Owner:TELEFON AB LM ERICSSON (PUBL)
Data processing device, semiconductor external view inspection device, and data volume increase alleviation method
ActiveUS9489324B2Suppress overflowProcessor architectures/configurationElectric digital data processingStack buffer overflowProcessor element
Provided is a data processing device with which, when a temporary network congestion occurs, it is possible to avoid a buffer overflow and sustain a process. When a request for retransmission of the same data with respect to a processor element from a buffer occurs continuously a prescribed number of iterations, a data processing device according to the present invention determines that it is possible that a buffer overflow occurs, and suppresses an increase in the volume of data which is accumulated in the buffer (see FIG. 1).
Owner:HITACHI HIGH-TECH CORP
An Adaptive Transmission Algorithm Based on Pi Controlled Streaming Media
ActiveCN106453270BAvoid utilizationPerceived quality experience is goodTransmissionSelective content distributionStack buffer overflowSelf adaptive
Owner:深圳云天畅想信息科技有限公司
Dynamic measuring method of buffer overflow on the basis of logic isolation
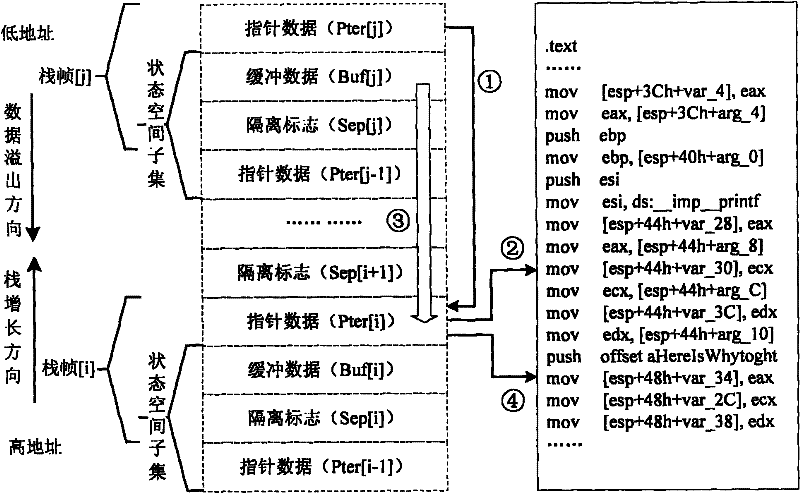
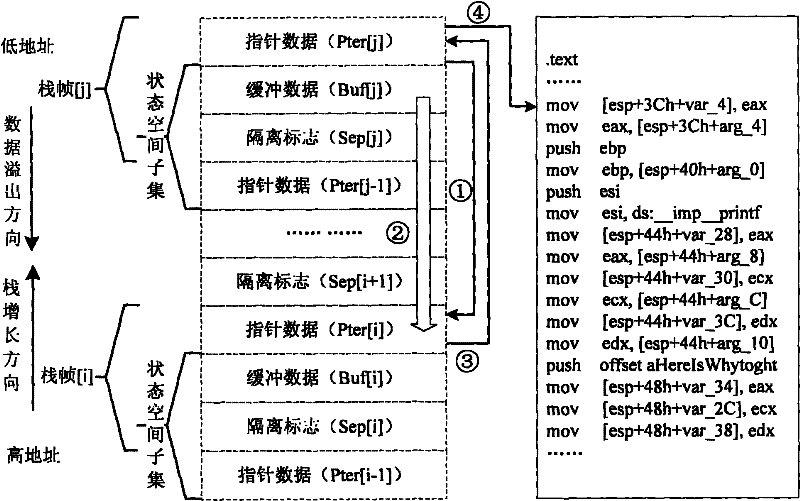
ActiveCN101694686BOvercome deficienciesPlatform integrity maintainanceStack buffer overflowPhysical space
The invention discloses a dynamic measuring method of buffer overflow on the basis of logic isolation, comprising the steps of logic isolation of buffer data and buffer dynamic measurement on the basis of the logic isolation in an operation process so as to detect the buffer overflow. Different data types are stored in continuous linear physical spaces without modifying the current structure of acomputer system. The dynamic measuring method comprises the following steps: by inserting an isolation mark, storing the buffer data in the low address direction of the isolation mark, and storing pointer data in the high address direction of the isolation mark to form a state space subset ranging from the low address to the high address of a memory, wherein a buffer comprises a plurality of continuous state space subsets; and based on the logic isolation, checking the completeness of the isolation mark by the dynamic measuring method to judge whether the buffer overflow occurs in or not. Thedynamic measuring method of buffer overflow on the basis of logic isolation can be applied to buffers with different applications, in particular to stacks. The method is optimized in measuring time and measuring range to overcome the defects of the traditional method.
