Dynamic stack memory management method
A memory management and stack technology, applied in the direction of platform integrity maintenance, can solve problems such as buffer overflow attacks, and achieve the effect of preventing stack buffer overflow
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0015] In order to further illustrate the present invention, further describe below in conjunction with accompanying drawing:
[0016] The above is the basic principle of the present invention, which can be implemented in multiple ways. For example, special memory devices (including software devices and hardware devices) can be used to implement. It can also be implemented using special computer systems. It is also possible to rewrite the compiler to generate an object program with the above functions. In short, various implementations within the spirit of the principles should be included. An example is given below to specifically illustrate the execution process of the program using this method.
[0017] Ⅰ. Execution process of normal program:
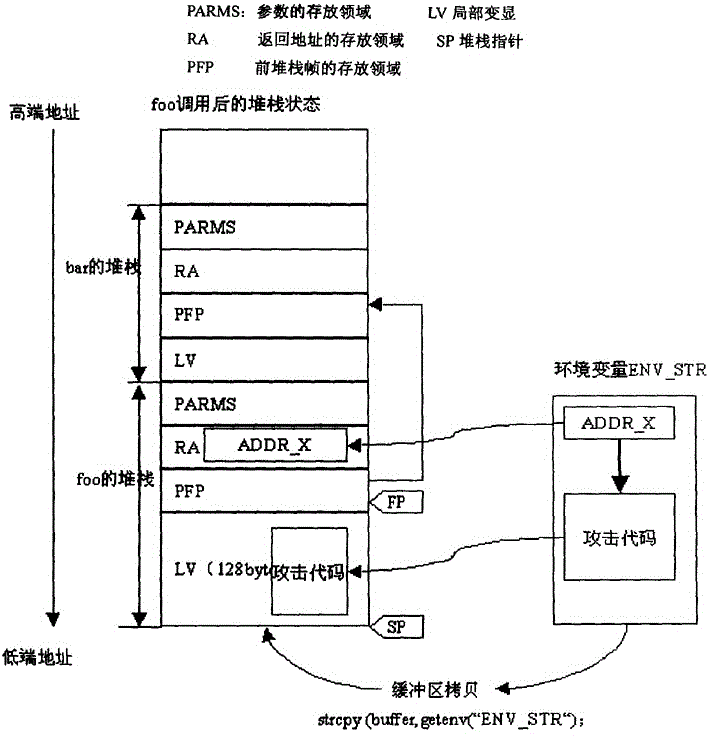
[0018] we take figure 2 As an example to illustrate the normal program execution flow. We use the example of the function foo being called by the function bar to illustrate. Assume that the stack frame grows from high address...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com