Detection method for buffer overflow of reconstructed CoSy intermediate representation
A buffer overflow and intermediate representation technology, applied in the field of information security, can solve the problems of inaccurate buffer state judgment method, inaccurate representation method, and inaccurate judgment results, so as to achieve comprehensive judgment results, reduce complexity, and accurately express Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
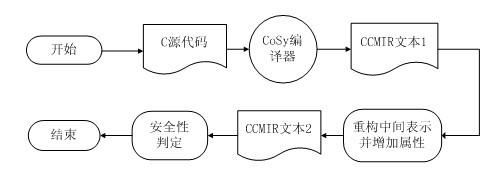
[0047] like figure 1 Shown, the buffer overflow detection method of reconstruction CoSy intermediate representation of the present invention, buffer overflow wherein refers to the buffer overflow on the stack, the concrete process of this method is as follows:
[0048] Step a, CoSy (compiler development tool of ACE company) compiler analyzes and scans the source program, and generates an intermediate representation CCMIR;
[0049] Step b. Reconstruct the CoSy intermediate representation CCMIR text, and add attributes to all non-static local variables for judging buffer overflow;
[0050] In step b, the method of reconstructing CCMIR is:
[0051] b1) Define DTD rules to convert CCMIR text into XML text storage;
[0052] The reason for converting to XML documents is because the CCMIR hierarchy is very suitable for XML documents, and XML docu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com