Owner:BEIJING UNIV OF TECH
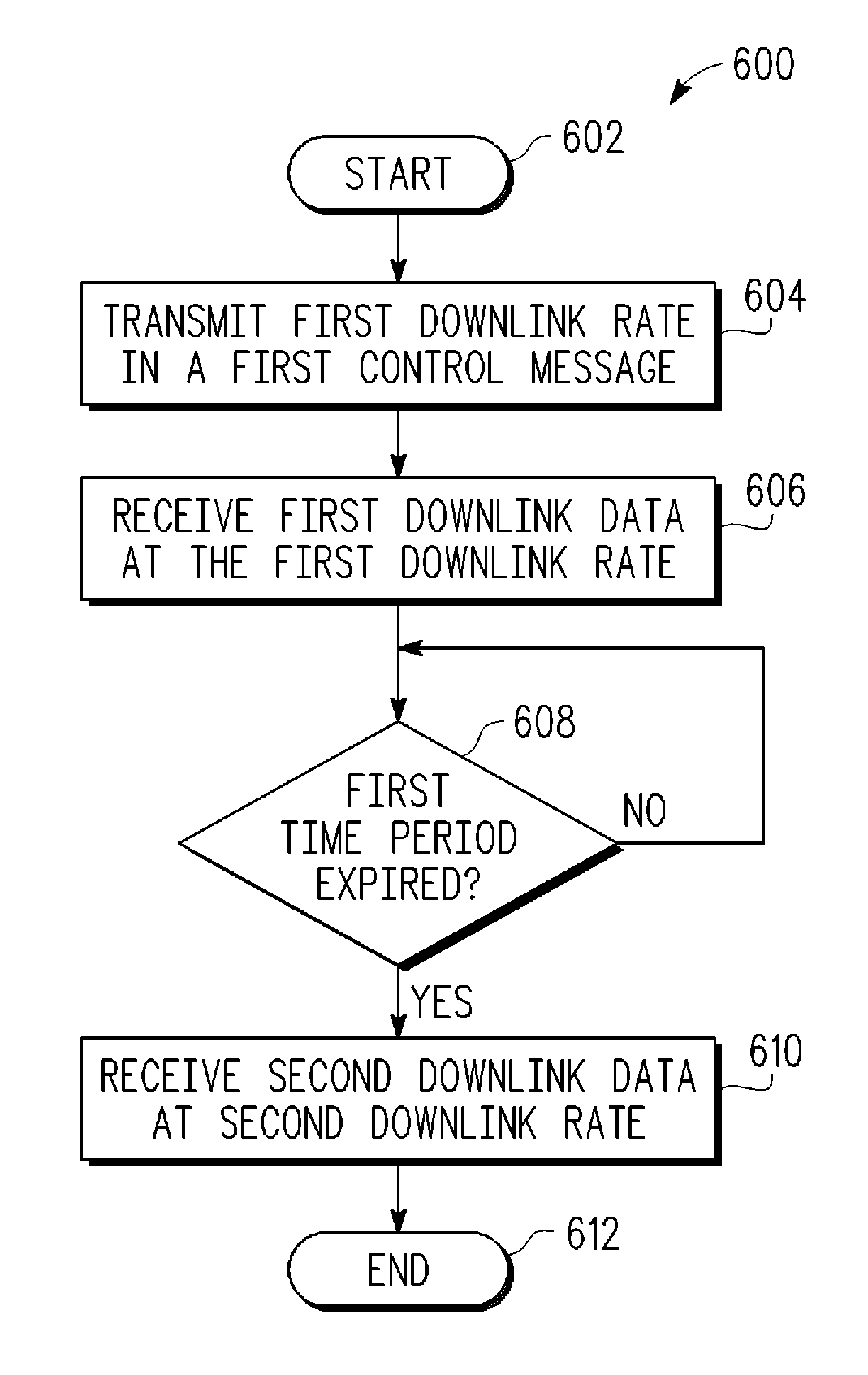
Techniques for reducing buffer overflow in a communication system
A technique for operating a wireless communication device includes transmitting a first downlink rate in a first control message. The first downlink rate is based on a latency of an inter-processor communication link associated with the wireless communication device. First downlink data at the first downlink rate is then received for a first time period. Following the first time period, second downlink data is received at a second downlink rate that is higher than the first downlink rate.
