Fault-tolerant method of software stack buffer overflow
A buffer overflow and buffer technology, applied in the field of computer security, can solve the problems of high false negative rate, inability to stack buffer overflow fault tolerance, strong conditions, etc., and achieve the effect of high flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
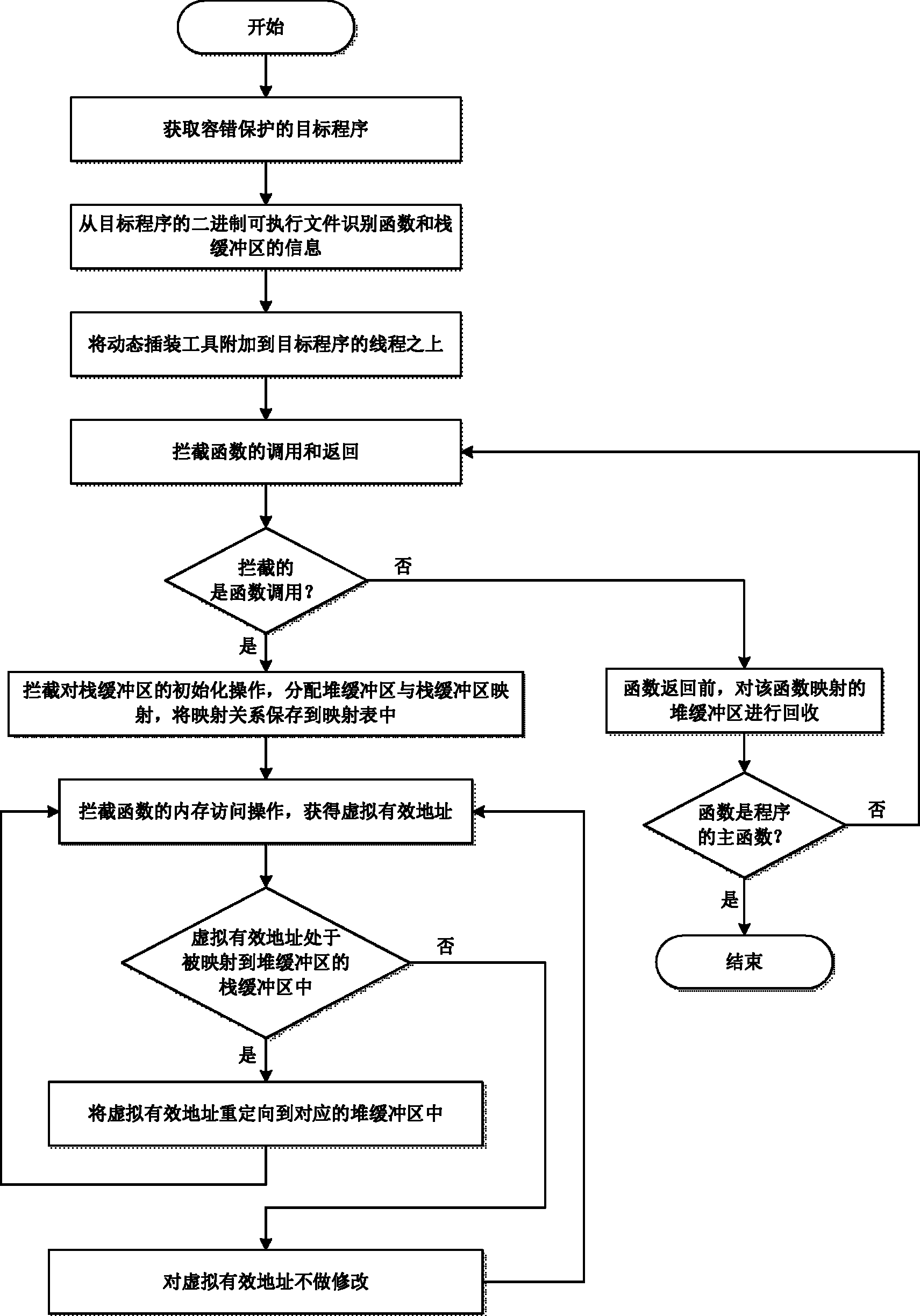
[0016] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
[0017] like figure 1 Shown, the inventive method comprises the following steps:
[0018] (1) obtain the target program of fault-tolerant protection;
[0019] (2) Perform object code analysis or debugging information analysis on the binary executable file of the fault-tolerant target program, and identify the set F of functions in the target program and the set I of the stack buffer information in the function. F={f 1 , f 2 ,..., f n}, where n is the number of functions contained in the target program, f i Represents a function. define f i The information set of the buffer contained in is B i ={b 1 , b 2 ,...,b m}, b j Represents information about a stack buffer. b j is a two-tuple {b j .o, b j .l}, b j .o is the starting offset address of the stack buffer, b j .l is the length of the stack buffer, a collection of stack buffer ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com