Owner:APPLE INC
Overflow attack defense method and system based on stack randomization
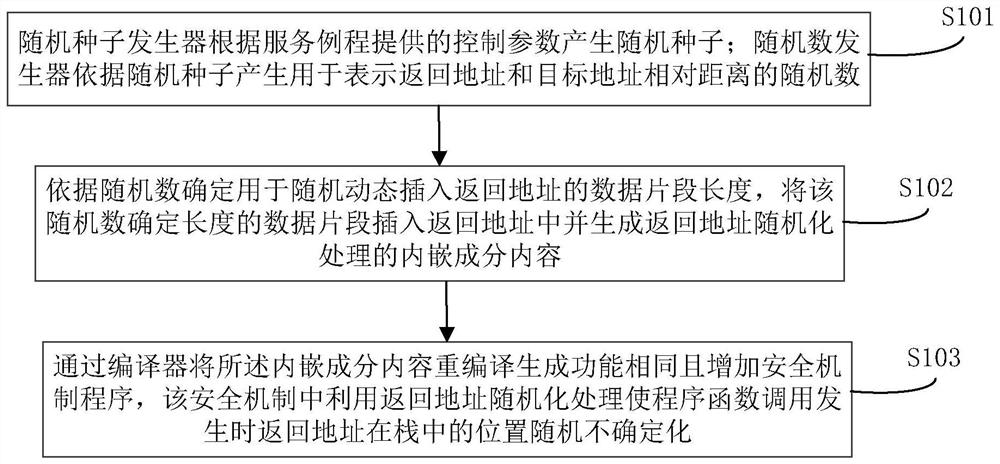
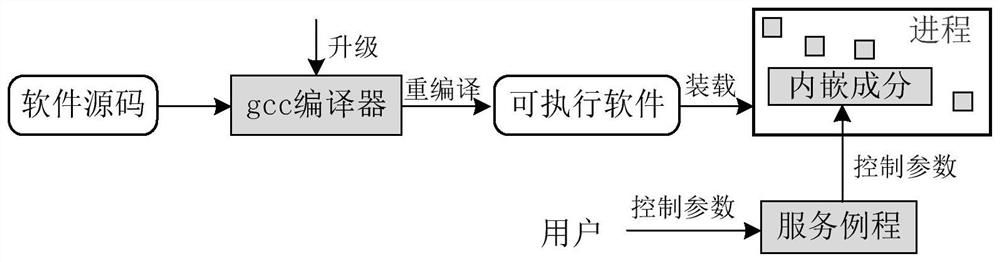
PendingCN114238942AIncrease the difficultyEasy to apply in actual scenariosPlatform integrity maintainanceAlgorithmAttack
The invention belongs to the technical field of computer security, and particularly relates to an overflow attack defense method and system based on stack randomization, and the method comprises the steps: a random seed generator generates a random seed according to a control parameter provided by a service routine; the random number generator generates a random number for representing a relative distance between a return address and a data overflow point according to the random seed; determining the length of a data fragment used for randomly and dynamically inserting a return address according to the random number, inserting the data fragment with the length determined by the random number into the return address, and generating an embedded component content for randomizing the return address; the content of the embedded component is recompiled through a compiler to generate programs with the same function and added with a security mechanism, and in the security mechanism, the position of a return address in a stack is randomly uncertain when program function calling occurs through return address randomization processing, so that the overflow attack difficulty of a stack buffer area is increased; return address integrity detection and other work are avoided, and the overall efficiency of return address protection is improved.
Owner:ZHONGYUAN ENGINEERING COLLEGE
Stack buffer overflow attack defense method and system based on dynamic shadow stack
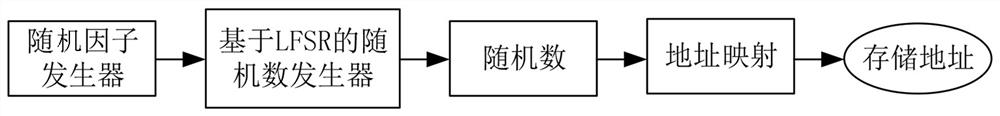
PendingCN114254400AImprove securityAchieve double protectionKey distribution for secure communicationInput/output to record carriersStack buffer overflowAttack
The invention belongs to the technical field of stack buffer overflow attack defense, and particularly relates to a stack buffer overflow attack defense method and system based on a dynamic shadow stack, and the method comprises the steps: applying for a large enough storage space in a process address space for storing shadow stack contents; dividing the content of the shadow stack into a plurality of shares for scattered storage by adopting a secret sharing method; a random number stream is generated based on a random factor generated by software and a shift feedback register, a storage address of a shadow stack which changes randomly is generated during each time of function calling, namely, a storage address of shares of the shadow stack which changes randomly is generated, and the shares are stored in specified positions of a storage space in a scattered mode. According to the method, dual protection of the shadow stack is achieved mainly through shadow stack content scattered storage and shadow stack address randomization, the attack difficulty is greatly increased, and therefore the security of the shadow stack is improved.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
A defense method of stack buffer overflow attack based on lbr
ActiveCN109858253BGuaranteed operating efficiencyPlatform integrity maintainanceStack buffer overflowAttack
The invention provides an LBR-based stack buffer overflow attack defense method. By using the set instruction set to replace the original call instruction and ret instruction, the hardware factor is introduced into the protection of the return address in the stack. The "address" stored in the stack is actually the software factor that generates the real return address. Only with processing The real return address can only be obtained after combining the hardware factors provided by the controller LBR, which makes the attacker's method of directly attacking the data in the stack invalid. Since the attacker does not have the ability to directly attack the physical system, the present invention can reasonably assume that the hard factor cannot be tampered with by the attack. Based on the credibility of the hard factor, combined with the anti-replay design of the random factor, the stack data protection scheme proposed by the present invention is effective. Different from the method of shadow stack or encrypted return address, the present invention does not rely on too much computational complexity and redundant space, but only adds several instructions, and the operating efficiency is guaranteed.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Equipment and method for preventing buffer overflow
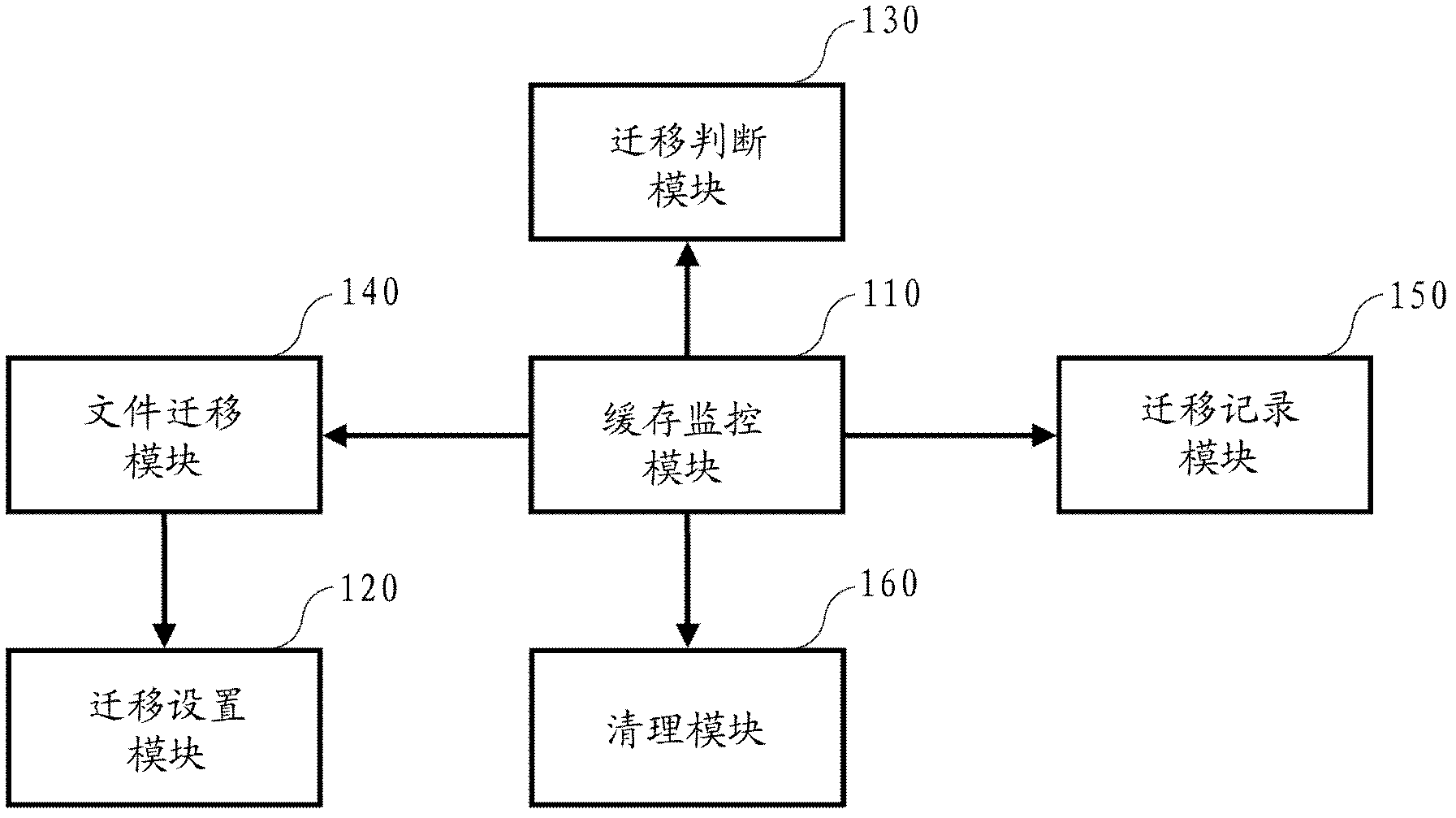
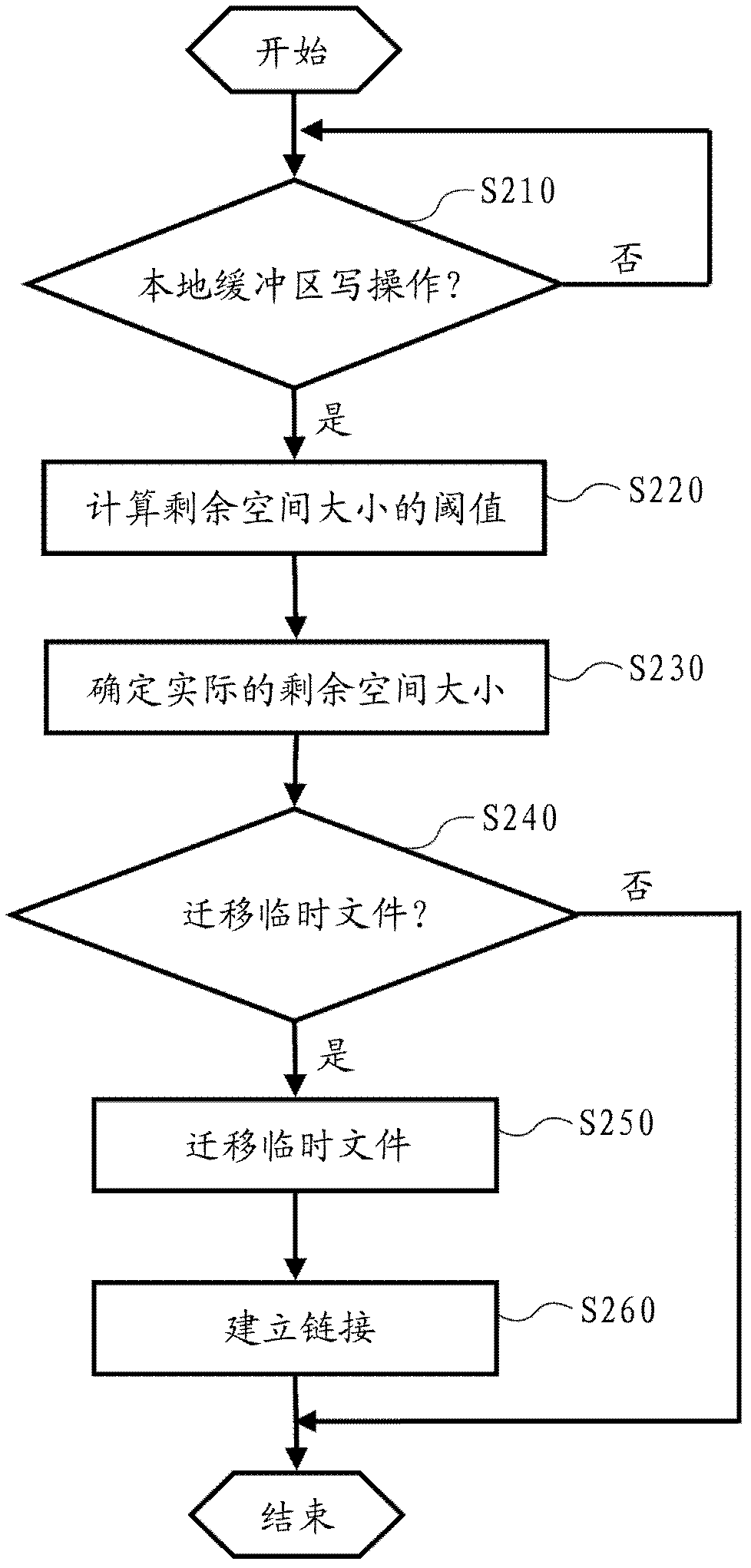
ActiveCN102693164BPrevent overflowEnsure that the operation is not significantly degradedError detection/correctionStack buffer overflowTemporary file
The invention provides equipment and a method for preventing buffer overflow. The equipment comprises: a migration determining module used to calculate a threshold of a free space in a local buffer area and calculate a actual free space in the current local buffer area, wherein the threshold of the free space is compared with the actual free space, and if the threshold of free space is greater than the actual free space, then the need to carry out temporary files migration is determined; a file migration module, by which the temporary files are migrated to a predetermined target directory, and soft links linking to the migrated temporary files are established in the directory of the local buffer area; and a buffer monitoring module which monitors operation on temporary files in the local buffer area by application tasks, when an writing operation upon the temporary files in the local buffer area is detected the migration determining module is controlled to determine whether to carry out temporary file migration or not, if the need to carry out temporary file migration is determined, then the file migration module is controlled to carry out temporary file migration.
Owner:BC P INC CHINA NAT PETROLEUM CORP +1
Fault-tolerant method of software stack buffer overflow
InactiveCN102521079BGuaranteed correctnessDo not overwrite each otherProgram controlRedundant operation error correctionFault toleranceStack buffer overflow
The invention provides a fault-tolerant method of software stack buffer overflow, which comprises the following steps of: obtaining a fault-tolerant-protection target program; parsing a binary executable file of the target program so as to identify functions in the target program and information of the stack buffer in the functions; attaching a dynamic instrumentation tool to all threads of the target program; using the dynamic instrumentation tool to intercept function call and function return; determining whether the intercept results are the function call of the target program or not, if so, using the dynamic instrumentation tool to intercept the initialization operation of the stack buffer, allocating a heap buffer in the heap space of the target program, so that the heap buffer is mapped with the stack buffer; saving a mapping relationship between the stack buffer and the heap buffer in a mapping table, and the mapping relationship comprising stack buffer information and heap buffer information; and using the dynamic instrumentation tool to intercept all memory access operations in order to obtain the virtual effective addresses of the memory access operation. The method realizes the fault tolerance of the stack buffer overflow.
Owner:HUAZHONG UNIV OF SCI & TECH
A method and device for locating buffer overflow vulnerabilities
ActiveCN106228065BSolve the damageRapid positioningPlatform integrity maintainanceStack buffer overflowData information
The invention relates to a method and an apparatus for locating buffer overflow vulnerability. According to the method and the apparatus, outdated data information on a stack can be used to reestablish a function calling relation chain in the case that buffer overflow at the stack covers a stack frame address and a function return address, and an overflow function can be further directly located by virtue of the reestablished function calling relation chain. The method comprises the following steps: when the buffer overflow occurs, allowing a current program to be interrupted by an error so as to avoid the execution of a malicious code; taking an address indicated by a current ESP register as a starting point, and successively finding and determining an outdated stack frame pointer and an outdated return address from outdated data on the stack, wherein a value of the outdated return address is the return address of a last sub-function called by the overflow function, and a function corresponding to the return address is the overflow function. According to the method and the apparatus, a novel way of directly locating the overflow function rather than the way of adopting a stack calling function for successively backtrackeing is used, a vulnerability function is located by using the outdated data on the stack, different situations are classified to be processed, so that the outdated data can be reused, and the overflow function and the overflow address can be rapidly located.
Owner:WUHAN GREENET INFORMATION SERVICE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com